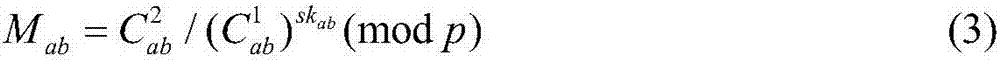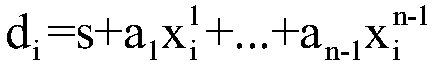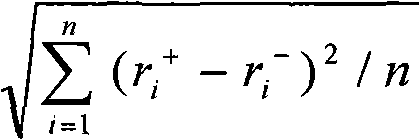Patents
Literature
415 results about "Data privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In a nutshell, data protection is about securing data against unauthorized access. Data privacy is about authorized access — who has it and who defines it. Another way to look at it is this: data protection is essentially a technical issue, whereas data privacy is a legal one.
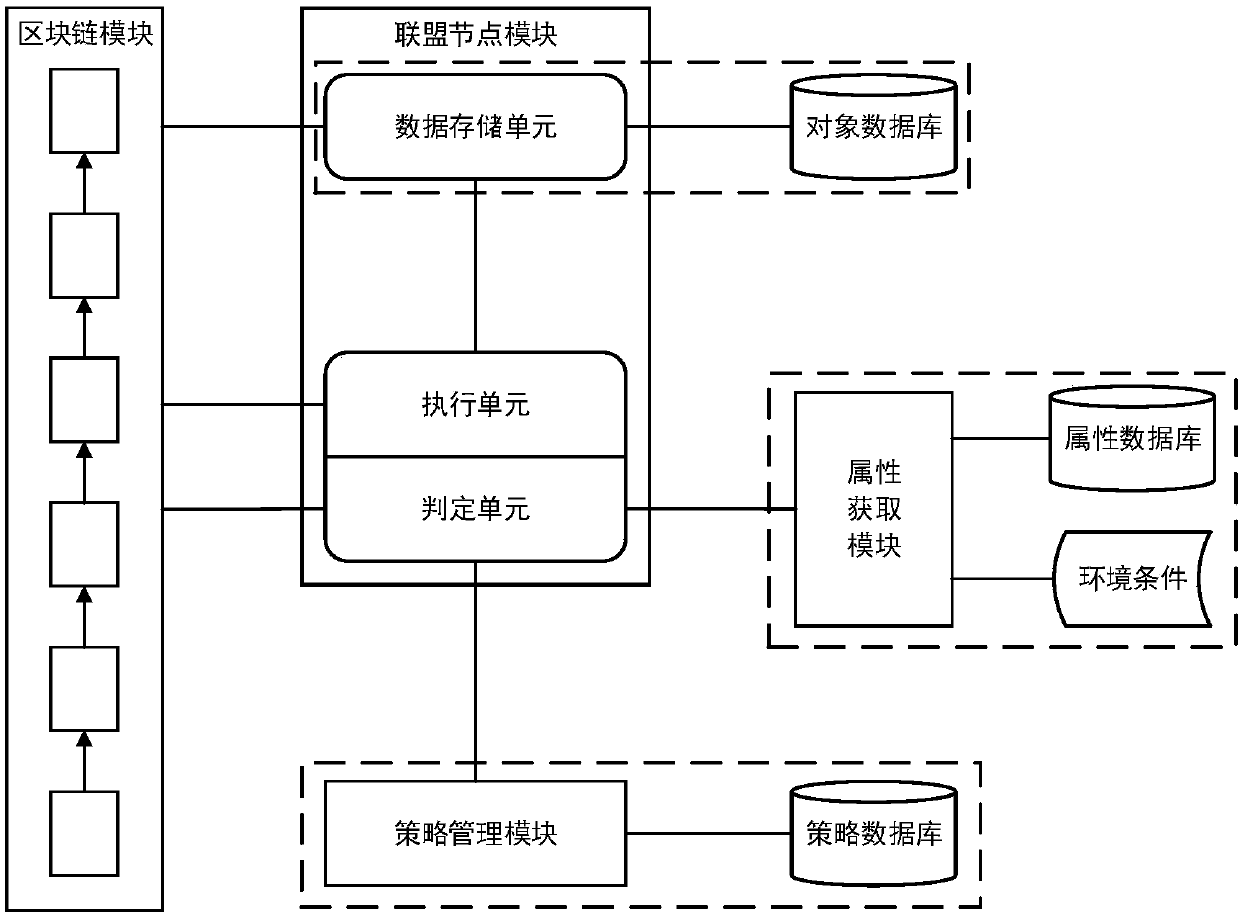
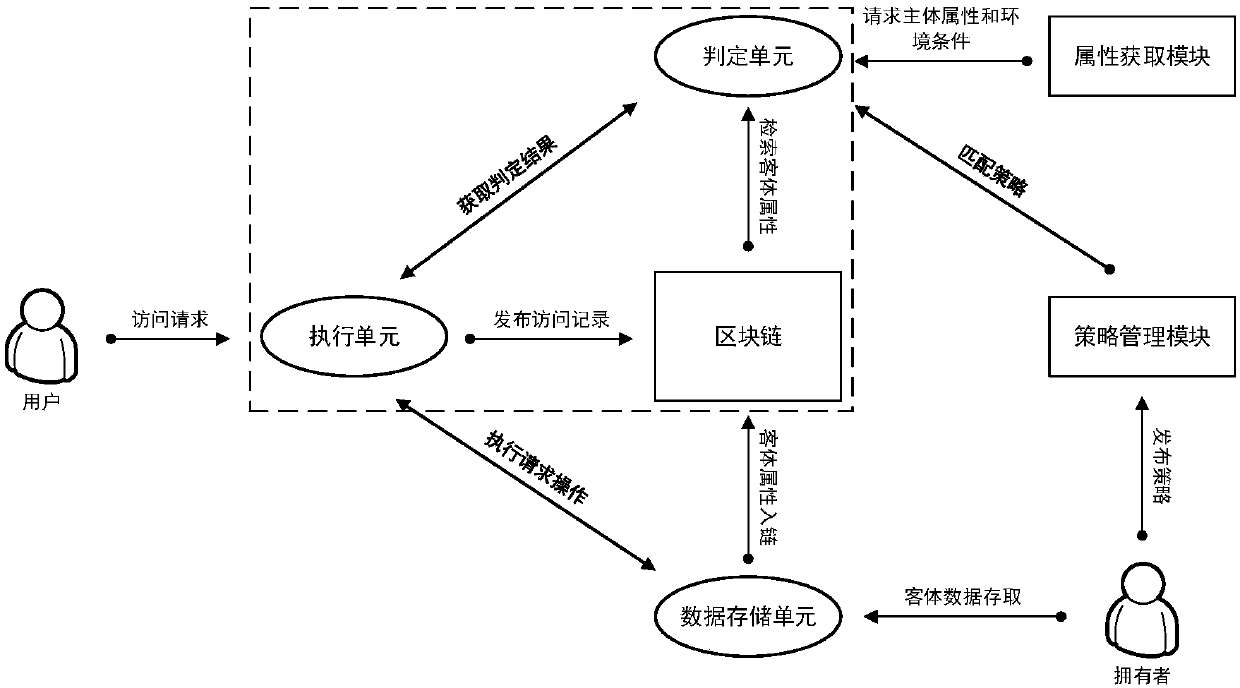
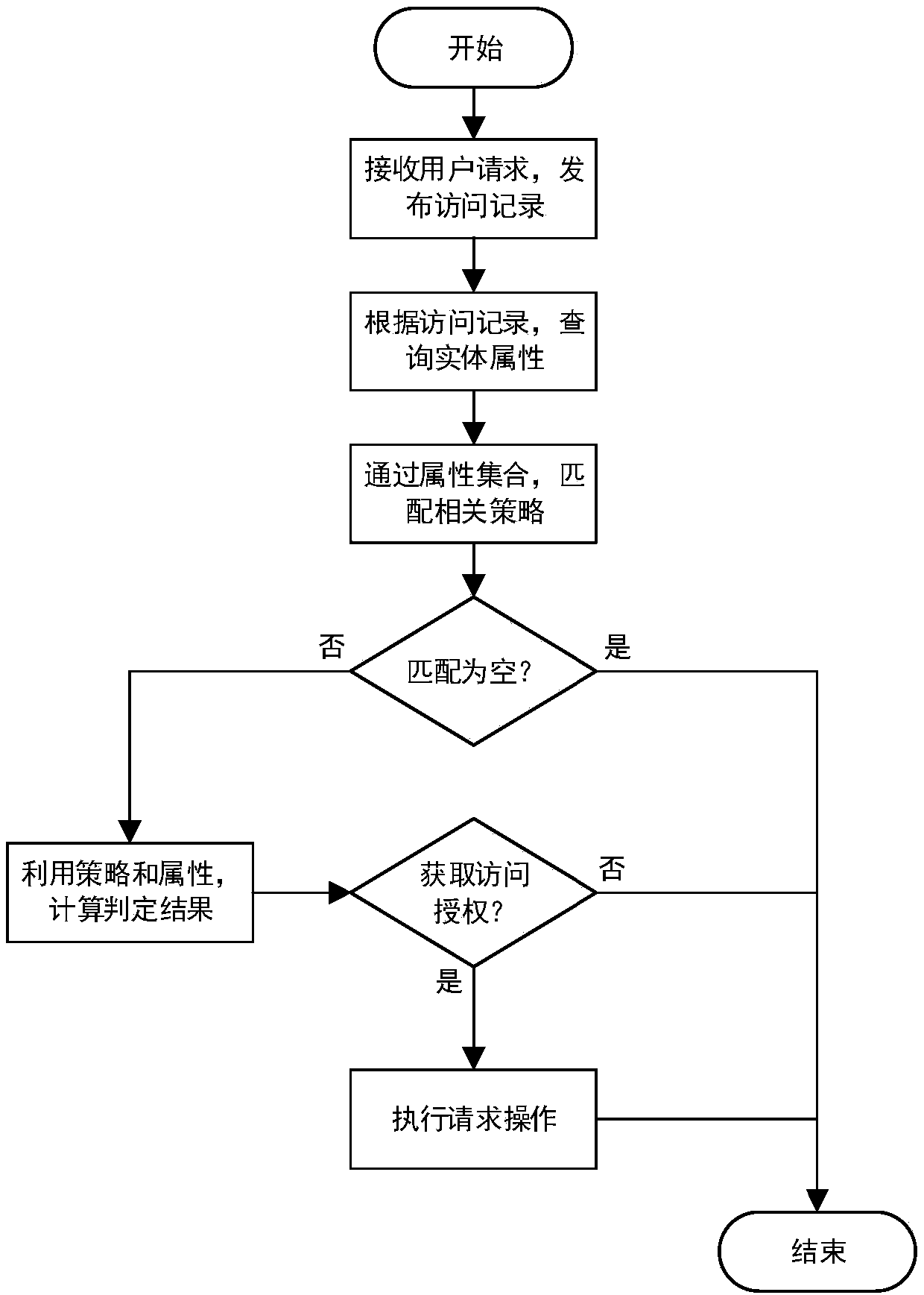
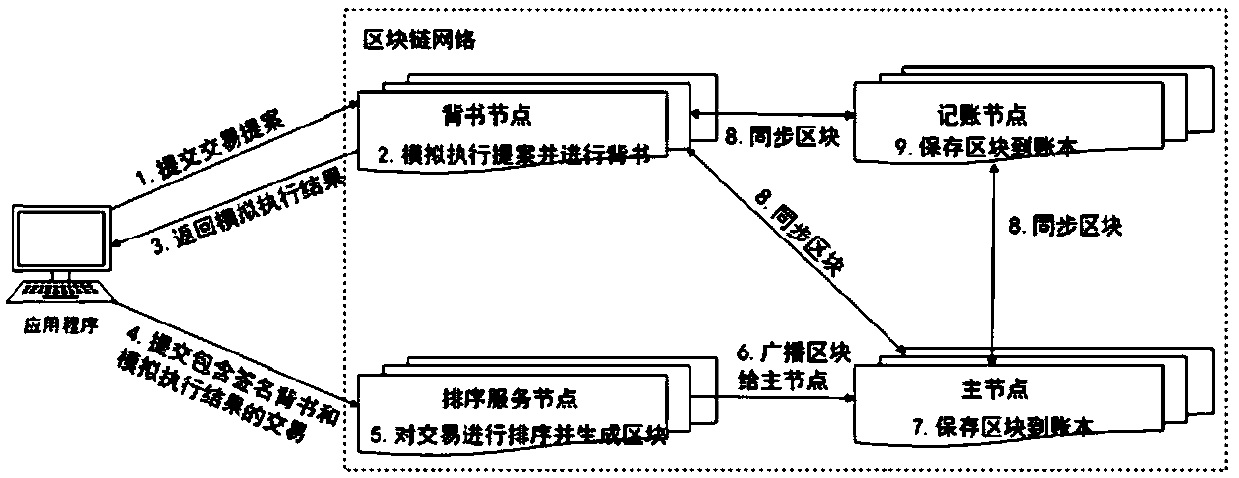
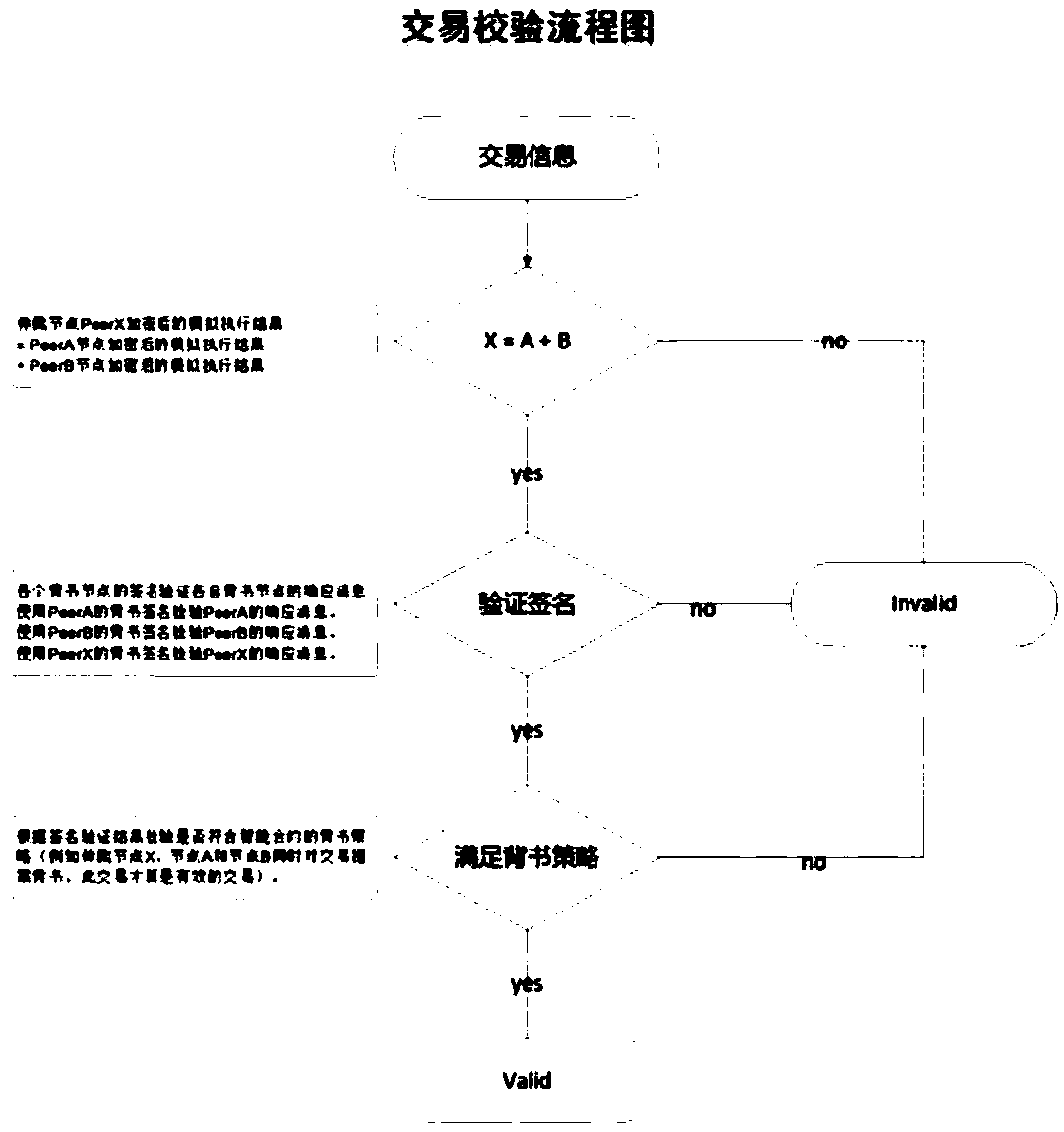
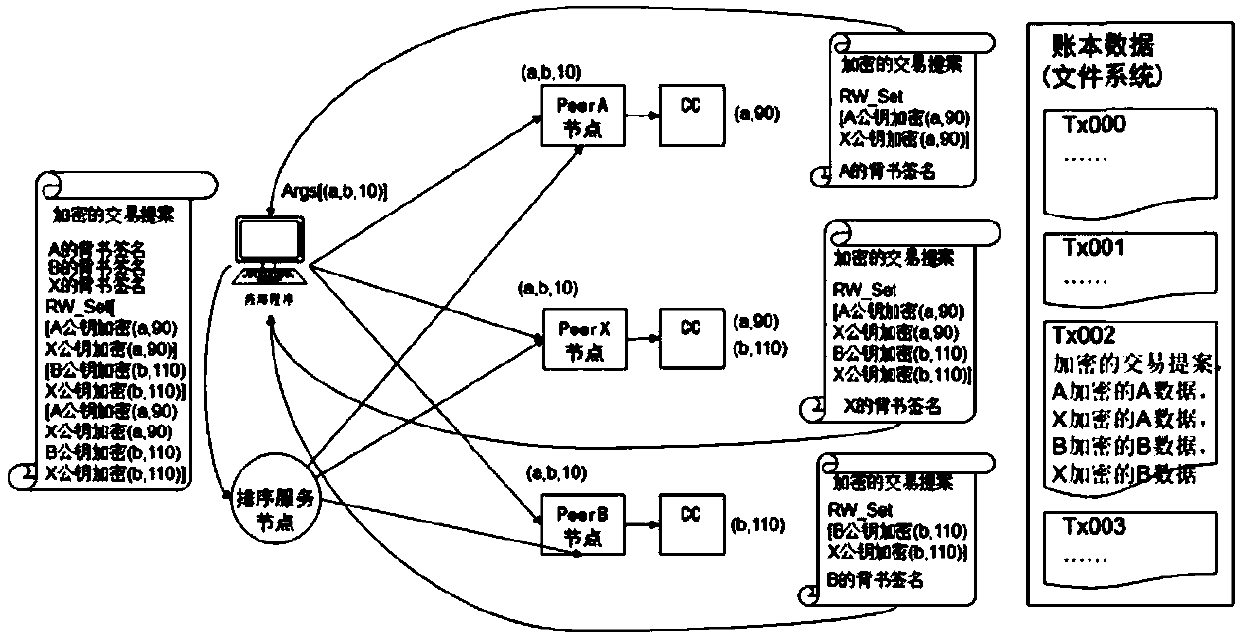
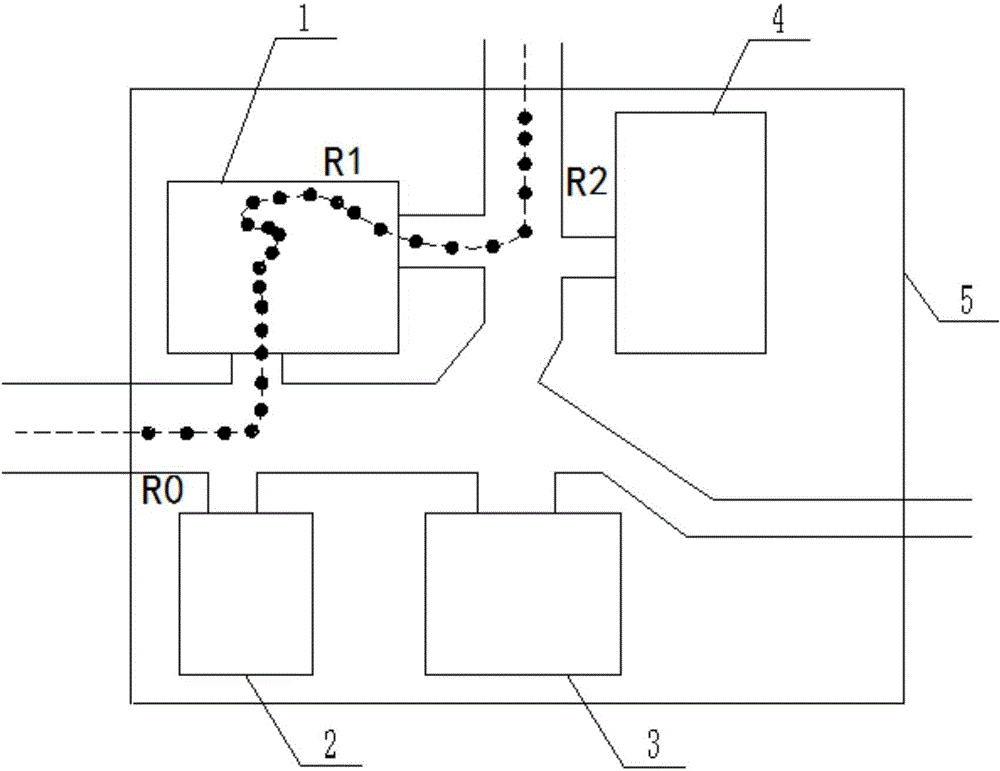
Access control method and system based on block chain technology
ActiveCN108123936AResistance to failureResist being attackedFinancePayment protocolsAuthorization ModeData privacy protection
The invention provides an access control method and system based on block chain technology. The block chain technology is combined with attribute-based access control in the method, and the method comprises the following steps: adding an object in a chain, binding a judgment process of attribute and strategy on all block chain nodes with reference to the strategy. The access authorization is converted from a centralized manner into a distributed manner, the consistency check of the judgment results in the whole network is achieved by using a consensus mechanism of the block chain, and the authorized operations for accessing the recorded transactions are permanently recorded on the block chain. The method has the advantages of anti-single point failure, flexible authorization mode, accurateaccess boundary, and record auditability. The access control method and system provided by the invention are applicable to operating environments such as enterprises and governments that have the need of data privacy protection and realize multi-branch cooperation work based on a block chain platform, the access permissions of users in the system can be dynamically and scalably managed, fine-grained permission management is achieved for the strategy and the attribute, and the access control method and system are of important practical significance for protecting the security of information systems in a distributed network environment.
