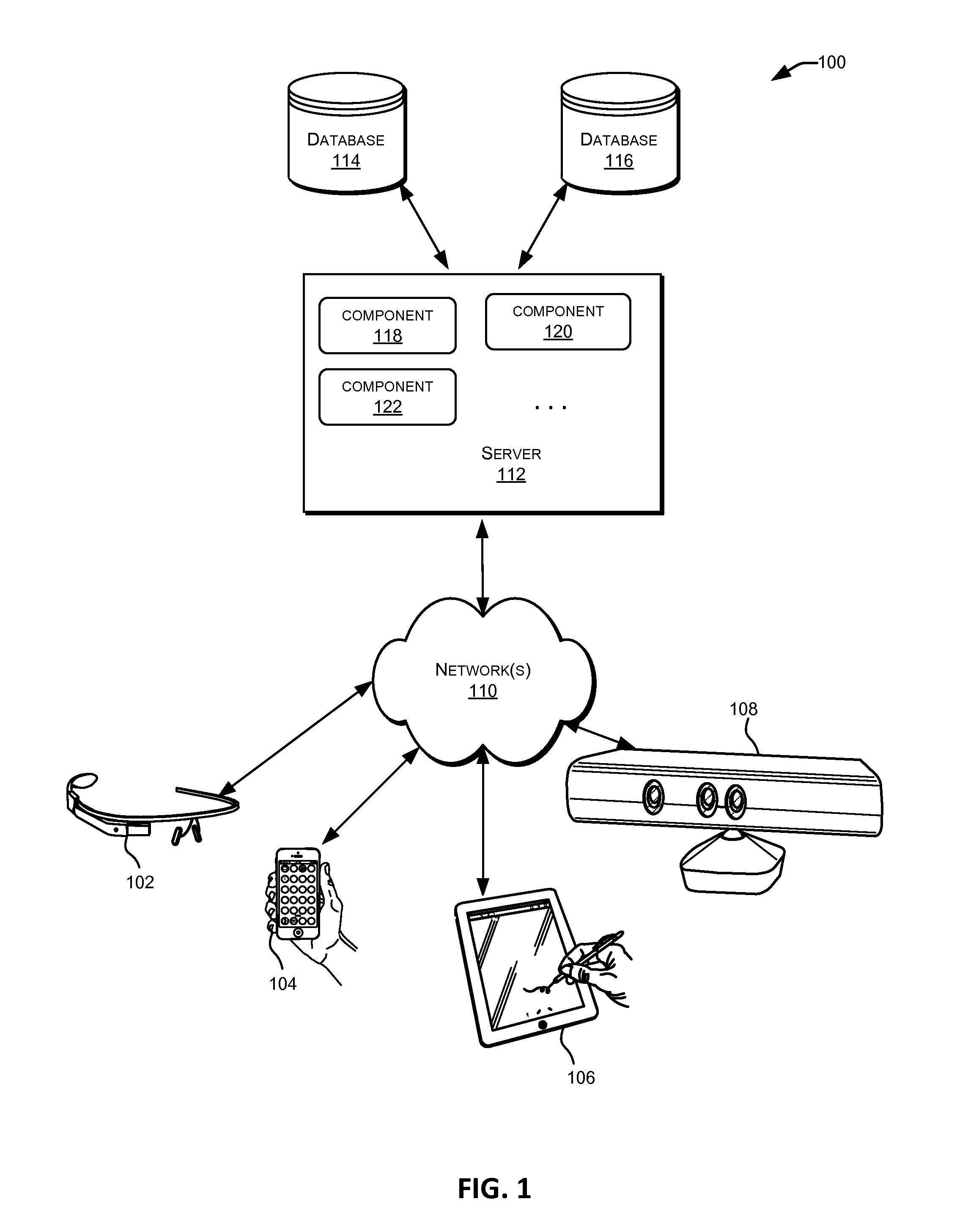
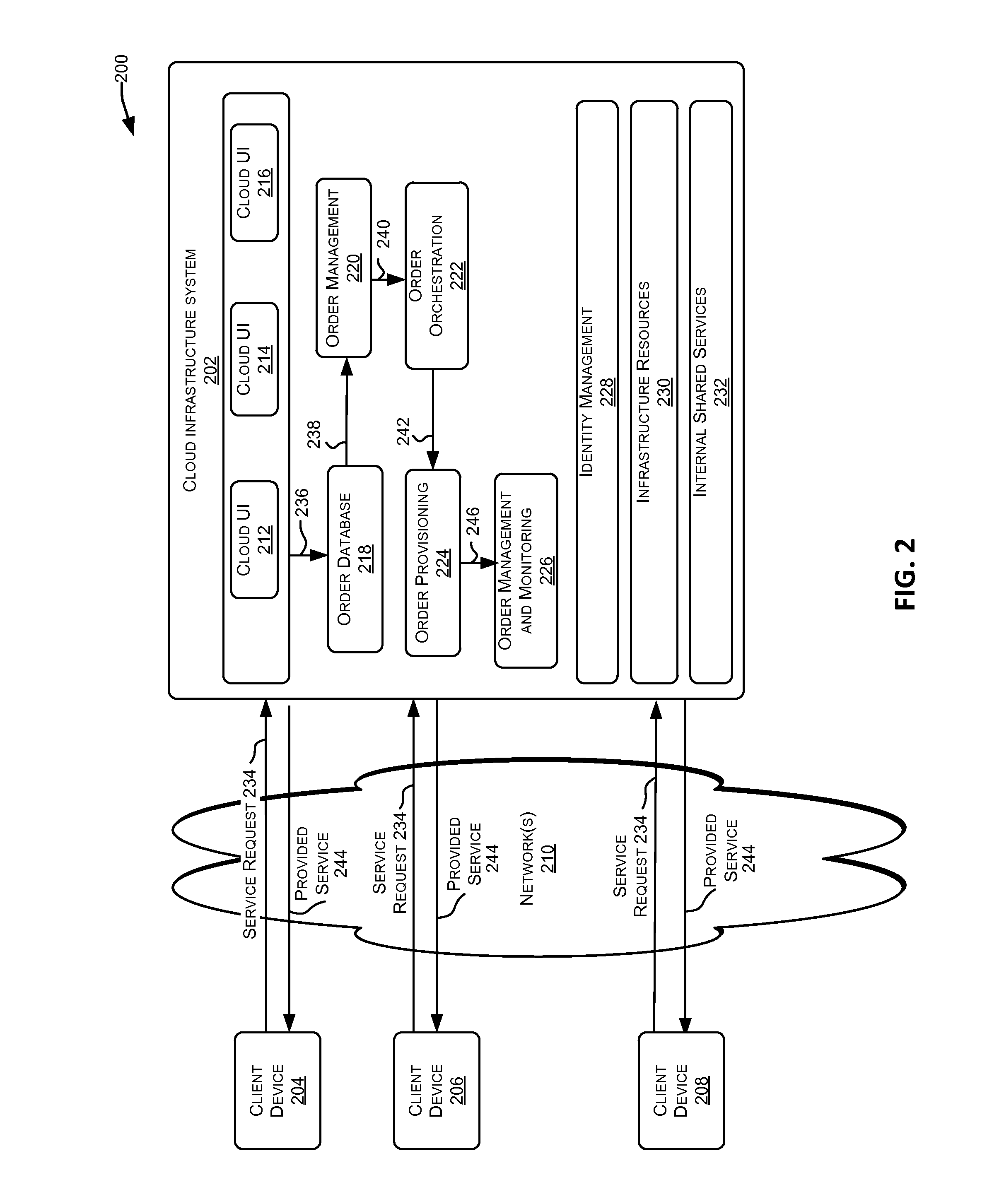
Patents
Literature
204 results about "Communication endpoint" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
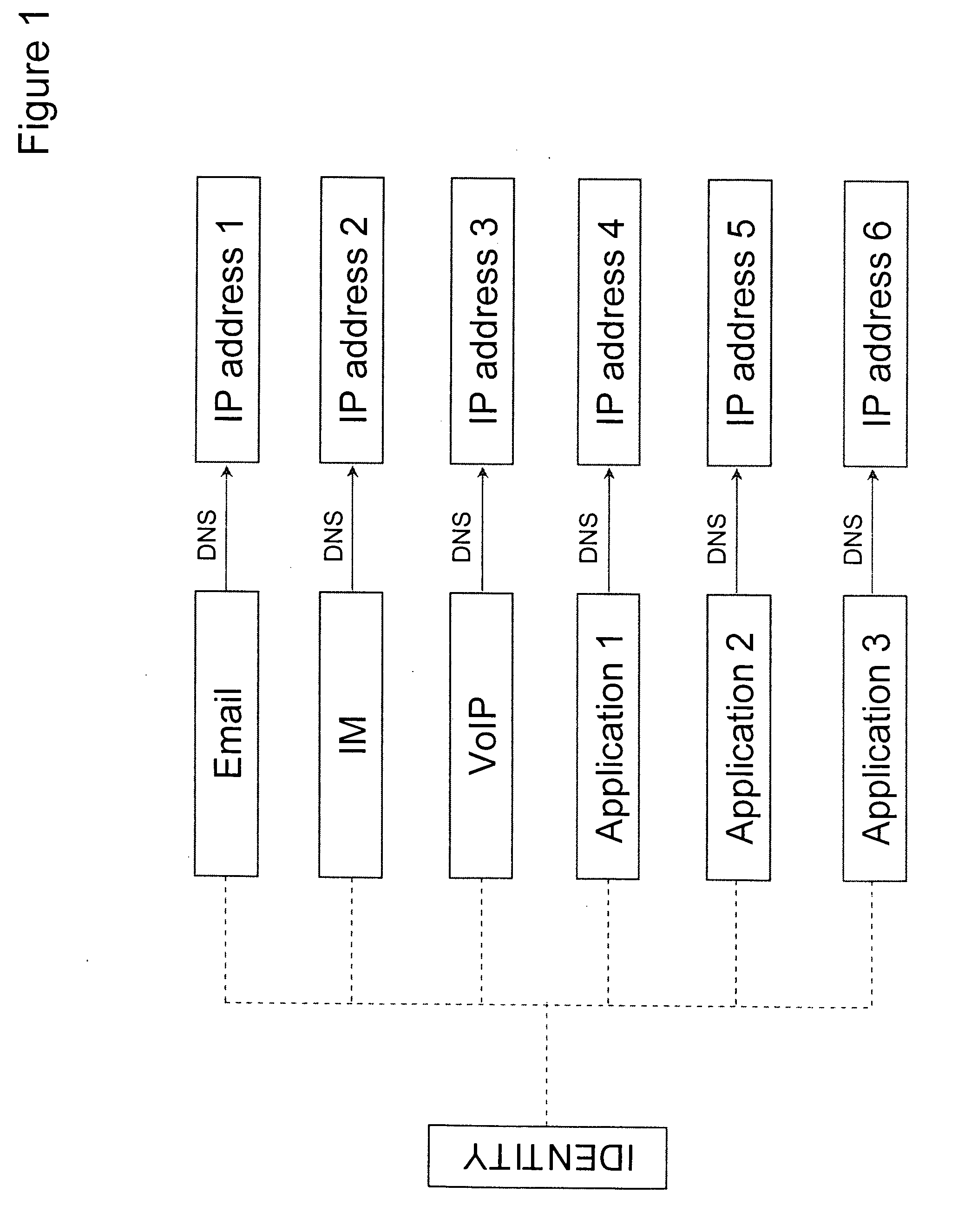
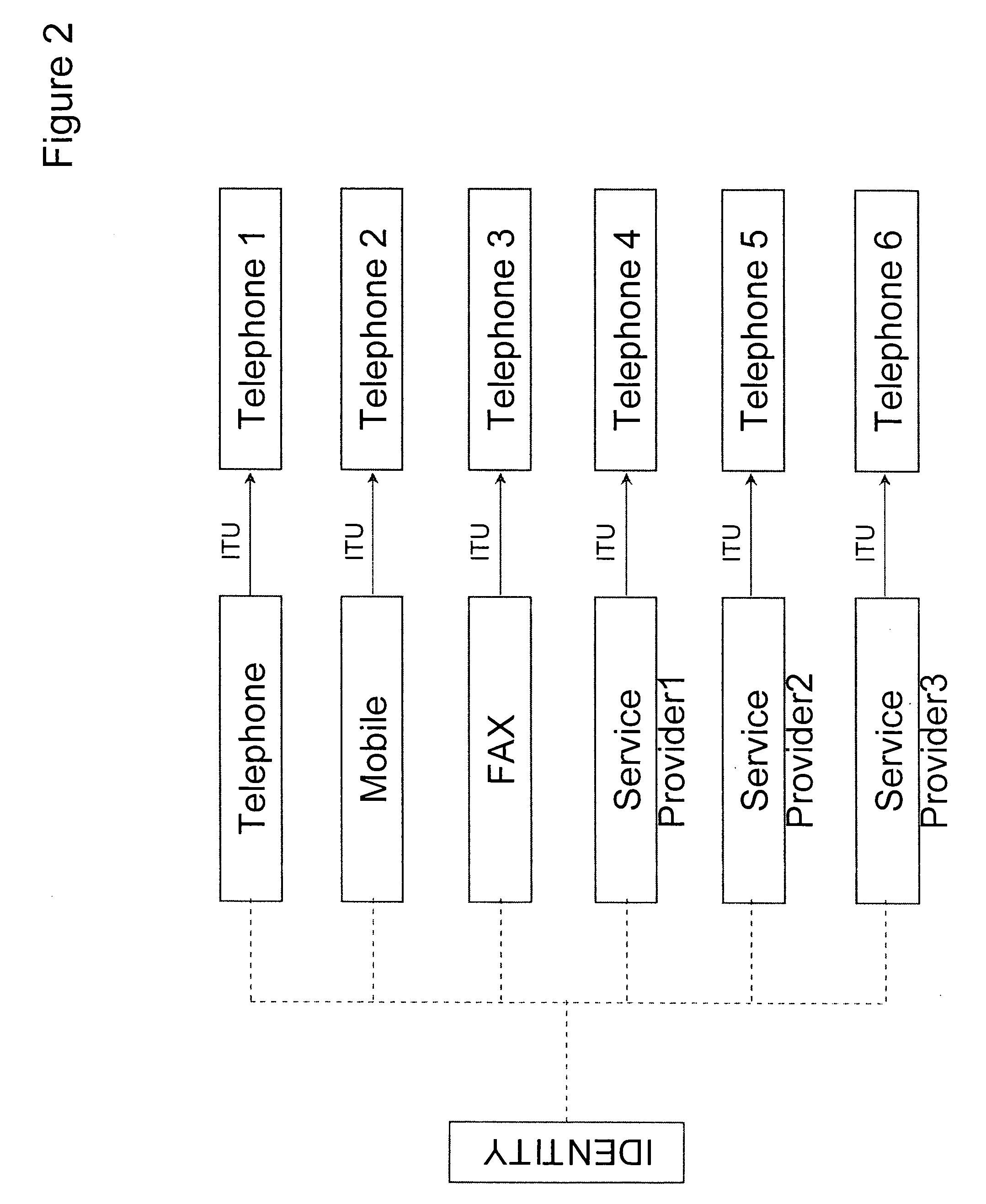
A communication endpoint is a type of communication network node. It is an interface exposed by a communicating party or by a communication channel. An example of the latter type of a communication endpoint is a publish-subscribe topic or a group in group communication systems.
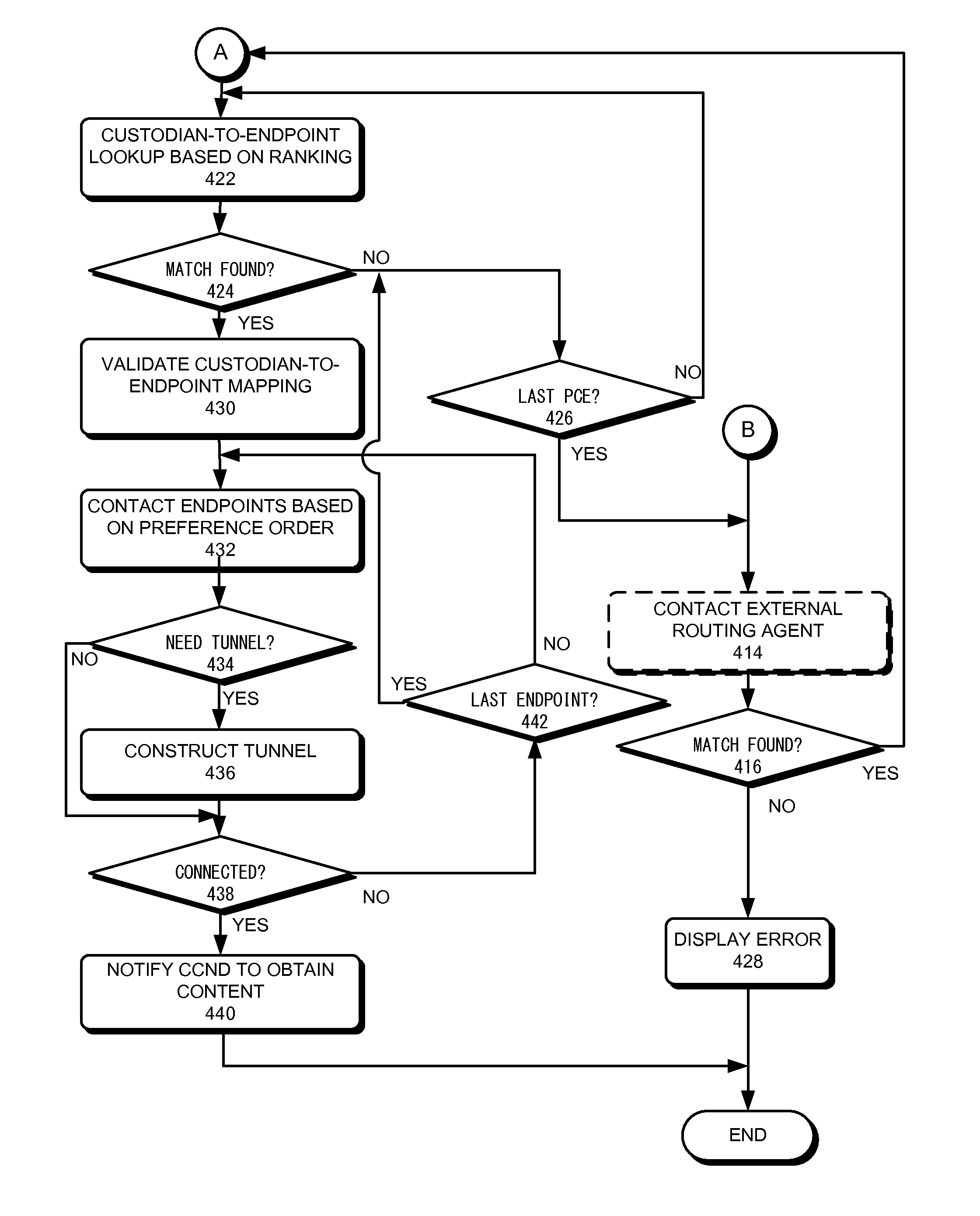
Custodian-based routing in content-centric networks
ActiveUS20120158973A1Easy to optimizeFacilitating custodian-based routingData switching by path configurationMultiple digital computer combinationsCommunication endpointComputer network
One embodiment of the present invention provides a system for facilitating custodian-based routing. During operation, the system receives, at a computing device, a request for a piece of content from a user, and determines whether the content is available locally. In response to the content not being available locally, the system identifies a remote custodian device that stores the content. The custodian device is not identified by its physical address. The system then identifies a communication endpoint associated with the identified custodian device, and maps a physical address corresponding to the identified communication endpoint. The system establishes a connection to the communication endpoint using the mapped physical address to obtain the requested content.
Owner:SAMSUNG ELECTRONICS CO LTD +1
System and method to control transactions on communication channels based on universal identifiers
InactiveUS20070073888A1Minimizing effect of changeMultiple digital computer combinationsTransmissionOutbound communicationAutomatic routing
The present invention is a method to control communication channels using universal and persistent identifiers in circuit / packet switched or converged networks. The method involves linking domain specific addresses or concrete identifiers of communication end points within or across channels, domains and networks with an abstract, persistent and universal identifier that represents the single point of contact or principal identity of the user. The principal identity can specify parameters of inbound / outbound communication relationships with other specified / unspecified users / entities inter-alia through default / specific levels of control in communication relationships on / across / through normal or alternate channels, domains, applications, networks, etc., based on universal / persistent identifiers such as XRI. All transactions originating from, or terminating on, the principal identity are authenticated, asserted securely and routed automatically to an appropriate channel based on the principal identity's current context (state, location, presence, etc.) and privileges (or contracts) defined in rules created by the principal identity for access, usage, privacy, synchronization, compliance, expiry, etc. The principal identity is also empowered with multi-level control over attributes and metadata including rules for what data to expose / share and what data to eclipse / hide for which user. Control / user data, or traffic, and program / client / sequence logic, may be resident / executed / exchanged / carried on, or across, diverse networks / channels / media / devices / domains etc.
Owner:AMSOFT SYST PTE LTD
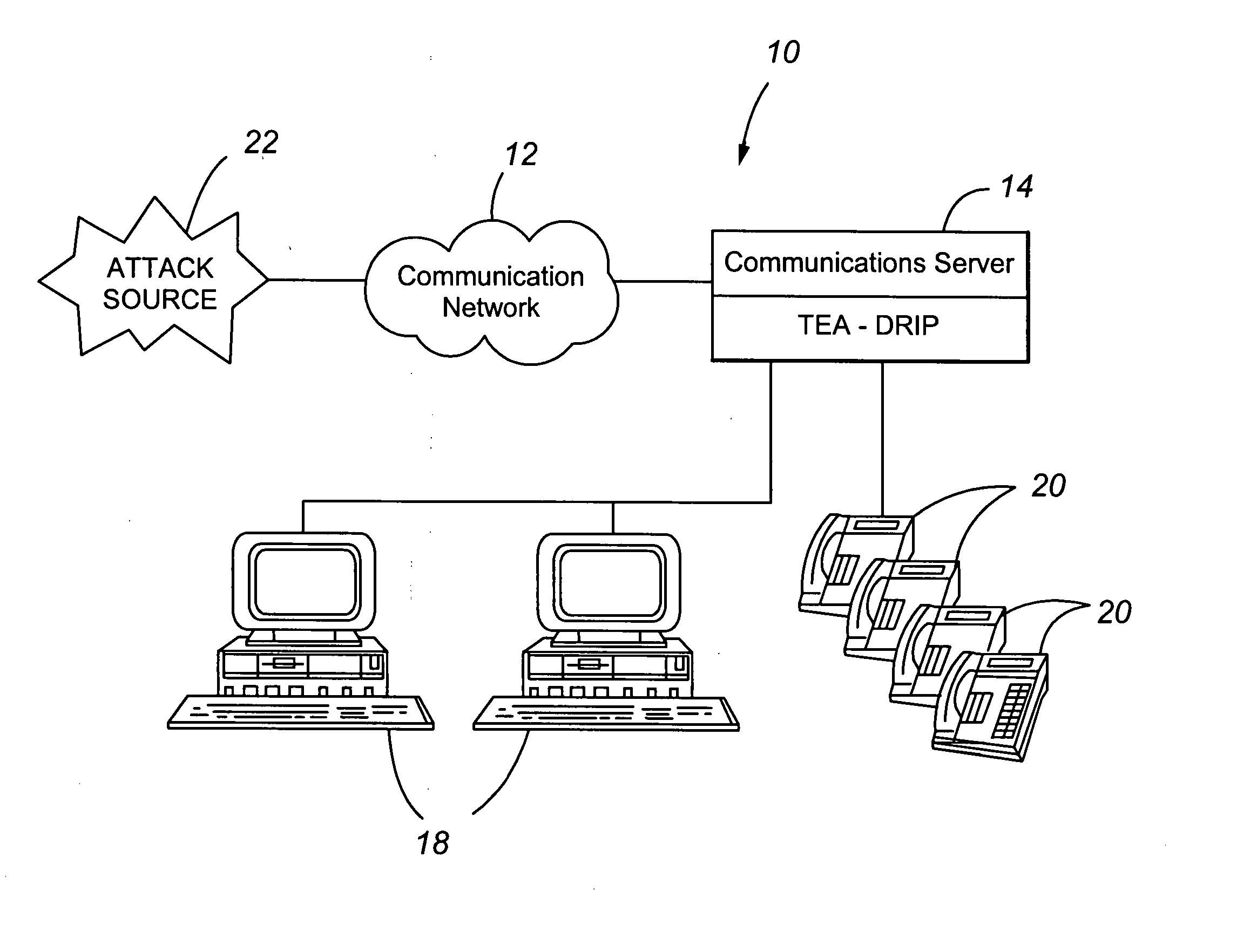
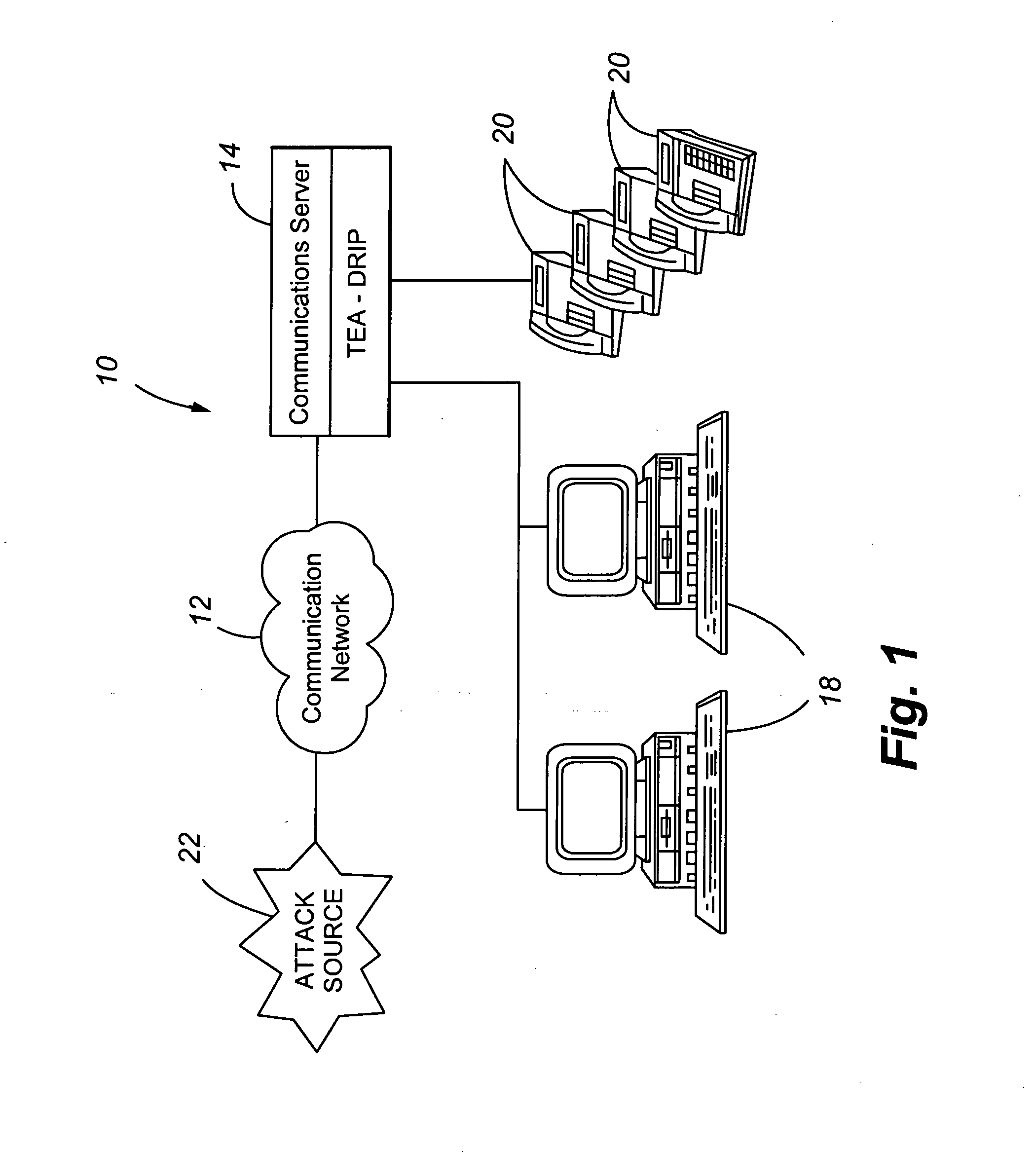
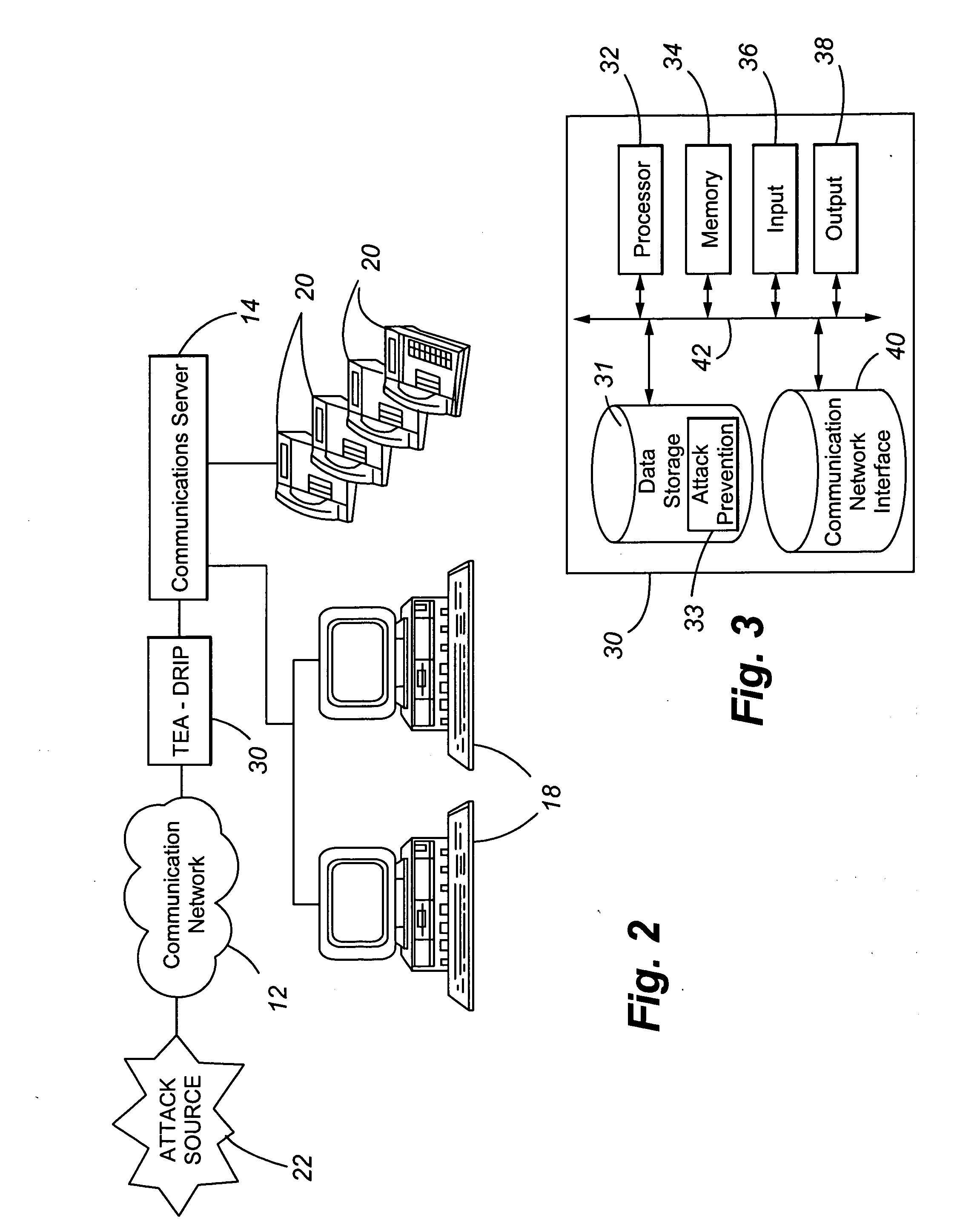
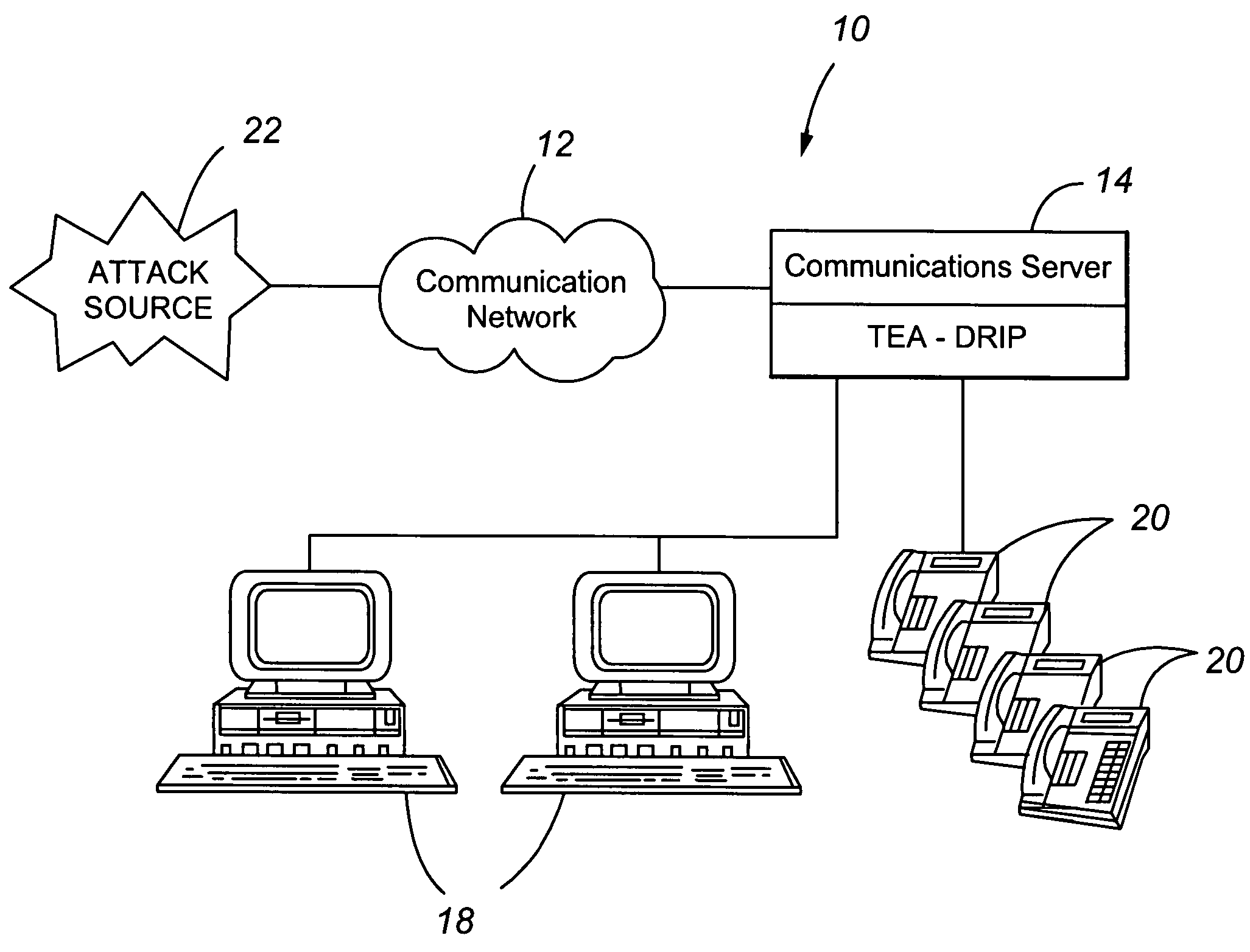
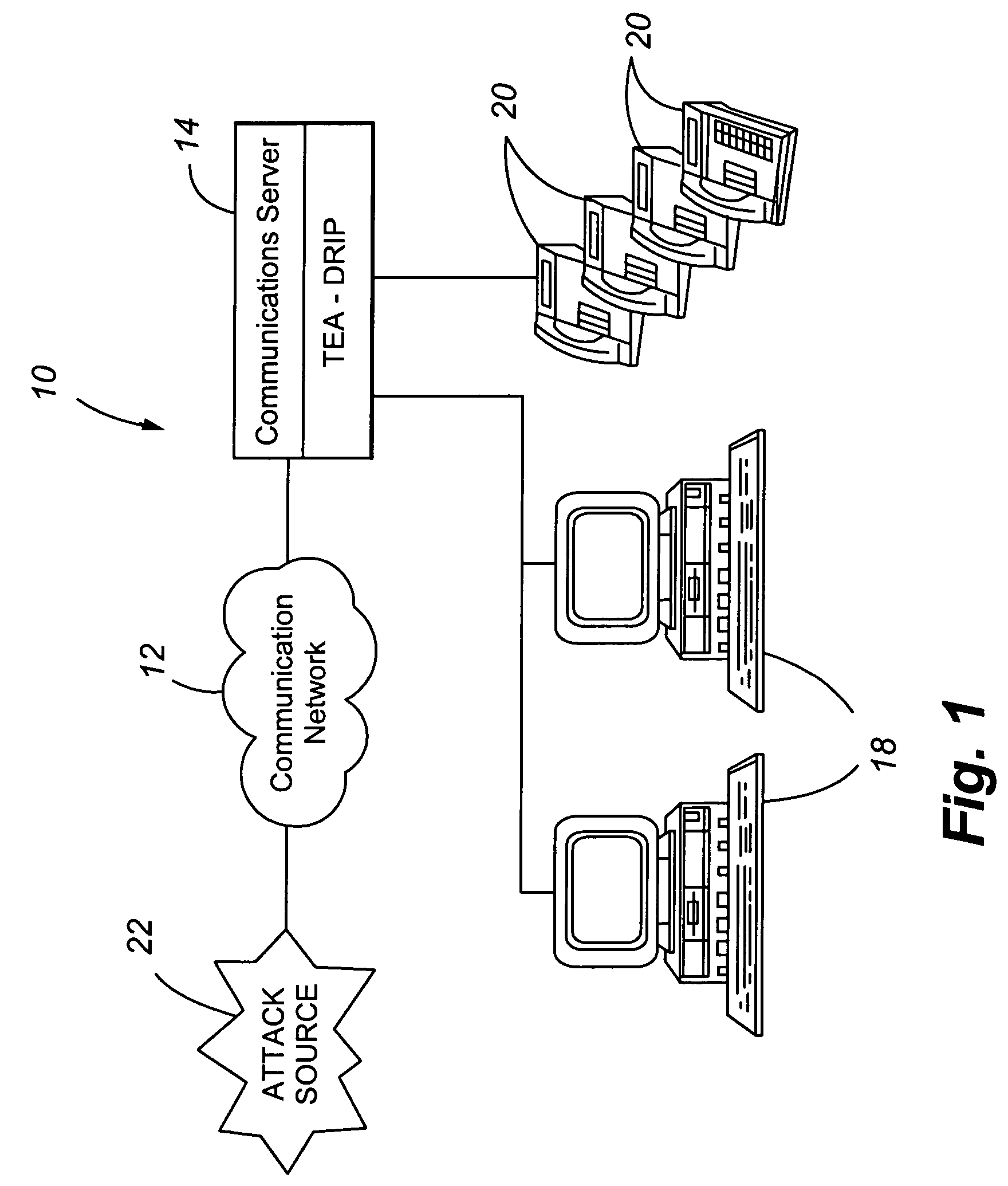
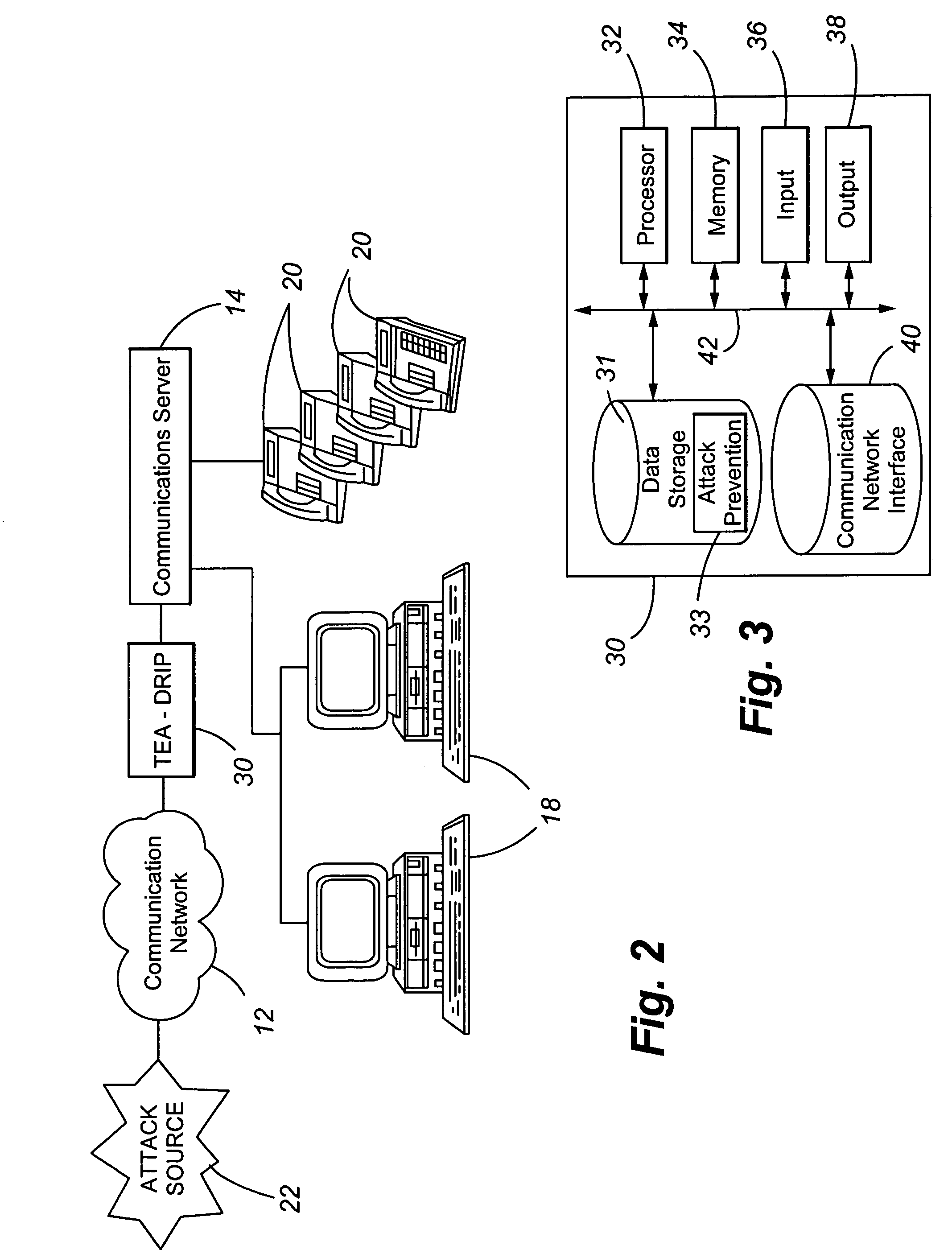
Telephony extension attack detection, recording, and intelligent prevention
ActiveUS20070036314A1Effectively prevent future attackAvoid attackData taking preventionAutomatic exchangesCommunication endpointRemedial action
A system and method are provided for detecting extension attacks made to a communication enterprise, and taking appropriate remedial action to prevent ongoing attacks and future attacks. One or more attributes of a suspect call are analyzed, and a risk is associated with each analyzed attribute. An overall risk or assessment is then made of the analyzed attributes, attack attributes are logged, and one or more remedial actions may be triggered as a result of the analyzed call attributes. The remedial actions may include recording the call, notifying an administrator of a suspect call, or isolating the communication enterprise from the attack by terminating the call or shutting down selected communication endpoints to prevent calls being made to those extensions. Rules may be applied to the analyzed attributes in order to trigger the appropriate remedial action. The call attributes analyzed may include call destination, call direction, call type, time of day of the call, call duration, whether a call source is spoofed, call volume from a particular call source, and hash values created for a suspect media stream.
