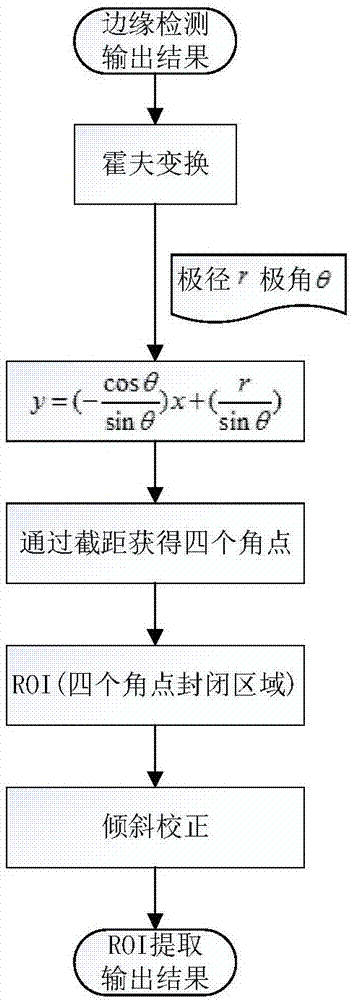
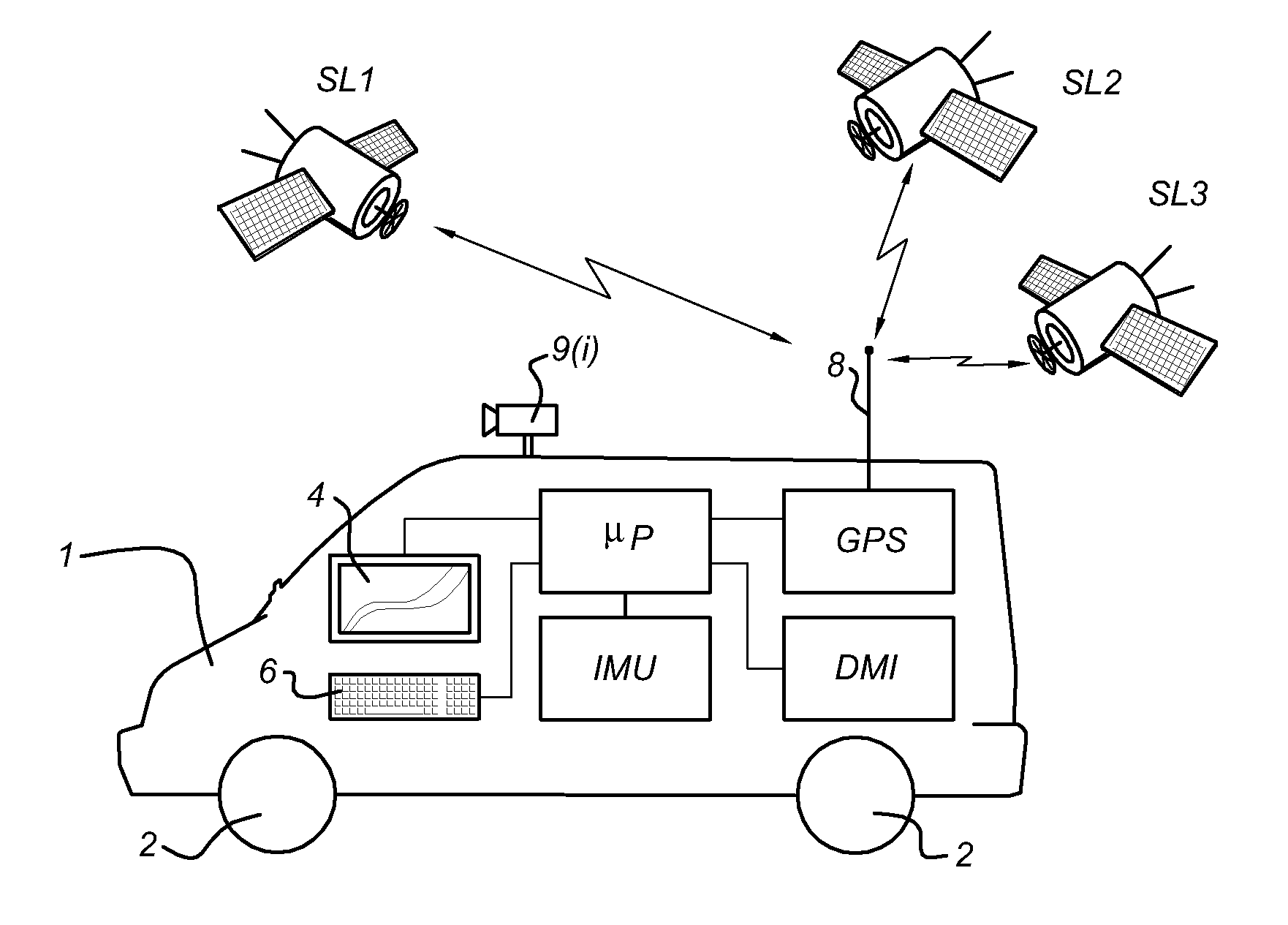
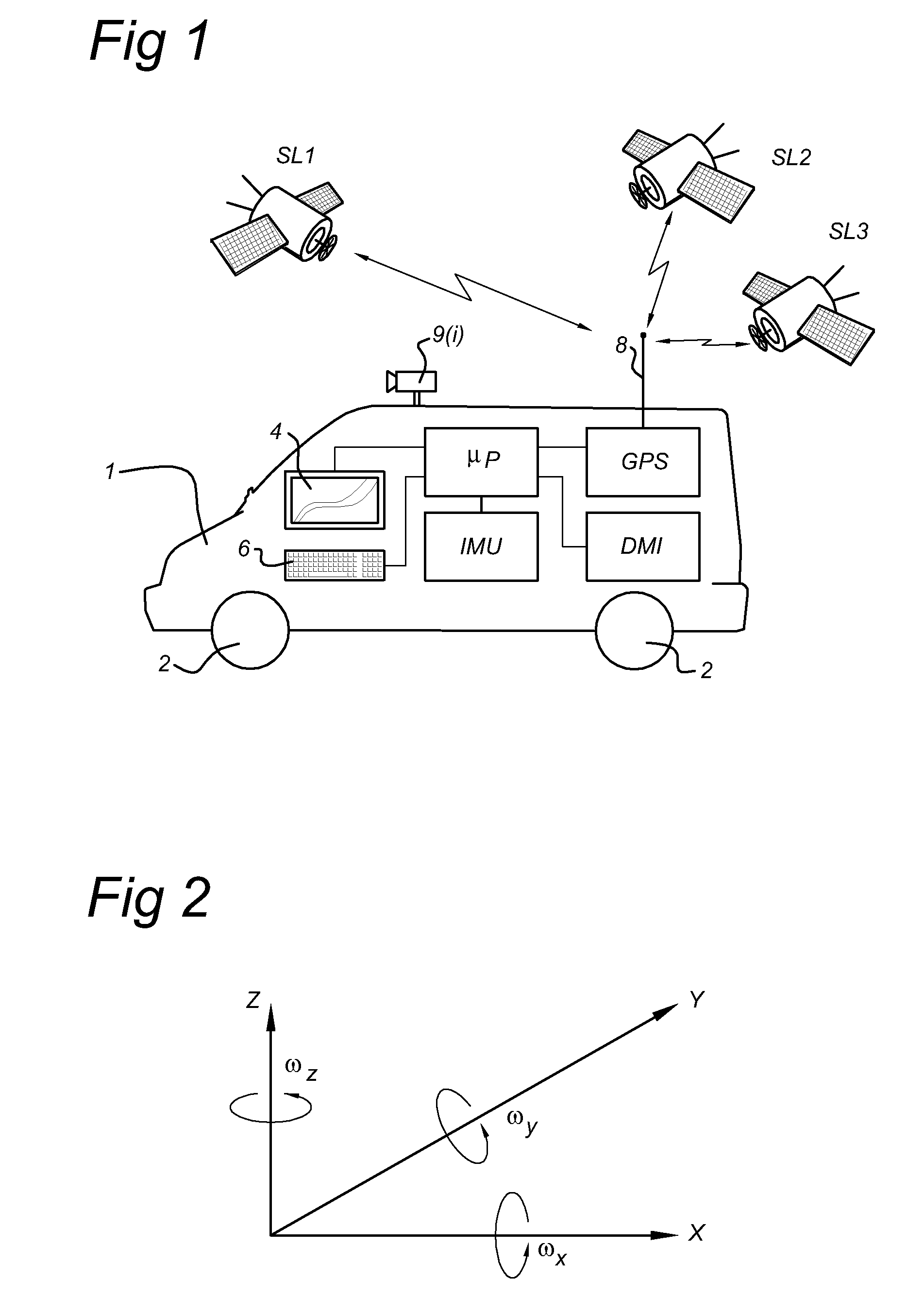
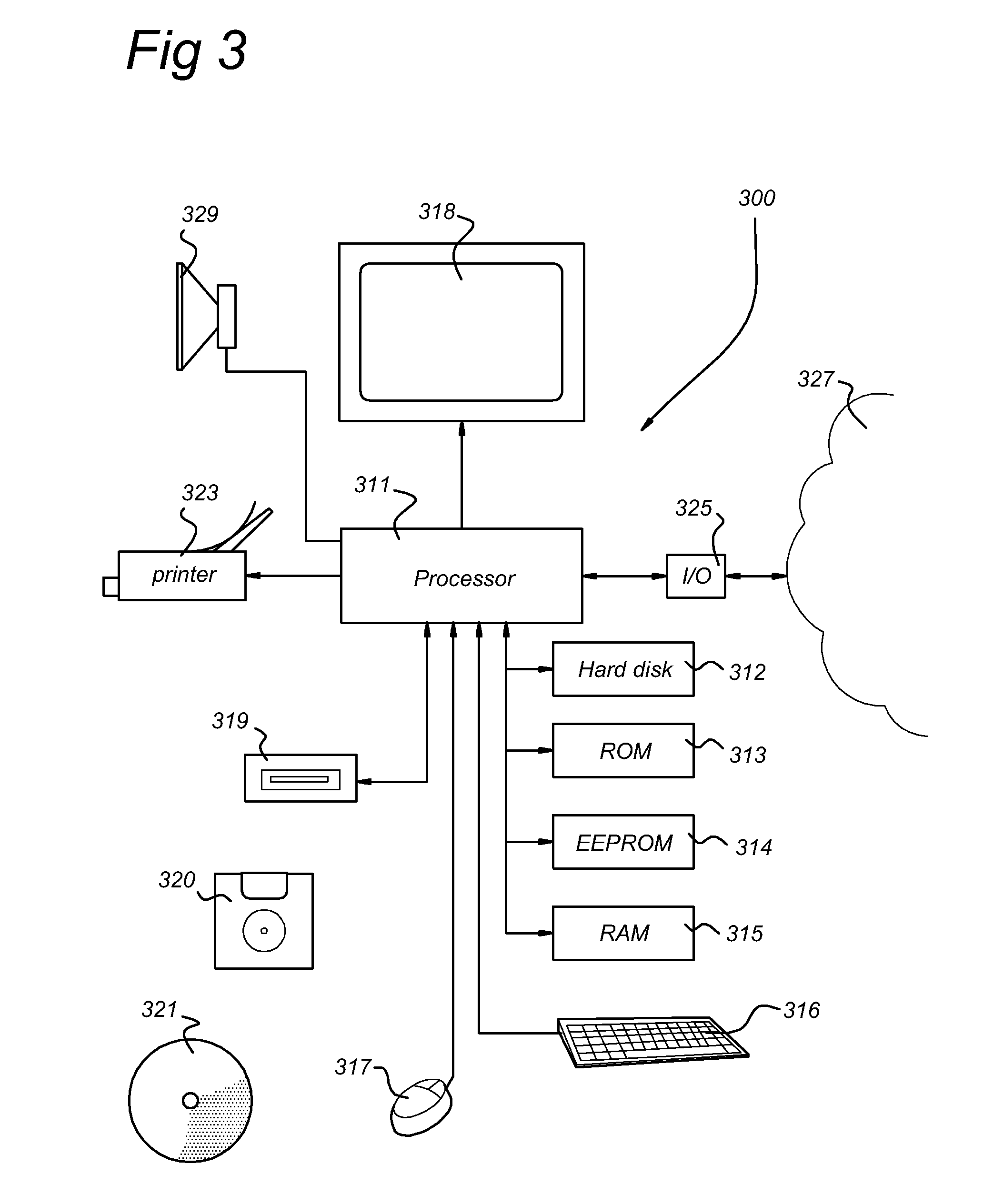
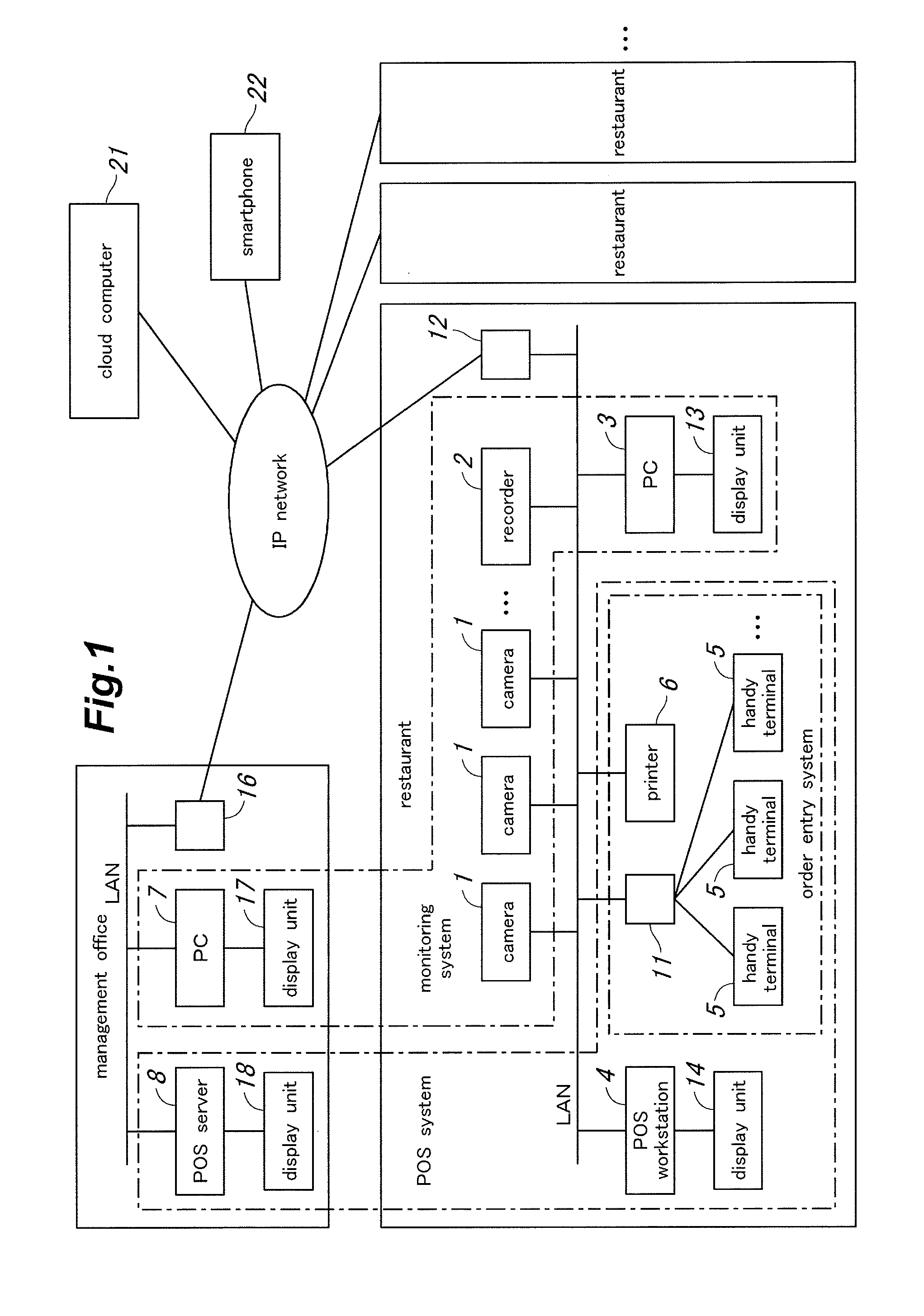
Patents
Literature
2411results about How to "Improve the detection rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
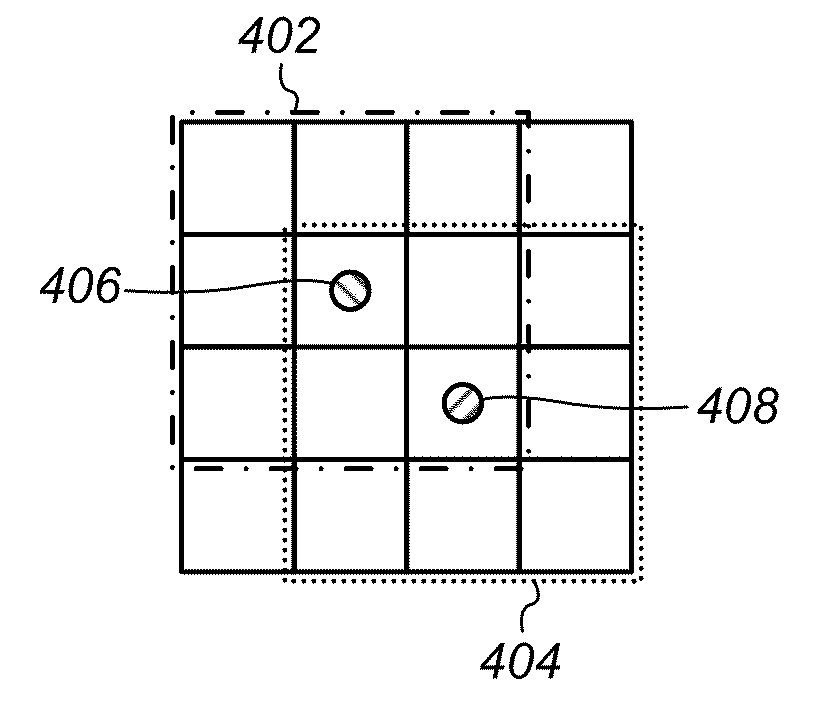
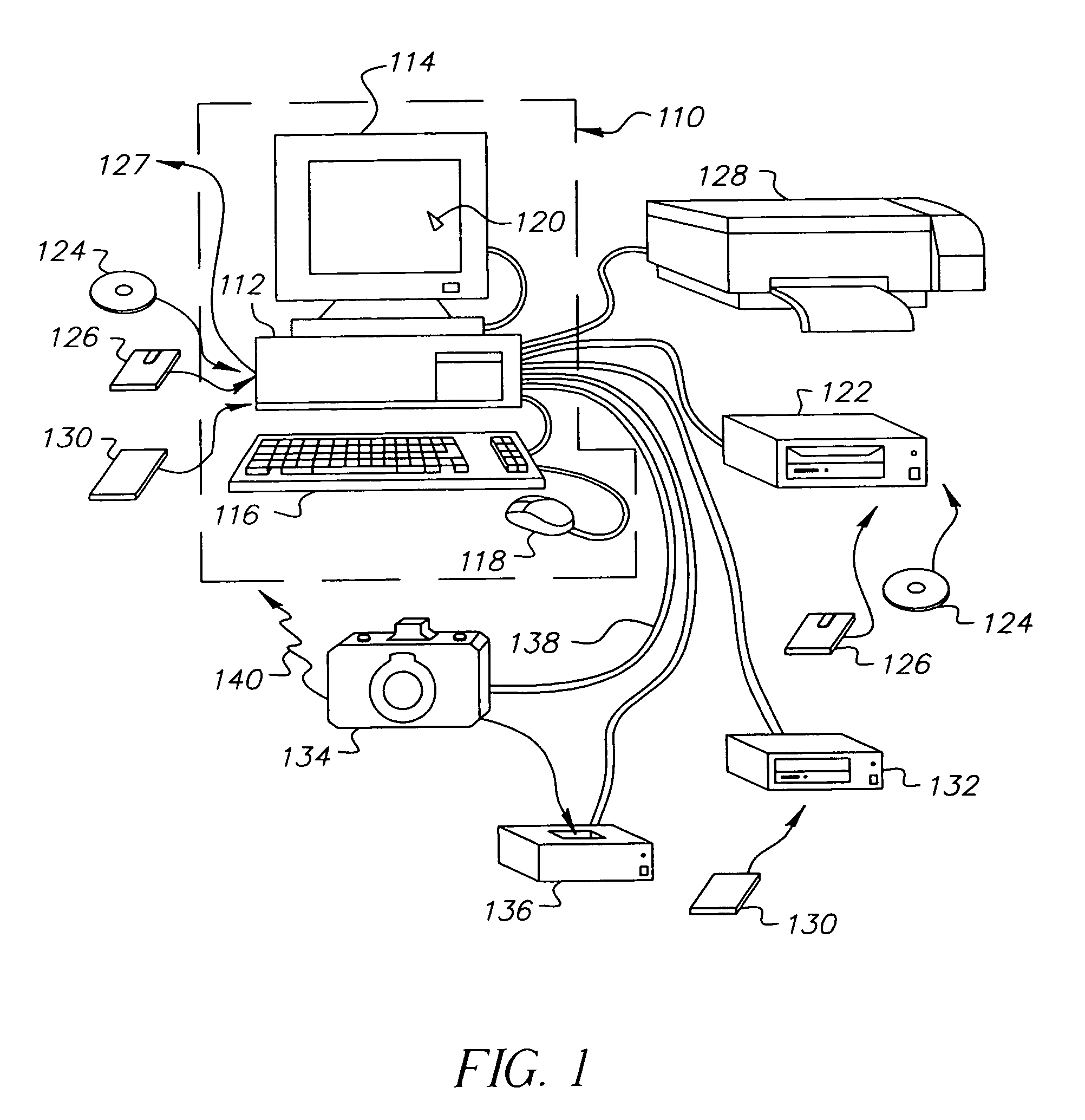
Detection of Defective Pixels in an Image Sensor
ActiveUS20110043668A1Efficient detectionImprove the detection rateTelevision system detailsColor signal processing circuitsPattern recognitionDefective pixel
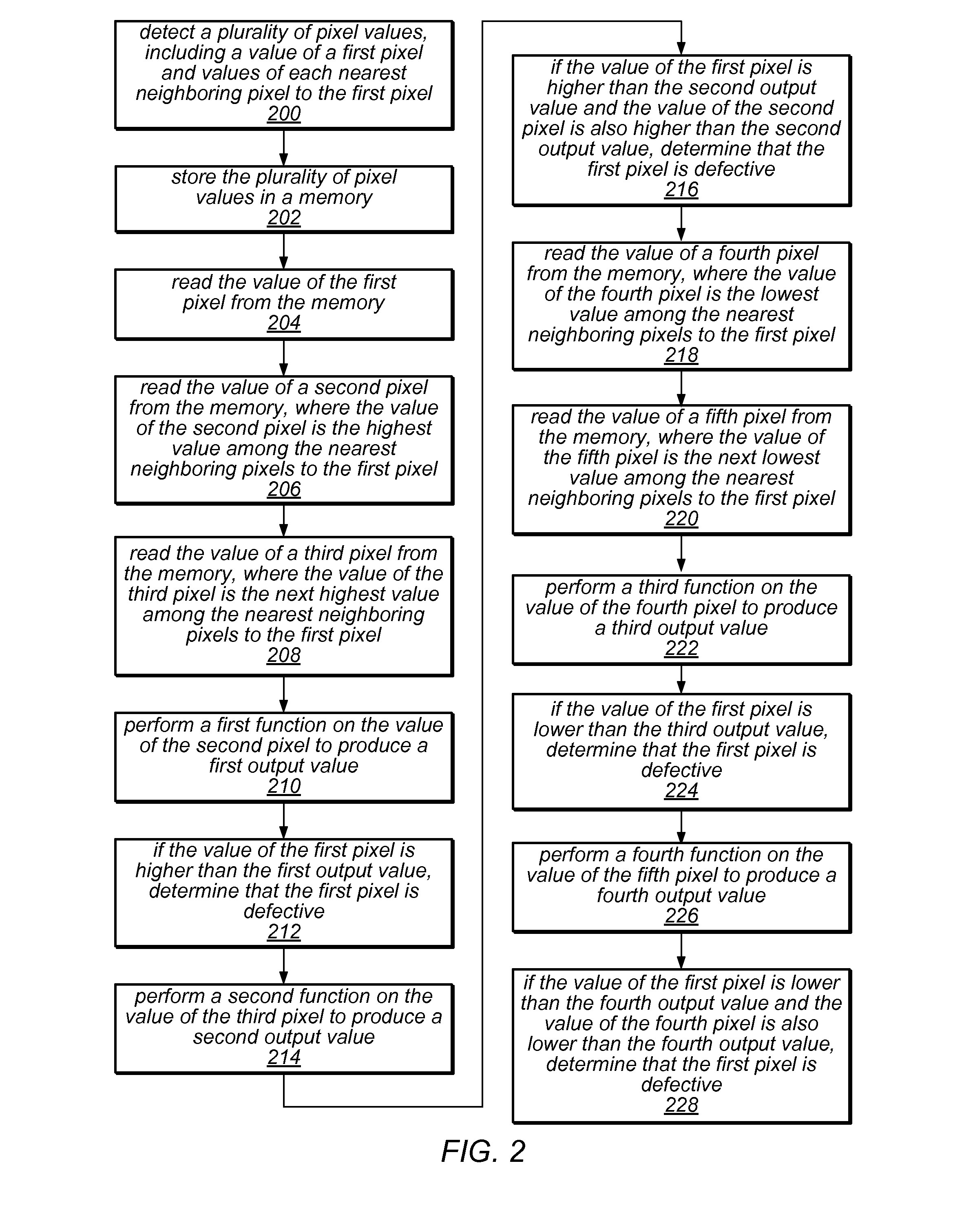
A system and method for detecting defective pixels in a sensor. A plurality of pixel values of the sensor may be detected. The values may include those of a first pixel and each nearest neighboring pixel to the first pixel. A second pixel may have the highest value of the neighboring pixels. A third pixel may have the next highest value of the neighboring pixels. A first function may be performed on the second pixel value, producing a first output value. A second function may be performed on the third pixel value, producing a second output value. If the first pixel value is higher than the first output value, or, if the first pixel value is higher than the second output value and the second pixel value is higher than the second output value, it may be determined that the first pixel is defective.
