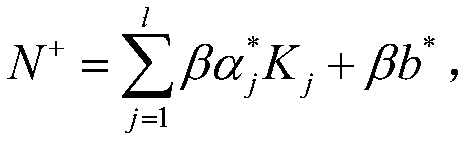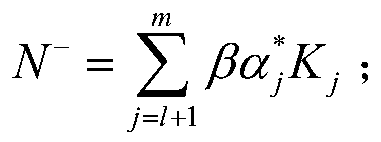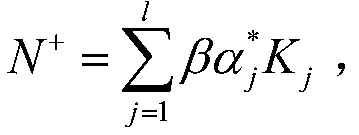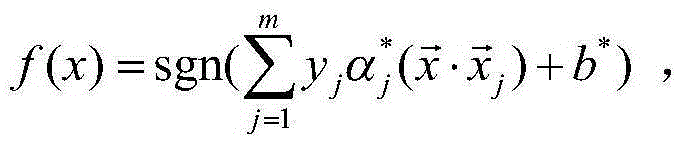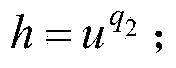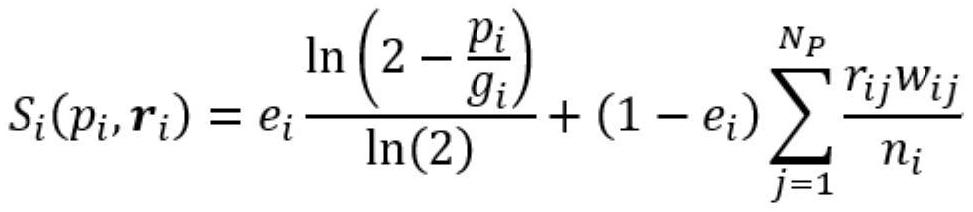Patents
Literature
46results about How to "Guaranteed privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
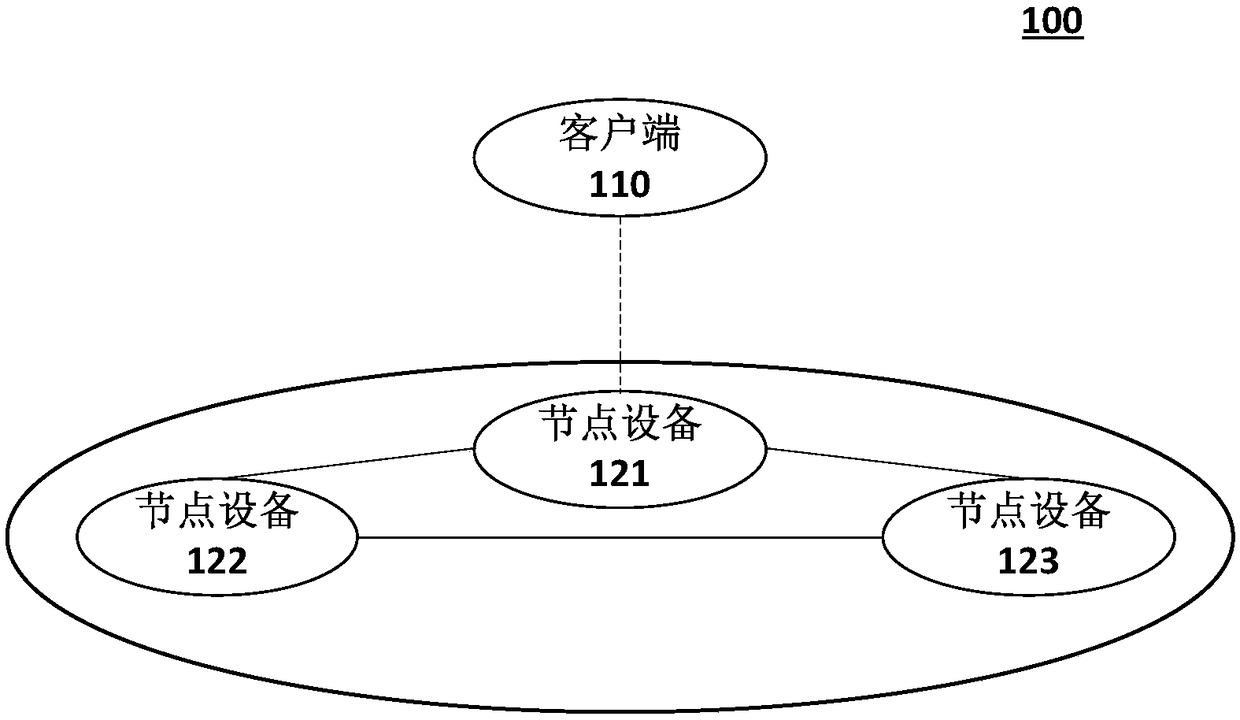
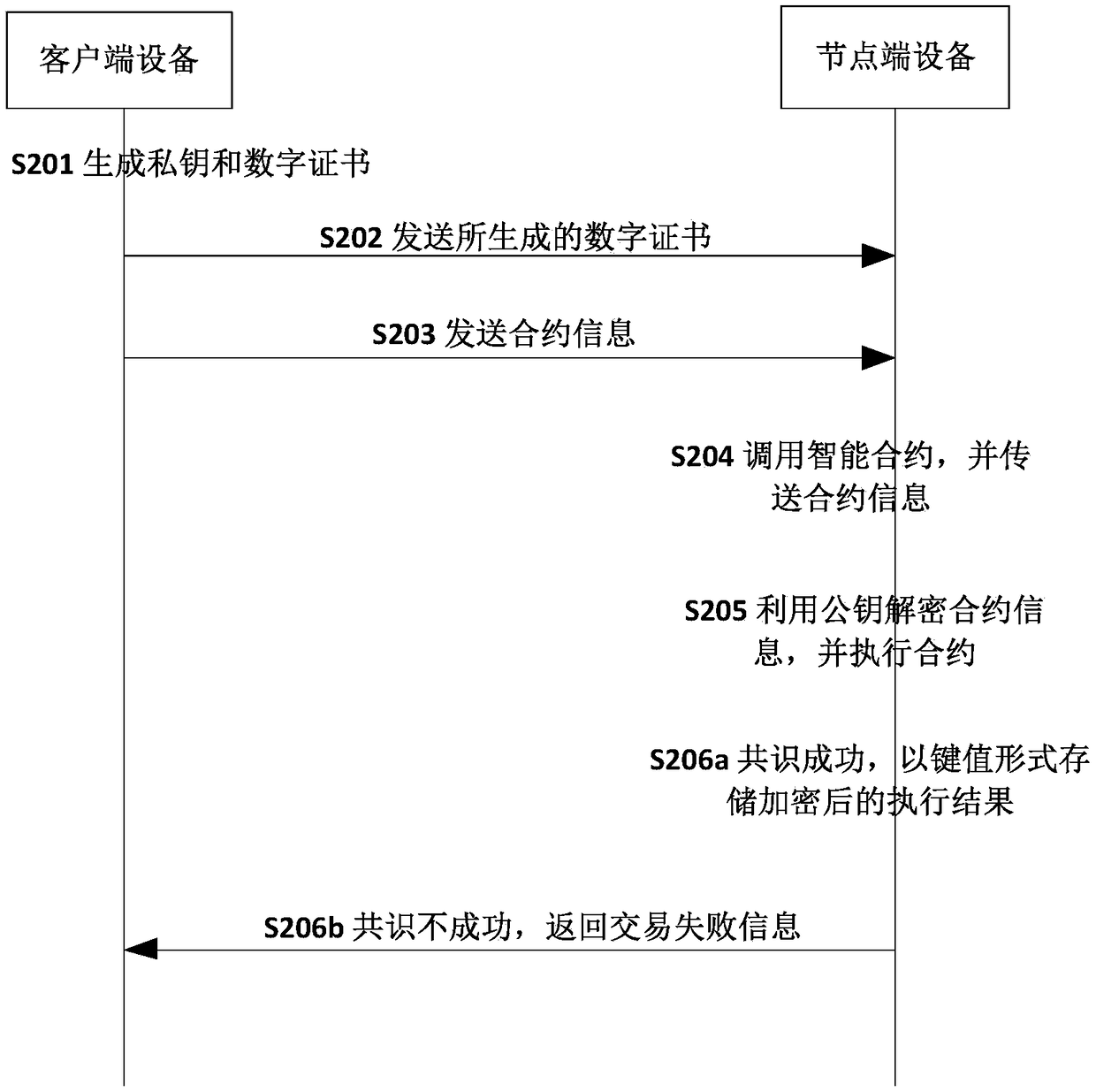
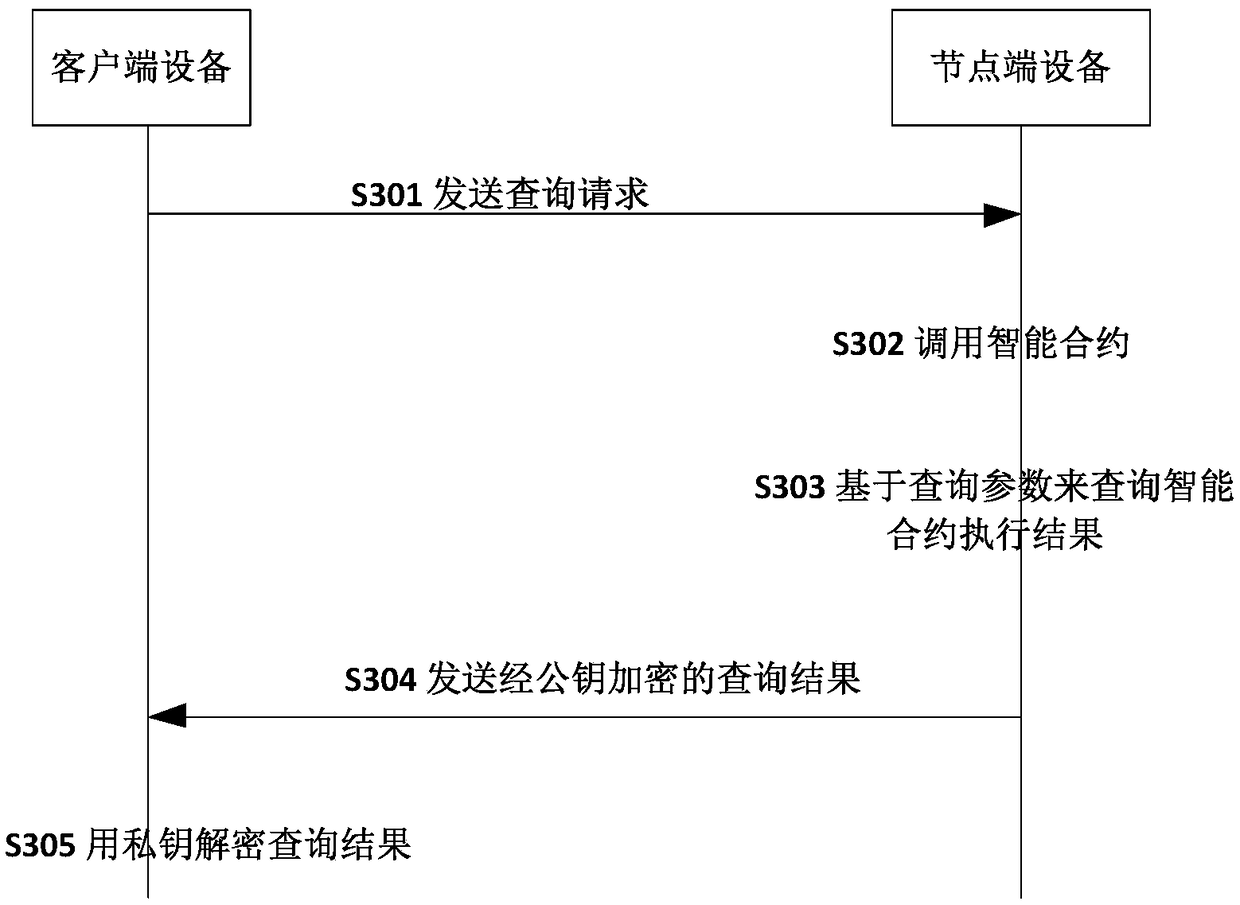
Secure transaction method and device based on a block chain
ActiveCN109493020AGuaranteed privacy protectionStrong encryptionFinancePayment protocolsPlaintextData privacy protection
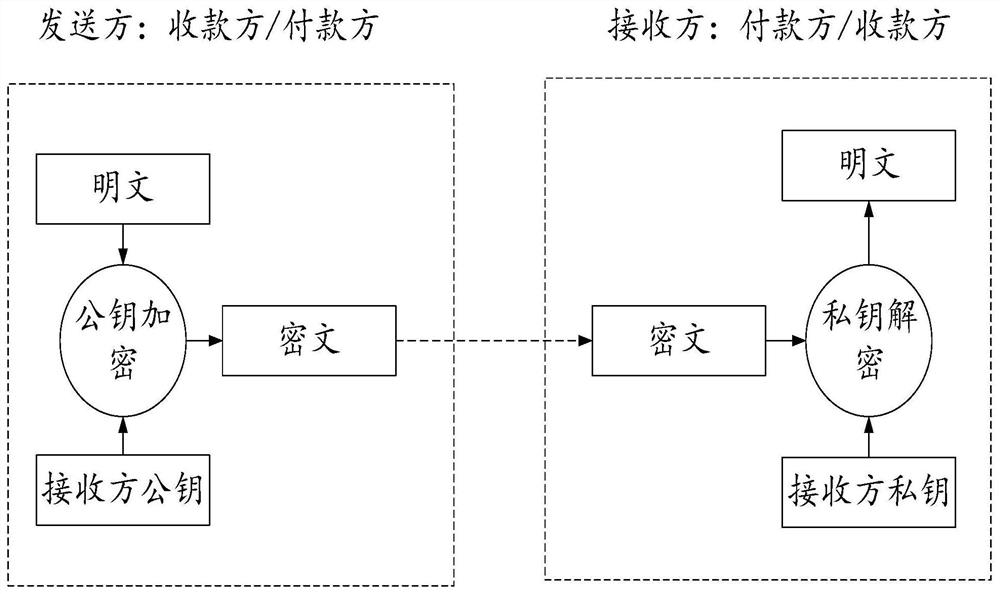
The invention discloses a secure transaction method and device based on a block chain. The node end equipment of the block chain calls the smart contract based on the contract information, the node end of the block chain decrypts the encrypted transaction parameters in the contract information by using the public key in the certificate, and executes the smart contract based on the transaction parameters; after the block chain node achieves consensus on the execution result in the block chain; wherein the node encrypts a key and a value based on the certificate public key and then writes the key and the value into the node database, the client inquires a transaction result through the blockchain node and needs to encrypt transaction parameters, the blockchain node needs to decrypt based onthe public key and then encrypt and return the transaction result, and the client decrypts based on the private key to obtain a plaintext result. Through the technical scheme of the invention, data security and data privacy protection for transaction and query can be formed.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
Decision tree classification service system and method supporting privacy protection
The invention belongs to the field of machine learning and privacy protection, and particularly relates to a decision tree classification service system and method supporting privacy protection. The service system comprises a model owner module, a client module, a cloud service module and a ciphertext operation module. The method comprises a preparation stage and a classification stage. The invention provides a decision tree classifier supporting privacy protection orienting cloud encryption data, and designs and implements a decision tree classification service system supporting privacy protection. Original data cannot be recovered through encrypted data uploaded by a user, privacy protection in the outsourcing calculation process is guaranteed, large-scale data are outsourced to a third-party server which is high in storage and calculation resource, local infrastructure investment and management of the user are reduced, and then more economic benefits are generated.
Owner:NORTHEASTERN UNIV
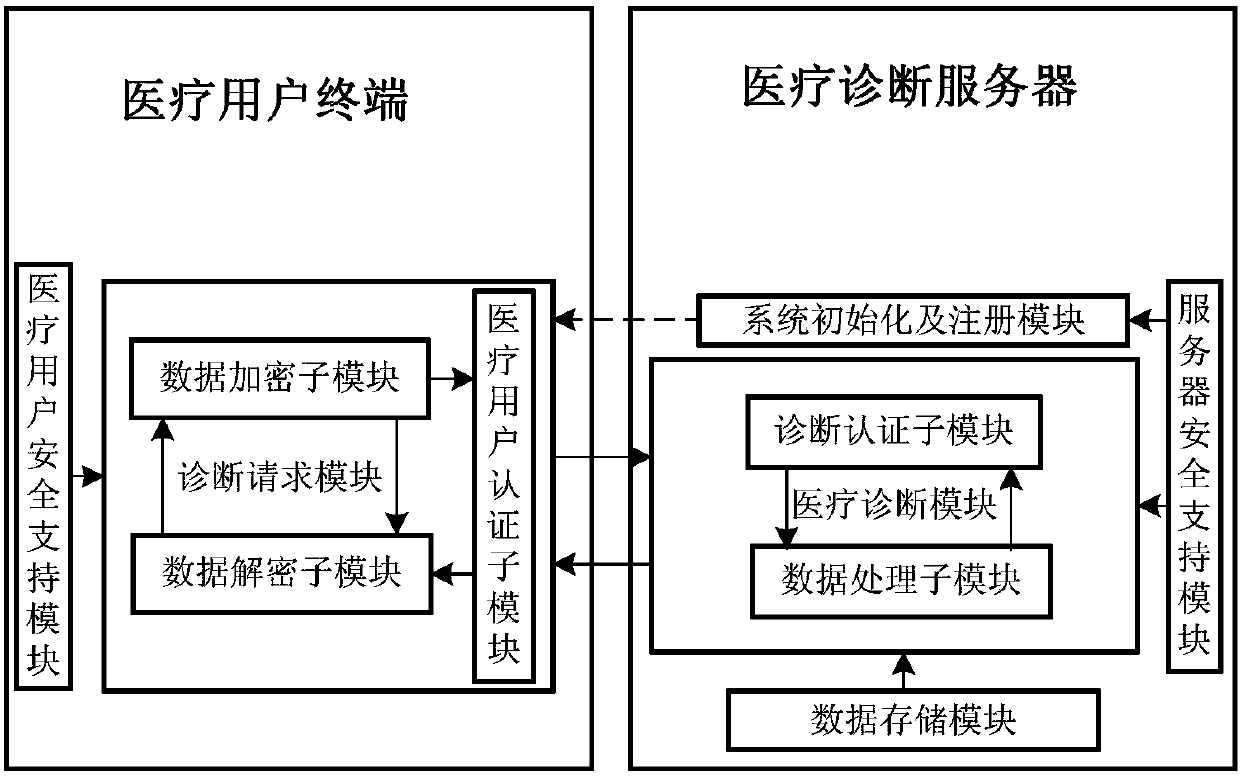
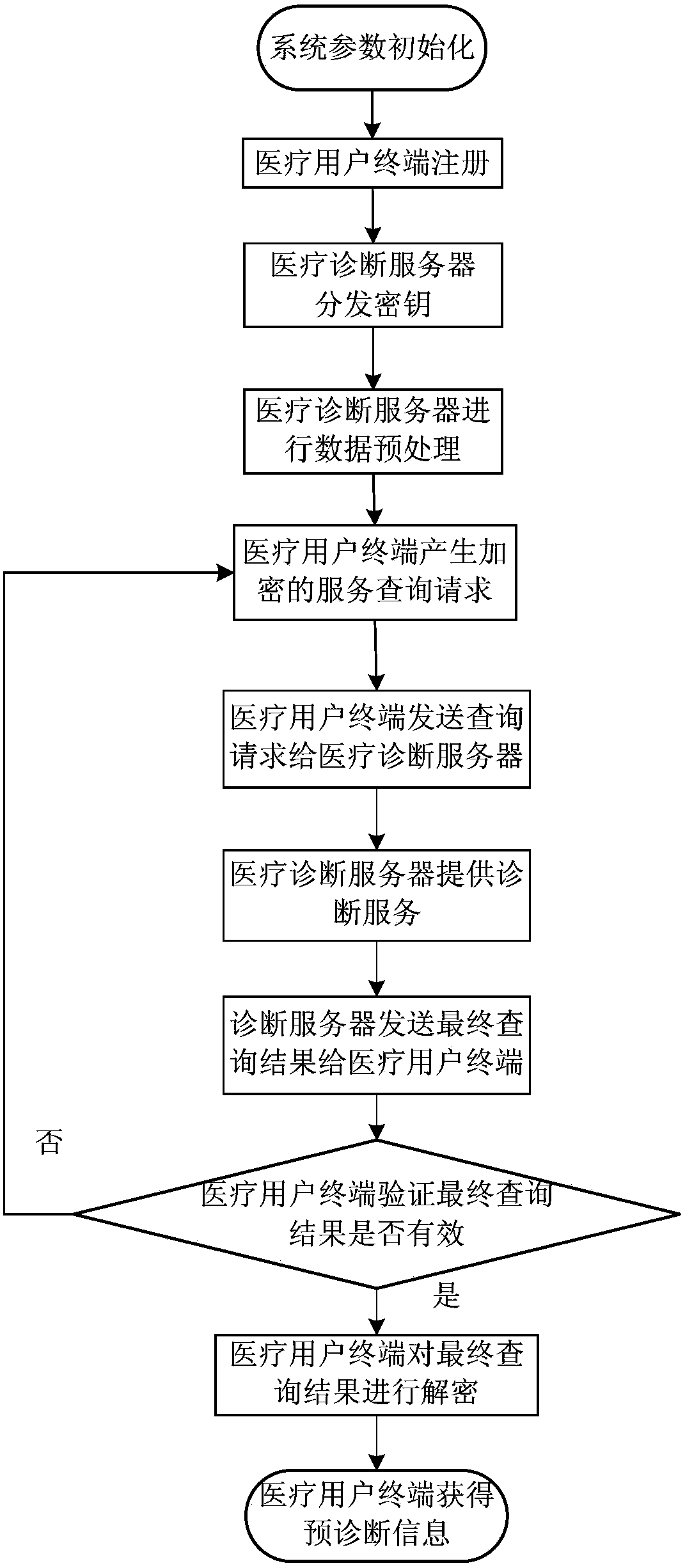
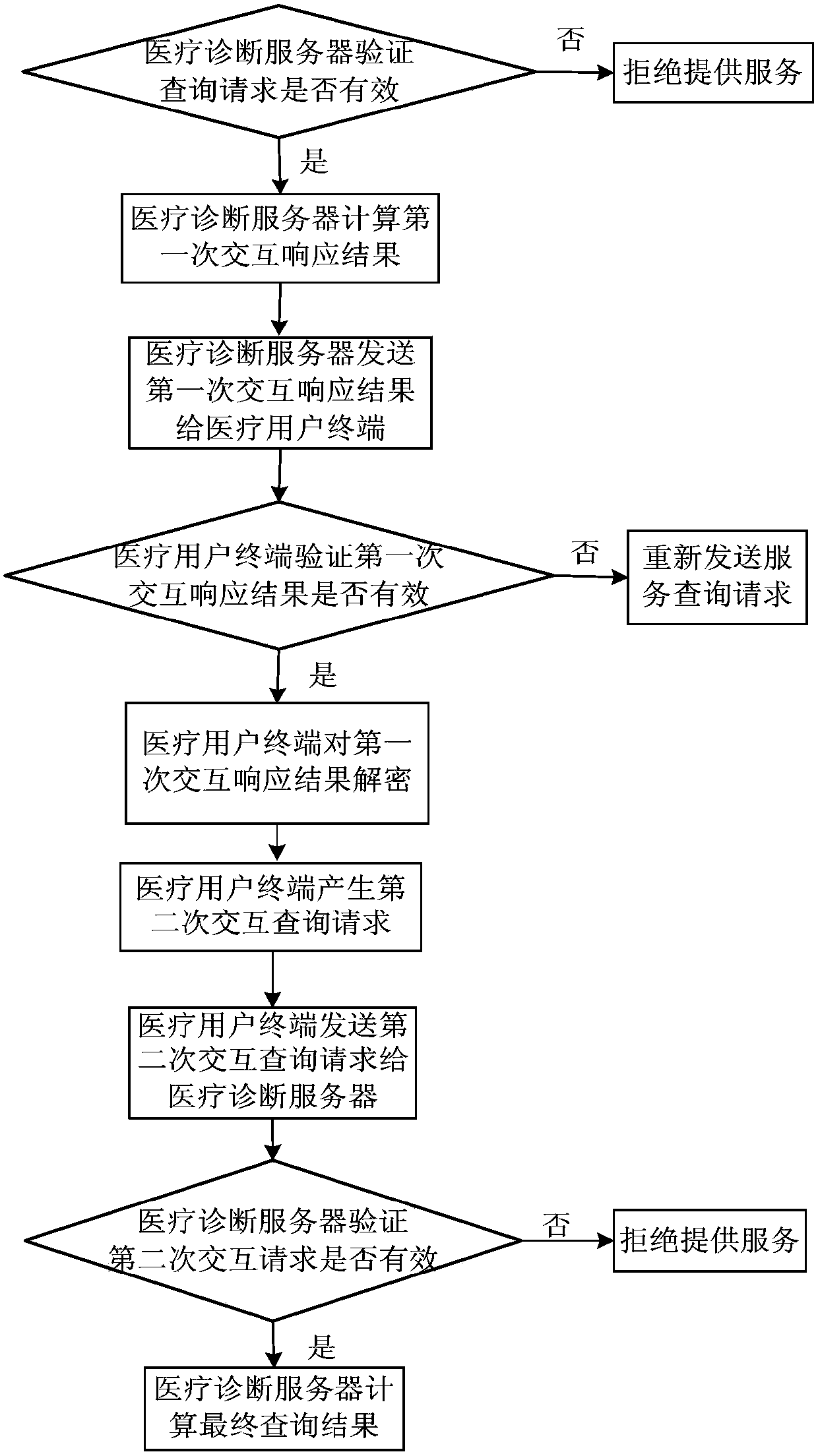
Two-way privacy protective system and method for inquiring medical diagnostic service
ActiveCN105577368ARealize privacy protectionGuaranteed privacy protectionKey distribution for secure communicationData processing applicationsDiseaseService provision
The invention discloses a two-way privacy protective system and method for inquiring a medical diagnostic service, used for mainly solving the problem that privacy protection of inquiry information of medical users and data resources of service providers are not related in the prior art. The system comprises a medical diagnostic server and a medical user terminal; the medical diagnostic server completes system initialization, provides login and distributes a secrete key to the medical user terminal, stores data of a nonlinear SVM model built by using the existing medical database, provides a privacy protective medical diagnostic service for the medical user terminal, and sends an inquiry response result to the user terminal; and the medical user terminal sends a service inquiry request to the medical diagnostic server and performs decryption and polynomial aggregation operation of the inquiry response result returned by the medical diagnostic server, such that a pre-diagnosis result is obtained. According to the invention, privacy protection of the inquiry information of the medical users and the data of the nonlinear SVM model can be realized; and the system and the method can be used for providing an online disease prediction service for the medical users.
