Patents
Literature
10859results about How to "Efficient detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
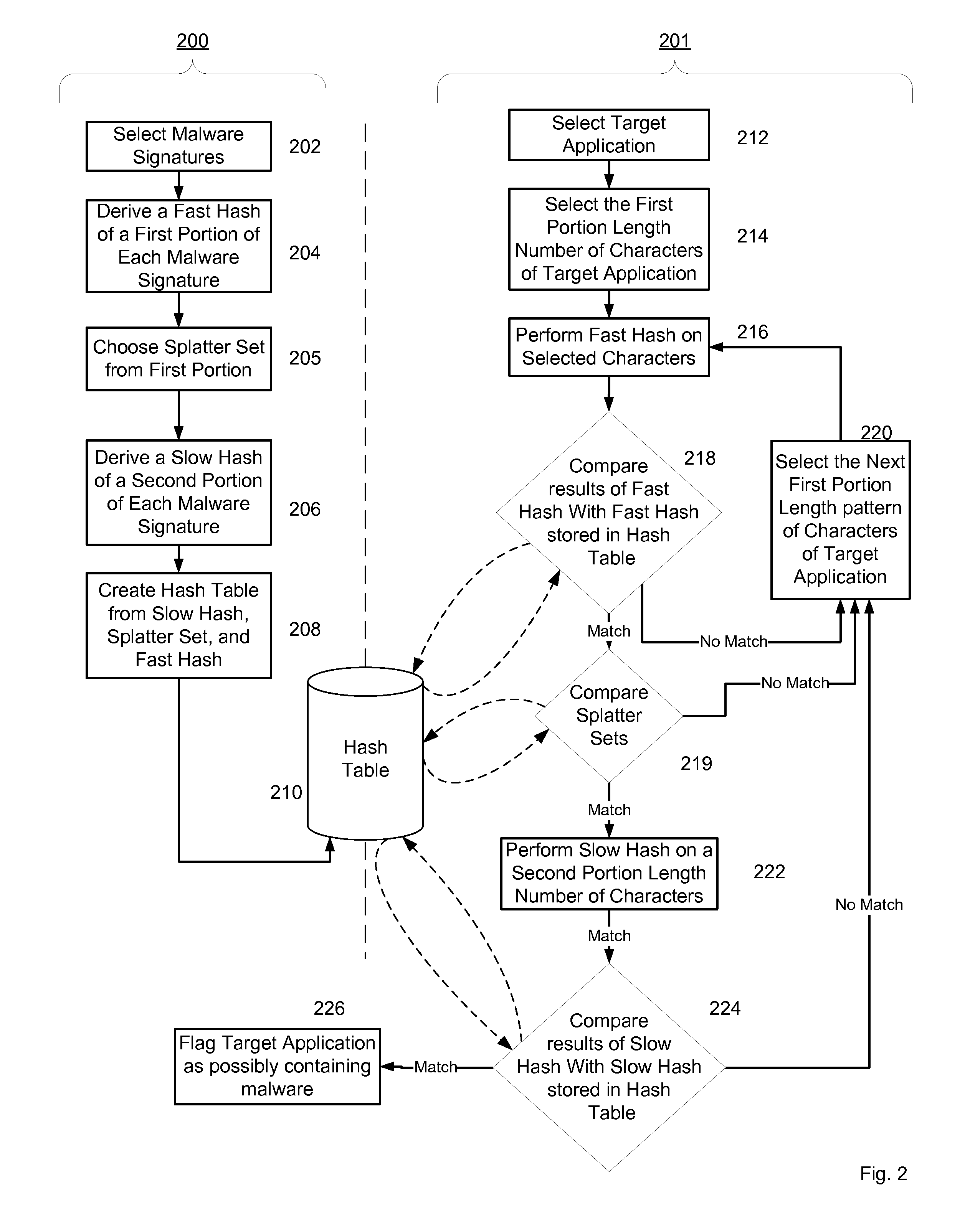
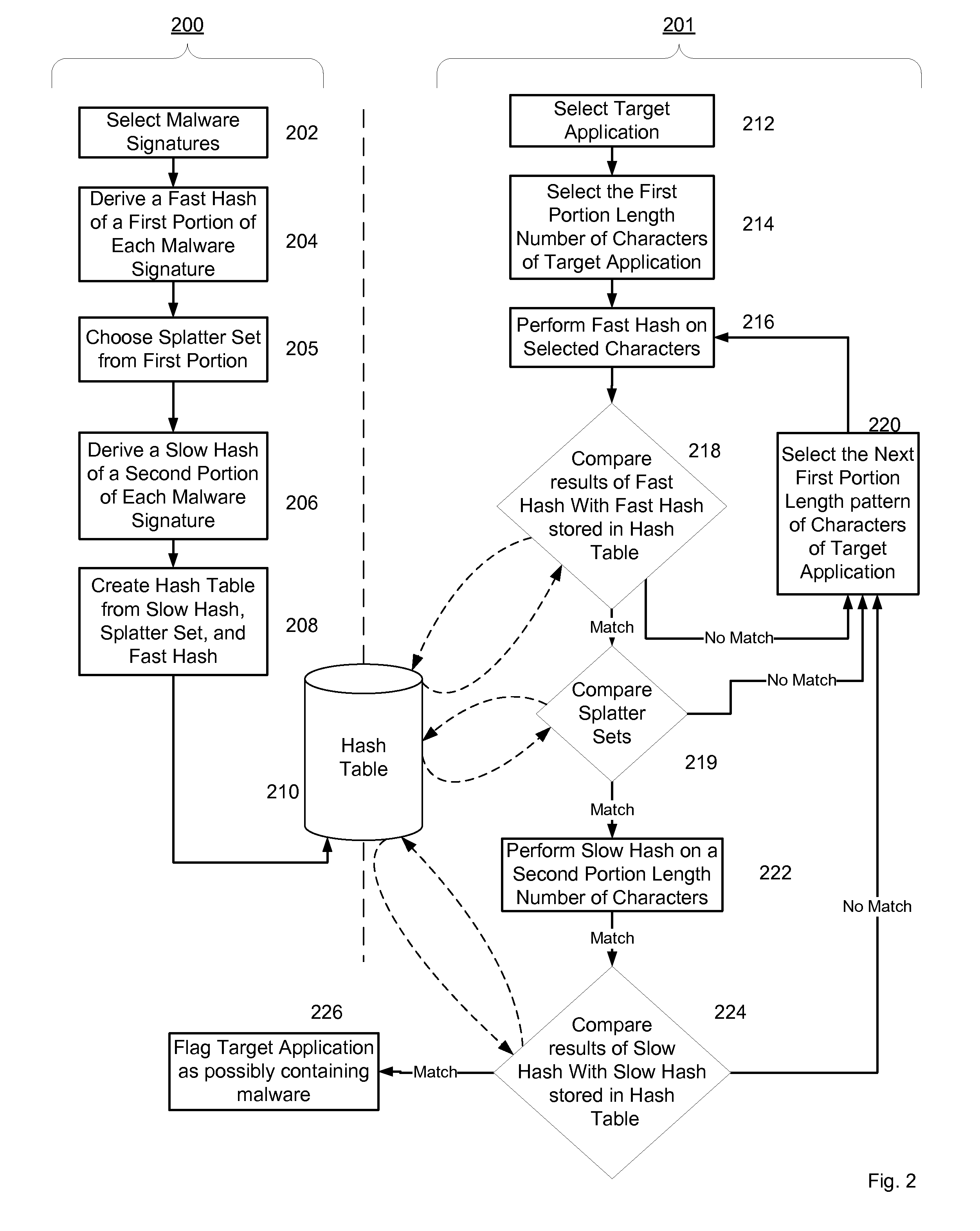
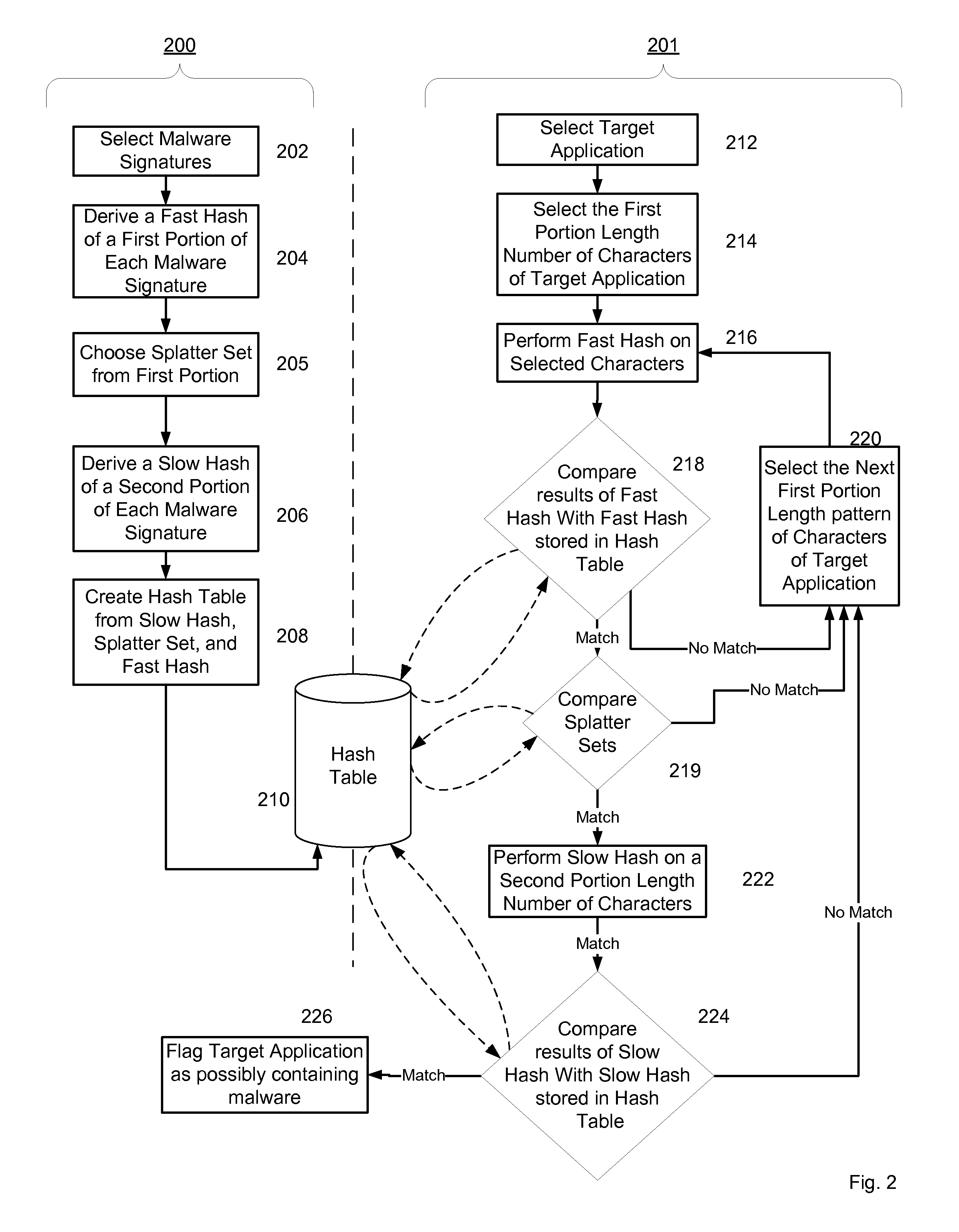
System and Method for Managing Malware Protection on Mobile Devices
InactiveUS20070240222A1Reliable detectionAmount of memory can be minimisedMemory loss protectionError detection/correctionClient-sideMalware
A system and method for providing malware protection on client mobile platforms in a mobile network. The system and method manages the malware scanning agents of the client mobile platforms from a management server using a device independent secure management protocol. The management server downloads new malware definitions to client mobile platforms and remotely initiates malware scanning on the client mobile platforms.
Owner:PULSE SECURE
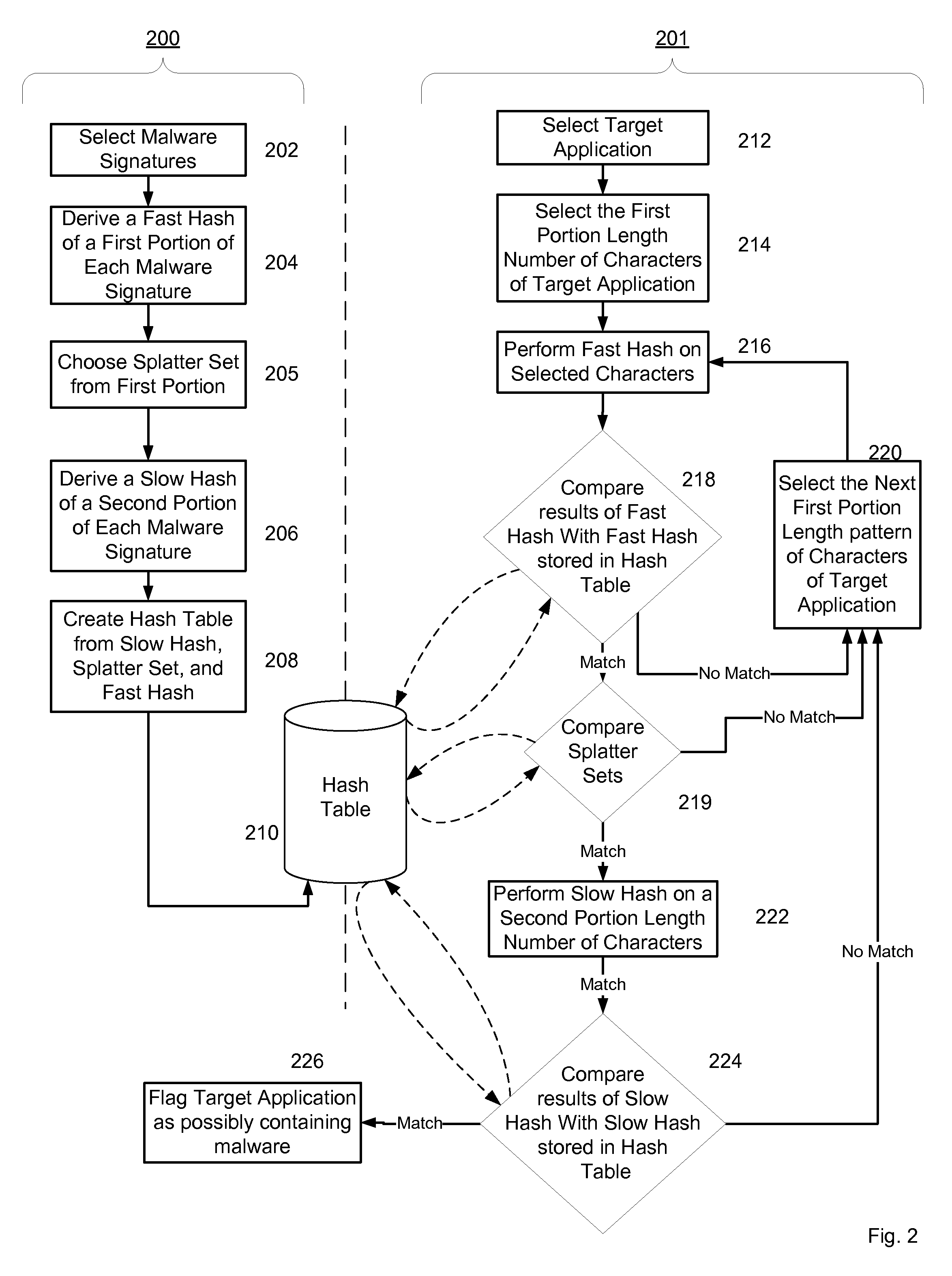
Malware Modeling Detection System And Method for Mobile Platforms
ActiveUS20070240217A1Suitable for useReliable detectionMemory loss protectionUser identity/authority verificationFeature setAlgorithm
A system and method for detecting malware by modeling the behavior of malware and comparing a suspect executable with the model. The system and method extracts feature elements from malware-infected applications, groups the feature elements into feature sets, and develops rules describing a malicious probability relationship between the feature elements. Using malware-free and malware-infected applications as training data, the system and method heuristically trains the rules and creates a probability model for identifying malware. To detect malware, the system and method scans the suspect executable for feature sets and applies the results to the probability model to determine the probability that the suspect executable is malware-infected.
Owner:PULSE SECURE
System and method for managing malware protection on mobile devices
ActiveUS20070240220A1Suitable for useReliable detectionMemory loss protectionError detection/correctionLimited accessFeature set
A system and method for detecting malware on a limited access mobile platform in a mobile network. The system and method uses one or more feature sets that describe various non-executable portions of malware-infected and malware-free applications, and compares a application on the limited access mobile platform to the features sets. A match of the features in a suspect application to one of the feature sets provides an indication as to whether the suspect application is malware-infected or malware-free.
