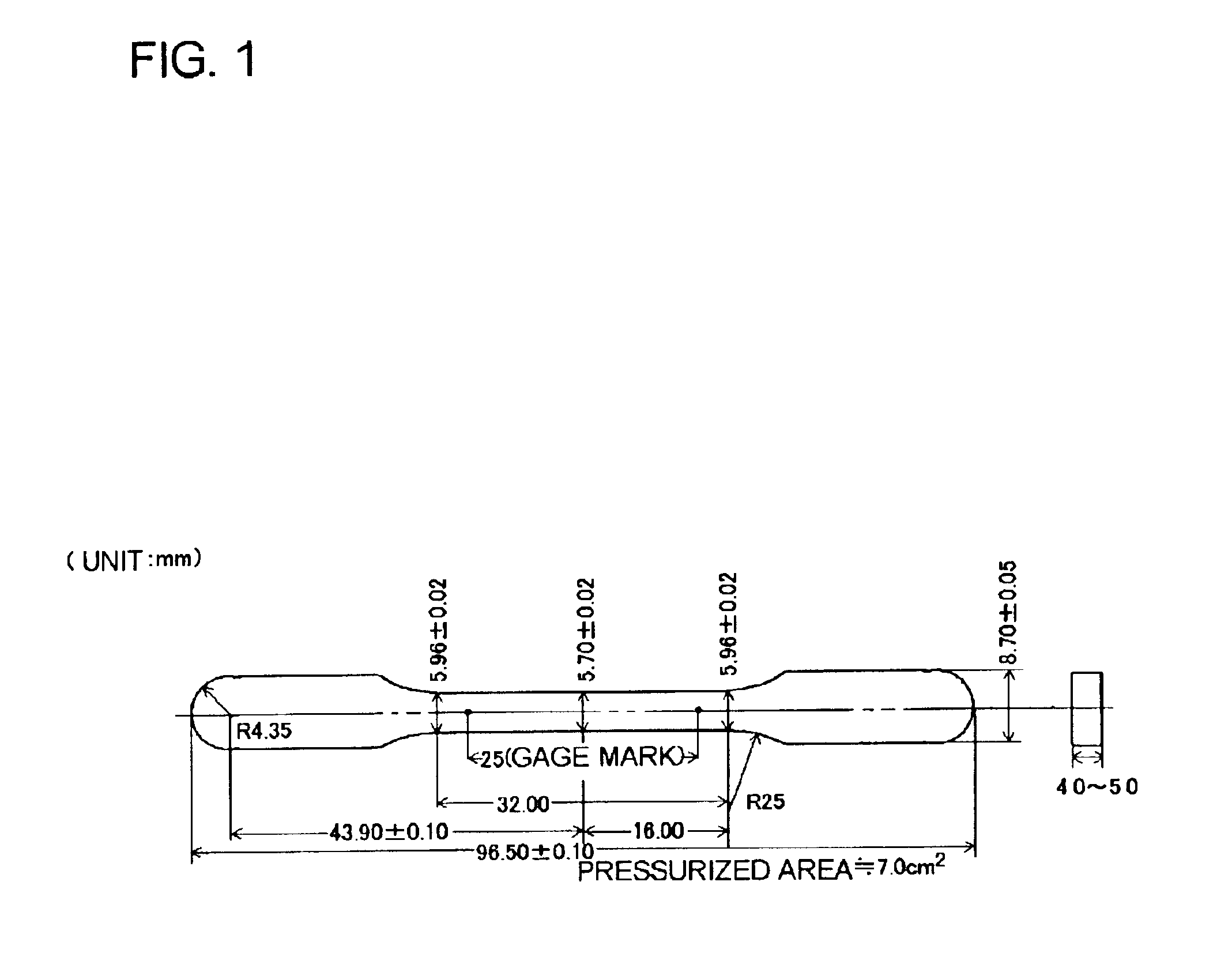
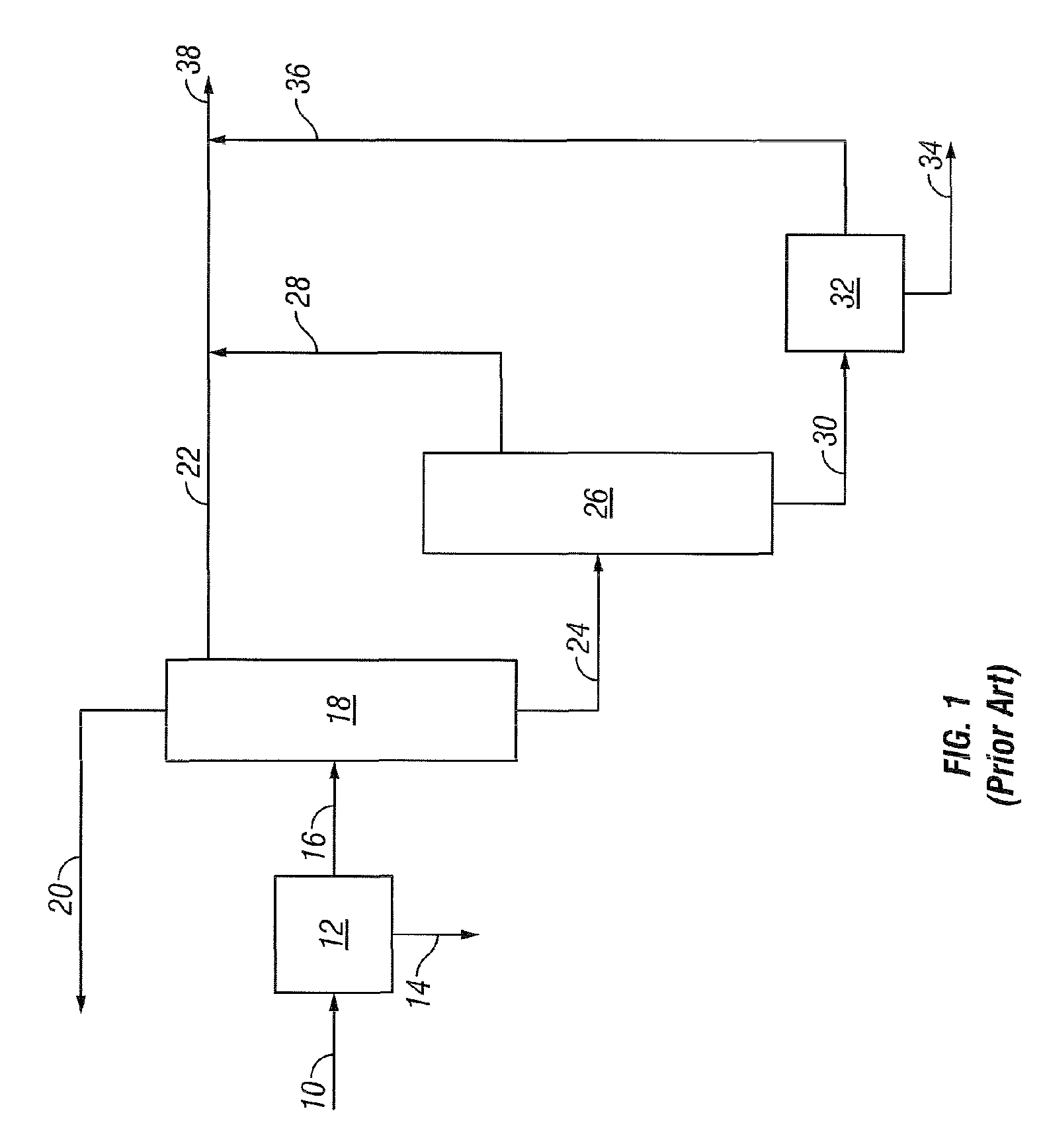
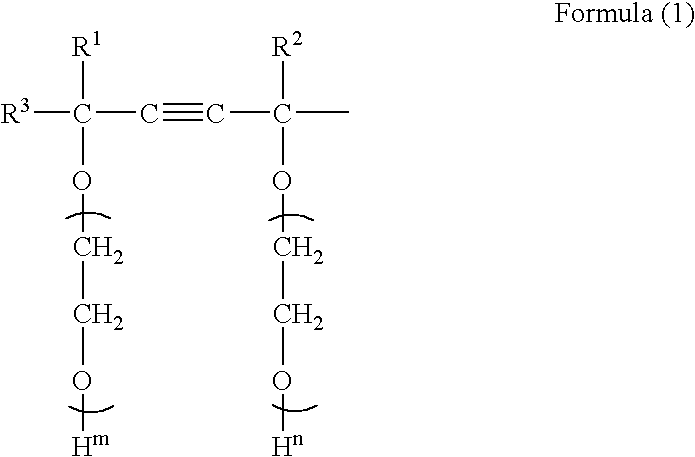
Patents
Literature
410results about How to "Reduce attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
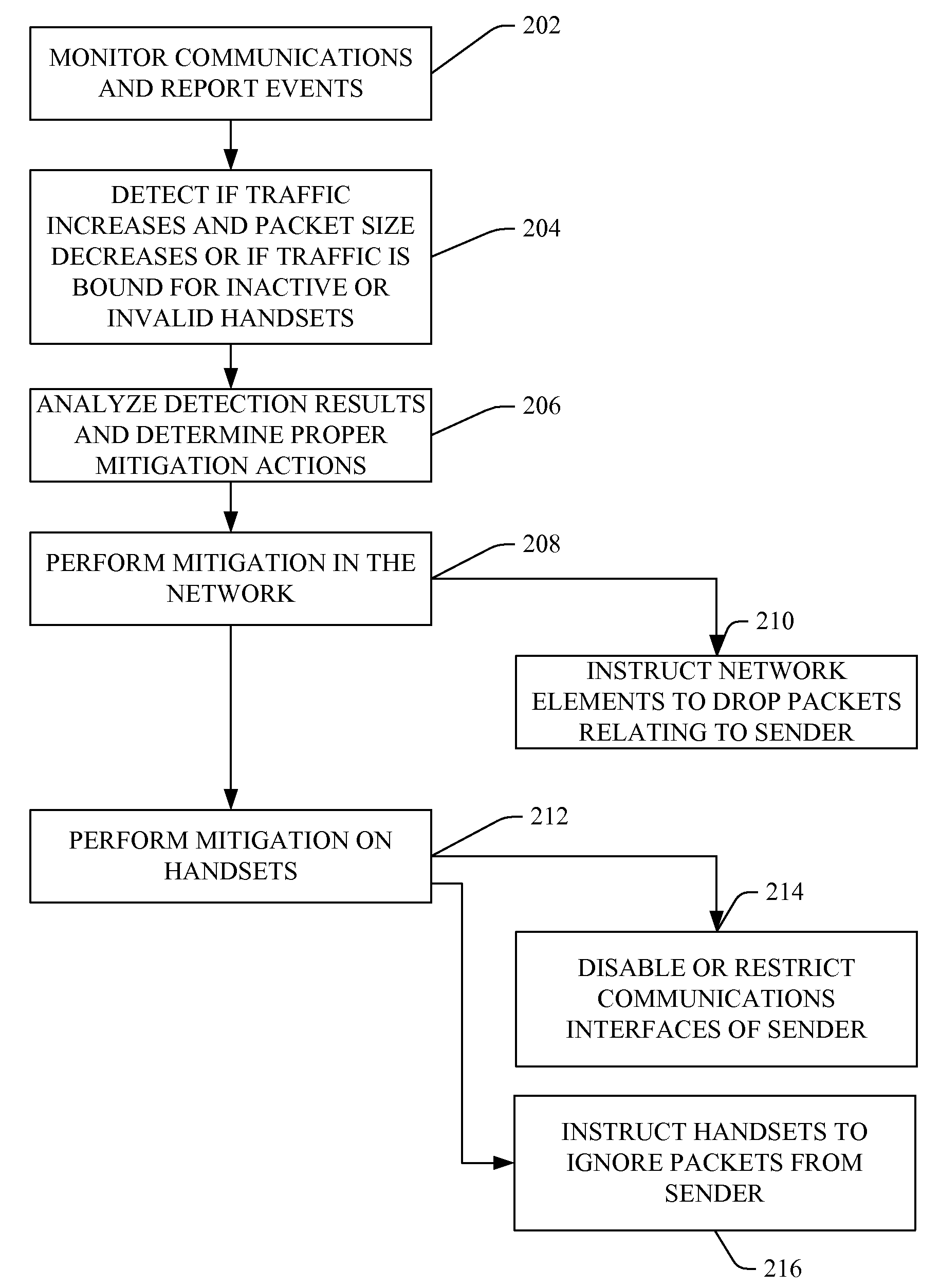
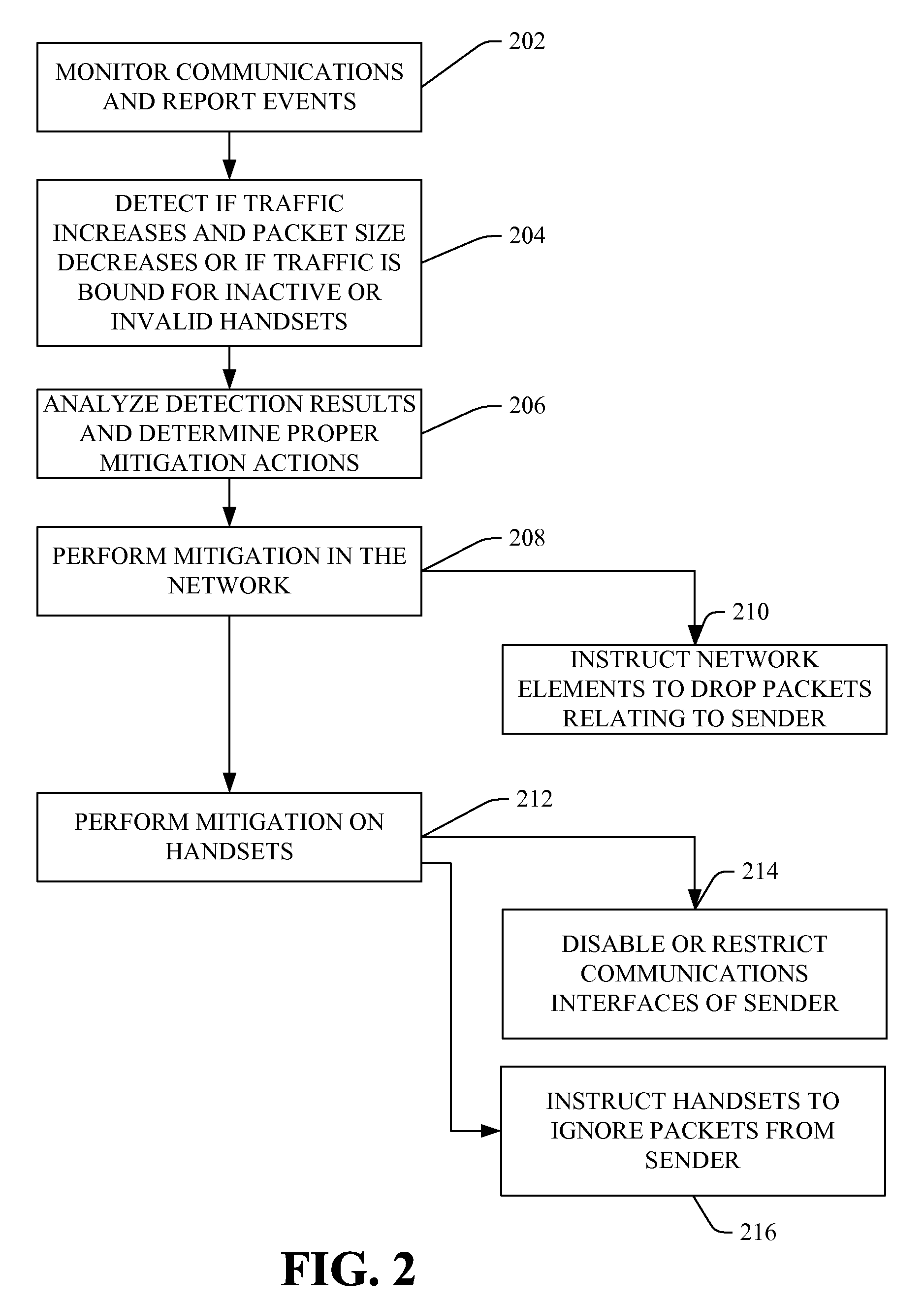
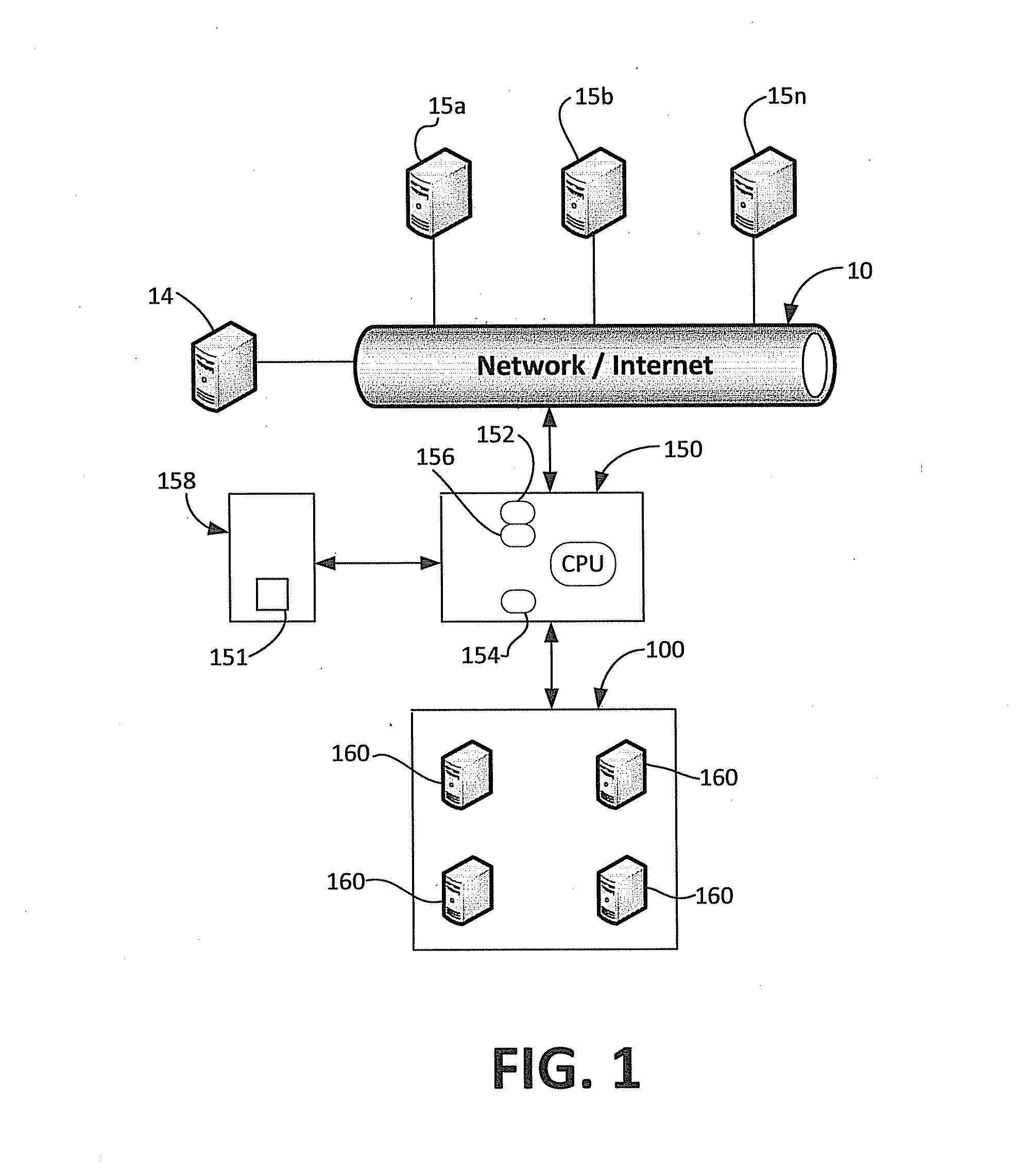
Wireless intrusion prevention system and method
ActiveUS20080178294A1Reduce transmissionReduce attackMemory loss protectionUnauthorised/fraudulent call preventionWireless intrusion prevention systemNetwork communication
A wireless intrusion prevention system and method to prevent, detect, and stop malware attacks is presented. The wireless intrusion prevention system monitors network communications for events characteristic of a malware attack, correlates a plurality of events to detect a malware attack, and performs mitigating actions to stop the malware attack.
Owner:PULSE SECURE
System and technique for situational awareness
InactiveUS20070060045A1Reduce the impactImproved GPS performanceBroadcast information characterisationBroadcast specific applicationsPerception systemCommunication device
A situational awareness system includes a first local network having a plurality of digital communication devices, each device capable of gathering information pertinent to an area in proximity of the device and providing information to a control station capable of collaborating the information and provide such information to the devices on the local network; a first regional network having a plurality of local networks, including the first local network, within an area of responsibility, the first regional network having a regional control station capable of collaborating information from the devices and provide said information to devices on the local network; and a central network having a plurality of regional networks including the first regional network, the central network having a central control station capable of collaborating information from the regional control stations and provide the information to devices on a local network.
Owner:PRAUTZSCH FRANK R
Method for etching a layer on a silicon semiconductor substrate
InactiveUS20100203739A1Increase selectivityHigh selectivitySemiconductor/solid-state device manufacturingMicrostructural device manufactureEtchingSemiconductor
A method for selective etching of an SiGe mixed semiconductor layer on a silicon semiconductor substrate by dry chemical etching of the SiGe mixed semiconductor layer with the aid of an etching gas selected from the group including ClF3 and / or ClF5, a gas selected from the group including Cl2 and / or HCl being added to the etching gas.
Owner:ROBERT BOSCH GMBH
System and Method for Denial of Service Attack Mitigation Using Cloud Services
ActiveUS20130055374A1Prevent flapMitigate such attackError detection/correctionMultiple digital computer combinationsTraffic volumeDenial-of-service attack
A method to mitigate attack by an upstream service provider using cloud mitigation services. An edge detection device, which located at the subscriber's network edge, is able to communicate information via status messages about attacks to an upstream service provider. The service provider is then able to mitigate attacks based on the status messages. There is a feedback loop whereby the amount of dropped traffic by the service provider is added to the network traffic to keep the mitigation request open and prevent flapping. Likewise, the detection device includes time-to-engage and time-to-disengage timers to further prevent flapping.