Owner:XIDIAN UNIV
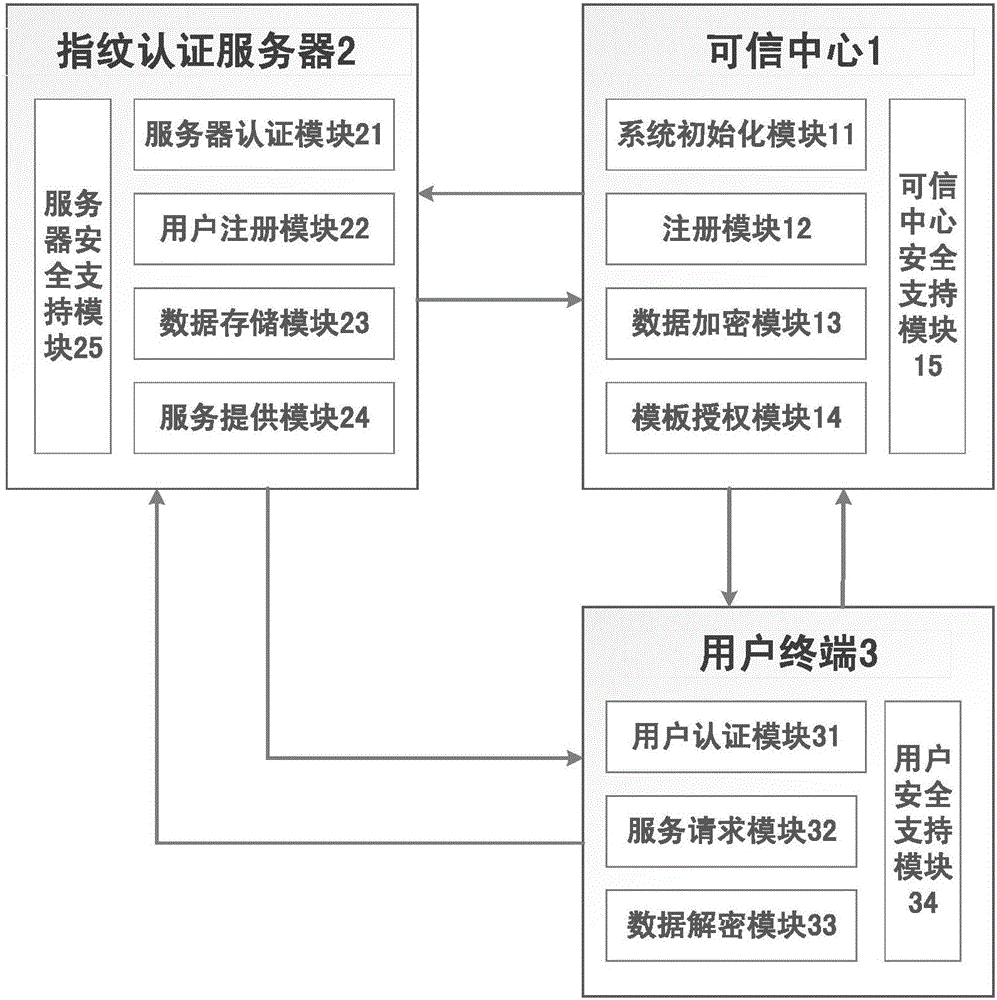
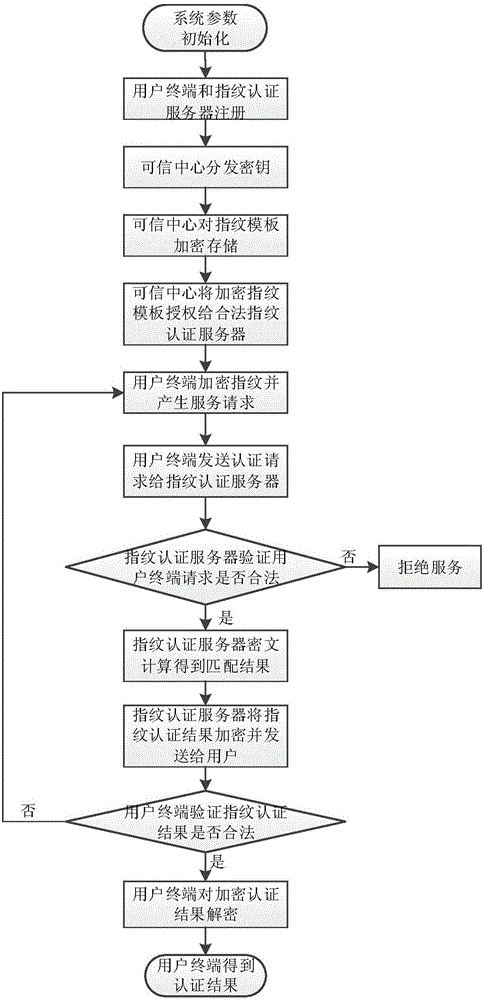
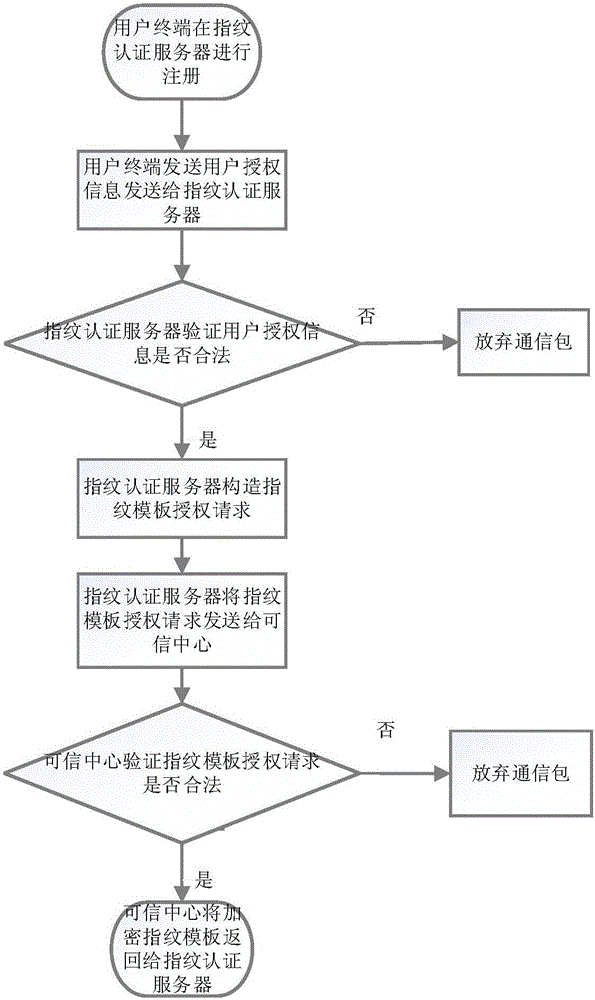
On-line fingerprint authentication system and method based on bidirectional privacy protection
ActiveCN106411533ARealize privacy protectionGuaranteed privacy protectionUser identity/authority verificationInternet Authentication ServiceCiphertext
The invention discloses an on-line fingerprint authentication system and method based on bidirectional privacy protection. With the system and method, a problem that bidirectional privacy protection of fingerprint data of the user and fingerprint template data is not involved in the prior art can be solved. The system is composed of a trusted center (1), a fingerprint authentication server (2), and a user terminal (3). The trusted center (1) completes system initialization, provides registration and secret key distribution for a user terminal and the fingerprint authentication server, collects a user fingerprint as an authentication template, and gives authorization of the template to a legal fingerprint authentication server in a ciphertext mode; the fingerprint authentication server (2) provides an on-line encryption fingerprint authentication service with privacy protection and returns an authentication result to the user terminal; and the user terminal (3) sends an encrypted fingerprint authentication request to the fingerprint authentication server and decrypts the reply of the fingerprint authentication server to obtain an authentication result. According to the invention, bidirectional privacy protection of the user fingerprint data and the fingerprint template data is realized and a secure on-line fingerprint authentication service is provided.
Owner:陕西嵩远明瑞信息技术有限公司
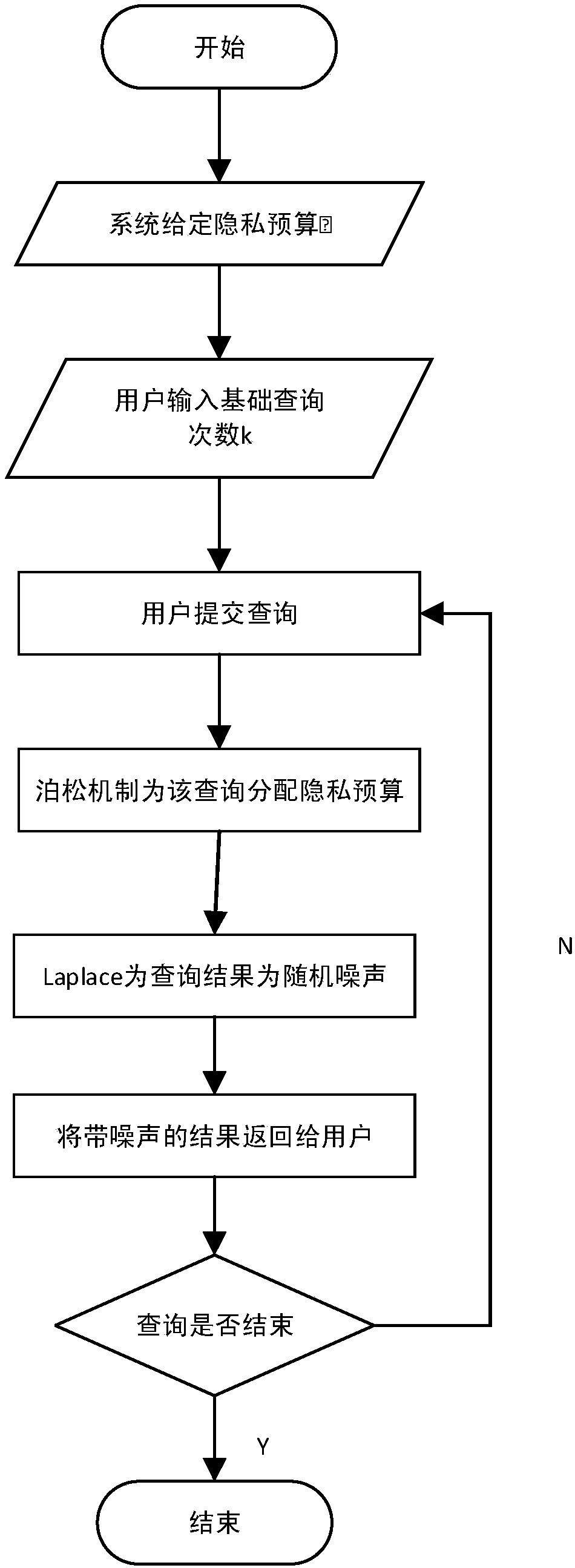
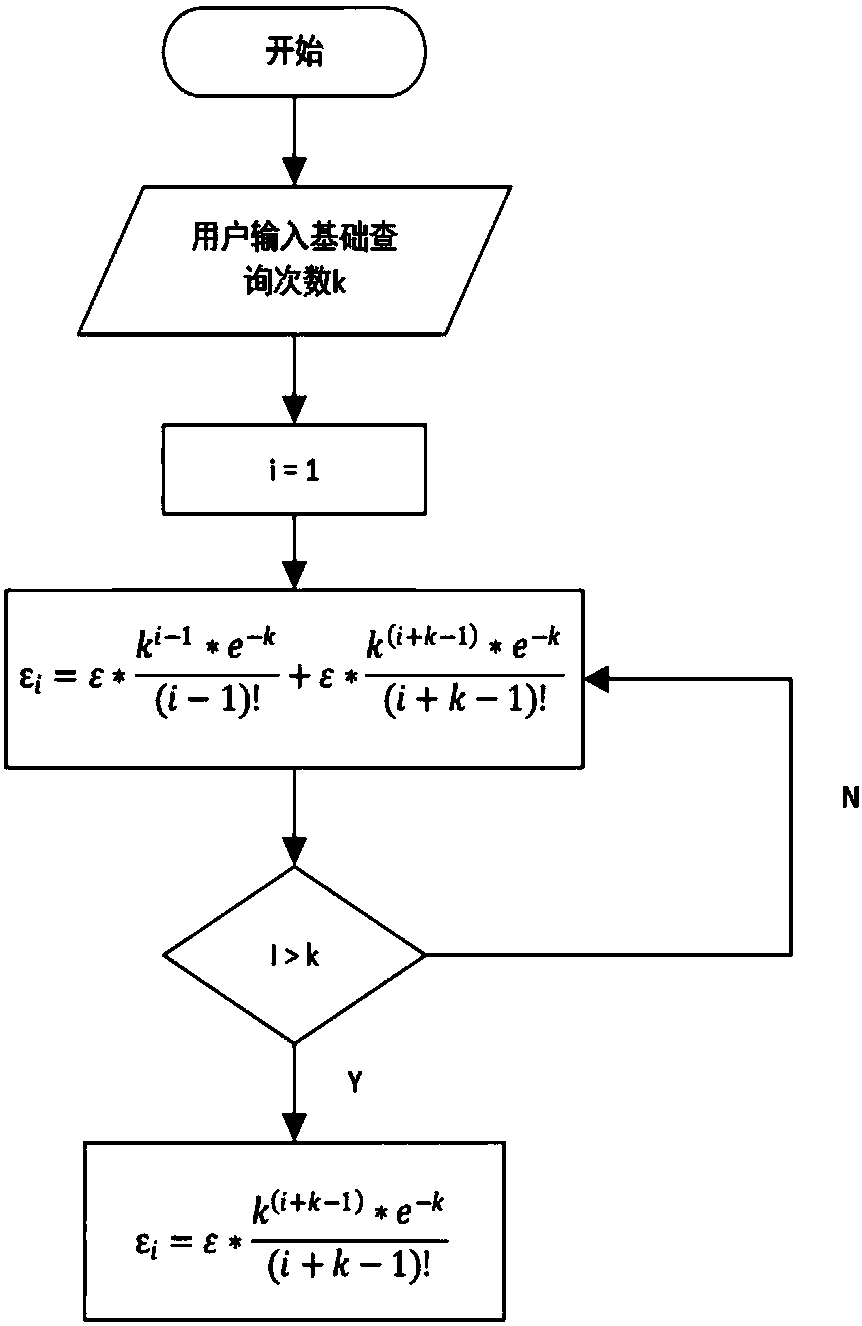
Privacy budget allocating and data publishing method and privacy budget allocating and data publishing system for protecting data query privacy
ActiveCN108537055APrivacy protectionGuaranteed availabilityDigital data protectionSpecial data processing applicationsAttackPrivacy protection
The invention discloses a privacy budget allocating and data publishing method for protecting the data query privacy. The privacy budget allocating and data publishing method includes steps of firstly, setting privacy budget parameters, to be more specific, giving privacy budgets of data by data administrators according to importance degrees of the data, denoting the privacy budgets of the data asepsilon, setting basic query frequencies of the data and denoting the basic query frequencies of the data as k; secondly, computing privacy budgets of each query; thirdly, acquiring the sensitivity delta f of the query according to the query f submitted by users, combining the sensitivity delta f with the privacy budget epsilon allocated to the query, and computing required-to-be-added noise forquery results by the aid of difference privacy protection algorithms so as to obtain query results with the noise; fourthly, returning the query results with the noise according to the query submittedby the users so as to protect the privacy of the data. The privacy budget allocating and data publishing method has the advantages that the privacy can be protected in data publishing procedures, accomplice attack can be resisted, the precision of first k times of query can be guaranteed, and the problem of excessively low data availability due to the fact that existing privacy budgets are infinitely allocated can be solved by the aid of the privacy budget allocating and data publishing method.