Owner:LIFESIZE INC
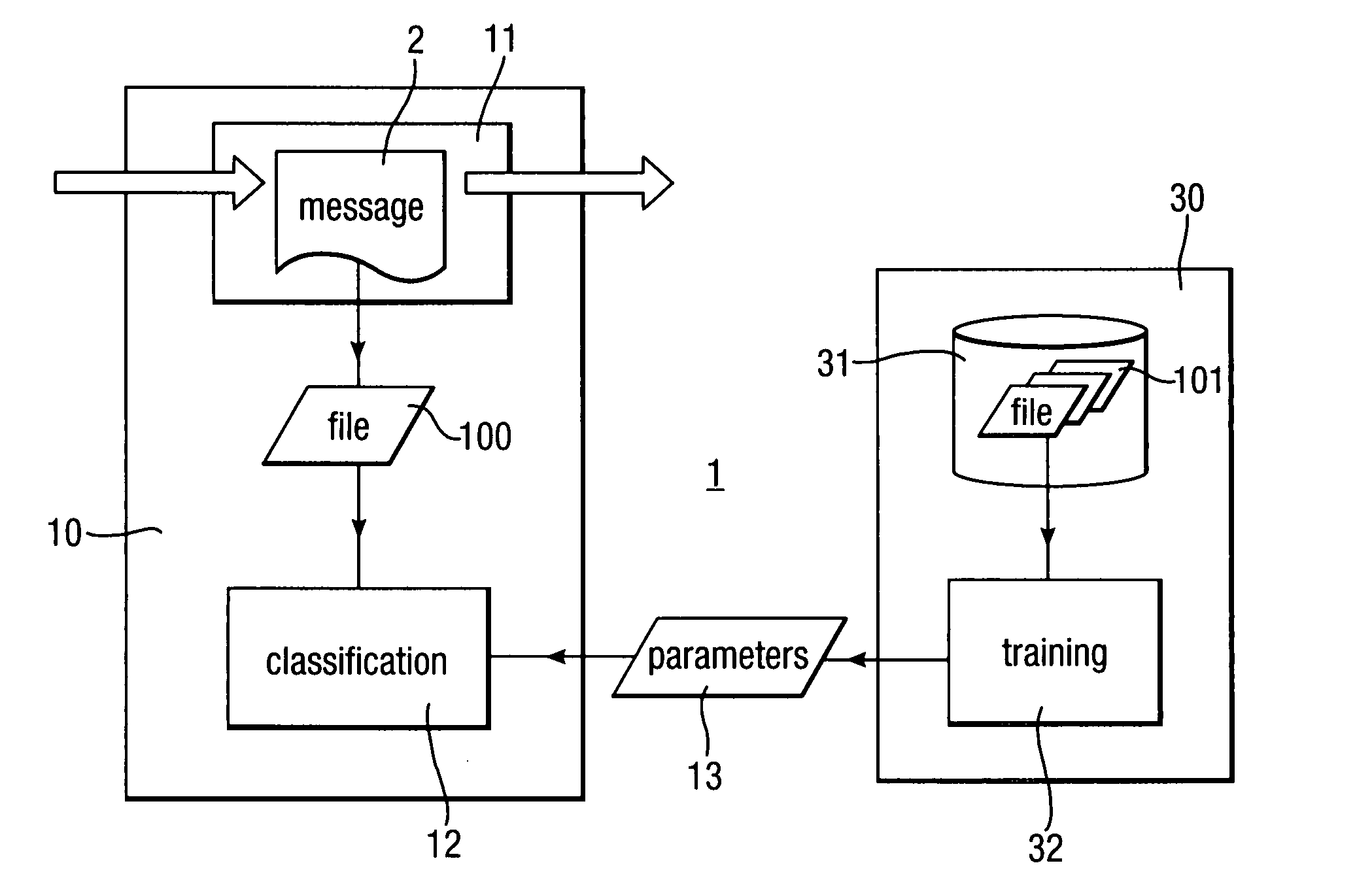
Heuristic detection of malicious code
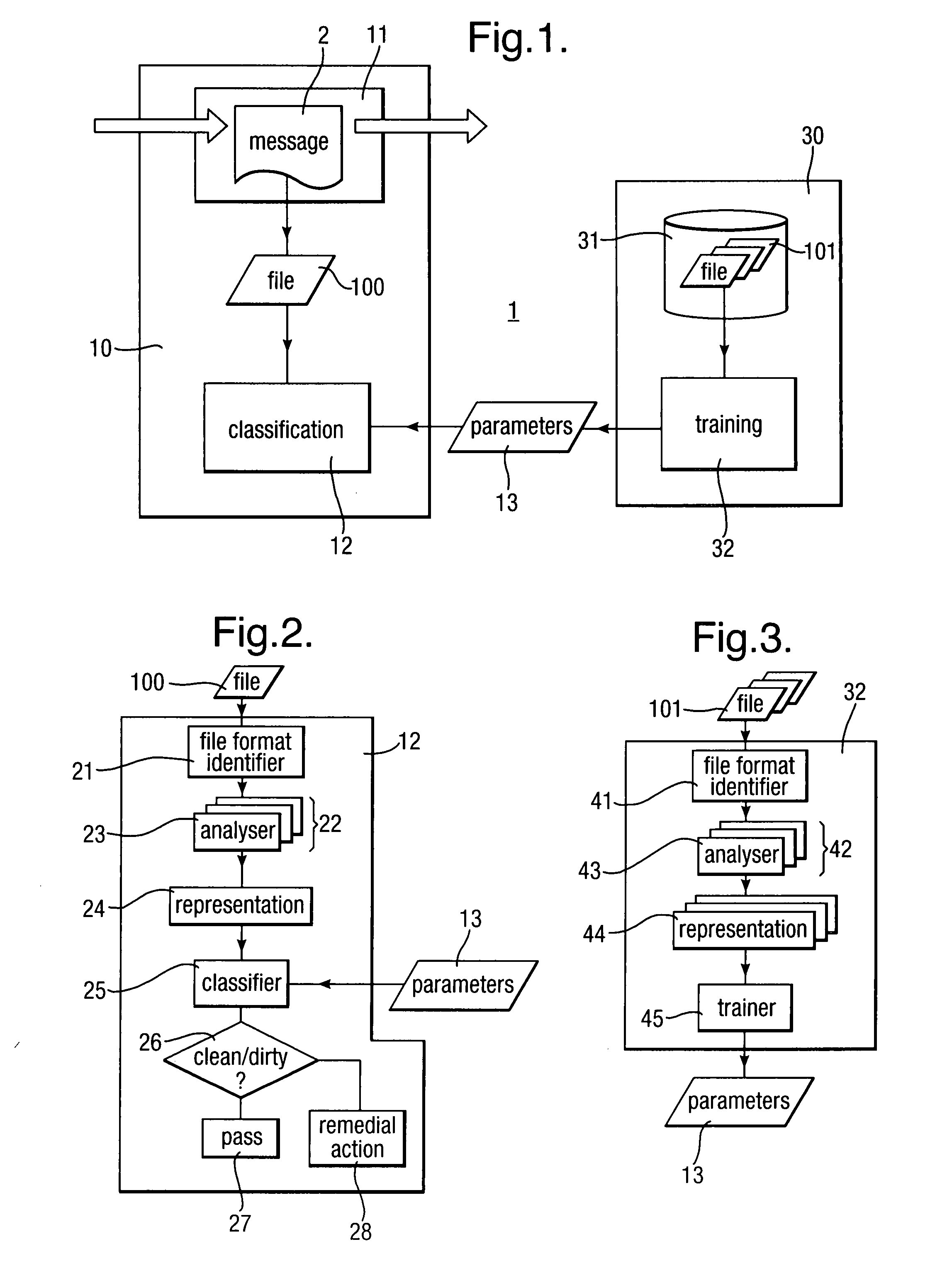
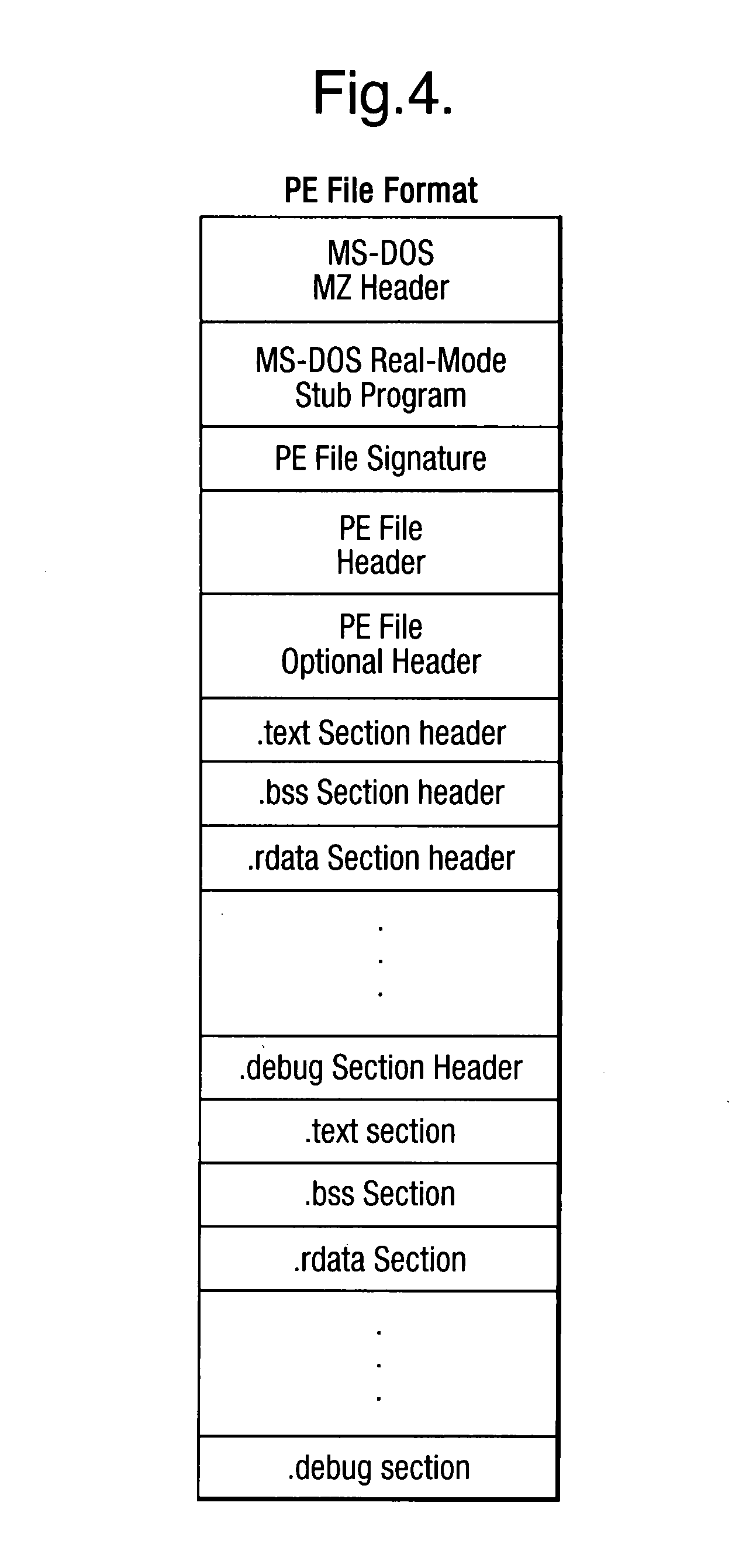
InactiveUS20090013405A1Avoid the needImprove the detection rateMemory loss protectionUnauthorized memory use protectionData fieldMalware
Scanning of computer files for malware uses a classifying technique to classify an input file as a clean file or a dirty file. The parameters of the classifying technique are derived to train the classification on a corpus of reference files including clean files known to be free of malware and dirty files known to contain malware. The classification is performed using a representation of the files in a feature space defined by a set of predetermined features for respective file formats, the features being a predetermined value or range of values for one or more data fields of given meanings. The representation of a file is derived by determining the file format, parsing the file on the basis of the structure of data fields in the determined file format to identify the data fields and their meaning, and determining, on the basis of the identified data fields, which of the set of predetermined features are present.
