Patents
Literature
2960 results about "Physical address" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
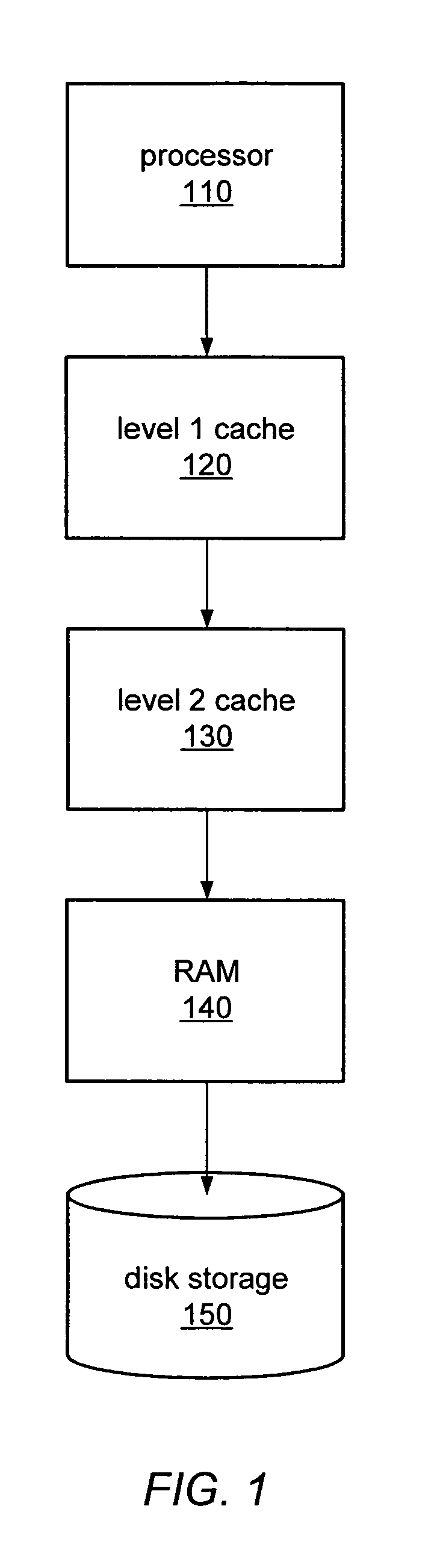
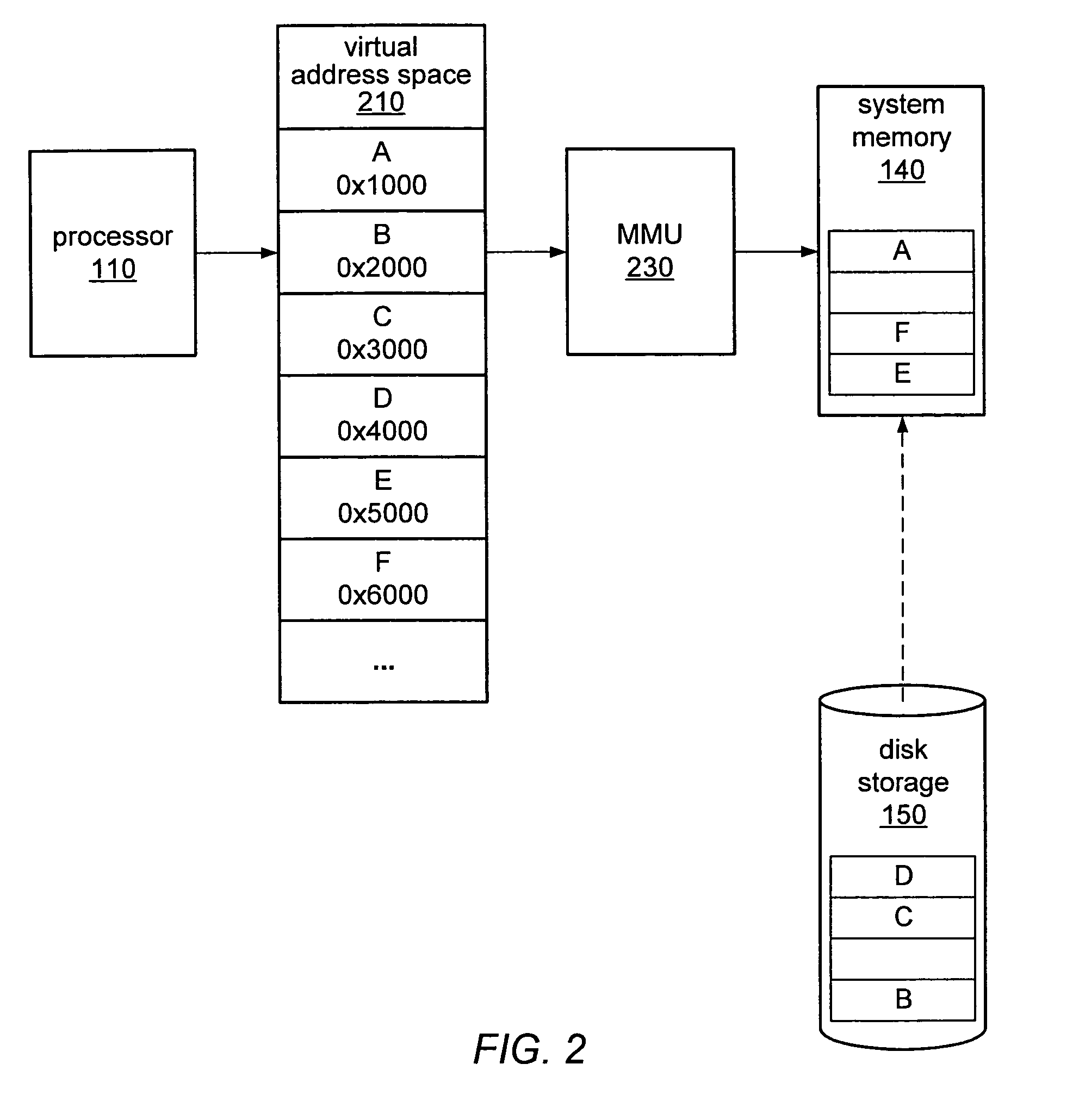
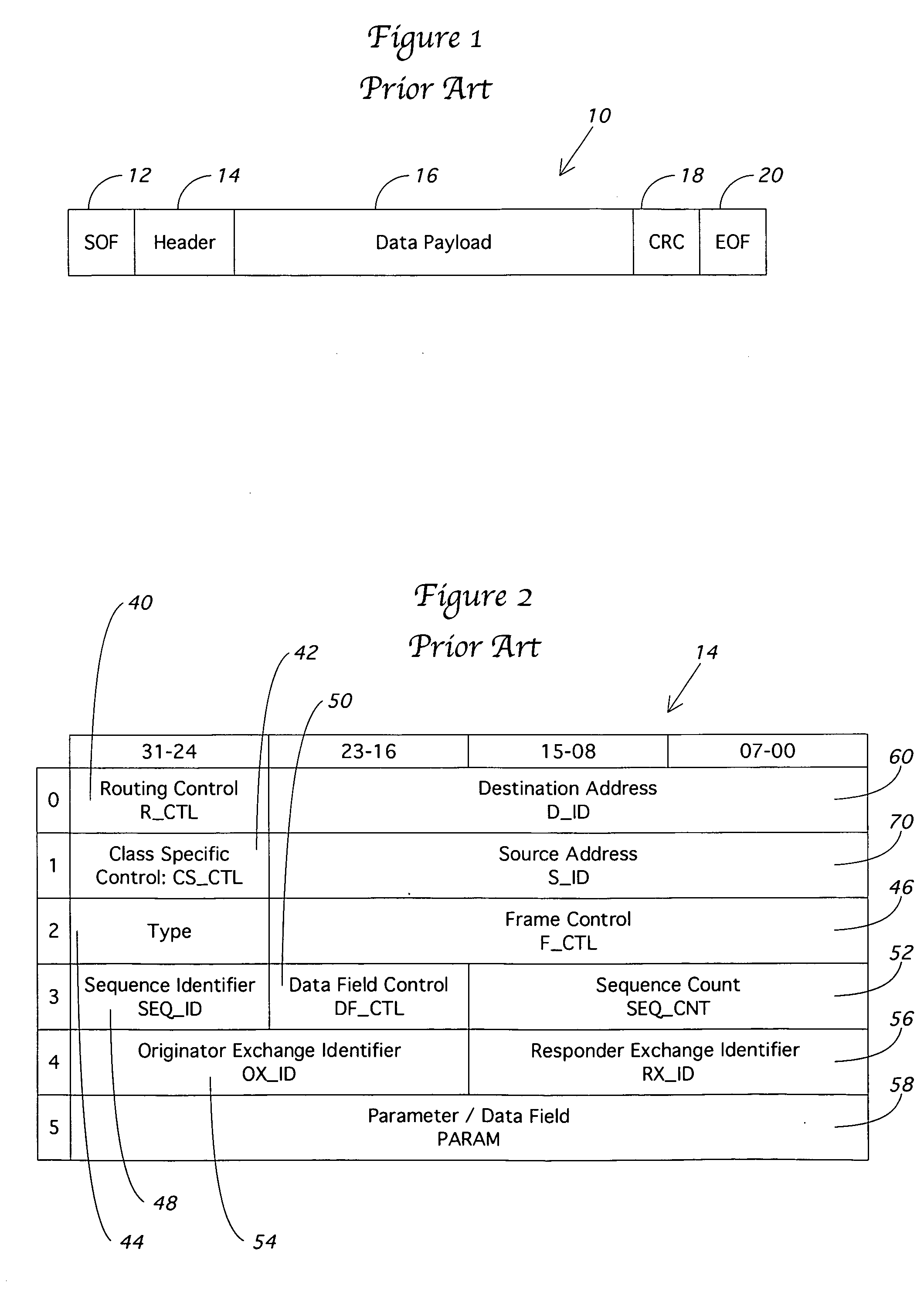
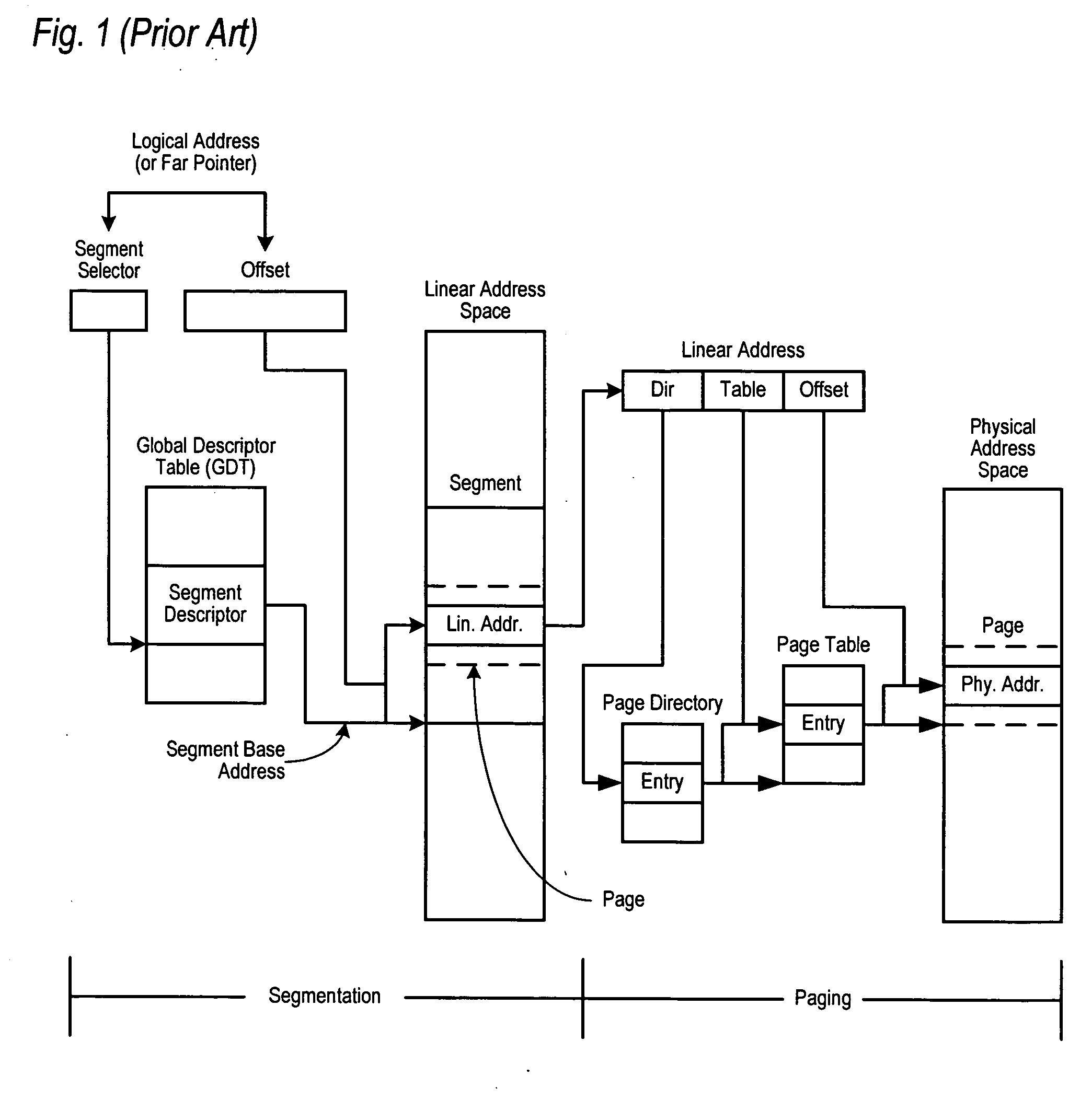
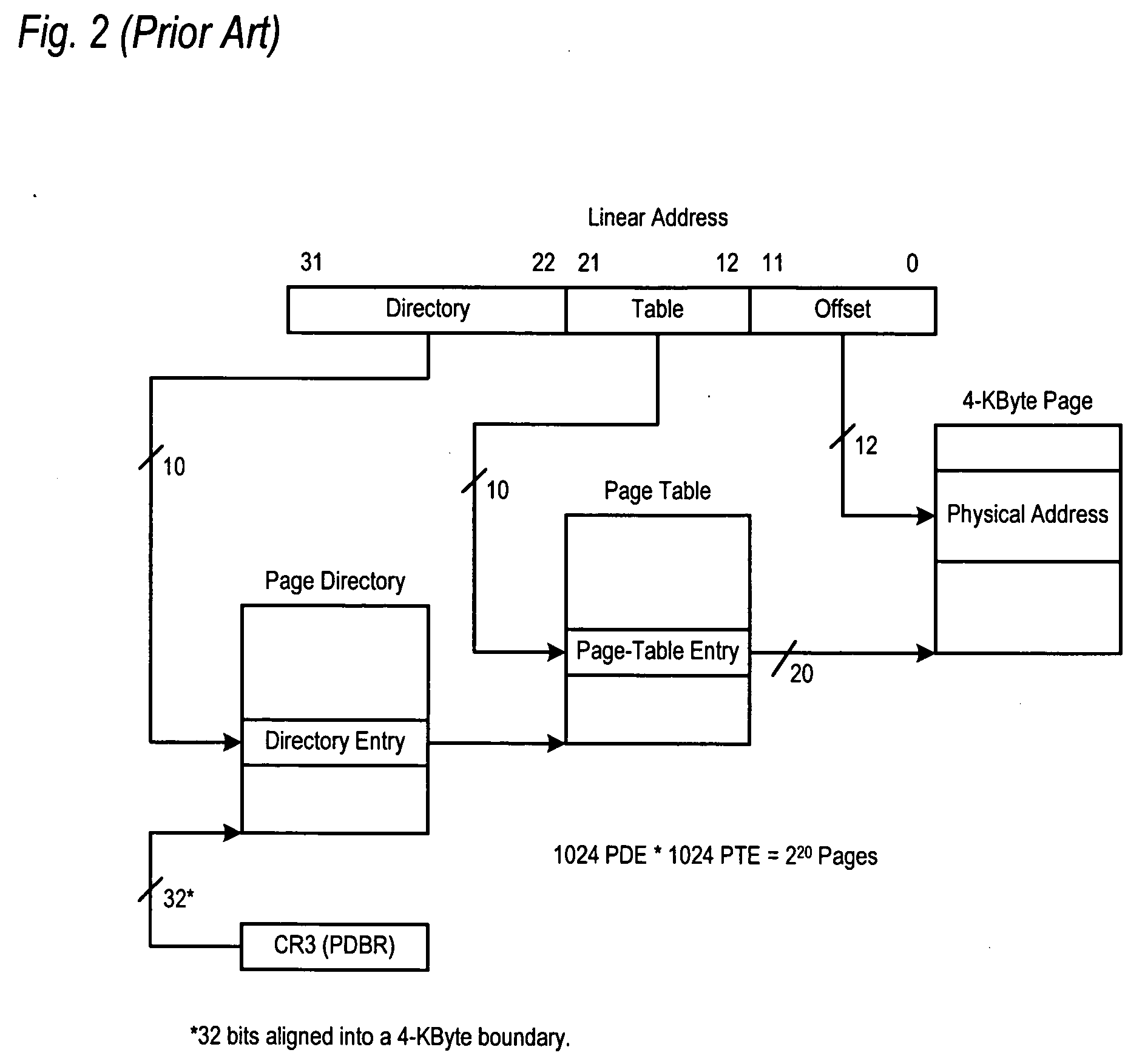
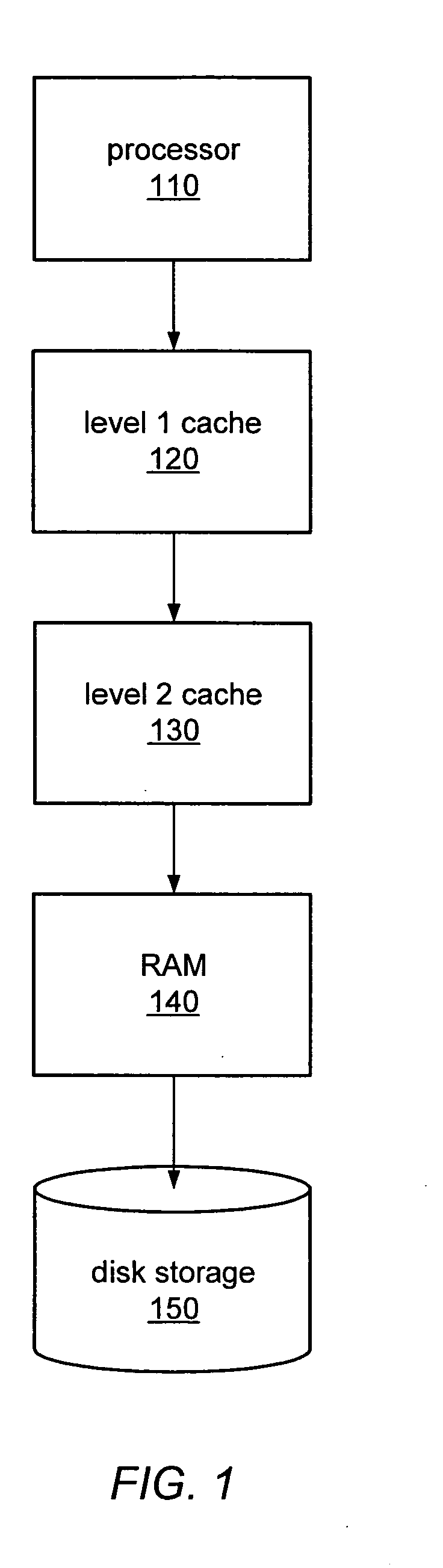
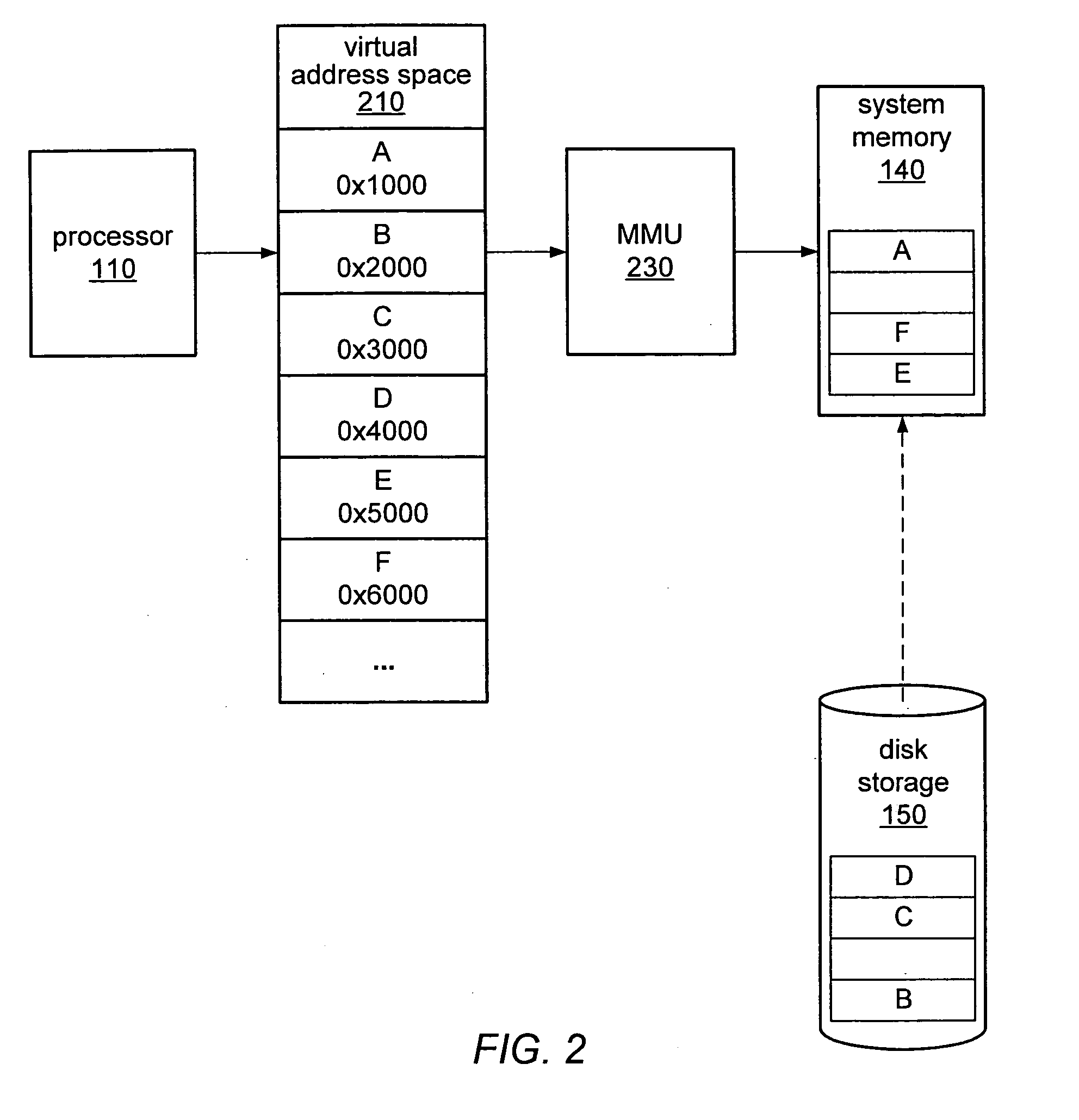
In computing, a physical address (also real address, or binary address), is a memory address that is represented in the form of a binary number on the address bus circuitry in order to enable the data bus to access a particular storage cell of main memory, or a register of memory mapped I/O device.
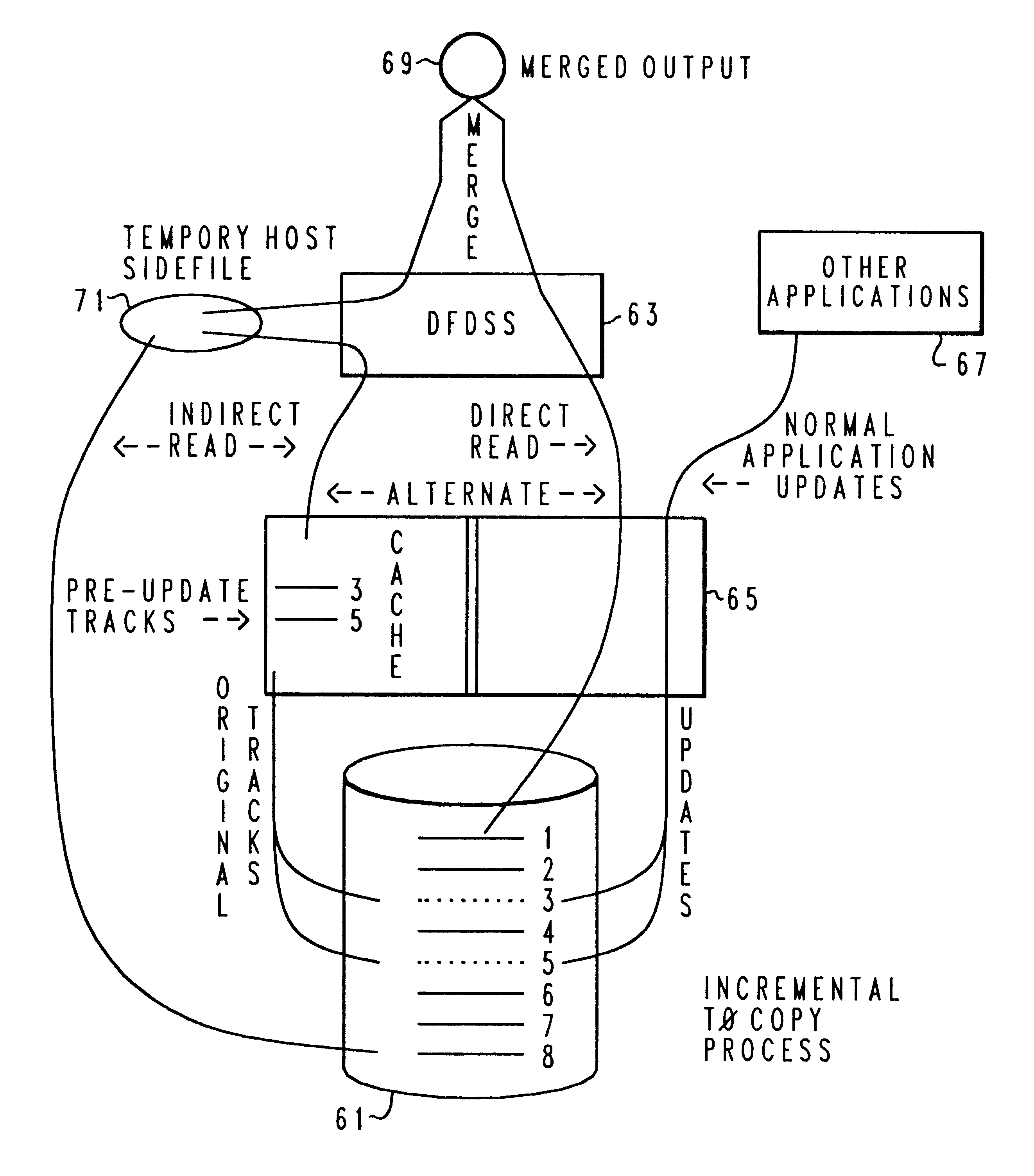
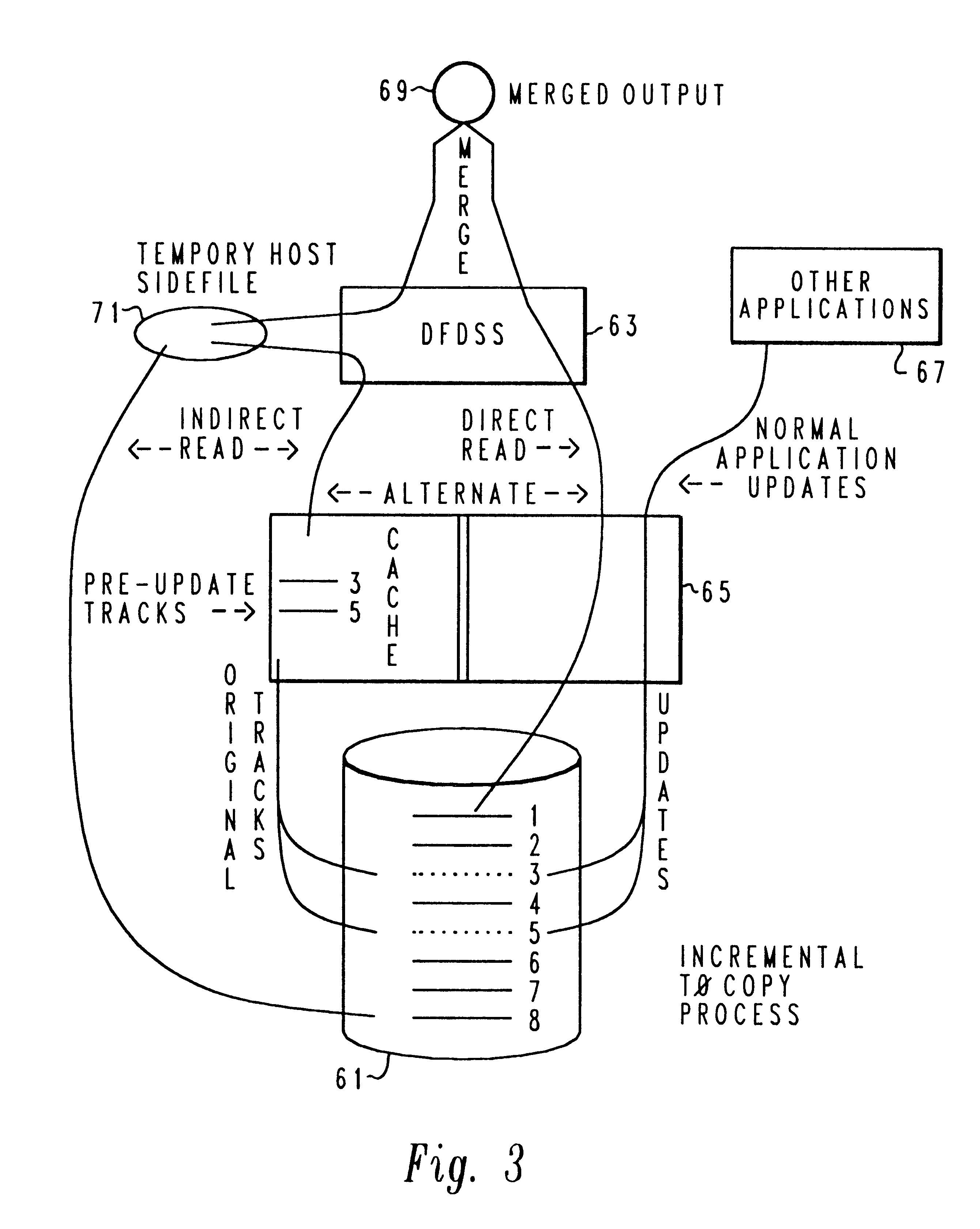
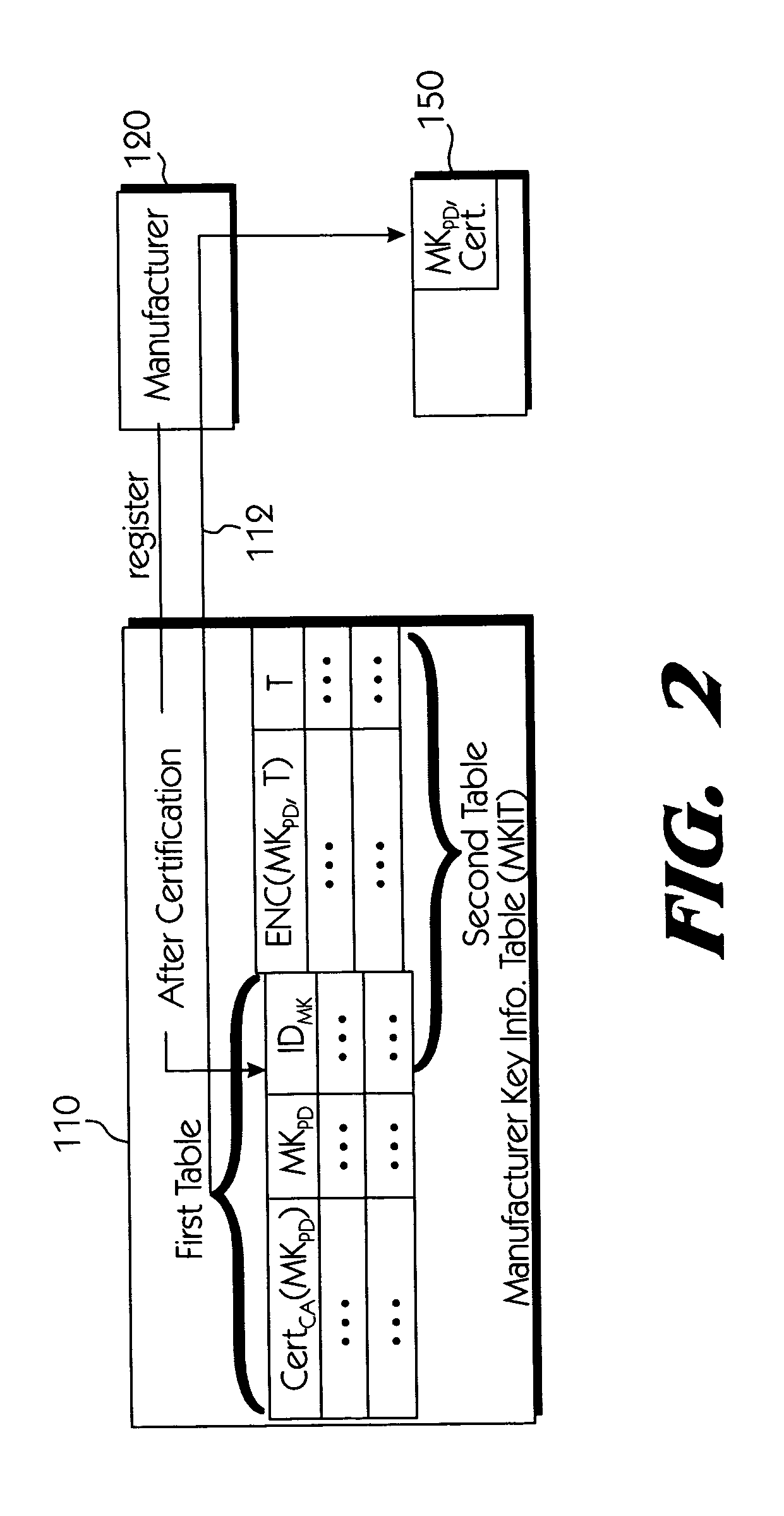
Method and system for incremental time zero backup copying of data
InactiveUSRE37601E1Maintaining continued availability of datasetsReduce suspensionRedundant operation error correctionMemory systemsData processing systemData set
Backup copying of designated datasets representing a first selected point in time consistency may be performed in a data processing system on an attached storage subsystem concurrent with data processing system application execution by first suspending application execution only long enough to form a logical-to-physical address concordance, and thereafter physically backing up the datasets on the storage subsystem on a scheduled or opportunistic basis. An indication of each update to a selected portion of the designated datasets which occurs after the first selected point in time is stored and application initiated updates to uncopied designated datasets are first buffered. Thereafter, sidefiles are made of the affected datasets, or portions thereof, the updates are then written through to the storage subsystem, and the sidefiles written to an alternate storage location in backup copy order, as controlled by the address concordance. At a subsequent point in time only those portions of the designated datasets which have been updated after the first selected period and time are copied, utilizing an identical technique.
