Patents
Literature
2339 results about "Data mapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing and data management, data mapping is the process of creating data element mappings between two distinct data models. For example, a company that would like to transmit and receive purchases and invoices with other companies might use data mapping to create data maps from a company's data to standardized ANSI ASC X12 messages for items such as purchase orders and invoices.
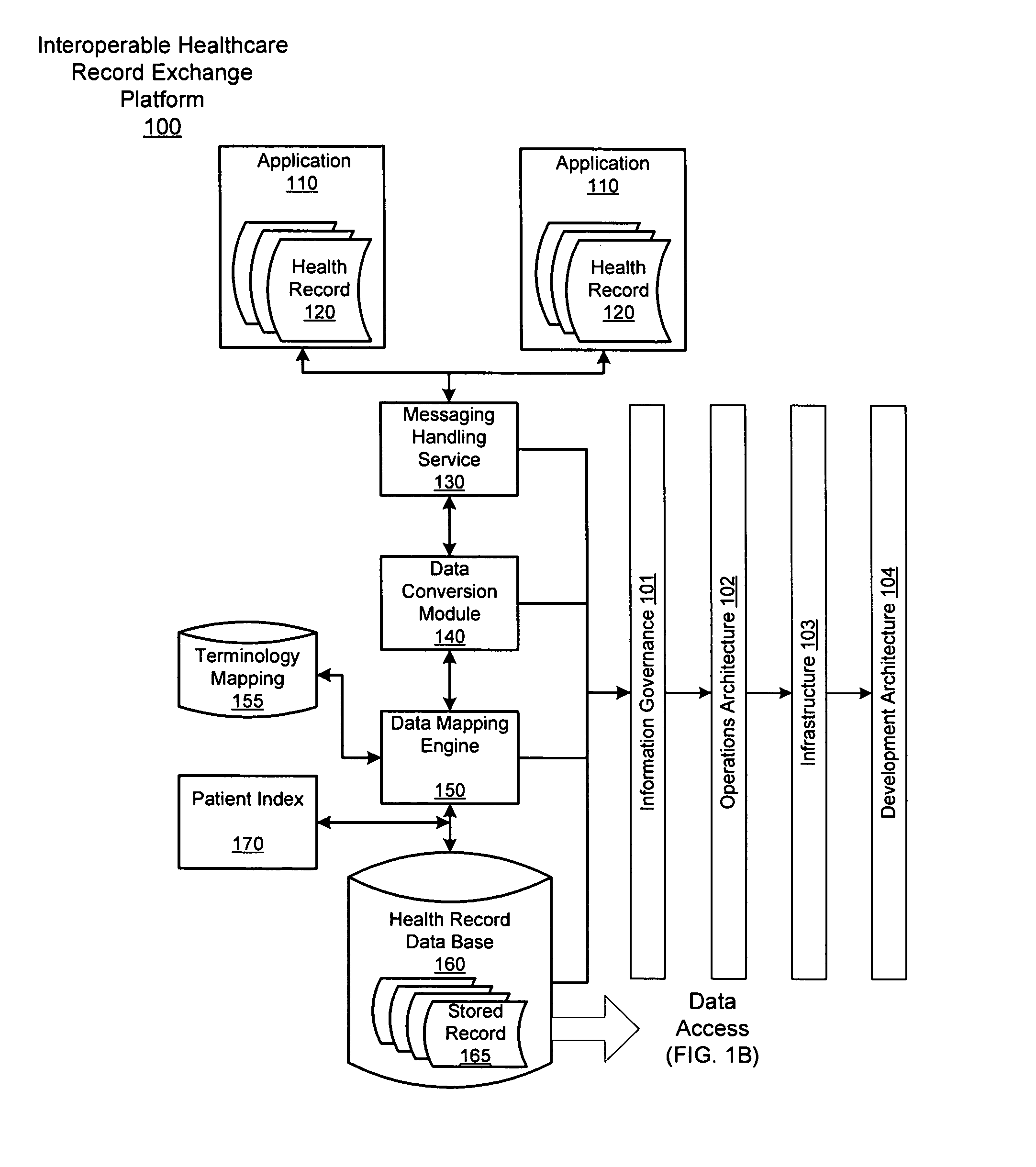
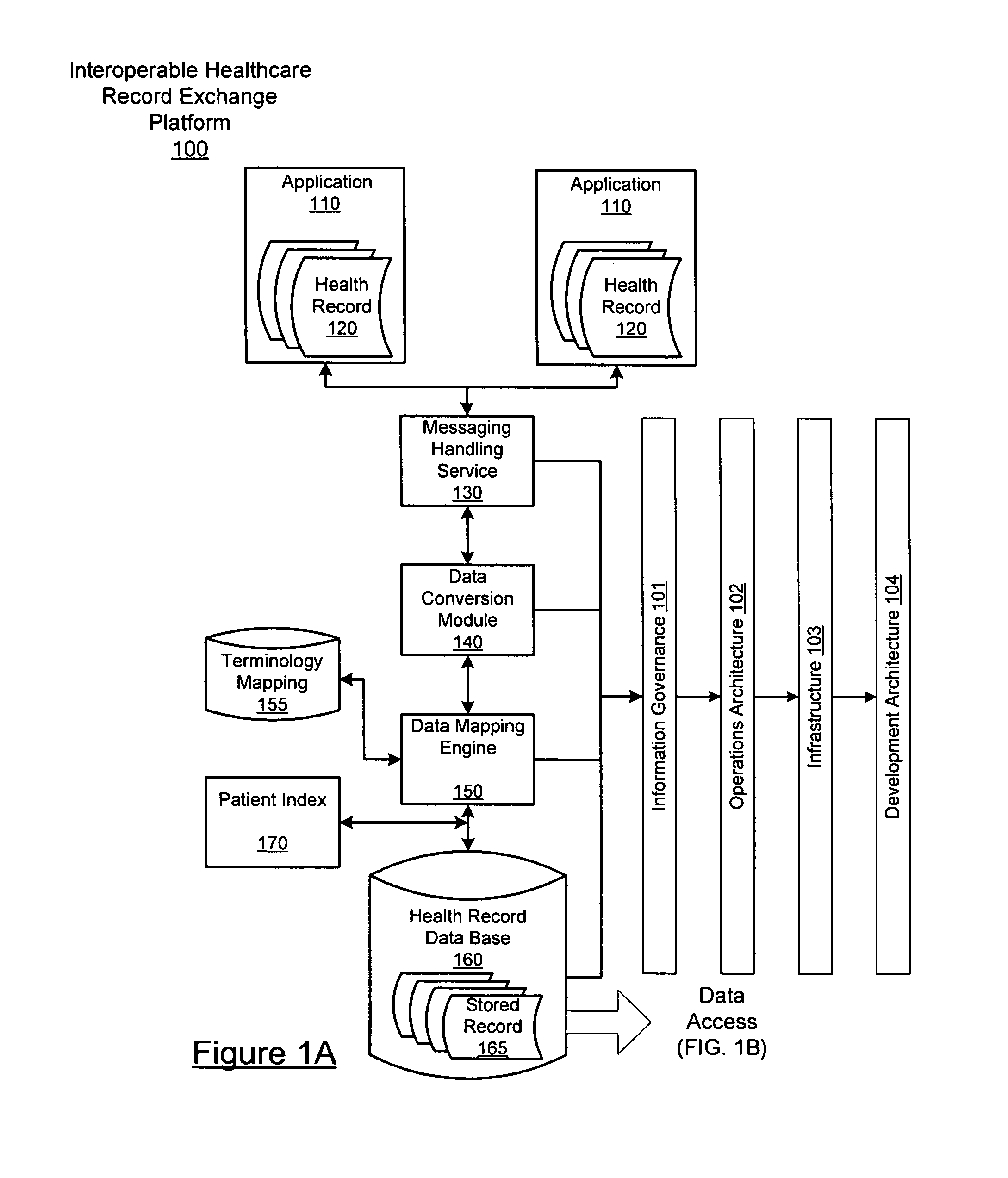
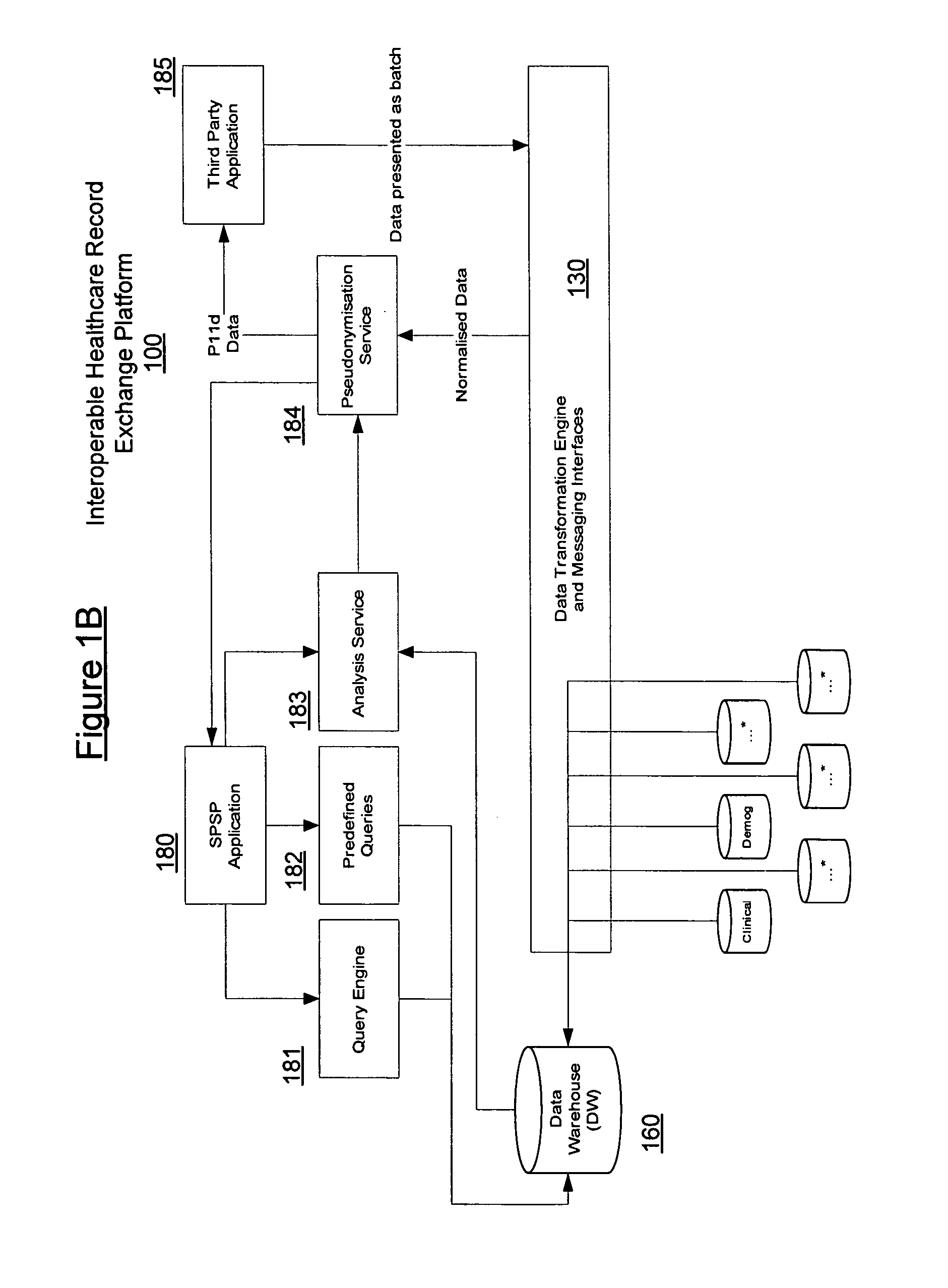
Platform for interoperable healthcare data exchange
InactiveUS20080046292A1Easy to controlData processing applicationsDatabase management systemsData exchangeData store
The interoperable healthcare data exchange platform seamlessly links a plurality of disparate, remote applications generally representing provider systems containing electronic health records (EHRs) to enable the real-time collection, processing and centralized storage of health records at a data store, along with enabling controlled access to the centralized storage. The central health records data store receives, in real time, substantially complete electronic medical data input from multiple, disparate providers and sources of health records. The platform enable semantic normalization of the health records by converting the data in the health records to standardized message formats using a data conversion engine and mapping the converted data to standard terminologies using mapping products.
Owner:ACCENTURE GLOBAL SERVICES LTD
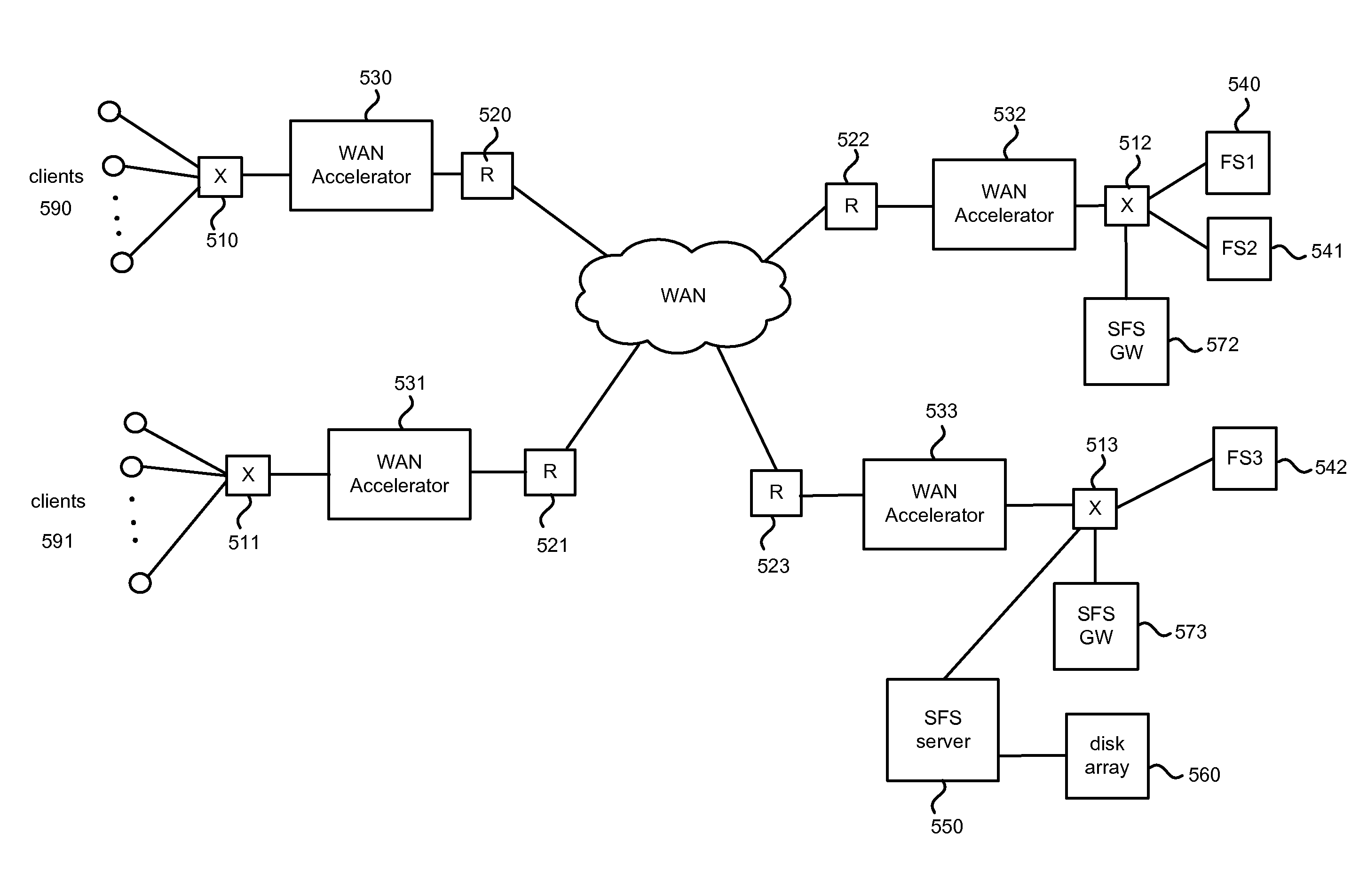
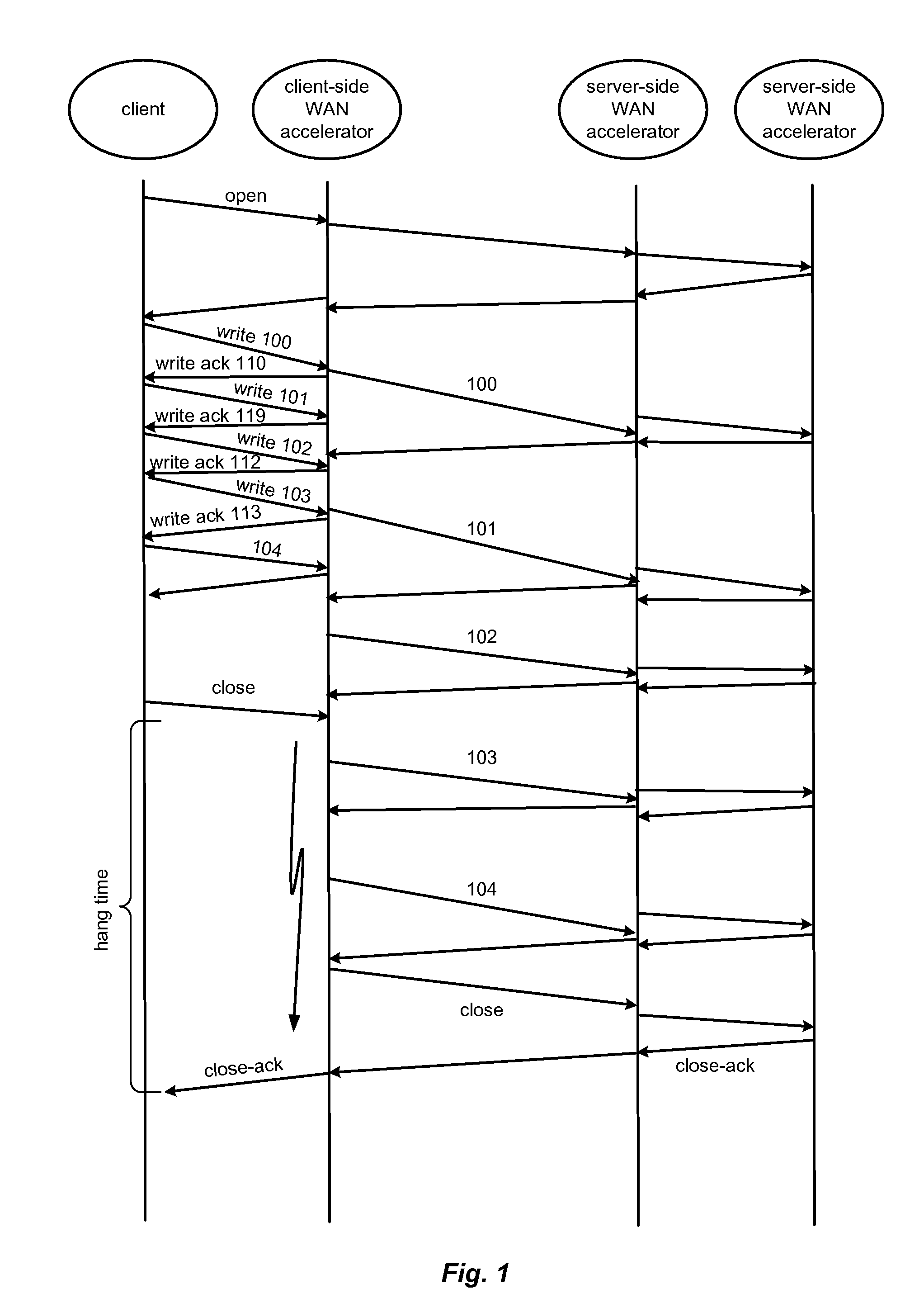
Hybrid segment-oriented file server and wan accelerator
ActiveUS20080281908A1Error detection/correctionComputer security arrangementsFile serverProtocol for Carrying Authentication for Network Access
In a network including WAN accelerators and segment-oriented file servers, a method comprises responding to a client request to manipulate a file via a network file protocol by receiving a first request at a first WAN accelerator, wherein the request is a request to open a file located at a file server that is a segment-oriented file server, sending a local request for the file, corresponding to the first request, from the WAN accelerator to the file server, using a segment-aware network request protocol, returning at least a portion of the requested file in the form of a representation of a data map corresponding to the at least a portion of the requested file stored on the file server and using a data map for reconstruction of the requested file.
Owner:RIVERBED TECH LLC
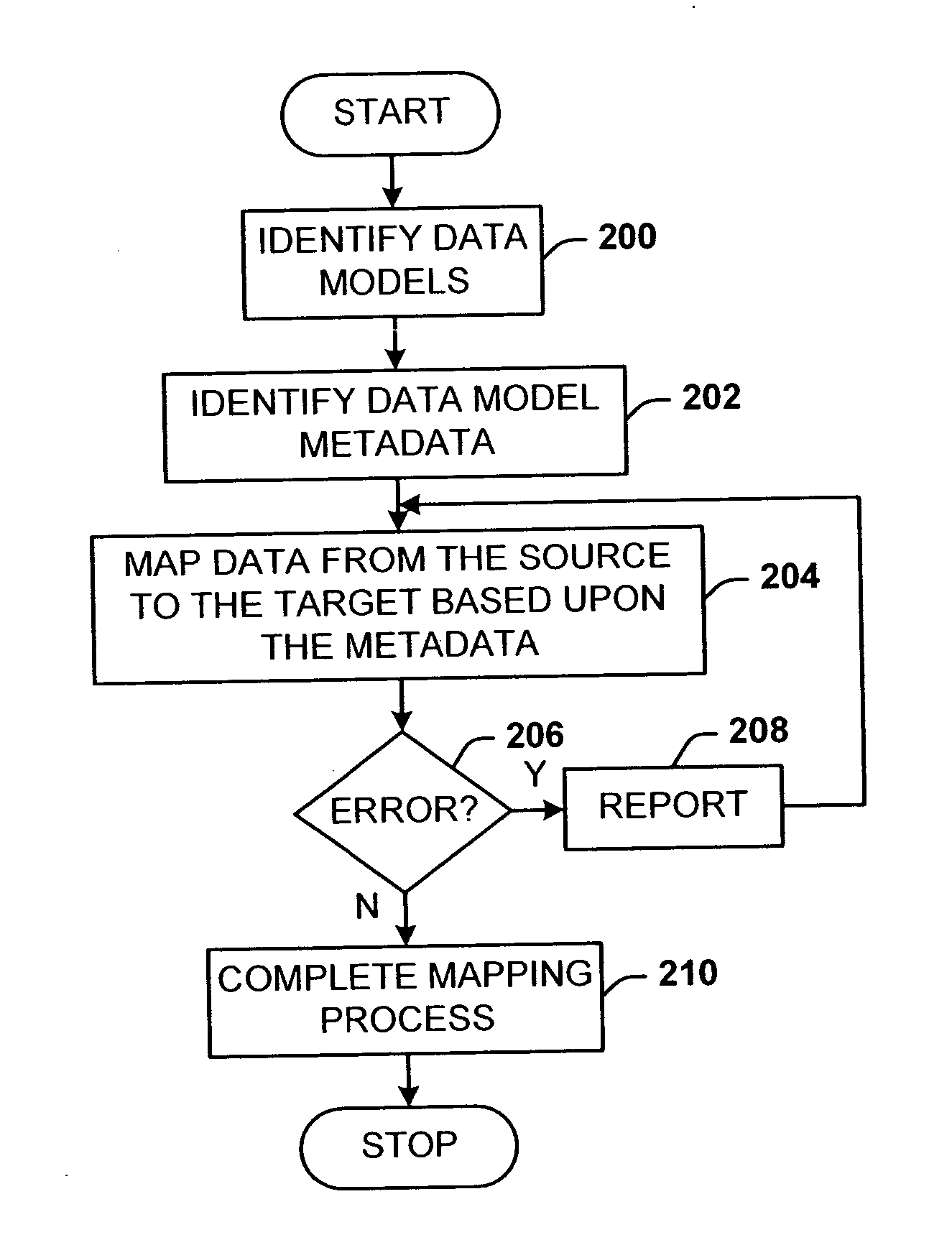
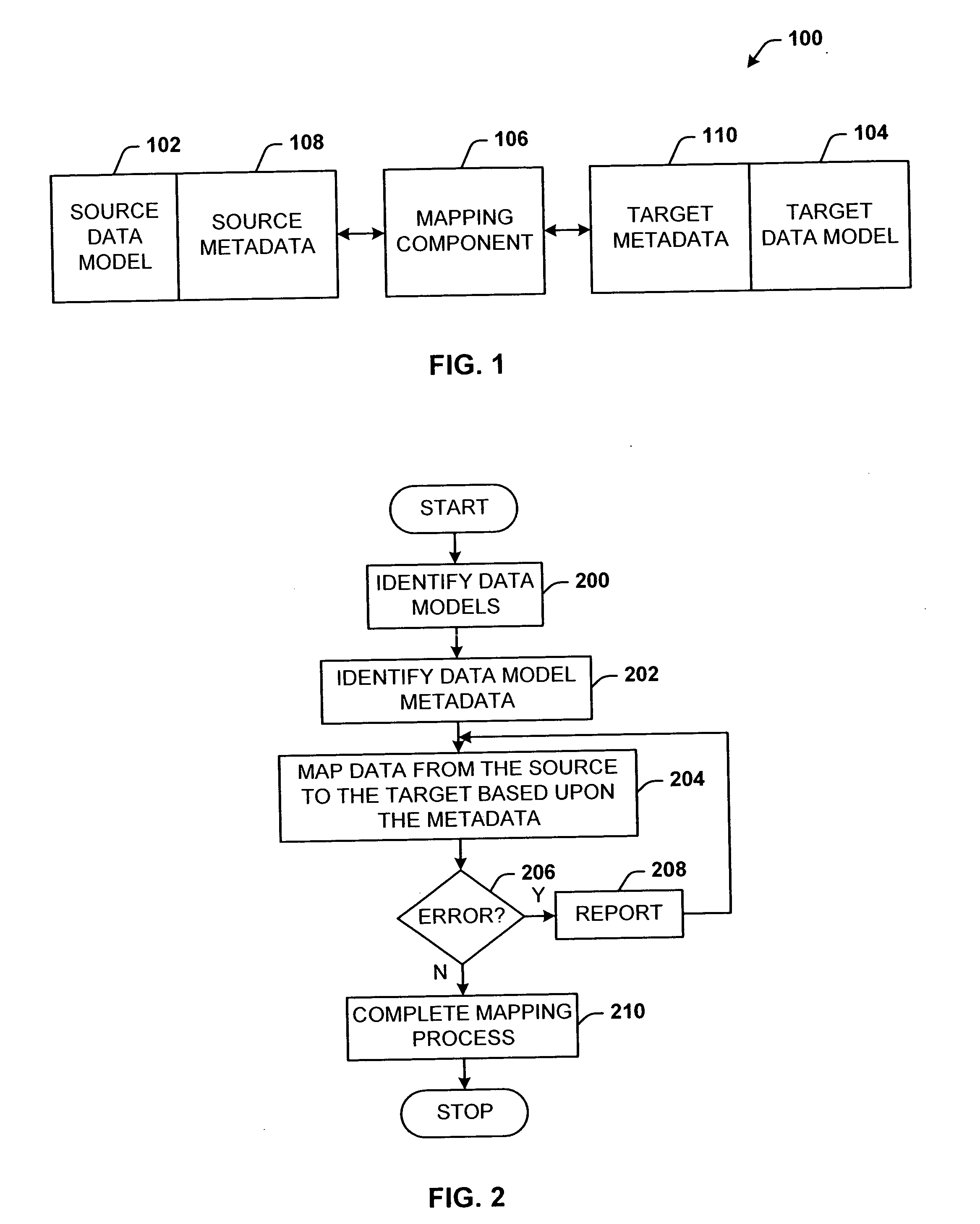
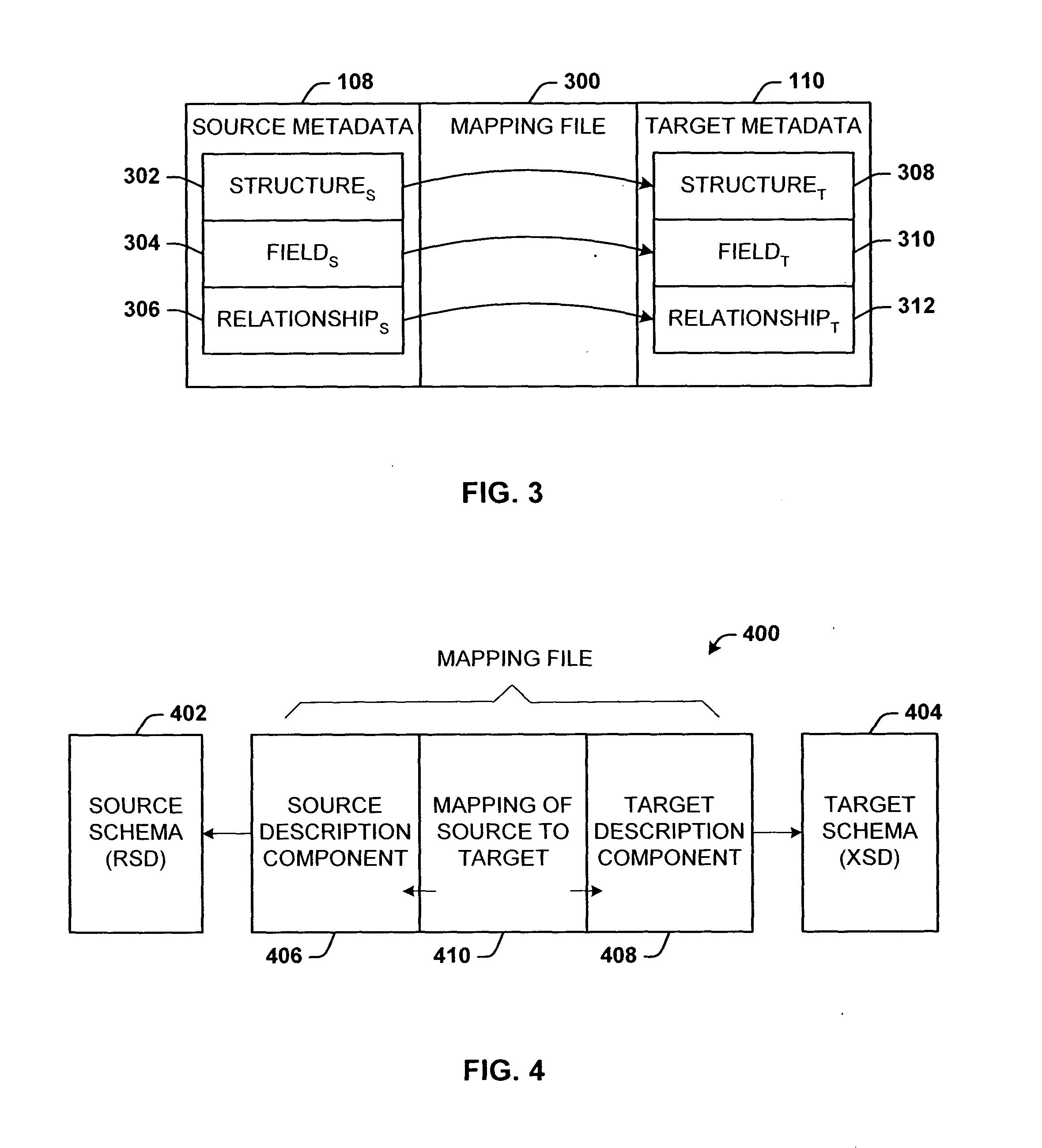
Mapping architecture for arbitrary data models
A data mapping architecture for mapping between two or more data sources without modifying the metadata or structure of the data sources themselves. Data mapping also supports updates. The architecture also supports at least the case where data sources that are being mapped, are given, their schemas predefined, and cannot be changed. The architecture includes a mapping component that receives respective metadata from at least two arbitrary data models, and maps expressions between the data models.
