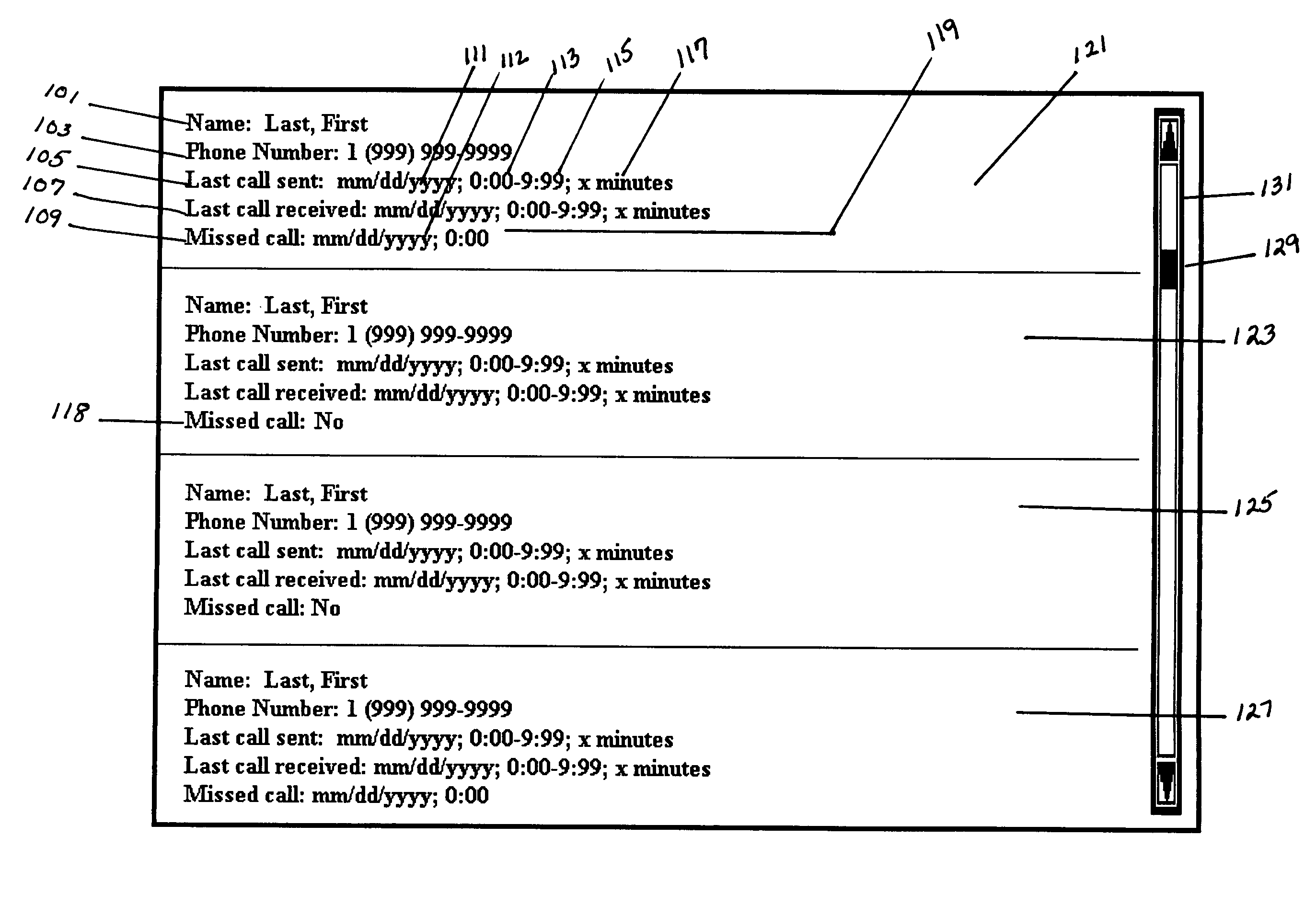
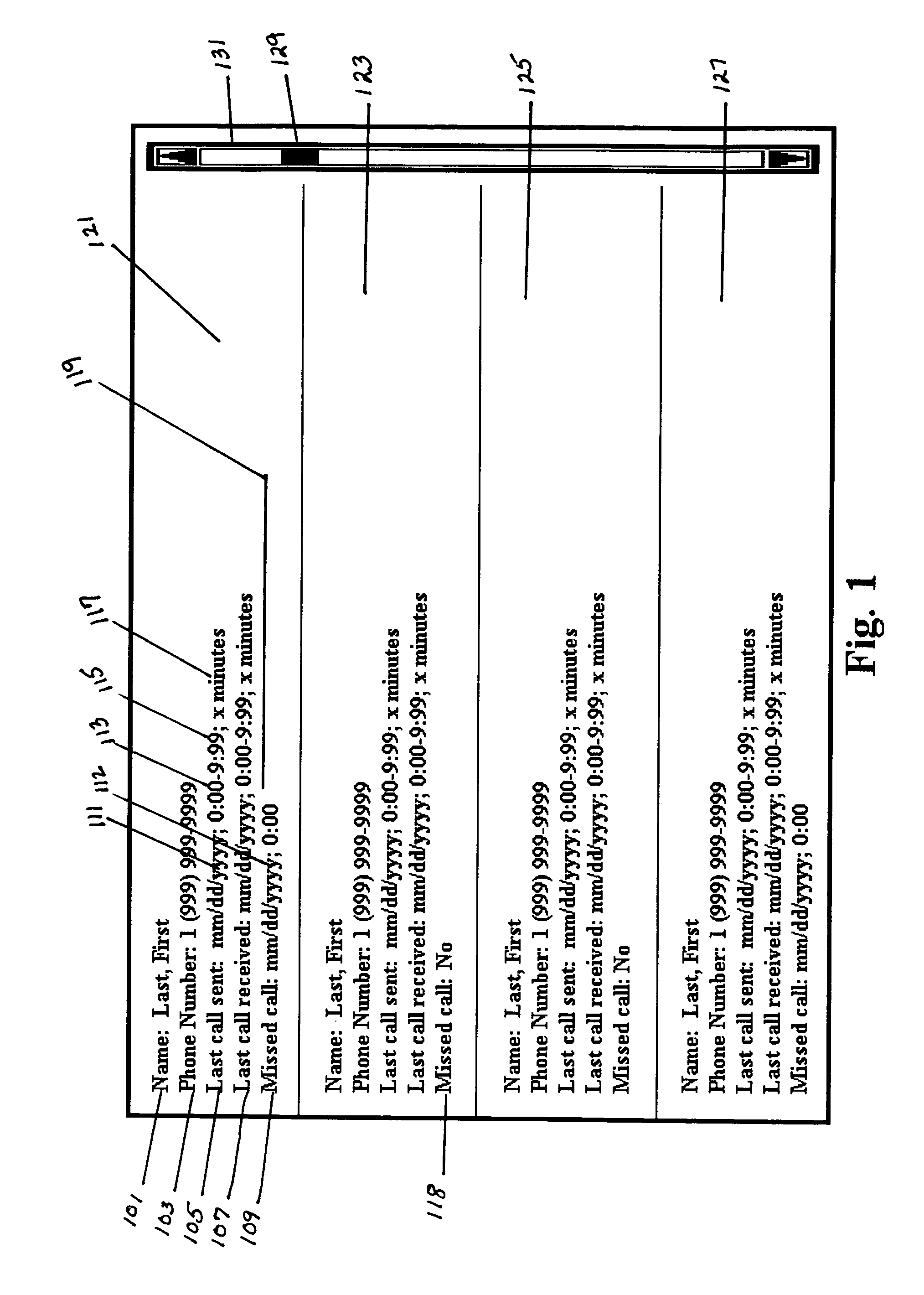
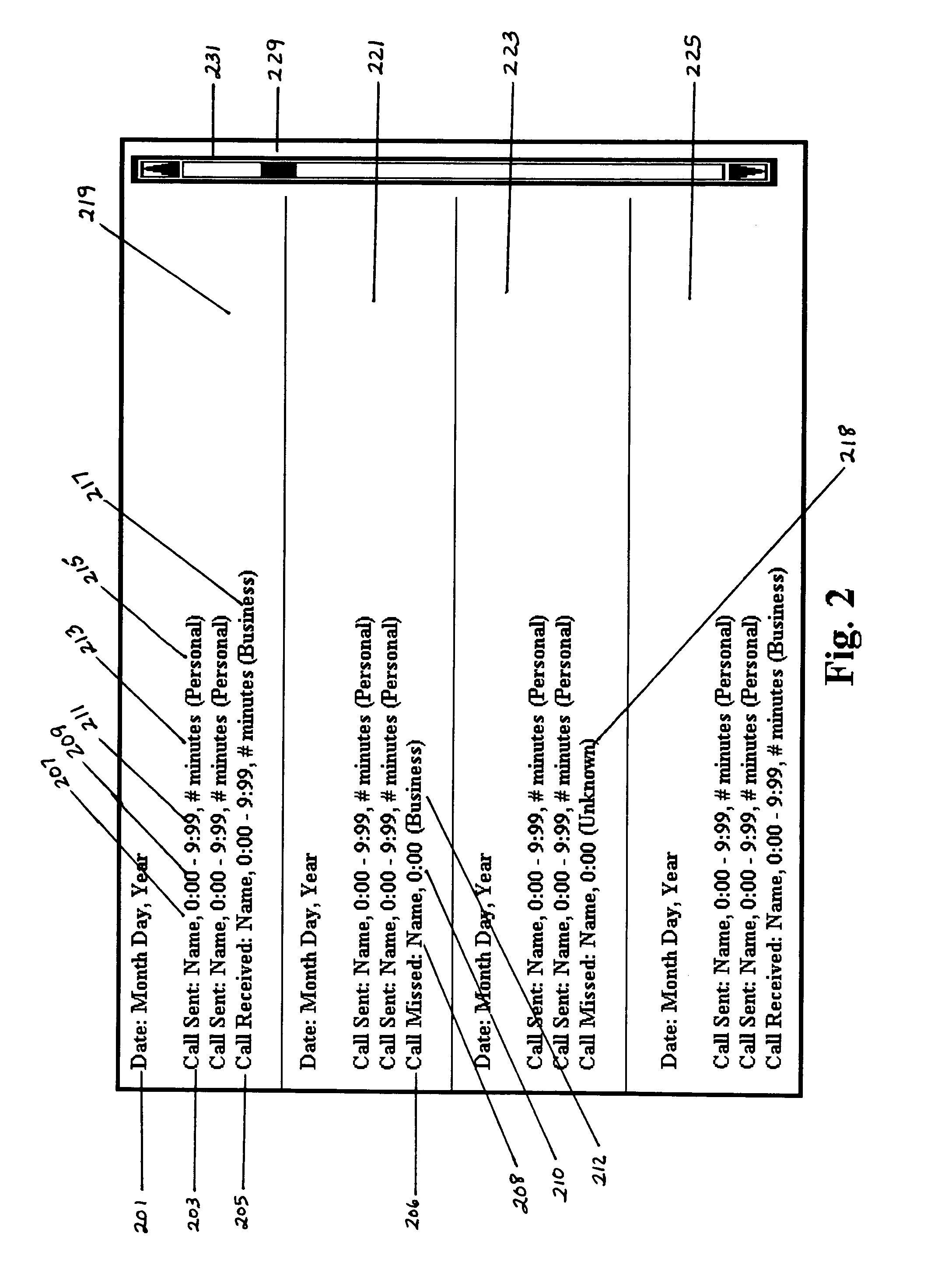
Patents
Literature
331 results about "Call duration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In telecommunications, the term call duration has the following meanings: In telephone systems, the time between the instant a circuit, i.e., off-hook condition at each end, is established between the call originator and the call receiver and the instant the call originator or the call receiver terminates the call. In data transmission, the duration of the information transfer phase of an information transfer transaction. Source: from Federal Standard 1037C
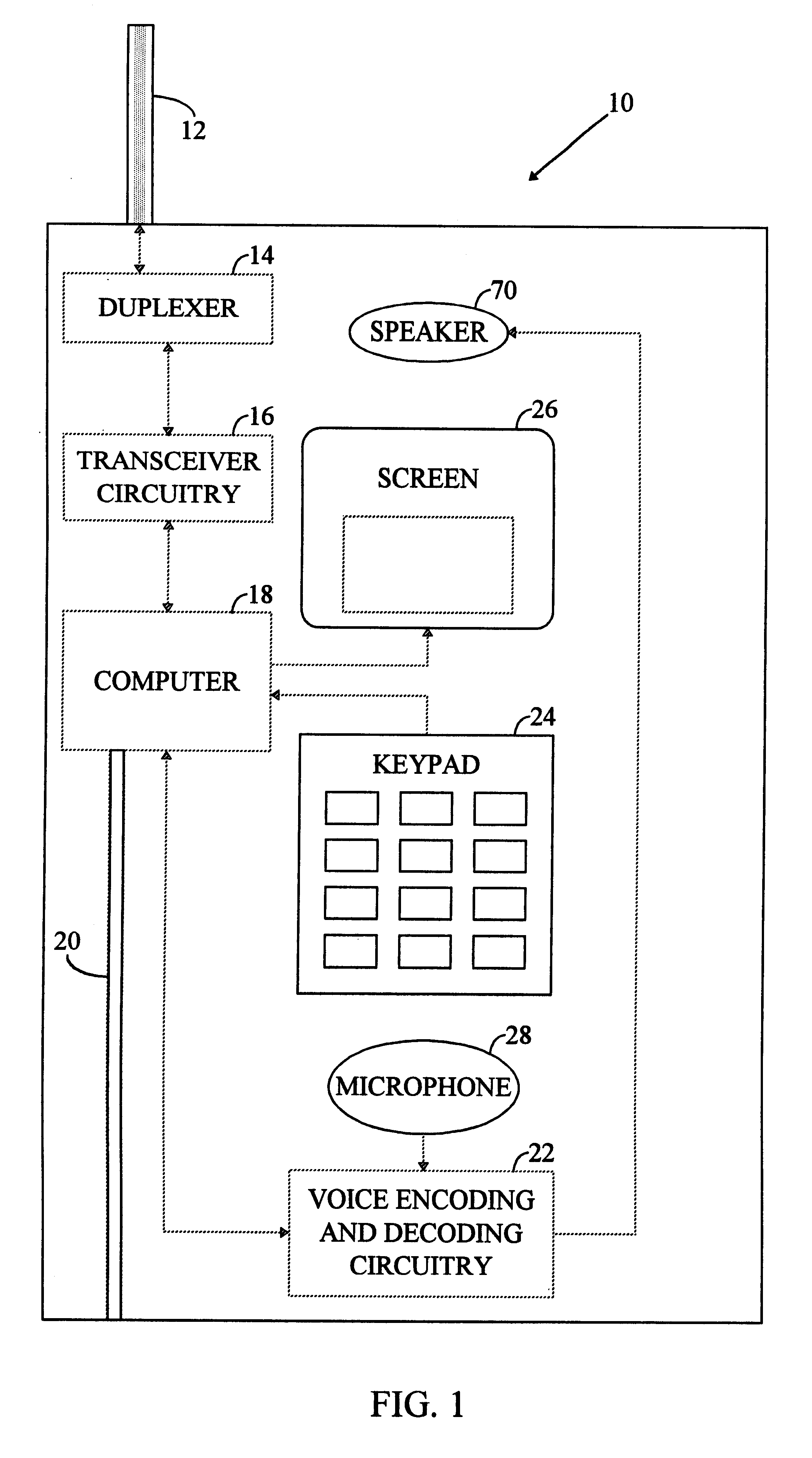
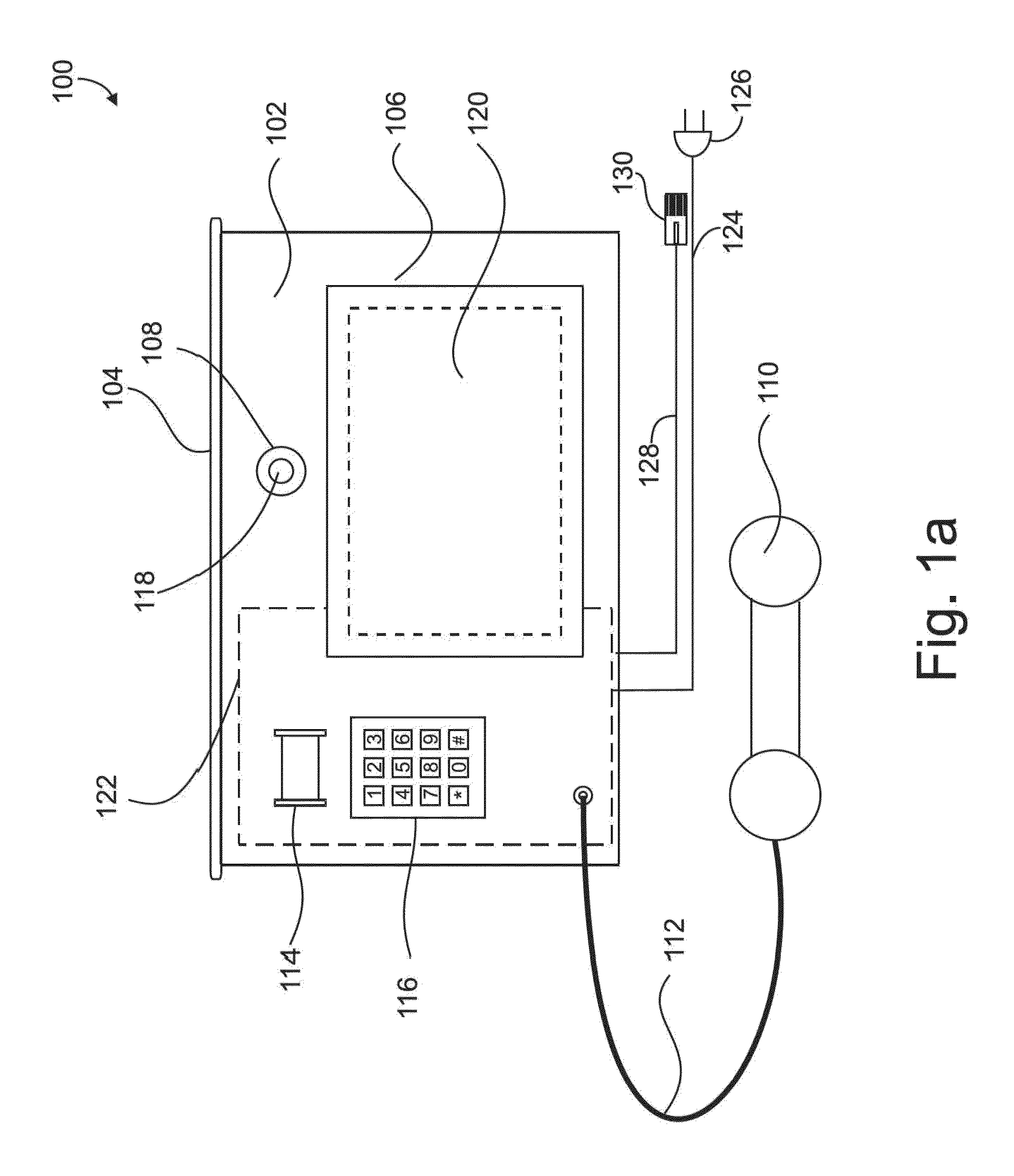
Method of and apparatus for communicating user related information using a wireless information device
InactiveUS7248677B2Special service for subscribersCalling susbscriber number recording/indicationTime scheduleRelevant information
A mobile telephone which can supply or post ‘pre-answer’ information which the device owner considers of relevance to a potential call recipient. This information enables a potential call recipient to be given useful information about a potential call before actually answering that call. The information is dynamic, unlike Caller ID information. Examples include: information about the subject of an intended voice call, a mood, a current activity, part or whole of a schedule of meetings or events, information about the urgency of an intended voice call, personal information, expected call duration, commercial inducements to a consumer to answer a call (special offers, loyalty points etc.), location information.
Owner:NOKIA TECHNOLOGLES OY
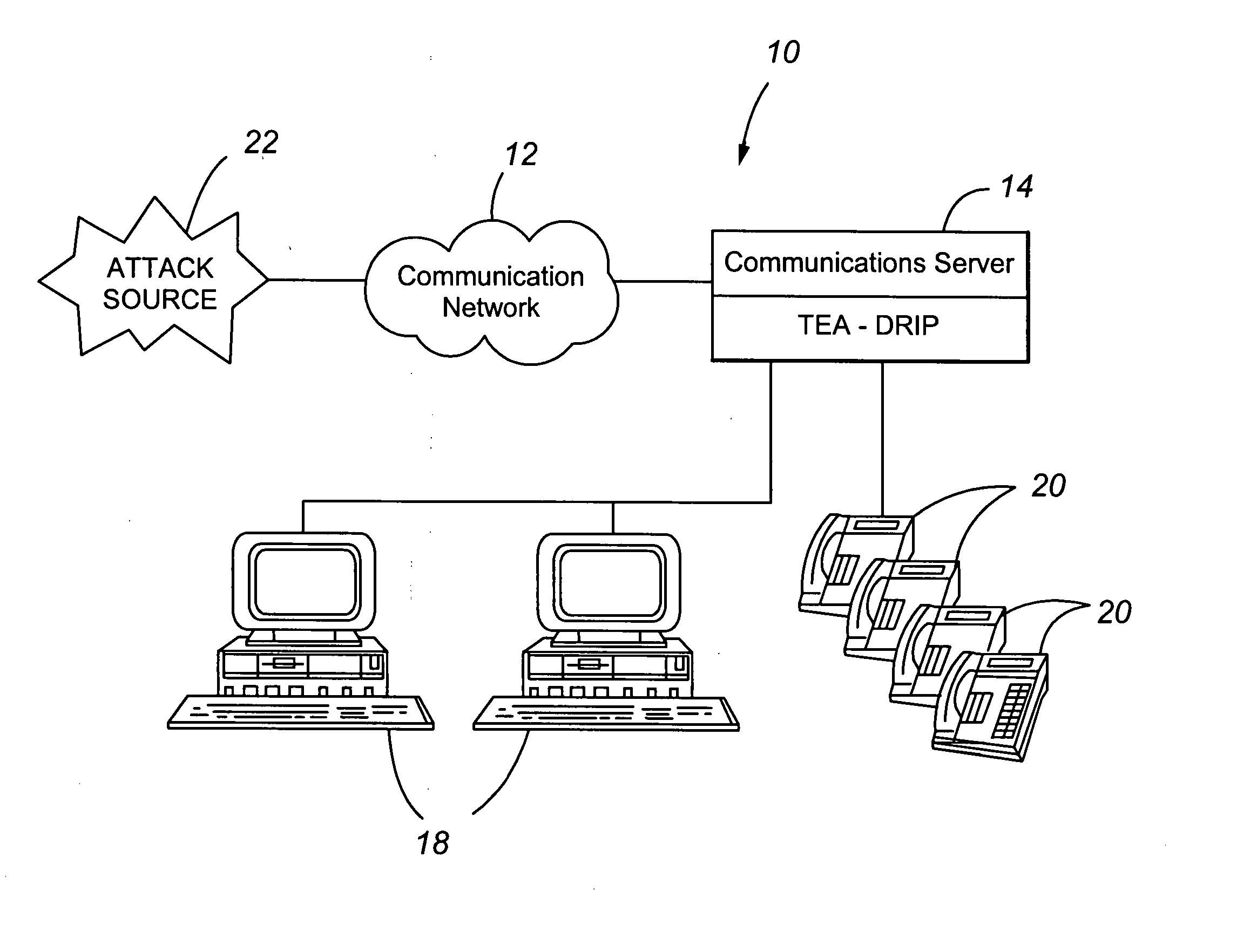
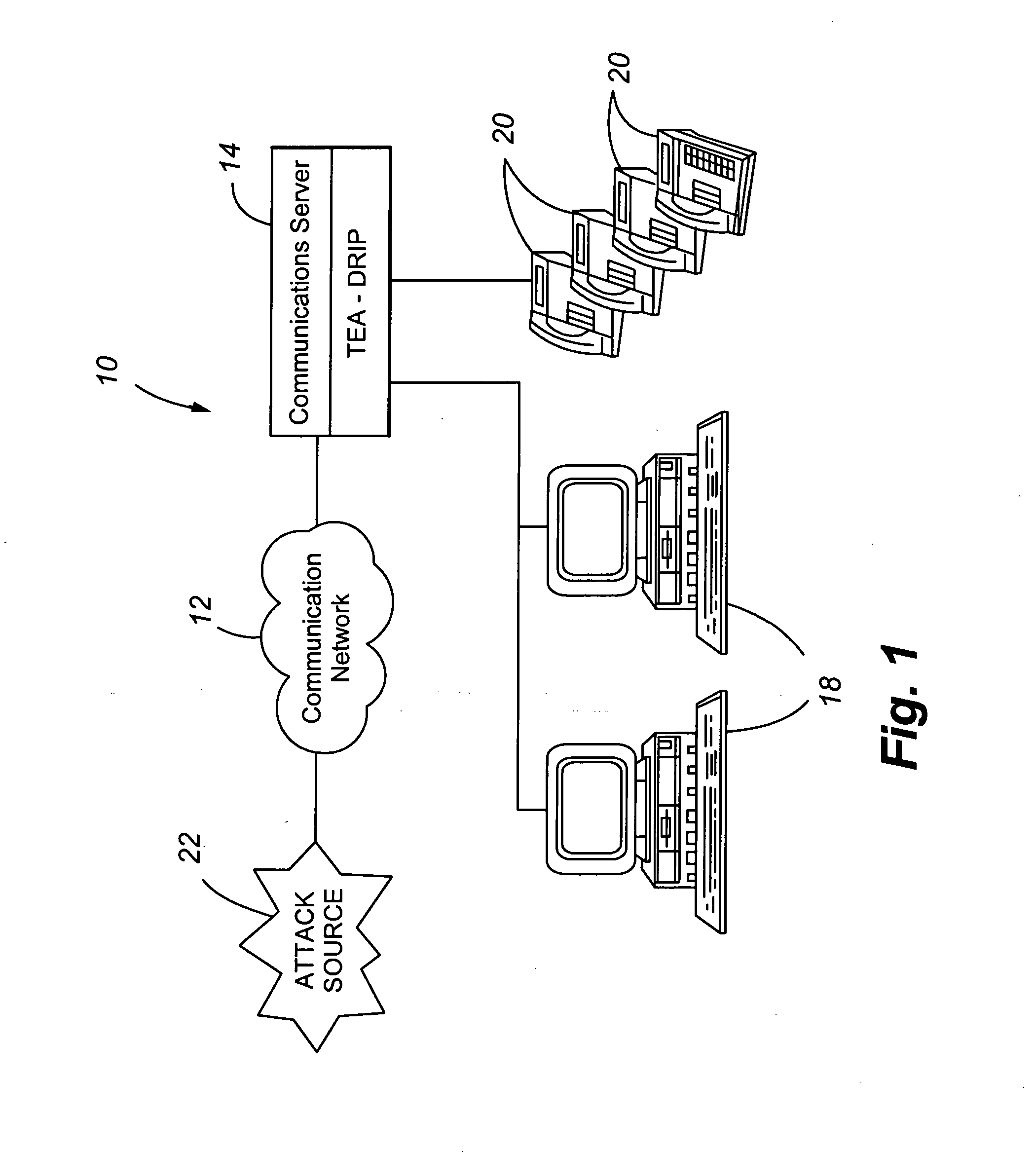
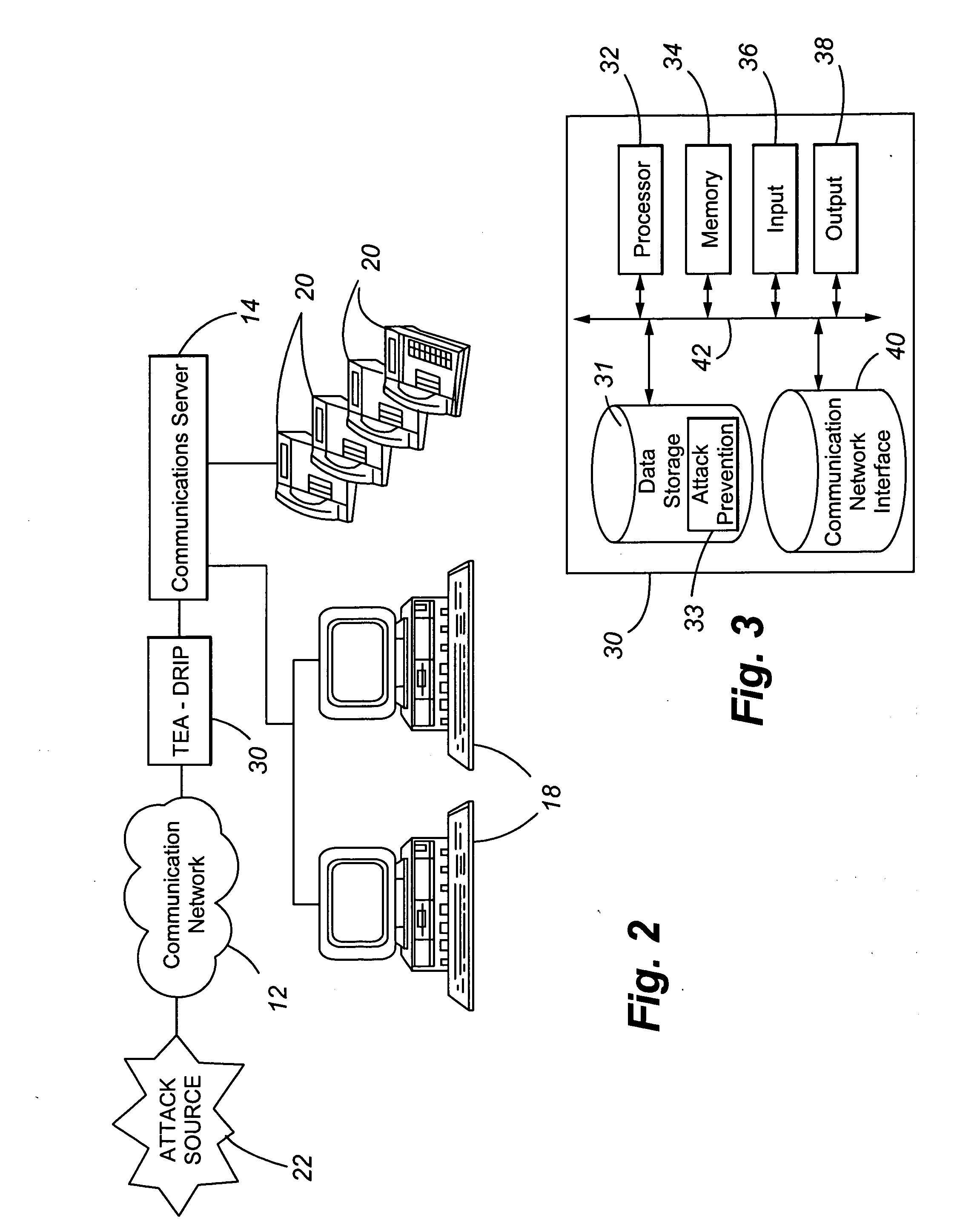
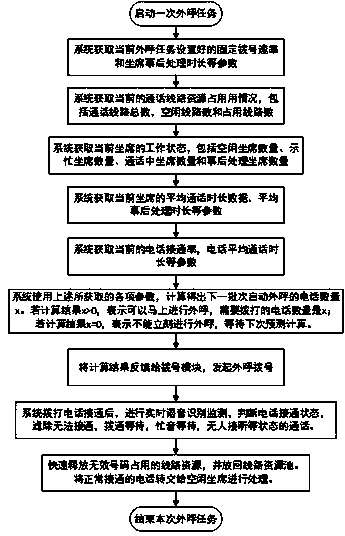
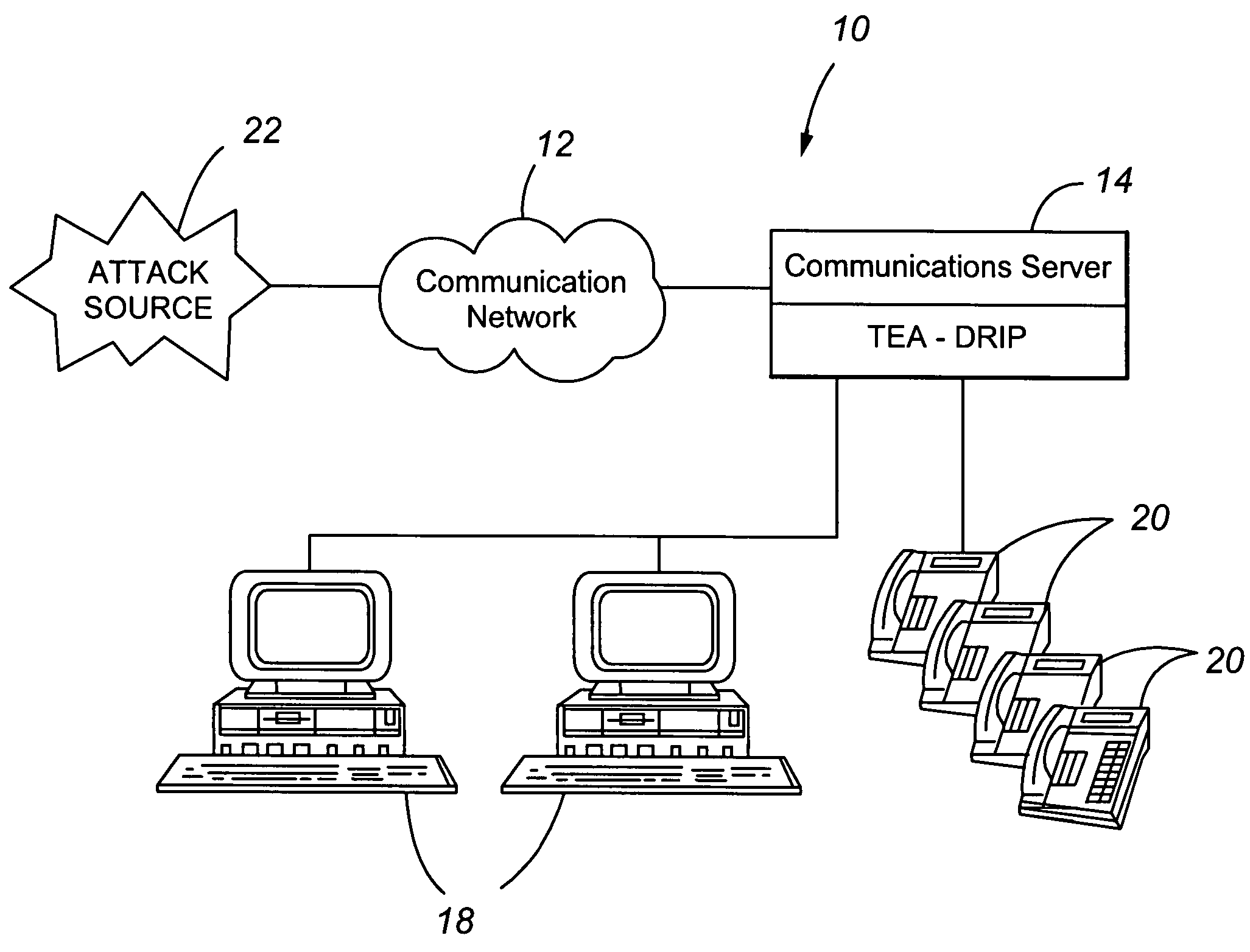
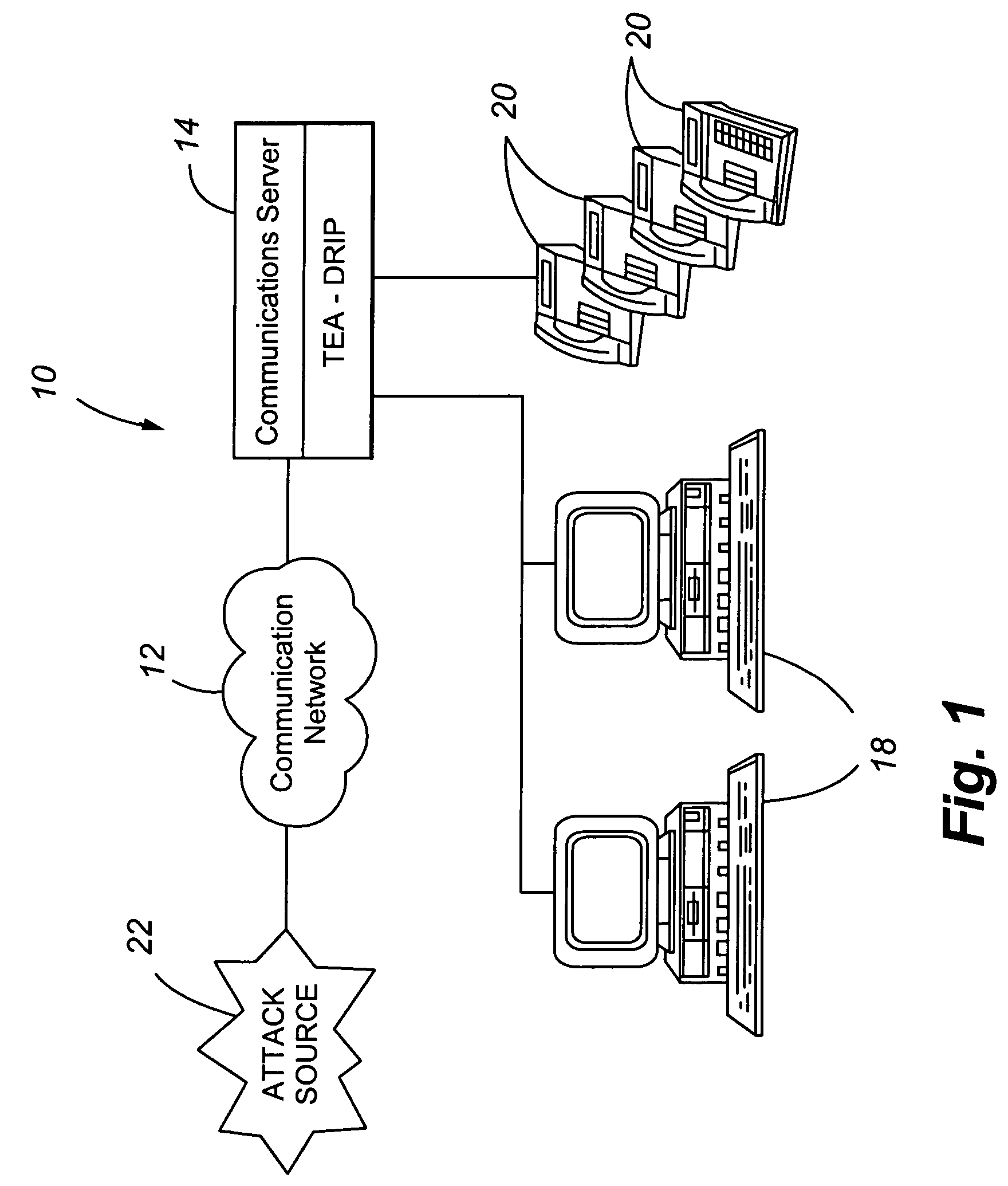
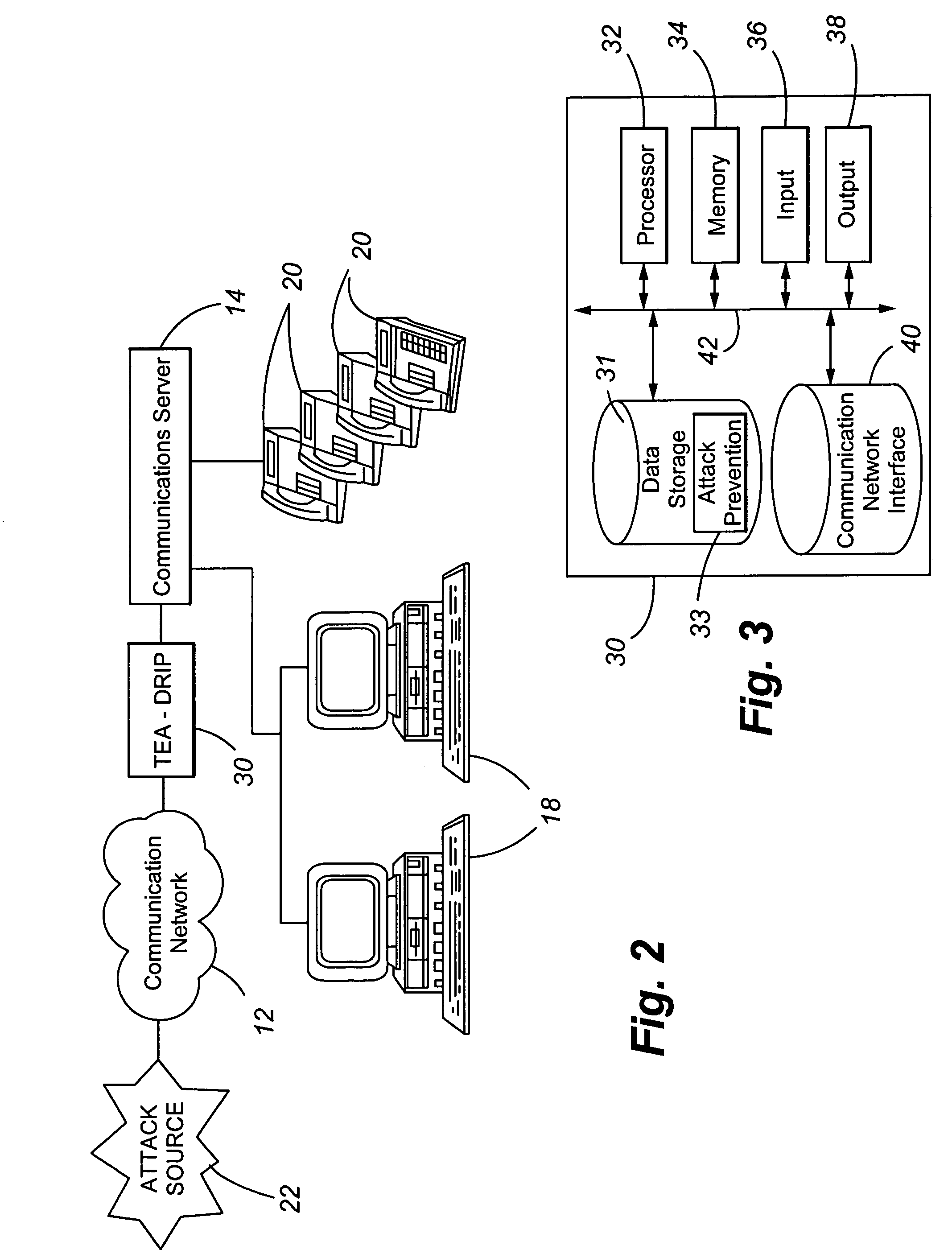
Telephony extension attack detection, recording, and intelligent prevention
ActiveUS20070036314A1Effectively prevent future attackAvoid attackData taking preventionAutomatic exchangesCommunication endpointRemedial action