Owner:IBM CORP
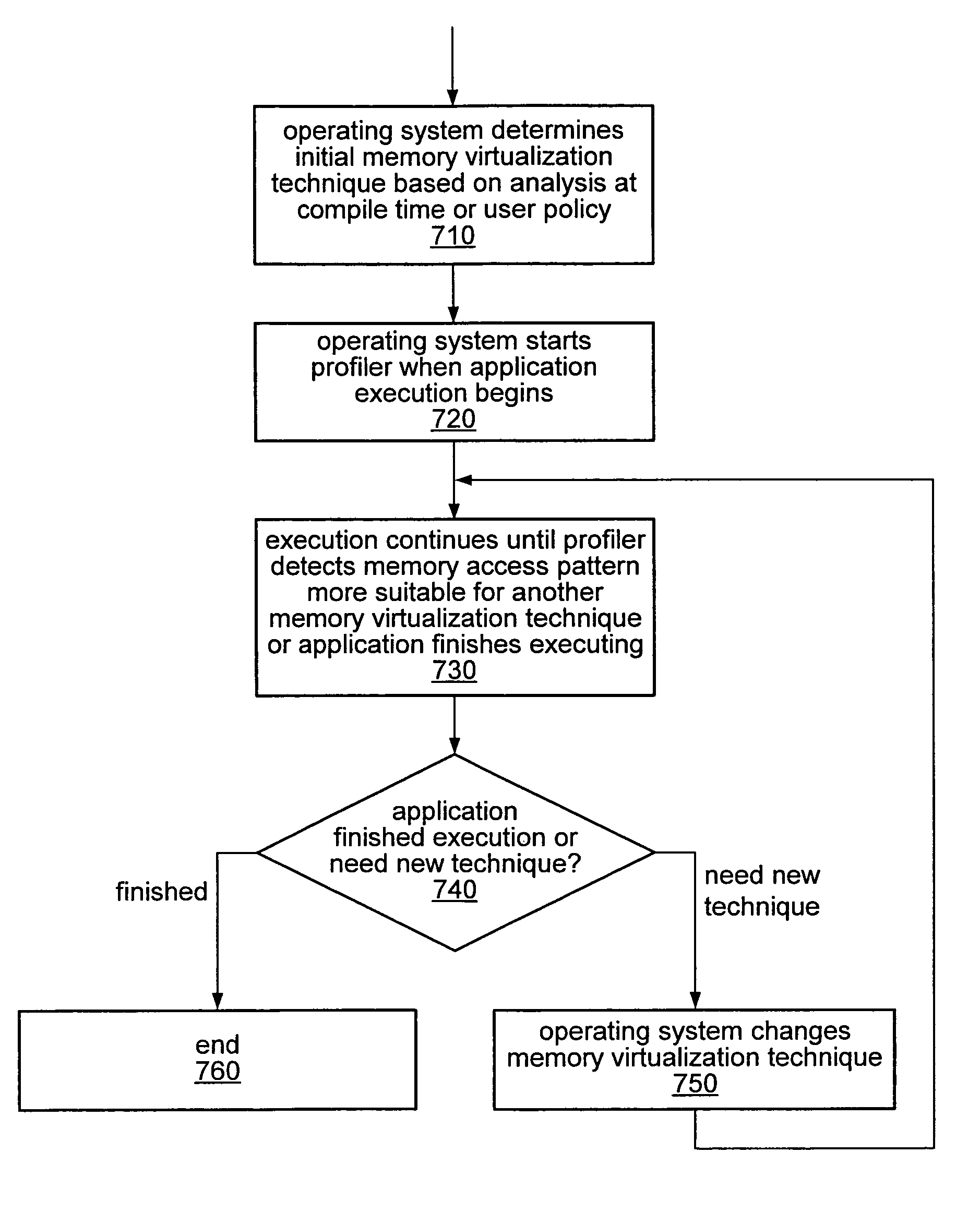
Dynamic selection of memory virtualization techniques
ActiveUS7752417B2Error detection/correctionMemory adressing/allocation/relocationVirtualizationComputerized system
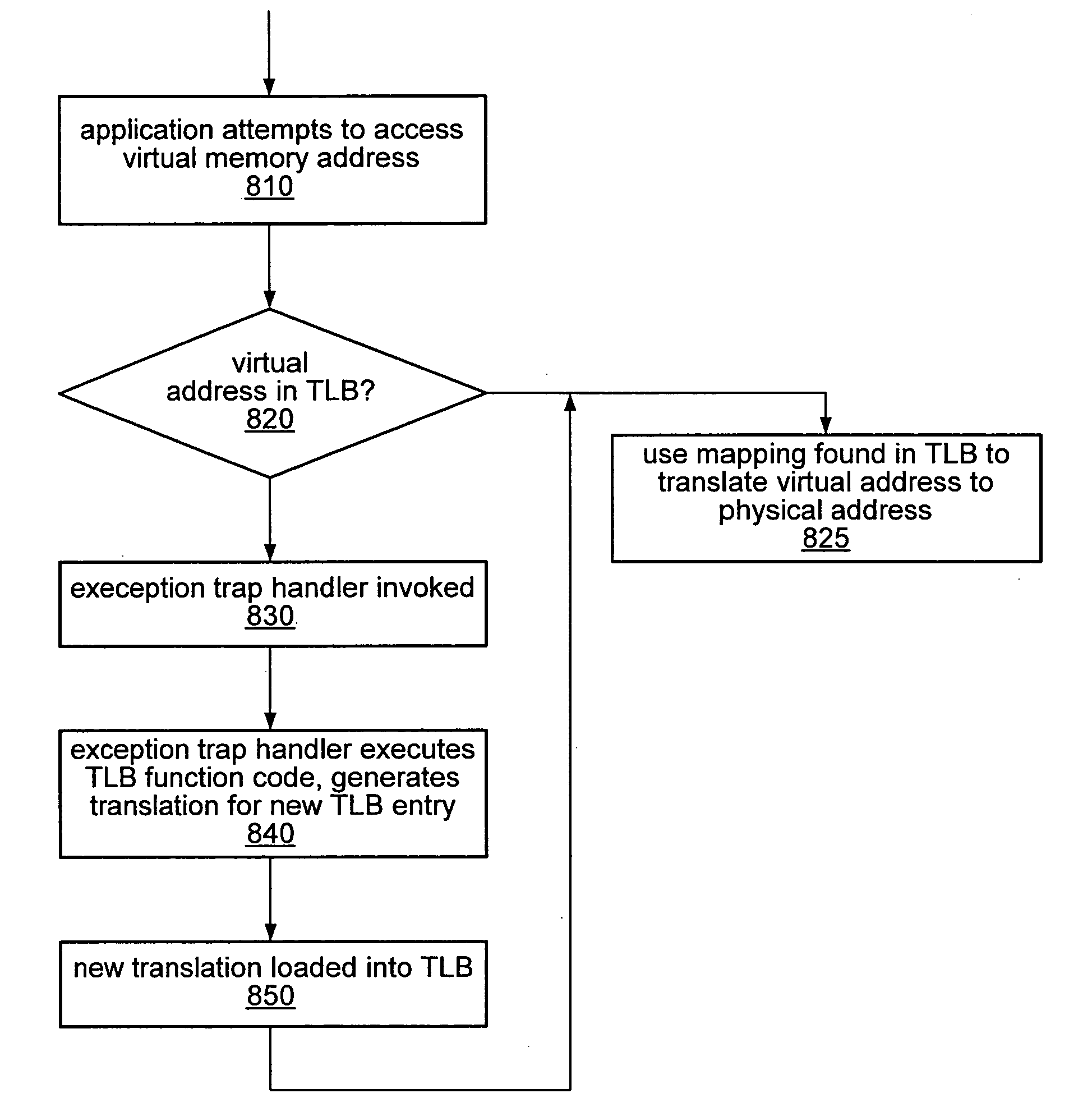
A computer system may be configured to dynamically select a memory virtualization and corresponding virtual-to-physical address translation technique during execution of an application and to dynamically employ the selected technique in place of a current technique without re-initializing the application. The computer system may be configured to determine that a current address translation technique incurs a high overhead for the application's current workload and may be configured to select a different technique dependent on various performance criteria and / or a user policy. Dynamically employing the selected technique may include reorganizing a memory, reorganizing a translation table, allocating a different block of memory to the application, changing a page or segment size, or moving to or from a page-based, segment-based, or function-based address translation technique. A selected translation technique may be dynamically employed for the application independent of a translation technique employed for a different application.
Owner:ORACLE INT CORP
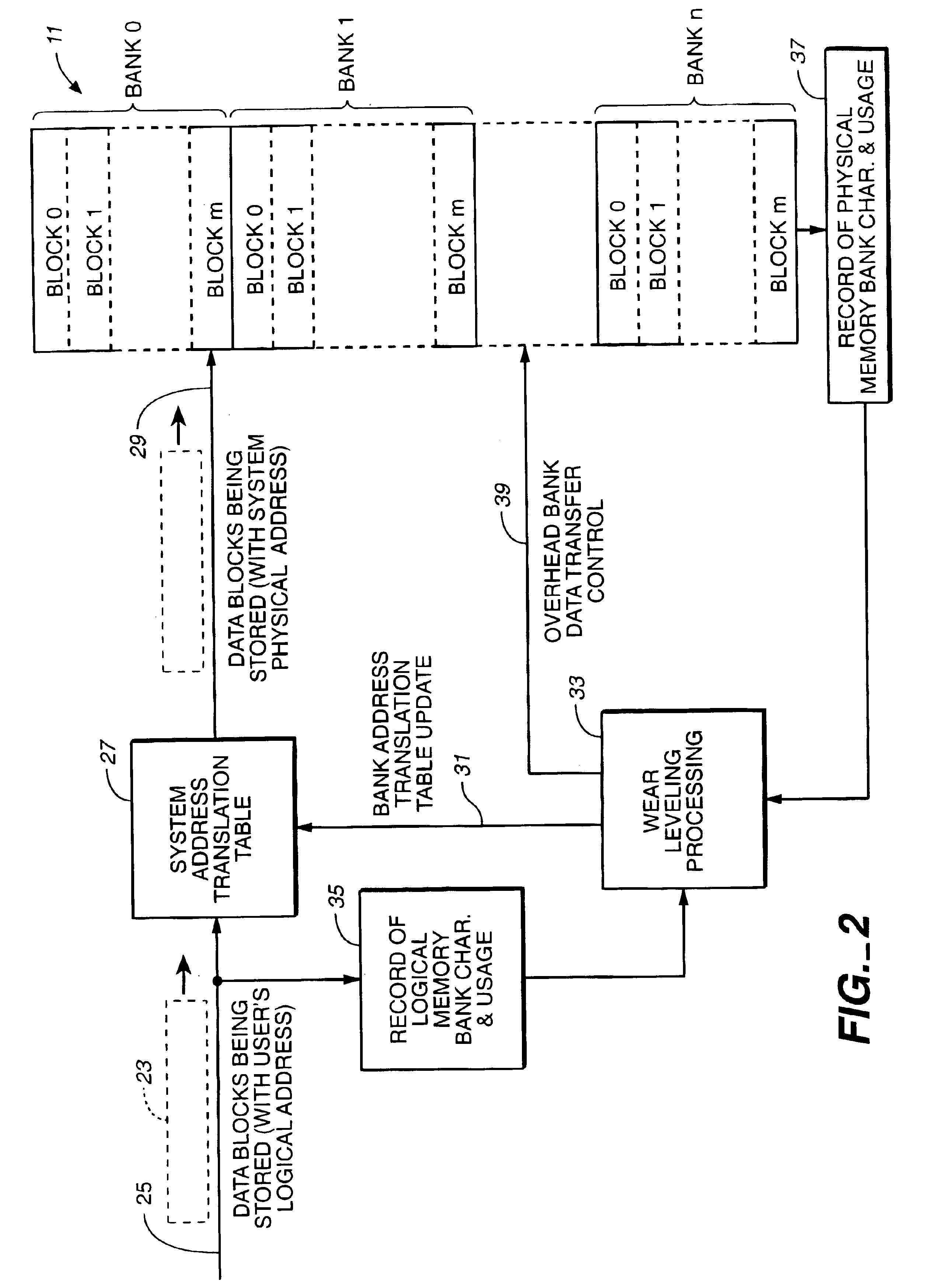
Wear leveling techniques for flash EEPROM systems
InactiveUS6850443B2Avoid uneven wearExtended service lifeMemory architecture accessing/allocationRead-only memoriesElectricityProgrammable read-only memory
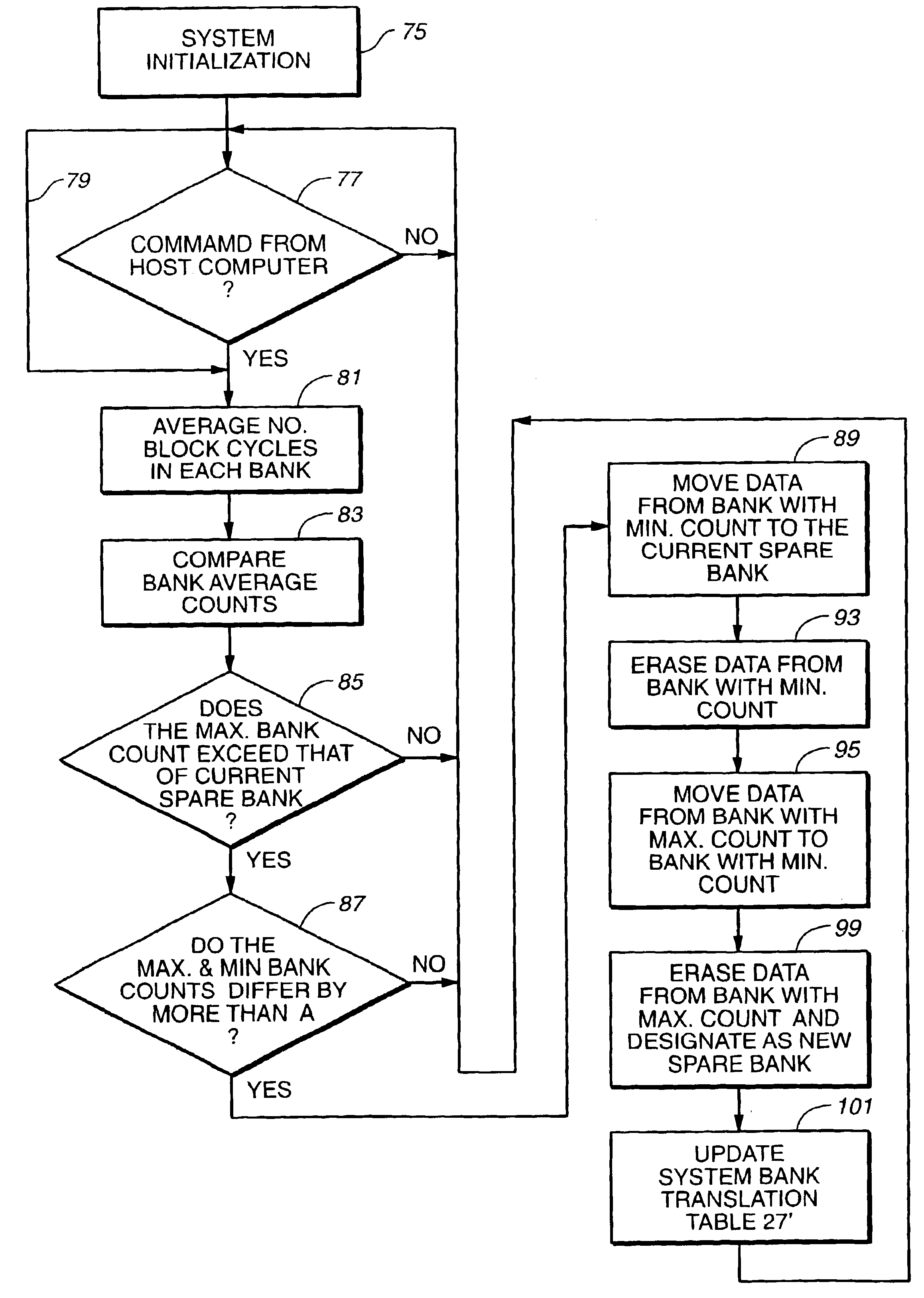
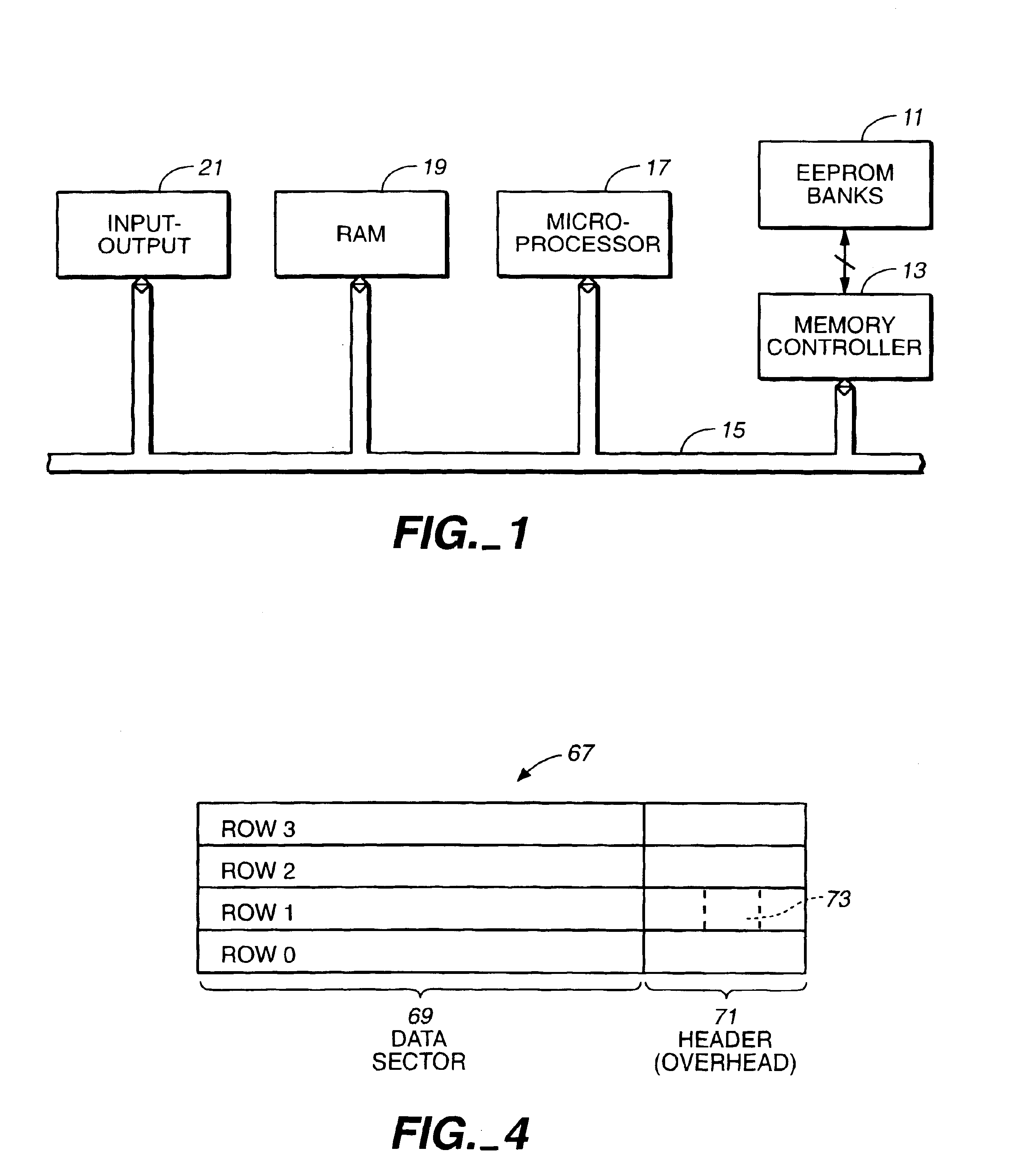
A mass storage system made of flash electrically erasable and programmable read only memory (“EEPROM”) cells organized into blocks, the blocks in turn being grouped into memory banks, is managed to even out the numbers of erase and rewrite cycles experienced by the memory banks in order to extend the service lifetime of the memory system. Since this type of memory cell becomes unusable after a finite number of erase and rewrite cycles, although in the tens of thousands of cycles, uneven use of the memory banks is avoided so that the entire memory does not become inoperative because one of its banks has reached its end of life while others of the banks are little used. Relative use of the memory banks is monitored and, in response to detection of uneven use, have their physical addresses periodically swapped for each other in order to even out their use over the lifetime of the memory.
Owner:SANDISK TECH LLC
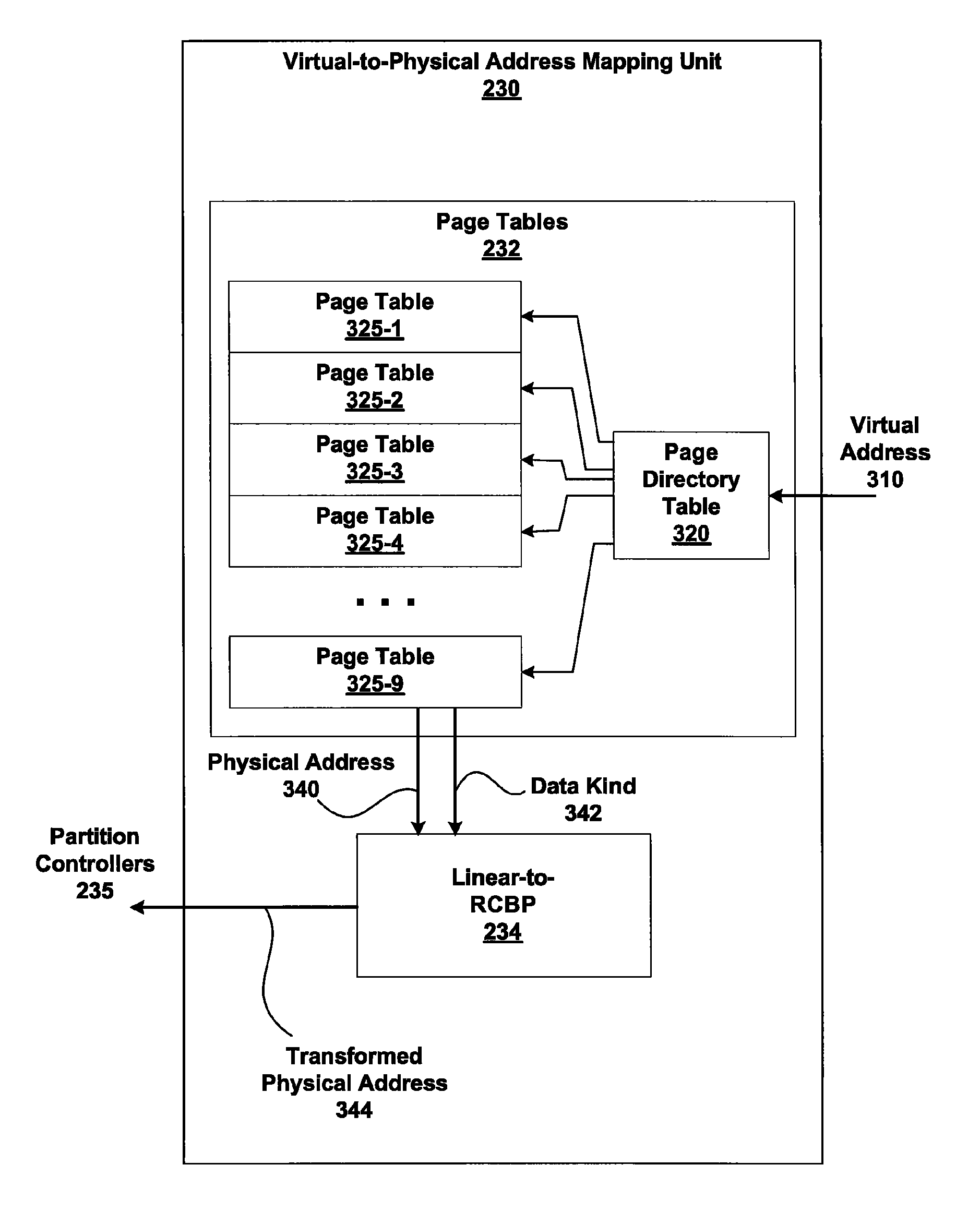
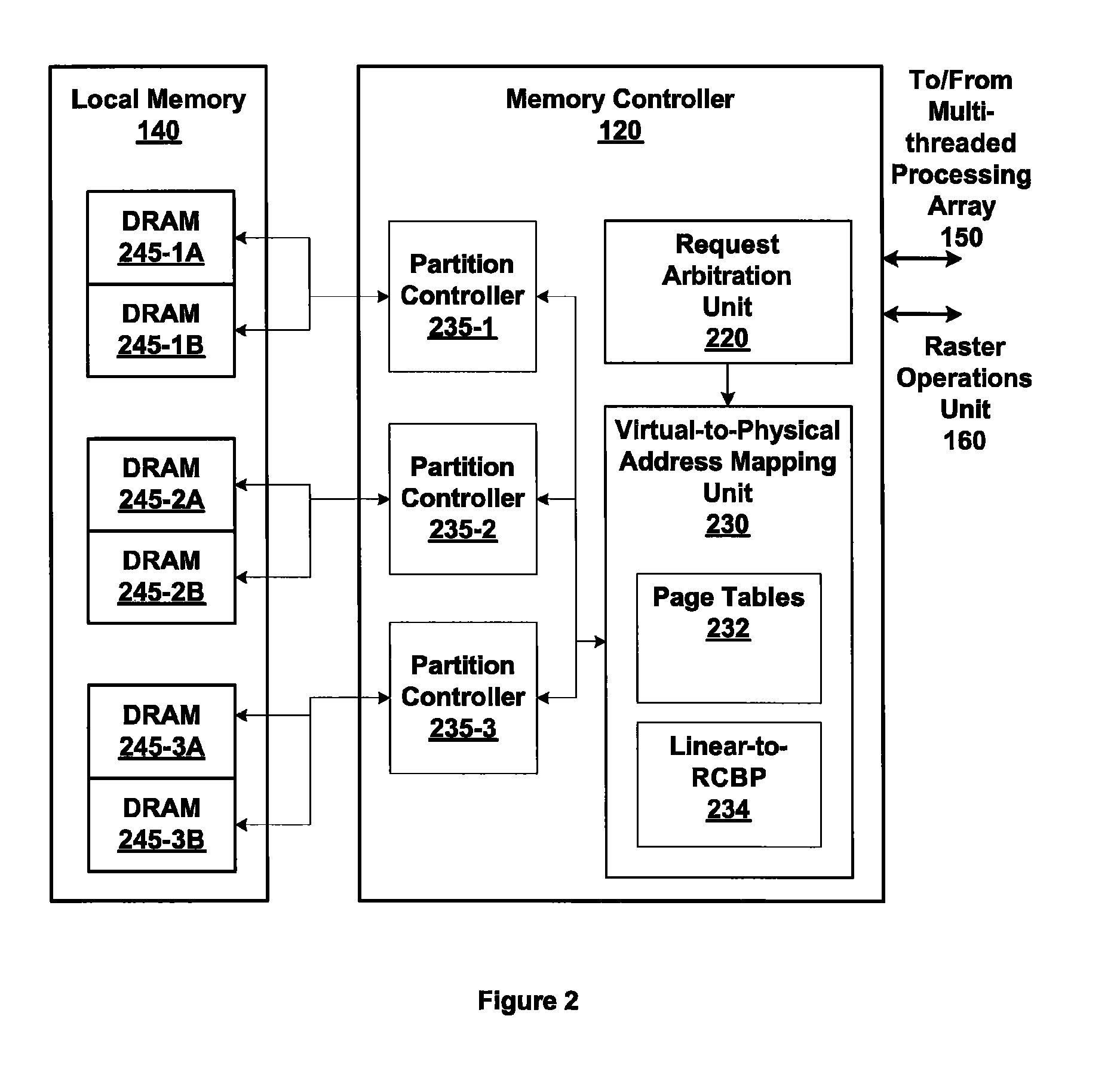
Memory addressing controlled by PTE fields
ActiveUS7805587B1Reduce accessMemory adressing/allocation/relocationComputer security arrangementsMemory addressDram memory
Embodiments of the present invention enable virtual-to-physical memory address translation using optimized bank and partition interleave patterns to improve memory bandwidth by distributing data accesses over multiple banks and multiple partitions. Each virtual page has a corresponding page table entry that specifies the physical address of the virtual page in linear physical address space. The page table entry also includes a data kind field that is used to guide and optimize the mapping process from the linear physical address space to the DRAM physical address space, which is used to directly access one or more DRAM. The DRAM physical address space includes a row, bank and column address. The data kind field is also used to optimize the starting partition number and partition interleave pattern that defines the organization of the selected physical page of memory within the DRAM memory system.