Owner:ARBOR NETWORKS
One-time pad Encryption key Distribution
InactiveUS6868495B1Ability can be reducedReduce attackKey distribution for secure communicationDigital data processing detailsPaymentSuccessful completion
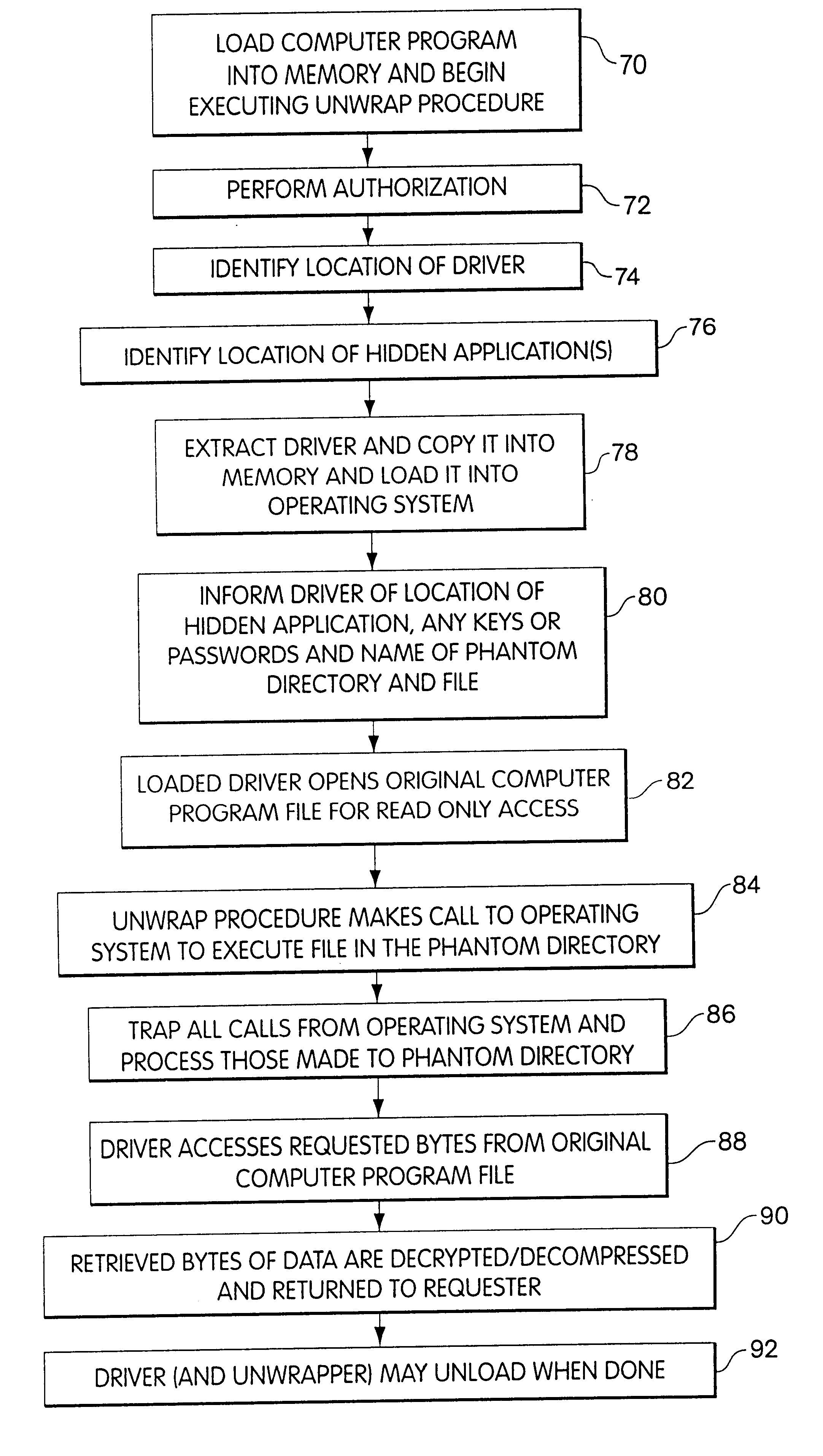
Some of these problems with digital information protection systems may be overcome by providing a mechanism which allows a content provider to encrypt digital information without requiring either a hardware or platform manufacturer or a content consumer to provide support for the specific form of corresponding decryption. This mechanism can be provided in a manner which allows the digital information to be copied easily for back-up purposes and to be transferred easily for distribution, but which should not permit copying of the digital information in decrypted form. In particular, the encrypted digital information is stored as an executable computer program which includes a decryption program that decrypts the encrypted information to provide the desired digital information, upon successful completion of an authorization procedure by the user. In combination with other mechanisms that track distribution, enforce royalty payments and control access to decryption keys, the present invention provides an improved method for identifying and detecting sources of unauthorized copies. Suitable authorization procedures also enable the digital information to be distributed for a limited number of uses and / or users, thus enabling per-use fees to be charged for the digital information.
Owner:RPX CORP
Lead frame structure, a packaging structure and a lighting unit thereof
ActiveUS20120074451A1Reduce moisture attackImprove bindingSemiconductor/solid-state device detailsSolid-state devicesEngineeringLead frame
A lead frame structure, a packaging structure and a lighting unit are disclosed. The lead frame structure includes at least two first lead frame units having a space therebetween, and the two first lead frame units are arranged in an opposite manner. Each the first lead frame unit has a first conducting portion, a second conducting portion, and a first connection portion between the first and the second conducting portions. Moreover, the first connection portion has at least two grooves on a surface thereof.
Owner:LITE ON ELECTRONICS (GUANGZHOU) LTD +1
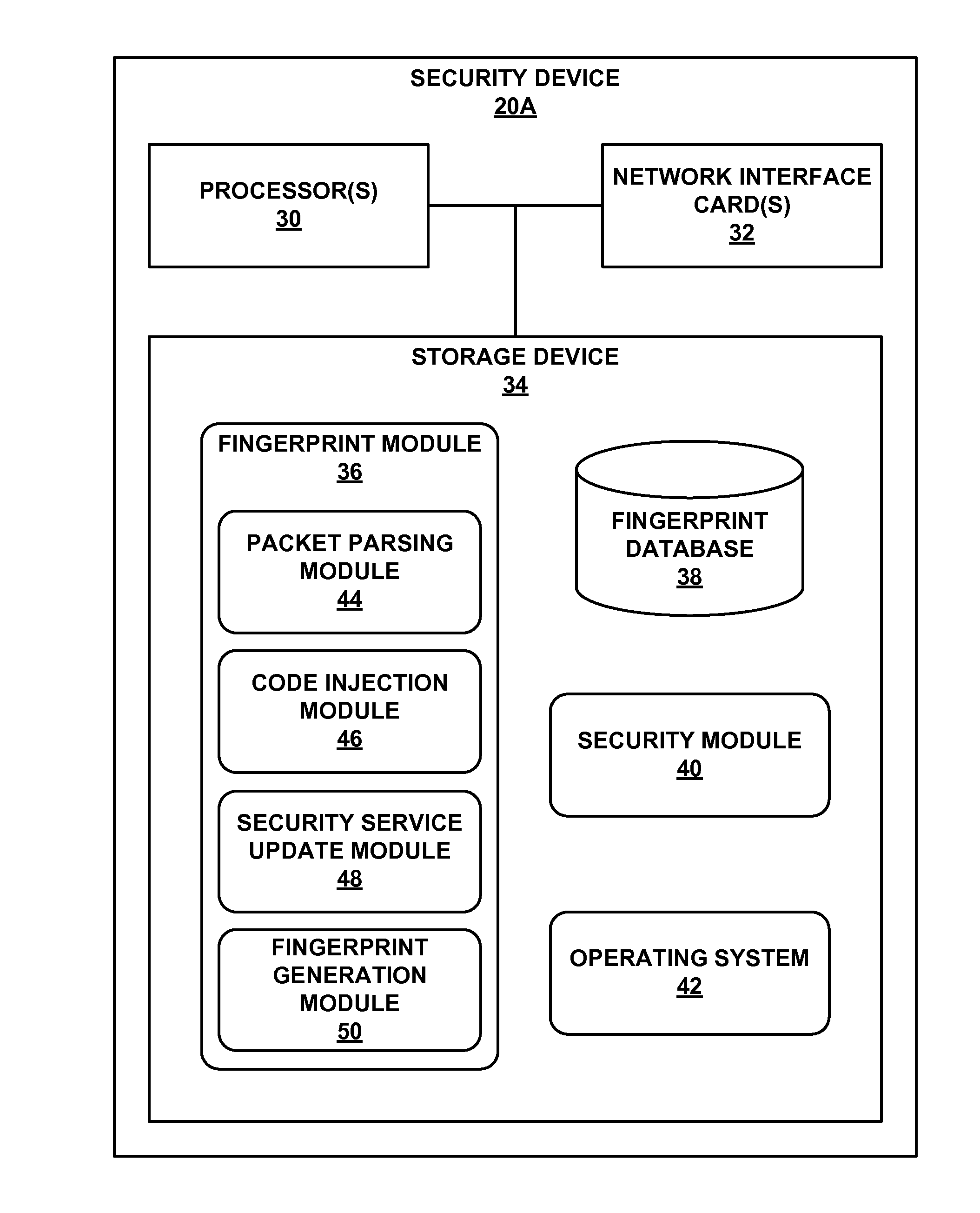
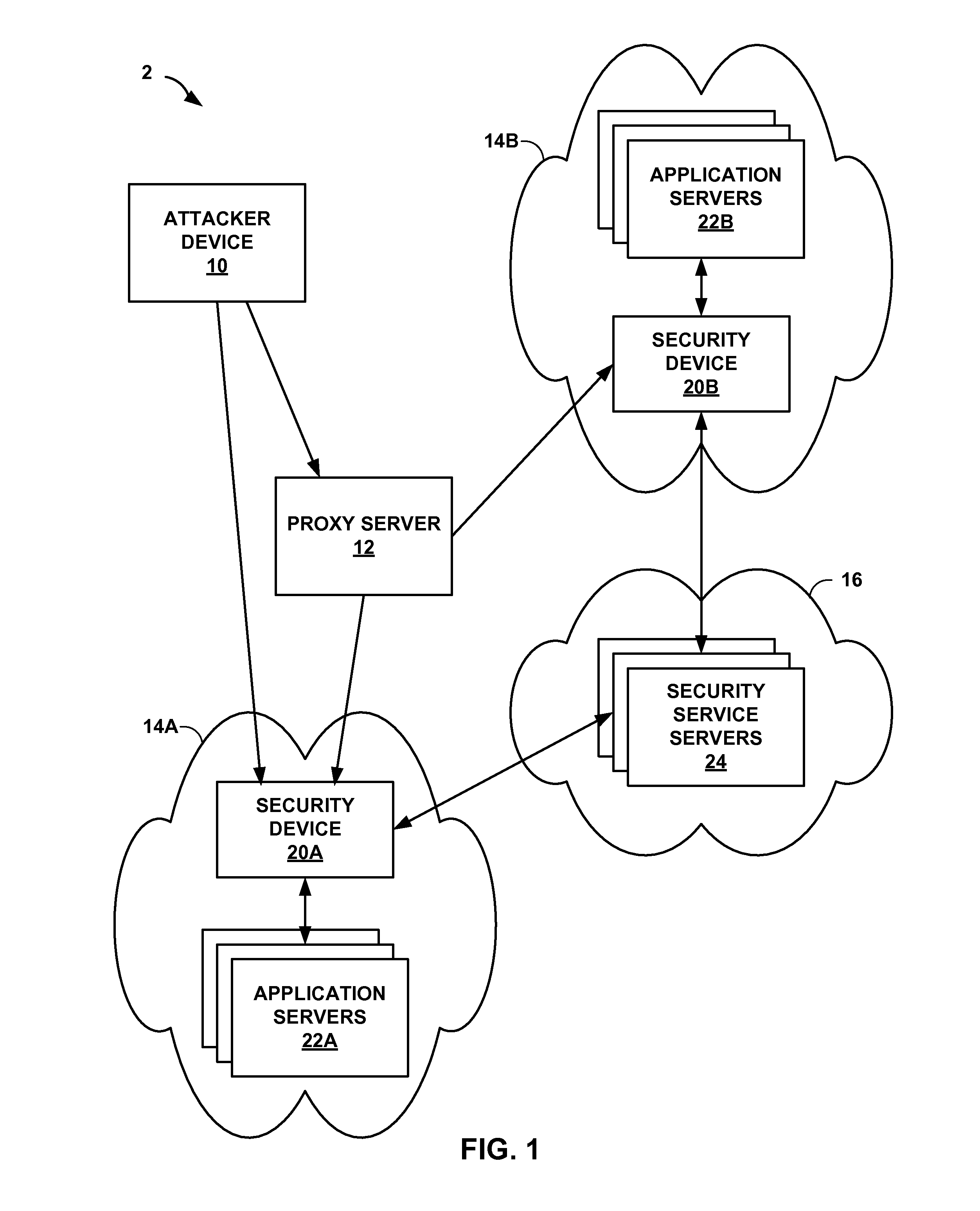
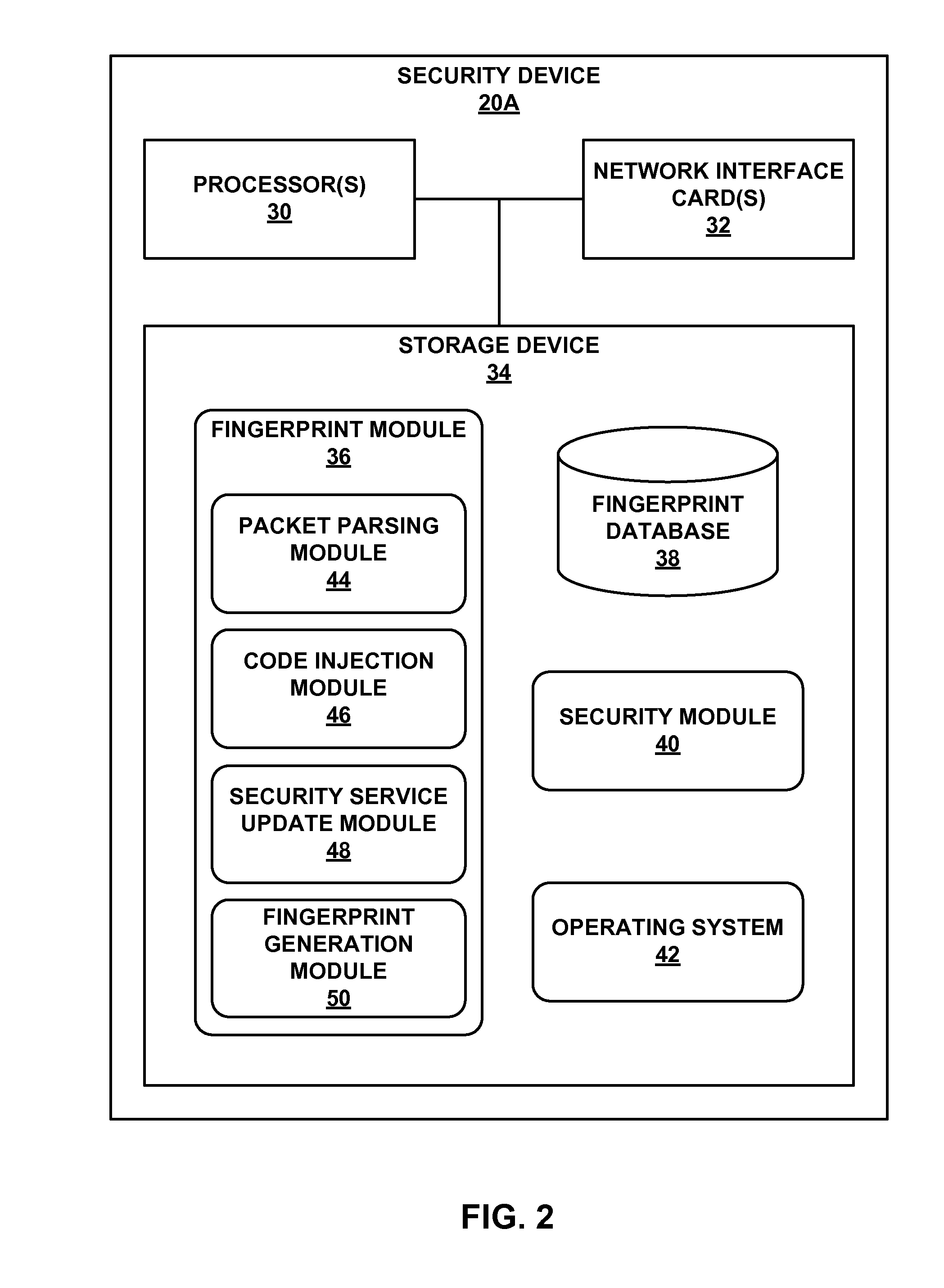
Attack detection and prevention using global device fingerprinting
ActiveUS20140283061A1Spread quicklyReduce attackMemory loss protectionError detection/correctionTraffic capacityComputer module
This disclosure describes a global attacker database that utilizes device fingerprinting to uniquely identify devices. For example, a device includes one or more processors and network interface cards to receive network traffic directed to one or more computing devices protected by the device, send, to the remote device, a request for data points of the remote device, wherein the data points include characteristics associated with the remote device, and receive at least a portion of the requested data points. The device also includes a fingerprint module to compare the received portion of the data points to sets of data points associated with known attacker devices, and determine, based on the comparison, whether a first set of data points of a first known attacker device satisfies a similarity threshold. The device also includes an security module to selectively manage, based on the determination, additional network traffic directed to the computing devices.
Owner:JUMIPER NETWORKS INC
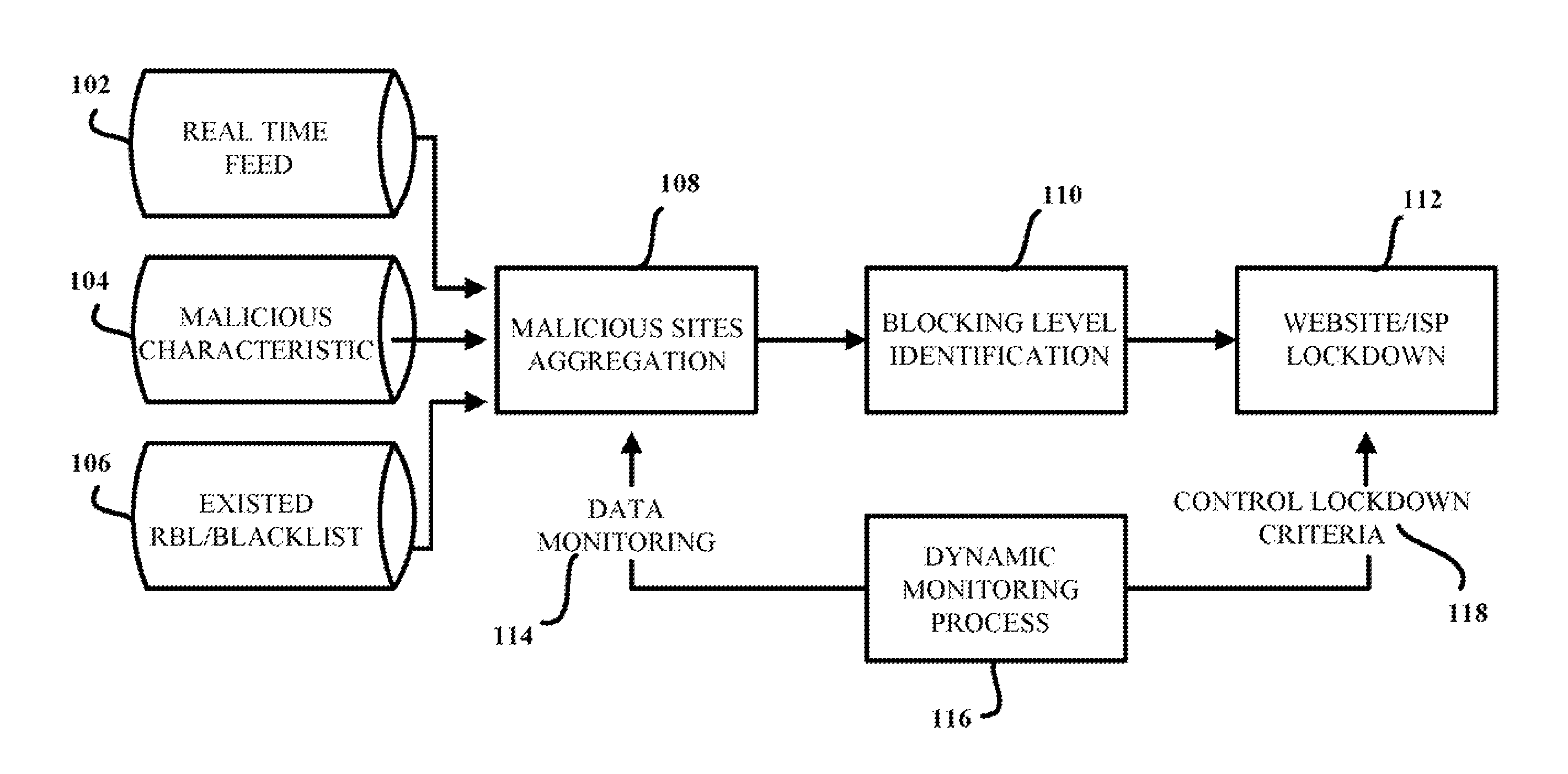
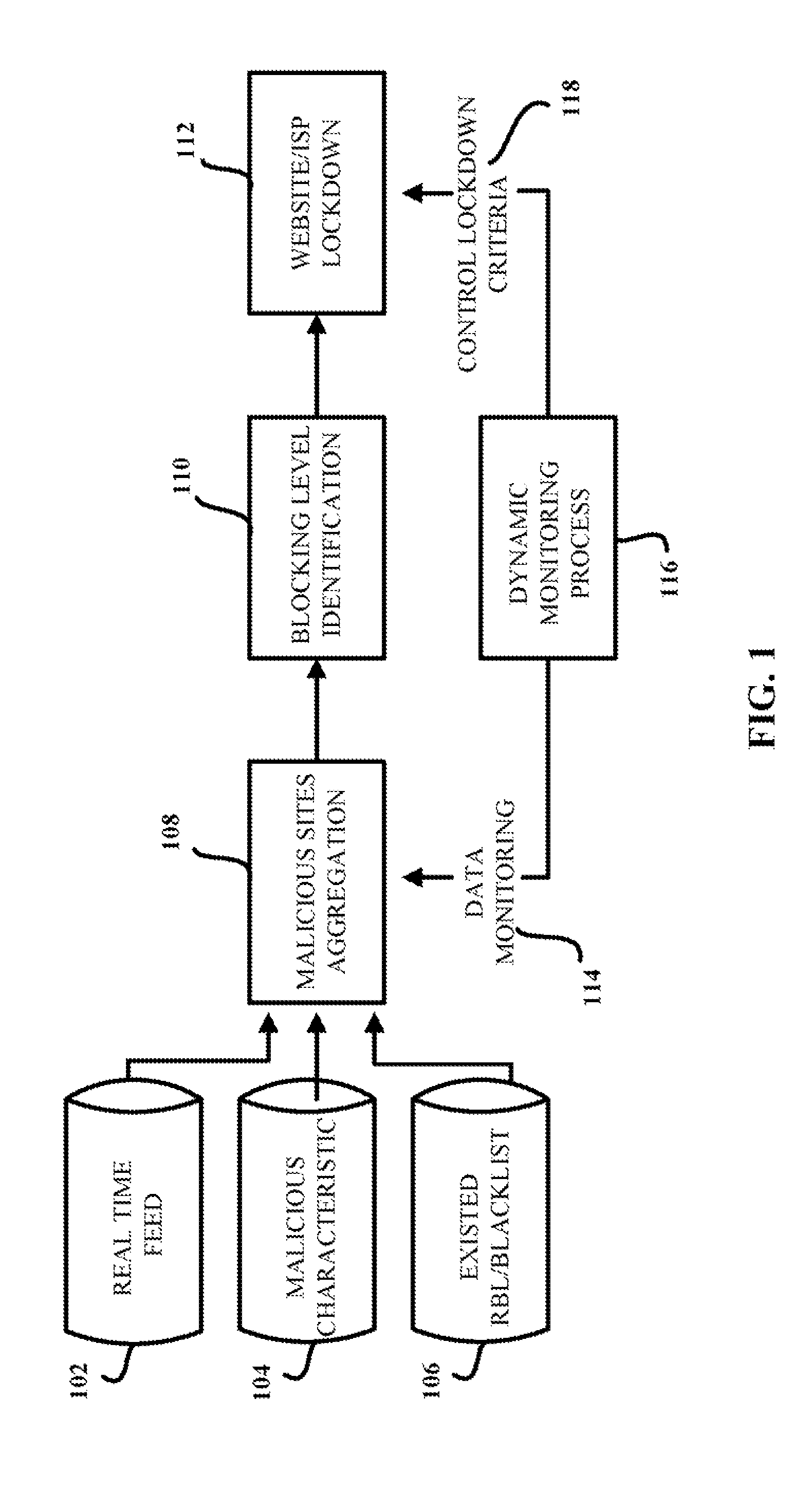
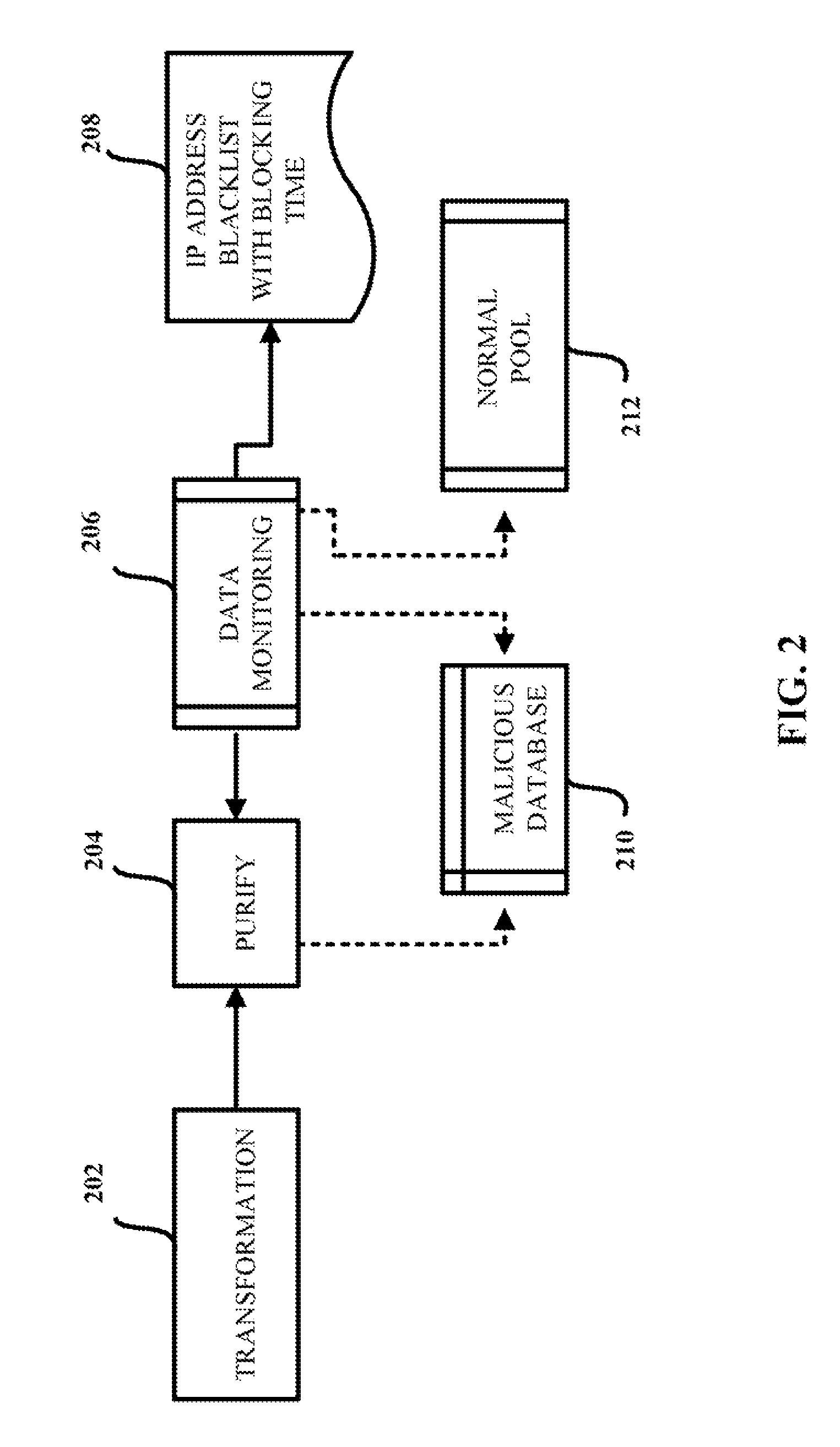
Aggregation-based phishing site detection
InactiveUS7854001B1Reduce in quantityReduce attackMemory loss protectionError detection/correctionWeb siteBlack list
A computer-implemented method for reducing phishing attacks that employ malicious websites is provided. The computer-implemented method includes gathering information about potentially malicious websites from a plurality of sources. The computer-implemented method also includes reducing the number of potentially malicious websites gathered; thereby creating a malicious website database that tracks at least a subset of the potentially malicious websites. In addition, the computer-implemented method includes generating a malicious website blacklist from the malicious website database, each website in the malicious website blacklist satisfying inclusion criteria, wherein the malicious website blacklist is employed to decide whether an access request to a given website is permitted.
