Patents
Literature
352 results about "Bit field" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A bit field is a data structure used in computer programming. It consists of a number of adjacent computer memory locations which have been allocated to hold a sequence of bits, stored so that any single bit or group of bits within the set can be addressed. A bit field is most commonly used to represent integral types of known, fixed bit-width.
Microprocessors
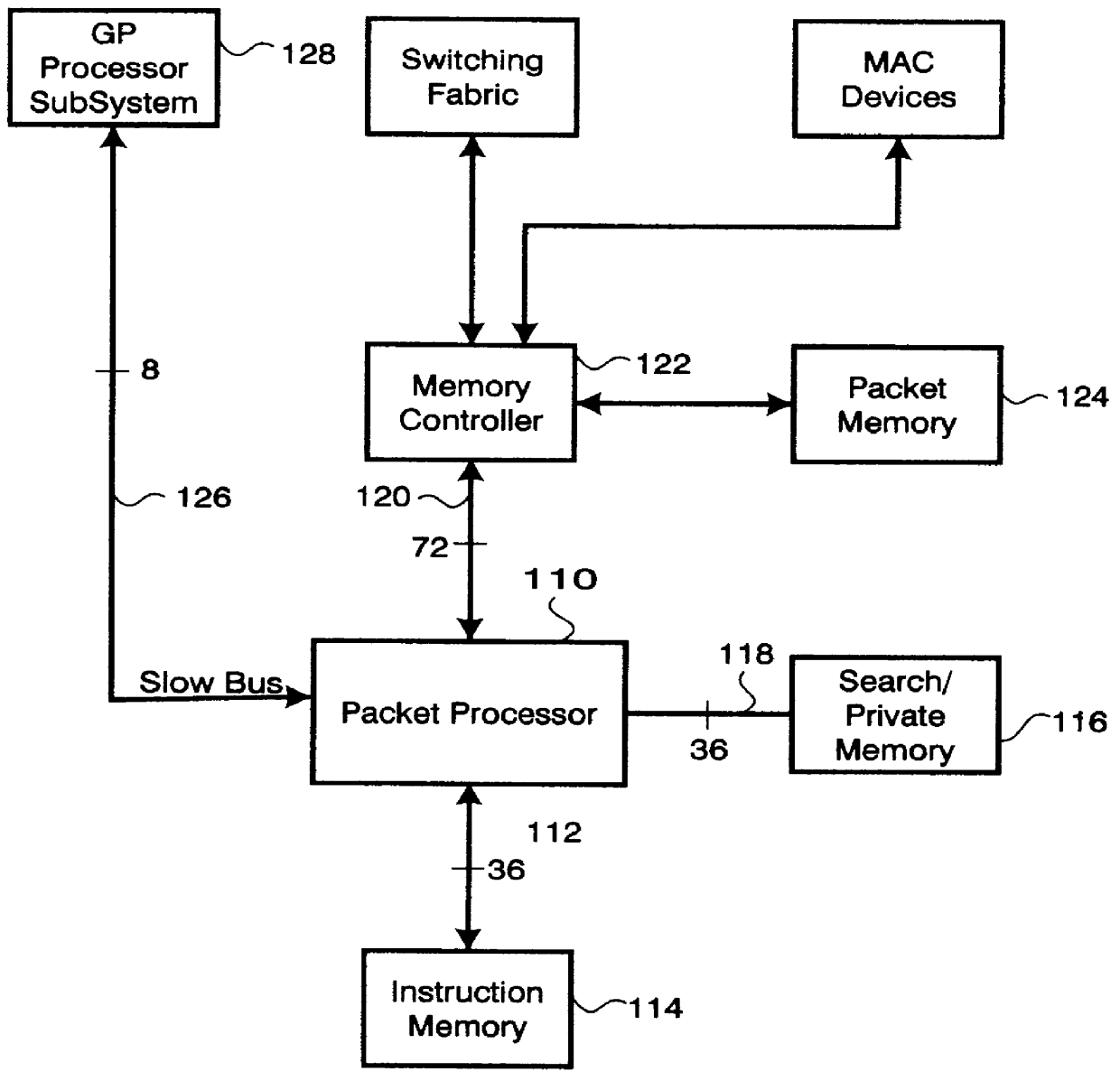
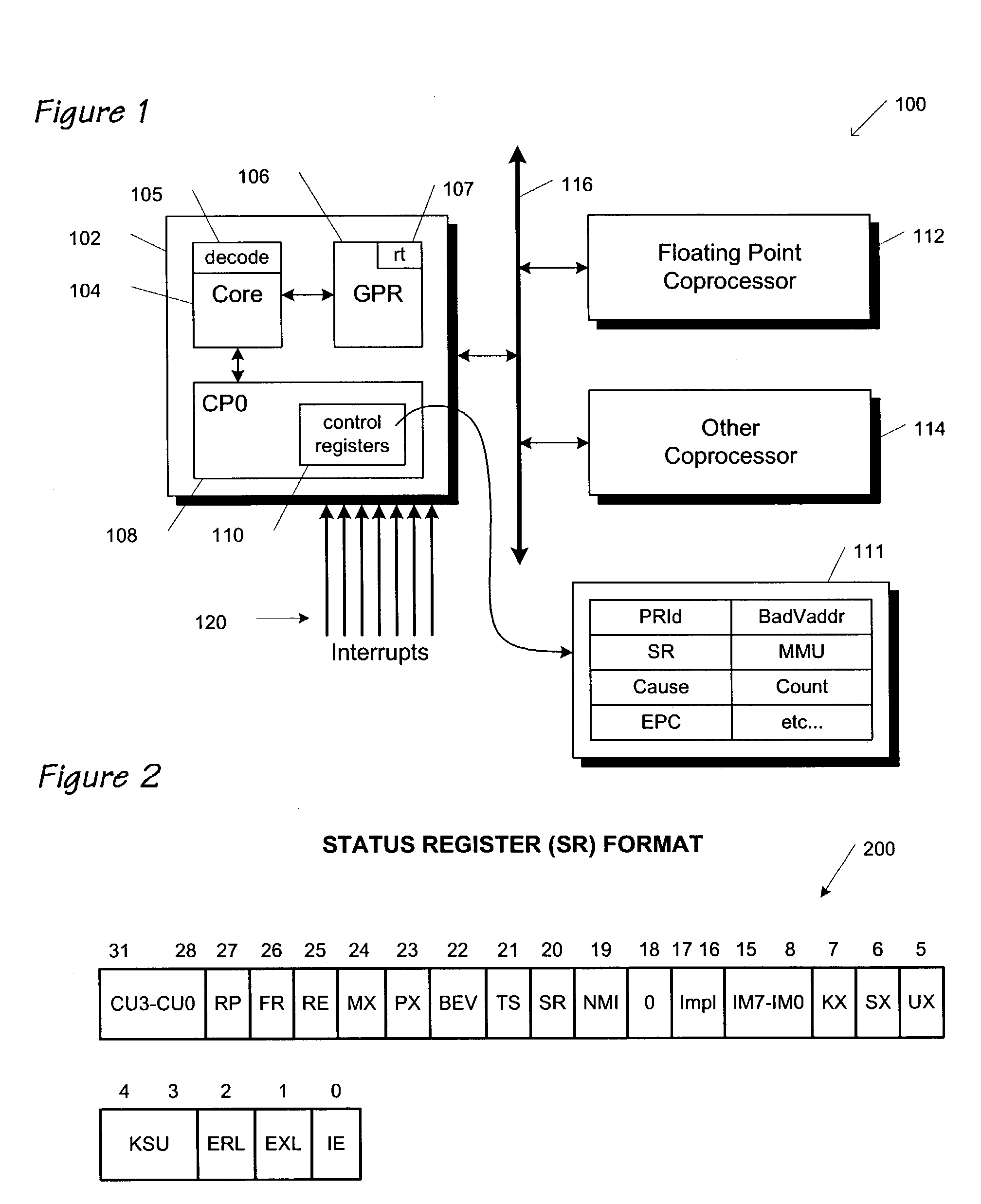
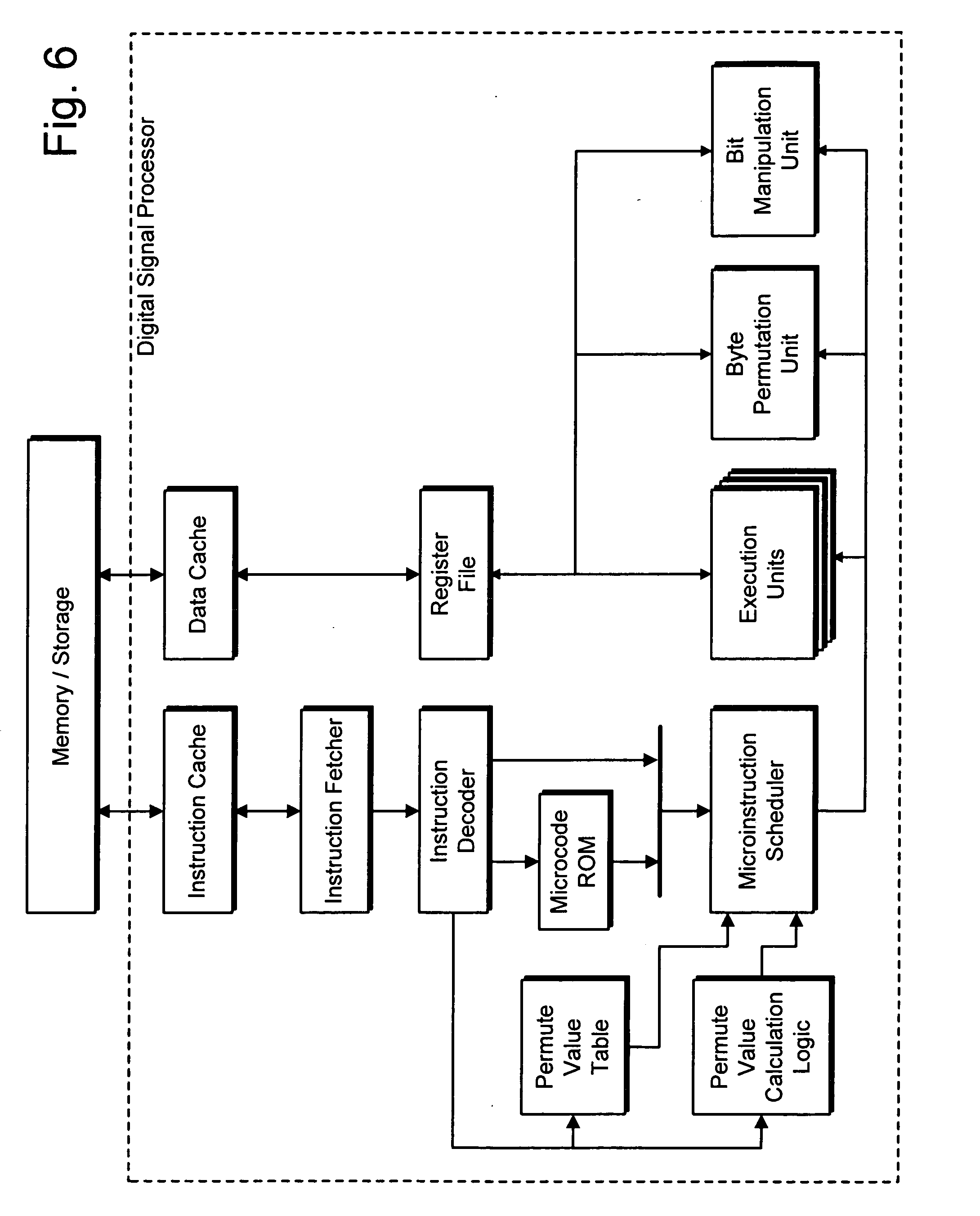
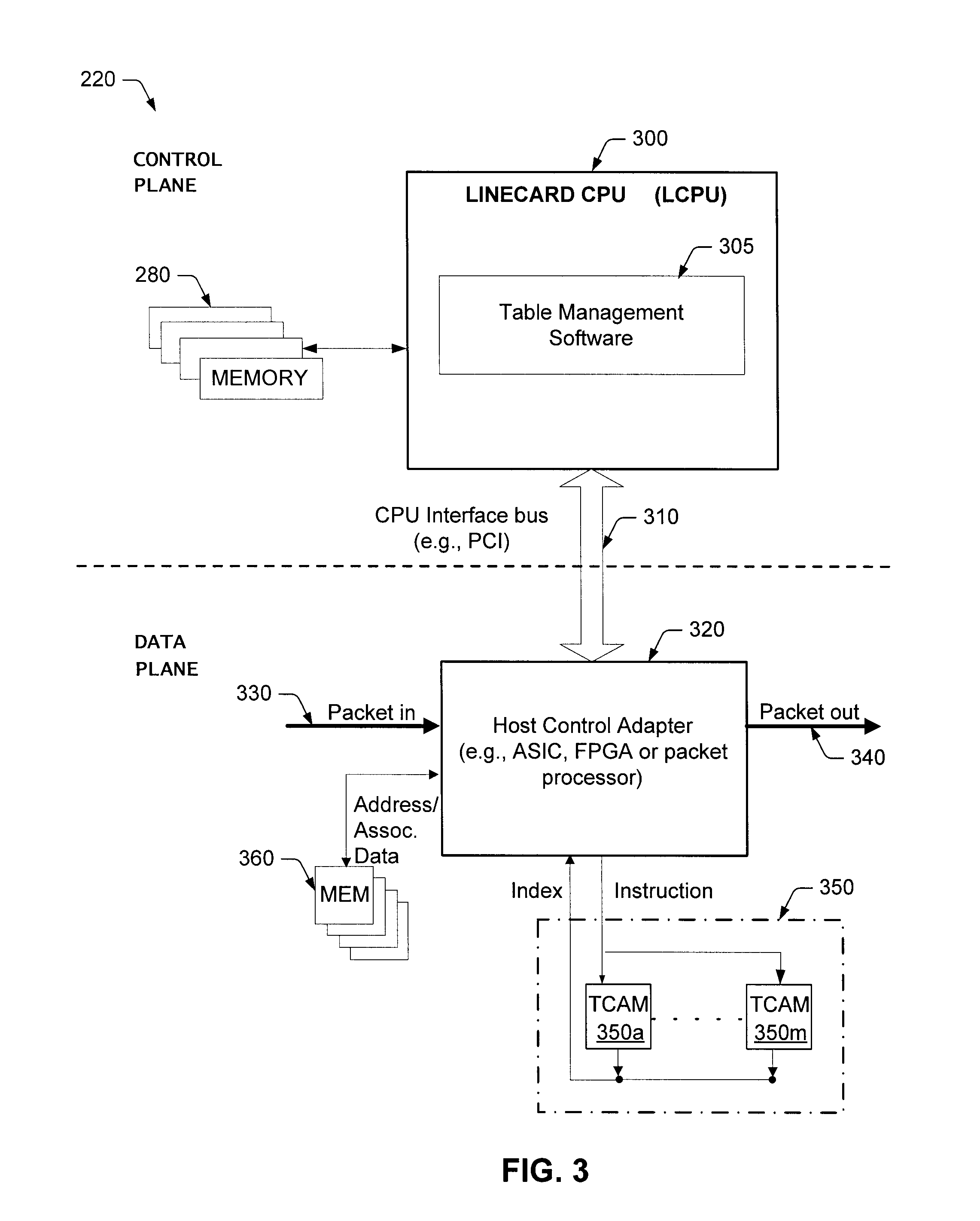
A processor (100) is provided that is a programmable fixed point digital signal processor (DSP) with variable instruction length, offering both high code density and easy programming. Architecture and instruction set are optimized for low power consumption and high efficiency execution of DSP algorithms, such as for wireless telephones, as well as pure control tasks. The processor includes an instruction buffer unit (106), a program flow control unit (108), an address / data flow unit (110), a data computation unit (112), and multiple interconnecting busses. Dual multiply-accumulate blocks improve processing performance. A memory interface unit (104) provides parallel access to data and instruction memories. The instruction buffer is operable to buffer single and compound instructions pending execution thereof. A decode mechanism is configured to decode instructions from the instruction buffer. The use of compound instructions enables effective use of the bandwidth available within the processor. A soft dual memory instruction can be compiled from separate first and second programmed memory instructions. Instructions can be conditionally executed or repeatedly executed. Bit field processing and various addressing modes, such as circular buffer addressing, further support execution of DSP algorithms. The processor includes a multistage execution pipeline with pipeline protection features. Various functional modules can be separately powered down to conserve power. The processor includes emulation and code debugging facilities with support for cache analysis.
Owner:TEXAS INSTR INC
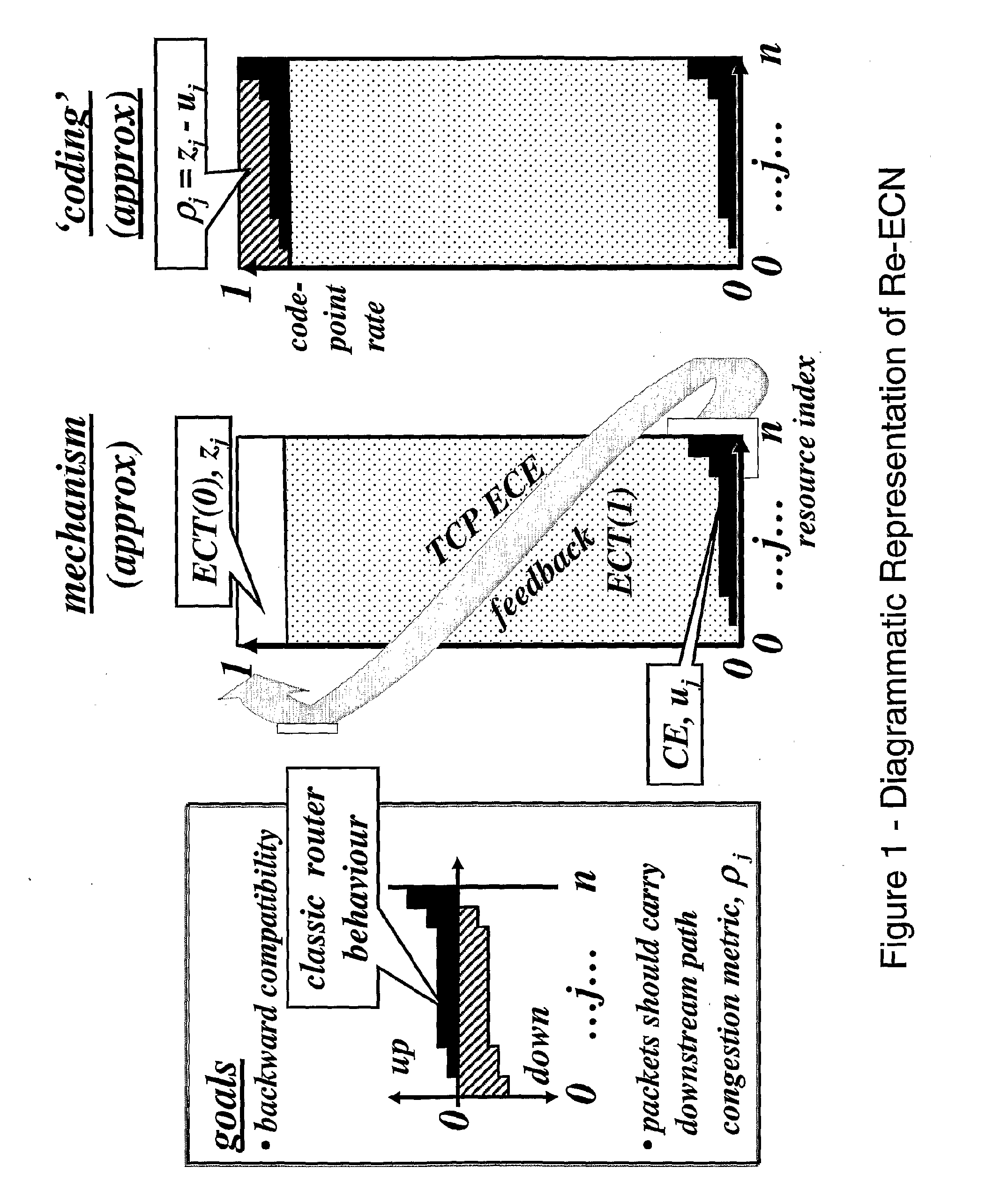
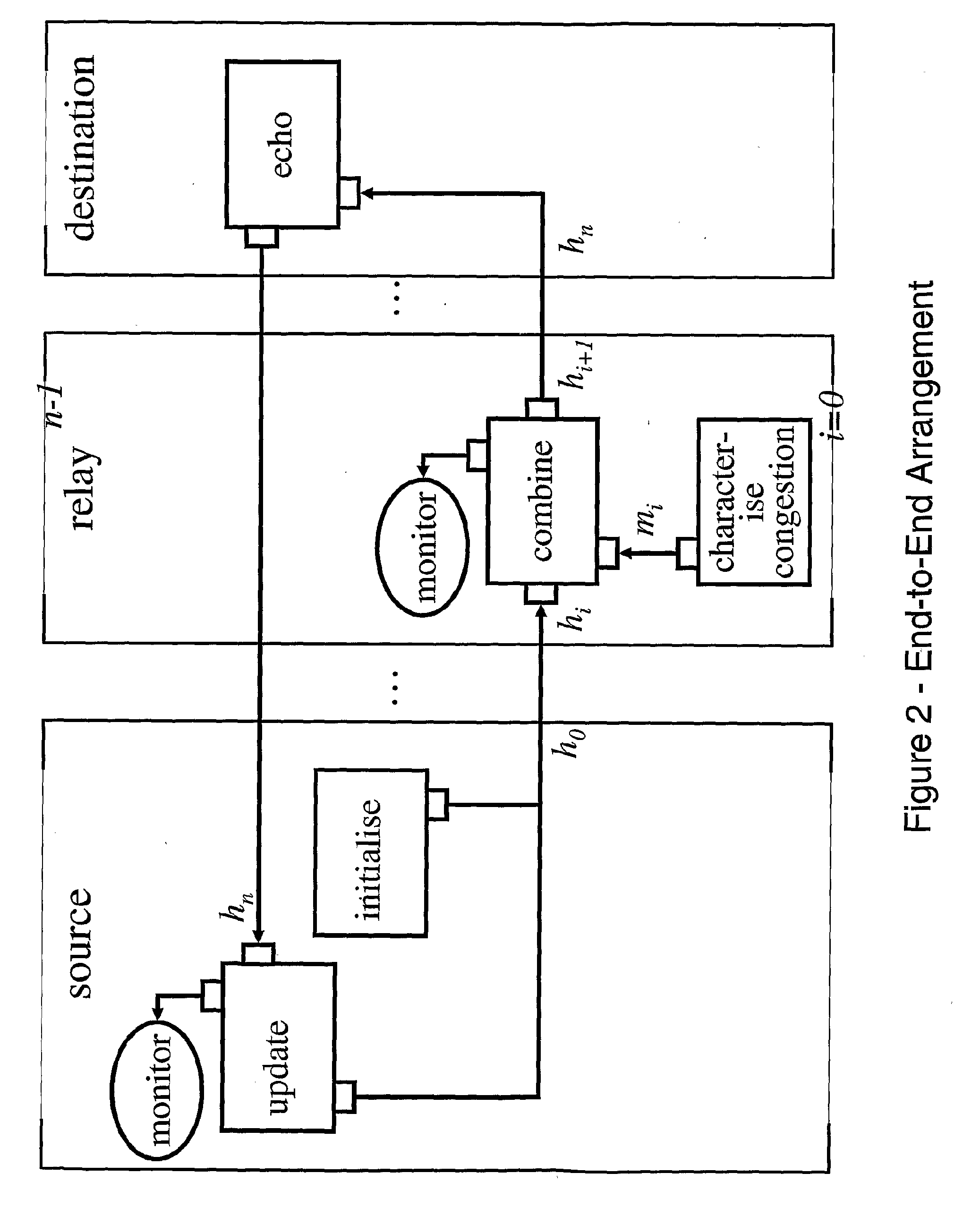
Rotationally invariant non-coherent burst coding
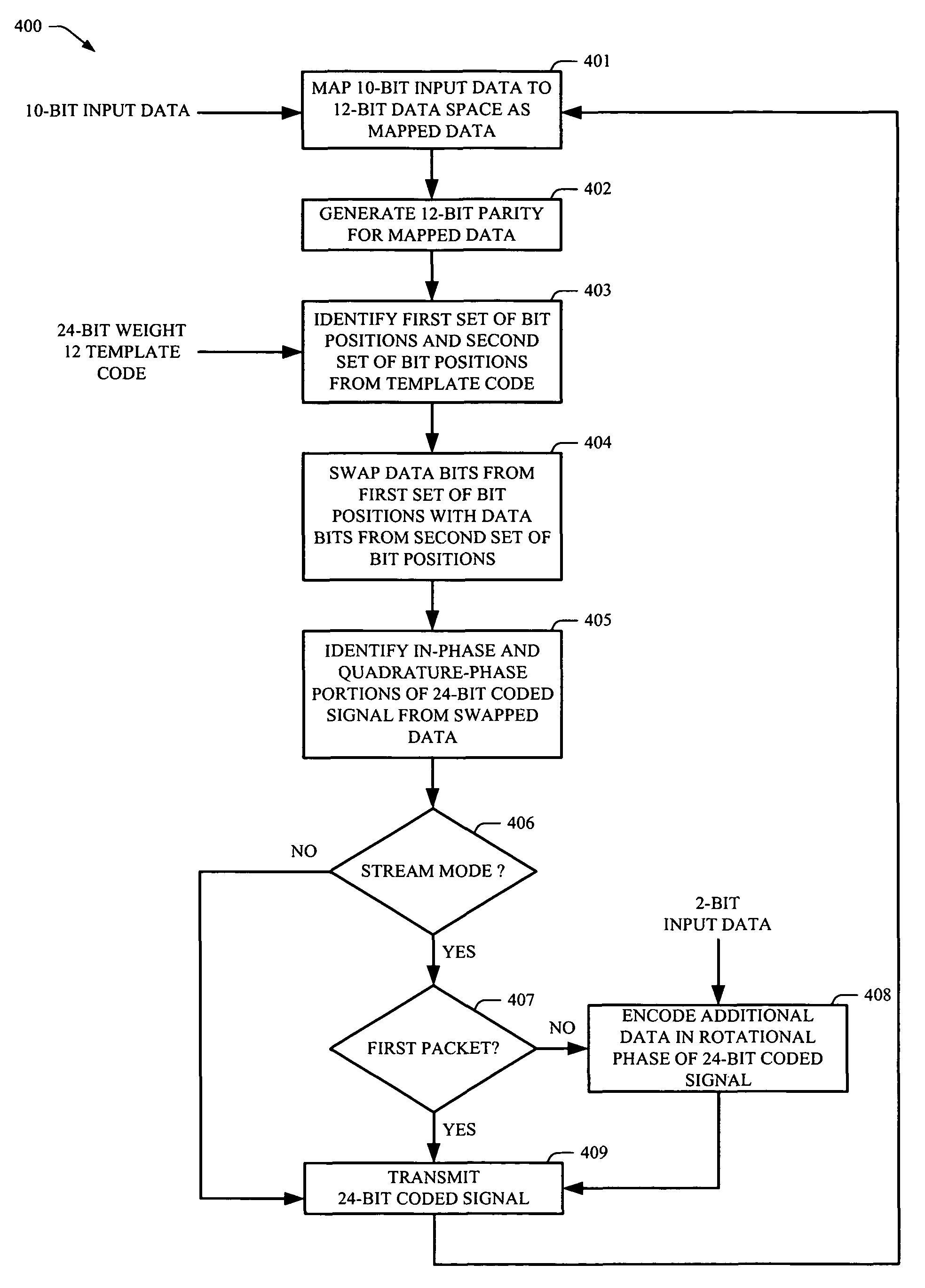
ActiveUS7779332B2Error correction/detection using block single space codingError preventionBit field24-bit
Owner:ALFRED E MANN FOUND FOR SCI RES
Dynamic Real-Time Tiered Client Access
ActiveUS20070174809A1Facilitate data exchangePower managementEnergy efficient ICTBit fieldClient-side
Wireless client devices within a wireless network exchange data with other wireless devices during particular time slots determined by the network. More particularly, the system generates and wirelessly broadcasts synchronization information to the client devices, where the synchronization information contains individual masks to be applied to bit fields of individual client devices, where said time slots are determined in accordance with the masked bit fields. In such a manner, client devices can be coordinated to communicate with the system in a dynamic real-time tiered manner.
