Patents
Literature
62results about How to "Strong encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
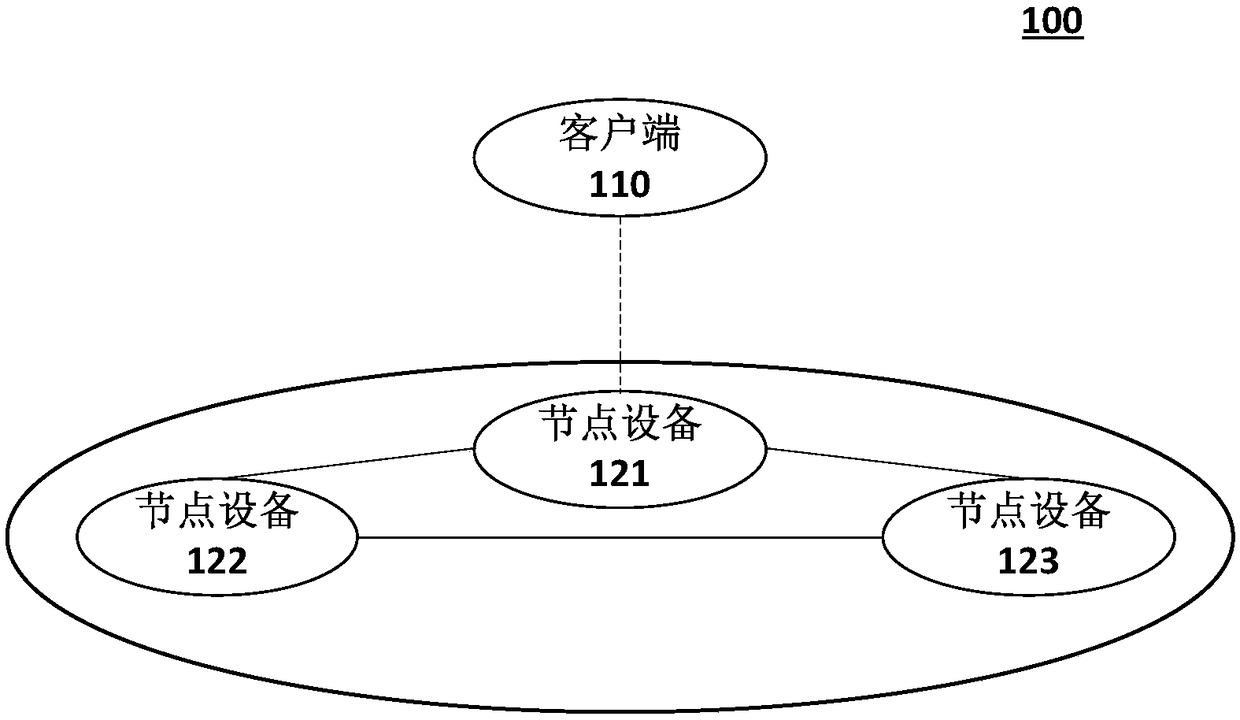
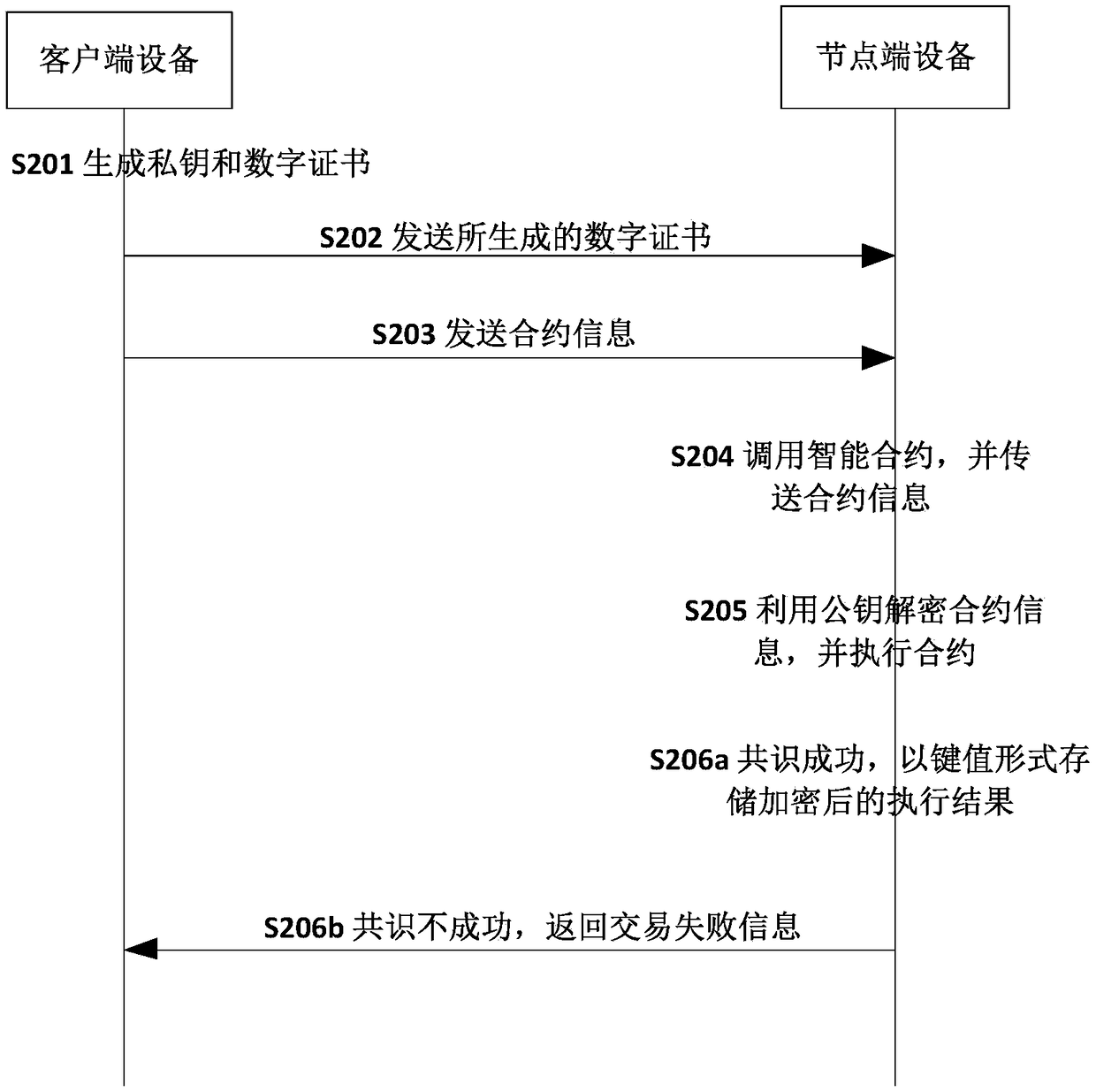
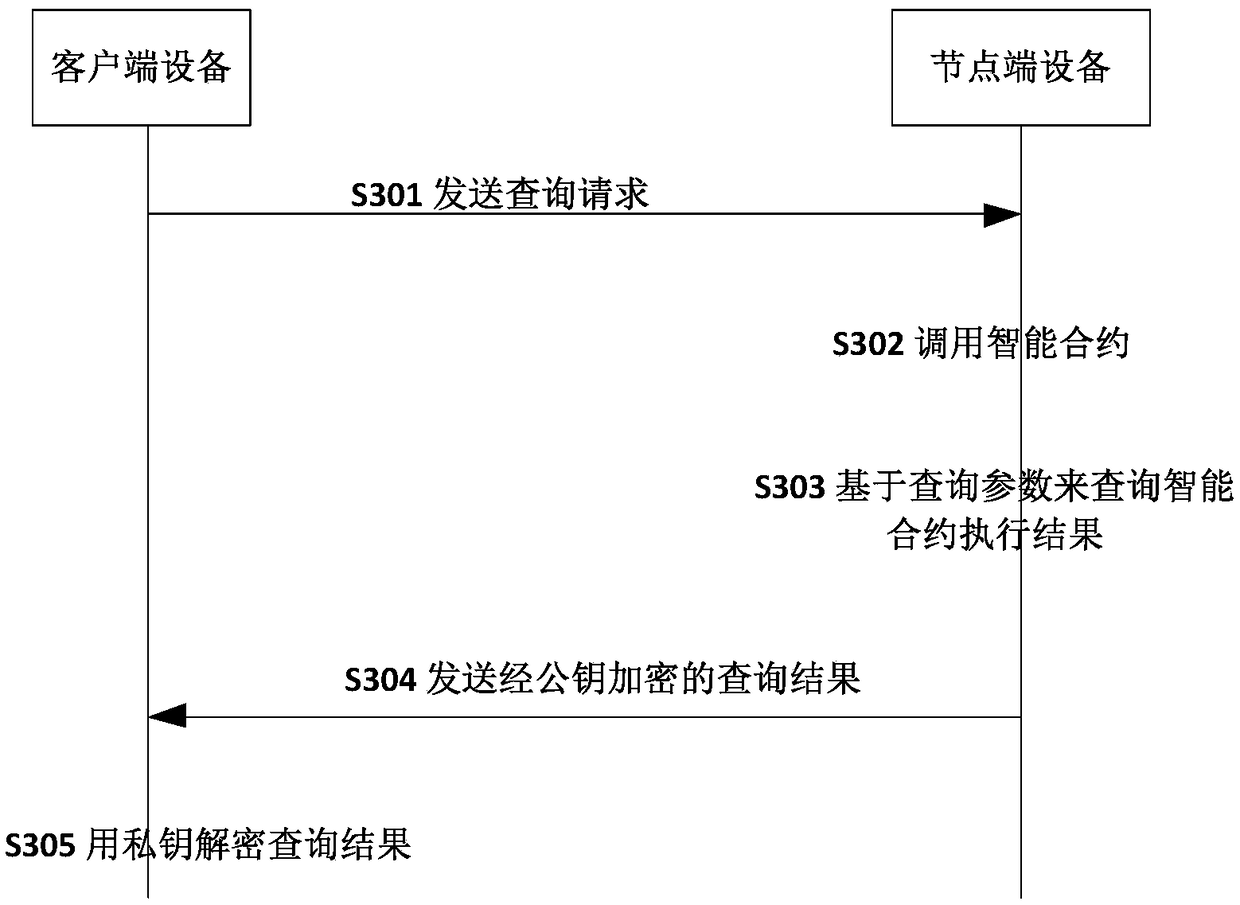
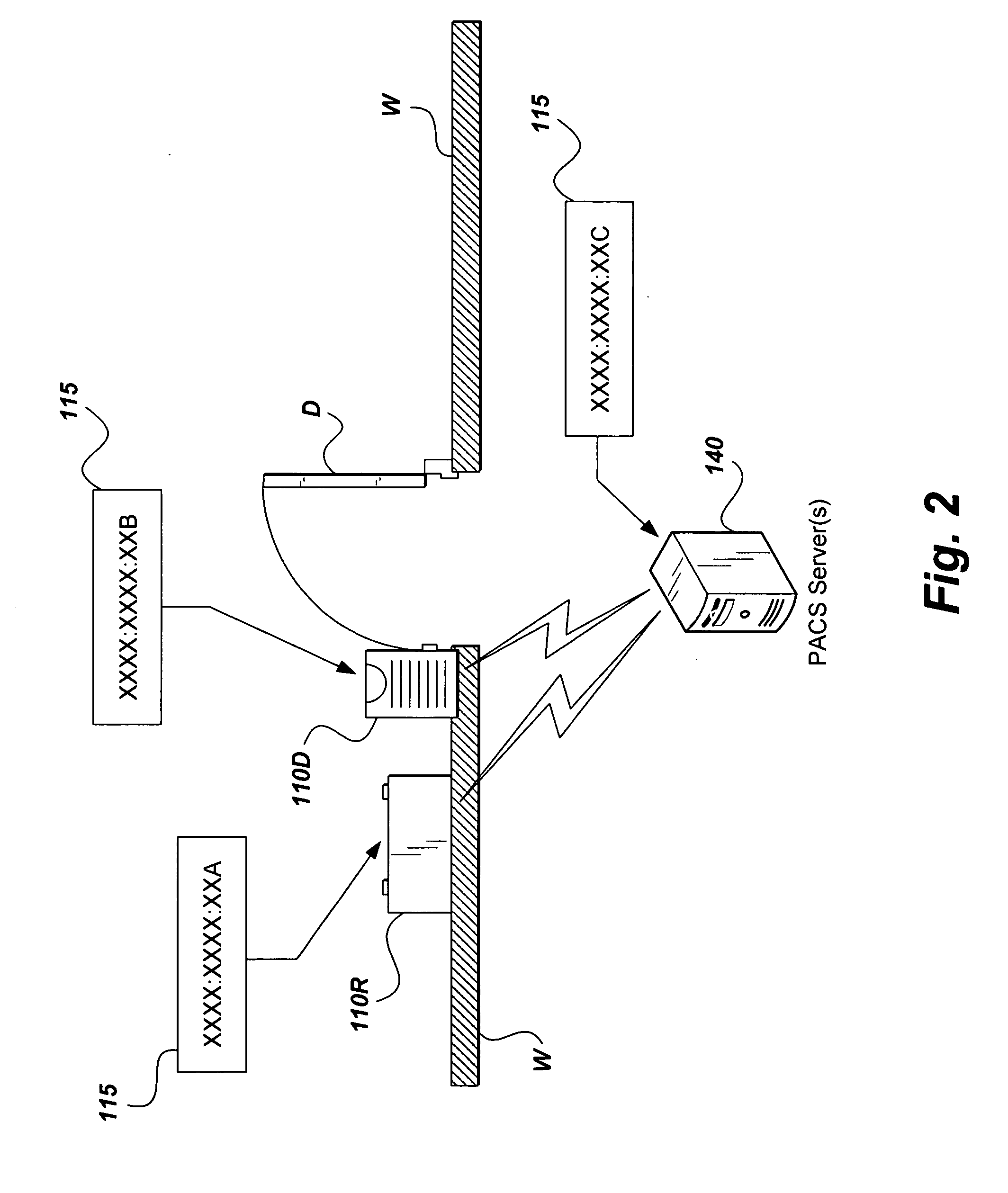
Secure transaction method and device based on a block chain
ActiveCN109493020AGuaranteed privacy protectionStrong encryptionFinancePayment protocolsPlaintextData privacy protection
The invention discloses a secure transaction method and device based on a block chain. The node end equipment of the block chain calls the smart contract based on the contract information, the node end of the block chain decrypts the encrypted transaction parameters in the contract information by using the public key in the certificate, and executes the smart contract based on the transaction parameters; after the block chain node achieves consensus on the execution result in the block chain; wherein the node encrypts a key and a value based on the certificate public key and then writes the key and the value into the node database, the client inquires a transaction result through the blockchain node and needs to encrypt transaction parameters, the blockchain node needs to decrypt based onthe public key and then encrypt and return the transaction result, and the client decrypts based on the private key to obtain a plaintext result. Through the technical scheme of the invention, data security and data privacy protection for transaction and query can be formed.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
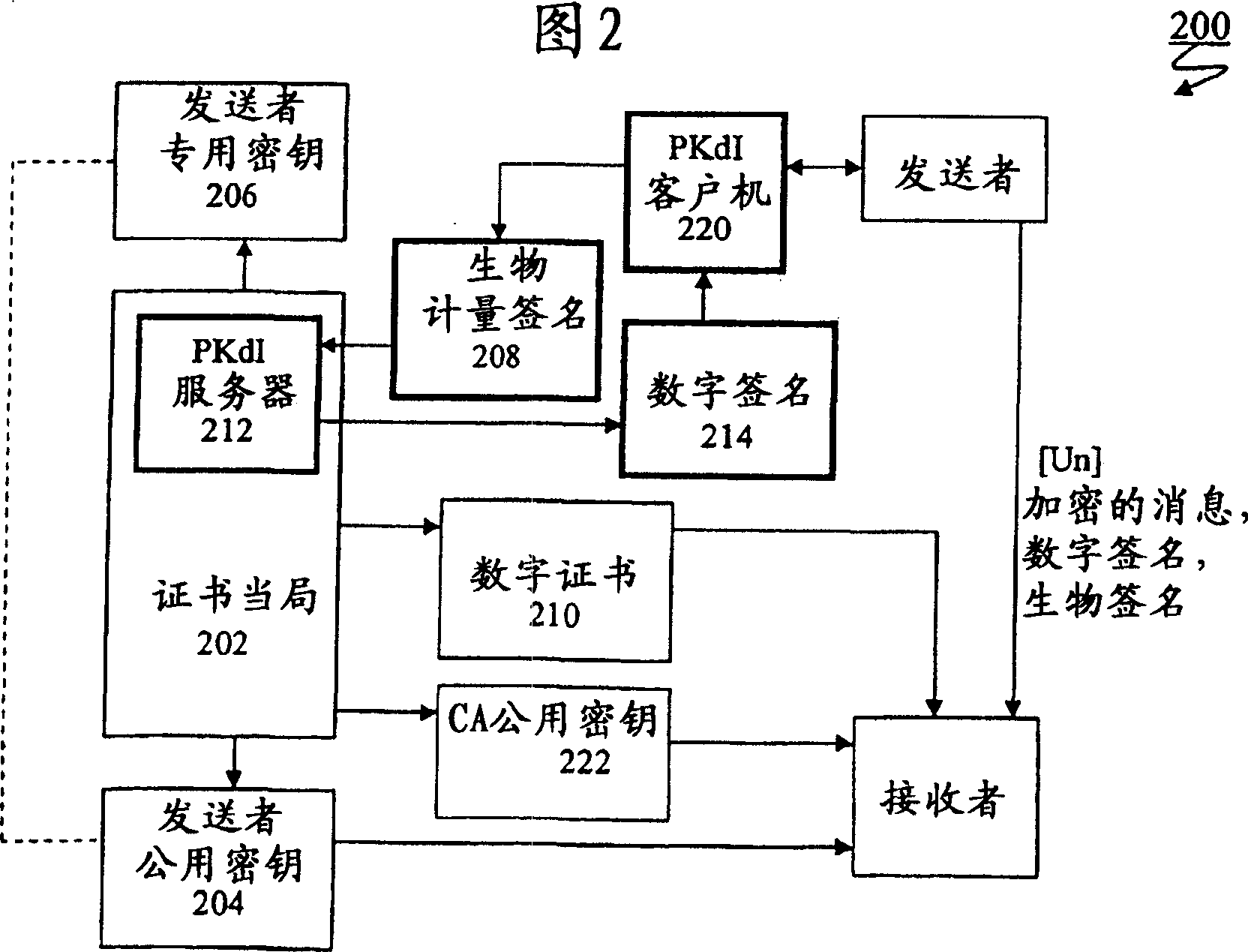
Biometric private key infrastructure
InactiveCN1705925AStrong encryptionKey distribution for secure communicationDigital data processing detailsData integrityDigital signature
In accordance with an aspect of providing trust and authentication for network communications and transactions, a network infrastructure is provided that employs biometric private keys (BioPKI). Generally, Bio PKI is a unique combination of two software solutions that validate electronic user authentication: a state-of-the-art biometric signature system, and a digital signature for data integrity. The combined solution allows networked businesses and merchants such as financial institutions to ensure that user authentication is conducted in a trusted, secure fashion within standard network environments. In one example implementation, a biometric signature augments standard digital signatures by adding an automated, non-reputable user authentication capability to the existing digital signature process. In contrast to simple verification in a pure biometric-based system or digital signature / certificate environment, BioPKI uses a combination of biometric technology to access private keys in order to create digital signatures based on biometric authentication and industry-standard PKI technologies. In one example, BioPKI utilizes public key cryptography technology to encrypt the biometric signature information for transmission to the BioPKI server. The encryption packet contains several layers of internal information to ensure that the biometric signature is secured and validated prior to accessing the individual's private key.