Owner:NANJING UNIV OF POSTS & TELECOMM
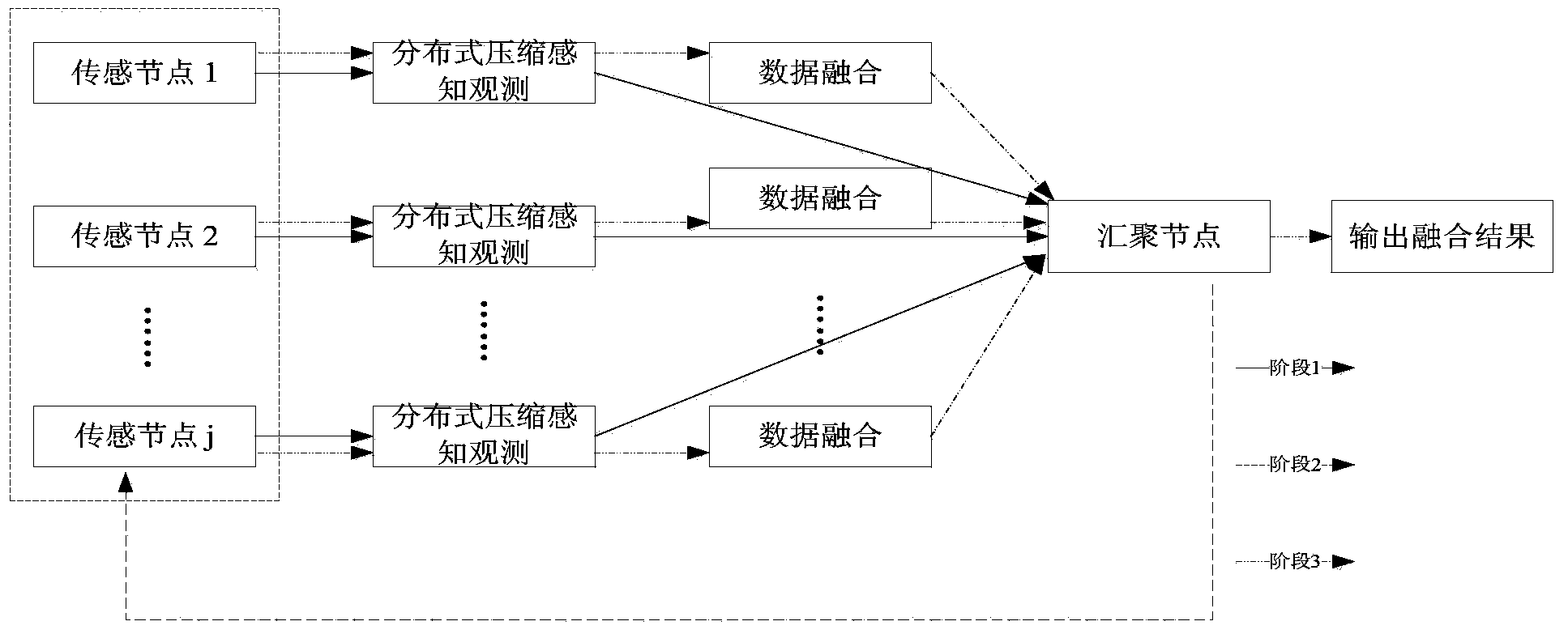
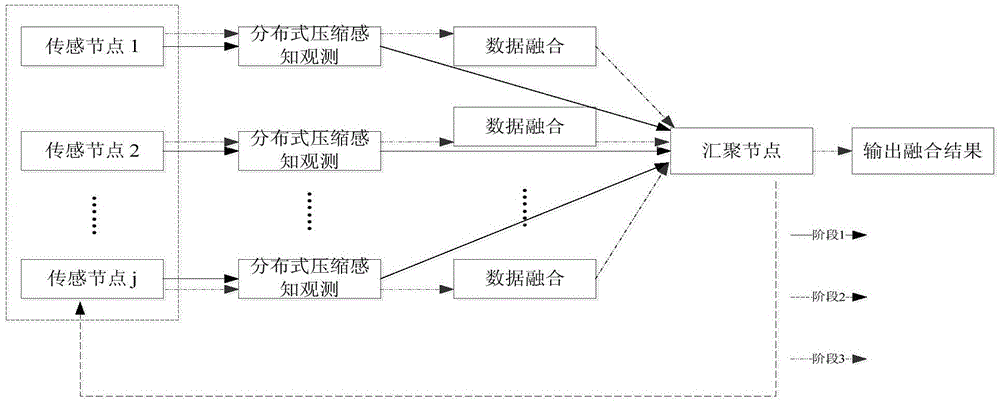
Distributed compressed sensing data fusion method having privacy protection effect
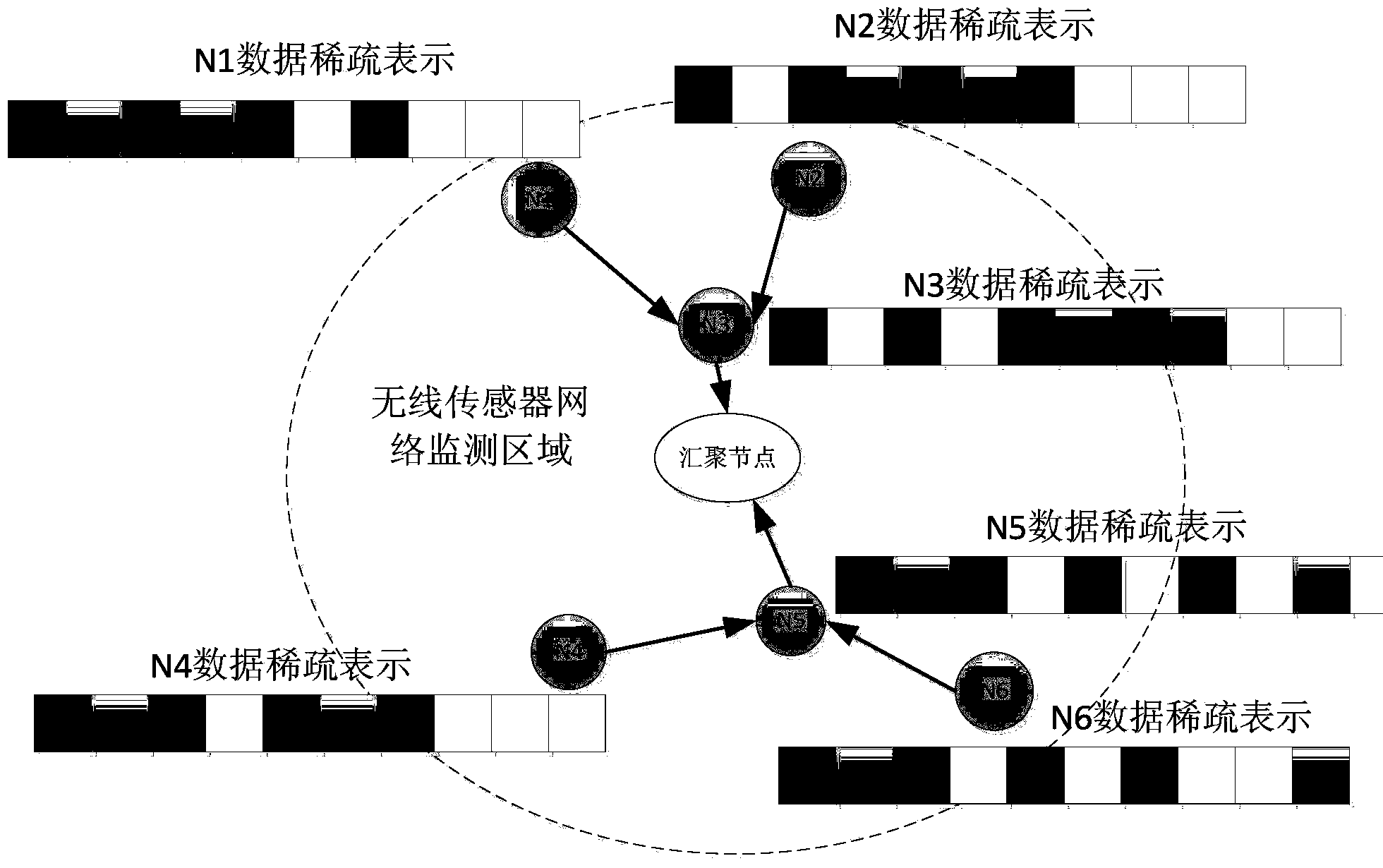
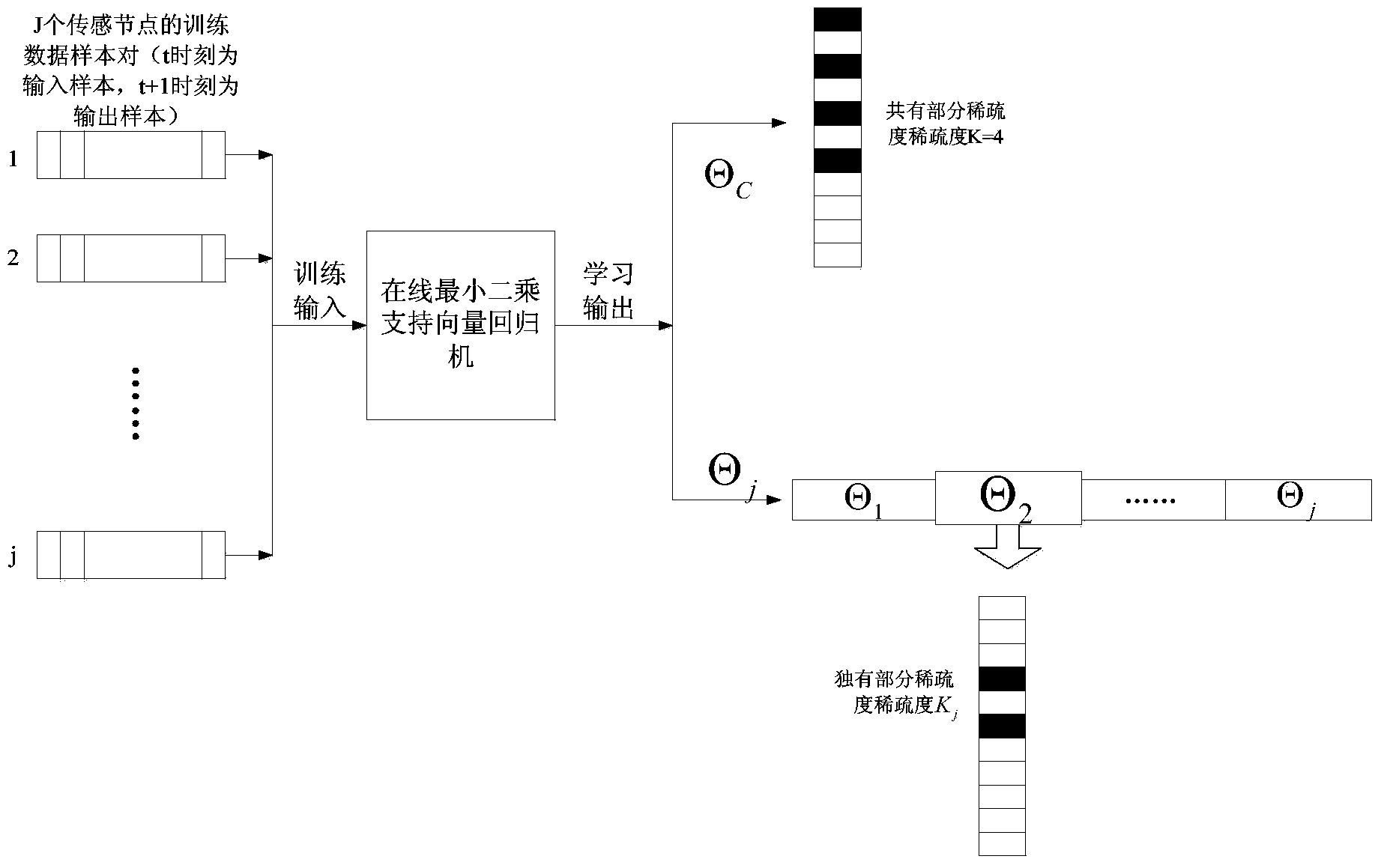
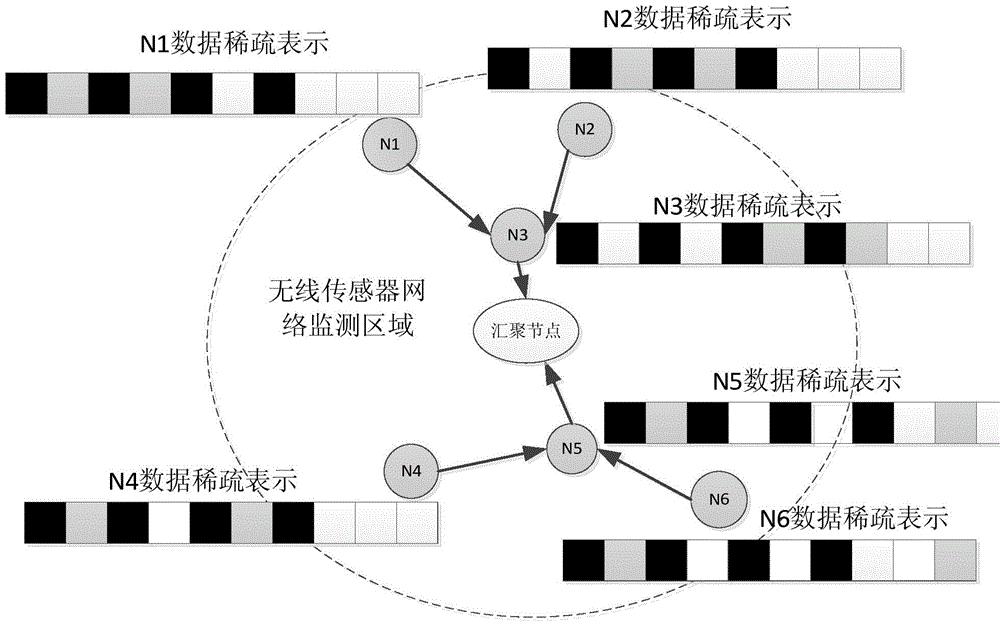
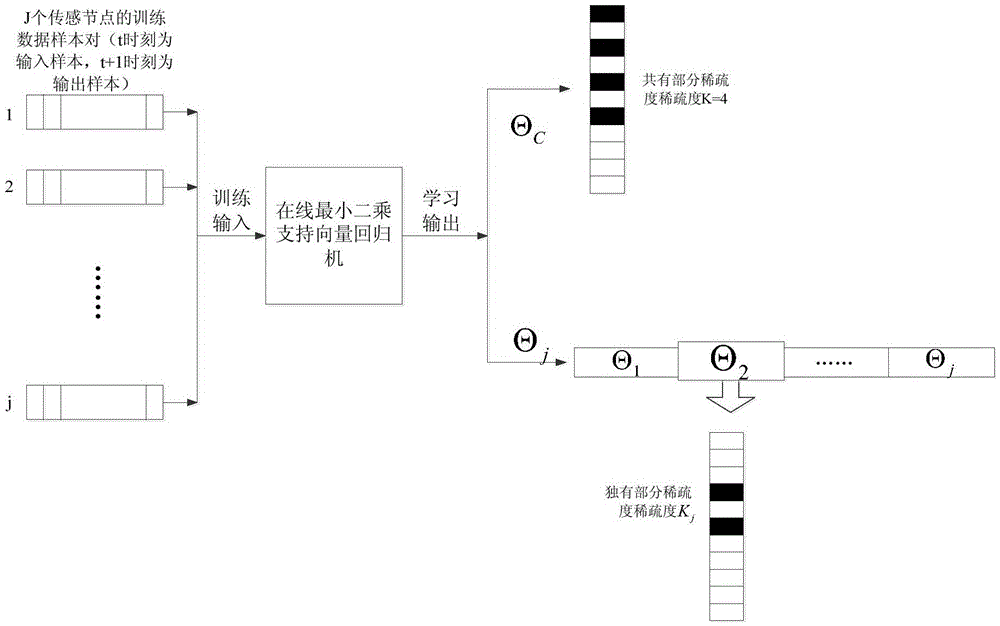
ActiveCN103476040AGuaranteed privacy protection effectReduce additional communication overheadNetwork planningHigh level techniquesCompressed sensingData processing
The invention provides a distributed compressed sensing data fusion method having the privacy protection effect and relates to the field of wireless networks. A privacy protection fusion method based on data sparsity position information hiding is designed in a distributed scene, and by the adoption of data sparsity support set feature learning, real data sparsity position hiding and distributed compressed sensing fusion observation, the additional communication cost brought by a traditional privacy protection fusion method is avoided, and data processing of sensor networks is facilitate. The data privacy protection fusion method has the obvious data privacy protection effect on the sensor networks, meanwhile can effectively reduce network energy consumption and improve the algorithm efficiency and the data processing performance by utilizing a distributed compressed sensing fusion strategy, and facilitates user management, network application and scale expanding.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
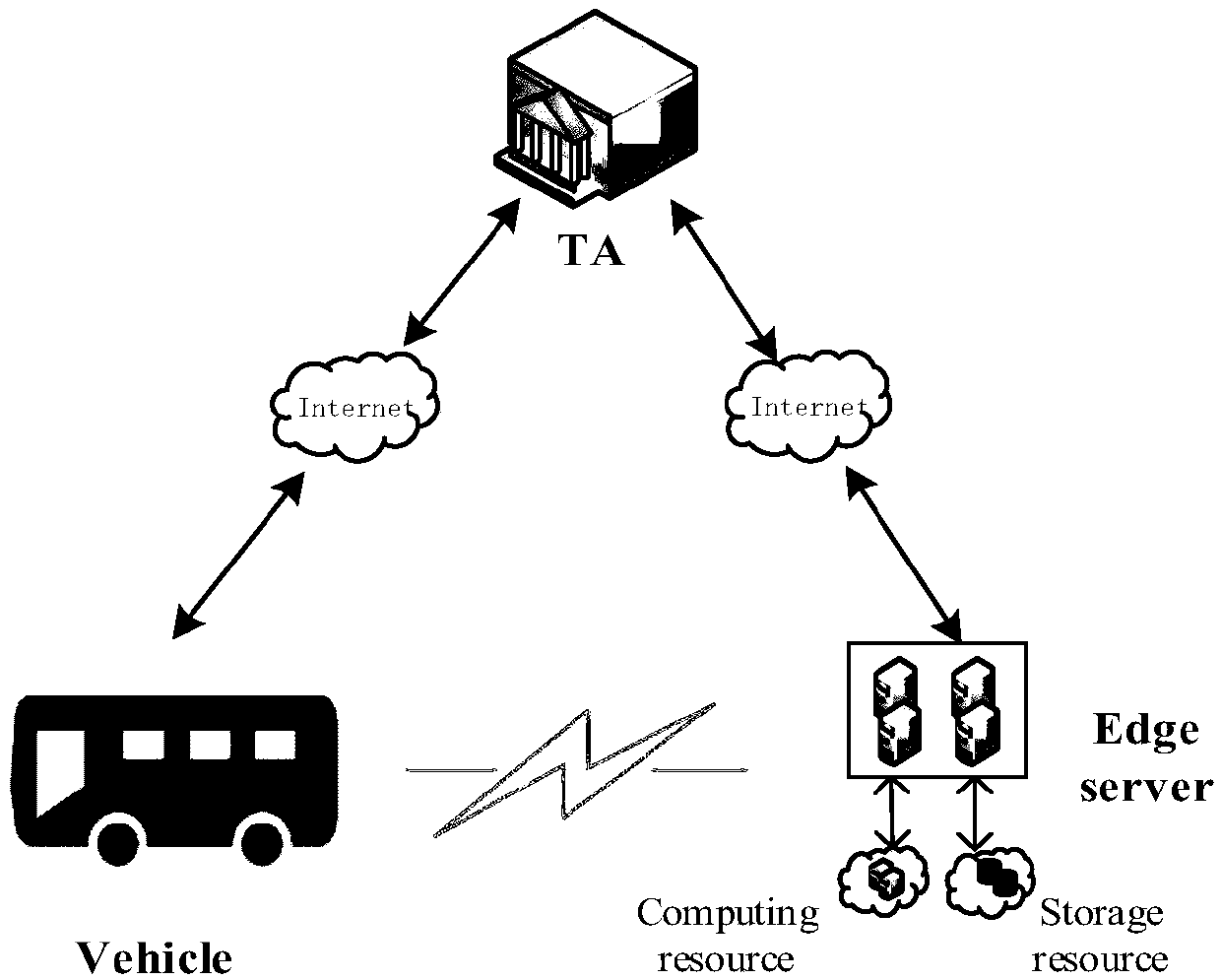
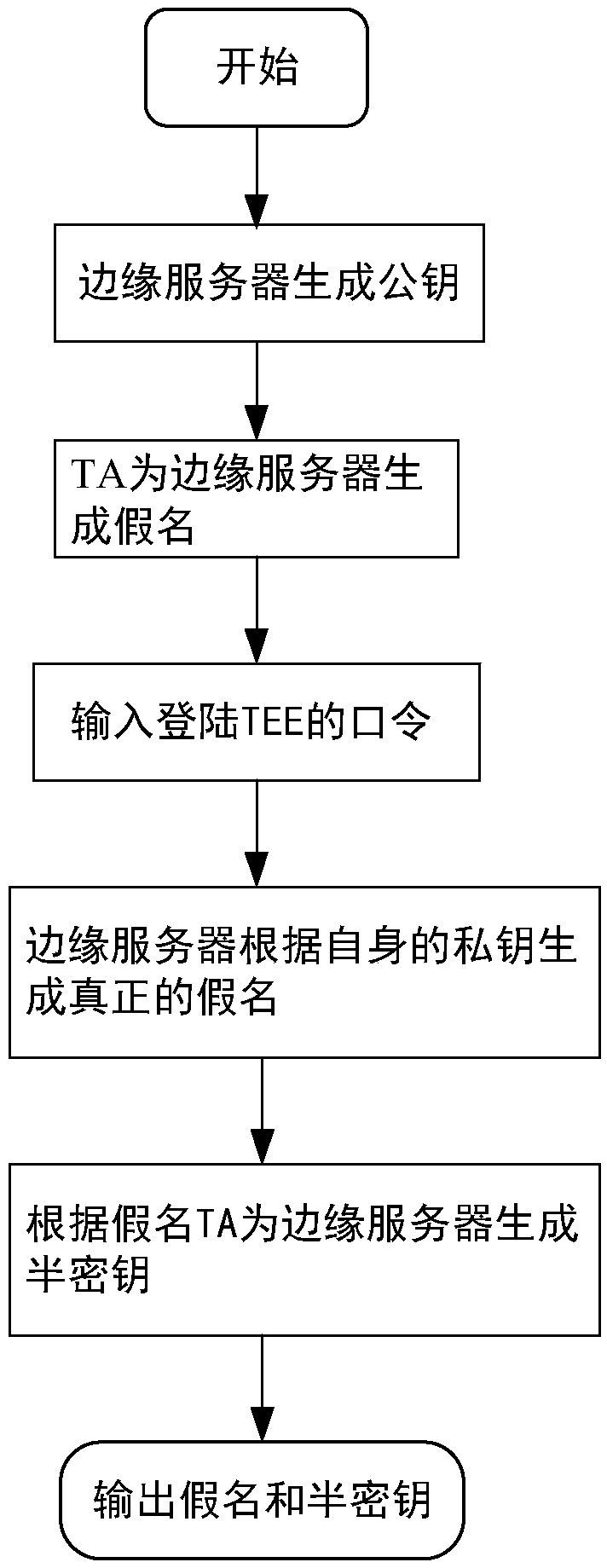
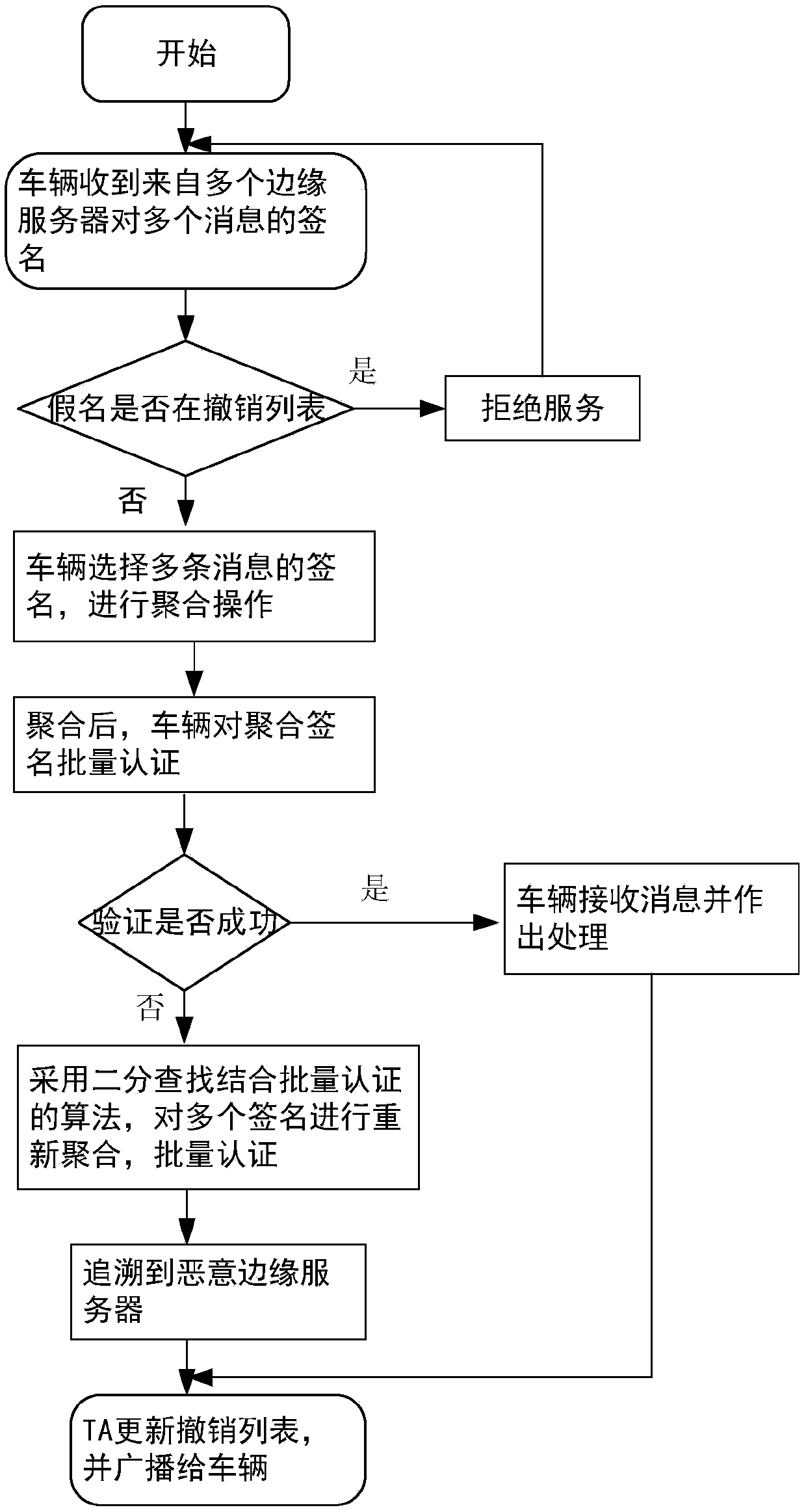
A message authentication method between an unmanned vehicle and a multi-mobile edge computing server
ActiveCN109005538ARealize privacy protectionReduce resource consumptionKey distribution for secure communicationUser identity/authority verificationEdge serverEdge computing
A message authentication method between an unmanned vehicle and a multi-mobile edge computing server is disclosed. The steps are system parameter generation, pseudonym generation for a mobile edge computing server and semi-key extraction, and authentication of a message between the mobile edge computing server and the vehicle. The step comprises: the vehicle migrates a large number of calculationor stored tasks to the mobile edge computing server, the mobile edge computing server performs ring signature on the message, and the vehicle authenticates the message in batch. The invention introduces the edge computing into the traditional vehicle-mounted ad hoc network, and the vehicle can migrate the computing or storage tasks to the edge server to execute instead of sending them to the cloudend for centralized processing. In the signature part of the invention, ring signature is combined with pseudonym, and the application of ring signature effectively protects the privacy of mobile edge computing server and traces the malicious mobile edge computing server through pseudonym.