Owner:PROXENSE
Magnetic disk having efficiently stored WRRO compensation value redundancy information and method for using the redundancy information
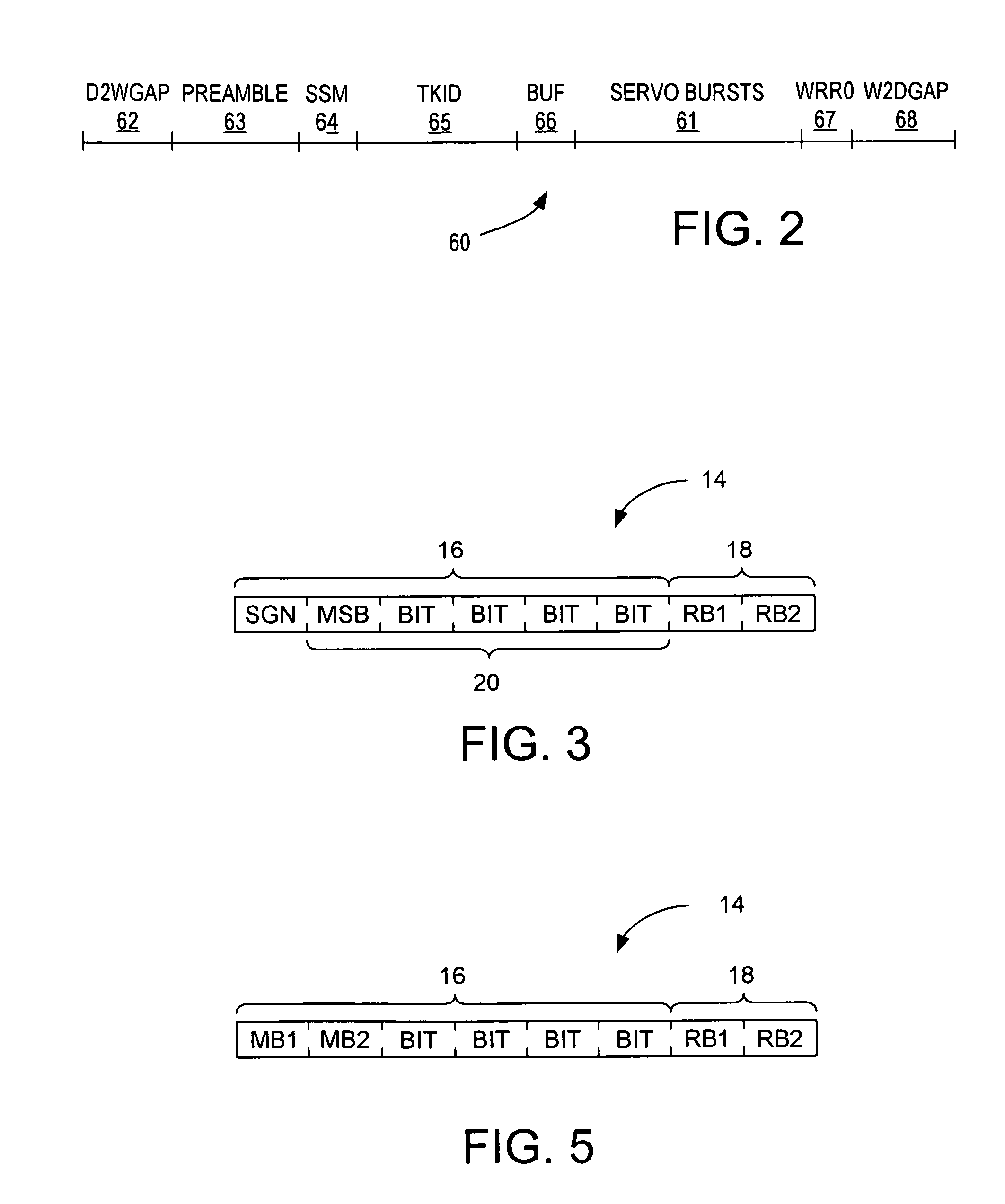
InactiveUS7580212B1Record information storageAlignment for track following on disksBit fieldSign bit
The present invention may be embodied in a magnetic disk, of a disk drive, having eight-bit fields storing wedge repeatable runout (WRRO) compensation values and redundancy information. The WRRO compensation value of each field includes a six-bit binary value of which five bits represent a compensation magnitude and one bit represents a sign bit indicating a compensation direction. The redundancy information of each field has a first bit based on the sign bit.
Owner:WESTERN DIGITAL TECH INC
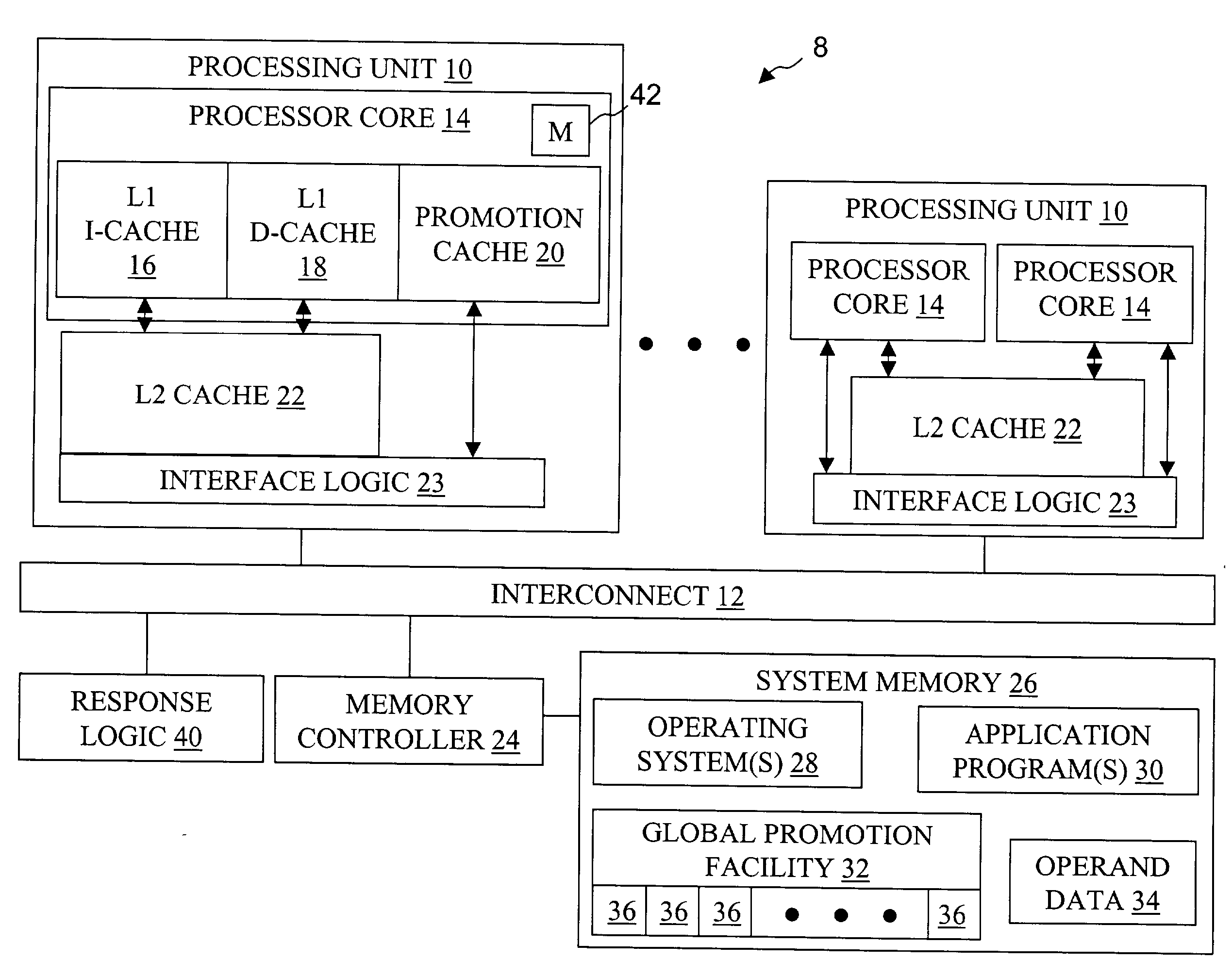
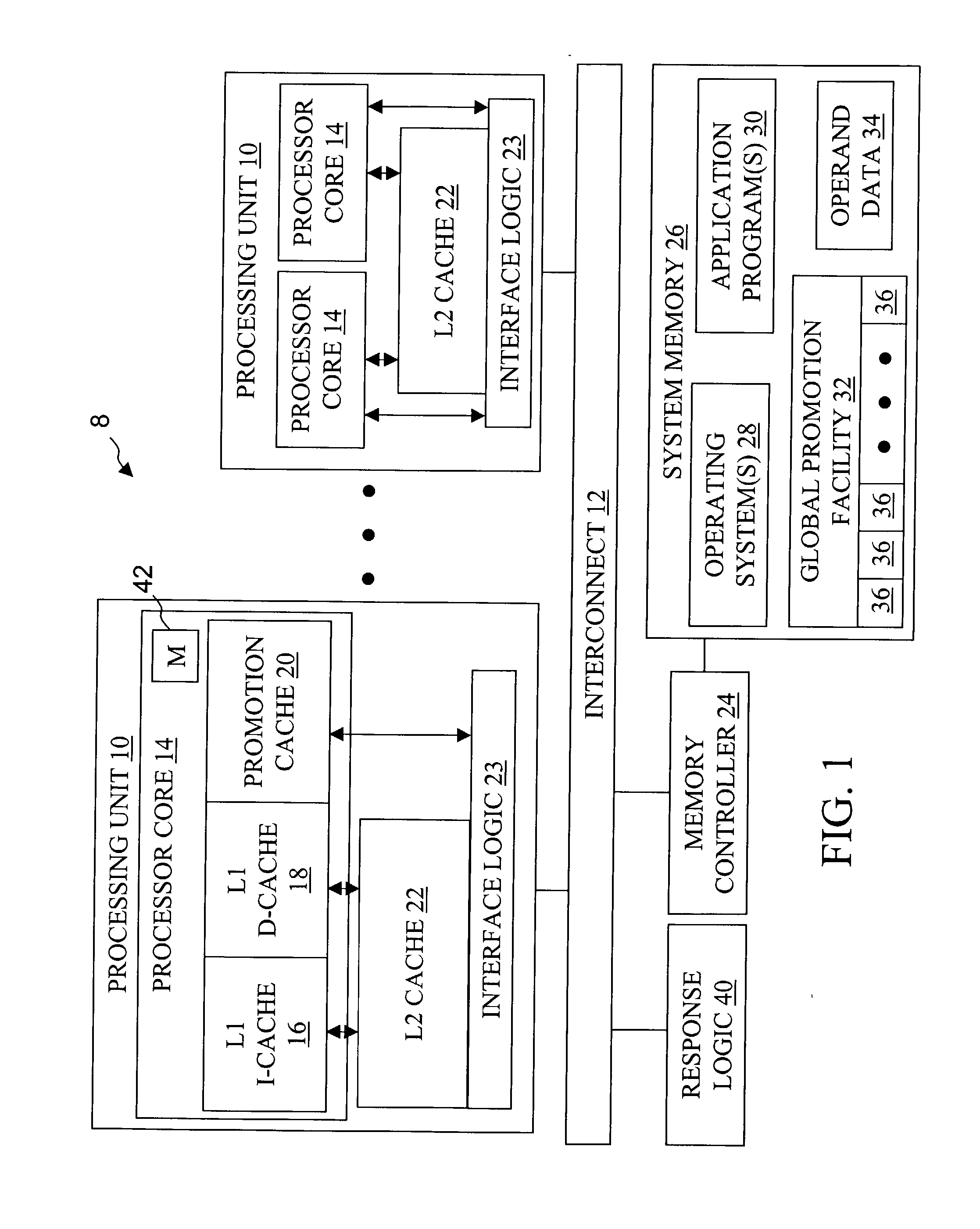
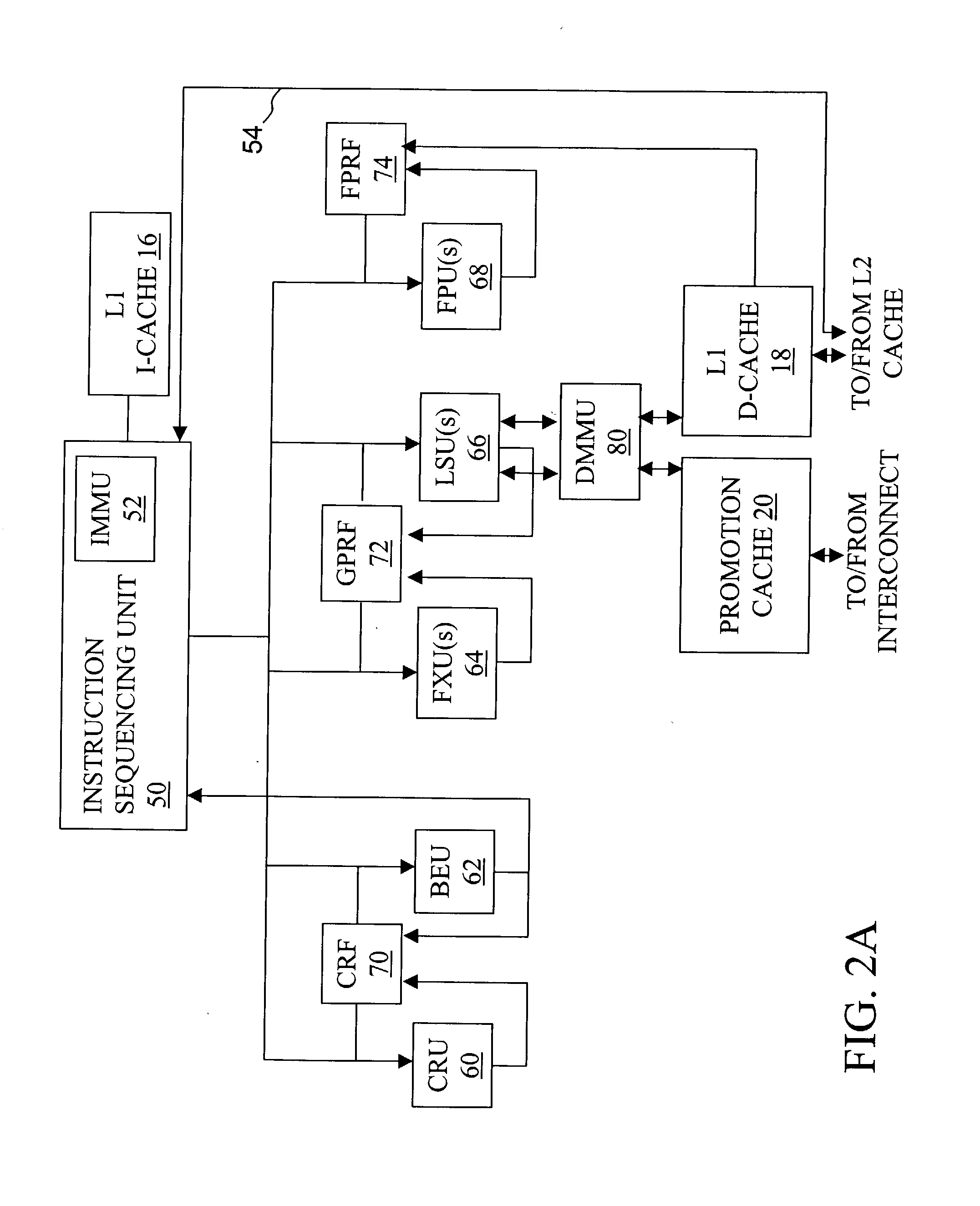
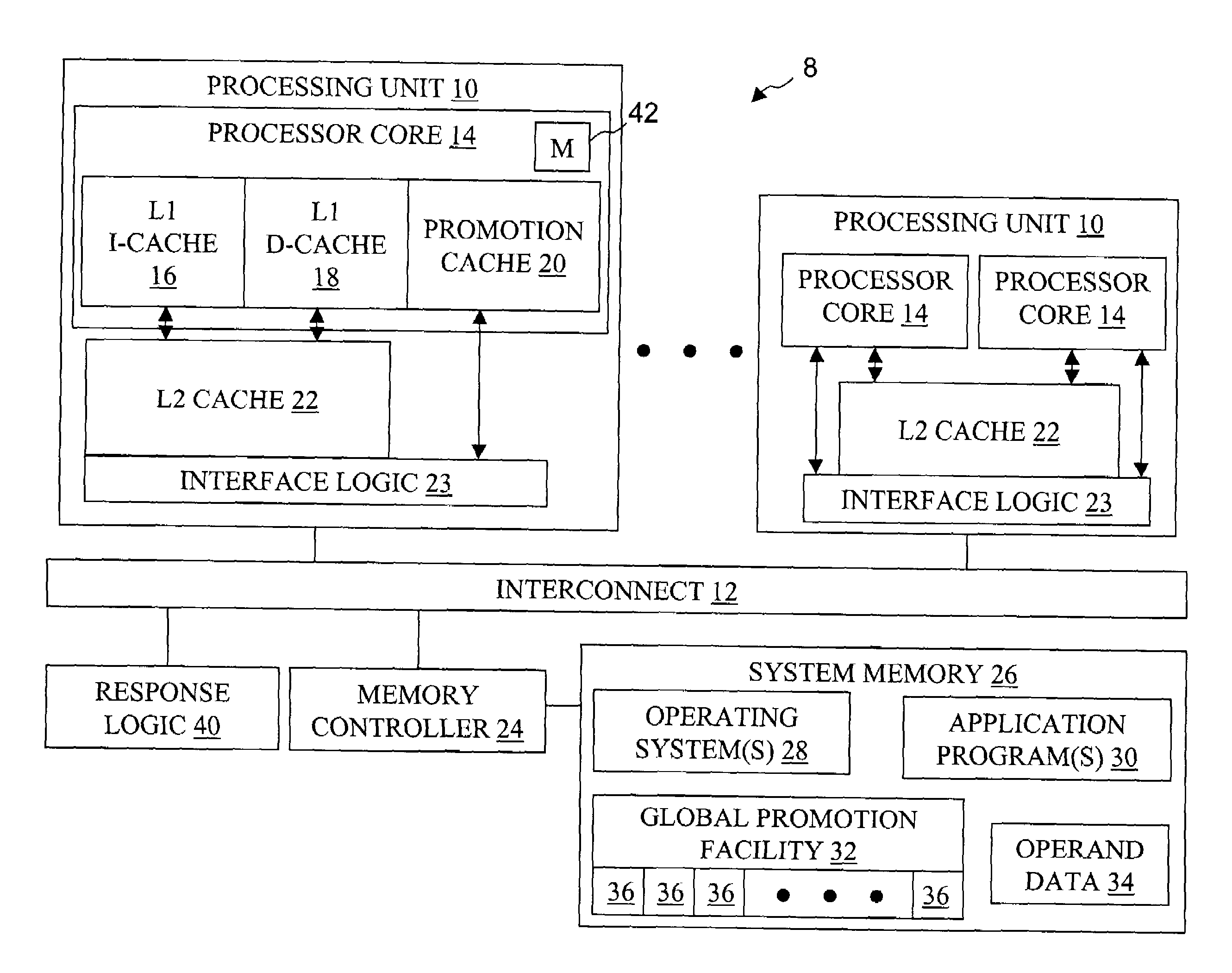
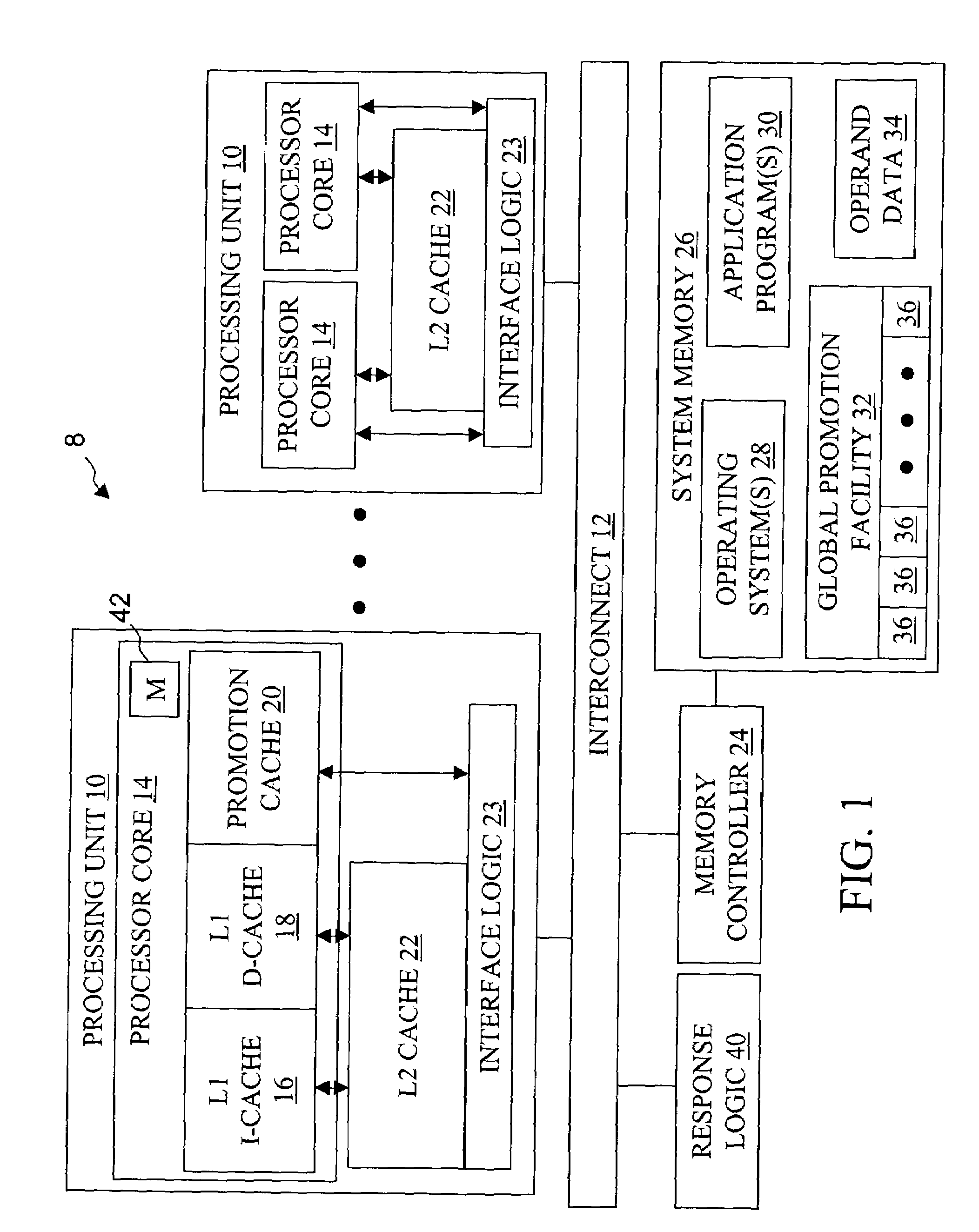
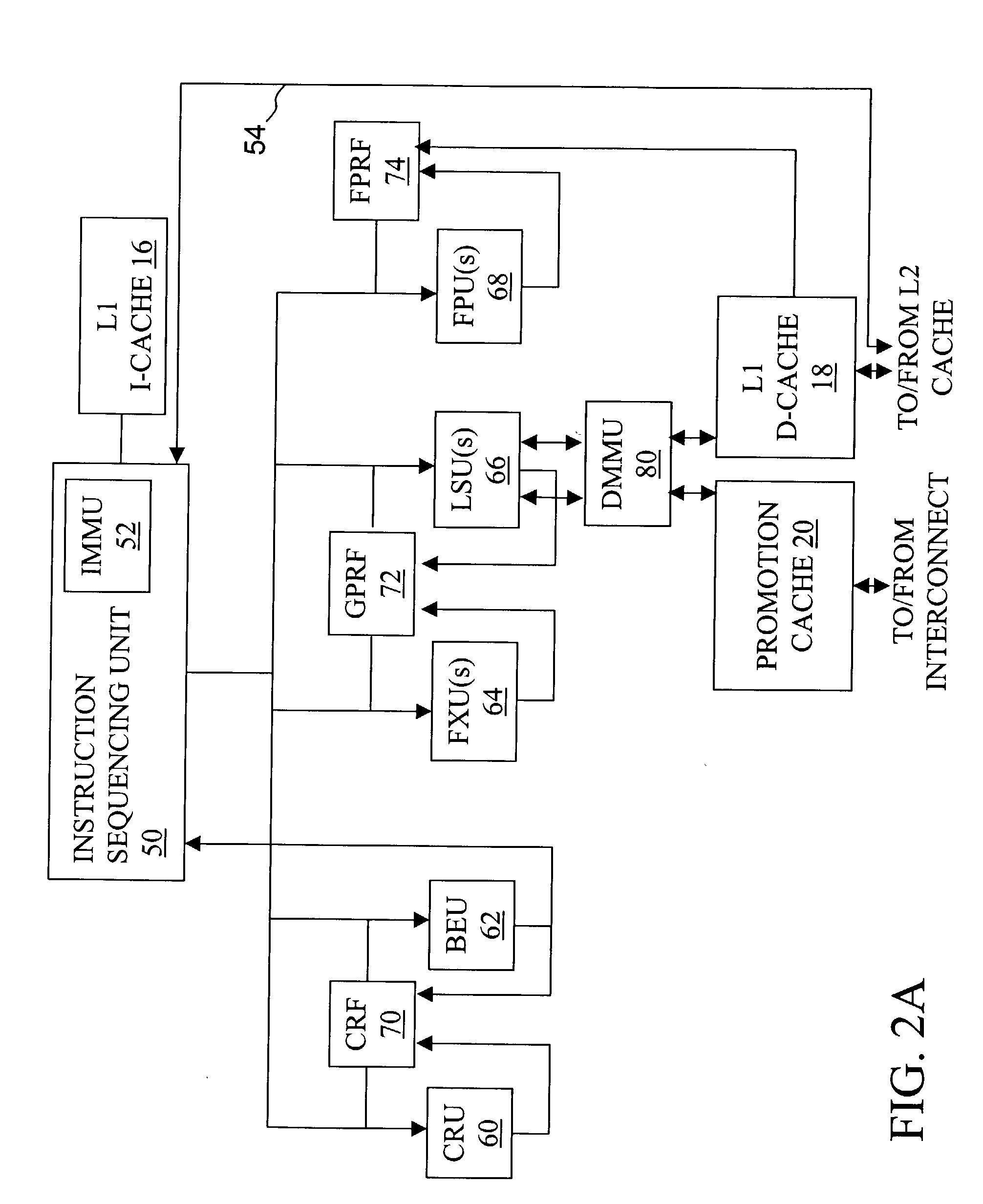
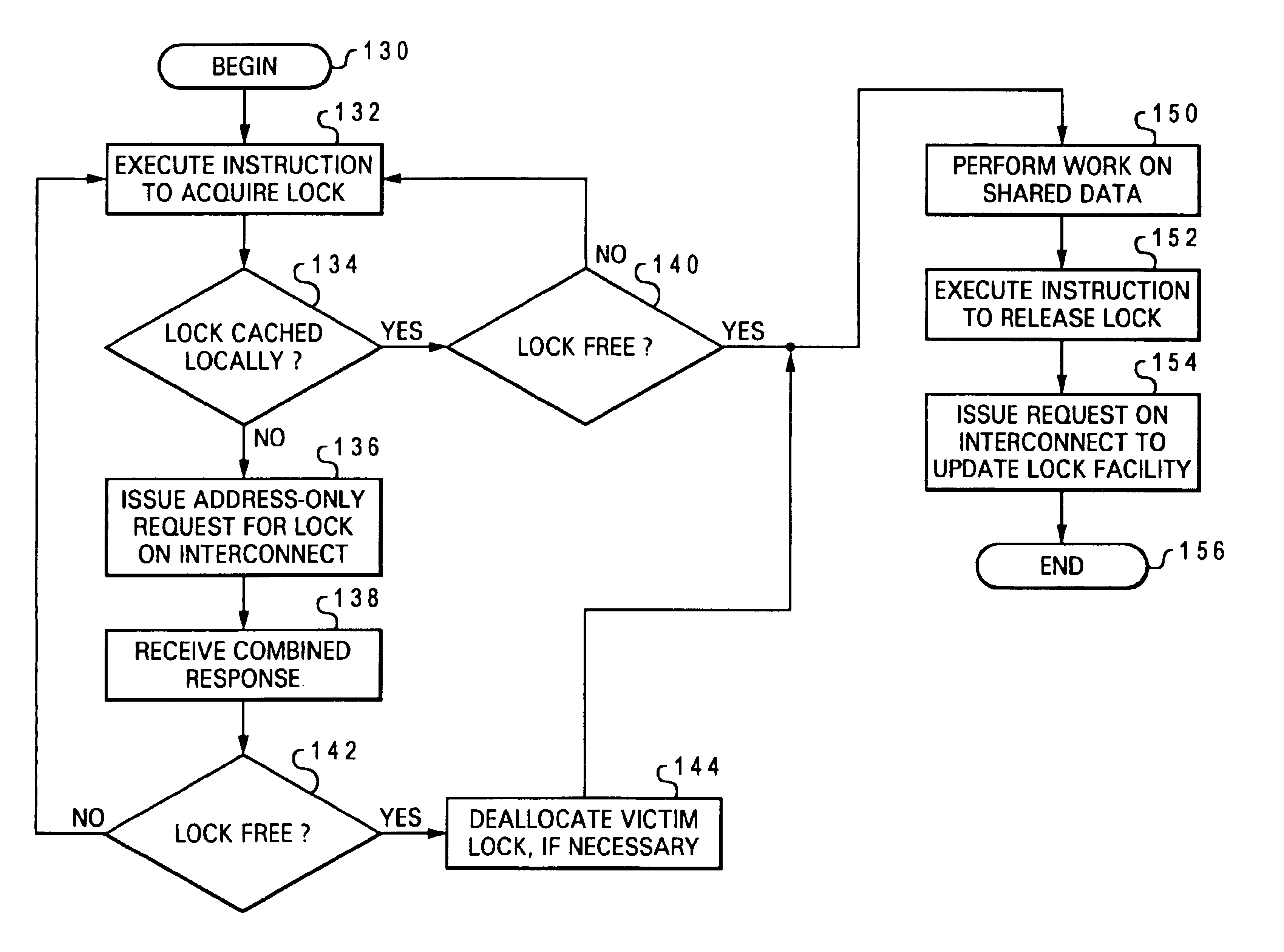
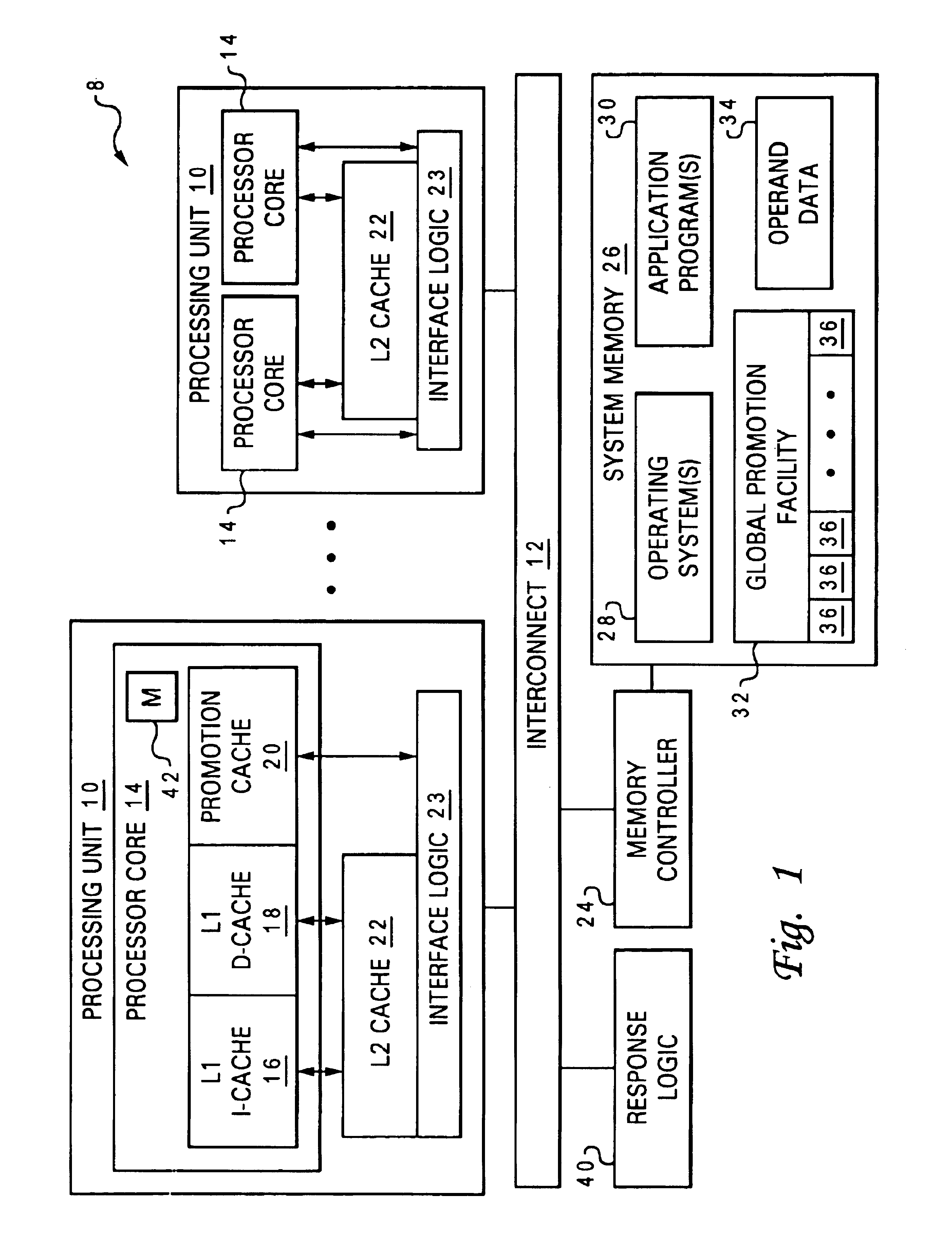
High speed promotion mechanism suitable for lock acquisition in a multiprocessor data processing system
InactiveUS20040073909A1Program synchronisationUnauthorized memory use protectionData processing systemBit field
A multiprocessor data processing system includes a plurality of processors coupled to an interconnect and to a global promotion facility containing at least one promotion bit field. A first processor executes a high speed instruction sequence including a load-type instruction to acquire a promotion bit field within the global promotion facility exclusive of at least a second processor. The request may be made visible to all processors coupled to the interconnect. In response to execution of the load-type instruction, a register of the first processor receives a register bit field indicating whether or not the promotion bit field was acquired by execution of the load-type instruction. While the first processor holds the promotion bit field exclusive of the second processor, the second processor is permitted to initiate a request on the interconnect. Advantageously, promotion bit fields are handled separately from data, and the communication of promotion bit fields does not entail the movement of data cache lines.
