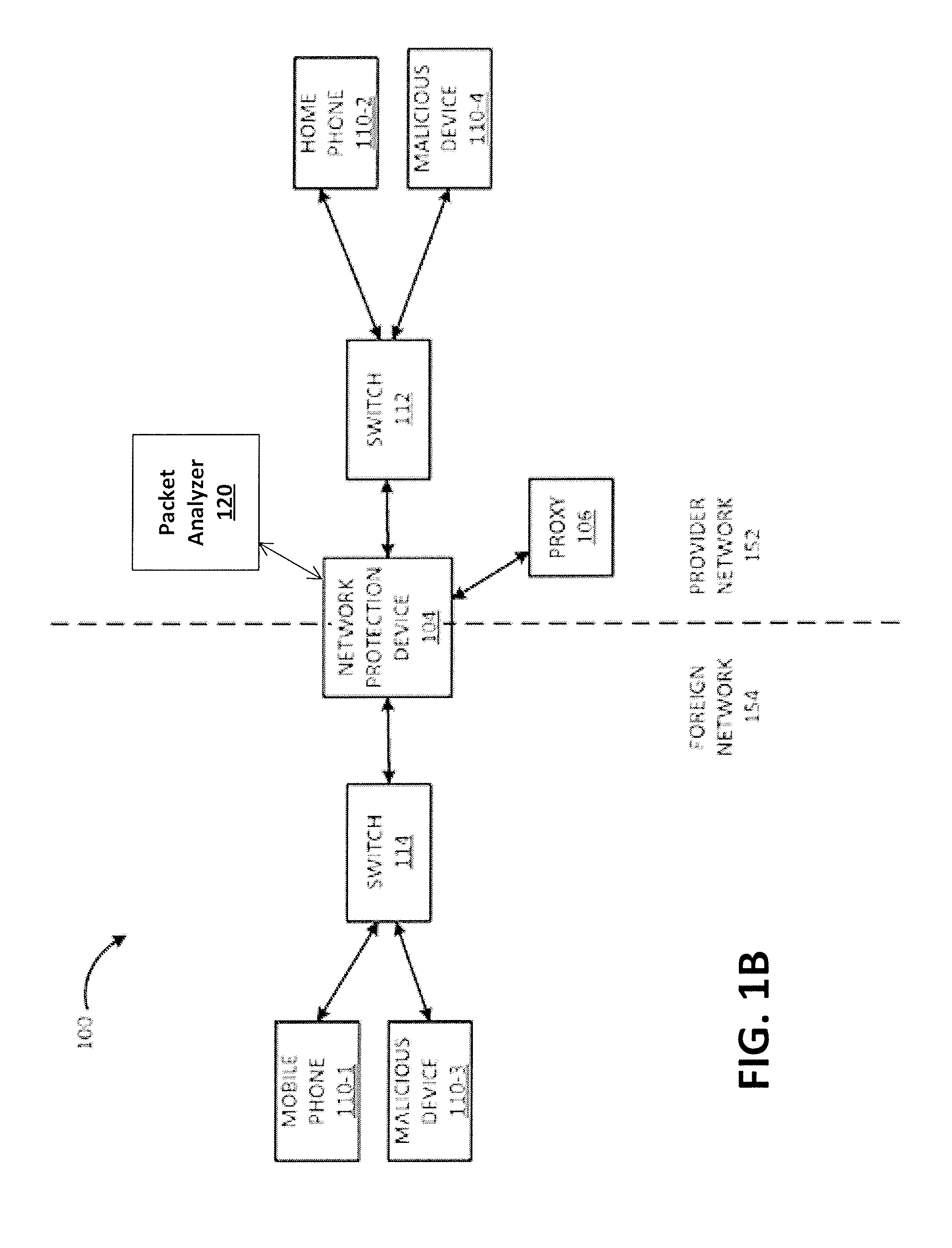
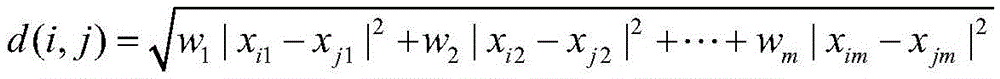Patents
Literature
2582 results about "Network attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
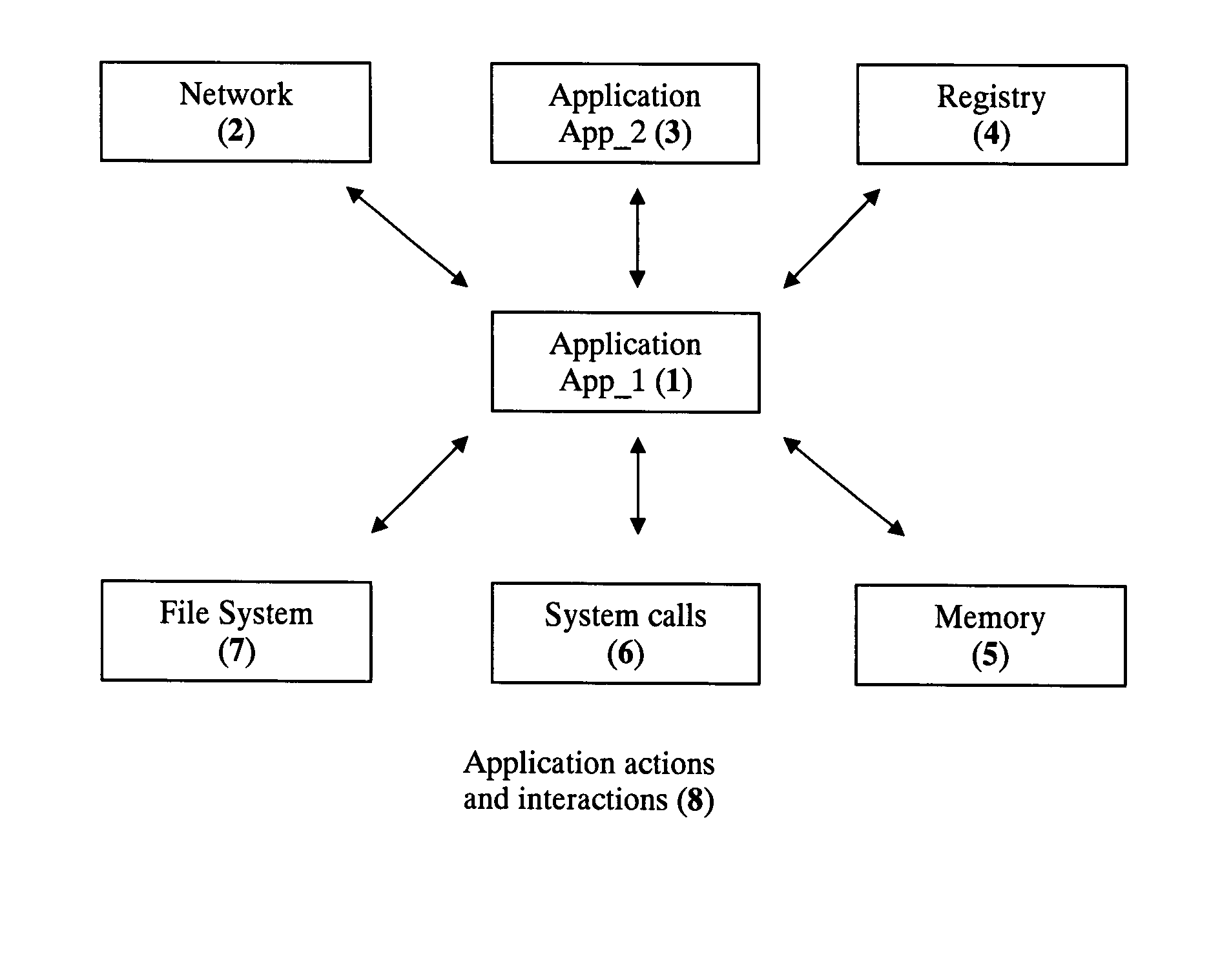
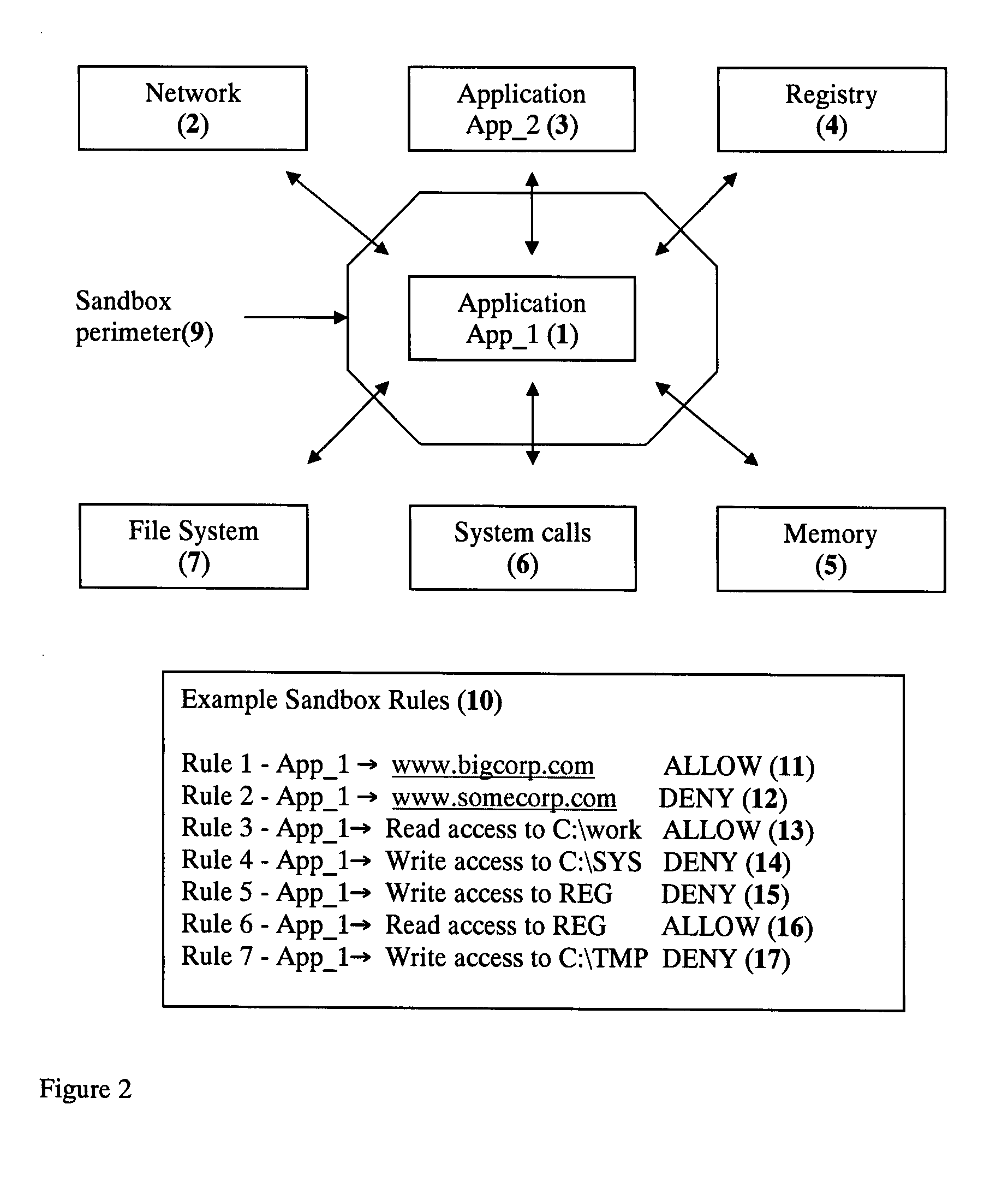
Application Sandbox to Detect, Remove, and Prevent Malware
InactiveUS20080016339A1Limit and eliminate attackRemove or neutralized malware on disk and in memoryPlatform integrity maintainanceSecuring communicationNetwork attackMalware
The disclosed invention is a new method and apparatus for protecting applications from local and network attacks. This method also detects and removes malware and is based on creating a sandbox at application and kernel layer. By monitoring and controlling the behavior and access privileges of the application and only selectively granting access, any attacks that try to take advantage of the application vulnerabilities are thwarted.
Owner:SHUKLA JAYANT
Mitigating network attacks using automatic signature generation
A computer-implemented method for mitigating attacks of malicious traffic in a computer network includes receiving a set of attack sequences, including first traffic sequences suspected of containing the malicious traffic, analyzing the attack sequences so as to automatically extract a regular expression that matches at least a portion of the attack sequences in the set, and comparing second traffic sequences to the regular expression in order to identify the second traffic sequences that contain the malicious traffic.
Owner:CISCO TECH INC
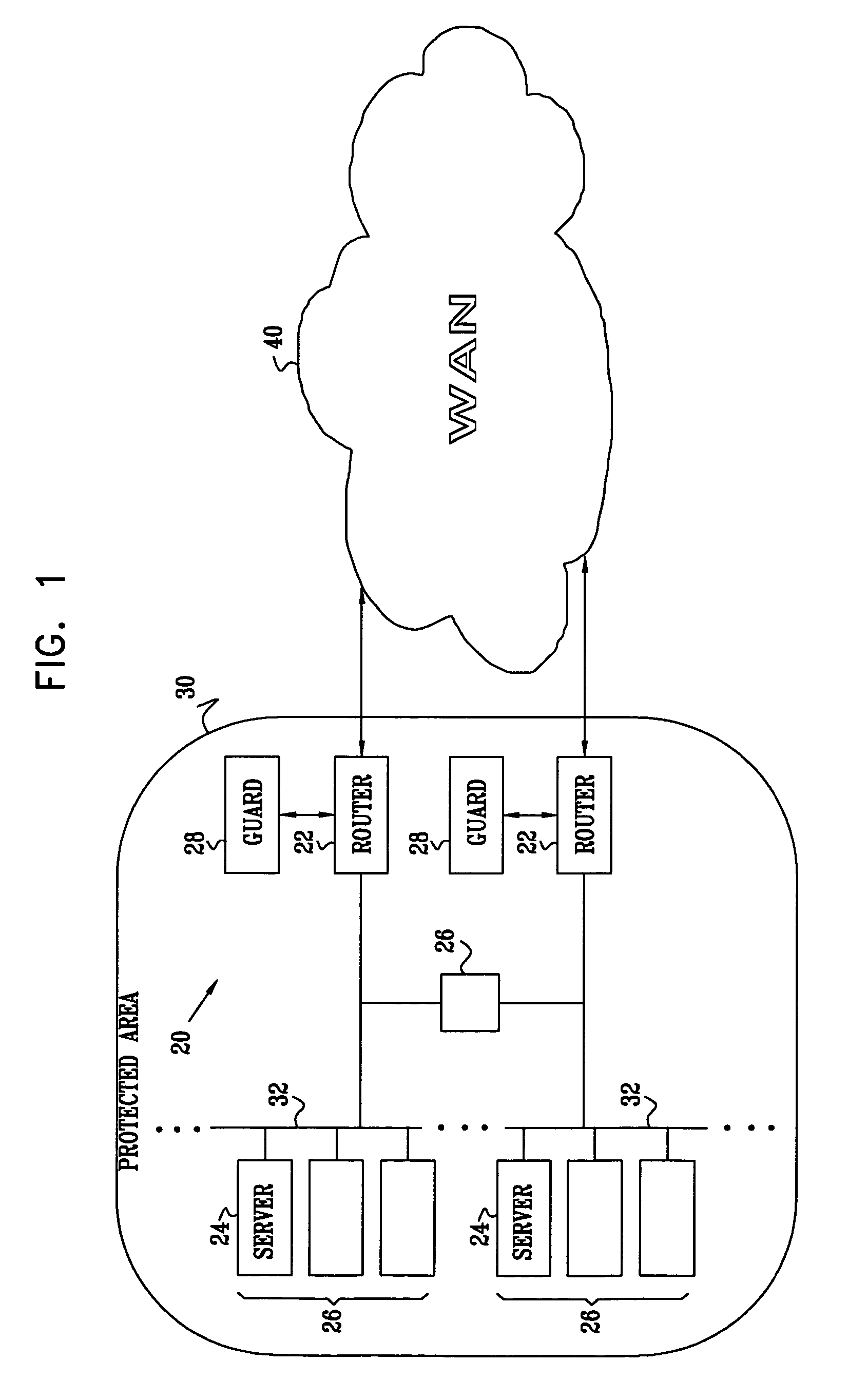
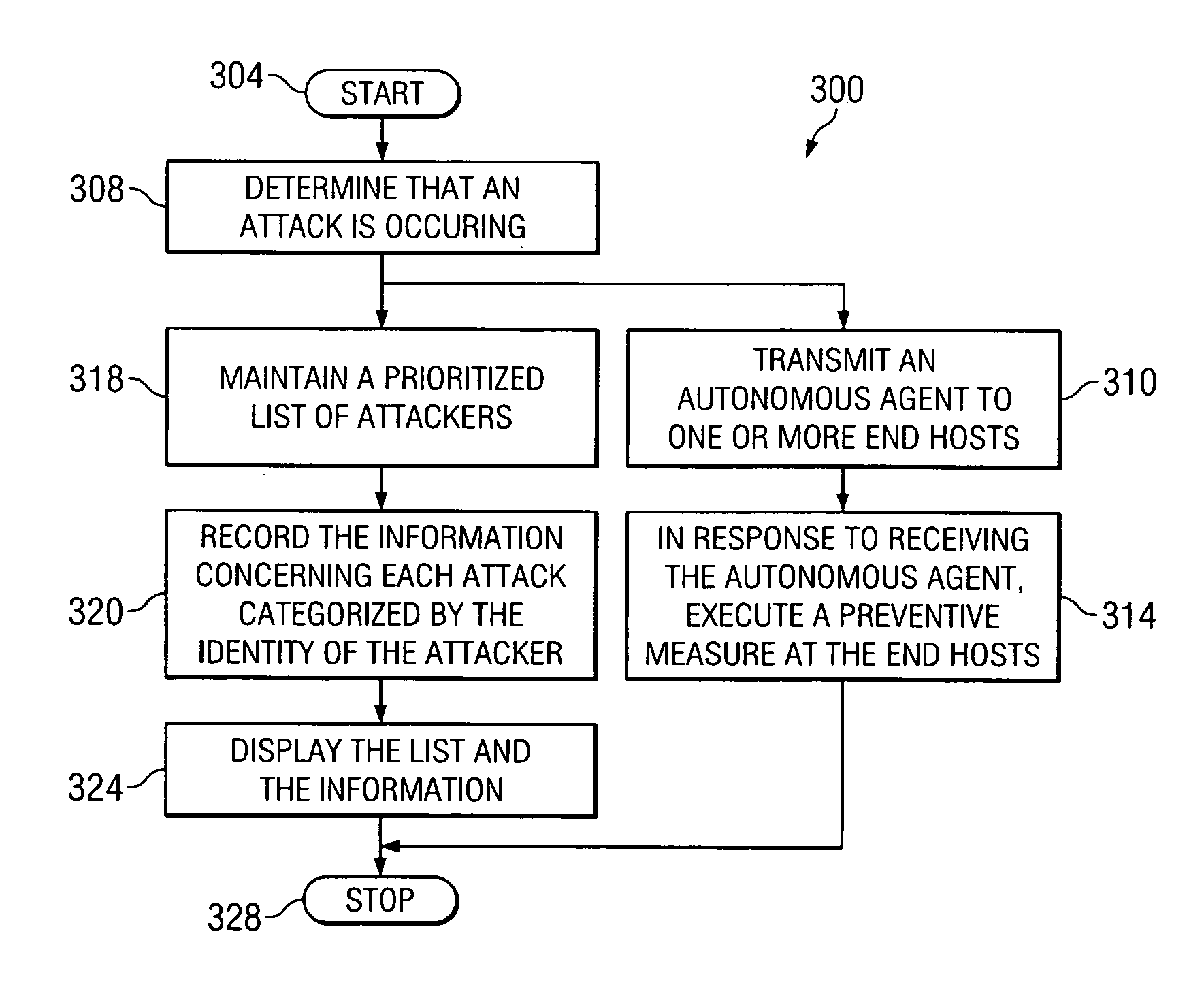
Network intrusion prevention
InactiveUS20060143709A1Avoid attackReduce the impactMemory loss protectionError detection/correctionComputer networkNetwork attack
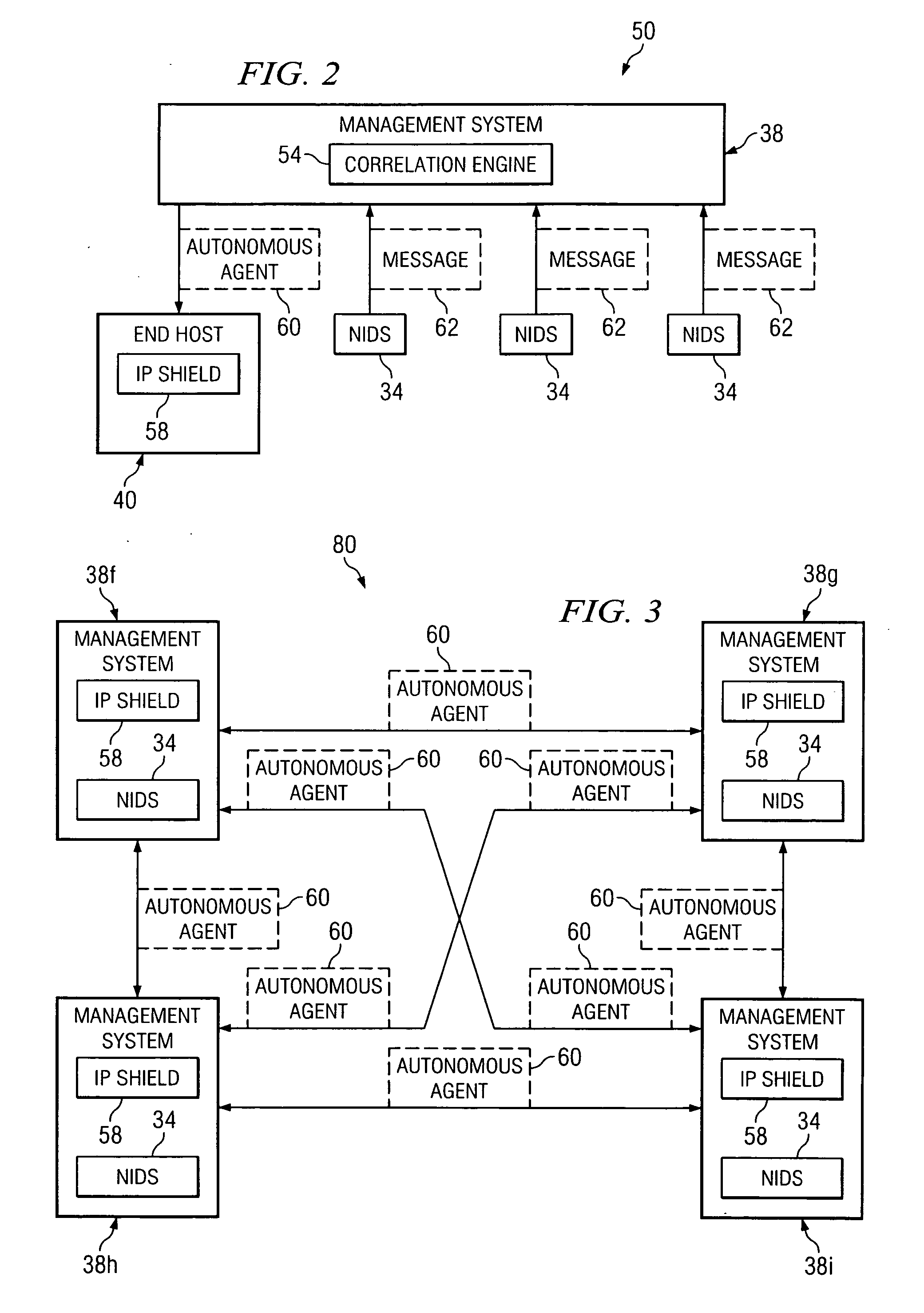
According to one embodiment of the invention, a system for preventing a network attack is provided. The system includes a computer having a processor and a computer-readable medium. The system also includes a shield program stored in the computer-readable medium. The shield program is operable, when executed by the processor, to transmit an agent to each of one or more nodes in a network in response to an attack directed to the network. The agent is operable to initiate a reduction of the effect of the attack on the node.
Owner:RAYTHEON CO
Mechanism to correlate the presence of worms in a network
ActiveUS20070094730A1Memory loss protectionError detection/correctionNetwork attackDistributed computing
A method and a system for preventing a network attack, the attack being cause by the presence of worms in the network, is provided. The method includes determining the number of packets being transmitted from each source in the network to a plurality of destinations, the packets being transmitted from a source with a set of characteristics. If the number of packets with the set of characteristics, being transmitted from a source, exceeds a predefined first threshold, then the signature of the packets is stored. Subsequently, if at least one of the pluralities of destinations of the packets identified with the source becomes a source of new packets, the new packets being transmitted to more than one destination; then the new packets are compared with the signature. If at least one new packet matches with the signature, then the worm is to be detected.
Owner:CISCO TECH INC
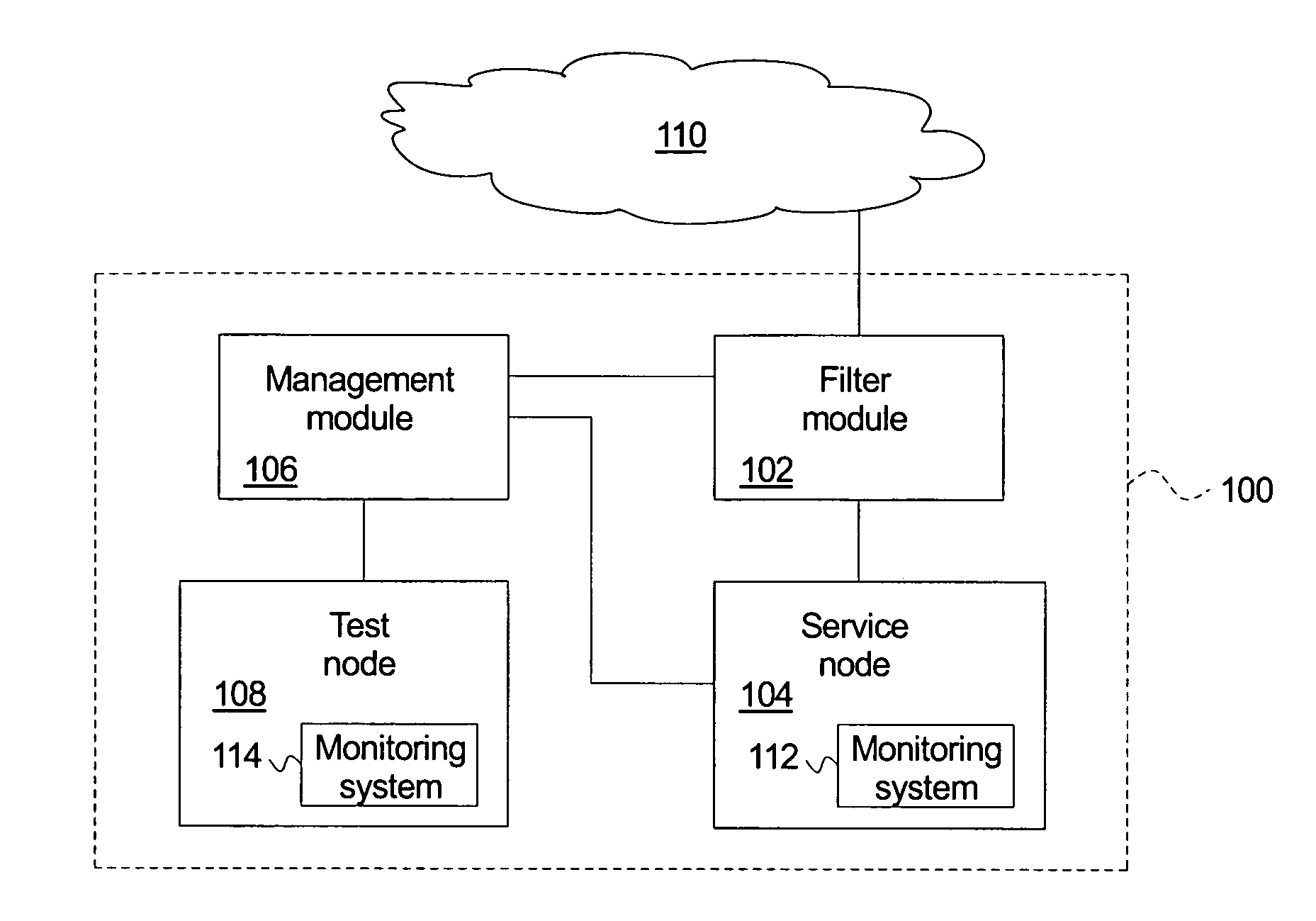
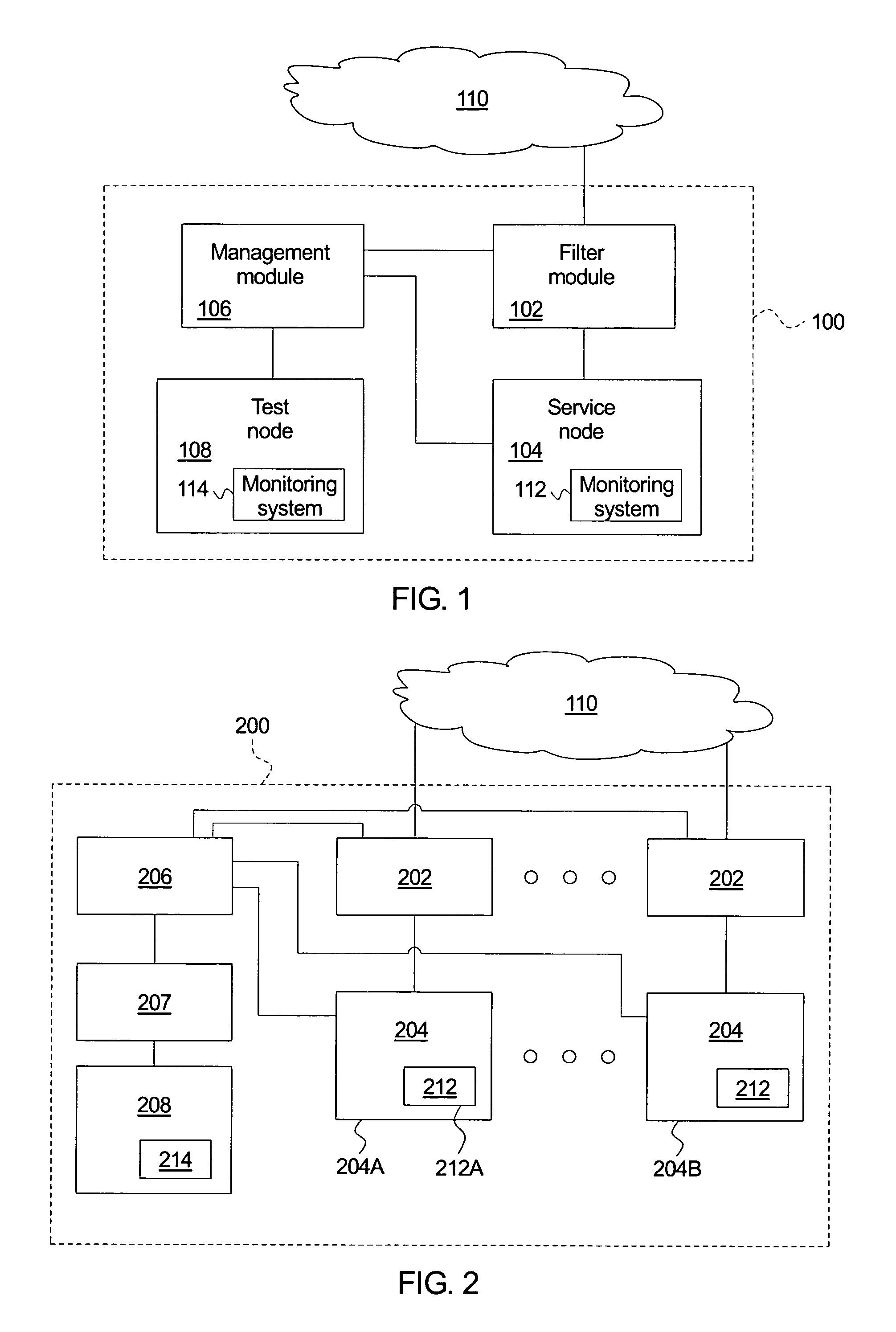
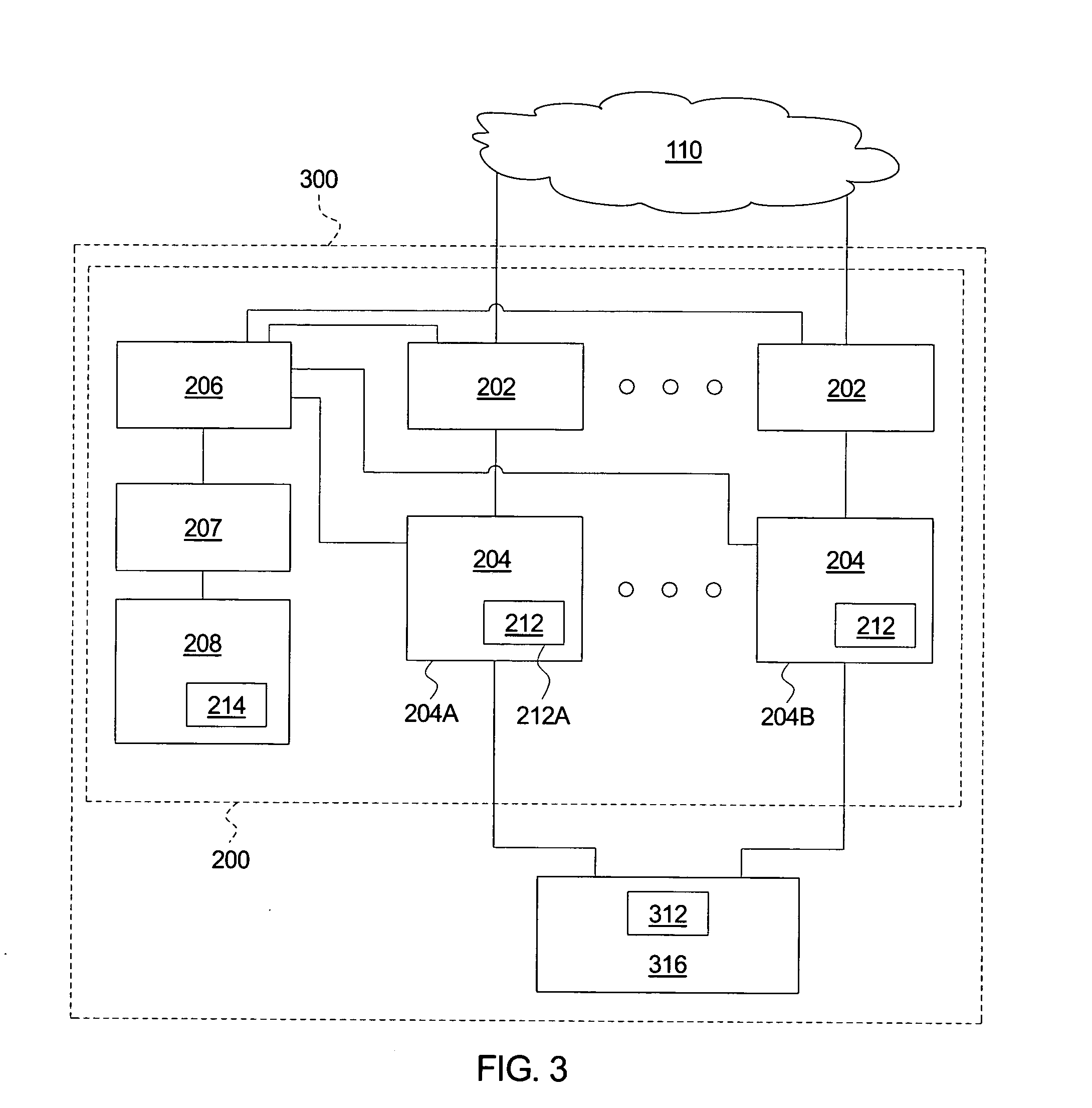
Automatically protecting network service from network attack
A system for detecting and responding to an attack comprises a filter module, a node, a management module, and a test node. The filter module allows questionable messages to proceed. The node receives the questionable messages and maintains logical operations associated with the questionable messages within a restricted region. The management module resets the service node upon a network attack. The test node replays the node questionable messages to identify a new attack. A method of protecting against a network attack logs questionable messages and directs the questionable messages to a node. The method maintains logical operations associated with the questionable messages within a restricted region and identifies a network attack upon the node, which triggers an intrusion response. The intrusion response resets the node, replays the questionable messages within a test node to identify a new attack message, and adds the new attack message to the known attack messages.