Owner:MICROSOFT TECH LICENSING LLC
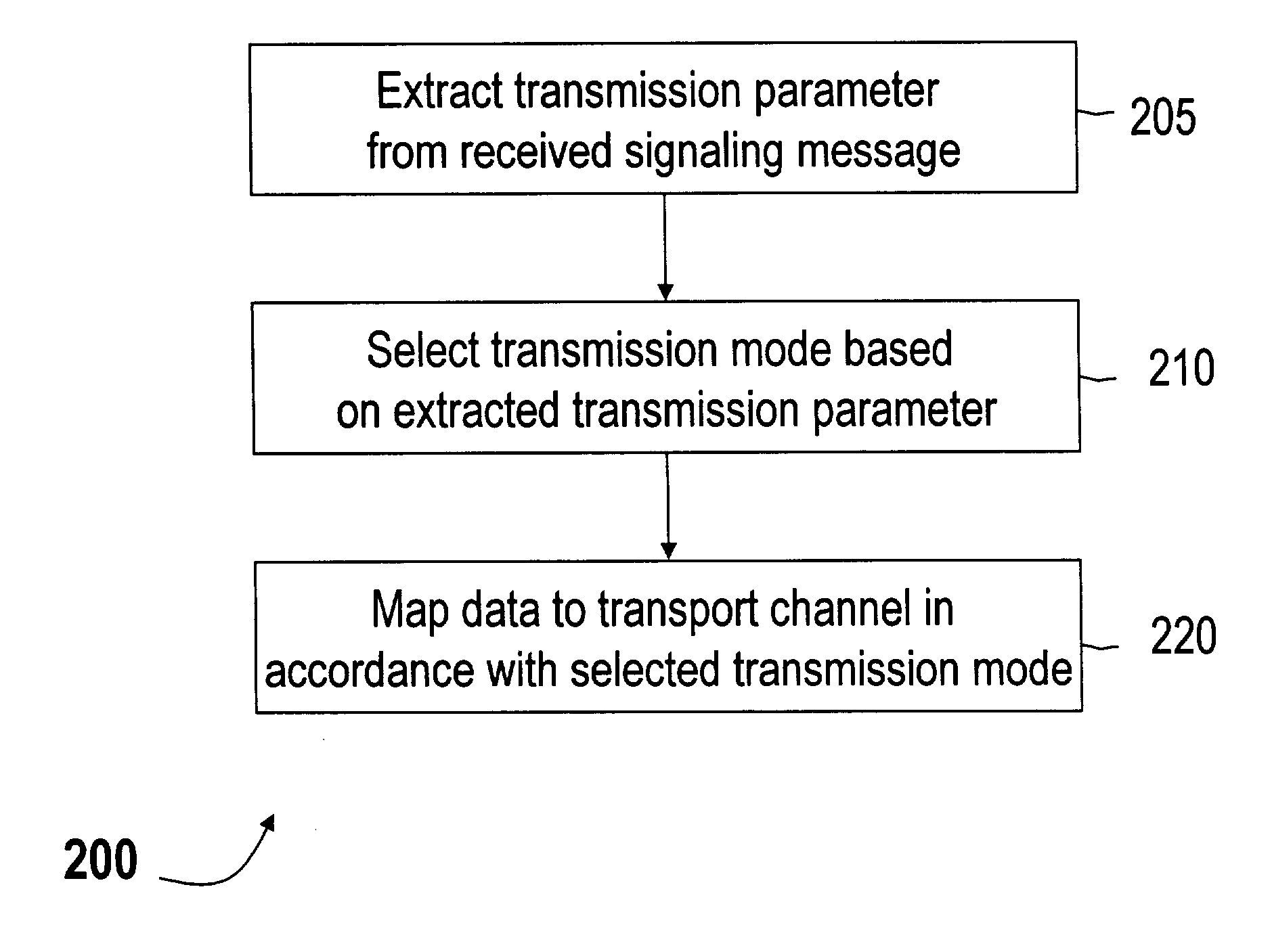
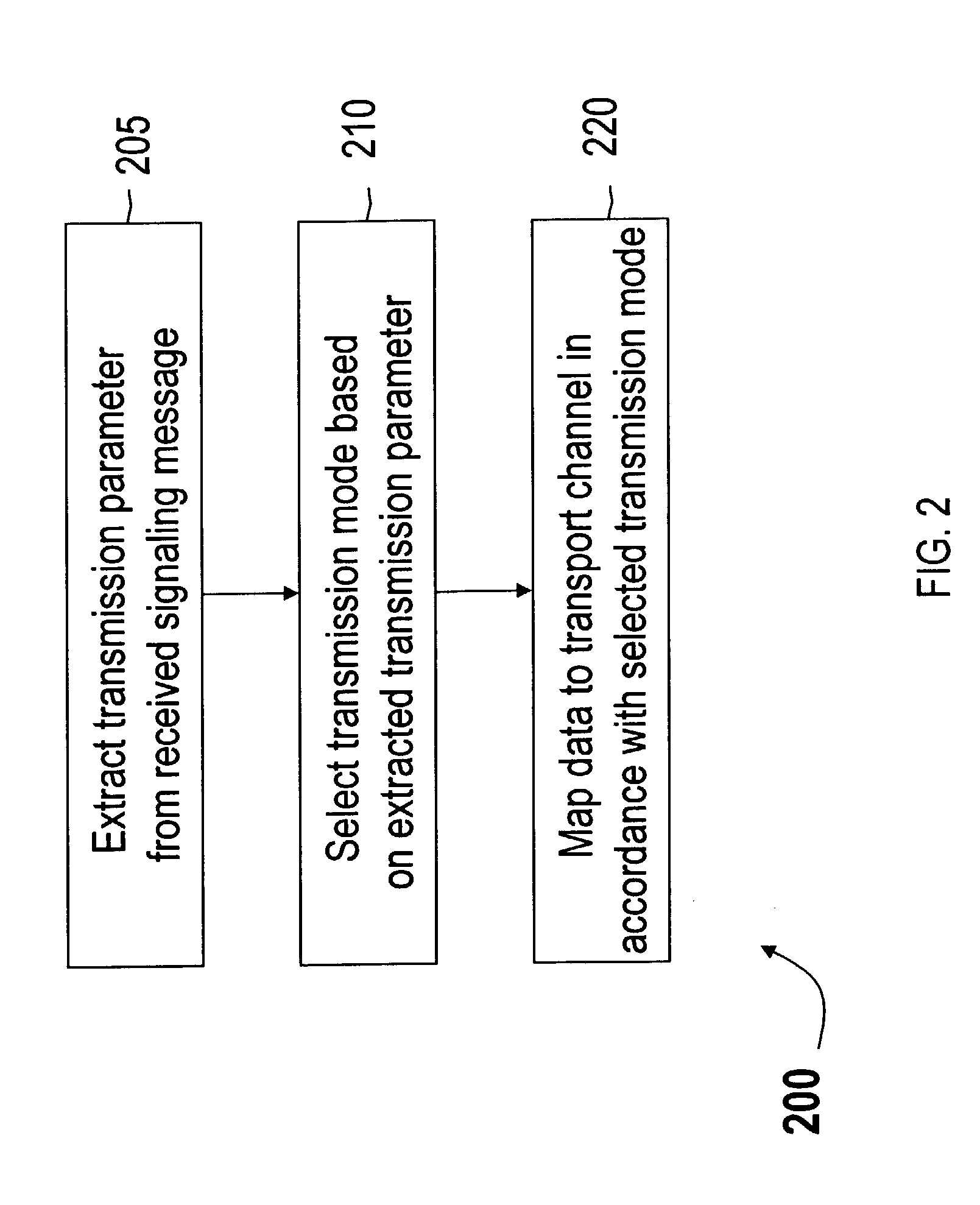
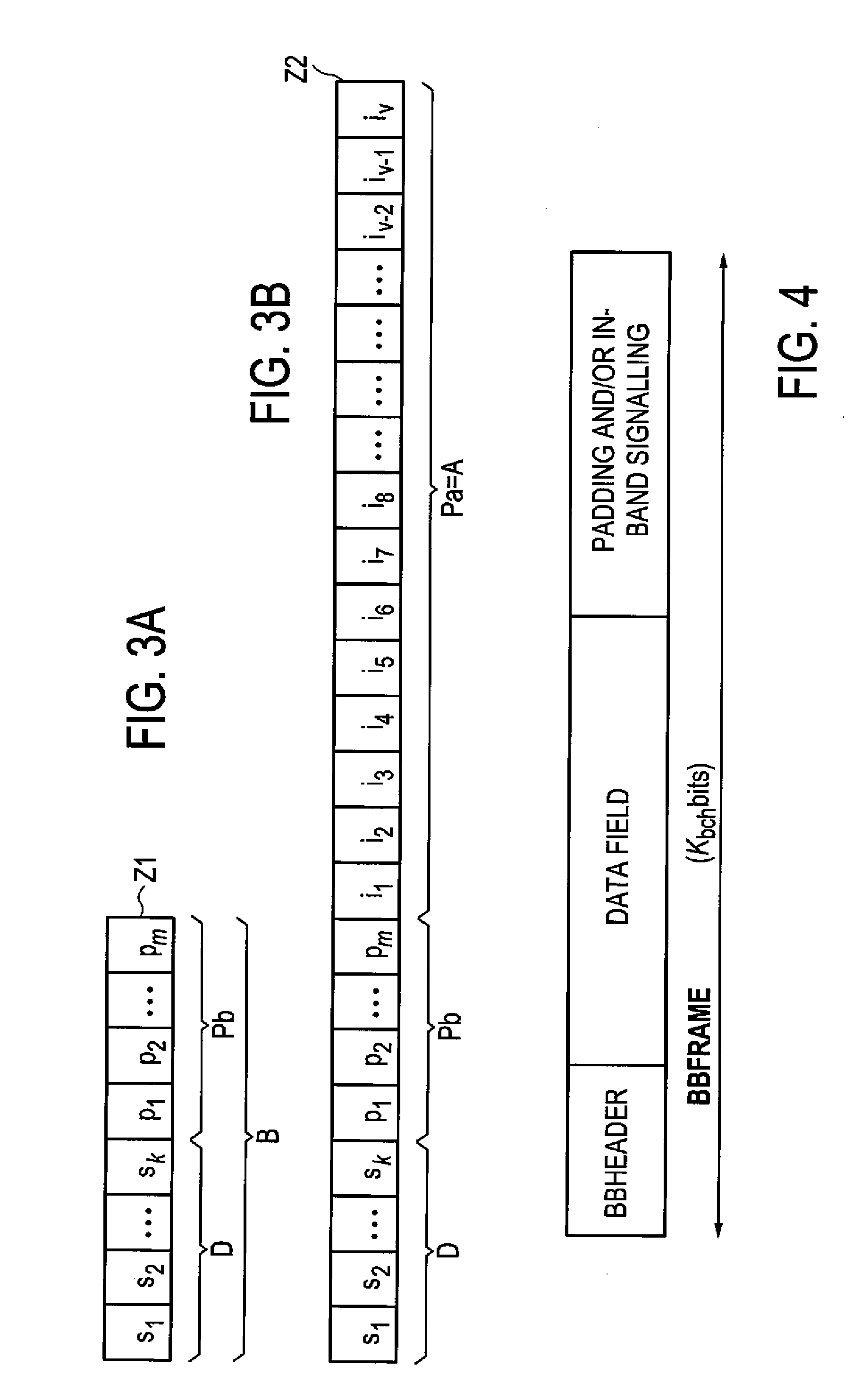
Method of mapping data for uplink transmission in communication systems
InactiveUS20040228313A1Error prevention/detection by using return channelData switching by path configurationCommunications systemUplink transmission
A method of mapping data for uplink transmission in a communication system maps data to a transport channel for uplink transmission in accordance with a selected transmission mode for uplink transmission. In the method, a transmission parameter may be extracted from a received signaling message, and a transmission mode for uplink transmission selected based on the extracted transmission parameter. The data, which may be high data rate uplink data, may me mapped from logical channels in a MAC layer to transport channels in a physical layer for transmission on the uplink. The transmission on the uplink may be performed from one of an autonomous transmission mode and a scheduled transmission mode, and the transmission parameter may be at least one of a priority indication parameter related to class priority of a service class of data to be transmitted on the uplink, and a radio channel condition.
Owner:LUCENT TECH INC
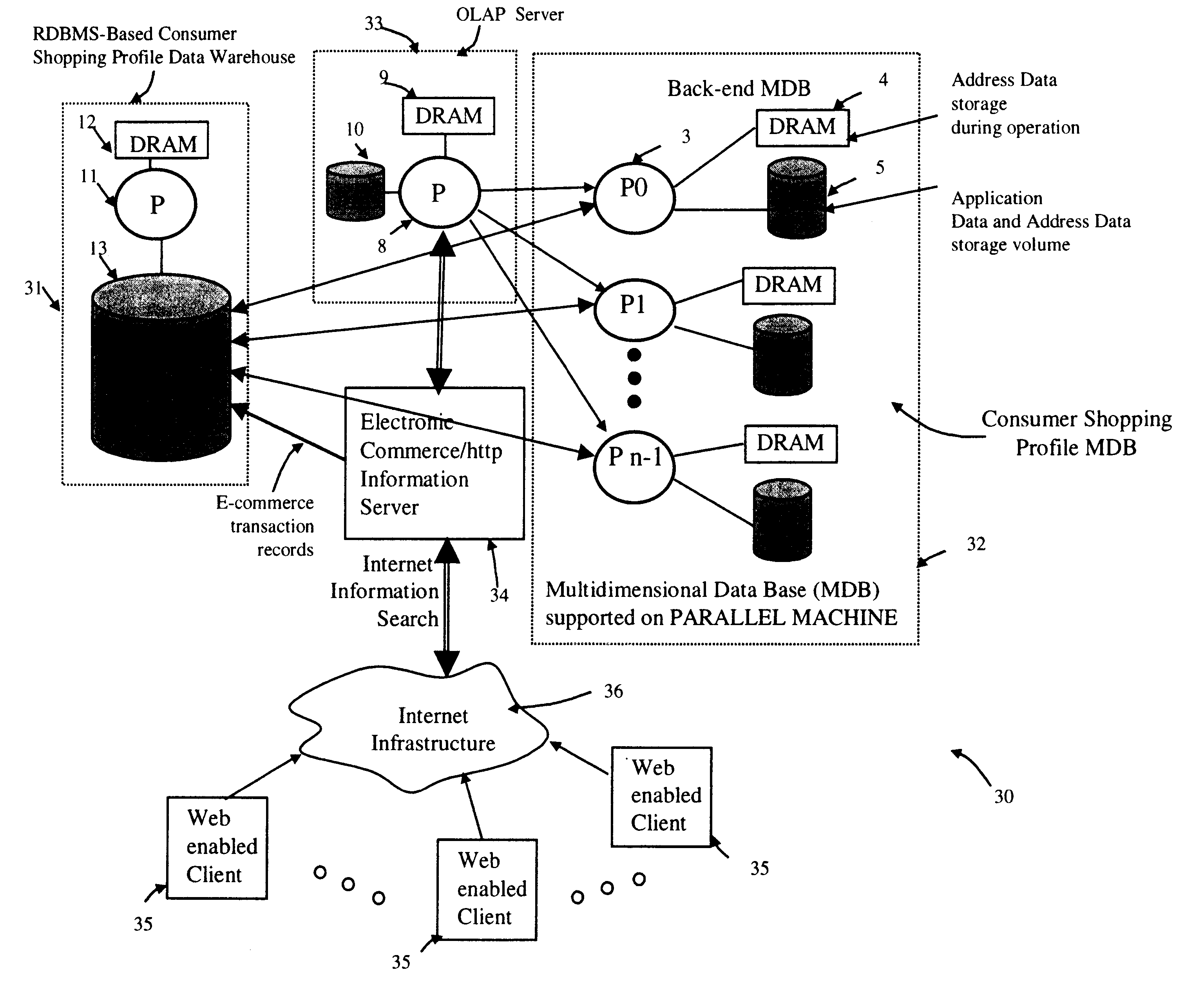
Method of and system for managing multi-dimensional databases using modular-arithmetic based address data mapping processes on integer-encoded business dimensions
InactiveUS6408292B1Improve performanceFast knowledge discoveryData processing applicationsMulti-dimensional databasesData warehouseThe Internet
An improved method of and a system for managing data elements in a multidimensional database (MDB) supported upon a parallel computing platform using modular-arithmetic based address data mapping (i.e. translation) processes on integer-encoded business dimensions. The parallel computing platform has a plurality of processors and one or more storage volumes for physically storing data elements therein at integer-encoded physical addresses in Processor Storage Space (i.e. physical address space in the one or more storage volumes associated with a given processor). The location of each data element in the MDB is specified in MDB Space by integer-encoded business dimensions associated with the data element. A data loading mechanism loads the integer-encoded business dimensions and associated data elements from a data warehouse. The address data mapping mechanism performs a two part address mapping processing. The first step maps the integer-encoded business dimensions associated with each data element to a given processor identifier (which uniquely identifies the processor amongst the plurality of processors of the parallel computing platform). The second step maps the integer-encoded business dimensions associated with each data element into an integer-encoded physical data storage address in Processor Storage Space associated with the processor identified by the processor identifier generated in the first mapping step. The mapping performed in this second step is based upon size of the integer encoded business dimensions. The data management mechanism manages the data elements stored in the storage volumes using the integer-encoded data storage addresses generated during the two-part address data mapping process. The use of modular-arithmetic functions in the two-part address data mapping mechanism ensures that the data elements in the MDB are uniformly distributed among the plurality of processors for balanced loading and processing. The present invention can be used to realize (i) an improved MDB for supporting on-line analytical processing (OLAP) operations, (ii) an improved Internet URL Directory for supporting on-line information searching operations by Web-enabled client machines, as well as (iii) diverse types of MDB-based systems for supporting real-time control of processes in response to complex states of information reflected in the MDB.
Owner:MEC MANAGEMENT LLC +1
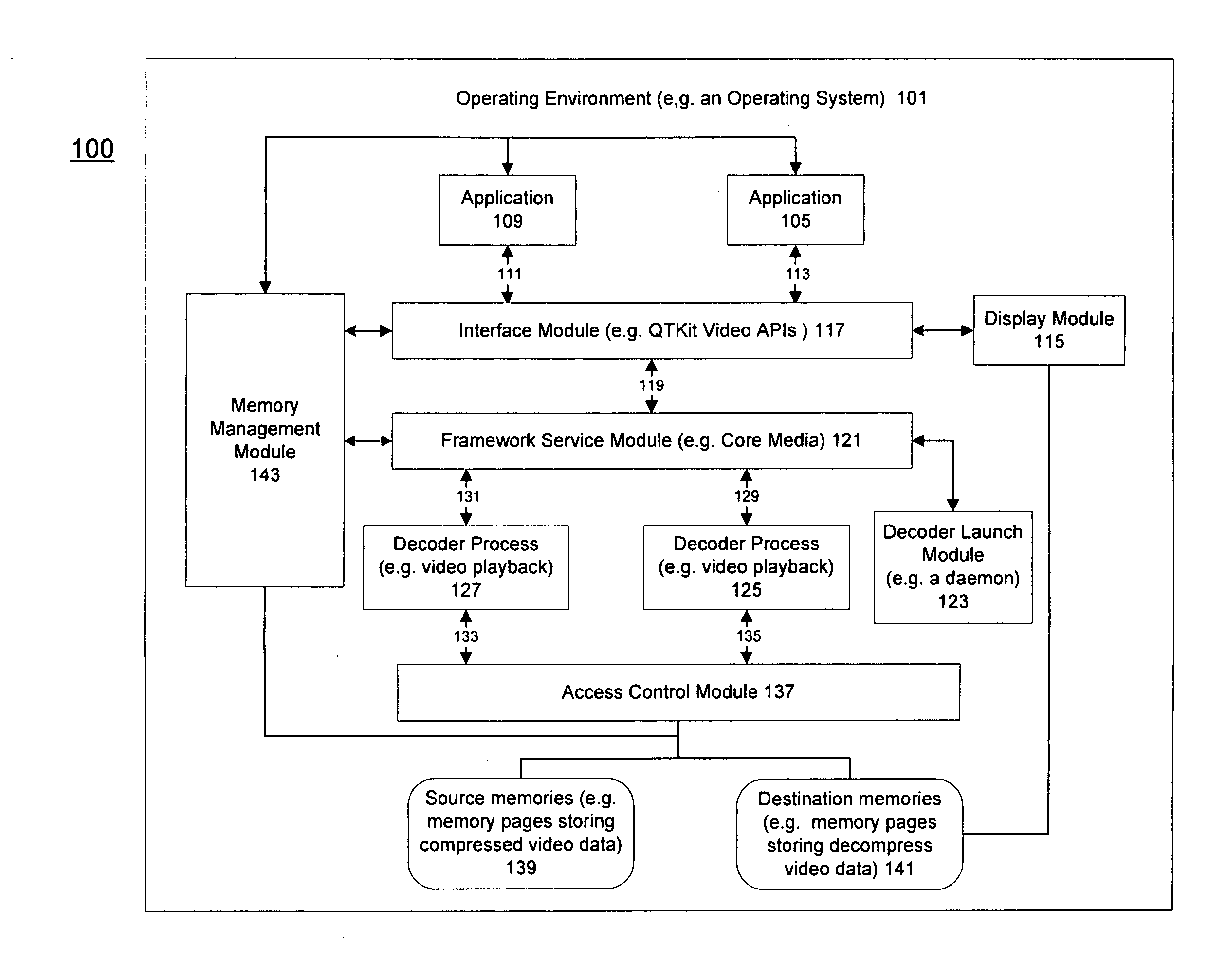
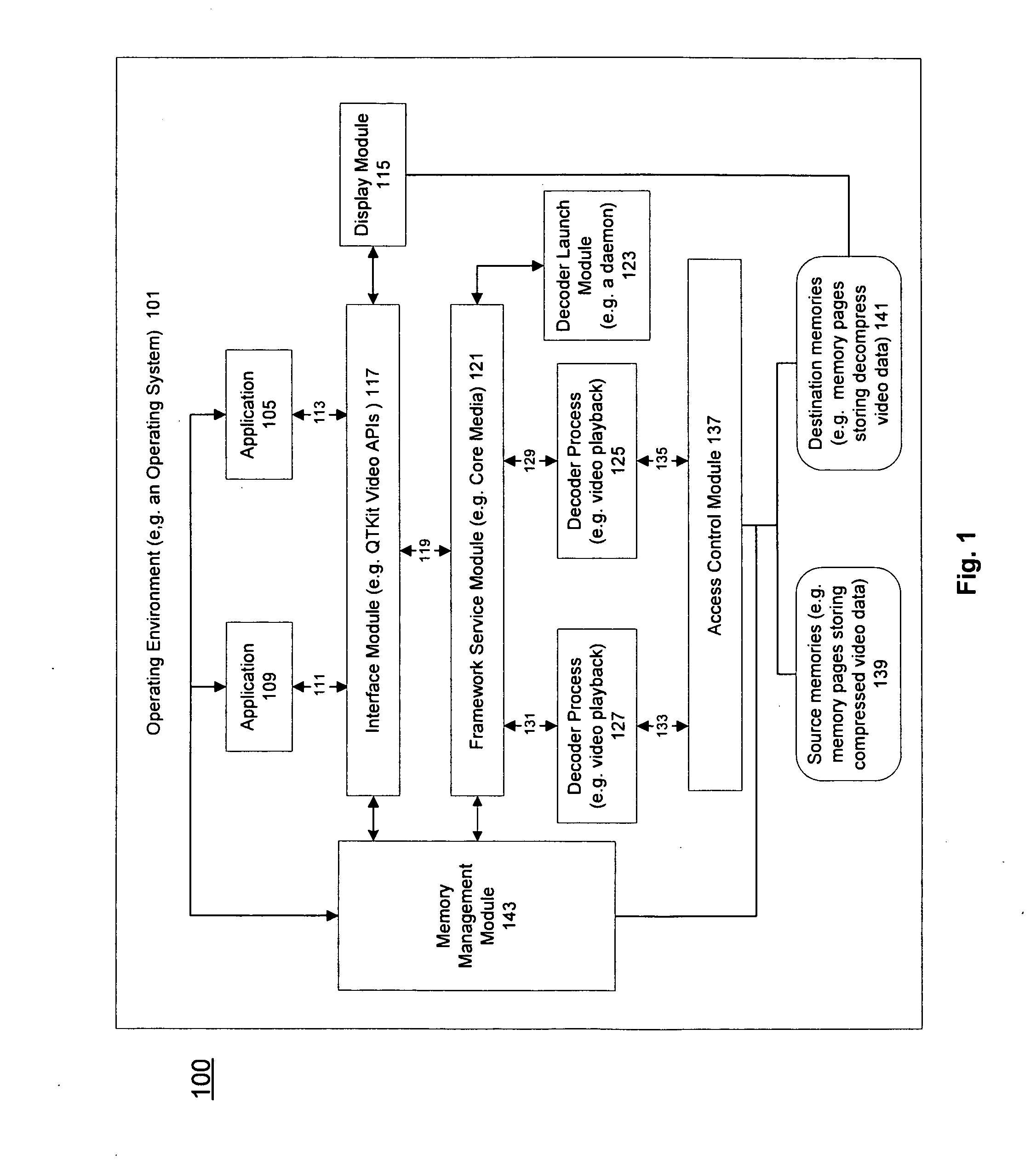
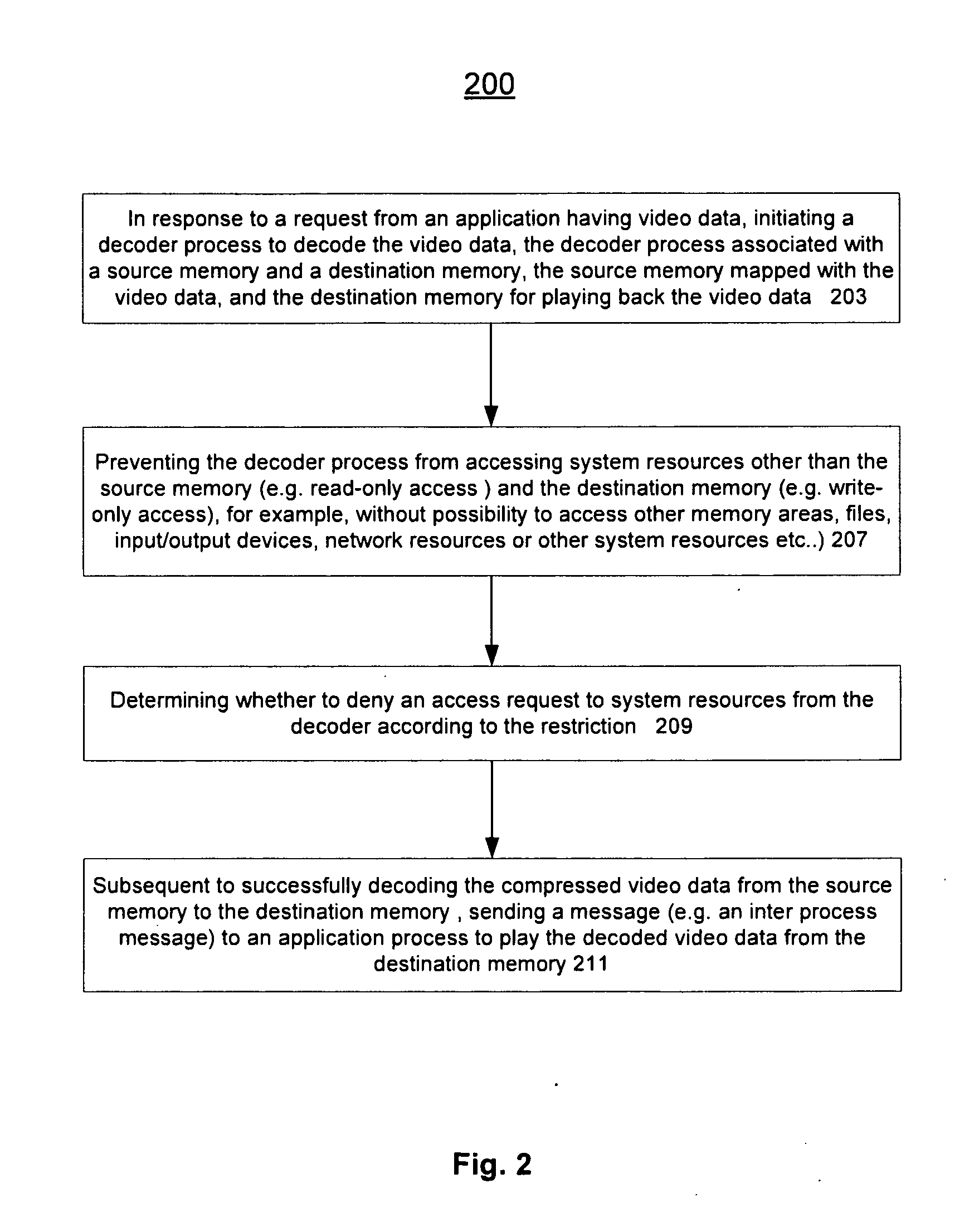
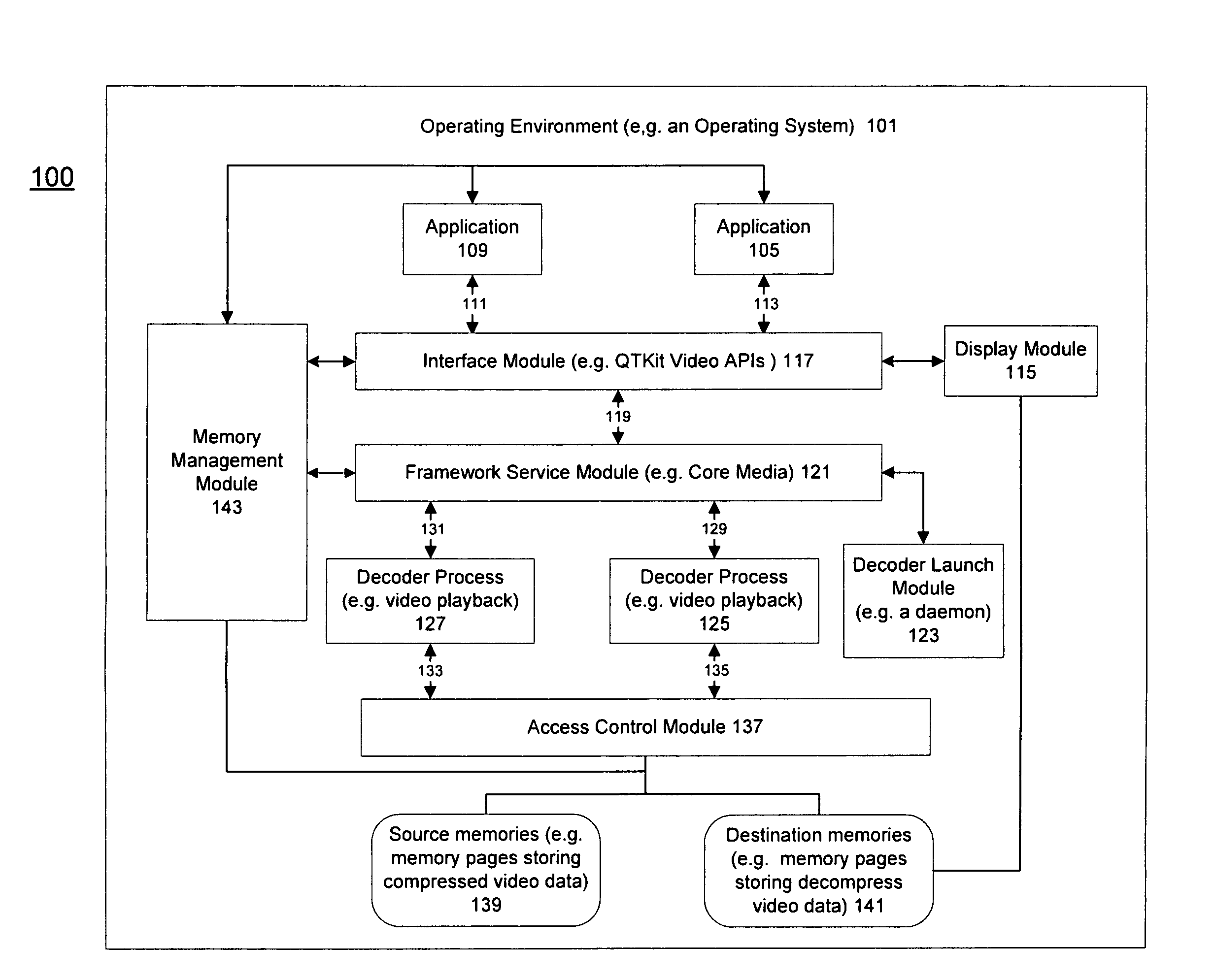
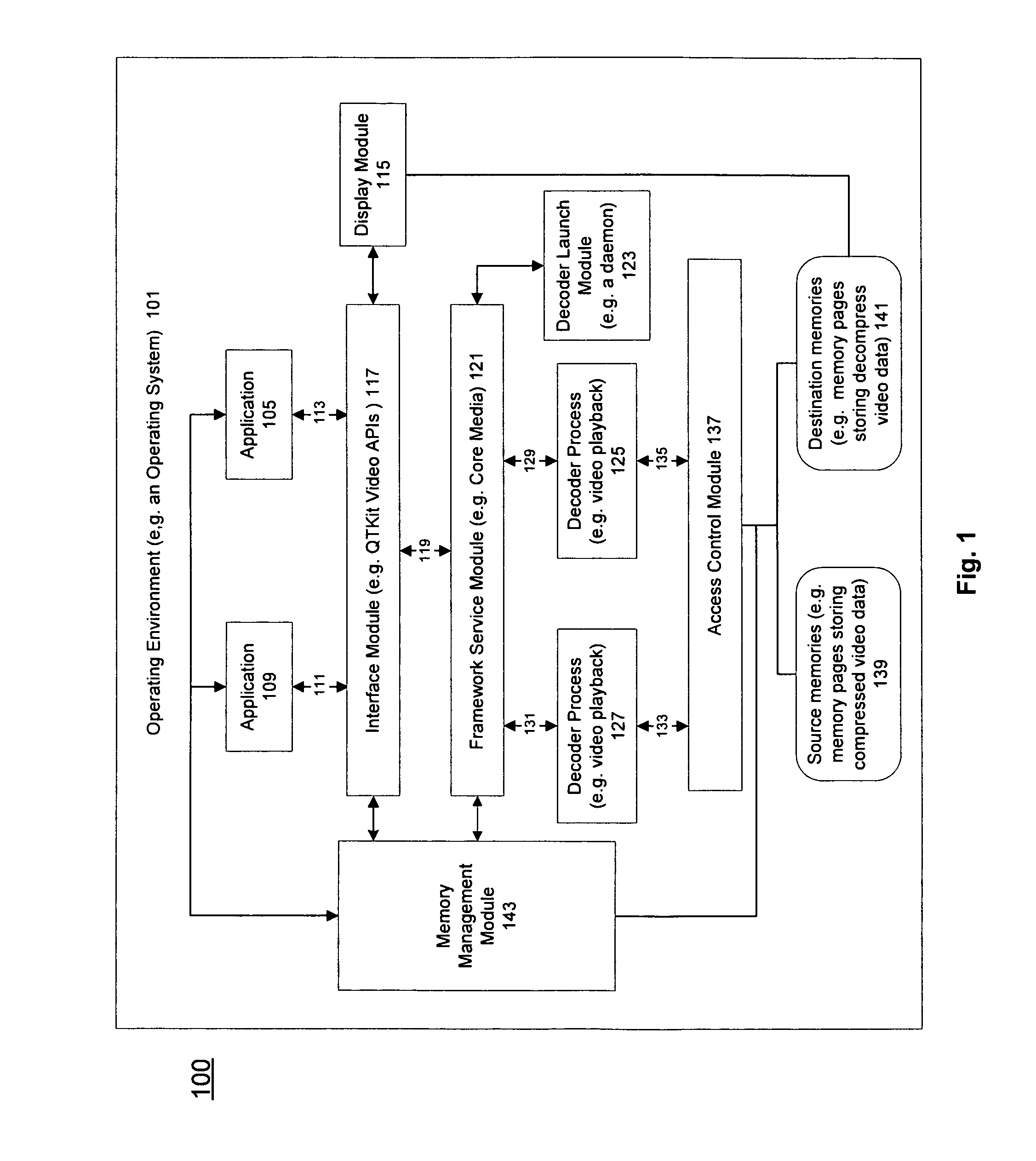
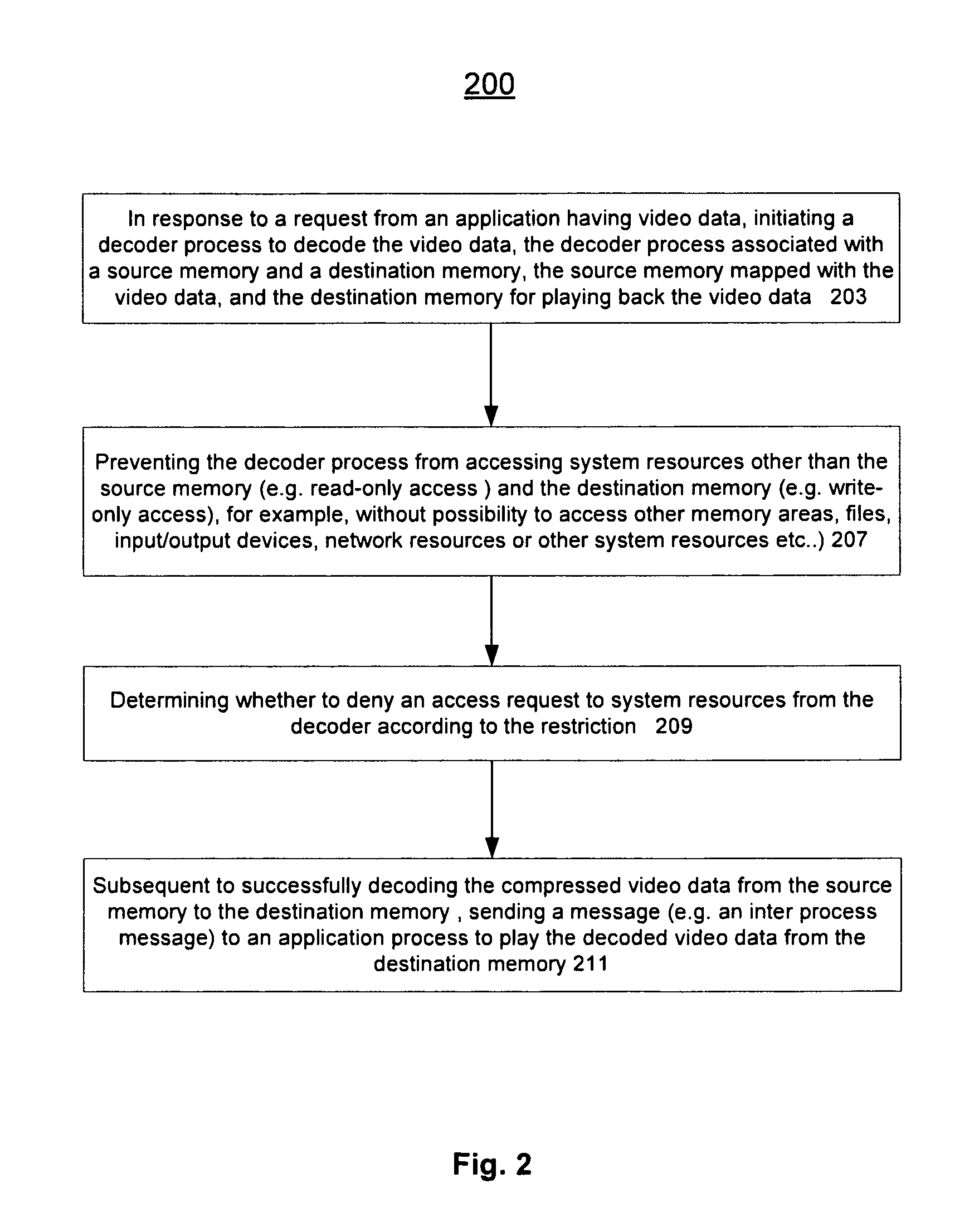
Method and apparatus for protected content data processing
ActiveUS20110004737A1Limited accessAvoid resourcesDigital data processing detailsUnauthorized memory use protectionComputer networkLimited access
Methods and an apparatuses that perform protected content data processing with limited access to system resources are described. One or more regions in a memory (including a source memory and a destination memory) can be allocated and unprocessed content data can be mapped to the source memory. A process can be initialized with the source and destination memories to process the content data. The process can be prevented from accessing resource other than the allocated regions in the memory. The processed content data can be stored in the destination memory. In one embodiment, the content data can include media content. A playing device can be instructed to play the media content based on the processed content data via the destination memory.