Owner:NVIDIA CORP
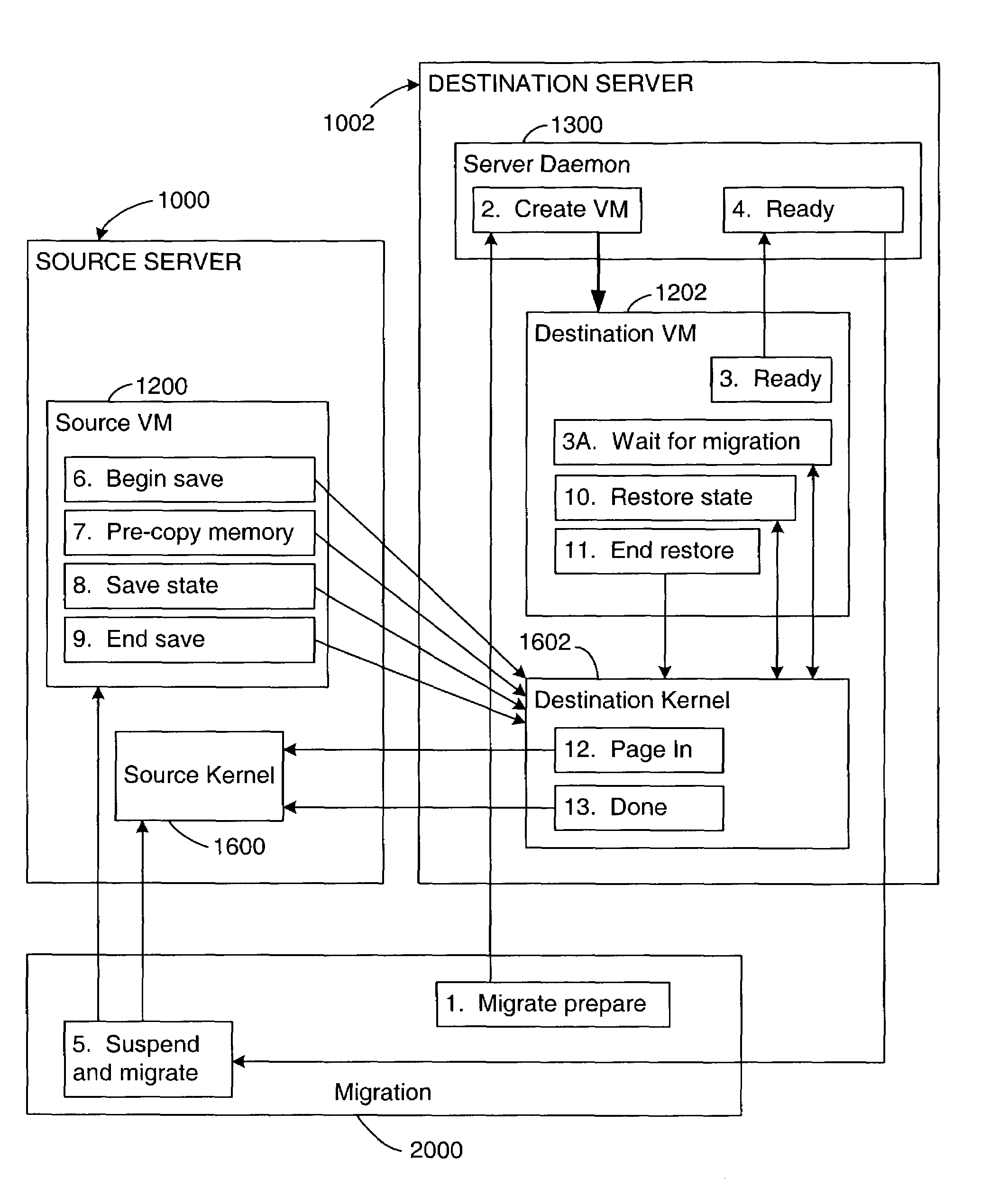
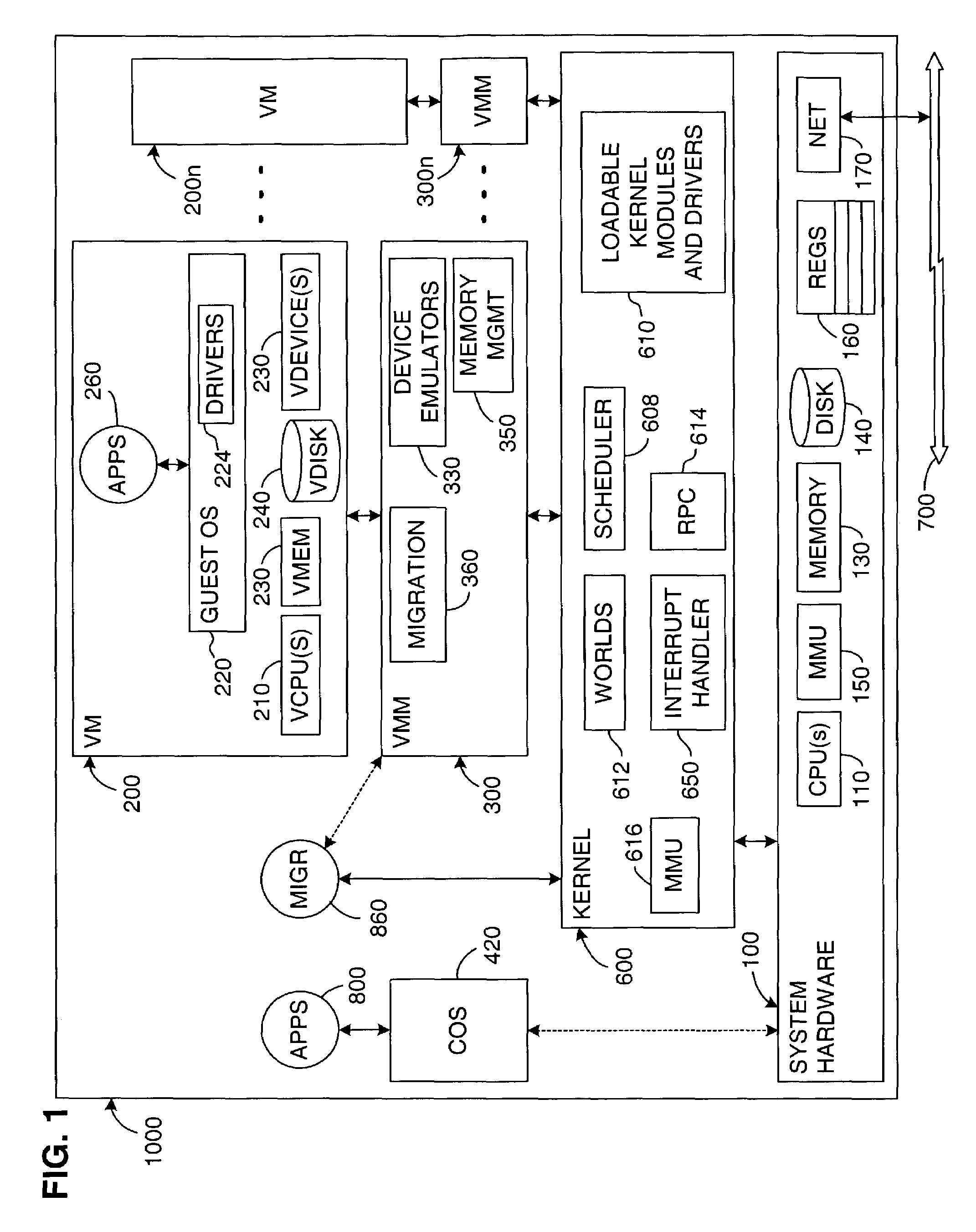
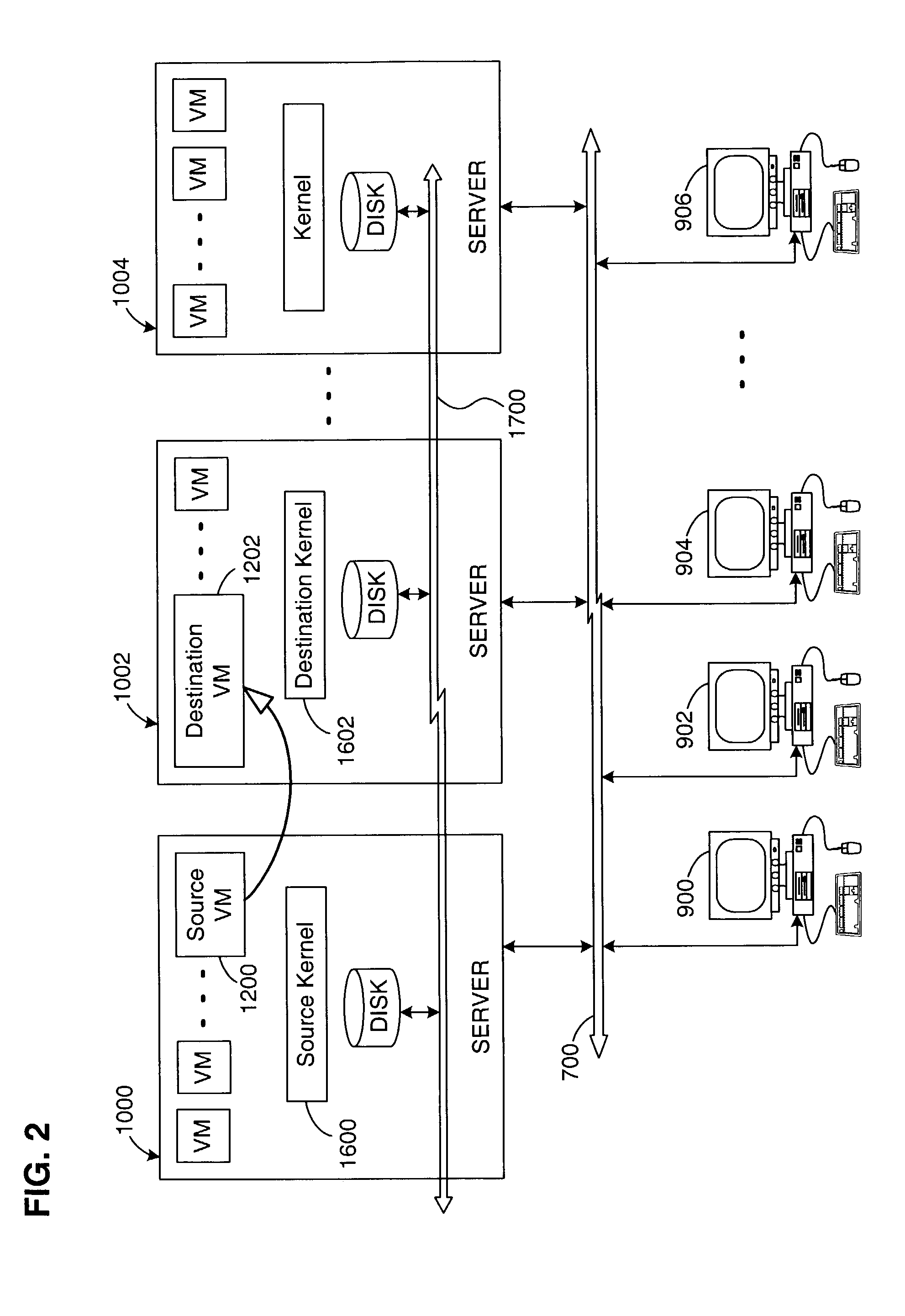
Virtual machine migration
A source virtual machine (VM) hosted on a source server is migrated to a destination VM on a destination server without first powering down the source VM. After optional pre-copying of the source VM's memory to the destination VM, the source VM is suspended and its non-memory state is transferred to the destination VM; the destination VM is then resumed from the transferred state. The source VM memory is either paged in to the destination VM on demand, or is transferred asynchronously by pre-copying and write-protecting the source VM memory, and then later transferring only the modified pages after the destination VM is resumed. The source and destination servers preferably share common storage, in which the source VM's virtual disk is stored; this avoids the need to transfer the virtual disk contents. Network connectivity is preferably also made transparent to the user by arranging the servers on a common subnet, with virtual network connection addresses generated from a common name space of physical addresses.
Owner:VMWARE INC
Locking technique for control and synchronization
InactiveUS6973549B1Digital data information retrievalMultiprogramming arrangementsFast pathLocking mechanism
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
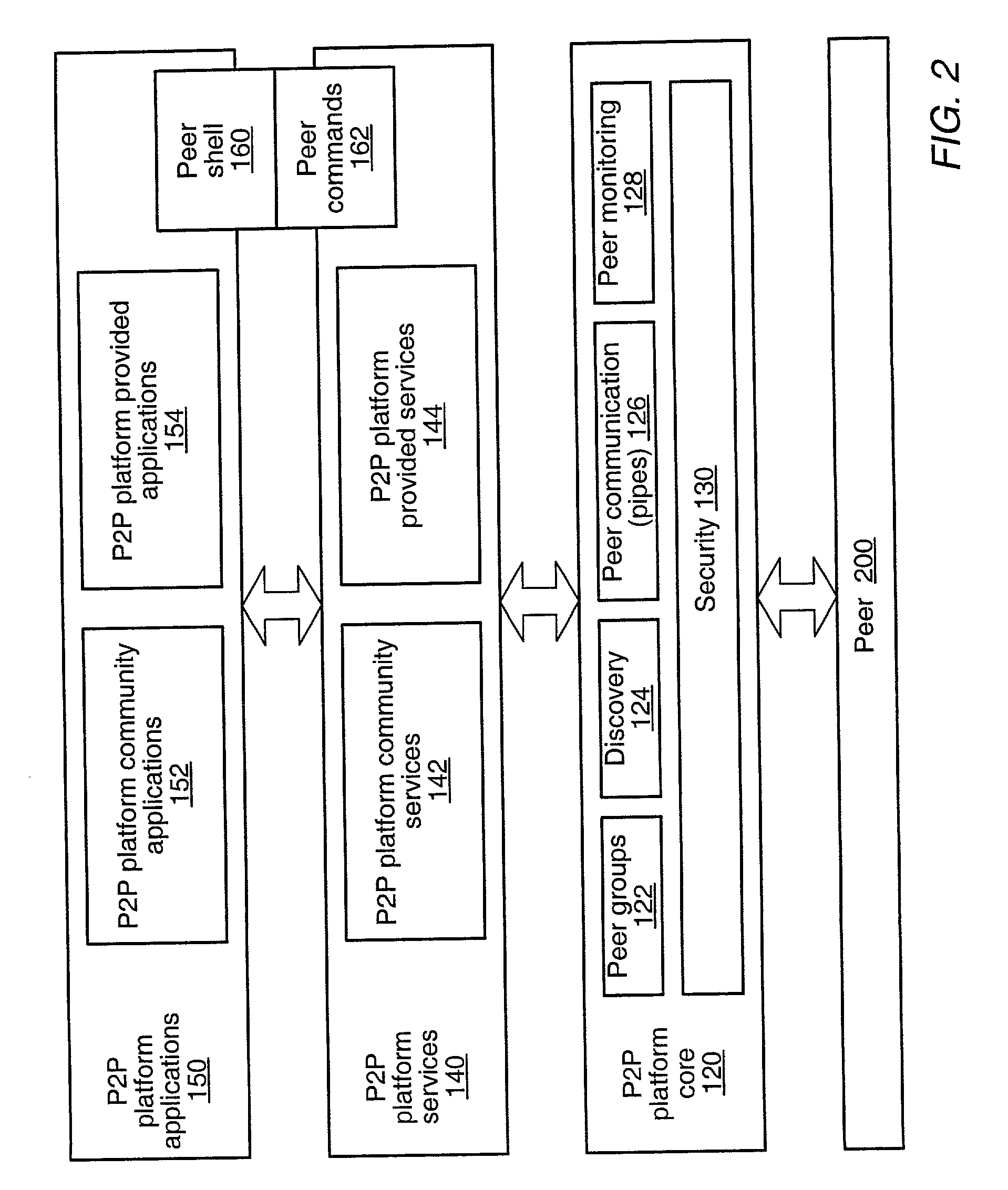
Peer-to-peer computing architecture
ActiveUS20020147771A1Multiprogramming arrangementsMultiple digital computer combinationsPhysical addressProtocol for Carrying Authentication for Network Access
A system and method for providing an open network computing platform designed for peer-to-peer computing. The peer-to-peer platform may provide protocols for peer-to-peer services and applications that allow peers to discover each other, communicate with each other, and cooperate with each other to form peer groups. The protocols may include a peer membership protocol, a peer discovery protocol, a peer resolver protocol, a peer information protocol, a pipe binding protocol, and a peer endpoint protocol. Services and applications that participate in the protocols may be provided to deal with higher-level concepts. Advertisements may be used to publish peer resources. The peer-to-peer platform provides the ability to replicate information toward end users and may enable peers to find content that is closest to them. The peer-to-peer protocols and unique peer identifiers may allow peer nodes to move to different locations and access services and other content independent of network physical addresses.
Owner:ORACLE INT CORP
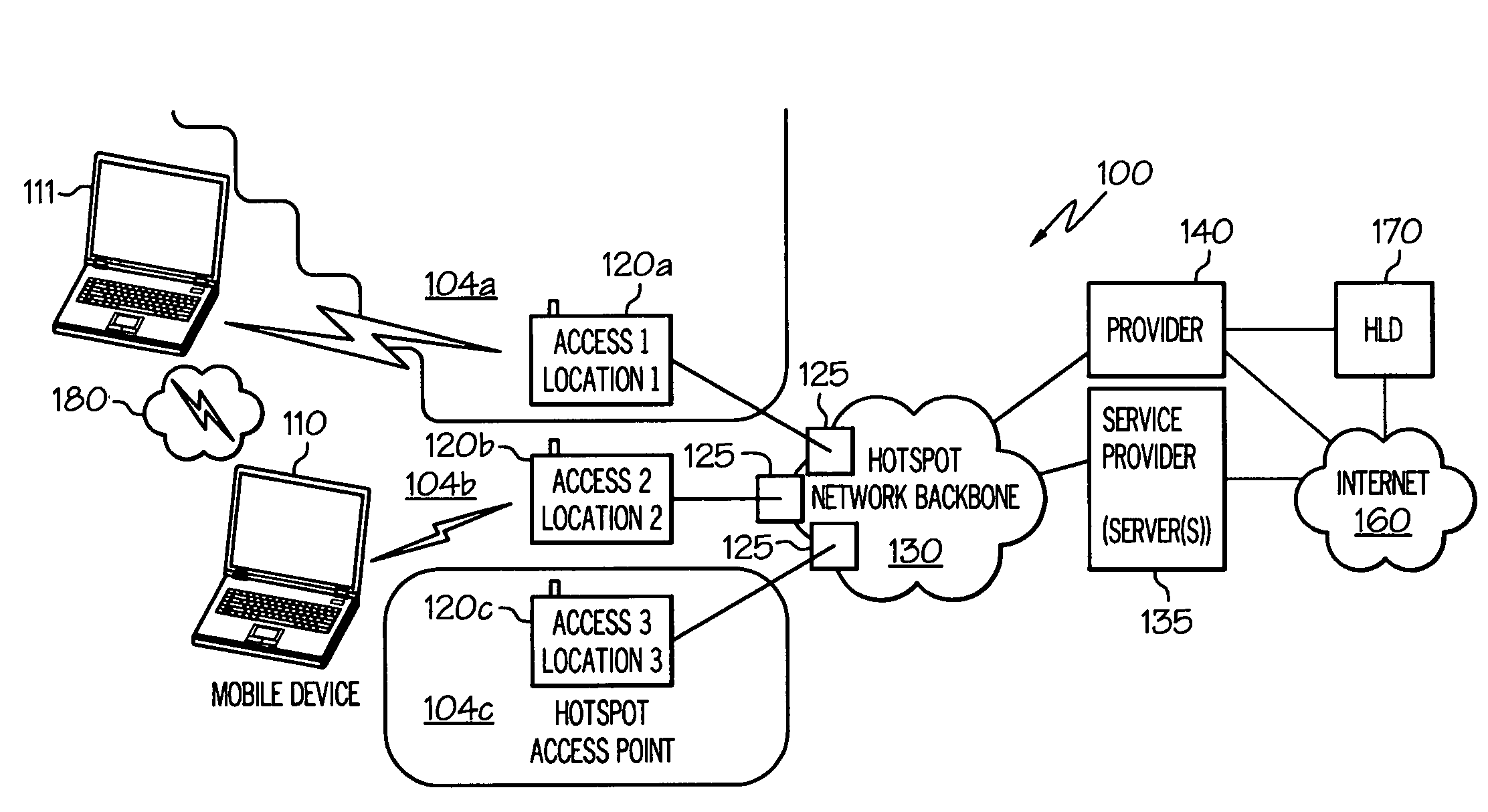
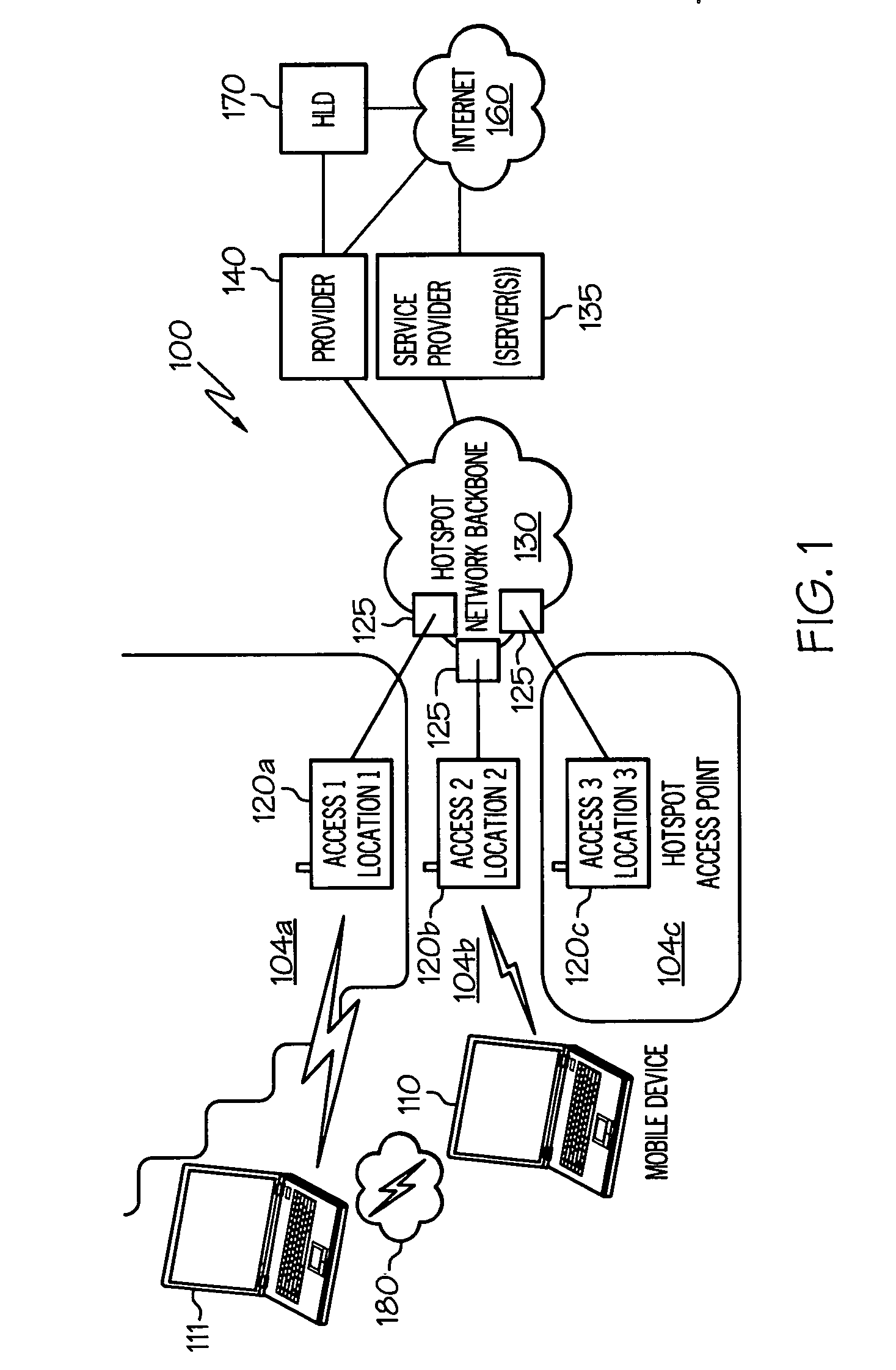
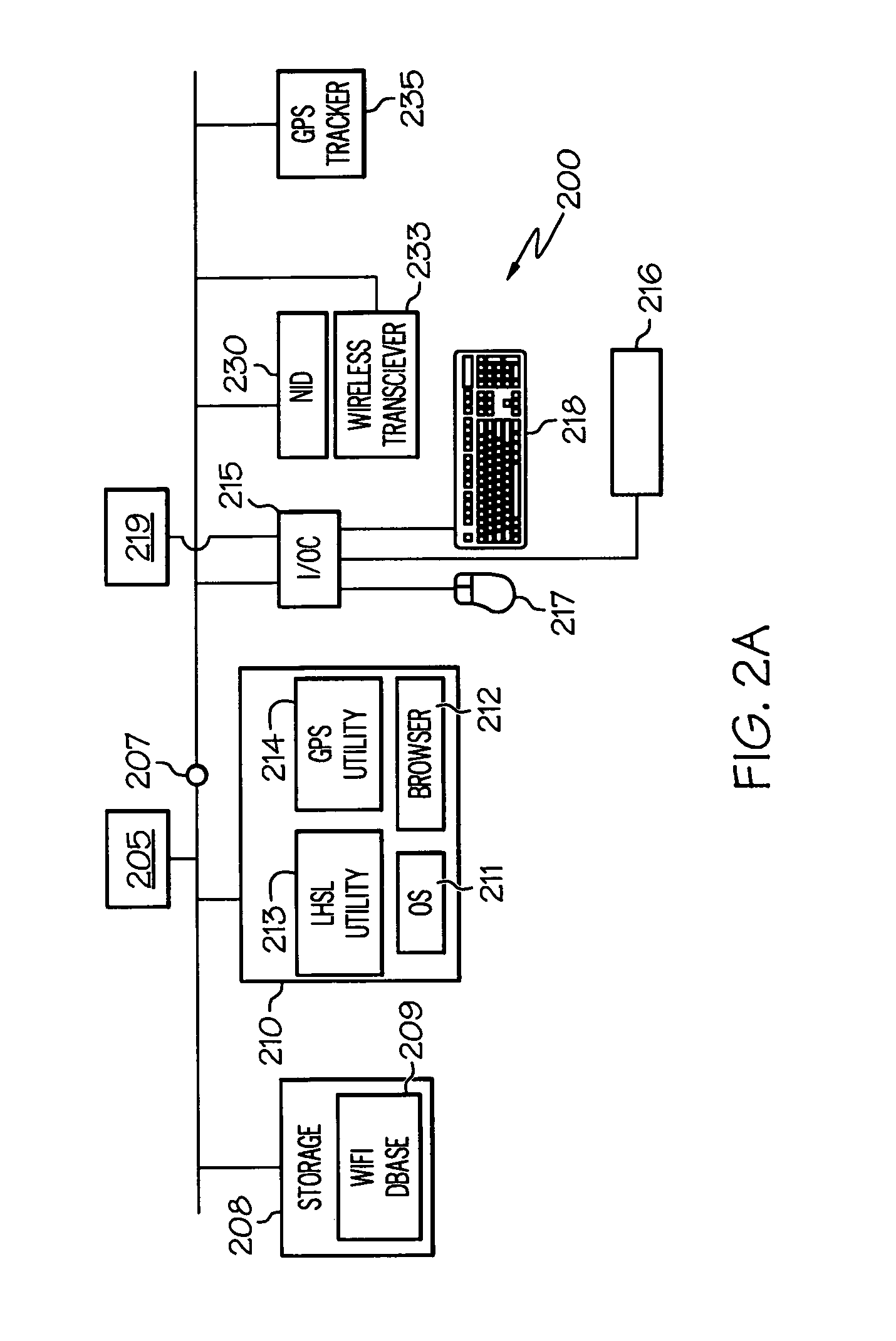
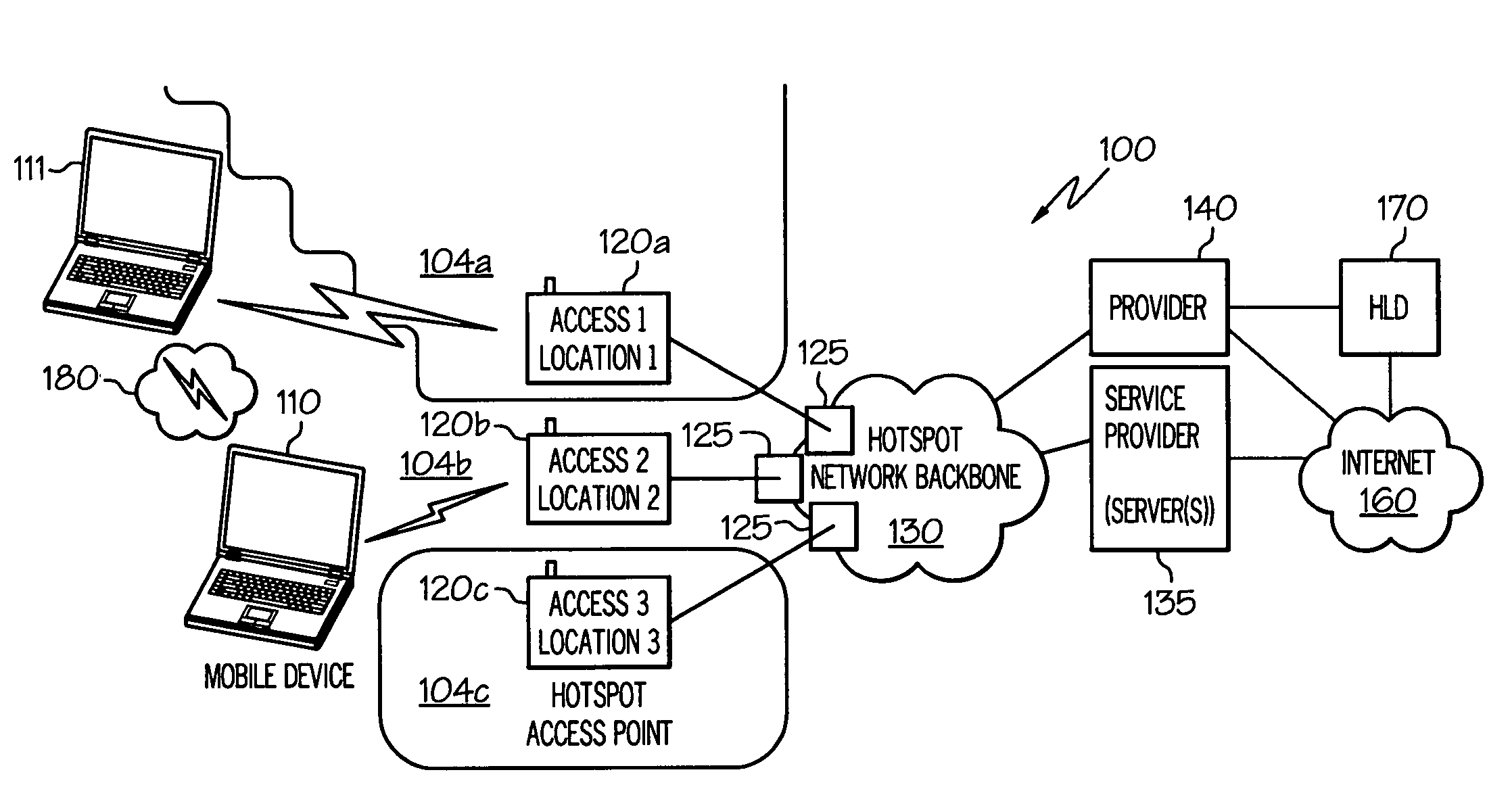
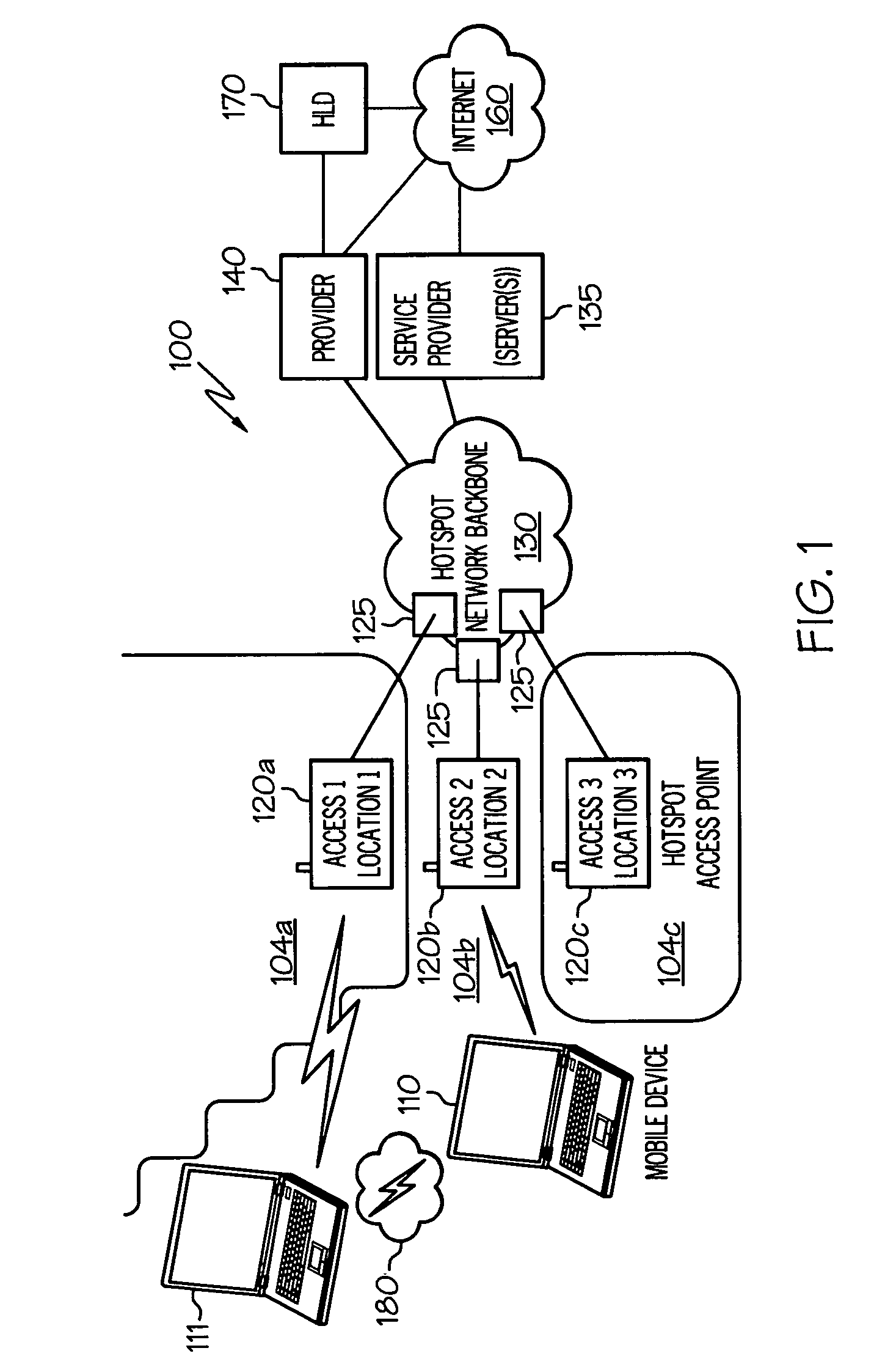
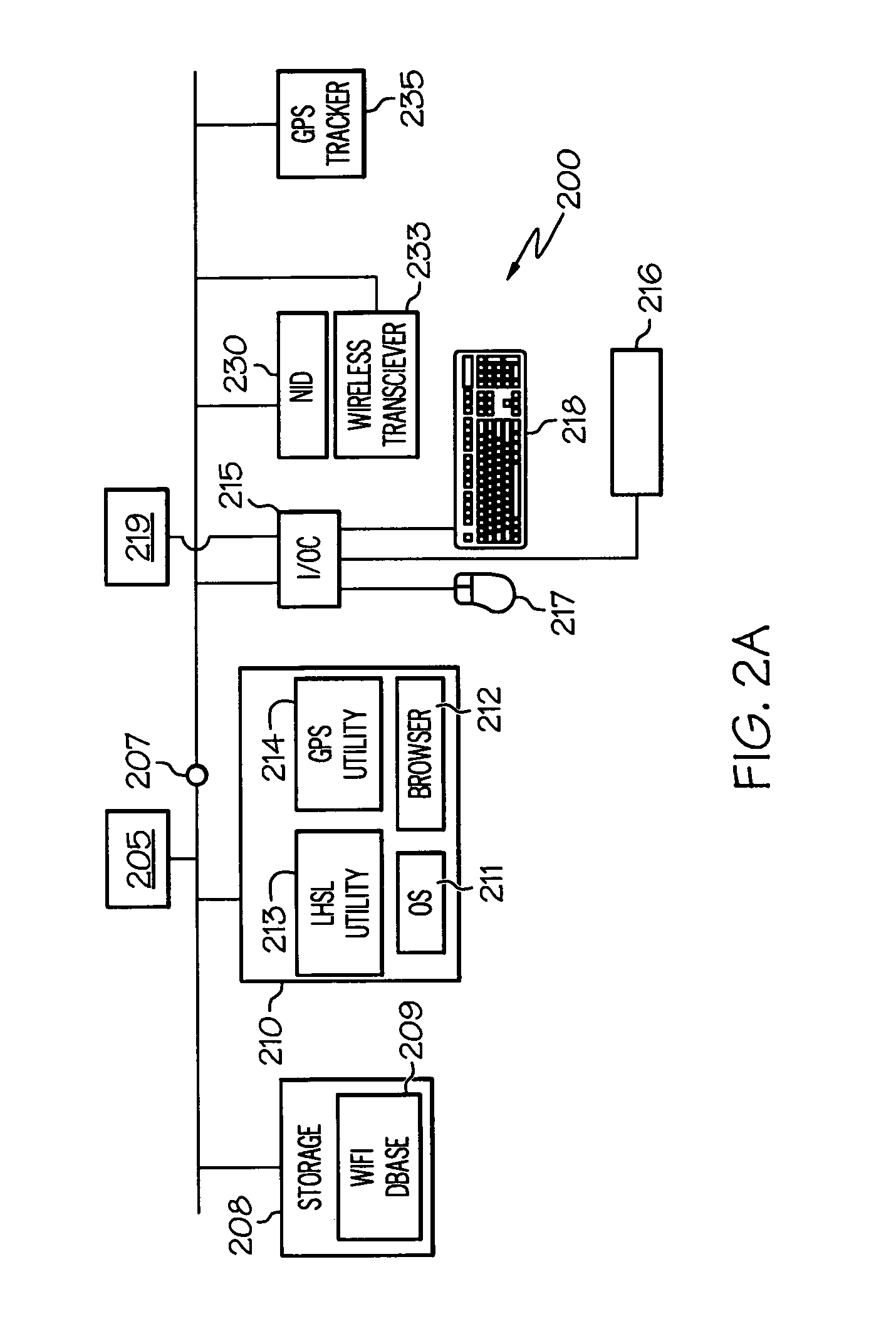
On-device mapping of WIFI hotspots via direct connection of WIFI-enabled and GPS-enabled mobile devices
InactiveUS20070167174A1Generate efficientlyRoad vehicles traffic controlError detection/correctionUser inputGeolocation
A WIFI-enabled and GPS-enabled user device executes a hotspot location utility, which enables the device to detect WIFI hotspots and update a locally-stored hotspot location database (LHLD) containing geographically-mapped hotspots. When a hotspot is detected, the device accesses the hotspot, retrieves identification information and usage terms from the hotspot, and measures performance metrics of the hotspot. The utility stores the identified hotspot with the current GPS coordinate as an entry within the LHLD. When a user later desires to locate hotspots within a particular geographic location, the user enters the physical address of the location, and hotspots with matching (or proximate) GPS coordinates of the entered address are presented to the user. The user may specify certain preferences for usage terms, performance metrics, and location criteria, and the utility filters all geographic hits and returns only hotspots in the geographic location that also satisfy these preferences.