Owner:HEWLETT PACKARD DEV CO LP
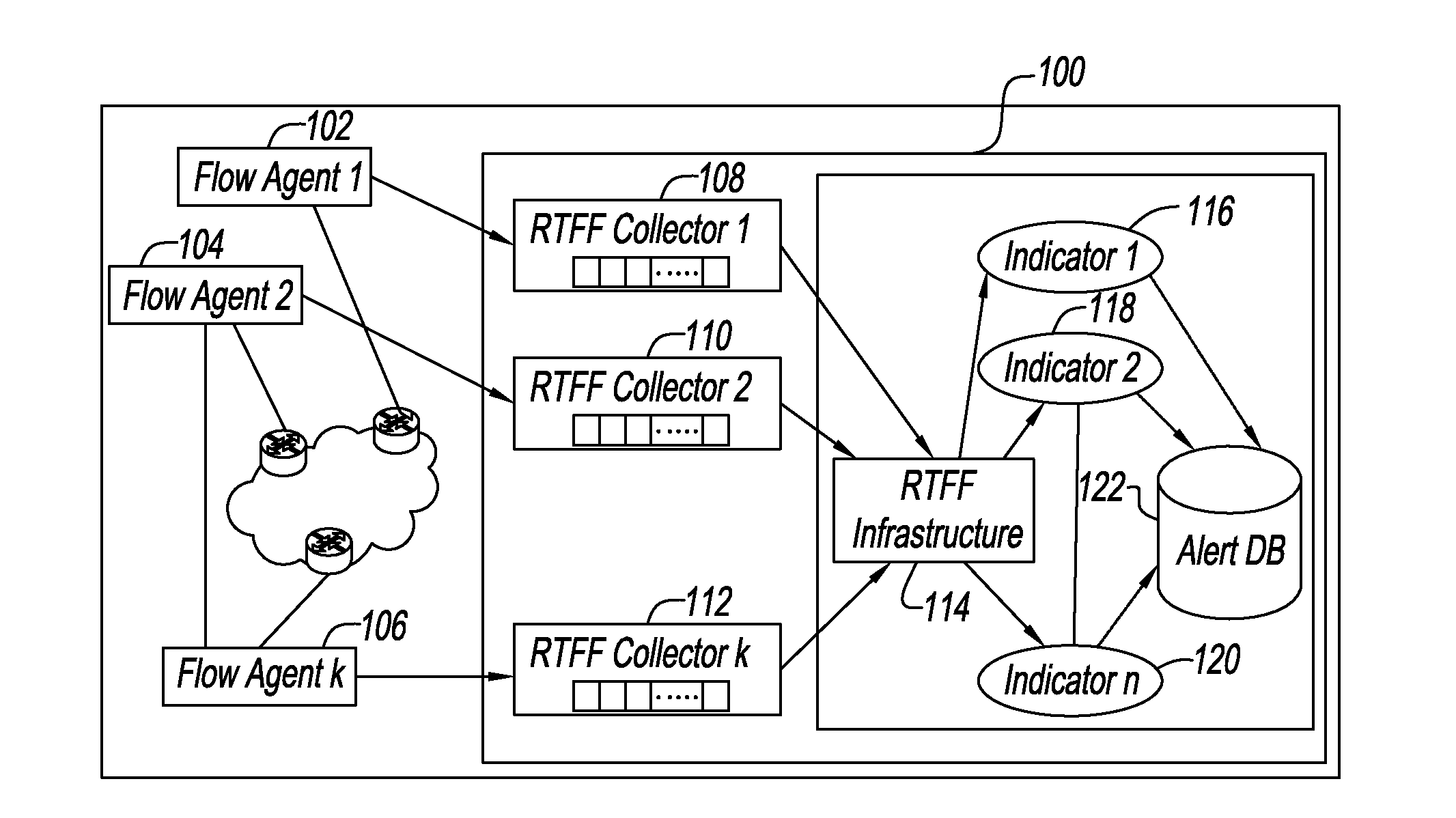
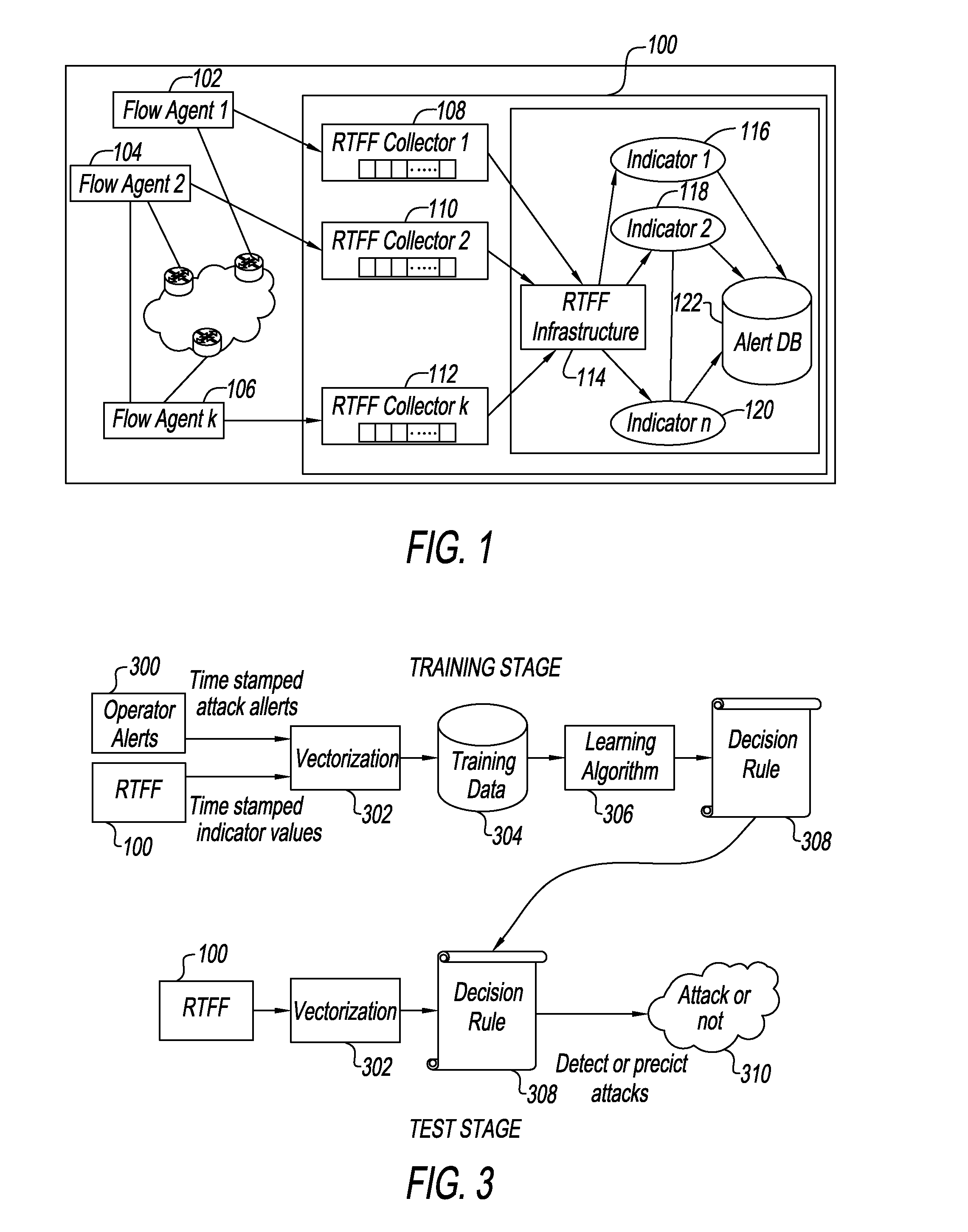
System and method for correlating historical attacks with diverse indicators to generate indicator profiles for detecting and predicting future network attacks
InactiveUS20140082730A1Reduce detectionAccurately detect and predictMemory loss protectionError detection/correctionTraffic characteristicAnomalous behavior
An apparatus and method predict and detect network attacks by using a diverse set of indicators to measure aspects of the traffic and by encoding traffic characteristics using these indicators of potential attacks or anomalous behavior. The set of indicators is analyzed by supervised learning to automatically learn a decision rule which examines the temporal patterns in the coded values of the set of indicators to accurately detect and predict network attacks. The rules automatically evolve in response to new attacks as the system updates its rules periodically by analyzing new data and feedback signals about attacks associated with that data. To assist human operators, the system also provides human interpretable explanations of detection and prediction rules by pointing to indicators whose values contribute to a decision that there is an existing network attack or an imminent network attack. When such indictors are detected, an operator can take remediation actions.
Owner:PERSPECTA LABS INC +1
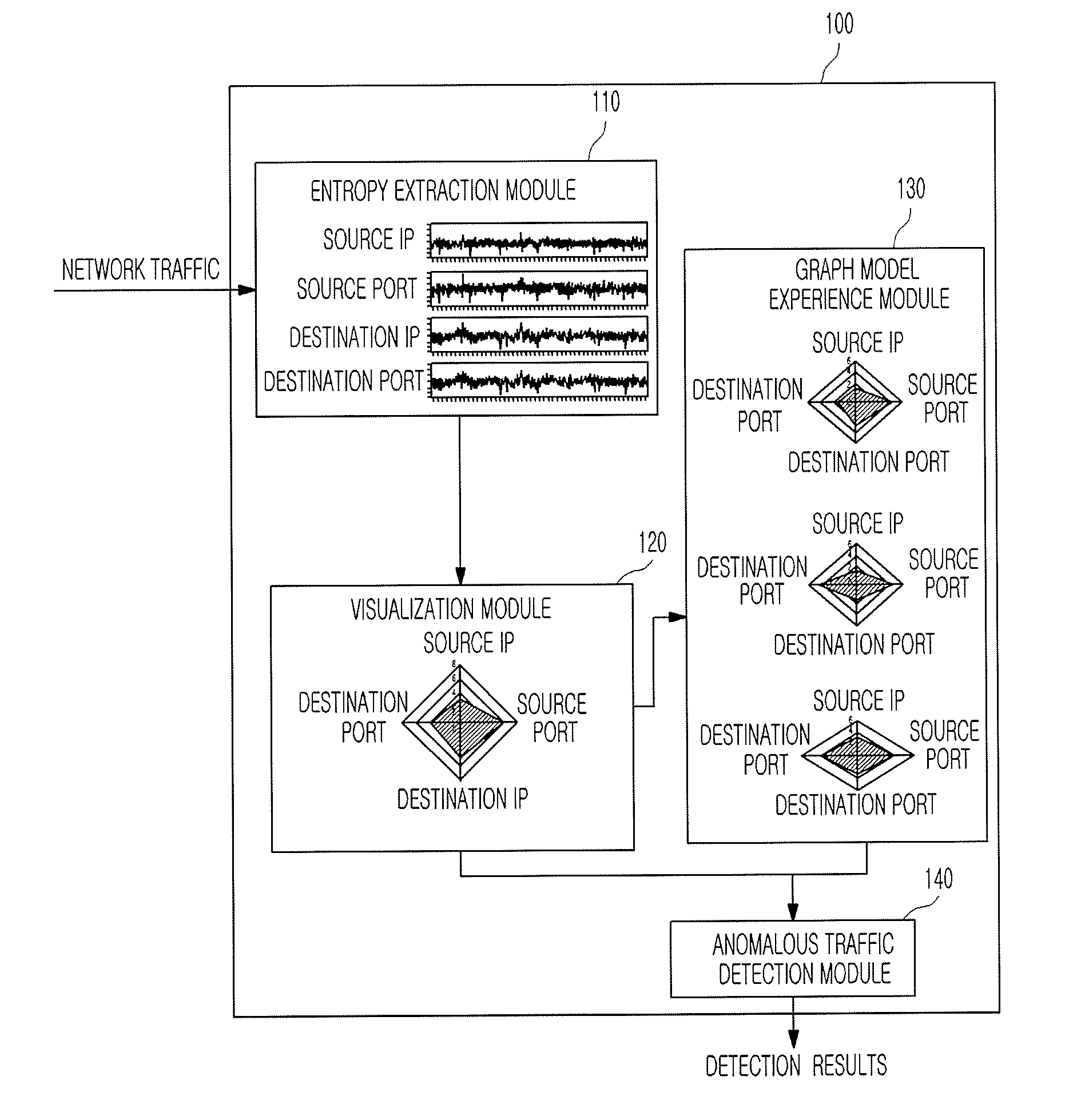
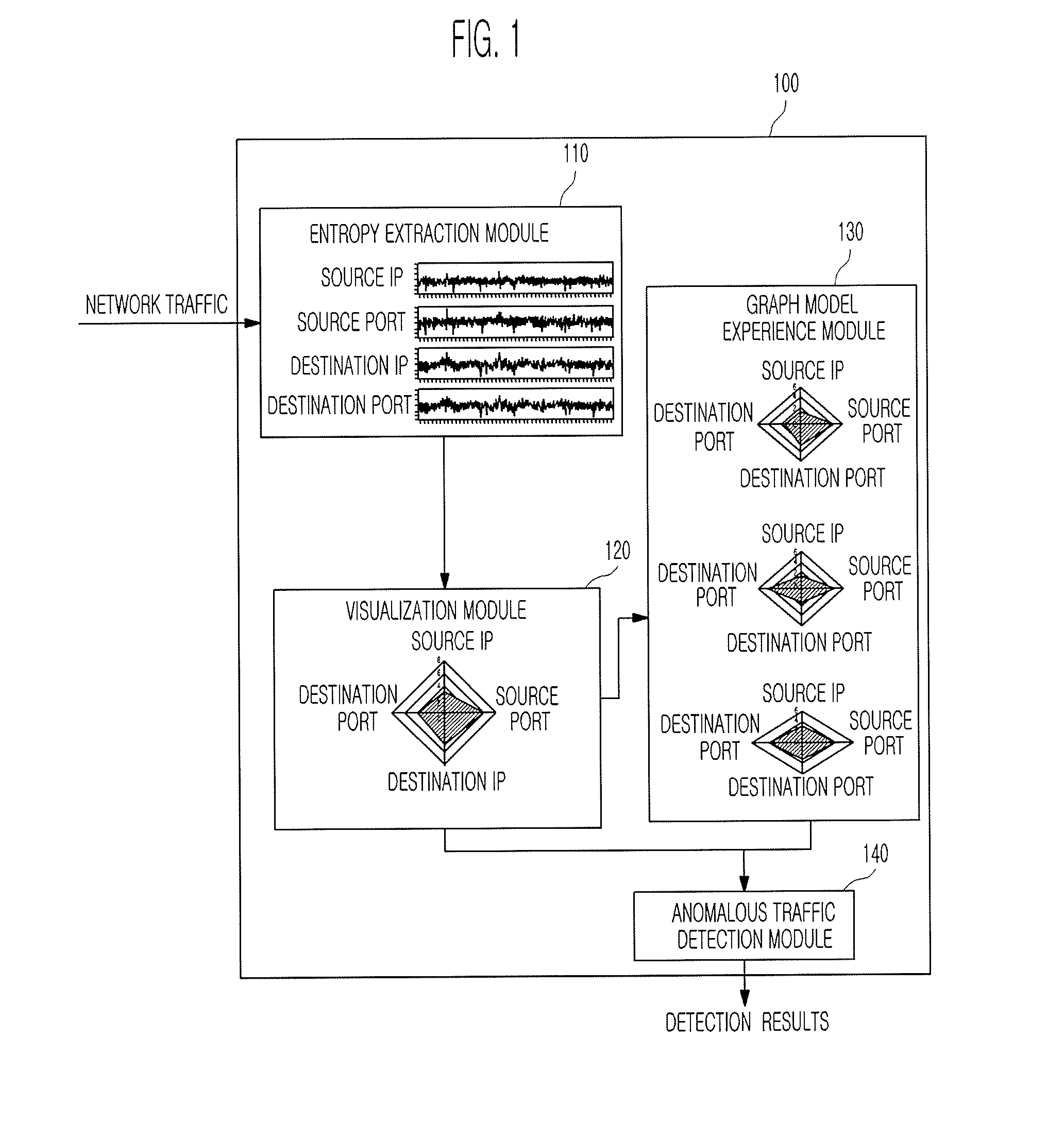
Apparatus and method for detecting anomalous traffic
InactiveUS20090138590A1Efficient and accurate detectionDetect anomalous traffic more accurately and efficientlyMultiple digital computer combinationsTransmissionNetwork entropyNetwork attack
An apparatus and method for detecting anomalous traffic are provided. More particularly, an apparatus and method for detecting anomalous traffic based on entropy of network traffic are provided. The apparatus of detecting anomalous traffic includes: an entropy extraction module for extracting entropy from network traffic; a visualization module for generating an entropy graph based on the entropy; a graph model experience module for updating a graph model for each network attack based on the entropy graph; and an anomalous traffic detection module for detecting anomalous traffic based on the entropy graph and the graph model for each network attack and outputting the detection results to a user. In the apparatus and method, anomalous traffic is detected based on network entropy rather than simple statistics based on the amount of traffic, so that a false alarm rate of the apparatus for detecting anomalous traffic can be reduced.