Owner:TREND MICRO INC
Semi Conductor Process Residue Removal Composition and Process
InactiveUS20090203566A1Efficient removalReduce attackOrganic detergent compounding agentsSurface-active detergent compositionsSemiconductorMetal
A composition that includes 2-(2-aminoethylamino)-ethanol, at least one of a chelating agent and a corrosion inhibitor, and water. The composition is capable of removing organic, organometallic and metal oxide residues from semiconductor substrates. The invention also relates to a method of removing etching residue from a semiconductor substrate.
Owner:EKC TECH
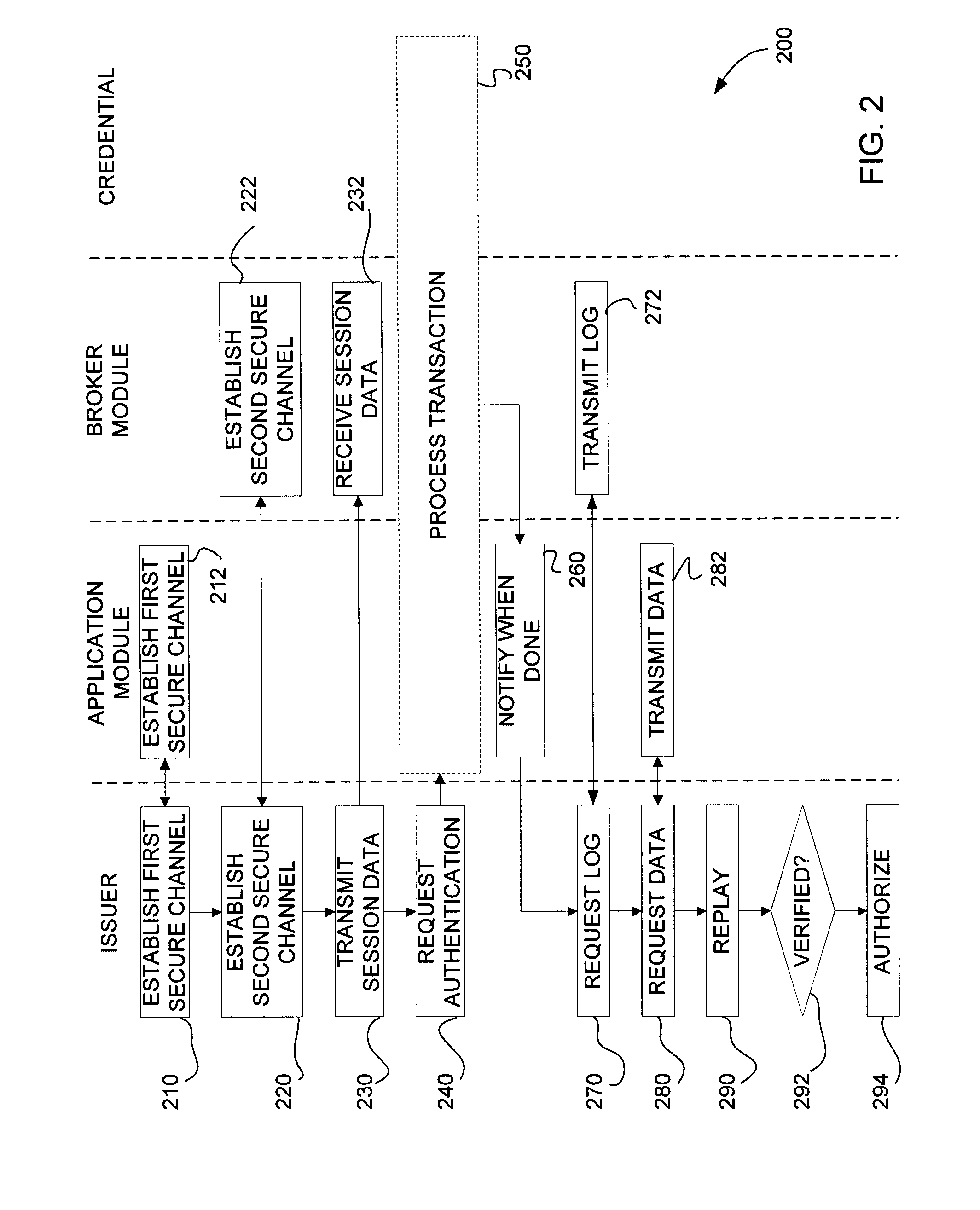
Credential authentication methods and systems
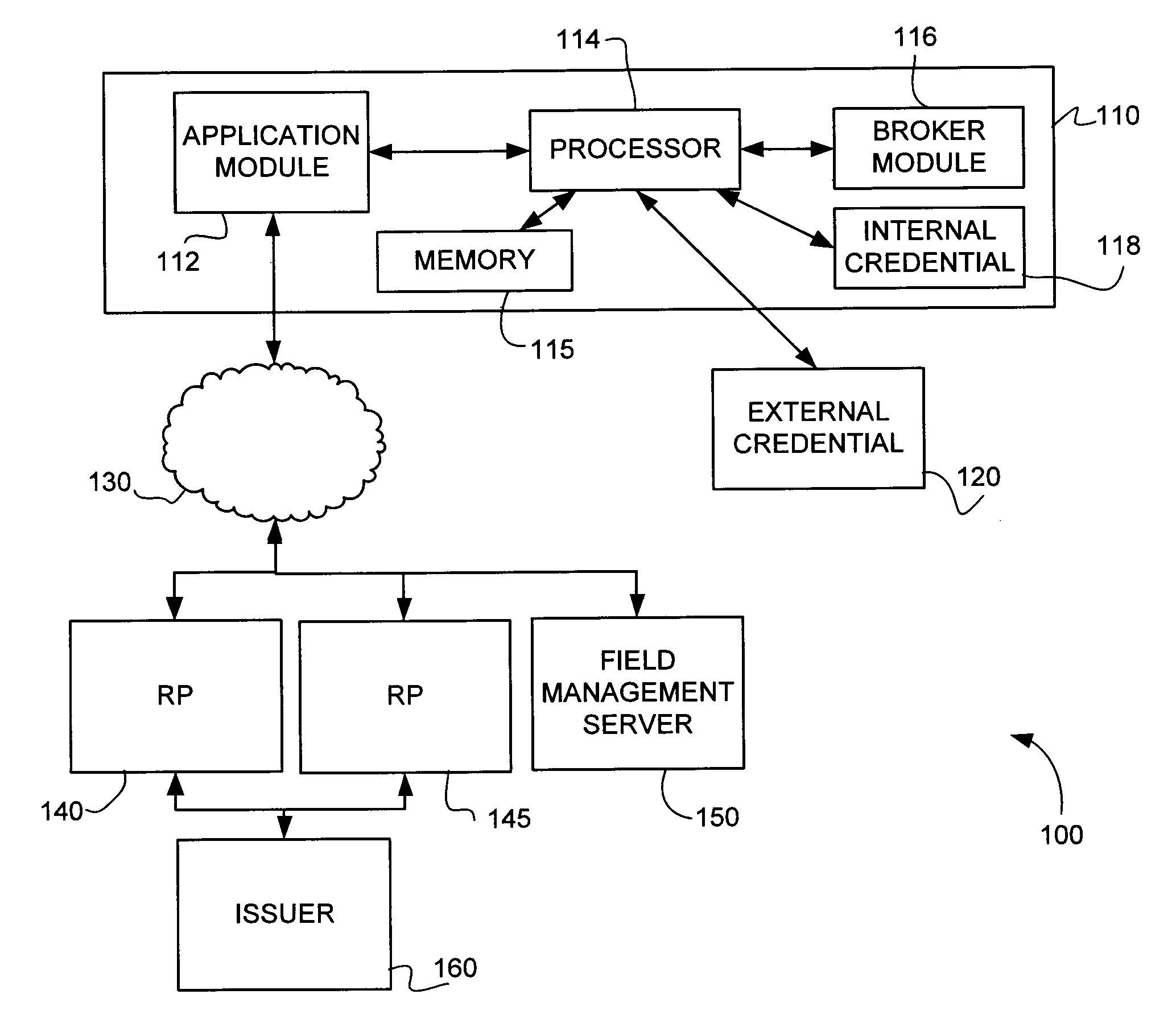
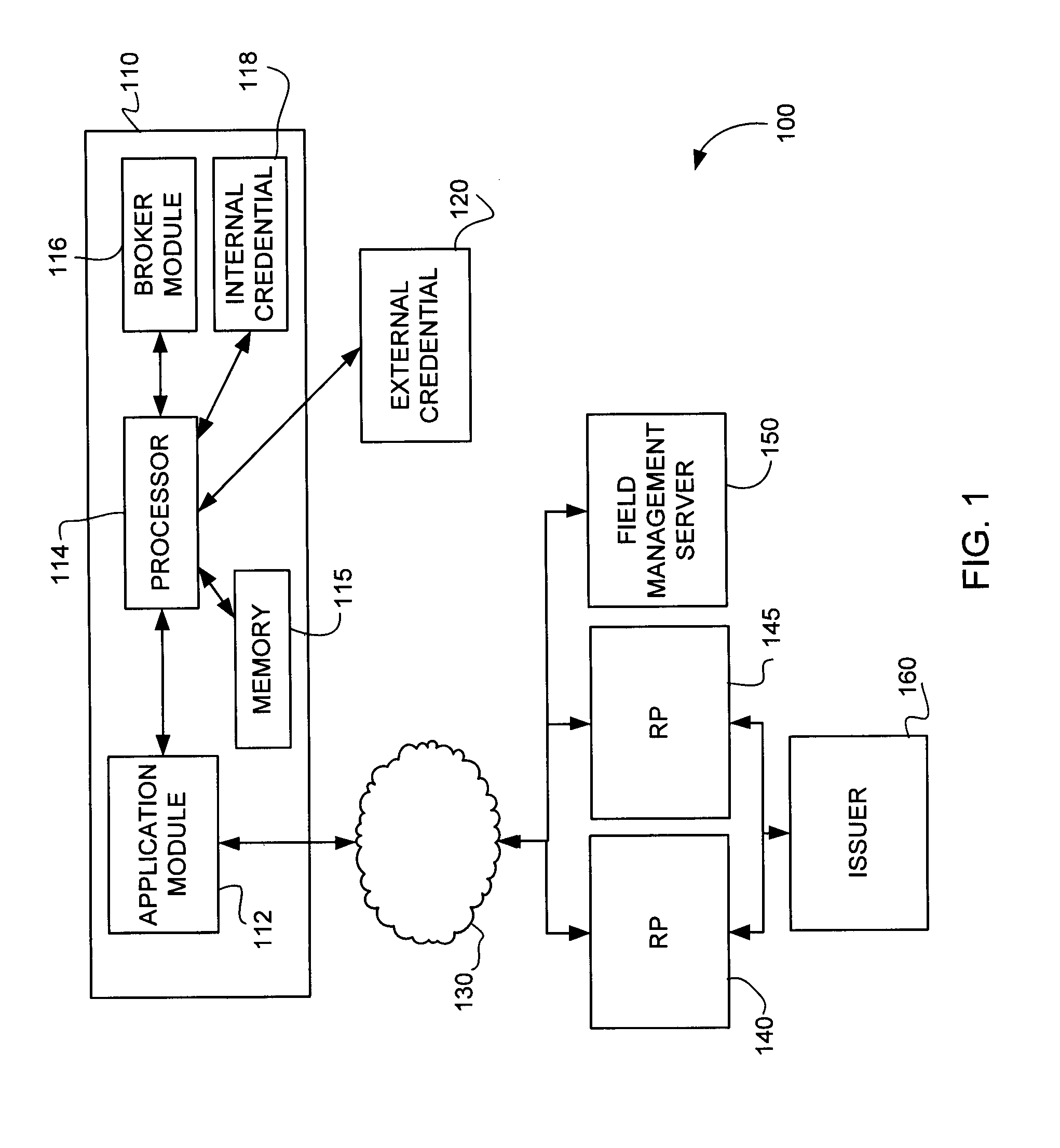
ActiveUS20140101734A1Great assuranceReduce attackDigital data processing detailsMultiple digital computer combinationsSmart cardApplication software
Methods and systems are provided for performing and verifying transactions involving authentication with a secure credential, such as a smart card, in an untrusted or semi-trusted environment. An application module, operating in an untrusted or semi-trusted environment can be denied access to sensitive data. The application module can determine a preliminary command to be sent to the credential and transmit the preliminary command to a broker module. The broker module, operating in a trusted environment, can supply sensitive data and transmit the command to the credential. Subsequently, the broker module can extract sensitive data from a response before it is transmitted to the application module. A verification server can audit the transaction to verify that it was carried out properly.
Owner:SECUREKEY TECH
System and method for initializing safety indicator of credible user interface
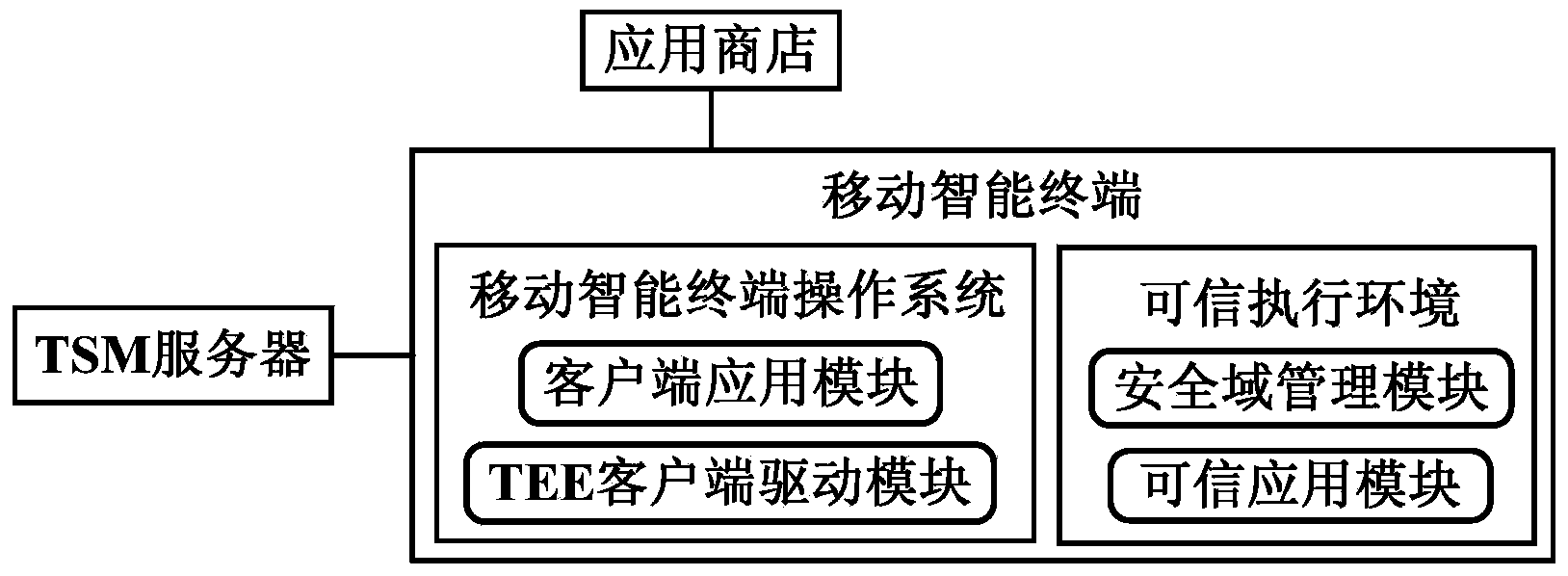
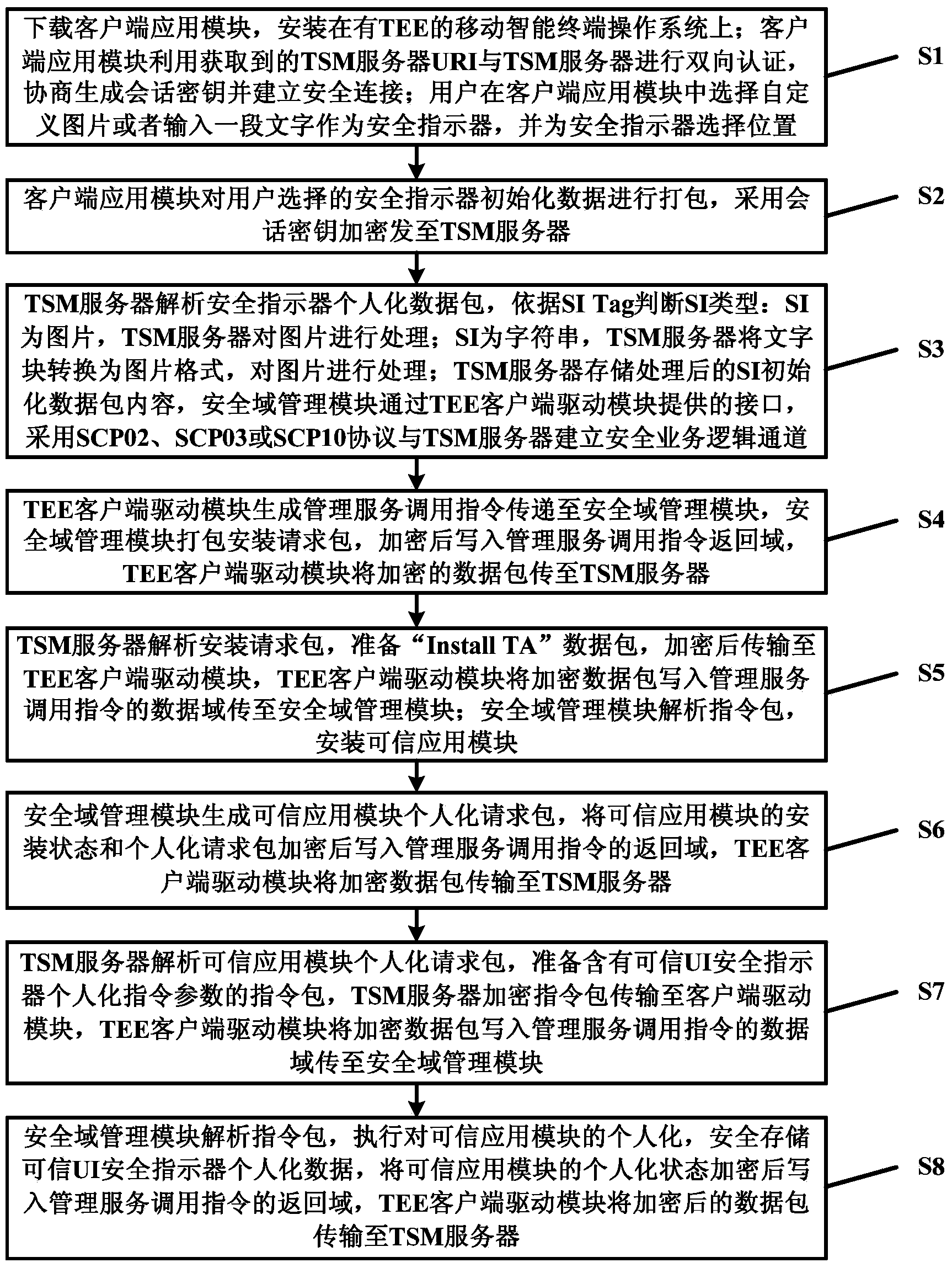
ActiveCN103856485AAchieve securityEnsure safetyTransmissionProgram/content distribution protectionOperational systemSafety indicators
The invention discloses a system and method for initializing a safety indicator of a credible user interface, and relates to the field of mobile intelligent terminals. The system comprises a TSM server, an application store and a mobile intelligent terminal. The mobile intelligent terminal comprises a mobile intelligent terminal operating system and a TEE. The mobile intelligent terminal operating system comprises a client side application module and a TEE client side drive module. The TEE provides a safe operation environment isolated from the mobile intelligent terminal operating system, the interior of the TEE is logically divided into a plurality of safety domains, and mutual isolation and independence of credible applications are guaranteed. Each safety domain is provided with a safety domain management module and a credible application module, and the TEE provides the safe operation environment for the safety domain management modules and the credible application modules. According to the system and method, individualization of the safety indicator in the credible UI provided for the credible application modules can be safely achieved, display credibility of the safety indicator is effectively improved, and the risk that the safety indicator is attacked and intercepted by malicious software is reduced.