A system and method are provided for detecting extension attacks made to a communication enterprise, and taking appropriate remedial action to prevent ongoing attacks and future attacks. One or more attributes of a suspect call are analyzed, and a risk is associated with each analyzed attribute. An overall risk or assessment is then made of the analyzed attributes, attack attributes are logged, and one or more remedial actions may be triggered as a result of the analyzed call attributes. The remedial actions may include recording the call, notifying an administrator of a suspect call, or isolating the communication enterprise from the attack by terminating the call or shutting down selected communication endpoints to prevent calls being made to those extensions. Rules may be applied to the analyzed attributes in order to trigger the appropriate remedial action. The call attributes analyzed may include call destination, call direction, call type, time of day of the call, call duration, whether a call source is spoofed, call volume from a particular call source, and hash values created for a suspect media stream.
Owner:AVAYA INC
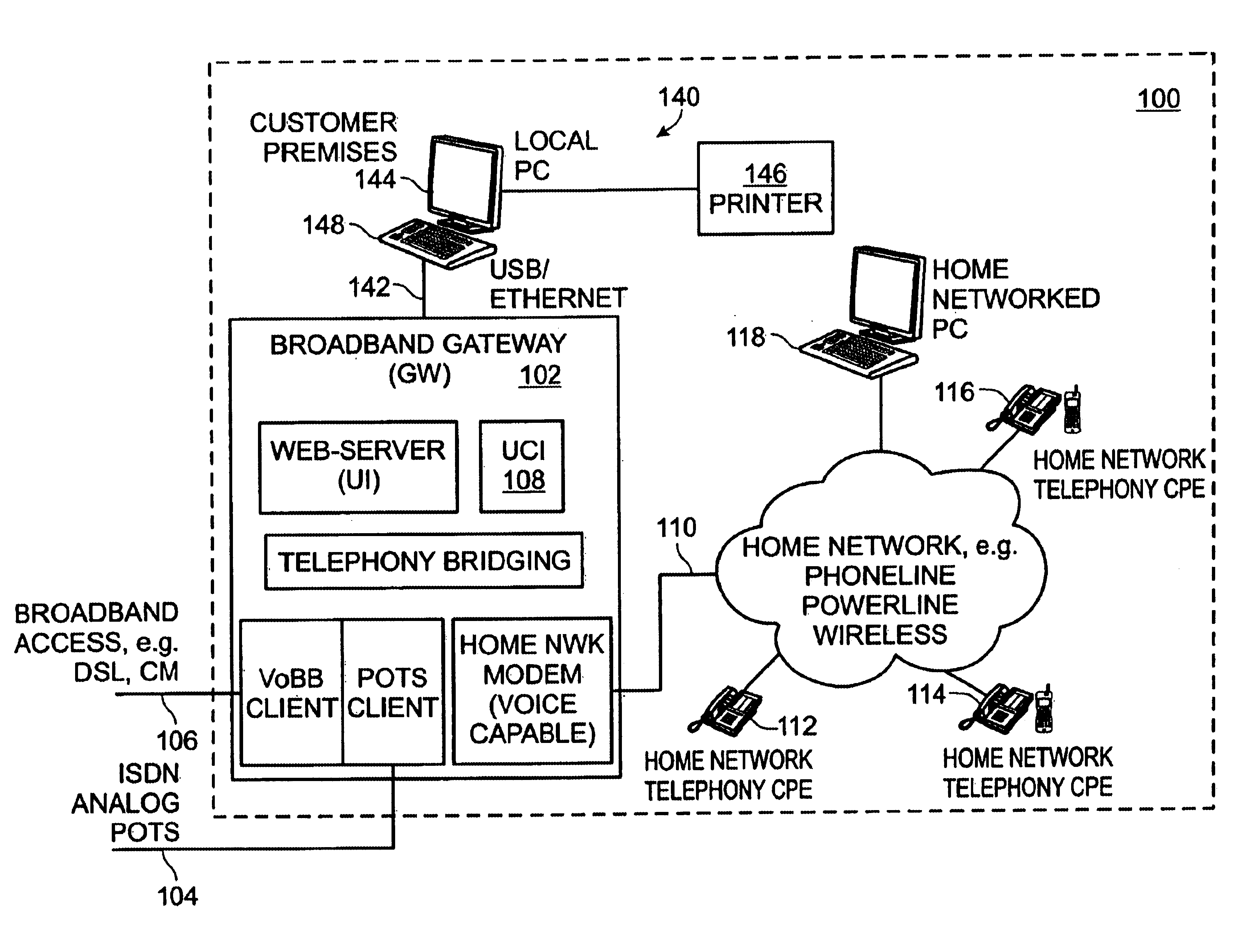
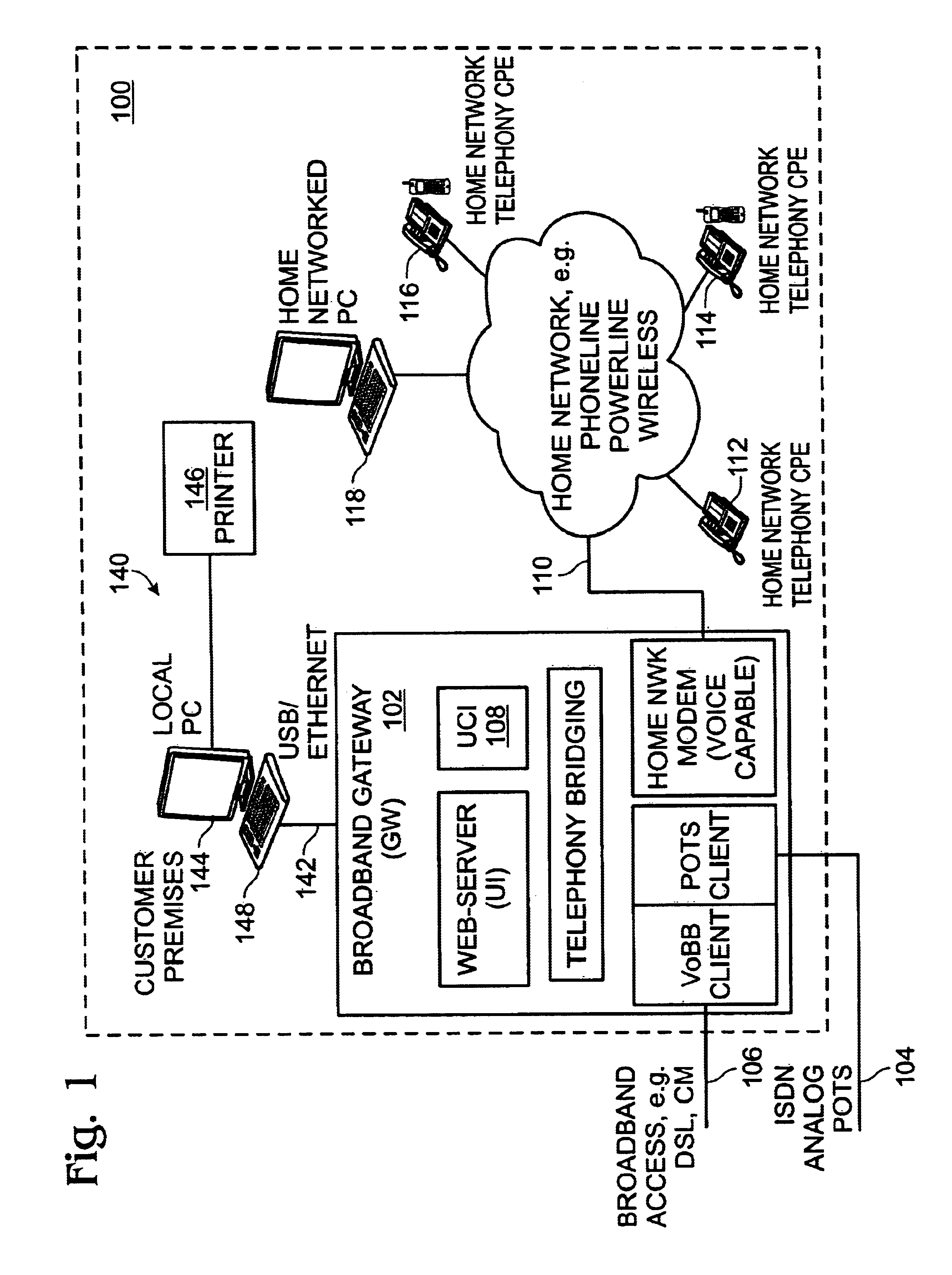
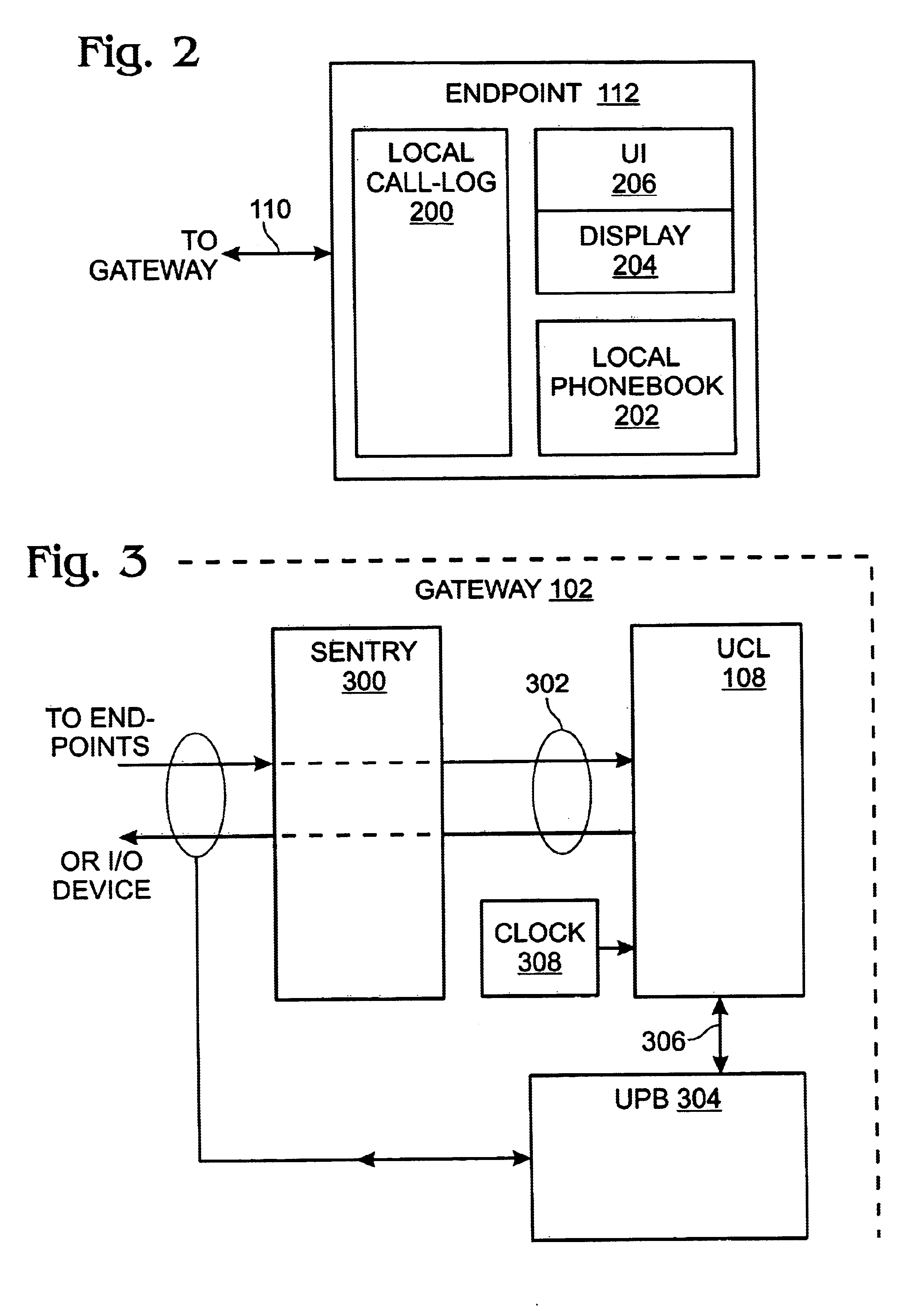
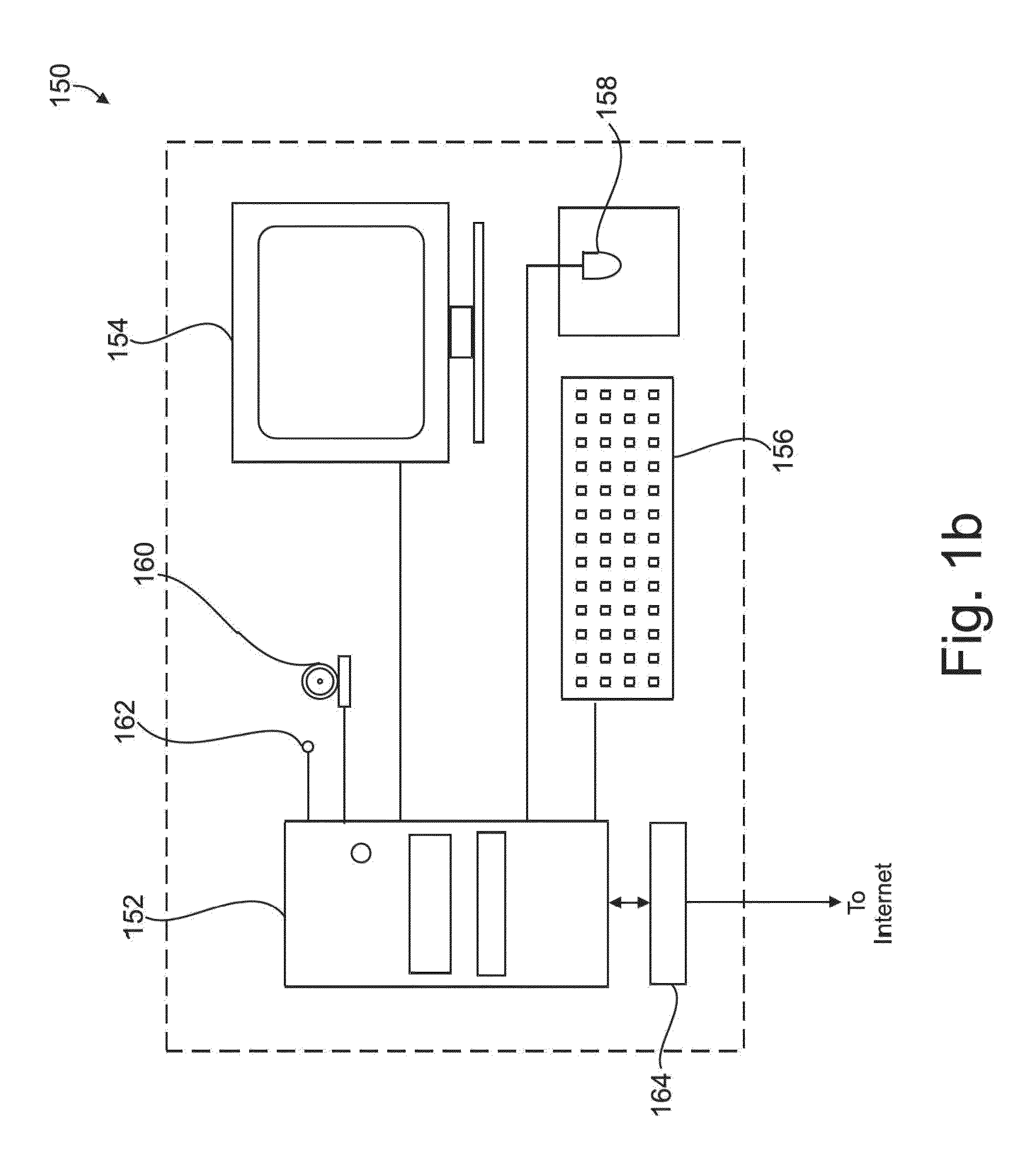
Universal call-log system and method for a home network telephone
InactiveUS6882714B2Easy accessCordless telephonesInterconnection arrangementsTelephone lineNetwork Endpoint
A system and method are provided for maintaining a universal call-log in a Home Network telephone system. The method comprises: transceiving calls on at least one external telephone line; bridging calls to a plurality Home Network endpoints; and, logging the bridged calls. Bridging calls to a plurality Home Network endpoints includes initiating an outgoing call from an endpoint. Then, the outgoing calls initiated from endpoints are logged. Likewise, incoming calls received on an external telephone line addressed to an endpoint and bridged, and logged. Logging the bridged calls includes cross-referencing entries such as call time, the call duration, the type of call, the external telephone involved, the external line telephone number from which an incoming call is received, the external telephone line telephone number to which an outgoing call is addressed, the endpoint to which an incoming call is addressed, and the endpoint initiating an outgoing call.