Owner:APPLE INC
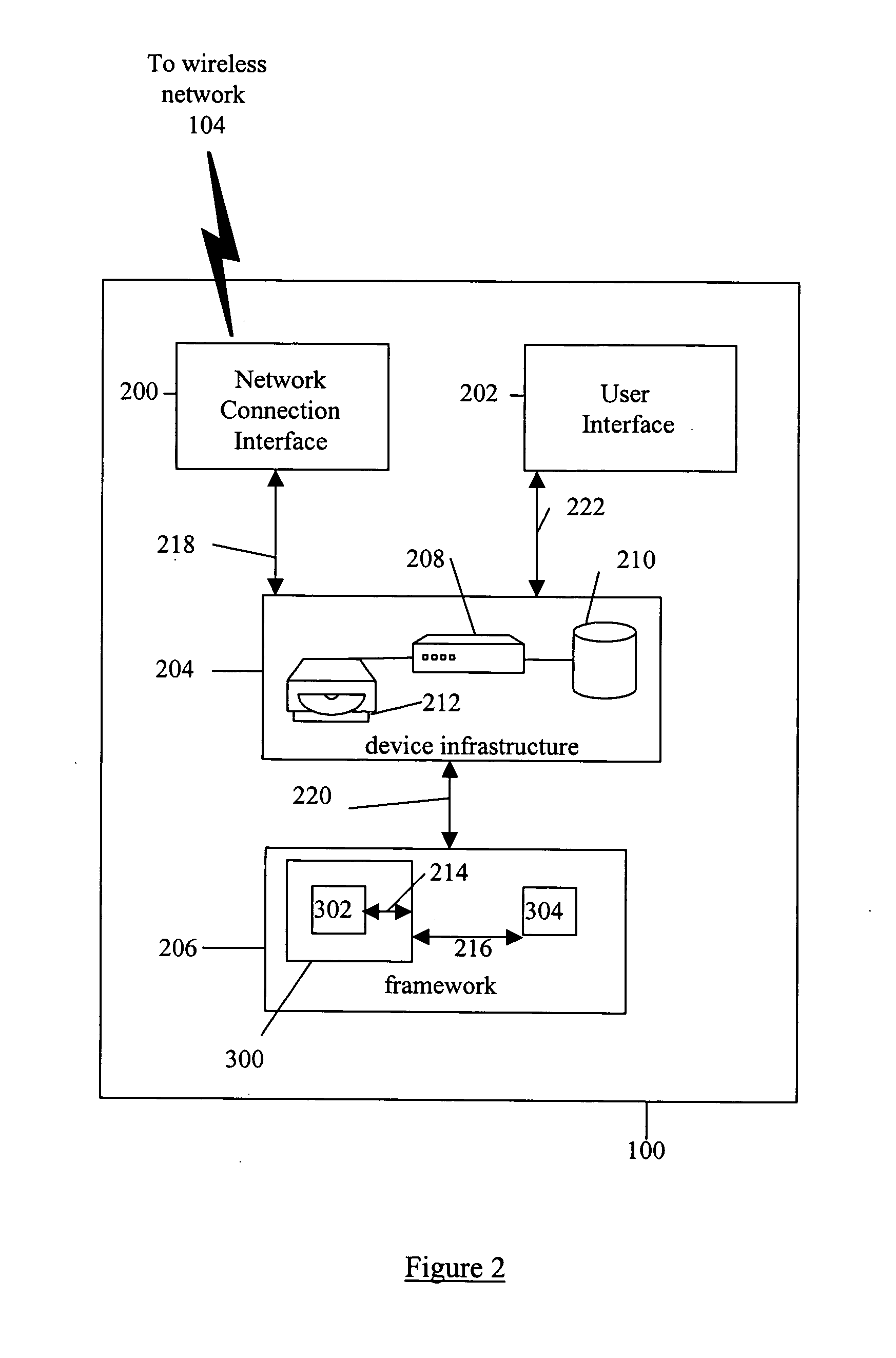
System and method for building wireless applications with intelligent mapping between user interface and data components
ActiveUS20050057560A1Reduce complexitySimplify development workDigital computer detailsMultiprogramming arrangementsData domainBasic service
A system and method is described for effective management of a User Interface (UI) of a wireless device by implementing direct mapping between the application data domain and UI screens and controls. The device has an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application, including a series of linked screen and data component definitions, and their interactions can simplify the development effort and reduce resource allocation. The data domain for this category of applications is defined using the atomic data component definitions. The communication between a device user interface and data components is defined using atomic screen component definitions. Both screen and data component definitions are described in metadata using a structured definition language such as XML. The relationships between the screen and data component definitions are embedded in the XML definitions in the form of screen / data mappings. Typically, rendered screens for display are derived from some underlying data component and screens controls affected by user events impact the current state (or data representation) of the application Changes to the application domain data are automatically synchronized with the user interface, and user-entered data is automatically reflected in the application domain data. The primary mechanism behind this synchronization is the mapping of screens and data. This mechanism enables creation of dynamic and interactive screens. All changes to the data component can be immediately reflected on the screen and vice versa. This model allows building effective wireless applications based on server-to-device notifications. The data updates asynchronously pushed from the server are instantaneously reflected at the UI screen.
Owner:GOOGLE TECH HLDG LLC
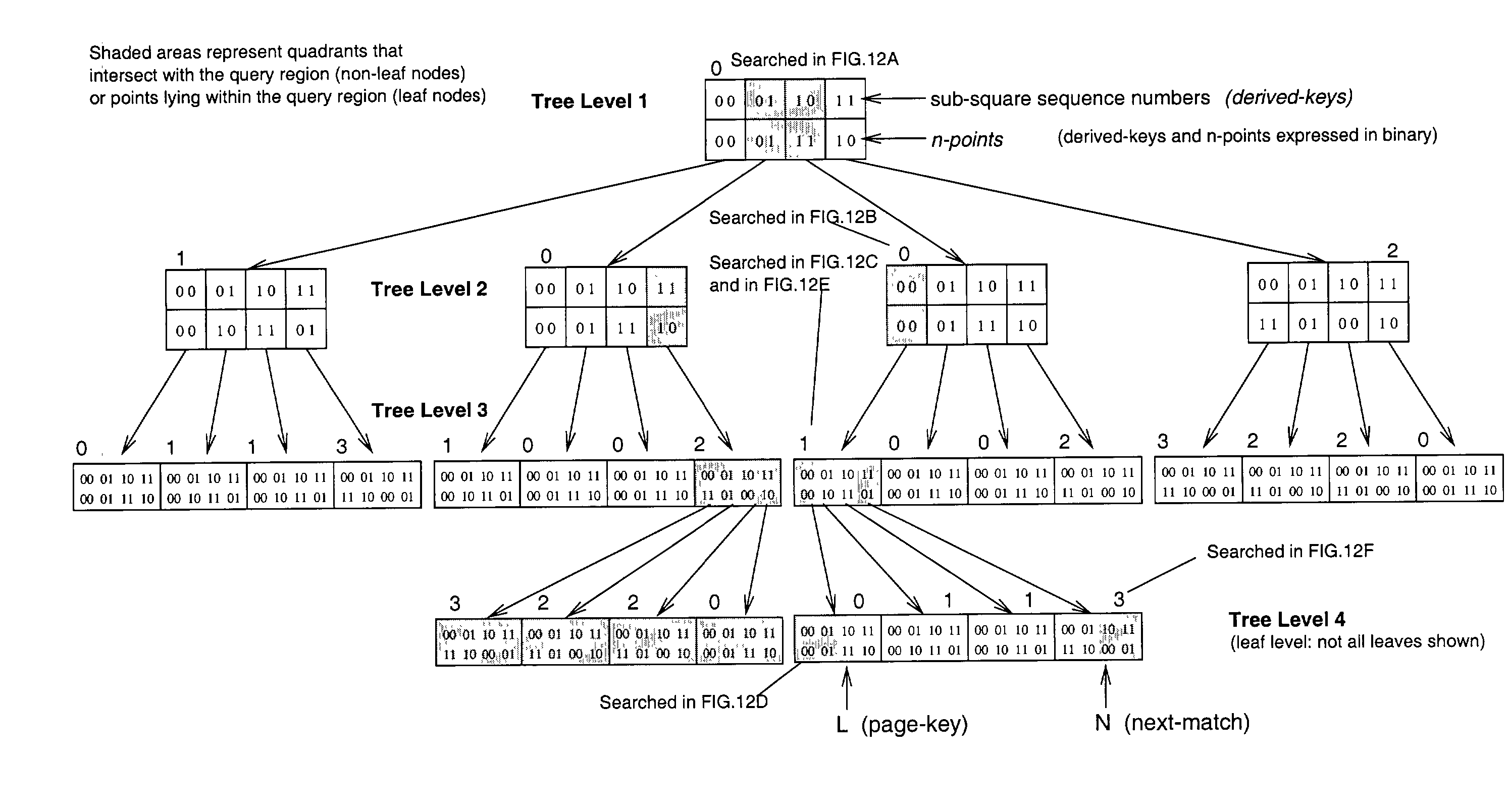
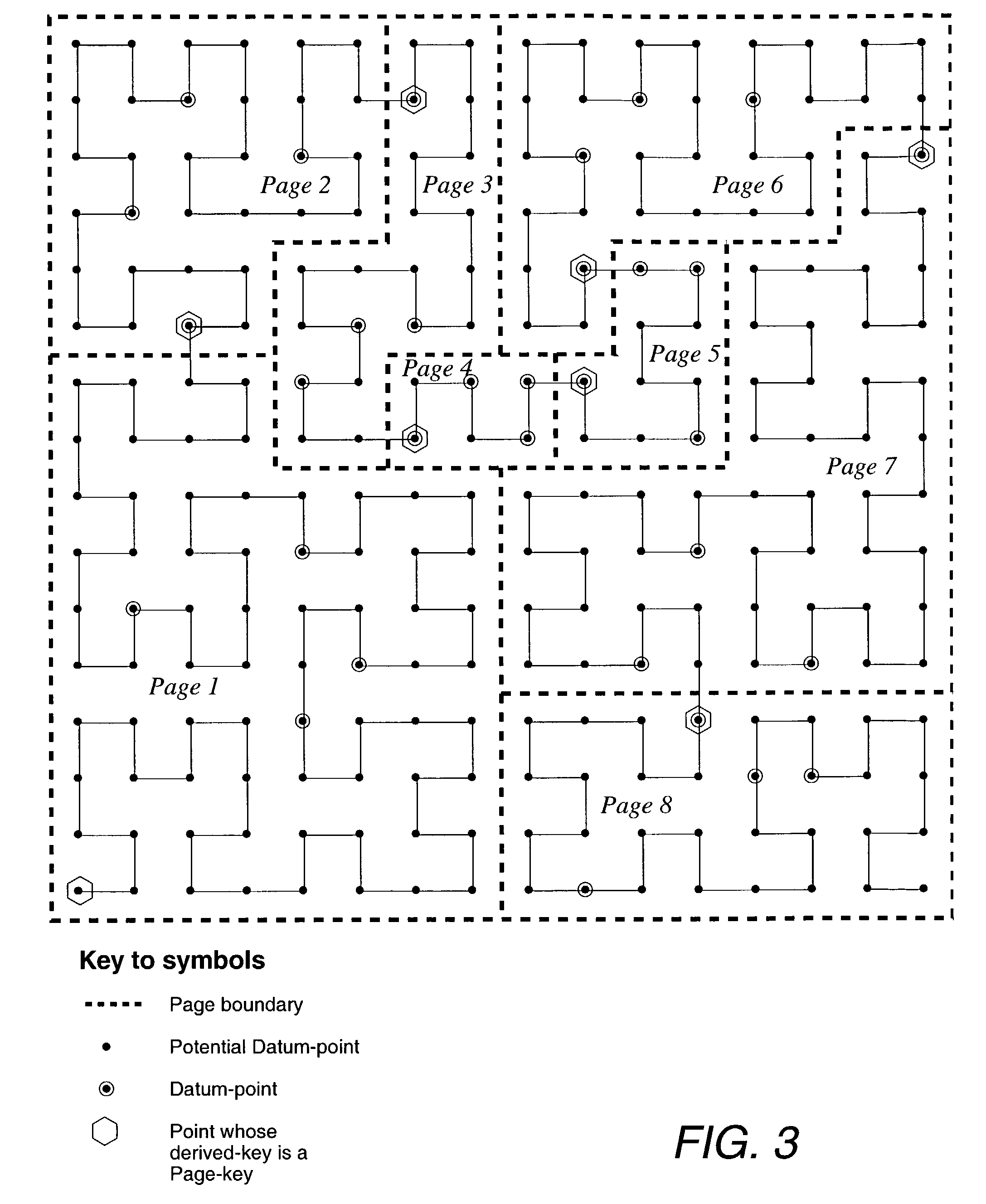
Method of storing and retrieving multi-dimensional data using the hilbert curve
InactiveUS20030004938A1Data processing applicationsDigital data information retrievalData spaceHilbert space
An improved method of partitioning and indexing multi-dimensional data that maps the data to one-dimensional values according to the sequence in which an approximation of a Hilbert space-filling curve passes through all of the points corresponding to potential multi-dimensional data in a data space. Data is partitioned into pages, each corresponding to a length of Hilbert curve. A page identifier is the sequence of the first point on its corresponding Hilbert curve section. The mapping orders data and also orders the data pages that contain data within a database. Mapping multi-dimensional data to one-dimensional values enables the data to be indexed using any one-dimensional index structure. The practical application of the indexing method is made viable and useful by the provision of a querying algorithm enabling data to be selectively retrieved in response to queries wherein all or some of the data that lies within a rectangular space within multi-dimensional space is required to be retrieved. The querying algorithm identifies pages whose corresponding curve sections intersect with a query region. The first intersecting page is found by calculating the lowest one-dimensional value corresponding to a possible multi-dimensional data value or point within the query region, and looking up in the index to find which page may contain this point. The next intersecting page, if it exists, is found by calculating the lowest one-dimensional value equal to or greater than the identifier of the next page to the one just identified. This new lowest one-dimensional, if found, is used to look up in the index and find the next page intersecting with the query region. Subsequent pages to be found, if any, are determined in a similar manner until no more are found. Pages found to intersect the query region can be searched for data lying within the query region.
Owner:LAWDER JONATHAN KEIR
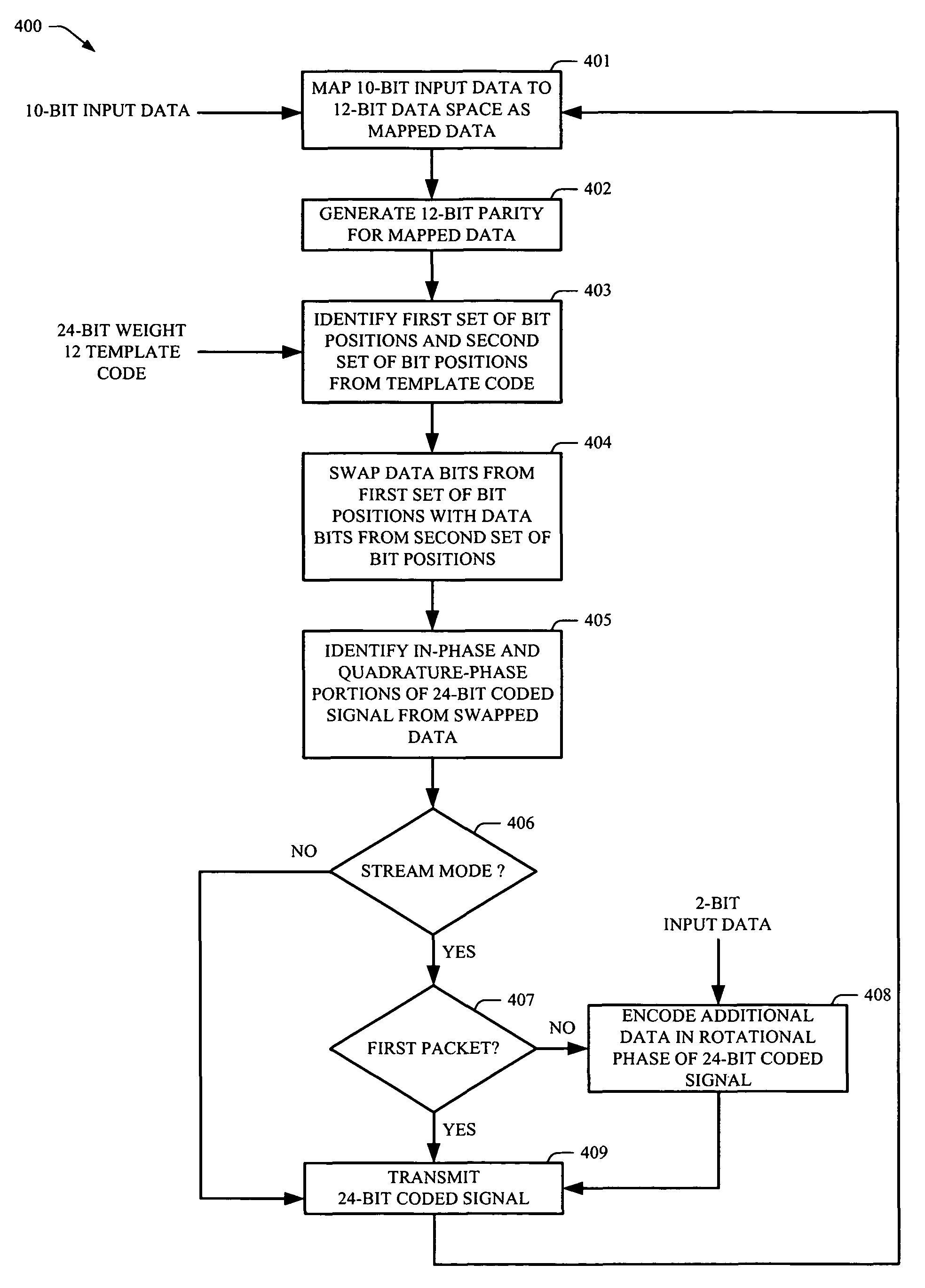
Rotationally invariant non-coherent burst coding
ActiveUS7779332B2Error correction/detection using block single space codingError preventionBit field24-bit
Owner:ALFRED E MANN FOUND FOR SCI RES
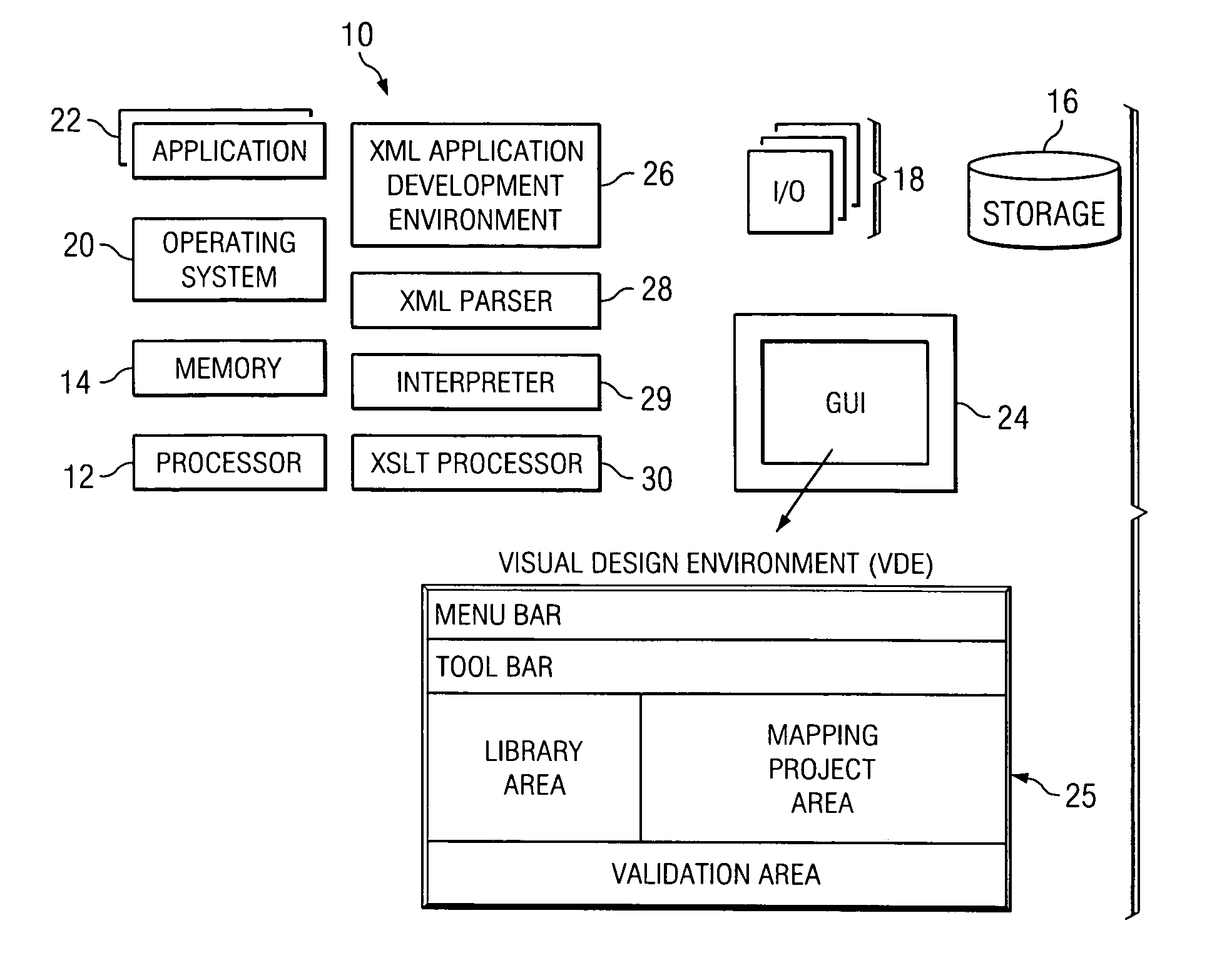
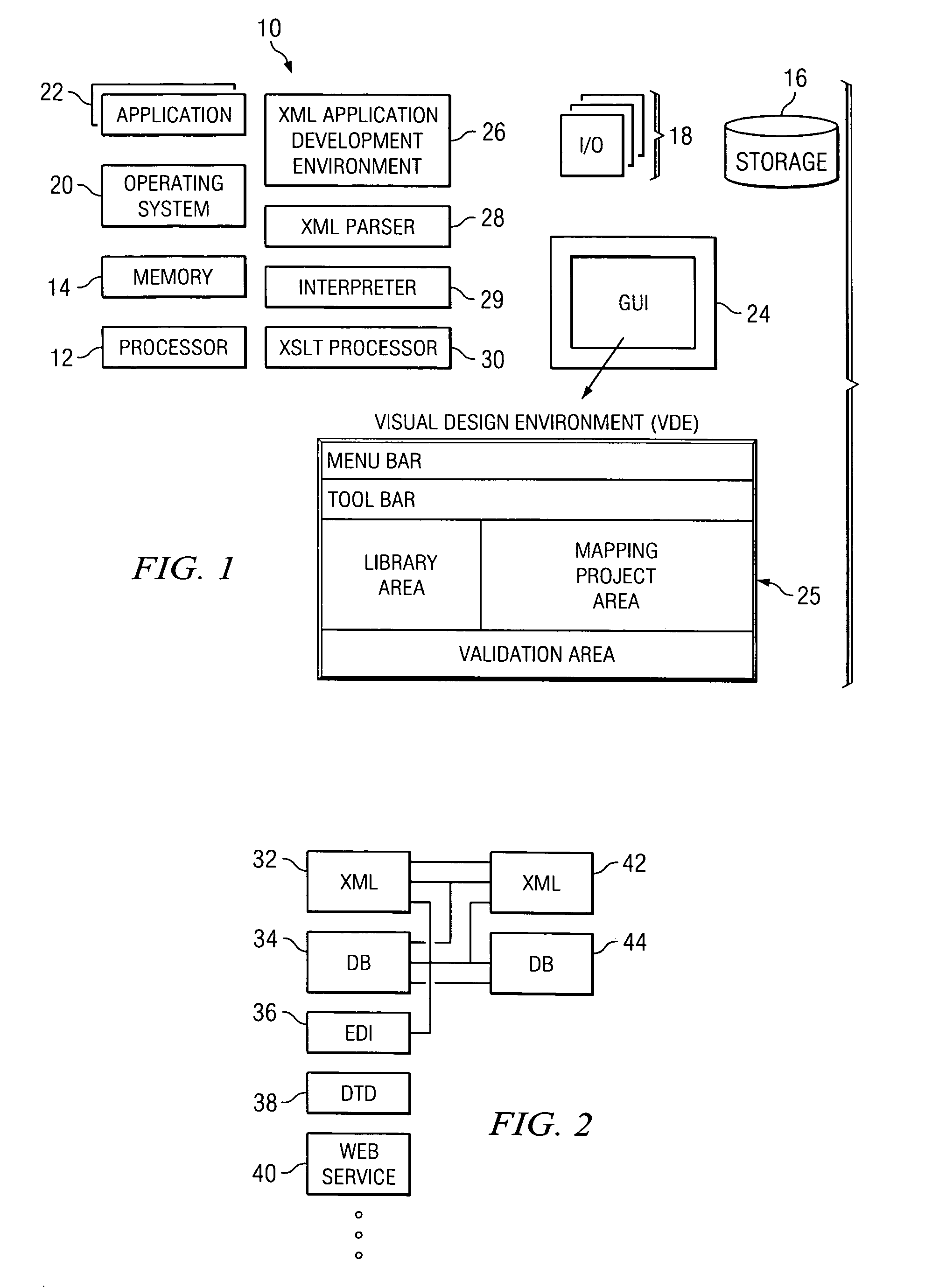
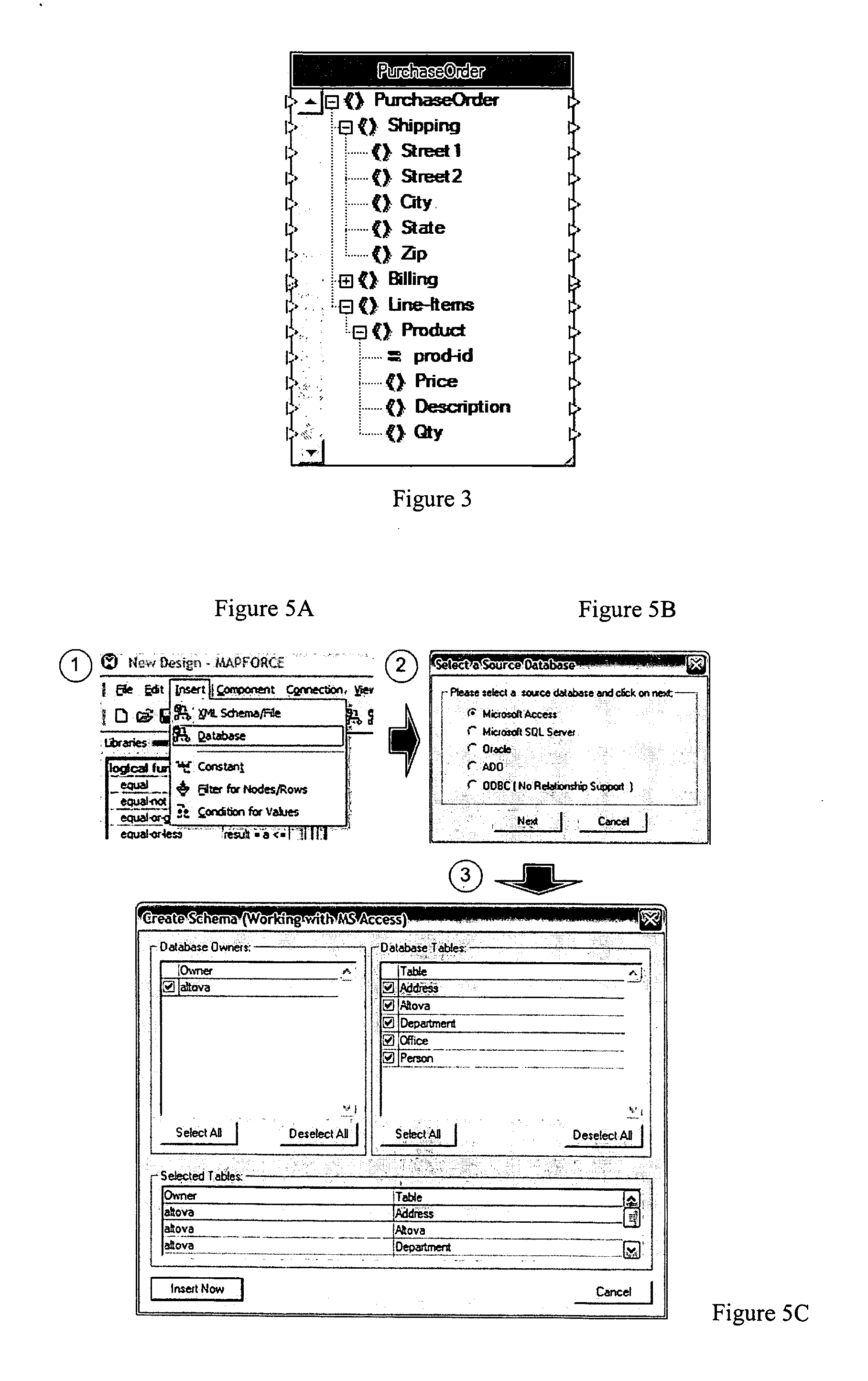
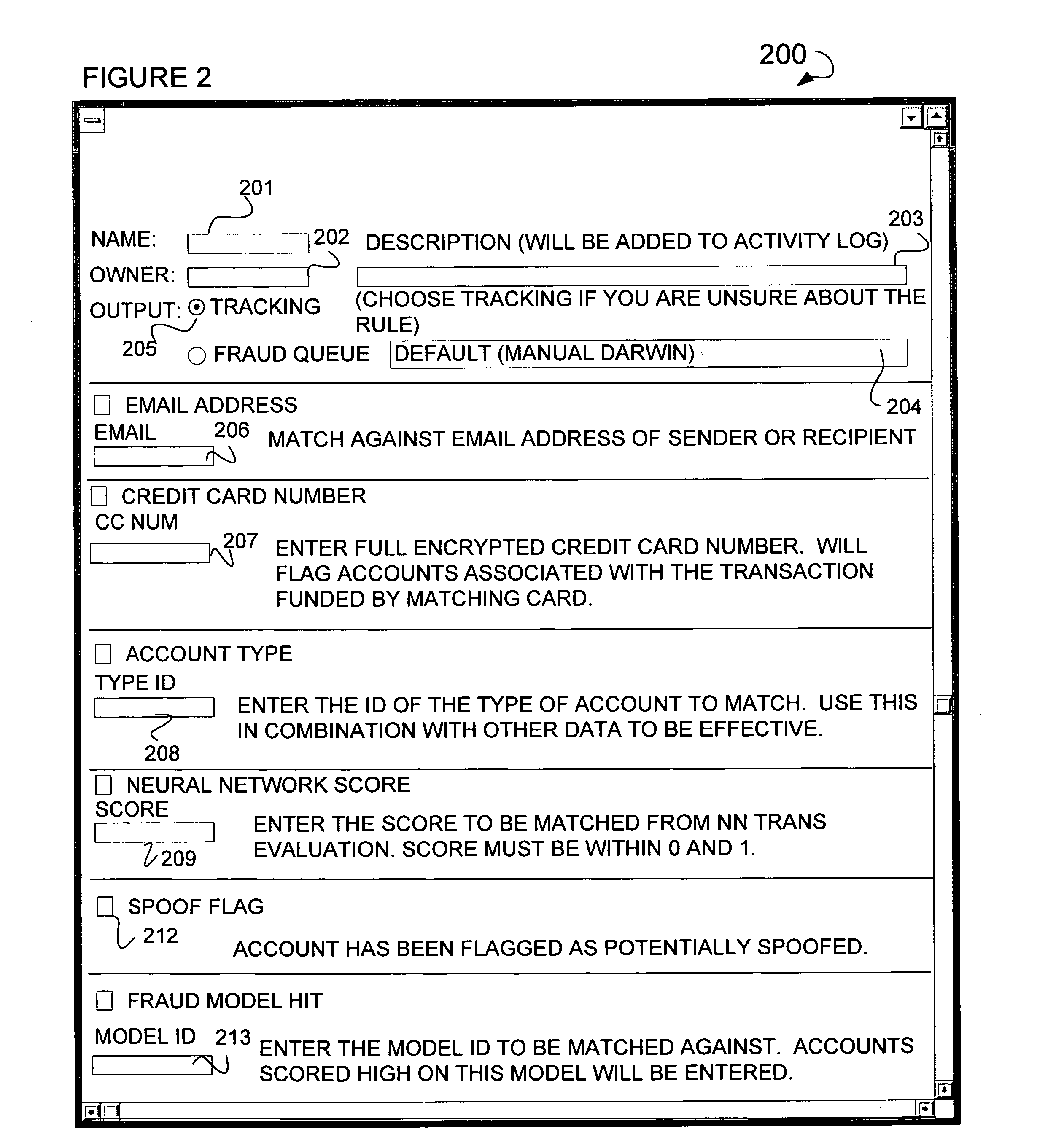
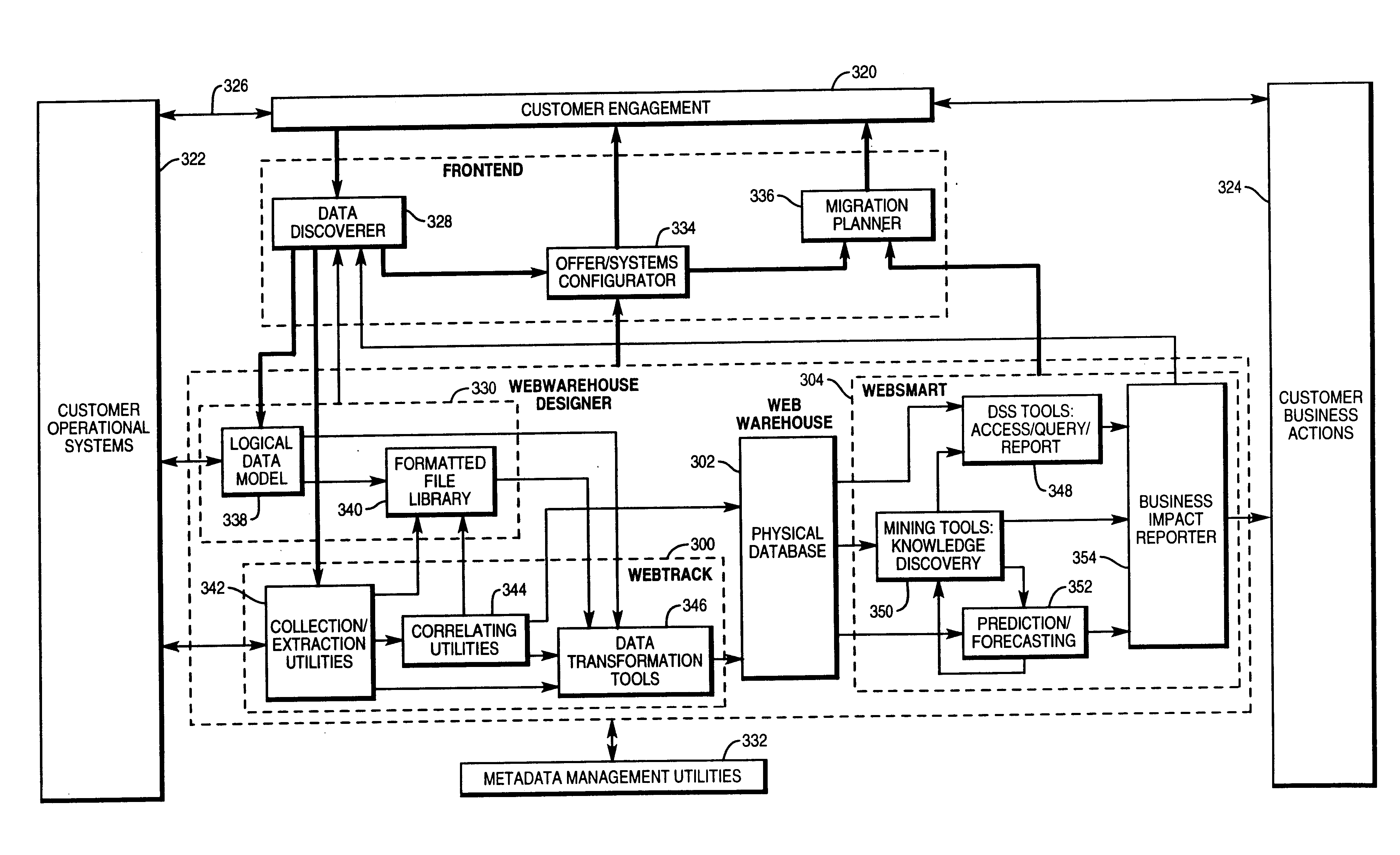
Method and system for visual data mapping and code generation to support data integration
InactiveUS20050257193A1Easy to createVisual/graphical programmingSpecific program execution arrangementsData architectPaper document
A data integration method and system that enables data architects and others to simply load structured data objects (e.g., XML schemas, database tables, EDI documents or other structured data objects) and to visually draw mappings between and among elements in the data objects. From there, the tool auto-generates software program code required, for example, to programmatically marshal data from a source data object to a target data object.