Owner:SYMANTEC CORP
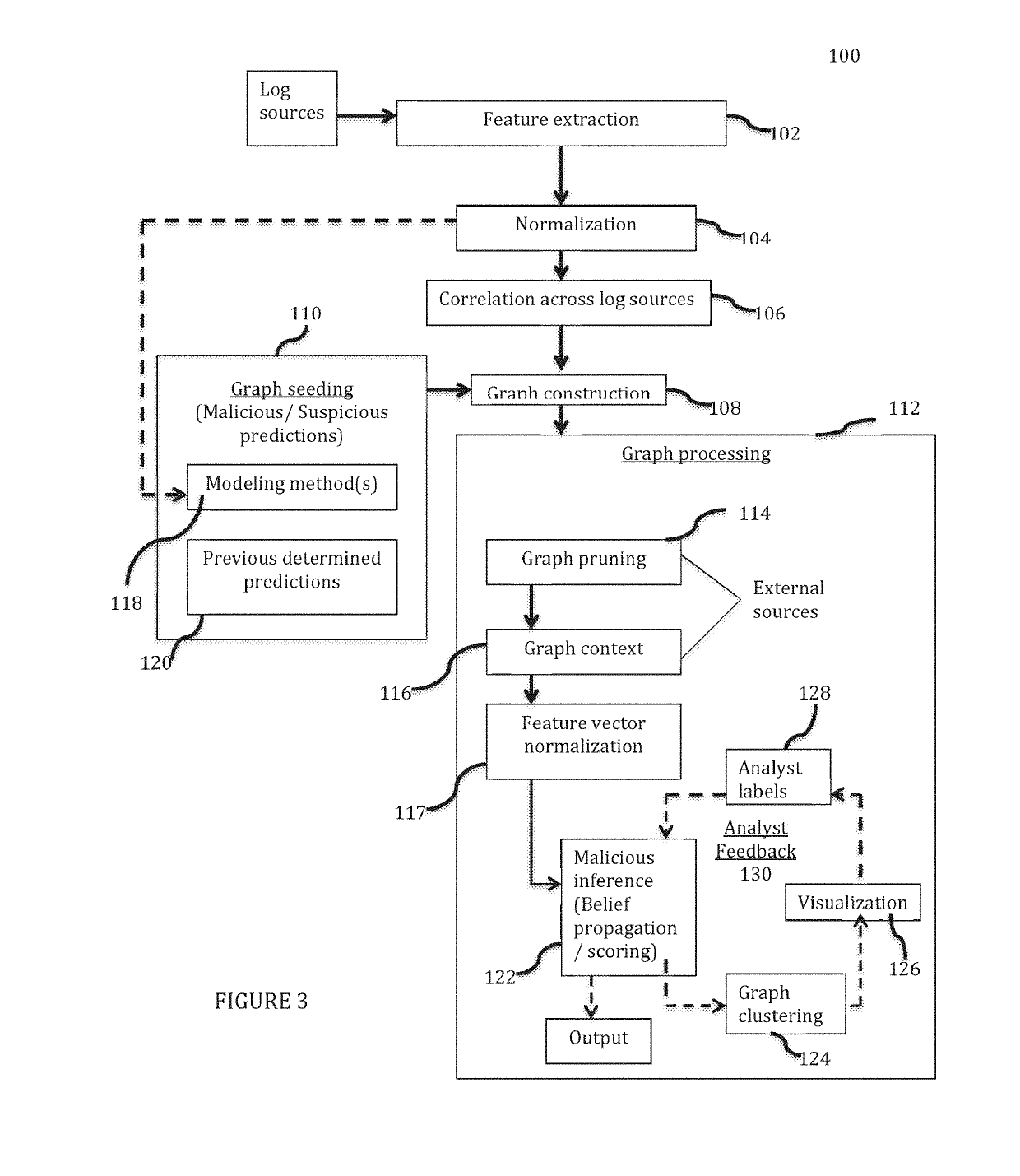
Method and system for employing graph analysis for detecting malicious activity in time evolving networks
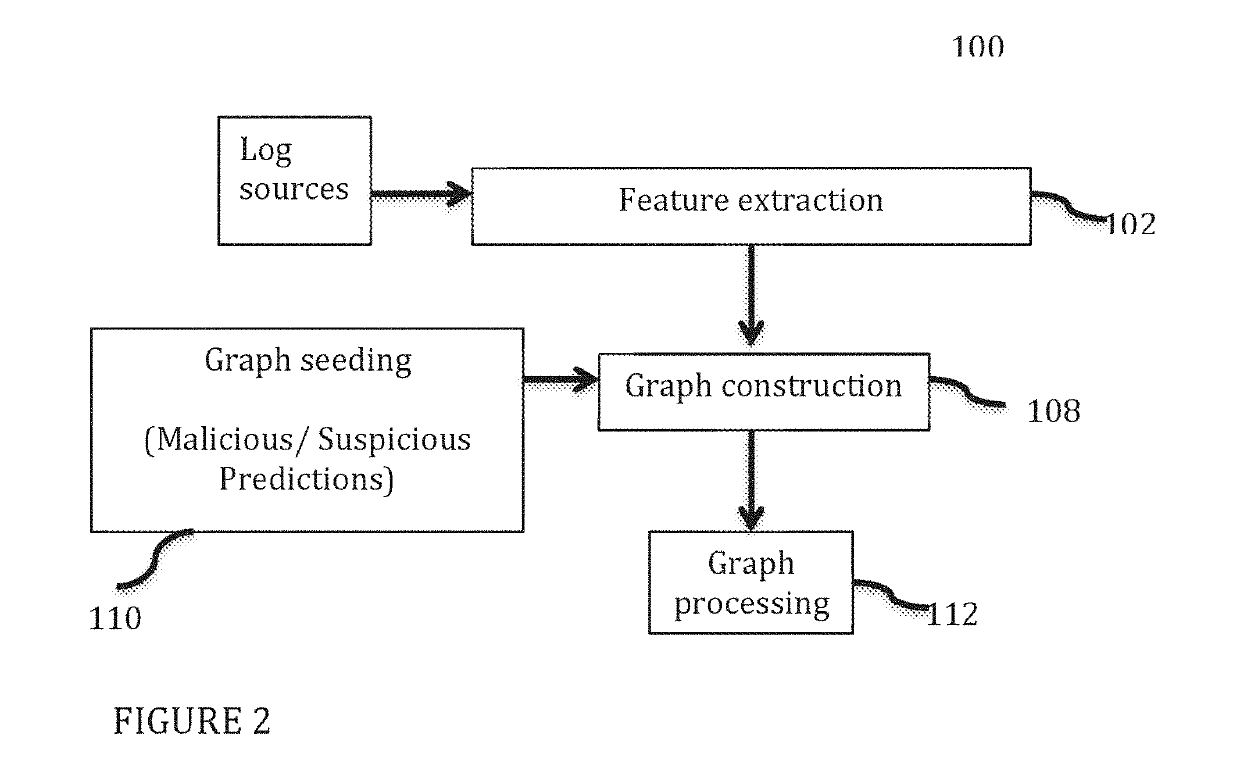
ActiveUS20190132344A1Demonstrate scalabilityDemonstrate effectivenessComputer security arrangementsProbabilistic networksGraph inferenceClassification methods
Disclosed is a method and system for detecting malicious entities and malicious behavior in a time evolving network via a graph framework by modeling activity in a network graph representing associations between entities. The system utilizes classification methods to give score predictions indicative of a degree of suspected maliciousness, and presents a unified graph inference method for surfacing previously undetected malicious entities that utilizes both the structure and behavioral features to detect malicious entities.
Owner:CORELIGHT INC
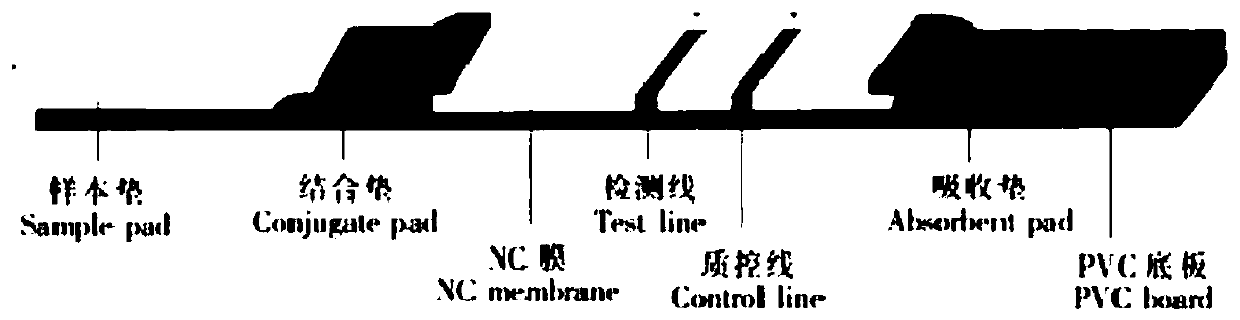
Colloidal gold immunochromatography device for combined detection of COVID-19 antigen and antibody and use method thereof
InactiveCN111024954AImprove the detection rateStrong specificityBiological testingImmunoassaysAntigenAntibody
The invention discloses a colloidal gold immunochromatography device for combined detection of a novel coronavirus COVID-19 antigen and antibody and a use method thereof. Through simultaneously detecting a novel coronavirus COVID-19 antigen and a specific IgM antibody and IgG antibody thereof, the immunology reaction state of the organism can be accurately judged, so that an accurate detection result is given according to the detection result, the detection rate of the new coronavirus is improved, a false negative result is avoided, missing detection is prevented, the detection accuracy is further improved, and help is provided for clinical diagnosis and treatment of the new coronavirus pneumonia. The colloidal gold immunochromatography device is high in specificity, high in detection speed and easy and convenient to operate, does not need special equipment or operation of professionals, and can be applied to preliminary screening of various places such as communities, primary hospitals, airports, customs and even families.