Owner:SHARP LAB OF AMERICA INC
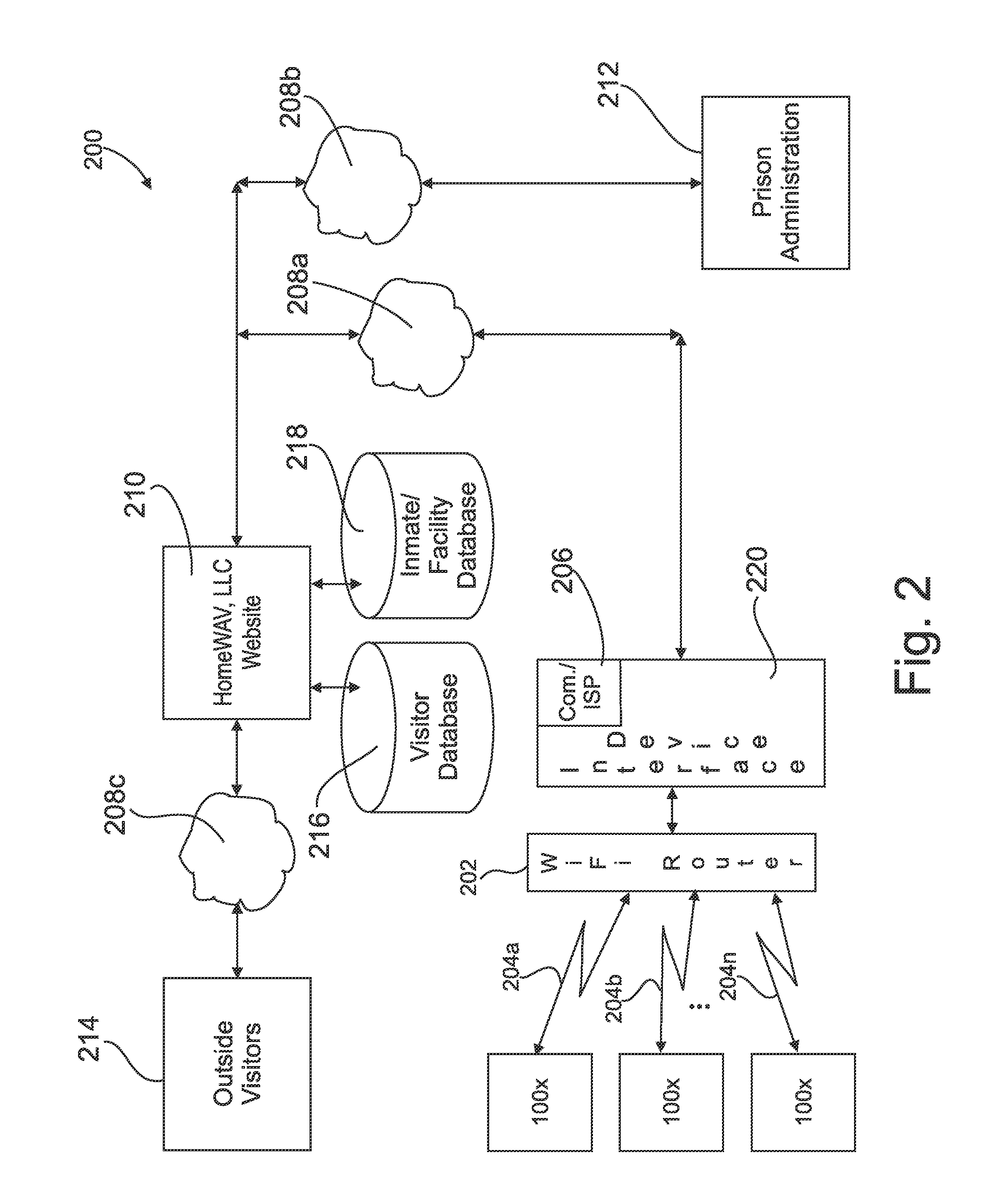
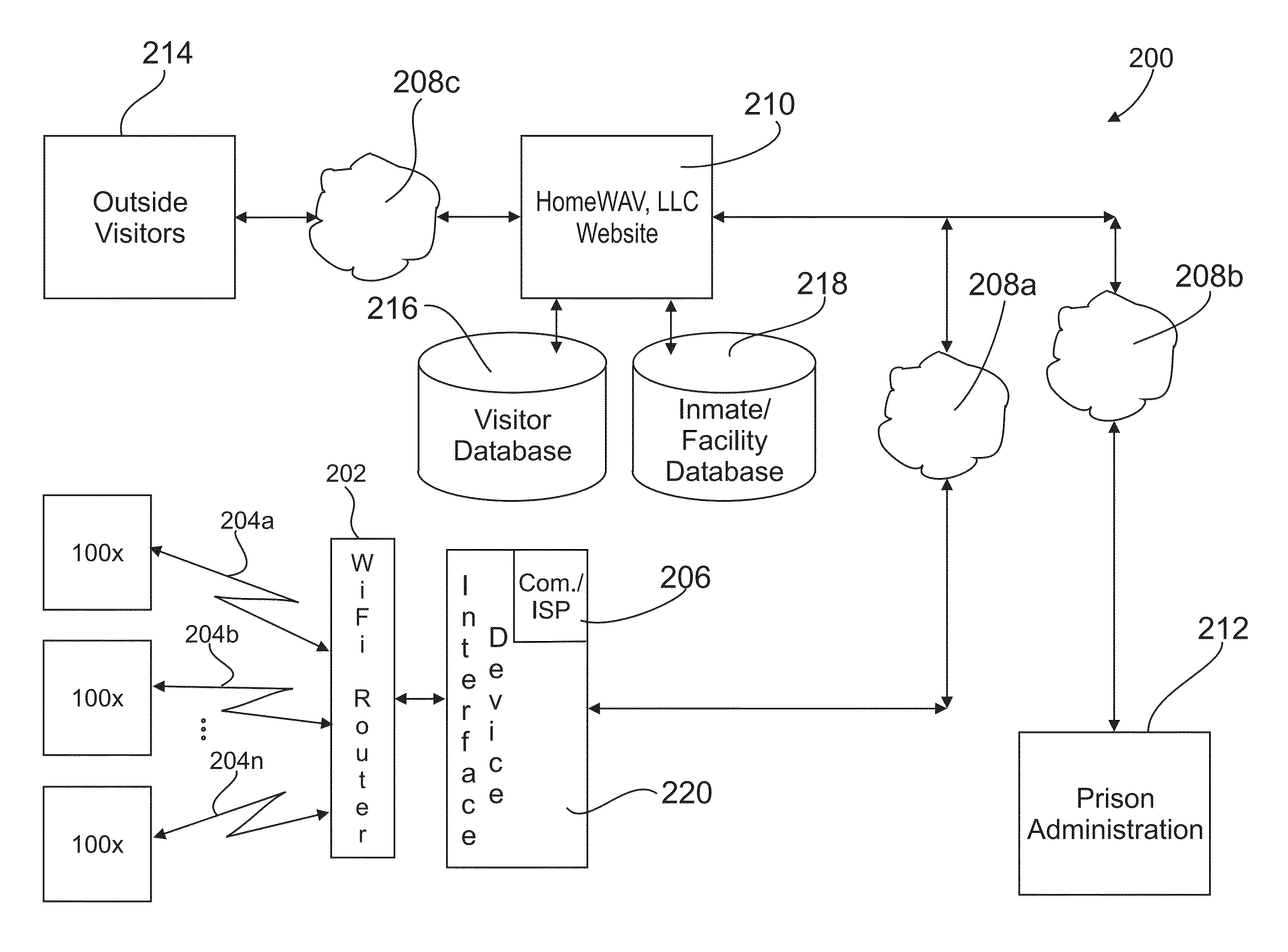
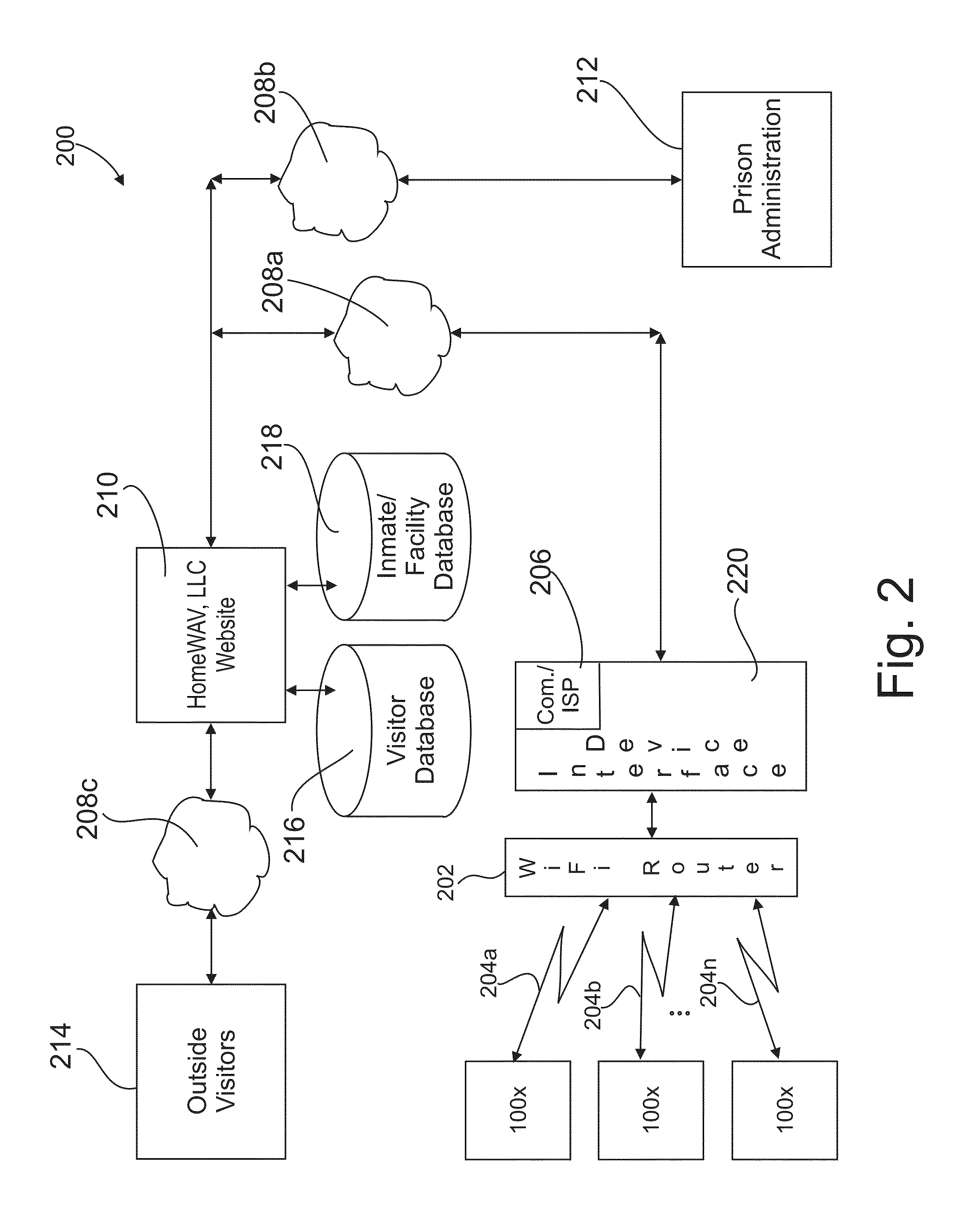
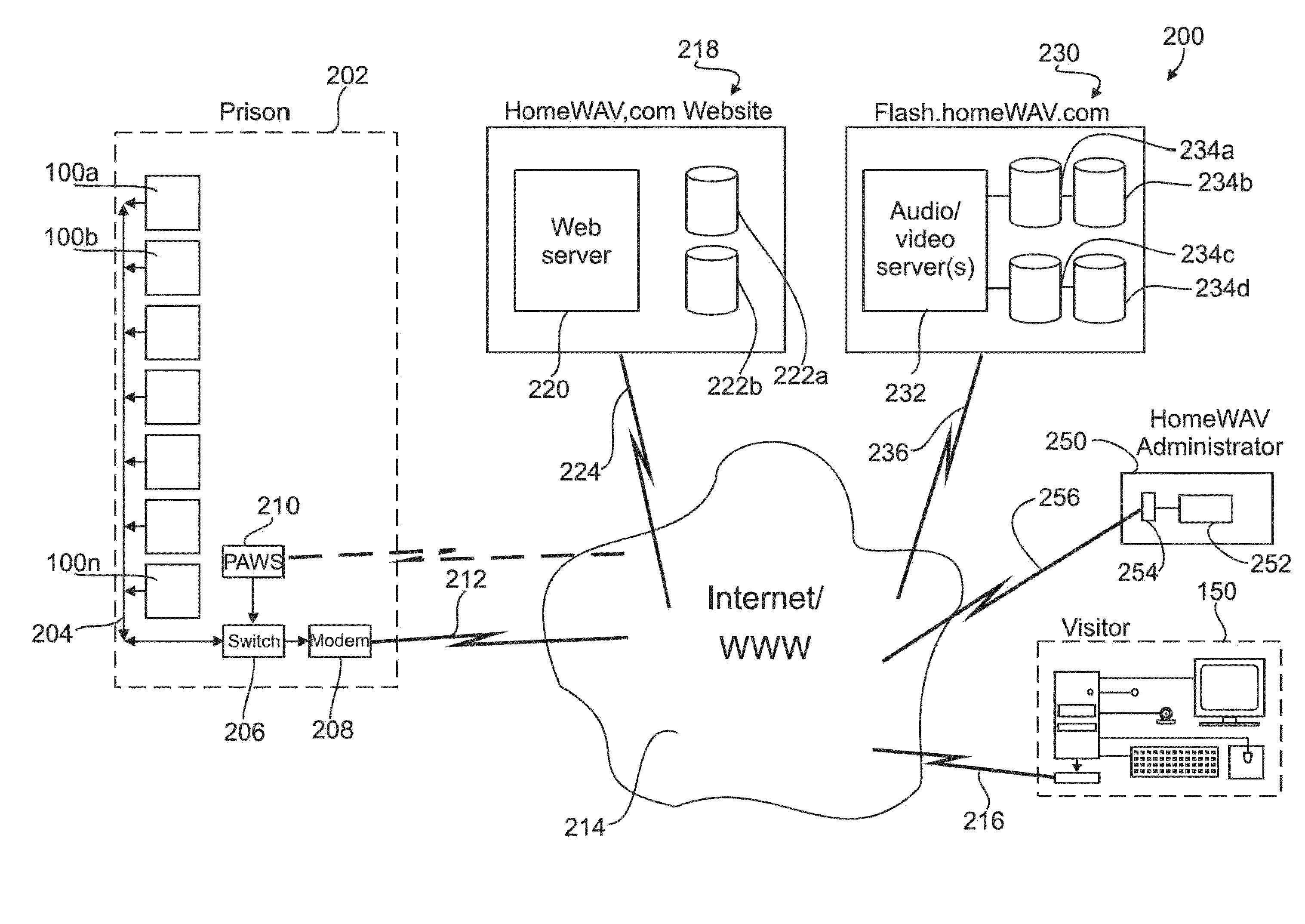
Method and apparatus for providing both audio/video visitation and VOIP telephonic visitation originated either by an inmate or by an outside visitor directly between inmates of a prison and an outside visitor without need of intervention by prison personnel
ActiveUS20130194377A1No costMetering/charging/biilling arrangementsAccounting/billing servicesPaymentInternet based
An Internet-based audio / video and VoIP telephone visitation system for prisons wherein audio / video and VoIP visitation may be originated by either an inmate or an outside visitor. An inmate uses an individual portable electronic device in his / her possession to communicate exclusively with the visitation system. Through the visitation system video messages, video visitations, and VoIP telecommunications may be exchanged between the inmate and a registered visitor having an Internet-enabled device. Communication requires no endpoint control by prison personnel. All communications may be subject to intervention, recordation, and monitoring by prison personnel. Payment for services is prepaid by visitors using an on-line payment service eliminating involvement of prison personnel. All non-privileged calls are recorded. All calls may be monitored. A fee-per-minute is charged. Time is tracked for each call. The call duration and time remaining for a call may be displayed for both the visitor and the inmate.
Owner:HOMEWAV
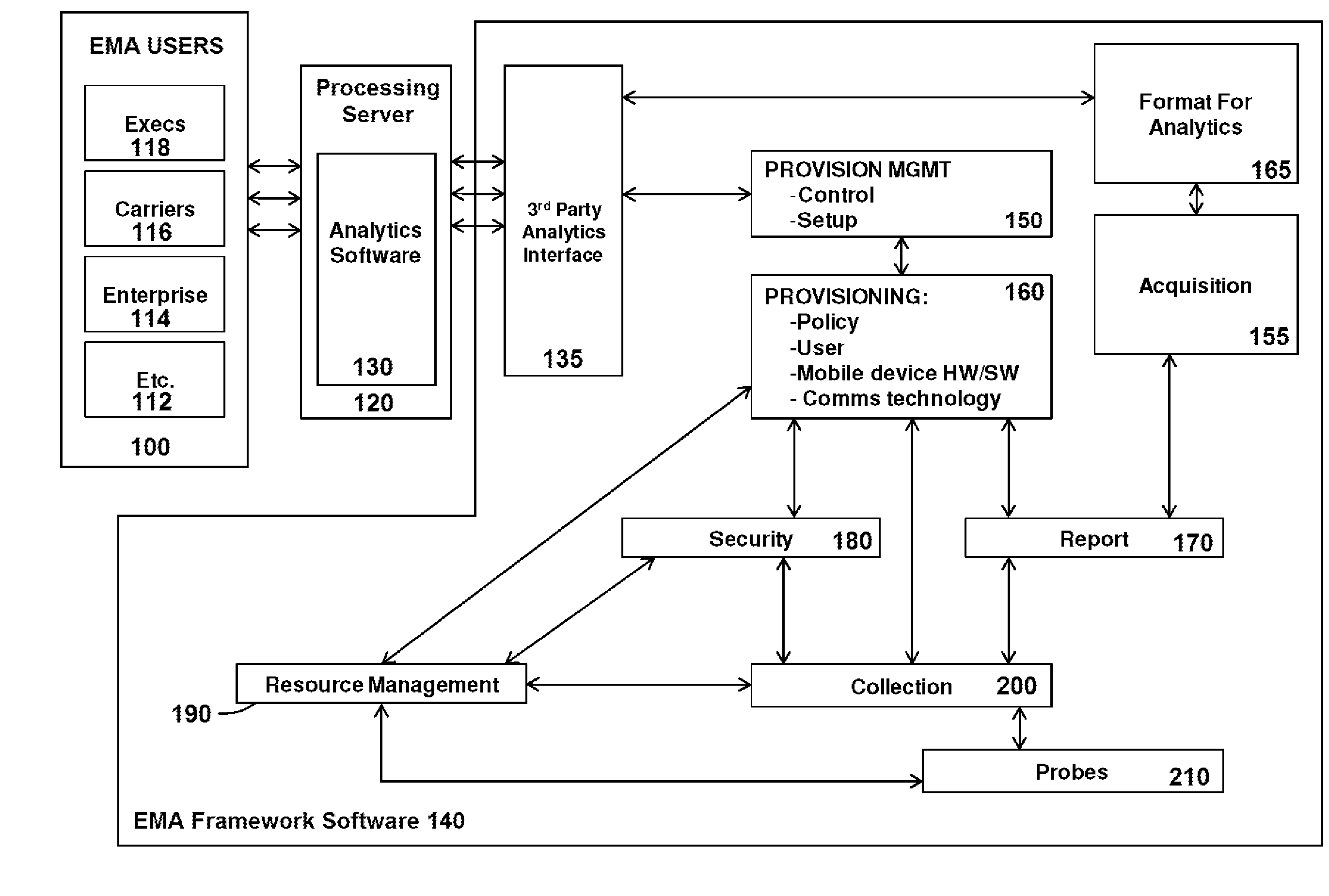
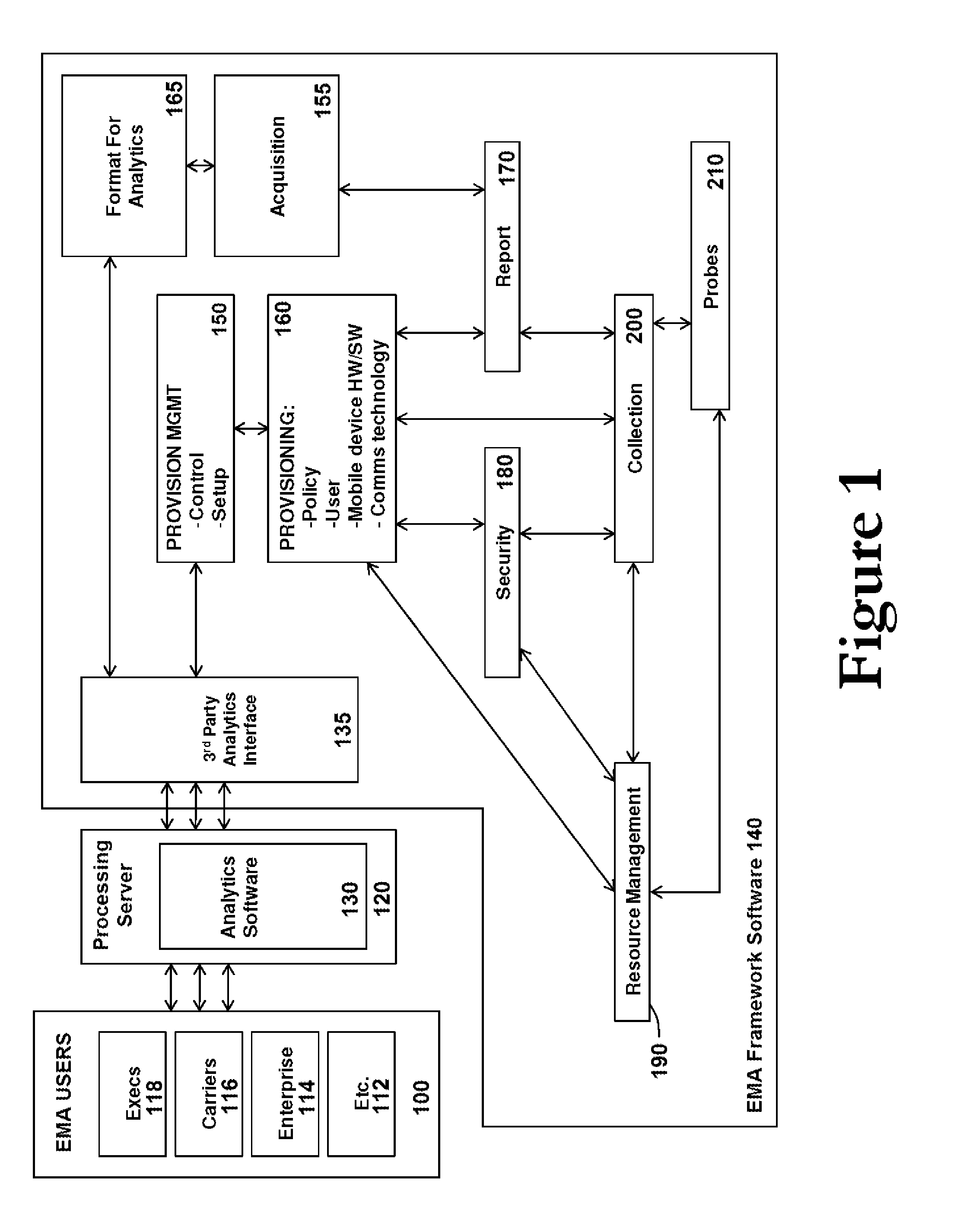
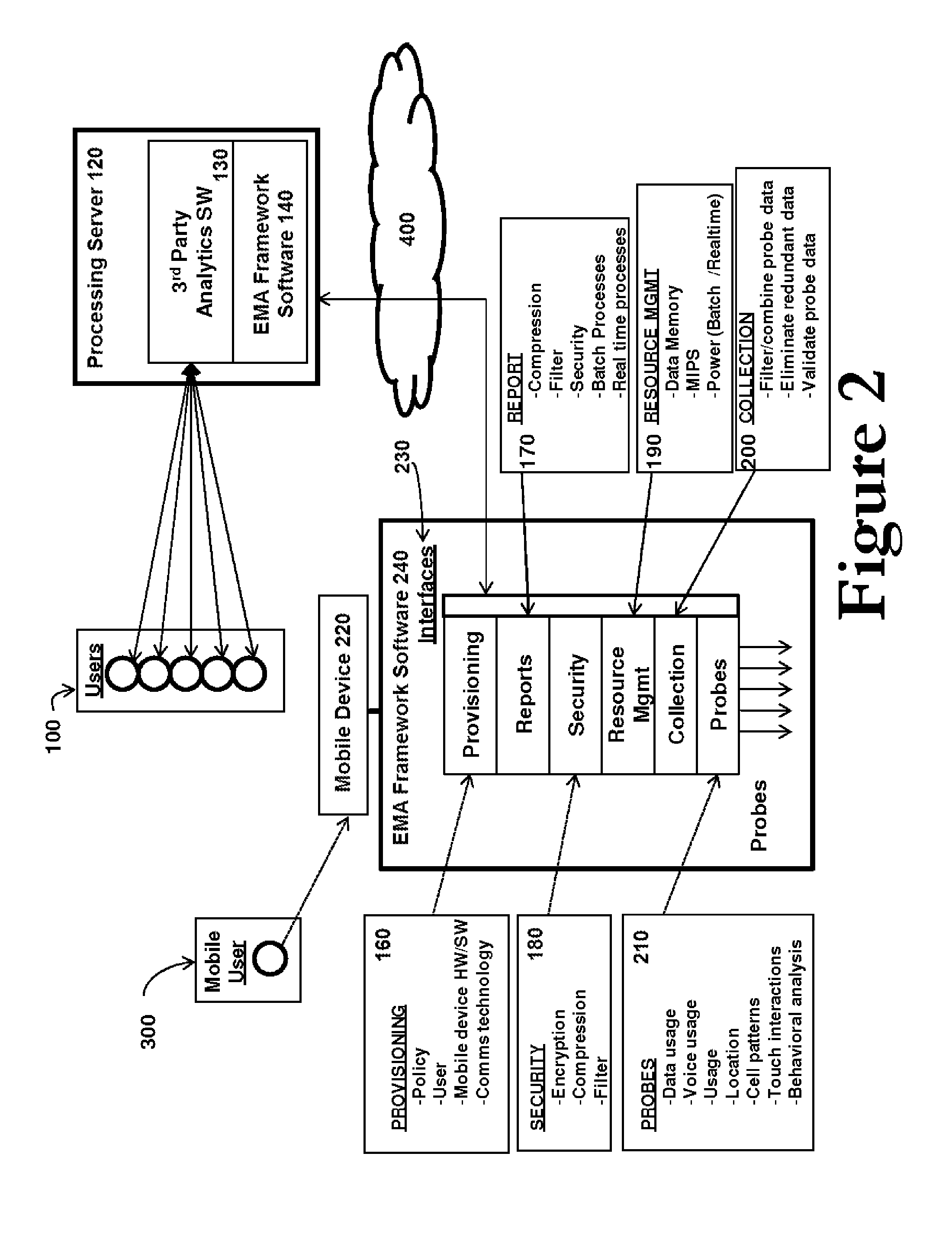
Embedded mobile analytics in a mobile device
InactiveUS20100041391A1Provide informationReduce in quantitySecurity arrangementThird generationUse of services
A method or process enables the collection of data from mobile devices and mobile networks using filtering, compression, encryption, memory management, and power management technologies to collect mobile device metrics at the mobile device (client side), and then transmit these metrics from the mobile device to a server for processing by analytics software. The analytics processing may also occur directly on the mobile device. Policies are determined and configured at the processing server to drive and control the mobile device metrics captured, which may include but are not limited to, data usage (e.g. time of day, amount of data sent / received), voice usage (e.g. time of day, calls in / out of network, dropped calls, call duration), the location of the mobile device, cell patterns (e.g. problem cells, roaming), touch interactions, behavioral analysis (programs used, services uses), battery performance, CPU usage, memory usage, network usage (e.g. 2G, 3G, 3.5G, 4G, Wi-Fi, WiMAX), and the like.