Owner:PULSE SECURE
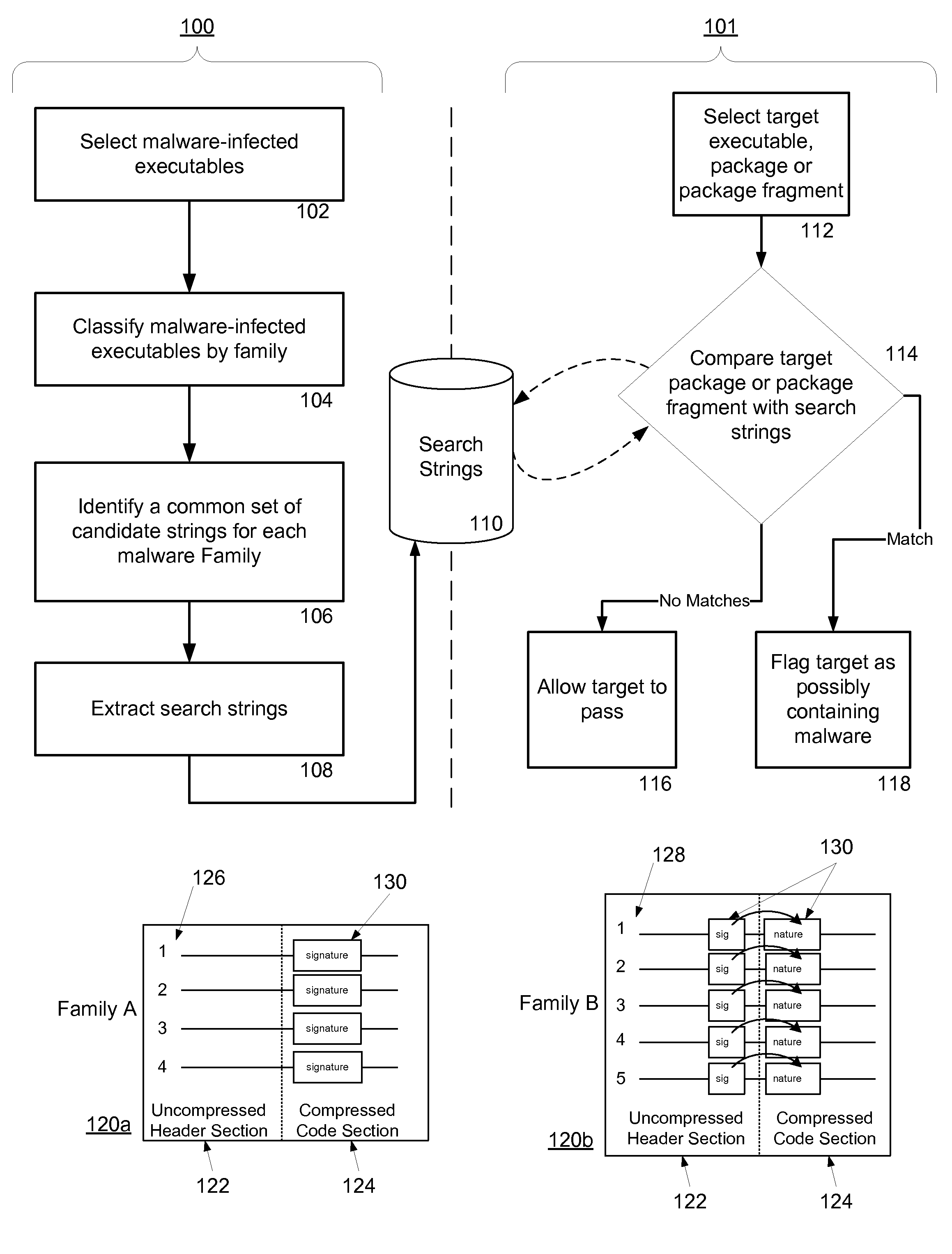
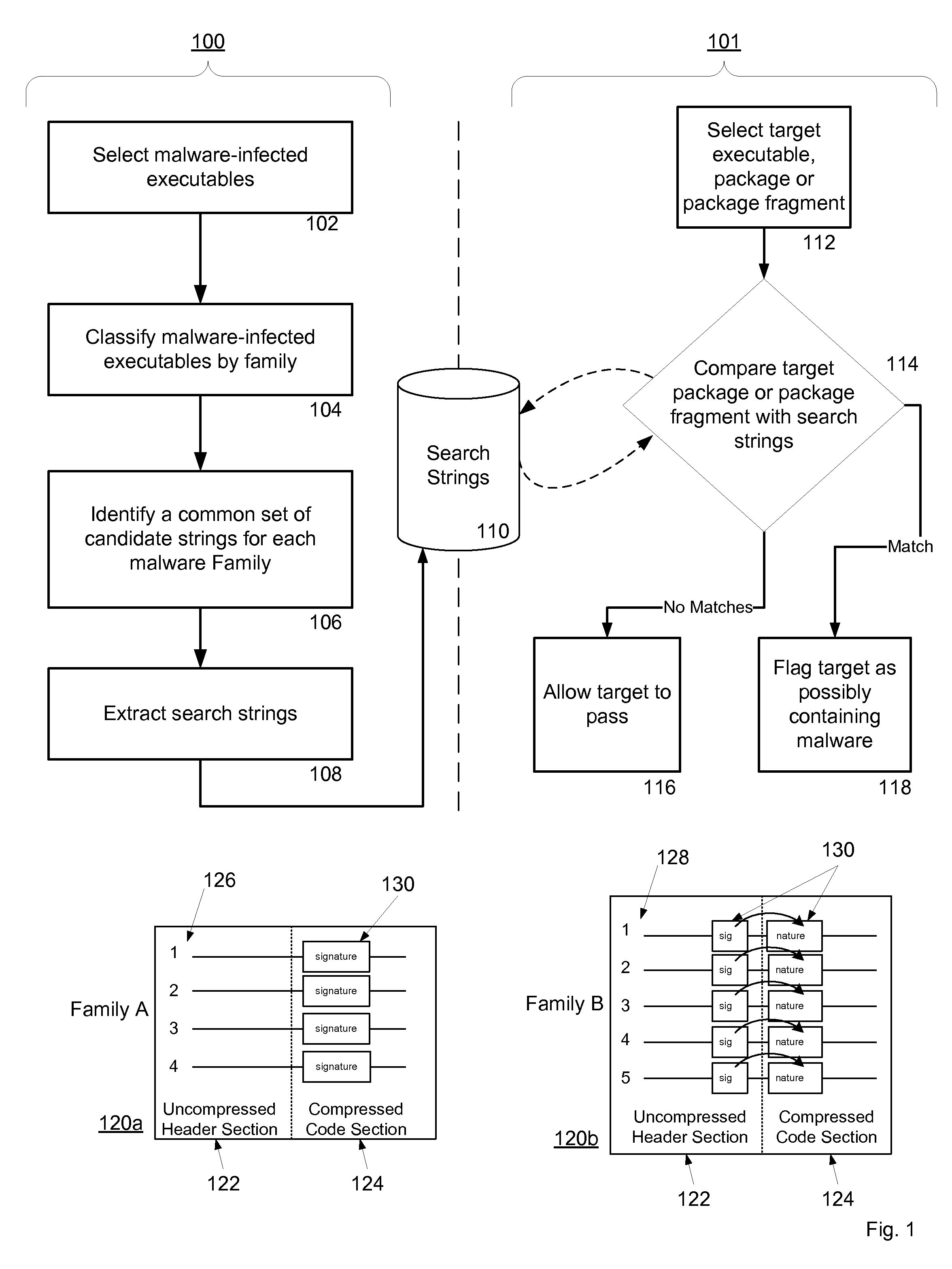
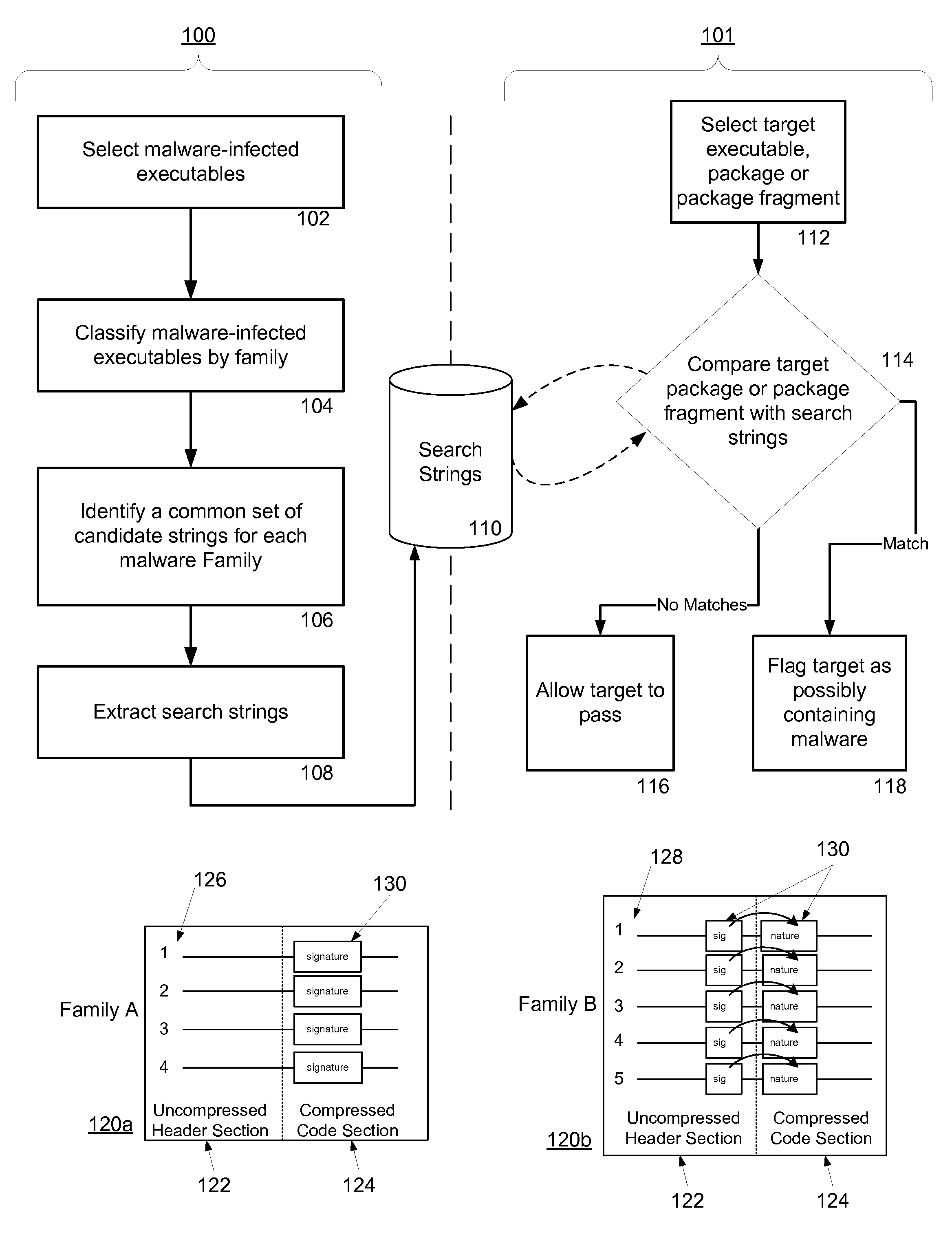
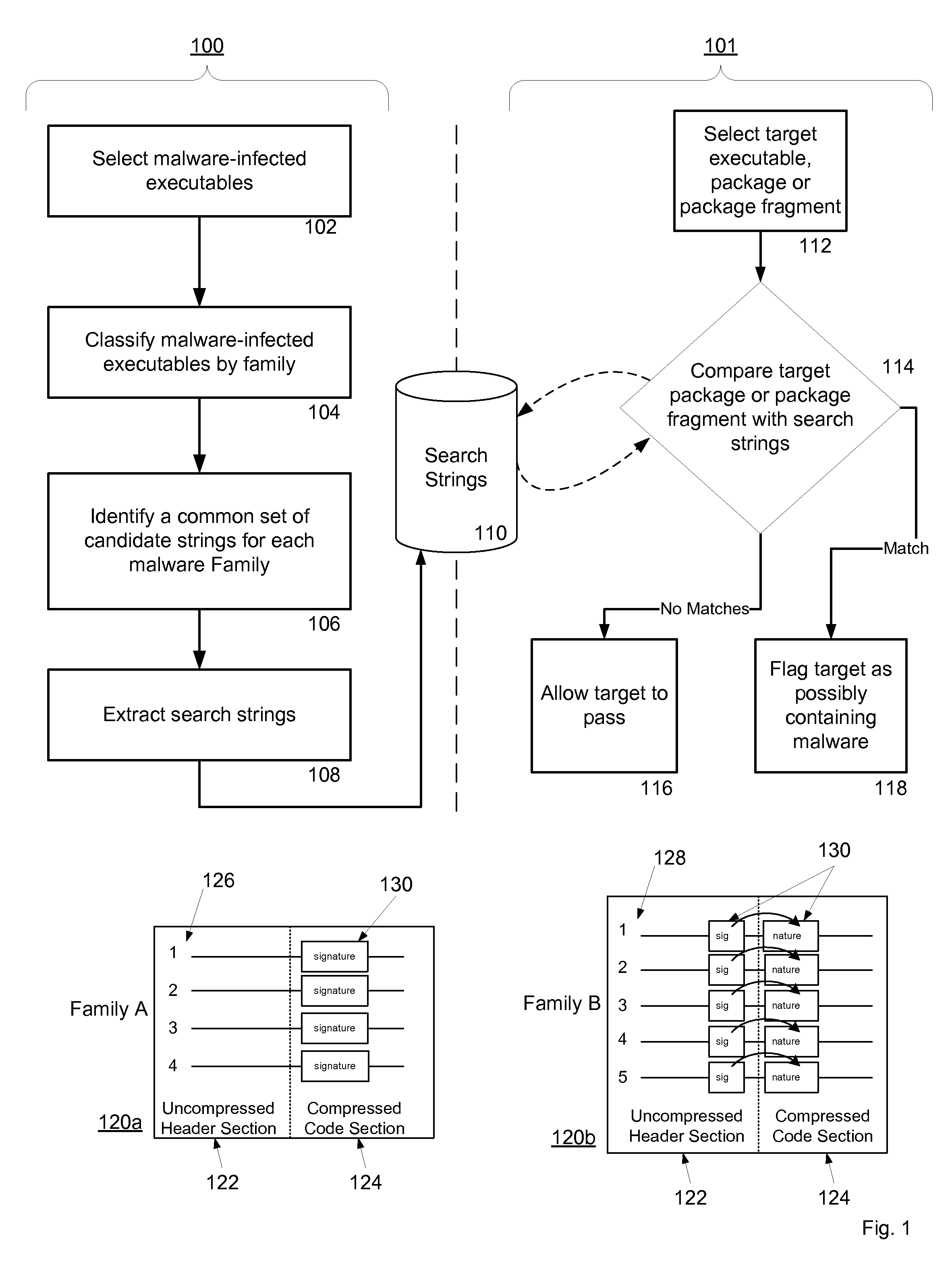
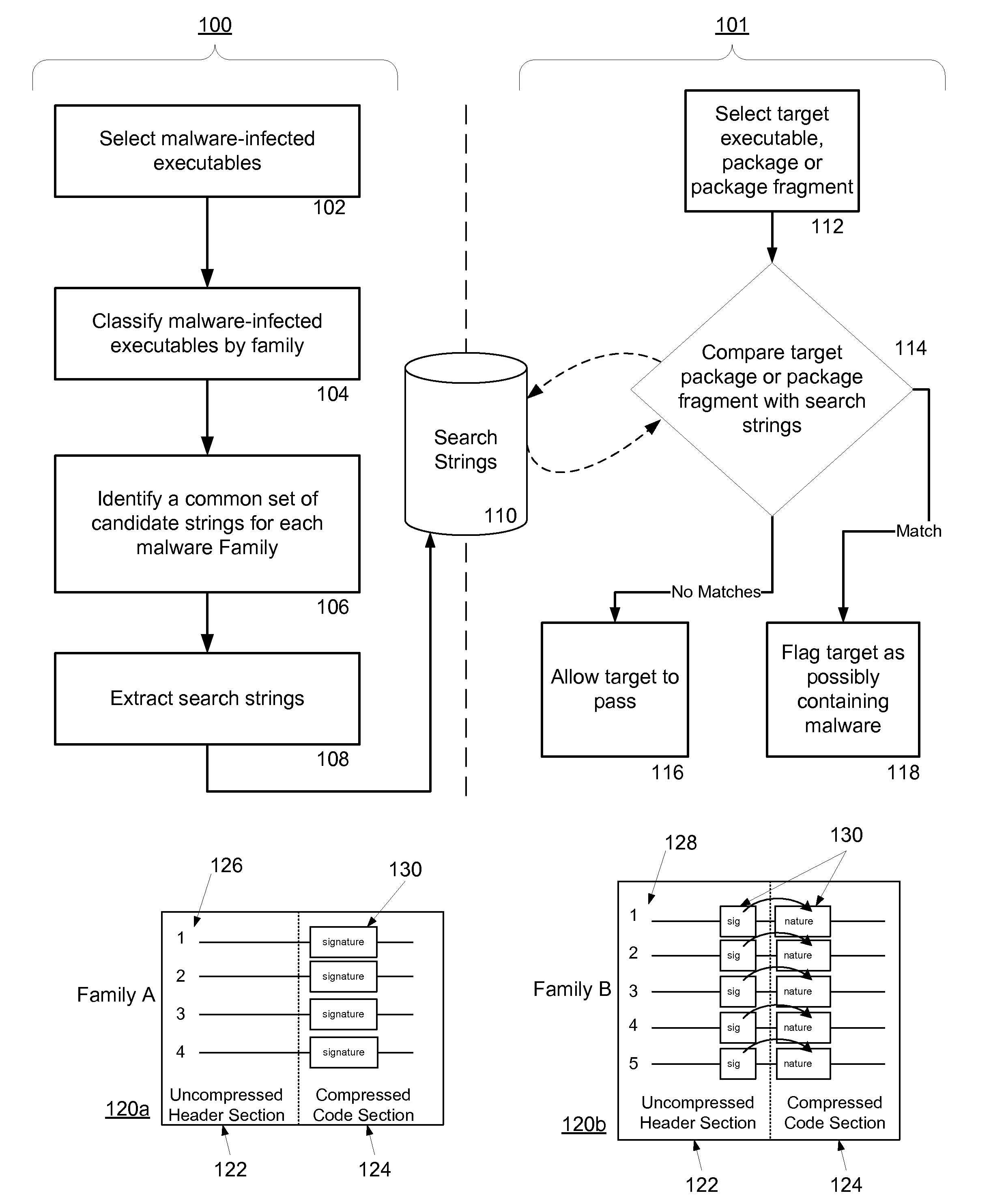
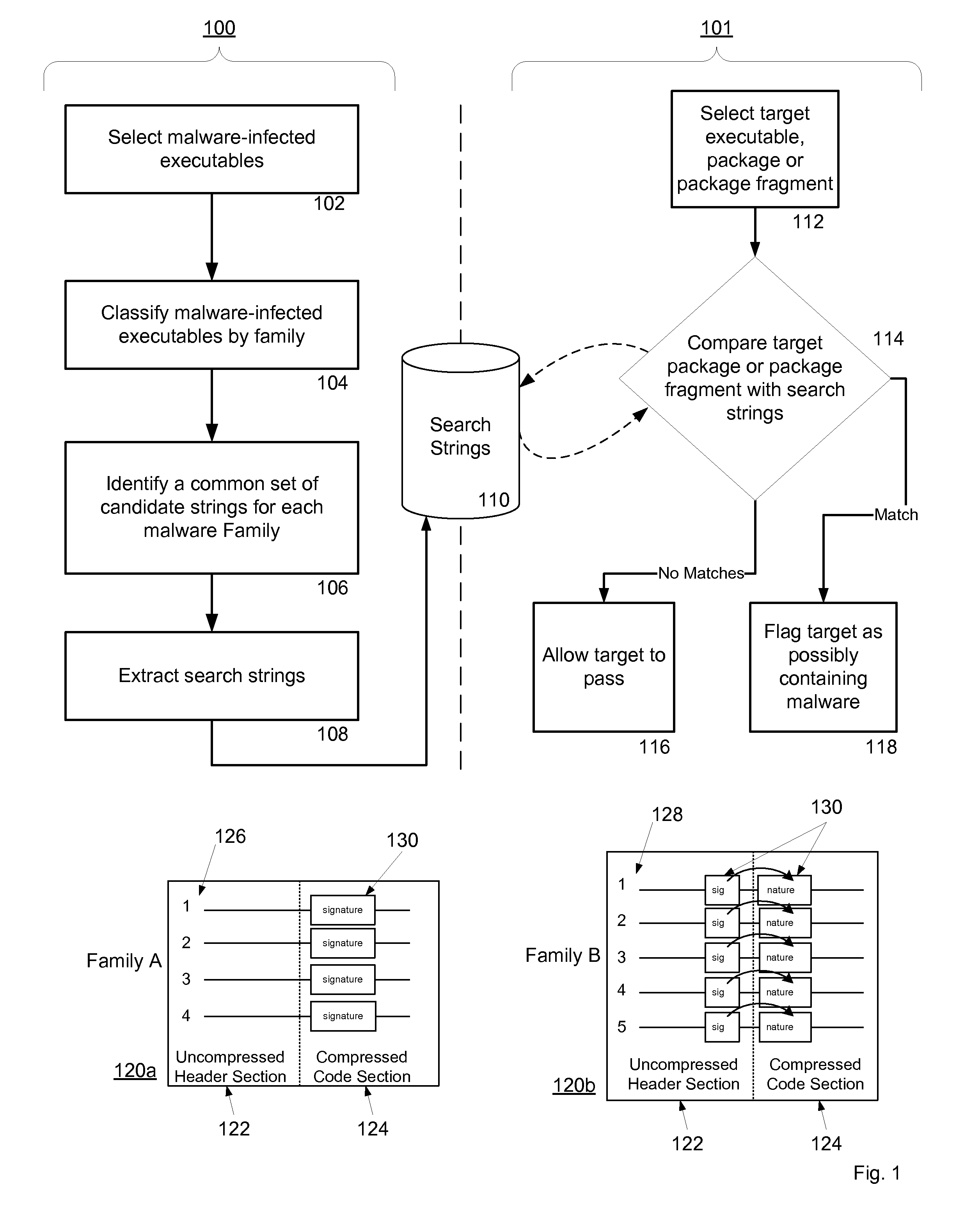
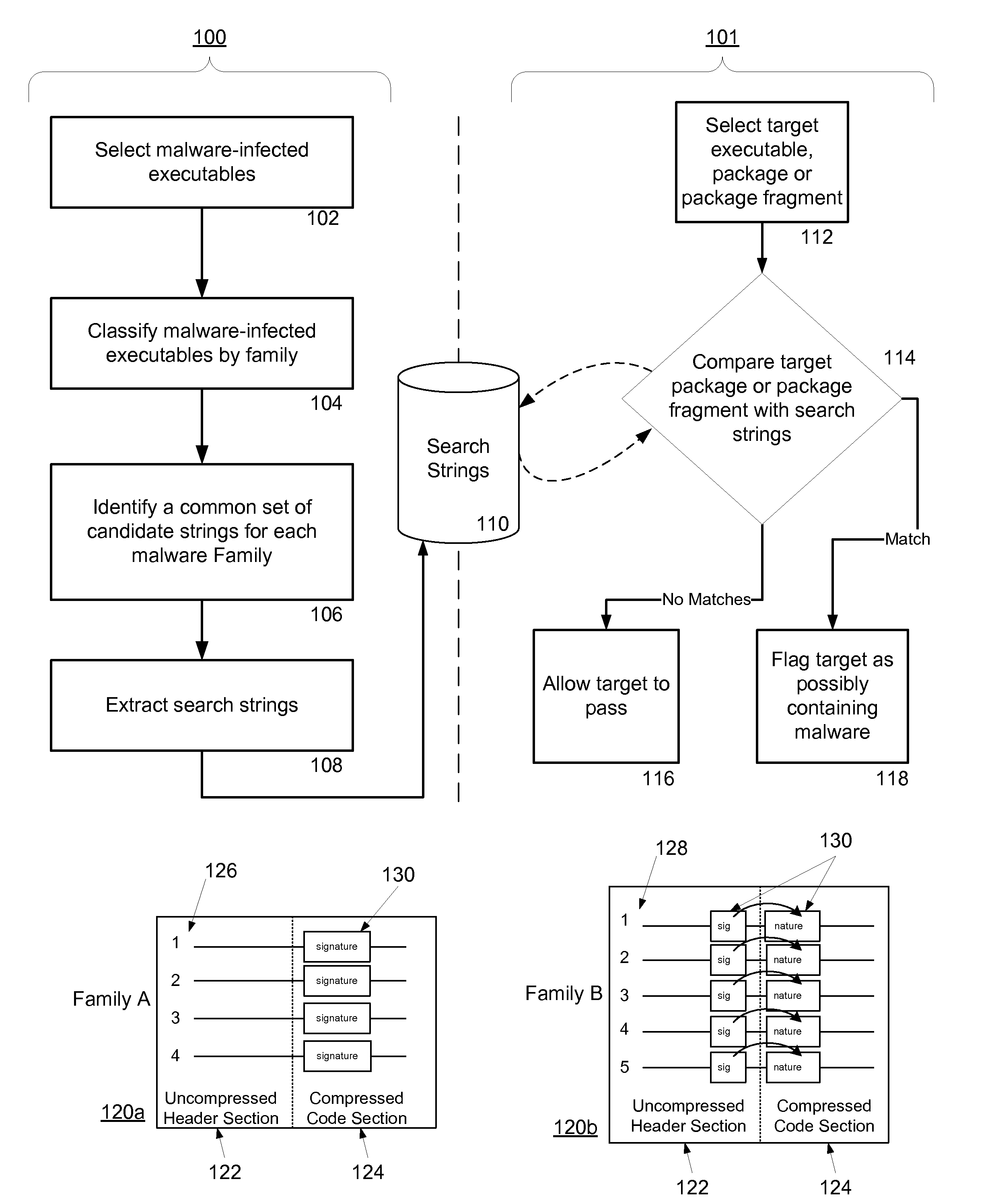
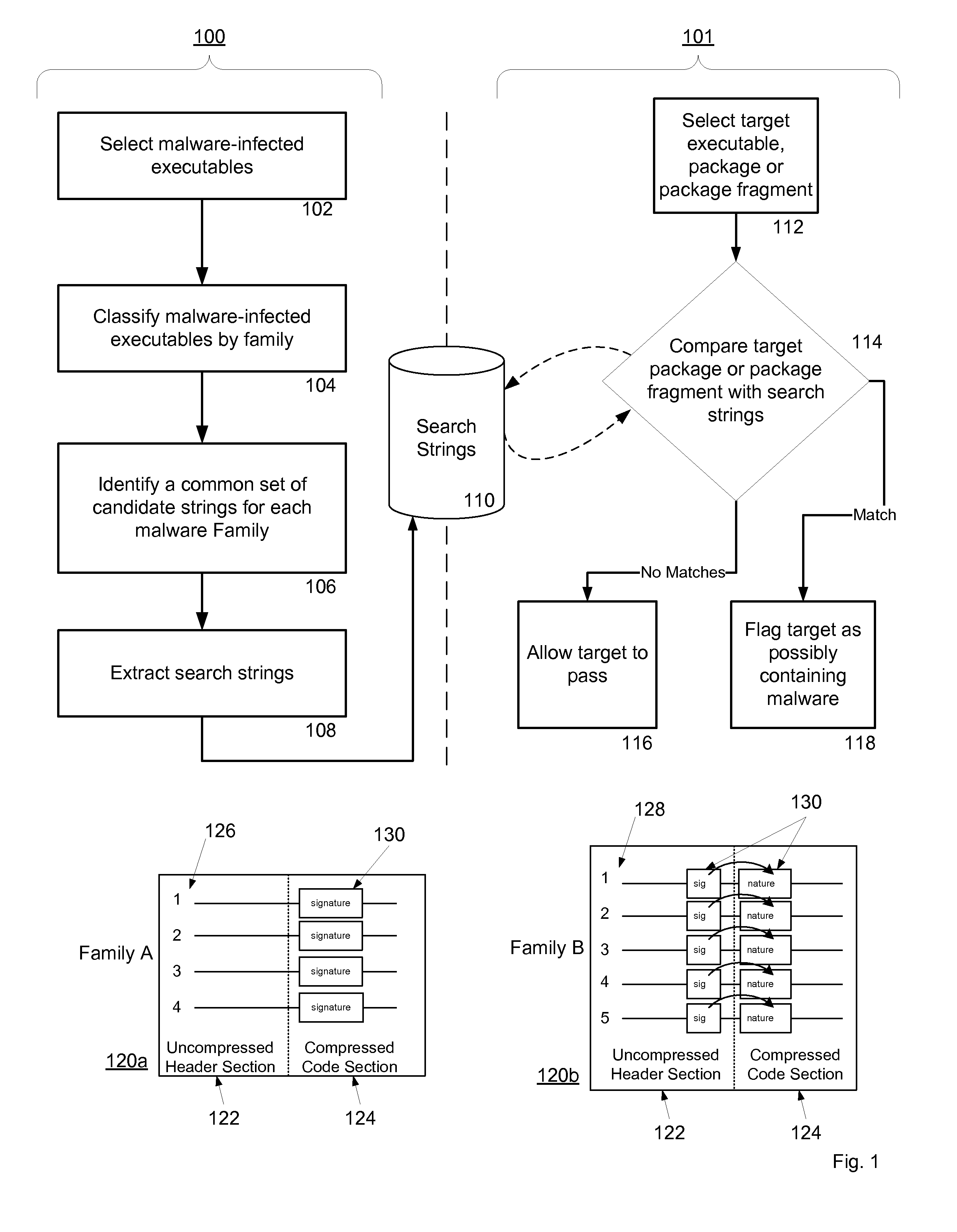
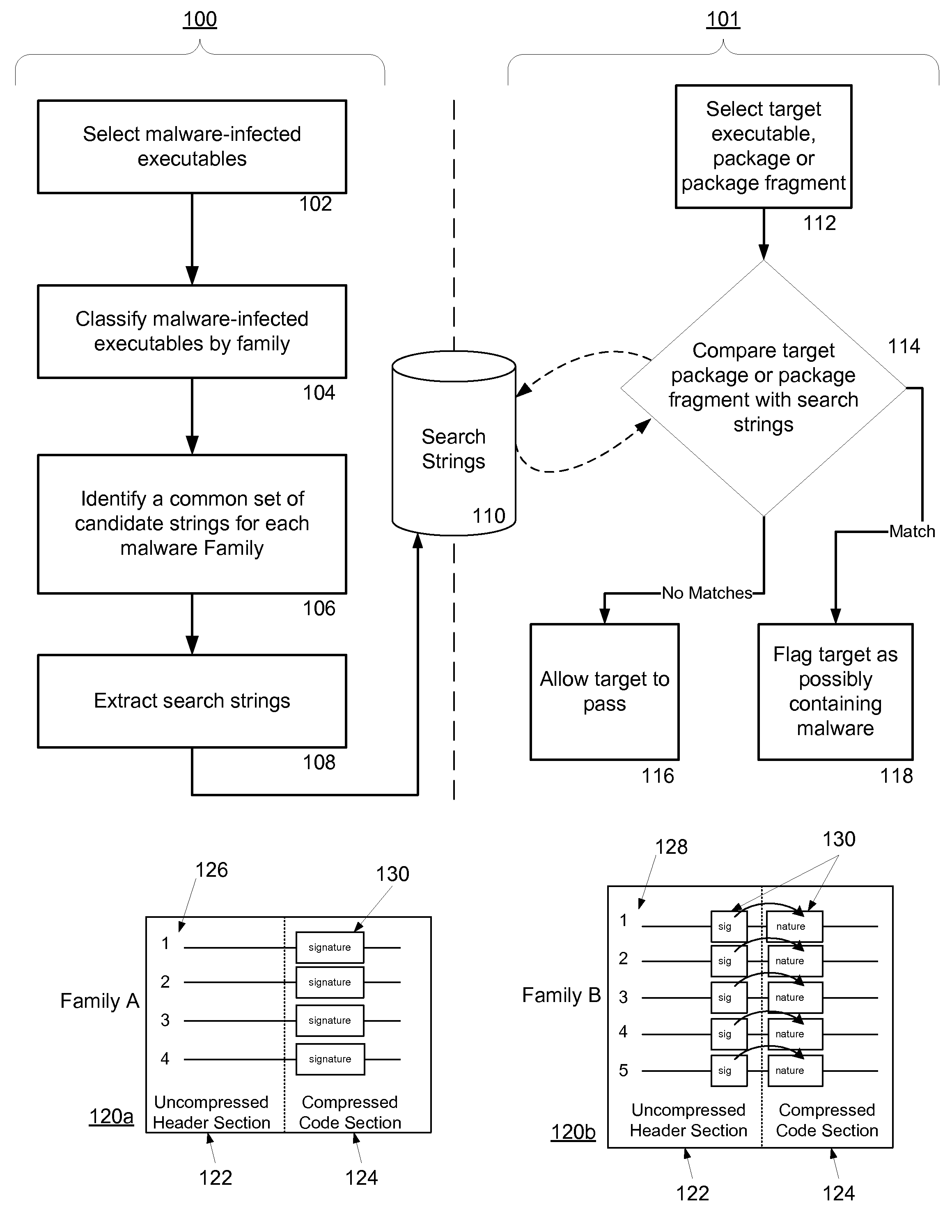
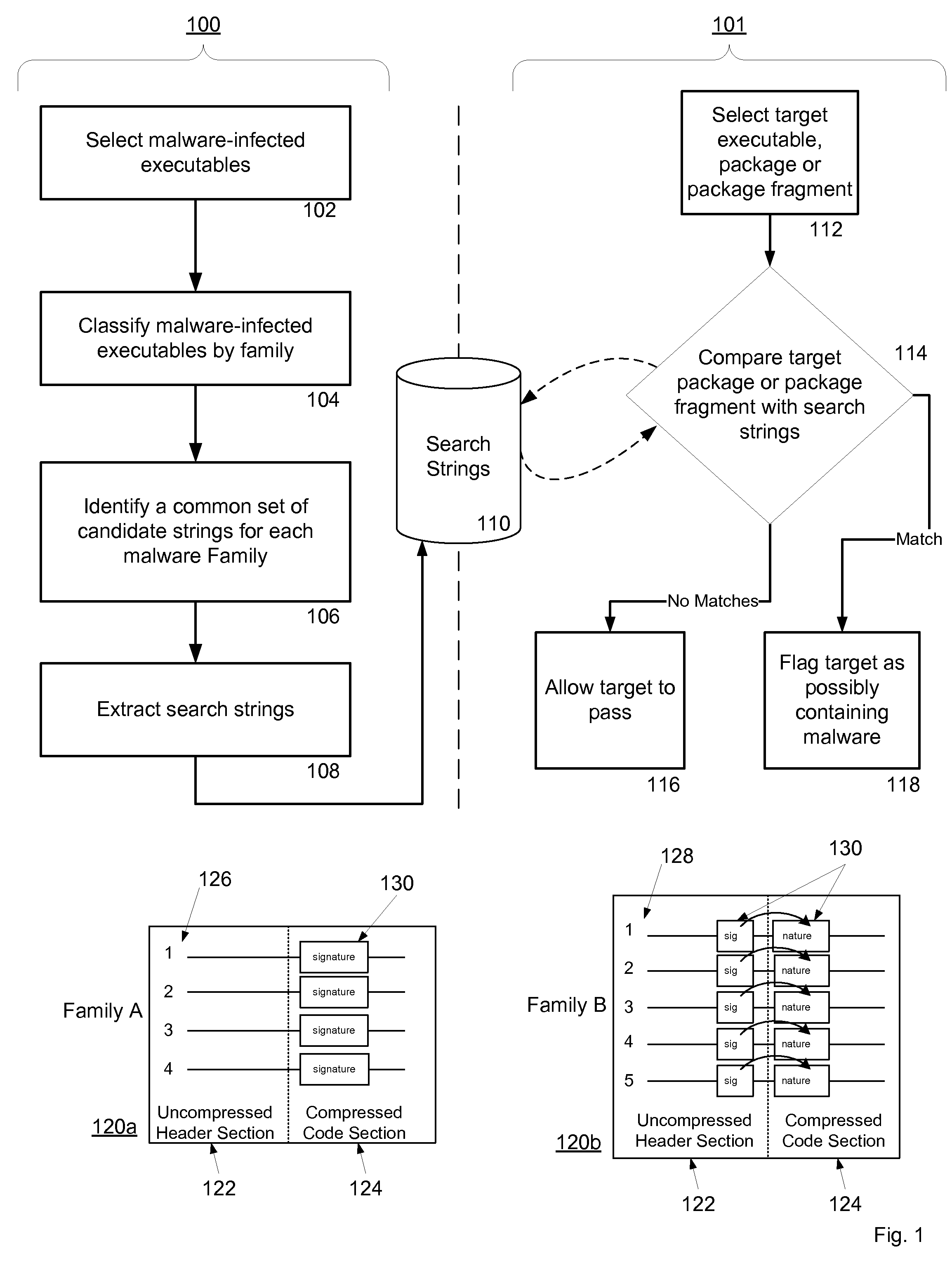
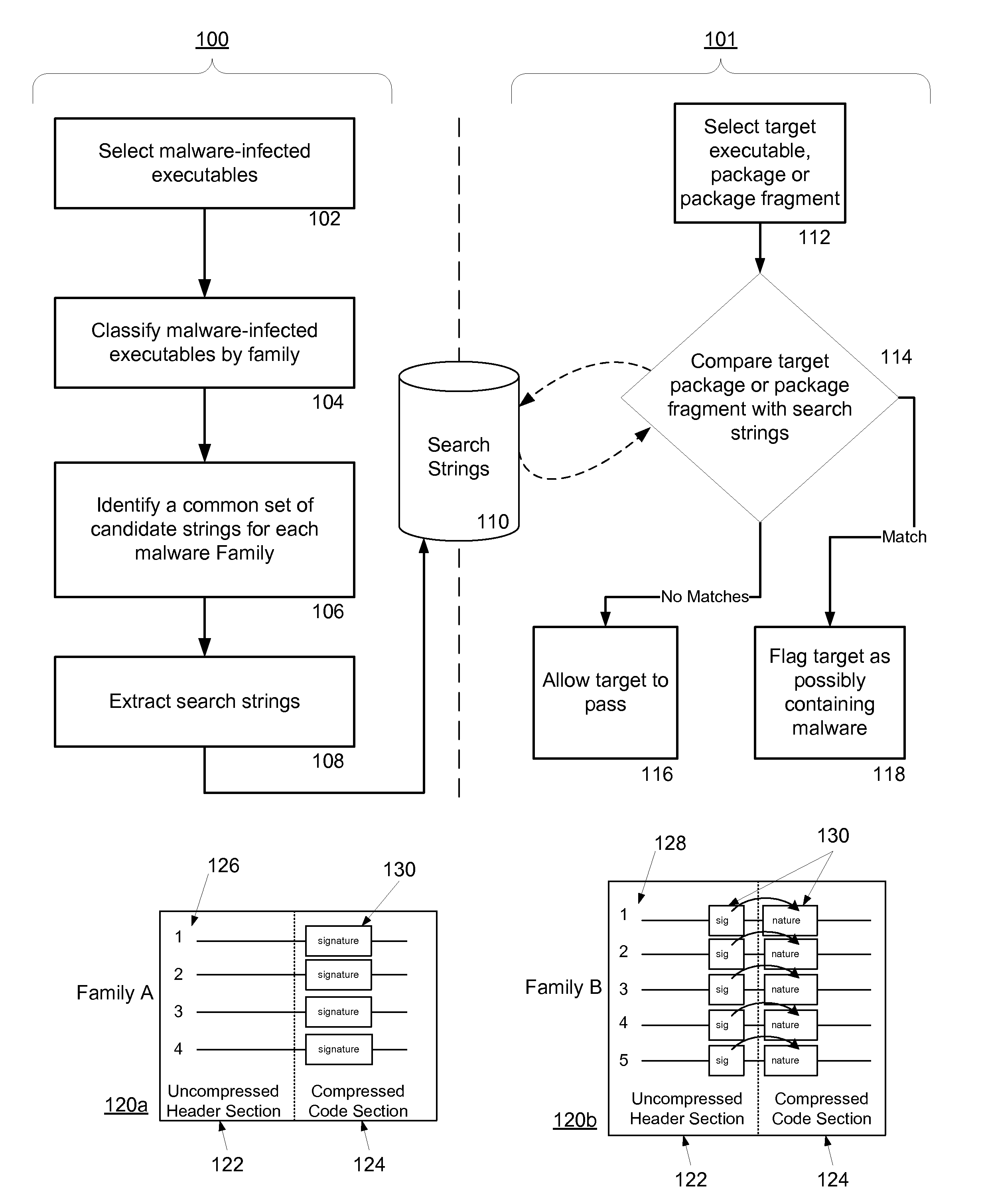
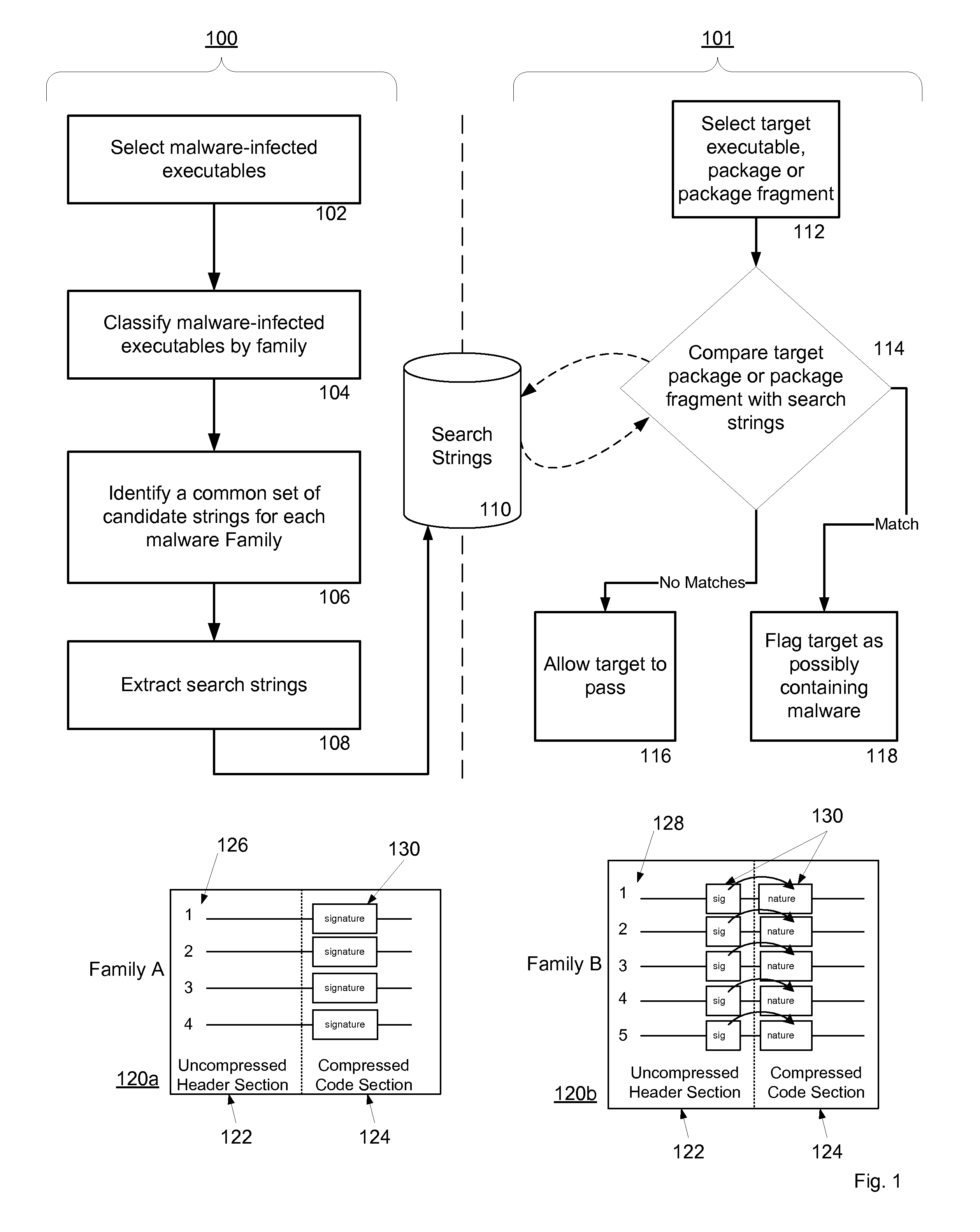
Malware Detection System And Method for Compressed Data on Mobile Platforms
ActiveUS20070240219A1Reliable detectionAmount of memory can be minimisedMemory loss protectionError detection/correctionMalwareExecutable
A system and method for detecting malware in compressed data. The system and method identifies a set of search strings extracted from compressed executables, each of which is infected with malware from a family of malware. The search strings detect the presence of the family of malware in other compressed executables, fragments of compressed executables, or data streams.
Owner:PULSE SECURE
Method and system for caching address translations from multiple address spaces in virtual machines
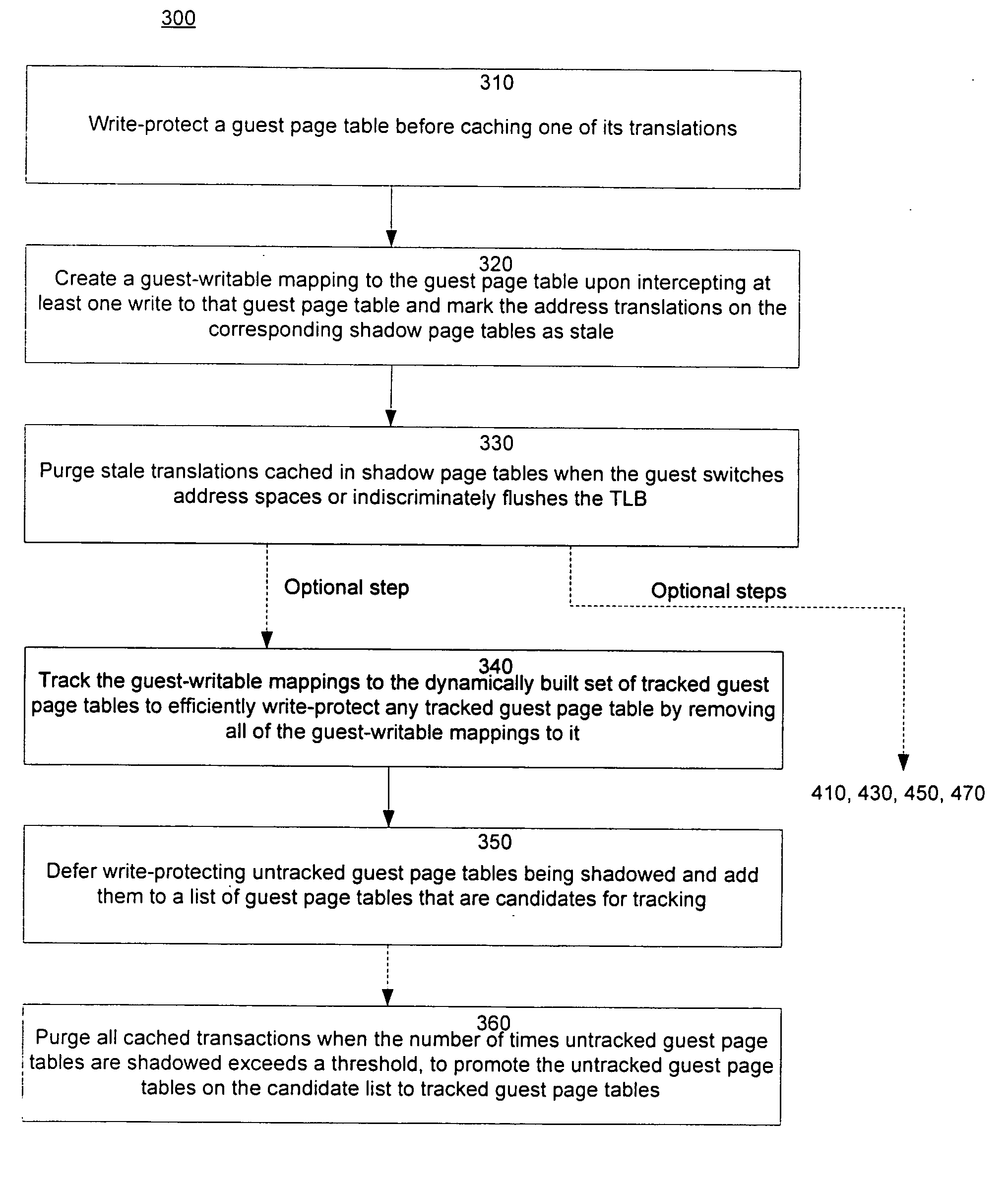
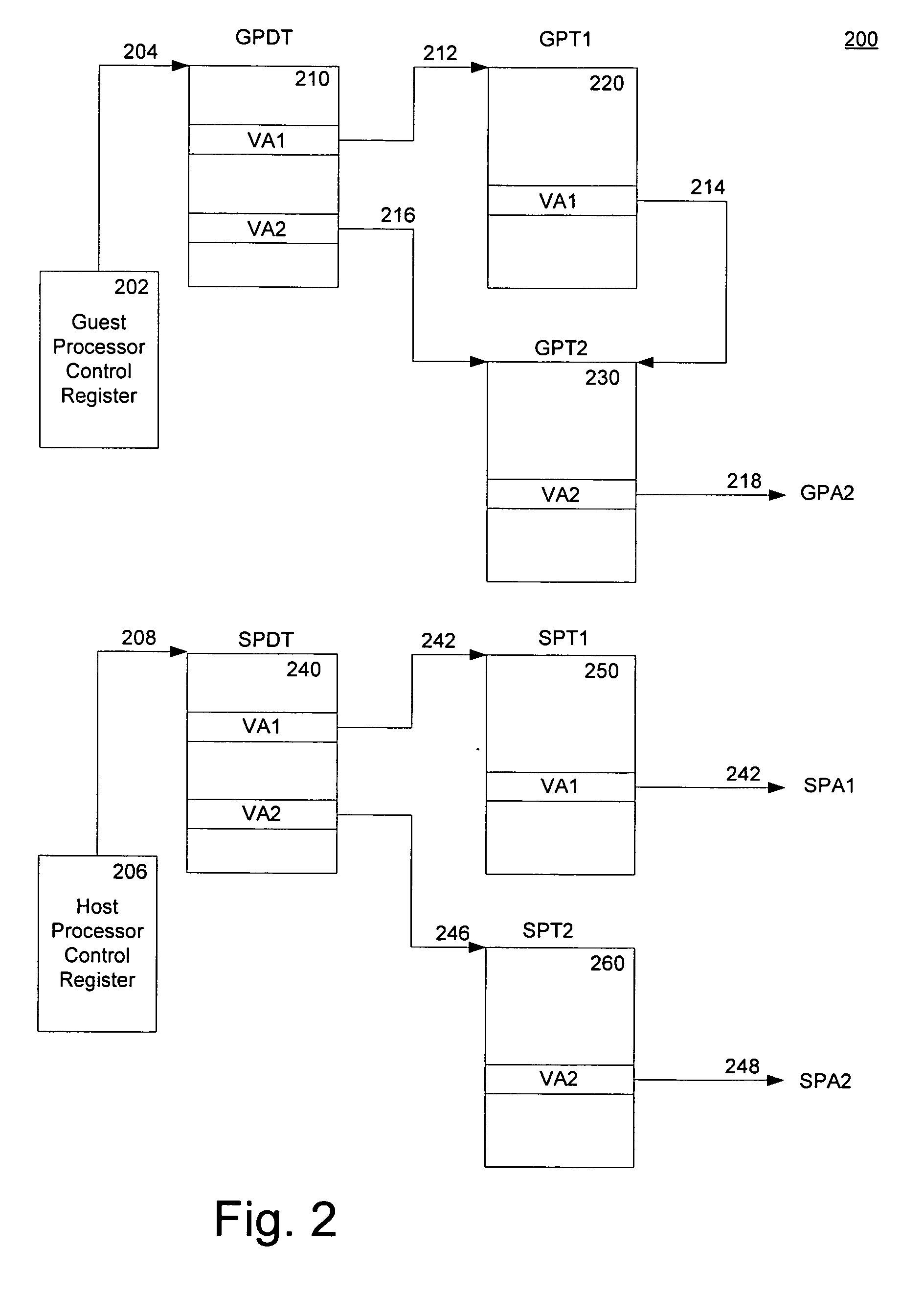
InactiveUS20060259734A1Reduce memory overheadLow costMemory architecture accessing/allocationMemory systemsVirtualizationPage table
A method of virtualizing memory through shadow page tables that cache translations from multiple guest address spaces in a virtual machine includes a software version of a hardware tagged translation look-aside buffer. Edits to guest page tables are detected by intercepting the creation of guest-writable mappings to guest page tables with translations cached in shadow page tables. The affected cached translations are marked as stale and purged upon an address space switch or an indiscriminate flush of translations by the guest. Thereby, non-stale translations remain cached but stale translations are discarded. The method includes tracking the guest-writable mappings to guest page tables, deferring discovery of such mappings to a guest page table for the first time until a purge of all cached translations when the number of untracked guest page tables exceeds a threshold, and sharing shadow page tables between shadow address spaces and between virtual processors.
