Patents
Literature
85 results about "Attack analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
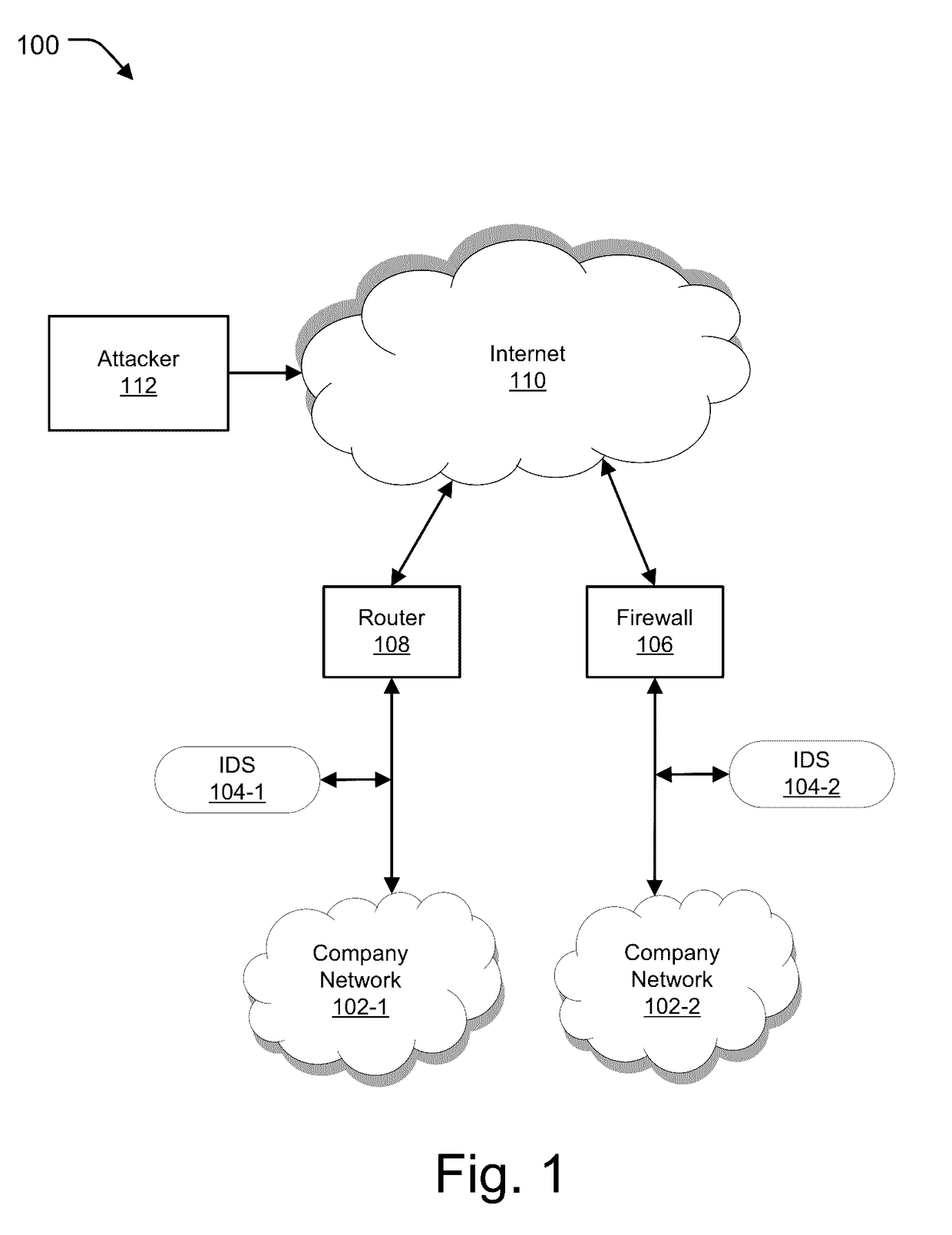
Attack surface analysis is an assessment of the total number of exploitable vulnerabilities in a system or network or other potential computer attack target. IT security workers and hackers both use attack surface analysis to detect security weaknesses in a system.
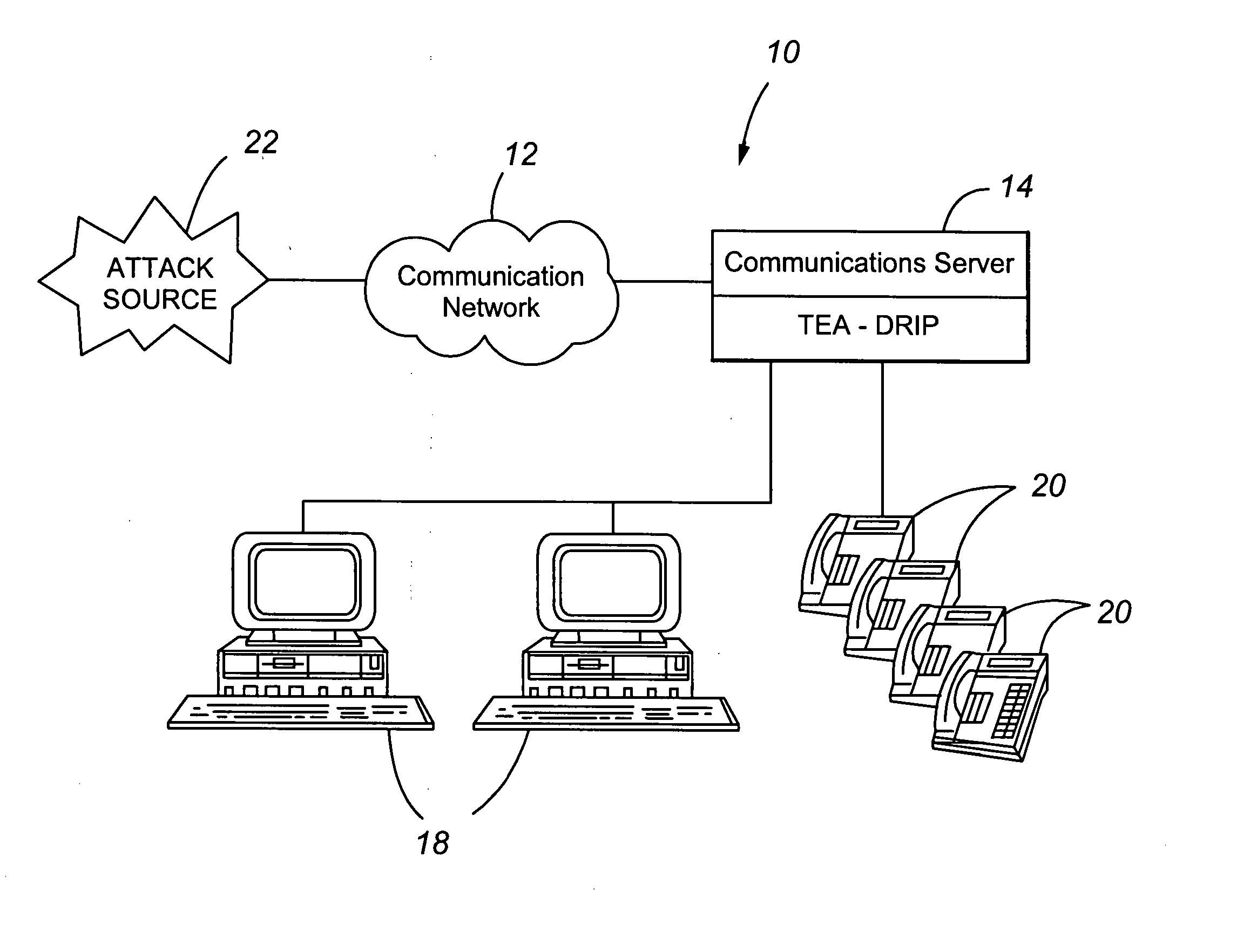
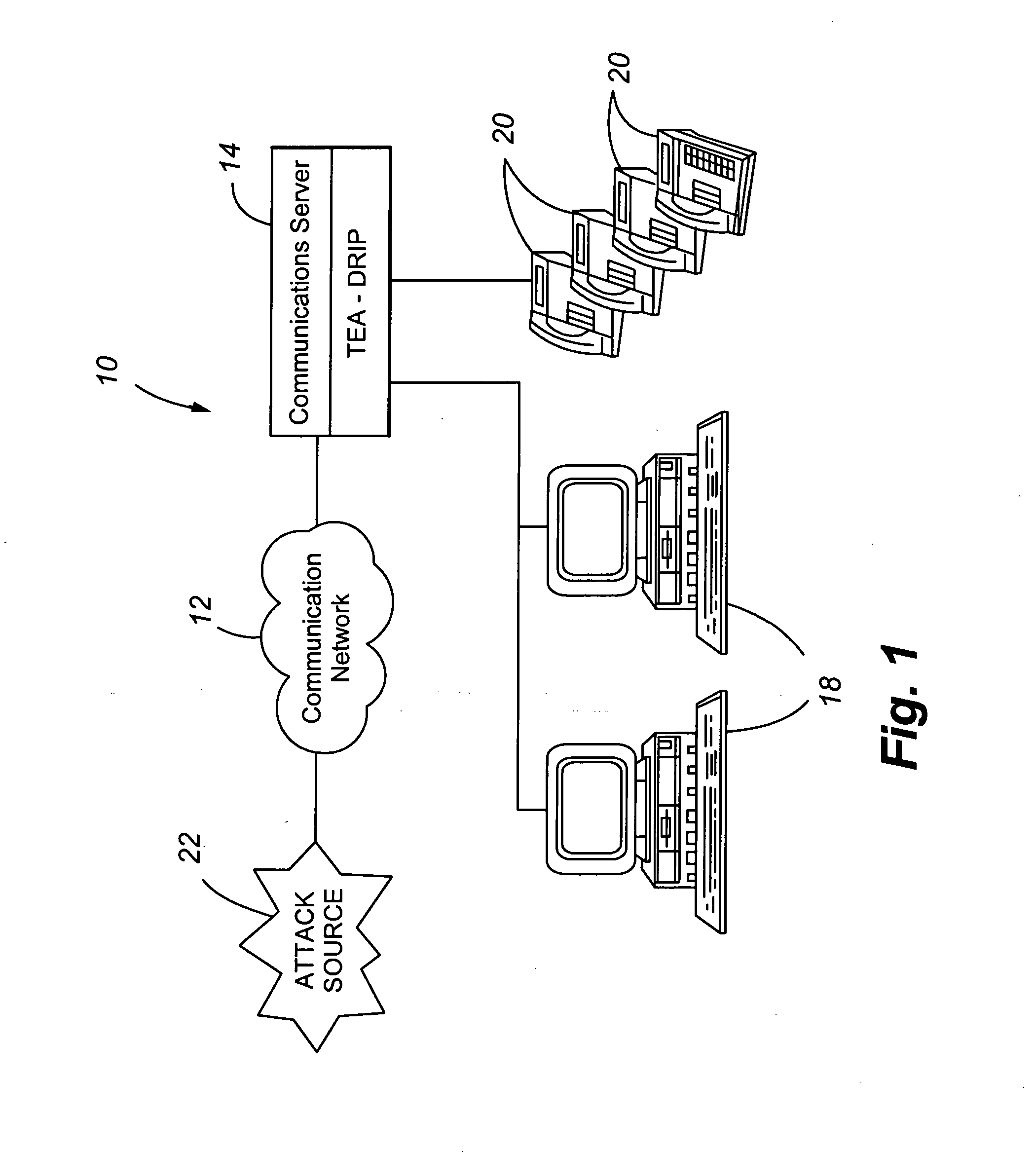
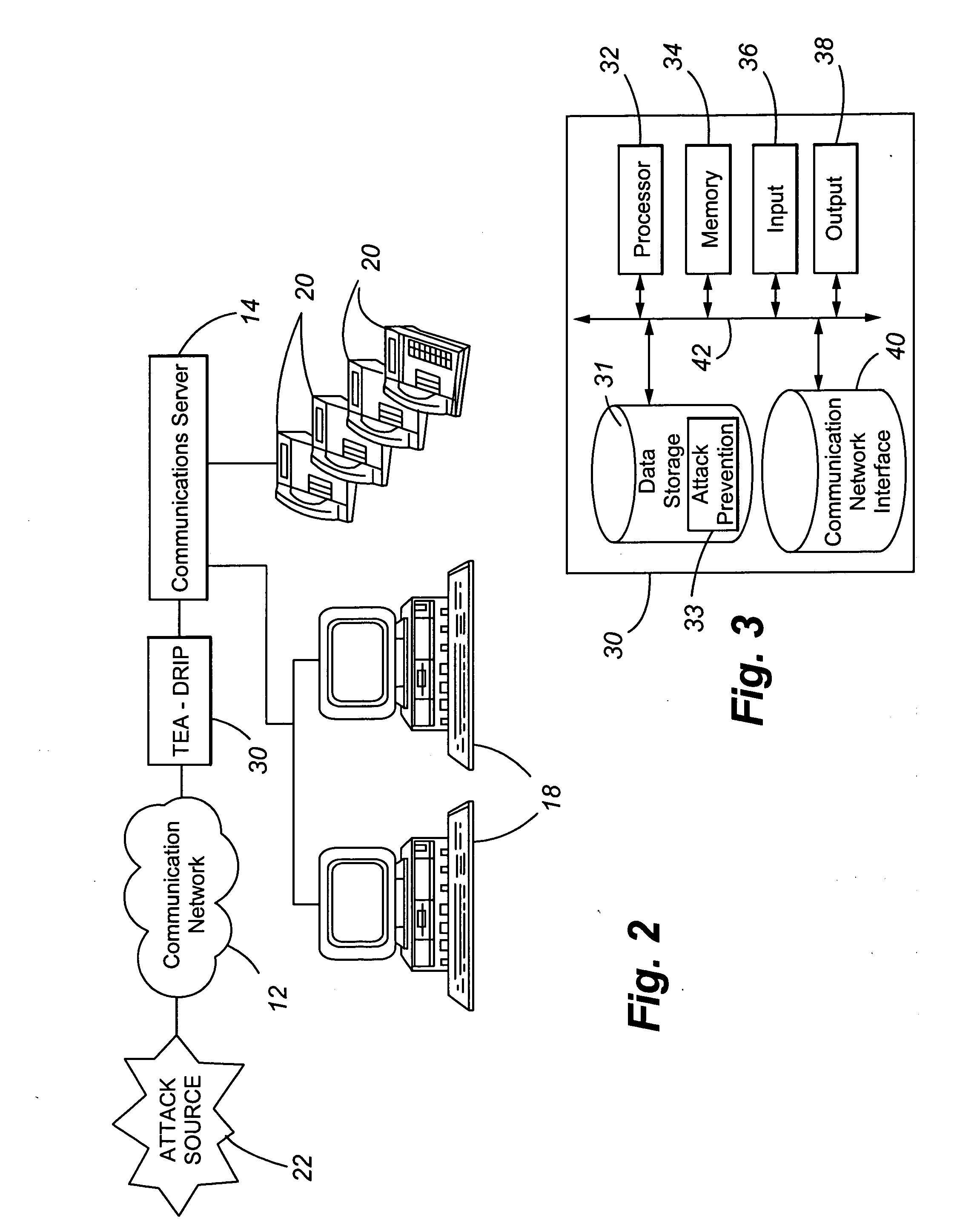
Telephony extension attack detection, recording, and intelligent prevention
ActiveUS20070036314A1Effectively prevent future attackAvoid attackData taking preventionAutomatic exchangesCommunication endpointRemedial action
A system and method are provided for detecting extension attacks made to a communication enterprise, and taking appropriate remedial action to prevent ongoing attacks and future attacks. One or more attributes of a suspect call are analyzed, and a risk is associated with each analyzed attribute. An overall risk or assessment is then made of the analyzed attributes, attack attributes are logged, and one or more remedial actions may be triggered as a result of the analyzed call attributes. The remedial actions may include recording the call, notifying an administrator of a suspect call, or isolating the communication enterprise from the attack by terminating the call or shutting down selected communication endpoints to prevent calls being made to those extensions. Rules may be applied to the analyzed attributes in order to trigger the appropriate remedial action. The call attributes analyzed may include call destination, call direction, call type, time of day of the call, call duration, whether a call source is spoofed, call volume from a particular call source, and hash values created for a suspect media stream.
Owner:AVAYA INC
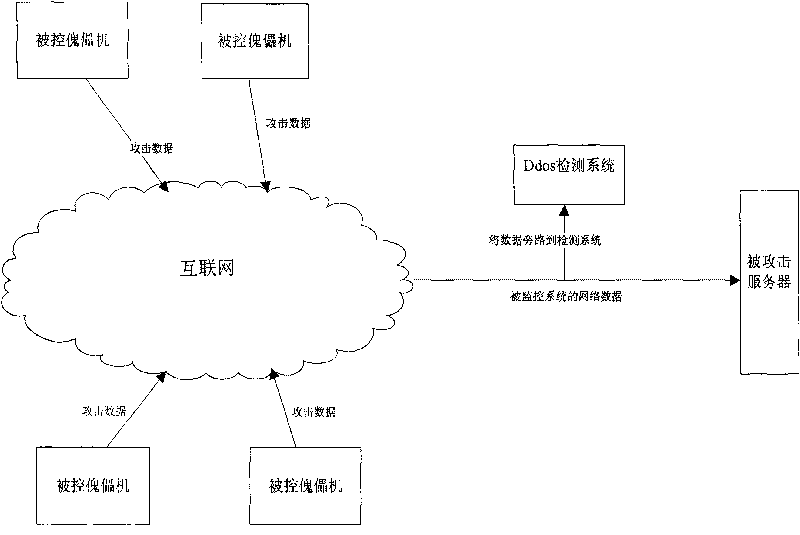
Detecting method of DDOS (distributed denial of service) attacks
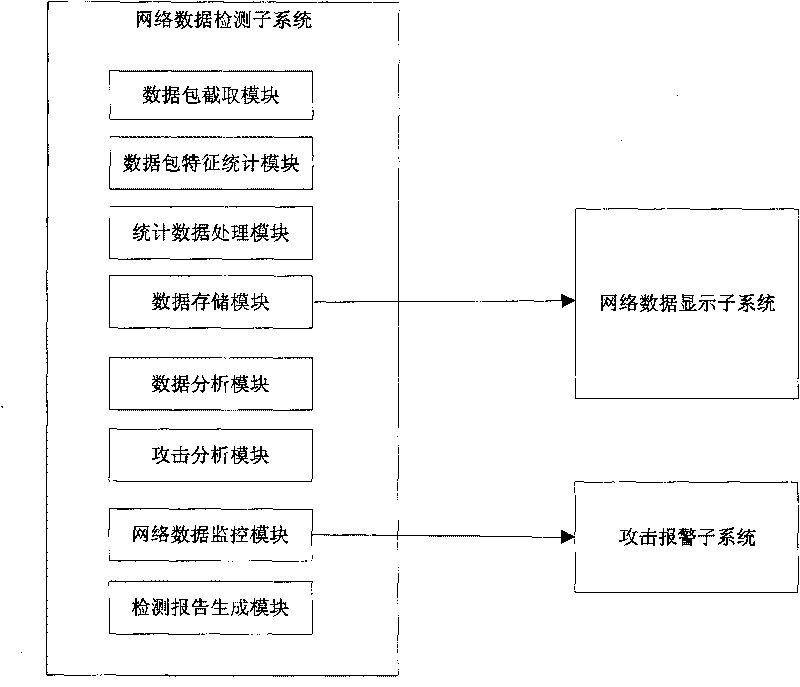
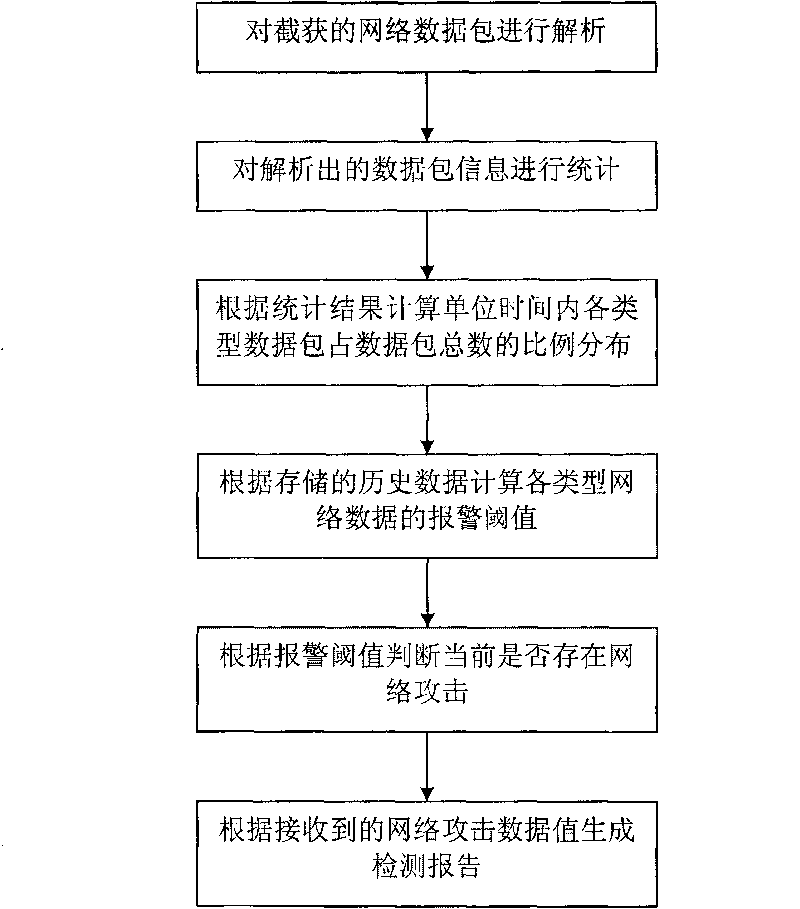
The invention discloses a detecting method of DDOS (distributed denial of service) attacks, belonging to the field of computer network safety and comprising the steps that, (1) a data packet interception module is used for analyzing accessed network data packet information; (2) a data packet feature statistic module is used for counting the analyzed network data packet information; (3) a statistical data processing module is used for computing the proportional distribution of all kinds of data packets relative to the total number of the data packets at unit time; (4) a data analyzing module is used for computing an alarm threshold of network data according to stored historical data computed in the steps (2) and (3); (5) the data analyzing module is used for judging whether a network data value at the current unit time exceeds the alarm threshold of the corresponding network data or not; if exceeds, the network data is submitted to an attack analyzing module; and (6) the attack analyzing module is used for generating a detection report according to the received network data value. Compared with the prior art, by integrating the historical data transmitted by a network, the invention carries out further analysis on the current network data, and can identify various ddos attacks.