Owner:IBM CORP
Hardware support for instruction set emulation
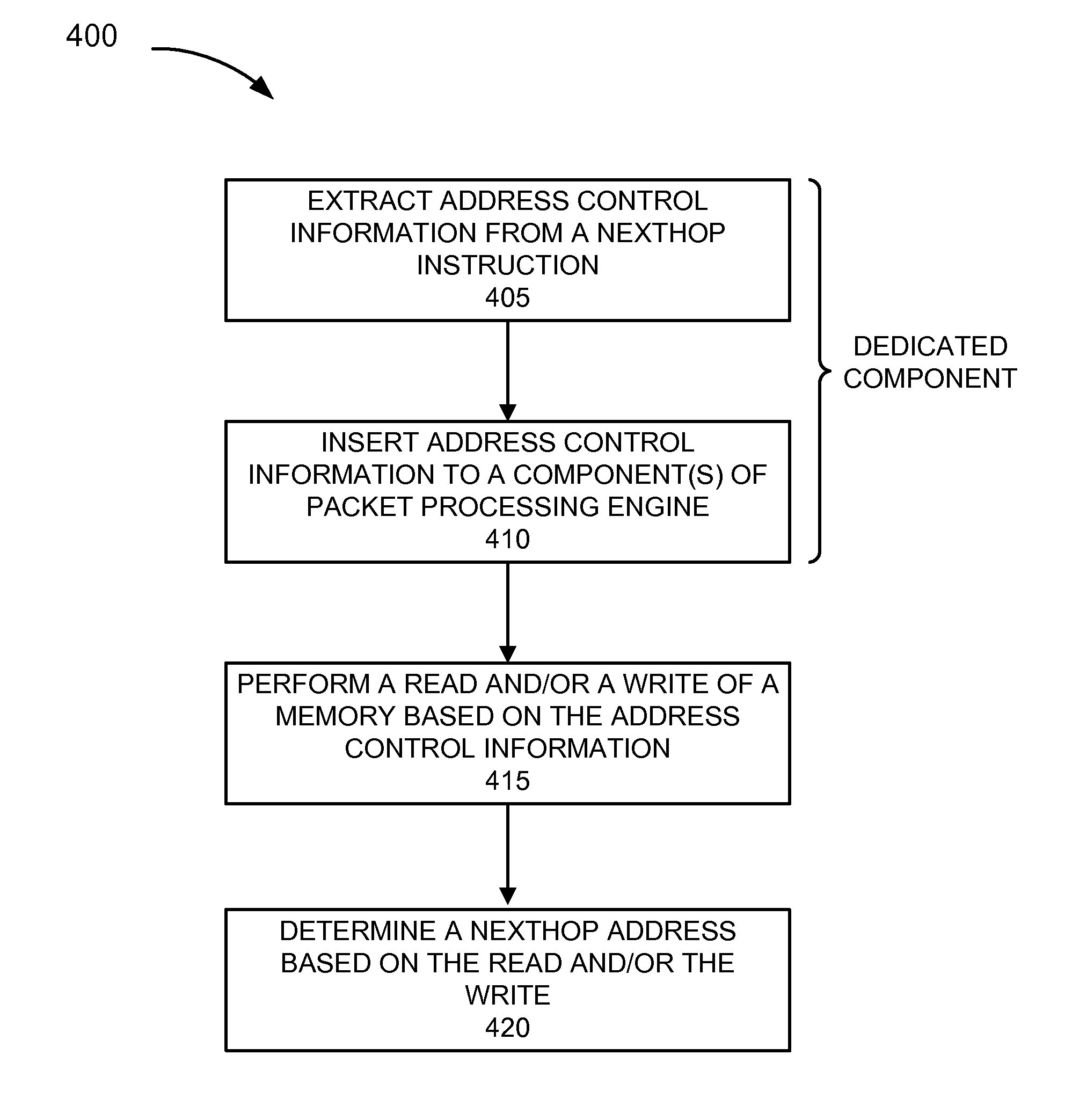
ActiveUS8069023B1Instruction analysisAnalogue computers for electric apparatusBit fieldNetwork addressing
A method for emulating a nexthop instruction in microcode with the assistance of dedicated hardware to extract read and write addressing from the nexthop instruction instead of performing this operation in microcode. A method for emulating a nexthop instruction in microcode with the assistance of dedicated hardware to compare a nexthop read address to a special value and to indicate whether the nexthop read address matches the special value, instead of performing this operation in microcode. A method for determining a network address by performing a single extraction of bit fields of a tree instruction to allow multiple tree search processes to be performed.
Owner:JUMIPER NETWORKS INC
Control of Data Flow in a Network
ActiveUS20080304413A1Easy networkingMinimize the numberError preventionFrequency-division multiplex detailsBit fieldData stream
Owner:BRITISH TELECOMM PLC
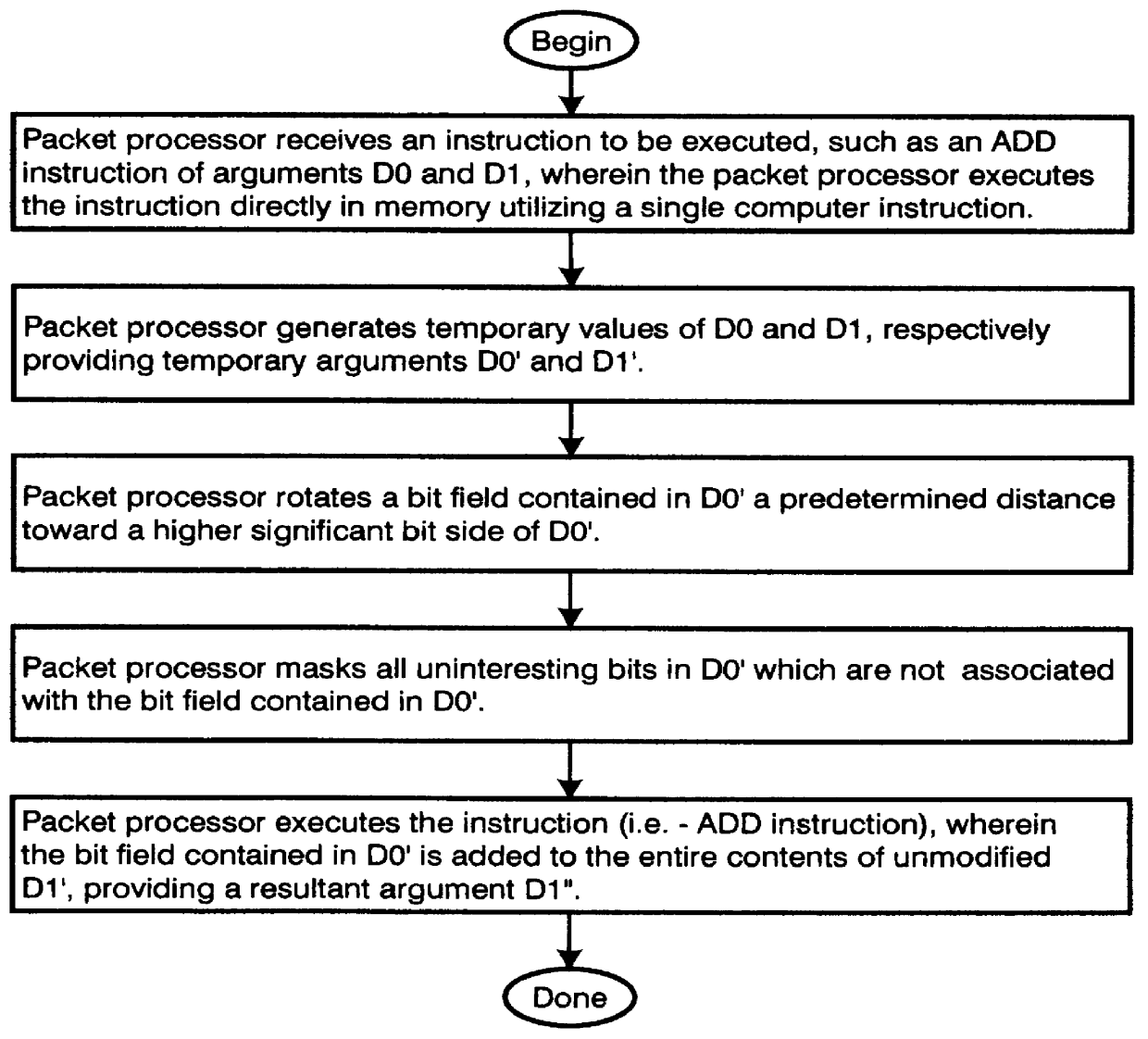
Method and apparatus for manipulation of bit fields directly in a memory source
InactiveUS6061783ADigital computer detailsSpecific program execution arrangementsBit fieldForward masking
A method and apparatus allowing for the direct manipulation of bit fields contained in a memory source. Logic circuitry performs a process wherein bit segments and bit fields contained in respective data strings are manipulated or moved along respective data strings, wherein the bit fields may not be aligned in accordance with data bytes contained in a respective data string. Additionally, the logic circuitry may mask any bits not associated with either the bit segment and the bit field in the respective data strings. The logic circuitry performs an arithmetic operation, wherein the masked respective data strings are arithmetically coupled to each other providing a resultant data string, the resultant data string containing the arithmetic result of the bit segment and the bit field segment as a bit field result. The logic circuitry can pass forward masks of the bit field result and any partially modified byte(s) instead of an entire mask of the respective data strings.
Owner:NORTEL NETWORKS LTD
High speed promotion mechanism suitable for lock acquisition in a multiprocessor data processing system
InactiveUS7213248B2Reduce percentageReduce the amount requiredProgram synchronisationUnauthorized memory use protectionData processing systemBit field
A multiprocessor data processing system includes a plurality of processors coupled to an interconnect and to a global promotion facility containing at least one promotion bit field. A first processor executes a high speed instruction sequence including a load-type instruction to acquire a promotion bit field within the global promotion facility exclusive of at least a second processor. The request may be made visible to all processors coupled to the interconnect. In response to execution of the load-type instruction, a register of the first processor receives a register bit field indicating whether or not the promotion bit field was acquired by execution of the load-type instruction. While the first processor holds the promotion bit field exclusive of the second processor, the second processor is permitted to initiate a request on the interconnect. Advantageously, promotion bit fields are handled separately from data, and the communication of promotion bit fields does not entail the movement of data cache lines.
Owner:INT BUSINESS MASCH CORP
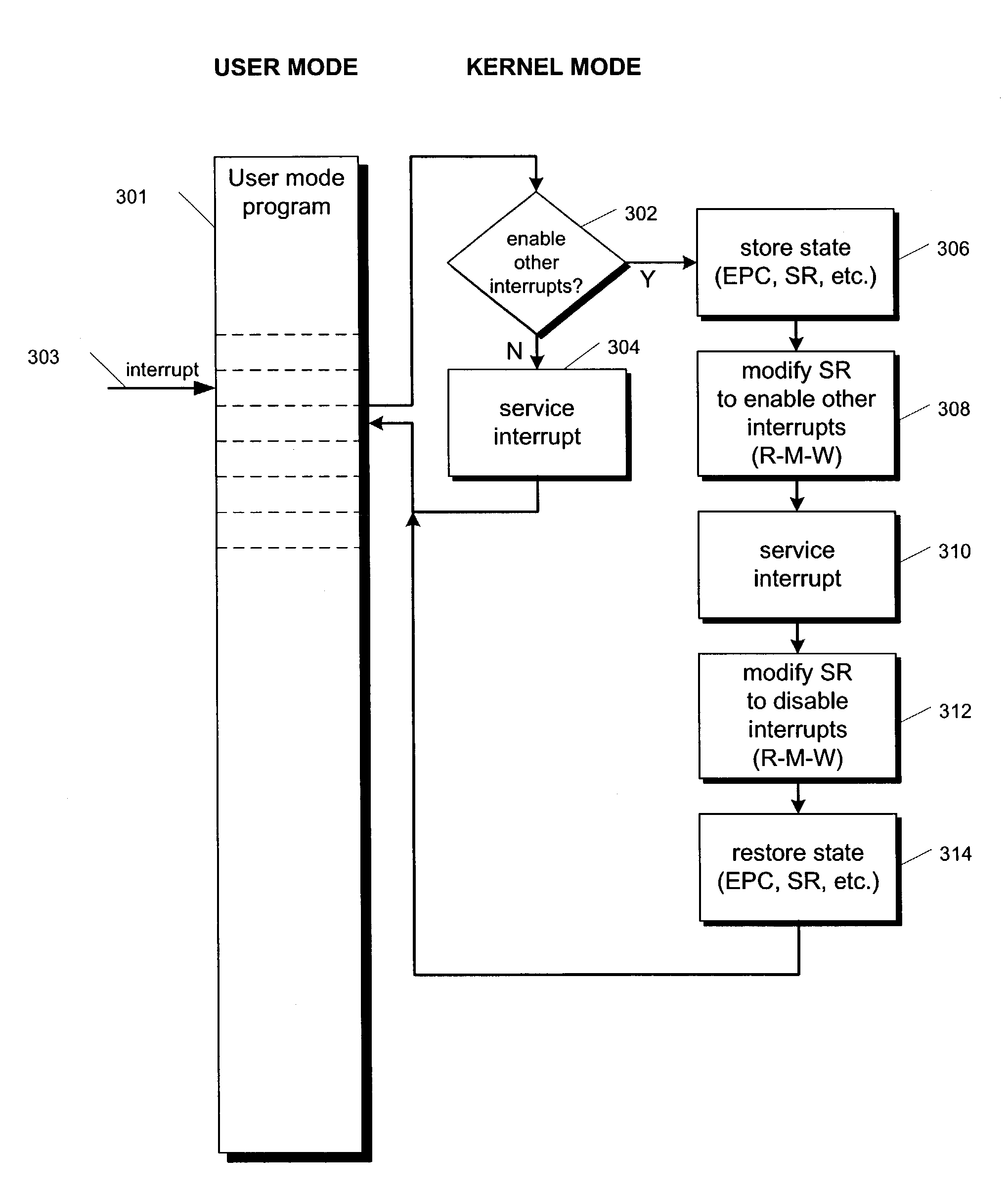
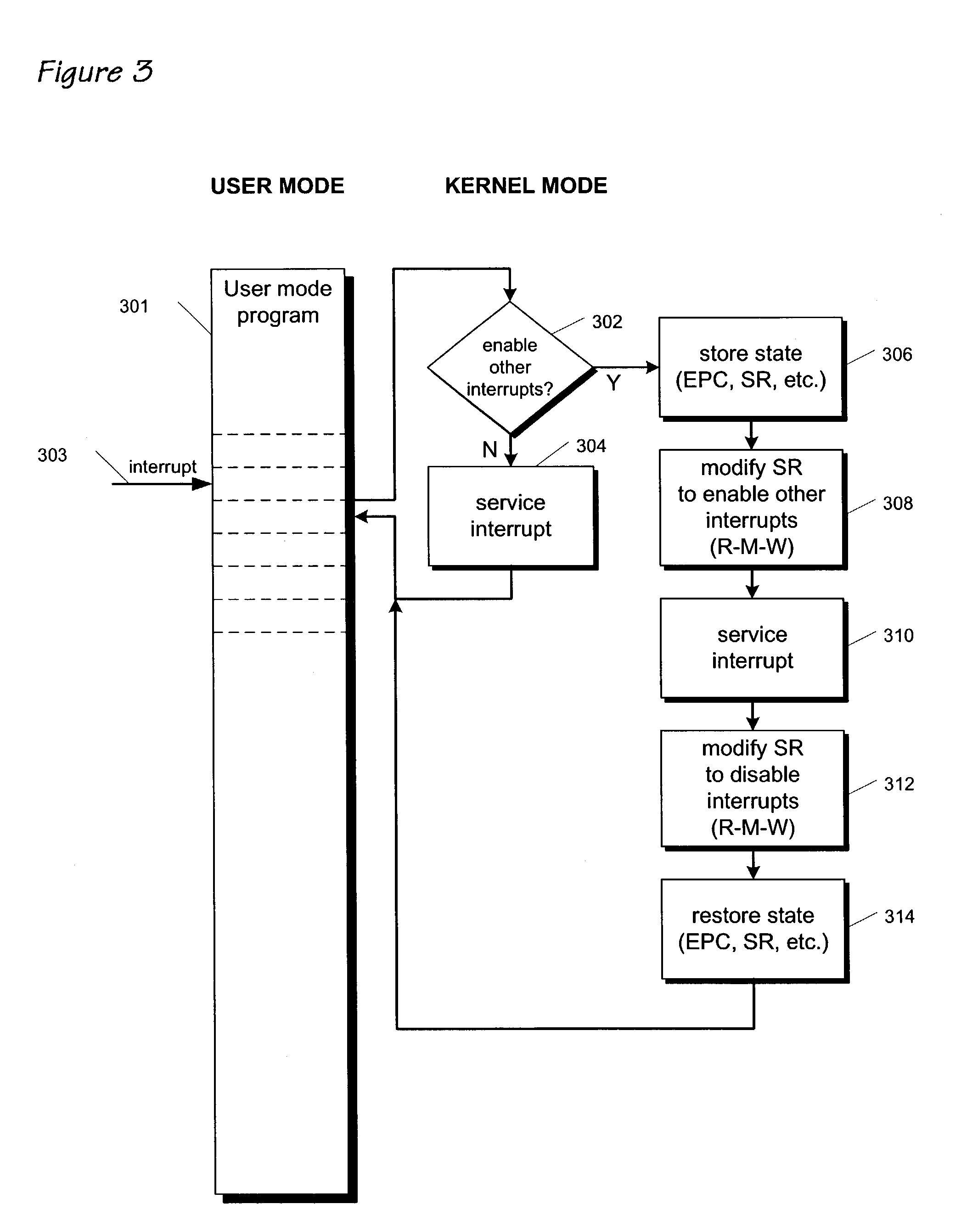
Instruction encoding for system register bit set and clear
ActiveUS7634638B1Digital computer detailsSpecific program execution arrangementsGeneral purposeComputer architecture
An instruction encoding architecture is provided for a microprocessor to allow atomic modification of privileged architecture registers. The instructions include an opcode that designates to the microprocessor that the instructions are to execute in privileged (kernel) state only, and that the instructions are to communicate with privileged control registers, a field for designating which of a plurality of privileged architecture registers is to be modified, a field for designating which bit fields within the designated privileged architecture register is to be modified, and a field to designate whether the designated bit fields are to be set or cleared. The instruction encoding allows a single instruction to atomically set or clear bit fields within privileged architecture registers, without reading the privileged architecture registers into a general purpose register. In addition, the instruction encoding allows a programmer to specify whether the previous content of a privileged architecture register is to be saved to a general purpose register during the atomic modification.