Owner:TAPROOT SYST
Method selecting actions or phases for an agent by analyzing conversation content and emotional inflection
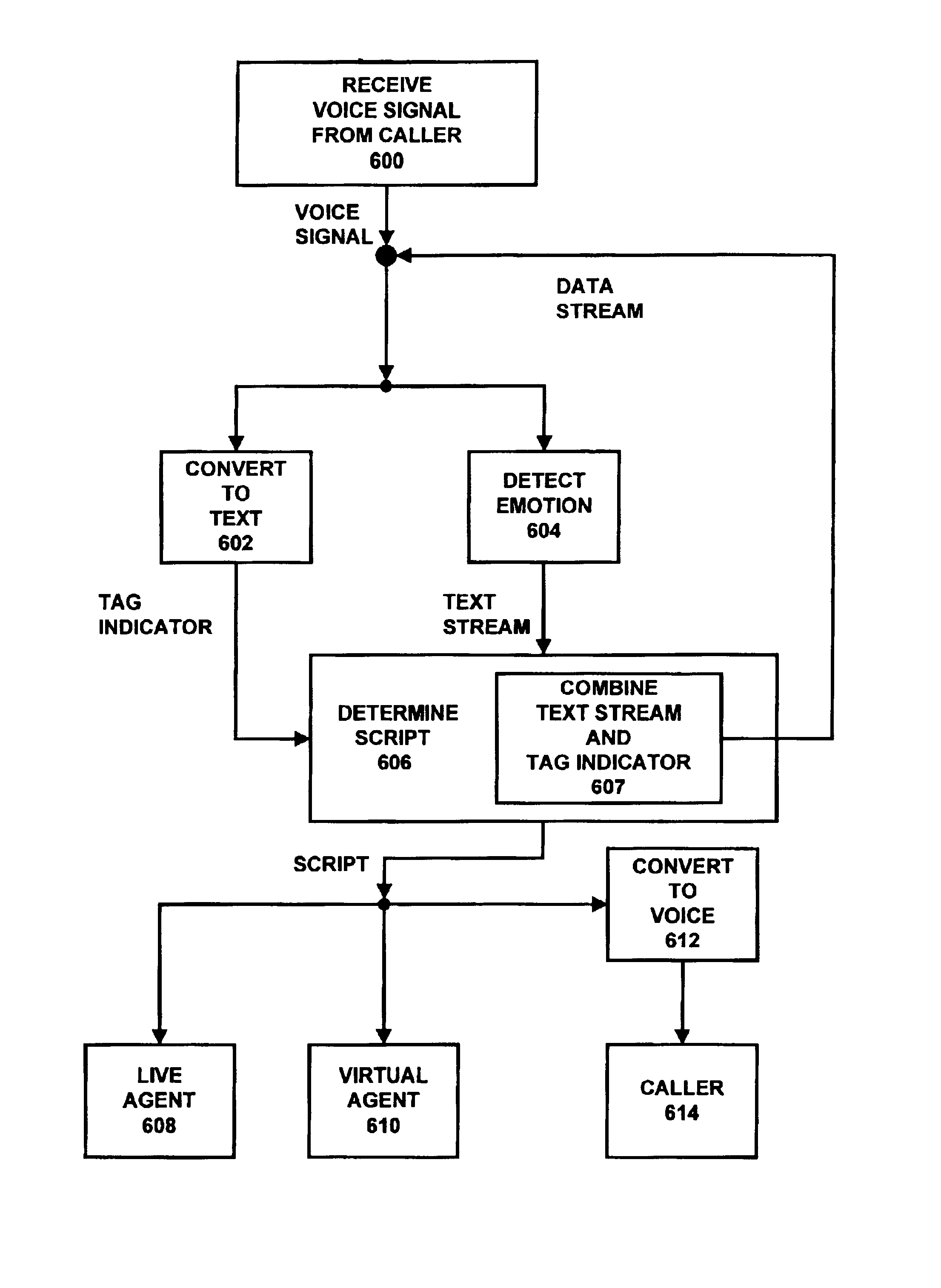
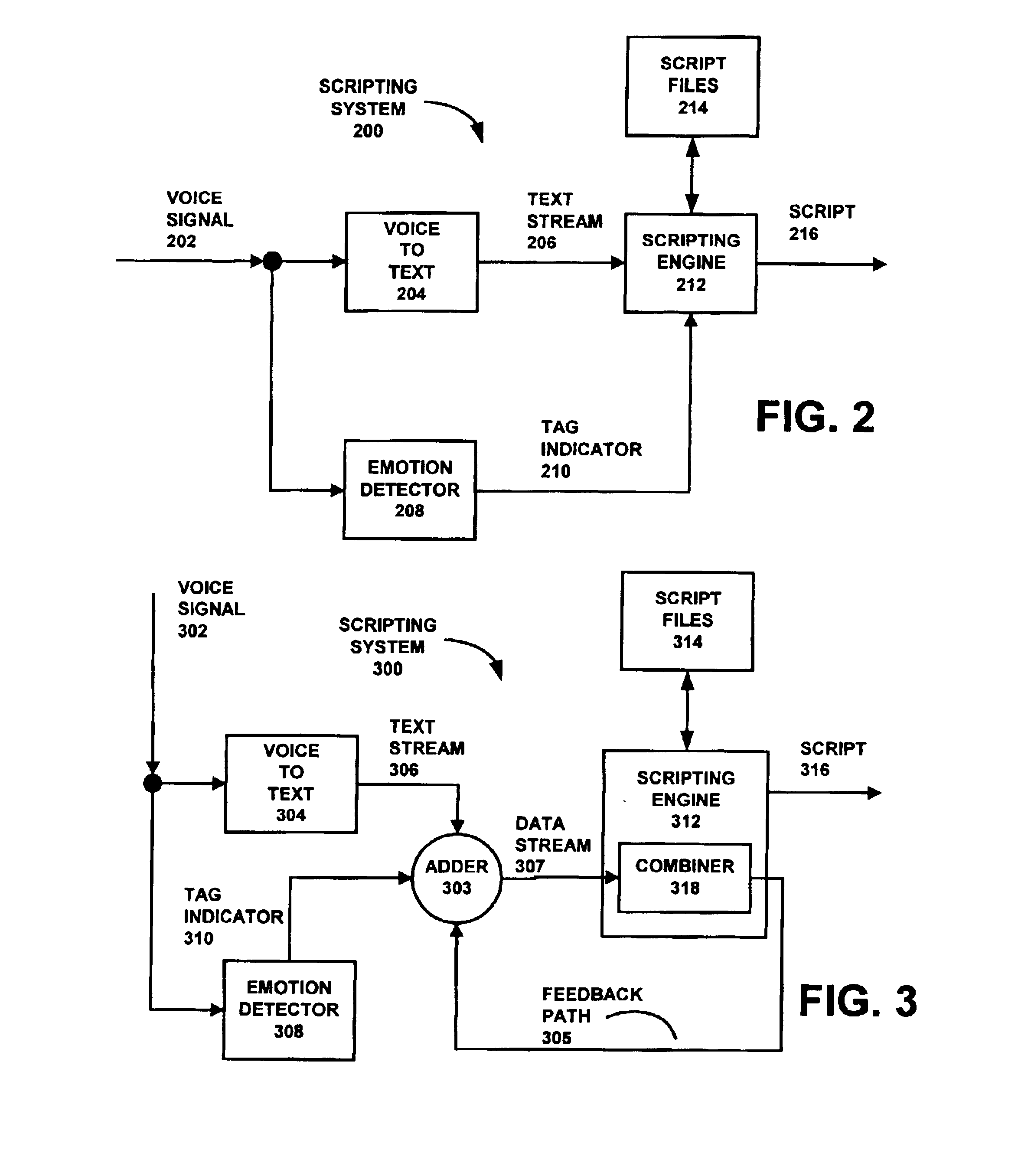
A method and apparatus are provided for accepting a call by an automatic call distributor and for automatic call handling of the call. The apparatus for automatic call handling has: a call receiving system that outputs at least one voice signal; a text voice converter having an input for the at least one voice signal, the text voice converter converting the voice signal to a text stream and providing the text stream on an output thereof; an emotion detector having an input for the at least one voice signal, the emotion detector detecting at least one emotional state in the voice signal and producing at least one tag indicator indicative thereof on an output of the emotion detector; and a scripting engine having inputs for the text stream and the at least one tag indicator, the scripting engine providing on an output thereof at least one response based on the text stream and on the at least one tag indicator. The method and apparatus provides the agents with scripts that are based on not only the content of the call from a caller, but that are also based upon the emotional state of the caller. As a result, there is a decrease in call duration, which decreases the cost of operating a call center. This decrease in the cost is a result in the amount of time an agent spends based on the agent's hourly rate and the costs associated with time usage of inbound phone lines or trunk lines.
Owner:FIRSTPOINT CONTACT TECH +1
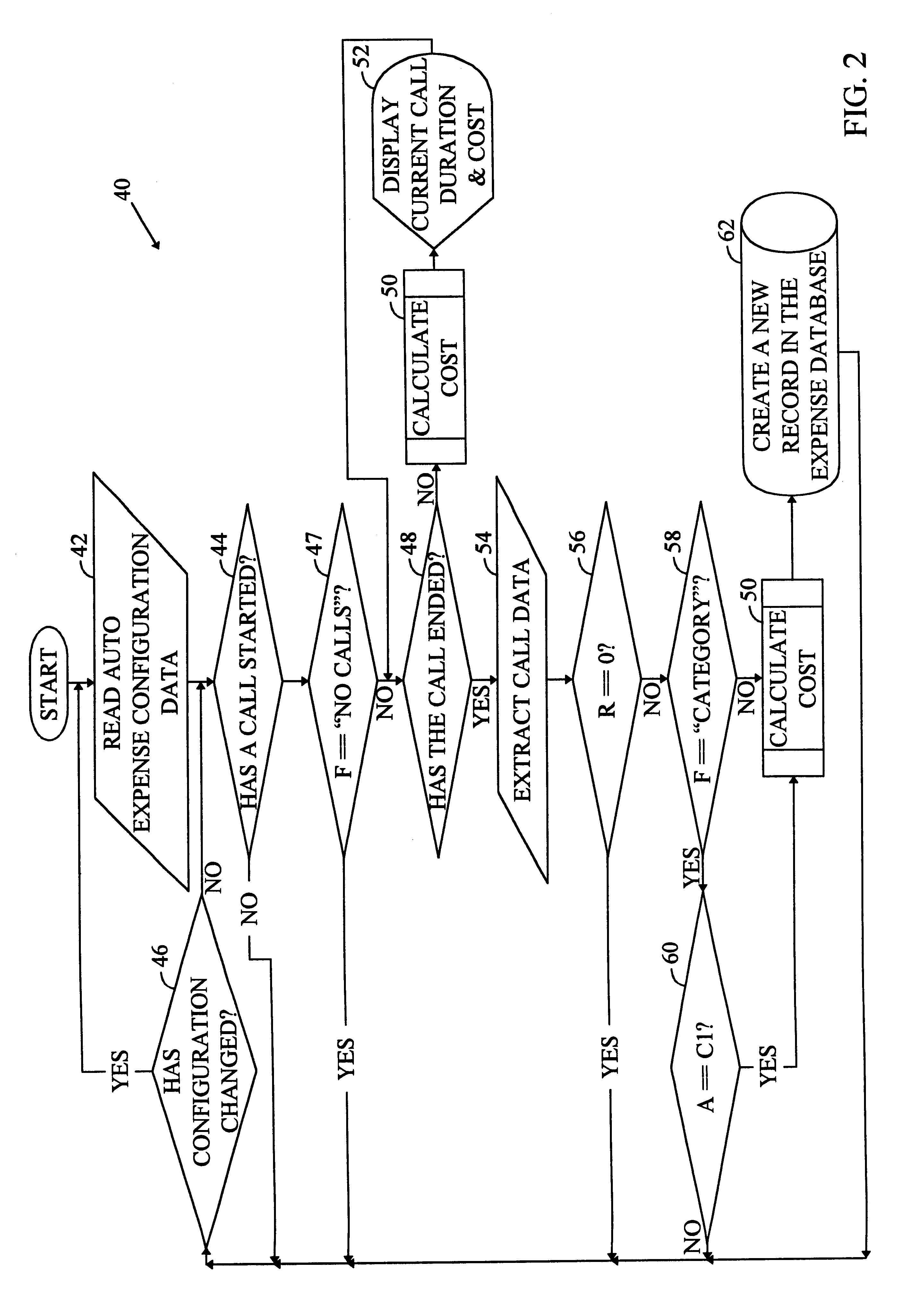
System and method for providing expense reports to wireless service subscribers
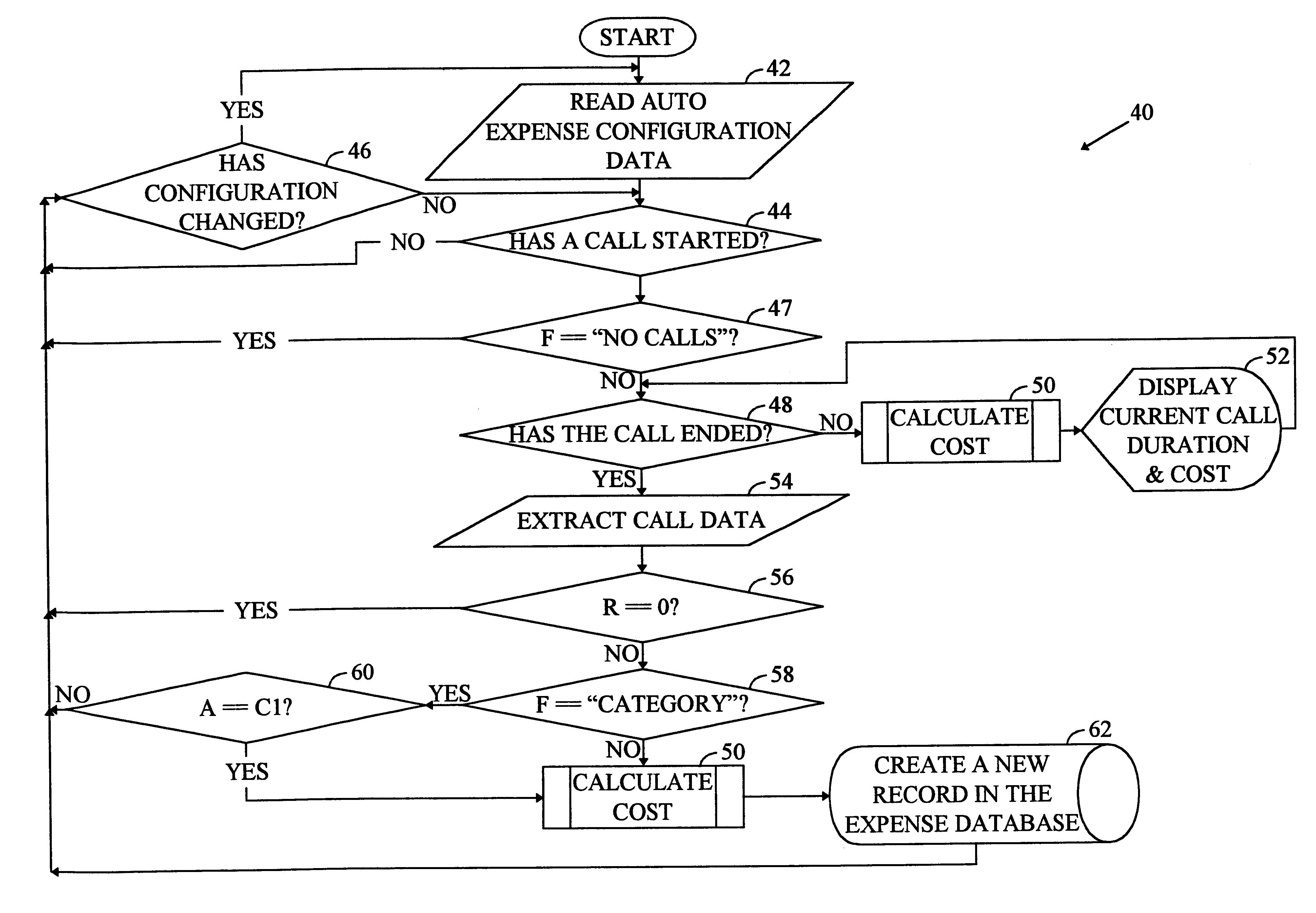
A system for providing immediate access to detailed information about a wireless call. The system includes a first mechanism for placing a wireless call. A second mechanism times the call to provide a call duration value. A third mechanism computes the detailed information from the call duration value and a predetermined value associated with the call. A fourth mechanism displays the detailed information. In a specific embodiment, the predetermine value is a billing rate associated with the call and the detailed information is expense information. The third mechanism includes a computer that runs software for computing the detailed information from the call duration value and the billing rate. The software includes a routine that detects when the wireless phone is being used for a call and times the call. The software also includes a mechanism for providing user-selectable parameters for controlling the third mechanism.The user-selectable parameters include a first parameter that indicates use of one or more address book categories or lack thereof. The address book categories each indicate one or more calls to be tracked by the system. The user-selectable parameters further include a category for association with newly provided detailed call information, a per-minute billing rate corresponding to the predetermined value, and a type of currency to be used by the third mechanism for computing expense information. The software generates an expense report listing the detailed information in response to the receipt of the user selectable parameters and any other received call identifiers. In the illustrative embodiment, the fourth mechanism includes mechanism for displaying the detailed information in approximately real-time and includes a mechanism for automatically displaying or storing the detailed information upon completion of the call.
Owner:QUALCOMM INC
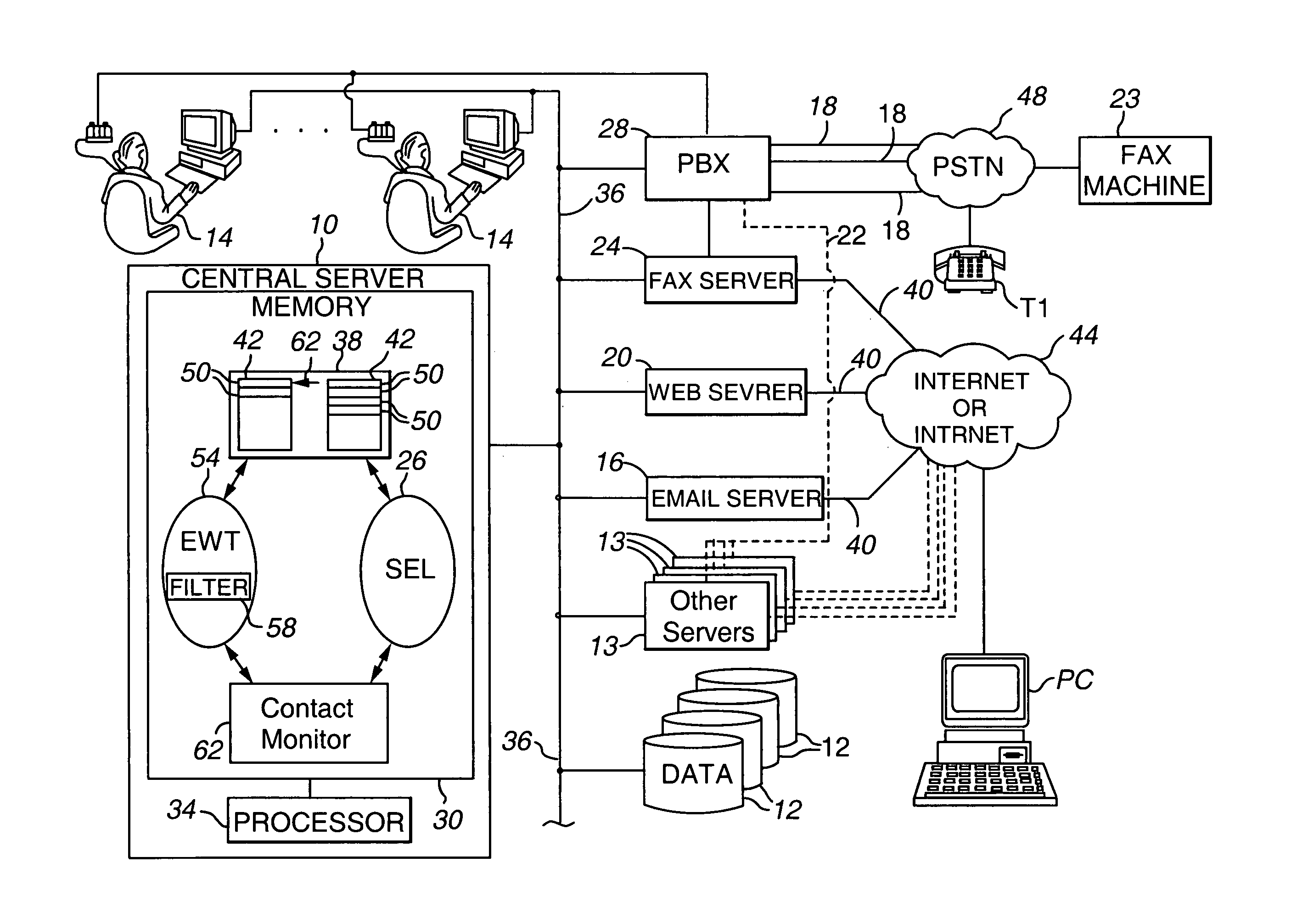
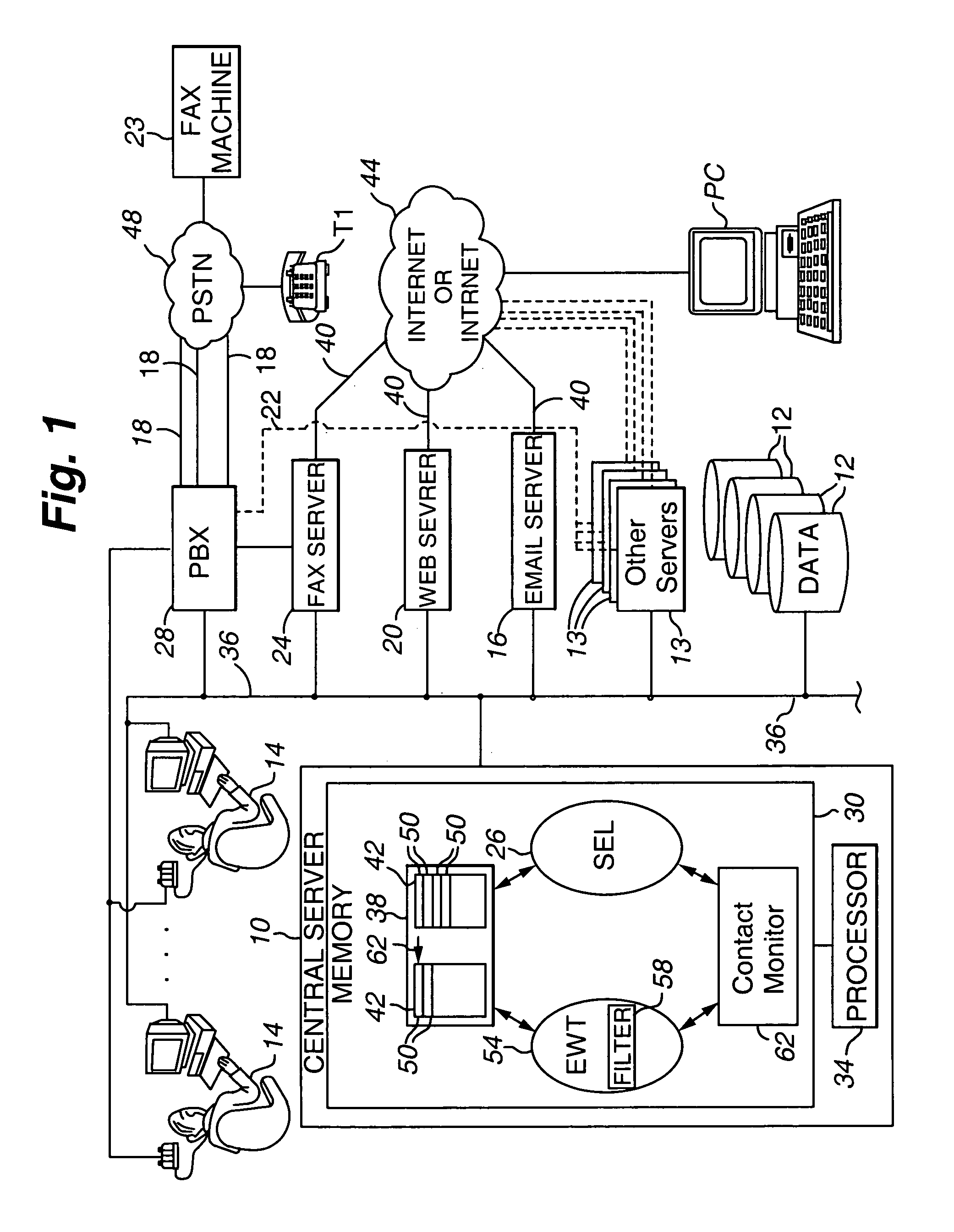
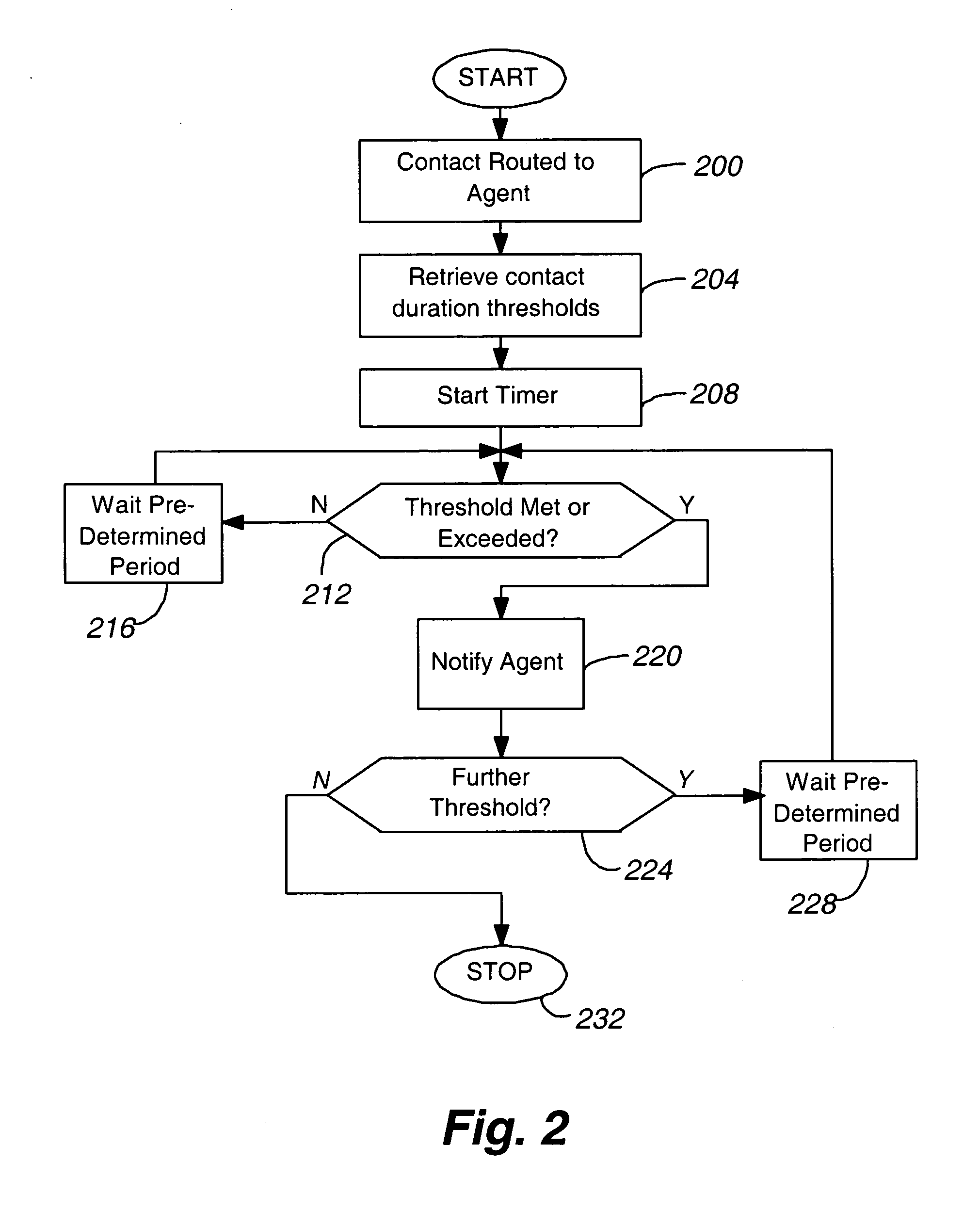
Call duration alert
ActiveUS7085367B1Higher of complianceImprove performanceSpecial service for subscribersManual exchangesContact centerEngineering
A contact center for servicing a contact is provided that includes (a) an input operable to receive a contact from a customer; (b) a selection function 26 operable to direct the contact to a human agent associated with the contact center for servicing; and (c) a contact monitor 62 operable (a) to track a service time required by the human agent to service the contact and (b), when the service time at least one of equals and exceeds a selected first threshold, notify the agent that the selected first threshold has been at least one of equaled and exceeded.
Owner:AVAYA INC
Method and apparatus for providing both audio/video visitation and VOIP telephonic visitation originated either by an inmate or by an outside visitor directly between inmates of a prison and an outside visitor without need of intervention by prison personnel
ActiveUS9124763B2No costMetering/charging/biilling arrangementsAccounting/billing servicesPaymentInternet based
An Internet-based audio / video and VoIP telephone visitation system for prisons wherein audio / video and VoIP visitation may be originated by either an inmate or an outside visitor. An inmate uses an individual portable electronic device in his / her possession to communicate exclusively with the visitation system. Through the visitation system video messages, video visitations, and VoIP telecommunications may be exchanged between the inmate and a registered visitor having an Internet-enabled device. Communication requires no endpoint control by prison personnel. All communications may be subject to intervention, recordation, and monitoring by prison personnel. Payment for services is prepaid by visitors using an on-line payment service eliminating involvement of prison personnel. All non-privileged calls are recorded. All calls may be monitored. A fee-per-minute is charged. Time is tracked for each call. The call duration and time remaining for a call may be displayed for both the visitor and the inmate.