Owner:IBM CORP
Router, frame forwarding method, and lower layer frame virtual forwarding system
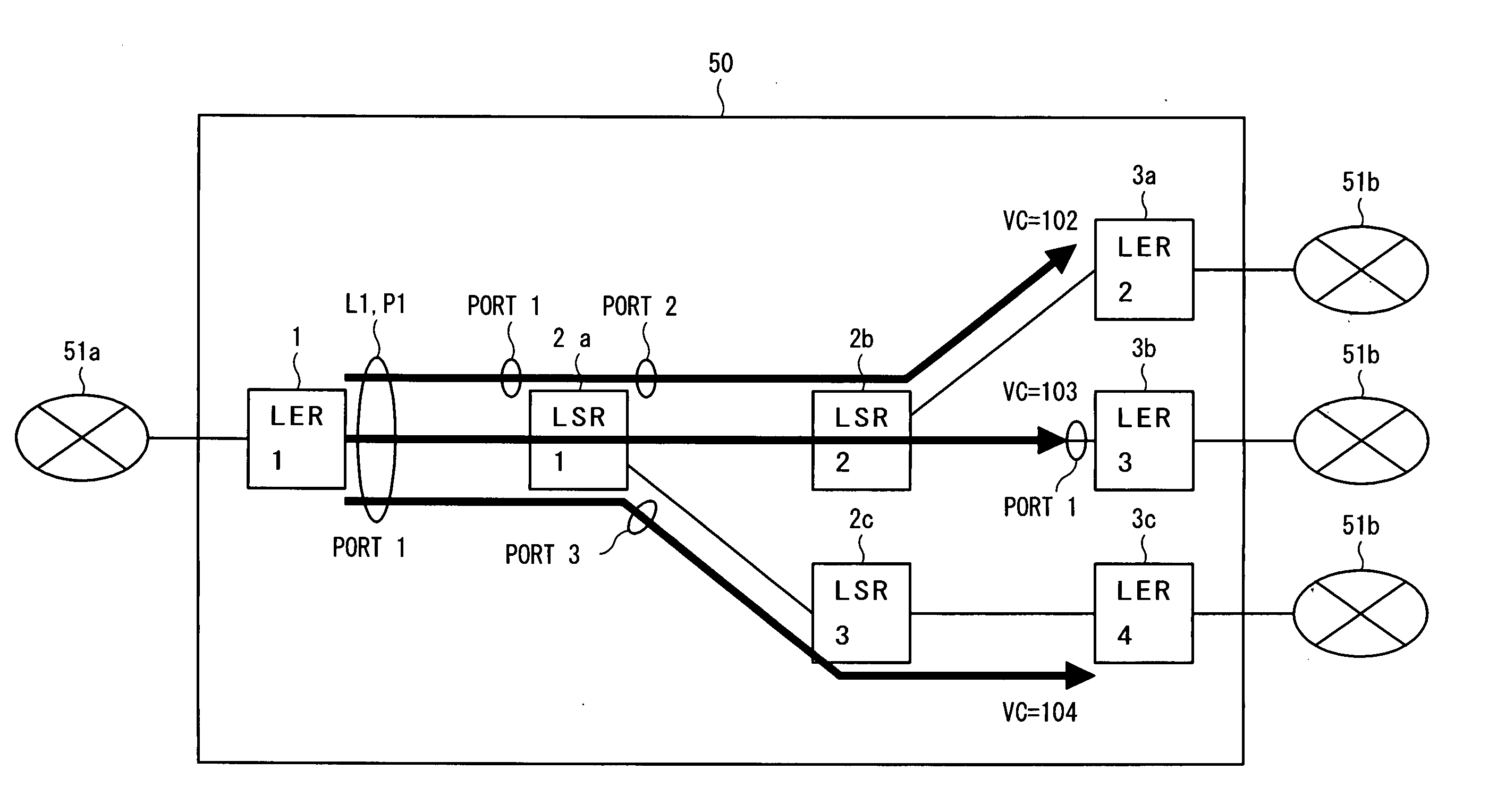
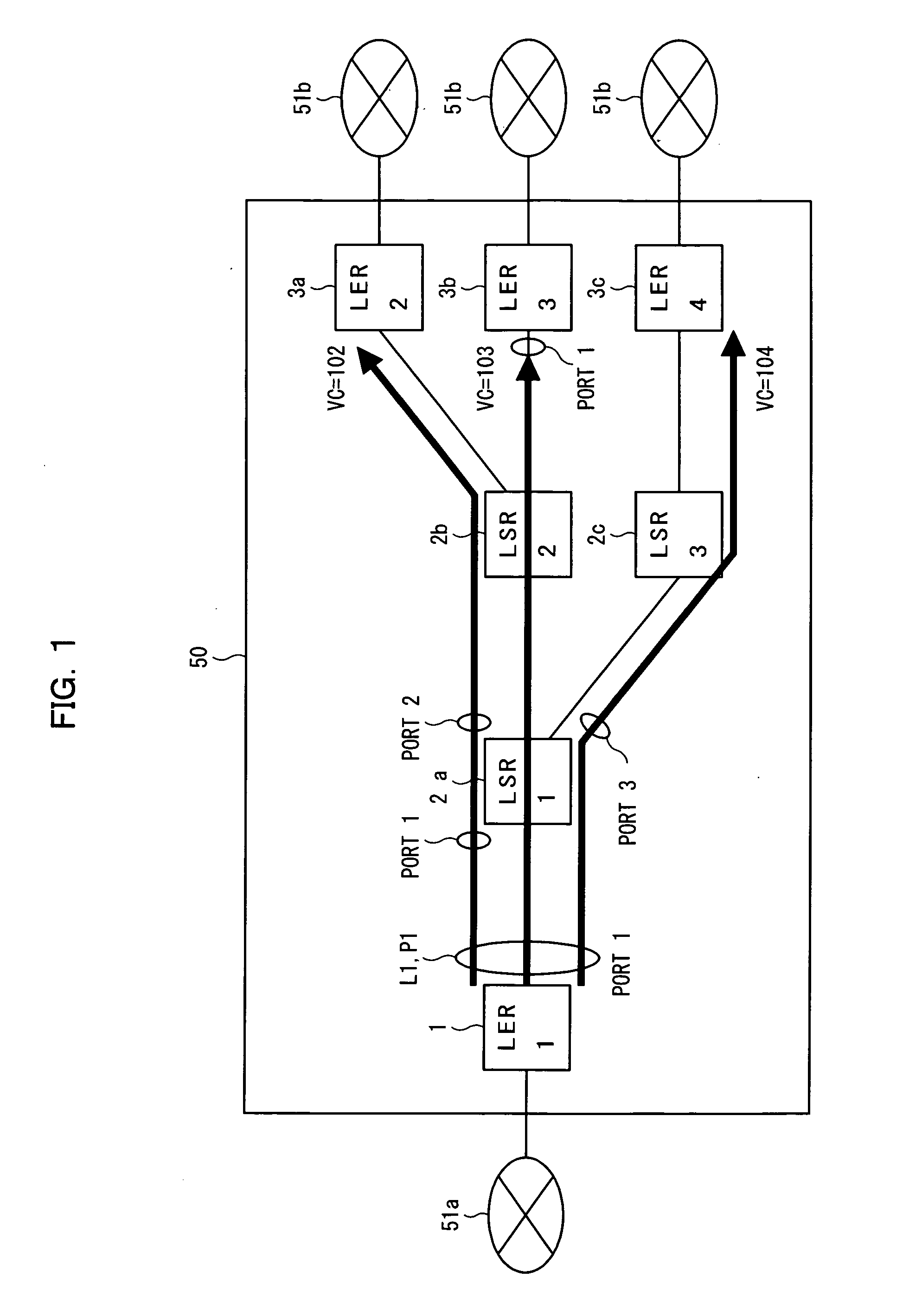
InactiveUS20050169270A1Avoid loadEasy to useTime-division multiplexNetworks interconnectionPhysical addressLabel switching
In an MPLS network, multicast, broadcast and address learning belonging to the layer 2 functions are realized. An ingress router comprises a frame receiving unit, a determining unit, a first frame transmitting unit, a physical address table for multicast, a label switching unit, a tunnel label table, a VCID giving unit, a L2 header creating unit and a second frame transmitting unit. The load on the network is suppressed, the band is efficiently used, and wasteful frame duplication and frame forwarding between edge routers are avoided.
Owner:FUJITSU LTD
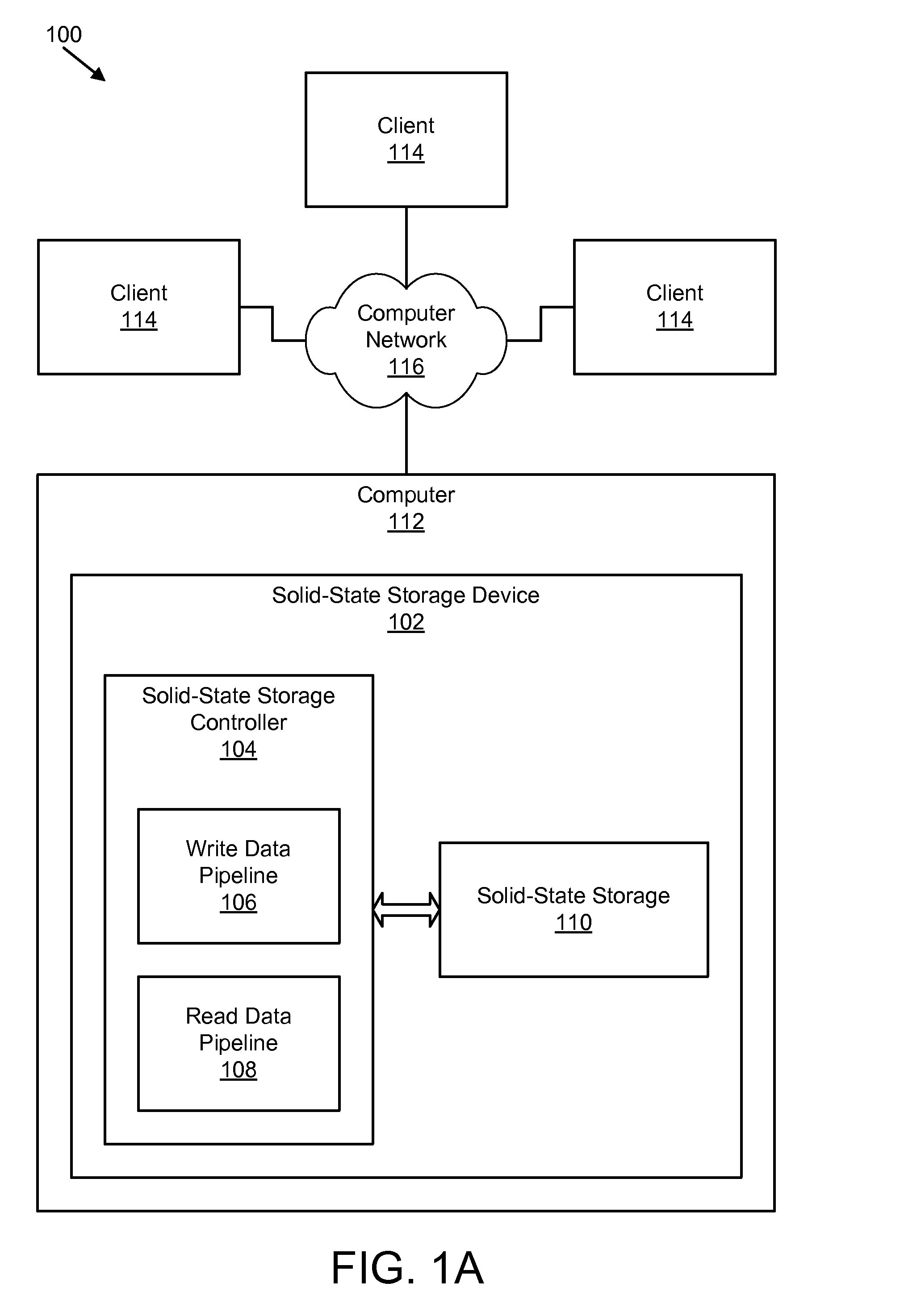
Apparatus, system, and method for storage space recovery after reaching a read count limit
ActiveUS20090125671A1Shorten the counting processReduce bit error rateMemory architecture accessing/allocationProgram synchronisationSolid-state storagePhysical address
An apparatus, system, and method are disclosed for storage space recovery after reaching a read count limit. A read module reads data in a storage division of solid-state storage. A read counter module then increments a read counter corresponding to the storage division. A read counter limit module determines if the read count exceeds a maximum read threshold, and if so, a storage division selection module selects the corresponding storage division for recovery. A data recovery module reads valid data packets from the selected storage division, stores the valid data packets in another storage division of the solid-state storage, and updates a logical index with a new physical address of the valid data.
Owner:UNIFICATION TECH LLC
Copy protection system for portable storage media
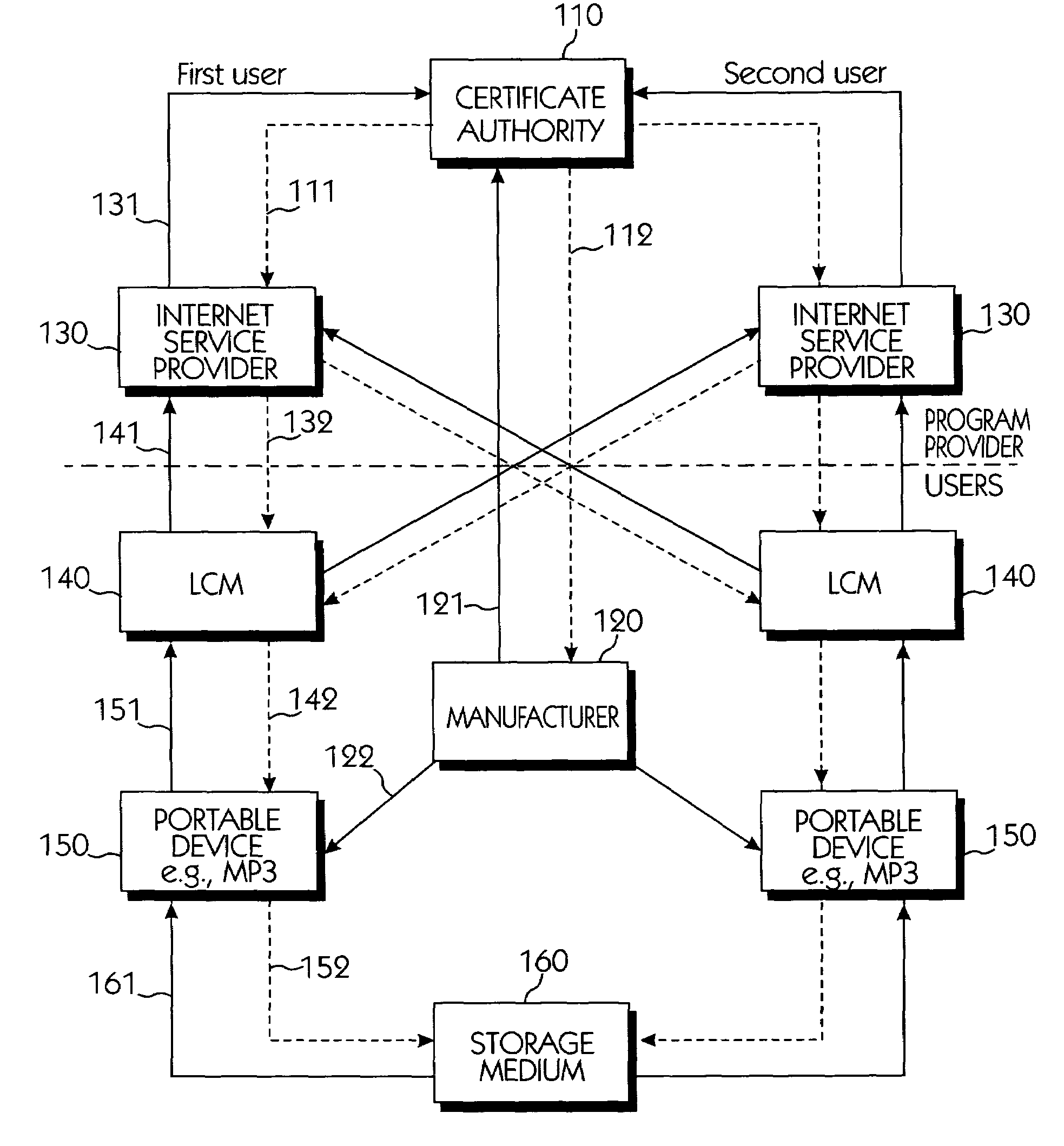
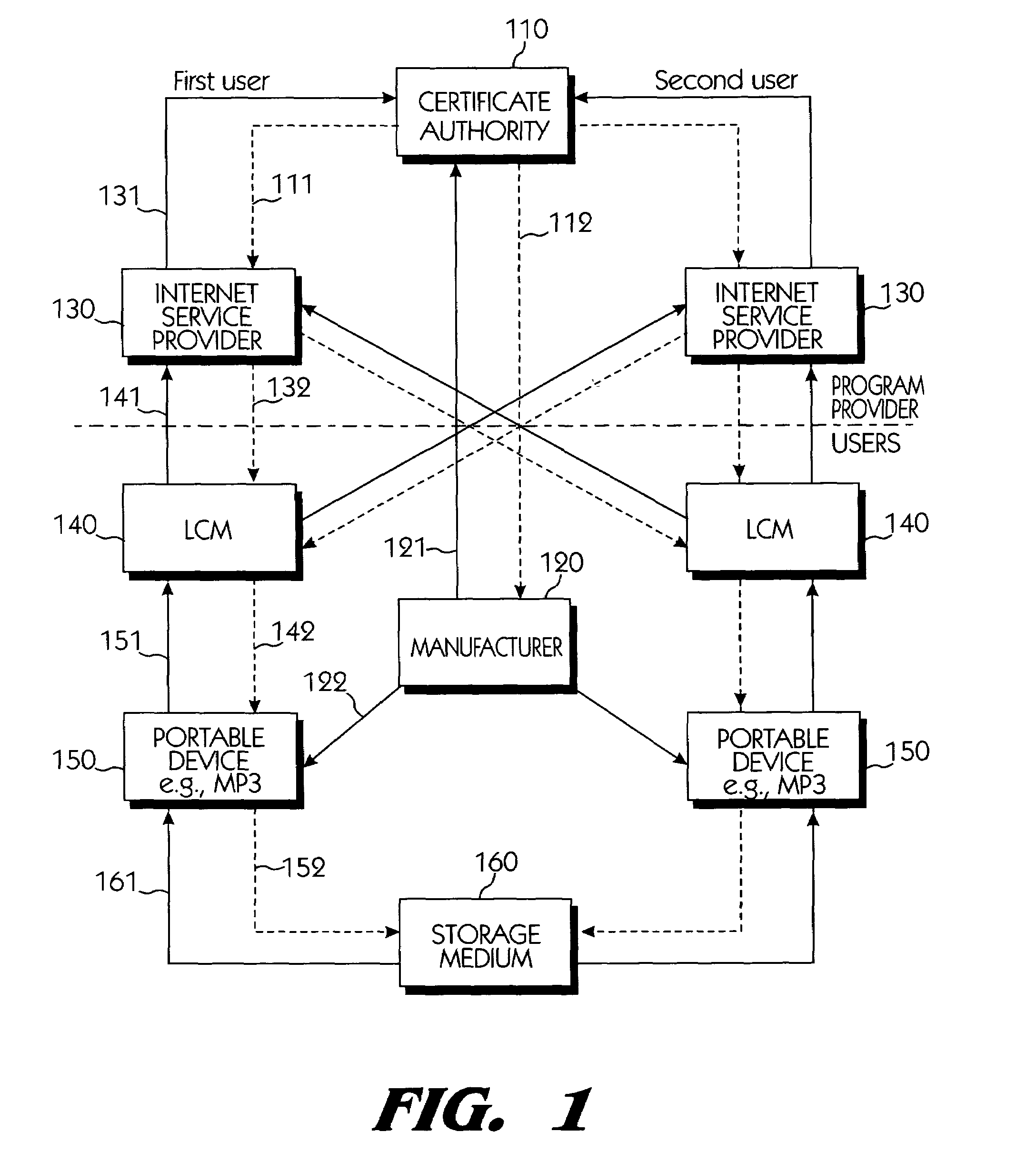
InactiveUS6950941B1Limited abilityKey distribution for secure communicationData processing applicationsDevice formDigital content
Systems connected to users generate a plurality of keys which are mutually shared, and download and upload digital contents by using secret channels formed between the systems. An information provider receives an authorization from a certificate authority. A licensed SDMI compliant module (LCM) is authenticated through the information provider, and the information provider and the LCM form a channel. A portable device is authenticated from the information provider through the LCM, and the LCM and the portable device form a channel. The digital content between the LCM and the portable device is downloaded and uploaded according to respective control state data of the LCM and the portable device. The system can use a physical address of a bad sector formed in the portable medium during the manufacturing process for preventing an illegal copy of the downloaded digital contents through the portable device after the digital contents have been downloaded.