Owner:AVAYA INC
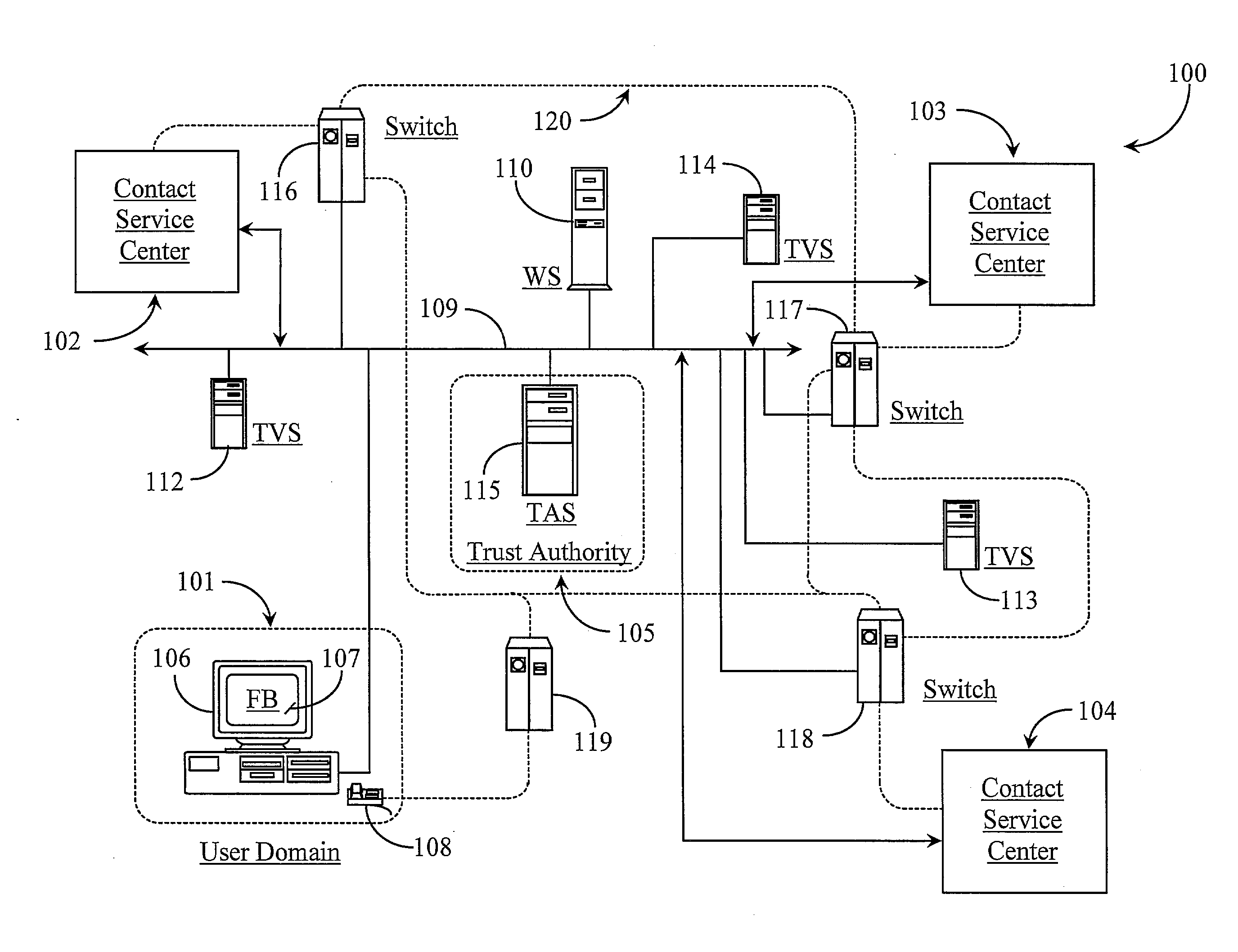
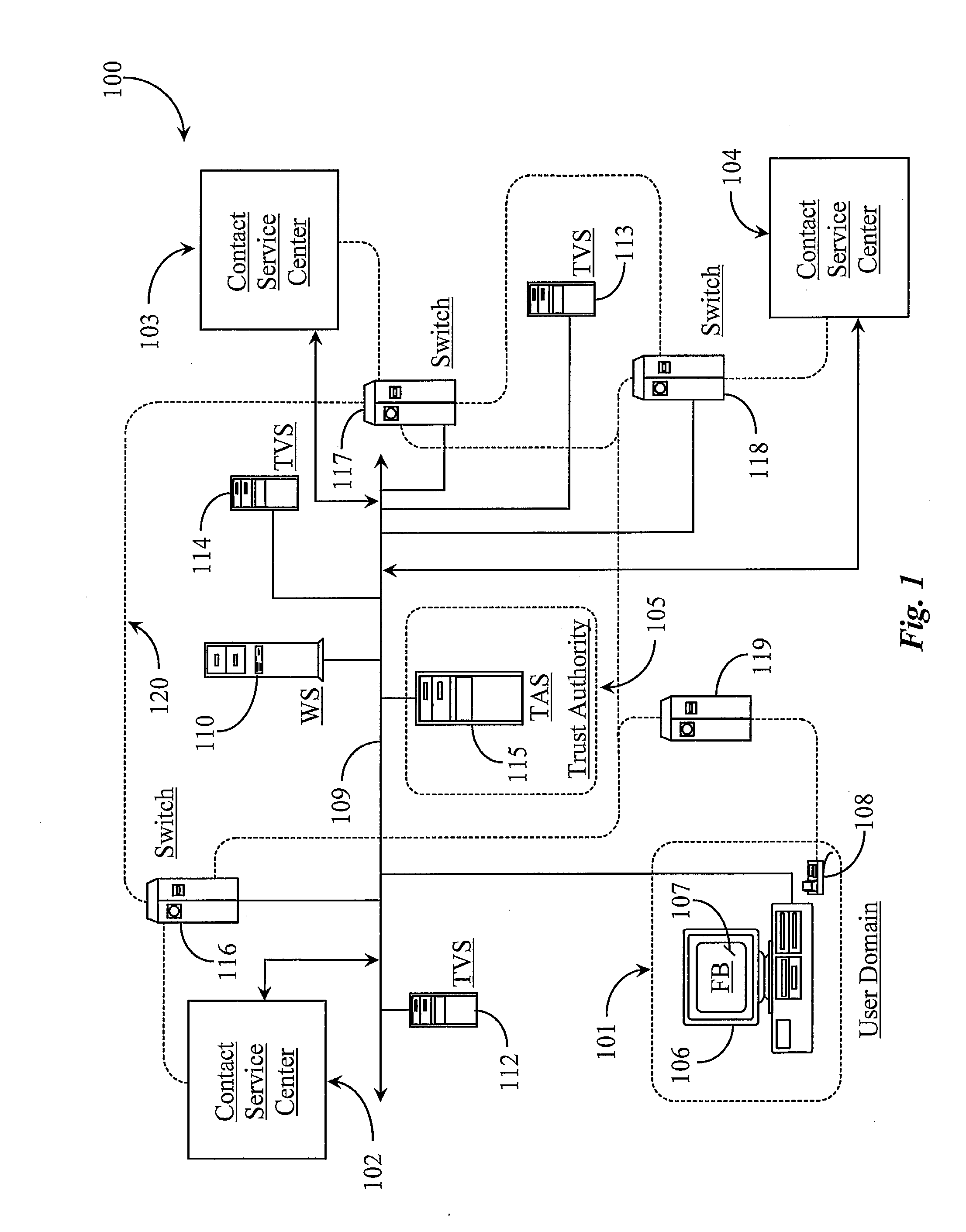
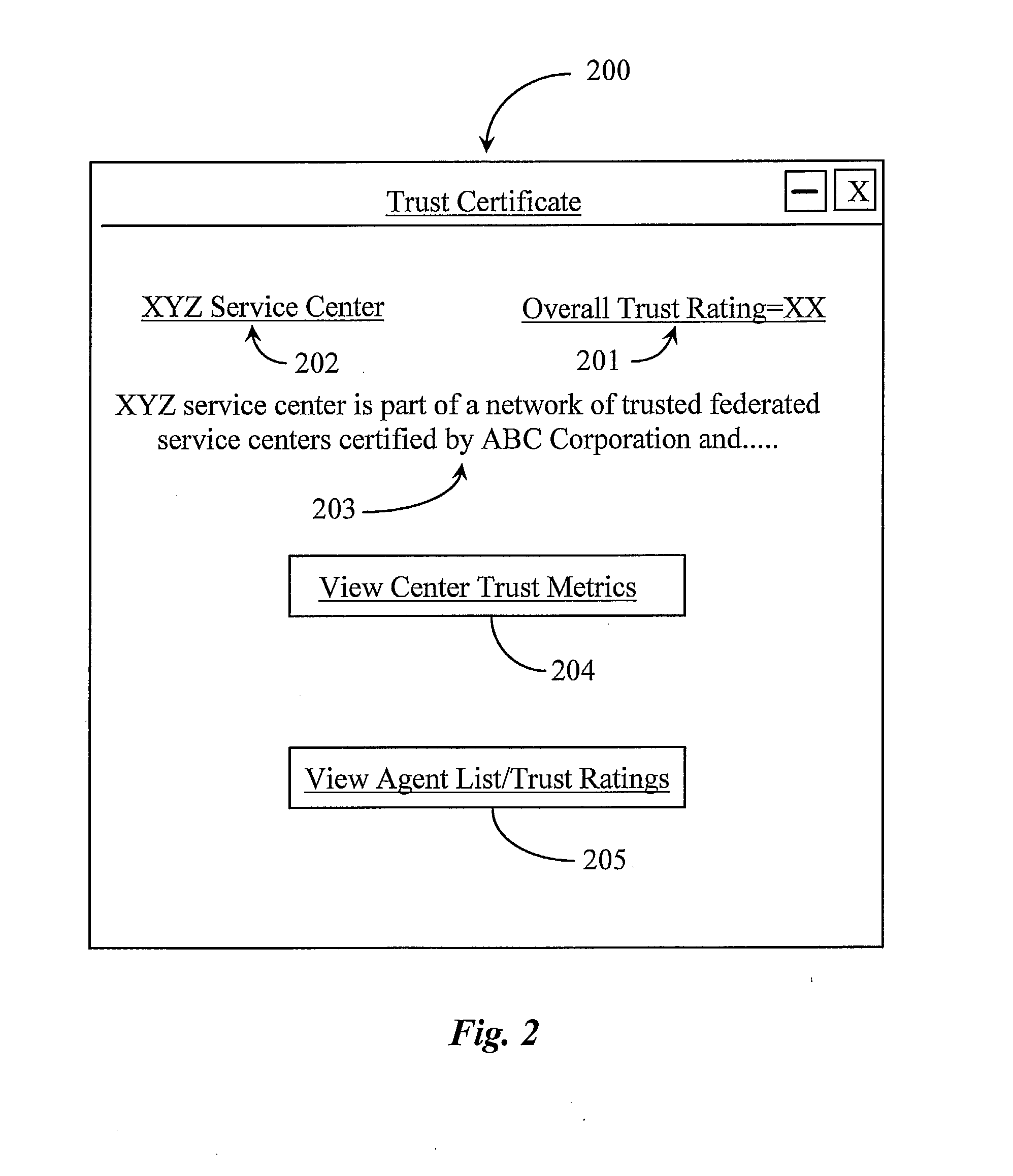
Method and System for Establishing and Managing Trust Metrics for Service Providers in a Federated Service Provider Network
InactiveUS20090172776A1Digital data processing detailsTelevision conference systemsCommunication interfaceCommunication endpoint
A system for issuing, validating, and managing trust between two or more entities authenticated to operate in a federated network includes one or more servers for issuing trust certificates based on one or more trust metrics, and one or more servers for validating issued trust certificates. Entities operating through a communications interface may be issued trust certificates pursuant to evaluation relative to certain trust metrics, the certificates accompanying communications between entities the certificates subject to validation at communication end points of interaction.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
High performance memory based communications interface
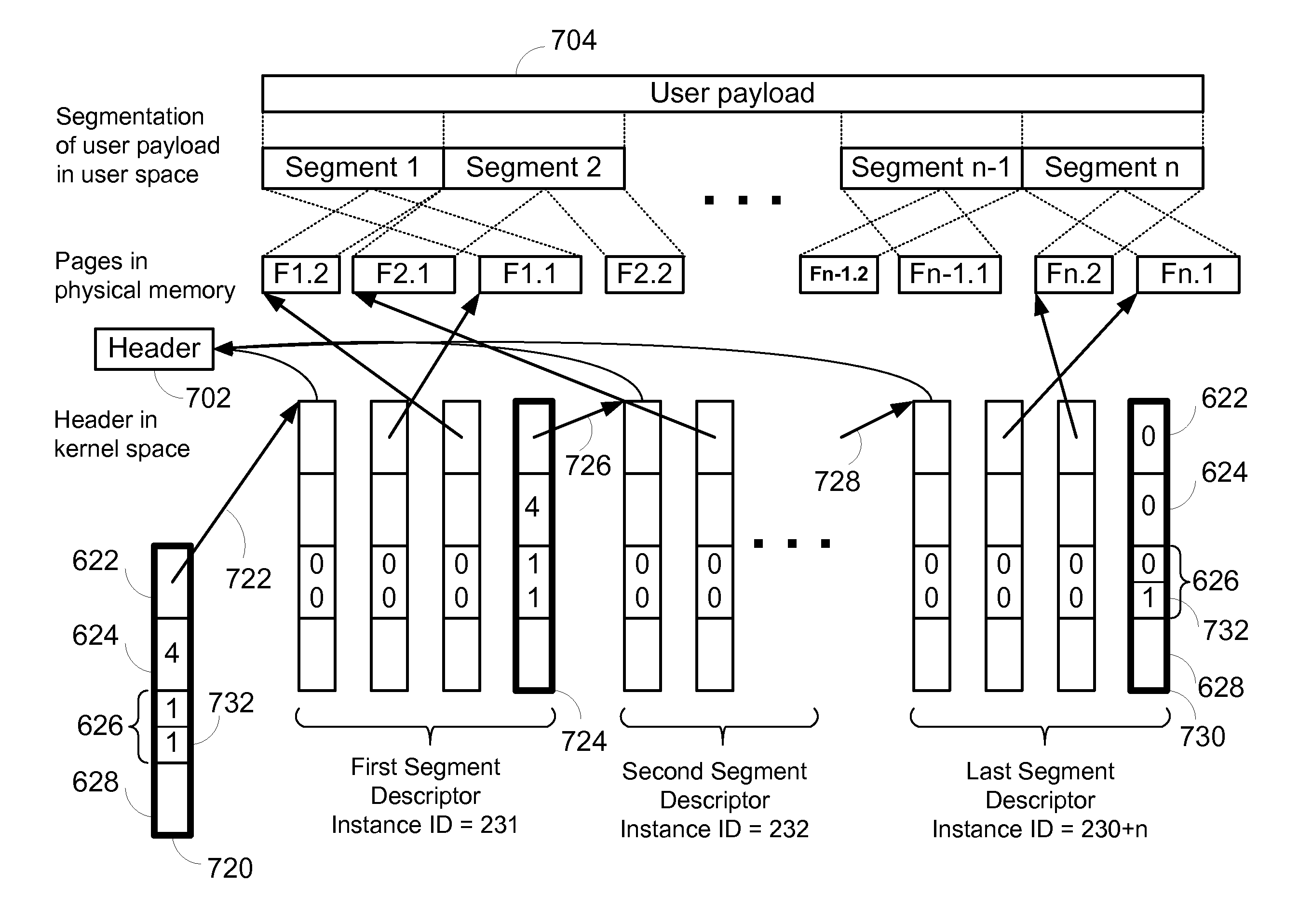
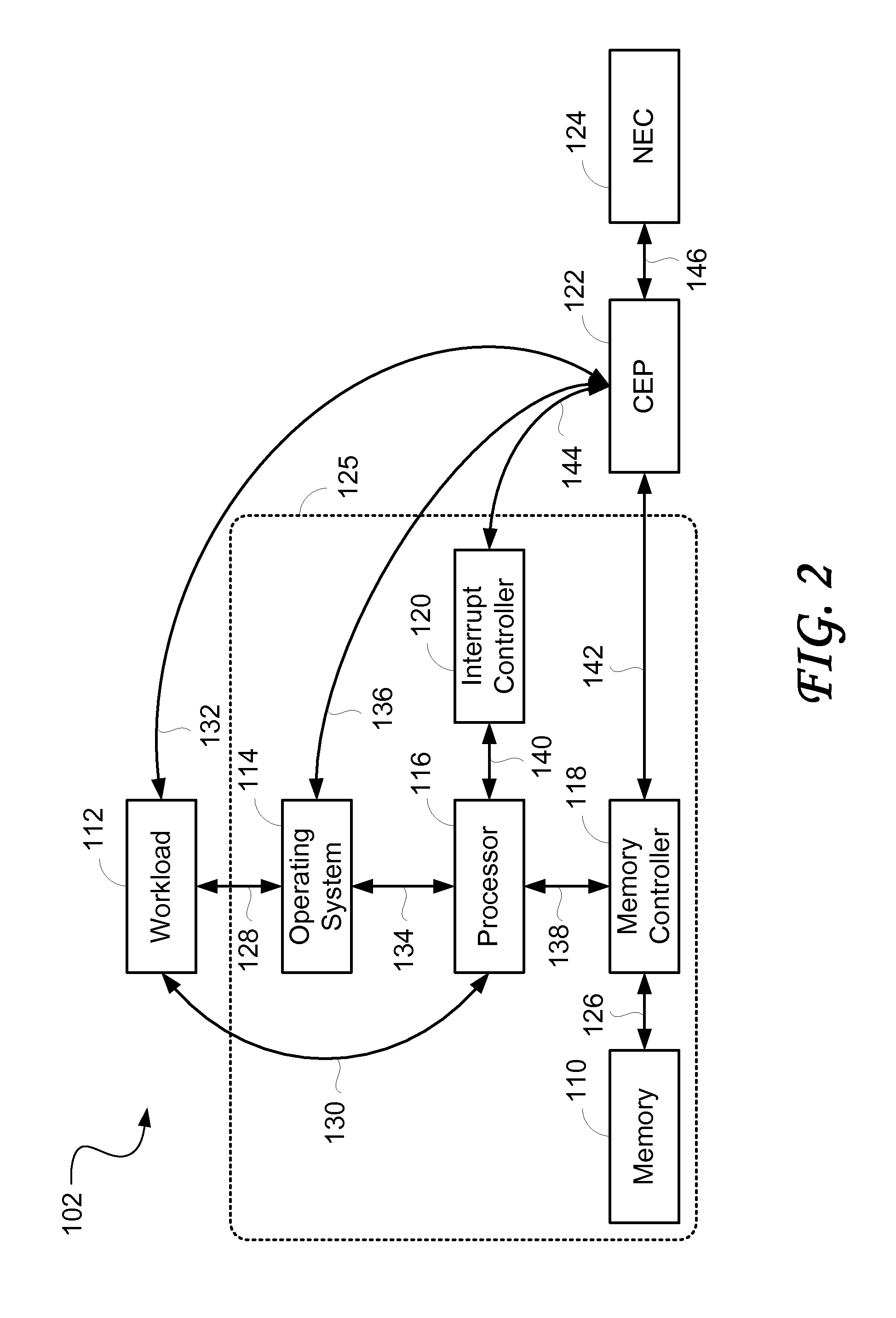
ActiveUS20070223483A1Improve performanceImprove throughputTime-division multiplexData switching by path configurationCommunication endpointMultiple frame
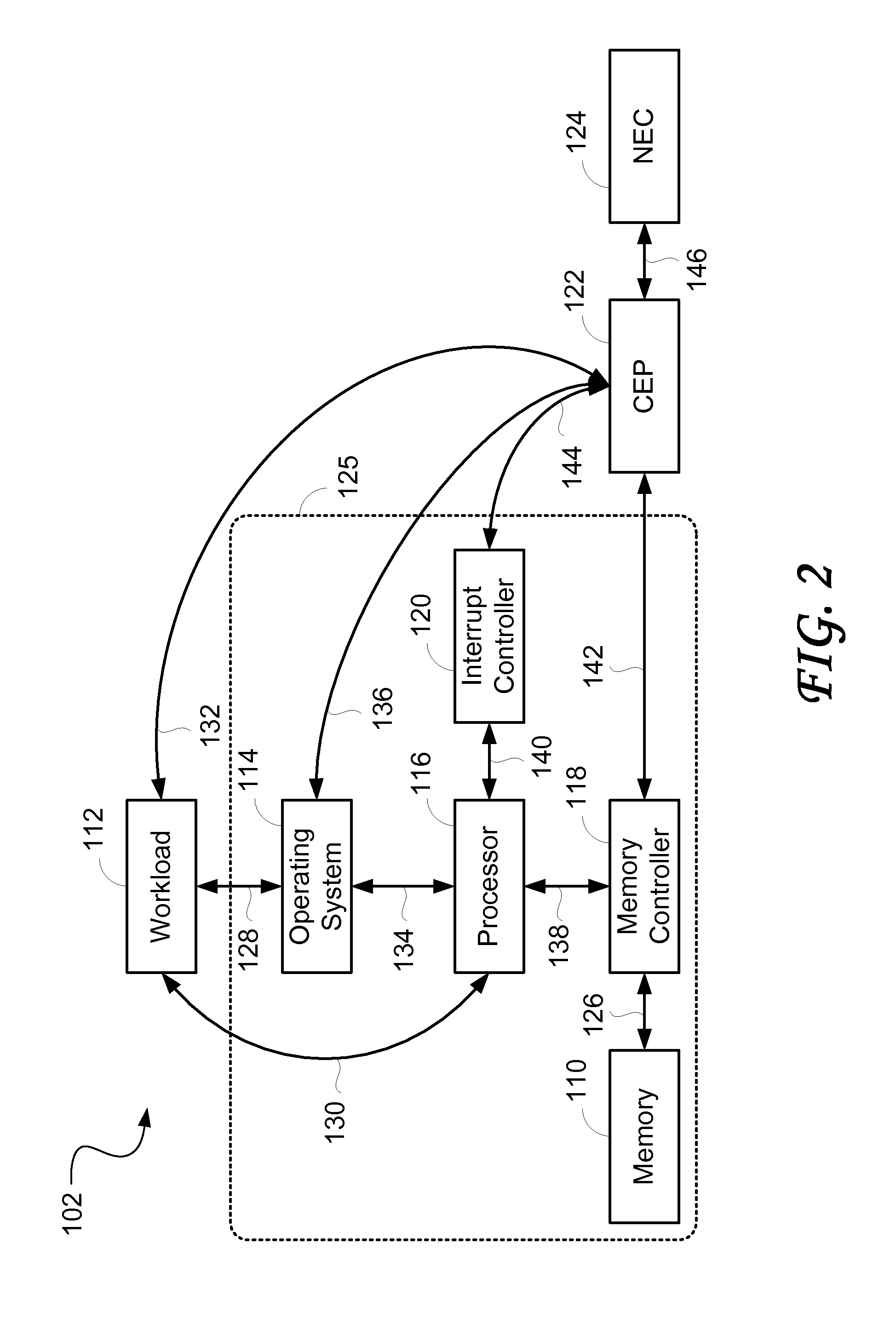
Embodiments of the present invention include enhanced functionalities and components within a Communication Endpoint Processor (CEP) that act as an interface between computational and communications domains. The embodiments disclosed herein deliver a complete memory mapped high performance interface that has the ability to support the simultaneous transmission of multiple frames of multiple sizes, and that has the ability to interrupt the transmission of lower priority frames in order to send higher priority frames.
Owner:III HLDG 1
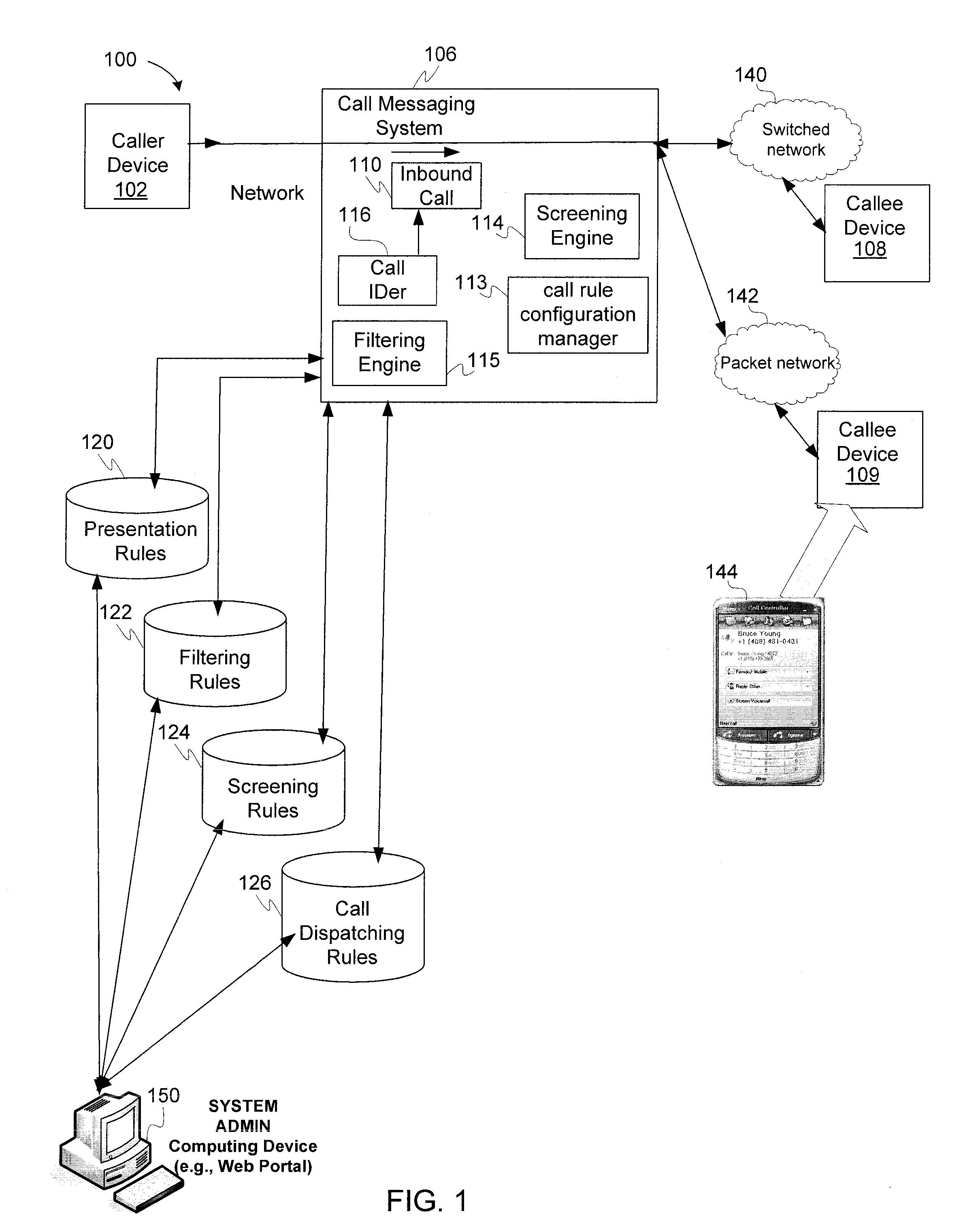
Active call filtering, screening and dispatching
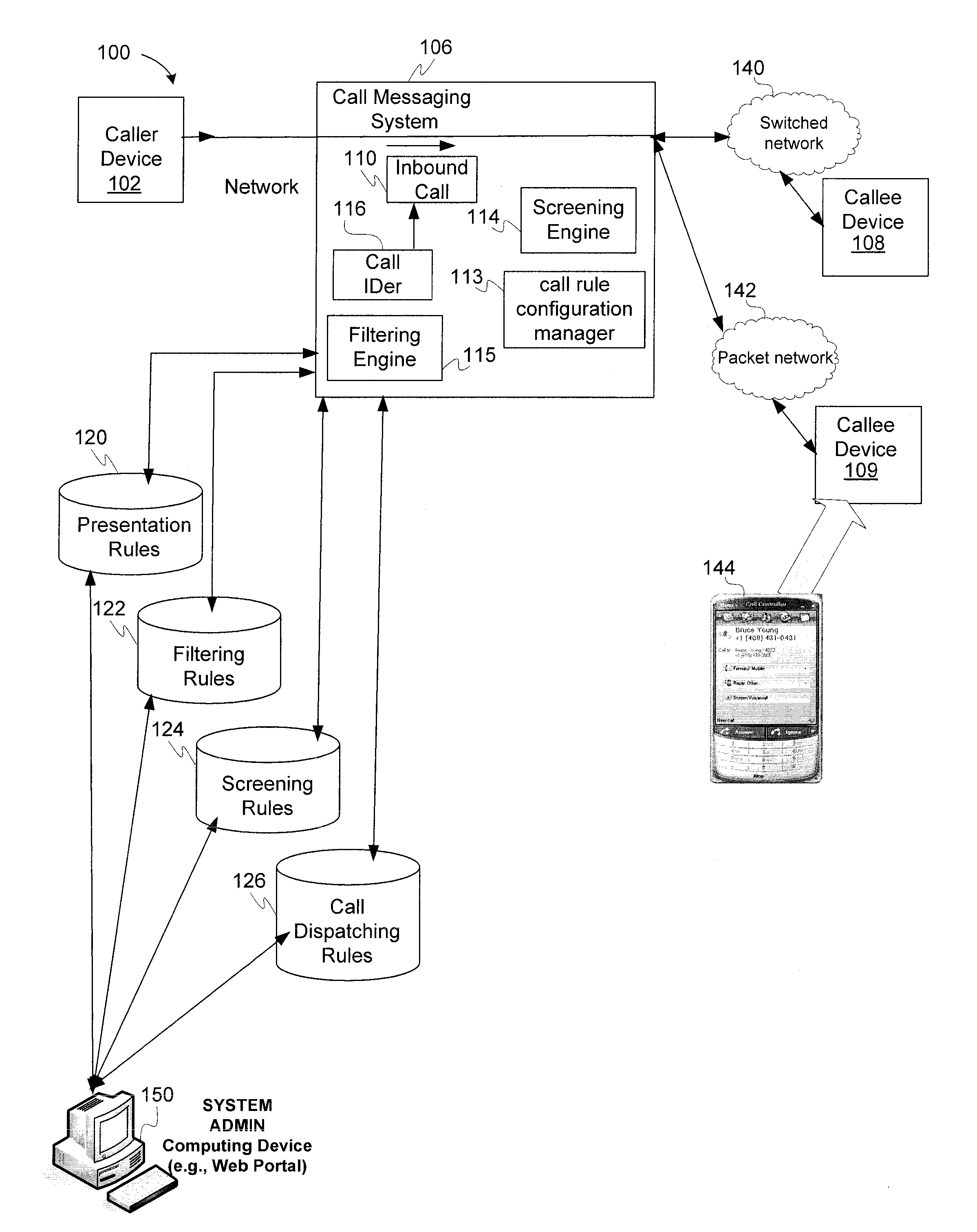
ActiveUS20090086953A1Application programming interface detailsSpecial service for subscribersCommunication endpointTelecommunications
An examples of active call filtering, screening and dispatching is described, including receiving data representing a call from a first communication endpoint; presenting at a second communication endpoint, prior to connecting to the call, a subset of prompts that specify dispatching actions for the call, at least one of the dispatching actions including transmitting a response via a communications network, detecting selection of a prompt that specifies a dispatching action for the call, and transmitting an instruction from the second communication endpoint to a call messaging system to perform the dispatching action. In some embodiments, a determination is made as to whether a bypass condition exists, the bypass condition specifying that one or more customized screening rules are to be bypassed. If the bypass condition exists, then a call messaging system can bypass the use of a subset of prompts.