Owner:WUHAN TIANYU INFORMATION IND
Secure framework for invoking server-side apis using ajax
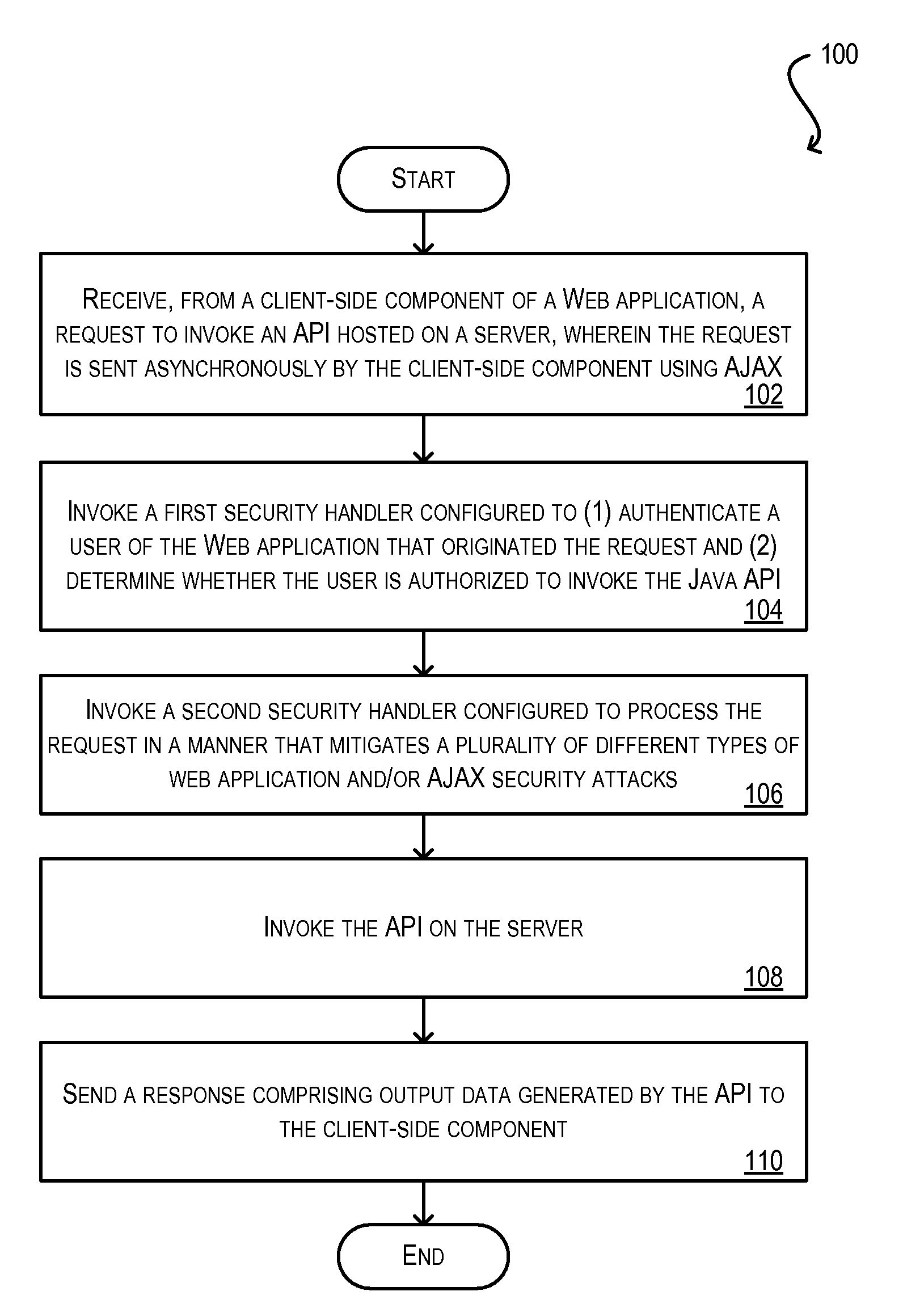
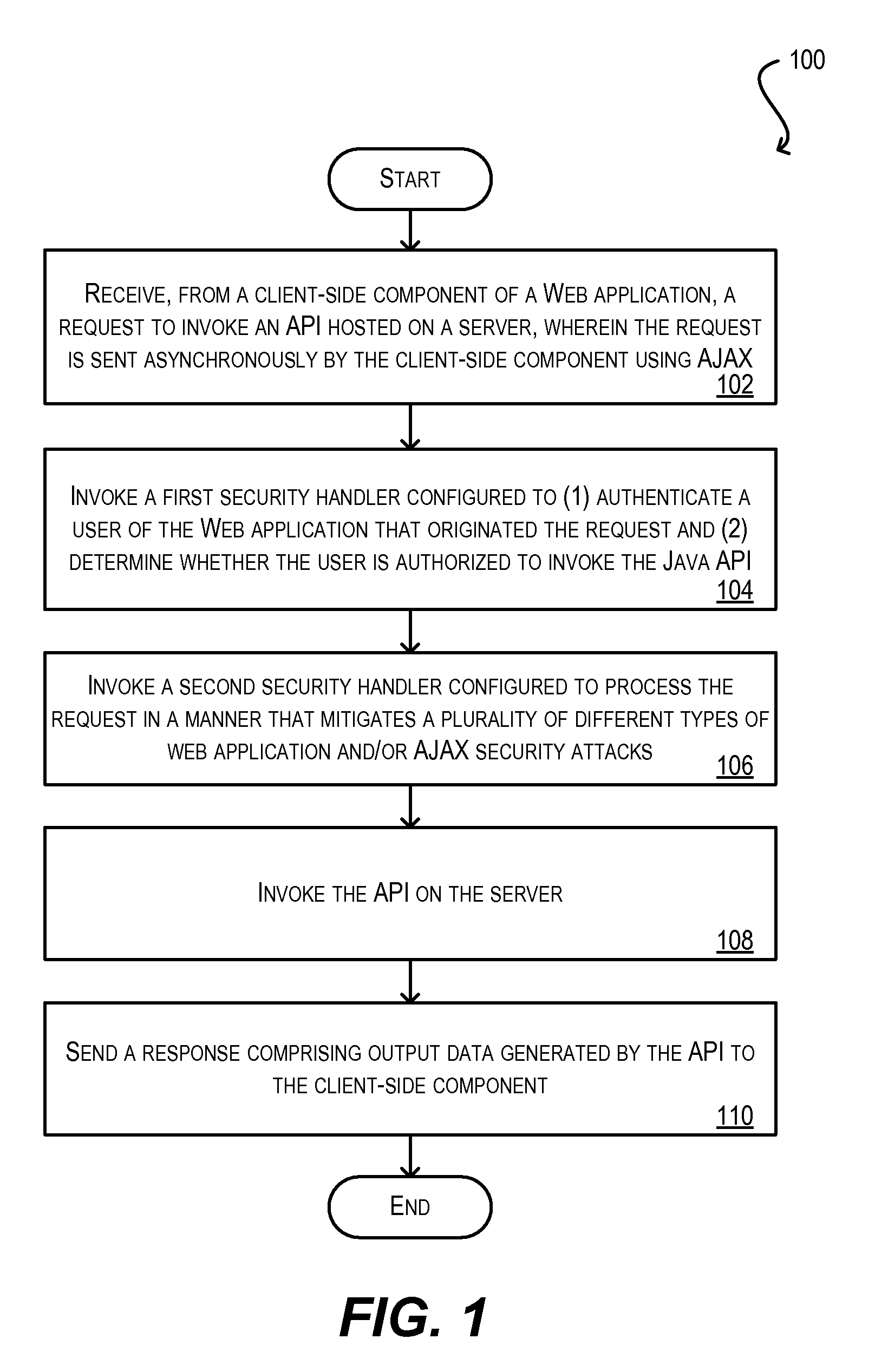
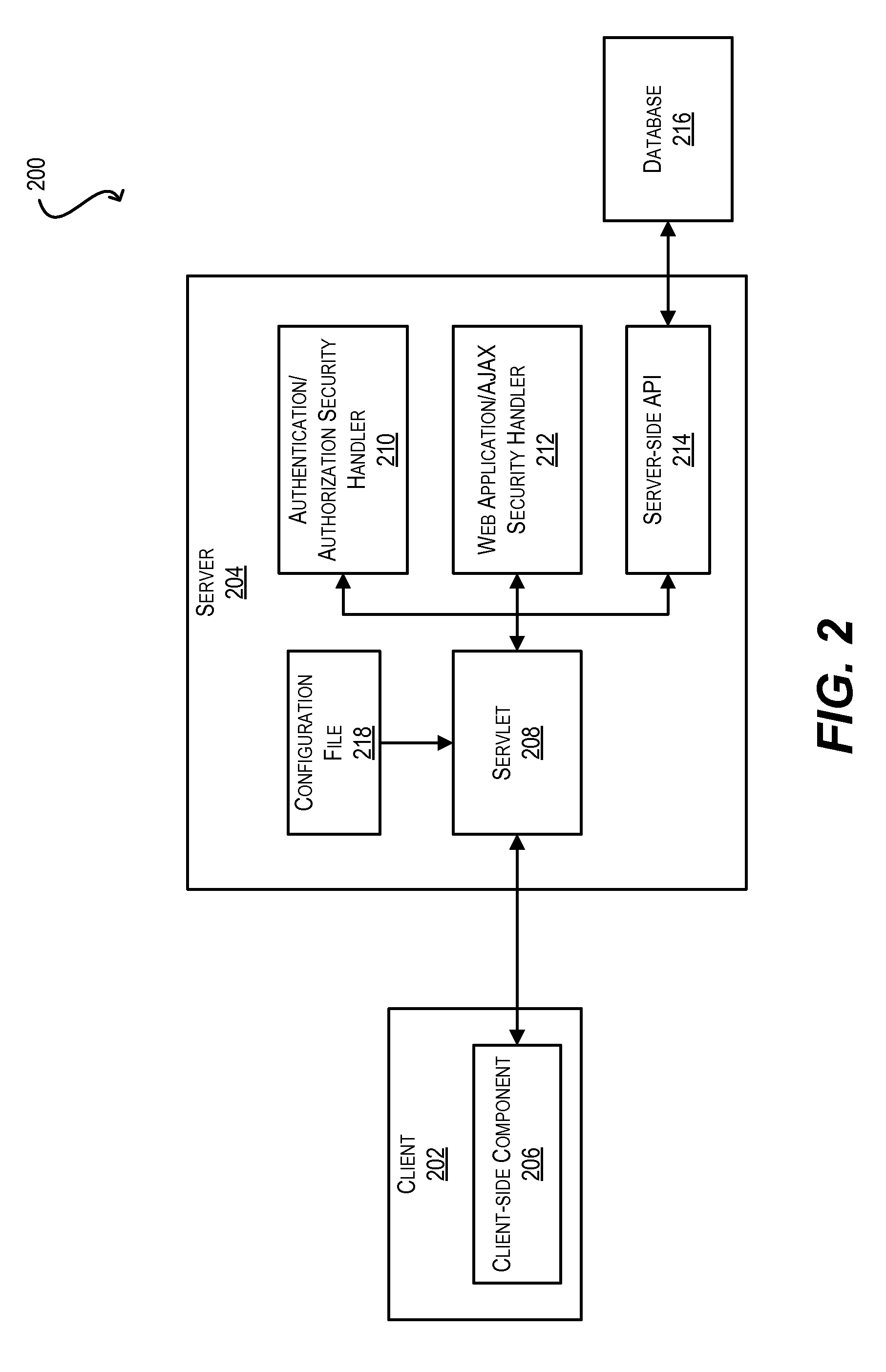
ActiveUS20100146291A1Mitigates security attackReduce attackMemory loss protectionDigital data processing detailsWeb applicationSecurity framework
Techniques for securely invoking a server-side API from client-side Web application code using AJAX. In one set of embodiments, a request to invoke a server-side API is received from a client-side component of a Web application, where the request is sent asynchronously using AJAX. One or more security handlers are then invoked to process the request in a manner that mitigates various security attacks. In one embodiment, a security handler is invoked to defend against a plurality of different types of Web application / AJAX security attacks. In another embodiment, authentication and authorization security handlers are invoked to authenticate a user of the Web application that originated the request and determine whether the user is authorized to call the server-side API. In yet another embodiment, configuration is implemented at the data storage tier to enforce user-access and data security on data that is retrieved / stored as a result of invoking the server-side API.
Owner:ORACLE INT CORP
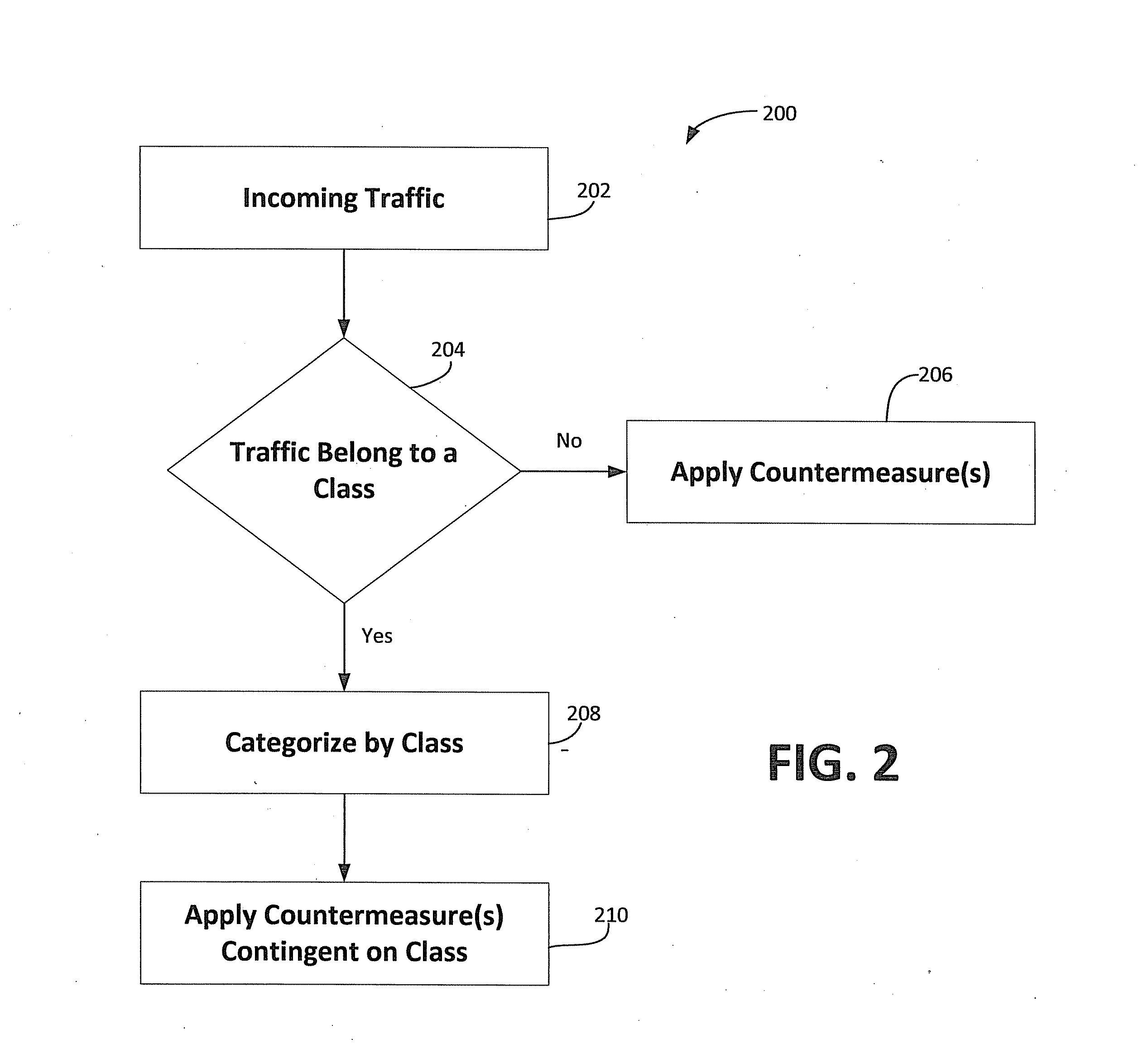
Adjusting ddos protection based on traffic type
ActiveUS20140325634A1Mitigating DDoS attackReduce generationMultiple digital computer combinationsProgram controlTraffic capacityCountermeasure
A system, method and computer readable storage medium that receives traffic / packets from external devices attempting to access protected devices in a protected network. A determination is made to whether a received packet belongs to one of a plurality of packet classifications. Each packet classification indicative of different classes of IP traffic. Countermeasures are applied to a received packet to prevent attack upon the protected devices. Applying a countermeasure to a received packet determined to belong to one of the plurality of packet classifications includes countermeasure modification / selection contingent upon the determined packet classification for the received packet.
Owner:ARBOR NETWORKS
Combining internet routing information with access logs to assess risk of user exposure
The present disclosure is directed towards systems and methods for evaluating or mitigating a network attack. A device determines one or more client internet protocol addresses associated with the attack on the service. The device assigns a severity score to the attack based on a type of the attack. The device identifies a probability of a user account accessing the service during an attack window based on the type of attack. The device generates an impact score for the user account based on the severity score and the probability of the user account accessing the service during the attack window. The device selects a mitigation policy for the user account based on the impact score.
Owner:CITRIX SYST INC
Network defense method and system based on honey pot technology
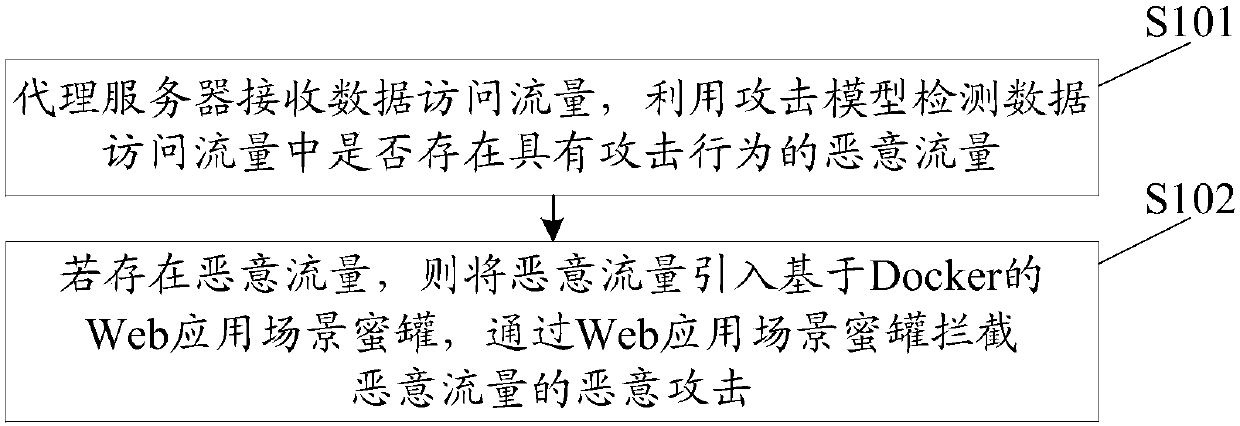
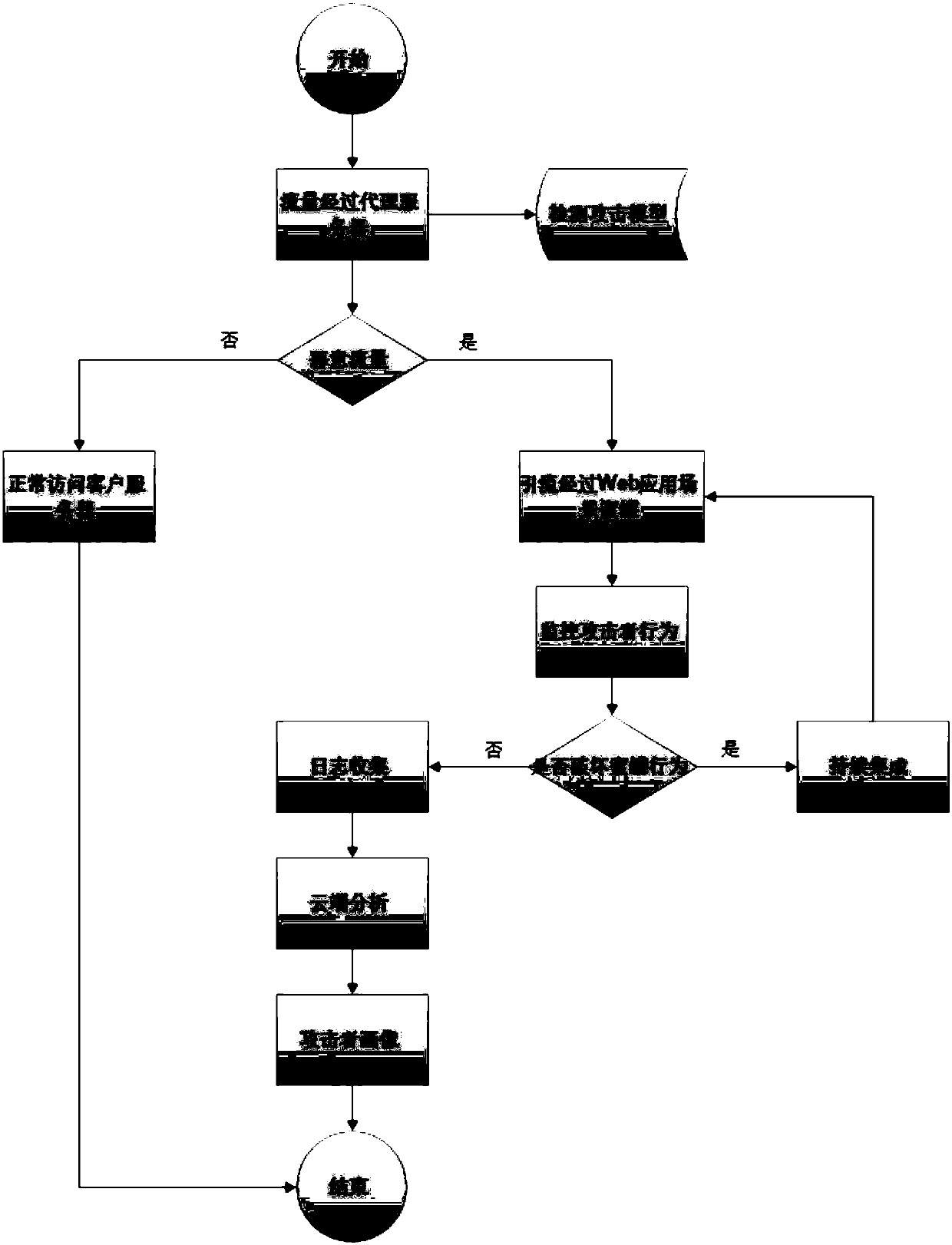
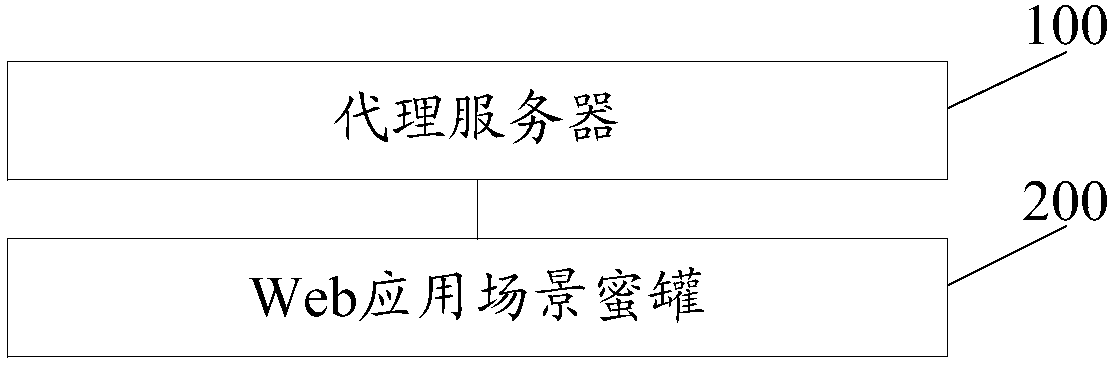
InactiveCN107707576AGuaranteed stabilityReduce attackTransmissionWeb applicationContinuous integration
The invention discloses a network defense method based on a honey pot technology. Malicious flor is introduced into a Web application scene honey pot based on Docker via a proxy server, malicious attack of malicious flow is intercepted through the Web application scene honey pot; thus, in the scheme, through deployment of the Web application scene honey pot based on Docker, network attack can be defensed actively, attack to a real goal by an attacker is delayed, the precious attack tracing time is provided for a defender. The Web application scene honey pot based on Docker also can effectivelyovercome the defect of inadaptability to real scenes of a customer, storage space is effectively reduced through a virtual Docker technology, the network is isolated, interference of honey pots is guaranteed, and the stability of the honey pot is guaranteed through continuous integration. The invention also discloses a network defense system based on the honey pot technology. The system also canhave the technical effects.