Owner:SAMSUNG ELECTRONICS CO LTD
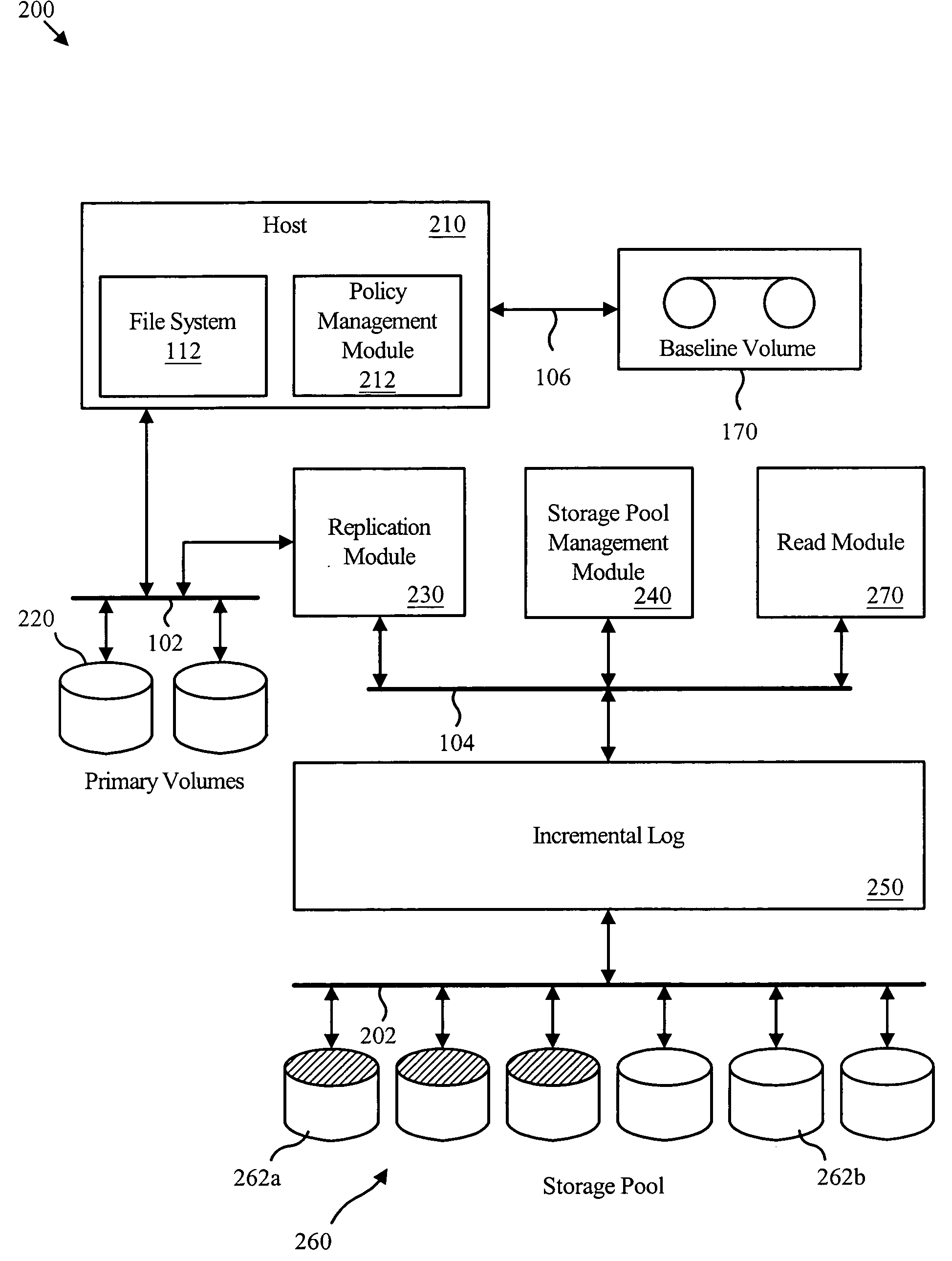
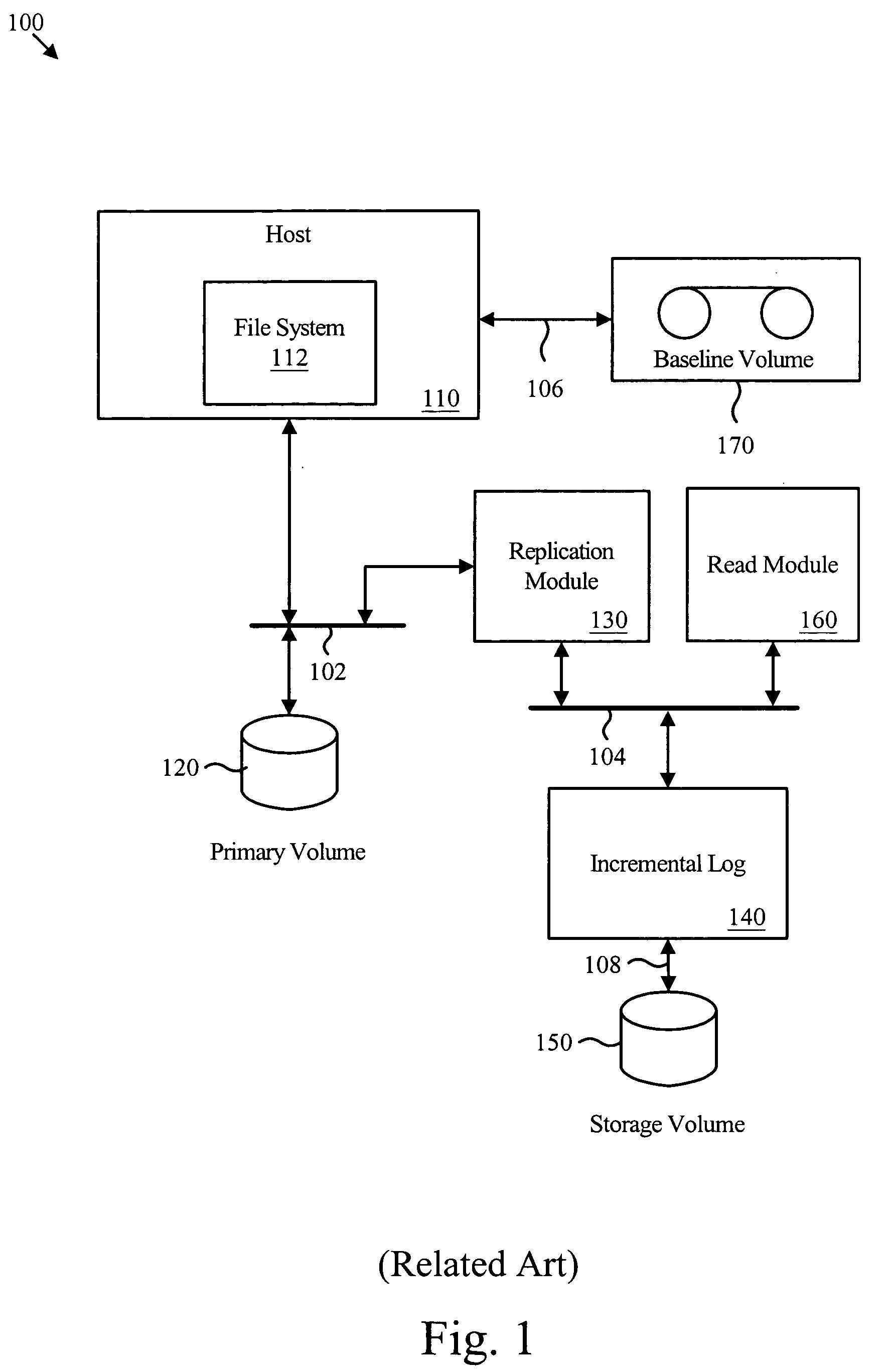
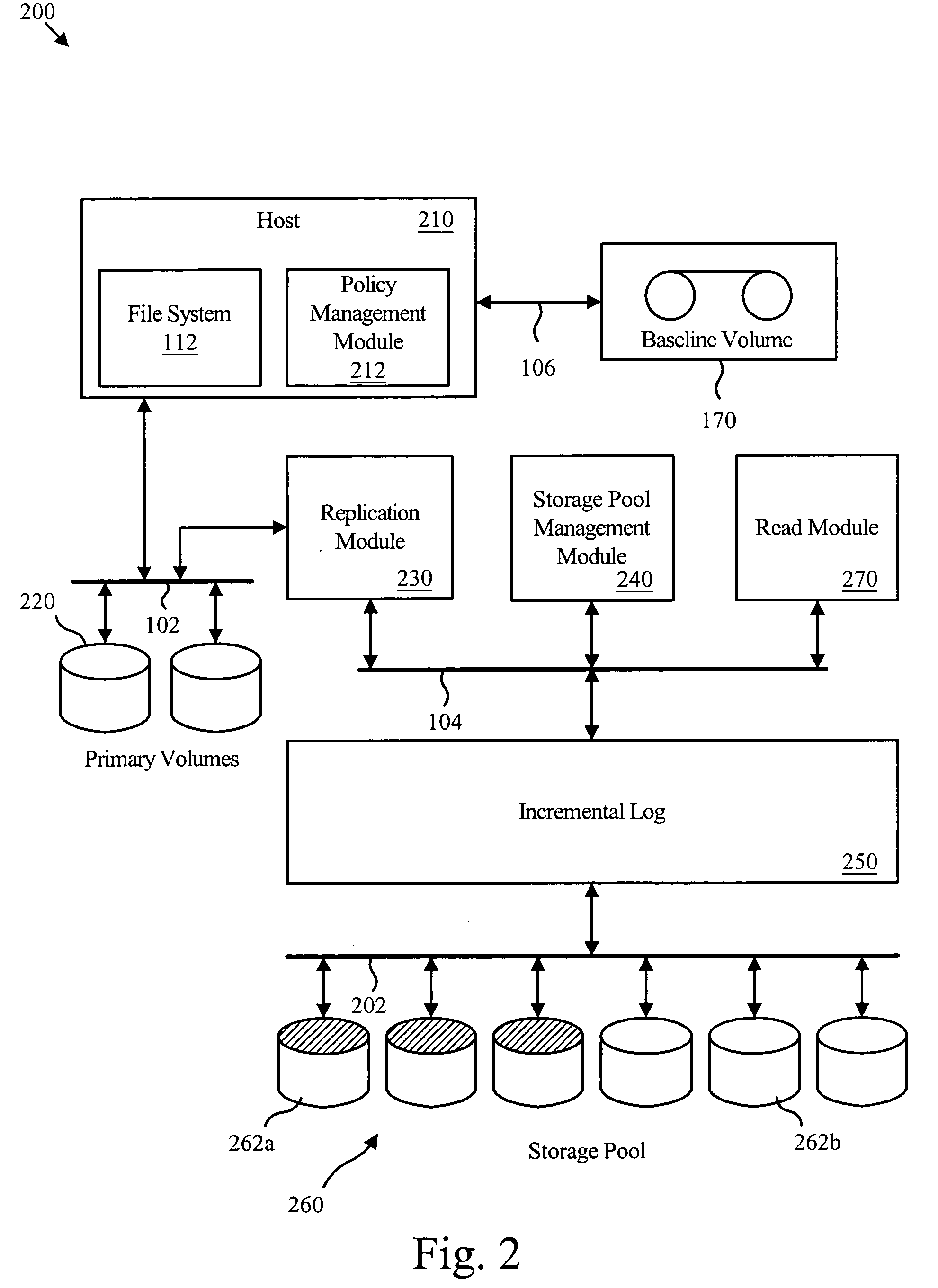
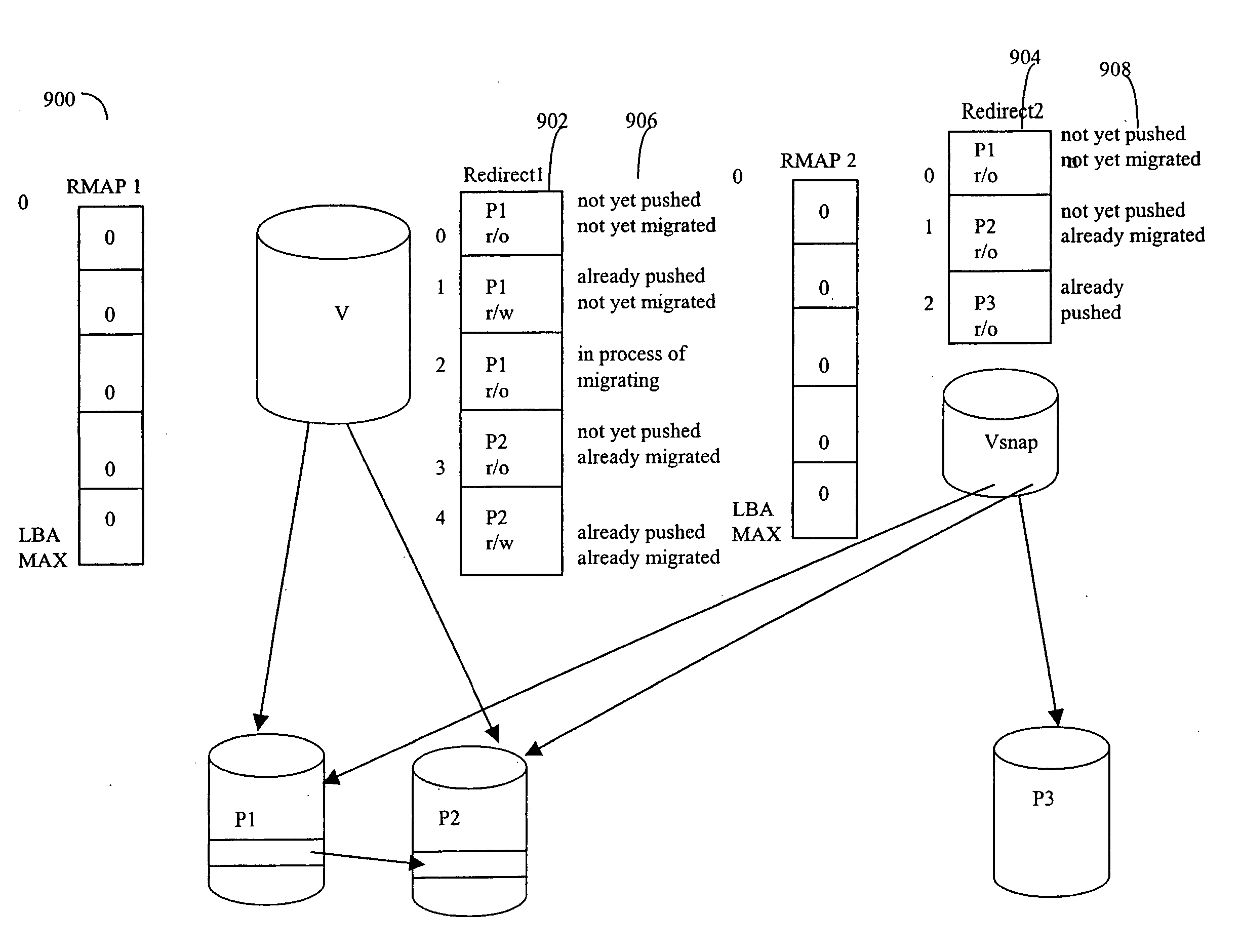
Virtual incremental storage apparatus method and system
InactiveUS20050108292A1The process is simple and effectiveSave storage spaceInput/output to record carriersError detection/correctionPhysical addressLookup table
An apparatus for managing incremental storage includes a storage pool management module that allocates storage volumes to a virtual volume. Also included is an incremental log corresponding to the virtual volume, which maps virtual addresses to storage addresses. The apparatus may also include a replication module that sends replicated data to the virtual volume and a policy management module that determines allocation criteria for the storage pool management module. In one embodiment, the incremental log includes a lookup table that translates read and write requests to physical addresses on storage volumes within the virtual volume. The replicated data may include incremental snapshot data corresponding to one or more primary volumes. The various embodiments of the virtual incremental storage apparatus, method, and system facilitate dynamic adjustment of the storage capacity of the virtual volume to accommodate changing amounts of storage utilization.
Owner:IBM CORP
System and method for detecting and eliminating IP spoofing in a data transmission network
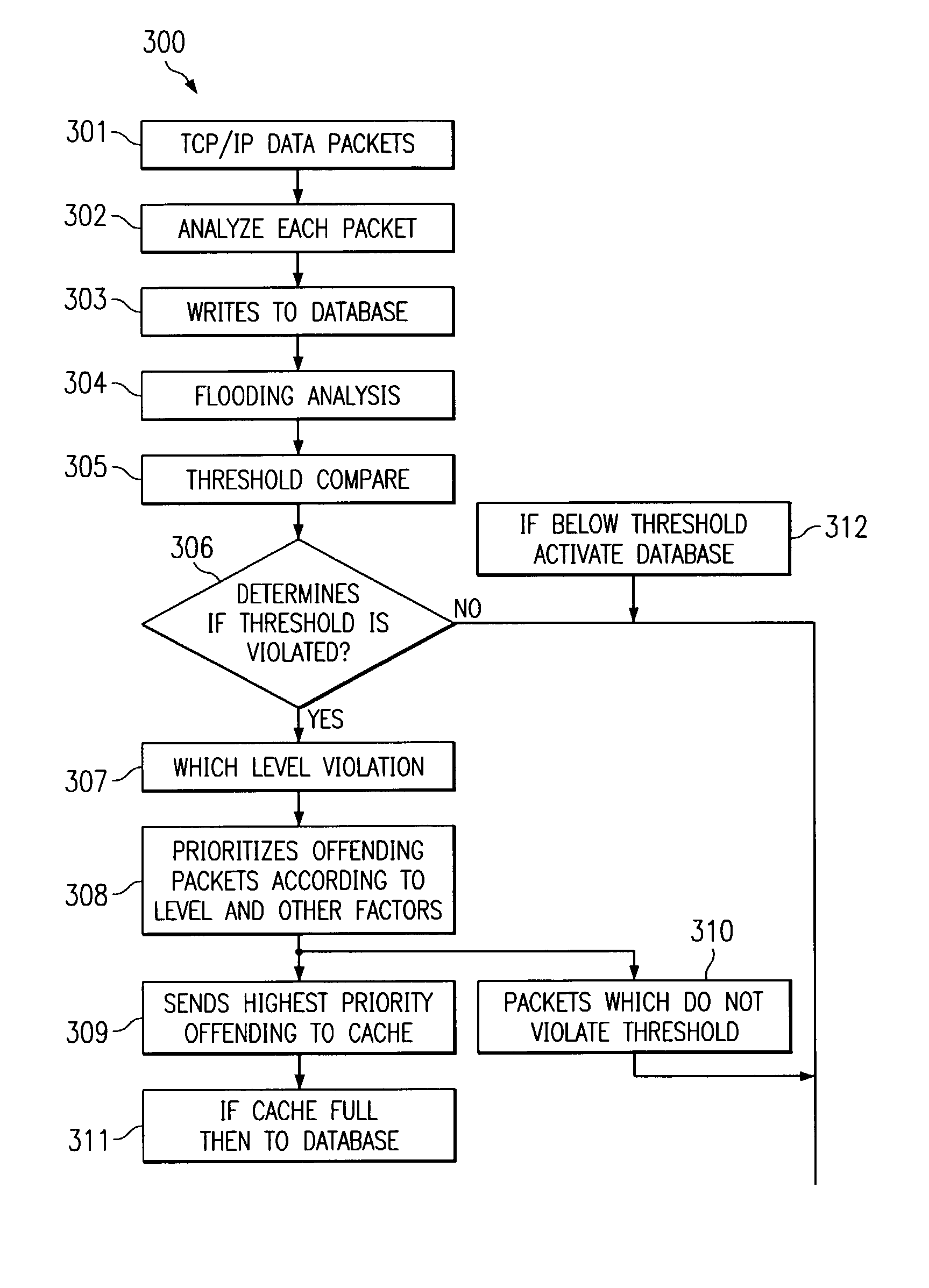
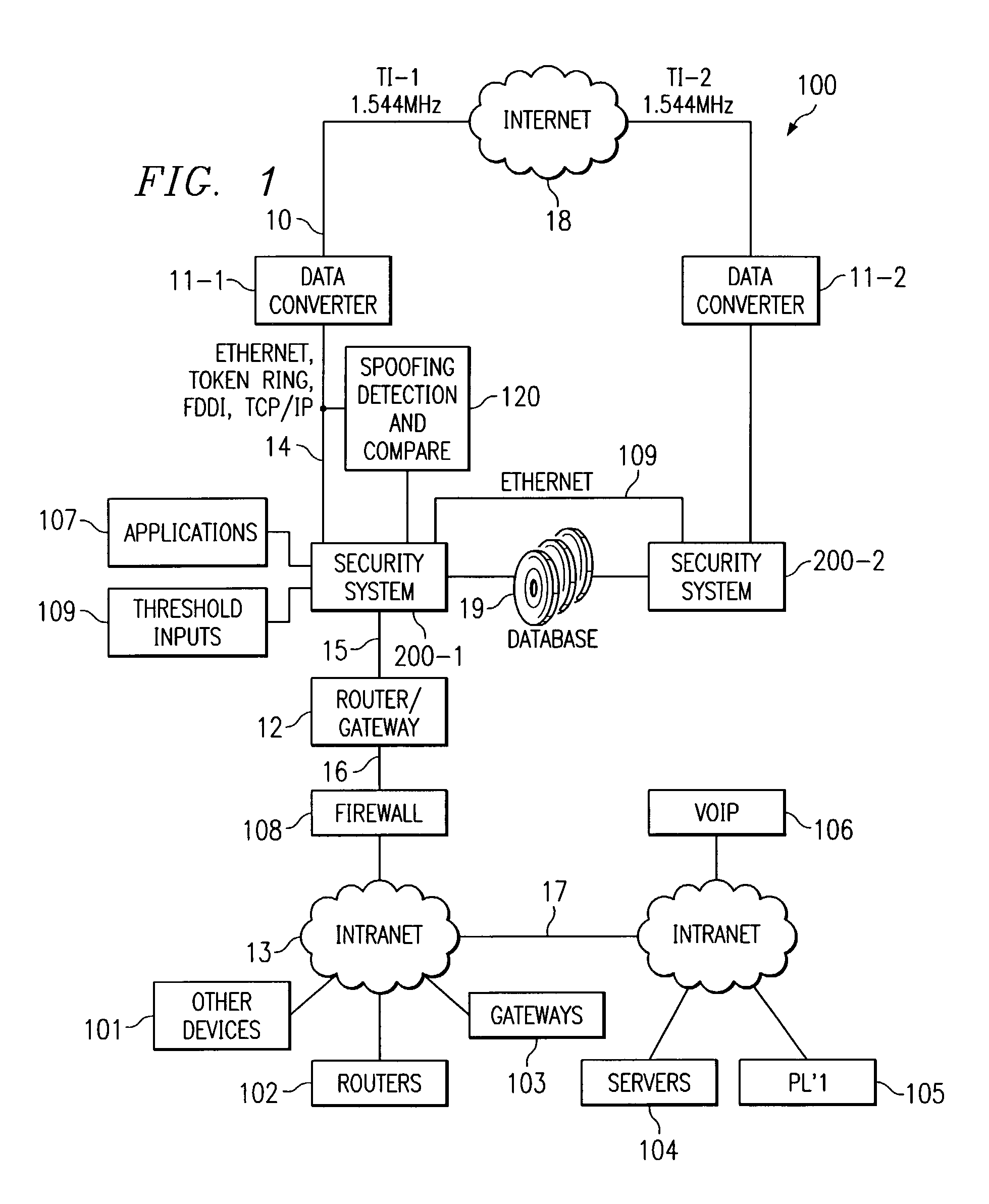
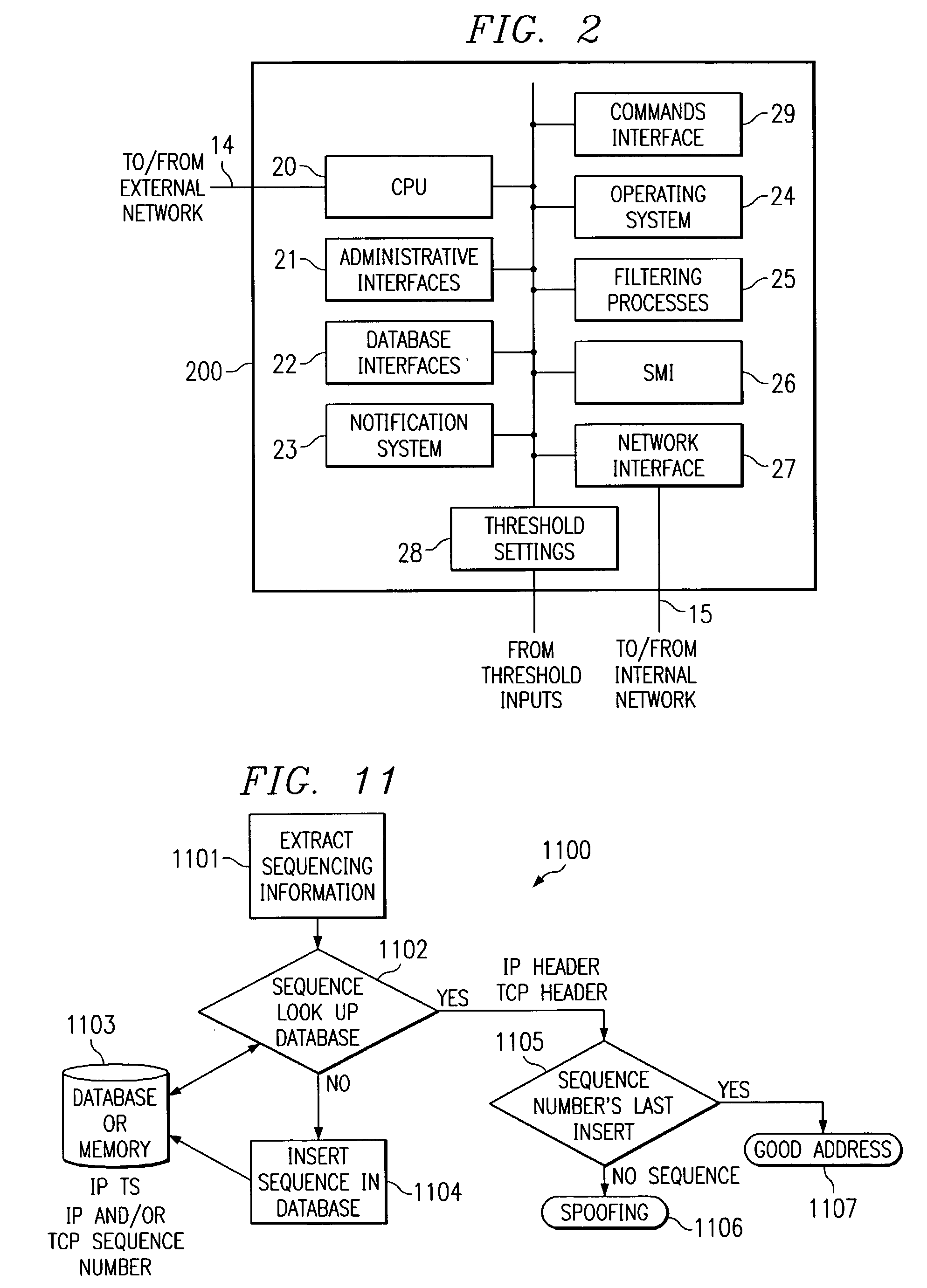
InactiveUS7380272B2Guaranteed uptimeAvoid flowMemory loss protectionError detection/correctionTraffic capacityIp address
A traffic management system sniffs data arriving at any point in a system. The sniffer operates to extract certain data from each address. This data could be, for example, the IP address data and the physical address data. The extracted data is then used to access different data bases to determine if matches occur. Time stamps, sequencing and other parameters of each piece of data entering a system are used to control data access.
Owner:TREND MICRO INC
Inter-fabric routing
InactiveUS20060034302A1More complicated routingLaser detailsTime-division multiplexComputer networkPhysical address
A method and apparatus is shown for communicating Fibre Channel frames between distinct fabrics. A proxy zone is established in each fabric with a physically present local device and a remote fabric device. A router creates a proxy device in each fabric for every device not physically connected to the fabric. The proxy devices appear to be directly attached to the router. The router handles all address translations between proxy and physical addresses. When multiple routers are encountered, the ingress router does all address translation. No routing or encapsulation headers are used except when routing between two routers. The source ID and the originator exchange identifier are stored at the egress router for all link requests that require special handling. When replies pass through that router, the destination ID and originator exchange identifier are compared with the stored information. On a match, the reply is specially handled.