Owner:ANHUI UNIVERSITY
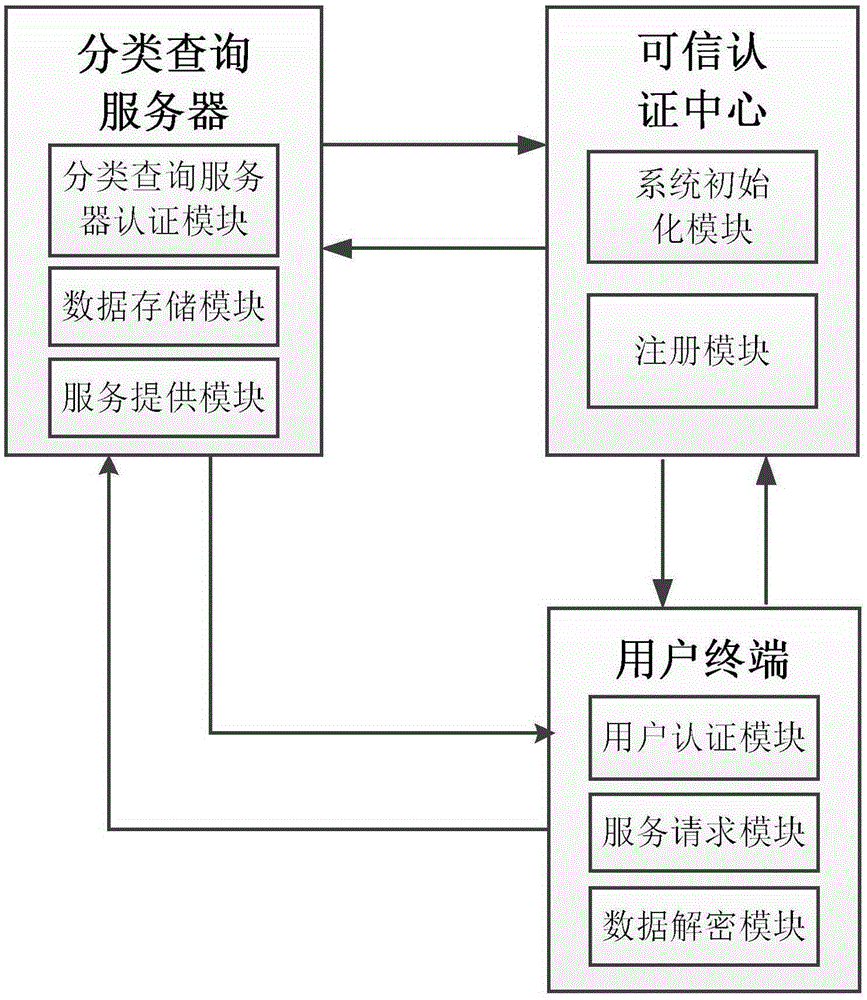
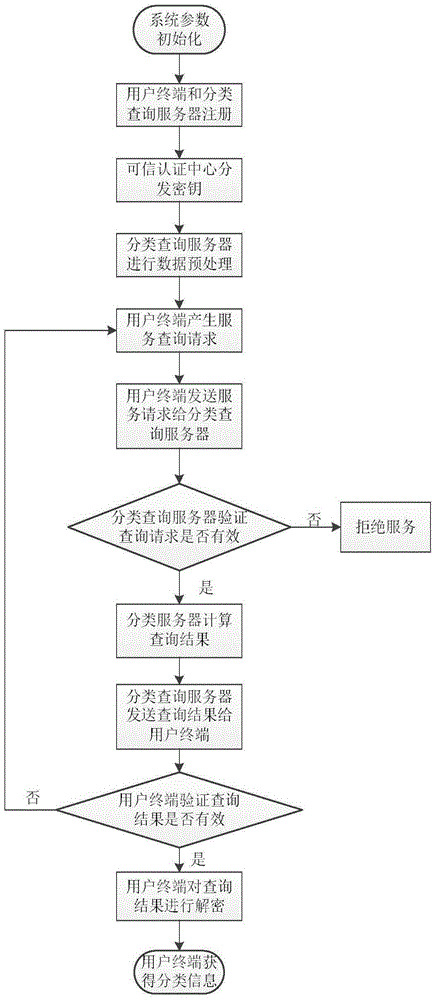
Linear SVM classification service query system and method with two-way privacy protection
ActiveCN105354233ARealize privacy protectionGuaranteed privacy protectionWeb data indexingDigital data protectionPrivacy protectionKey distribution
The present invention discloses a linear SVM (support vector machine) classification service query system and method with two-way privacy protection, for mainly solving the privacy protection problems of user query information and SVM model data which are not involved in the prior art. The system comprises a trusted authentication center, a classification query server and a user terminal. The trusted authentication center completes system initialization to provide registration and key distribution for the user terminal and the classification query server. The classification query server stores linear SVM classifier model data that have been establised, provides a classification query service of the privacy protection for the user terminal, and sends a query result to the user terminal. The user terminal sends a query service request to the classification query server, performs decryption and polynomial aggregation operation to the query result returned by the classification query server, and obtains final classification information. According to the system and the method provided by the present invention, the privacy protection of the user query information and the linear SVM model data is implemented. The system and the method can be used to provide a user with an online DNA query and a disease prediction service.
Owner:XIDIAN UNIV
Privacy protection method and system of data release
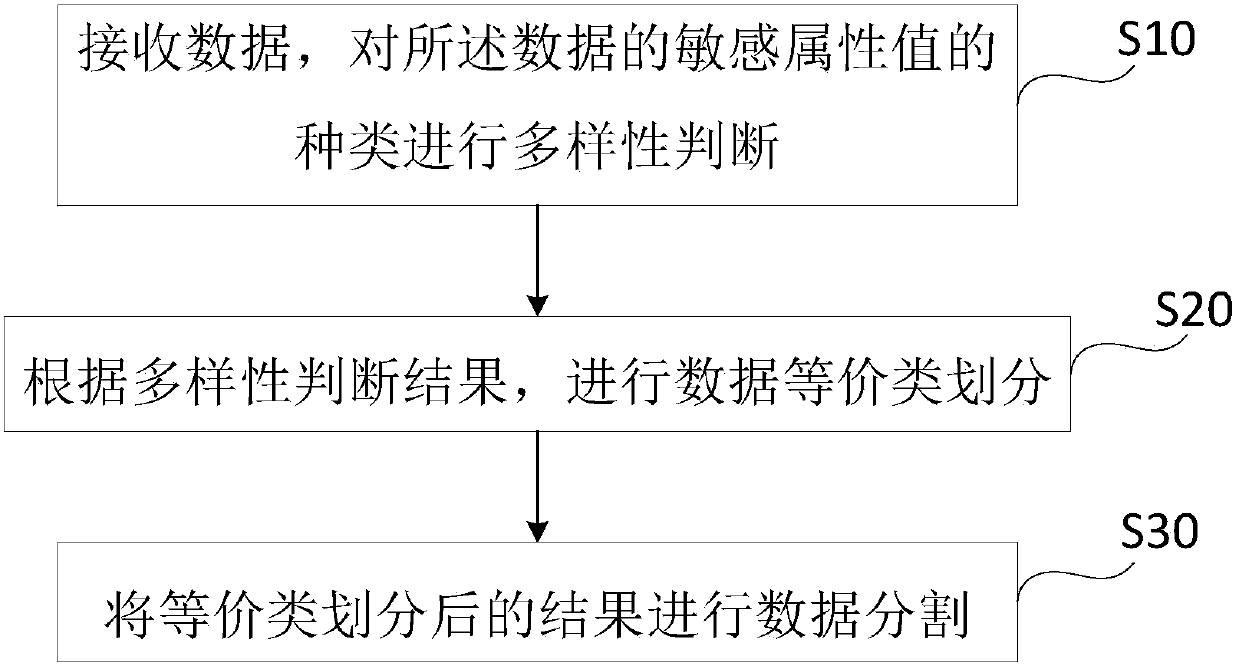
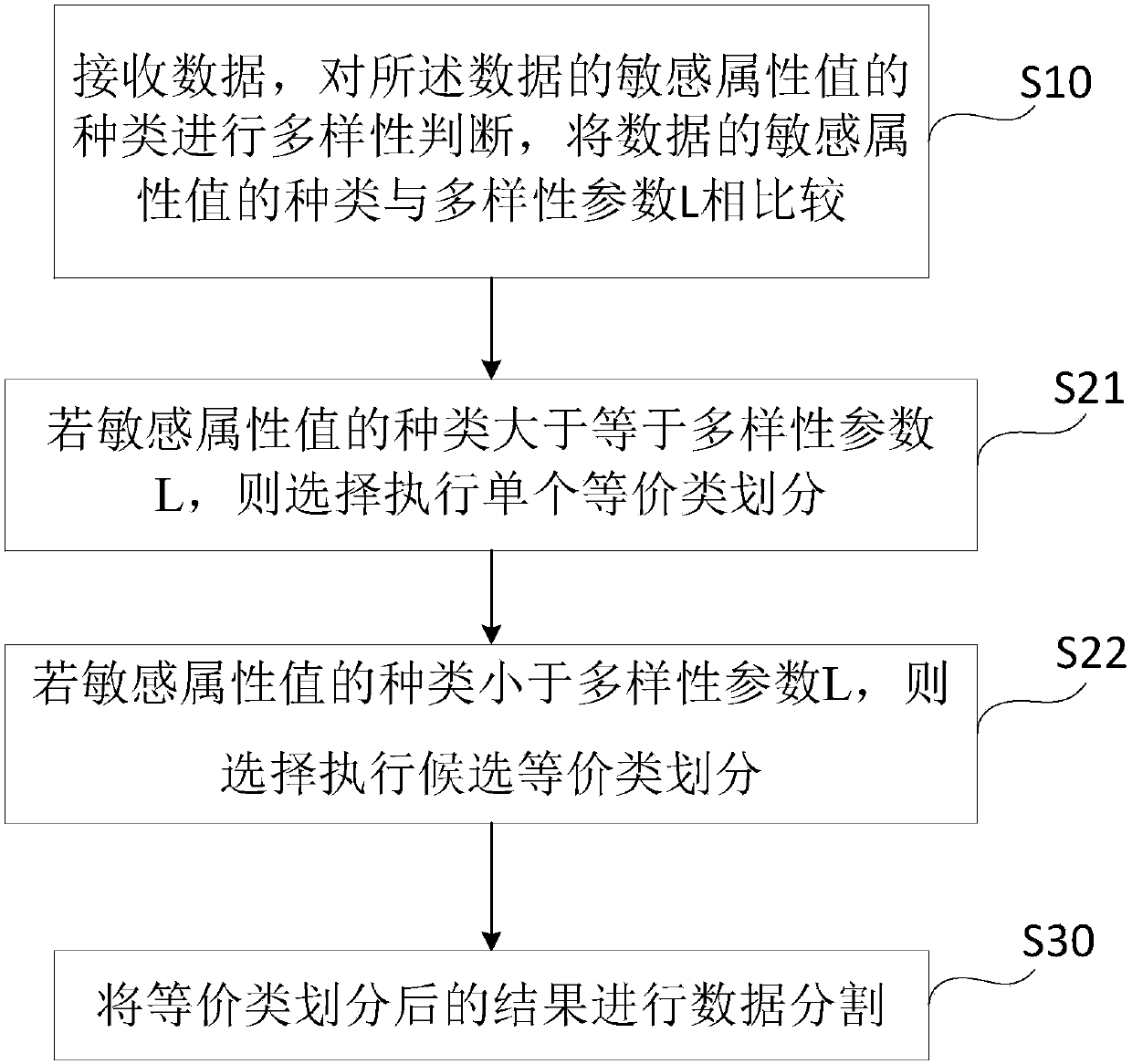
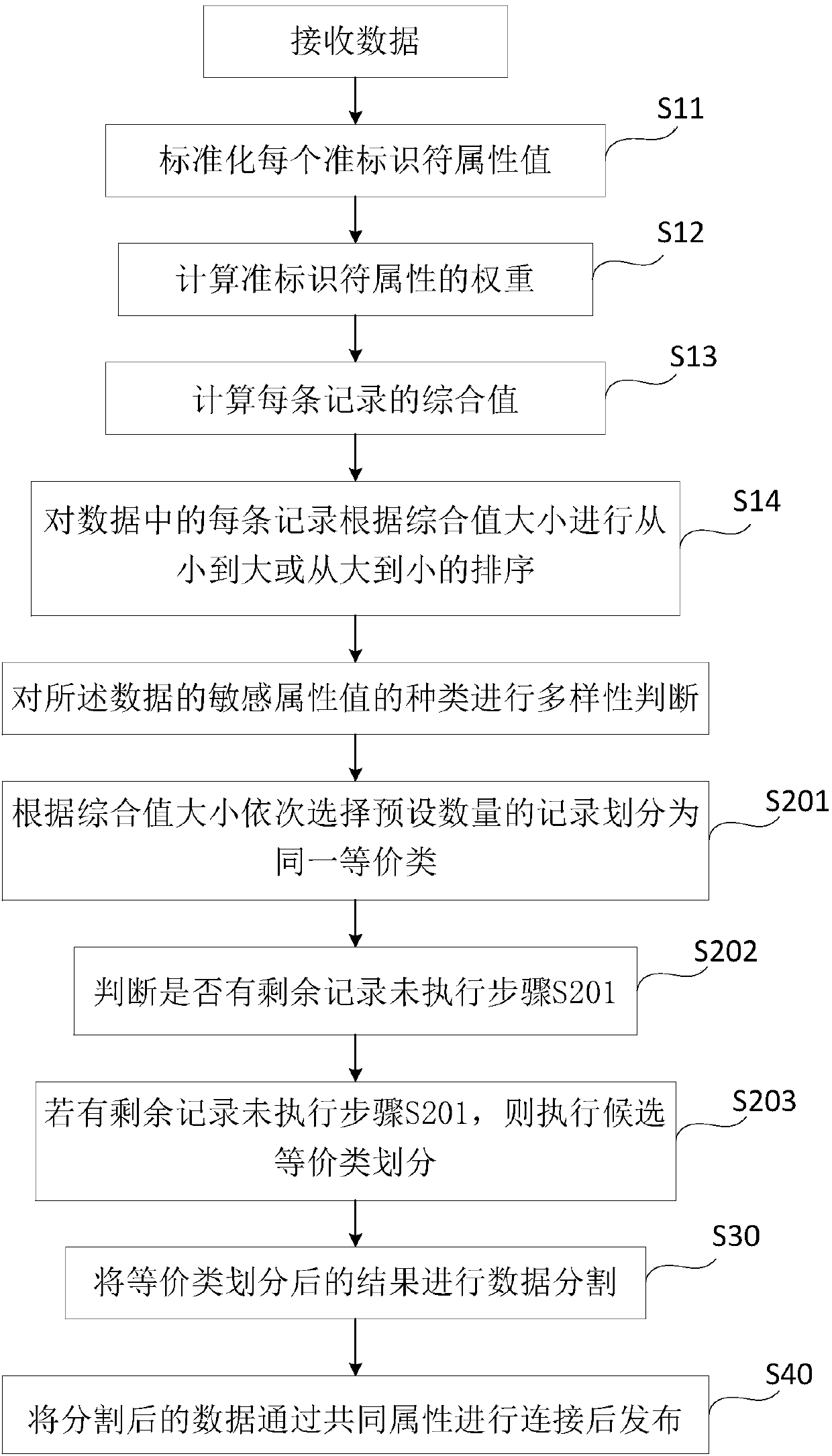
InactiveCN107832631AImprove usabilityReduce contactDigital data protectionPrivacy protectionEquivalence partitioning
The invention discloses a privacy protection method and system of data release. The privacy protection method includes the following steps: S10, receiving data, and performing diversity determinationon the types of sensitive attribute values of the data, and ensuring that later equivalence partitioning has the same diversity; S20: performing data equivalence partitioning according to the diversity determination result; and S30: and performing data partitioning on the equivalence partitioning result. The privacy protection method and system are easy to implement; the processed data has high privacy protection degree, low information loss degree, good availability, and high practicability, and can resist various privacy prying attacks.
Owner:台州市吉吉知识产权运营有限公司
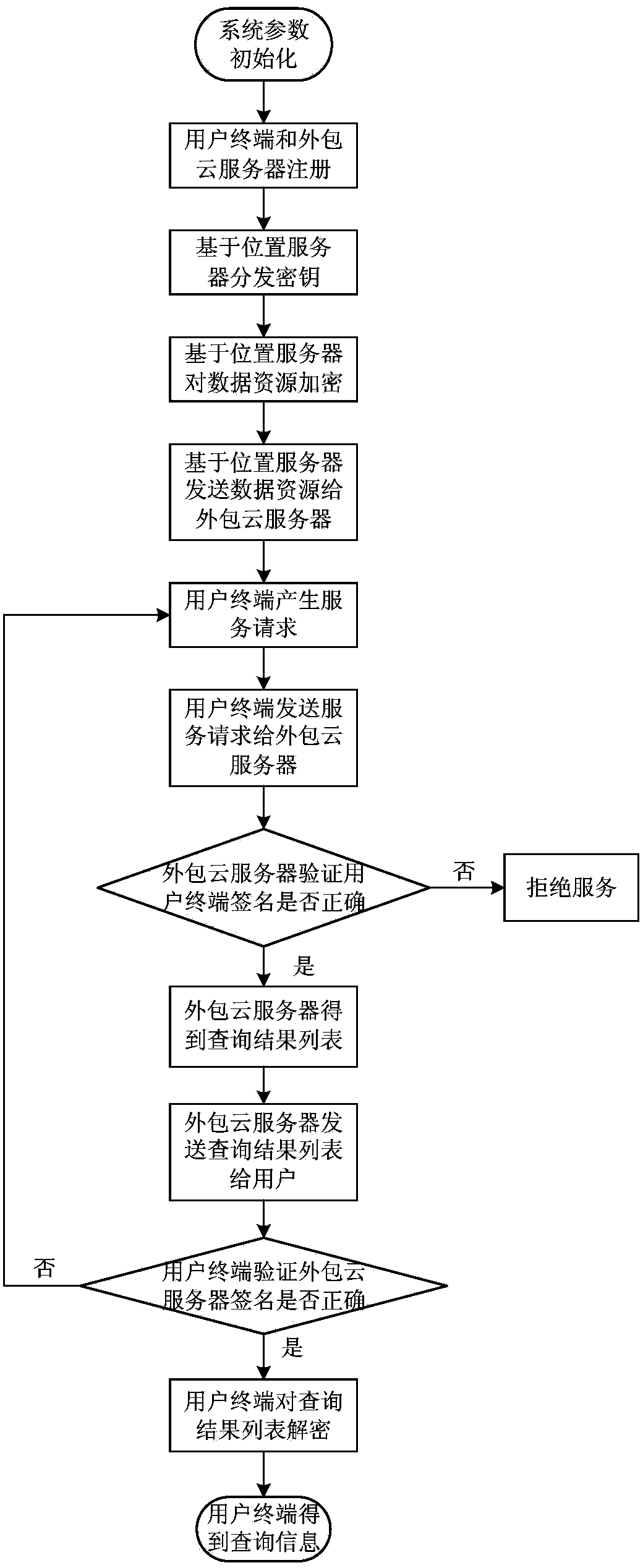
System and method for location based service-orientated user privacy protection
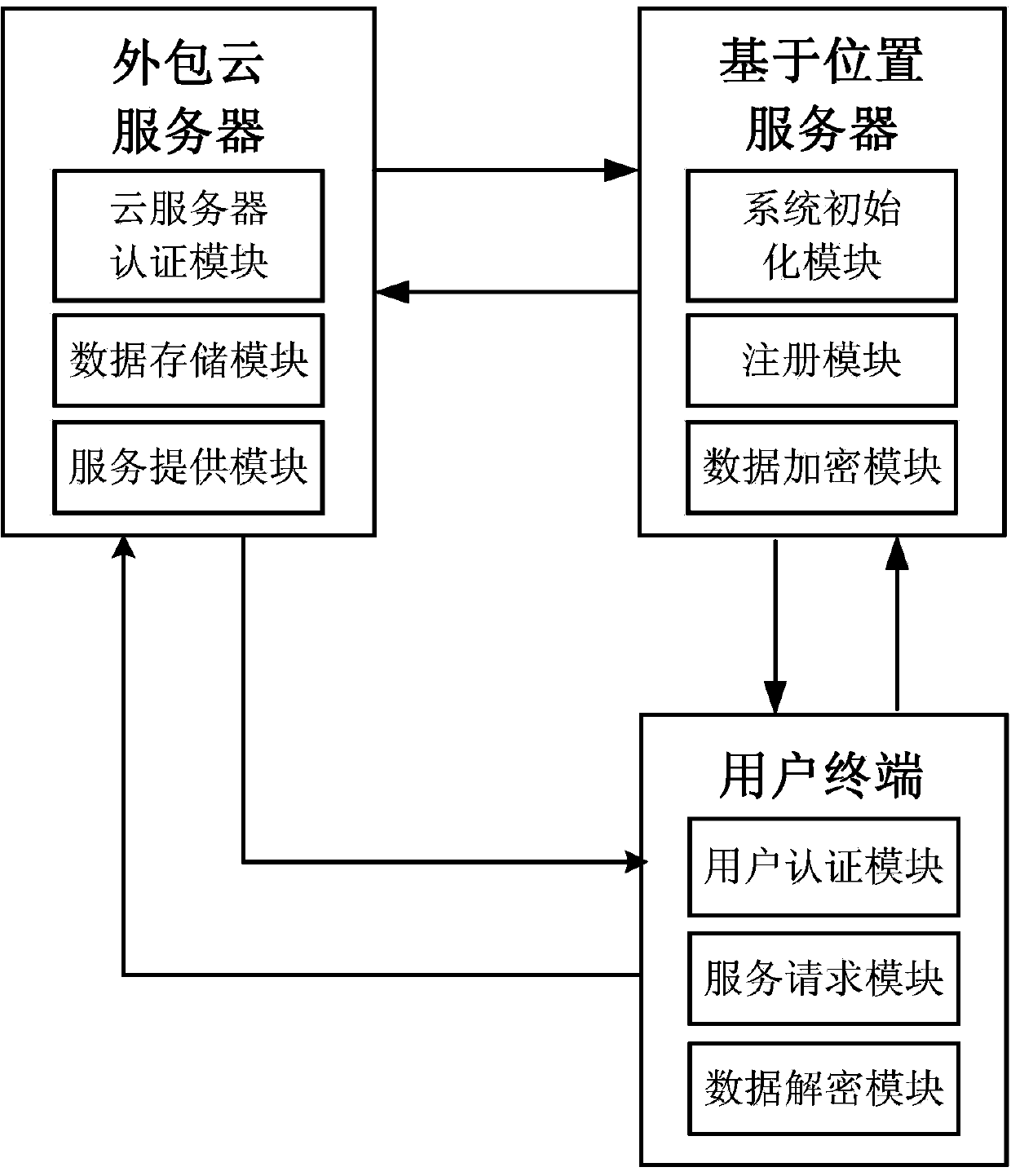
ActiveCN104219245AEfficient serviceStrong computing powerTransmissionData informationPrivacy protection
The invention discloses a system and a method for location based service-orientated user privacy protection, which mainly solve the problems of poor safety and low processing efficiency of the existing scheme. The system comprises a location based server, an outsourced cloud server and a user terminal, wherein the location based server is used for finishing system initialization, providing registration and secret key distribution for the user terminal and the outsourced cloud server; the outsourced cloud server is used for storing enciphered data resources, calculating for the user terminal to obtain the query result needed by a user and sending the query result to the user terminal; the user terminal is used for sending a service request to the outsourced cloud server, and decrypting the data information list returned by the outsourced cloud server to obtain the query result; the user terminal and the outsourced cloud server carry out bidirectional authentication in a service. The system and the method disclosed by the invention realize privacy protection for the location information of the user and data resources, increases the system efficiency, and can be used for providing safe and fast dinning, entertainment and travel information for the user in actual life.