Owner:HOMEWAV
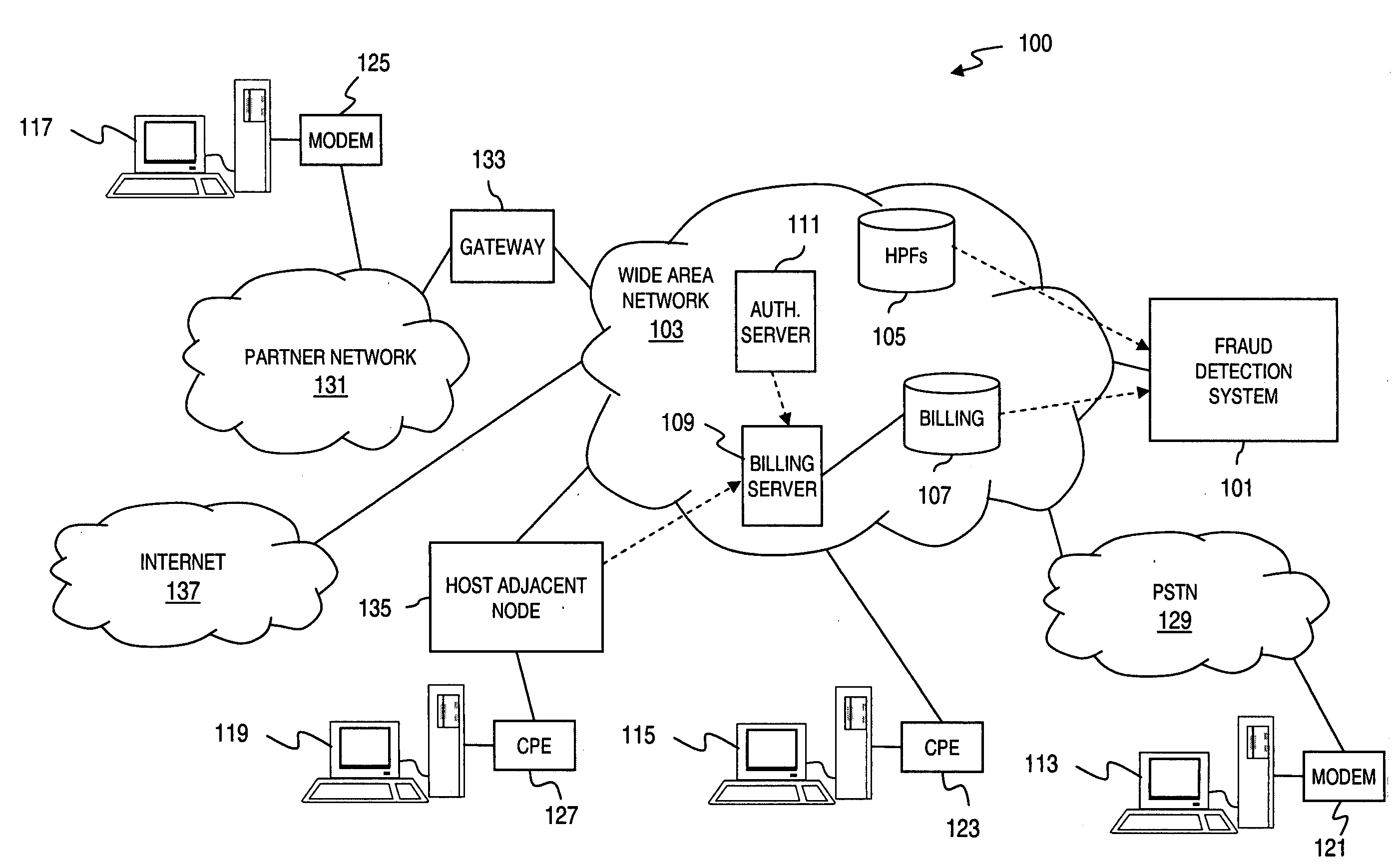
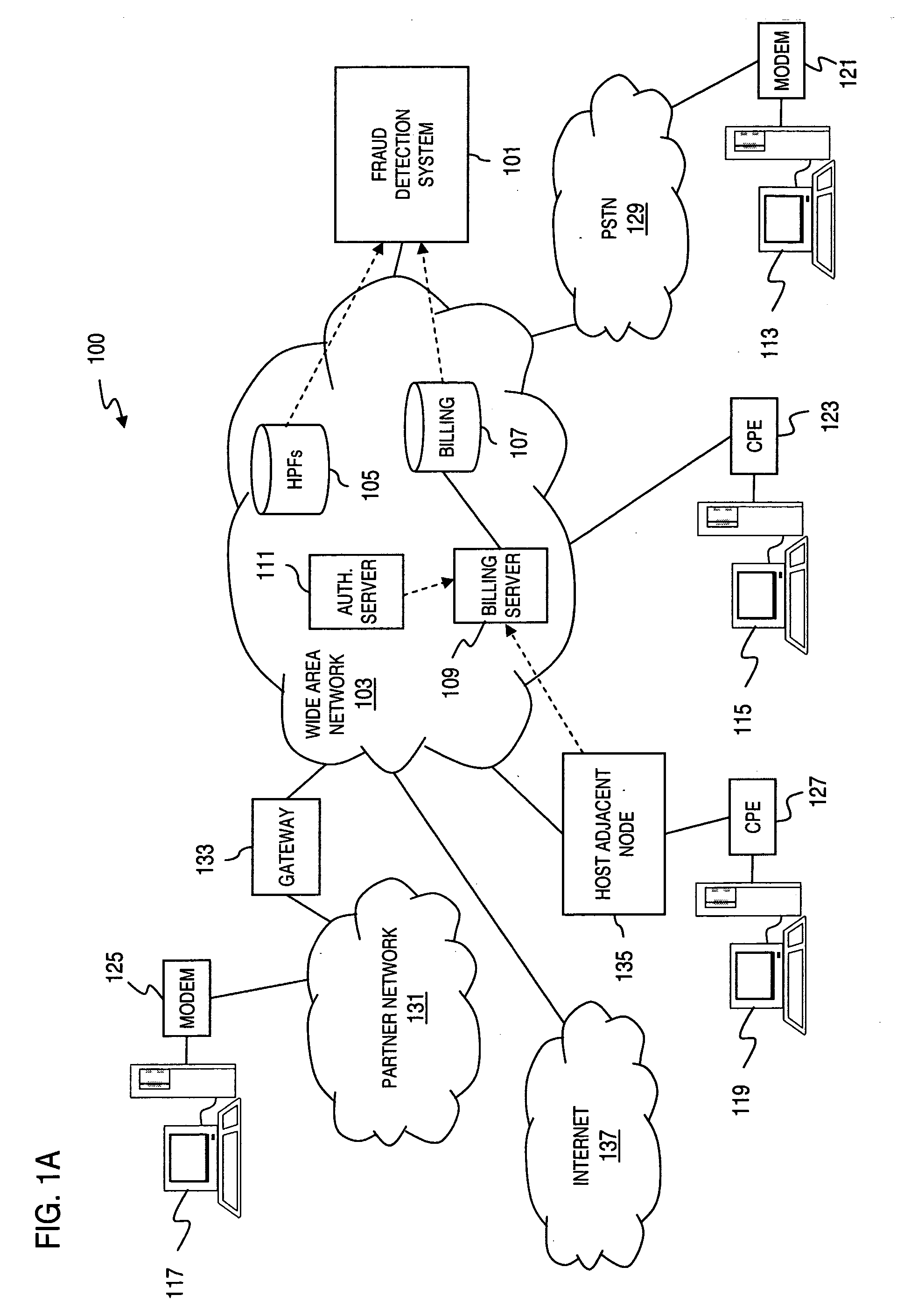
Method and apparatus for providing fraud detection using geographically differentiated connection duration thresholds
InactiveUS20050249341A1Reduces heavy costFacilitate fraud detectionUser identity/authority verificationDigital computer detailsData miningDuration time
An approach provides fraud detection in support of data communication services. A threshold corresponding to a geographic location is set. The threshold corresponds to duration of a call supporting data communications. It is determined whether the call duration exceeds the threshold. A fraud alert is generated if the monitored call duration exceeds the threshold.
Owner:VERIZON PATENT & LICENSING INC
Method of and Apparatus for Communicating User Related Information Using a Wireless Information Device
InactiveUS20080045184A1Special service for subscribersSubstation equipmentTime scheduleRelevant information
A mobile telephone which can supply or post 'pre-answer' information which the device owner considers of relevance to a potential call recipient. This information enables a potential call recipient to be given useful information about a potential call before actually answering that call. The information is dynamic, unlike Caller ID information. Examples include: information about the subject of an intended voice call, a mood, a current activity, part or whole of a schedule of meetings or events, information about the urgency of an intended voice call, personal information, expected call duration, commercial inducements to a consumer to answer a call (special offers, loyalty points etc.), location information.
Owner:NOKIA TECHNOLOGLES OY
Remote web-based visitation system for prisons
A web-based video conferencing system and method for providing remote visitation with inmates incarnated in a prison. All visitations are initiated by the inmates and no endpoint control by prison personnel is required. “Jail-hardened” terminals in the prison communicate via Internet with visitor Internet-enabled devices. Payment for services is paid by visitors using an on-line payment service relieving prison personnel of any handling of money. All calls (excluding clergy, lawyers, etc.) are typically recorded and no routine monitoring is required by prison personnel. Inmates use the “jail-hardened” terminals to initiate video conference using only a 12-key telephone style keypad. A fee-per-minute is charged. Time is tracked for each call and the call duration and remaining time for a call based upon the maximum allowed call length and an inmate's available minutes are displayed for both the visitor and the inmate.
Owner:HOMEWAV
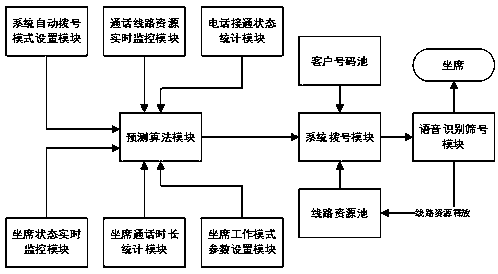
Intelligent auto-dial outbound system and intelligent auto-dial outbound method
ActiveCN108156331ASolve the problem of low efficiency and ineffective use of resourcesTake advantage ofSpecial service for subscribersSupervisory/monitoring/testing arrangementsResource poolOptical Module
The invention relates to an intelligent auto-dial outbound system, the system comprises a system dialing module, a client number pool module, a line resource pool module, a system auto-dial mode setting module, a conversation line resource real-time monitoring module, a call connection state statistics module, an agent state real-time monitoring module, an agent call duration statistics module, anagent work mode parameter setting module and an outbound quantity prediction calculation module. The invention also discloses an intelligent auto-dial outbound method, and the method comprises stepsof acquiring parameters, calculating dialing quantity, dialing by the system, answering by agents, and so on. In the system and the method provided by the invention, the quantity of dialing outbound is predicted according to real-time external parameters through an intelligent algorithm, and the system and the method have the characteristics of being efficient and capable of making full use of resources.
Owner:大连金慧融智科技股份有限公司
Telephony extension attack detection, recording, and intelligent prevention
ActiveUS7653188B2Avoid attackData taking preventionAutomatic exchangesCommunication endpointRemedial action
A system and method are provided for detecting extension attacks made to a communication enterprise, and taking appropriate remedial action to prevent ongoing attacks and future attacks. One or more attributes of a suspect call are analyzed, and a risk is associated with each analyzed attribute. An overall risk or assessment is then made of the analyzed attributes, attack attributes are logged, and one or more remedial actions may be triggered as a result of the analyzed call attributes. The remedial actions may include recording the call, notifying an administrator of a suspect call, or isolating the communication enterprise from the attack by terminating the call or shutting down selected communication endpoints to prevent calls being made to those extensions. Rules may be applied to the analyzed attributes in order to trigger the appropriate remedial action. The call attributes analyzed may include call destination, call direction, call type, time of day of the call, call duration, whether a call source is spoofed, call volume from a particular call source, and hash values created for a suspect media stream.
Owner:AVAYA INC
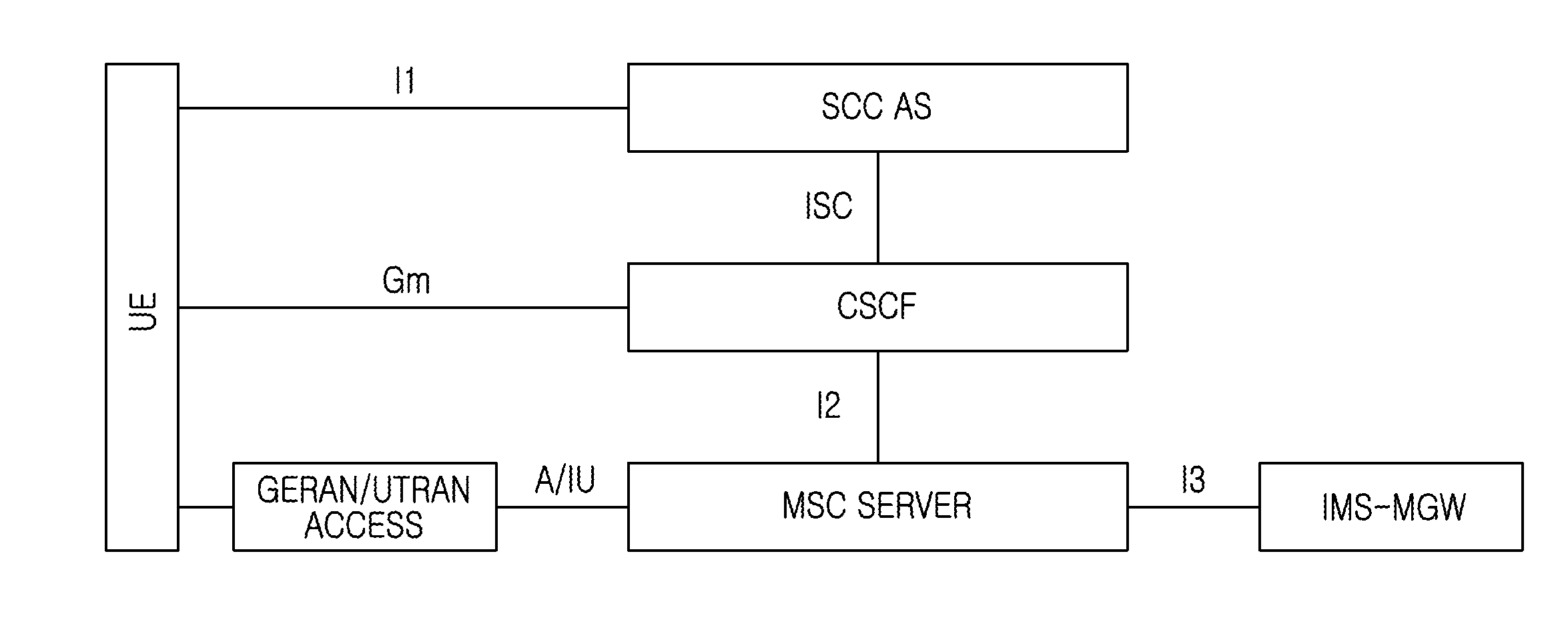
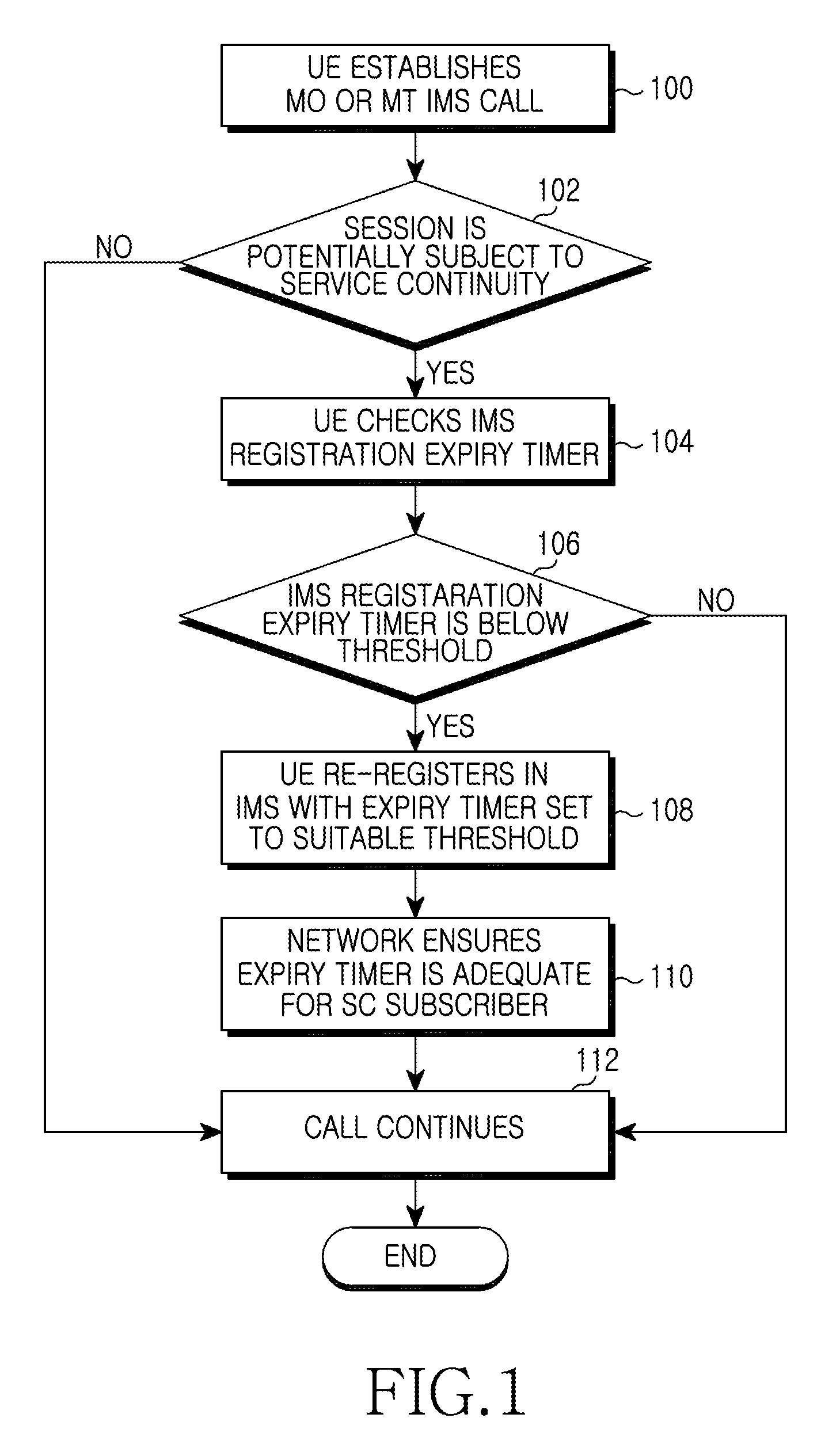
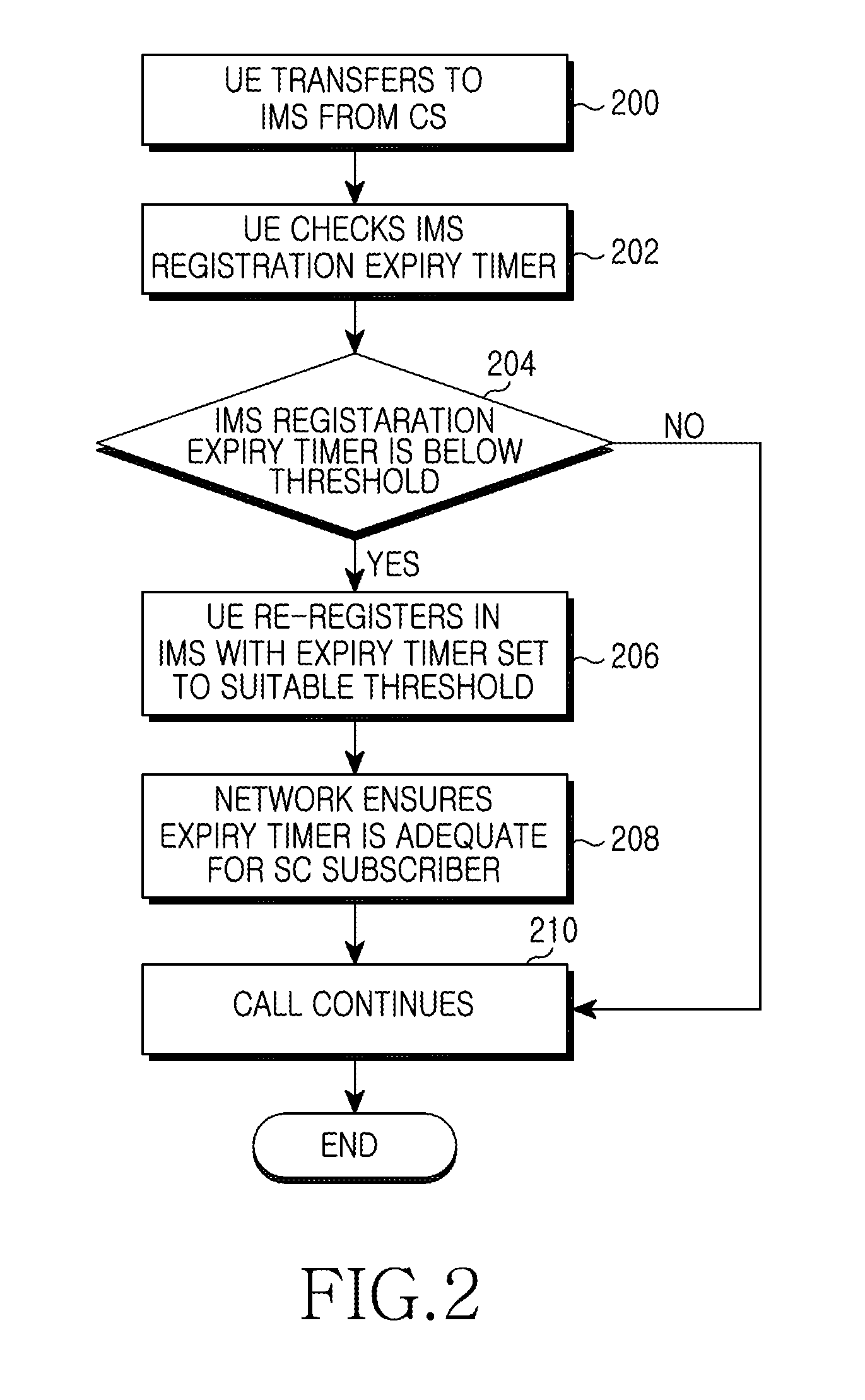
Reducing occurrence of user equipment registration expiry during calls
ActiveUS20090276532A1Reduce generationReduce probabilityMultiple digital computer combinationsTransmissionComputer scienceUser equipment
Methods, systems, User Equipment (UE), and computer readable medium for reducing the occurrence of UE registration expiry are provided. A method of reducing the occurrence of UE registration expiry during calls includes registering a UE with a network for a registration period, determining a re-registration threshold time period, comparing a duration of a remaining portion of the registration period at a particular time with the re-registration threshold time period, and attempting to re-register the UE with the network for a further registration period if the remaining portion is less than or equal to the re-registration threshold time period, wherein the determining of the re-registration threshold time period includes at least one of setting the threshold time period to a value greater than 600 seconds, determining the threshold time period according to a remaining talk time of the UE at the particular time, determining the threshold time period according to a state of the UE at the particular time, determining the threshold time period according to a duration of at least one previous call made by the UE, determining the threshold time period according to a statistical parameter of a plurality of calls made by the UE, determining the threshold time period according to a statistical parameter of a plurality of calls made by at least one UE, determining the threshold time period according to a predefined maximum call duration, and determining the threshold time period independently of a length of the registration period.
Owner:SAMSUNG ELECTRONICS CO LTD
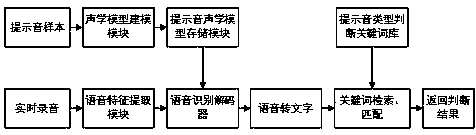
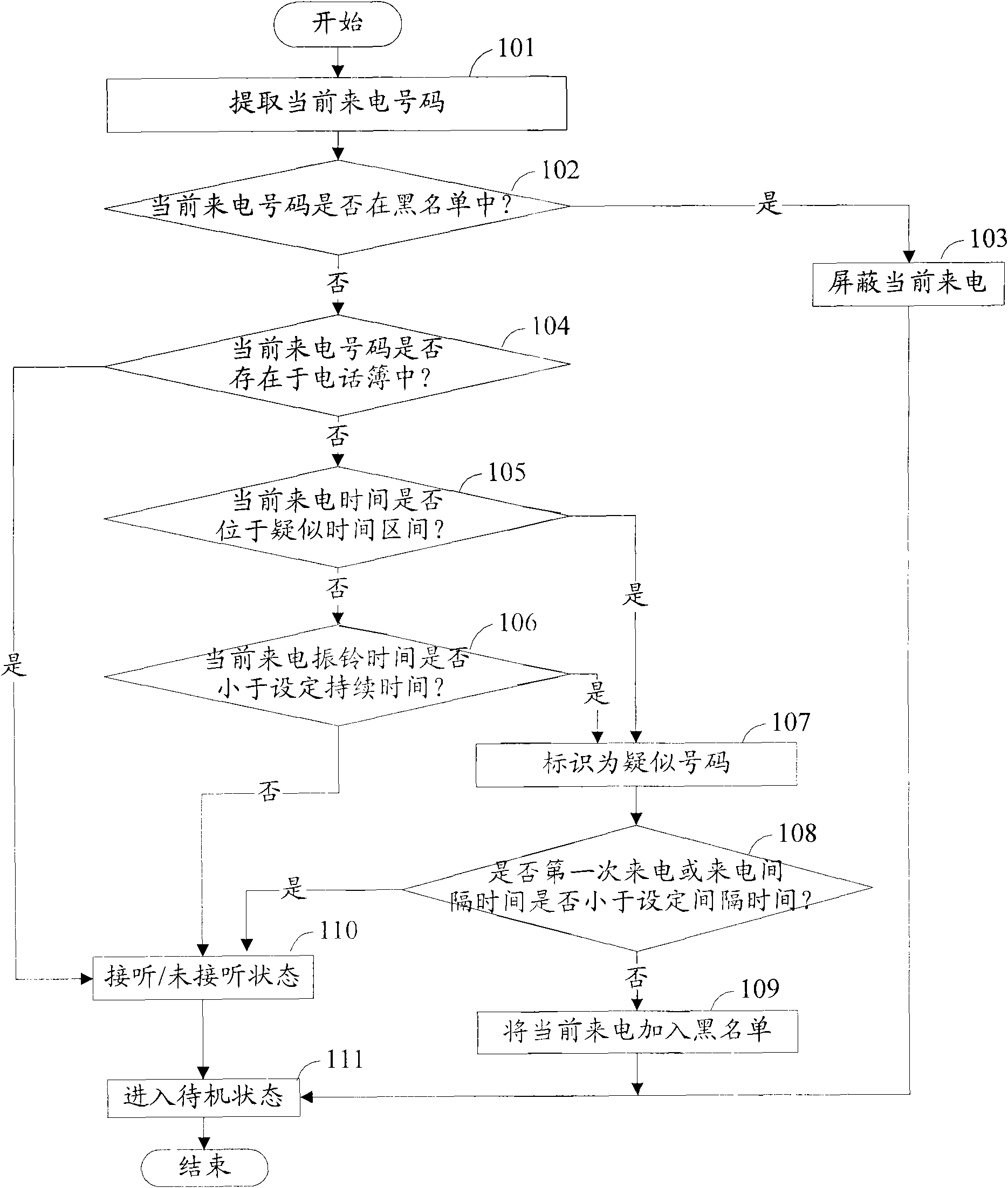
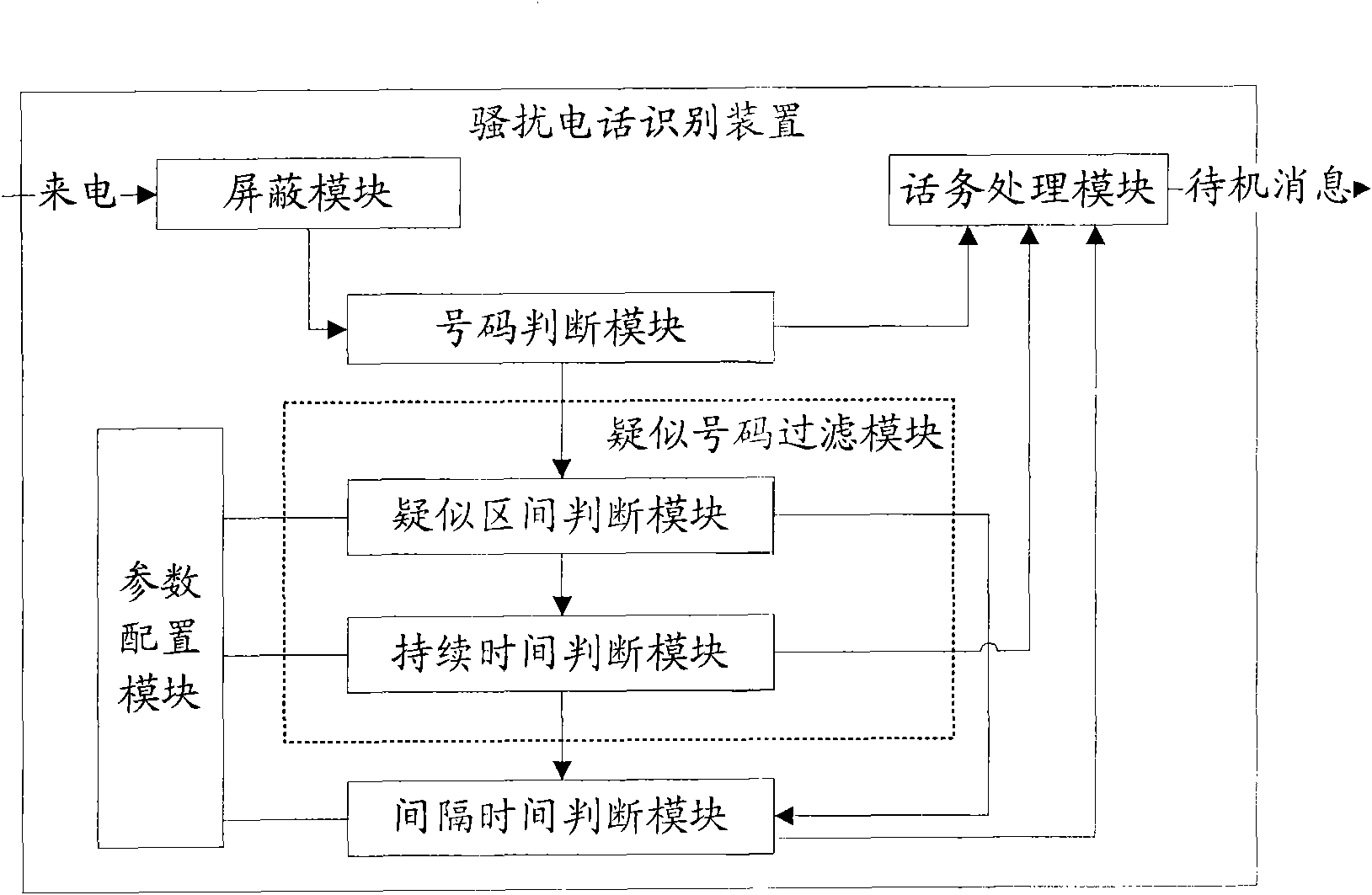
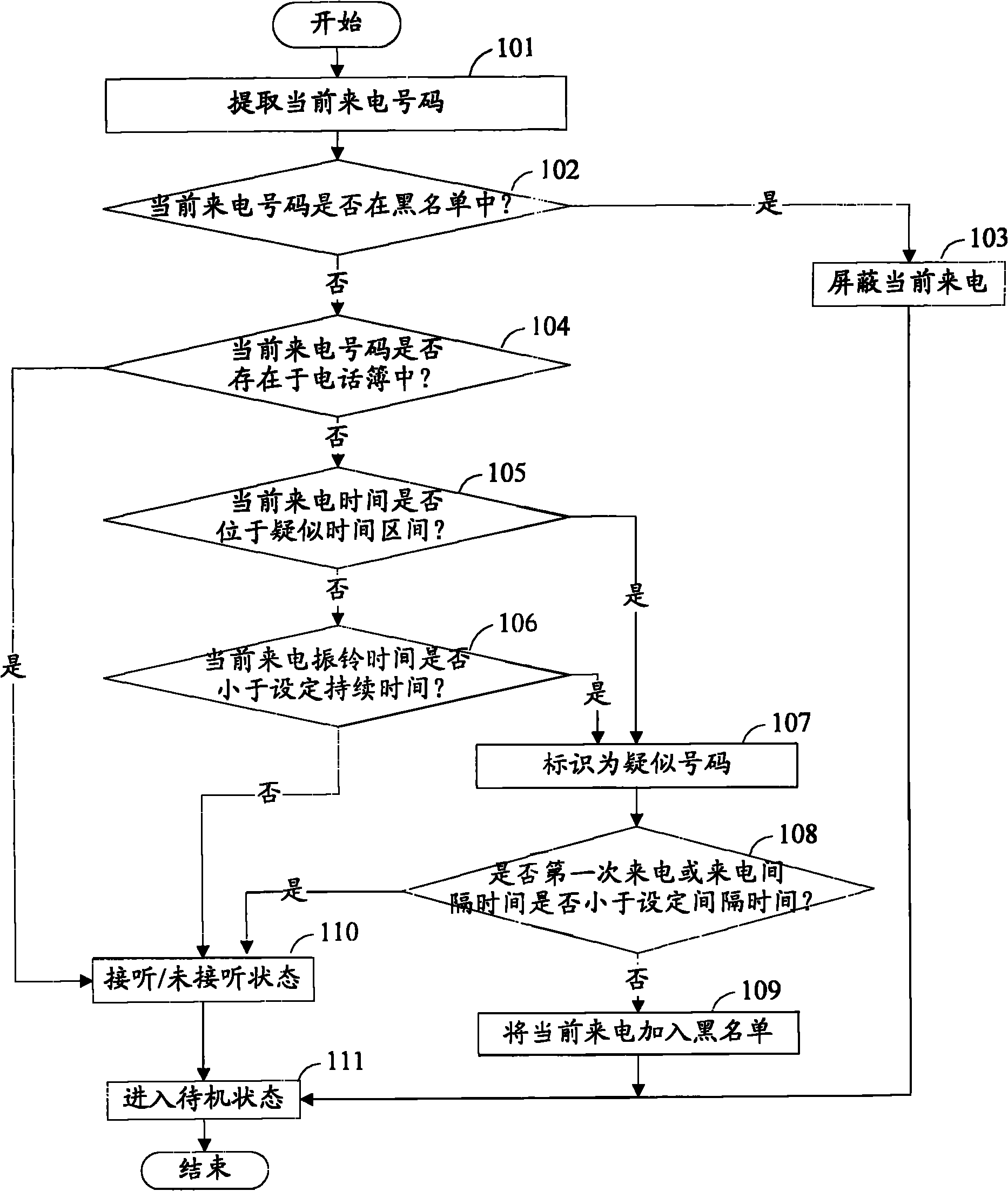
Recognition method and device of harassing calls
ActiveCN101827367AImprove satisfactionImprove accuracyAssess restrictionSubstation equipmentMobile telephonyDuration time
The invention discloses a recognition method and a device of harassing calls, which are used for solving the technical problems of inaccurate harassing call recognition and user use influence caused by easy error judgment. The invention introduces the recognition processing on unfamiliar telephone numbers into mobile phones, and carries out automatic comparison on the judgment rule through the statistics on the calling time intervals, the calling duration time length and the calling times of unfamiliar telephone numbers, the harassing calls can be recognized, the recognition accuracy is high, the error judgment times are few, the setting is simple and flexible, and the satisfaction degree of users is improved.