Owner:AVAGO TECH INT SALES PTE LTD
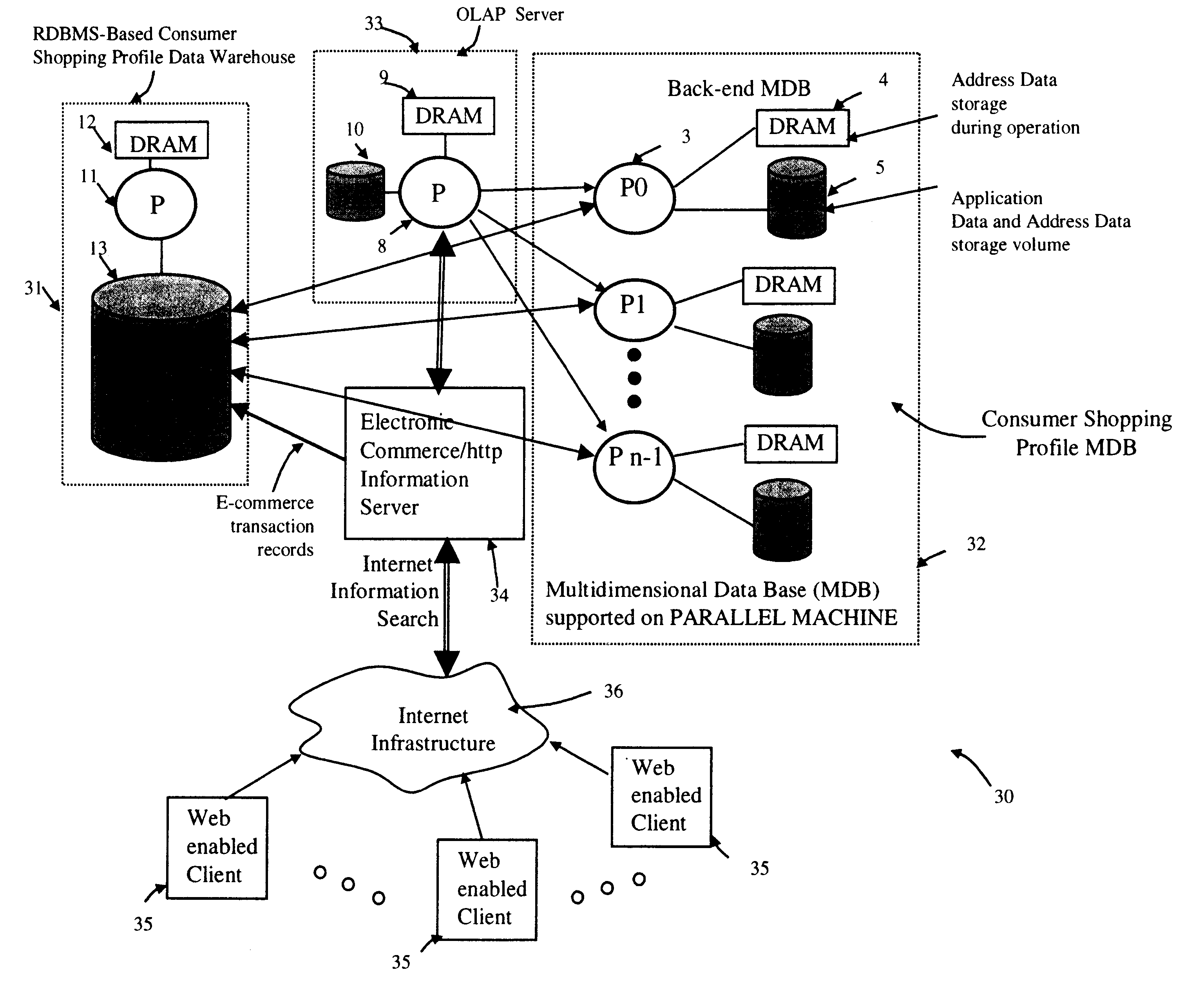
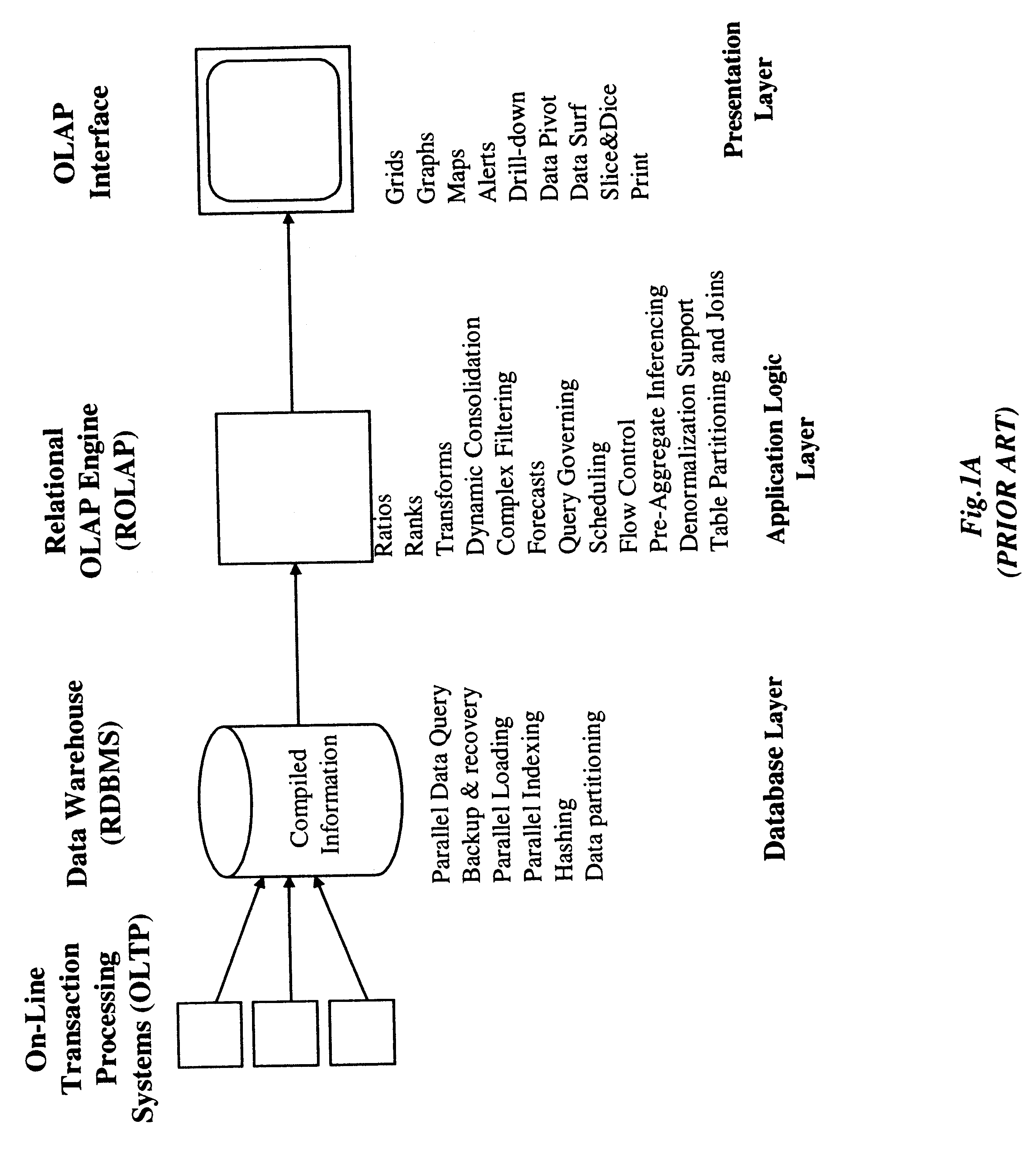
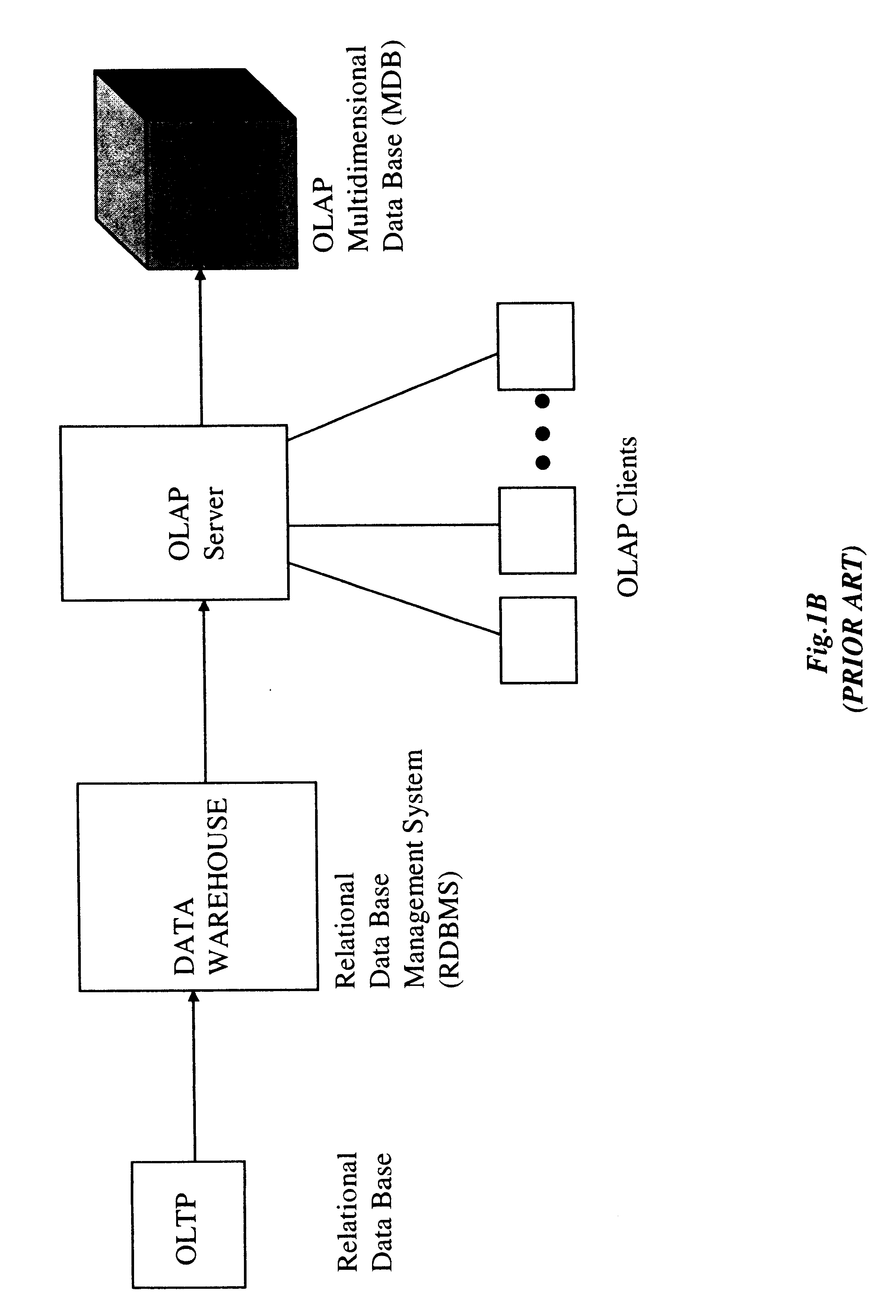
Method of and system for managing multi-dimensional databases using modular-arithmetic based address data mapping processes on integer-encoded business dimensions
InactiveUS6408292B1Improve performanceFast knowledge discoveryData processing applicationsMulti-dimensional databasesData warehouseThe Internet
An improved method of and a system for managing data elements in a multidimensional database (MDB) supported upon a parallel computing platform using modular-arithmetic based address data mapping (i.e. translation) processes on integer-encoded business dimensions. The parallel computing platform has a plurality of processors and one or more storage volumes for physically storing data elements therein at integer-encoded physical addresses in Processor Storage Space (i.e. physical address space in the one or more storage volumes associated with a given processor). The location of each data element in the MDB is specified in MDB Space by integer-encoded business dimensions associated with the data element. A data loading mechanism loads the integer-encoded business dimensions and associated data elements from a data warehouse. The address data mapping mechanism performs a two part address mapping processing. The first step maps the integer-encoded business dimensions associated with each data element to a given processor identifier (which uniquely identifies the processor amongst the plurality of processors of the parallel computing platform). The second step maps the integer-encoded business dimensions associated with each data element into an integer-encoded physical data storage address in Processor Storage Space associated with the processor identified by the processor identifier generated in the first mapping step. The mapping performed in this second step is based upon size of the integer encoded business dimensions. The data management mechanism manages the data elements stored in the storage volumes using the integer-encoded data storage addresses generated during the two-part address data mapping process. The use of modular-arithmetic functions in the two-part address data mapping mechanism ensures that the data elements in the MDB are uniformly distributed among the plurality of processors for balanced loading and processing. The present invention can be used to realize (i) an improved MDB for supporting on-line analytical processing (OLAP) operations, (ii) an improved Internet URL Directory for supporting on-line information searching operations by Web-enabled client machines, as well as (iii) diverse types of MDB-based systems for supporting real-time control of processes in response to complex states of information reflected in the MDB.
Owner:MEC MANAGEMENT LLC +1
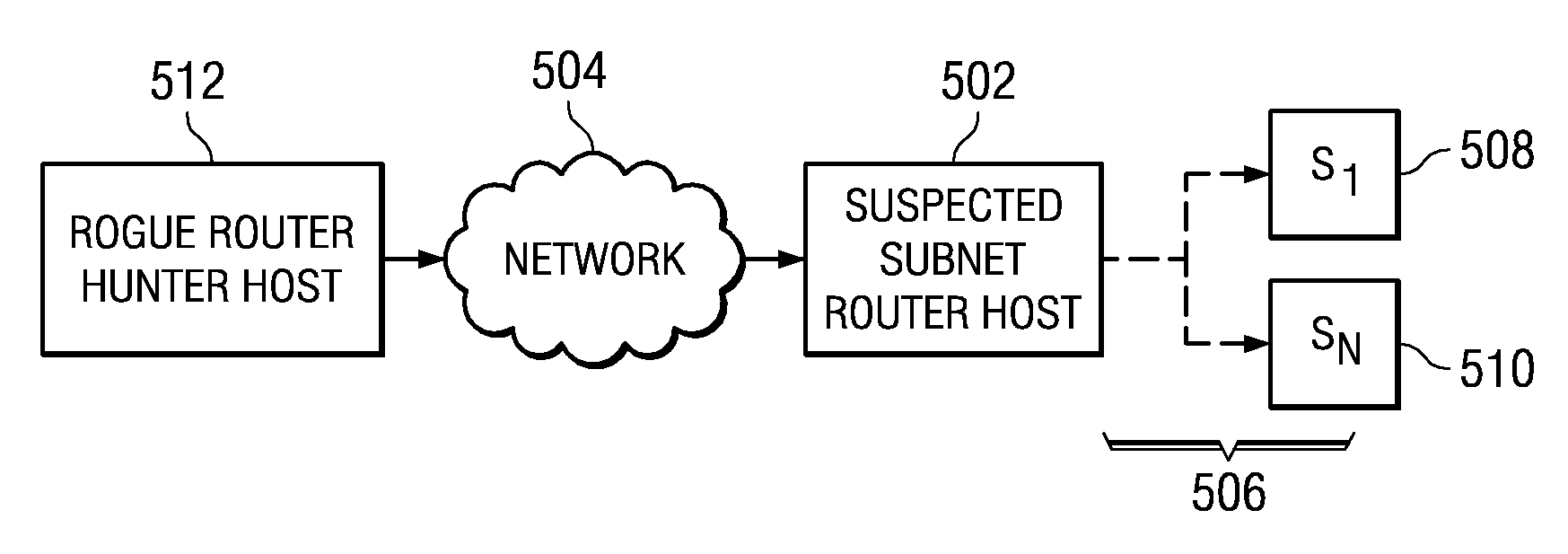
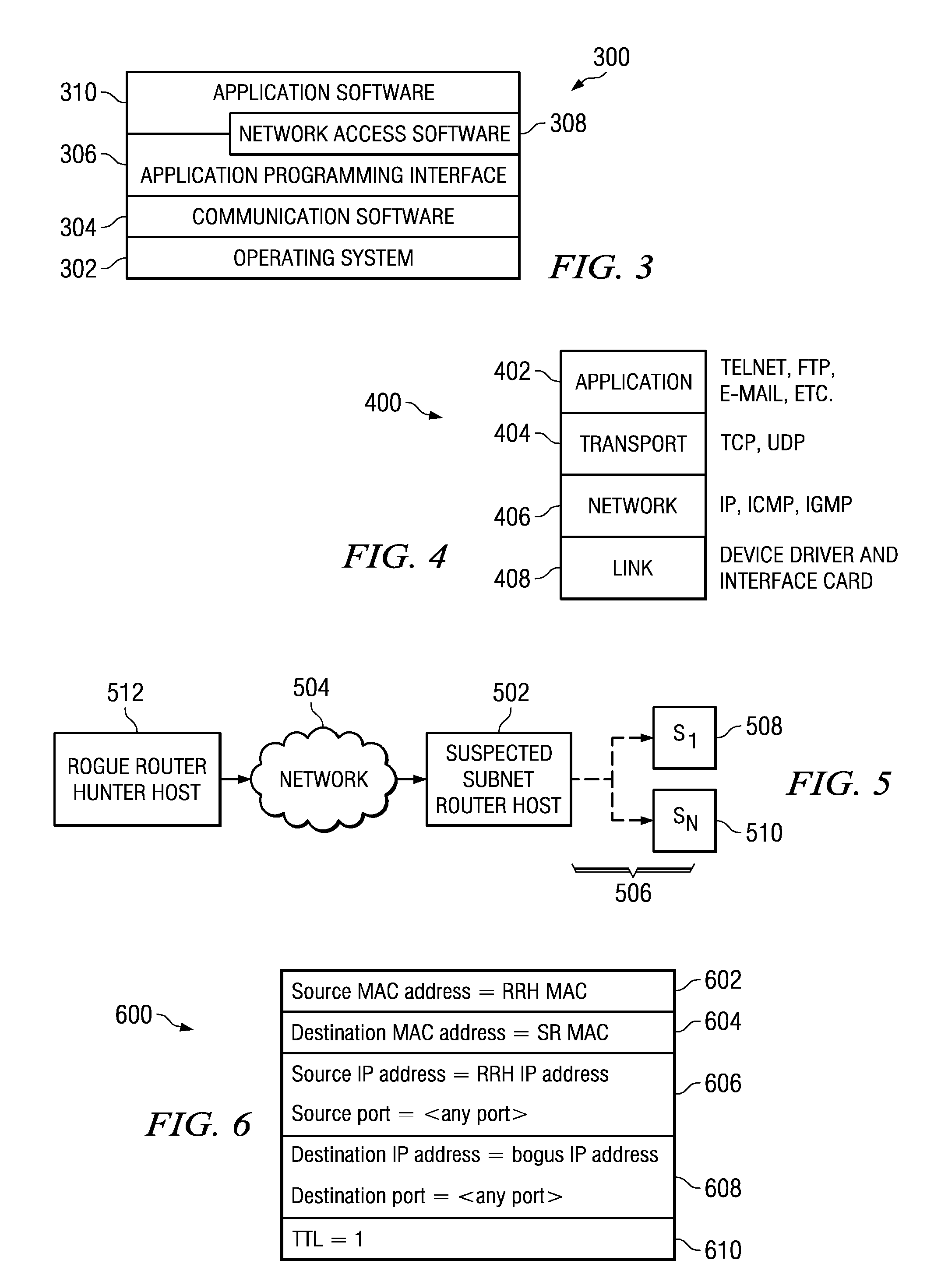
Rogue router hunter
InactiveUS7991877B2Digital computer detailsPlatform integrity maintainanceData processing systemTime limit
A computer implemented method, data processing system, and computer program product for discovering an unauthorized router in a network. The process in the illustrative embodiments first obtains a physical address of a suspected router or destination device. A data packet is created which comprises at least a destination media access control field, a destination internet protocol field, and a time-to-live field, wherein the destination media access control field comprises the physical address of the destination device, wherein the destination internet protocol field comprises a bogus internet protocol address, and wherein the time-to-live field comprises a value indicating the data packet has exceeded a time limit. The data packet is sent to the destination device using the physical address in the destination media access control field. If a time exceeded message is received from the destination device, the destination device is determined to be enabled for routing.
Owner:INT BUSINESS MASCH CORP
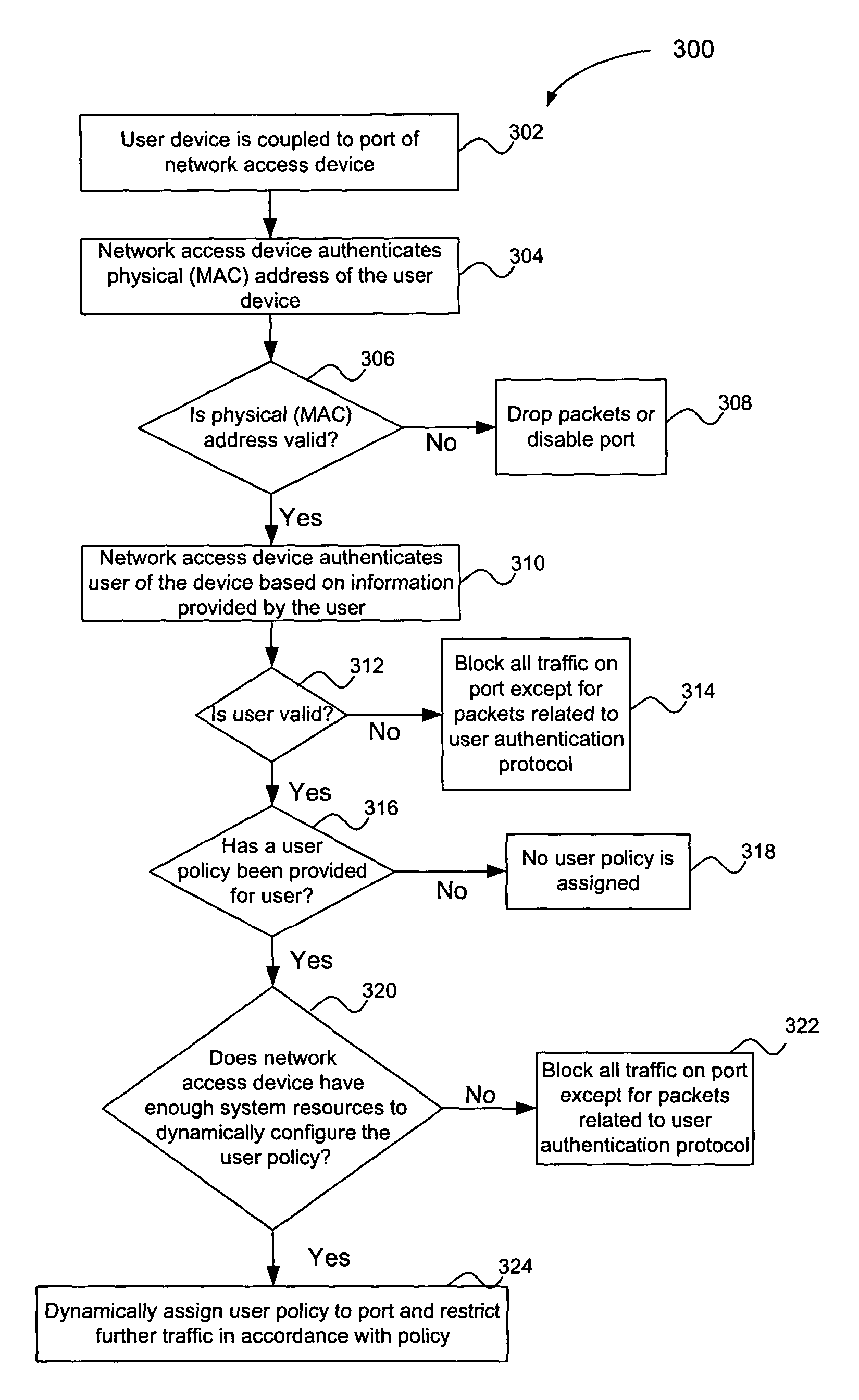
Multiple tiered network security system, method and apparatus using dynamic user policy assignment
InactiveUS20050055570A1Improve network securityEfficiently provideUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThree levelPhysical address
A multiple key, multiple tiered network security system, method and apparatus provides at least three levels of security. The first level of security includes physical (MAC) address authentication of a user device being attached to the network, such as a user device being attached to a port of a network access device. The second level includes authentication of the user of the user device, such as user authentication in accordance with the IEEE 802.1x standard. The third level includes dynamic assignment of a user policy to the port based on the identity of the user, wherein the user policy is used to selectively control access to the port. The user policy may identify or include an access control list (ACL) or MAC address filter. Also, the user policy is not dynamically assigned if insufficient system resources are available to do so. Failure to pass a lower security level results in a denial of access to subsequent levels of authentication.
Owner:AVAGO TECH INT SALES PTE LTD
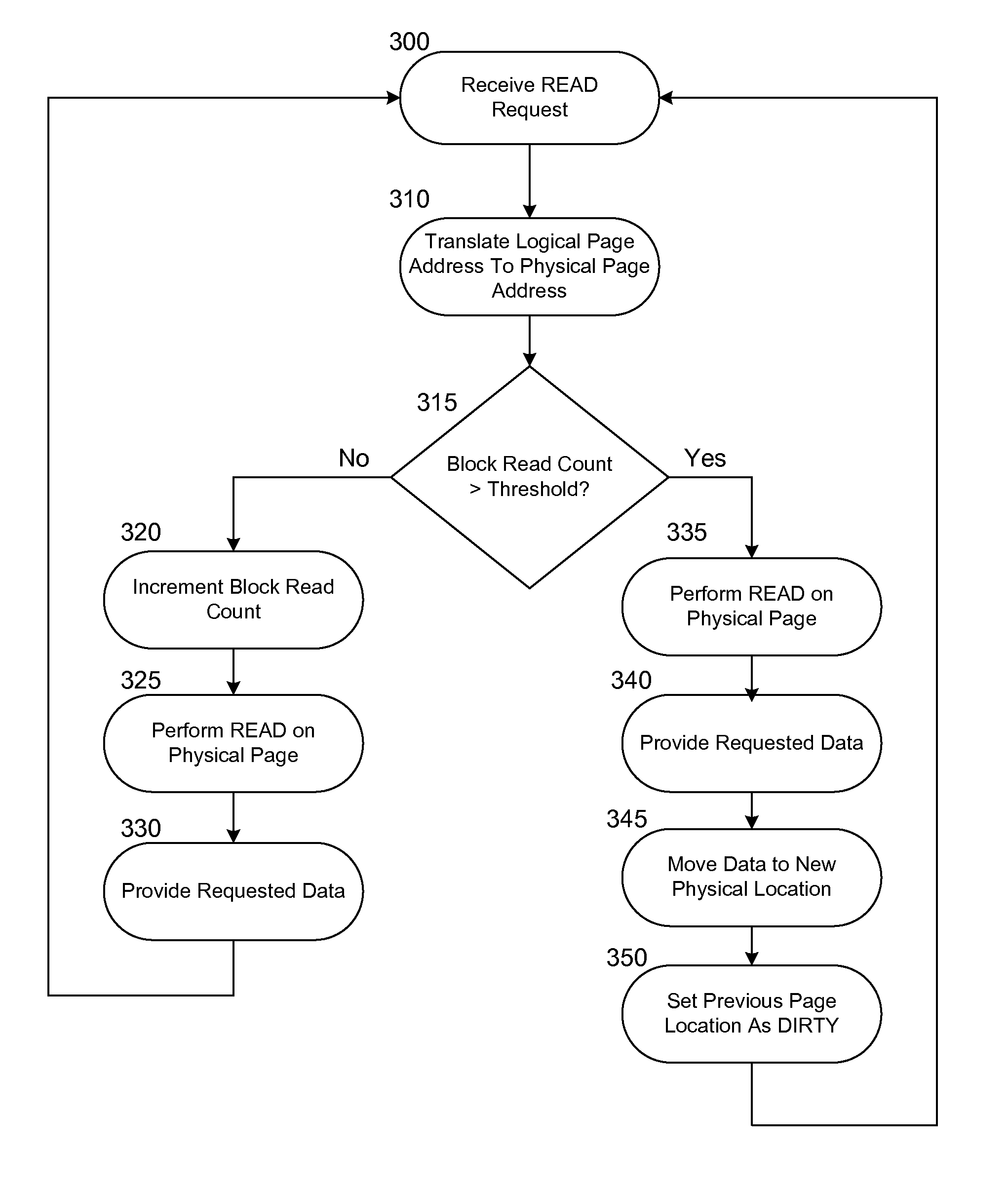
Efficient reduction of read disturb errors in NAND FLASH memory
InactiveUS7818525B1Disturb errorEfficient reduction of Read Disturb errorMemory architecture accessing/allocationRead-only memoriesPhysical addressTranslation table
Methods and apparatuses for reduction of Read Disturb errors in a NAND FLASH memory system comprise a controller configured to organize FLASH memory devices into blocks, each block having a plurality of pages, and each page defining an individually addressable physical memory location. The controller is further configured to accumulate a Block READ Count corresponding to the number of times any pages in a first block of pages have been read since the first block was last erased. Once the READ count reaches a predetermined number, the controller responds to subsequent READ requests for pages within the first block by moving data associated with a requested page to a page in a second, different block without moving data associated with other pages in the first block, and modifying a logical-to-physical translation table to associate the moved data with the physical address of the page in the second block.
Owner:IBM CORP
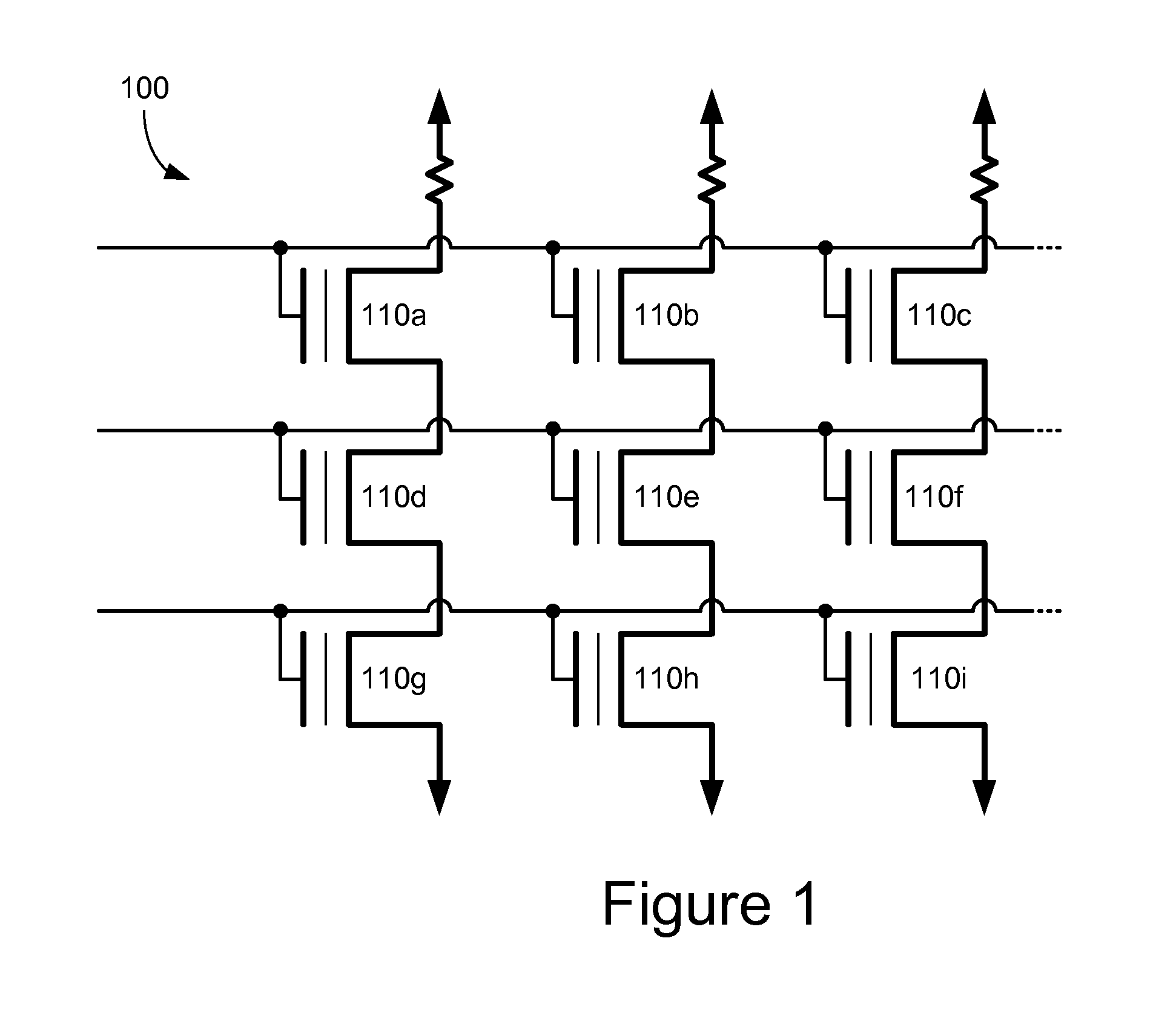
Custodian-based routing in content-centric networks
ActiveUS20120158973A1Easy to optimizeFacilitating custodian-based routingData switching by path configurationMultiple digital computer combinationsCommunication endpointComputer network
One embodiment of the present invention provides a system for facilitating custodian-based routing. During operation, the system receives, at a computing device, a request for a piece of content from a user, and determines whether the content is available locally. In response to the content not being available locally, the system identifies a remote custodian device that stores the content. The custodian device is not identified by its physical address. The system then identifies a communication endpoint associated with the identified custodian device, and maps a physical address corresponding to the identified communication endpoint. The system establishes a connection to the communication endpoint using the mapped physical address to obtain the requested content.