Owner:SANGFOR TECH INC
Authentication system and device including physical unclonable function and threshold cryptography
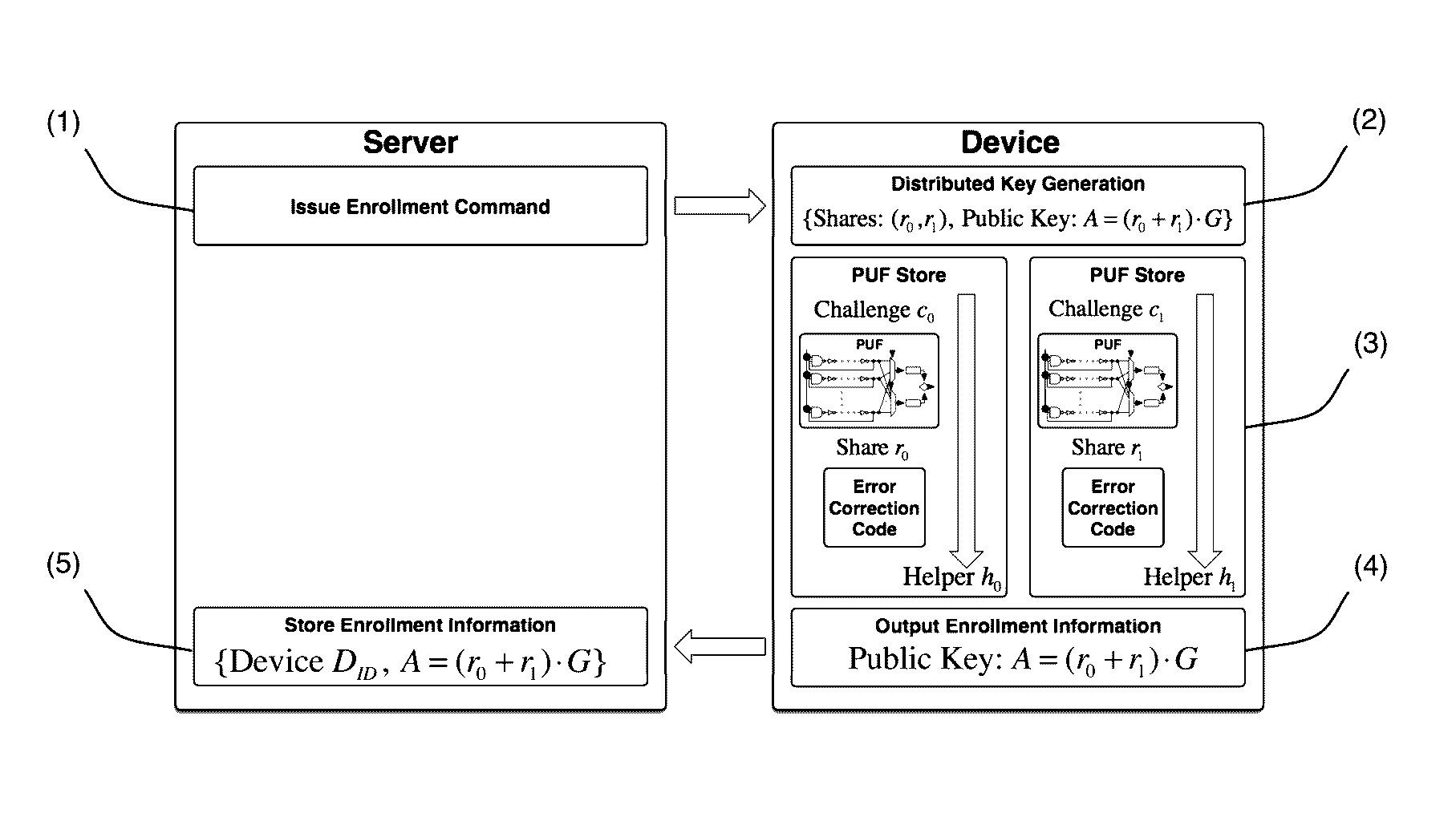
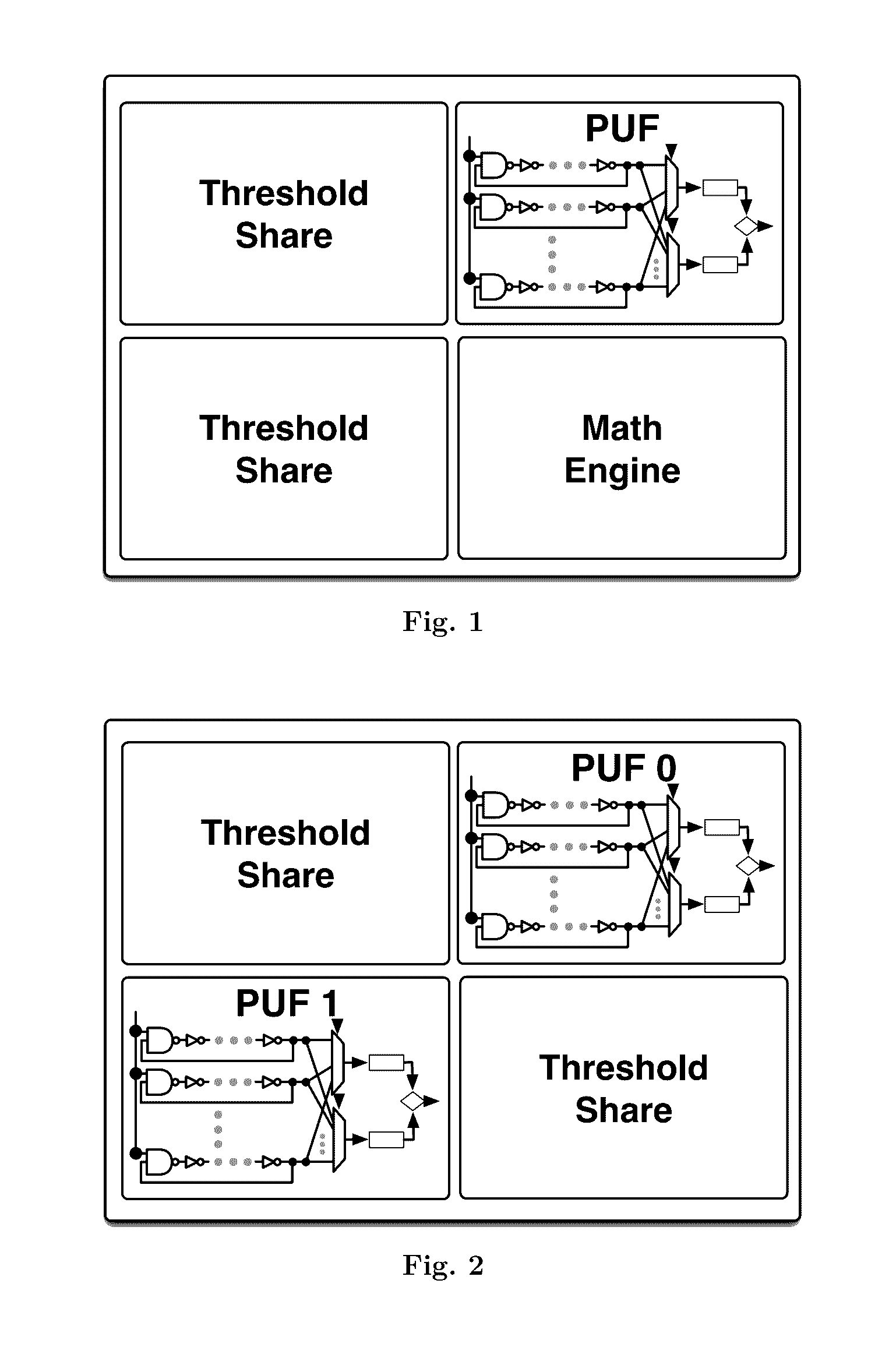
ActiveUS20170063559A1Mitigate side-channel attackEliminate needKey distribution for secure communicationData stream serial/continuous modificationPhysical unclonable functionAuthentication system
An authentication system and device including physical unclonable function (PUF) and threshold cryptography comprising: a PUF device having a PUF input and a PUF output and constructed to generate, in response to the input of a challenge, an output value characteristic to the PUF and the challenge; and a processor having a processor input that is connected to the PUF output, and having a processor output connected to the PUF input, the processor configured to: control the issuance of challenges to the PUF input via the processor output, receive output from the PUF output, combine multiple received PUF output values each corresponding to a share of a private key or secret, and perform threshold cryptographic operations. The system and device may be configured so that shares are refreshable, and may be configured to perform staggered share refreshing.
Owner:ANALOG DEVICES INC
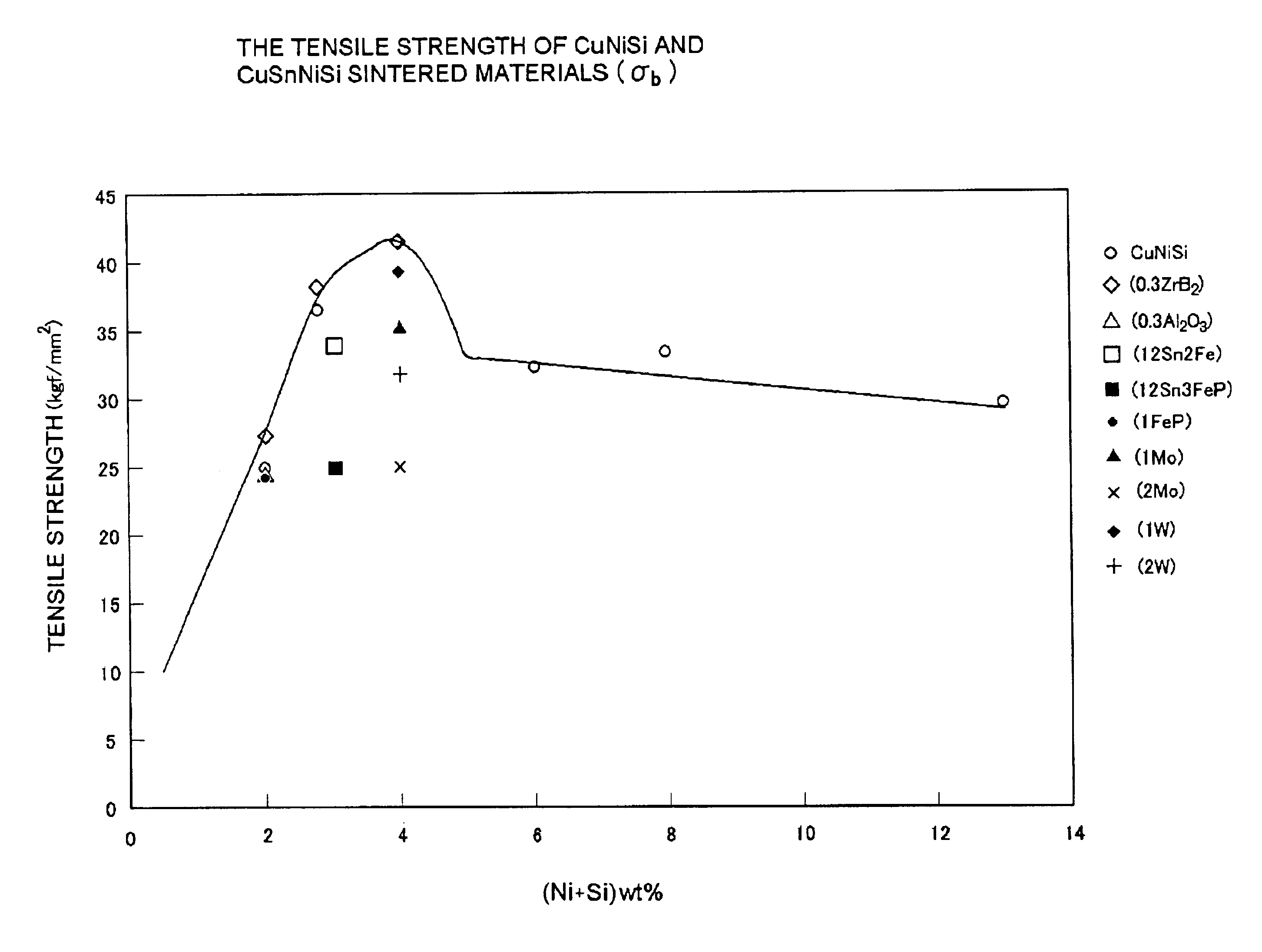
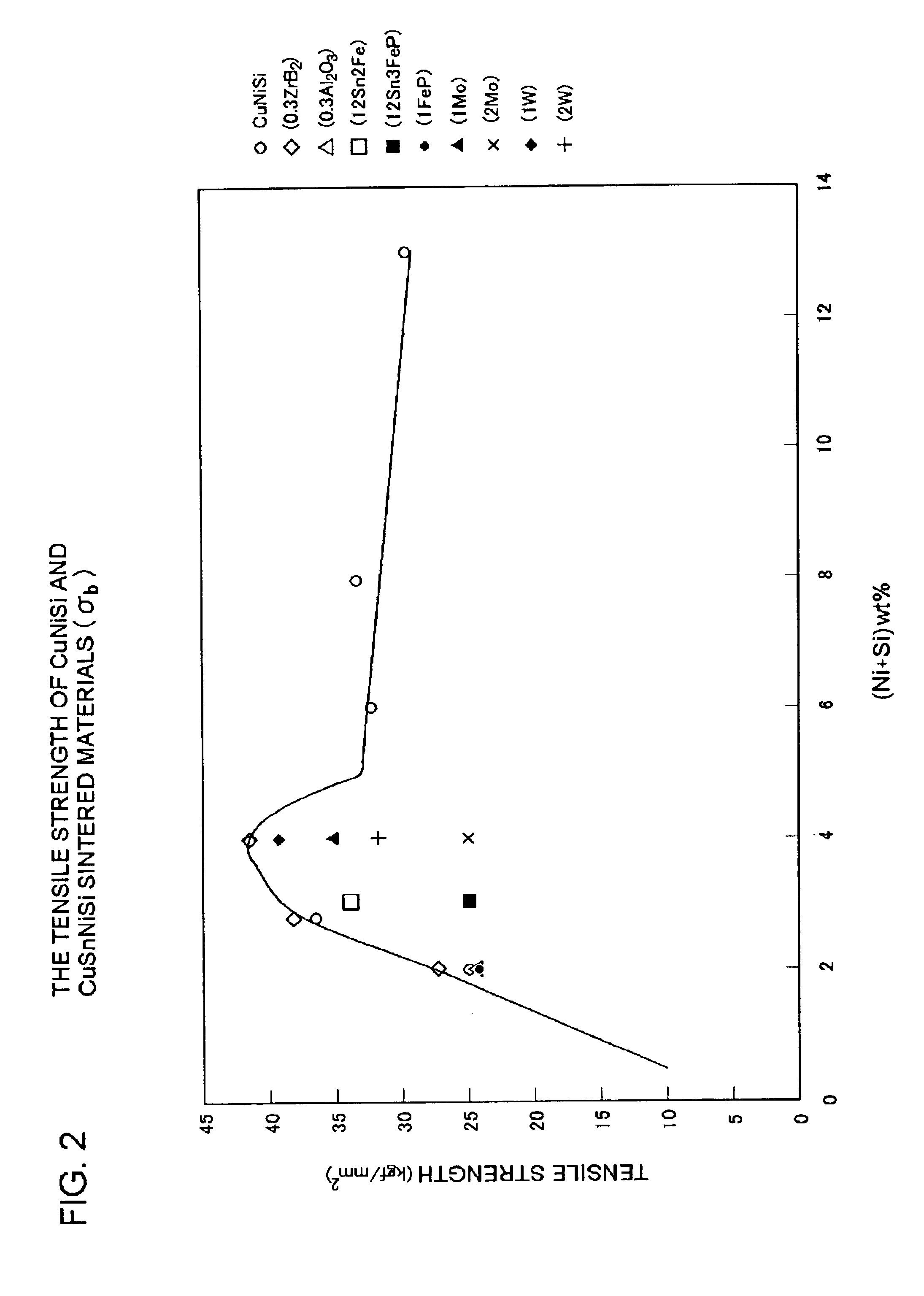
Copper based sintered contact material and double-layered sintered contact member
With the objectives of alleviating the property of attacking on the mating member by scratching-off of local agglutinates on the sliding contact surface, achieving improved wear resistance, and achieving improved seizure resistance through restraint of frictional heat generation by a hard phase, a copper based sintered contact material contains shock-resistant ceramics in an amount of 0.05 to less than 0.5 wt % as non-metallic particles composed of one or more substances selected from pulverized oxides, carbides and nitrides. The shock-resistant ceramics are comprised of SiO2 and / or two or more substances selected from SiO2, Al2O3, LiO2, TiO2 and MgO.