Owner:SHENZHEN BIOEASY BIOTECHNOLOGY CO LTD
Multiple-sensor and multiple-object information fusing method
InactiveCN1389710AExpand coverageImprove the detection rateBeacon systems using radio wavesAiming meansFeature extractionAlgorithm
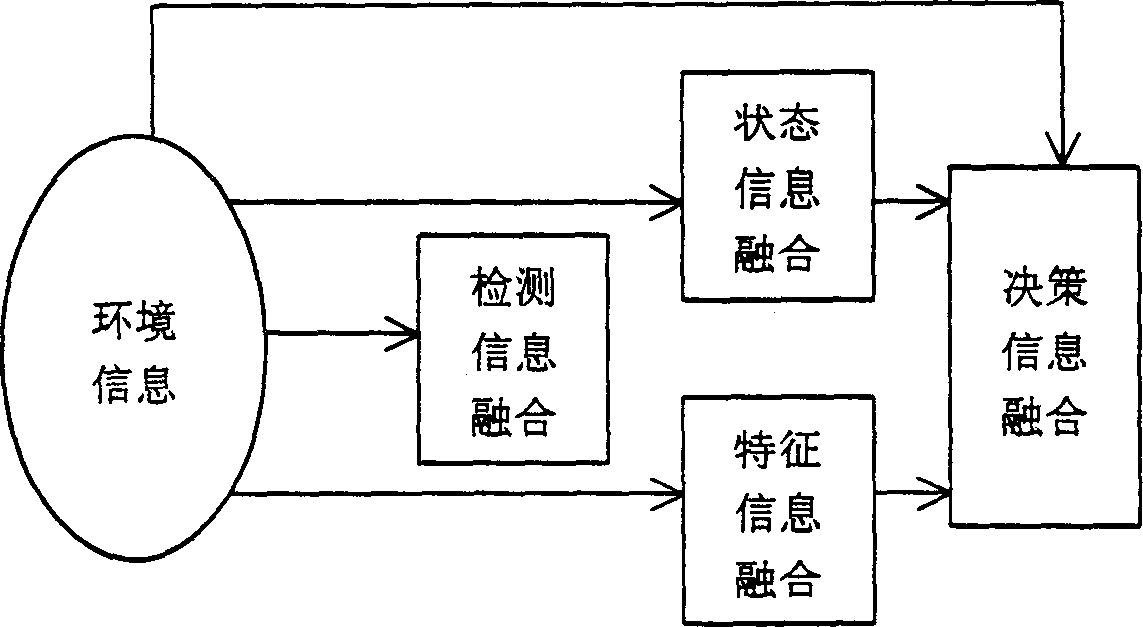
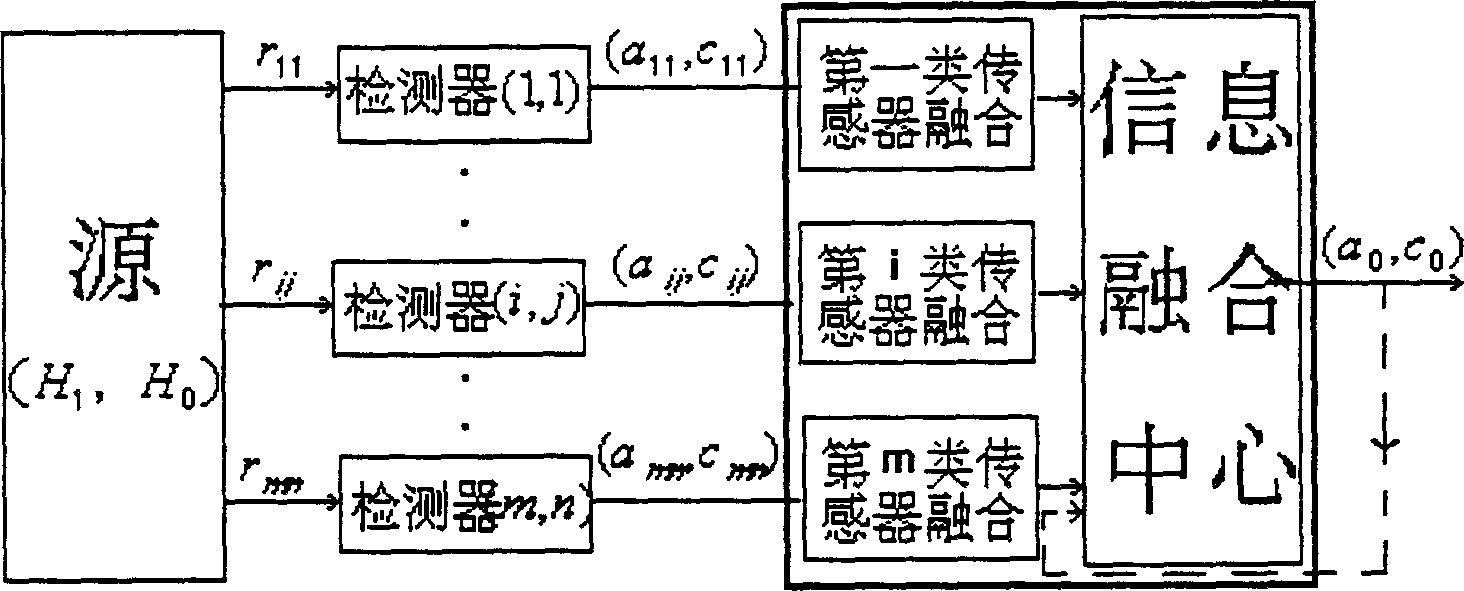
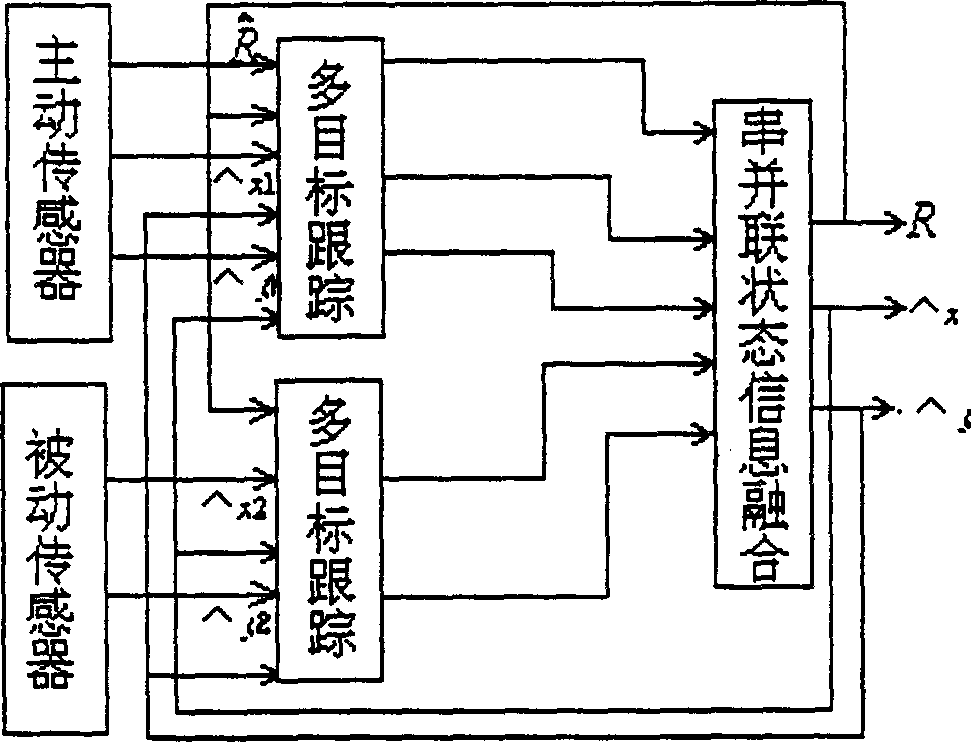
Transducers of different distributions detect the existence of targets of environment first and a test information composition system mixes the results detected by transducers to follow up the state and pick-up the character of the target. The state information composition system and the character dinformation composition system composite the traced states and identification results of character vector separately by each transducer to get relative accurate state parameter and identified results and information composition makes the entire systematic composition to provide favorable decision for next step, to increase systematic detecting probability, estimated accuracy and identified probability and more resonable algorithm.
Owner:SHANGHAI JIAO TONG UNIV
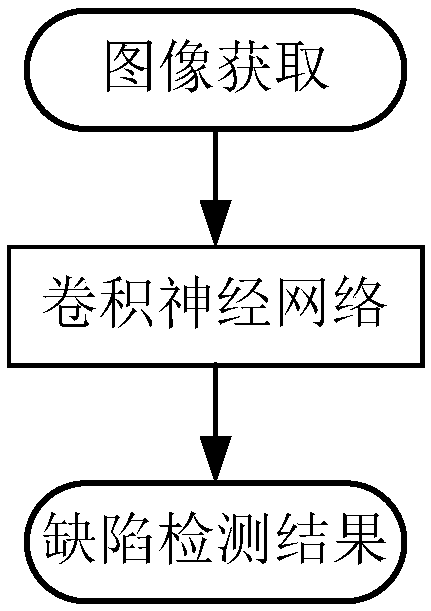
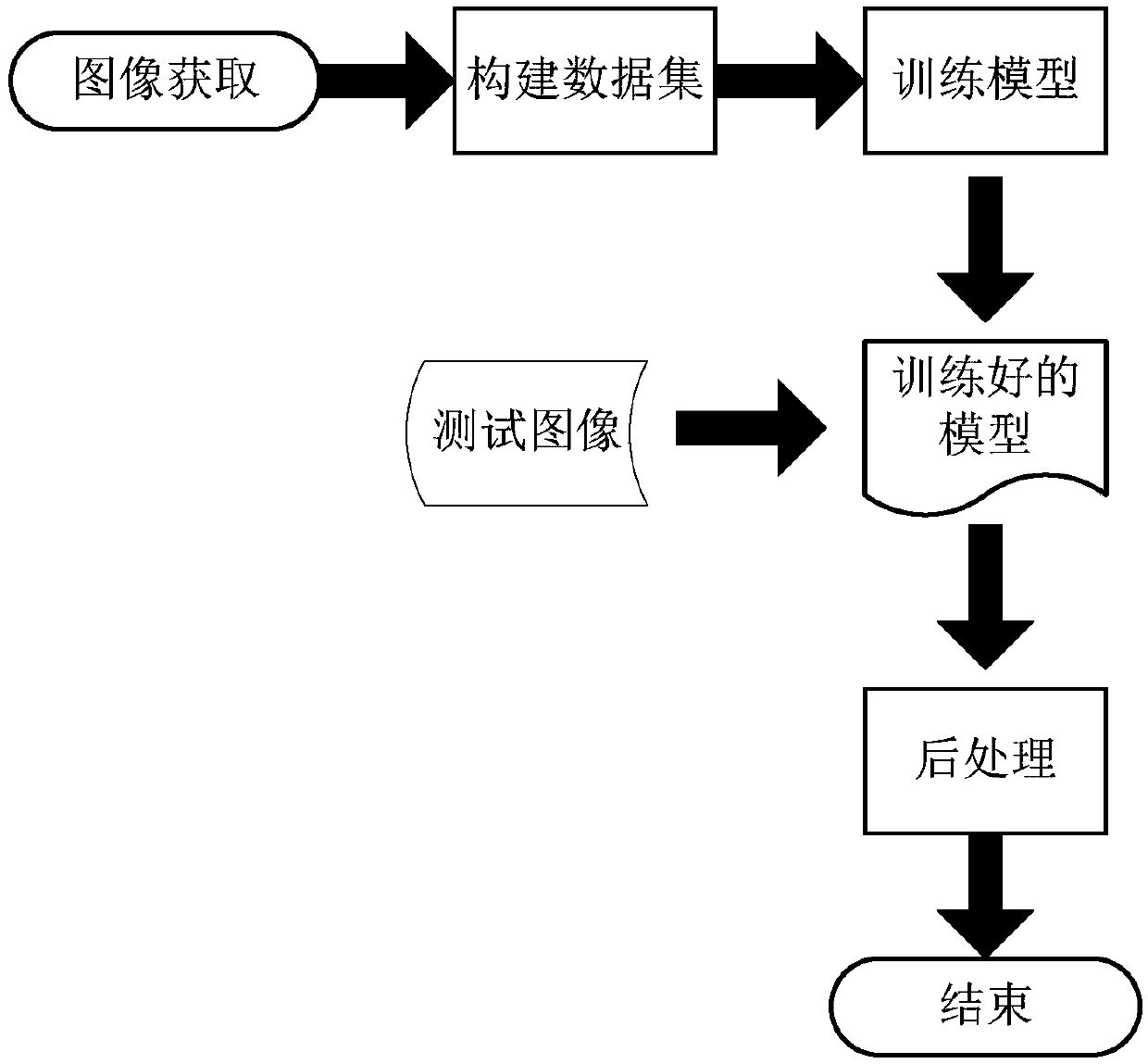
Mobile phone casing defect detecting method based on depth learning
ActiveCN106875381AImprove detection accuracyReliable test resultsImage analysisGeometric image transformationFeature extractionMobile phone
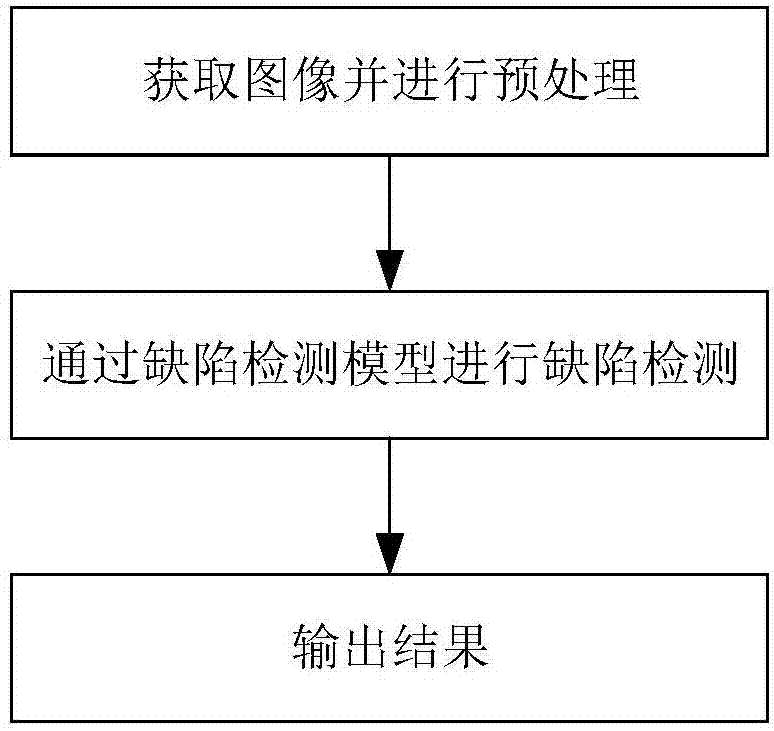
The invention relates to a mobile phone casing defect detecting method based on depth learning. The method comprises the steps that (1) the image of a mobile phone casing to be detected is acquired and pre-processed; and (2) the pre-processed image is input into a pre-trained defect detection model for defect detecting to acquire the position of a defect on the mobile phone casing, and the confidence of the position as the defect is provided. The defect detection model is a depth network based on depth learning, and comprises a feature extraction network and a classifier and regression device network, wherein the feature extraction network and the classifier and regression device network are in successive cascade. The feature extraction network carries out feature extraction on the pre-processed image to acquire a feature image. The classifier and regression device network classifies and regresses the feature image to acquire the defect position and the confidence of the mobile phone casing. Compared with the prior art, the method provided by the invention has the advantages of high detection precision and accurate and reliable detection result.