Owner:MICROSOFT TECH LICENSING LLC
System and method for rapidly tracking multiple faces
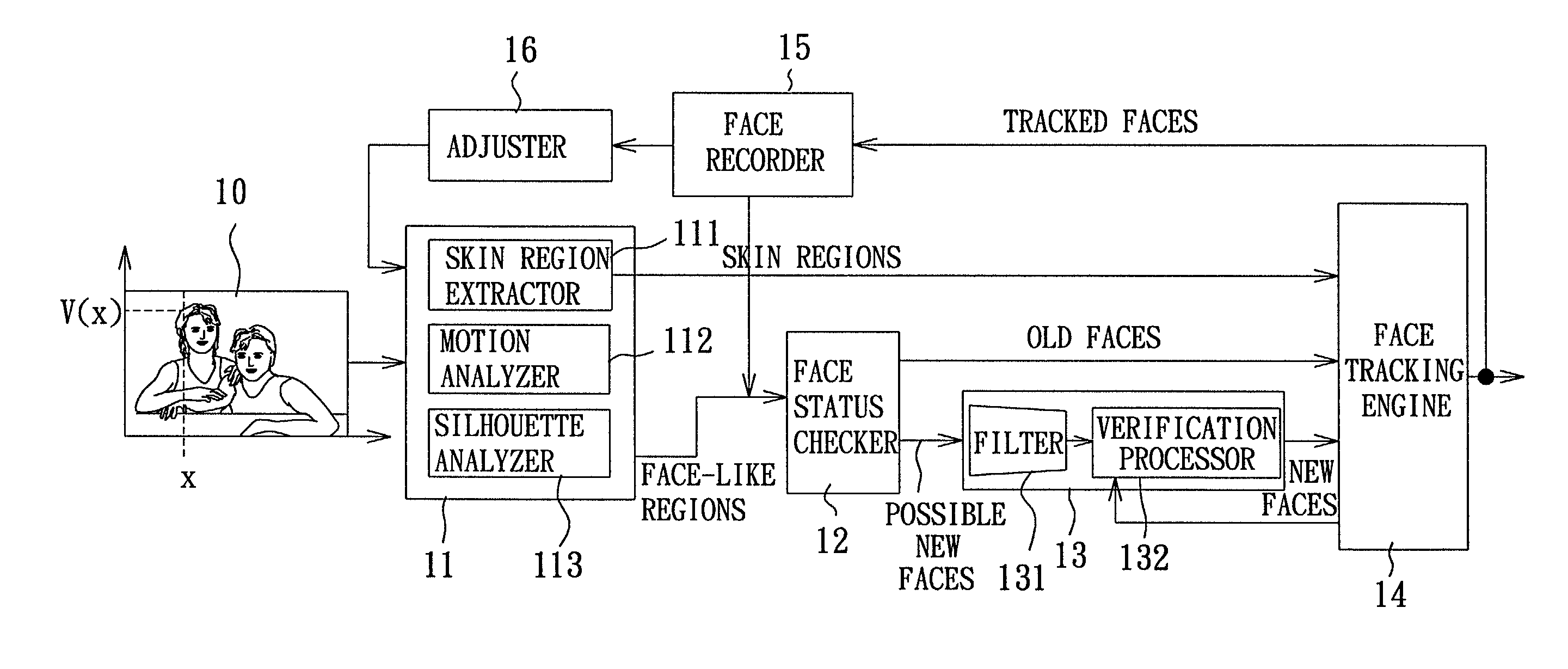
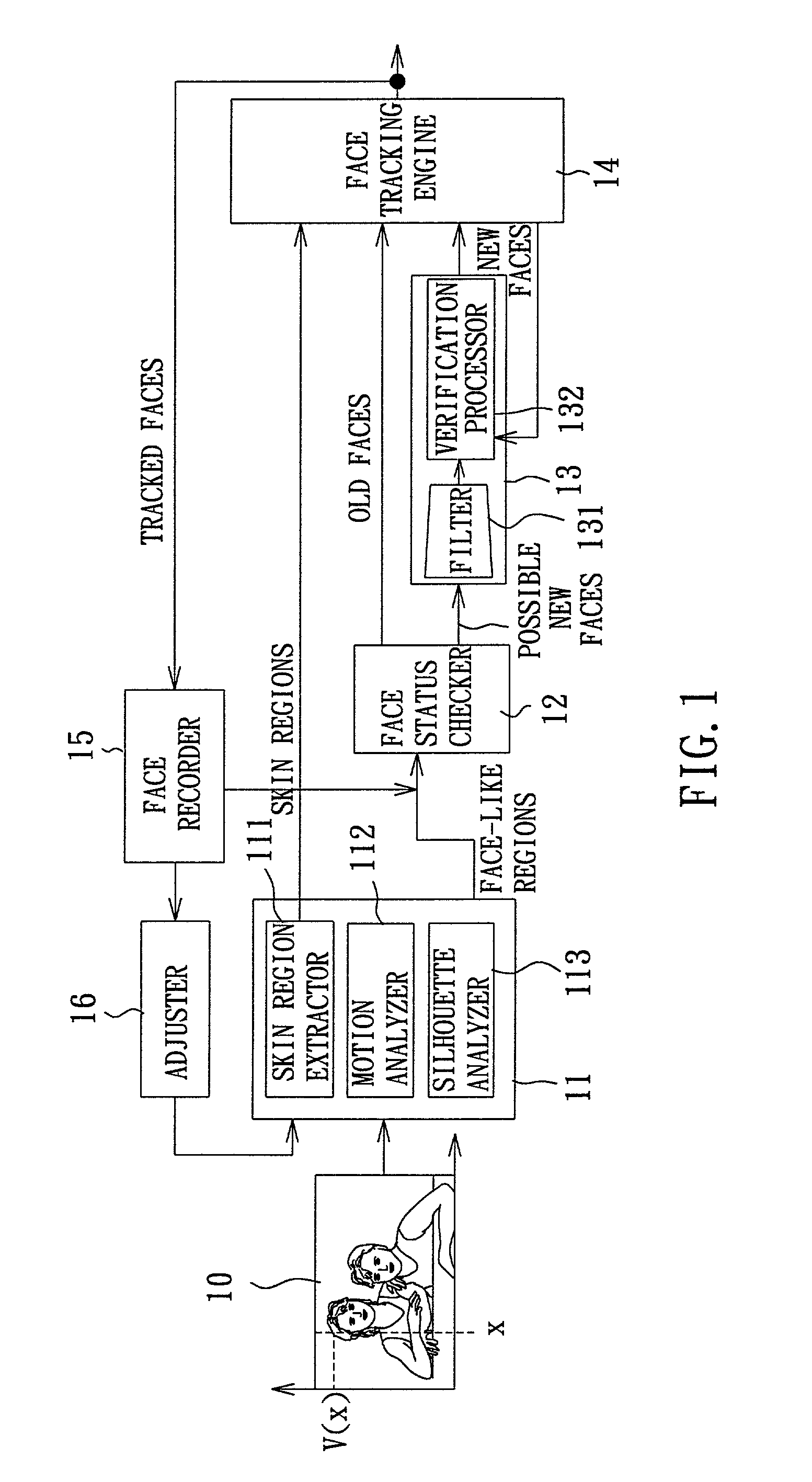
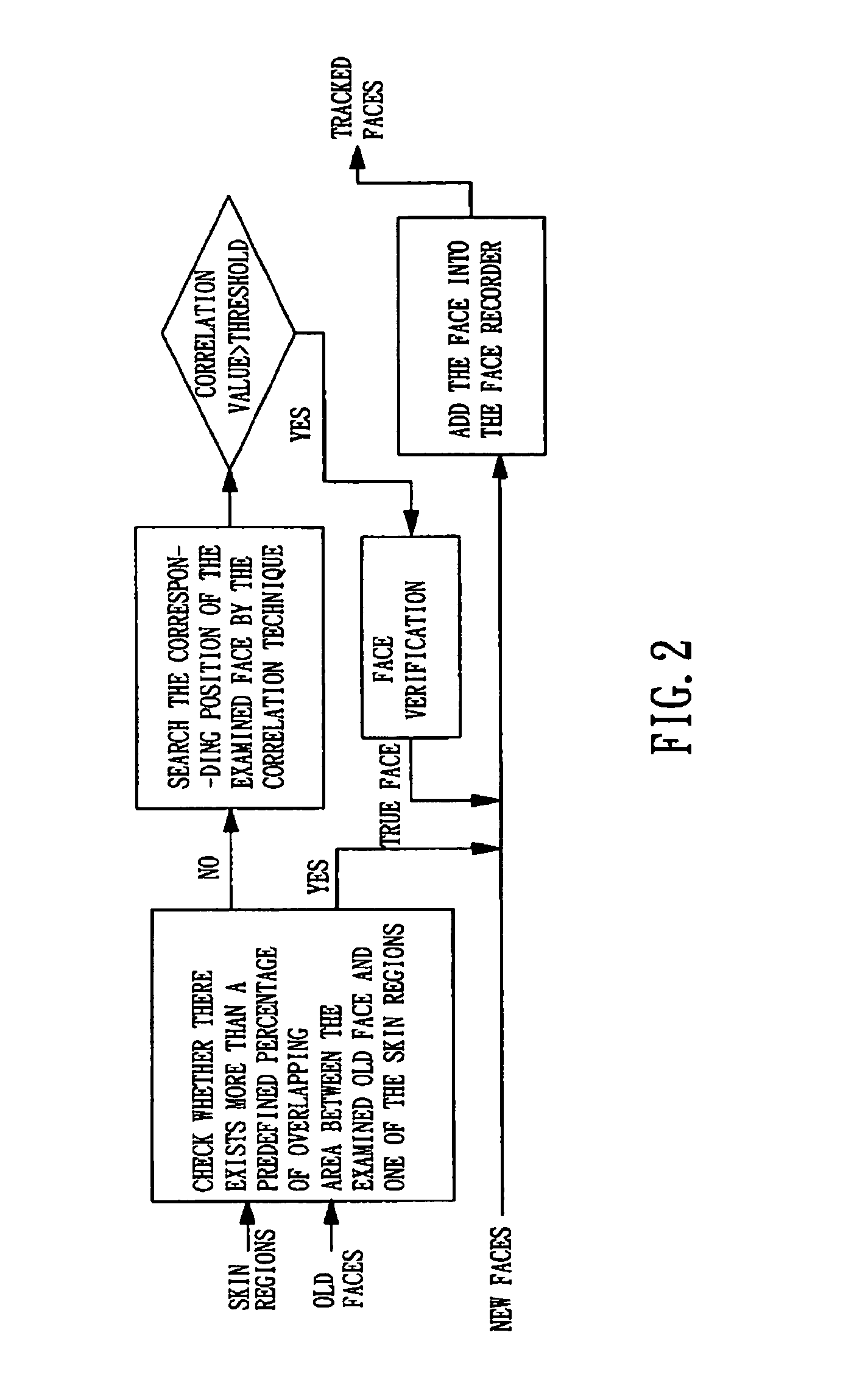
InactiveUS7003135B2Efficient detectionEffective trackingImage analysisCharacter and pattern recognitionSkin colorFace verification
A system and a method for rapidly tracking multiple faces uses a face-like region generator to find a face-like region by skin color, motion, and silhouette information. A face tracking engine tracks faces based on new and old faces, and skin colors provided by the face-like regions. The tracked face is fed into a face status checker for determining whether the face-like regions are old faces tracked in a previous frame or are possible new faces. If the face-like regions are old faces, a face verification engine checks whether there exists a predefined percentage of overlapping area between an old face and a skin region. If yes, the old face is still in the current frame and its position is in the center of the skin region, otherwise, the position of the old face is found by a correlation operation.
Owner:IND TECH RES INST
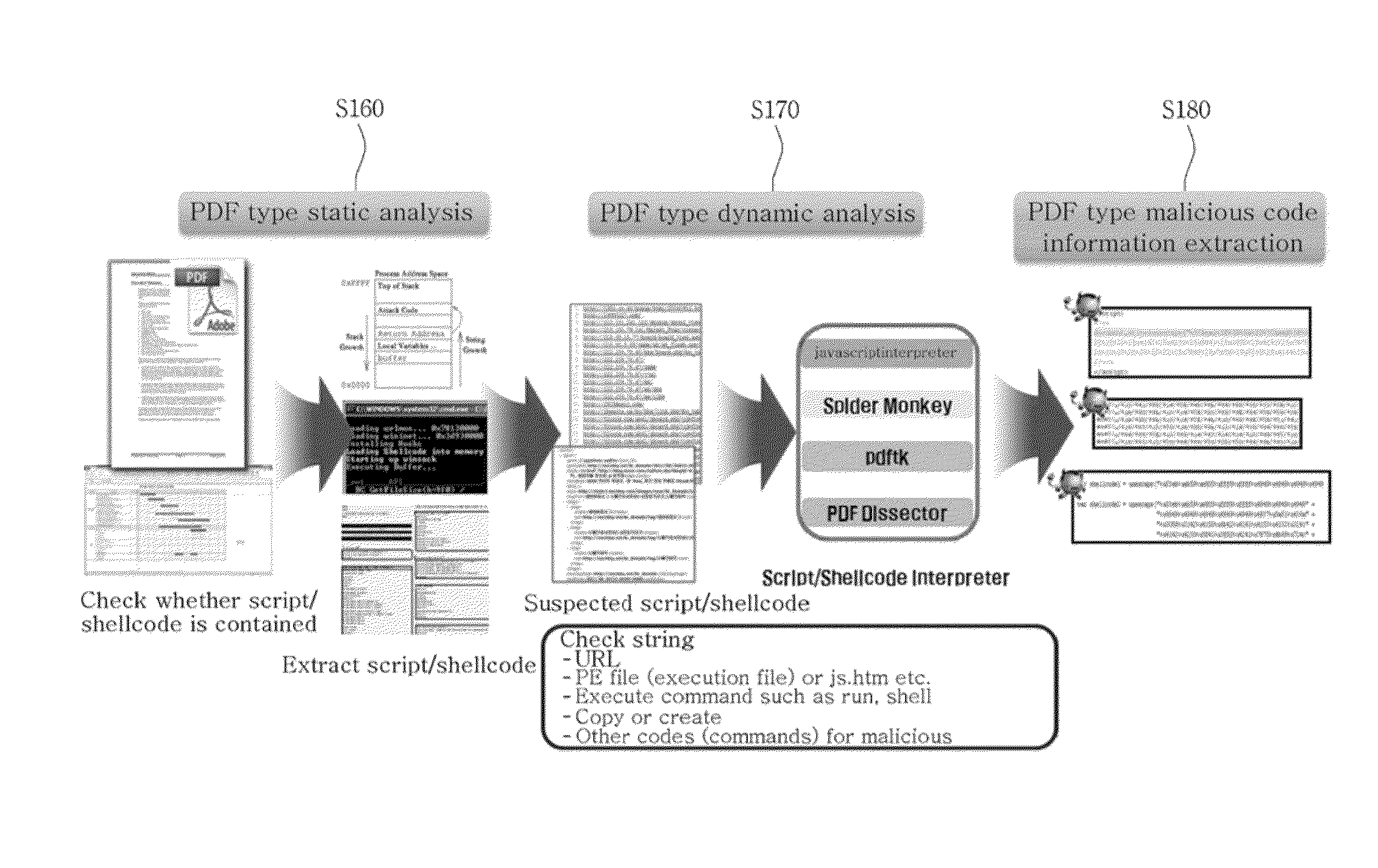
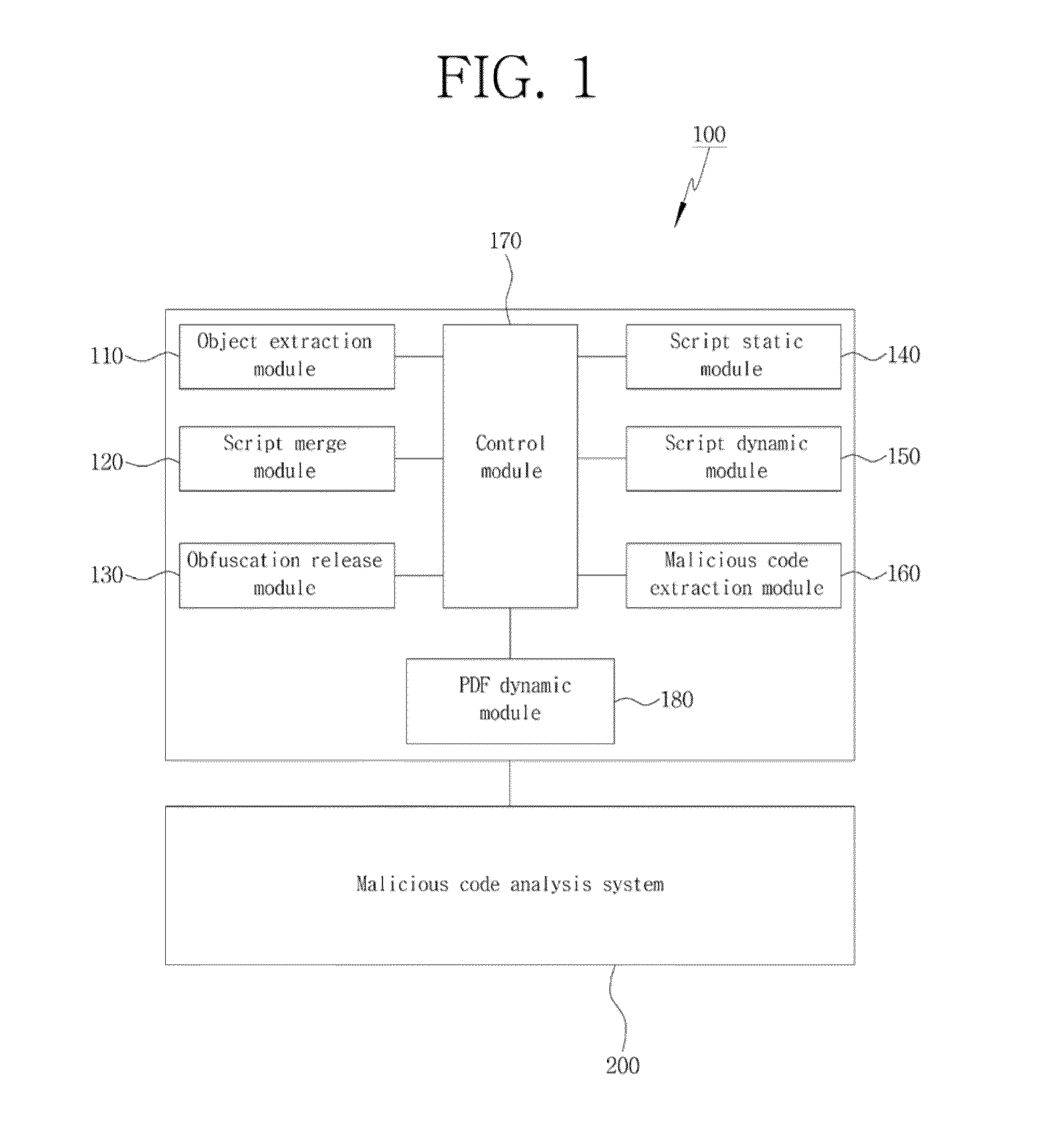
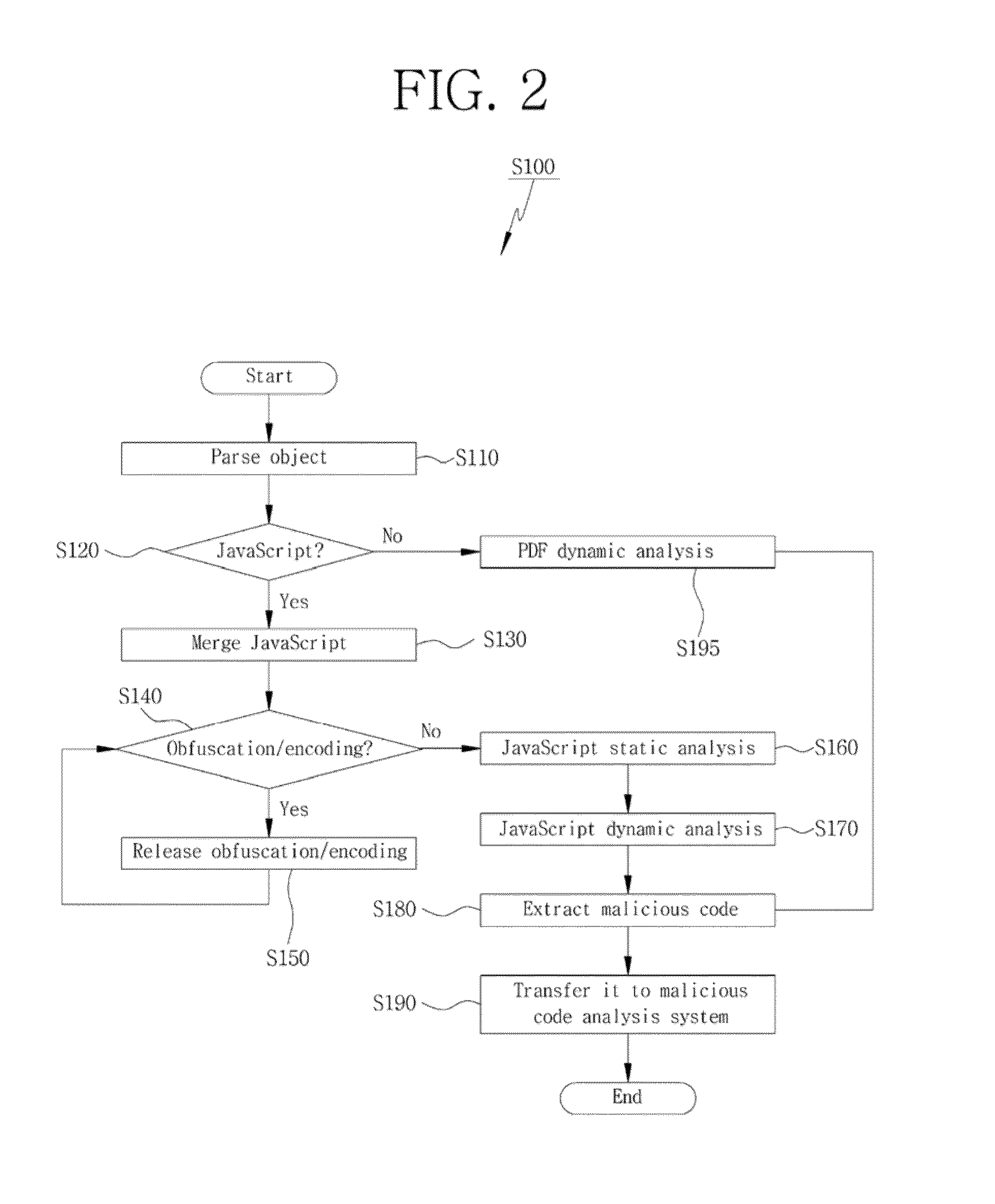
System and method for detecting malicious code of pdf document type
InactiveUS20130160127A1Efficient extractionEfficient detectionMemory loss protectionError detection/correctionDatabaseJavaScript
Disclosed herein is a PDF document type malicious code detection system for efficiently detecting a malicious code embedded in a document type and a method thereof. The present invention may perform a dynamic and static analysis on JavaScript within a PDF document, and execute the PDF document to perform a PDF dynamic analysis, thereby achieving an effect of efficiently extracting a malicious code embedded in the PDF document.
Owner:KOREA INTERNET & SECURITY AGENCY
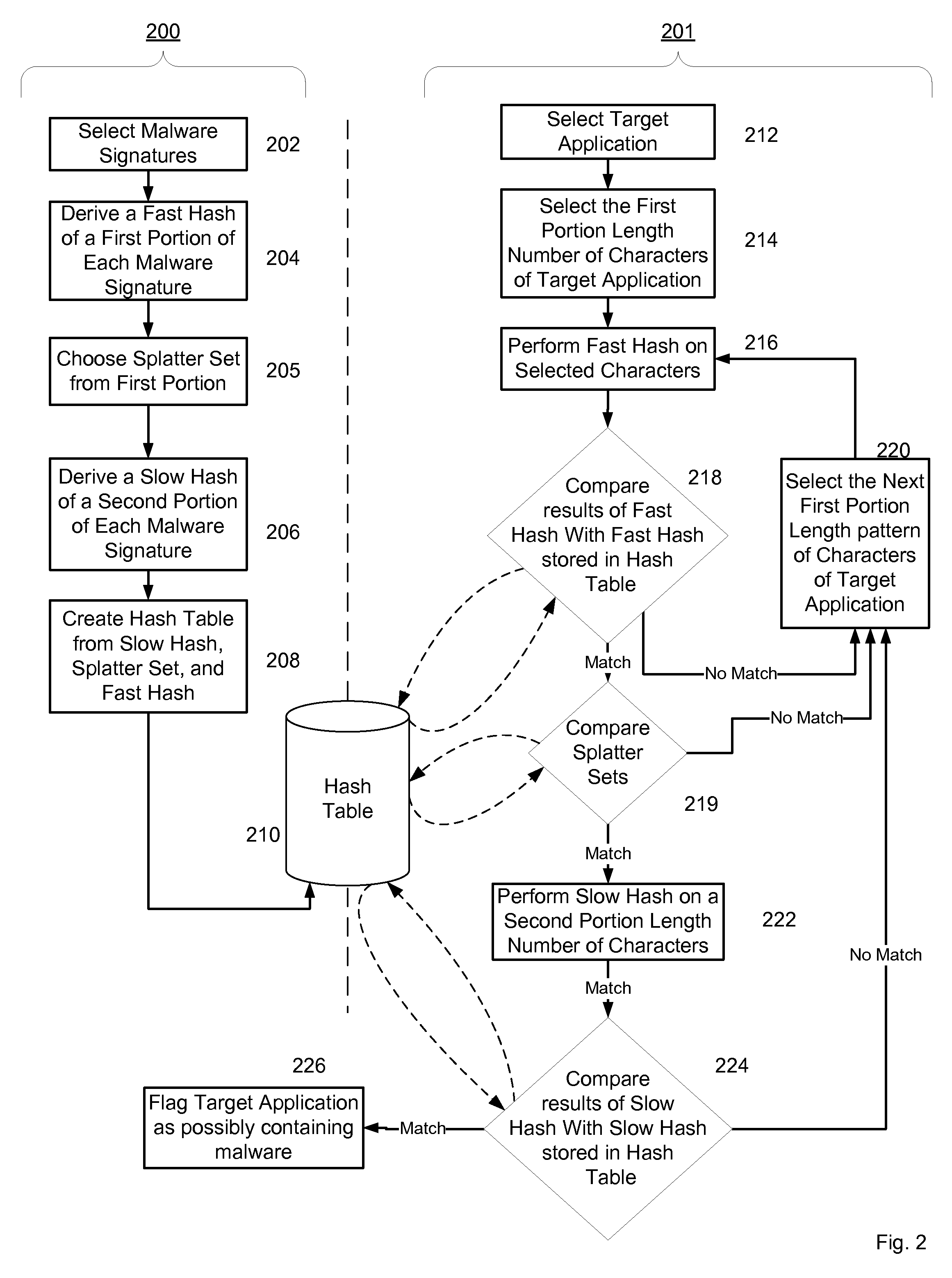
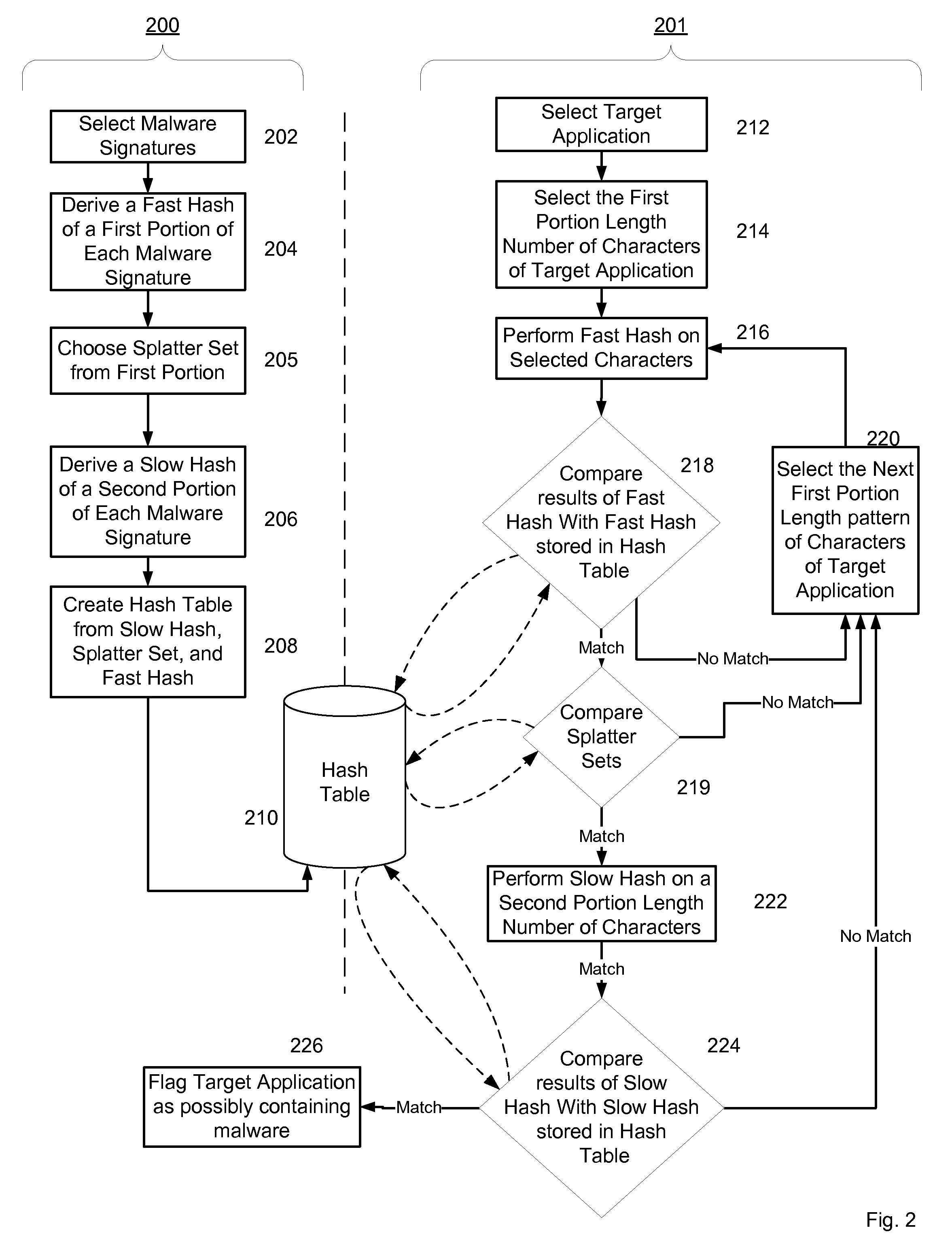
Non-Signature Malware Detection System and Method for Mobile Platforms
ActiveUS20070240221A1Suitable for useReliable detectionMemory loss protectionError detection/correctionEntry pointChecksum
A system and method for detecting malware on a mobile platform in a mobile network. The system and method verifies that an executable is malware-free by computing the checksum of the executable and comparing that checksum with a checksum obtained from a malware-free copy of the executable. The checksum is a sum of all 32-bit values in a code section and an import section of said executable, a byte sequence at an entry point in said executable, a size descriptor of an import table, a size descriptor of said import section, a cyclic redundancy check of said executable, or a combination thereof.
Owner:PULSE SECURE
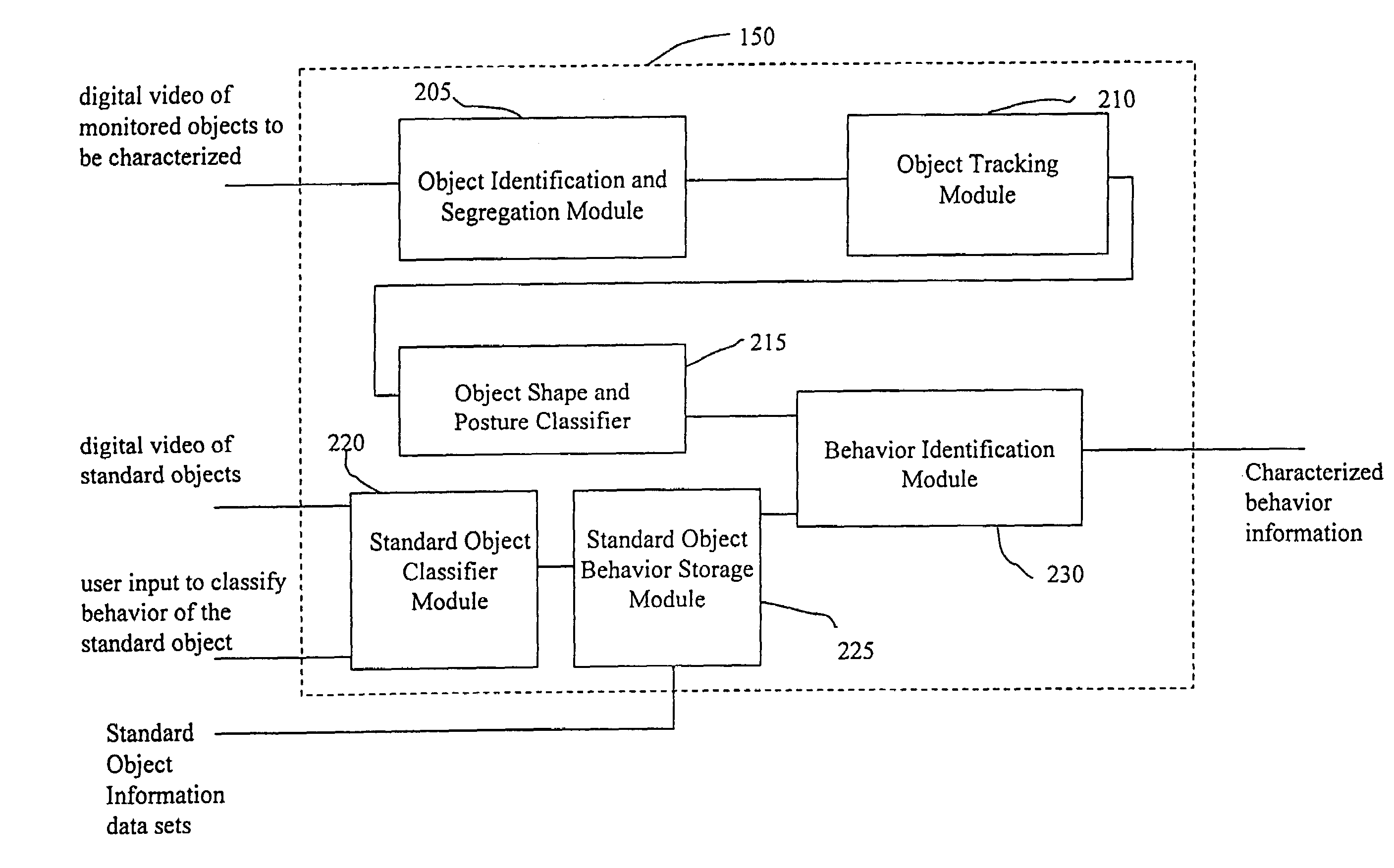
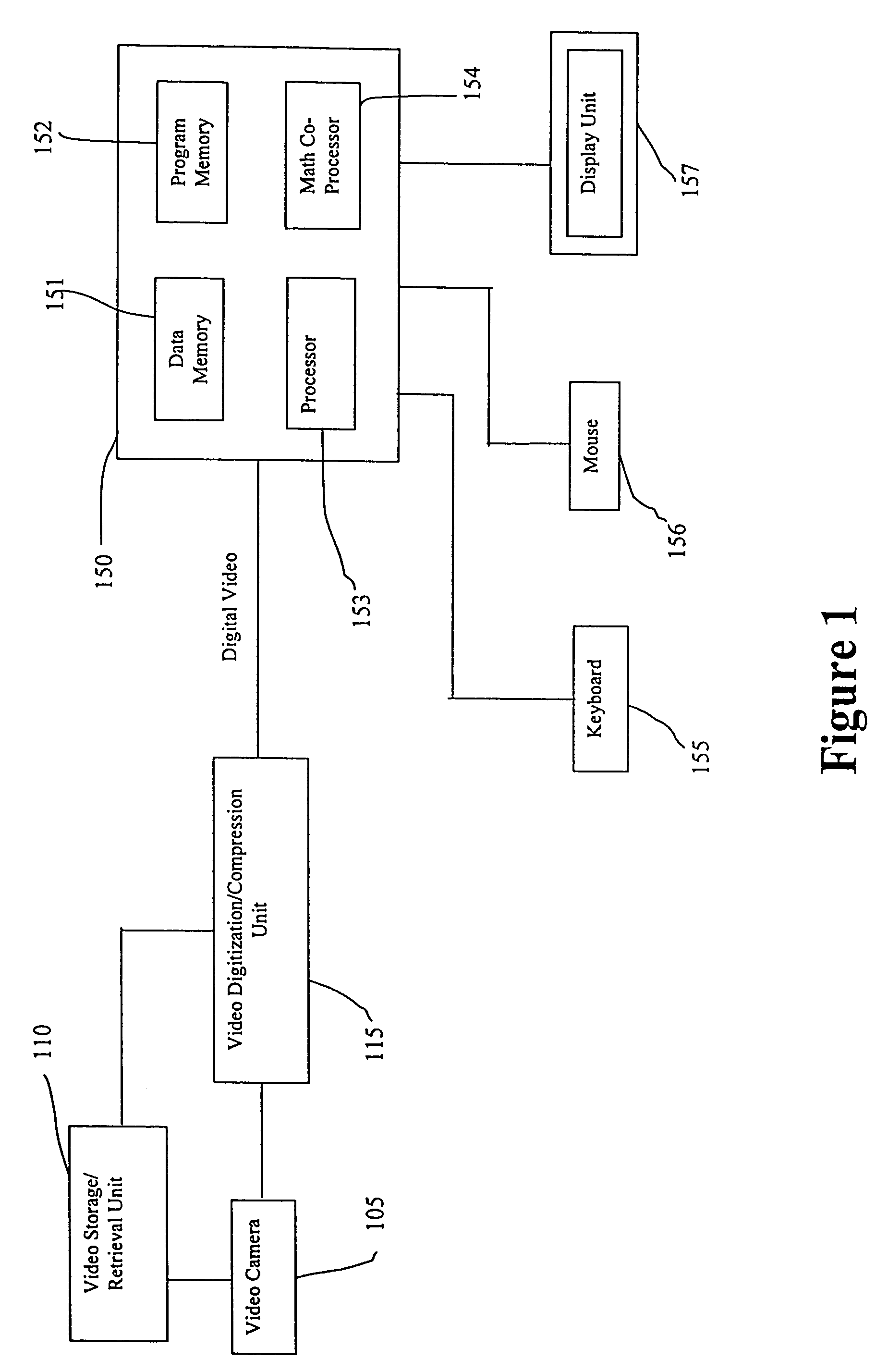
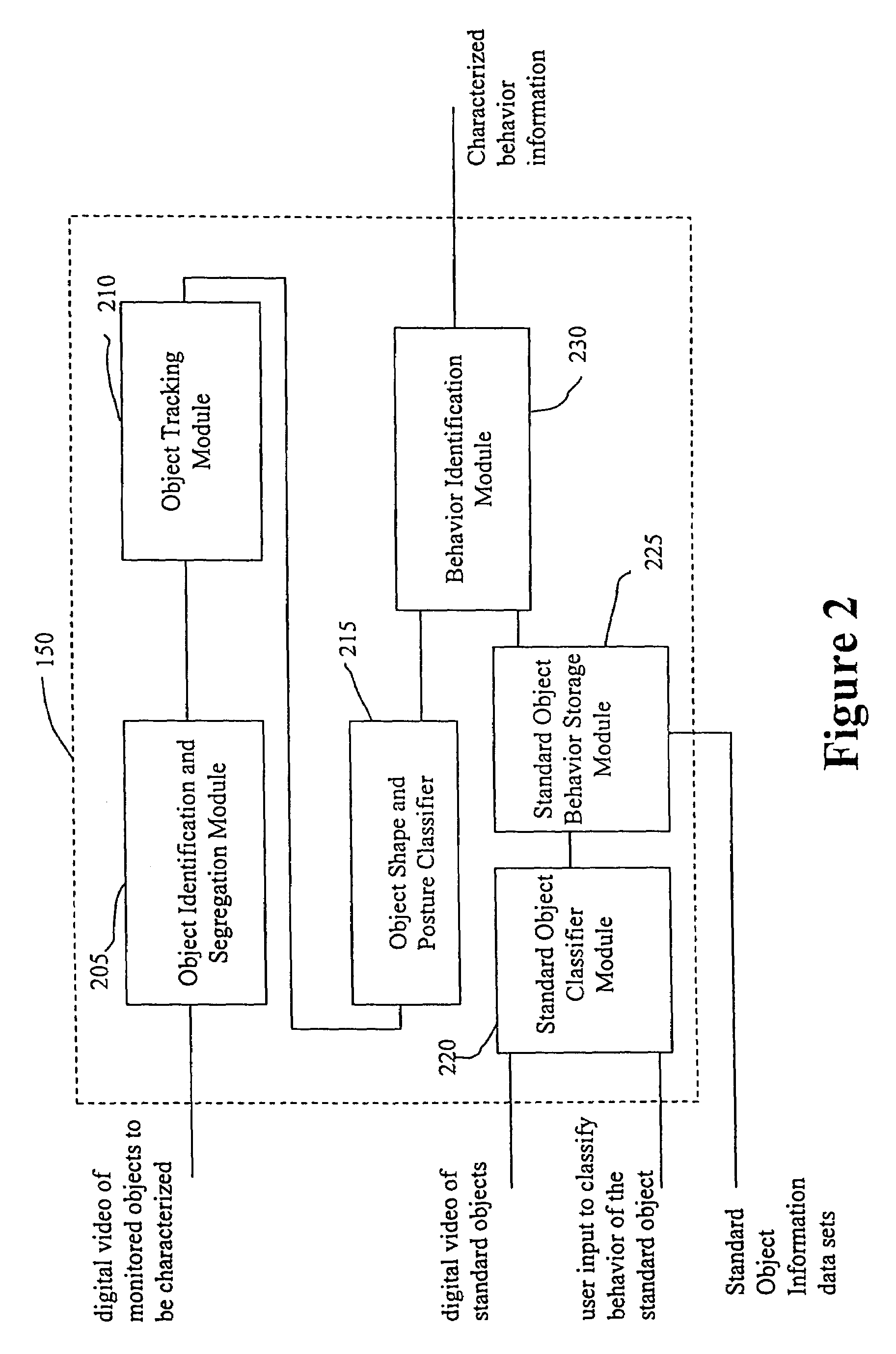
System and method for object identification and behavior characterization using video analysis
InactiveUS7068842B2Accurate identificationEfficient detectionImage enhancementImage analysisProbabilistic methodAnimal behavior
In general, the present invention is directed to systems and methods for finding the position and shape of an object using video. The invention includes a system with a video camera coupled to a computer in which the computer is configured to automatically provide object segmentation and identification, object motion tracking (for moving objects), object position classification, and behavior identification. In a preferred embodiment, the present invention may use background subtraction for object identification and tracking, probabilistic approach with expectation-maximization for tracking the motion detection and object classification, and decision tree classification for behavior identification. Thus, the present invention is capable of automatically monitoring a video image to identify, track and classify the actions of various objects and the object's movements within the image. The image may be provided in real time or from storage. The invention is particularly useful for monitoring and classifying animal behavior for testing drugs and genetic mutations, but may be used in any of a number of other surveillance applications.