Owner:AURORA WIRELESS TECH
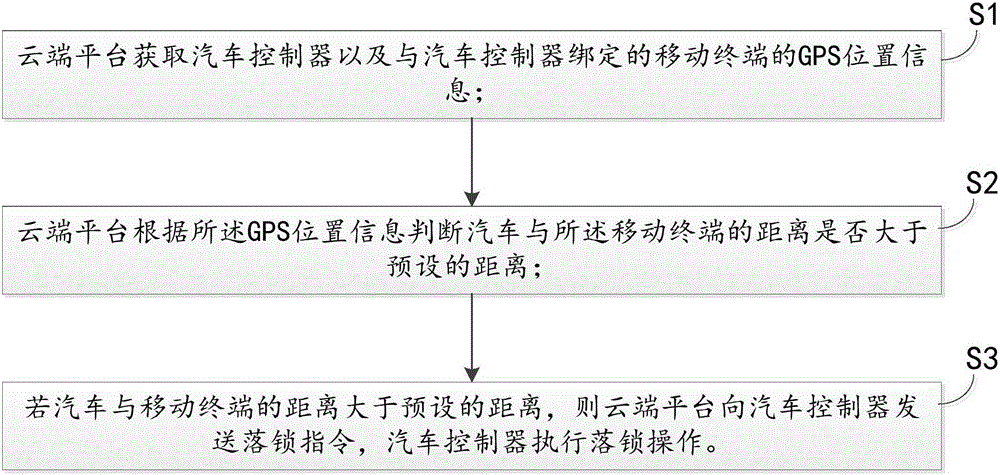
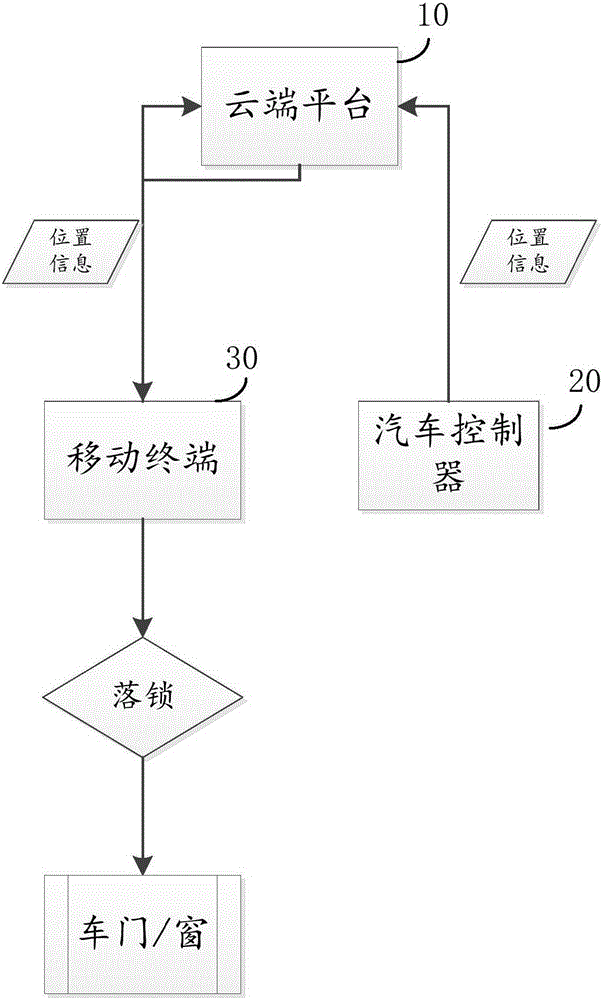
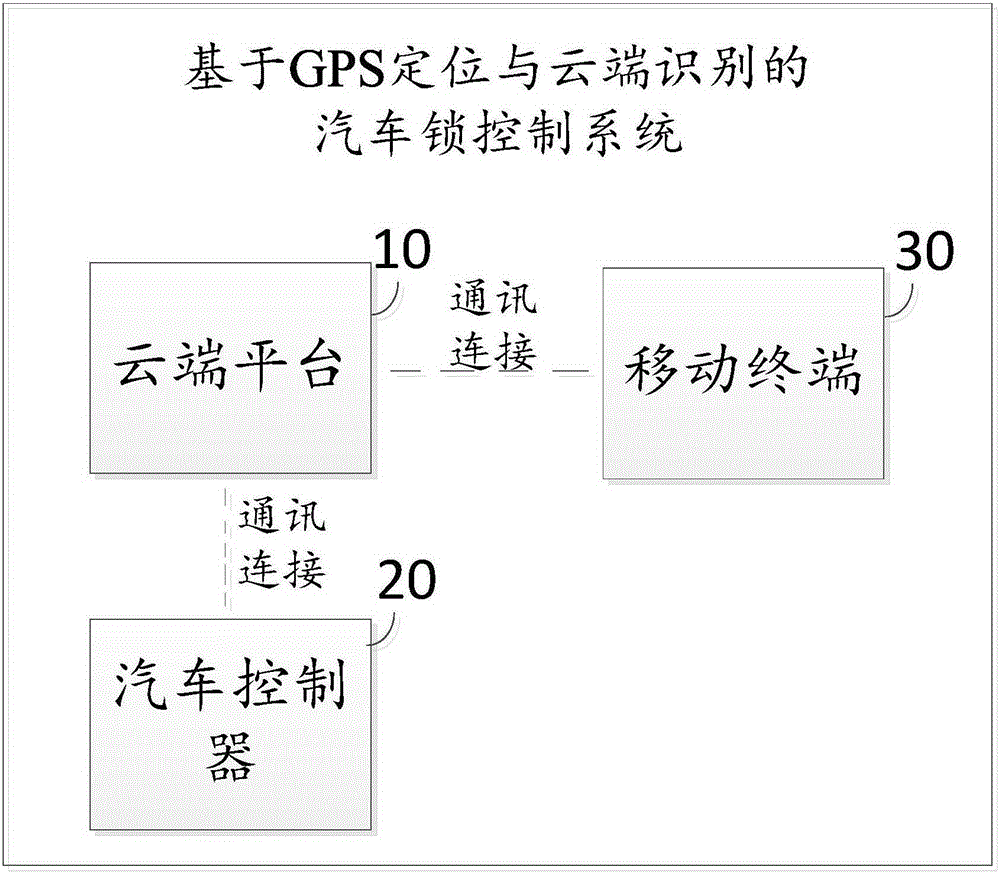
Automobile lock control method and device based on GPS positioning and cloud recognizing
InactiveCN105235645AImprove convenienceImprove the safety of useAnti-theft devicesAutomotive engineeringGps positioning
The invention discloses an automobile lock control method and device based on GPS positioning and cloud recognizing. The automobile lock control method comprises the following steps: acquiring GPS position information of an automobile controller and a mobile terminal bound with the automobile controller through a cloud platform; determining whether the distance from an automobile to the mobile terminal exceeds a preset distance through the cloud platform according to the GPS position information; if the distance from the automobile to the mobile terminal exceeds the preset distance, sending a locking command to the automobile controller through the cloud platform, and then locking through the automobile controller. With the adoption of the method and device, the convenience and safety of locking and unlocking of the automobile can be improved.
Owner:FJ MOTOR GRP YUDO NEW ENERGY AUTOMOBILE CO LTD
Spring lock without spring
The invention provides a spring lock without a spring, which consists of a lock body, a lock core, a ball and a paired key. In the spring lock, a ball spring of the conventional known spring lock is removed, so the spring lock overcomes the defect of rustiness in the spring and is particularly suitable for occasions where the lock often contacts water, for example wrist strap clamp locks, which are compelled to wear continuously, of a wrist strap electronic monitoring terminal in specific people inside and outside prisons and cylindrical handcuffs in the improved known technology; more importantly, the spring lock is not provided with the ball spring, only one ball is arranged in each ball hole channel, the balls stay in the ball hole channels randomly, and the position is uncertain, so staff who know a lockset structure still cannot unlock illegally.
Owner:CHONGQING SHUAINENG SCI & TECH
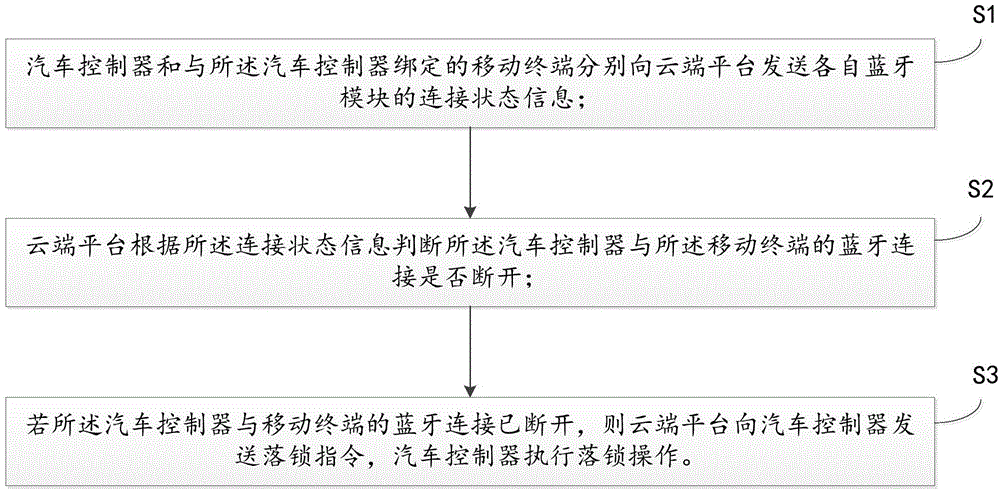
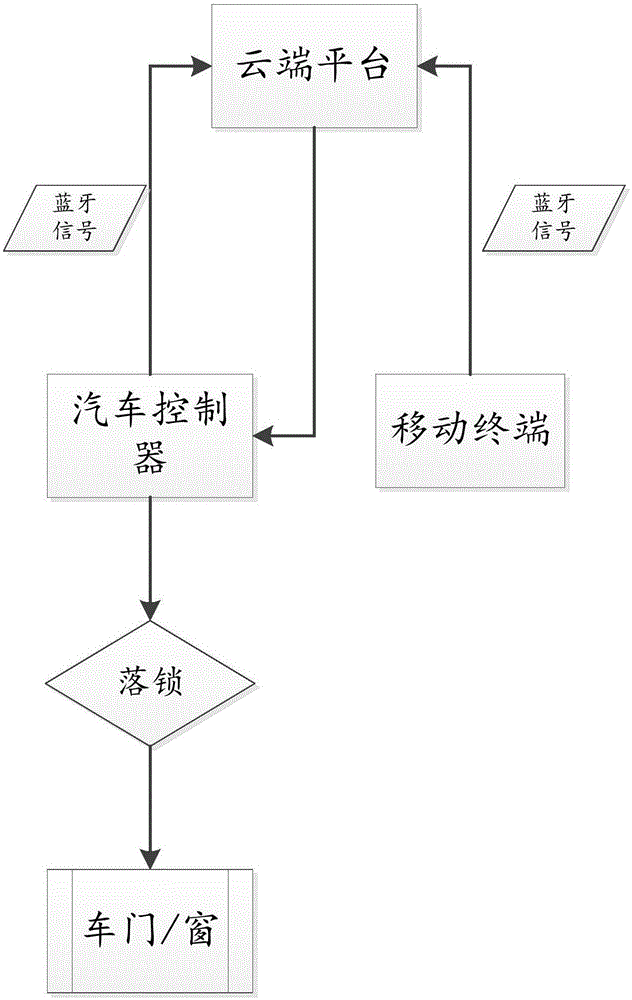
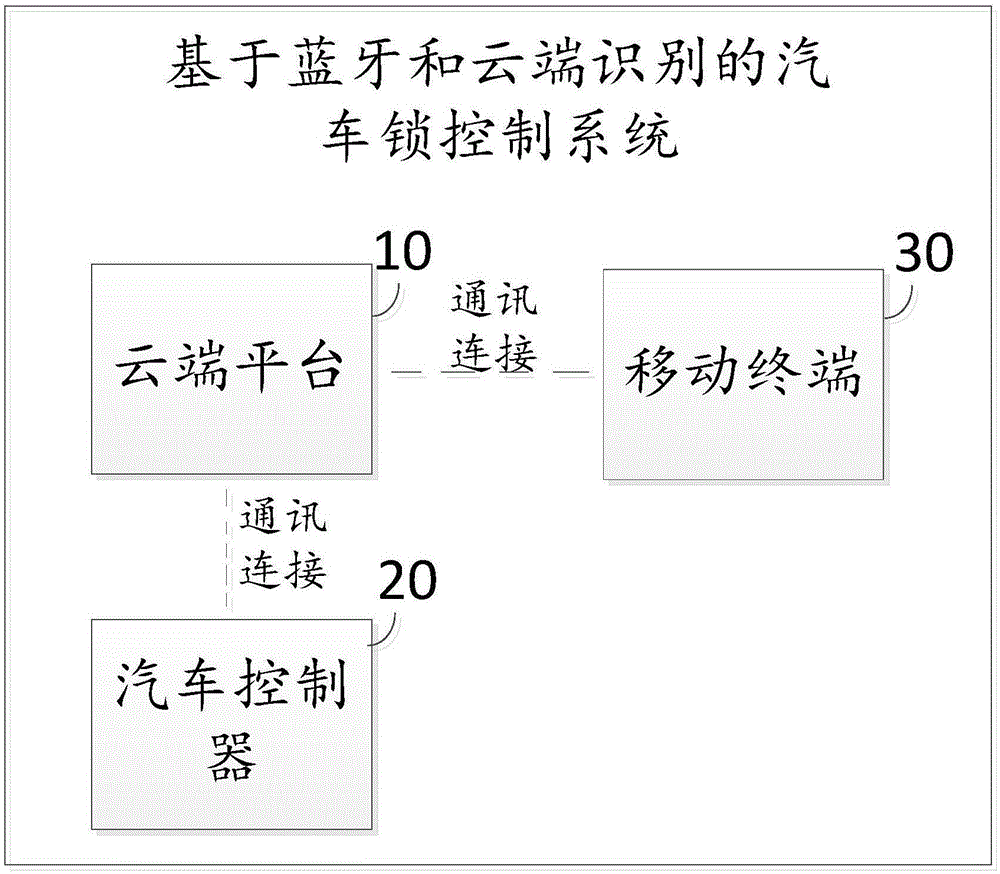
Automobile lock control method and system based on Bluetooth and cloud recognition
InactiveCN105160745AImprove the safety of useImprove convenienceAnti-theft devicesIndividual entry/exit registersControl systemComputer module
The invention discloses an automobile lock control method and an automobile lock control system based on Bluetooth and cloud recognition. The automobile lock control method comprises the following steps: transmitting connection state information of respective Bluetooth modules of an automobile controller and a mobile terminal bound with the automobile controller to a cloud platform respectively; judging whether the Bluetooth of the automobile controller and the mobile terminal is disconnected or not by the cloud platform according to the connection state information; and if the Bluetooth connection of the automobile controller and the mobile terminal is broken, transmitting a locking instruction to the automobile controller by the cloud platform and executing locking operation by the automobile controller. With the adoption of the automobile lock control method and system, the portability and security of locking and unlocking operation of an automobile are improved.
