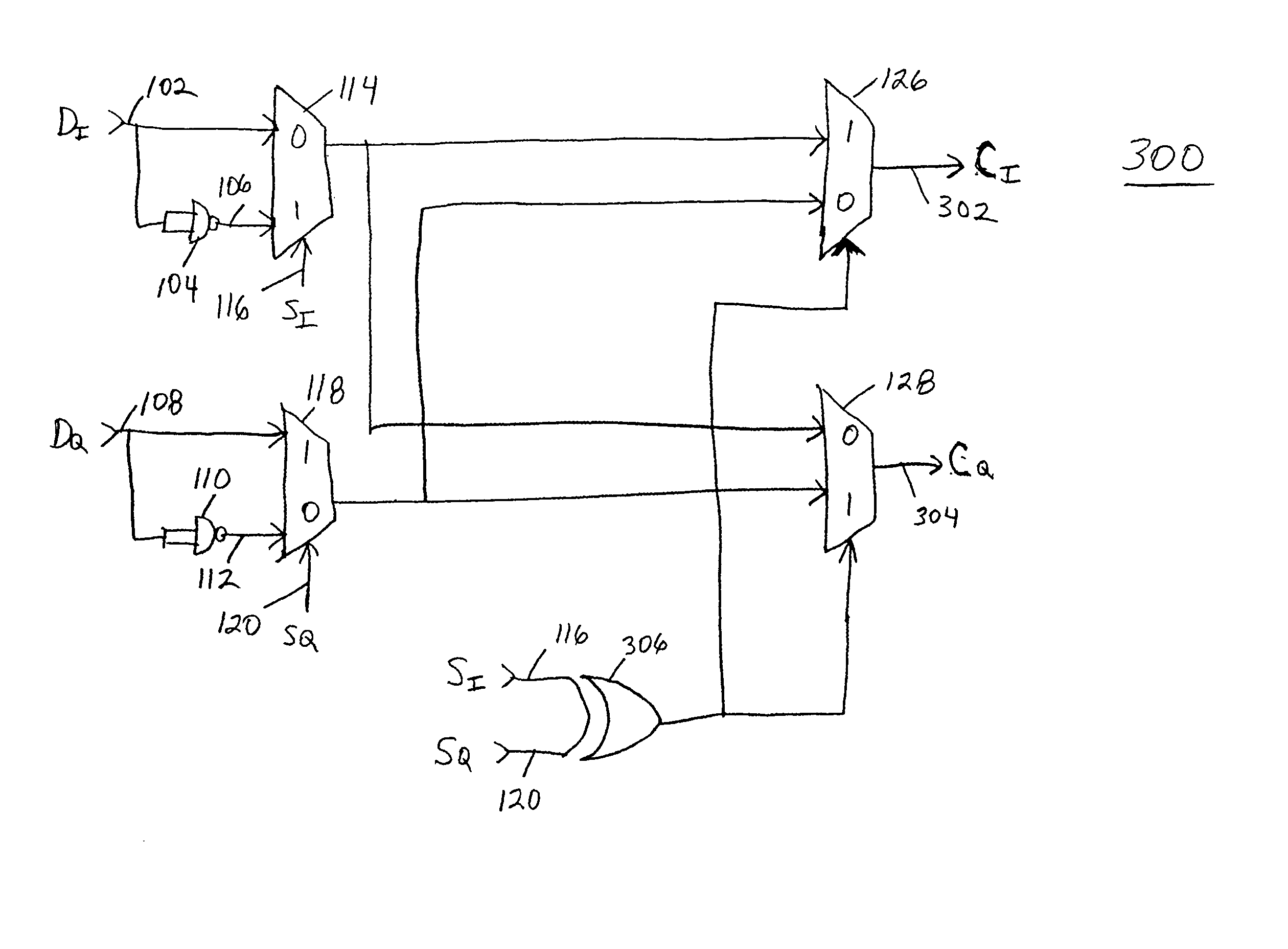
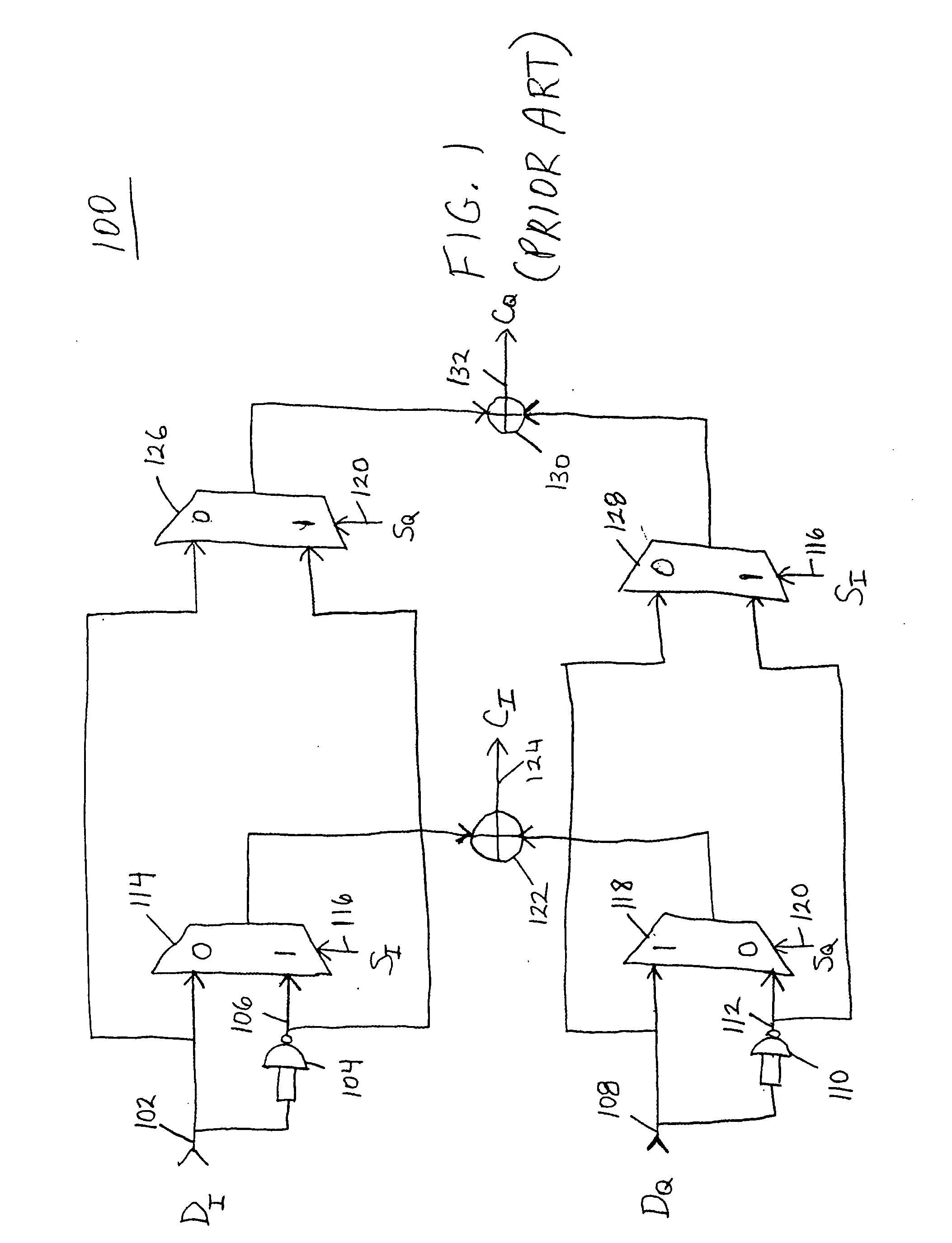
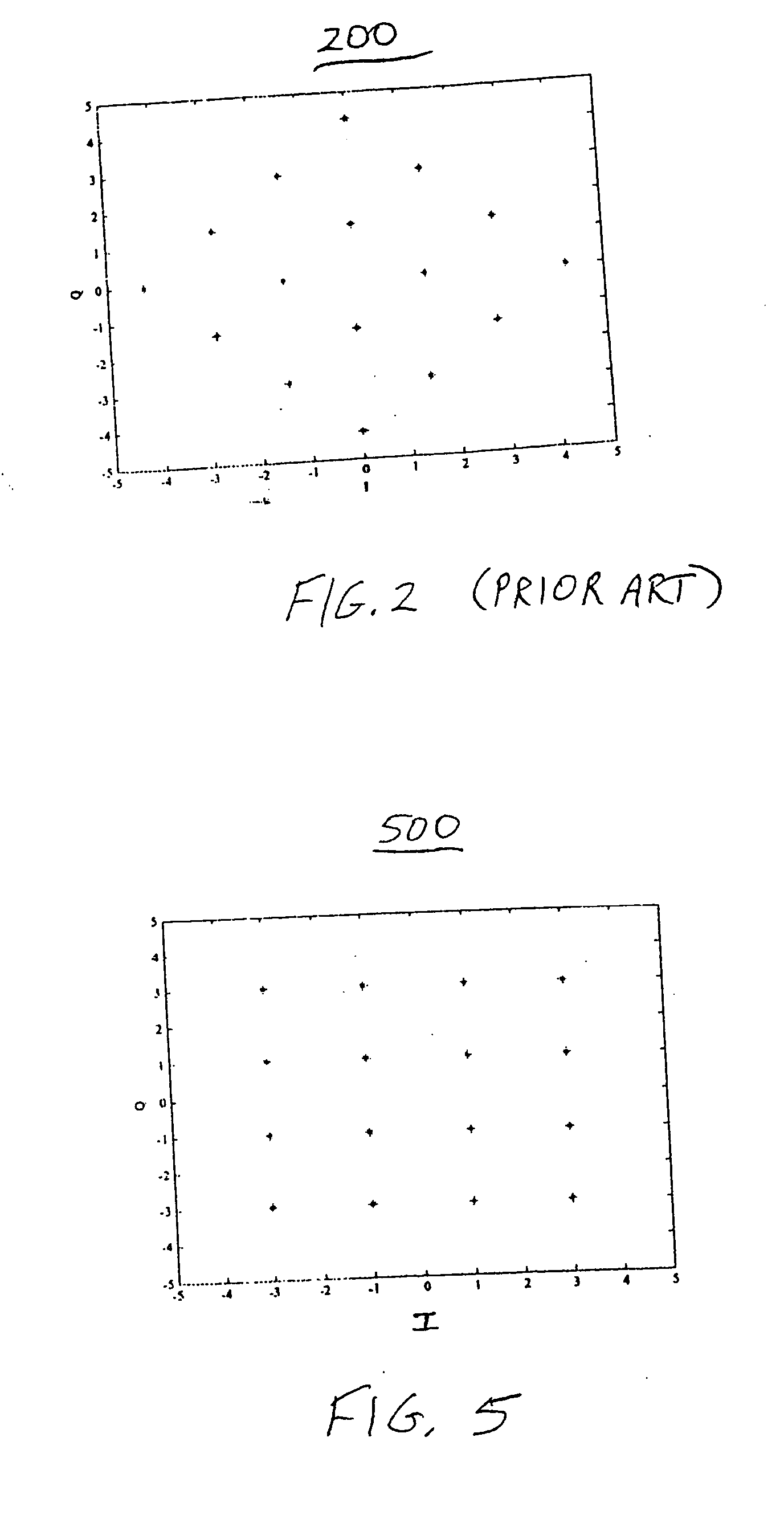
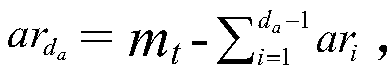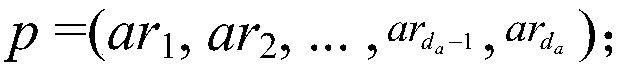Patents
Literature
333 results about "Real arithmetic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
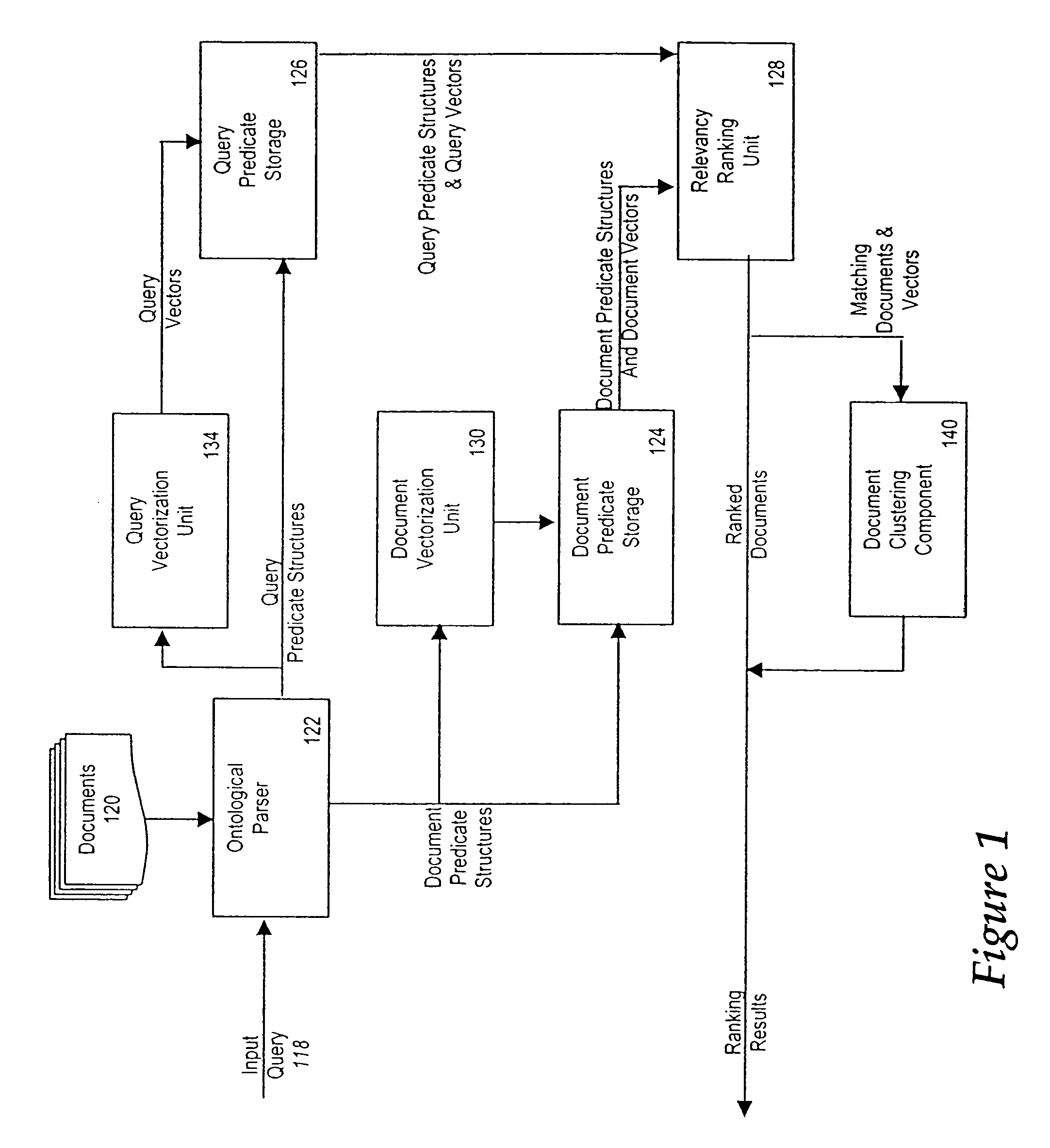
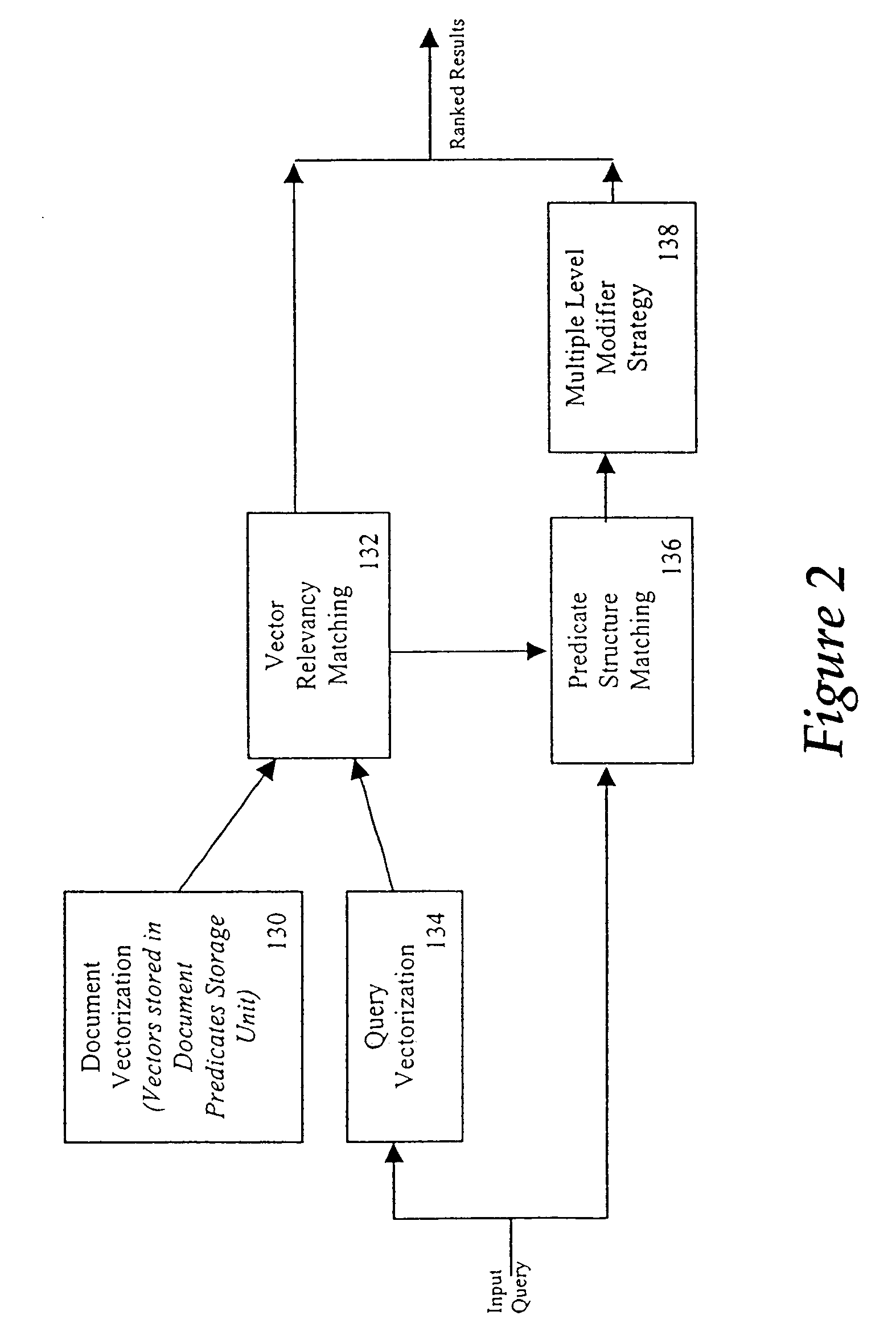
Method and system of ranking and clustering for document indexing and retrieval
InactiveUS20020129015A1Increase weightReduce weightData processing applicationsDigital data processing detailsReal arithmeticInformation retrieval
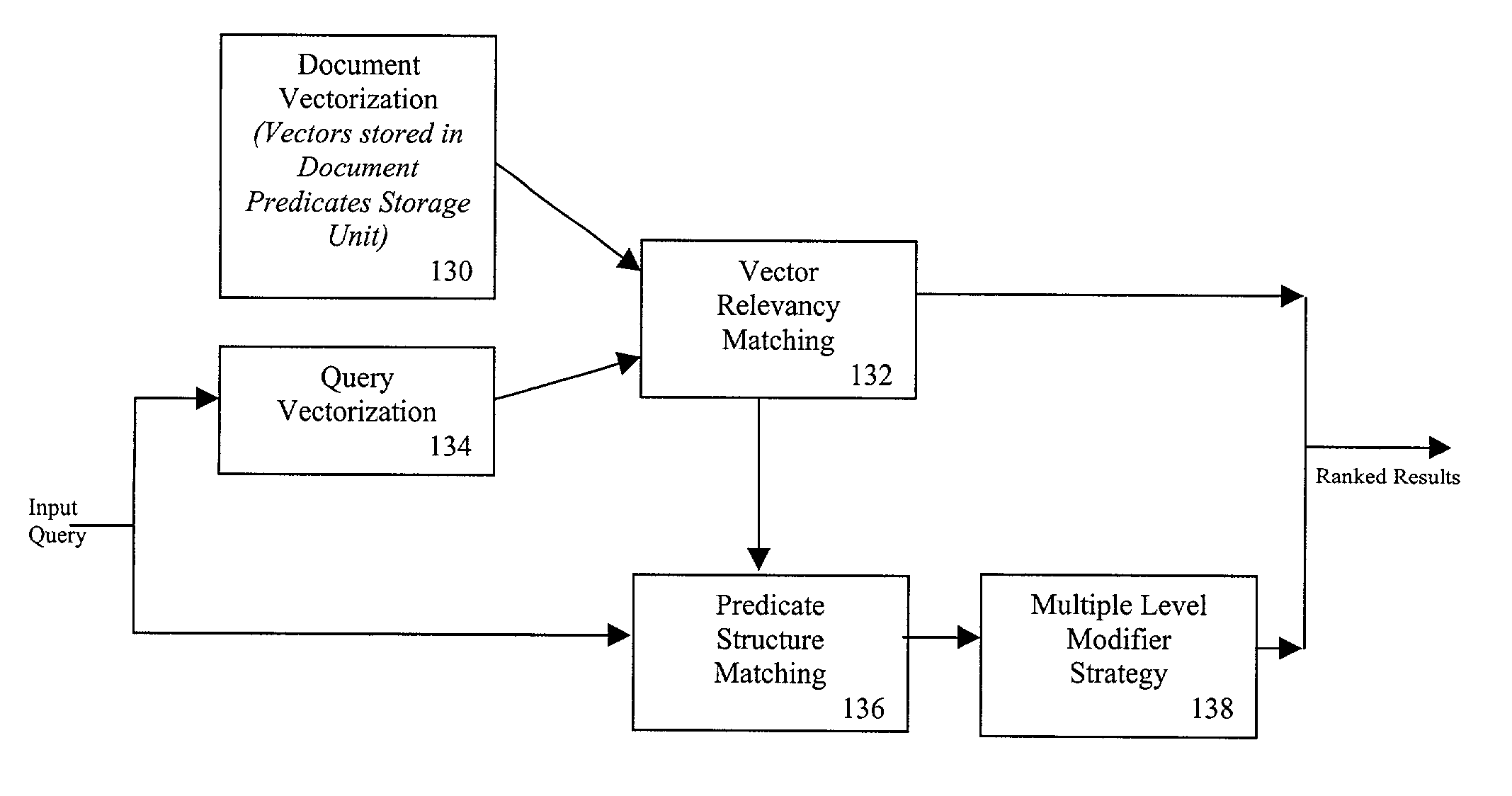
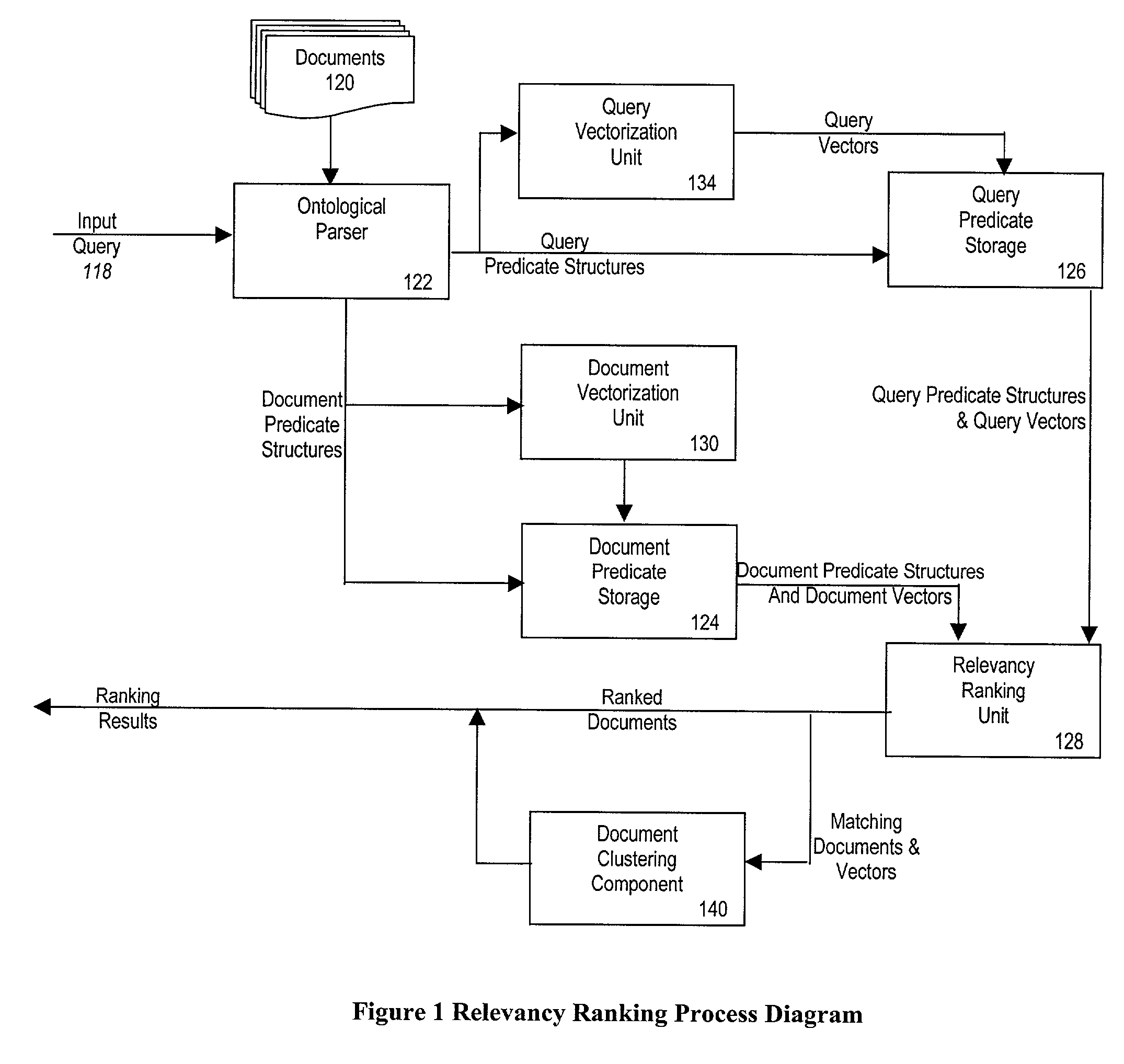
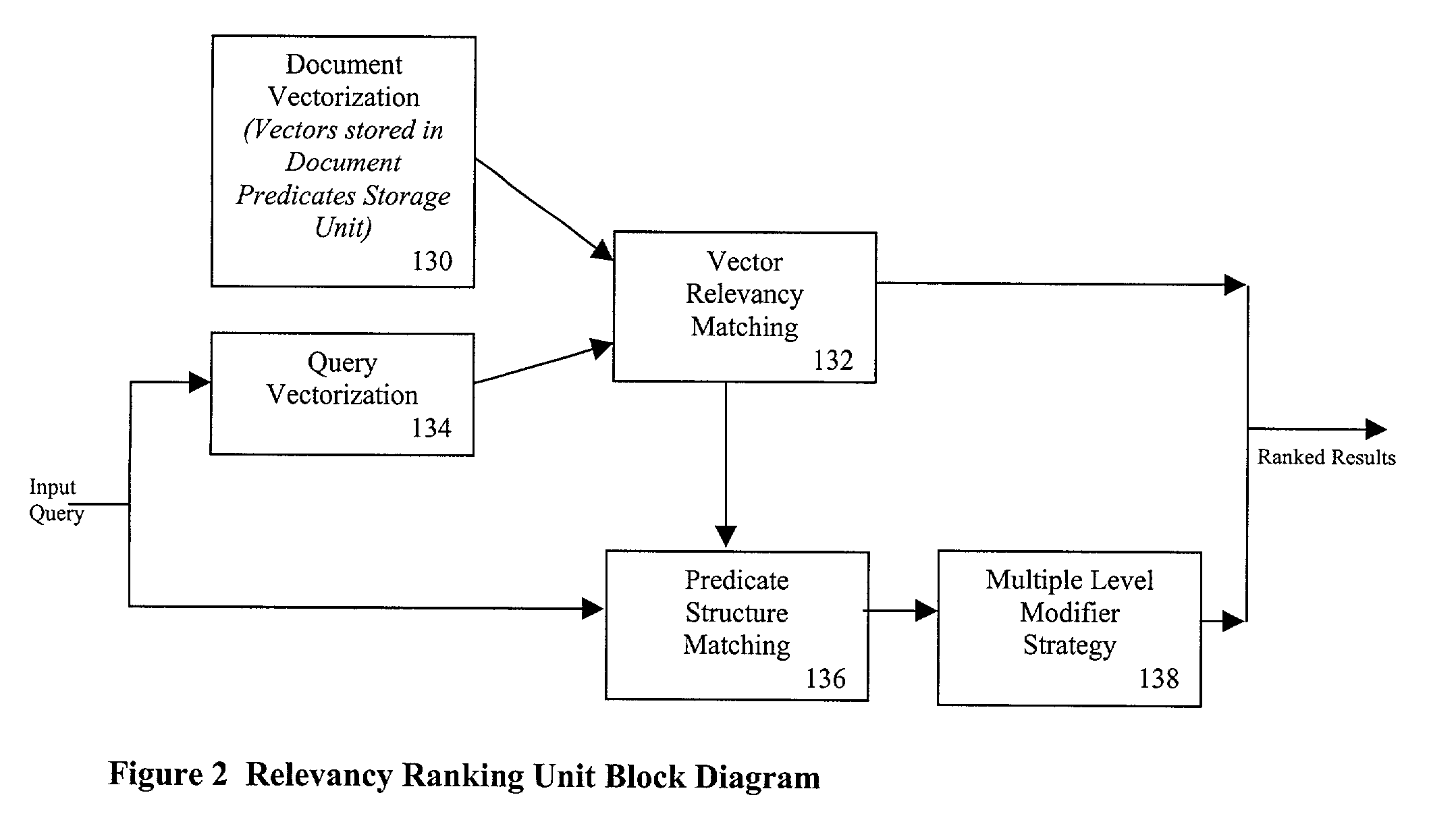
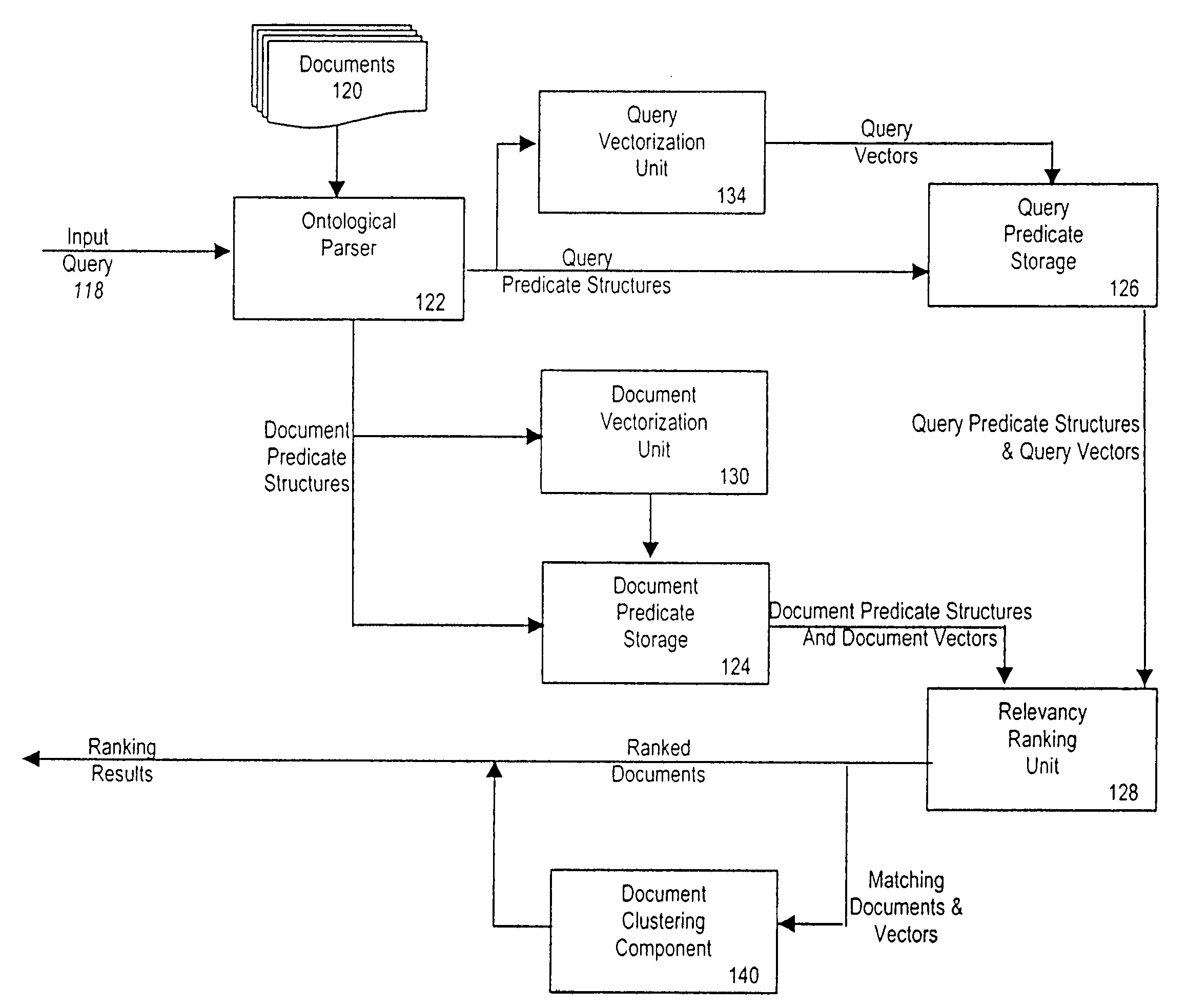
A relevancy ranking and clustering method and system that determines the relevance of a document relative to a user's query using a similarity comparison process. Input queries are parsed into one or more query predicate structures using an ontological parser. The ontological parser parses a set of known documents to generate one or more document predicate structures. A comparison of each query predicate structure with each document predicate structure is performed to determine a matching degree, represented by a real number. A multilevel modifier strategy is implemented to assign different relevance values to the different parts of each predicate structure match to calculate the predicate structure's matching degree. The relevance of a document to a user's query is determined by calculating a similarity coefficient, based on the structures of each pair of query predicates and document predicates. Documents are autonomously clustered using a self-organizing neural network that provides a coordinate system that makes judgments in a non-subjective fashion.