Owner:XIDIAN UNIV
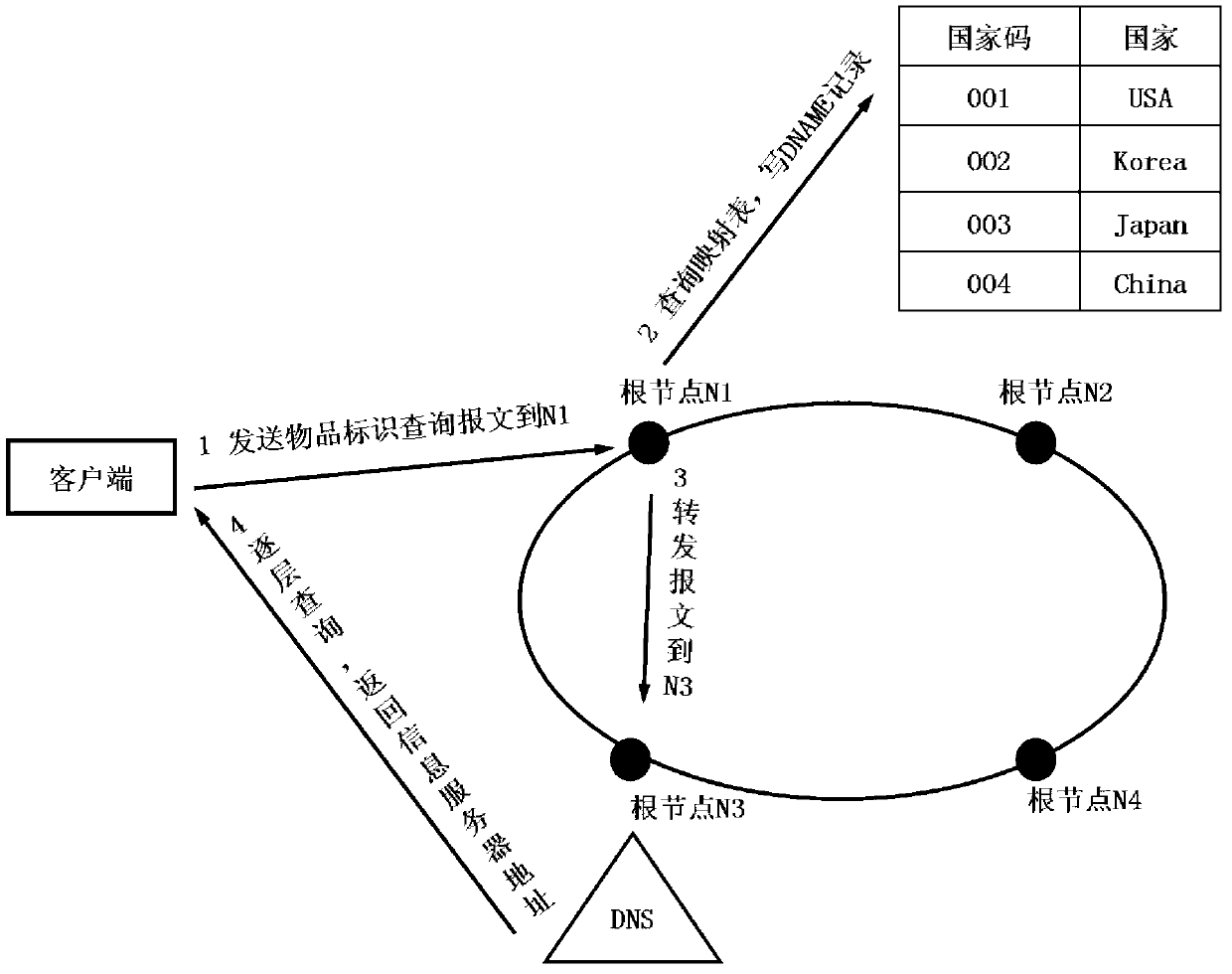
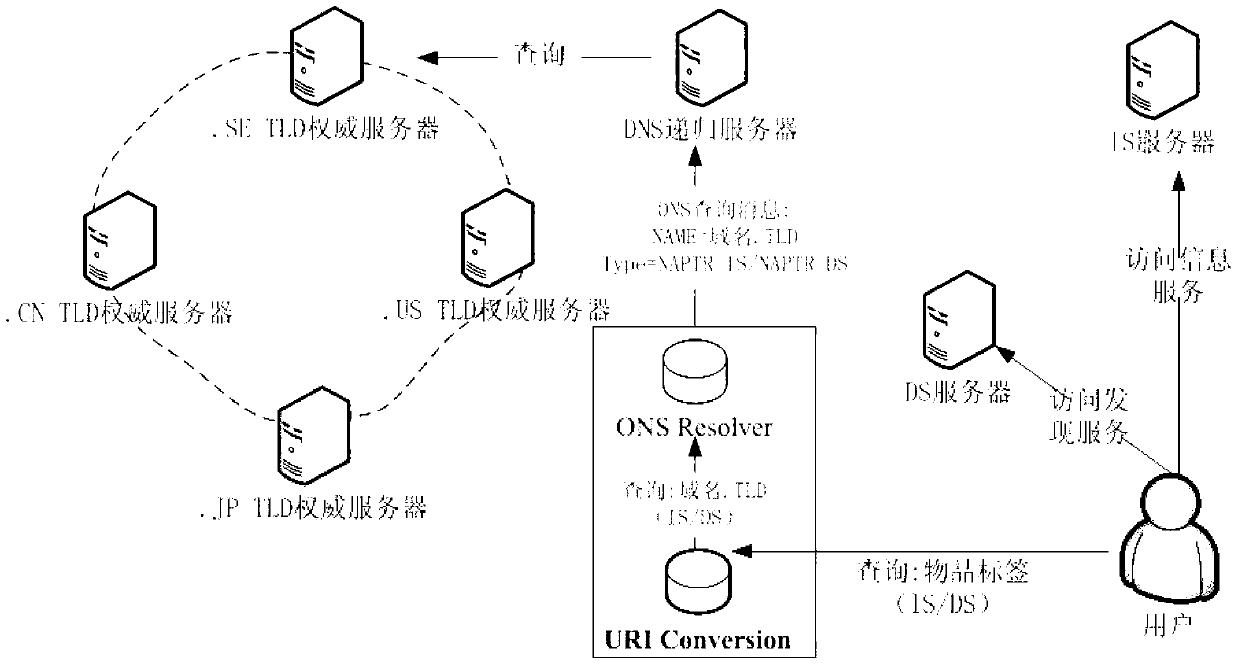
ONS architecture with decentralized management-based EPC parsing method
The invention relates to an object naming service (ONS) architecture with decentralized management-based electronic produce code (EPC) parsing method. The EPC parsing method comprises the following steps that: firstly, a URI Conversion unit reads a company prefix in an object code and determines a country code top level domain (ccTLD) area which the object code is located at; secondly, the URI Conversion unit carries out conversion on the object code, adds the ccTLD information, and constructs a complete domain name; thirdly, an ONS resolver unit receives the converted domain name and carries out parsing according to a normal DNS query flow until a name server of the domain name returns a corresponding naming authority pointer (NAPTR) record; and fourthly, a Local System unit accesses a corresponding an EPC information server (EPC IS) or EPC discovery server (EPC DS) according to the NAPTR record so as to obtain related information of the object. According to the invention, querying time delay and expenditure of the ONS can be optimized; and privacy protection of object information by all sovereign states and areas can be guaranteed.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Mobile application recommendation system and method with privacy protection function under cloud services
ActiveCN107248980AProtect data privacyPrivacy protectionCommunication with homomorphic encryptionPrivacy protectionClient-side
The invention discloses a mobile application recommendation system and method with a privacy protection function under cloud services, and belongs to the technical fields of cloud service, information safety trust management and privacy protection technologies. Authentication registration is carried out on an authentication center, a safety parameter s is received from the authentication center, and an initiation operation is completed; a client is operated in user equipment, and trust behavior data that a user uses a mobile phone application is collected automatically and continuously; the trust behavior data of the user is formalized to obtain trust data of the user; and via client software, a user sends a request for application recommendation to a cloud server by using an anonymous identity; and the cloud end authenticates the user with the recommendation request to the authentication center, and after authentication passes, interactive communication with the client is carried out. Thus, data of the user is protected, so that accurate mobile applications are recommended for the user, and the data privacy of the user can be protected effectively.
Owner:XIDIAN UNIV
Intelligent auto-induction dimming glass system for household toilet
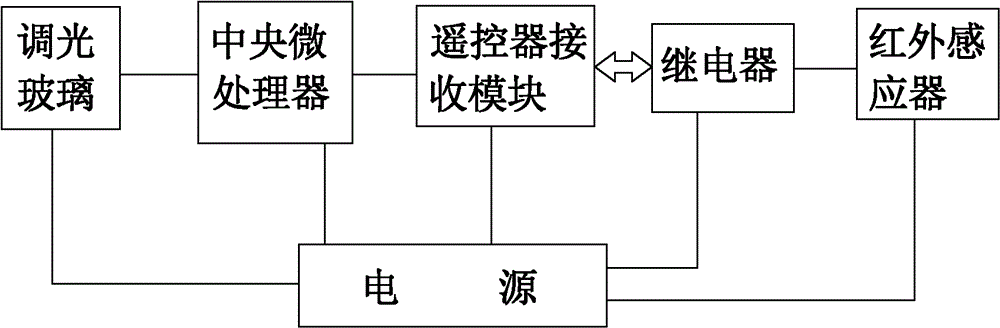
InactiveCN102747809AGuaranteed open-ended effectGuaranteed privacy protectionStatic indicating devicesBuilding componentsMicrocontrollerAutomatic control
The invention relates to an auto-induction dimming glass system for a toilet, in particular to a device control system of an auto-induction dimming glass system for the toilet. The intelligent auto-induction dimming glass system for the household toilet comprises dimming glass, a central microprocessor, a remote controller receiving module, a relay, an infrared inductor and a power supply, wherein the dimming glass and the remote controller receiving module are electrically connected with the central microprocessor respectively; the remote controller receiving module is communicated with the infrared inductor through the relay; and the dimming glass, the central microprocessor, the remote controller receiving module, the relay and the infrared inductor are connected with the power supply respectively. The auto-induction dimming glass system is an automatic control system integrating the various technologies such as the dimming glass technology, the infrared sensor technology, the radio-frequency communication technology and the singlechip technology.
Owner:QINGDAO PENGHAI SOFT CO LTD
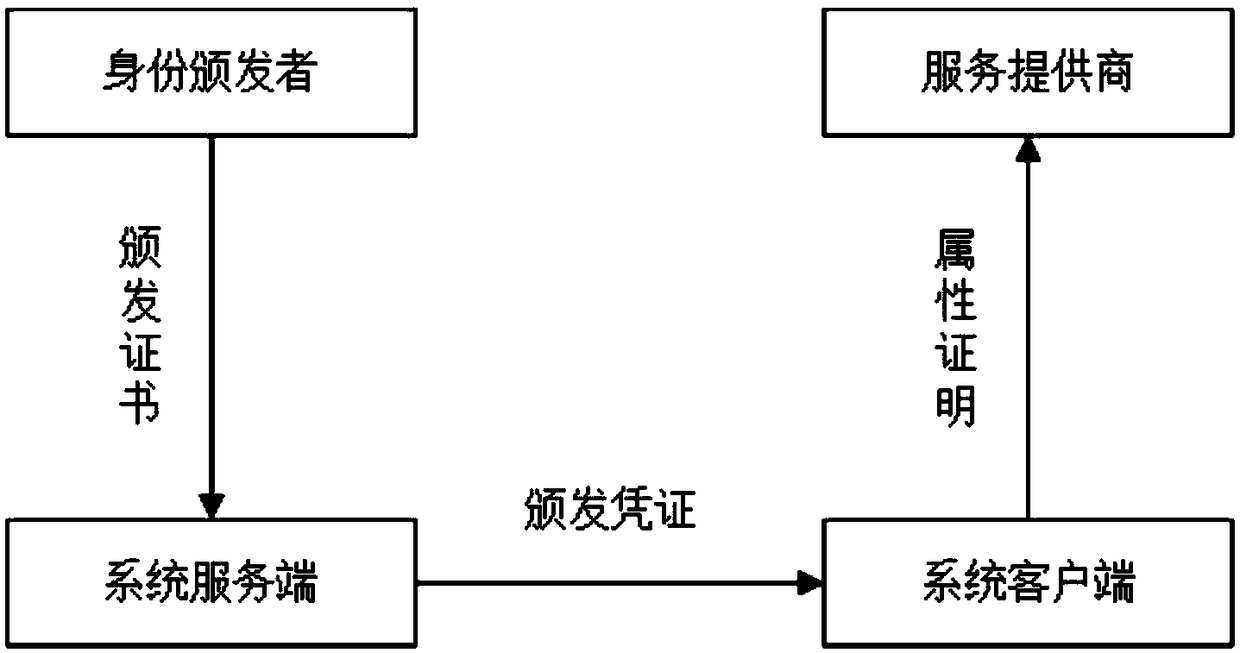
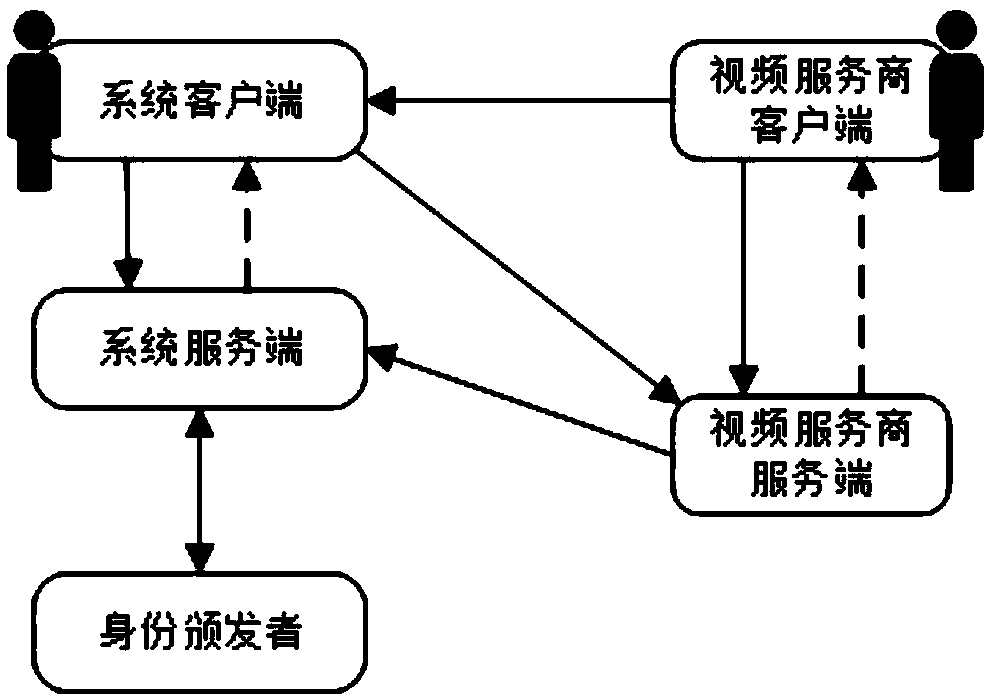
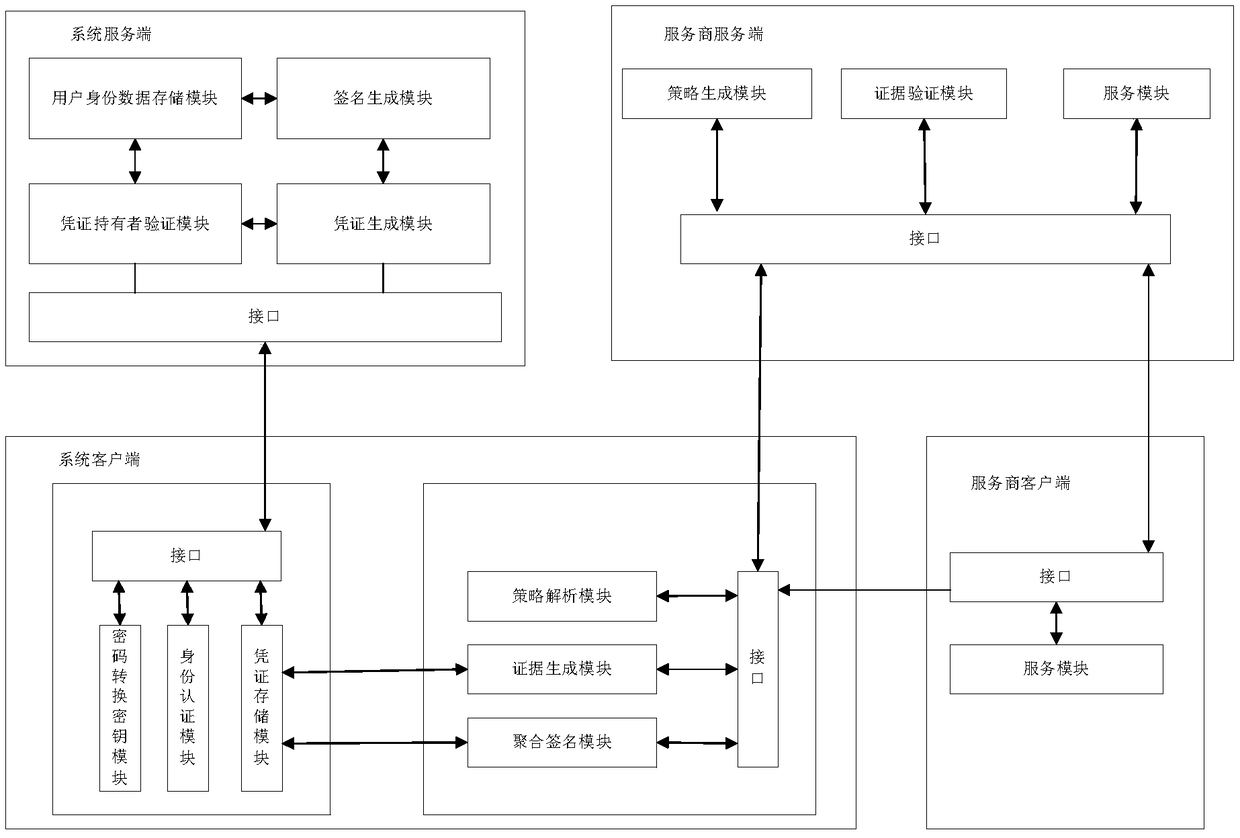
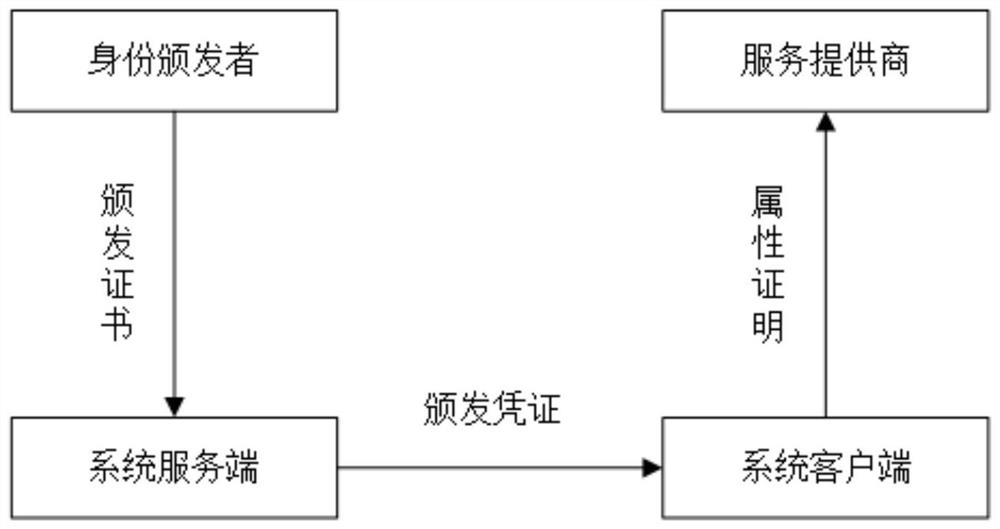
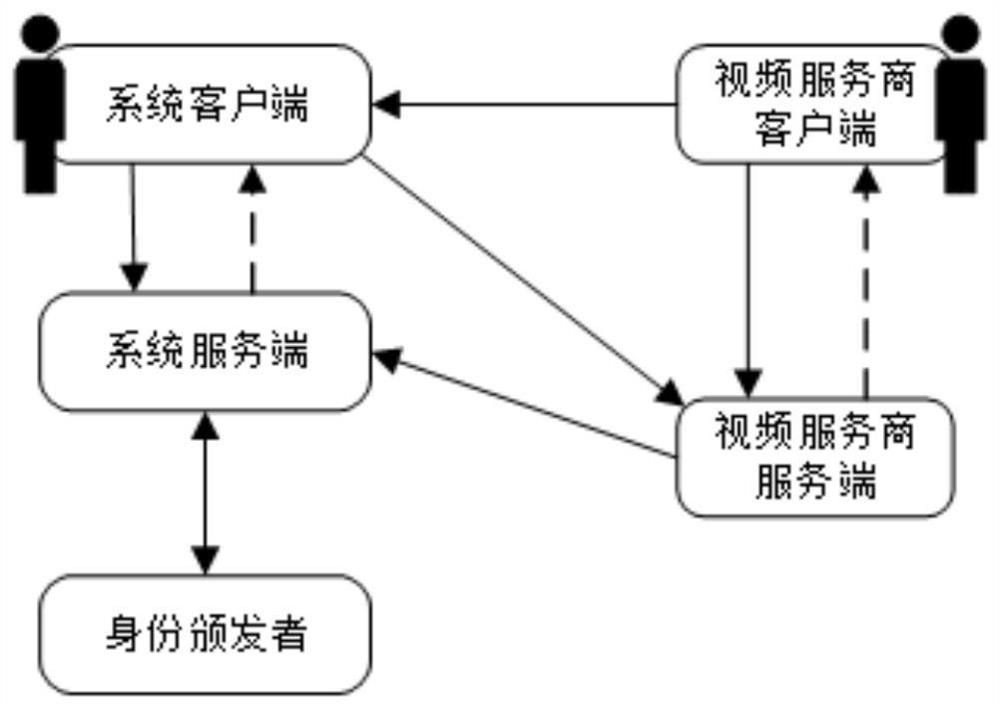
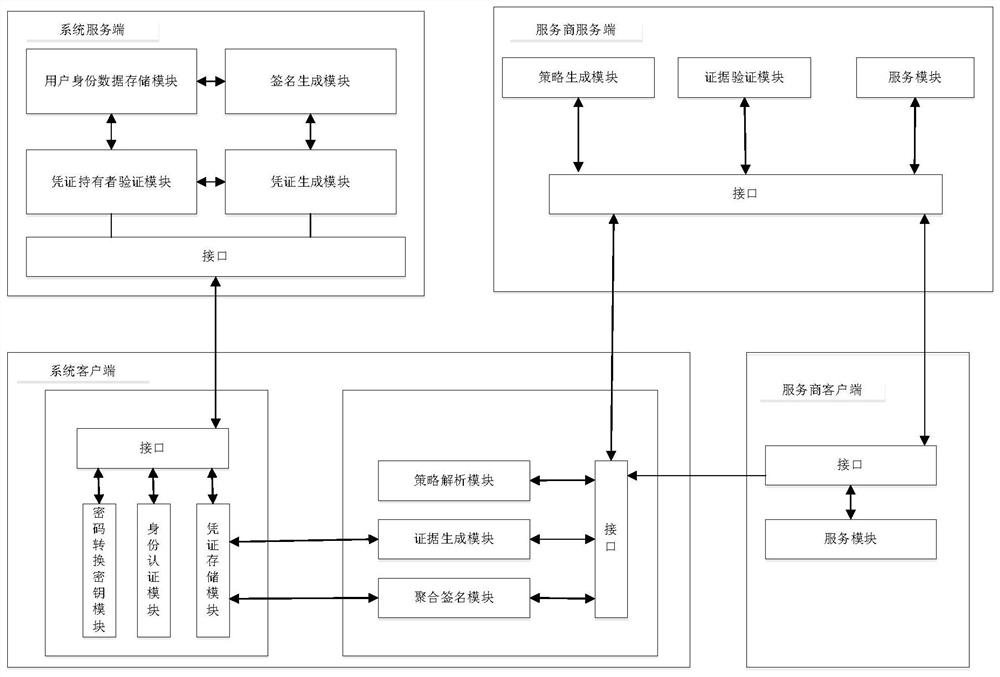
Identity attribute certification system and method for privacy protection
ActiveCN108769020AGuaranteed privacy protectionPrevent forgeryUser identity/authority verificationPrivacy protectionClient-side
The invention provides an identity attribute certification system and method for privacy protection. The system comprises a service-provider server, a service-provider client, a system server and a system client, wherein the service-provider server generates an access strategy of a service, sends the access strategy to the service-provider client, and performs verification on an evidence; the service-provider client sends a service request to the service-provider server, redirects the service request to the system client and forwards the access strategy to the system client; the system serverrequests a certificate of an attribute, re-signs the attribute in the certificate, generates a voucher of the attribute and issues the voucher to the system client; the system client retrieves an attribute label in the access strategy; if the voucher of the attribute is not stored in the system client, the system client applies to the system server for the voucher of the attribute; and the evidence for attribute certification is generated via an aggregate signature and is sent to the service-provider server. A service provider cannot obtain real attribute information of a user, so a privacy ofthe user is protected.