Owner:KOMATSU LTD
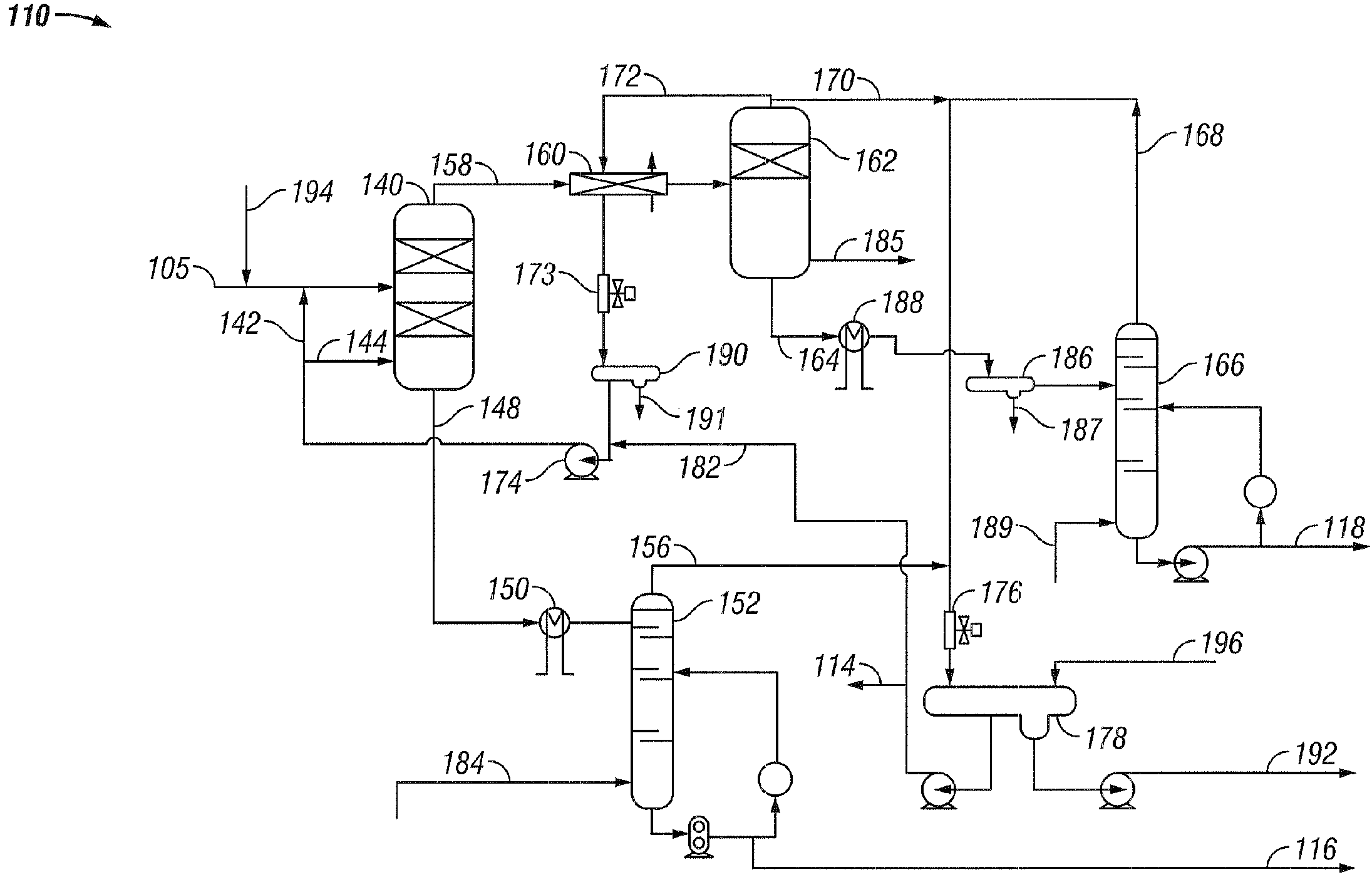
Bitumen production-upgrade with common or different solvents
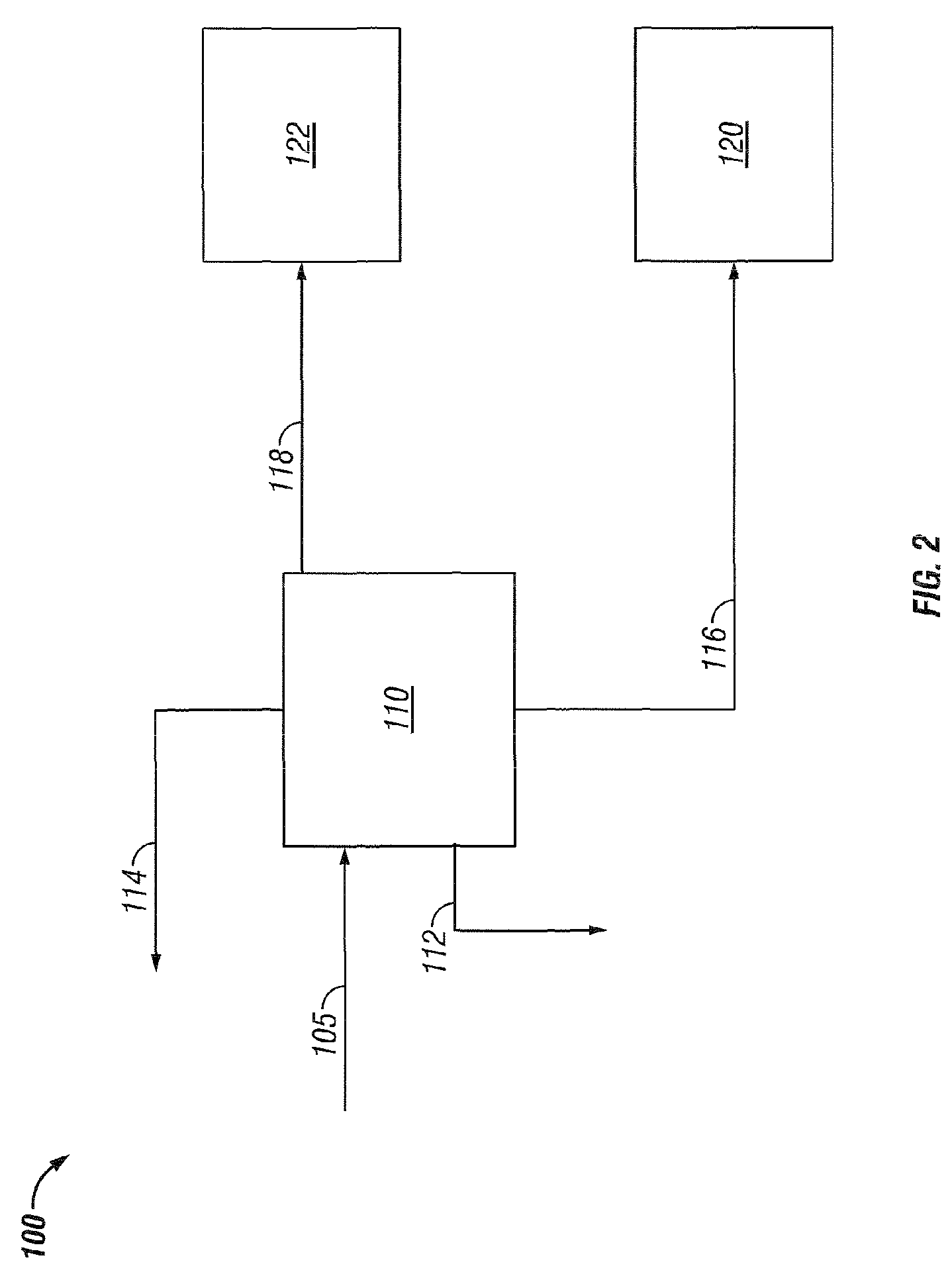
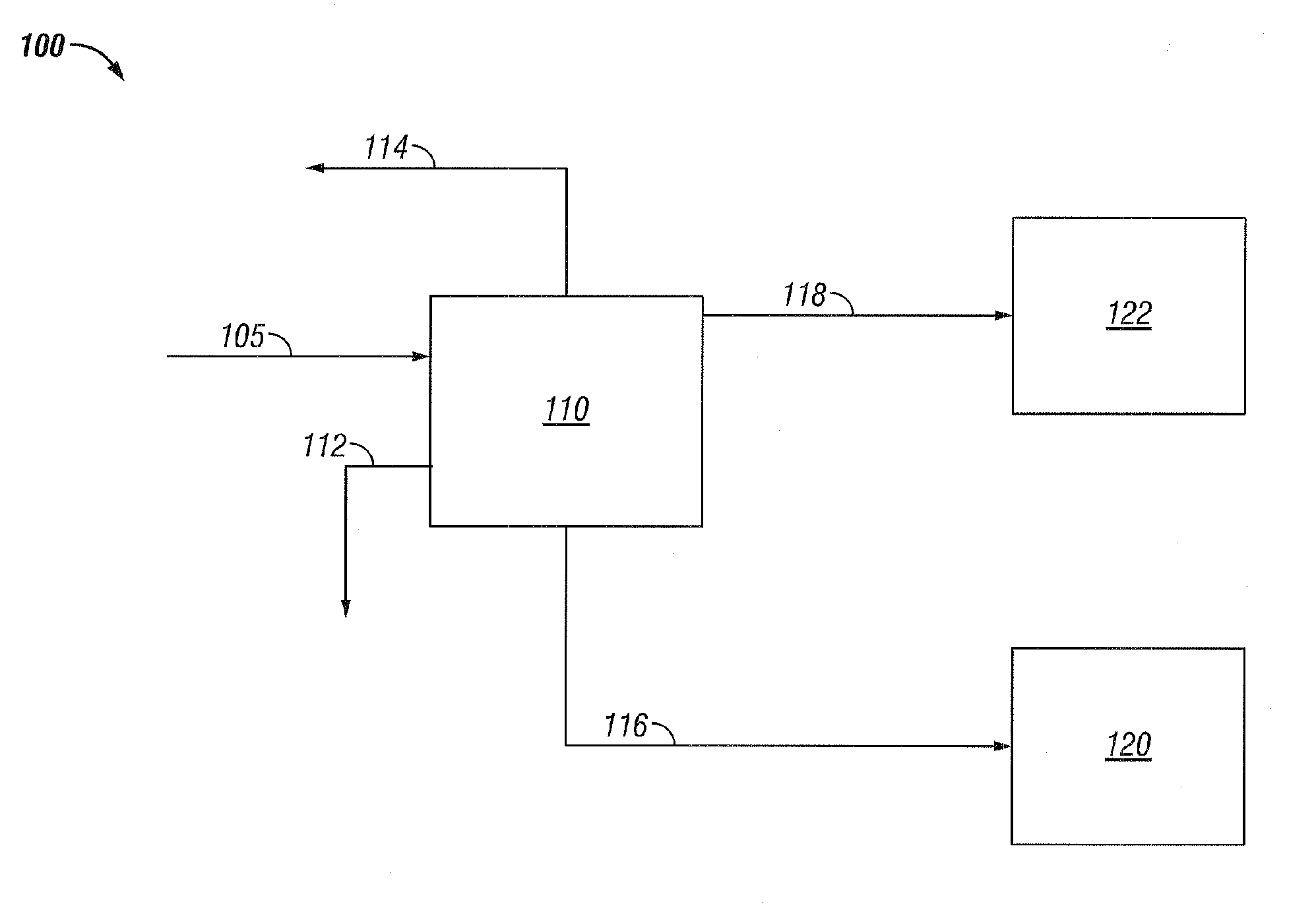
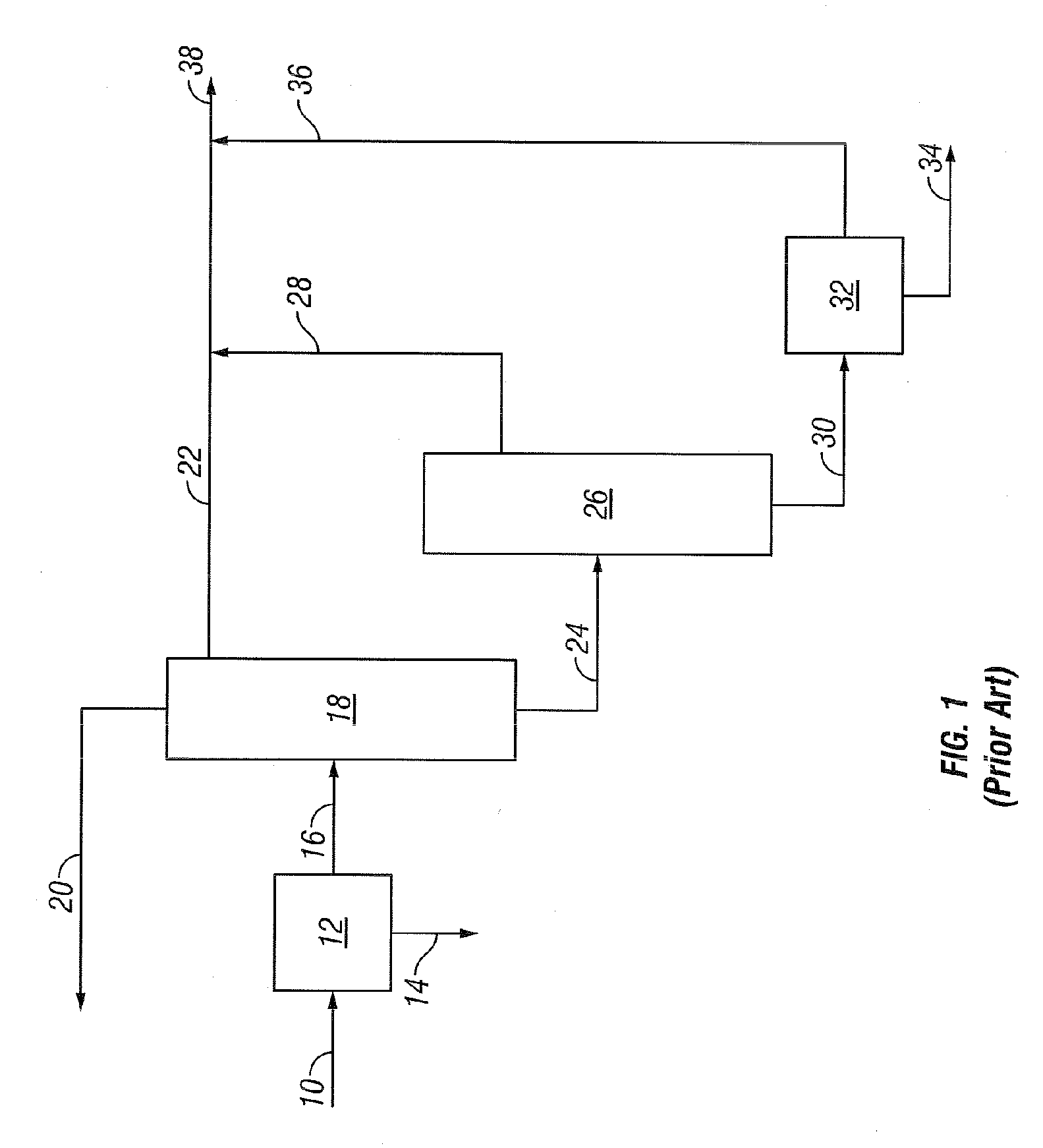
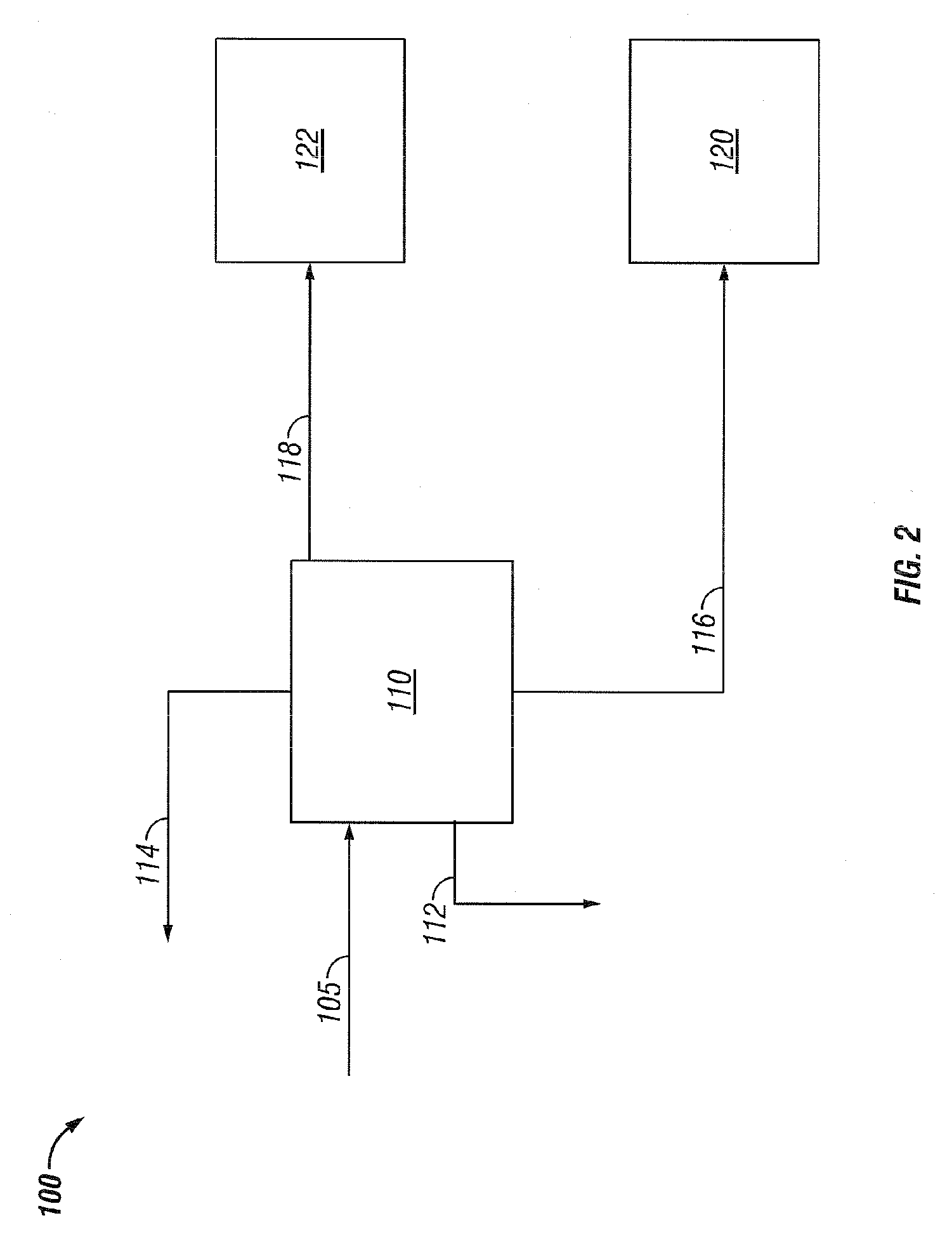
ActiveUS7749378B2Reduce capital investmentReduce operating expensesWorking-up pitch/asphalt/bitumen by selective extractionRefining by water treatmentDiluentWater fraction
Disclosed is a process for the upgrading of heavy oils and bitumens, where the total feed to the process can include heavy oil or bitumen, water, and diluent. The process can include the steps of solvent deasphalting 110 the total feed 105 to recover an asphaltene fraction 116, a deasphalted oil fraction 118 essentially free of asphaltenes, a water fraction 112, and a solvent fraction 114. The process allows removal of salts from the heavy oils and bitumens either into the aqueous products or with the asphaltene product.
Owner:KELLOGG BROWN & ROOT LLC
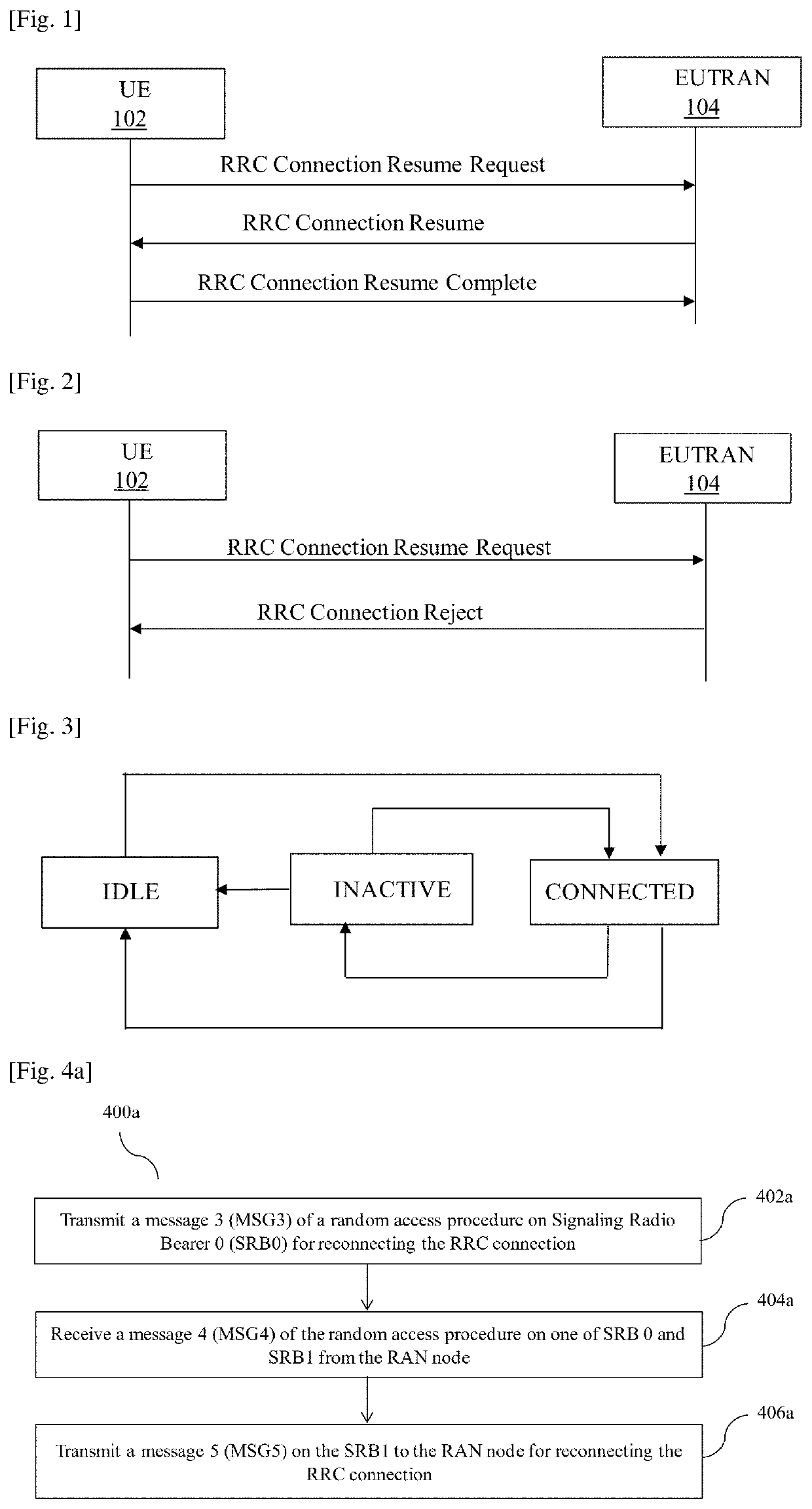
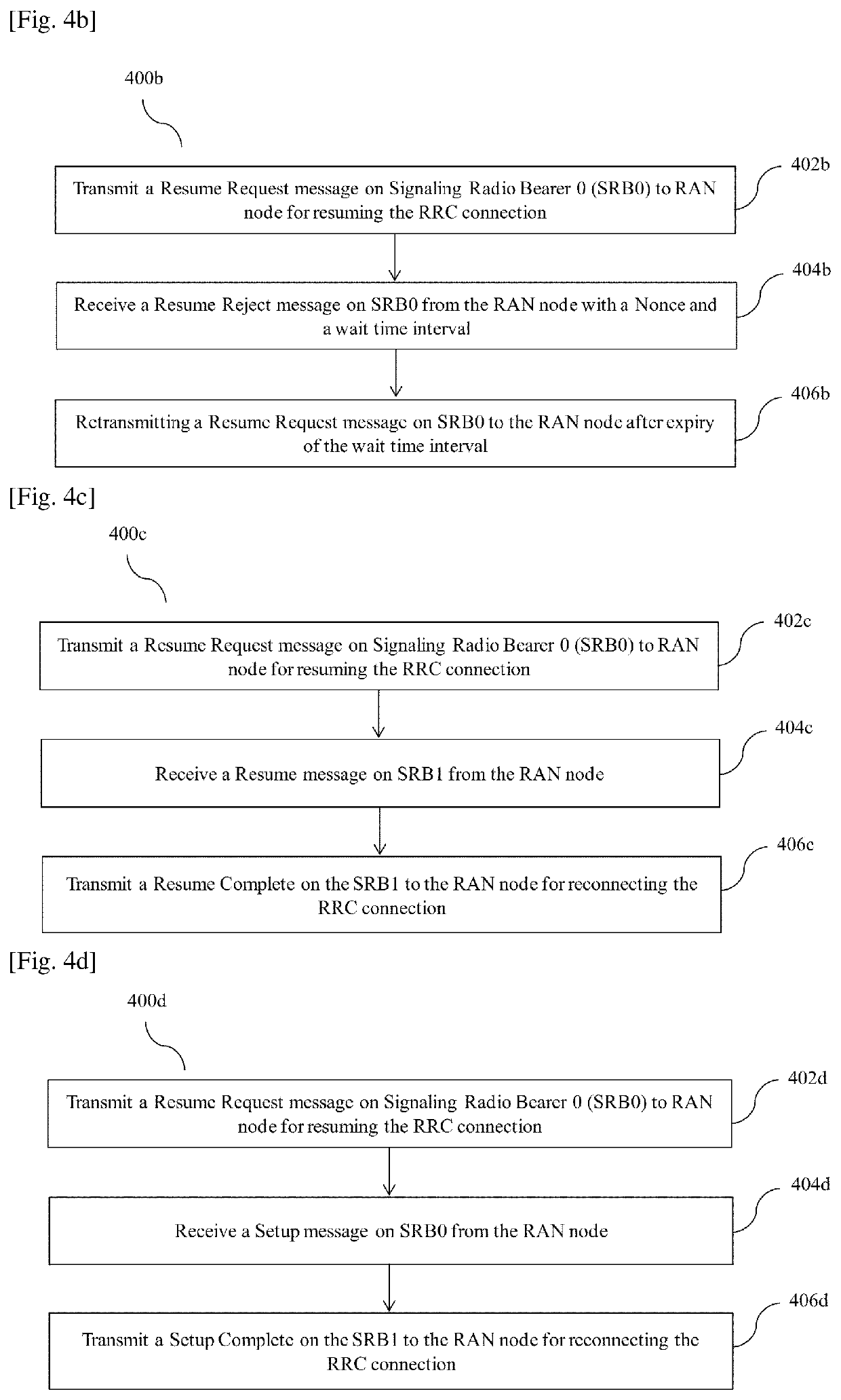
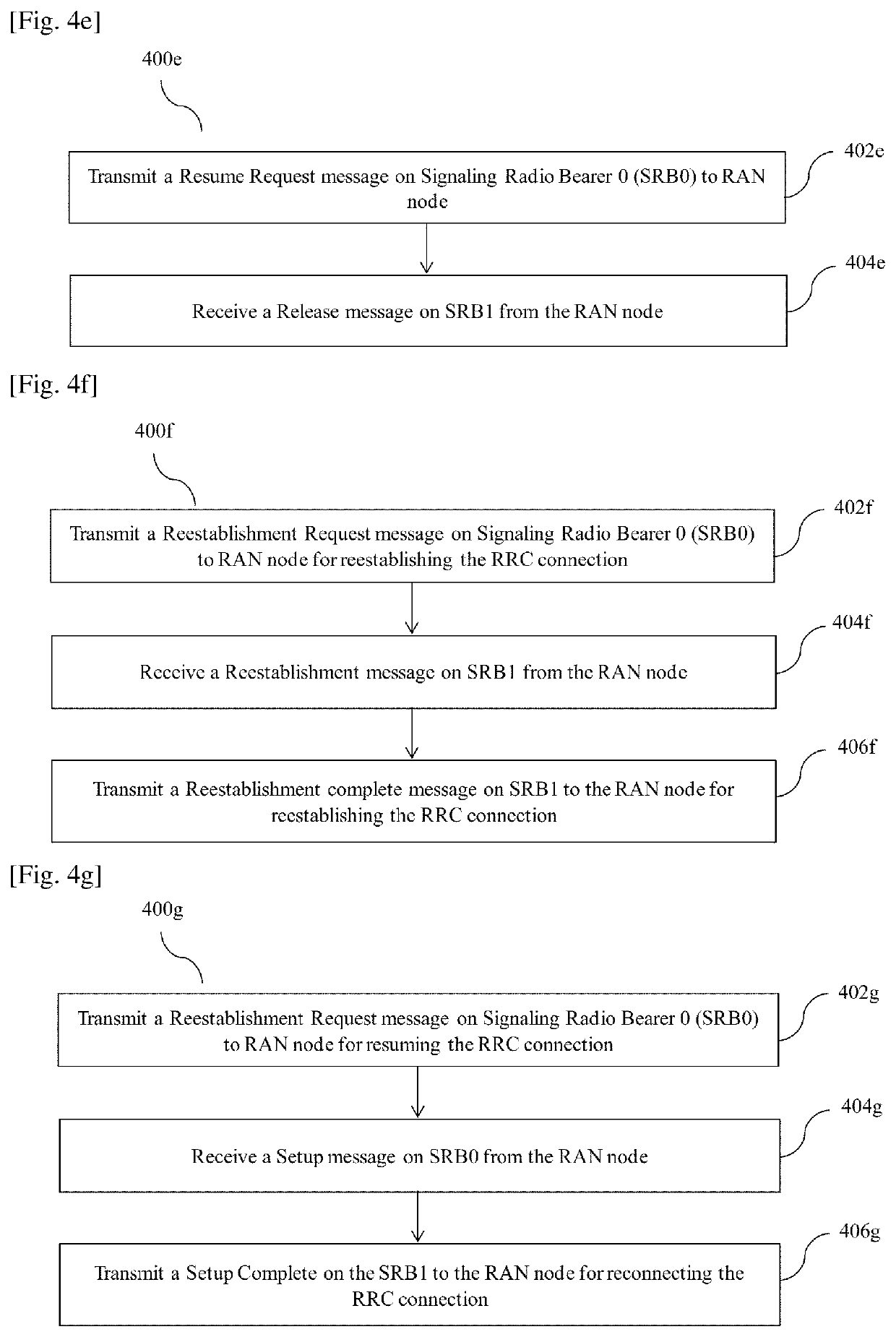
Method and user equipment (UE) for reconnecting rrc connection with radio access network (RAN) node
InactiveUS20200214070A1Reduce attackConnection managementSecurity arrangementAccess networkCommunications system
Accordingly the embodiments herein provide a method for reconnecting a Radio Resource Control (RRC) connection with a Radio Access Network (RAN) node by a User Equipment (UE) in a wireless communication system. The method includes transmitting a message 3 (MSG3) of a random access procedure on Signaling Radio Bearer 0 (SRB0) for reconnecting the RRC connection. The MSG3 is a request message to the RAN node with set of connection parameters. Further, the method includes receiving a message 4 (MSG4) of the random access procedure from the RAN node. The MSG4 is received on a SRB0 or a Signaling Radio Bearer 1 (SRB1). Furthermore, the method includes transmitting a message 5 (MSG5) on the SRB1 to RAN node for reconnecting RRC connection. The proposed method can be used to mitigate a replay attack on the UE in a inactive state using a nonce and a wait time interval.