Owner:LEIDOS
Method and system of ranking and clustering for document indexing and retrieval
InactiveUS7496561B2Provide efficiencyData processing applicationsDigital data information retrievalReal arithmeticDocumentation
A relevancy ranking and clustering method and system that determines the relevance of a document relative to a user's query using a similarity comparison process. Input queries are parsed into one or more query predicate structures using an ontological parser. The ontological parser parses a set of known documents to generate one or more document predicate structures. A comparison of each query predicate structure with each document predicate structure is performed to determine a matching degree, represented by a real number. A multilevel modifier strategy is implemented to assign different relevance values to the different parts of each predicate structure match to calculate the predicate structure's matching degree. The relevance of a document to a user's query is determined by calculating a similarity coefficient, based on the structures of each pair of query predicates and document predicates. Documents are autonomously clustered using a self-organizing neural network that provides a coordinate system that makes judgments in a non-subjective fashion.
Owner:LEIDOS
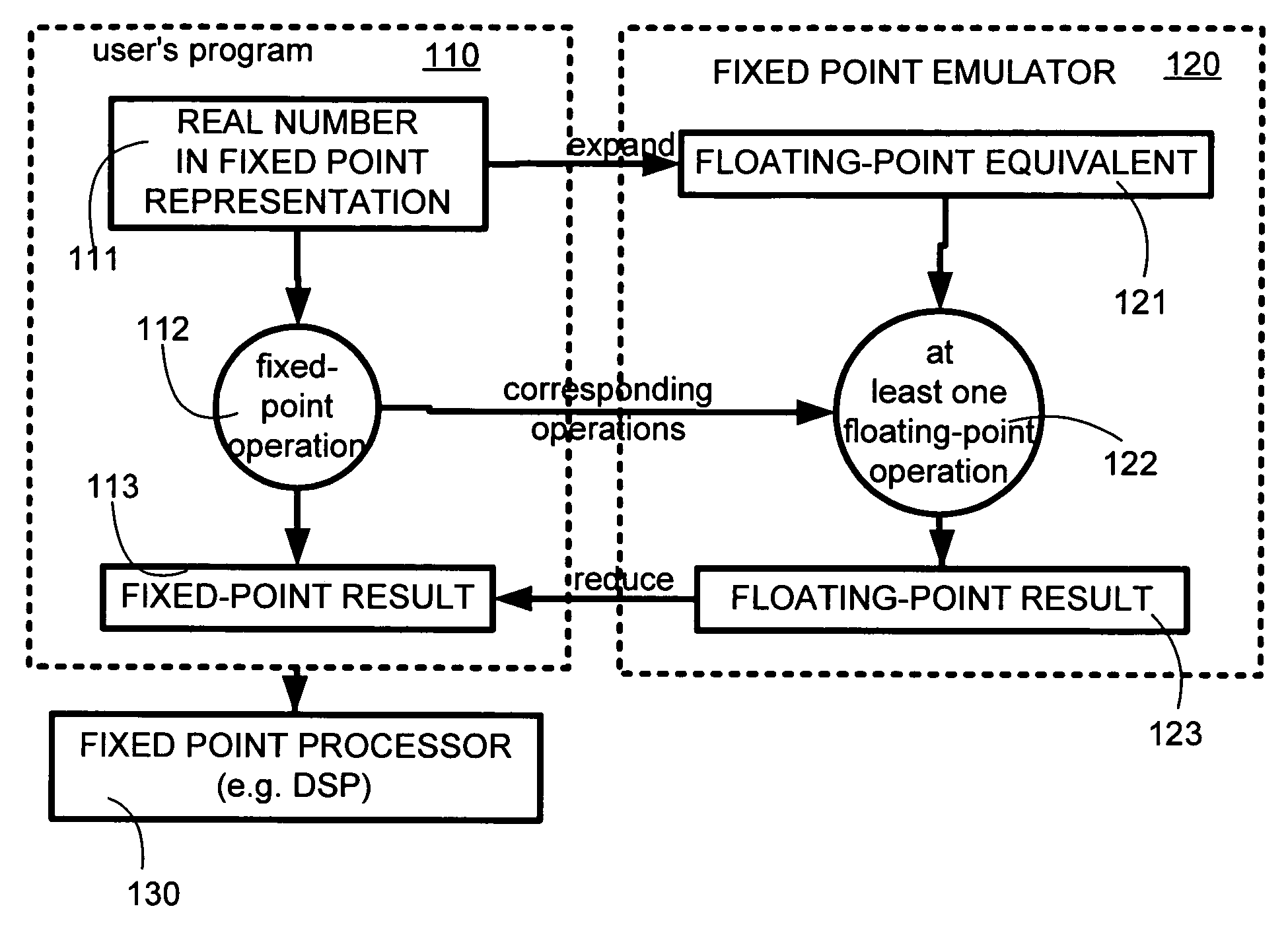
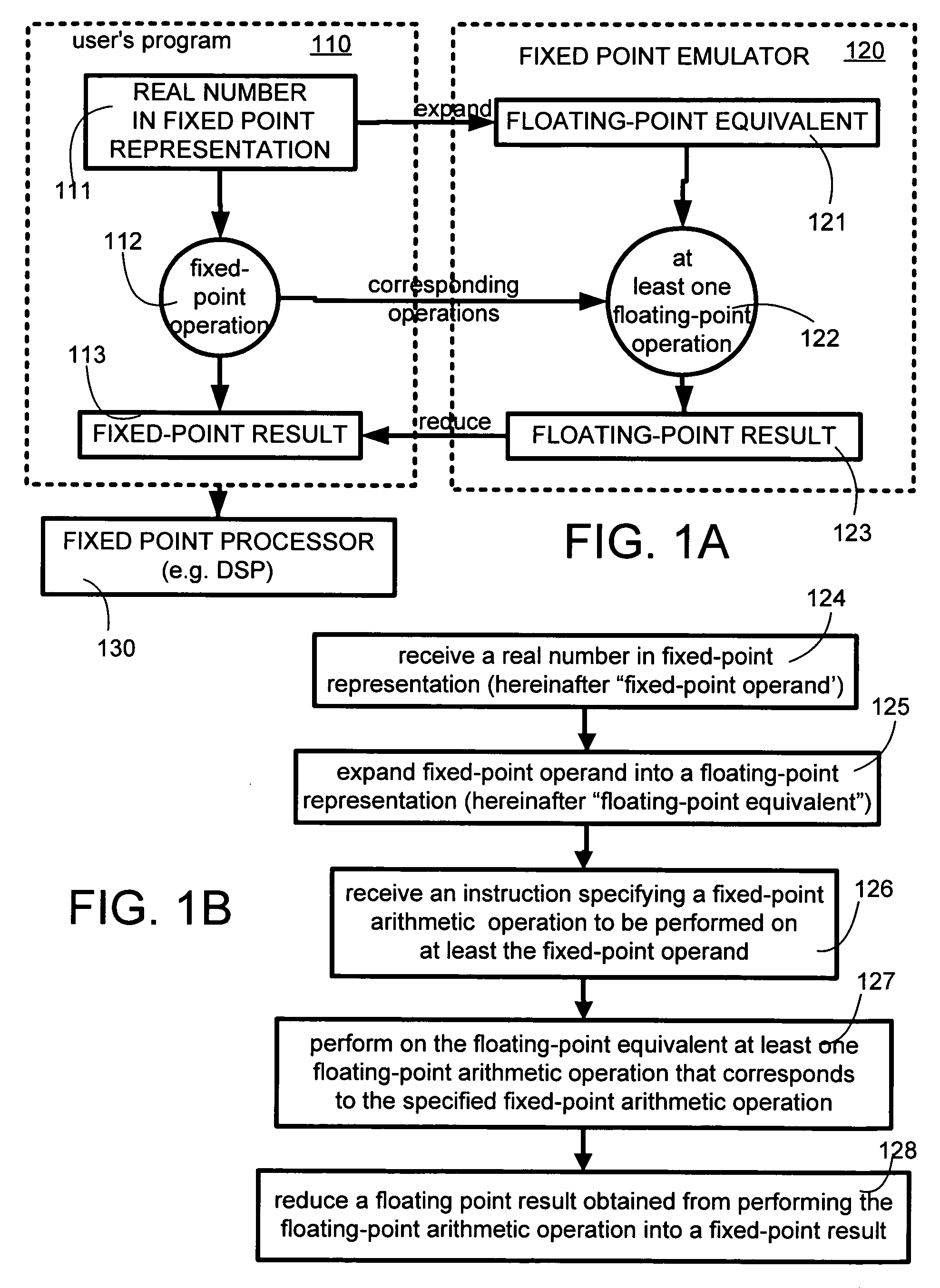
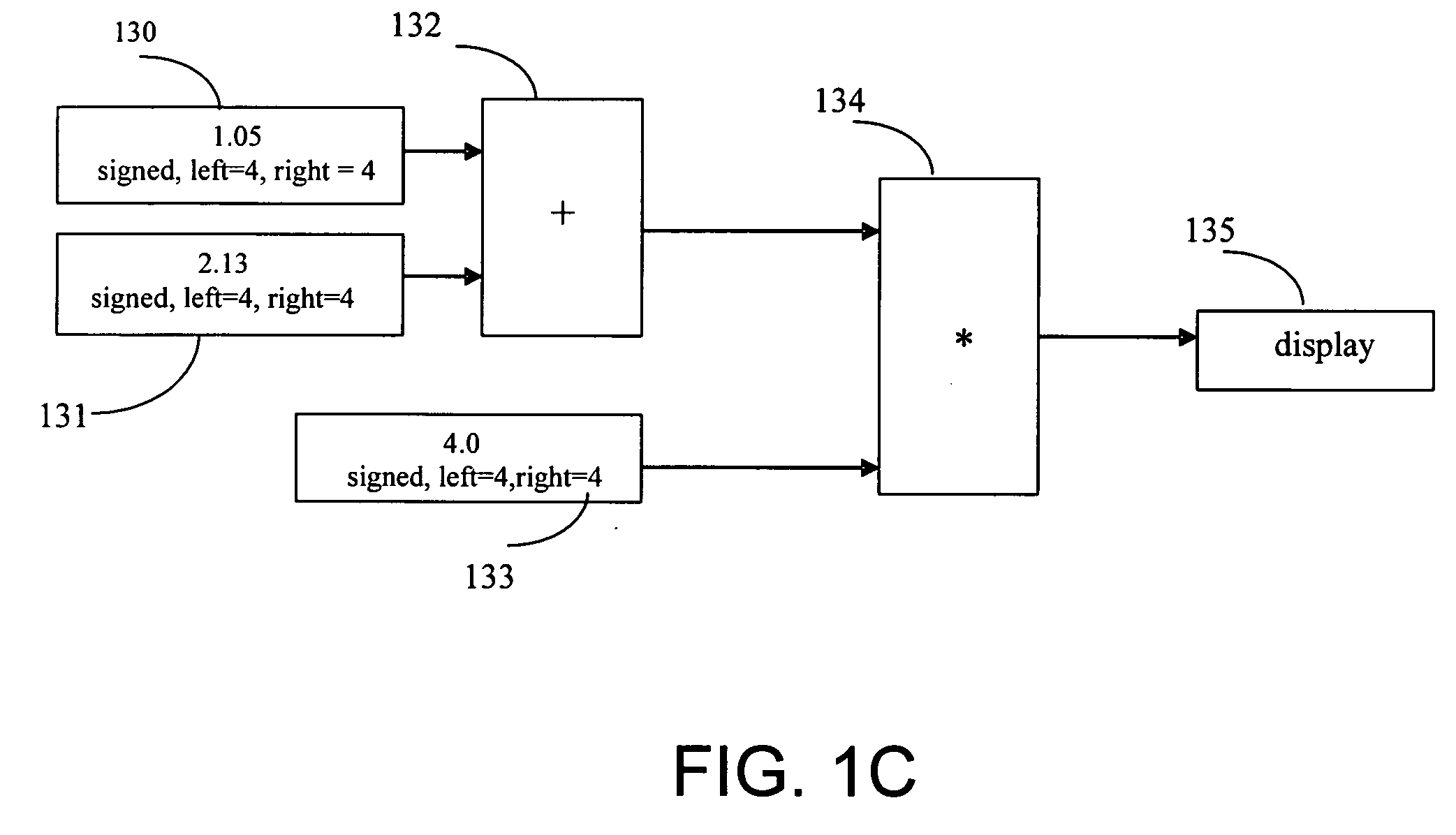
Emulation of a fixed point operation using a corresponding floating point operation
InactiveUS20050065990A1Simpler and more readableNot easy to make mistakesSoftware simulation/interpretation/emulationMemory systemsOperator overloadingReal arithmetic
A computer is programmed to emulate a fixed-point operation that is normally performed on fixed-point operands, by use of a floating-point operation that is normally performed on floating-point operands. Several embodiments of the just-described computer emulate a fixed-point operation by: expanding at least one fixed-point operand into a floating-point representation (also called “floating-point equivalent”), performing, on the floating-point equivalent, a floating-point operation that corresponds to the fixed-point operation, and reducing a floating-point result into a fixed-point result. The just-described fixed-point result may have the same representation as the fixed-point operand(s) and / or any user-specified fixed-point representation, depending on the embodiment. Also depending on the embodiment, the operands and the result may be either real or complex, and may be either scalar or vector. The above-described emulation may be performed either with an interpreter or with a compiler, depending on the embodiment. A conventional interpreter for an object-oriented language (such as MATLAB version 6) may be extended with a toolbox to perform the emulation. Use of type propagation and operator overloading minimizes the number of changes that a user must make to their program, in order to be able to use such emulation.
Owner:AGILITY DESIGN SOLUTIONS
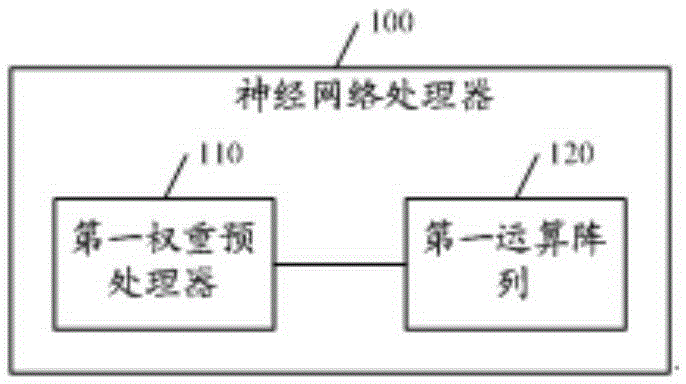
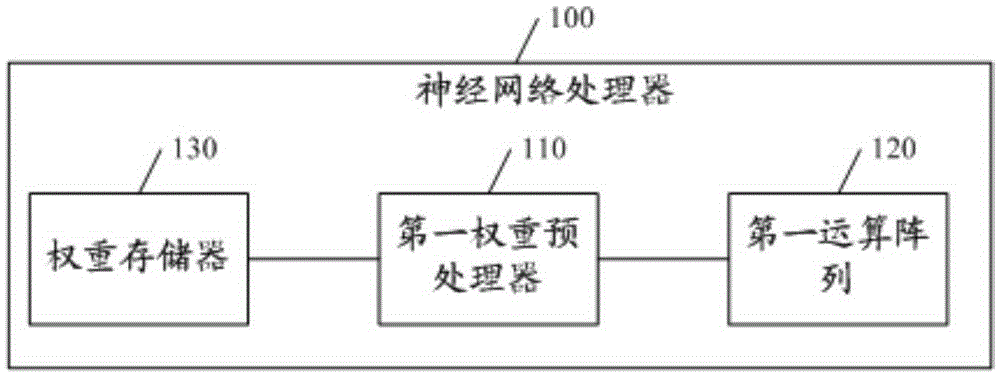
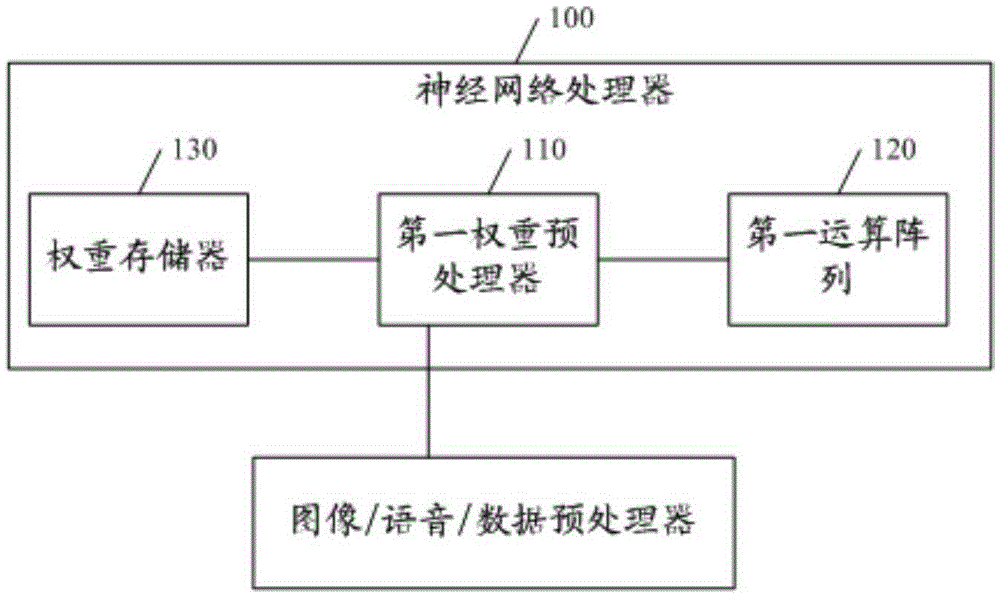
Neural network processor and convolutional neural network processor
ActiveCN105260776ARange space expansionMeet precision requirementsPhysical realisationReal arithmeticDomain space
The embodiment of the invention discloses a neural network processor and a convolutional neural network processor. The neural network processor can comprise a first weight preprocessor and a first operation array, wherein the first weight preprocessor is used for receiving a vector V<x> including M elements; the normalized value domain space of the element V(x-i) of the vector V<x> is a real number which is greater than or equal to 0 and is smaller than or equal to 1; an M*P weight vector matrix Q<x> is used for performing weighting operation on the M elements of the vector V<x> to obtain M weighting operation result vectors; the first operation array is used for accumulating the elements with the same positions in the M weighting operation result vectors to obtain P accumulated values; a vector V<y> including P elements is obtained according to the P accumulated values; and the vector V<y> is output. The technical scheme provided by the embodiment has the advantage that the expansion of the application range of neural network operation is facilitated.