Owner:CLEVER SYS
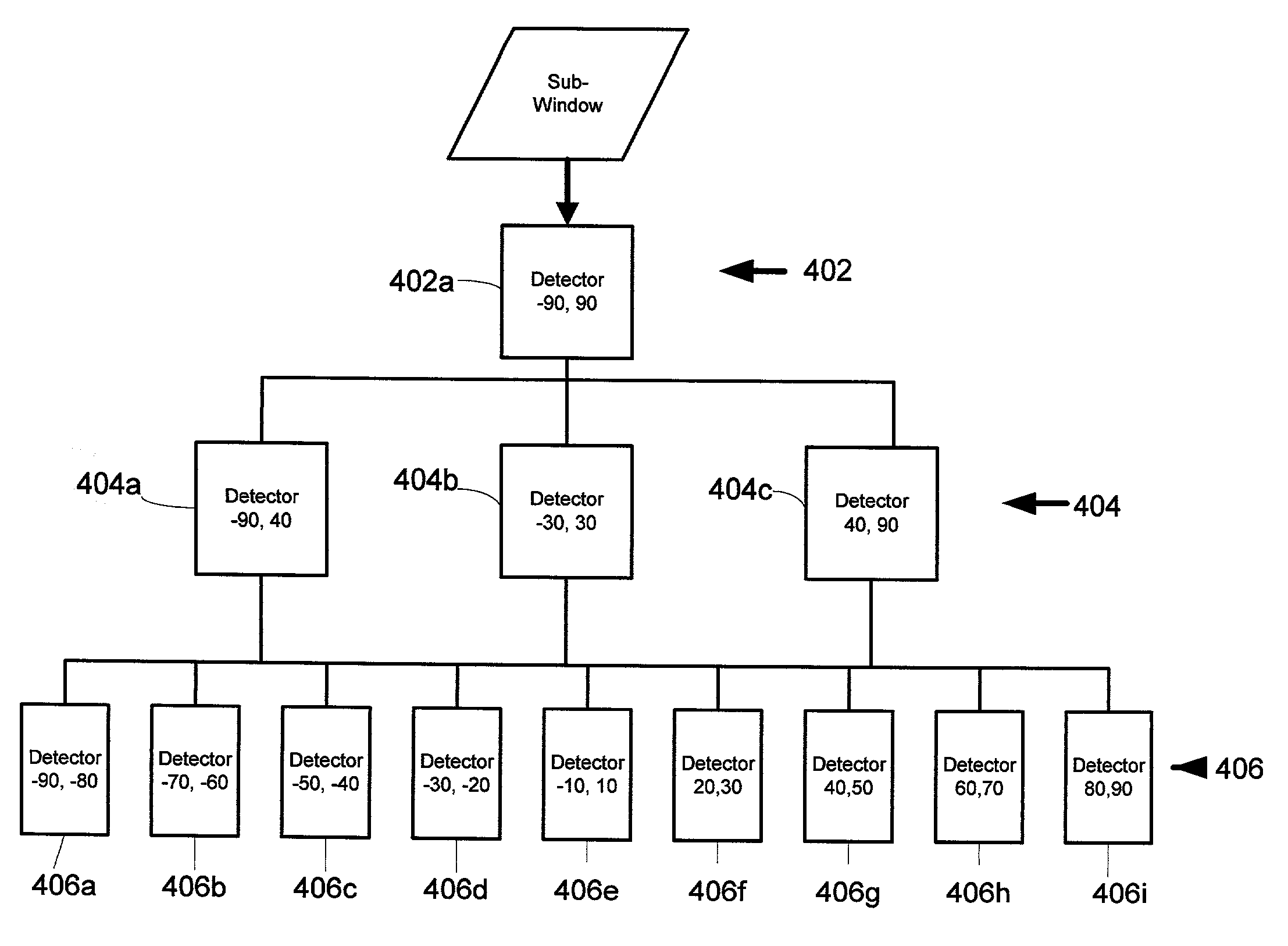
System and method for multi-view face detection
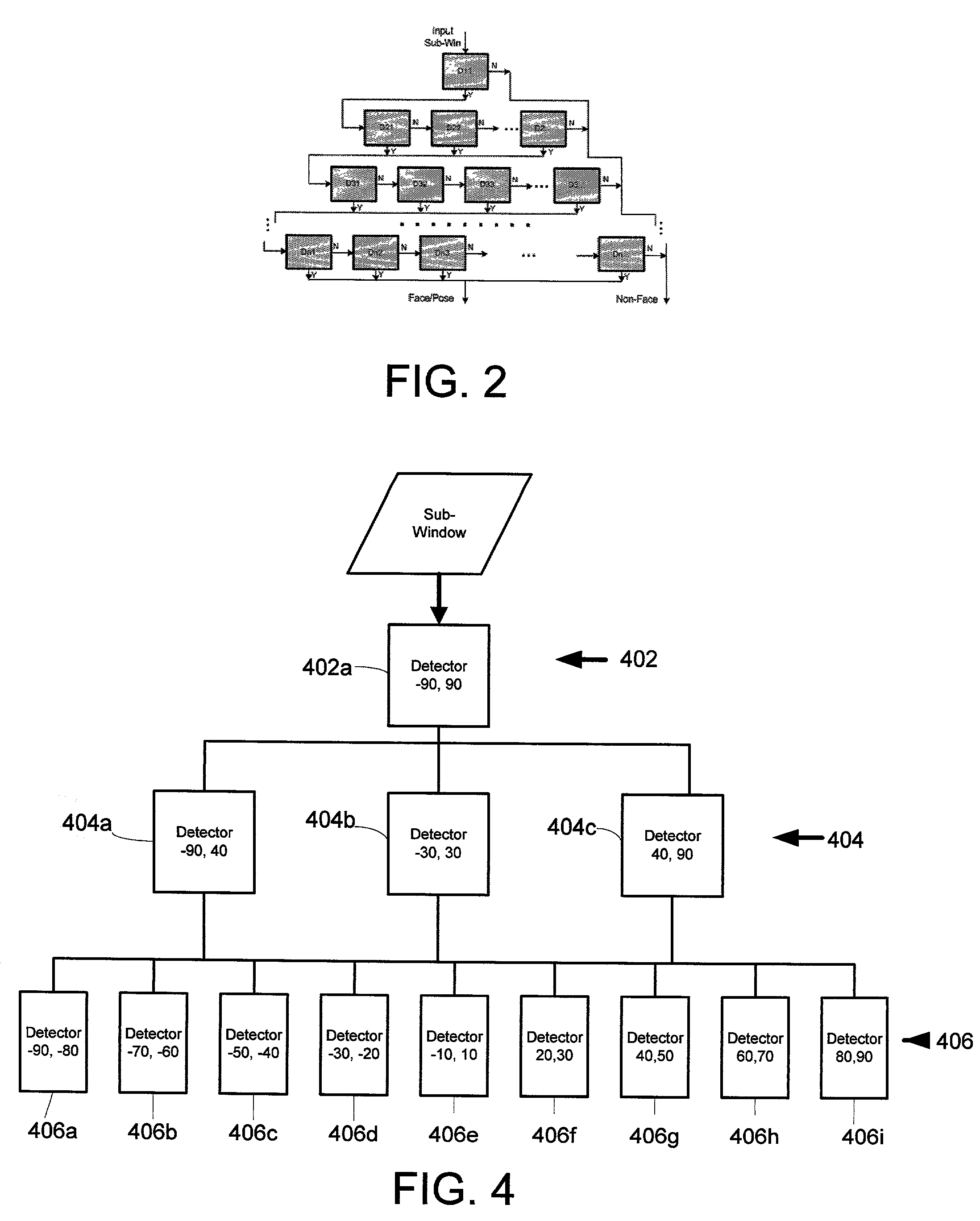
InactiveUS7050607B2Overcome limitationsOptimization rangeCharacter and pattern recognitionFace detectionState of art
A system and method for real-time multi-view (i.e. not just frontal view) face detection. The system and method uses a sequence of detectors of increasing complexity and face / non-face discriminating thresholds to quickly discard non-faces at the earliest stage possible, thus saving much computation compared to prior art systems. The detector-pyramid architecture for multi-view face detection uses a coarse-to-fine and simple-to-complex scheme. This architecture solves the problem of lengthy processing that precludes real-time face detection effectively and efficiently by discarding most of non-face sub-windows using the simplest possible features at the earliest possible stage. This leads to the first real-time multi-view face detection system which has the accuracy almost as good as the state-of-the-art system yet 270 times faster, allowing real-time performance.
Owner:MICROSOFT TECH LICENSING LLC
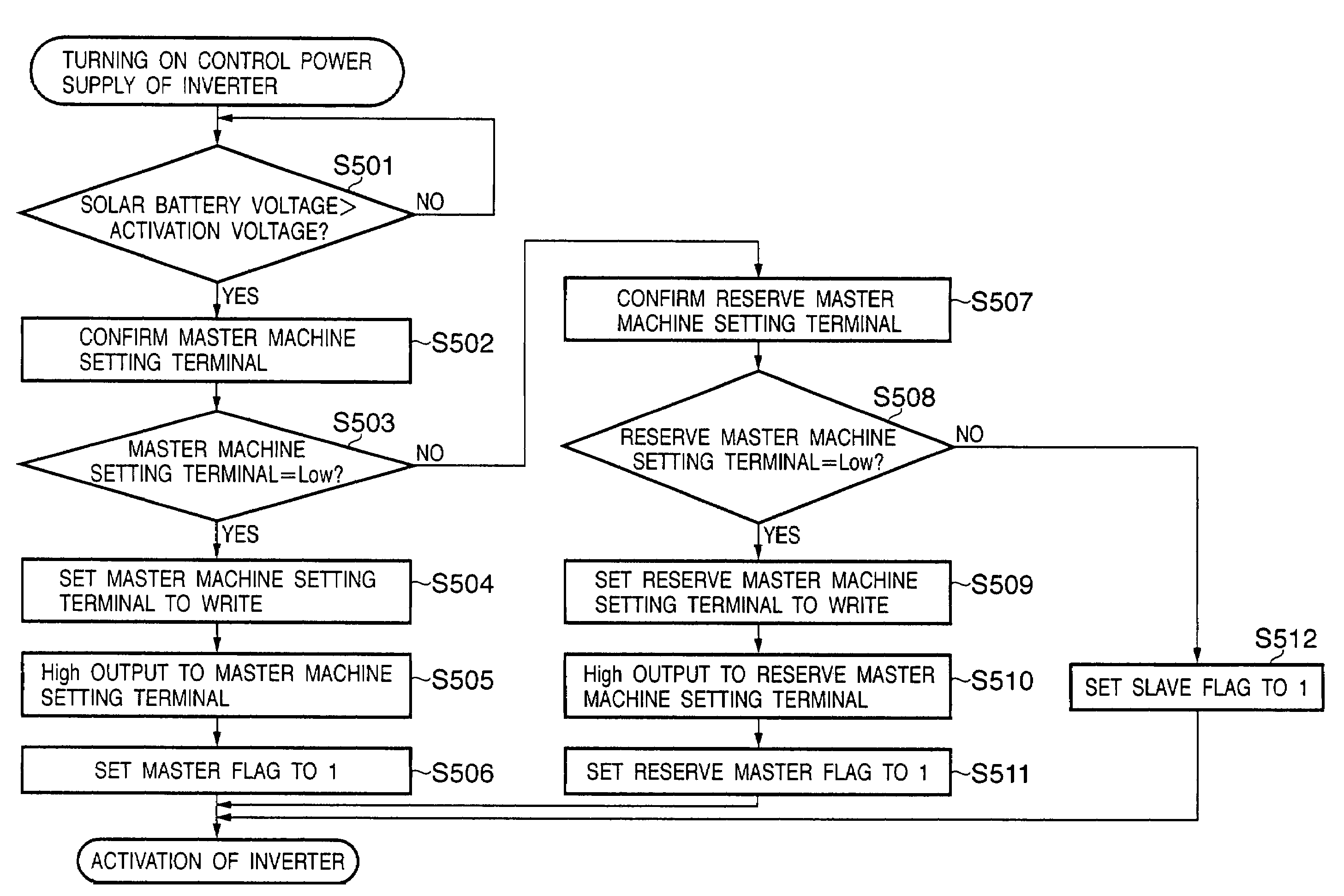
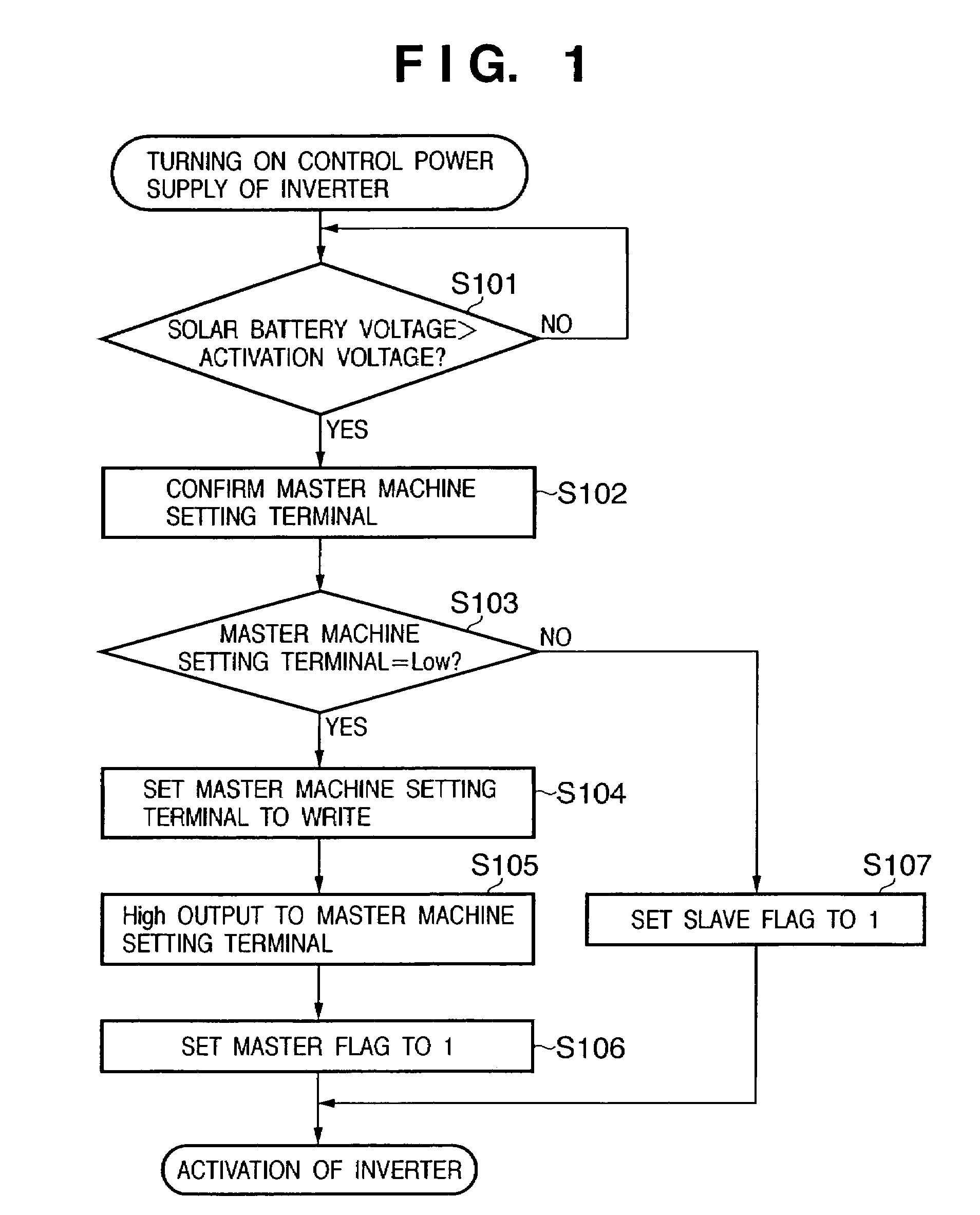
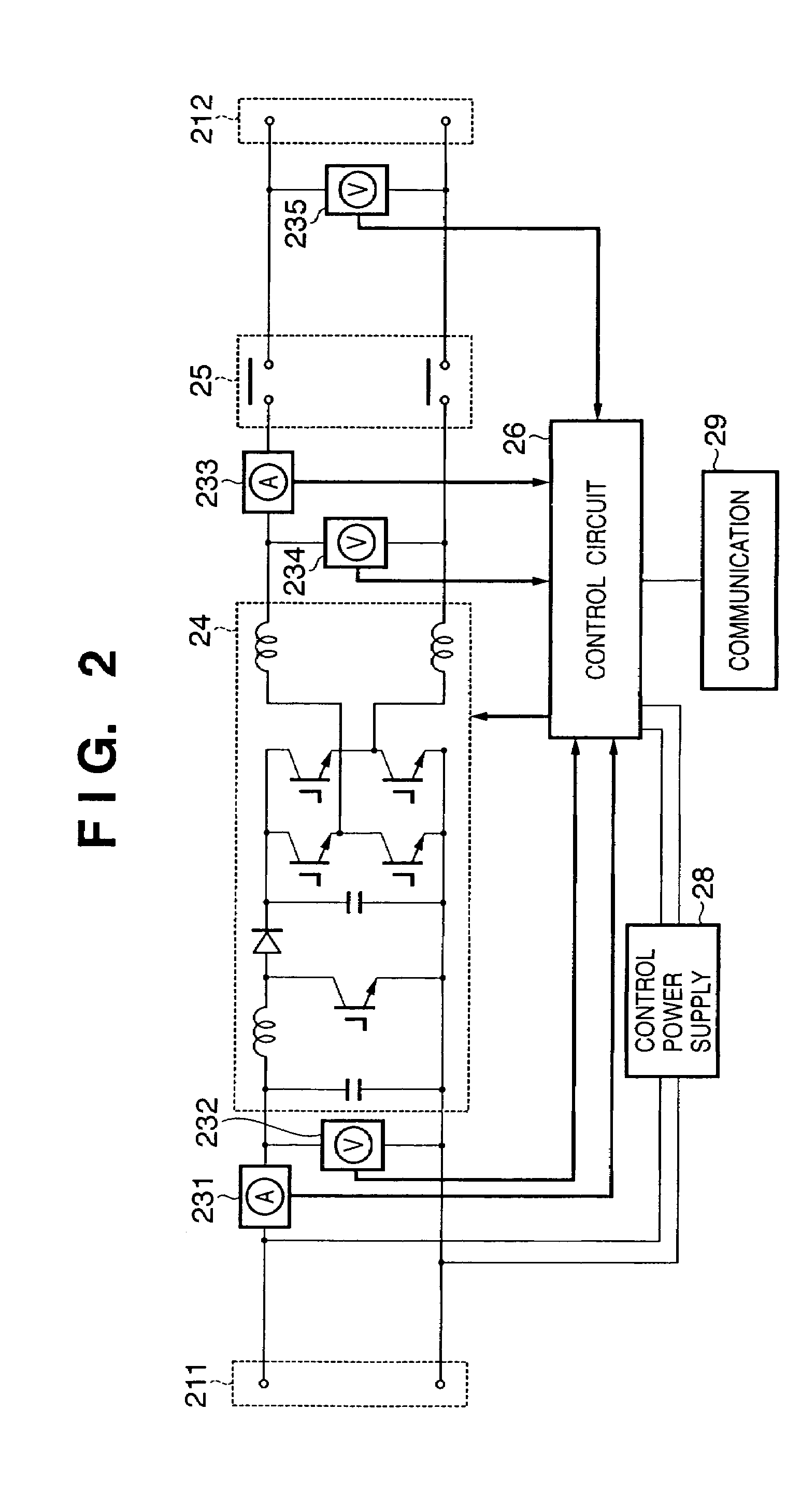
Power generation system, and administration apparatus and administration method of power generation system
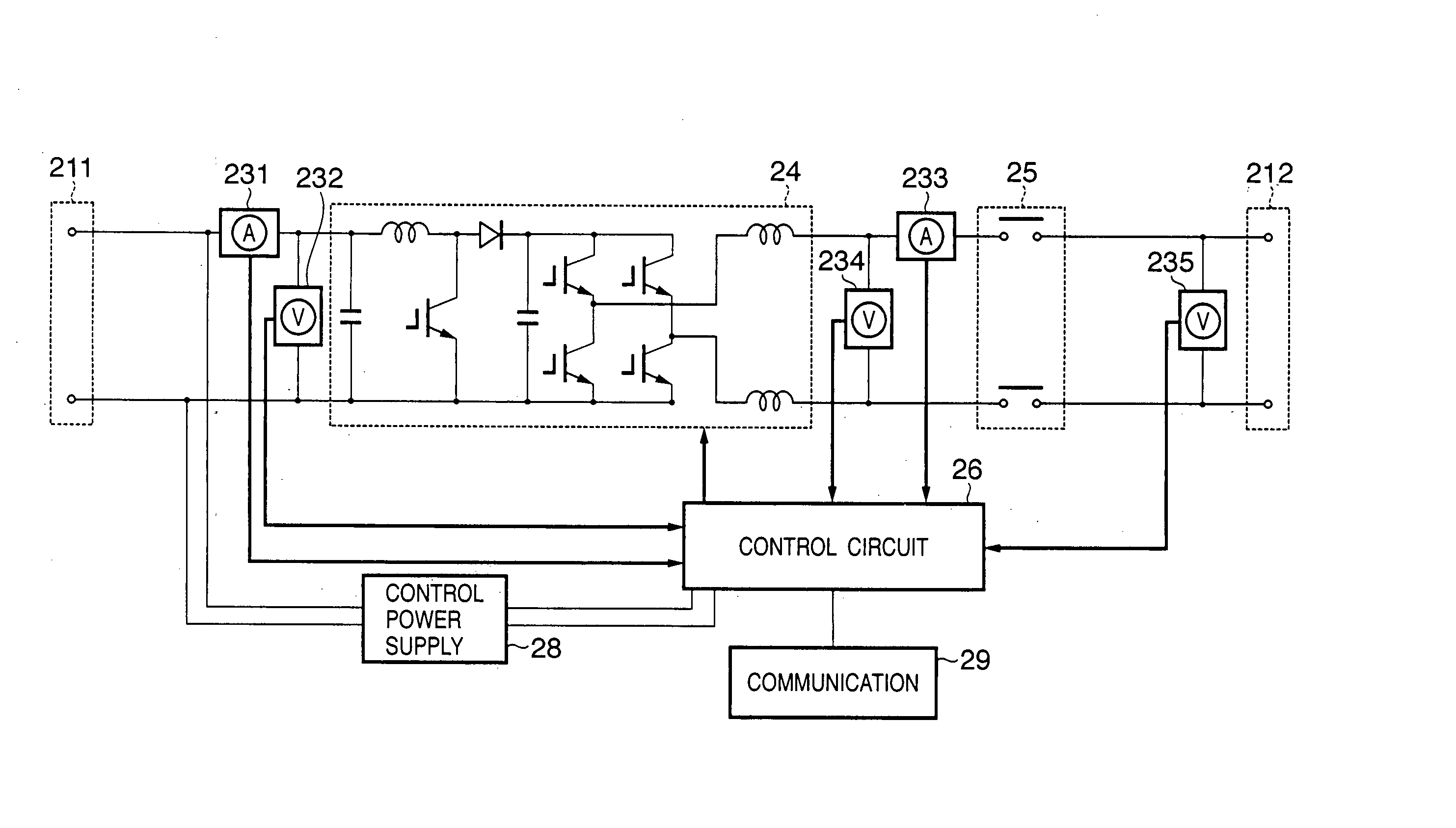
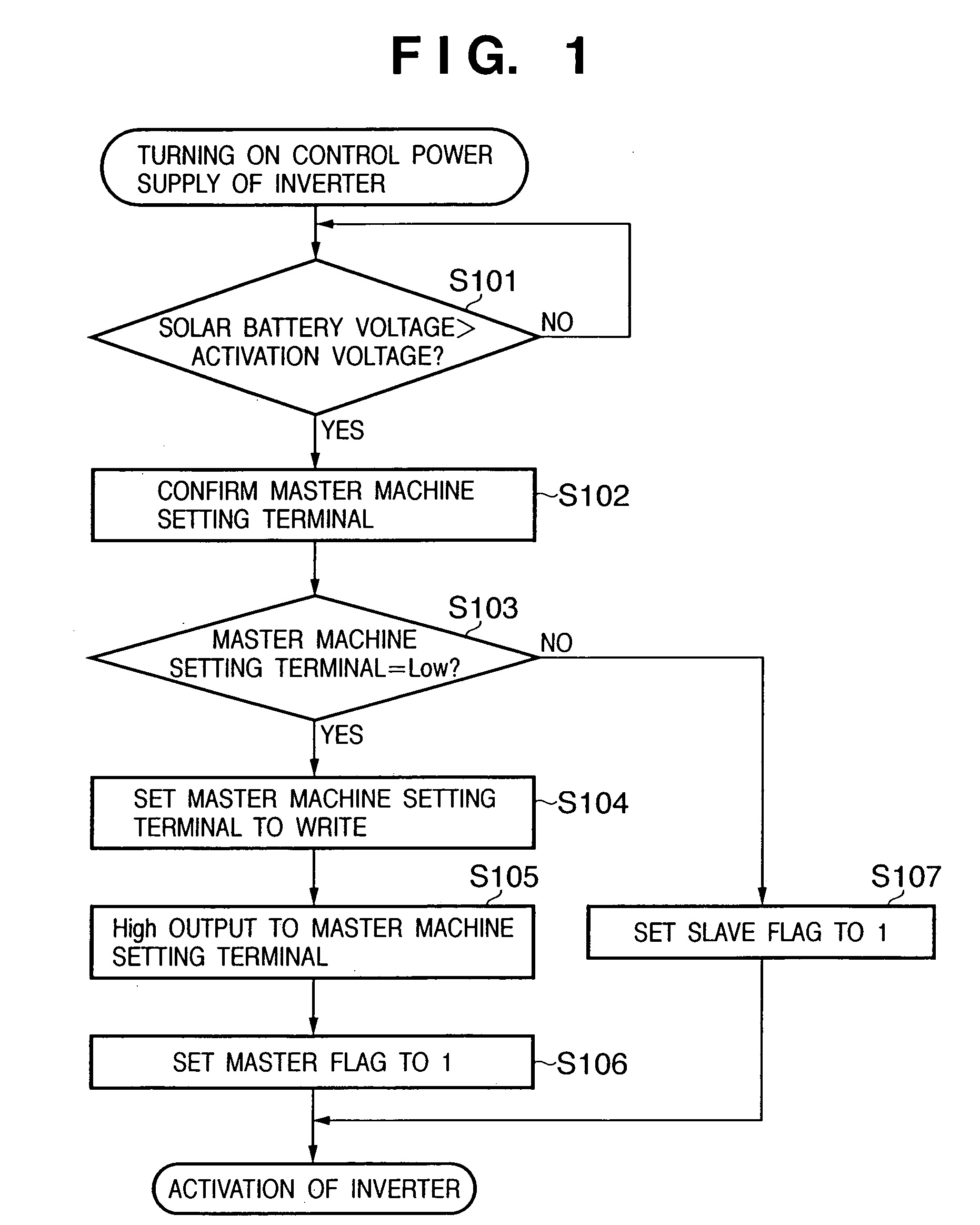
InactiveUS20050213272A1Improve reliabilityEfficient detectionDc network circuit arrangementsAc-dc conversionIslandingEngineering
In a power generation system which includes a plurality of sets of direct current power sources and power converters which are connected to the direct current power sources to convert a direct current power into an alternative current power, the power converters being connected in parallel to supply the alternative current power to a system power supply, from the plurality of power converters in the system, one power converter is set as a master machine which detects an islanding operation state in which power supply from the system power supply is stopped, and setting is executed so as to cause the remaining power converters not to detect the islanding operation state. When the master machine is not present among the power converters in operation, the master machine is selected from the power converters in operation in accordance with a predetermined condition.
Owner:CANON KK
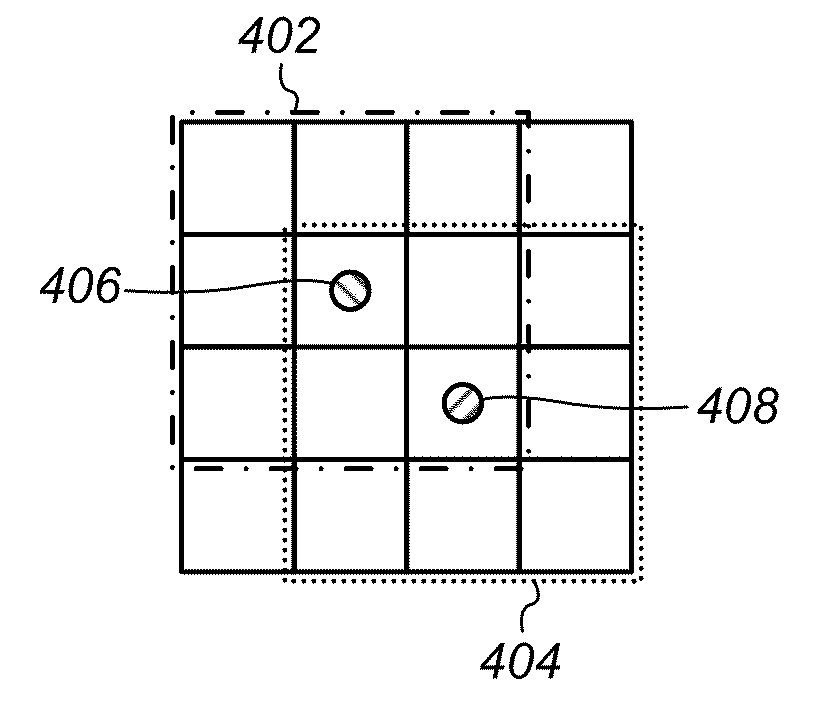
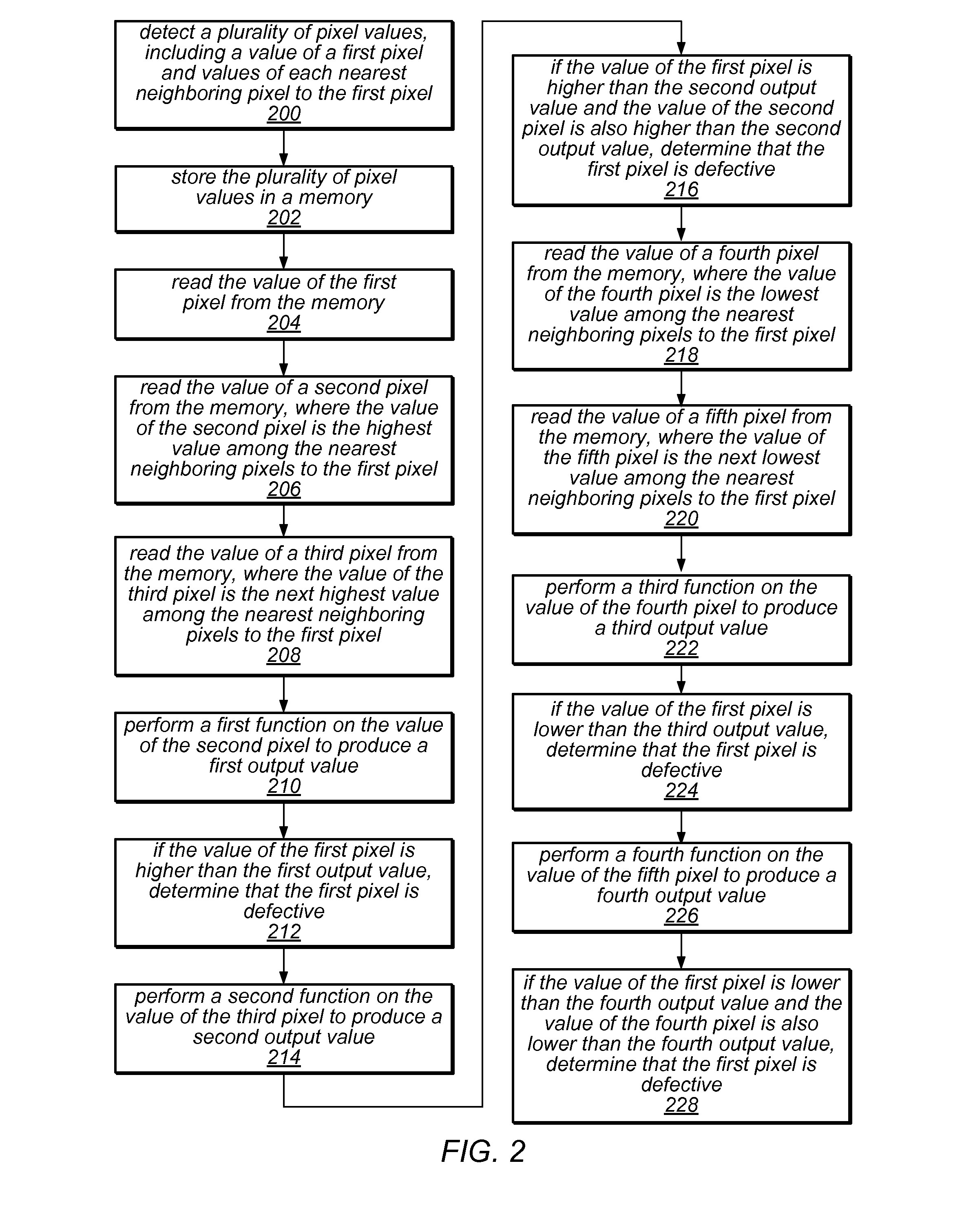
Detection of Defective Pixels in an Image Sensor
ActiveUS20110043668A1Efficient detectionImprove the detection rateTelevision system detailsColor signal processing circuitsPattern recognitionDefective pixel
A system and method for detecting defective pixels in a sensor. A plurality of pixel values of the sensor may be detected. The values may include those of a first pixel and each nearest neighboring pixel to the first pixel. A second pixel may have the highest value of the neighboring pixels. A third pixel may have the next highest value of the neighboring pixels. A first function may be performed on the second pixel value, producing a first output value. A second function may be performed on the third pixel value, producing a second output value. If the first pixel value is higher than the first output value, or, if the first pixel value is higher than the second output value and the second pixel value is higher than the second output value, it may be determined that the first pixel is defective.