Owner:ZTE CORP
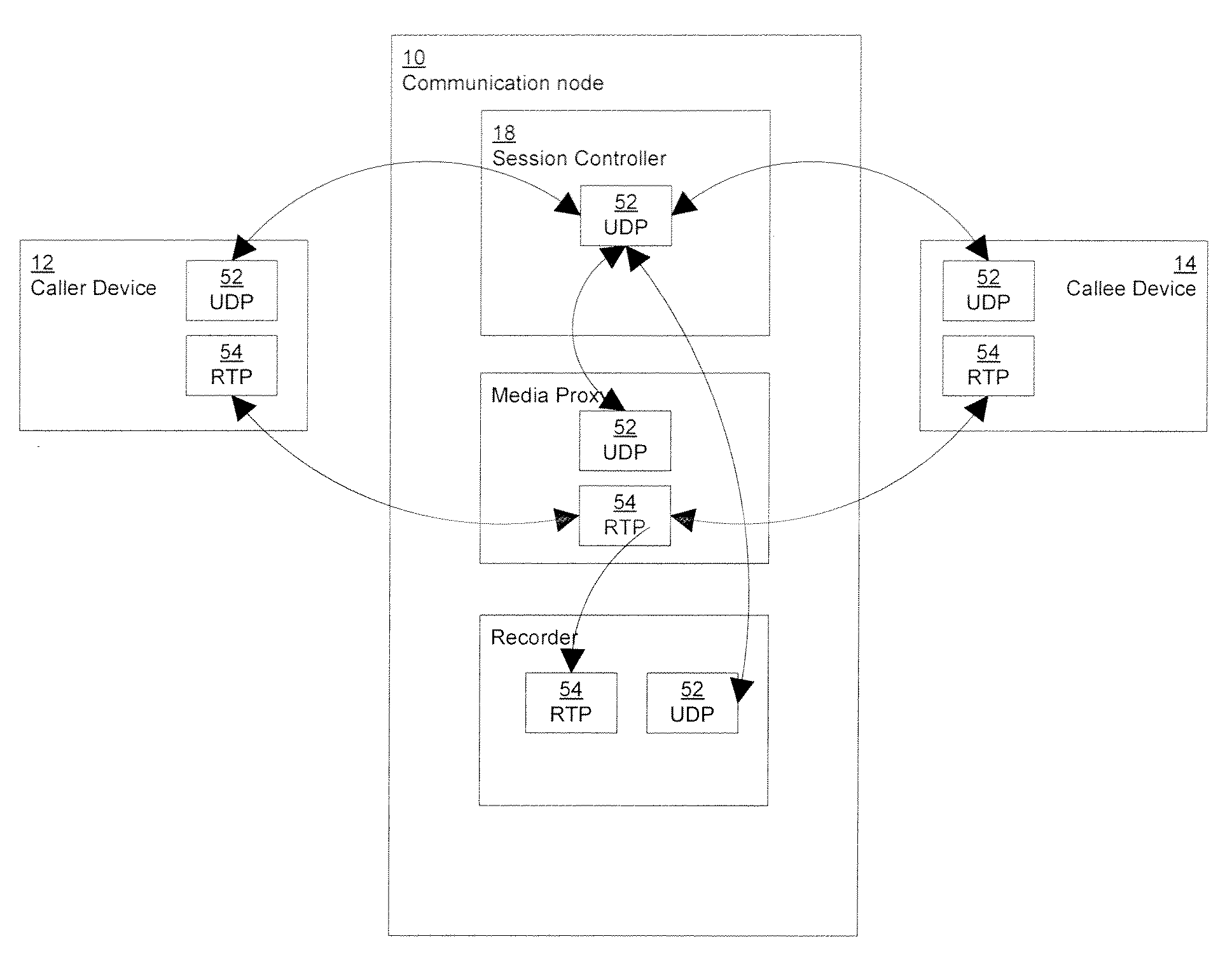
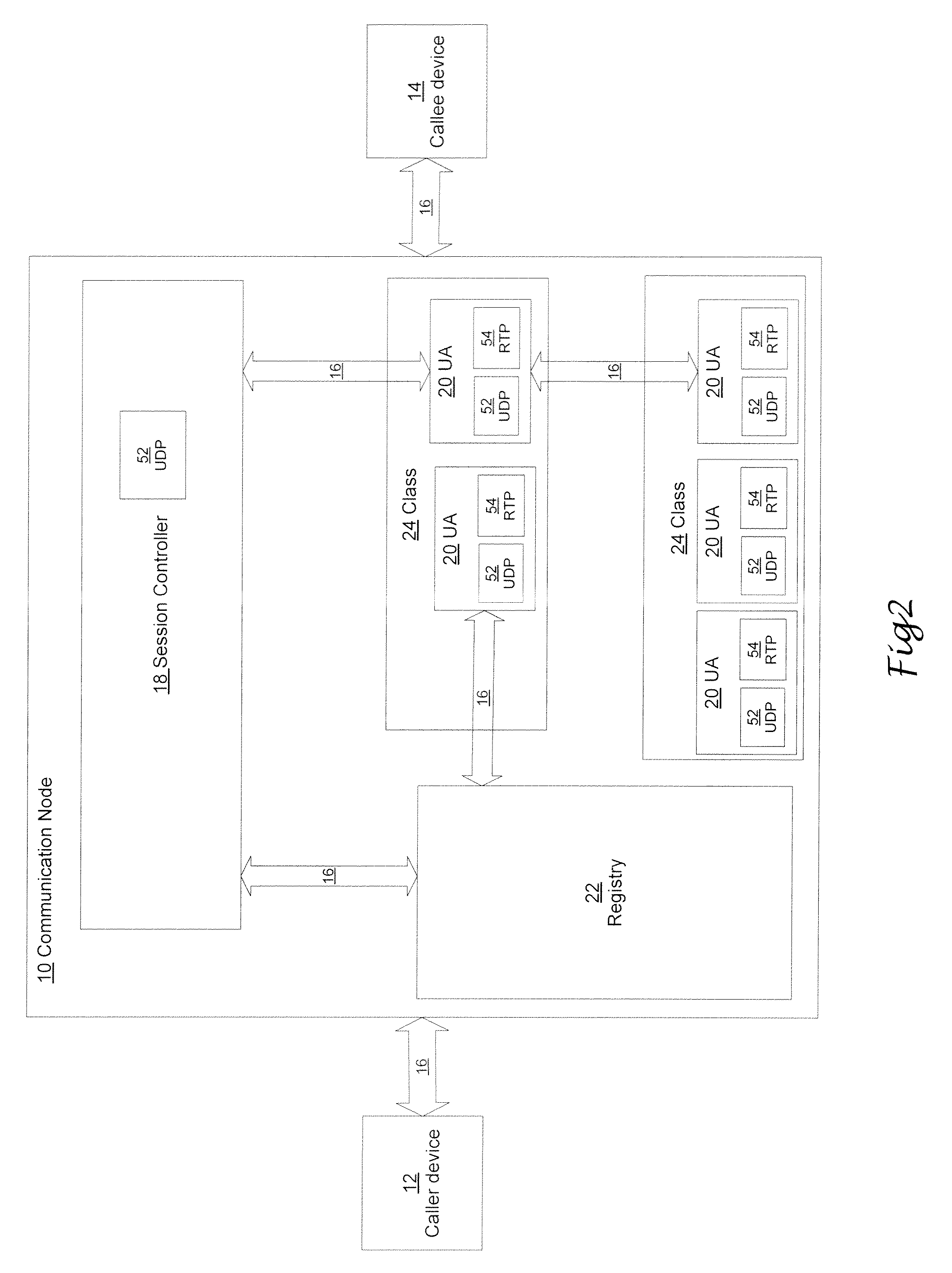
Communication node and method for handling sip communication
The present invention relates to a communication node and method for connecting and maintaining a call between a caller device and a callee device. The communication node comprises a session controller module and a plurality of internal SIP UA (Session Initiation Protocol User Agent) servers. The session controller module is adapted to remain in communication with the caller device and the callee device through a whole duration of the call. The plurality of internal SIP UA servers is adapted to communicate with the session controller module by open protocol.
Owner:PARAXIP TECH
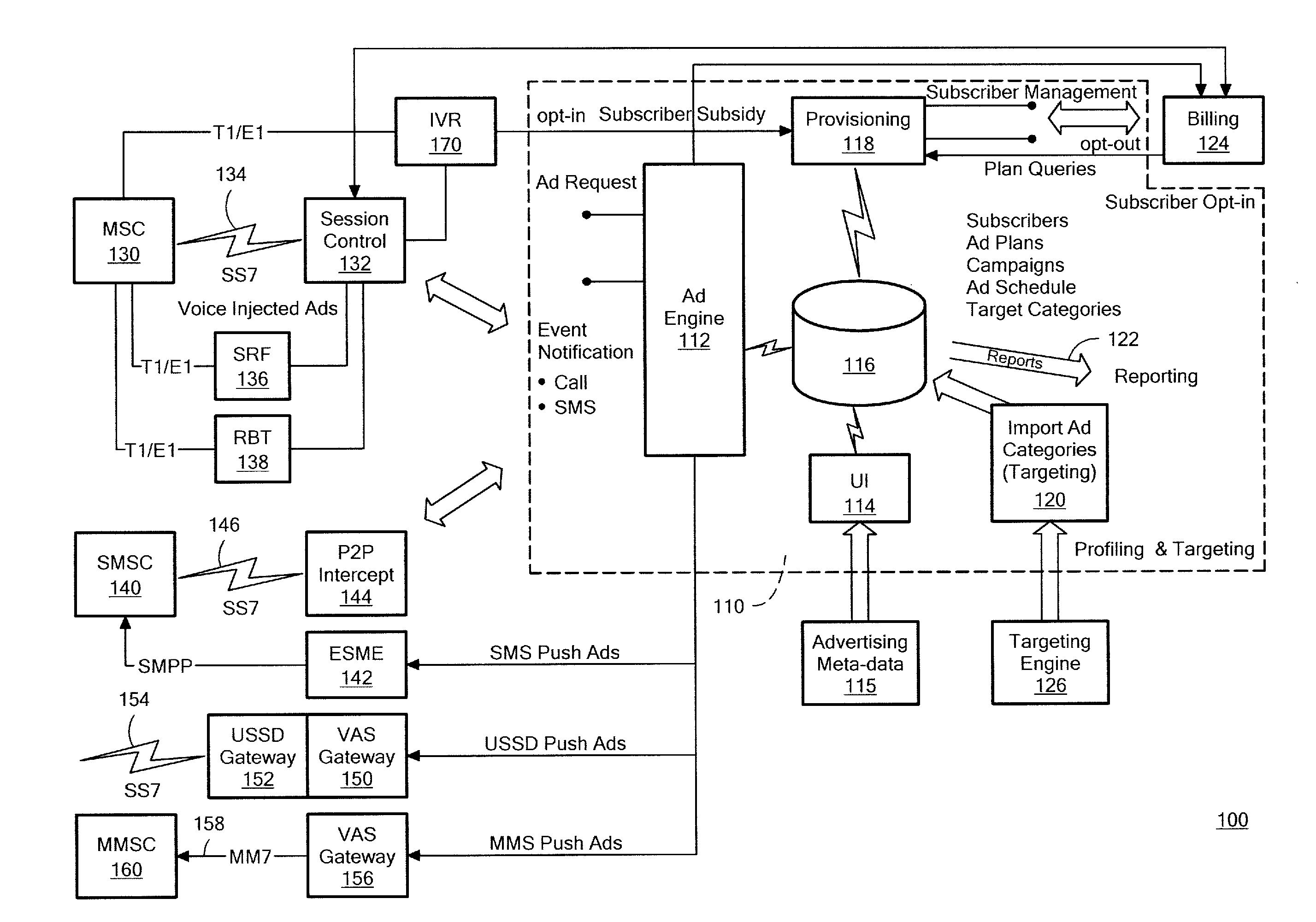
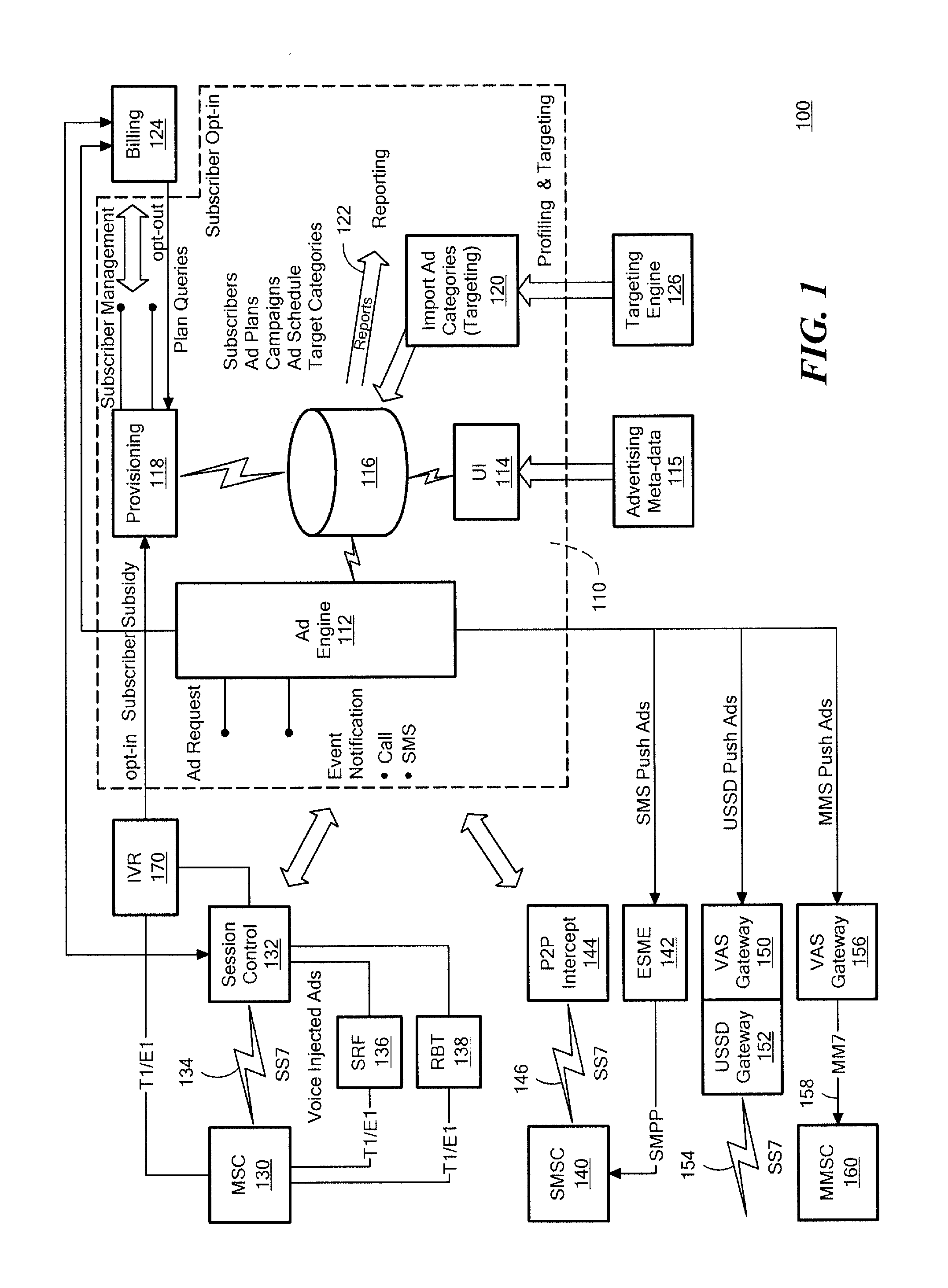
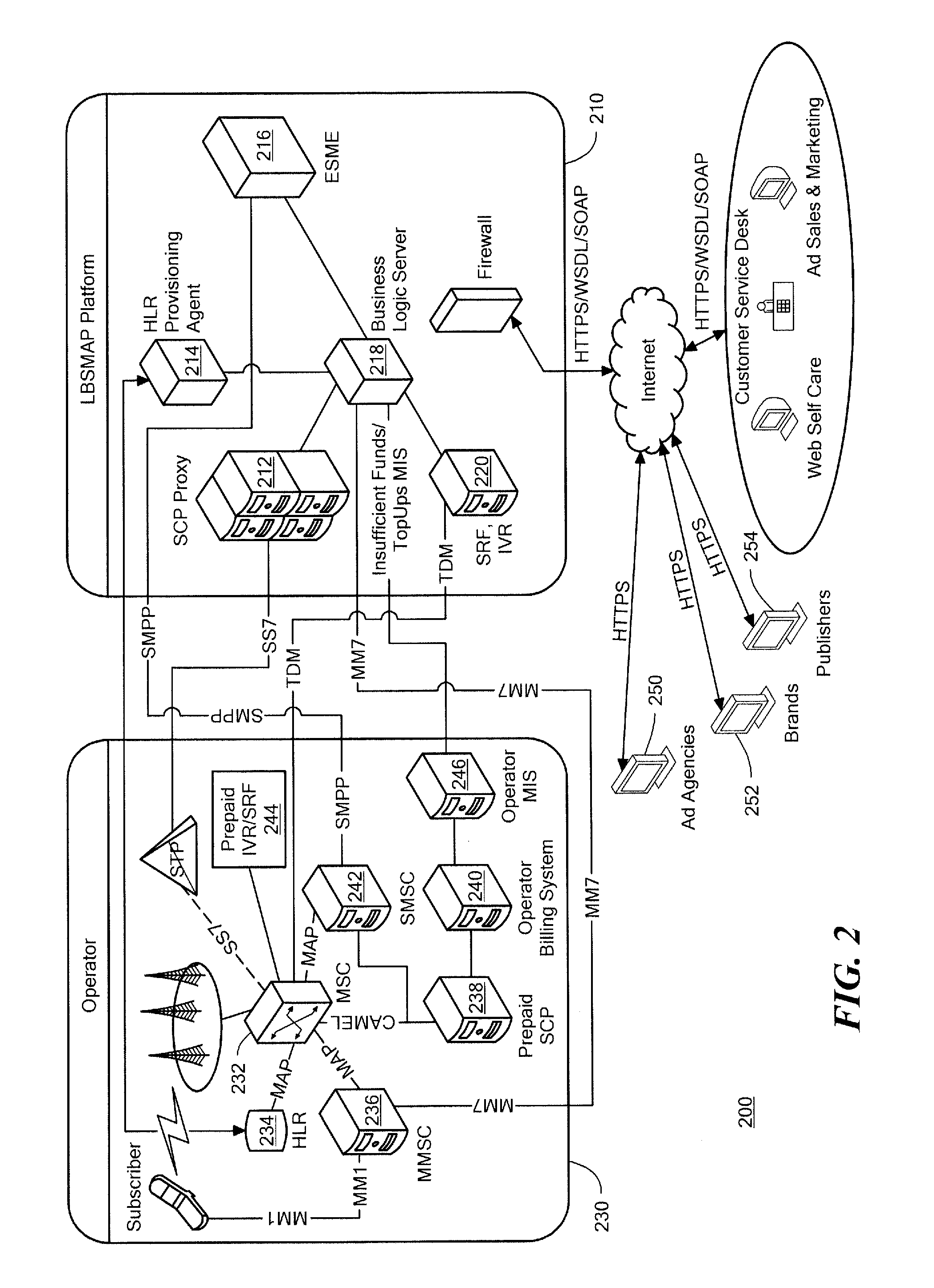
Method and apparatus for rule triggered mobile advertising
An advertising subsidized communication service is provided that can be utilized by eligible subscribers in instances designated by mobile operators or advertisers. An eligible subscriber that meets certain criteria, such as having a low pre-paid balance, can opt-in to an advertising subsidized service initiated through an SCP proxy for the advertising service platform. The subscriber receives advertising through selected channels, such as voice injection, text messaging or other media, which advertising subsidizes subscriber communication service. The subsidized service may be limited in some regard to number of calls, call duration or incoming calls, as examples. The subscriber may be automatically opted-out of the subsidized service upon payment being applied to a pre-paid for post-paid service account. The opt-in process for subsidized service occurs in real-time and may be prompted through a number of channels, such as voice or text messages.
Owner:XIUS CORP
Method and device for analyzing user social relation
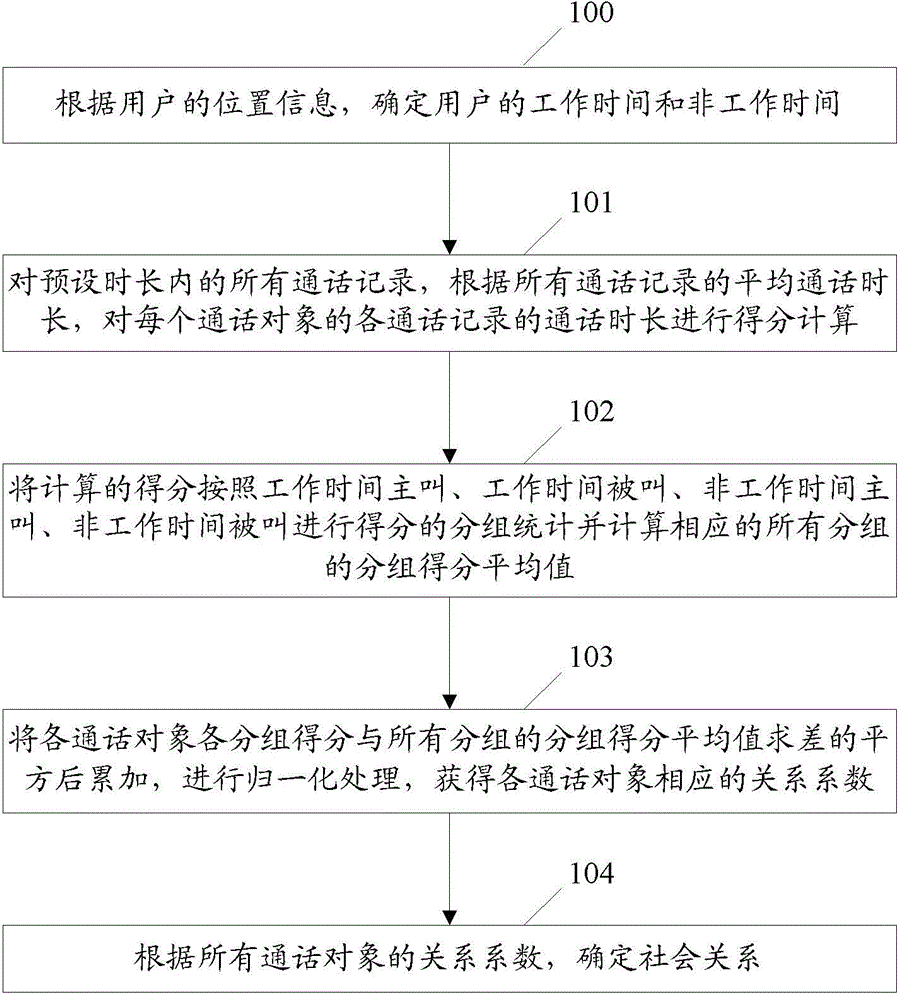
ActiveCN104636439APrecise positioningSpecial data processing applicationsMarketingWork periodComputer science
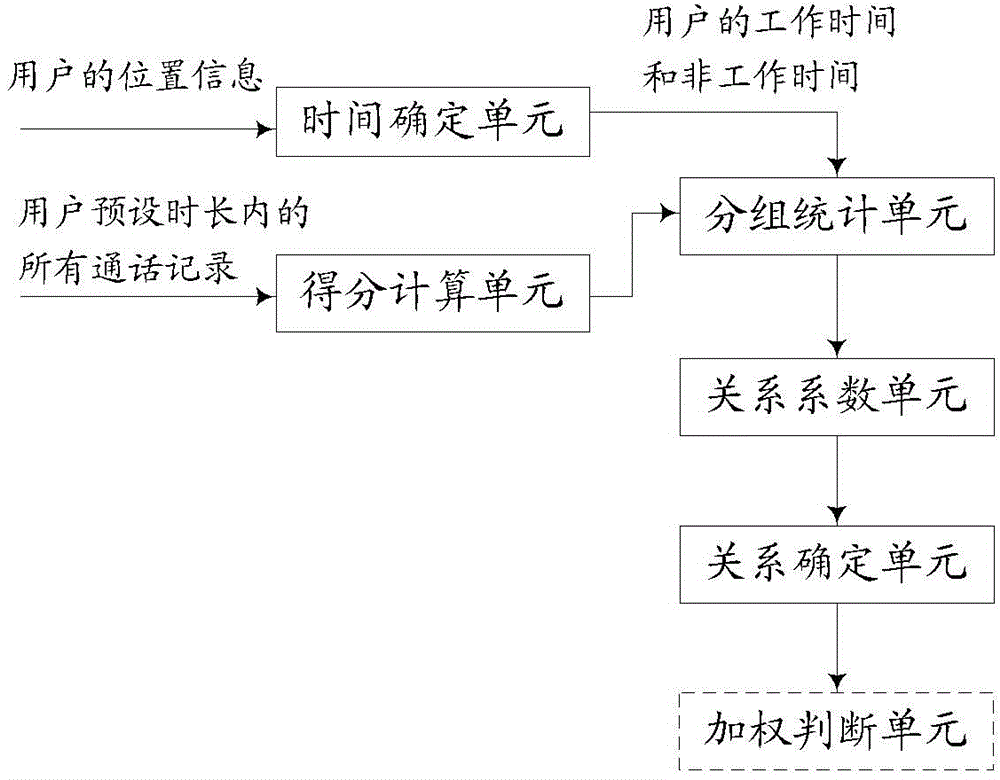
The invention discloses a method and device for analyzing the user social relation. The method comprises the steps that according to position information of a user, working time and non-working time of the user are determined; according to average call duration of all call records within the preset duration, scoring calculation is carried out on the call duration of all the call records of each call object; according to an originating call at the working time, an incoming call of the working time, an originating call of the non-working time and an incoming call of the non-working time, scoring grouping statistics is carried out, and grouped score average values of all groups are calculated; the square of the difference is carried out on the grouped scores of the call objects and the grouped score average value of the all groups, accumulation and normalization processing are carried out, and corresponding relation coefficients of all the call objects are obtained; according to the relation coefficients of all the call objects, the social relation is determined. Grouped statistics is carried out on the call records of the user, the social relation is accurately located according to the obtained relation coefficients, the basis is provided for service popularization of an operator, and the important reference basis is provided for applying and checking of relevant services.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Communication terminal and address book ordering method thereof
InactiveCN102780803AOperation conforms toThe sorting result is reasonableSubstation equipmentAddress bookData acquisition
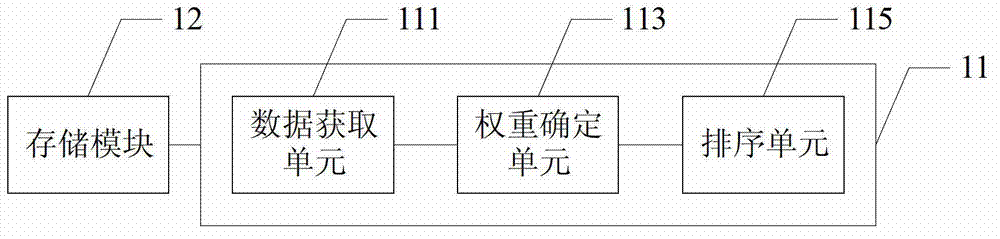
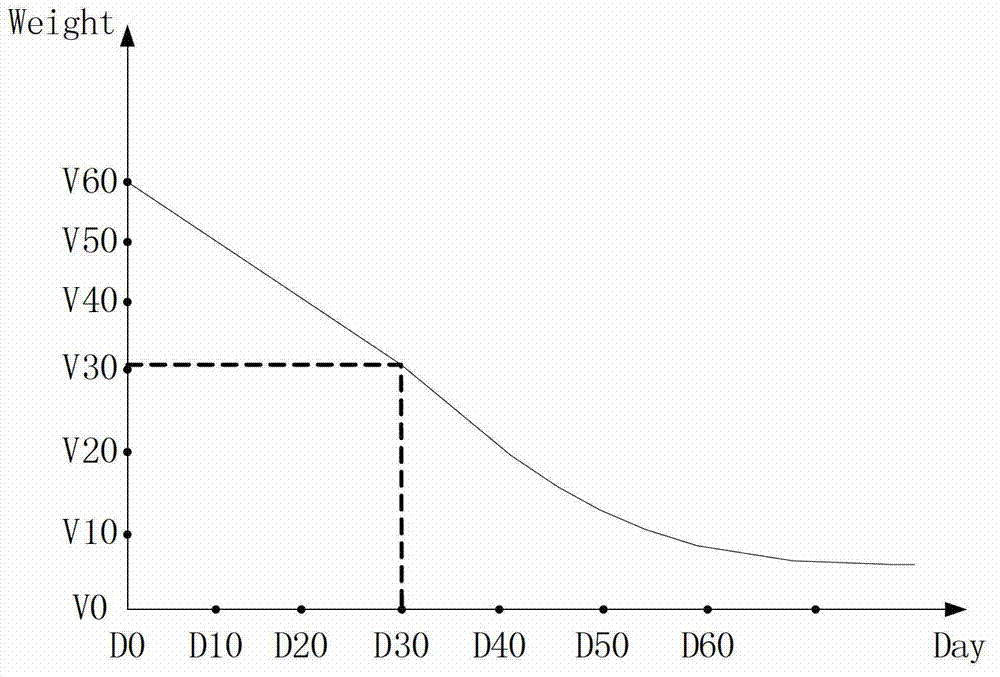
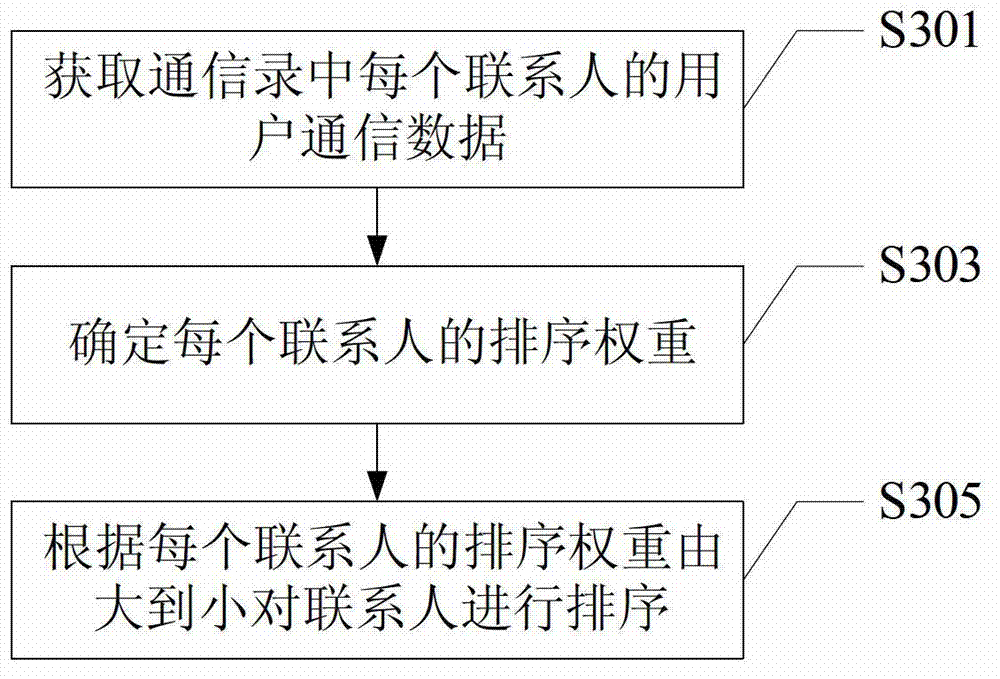
The invention discloses an address book ordering method for a communication terminal and the communication terminal. The method comprises the following steps of: a data acquisition step, namely acquiring user communication data of each contact in an address book, wherein the user communication data of each contact comprises the communication frequency, the communication occurrence time and the call duration of the communication between the communication terminal and the contact; a weight determination step, namely determining the ordering weight of each contact according to the acquired user communication data; and an ordering step, namely ordering contacts according to the order weights of each of the contacts from large to small. The ordering weights provided by the invention are determined according to the communication time length, the communication frequency, the interval length between the communication occurrence time at each time and the current time and the like, namely various factors which influence the ordering of the communication book are considered synthetically in the ordering of the address book, and a certain aspect of the influence factors is not biased, so that the ordering result is more reasonable; and therefore, the operation of the address book of the communication terminal is more accordance with actual need.