Owner:FJ MOTOR GRP YUDO NEW ENERGY AUTOMOBILE CO LTD
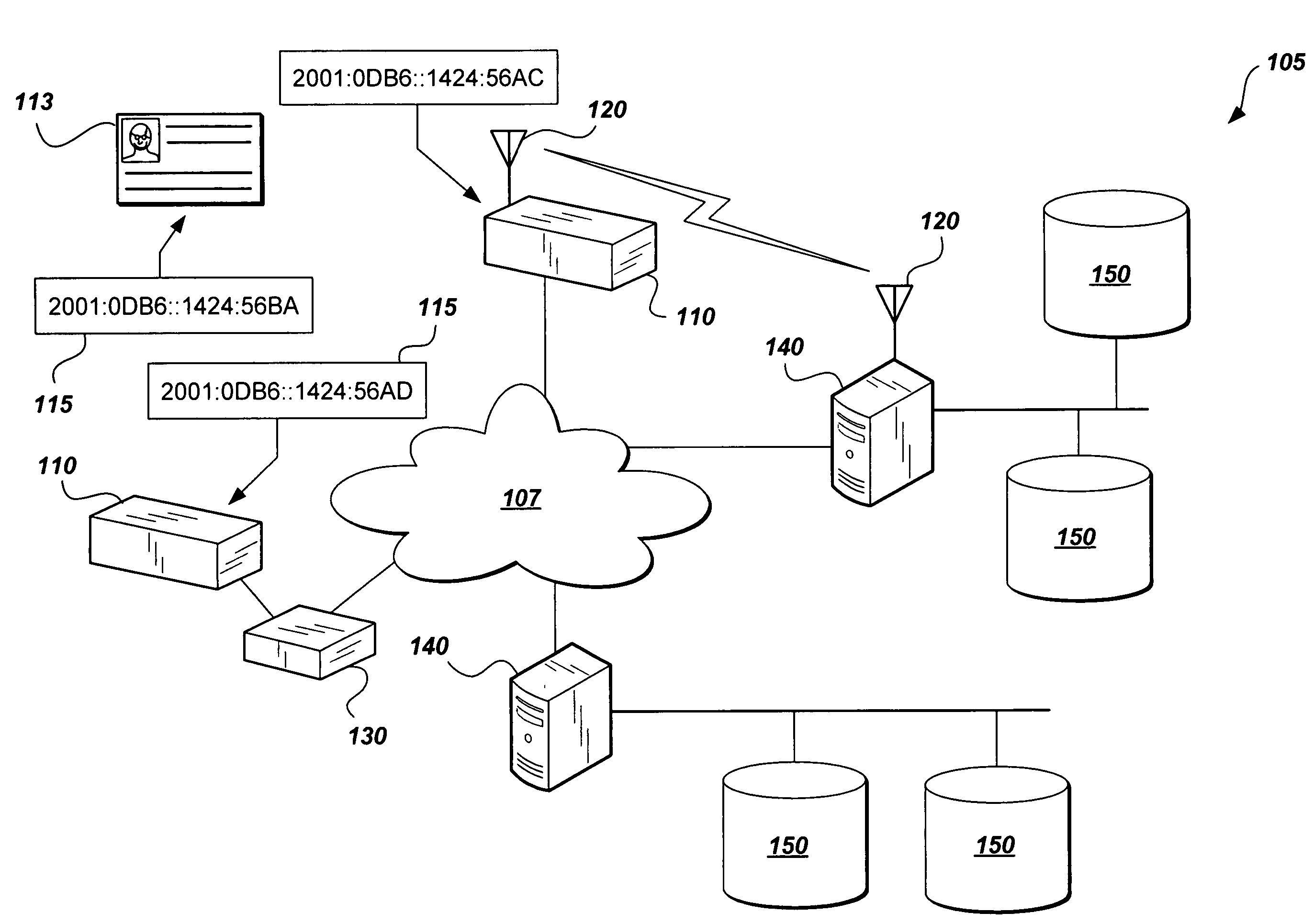
System and method for global access control
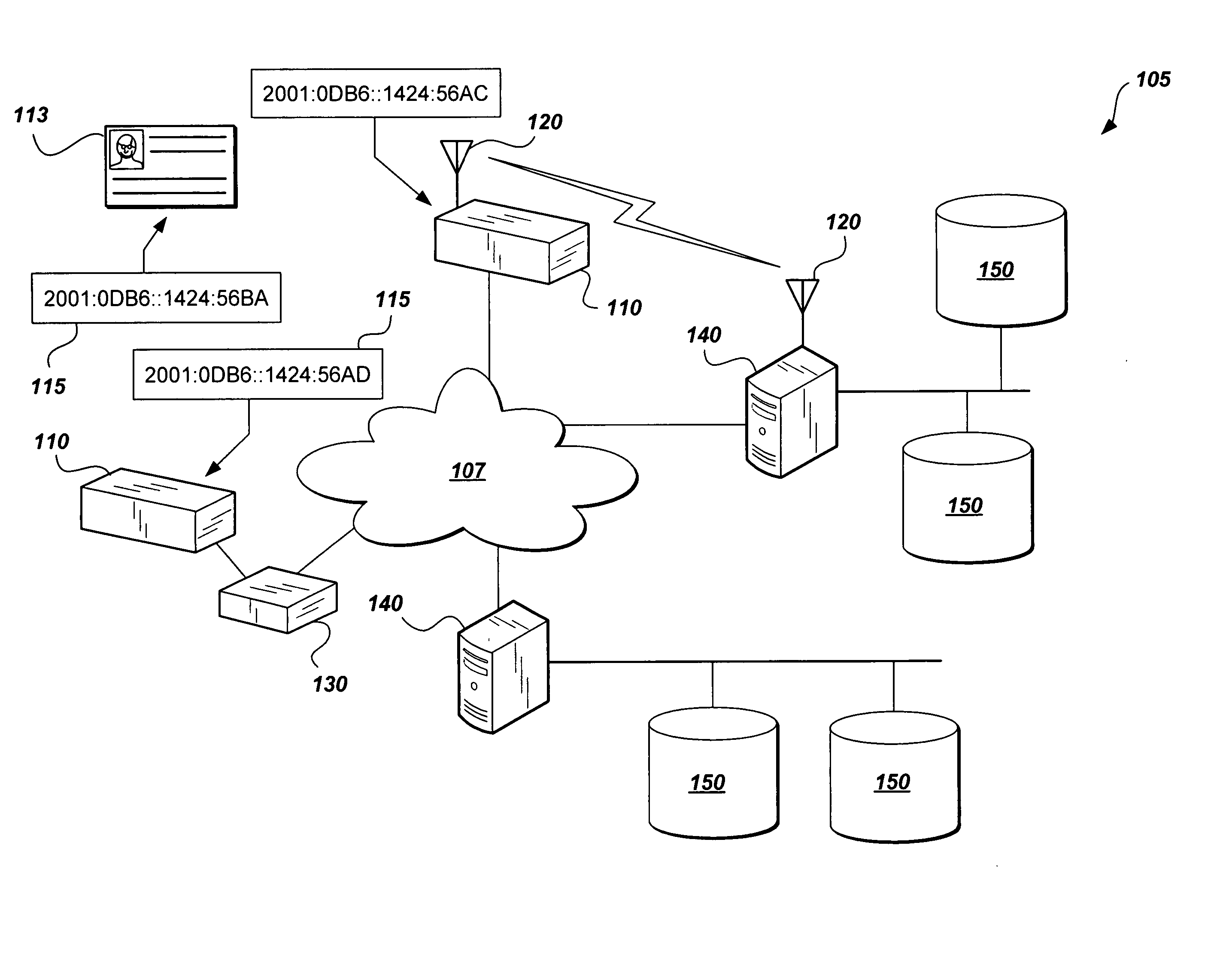
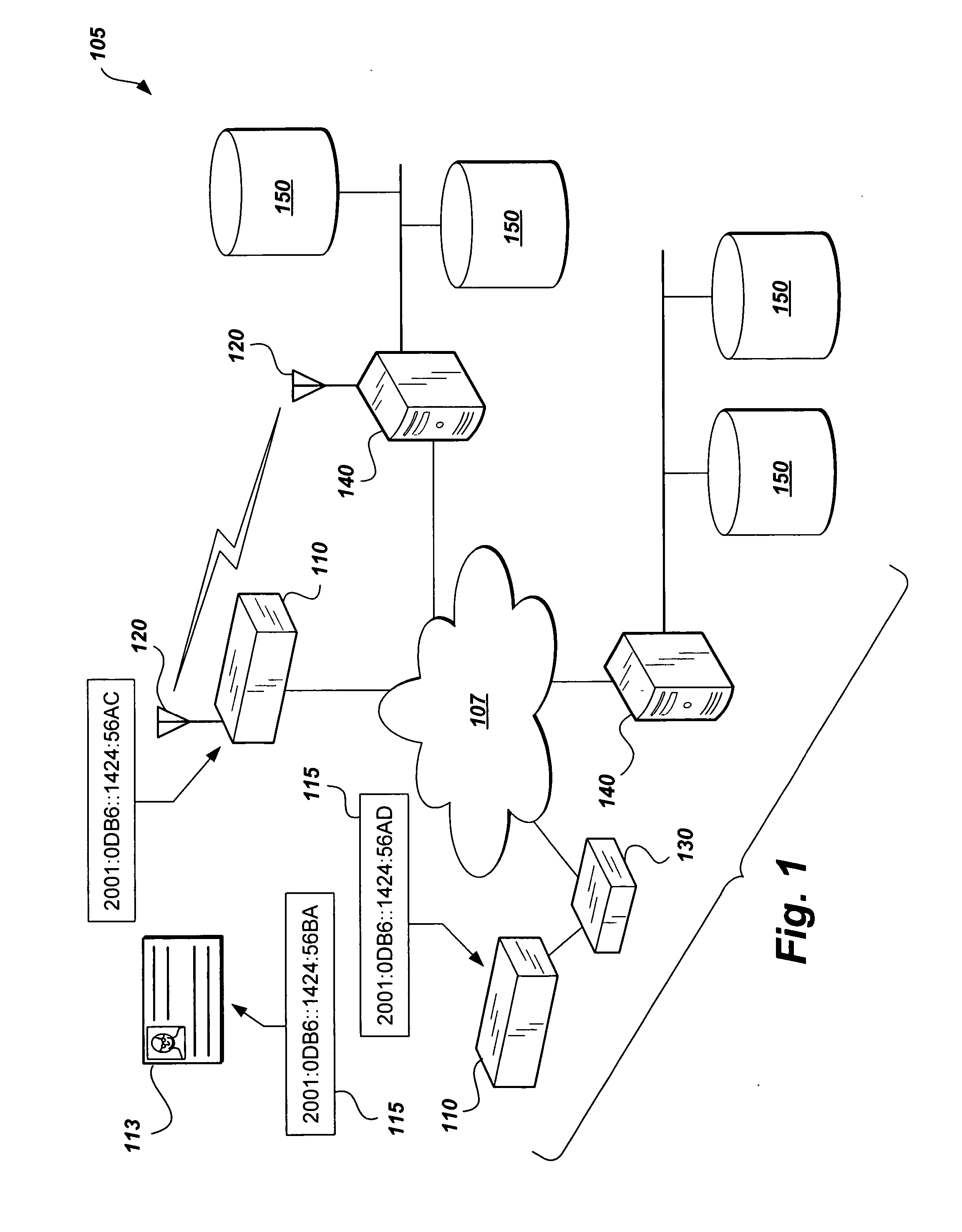
InactiveUS7818783B2Efficient searching and auditing of devicesReduce necessityElectric signal transmission systemsMultiple keys/algorithms usageInformation processingControl system
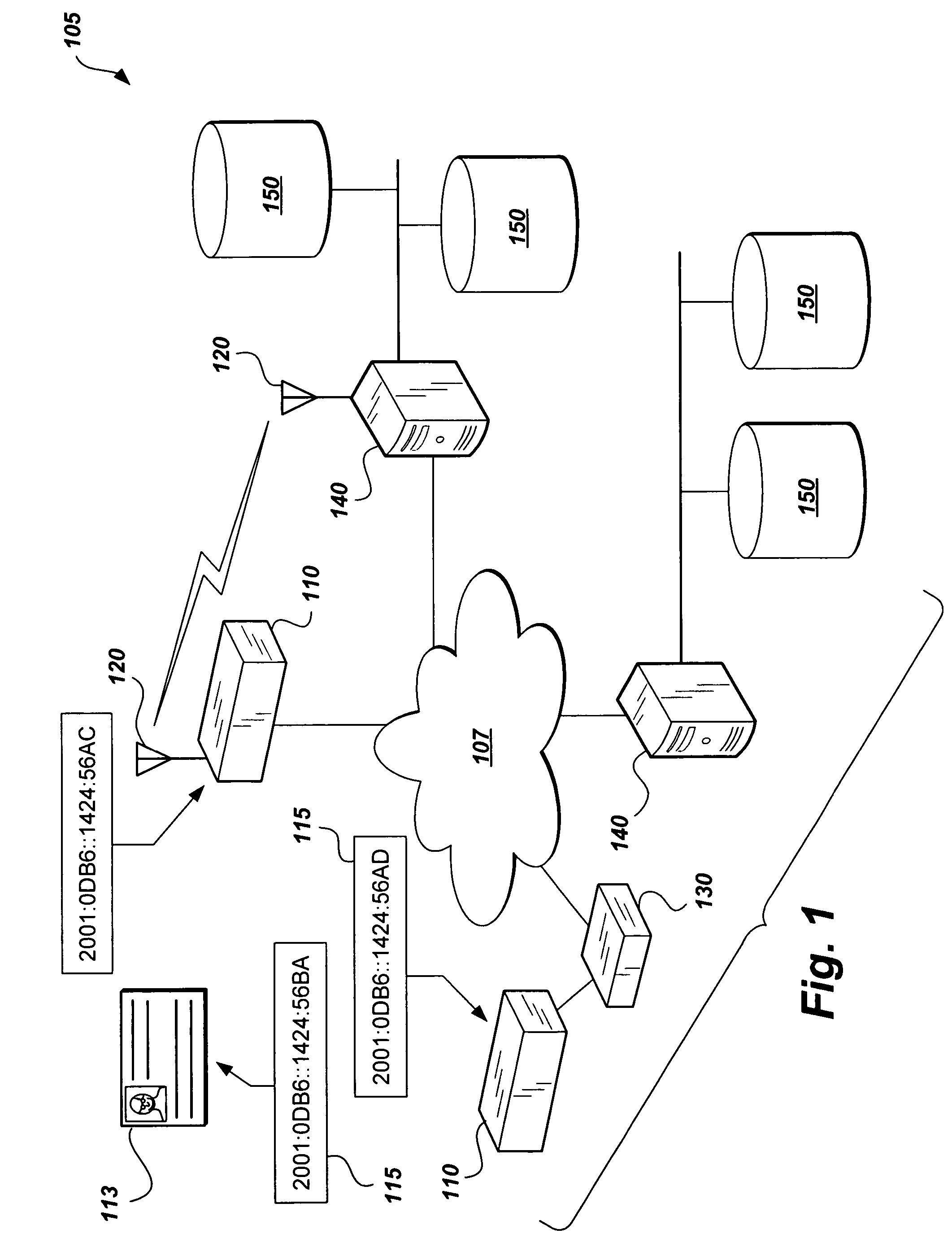
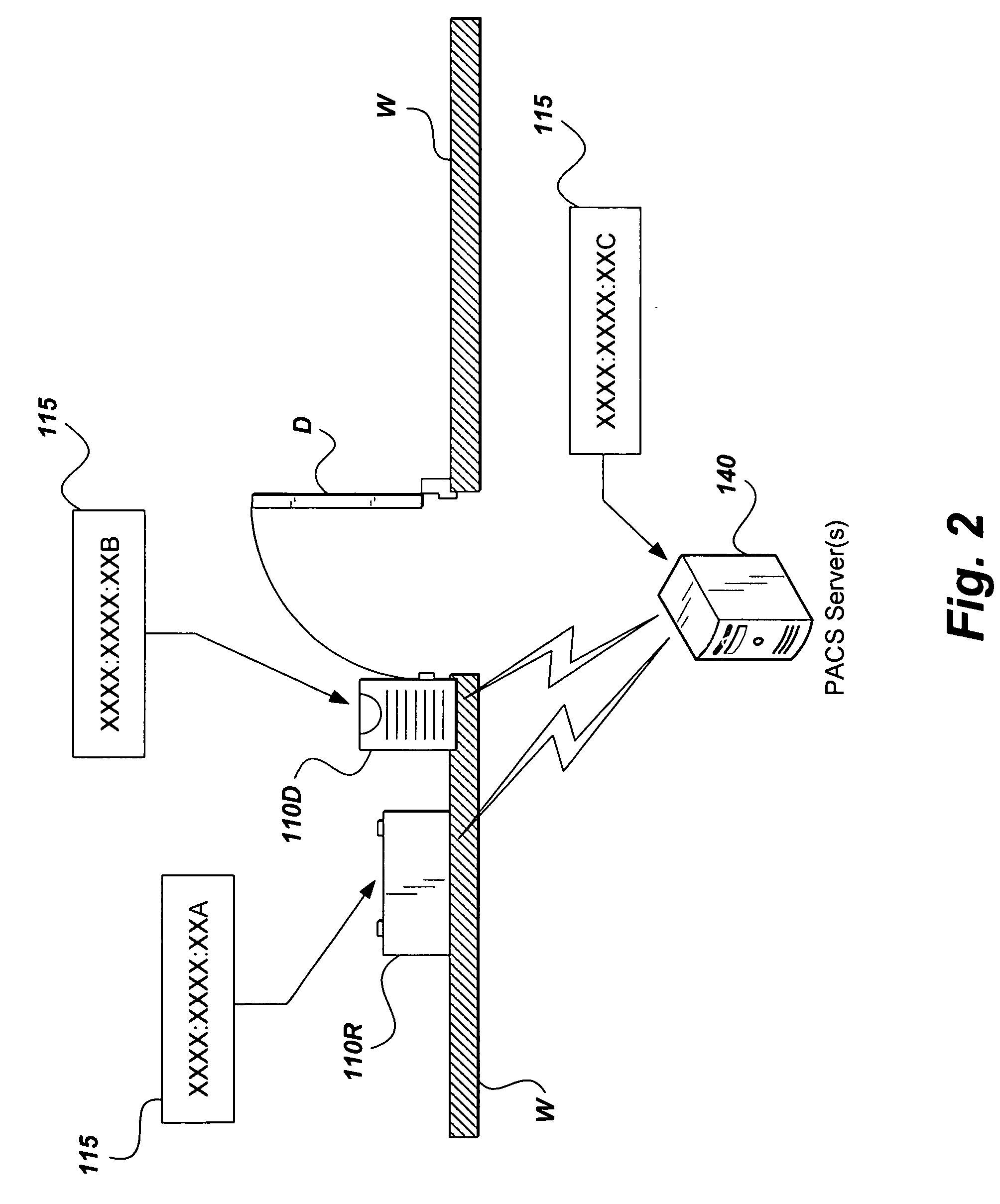
The global access control system and method presents a solution to synchronizing the physical access devices that federal agencies must try to meet Federal Information Processing Standards (FIPS) 201 requirements. The method encompasses wire and wireless technology, IP Security (IPSec), the assignment of IPv6 addresses to every device, integrating with logical access control systems, and providing a homogeneous audit and control format. As part of FIPS 201, Government identification badges (Personal Identity Verification (PIV) cards) will include an IPv6 address that uniquely identifies every card holder. By assigning an IPv6 address to every access device and using the card holder's IPv6 address, every access device can be used for global access control. Moreover, common and interoperable audit records throughout an entire enterprise (logical and physical) are possible. This unique combination of technologies provides a mechanism for integrating heterogeneous systems to provide merging of physical and logical access control systems.
Owner:DAVIS RUSSELL J
Four-dimensional code, image identification system and method as well as retrieval system and method based on four-dimensional code
ActiveCN104820817ABig amount of dataStrong encryptionCharacter and pattern recognitionSpecial data processing applicationsElectronic documentFault tolerance
Owner:崔明 +1
USB flash disk fingerprint authentication encryption method
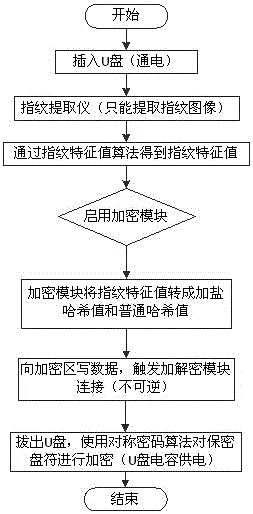
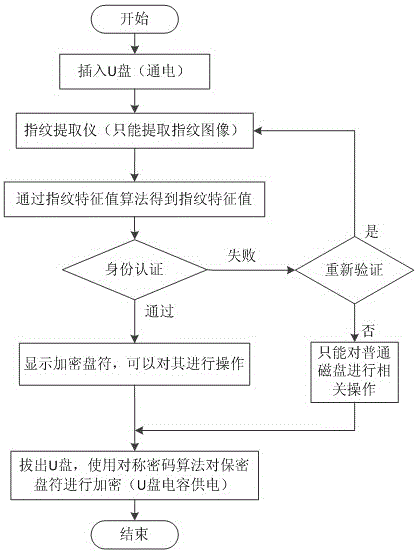
InactiveCN105809070AReduce occupancyPrevent leakageDigital data protectionInternal/peripheral component protectionInformation quantityUSB
The invention discloses a USB flash disk fingerprint authentication encryption method. According to the method, fingerprint features of a user are extracted; a hash value is converted by adopting a hash algorithm; registering encryption is carried out by adopting a symmetric encryption algorithm; and when a USB flash disk is used next time, conversion is carried by using the extracted fingerprint features, thus realizing the comparison decryption process of the hash value. According to the method, the extracted fingerprint features are used for producing a secret key through adoption of the pseudo-random number generation symmetric encryption algorithm; a file is encrypted and decrypted by using the secrete key; in this way, only a fingerprint feature value needs to be stored; the occupancy of a storage space is recued; an information quantity is reduced; the possibility of exposing the effective information is reduced; the security of a system is improved; and the secrete quantity of the symmetric encryption algorithm reaches 128 bits, therefore, the encryption performance is high, the security is high, and the information is effectively prevented from being leaked.