Owner:RUN TECH CO LTD BEIJING
Security defensive system and defensive method based on software-defined network
ActiveCN104023034AGuaranteed service qualityReduce distractionsTransmissionNetwork controlAttack analysis
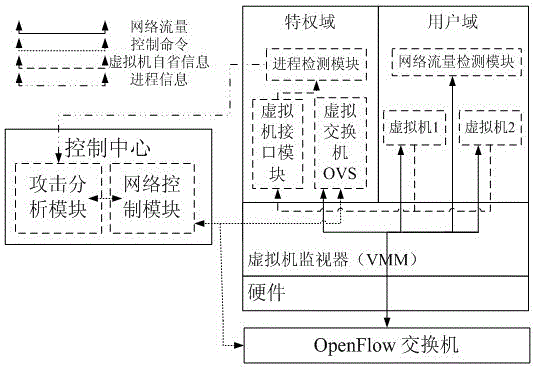
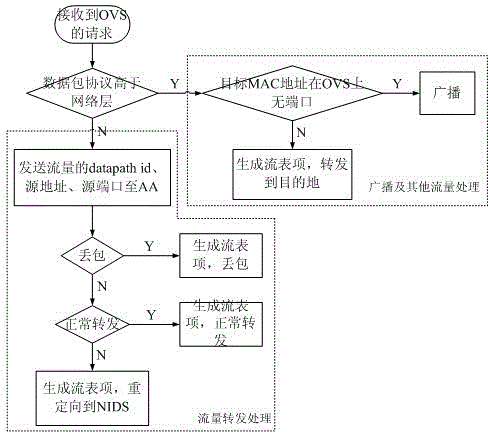
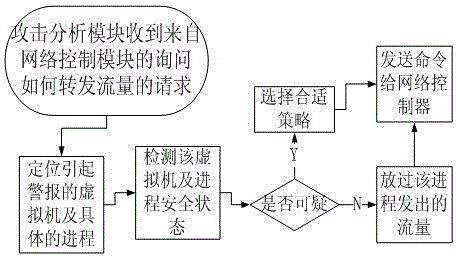
The invention relates to the technical field of computer security, and in particular to a security defensive system and a defensive method based on a software-defined network. The security defensive system comprises a network control module, an attack analysis module, a progress detection module and a network flow detection module, wherein the network control module is used for intercepting a network data packet between virtual machines and used for forwarding acquired flow information to the attack analysis module; the attack analysis module is used for receiving flow information from the virtual machines of the network control module, used for scheduling the progress detection module to detect whether the progress is questionable, and used for scheduling the network flow detection module to execute deep detection on questionable flow if necessary. Aiming at expansion of virtual switches for flow forwarding among virtual machines in a conventional virtual machine server, the invention discloses a deep defensive system which is capable of intercepting, detecting and reorienting the flow, and the purposes of preventing and stopping attack behaviors of virtual machines of a network cluster are achieved.
Owner:WUHAN UNIV
Apparatus and method for detecting network attack based on visual data analysis
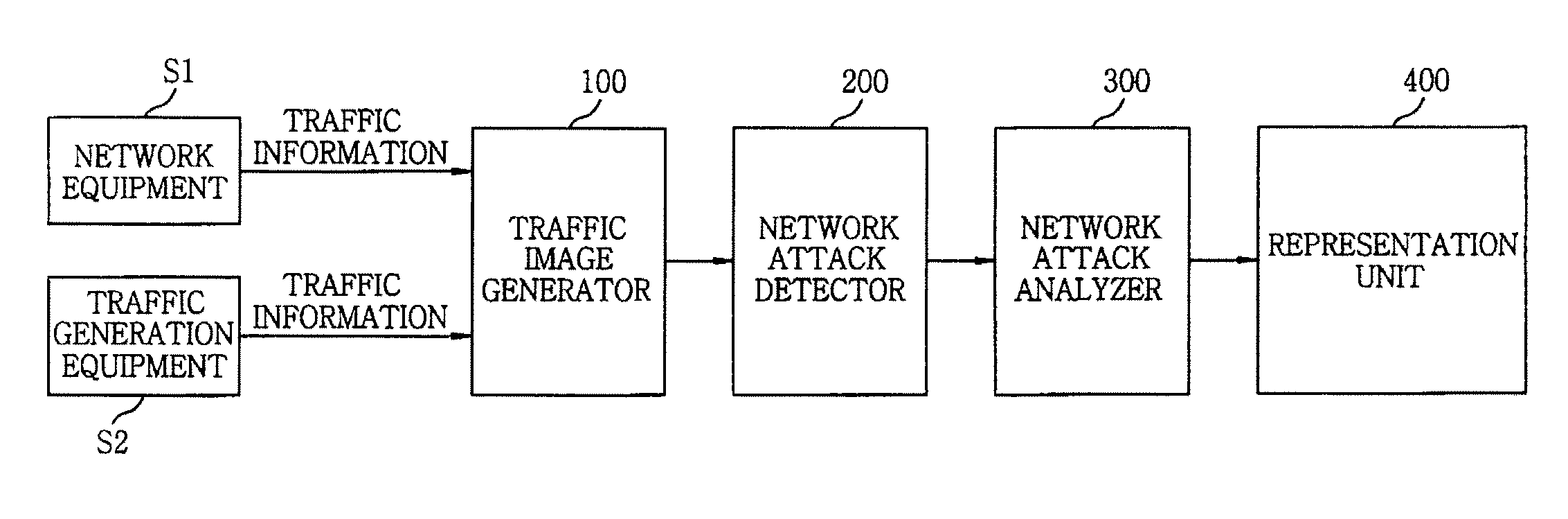
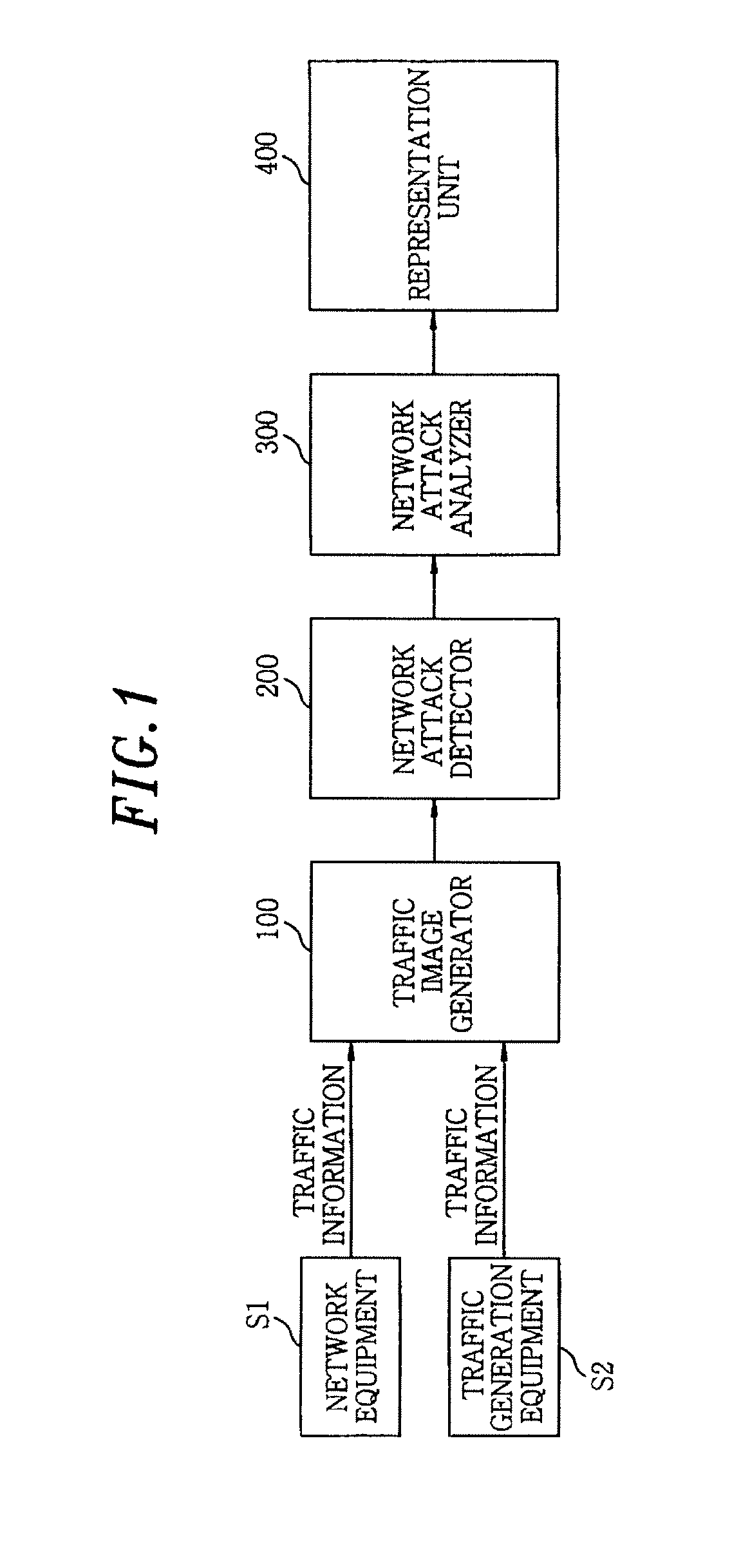
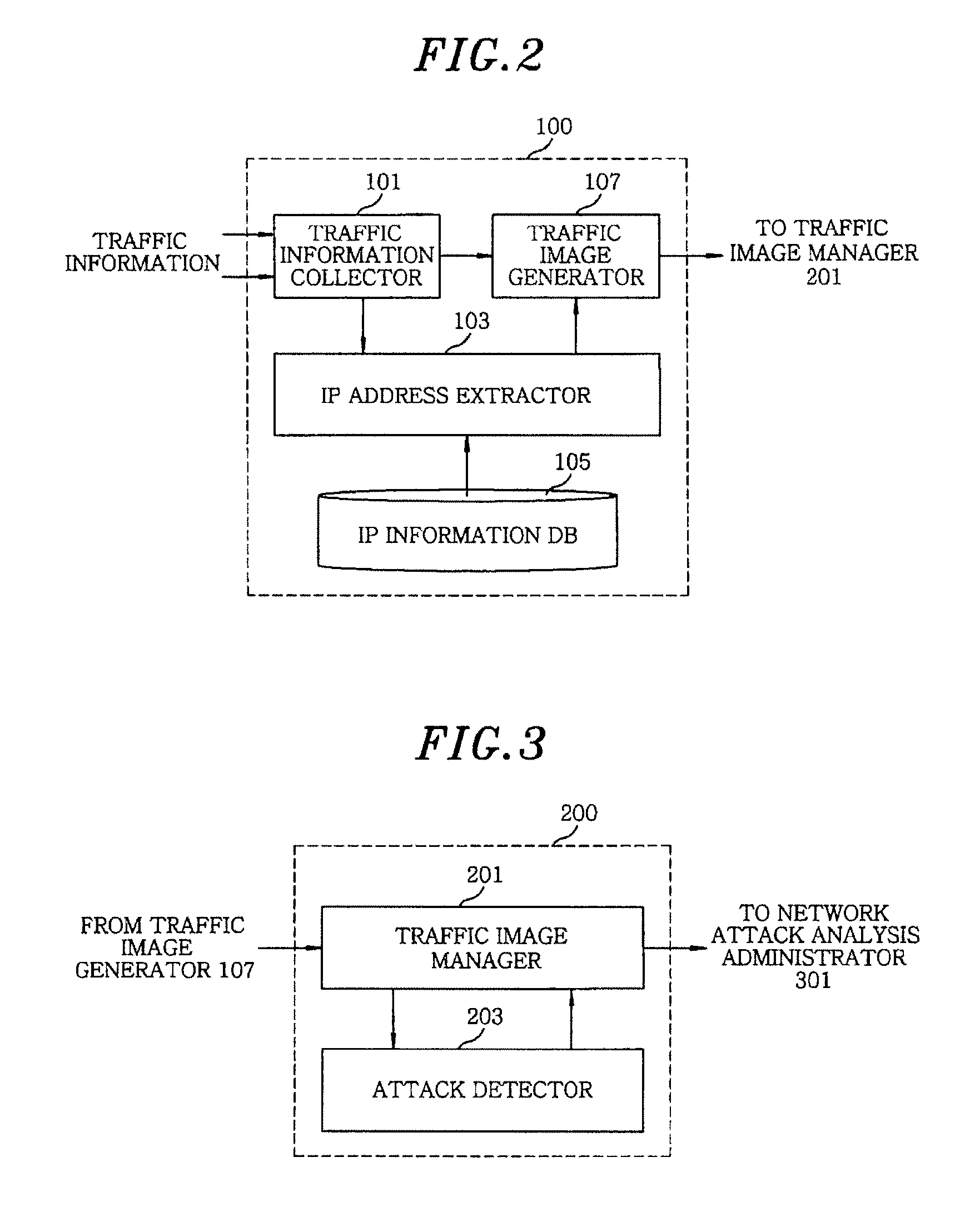
An apparatus for detecting a network attack includes a traffic image generator for generating a traffic image using traffic information and additional IP information extracted from the traffic information; a network attack detector for comparing similarities between the traffic image and a previously generated traffic image based on a predetermined similarity threshold to detect the presence of the network attack; and a network attack analyzer for analyzing the traffic image at a time when the network attack is detected to detect network attack information and pattern information of the network attack. A representation unit for visualizing the network attack information and the pattern information of the network attack.
Owner:ELECTRONICS & TELECOMM RES INST
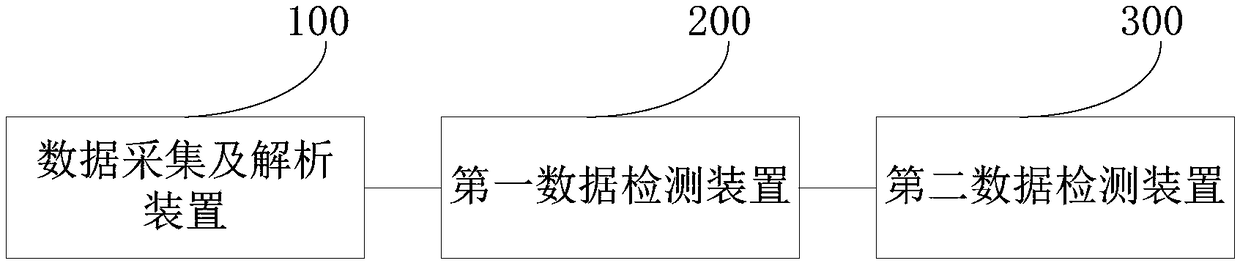
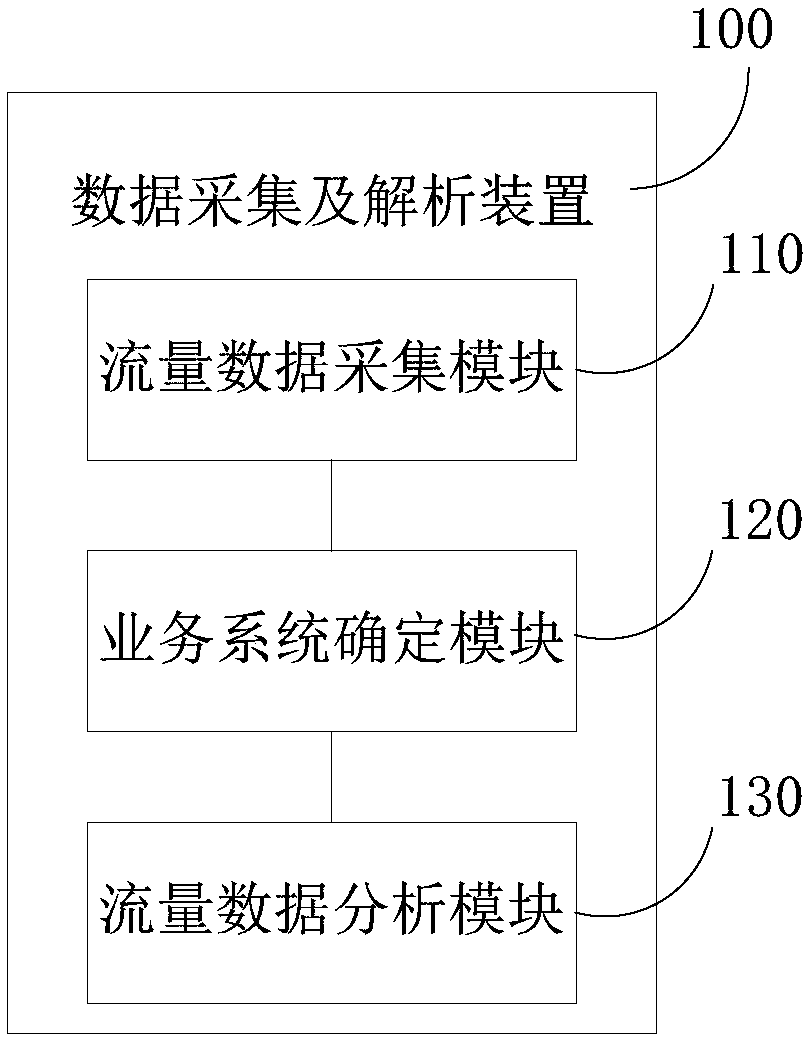
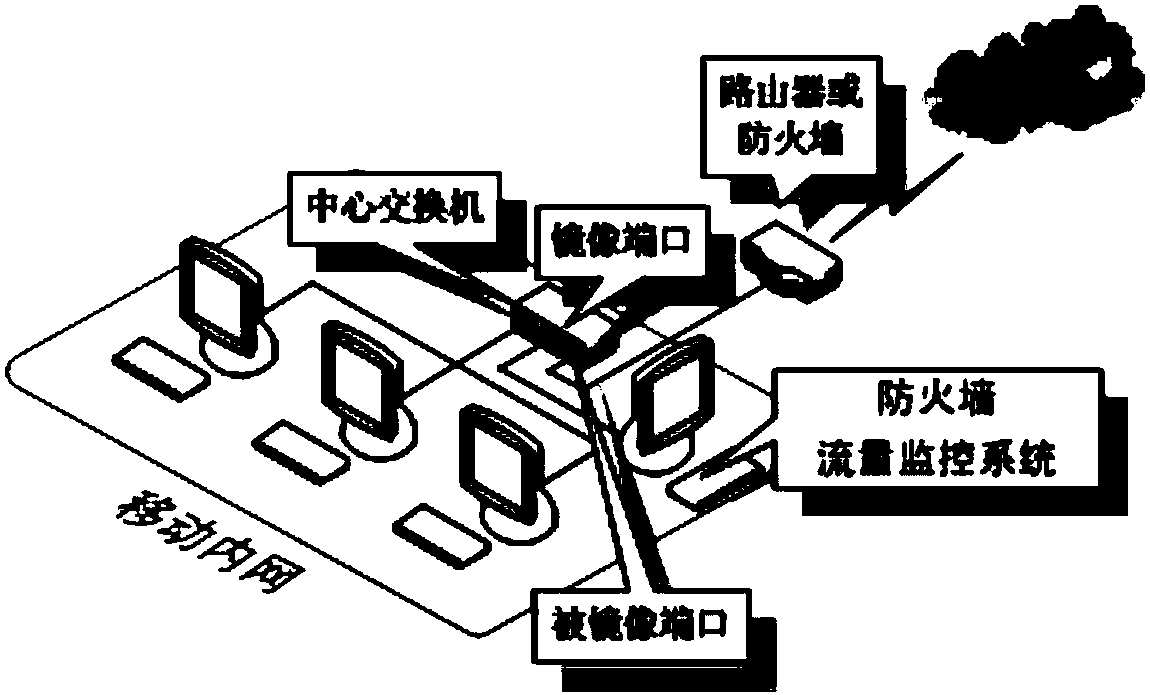
Abnormal flow detection system and abnormal flow detection method based on service model
ActiveCN108289088AEasy to detectImprove the protective effectTransmissionService modelData acquisition
The invention discloses an abnormal flow detection system and an abnormal flow detection method based on a service model. The abnormal flow detection system comprises a data acquisition and analysis device, a first data detection device, and a second data detection device. The data acquisition and analysis device is used for acquisition and analysis of original target flow data of a target networkport. The first data detection device is used to filter the analyzed target flow data according to a preset flow information white list and a preset flow information black list, and is used to transmit the first flow data of the original target flow data, which is not matched with the flow information white list and the flow information black list, to the second data detection device. The seconddata detection device is used to carry out the flow attack determining of the first flow data according to a preset flow attack analysis module, and is used to identify abnormal flow data from the first flow data. By adopting the method and the system provided by the invention, problems of conventional abnormal flow detection methods such as detection lag, high detection costs, and limited detection capability are effectively solved.