Owner:RINGCENTRAL INC
Packet based communications
InactiveUS20100014510A1Raise the ratioImprove efficiencyNetwork connectionsData trafficCommunication endpoint
This invention is applicable to packet based, rate limited radio links, such as satellite or terrestrial wireless digital communications systems. These communications networks concurrently carry time-critical traffic, such as voice or multimedia, and non time-critical traffic, such as generic data traffic, between two or more communication end points. The communication end points may be connected through a number of heterogenous networks and the end to end throughput characteristics may vary over time. A first aspect of the invention concerns a method for generating packets. In other aspects the invention concerns a computer system for use in packet based communications, a computer protocol for packet based communications and a communications packet. The invention involves determining a “time slice” packet size from the link speed and the interval of time extending between the times at which packets are selected for output from a buffer to the transmission interface. It also involves creating a network packet from frames of time-critical data generated during the interval, where the packet is synchronised to both existing timing requirements of the time-critical frames and the link speed. Then, adding non time-critical data to the network packet if its size had not exceeded the determined “time slice” packet size.
Owner:NAT ICT AUSTRALIA
High performance memory based communications interface
ActiveUS7773630B2Quality of serviceProvide qualityTime-division multiplexTransmissionCommunication endpointMultiple frame
Owner:III HLDG 1
Individual participant identification in shared video resources
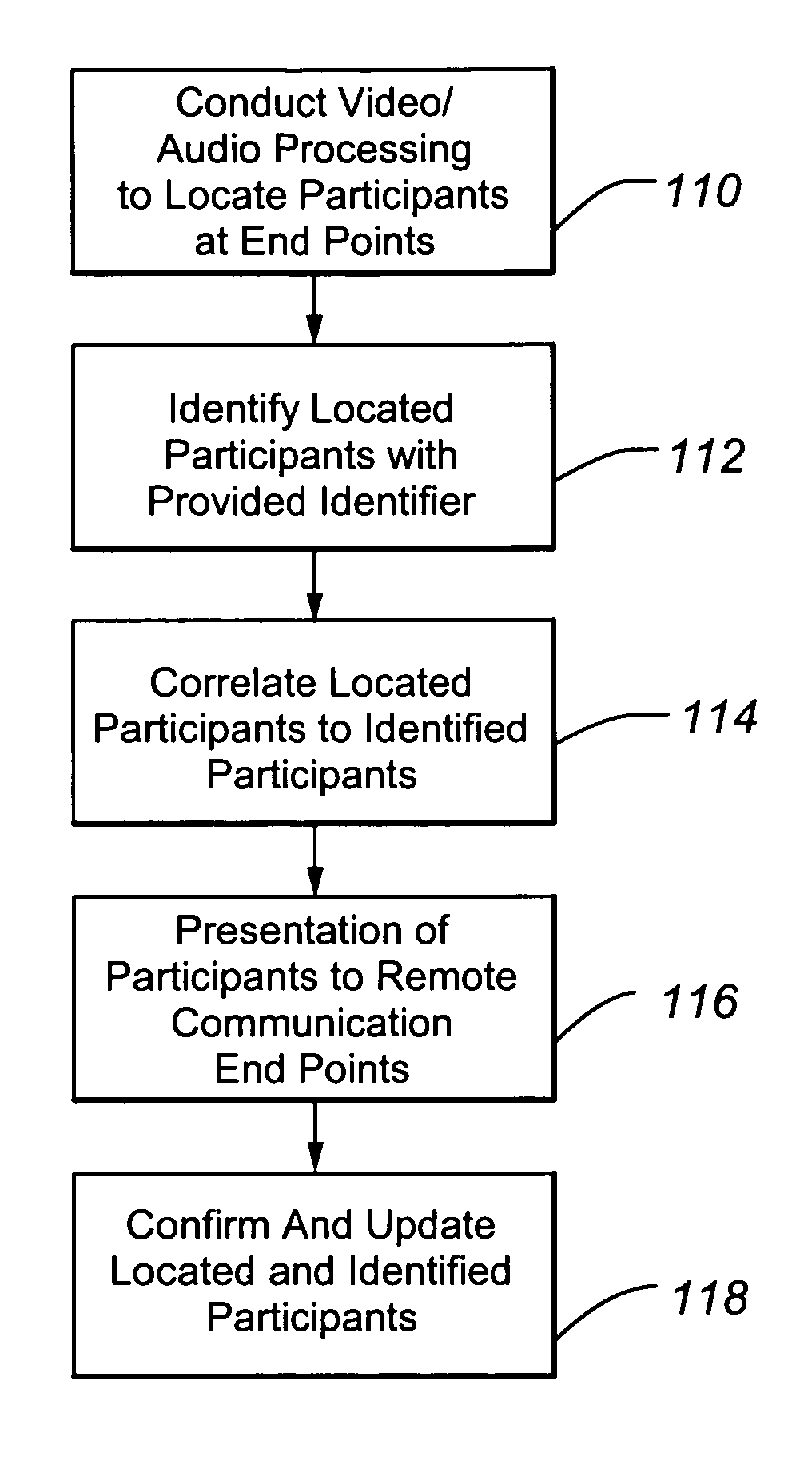
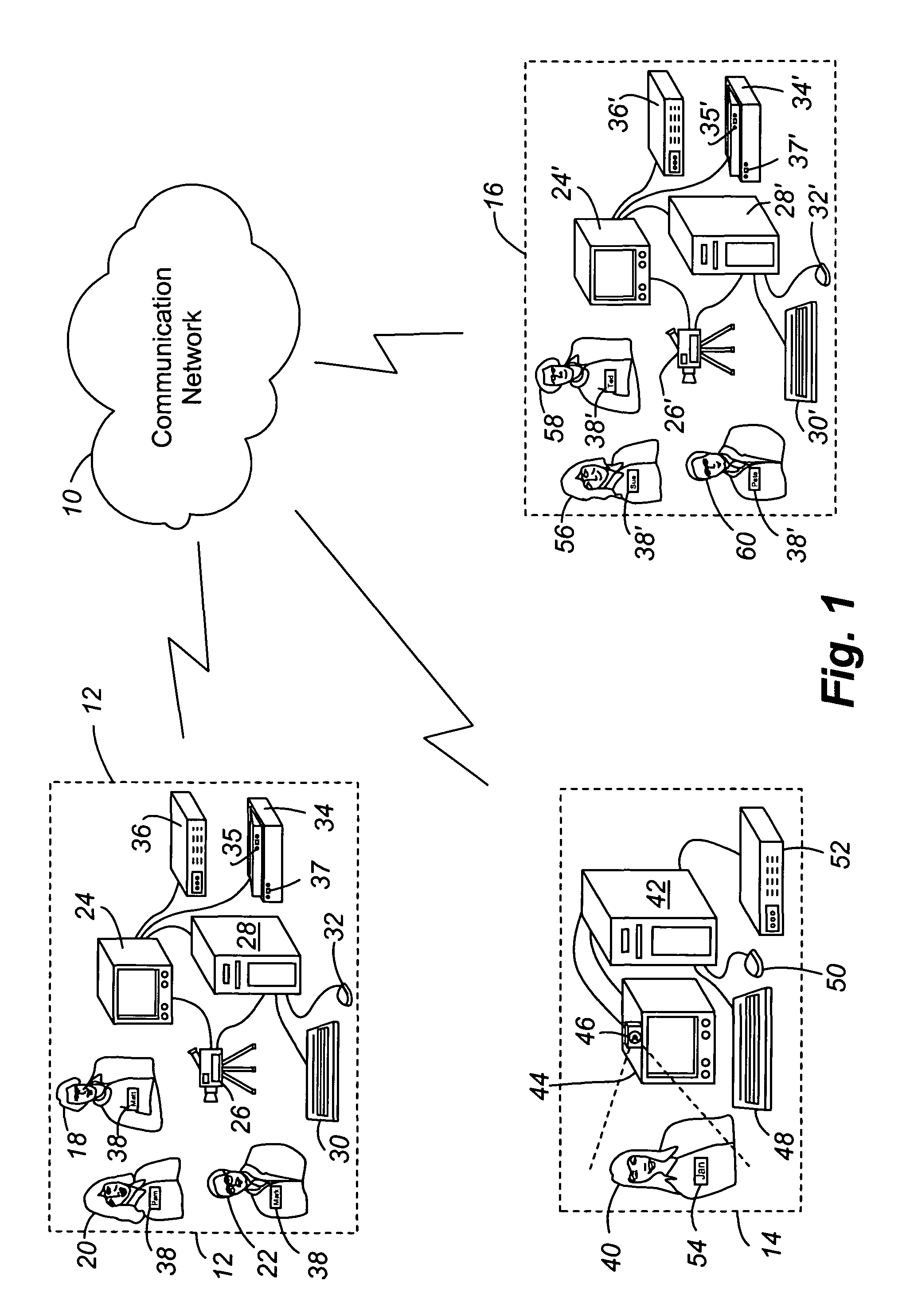
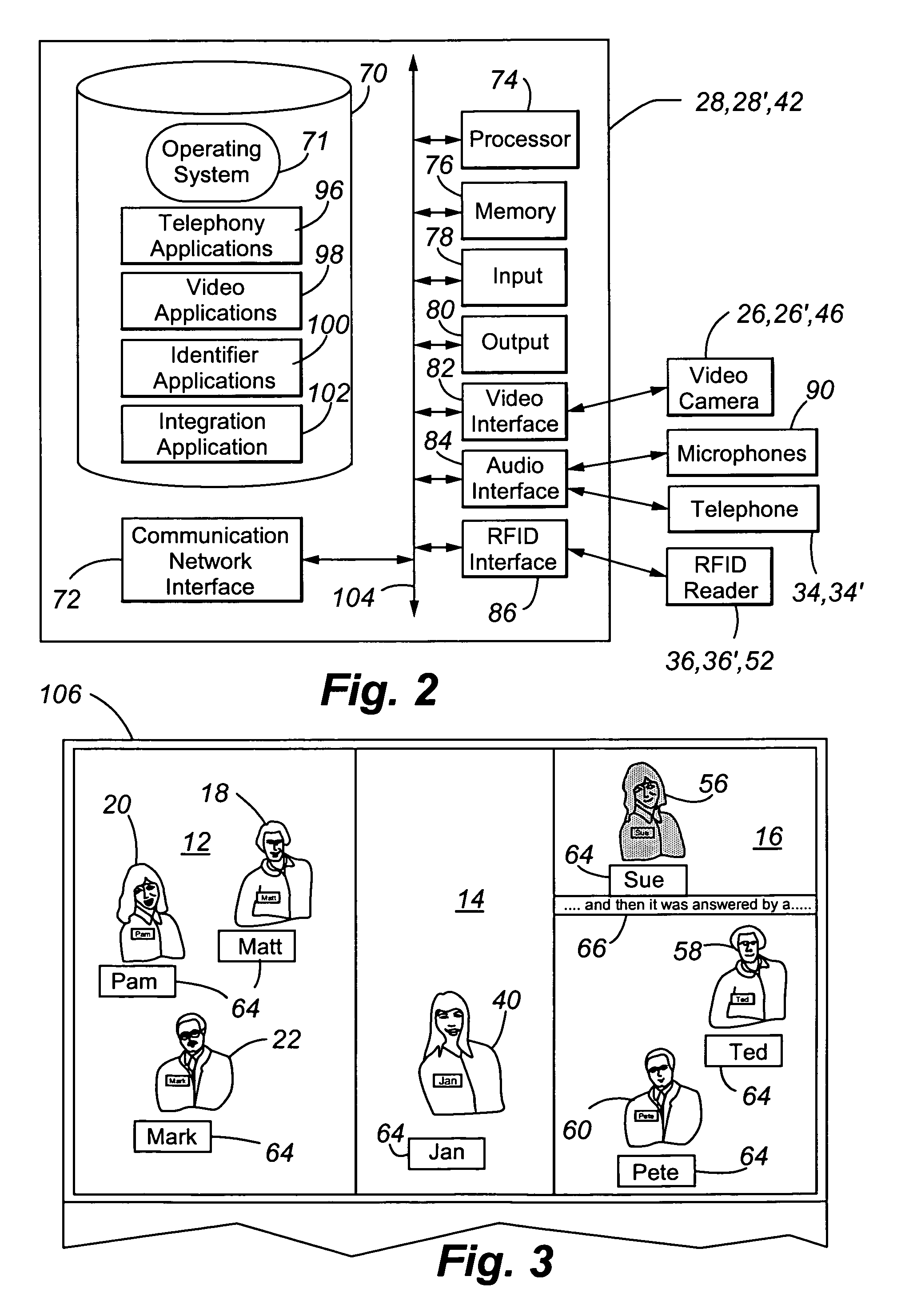
ActiveUS7920158B1Effective coverageTelevision system detailsTelevision conference systemsCommunication endpointCommunications system
An integrated communications system is provided wherein video conferencing is conducted and participants sharing a video resource may be identified. Application of the present invention is particularly suited for videoconferencing when there are a plurality of communication endpoints, and at least one of the communication endpoints includes multiple participants at the shared video resource. A video or audio processing technique takes place to identify locations of conference participants at the communication endpoints. Each participant has an assigned RFID identifier during the conference. The RFID identifiers are interrogated by an RFID reader that downloads data from the identifiers to the system. The gathered RFID data is then matched with the processed video or audio data in order to identify each of the conference participants. A user interface is provided to allow the participants to view the other remote participants along with the identifying data of the remote participants. The data may include, for example, each remote participant's name displayed directly below the video image of that remote participant. As time progresses during the conference, participant identity is tracked and updated by repeating the video / audio processing technique and repeating the interrogation of the RFID identifiers.
Owner:AVAYA INC
Services within reverse proxy servers
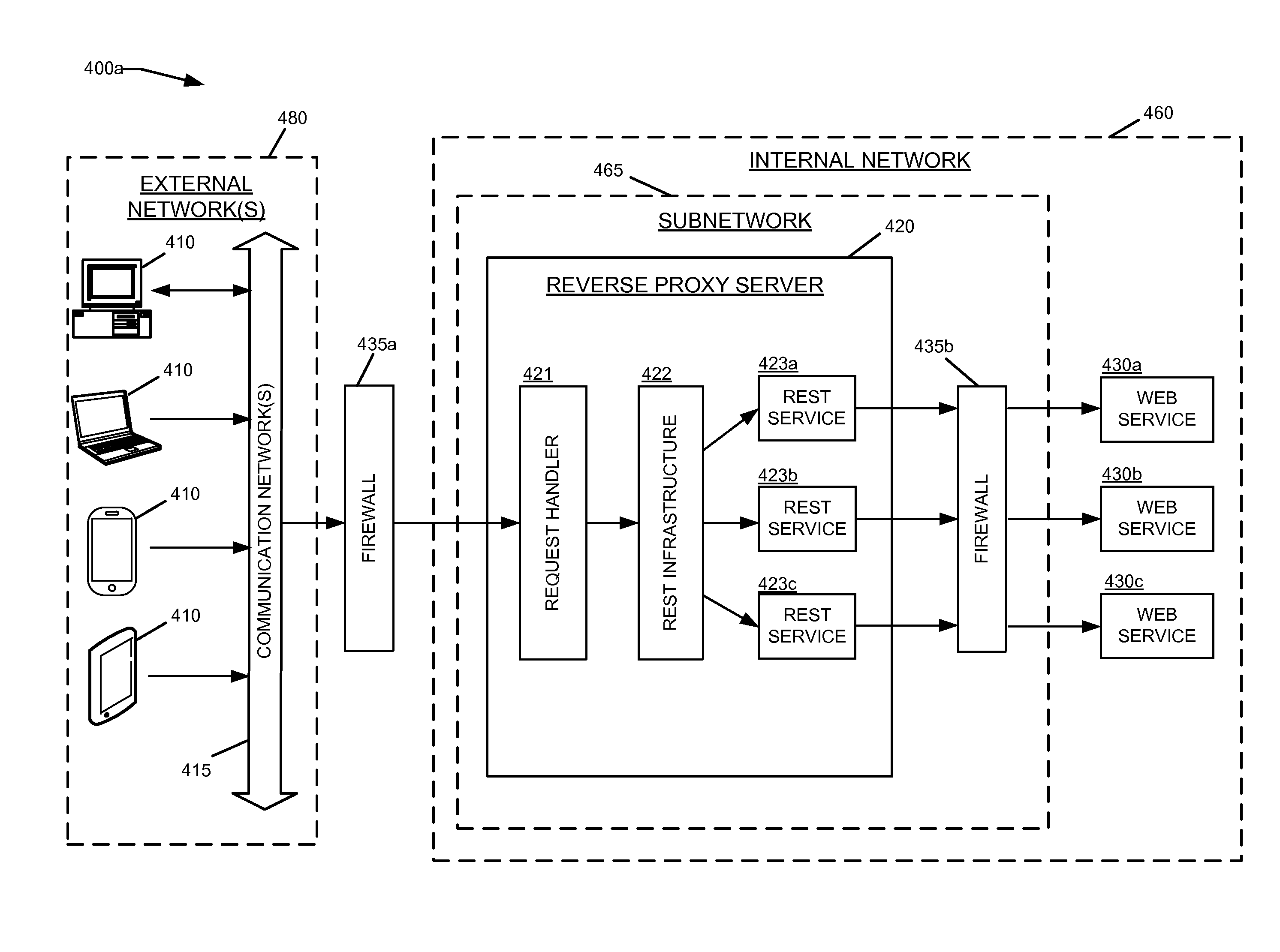
ActiveUS20160088023A1Multiple digital computer combinationsWebsite content managementCommunication endpointRepresentational state transfer
Embodiments of the invention provide techniques for processing messages transmitted between computer networks. Messages, such as requests from client devices for web services and other web content may be transmitted between multiple computer networks. Intermediary devices or applications such as proxy servers may receive, process, and transmit the messages between the communication endpoints. In some embodiments, a reverse proxy server may be configured to dynamically generate Representational State Transfer (REST) services and REST resources within the reverse proxy server. The REST services and REST resources within the reverse proxy server may handle incoming requests from client devices and invoke backend web services, thereby allowing design abstraction and / or enforcement of various security policies on the reverse proxy server.
Owner:ORACLE INT CORP
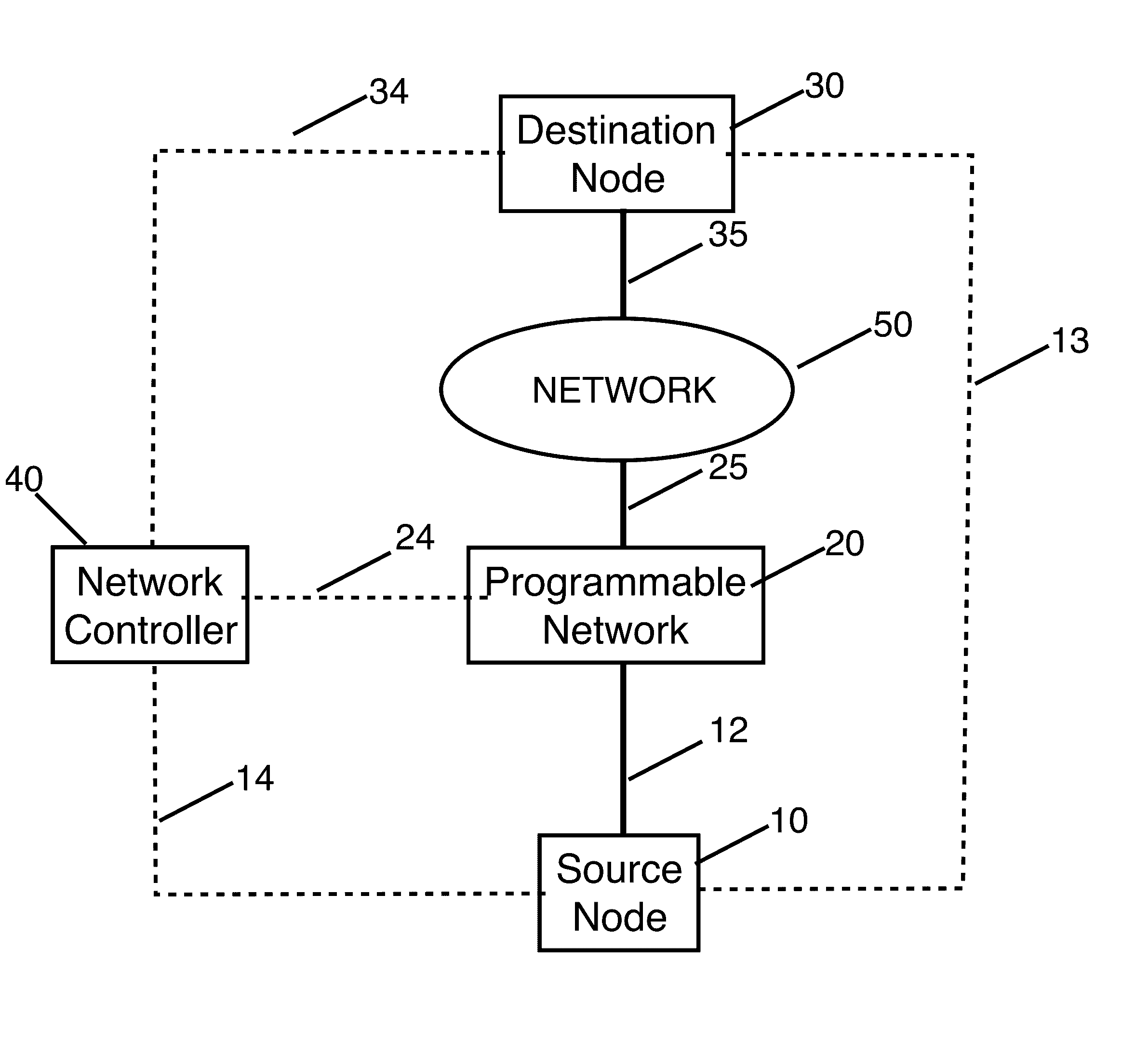
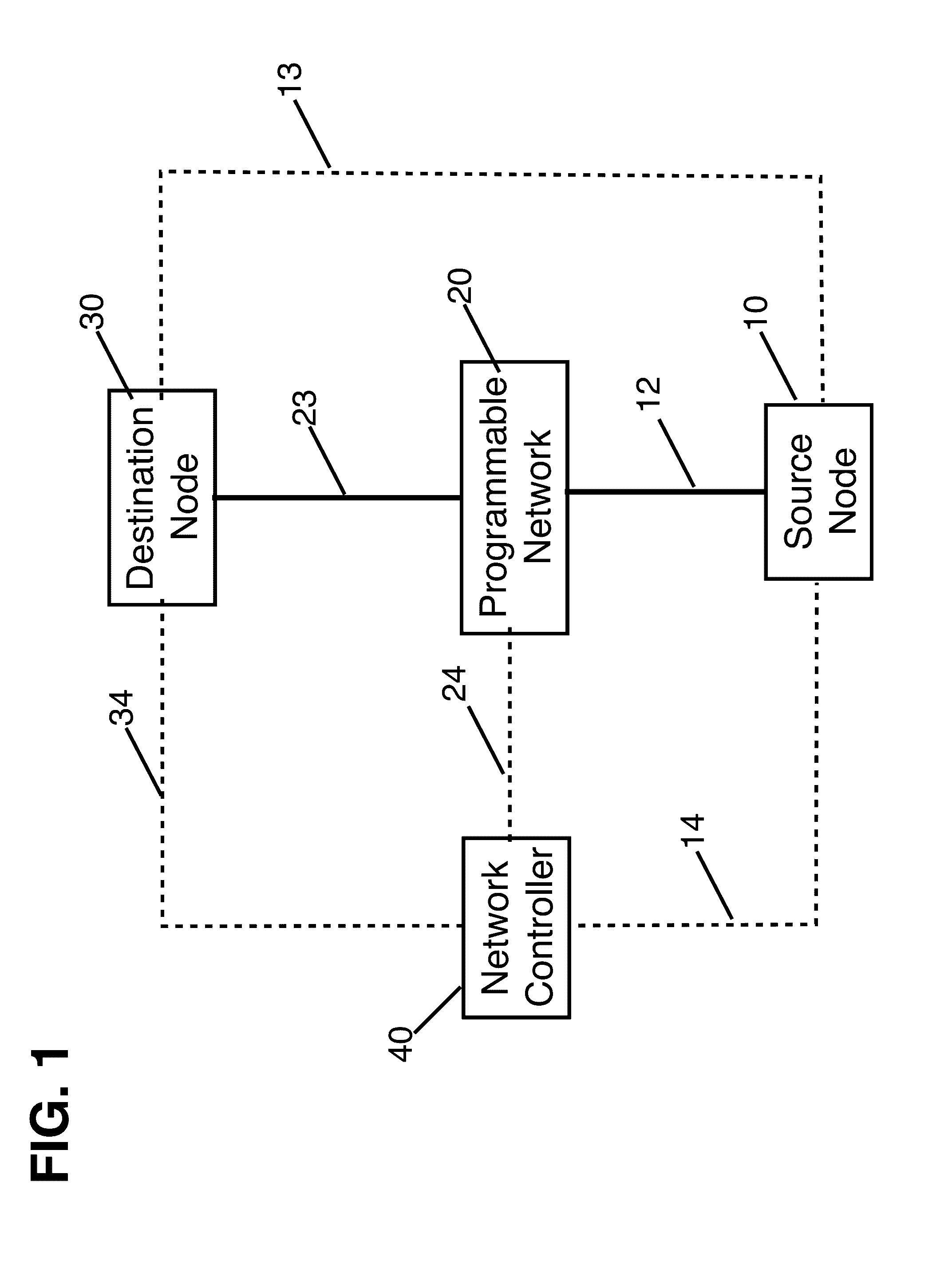
Method for forwarding rule hopping based secure communication
One or both end points of the communication and a network controller of a software defined network (SDN) agree on a definition of a traffic flow that varies as a function of time, where communicating end points vary one or more fields of the packet headers at the sender side before sending the flow packets to the network according to an agreed upon procedure with the network controller. The network controller dynamically updates the forwarding tables in forwarding elements such that whenever source node transitions into the next epoch, and thus alter the header fields, a corresponding forwarding rule is already installed onto the forwarding elements along the route of the packet towards the other end point of the communication, referred to as destination node.
Owner:NETSIA INC
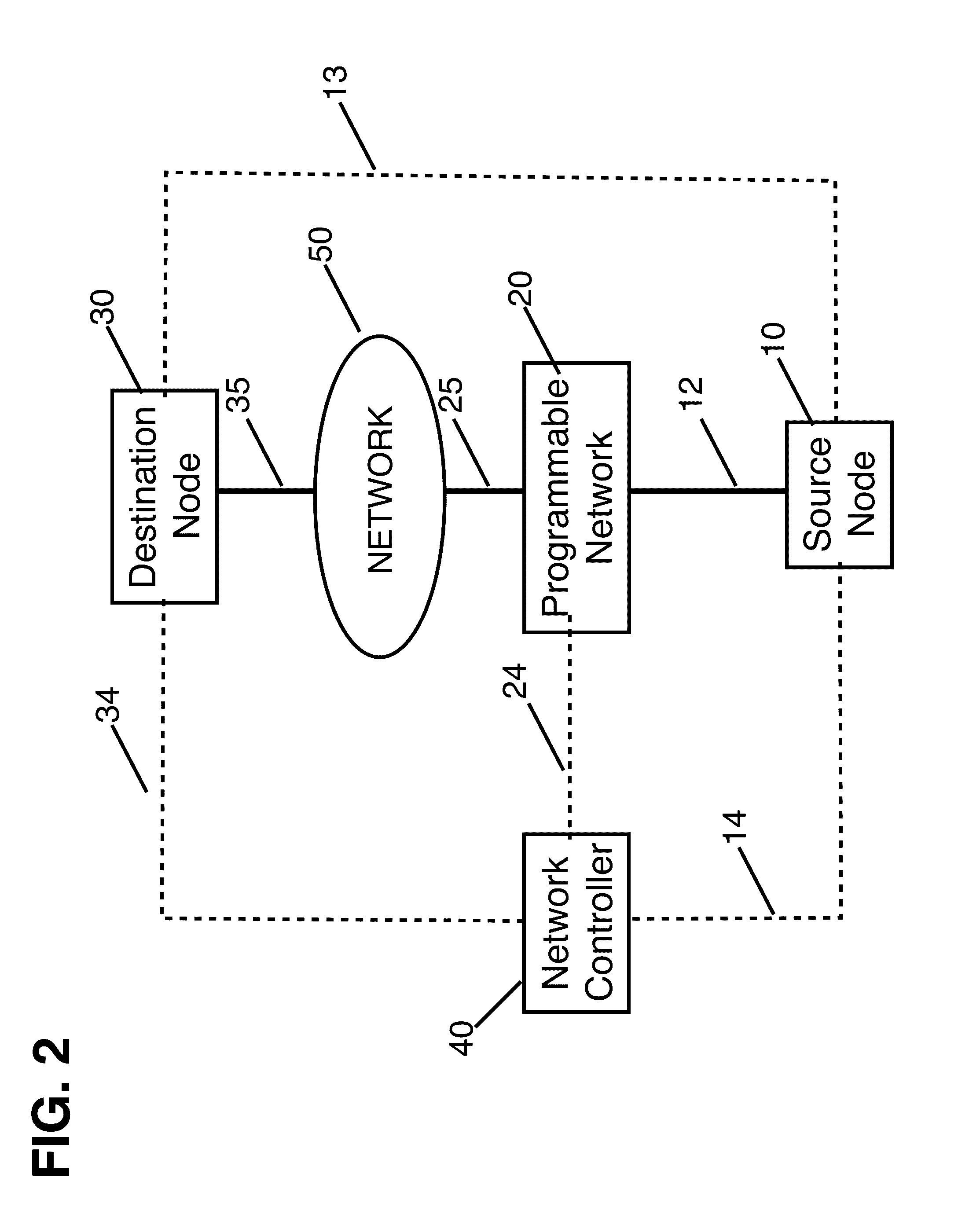
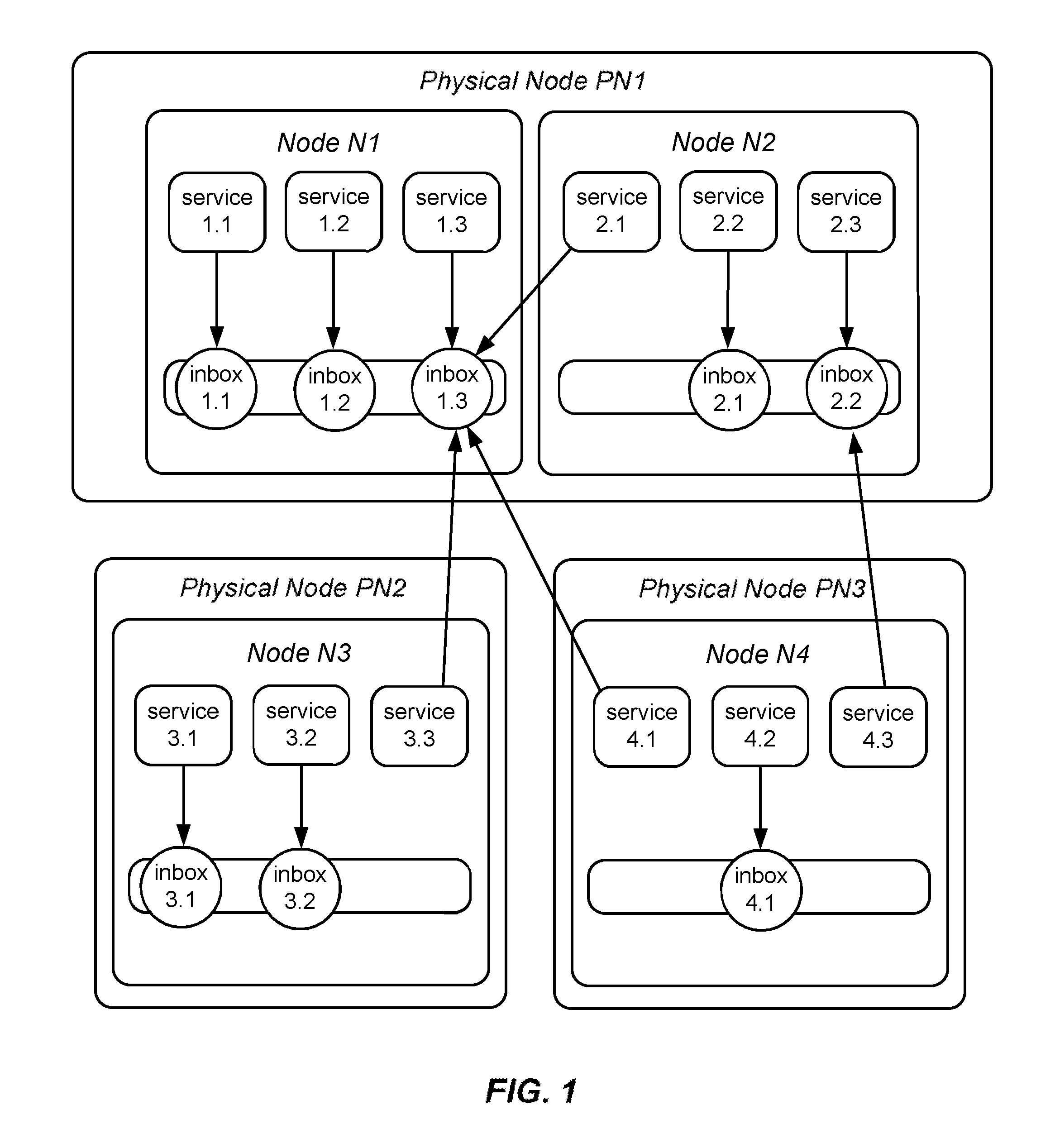
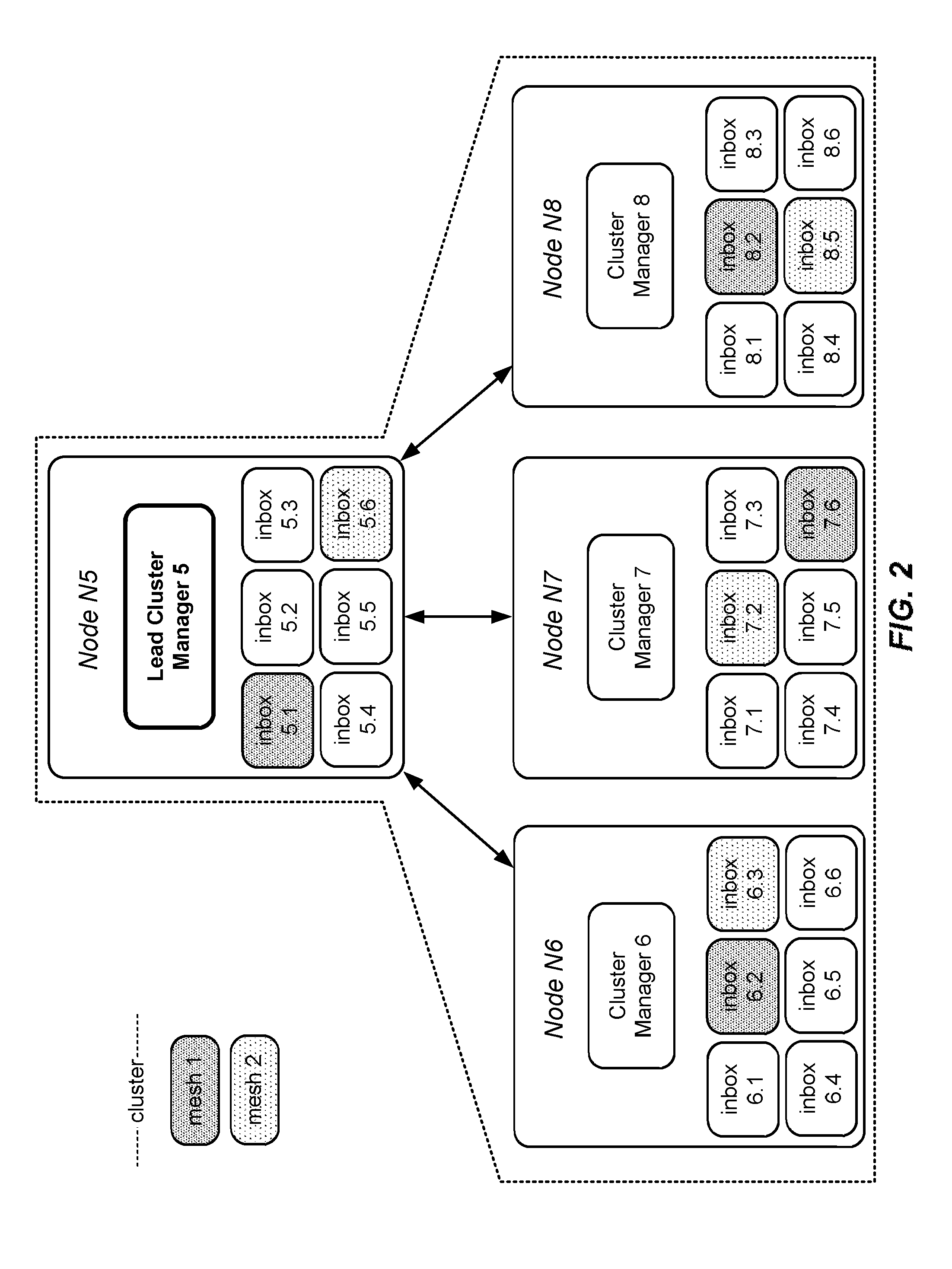
Federated, policy-driven service meshes for distributed software systems
ActiveUS20130103837A1Improve usabilityReduce processMultiple digital computer combinationsProgram controlCommunication endpointDynamic management
Platforms, systems, software, and methods for deploying and maintaining distributed computing, networking and storage comprising a configuration of dedicated service meshes. The invention further comprising a module for dynamically managing physical nodes; a module for dynamically managing nodes on physical nodes; a module for dynamically managing services / workers on nodes; a module for governing communication within the system and with the system; a plurality of communication endpoints; a plurality of services, wherein each service is associated with one or more endpoints, wherein services communicate by message exchange via their endpoints; a module for grouping nodes into clusters; a module for grouping endpoints into meshes such that all member services of a mesh can be addressed as a whole or as pertinent subsets thereof; and a module for dynamically effecting topology changes.