Owner:GUIZHOU UNIV
Multi-wavelength fluorescent quantum dot anti-counterfeiting method
The invention discloses a multi-wavelength fluorescent quantum dot anti-counterfeiting method, comprising the following steps of (1) selecting a plurality of fluorescent quantum dots with various grain diameter types, wherein the fluorescence emission spectrums of the fluorescent quantum dots are evenly distributed within a near-infrared area; moreover, no wave bands overlap; and the type of the selected quantum dots is in a number equal to that of the ink boxes of a selected printer, and further is corresponding to the ink boxes of the selected printer one to one; (2) coding a plurality of fluorescent quantum dots of various types in each black bar according to bar codes through the utilization of the presence or absence of the fluorescence peaks of the fluorescent quantum dots of various type within a given wave band; (3) evenly mixing the quantum dots with ink in the corresponding printer ink box; and (4) printing an anti-counterfeiting marker with the ink containing the quantum dots in the step (3) so as to realize the highly anti-counterfeiting of commodities. The anti-counterfeiting marker made by such an anti-counterfeiting method has the advantages of high precision, good hiddenness and large information capacity, and further can be set and assigned by a manufacturer.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
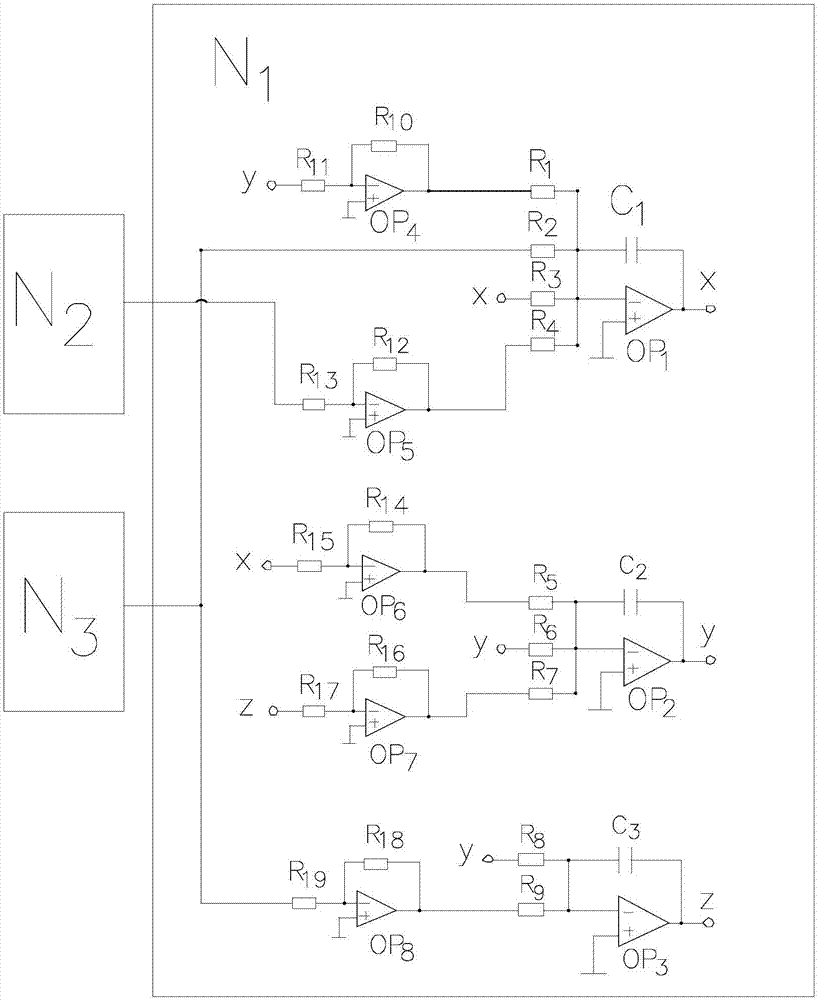
Three-dimensional multi-scroll chaotic signal generator
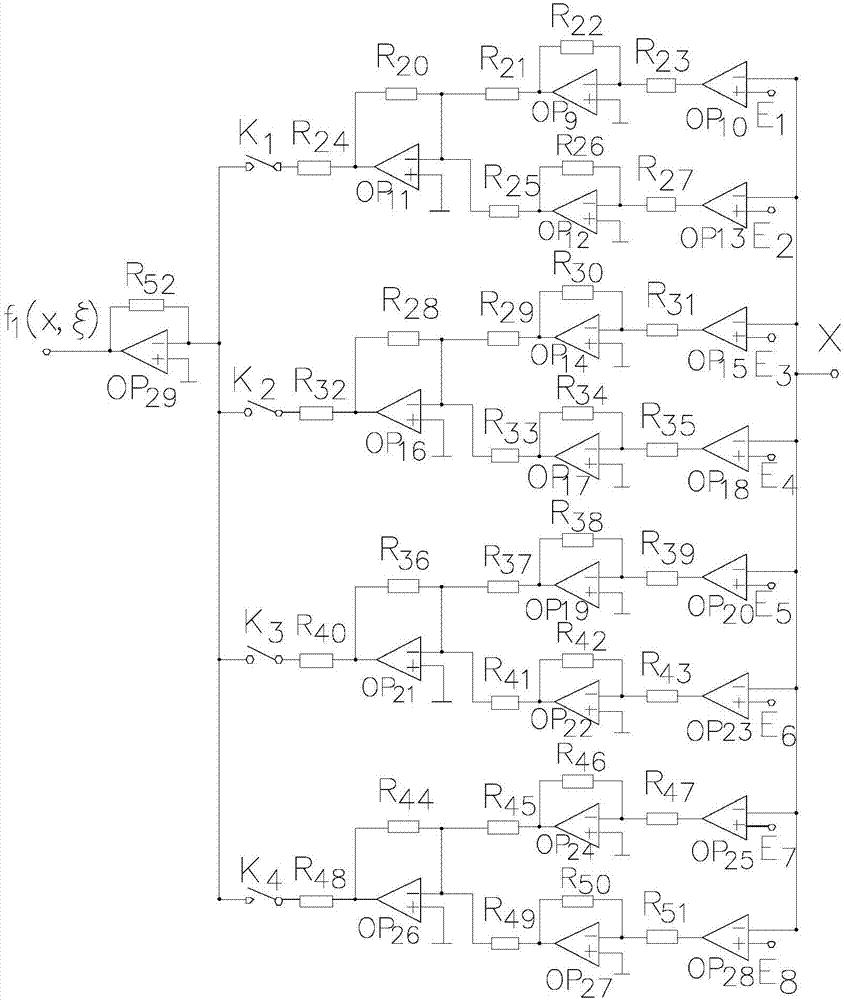
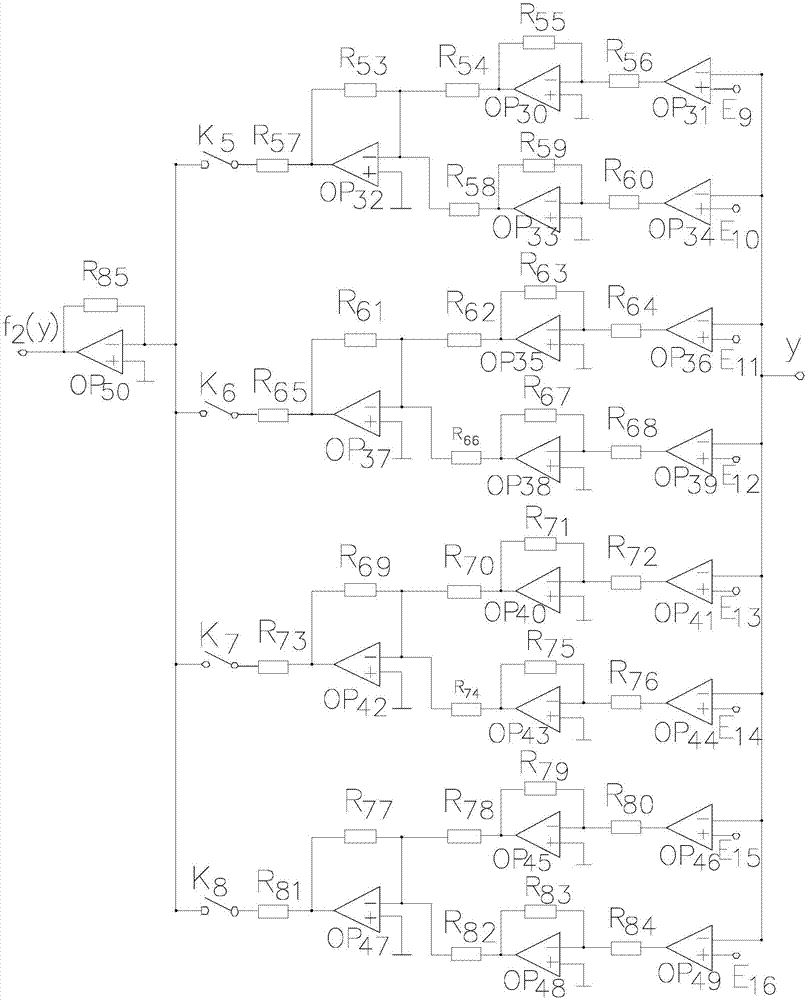
ActiveCN107294699ASimple hardwareStrong encryptionSecuring communication by chaotic signalsSignal productionHandoff control
The invention discloses a three-dimensional multi-scroll chaotic signal generator. The generator comprises a basic chaotic signal generation circuit N1, a sequence generator N2 used for generating a switching control function f1(x, xi) and a sequence generator N3 used for generating a switching control function f2(y). An output terminal of the basic chaotic signal generation circuit N1 is connected to input terminals of the sequence generator N2 and the sequence generator N3 respectively. Output terminals of the sequence generator N2 and the sequence generator N3 are connected to an input terminal of the basic chaotic signal generation circuit N1. After effects of the sequence generator N2 and the sequence generator N3, a three-dimensional multi-scroll chaotic signal can be acquired; the sequence generator generating the switching control function is adopted to the circuit so that hardware of a composite chaotic signal generator is easy to realize and chaotic encryption performance is high.
Owner:FOSHAN UNIVERSITY
System and method for global access control
InactiveUS20070214493A1Efficient searching and auditing of devicesReduce necessityElectric signal transmission systemsMultiple keys/algorithms usageInformation processingControl system
The global access control system and method presents a solution to synchronizing the physical access devices that federal agencies must try to meet Federal Information Processing Standards (FIPS) 201 requirements. The method encompasses wire and wireless technology, IP Security (IPSec), the assignment of IPv6 addresses to every device, integrating with logical access control systems, and providing a homogeneous audit and control format. As part of FIPS 201, Government identification badges (Personal Identity Verification (PIV) cards) will include an IPv6 address that uniquely identifies every card holder. By assigning an IPv6 address to every access device and using the card holder's IPv6 address, every access device can be used for global access control. Moreover, common and interoperable audit records throughout an entire enterprise (logical and physical) are possible. This unique combination of technologies provides a mechanism for integrating heterogeneous systems to provide merging of physical and logical access control systems.
Owner:DAVIS RUSSELL J
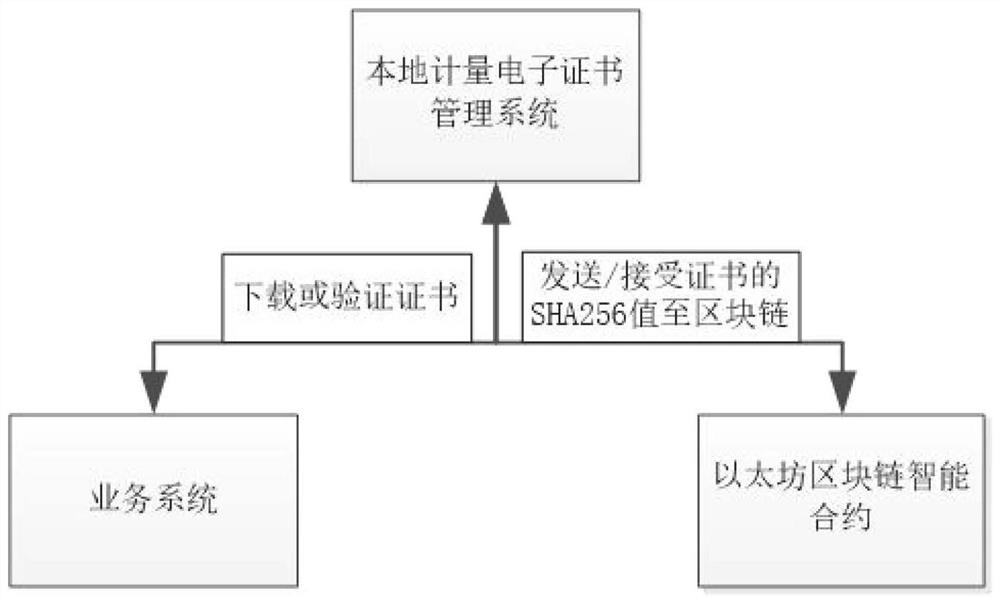
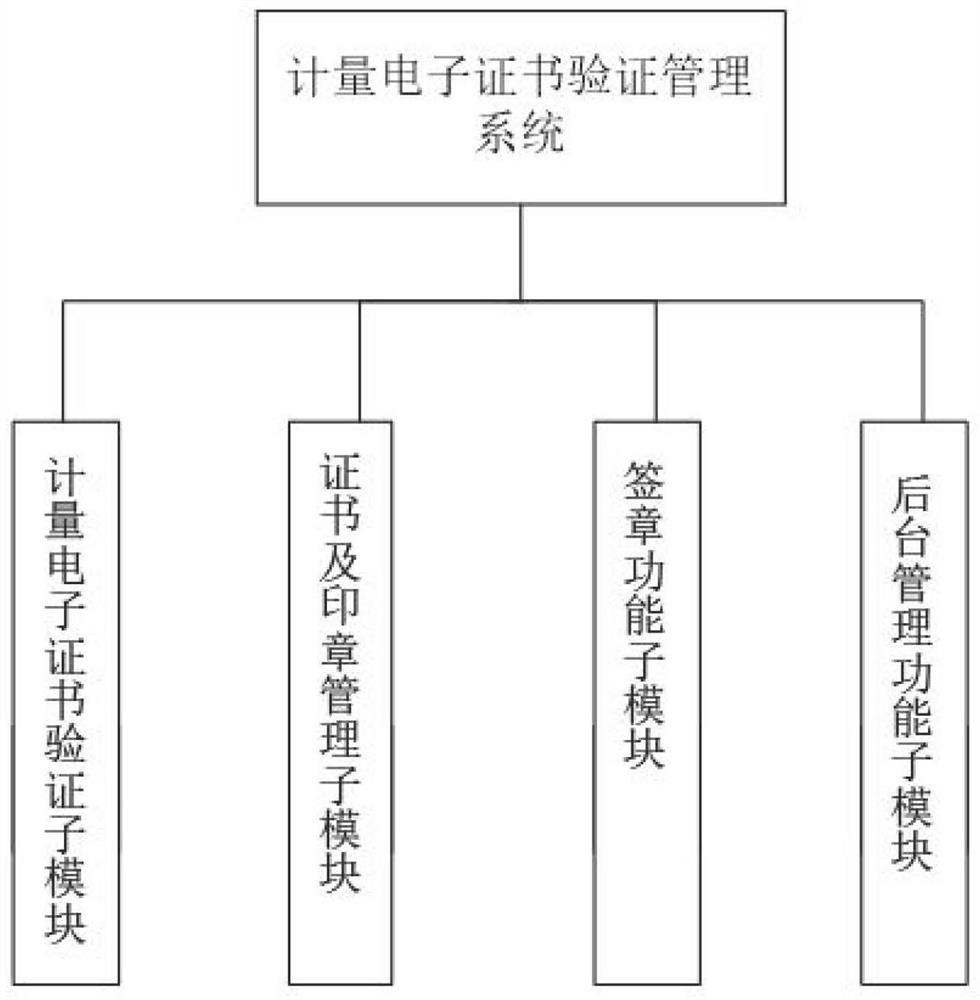
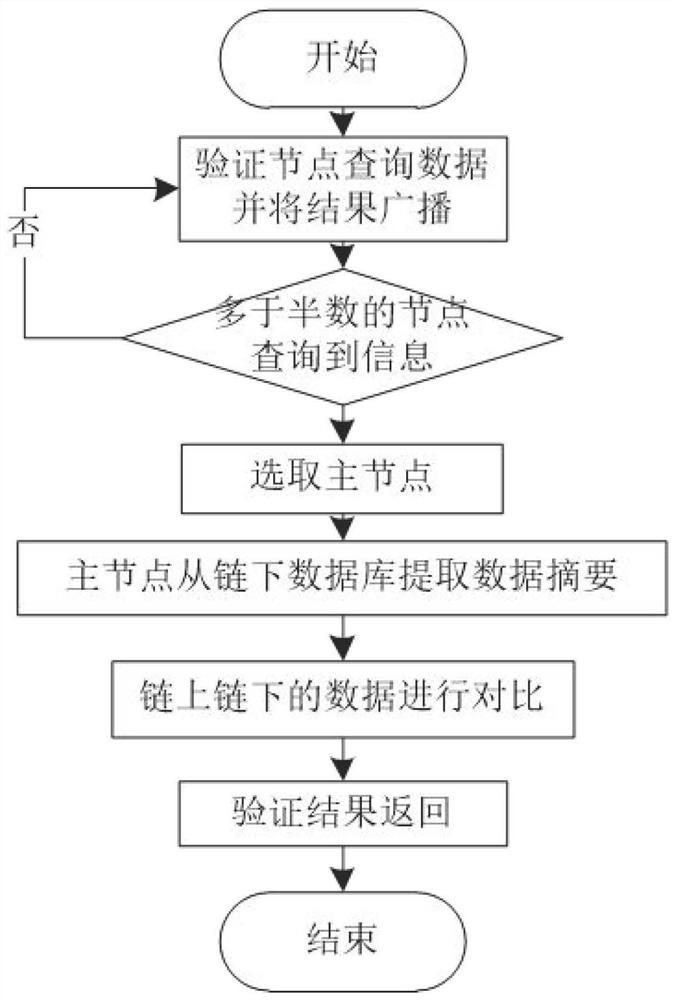
Metering electronic certificate verification management system based on block chain
PendingCN112685717AEasy to storeEasy to manage digitallyDigital data protectionDigital data authenticationHTML5Python language
The invention discloses a metering electronic certificate verification management system based on a block chain, and the system comprises the following contents: a system technical scheme: a Bootstrap framework and an HTML5 / CSS / JavaScript language are used at the front end of the system, a Django framework based on a Python language is used at the rear end of the system, the block chain is an Ethereum public chain, and a file feature value calculation algorithm is an SHA256 algorithm; the system module comprises a metering electronic certificate verification sub-module, a certificate and seal management sub-module, a signature function sub-module and a background management function sub-module. According to the metering electronic certificate verification management system based on the block chain, data of the metering electronic certificate can be verified and cannot be tampered, the credibility of the metering electronic system is improved, meanwhile, malicious users can be prevented from tampering the metering electronic certificate of the system, and the safety of the metering electronic certificate system is improved.
Owner:SD STEEL RIZHAO CO LTD
Self-networking system and method realizing reselection switch, self organization and self restoration
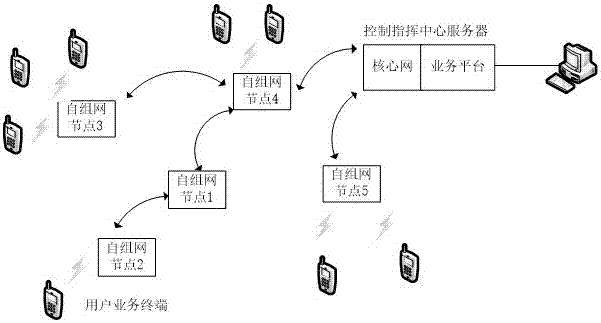
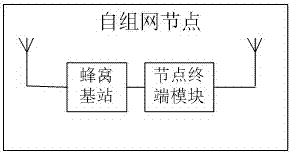
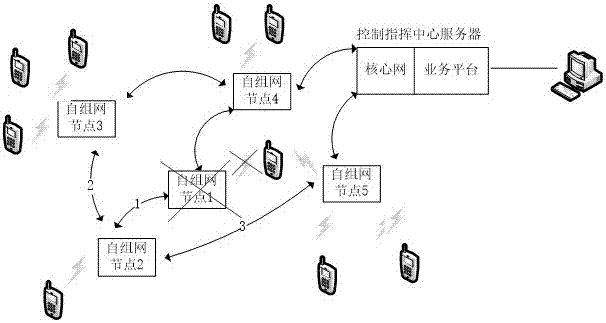
InactiveCN107231626AExpand coverageStrong authenticationNetwork topologiesSecurity arrangementSystem capacityHigh bandwidth
The invention discloses a self-networking system and method realizing reselection switch, self organization and self restoration. The system comprises a command and control center server, self-networking nodes and a user service terminal, wherein each self-networking node separately comprises a cellular base station system and a node terminal module, the cellular base station system is used for accessing the user service terminal and the node terminal module to realize a communication function of a wireless user; and the node terminal module serves as a connection and routing of the self-networking system to increase a corresponding routing judgment function. According to the self-networking system and method, the mobile communication base station technology is imported to the self-networking to make full use the advantages of the both to form a brand new network structure that can realize free switch and reselection and has self organization and self restoration functions, and the coverage can be greatly improved by using relatively small node power; the system has a huge authentication and encryption function to prevent the information from being broken and intercepted; and the cost of the user service terminal is greatly reduced, the network system capacity is greatly expanded, and the service access with large capacity and high bandwidth is satisfied.
Owner:苏州智铸通信科技股份有限公司
Encryption component applied to safe transmission of communication data
ActiveCN111641509AIngenious structureThe principle is simpleMechanically effected encryptionMagnetic switchControl theory
The invention provides an encryption component applied to safe transmission of communication data, which comprises an output encryption device connected with a memory to directly establish a data communication channel; in an initial state, a communication channel in the output encryption device is disconnected; the output encryption device comprises a cylindrical mounting shell with an opening inone end, an output contact, an output wire, an electromagnetic switch and a power generation winding; a circular end cover for sealing the mounting shell is coaxially and fixedly arranged at the opening of the mounting shell; the output contact is mounted on the base block in a floating manner and penetrates to the outer side end surface of the end cover; the output wire is connected between the memory and the output contact; the electromagnetic switch is connected to the output wire in series and can control on-off of the output wire, the power generation winding is fixedly installed on the end face of the inner side of the end cover and can generate power under the action of the butt joint decryption device to form the current with the set value, and the electromagnetic switch can be promoted to be turned on when the current with the set value of the power generation winding is small.