Owner:HUAWEI TECH CO LTD
Seismic data interpolation system
InactiveUS7027929B2Computation timeReduce random noiseSeismic signal processingSpecial data processing applicationsReal arithmeticData set
Owner:DIVESTCO
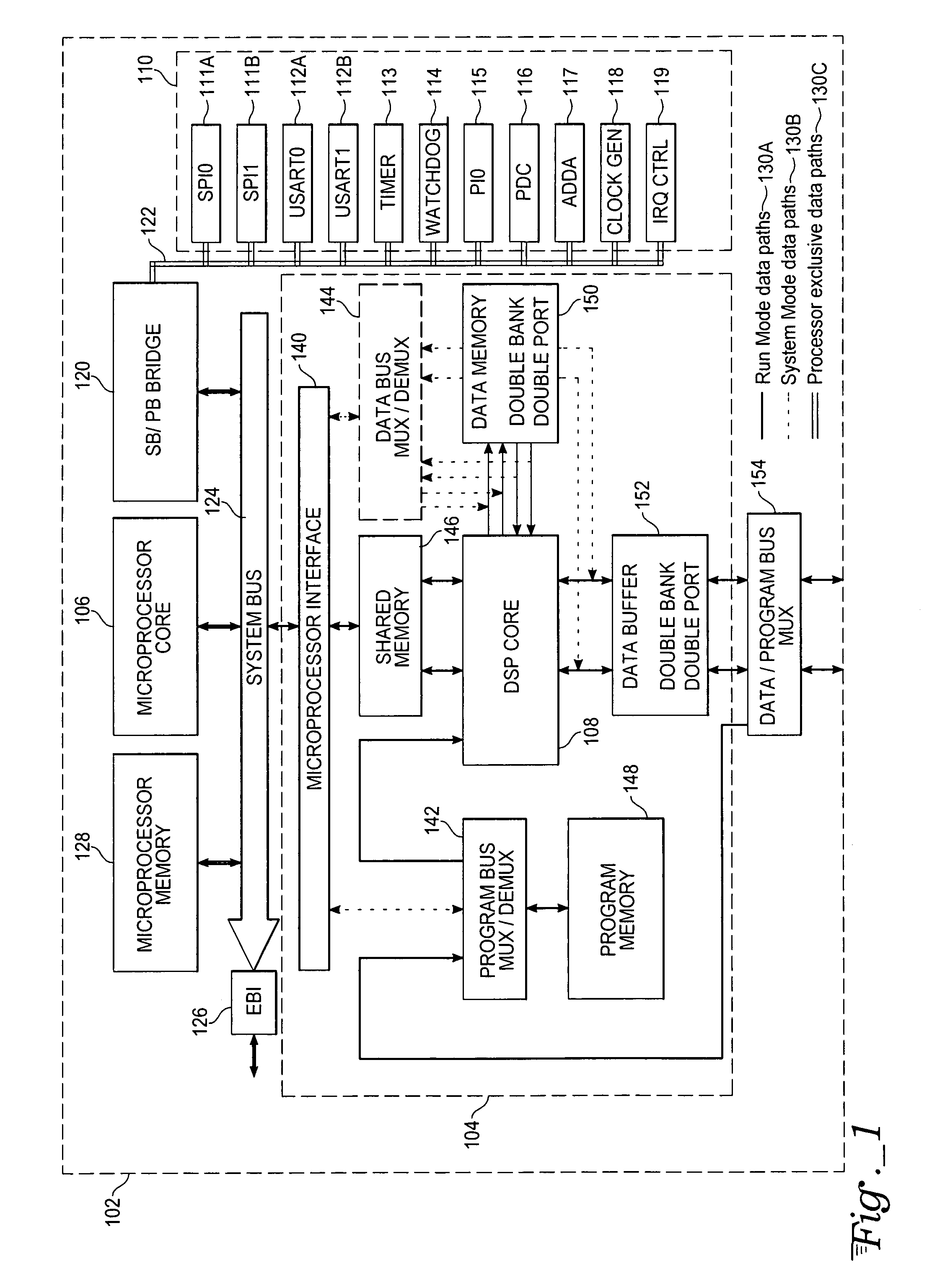
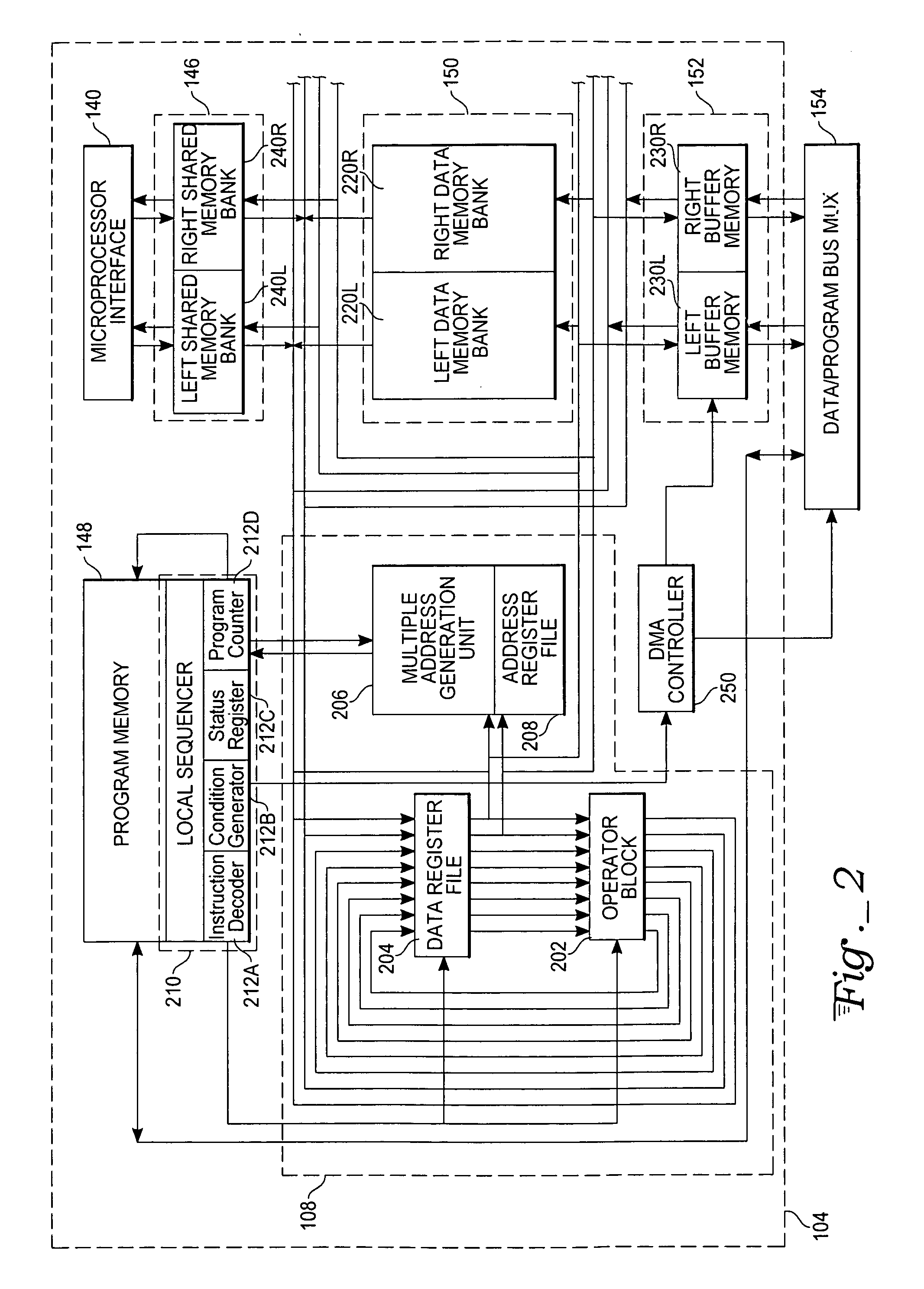
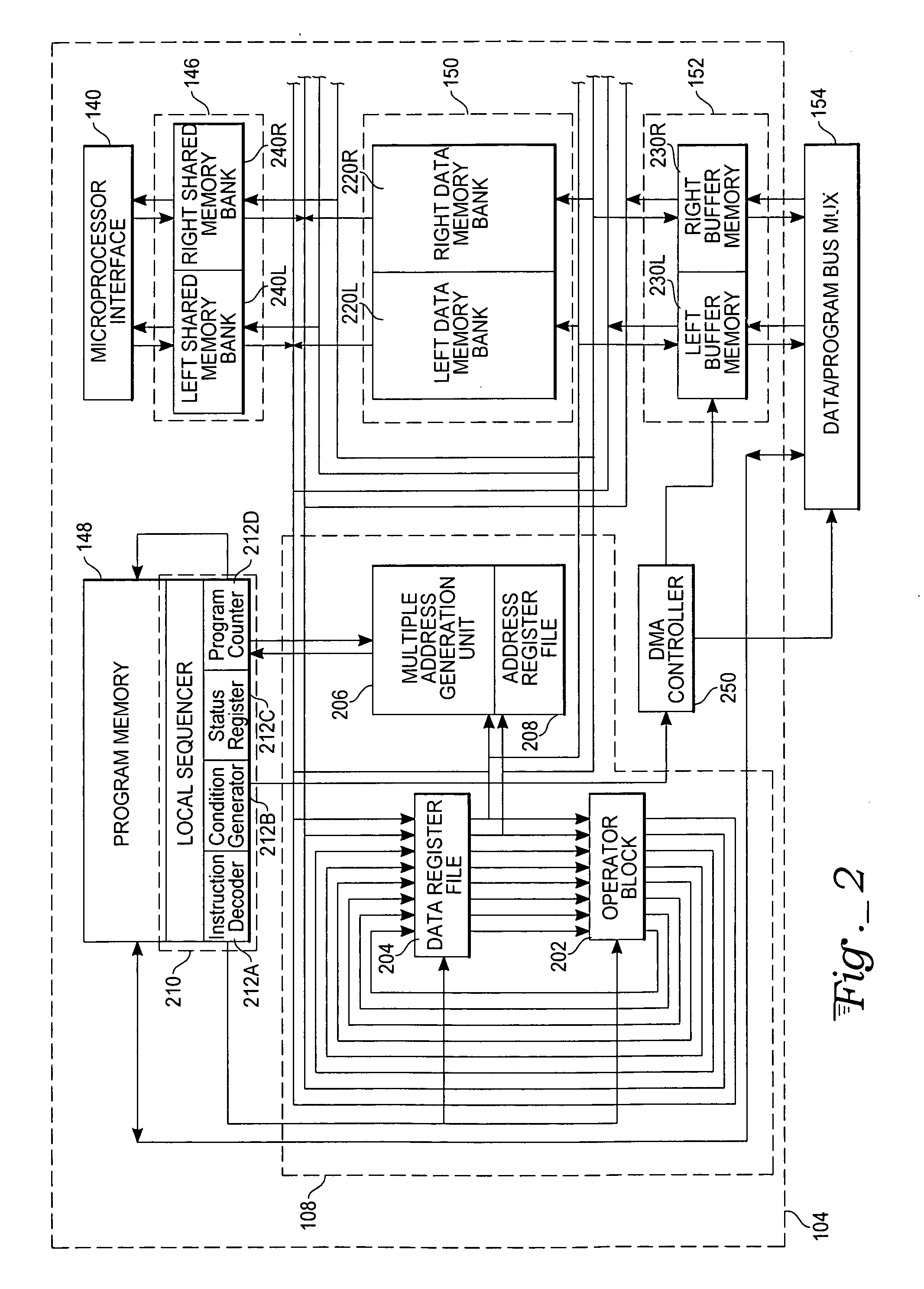
Complex domain floating point VLIW DSP with data/program bus multiplexer and microprocessor interface
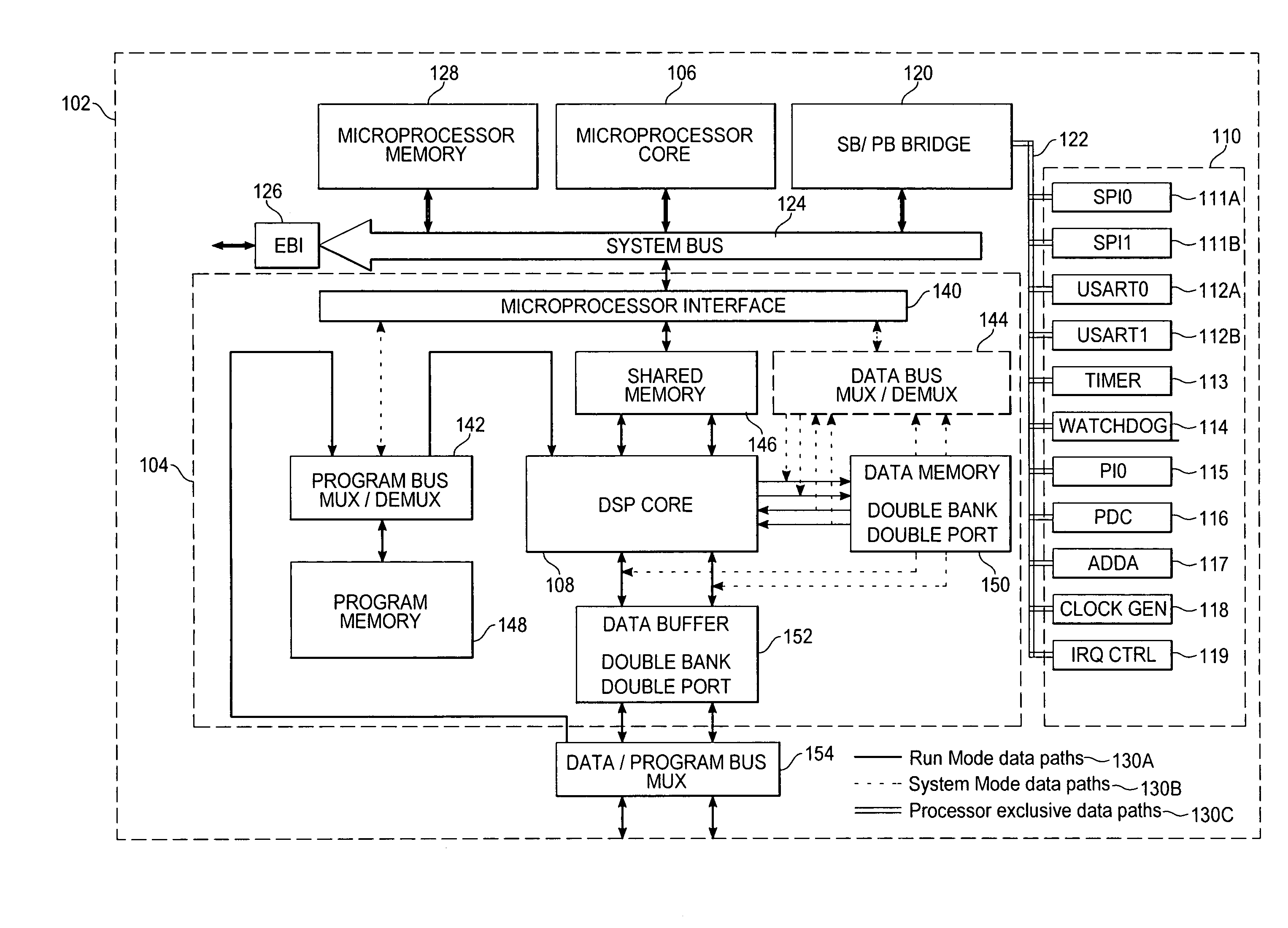
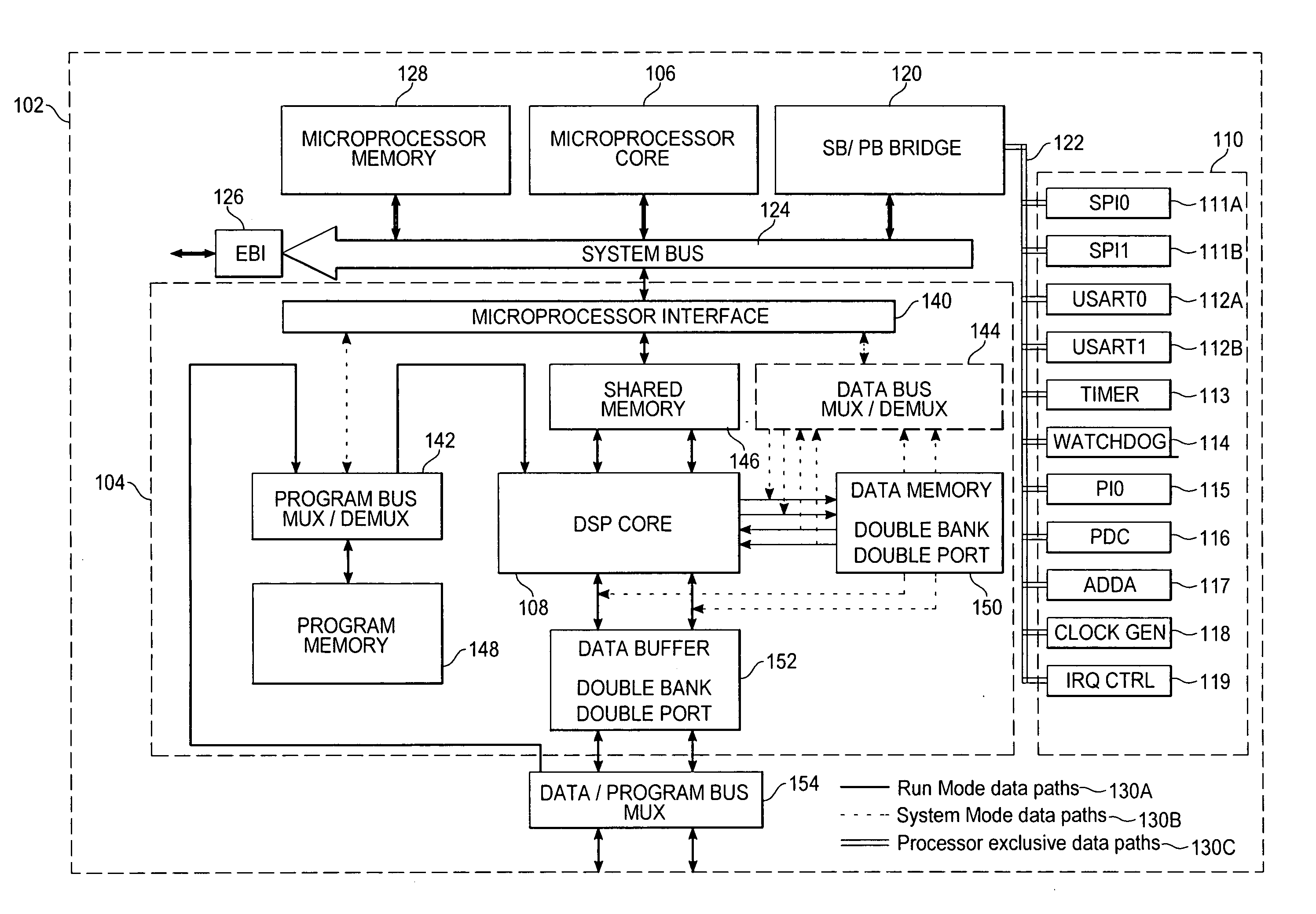
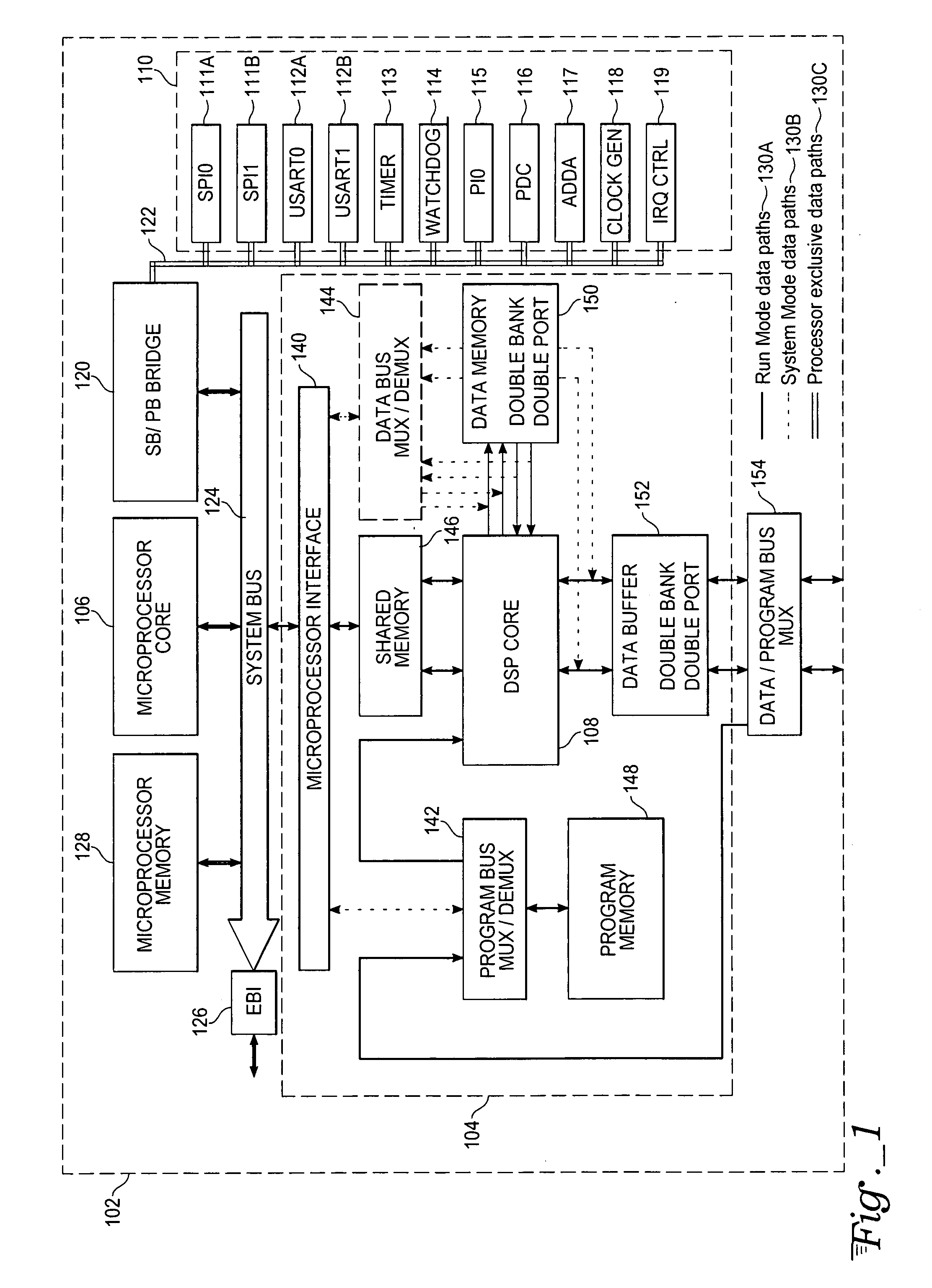
ActiveUS7437540B2No performance lossReduce in quantityArchitecture with single central processing unitSpecific program execution arrangementsDigital signal processingProcessing core
A system for digital signal processing, configured as a system on chip (SoC), combines a microprocessor core and digital signal processor (DSP) core with floating-point data processing capability. The DSP core can perform operations on floating-point data in a complex domain and is capable of producing real and imaginary arithmetic results simultaneously. This capability allows a single-cycle execution of, for example, FFT butterflies, complex domain simultaneous addition and subtraction, complex multiply accumulate (MULACC), and real domain dual multiply-accumulators (MACs). The SoC may be programmed entirely from a microprocessor programming interface, using calls from a DSP library to execute DSP functions. The cores may also be programmed separately. Capability for programming and simulating the entire SoC are provided by a separate programming environment. The SoC may have heterogeneous processing cores in which either processing core may act as master or slave, or both cores may operate simultaneously and independently.
Owner:ATMEL CORP
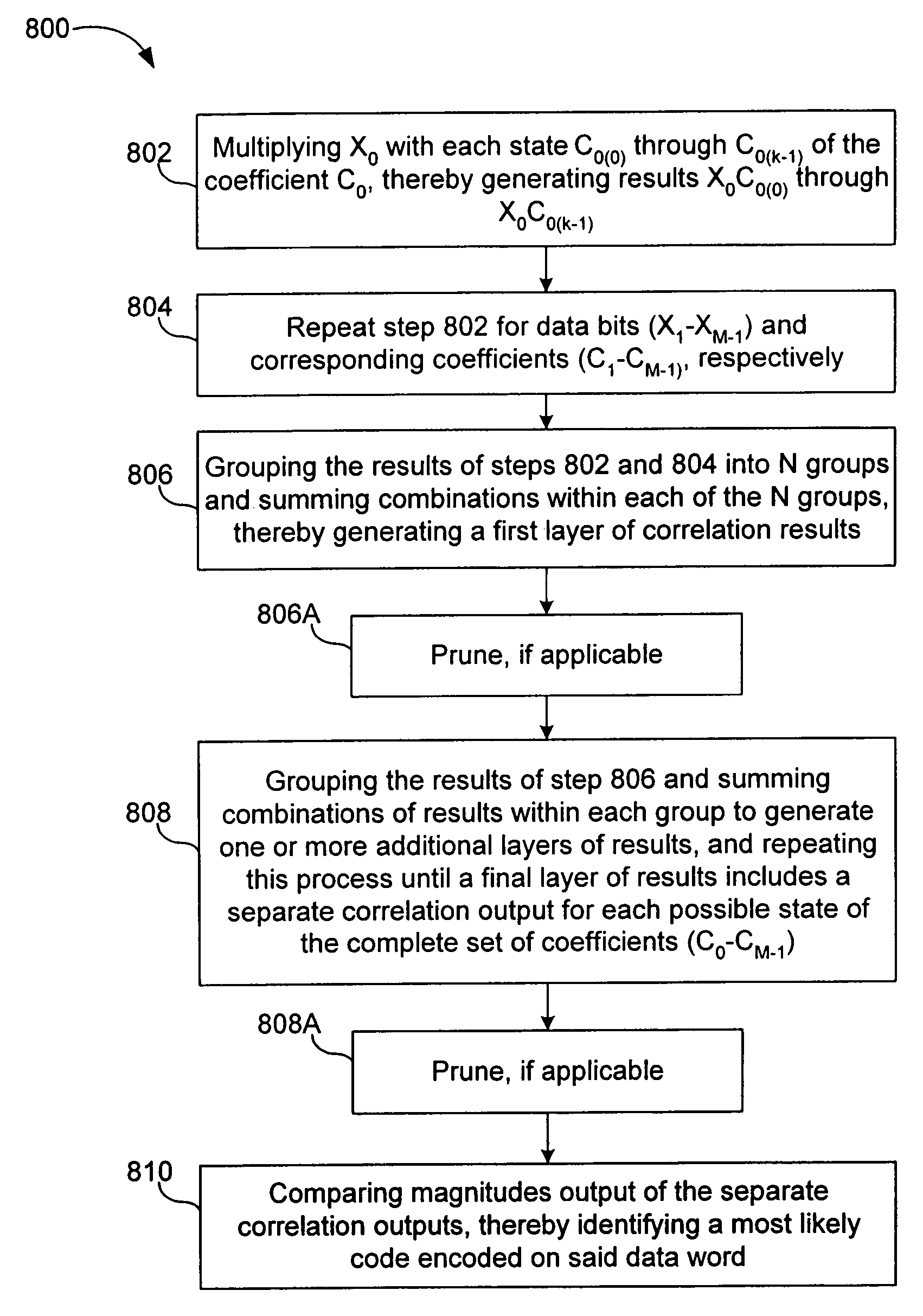
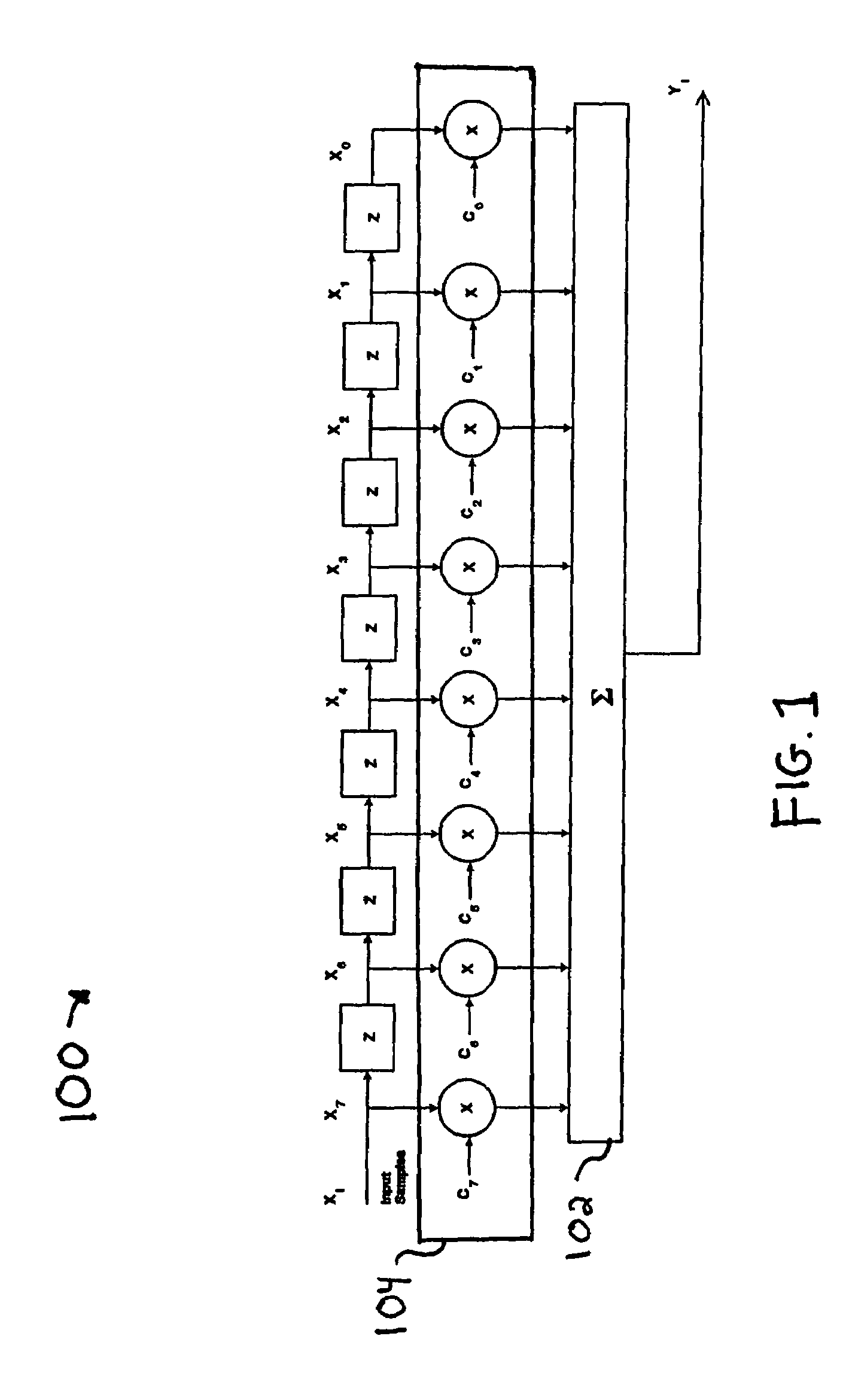
Methods, systems, and computer program products for parallel correlation and applications thereof
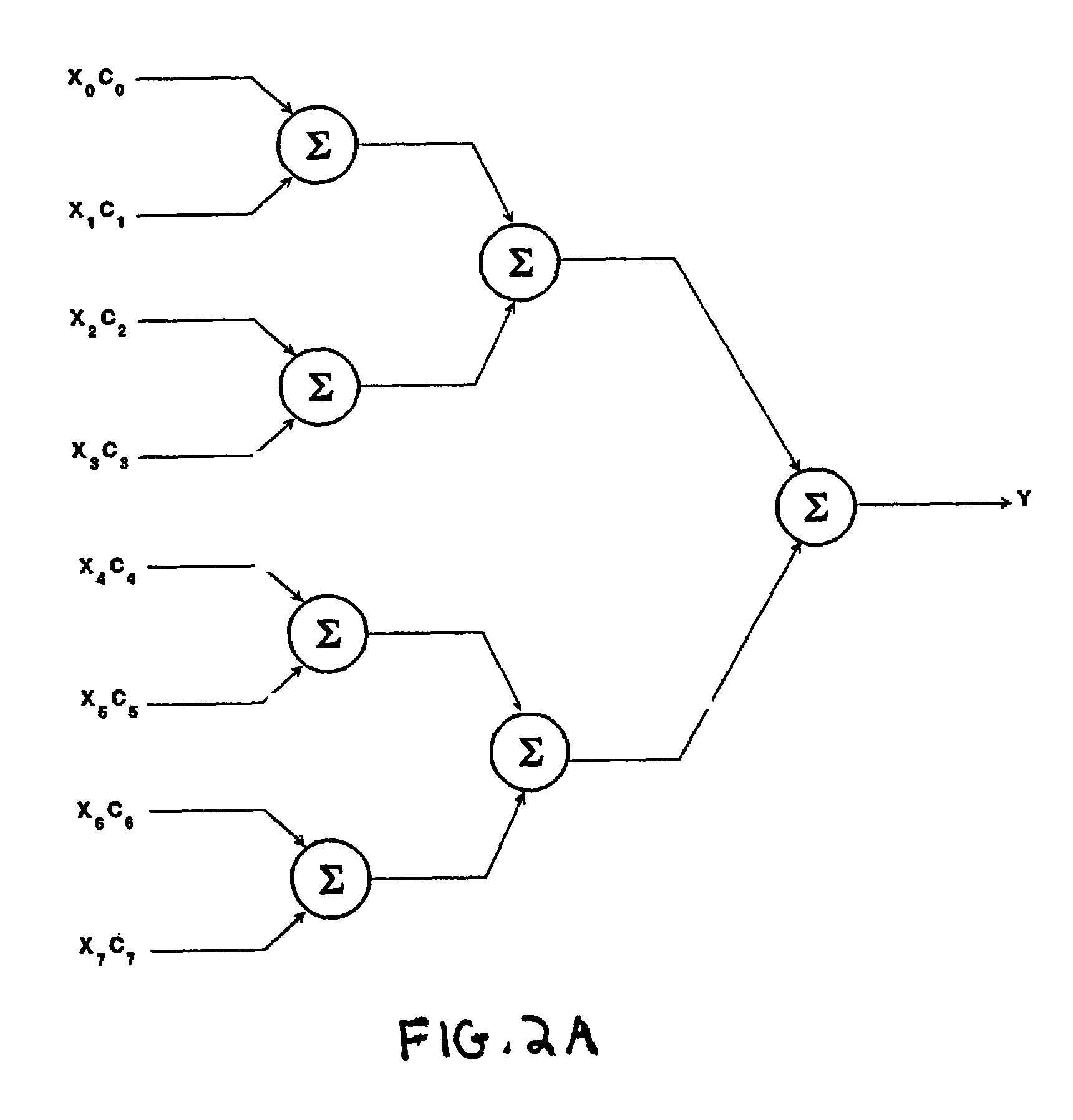
A fast correlator transform (FCT) algorithm and methods and systems for implementing same, correlate an encoded data word (X0-XM−1) with encoding coefficients (C0-CM−1), wherein each of (X0-XM−1) is represented by one or more bits and each said coefficient is represented by one or more bits, wherein each coefficient has k possible states, and wherein M is greater than 1. X0 is multiplied by each state (C0(0) through C0(k−1)) of the coefficient C0, thereby generating results X0C0(0) through X0C0(k−1). This is repeated for data bits (X1-XM−1) and corresponding coefficients (C1-CM−1), respectively. The results are grouped into N groups. Members of each of the N groups are added to one another, thereby generating a first layer of correlation results. The first layer of results is grouped and the members of each group are summed with one another to generate a second layer of results. This process is repeated until a final layer of results is generated. The final layer of results includes a separate correlation output for each possible state of the complete set of coefficients (C0-CM−1). The final layer of results is compared to identify a most likely code encoded on the data word. The summations can be optimized to exclude summations that would result in invalid combinations of the encoding coefficients (C0-CM−1). Substantially the same hardware can be utilized for processing in-phase and quadrature phase components of the data word (X0-XM−1). The coefficients (C0-CM−1) can represent real numbers and / or complex numbers. The coefficients (C0-CM−1) can be represented with a single bit or with multiple bits (e.g., magnitude). The coefficients (C0-CM−1) represent, for example, a cyclic code keying (“CCK”) code set substantially in accordance with IEEE 802.11 WLAN standard.