Owner:LIFESIZE INC
System for measuring vital signs during hemodialysis
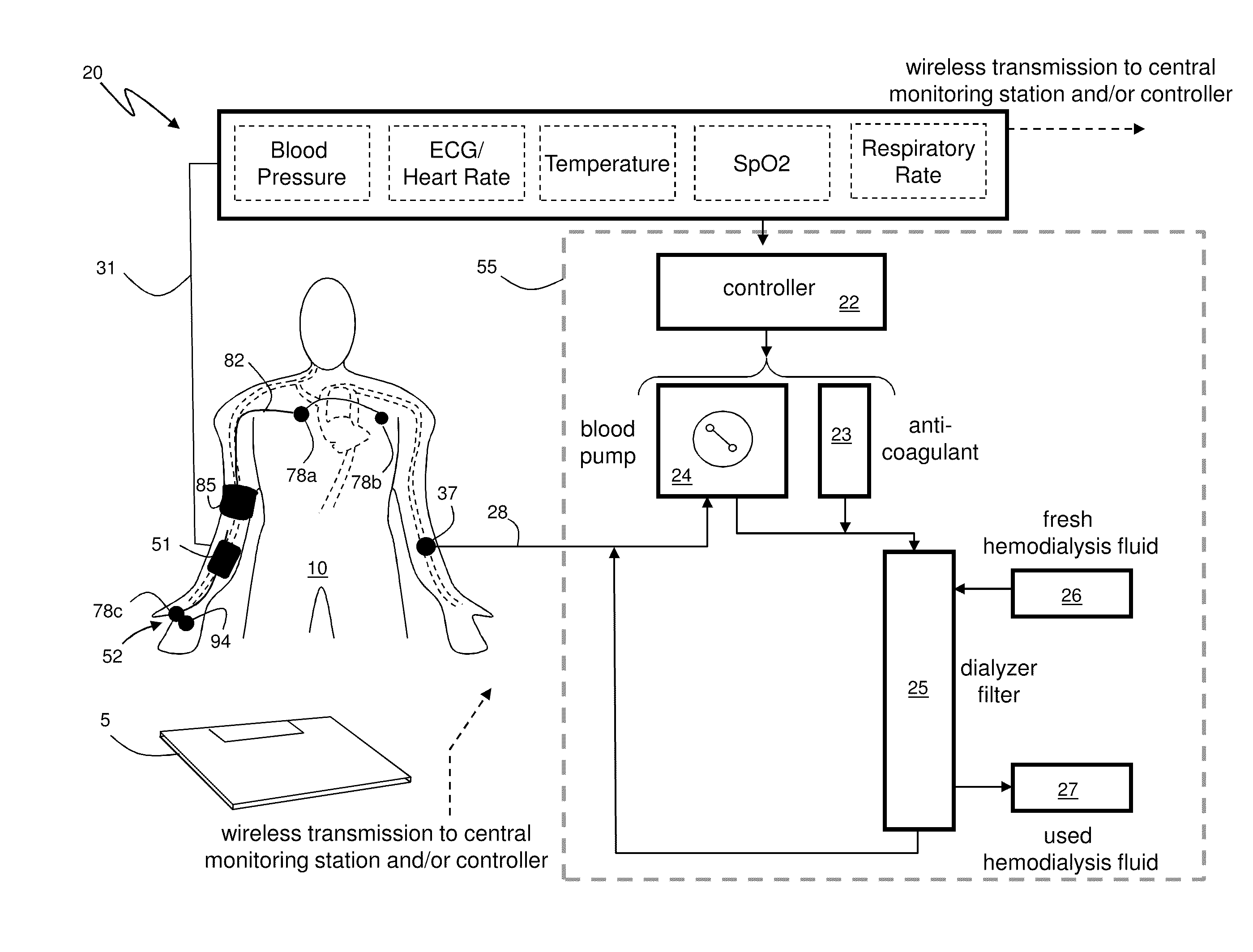
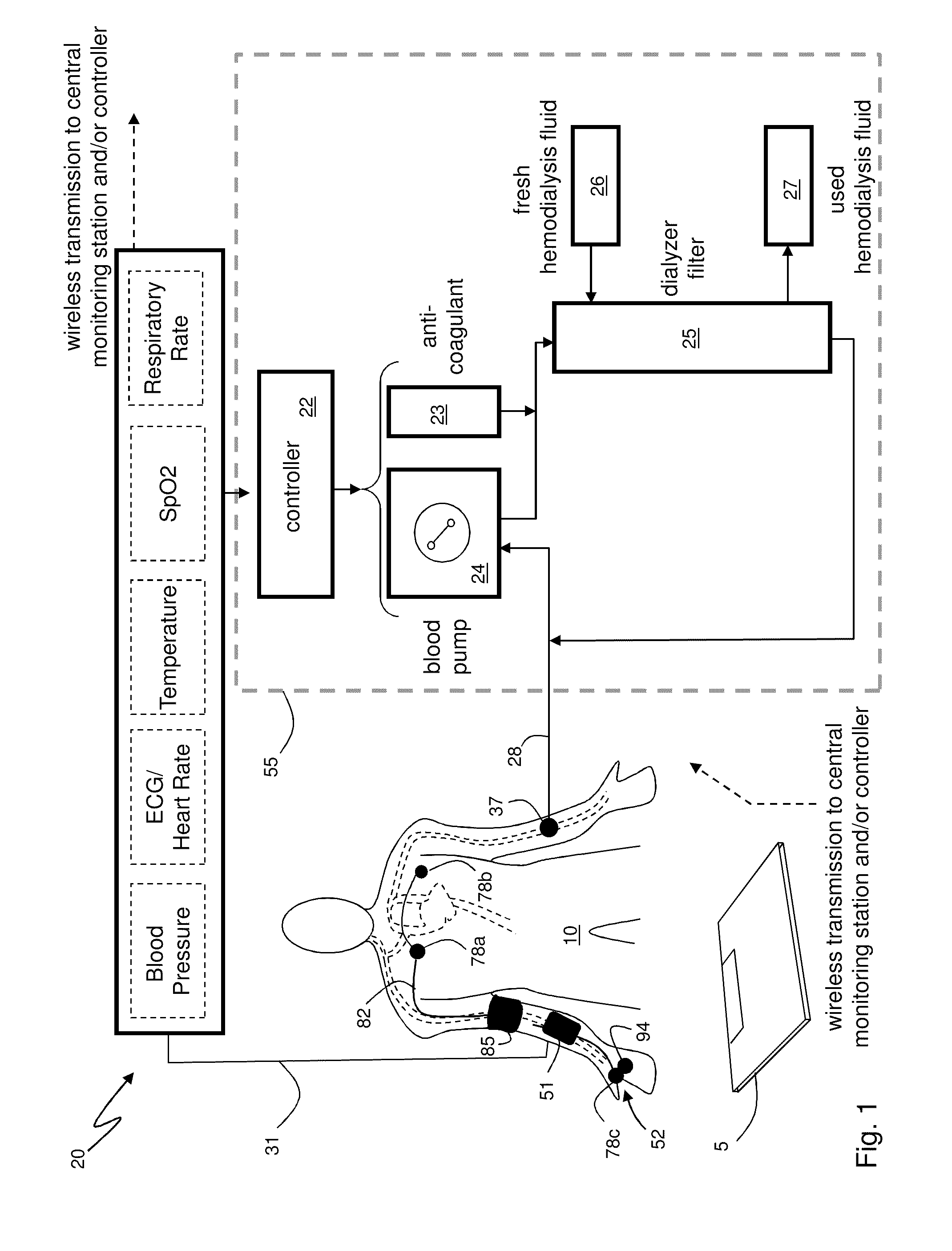
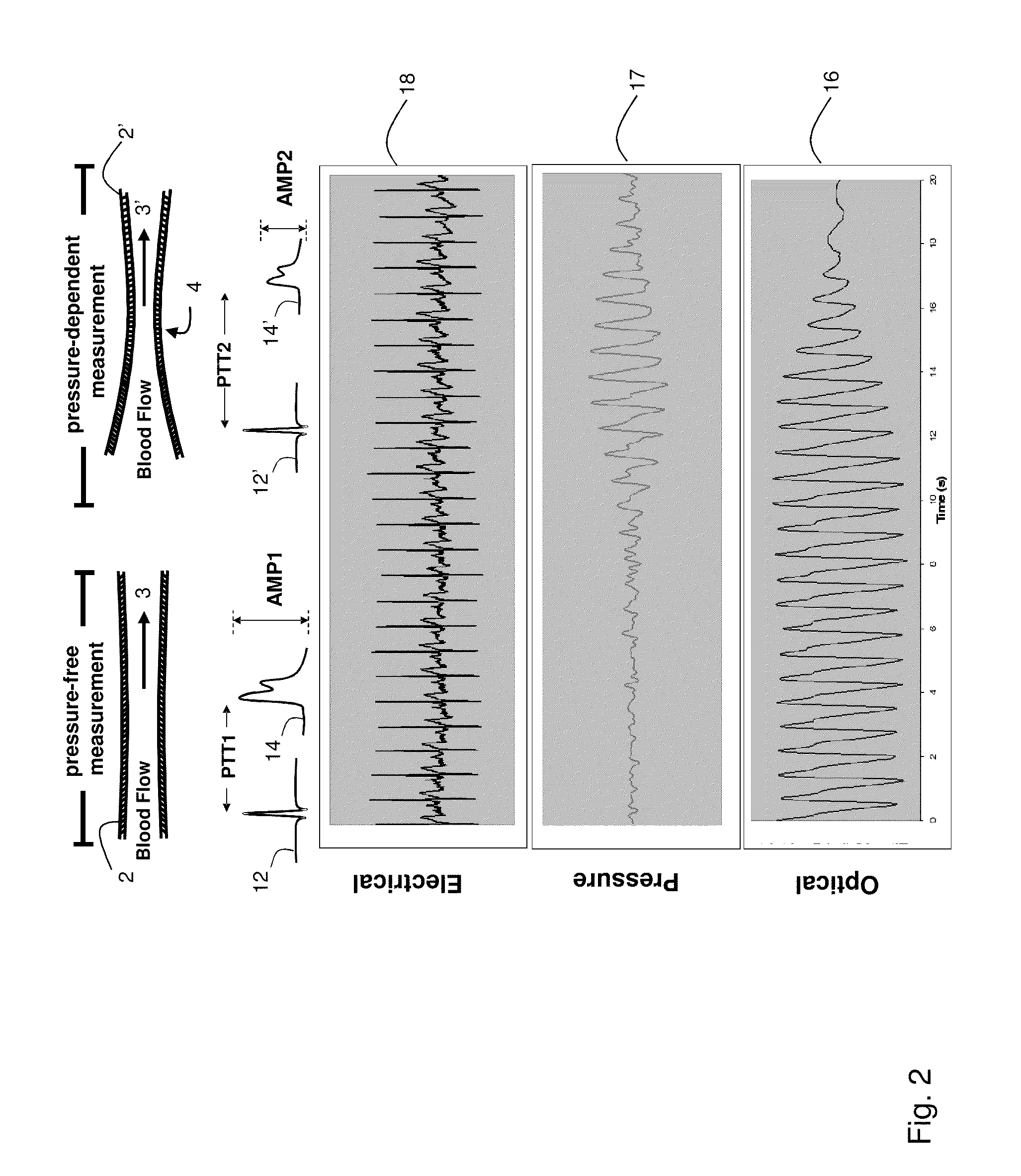
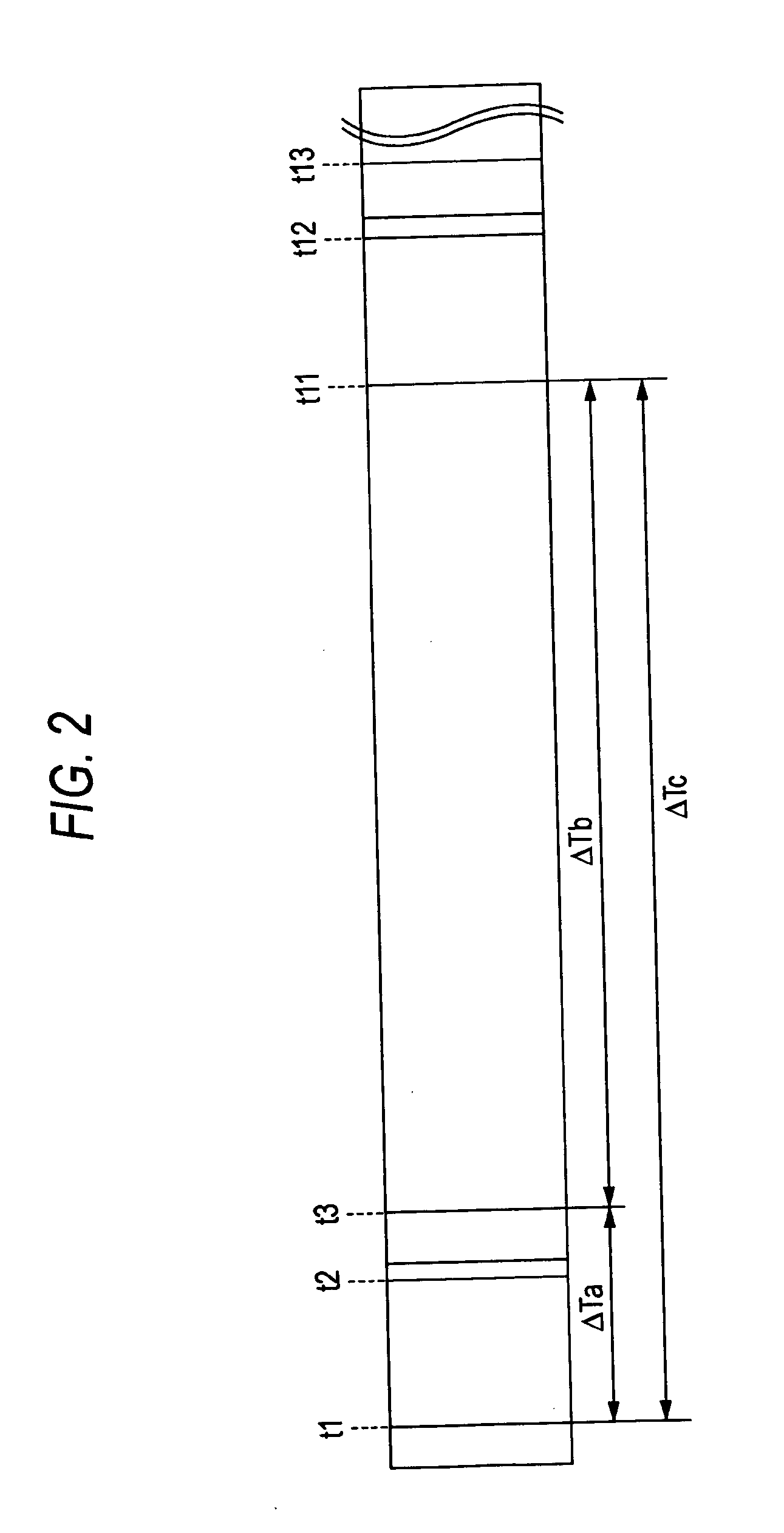
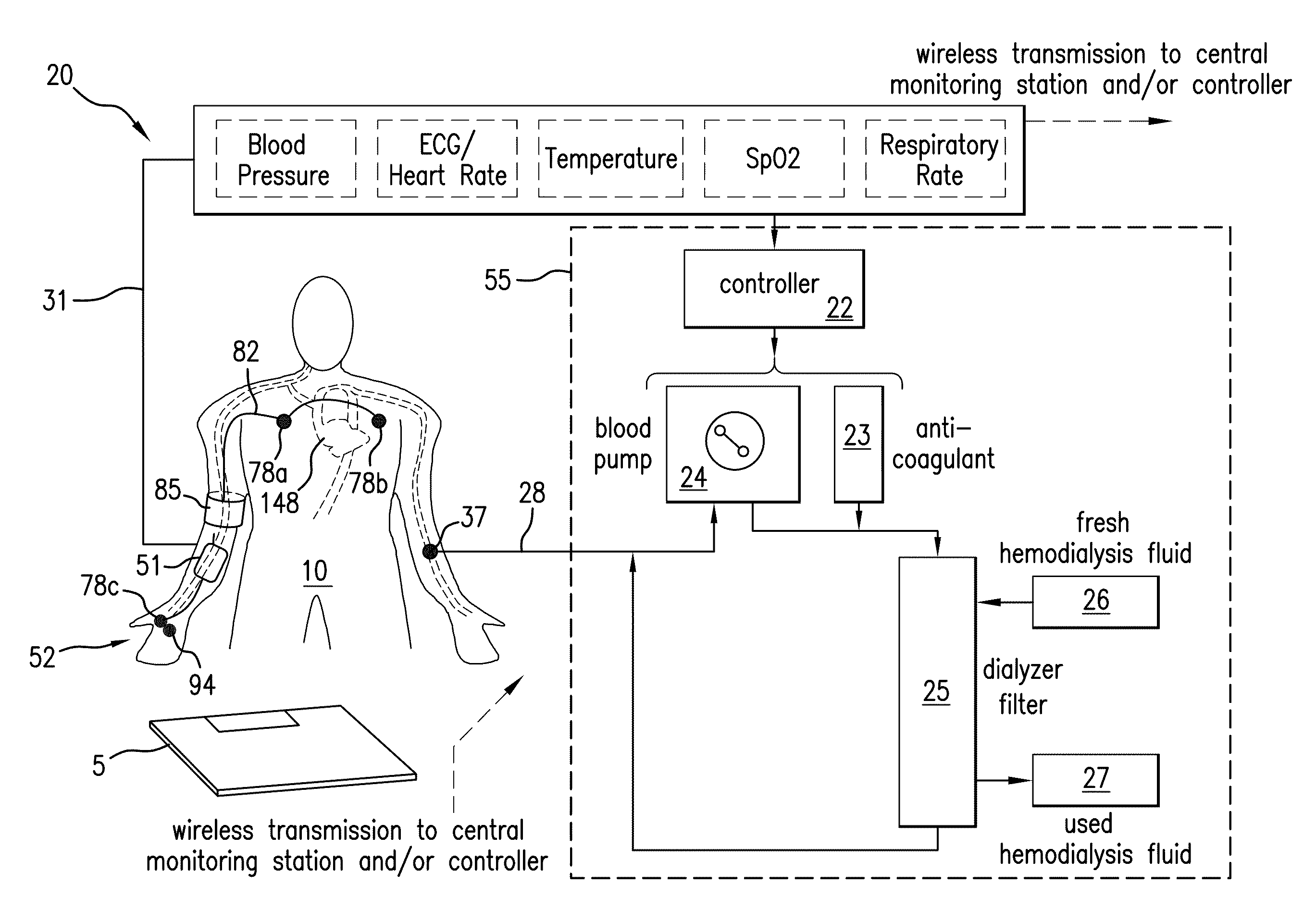
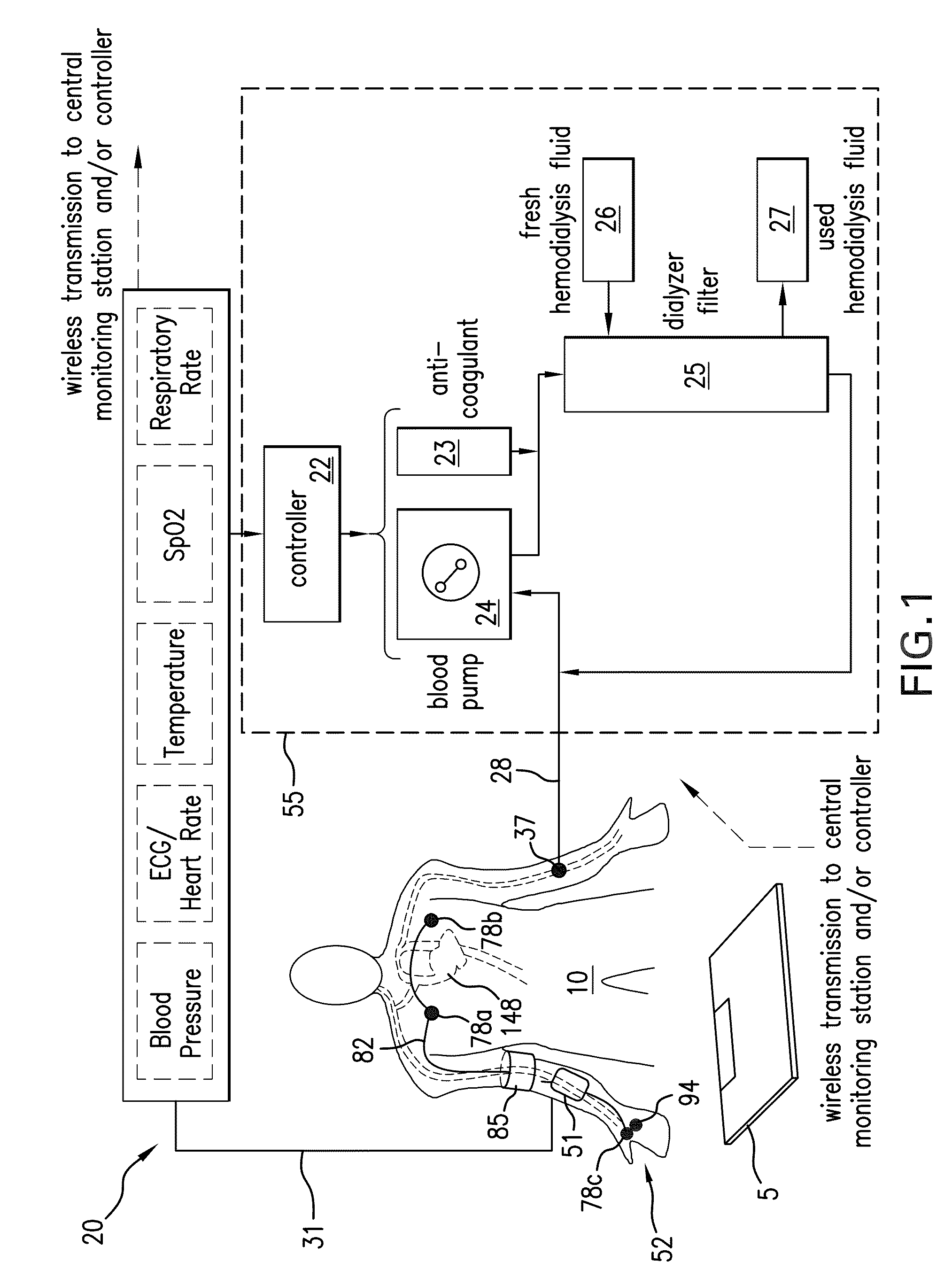
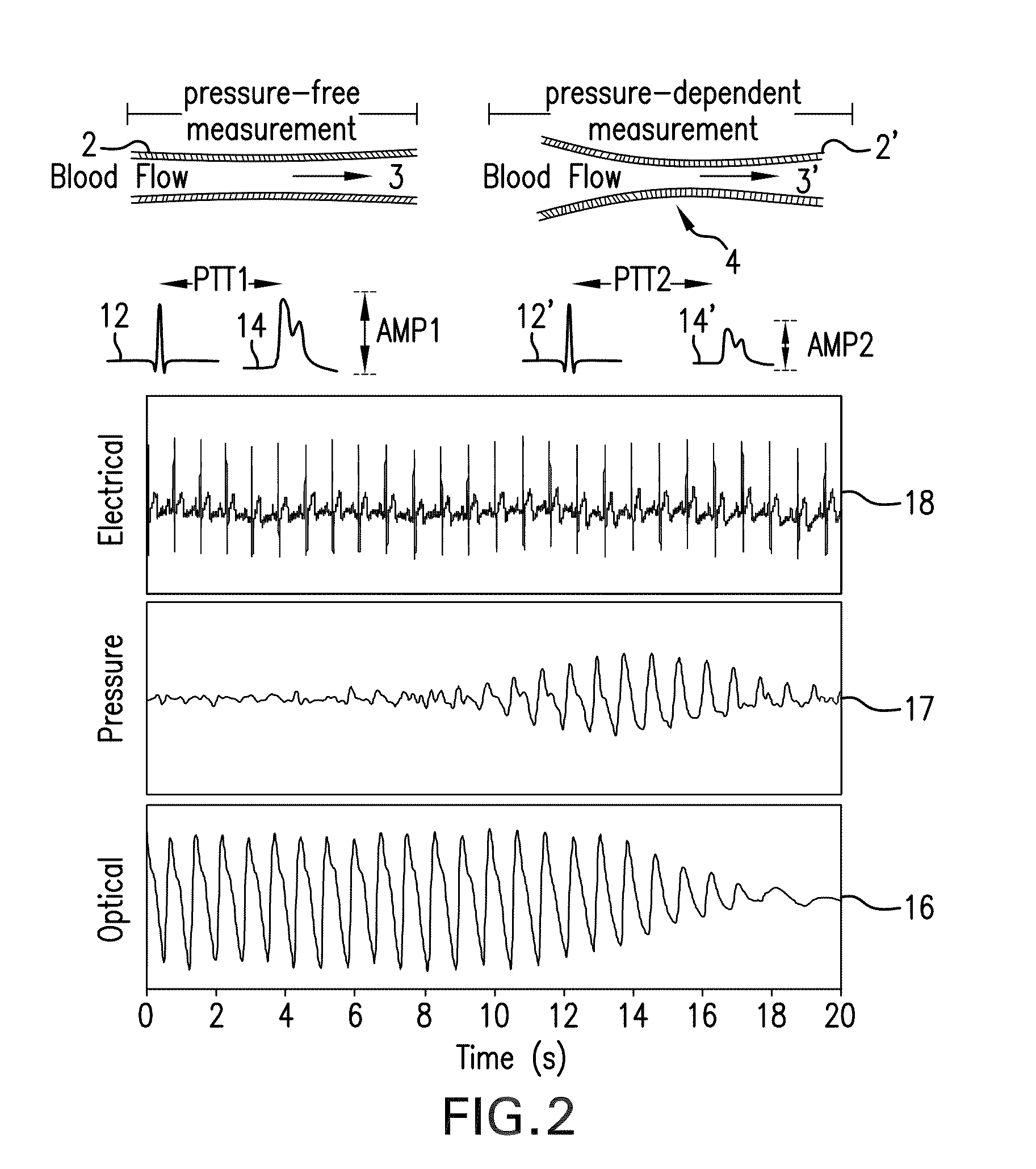
InactiveUS20110066043A1Simplifies and expedites applicationEfficient detectionDialysis systemsMedical devicesTransit timeSerial port
The invention provides a system for continuously monitoring a patient during hemodialysis. The system includes a hemodialysis machine for performing the hemodialysis process that features a controller, a pump, a dialyzer filter, a lumen, and an interface to a body-worn monitor. A patient attaches to the dialysis machine through the lumen, and wears a body-worn monitor for continuously measuring blood pressure. The monitor includes an optical system for measuring an optical waveform, an electrical system for measuring an electrical waveform, and a processing component for determining a transit time between the optical and electrical waveforms and then calculating a blood pressure value from the transit time. The body-worn monitor features an interface (e.g. a wired serial interface, or a wireless interface) to transmit the blood pressure value to the controller within the hemodialysis machine. The controller is configured to receive the blood pressure value, analyze it, and in response adjust the dialysis process.
Owner:SOTERA WIRELESS
Object position and orientation detection system
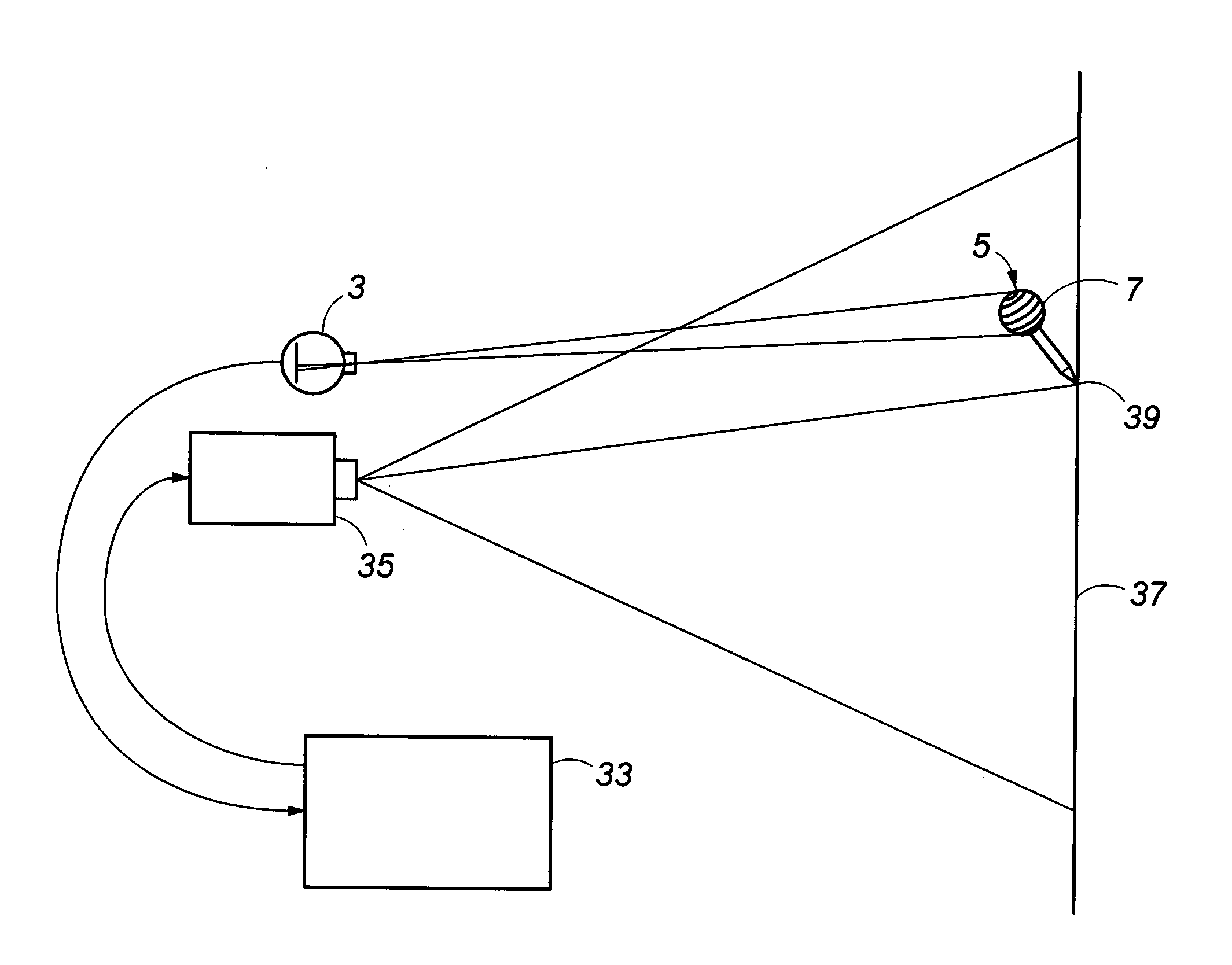
ActiveUS20100091112A1Image be preventEfficient detectionTelevision system detailsCharacter and pattern recognitionWhiteboardDisplay device
An object position and orientation detection system and in particular one which is capable of describing observed movement in 3 dimensions. In one example, a spherical patterned marker with concentric rings is imaged using one or more digital cameras, and the resulting images are processed to determine the position and orientation of an object to which the patterned marker is attached. The method of optical tracking employed by the system allows motion to be determined in six degrees of freedom. In conjunction with a suitable display, such as a projector, an interactive white board or similar application can be realised.
Owner:CARL ZEISS IND MESSTECHN GMBH +1
Malware detection system and method for mobile platforms
InactiveUS20110179484A1Reliable detectionAmount of memory can be minimisedMemory loss protectionError detection/correctionMalwareProtocol for Carrying Authentication for Network Access
In one example, a management server is configured to provide malware protection for one or more client mobile platforms in communication with the management server via a mobile network. In the example, the management server includes a processor configured to detect malware in the mobile network, select a client mobile platform having a malware scanning agent, and, manage the malware scanning agent of the client mobile platform using a device independent secure management protocol based at least in part on the malware detected in the mobile network.
Owner:JUMIPER NETWORKS INC
Power generation system, and administration apparatus and administration method of power generation system
InactiveUS7456523B2Improve reliabilityEfficient detectionDc network circuit arrangementsAc-dc conversionIslandingEngineering
In a power generation system which includes a plurality of sets of direct current power sources and power converters which are connected to the direct current power sources to convert a direct current power into an alternating current power, the power converters being connected in parallel to supply the alternating current power to a system power supply, from the plurality of power converters in the system, one power converter is set as a master machine which detects an islanding operation state in which power supply from the system power supply is stopped, and setting is executed so as to cause the remaining power converters not to detect the islanding operation state. When the master machine is not present among the power converters in operation, the master machine is selected from the power converters in operation in accordance with a predetermined condition.