Owner:UNIV OF SCI & TECH BEIJING
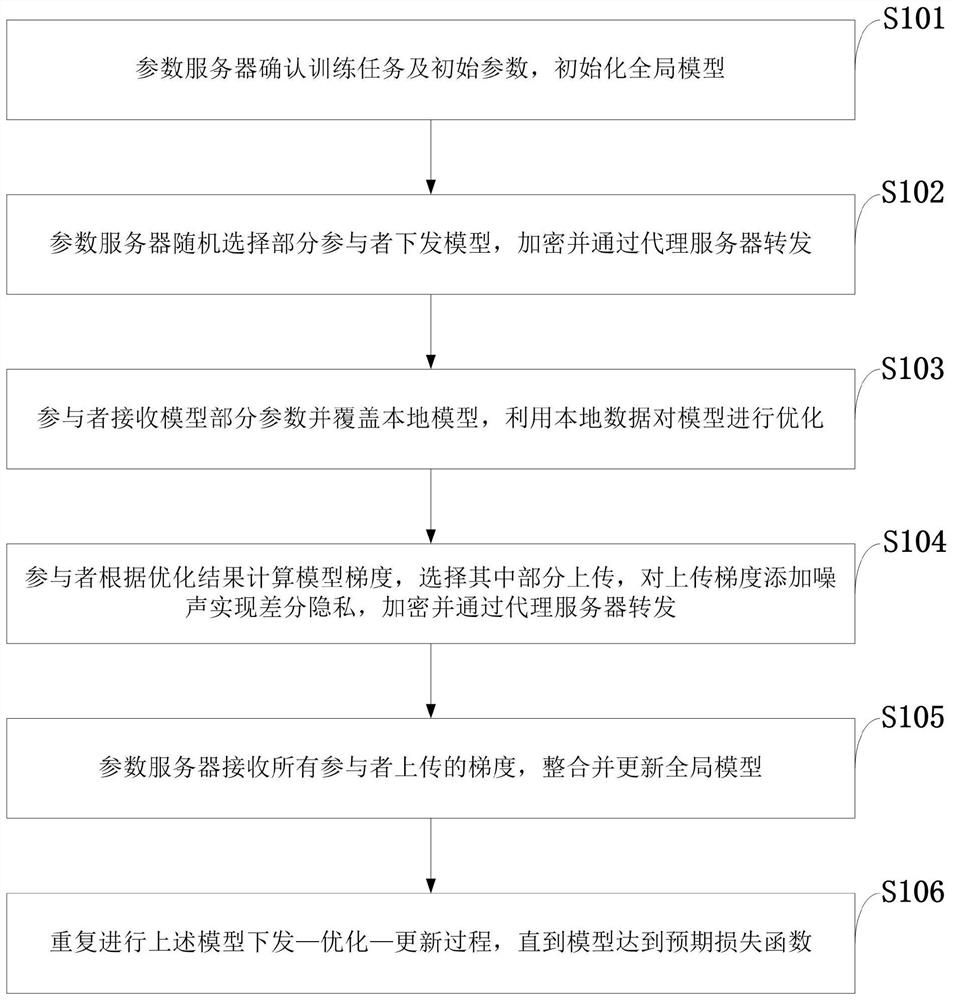
Federated learning information processing method and system, storage medium, program and terminal
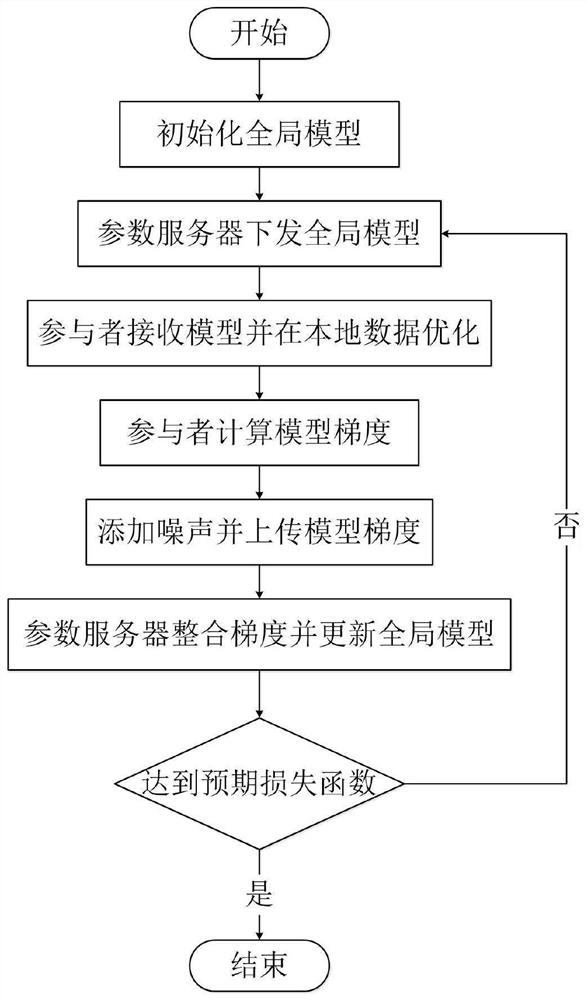
ActiveCN111611610ARealize identity anonymityGuaranteed separation effectDigital data protectionNeural architecturesInformation processingData privacy protection
The invention belongs to the technical field of wireless communication networks, and discloses a federated learning information processing method and system, a storage medium, a program, and a terminal. A parameter serve confirms a training task and an initial parameter and initialize a global model. The parameter server randomly selects part of participants to issue model parameters, encrypts themodel parameters and forwards the model parameters through the proxy server; the participants receive part of parameters of the model and cover the local model, and the model is optimized by using local data; the participant calculates a model gradient according to an optimization result, selects a part of the model gradient for uploading, adds noise to the uploading gradient to realize differential privacy, encrypts the uploading gradient and forwards the uploading gradient through the proxy server; the parameter server receives the gradients of all participants, and integrates and updates the global model; and the issuing-training-updating process of the model is repeated until an expected loss function is achieved. According to the invention, data privacy protection is realized; the communication overhead of a parameter server is reduced, and anonymity of participants is realized.
Owner:XIDIAN UNIV
Block chain network for partitions and method for realizing partition storage
InactiveCN107766540AReduce the spreadImprove privacy protectionFinanceDatabase distribution/replicationData privacy protectionTransaction data
The invention discloses a block chain network for partitions. The block chain network consists of a plurality of nodes, wherein a part of the nodes or all the nodes are divided in one or more partitions according to visible authorities, for different pieces of transaction data, of each node; in a same partition, the transaction data is completely visible, and between different partitions, the transaction data is invisible; all the nodes are classified into global consensus nodes, partition consensus nodes and synchronous nodes according to authority, for participating a consensus process, of each node; the global consensus nodes store all the pieces of transaction data which passes verification in the whole network via a block chain data structure; and both the partition consensus nodes and the synchronous nodes store all the pieces of transaction data which passes verification in the partition and transaction fingerprints of all the pieces of transaction data which passes verificationin the other partitions via the block chain data structure. According to the block chain network, the nodes in the block chain network are partitioned and classified, so that the storage node range of the transaction data which passes verification is limited, and the data privacy protection effect is improved.
Owner:上海分布信息科技有限公司
Privacy protection transaction method based on blockchain technology in electronic commerce
ActiveCN108389046AEase of evaluationMeet privacy requirementsFinanceDigital data protectionData privacy protectionLogistics management
The invention discloses a privacy protection transaction method based on a blockchain technology in electronic commerce. The method comprises the following steps that: adopting the blockchain technology which comprises a privacy smart contract and a zero-knowledge proof to protect the private information of a user; taking the privacy smart contract as a bridge between a buyer and a seller in a transaction period; adopting the zero-knowledge proof to issue a confidentiality token and create a confidentiality transaction; and combining the blockchain, an industrial data space and the Internet ofThings technology to establish infrastructure, and establishing an integrated platform for logistics business management in a distribution way. By use of the method, private information can be hiddenfor dispatchers, private information, including, identity, address, telephone number and the like, can be hidden for sellers, in addition, the method also can be used for other blockchain applicationscenes with a data privacy protection requirement, in addition, blockchain characteristics can be fully utilized, and therefore, the evaluation problem of an electronic commerce platform can be improved.
Owner:XI AN JIAOTONG UNIV
Partitioned blockchain network and method of realizing partition consensus thereby
InactiveCN107807984AReduce the spreadImprove privacy protectionFinanceDatabase distribution/replicationData privacy protectionTransaction data
The application discloses a partitioned blockchain network. The network is formed by multiple nodes; part or all of the nodes are divided into one or more partitions according to visible authority ofeach node on different transaction data; the transaction data inside the same partition are completely visible to the inside of the same partition, and the transaction data in the partition are invisible to the other different partitions; all the nodes are also classified according to authority of each node on participating in consensus processes: the nodes which can participate in the consensus processes of all the partitions are global consensus nodes, the nodes which can only participate in the consensus processes of the local partitions are partition consensus nodes, and the nodes which cannot participate in any consensus process are synchronization nodes; and transaction data waiting for confirmation are verified only by the global consensus nodes and the partition consensus nodes ofthe local partition. According to the network, a range of the nodes participating in the consensus processes is limited through partitioning and classifying all the nodes in the blockchain network, thus a spreading range of the transaction data waiting for confirmation is enabled to be greatly reduced, and a data privacy protection effect is improved.
Owner:上海分布信息科技有限公司
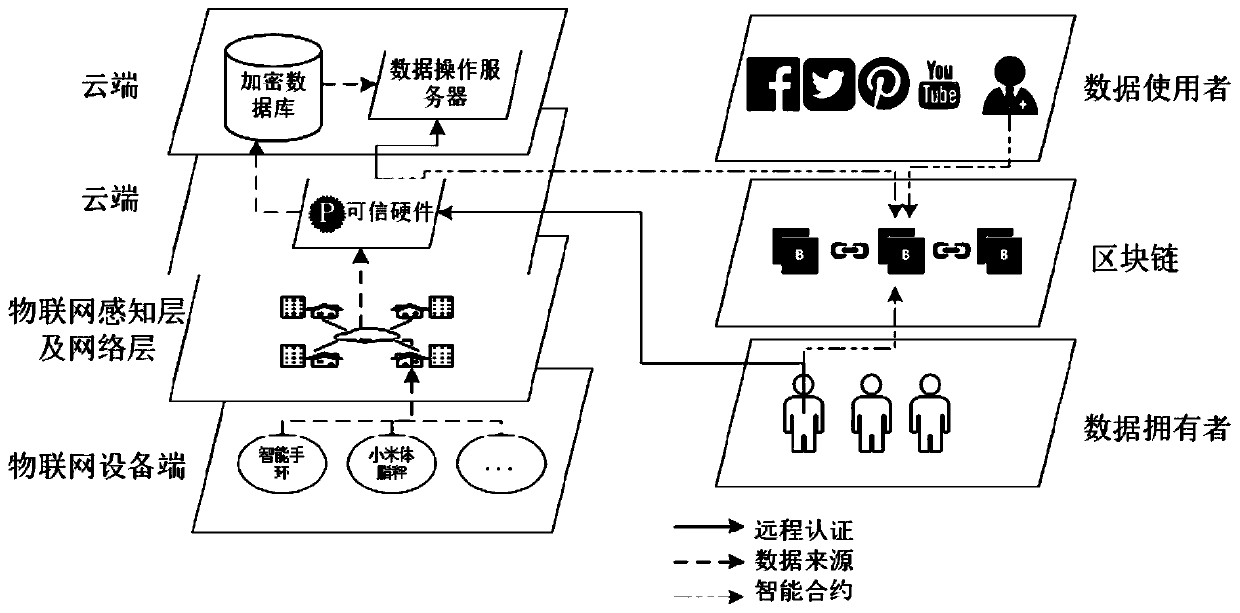
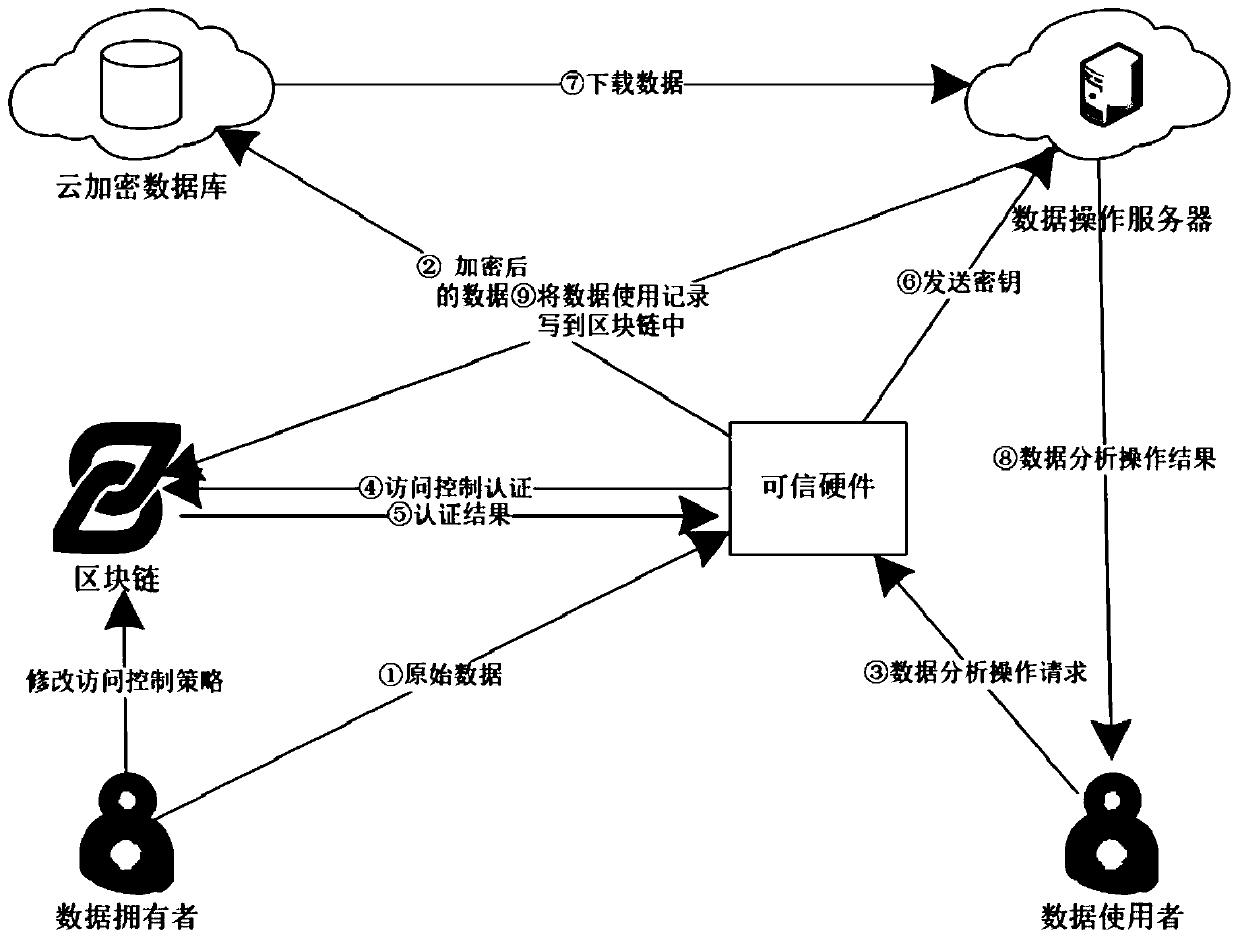
Internet of Things data privacy protection method based on block chain and trusted hardware
ActiveCN110086804AEnsure safetyGuaranteed reliabilityUser identity/authority verificationDigital data protectionData privacy protectionTrusted hardware
The invention relates to an Internet of Things data privacy protection method based on a block chain and the trusted hardware. The method comprises three stages of secret key management and data generation, data access control strategy definition and intelligent contract deployment and data access and intelligent contract execution, and Internet of Things data is encrypted by a hardware trusted entity IDA and uploaded to a cloud for storage; when there is an operation request, the trusted entity calls an access control authentication interface of the smart contract to carry out authority authentication; after the authority authentication passes, the trusted entity carries out security authentication on the operation execution server and sends the secret key to the data operation executionserver through a security channel; and the server downloads the data from the cloud, then decrypts the data and executes the operation, and writes the data use record into the block chain after the data analysis operation is completed. According to the scheme, the block chain is combined with the trusted entity, the data is effectively operated under the condition that the original data privacy isnot leaked, and the integrity and the safety of the data use records are guaranteed.
Owner:GUANGZHOU UNIVERSITY
Partitioned block chain network and method for realizing partition query by same
ActiveCN107766542AReduce the spreadImprove privacy protectionFinanceDigital data protectionData privacy protectionTransaction data
The invention discloses a partitioned block chain network. The block chain network consists of multiple nodes; according to visible permissions of the nodes to different transaction data, part or allof the nodes are divided in one or more partitions; the interior of the same partition is completely visible for the transaction data, and different partitions are invisible for the transaction data;according to the permissions of the nodes participating in a consensus process, all the nodes are classified: the nodes capable of participating in the consensus process of all the partitions are global consensus nodes, the nodes only capable of participating in the consensus process of the partitions where the nodes are located are partition consensus nodes, and the nodes incapable of participating in any consensus process are synchronous nodes; each node has a partition identifier; and each node stores transaction fingerprints of all historical transaction data. By partitioning and classifying the nodes in the block chain network, the query of the historical transaction data is limited in the same partition, so that the propagation range of the historical transaction data is greatly reduced and the data privacy protection effect is improved.
Owner:上海分布信息科技有限公司
Method and a system for constructing a smart contract in a block chain
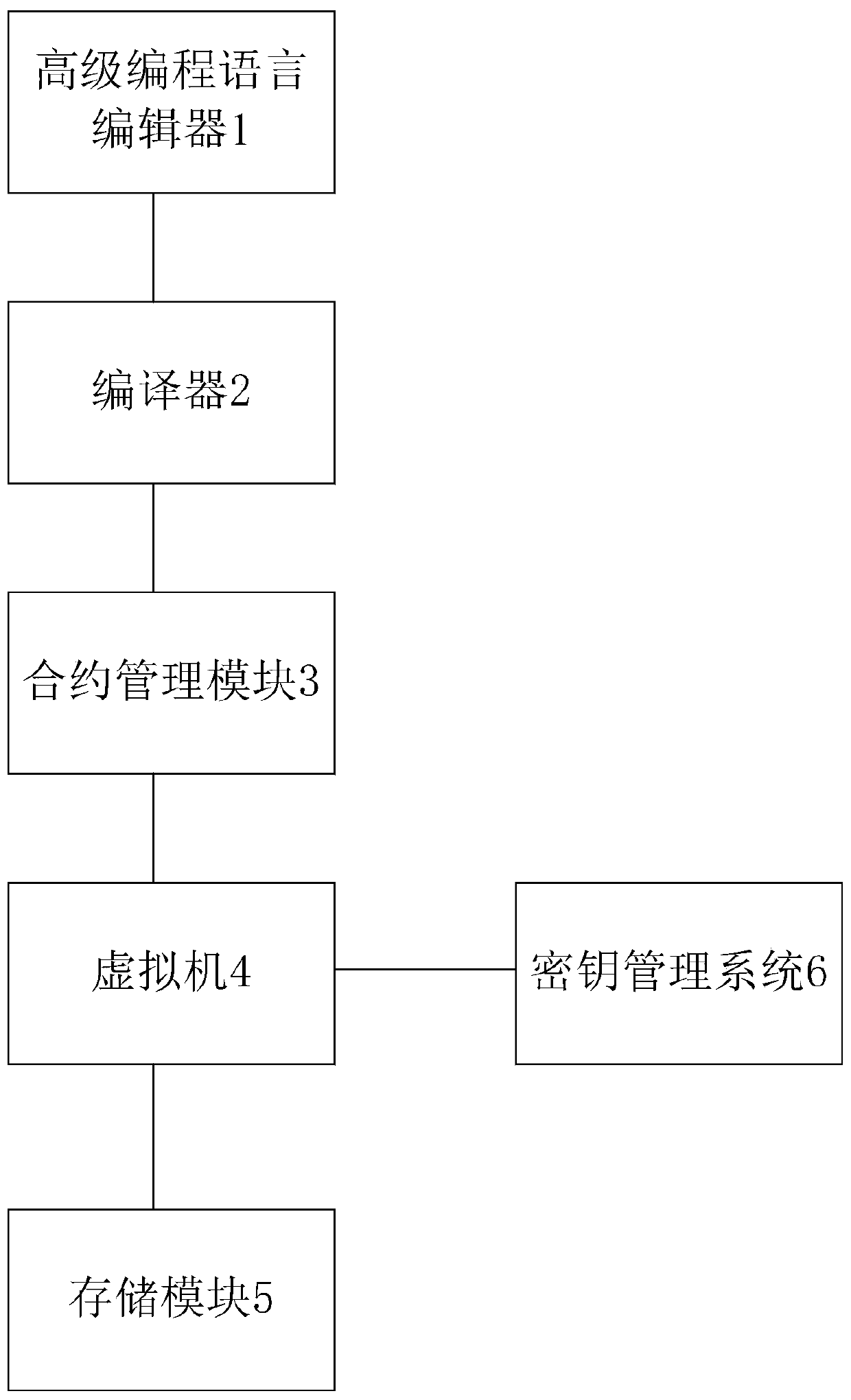
ActiveCN109766722APerformance bottleneckLow execution efficiencyDigital data protectionCode compilationData privacy protectionSmart contract
The invention relates to a method and a system for constructing an intelligent contract in a block chain. The method comprises the steps of 1, constructing an intelligent contract core system in the block chain; Step 2, contract upgrading based on the intelligent contract core system; Step 3, contract execution based on the intelligent contract core system; And step 4, performing data privacy protection based on the intelligent contract core system. The characteristics of data isolation, contract upgradable and data privacy protection are provided, and the requirements of enterprise organizations for service iterative upgrade, data governance and data security are better met.