Owner:SHENZHEN POWER SUPPLY BUREAU
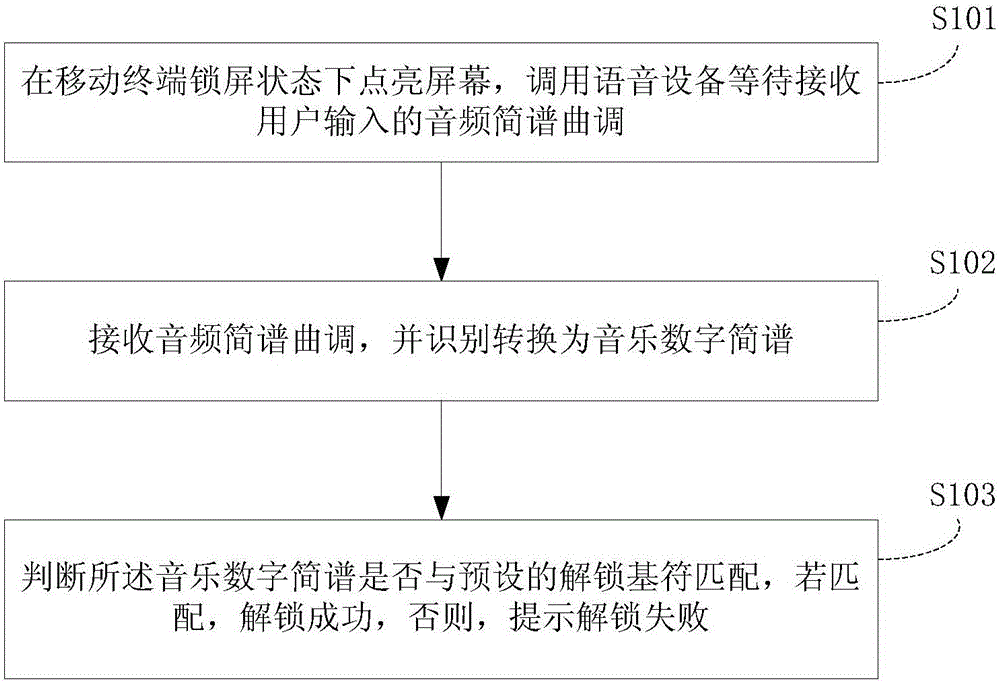
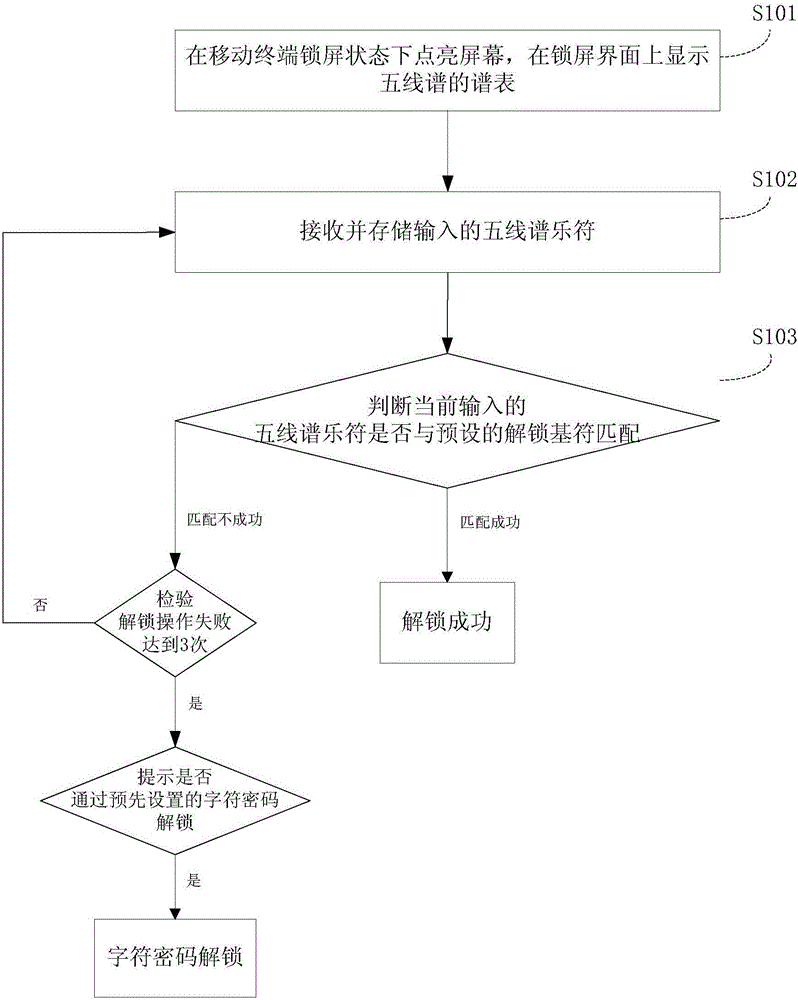
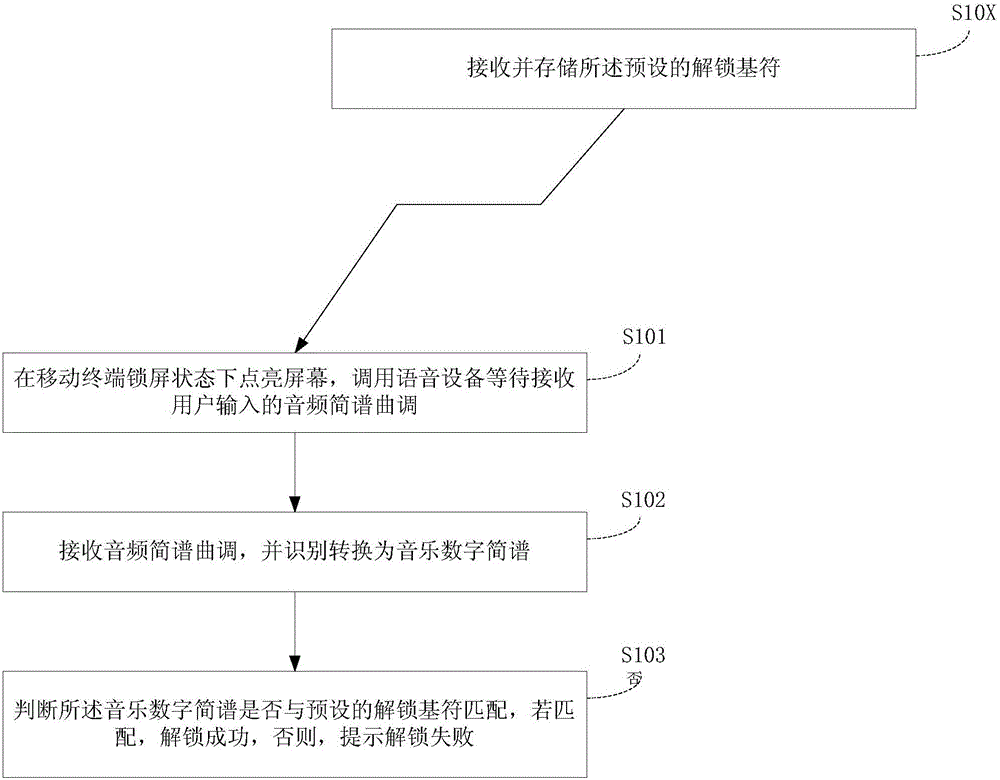
Display screen unlocking method, device and mobile terminal based on music identifier
InactiveCN105893825AImprove experienceImprove practicalityDigital data authenticationDigital numberUser input
The invention discloses a display screen unlocking method, device and mobile terminal based on a music identifier. The display screen unlocking method comprises the following steps: lightening the screen in a screen-locked state of the mobile terminal, and calling voice equipment to wait for receiving the audio numbered musical notation tune input by a user; receiving the audio numbered musical notation tune and identifying and converting into music digital numbered musical notation; and judging whether the music digital numbered musical notation is matched with the preset unlocking base identifier, wherein if so, the unlocking succeeds; otherwise, the unlocking failure is prompted. In the invention, the music numbered musical notation identifier is used as the unlocking base identifier, and the audio numbered musical notation tune is input in an input form of user speaking / singing, thus the unlocking experience of the user is effectively improved; when both hands of the user are busy, unlocking can be realized through the music numbered musical notation tune; meanwhile, a relatively long complicated password can be set, the password is convenient to memorize for specific users understanding music, and the science and technology impression as well as humanity is improved; and moreover, the encryption way is novel and unique and has strong encryption ability, and the password is hard to crack.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Gate lock regulated and controlled by mobile phone
InactiveCN103161357AStrong encryptionGood anti-theft performanceTelephonic communicationElectric permutation locksEngineeringMicrocomputer
The invention provides a gate lock regulated and controlled by a mobile phone. A single chip microcomputer is arranged in the gate lock. One end of the single chip microcomputer is connected with a gate lock demodulation circuit and a mobile phone signal circuit, and the other end of the single chip microcomputer is connected with a power amplification circuit and a mechanical execution component. The end tip of the single chip microcomputer is connected with a secret key preset and reset circuit. The single chip microcomputer is further connected with a warning circuit. When the gate lock regulated and controlled by the mobile phone is used after being installed, the mobile phone can be used to be aimed at a gate lock signal reception circuit to issue a password command, so that the gate lock can be unlocked. Due to adoption of scientific combination of the gate lock and the general mobile phone, usage of the gate lock is very convenient. Due to the fact that the mobile phone can be encrypted as needed, the antitheft effect is good.
Owner:XIANGFAN UNIVERSITY
Method for establishing encrypted data transmission channel
InactiveCN111666612AIngenious structureThe principle is simpleCoupling device detailsInternal/peripheral component protectionElectric machineTransmission channel
The invention provides a method for establishing an encrypted data transmission channel, which comprises the following steps that firstly, a power input contact and a power output contact are matchedand butted, and a signal input contact and a signal output contact are matched and butted; then, the memory supplies power to the servo motor, the servo motor drives the magnet to perform centrifugalmotion and directly face the winding I and the winding II, and the magnet generates a changing magnetic field and performs relative cutting motion with the winding I and the winding II; then, the loading voltage of the servo motor is adjusted, the voltage value is a certain determined value matched with M and N, at the moment, the numerical value of the current generated in the first winding is M,the numerical value of the current generated in the second winding is N, the first electromagnetic switch and the second electromagnetic switch are turned on, and decryption is completed; and finally, the signal output wire is conducted, a communication channel in the output encryption device is conducted, and data in the memory is transmitted to the receiver through the signal output wire, the signal output contact, the signal input contact and the signal input wire.
Owner:安徽拔沃乎机电科技有限公司
A Digital Signal Encryption Method Using Multi-matrix
InactiveCN102271036AEasy to operateStrong encryptionEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
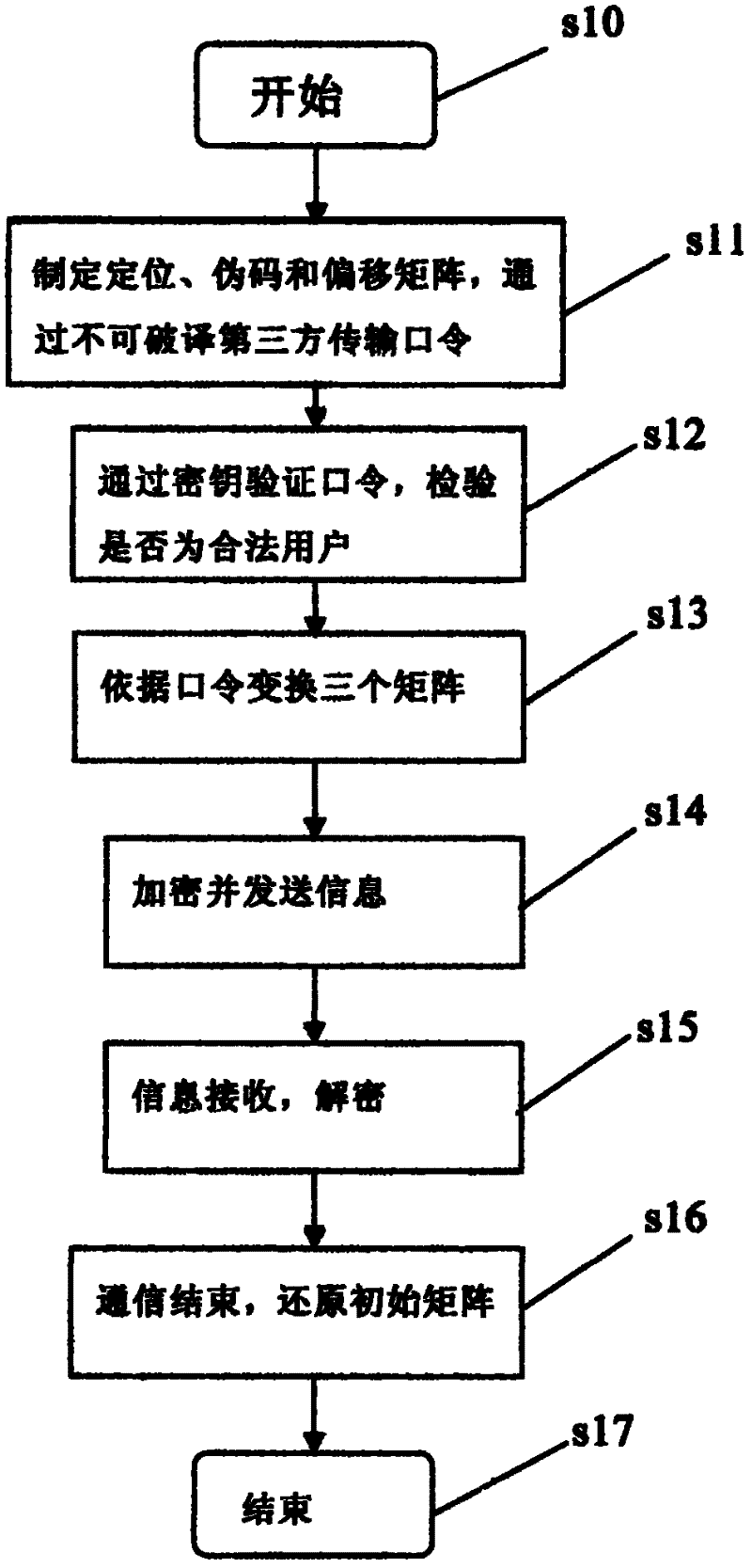
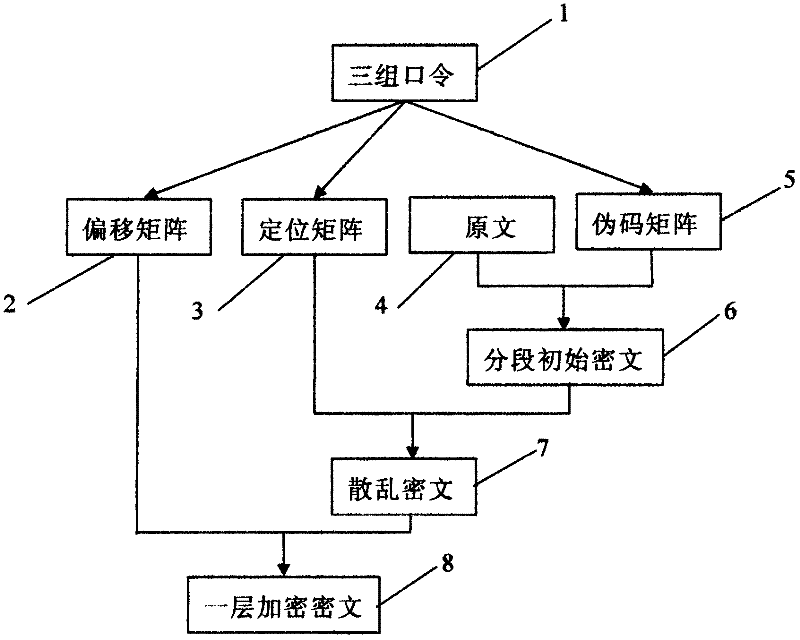
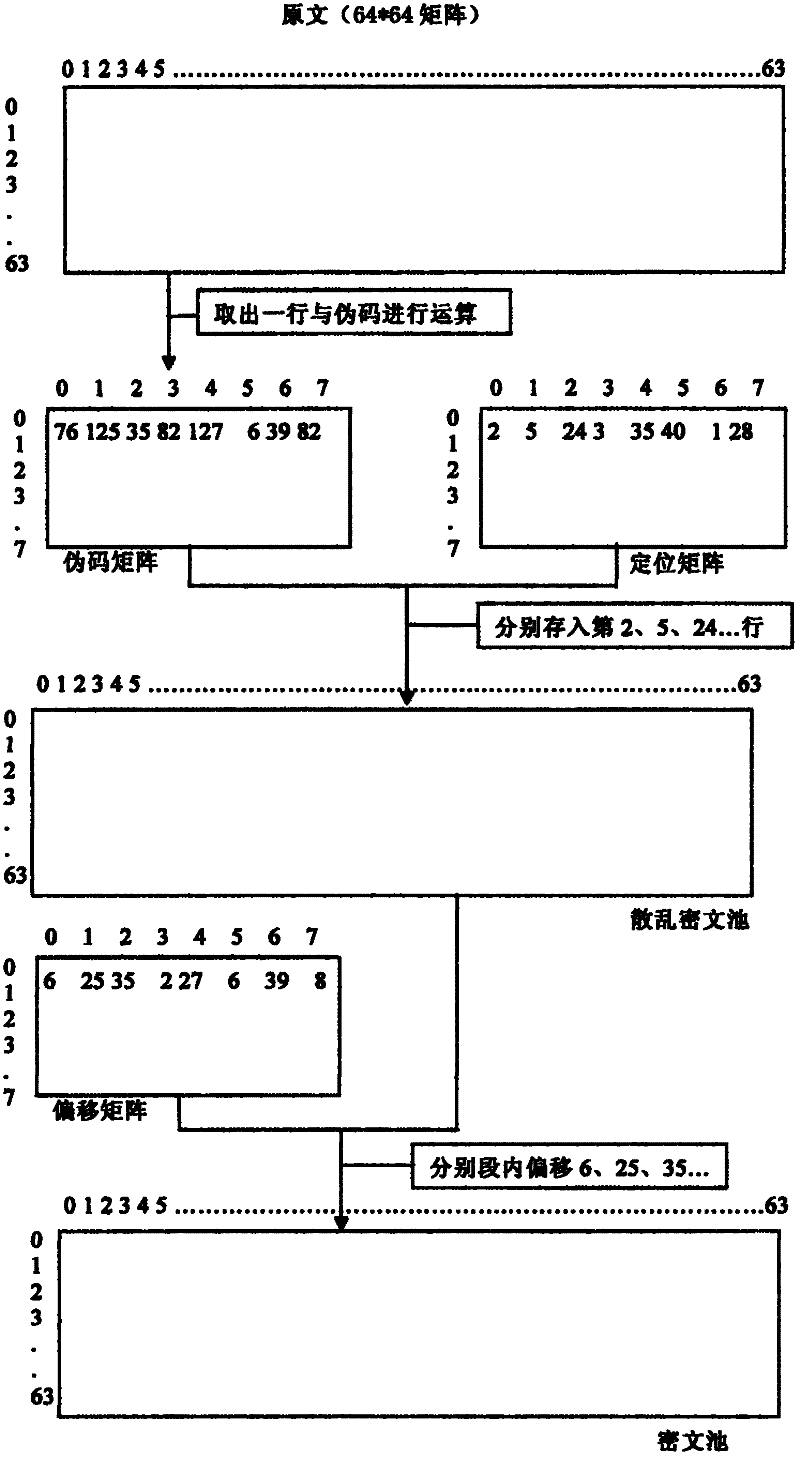
The invention discloses a digital signal encryption method utilizing multiple matrices, comprising the following steps: inputting a password, respectively transforming a positioning matrix, a pseudo-code matrix and an offset matrix according to the password, and performing segmental calculation with the data of the pseudo-code matrix and the original text after completion Obtain segmented ciphertext, and rearrange the ciphertext according to the positioning matrix. After completion, divide the ciphertext into segments, which can be of equal length or unequal length, and then divide the divided segments according to the value of the offset matrix Perform intra-segment offset and save the offset result. The method can well strengthen the confidentiality of mutual communication, and the password-controlled matrix transformation can eliminate the security threat of a third party to mutual communication. This encryption method avoids the shortcomings of other encryption methods in the past that cannot verify the user's identity and that a set of encryption methods is easy to leak when used by multiple people, and it solves the information security problem in the communication process well.