Owner:IZEX +1
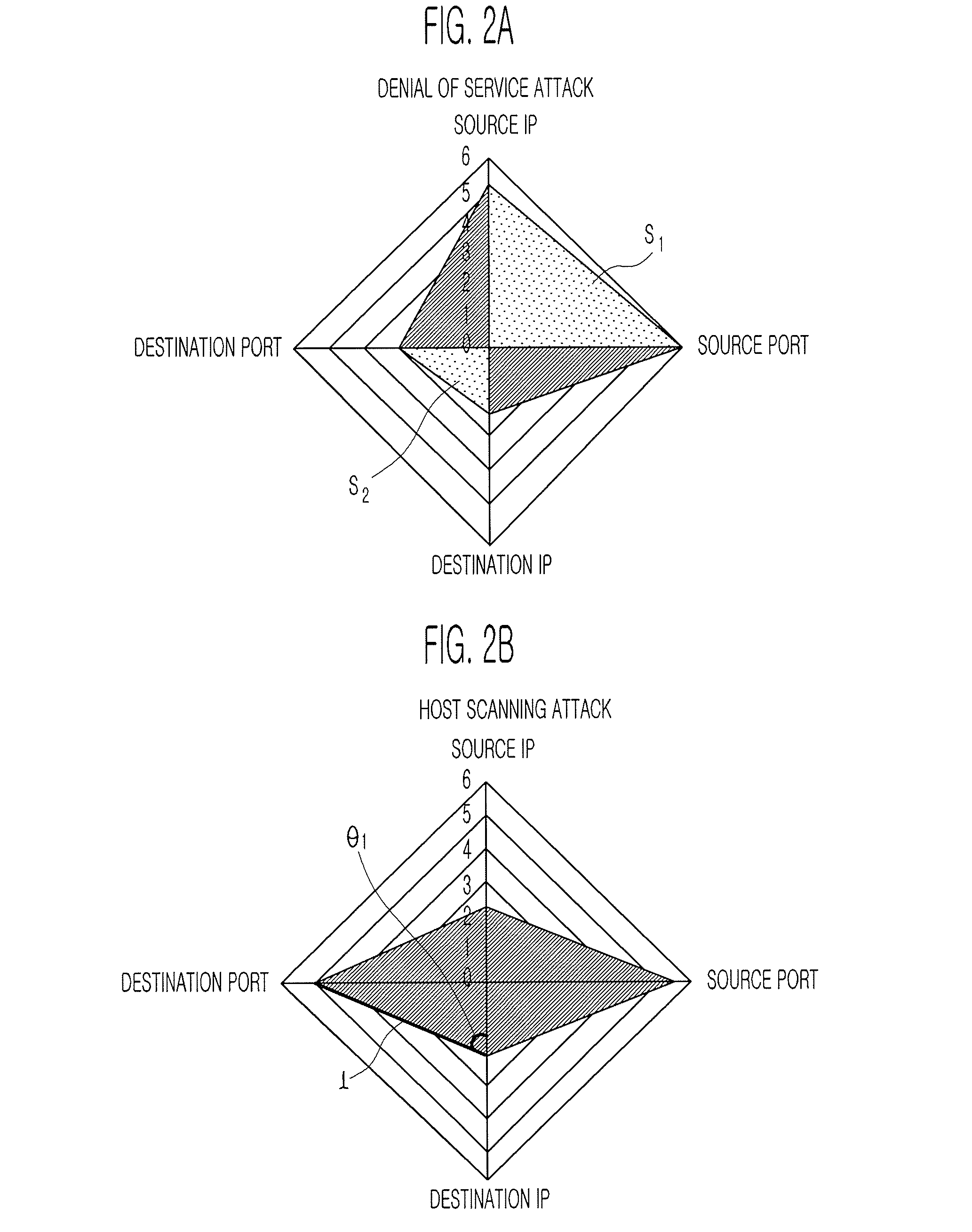
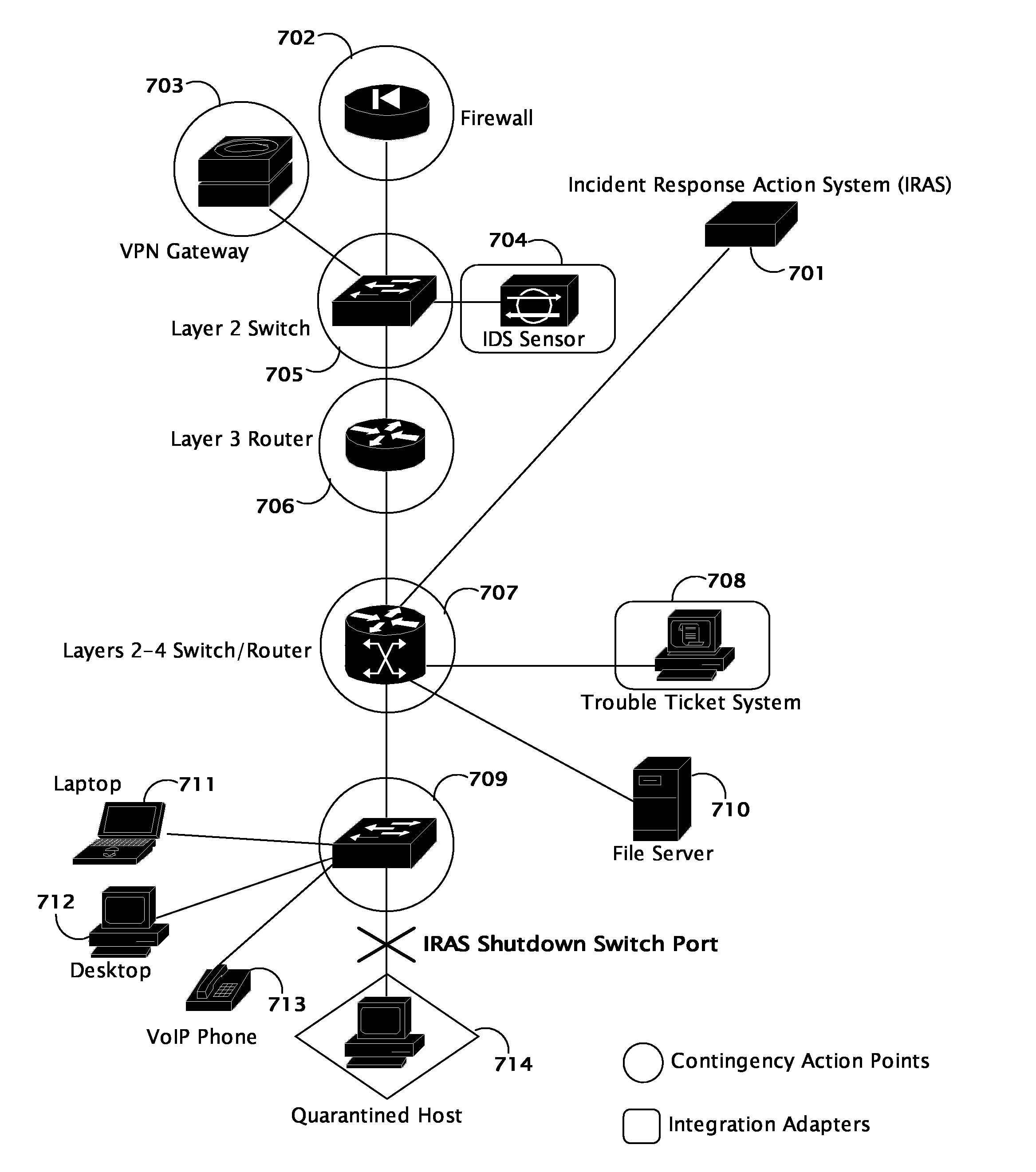
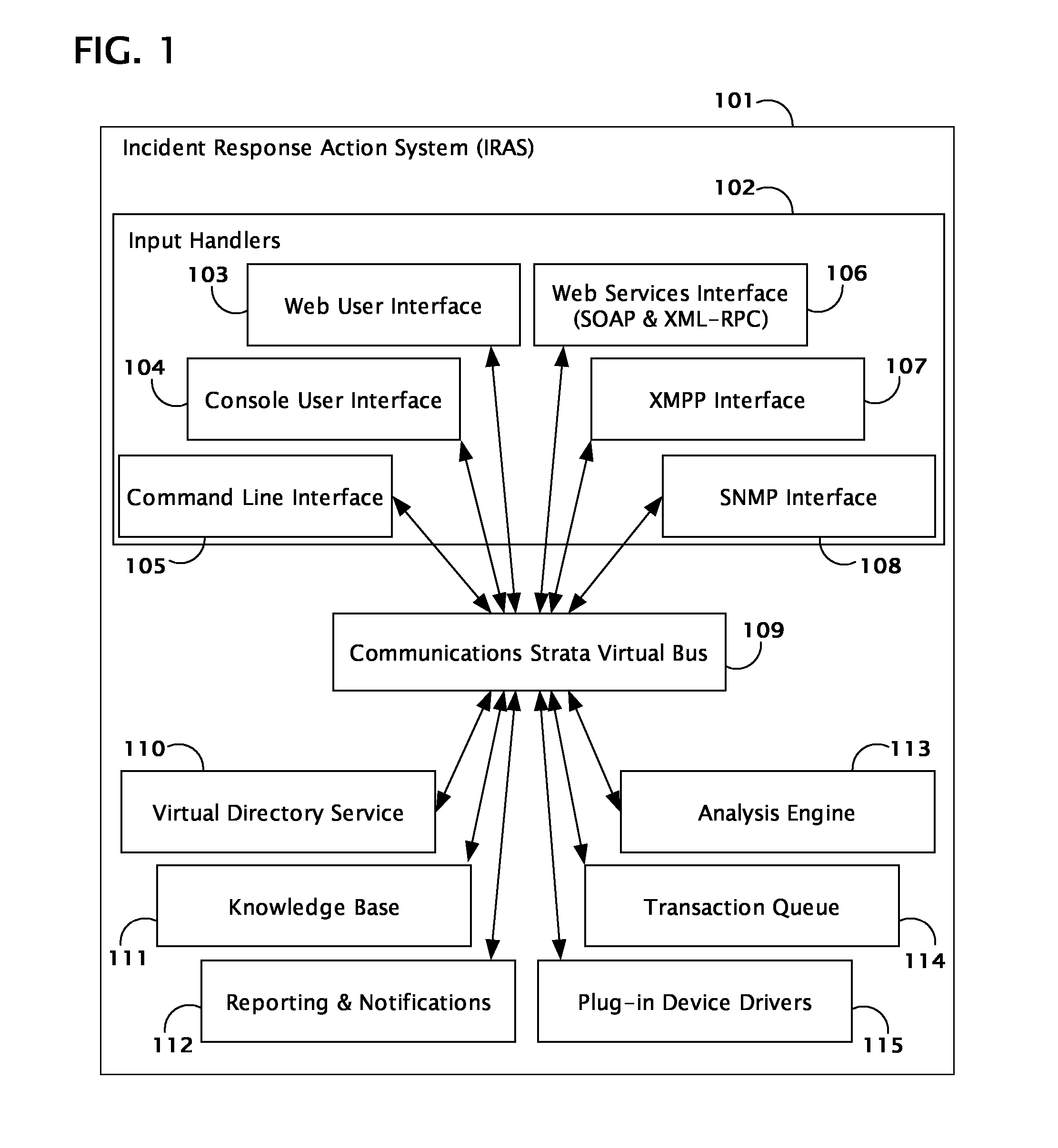
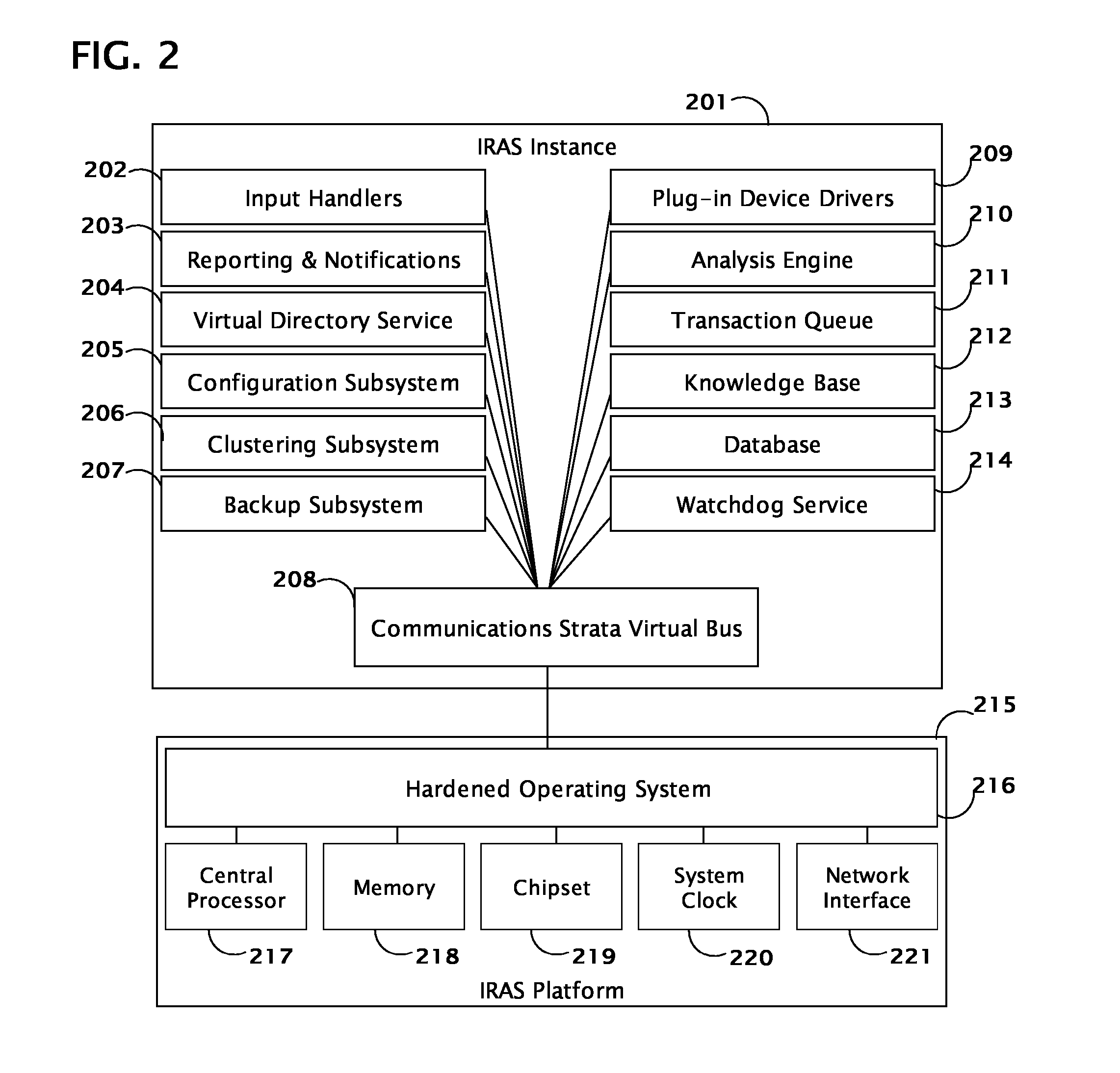
System and method for coordinating network incident response activities
ActiveUS20060212932A1Improve responseReduce decreaseMemory loss protectionError detection/correctionCountermeasureNetwork connection
The present invention provides a system and method to process information regarding a network attack through an automated workflow that actively reconfigures a plurality of heterogeneous network-attached devices and applications to dynamically counter the attack using the network's own self-defense mechanisms. The present invention leverages the security capabilities present within existing and new network-attached devices and applications to affect a distributed defense that immediately quarantines and / or mitigates attacks from hostile sources at multiple points simultaneously throughout the network. In a preferred embodiment, deployed countermeasures are automatically lifted following remediation activities.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Apparatus and method for monitoring network using the parallel coordinate system
InactiveUS20070044147A1Data switching by path configurationMultiple digital computer combinationsData packNetwork attack
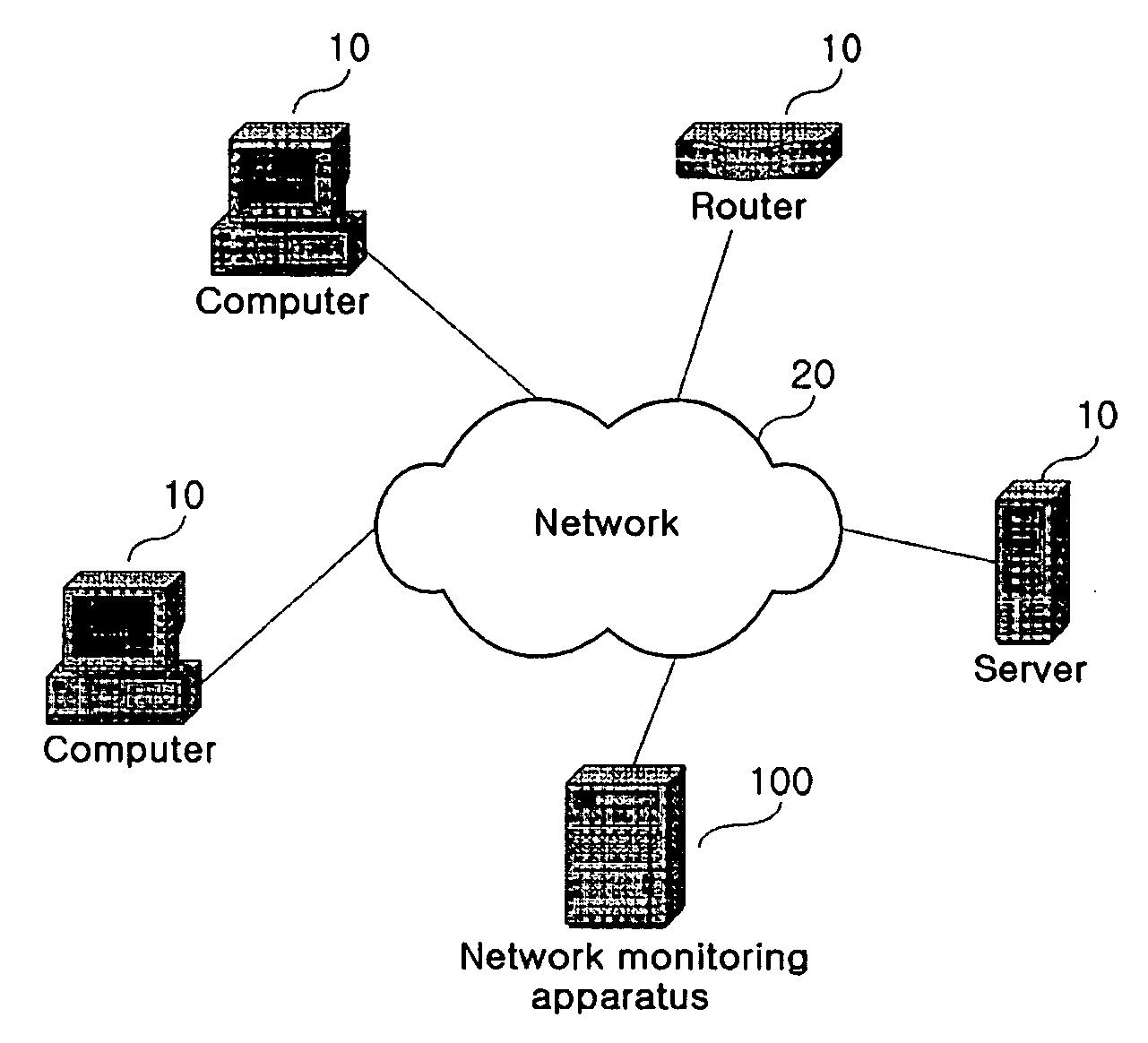
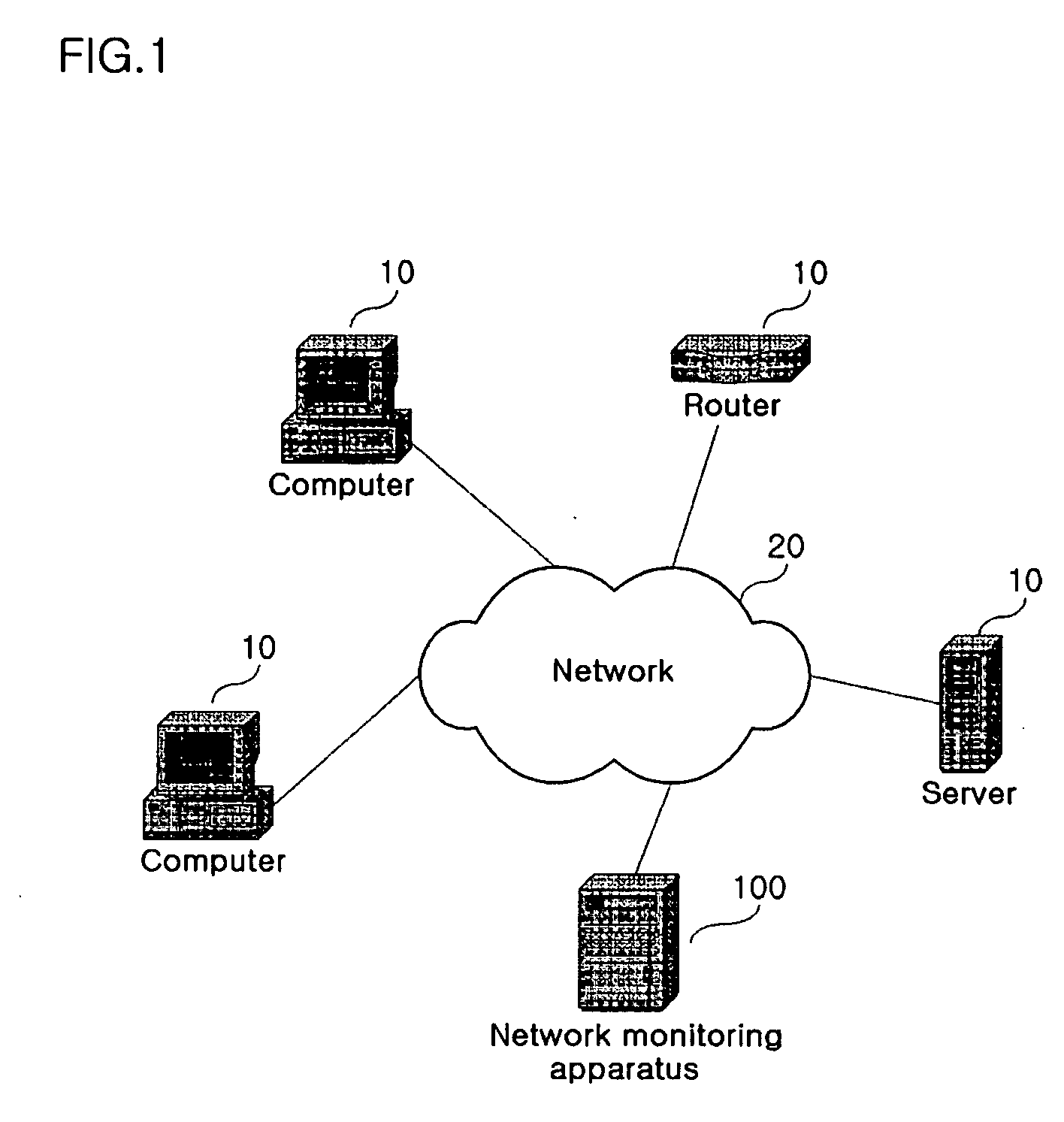
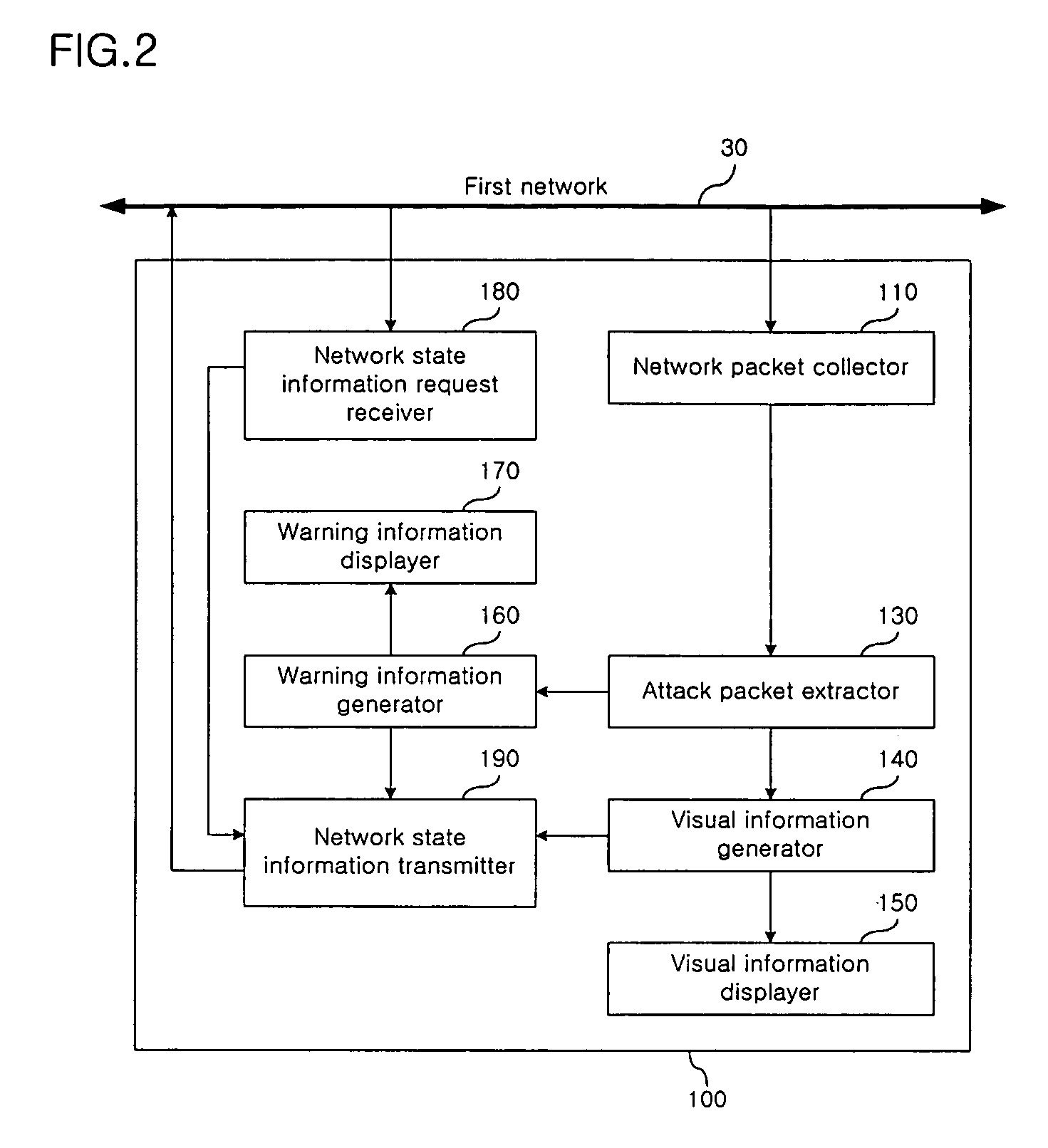
A network monitoring apparatus collects packets of a first network, and generates visual information by displaying the packets on a parallel coordinate system which has one or more parallel axis for parameters of the packets. The network monitoring apparatus may extract attack packets from the packet, and the network monitoring apparatus may transmit the visual information to a remote server. Through the network monitoring apparatus, the network manager can visually grasp the state of the network or the existence of a network attack.
Owner:KOREA UNIV IND & ACAD COLLABORATION FOUNDATION
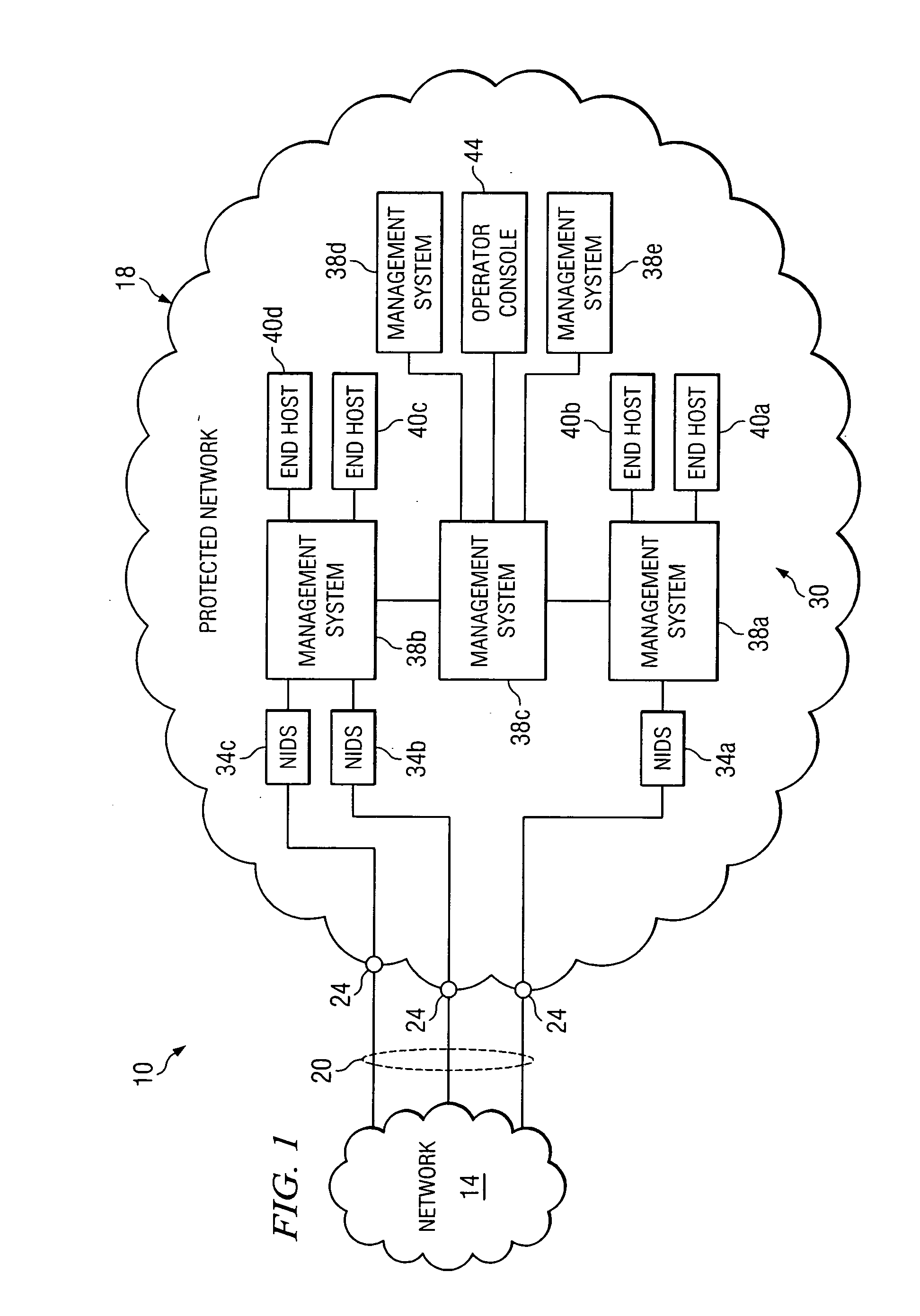
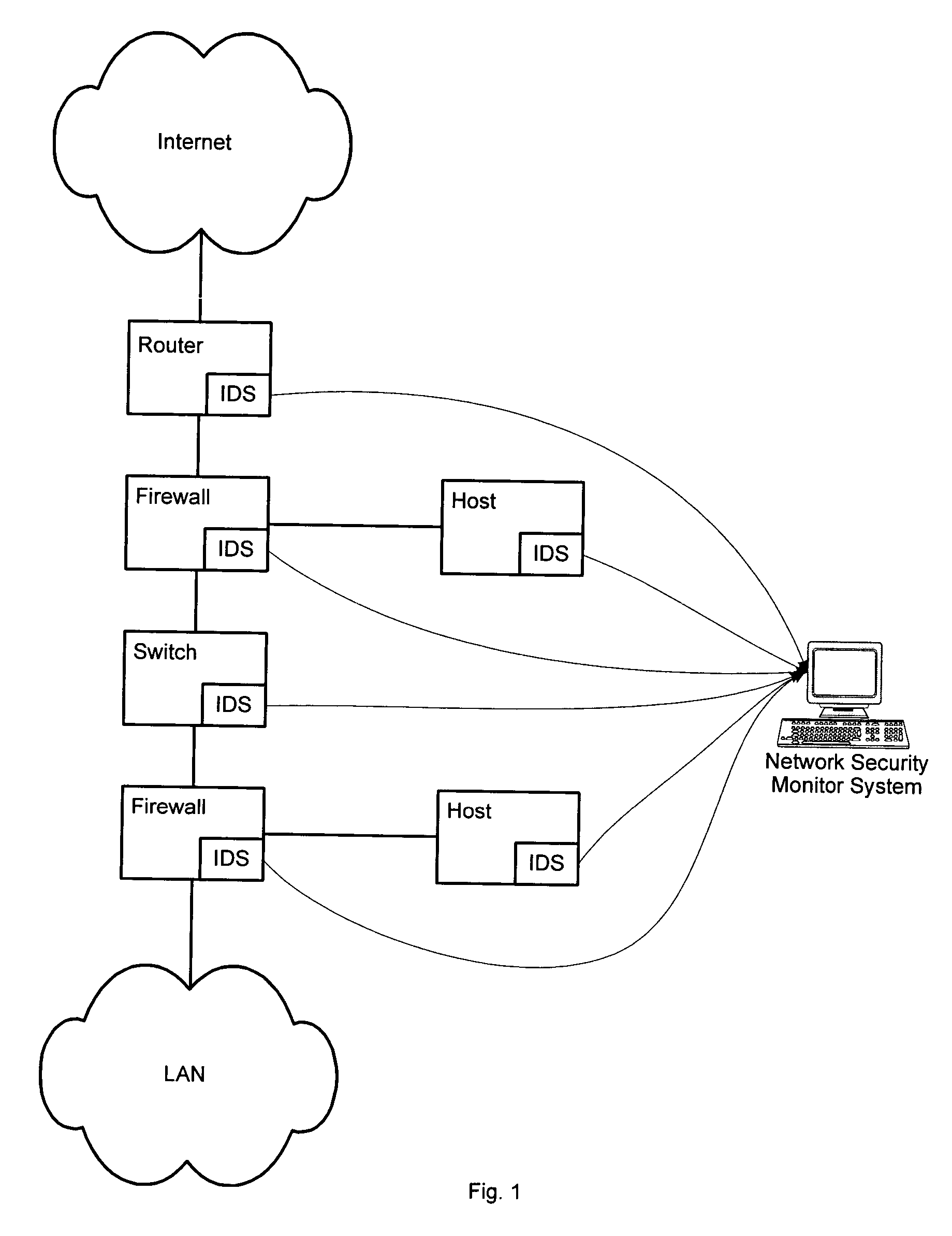
Method and system for displaying network security incidents
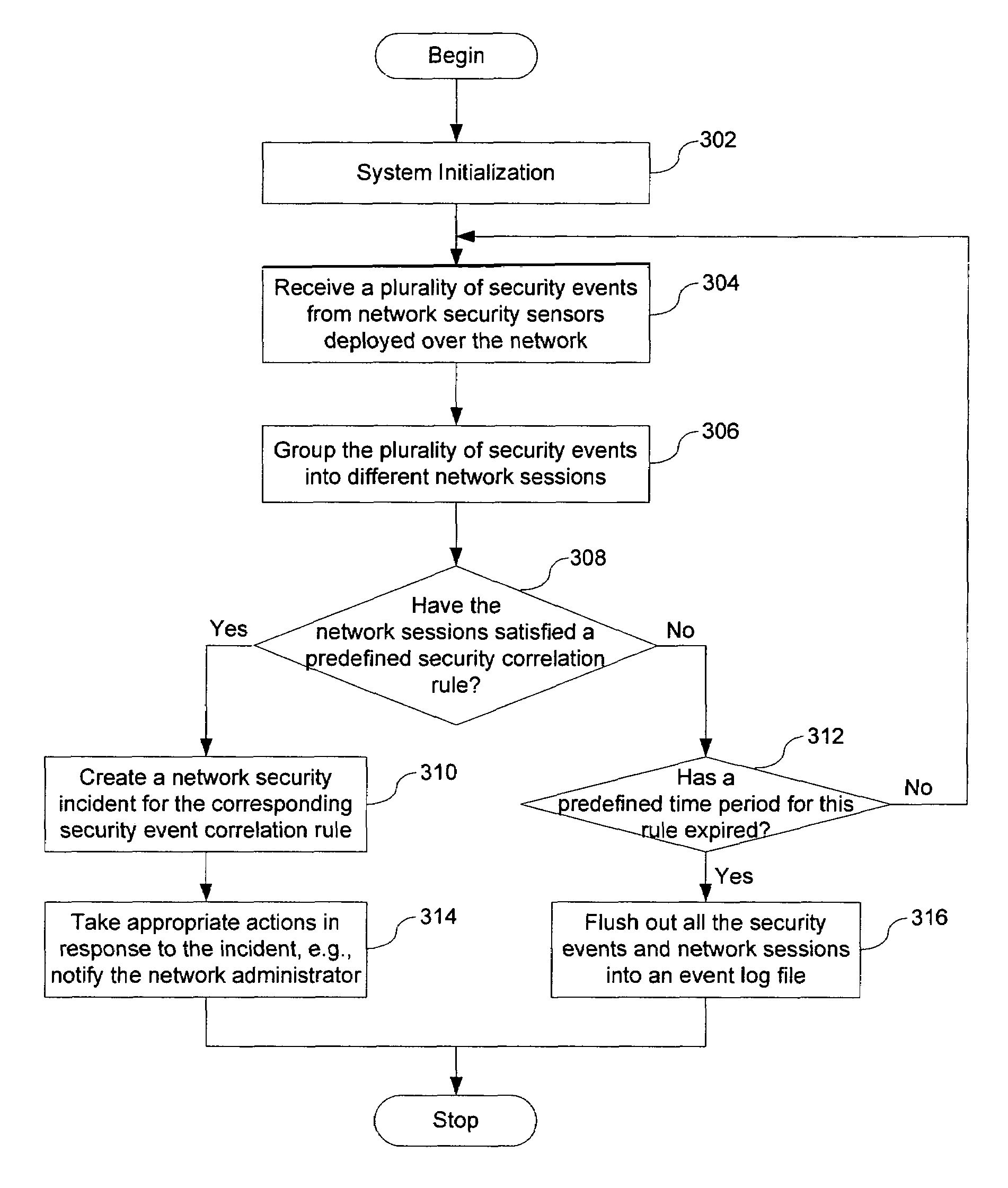
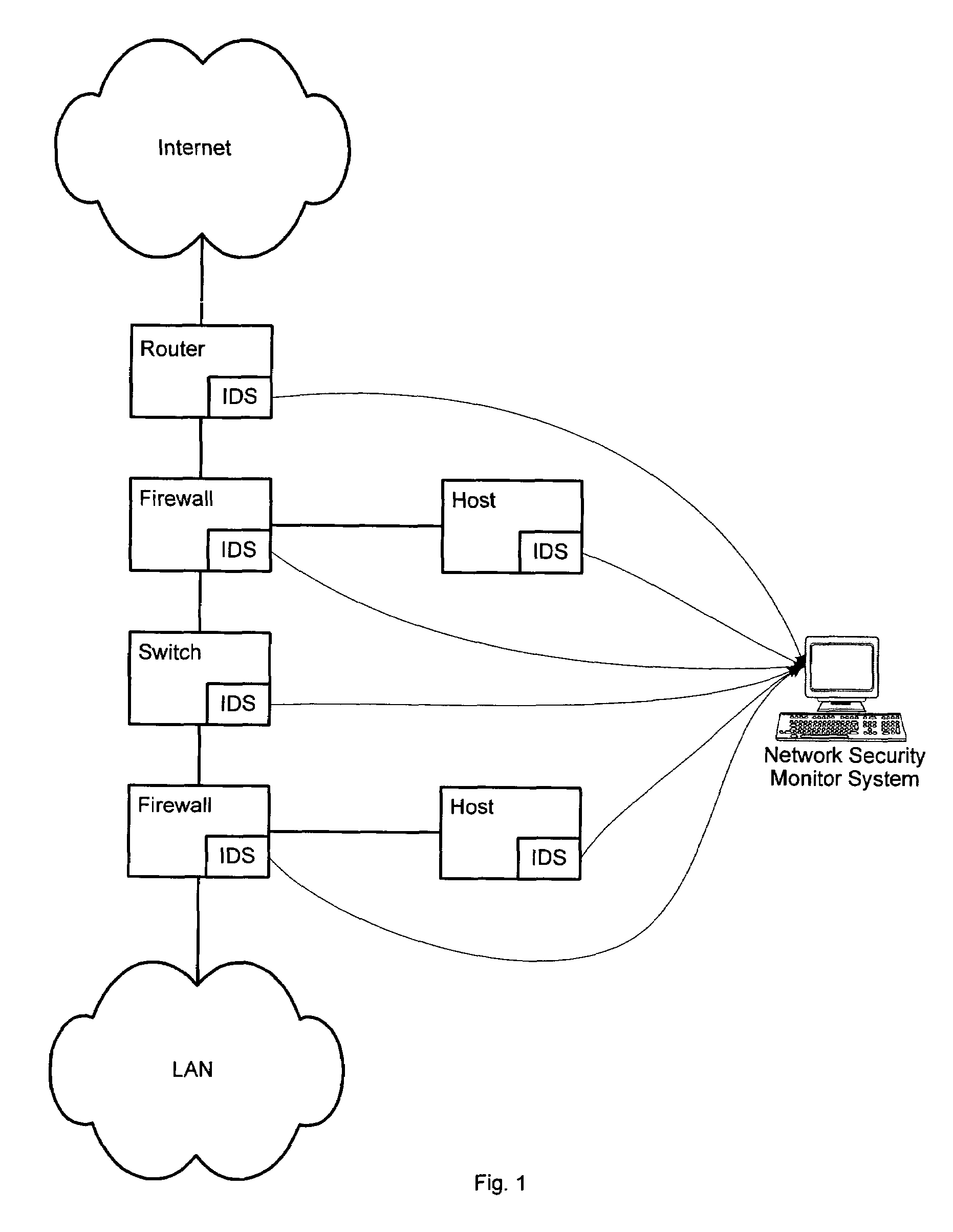
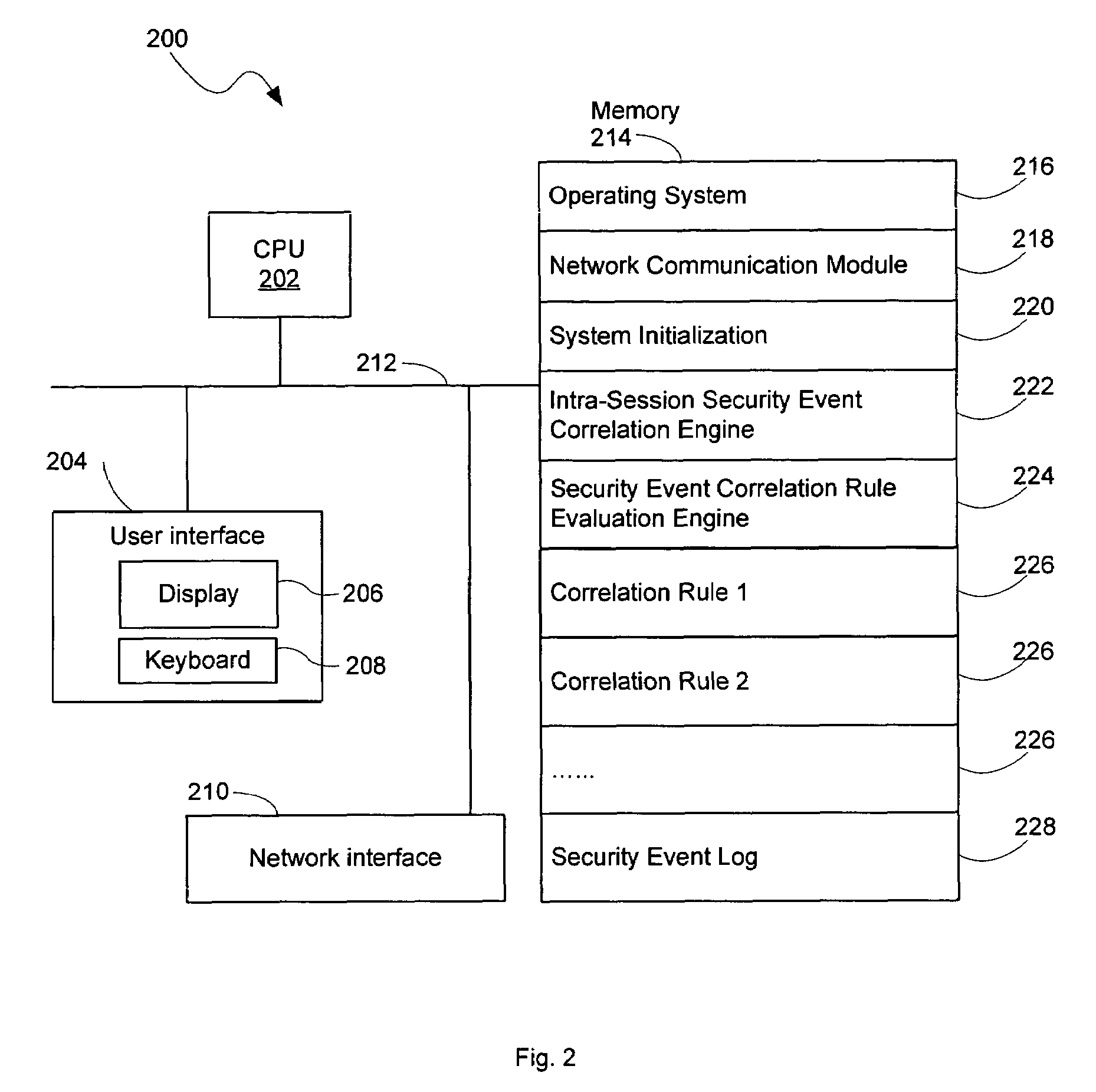
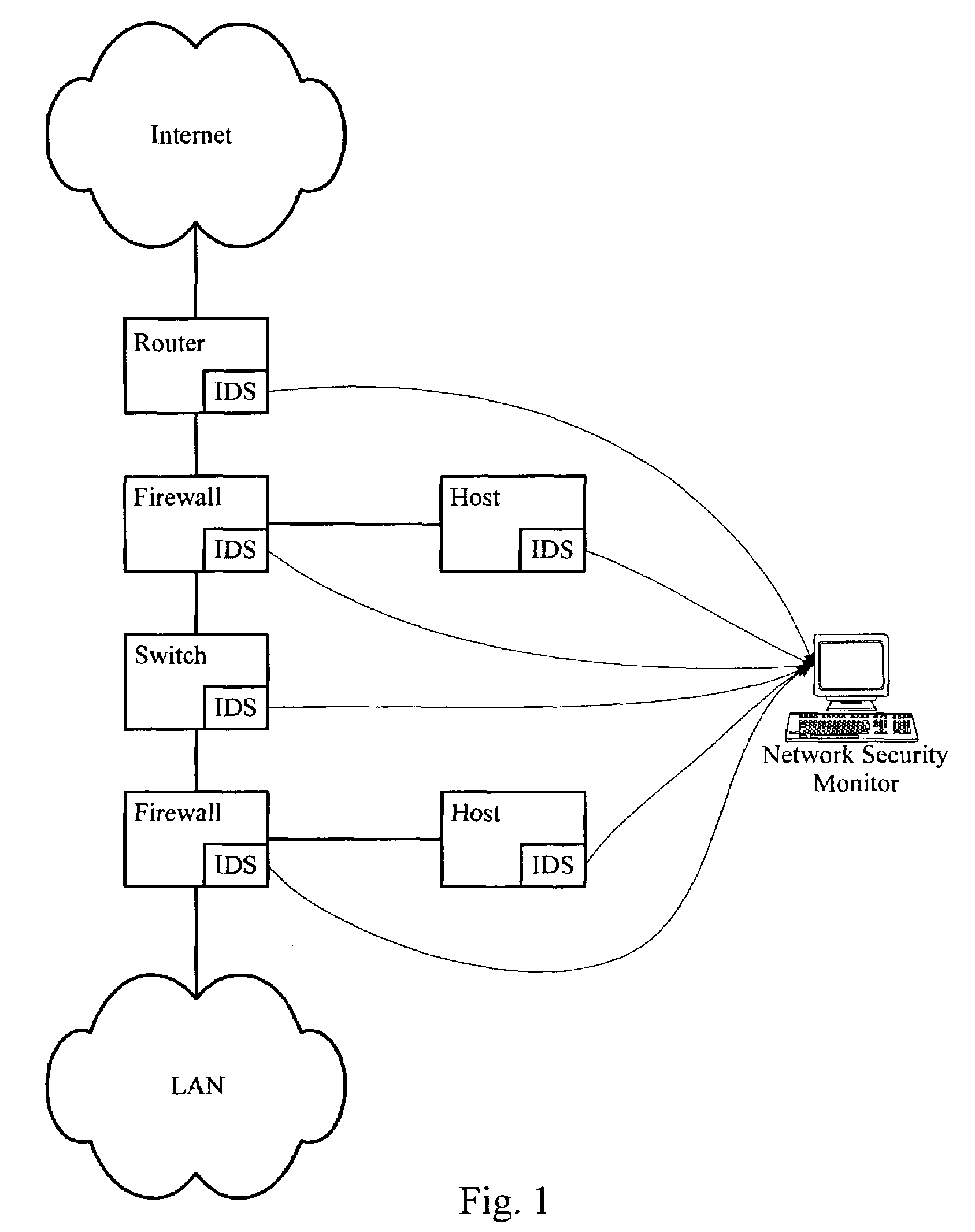
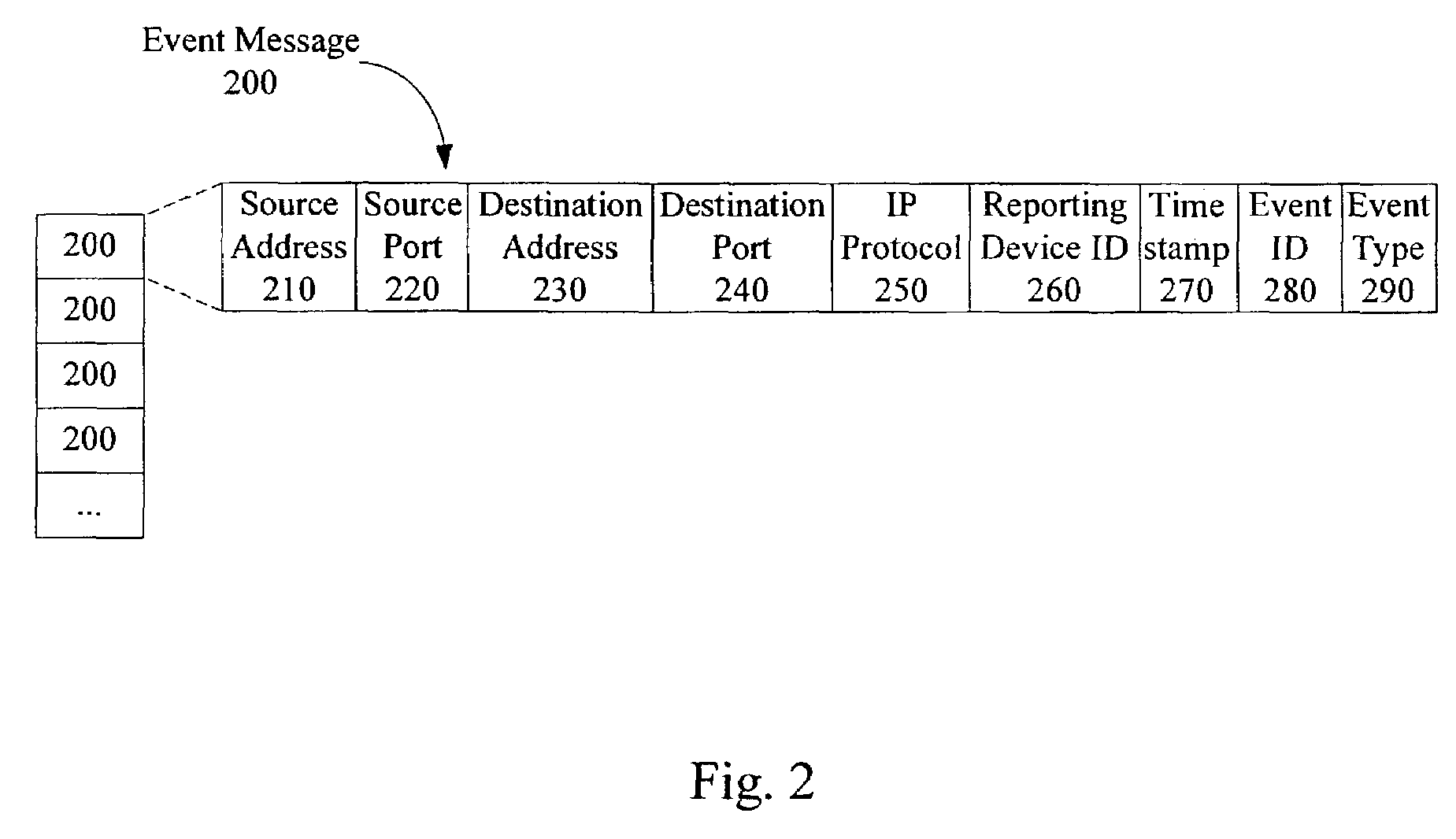
InactiveUS20050060562A1Digital data processing detailsDigital computer detailsNetwork attackSafety monitoring
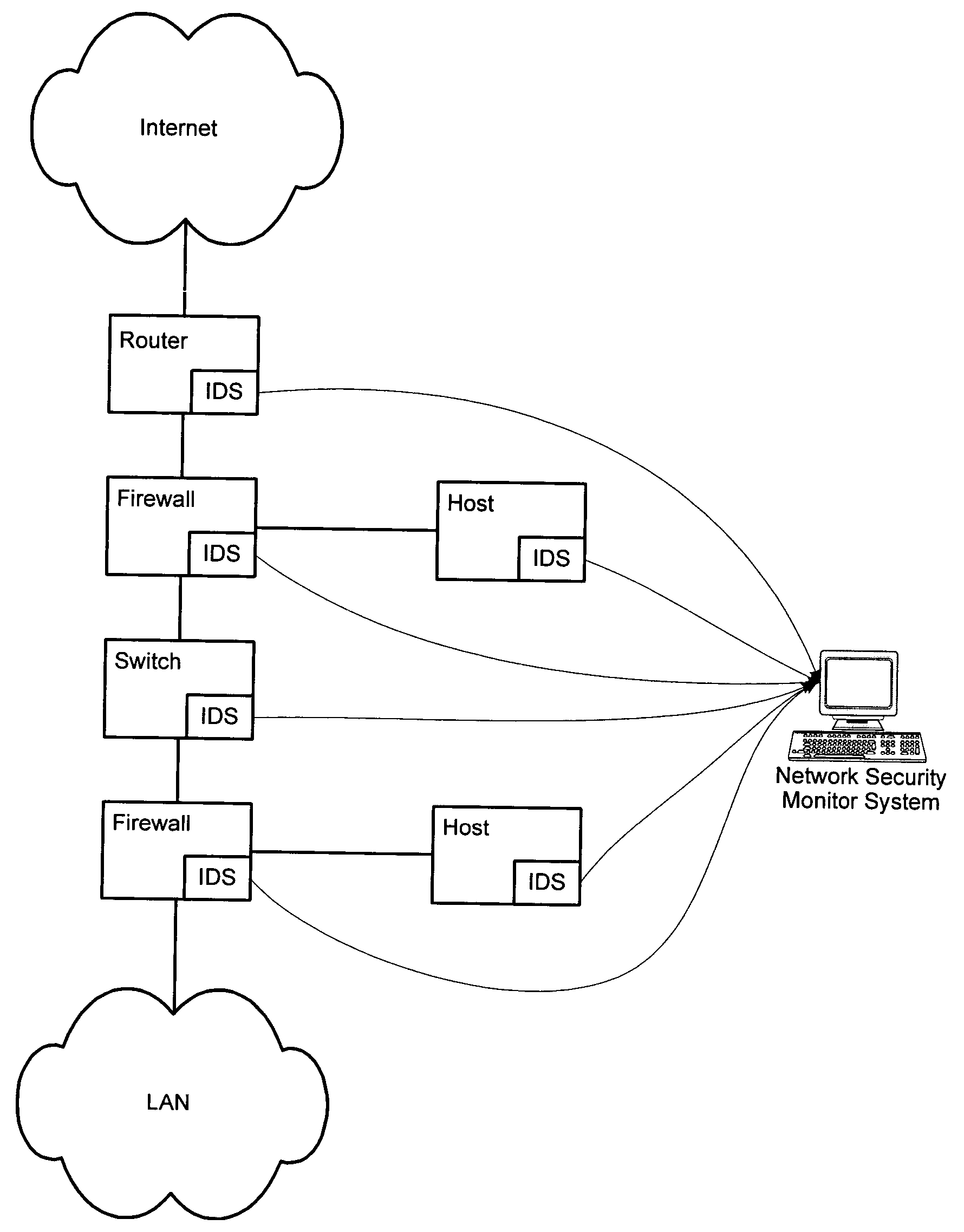
A network security monitor system groups a plurality of security events into network sessions, correlates the network sessions according to a set of predefined network security event correlation rules and generates a security incident for the network sessions that satisfy one of the network security event correlation rules. The system then presents the information of the network sessions and security incidents to a user of the system in an intuitive form. The user is able to not only learn the details of a possible network attack, but also creates new security event correlation rules intuitively, including drop rules for dropping a particular type of events.