Owner:NORTHEASTERN UNIV
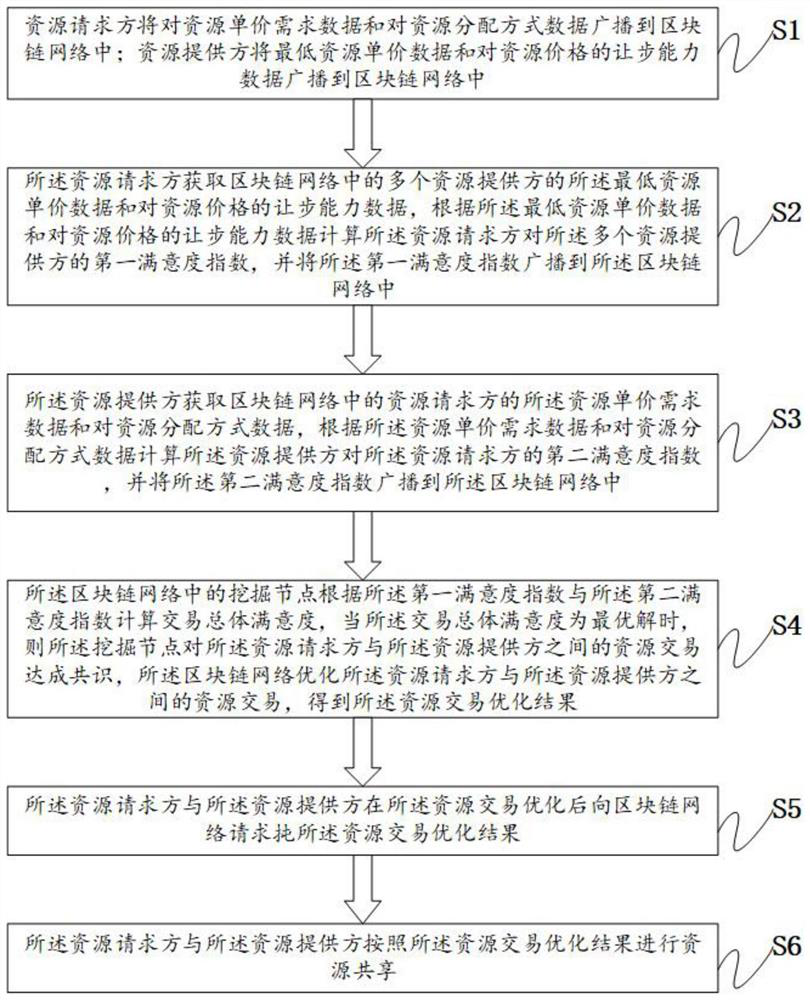
Edge cloud collaborative computing resources transaction method, computer equipment and storage medium
PendingCN111950858AEnsure safetyGuaranteed privacy protectionSpecial service provision for substationDatabase distribution/replicationResource ProviderFinancial transaction
The invention provides an edge cloud collaborative computing resources transaction method, computer equipment and a storage medium, and the method comprises the steps that S1, a resources requester broadcasts resources unit price demand data and resources distribution mode data, and resources providers broadcast lowest resources unit price data and yielding capability data for resources prices toa blockchain network; S2, the resource requester calculates a first satisfaction index for the plurality of resources providers; S3, the resource providers calculate a second satisfaction index of theresource requester; S4, the overall satisfaction degree of the transactions is calculated in a blockchain network, and when the overall satisfaction degree of the transactions is an optimal solution,resources transactions reach agreements and the resources transactions are optimized; S5, the blockchain network is requested for a resources transaction optimization result; and S6, the resource requester and the resource providers share resources according to the optimization result. According to the invention, all parties participating in sharing can obtain the maximum benefit sum.
Owner:SHENZHEN POWER SUPPLY BUREAU
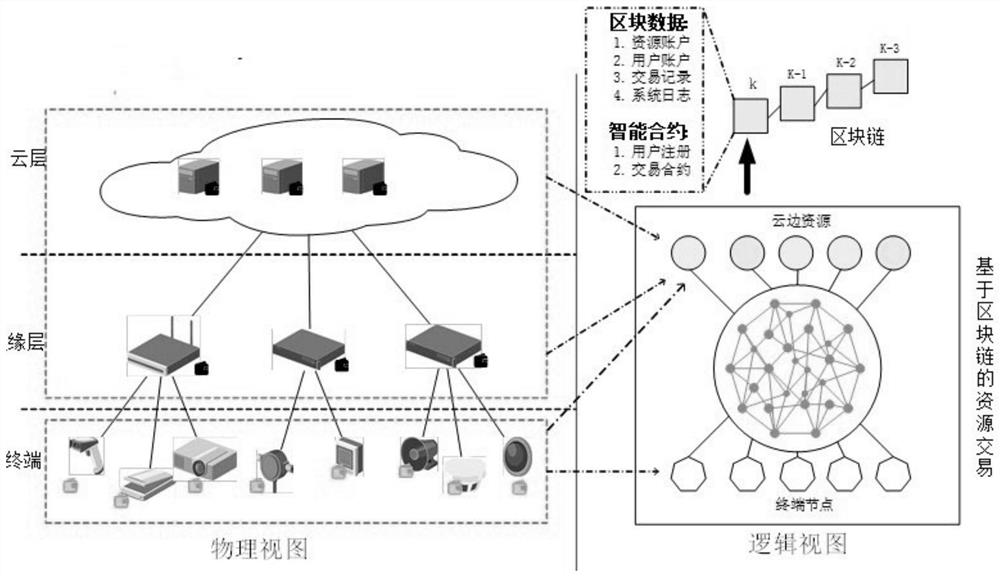
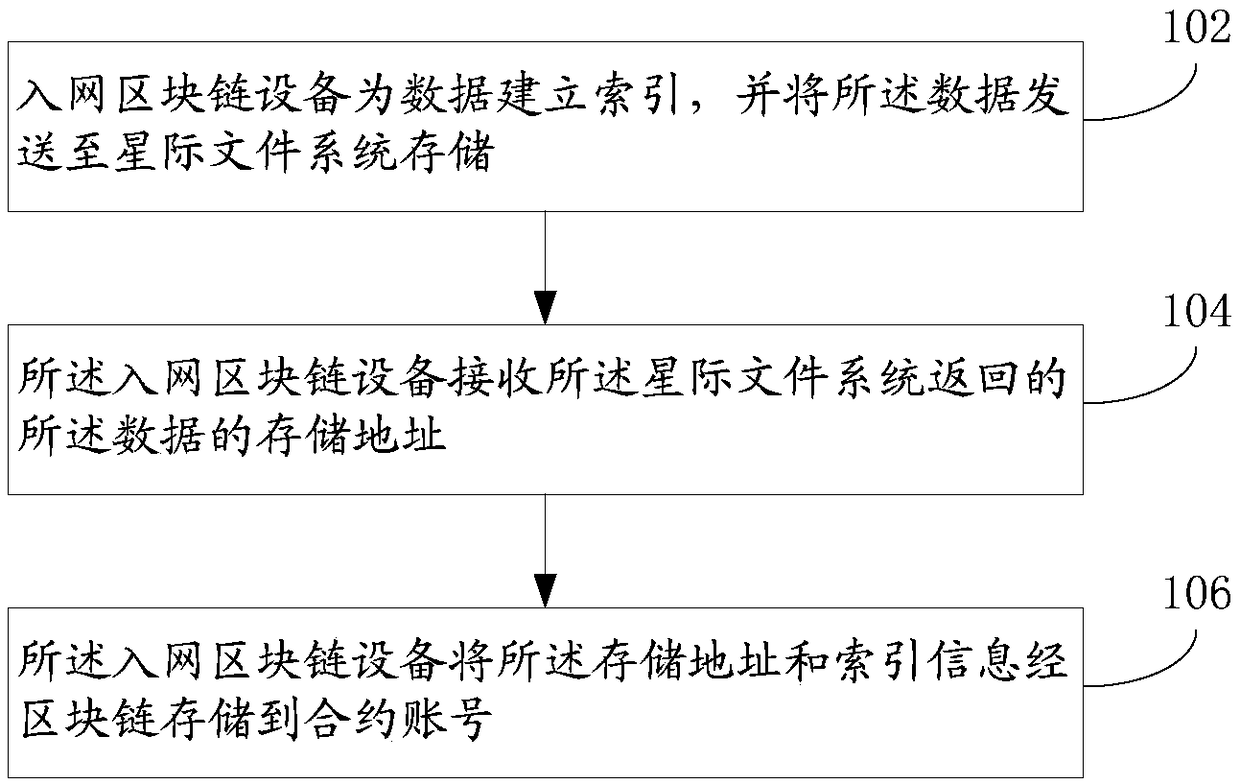
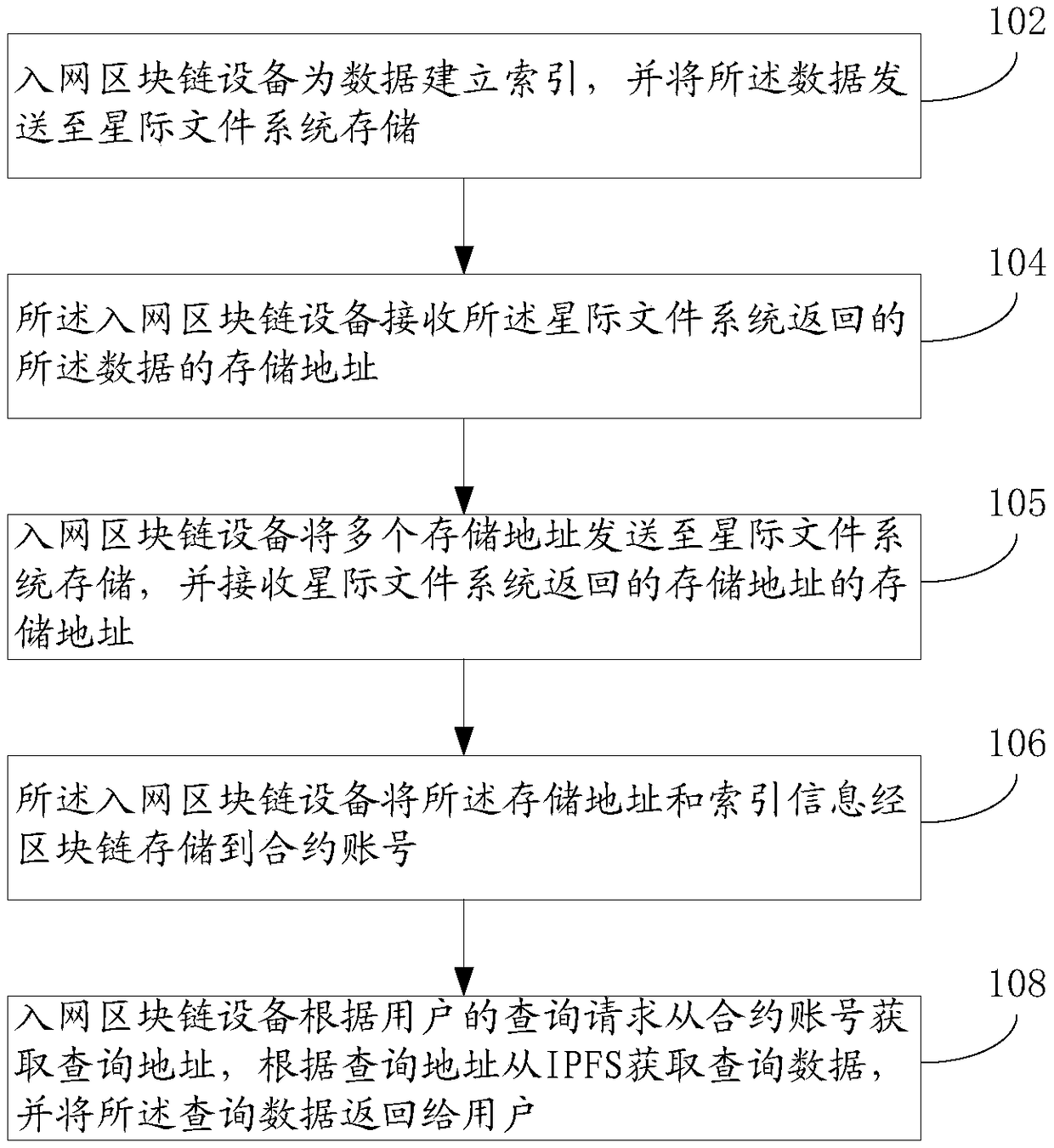
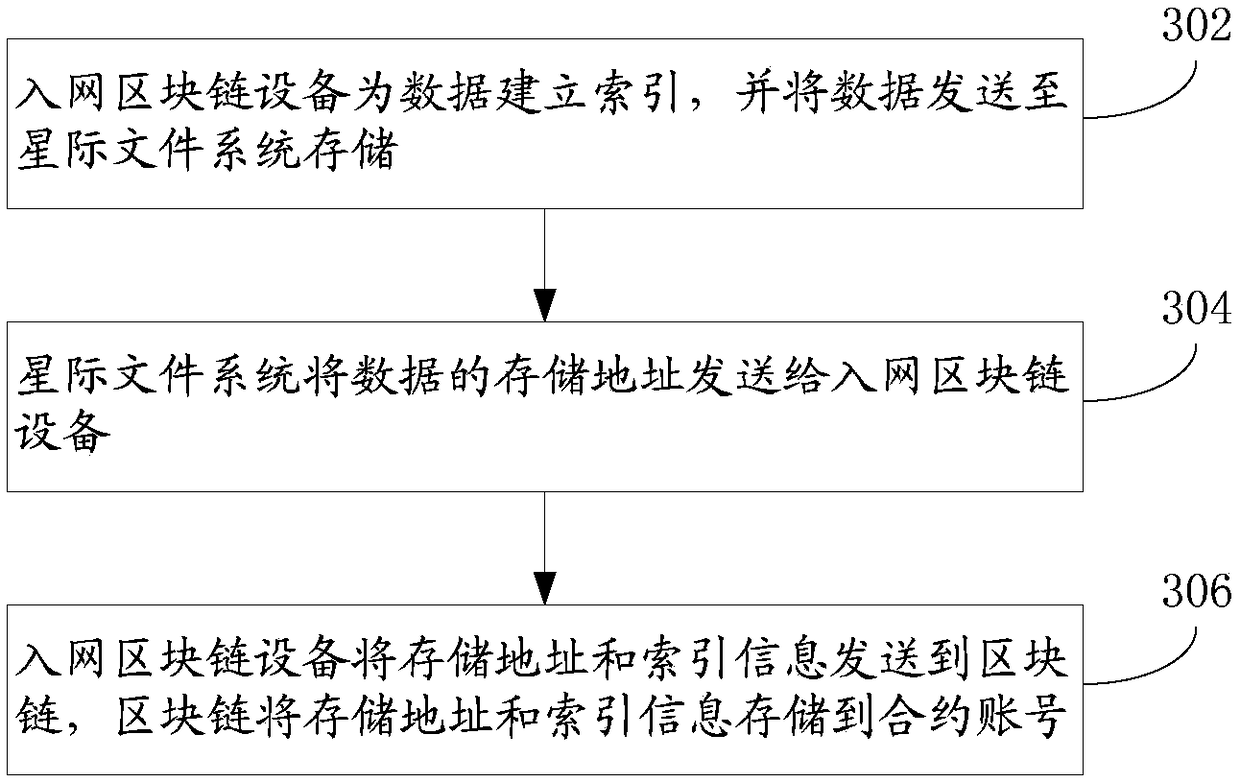
Network access block chain equipment based on block chain and data processing method and device
The invention discloses a network access block chain equipment based on block chain and data processing method and device, and the method comprises the steps: the network access block chain equipmentestablishes an index for data, and sends the data to an interstellar file system for storage; the network access block chain device receives a storage address of the data returned by the interstellarfile system; and the network access block chain device stores the storage address and the index information to a contract account through a block chain. According to the embodiment of the invention, the method comprises the following steps that: network access block chain equipment establishes an index for data, and sends the data to an interstellar file system for storage; the network access block chain device stores the storage address and the index information to the contract account through the block chain, so that the data is stored through the interstellar file system, the decentration of the storage is realized, and the privacy protection of the data can be ensured.
Owner:SHENZHEN ZTE NETVIEW TECH
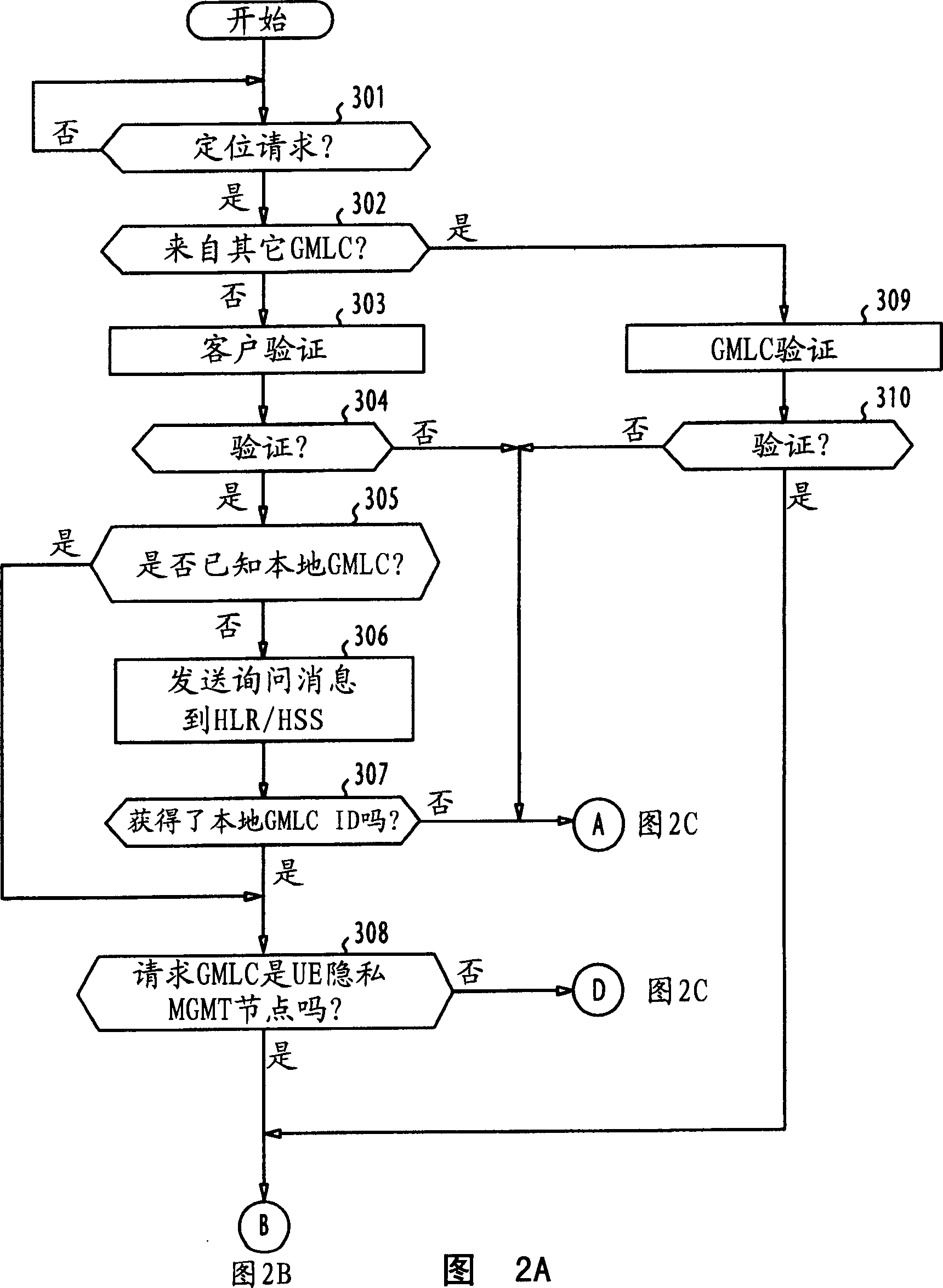
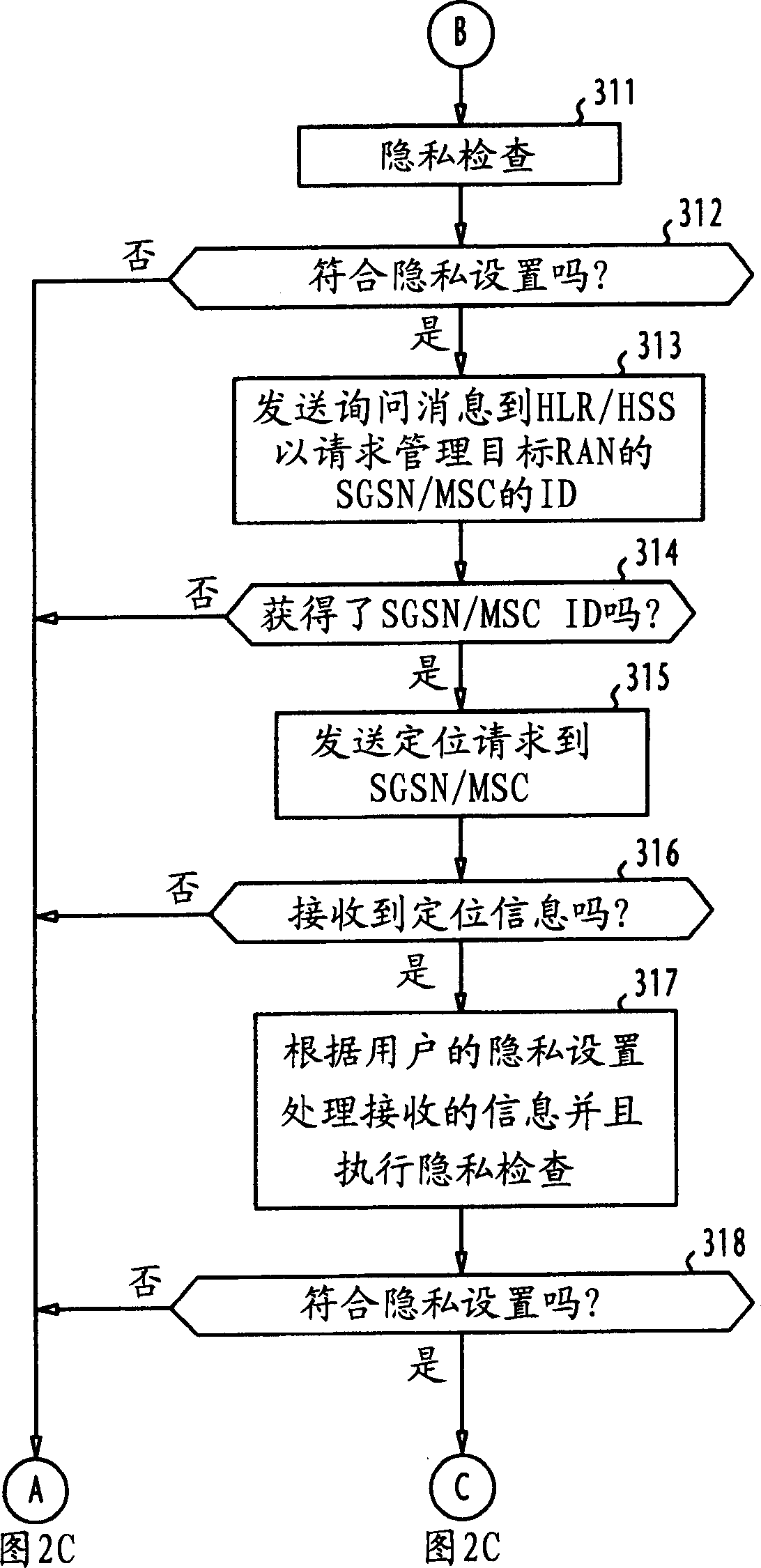
Location system with enhanced security
InactiveCN1449218AGuaranteed privacy protectionPosition fixationRadio/inductive link selection arrangementsInternet privacyPositioning system
In a location system, gateways maintain privacy settings of mobile terminals. On receiving a location request from a client terminal, each gateway determines which of the gateways maintains the privacy settings of a target mobile terminal specified in the request, and transmits the location request to a gateway if the latter maintains the privacy settings of the specified target mobile terminal. The gateway performs a first privacy check on a location request received either from the client terminal or from other gateway using the privacy settings of the target mobile terminal, transmits the request to a positioning system to obtain a measurement result indicating the location of the target mobile terminal if the request conforms to the privacy settings, and performs a second privacy check on the measurement result using the privacy settings. A result of the second privacy check is then communicated to the client terminal.