Owner:梧桐链数字科技研究院(苏州)有限公司
Secure transaction method and device based on a block chain
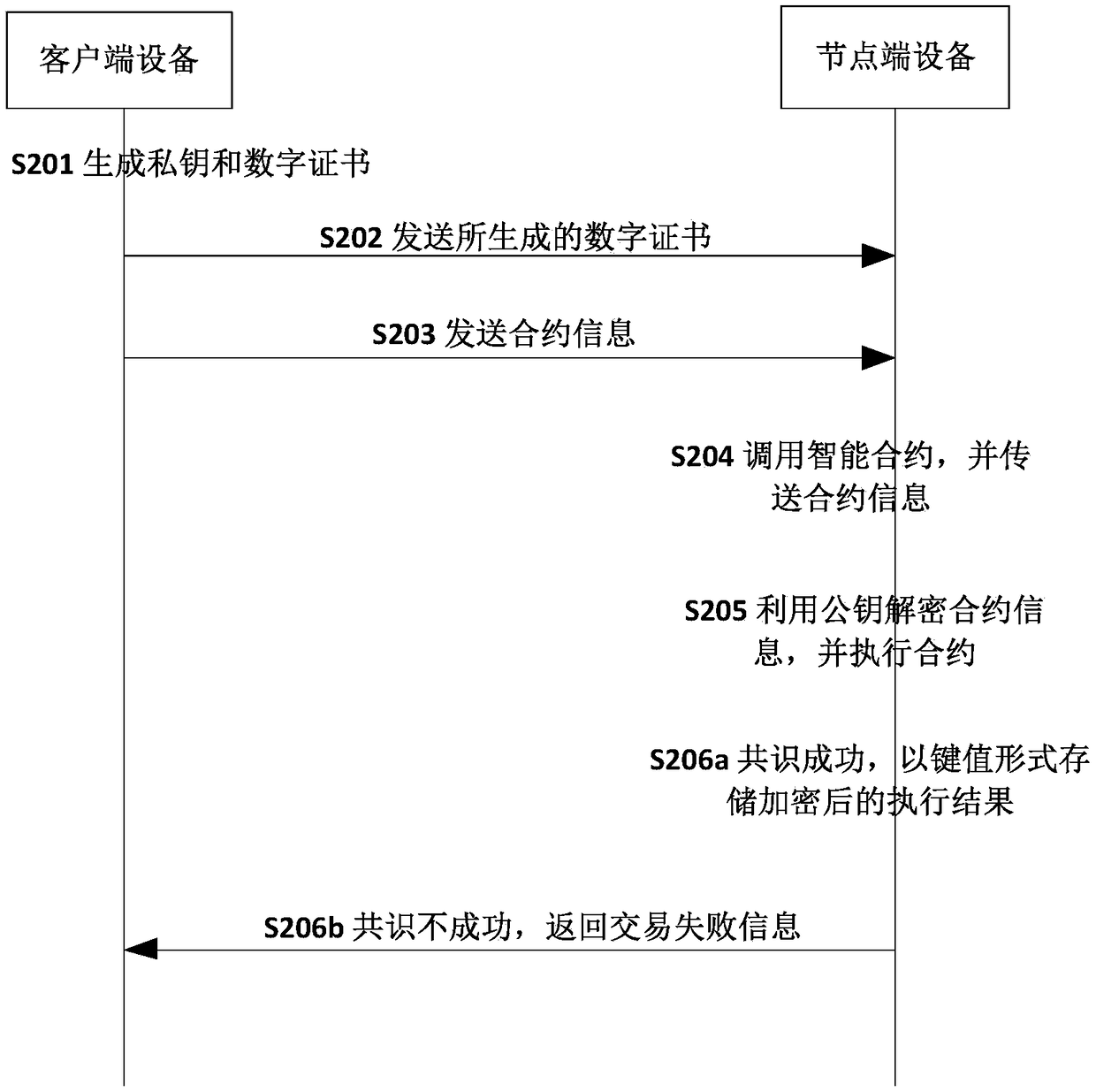
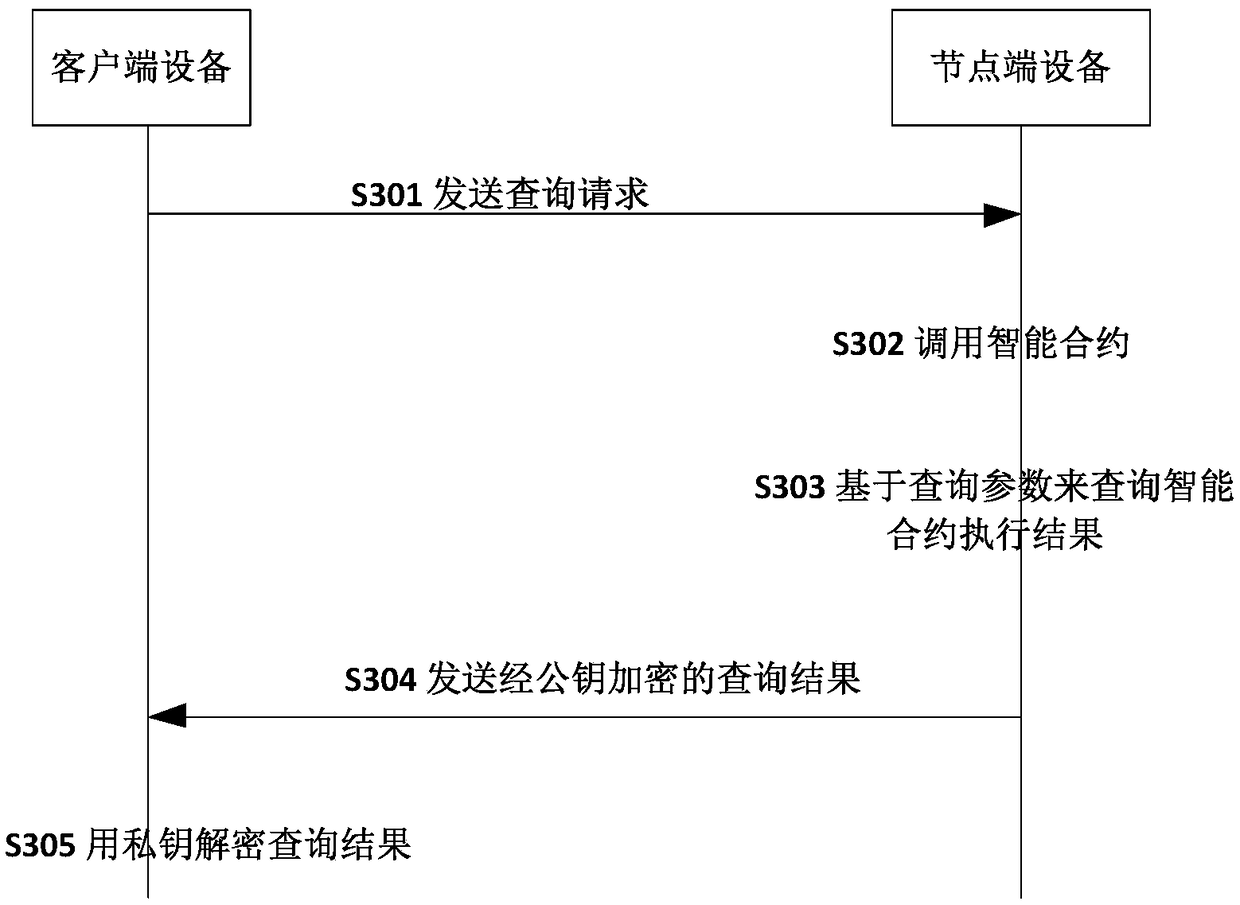
ActiveCN109493020AGuaranteed privacy protectionStrong encryptionFinancePayment protocolsPlaintextData privacy protection
The invention discloses a secure transaction method and device based on a block chain. The node end equipment of the block chain calls the smart contract based on the contract information, the node end of the block chain decrypts the encrypted transaction parameters in the contract information by using the public key in the certificate, and executes the smart contract based on the transaction parameters; after the block chain node achieves consensus on the execution result in the block chain; wherein the node encrypts a key and a value based on the certificate public key and then writes the key and the value into the node database, the client inquires a transaction result through the blockchain node and needs to encrypt transaction parameters, the blockchain node needs to decrypt based onthe public key and then encrypt and return the transaction result, and the client decrypts based on the private key to obtain a plaintext result. Through the technical scheme of the invention, data security and data privacy protection for transaction and query can be formed.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
Quasi-fully homomorphic ciphertext data operation method and system
InactiveCN107592195AAvoid insecuritySolving inefficienciesSecuring communicationThird partyCiphertext
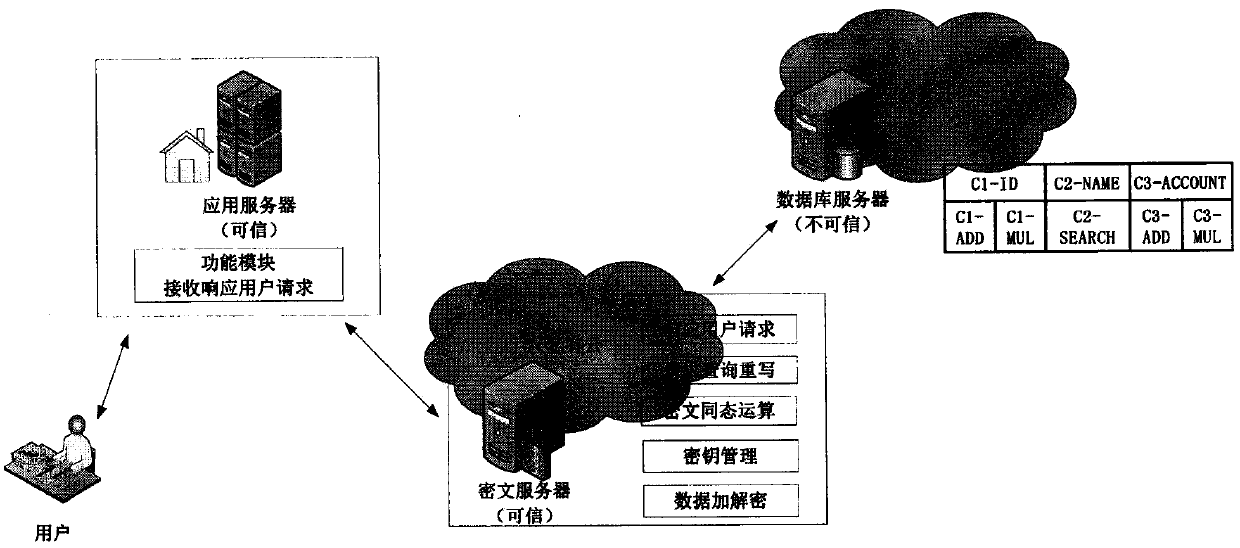
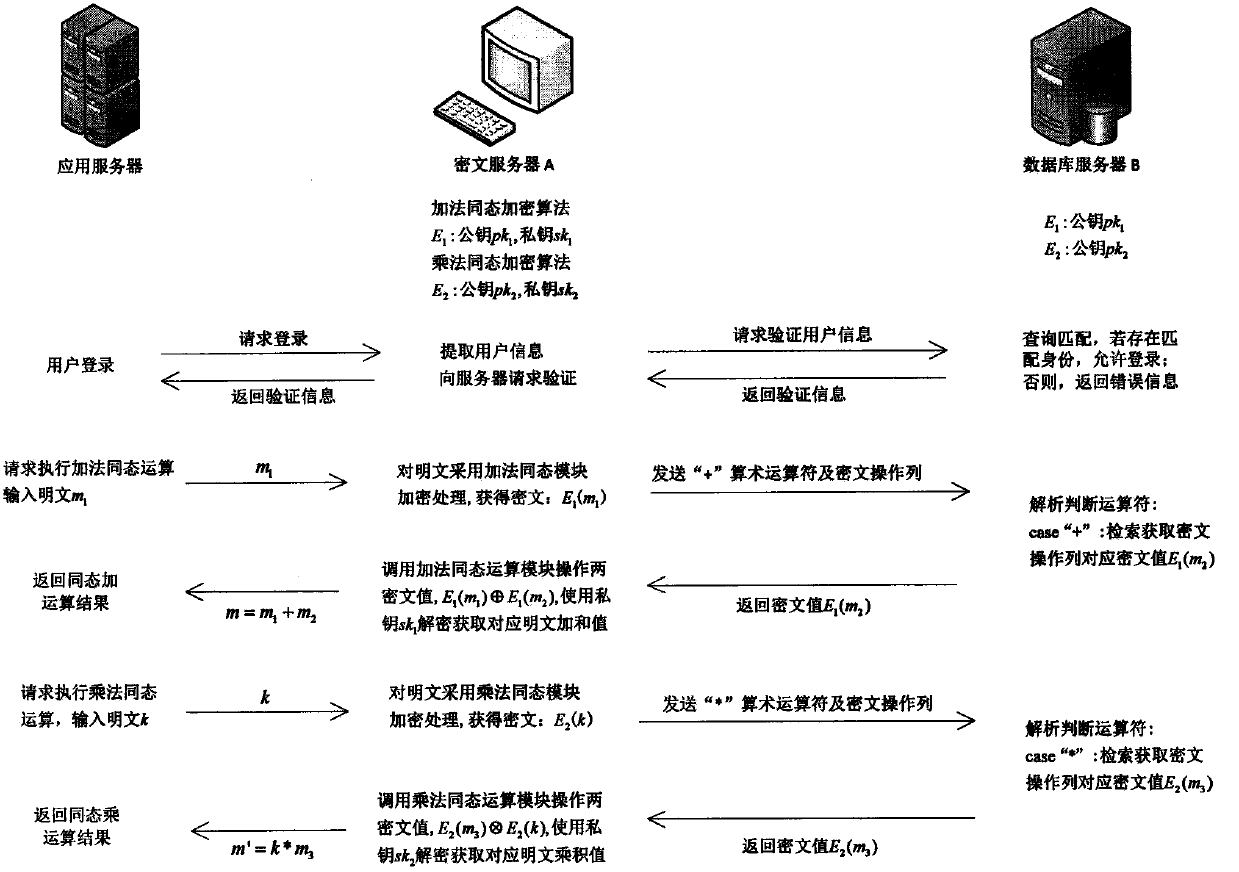
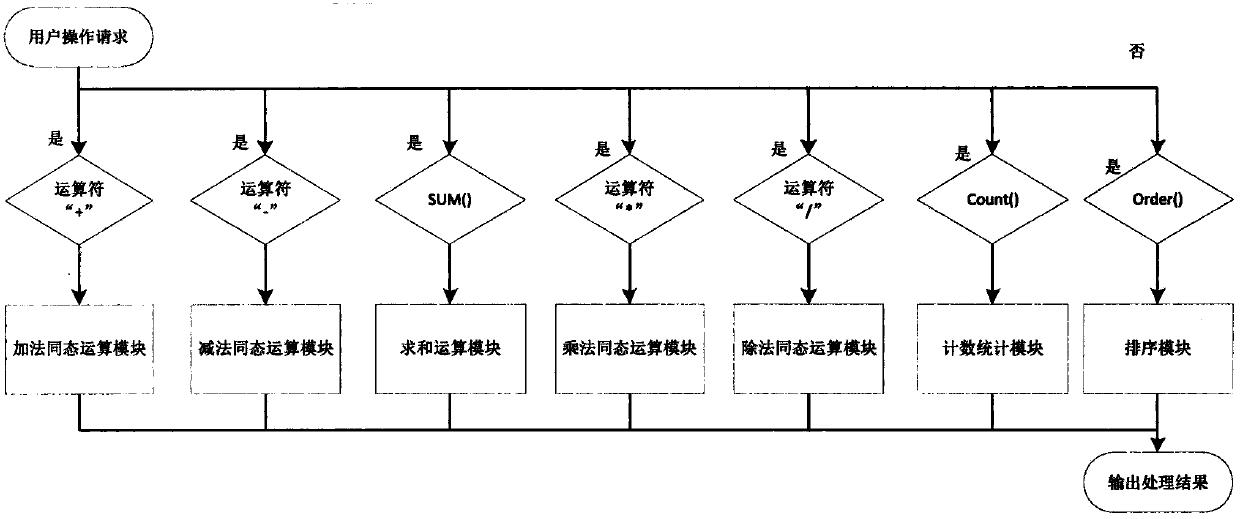
The present invention discloses a quasi-fully homomorphic ciphertext data operation method and system and belongs to the ciphertext database and network data privacy protection technical field. The fully homomorphic cipher operation-based hybrid cloud platform architecture is provided, existing database configurations are not needed to be drastically modified, and therefore, a construction mode issimple; a ciphertext server is defined to support homomorphic calculation, query interception rewriting, data encryption and decryption, key management and other functions, is deployed at the privatecloud platform of a local data center and can establish a connection between the local data center and a third-party public cloud platform; a classified field extension mode is adopted, field extension is performed on numerical value data and character type data; by means of mode innovation, quasi-fully homomorphic ciphertext conventional arithmetic calculation is performed on the numerical valuedata through a functional demand-based cipher service strategy; query / operation is directly performed on ciphertext data; and therefore, the processing efficiency of the data and the security of thestorage and retrieval of the data can be improved.
Owner:BEIJING ELECTRONICS SCI & TECH INST
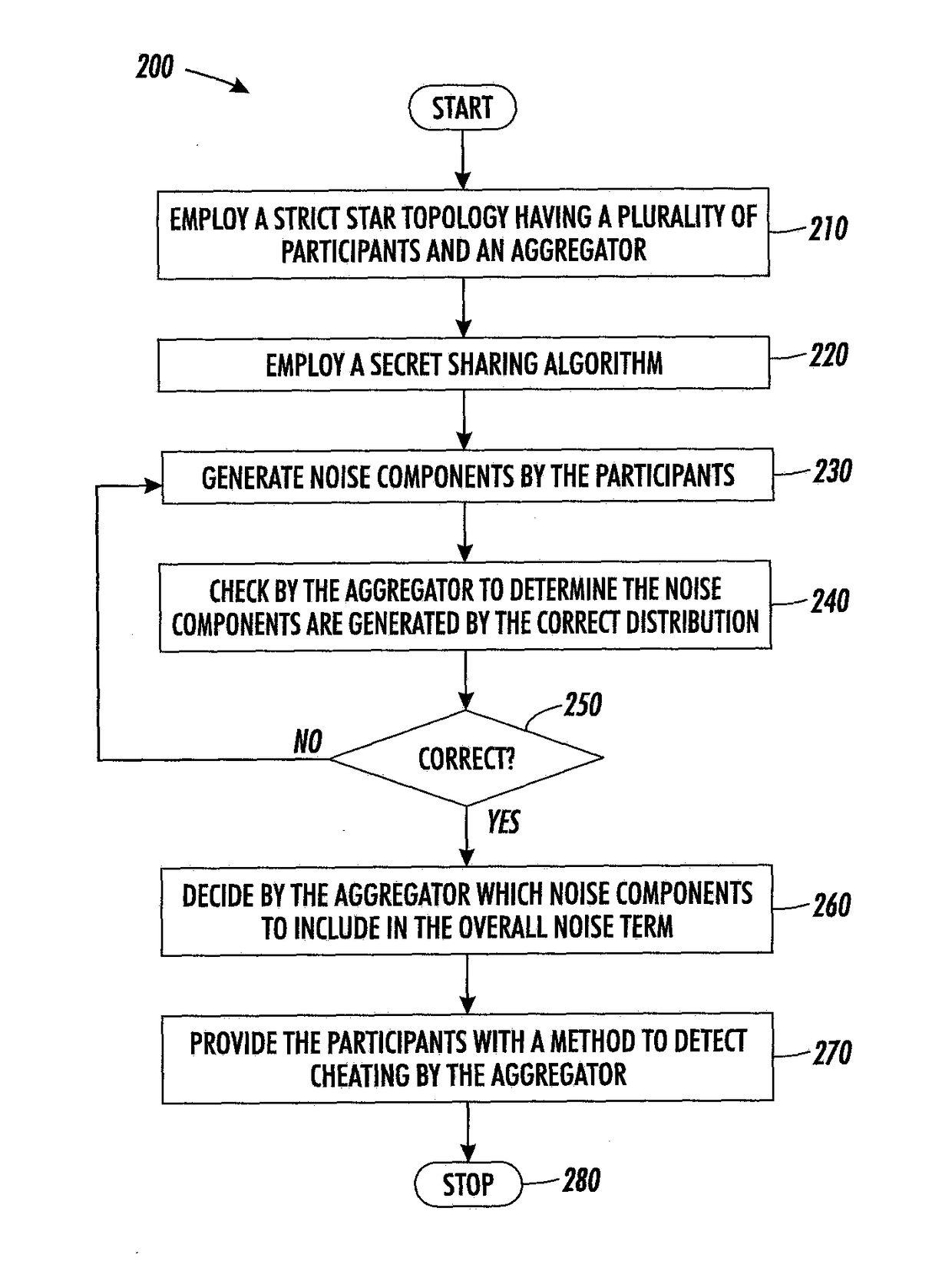
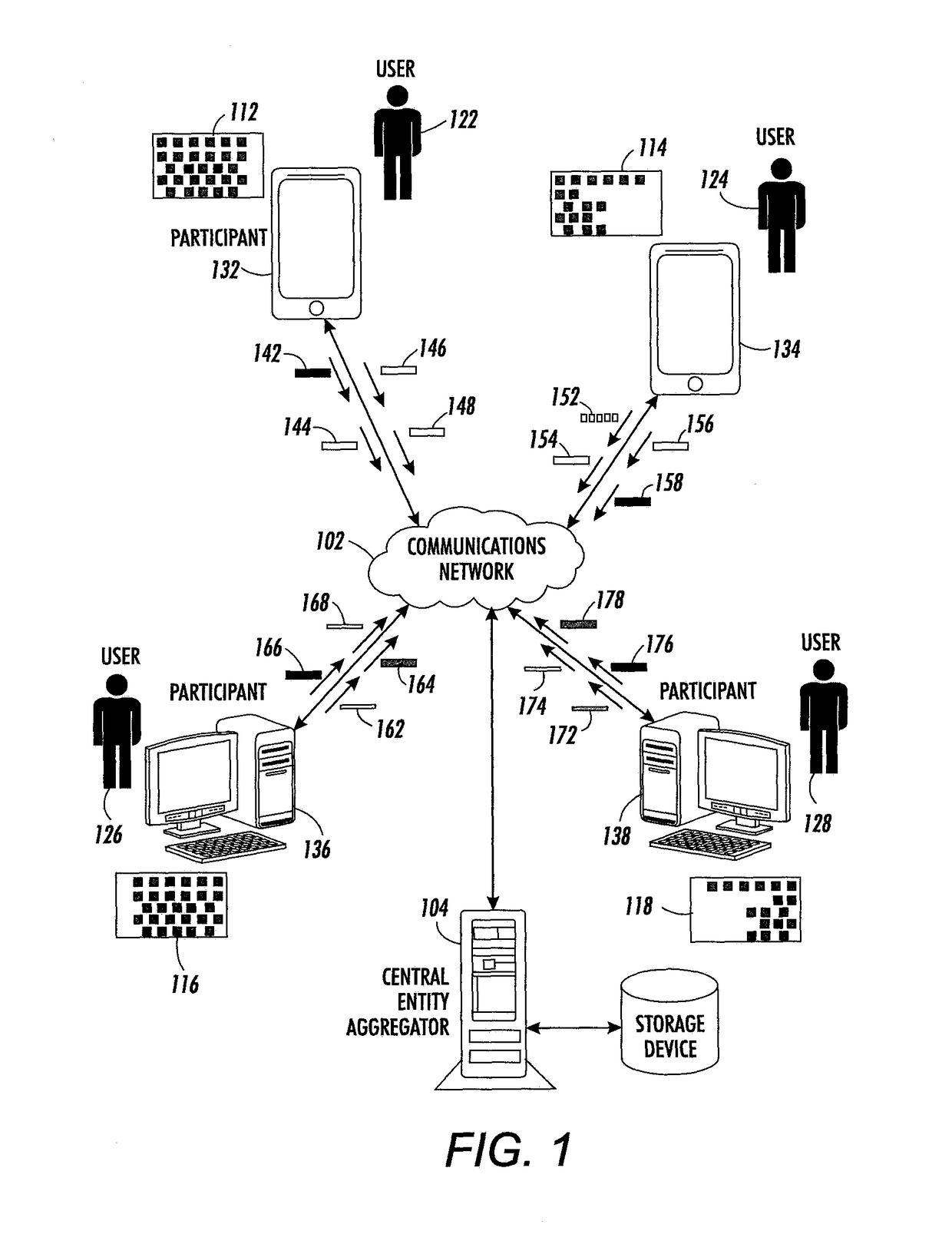
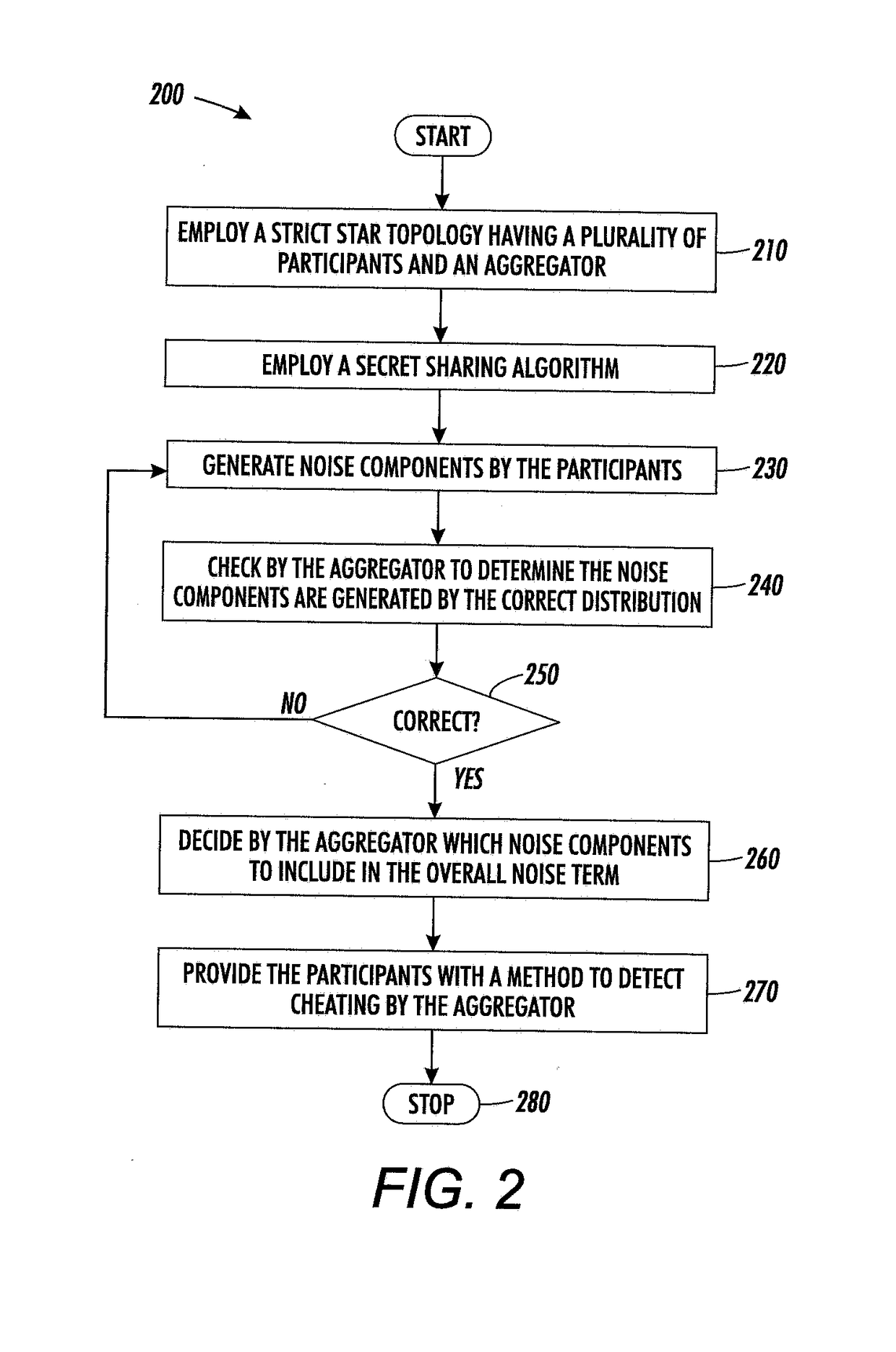
Method for differentially private aggregation in a star topology under a realistic adversarial model
ActiveUS20180101697A1Key distribution for secure communicationDigital data protectionPattern recognitionData privacy protection
One embodiment provides a system for noise addition to enforce data privacy protection in a star network. In operation, participants may add a noise component to a dataset. An aggregator may receive the noise components from the plurality of participants, compute an overall noise term based on the received noise components, and aggregate values using the noise components and overall noise term.