Owner:田耕
Railway early warning system and early warning method based on mobile communication
InactiveCN102039918AAlert at any timeAutomatic warningAutomatic systemsWireless commuication servicesEarly warning systemCommunication unit
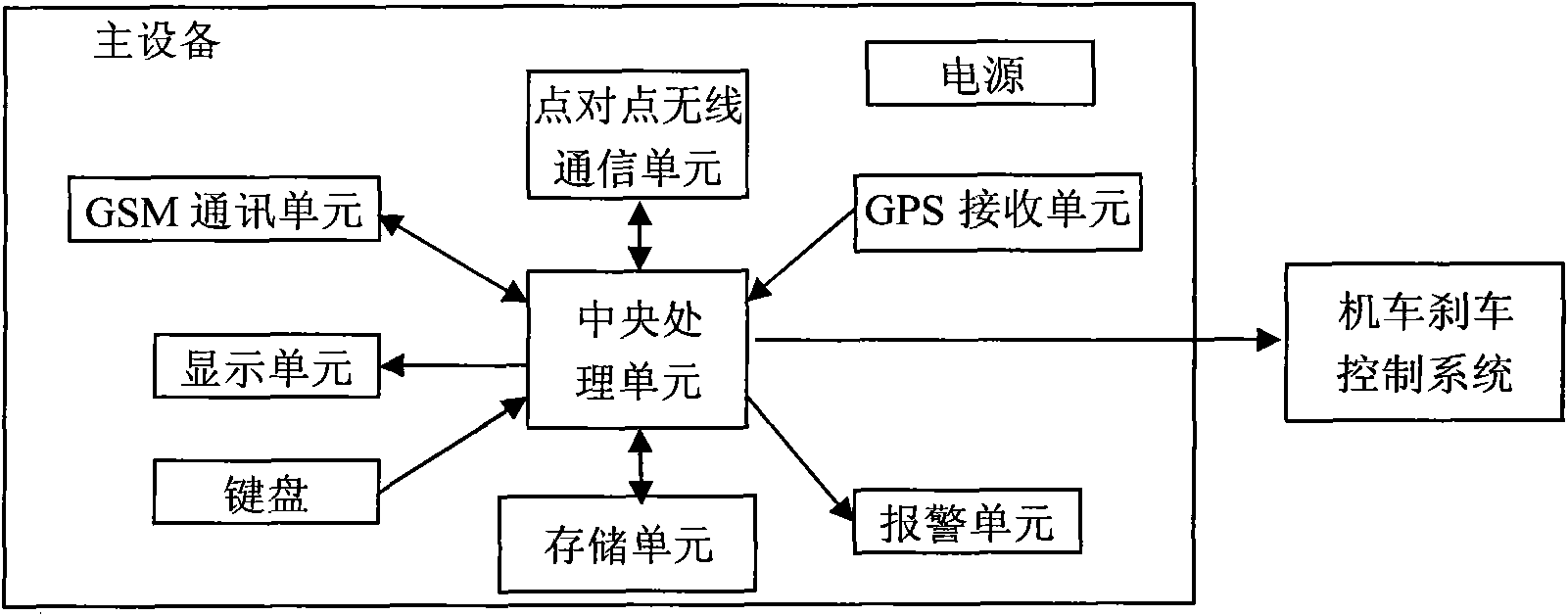
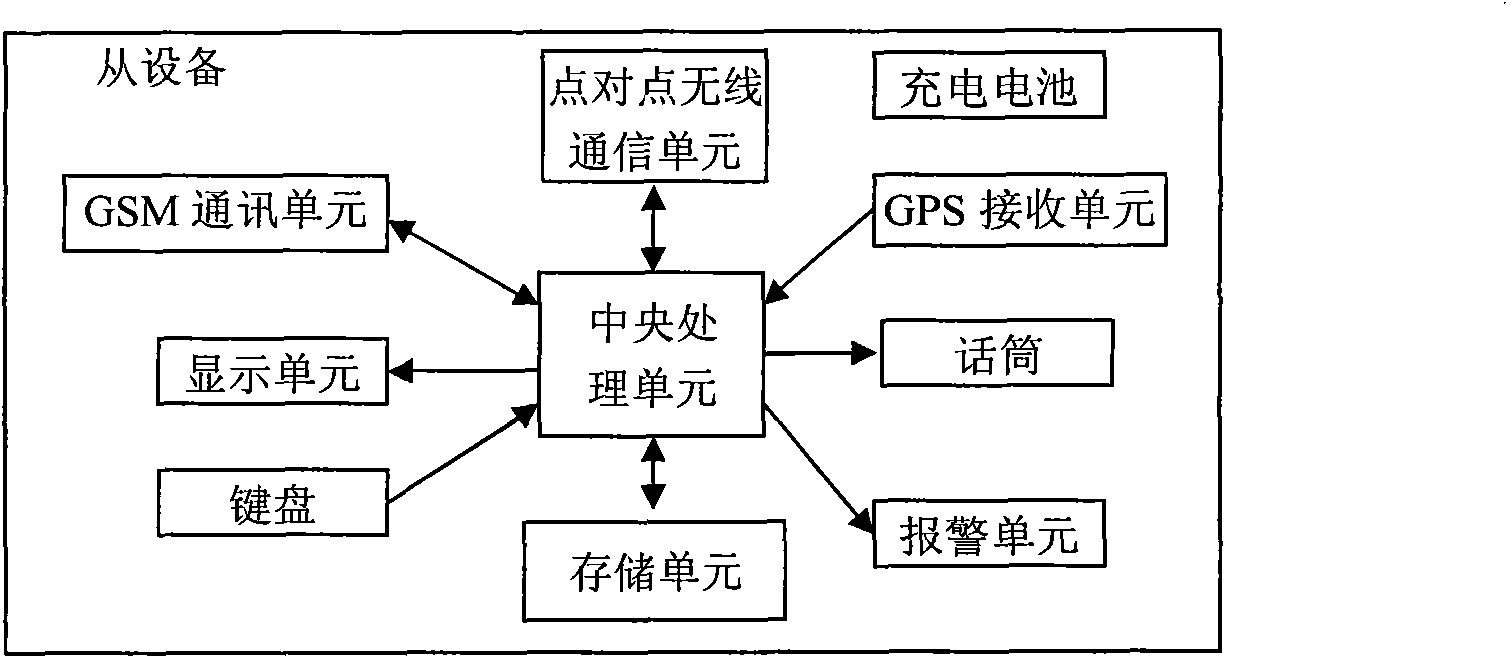
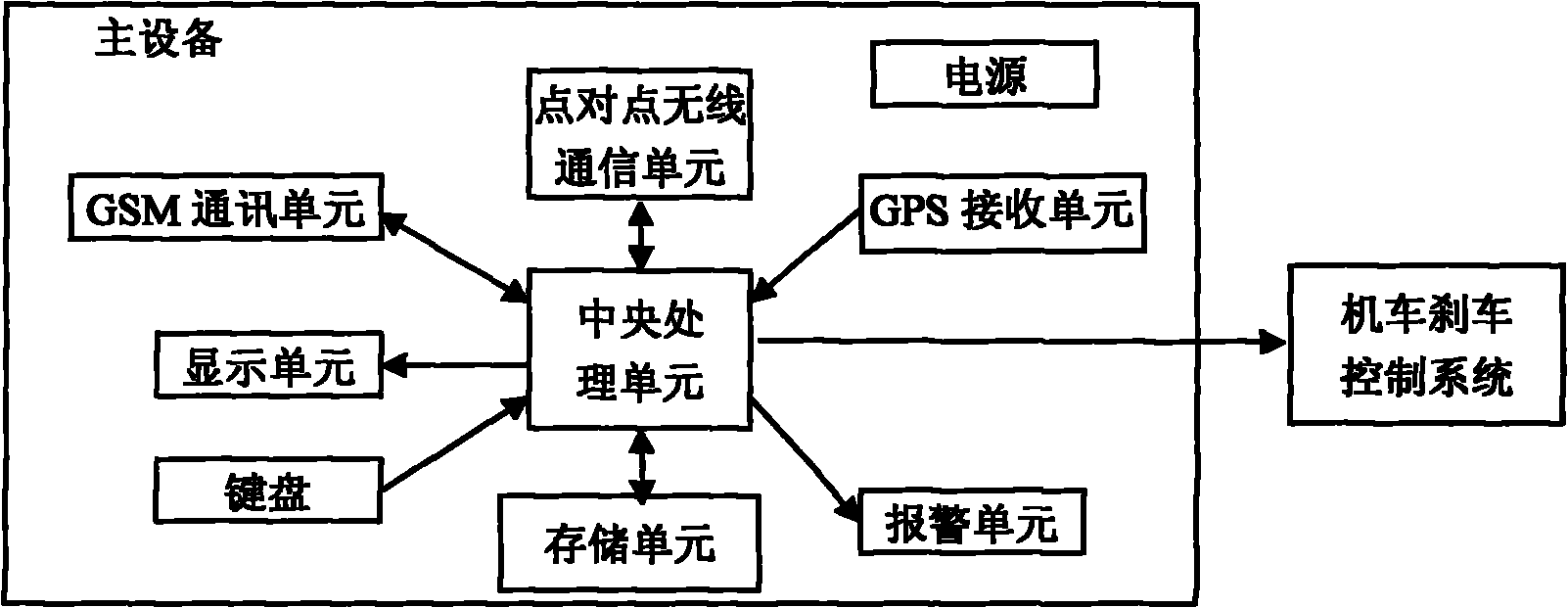
The invention relates to a railway early warning system and an early warning method based on mobile communication. The railway early warning system comprises at least one main device and at least one slave device, wherein the main device is mounted on a locomotive head; the slave device is a portable mobile device; the main device comprises a power supply, a central processing unit, a keyboard, a display unit, an alarming unit and a point-to-point wireless communication unit, wherein the keyboard, the display unit, the alarming unit and the point-to-point wireless communication unit are respectively connected with the central processing unit; the slave device comprises a rechargeable battery, a central processing unit, a keyboard, a microphone, a display unit, a alarming unit and a point-to-point wireless communication unit, wherein the keyboard, the microphone, the display unit, the alarming unit and the point-to-point wireless communication unit are respectively connected with the central processing unit; and the point-to-point wireless communication unit of the main device and the point-to-point wireless communication unit of the slave device form a point-to-point wireless communication system. The invention solves the technical problem that the traditional railway early warning system only can be used for static fixed occasions. The invention can effectively prevent the occurrences of events, achieve random, automatic and fast early warning, and immediately stop or minimize the possible accidents.
Owner:XIAN XISHENG ELECTRONICS TECH
Multiple chaotic attractor time-sharing switching method and device for communication encryption
InactiveCN103684741AIncrease diversityTime-varyingSecuring communicationHandoff controlControl signal
The invention relates to a multiple chaotic attractor time-sharing switching method and device for communication encryption, belongs to the technical field of communication encryption and solves the problem that the existing multiple chaotic attractor switching software system is unavailable for fast time-sharing switching of different chaotic system attractors. A switching chaotic system is built in an FPGA; subsystem control characters are entered to a single-chip microcomputer through a soft keyboard; the single-chip microcomputer converts the subsystem control characters into subsystem switching control signals which are transmitted to the FPGA; the FPGA selects one subsystem of the switching chaotic system according to the subsystem switching control signals; split-phase control characters are entered to the single-chip microcomputer through the soft keyboard; the single-chip microcomputer converts the split-phase control characters into split-phase switching control signals which are transmitted to the FPGA; the FPGA selects two of three phases or four phases of the selected subsystem for outputting, according to the split-phase switching control signals. Time-varying, diverse and complex chaotic signals are provided. Encryption effect and decryption resistance are improved, and multiple chaotic attractors can be subjected to fast time-sharing switching anytime.
Owner:HARBIN UNIV OF SCI & TECH
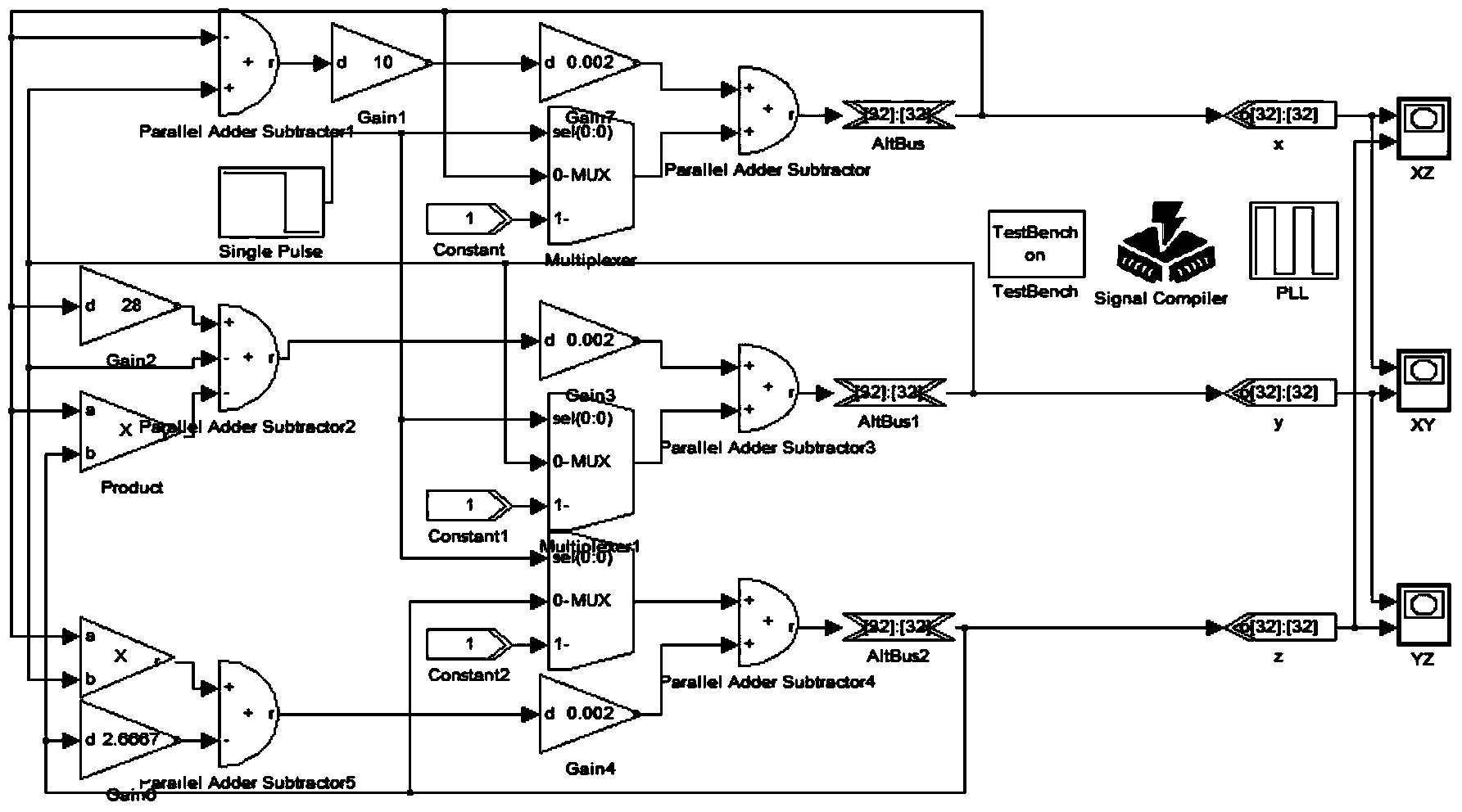
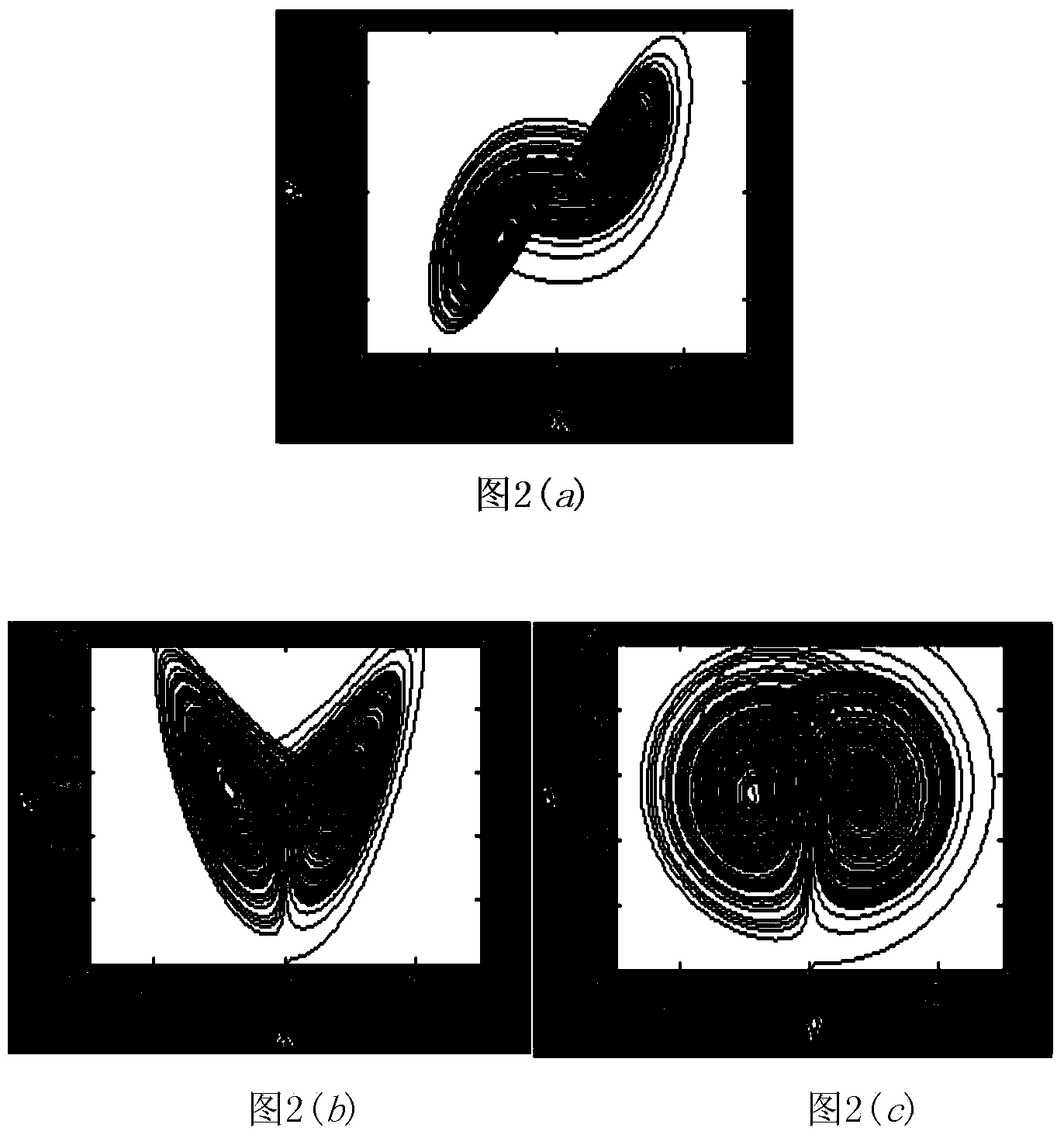
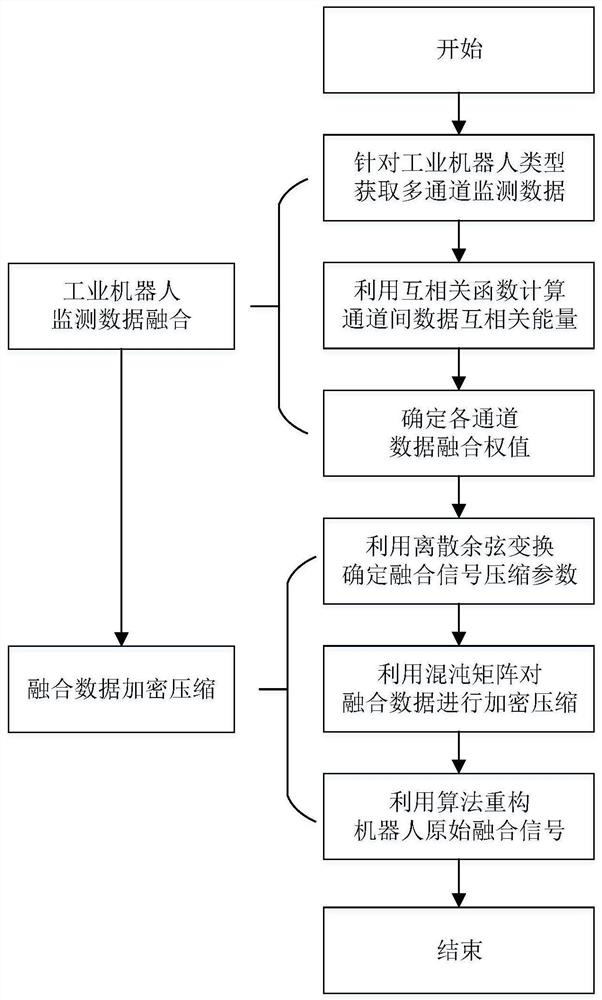
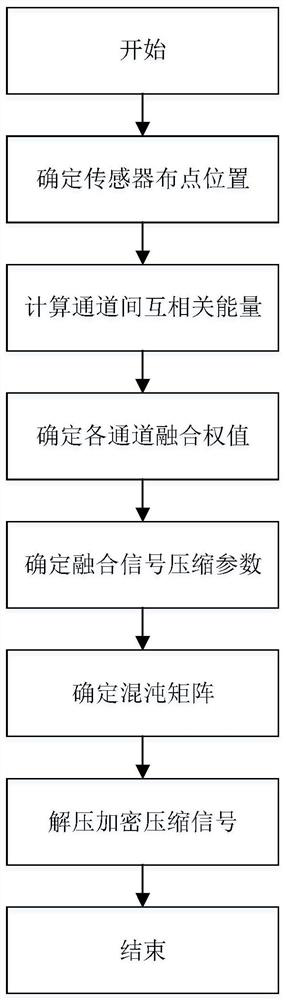
Multi-channel monitoring data compression method and system for industrial robot
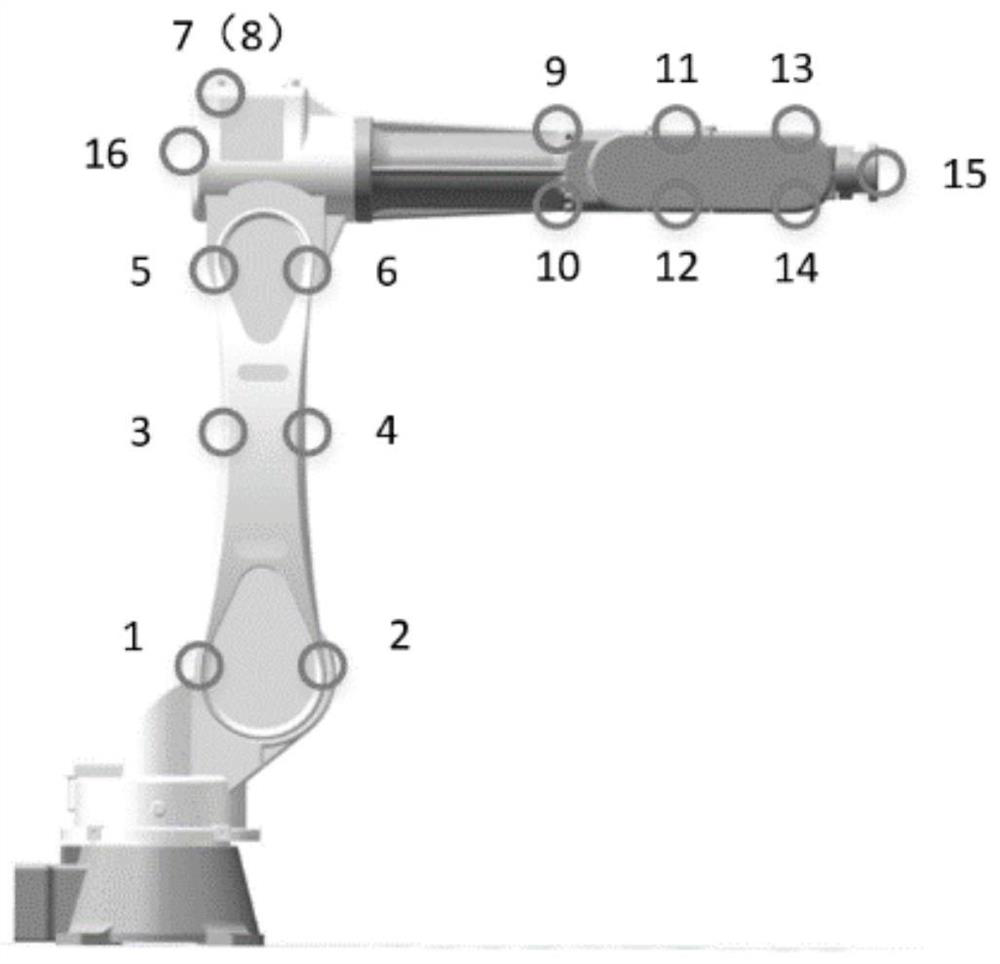
ActiveCN113225089ASafe and Efficient TransmissionReduce Signal RedundancyCode conversionData compressionChannel data
The invention discloses a multi-channel monitoring data compression method and system for an industrial robot, and the method comprises the steps: fusing the multi-channel data only containing the local state information of the robot into a comprehensive signal with the global information through a cross-correlation function fusion algorithm according to the correlation characteristics between the monitoring data of each channel of the industrial robot, signal redundancy between data of each channel sensor is obviously reduced, and signal quality is improved. The comprehensive signal is encrypted and compressed through the composite chaos matrix and is transmitted to a remote maintenance center through a network, and the remote maintenance center recovers an original signal by using a secret key in combination with an orthogonal matching pursuit algorithm, so that safe and efficient transmission of the signal is realized. According to the invention, the efficiency and safety of signal transmission can be improved, the problem that a large amount of redundant mass vibration data generated by multi-channel real-time monitoring of the industrial robot cannot be safely and efficiently transmitted to a remote maintenance center is solved, and meanwhile, a data basis is provided for fault diagnosis and health assessment of the industrial robot.
Owner:XI AN JIAOTONG UNIV
Method for improving encrypted data security transmission level
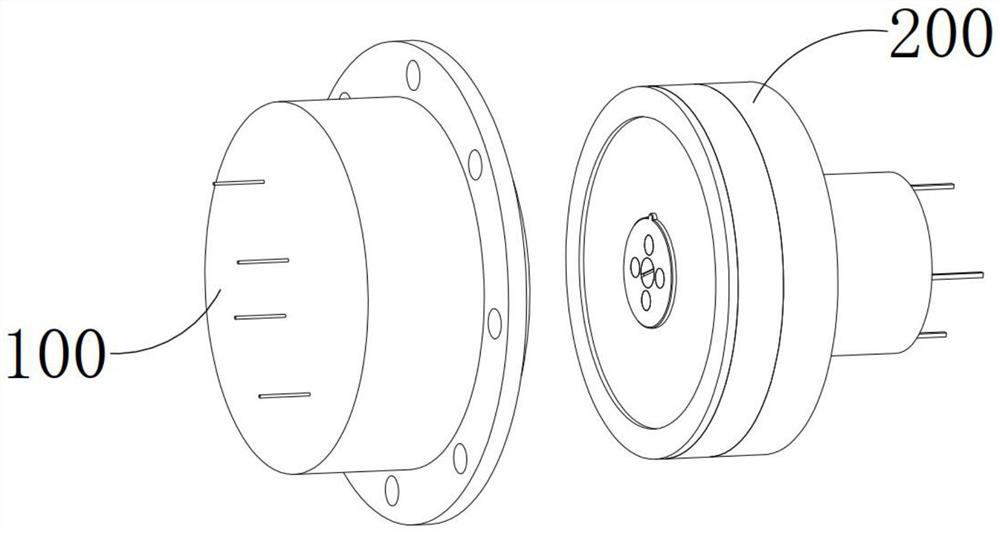
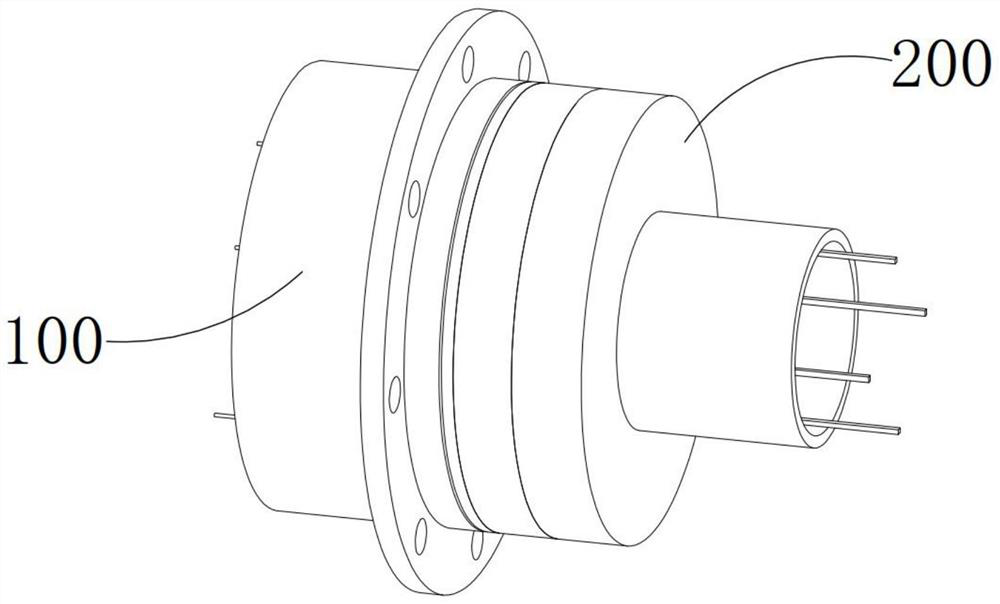
InactiveCN111666611ACompact structureThe principle is simple and reliableCoupling device detailsTwo-part coupling devicesComputer hardwareSecure transmission