Owner:HANDAN BRANCH OF CHINA MOBILE GRP HEBEI COMPANYLIMITED +1
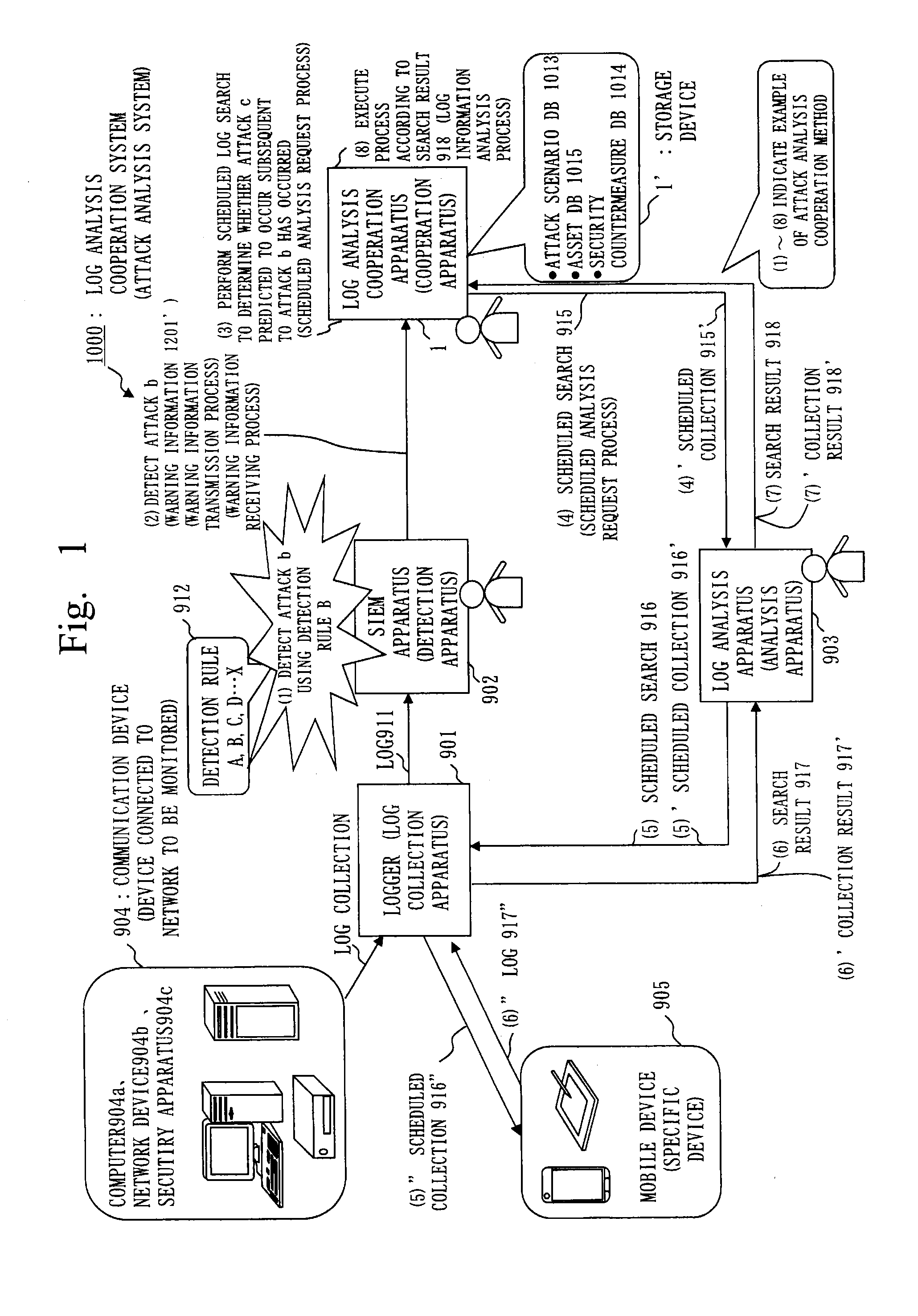
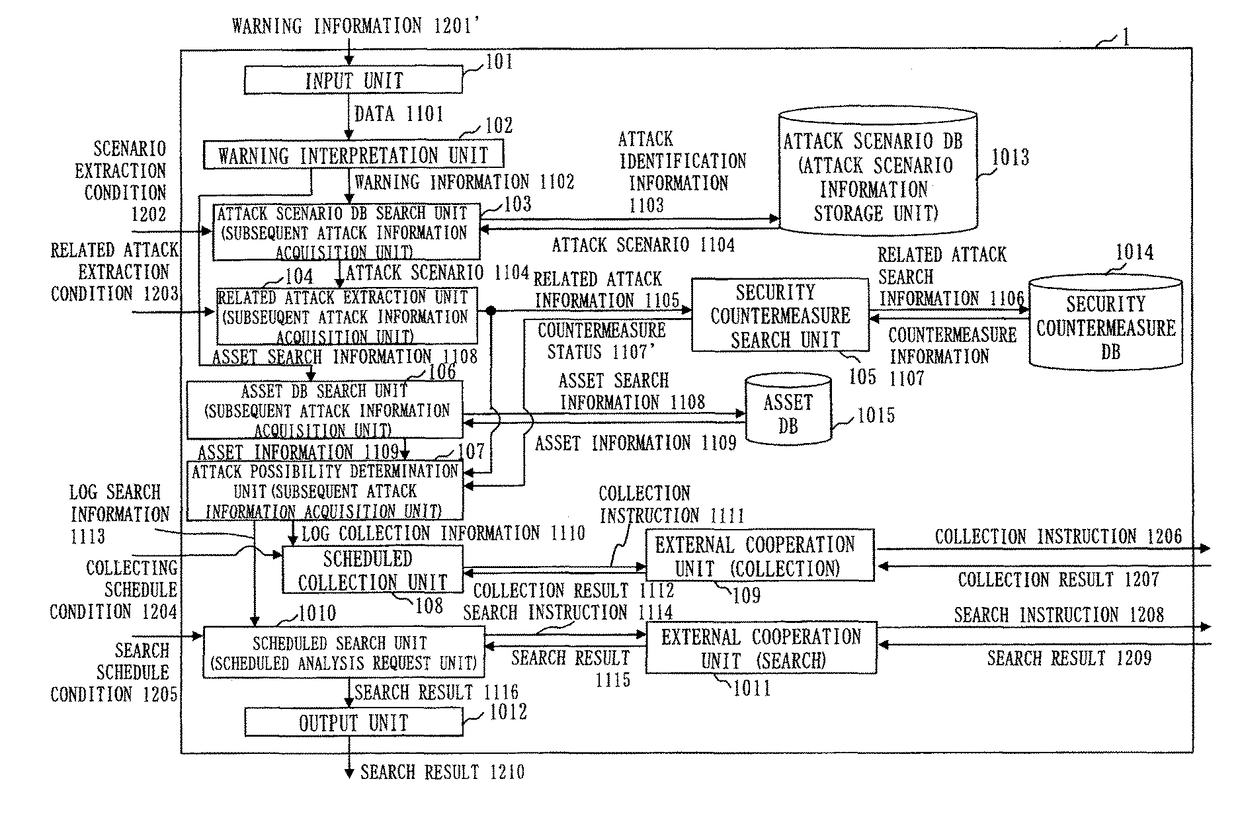
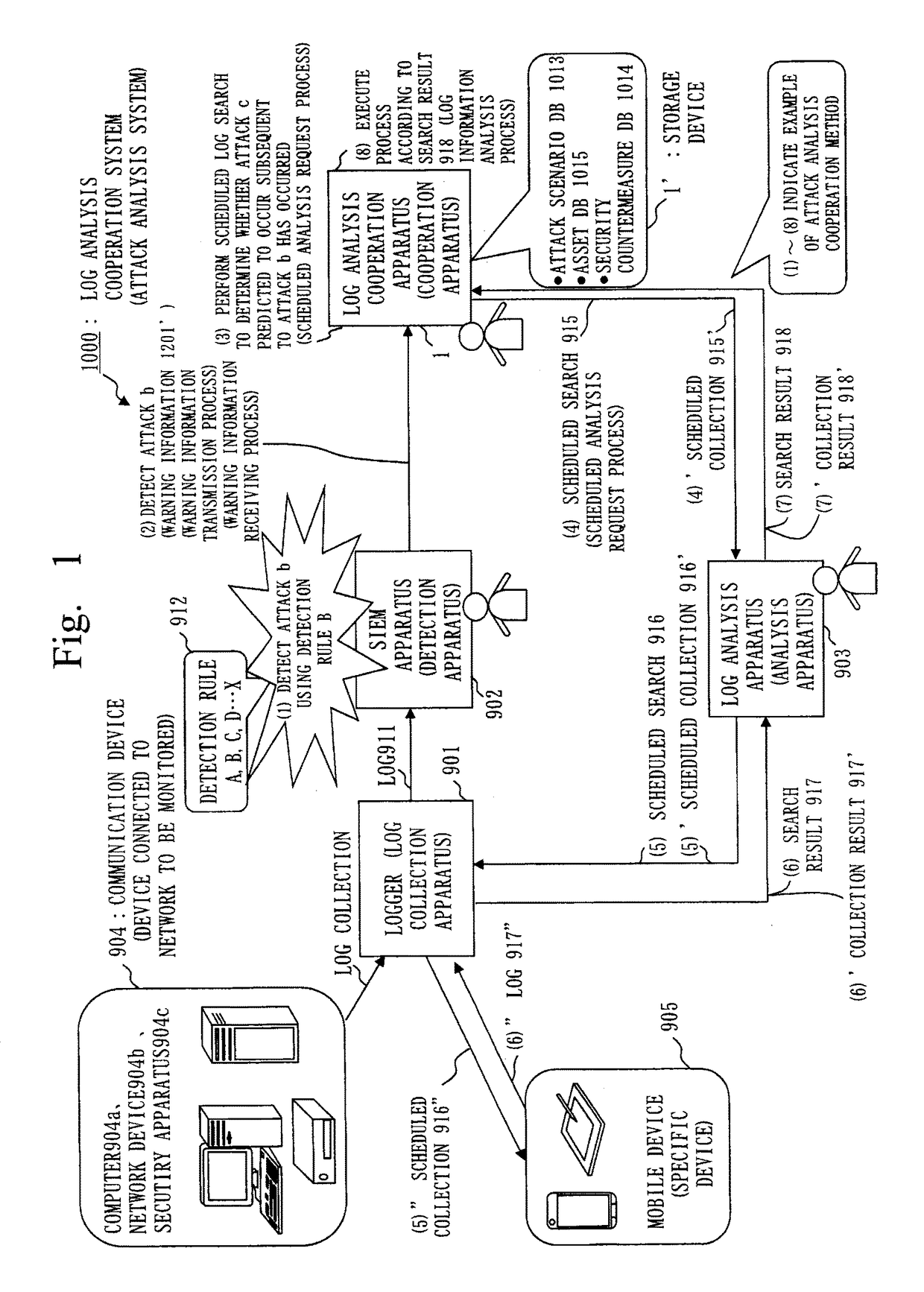
Attack analysis system, cooperation apparatus, attack analysis cooperation method, and program
ActiveUS20150256554A1Efficient discoveryMemory loss protectionUnauthorized memory use protectionAttack analysisData mining
In a log analysis cooperation system including a logger that collects a log of a communication device and stores the log in a storage device, a SIEM apparatus that detects an attack, and a log analysis apparatus that analyzes the log collected by the logger, a log analysis cooperation apparatus stores an attack scenario in a storage device, receives from the SIEM apparatus warning information including information on the detected attack, computes a predicted occurrence time of an attack predicted to occur subsequent to the detected attack based on the warning information and the attack scenario, and transmits to the log analysis apparatus a scheduled search to search the log at predicted occurrence time computed. The log analysis apparatus transmits a scheduled search to the logger to search the log at the predicted occurrence time.
Owner:MITSUBISHI ELECTRIC CORP
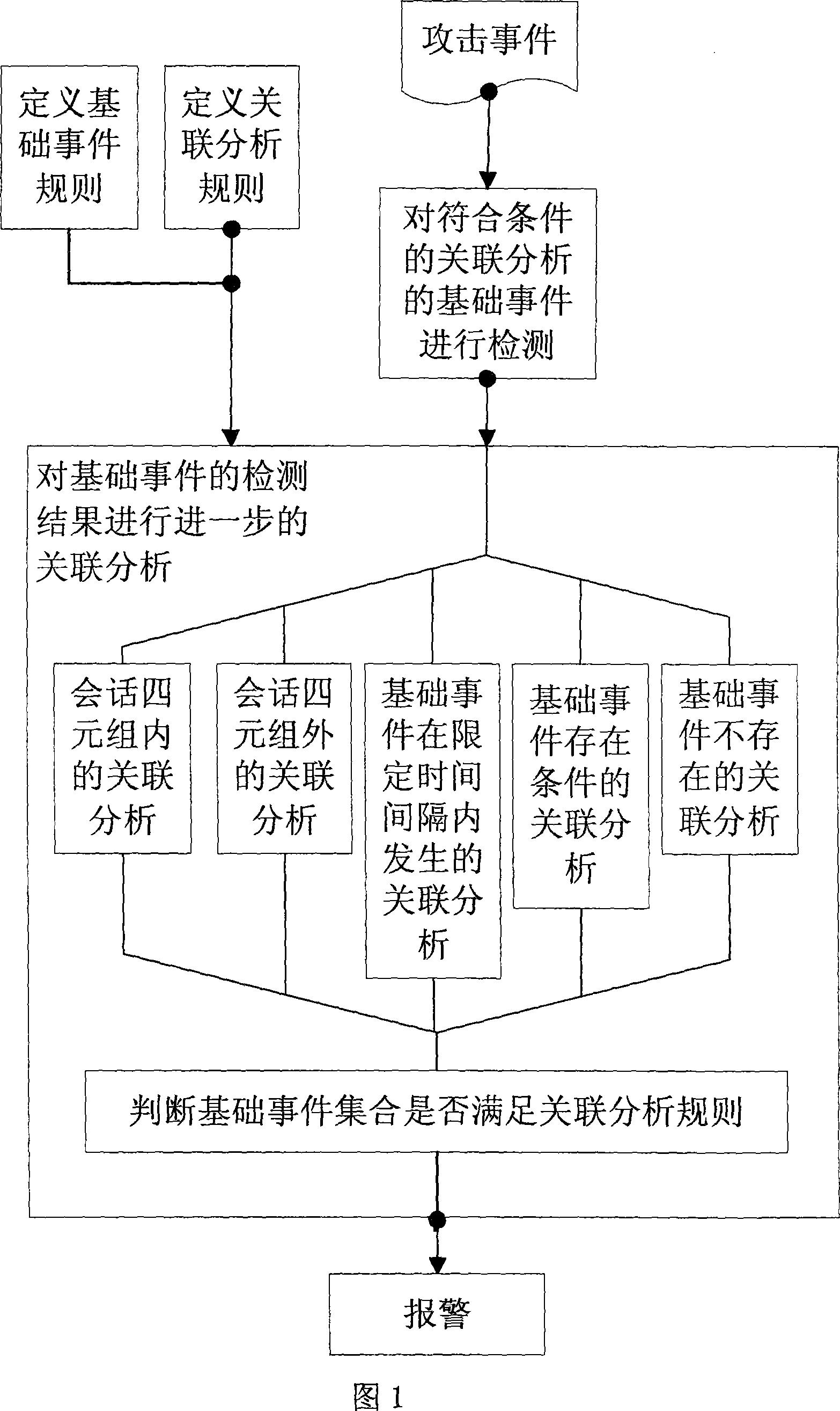
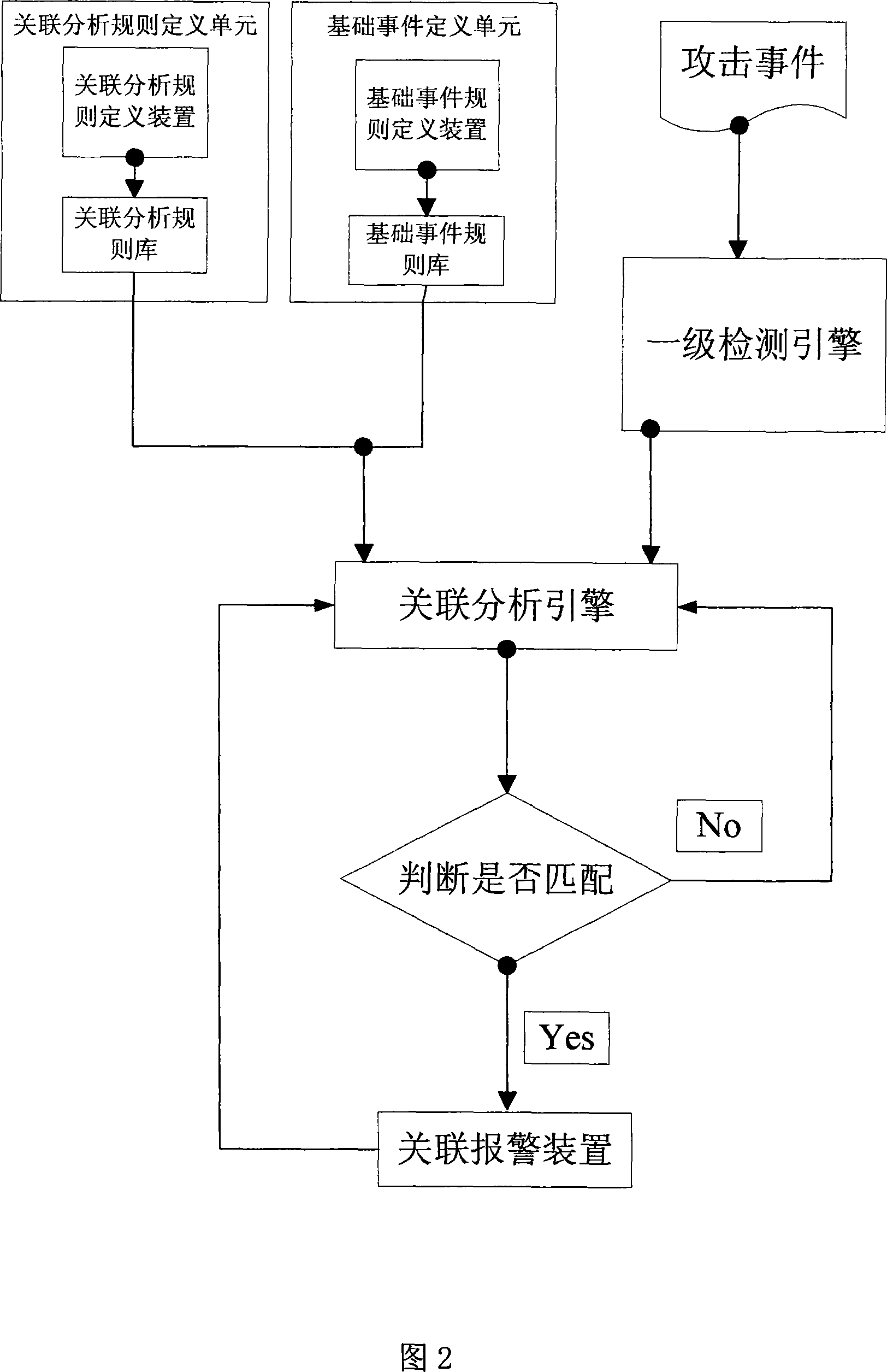
Associative attack analysis and detection method and device based on the time sequence and event sequence
InactiveCN101034974AAccurate detectionComprehensive descriptionData switching networksSecuring communicationCorrelation analysisAttack analysis
This invention is based on the time and events sequence to analysis attacking detection methods and devices involved in exchange for the function of the network. It is a methods and devices to prevent removing data from the data transmission channel without permission .The method provides a complex text-based attack description language to make the user can amend the built-related characteristics, and add new features of related events. The present invention include: basic rules of the incident, the rules of the association, first level detection engine, correlation analysis engine. The whole process of attacking are described more comprehensive and reasonable taking into account the time factor and the order of events Such description and testing which distinct the basic incidents more carefully are more in line with the requirements of detecting attacks. The invention also describes the relation between alarm incident and not alarm incident.