Owner:TONGJI UNIV
Method and apparatus for producing lane information
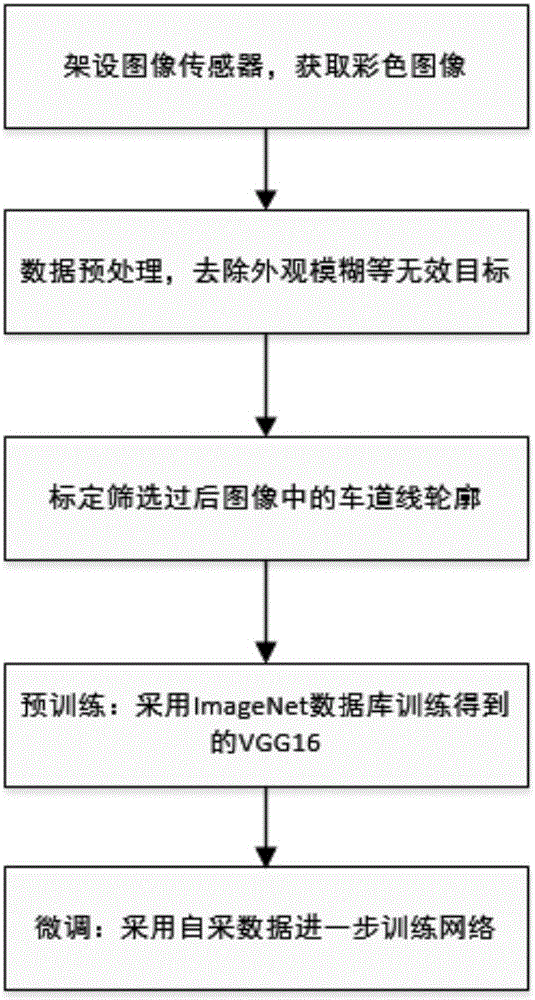
ActiveUS20100266161A1Easy to numberAccurate detectionImage enhancementInstruments for road network navigationRoad surfaceSource image
A method of producing lane information for use in a map database is disclosed. In at least one embodiment, the method includes acquiring one or more source images of a road surface and associated position and orientation data, the road having a direction and lane markings parallel to the direction of the road; acquiring road information representative of the direction of said road; transforming the one or more source images to obtain a transformed image in dependence of the road information, wherein each column of pixels of the transformed image corresponds to a surface parallel to the direction of said road; applying a filter with asymmetrical mask on the transformed image to obtain a filtered image; and producing lane information from the filtered image in dependence of the position and orientation data associated with the one or more source images.
Owner:TOMTOM GLOBAL CONTENT
Intrusion detection in communication networks
ActiveUS20120278890A1Increase the number ofSolve the high false alarm rateMemory loss protectionError detection/correctionNetwork activityInternet traffic
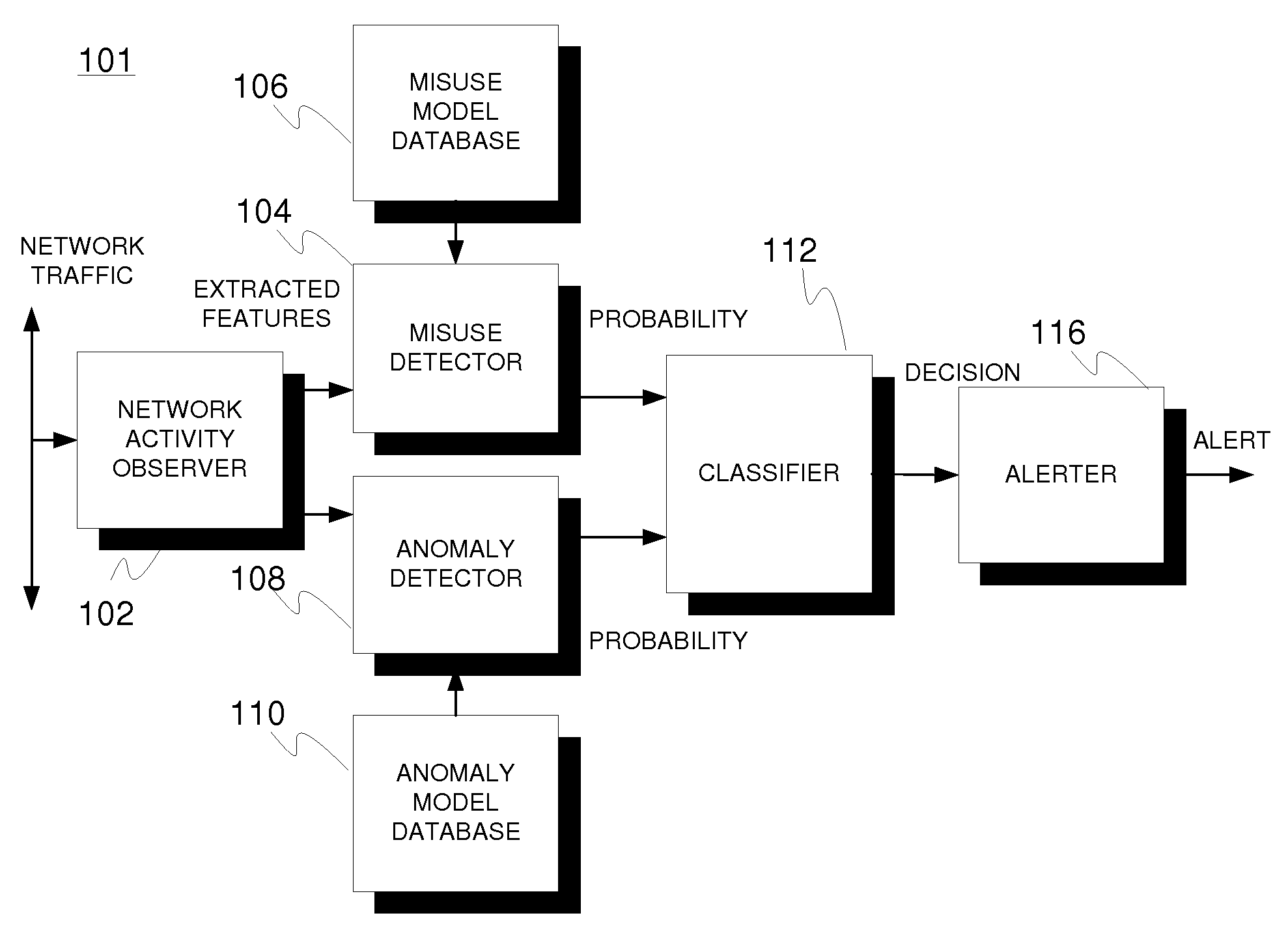
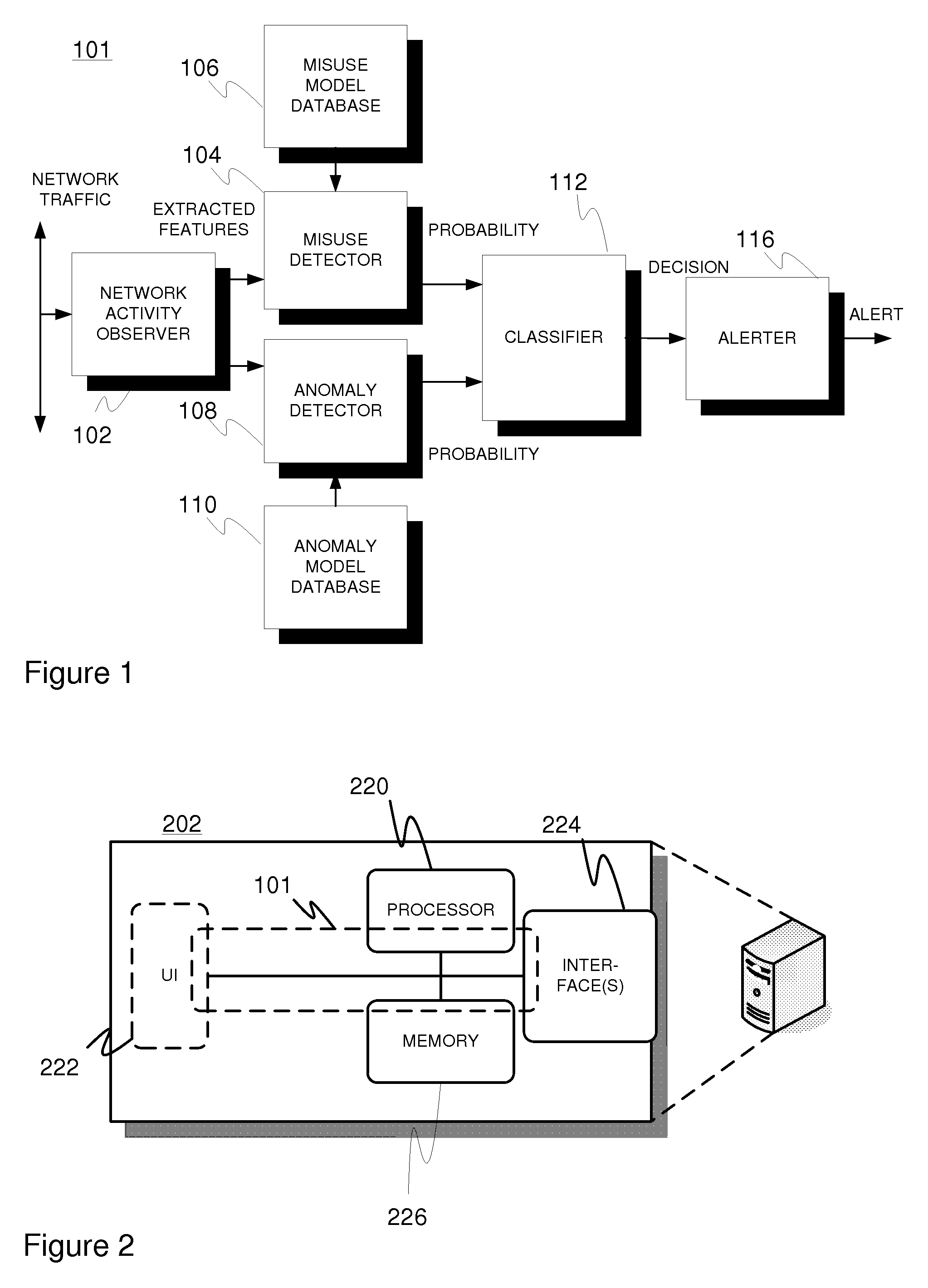
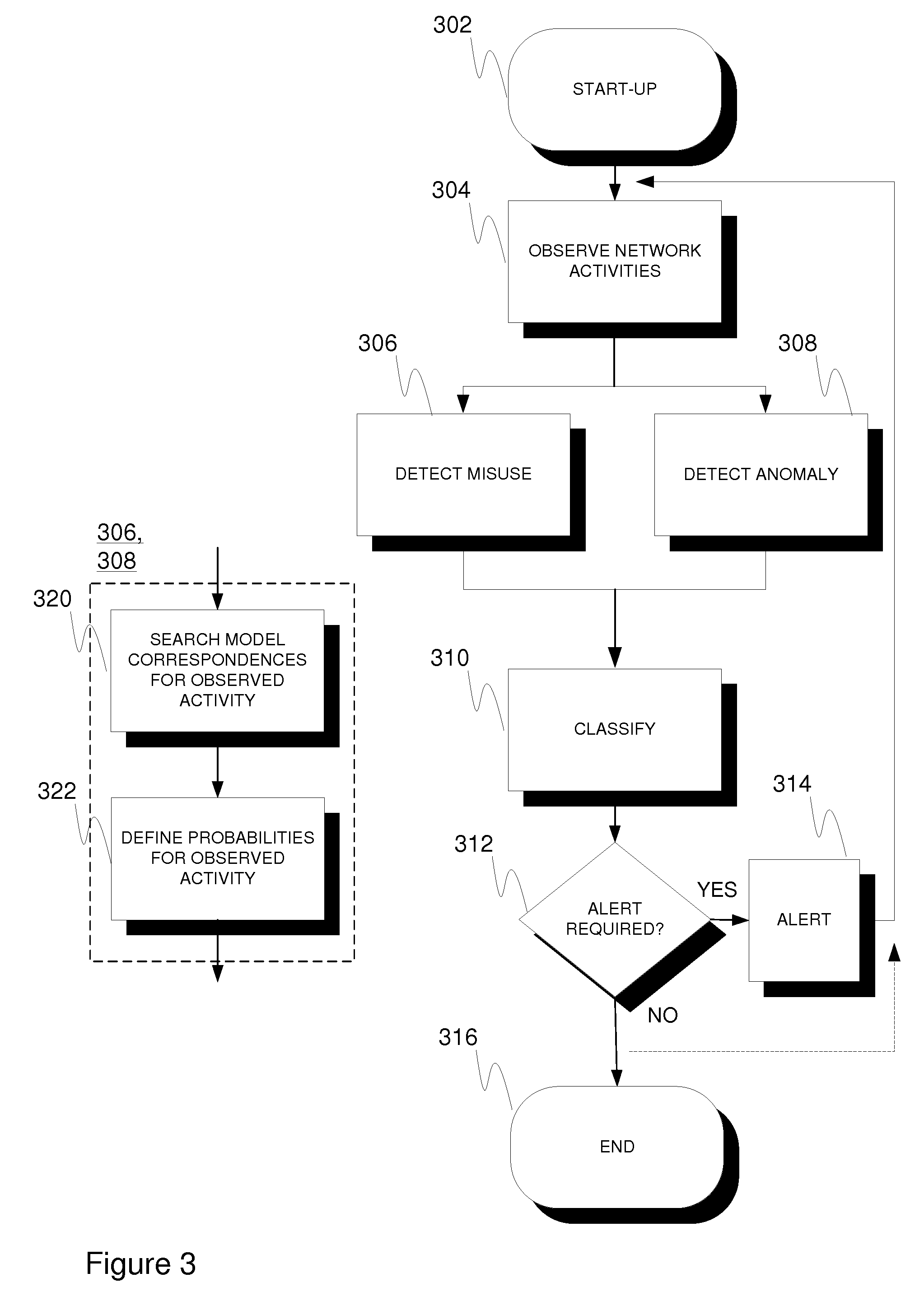
An intrusion detection arrangement (101) for communication networks comprising a network activity observer (102) configured to monitor network traffic by the related traffic elements, such as data packets, thereof and to establish traffic profiles relative to the monitored traffic elements, such as one profile per each monitored traffic element, a misuse detector (104) configured to determine a first indication of a probability of the profiled traffic representing malicious activity through co-operation with a model repository (106) comprising at least one model characterizing a known intrusion attack, an anomaly detector (108) configured to determine, at least logically in parallel with the misuse detector, a second indication of a probability of the profiled traffic representing anomalous activity through cooperation with a model repository (110) comprising at least one model characterizing legitimate network activity, and a classifier (112) configured to operate on said first and second indications to generate a classification decision on the nature of the profiled traffic, wherein the applied classification space includes at least one class for legitimate traffic and at least one other class for other traffic such as malicious and / or anomalous traffic. A corresponding method is presented.