Owner:NEC CORP
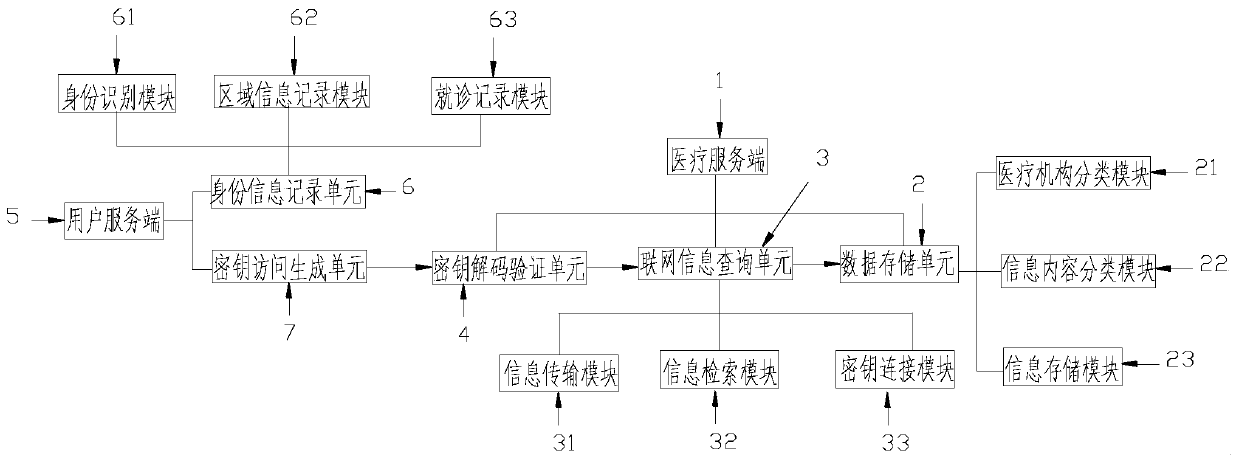
Regional medical information sharing and query system
PendingCN111241375AQuick searchGuaranteed privacy protectionWeb data indexingDigital data protectionIdentity recognitionInternet privacy
The invention relates to the field of medical information query, in particular to a regional medical information sharing and query system, which comprises a medical server, a data storage unit, a networking information query unit, a secret key decoding verification unit, a user server, an identity information recording unit and a secret key access generation unit, wherein the user server is a mobile server for patients; the identity information recording unit records identity information of each patient, generates a unique identity identification code and records regional information and treatment records of the patients at the same time; the identities of the patients are identified through using the secret key access generation unit, unique access keys are generated according to an encryption algorithm, the secret key decoding verification unit carries out decoding calculation on the access secret keys and is connected to the networking information query unit after verification, thenetworking information query unit carries out access connection on the corresponding secret keys and carries out information query according to requirements, and the medical service terminal is arranged on a networking server of each medical institution.
Owner:KUNMING UNIONSCIENCE TECH CO LTD
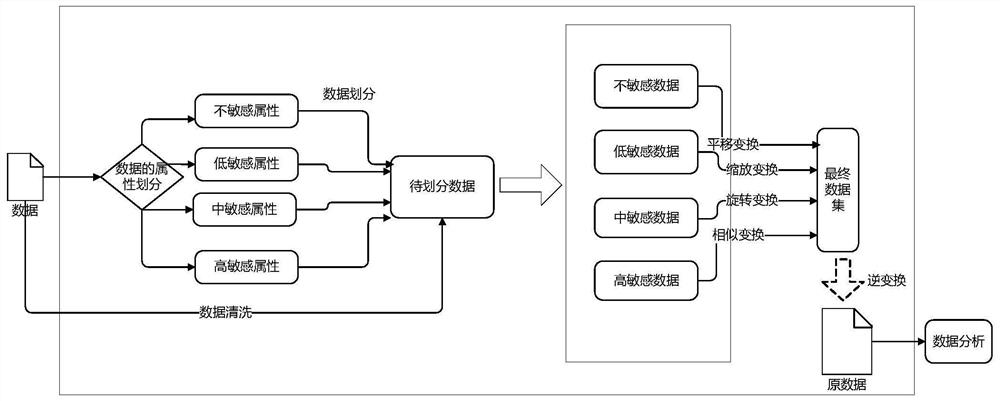
Big data security privacy protection method based on geometric deformation and storage medium
InactiveCN112231745AEffective protectionTo achieve the purpose of privacy protectionDigital data protectionData privacy protectionData set
The invention relates to the field of big data processing, and discloses a big data security privacy protection method based on geometric deformation and a storage medium. The method comprises the following steps: establishing an attribute sensitive set: dividing attributes of data into four sets which represent four sensitive degrees; cleaning data: deleting incomplete data entries, and serializing discrete data to obtain to-be-divided data; dividing data: screening out data corresponding to all attributes in the same sensitive set, and classifying the data into different columns of the samematrix to form a homosensitive data set; carrying out geometric deformation: carrying out corresponding translation, scaling, rotation or similar transformation processing on the homosensitive data set, and recording transformation parameters so as to be used in subsequent inverse transformation processing; and obtaining a final data set, wherein the four data sets after transformation processingare one data set. A concise, efficient and graded data privacy protection method can be provided for release and transmission of mass data, and data restoration can be achieved through geometric deformation inverse transformation.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Privacy protection method for position density distribution attack
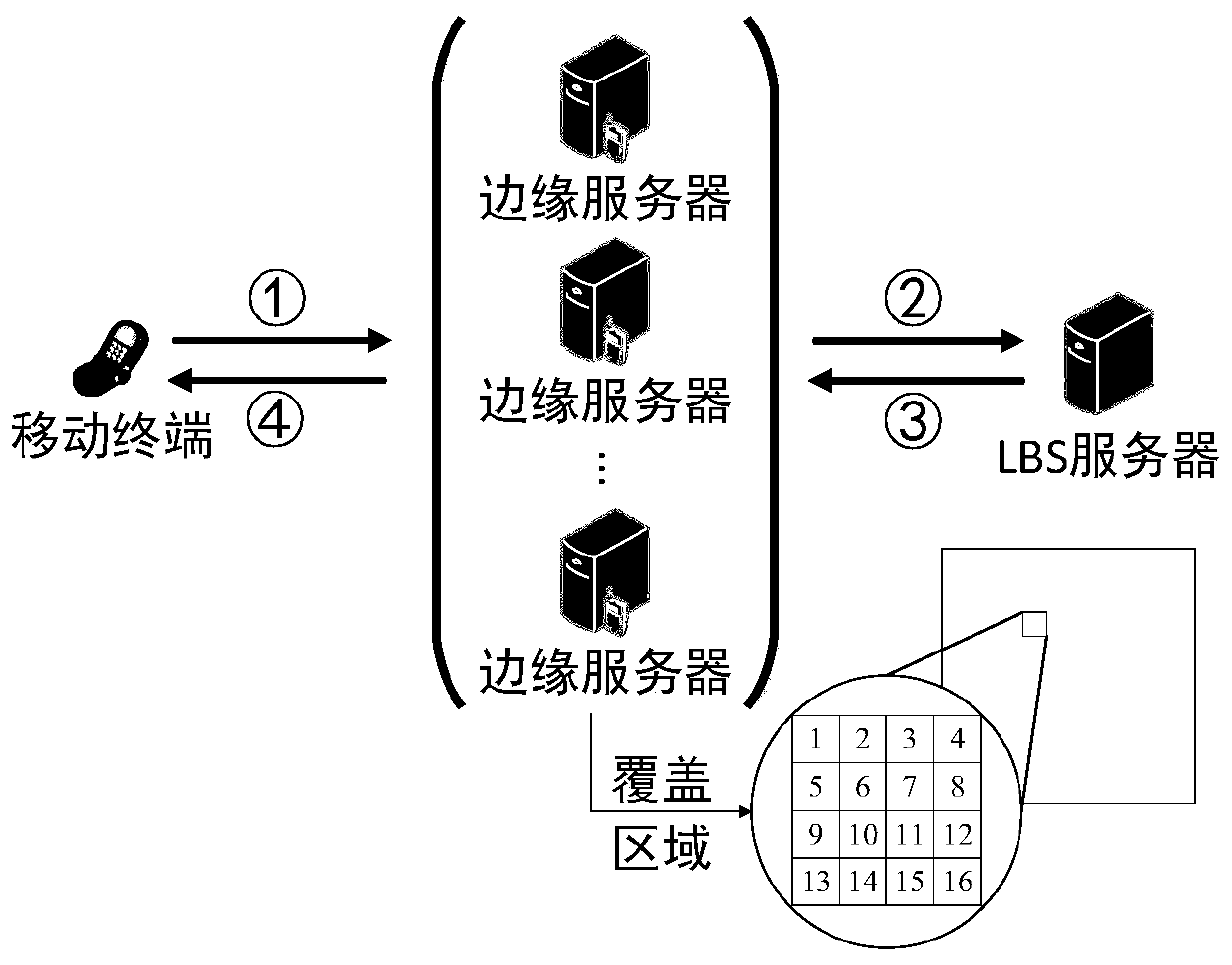
ActiveCN110213763AReduce computing costReduce communication overheadTransmissionSecurity arrangementEdge serverDensity distribution
The invention provides a privacy protection method for position density distribution attacks, and provides a privacy protection scheme for the position density distribution attacks of regional privacy. The method comprises: using an edge server to divide the service area, and counting the service requests in each area; then, detecting the difference of preset values of the sub-regions and the range level difference of neighborhoods of the sub-regions, and determining an abnormal state; and finally, calculating the number of noise added through an improved differential privacy method, and adding noise to the abnormal area, thereby reducing privacy protection budget, controlling noise cost, and reducing attacks caused by background knowledge to area privacy until abnormities completely disappear. The privacy disclosure problem caused by the position density distribution attack can be effectively reduced.
Owner:NANJING UNIV OF TECH
Hospital portrait construction method, device and equipment, and storage medium
PendingCN113657809AFix the angle problemGuaranteed privacy protectionDigital data protectionResourcesPatient IssueData set
The invention relates to the field of big data, is applied to the field of intelligent medical treatment, provides a hospital portrait construction method, device and equipment and a storage medium, and aims at solving the problem that a hospital portrait cannot visually present information of all dimensions required by a patient under the condition that privacy protection of related medical sensitive data in a hospital is guaranteed. The hospital portrait construction method comprises the steps of creating an initial hospital portrait according to patient issue module information and to-be-analyzed hospital information; carrying out efficiency calculation through a data envelope analysis algorithm, the index factors corresponding to patient issue module labels and hospital data sets corresponding to the hospital labels to calculate patient issue module label score values corresponding to the hospital labels; sorting the plurality of hospital labels according to the label score value of the patient issue module to obtain a hospital label sequence; and updating the initial hospital portrait through the hospital label sequence to obtain a target hospital portrait. In addition, the invention also relates to a block chain technology, and the target hospital portrait can be stored in a block chain.
Owner:深圳平安医疗健康科技服务有限公司
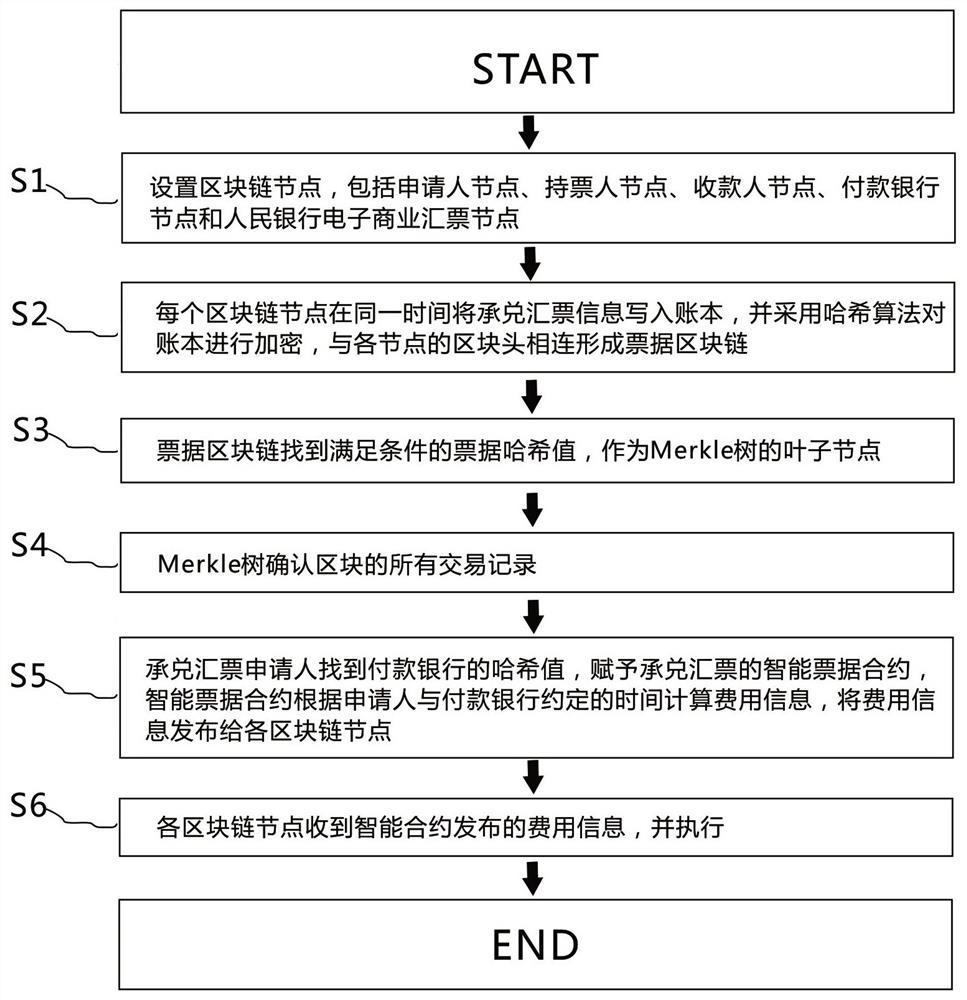
Acceptance bill management method based on block chain
ActiveCN111967985AEasy to counterfeitSlow to resolve transactionsFinanceWeb data indexingTicketConfidentiality
The invention discloses an acceptance bill management method based on a block chain. The method enables the block chain technology to be applied to bank acceptance bill business, and solves problems that a conventional bank acceptance bill business is liable to be counterfeited, is slow in transaction, achieves the illegal transaction, is discontinuous in endorsement, and is large in resource consumption. Meanwhile, secure multi-party computing technology is applied to the bank acceptance bill business, privacy protection of account book information of all nodes is guaranteed, and the problemthat traditional bank acceptance bill business is poor in confidentiality is solved. Meanwhile, applicant information is obtained, applicant credit is verified, risk judgment is provided for the ticket holder, and unnecessary loss of the ticket holder is further reduced or prevented.
Owner:四川川投云链科技有限公司
Distributed Compressed Sensing Data Fusion Method with Privacy Preservation
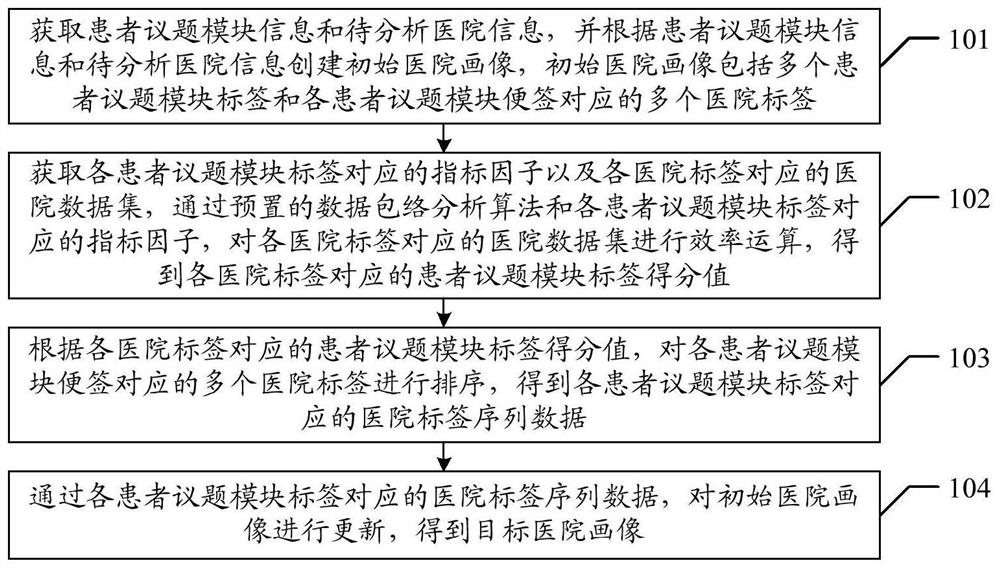
ActiveCN103476040BAccurately obtain sparse featuresGet sparse featuresNetwork planningHigh level techniquesData privacy protectionFeature learning
The invention provides a distributed compressed sensing data fusion method having the privacy protection effect and relates to the field of wireless networks. A privacy protection fusion method based on data sparsity position information hiding is designed in a distributed scene, and by the adoption of data sparsity support set feature learning, real data sparsity position hiding and distributed compressed sensing fusion observation, the additional communication cost brought by a traditional privacy protection fusion method is avoided, and data processing of sensor networks is facilitate. The data privacy protection fusion method has the obvious data privacy protection effect on the sensor networks, meanwhile can effectively reduce network energy consumption and improve the algorithm efficiency and the data processing performance by utilizing a distributed compressed sensing fusion strategy, and facilitates user management, network application and scale expanding.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Cloud medical record management method for CT scanning images based on artificial intelligence
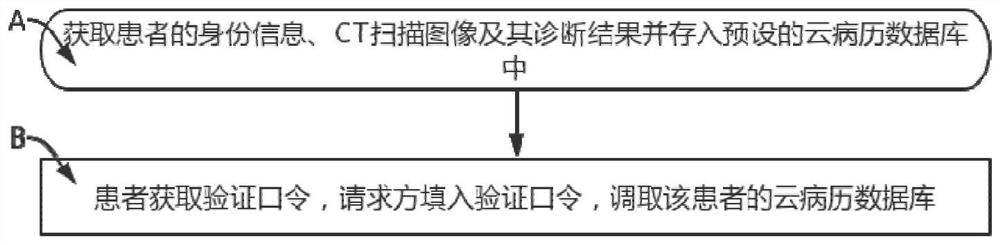
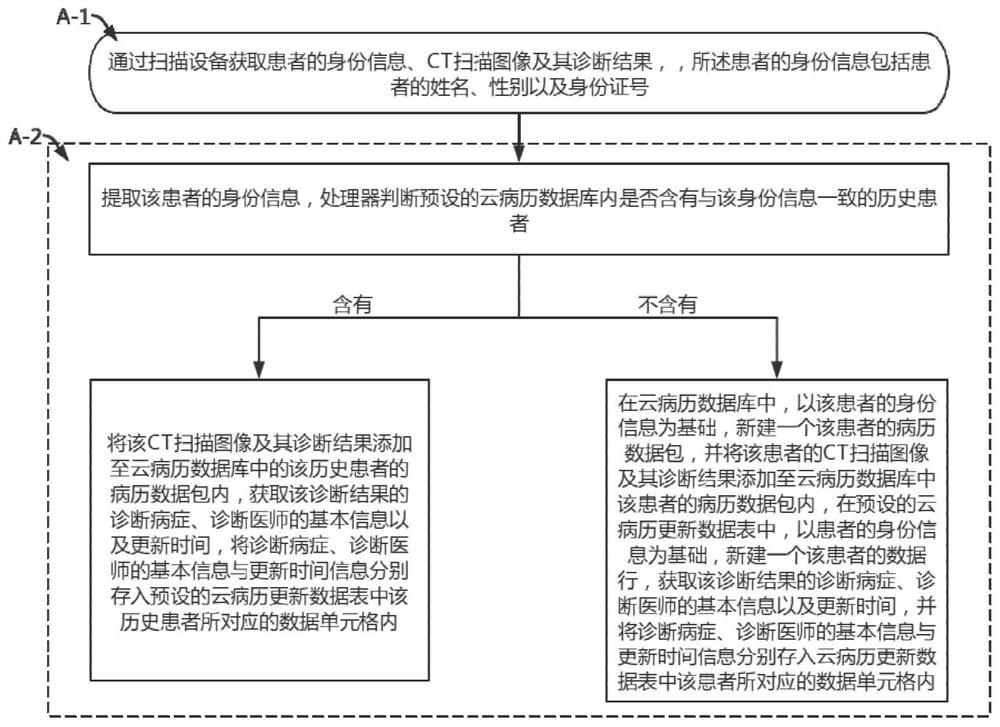
PendingCN113571144AGuaranteed privacy protectionAvoid being randomly calledMedical data miningMedical imagesMedical recordPrivacy protection
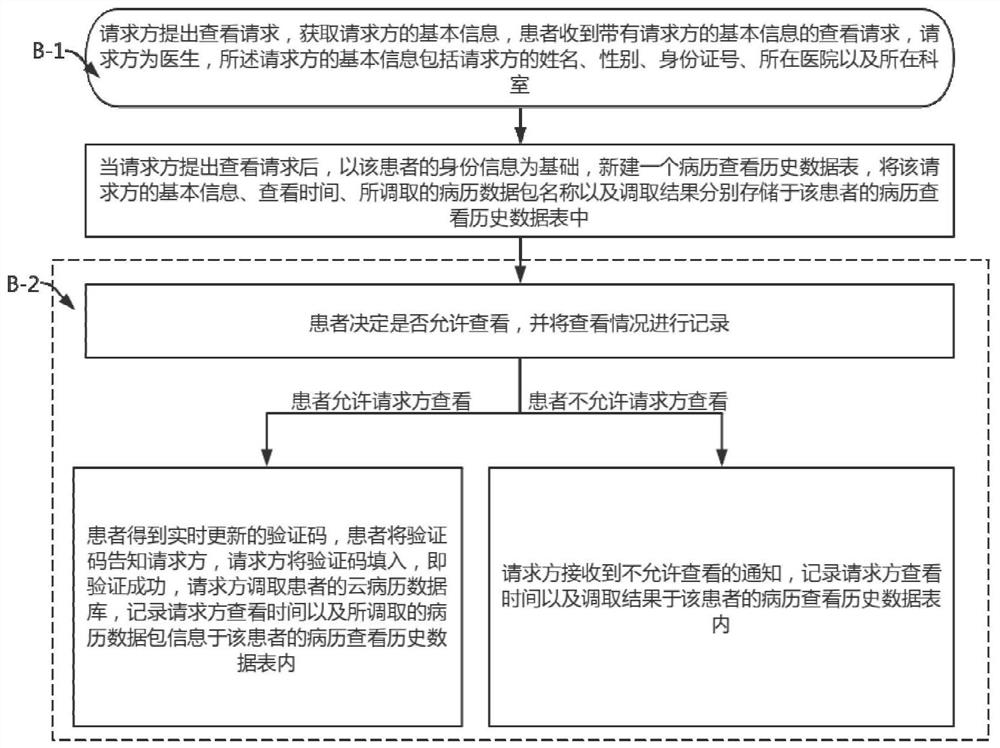
The invention provides a cloud medical record management method for CT scanning images based on artificial intelligence. The cloud medical record management method comprises the steps that the CT scanning images and related information of a patient are acquired; whether a preset cloud medical record database contains patients with consistent related information or not is judged, if yes, the cloud medical records are added to cloud medical records of historical patients, and if not, new cloud medical records are created and stored in the cloud medical record database; a requester requests to call and whether a patient agrees is judged, if the patient agrees, verification codes are provided, verification is successful, and calling and recording are carried out; and if the patient does not agree, recording is carried out. According to the invention, by recording the calling condition of a doctor and verifying the patient, the accurate management of the cloud medical record of the patient and the calling of the cloud medical record of the patient by the doctor is realized, the condition that the cloud medical record of the patient is randomly called is avoided, and the privacy protection of the related information of the patient is ensured; by performing specific storage on the cloud medical record data of the patient, the accuracy of medical record storage of the patient is ensured, and the safety of the cloud medical record of the patient is ensured.