Owner:BEIJING VENUS INFORMATION TECH
Industrial radio control system semi-physical security experiment platform
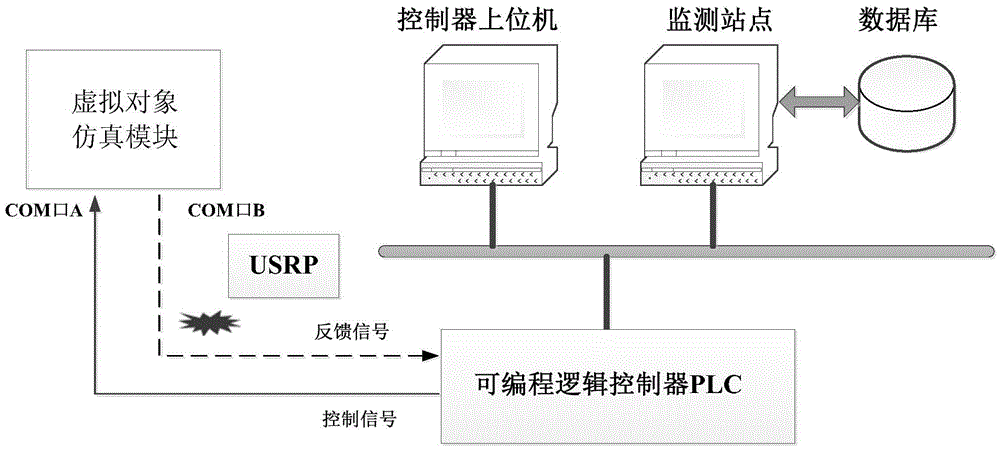
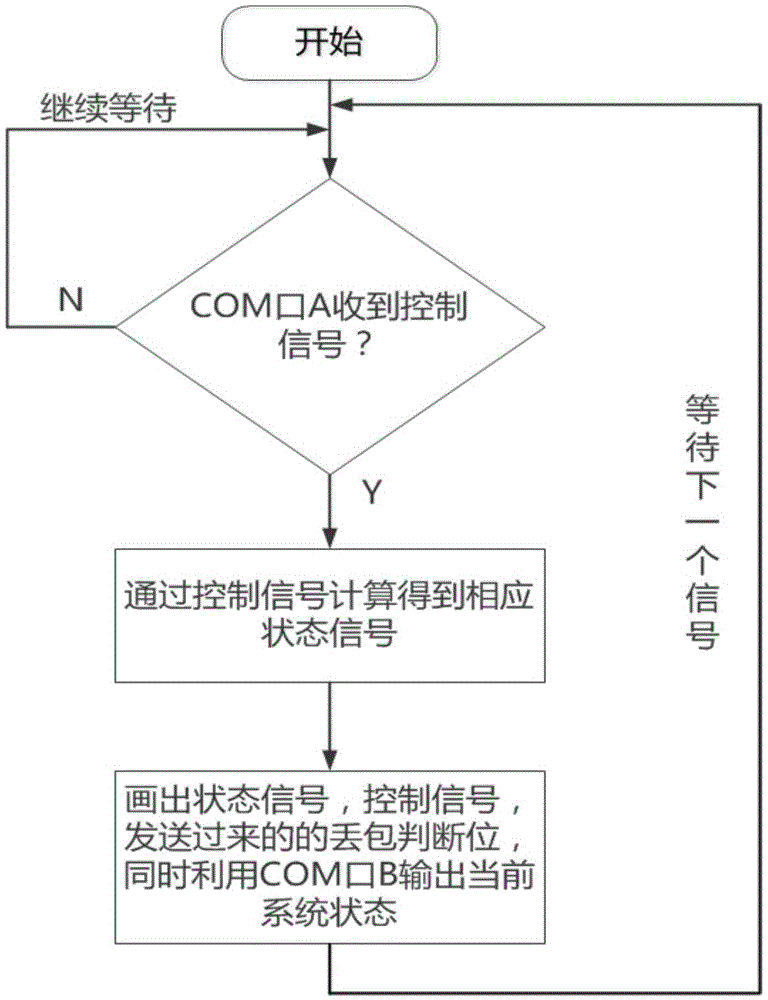
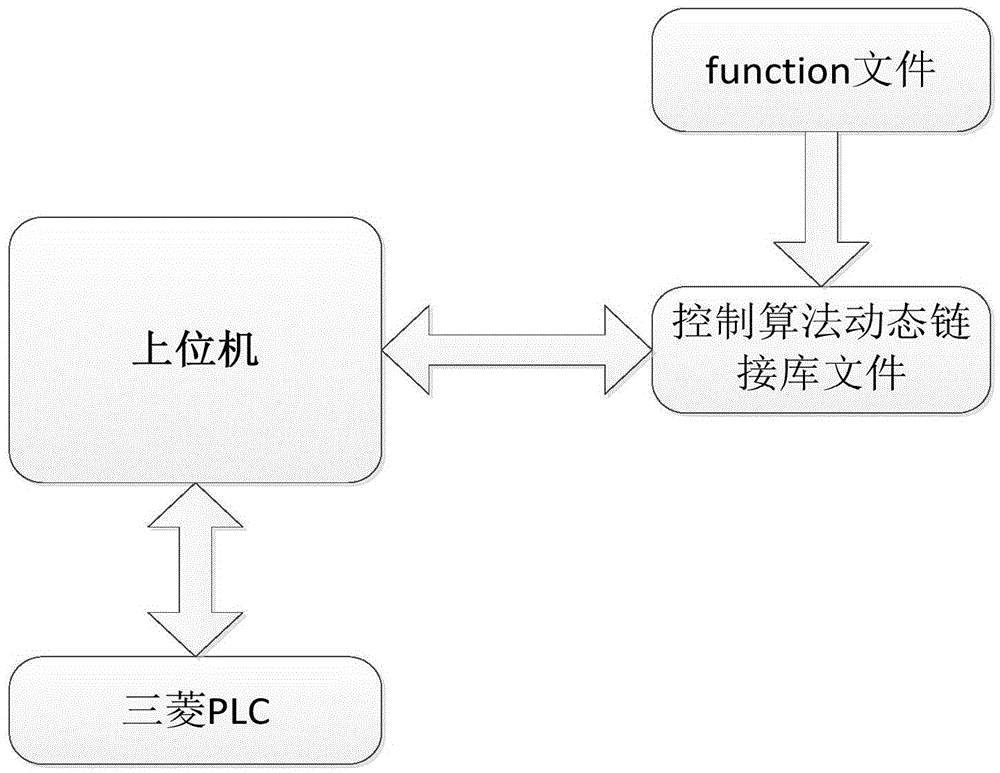
ActiveCN105607509ATesting and Analyzing SecurityTesting and Analyzing VulnerabilitiesSimulator controlPhysical securityControl signal
The invention discloses an industrial radio control system semi-physical security experiment platform. The platform comprises a simulation module, a controller host computer, a monitoring site, a programmable logic controller (PLC), an industrial radio communication device and a universal software radio peripheral (USRP) for simulating attacks. The simulation module is used for erecting a virtual controlled object and simulating different industrial scenes. The controller host computer is used for simulating different control algorithms. The monitoring site monitors in real time state signals, control signals and the like in a system operation process and stores correlation data in a database. The USRP is used for simulating a typical industrial radio attack mode. According to the experimental platform, through simulating a typical industrial object and a control algorithm, an attack on an industrial radio channel is simulated by use of the USRP, and the security of an industrial radio protocol and the control system performance under a typical attack are analyzed. The industrial radio control system semi-physical security experiment platform is low in system cost and can be applied to simulation of a typical industrial control object and a corresponding control algorithm and evaluation of the influence of a typical industrial radio attack on an industrial control system.
Owner:ZHEJIANG UNIV
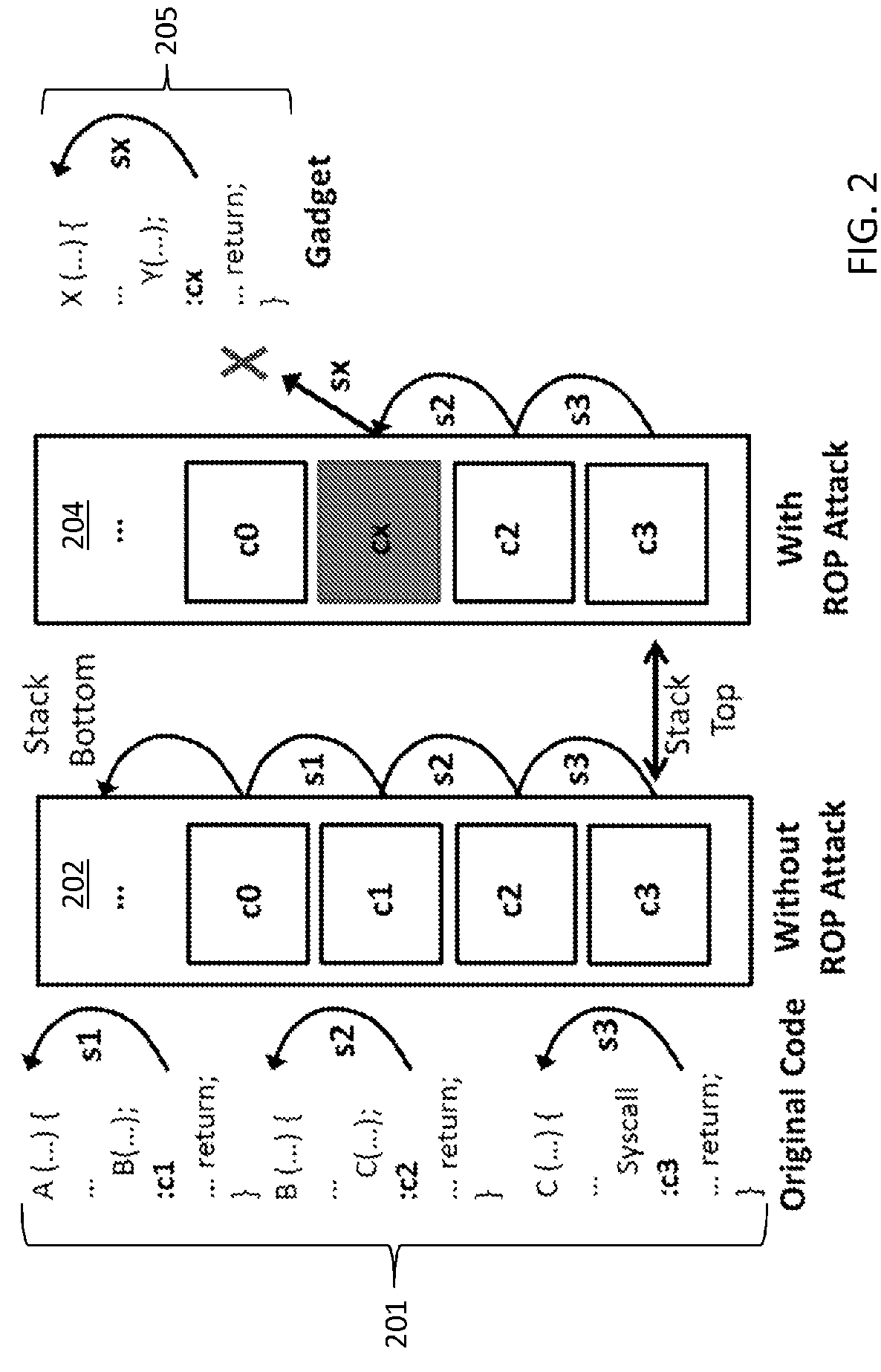
Transparent detection and extraction of return-oriented-programming attacks
Systems and methods for detection and prevention of Return-Oriented-Programming (ROP) attacks in one or more applications, including an attack detection device and a stack inspection device for performing stack inspection to detect ROP gadgets in a stack. The stack inspection includes stack walking from a stack frame at a top of the stack toward a bottom of the stack to detect one or more failure conditions, determining whether a valid stack frame and return code address is present; and determining a failure condition type if no valid stack frame and return code is present, with Type III failure conditions indicating an ROP attack. The ROP attack is contained using a containment device, and the ROP gadgets detected in the stack during the ROP attack are analyzed using an attack analysis device.
Owner:NEC CORP
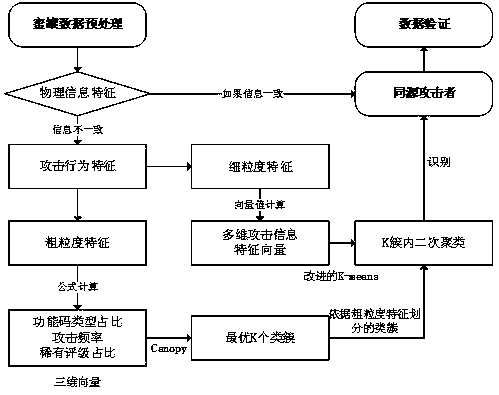
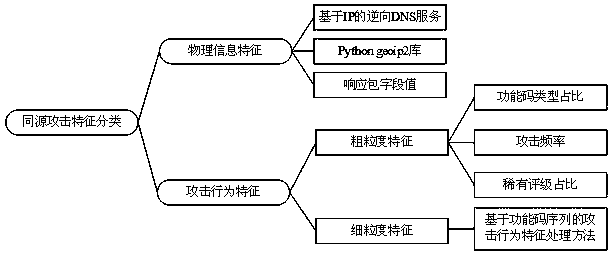
Homologous attack analysis method for industrial control honeypot
The invention discloses a homologous attack analysis method for an industrial control honeypot, and the method comprises the steps: introducing coarse-grained and fine-grained attack behavior featuresthrough the physical position features of an attacker, converting the information of the attacker into a group of multi-dimensional attack behavior feature vectors, finding an optimal K value by using a Canopy method according to the coarse-grained attack information of the attacker, and determining attackers or attack organizations with close Euclidean distances as homologous attacks by using animproved K-means clustering method according to the fine-grained attack information of the attacker. According to the method and the system, the behavior characteristics of the homologous attacker can be modeled into the characteristic vector based on the function code sequence, and the method and the system are suitable for analyzing various industrial control protocol honeypot data with function code characteristics; a verification method is provided for solving the problem that it is difficult to judge and verify the same attack source of honeypot data, for some unknown enterprise scannersor attackers, an open source abuse IP database is used for query, and the traditional attacker information of the other unknown attackers is verified.
Owner:山西星泽汇联科技有限公司
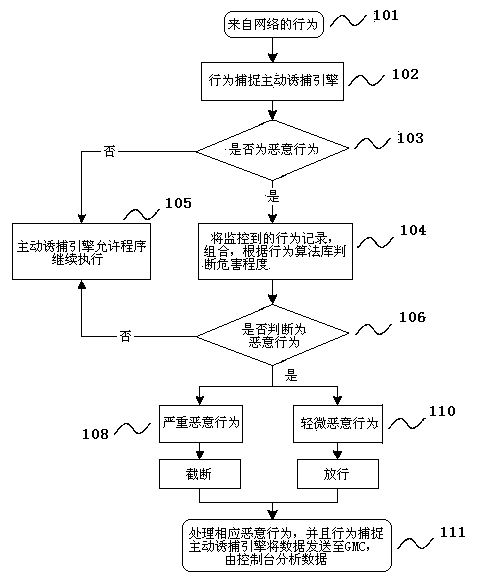
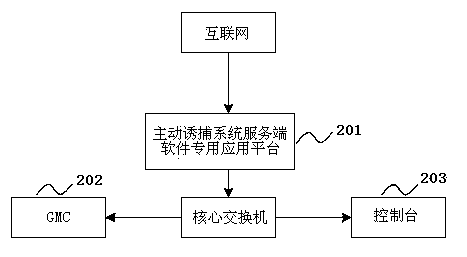
Active trapping method based on behavior capturing
InactiveCN103581104APrevent intrusionAvoid attackPlatform integrity maintainanceTransmissionFeature extractionTrapping
The invention brings forward an active trapping method based on behavior capturing. A trapping system is established in a formulated network area. The active trapping method comprises the following three links: (1) an active trapping system is established in an advance defense of a network defense system, and an active trapping engine technology is adopted; an active trapping engine, target cheating, attack capturing, attack control, attack analysis and characteristic extracting are established in multiple systems included by a computer; (2) a dynamic depth target cheating attack behavior is utilized to trap a real attack objective of an attacker; (3) and the active trapping system makes the attacker be sure of the attack target according to the aforementioned judgment results so that the real attack objective of the attacker is trapped. According to the active trapping method based on behavior capturing, known and unknown attack behaviors can be captured, the security state of the whole network is mastered and the network security level is enhanced.