Owner:MIPS TECH INC
Method, apparatus and system for acquiring a global promotion facility utilizing a data-less transaction
InactiveUS6829698B2Data processing applicationsProgram synchronisationData processing systemBit field
Owner:INT BUSINESS MASCH CORP
A coding method and device and system for multi-dimension address
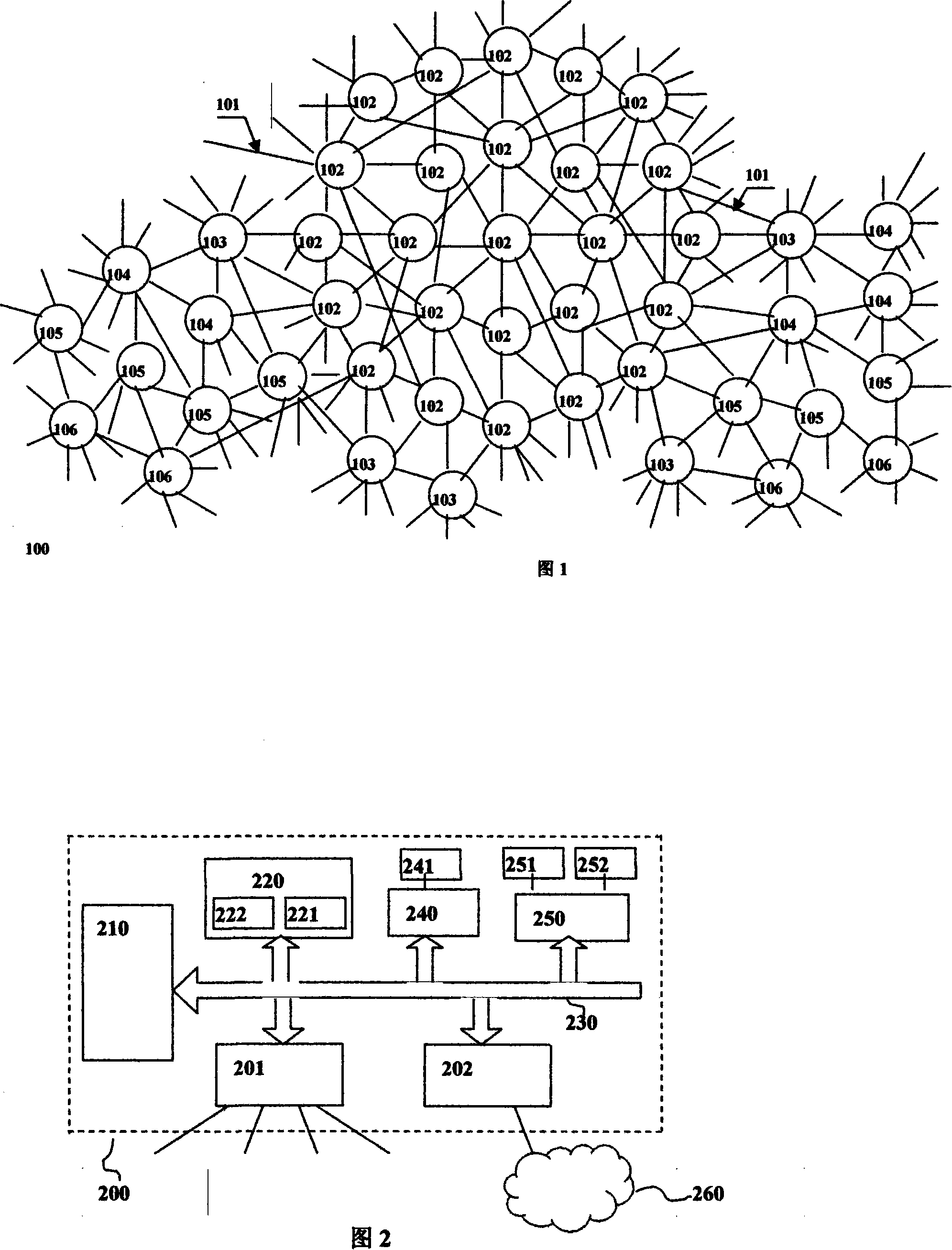
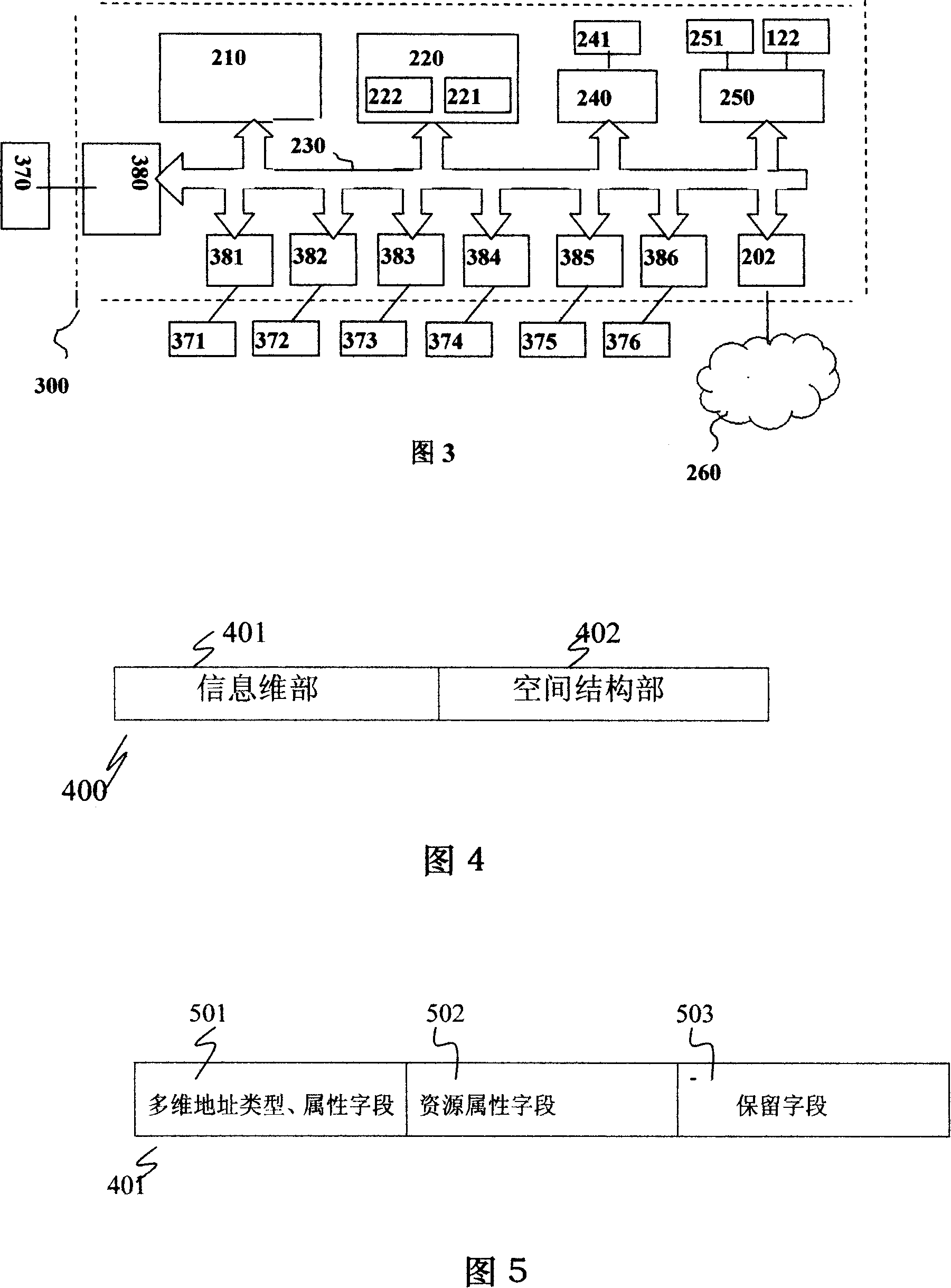
ActiveCN101123613AReduce transfer volumeFunction increaseTransmissionSpecial data processing applicationsBit fieldSpatial structure
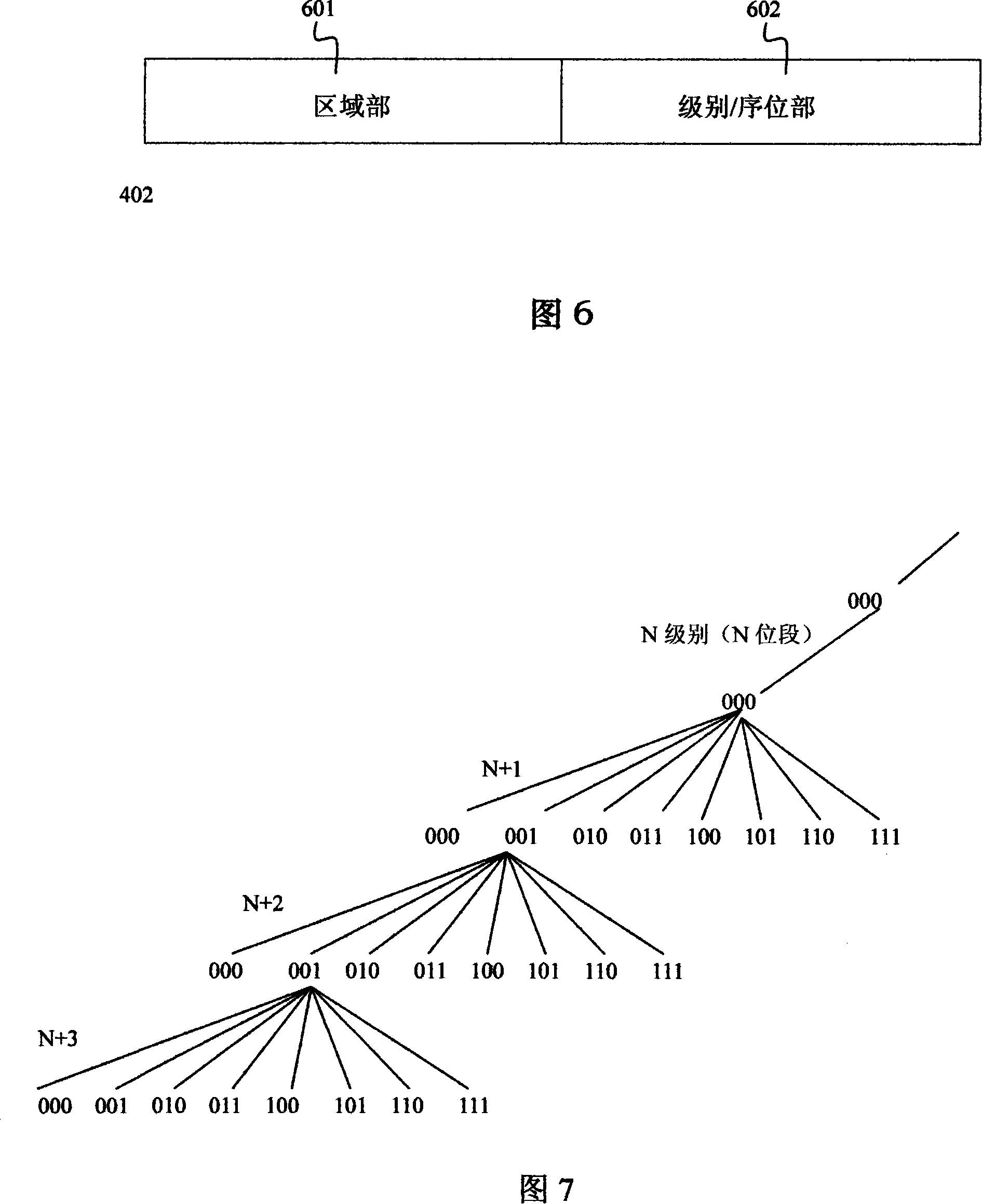
The invention discloses a method, a device and a system for addressing a multi-dimensional address. The invention comprises that through establishing a standard of format, grammar and type of the multi-dimensional address data, an effective multi-dimensional address format, which is generated by a first resource, can be output, input, processed and stored by the first and the second resources. The invention also comprises that the multi-dimensional address is defined by a binary digit series identifier, and the length of the binary digit series identifier is an arbitrary digit number from 1 bit to 1536 bit. An information dimension part is included in the multi-dimensional address through the bit segment division; the invention comprises that the object and attribute data is constructed through the bit, the bit segment and the data in the information dimension part; a virtual space structural part is also included in the multi-dimensional address; the invention comprises that the space structure and relation data of the object and attribute data is constructed through the bit, and the bit segment and the data in the virtual space structural part. The invention also comprises that each bit segment is seperated by a symbol; each bit segment carries out an automatic conversion of carry counting system; a leading zero of each bit segment is compressed; and the zero of an all -zerocontinuous bit segment in the multi-dimensional address carries out zero compression.
Owner:张建中
Method and system for sharing a computer resource between instruction threads of a multi-threaded process
InactiveUS7131125B2Program initiation/switchingData switching by path configurationComputer resourcesExternal storage
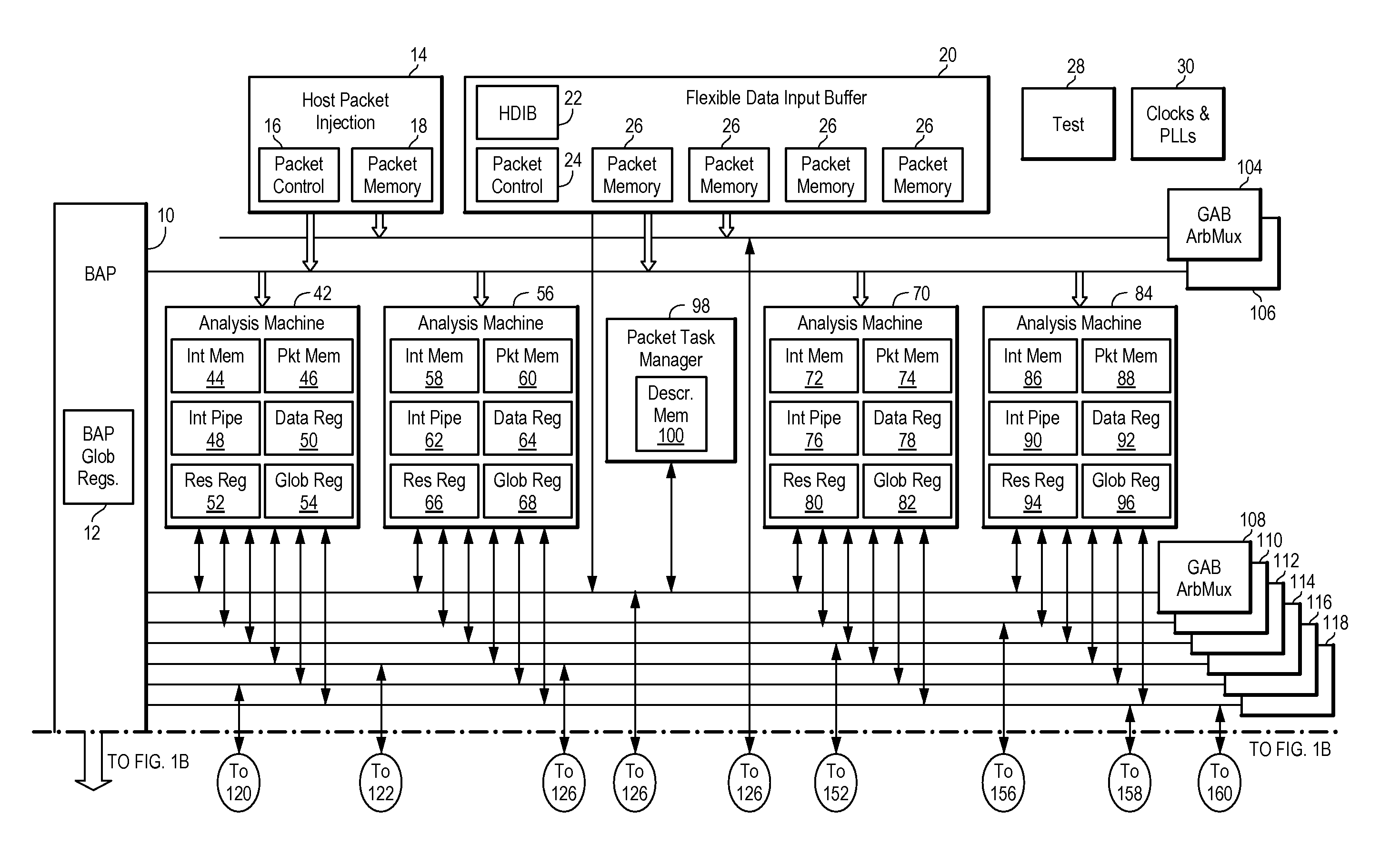
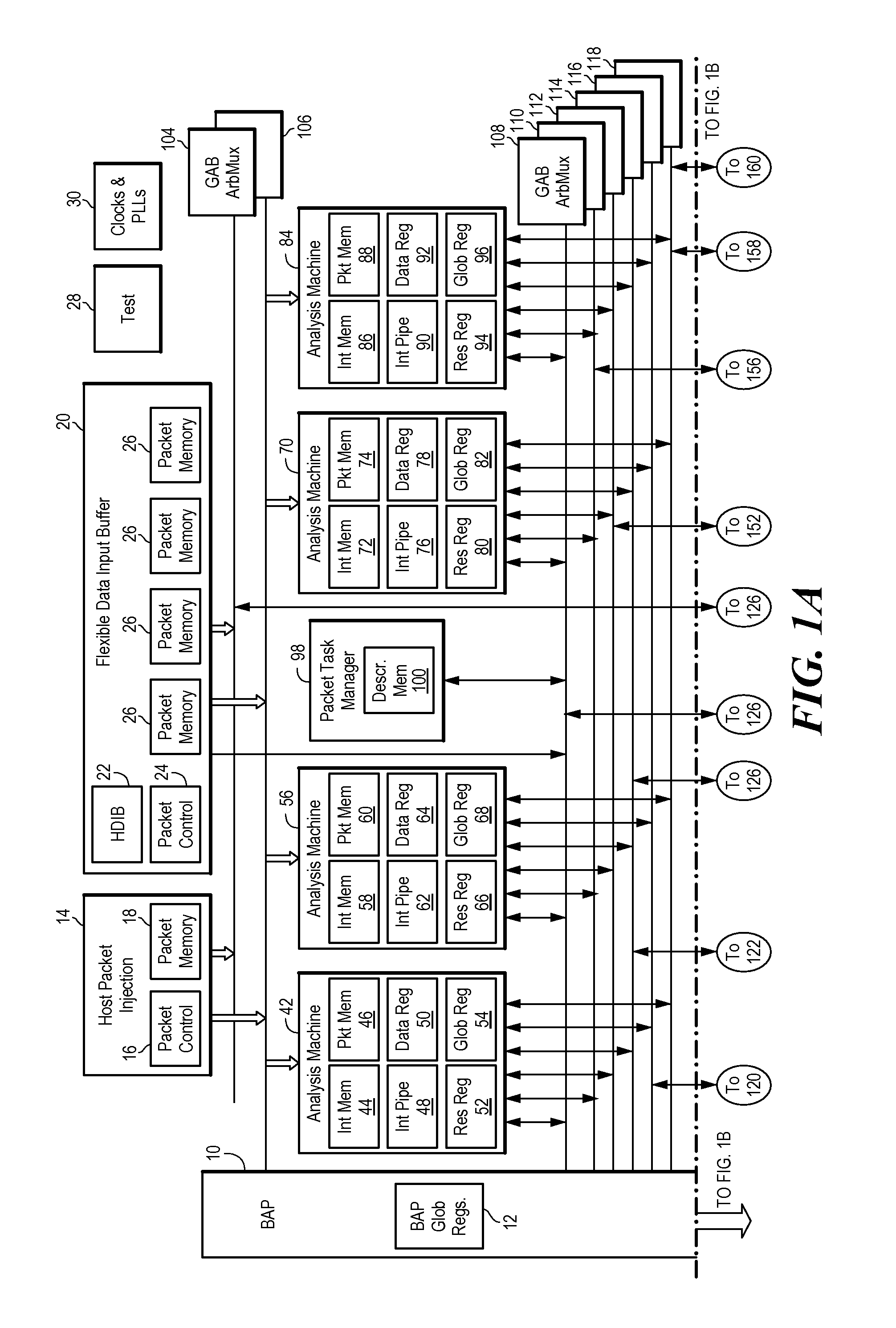
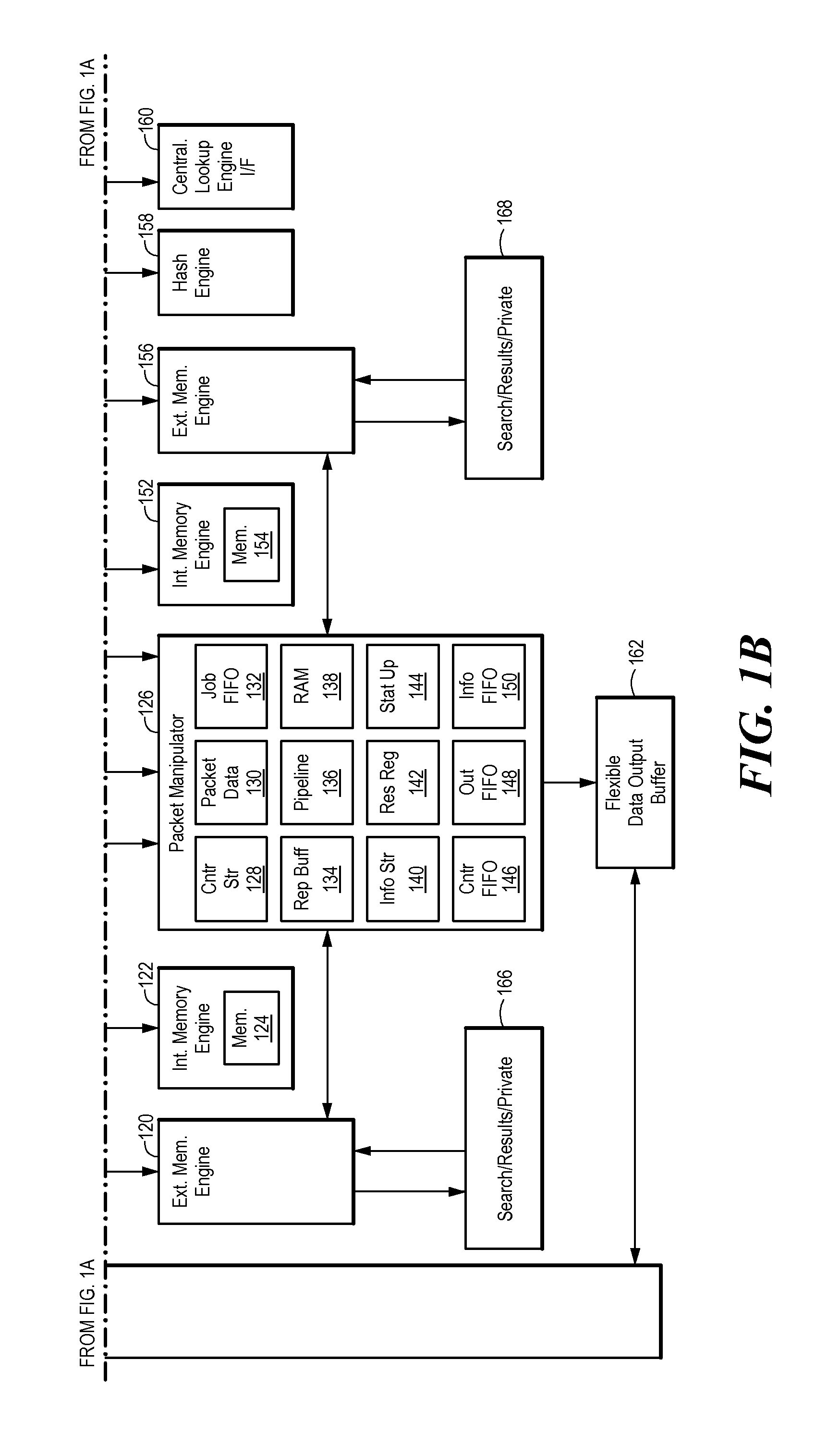
Route switch packet architecture processes data packets using a multi-threaded pipelined machine wherein no instruction depends on a preceding instruction because each instruction in the pipeline is executed for a different thread. The route switch packet architecture transfers a data packet from a flexible data input buffer to a packet task manager, dispatches the data packet from the packet task manager to a multi-threaded pipelined analysis machine, classifies the data packet in the analysis machine, modifies and forwards the data packet in a packet manipulator. The route switch packet architecture includes an analysis machine having multiple pipelines, wherein one pipeline is dedicated to directly manipulating individual data bits of a bit field, a packet task manager, a packet manipulator, a global access bus including a master request bus and a slave request bus separated from each other and pipelined, an external memory engine, and a hash engine.
Owner:AVAYA MANAGEMENT LP
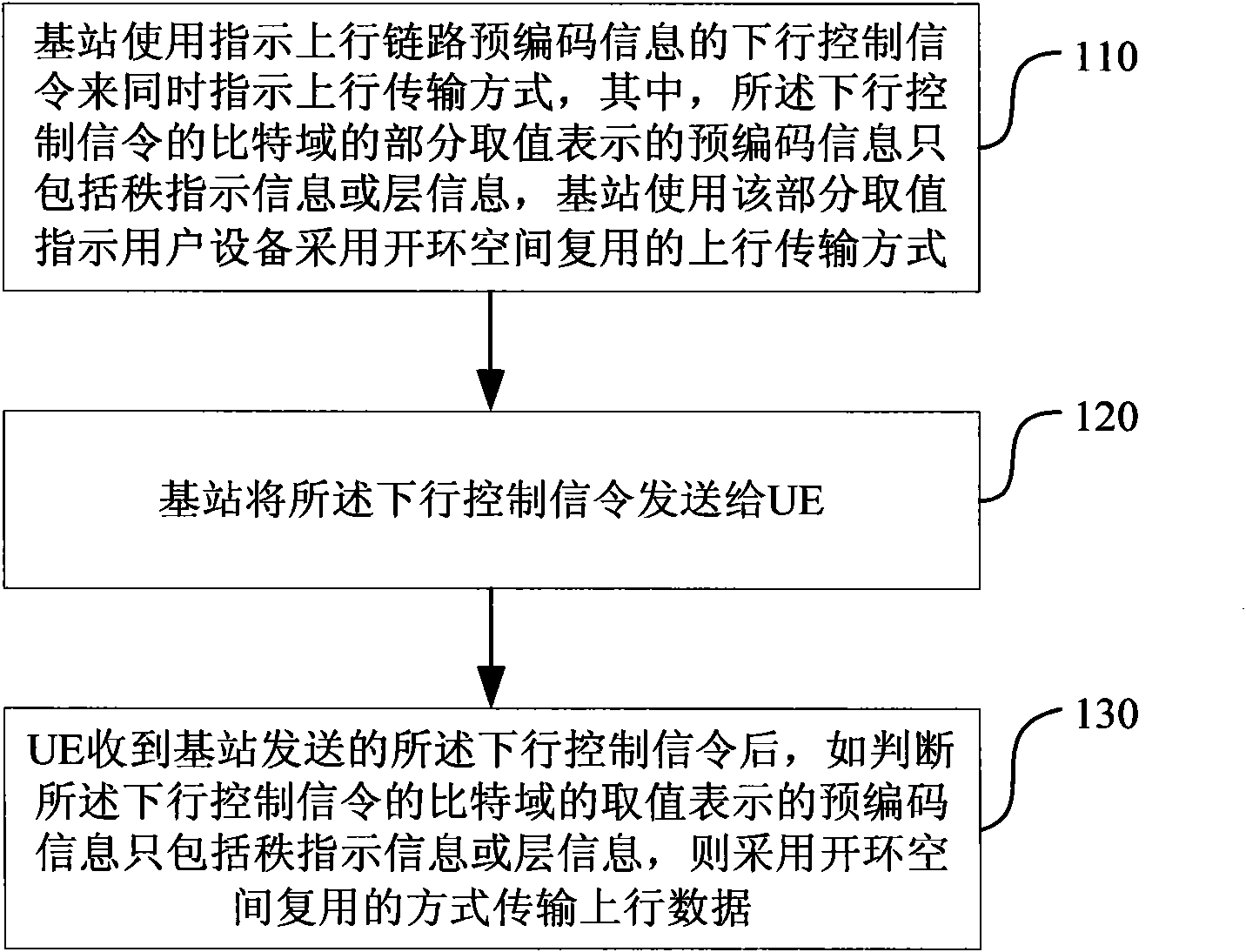
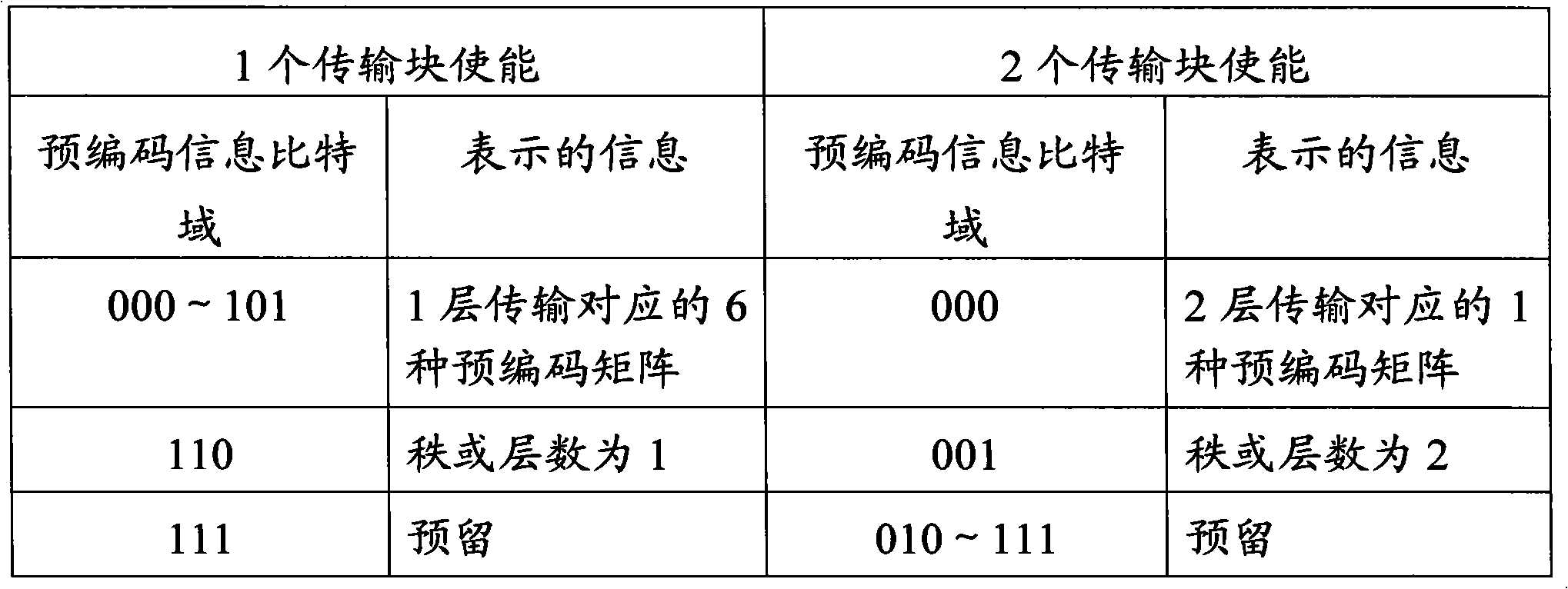
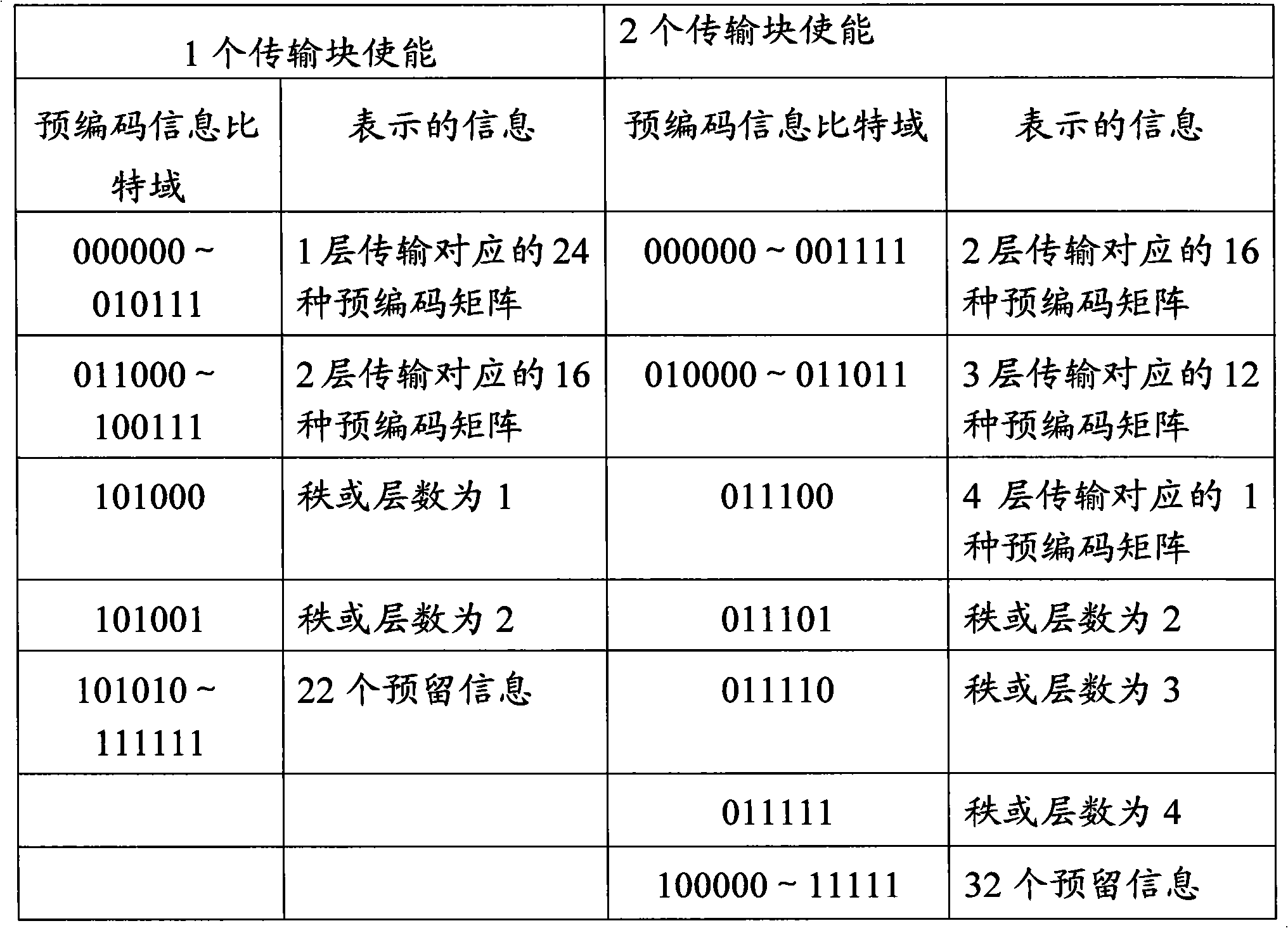
Method and system for indicating and determining uplink transmission mode
ActiveCN101938336AConvenient Uplink SchedulingTransmission path divisionWireless communicationPrecodingBit field
The invention discloses a method and a system for indicating and determining an uplink transmission mode, which is used for an advanced long-term evolution (LTE-A) system. The indication method comprises the following steps: a base station uses a downlink control signaling indicating the uplink precoding information to indicate the uplink transmission mode at the same time, wherein, the precoding information indicated by the partial value of a bit field of the downlink control signaling only comprises order indication information or layer information; the base station uses the partial value to indicate the user equipment to adopt the uplink transmission mode multiplexed by the open-loop space; and the base station transmits the downlink control signaling to the user equipment. The indication method of the invention can solve the problem that the base station can not indicate the uplink transmission mode to the user equipment. The invention also provides a determination method of the uplink transmission mode based on the indication method of the uplink transmission mode and a corresponding system; and the user equipment determines the uplink transmission mode needing to be adopted according to the downlink control signaling, and can carry out corresponding precoding processing.
