Protective method for network attack
A network attack and network equipment technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., to achieve the effect of reducing attacks, saving hardware resources, and improving response speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
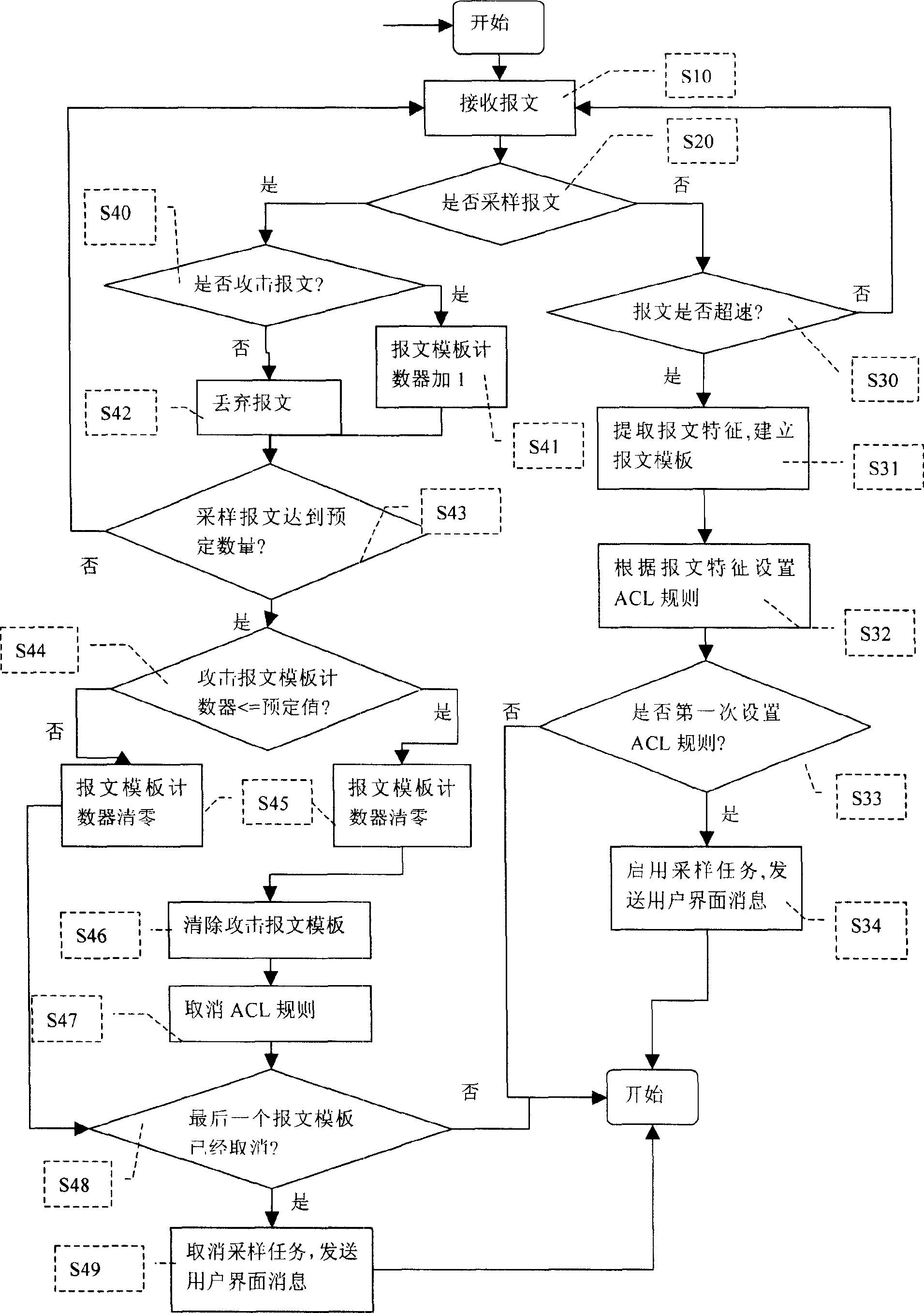
[0037] The core idea of the present invention is to make full use of the characteristics of the hardware and the flexible control of the software, automatically set the ACL rules of the chip to filter the messages under the analysis of the software, and use the sampling technology to analyze the abnormal messages to judge when the attack ends. When the attack is over, the function of the port is restored, and the issued ACL rules are cancelled, so as to achieve the purpose of CPU anti-attack.
[0038] Specifically, the network packet receiving module driven by the bottom layer of the network device detects the received packets. If an abnormal packet is received, for example, a port with a large flow of packets is detected in a short period of time, it can be considered as If there is a packet attack on this port, an alarm message will be issued to remind the user. At the same time, the packet characteristics will be extracted from the packet received by the attacked port and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com