Owner:SAMSUNG ELECTRONICS CO LTD
Aqueous ink composition
InactiveUS7294659B2Improve printing qualityGood colorDuplicating/marking methodsInksMethacrylateWater dispersible
Owner:SEIKO EPSON CORP
Use of human amniotic mesenchymal stem cell exosome
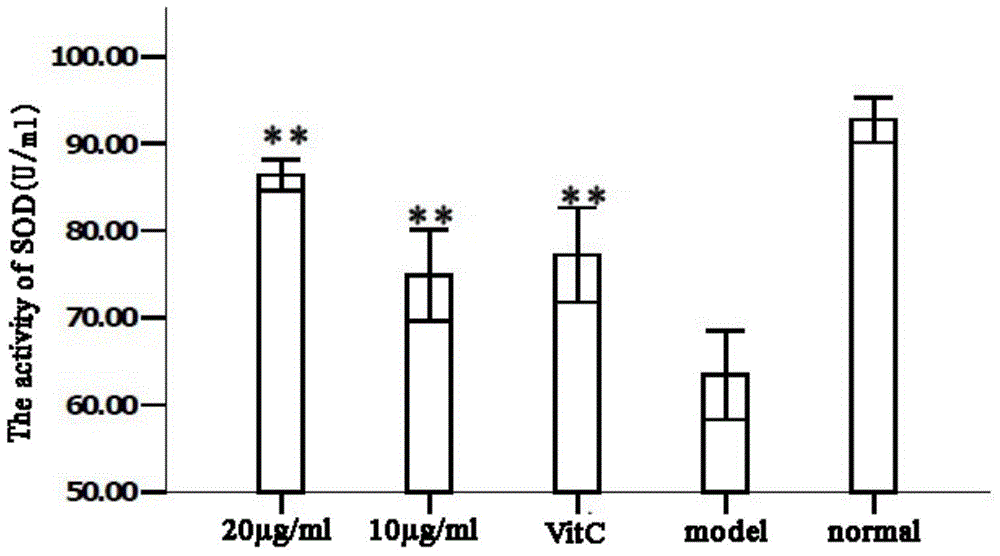
InactiveCN104382827AReduce attackAvoid damageCosmetic preparationsPowder deliveryMortality rateMesenchymal stem cell
The invention relates to the field of stem cells, and discloses novel use of a stem cell exosome, and particularly discloses novel use of a human amniotic mesenchymal stem cell exosome. The experiment result shows that a human amniotic mesenchymal stem cell is capable of promoting growth of HDF cells, improving the activity of SOD (Superoxide Dismutase) enzyme in the cells, reducing attacks and damages to the cells caused by oxygen radicals generated by ultraviolet radiation induction, and reducing the death rate of the cells. The use shows that the human amniotic mesenchymal stem cell exosome has an anti-photoaging effect, and meanwhile, the human amniotic mesenchymal stem cell exosome is free of phototoxicity, so that application of the human amniotic mesenchymal stem cell exosome in preparation of an anti-ageing preparation is provided. The invention also provides an anti-ageing preparation of the human amniotic mesenchymal stem cell exosome.
Owner:GUANGZHOU SALIAI STEMCELL SCI & TECH CO LTD
Protective method for network attack
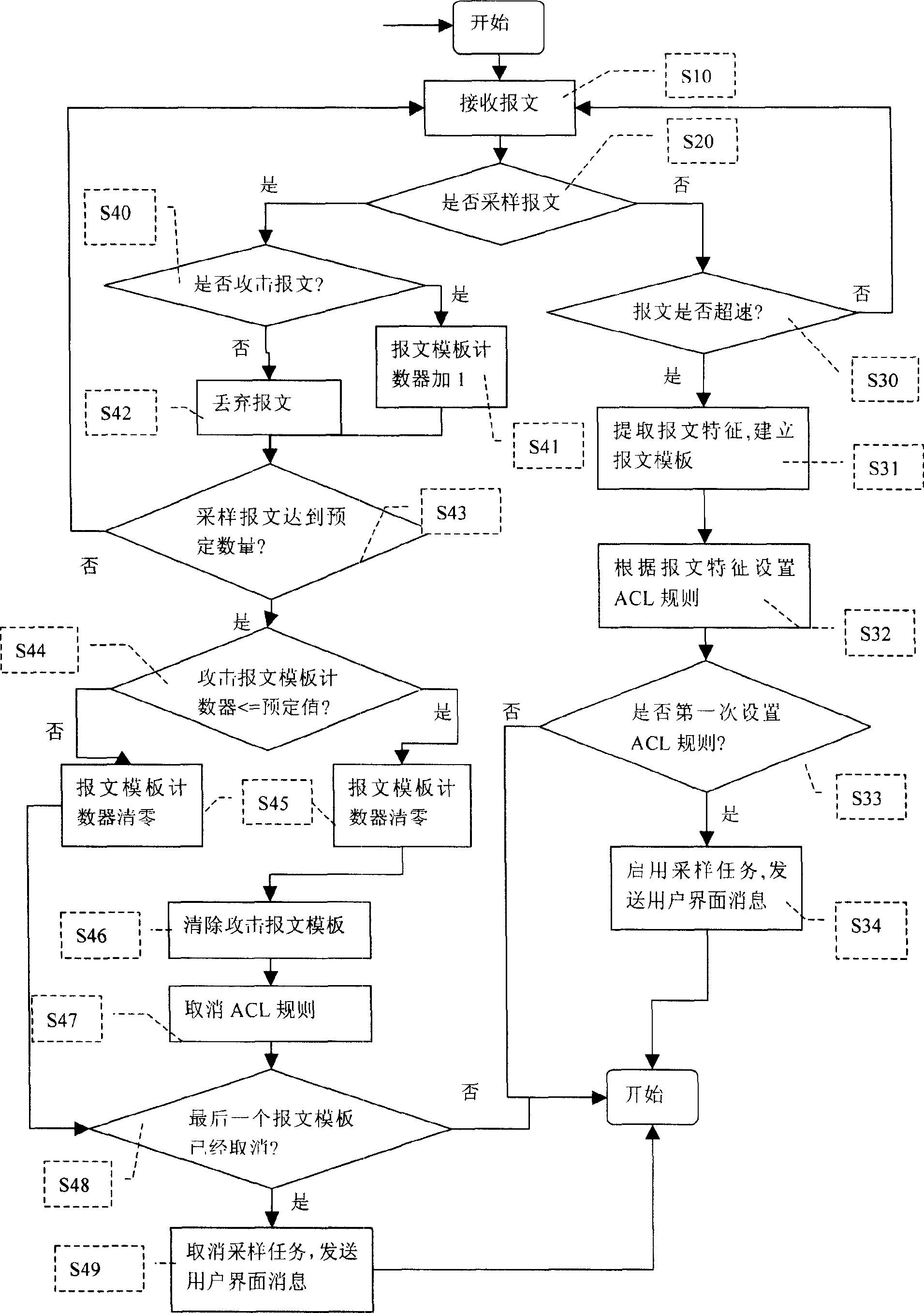
ActiveCN1878082ATo achieve the purpose of anti-attackEasy to integrateData switching networksComputer hardwareNetwork attack
The invention discloses a protective method of network attack in the CPU network equipment, which comprises the following steps: detecting port report of network equipment; building report form when finding abnormal report; setting ACL access regulation at the port; starting the sampling mechanism; comparing the feature of abnormal report with sampled and reserved report form; cancelling ACL regulation when the abnormal report doesn't exist. The invention can utilize hardware character completely and software control flexibly, which solves defect of attack for hardware and software simply.
Owner:NEW H3C TECH CO LTD
Programming of cells for tolerogenic therapies
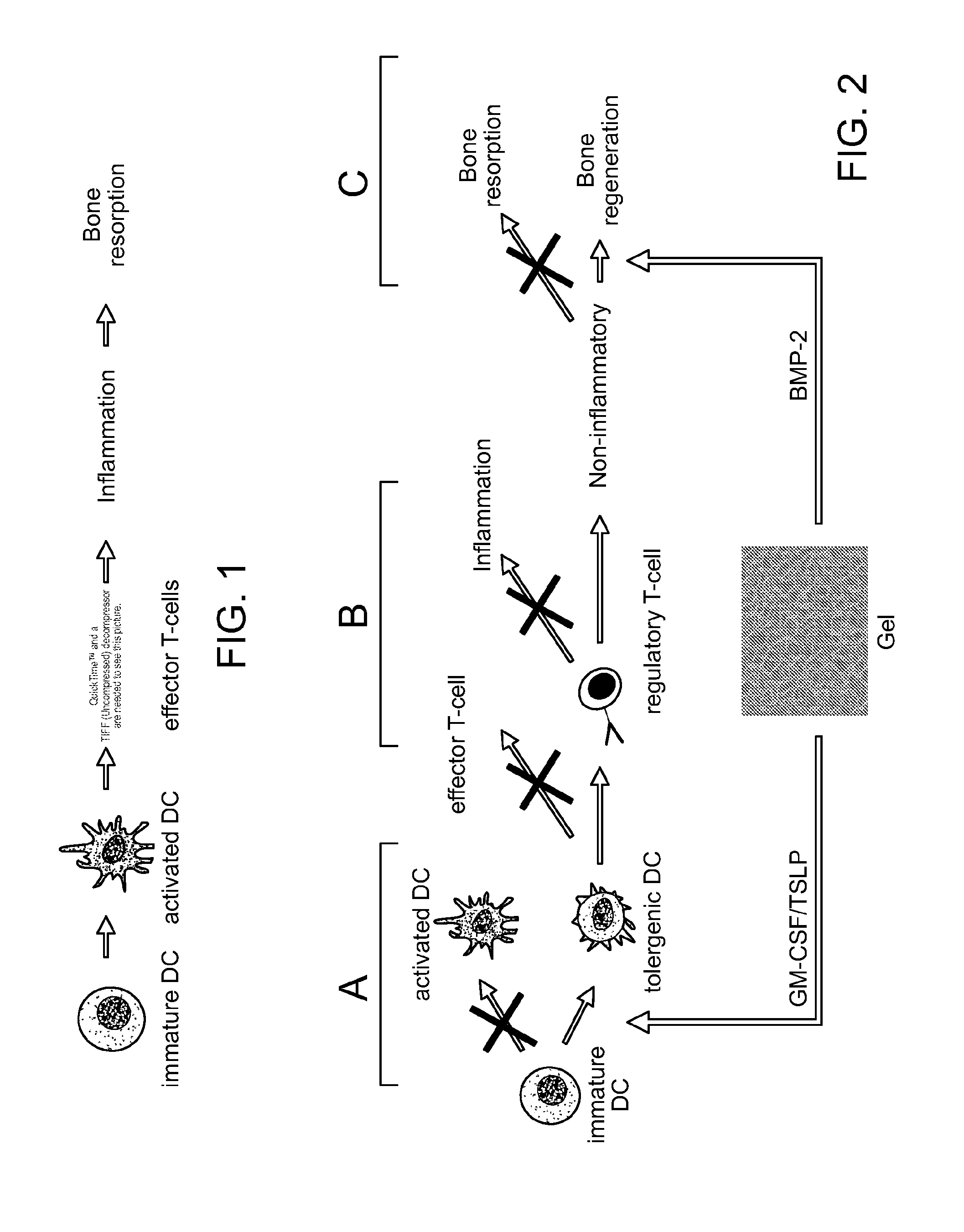
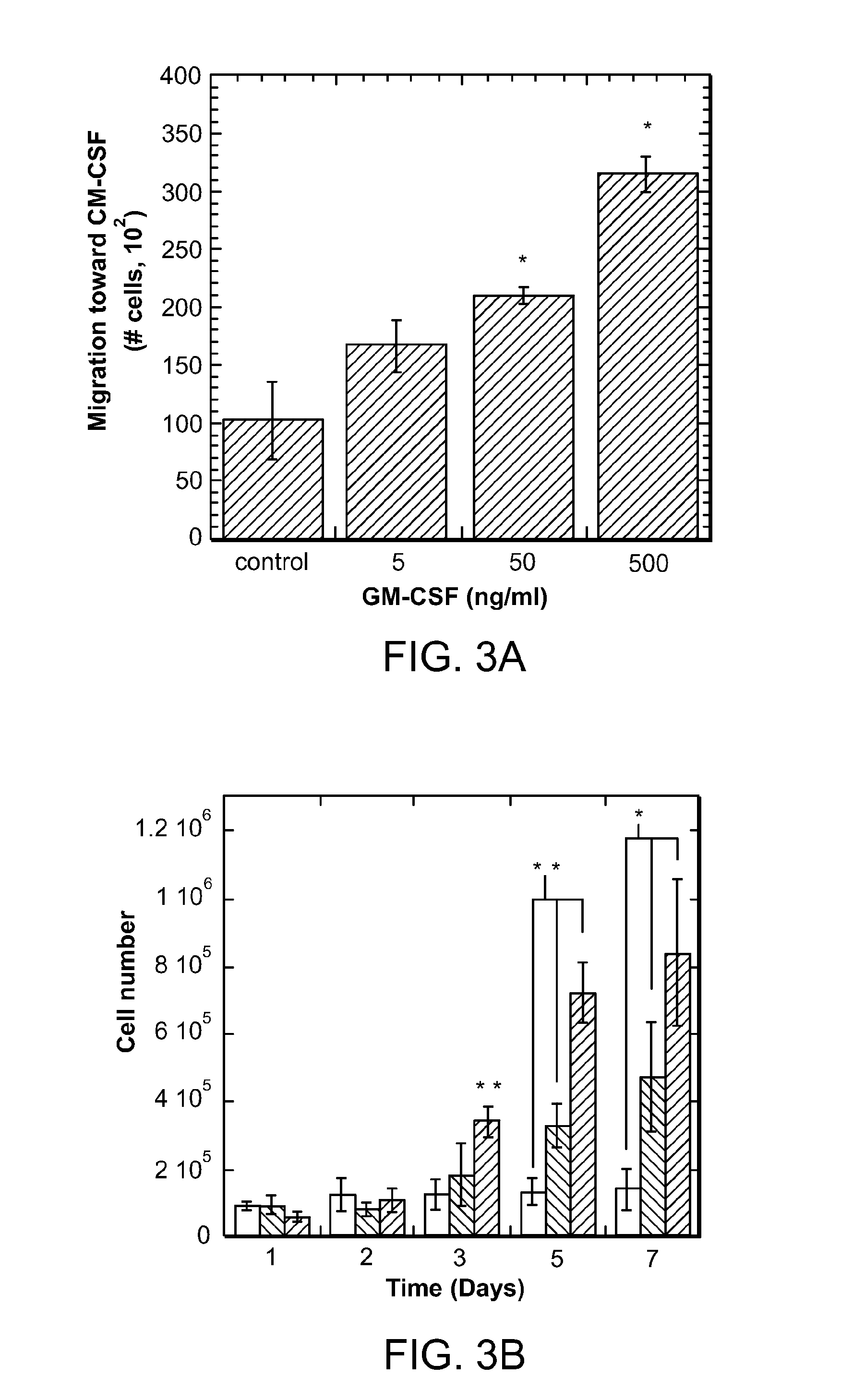
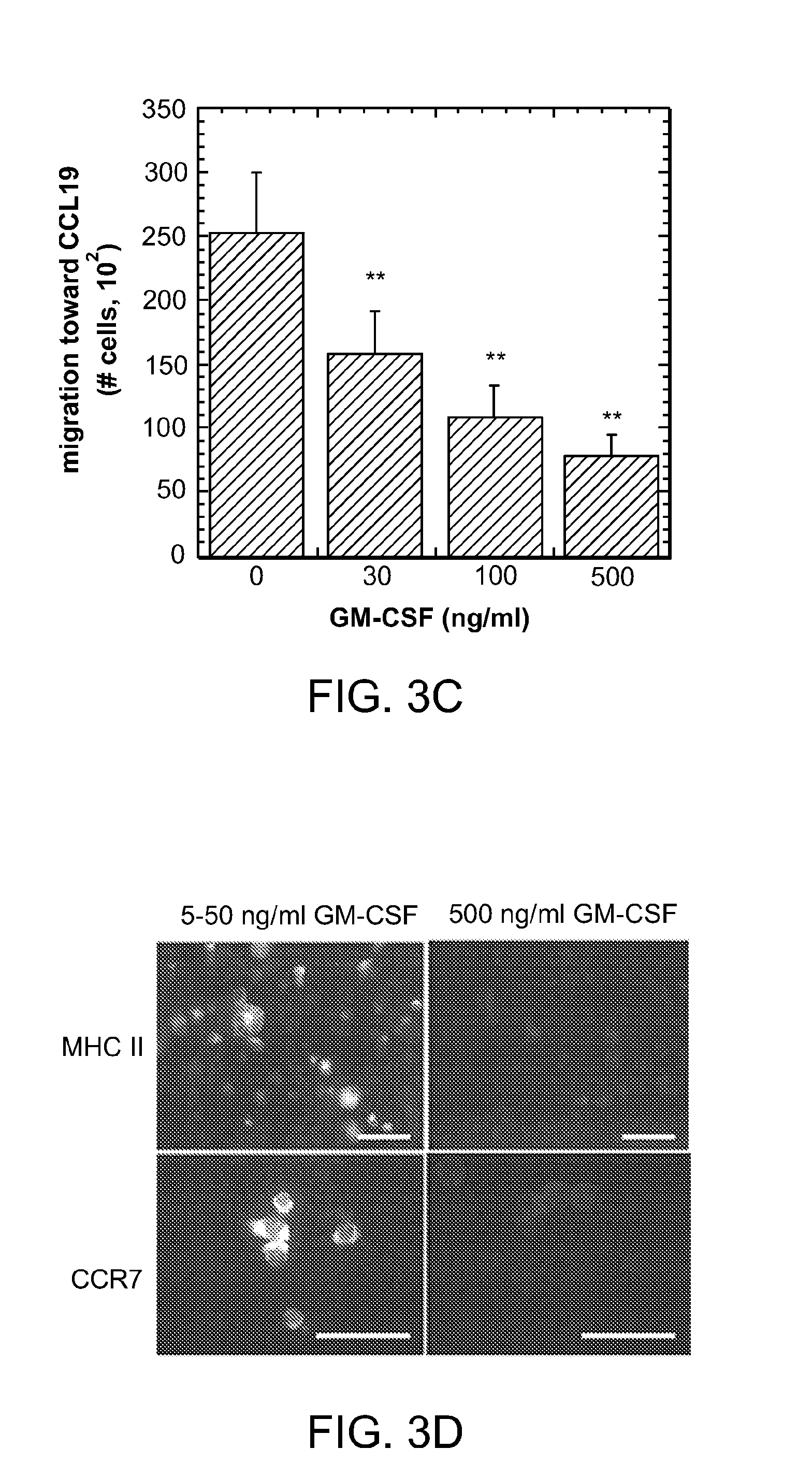
ActiveUS8728456B2Reduce severityReduce attackNervous disorderPeptide/protein ingredientsTolerogenic therapyAutoimmune responses
Biomaterial systems, e.g., gel scaffolds, are used in vivo to recruit immune cells and promote their activation towards a non-inflammatory phenotype, thereby leading suppression of inflammation. The compositions and methods are useful to reduce the severity of autoimmunity, chronic inflammation, allergy, and periodontal disease.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE +1
Semiconductor process residue removal composition and process
InactiveUS7528098B2Efficient removalReduce rateOrganic detergent compounding agentsDetergent mixture composition preparationHydroxylamineGallic acid ester
A residue remover for removing polymeric material and etch residue includes 2-(2-aminoethylamino)-ethanol and optionally another two-carbon atom linkage alkanolamine compound, gallic acid or catechol, water, a polar organic solvent, and hydroxylamine. A process for removing photoresist or other residue from a substrate, such as an integrated circuit semiconductor wafer including titanium metallurgy, includes the steps of contacting the substrate with the above composition for a time and at a temperature sufficient to remove the photoresist or other residue from the substrate. Use of 2-(2-aminoethylamino)-ethanol in the composition and process provides superior residue removal without attacking titanium or other metallurgy on the substrate. The composition preferably has a flash point greater than about 130° C.