Owner:VIASAT INC
Systems, Methods and Computer-Readable Media for Regulating Remote Access to a Data Network
InactiveUS20080276305A1Memory loss protectionError detection/correctionCommunication endpointIdenticon
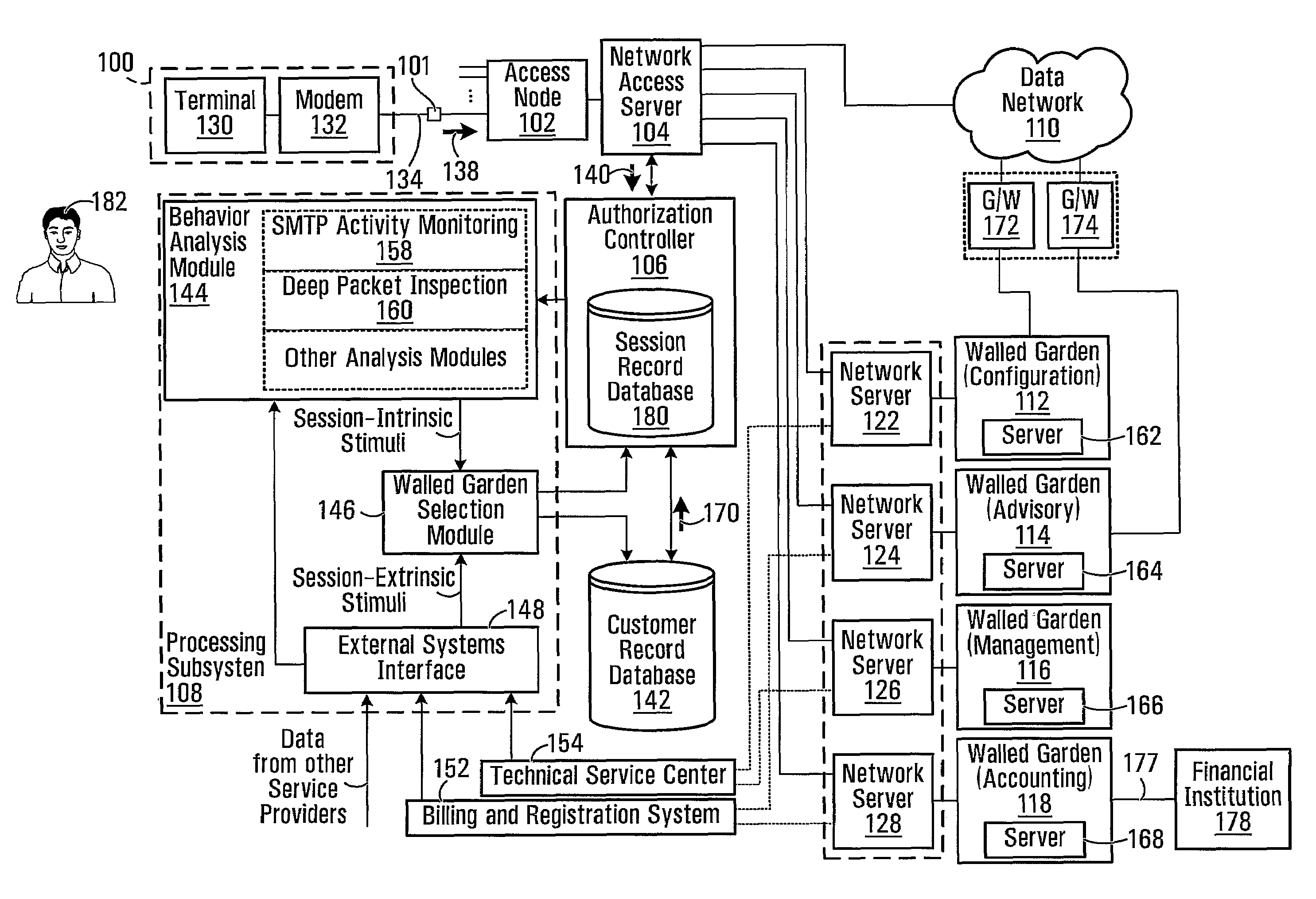
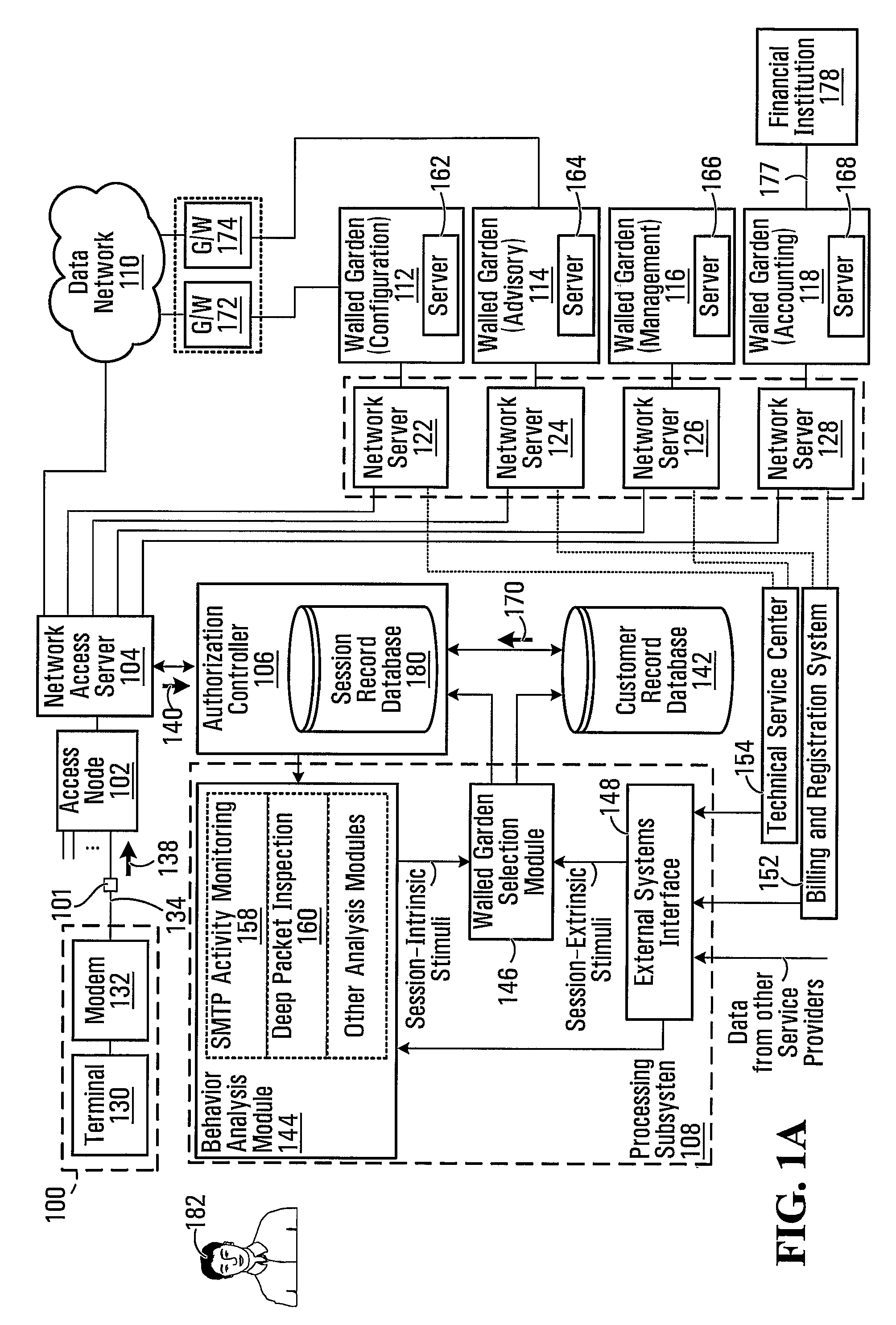
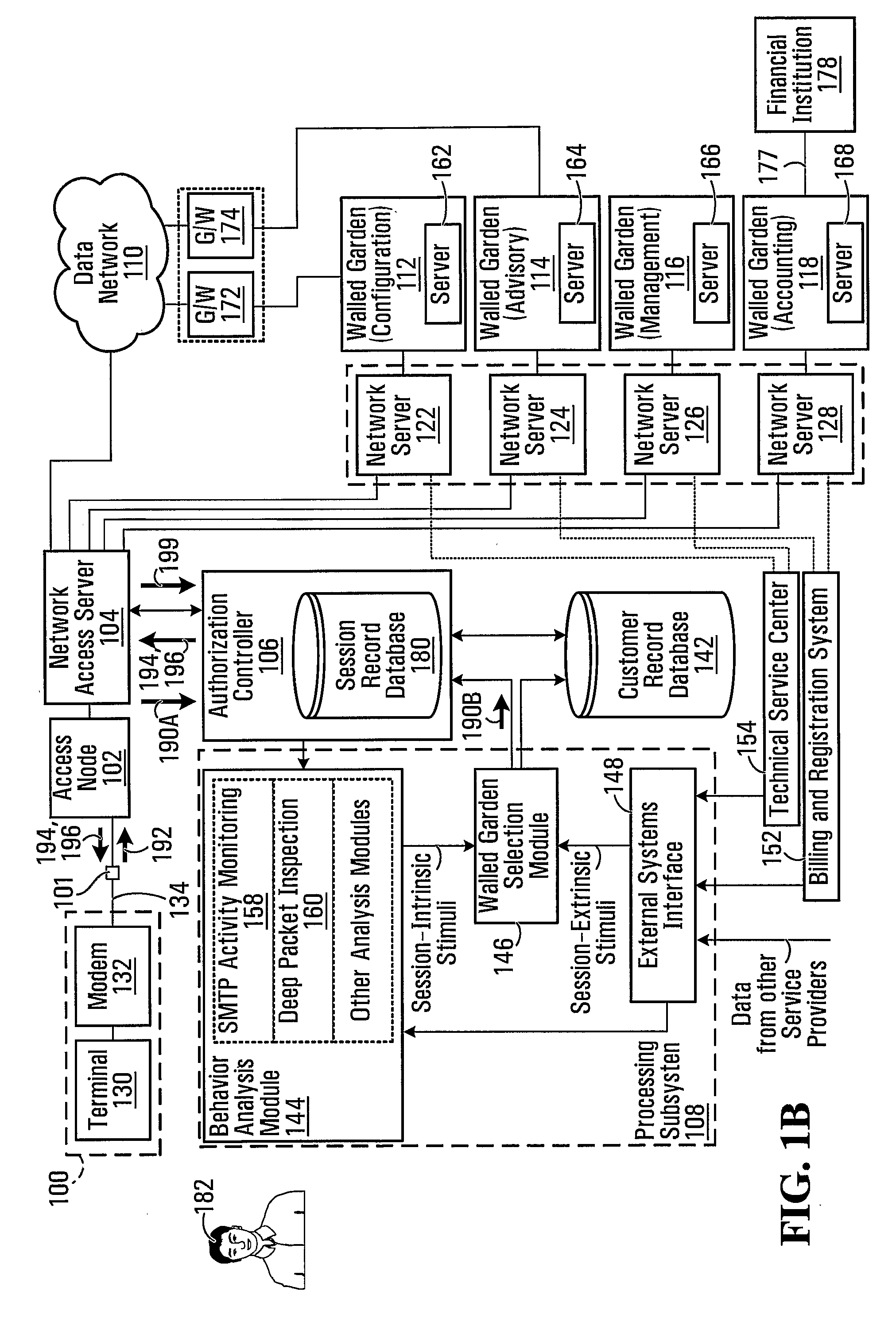
A system, which comprises an authorization controller operable for regulating establishment of user sessions over a data network; a processing subsystem operable for monitoring the user sessions and applying a walled garden policy, wherein application of the walled garden policy respectively associates each user in a certain subset of users with a respective walled garden selected from a common plurality of walled gardens; and a database for storing, in association with each said user in the certain subset of users, a respective identifier corresponding to the respectively associated walled garden. The authorization controller is further operable for responding to receipt of an access request identifying a particular user in the certain subset of users and received from a communication endpoint by (I) consulting the database to identify the walled garden respectively associated with said particular user and (II) directing the communication endpoint to said walled garden respectively associated with said particular user.