Owner:PARKER VISION INC
Method and apparatus for SIMD complex arithmetic
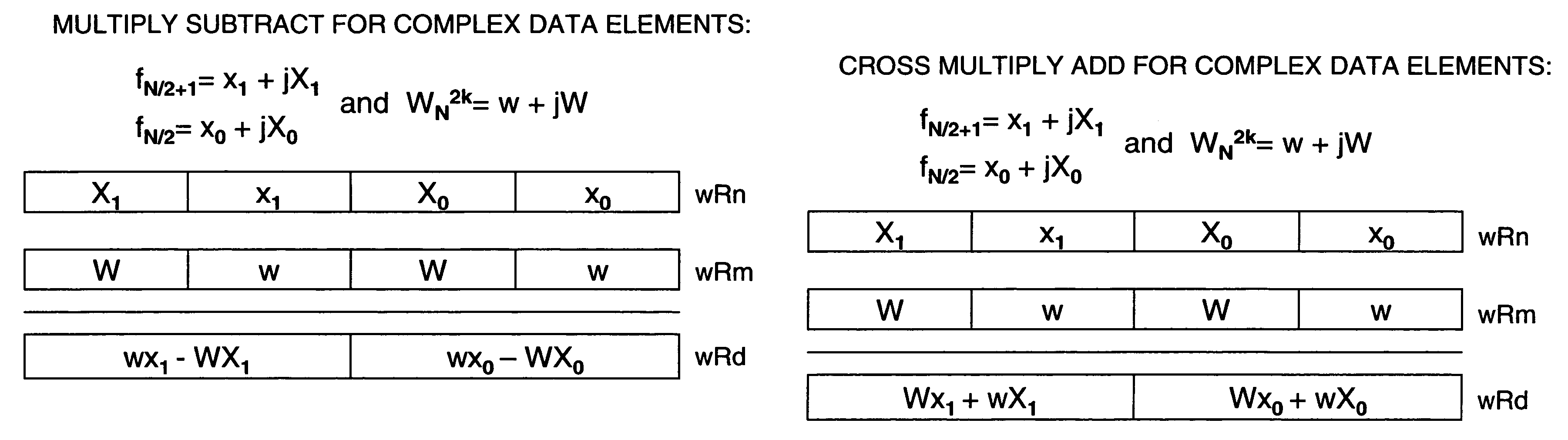
Methods and apparatus for calculating Single-Instruction-Multiple-Data (SIMD) complex arithmetic. A coprocessor instruction has a format identifying a multiply and subtract instruction to generate real components for complex multiplication of first operand complex data and corresponding second operand complex data, a cross multiply and add instruction to generate imaginary components for complex multiplication of the first operand complex data and the corresponding second operand complex data, an add-subtract instruction to add real components of the first operand to imaginary components of the second operand and to subtract real components of the second operand from imaginary components of the first operand, and a subtract-add instruction to subtract the real components of the second operand from the imaginary components of the first operand and to add the real components of the first operand to the imaginary components of the second operand.
Owner:MARVELL ASIA PTE LTD
Cross multiply and add instruction and multiply and subtract instruction SIMD execution on real and imaginary components of a plurality of complex data elements
Methods and apparatus for calculating Single-Instruction-Multiple-Data (SIMD) complex arithmetic. A coprocessor instruction has a format identifying a multiply and subtract instruction to generate real components for complex multiplication of first operand complex data and corresponding second operand complex data, a cross multiply and add instruction to generate imaginary components for complex multiplication of the first operand complex data and the corresponding second operand complex data, an add-subtract instruction to add real components of the first operand to imaginary components of the second operand and to subtract real components of the second operand from imaginary components of the first operand, and a subtract-add instruction to subtract the real components of the second operand from the imaginary components of the first operand and to add the real components of the first operand to the imaginary components of the second operand.
Owner:MARVELL ASIA PTE LTD
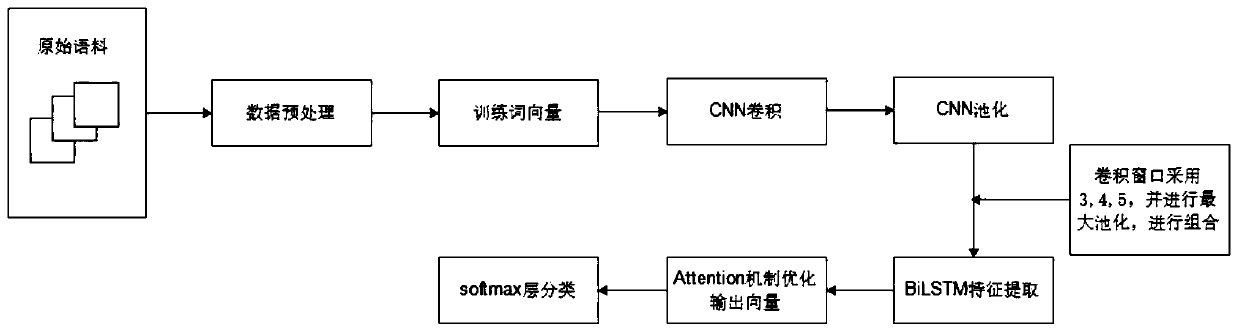
A text sentiment analysis method combining BiLSTM with an Attention mechanism
PendingCN109740148ACharacter and pattern recognitionNeural architecturesReal arithmeticFeature extraction
The invention provides a short text sentiment tendency analysis method combining BiLSTM with an Attention mechanism. A model combining a convolutional bidirectional long-short time memory network withan attention mechanism is constructed; for the problems that high dimensions represented by data in text classification are difficult to train and vector representation features are irrelevant, the text data are mapped to a low-dimension real number vector, and the problem that a model is subjected to dimension disasters due to high-dimension input is avoided; and for the feature selection problem, constructing a feature extraction model, and carrying out text sentiment classification on the extracted features.
Owner:BEIJING UNIV OF TECH
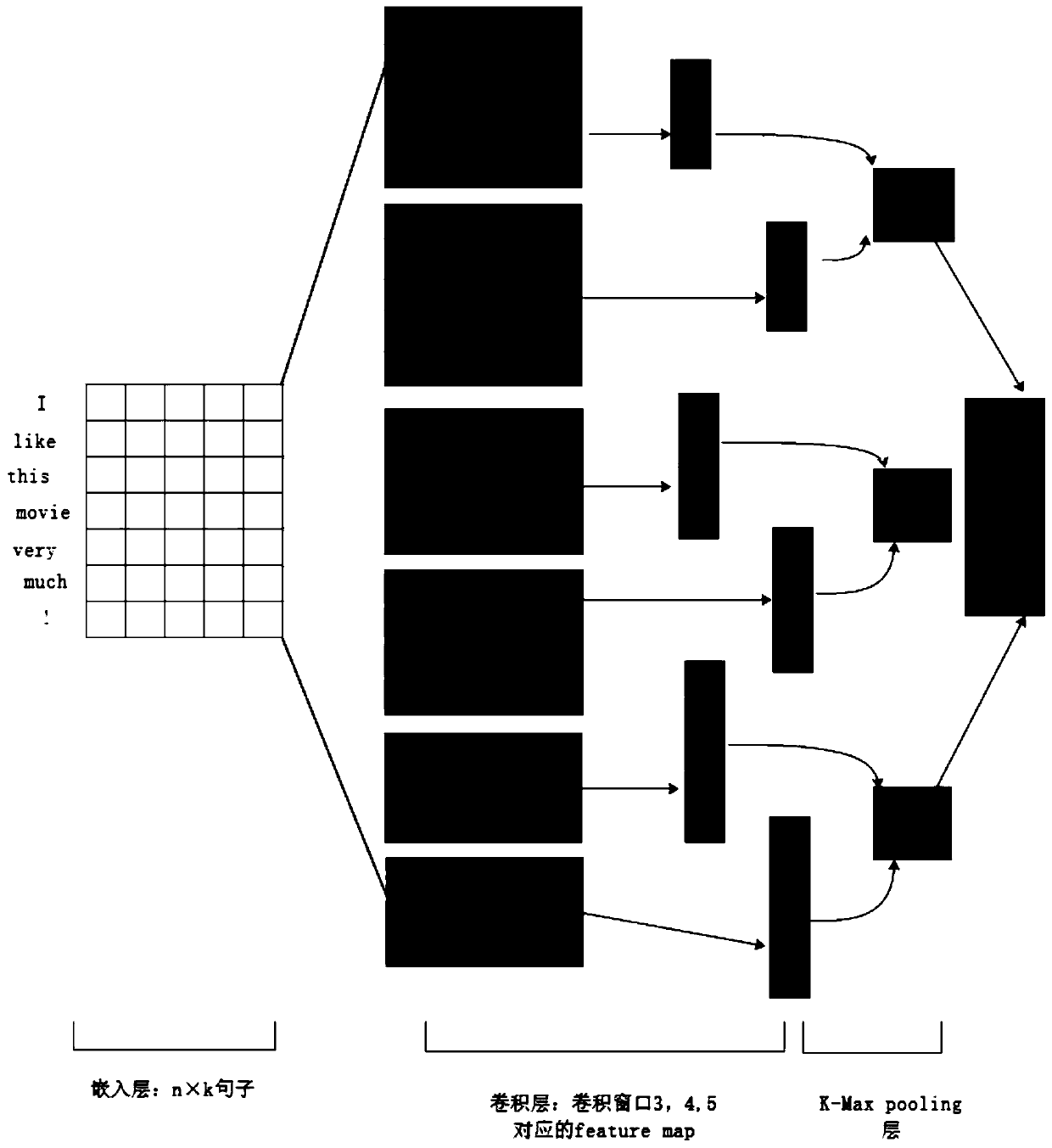
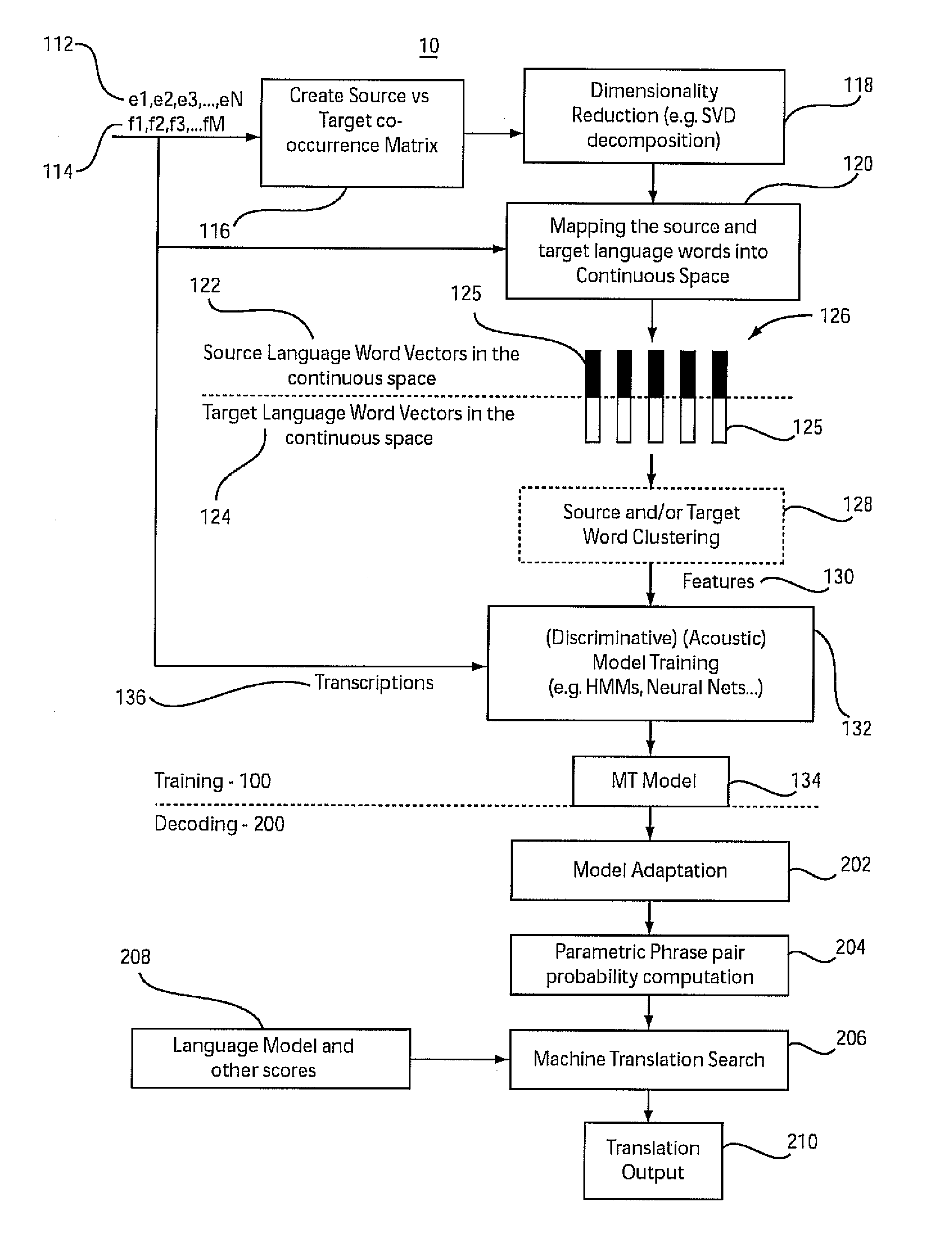
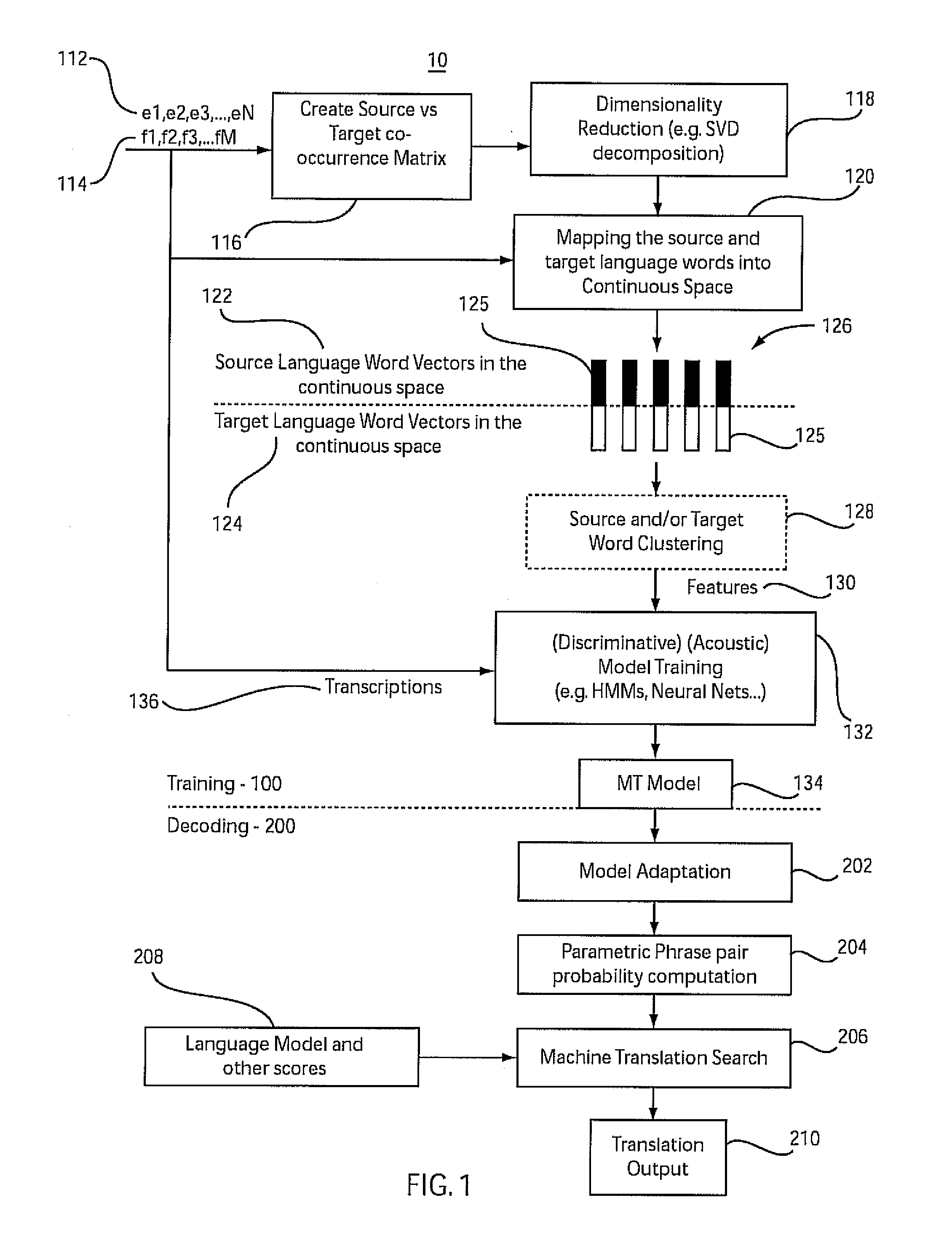
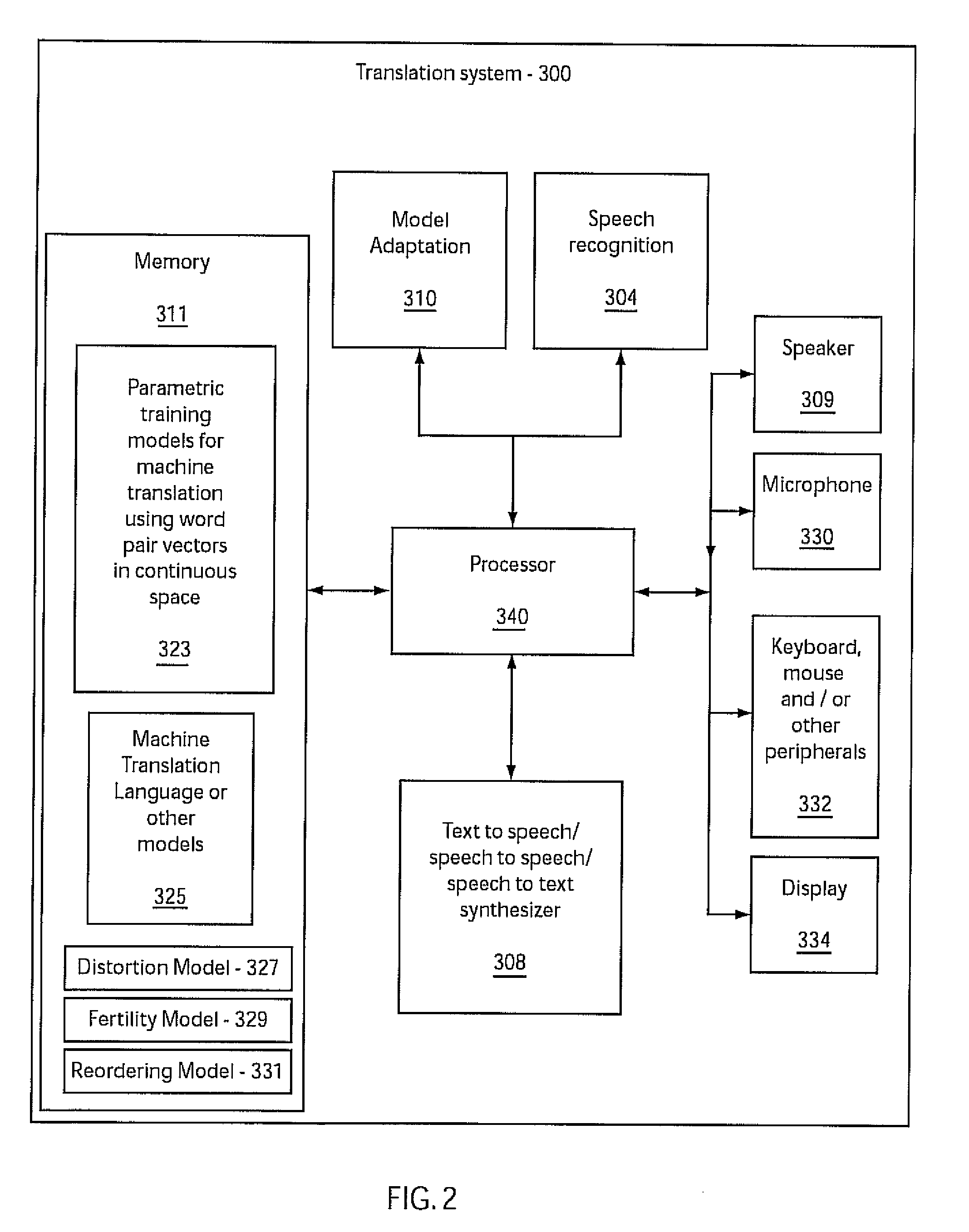
Machine translation in continuous space
A system and method for training a statistical machine translation model and decoding or translating using the same is disclosed. A source word versus target word co-occurrence matrix is created to define word pairs. Dimensionality of the matrix may be reduced. Word pairs are mapped as vectors into continuous space where the word pairs are vectors of continuous real numbers and not discrete entities in the continuous space. A machine translation parametric model is trained using an acoustic model training method based on word pair vectors in the continuous space.