Owner:XEROX CORP
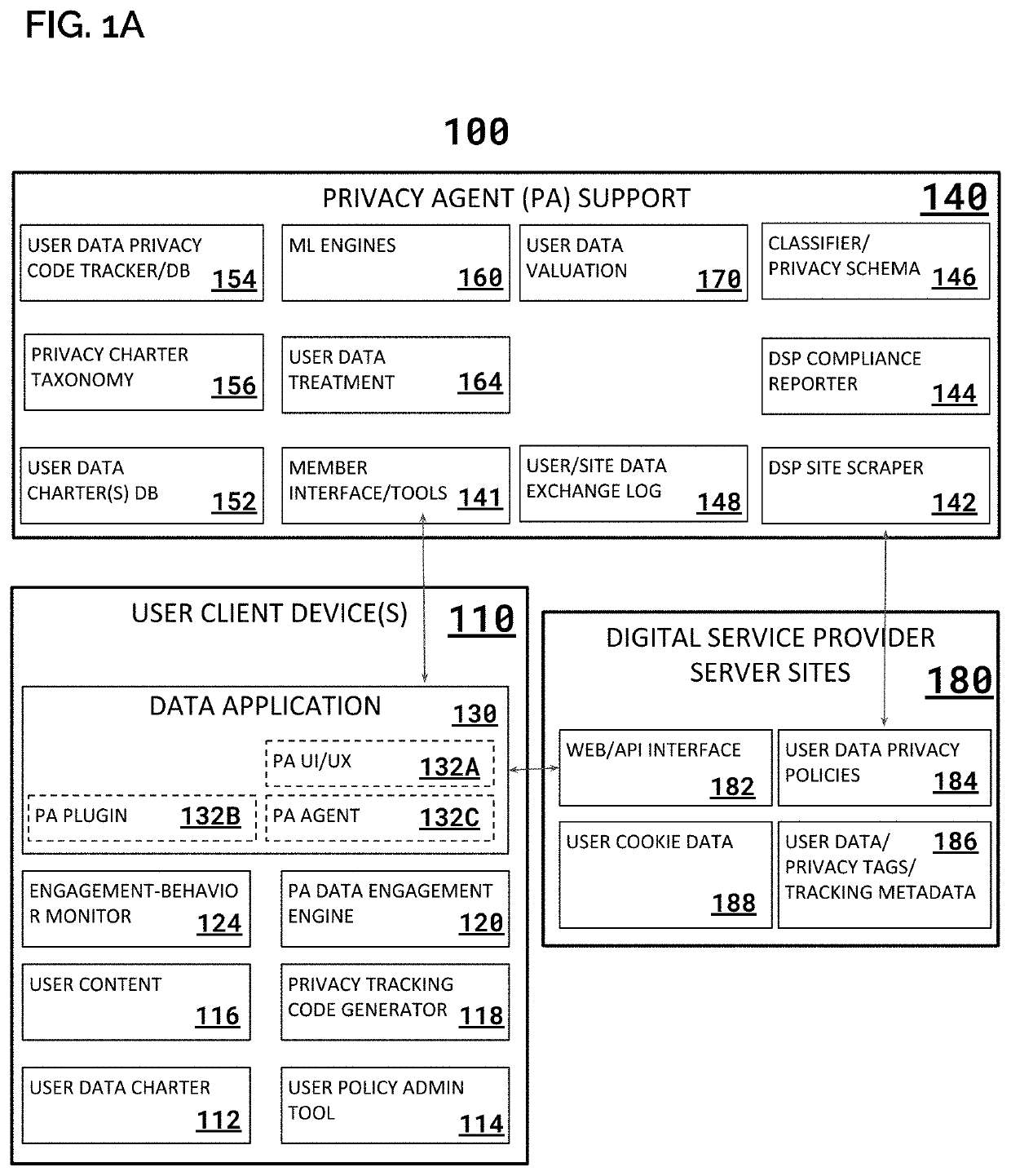
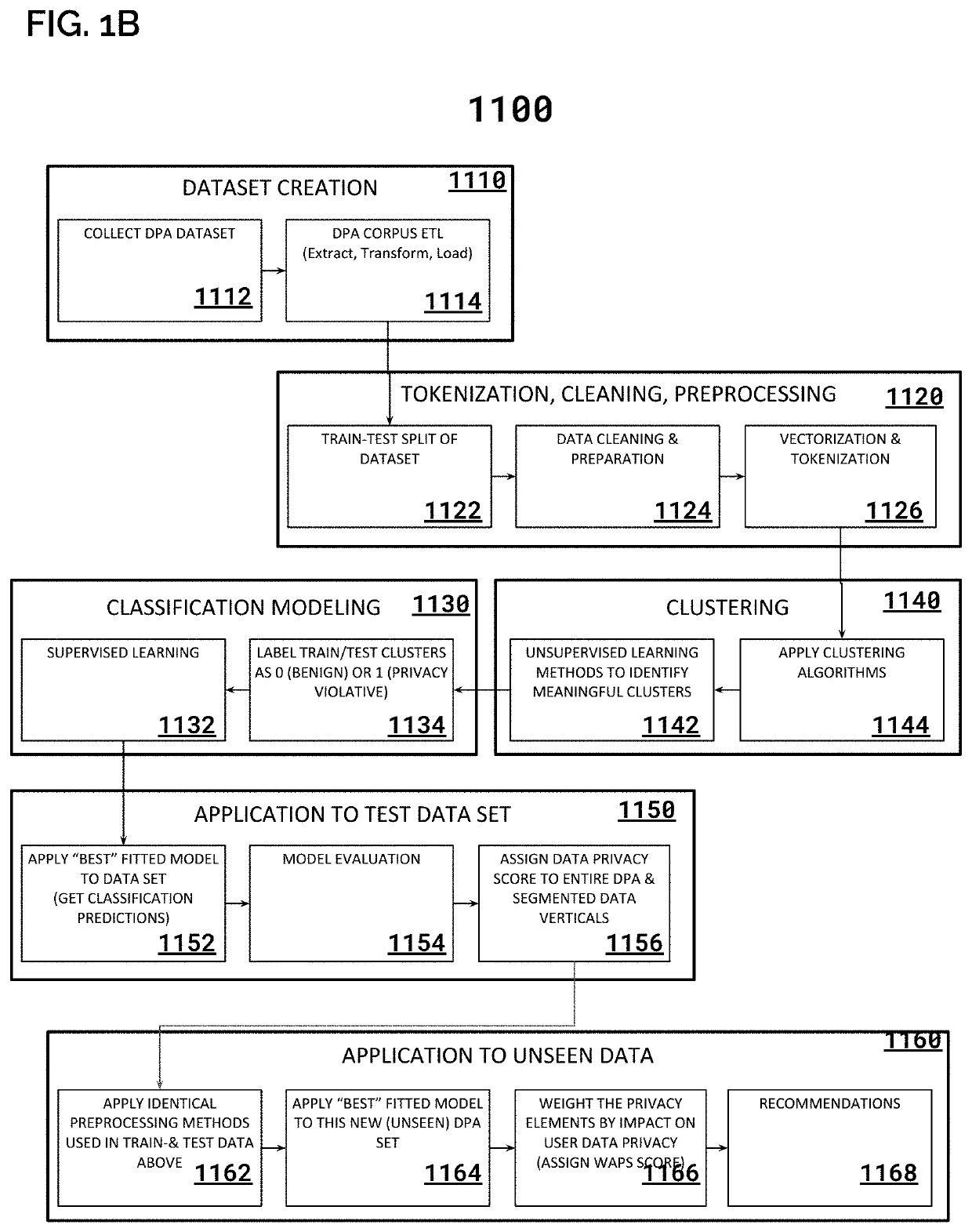
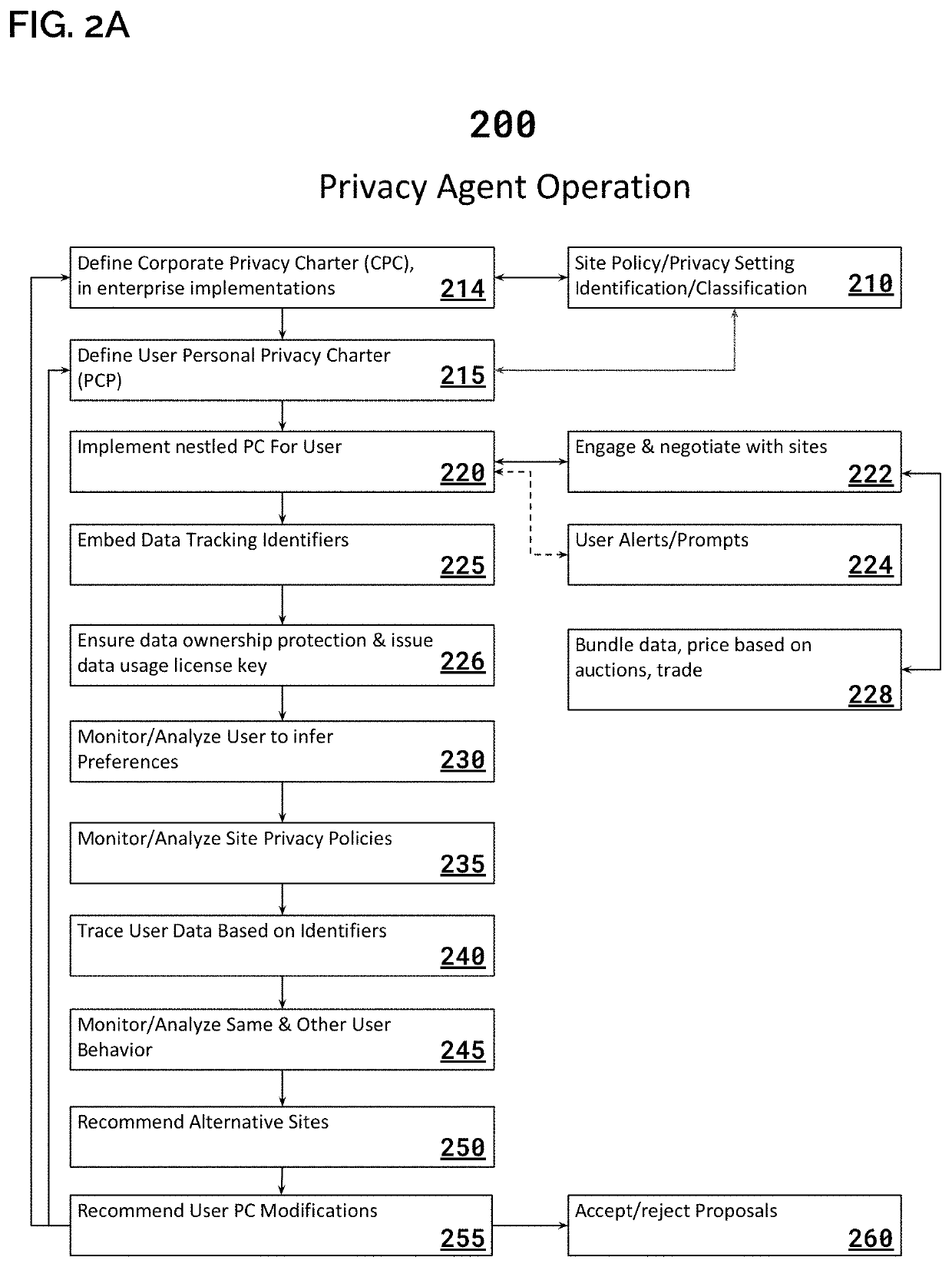
System & Method for Analyzing Privacy Policies
PendingUS20210192651A1Simplifies privacyEfficient settingsMarket predictionsEnsemble learningData privacy protectionEngineering
A natural language processing system is adapted to locate, extract and analyze content and meaning of provisions in user data management agreements employed by digital service providers (DSPs) and related entities. The resulting analysis can be used to inform (and as part of a) data privacy protection systems that utilize personal / corporate privacy policies to engage with DSPs according to a desired set of protection parameters.
Owner:CAMBRIAN DESIGNS INC
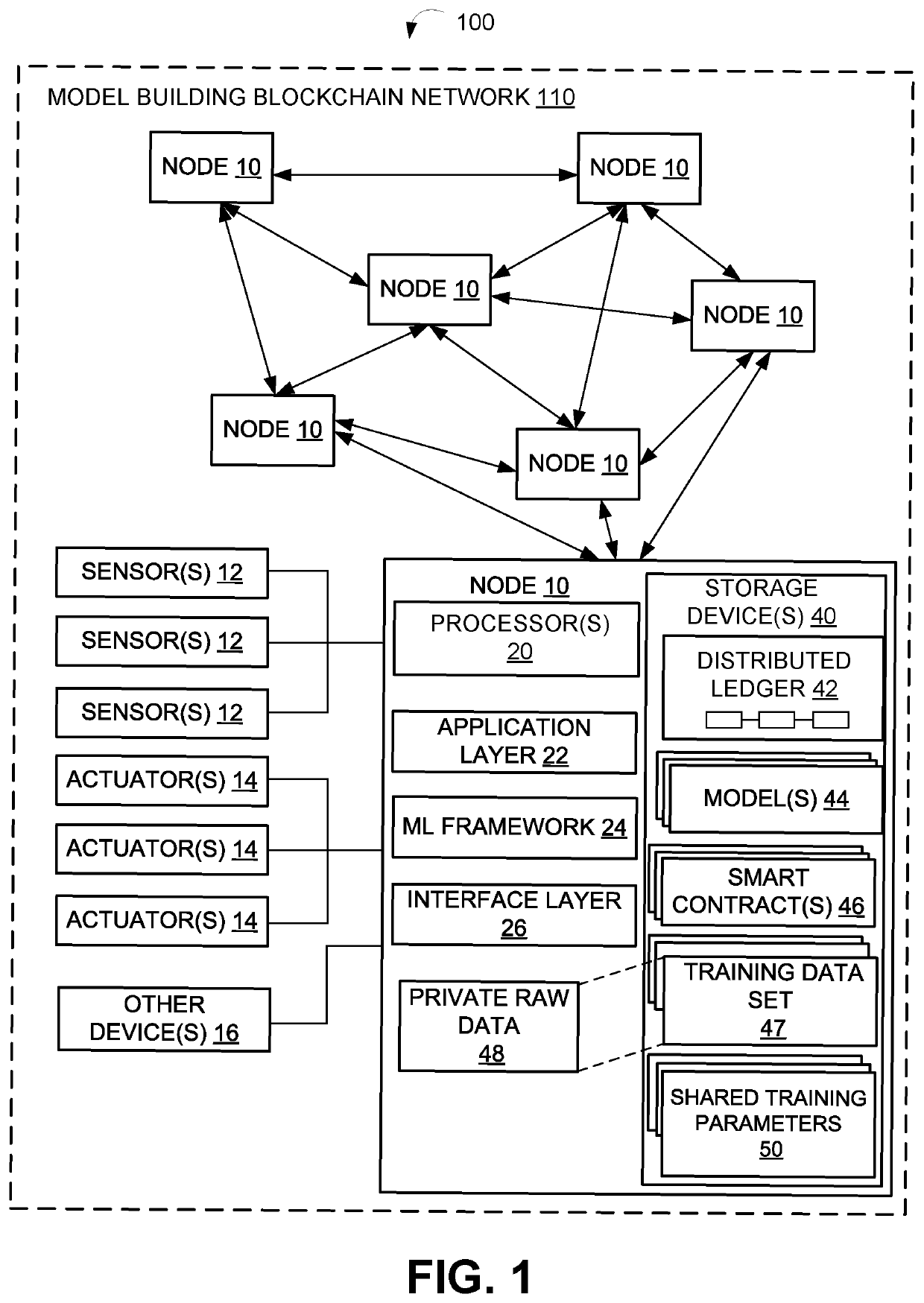
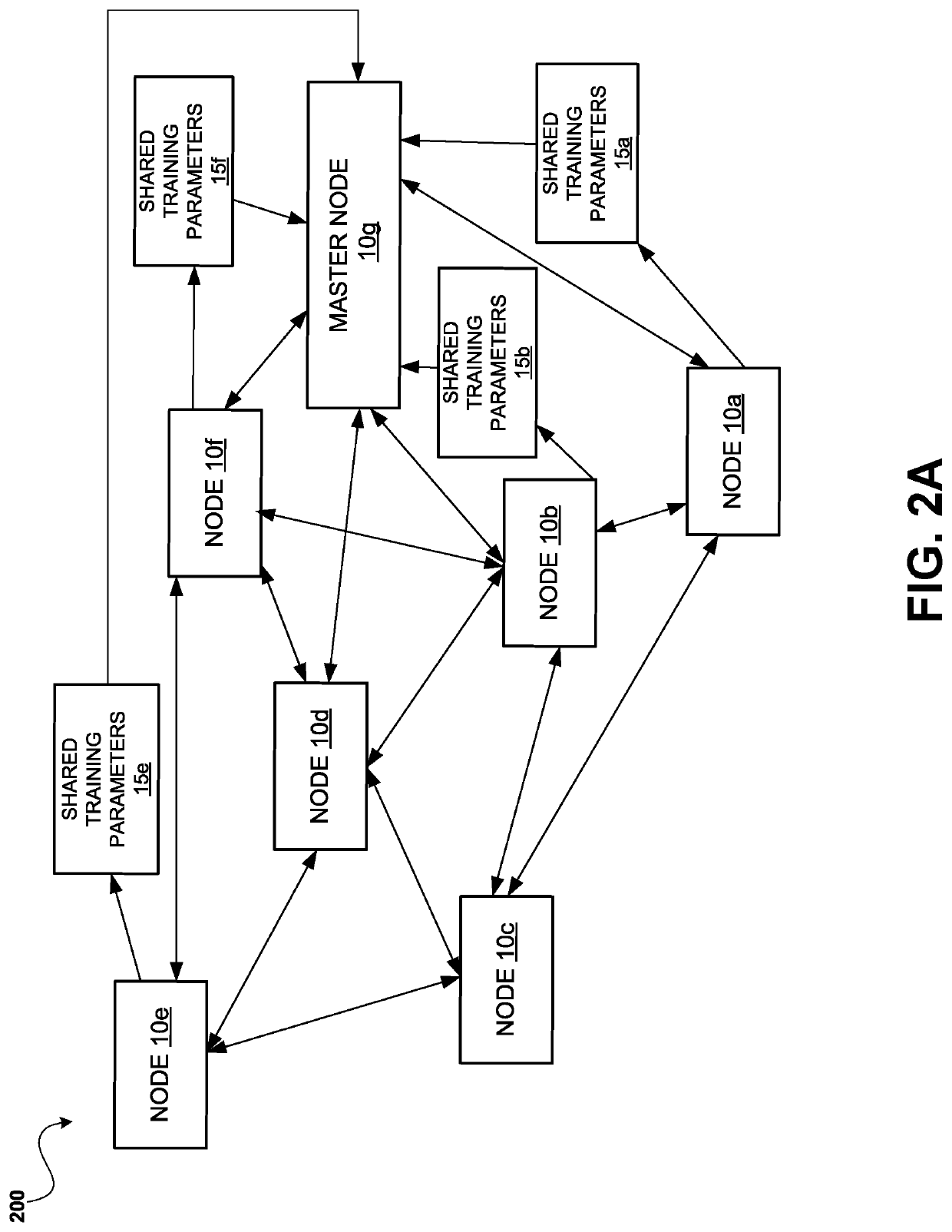
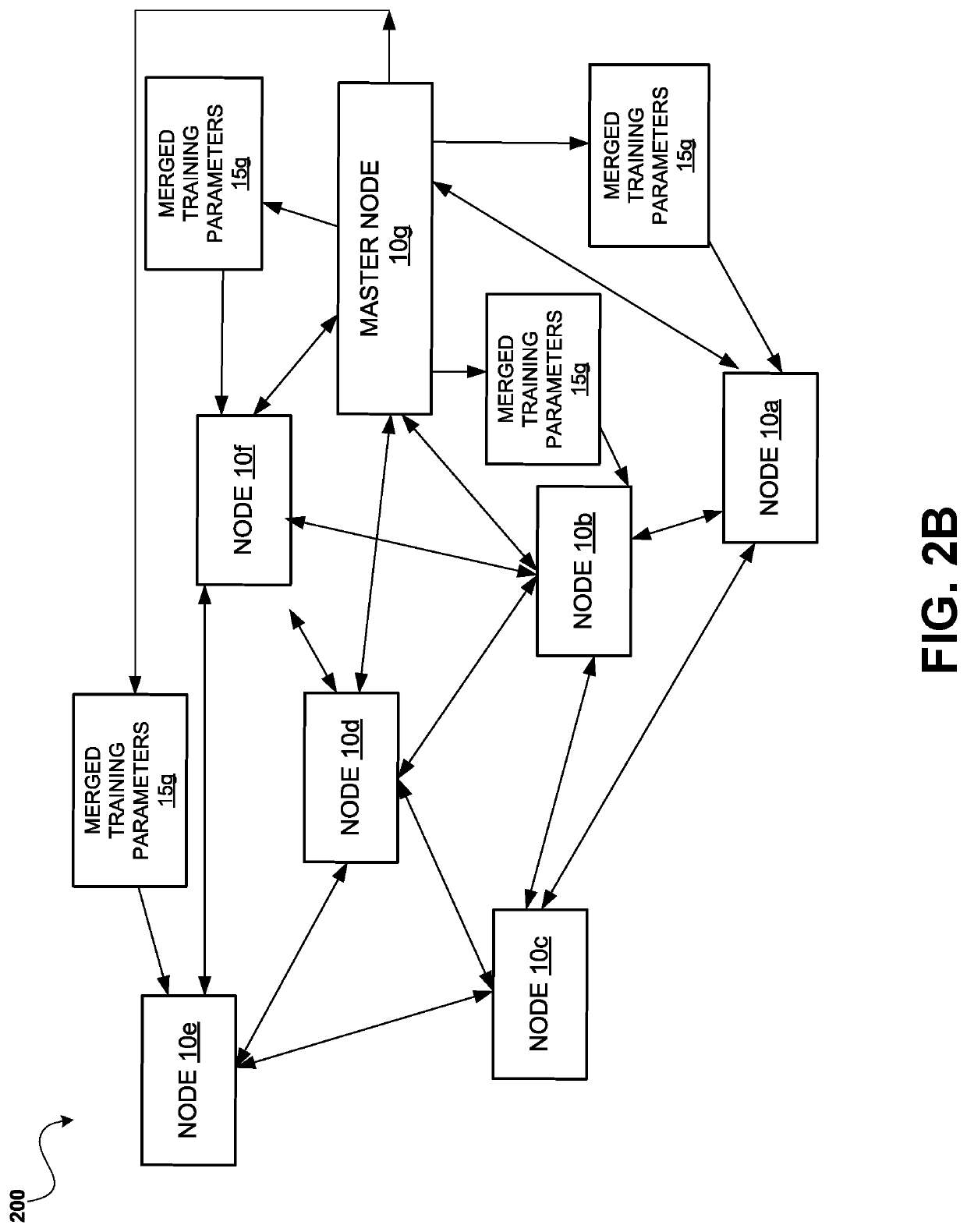
System and method of decentralized model building for machine learning and data privacy preserving using blockchain
InactiveUS20200272945A1Encryption apparatus with shift registers/memoriesKernel methodsData privacy protectionEngineering
Decentralized machine learning to build models is performed at nodes where local training datasets are generated. A blockchain platform may be used to coordinate decentralized machine learning over a series of iterations. For each iteration, a distributed ledger may be used to coordinate the nodes communicating via a blockchain network. A node can have a local training dataset that includes raw data, where the raw data is accessible locally at the computing node. Further, a node can train a local model based on the local training dataset during a first iteration of training a machine-learned model. The node can generate shared training parameters based on the local model in a manner that precludes any requirement for the raw data to be accessible by each of the other nodes on the blockchain network to perform the decentralized machine learning, while preserving privacy of the raw data.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
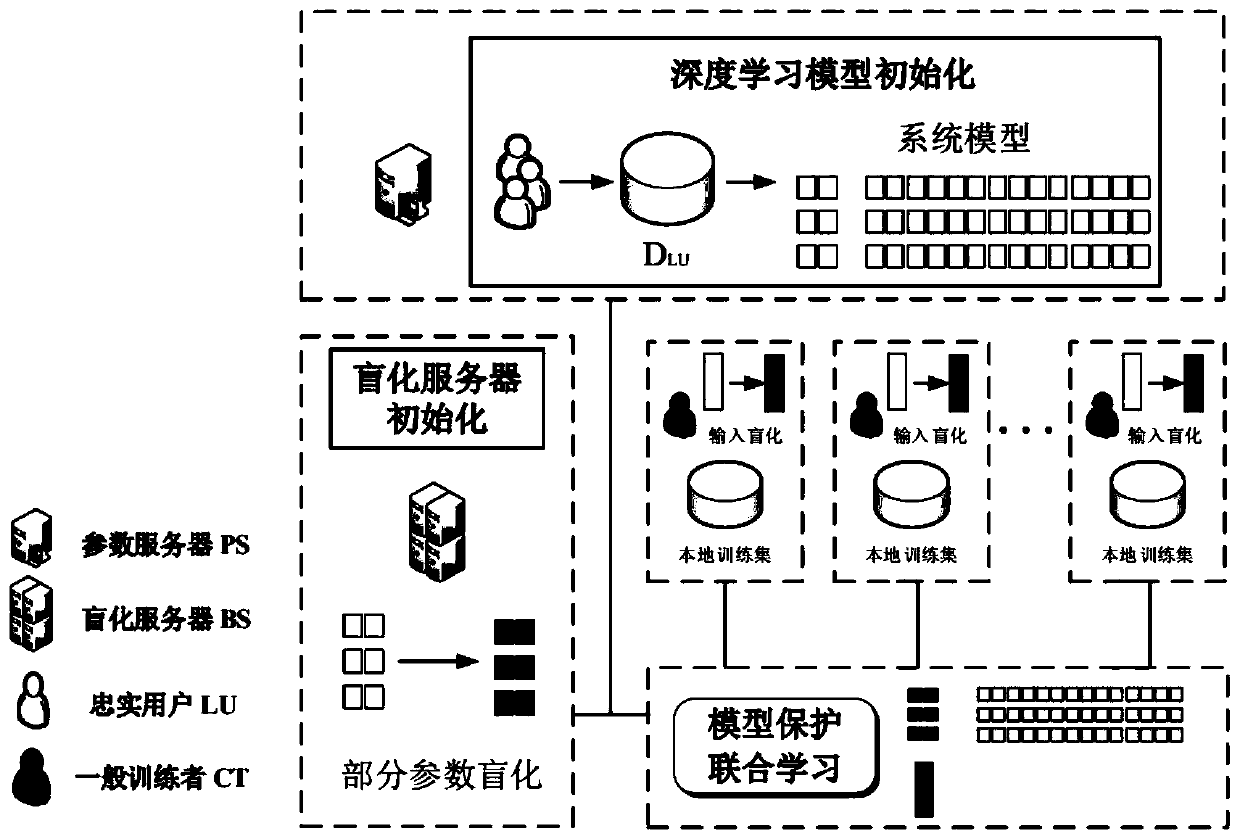
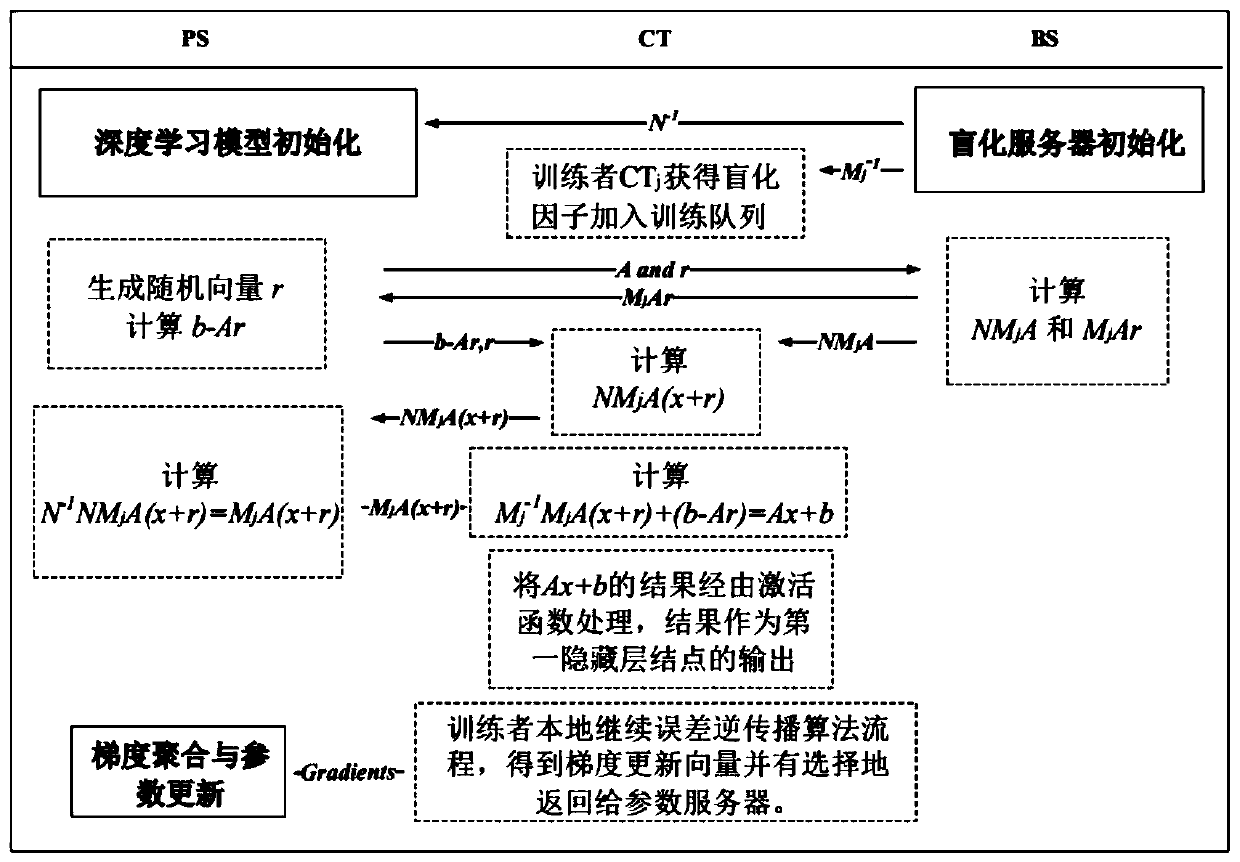
Joint deep learning method capable of resisting generative adversarial network attacks
ActiveCN110460600ARealize privacy protectionLimit the ability to use system models independentlyData switching networksPattern recognitionStochastic gradient descent
The invention provides a joint deep learning method capable of resisting GAN (Generative Adversarial Network) attacks. The joint deep learning method comprises the following steps: initializing a deeplearning model; performing blind server initialization; and performing model protection joint learning and the like. By combining a matrix blinding technology and a random gradient descent method, blinding of input vectors and part of model parameters can be realized. According to the method, modeling and updating of an attacker local generative adversarial network are limited; meanwhile, the modes such as deep learning model right of use are limited, distributed trainees are allowed to utilize private data sets locally to train to obtain gradient update of model parameters, gradient update of each trainee is aggregated by a parameter server, and global update of a system model is achieved. According to the method, the GAN attack is resisted, the joint deep learning system model is protected, and the model accuracy and training data privacy protection requirements are greatly balanced.