Owner:ZTE CORP
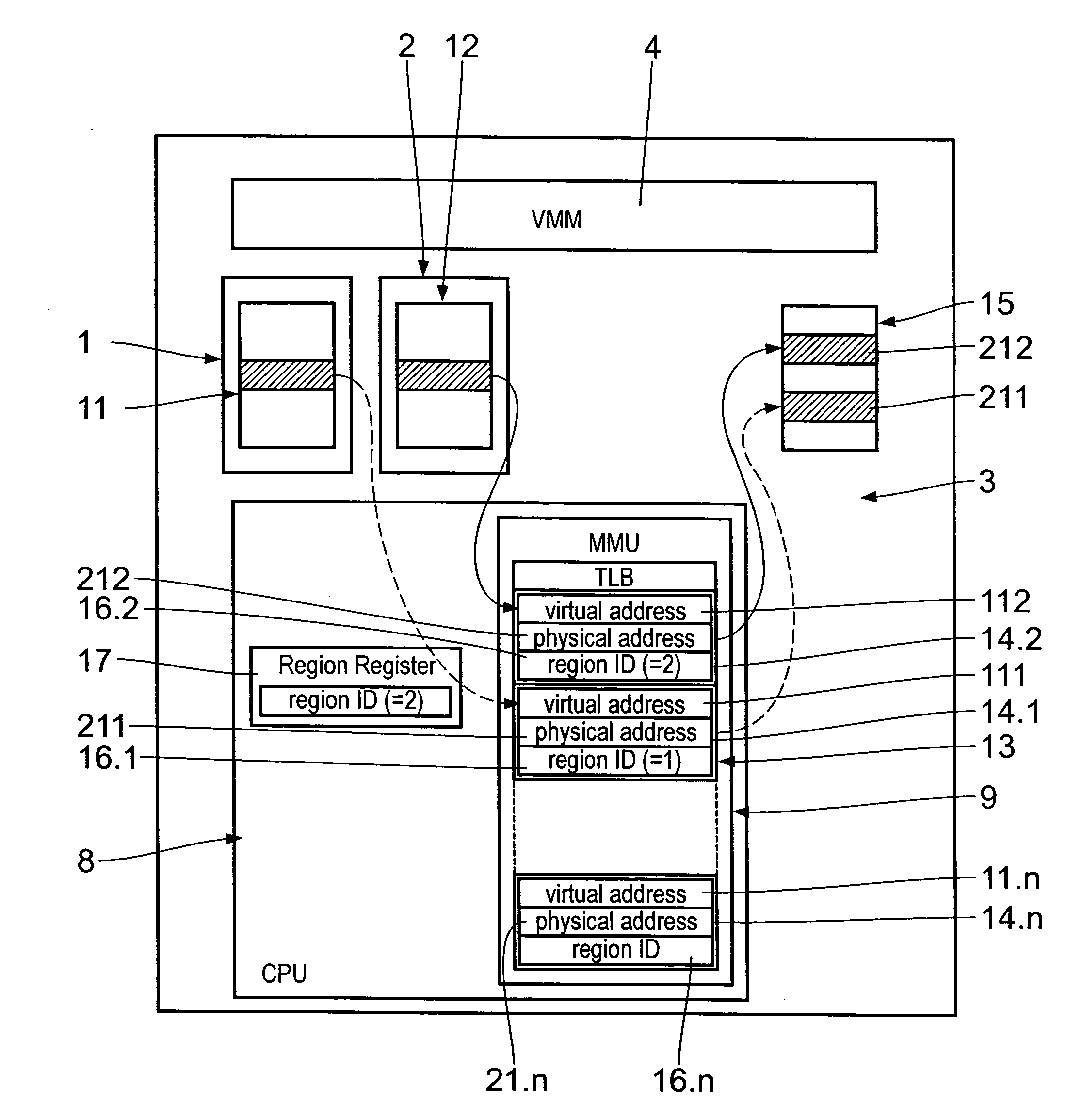
Virtual machine computer system for running guest operating system on a central processing means virtualized by a host system using region ID virtual memory option
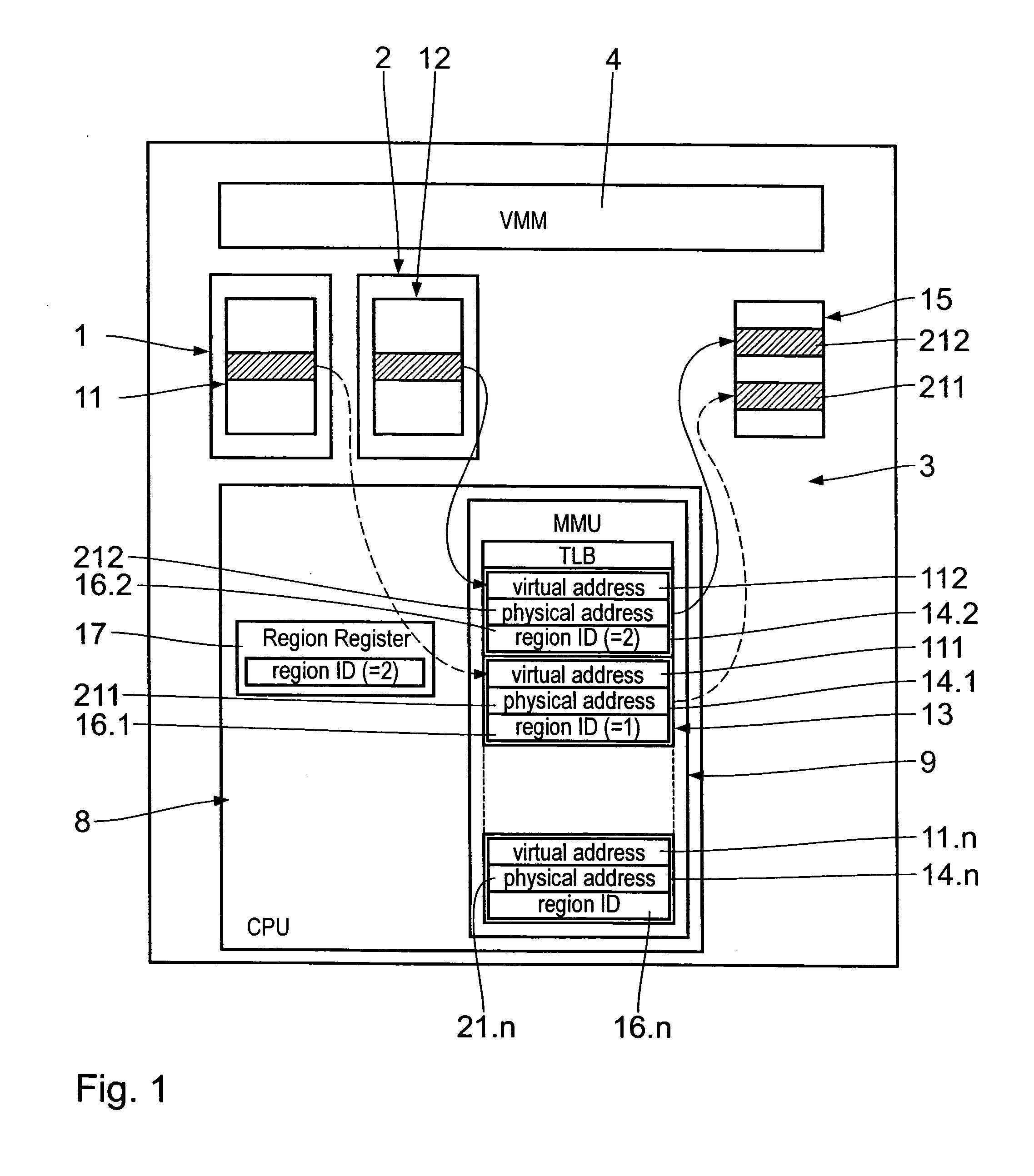
InactiveUS20060112212A1Improve performanceComputer security arrangementsProgram controlVirtual memoryVirtualization
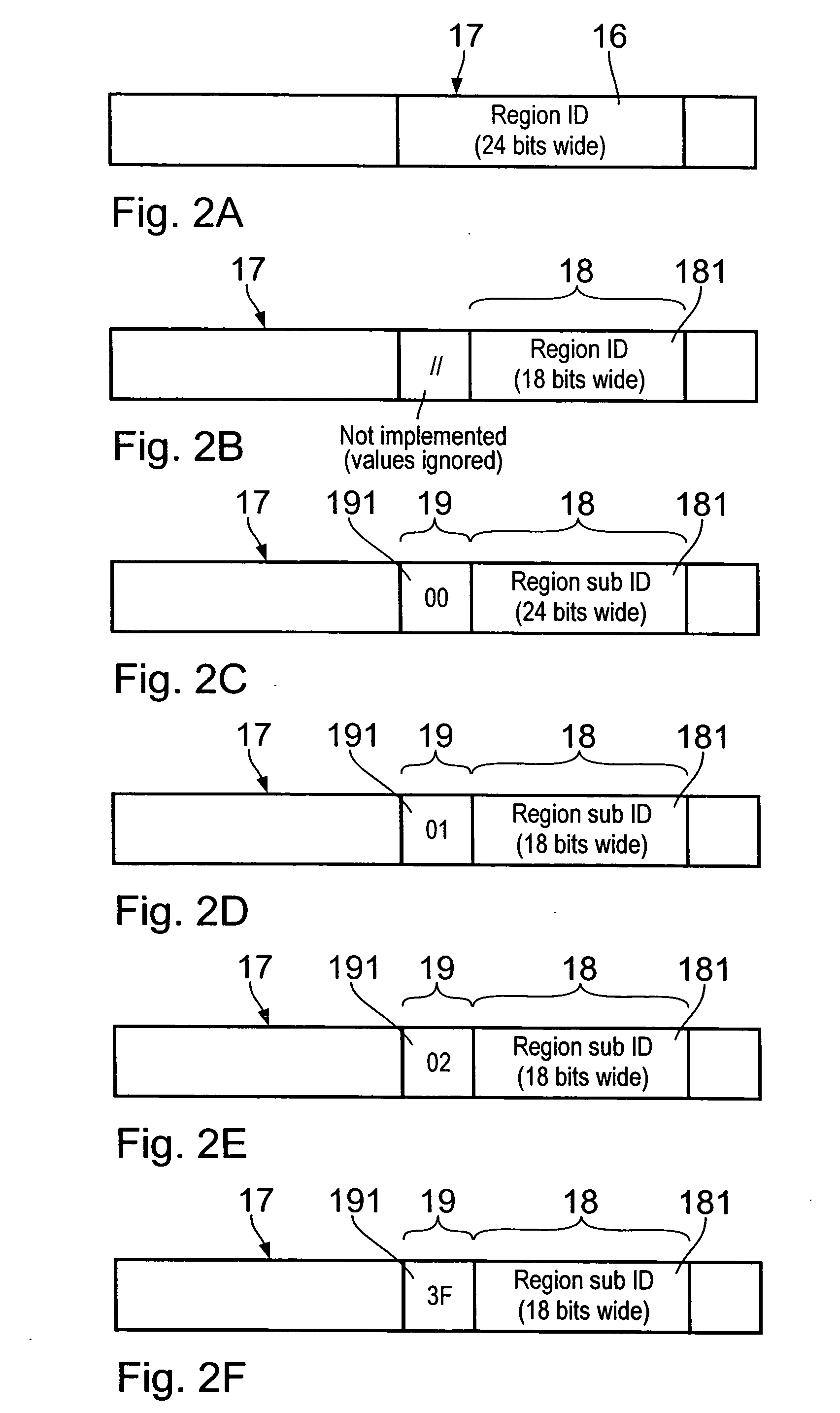
The virtual machine system for running computer guest processes on a central processing means 8 virtualized by the virtual machine monitor (VMM) includes a host central processing unit 8 on which a host memory management unit 9 is implemented. The latter has a translation look-aside buffer 13 with a plurality of entries 14 each of which consists of a virtual address value 111, a physical address value 211 and a region identification value 16. The region register 17 in the host CPU 8 contains the region ID 16 of the currently running guest process. The region ID 16 is composed of a guest allocated bit field 18, in which a region sub ID is entered, and a guest system identifier bit field 19, in which an identification value uniquely identifying an associated guest system is entered.
Owner:HOB GMBH & CO KG
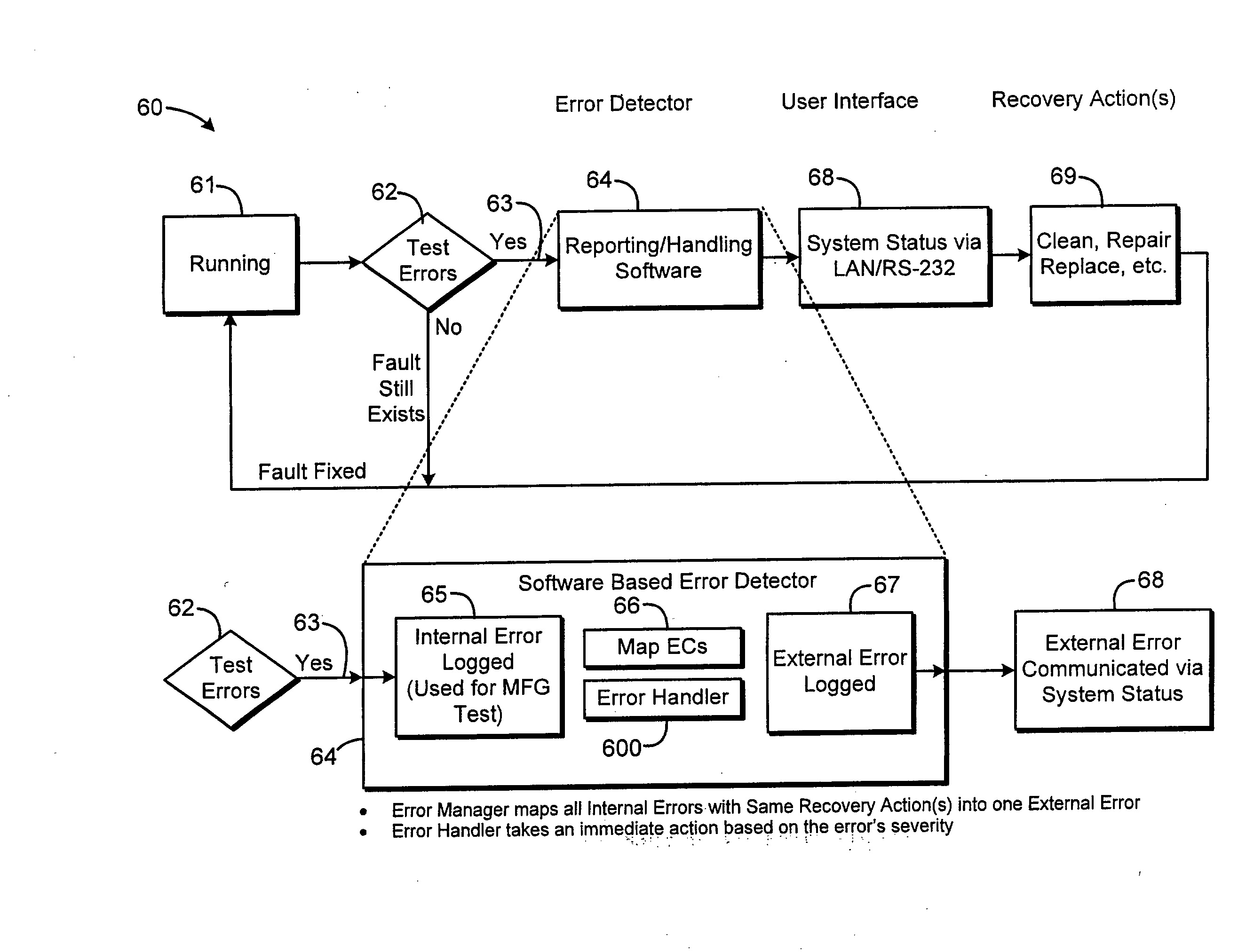
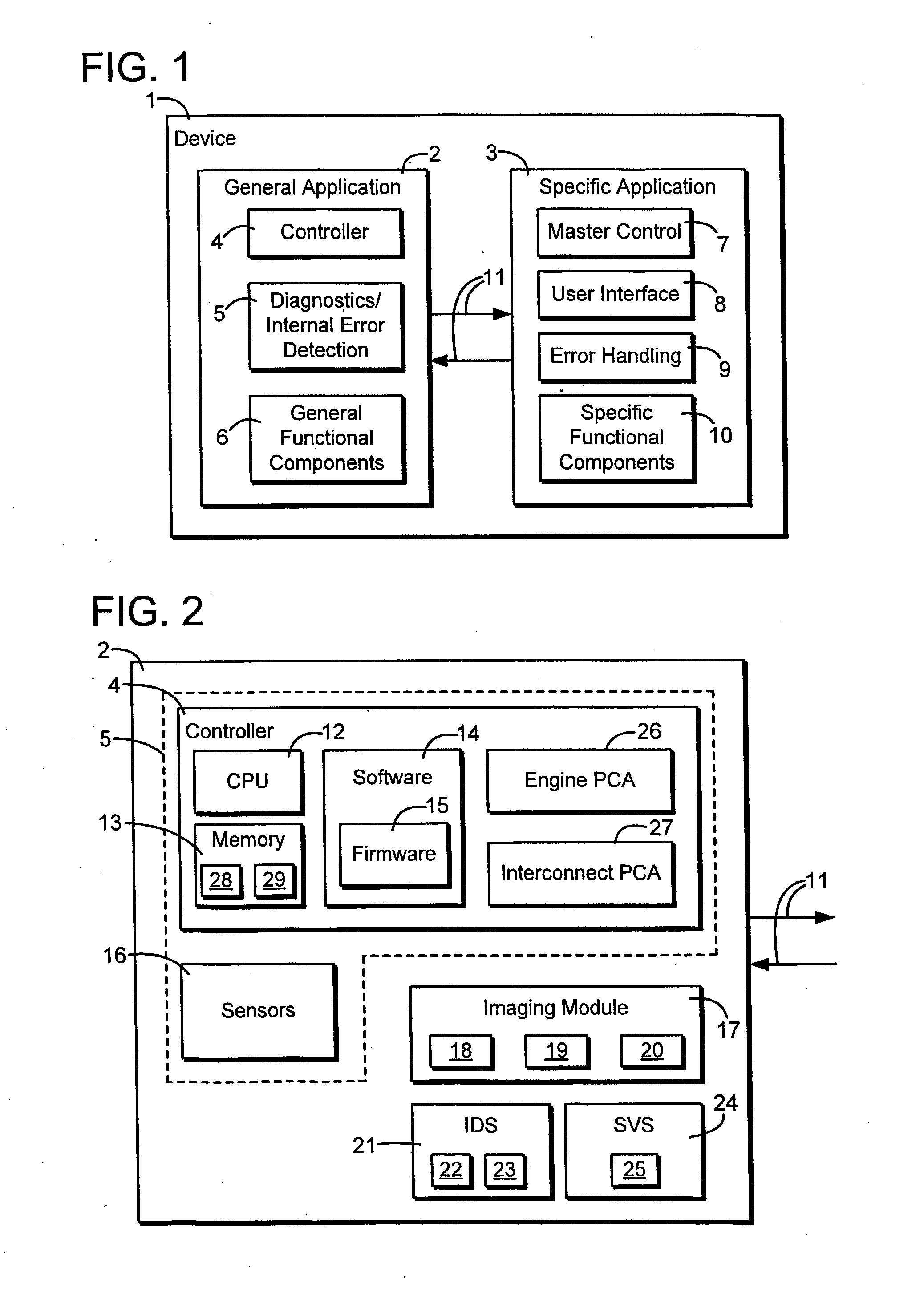
System and Method of Reporting Error Codes in an Electronically Controlled Device
A method of reporting errors in an electronically controlled device, comprises generating a first bit field representative of a severity of an internal error, generating a second bit field representative of a location of the internal error; and generating a third bit field representative of a cause of the internal error. The method also comprises structuring an internal error code, wherein the internal error code includes the first, second, and third bit fields.
Owner:HEWLETT PACKARD DEV CO LP
Method for dynamic interpretation of transport block size
ActiveUS20080313521A1Small sizeImprove performanceError prevention/detection by using return channelTransmission systemsBit fieldControl channel
A system and method is provided which allows for the dynamic interpretation of a transport block size field in a Layer 1 / Layer 2 (L1 / L2) control channel, such that for any first H-ARQ transmission, the transport block size indication field will indicate the size of the transport block. For any retransmission, the transport block size indication bits can be transformed into dedicated bits for indicating the RV used as it relates to circular buffering. A robust bit field for indicating new data transmission (e,g, new data indication (NDI)) is therefore introduced, and from a UE perspective it is possible to determine how to interpret the transport block size field.
Owner:HMD GLOBAL
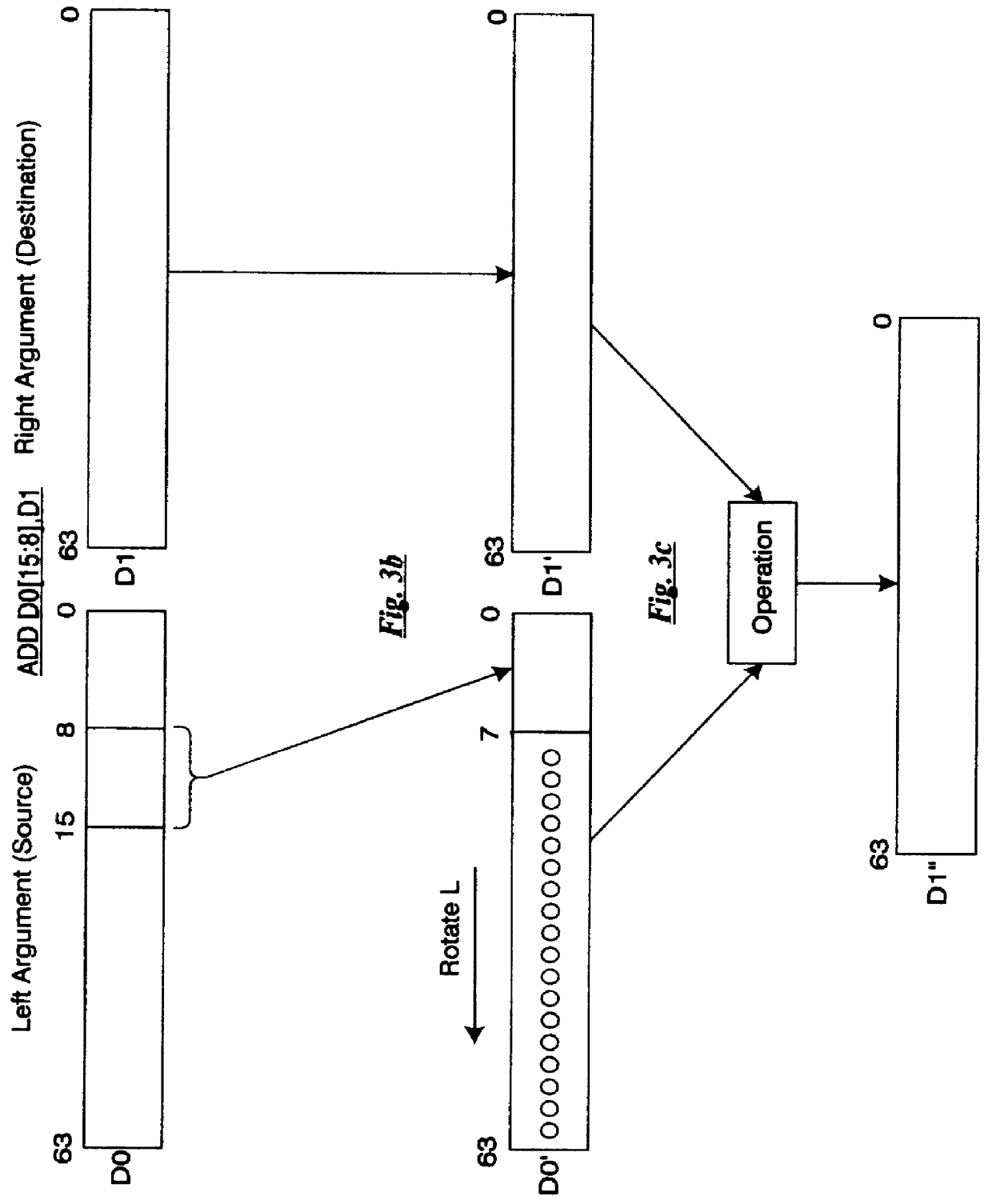
Bit field selection instruction
A digital signal processor having a generalized bit field extraction instruction which can be used to perform a bit field selection operation, a rotate left operation, a rotate right operation, a shift left operation, a logical shift right operation, an arithmetic shift right operation, and so forth.