Owner:BCE
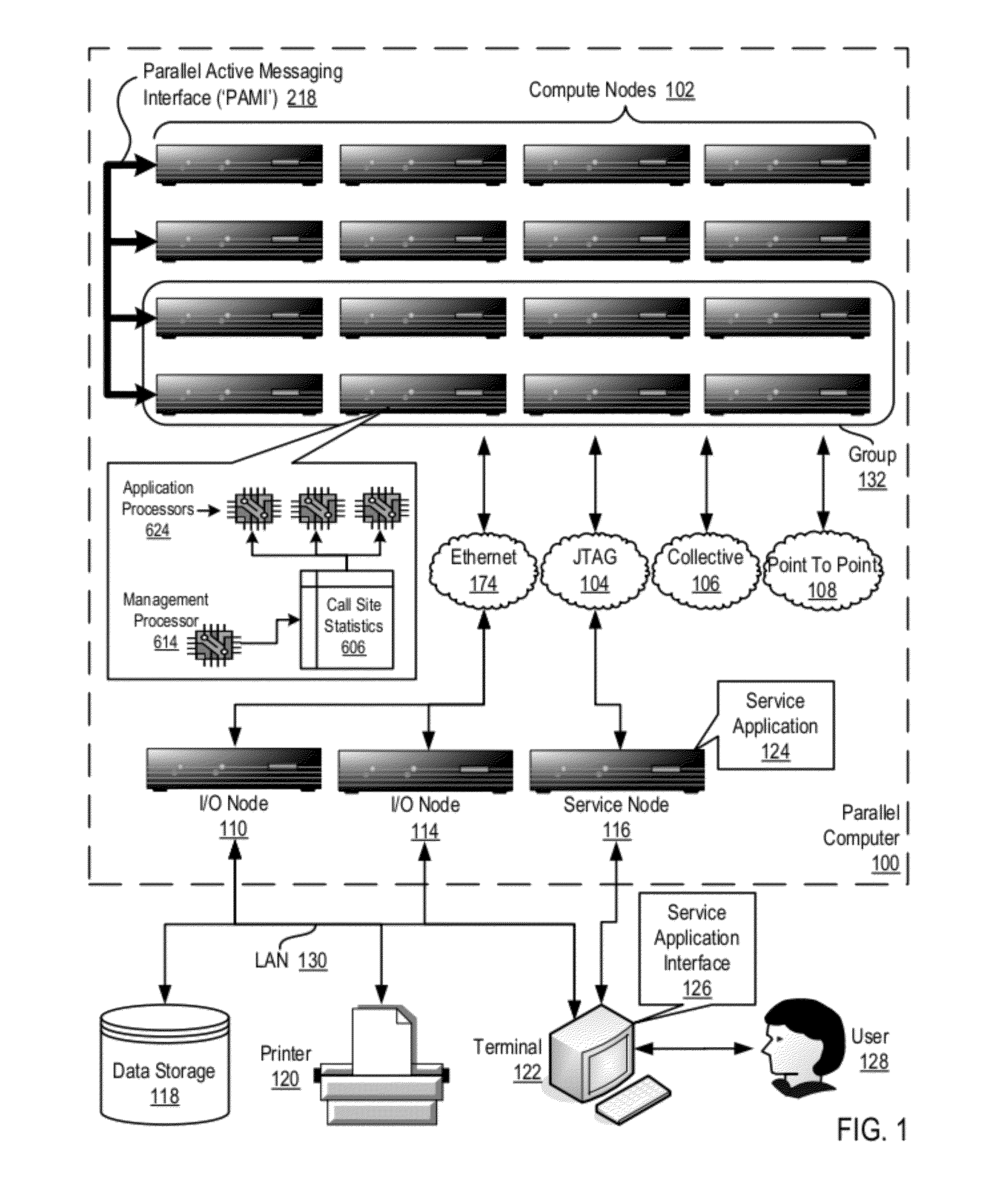
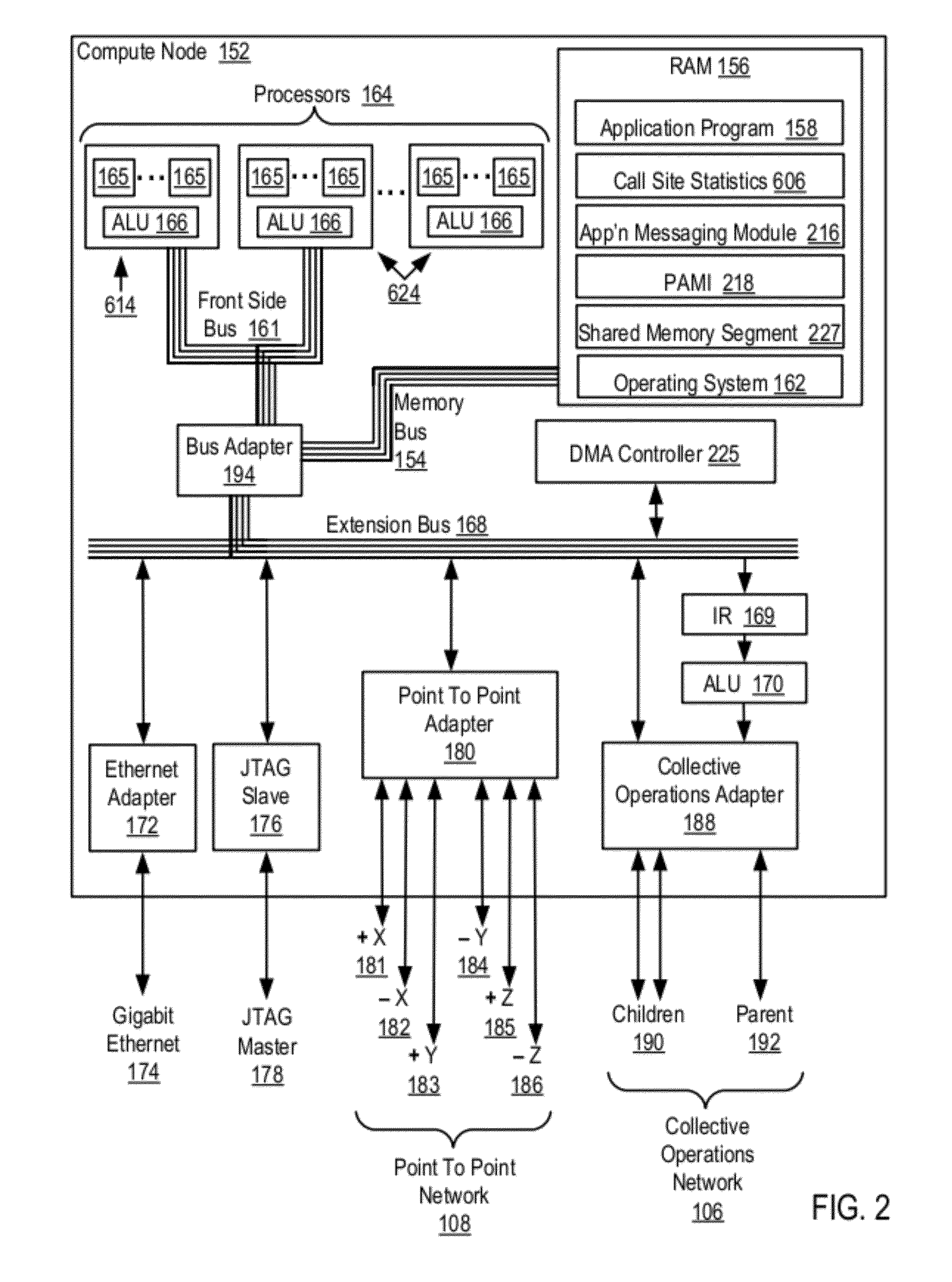
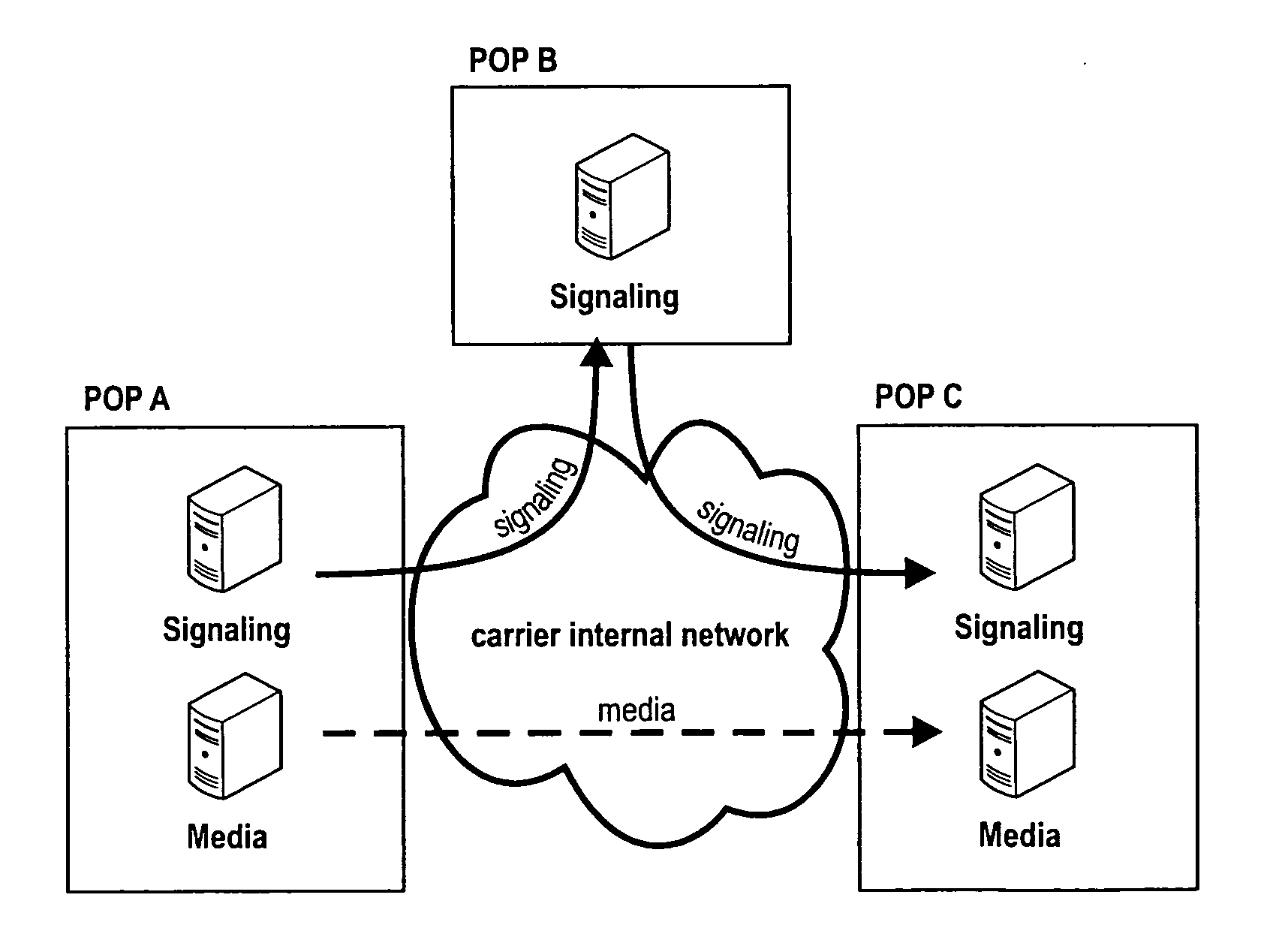
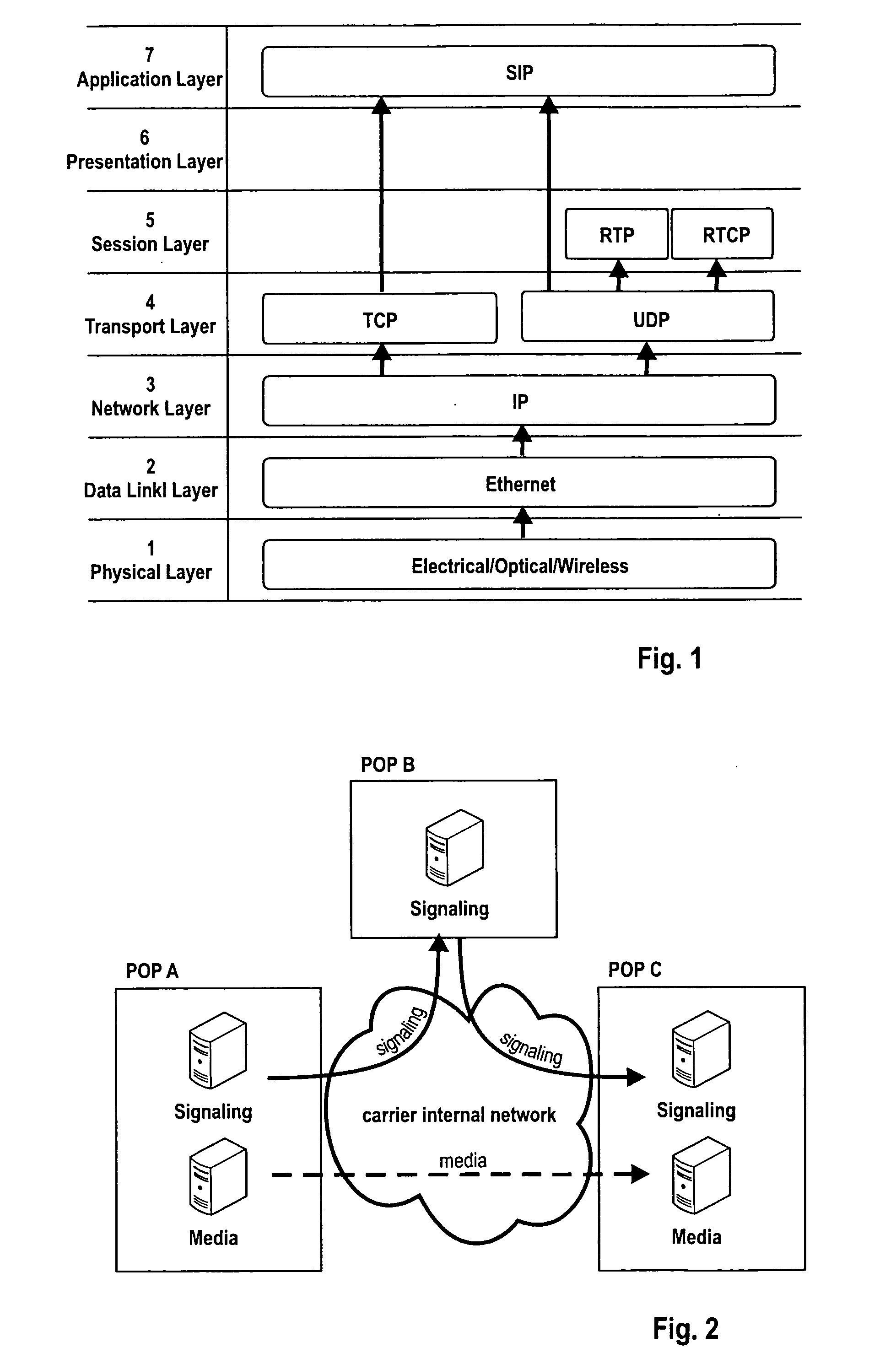
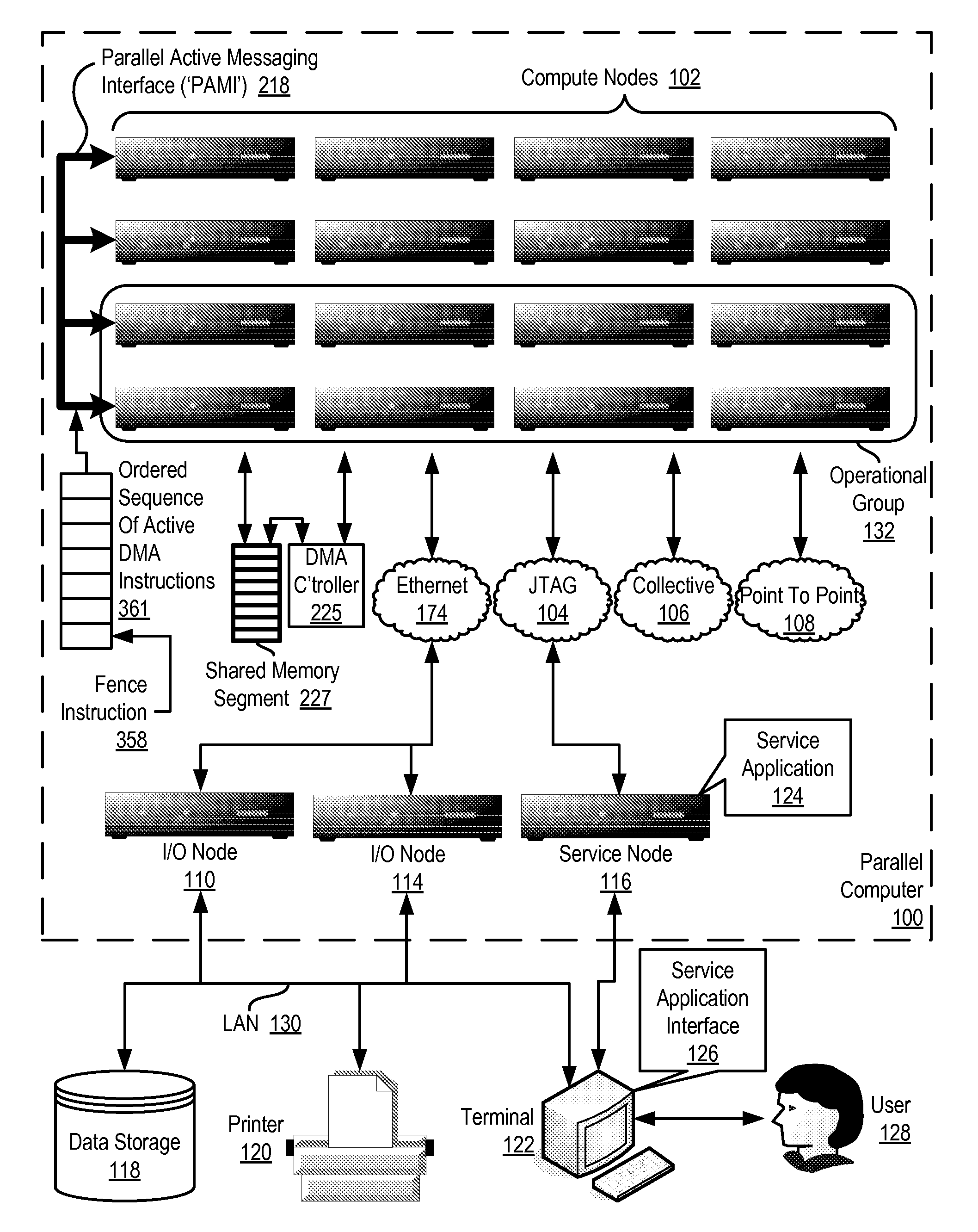
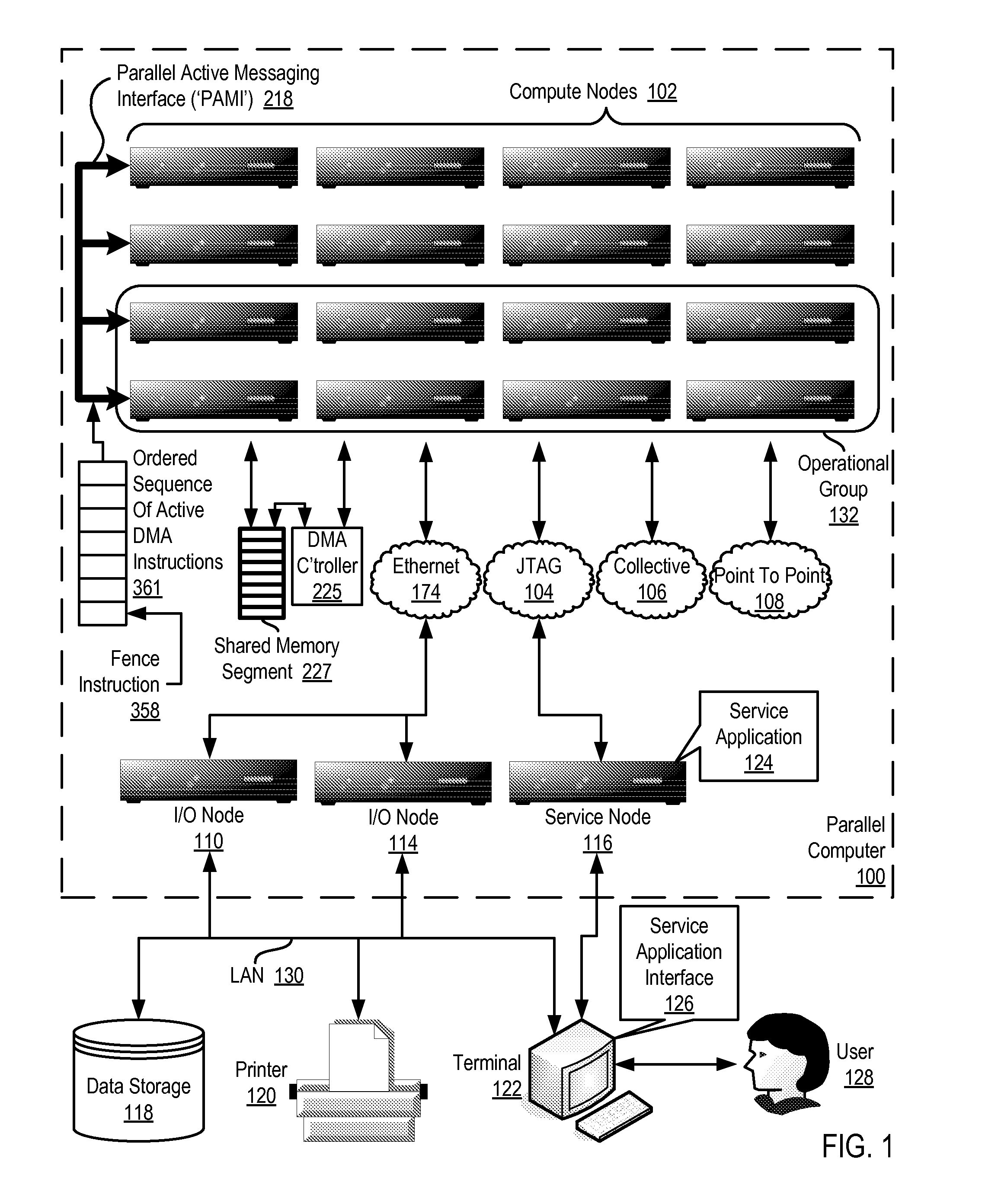
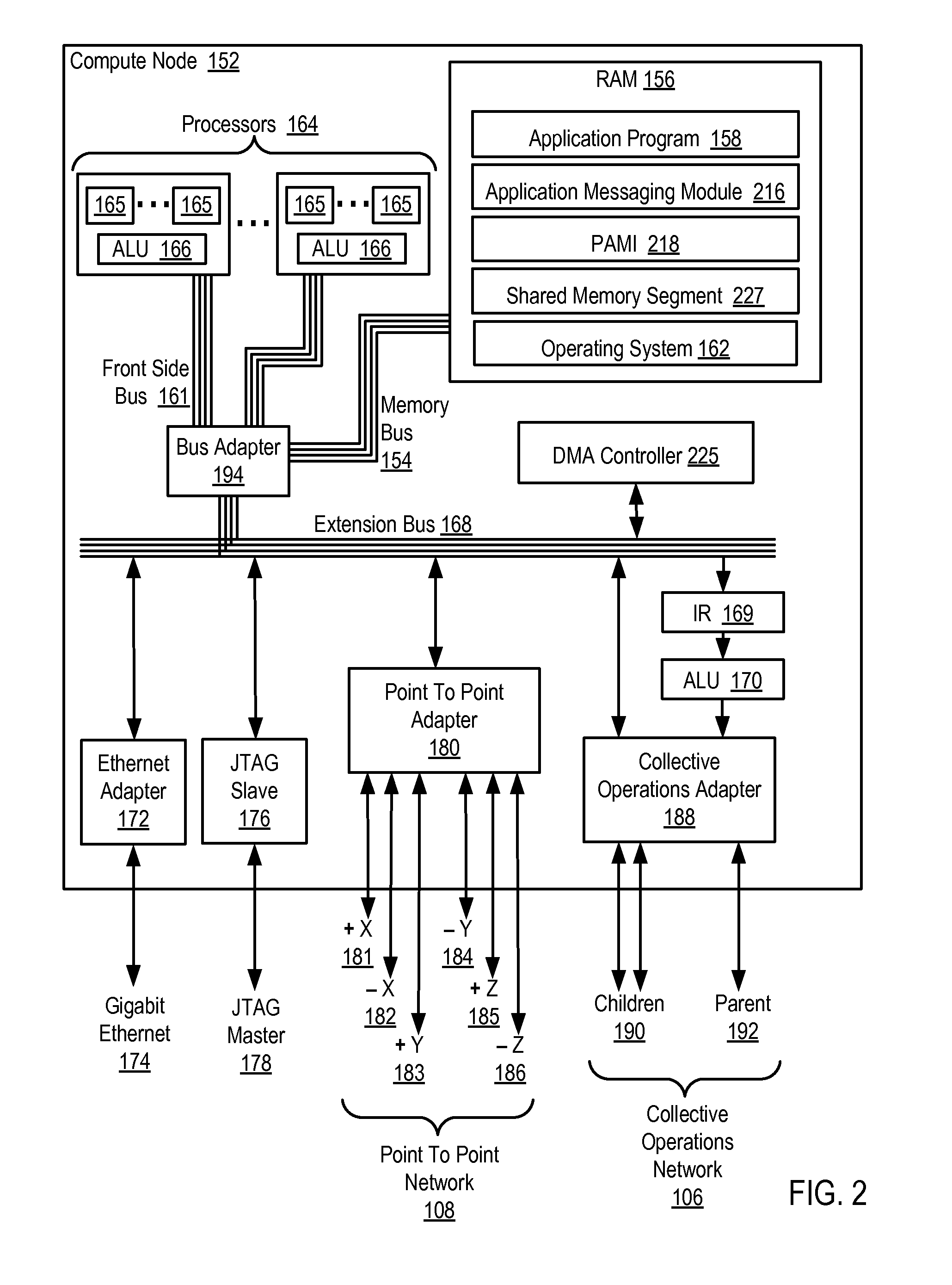
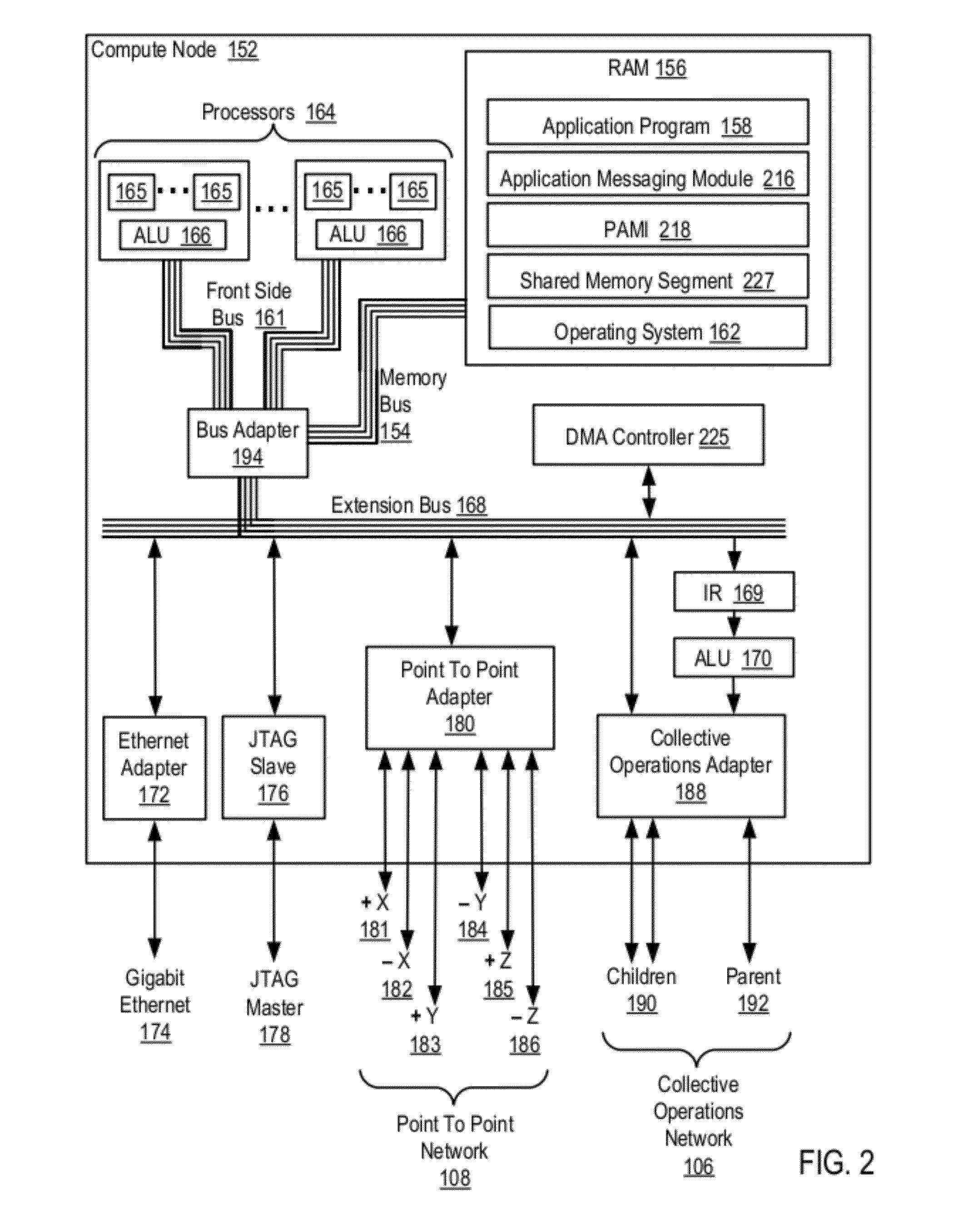
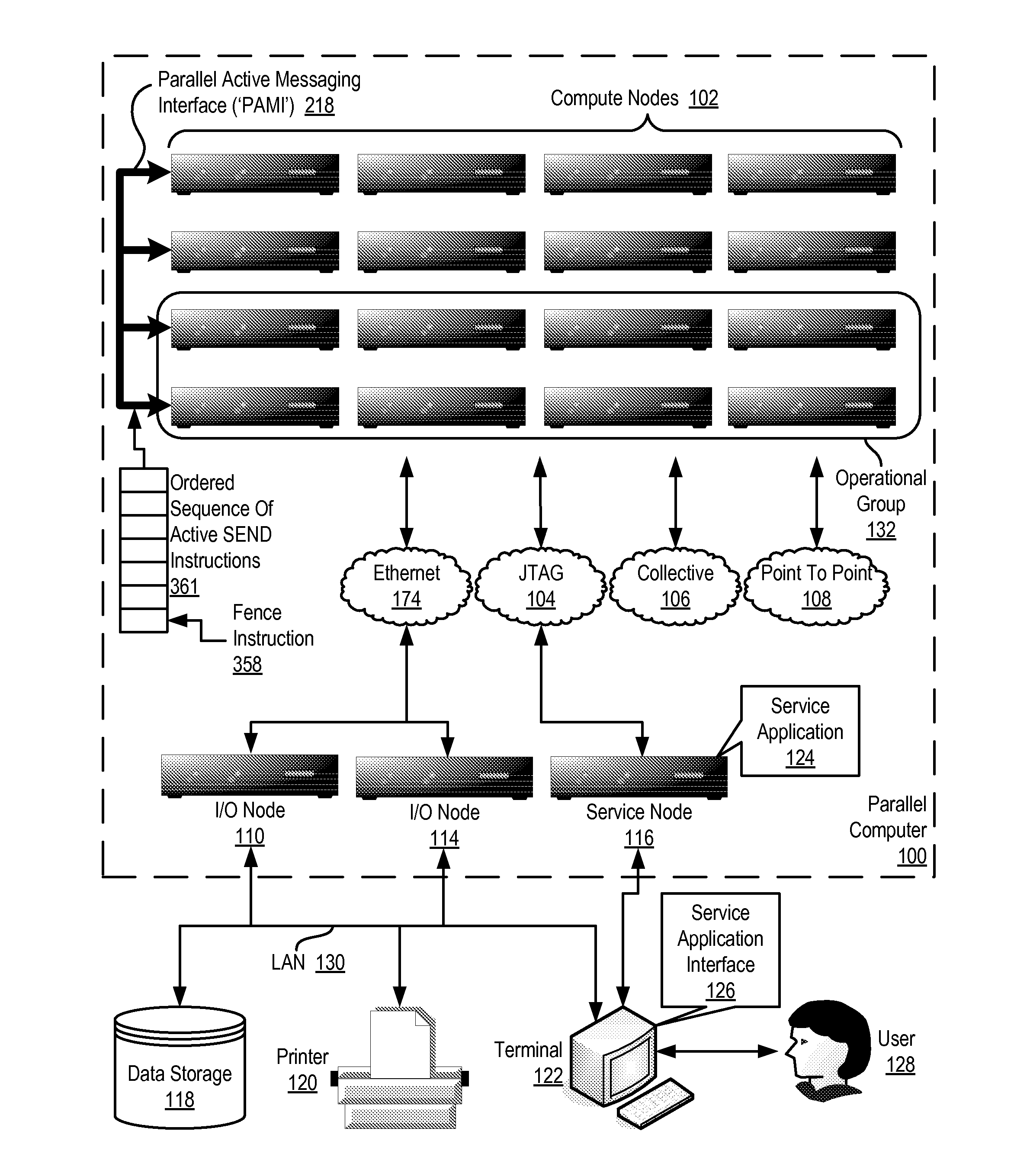
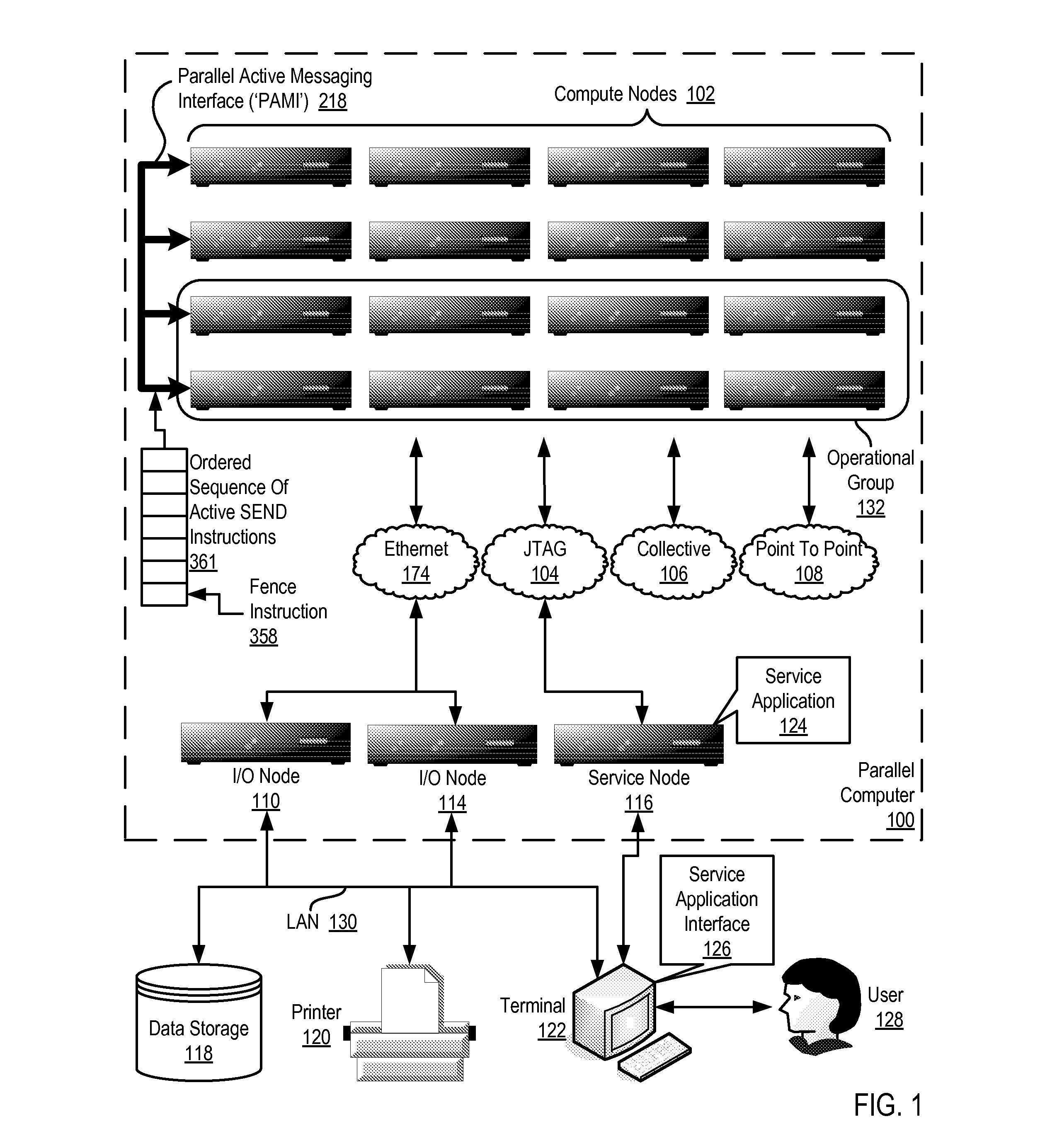
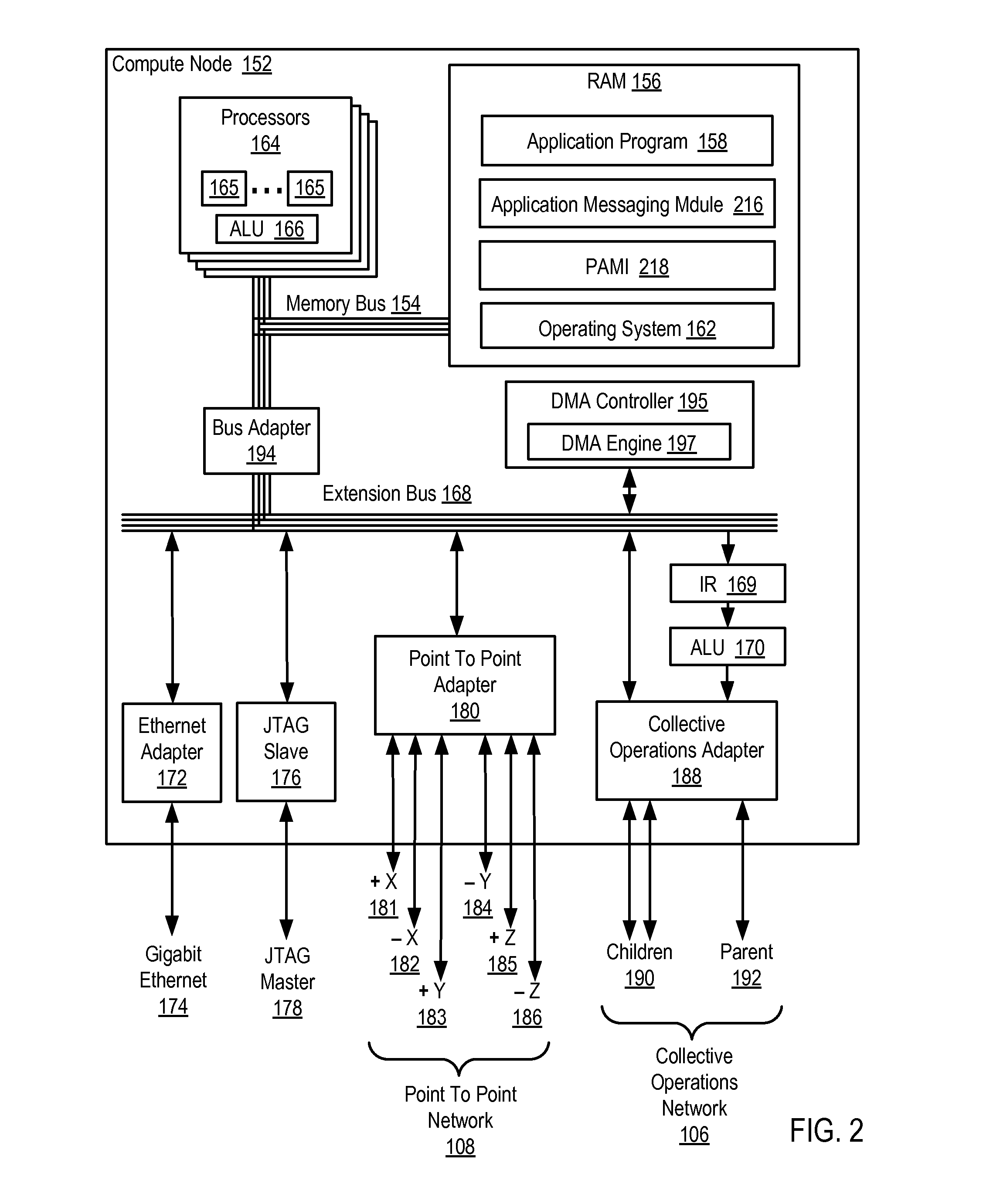
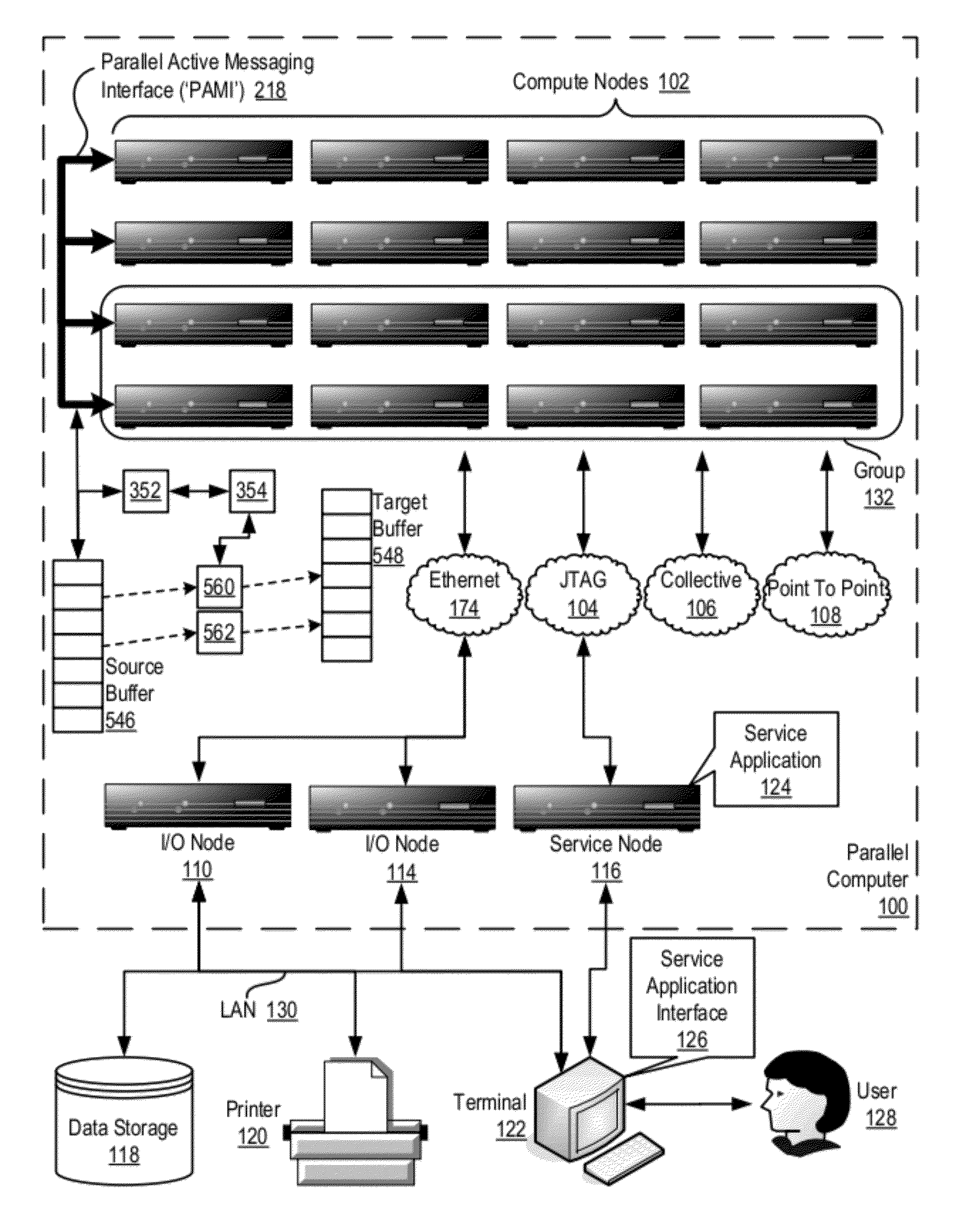
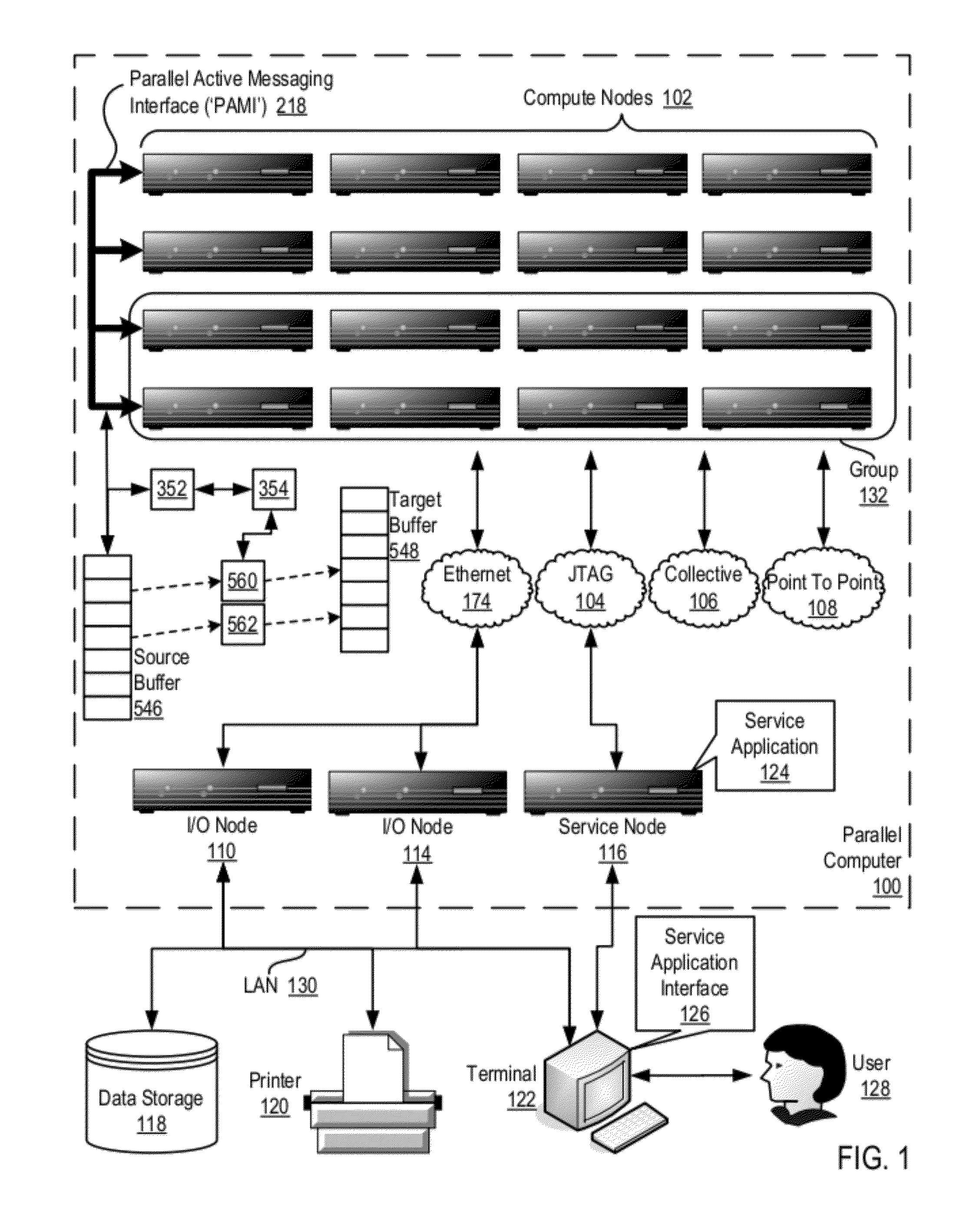
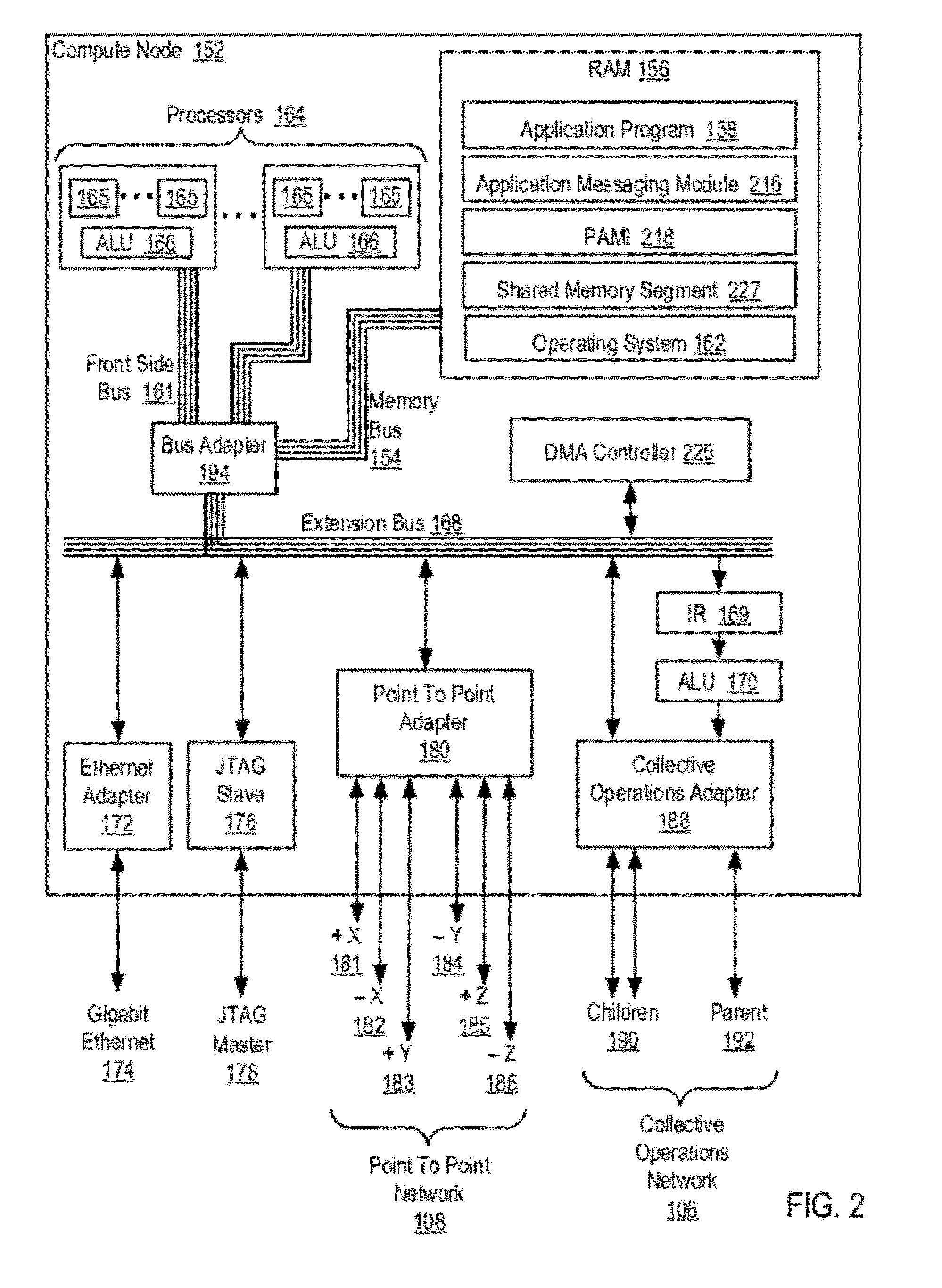
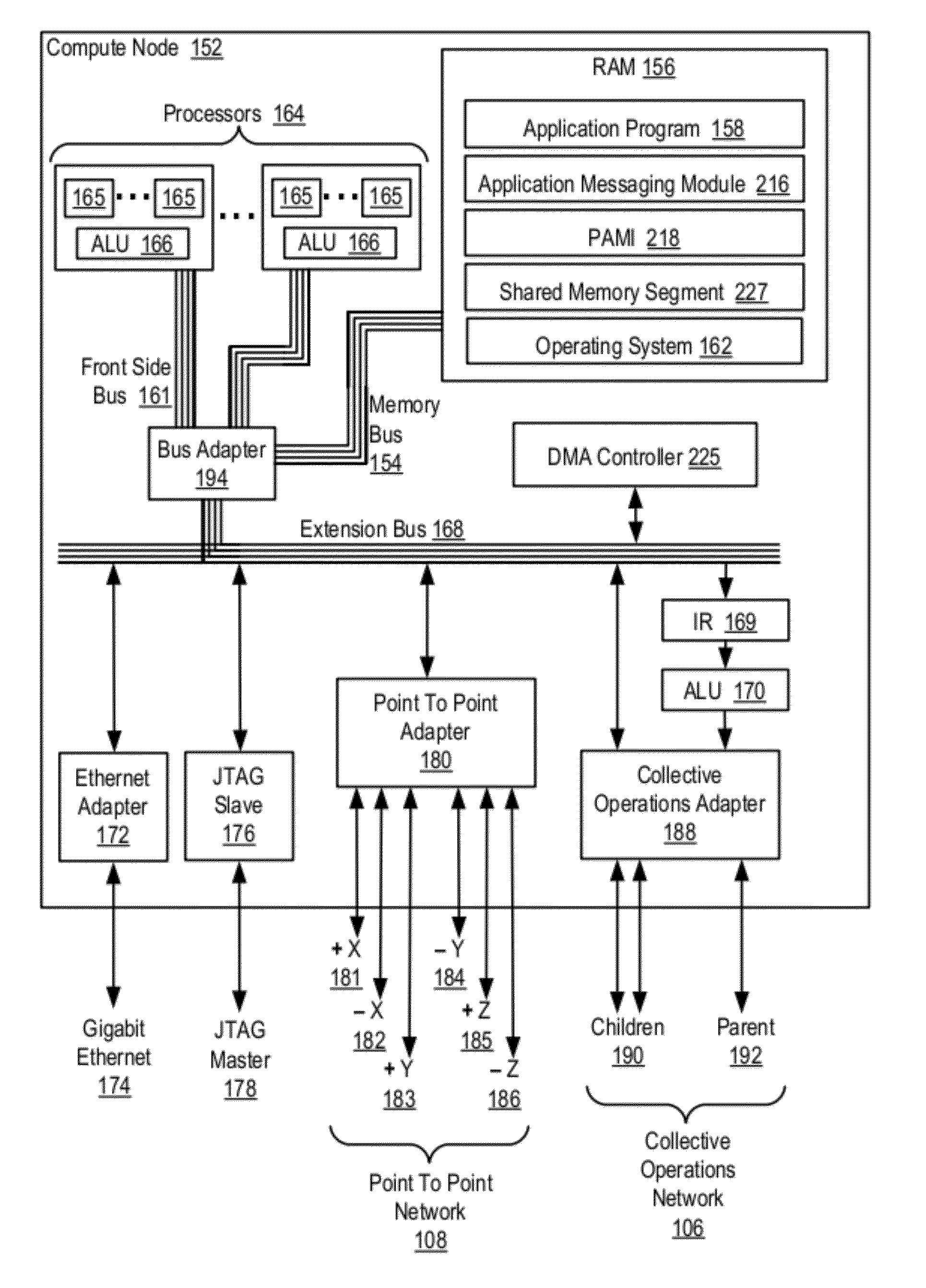
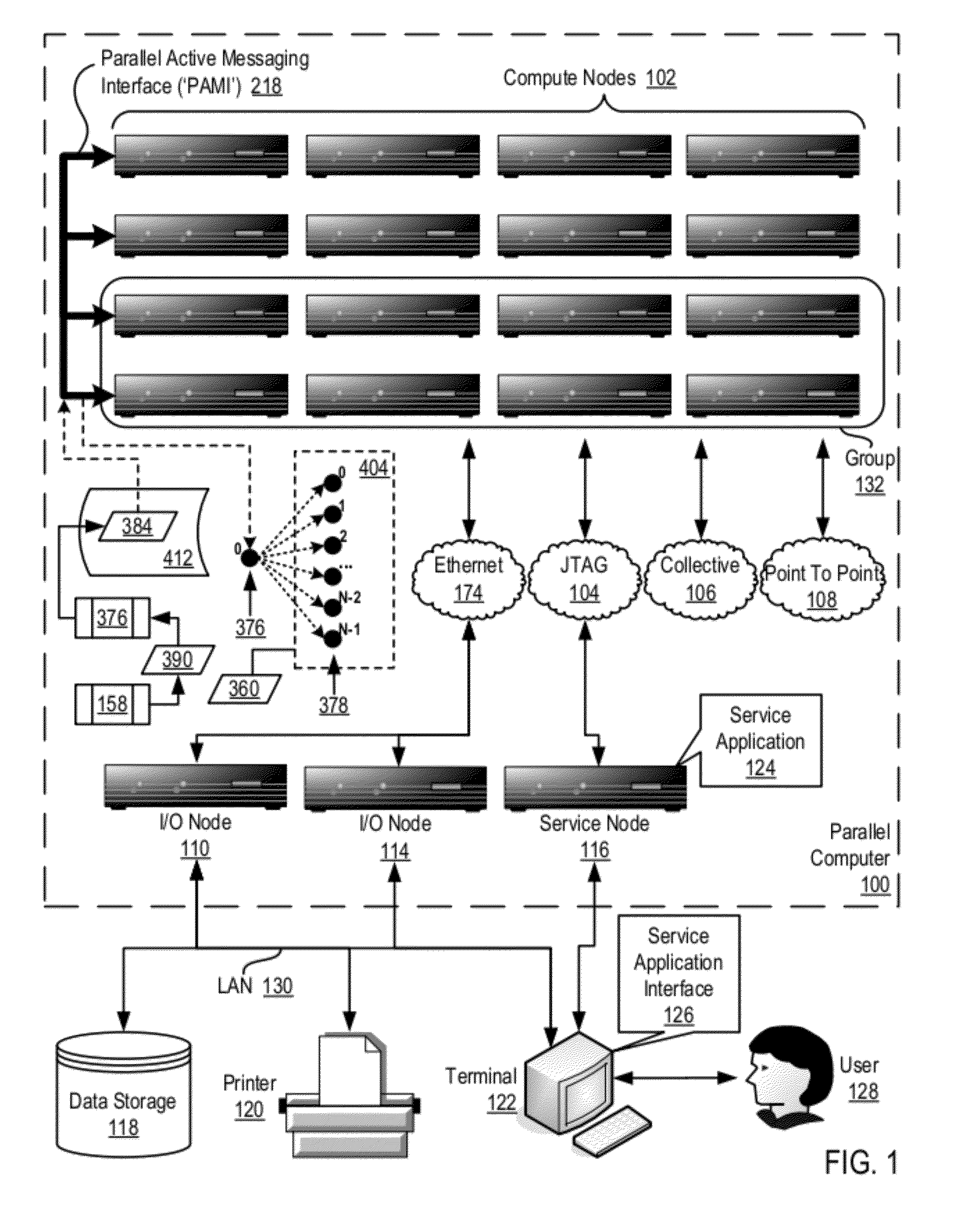
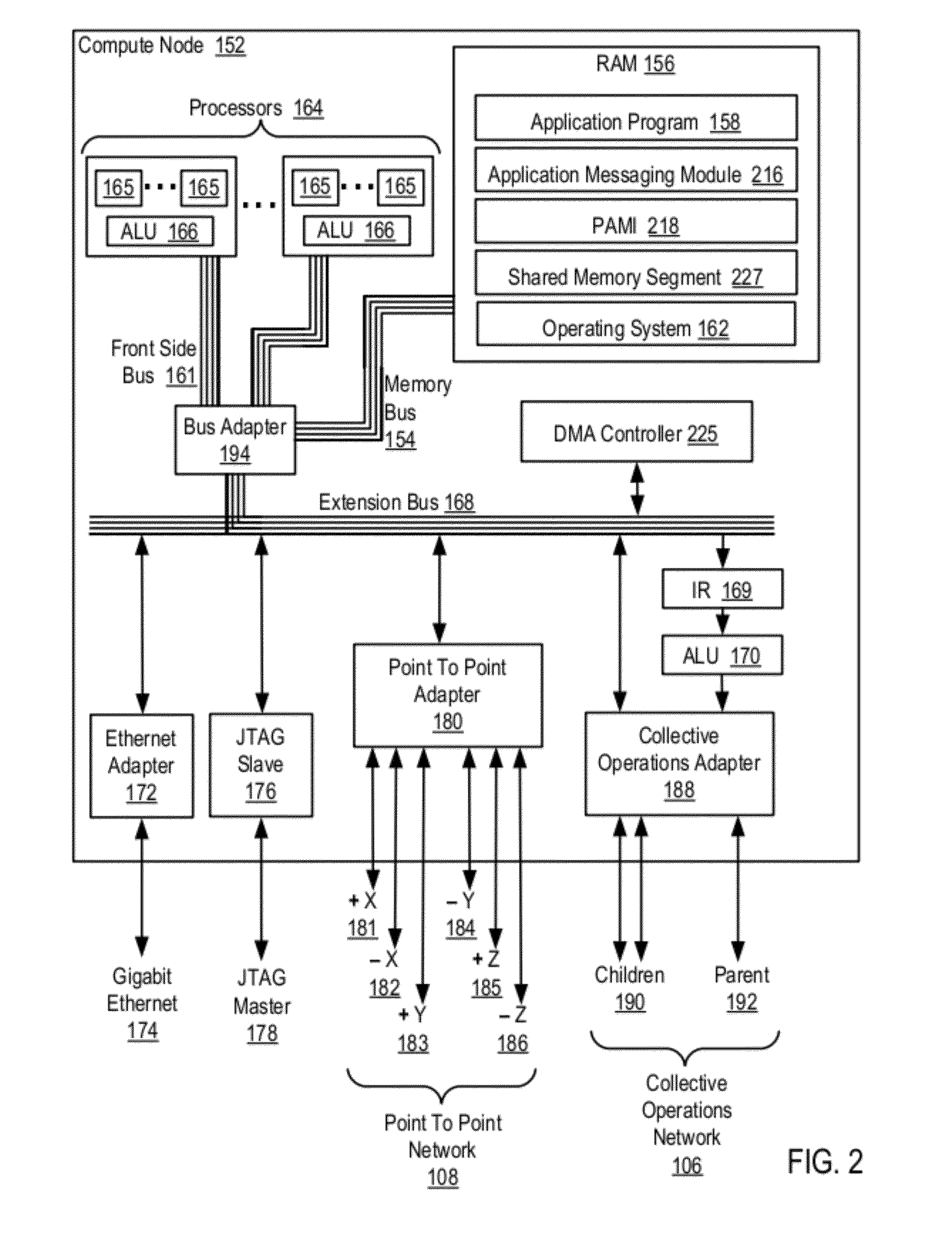
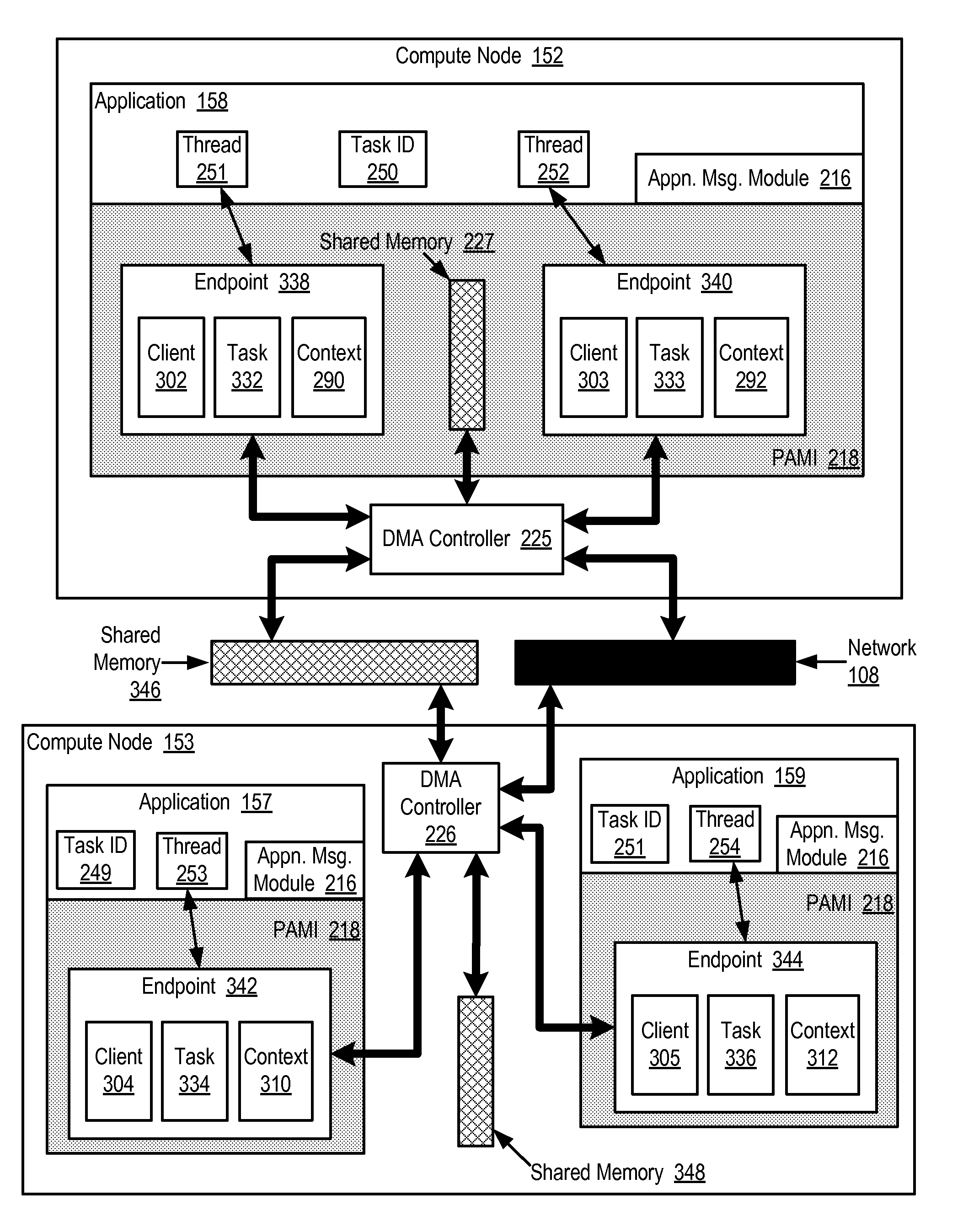
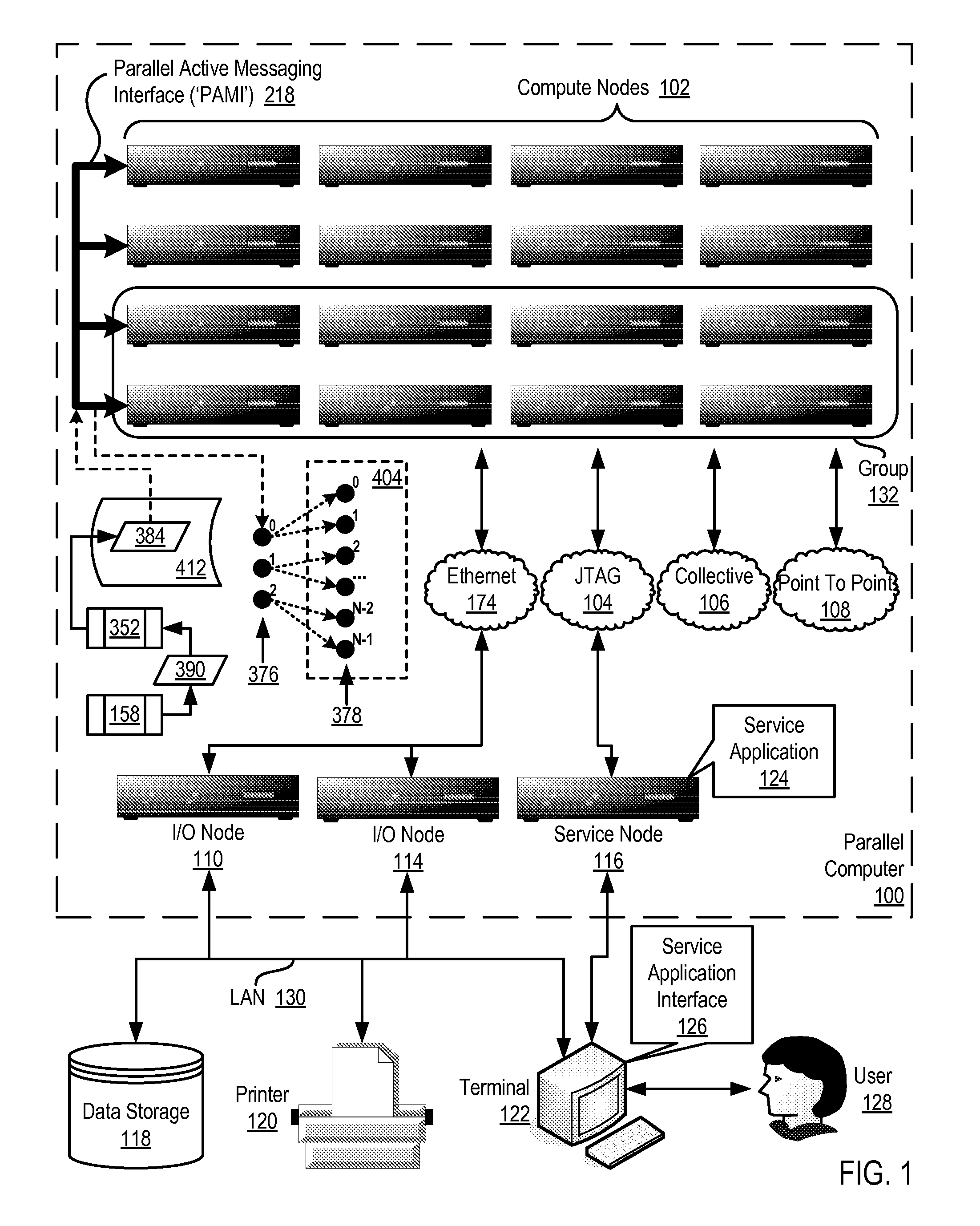
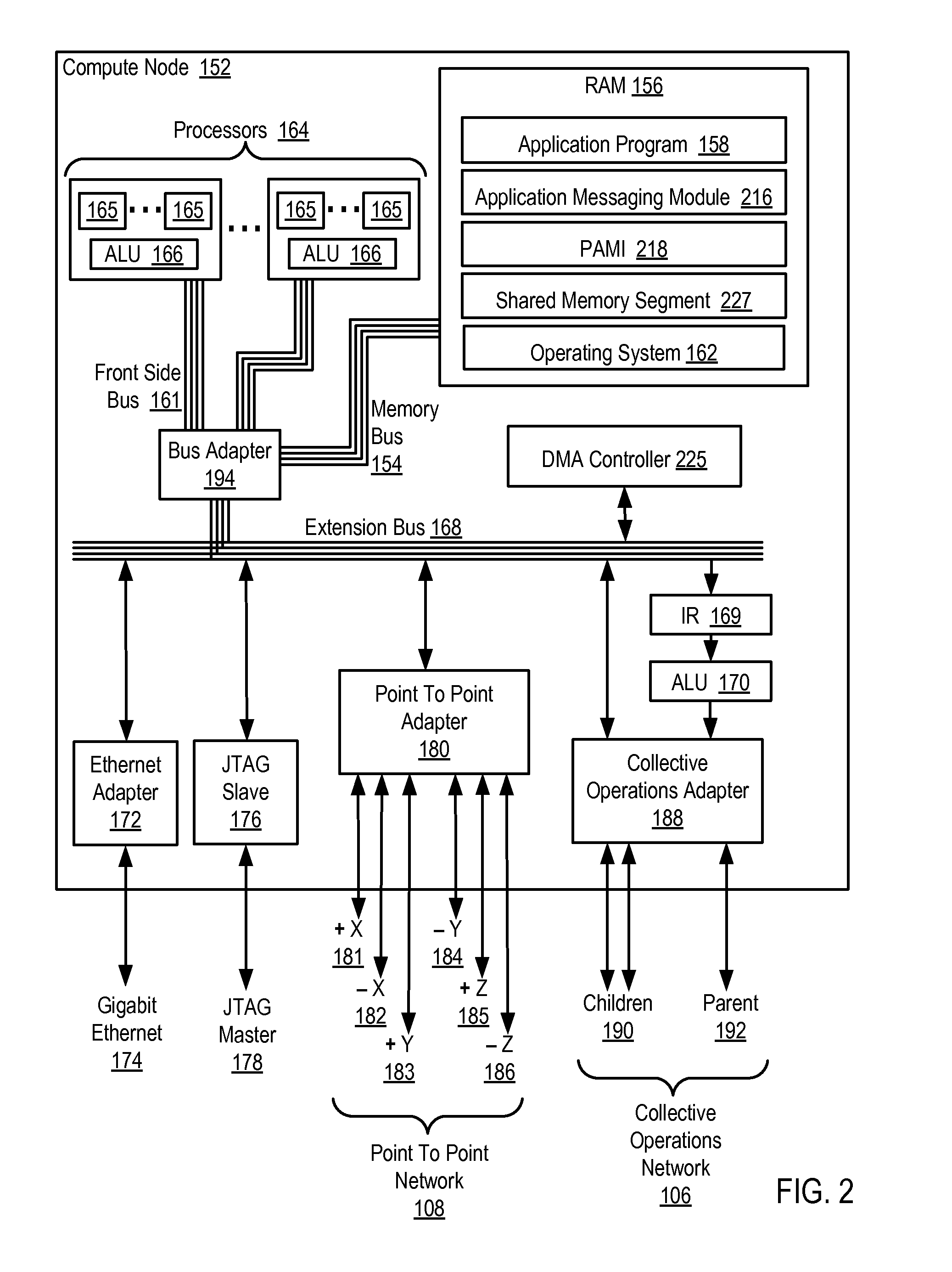
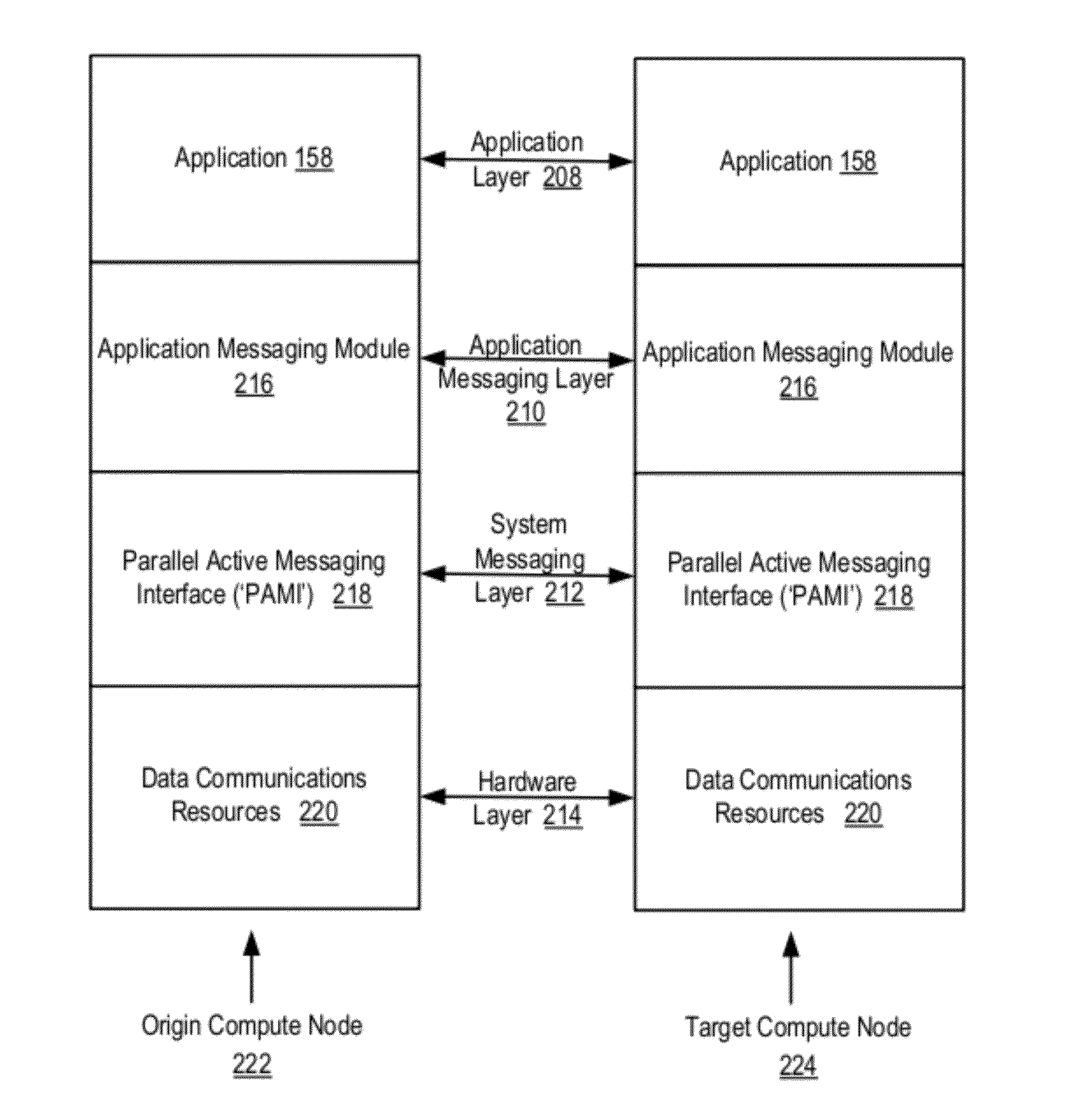
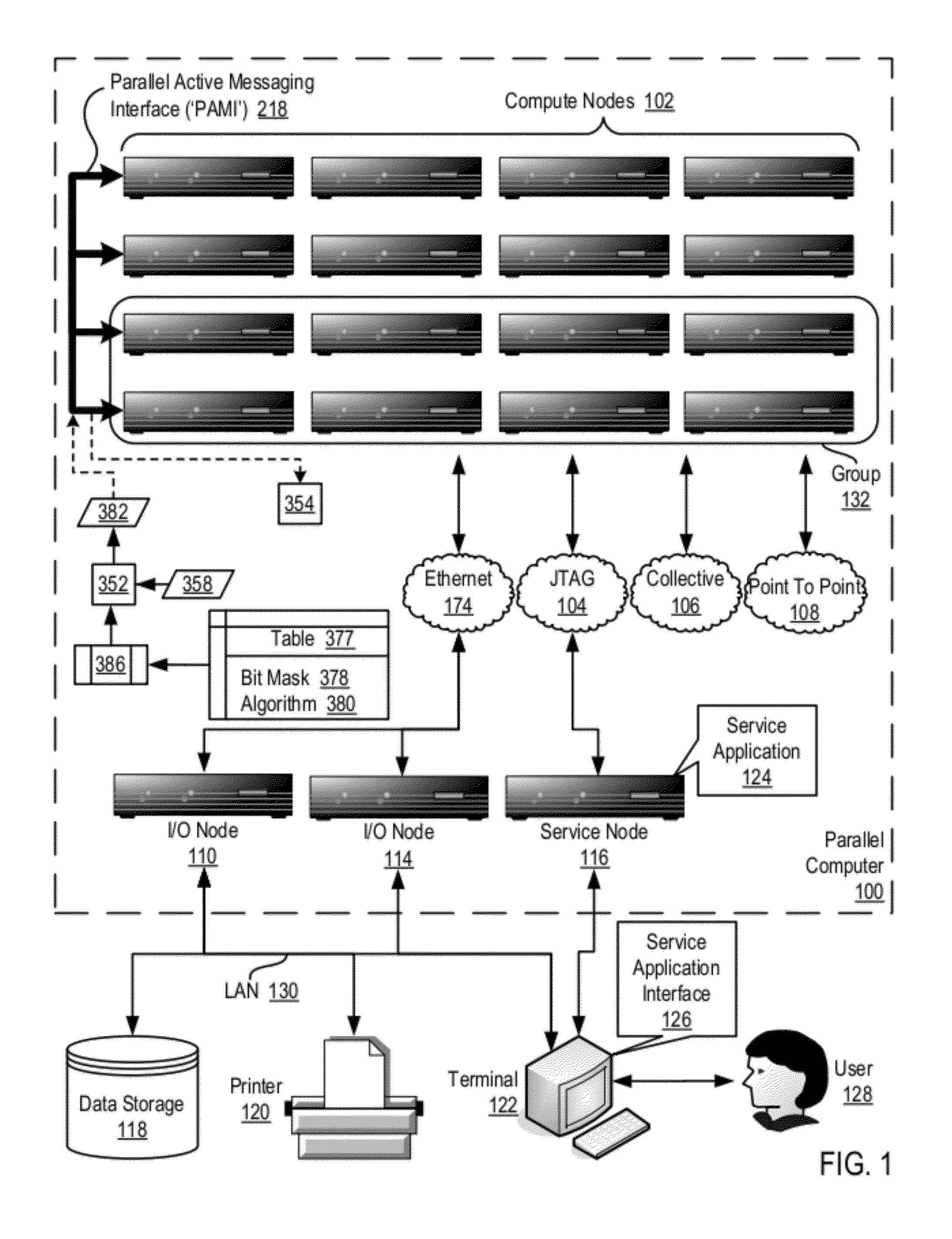
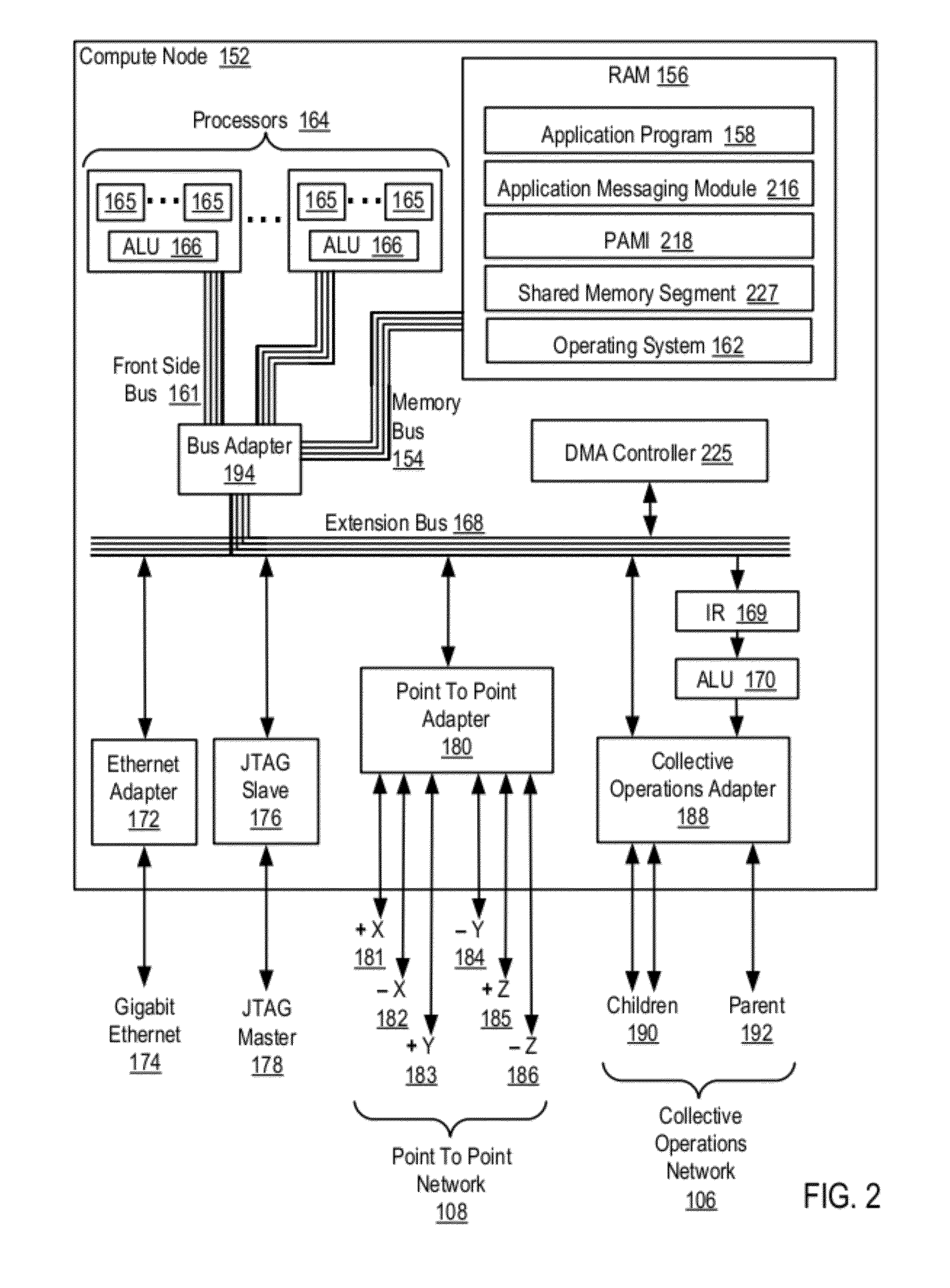
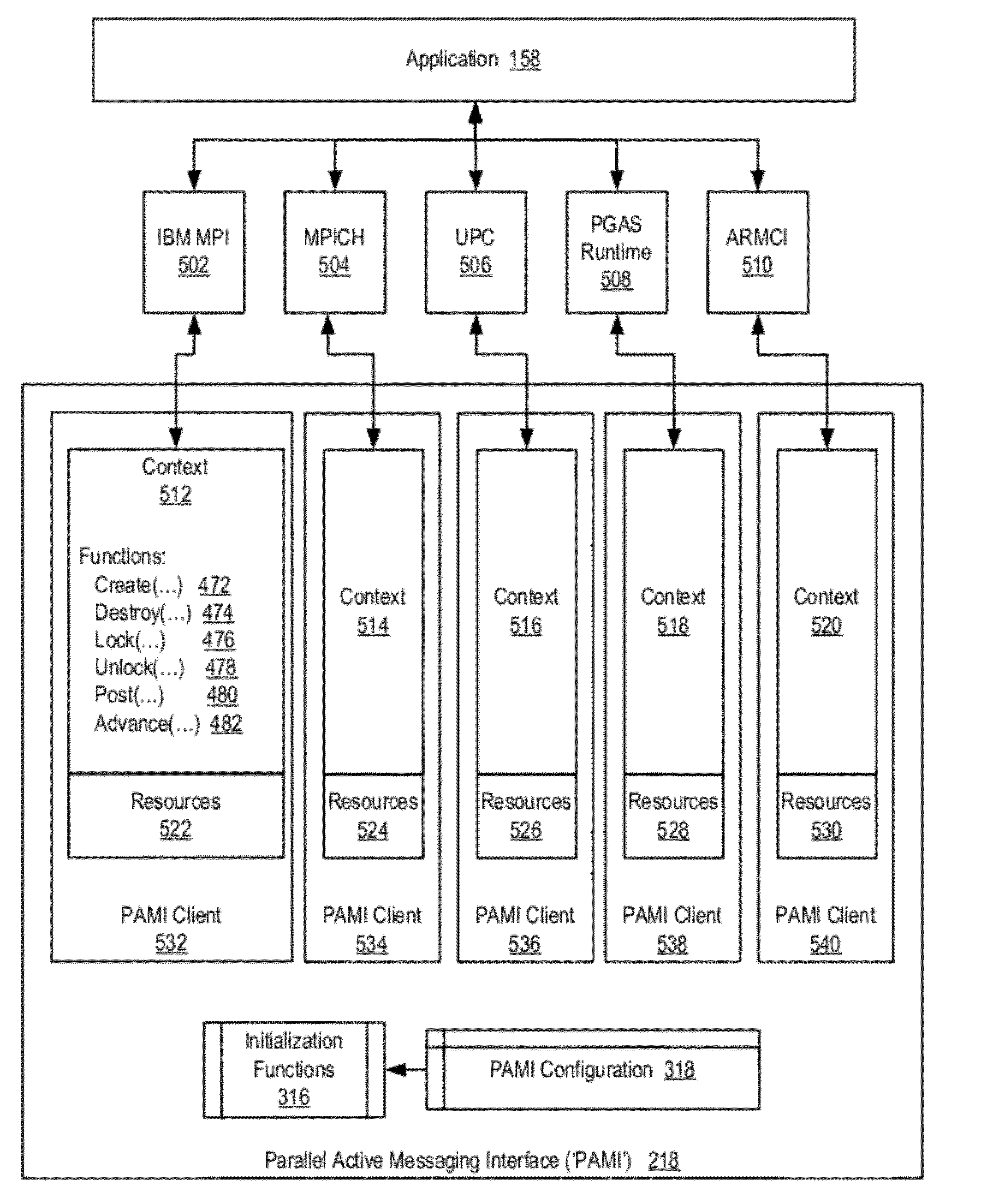
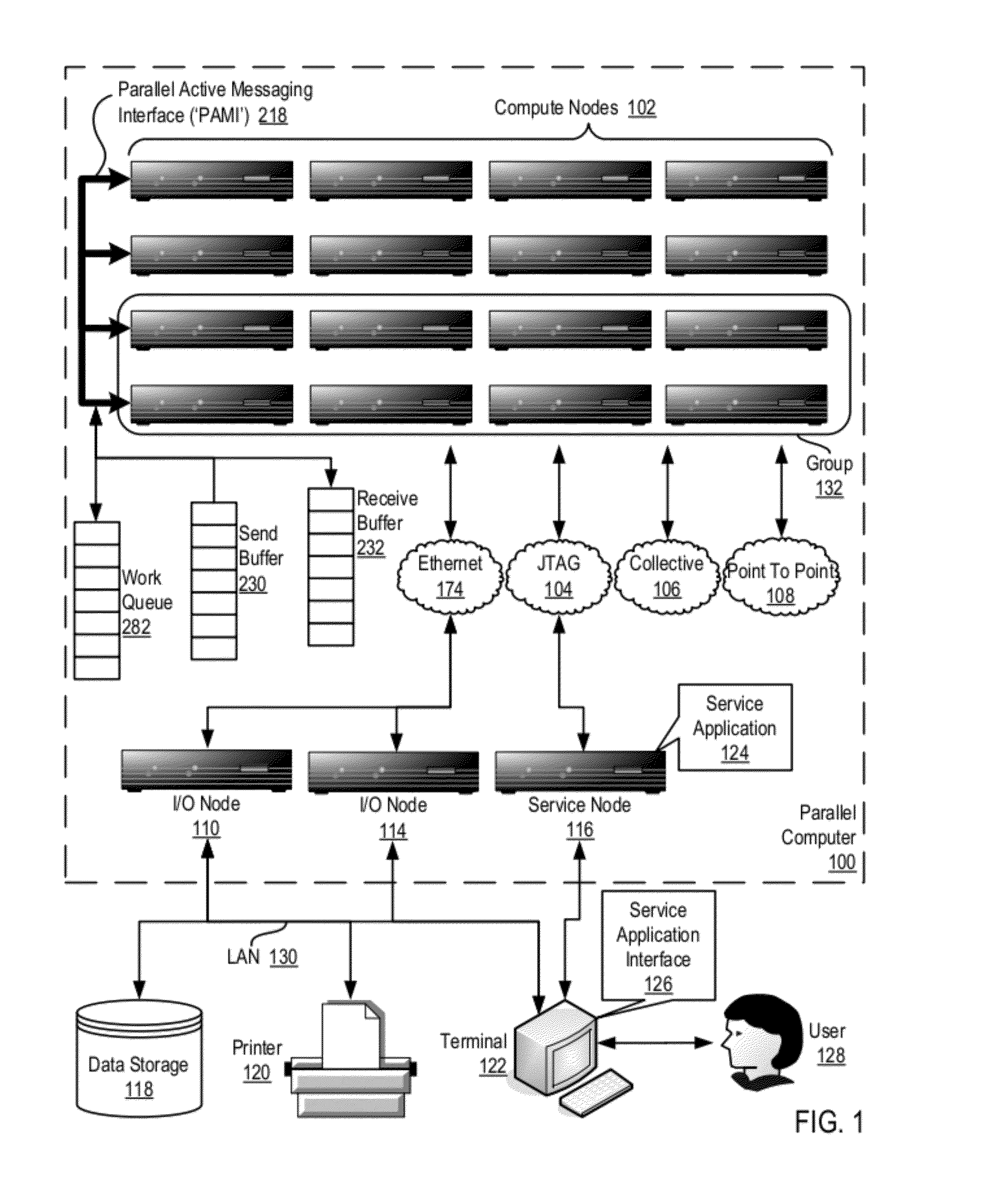
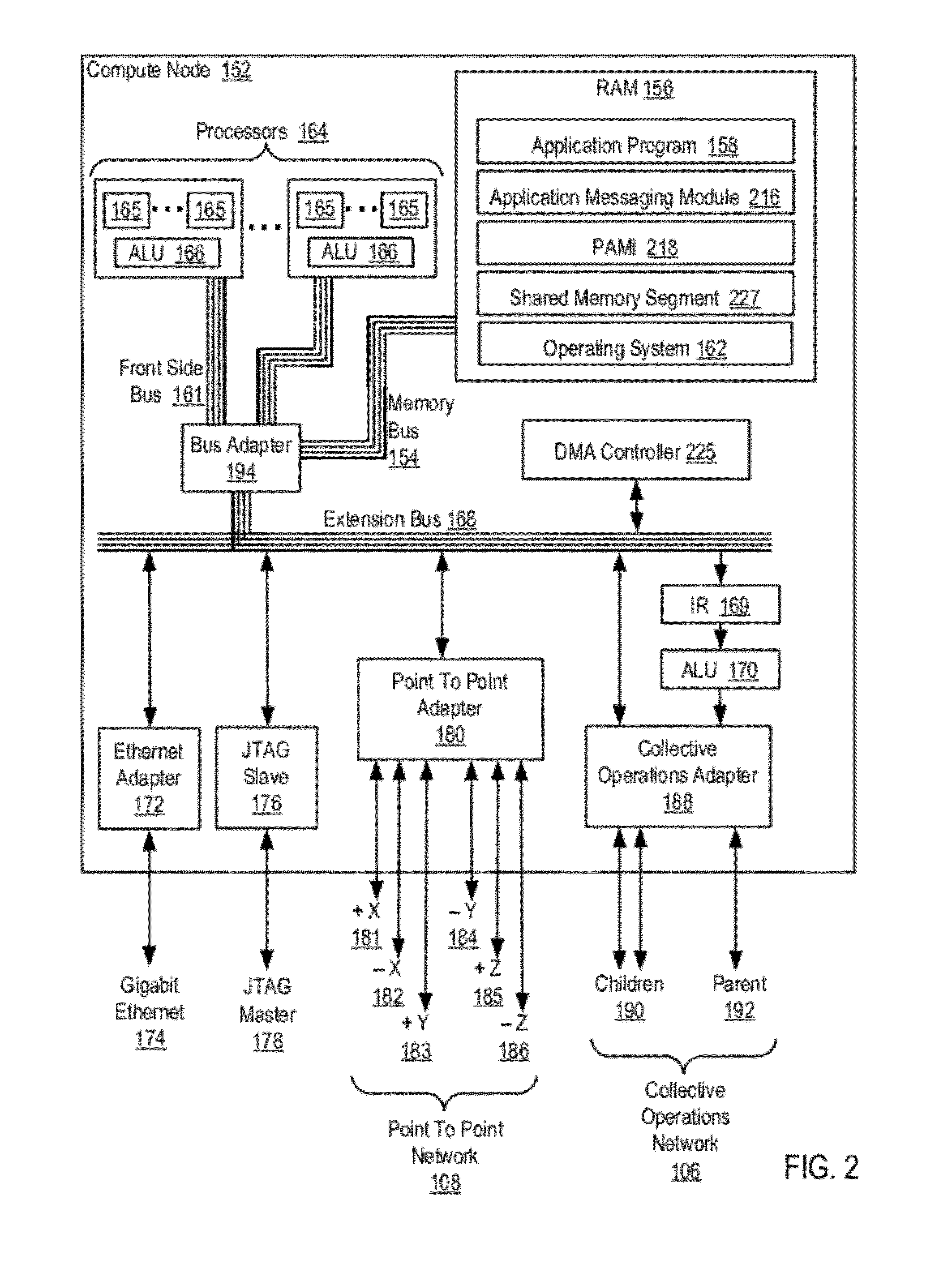