Owner:SHANGHAI FIRST PEOPLES HOSPITAL
Smart city cross-department information interaction architecture system and method
ActiveCN113905051ARealize trusted shared deliveryGuaranteed privacy protectionClimate change adaptationUser identity/authority verificationSoftware engineeringPrivacy protection
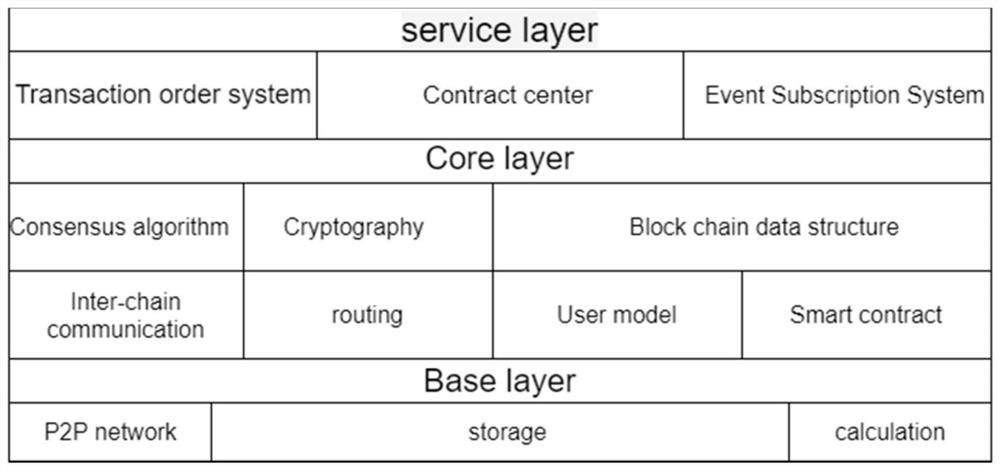
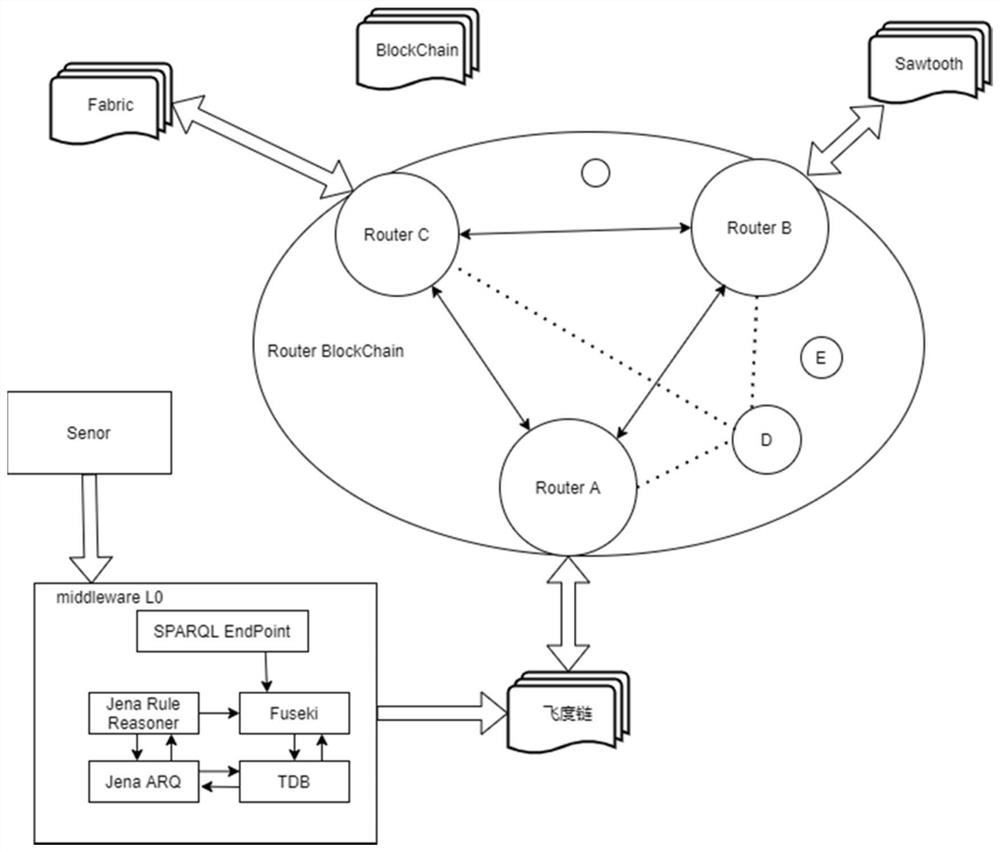
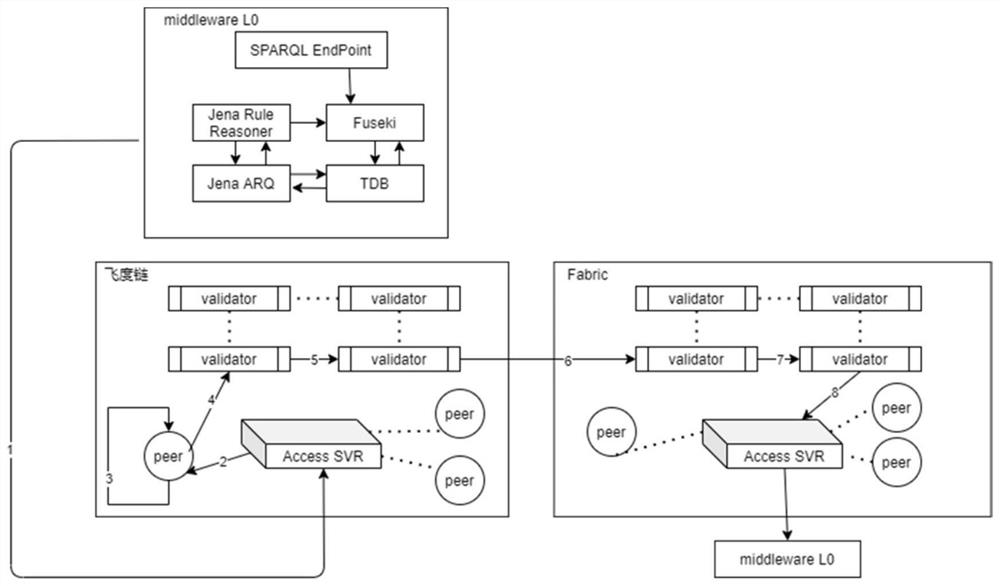
The invention relates to a smart city cross-department information interaction architecture system and method, the system is used for realizing cross-department data trusted security access and privacy protection, and the system comprises a sensor or hardware module used for obtaining data; a semantic middleware Middleware L0 module used for processing and transmitting data to a block chain module; and the block chain module which is constructed by adopting an isomorphic multi-chain technology and is used for receiving the data information and performing verification and consensus. Compared with the prior art, the method has the advantages that data trusted security access and privacy protection are realized, and the method is high in security and quick in information interaction.
Owner:TONGJI UNIV
A privacy-protected identity attribute certification system and method
ActiveCN108769020BGuaranteed privacy protectionPrevent forgeryUser identity/authority verificationPrivacy protectionUser privacy
The present invention provides a privacy-protected identity attribute certification system and method. The system includes: the server of the service provider generates an access strategy for the service, sends the access strategy to the client of the service provider, and the server of the service provider verifies the evidence; the client of the service provider The client sends a service request to the server of the service provider, redirects to the system client, and forwards the access policy to it; the system server requests the certificate of the attribute; re-signs the attribute in the certificate, generates a certificate of the attribute, and issues it to the system client ;The system client retrieves the attribute label in the access policy: if the certificate of the attribute is not saved in the system client, the system client applies for the certificate of the attribute from the system server; And send it to the service provider server. The service provider cannot obtain the real attribute information of the user, and the privacy of the user is protected.
Owner:NORTHEASTERN UNIV LIAONING
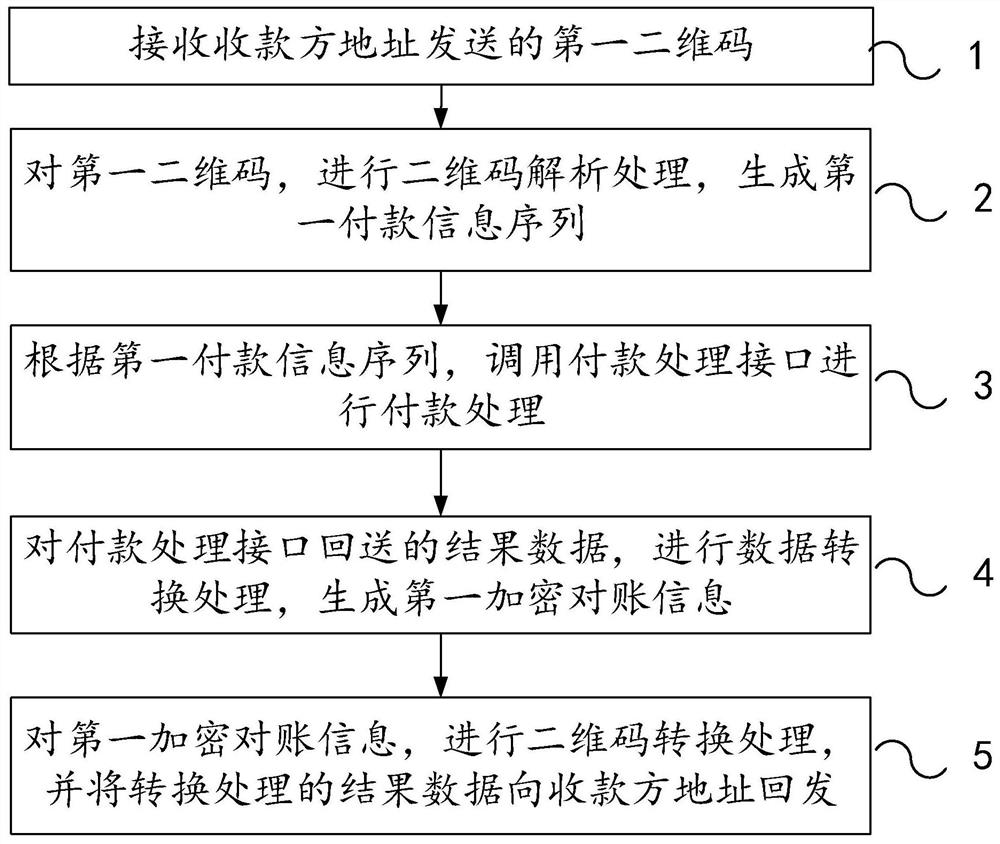
Payment information processing method and device thereof
PendingCN112700238AGuaranteed privacy protectionAvoid manual operationCo-operative working arrangementsPayment protocolsPaymentData transformation
The invention relates to a payment information processing method and a device thereof. The method comprises the following steps: receiving a first two-dimensional code sent by a payee address; performing two-dimensional code analysis processing on the first two-dimensional code to generate a first payment information sequence; calling a payment processing interface to perform payment processing according to the first payment information sequence; performing data conversion processing on result data returned by the payment processing interface to generate first encrypted reconciliation information; performing two-dimensional code conversion processing on the first encrypted reconciliation information, and sending back conversion processing result data to the address of the payee; according to the embodiment of the invention, the security and privacy of data transmission are ensured, and the payment efficiency is improved.
Owner:能链物流科技有限公司
A method and system for realizing data set desensitization based on k-anonymity algorithm
ActiveCN110543782BImprove area corner problemLow degree of generalizationDigital data protectionComplex mathematical operationsData setReal arithmetic
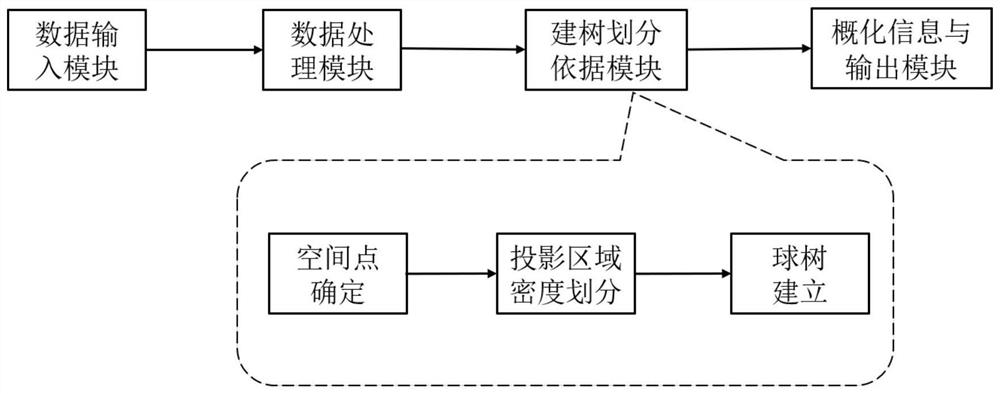
The invention discloses a method and system for desensitizing a data set based on a k-anonymity algorithm, comprising the following steps: obtaining a data set that has not been desensitized; deleting the display identifier of the data set; Each attribute takes the order of the value domain to make it an ordered domain; maps the ordered domain to the real number domain one by one; defines the distance of each data point in space and calculates the relative distance, and divides it according to the relative distance combined with the projection area density The algorithm determines the division point of the data set, calculates the division points at all levels recursively, and finally establishes the hypersphere group; generalizes the point information contained in each hypersphere in the hypersphere group, so that the accuracy of all records The values of the identifiers are the same, and the desensitization process is completed. The present invention can improve the area corner problem existing in the rectangle, and can take into account the distance between adjacent points in the temporary anonymous group, so that more anonymous groups can be obtained under the premise of ensuring privacy protection, and the degree of generalization of data can be improved. The lower the value, the greater the availability of data.
Owner:JINAN UNIVERSITY
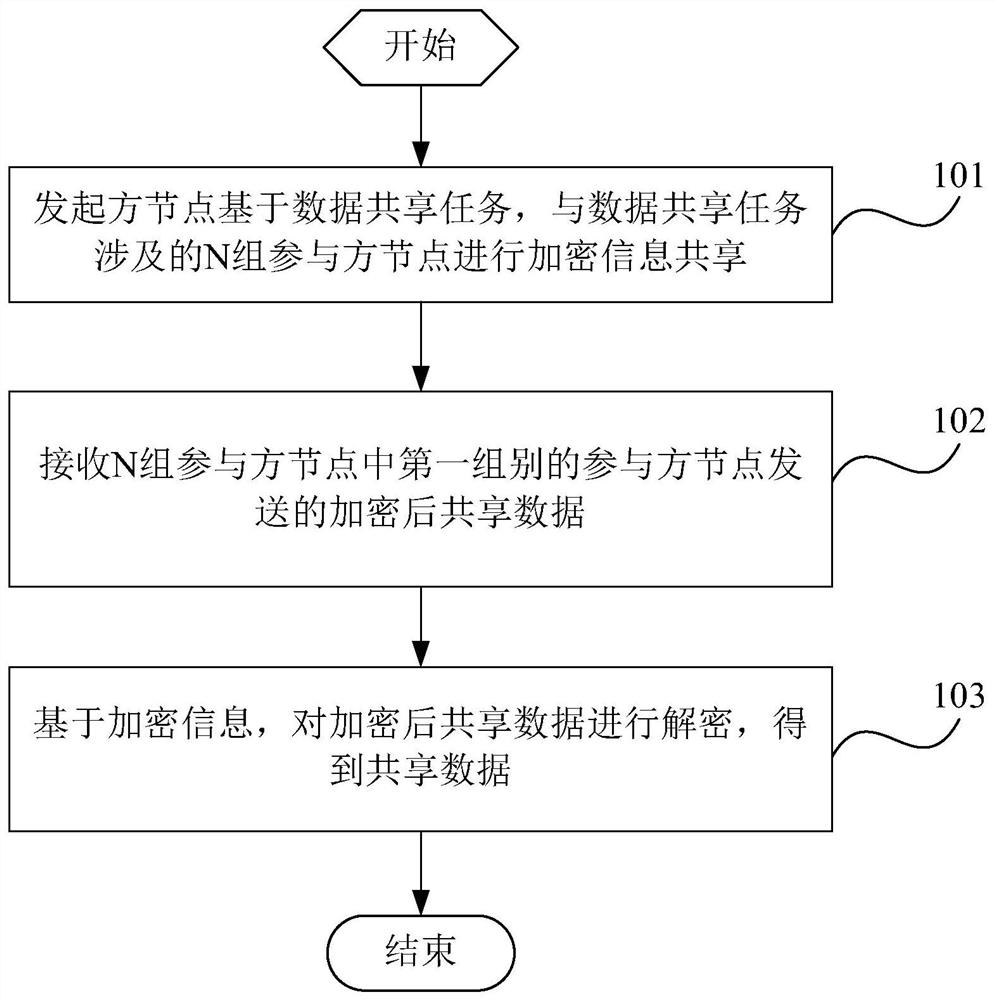
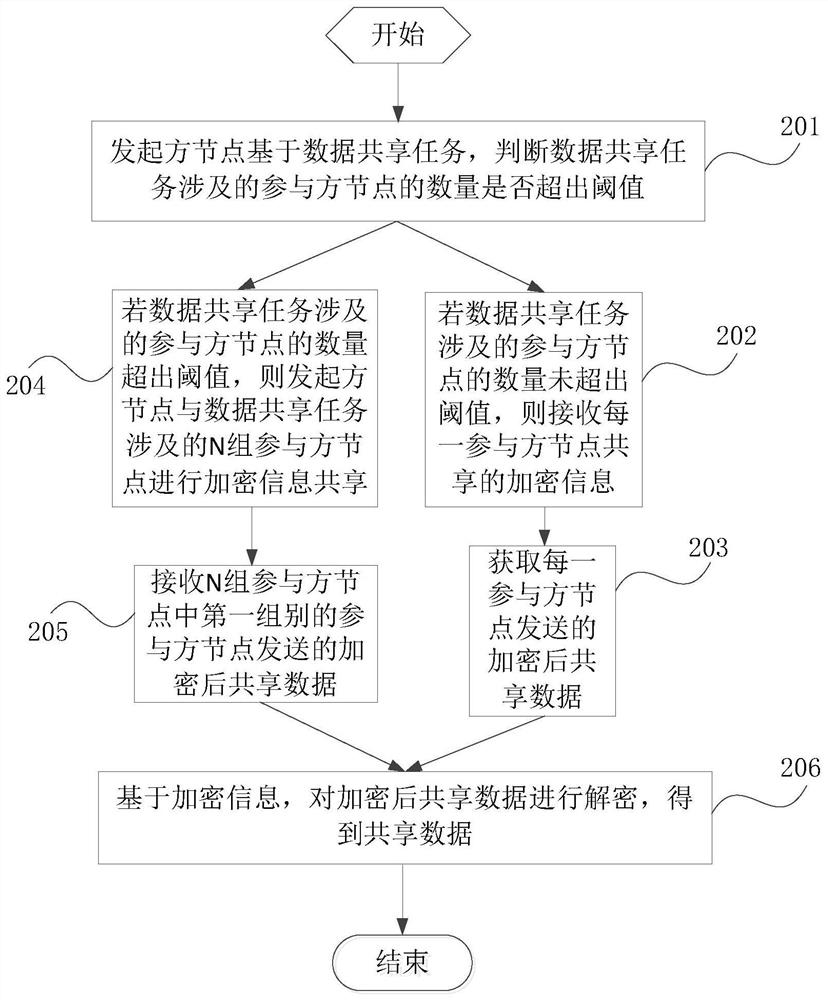
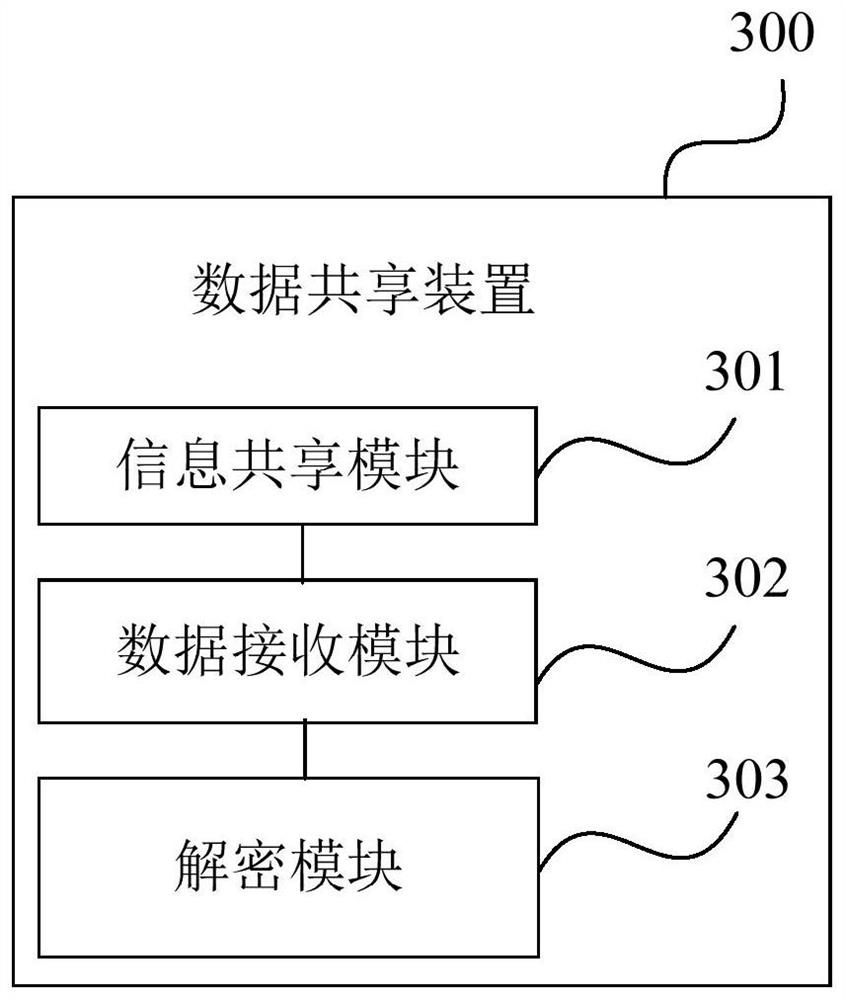
Data sharing method and device, terminal and storage medium
PendingCN113536336AGuaranteed privacy protectionEnsure safetyDigital data protectionInformation sharingComputer science
The invention is suitable for the technical field of block chains, and provides a data sharing method and device, a terminal and a storage medium. The method comprises the steps: initiating, by an initiator node, encrypted information sharing with N groups of participant nodes related to a data sharing task based on the data sharing task; and receiving encrypted shared data sent by the first group of participant nodes in the N groups of participant nodes, and decrypting the encrypted shared data based on the encryption information to obtain shared data. According to the scheme, the operation efficiency can be improved on the premise of ensuring the algorithm security.
Owner:HANGZHOU QULIAN TECH CO LTD
Two-way privacy-protected medical diagnosis service query system and method
ActiveCN105577368BRealize privacy protectionGuaranteed privacy protectionKey distribution for secure communicationData processing applicationsDiseaseService provision
The invention discloses a two-way privacy protective system and method for inquiring a medical diagnostic service, used for mainly solving the problem that privacy protection of inquiry information of medical users and data resources of service providers are not related in the prior art. The system comprises a medical diagnostic server and a medical user terminal; the medical diagnostic server completes system initialization, provides login and distributes a secrete key to the medical user terminal, stores data of a nonlinear SVM model built by using the existing medical database, provides a privacy protective medical diagnostic service for the medical user terminal, and sends an inquiry response result to the user terminal; and the medical user terminal sends a service inquiry request to the medical diagnostic server and performs decryption and polynomial aggregation operation of the inquiry response result returned by the medical diagnostic server, such that a pre-diagnosis result is obtained. According to the invention, privacy protection of the inquiry information of the medical users and the data of the nonlinear SVM model can be realized; and the system and the method can be used for providing an online disease prediction service for the medical users.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com