Owner:NANJING UNIV OF SCI & TECH
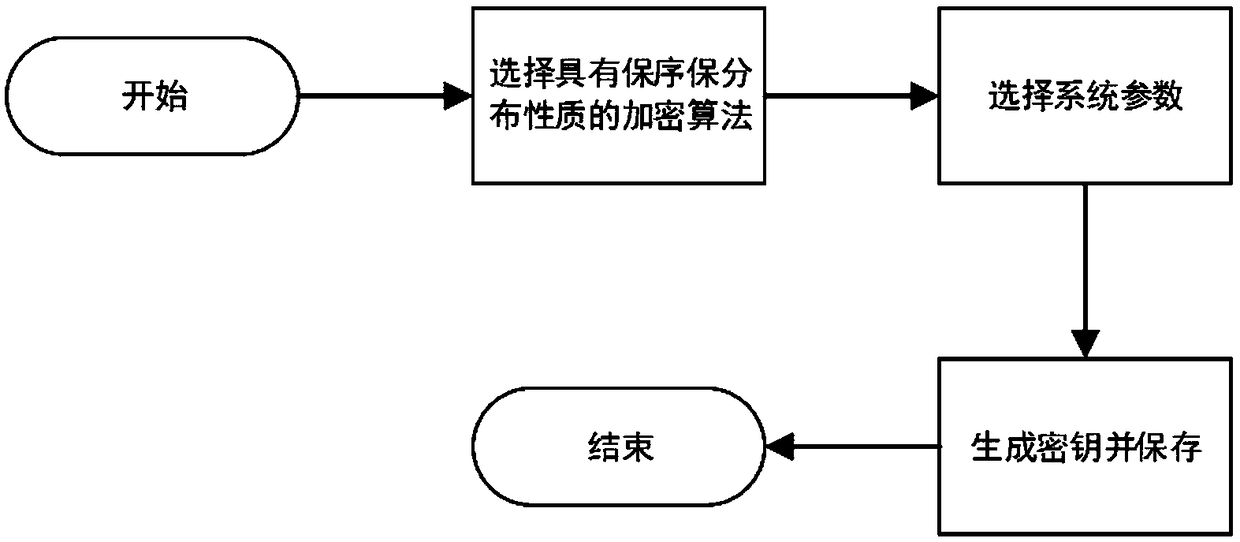
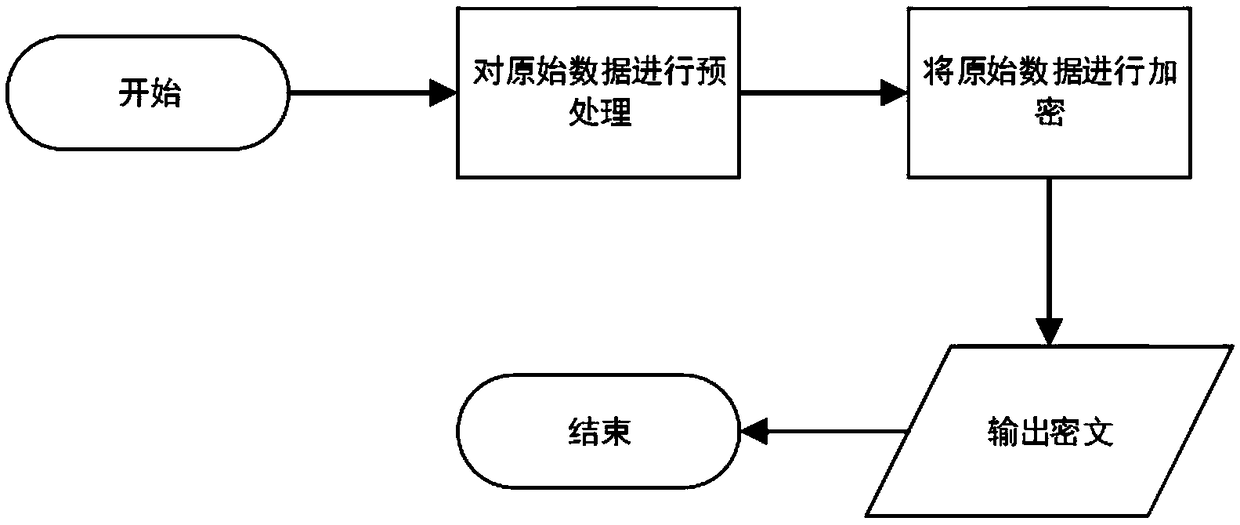
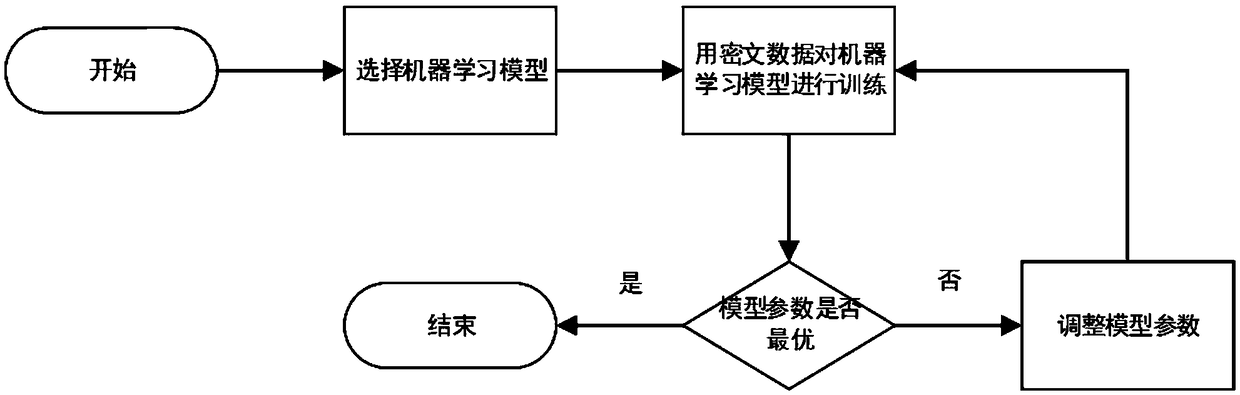
Data privacy protection method and system in machine learning
ActiveCN108717514AThe degree of ciphertext expansion is smallPracticalDigital data protectionTransmissionPlaintextData privacy protection
The invention relates to a data privacy protection method and system in machine learning. The method is characterized by comprising the following steps of: 1) selecting a to-be-used encryption algorithm and system parameters to generate a secret key; 2) encrypting original data to generate corresponding cyphertext data; 3) carrying out training and parameter adjustment on a to-be-used machine learning model by using the cyphertext data so as to obtain an optimal machine learning model; and 4) encrypting to-be-predicted or classified original data by using the secret key in the step 1) by adoption of the method in the step 2) , and inputting the to-be-predicted or classified original data into the optimal machine learning model to obtain a prediction or classification result. According to the method and system, an order preserving / distribution property preserving encryption algorithm and the machine learning model are combined, so that the original data and the machine learning model can be protected. The swelling degree of cyphertext output by the order preserving / distribution property preserving encryption algorithm is far lower than that of a full-homomorphic encryption algorithm, and certain distribution features in plaintext features can be kept, so that the machine learning is relatively high in efficiency and has relatively good expansibility.
Owner:RENMIN UNIVERSITY OF CHINA
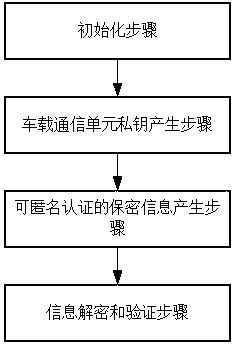
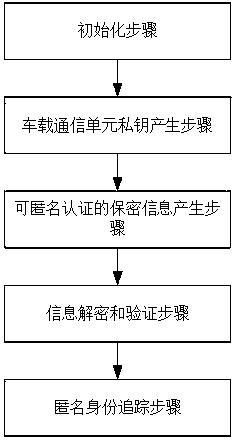
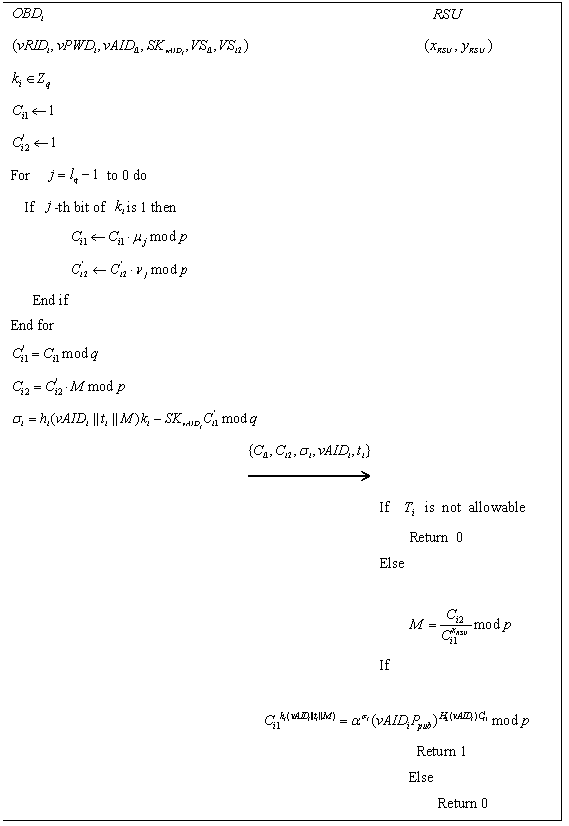
Lightweight anonymity authentication method with privacy protection and based on Internet of Vehicles
ActiveCN108964919AImplement encrypted transmissionSatisfy forward securityUser identity/authority verificationData privacy protectionCommunication unit
The invention discloses a lightweight anonymity authentication method with privacy protection and based on Internet of Vehicles. The method comprises the steps of initialization, generation of a private key of a vehicle-mounted communication unit, generation of secrecy information capable of anonymity authentication, information decryption and verification, and tracking of anonymous identity. A trustable center generates an anonymous identity for an intelligent vehicle as well as the private key of the anonymous identity, an ElGamaL encryption algorithm and a modified Schnorr signature algorithm are combined to generate the information capable of anonymity, transmission information is transmitted in an encrypted way in authentication protocols, and the information cannot be decrypted unless using the secret key of a roadside base station unit; when a dispute of a traffic accident occurs, the anonymous identity can be tracked; and the method has prospects in practical application.
Owner:SOUTHWEST PETROLEUM UNIV
Location privacy protection method based on the cloud server
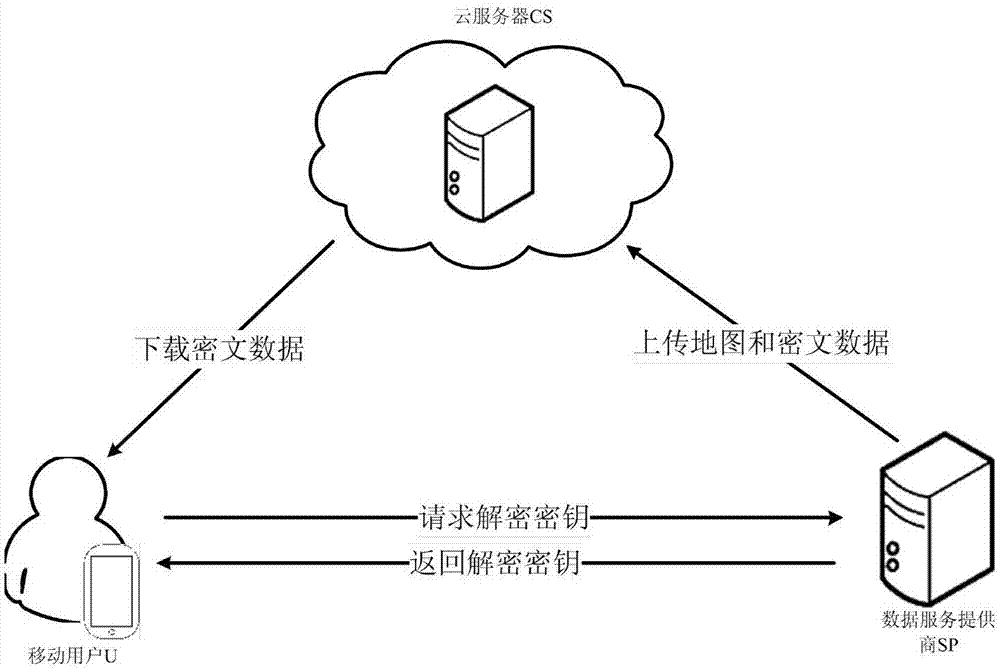
ActiveCN107347096ALow storage costProtect data privacyDigital data protectionTransmissionData privacy protectionUser privacy
The invention discloses a location privacy protection method based on a cloud server. The method is characterized in that a cloud server, a data service provider and a number of mobile users exist; the data service provider defines a data format uniformly, carries out data segmentation and encryption, stores data into the cloud server, and secretly stores a decryption key; a user obtains an encrypted data block from the cloud server at a position of the user, the data service provider transmits the decryption key to the user according to an oblivious transfer protocol, and finally the user carries out decryption to obtain plaintext block data. The position information of the user is not exposed in a whole process, and thus the protection of position privacy is realized. According to the method, a problem of data privacy and position privacy protection based on position service can be effectively solved, at the same time, the storage cost, calculation cost and communication cost of the data service provider are reduced, and thus the system overhead is reduced while the user privacy is protected.
Owner:ANHUI UNIVERSITY
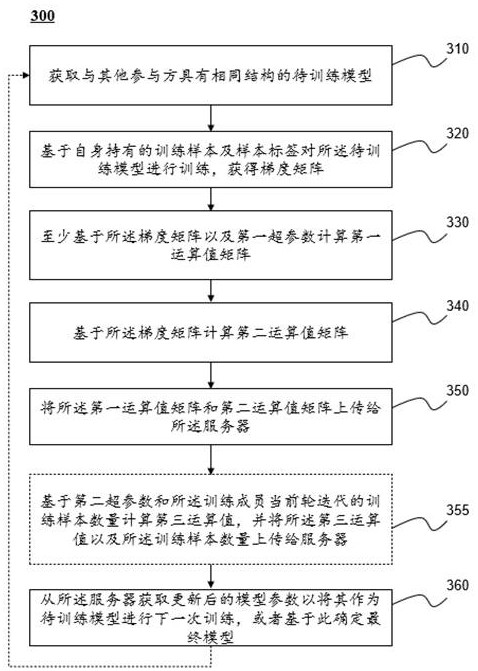
Method, system and device for updating model parameters based on federated learning
The invention relates to a method, system and device for updating model parameters based on federated learning. The method, system and device can be used for data privacy protection. The method is realized by any training member in participants, and the method comprises the following steps: carrying out multiple rounds of iterative updating on model parameters, wherein one round of iterative updating comprises the following steps: obtaining a to-be-trained model with the same structure as other participants; training the to-be-trained model based on a self-held training sample and a sample label to obtain a gradient matrix; calculating a first operation value matrix at least based on the gradient matrix and a first hyper-parameter; calculating a second operation value matrix based on the gradient matrix; uploading the first operation value matrix and the second operation value matrix to the server, so that the server updates model parameters of a to-be-trained model of a server side; and obtaining updated model parameters from the server so as to take the updated model parameters as a to-be-trained model for the next round of iterative update, or determining a final model based onthe updated model parameters.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
A blockchain data privacy protection method with introduction of an arbitration mechanism
PendingCN109598616AAchieve isolationProtection securityFinanceDigital data protectionData privacy protectionData information
The invention discloses a blockchain data privacy protection method with introduction of an arbitration mechanism. data isolation is realized, and each node can only obtain a data result related to its own node by calling a smart contract. Meanwhile, the data transmitted in the block chain network and the data stored in the block chain account book are encrypted and decrypted, the transmission safety of the data information in the block chain network is protected, and malicious attacks and tampering are prevented. And meanwhile, the privacy of the account book data recorded in the block chainis protected, and the real meaning of the data is not known by other nodes. The verification of the authenticity and effectiveness of the transaction is realized through the introduced arbitration node, and meanwhile, the arbitration node can be used for auditing and monitoring. According to the invention, the detection of the effectiveness of the online transaction is realized, the online transaction is ensured to be real and effective, the high privacy of the online data is realized, and only the owner of the data can access and operate the real data.
Owner:DALIAN FUTURES INFORMATION TECH
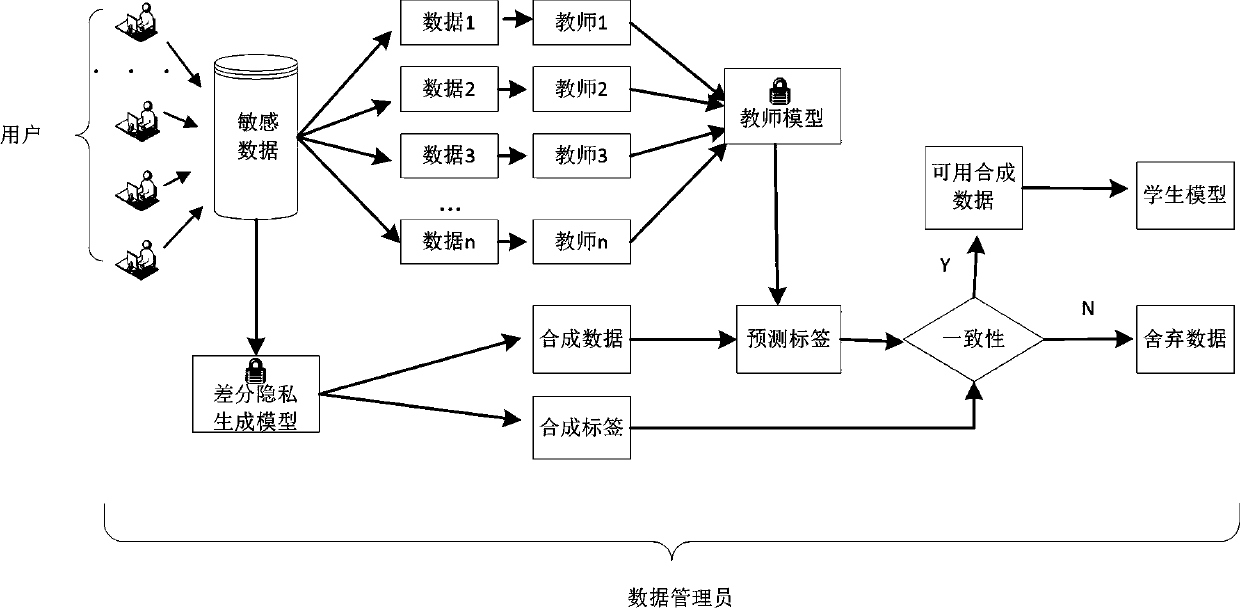
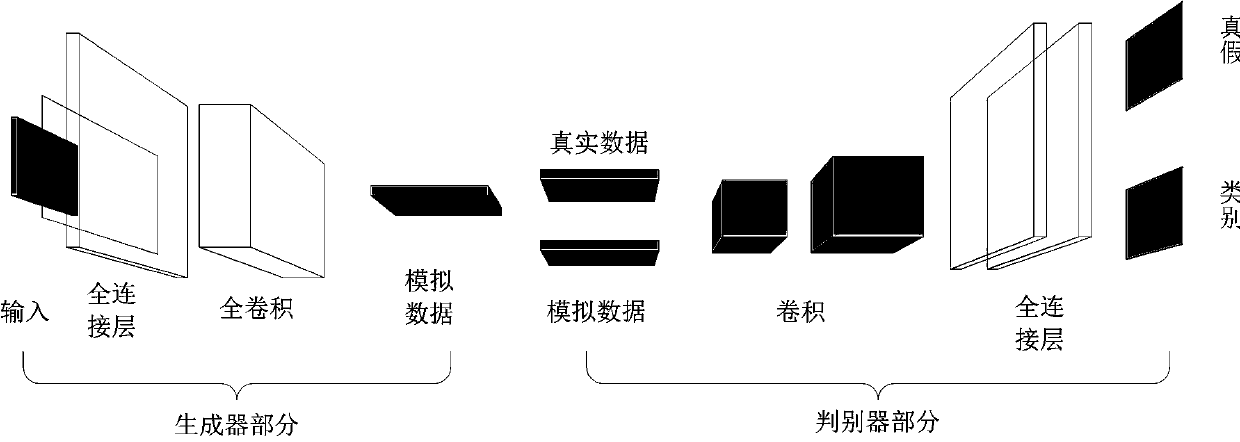
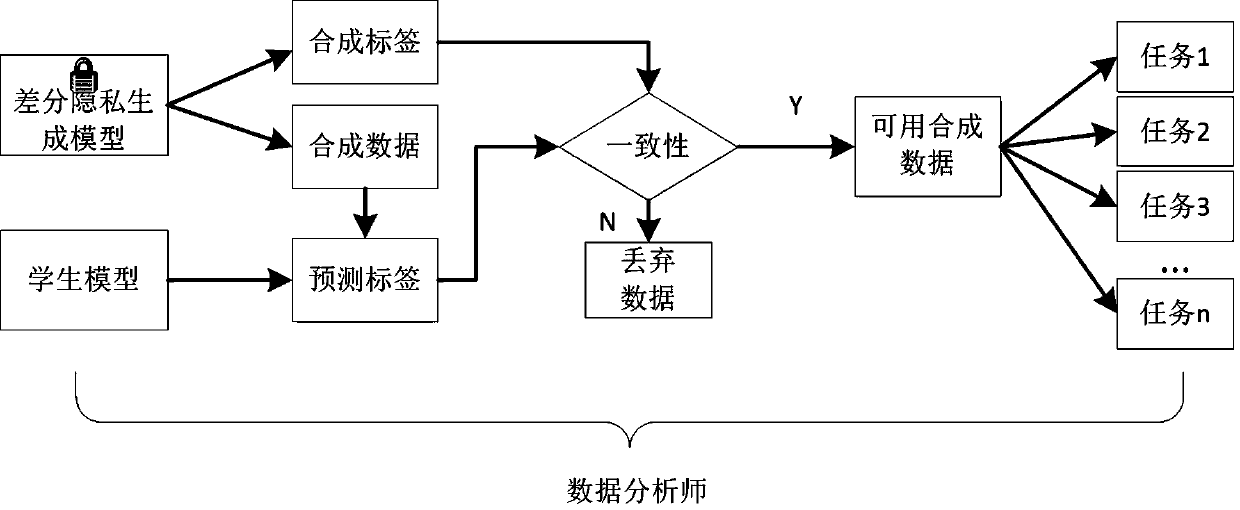
Form data privacy protection method fusing differential privacy GAN model and PATE model
ActiveCN109784091ARealize privacy protectionCharacter and pattern recognitionDigital data protectionData privacy protectionData set
The invention relates to a form data privacy protection method fusing a differential privacy GAN model and a PATE model. The method comprises the steps of 1, training a differential privacy generationmodel by using original table data; 2, training a teacher classifier under the differential privacy budget by using the original table data; Step 3, generating 'false' table data by using the generation model, predicting labels of the 'false' table data by using a teacher classifier, selecting data with consistent prediction labels and generated labels, defining an 'available' data set, and training a student classifier by using the 'available' data set; and step 4, releasing the generation model and the student classifier, synthesizing data by using the generation model, selecting the data by using the student model, and finishing a data analysis task. According to the method, privacy protection is carried out on the table data in the data release stage, a data analyst cannot restore original training data through a generation model and cannot speculate the original training data through a student model, protection on the original table data is achieved, and the requirement of the data analyst for the data is met.