Owner:江苏中科慧创信息安全技术有限公司
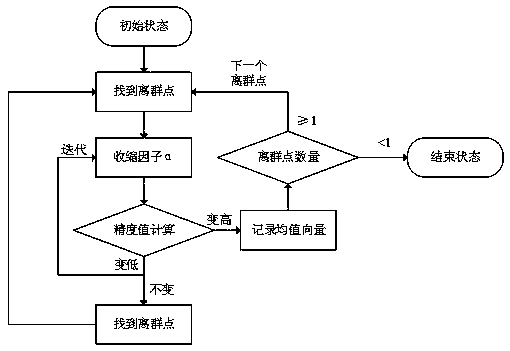
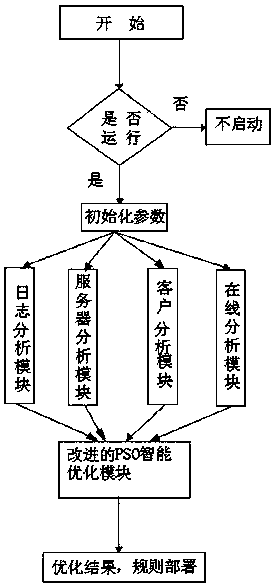
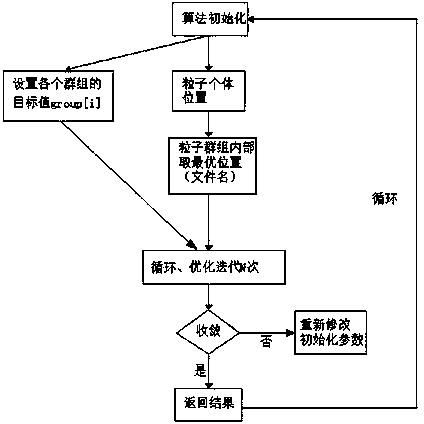
Information security defense rule intelligent deployment method based on improved particle swarm optimization
InactiveCN103973702AImprove defense targetingReduce overheadTransmissionNetwork conditionsSecurity rule
The invention discloses an information security defense rule intelligent deployment method based on an improved particle swarm optimization. The method comprises the steps of deployment strategies of the intelligent learning algorithm and security rules; according to attack frequency and type and potential attacks in parametric improved particle swarm optimization system logs, the intelligent learning algorithm is adopted for deployment on the condition that normal resource overheads of a security defense system are not influenced, rule deployment is conducted for the actual environment of the network, an access log attack analysis engine which can defend existing attacks and see through the potential attacks according to network conditions and has the independent attack analysis ability is adopted, and common attacks can be recognized through the access logs. According to the information security defense rule intelligent deployment method, on the condition that an existing security rule defense flow or principle is not influenced, intelligent deployment is conducted on the rules, and the intelligent deployment is different from manual deployment. On the basis of the existing manual deployment, defense pertinence of security products is improved, and server overheads are reduced to a greater degree.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
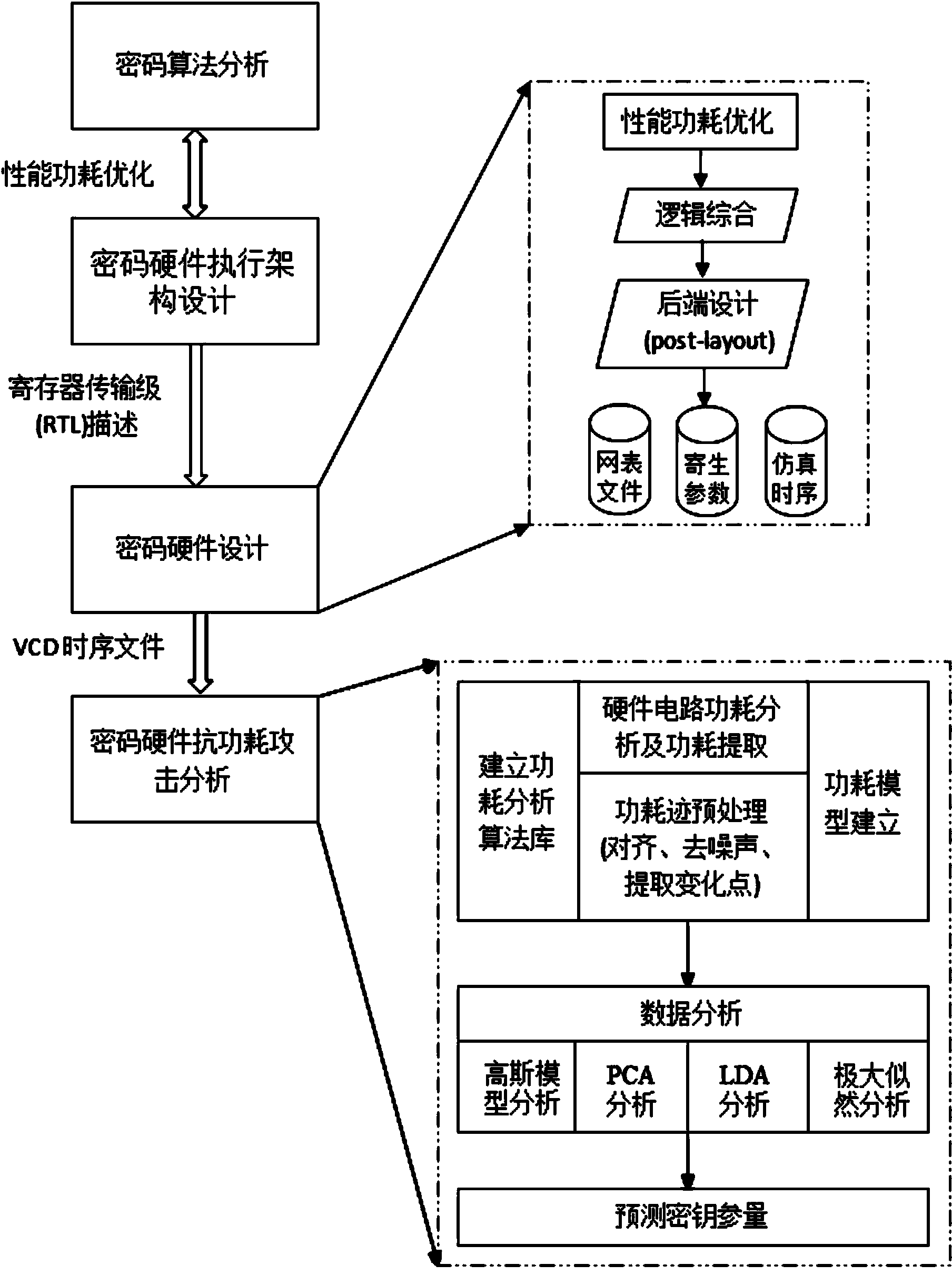
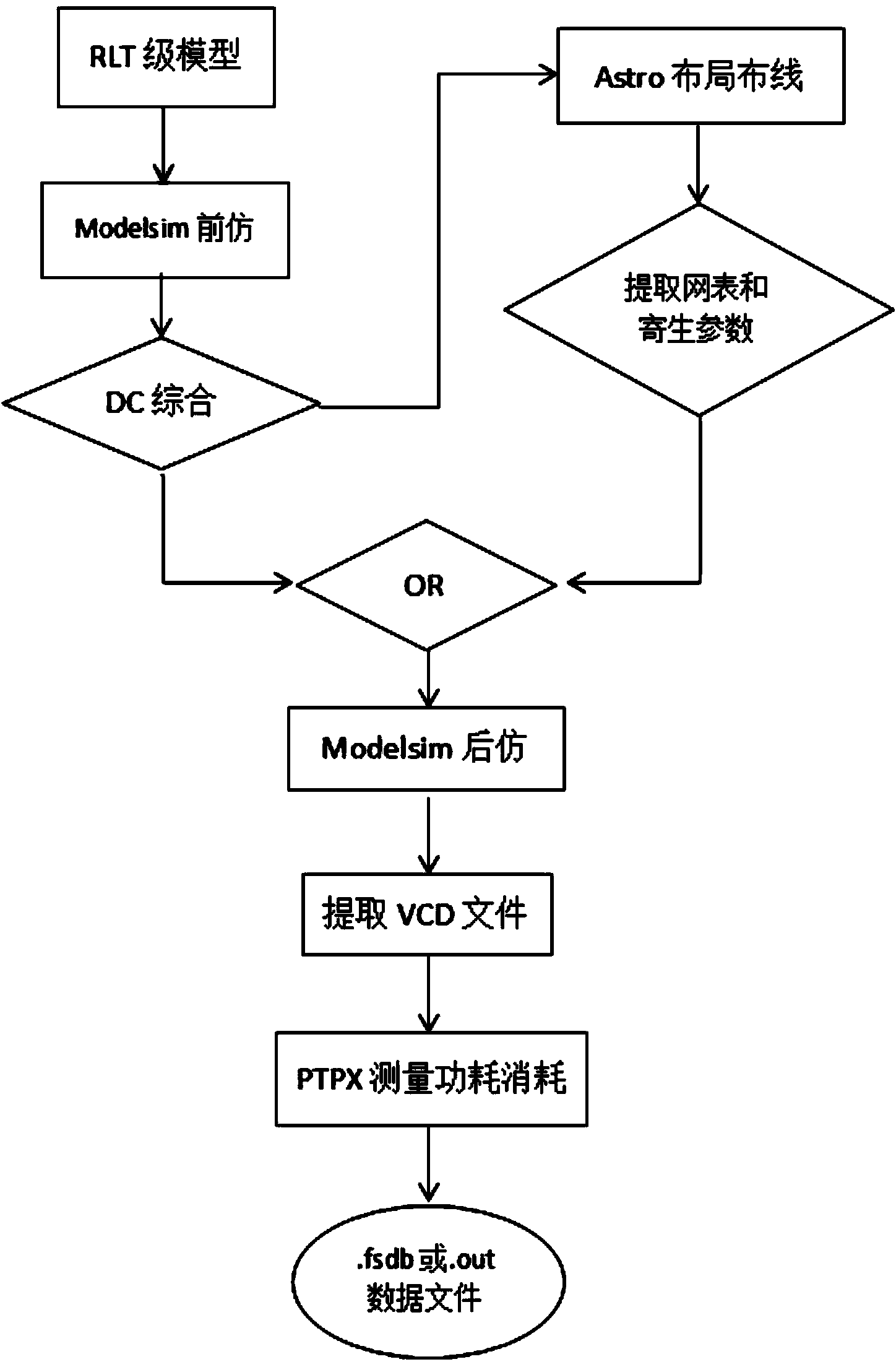
Security detection method for design of cryptographic algorithm hardware
InactiveCN103812642ALow costPrecise power consumptionEncryption apparatus with shift registers/memoriesPasswordSecret code
The invention discloses a security detection method for the design of cryptographic algorithm hardware. The method comprises the steps of analyzing cryptographic algorithm, and adding protective measures into the cryptographic algorithm according to an analyzing result; performing architectural design on password hardware, and formulating and adding the hardware protective measures; programming the password hardware, and generating an ASIC (Application Specific Integrated Circuit) password chip circuit layout according to the programming result; and performing power resistance analysis on the password chip, and verifying the security of the chip, including the acquiring of power consumption information and the analysis of data. According to the method, the characteristic of an EDA (Electronic Design Automation) tool capable of stimulating the chip operation power consumption to obtain the stimulated power consumption of the chip at a chip design early stage can be maximally utilized, so that the stimulated power consumption is more accurate in operation, lower in noise, simpler in power alignment, and is more likely to perform power consumption attack analysis in comparison with the operation consumption of the chip. The stimulated and synthesized results are only analyzed and the real chip is not needed, so that the research cost is low, and the total cost for producing the password chips in a company can be reduced.
Owner:TIANJIN UNIV
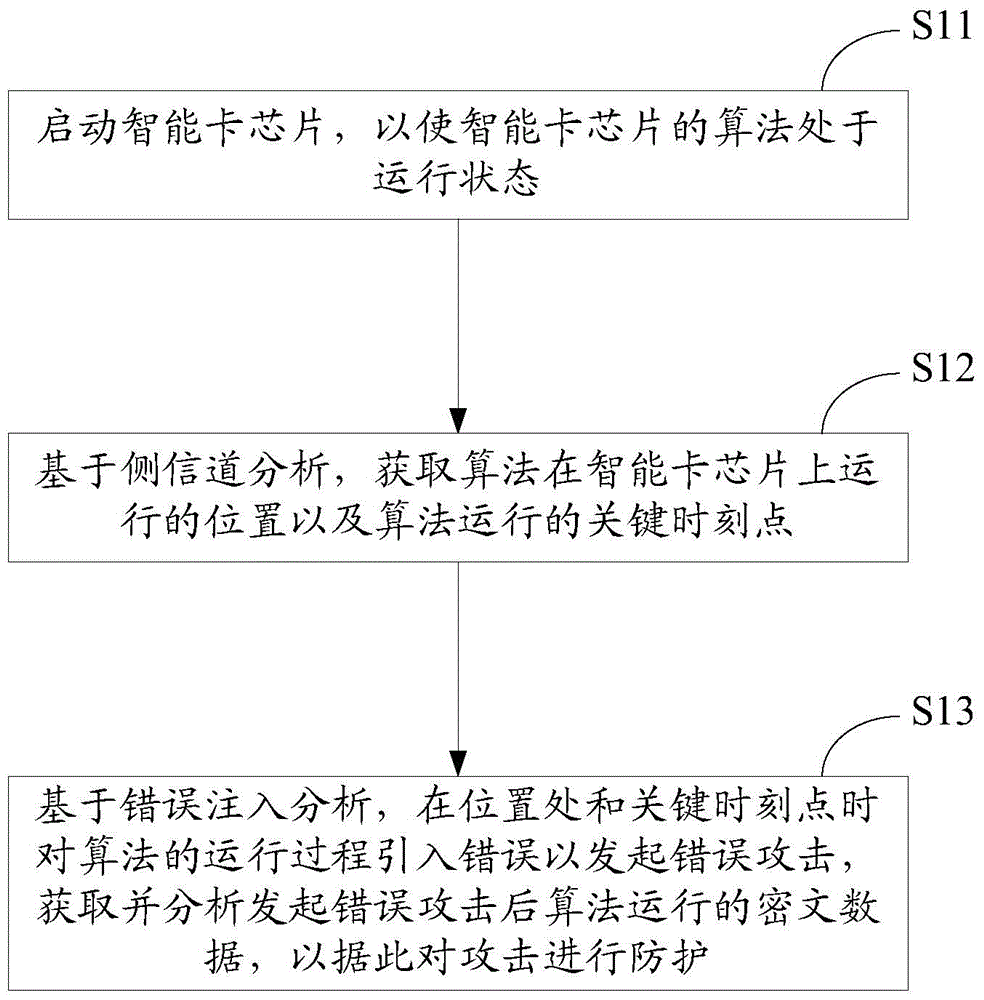
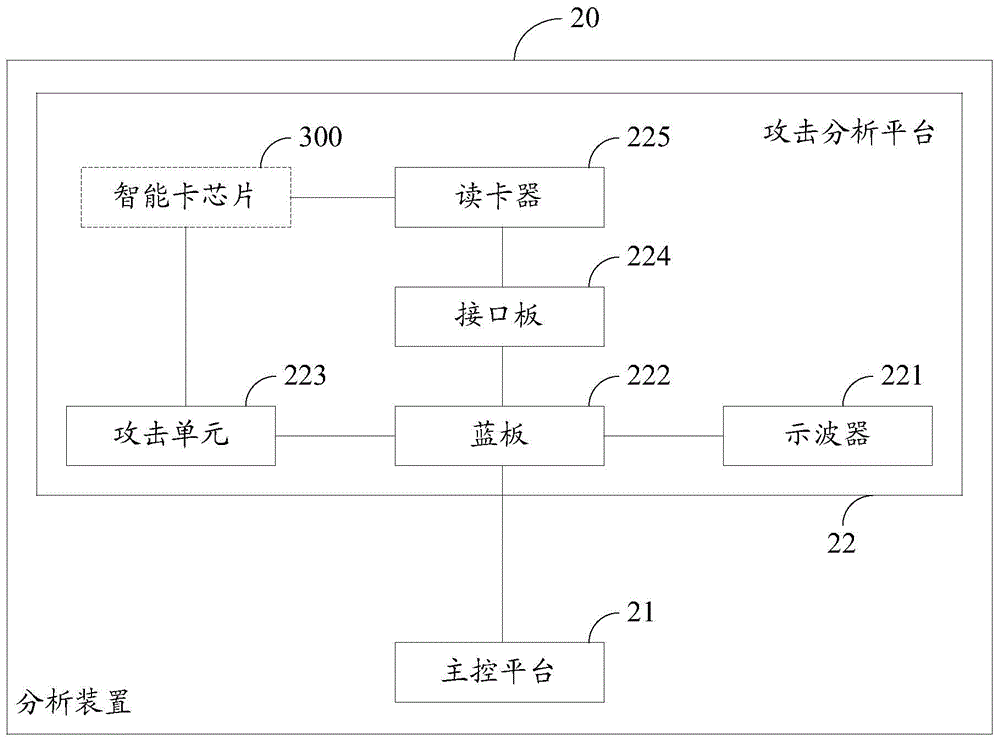
Method and device for analyzing attack on smart card chip
ActiveCN105095750AControl precisionReduce attackPlatform integrity maintainanceCritical timeSmart card
The invention provides a method and device for analyzing an attack on a smart card chip. The method comprises the following steps: starting the smart card chip, so that the algorithm of the smart card chip is in an operation state; obtaining the operation position of the algorithm on the smart card chip and a critical time point when the algorithm is operated based on analysis of a side channel; and introducing error into the operation process of the algorithm in the position at the critical time point based on analysis of error injection so as to initiate an error attack, and obtaining and analyzing operation encryption data of the algorithm after the error attack is initiated so as to protect the attack. By means of the manner, in combination with the side channel attack and the error injection attack, the attack is precisely controlled in time and space; the error injection precision can be controlled; the attack analysis cost is reduced; the analysis efficiency and the success rate are increased; and thus, effective protection to the attack can be realized.
Owner:NATIONZ TECH INC
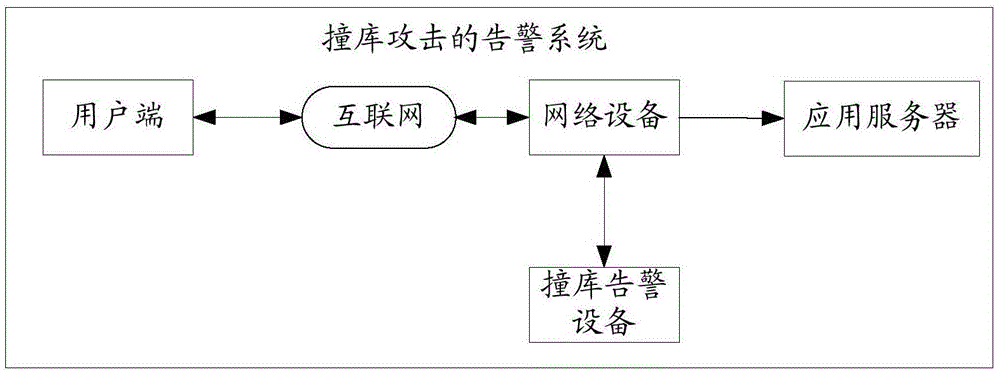
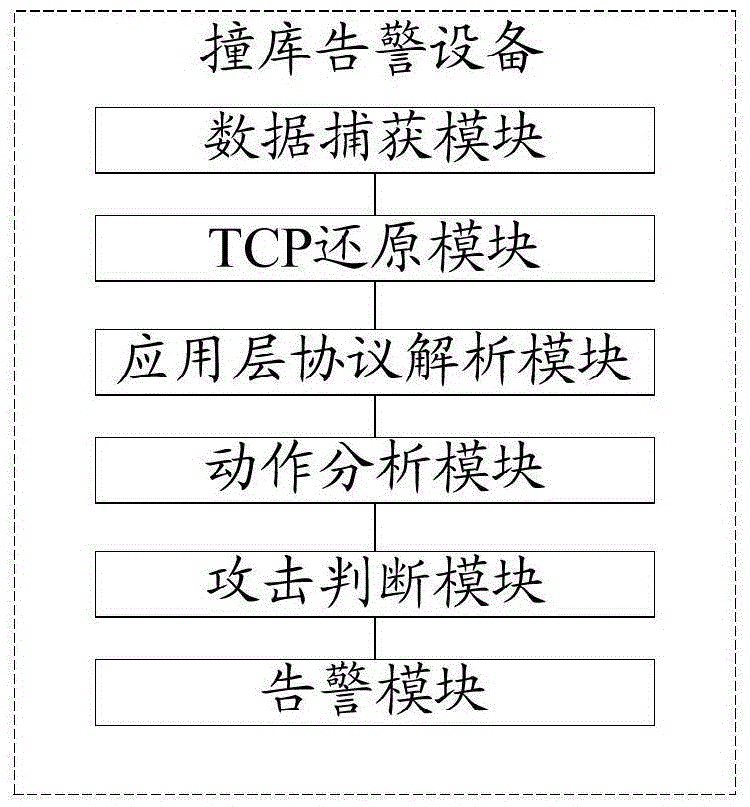
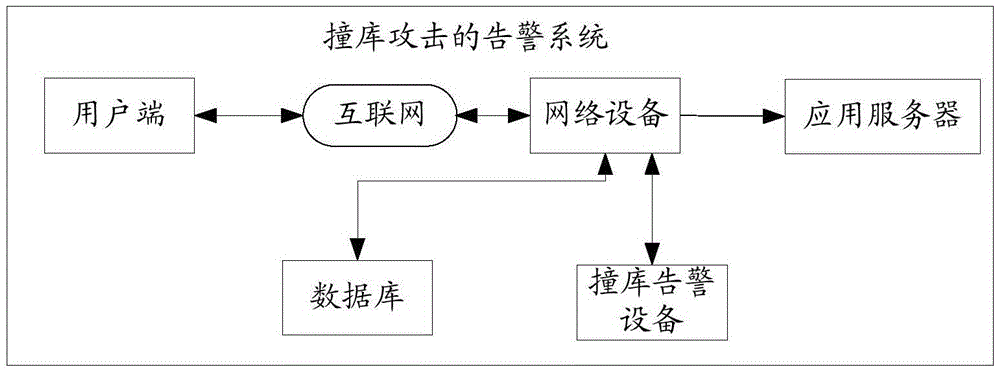
Warning system of database-hit attack
ActiveCN105577670ARealize information security protectionReduce subsequent lossesData switching networksApplication serverThe Internet
This invention discloses a warning system of a database-hit attack. The warning system is used for finding a database-hit attack of an application server in the internet. The warning system of the database-hit attack comprises a client, an application server, a network device and a database-hit attack analyzing device, wherein the client is connected with the network device through the internet; the network device is connected with the application server and the database-hit attack analyzing device; the network device is used for performing a mirroring process to communication data transmitted between the client and the application server so as to generate mirror data corresponding to the communication data, and sending the mirror data to the database-hit attack analyzing device; the database-hit attack analyzing device is used for acquiring the mirror data from the network device; a user access action corresponding to the communication data is acquired according to the mirror data; according to the user access action, judge whether the application server is suffering the database-hit attack or not; if so, a warning is sent in real time.