Data Communications In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120185873A1Digital computer detailsMultiprogramming arrangementsCommunication endpointParallel computing
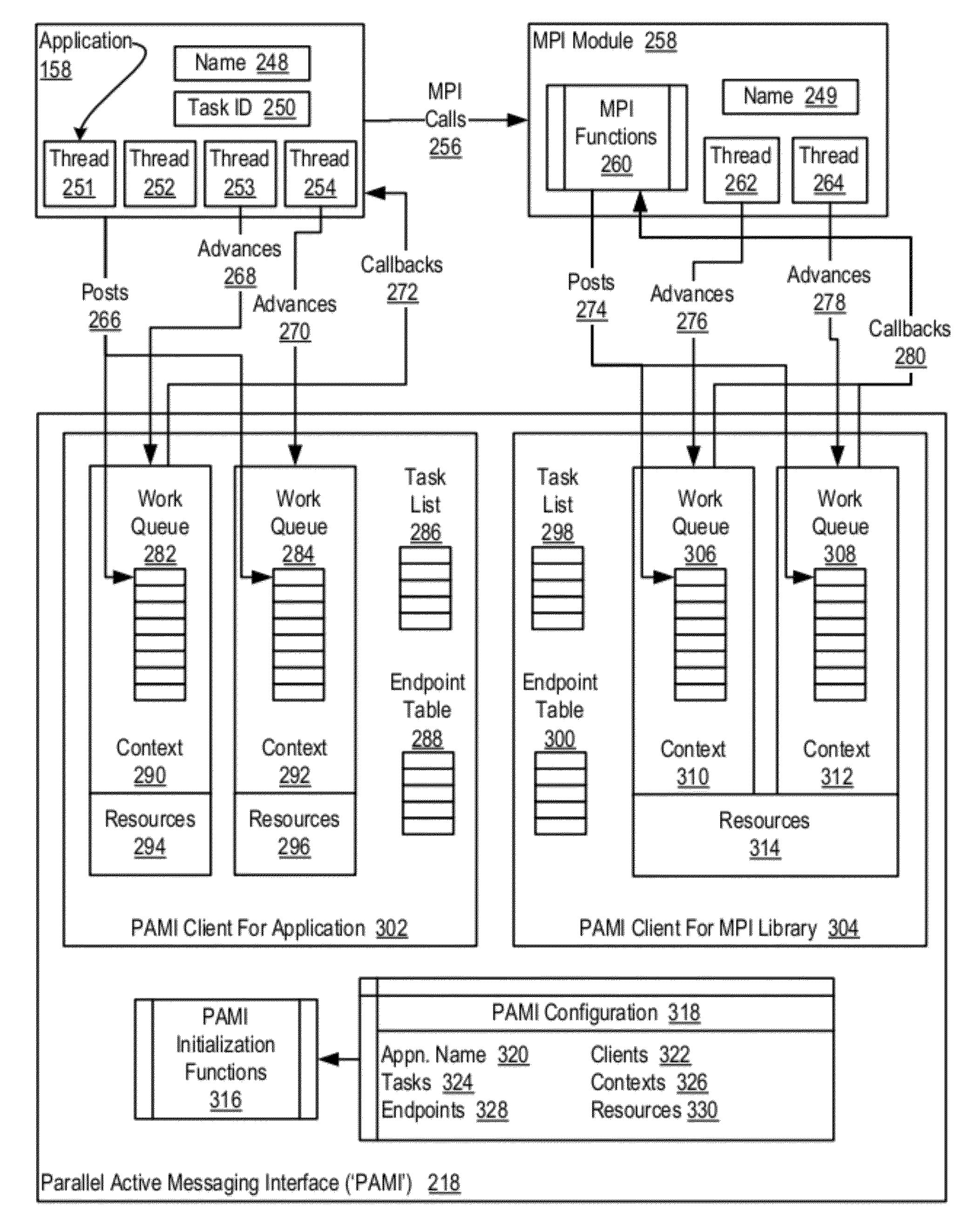
Data communications in a parallel active messaging interface (‘PAMI’) of a parallel computer composed of compute nodes that execute a parallel application, each compute node including application processors that execute the parallel application and at least one management processor dedicated to gathering information regarding data communications. The PAMI is composed of data communications endpoints, each endpoint composed of a specification of data communications parameters for a thread of execution on a compute node, including specifications of a client, a context, and a task, the compute nodes and the endpoints coupled for data communications through the PAMI and through data communications resources. Embodiments function by gathering call site statistics describing data communications resulting from execution of data communications instructions and identifying in dependence upon the call cite statistics a data communications algorithm for use in executing a data communications instruction at a call site in the parallel application.