Owner:ADVANCED MICRO DEVICES INC
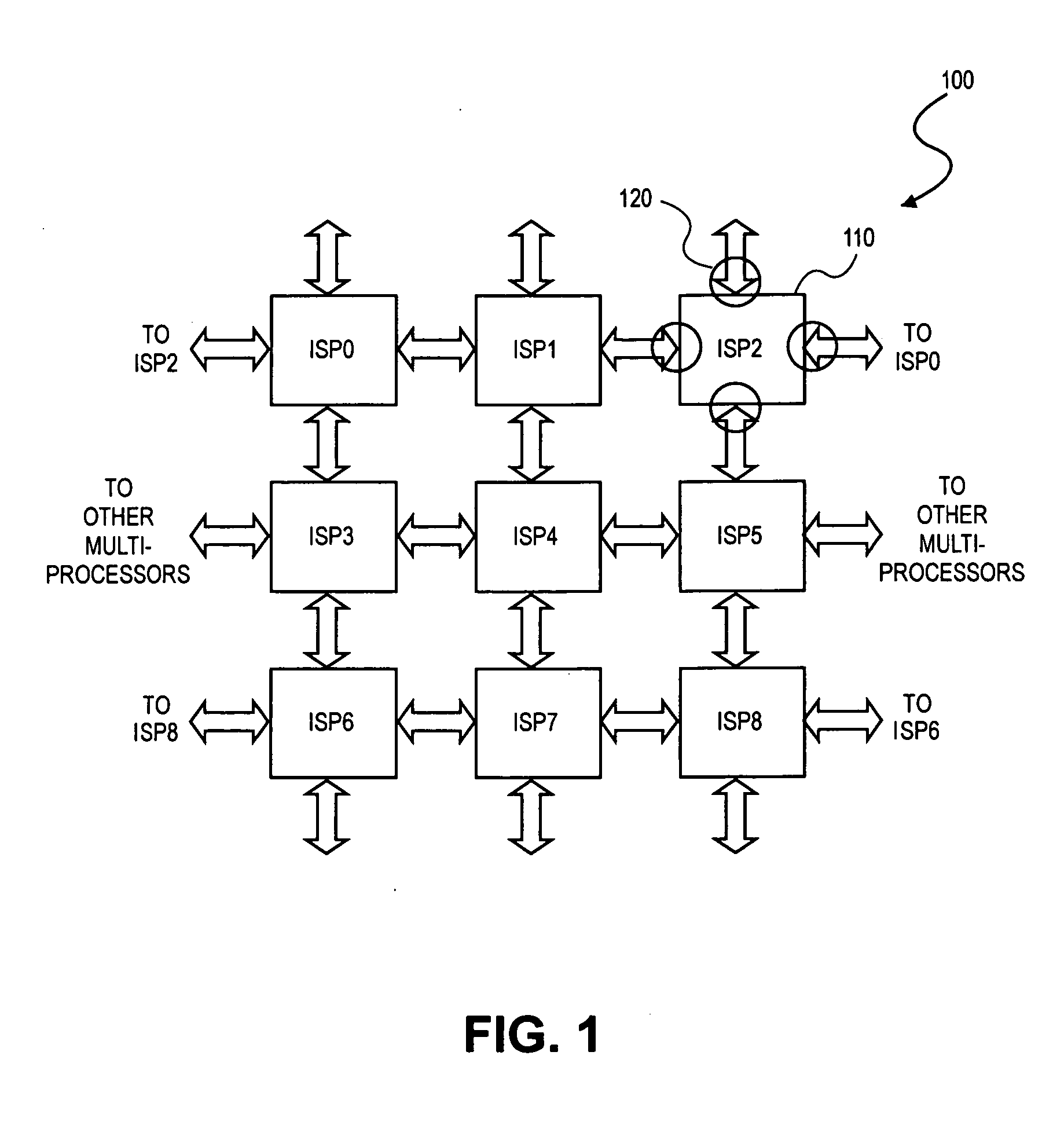
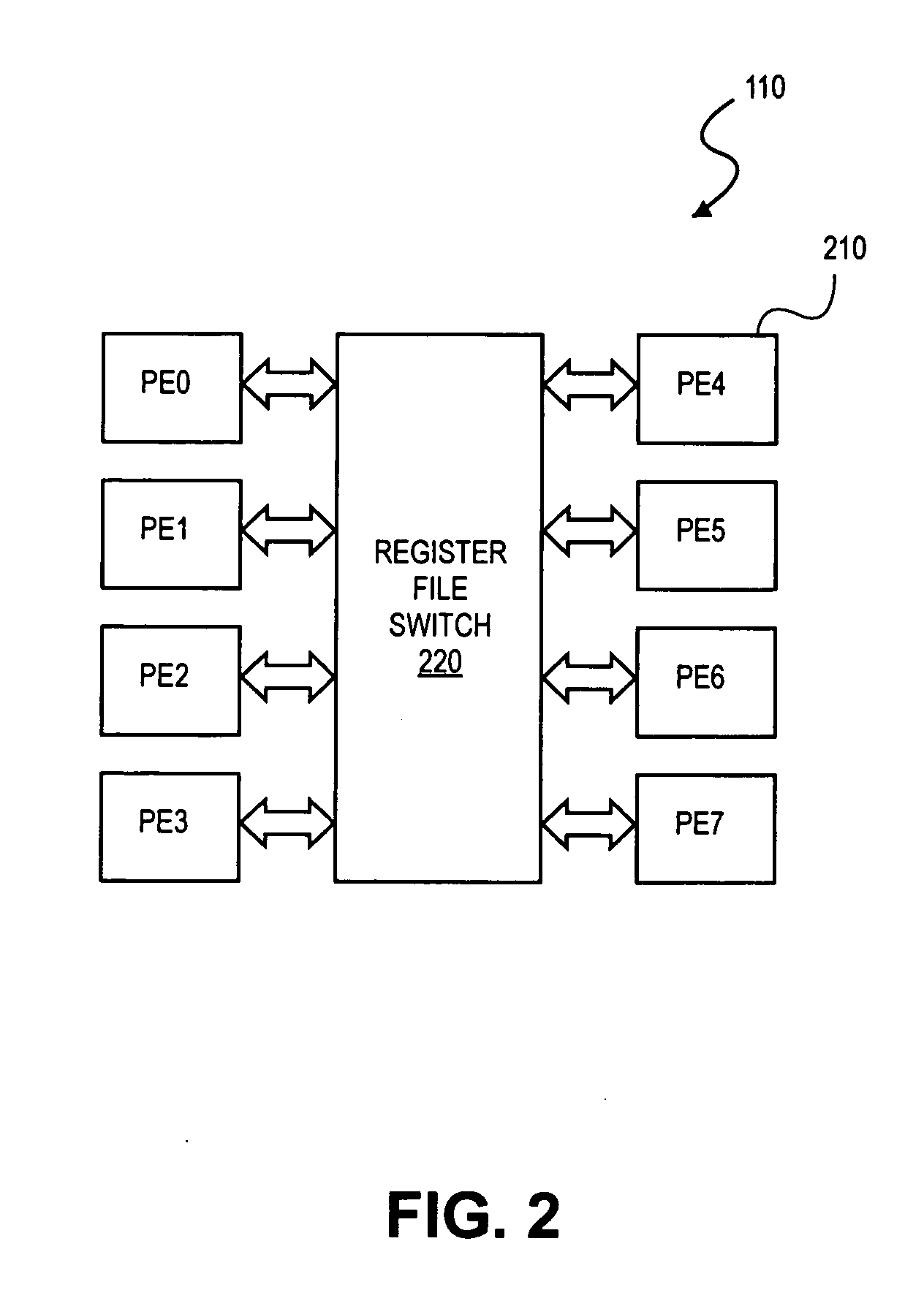
Method and apparatus for multiprocessor debug support
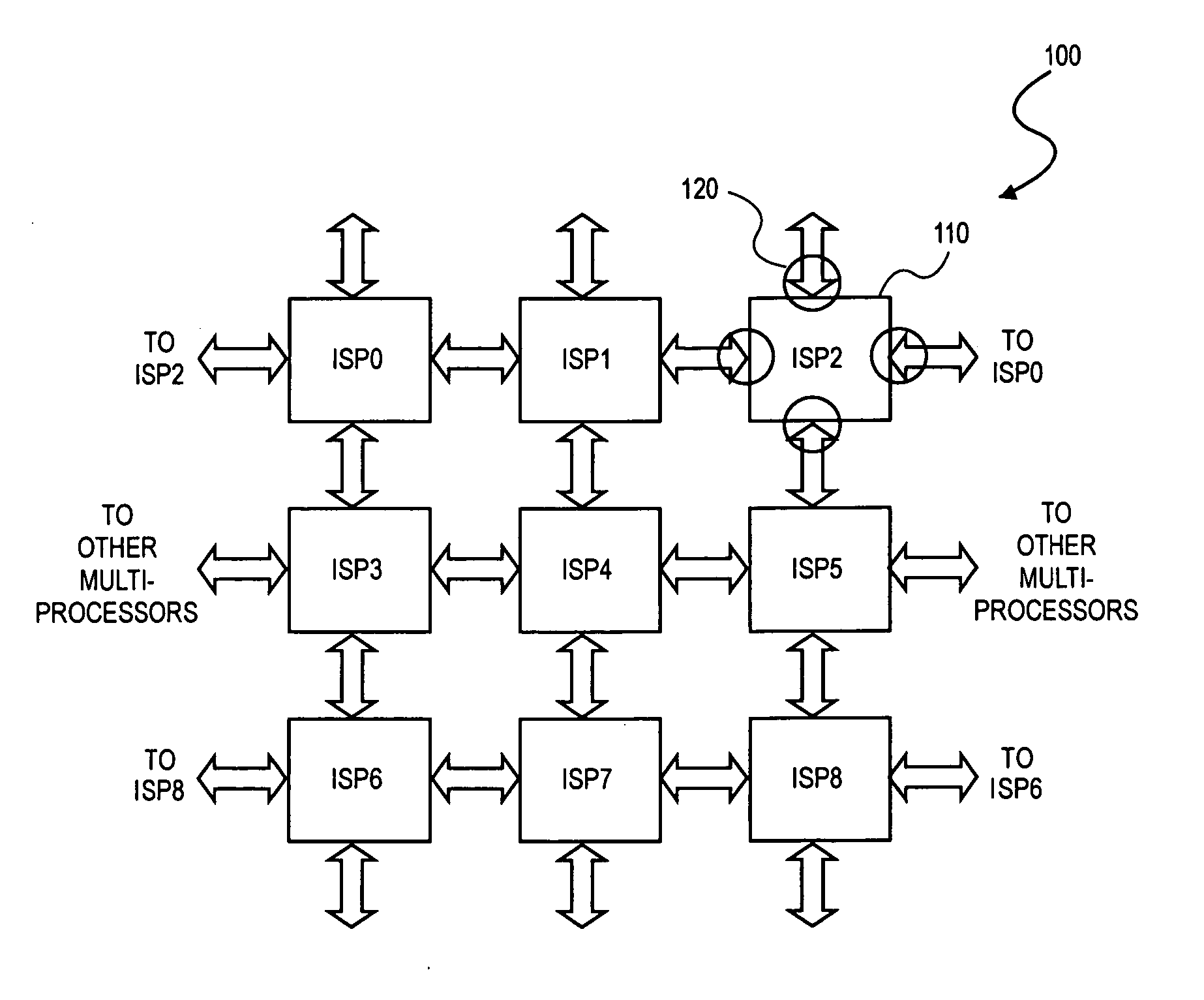
A device having at least one processor connected a controller and a memory; where the controller to execute a debug process. The debug process attaches a breakpoint bit field to each instruction. A system having image signal processors (ISPs), each ISP including processor elements (PEs). The ISPs include a debug instruction register connected to a first mux element. An instruction memory is connected to an instruction register. A decoder is connected to the instruction register. An execution unit is connected to the decoder. A debug executive unit is connected to the instruction memory, and a second mux element is connected to the execution unit and local registers. The decoder decodes a breakpoint bit field of each instruction.
Owner:INTEL CORP
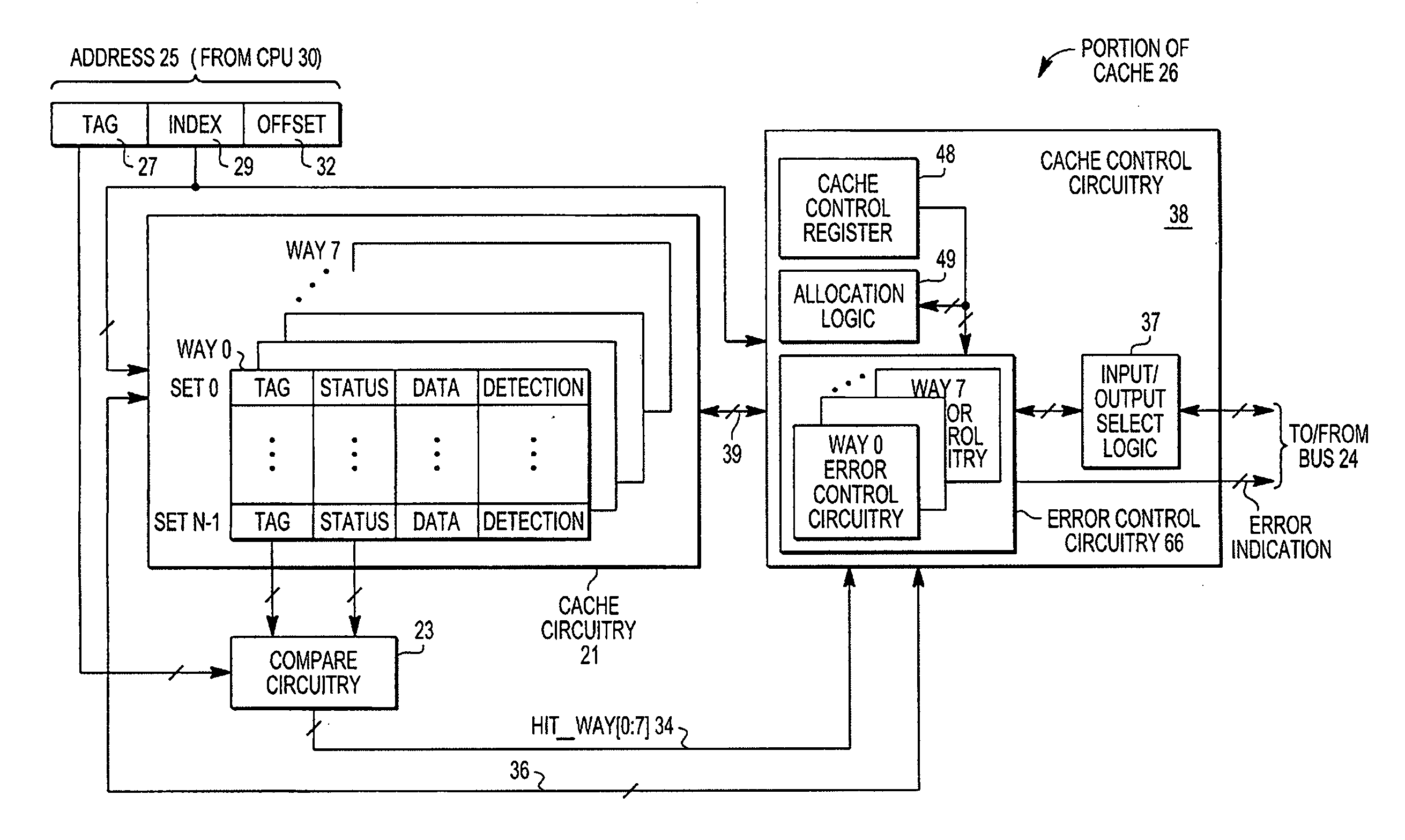
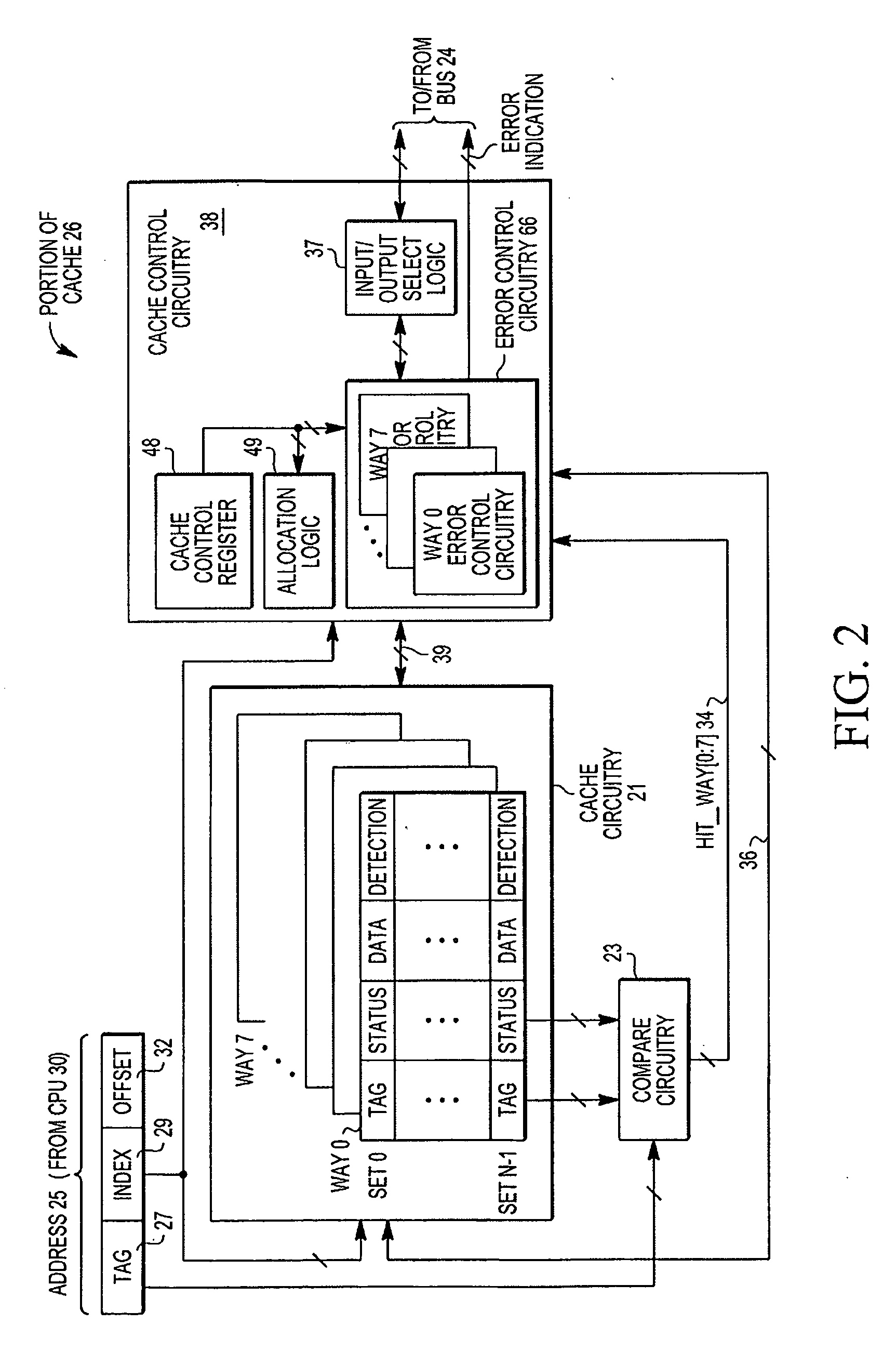
Implementation of multiple error detection schemes for a cache
A cache includes a plurality of cache lines, where each cache line includes a detection type field, corresponding cache data field, a detection field, and a corresponding tag field. The detection type field indicates an error detection scheme from a plurality of error detection schemes currently in use for the corresponding cache data field. One example of an error detection scheme is a multiple bit error detection scheme (e.g. an error detection coding (EDC) or an error correction coding (ECC)). Another type is a single bit error detection scheme (e.g. parity error detection). The detection bits field stores parity bits if parity error detection is used. The detection bits field stores checking bits if EDC coding is used.
Owner:NORTH STAR INNOVATIONS
Variable bit field encoding
InactiveUS7119813B1Improve image qualityHigh color resolutionTexturing/coloringCathode-ray tube indicatorsBit fieldImage resolution
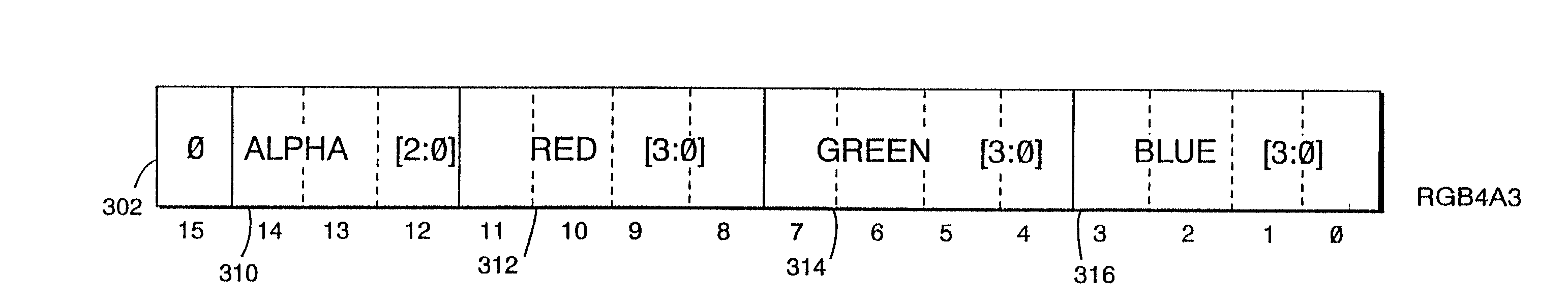
A compact image element encoding format selectively allocates a bit field within the format to alternately encode either multi-bit alpha resolution or increased color resolution. This encoding technique may be advantageously used to allocate encoding bits to model semi-transparency while using those same bits for other purposes (e.g., higher color resolution) in instances where semi-transparency is not required (e.g., for opaque image elements). In one advantageous embodiment, the same encoding format can provide either RGB5 or RGB4A3, on an image-element-by-image-element basis. Applications include but are not limited to texture mapping in a 3D computer graphics system such as a home video game system or a personal computer.
Owner:NINTENDO CO LTD
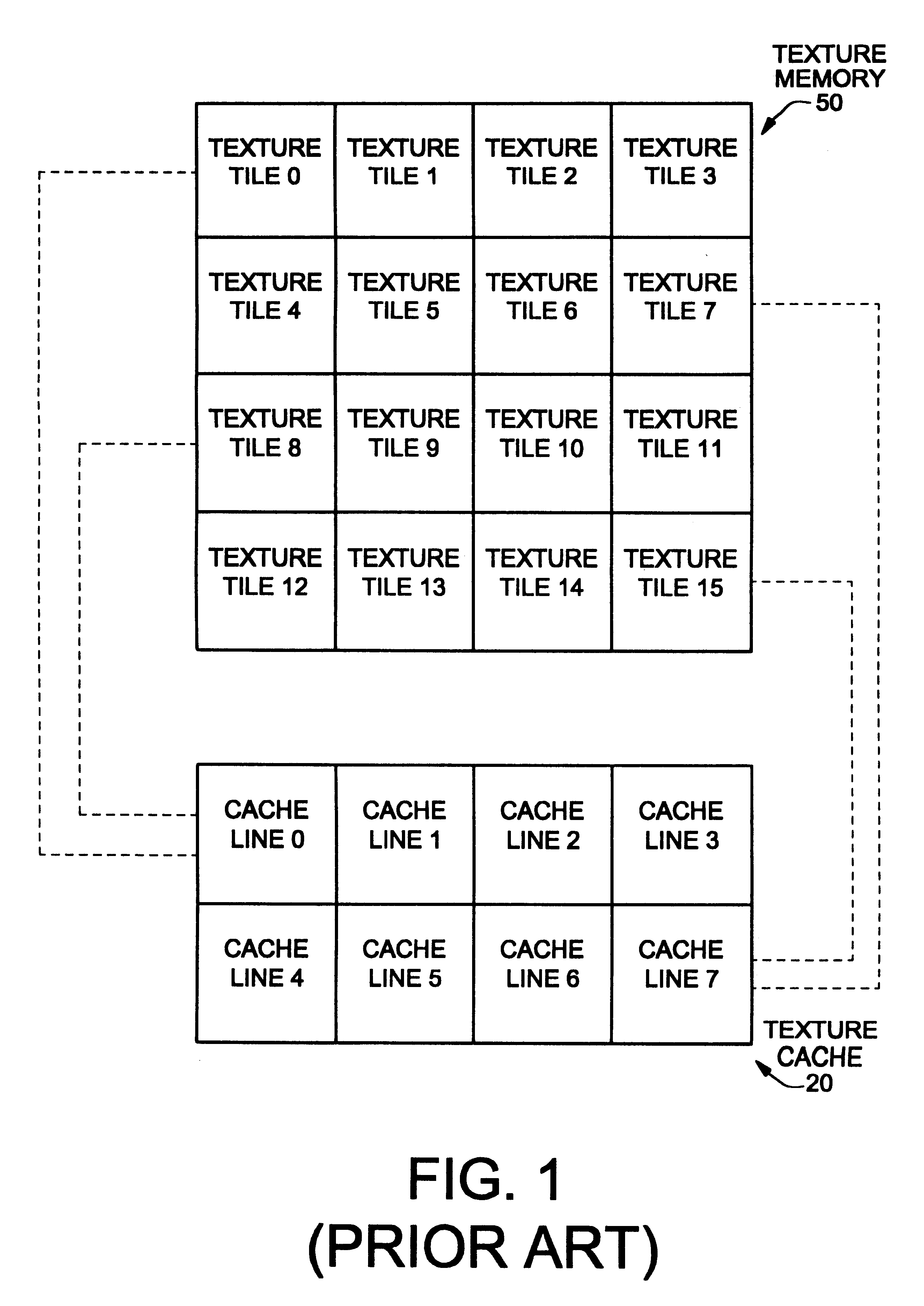
Hashed direct-mapped texture cache
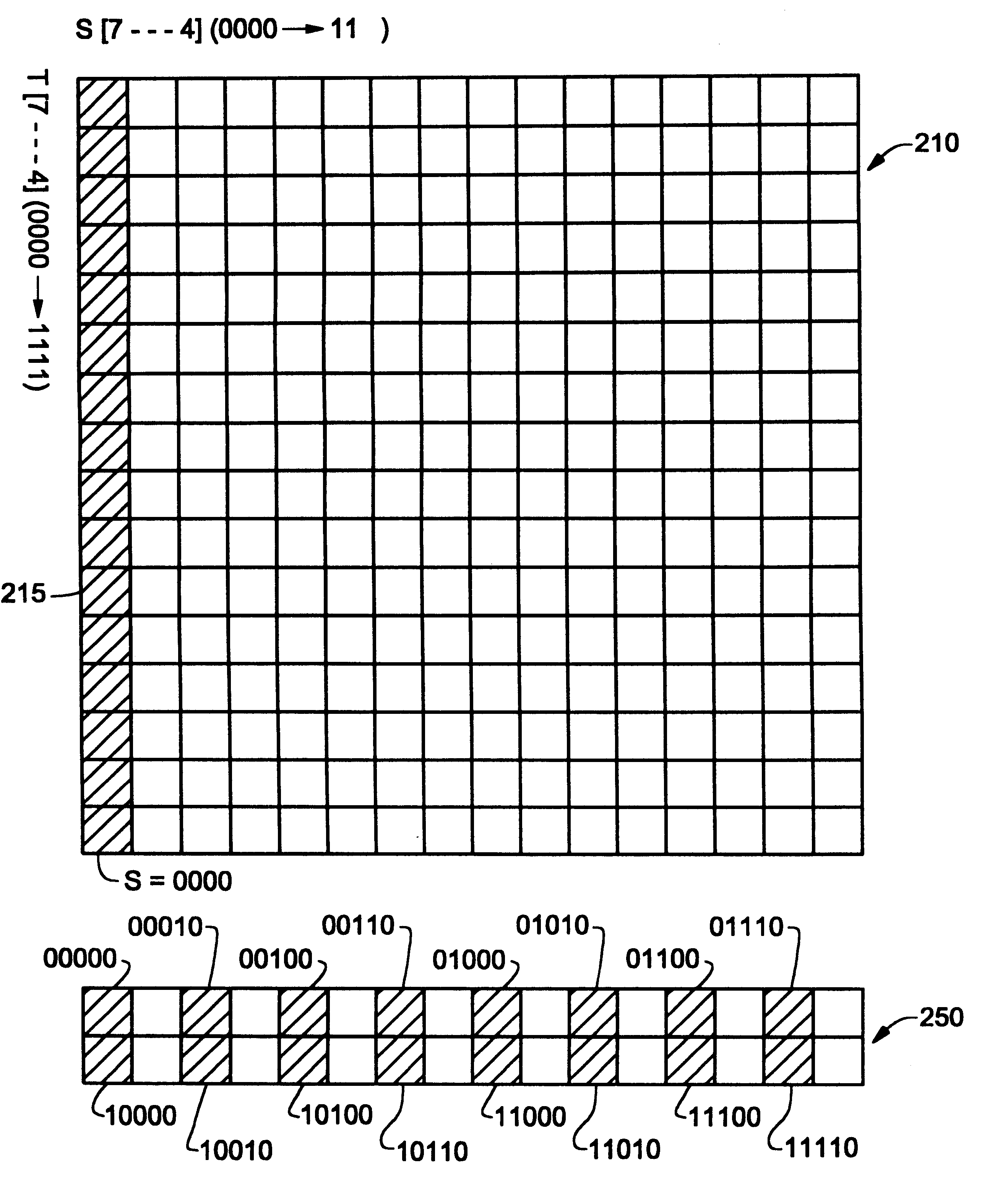
InactiveUS6233647B1Memory adressing/allocation/relocationCathode-ray tube indicatorsBit fieldParallel computing
The present invention pertains to an apparatus for and method of mapping texture memory to a texture cache such that cache contention is minimized. Significantly, in one embodiment of the present invention, addresses of the texture memory are mapped to entries of the texture cache according to a predetermined hashing scheme. According to the one embodiment, texture memory is addressed as a virtually contiguous address space by a multi-dimensional index. The multi-dimensional index is further partitioned into a low order bit field and a high order bit field. Low order bits of the multi-dimensional index are directly mapped to low order bits of the cache address. High order bits of the multi-dimensional index are mapped to high order bits of the cache address according to a predetermined address-hashing scheme. Particularly, in one embodiment, high order bits of the multi-dimensional index are selectively "exclusive-or-ed" to generate corresponding addresses of the texture cache.