Owner:ALTOVA
Method for extending a network map
ActiveUS7028083B2Reduce dimensionalityOvercome problemsMultiple digital computer combinationsData switching networksSystem usageIp address
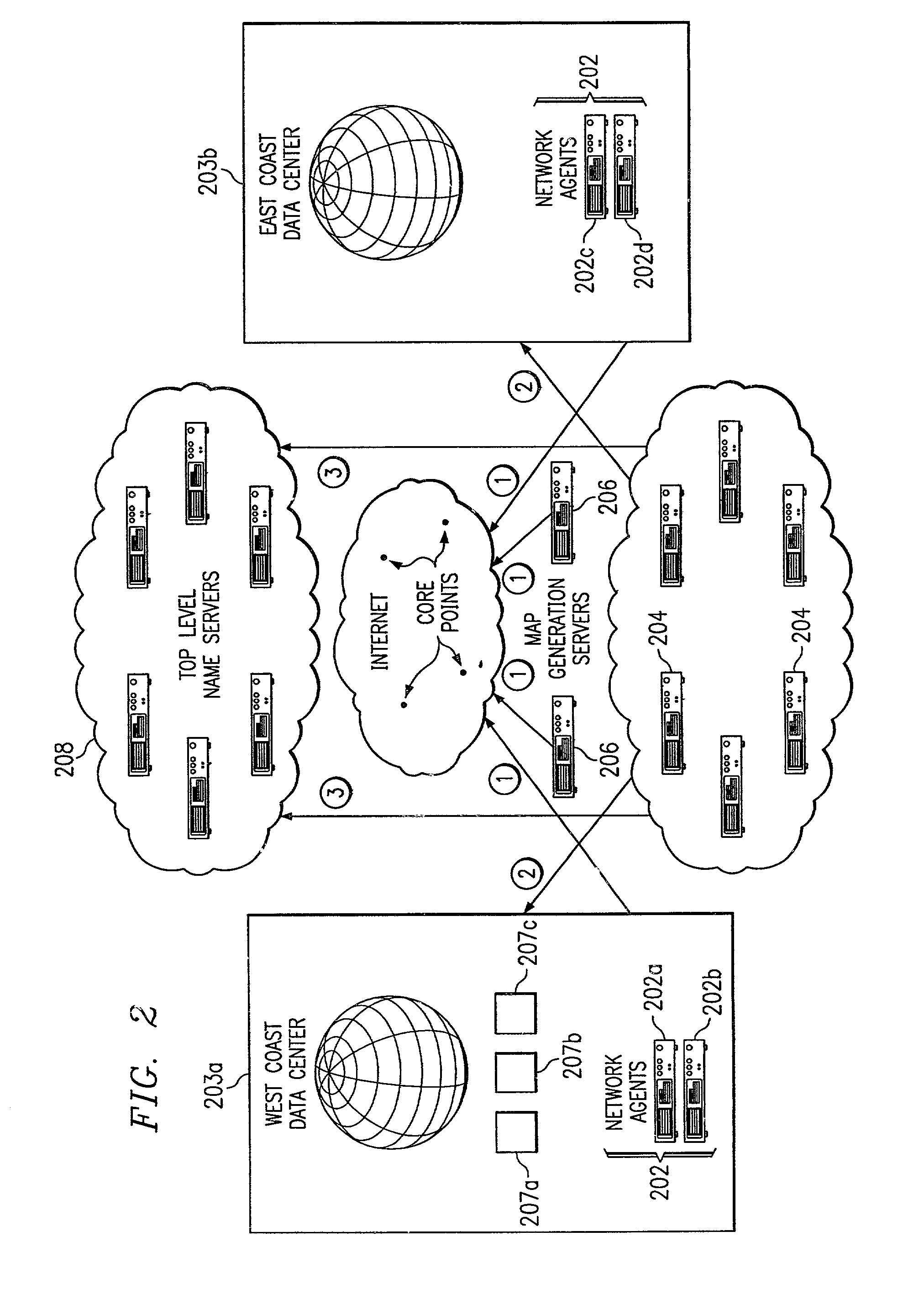
An intelligent traffic redirection system performs global load balancing. The system uses a network map that is generated in part by extending a “sparse” IP address data map. In particular, a method of extending an IP address block map begins by defining a set of one or more upper bound block(s). These upper bound blocks are then used to partition a space of IP addresses into subsets or “territories”, wherein each territory represents a largest set of IP addresses to which a piece of mapping data may be extended. The “piece” of mapping data typically consists of a host (usually a “name server” identified by the core point discovery process) IP address and some data about that host, namely, a “nearest” data center or a flag indicating that either “no data” exists for that host or that the system is “indifferent” as to which of a set of mirrored data centers the host should be mapped. A unification algorithm partitions the territory of each upper bound block into the largest possible sub-blocks in which a given unanimity criterion is satisfied and extends the mapping data in each such sub-block to all of the territory of that sub-block.
Owner:AKAMAI TECH INC
Cash dispensing automated banking machine system and communication method
InactiveUS7606767B1Easy to operateMaintain securityFinancePayment architectureApplication serverMachining system
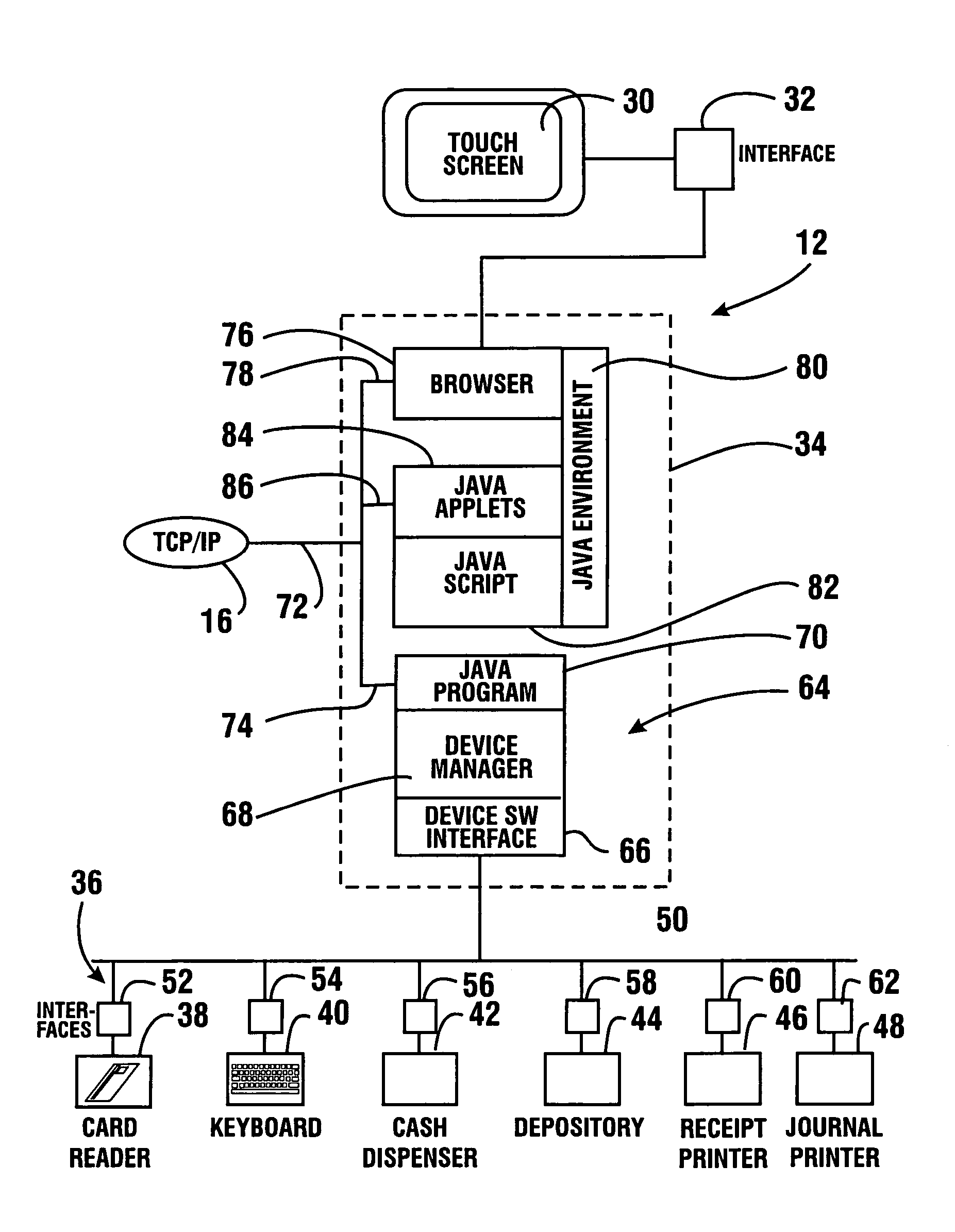
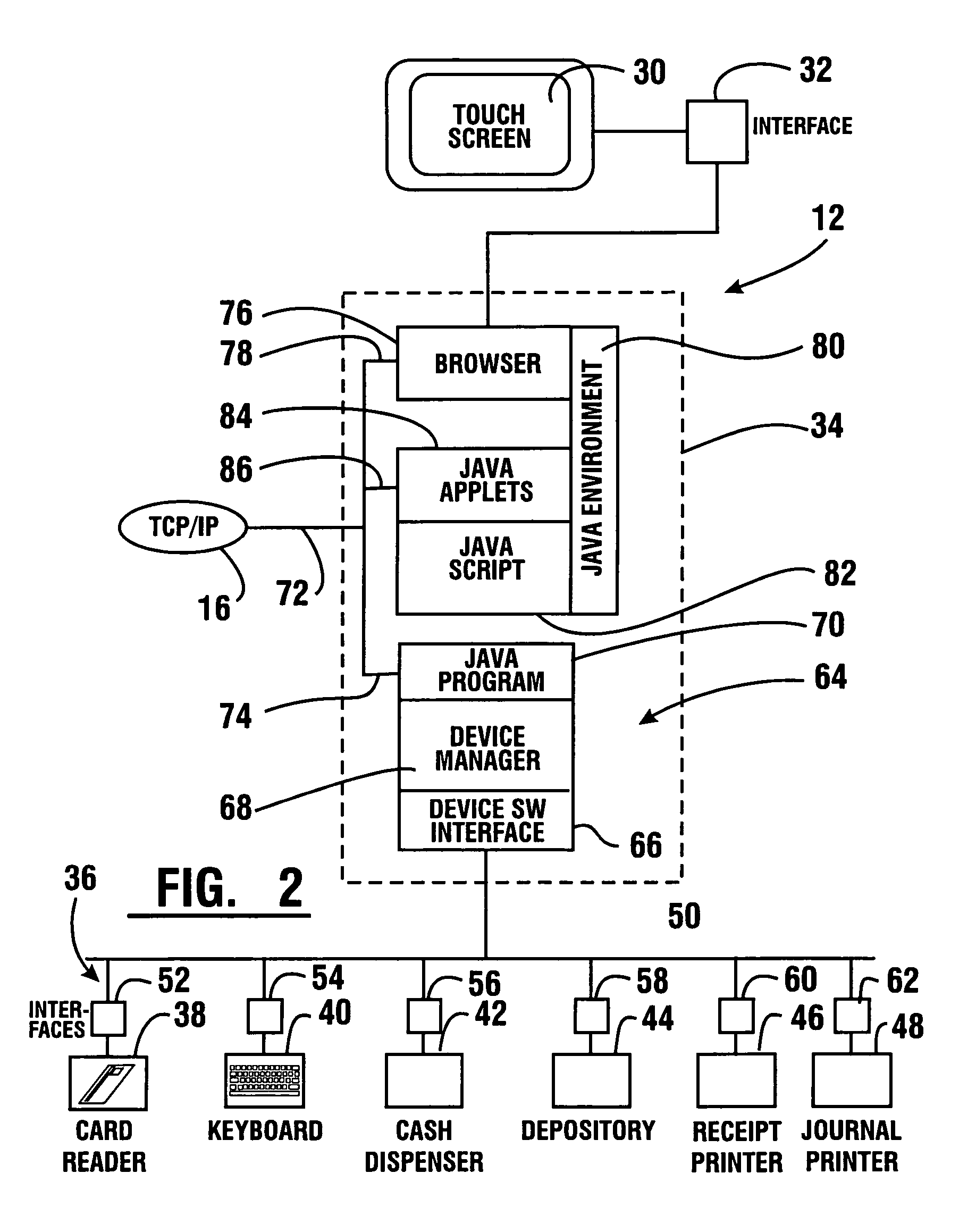
A method of operating an automated banking machine is provided. The method comprises sending a configuration XML message to an ATM from an application server, wherein the configuration XML data includes configuration data targeted to the ATM. The method also includes sending with the application server an application XML message to the ATM, wherein the application XML message includes application data. In addition, the method includes mapping the application data to at least one corresponding resource on the ATM responsive to the configuration data. In addition, the method includes performing a banking transaction using the at least one resource on the ATM responsive to the application XML message.
Owner:DIEBOLD NIXDORF
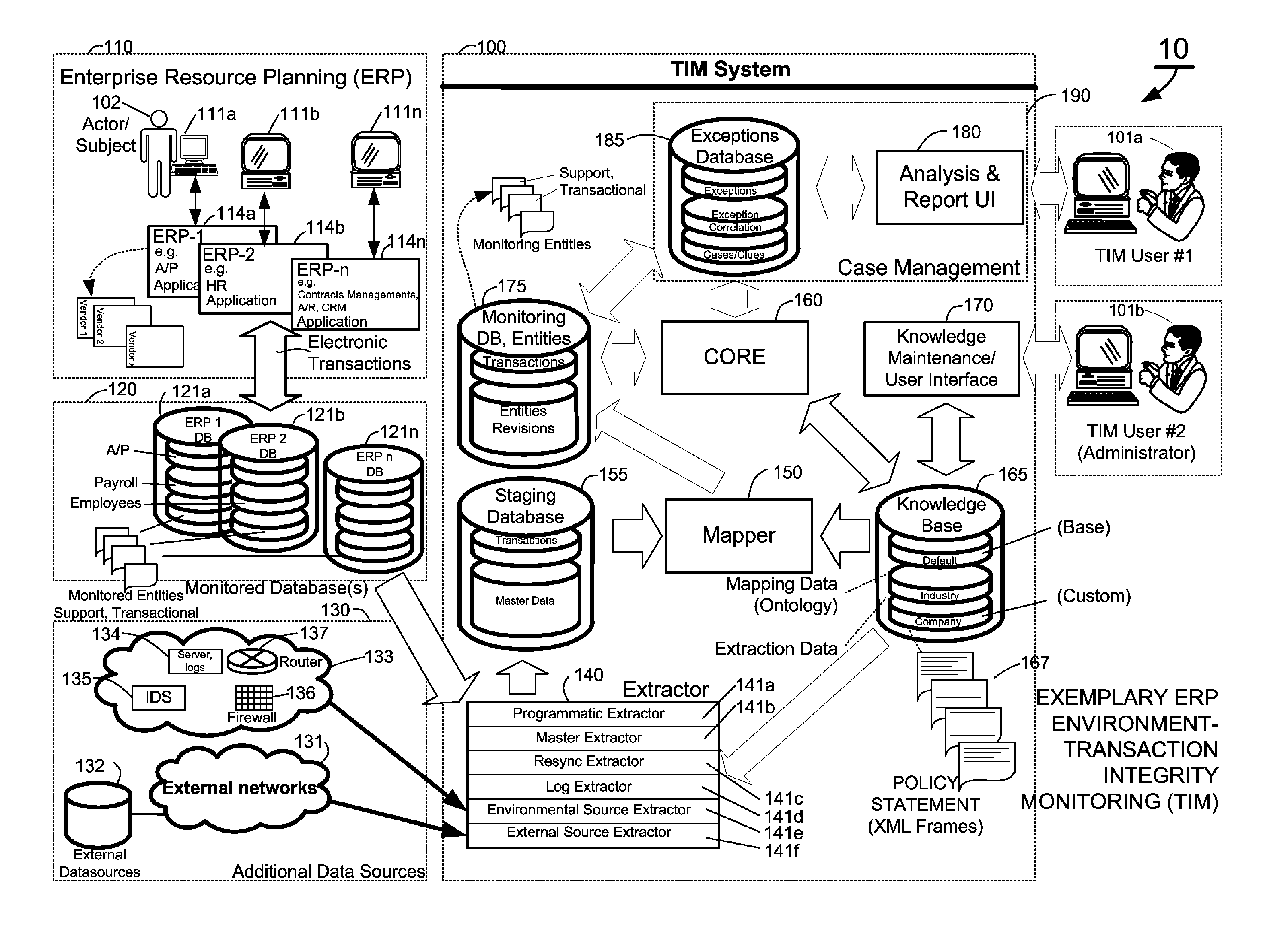
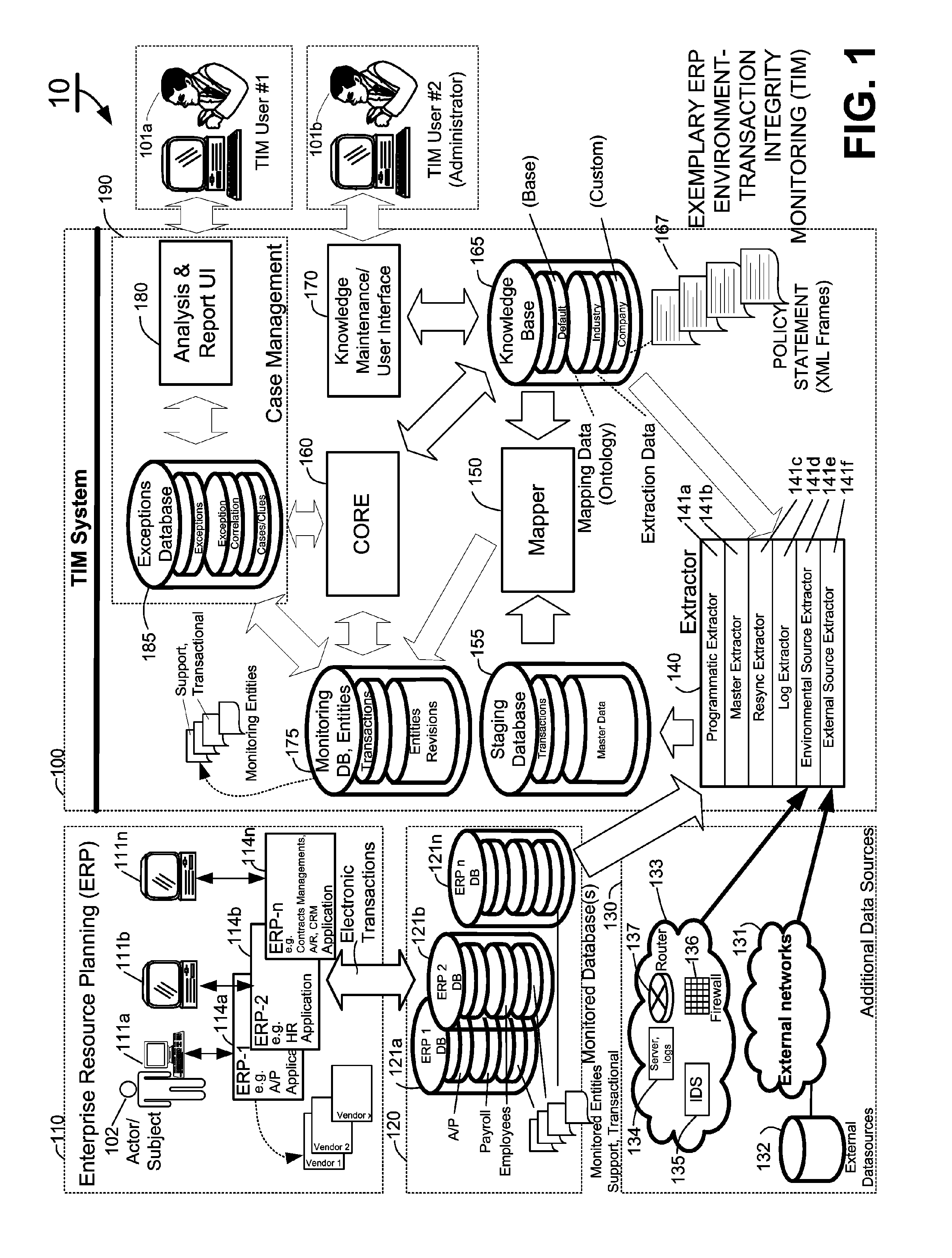
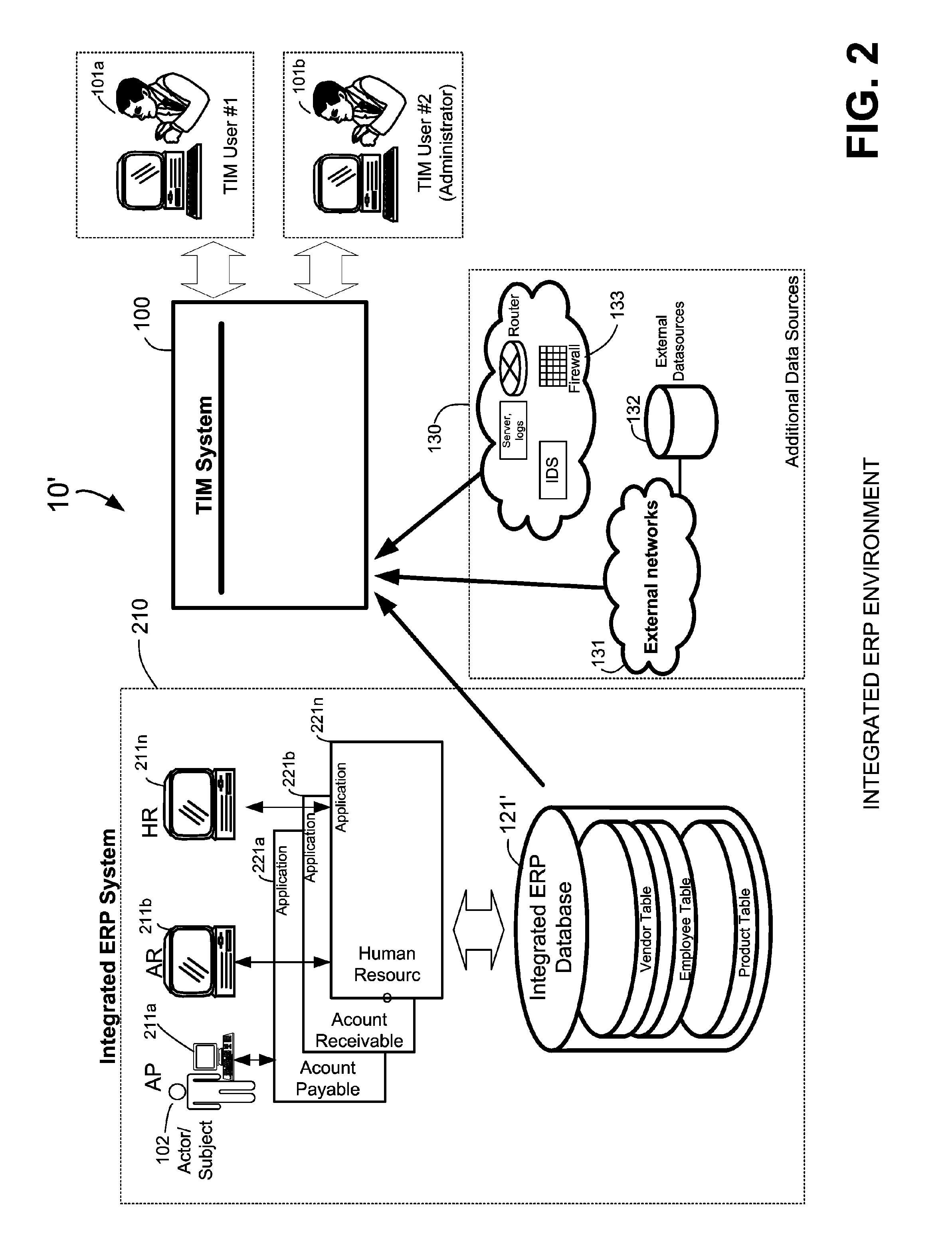
Methods and systems for mapping transaction data to common ontology for compliance monitoring
InactiveUS20080082374A1Improve performanceMinimizes financial lossDigital data information retrievalFinanceCompliance MonitoringData source
An automated transaction integrity monitoring system operative to monitor electronic transactions of an enterprise and detect exceptions indicating noncompliance with enterprise policies. The system allows establishment, codification, and maintenance of enterprise policies, monitors electronic transactions of the enterprise from various and possibly heterogeneous data sources, detects exceptions to established policies, reports such exceptions to authorized users such as managers and auditors, and / or provides a case management system for tracking such exceptions and their underlying transactions. The invention specifically relates to systems and methods for transforming or mapping information from a data source relating to a transactional entity associated with an enterprise into a form for processing by a transaction analysis engine operative upon data expressed in a predetermined ontology. The ontology expresses data items in a manner common across plural heterogeneous databases. The enterprise policies are expressed in terms of the ontology.