Owner:CISCO TECH INC
Denial of service (DOS) attack detection systems and methods
ActiveUS20150007314A1Memory loss protectionError detection/correctionNetwork attackDenial-of-service attack
Methods, systems, and apparatus that enable identification of network attacks such as denial of service attacks are disclosed. A network attack may be identified by monitoring packets received for delivery to devices on a network, and developing a historic packet profile by examining the monitored packets received during a number of time periods preceding an instant time period. An instant packet profile is developed by examining the monitored packets during the instant time period. The instant packet profile is compared to the historic packet profile to determine whether a deviation exceeding a predetermined statistical threshold deviation between the instant packet profile and the historic packet profile is present. The existence of a network attack is identified in response to determining that the deviation exceeds the predetermined statistical threshold deviation.
Owner:CELLCO PARTNERSHIP INC
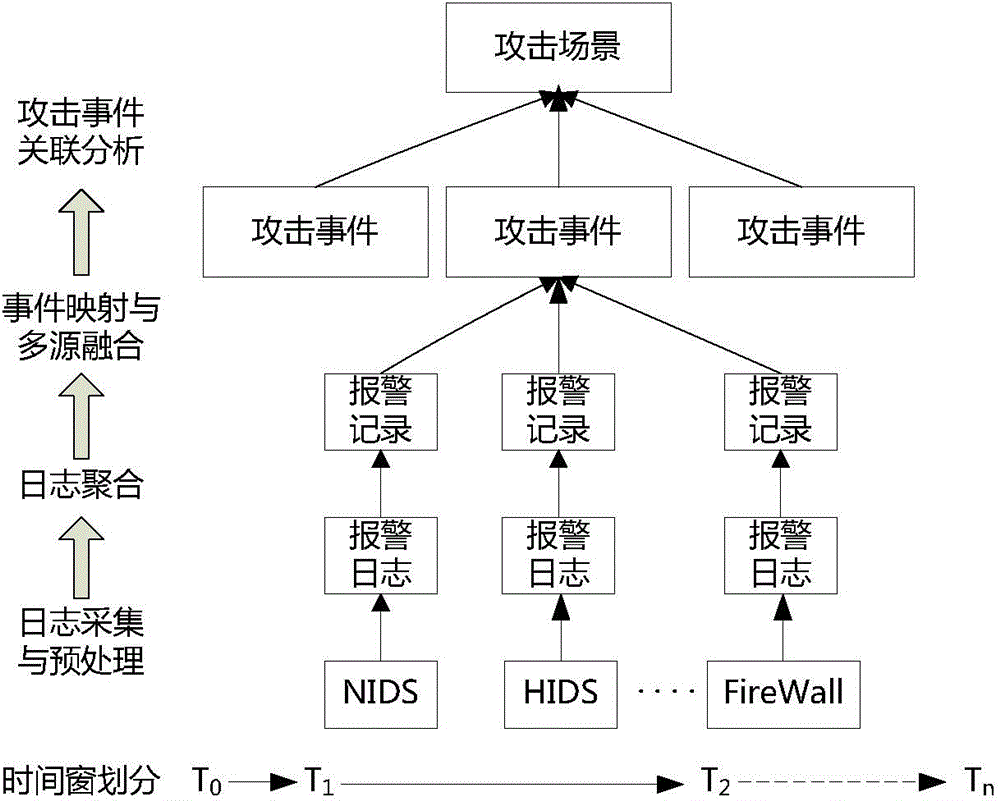
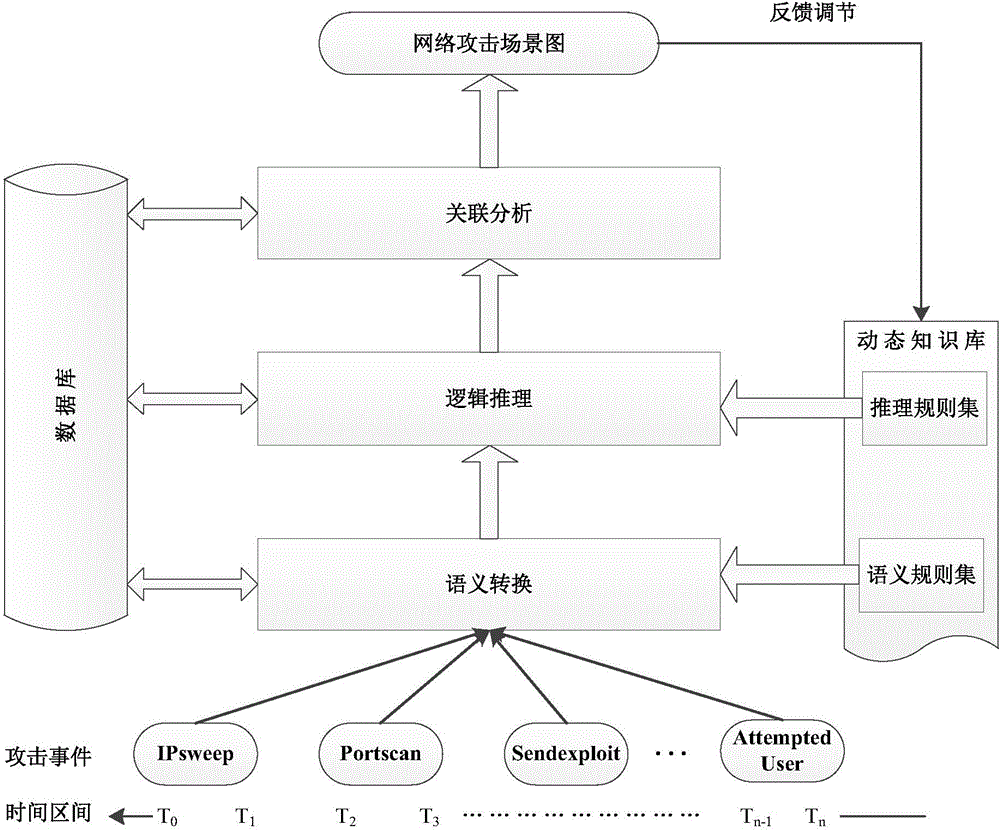
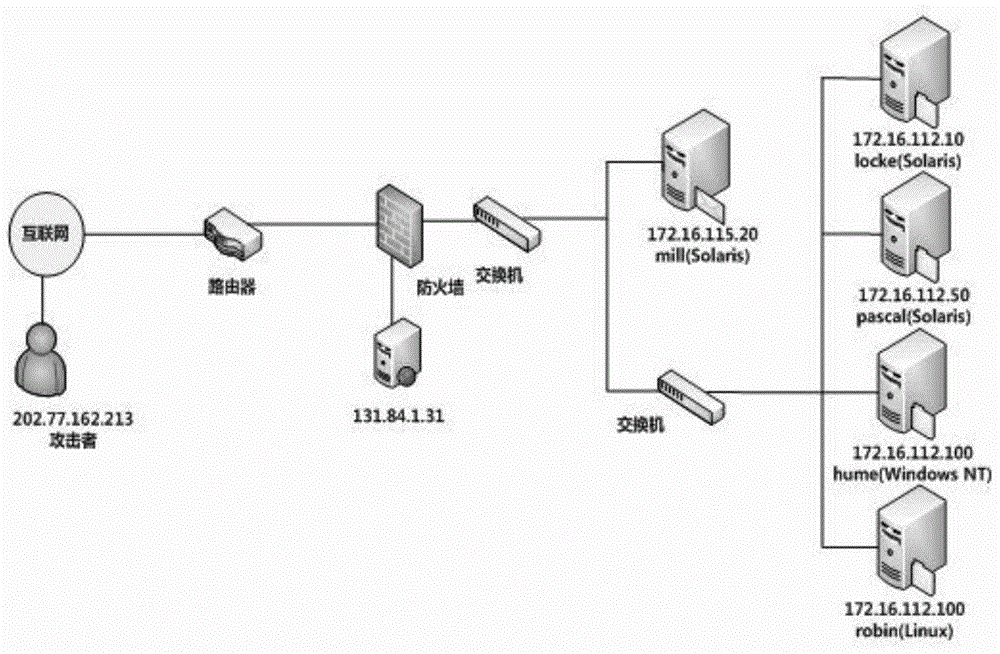
Network attack scene generating method based on multi-source alarm logs
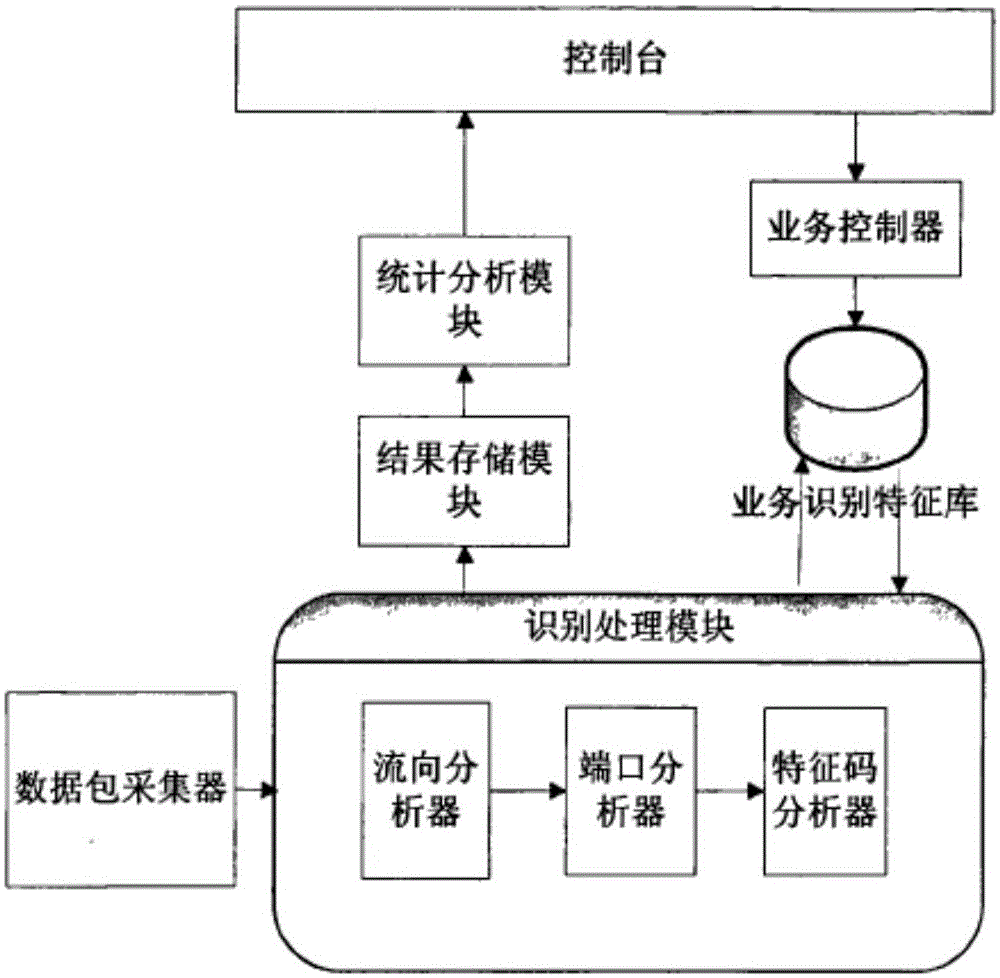
InactiveCN104539626AReflects security threat statusShow intentData switching networksCorrelation analysisNetwork attack
The invention relates to a network attack scene generating method based on multi-source alarm logs. The network attack scene generating method includes the steps that firstly, the alarm logs generated by multiple network security protection devices are collected, effective alarm log data are extracted through preprocessing, and noise, redundancy or ineffective logs are removed; for the effective alarm logs acquired by one device, log format differences of different devices are shielded through single-source log aggregation and mapping, and attack event information is analyzed and extracted; attack events extracted from different sources are fused and analyzed, and network attack events with high credibility are generated; then through correlation analysis of the attack events, a network attack scene graph is generated, and the whole attack process of one attack operation is analyzed. Due to the fact that the multi-source logs are fused, the analyzed attack event information can more completely and more reliably depict attacks to which a network is subject, attack scenes are acquired through correlation analysis of the attack events, the intentions of attackers can be more clearly shown, and the security threat state of the network can be more clearly reflected.