The invention provides a method for improving the security transmission level of encrypted data, which comprises the following steps that firstly, a decryption cylinder is inserted into a mounting cylinder and matching butt joint is completed, an output component and an input component are connected in a butt joint manner, and a decryption mechanism is over against an encryption switch; thereafter, the decryption mechanism is operated, a first sleeving cylinder in threaded connection fit with the decryption cylinder moves close to a second sleeving cylinder, a supporting arm supports a triggering arm and forces the triggering arm to be unfolded, the triggering arm penetrates through a through groove from a folded state to be switched into an unfolded state, meanwhile, the triggering arm slides through a channel to enter an inner cavity and pushes and presses an ejector rod, and an encryption switch is switched into an opened state from a disconnected state; and finally, the interior ofthe output component is conducted, the communication channel in the encryption socket is conducted, the data is transmitted to the memory by the computer through the output component and the input component in sequence to perform encryption transmission on the data. The significance is that only when all encryption switches are turned on, the communication channel can be conducted, the encryptionperformance is strong, and matching and butt joint are facilitated.
Owner:安徽拔沃乎机电科技有限公司
Streaming media information safety guarantee method and system
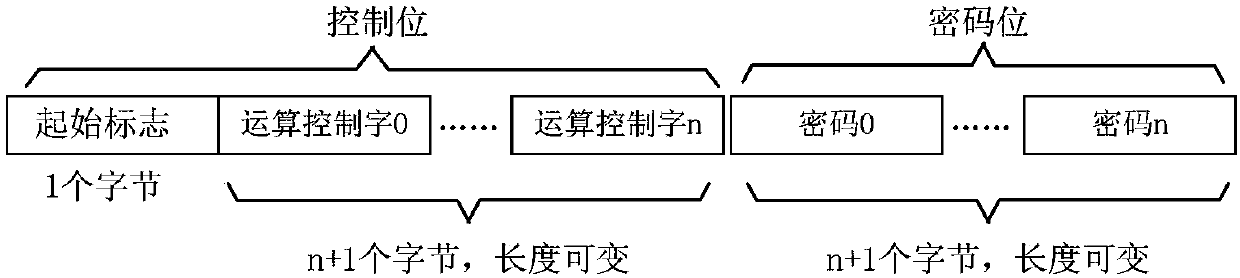
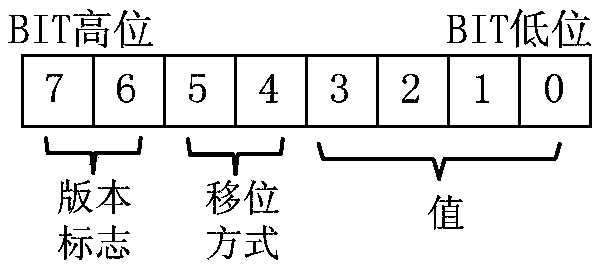
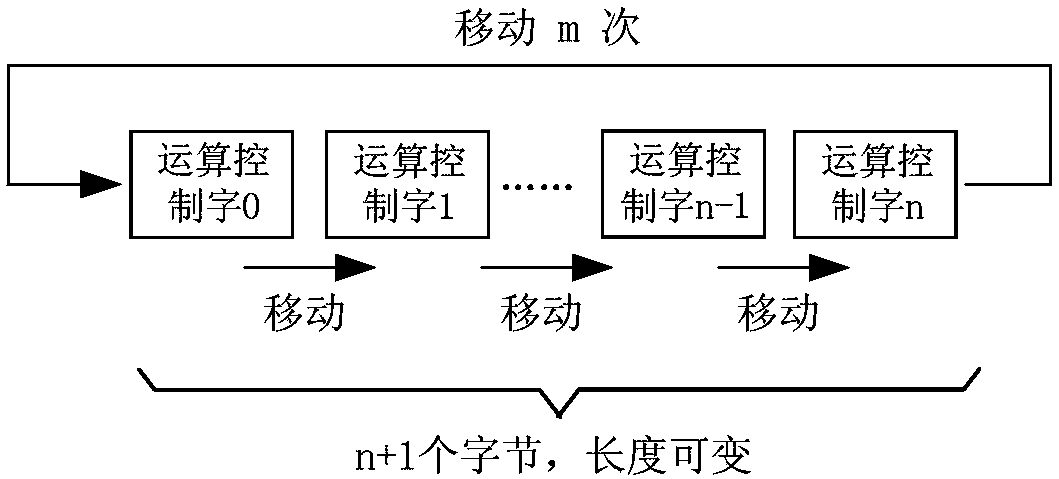
The invention discloses a streaming media information safety guarantee method. The method is a symmetrical encryption algorithm and comprises the following steps during encryption: (1) reading in passwords, and analyzing a start flag, an operation control word and the passwords, if a mistake is made during analyzing, quitting and giving out an error-reporting message, and if the analyzing is correct, executing a step (2); (2) aligning the operation control word and the passwords according to an analytic value of the start flag; (3) carrying out marshalling calculation on the password controlled by each control operation word, and forming final password groups; (4) according to the length of each password group, grouping to-be-encrypted plaintext, and forming a grouping set; and (5) according to encryption operation rules designated by an operation rule field of the operation control word, carrying out encryption calculation on the to-be-encrypted plaintext with the corresponding password, and finally generating ciphertext. The invention also discloses a streaming media information safety guarantee system.
Owner:唐常芳
Special socket component for improving data encryption level
InactiveCN111682949ACompact structureThe principle is simple and reliableData switching detailsCoupling device detailsComputer hardwareMultiple encryption
The invention provides a special socket component for improving a data encryption level. The special socket component comprises a mounting cylinder, an output component and a plurality of encryption switches, wherein the output component and the encryption switches are both mounted in the mounting cylinder; the encryption switches are connected to the output component in series, and the multiple encryption switches are turned on at the same time to turn on the output component; the encryption switches are turned off in an initial state; the mounting cylinder is composed of a mounting cylinderI and a mounting cylinder II which are coaxially and fixedly connected; one end of the mounting cylinder I is a fixed end, and the other end of the mounting cylinder I is a connection end; one end ofthe mounting cylinder II is a fixed end, and the other end of the mounting cylinder II is connected with a connection end; the connection end of the mounting cylinder I is coaxially and fixedly connected with the connection end of the mounting cylinder II; the output component is mounted at the fixed end of the mounting cylinder I; and the encryption switches are mounted at the fixed end of the mounting cylinder II. The beneficial effects are that the structure is compact, the principle is simple and reliable, on-off of communication channels in the encryption socket is controlled through theplurality of switches, only when all switches are turned on, the communication channels can be turned on, and the encryption performance is high.
Owner:安徽拔沃乎机电科技有限公司
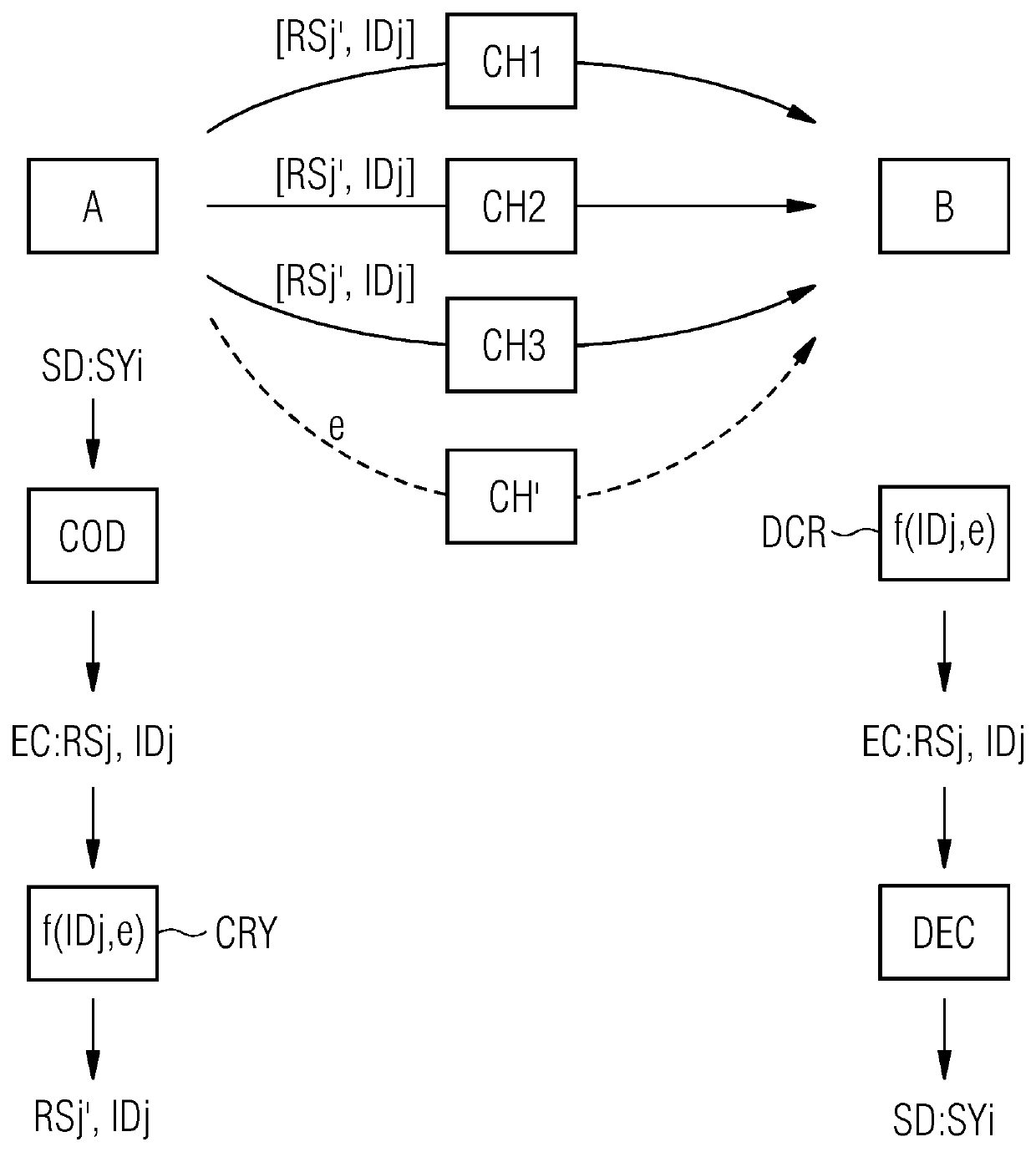
A method for sending digital data over a number of channels
ActiveUS20200204354A1Strong encryptionEfficient implementationKey distribution for secure communicationError preventionSource dataDigital data
Provided is a method for sending digital data over a number of channels wherein a sender performs the following steps: encoding source data having a first number of source symbols, the encoding being such that an error correction code is generated from the source data, the error correction code comprising a second number of repair symbols higher than the first number as well as identifiers where each identifier is assigned to a corresponding repair symbol, the error correction code adding redundancy to the source data; encrypting each repair symbol by an encryption process which is based on a shared secret between the sender and a receiver, where the encryption process for a respective repair symbol depends on the identifier assigned to the respective repair symbol; feeding pairs of the encrypted repair symbols and the assigned identifiers to the number of channels which are connected to the receiver.