Owner:KENNIS PETER H +7
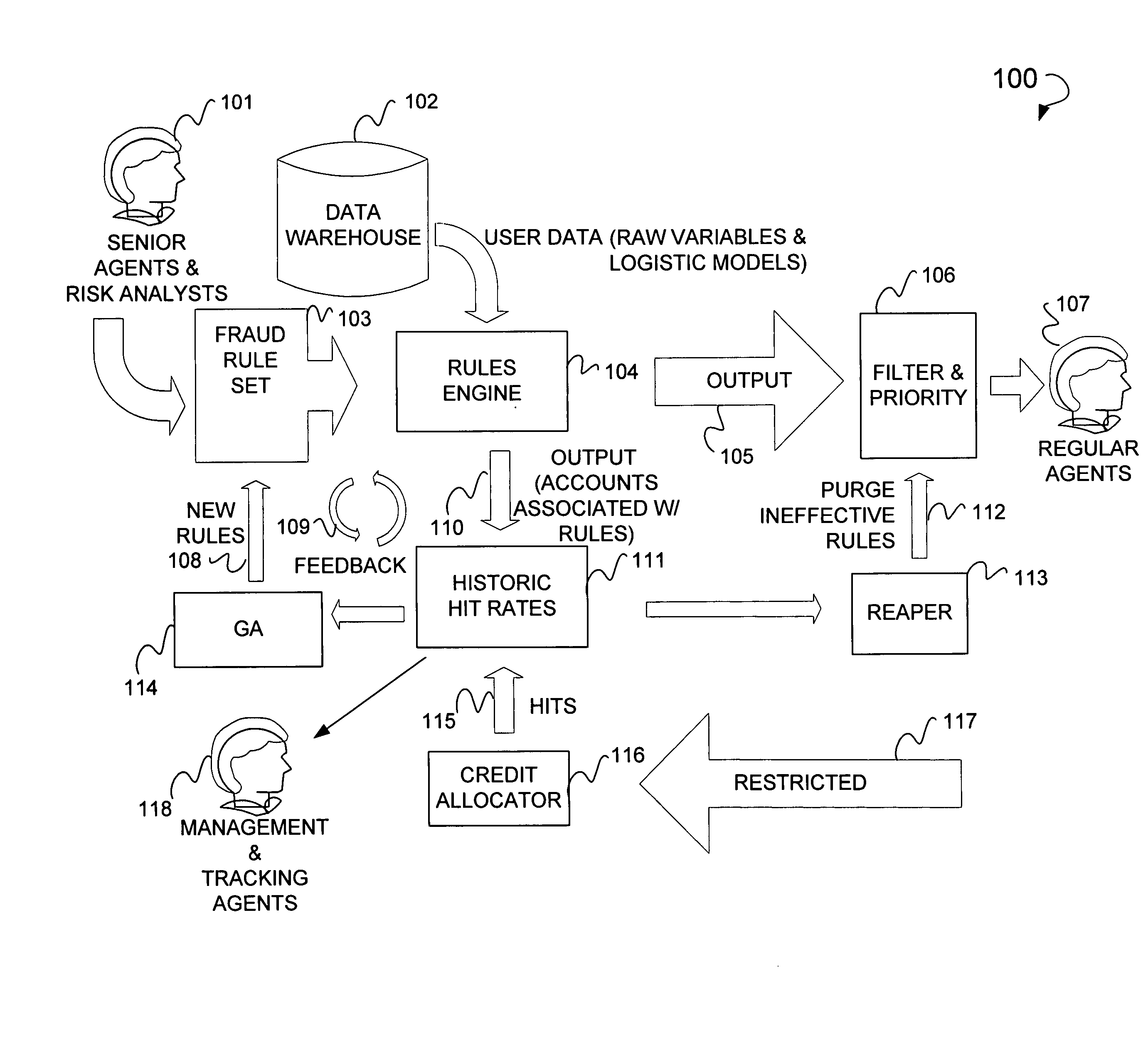
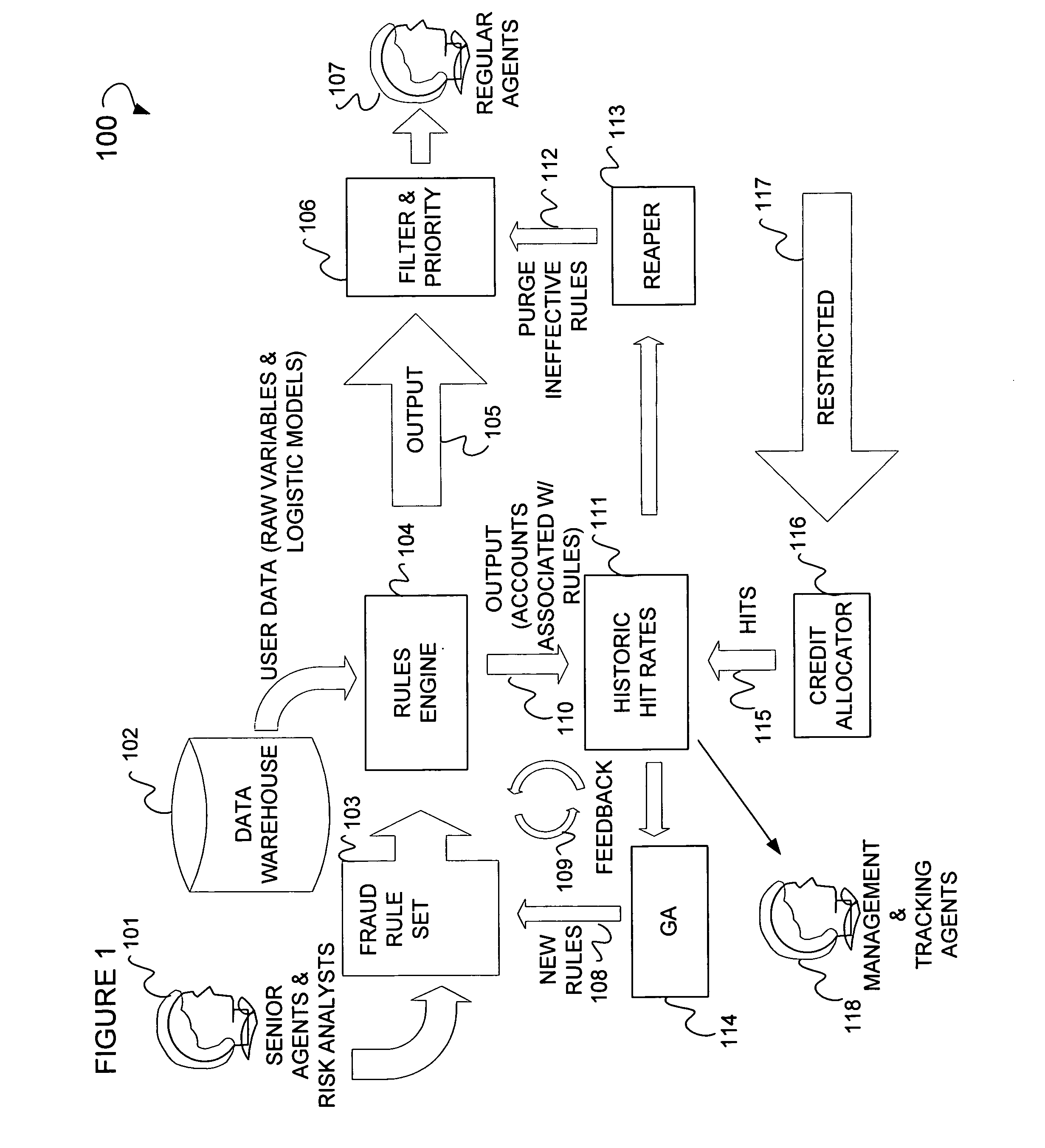
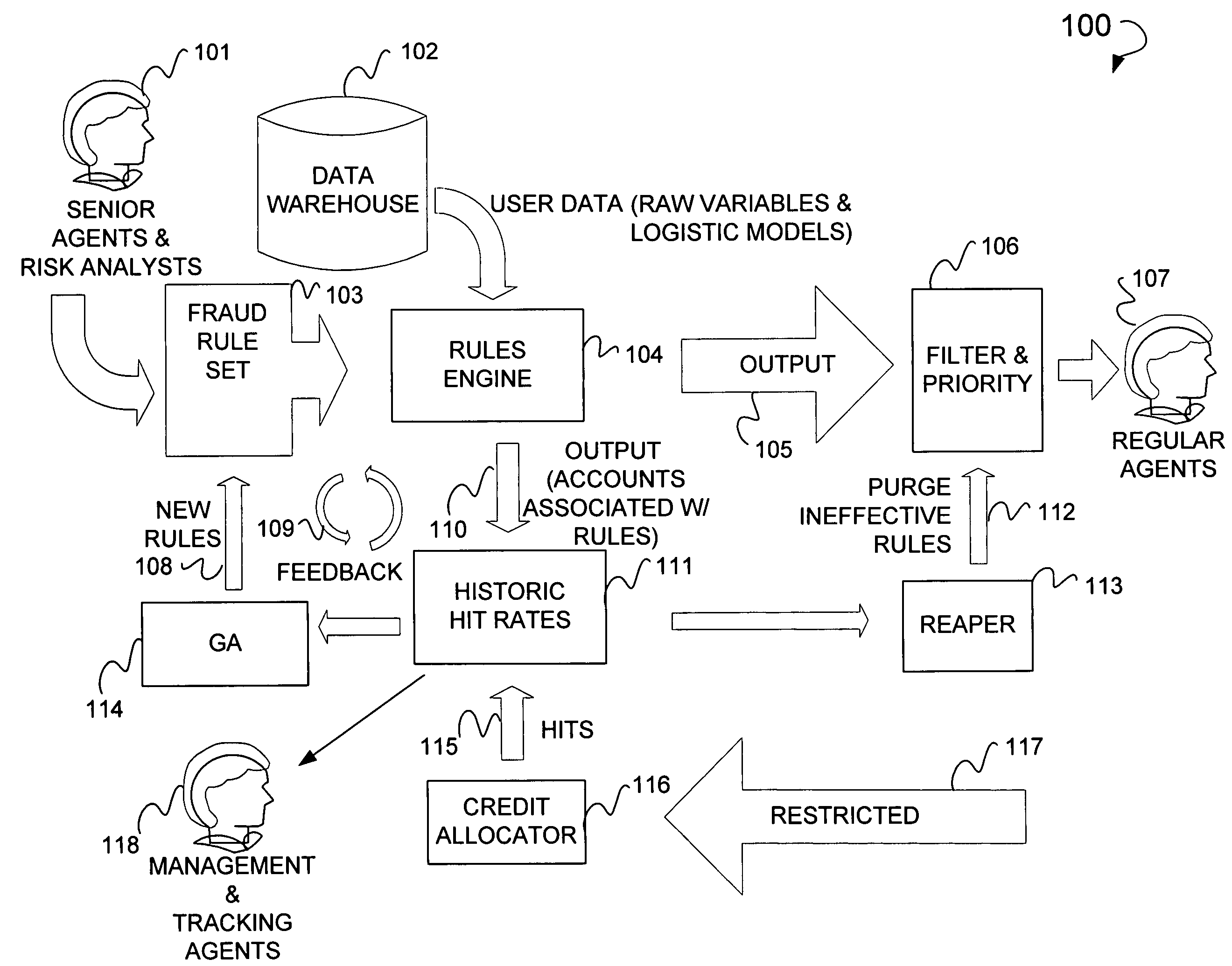
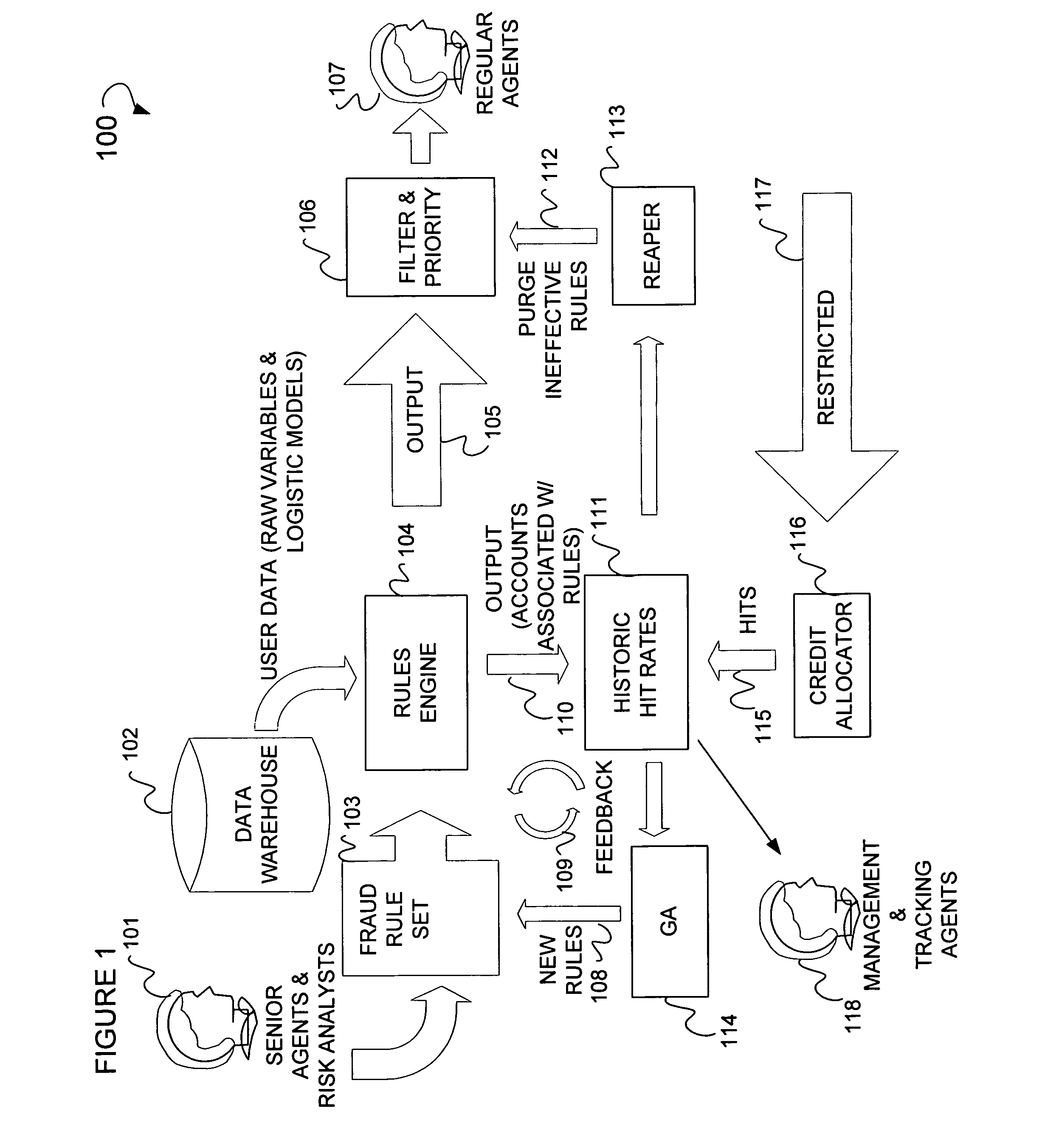
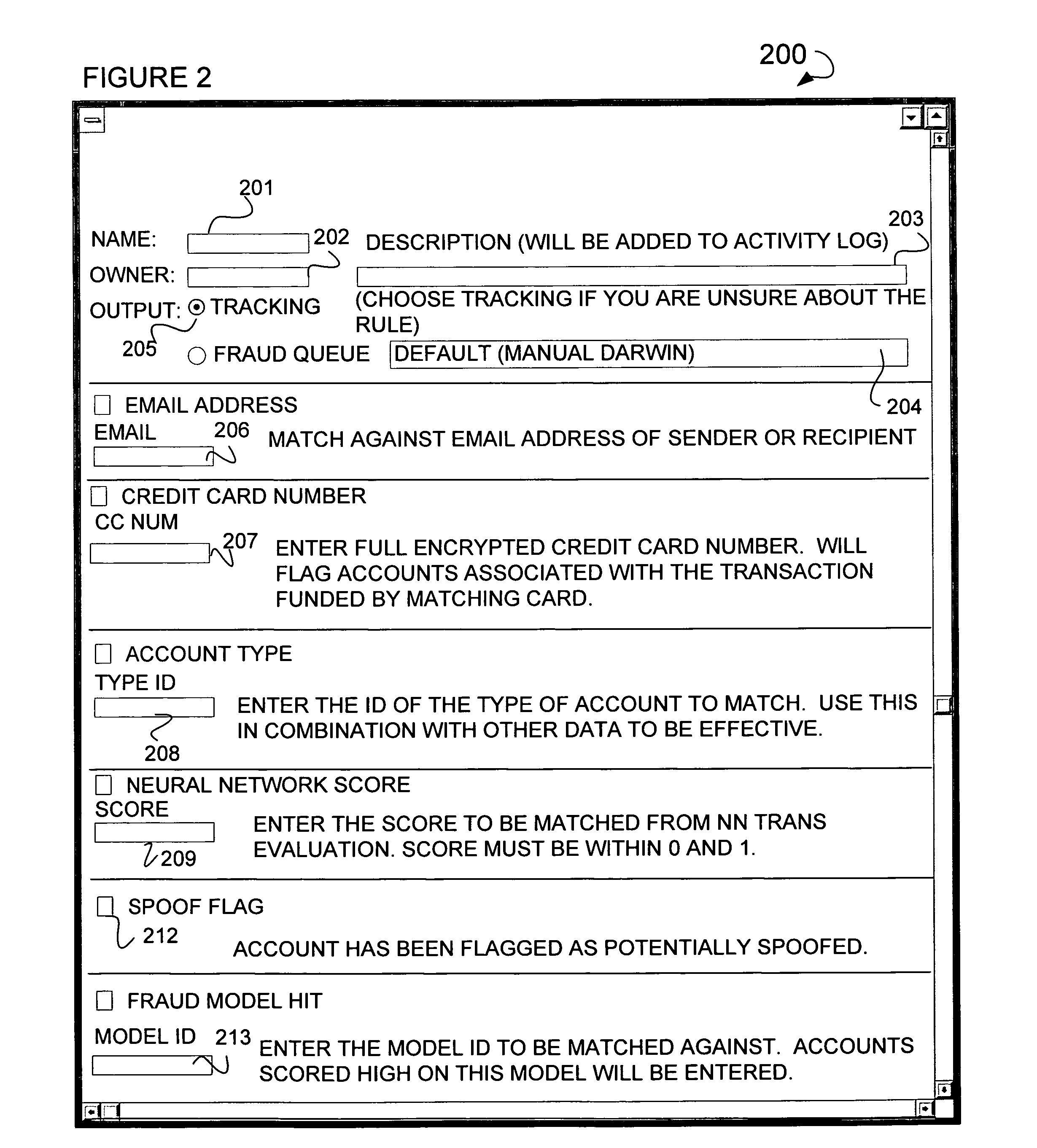
Online fraud prevention using genetic algorithm solution
Online fraud prevention including receiving a rules set to detect fraud, mapping the rules set to a data set, mapping success data to members of the rules set, filtering the members of the rules set, and ordering members of the data set by giving priority to those members of the data set with a greater probability for being fraudulent based upon the success data of each member of the rule set in detecting fraud. Further, a receiver coupled to an application server to receive a rules set to detect fraud, and a server coupled to the application server, to map the rules set to a data set, and to map the success data to each members of the rules set. The server is used to order the various members of the data set by giving priority to those members of the data set with a greatest probability for being fraudulent.
Owner:PAYPAL INC
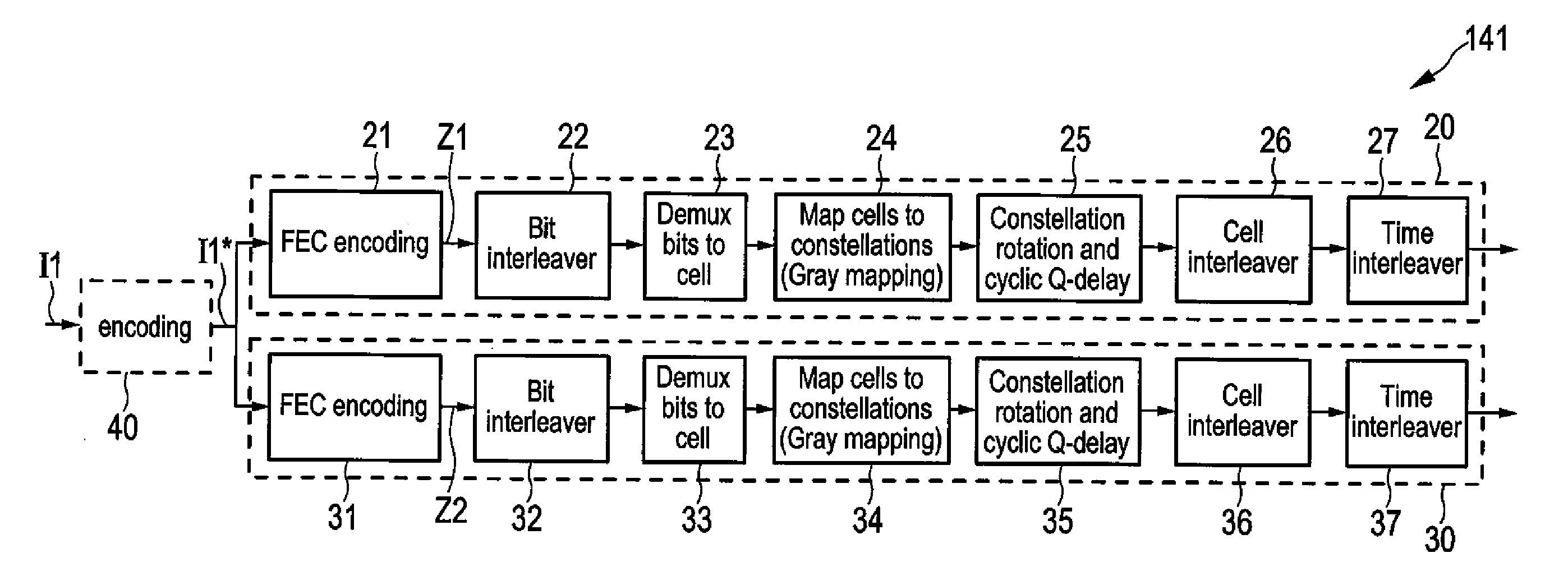
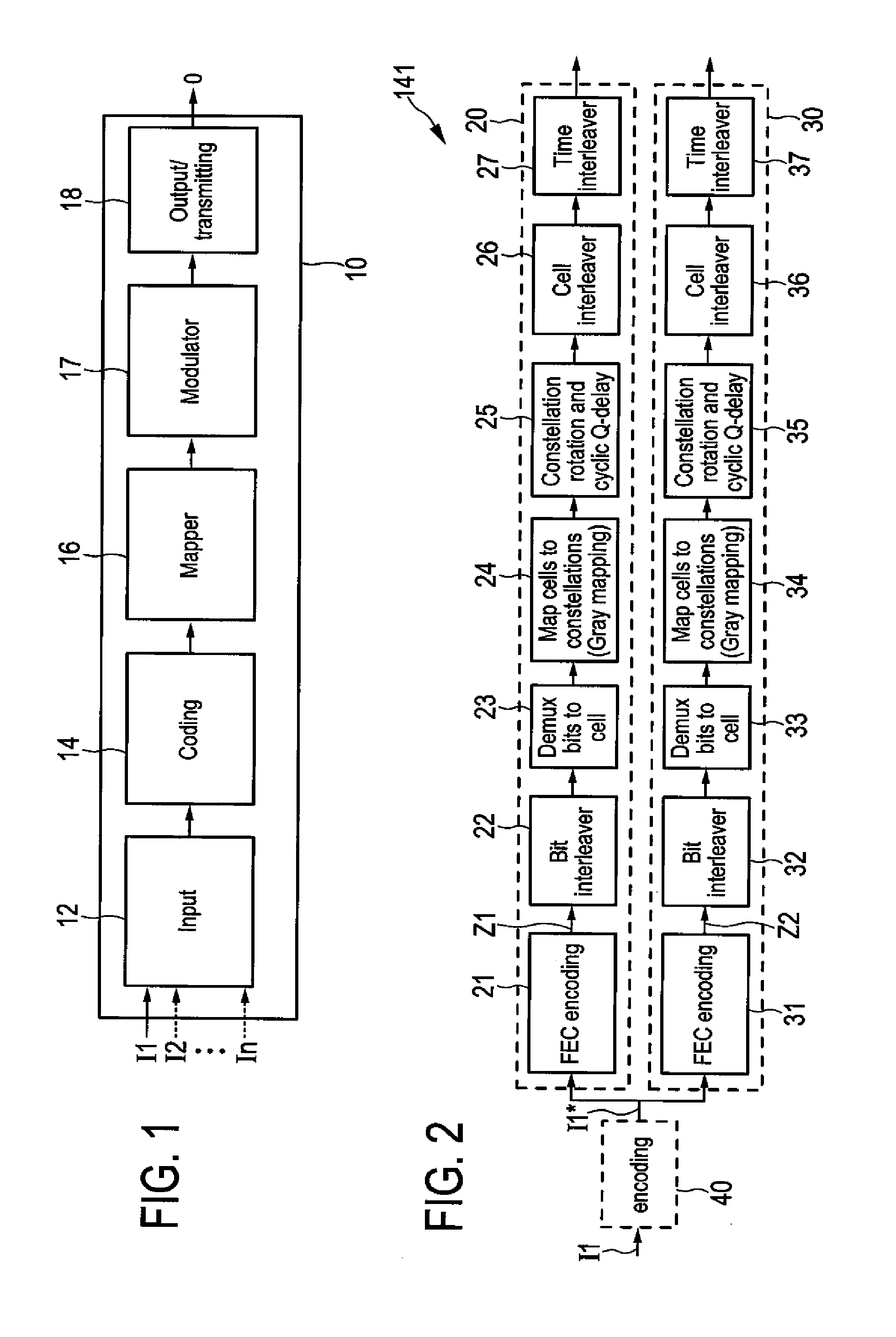
Transmitter and receiver for broadcasting data and providing incremental redundancy
ActiveUS20120272117A1Increase probabilityImprove robustnessError prevention/detection by using return channelCode conversionData streamBroadcast data
A transmitter for broadcasting data in a broadcasting system that improves the decoding quality, if needed, comprises a data input, and an encoder for error correction code encoding the input data words into codewords, a codeword comprising a basic codeword portion and an auxiliary codeword portion, wherein said encoder is adapted for generating said basic codeword portion from an input data word according to a first code and for generating said auxiliary codeword portion from an input data word according to a second code, said basic codeword portion being provided for regular decoding and said auxiliary codeword portion being provided as incremental redundancy if regular decoding of the codeword by use of the basic codeword portion is erroneous. Further, the transmitter comprises a data mapper for mapping the codewords onto frames of a transmitter output data stream, and a transmitter unit for transmitting said transmitter output data stream.
Owner:SATURN LICENSING LLC
Method and system for providing a user interface that enables control of a device via respiratory and/or tactual input
A method and system are provided for a user interface that enables control of a device via respiratory and / or tactual input. A mobile device comprising a graphical user interface may receive data from a second device and / or locally from within the mobile device. The data may be associated with and / or mapped to multimedia content that may be retrievable from a content source. The content source may be external to the mobile device and the second device. The associating and / or mapping may occur at either the mobile device or the second device and the associated or mapped data may be operable to function as at least a portion of the graphical user interface of the mobile device. The graphical user interface may be customized utilizing the data that is associated and / or mapped to the media content. The second device may map the received data to the media content.
Owner:BONNAT PIERRE
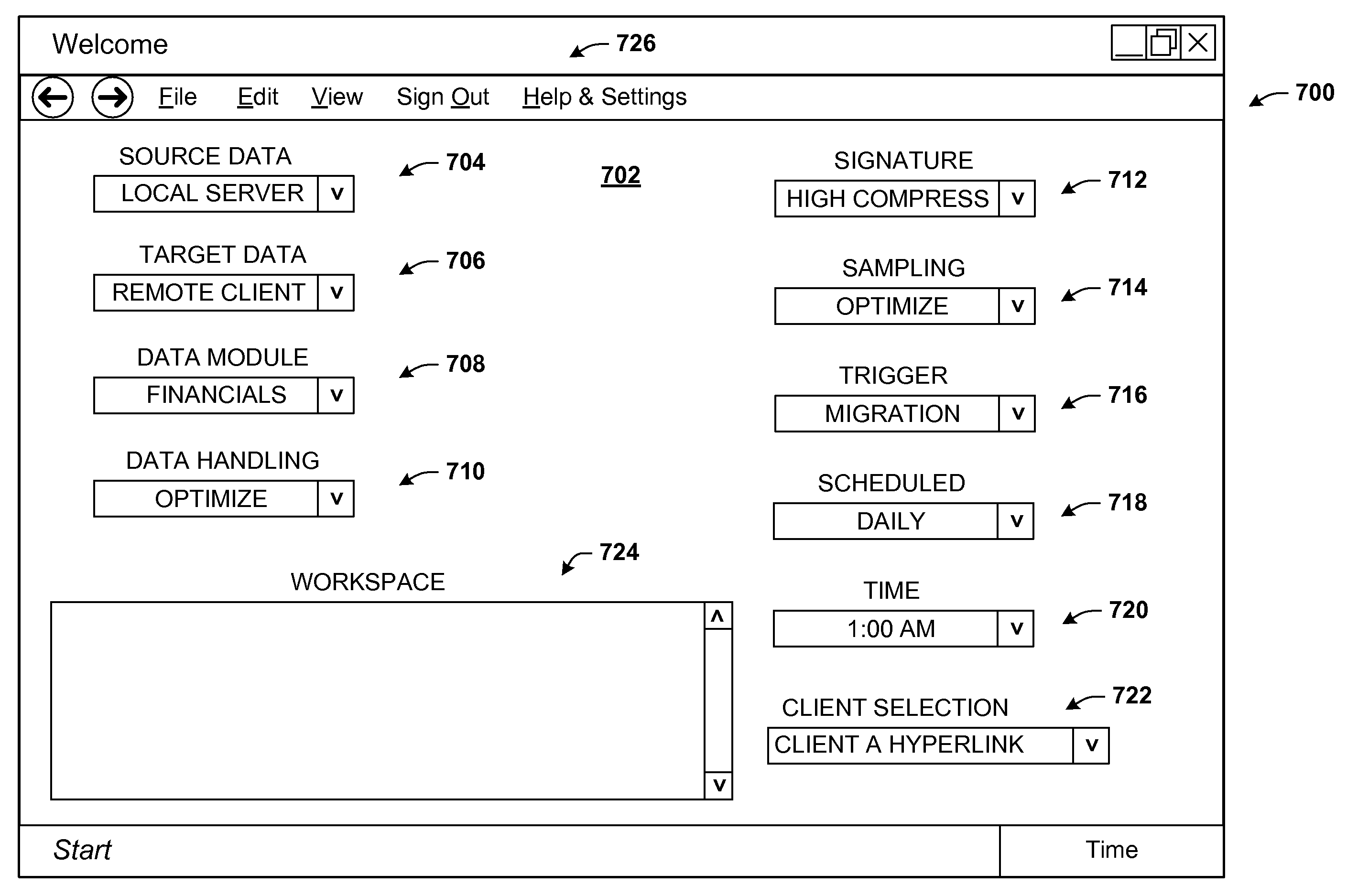
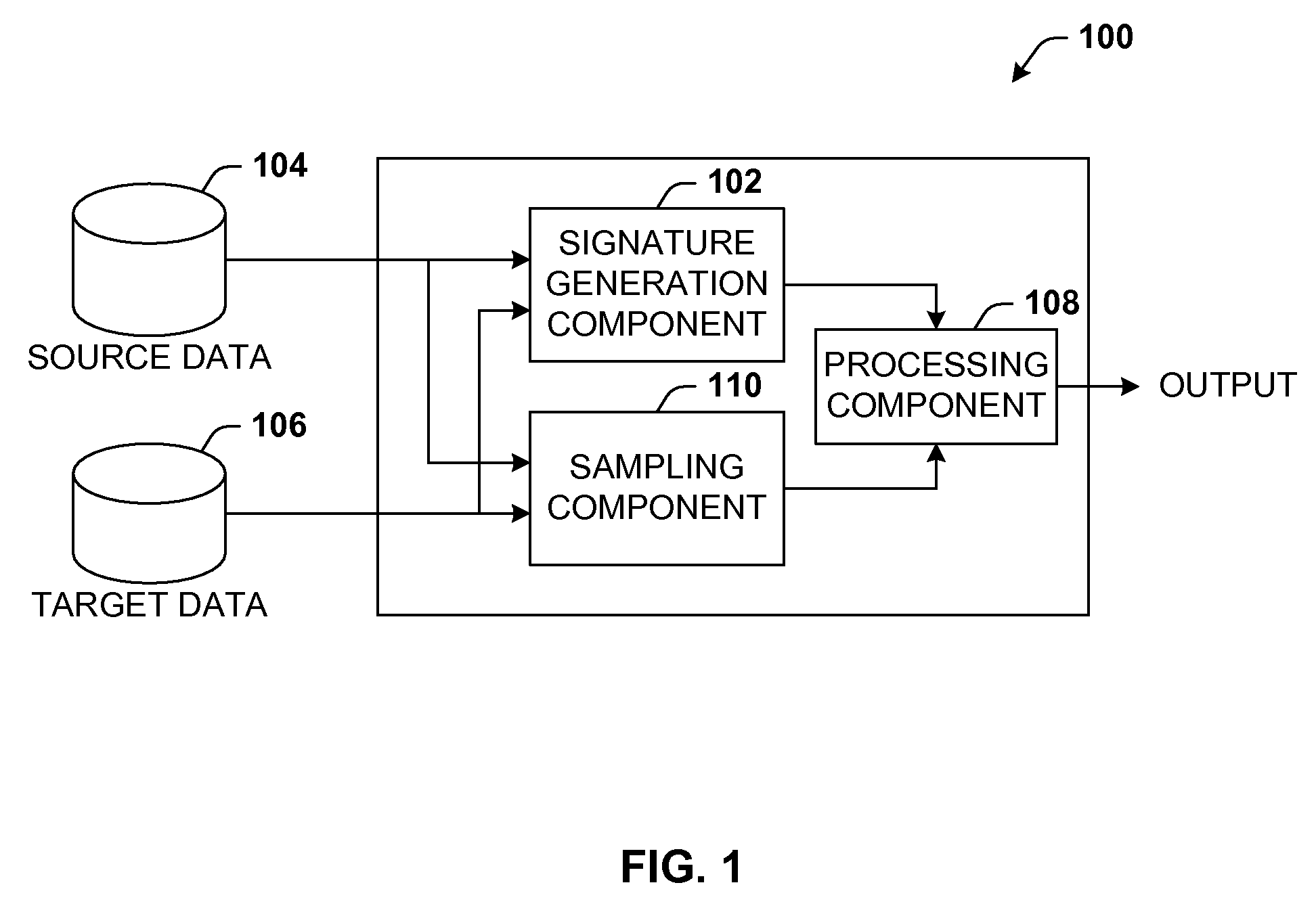
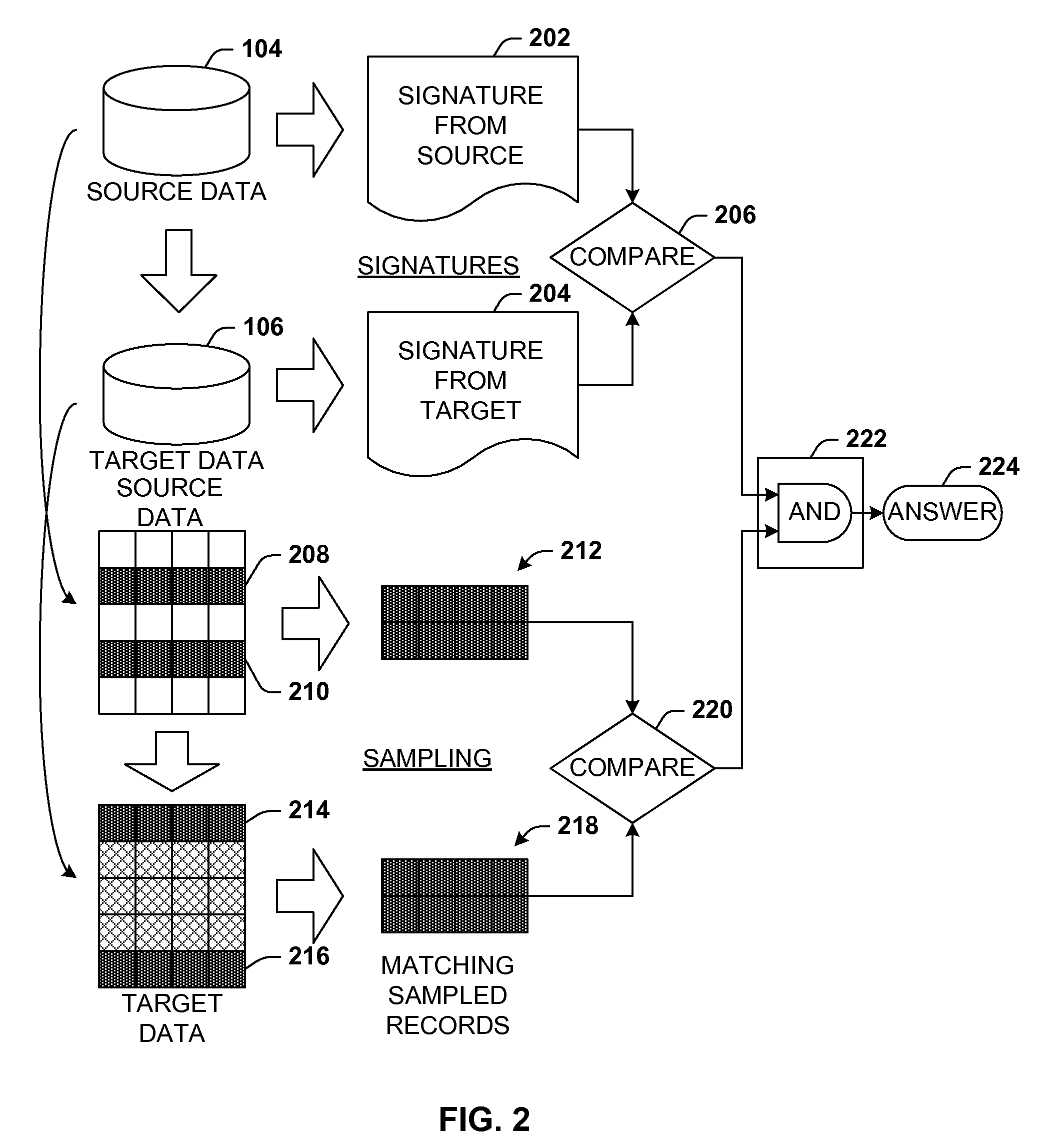
Data validation using signatures and sampling
InactiveUS20090132955A1User identity/authority verificationCharacter and pattern recognitionData validationSource Data Verification
Architecture that facilitates validation of a data mapping of data from a data source to a data target. There is included a signature generation component that generates a source signature of all or a portion of the data source and a target signature of all or a corresponding portion of the data target, and a sampling component that obtains a sample of the source data a corresponding sample of the target data. The data signatures and data samples are compared respectively and processed with a processing component to determine the status of the validation process.