Owner:IBM CORP
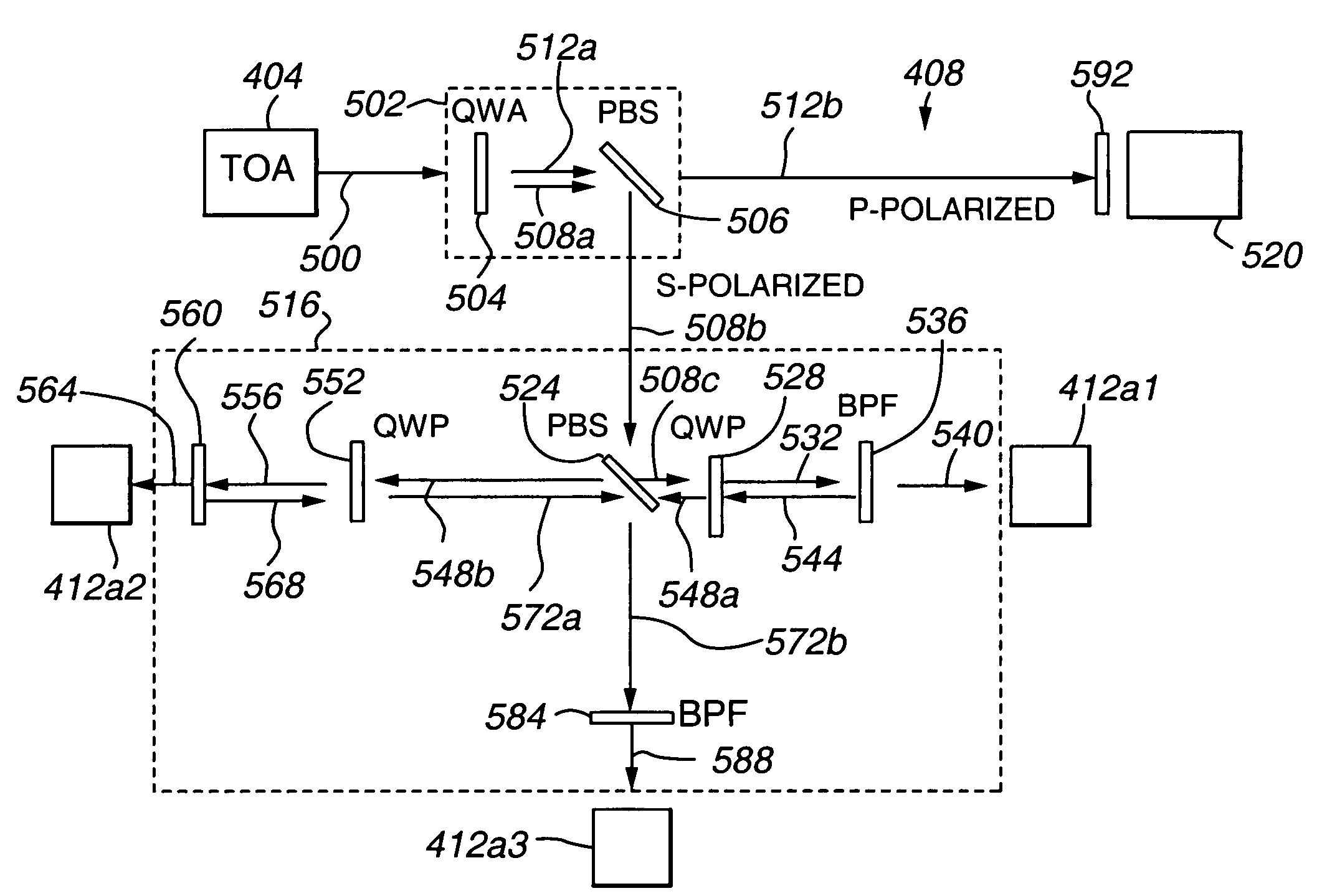
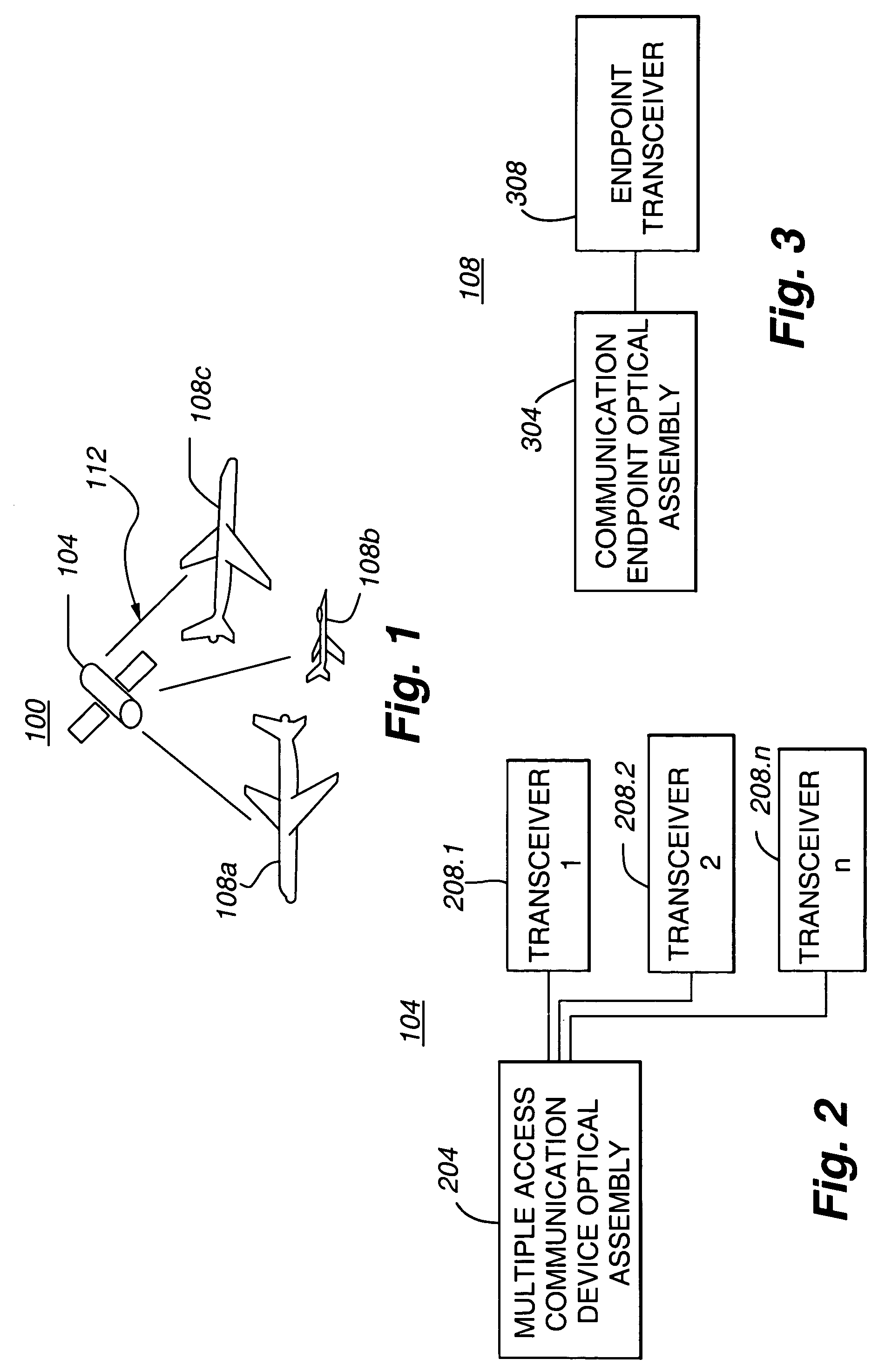
Multiple access space communications optical system using a common telescope aperture
ActiveUS7277641B1Reliable distinctionWavelength-division multiplex systemsSatellite communication transmissionBandpass filteringCommunication endpoint
Owner:BALL AEROSPACE & TECHNOLOGIES
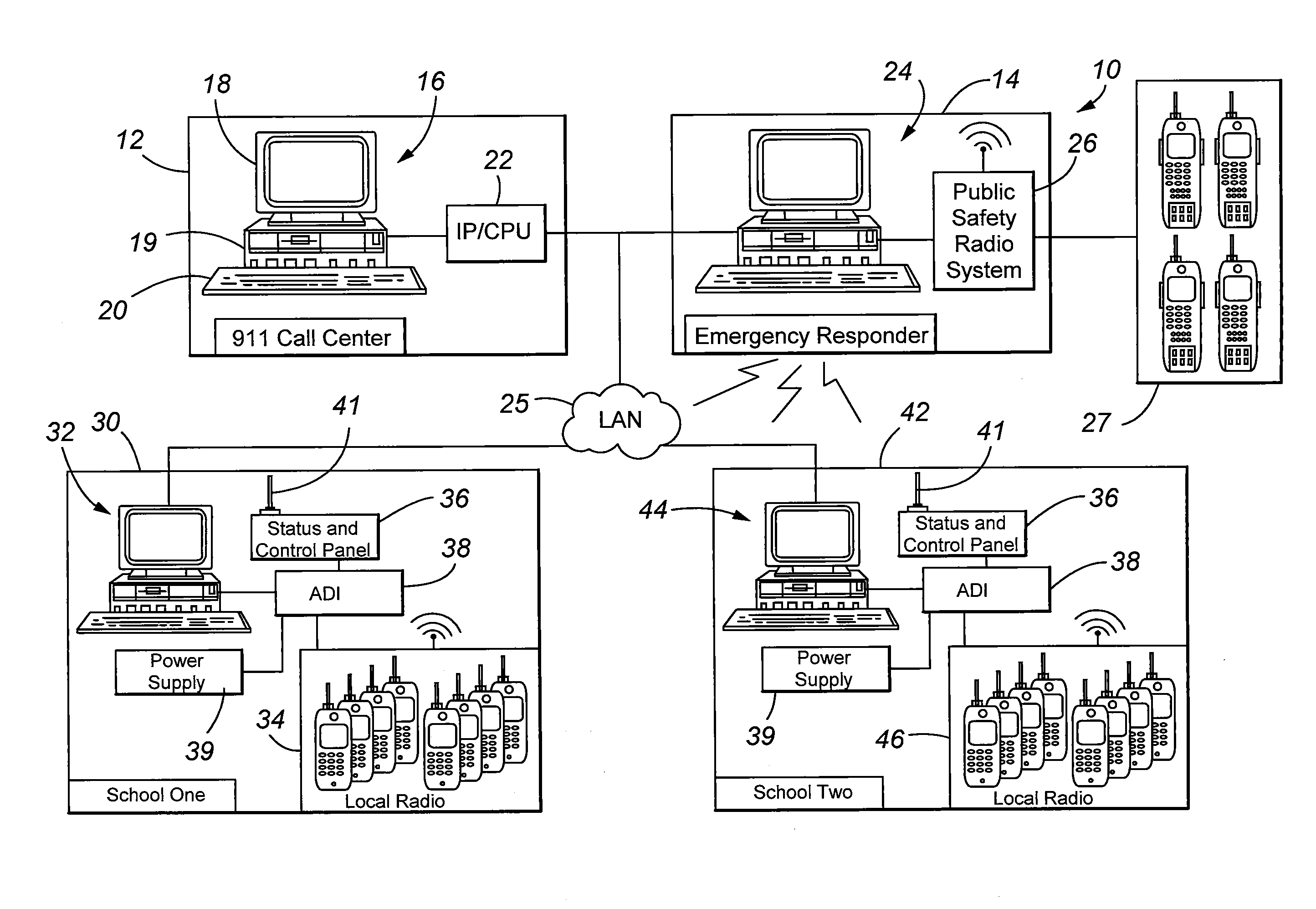
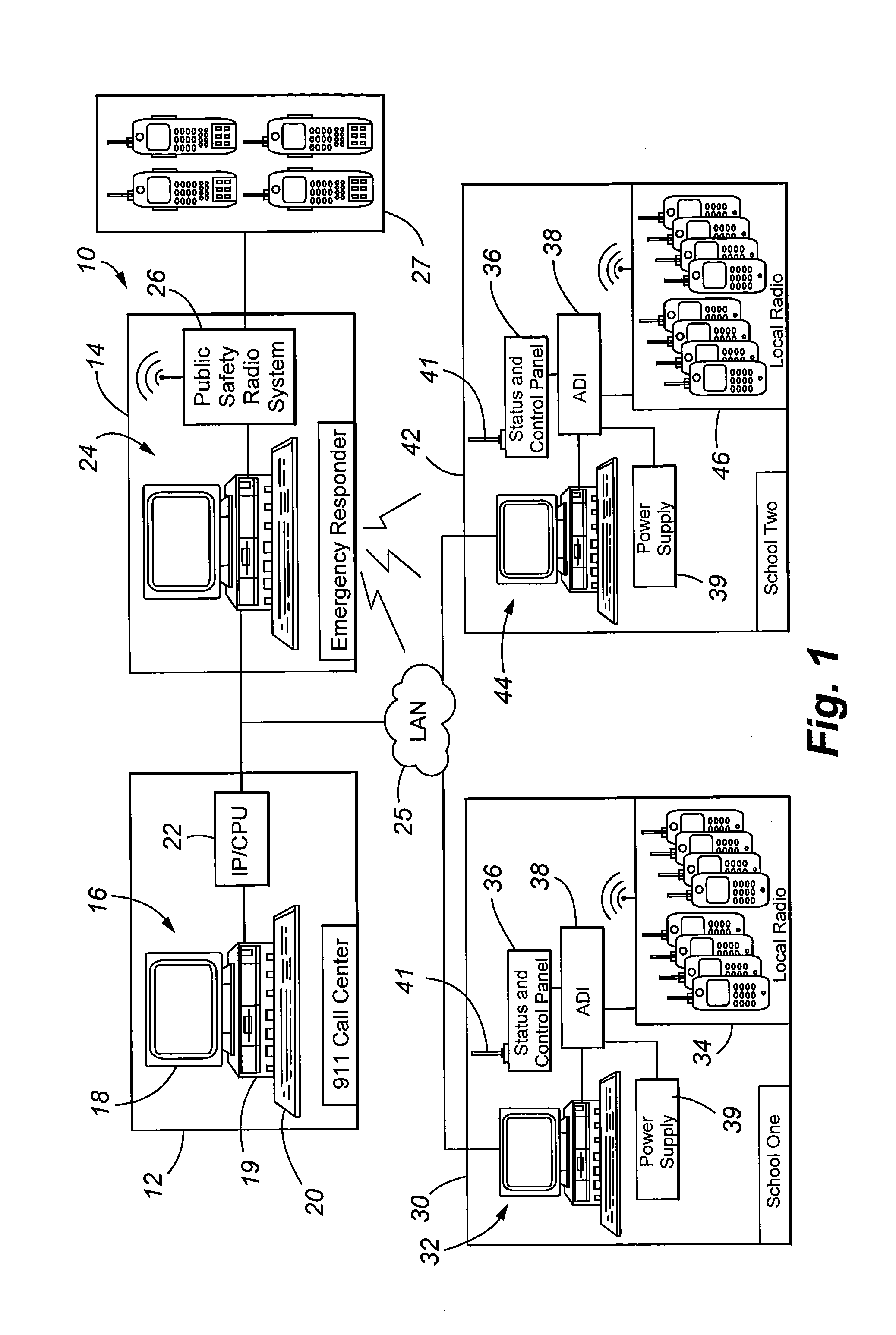
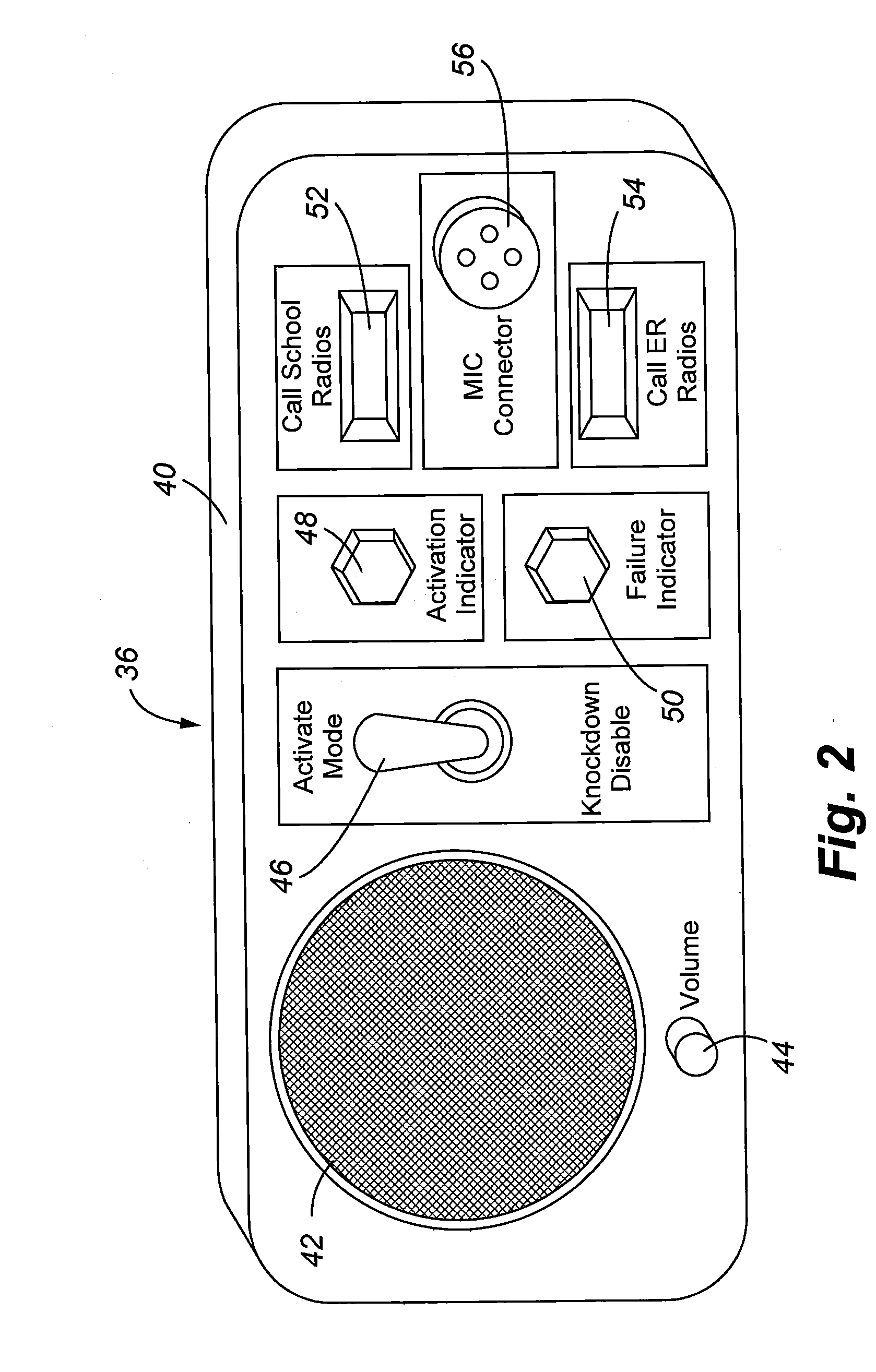
Emergency Communications System
ActiveUS20090041206A1Increase speedEmergency connection handlingUnbalanced current interference reductionCommunication endpointCommunications system
A communication system and method is provided for handling emergency situations wherein complex public safety radio systems can be used to directly communicate with normally incompatible radio systems used by organizations such as schools, hospital, and other facilities. The system includes a radio communication bridge that is selectively activated by emergency personnel to contact selected organizations. The bridge is activated via a TCP / IP command sent from an organization having activation privileges to the selected communication endpoints. Computer software or firmware installed at various communication endpoints, emergency responder locations, and at an emergency call center is used to facilitate functionality of the system to include emergency notifications, dissemination of information associated with a particular emergency, and the status of the system to include activation and deactivation of the radio bridge.
Owner:SAFECOM 911
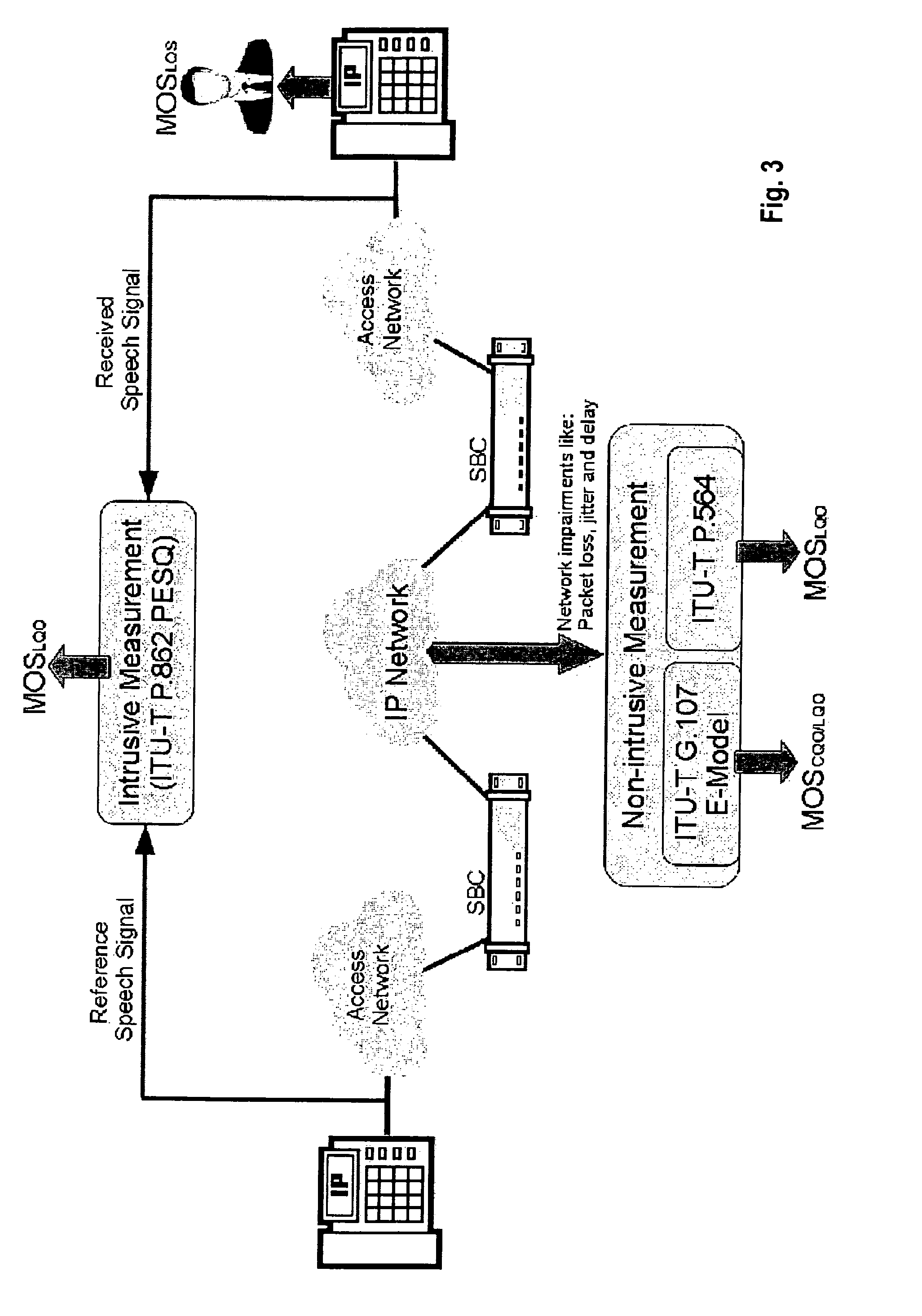
VOIP quality measurement enhancements using the internet control message protocol
ActiveUS20130329595A1Improve quality monitoringError preventionTransmission systemsCommunication endpointTTEthernet
This invention relates to a method for enhancing the quality information of a VoIP session by deducting information from received ICMP messages, in addition to quality information already collected from media streams and / or signaling streams of the same VoIP session. ICMP messages passing on the network link are monitored and correlated with an existing and ongoing VoIP session, i.e. media stream, already monitored by a media plane monitoring unit. A data record for the media stream(s) is expanded with information from the ICMP messages, thus giving a better and more complete quality feedback of the media stream reception at the two communication endpoints.
Owner:VOIPFUTURE
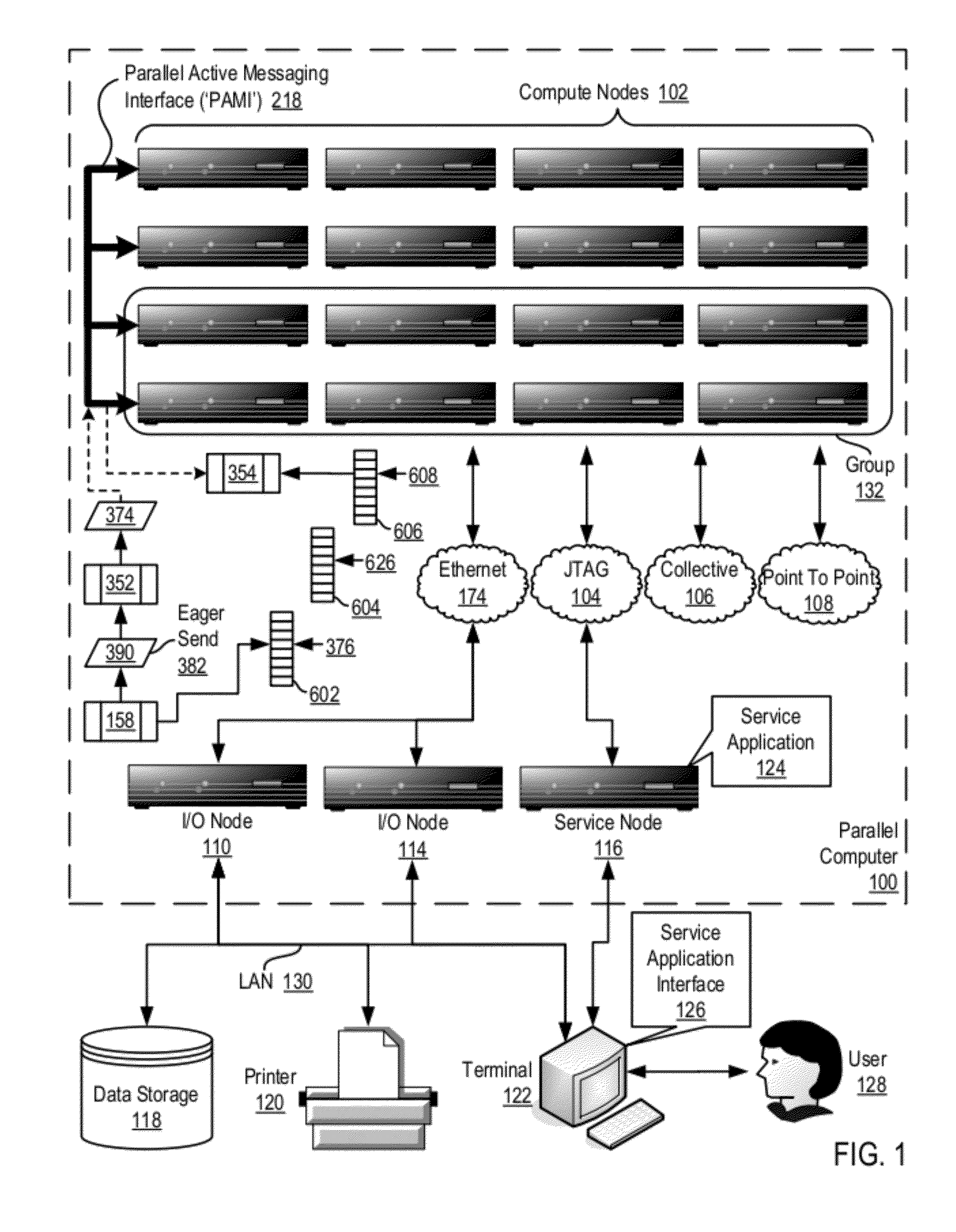
Fencing Direct Memory Access Data Transfers In A Parallel Active Messaging Interface Of A Parallel Computer
Fencing direct memory access (‘DMA’) data transfers in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI including data communications endpoints, each endpoint including specifications of a client, a context, and a task, the endpoints coupled for data communications through the PAMI and through DMA controllers operatively coupled to segments of shared random access memory through which the DMA controllers deliver data communications deterministically, including initiating execution through the PAMI of an ordered sequence of active DMA instructions for DMA data transfers between two endpoints, effecting deterministic DMA data transfers through a DMA controller and a segment of shared memory; and executing through the PAMI, with no FENCE accounting for DMA data transfers, an active FENCE instruction, the FENCE instruction completing execution only after completion of all DMA instructions initiated prior to execution of the FENCE instruction for DMA data transfers between the two endpoints.