Owner:FUZHOU UNIV
Privacy protection method based on blockchain cloud outsourcing computing data
ActiveCN108712429AOvercoming scalabilityOvercome securityPublic key for secure communicationExtensibilityData privacy protection
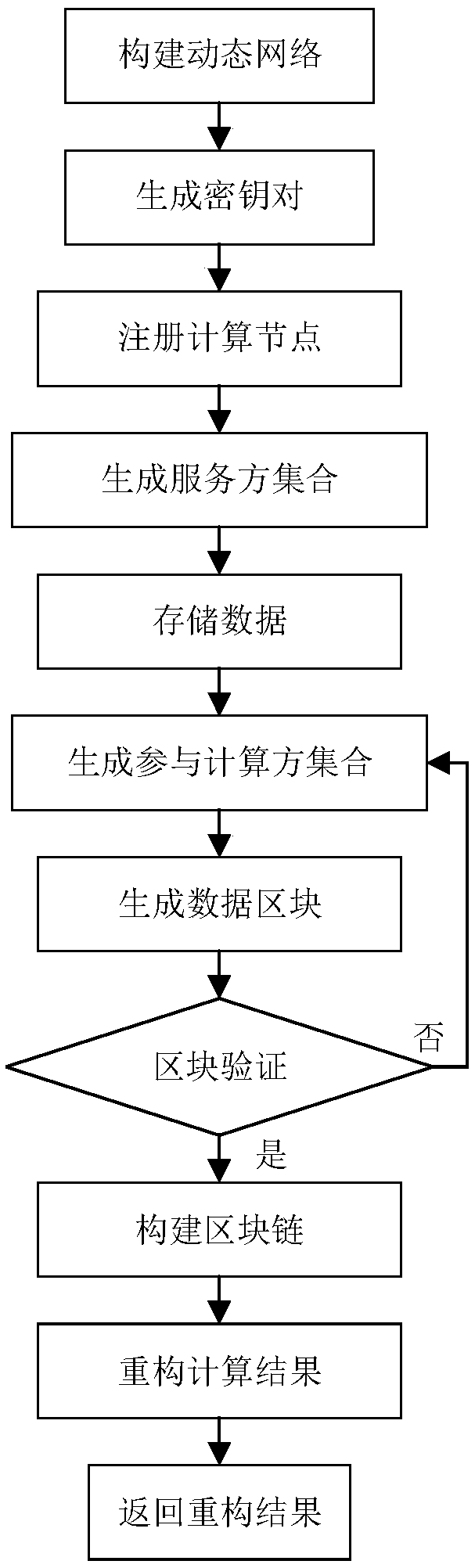
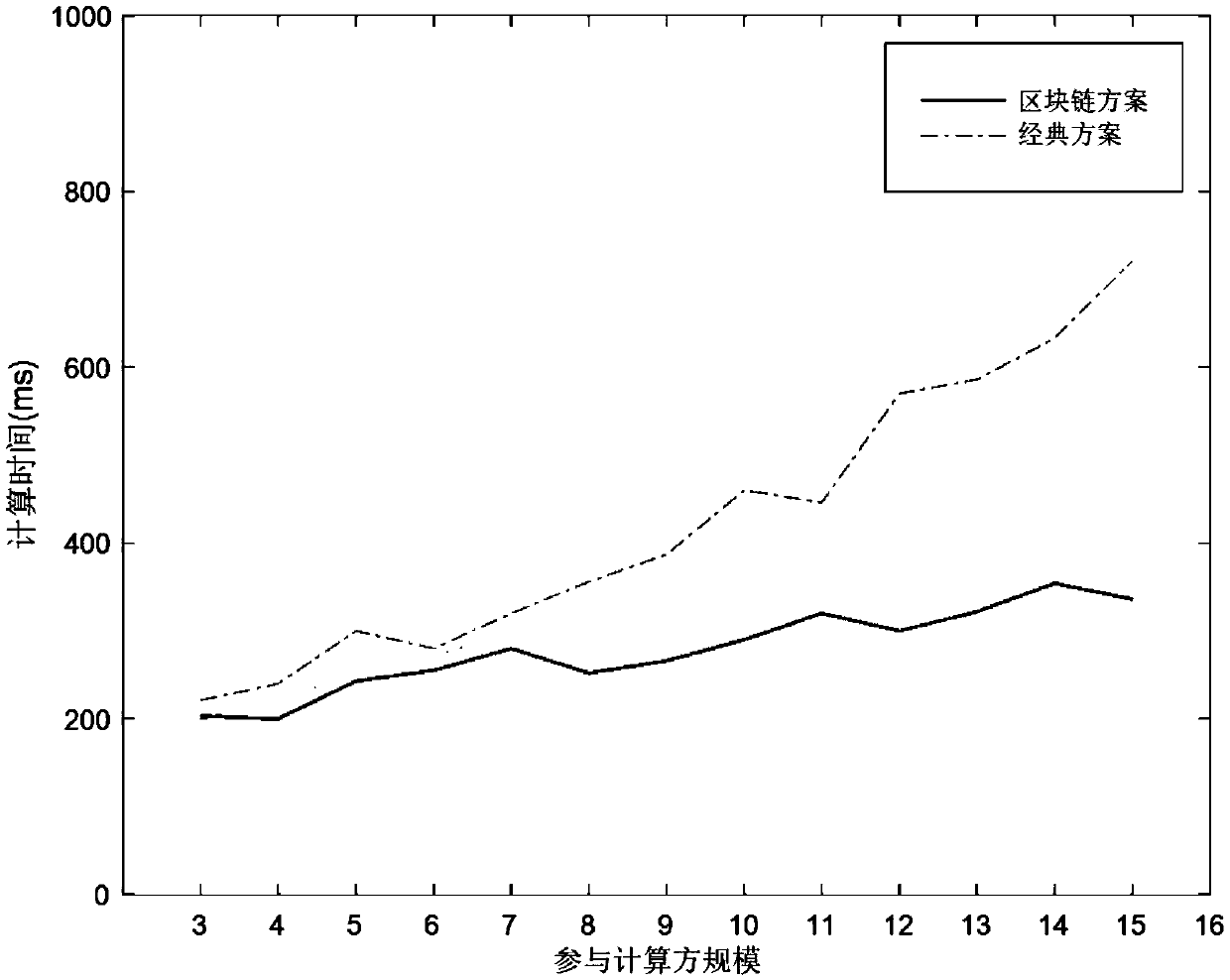
The invention discloses a privacy protection method based on blockchain cloud outsourcing computing data, and mainly solves the problem of high time complexity and scalability of the data privacy protection technology in the current cloud outsourcing computing process. The technical scheme is of using log information of a computing node to construct a blockchain, and using the blockchain technology to perform secure storage verification of the computing data; using the quorum technology to select a suitable computing node set for each round of computing to complete the computing task; and adopting a secure multi-party computing method based on threshold secret sharing to segment and reconstruct secret information. The privacy protection method based on blockchain cloud outsourcing computing data in the invention overcomes the problem that in the prior art, the computing network lacks the scalability and security and the complexity of the data verification process is high; and the scalability of the computing network and the efficiency of the computing process are greatly improved while the data privacy can be effectively ensured.
Owner:XIDIAN UNIV
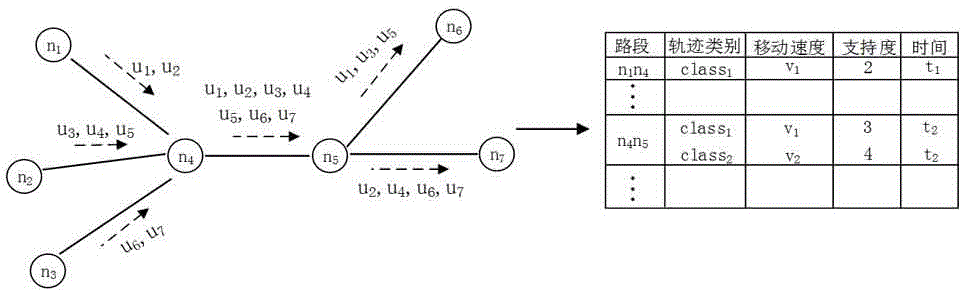
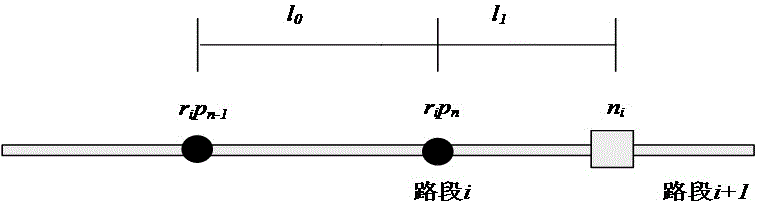
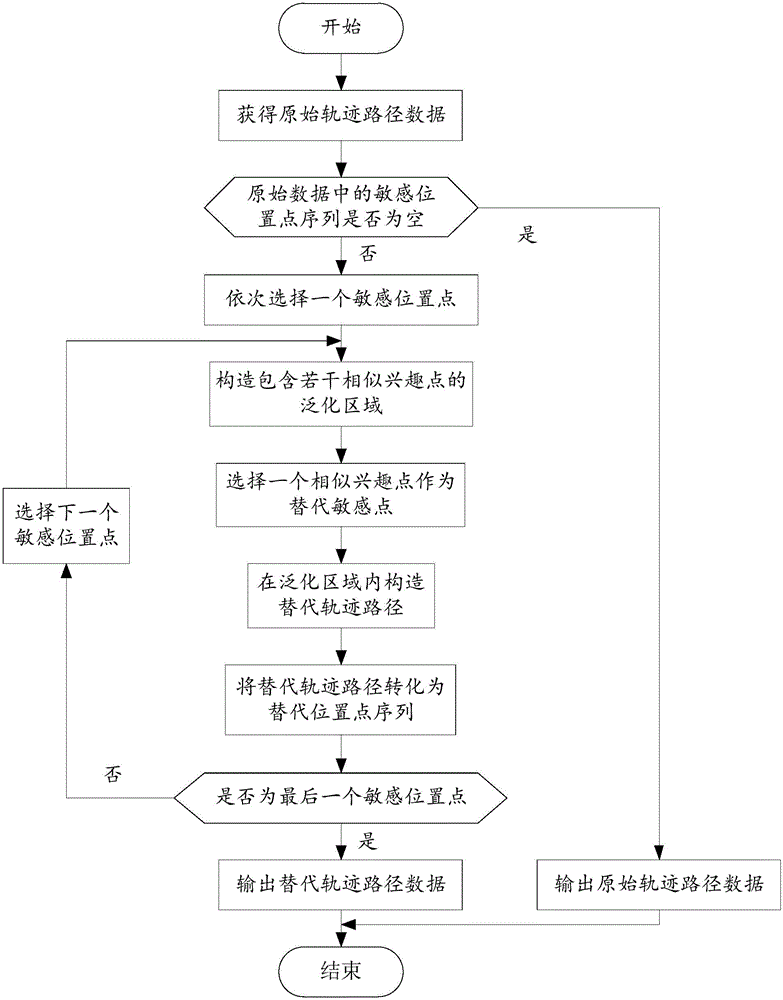
Trajectory data privacy protection method based on road network
InactiveCN105760780AEnsure safetyImprove usabilityDigital data protectionTemporal informationData set
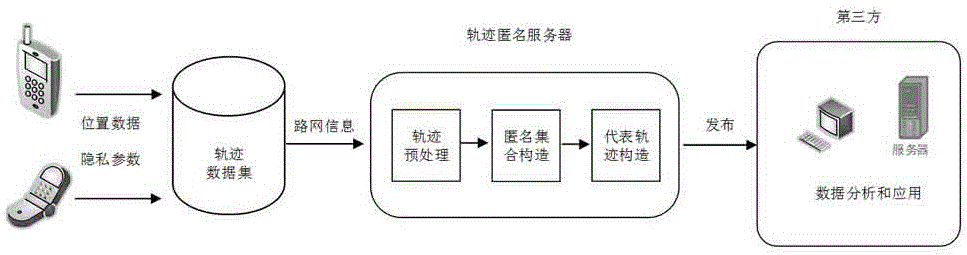
The invention relates to a trajectory data privacy protection method based on a road network.The method includes the steps that in a trajectory data dissemination and application scene, a trajectory is pretreated first; according to road network information, the original integral trajectory is divided into multiple subtrajectory segments according to road segments, and the subtrajectory segments on the same road segment are grouped according to time information; privacy needs of users and movement speed information are combined to cluster trajectory segment sets in the same group, and the trajectory segments in each equivalence class form an anonymous set; a suitable representative trajectory is constructed in the anonymous set to be issued, and privacy protection treatment on a trajectory data set is achieved.While safety of the issued trajectory data set is ensured, data usability is promoted.
Owner:FUJIAN NORMAL UNIV
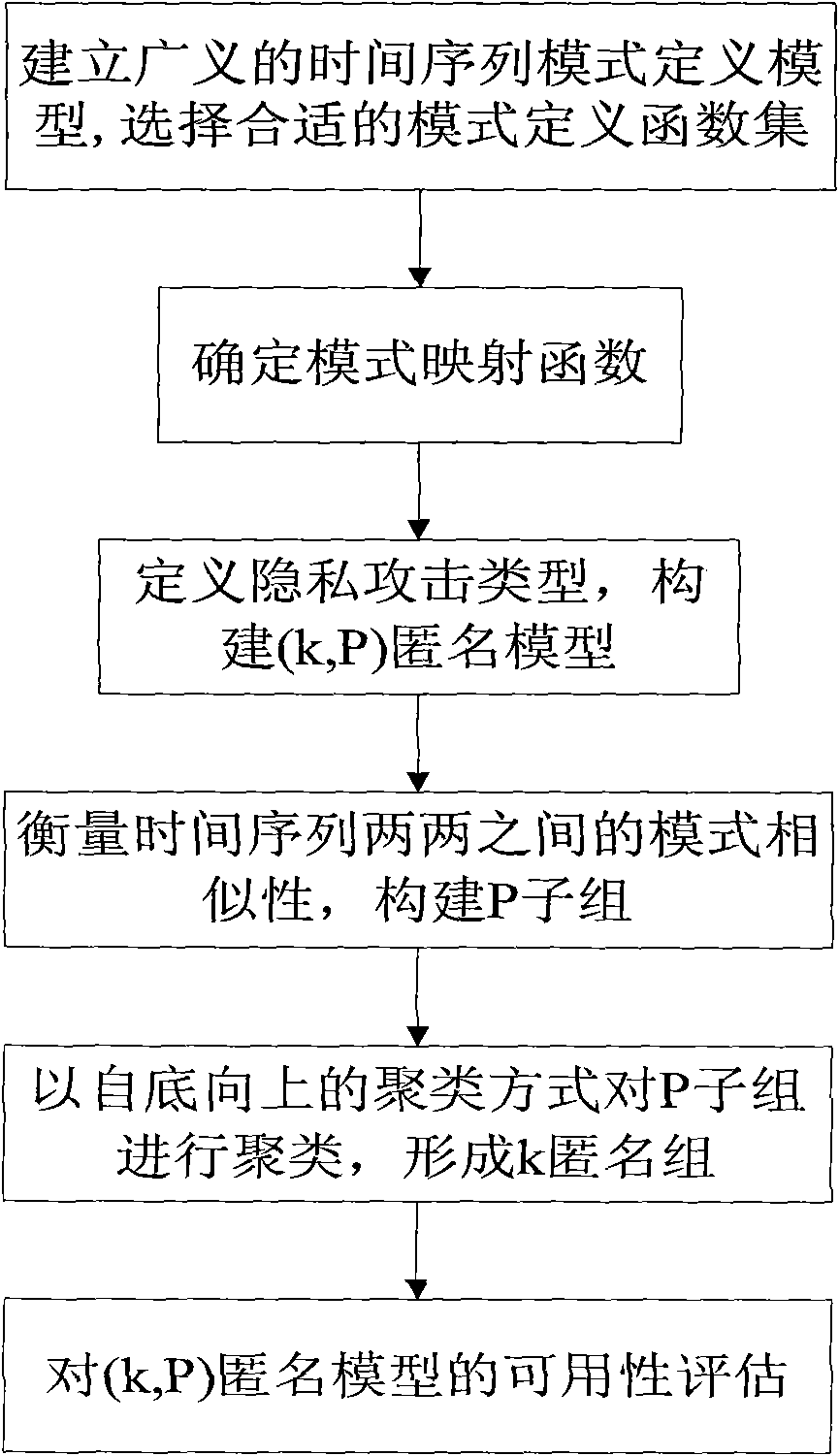
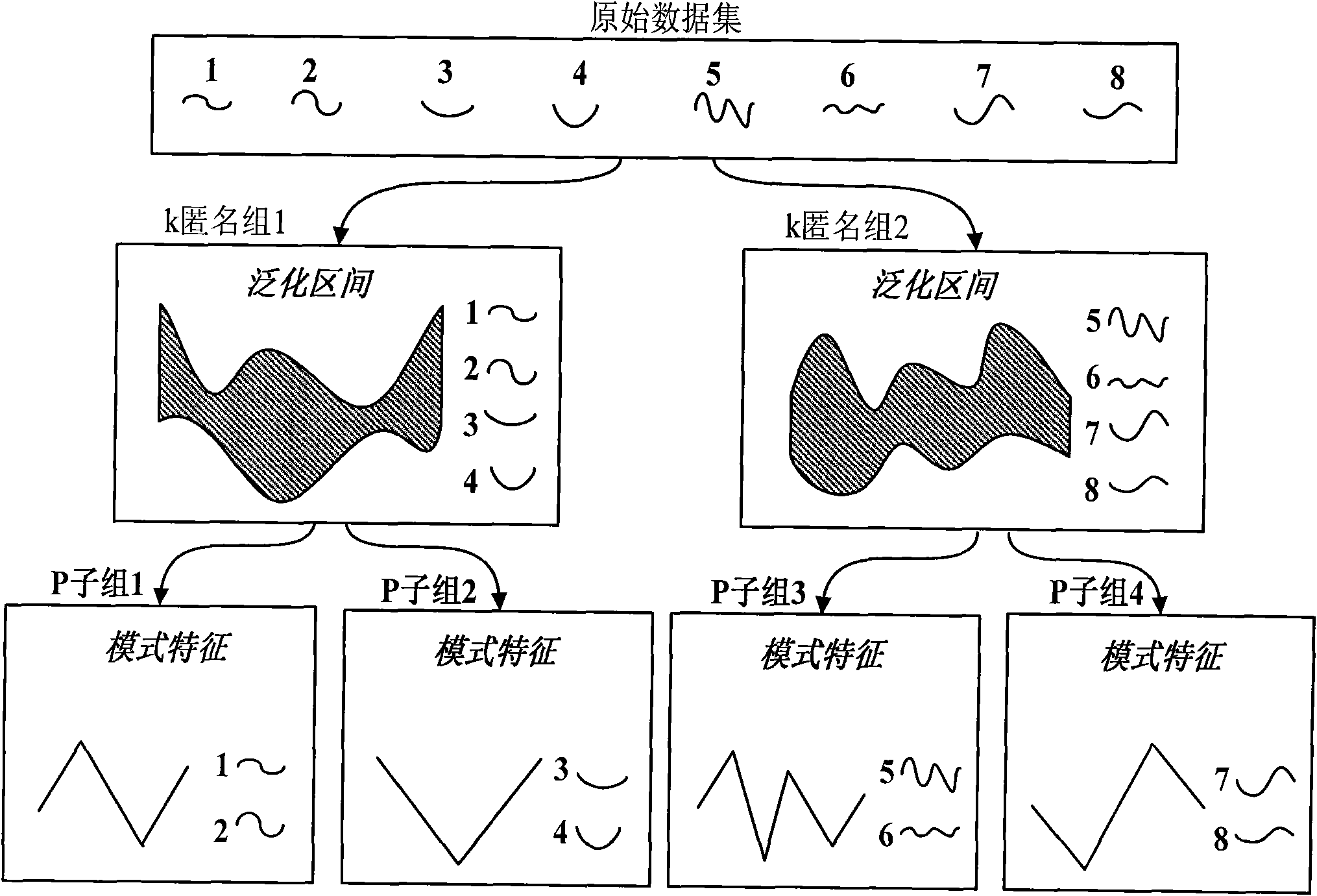
Privacy protection method for mode information loss minimized sequence data
InactiveCN101964034AGuaranteed availabilityDigital data protectionSpecial data processing applicationsK-anonymityData privacy protection
The invention discloses a privacy protection method for mode information loss minimized sequence data. The method comprises the following steps of: confirming a model defined function set based on a generalized mode definition model and a practical application requirement, based on which selecting a mode mapping function capable of realizing minimized mode information loss so as to extract a mode feature, confirming the privacy attack type based on the background knowledge of an attacker, and exerting a (k, P) anonymity mode on a QI attribute value of a time sequence and the mode feature based on a k anonymity technique, wherein the mode separately releases the attribute generalized region of the time sequence and the mode feature, minimizes the mode information loss of the time sequence based on ensuring the data privacy and ensures the usability of the data. The (k, P) anonymity mode is compatible with various mode definition ways and has a set of complete usability evaluating system, the integrity and effectiveness of which results in that the (k, P) anonymity mode is extremely relied and widely applied.