Owner:SHENZHEN TINNO WIRELESS TECH
Apparatus and method for recording incoming call information
InactiveUS6961420B2Cordless telephonesSpecial service for subscribersStart timeIdentification device
A method for interrelating call information between programs of a data processing device. Call information including a caller's name, phone number, the date of the call, start time of the call, finish time of the call, the call duration, and the type of call, may be organized and accessed by several different programs running on a data processing device. Information such as a caller's name and phone number may be accessed by a caller identification device coupled to the data processing device. Information such as the start time and finish time may be accessed by a clock coupled to the data processing device. The call duration may be calculated from the start and finish times or may be accessed from a timer coupled to the data processing device.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for improving cluster performance through minimization of method variation
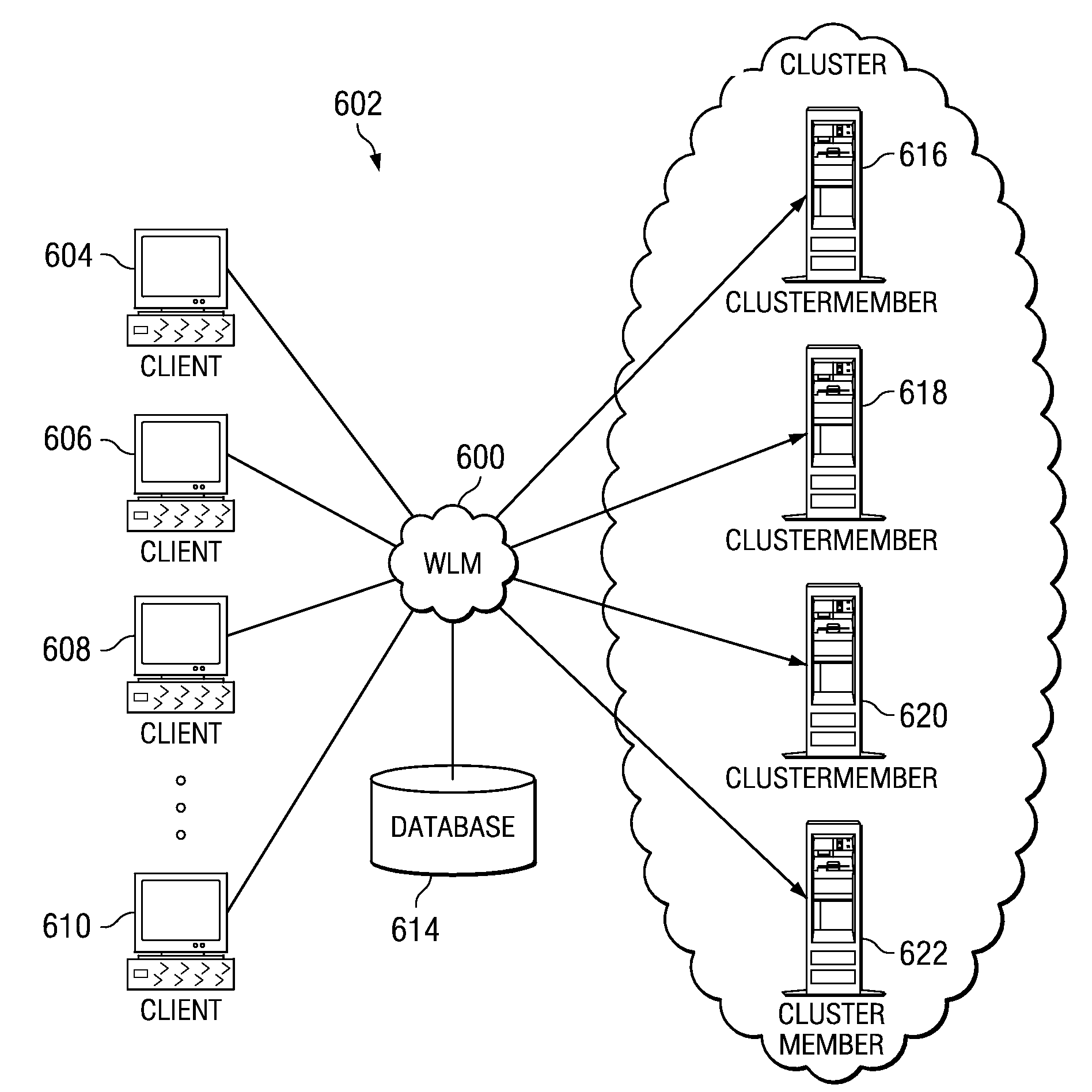
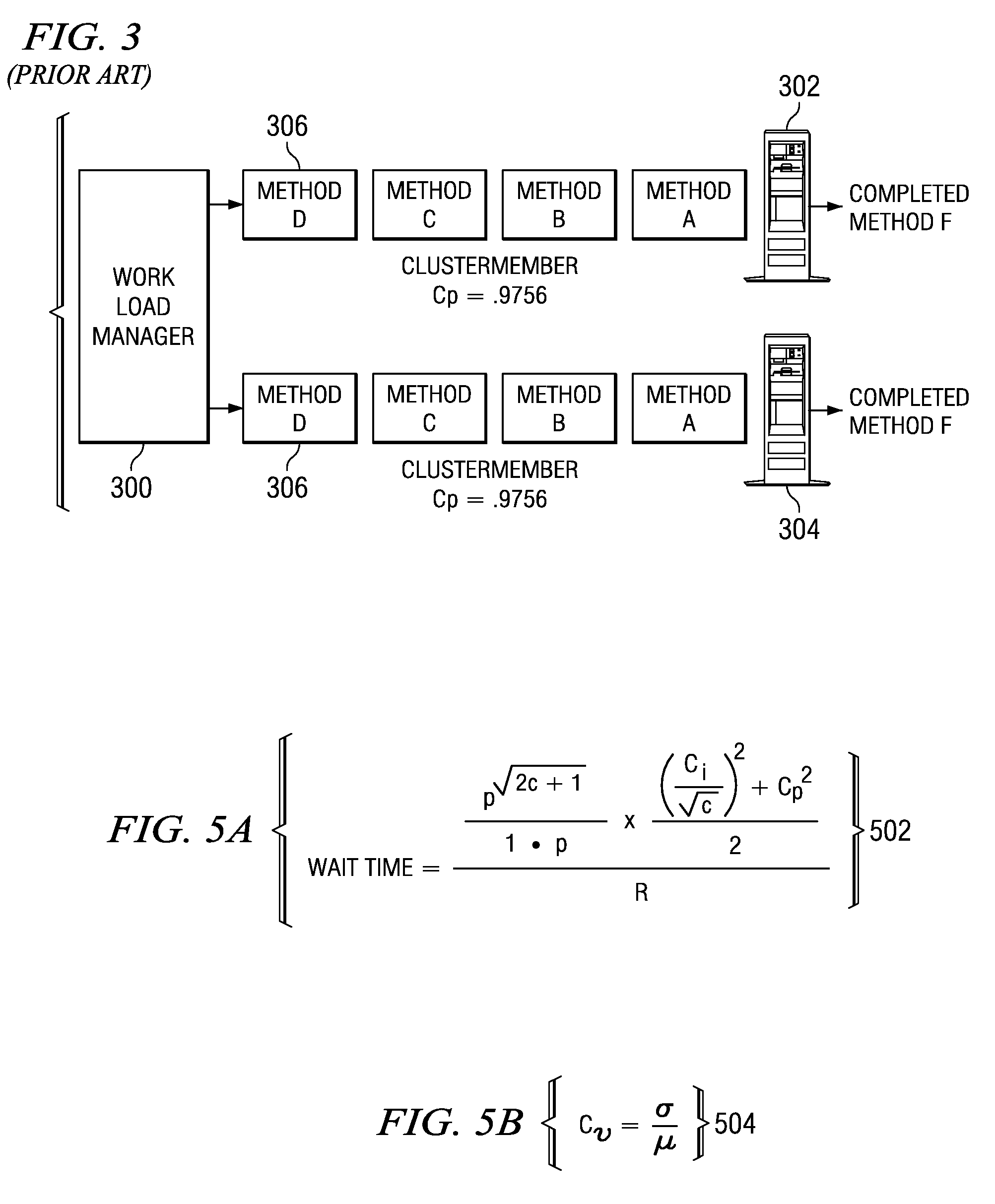
InactiveUS20080021988A1Reduces coefficient of variationReduce variationDigital computer detailsTransmissionCoefficient of variationOperating system
A computer implemented method, apparatus, and computer usable program code for managing a server cluster. The process identifies a plurality of average method call durations corresponding to calls to a plurality of methods associated with an application on the server cluster to form a plurality of identified average method call durations. The process groups the plurality of methods based on the plurality of identified average method call durations to form a plurality of grouped methods. Each method in the plurality of grouped methods is executed by a particular cluster member in the server cluster. The manner in which the plurality of grouped cluster members is grouped reduces a coefficient of variation on each cluster member in the server cluster. The process executes a method in a selected cluster member associated with the method in response to receiving a call for the method.
Owner:LINKEDIN
Implement method and device of terminal call firewall
InactiveUS20110283349A1Easy to implementSimple and efficientComputer security arrangementsMultiple digital computer combinationsStart timeBlack list
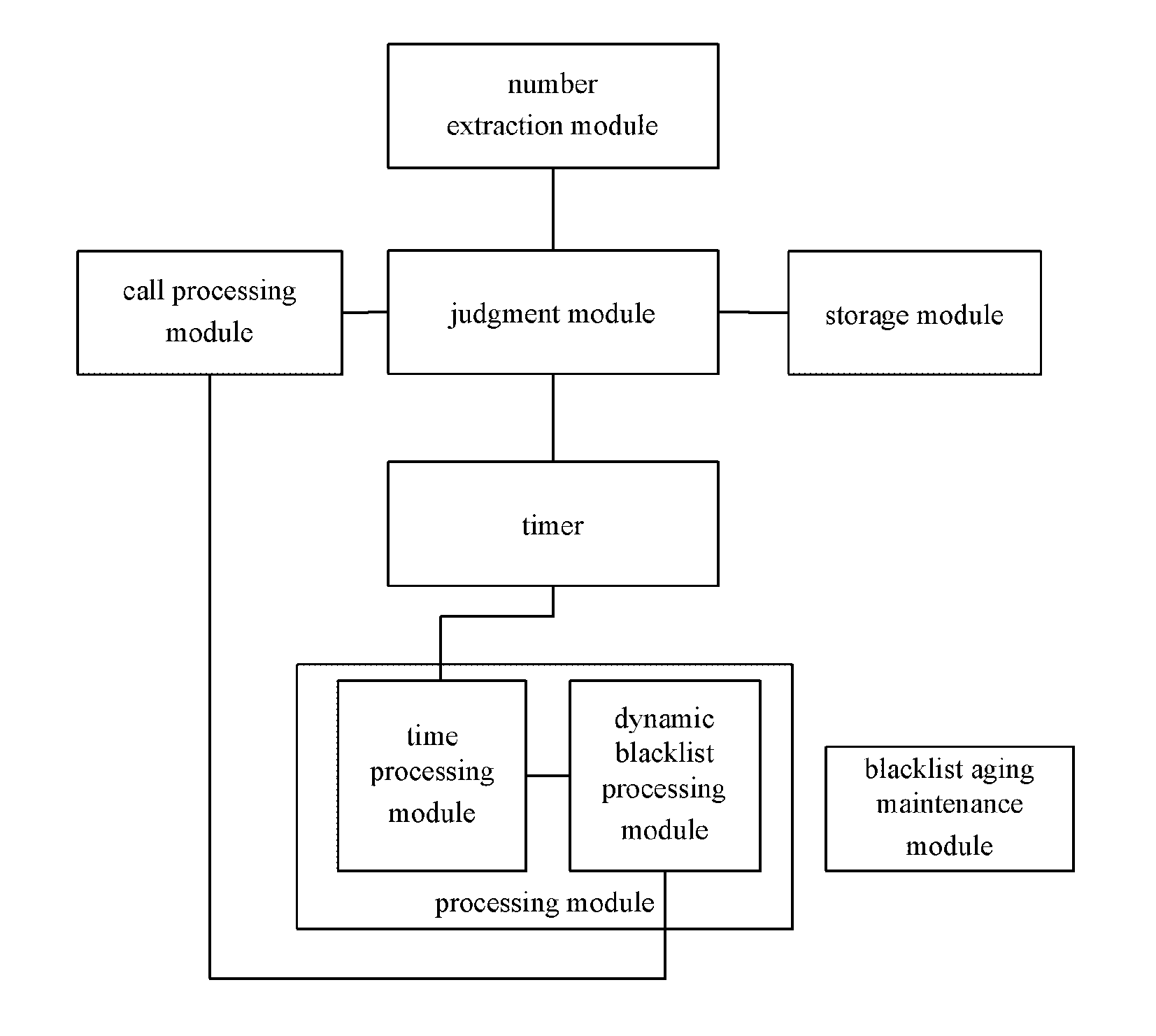
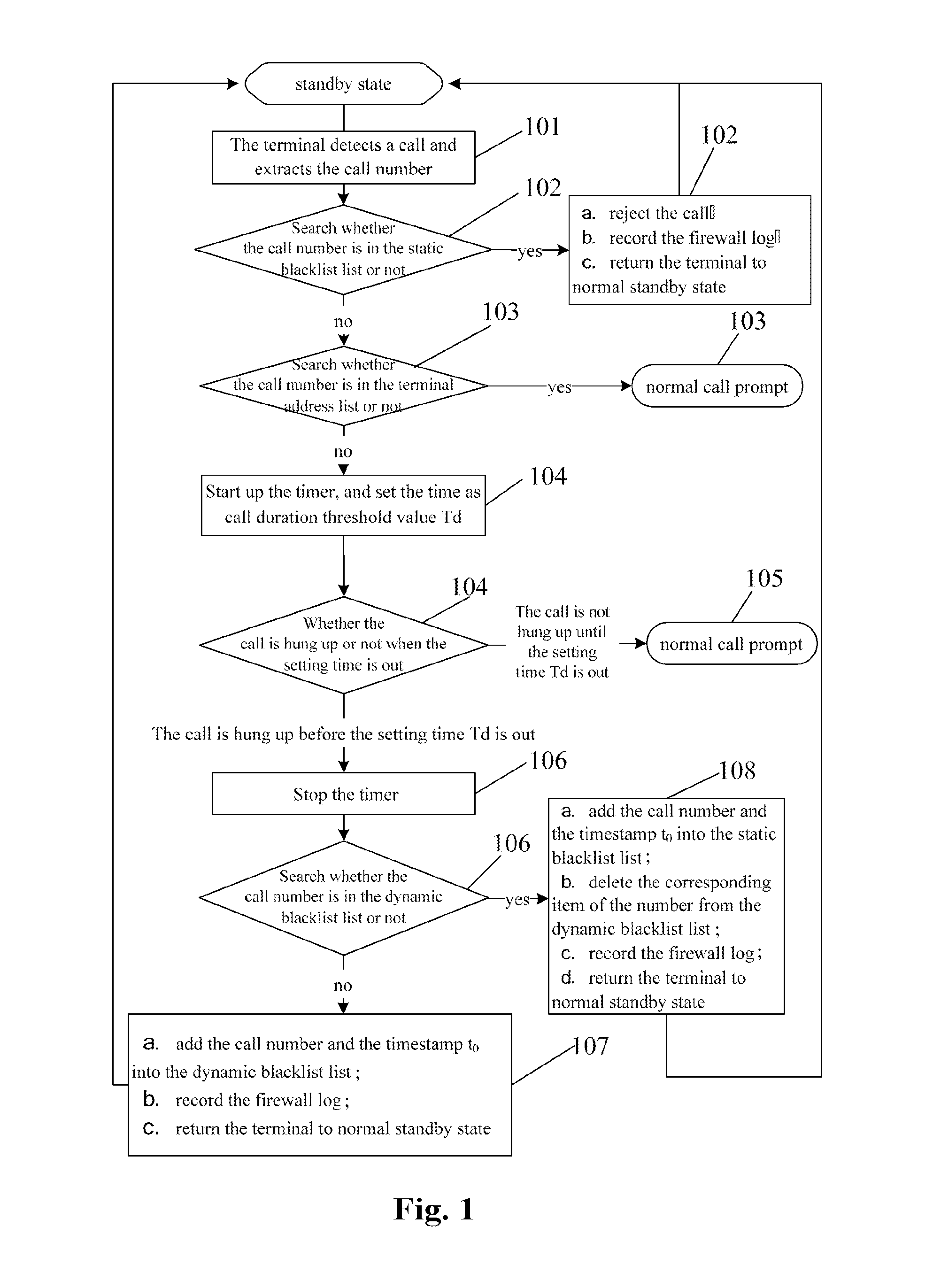
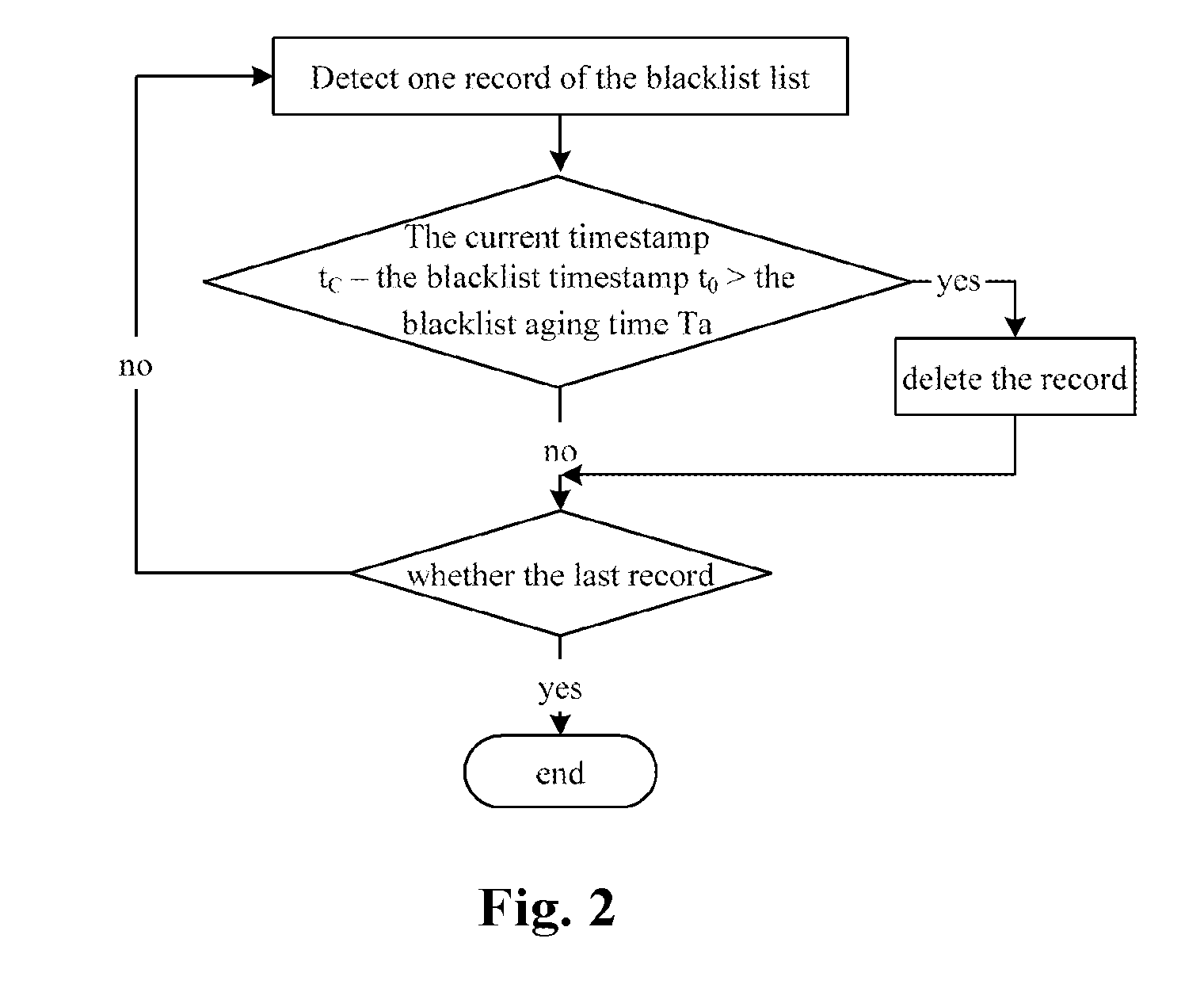
The present invention discloses an implement method and device of a terminal call firewall. The method comprises: adding a call number into a blacklist list, when it is determined that the call number is not in the blacklist list stored and an address list and it is determined that a call duration is less than a set call duration threshold. The device comprises: a storage module, which is connected with a judgment module, and configured to store a blacklist list and an address list; the judgment module, which is connected with a storage module and a timer, and configured to start up the timer to start timing when a call number is determined not in the blacklist list and the address list; the timer, which is connected with the judgment module and a processing module, and configured to make timing for a time length of a call duration threshold; the processing module, which is connected with the timer, and configured to add the call number into the blacklist list when the duration of the call is determined less than the call duration threshold. Through the method and the device, the present invention can ensure the terminal to identify unknown harassing call automatically during operation, can add the number of the call directly into the blacklist list, does not bother the user by ringing or prompting the user of the call, is simple and convenient to be used, and has remarkable practical effect.