Owner:MICROSOFT TECH LICENSING LLC
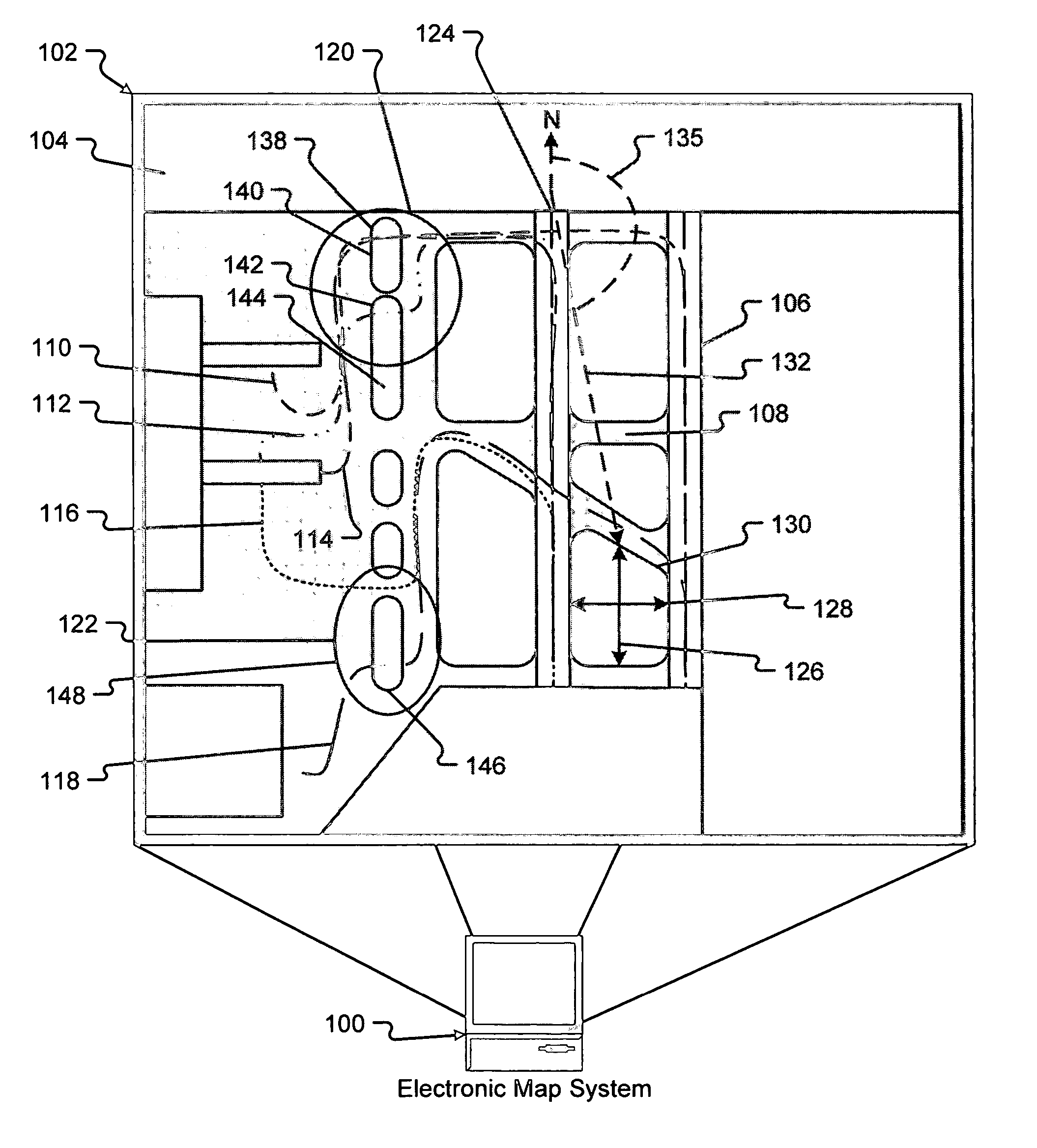
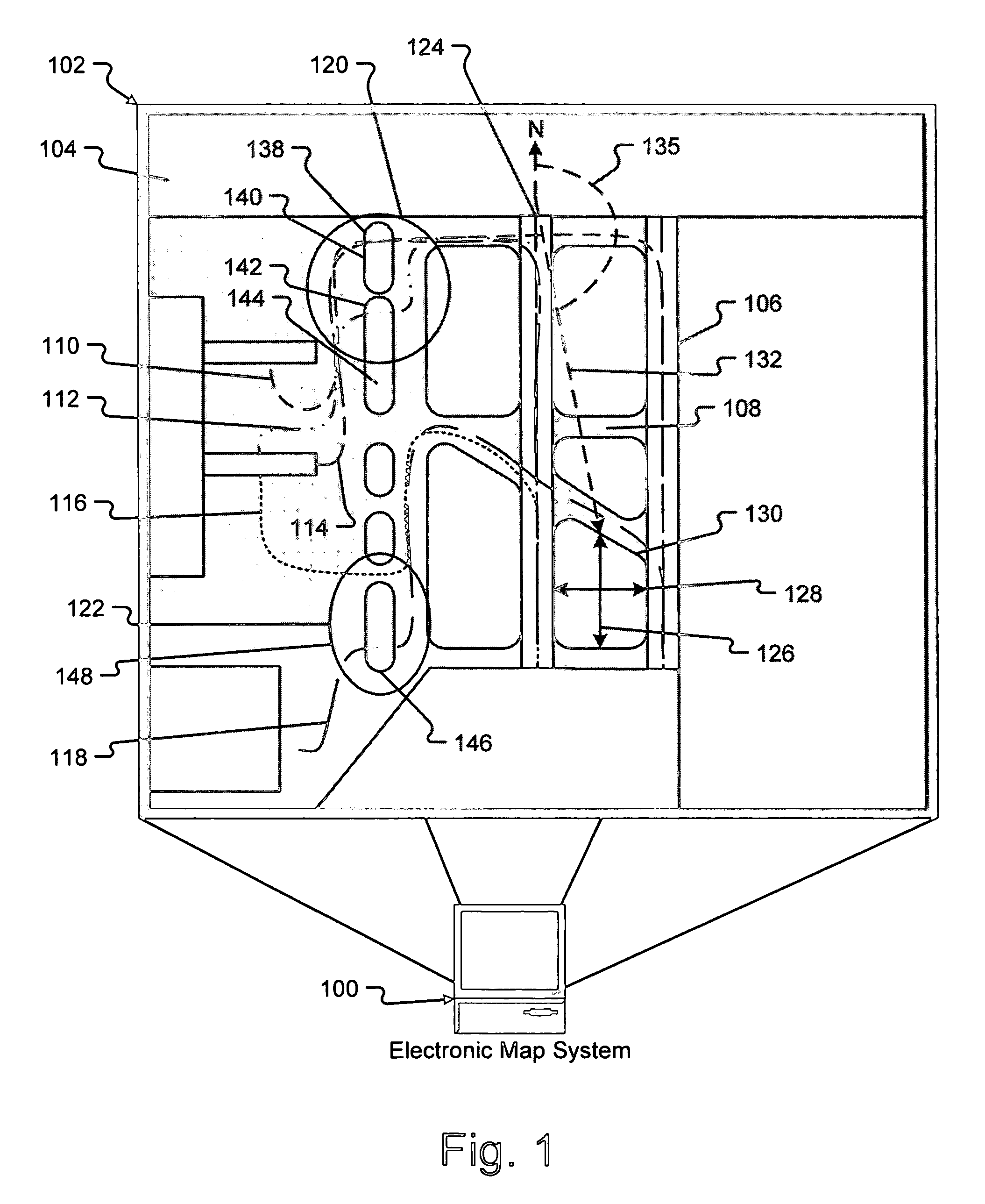
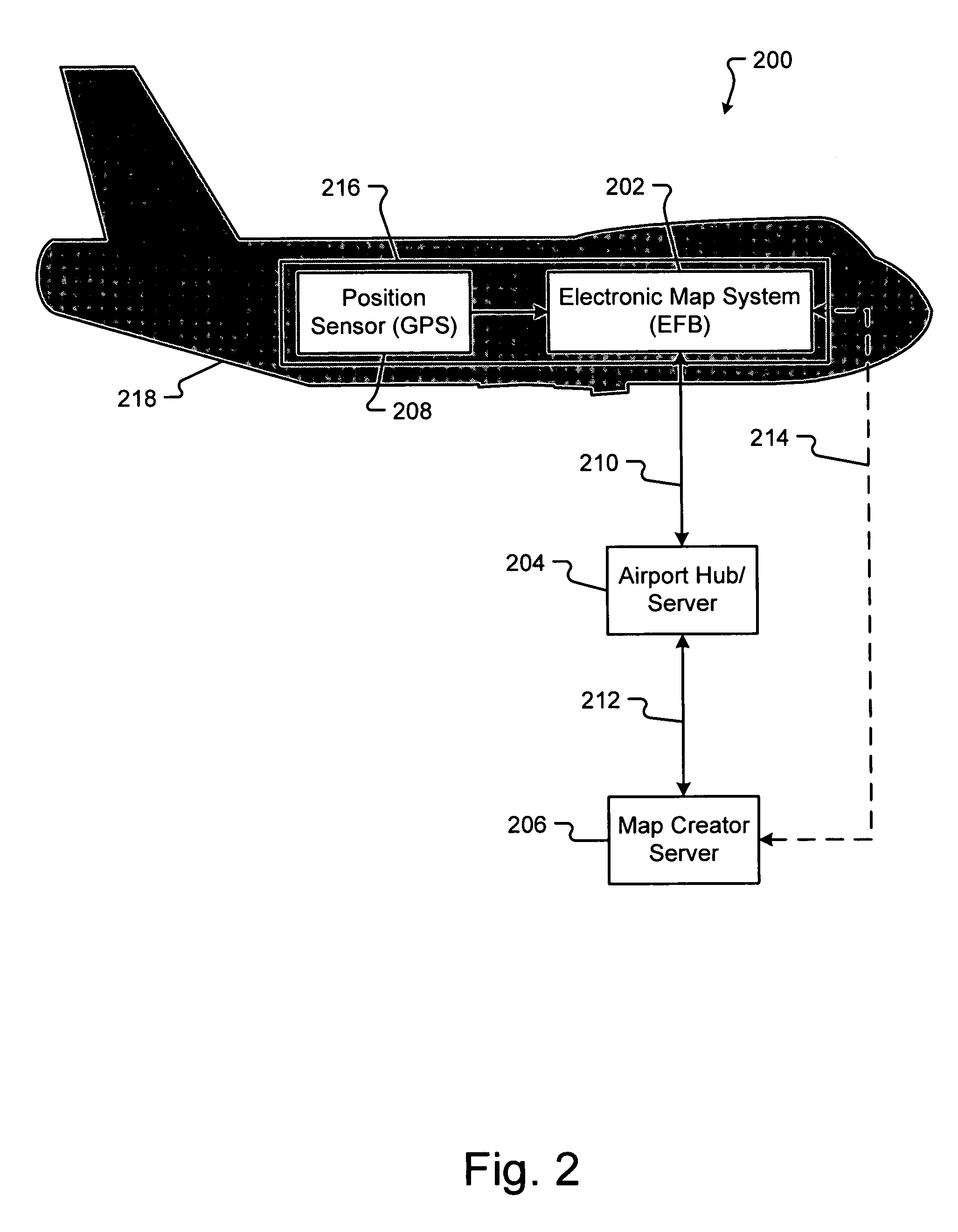
System and method for data mapping and map discrepancy reporting
ActiveUS20070021908A1Eliminate differencesEliminating discrepancies in electronic mapsInstruments for road network navigationRoad vehicles traffic controlComputer scienceElectronic map
Embodiments of the present invention generally relate to systems and methods for identifying and eliminating discrepancies in electronic maps. Embodiments of a method and system for correcting discrepancies in an electronic map includes receiving location information from one or more computing devices using the electronic map, identifying a discrepancy between the electronic map and the location information, and altering the electronic map to eliminate the discrepancy.
Owner:THE BOEING CO
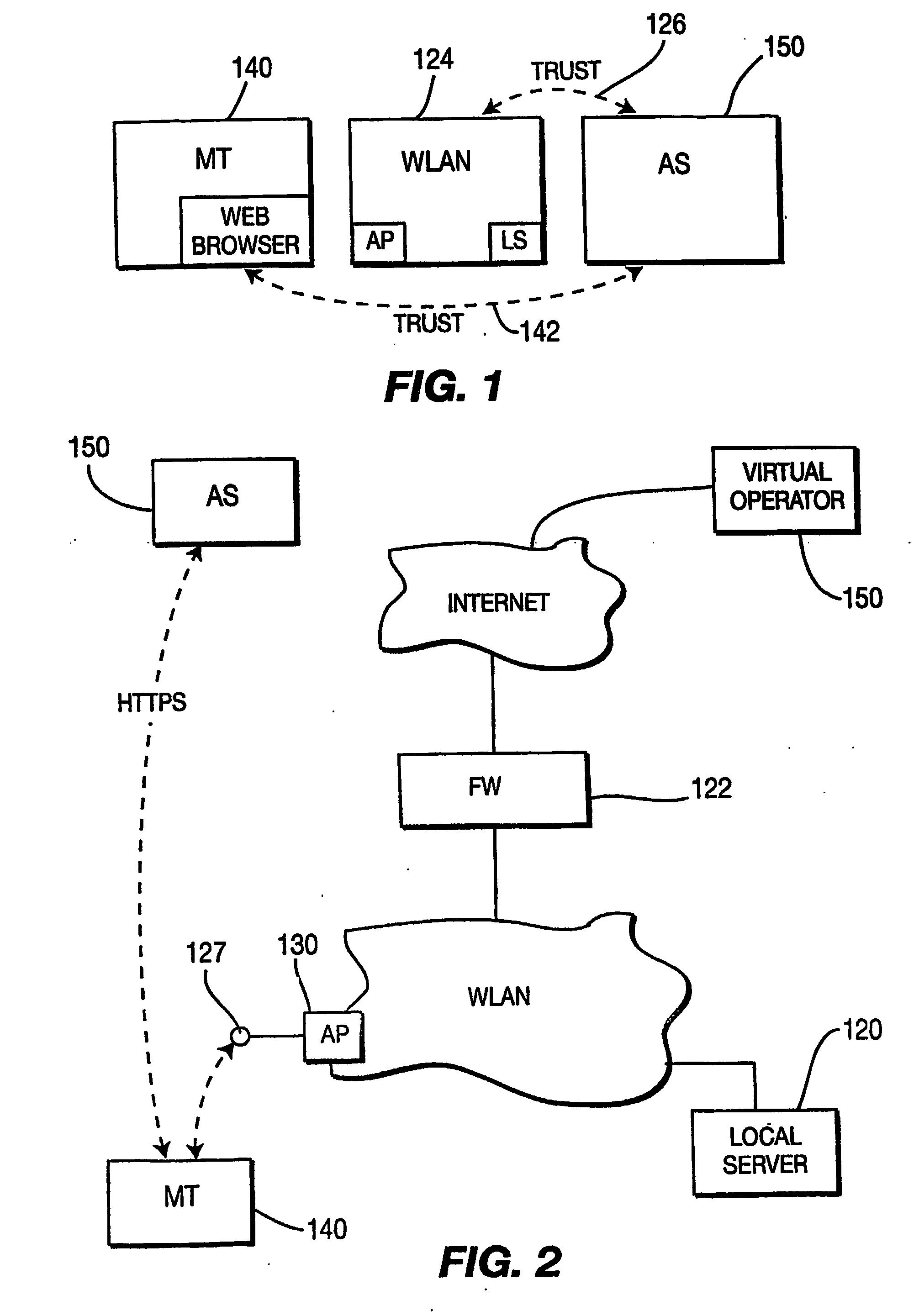
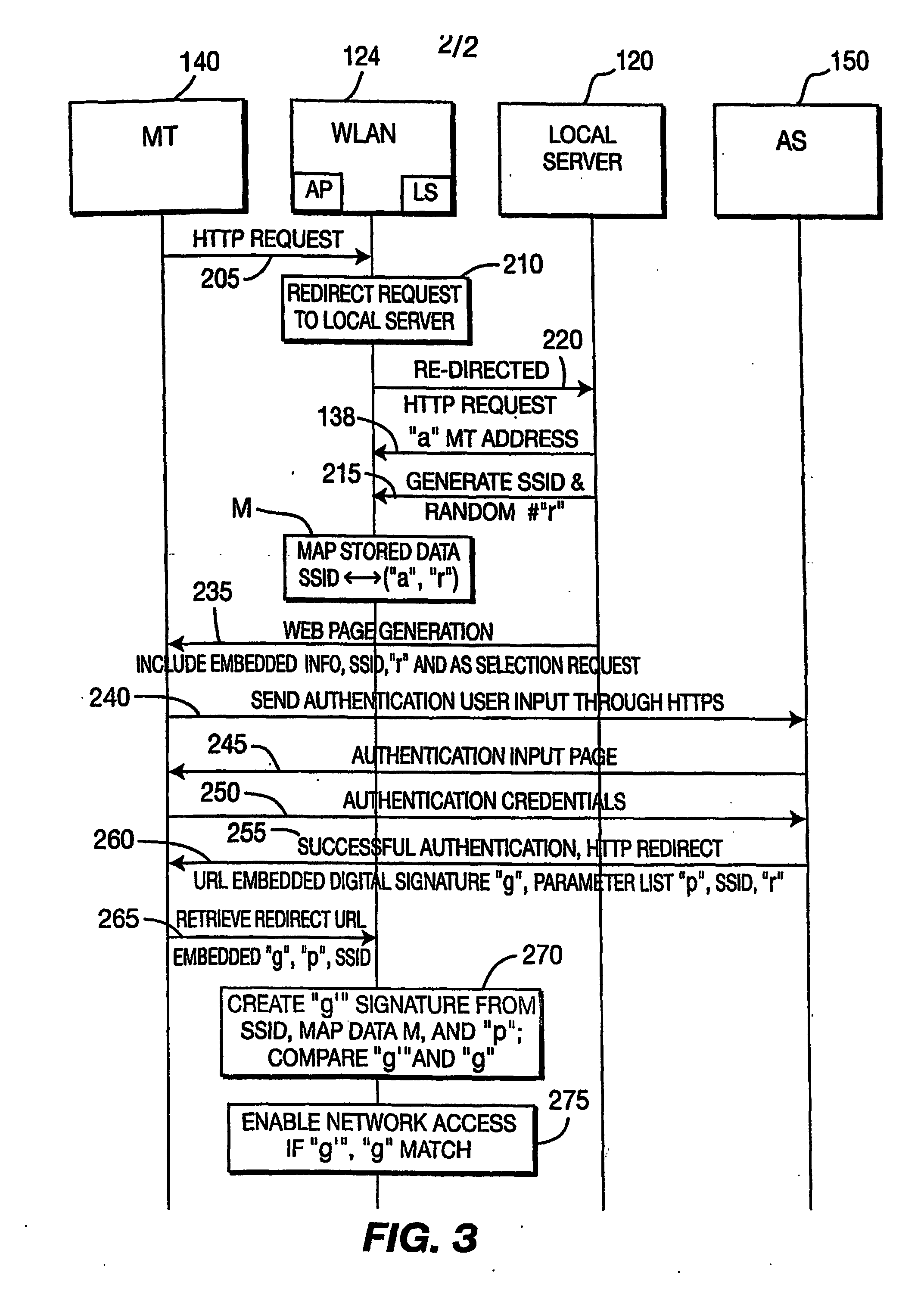
Controlling access to a network using redirection
InactiveUS20070113269A1Error prevention/detection by using return channelAssess restrictionWeb browserDigital signature
A mechanism to improve the security and access control over a network, such as a wireless local area network (“WLAN”), that takes advantage of web browser interactions without requiring explicit separate communication session between a hot spot network and a service provider network. The method comprises receiving a request to access the WLAN from a mobile terminal (MT) / client disposed within a coverage area of the WLAN. The access point (AP) of the network associates a session ID and randomized number with an identifier associated with the MT and stores data mapping the session ID to the identifier of the MT and randomized number. The local server transmits an authentication request in the form of a web page, which includes the session ID and randomized number, to the MT. The AP receives from the MT a digitally signed authentication message, a parameter list containing user credential information, session ID, and randomized number concerning the MT, the authentication message being digitally signed using the session ID and randomized number together with the parameter list. The AP correlates the session ID and parameter list received from the MT and, using the stored mapping data, generates a local digital signature for comparison with the received digitally signed authentication message for controlling access of the MT to the WLAN.
Owner:THOMSON LICENSING SA
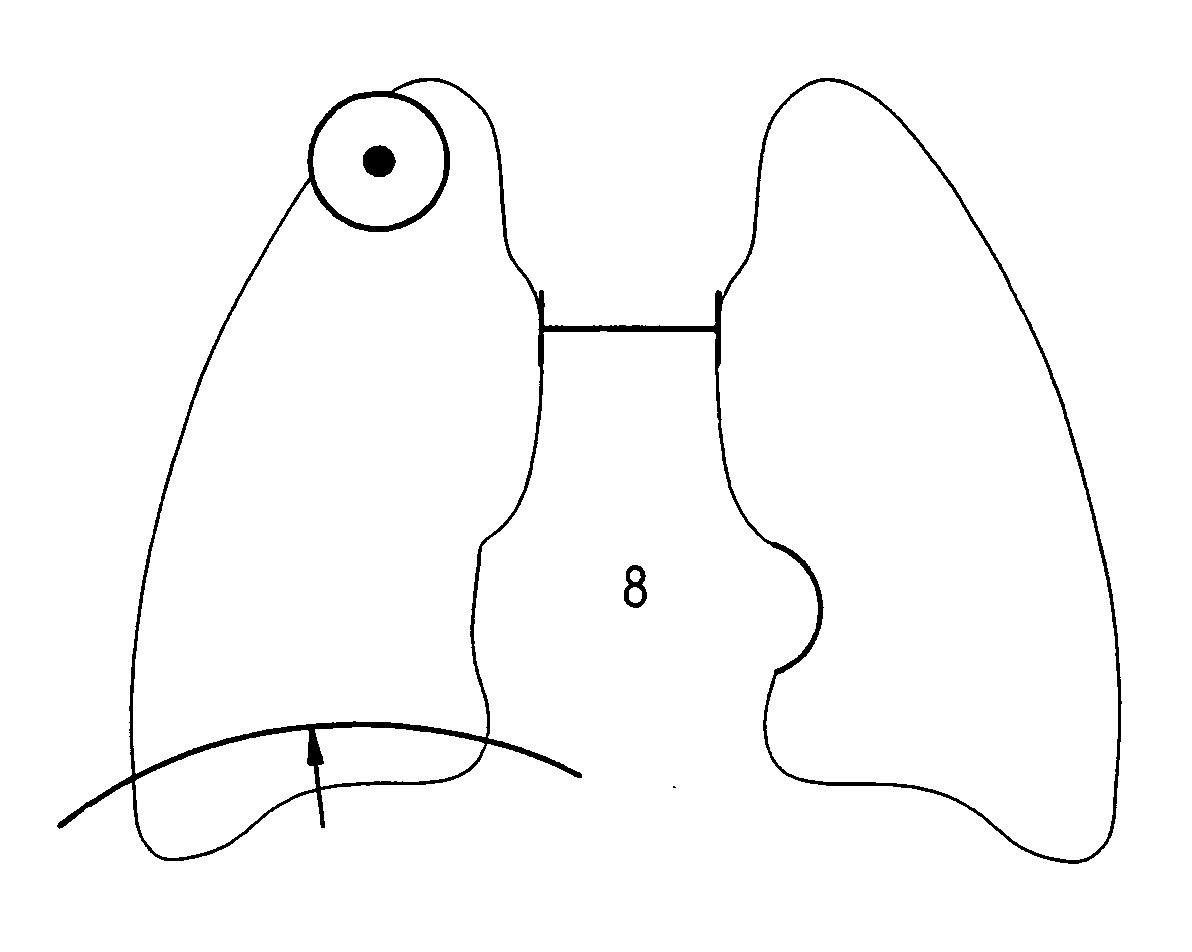
Gesture-based communication and reporting system
ActiveUS20090018867A1Avoid mistakesFacilitate communicationData processing applicationsMechanical/radiation/invasive therapiesData dredgingImaging quality
The present invention relates to a gesture-based reporting method and system, including a critical results reporting pathway, which is used to communicate critical findings to users according to predetermined methods (i.e., e-mail, facsimile, etc.), and create an electronic auditing trail to document receipt, understanding, bi-directional queries, and track clinical outcomes. Based on a predetermined rule set, predetermined data elements within the structured database could trigger the critical results reporting pathway. There is a quality assurance component to the invention, such that technical deficiencies in an imaging quality can be noted, analyzed, and tracked. There is a workflow and data analysis portion to the invention, wherein workflow is enhanced, and structured data is mapped to a standardized lexicon, such that data mining can be performed. Thus, the present invention extends beyond reporting alone and is a tool to facilitate electronic communication, consultation, education / training, and data mining for quality assurance.
Owner:IMPRIVATA
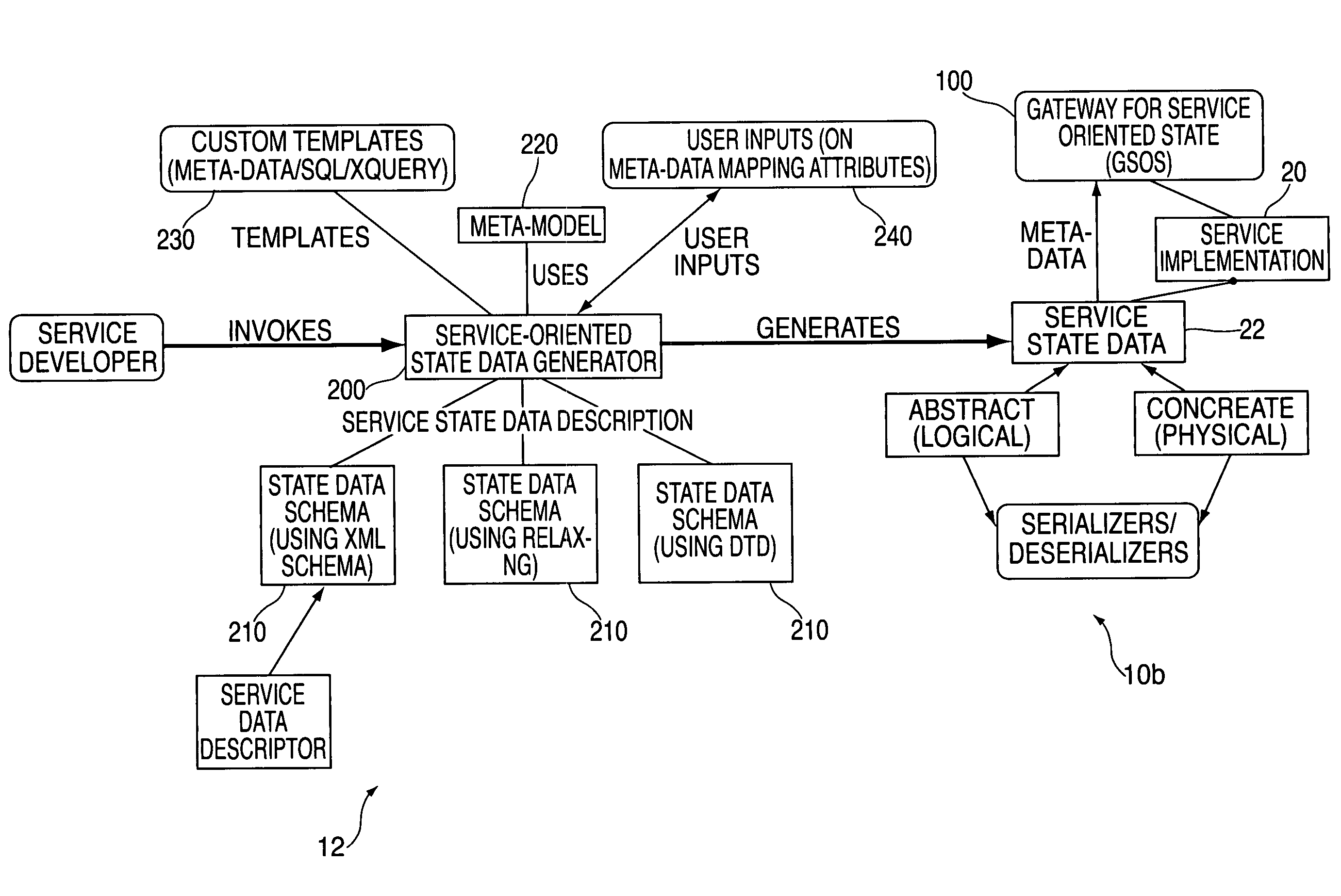
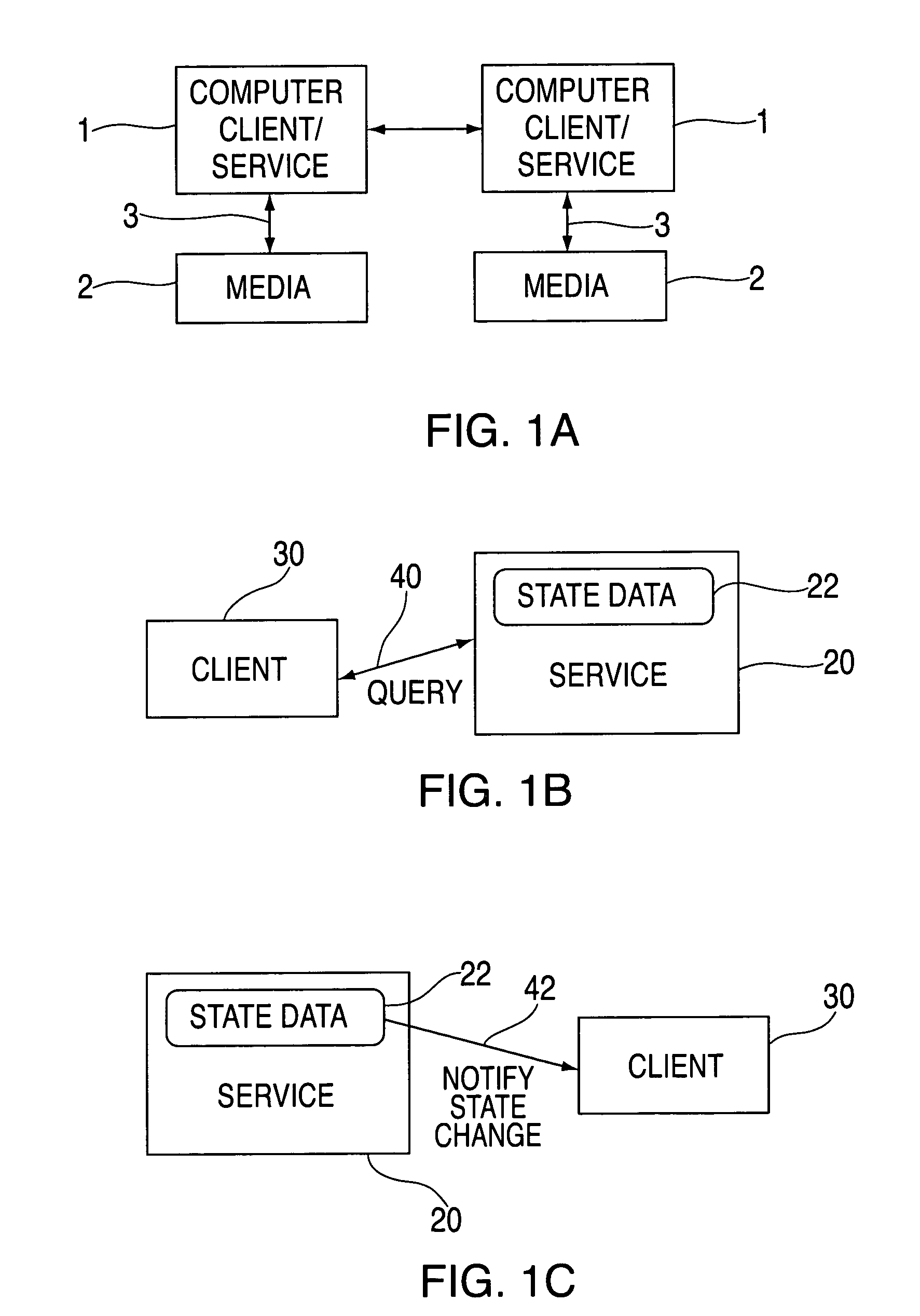
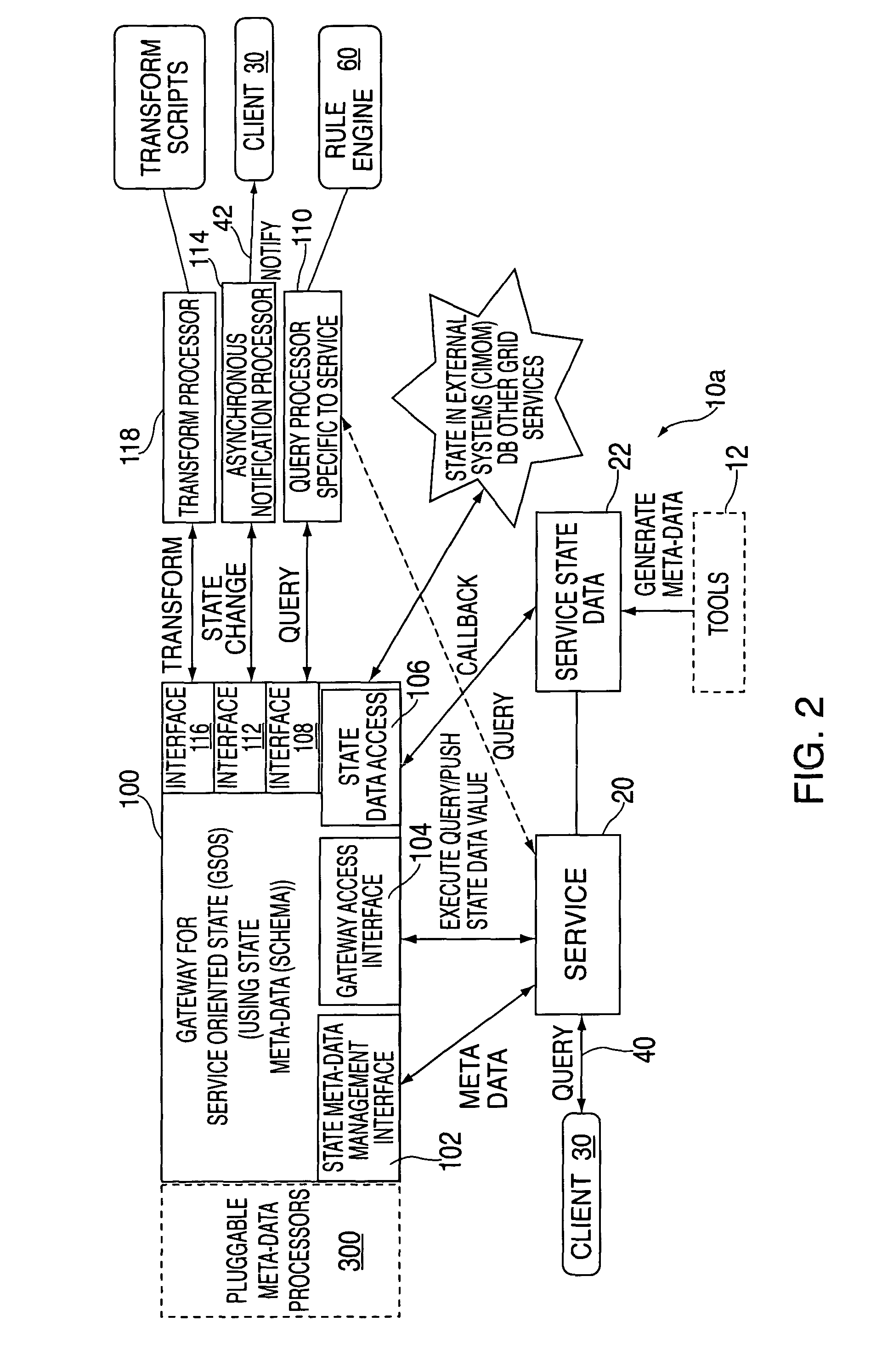
Method and apparatus for generating service oriented state data mapping between extensible meta-data model and state data including logical abstraction
InactiveUS7287037B2Data processing applicationsMultiple digital computer combinationsData descriptionData information
A method and apparatus for generating service state data and extensible meta-data information with a service oriented state data generator (SSDG) comprising: establishing a platform independent, extensible meta-data model for the meta-data information; obtaining state data schema based on a service state data description; defining an extensible set of meta-data attributes and templates corresponding to the meta data based on requirements of a service; and utilizing the meta-data model and based on the state data schema and the attributes, generating service state data based on the service state data schema; and The service state data including at least one of: state data, state data logical mapping, state data physical mapping, meta-data associated with the service state data and meta-data model correlations associated with the meta-data.