Owner:LINEWELL SOFTWARE
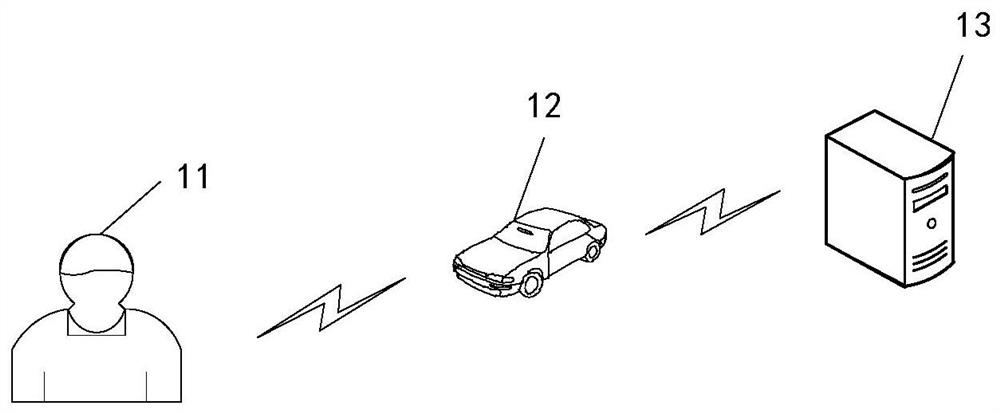
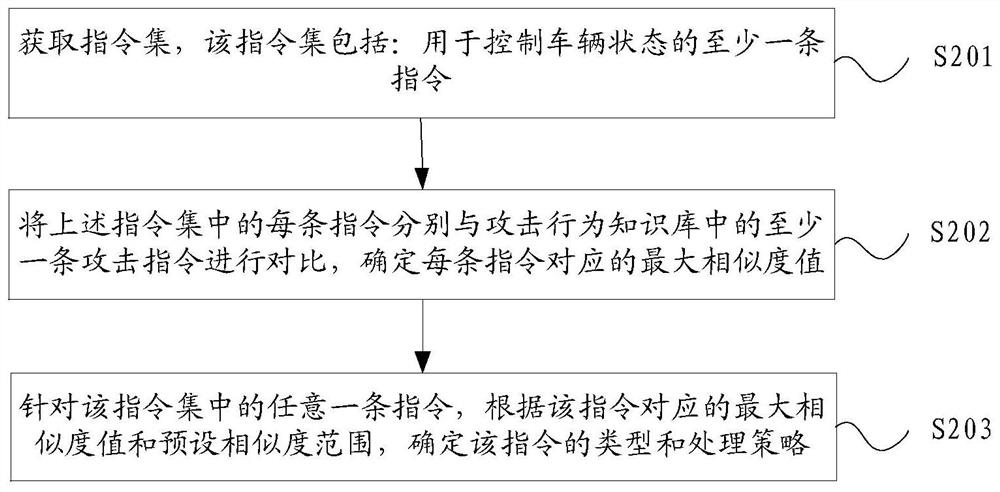
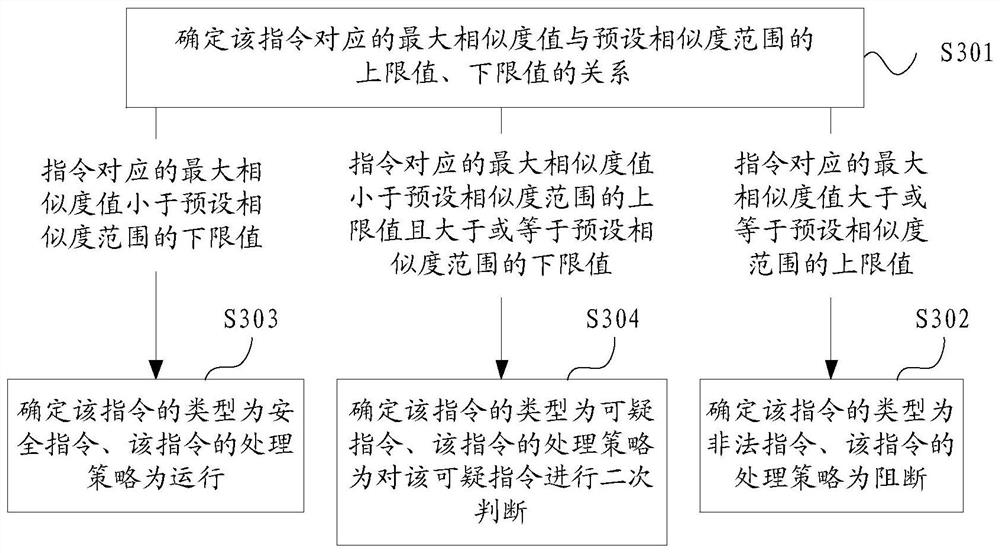
Attack defense method, device and equipment and storage medium
PendingCN111726774AParticular environment based servicesVehicle wireless communication serviceData setAttack
The invention discloses an attack defense method, device and equipment and a storage medium, relates to the technical field of information safety, and the method and the device can be used for intelligent transportation or automatic driving scenes. According to the specific implementation scheme, the method comprises the steps of obtaining an instruction set comprising at least one instruction forcontrolling the state of the vehicle, and respectively comparing each instruction in the instruction set with at least one attack instruction in an attack behavior knowledge base, determining a maximum similarity value corresponding to each instruction, and determining the type and processing strategy of each instruction according to the maximum similarity value corresponding to each instructionand a preset similarity range. According to the technical scheme, each attack instruction in the attack behavior knowledge base is obtained by performing attack analysis on the chain type data set ofat least one vehicle-mounted component, and the context data of the source data is associated when the attack instruction is generated, so that the accuracy of the determined instruction type and theattack defense precision are improved.
Owner:APOLLO INTELLIGENT CONNECTIVITY (BEIJING) TECH CO LTD
Method for verifying safety of SM2 signature algorithm based on improved difference error attack
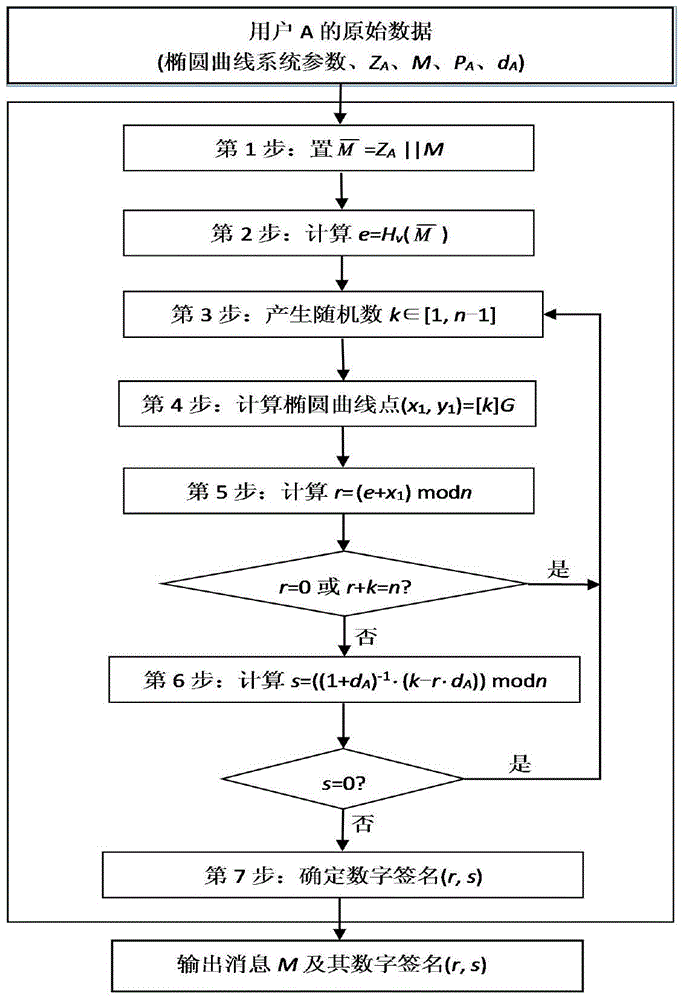
ActiveCN104836808AComprehensive analysis of security capabilitiesEasy injection of errorsUser identity/authority verificationValidation methodsDigital Signature Algorithm
The invention discloses a method for verifying safety of an SM2 signature algorithm based on an improved difference error attack, wherein the method comprises the steps as follows: 1) using the SM2 signature algorithm to sign a message M, injecting an error when scalar multiplication of a generated random number k and an elliptic curve base point G of the SM2 signature algorithm is iterated to the No.i times so as to change part of bit value of y coordinate of a medium value in the No.i times; 2) recovering the continuous bit value of the random number k by using the signature result obtained in the step 1), an attestation public key PA and a message M hashing value e; 3) configuring an HNP problem by using the continuous bit value and a wrong signature result, and analyzing a private key by using a lattice attack, and judging whether the current SM2 signature algorithm is safe according to the private key. The method of the invention can insert error more simply and comprehensively analyze the safety that the SM2 signature algorithm resists an attack.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +2
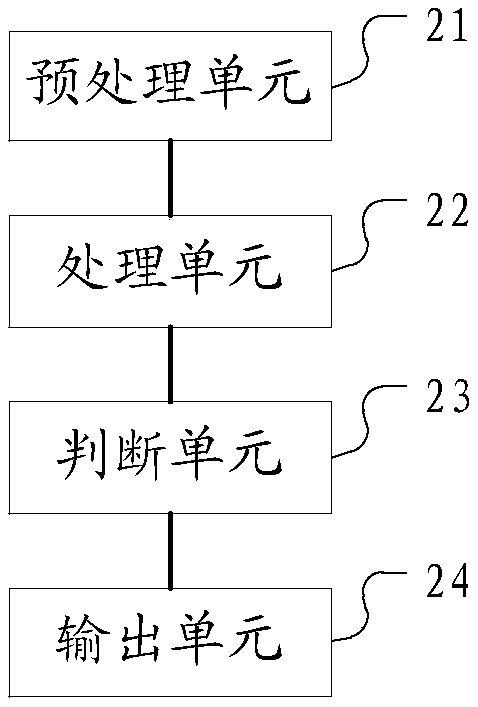
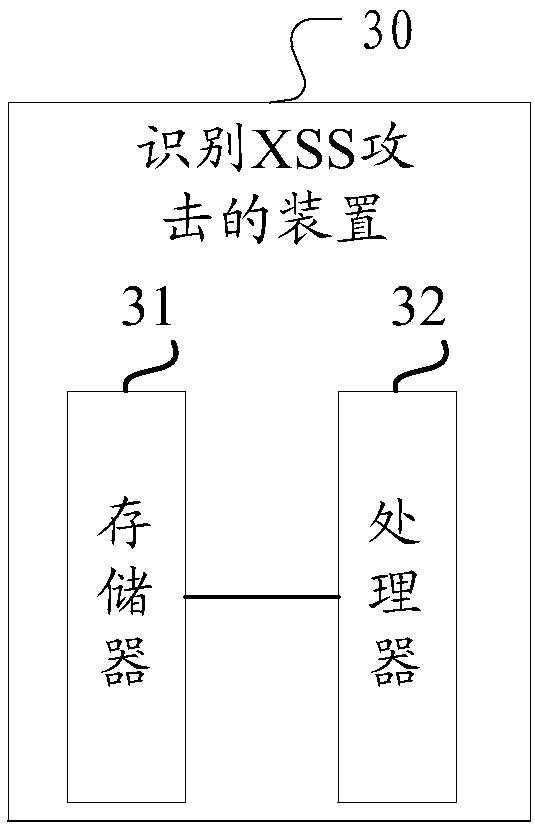
Method and device for identifying XSS attack, and computer readable storage medium
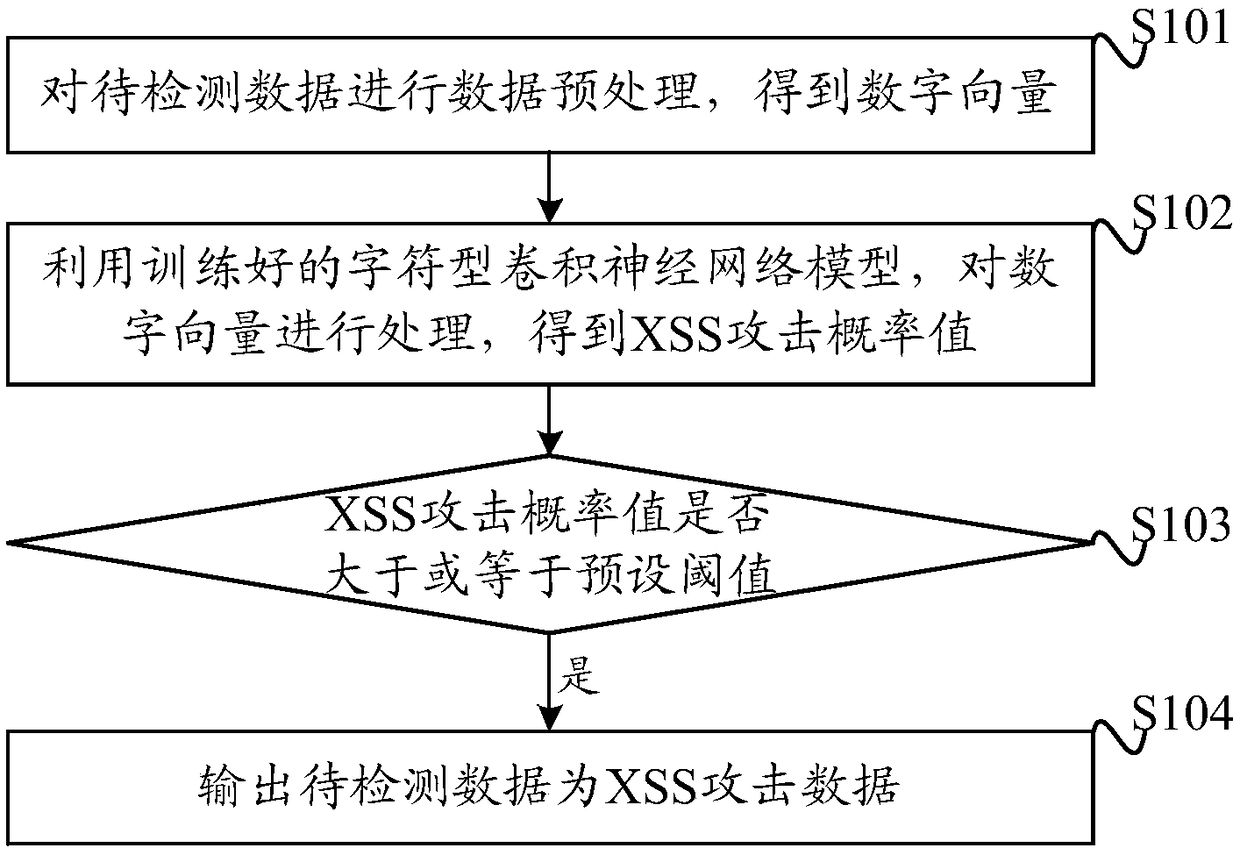
InactiveCN109388943ARobustImprove generalization abilityPlatform integrity maintainanceNeural architecturesSemanticsNetwork structure
The embodiment of the invention discloses a method and device for identifying an XSS attack, and a computer-readable storage medium. The data to be detected is preprocessed to obtain a digital vector. the trained character-based convolutional neural network model is used to process the digital vector to obtain the attack probability of XSS. When the XSS attack probability value is greater than orequal to the preset threshold, the output data to be detected is XSS attack data. Compared with the prior art, the technical scheme does not need to make rules artificially, and only needs to use thetrained character-type convolution neural network model for XSS attack analysis. The model uses the network structure of convolution neural network, and can identify some attacks with similar structure, which improves the generalization ability of the model. And the character-based convolution neural network model can take each character as the smallest processing unit. Compared with word segmentation processing, it can learn deeper semantics and improve the accuracy of XSS attack recognition.
Owner:HANGZHOU SHIQU INFORMATION TECH CO LTD
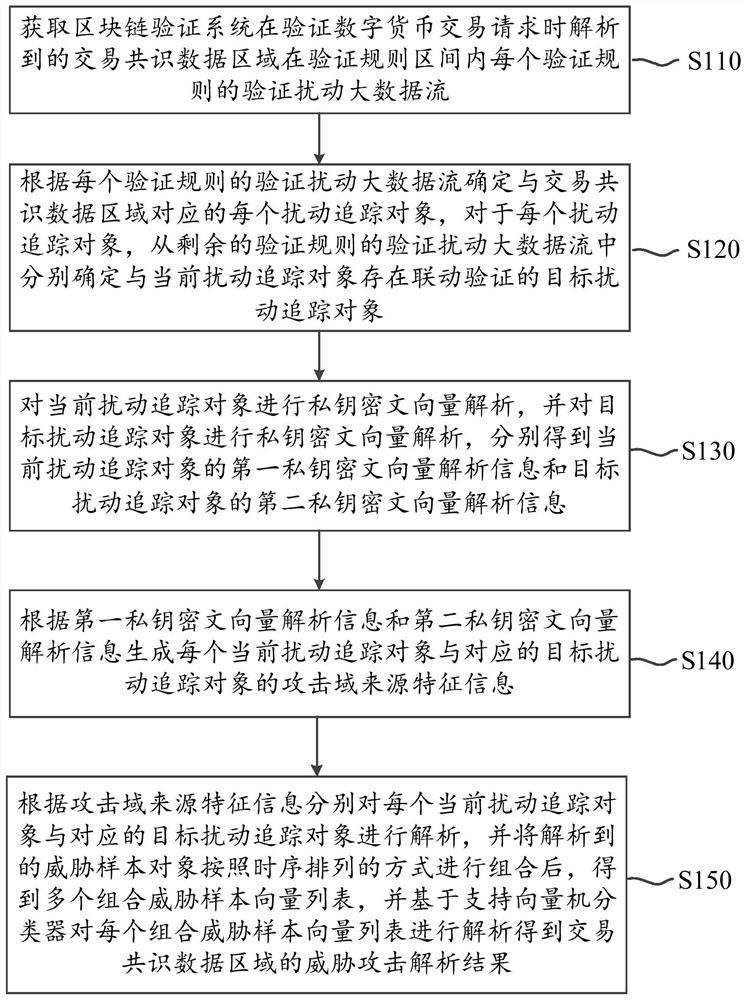
Data flow monitoring method based on block chain and big data and cloud computing service platform
InactiveCN111932226AHigh discrimination accuracyImprove accuracyFinanceCharacter and pattern recognitionData streamCiphertext
The embodiment of the invention provides a data flow monitoring method based on a block chain and big data and a cloud computing service platform. Each disturbance tracking object of each verificationrule and a target disturbance tracking object in linkage verification with the current disturbance tracking object are determined; therefore, private key ciphertext vector analysis can be carried outbased on the association relationship between the disturbance tracking object and the target disturbance tracking object; threat attack analysis is carried out through the support vector machine classifier, so that the judgment accuracy of the threat attack behavior of the transaction consensus data area on the blockchain encryption node in the verification rule interval can be improved, and theaccuracy of threat attack identification is improved.