Owner:THE PLA INFORMATION ENG UNIV
System and method for simulating computer network attacks
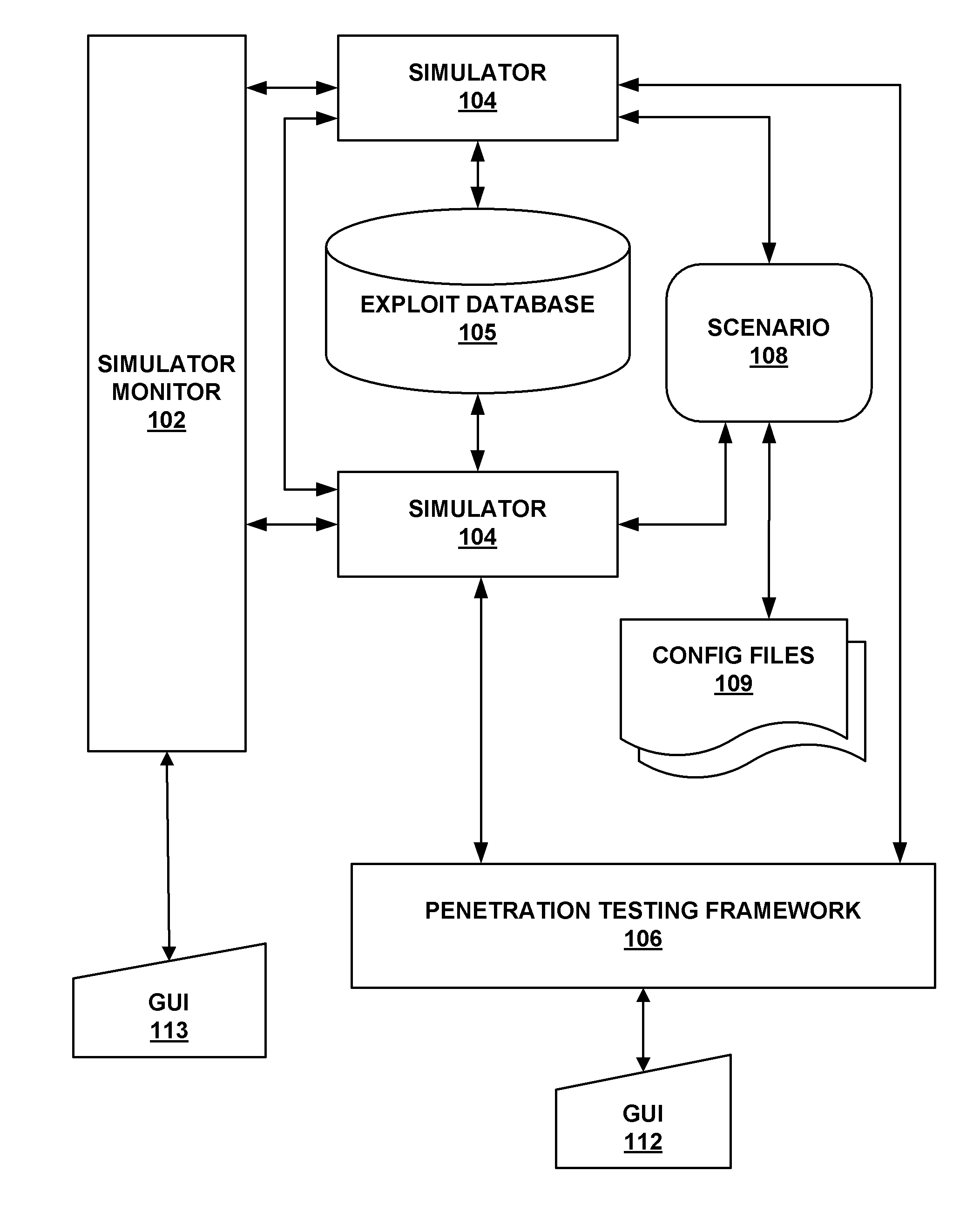
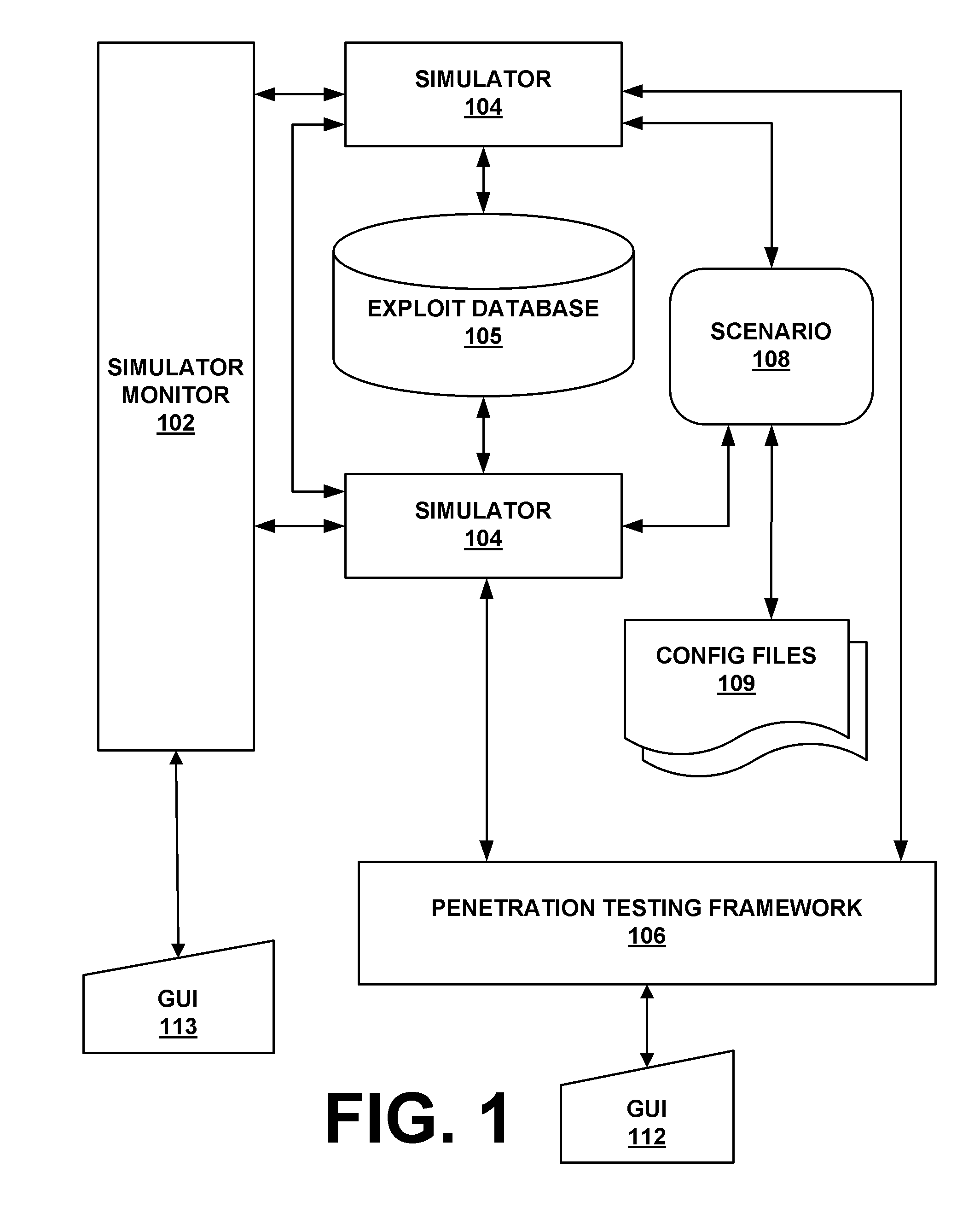
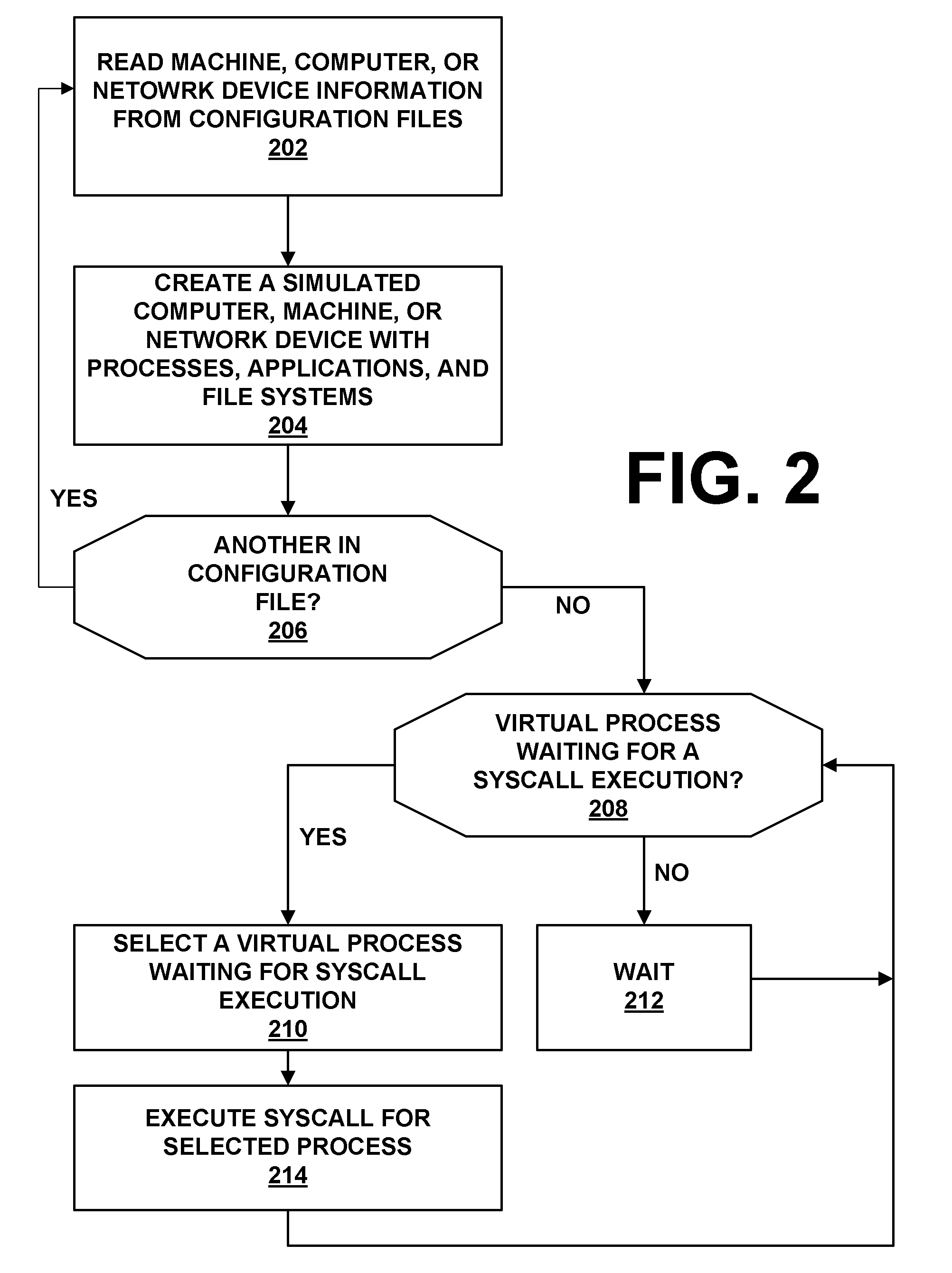
ActiveUS20090007270A1Memory loss protectionError detection/correctionOperational systemNetwork agent
The present invention provides a system and method for providing computer network attack simulation. The method includes the steps of: receiving a network configuration and setup description; simulating the network configuration based on the received network configuration; receiving at least one confirmed vulnerability of at least one computer, machine, or network device in the simulated network; receiving a method for compromising the confirmed vulnerability of the at least one computer, machine, or network device; and virtually installing a network agent on the at least one computer, machine, or network device, wherein the network agent allows a penetration tester to execute arbitrary operating system calls on the at least one computer, machine, or network device.
Owner:FORTRA LLC
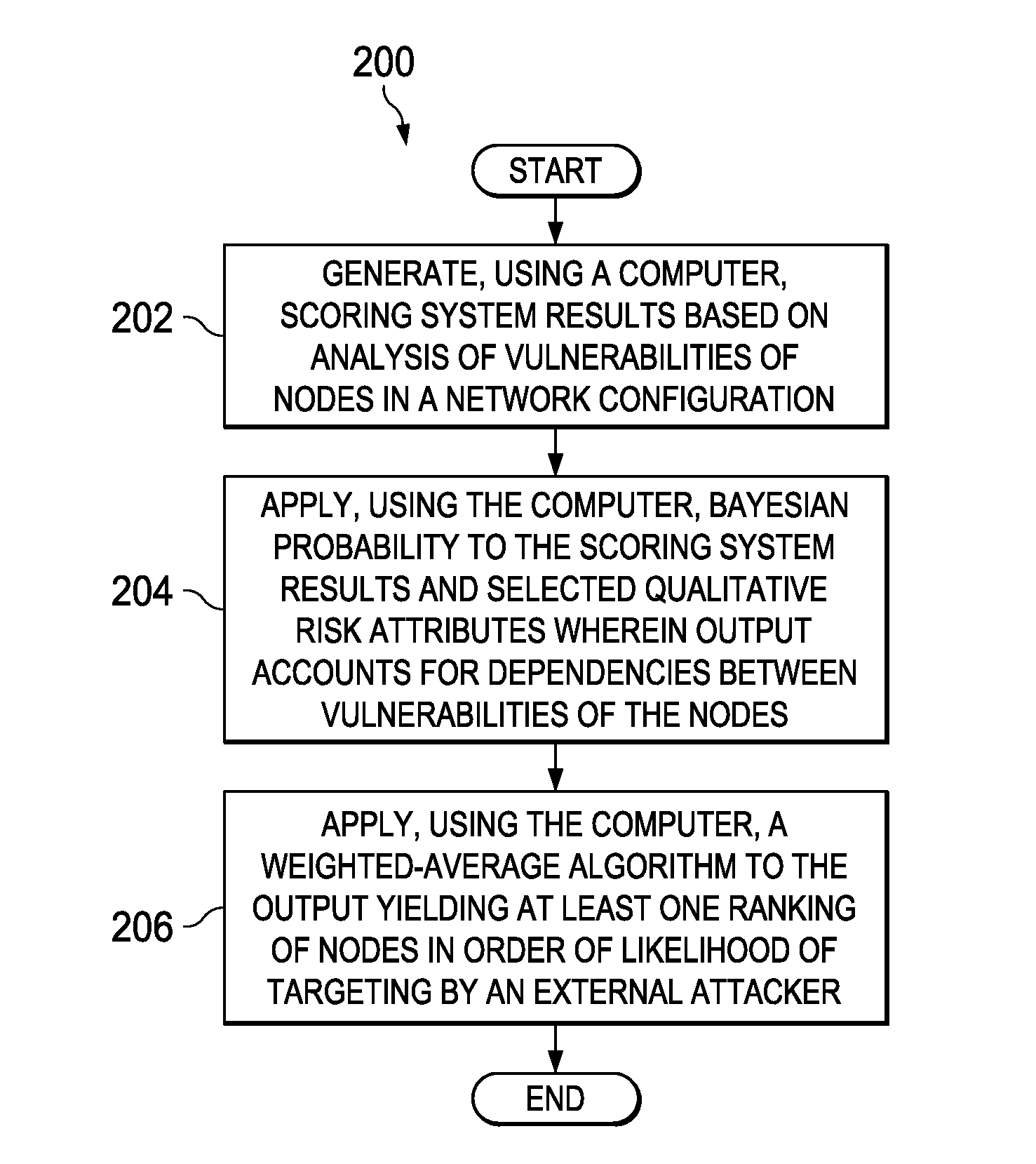
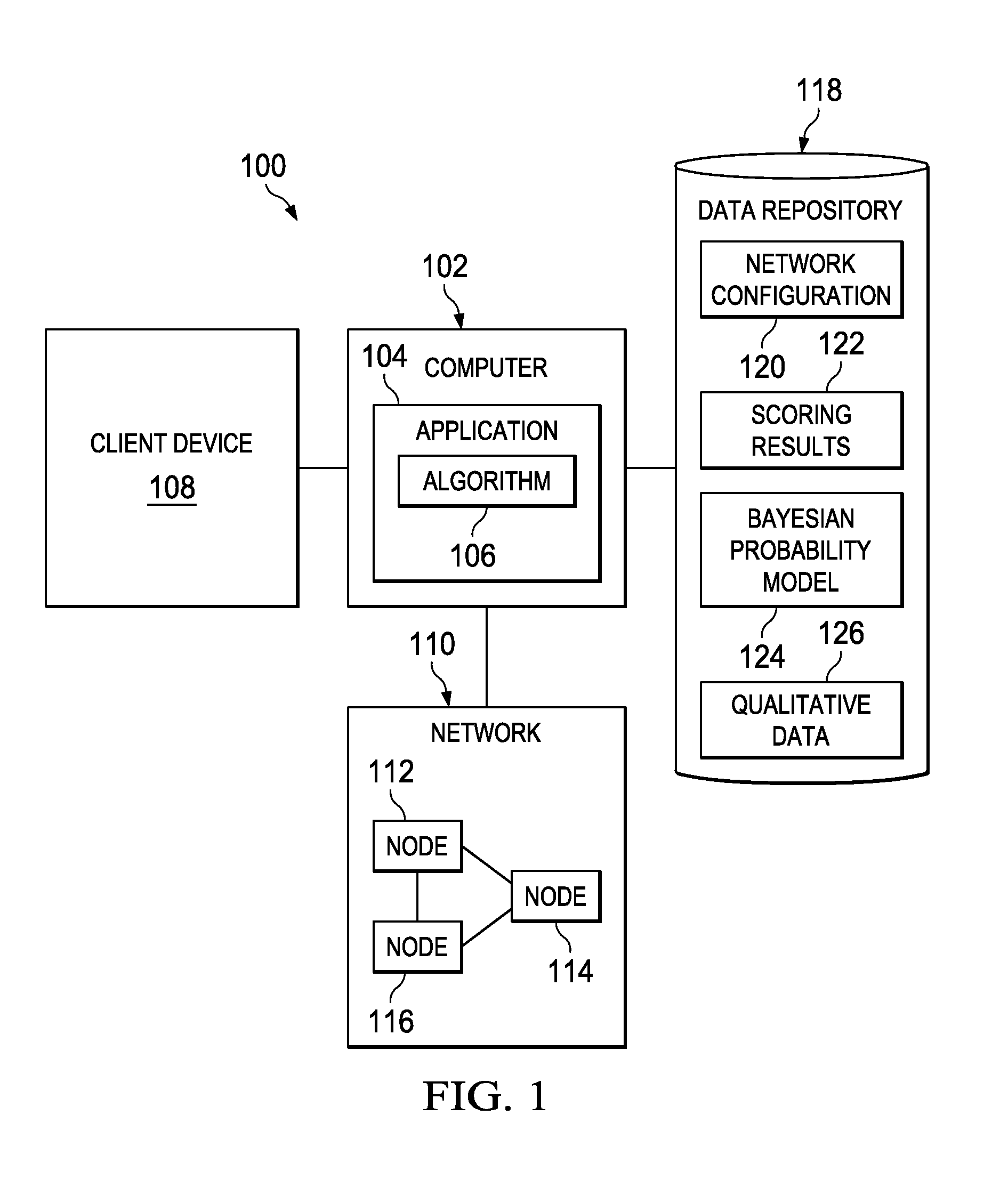
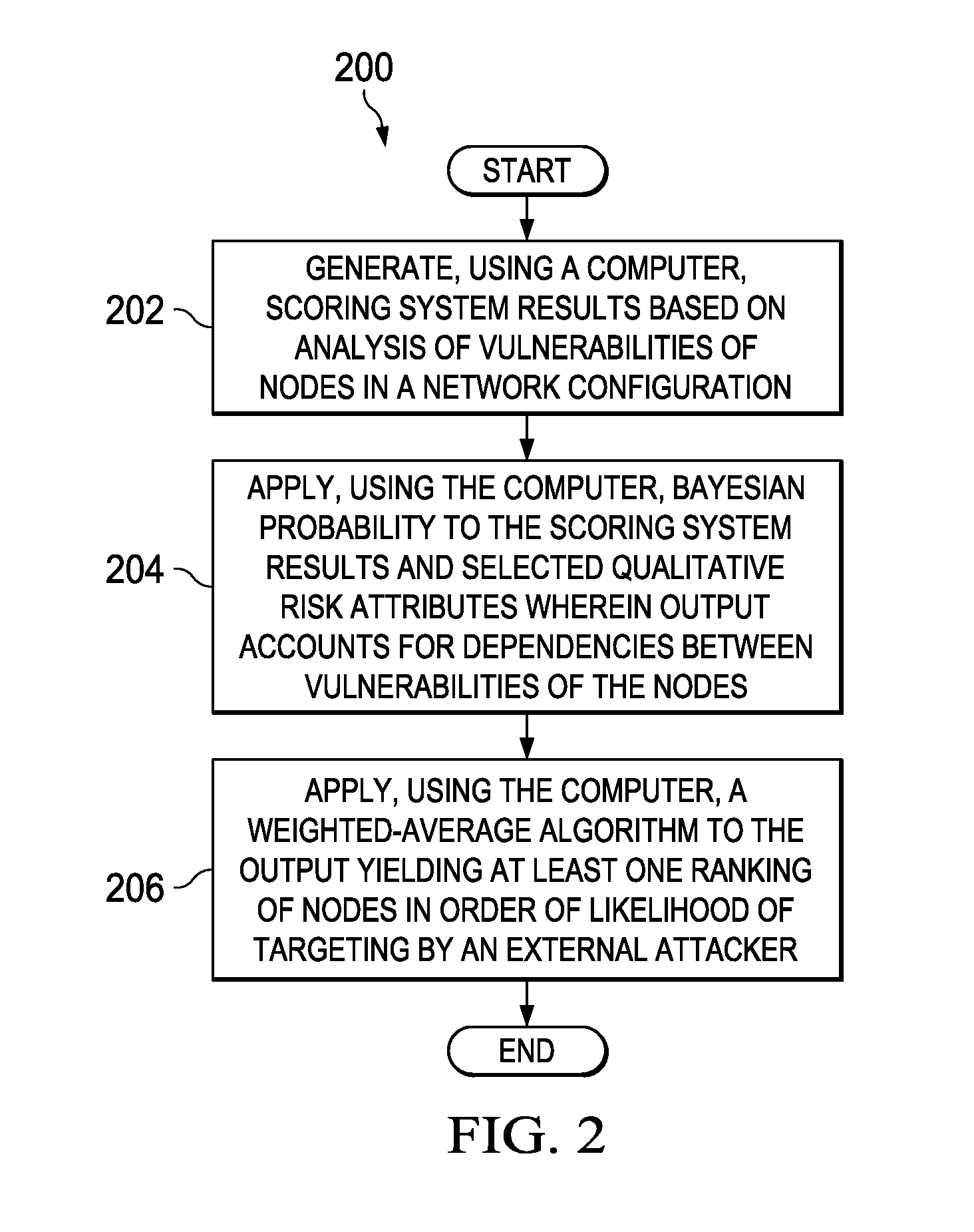
System and method for discovering optimal network attack paths
A computer-implemented method for discovering network attack paths is provided. The method includes a computer generating scoring system results based on analysis of vulnerabilities of nodes in a network configuration. The method also includes the computer applying Bayesian probability to the scoring system results and selected qualitative risk attributes wherein output accounts for dependencies between vulnerabilities of the nodes. The method also includes the computer applying a weighted-average algorithm to the output yielding at least one ranking of nodes in order of likelihood of targeting by an external attacker.
Owner:THE BOEING CO
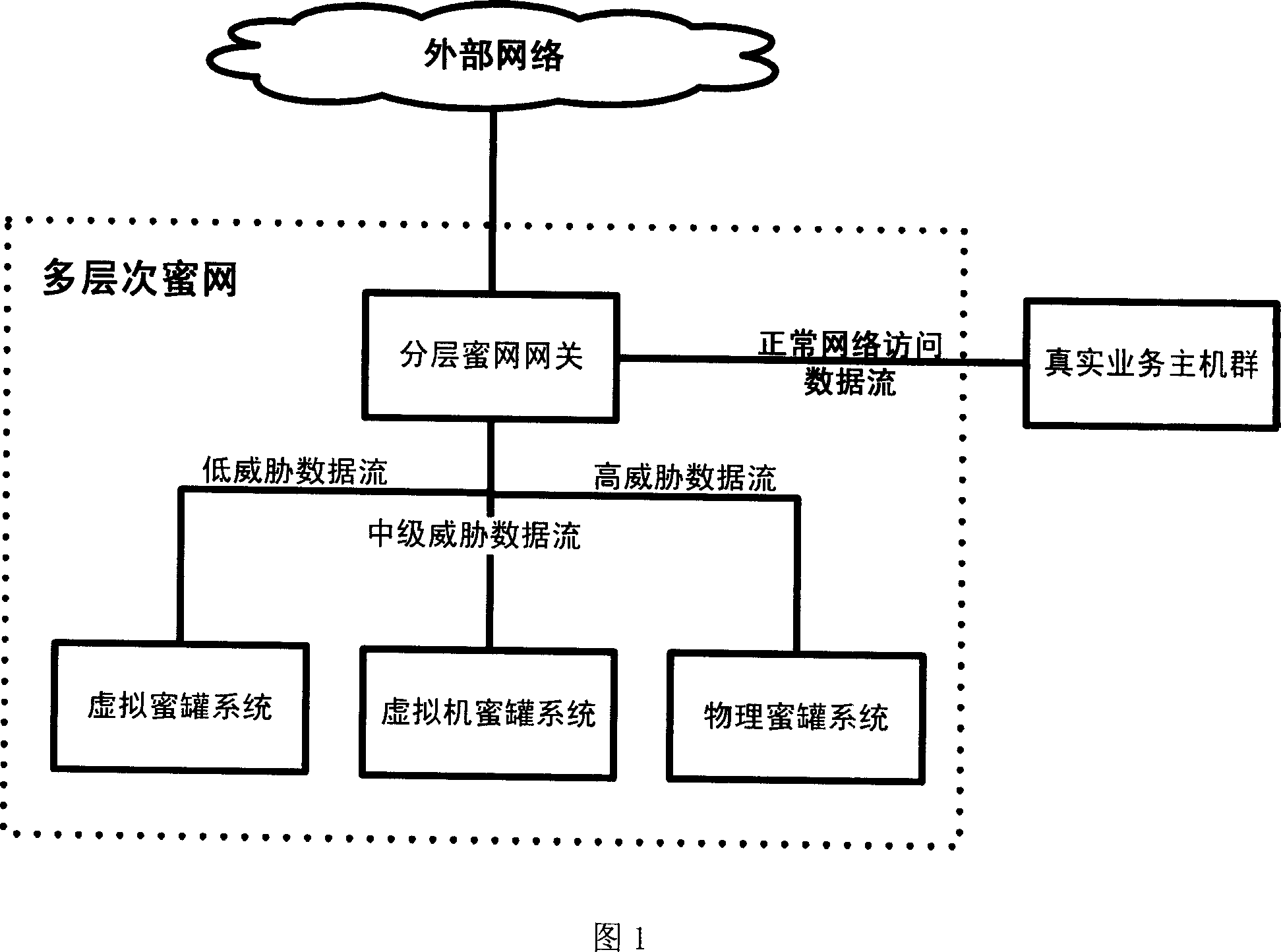
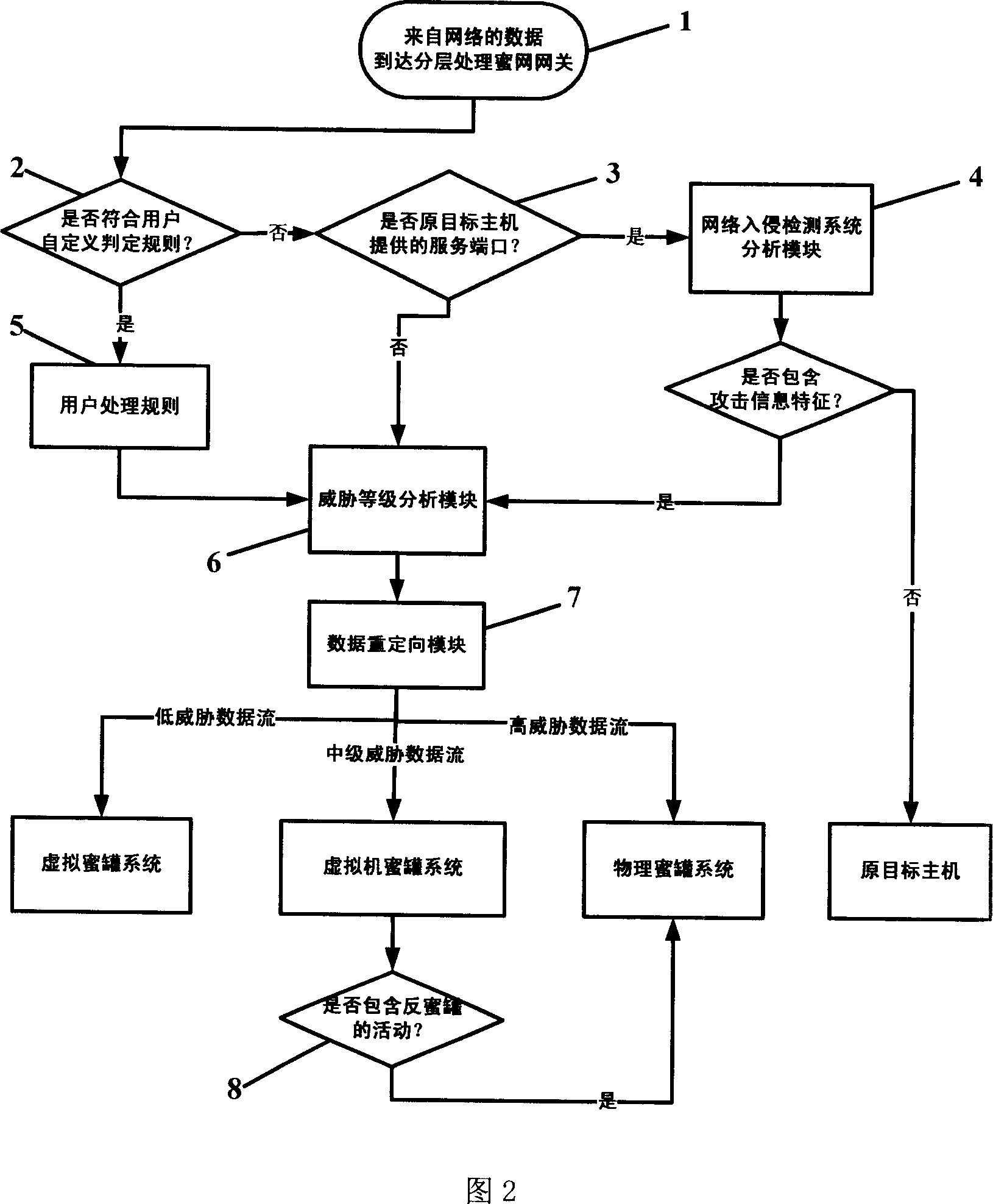
Multi-layer honey network data transmission method and system
InactiveCN101087196AIncrease reachSave resourcesNetwork connectionsSecuring communicationData streamNonnormal data
The invention relates to multilayer honey-net data transmission method and system, and the gateway of honey-net receives the data flow of external network; the gateway of honey-net detects the network intrusion for the received data flow; the normal data flow can pass, which is sent to the target host computer; and the informal data flow is divide into high, middle and low according to dangerous level; and the data flow with high level is sent to physical honey-tank system, the data flow with middle level is sent to virtual machine honey-tank system, and the data floe with low level is sent to virtual honey-tank system. The invention can utilize the advantages of low interactive honey-tank system and high interactive honey-tank system, save system source, and improve the covering area of honey-tank system and the ability of obtaining the movable information of network attack and capturing the malice code; it can defeat the anti-honey tank technique. And it can be used in security field of computer network.