Owner:IBM CORP
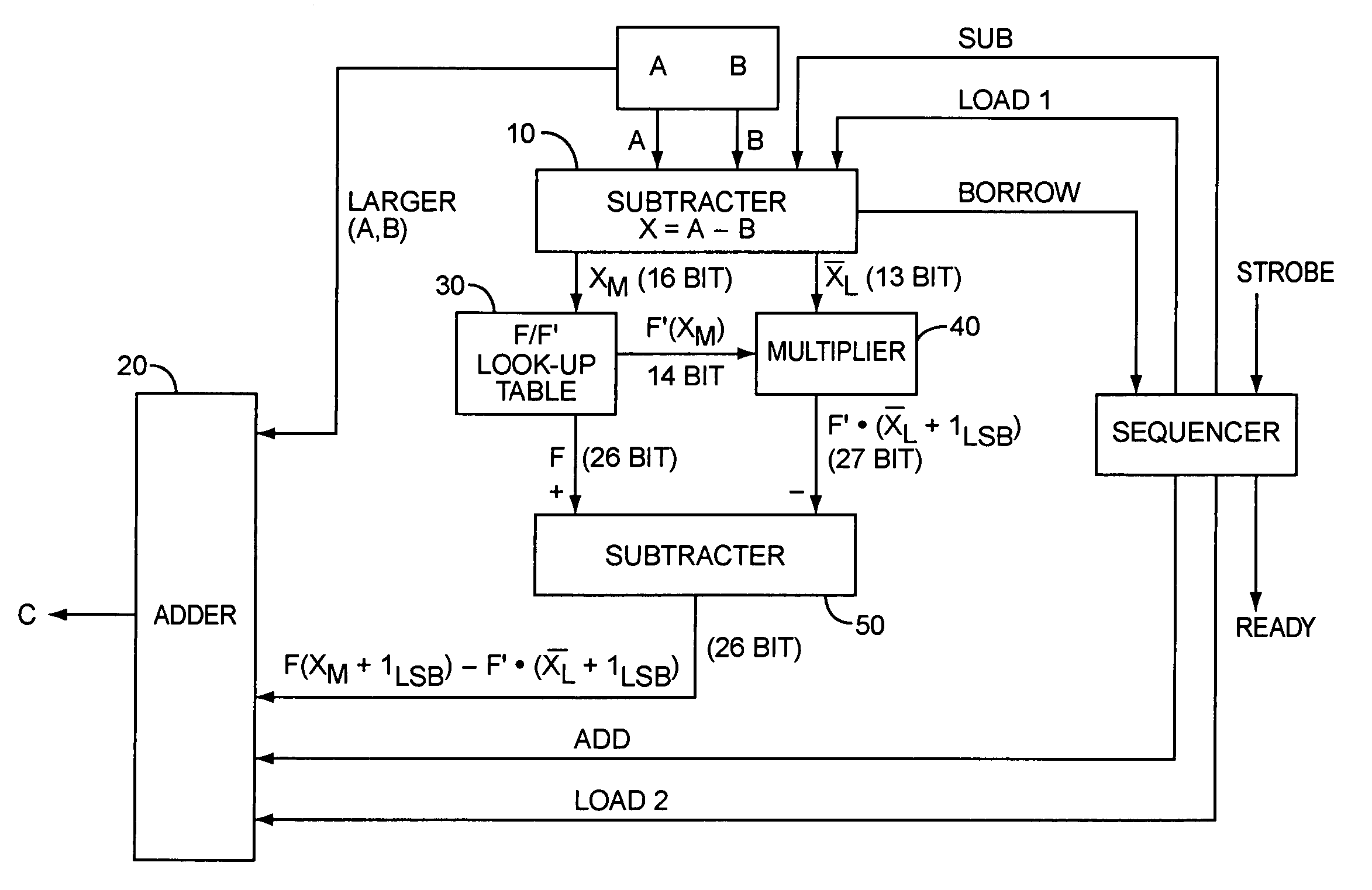
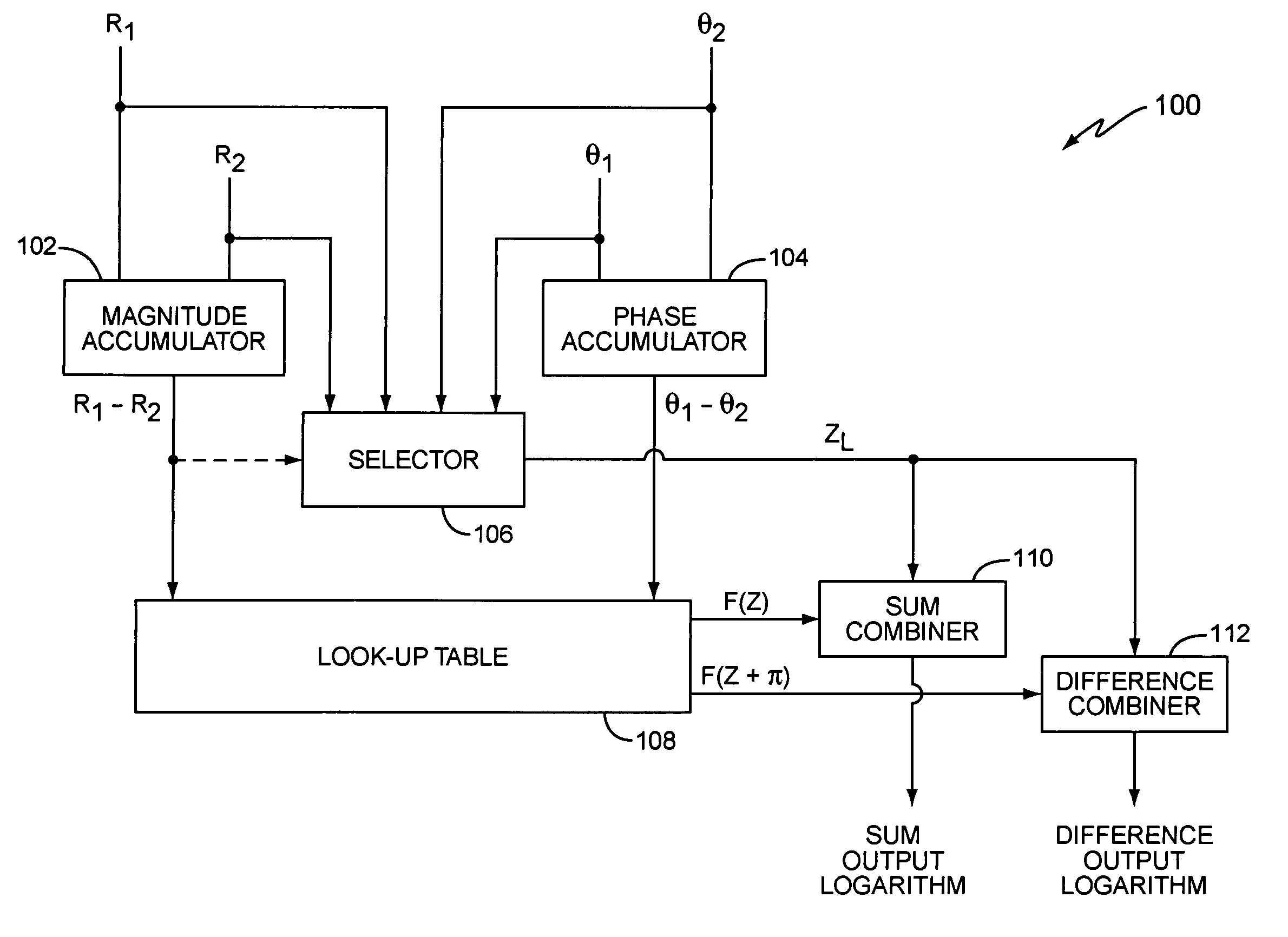
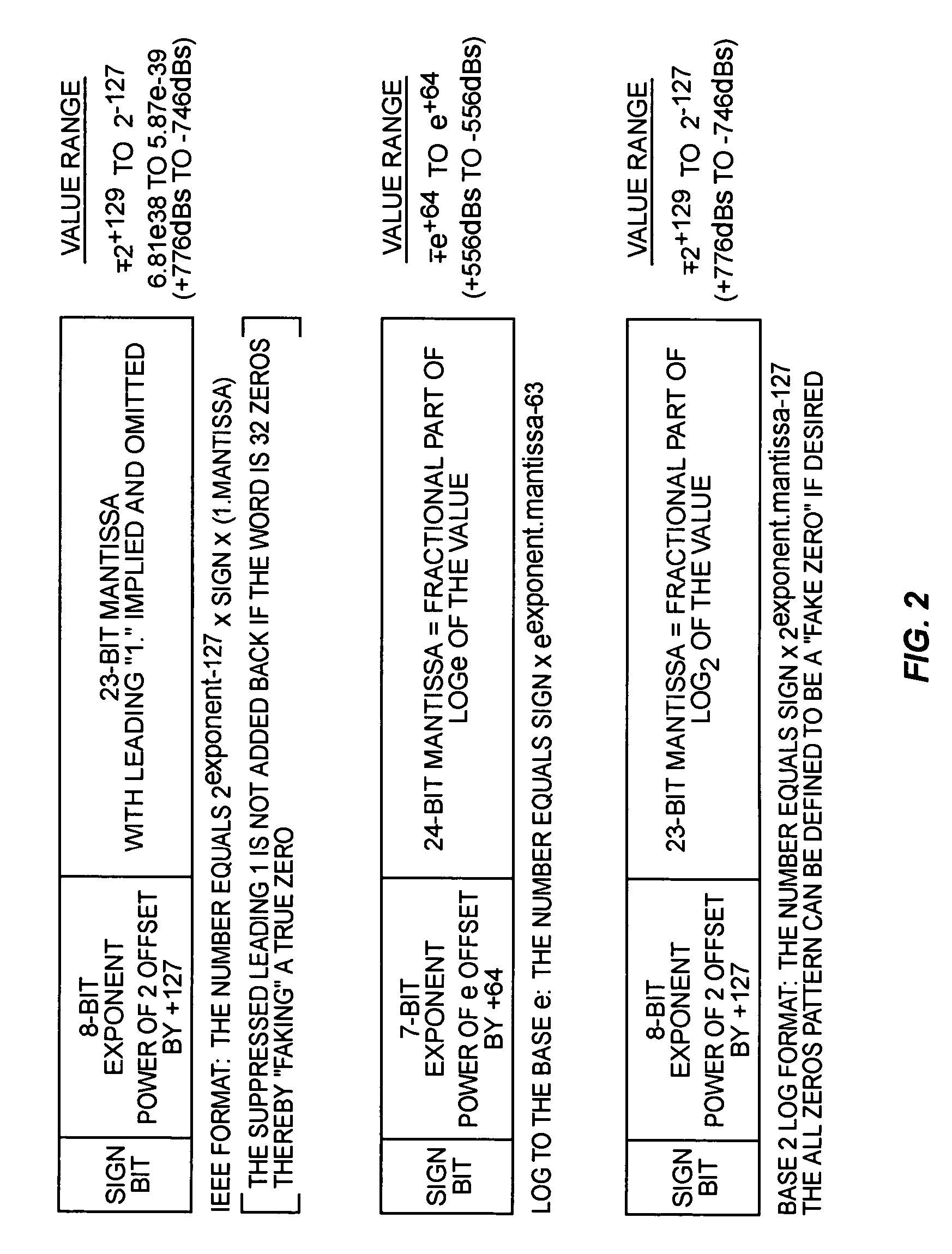
Complex logarithmic ALU
InactiveUS20050273483A1Simplifies divisionSimplifies multiplicationComputation using non-contact making devicesDigital computer detailsReal arithmeticLogit
Owner:OPTIS WIRELESS TECH LLC
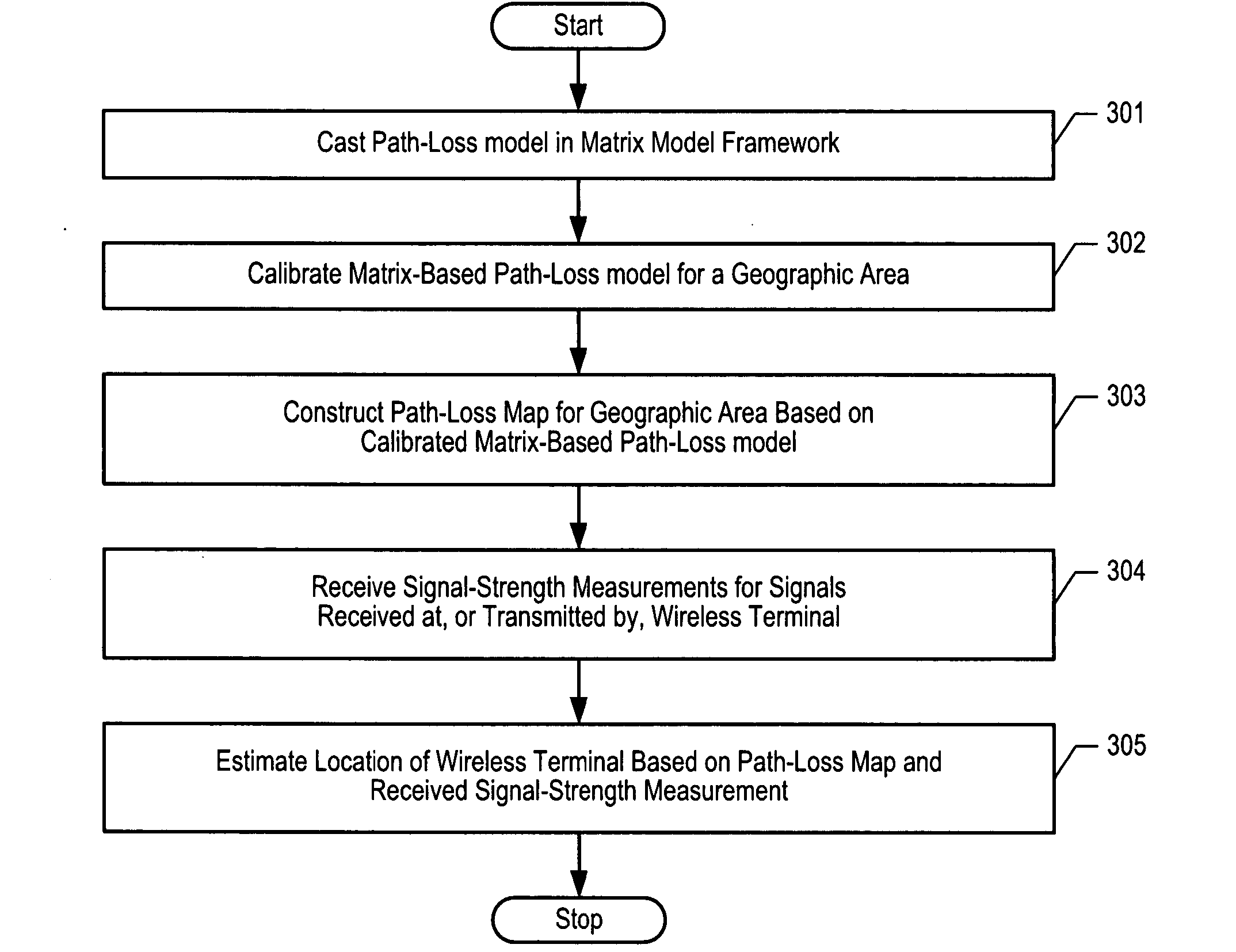
Electro-magnetic propagation modeling
ActiveUS20060199546A1Tuning is slowEfficient of admissibilityDirection finders using radio wavesTransmission monitoringReal arithmeticLinear matrix
A generalized framework is disclosed in which a wide variety of propagation models can be cast in a matrix-based format using arbitrary matrix coefficients (e.g., real numbers, integers, etc.). Casting propagation models in the matrix-based framework enables efficient computer implementation and calculation, ease of tuning, admissibility (i.e., the tuned parameters of a linear matrix model are guaranteed to be the global optimum), and aggregating multiple propagation models into a single matrix-based model. Matrix-based propagation models based on transmitter-receiver azimuth orientation, transmitter antenna height, terrain elevation, and clutter are also disclosed. The propagation models can be used in conjunction with automated data acquisition from information sources such as topographic maps, clutter maps, etc.
Owner:POLARIS WIRELESS
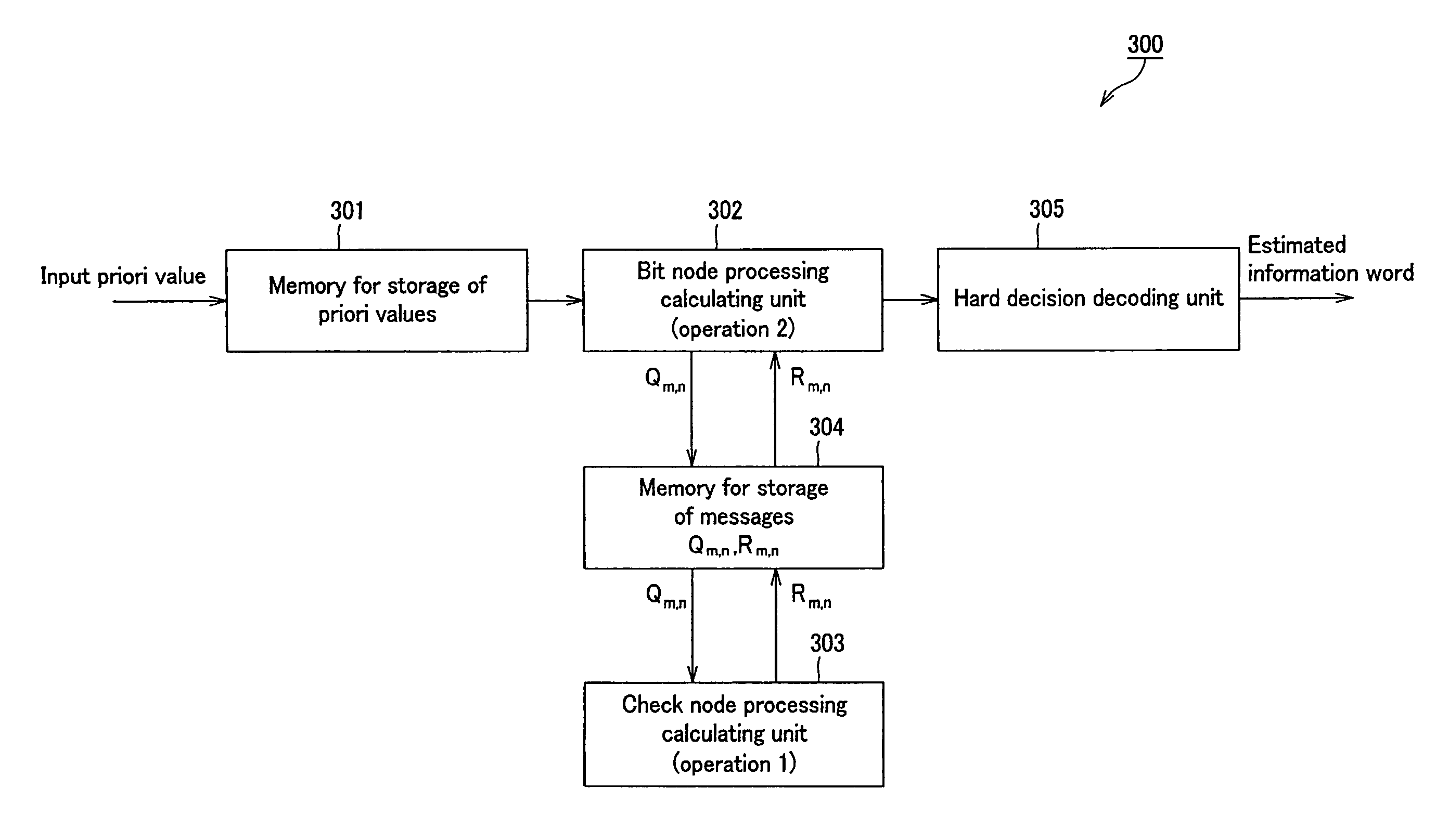
Decoding apparatus and method and information processing apparatus and method
InactiveUS7676734B2Simple calculationOther decoding techniquesCode conversionInformation processingReal arithmetic
A decoding apparatus, decoding the LDPC code using a message passing algorithm, sets a message as a log likelihood ratio having, as a base, a real number “a” which is a power of 2, and includes a check node processing calculating unit for receiving a message from a bit node to calculate a message from a check node. The check node processing calculating unit includes a converter for converting an absolute value x of the message to output f (x) and a converting unit supplied as an input y with a sum of the absolute values x of the message from the totality of the bit nodes less one, converted by the converter, subdividing the input y in preset domains and for converting the number in the domain into g (y), and expresses the boundary values of the domains of the input y and f (x) by a power of 2.
Owner:SONY CORP
Dual-processor complex domain floating-point DSP system on chip
ActiveUS20050216702A1No performance lossReduce in quantityArchitecture with single central processing unitSpecific program execution arrangementsProcessing coreReal arithmetic
A system for digital signal processing, configured as a system on chip (SoC), combines a microprocessor core and digital signal processor (DSP) core with floating-point data processing capability. The DSP core can perform operations on floating-point data in a complex domain and is capable of producing real and imaginary arithmetic results simultaneously. This capability allows a single-cycle execution of, for example, FFT butterflies, complex domain simultaneous addition and subtraction, complex multiply accumulate (MULACC), and real domain dual multiply-accumulators (MACs). The SoC may be programmed entirely from a microprocessor programming interface, using calls from a DSP library to execute DSP functions. The cores may also be programmed separately. Capability for programming and simulating the entire SoC are provided by a separate programming environment. The SoC may have heterogeneous processing cores in which either processing core may act as master or slave, or both cores may operate simultaneously and independently.
Owner:ATMEL CORP
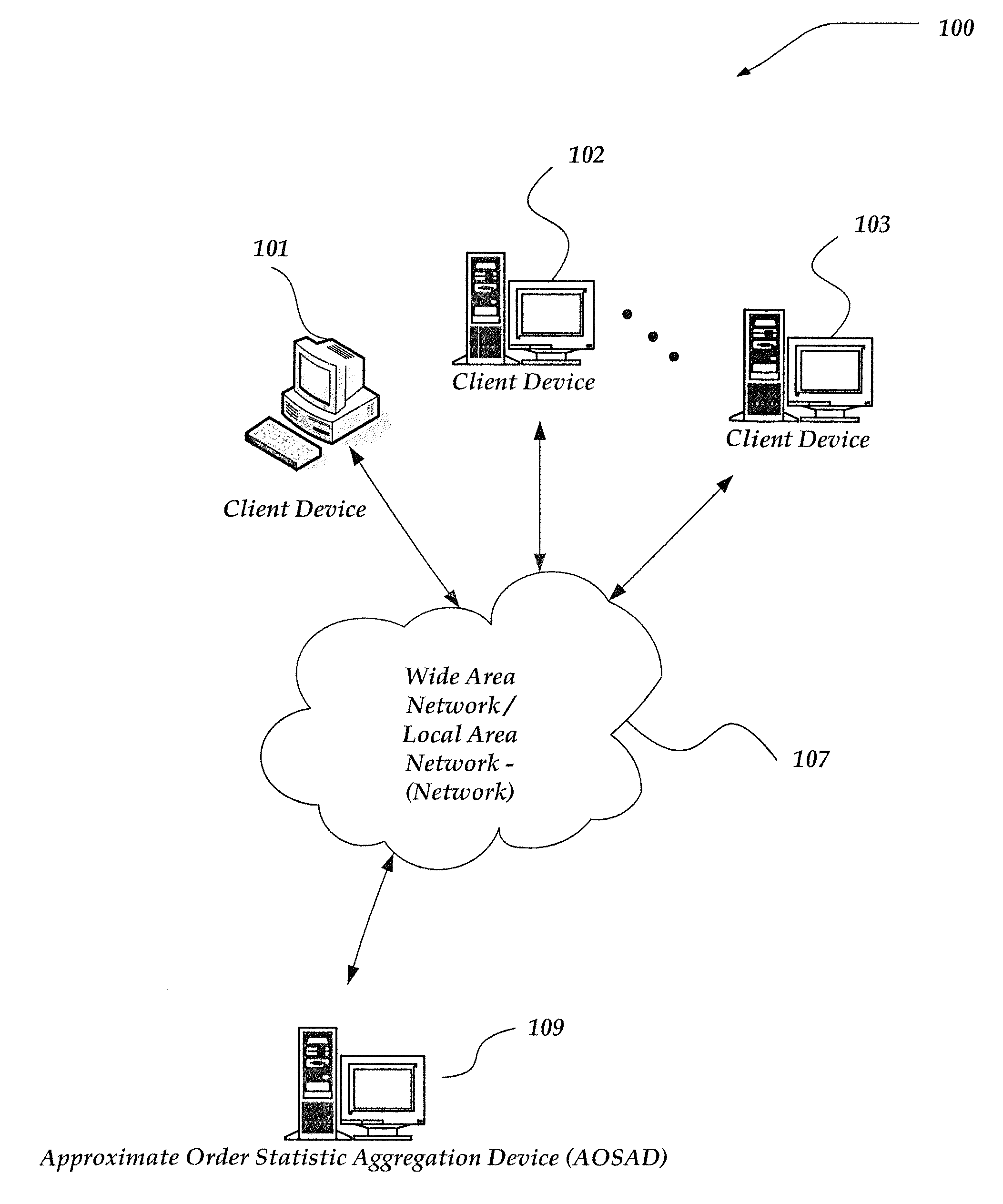
Approximate order statistics of real numbers in generic data
ActiveUS20130054660A1Digital data processing detailsDigital computer detailsReal arithmeticTheoretical computer science
A method, system, and processor-readable storage medium are directed towards calculating approximate order statistics on a collection of real numbers. In one embodiment, the collection of real numbers is processed to create a digest comprising hierarchy of buckets. Each bucket is assigned a real number N having P digits of precision and ordinality O. The hierarchy is defined by grouping buckets into levels, where each level contains all buckets of a given ordinality. Each individual bucket in the hierarchy defines a range of numbers—all numbers that, after being truncated to that bucket's P digits of precision, are equal to that bucket's N. Each bucket additionally maintains a count of how many numbers have fallen within that bucket's range. Approximate order statistics may then be calculated by traversing the hierarchy and performing an operation on some or all of the ranges and counts associated with each bucket.
Owner:SPLUNK INC
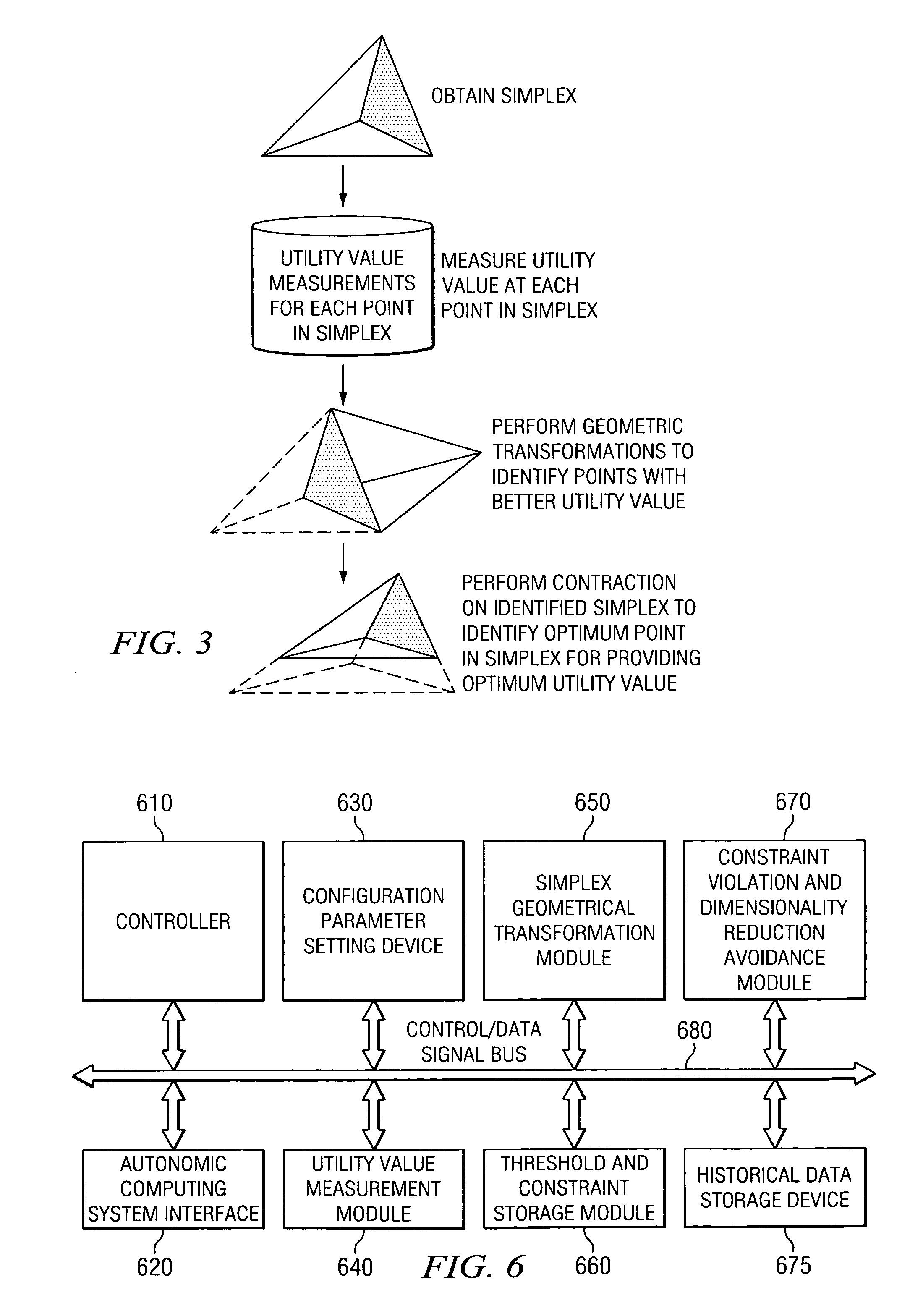
Dynamic online multi-parameter optimization system and method for autonomic computing systems
InactiveUS20050010388A1Improve system performanceSmall sizeError detection/correctionProgram controlReal arithmeticImproved method
An improved method and system for performing dynamic online multi-parameter optimization for autonomic computing systems are provided. With the method and system of the present invention, a simplex, i.e. a set of points in the parameter space that has been directly sampled, is maintained. The system's performance with regard to a particular utility value is measured for the particular setting of configuration parameters associated with each point in the simplex. A new sample point is determined using the geometric transformations of the simplex. The method and system provide mechanisms for limiting the size of the simplex that is generated through these geometric transformations so that the present invention may be implemented in noisy environments in which the same configuration settings may lead to different results with regard to the utility value. In addition, mechanisms are provided for resampling a current best point in the simplex to determine if the environment has changed. If a sufficiently different utility value is obtained from a previously sampled utility value for the point in the simplex, then rather than contracting, the simplex is expanded. If the difference between utility values is not sufficient enough, then contraction of the simplex is performed. In addition, in order to allow for both real and integer valued parameters in the simplex, a mechanism is provided by which invalid valued parameters that are generated by geometric transformations being performed on the simplex are mapped to a nearest valid value. Similarly, parameter values that violate constraints are mapped to values that satisfy constraints taking care that the dimensionality of the simplex is not reduced.