Owner:ZHEJIANG UNIV
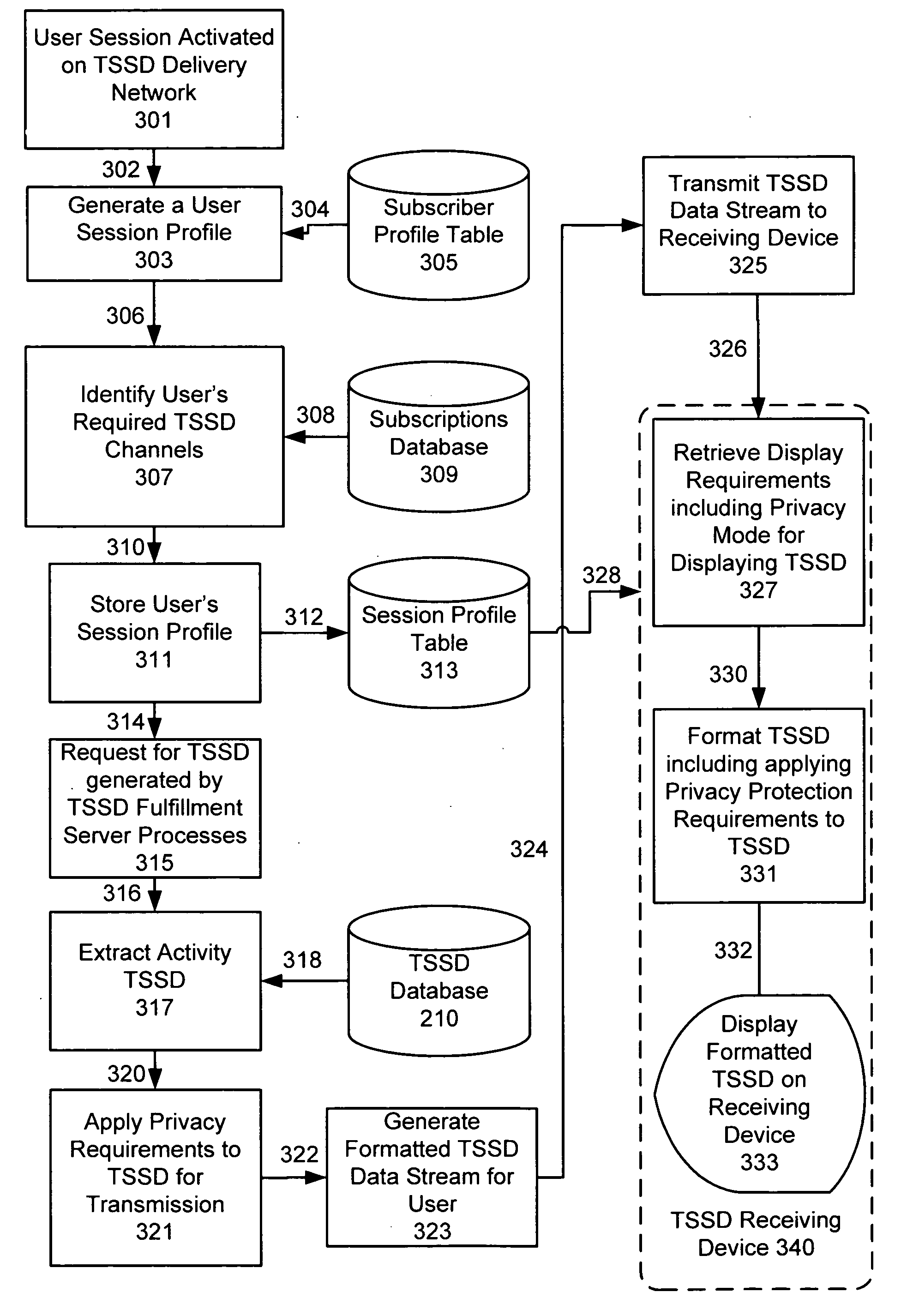
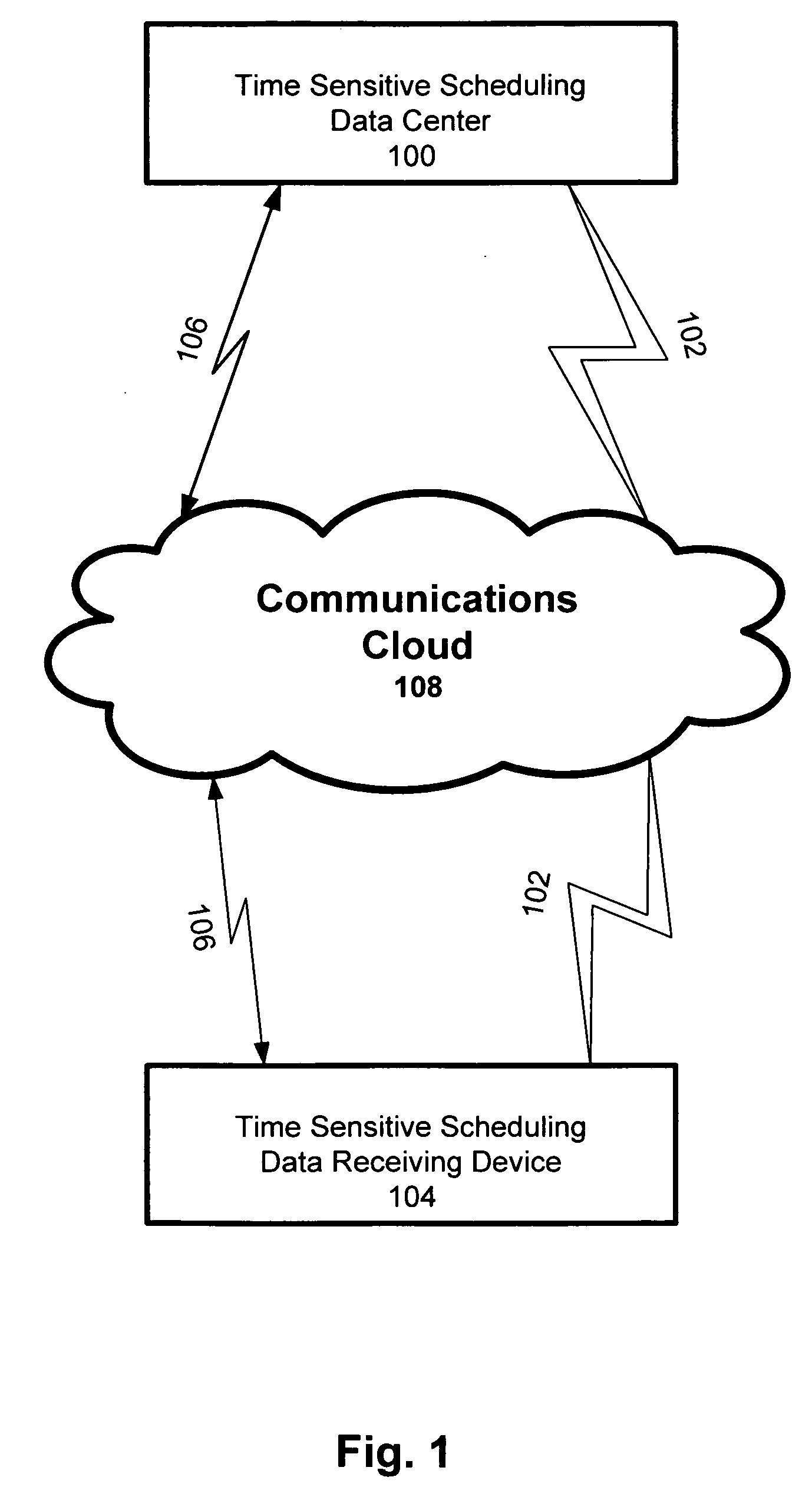
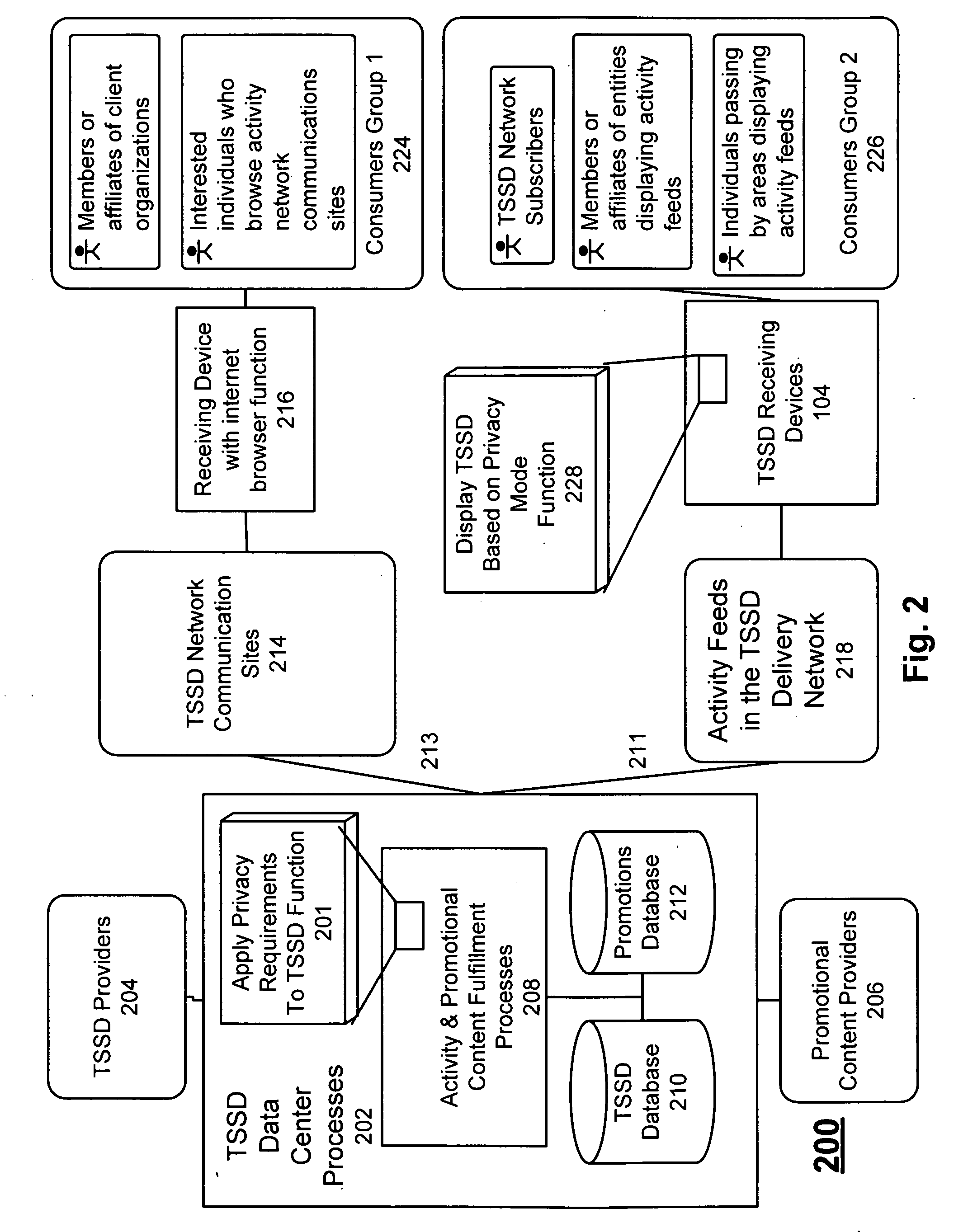
System and method for Time Sensitive Scheduling Data privacy protection
InactiveUS20090106848A1Digital data processing detailsAnalogue secracy/subscription systemsData streamData privacy protection
Providing privacy protection to an entity related to the passive delivery of time sensitive scheduling data via a Time Sensitive Scheduling Data Delivery Network is described. A communications network based passive delivery of privacy protected time sensitive scheduling data is accommodated to an entity. Specific privacy protected time sensitive scheduling data from sources including originating organizations, affiliated groups of individuals, and individuals are aggregated into time sensitive scheduling data streams. Then the specific privacy protected time sensitive scheduling data streams aggregated from sources including multiple originating organizations, affiliated groups of individuals, and individuals are transmitted via the communications network to the entity. Finally the time sensitive scheduling data is presented in a manner affording privacy based on content privacy states which determine the representation of a time sensitive scheduling data item being presented.
Owner:KEEP IN TOUCH SYST
Frequent item set mining method and system supporting differential privacy
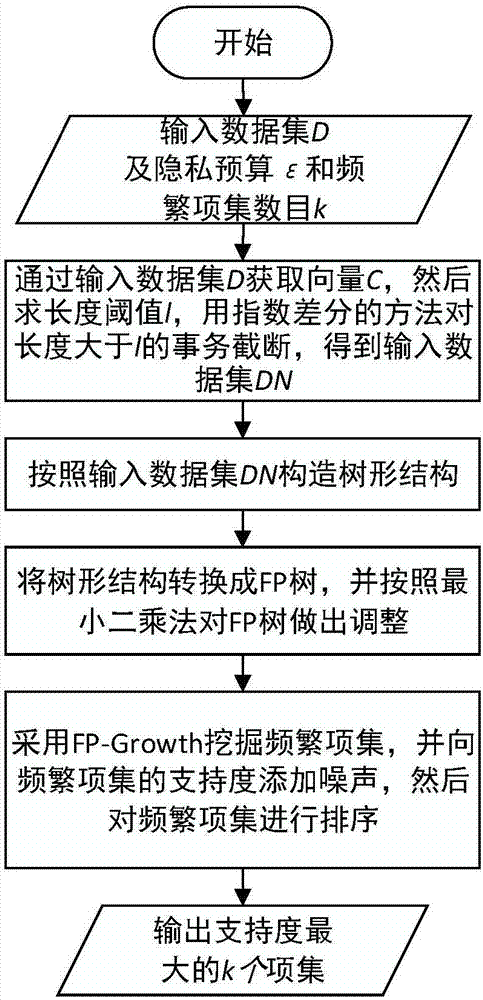
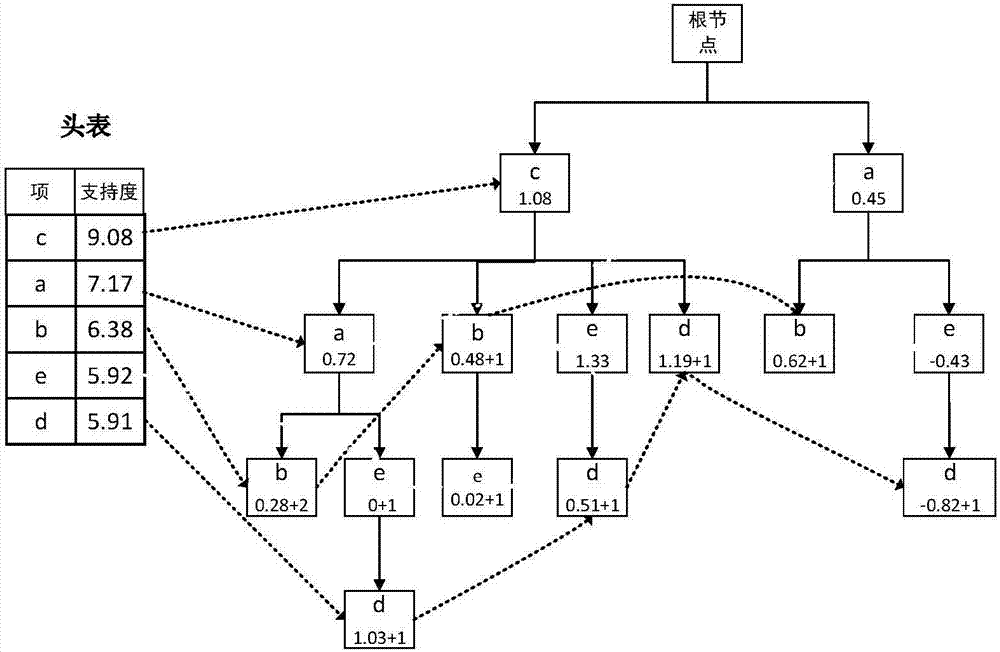
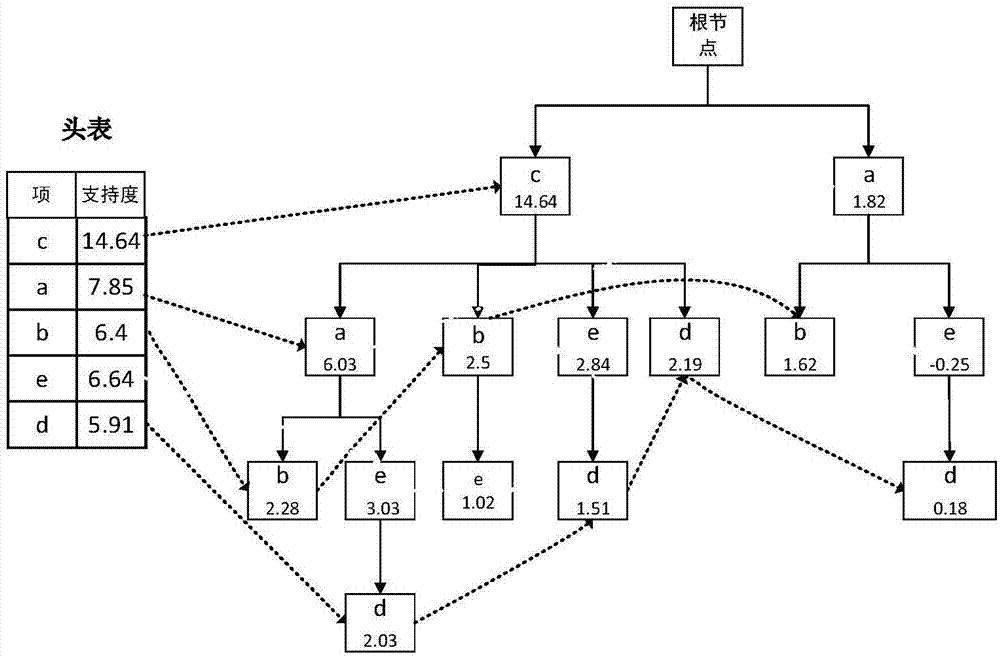
InactiveCN107092837AFix technical inefficienciesImprove digging efficiencyDigital data protectionData setData privacy protection
The invention discloses a frequent item set mining method and system supporting differential privacy, and belongs to the field of computer data privacy protection and data mining. The method comprises the steps of processing an original data set by adopting a transaction truncation method, and avoiding privacy leakage in the truncation process by using an exponential difference mechanism-based method; then constructing a tree structure, wherein each node corresponds to an item of a transaction, frequent information on the transaction is stored in a node corresponding to the last item of the transaction, and the support degree of each node is initialized by using Laplace noise to avoid the privacy leakage in the tree construction process; and converting the constructed tree into an FP tree, so that a frequent item set can be mined by using an FP-Growth method. According to the method and the system, the released frequent item set can meet security demands of the differential privacy; compared with an original frequent item set, the released frequent item set has relatively high similarity with the original frequent item set and relatively high data availability; and compared with a conventional algorithm, higher efficiency is achieved.
Owner:HUAZHONG UNIV OF SCI & TECH
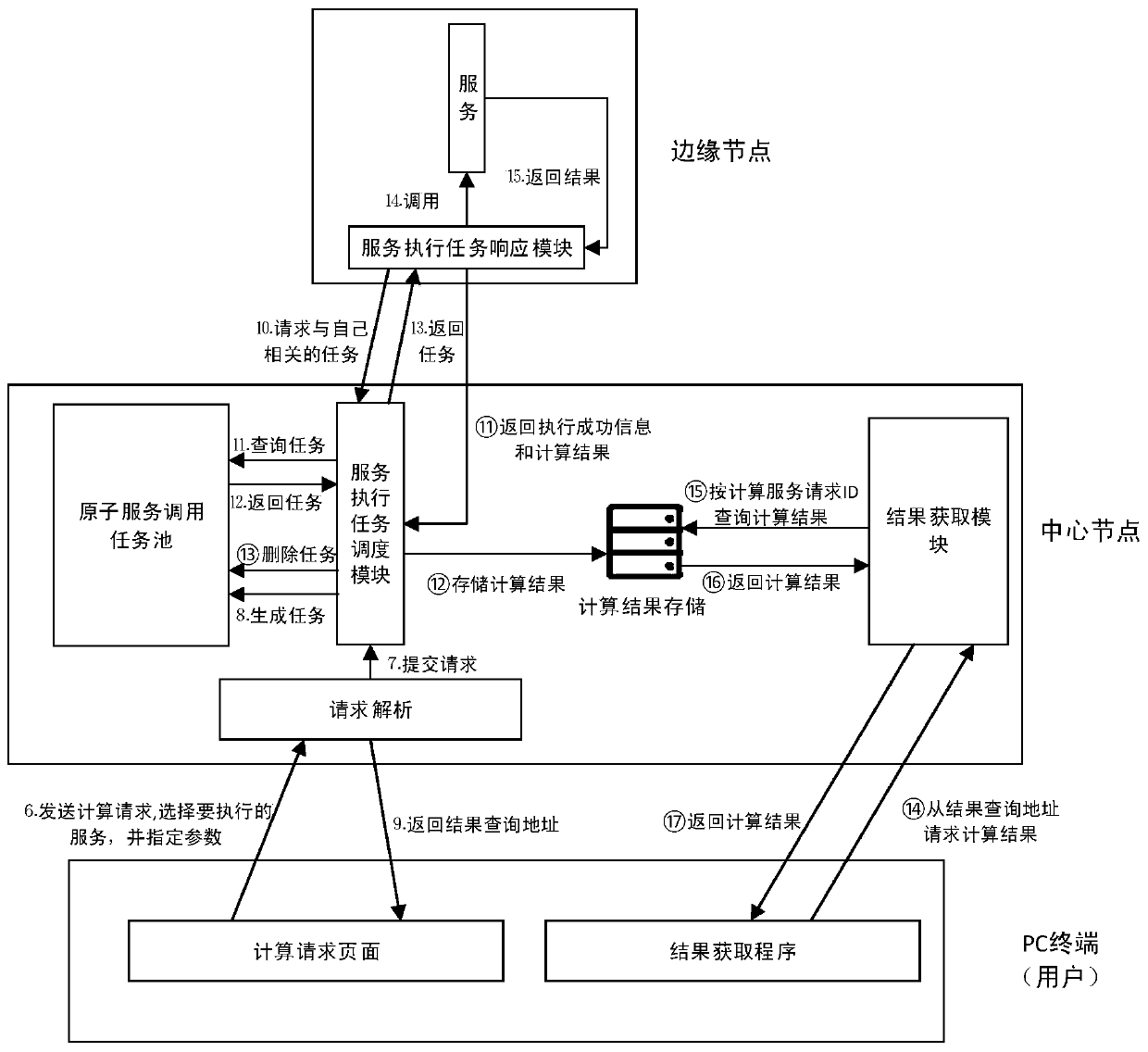
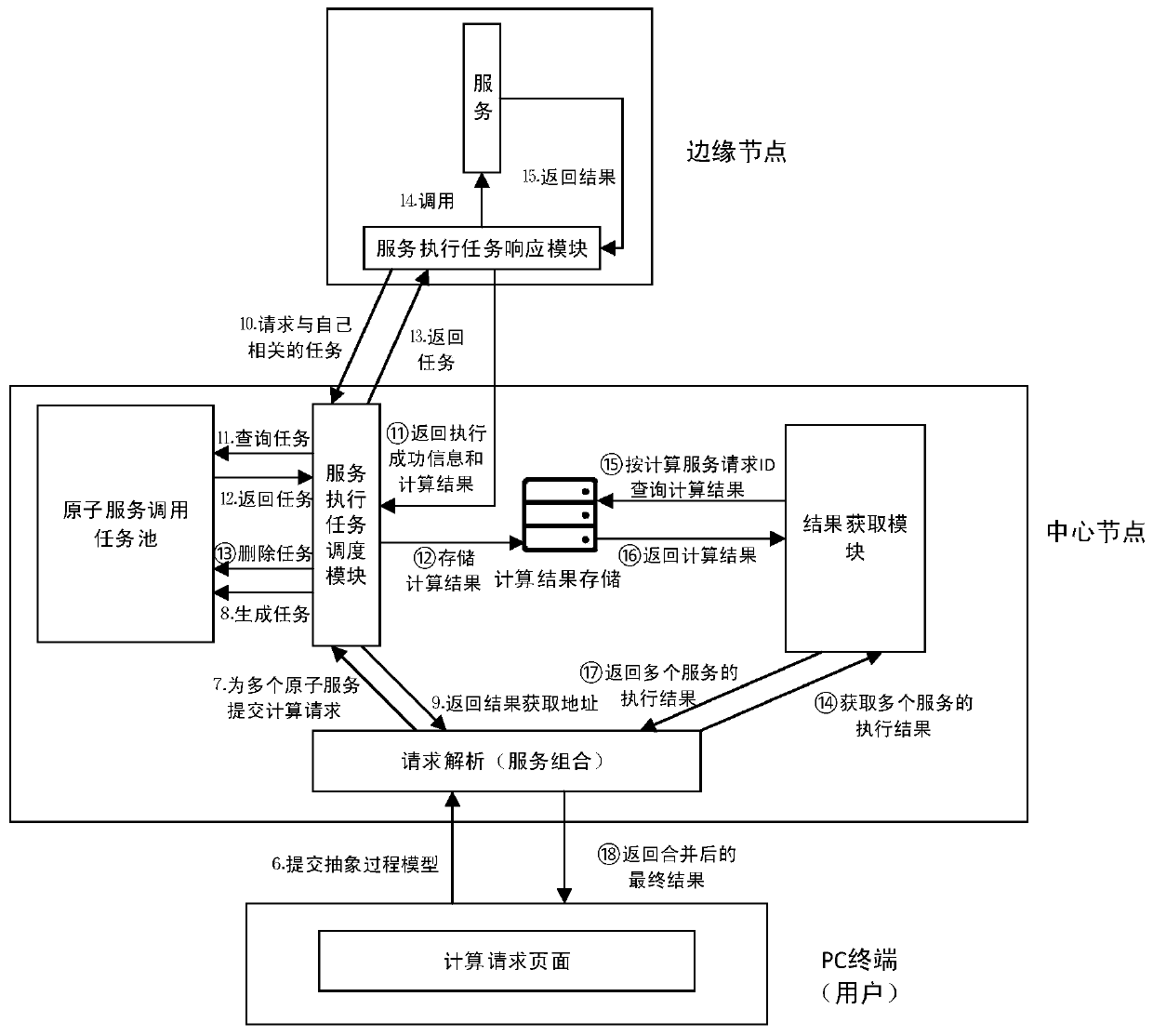
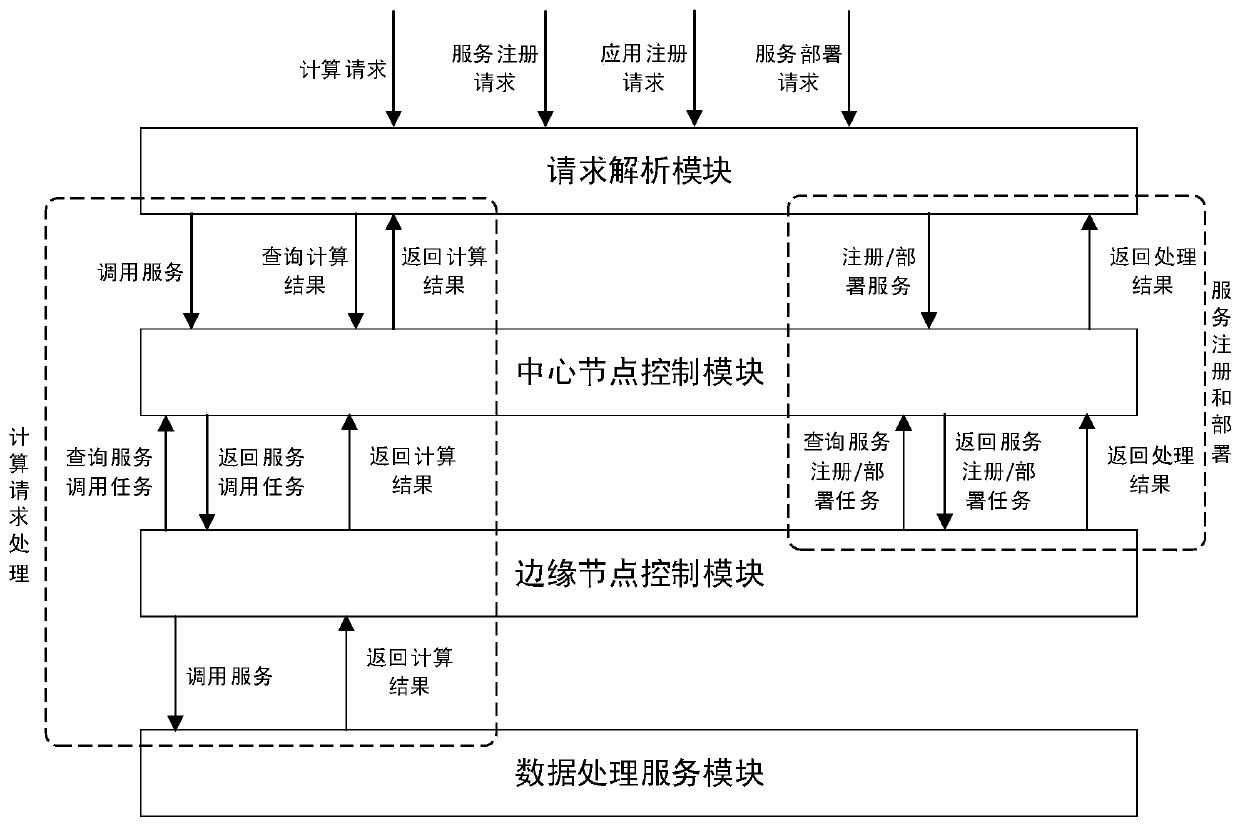
Collaborative computing platform system and method in edge environment
ActiveCN109889575AImprove scalabilityPerfect data processing functionProgram initiation/switchingTransmissionStreaming dataData privacy protection
The invention relates to a collaborative computing platform system and method in an edge environment. The collaborative computing platform system comprises a request analysis module, a central node, an edge node control module and a data processing service module. The system and the method are based on a computing model in an edge environment, and computing is completed by a central node responsible for computing task distribution and a plurality of edge nodes responsible for computing task execution in a cooperative manner. Streaming data and non-streaming data processing under the edge environment is achieved, compared with a traditional computing platform based on a centralization model, the computing platform has higher computing efficiency, and the appeal of data privacy protection ofa data provider is met.