Owner:SAMSUNG ELECTRONICS CO LTD +1
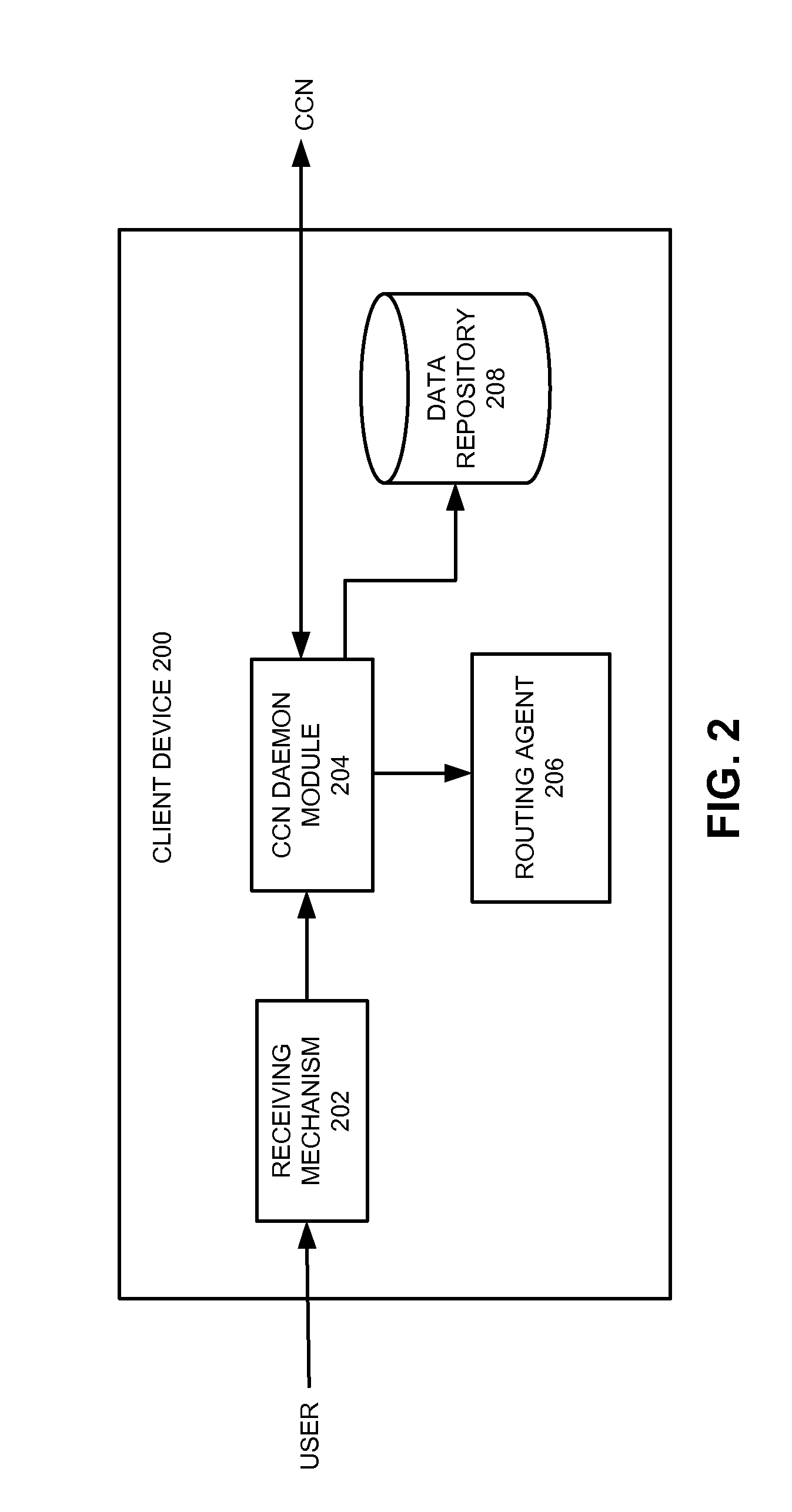
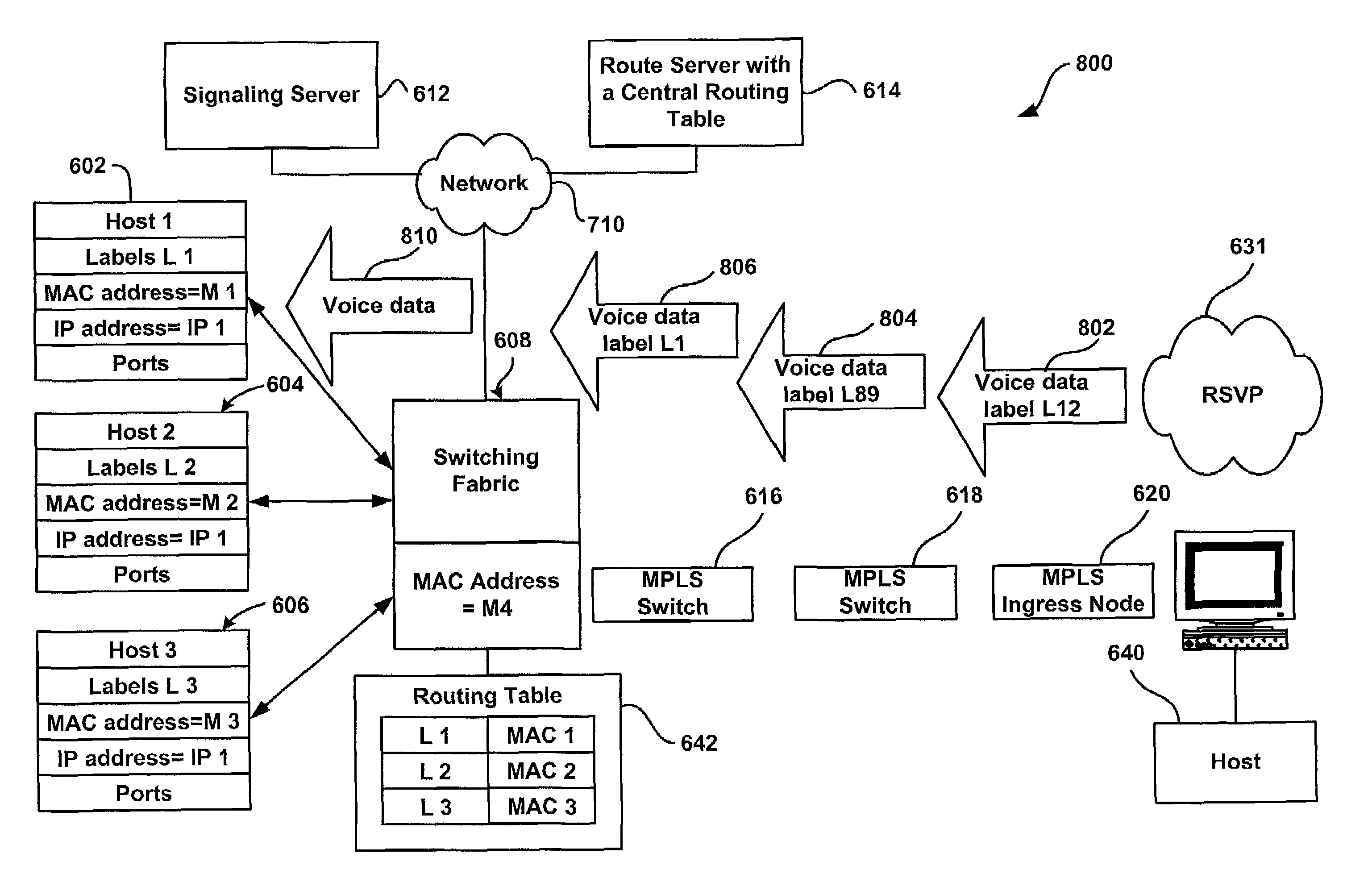
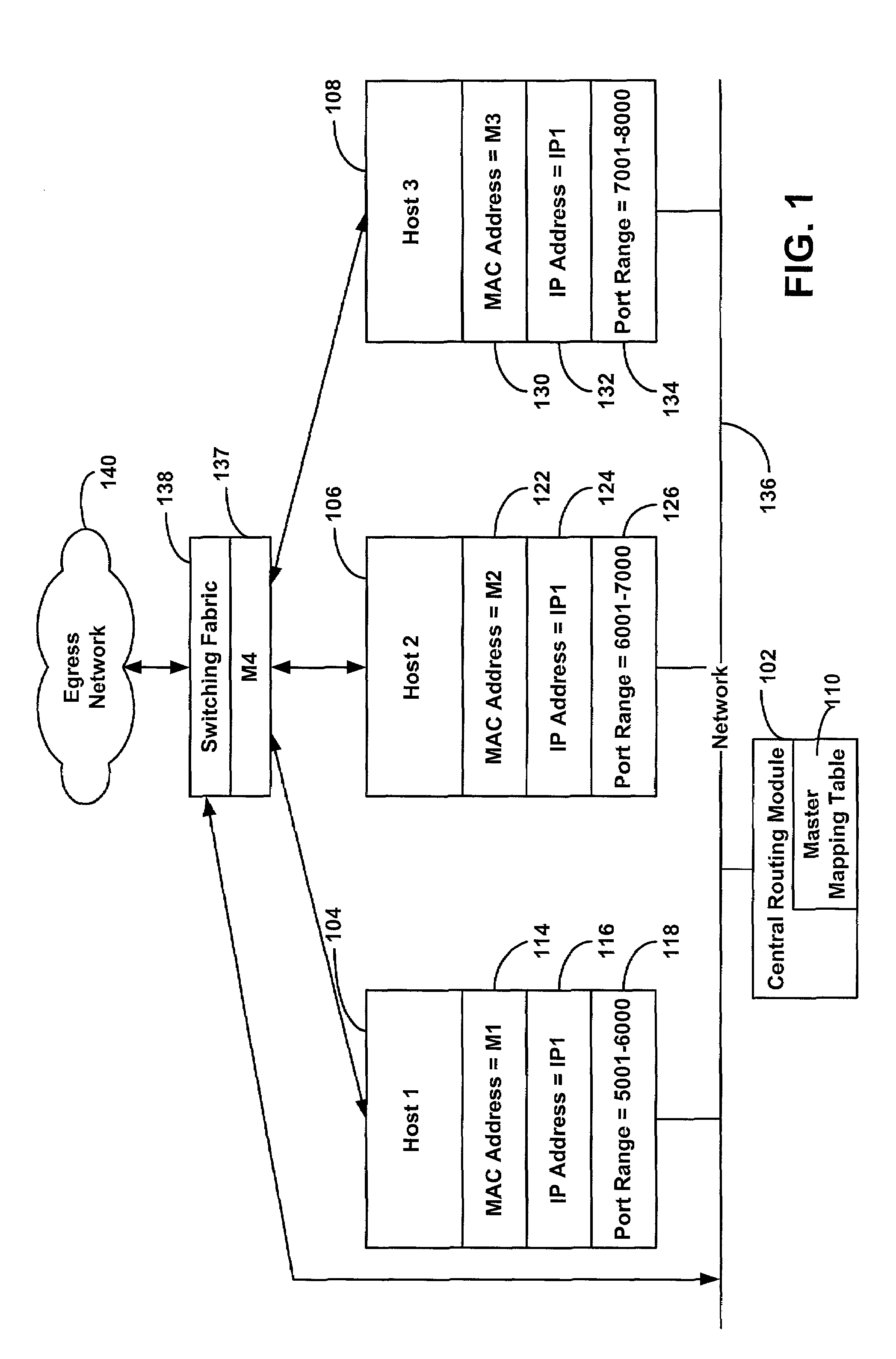
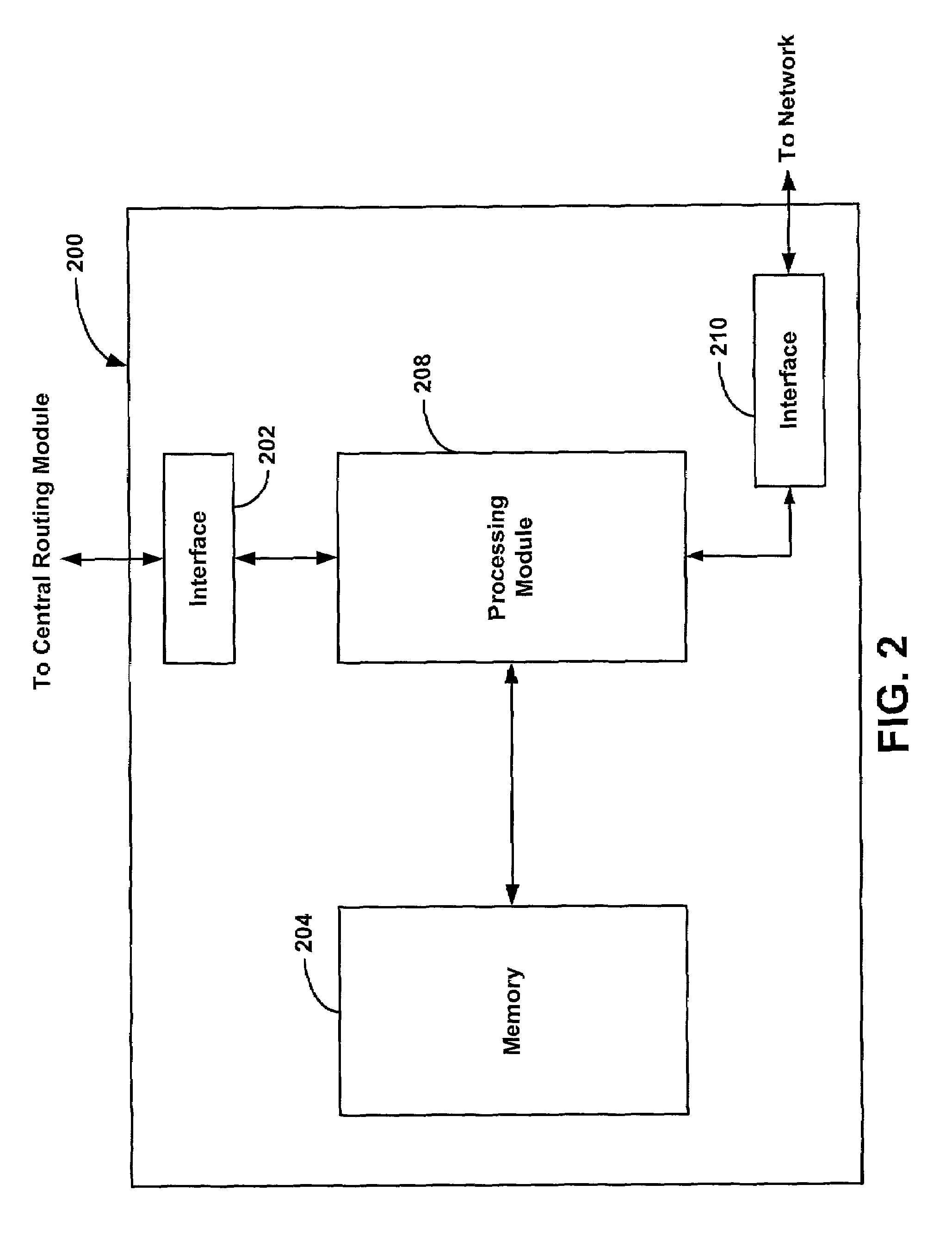
System and method for providing masquerading using a multiprotocol label switching
A system and method for transmitting information between a source host and a destination host. A source host generates a message and forwards the message via a label switched path to the destination host so that when a central routing module receives the message, the message includes a label. A central routing module establishes a local master mapping table including a plurality of physical addresses, and each of the plurality of physical addresses is associated with a unique identifier such as a label. When a switch egress module receives the message with the label, the switch egress module determines a physical address associated with the label, maps the physical address to the message, and forwards the message to the destination host associated with the label.
Owner:VALTRUS INNOVATIONS LTD
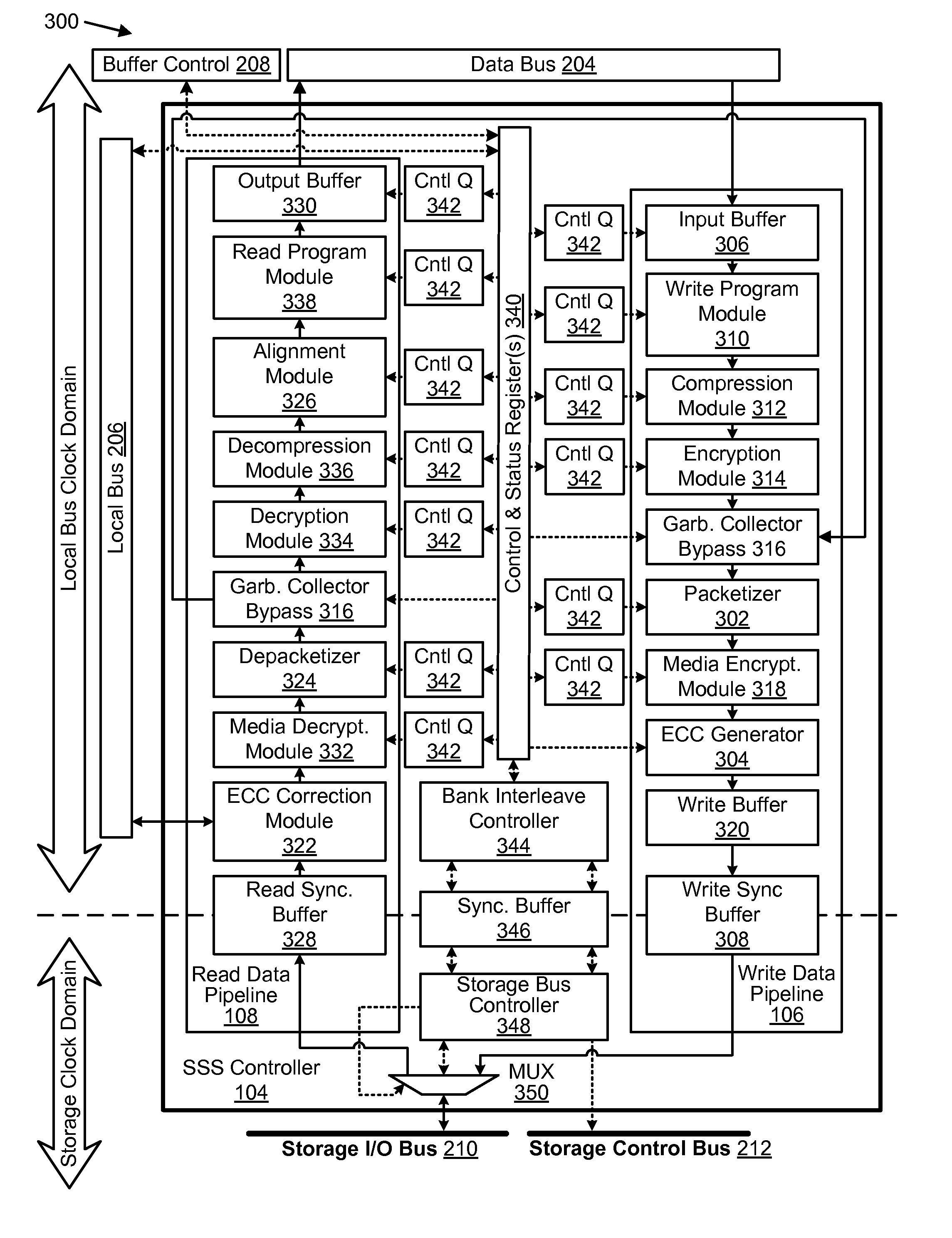
RDMA enabled I/O adapter performing efficient memory management
InactiveUS20060236063A1Reduce the numberReduce the amount requiredMemory systemsPhysical addressTerm memory
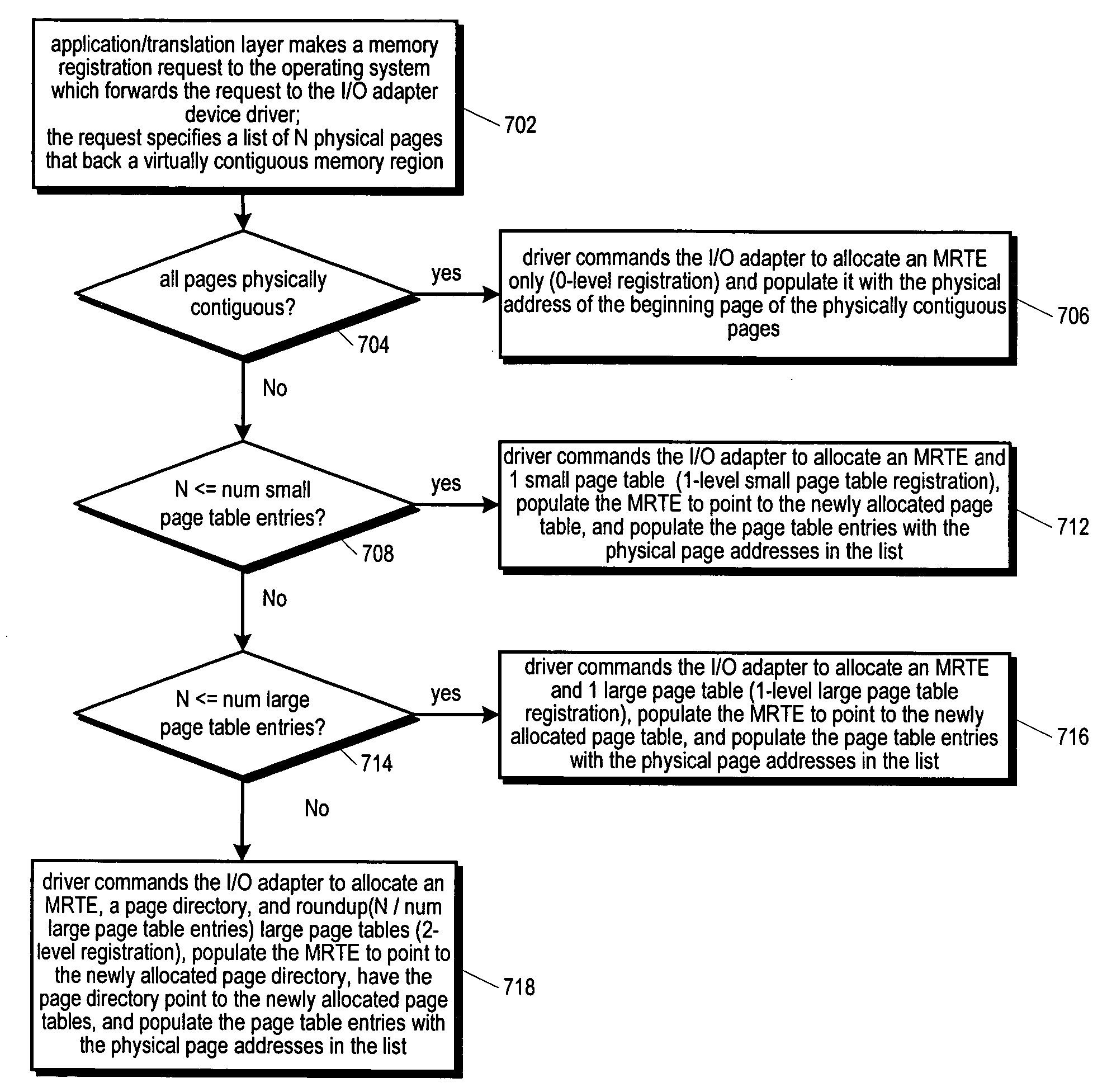
An RDMA enabled I / O adapter and device driver is disclosed. In response to a memory registration that includes a list of physical memory pages backing a virtually contiguous memory region, an entry in a table in the adapter memory is allocated. A variable size data structure to store the physical addresses of the pages is also allocated as follows: if the pages are physically contiguous, the physical page address of the beginning page is stored directly in the table entry and no other allocations are made; otherwise, one small page table is allocated if the addresses will fit in a small page table; otherwise, one large page table is allocated if the addresses will fit in a large page table; otherwise, a page directory is allocated and enough page tables to store the addresses are allocated. The size and number of the small and large page tables is programmable.
Owner:INTEL CORP
Dynamic selection of memory virtualization techniques
ActiveUS20070283125A1Error detection/correctionMemory adressing/allocation/relocationVirtualizationComputerized system
A computer system may be configured to dynamically select a memory virtualization and corresponding virtual-to-physical address translation technique during execution of an application and to dynamically employ the selected technique in place of a current technique without re-initializing the application. The computer system may be configured to determine that a current address translation technique incurs a high overhead for the application's current workload and may be configured to select a different technique dependent on various performance criteria and / or a user policy. Dynamically employing the selected technique may include reorganizing a memory, reorganizing a translation table, allocating a different block of memory to the application, changing a page or segment size, or moving to or from a page-based, segment-based, or function-based address translation technique. A selected translation technique may be dynamically employed for the application independent of a translation technique employed for a different application.
Owner:ORACLE INT CORP
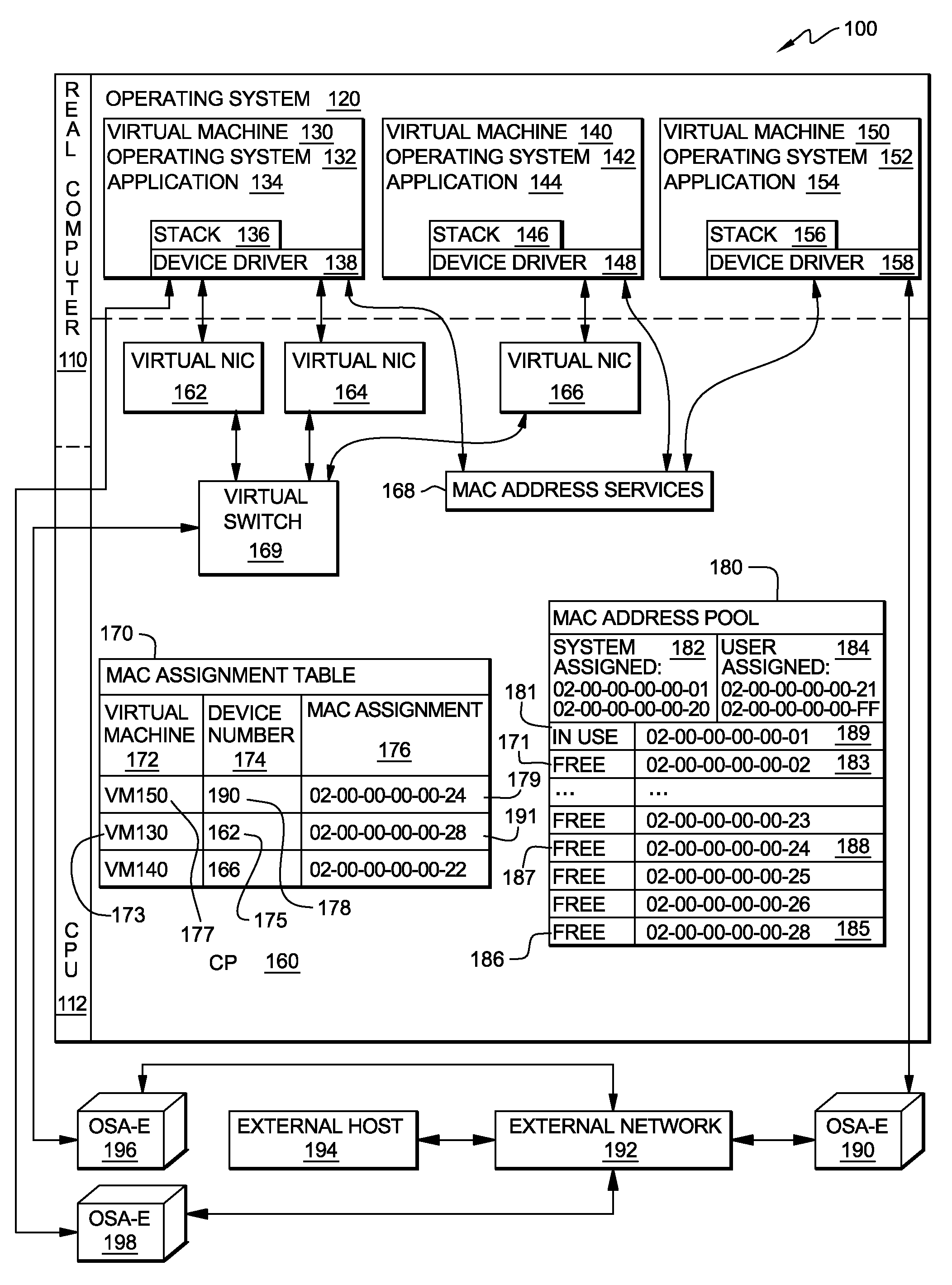
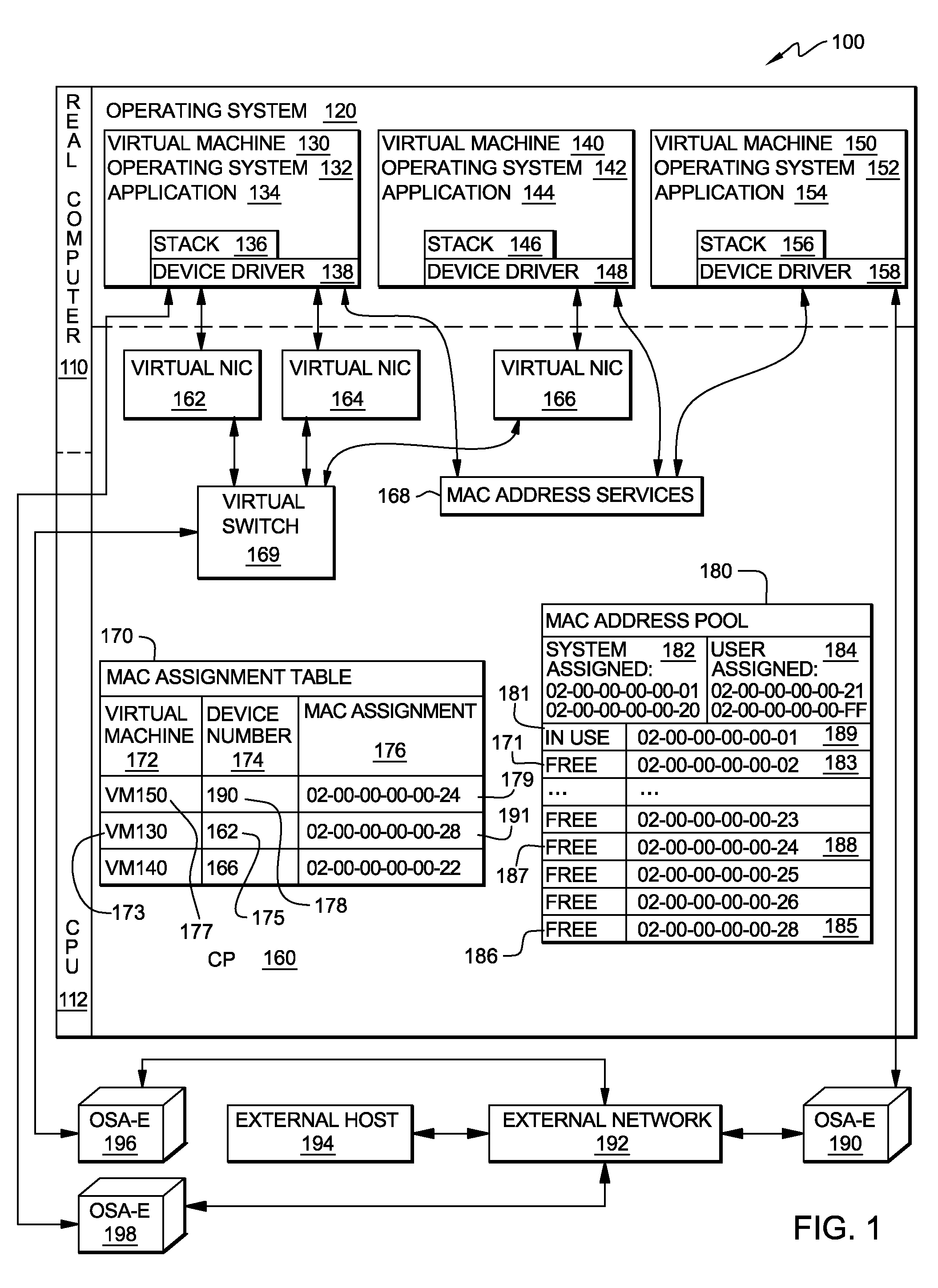
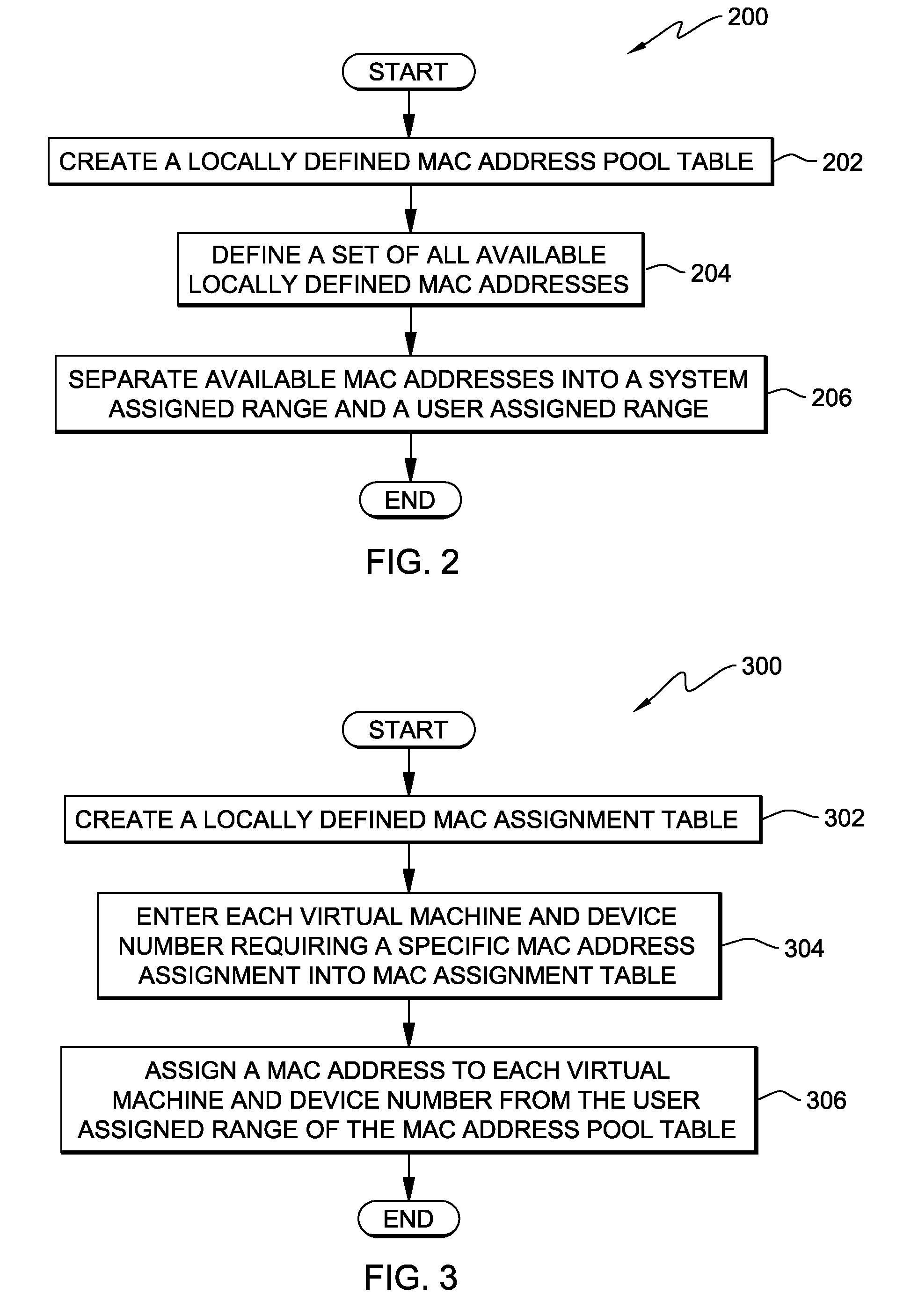
Method, system and program product for managing assignment of mac addresses in a virtual machine environment
InactiveUS20090327462A1Multiprogramming arrangementsMultiple digital computer combinationsVirtual memoryOperational system
A method, system and program product for managing assignment of virtual physical addresses. The method includes requesting, using a services function provided by a virtual machine operating system, a MAC address assignment for a real device and searching, in a MAC assignment table created and stored within a virtual memory space, to determine whether or not an explicit MAC address is assigned to the device. If an explicit MAC address is determined to be assigned to the device, retrieving the explicit MAC address upon verifying that the MAC address is not in use by another device and forwarding, using the services function, the explicit MAC address retrieved for assignment to the real device. If an explicit MAC address is not assigned to the device, retrieving an available MAC address from a MAC address pool table and forwarding the available MAC address retrieved for assignment to the real device.