Owner:IBM CORP
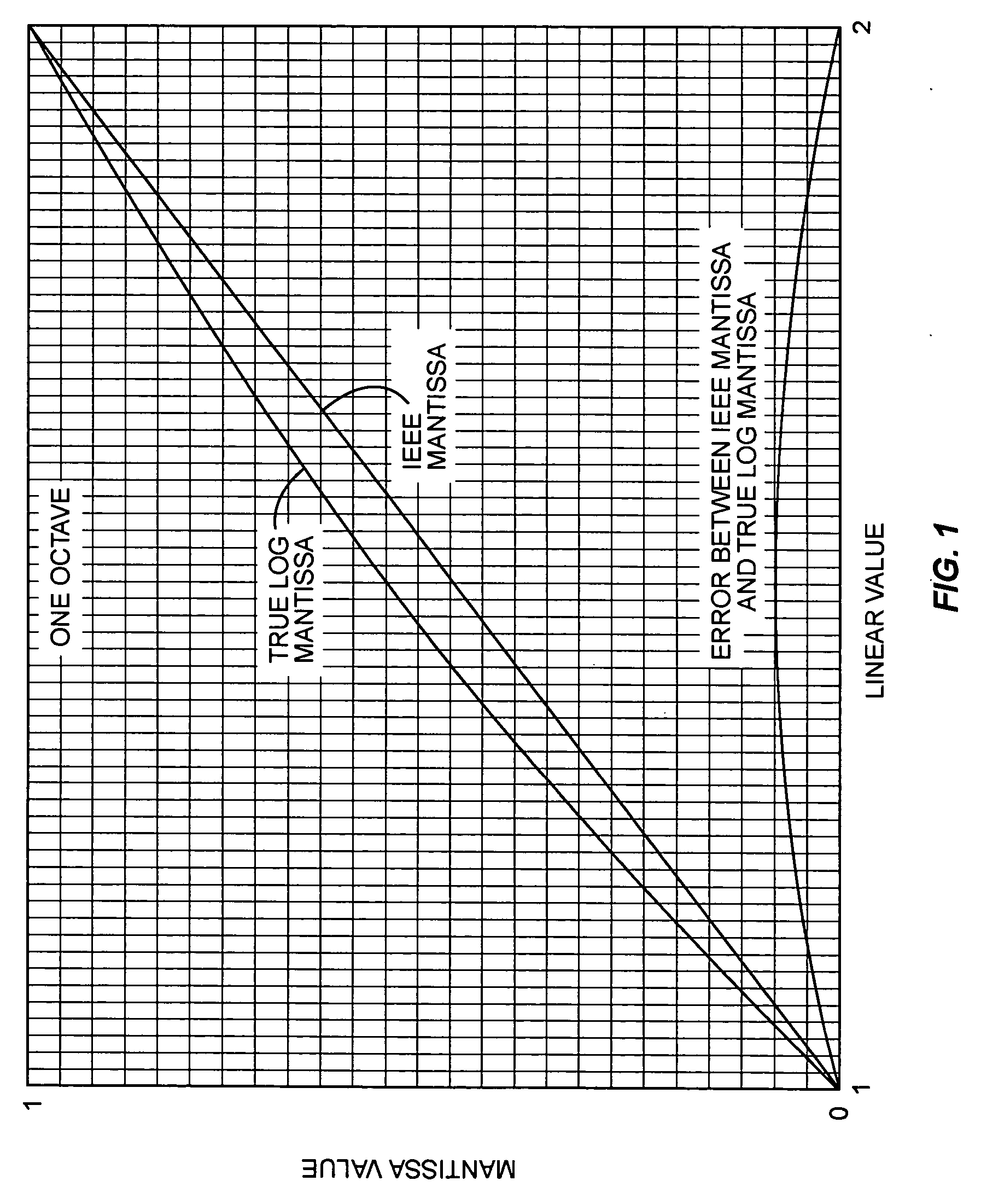
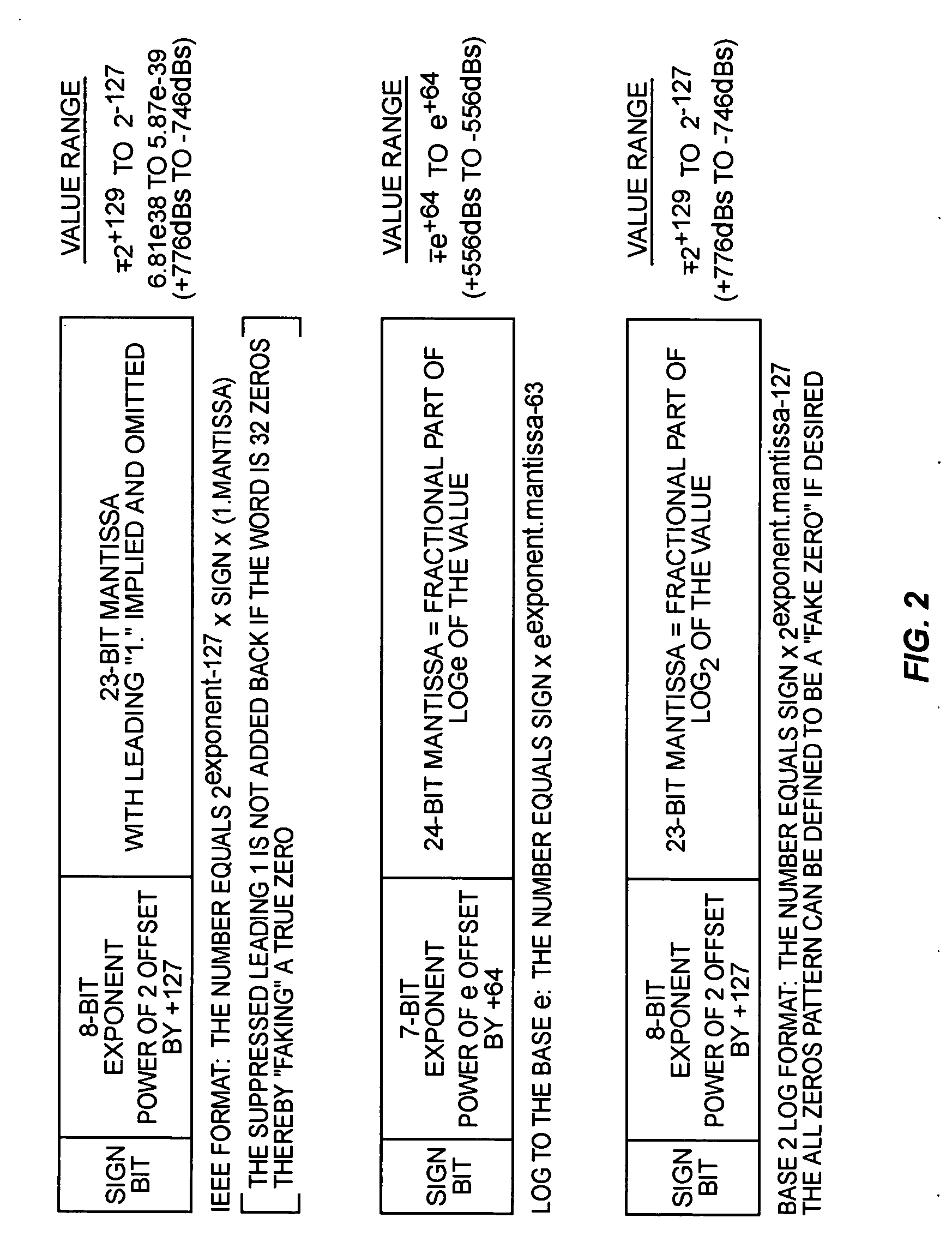
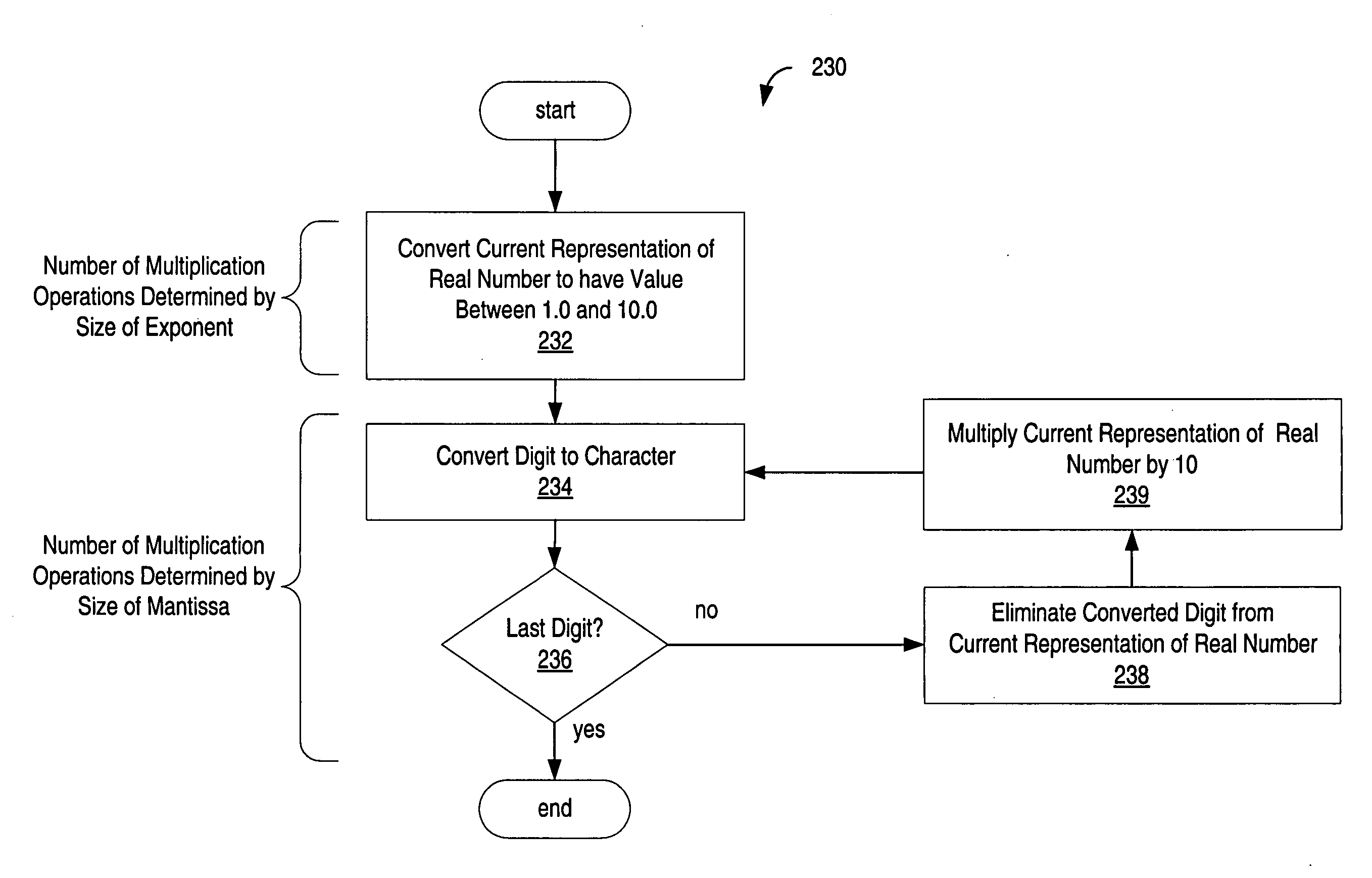
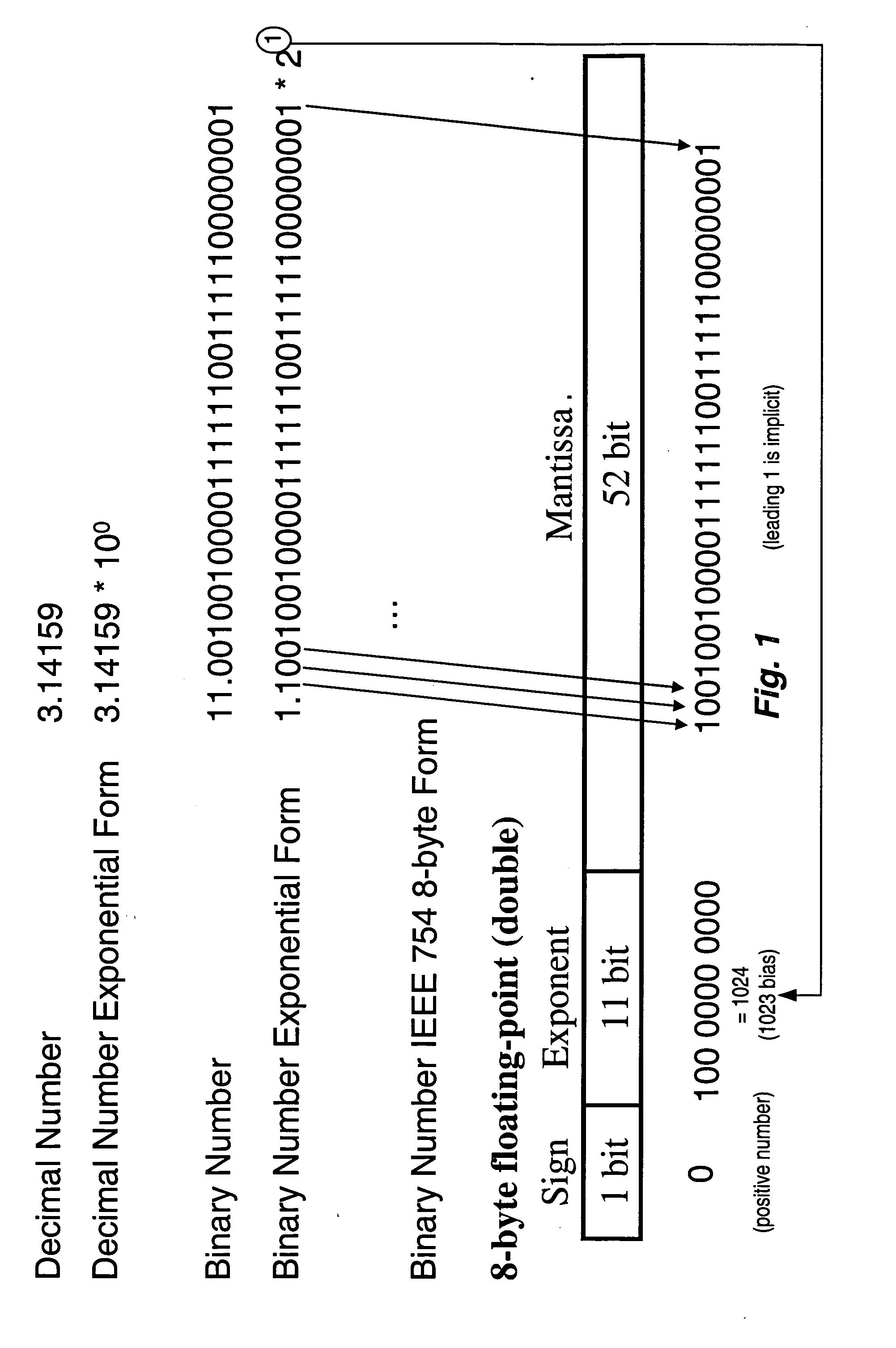
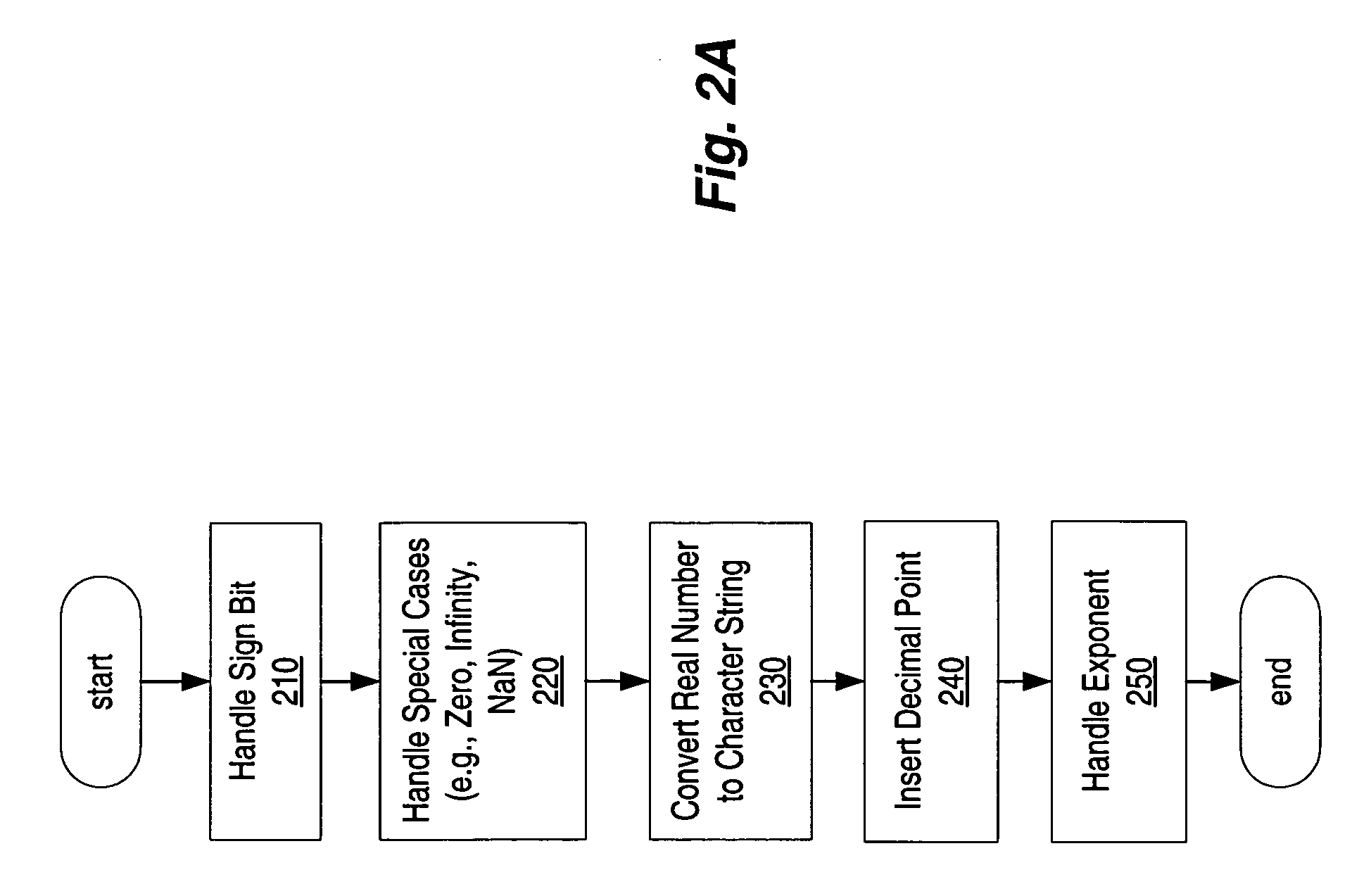
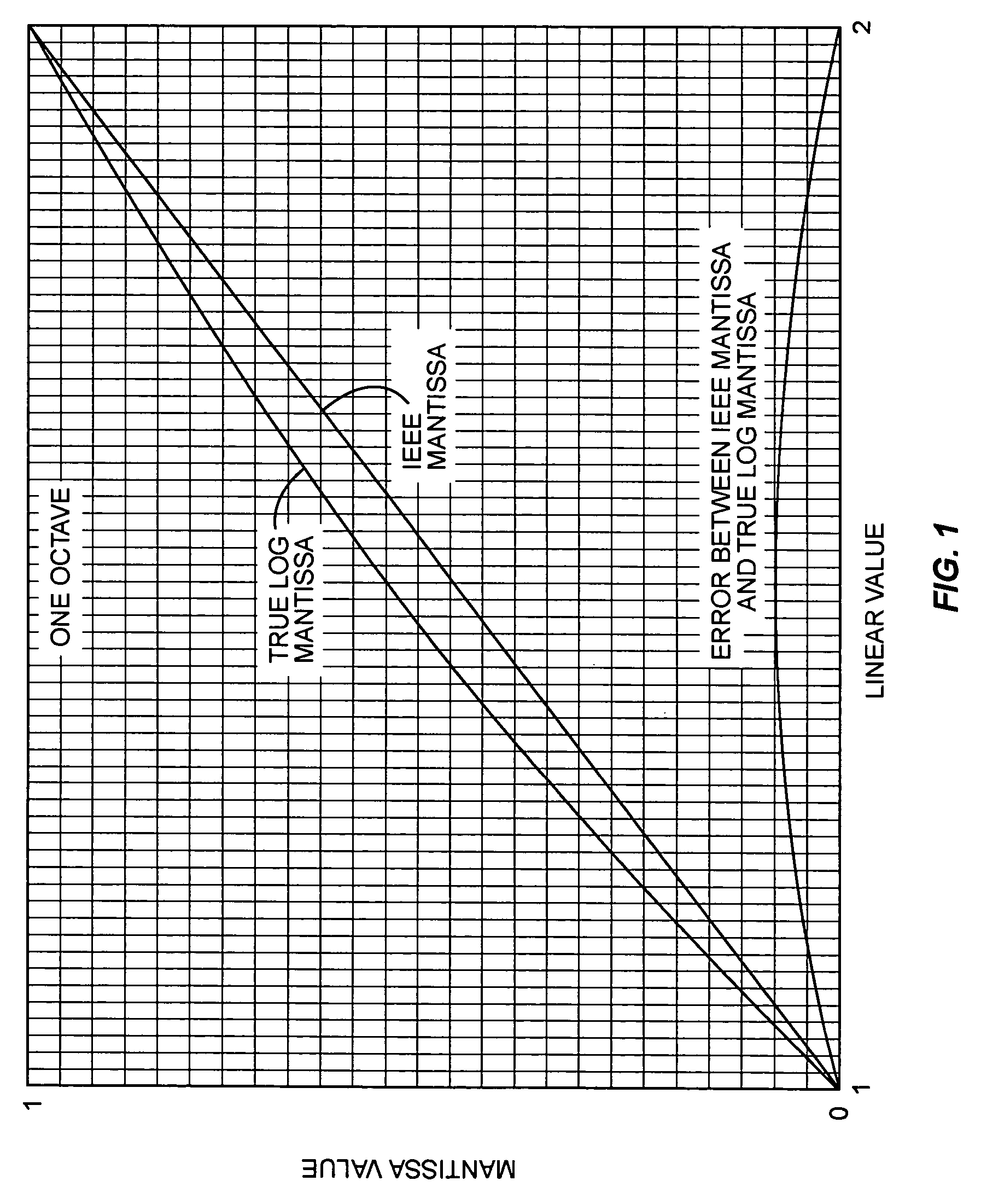
Conversion of floating-point numbers from binary into string format
ActiveUS20070203965A1Digital data processing detailsDigital computer detailsReal arithmeticFloating point
A method, system, and computer program product that convert a real number from a floating point representation to a character string. Mantissa bits are extracted from the floating-point representation of a value into an integer format. The mantissa bits of the integer format may be shifted left by a number of positions that is equal to a base 2 exponent of a first representation of the value. Prior to converting the value, the floating-point representation of the value can be divided by 2n, where n is the number of the mantissa bits in the floating-point representation of the value. A set of operations can then be performed to convert a result of the division to a number greater than or equal to 1.0 and less than 10.0. The set of operations may include multiplication operations and / or retrieving a constant from a lookup table.
Owner:ORACLE INT CORP
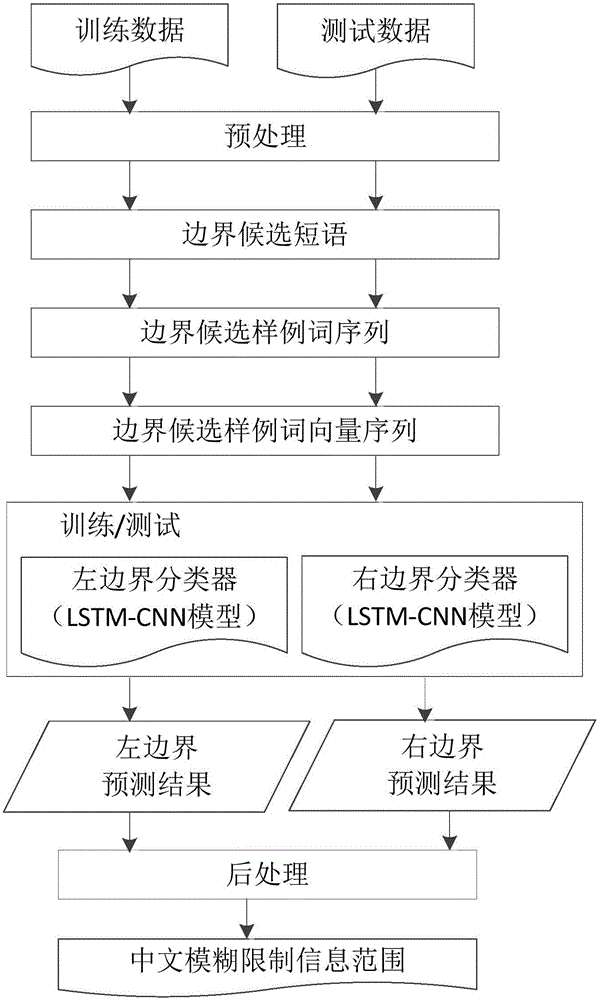
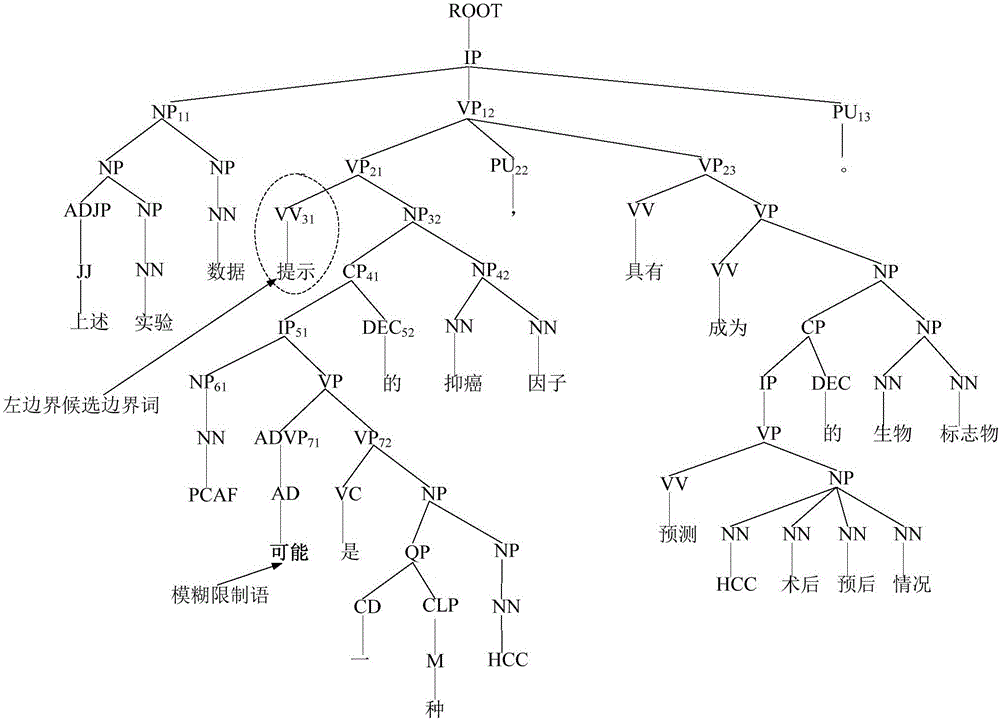
Chinese hedge scope detection method based on stacked neural network
The invention discloses a Chinese hedge scope detection method based on a stacked neural network. The Chinese hedge scope detection method is characterized by comprising the following steps: carrying out word segmentation processing on sentences which contain hedges in a to-be-analyzed experimental corpus; carrying out syntactic parsing on the sentences after the word segmentation processing by employing a syntactic parser to obtain a phrase structure tree of the sentences; finding candidate phrases via a phrase-based candidate sample screening strategy, thereby determining boundary words of the candidate phrases, including left boundary words and right boundary words; respectively filtering the left and right boundary words as well as context information of the hedges by employing filtering windows; taking the left and right boundary words as well as the context information of the hedges as candidate sample word sequences and mapping to a real number vector space to convert into a word vector form; inputting a stacked learning model LSTM (Long Short Term Memory networks)-CNN (Convolutional Neural Network) based on a combination of the LSTM and the CNN for learning to obtain boundary classifiers; and carrying out classification on test data to obtain classification results of left and right boundaries.
Owner:DALIAN UNIV OF TECH
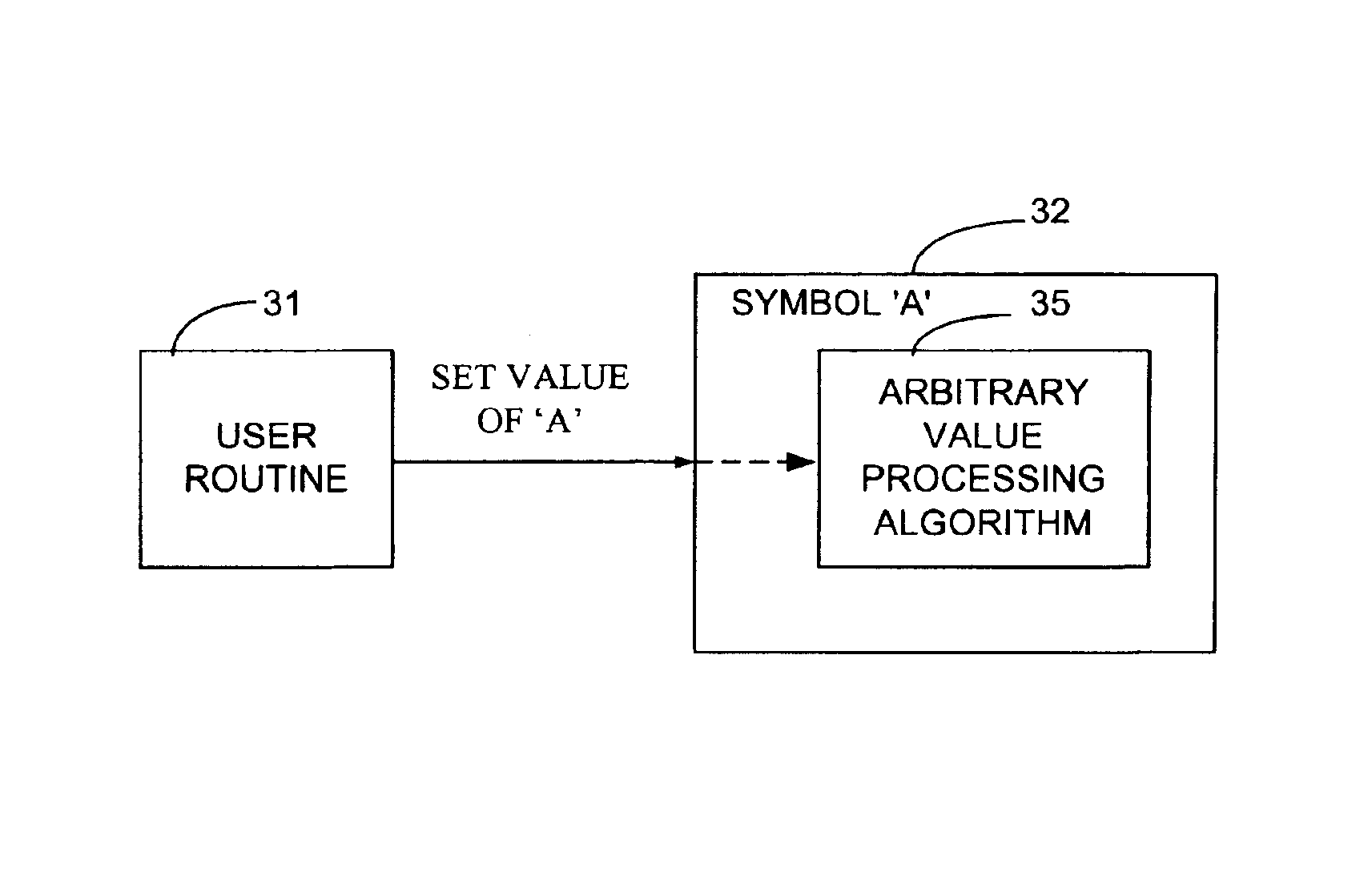
Active data type variable for use in software routines that facilitates customization of software routines and efficient triggering of variable processing
InactiveUS6880148B1Programming languages/paradigmsSpecific program execution arrangementsReal arithmeticData mining
The present invention provides an active data type for use in a computer program. The active data type has an identifier and at least one algorithm associated therewith. The identifier is utilized by the computer program to identify the instance of the active data type. The algorithm is configured to be automatically executed when an attempt to access a value associated with the active data type instance is made by a routine or otherwise. When a particular routine that uses an instance of the active data type attempts to access the value associated with the active data type, the algorithm determines the value associated with the active data type before the routine obtains access to the value. The active data type may be a real, an integer, or a string, for example. The algorithm automatically determines the current value associated with the active data type instance. Preferably, the active data type has an identifier, a first algorithm and a second algorithm associated therewith. The first algorithm preferably automatically determines the current value of the instance of the active data type when a routine that utilizes the value of the active data type instance attempts to access the value. When the value of the instance of the active data type is set, the second algorithm preferably automatically post-processes the value to which the active data type instance has been set. A locking / unlocking mechanism sets the value of the active data type instance prior to the first algorithm invoking the particular routine, suspends active data type algorithm processing while the routine executes, and processes the value of the active data type instance using the second algorithm once the routine has returned in order to post-process any changes to the value of the active data type instance.
Owner:AGILENT TECH INC
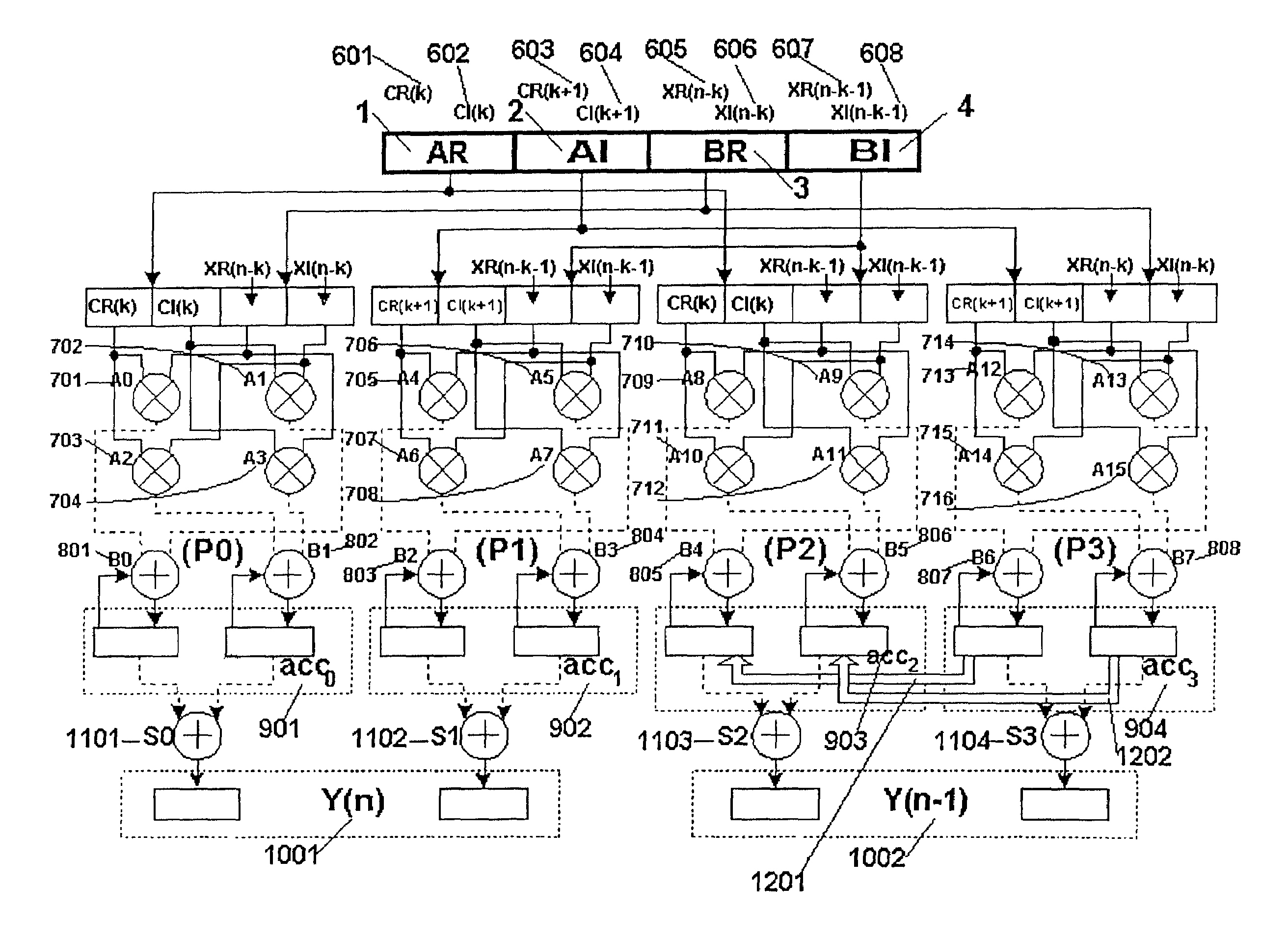
Complex-valued multiplier-and-accumulator
InactiveUS7113970B2Omit stepsComputation using non-contact making devicesLogic circuitsReal arithmeticBinary multiplier
The multi-mode Multiplier-And-Accumulator of the present invention is used with the double-precision Complex-Valued Multiplier-And Accumulator as a main configuration, and the different precisions and digital modes make it more flexible, compared to the traditional real number Multiplier-And-Accumulator. In addition, it does not have a data alignment problem which occurs in the traditional application of different precision Subword Parallel processors. This kind of Multiplier-And-Accumulator takes a double-precision Complex-Valued Multiplier-And- Accumulator as the main configuration, with four double-precision real-valued multipliers and several groups of accumulators to assist in different modes ofoperation. Each double-precision real- valued multiplier can be segmented into four single-precision multipliers, and then double-precision multiplier products are obtained by means of displacement addition. If two real numbers which are continuous in time sequence are taken as the real number input and imaginary number input for the original complex-valued multipliers, the accumulated products include not only the present output accumulated product summation but also the output accumulated product summation of the previous time and the next time.