Owner:周浩
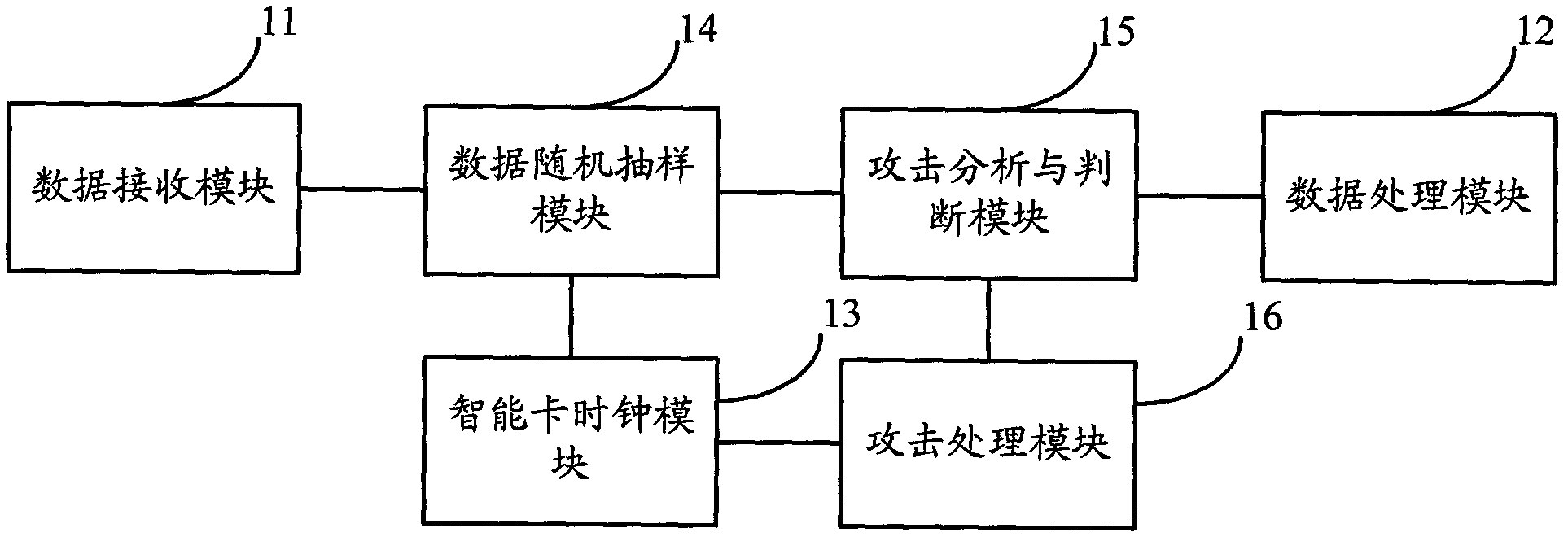
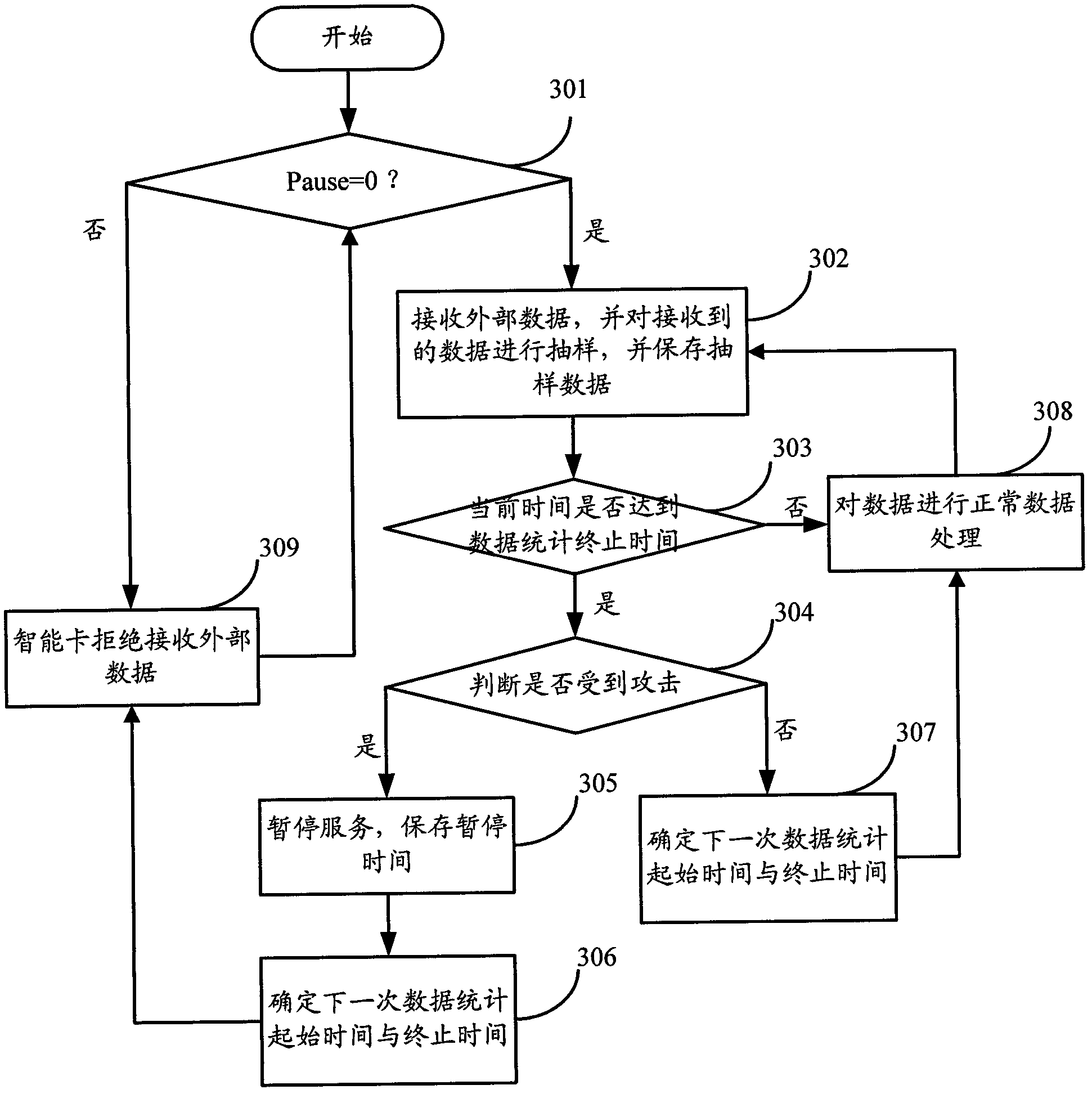
Smart card and safety protection method thereof
The invention discloses a smart card and a safety protection method of the smart card. The smart card comprises a smart card clock module, a data random sampling module, an attack analysis and judgment module and an attack processing module, wherein the smart card clock module is used for timing according to a received external level signal; the data random sampling module is used for determining the data statistics beginning time and the data statistics terminating time at random, and sampling the received data according to the data statistics beginning time and the data statistics terminating data; the attack analysis and judgment module is used for judging whether the smart card is attacked according to the obtained data sampled by the data random sampling module, and the corresponding data statistics beginning time and data statistics terminating time; and the attack processing module is used for carrying out anti-attack treatment when the attack analysis and judgment module judges the smart card is attacked. According to the safety protection method of the smart card, whether the smart card is attached can be more effectively judged.
Owner:CHINA MOBILE COMM GRP CO LTD
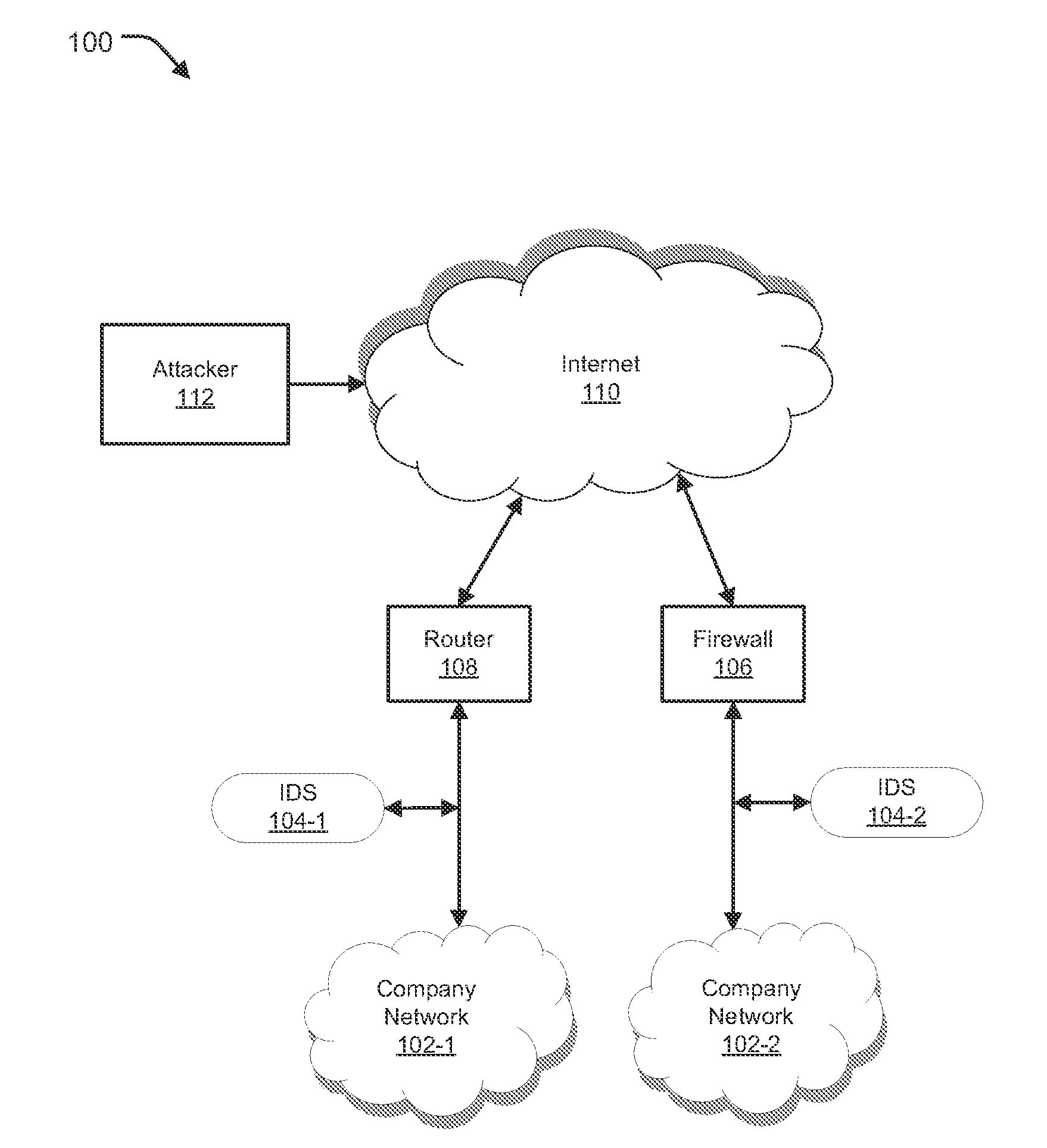
Logging attack context data
ActiveUS20150180887A1Data augmentationEasy to analyzeMemory loss protectionError detection/correctionNetwork packetContext data
Owner:FORTINET
DDOS attack detection method with high accuracy
The invention discloses a high-accuracy DDOS attack detection method, which belongs to the field of computer network security. The method is as follows: the data packet interception module analyzes the access network data packet information; the data packet feature statistics module performs statistics on the parsed network data packet information; The proportion distribution of the total number of packets; the data analysis module calculates the alarm threshold of network data according to the calculated historical data stored; Submit it to the attack analysis module; the attack analysis module generates a detection report according to the received network data value. Compared with the prior art, the present invention integrates the historical data of network transmission, deeply analyzes the current network data, and can identify various DDOS attacks.
Owner:蔡昌菊
Logging attack context data
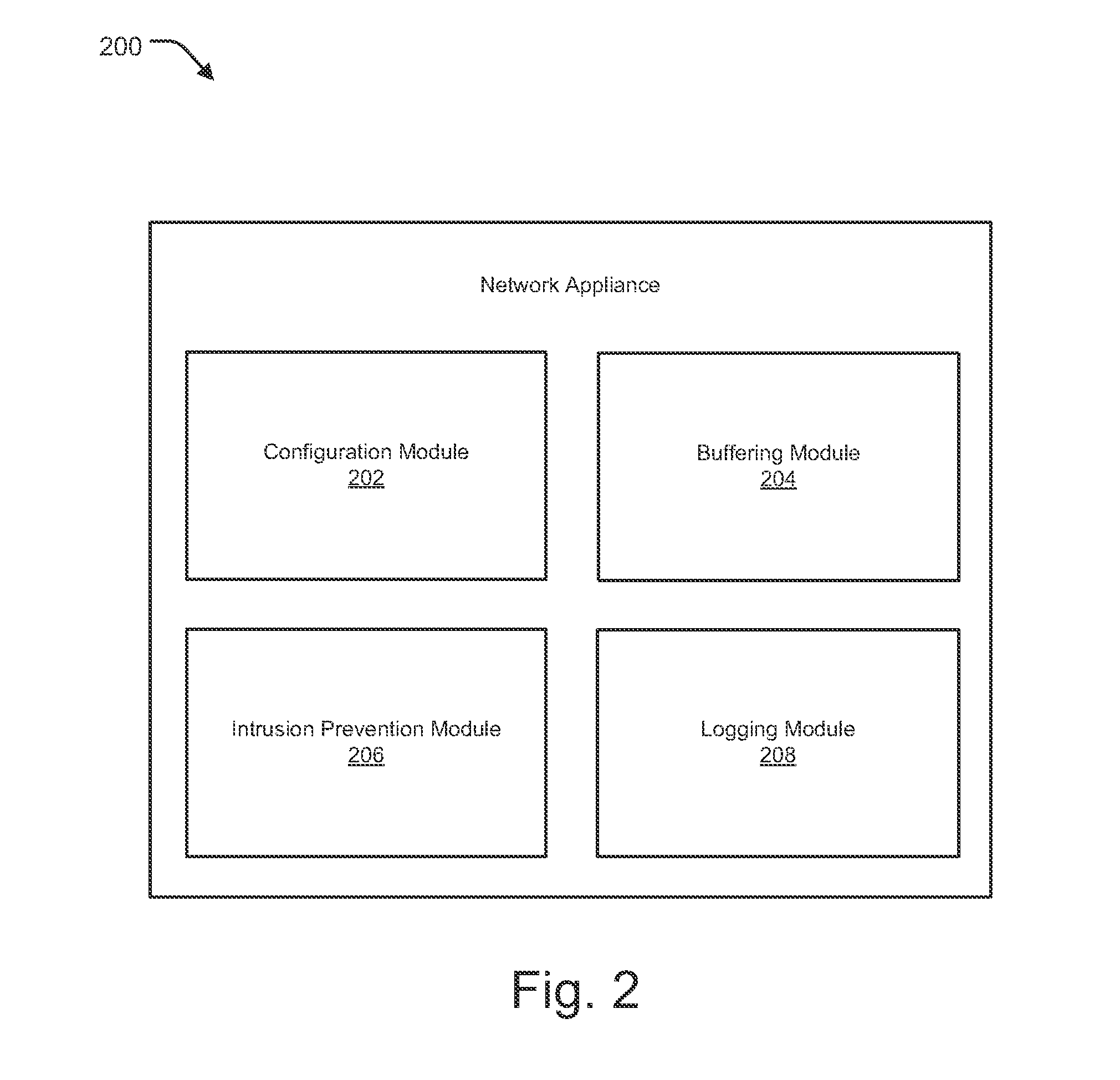
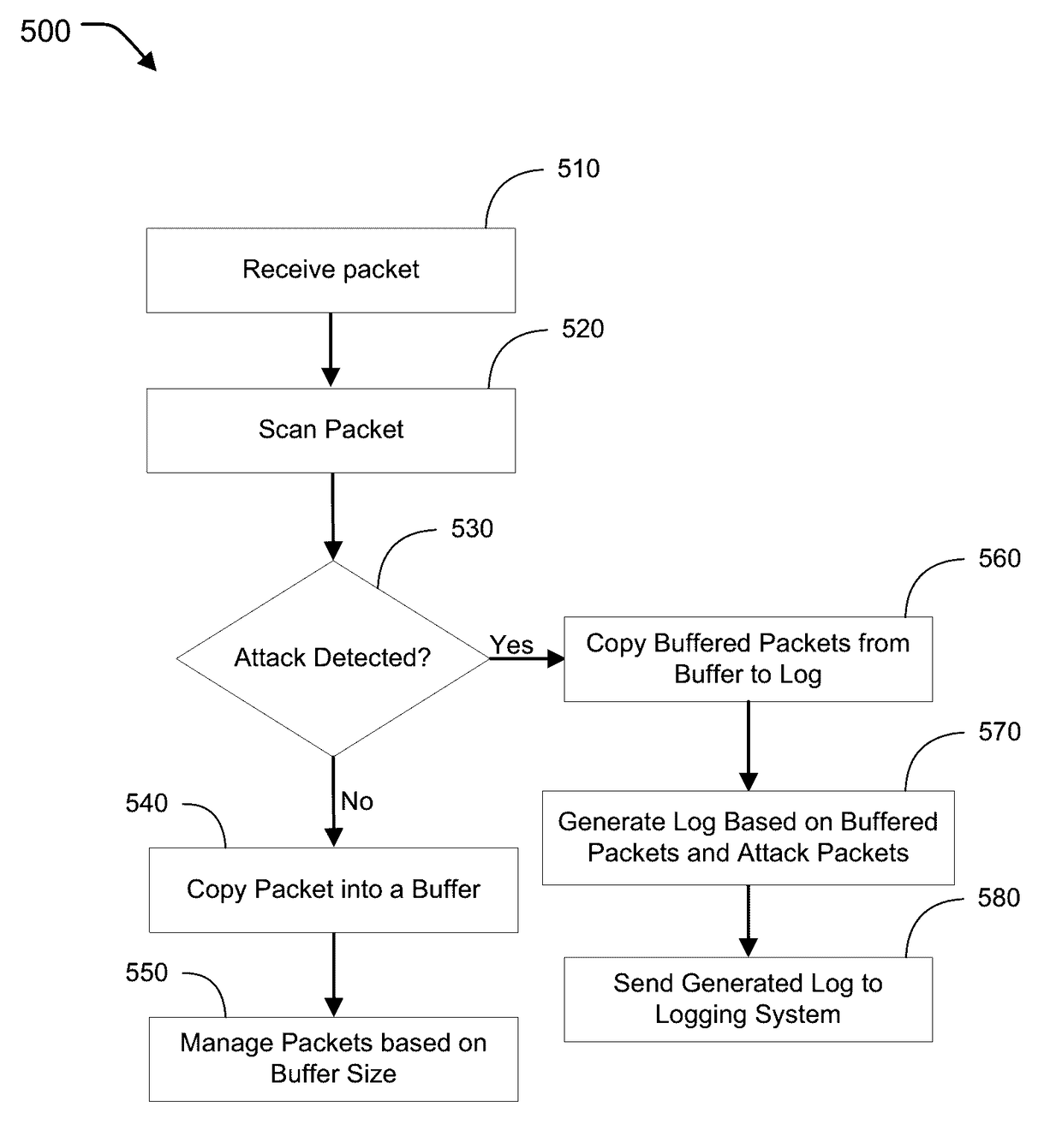
Methods and systems for improved attack context data logging are provided. According to one embodiment, configuration information is received from an administrator of a network security device. The configuration information includes information indicative of a quantity of packets to be captured for post attack analysis. Responsive to receipt of the configuration information, a size of a circular buffer is configured based thereon. Multiple packets directed to a network protected by the network security device are received from an external network. The received packets are temporarily buffered within the circular buffer. An analysis is performed to determine whether one of the received packets is potentially associated with a threat or undesired activity (“trigger packet”). Responsive to an affirmative determination, contextual information is captured by extracting information regarding at least a portion of the configured quantity of packets from the circular buffer and storing the contextual information within a log.