Owner:MORGAN STANLEY +1
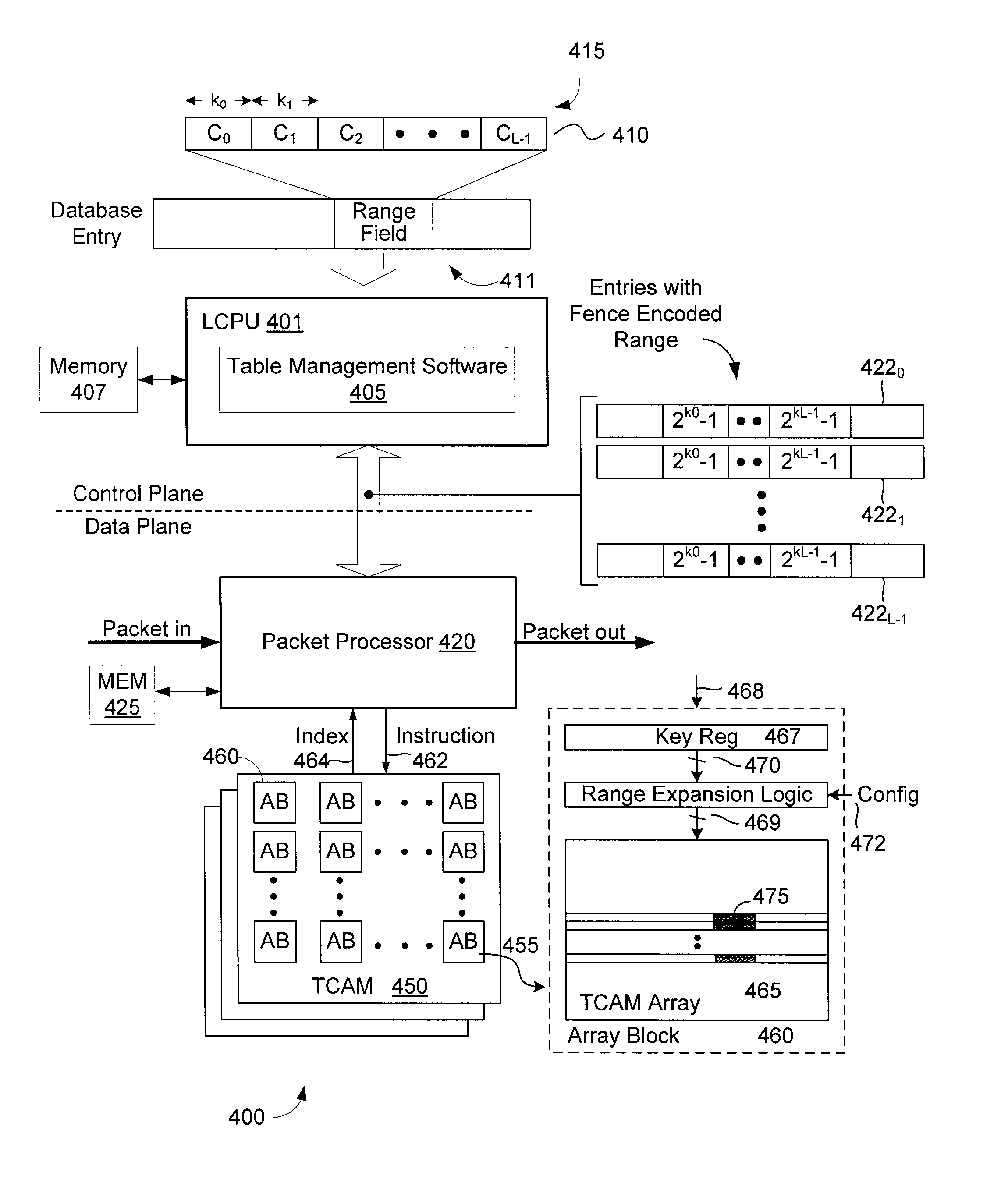
Range representation in a content addressable memory (CAM) using an improved encoding scheme
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
System and method of reporting error codes in an electronically controlled device
A method of reporting errors in an electronically controlled device, comprises generating a first bit field representative of a severity of an internal error, generating a second bit field representative of a location of the internal error; and generating a third bit field representative of a cause of the internal error. The method also comprises structuring an internal error code, wherein the internal error code includes the first, second, and third bit fields.
Owner:HEWLETT PACKARD DEV CO LP
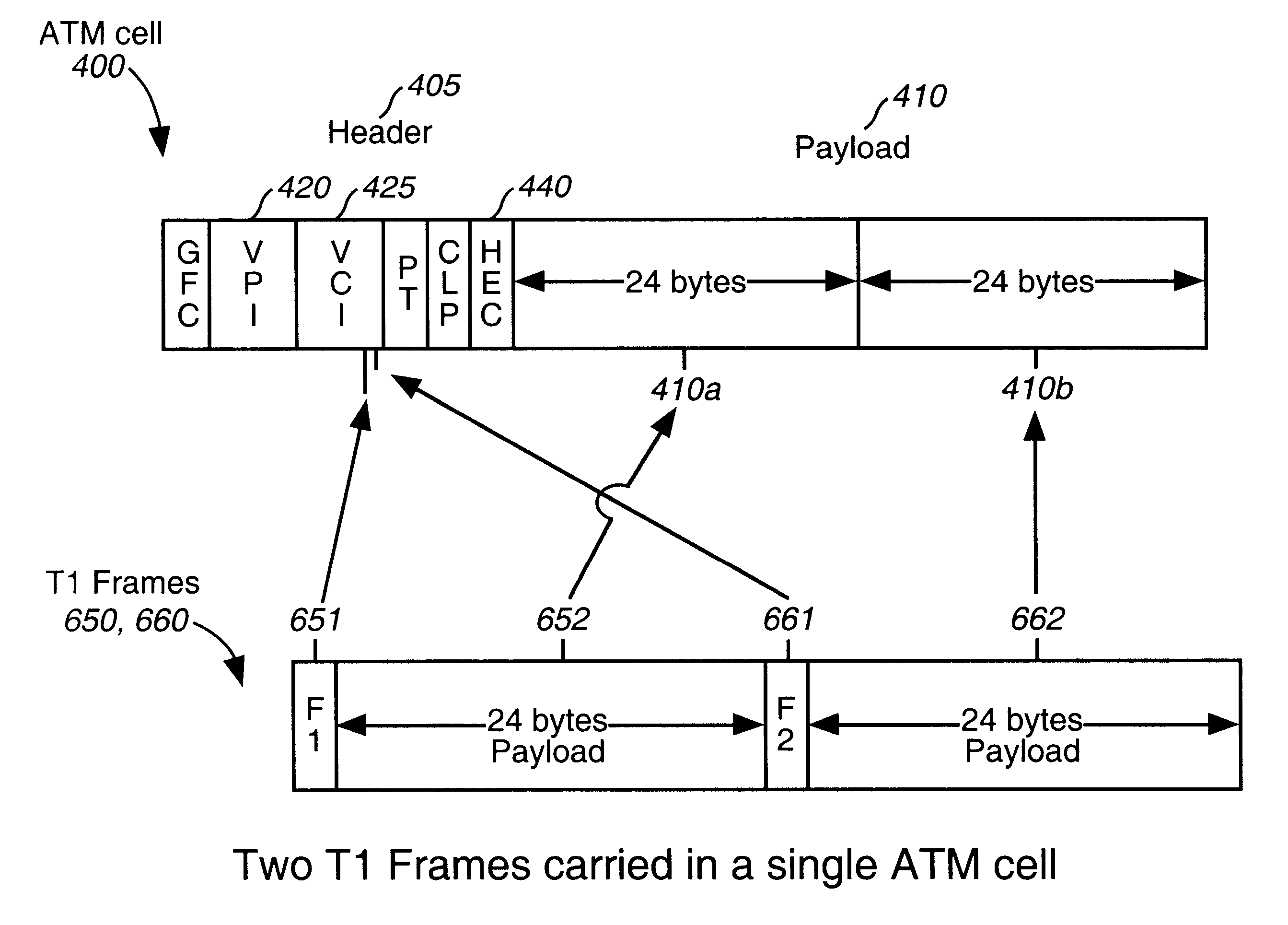
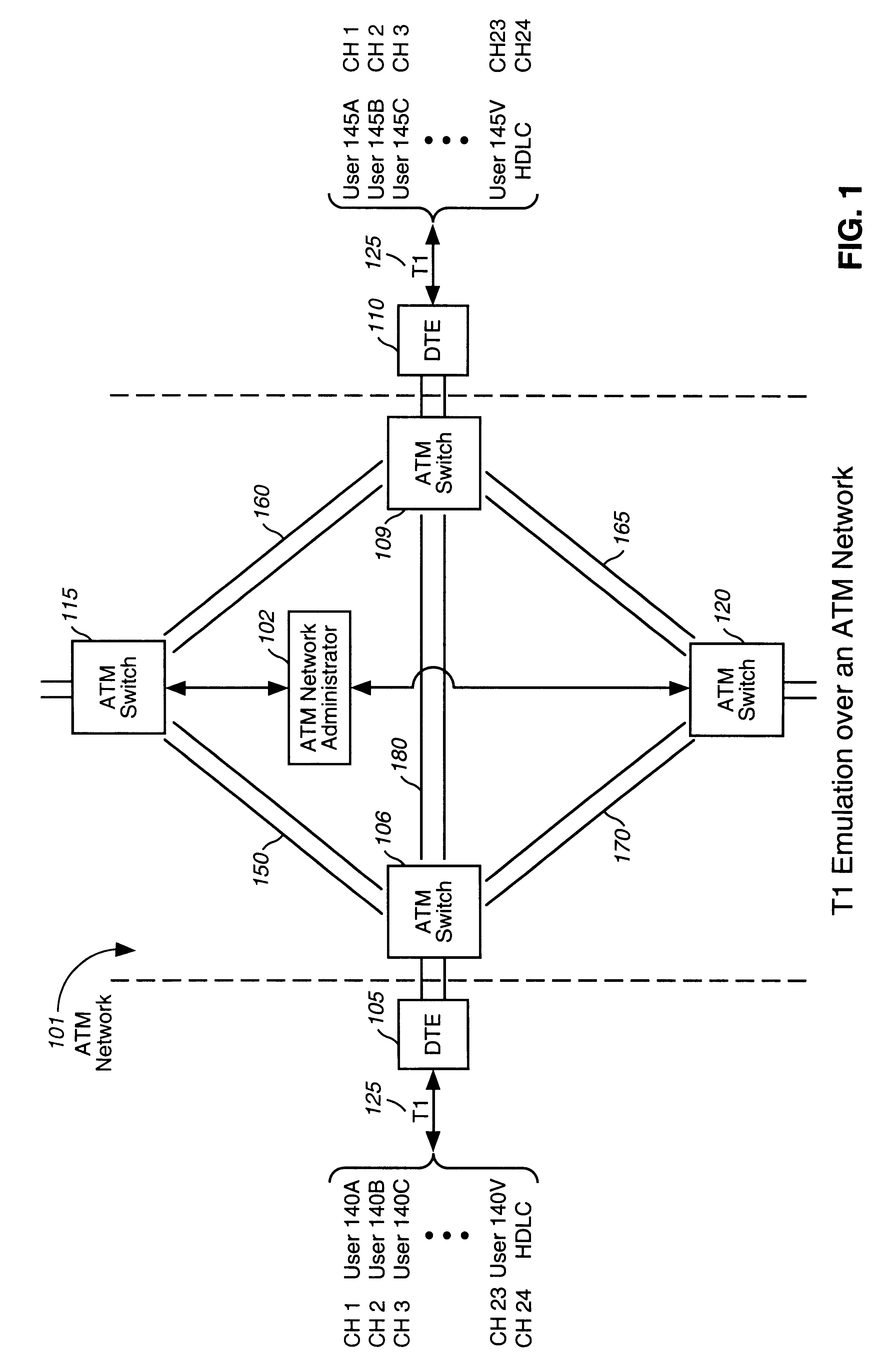
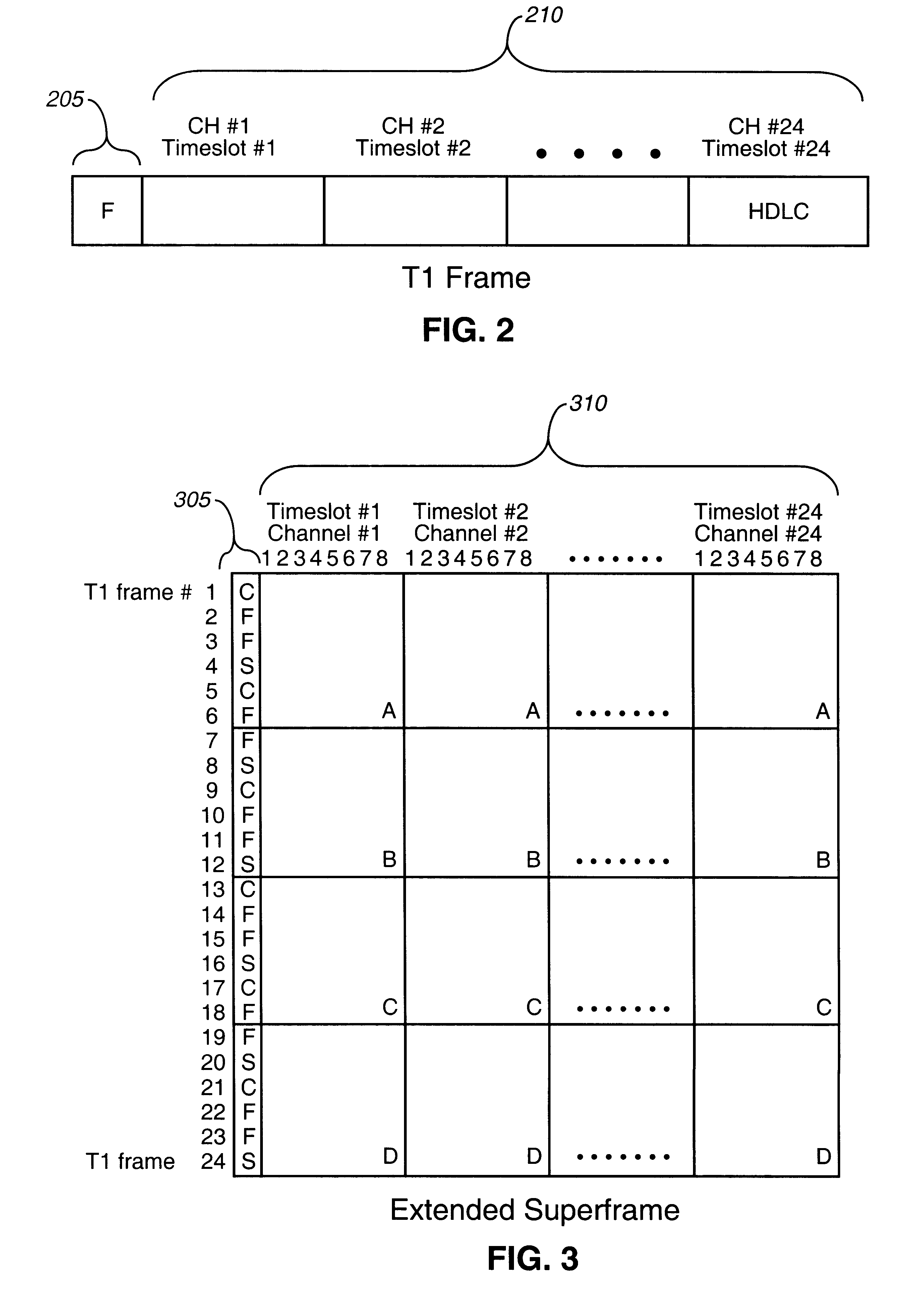
Method and system for emulating a T1 link over an ATM network
InactiveUS6272128B1Time-division multiplexData switching by path configurationBit fieldLeast significant bit
A method and system of emulating a T1 link over an ATM network. A T1 line carrying a stream of T1 frames is terminated at a first ATM Data Terminating Equipment (DTE). T1 frames are loaded into ATM cells and sent over an ATM network to a second ATM DTE. The T1 frames are unloaded at the second ATM DTE, and sent to a switch matrix to be de-multiplexed. In one example of T1 emulation, two T1 payloads are inserted in each ATM cell payload. The corresponding T1 frame bits replace the two least significant bits in the VCI field of the ATM cell header. For quasi-fractional T1 emulation, three or four quasi-fractional T1 payloads can be carried in the ATM cell payload. For fractional T1 emulation, multiple fractional T1 payloads are carried in a fractional payload field, and a frame bit field is created in the ATM cell payload to carry the T1 frame bits. The use of a T1 framer at the second DTE is avoided by insuring the T1 frame bit positions are constant over successive ATM cells.
Owner:VERIZON PATENT & LICENSING INC
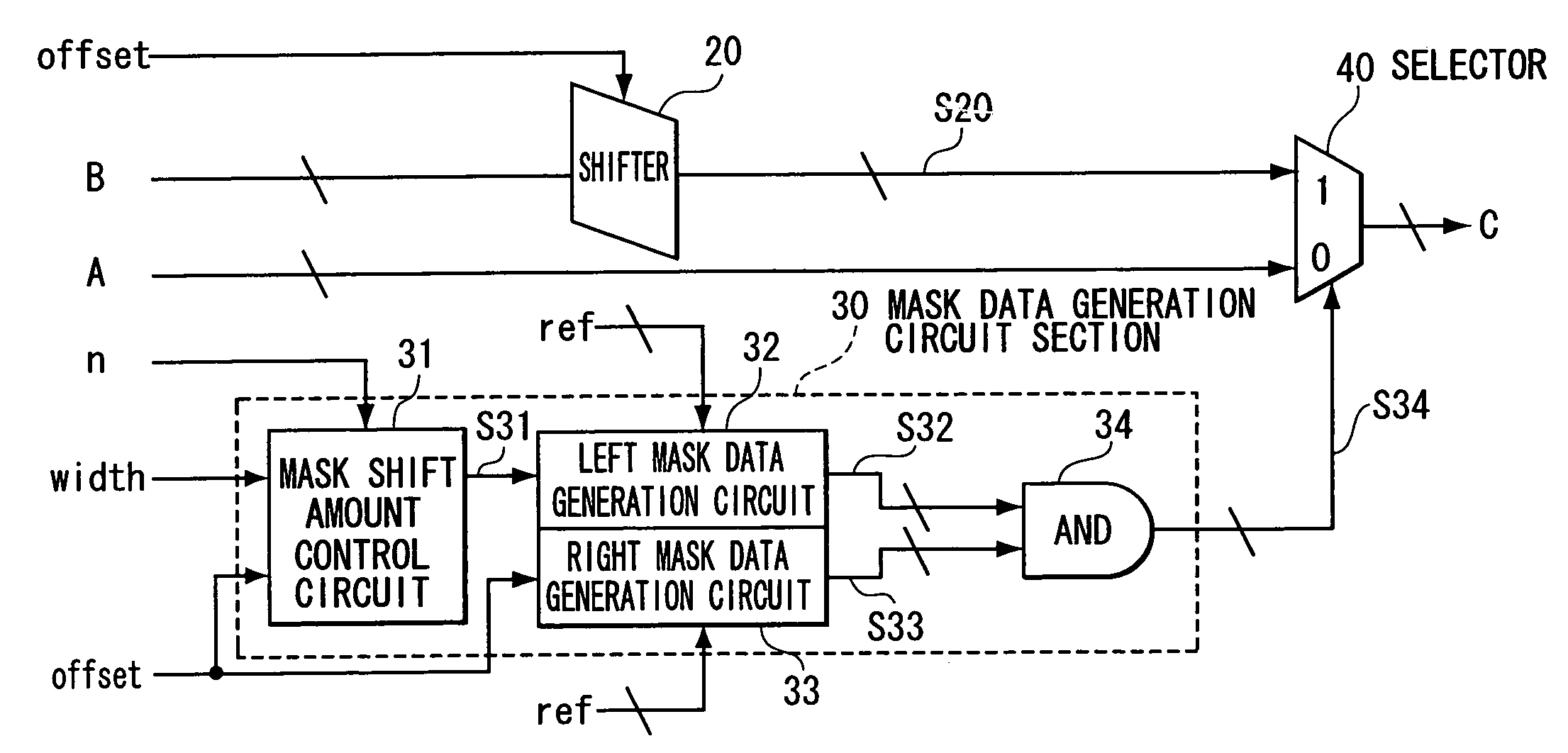
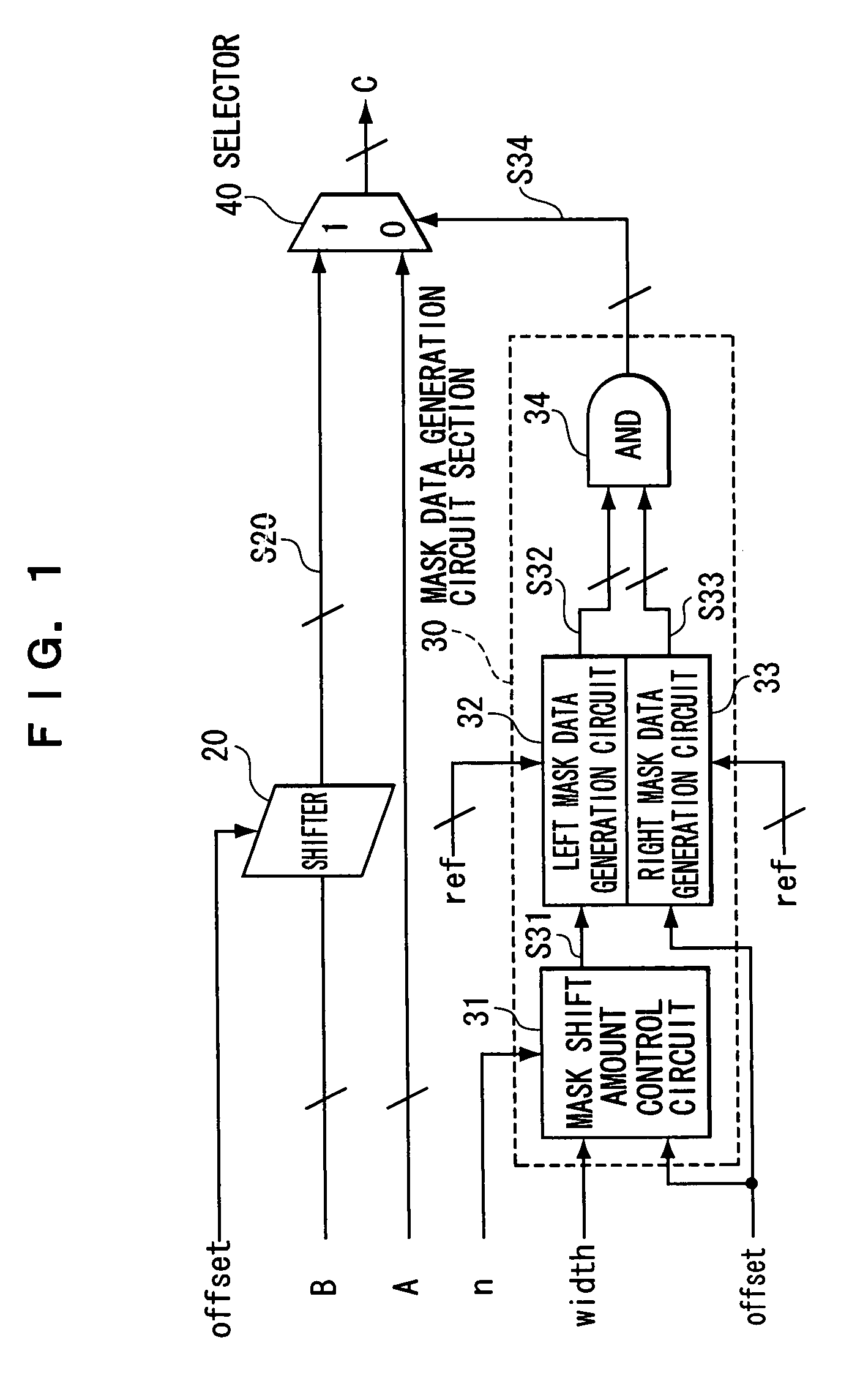
Bit field operation circuit
InactiveUS20080077643A1Digital computer detailsSpecific program execution arrangementsEngineeringBit field
A bit field operation circuit has a first shift unit, a mask shift amount control circuit, a second shift unit, a logic operation unit, and a selection unit. The first shift unit outputs a first intermediate data based on a first control signal. The mask shift amount control circuit outputs a mask shift control signal in accordance with a mask shift amount. The second shift unit outputs a second intermediate data based on a mask shift control signal. The third shift unit outputs a third intermediate data based on the first control signal. The logic operation unit performs logical operation of the second intermediate data and the third intermediate data, and outputs a mask selection data. The selection unit selects either one of the first intermediate data or the second input data based on the mask selection data to output as output data.
Owner:LAPIS SEMICON CO LTD
Method and system for clearing dependent speculations from a request queue
InactiveUS6487637B1Memory adressing/allocation/relocationConcurrent instruction executionMemory hierarchyBit field
A method of operating a multi-level memory hierarchy of a computer system and apparatus embodying the method, wherein instructions issue having an explicit prefetch request directly from an instruction sequence unit to a prefetch unit of the processing unit. The invention applies to values that are either operand data or instructions. These prefetch requests can be demand load requests, where the processing unit will need the operand data or instructions, or speculative load requests, where the processing unit may or may not need the operand data or instructions, but a branch prediction or stream association predicts that they might be needed. Further branch predictions or stream associations that were made based on an earlier speculative choice are linked by using a tag pool which assigns a bit fields in the tag pool entries to the level of speculation depth. Each entry shares in common the bit field values associated with earlier branches or stream associations. When a branch or stream predicted entry is no longer needed, that entry can be cancelled and all entries that were to be loaded dependent on that entry can likewise be cancelled by walking through all entries sharing the bit fields corresponding to the speculation depth of the cancelled entry and tagging those entries as invalid.