Owner:NAT SCI COUNCIL
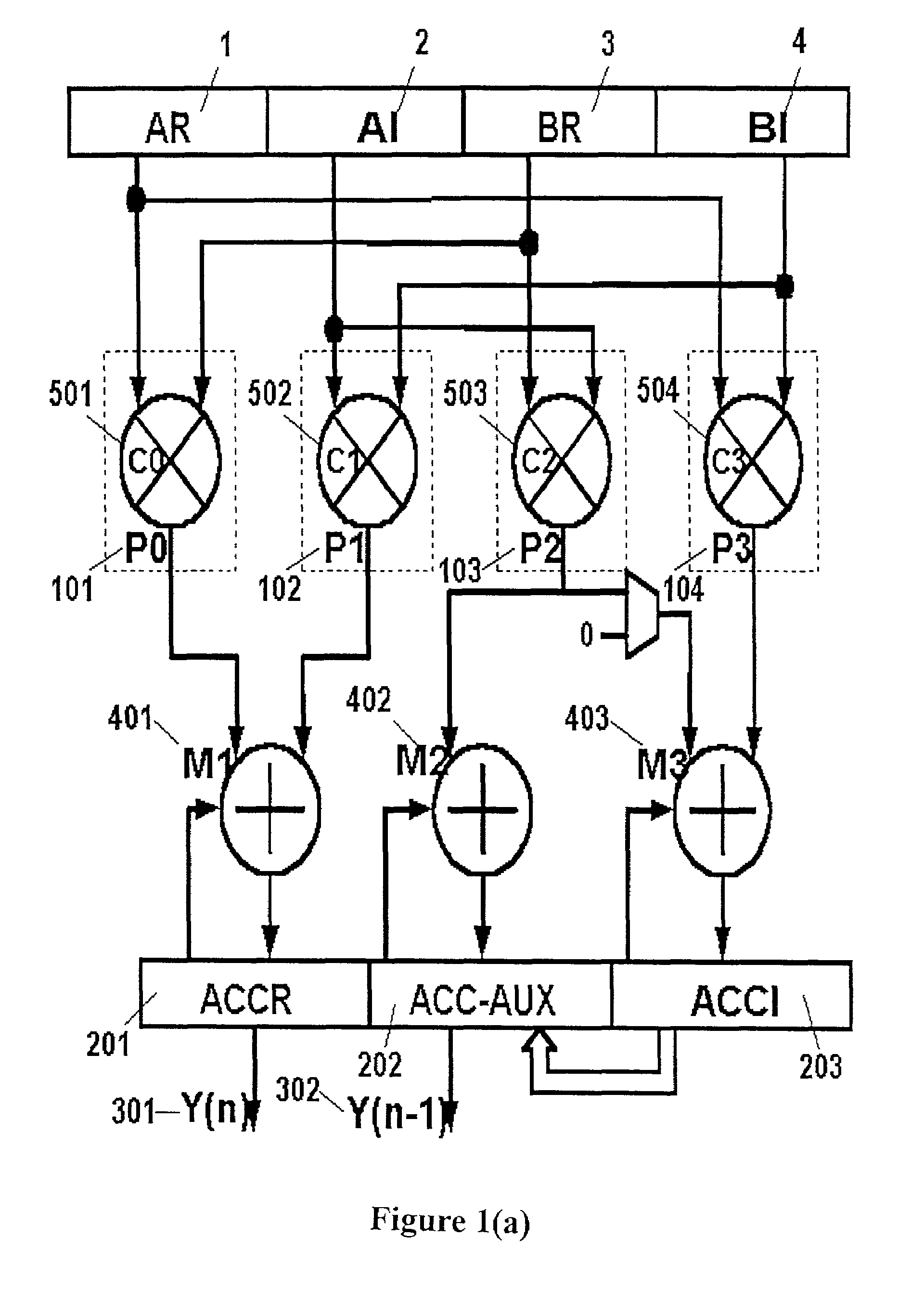
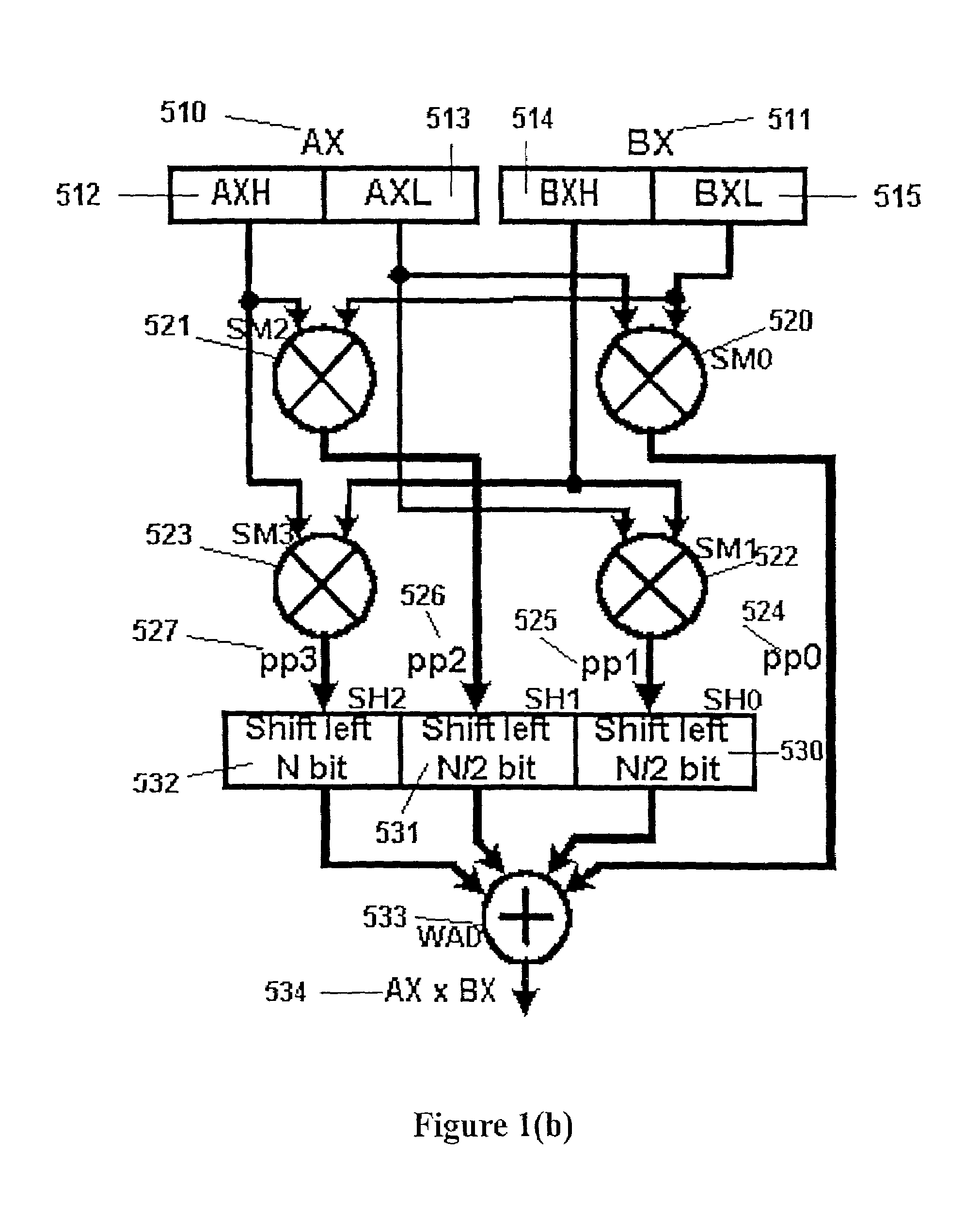
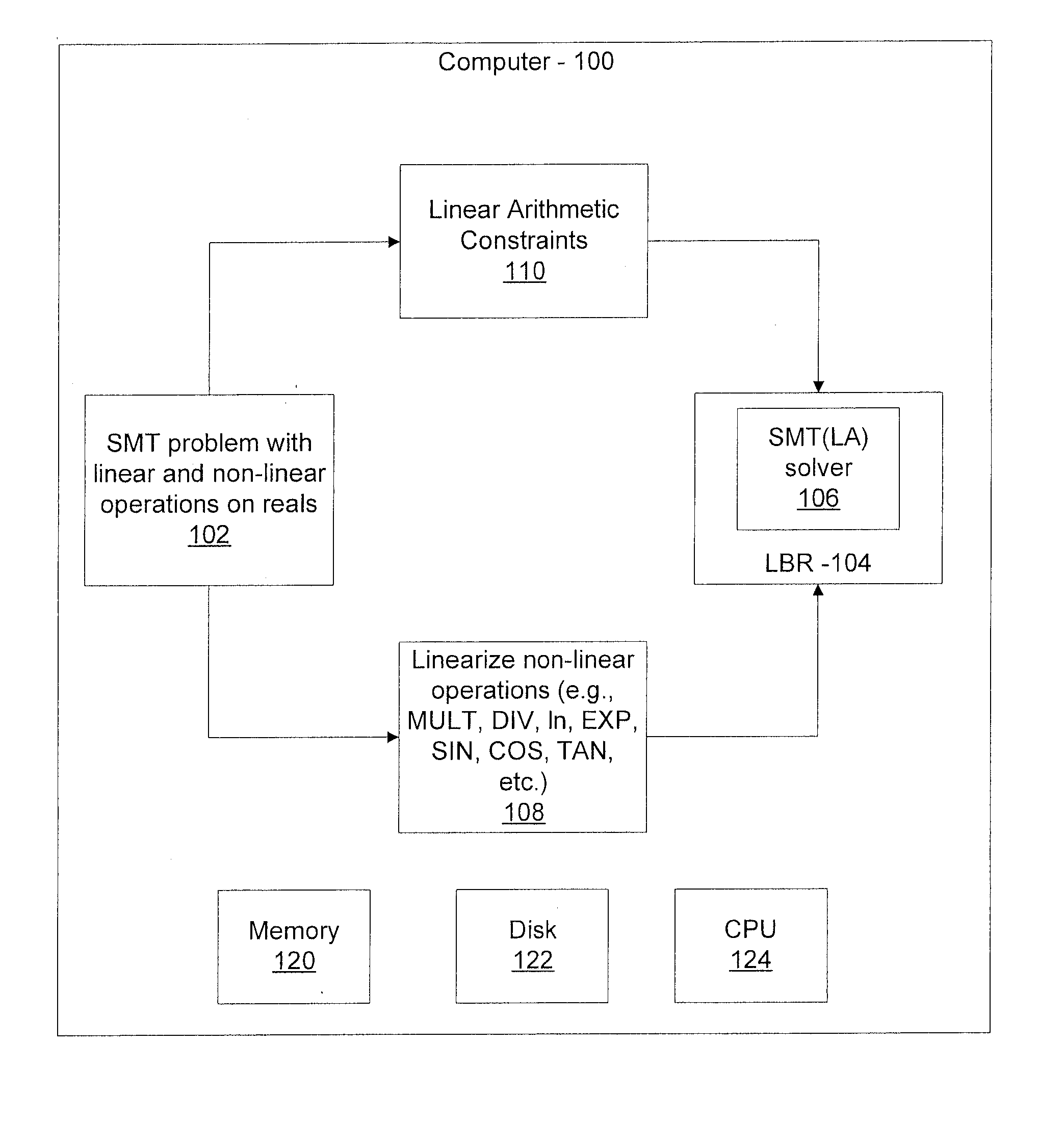
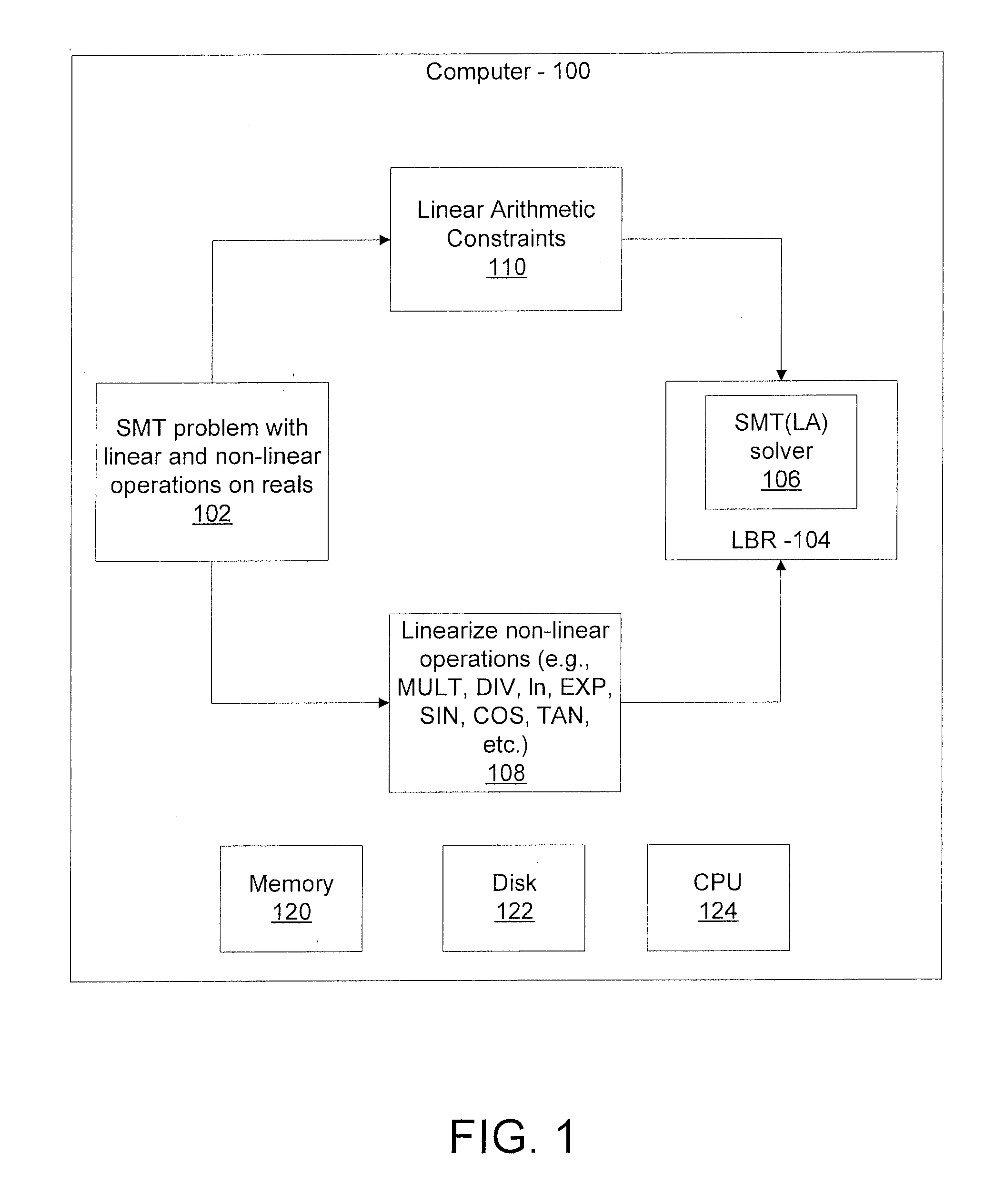
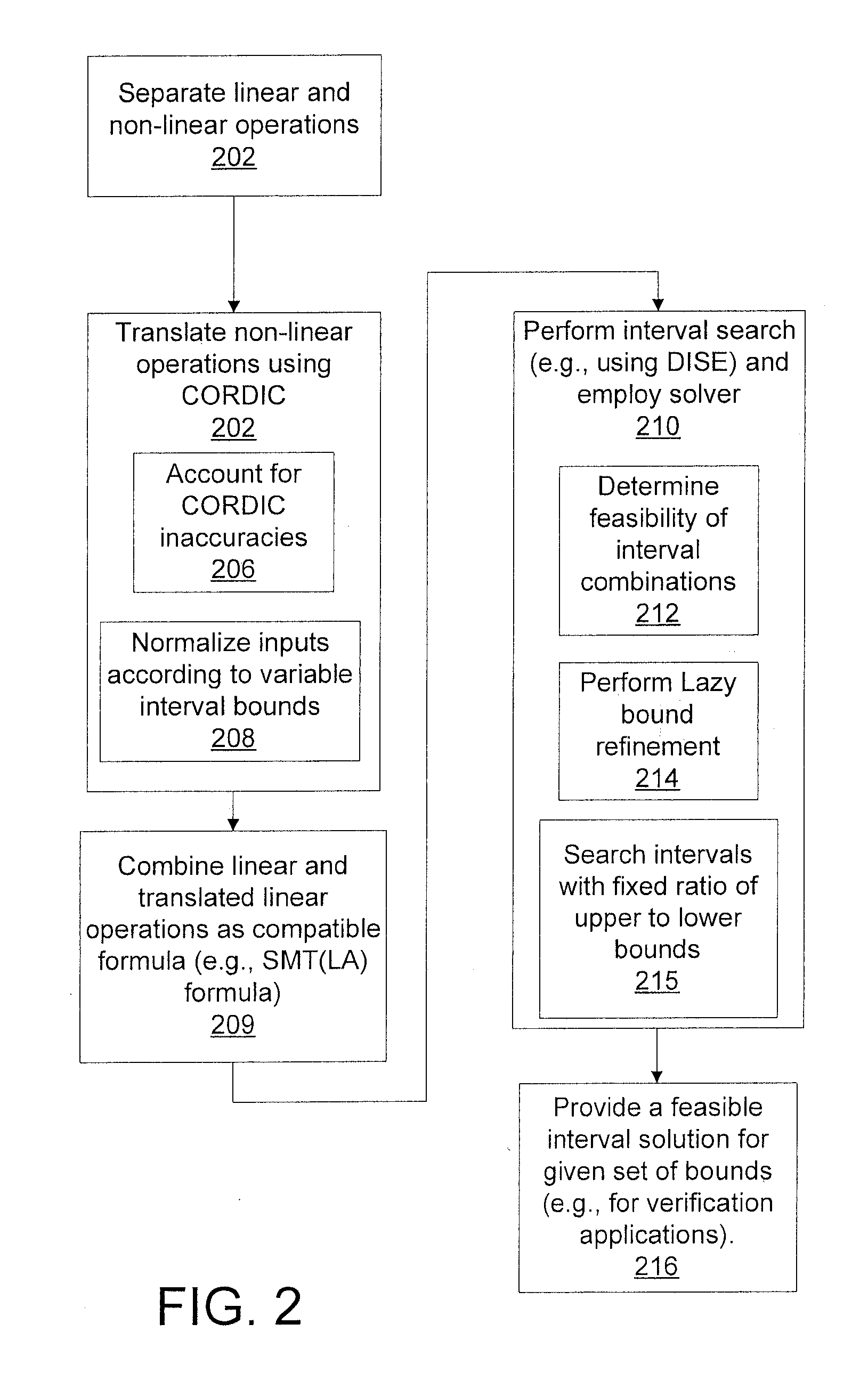
Efficient decision method for real non-linear arithmetic constraints
InactiveUS20100281086A1Digital computer detailsKnowledge representationReal arithmeticOperational transformation
A system and method for solving a decision problem having Boolean combinations of linear and non-linear operations includes translating the non-linear real operations using a COordinate Rotation DIgital Computer (CORDIC) method programmed on a computer device into linear operations maintaining a given accuracy. Linear and translated linear operations are combined into a formula. Satisfiablity of the formula is solved using a decision procedure for Boolean combinations of linear operations over integers and reals.
Owner:NEC CORP
Method for Transforming Data by Look-Up Table
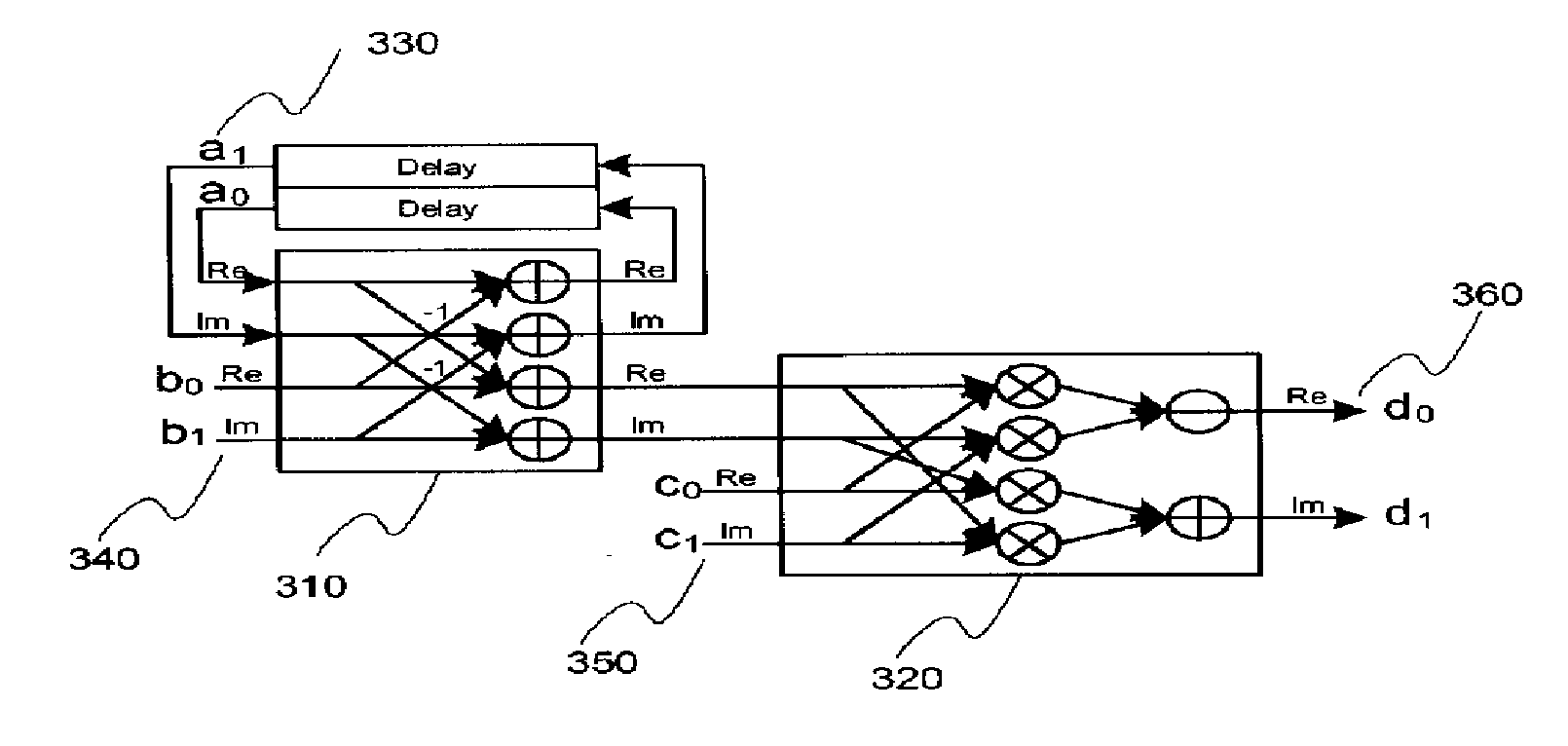
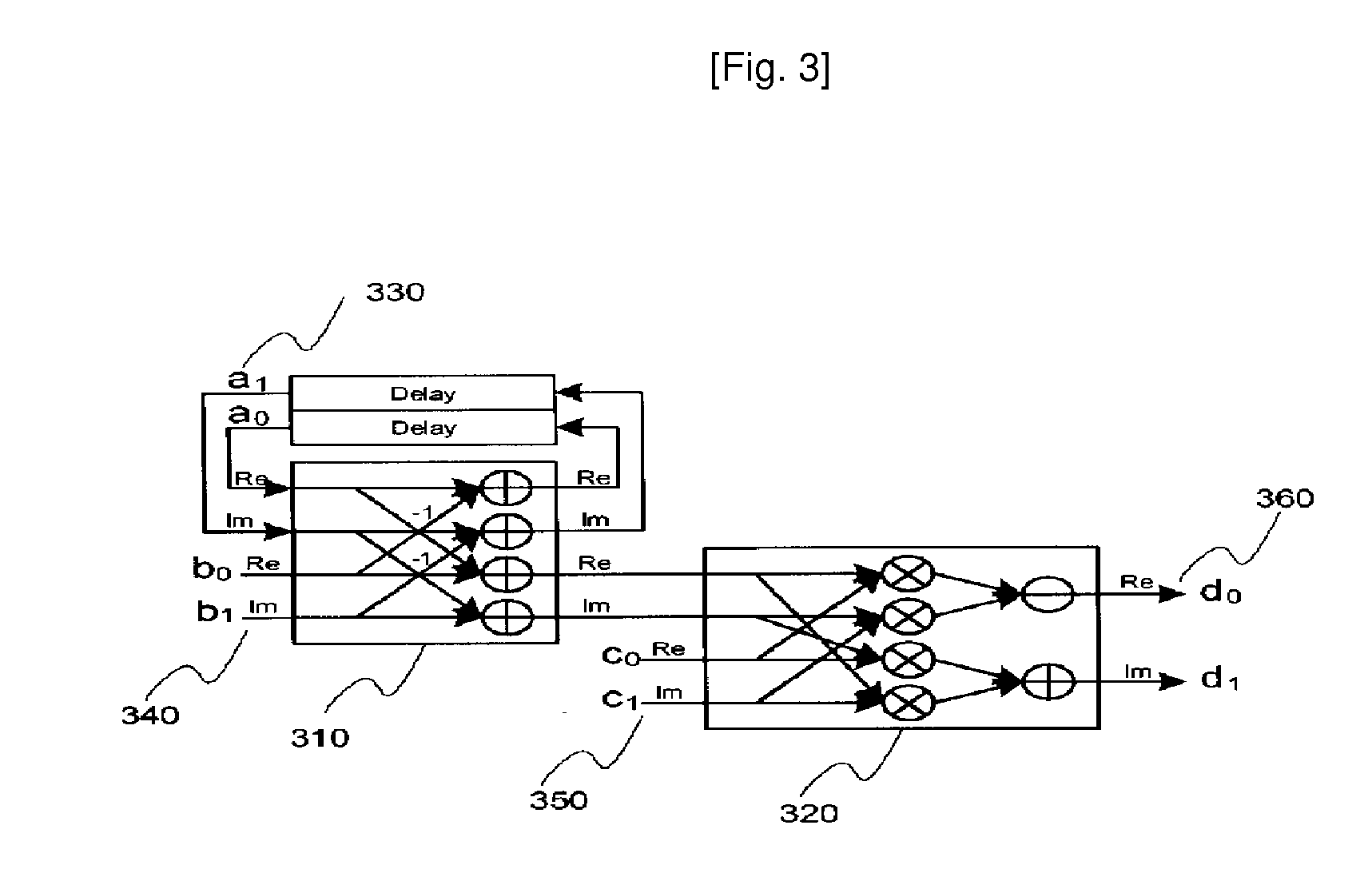
InactiveUS20080071847A1Reduce hardware sizeLow power operationModulated-carrier systemsComputation using non-contact making devicesFour quadrantsReal arithmetic
Provided is a method for transforming data using a look-up table. The method includes the steps of: (a) mapping preprocessed input binary data to a constellation diagram divided into four quadrants to output a first complex number; (b) performing addition / subtraction operations between real numbers and between imaginary numbers with respect to the first complex number and a second complex number; and (c) reading a fourth complex from a look-up table in response to the first complex number, the second complex number and a third complex number, the look-up table outputting the fourth complex by performing a subtraction operation on multiplication results between real numbers and between imaginary numbers and an addition operation on multiplication results between the real numbers and the imaginary numbers with respect to the result value of the step (b) and the third complex number. Accordingly, it is possible to reduce the hardware size at the time of IFFT / FFT design and to provide a high-speed, low-power operation.