Owner:PEKING UNIV
Method and system for displaying network security incidents
InactiveUS7644365B2Digital data processing detailsDigital computer detailsNetwork attackEvent correlation
A network security monitor system groups a plurality of security events into network sessions, correlates the network sessions according to a set of predefined network security event correlation rules and generates a security incident for the network sessions that satisfy one of the network security event correlation rules. The system then presents the information of the network sessions and security incidents to a user of the system in an intuitive form. The user is able to not only learn the details of a possible network attack, but also creates new security event correlation rules intuitively, including drop rules for dropping a particular type of events.
Owner:CISCO TECH INC
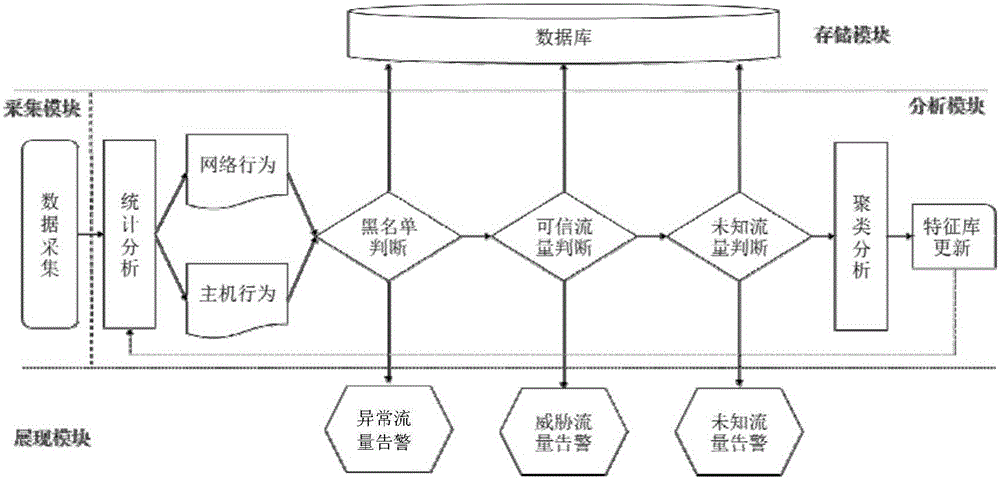
Method and system for detecting network security threat based on trusted business flow
The invention discloses a method and a system for detecting a network security threat based on trusted business flow. The method comprises the following steps of establishing a blacklist and a white list of network flow and constructing a baseline model, wherein the white list is the trusted business flow and is a feature contour library of normal network behavior and host behavior; comparing real-time monitoring flow data and the baseline model; when the real-time data is matched with the blacklist, outputting an abnormal flow alarm; when the real-time data is matched with the white list and a deviation exceeds a preset threshold, outputting a threat flow alarm; and when the real-time data is mismatched with the blacklist and the white list, treating as a gray list and outputting an unknown flow alarm. According to the method and the system, the network security threat can be comprehensively and effectively detected at a low false alarm rate and high anti-virus efficiency, and the method and the system can adapt to a more granular network attack and defense confrontation environment.
Owner:STATE GRID CORP OF CHINA +1
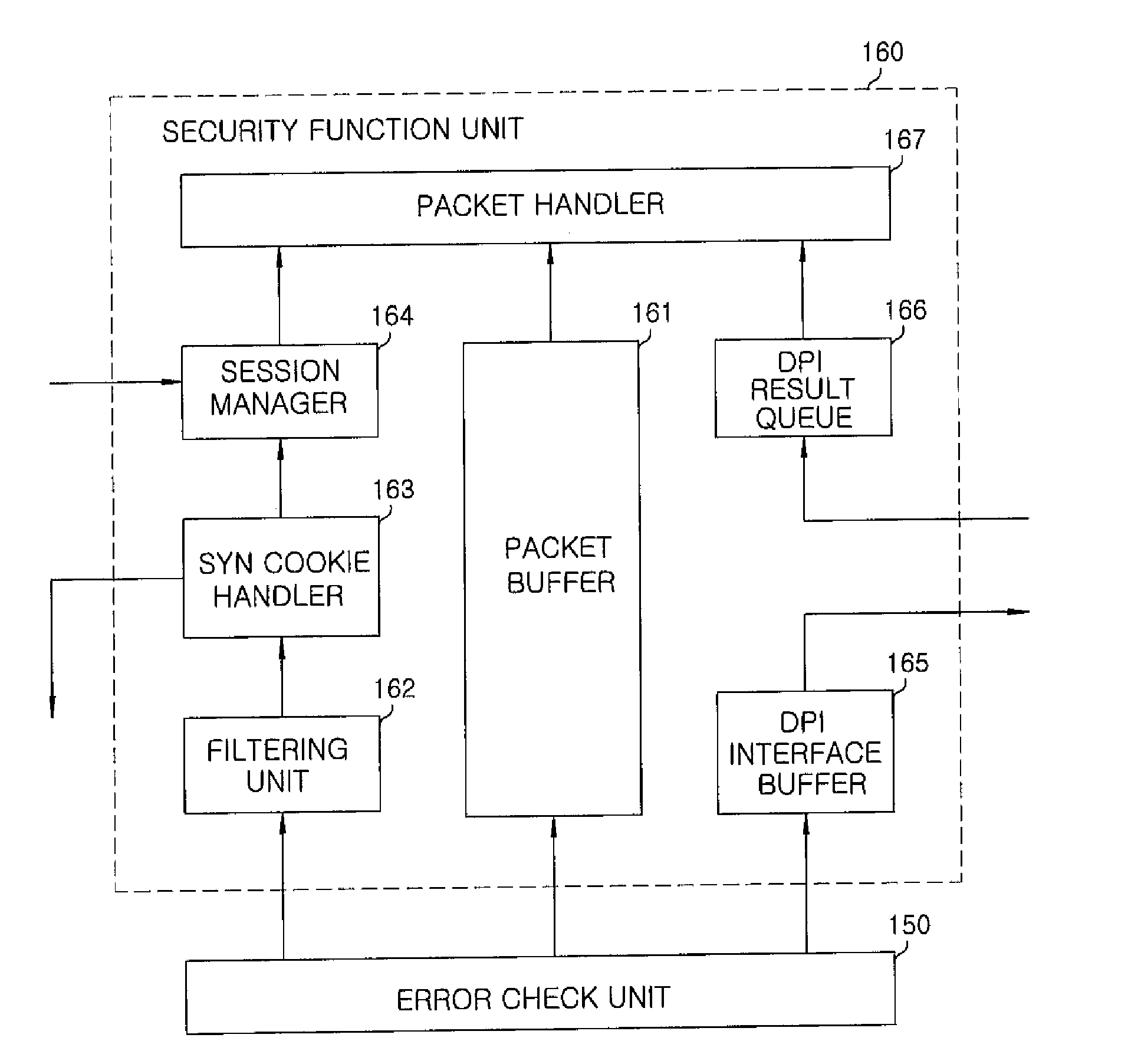
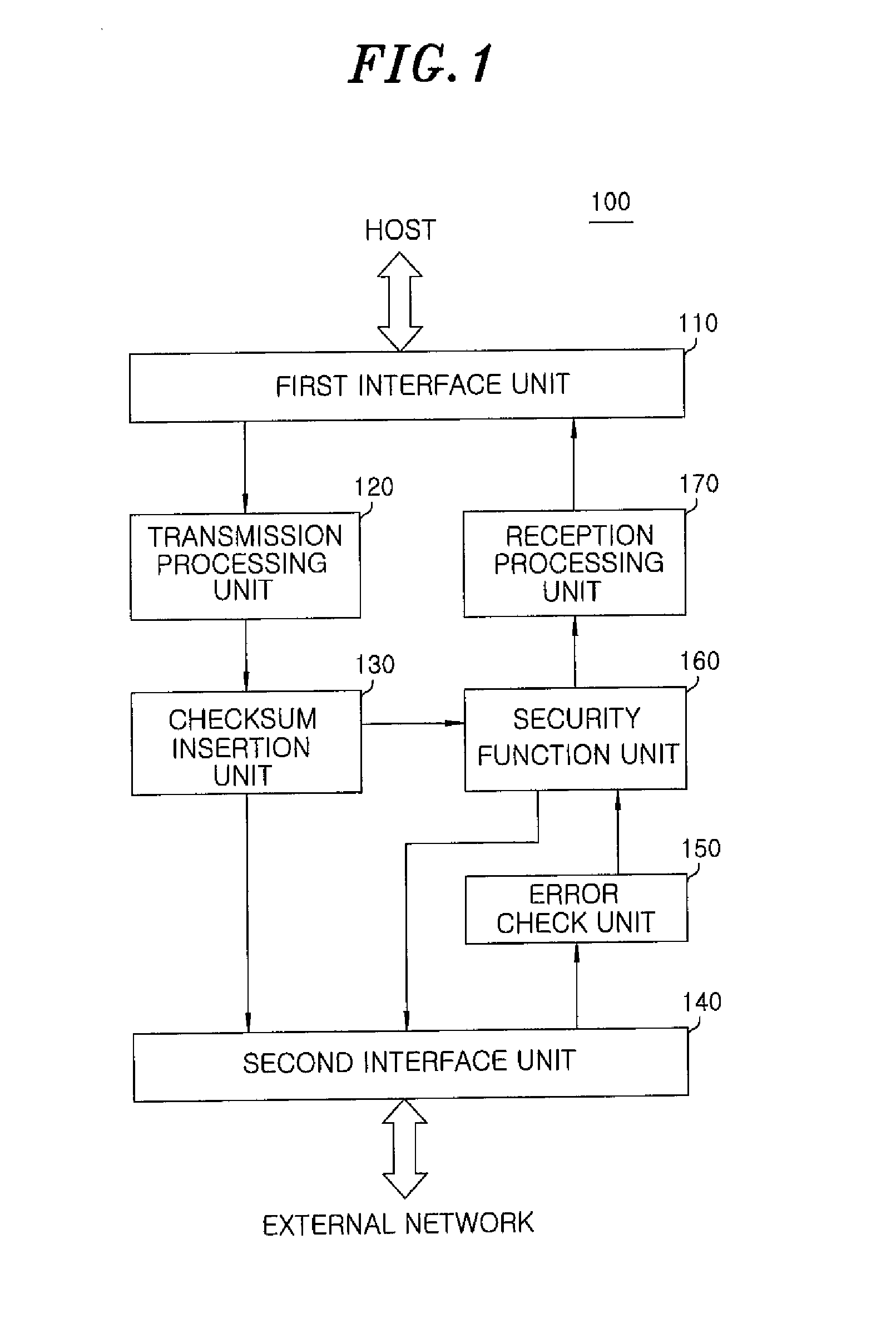
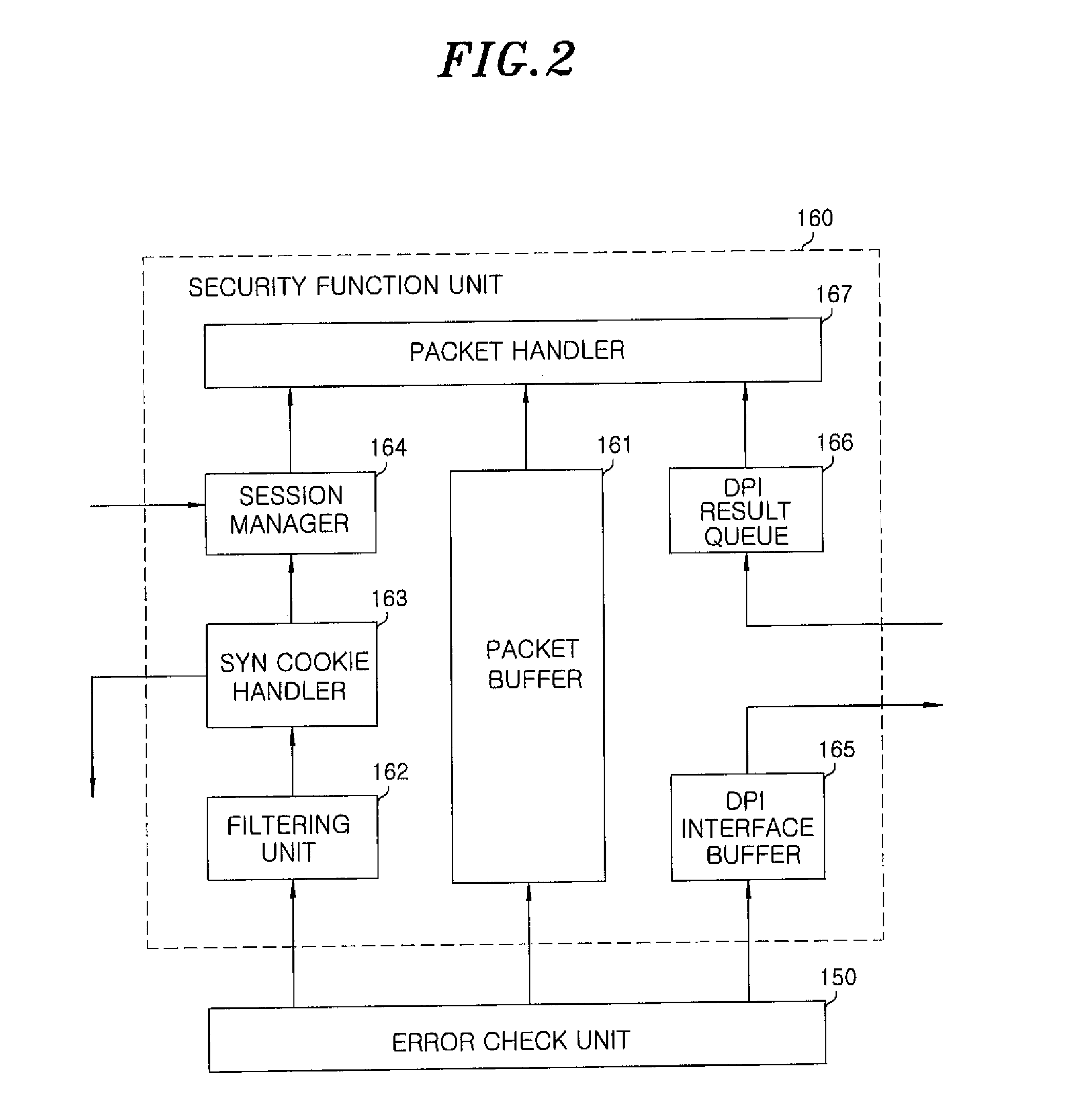
Apparatus and method for preventing network attacks, and packet transmission and reception processing apparatus and method using the same
InactiveUS20110131646A1Prevent cyber attacksData taking preventionMultiple digital computer combinationsSession managementNetwork attack
An apparatus for preventing network attacks includes: a packet buffer for storing received packets from a network; a filtering unit for filtering harmful packets based on a result of comparison between information of the received packets and preset filtering information to select a first filtering target packet; an SYN cookie handler for selecting a second filtering target packet using an SYN cookie if it is determined that there is a TCP SYN flooding attack based on the information of the received packets after said filtering; and a session manager for selecting a third filtering target packet through session management if there is a TCP flag flooding attack based on the information of the received packets after said filtering. The apparatus further includes a packet transmission and receipt processing method and apparatus using above.
Owner:ELECTRONICS & TELECOMM RES INST
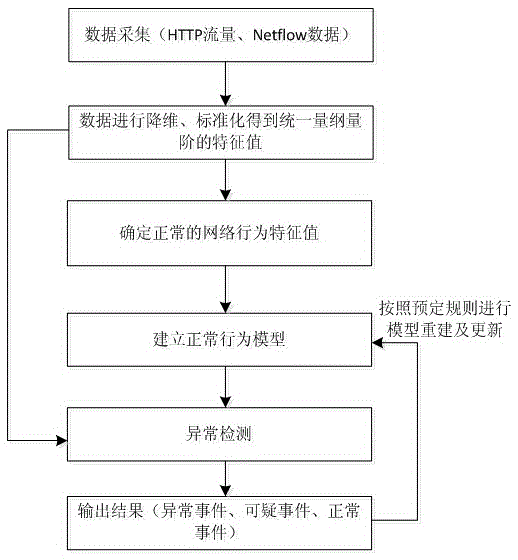
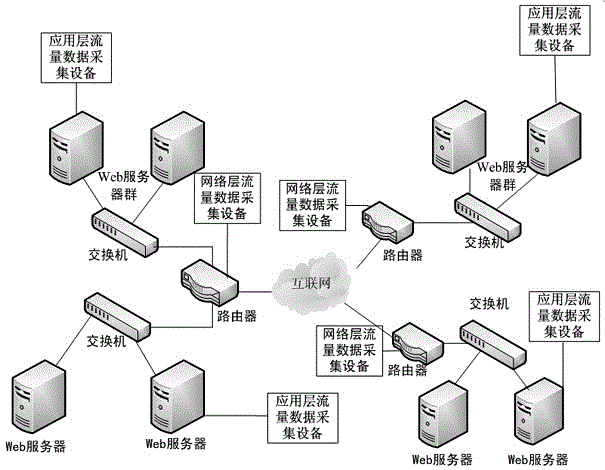
Network attack abnormality detection method
ActiveCN105553998AReduce false alarm rateAuto rebuildTransmissionNetwork behaviorDimensionality reduction
The invention discloses a network attack abnormality detection method, and relates to the technical field of information security. The technical point of the network attack abnormality detection method disclosed by the invention is as follows: a step 1, deploying a traffic data collection device at a network traffic aggregation node; a step 2, extracting a network behavior feature value from the collected traffic data; a step 3, carrying out dimensionality reduction and standardization on the network behavior feature value; a step 4, determining normal network behavior feature values, and establishing a normal behavior model based on a set of the normal network behavior feature values; and a step 5, detecting other network behavior feature values based on the normal behavior model, and judging whether abnormal network behaviors occur; and when detecting abnormal network behaviors, updating the normal behavior model according to a new normal network behavior feature value.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Network access control method and system based on IP access behaviors
ActiveCN103475637ASolve efficiency problemsSolve the cumbersome configurationTransmissionQuality of serviceData access control
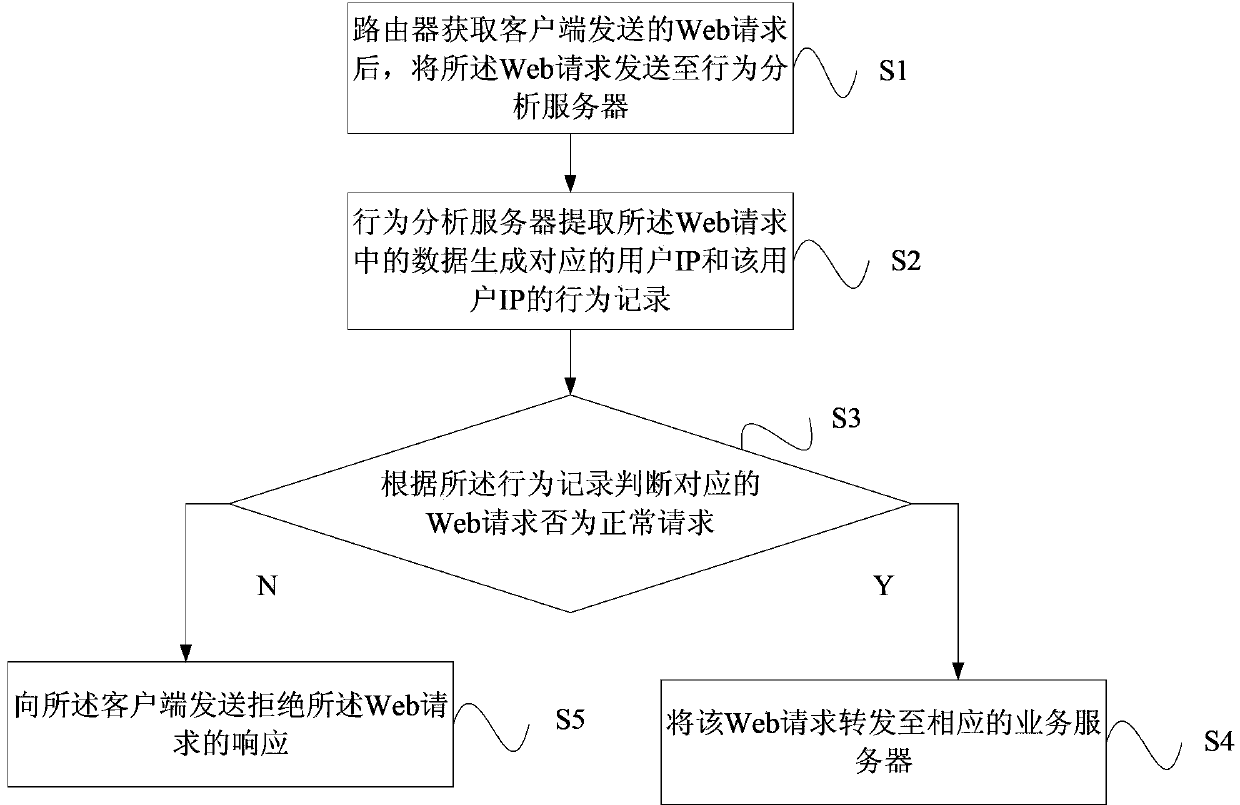
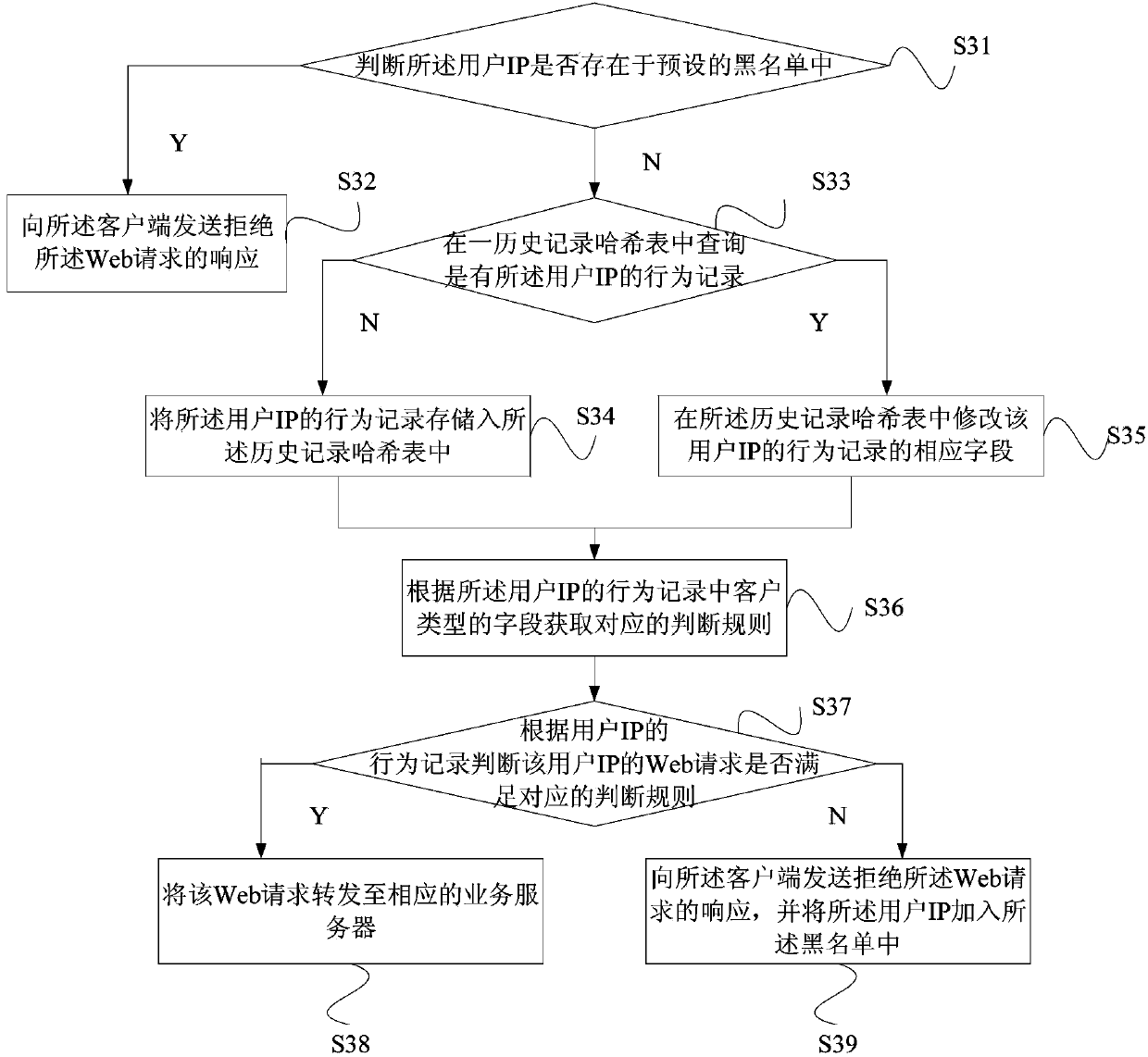
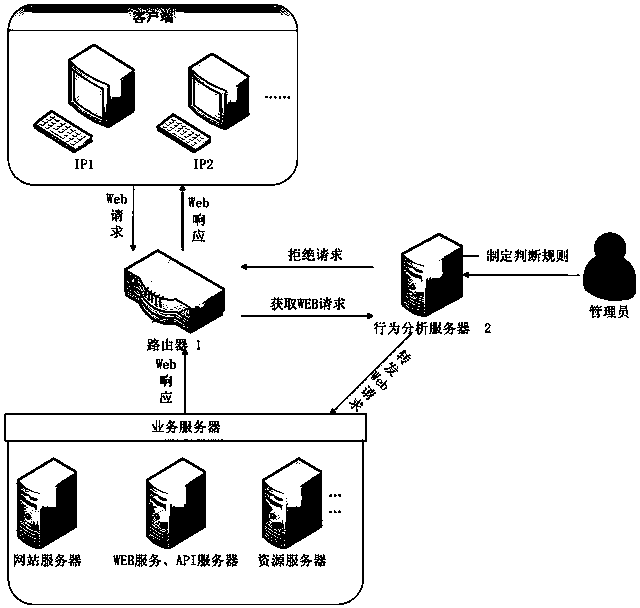
The invention provides a network access control method and system based on IP access behaviors. The method includes: after a Web request sent by a client is acquired through a router, the Web request is sent to a behavior analyzing server; data in the Web request are extracted by the behavior analyzing server and a corresponding user IP and a behavior record of the user IP are generated and whether the Web request is a normal request is judged according to the behavior record; if the Web request is a normal request, then the Web request is forwarded to a corresponding service server and if not, then a response refusing the Web request is sent to the client so that access control on unknown IPs can be carried out dynamically and problems such as low efficiency, tedious configuration and poor dynamic instantaneity and the like in traditional IP access control are solved. At the same time, the network access control method and system also aim at restraining network attacks, regulating crawler behaviors, improving website or API service qualities and enhancing website stability and usability.