Owner:BEIHANG UNIV
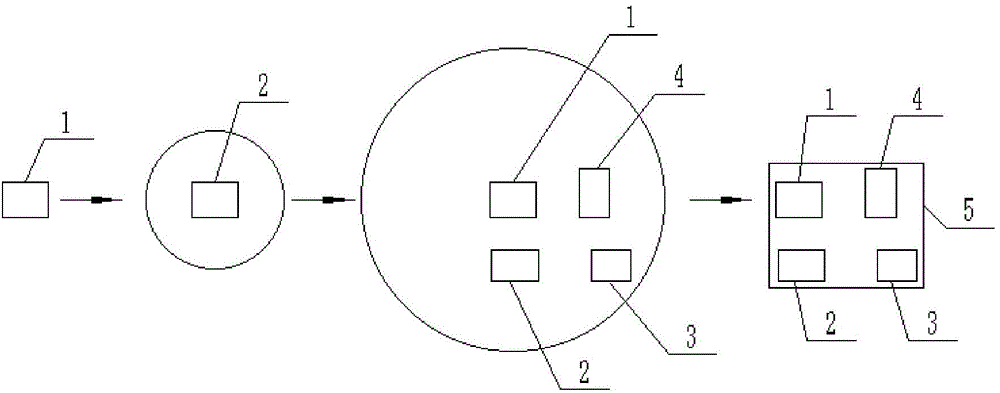
Personalized track data privacy protection method based on semantics
InactiveCN104680072AMeet privacy protection needsImprove utilizationDigital data protectionSpecial data processing applicationsPersonalizationData privacy protection
The invention provides a personalized track data privacy protection method based on semantics. According to the method, a generalization region comprising a plurality of similar interested points is respectively constructed according to each sensitive position point provided by users, one similar interested point is selected for replacing the sensitive position point, and in addition, a reasonable replacing track path and a replacing position point sequence are constructed in the generalization region. The personalized track data privacy protection method has the advantages that the requirement of personalized track data privacy protection of the users is met, and meanwhile, the replacing track path data can be enabled to have higher effectiveness.
Owner:FUJIAN NORMAL UNIV
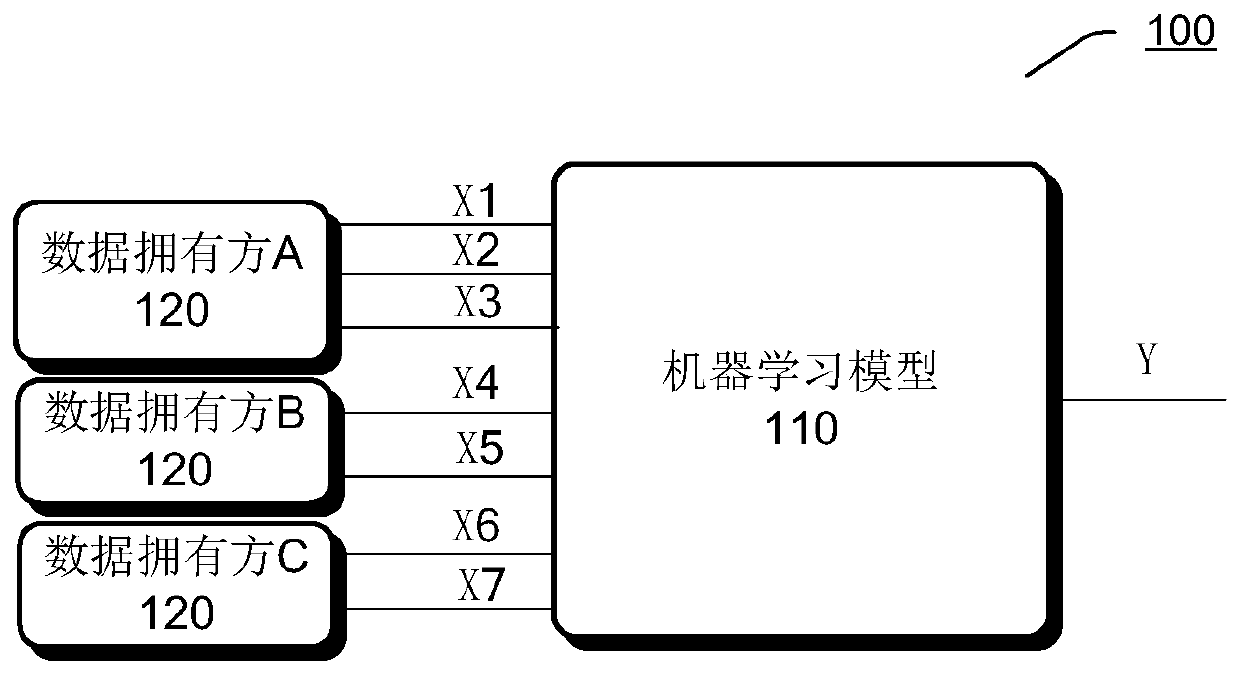
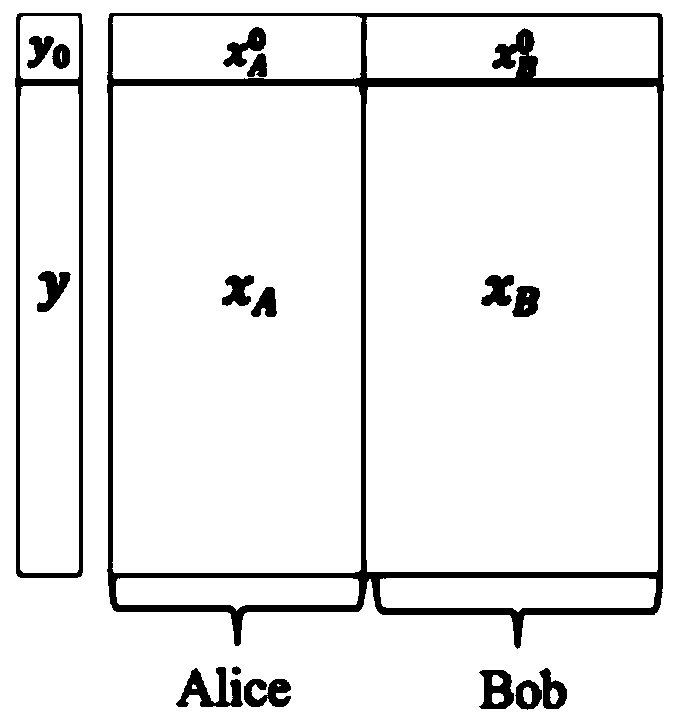
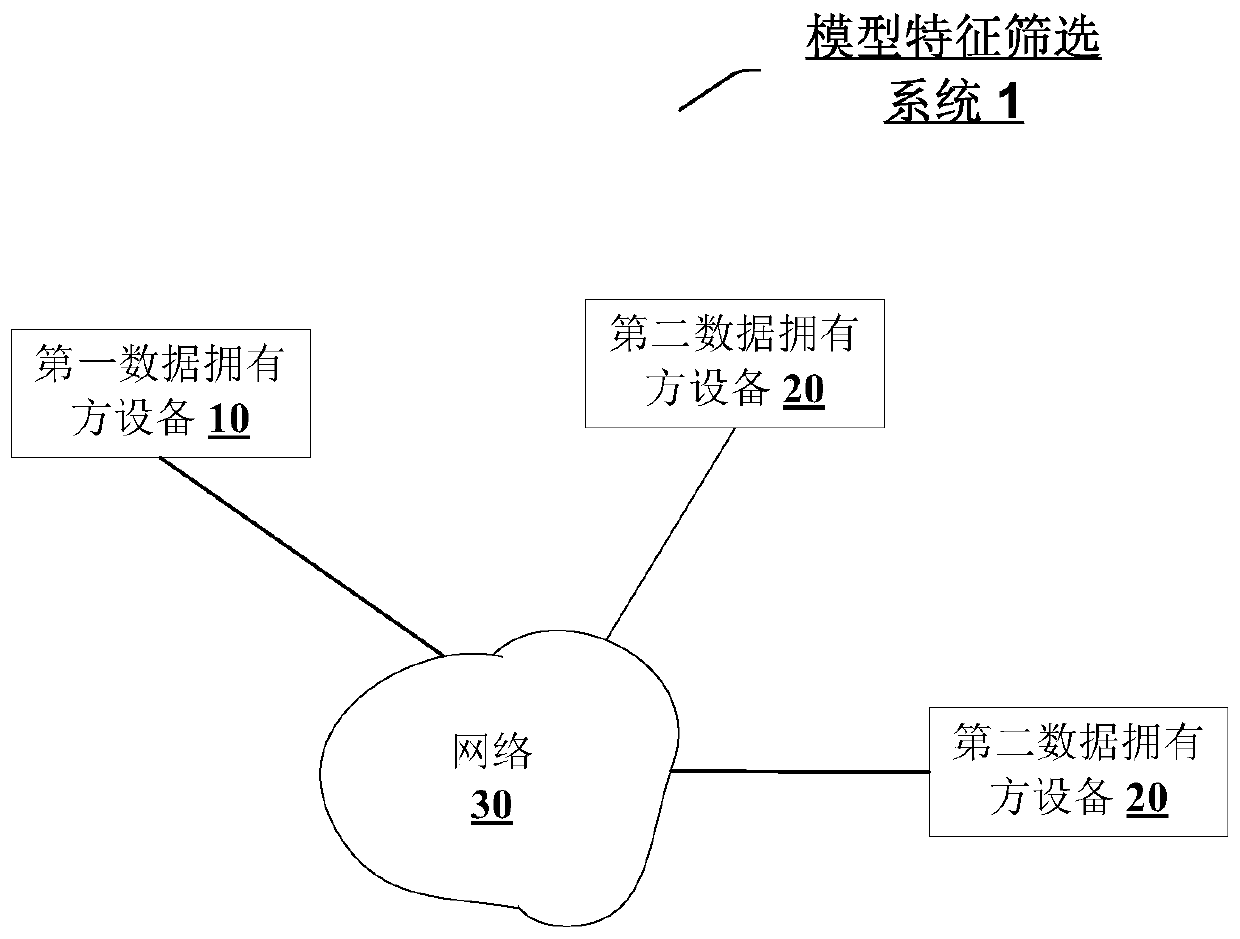
Machine learning model feature screening method and device based on data privacy protection
ActiveCN111062487ACharacter and pattern recognitionMachine learningData privacy protectionEngineering
The embodiment of the invention provides a machine learning model feature screening method based on data privacy protection. The machine learning model has a set of model features, and feature data ofthe machine learning model is distributed vertically segmented at a first data owner and at least one second data owner, each data owner having feature data corresponding to a subset of model features of the set of model features; the first data owner has the feature data of the to-be-screened model features, and the second data owner does not have the feature data of the to-be-screened model features. And the first data owner and the at least one second data owner cooperatively use the respective feature data to perform multi-party security calculation so as to train a prediction model of the to-be-screened model features. A variance expansion factor of the to-be-screened model feature is determined based on the prediction difference value of the to-be-screened model feature at the firstdata owner so as to perform model feature screening processing.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Data privacy protection-oriented machine learning prediction method and system
ActiveCN111275202APrevent theftReliable two-way securityDigital data protectionMachine learningData privacy protectionEngineering
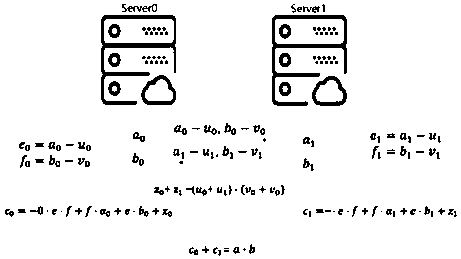
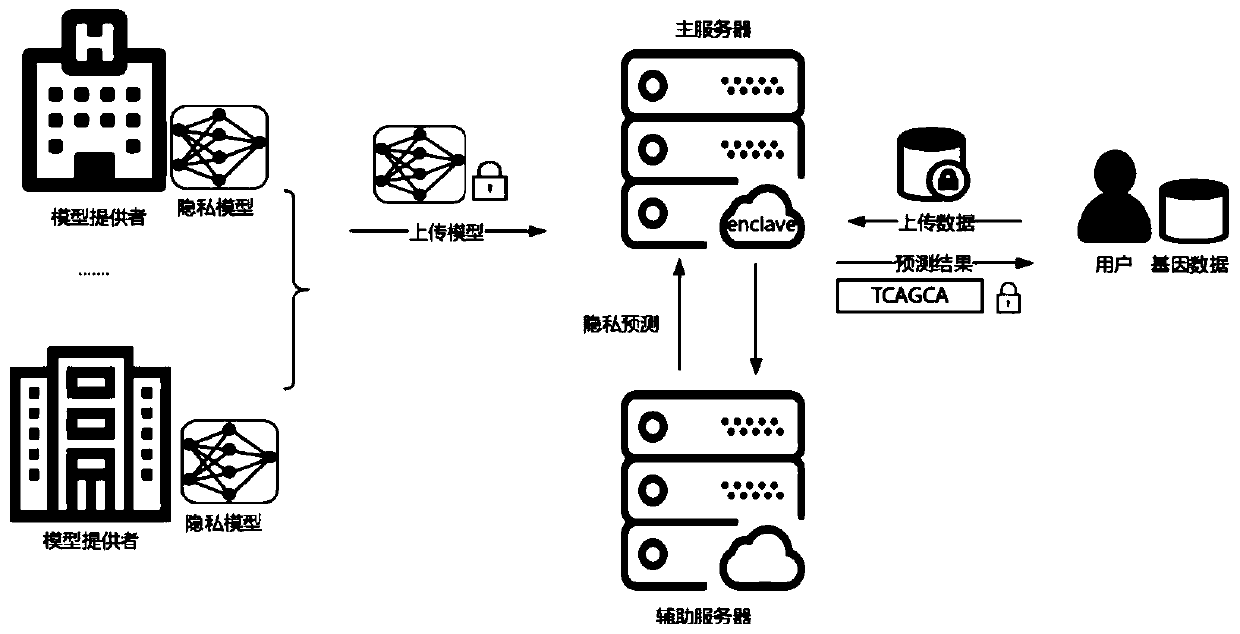
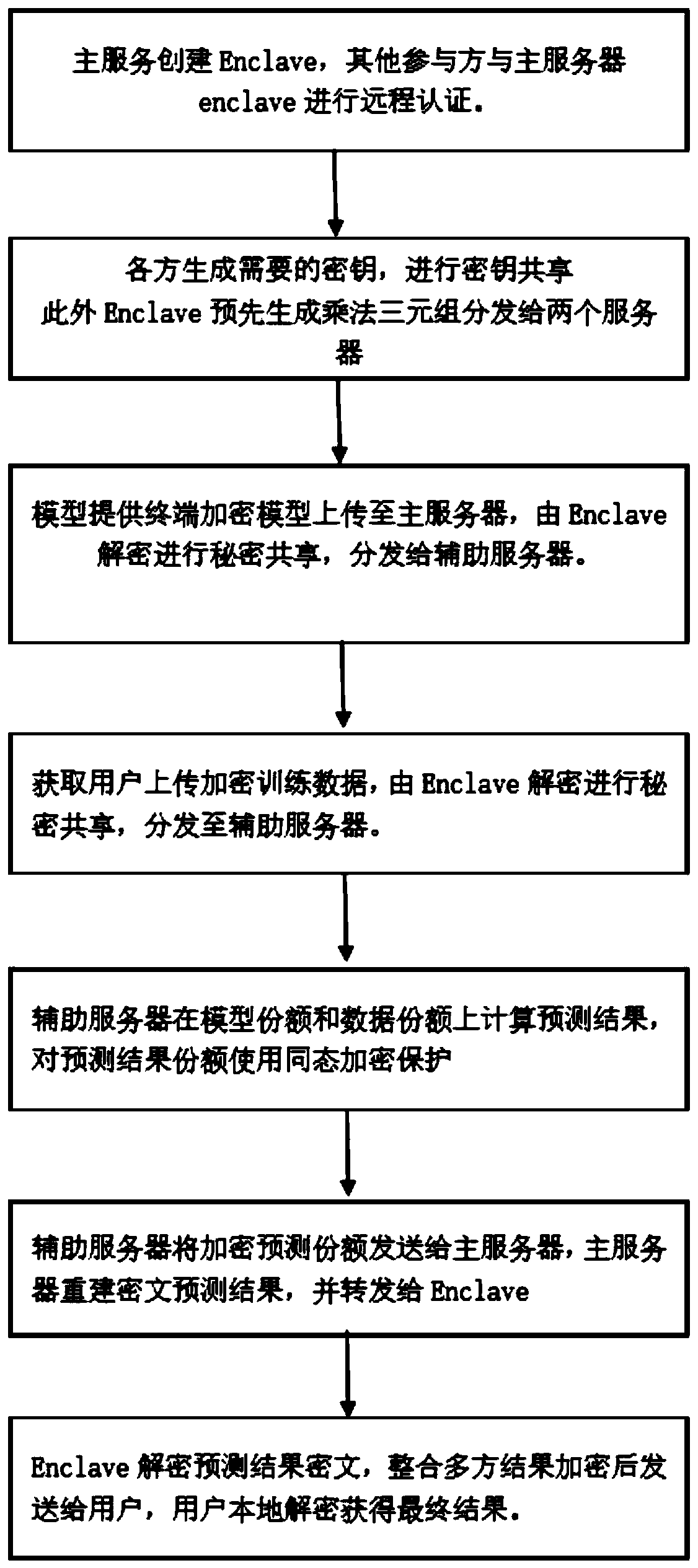
The invention provides a data privacy protection-oriented machine learning prediction method and system. The method comprises the following steps of obtaining encrypted data; the main server creates acredible area, and decrypts the obtained to-be-predicted data and the prediction model in the credible area; the main server carries out secret sharing on the decrypted to-be-predicted data and the prediction model to obtain a data secret share and a model share respectively, and distributes the data secret share and the model share to an unconspired auxiliary server and the main server; the auxiliary server and the main server respectively perform prediction calculation to obtain a prediction result share; and the main server carries out secret reconstruction on all the prediction result shares, forwards the reconstructed prediction result shares to the trusted area for integration and encryption, and sends the reconstructed prediction result shares to the to-be-predicted data providingterminal, and the data providing terminal decrypts the reconstructed prediction result shares to obtain a prediction result predicted according to the model. Privacy security of the two parties is protected by combining secure multi-party computing and an SGX technology, and the security problem in the prediction service providing process is solved.
Owner:UNIV OF JINAN
Medical data joint learning system and method based on trusted computing and privacy protection
ActiveCN110197084AStrict and flexible authorization authenticationRealize deep miningMedical data miningDigital data protectionInteraction layerData privacy protection
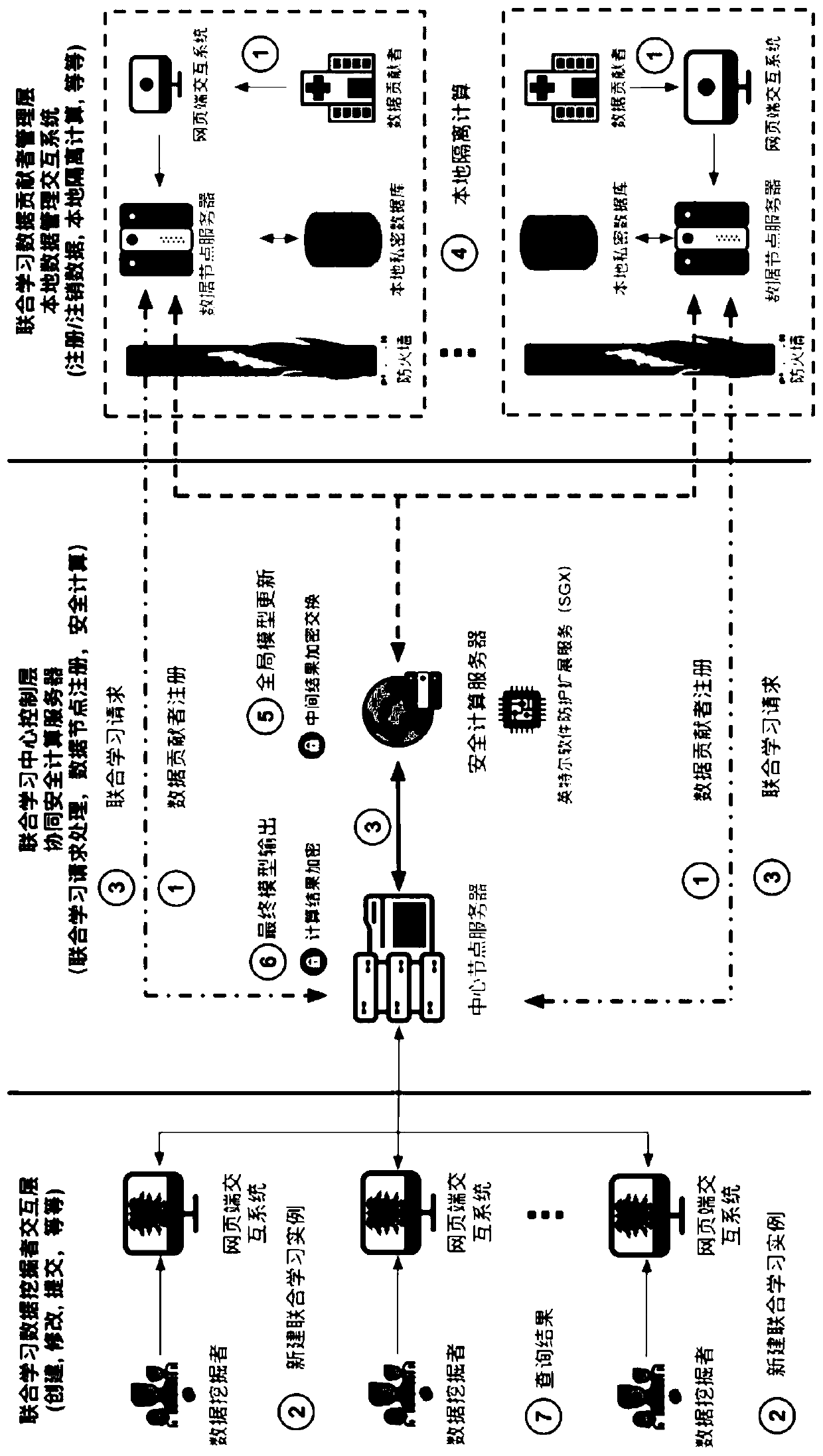
The invention relates to a medical data joint learning system and method based on trusted computing and privacy protection. A joint learning center control layer receives non-sensitive meta-information uploaded by a data contributor through a data contributor management layer of a data node where the joint learning center control layer is located for filing, and original data is locally registered, stored and subjected to isolation calculation; and the joint learning center control layer processes a joint learning request initiated by the data miner through the data miner interaction layer, summarizes insensitive intermediate results obtained by performing local isolation calculation on the data nodes based on the original data in a safe calculation area, and returns a final joint learningresult to the data miner interaction layer. The invention provides a whole set of service system based on medical big data security sharing, trusted computing, deep mining, authority authentication and multi-platform joint learning, and solves the problems of scattered, single and incomplete medical data privacy protection and data mining at the present stage.
Owner:上海锘崴信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com