Owner:IBM CORP
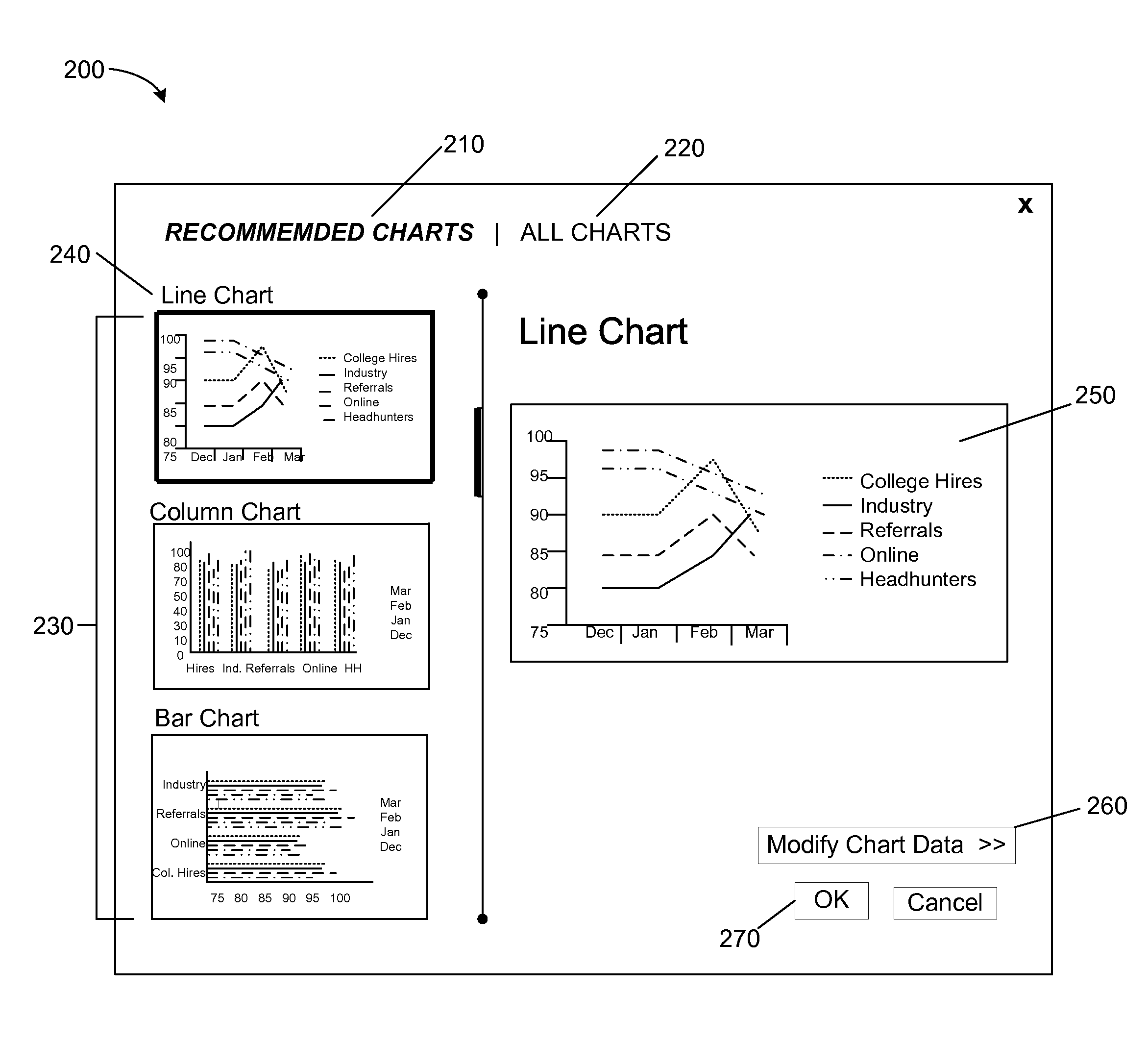
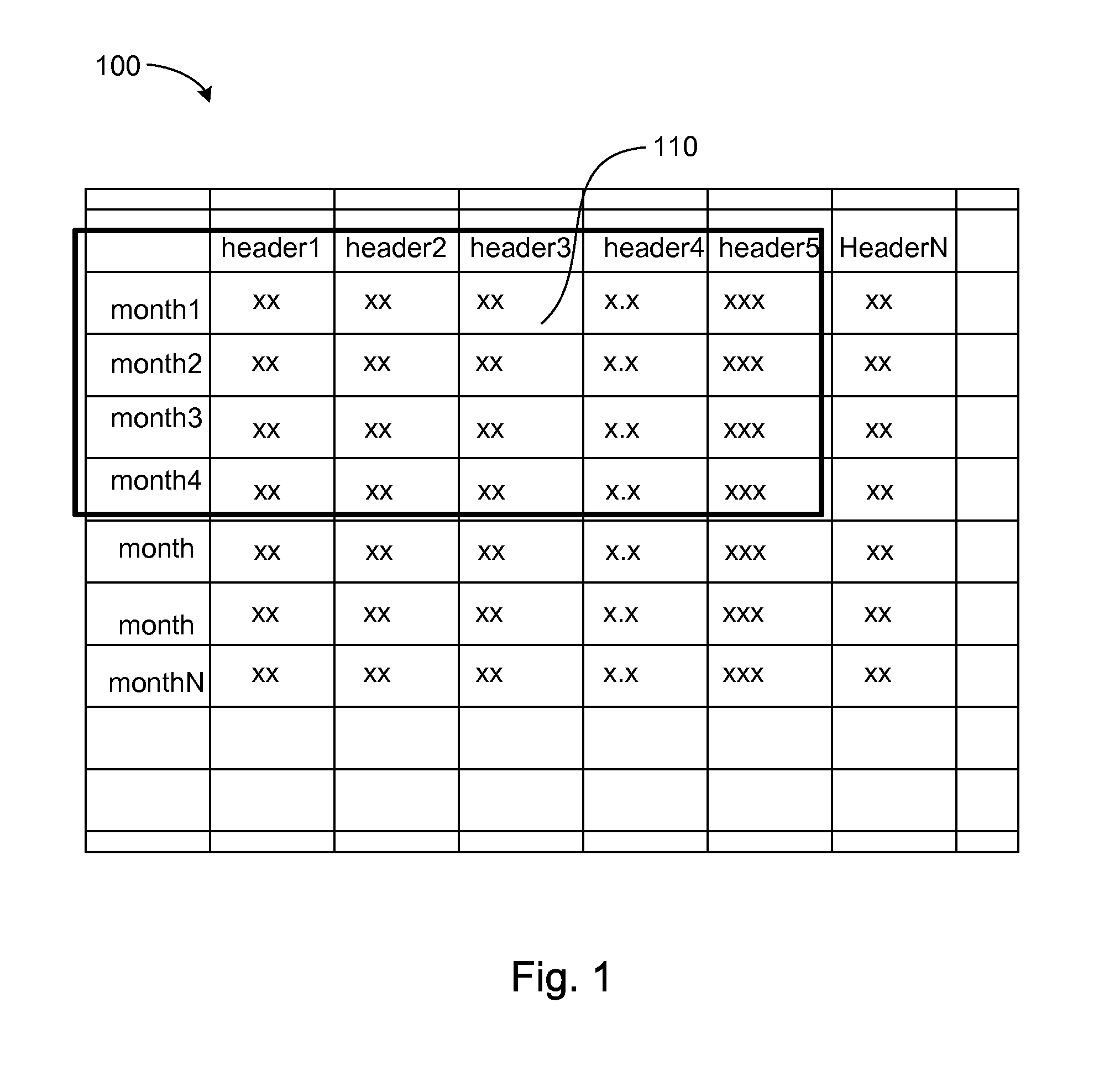
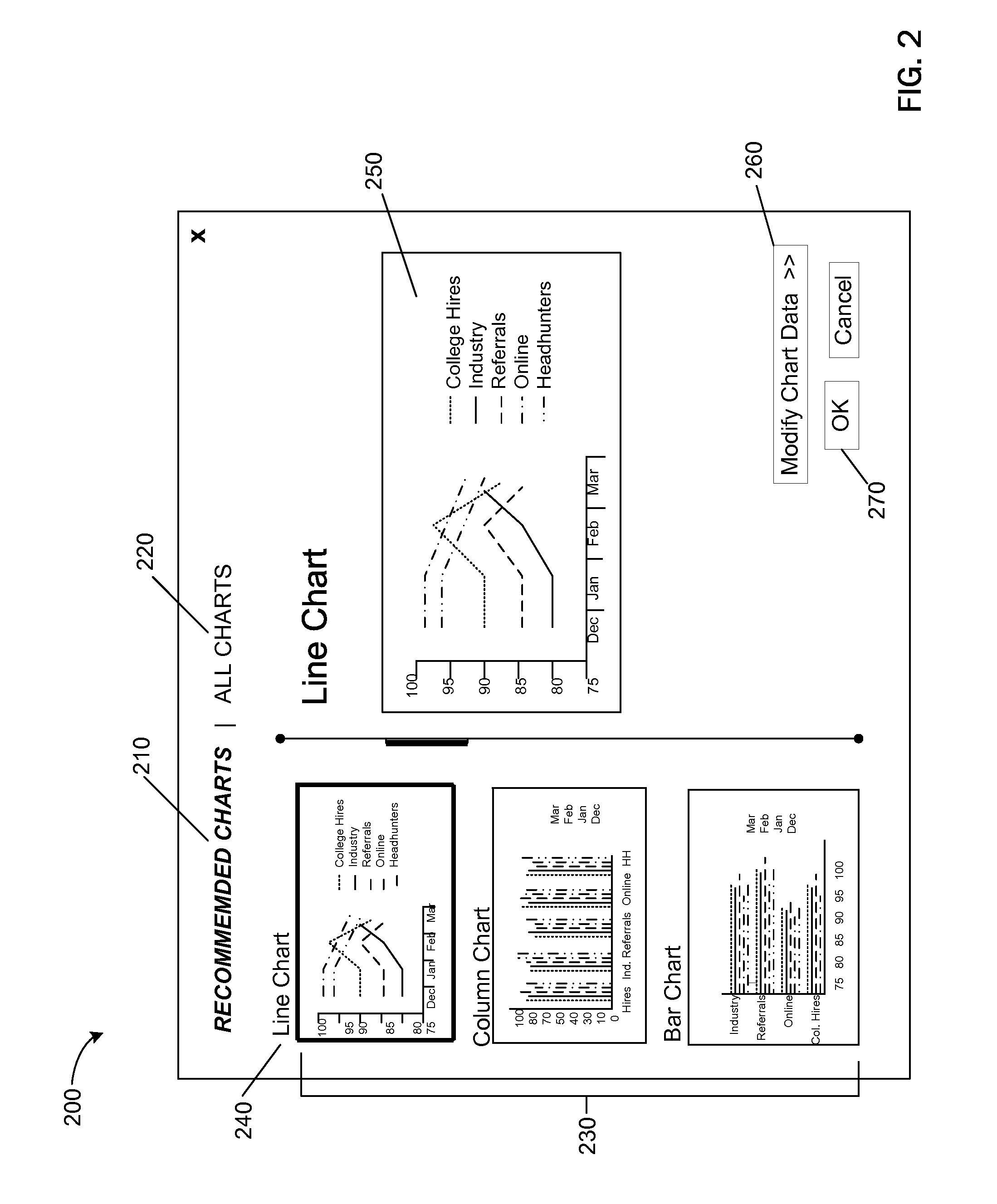
Suggesting alternate data mappings for charts
ActiveUS20130097177A1Avoid difficult choicesDigital data processing detailsText processingData setRanking
Data mapping alternatives for creating a visual representation of a set of data are presented. A set of data is identified for analysis. The identified set of data and properties associated with the identified set of data are analyzed. Based on the analysis, data mapping alternatives for the identified set of data are determined. The determined data mapping alternatives for the identified set of data are ranked. The determined data mapping alternatives are presented in an order according to the ranking of the determined data mapping alternatives.
Owner:MICROSOFT TECH LICENSING LLC
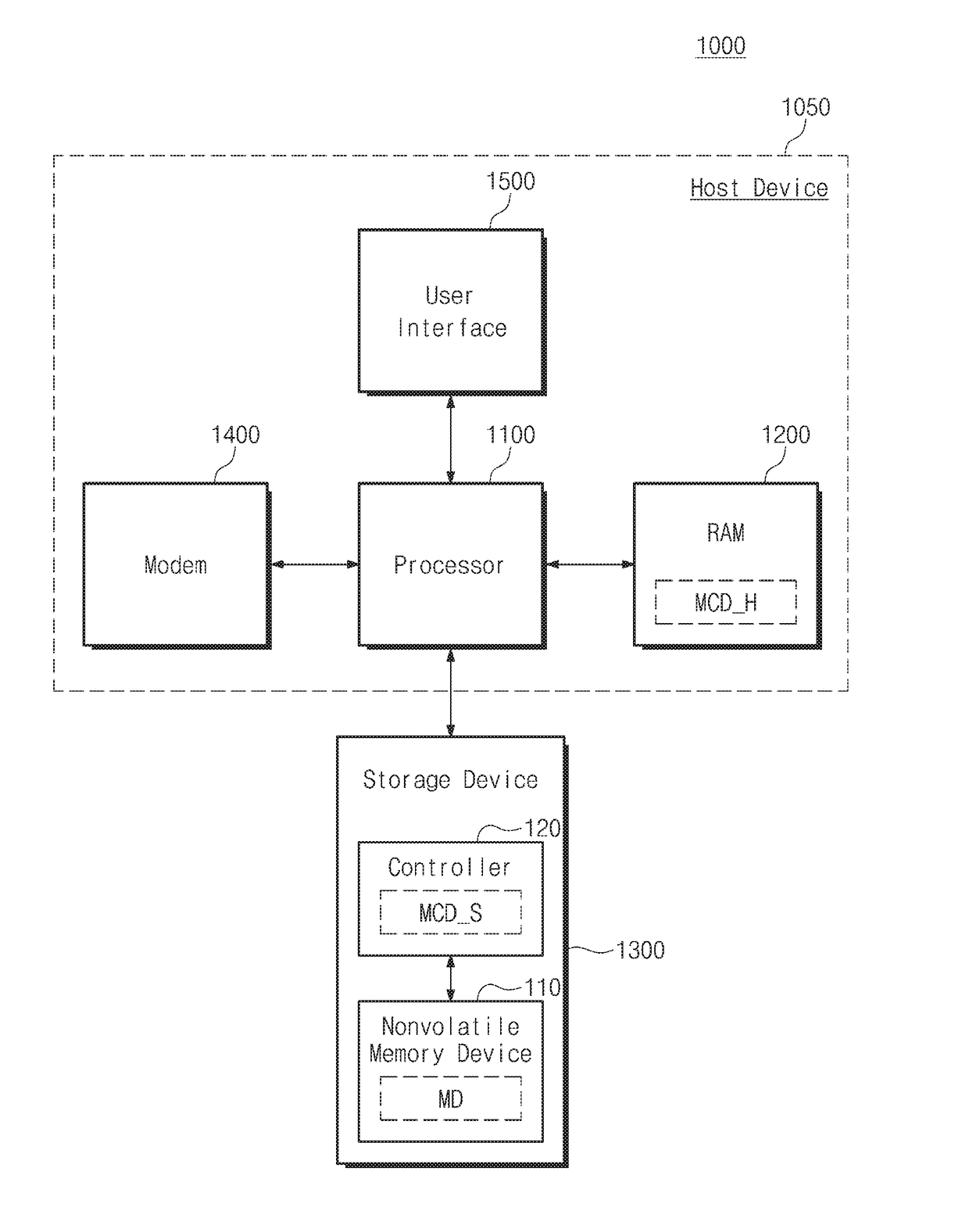
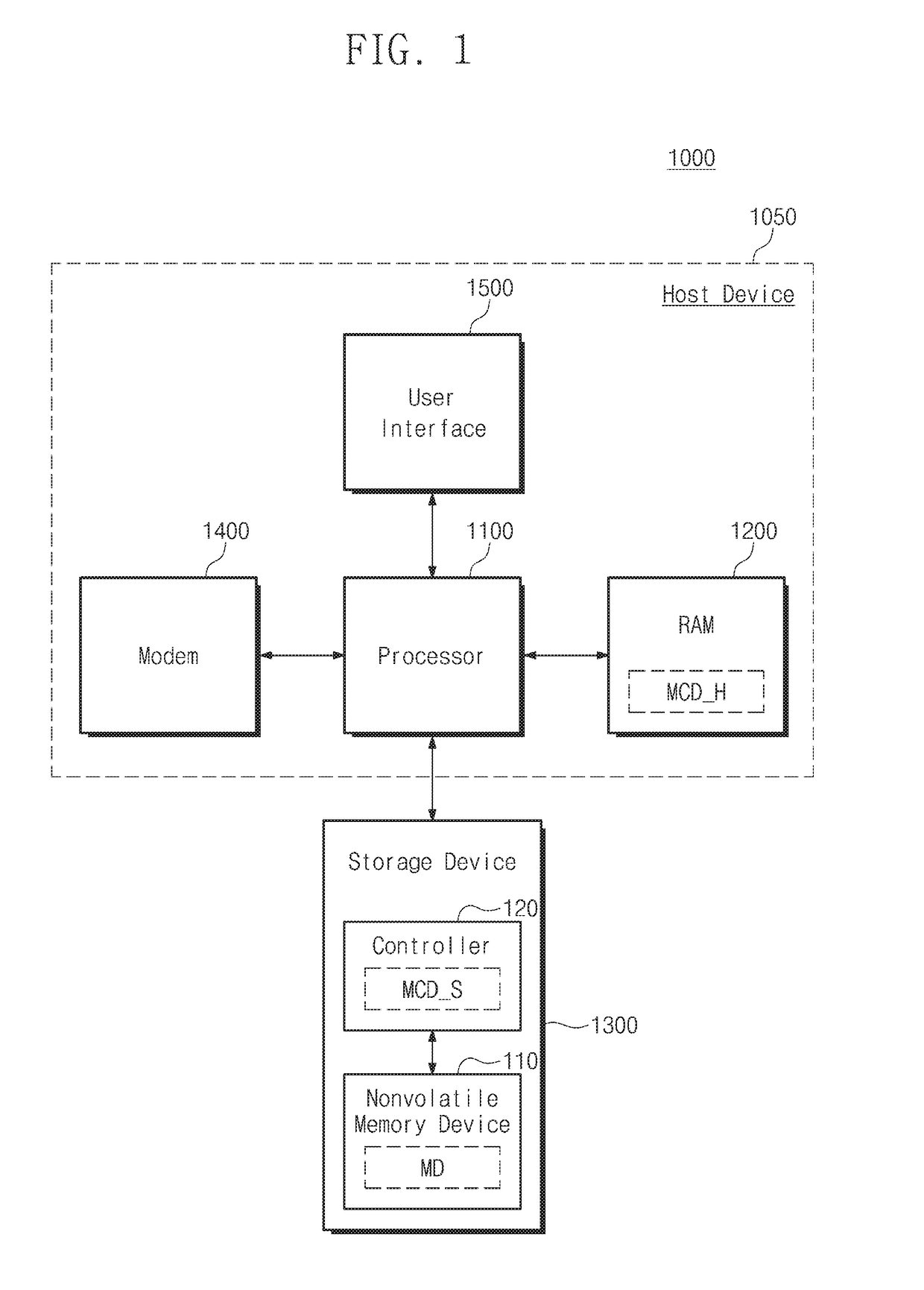
Storage device including nonvolatile memory device and controller, operating method of storage device, and method for accessing storage device
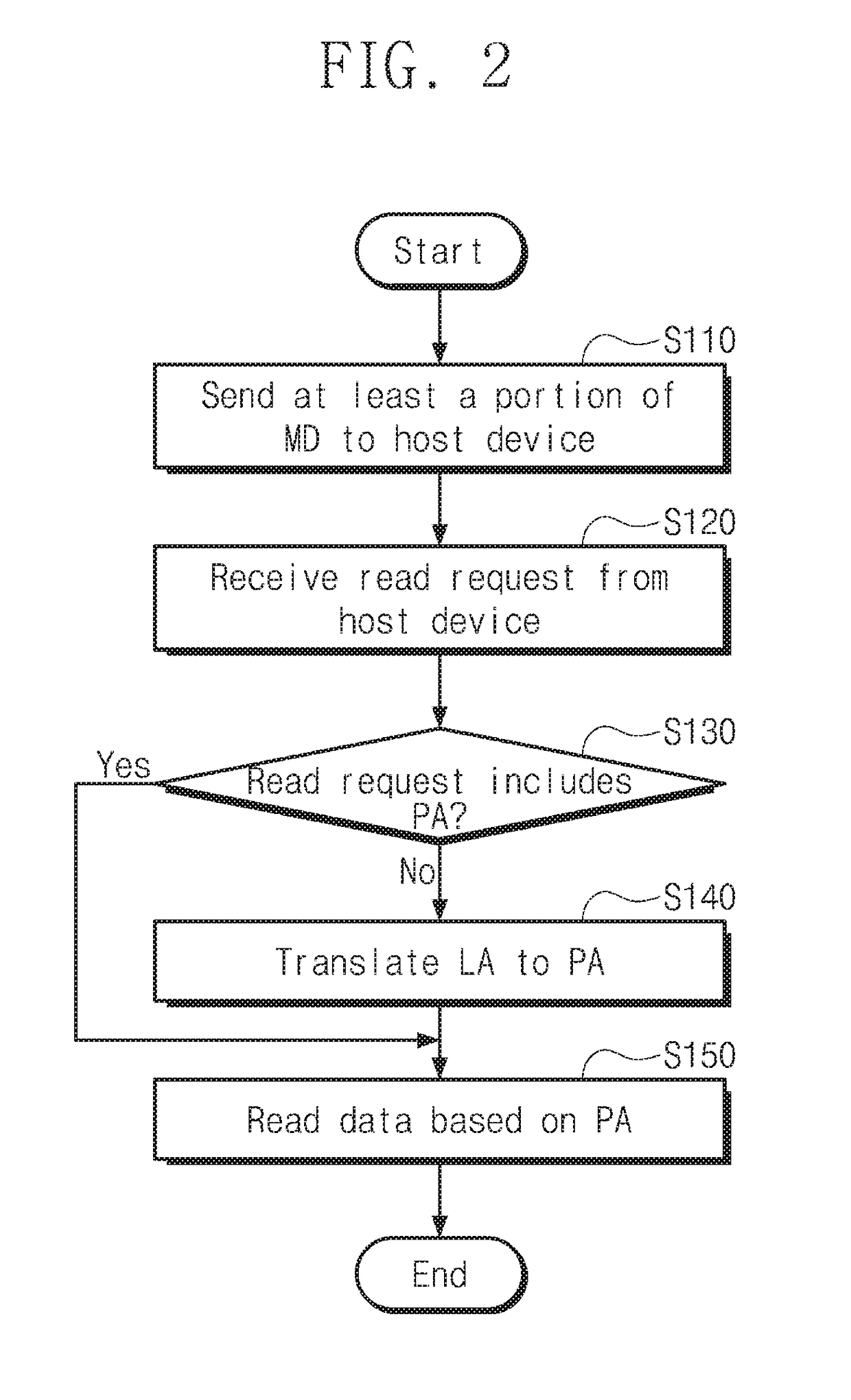
ActiveUS20170192902A1High speedMemory architecture accessing/allocationMemory adressing/allocation/relocationNon-volatile memoryHost machine
An operating method of a storage device that includes a nonvolatile memory device and a controller configured to control the nonvolatile memory device includes sending map data from the storage device to a host device, the map data mapping one or more of a plurality of physical addresses of the nonvolatile memory device to one or more of a plurality of logical addresses of the host device; receiving, at the storage device, a read request from the host device; if the read request includes a physical address, reading data from the nonvolatile memory device based on the included physical address; and if the read request does not include a physical address, translating a logical address of the read request into a first physical address, and reading data from the nonvolatile memory device based on the translated first physical address.
Owner:SAMSUNG ELECTRONICS CO LTD
Computer architecture and method for supporting and analyzing electronic commerce over the world wide web for commerce service providers and/or internet service providers
InactiveUS6934687B1Designed for such useFacilitate communicationSpecial data processing applicationsMarket data gatheringData warehousePayment service provider
A computer system that supports and analyzes Internet and / or electronic commerce data includes at least one user station transmitting a user request, and at least one Internet server, connectable to the user station, and providing the user station access to external data sources. The computer system also includes at least one data collection and analysis system. The data collection and analysis system includes at least one analysis module performing statistical and analytical analysis of the Internet and / or electronic commerce data for use by a user in performing one or more business decisions, and at least one Internet and / or electronic commerce data warehouse which is responsively connected to the analysis module and separated from external systems. The data warehouse receives the Internet and / or electronic commerce data, and provides access to the Internet and / or electronic commerce data by the user. The data collection and analysis system also includes at least one data mapping module which searches, collects and transforms the Internet and / or electronic commerce data, and transmits the same to the data warehouse for storage.
Owner:NCR CORP
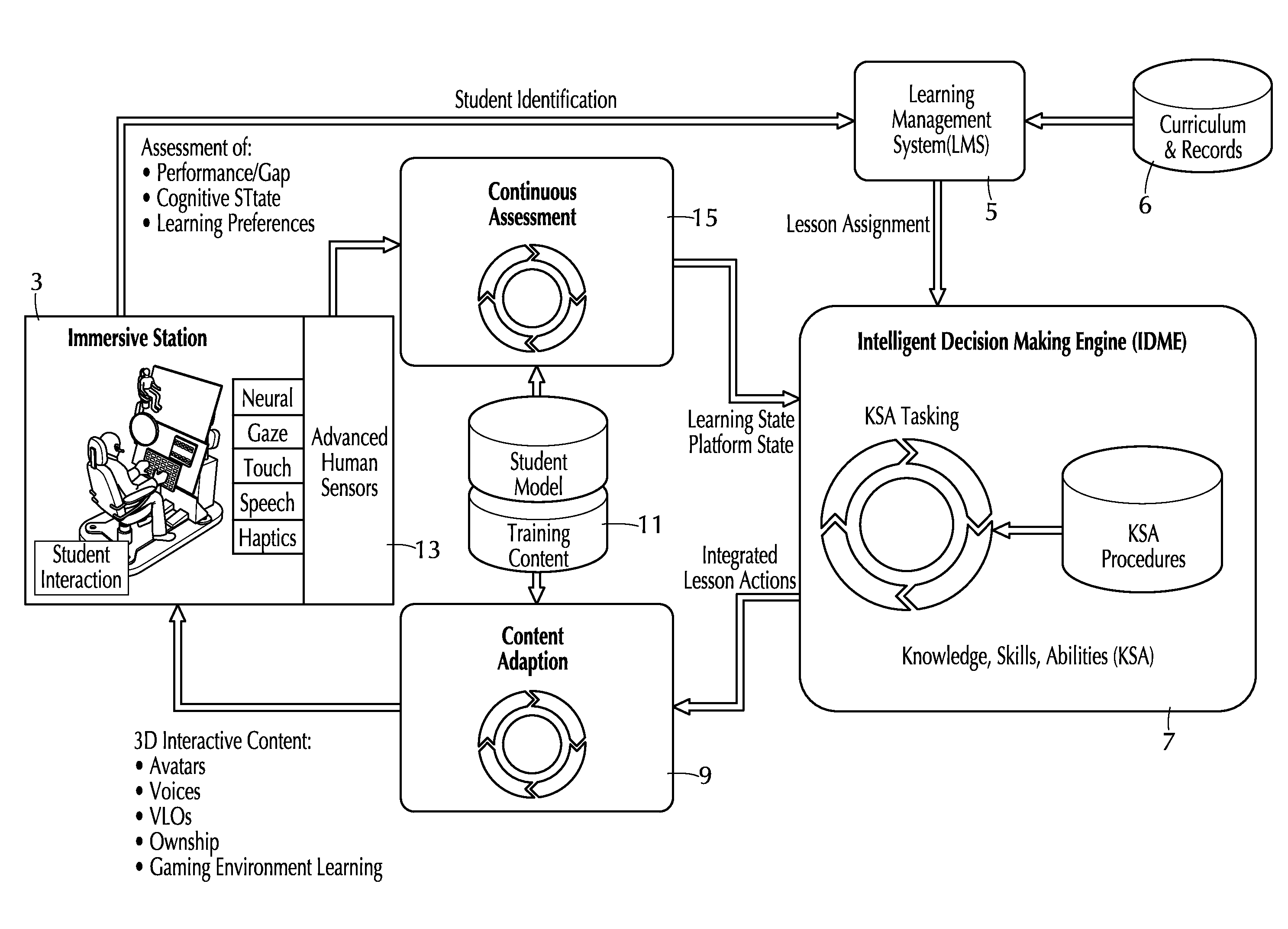
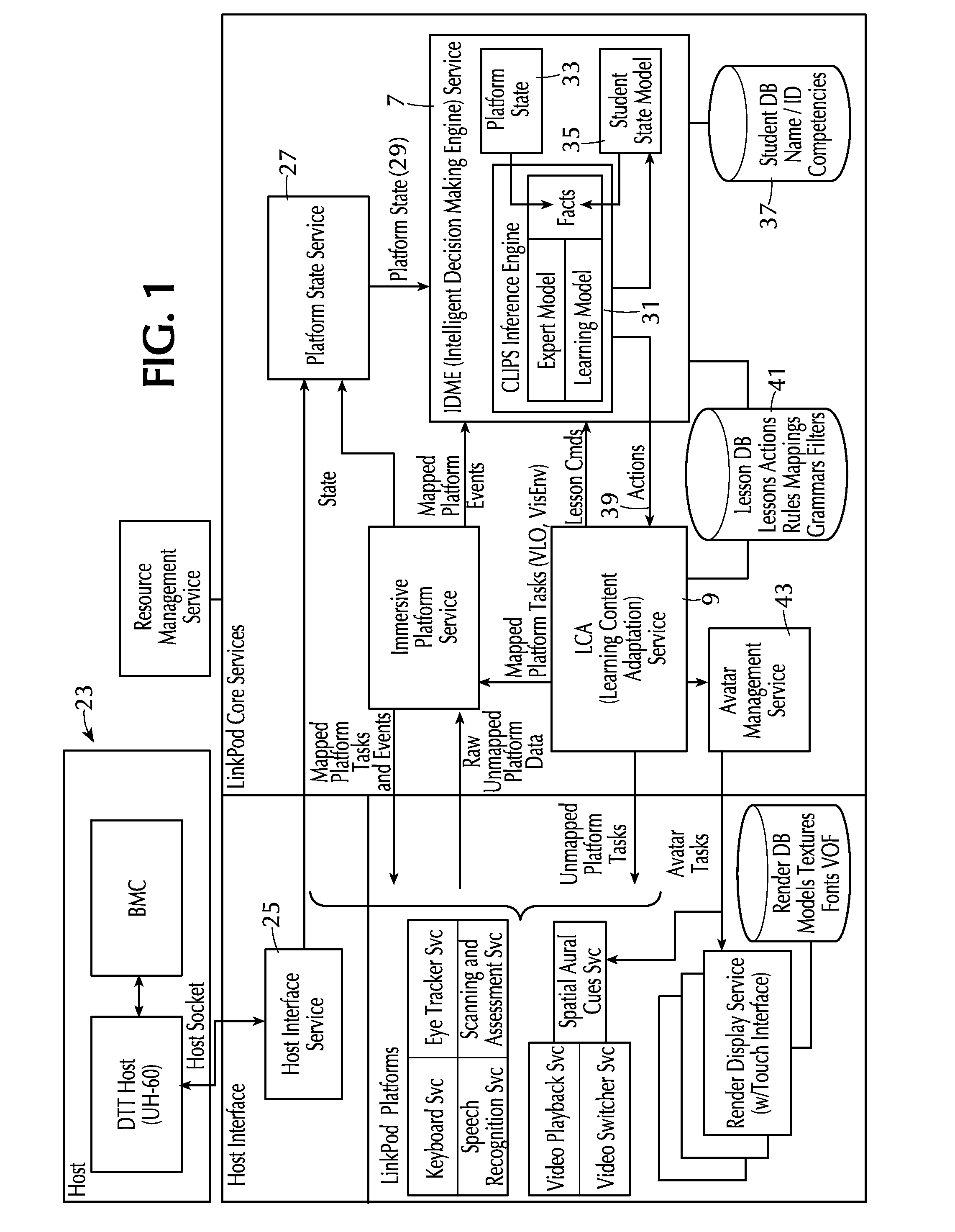
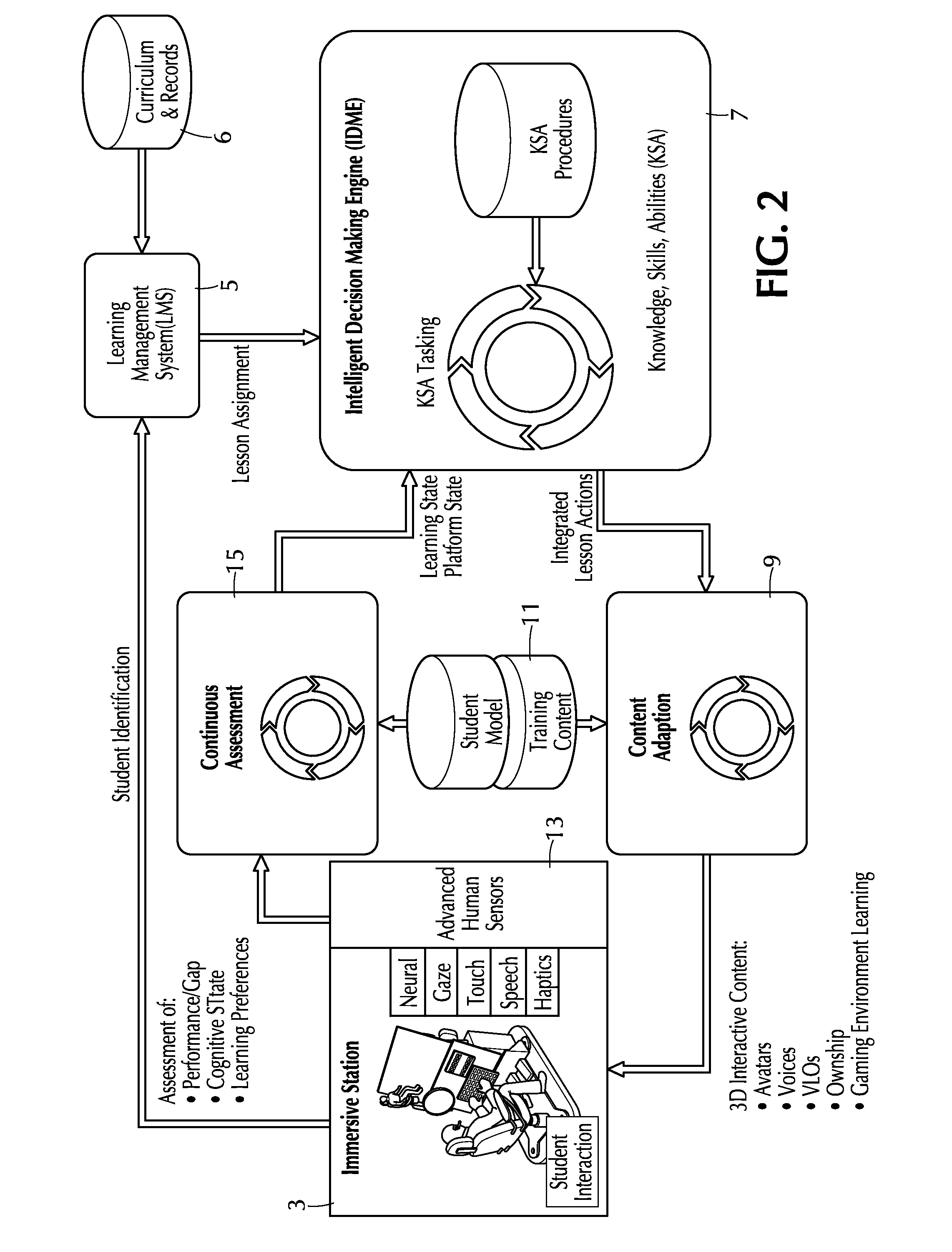
Adaptive training system, method and apparatus
ActiveUS20150050623A1Effective instructionEffective trainingCosmonautic condition simulationsBatteries circuit arrangementsComputerized systemData memory
A system and method for training a student employ a simulation station that displays output to the student and receives input. The computer system has a rules engine operating on it and computer accessible data storage storing (i) learning object data including learning objects configured to provide interaction with the student at the simulation system and (ii) rule data defining a plurality of rules accessed by the rules engine. The rules data includes, for each rule, respective (a) if-portion data defining a condition of data and (o) then-portion data defining an action to be performed at the simulation station. The rules engine causes the computer system to perform the action when the condition of data is present in the data storage. For at least some of the rules, the action comprises output of one of the learning objects so as to interact with the student. The system may be networked with middleware and adapters that map data received over the network to rules engine memory.