Owner:SIEMENS AG
Encrypted data port for constructing transmission channel special for encrypted data
InactiveCN111666603ACompact structureThe principle is simple and reliableCoupling device detailsTwo-part coupling devicesData portTransmission channel
The invention provides an encrypted data port for constructing a transmission channel special for encrypted data. The encrypted data port includes an encryption socket connected with a computer, wherein an internal communication channel is disconnected under the initial state of the encryption socket, and a decryption plug connected with a memory, wherein the communication channel in the decryption plug is conducted. The decryption plug decrypts the encryption socket, so that a communication channel in the encryption channel is switched from disconnection to connection, data in the computer istransmitted into the memory through the encryption socket and the decryption plug, and the encryption socket comprises a mounting cylinder, an output component and a plurality of encryption switches;the decryption mechanism comprises a decryption cylinder used for being inserted into the mounting cylinder, an output component used for being in butt joint with the input component, and a decryption mechanism used for decrypting the encryption switch and switching the encryption switch from closing to opening; the beneficial effects of the invention are that the interior of the encryption socket controls the on-off of the communication channels in the plurality of switches, only when all switches are turned on, the communication channels can be turned on, and the encryption performance is high.
Owner:安徽拔沃乎机电科技有限公司
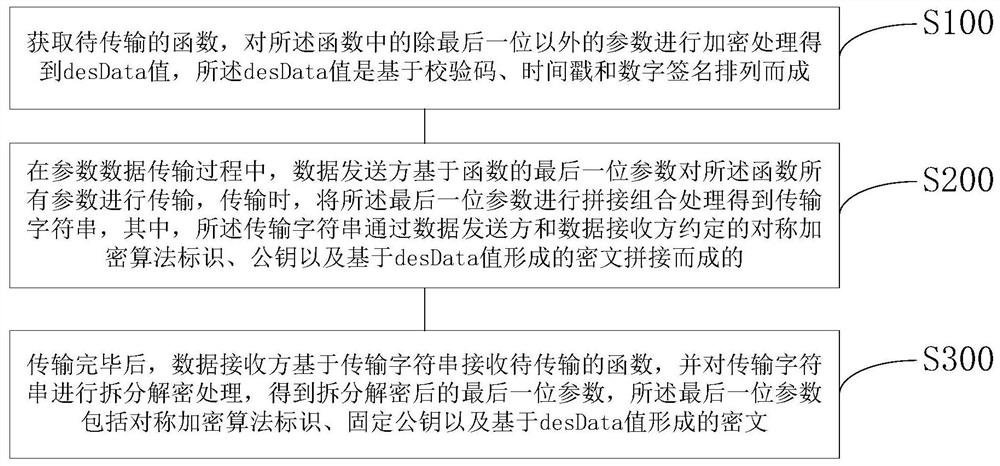
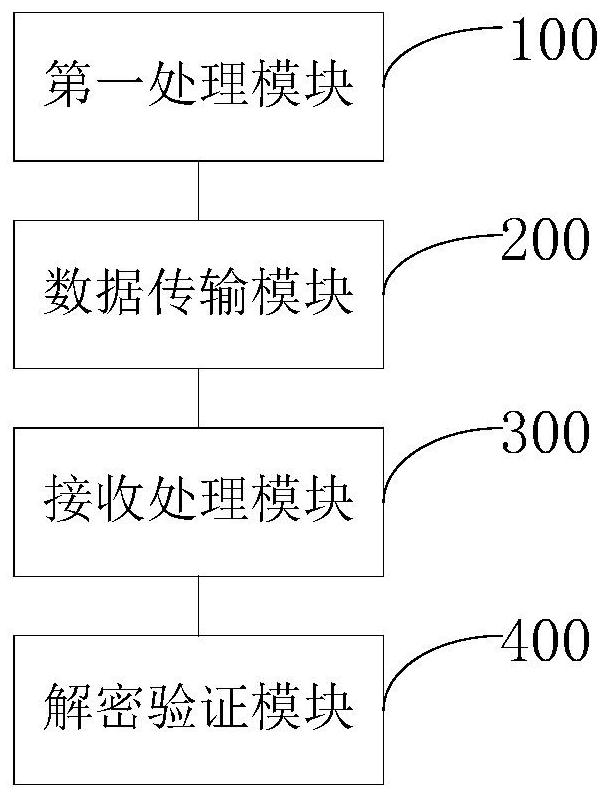
Function parameter data transmission encryption method, system and device and readable storage medium
ActiveCN112383522AGood technical effectQuick discoveryError preventionUser identity/authority verificationTimestampDigital signature
The invention discloses a function parameter data transmission encryption method, which comprises the following steps of: a function to be transmitted is acquired, and parameters except the last bit in the function are encrypted to obtain a desData value; in the parameter data transmission process, a data sender transmits all parameters of the function based on the last bit parameter of the function, and during transmission, the last bit parameter is spliced and combined to obtain a transmission character string; and after the transmission is finished, a data receiver receives the function tobe transmitted and splits and decrypts the transmission character string to obtain the last bit parameter after split and decryption. All the parameters can be encrypted in a unified mode, and all theparameters are encrypted at a time; cyclic redundancy check + timestamp and digital signature encryption and symmetric encryption algorithms are adopted, so that the encryption speed is high, and thedata transmission efficiency is not influenced; the related encryption algorithm is a symmetric encryption algorithm, random matching is carried out according to an agreed identifier without limitation, the encryption strength is higher, and the encryption algorithm is not easy to crack.
Owner:ZHEJIANG CANGNAN INSTR GRP CO LTD
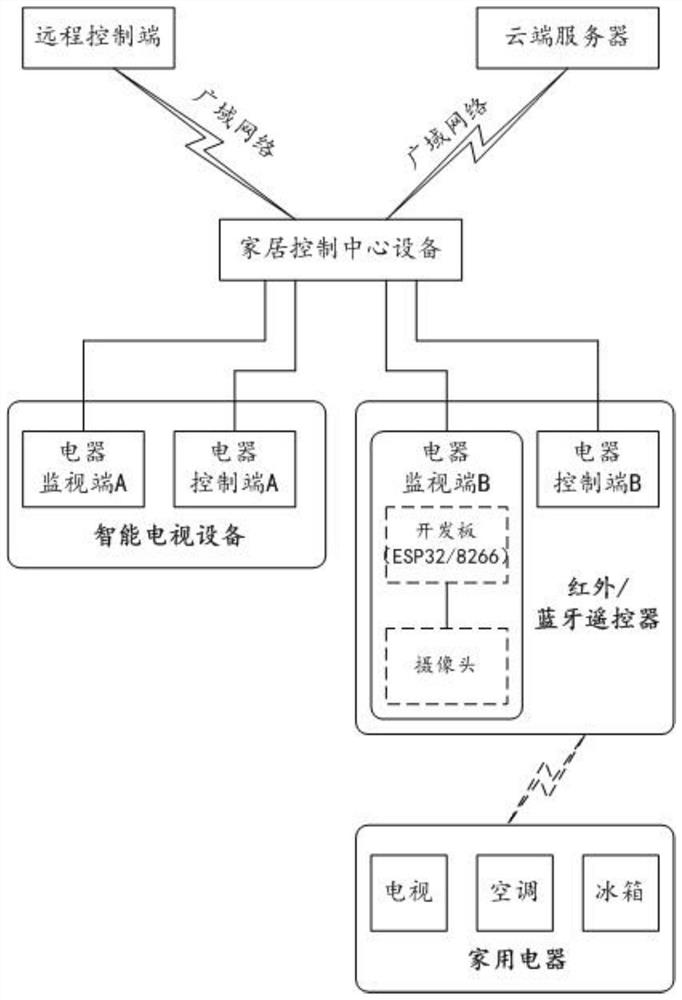
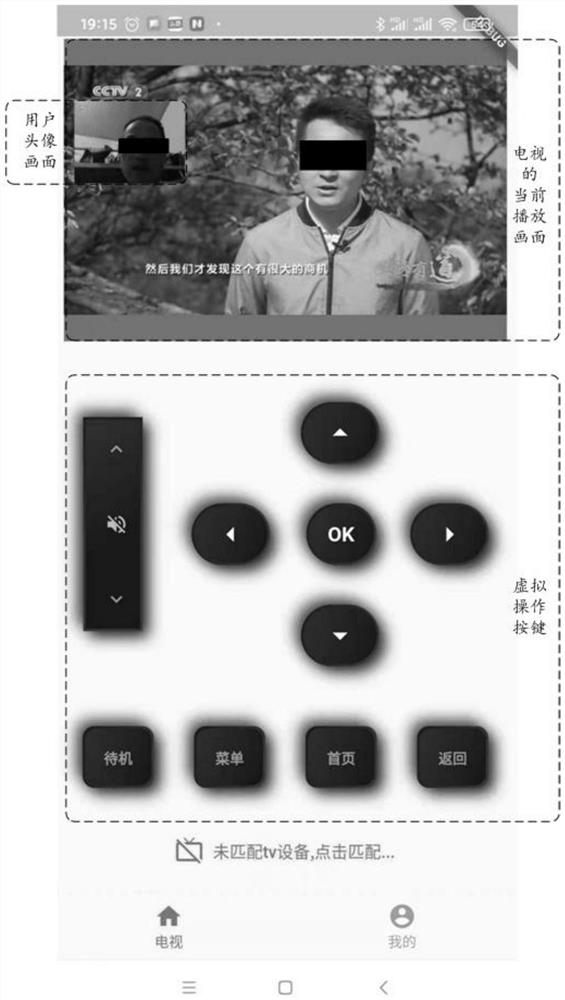
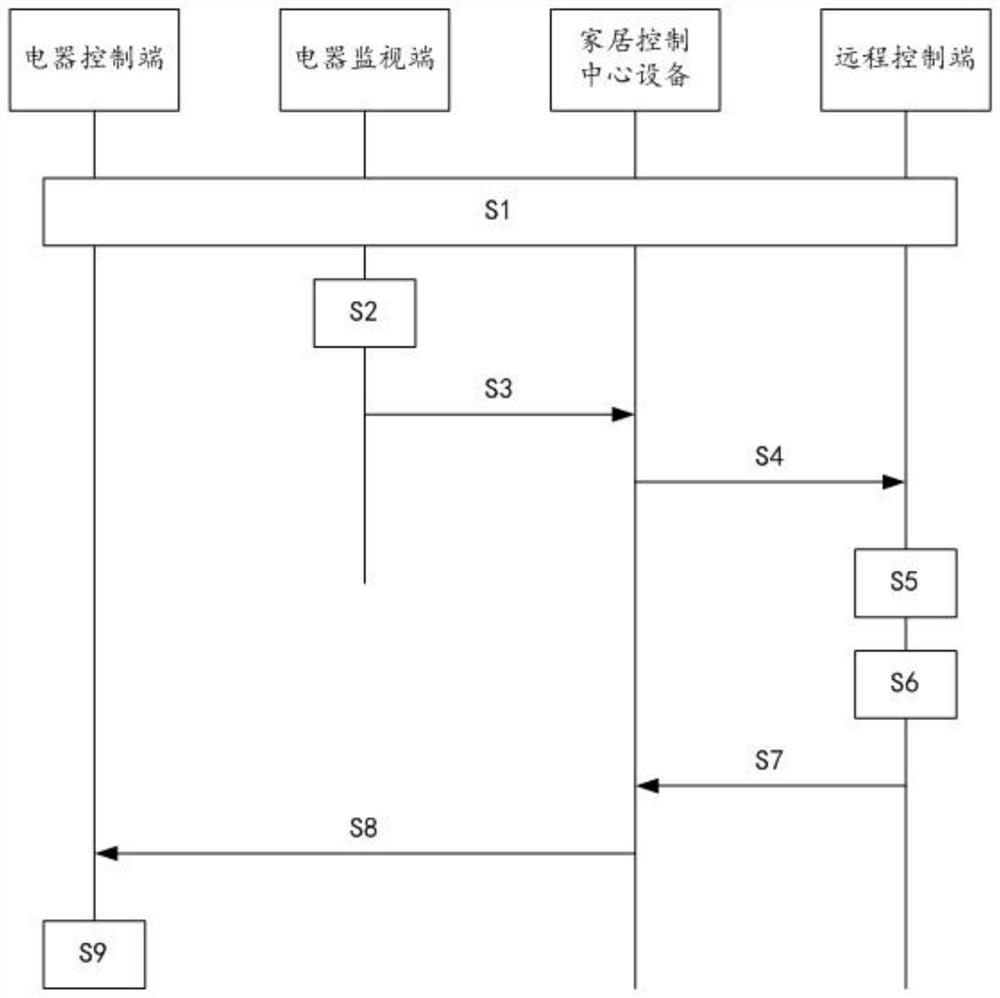
Wide area network intelligent home remote control system and working method thereof
ActiveCN113452589AEasy to useTo achieve the purpose of distance educationData switching by path configurationTotal factory controlData displayHome use
The invention relates to the technical field of smart home remote control, and discloses a wide area network smart home remote control system and a working method thereof. On the one hand, the working monitoring data of a household electrical appliance is acquired through an electrical appliance monitoring end, and the working monitoring data is transmitted to a remote control end for data display through a home control center equipment and a wide area network, so that a user can remotely sense the current use condition of the household electrical appliance, and then a correct electrical appliance operation instruction is issued; on the other hand, electric appliance control information generated by operation can be transmitted to an electric appliance control end for control execution through the home control center equipment and a wide area network, and finally, the purpose of remotely controlling the home electric appliances is achieved, so a user can control the home electric appliances anytime and anywhere, and home use is facilitated. The method is particularly suitable for scenes where left-behind children need to be limited to use household appliances (such as televisions and the like) in a limited mode, body health of the children is guaranteed, the pain point of current children education is solved, and good practicability and expansibility are achieved.
Owner:张 挺
A color two-dimensional code and its generation method, generation system and a printed matter
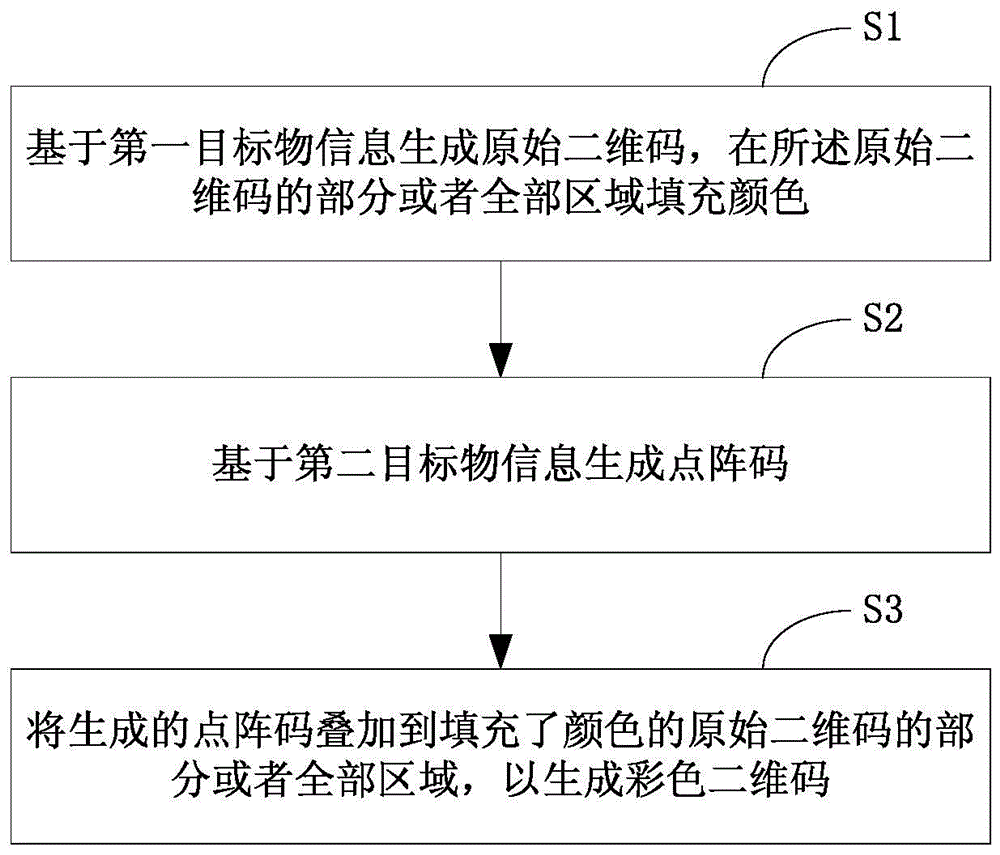
ActiveCN103489026BHigh coding densityEasy to crackRecord carriers used with machinesDot matrixTheoretical computer science
The invention discloses a colorful two-dimension code, a generating method and generating system thereof and a printed article. The colorful two-dimension code is printed on the printed article, and the system comprises an original two-dimension code generating module, a dot matrix code generating module and an overlaying module. The method comprises the steps that S1, an original two-dimension code is generated on the basis of first target article information, and part of or all areas of the original two-dimension code are filled with colors; S2, a dot matrix code is generated on the basis of second target article information; S3, the dot matrix code is overlaid to the part or all the areas of the original two-dimension code, filled with the colors, so that the colorful two-dimension code is generated. The generated colorful two-dimension code is large in coding density, and high in decoding difficulty and imitation difficulty.
Owner:SHENZHEN CHINACHOICE SCI & TECH CO LTD
WVEFC fast coding method based on flight ad hoc network
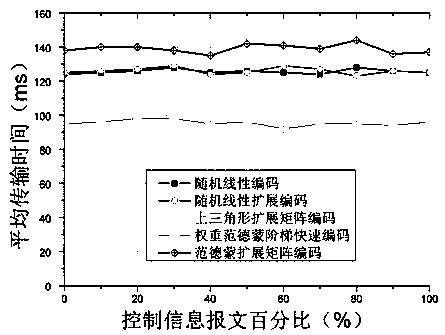
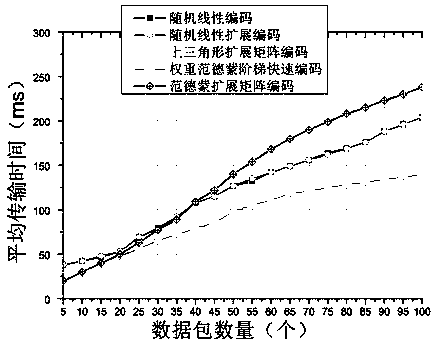
InactiveCN107947903AStrong encryptionShorten the timeNetwork topologiesChannel coding adaptationDelivery PerformanceNetwork packet
The invention discloses a WVEFC fast coding method based on a flight ad hoc network and aims at a characteristic that the requirements of different data packets in the flight ad hoc network for the real-time performance and the safety are different. According to the method, linear independence of a Vandermonde matrix is utilized, an expanded Vandermonde step coding matrix is constructed by takingthe Vandermonde matrix as a basic structure, and coding transmission is carried out on data by using the matrix. According to the method, the robustness of the flight ad hoc network is improved, and afinal discrete event simulation experiment also verifies excellent rapid delivery performance of coding.
Owner:NANJING UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com