Owner:CANON KK
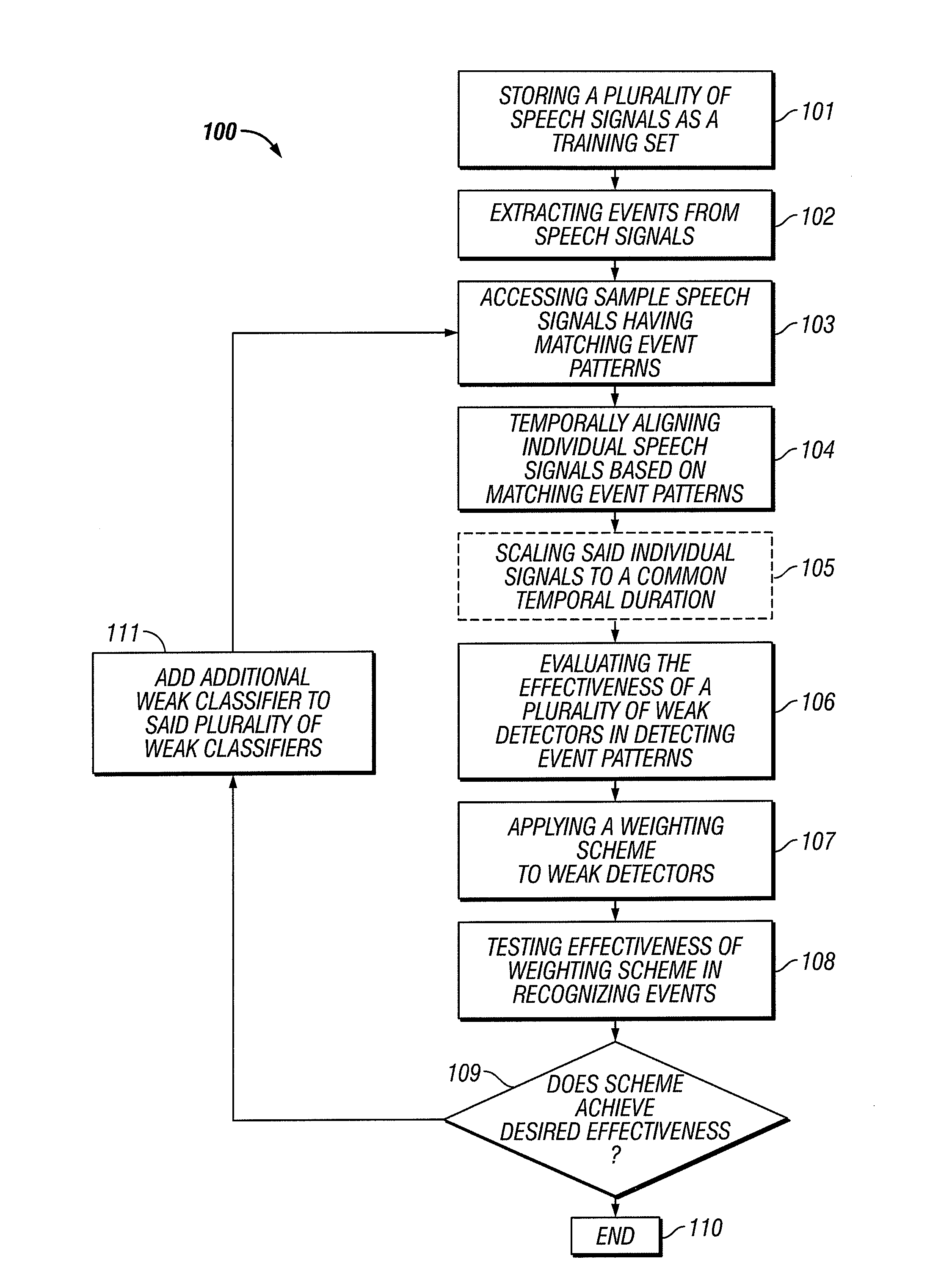
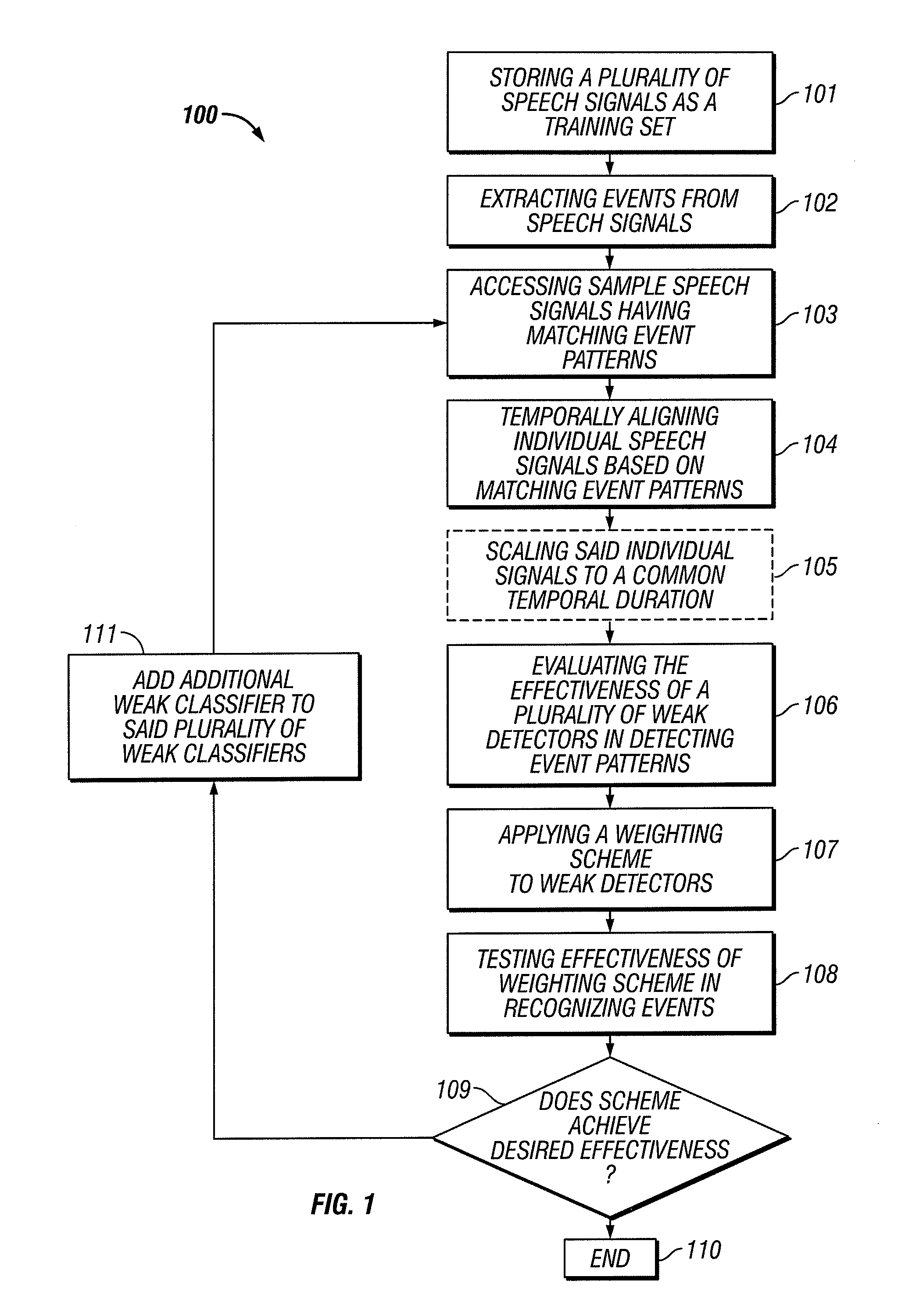
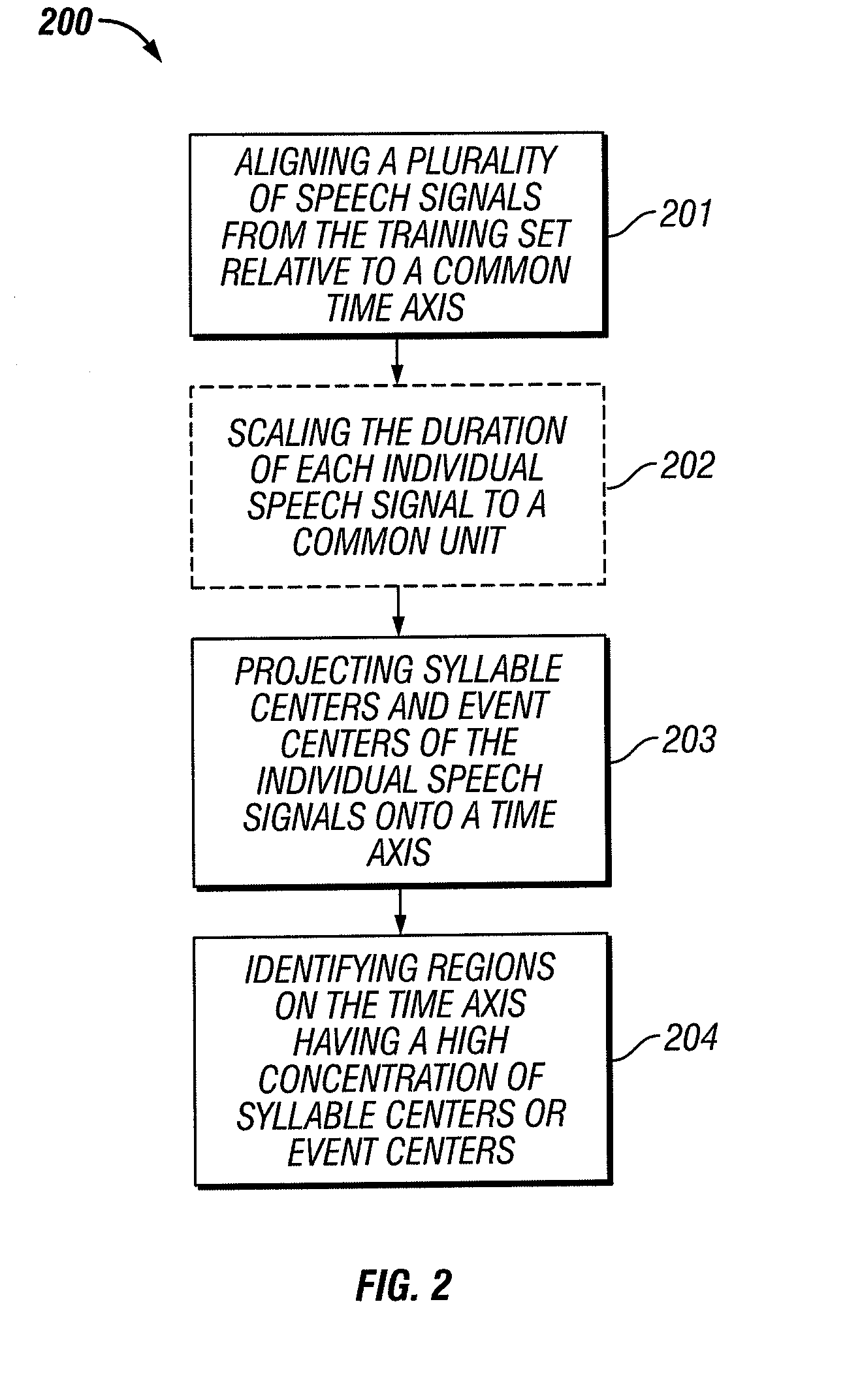
System and method for automatic speech to text conversion
ActiveUS20100121638A1Easy to identifyReduce complexitySpeech recognitionText streamSpeech identification
Speech recognition is performed in near-real-time and improved by exploiting events and event sequences, employing machine learning techniques including boosted classifiers, ensembles, detectors and cascades and using perceptual clusters. Speech recognition is also improved using tandem processing. An automatic punctuator injects punctuation into recognized text streams.
Owner:SCTI HLDG INC
Watermarking with random zero-mean patches for printer tracking
InactiveUS6556688B1Efficient detectionUser identity/authority verificationCharacter and pattern recognitionVirtual cellControl signal
A steganographic method embeds hidden information like digital watermarks and digital fingerprints into an image by applying one or more zero-mean patches to a digital signal that conveys the image. Each zero-mean patch comprises elements having an average value substantially equal to zero. A printer tracking system is implemented by selecting a plurality of zero-mean patches according to a string of bits representing a printer serial number, and modifying printer control signals to embed the plurality of patches in each of a number of virtual cells within the image to be printed. The offset of the virtual cells with respect to the boundaries of the image and the location of the patches within each virtual cell are established in pseudo-random fashion. The printer tracking system further includes a technique for subsequently detecting the printer serial number by scanning the printed image and running a detection algorithm on the scanned data to recover the string of bits embedded in the zero-mean patches.
Owner:SEIKO EPSON CORP
Logical Group Endpoint Discovery for Data Communication Network
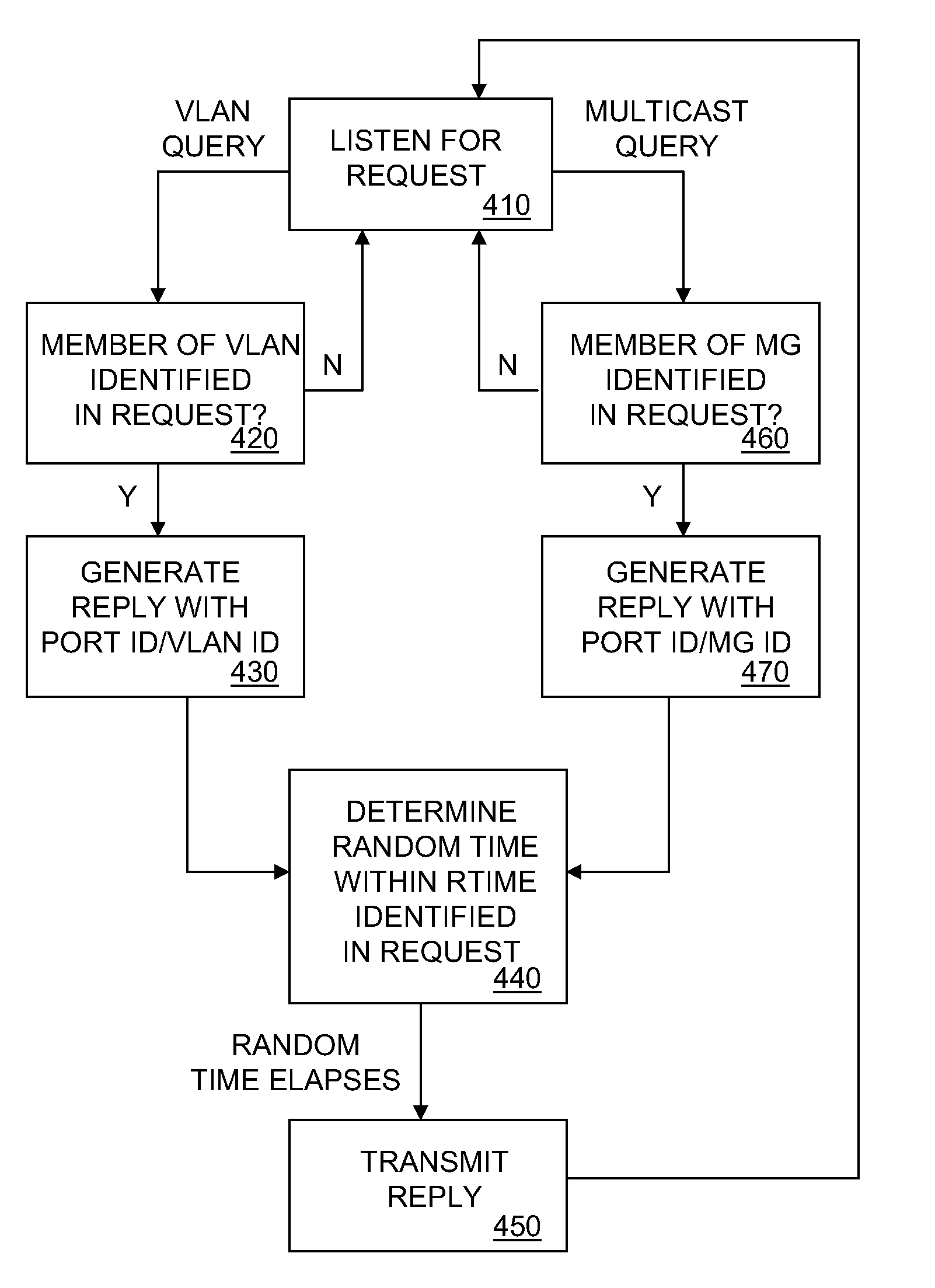
InactiveUS20070223493A1Efficient learning processEfficient detectionNetworks interconnectionMulticast addressDistributed computing
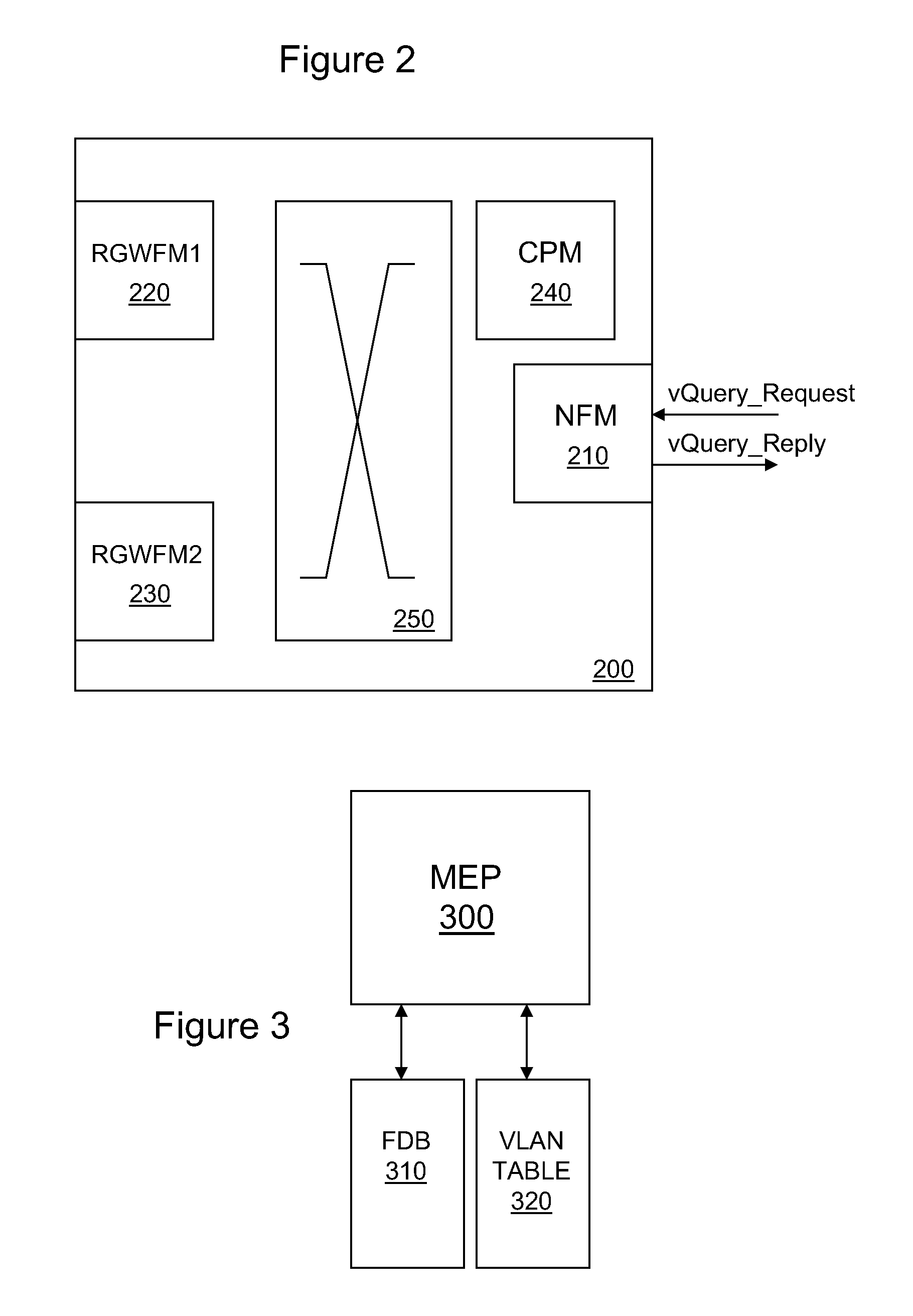
A method and system for logical group endpoint discovery in a data communication network is disclosed. A network endpoint receives from a source a request identifying a logical group and determines whether a port associated with the endpoint is a member of the logical group. If a port associated with the endpoint is a member of the logical group, the endpoint transmits to the source a reply identifying the port and the logical group. The request may be multicast while the reply may be unicast. The logical group may be a VLAN or a multicast group. The source and endpoint are preferably 802.1 ag maintenance endpoints. The request may include an IEEE 802.1 ag continuity check multicast address as a destination address.
Owner:ALCATEL LUCENT SAS
Apparatus and method for event correlation and problem reporting
InactiveUS7107185B1Effective monitoringImprove efficiencyNuclear monitoringDigital computer detailsComplex systemComputer science
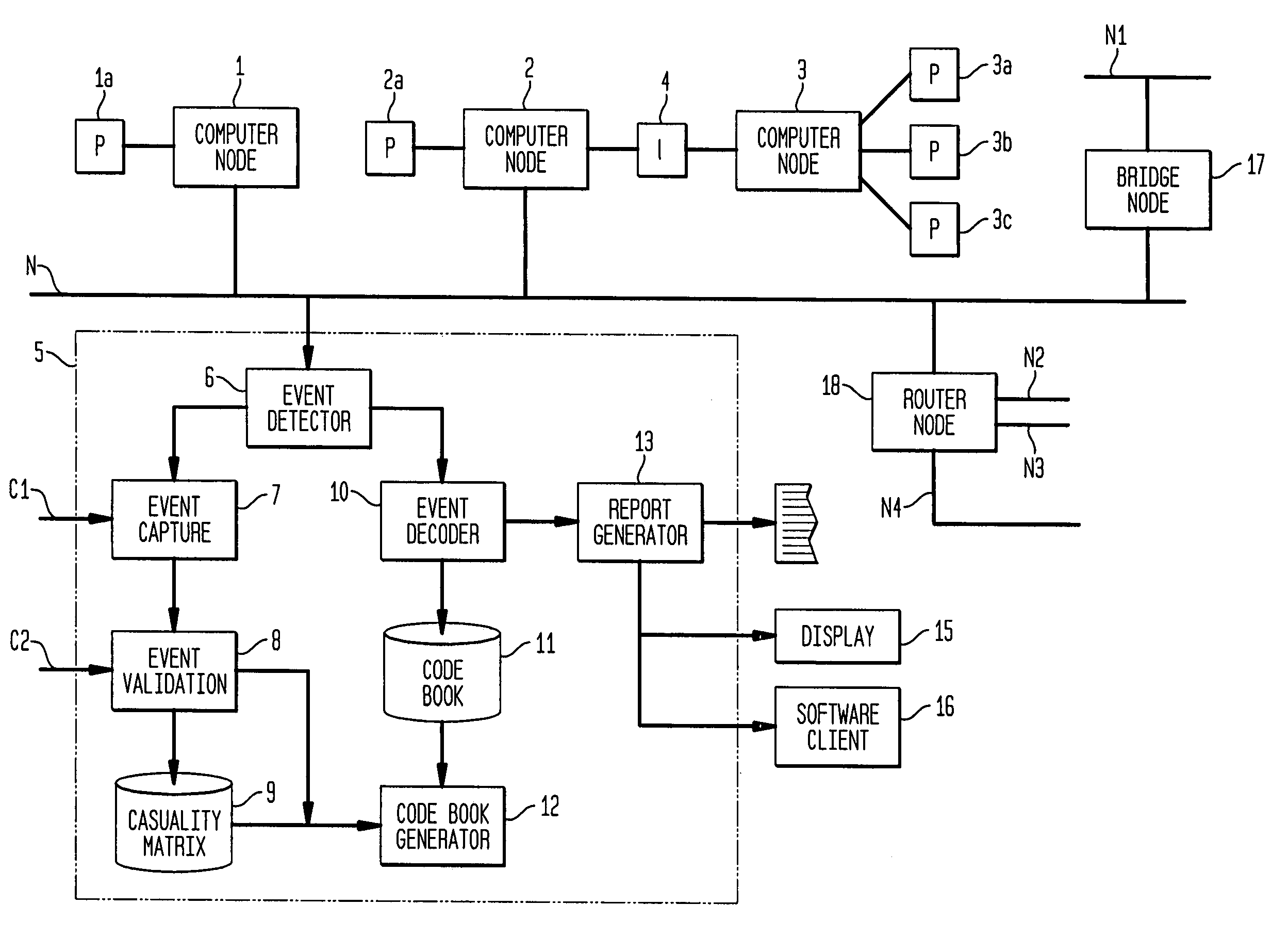
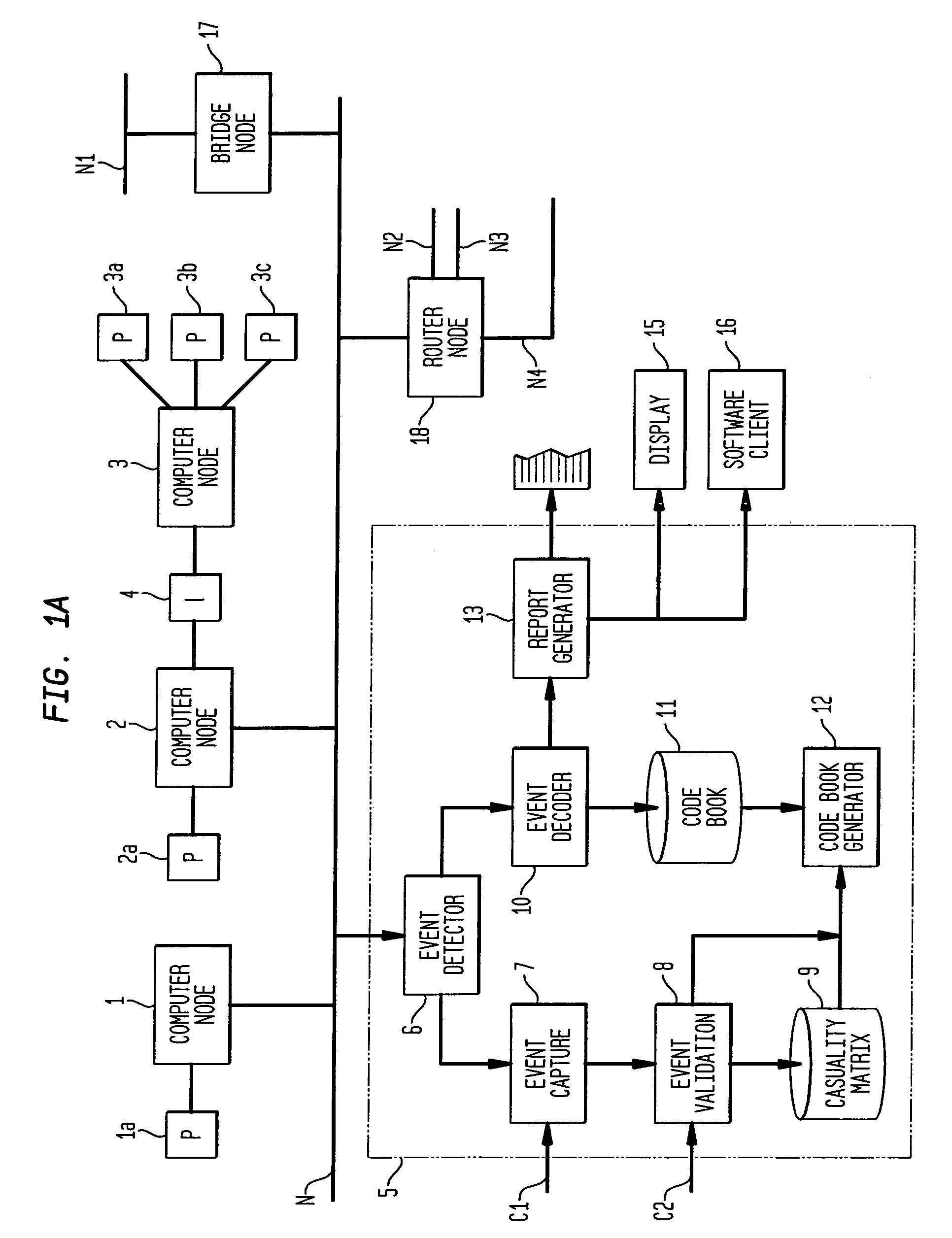
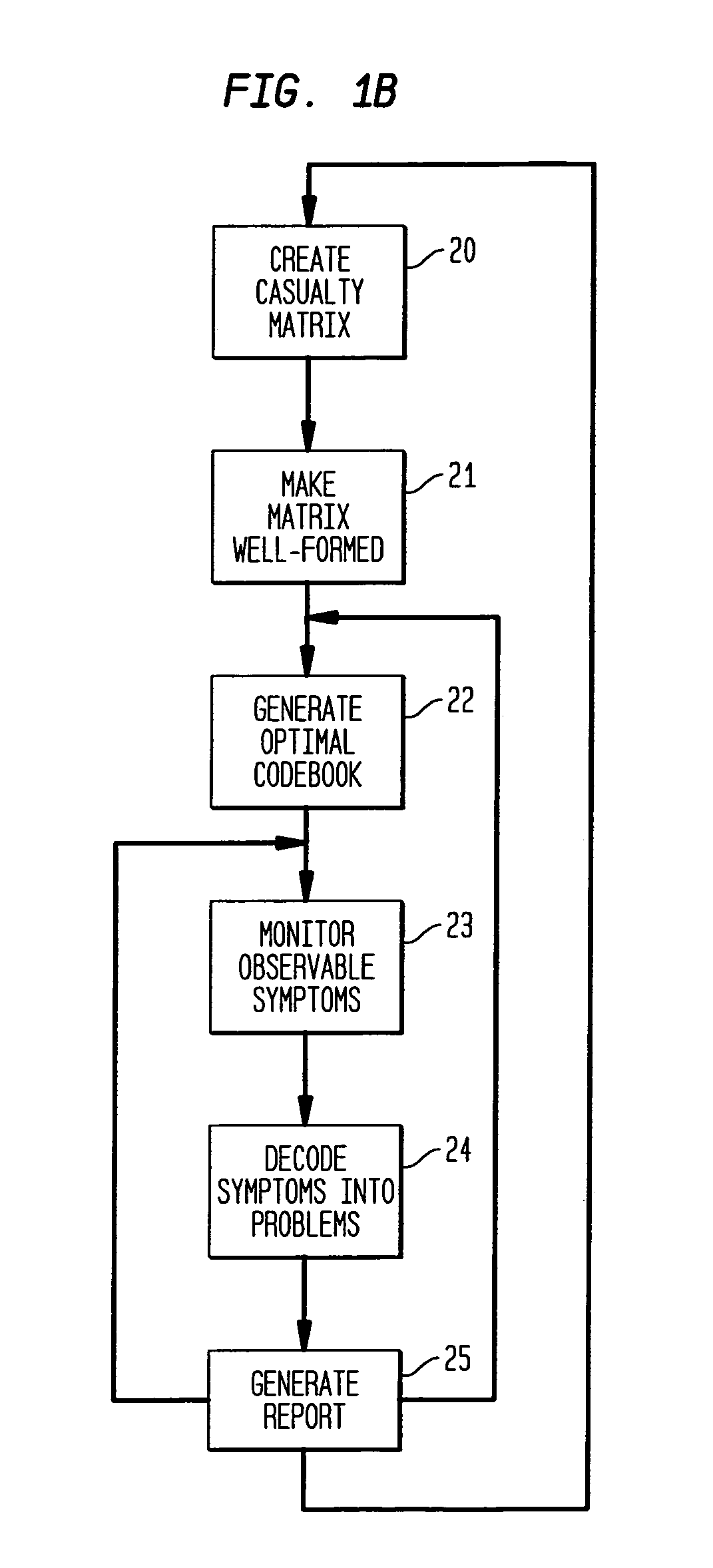
A computer implemented method on a computer readable media is provided for determining the source of a problem in a complex system of managed components based upon symptoms. The problem source identification process is split into different activities. Explicit configuration non-specific representations of types of managed components, their problems, symptoms and the relations along which the problems or symptoms propagate are created that can be manipulated by executable computer code. A data structure is produced for determining the source of a problem by combining one or more of the representations based on information of specific instances of managed components in the system. Computer code is then executed which uses the data structure to determine the source of the problem from one or more symptoms.