Owner:FORTINET
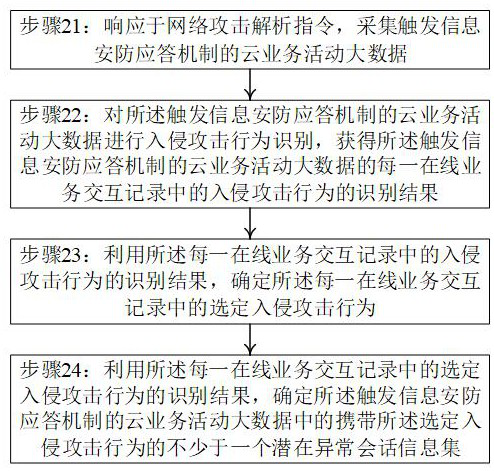
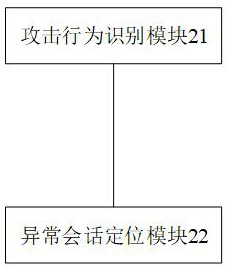
Data analysis method for coping with cloud computing network attack and server
ActiveCN114726654AReduce overheadReduce the computational load of attack identificationSecuring communicationAttackEngineering
The invention provides a data analysis method for coping with a cloud computing network attack and a server, which can intelligently respond to a network attack analysis instruction and collect a potential abnormal session information set in cloud service activity big data triggering an information security response mechanism. Then, the method can be used for guiding a big data attack analysis network to identify cloud service activity big data triggering an information security response mechanism based on the potential abnormal session information set, so that the attack identification operand of the big data attack analysis network is reduced; compared with a traditional thought of manually positioning the potential abnormal session information set for a big data attack analysis network, the method has the advantages that the intelligent degree of network attack identification for cloud service activity big data can be improved; and unnecessary resource overhead is reduced.
Owner:北京徽享科技有限公司
Attack analysis system, cooperation apparatus, attack analysis cooperation method, and program
ActiveUS9853994B2Efficient discoveryHardware monitoringPlatform integrity maintainanceAttack analysisData mining
In a log analysis cooperation system including a logger that collects a log of a communication device and stores the log in a storage device, a SIEM apparatus that detects an attack, and a log analysis apparatus that analyzes the log collected by the logger, a log analysis cooperation apparatus stores an attack scenario in a storage device, receives from the SIEM apparatus warning information including information on the detected attack, computes a predicted occurrence time of an attack predicted to occur subsequent to the detected attack based on the warning information and the attack scenario, and transmits to the log analysis apparatus a scheduled search to search the log at predicted occurrence time computed. The log analysis apparatus transmits a scheduled search to the logger to search the log at the predicted occurrence time.
Owner:MITSUBISHI ELECTRIC CORP
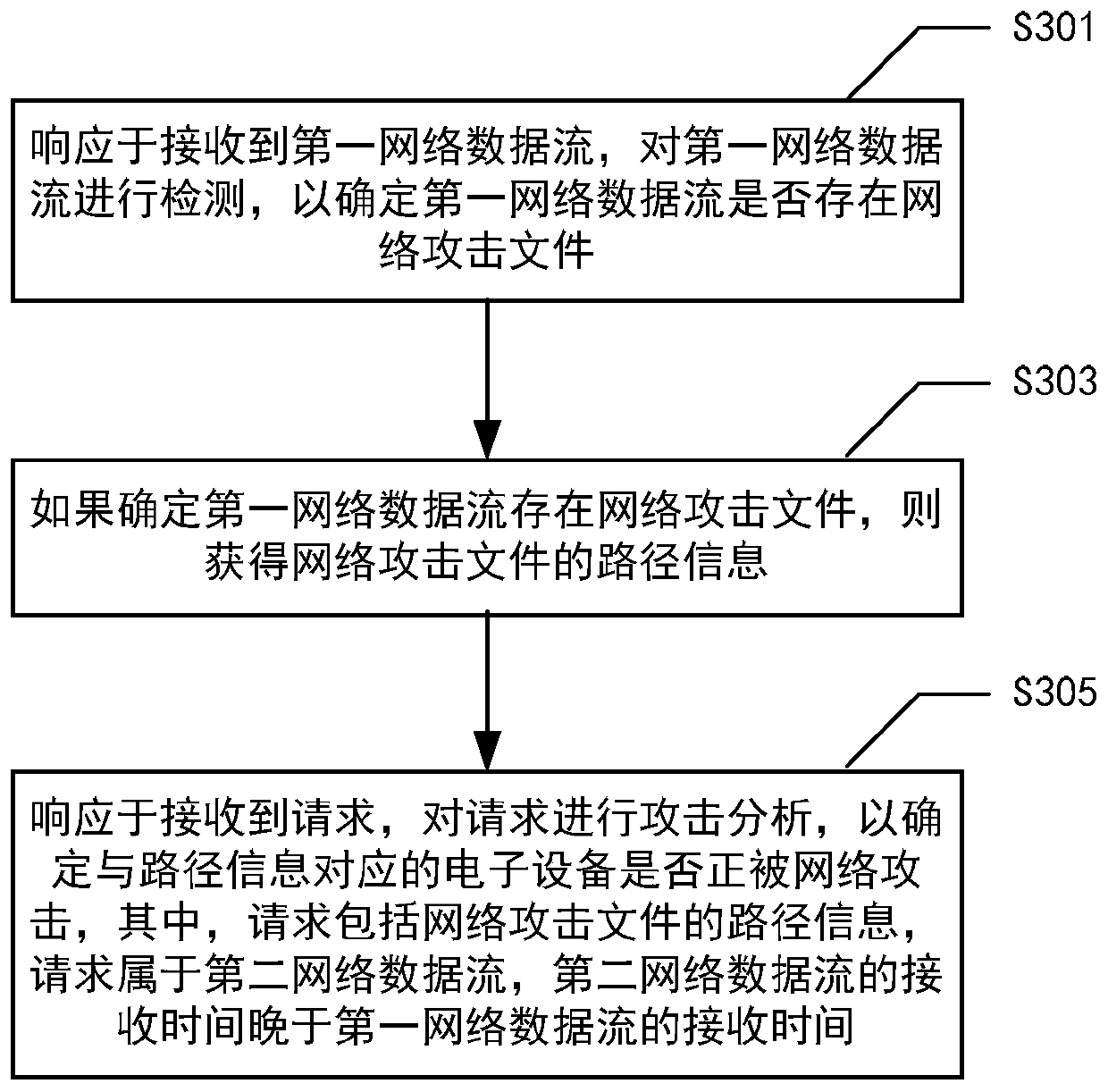
Network attack analysis method, network attack analysis device, computing equipment and medium
The invention provides a network attack analysis method, a network attack analysis device, computing equipment and a medium. The method comprises the following steps: detecting a first network data flow in response to the received first network data flow to determine whether the first network data flow has a network attack file or not; if it is determined that the network attack file exists in thefirst network data stream, obtaining path information of the network attack file; and in response to receiving the request, performing attack analysis on the request to determine whether the electronic device corresponding to the path information is being attacked by the network, the request including the path information of the network attack file and the request belonging to the second networkdata flow, and the receiving time of the second network data flow being later than the receiving time of the first network data flow.
Owner:BEIJING QIANXIN TECH +1
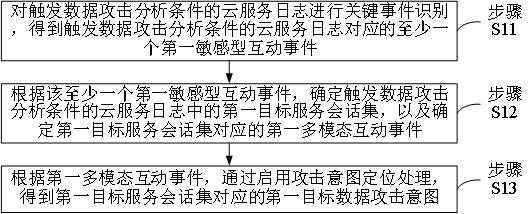
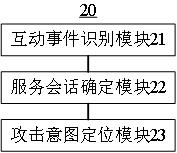
Data attack analysis method applied to cloud service and server
InactiveCN113949577AEfficient and accurate intent analysisCharacter and pattern recognitionNeural architecturesAttackLog trigger
The invention relates to the technical field of cloud services and data attack analysis, in particular to a data attack analysis method applied to cloud services and a server. Due to the fact that in the attack intention analysis process, service event positioning processing can analyze a random and changeable service environment, according to at least one first sensitive interaction event, the first target service session set in the cloud service log triggering the data attack analysis condition is determined, and the first multi-modal interaction event corresponding to the first target service session set is determined, that is, the intention analysis result in the attack intention analysis process is obtained, according to the first multi-modal interaction event, attack intention positioning processing is started, so that a first target data attack intention corresponding to the first target service session set in the service scene can be obtained, so that the intention analysis of the service session sets in different states in the cloud service log triggering the data attack analysis condition can be efficiently and accurately realized.
Owner:广州酷风技术开发有限公司
APT attack analysis method and system, and server
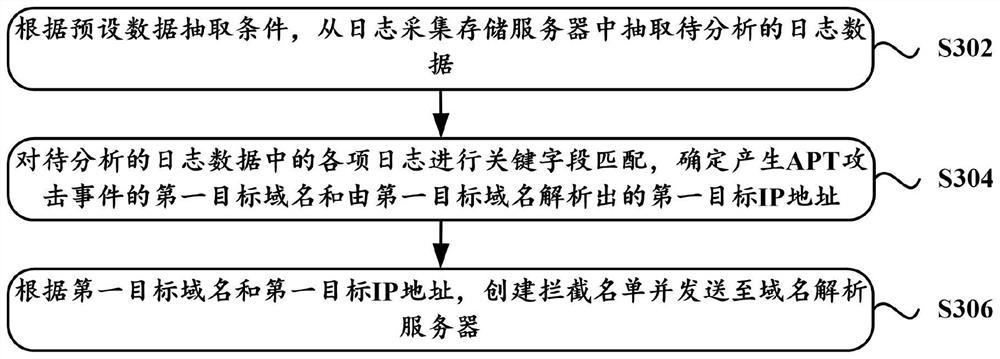
ActiveCN112165451AAvoid lossRealize association analysisTransmissionEnergy efficient computingDomain nameIp address
The embodiment of the invention discloses an APT attack analysis method and system and a server, and the method is used for solving the problem that in the prior art, correlation analysis is difficultto be carried out on a domain name resolution log and an APT attack event. The method comprises the steps of extracting to-be-analyzed log data from a log collection and storage server according to apreset data extraction condition; performing key field matching on each log in the to-be-analyzed log data, and determining a first target domain name generating an APT attack event and a first target IP address resolved by the first target domain name; and according to the first target domain name and the first target IP address, creating an interception list and sending the interception list toa domain name resolution server, so that the domain name resolution server determines whether to respond to a domain name resolution request initiated by a client according to the interception list.According to the technical scheme, correlation analysis between the domain name resolution log and the APT attack event is realized, so that log data for data backup plays a role in discovering APT attacks.
Owner:新浪技术(中国)有限公司
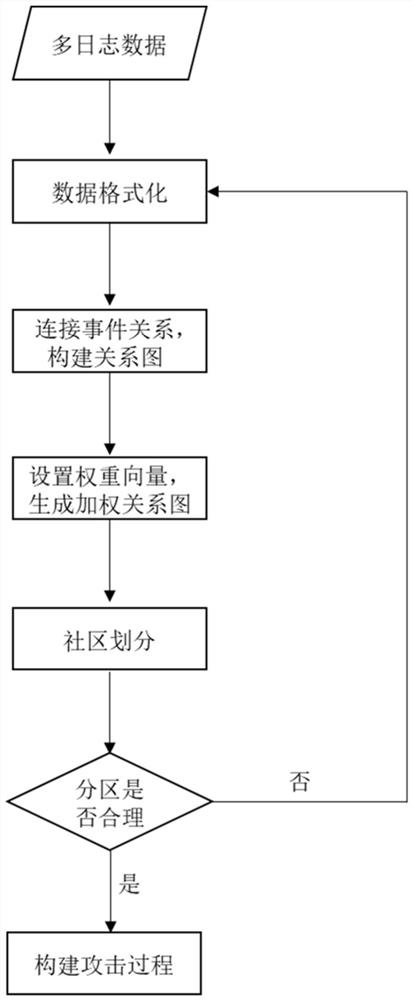
Multi-step attack tracing method and system, terminal and readable storage medium
ActiveCN112182567AReduce connectionsImprove accuracyWeb data indexingCharacter and pattern recognitionRelation graphAttack
The invention discloses a multi-step attack tracing method and system, a terminal and a readable storage medium. The tracing method comprises the following steps: formatting a log, extracting event features from the log, establishing a feature relationship, and constructing an event relationship graph according to the feature relationship; weighting the event relation graph through the weight vector to obtain a weighted relation graph; transmitting the weighted relation graph to a community detection module, performing relation division on the weighted relation graph through a community discovery algorithm, and discovering an attack community; after the community is found, based on the obtained attack community, according to the event logic relationship, establishing a sequence, and constructing an attack process. The invention also provides a system, a terminal and a readable storage medium for realizing the method, the problem of state explosion caused by relationship connection canbe solved by utilizing multiple log association analysis, the attack process of multi-step attack can be effectively analyzed, and the method can be used for multi-log-based attack analysis in varioussystems.
Owner:XIDIAN UNIV
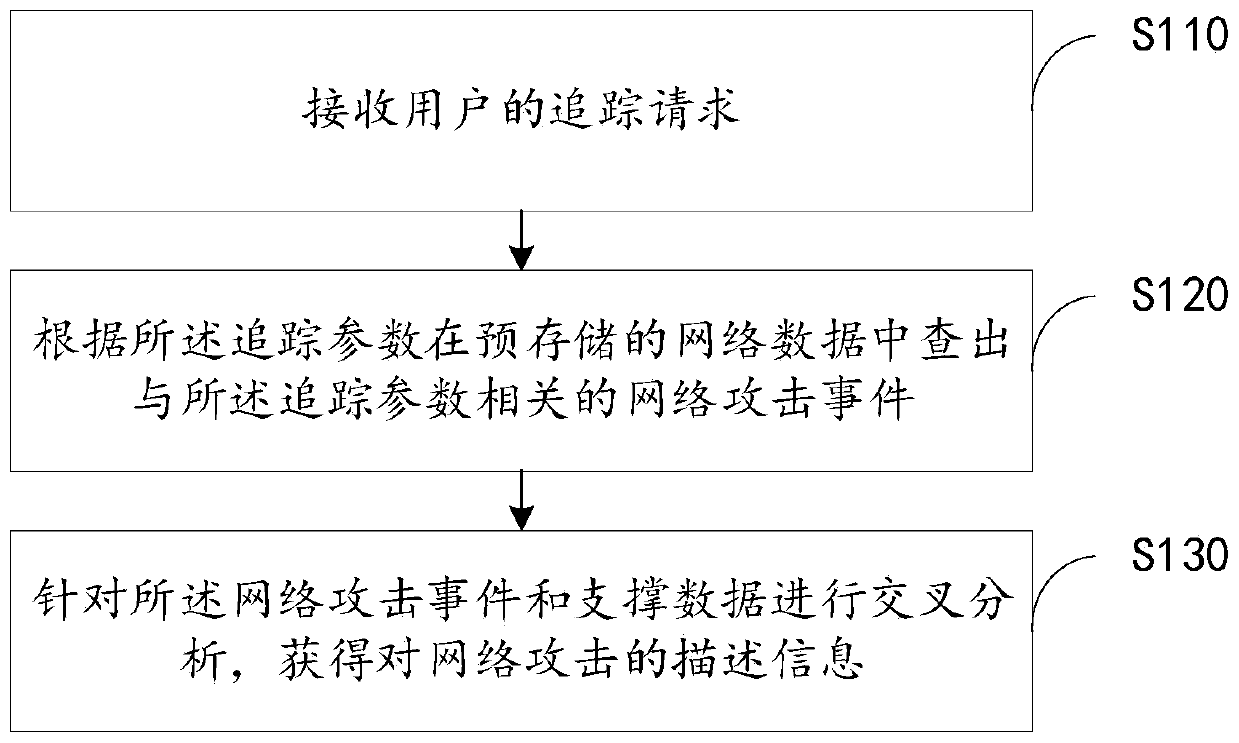
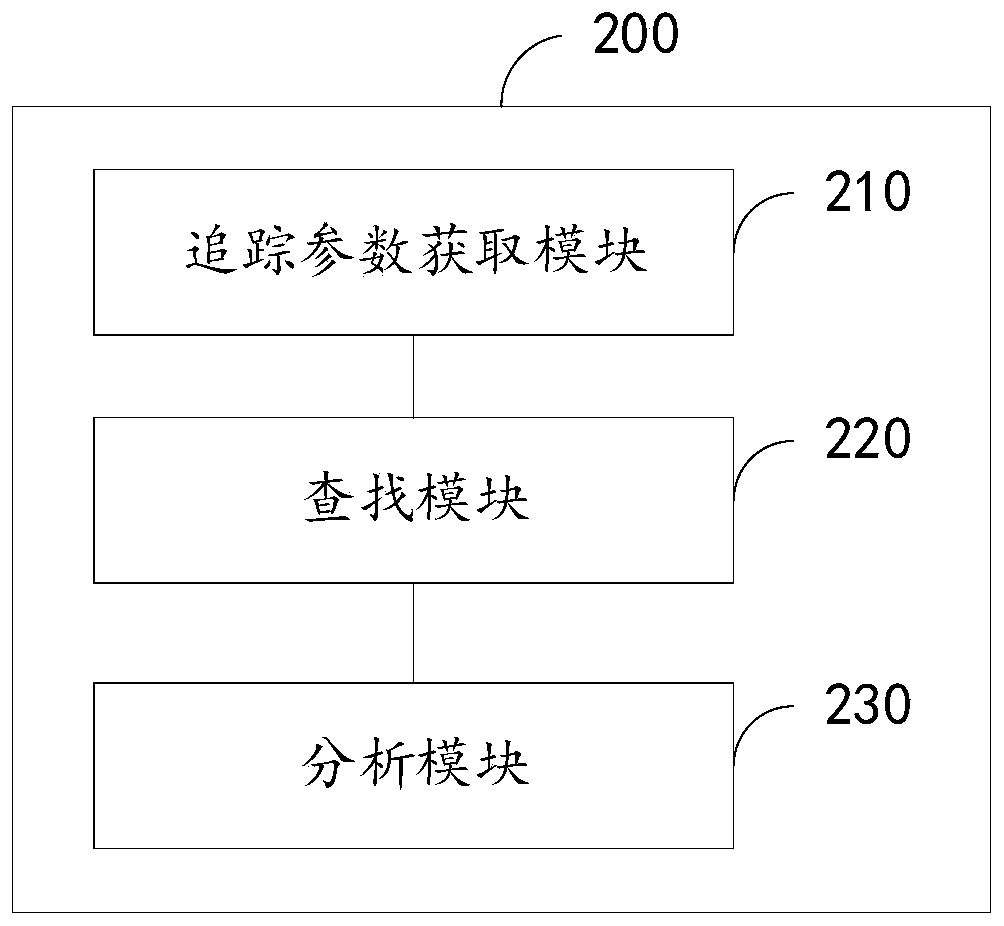
Network attack tracking method and device, electronic device and readable storage medium
The invention provides a network attack tracking method and device, an electronic device and a readable storage medium, and relates to the field of network communication. The method comprises the following steps of receiving a tracking request of a user, wherein the tracking request comprises a tracking parameter; searching a network attack event related to the tracking parameter in the pre-storednetwork data according to the tracking parameter; and performing cross analysis on the network attack event and the support data to obtain the description information of the network attack, wherein the support data is the analysis data related to the network attack except the network data. According to the scheme, the network attack event related to the tracking parameter is firstly retrieved byusing the network data, and then the cross data is performed with other support data related to the network attack, so that the data sources participating in the network attack analysis are more, andmore comprehensive analysis of the network attack can be realized.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com