Owner:PATTINGTON IP LLC
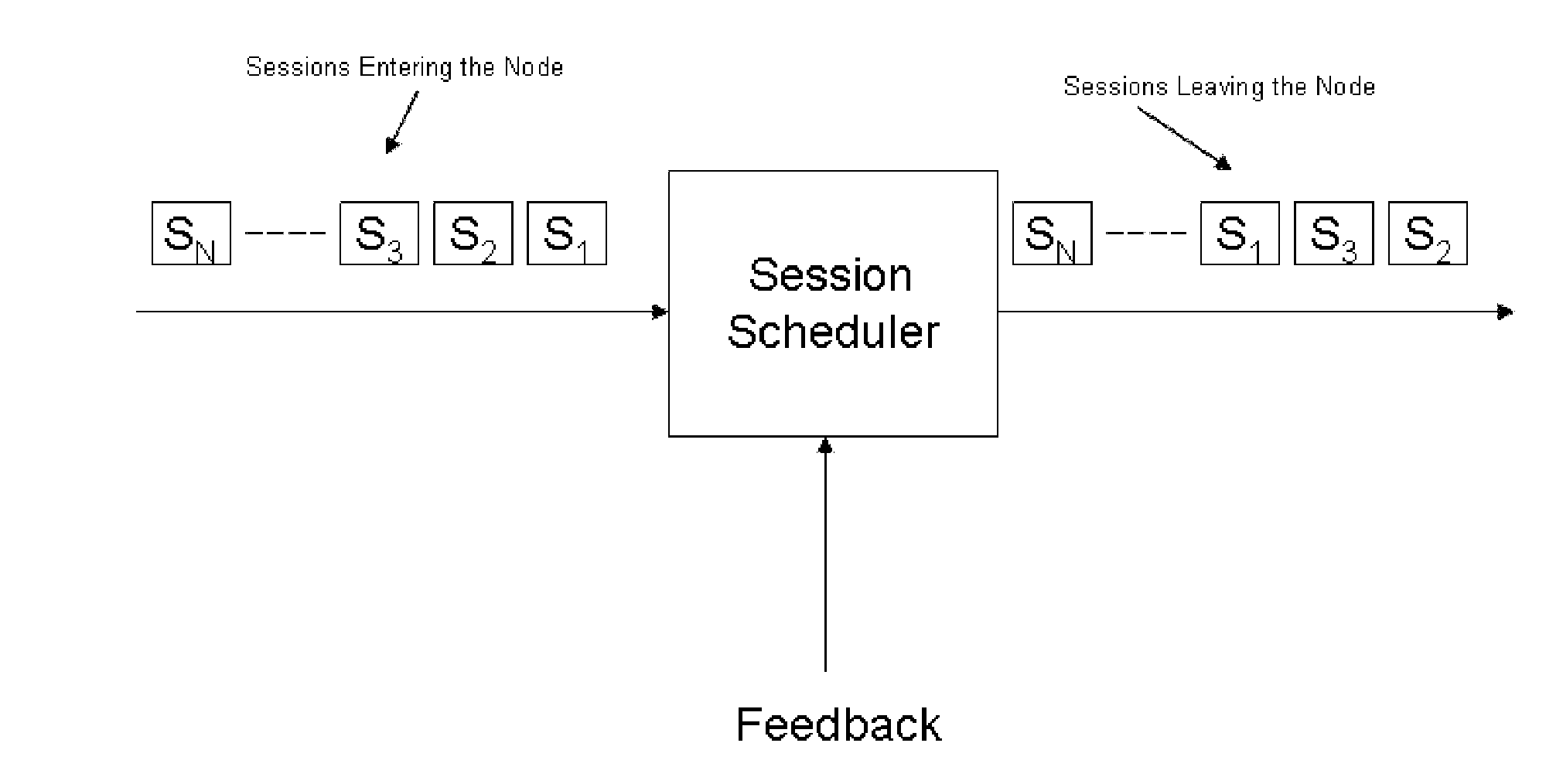
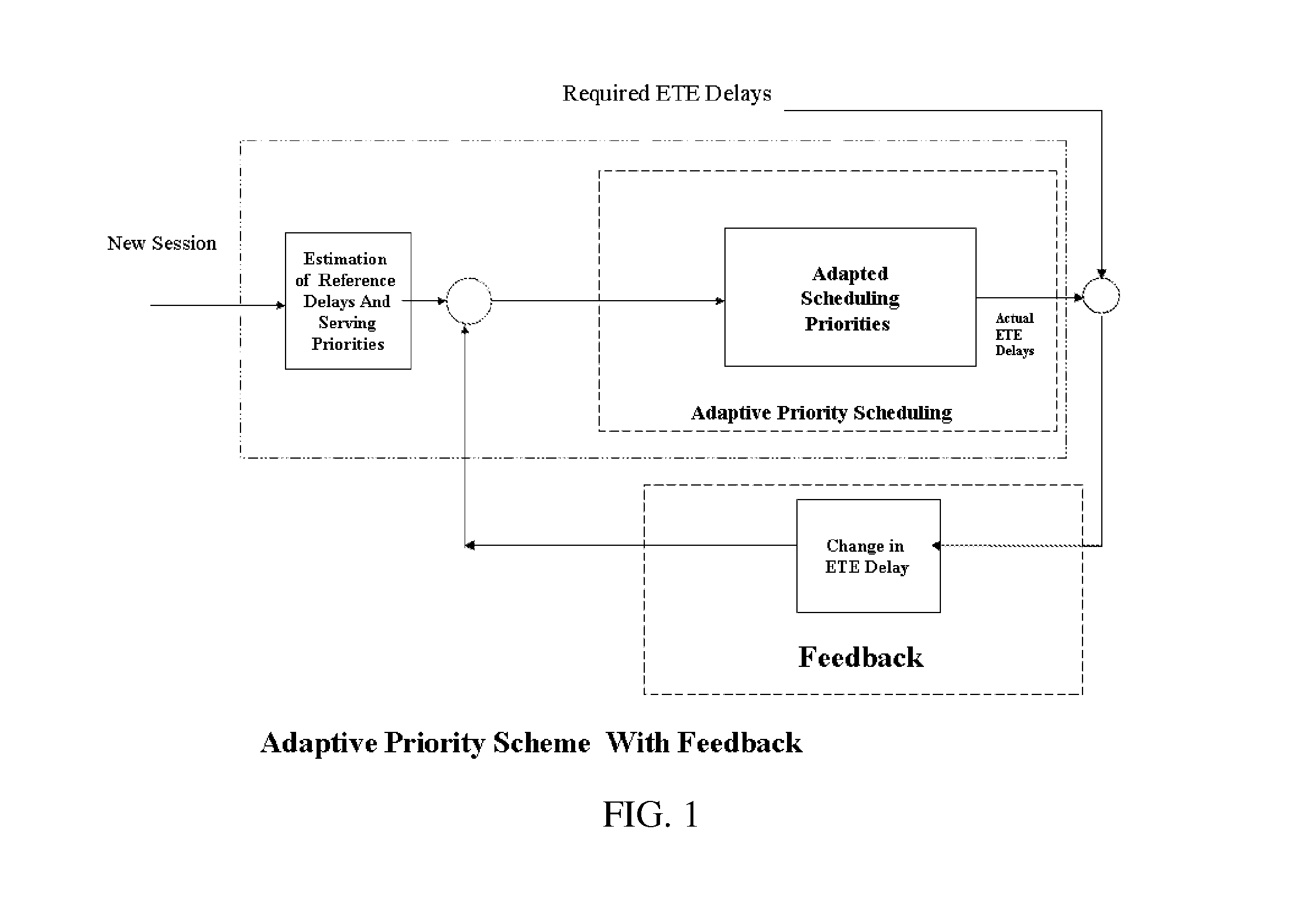
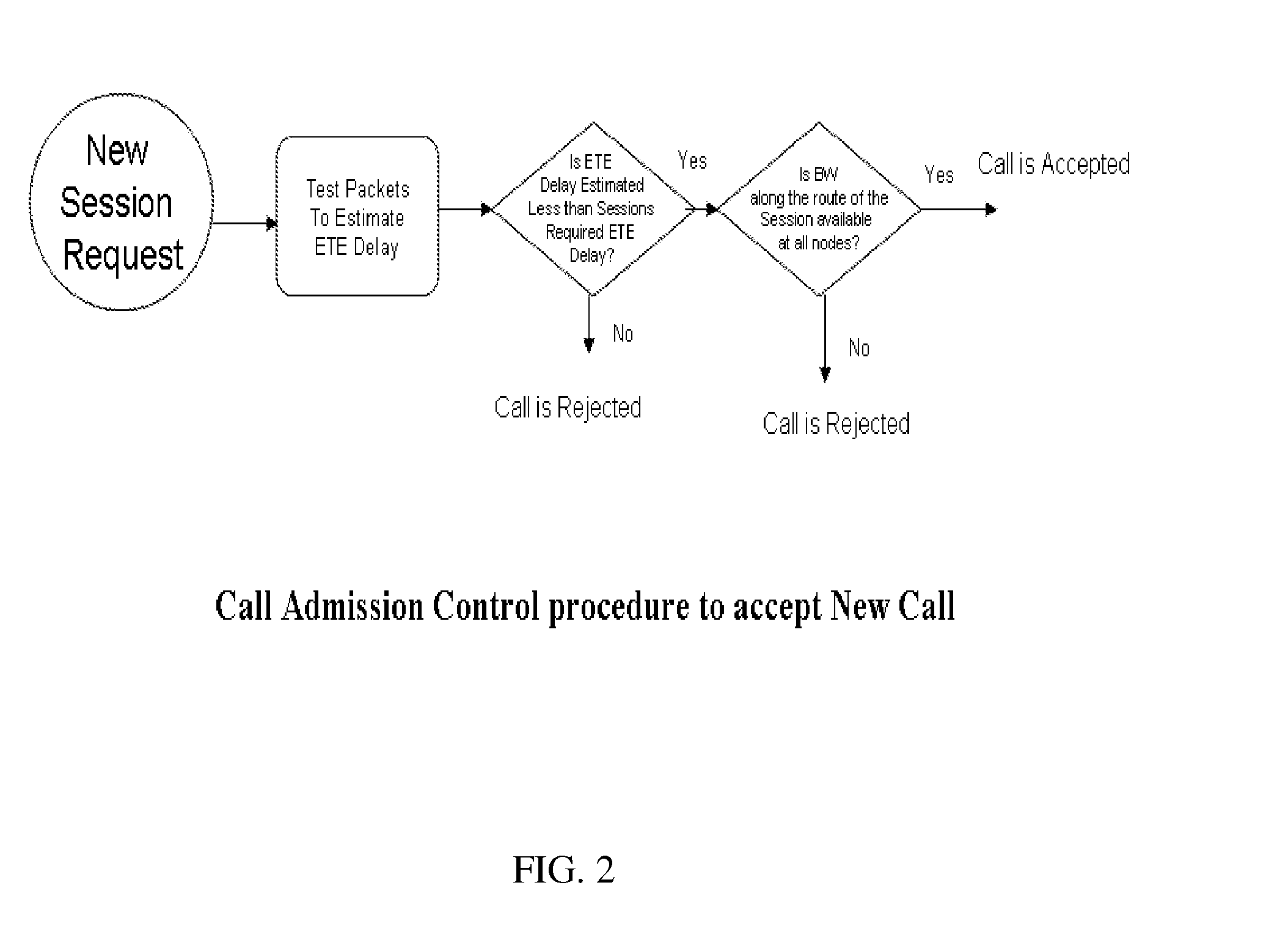
Control of end-to-end delay for delay sensitive IP traffics using feedback controlled adaptive priority scheme
When transporting delay-sensitive traffics such as voice, video and radar data over Internet Protocol (IP), control of end-to-end delay becomes a challenge. Typical approaches tie up bandwidths for entire duration of call. Second thing they do, is prioritization of certain classes over others, to control queuing delays, but this prioritization, remains at class-level and does not go to individual session-levels. As a result certain sessions within a class get more delay than others. Depending upon situation, it can cause adverse effects to certain QoS sessions. In our invention we have developed an intelligent priority scheme which adapts serving priorities of sessions to control ETE delay of each individual QoS session. Priority adapting mechanism is based on feedback control which measures ETE delay of QoS session at destination node and broadcasts it to all nodes along the route of the session to adapt session's priorities to control ETE delay.
Owner:AHMED FAHEEM
Network expansion method and network expansion evaluation device
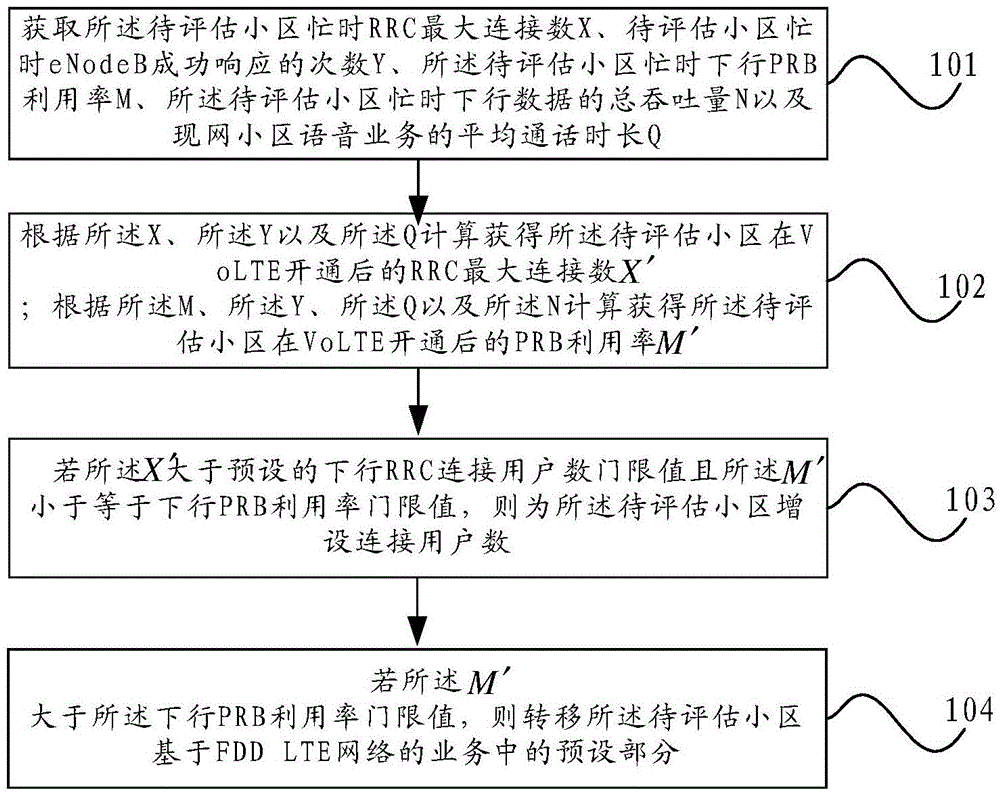
ActiveCN105611546AReduce business loadEnsure perceptionNetwork traffic/resource managementNetwork planningResource blockTime evolution
The invention provides a network expansion method and a network expansion evaluation device, which relate to the technical field of communications and are applied to cell network expansion. The network expansion method comprises the steps: obtaining a busy-hour RRC (Radio Resource Control)maximum connection number X, busy-hour eNodeB successful response times Y, a busy-hour downlink PRB (Physical Resource Block)utilization rate Mand busy-hour downlink data total throughput N of a to-be-evaluated cell,and average call duration Q of a voice service of an existing network cell; according to the X, Y and Q, calculating to obtain an RRC maximum connection number X' of the to-be-evaluated cell after VoLTE (Voice over LTE)is opened; according to the M, Y, Q and N, calculating to obtain a PRB utilization rate M' of the to-be-evaluated cell after the VoLTE is opened; if the X' is larger than a preset downlink RRC user connection number threshold and the M' is smaller than or equal to a downlink PRB utilization rate threshold, additionally configuring a user connection number for the to-be-evaluated cell; if the M' is larger than the downlink PRB utilization rate threshold, transferring preset parts of services of the to-be-evaluated cell based on FDD LTE(Frequency Division Duplexing Long Time Evolution) network.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
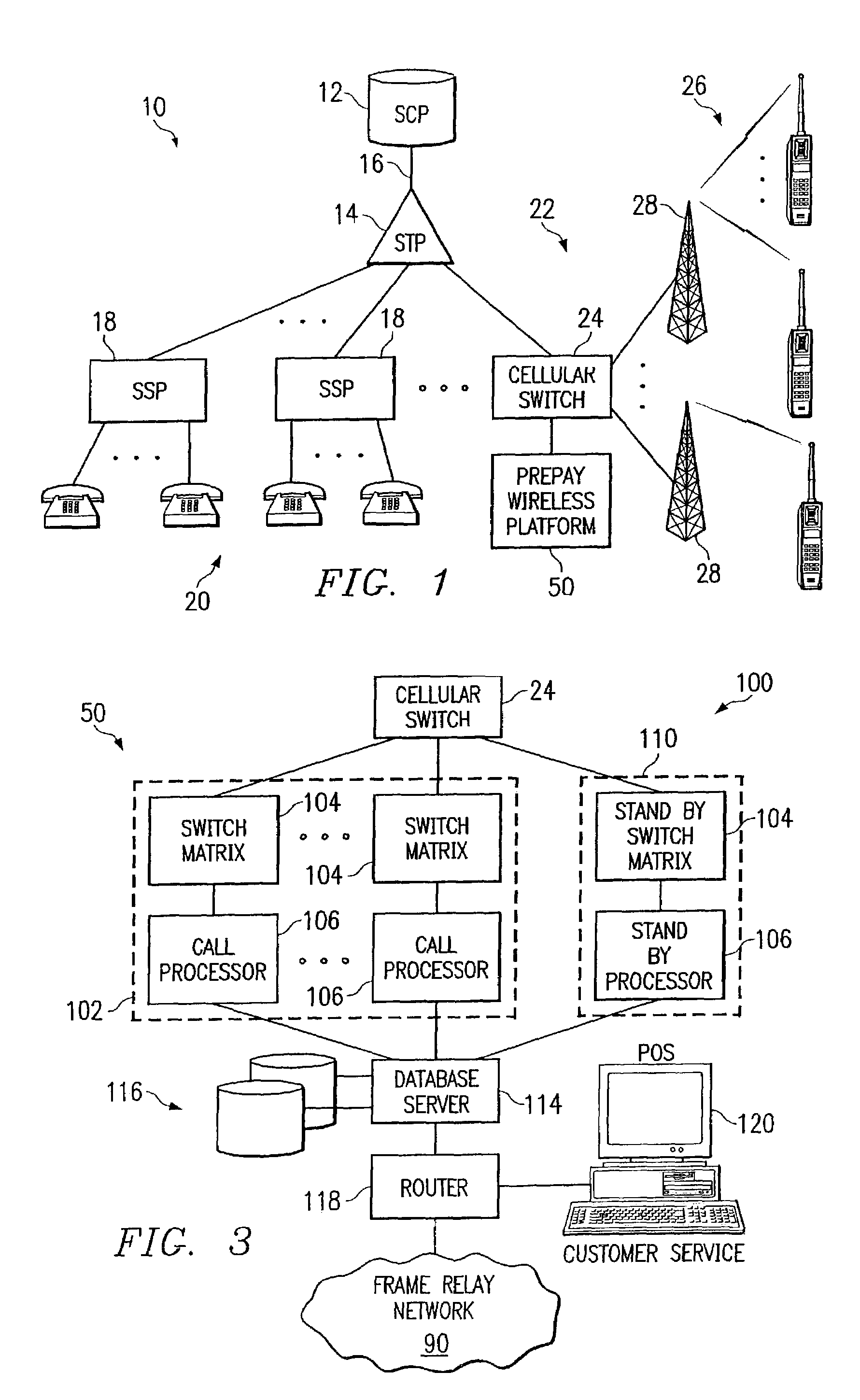
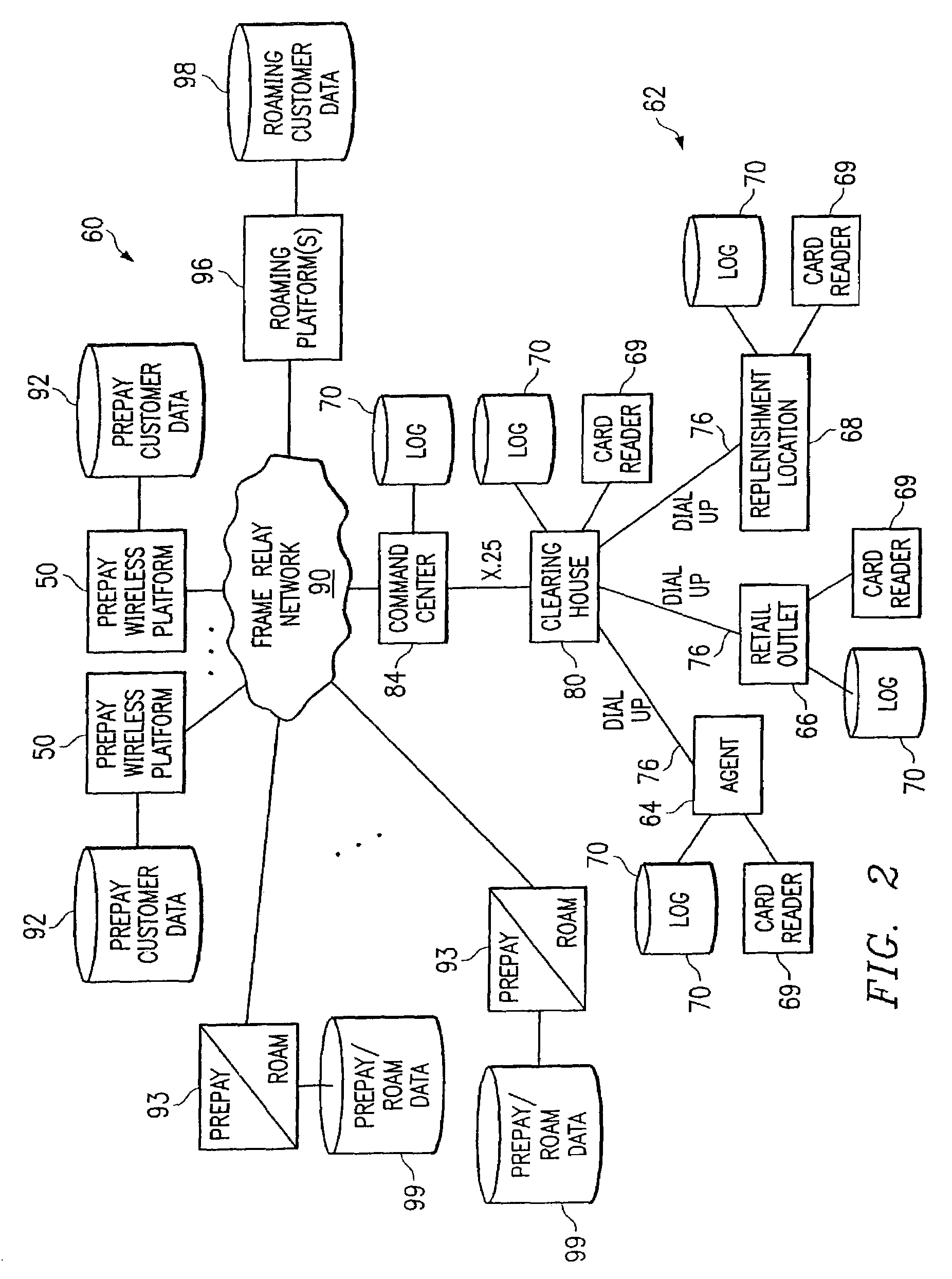
Prepay telecommunications system
InactiveUS7162220B2Reduce usageAccounting/billing servicesRadio/inductive link selection arrangementsMobile identification numberTimer
Owner:FREEDOM WIRELESS
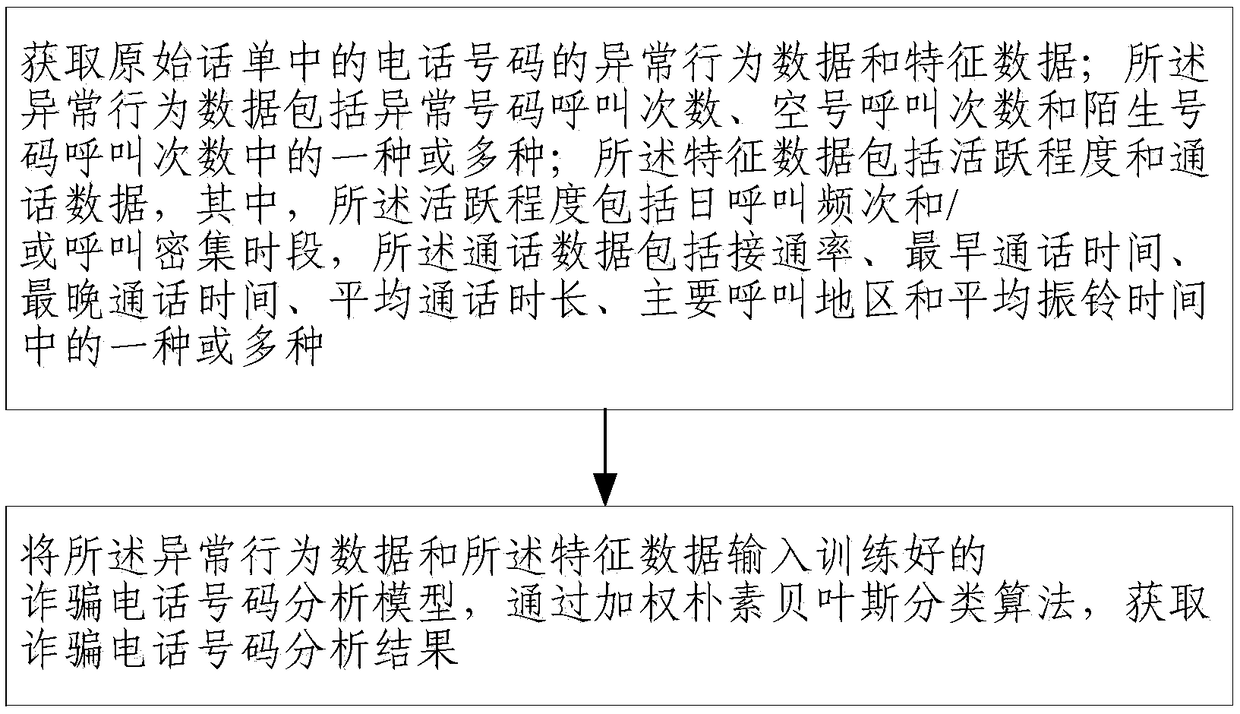
Fraudulent telephone number analysis method and equipment
InactiveCN108093405AAccurate analysisEasy to analyzeSecurity arrangementNetwork planningFeature dataAnalysis method
The invention provides a fraudulent telephone number analysis method and equipment. The analysis method comprises the following steps: acquiring abnormal behavior data and feature data of telephone numbers in an original telephone bill, wherein the abnormal behavior data include one or more of number of calls of abnormal numbers, number of calls of vacant numbers, and number of calls of strange numbers, and the feature data comprise activity degree and call data, wherein the activity degree comprises the daily call frequency and / or a call intensive time period, and the call data comprise one or more of call completing rate, earliest call time, latest call time, average call duration, main call area and average ring time; and inputting two kinds of data into a trained fraudulent telephone number analysis model, and acquiring a fraudulent telephone number analysis result through a weighted naive Bayesian classification algorithm. The fraudulent telephone number analysis method provided by the invention can accurately analyze whether a telephone number is a fraudulent telephone number, and a multi-dimensional fraudulent telephone number analysis model is obtained, so that whether thetelephone number is the fraudulent telephone number can be comprehensively analyzed.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method for carrying out real-time fee deduction during instant messaging
InactiveCN101527640AReduce intermediate linksMetering/charging/biilling arrangementsE-commerceClient-side
The invention discloses a method for carrying out real-time fee deduction on the user during instant messaging which belongs to the network technical field. An adopted technical proposal is as follows: a flash chat window, a background socket server and a background database are adopted to realize the fee deduction process concretely by a server script and a control component. Firstly, two chatting parties open the chat window to chat, free of charging, if charging is required, the user can carry out the real-time fee deduction on a user account just by clicking a charging-starting button, which is similar as the fee deduction mechanism of telephone, and the difference is that on-line chatting deducts fees from one party and supplements the sum of money to an account of the other party at real time simultaneously. In addition, the system can adjust chatting modes at any time according to the balance of the account automatically and carries out the classified statistic of call duration according to the current mode of the user. The invention does not require the user to install any client end software and promotes the popularization and application of instant communication tools in the field of e-business.
Owner:周佺喜
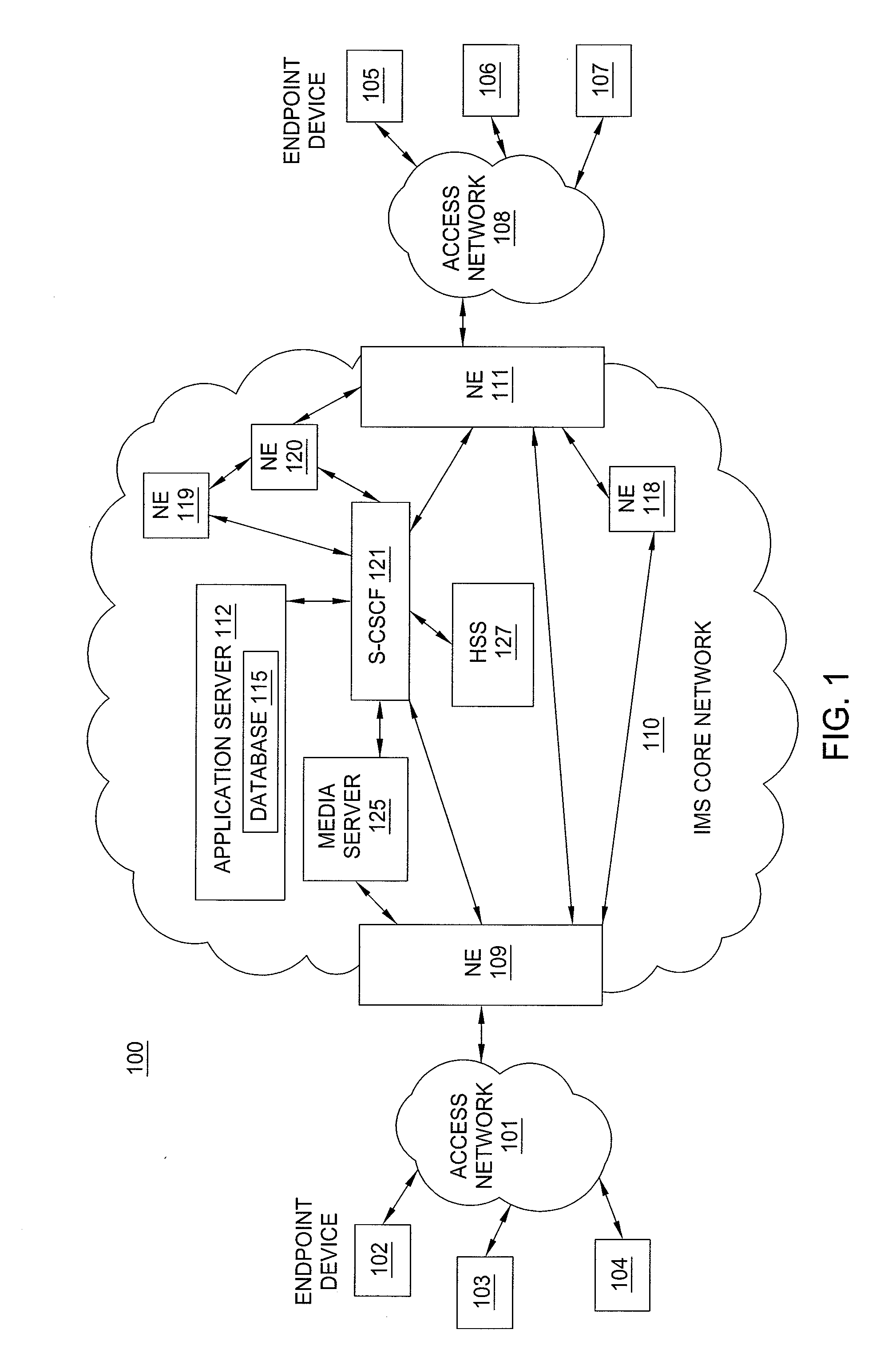
Method and system for determining service metrics in a wireless network
A method and system for determining service metrics in a communications network are disclosed. The method measures a speed of a wireless endpoint device in an ongoing call, and collects call performance data. The method deems the ongoing call as being associated with a user who is mobile if the speed of the wireless endpoint device exceeds a speed threshold at any time during the ongoing call, or as being associated with a user who is stationary if the speed of the wireless endpoint device does not exceed or is equal to the speed threshold over a call duration. The method adds the call performance data to an aggregate service metrics for mobile users if the ongoing call is deemed as being associated with a user who is mobile, or to an aggregate service metrics for stationary users if the ongoing call is deemed as being associated with a user who is stationary.
Owner:AT&T MOBILITY II LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com