Owner:VMWARE INC
Detection and correction of block-level data corruption in fault-tolerant data-storage systems
ActiveUS20080115017A1Eliminate needEfficient detectionStatic storageRedundant data error correctionRAIDDisk controller
Various embodiments of the present invention provide fault-tolerant, redundancy-based data-storage systems that rely on disk-controller-implemented error detection and error correction, at the disk-block level, and RAID-controller-implemented data-redundancy methods, at the disk and disk-stripe level, in order to provide comprehensive, efficient, and system-wide error detection and error correction. Embodiments of the present invention use disk-level and stripe-level data redundancy to provide error detection and error correction for stored data objects, obviating the need for certain costly, intermediate levels of error detection and error correction commonly employed in currently available fault-tolerant, redundancy-based data-storage systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
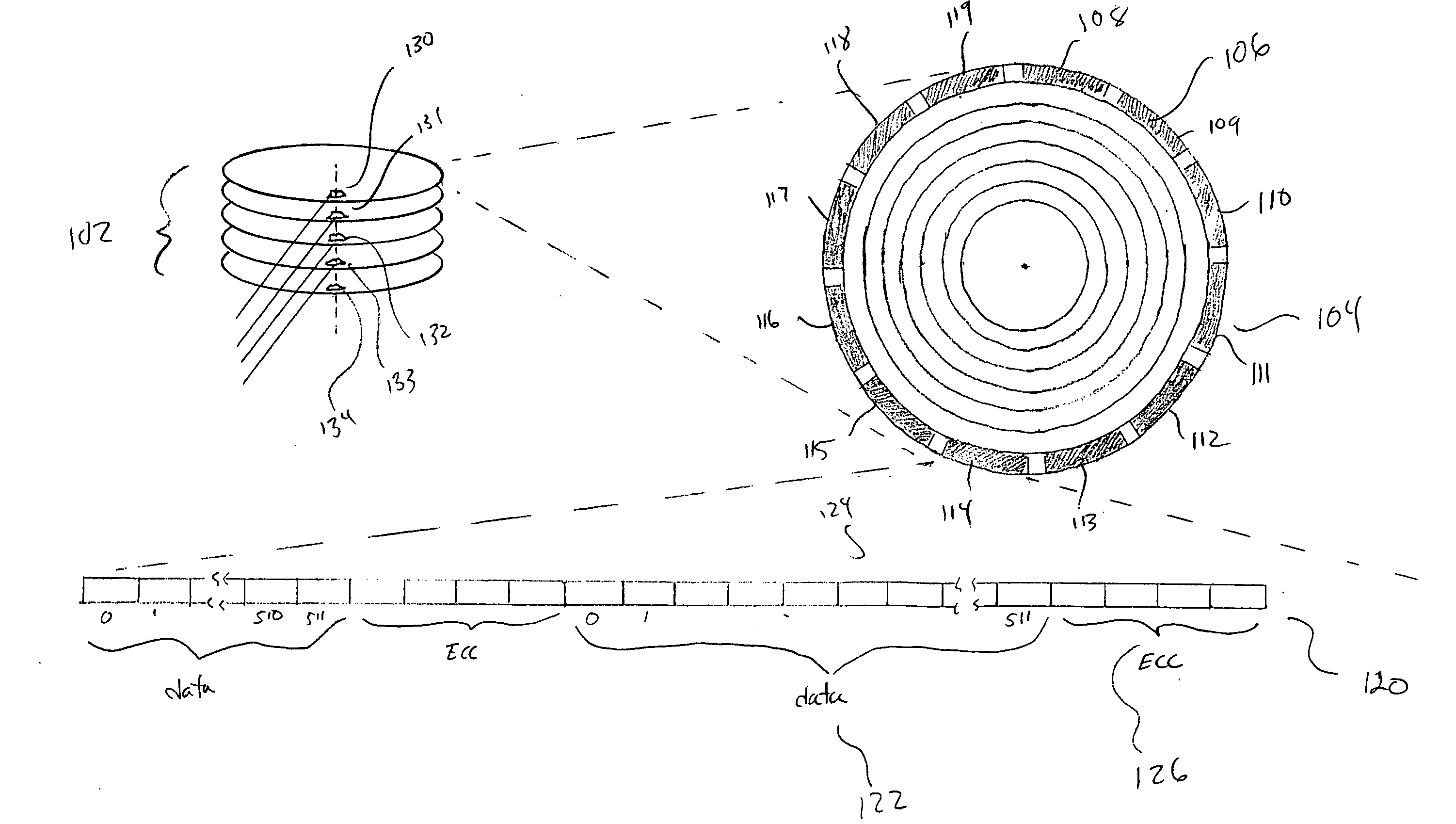
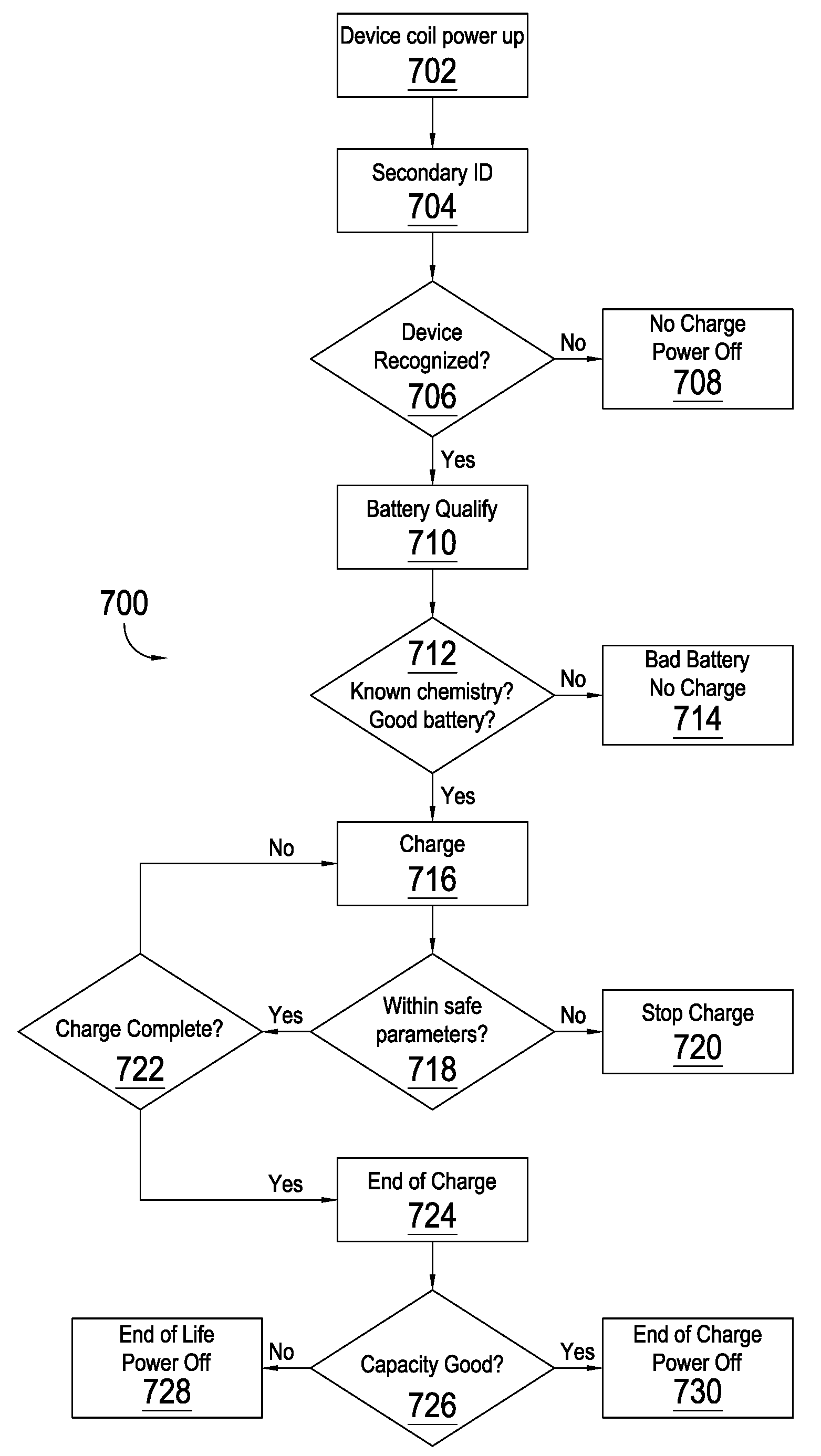
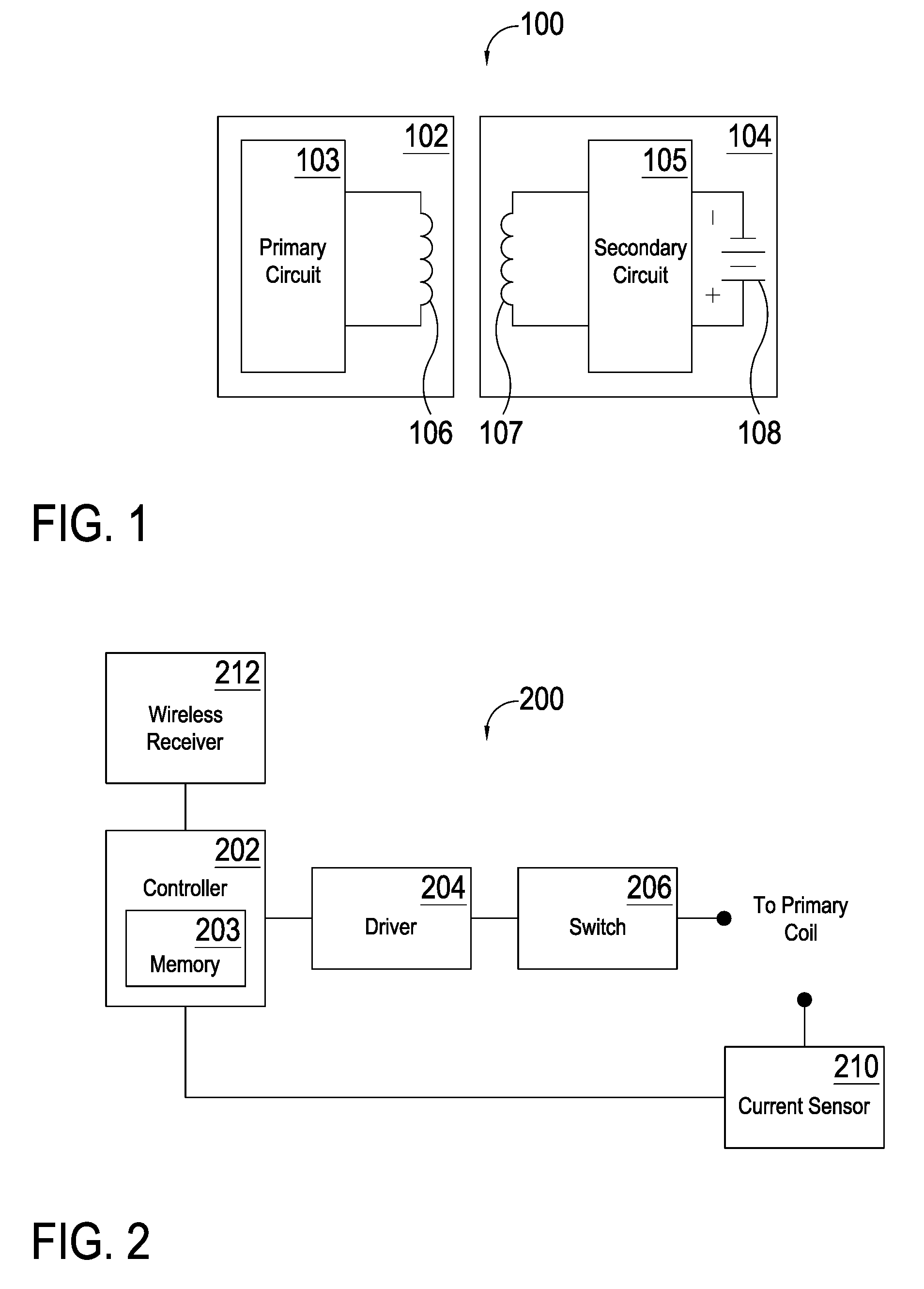
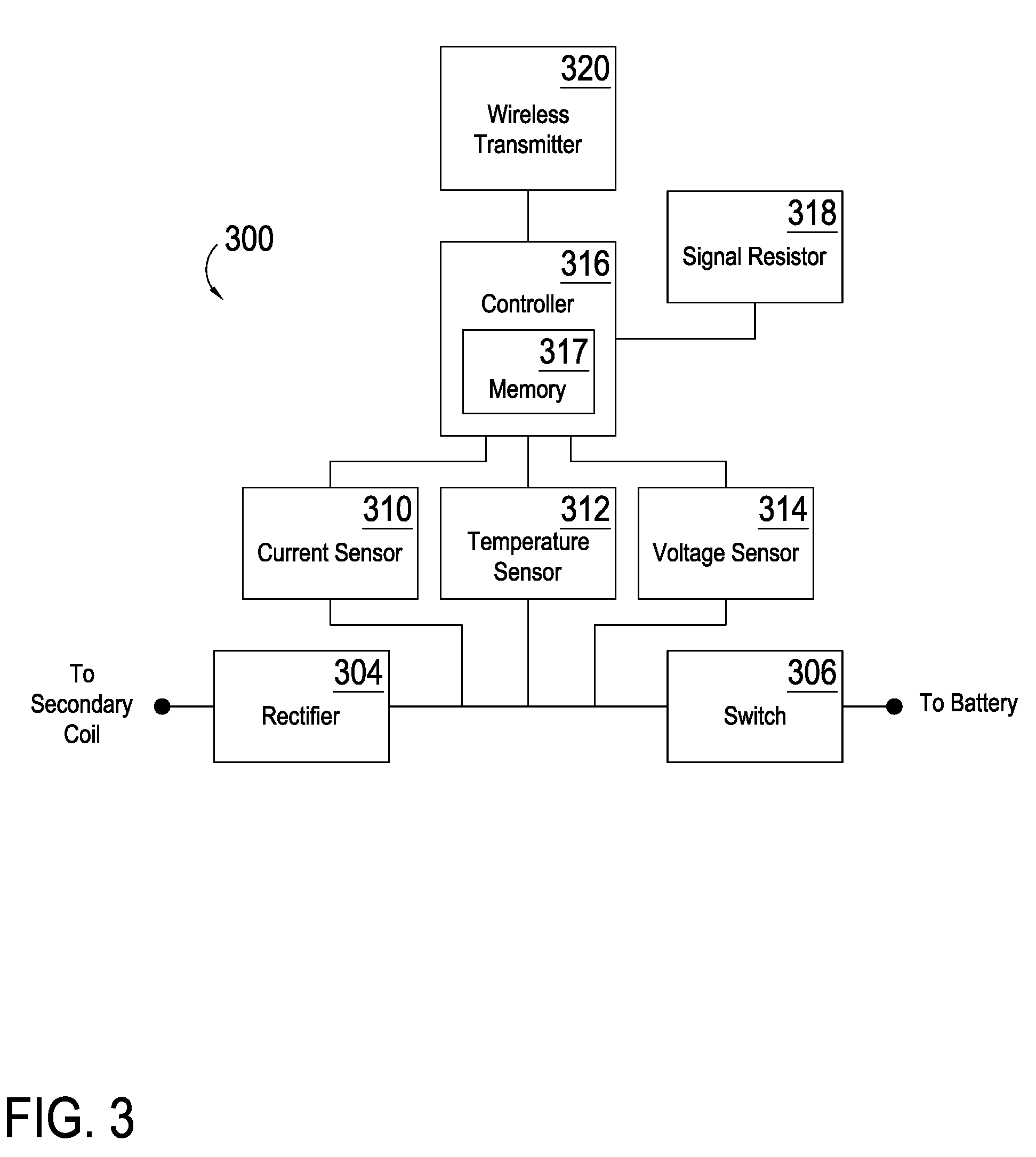
Inductive power supply system with battery type detection
ActiveUS20090212736A1Simple and effective methodAdditional flexibility and transparencyNear-field transmissionTransformersInductive chargingEngineering
An inductive power supply system to wirelessly charge a remote device based on detected battery characteristics. The system includes an inductive power supply with a primary coil capable of inductively providing power to a secondary coil in a remote device. The inductive power supply and remote device include communication means for wirelessly communicating. The system further includes a remote device, having a battery with detectable battery characteristics. In operation, the remote device is capable of detecting the battery characteristics by applying a qualification charge to the battery. The inductive power supply system is capable of identifying the battery installed in the remote device by analyzing the detected battery characteristics. The inductive power supply system selects an appropriate charging algorithm based on the analyzed characteristics.
Owner:PHILIPS IP VENTURES BV
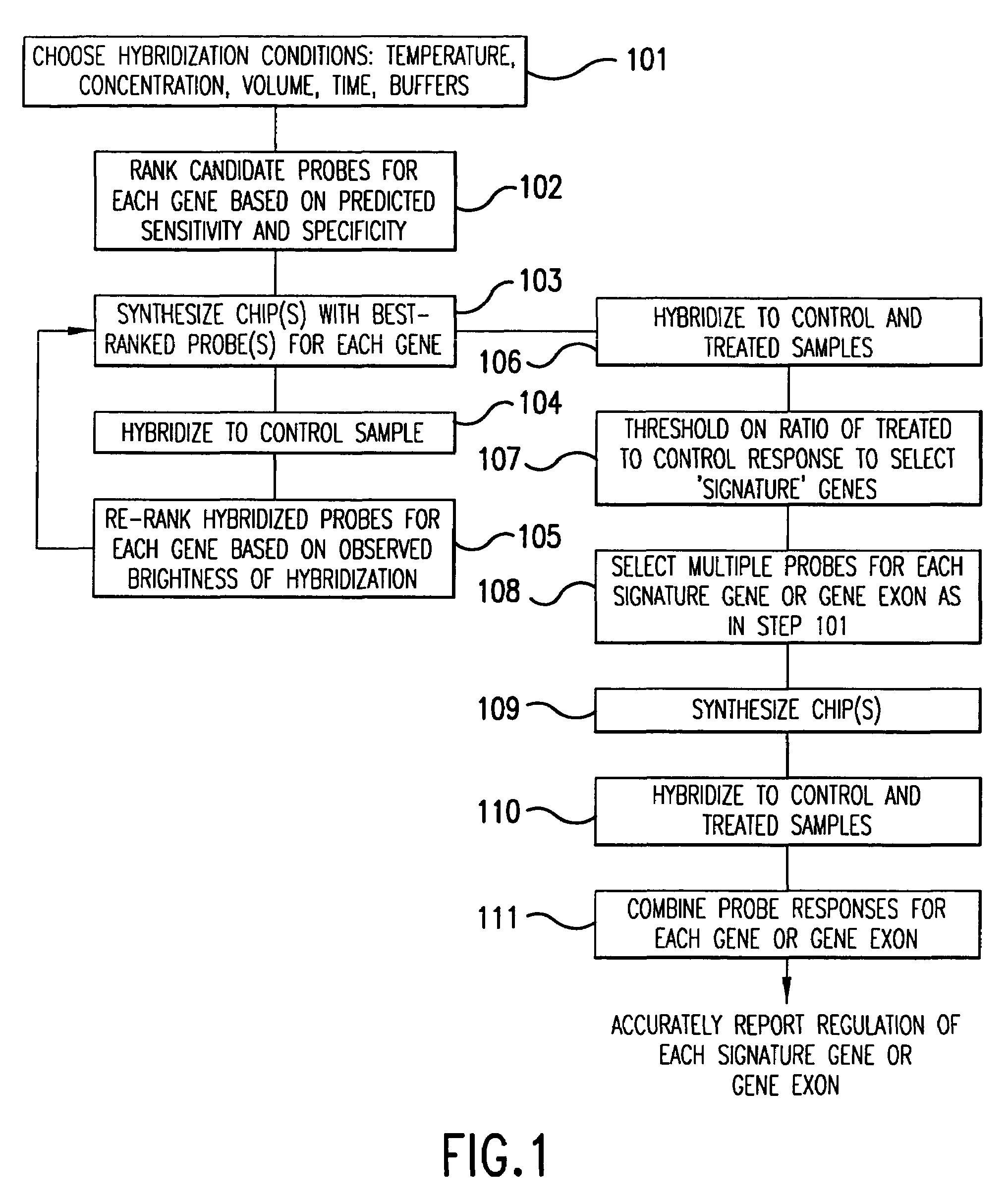
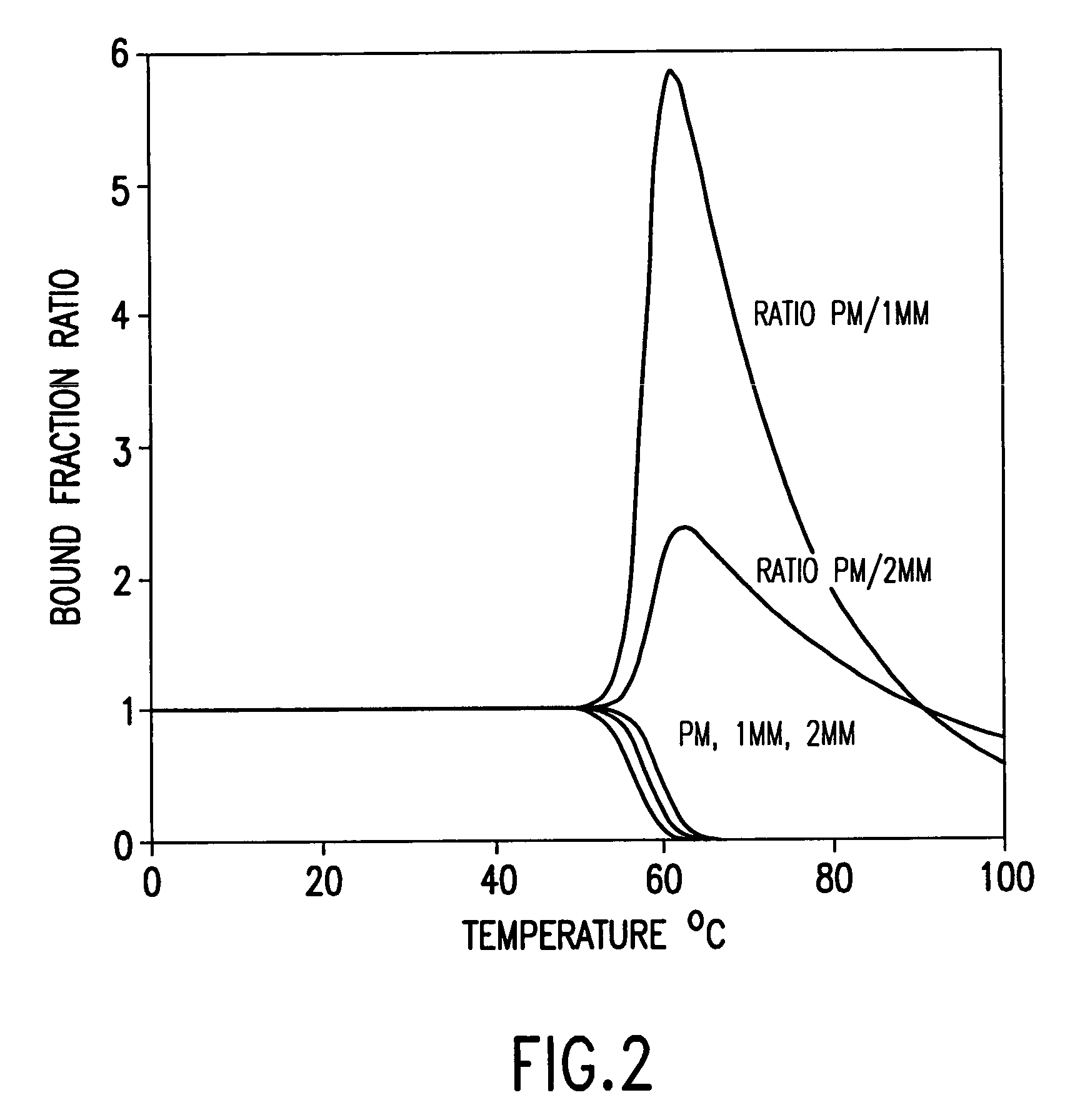
Iterative probe design and detailed expression profiling with flexible in-situ synthesis arrays
InactiveUS7013221B1Efficient changeEfficient detectionBioreactor/fermenter combinationsBiological substance pretreatmentsBiological bodyNucleotide
Methods and compositions are provided that are useful for detecting and reporting a plurality of different target polynucleotide sequences in a sample, such as polynucleotides corresponding to a plurality of different genes expressed by a cell or cells. In particular, the invention provides methods for screening a plurality of candidate polynucleotide probes to evaluate both the sensitivity and the specificity with which each candidate probe hybridizes to a target polynucleoide sequence. Candidate polynucleotide probes can then be ranked according to both their sensitivity and specificity, and probes that have optimal sensitivity and specificity for a target polynucleotide sequence can be selected. In one embodiment, polynucleotide probes can be selected according to the methods described herein to prepare “screening chips” wherein a large number of target polynucleotide sequences are detected using a single microarray have a few (e.g., 1–5) probes for each target polynucleotide sequence. In a particularly preferred embodiment, the invention provides a screening chip that can detect genetic transcripts from the entire genome of an organism. In an alternative embodiment, polynucleotide probes can be selected according to the methods described herein to prepare “signature chips” to more accurately detect certain selected “signature genes” using several polynucleotide probes (e.g., 10–20) for each signature gene. The invention additionally provides microarrays containing polynucleotide probes for a large number of genes expressed by a cell or organism. Further, methods for detecting a plurality of polynucleotide molecules, including a large number of genes expressed by a cell or organism, are also provided.
Owner:MERCK & CO INC
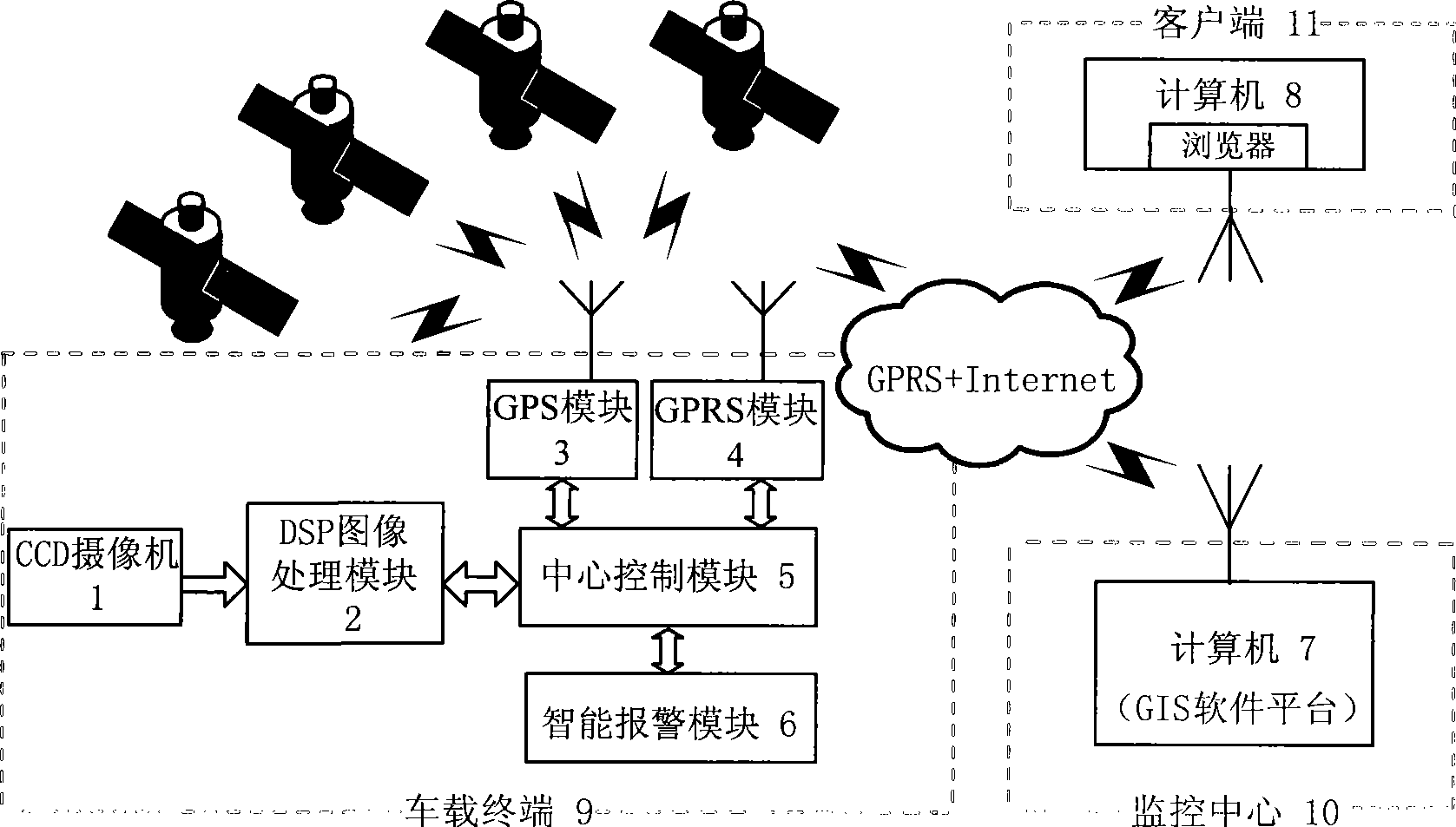
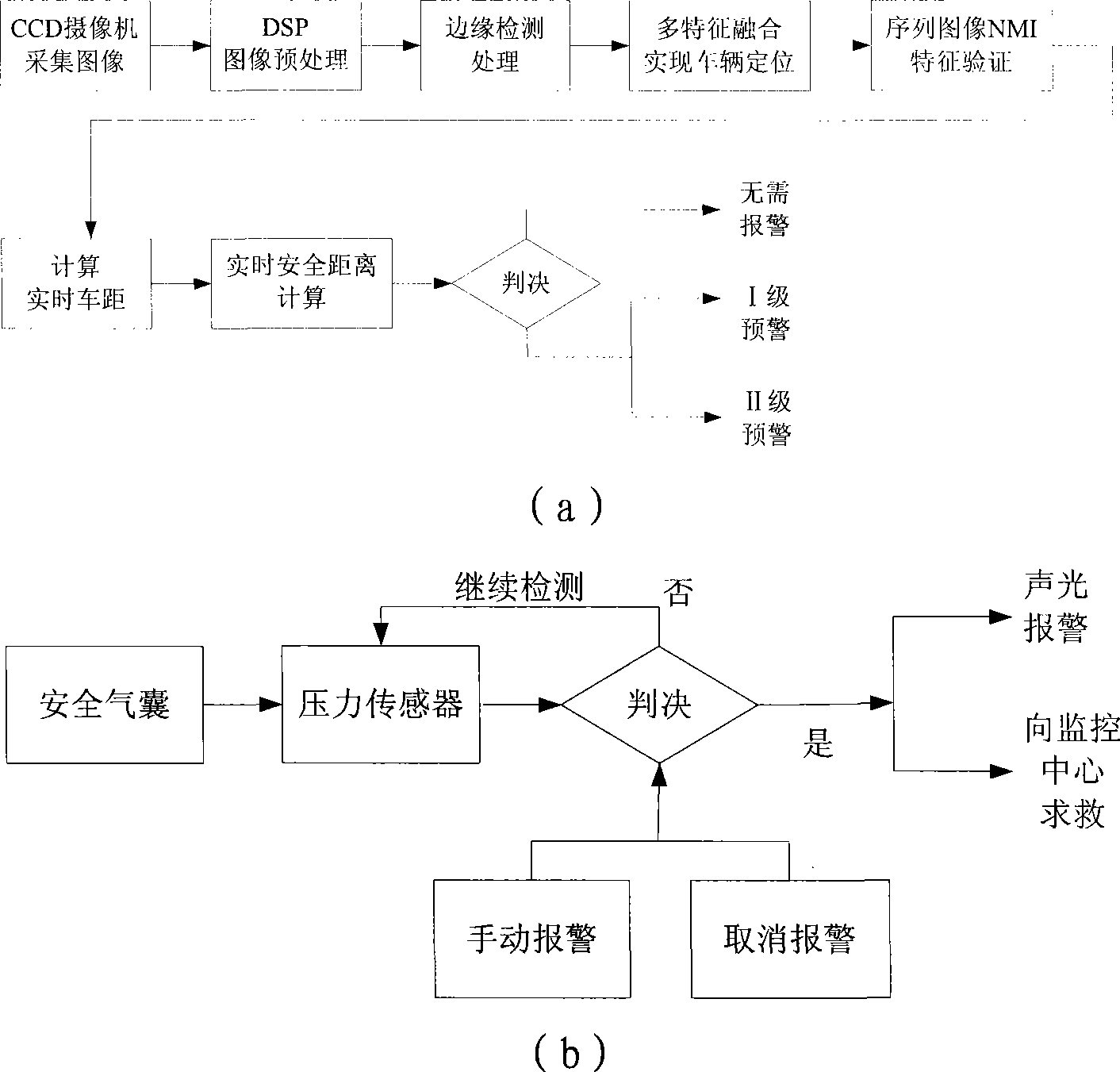
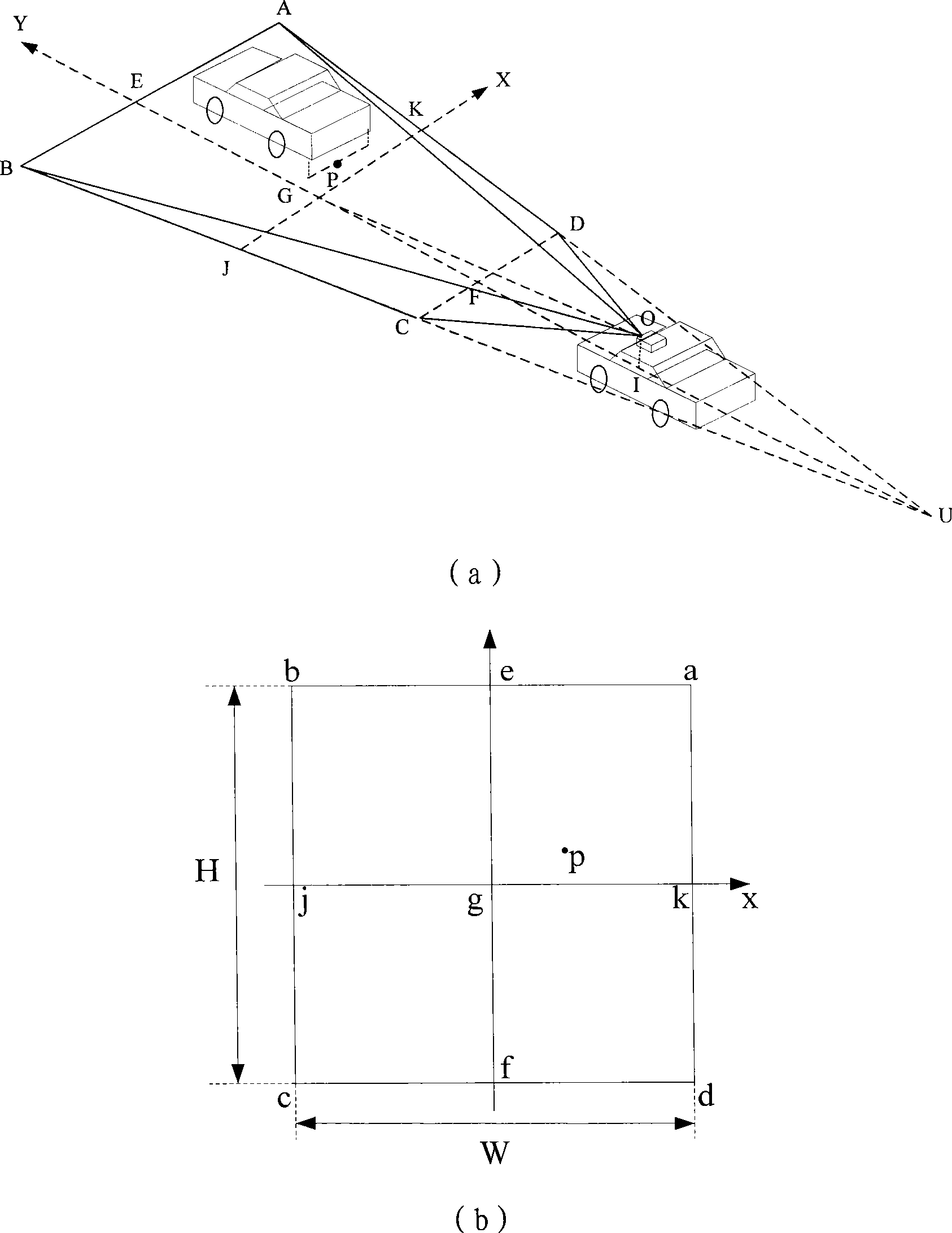
Vehicle intelligent alarming method and device
InactiveCN101391589AImprove securityEfficient detectionPedestrian/occupant safety arrangementSignalling/lighting devicesMobile vehicleMachine vision
The invention relates to an on-board intelligent alarming method and a device, wherein, the method combines a longitudinal anti-collision pre-warning method based on the single-eye vision and an accident automatic help-calling method, realizes preventing the rear-end accidents, strives for helping time, reduces injuries and deaths, effectively prevents the collision accidents and personnel deaths caused by the collision, and improves the running safety of the automobile; the device mainly comprises three parts: an on-board terminal, a monitoring center and a user end; the method and the device use the machine vision technique to differentiate the moving vehicles in the front, have high precision and wide visible range, can effectively probe the obstacles, reduce the error reporting possibility and prevent the collision accidents. The method and the device can improve the safety of the vehicle, thus having extremely large application value and prospect.
Owner:SHANGHAI UNIV
Method and apparatus for detecting doubled bills in a currency handling device
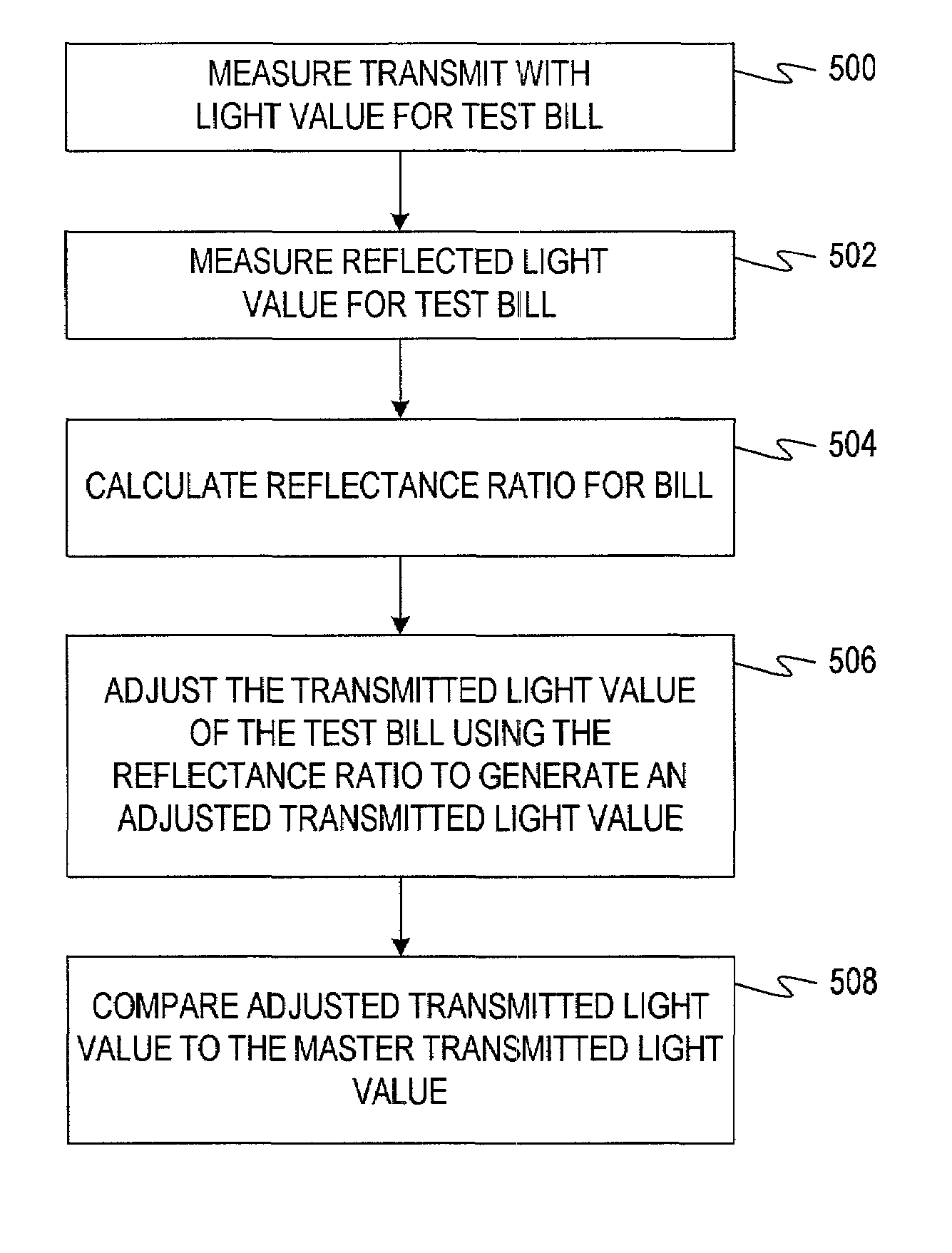
InactiveUS7103206B2Simple systemEfficient detectionPaper-money testing devicesCharacter and pattern recognitionReflectivityLight source
A doubles detection system for detecting doubled documents. The system comprises one or more light sources disposed on a first side of a test document and one or more reflected light sensors disposed along the first side of the test document. The reflected light sensors are adapted to generate reflected light signals. The system also comprises one or more transmitted light sensors disposed along a second side of the test document which are adapted to generate transmitted light signals. The system also comprises a memory having a master reflected light value and a master transmitted light value stored therein. The system comprises a processor adapted to receive the reflected light signal, generate a reflected light value for the test document, and calculate a reflectance ratio between the reflected light value of the test document and a master reflected light value. The processor is also adapted to receive the transmitted light signal, generate a transmitted light value for the test document, and adjust the transmitted light value for the test document based on the reflectance ratio. The processor is adapted to compare the adjusted transmitted light value for the test document to the master transmitted light value and generate a doubles signal if the comparison of the adjusted transmitted light value for the test document with the master transmitted light value indicates that more than one document is present.