Owner:BIN 2022 SERIES 822 OF ALLIED SECURITY TRUST I
Method and apparatus for detecting objects from terrestrial based mobile mapping data
ActiveUS20100020074A1Efficient processingEffectively scaledImage enhancementInstruments for road network navigationMobile mapping3d image
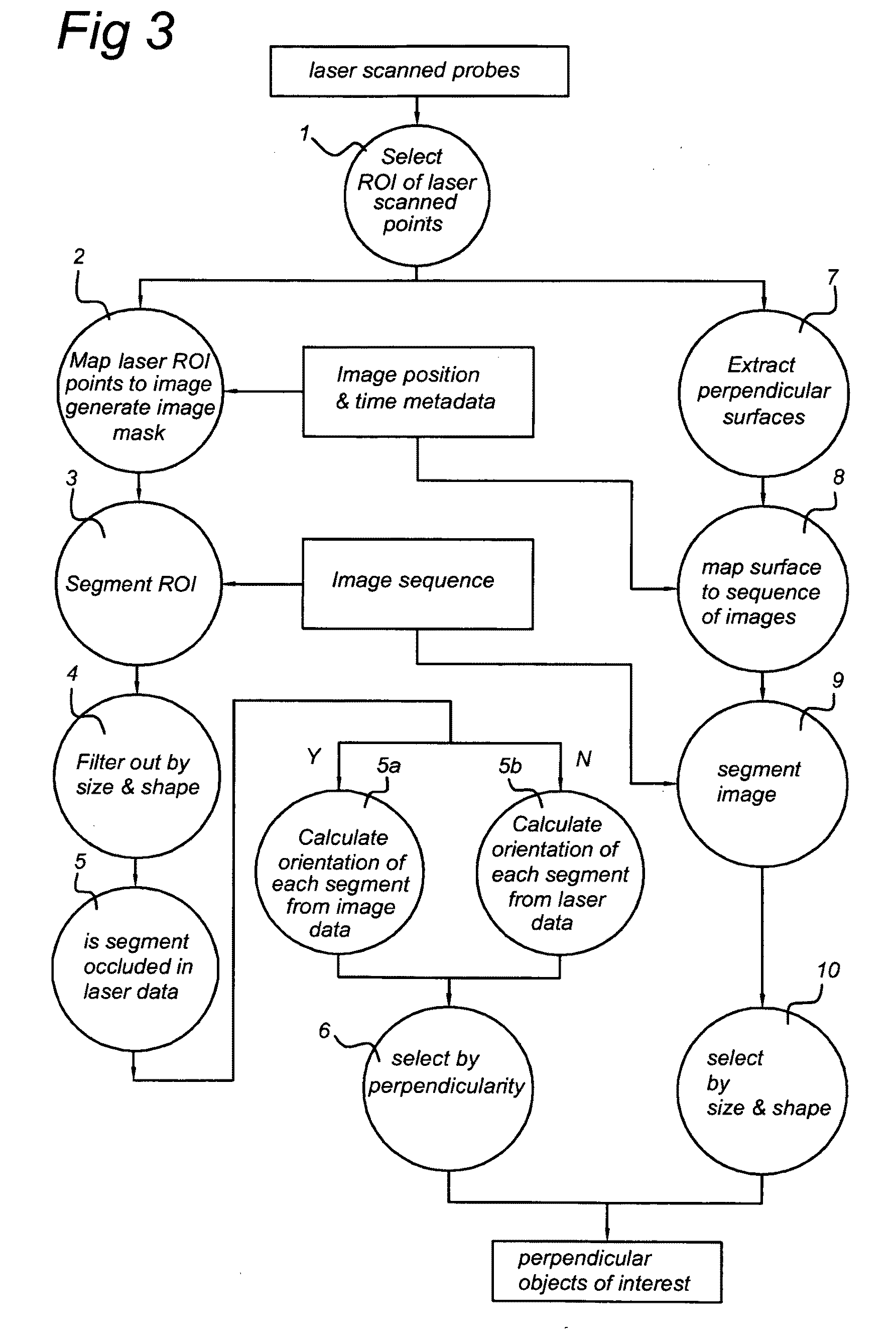
A method of detecting objects from terrestrial based mobile mapping data is disclosed, wherein the terrestrial based mobile mapping data has been captured by way of a terrestrial based mobile mapping vehicle driving on a road having a driving direction, the mobile mapping data including laser scanner data, source images obtained by at least one camera and position and orientation data of the vehicle, wherein the laser scanner data includes laser points, each laser point having associated position and orientation data, and each source image comprises associated position and orientation data. In at least one embodiment, the method includes: retrieving a position and orientation of the vehicle; filtering the laser scanner data in dependence of the position and orientation of the vehicle to obtain laser points corresponding to regions of interest; retrieving a source image associated with the position and orientation of the vehicle; mapping the laser points corresponding to regions of interest to image coordinates of the source image to generate a recognition mask; combining the recognition mask and the source image to obtain candidate 3D images representative of possible objects within the regions of interest; and, detecting a group of objects from the candidate 3D images. By combining image recognition and laser scanner recognition the detection rate can be increased to a very high percentage, thereby substantially reducing human effort. Furthermore, the generating of regions of interest in the laser data, enables a significant reduction of the processing power and / or the processing time needed to detect the objects in the images.
Owner:TOMTOM GLOBAL CONTENT
Small target rapid detection method based on deep convolution neural network
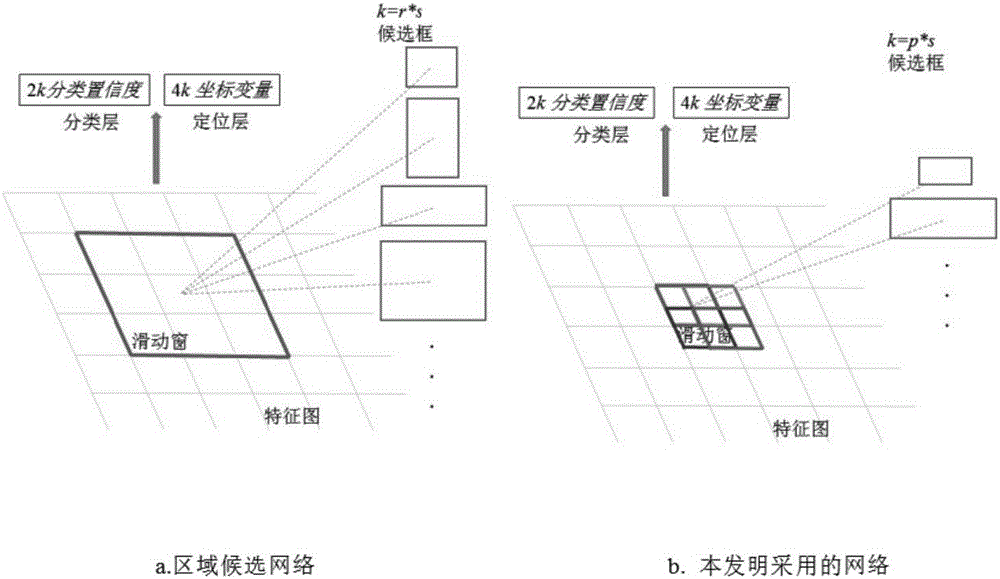
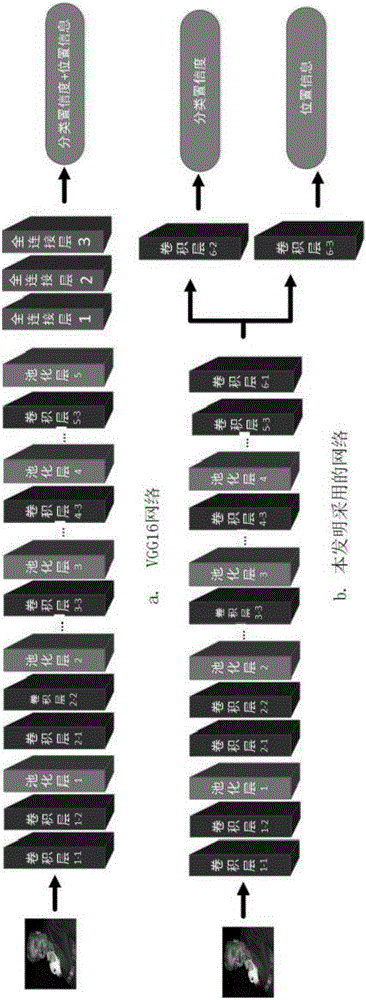
InactiveCN106599827AIncrease the number ofReduce computational complexityBiological neural network modelsScene recognitionNerve networkComputation complexity
The invention discloses a small target rapid detection method based on a deep convolution neural network. The deep convolution neural network is improved by the following steps: selecting the sliding windows on the convolution feature map of the last shared convolution layer of a VGG16 network as candidate boxes, wherein the sliding windows adopted are half-pixel precision sliding window; deleting a fifth pooling layer, and retaining other convolution layers and pooling layers; adding a convolution layer with a 3*3 convolution kernel; and using two convolution layers with 1*1 convolution kernels to replace all full-connection layers in the network to get the network adopted in the invention, training the network using collected data to get a small target classification model, and using the model to detect small targets. By using the method, the computational complexity is reduced, and the detection rate of small targets is improved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY +1
