Location privacy protection method based on location sensitivity and hot degree in road network
A privacy-preserving and sensitive technology, applied in location-based services, security devices, electrical components, etc., to achieve good performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
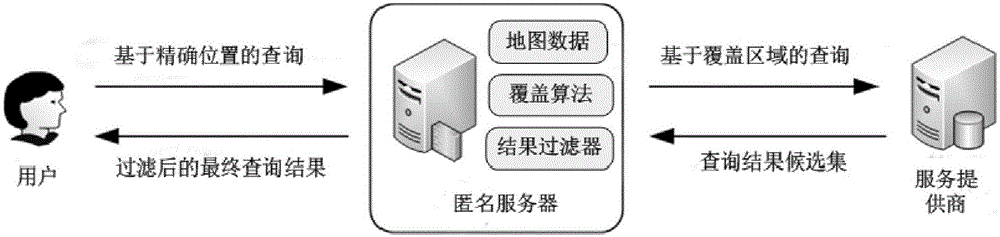
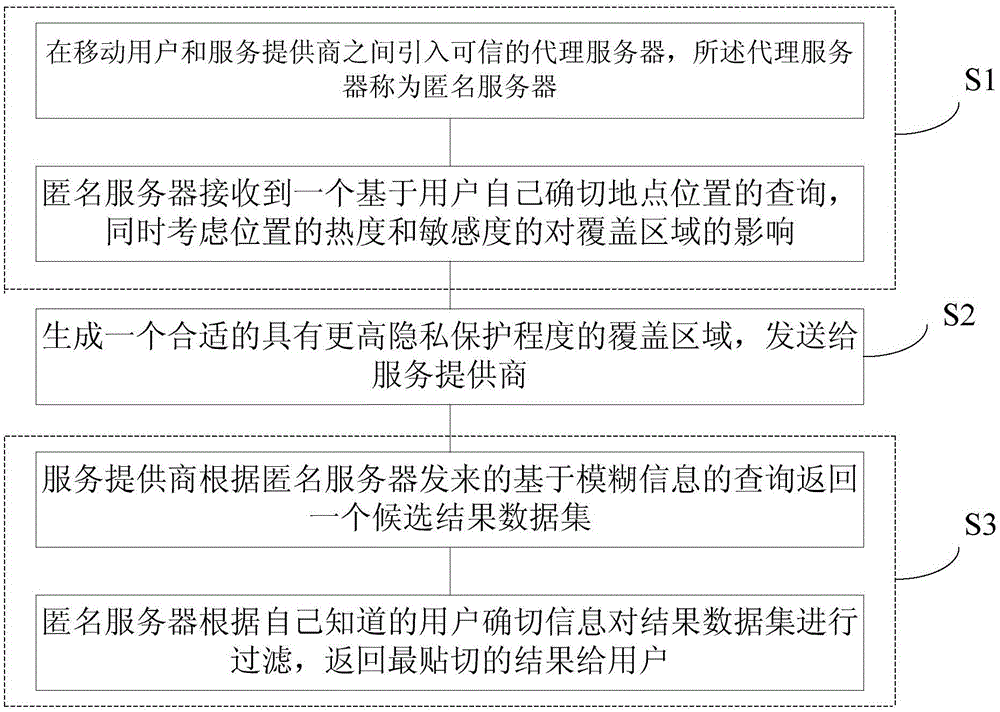
[0035] The system architecture of the present invention is as figure 2 As shown, a trusted proxy server, called an anonymous server, is introduced between the mobile user and the service provider. The whole protection process is as image 3 Shown:
[0036] S1, introducing a credible proxy server between the mobile user and the service provider, the proxy server is called an anonymous server;
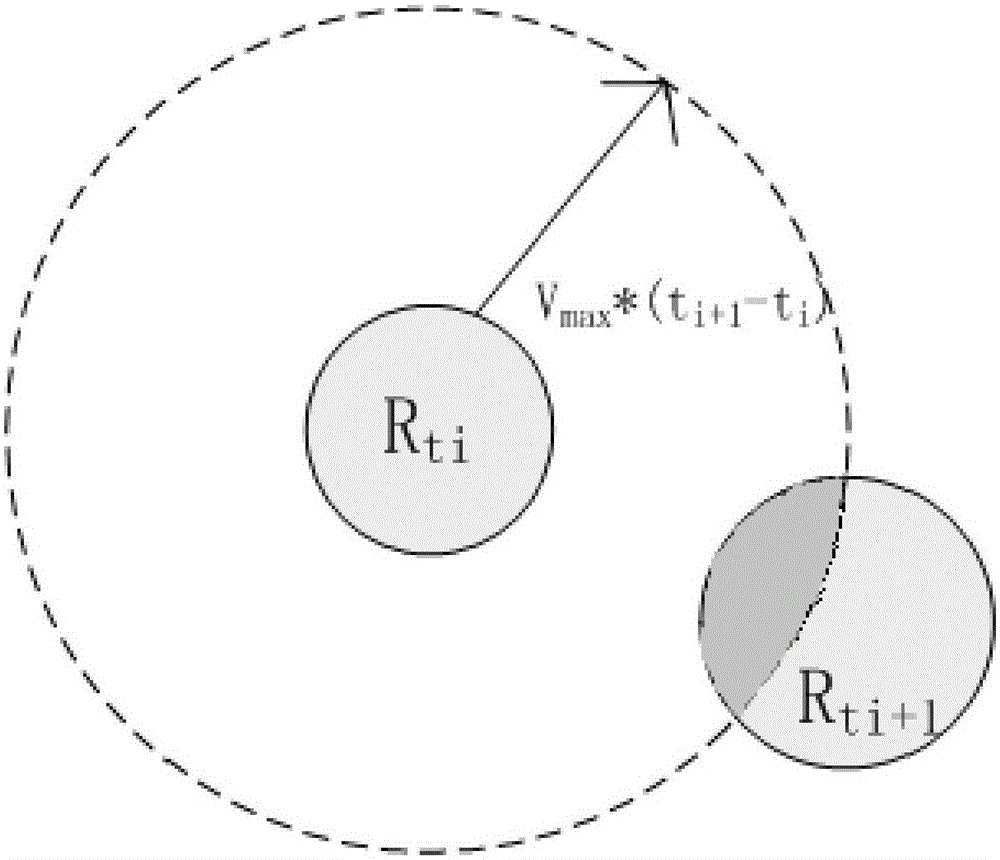
[0037] S2. The anonymous server receives a query based on the exact location of the user, and considers the influence of the heat and sensitivity of the location on the coverage area, thereby generating a suitable coverage area with a higher degree of privacy protection and sending it to the service provider business;
[0038] S3. The service provider returns a candidate result data set according to the query based on fuzzy information sent by the anonymous server. The anonymous server filters the result data set according to the exact information of the user it knows, and returns th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com