Owner:EKC TECH
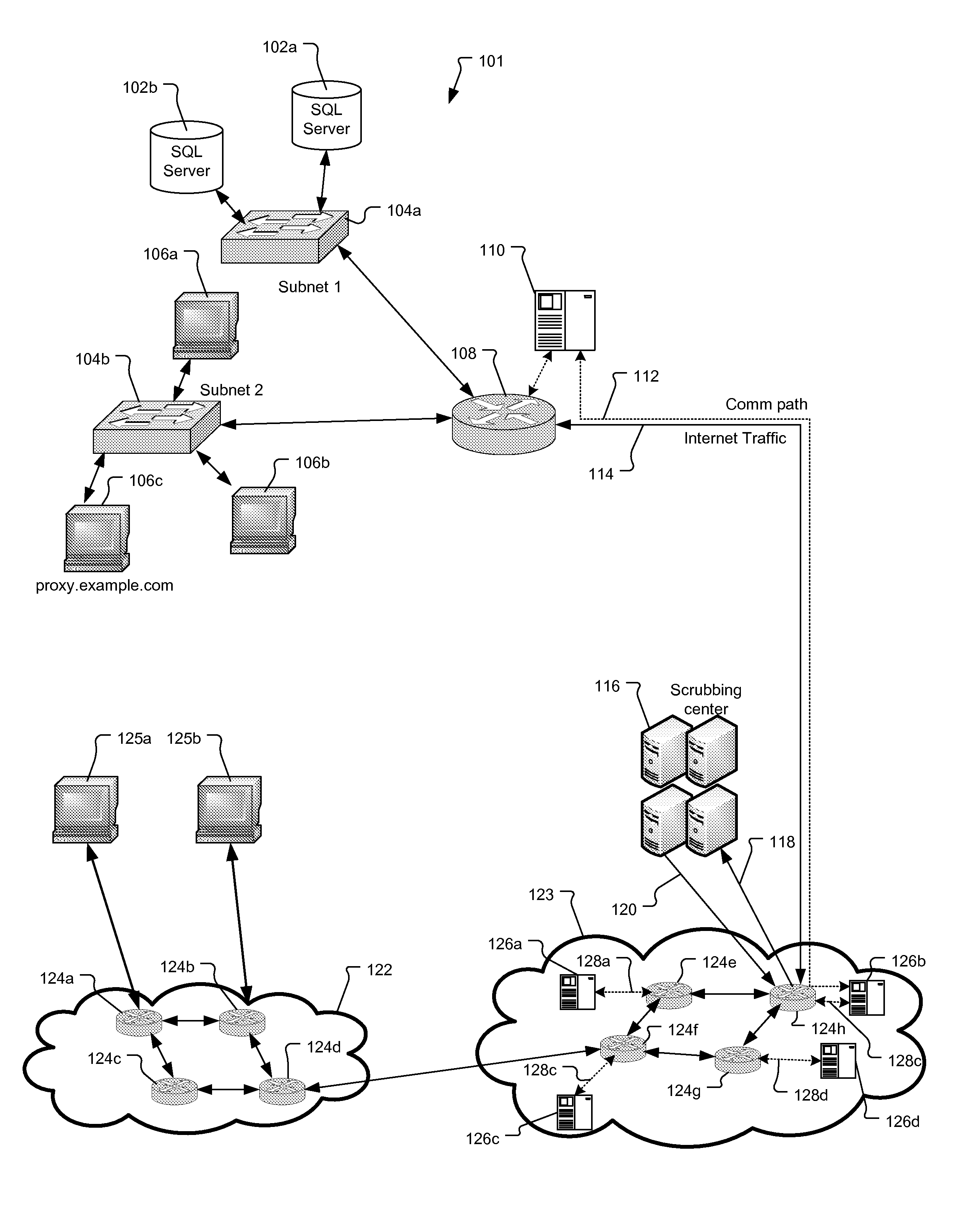
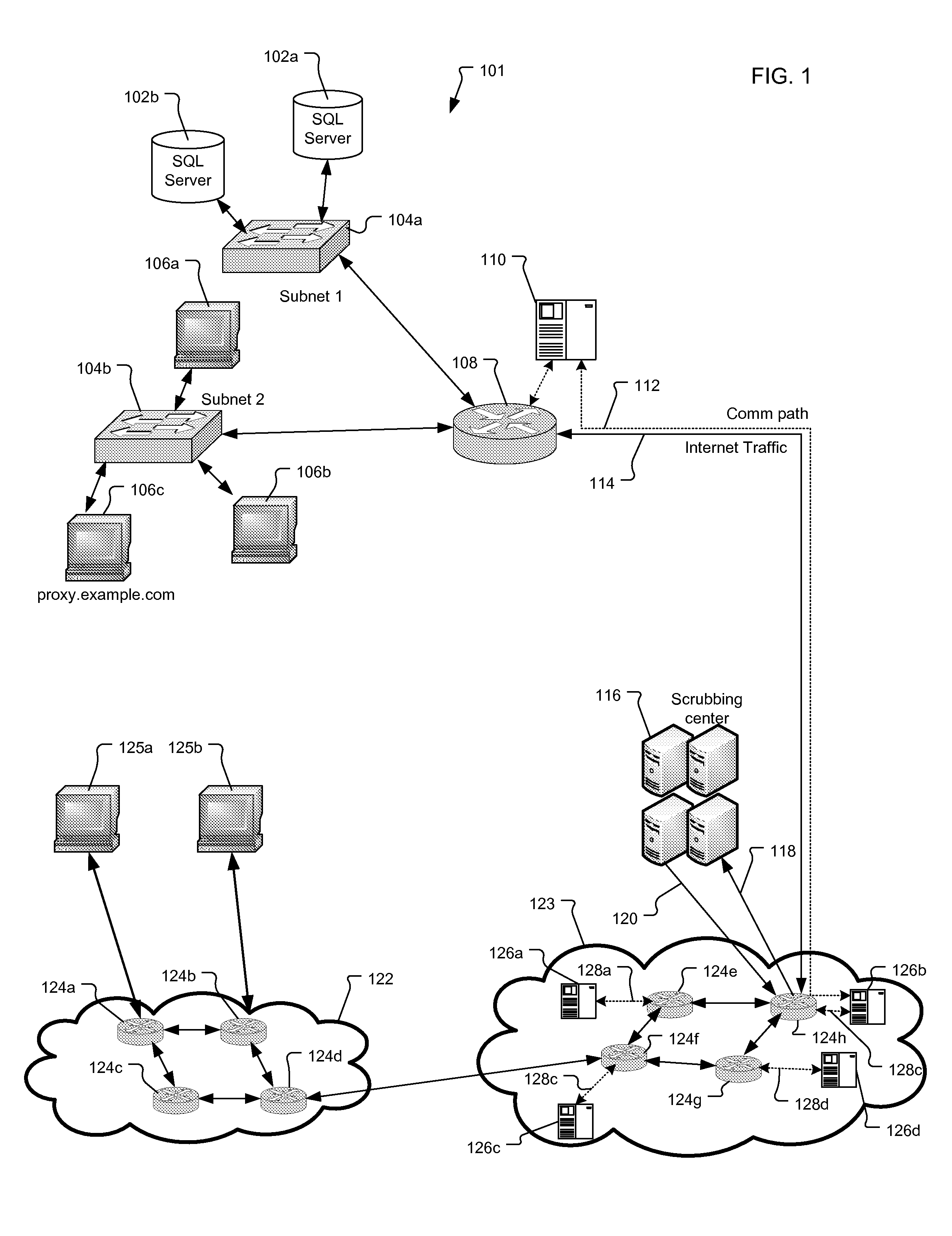
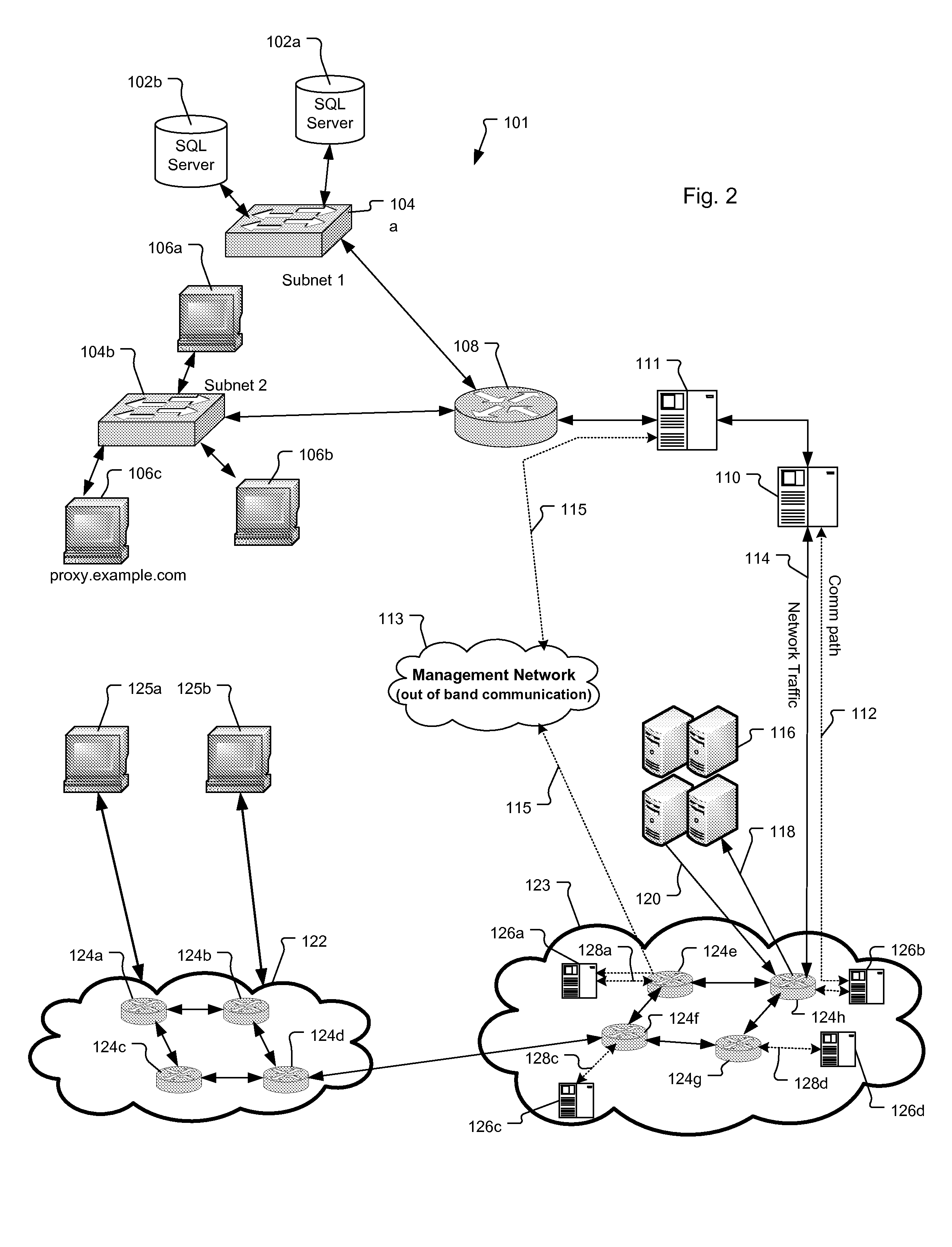
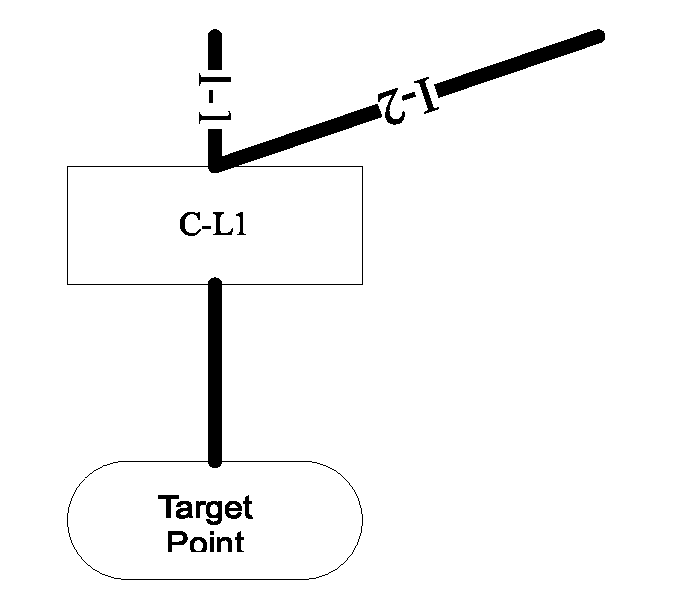
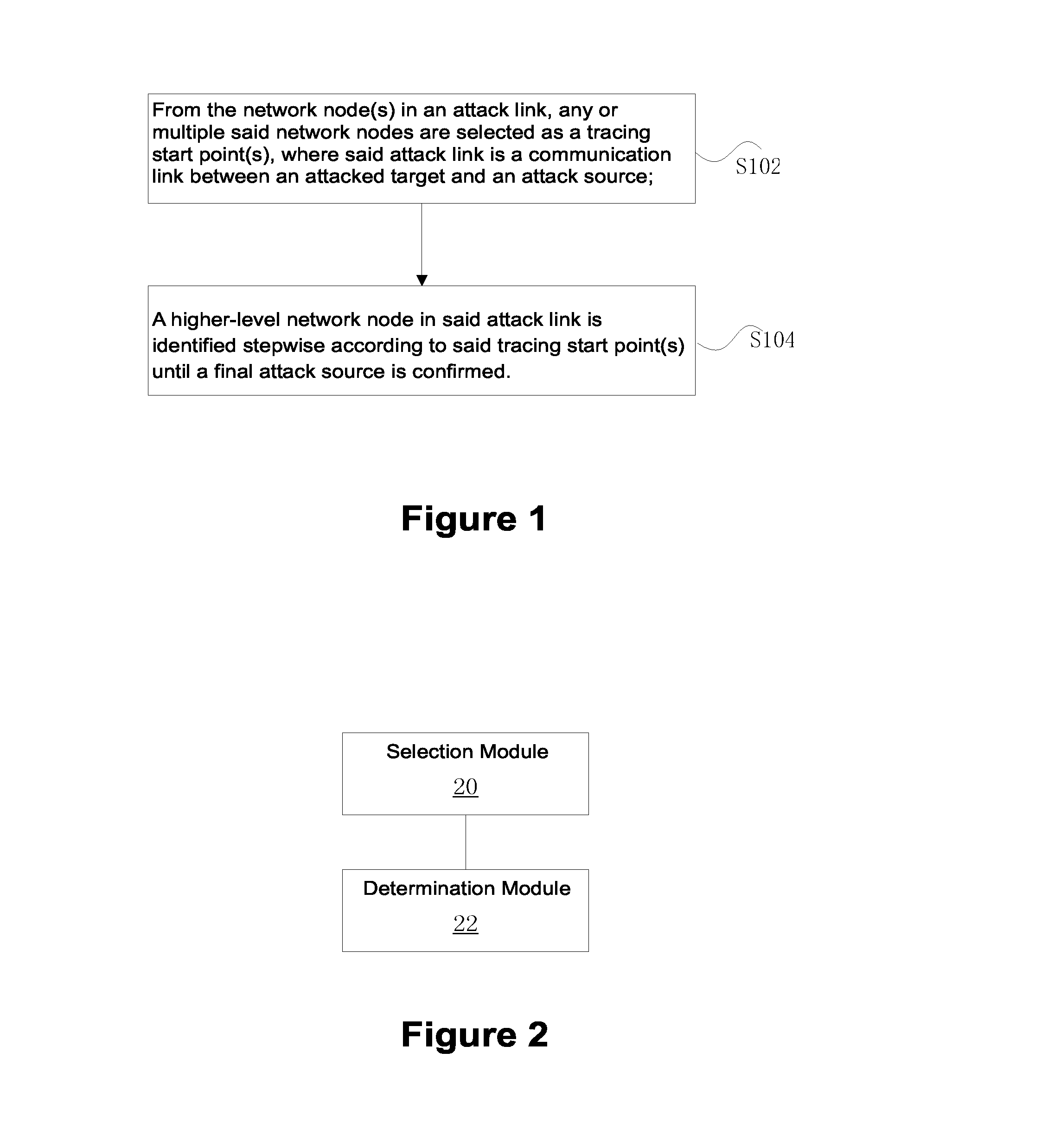
Method and Apparatus for Tracing Attack Source of Abnormal Network Traffic
ActiveUS20140230059A1Reduce attackAchieve effectMemory loss protectionError detection/correctionTelecommunications linkCommunication link
The present invention provides a method and an apparatus for tracing an attack source in the case of an abnormal network traffic, where said method comprises: from the network node(s) of an attack link, any or multiple said network nodes are selected as a tracing start point(s) and there into, said attack link is a communication link between an attacked target and an attack source. According to said tracing start point(s), a higher-level network node of said attack link is identified stepwise until a final attack source is confirmed. By adopting said technical solution provided by the present invention, the problems that the network security mechanisms in related technologies can only alleviate a network attack rather than position an attack source are solved, thus an effect can be achieved to trace and position the attack source in a reverse direction.
Owner:BEIJING RUNSTONE TECH
HTTP relocation method for WEB identification
InactiveCN1538706ASimplified WEB authentication operationSolve the problem of remembering the authentication server addressUser identity/authority verificationData switching networksDomain nameDigest access authentication
The invention is applicable to access authentication based on WEB browser. Thus, it is possible to complete authentication without asking user to remember IP address and domain name. The method includes steps: (1) filtering packet function of peripheral access router of ISP captures HTTP message from not authenticated user; (2) the access router is 'masquerading' as target host user accesses, and builds TCP connection with the host of not authenticated user; (3) the access router redirects HTTP request of user to pointed authentication server. The authentication server transfers HTML page in use for authentication to browser at user side. Based on hint on the HTML page, user completes authentication.
Owner:HUAWEI TECH CO LTD
System and Method for Secure Password-Based Authentication
ActiveUS20130125221A1Prevent or reduce social engineering attacksAmount of necessaryDigital data processing detailsUser identity/authority verificationWeb browserPassword
Various embodiments of a system and method for secure password-based authentication are described. The system and method for secure password-based authentication may include an authentication component configured to request and receive authentication from an authenticating system according to a secure password-based authentication protocol. The authentication component may be configured to participate in an attack-resistant password-based authentication protocol such that an attacker who has compromised the authorizing system and / or a communication channel between the authentication component and the authenticating system may not determine a user's password and / or impersonate the user. In one embodiment, the authentication component may be configured to provide its attack-resistant password-based authentication functionality to an application (e.g., through a stand-alone application, plugin, or application extension). For instance, the authentication component may enable a web browser to participate in the attack-resistant password-based authentication protocol in order to access an online bank account from a web server.
Owner:ADOBE SYST INC
Method for coating a metal with a ceramic coating, electrolyte used therefor, ceramic coating, and metal material
InactiveUS20100025253A1Excellent abrasion resistanceReduce attackAnodisationElectrolytic inorganic material coatingElectrolysisCeramic coating
This invention provides a method for coating a ceramic film on a metal, which can form dense films on various bases of metals such as magnesium alloys. The formed ceramic film has excellent abrasion resistance, causes no significant attack against a counter material, and has excellent corrosion resistance. The method comprises electrolyzing a metallic base in an electrolysis solution using the metallic base as a working electrode while causing glow discharge and / or arc discharge on the surface of the metallic base to form a ceramic film on the surface of the metallic base. The electrolysis solution contains zirconium oxide particles having an average diameter of not more than 1 μm, satisfies the following formulae (1) to (3): 0.05 g / L≦X≦500 g / L (1), 0 g / L≦Y≦500 g / L (2), and 0≦Y / X≦10 (3); and has a pH value of not less than pH 7.0. In the formulae (1) to (3), X represents the content of zirconium oxide particles in the electrolysis solution; and Y represents the content of a compound of at least one element selected from the group consisting of Mg and the like, other than zirconium oxide.
Owner:NIHON PARKERIZING
Method for planting organic arabian jasmine flowers
The invention discloses a method for planting organic arabian jasmine flowers. The method comprises the steps of seed selection of the arabian jasmine flowers, soil ph adjustment, seedling growing, soil preparation, planting, pruning and cutting, weeding, fertilization and plant disease and insect pest prevention, the method mainly aims to produce the high-quality organic arabian jasmine flowers free of pesticides, hormones and chemical pollution and meet the needs of providing and producing various high-end organic jasmine tea and producing edible fresh and dry arabian jasmine flowers or arabian jasmine flower spices, and the arabian jasmine flowers obtained through the full-ecological technology planting method are purely natural, have fragrance, are free of peculiar smells, and are pure white in color.
Owner:横县生产力促进中心
Bitumen Production-Upgrade with Common or Different Solvents
ActiveUS20060283776A1Reduce operating expensesOperational reliability is increasedWorking-up pitch/asphalt/bitumen by selective extractionRefining by water treatmentDiluentFuel oil
Disclosed is a process for the upgrading of heavy oils and bitumens, where the total feed to the process can include heavy oil or bitumen, water, and diluent. The process can include the steps of solvent deasphalting 110 the total feed 105 to recover an asphaltene fraction 116, a deasphalted oil fraction 118 essentially free of asphaltenes, a water fraction 112, and a solvent fraction 114. The process allows removal of salts from the heavy oils and bitumens either into the aqueous products or with the asphaltene product.
Owner:KELLOGG BROWN & ROOT LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com