Owner:IBM CORP
Fast path for performing data operations
InactiveUS20070016754A1Multiplex system selection arrangementsUnauthorized memory use protectionFast pathData operations
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
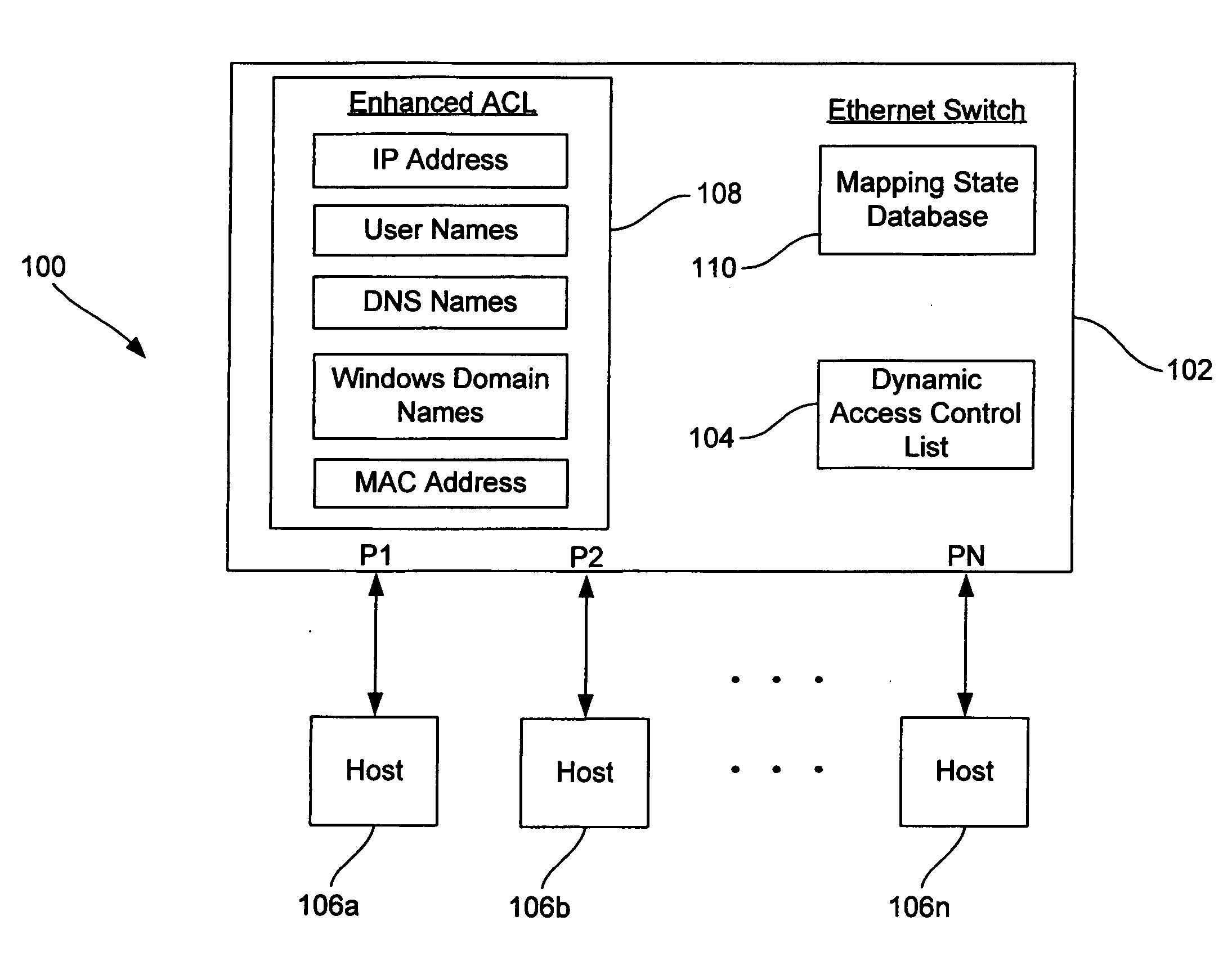
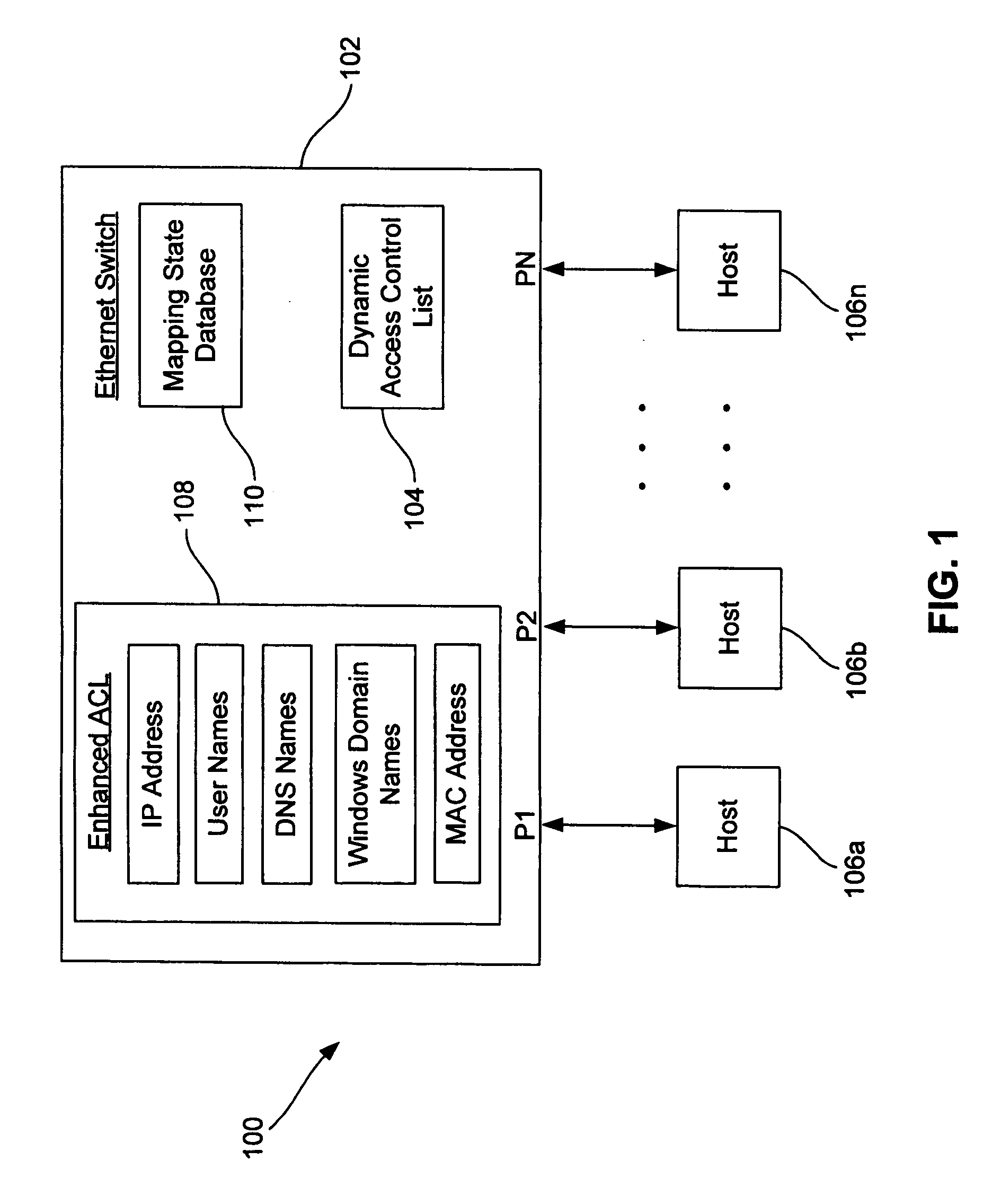
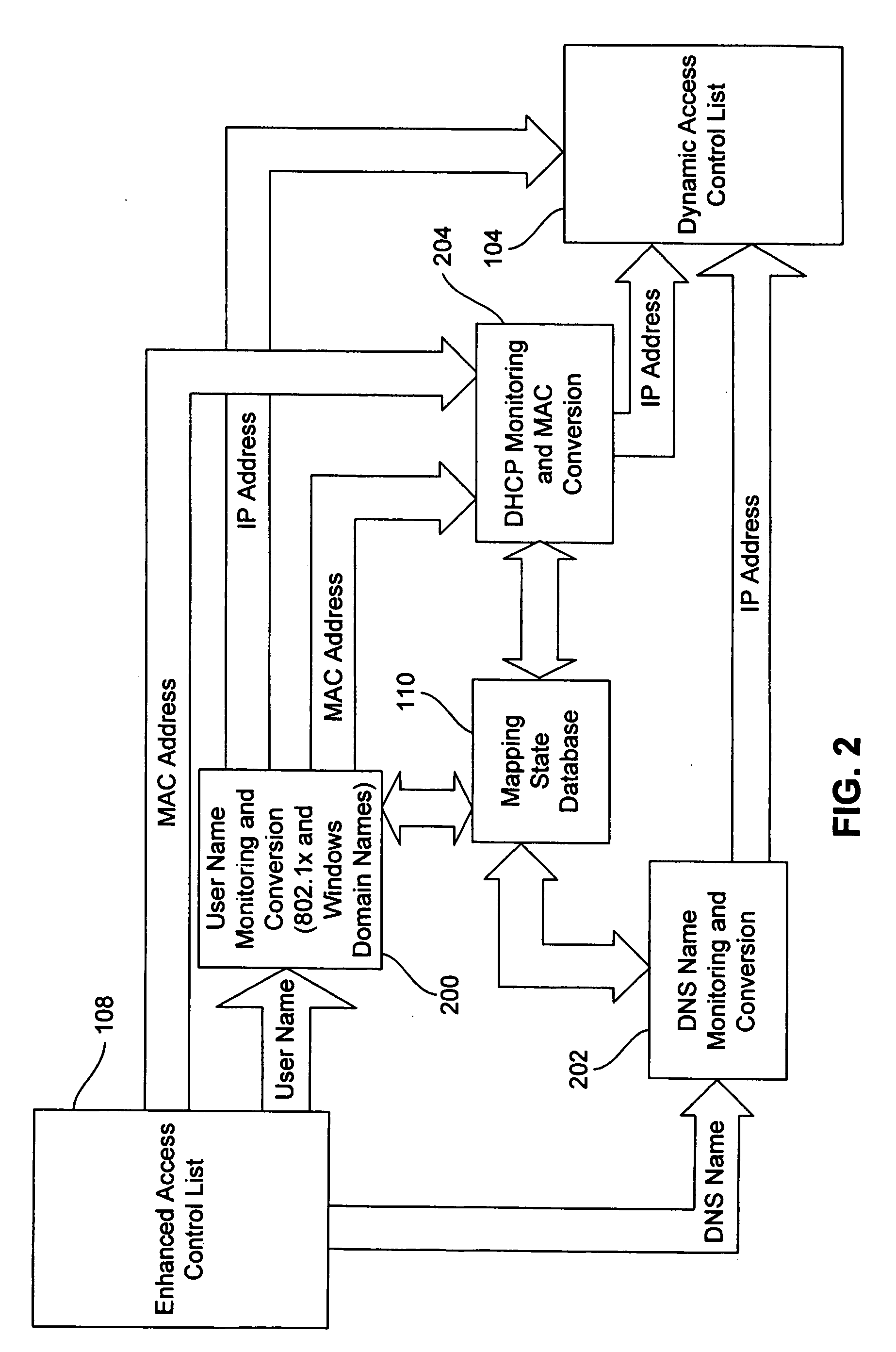
Dynamic access control lists
ActiveUS20050259654A1Data switching by path configurationMultiple digital computer combinationsDomain nameIp address
A method controls access of a user to a network including a plurality of hosts coupled together through a network switch. The method includes storing in the network switch an enhanced access control list containing data related to at least one of user names, DNS names, domain names, and physical addresses. A dynamic access control list is generated from the enhanced access control list, with the dynamic access control list containing a plurality of IP addresses that restrict access of the user to the network.
Owner:LIONRA TECH LTD
Method and apparatus for securing portions of memory
ActiveUS20020147916A1User identity/authority verificationUnauthorized memory use protectionPhysical addressComputer security
The present invention provides a method and apparatus for securing portions of a memory. The method includes identifying information for protection and indicating at least one physical address of a memory that houses the information as at least one of read and write disabled. The method includes receiving a request from a program to access the information. The method further includes accessing the information in response to determining that the program has the authority to access the information. The apparatus includes a memory comprising a privileged code. The privileged code is capable of receiving a request to protect selected information and indicating at least one physical address of a memory housing the information as at least one of read and write disabled. The privileged code is capable of receiving a request from a program to access the information. The privileged code is further capable of accessing the information in response to determining that the program has the authority to access the information.
Owner:MEDIATEK INC
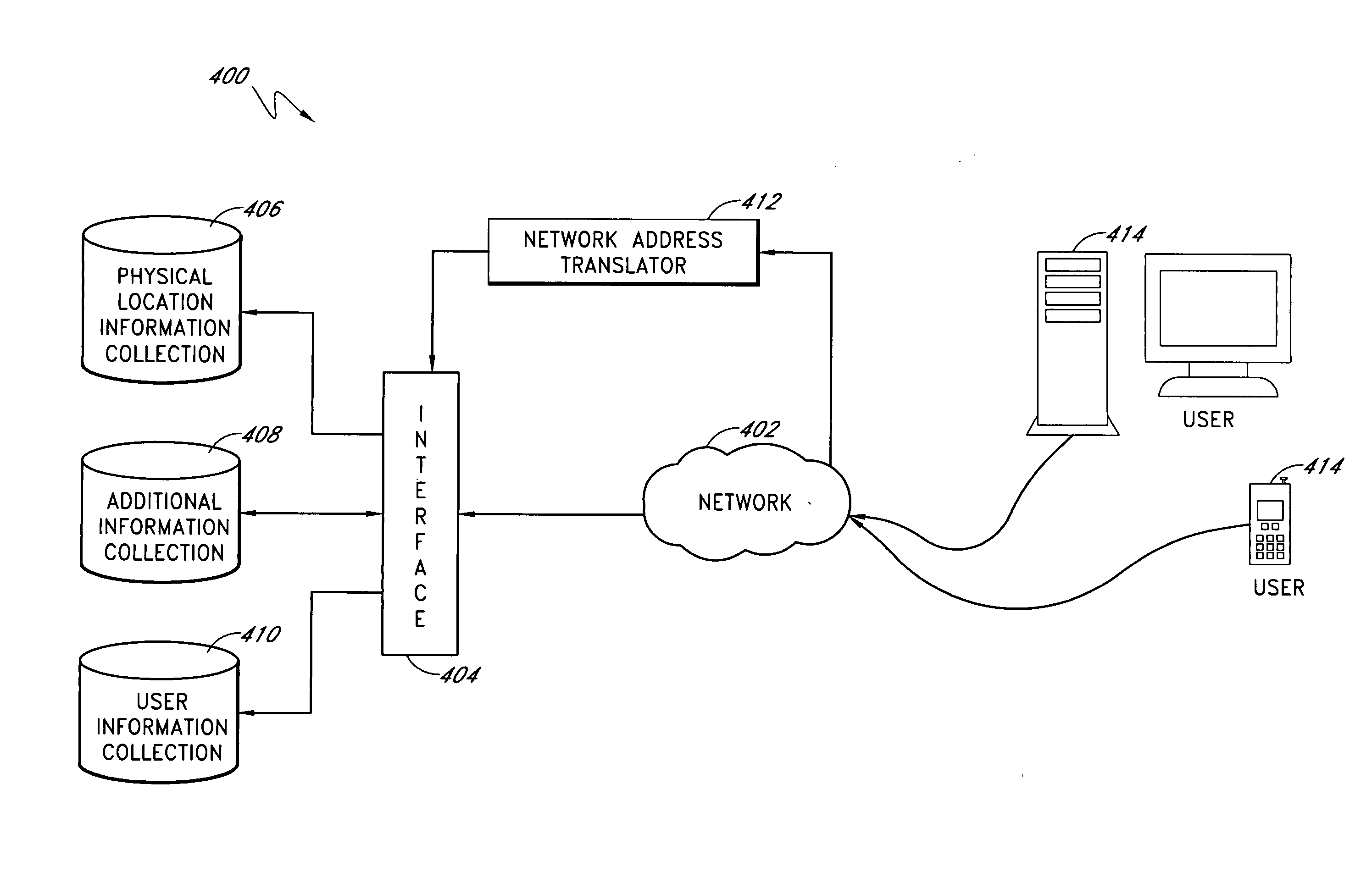
System and method of virtualizing physical locations
InactiveUS20050192999A1Easy accessMultiple digital computer combinationsGeographical information databasesDomain nameVirtualization
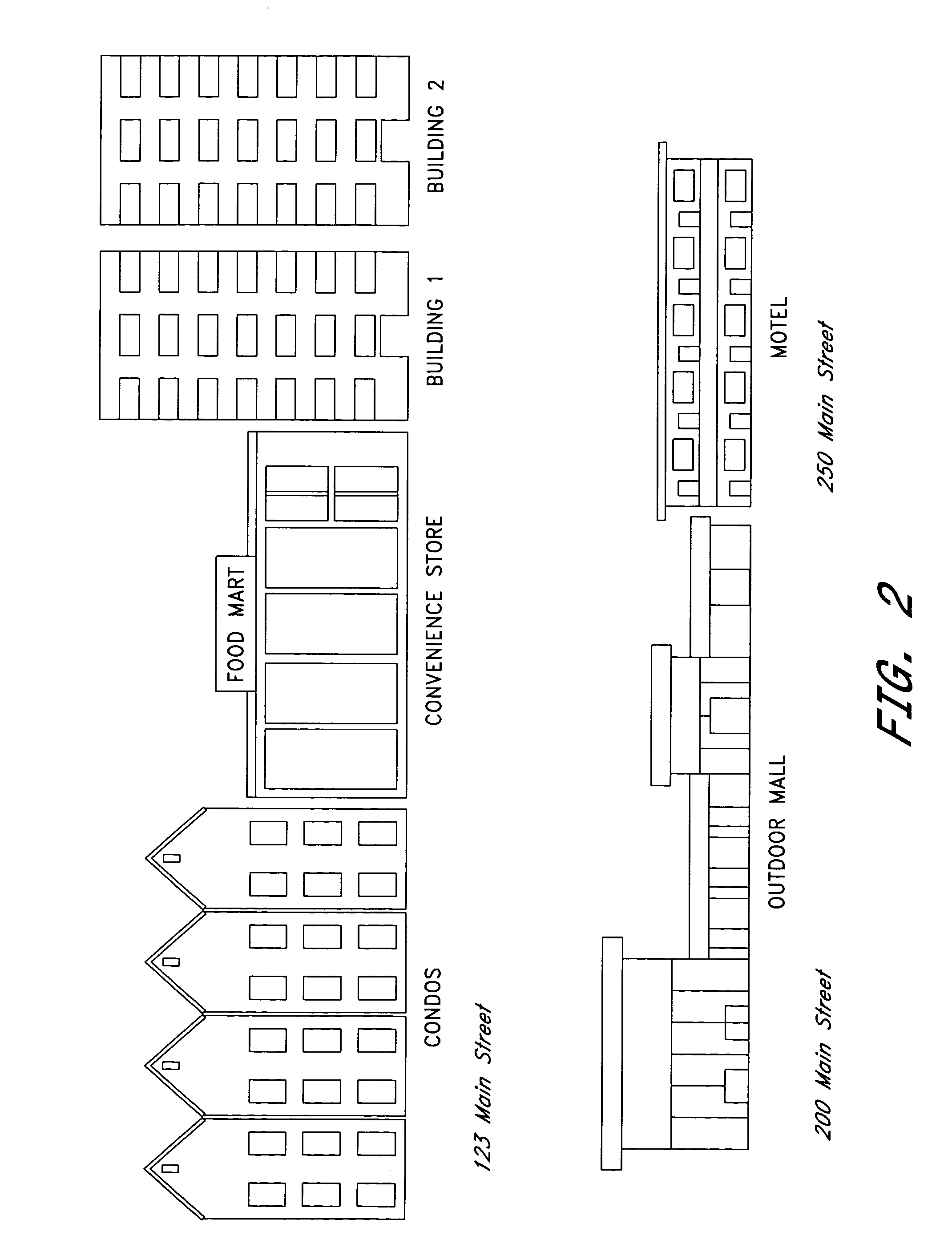
The system and method provide an intuitive and user-friendly way to store information about physical locations on a computer network. In particular, a physical location information collection is created and stored on a computer network at a network address that corresponds to the physical address of the physical location to which the information pertains. The network address for information about the physical location at 123 Main Street, for example, incorporates at least a portion of 123 Main Street. The physical address can be incorporated into a Uniform Resource Locator (“URL”) domain name, such as, for example, www.123mainstreet.com. Alternatively, the physical address can be incorporated into another portion of a network address, such as, for example, www.buildingaddress.com / 123mainstreet / .
Owner:BUILDING ADDRESS
On-device mapping of WIFI hotspots via direct connection of WIFI-enabled and GPS-enabled mobile devices
InactiveUS7466986B2Generate efficientlyAssess restrictionError detection/correctionUser inputGeolocation
A WIFI-enabled and GPS-enabled user device executes a hotspot location utility, which enables the device to detect WIFI hotspots and update a locally-stored hotspot location database (LHLD) containing geographically-mapped hotspots. When a hotspot is detected, the device accesses the hotspot, retrieves identification information and usage terms from the hotspot, and measures performance metrics of the hotspot. The utility stores the identified hotspot with the current GPS coordinate as an entry within the LHLD. When a user later desires to locate hotspots within a particular geographic location, the user enters the physical address of the location, and hotspots with matching (or proximate) GPS coordinates of the entered address are presented to the user. The user may specify certain preferences for usage terms, performance metrics, and location criteria, and the utility filters all geographic hits and returns only hotspots in the geographic location that also satisfy these preferences.
Owner:INT BUSINESS MASCH CORP
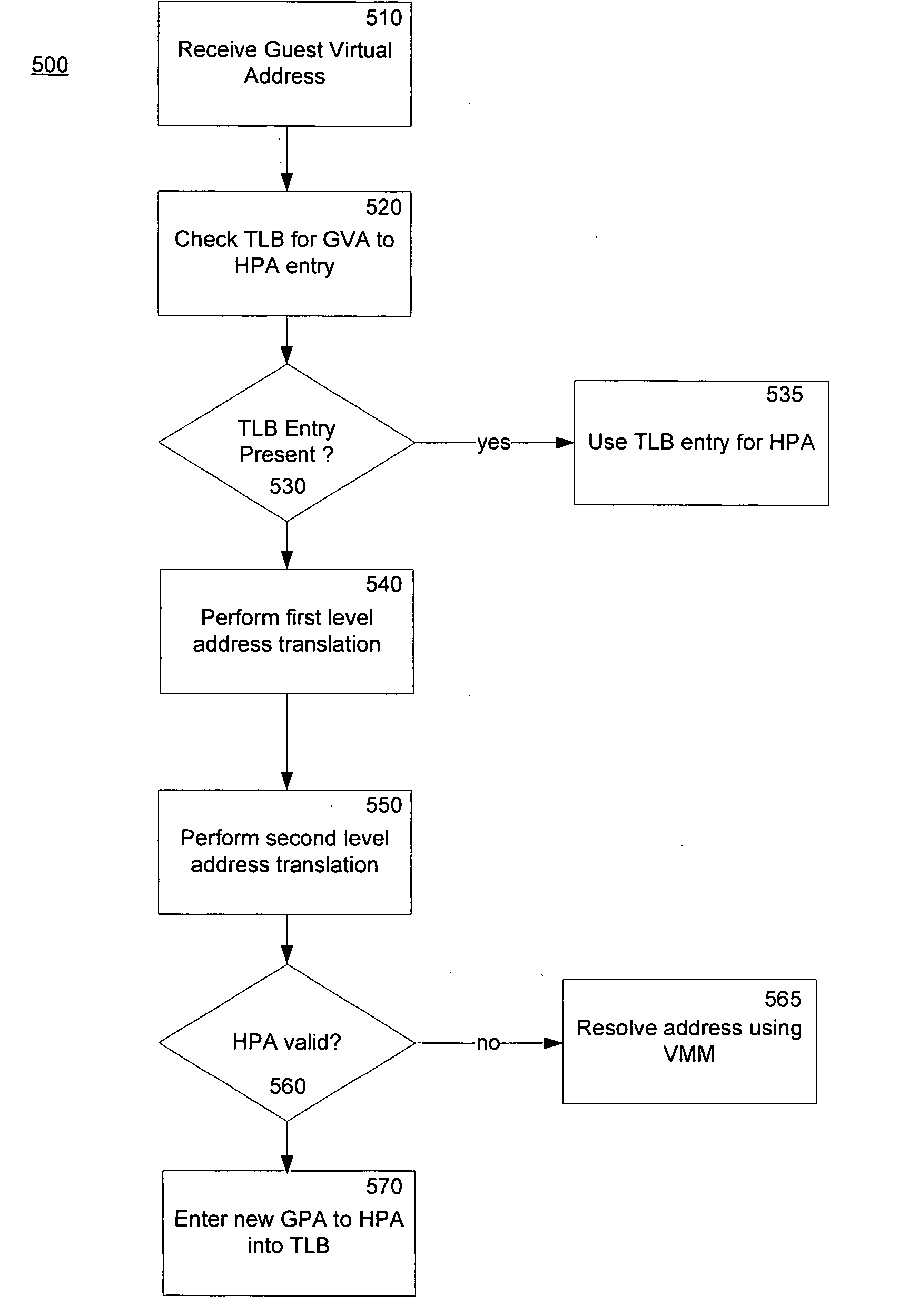
Method and system for a second level address translation in a virtual machine environment
ActiveUS20060206687A1Increase speedReduce usageMemory architecture accessing/allocationMemory adressing/allocation/relocationPhysical addressHost memory
A method of performing a translation from a guest virtual address to a host physical address in a virtual machine environment includes receiving a guest virtual address from a host computer executing a guest virtual machine program and using the hardware oriented method of the host CPU to determine the guest physical address. A second level address translation to a host physical address is then performed. In one embodiment, a multiple tier tree is traversed which translates the guest physical address into a host physical address. In another embodiment, the second level of address translation is performed by employing a hash function of the guest physical address and a reference to a hash table. One aspect of the invention is the incorporation of access overrides associated with the host physical address which can control the access permissions of the host memory.
Owner:MICROSOFT TECH LICENSING LLC
Method and systems for providing a secure electronic mailbox
InactiveUS20020029248A1User identity/authority verificationUnauthorized memory use protectionPaymentInternet privacy
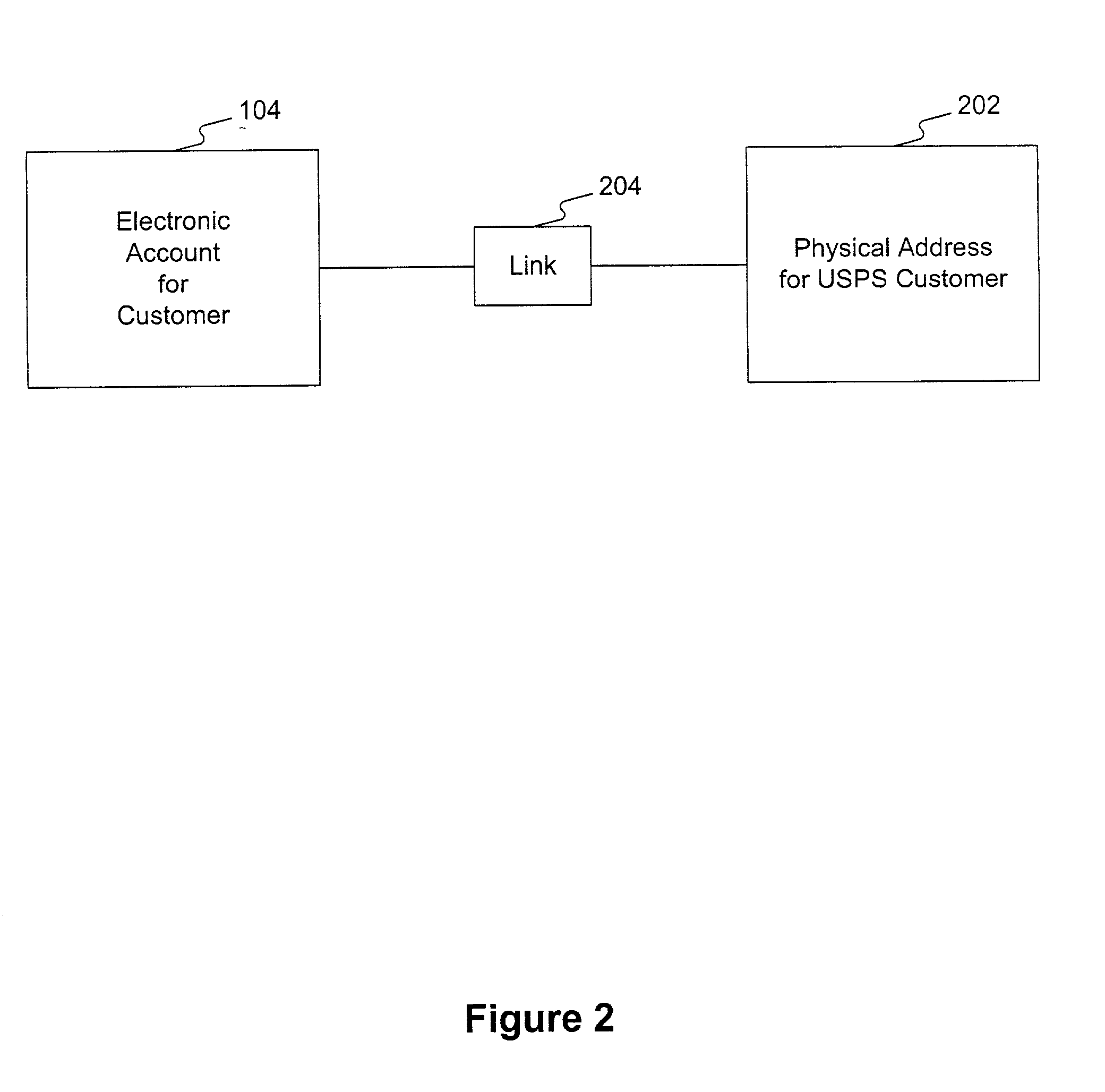
A secure electronic mailbox is provided to a customer having an electronic account. The electronic account links the secure electronic mailbox to a physical address of the customer. The customer can send and receive secure and nonsecure messages via the secure electronic mailbox. The customer can also access electronic services such as electronic bill presentment and payment using the secure electronic mailbox.
Owner:US POSTAL SERVICE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com