Owner:CUMMINS-ALLISON CORP
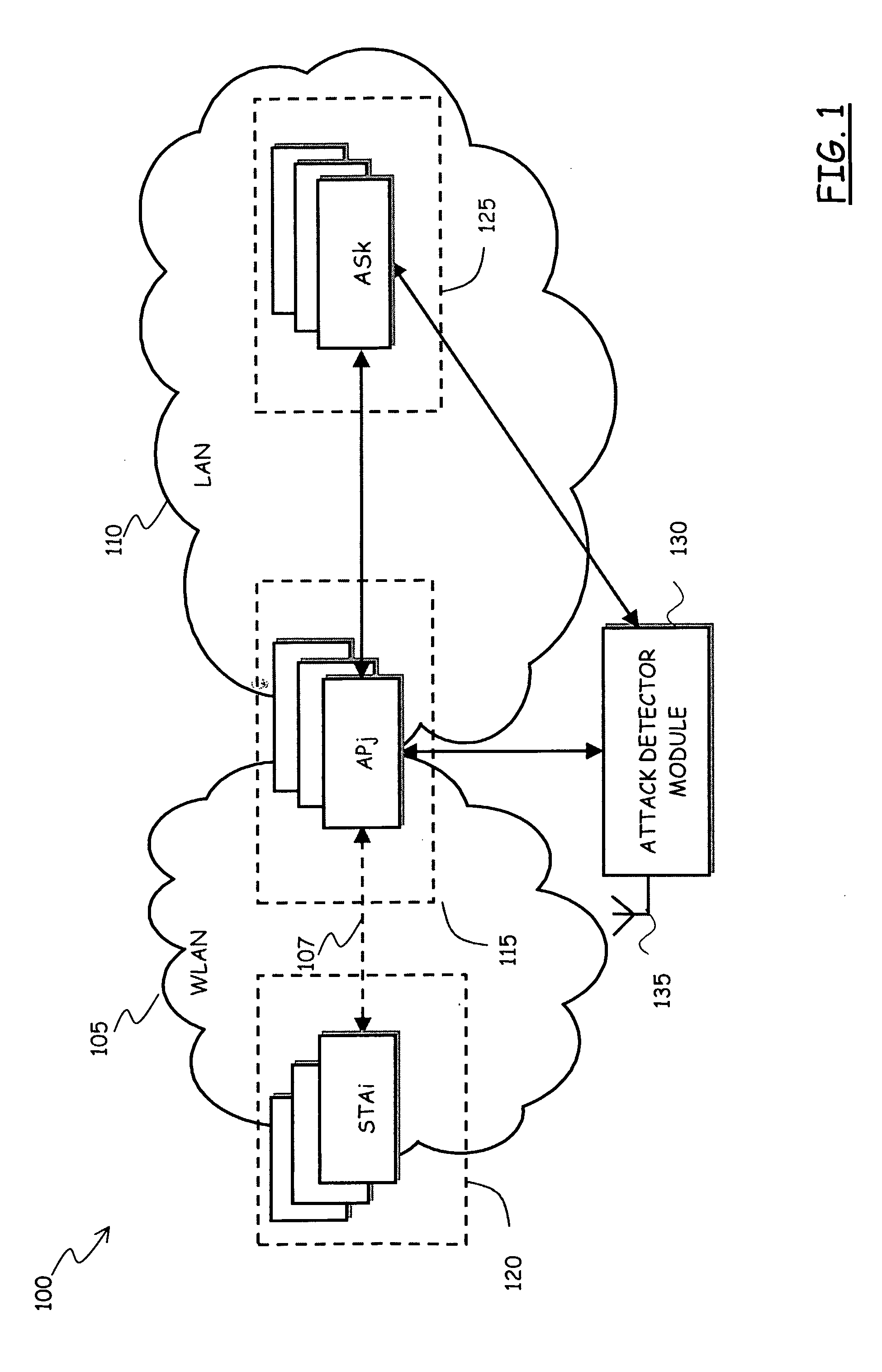
Method and System for Detecting Attacks in Wireless Data Communications Networks
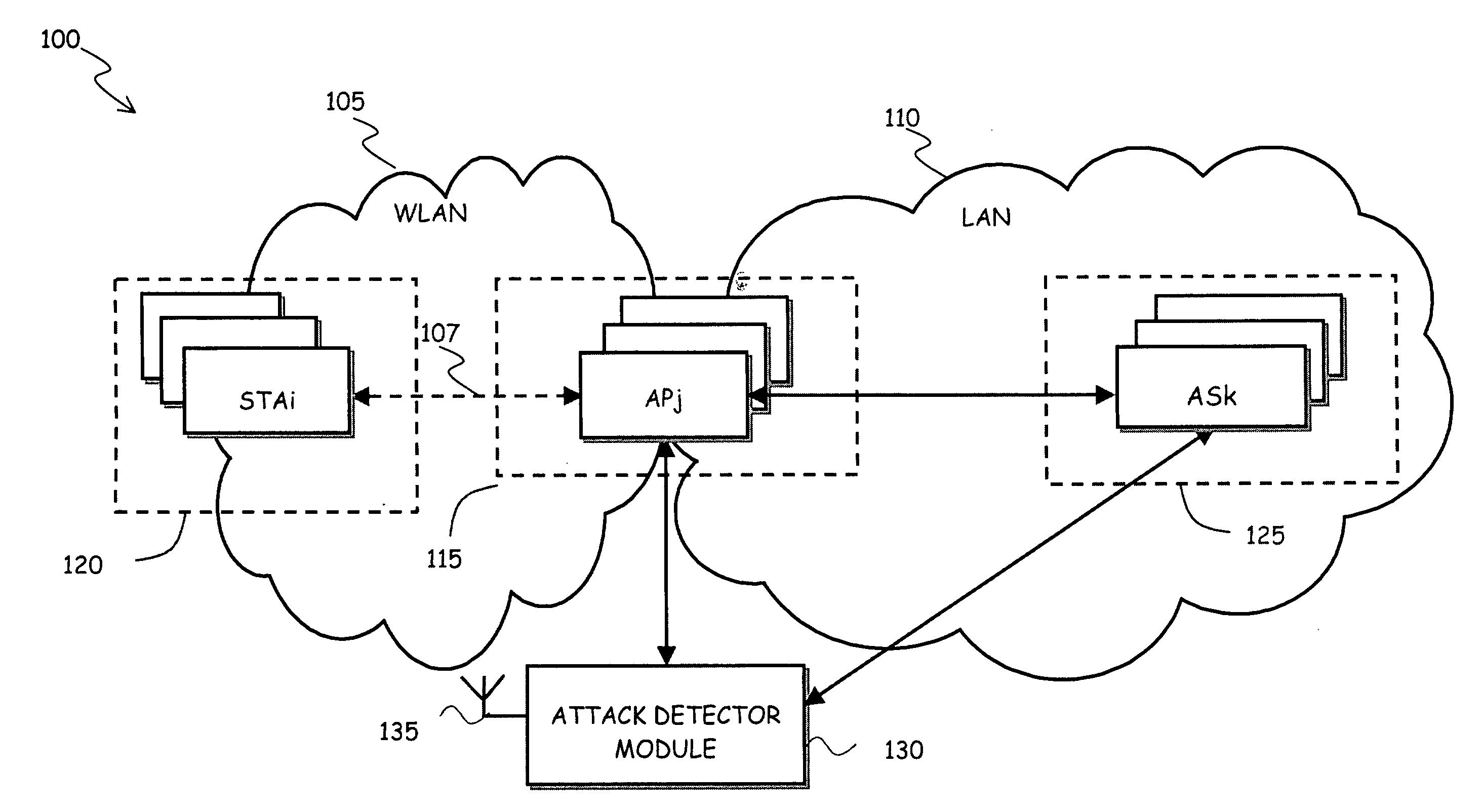
ActiveUS20080043686A1Efficient detectionReliable basisUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTraffic volumeWireless data
A method of detecting attacks in a wireless data communications network, includes: monitoring wireless traffic over the wireless data communications network; deriving a first network state from the monitored wireless traffic; acquiring trusted information indicative of a wireless network state from at least one apparatus of a network infrastructure; establishing a second network state based on the acquired trusted information; comparing the derived first network state with the second network state, and determining a wireless network attack in case of incoherence between the derived first network state compared to the second network state.
Owner:TELECOM ITALIA SPA
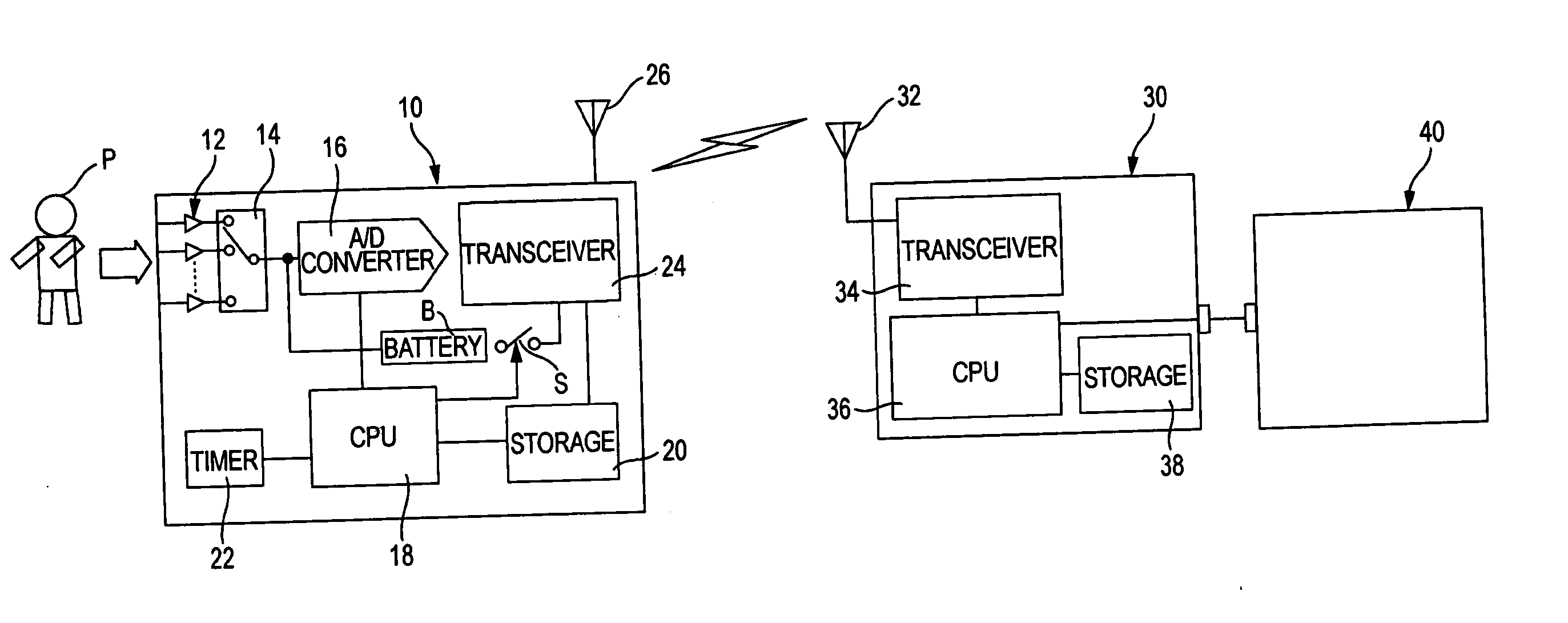
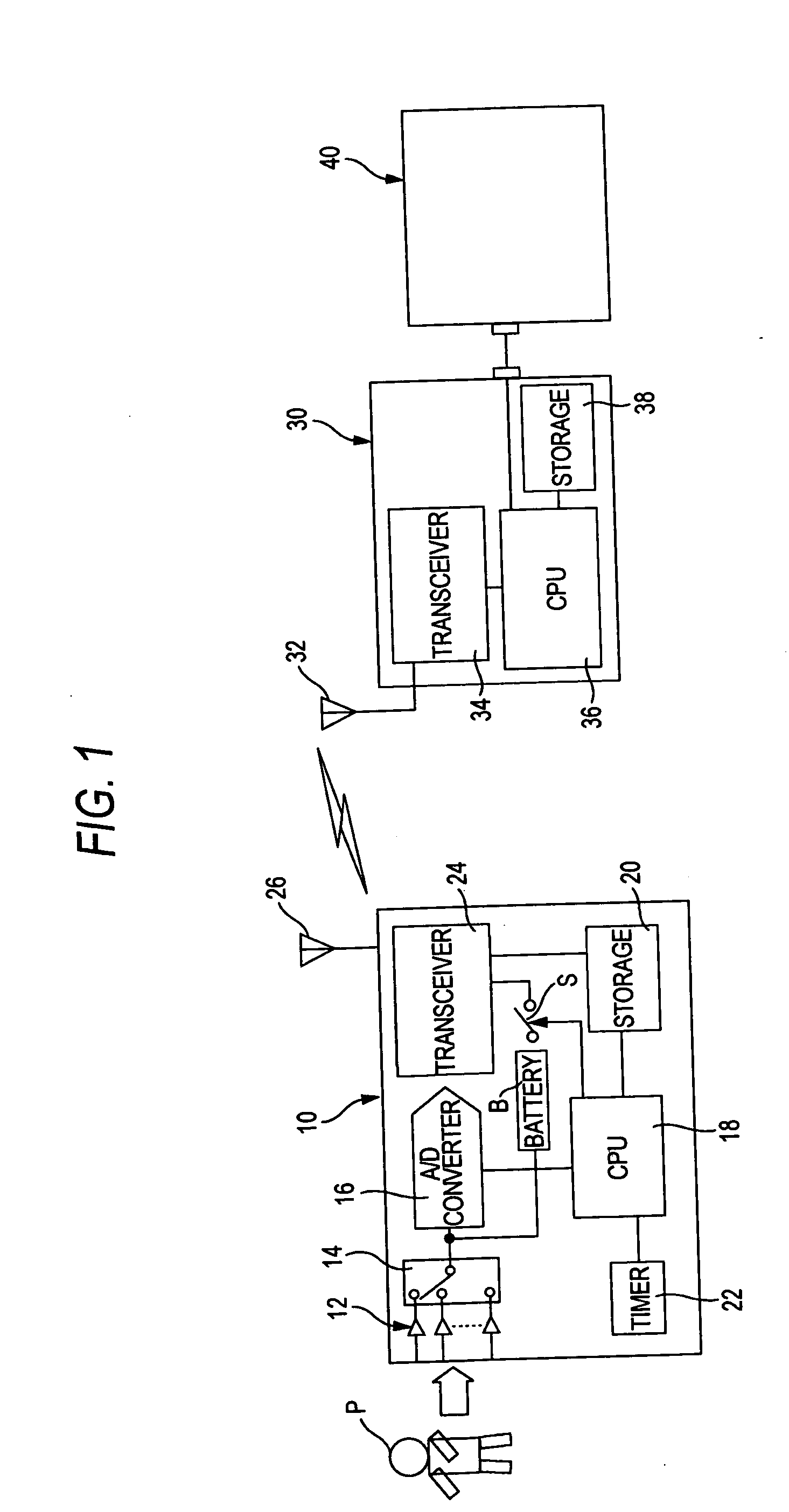
Multi-channel biological signal telemetry systems
ActiveUS20050085872A1Reduce the amount of solutionSimple and flexible and accurate analysisElectrotherapySurgeryDigital dataTransceiver
A system for performing telemetry of multi-channel biological signals obtained from electrodes attached to a subject, is provided with a transmitter and a receiver. In the transmitter, a converter converts the multi-channel biological signals to digital data, and a storage stores the digital data. In the transmitter, a first transceiver is operable to transmit a prescribed amount of the digital data stored in the storage, and a battery is operable to supply a battery voltage to the first transceiver. In the transmitter, a switch places the battery in either a first state where the battery voltage is supplied to the first transceiver or a second state where the battery voltage is not supplied to the first transceiver, so that the first transceiver intermittently transmits the digital data. In the receiver, a second transceiver is operable to receive the digital data transmitted from the first transceiver. The received digital data is to be reproduced multi-channel biological signals at an output device.
Owner:NIHON KOHDEN CORP
System for measuring vital signs during hemodialysis
ActiveUS20110066006A1Simplifies and expedites applicationEfficient detectionElectrocardiographyMedical devicesHemodialysisBlood pressure
The invention provides a system for continuously monitoring a patient during hemodialysis. The system includes a hemodialysis machine for performing the hemodialysis process that features a controller, a pump, a dialyzer filter, a lumen, and an interface to a body-worn monitor. A patient attaches to the dialysis machine through the lumen, and wears a body-worn monitor for continuously measuring blood pressure. The monitor includes an optical system for measuring an optical waveform, an electrical system for measuring an electrical waveform, and a processing component for determining a transit time between the optical and electrical waveforms and then calculating a blood pressure value from the transit time. The body-worn monitor features an interface (e.g. a wired serial interface, or a wireless interface) to transmit the blood pressure value to the controller within the hemodialysis machine. The controller is configured to receive the blood pressure value, analyze it, and in response adjust the dialysis process.
Owner:SOTERA WIRELESS
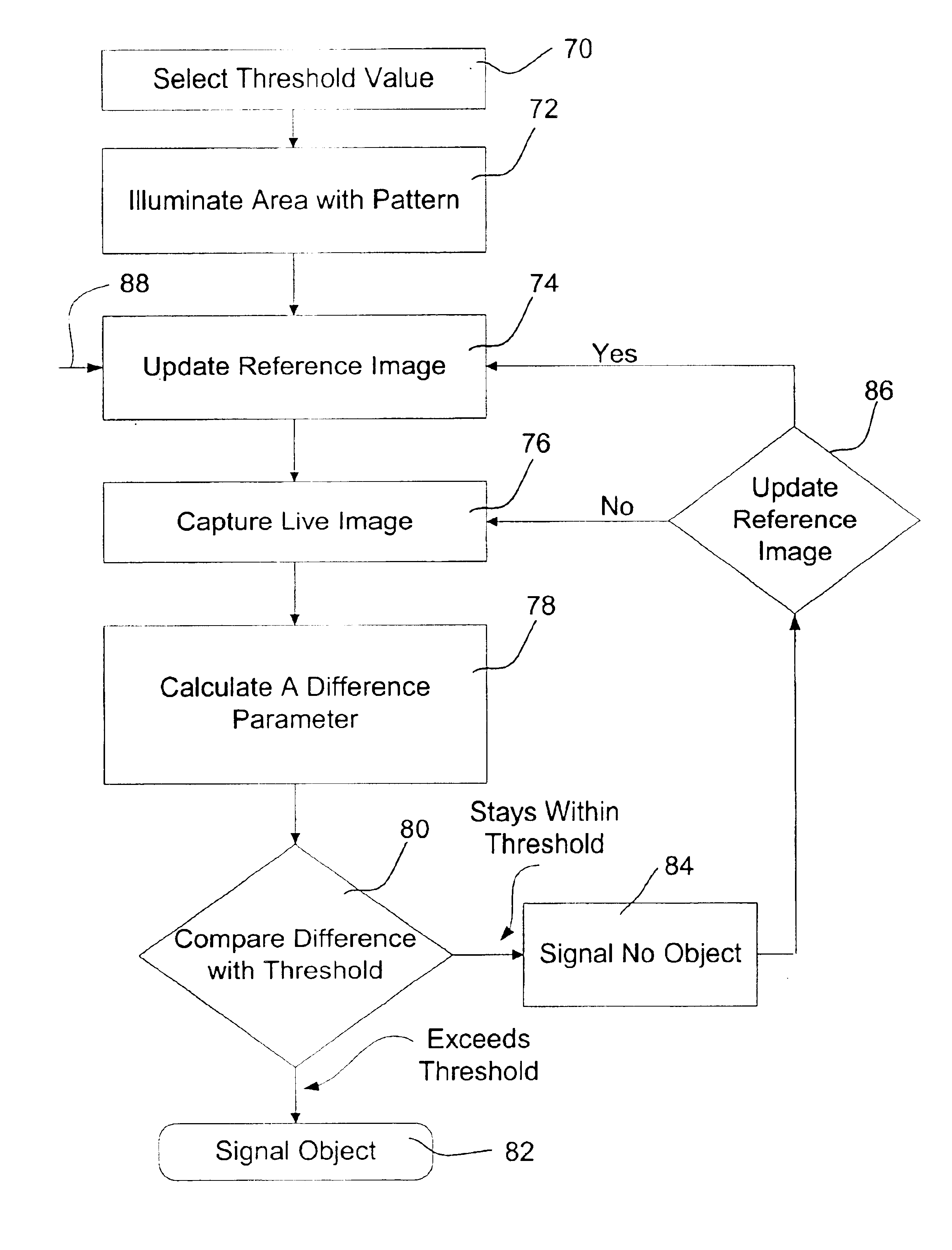
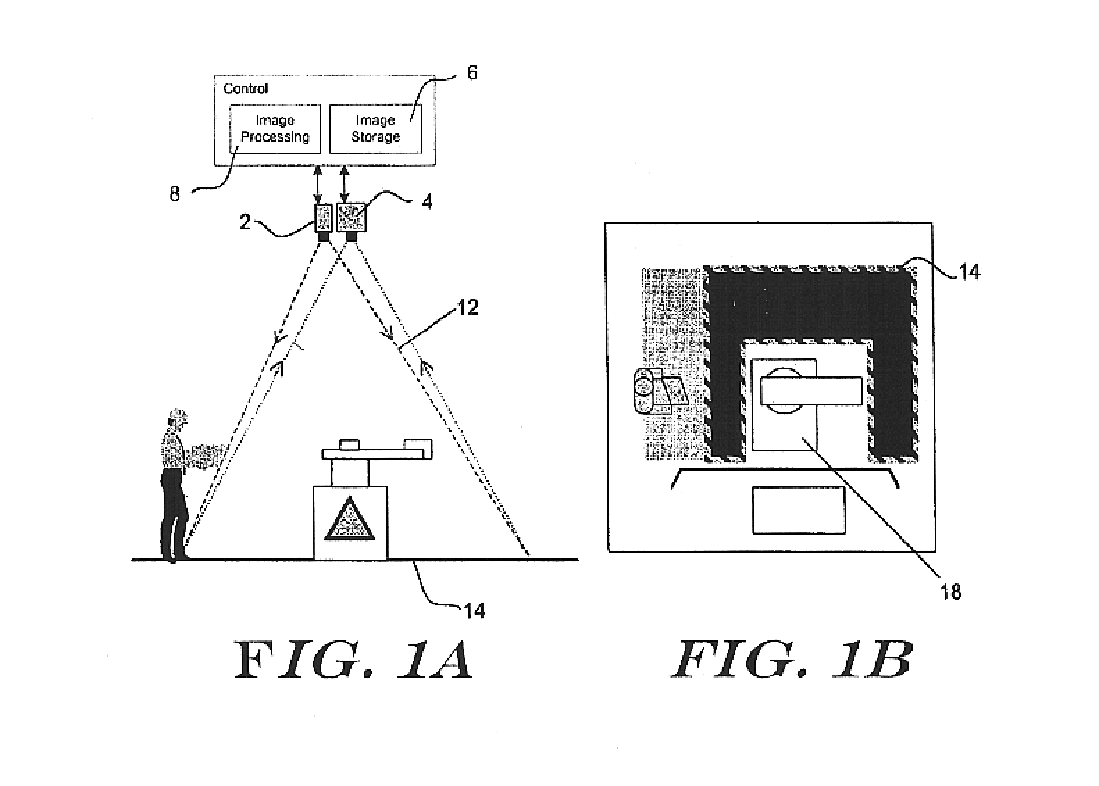
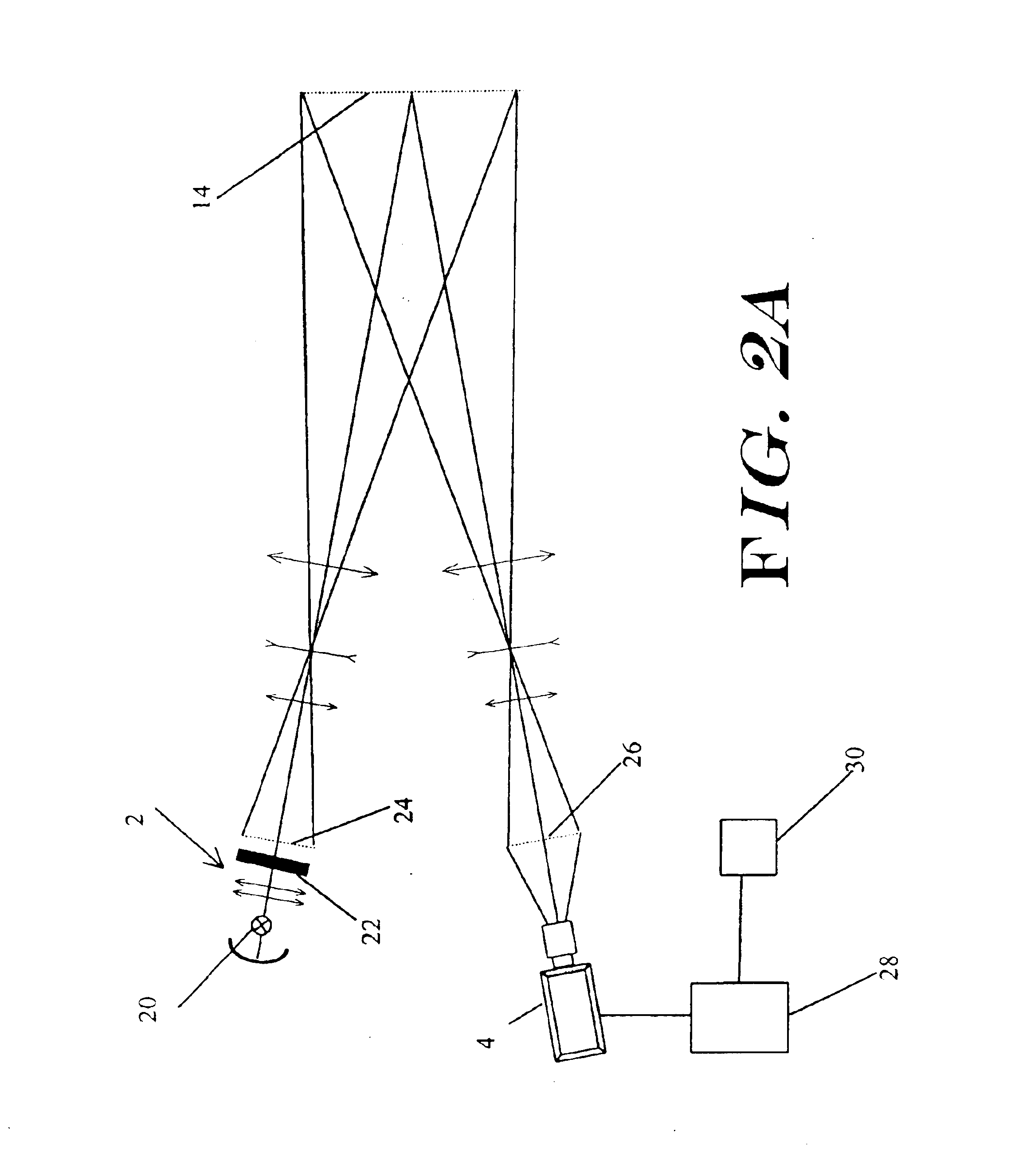
Method and apparatus for detecting objects
InactiveUS6841780B2Less effect efficacyHighly effectiveRadiation pyrometryImage analysisObject motionComputer science
An object detection system is provided that projects one or more patterns onto a monitored area, captures one or more live images of the monitored area, and detects objects that enter the monitored area by detecting changes in the one or more patterns in the live images. Such an object detection system may be less susceptible to dynamic lighting conditions, and more sensitive to object motion and / or presence.
Owner:HONEYWELL INT INC
High-efficiency neutron detectors and methods of making same
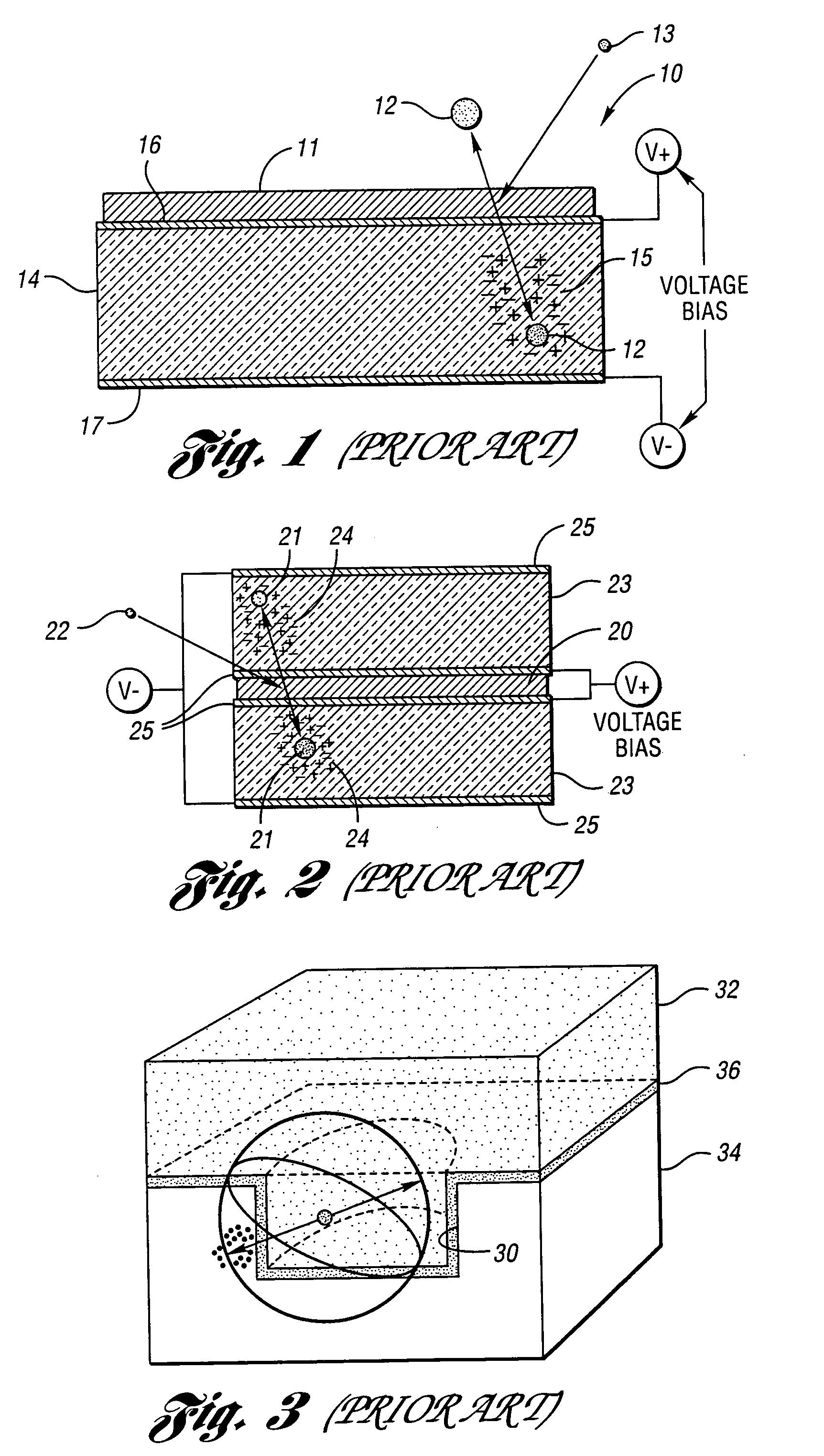
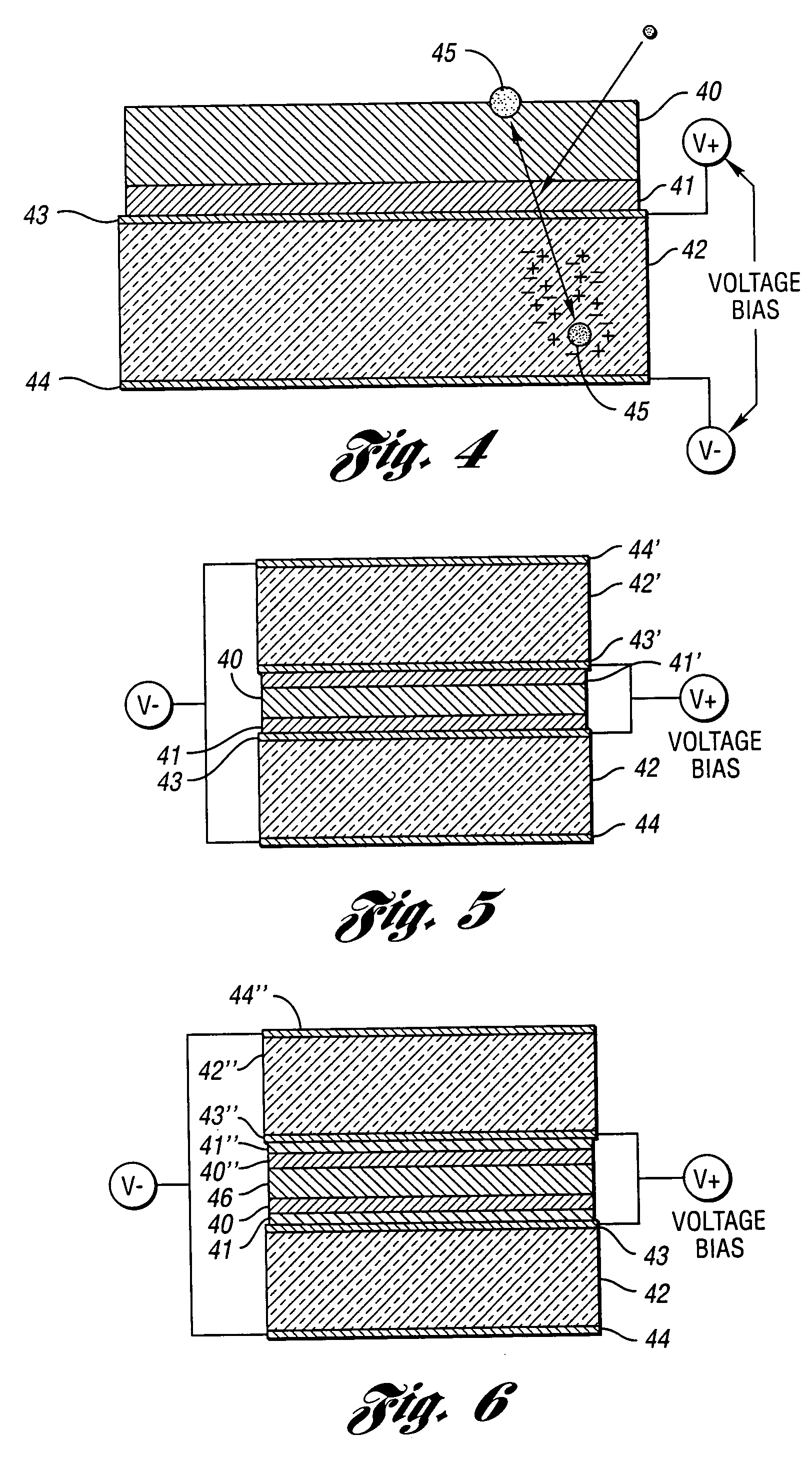
ActiveUS20050258372A1Efficient detectionThin and compactMeasurement with semiconductor devicesMaterial analysis by optical meansRoom temperatureReactive material
Neutron detectors, advanced detector process techniques and advanced compound film designs have greatly increased neutron-detection efficiency. One embodiment of the detectors utilizes a semiconductor wafer with a matrix of spaced cavities filled with one or more types of neutron reactive material such as 10B or 6LiF. The cavities are etched into both the front and back surfaces of the device such that the cavities from one side surround the cavities from the other side. The cavities may be etched via holes or etched slots or trenches. In another embodiment, the cavities are different-sized and the smaller cavities extend into the wafer from the lower surfaces of the larger cavities. In a third embodiment, multiple layers of different neutron-responsive material are formed on one or more sides of the wafer. The new devices operate at room temperature, are compact, rugged, and reliable in design.
Owner:RGT UNIV OF MICHIGAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com