Owner:ELECTRONICS & TELECOMM RES INST
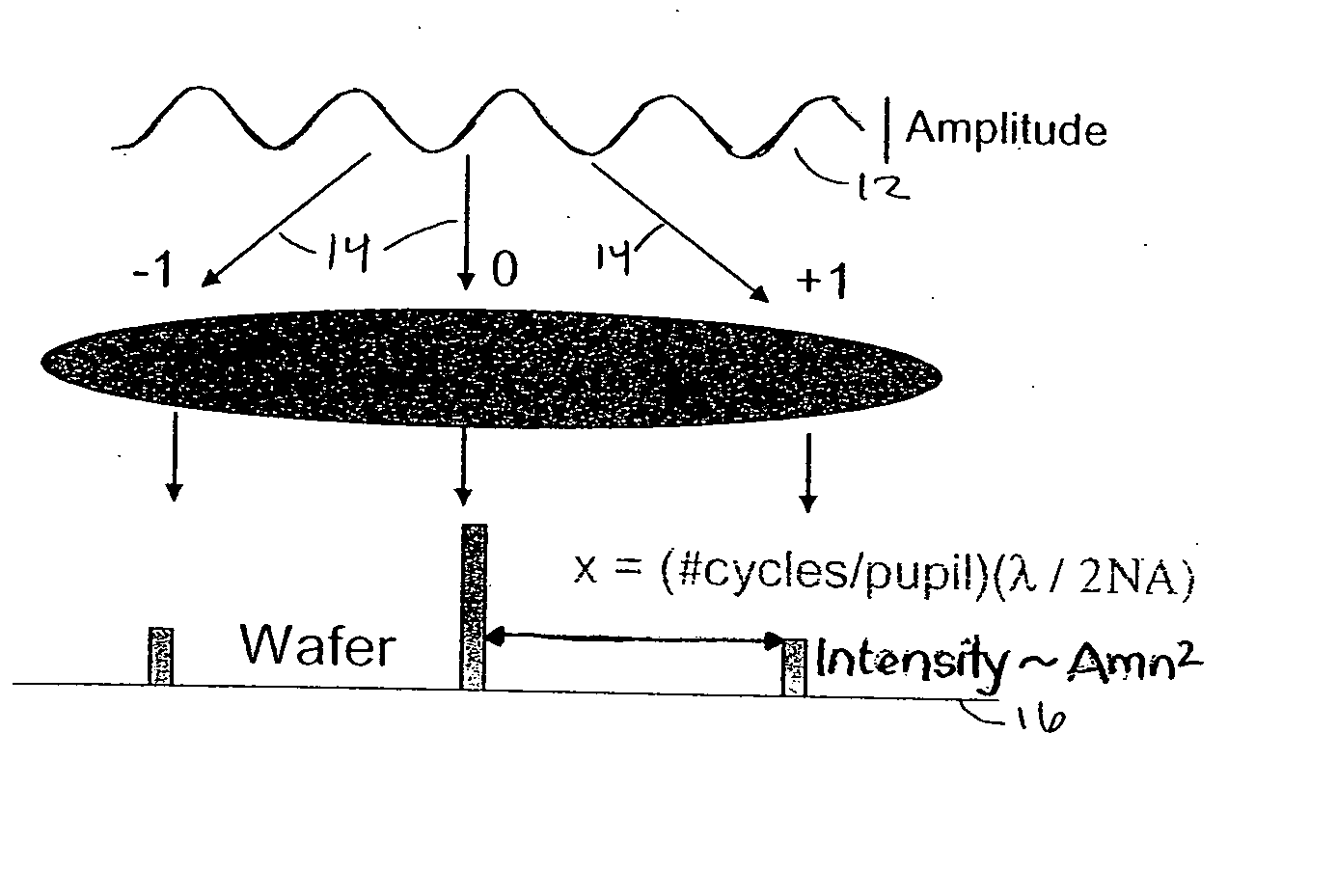
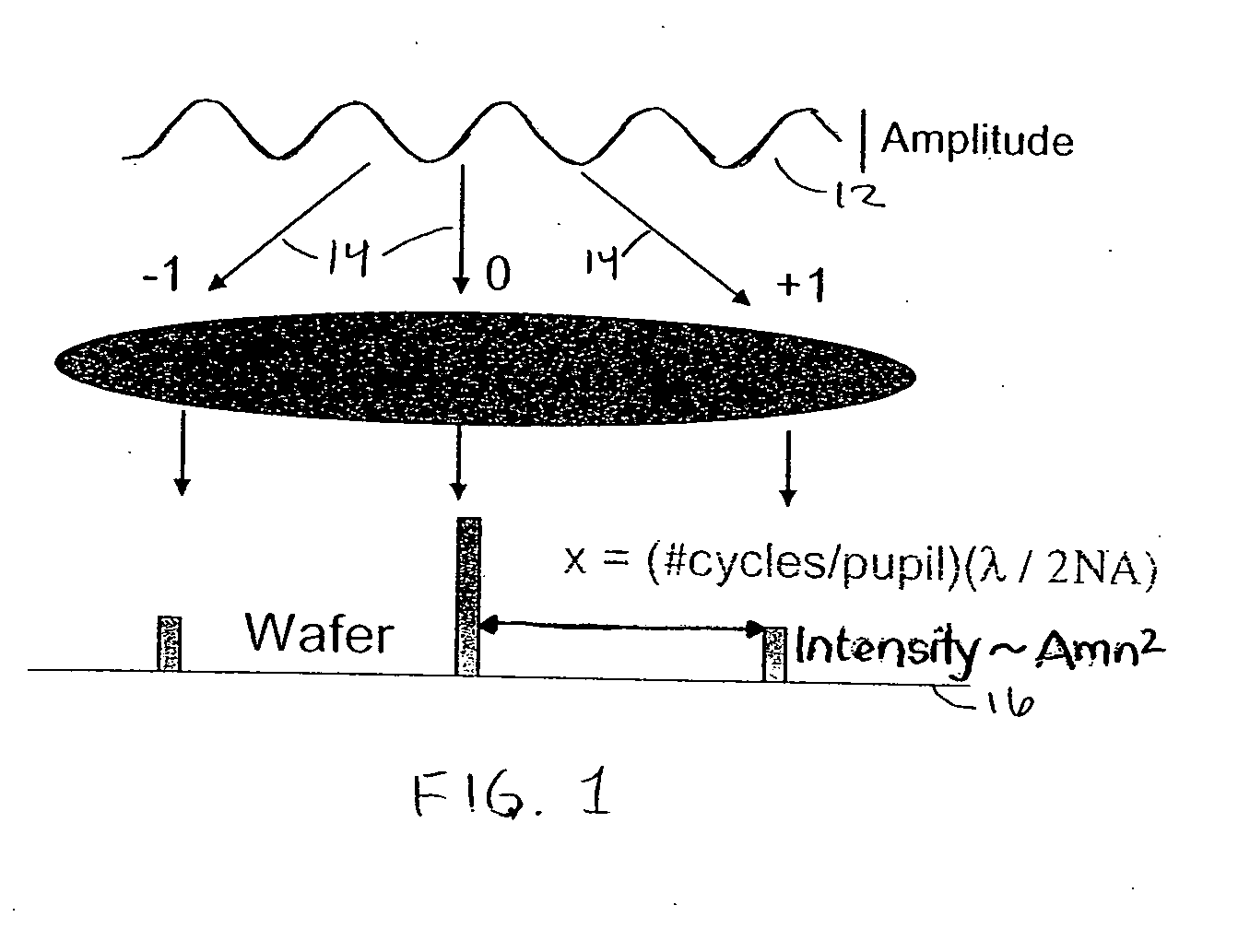
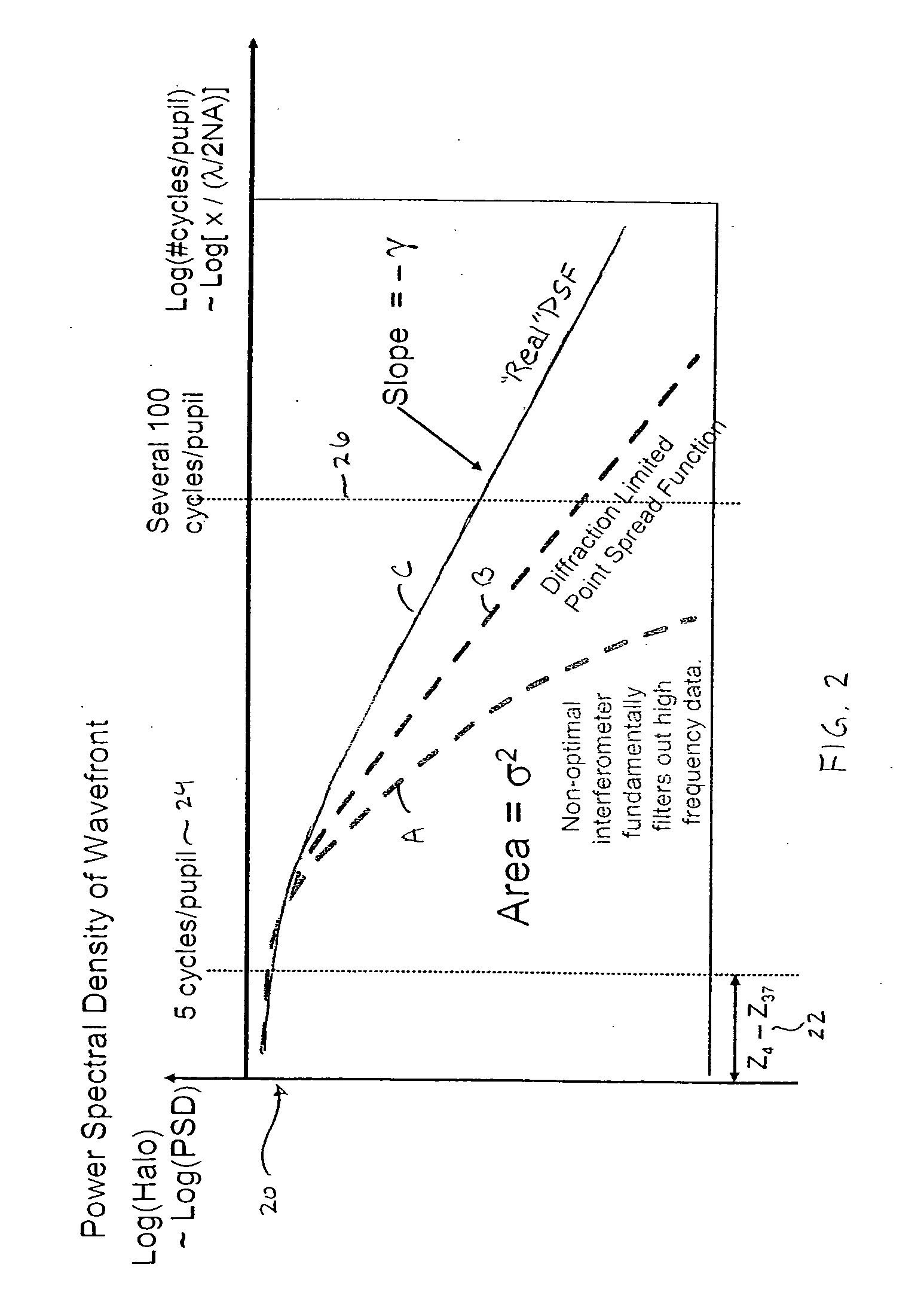
Incorporation of a phase map into fast model-based optical proximity correction simulation kernels to account for near and mid-range flare
InactiveUS20050091013A1Analogue computers for electric apparatusSemiconductor/solid-state device manufacturingFast Fourier transformReal arithmetic
A first method to compute a phase map within an optical proximity correction simulation kernel utilizes simulated wavefront information from randomly generated data. A second method uses measured data from optical tools. A phase map is created by analytically embedding a randomly generated two-dimensional array of complex numbers of wavefront information, and performing an inverse Fourier Transform on the resultant array. A filtering function requires the amplitude of each element of the array to be multiplied by a Gaussian function. A power law is then applied to the array. The elements of the array are shuffled, and converted from the phasor form to real / imaginary form. A two-dimensional Fast Fourier Transform is applied. The array is then unshuffled, and converted back to phasor form.
Owner:GLOBALFOUNDRIES INC
A verifiable fully homomorphic encryption method based on matrix operation
ActiveCN109787743AVerifiableImprove efficiencyKey distribution for secure communicationPlaintextComputer science
The invention discloses a verifiable fully homomorphic encryption method based on matrix operation. The method comprises the following steps: preprocessing and converting plaintext data into vectors to obtain a vector set; Then selecting a non-zero random real number and each vector to construct a triangular matrix, and encrypting each triangular matrix to obtain an encrypted matrix set; Generating verification evidences by utilizing the triangular matrix set according to the calculation function type; Performing matrix operation on each encryption matrix according to a certain rule to obtainan encrypted operation result; And finally, decrypting the encrypted operation result to obtain a plaintext of the result, and verifying the correctness of the result by comparing whether the verification evidence is equal to the value of the calculation result. The method has privacy security and result verifiability; Simulation experiment results show that the method has high efficiency in the stages of secret key generation, decryption and verifiability, and the effectiveness and feasibility of the scheme are shown.
Owner:GUANGXI UNIV
Complex multiplication method and apparatus with phase rotation
ActiveUS20040267860A1Computation using non-contact making devicesTransmissionNegationComputer science
A method and apparatus for complex multiplication includes steps of: (a) receiving a complex multiplicand having a real value and an imaginary value (704); (b) generating a negation of the real value of the complex multiplicand (706); (c) generating a negation of the imaginary value of the complex multiplicand (708); (d) receiving a complex multiplier (710); and (e) selecting a phasor constant having a value wherein a complex product of the complex multiplicand times the complex multiplier times the phasor constant has a real value equal to one of the real value of the complex multiplicand, the imaginary value of the complex multiplicand, the negation of the real value of the complex multiplicand, and the negation of the imaginary value of the complex multiplicand (712).
Owner:GOOGLE TECH HLDG LLC
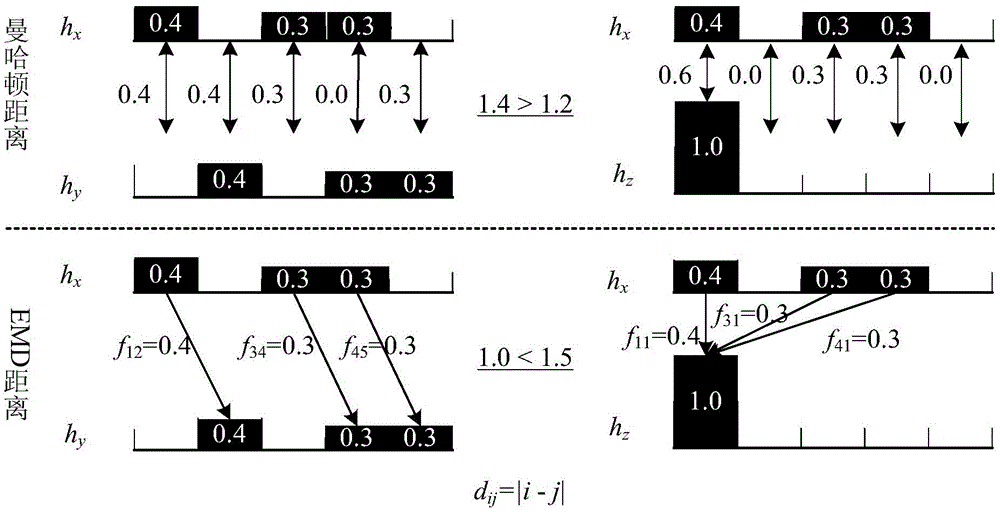
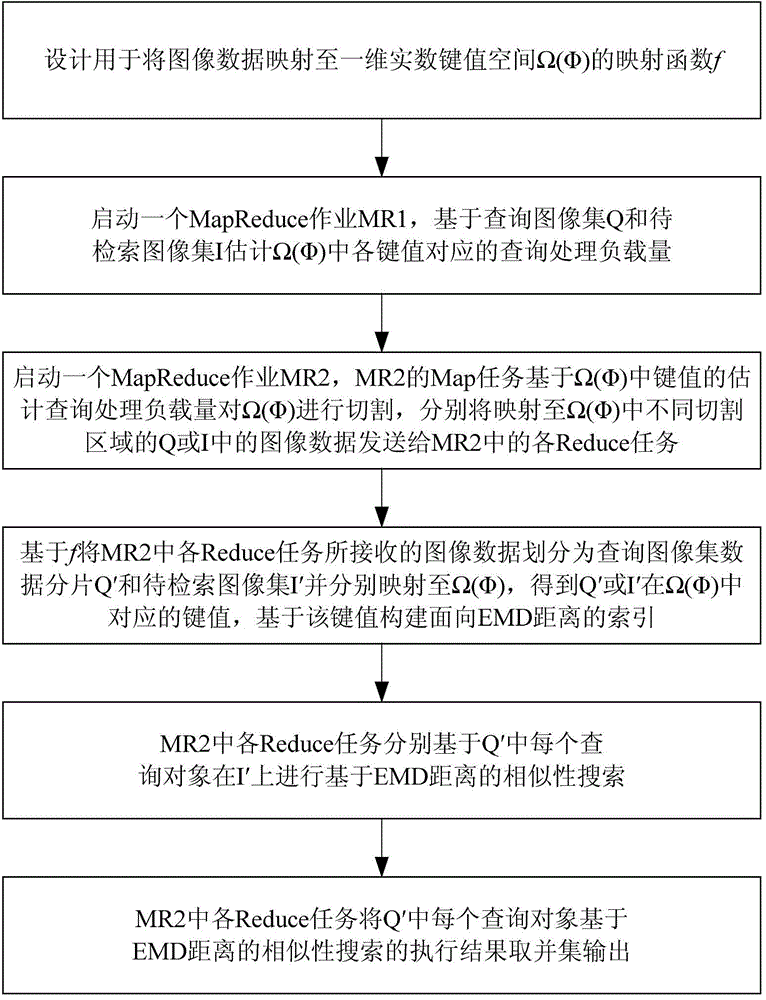
Large-scale image data similarity searching method based on EMD (earth mover's distance)
ActiveCN104679887ABalance query processing runtimeImprove scalabilitySpecial data processing applicationsExtensibilityReal arithmetic
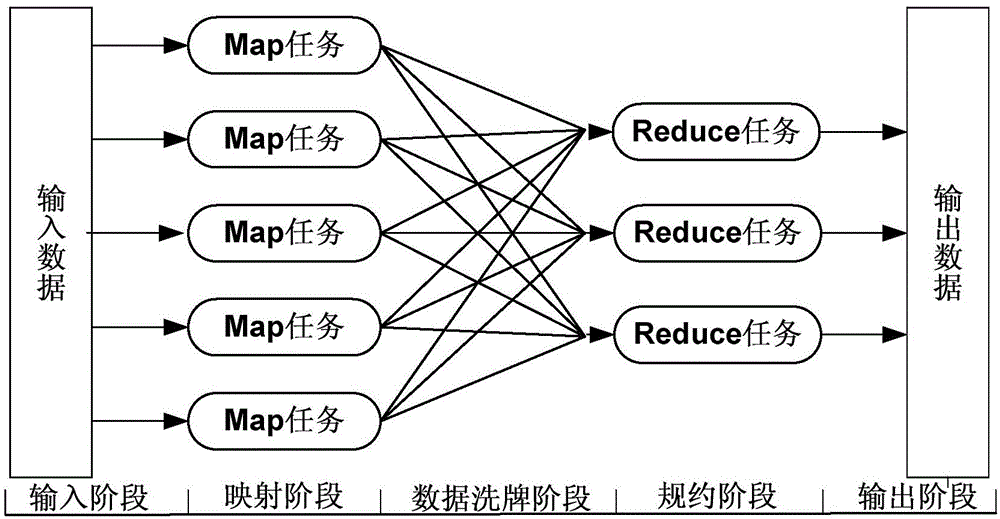
The invention discloses a large-scale image data similarity searching method based on an EMD (earth mover's distance). The method comprises the following steps that an image data mapping function f used for mapping to a one-dimension real number key value space Omega(phi) is designed; an operation MR1 is started, and a load of each key value in the Omega(phi) is estimated; the operation MR2 is started, the cutting is carried out on the Omega(phi) through a Map task on the basis of the estimated key value load, and data corresponding to the cutting region are sent to a Reduce task in a segmented way; image data received by each Reduce task is mapped to the key values in the Omega(phi) on the basis of f, and an index structure oriented to the EMD is built on the basis of the key values; the similarity searching based on the EMD is executed on the basis of the index structure; execution results of each Reduce task based on EMD similarity searching in the MR2 are subjected to union set taking and output. The large-scale image data similarity searching method has the advantages that the network transmission data quantity is lower, the calculation load distribution is more balanced, the similarity searching efficiency is higher, and the big data set analysis and processing expandability is better.
Owner:GUANGXI UNIV
Complex logarithmic ALU
InactiveUS7689639B2Simplifies divisionSimplifies multiplicationComputation using non-contact making devicesDigital computer detailsReal arithmeticLogit
Owner:OPTIS WIRELESS TECH LLC
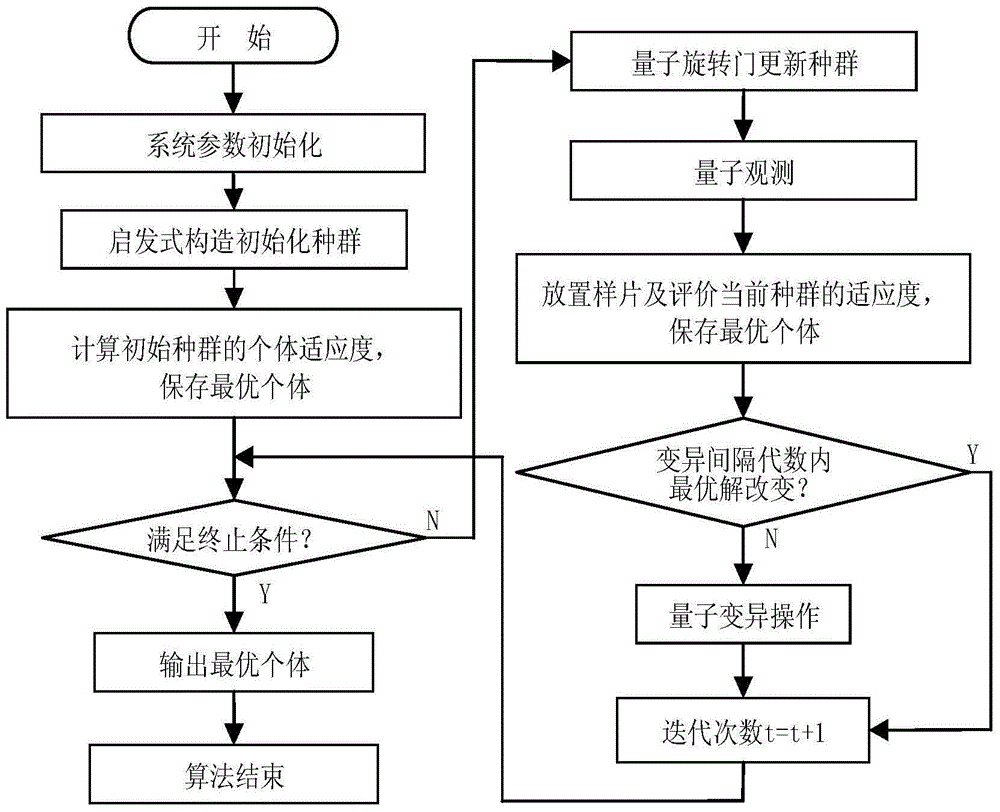
Irregular layout method based on real-coded quantum evolutionary algorithm
InactiveCN105740953AReduce code lengthReduce layout timeGenetic algorithmsQuantum evolutionary algorithmReal arithmetic
The invention belongs to the technical field of the computer-aided layout technology, and relates to an irregular layout method based on a real-coded quantum evolutionary algorithm. The irregular layout method comprises the following steps: S1: utilizing a real-coded quantum probability amplitude to carry out uniform coding on a layout number sequence and a rotation angle sequence; S2: carrying out system initialization; S3: calculating the fitness of a population individual, and storing an optimal individual; S4: updating a quantum population; S5: carrying out quantum observation; S6: arranging a print into a mother board, carrying out individual fitness evaluation again, and updating the optimal individual; and S7: judging a termination condition. Since the quantum evolutionary algorithm is applied for solving an irregular layout problem, the irregular layout method has the advantages that layout time can be effectively shortened, the search precision of layout is improved and the use ratio of raw materials is improved, and the irregular layout method can be used for the layout in production and processing including glass cutting, clothes and leather cutting and the like.
Owner:WENZHOU UNIVERSITY
LP method and apparatus for identifying route propagations
InactiveUS6883154B2Record information storageData switching by path configurationSub regionLinear programming
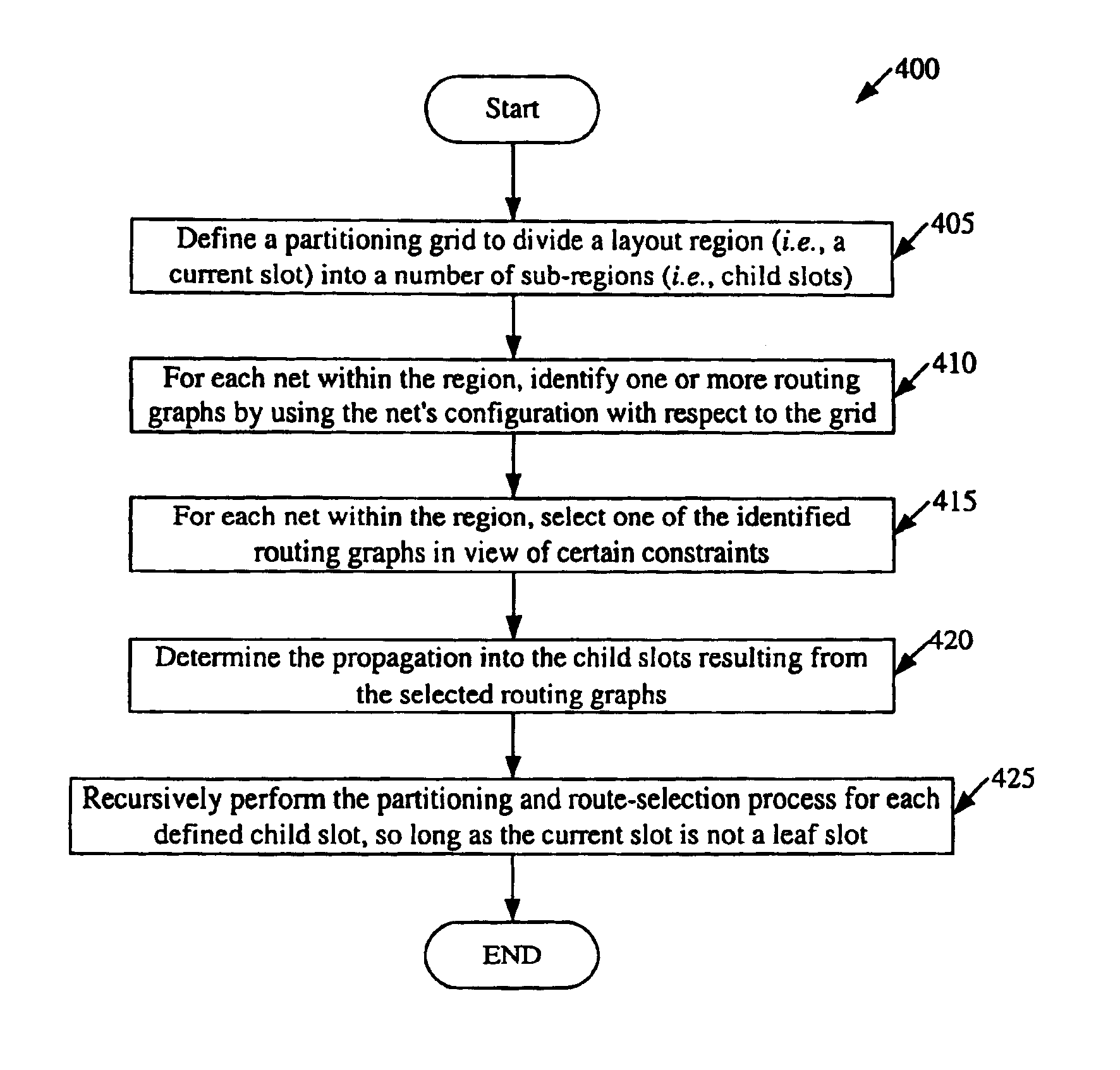
Some embodiments provide an LP method that identifies route propagations. In some embodiments, this method is used by a router that hierarchically defines routes for nets within a region of a design layout. The router (1) partitions the region into a first set of sub-regions, and (2) for each particular net, identifies a route that traverses a set of the first-set sub-regions. In some embodiments, the invention's method partitions the first set of sub-regions into a second set of smaller sub-regions. It then identifies a plurality of propagation possibilities for propagating each route into the second set of smaller sub-regions of the first set sub-regions. The method next formulates a linear-programming (“LP”) problem based on the identified propagation possibilities. The method then solves the LP problem. In some embodiments, the formulated LP problem is an integer-linear-programming (“ILP”) problem, and solving the ILP problem returns integer solutions that specify one propagation permutation for each route in each first-set sub-region traversed by the route. In other embodiments, solving the LP problem returns real-numbered solutions. In some of these embodiments, the method converts the real-number solutions into integer solutions that specify one identified propagation permutation for each route in each first-set sub-region traversed by the route.
Owner:CADENCE DESIGN SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com