Owner:IBM CORP
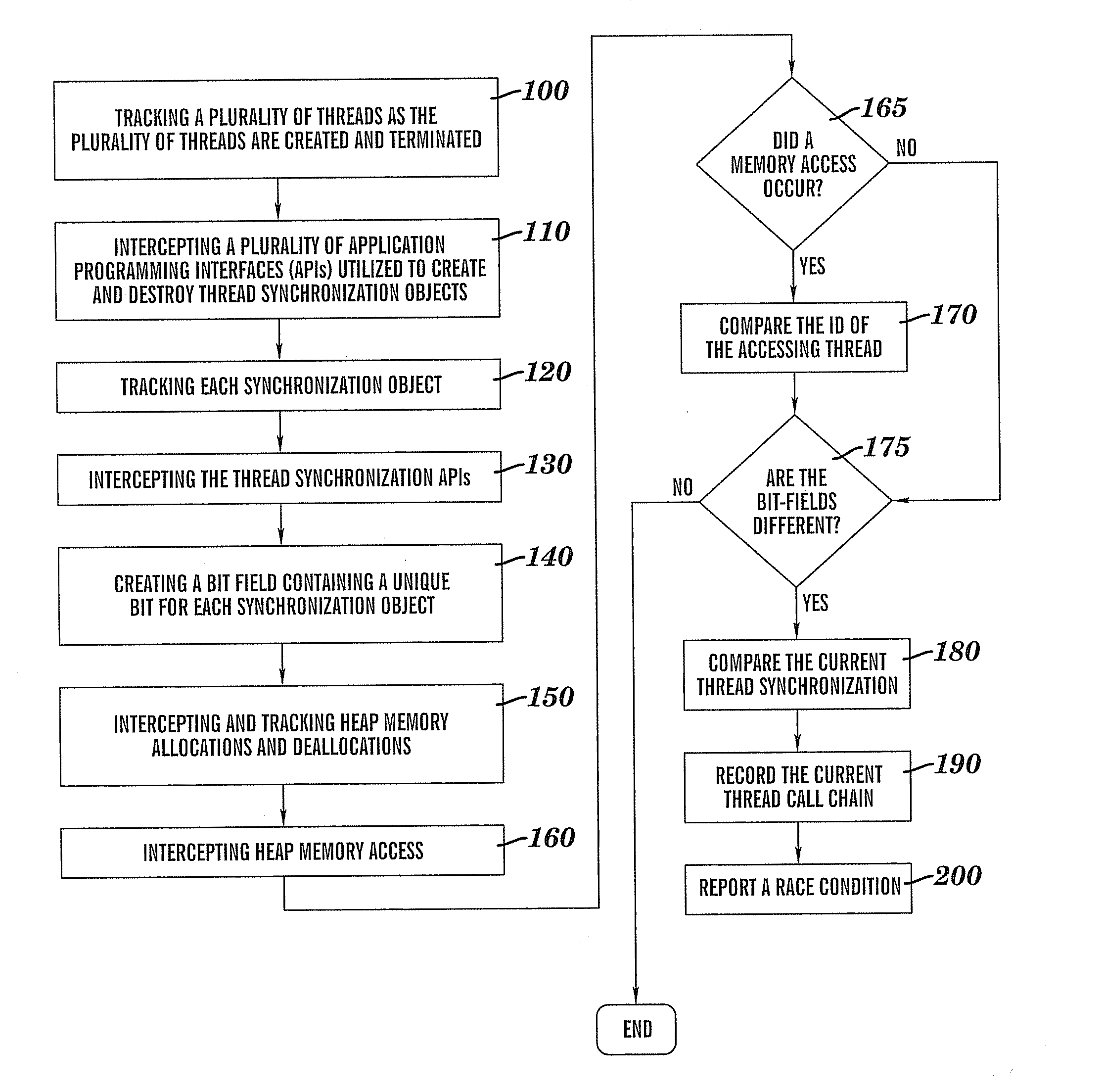
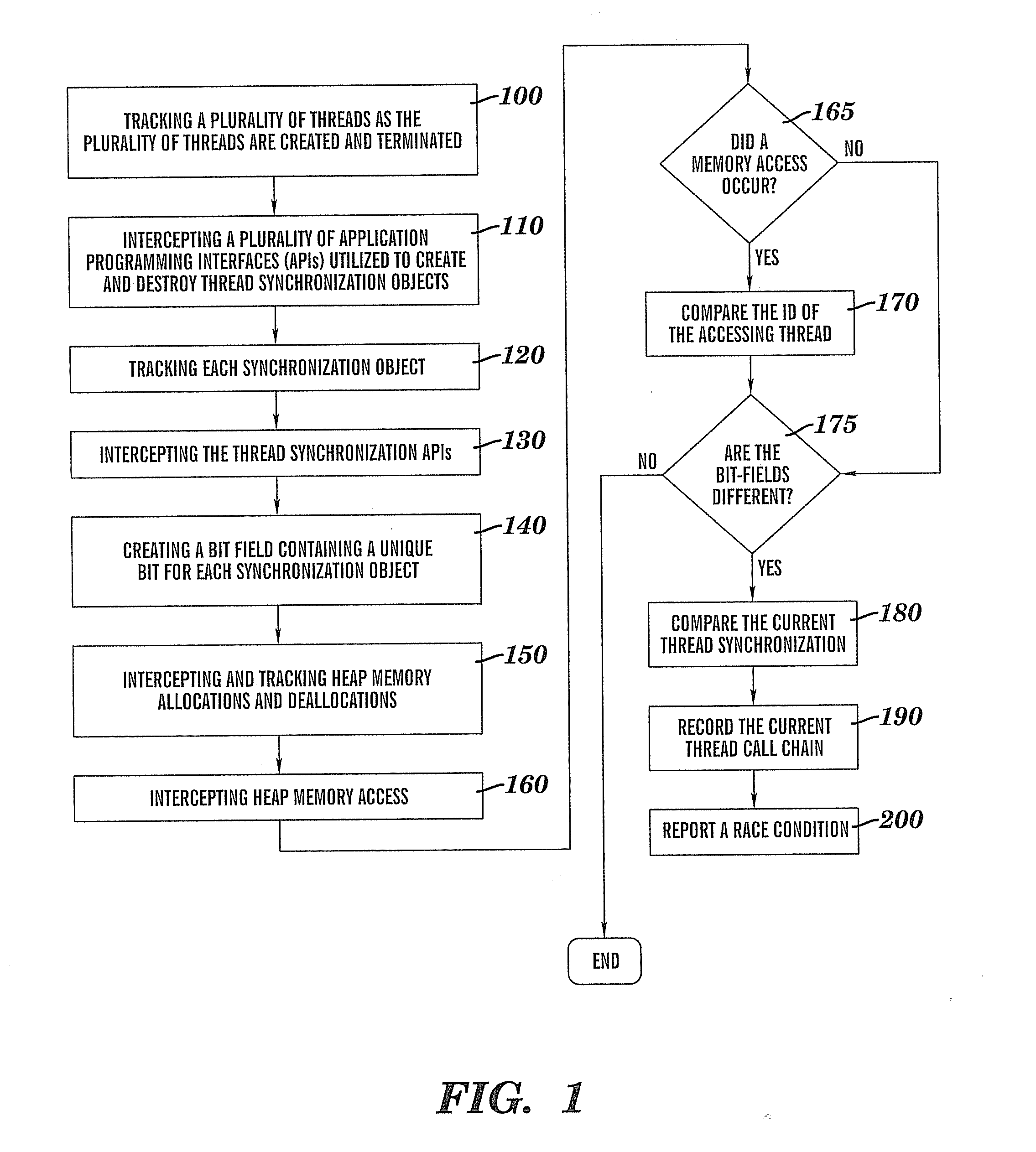
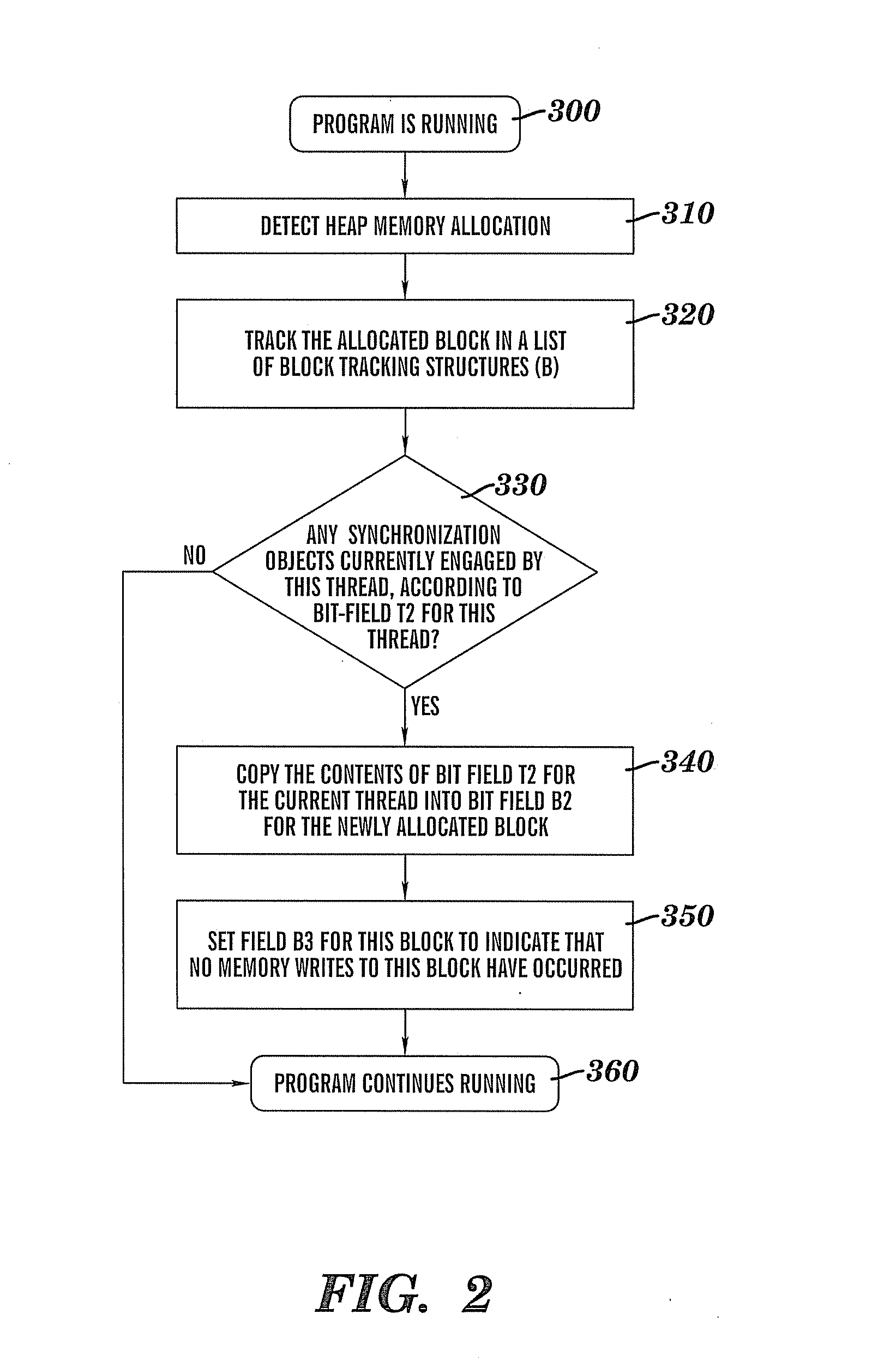
Method for detecting race conditions involving heap memory access
InactiveUS20080120627A1Error detection/correctionMultiprogramming arrangementsBit fieldParallel computing
A method for detecting race conditions involving heap memory access including a plurality of threads being tracked. At runtime a plurality of APIs utilized to create and destroy thread synchronization objects are intercepted, and each synchronization object created via the APIs is tracked. A bit field is created that contains a unique bit for each synchronization object. Heap memory allocations and deallocations are intercepted and tracked. The heap memory access is intercepted, and at that time, the ID of the accessing thread is compared with the last thread ID associated with that memory block when it was last accessed. If the thread IDs do not match, then the current thread synchronization object bit field is compared with the last synchronization object bit field associated with thread memory block. Provided the bit fields are different, a race condition warning is reported that is displayable to the user having the call chains.
Owner:GLOBALFOUNDRIES INC
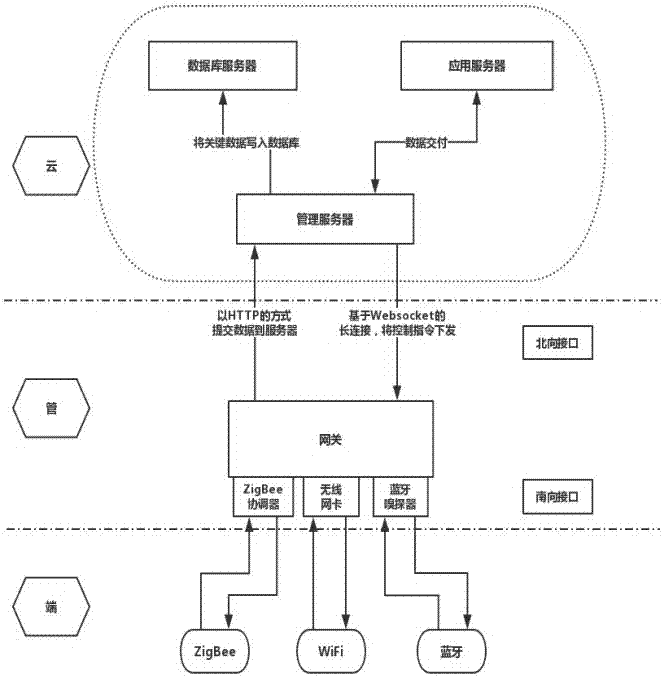
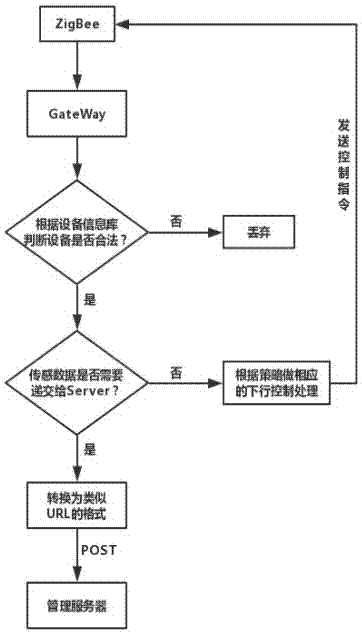
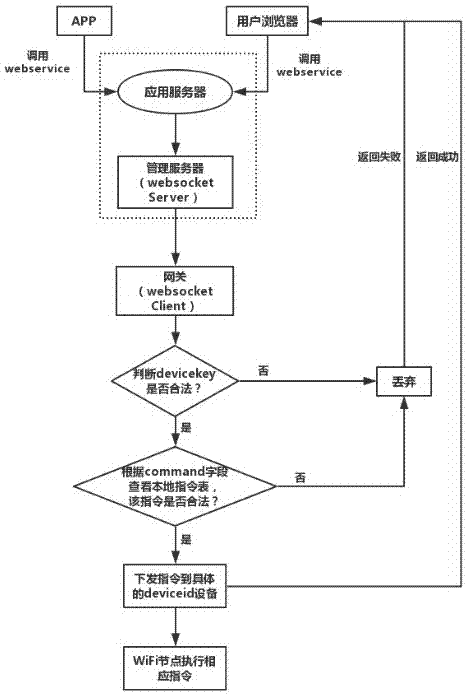
Internet of Things device discovery and management method
InactiveCN107172051ARealize the authentication functionImplement forwarding orientationTransmissionInformation repositoryBit field
The invention discloses an Internet of Things device discovery and management method. The method comprises the following steps: collecting and uploading a data message by a bottom layer sensing device to a gateway; pre-establishing and storing a device information database, a policy information database and an instruction information database by the gateway; calling device information in the data message uploaded by the bottom layer sensing device and matching the device information in the device information database to judge whether the bottom layer sensing device has a device security check code by the gateway; extracting a data bit field and matching the data bit field in the policy information database to obtain a control policy; performing format conversion, and uploading the data message to a server, receiving and storing the data message uploaded by the gateway, generating an application instruction and allocating the application instruction to the gateway by the server, receiving the application instruction, extracting the device information in the application instruction and matching the device information in the device information database by the gateway to extract a logic instruction in the application instruction and match the logic instruction in the instruction information database so as to obtain a corresponding control instruction and execute the control instruction on the corresponding bottom layer sensing device. By adoption of the Internet of Things device discovery and management method disclosed by the invention, a data authentication function, a data forwarding direction and a control instruction acquisition function can be realized.
Owner:NANJING UNIV OF POSTS & TELECOMM
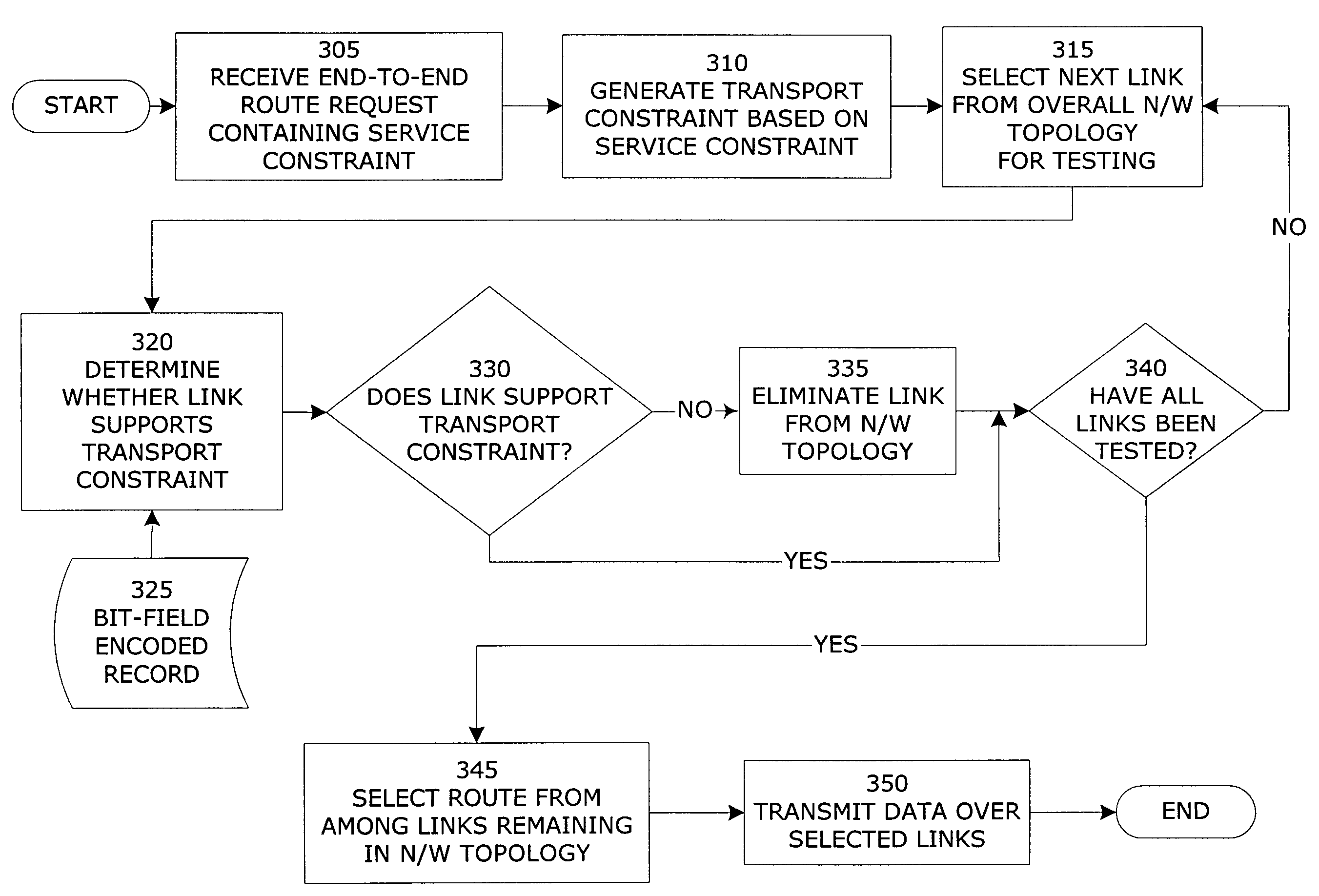
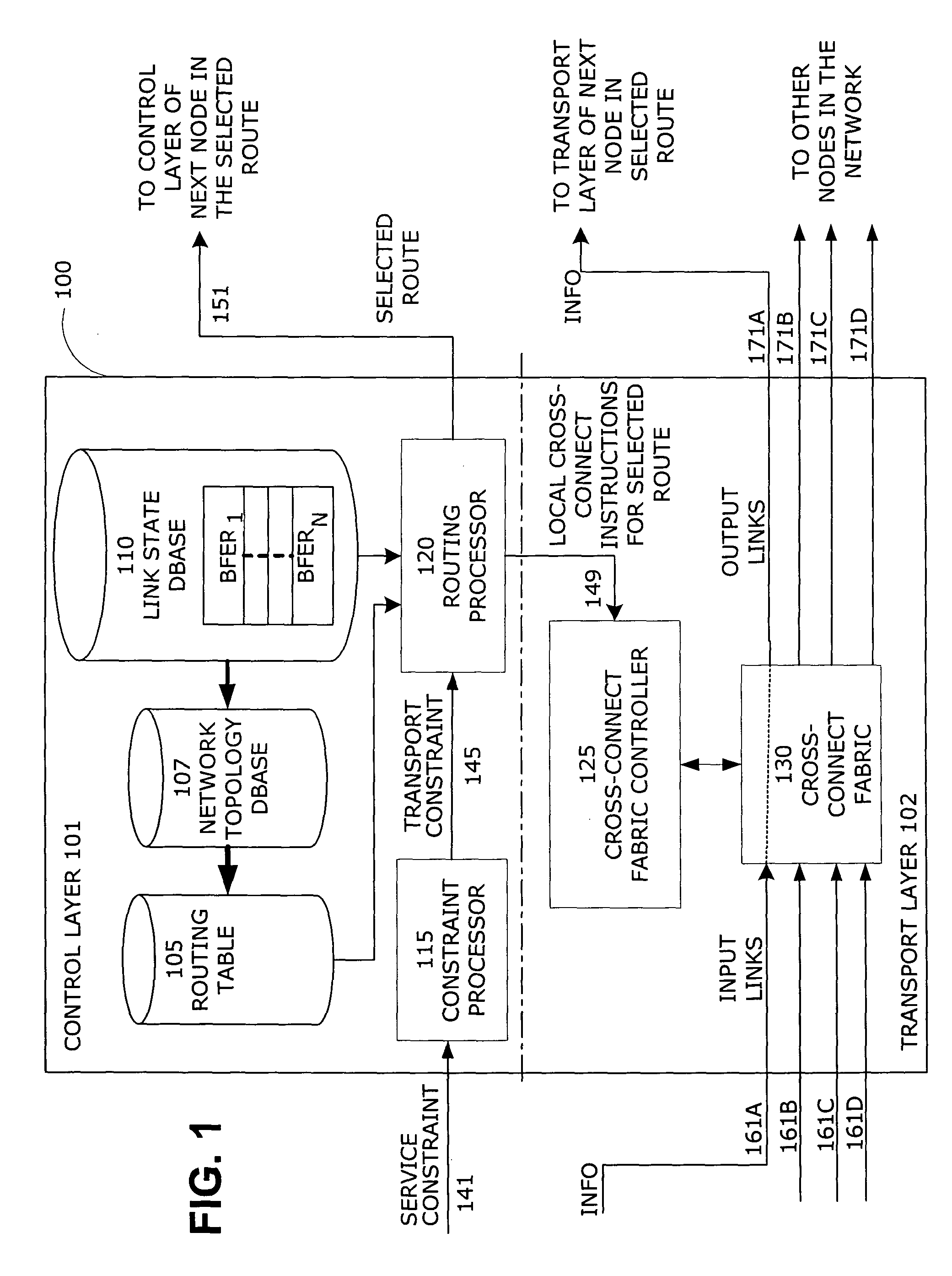
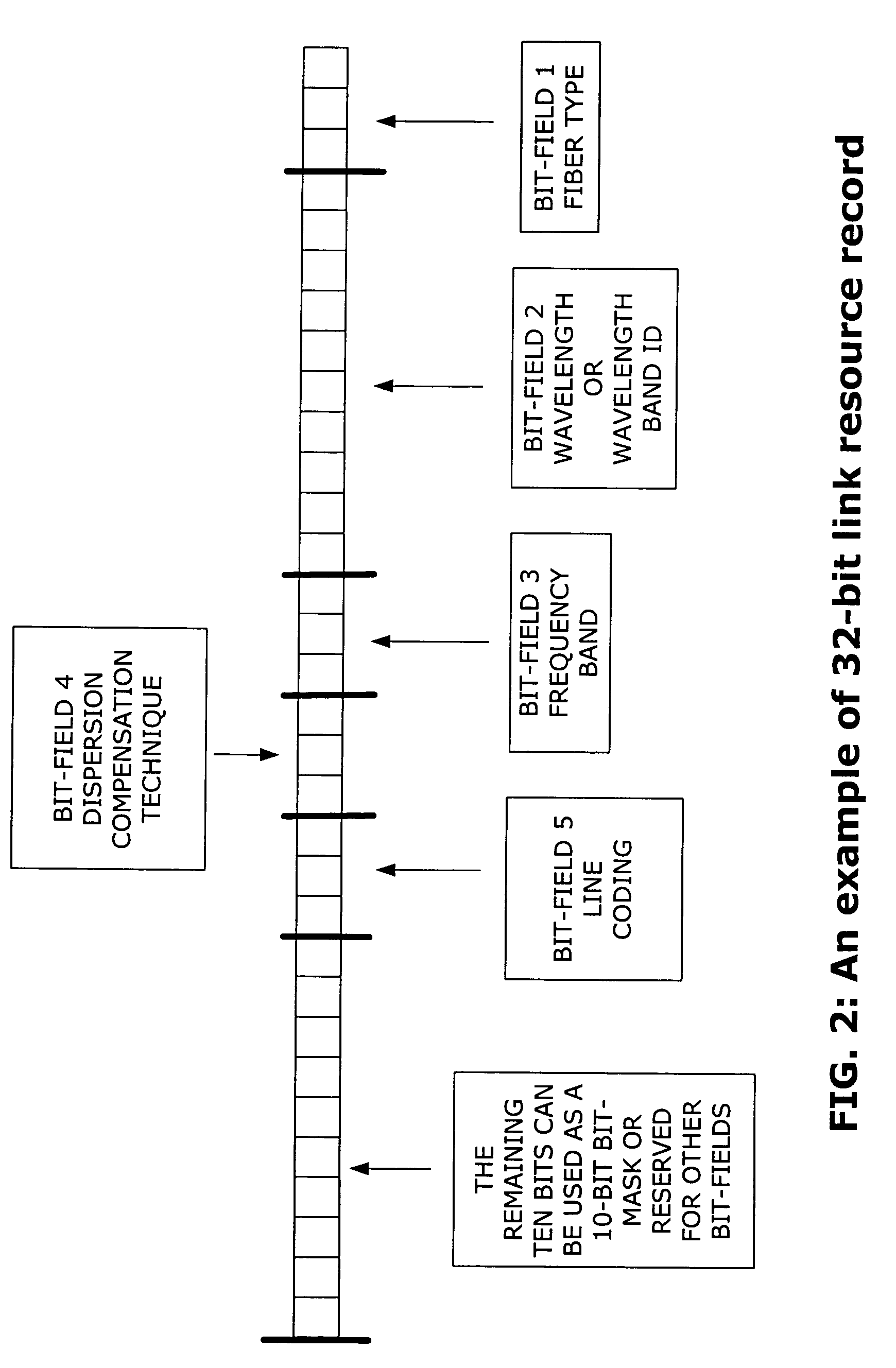
Bit-field-encoded resource record for determining a transmission path in a communications network
ActiveUS7336617B1Avoid less flexibilityIncrease the number ofError preventionTransmission systemsInformation transmissionBit field
Method and apparatus for tracking, recording and distributing link state characteristics over communications networks. The invention allows network operators to efficiently define, track, store and disseminate link state characteristics using a bit-field-encoded resource record that is capable of representing many more link state characteristics than the bit-mask-encoded records used in existing systems. As a result, the present invention, when used in conjunction with standard routing and network maintenance algorithms, provides a much more efficient method than existing systems provide, for performing sophisticated networking tasks, such as handling complicated information transmission requests, setting up and tearing down network paths, and making dynamic routing decisions.
Owner:VERIZON PATENT & LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com