Owner:CAE USA INC
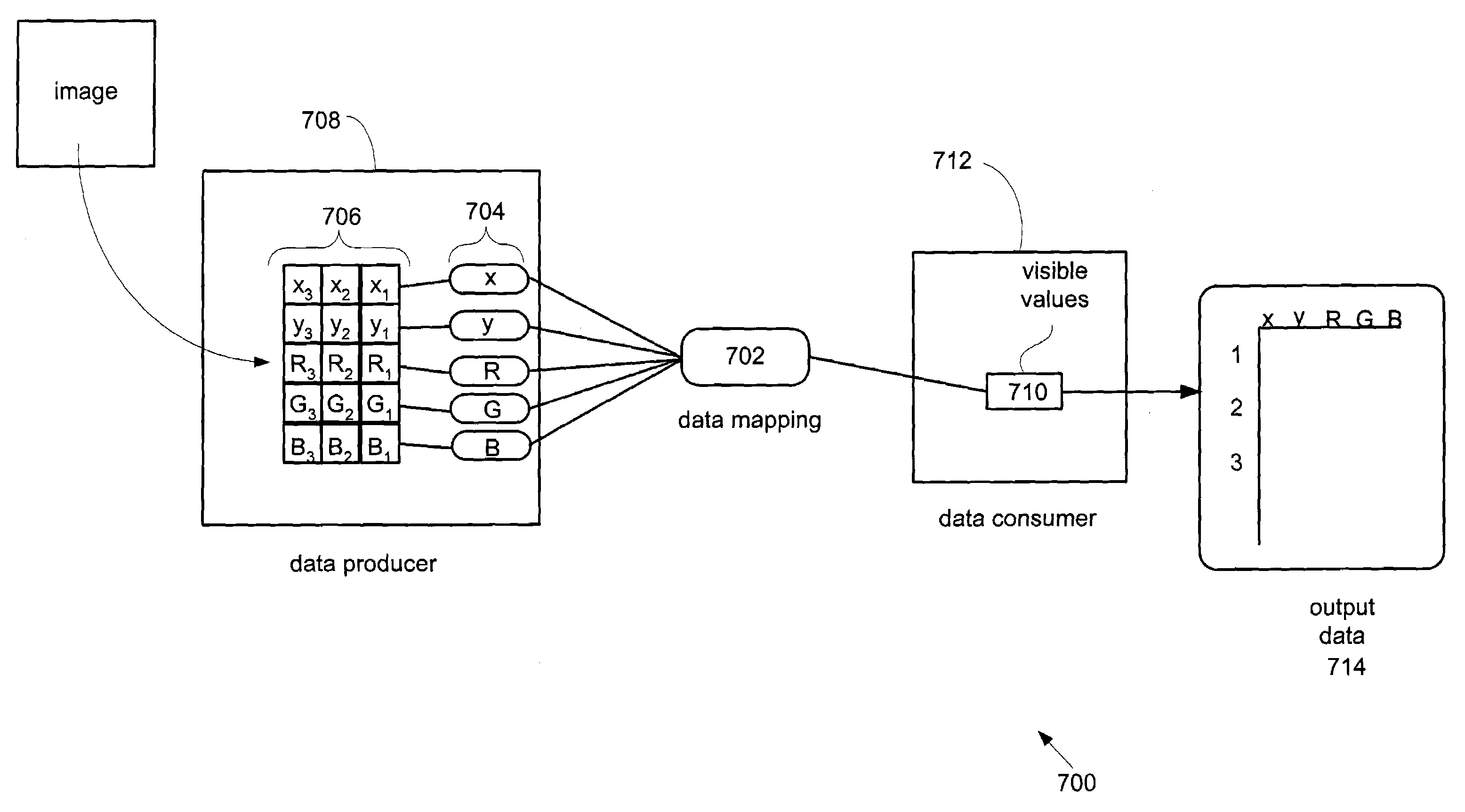
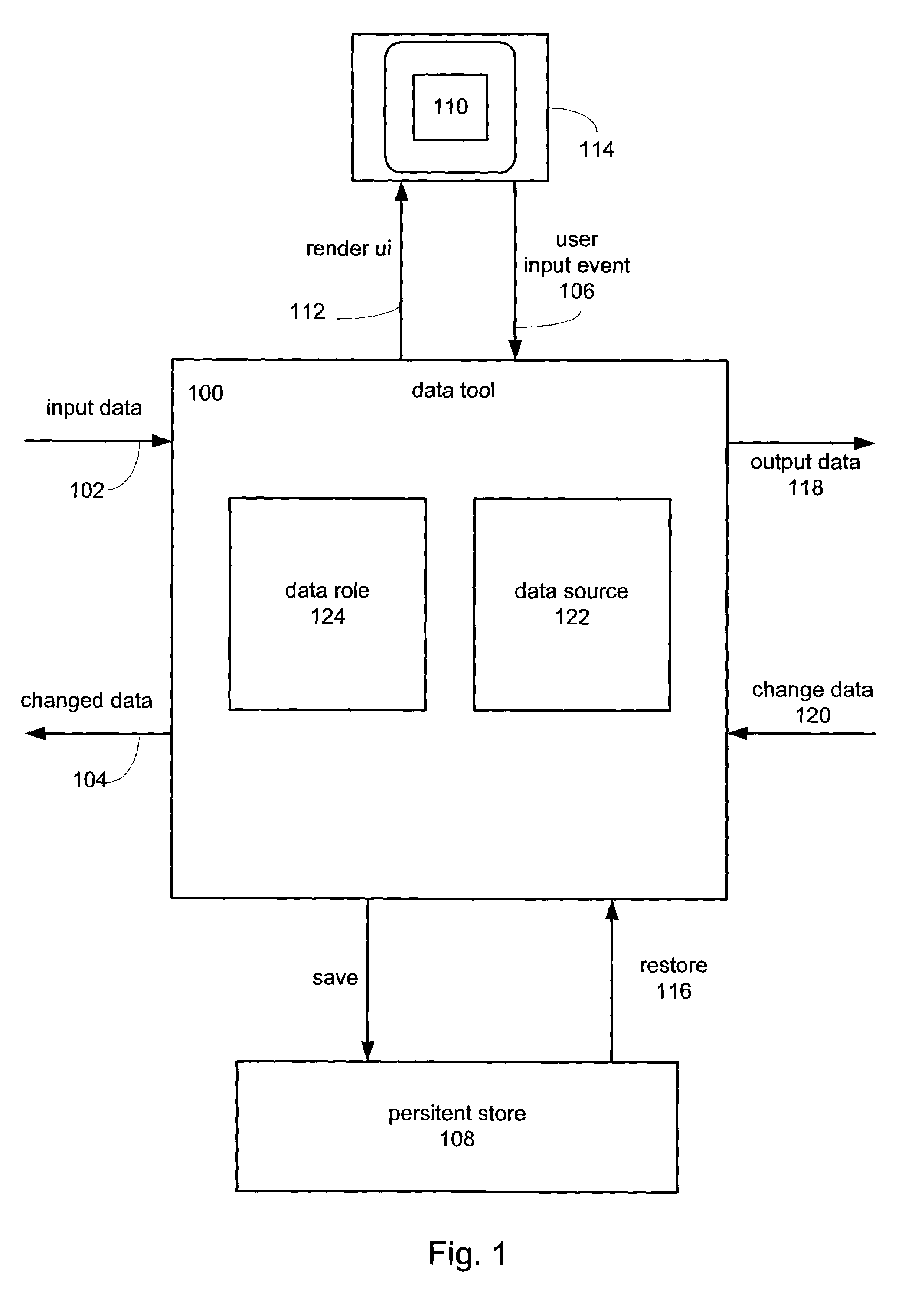
Architecture for developing and reusing analytic and visualization components and methods of use thereof
An interactive and dynamic data analysis tool that helps interactive analysis in real time on medium size datasets having complex structure is described. In one aspect, the data analysis tool is capable of being configured to act as a data producer tool arranged to provide a data source. The data analysis tool can also be configured as a data consumer tool capable of receiving and processing a particular data source. The data source tool and the data consumer tool are connected together to form a framework that takes the form of a data mapping context that mediates the data provided by the data source and a particular data role.
Owner:PERLEGEN SCIENCES INC
Method and apparatus for protected content data processing
ActiveUS8225061B2Digital data processing detailsUnauthorized memory use protectionLimited accessComputer network
Owner:APPLE INC
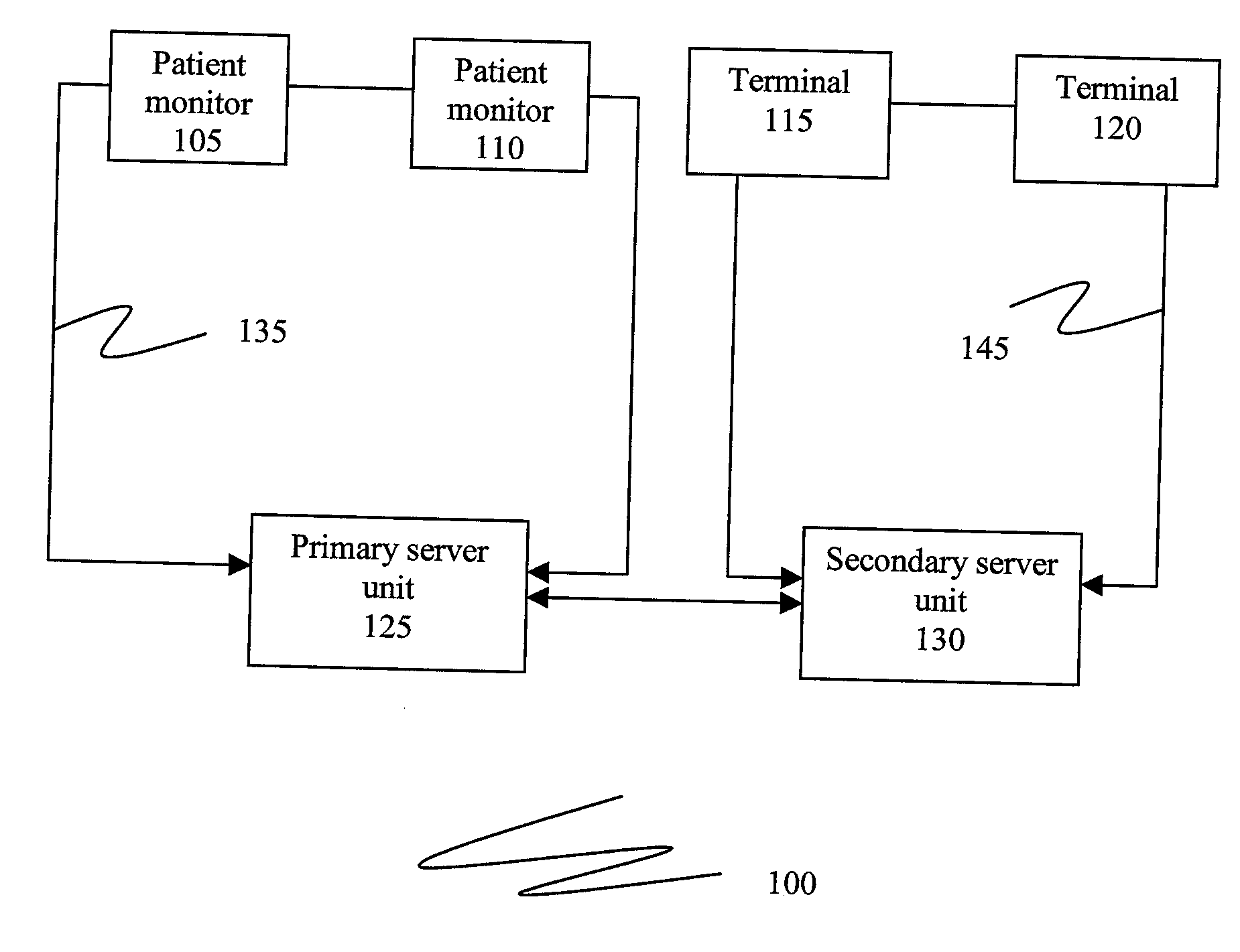
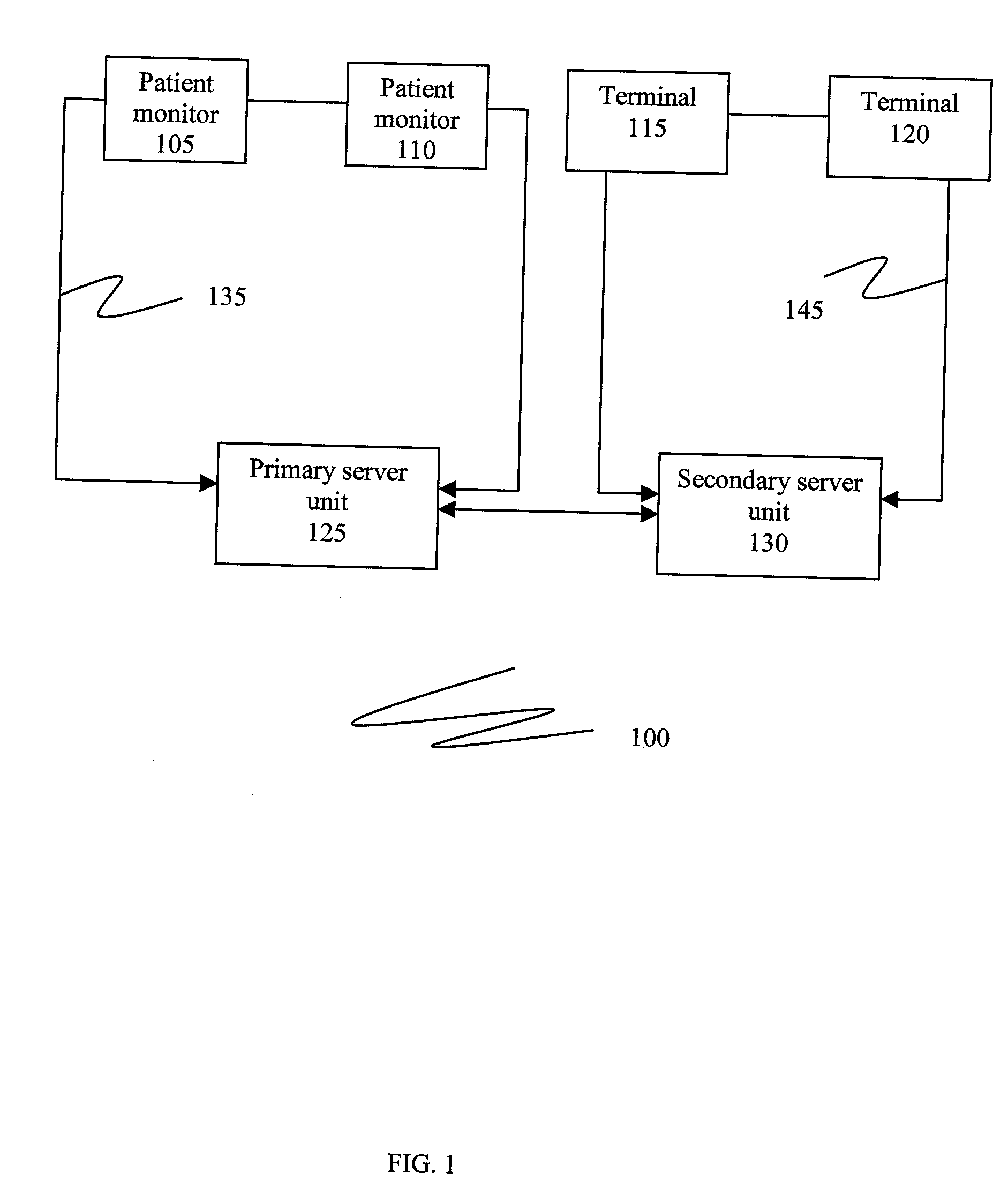
Patient monitoring network and method of using the patient monitoring network
InactiveUS20090177641A1Digital data processing detailsMultiple digital computer combinationsCaregiver personData display
In one embodiment, a method of using a patient monitoring network is provided. The method comprises steps of storing an association data at a primary server unit, the association data mapping a caregiver with at least one patient associated with the caregiver, storing an object data of at least one patient at a patient monitor coupled to the primary server unit, the object data comprising an identification data and a patient data of the patient, receiving a query at the patient monitor by the caregiver, fetching the association data of the caregiver from the primary server unit, displaying the identification data of at least one patient associated with the caregiver at the patient monitor, obtaining a selection for the patient at the patient monitor and displaying the patient data of the patient at the patient monitor.
Owner:GENERAL ELECTRIC CO
Online fraud prevention using genetic algorithm solution
Online fraud prevention including receiving a rules set to detect fraud, mapping the rules set to a data set, mapping success data to members of the rules set, filtering the members of the rules set, and ordering members of the data set by giving priority to those members of the data set with a greater probability for being fraudulent based upon the success data of each member of the rule set in detecting fraud. Further, a receiver coupled to an application server to receive a rules set to detect fraud, and a server coupled to the application server, to map the rules set to a data set, and to map the success data to each members of the rules set. The server is used to order the various members of the data set by giving priority to those members of the data set with a greatest probability for being fraudulent.
Owner:PAYPAL INC
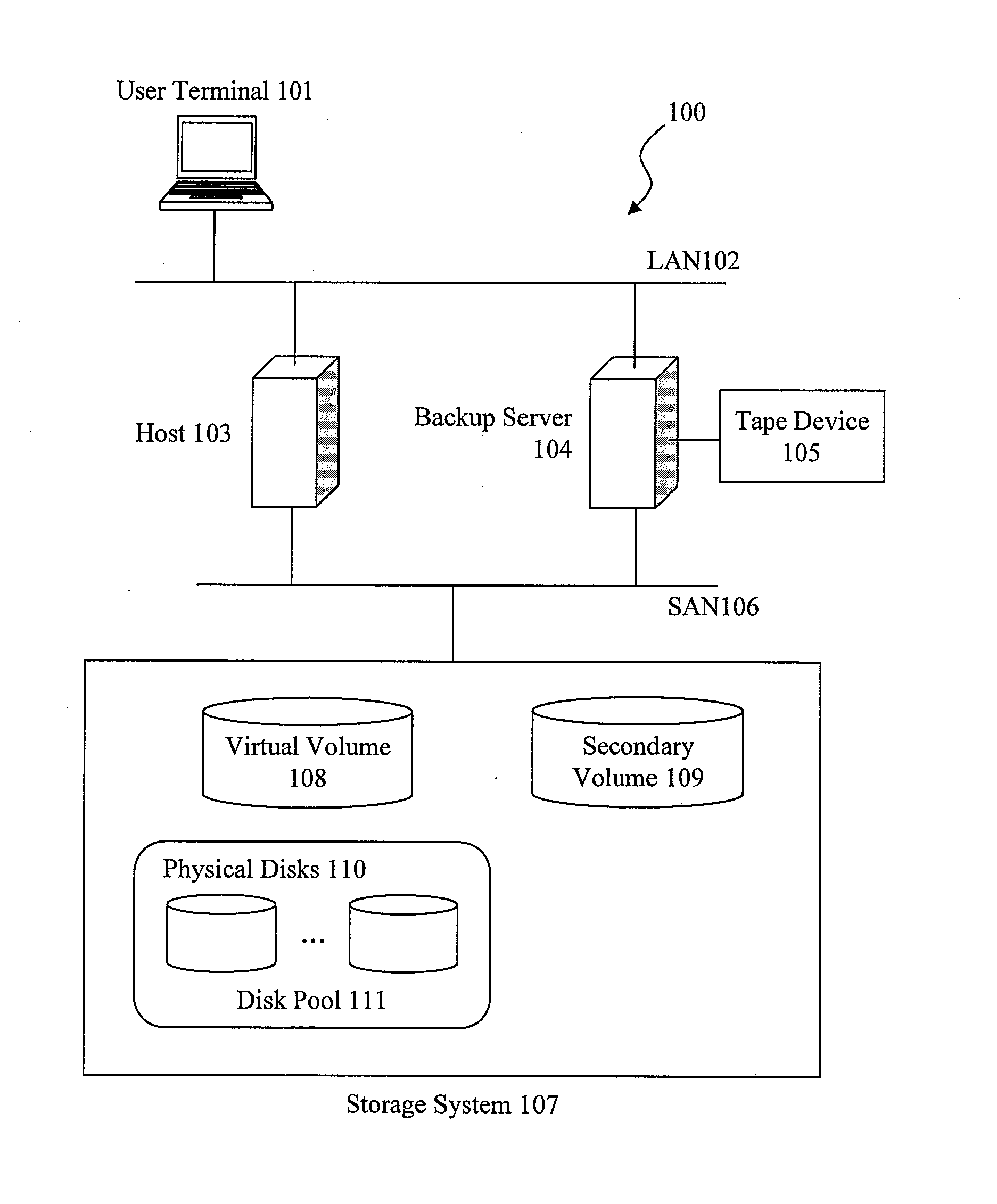
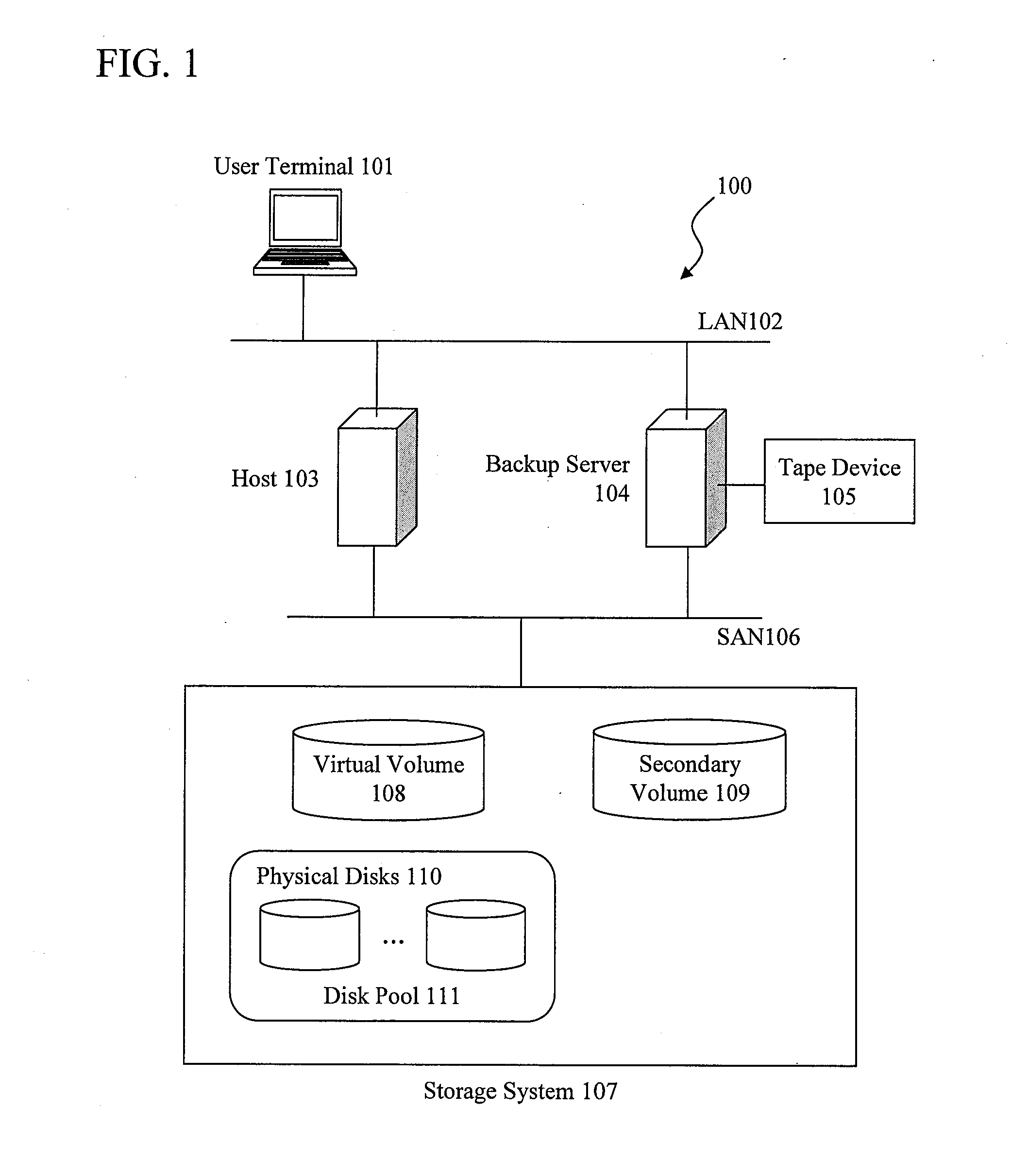
Information backup/restoration processing apparatus and information backup/restoration processing system
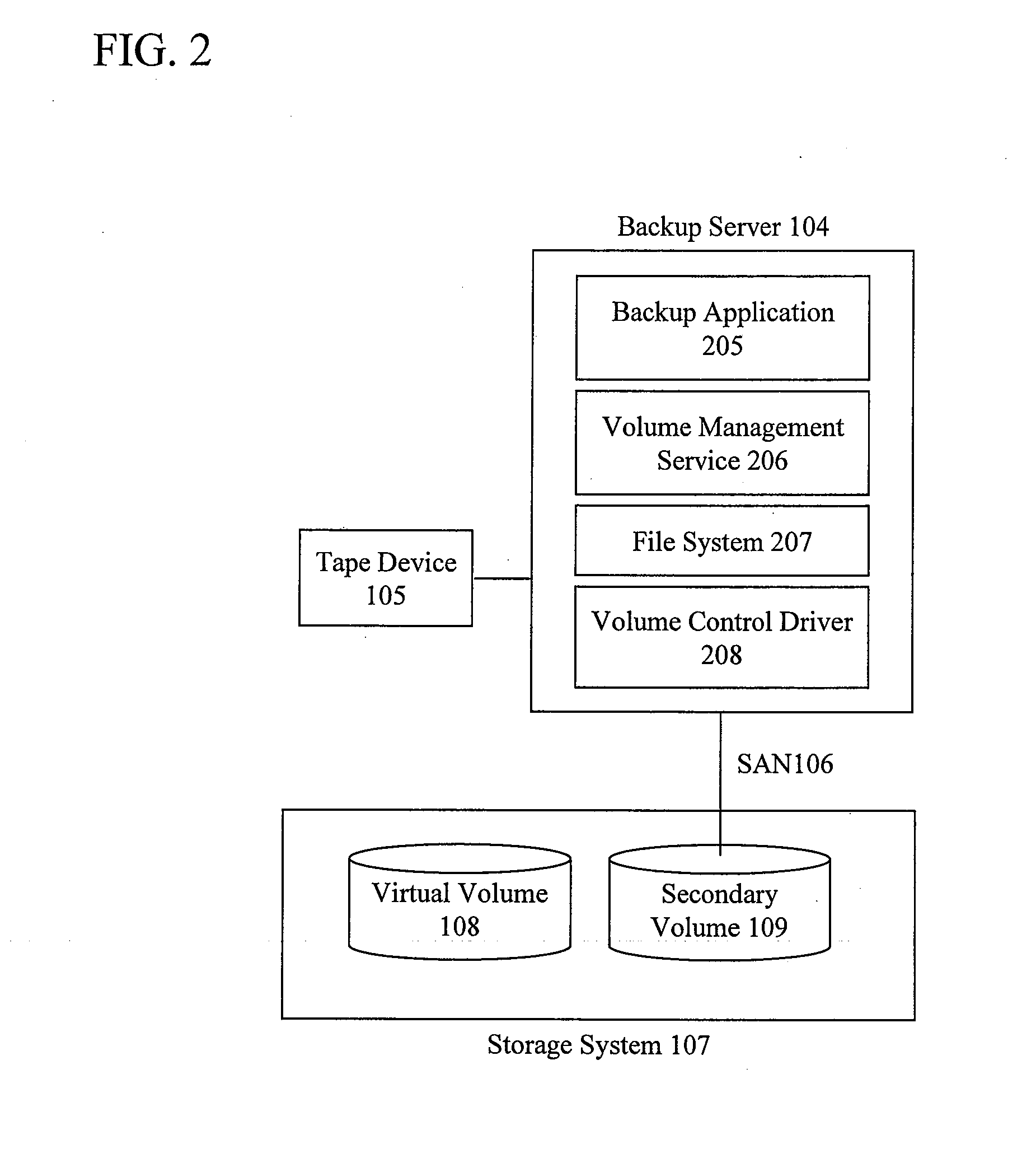
InactiveUS20110022811A1Efficiently restoredMemory loss protectionError detection/correctionFile systemBackup
To reduce the size of backup data, increase the backup speed, and solve a problem that the amount of unnecessary writing could undesirably increase in a restoration process, which would otherwise require physical disks with a capacity greater than the size of a virtual volume. On a backup server having mounted thereon a virtual volume that is the target to be backed up and restored, read / write access to only the blocks of data areas is performed by a device driver that filters I / O access to a device from a file system on the basis of the data mapping information of the virtual volume, whereby read / write access to unnecessary portions is avoided. Thus, it is possible to reduce the size of backup data, increase the backup speed, and prevent an increase in the amount of unnecessary writing to the virtual volume in a restoration process.
Owner:HITACHI SOFTWARE ENG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com