Owner:IBM CORP
Data Communications In A Parallel Active Messaging Interface Of A Parallel Computer
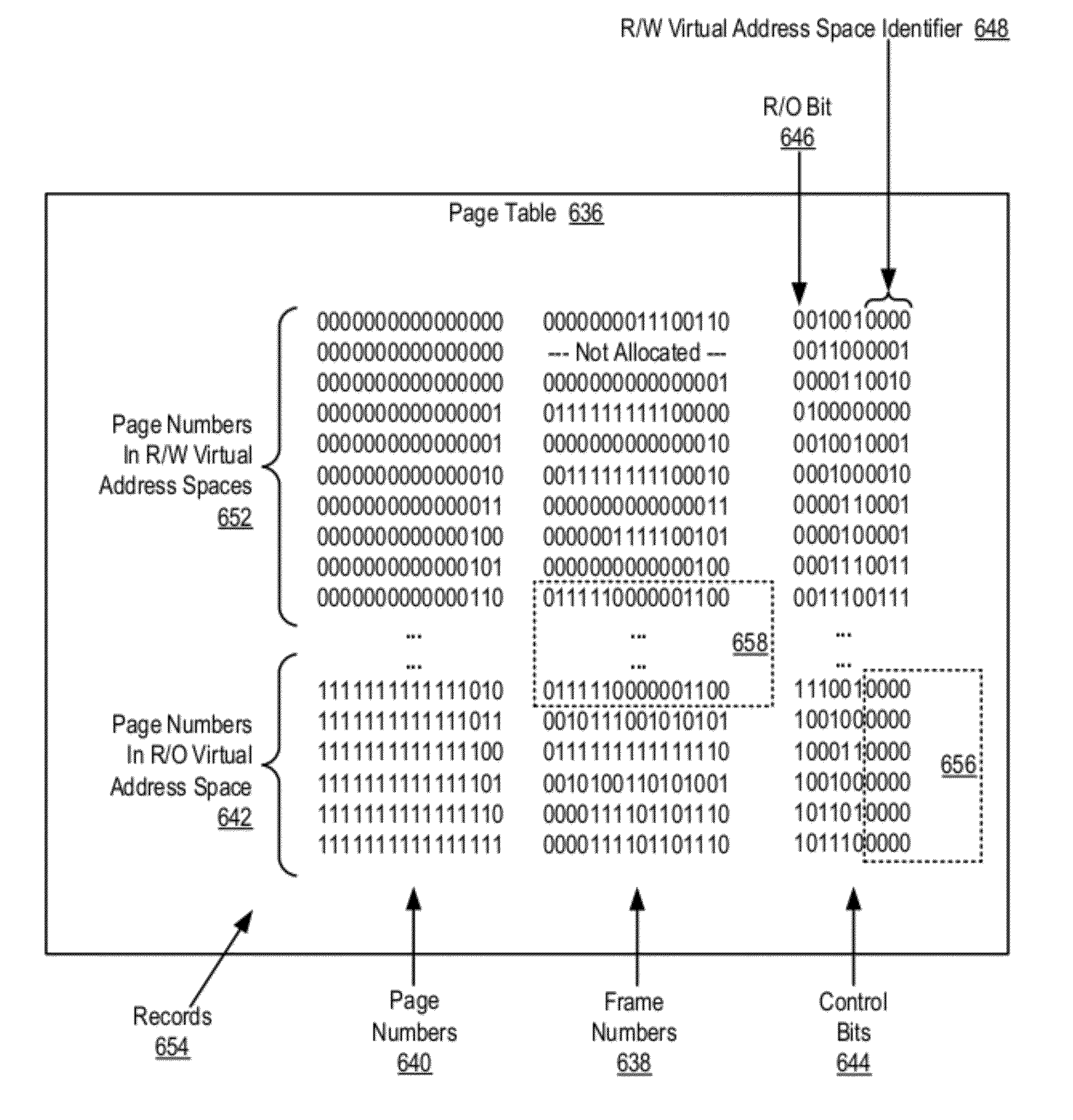
InactiveUS20120210094A1Memory adressing/allocation/relocationDigital computer detailsVirtual memoryMemory address
Eager send data communications in a parallel active messaging interface (PAMI) of a parallel computer, the PAMI composed of data communications endpoints that specify a client, a context, and a task, including receiving an eager send data communications instruction with transfer data disposed in a send buffer characterized by a read / write send buffer memory address in a read / write virtual address space of the origin endpoint; determining for the send buffer a read-only send buffer memory address in a read-only virtual address space, the read-only virtual address space shared by both the origin endpoint and the target endpoint, with all frames of physical memory mapped to pages of virtual memory in the read-only virtual address space; and communicating by the origin endpoint to the target endpoint an eager send message header that includes the read-only send buffer memory address.
Owner:IBM CORP
Fencing Data Transfers In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120117211A1Multiple digital computer combinationsProgram controlCommunication endpointParallel computing
Fencing data transfers in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI including data communications endpoints, each endpoint comprising a specification of data communications parameters for a thread of execution on a compute node, including specifications of a client, a context, and a task, the compute nodes coupled for data communications through the PAMI and through data communications resources including a deterministic data communications network, including initiating execution through the PAMI of an ordered sequence of active SEND instructions for SEND data transfers between two endpoints, effecting deterministic SEND data transfers; and executing through the PAMI, with no FENCE accounting for SEND data transfers, an active FENCE instruction, the FENCE instruction completing execution only after completion of all SEND instructions initiated prior to execution of the FENCE instruction for SEND data transfers between the two endpoints.
Owner:IBM CORP
Telephony extension attack detection, recording, and intelligent prevention
ActiveUS7653188B2Avoid attackData taking preventionAutomatic exchangesCommunication endpointRemedial action
A system and method are provided for detecting extension attacks made to a communication enterprise, and taking appropriate remedial action to prevent ongoing attacks and future attacks. One or more attributes of a suspect call are analyzed, and a risk is associated with each analyzed attribute. An overall risk or assessment is then made of the analyzed attributes, attack attributes are logged, and one or more remedial actions may be triggered as a result of the analyzed call attributes. The remedial actions may include recording the call, notifying an administrator of a suspect call, or isolating the communication enterprise from the attack by terminating the call or shutting down selected communication endpoints to prevent calls being made to those extensions. Rules may be applied to the analyzed attributes in order to trigger the appropriate remedial action. The call attributes analyzed may include call destination, call direction, call type, time of day of the call, call duration, whether a call source is spoofed, call volume from a particular call source, and hash values created for a suspect media stream.
Owner:AVAYA INC
Data Communications In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120137294A1Multiprogramming arrangementsMemory systemsCommunication endpointParallel computing
Data communications in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI composed of data communications endpoints, each endpoint including a specification of data communications parameters for a thread of execution on a compute node, including specifications of a client, a context, and a task, endpoints coupled for data communications through the PAMI and through data communications resources, including receiving in an origin endpoint of the PAMI a SEND instruction, the SEND instruction specifying a transmission of transfer data from the origin endpoint to a first target endpoint; transmitting from the origin endpoint to the first target endpoint a Request-To-Send (‘RTS’) message advising the first target endpoint of the location and size of the transfer data; assigning by the first target endpoint to each of a plurality of target endpoints separate portions of the transfer data; and receiving by the plurality of target endpoints the transfer data.
Owner:IBM CORP
Socket-like communication API for Java
ActiveUS20060129981A1Multiprogramming arrangementsSpecific program execution arrangementsCommunication endpointApplication programming interface
A system and method are described for performing data processing using shared memory and socket-like application programming interface. In one embodiment, a plurality of handles is employed and associated with a plurality of processes. The plurality of handles may serve as communication end-points for communication of data. Further, an application programming interface is employed to present the plurality of handles as the application programming interface for sockets for facilitating the communication of data compatible with a programming language. The data is communicated between the plurality of processes via the socket-like plurality of handles.
Owner:SAP AG
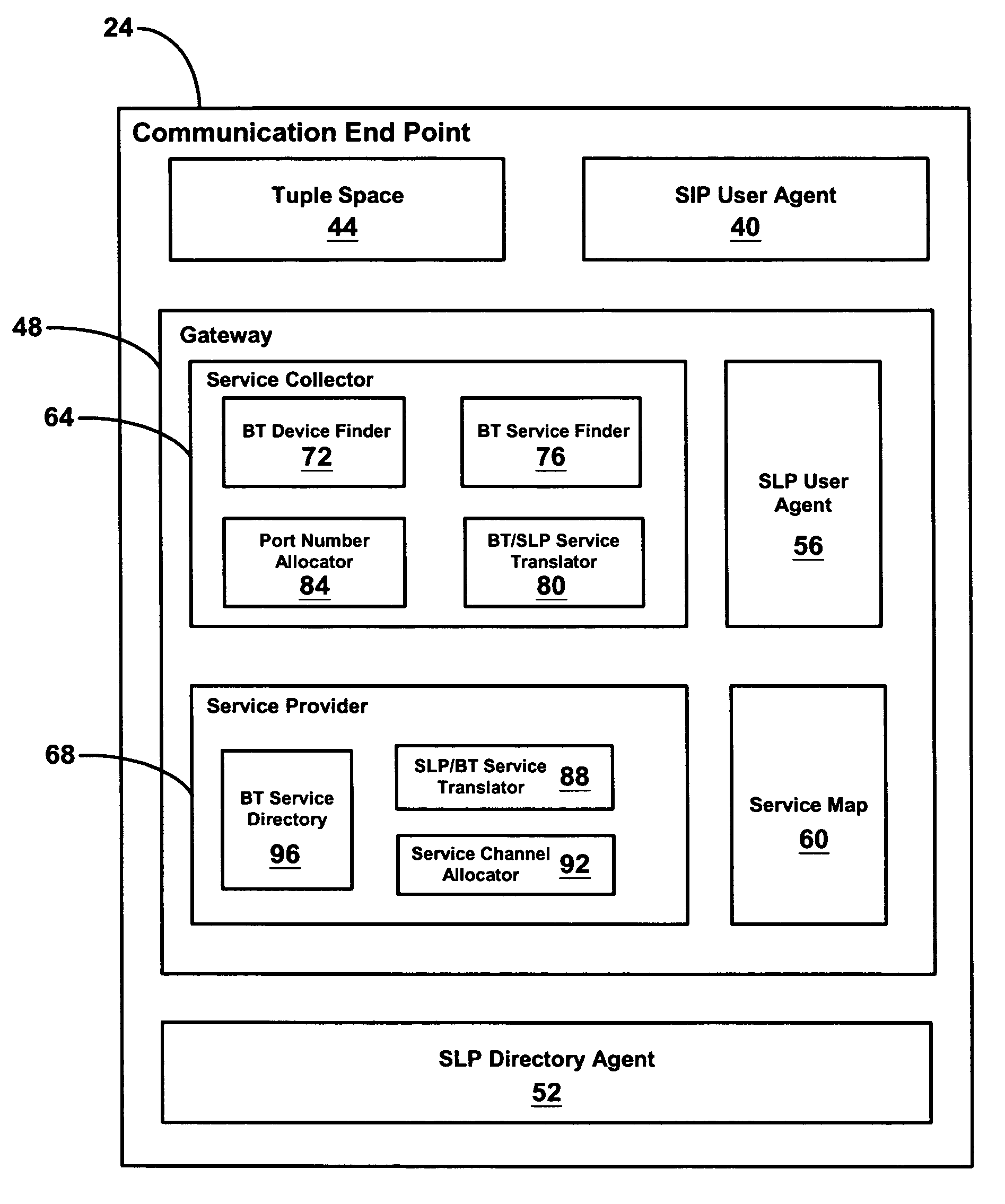
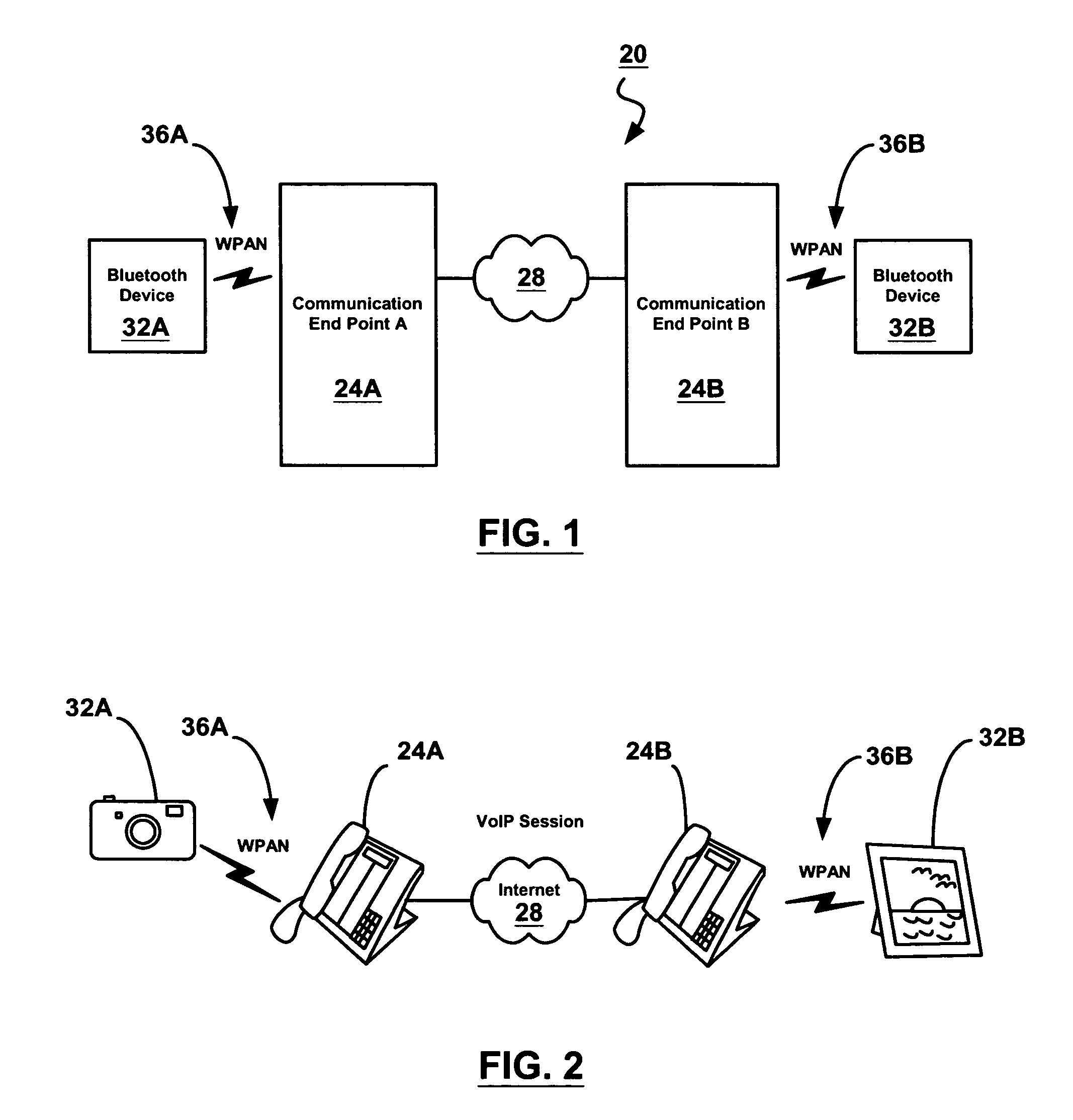
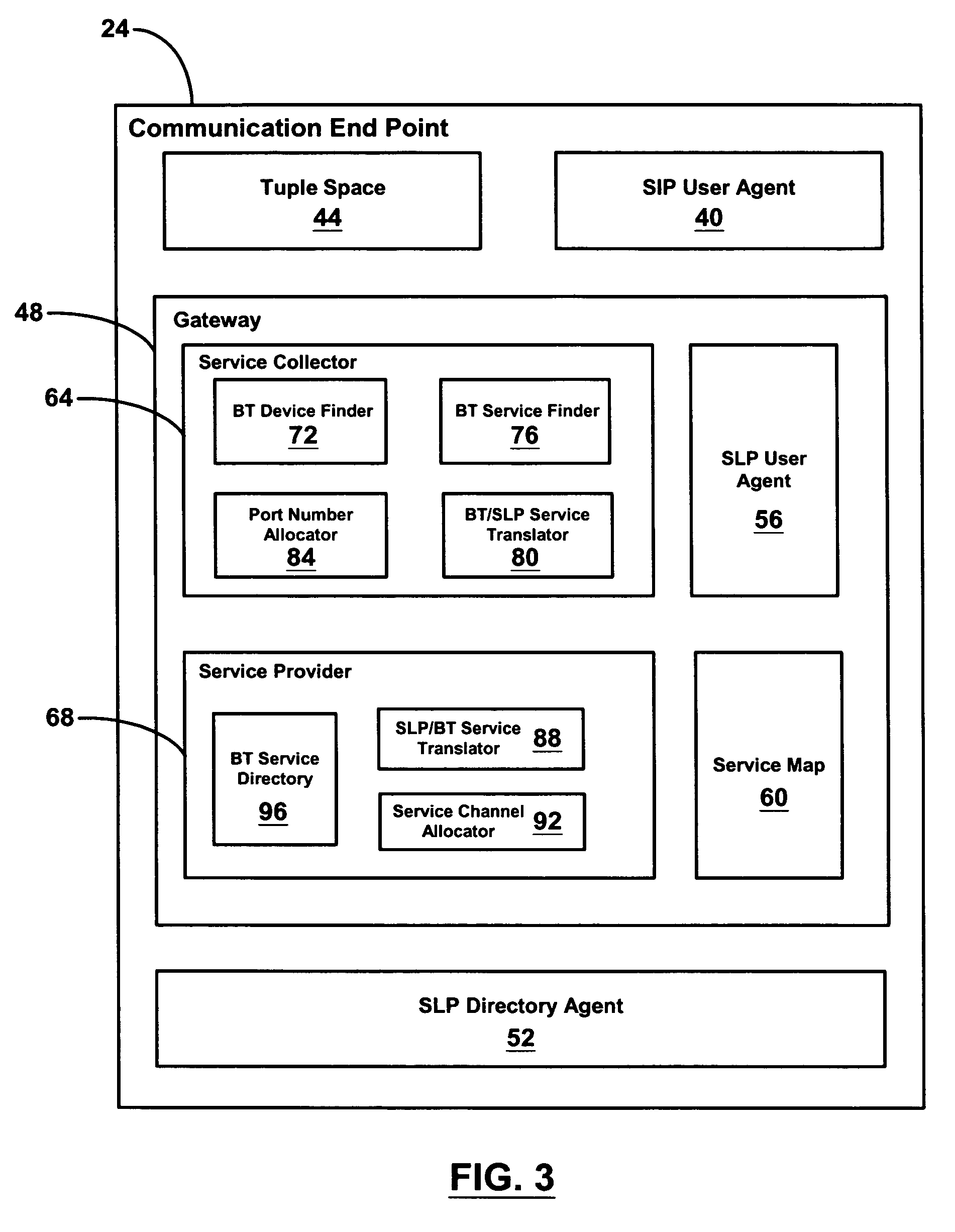
Spontaneous discovery of remote service profiles
A system for providing spontaneous discovery of remote service profiles is provided. A Bluetooth-enabled communication end point registers the service profiles available on Bluetooth devices in communication with the end point over a personal area network. The end point then translates the service profiles to a format supported over a second network and transmits them to other end points. The other end point then registers the service profiles and translates them to a format understood by Bluetooth devices. Bluetooth devices local to the second end point can then communicate with the remote Bluetooth devices via the translated service profiles.
Owner:MITEL
Endpoint-Based Parallel Data Processing With Non-Blocking Collective Instructions In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120185679A1Interprogram communicationDigital computer detailsCommunication endpointConcurrent computation
Endpoint-based parallel data processing with non-blocking collective instructions in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI composed of data communications endpoints, each endpoint including a specification of data communications parameters for a thread of execution on a compute node, including specifications of a client, a context, and a task, the compute nodes coupled for data communications through the PAMI, including establishing by the parallel application a data communications geometry, the geometry specifying a set of endpoints that are used in collective operations of the PAMI, including associating with the geometry a list of collective algorithms valid for use with the endpoints of the geometry; registering in each endpoint in the geometry a dispatch callback function for a collective operation; and executing without blocking, through a single one of the endpoints in the geometry, an instruction for the collective operation.
Owner:IBM CORP
Endpoint-Based Parallel Data Processing In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120254344A1Multiple digital computer combinationsProgram controlCommunication endpointApplication software
Endpoint-based parallel data processing in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI composed of data communications endpoints, each endpoint including a specification of data communications parameters for a thread of execution on a compute node, including specifications of a client, a context, and a task, the compute nodes coupled for data communications through the PAMI, including establishing a data communications geometry, the geometry specifying, for tasks representing processes of execution of the parallel application, a set of endpoints that are used in collective operations of the PAMI including a plurality of endpoints for one of the tasks; receiving in endpoints of the geometry an instruction for a collective operation; and executing the instruction for a collective operation through the endpoints in dependence upon the geometry, including dividing data communications operations among the plurality of endpoints for one of the tasks.
Owner:IBM CORP
Multi-media communication system having programmable speed dial control indicia
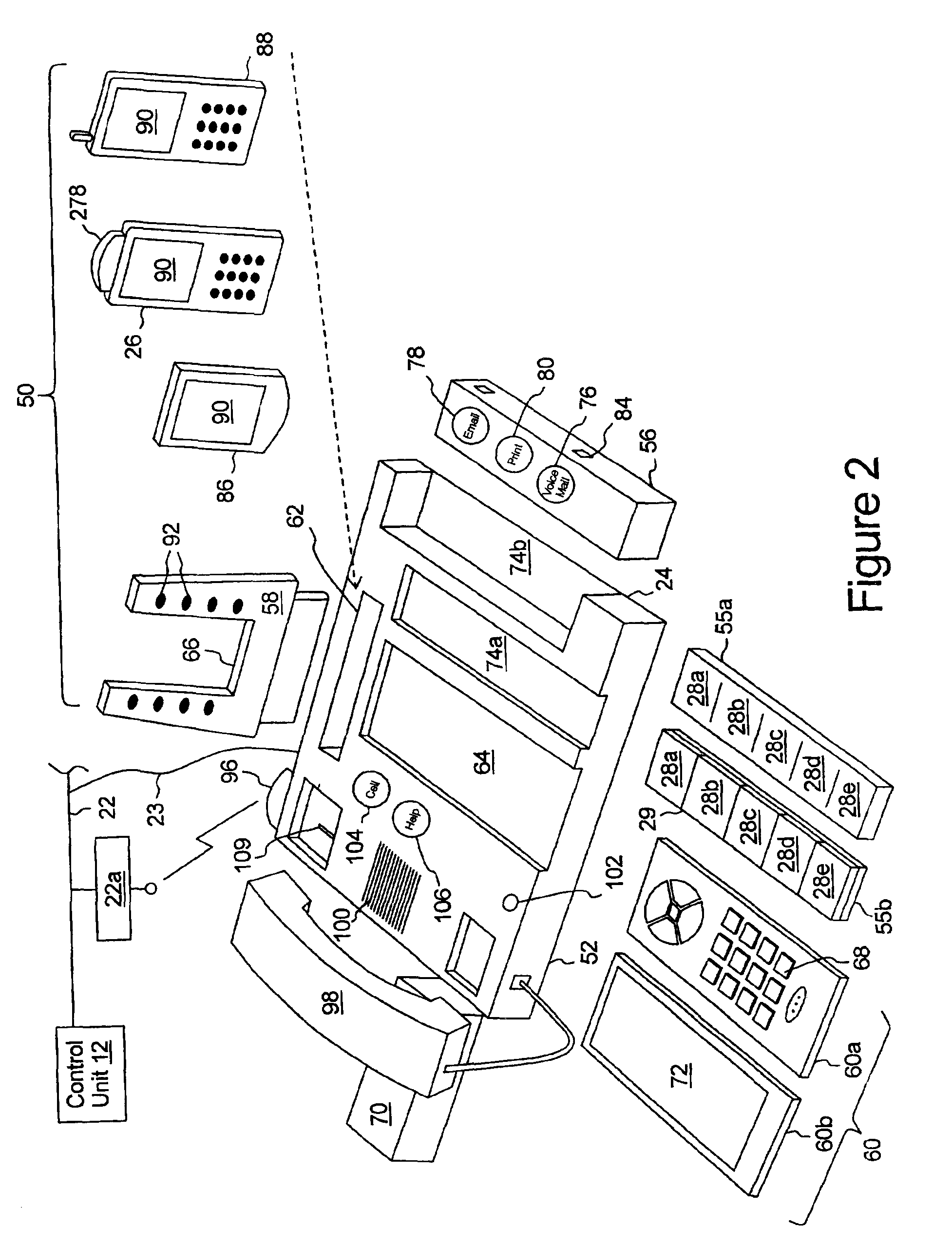
InactiveUS6970556B2Easy to startSpecial service provision for substationSpecial service for subscribersCommunication endpointDisplay device
The present multi-media subscriber station has control unit and a plurality of communication devices. Each communication device includes speed dial controls which, when activated but a user, provide for establishing a communication session to a communication end point associated with the speed dial control. Each speed dial control is associated with a programmable image display on which an image associated with the communication end point may be displayed.
Owner:TELEWARE
Data Communications For A Collective Operation In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120144401A1Interprogram communicationDigital computer detailsCommunication endpointClient-side
Algorithm selection for data communications in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI composed of data communications endpoints, each endpoint including specifications of a client, a context, and a task, endpoints coupled for data communications through the PAMI, including associating in the PAMI data communications algorithms and bit masks; receiving in an origin endpoint of the PAMI a collective instruction, the instruction specifying transmission of a data communications message from the origin endpoint to a target endpoint; constructing a bit mask for the received collective instruction; selecting, from among the associated algorithms and bit masks, a data communications algorithm in dependence upon the constructed bit mask; and executing the collective instruction, transmitting, according to the selected data communications algorithm from the origin endpoint to the target endpoint, the data communications message.
Owner:IBM CORP
Processing Data Communications Events In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120117361A1Decreasing message latencyPowerful processorProgram synchronisationInterprogram communicationCommunication endpointParallel computing
Processing data communications events in a parallel active messaging interface (‘PAMI’) of a parallel computer that includes compute nodes that execute a parallel application, with the PAMI including data communications endpoints, and the endpoints are coupled for data communications through the PAMI and through other data communications resources, including determining by an advance function that there are no actionable data communications events pending for its context, placing by the advance function its thread of execution into a wait state, waiting for a subsequent data communications event for the context; responsive to occurrence of a subsequent data communications event for the context, awakening by the thread from the wait state; and processing by the advance function the subsequent data communications event now pending for the context.
Owner:IBM CORP
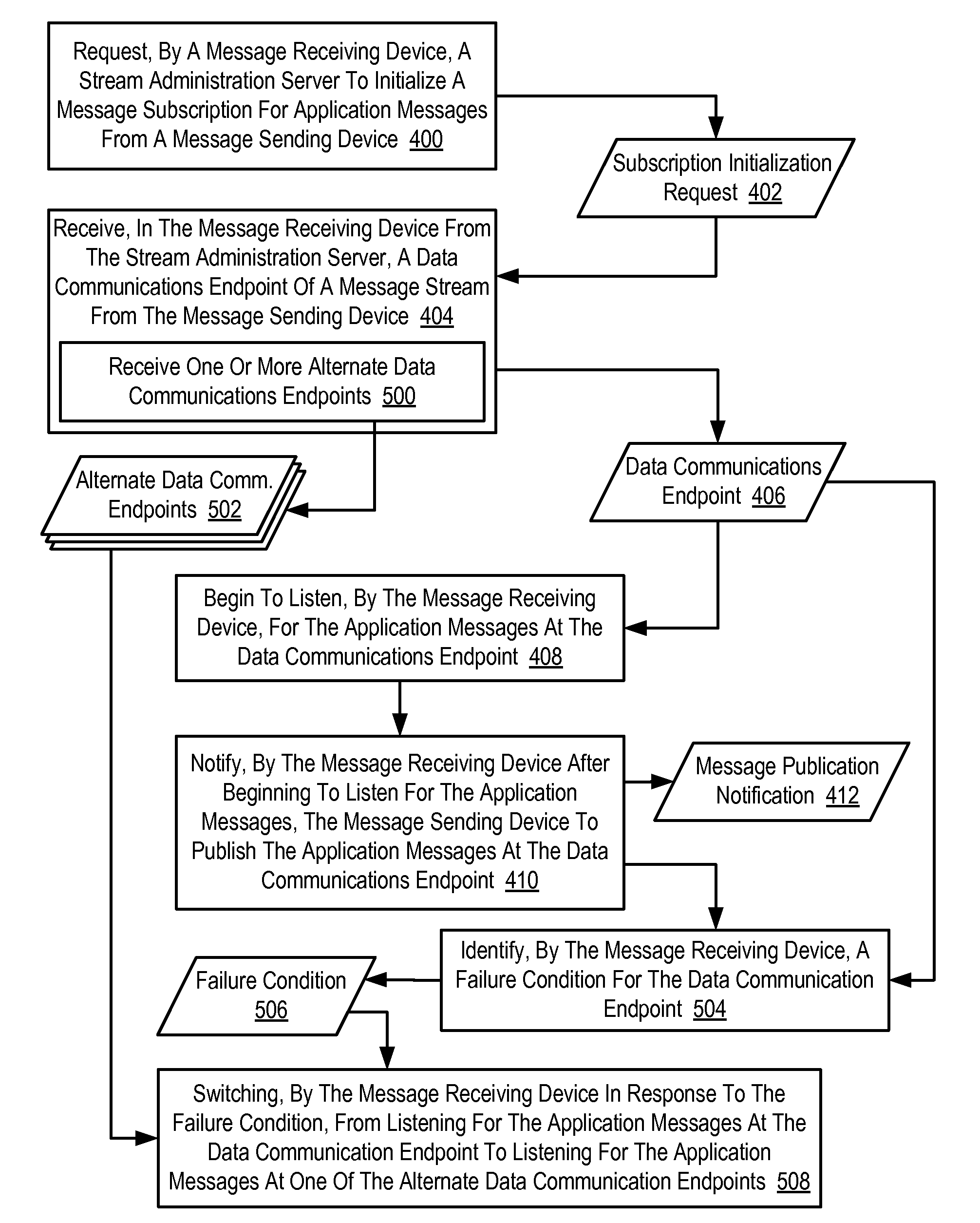
Subscribing For Application Messages In A Multicast Messaging Environment
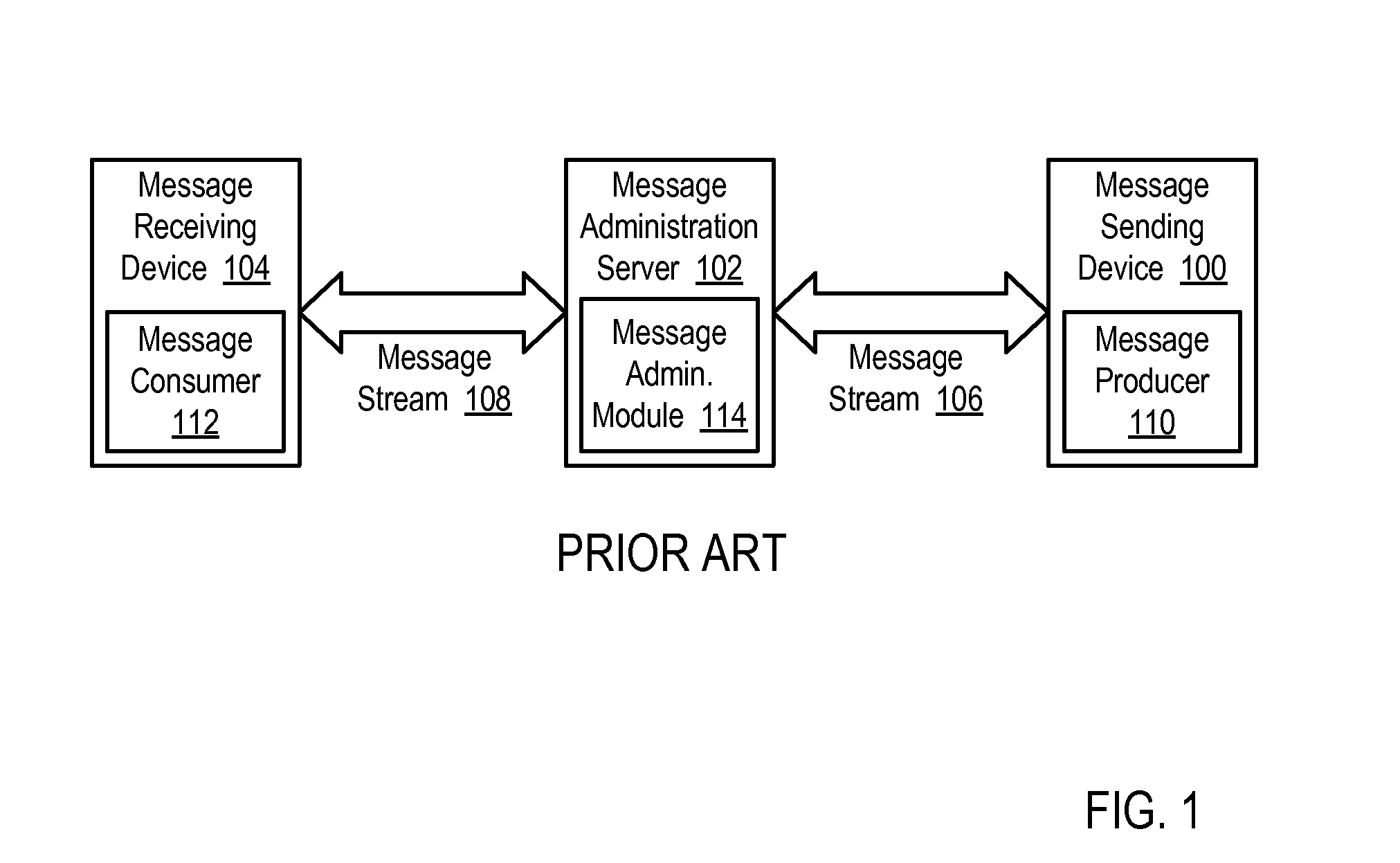
Methods, systems, and products for subscribing for application messages in a multicast messaging environment as disclosed that include: requesting, by a message receiving device, a stream administration server to initialize a message subscription for application messages from a message sending device; receiving, in the message receiving device from the stream administration server, a data communications endpoint of a multicast message stream from the message sending device; beginning to listen, by the message receiving device, for the application messages at the data communications endpoint; and notifying, by the message receiving device after beginning to listen for the application messages, the message sending device to publish the application messages at the data communications endpoint.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com