Owner:CTRIP COMP TECH SHANGHAI
Network attack detection method and device thereof
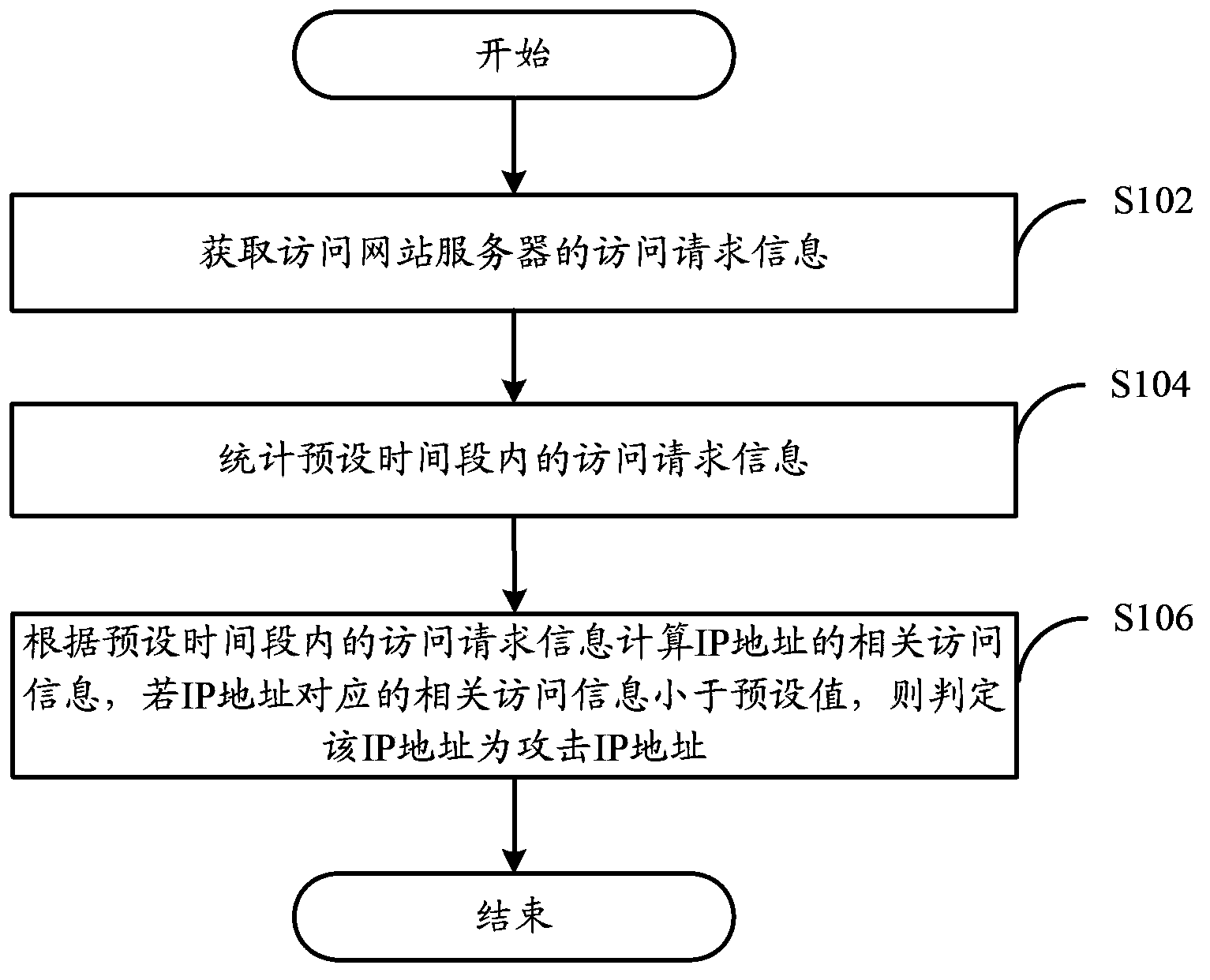
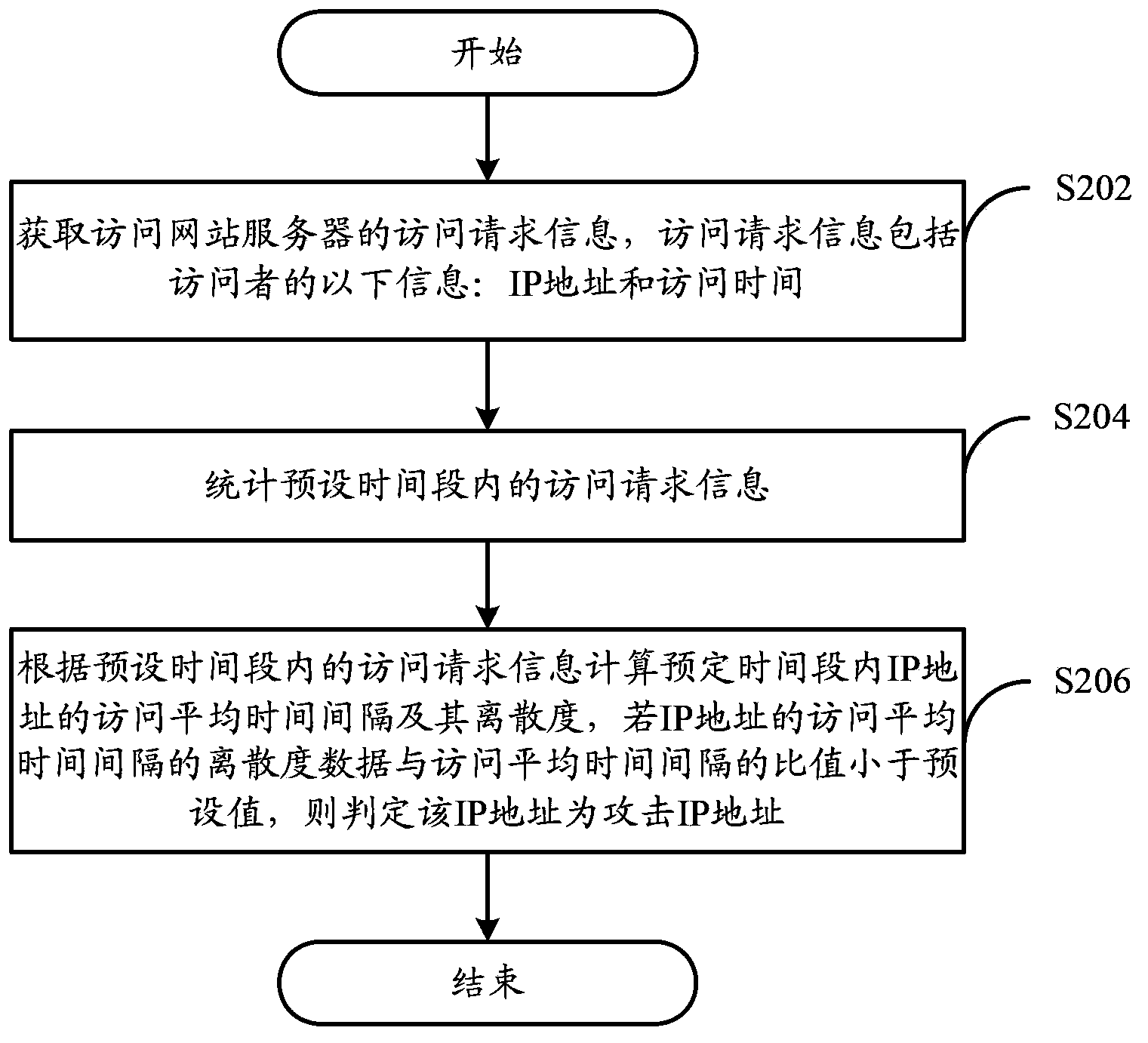
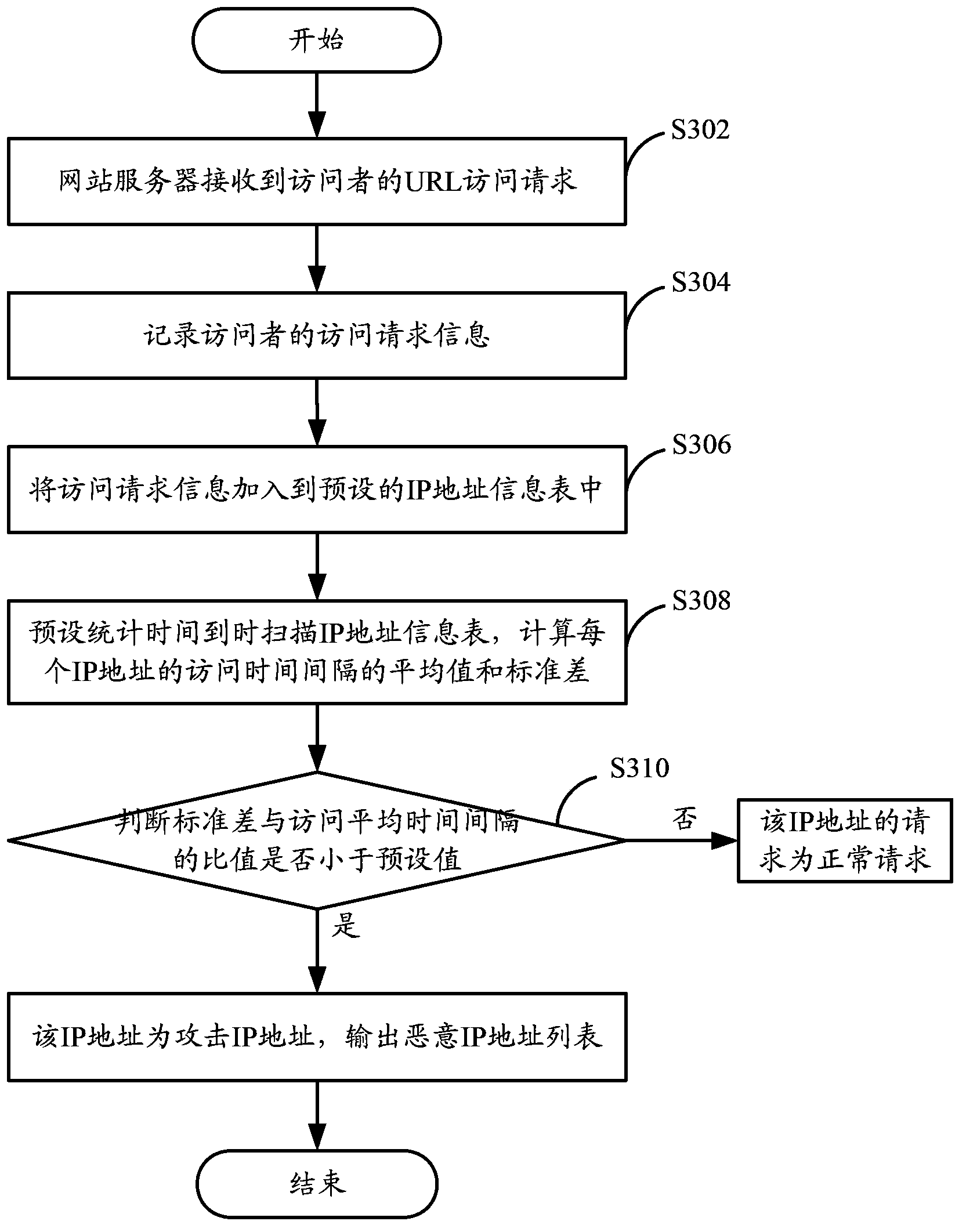
The application discloses a network attack detection method and a device thereof. The network attack detection method of the embodiment of the application comprises the steps that access request information of an access website server is acquired; statistics is performed on the access request information within a preset time period; and related access information of an IP address is calculated according to the access request information within the preset time period, and if the related access information corresponding to the IP address is less than a preset value, the IP address is an attack IP address through judgment. Over intervention of operation and maintenance personnel is not needed, and the method is completely decoupled from services so that accurate detection of HTTP-Flood attack is realized.
Owner:ALIBABA GRP HLDG LTD
Correlation engine for detecting network attacks and detection method
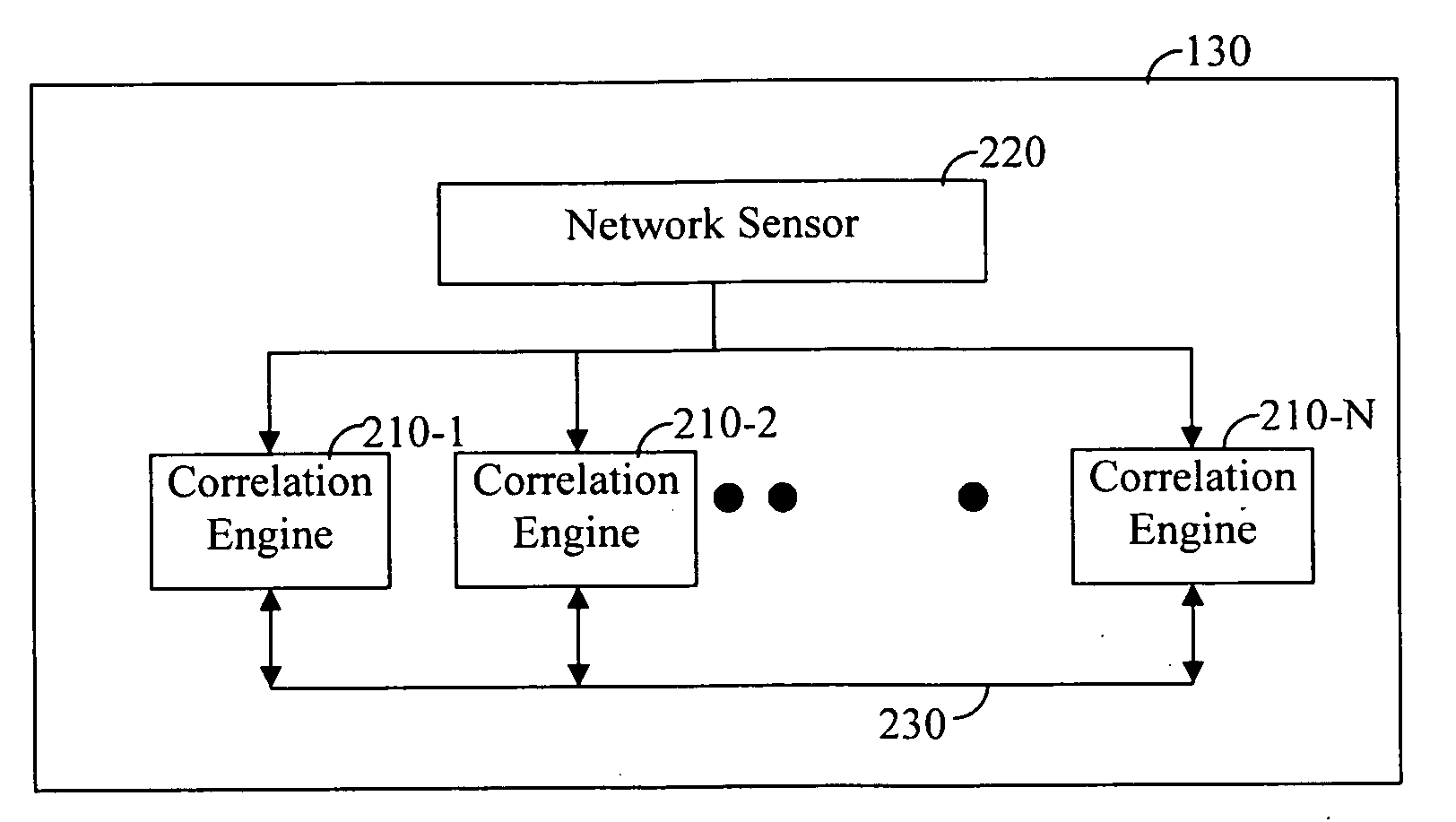
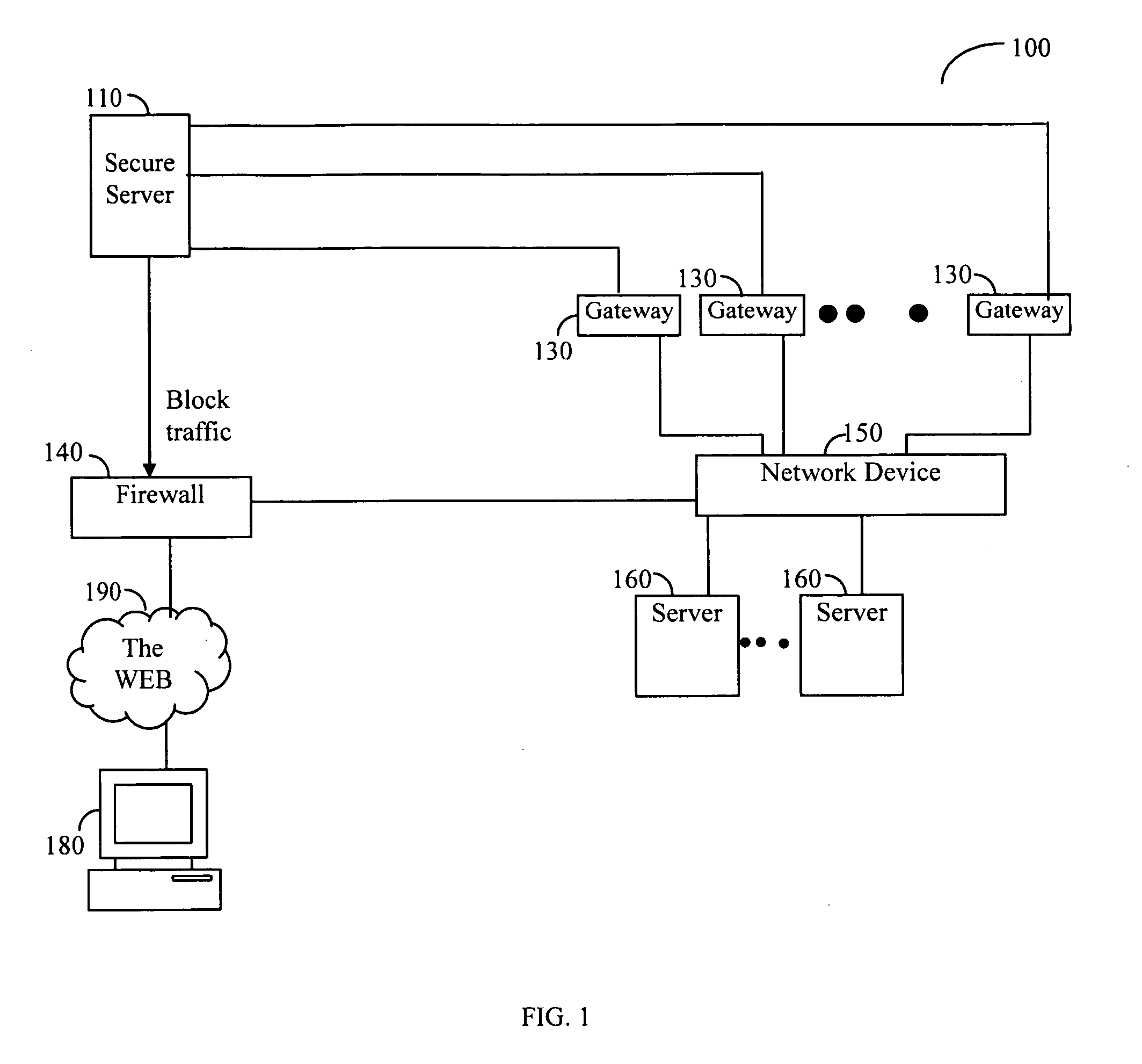
ActiveUS20070214503A1Memory loss protectionUser identity/authority verificationNetwork attackComputer program
A method for detecting network attacks is provided. In one implementation, the method receives a plurality of attack indications based on data transmitted on the network and applies rules to the plurality of attack indications. Also, the method generates an alert if an application of at least a subset of the rules on the plurality of attack indications indicates a potential attack. In addition, a network device that performs the method and a computer program corresponding to the method are provided.
Owner:IMPERVA
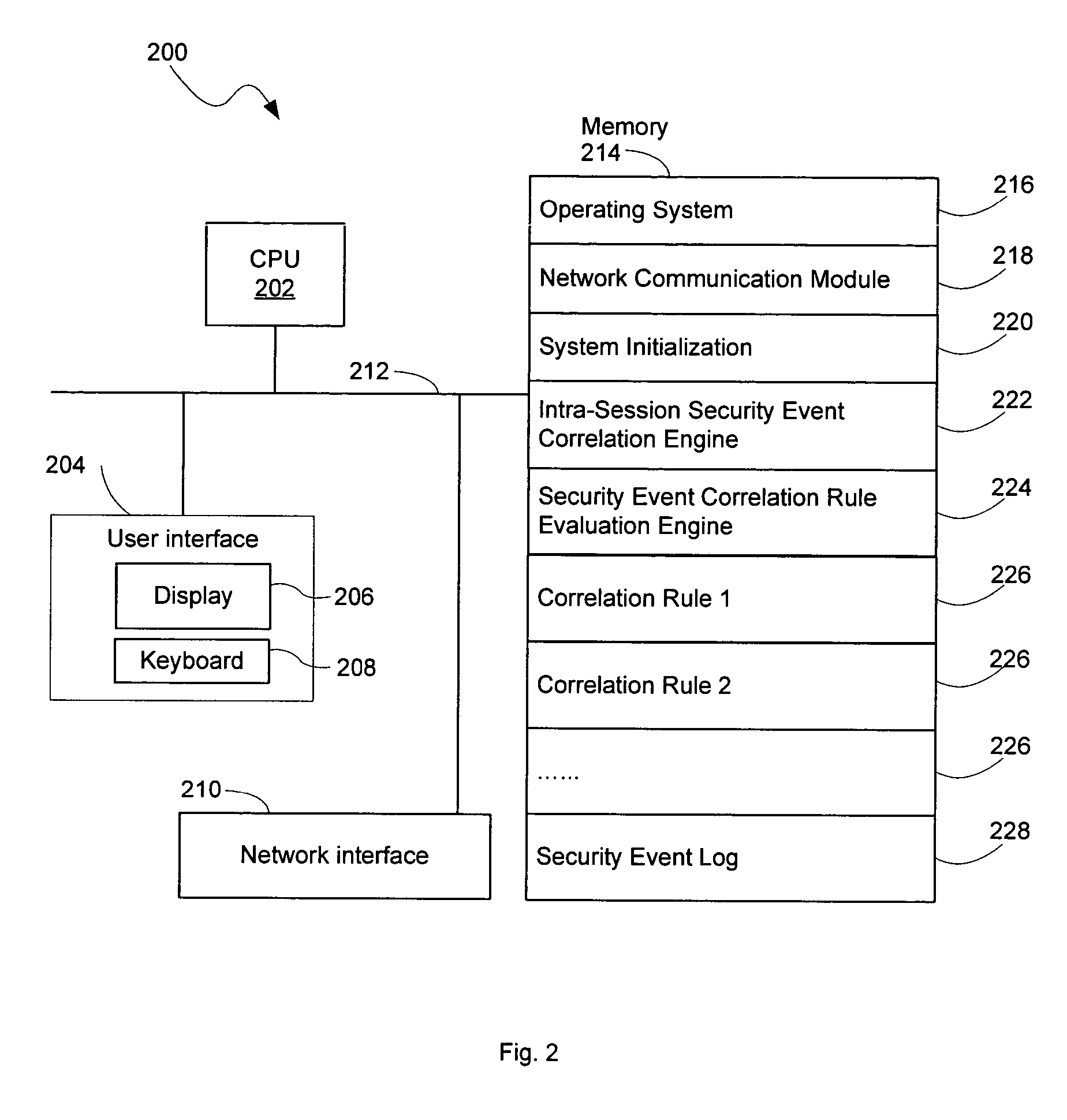
Network security monitoring system
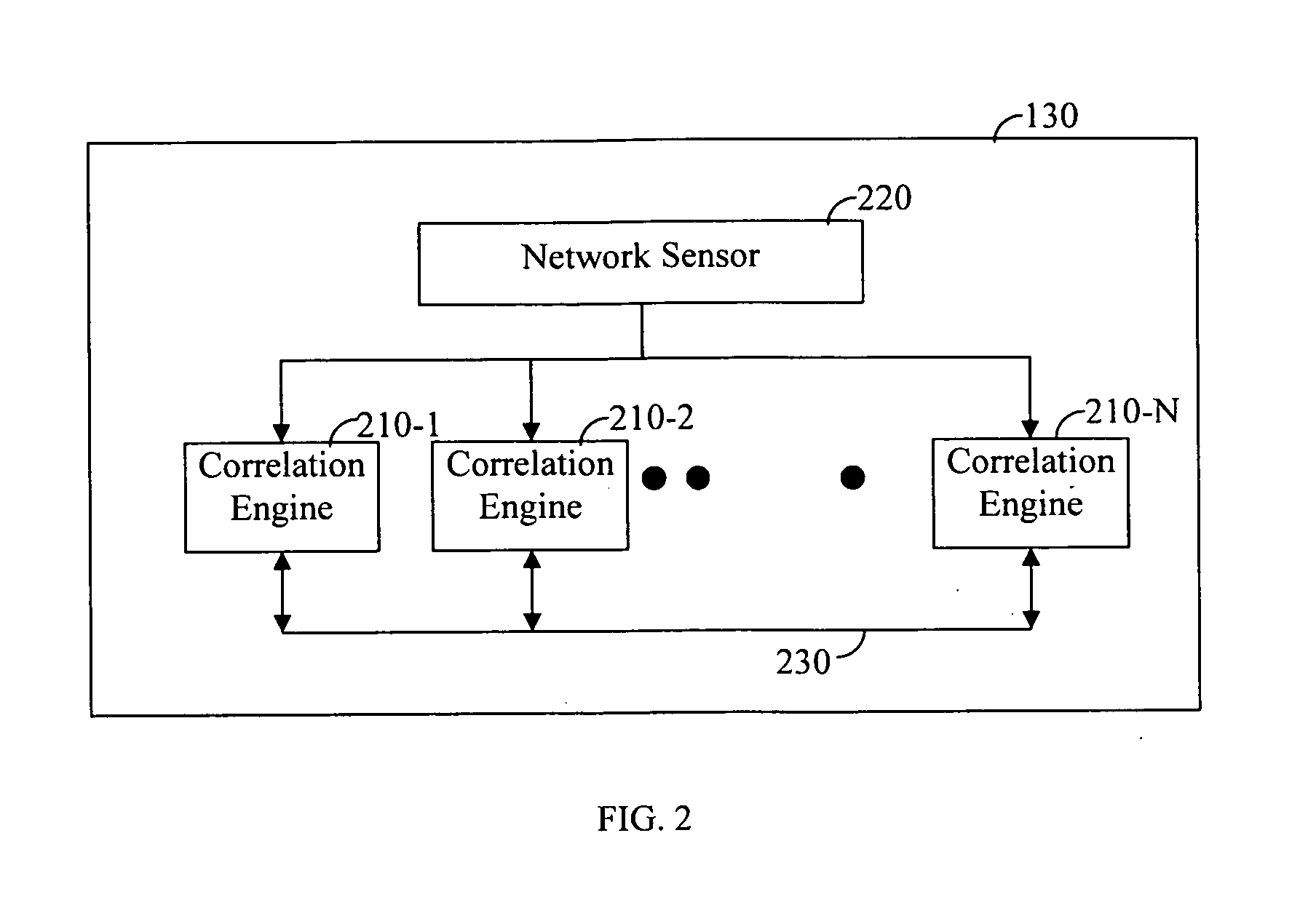
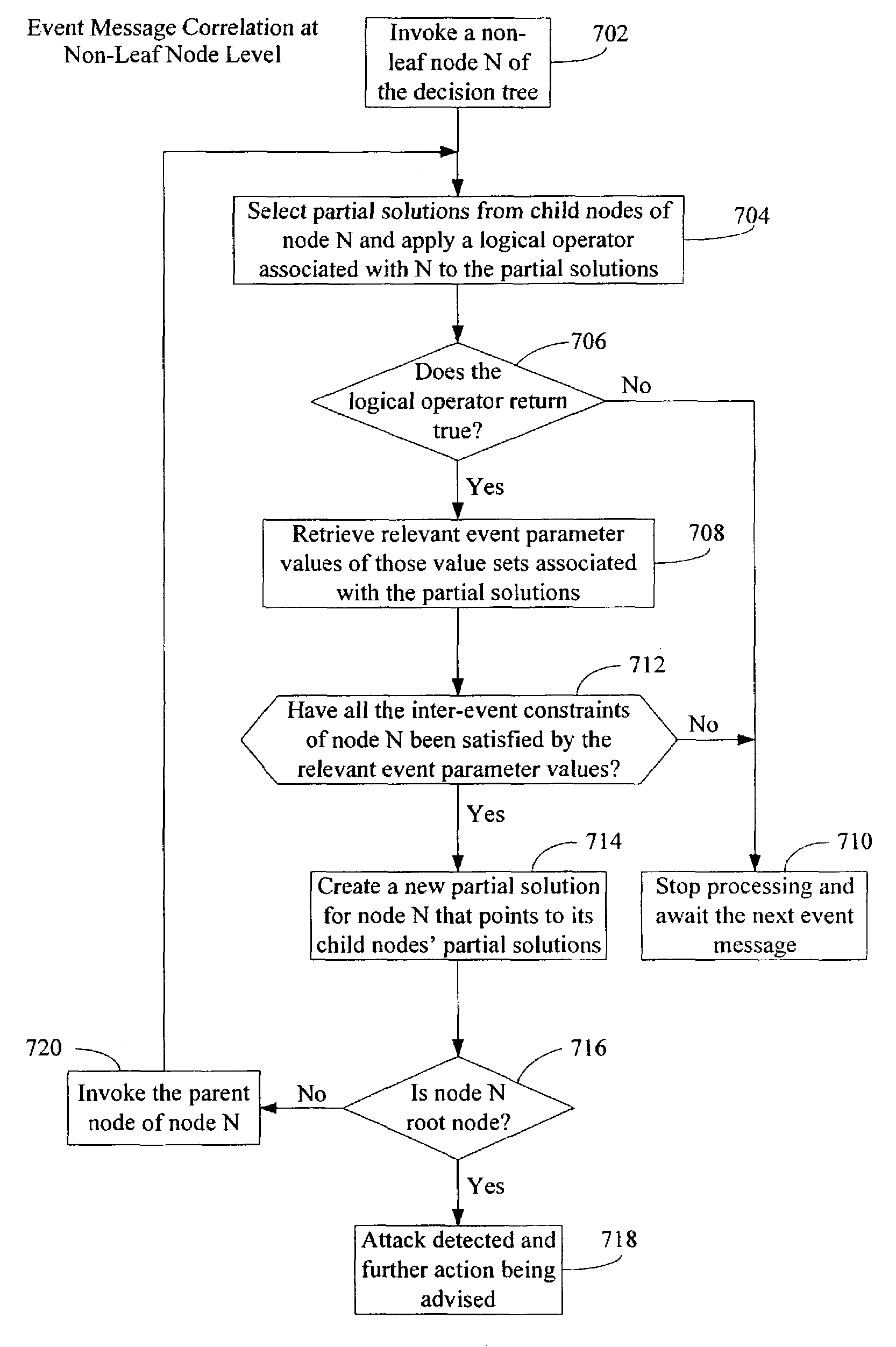
InactiveUS7483972B2Memory loss protectionError detection/correctionMonitoring systemPartial solution
A security monitoring system processes event messages related to computer network security in real time, evaluating inter-event constraints so as to identify combinations of events that are partial solutions to a predefined event correlation rule, and furthermore evaluating combinations of the partial solutions do determine if they together satisfy the predefined event correlation rule. A decision tree is formed based on the rule. Event messages are categorized into groups at leaf nodes of the tree in accordance with a plurality of intra-event constraints, and then the messages are correlated in accordance with a plurality of inter-event constraints at non-leaf nodes of the tree. When the inter-event constraint at a root node of the tree has been satisfied, a network attack alert is issued and protective actions may be taken.
Owner:CISCO TECH INC
Systems and methods that identify normal traffic during network attacks
A system protects against loss of communication during network attacks. In a first implementation, a system (120) models the behavior of normal users in a network in response to an application of a first packet filtering technique. The system (120) receives a group of packets from a first user subsequent to the application of the first packet filtering technique and creates one or more models reflecting the behavior of the first user based on the received packets. In another implementation, a system (130) receives a stream of packets subsequent to a filtering technique being applied, partitions the packets into groups, where each group corresponds to more than one packet, and classifies each group of packets as a normal group or an attack group using one or more models. Each model reflects a normal response to an application of the filtering technique. The system (130) forwards groups classified as normal groups, thus preventing network attacks from choking off all communication in the network.
Owner:TRI COUNTY EXCELSIOR FOUND +1
System and method for probabilistic attack planning
ActiveUS8490193B2Memory loss protectionUnauthorized memory use protectionProgram planningNetwork attack
Owner:FORTRA LLC
Network security accident classification and predicting method and system
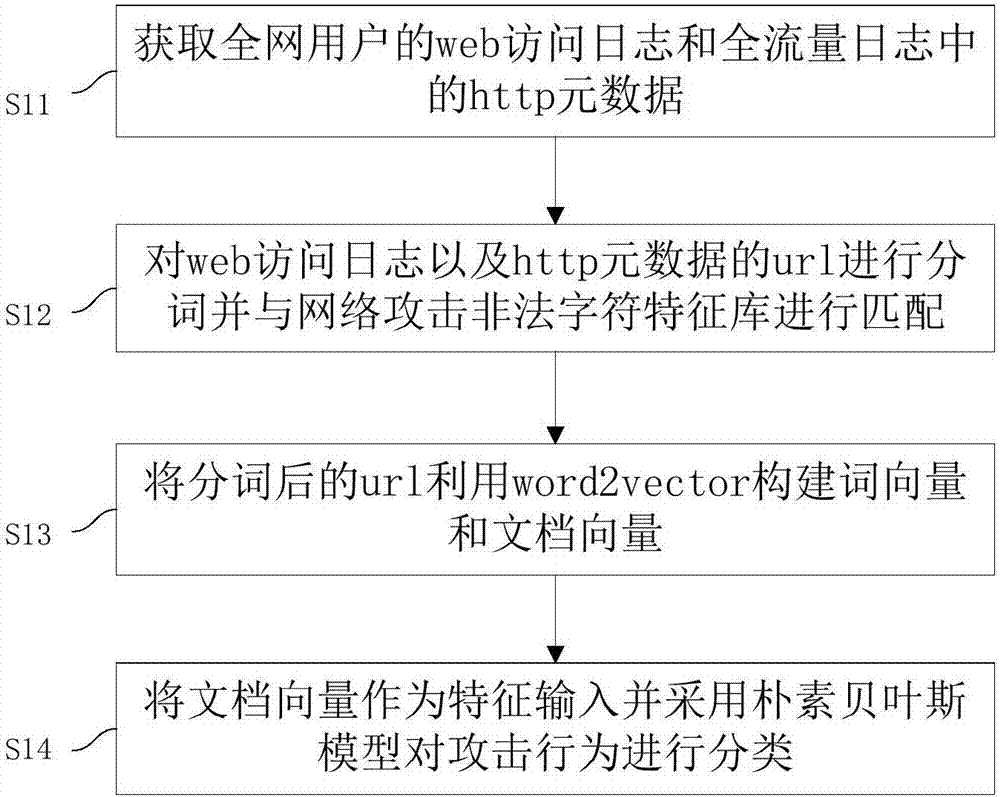
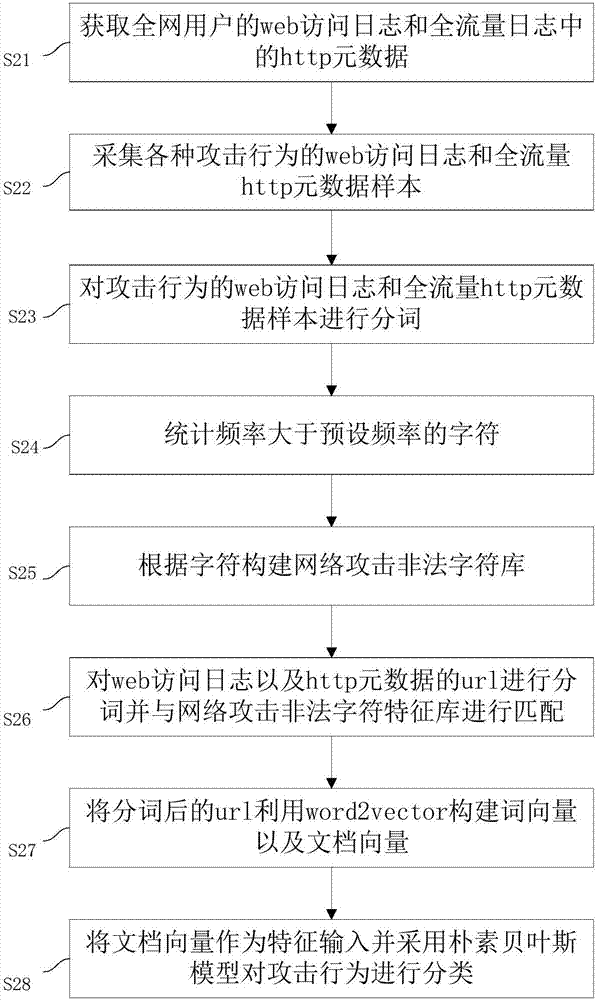
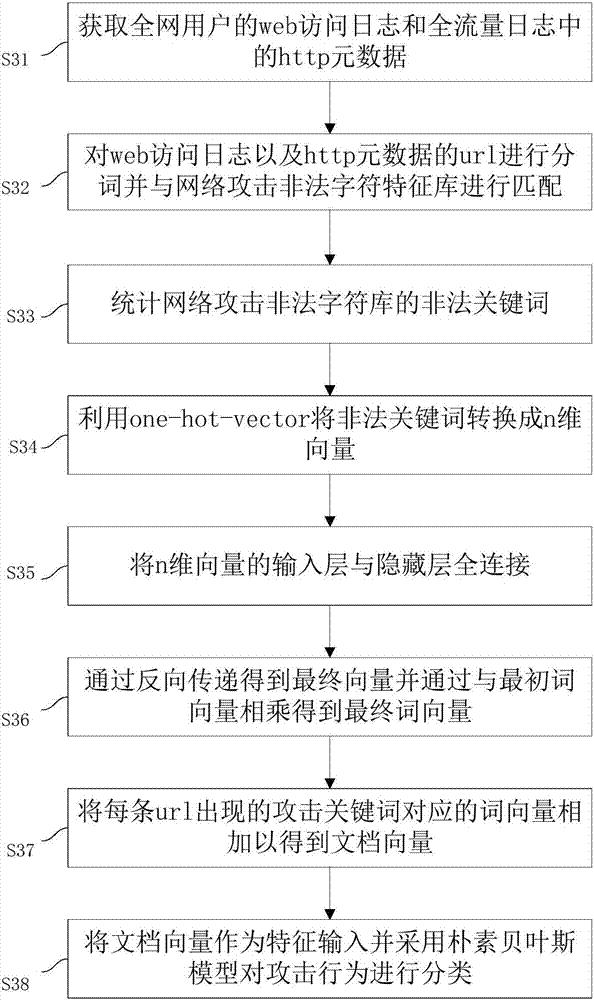
ActiveCN107241352AImprove classification efficiencySave time and costTransmissionNetwork attackTime cost
The invention discloses a network security accident classification and predicting method and a system, which are used for solving the problems of the prior art on lacking the capability of timely finding the characteristics of attack behaviors and accurately classifying the attack behaviors. The method comprises the following steps: S1. acquiring web access log of users in a whole network and http metadata in full-flow log; S2. segmenting the web access log and the url of the http metadata, and matching with a network attach illegal character feature library; S3. constructing a word vector and a document vector of the segmented url by utilizing word2vector; and S4. inputting the document vector as a feature and classifying the attack behavior by adopting a naive bayes model. The real-time monitoring of key points can be realized, the abnormal behavior carrying mainstream attack feature can be found by means of machine learning, the classification efficiency of network attack behaviors can be improved, and the time cost of manual check can be lowered, continuously changed attack behaviors can be adapted, and the classification detection accuracy can be enhanced, thus providing guarantee for network security.
Owner:ZHEJIANG PONSHINE INFORMATION TECH CO LTD
Industrial control network security protection method and system
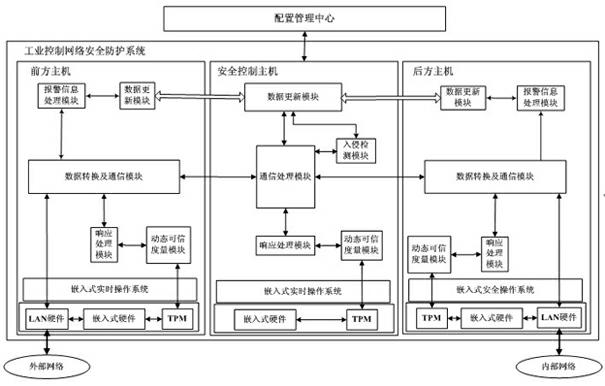
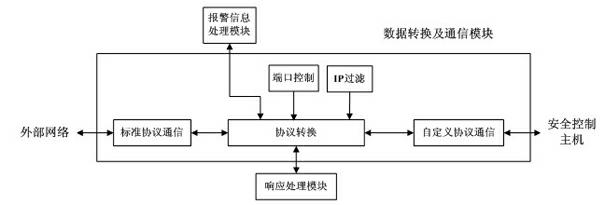
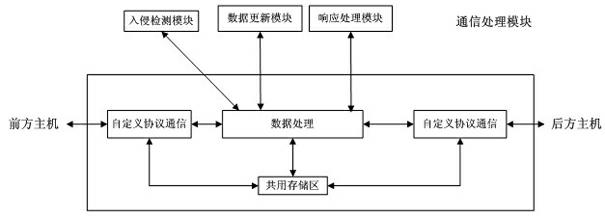
InactiveCN102438026AImprove resistance to attackImprove securityUser identity/authority verificationData switching networksSystem transformationNetwork attack
The invention discloses an industrial control network security protection method and an industrial control network security protection system. The method comprises the following steps that: aiming at an external network attack, a front host performs first layer data filter and access control on external network data; a security control host caches data through a common storage region, performs intrusion detection on the data, timely alarms illegal data and informs hosts on two sides; a rear host performs deep filter and access control on the data and causes the legal data to enter an internal network; aiming at an internal network attack, the rear host performs the first data filter and access control on internal network data; the security control host caches the data through the common storage region, performs the intrusion detection on the data, timely alarms the illegal data and informs the hosts on the two sides; and the front host performs the deep filter and access control on the data and causes the legal data to enter an external network. By the method and the system, the network security level of an industrial control system is increased, and the cost on investment, system transformation and management is reduced.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
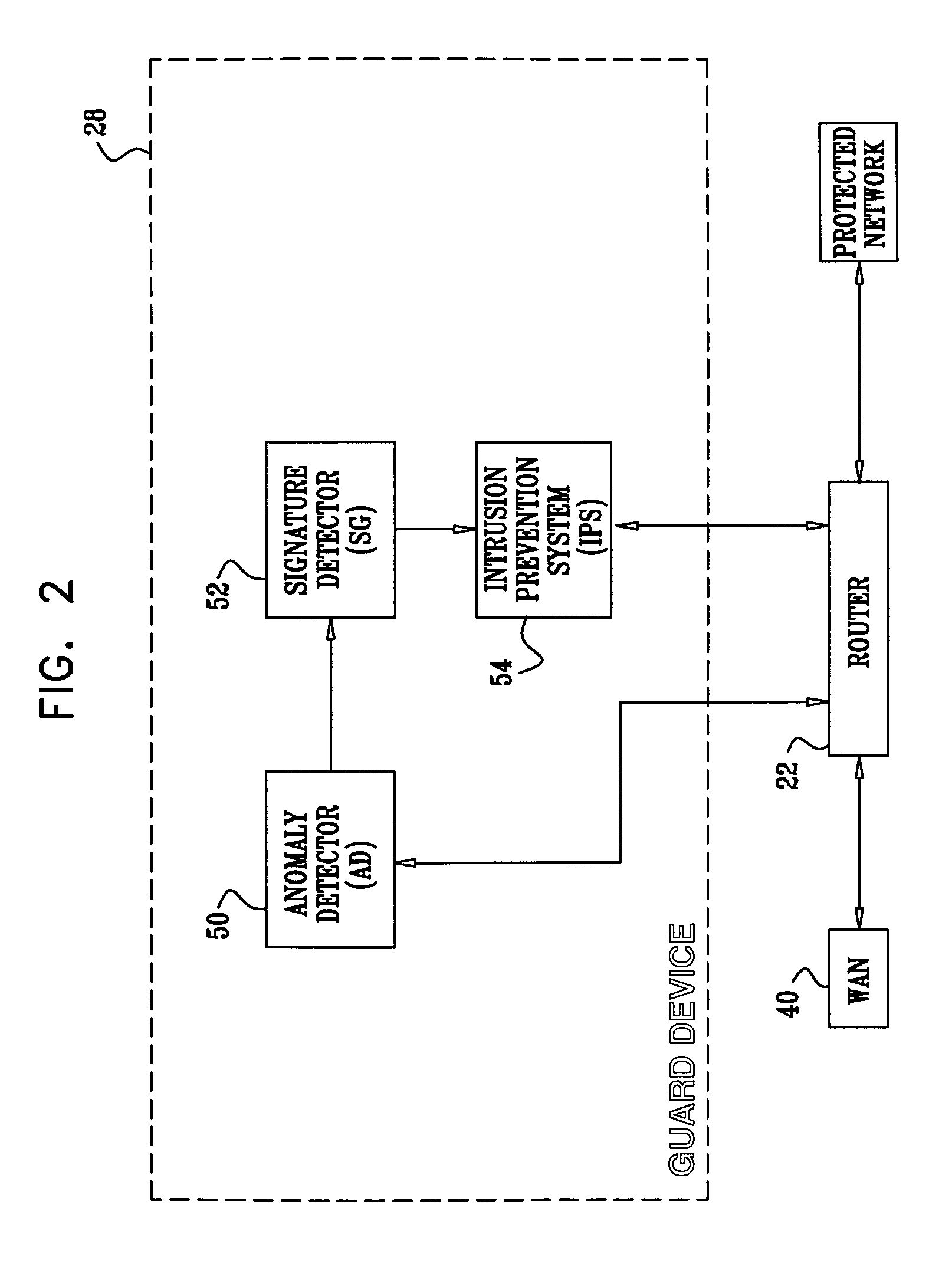
Network intrusion detection and prevention system and method thereof
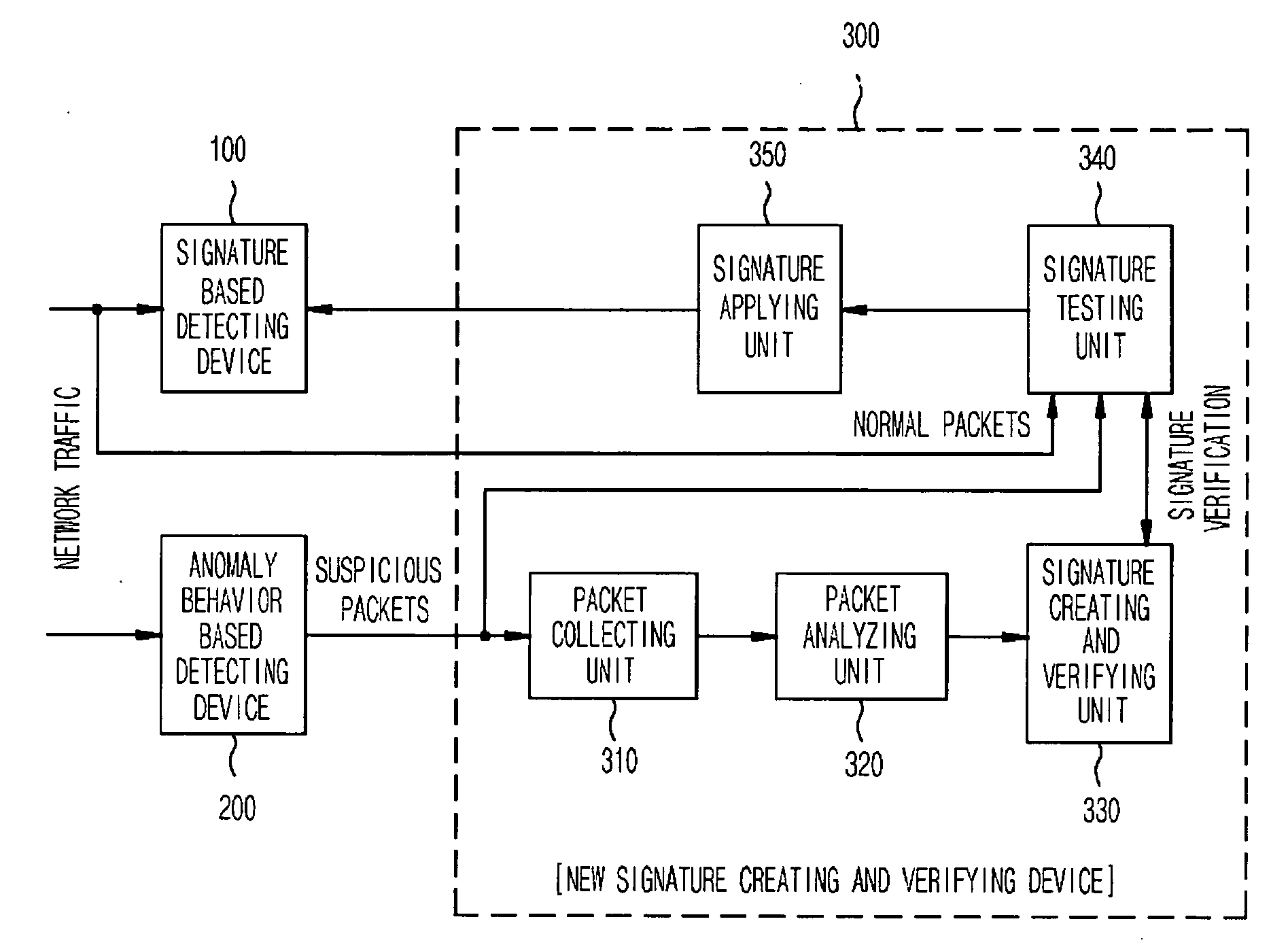
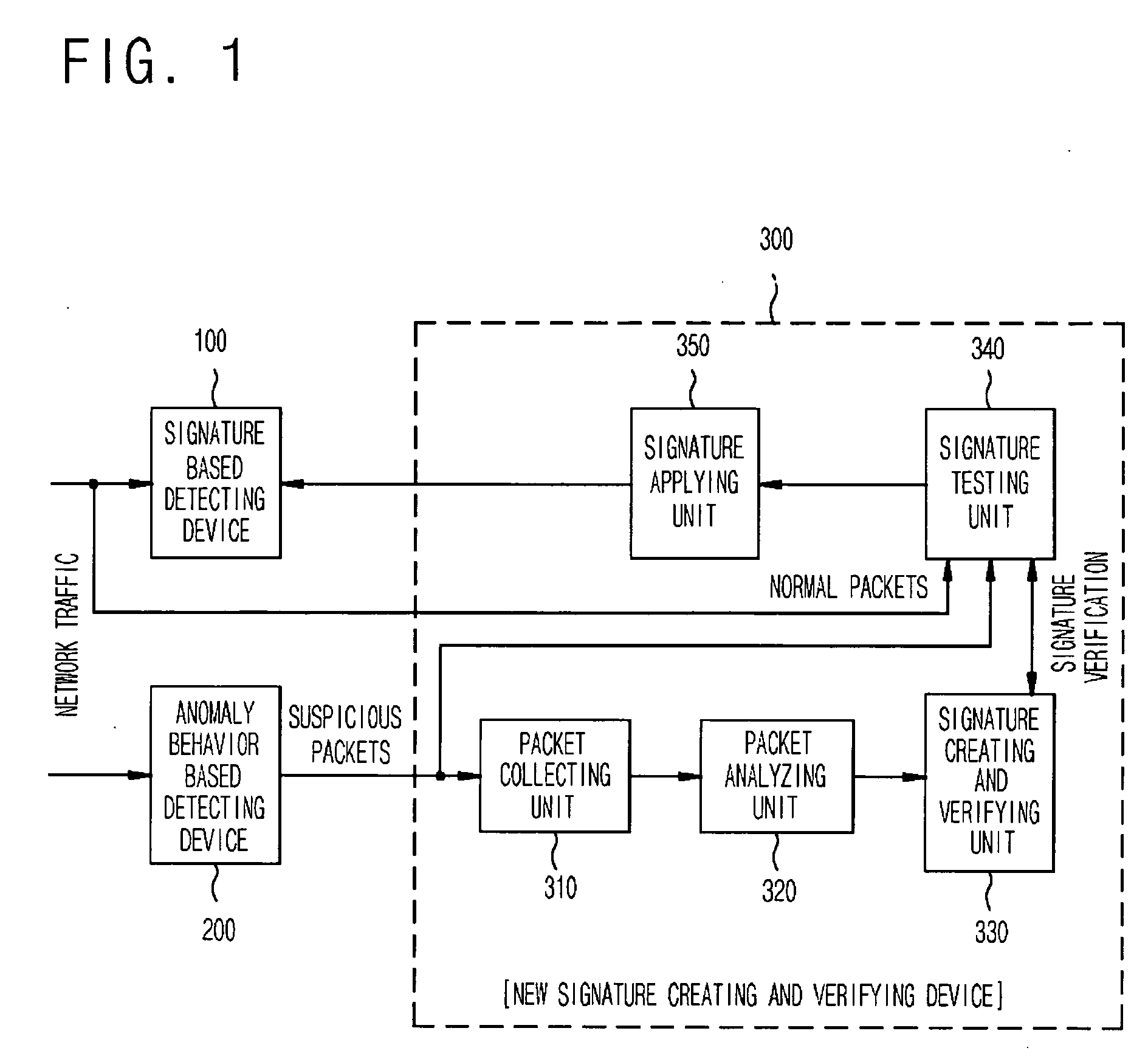
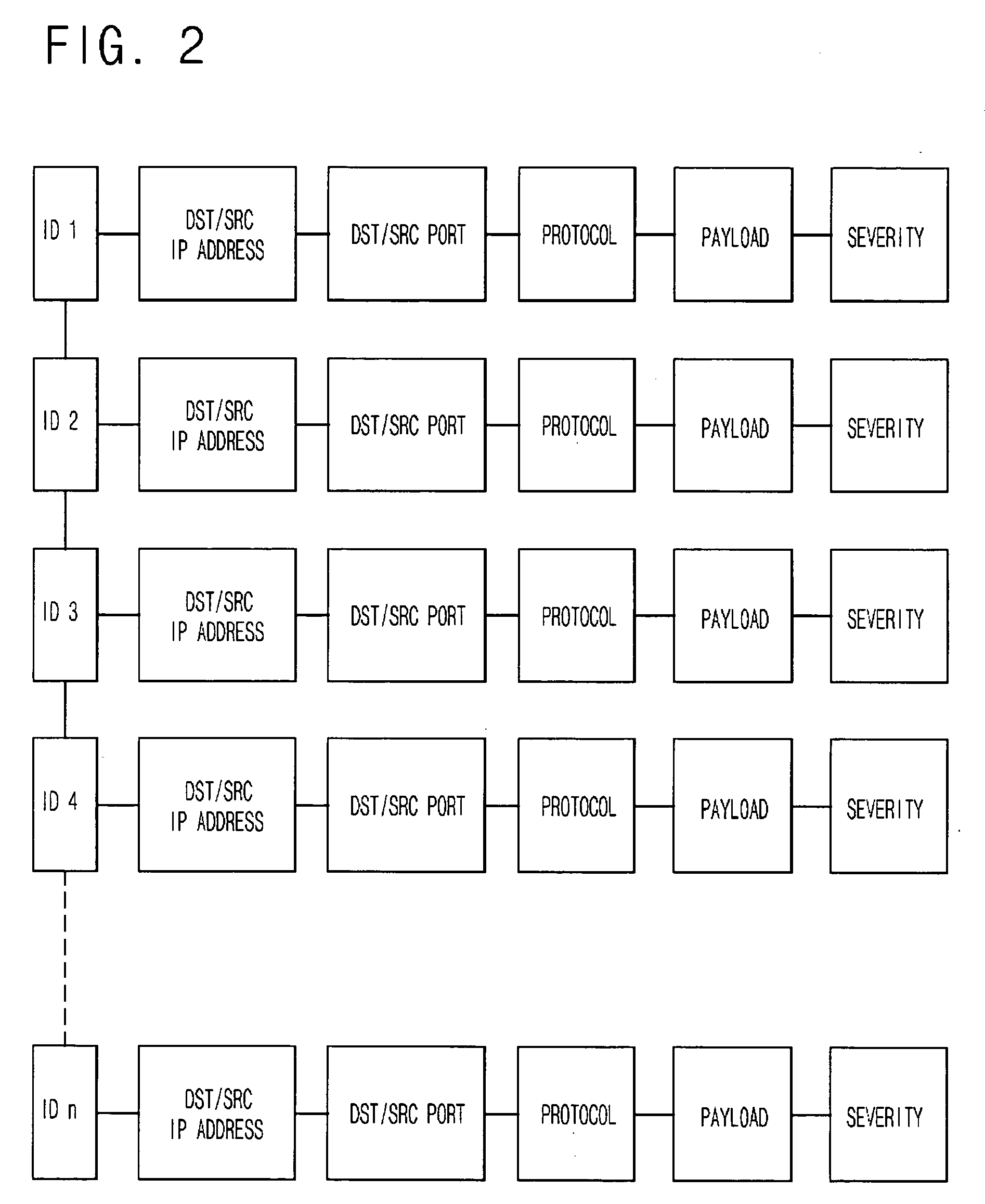
InactiveUS20060085855A1Maximize the effectCritical damageMemory loss protectionData taking preventionData packPublic information
The present invention relates to a network intrusion detection and prevention system. The system includes: a signature based detecting device; an anomaly behavior based detecting device; and a new signature creating and verifying device disposed between the signature based detecting device and the anomaly behavior based detecting device, wherein if the anomaly behavior based detecting device detects network-attack-suspicious packets, the new signature creating and verifying device collects and searches the detected suspicious packets for common information, and then creates a new signature on the basis of the searched common information and at the same time, verifies whether or not the created new signature is applicable to the signature based detecting device, and then registers the created new signature to the signature based detecting device if it is determined that the created new signature is applicable.
Owner:ELECTRONICS & TELECOMM RES INST
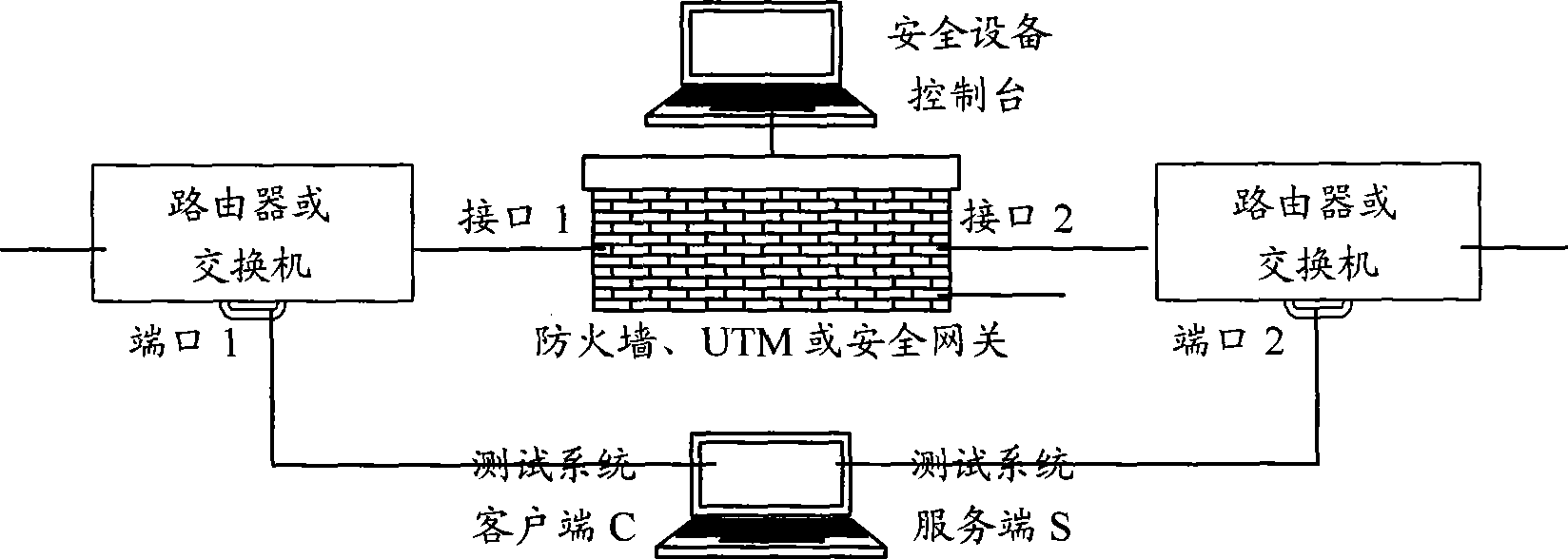
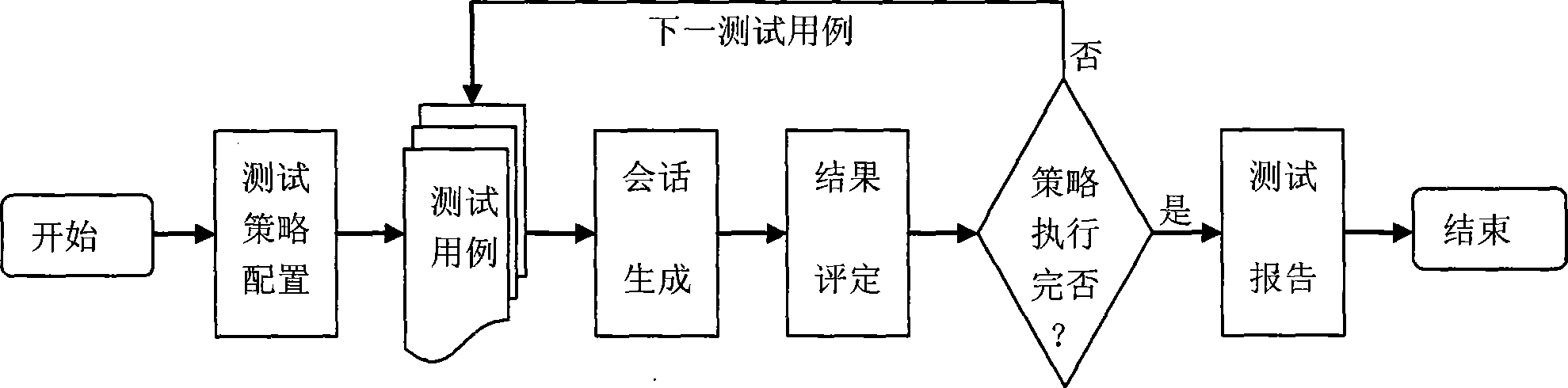
Test system used for network safety product and test method thereof
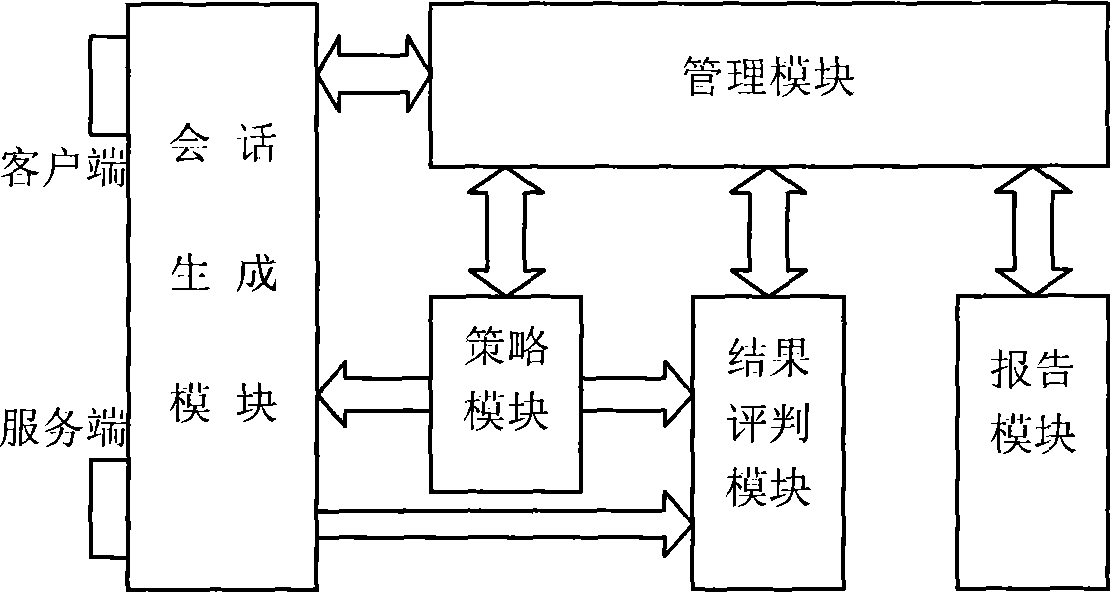
InactiveCN101447898AAchieving Policy Configuration ValidityAchieve effectivenessNetwork connectionsNetwork packetClient-side
The invention discloses a test system used for a network safety product and a test method thereof. The test system comprises a policy module, a session generating module, a result judge module and a reporting module. The test method comprises the steps as follows: (a) a data structure linked list of a test rule is filled to generate a concrete test case; (b) a client end and a server end program are constructed for respectively simulating hosts in two networks isolated by the network safety product and transferring a test plug-in corresponding to the test case by the client end and server endprogram to generate a corresponding data packet at real time to be transferred to a client end or a server end for sending, thereby generating a network session or a network attack session; and (c) atest result of the test case is judged according to the session finishing status and the network safety product behavioral parameter in the test case. The invention can realize the automatic real-time online detection of the policy configuration effectivity, the anti-attack penetration effectivity and the updating effectivity of the network safety product.
Owner:中国人民解放军信息安全测评认证中心
Attack signature generation
InactiveUS20070094728A1Raise the possibilityAccurate detectionMetering/charging/biilling arrangementsMemory loss protectionData processing systemNetwork addressing
The present invention provides a method for generating from requests from a first data network attack signatures for use in a second data network having a plurality of addresses assigned to data processing systems, the method comprising receiving data traffic from the first data network addressed to a number of unassigned addresses in a third data network; inspecting several incidents of the received data traffic for a common data pattern, upon finding a said data pattern, determining from the corresponding data traffic the attack signature for use in detecting attacks for the second data network. The invention also provides an apparatus for generating from requests on a first data network attack signatures for use in a second data network having a plurality of addresses assigned to data processing systems. The present invention further extends to a computer program element comprising computer program code means which, when loaded in a processor of a data processing system, configures the processor to perform a method for detecting attacks on a data network as hereinbefore described. The present invention further extends to a method of supporting an entity in the handling of a detected attack.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com