Image display device and method of driving image display device
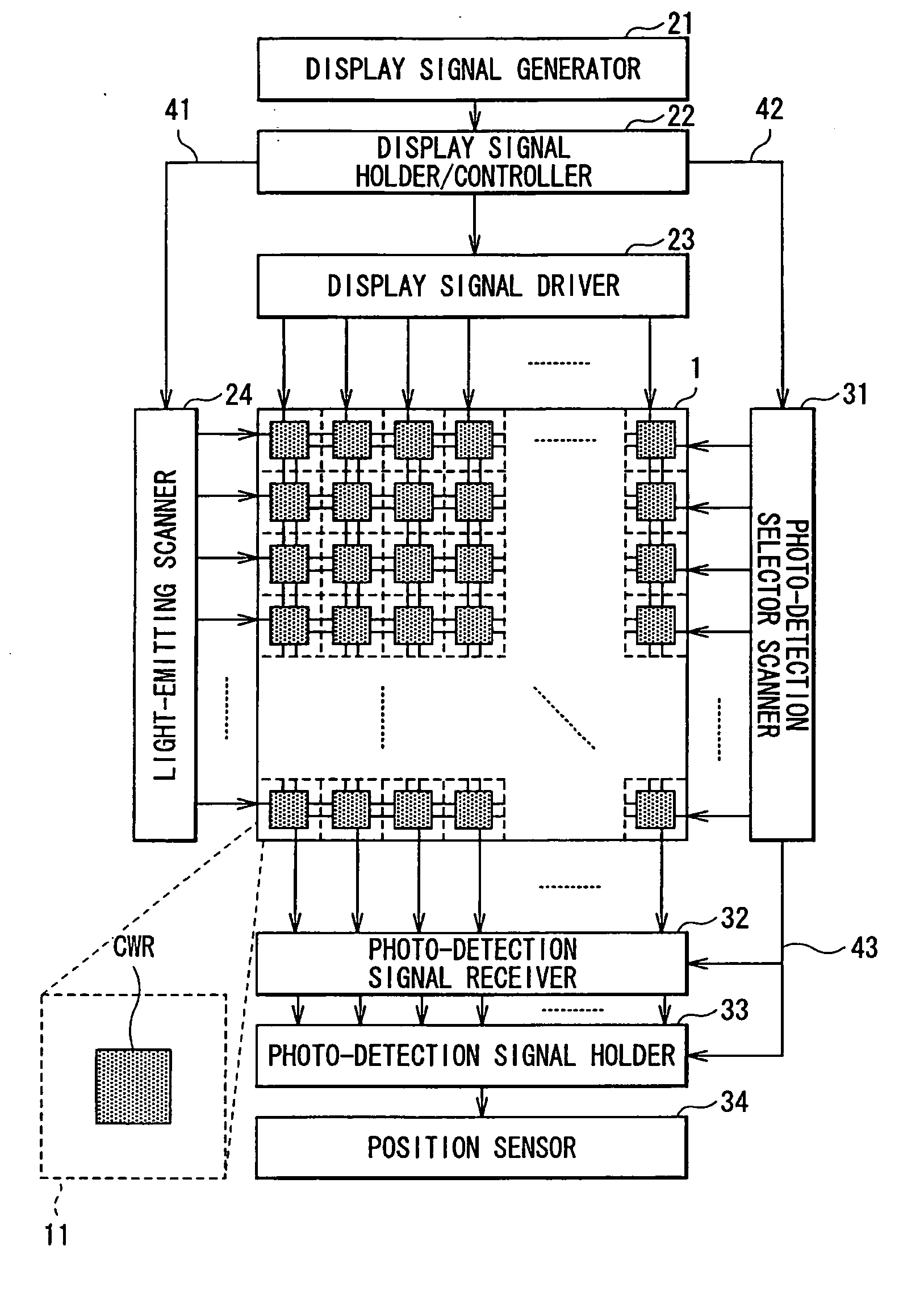
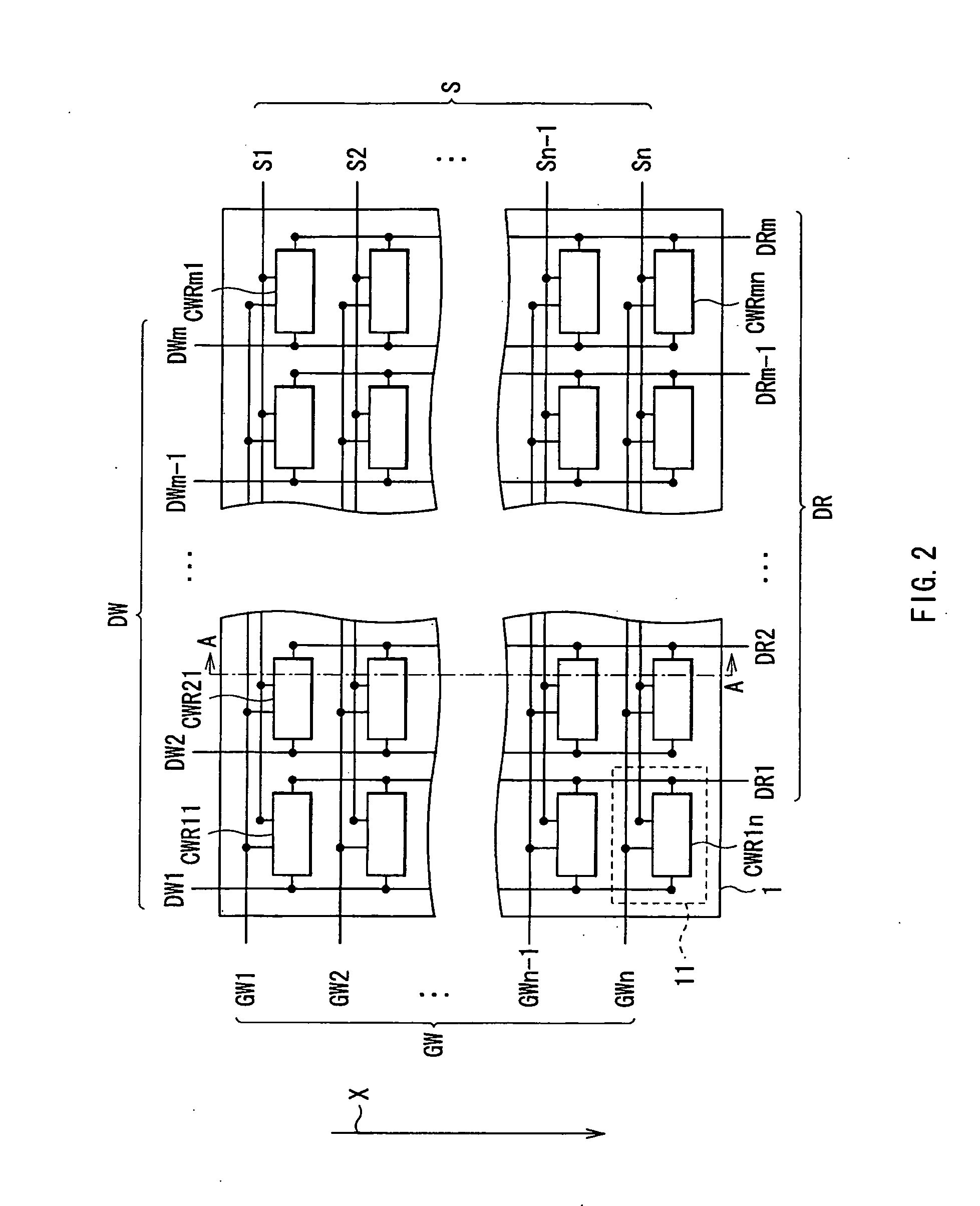
InactiveUS20050219229A1Increase in the amount of photo-detection signalRaise the ratioCathode-ray tube indicatorsInput/output processes for data processingDisplay deviceComputer science
There is provided an image display device and a method of driving an image display device, which enable detecting an object position and the like without image degradation using a simple structure while ensuring convenience. The image display device includes: a plurality of light-emitting / photo-detection devices each having both light-emitting and photo-detection functions; light-emission driving section driving the light-emitting / photo-detection devices for light emission in accordance with image data; photo-detection driving section driving one or more light-emitting / photo-detection devices for photo-detection, other than a light-emitting / photo-detection device which is emitting light in accordance with the image data, so that the one or more light-emitting / photo-detection devices detect light emitted from the light-emitting / photo-detection device and reflected from a target object; and detecting section detecting the target object in accordance with one or more photo-detection signals obtained from the one or more light-emitting / photo-detection devices.
Owner:JAPAN DISPLAY WEST
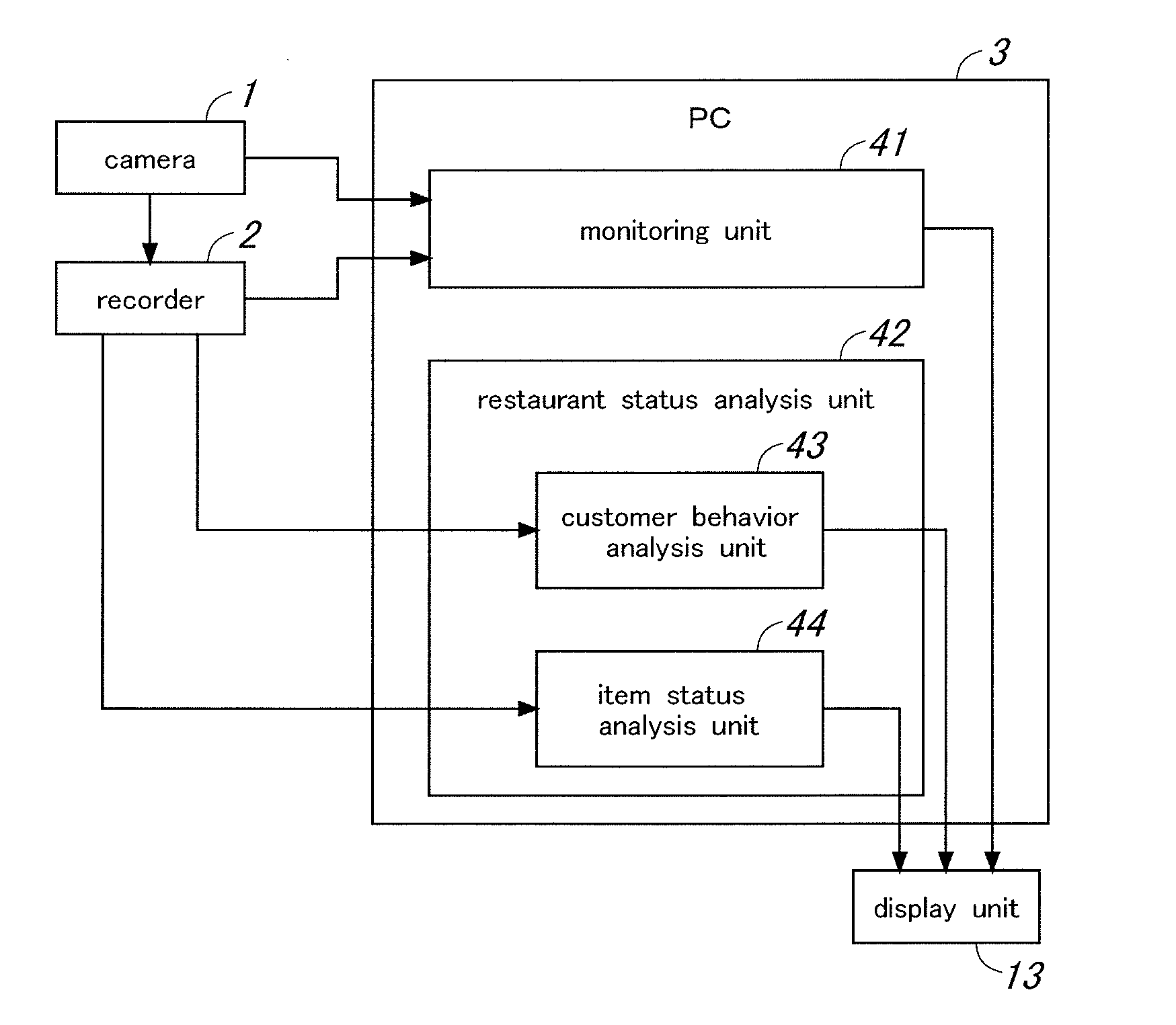
Customer behavior analysis device, customer behavior analysis system and customer behavior analysis method
InactiveUS20140222501A1Easy to knowAvoid complainingMarket data gatheringBehavioral analyticsAnalysis method
A customer behavior analysis device includes: a tracking unit configured to track persons moving in an area around a self-service area where items are provided for self-service, based on image information provided by an imaging device capturing images of the area around the self-service area; a detection unit configured to obtain, based on a result of tracking performed by the tracking unit, a moving direction of each person relative to an access area, which a customer needs to enter to choose and pick up items from the self-service area, and a staying time of the person in the access area, and to detect non-completing persons who gave up completing self-service action based on the moving direction and the staying time; and an output information generation unit configured to generate output information representing a result of analysis based on a result of detection performed by the detection unit.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
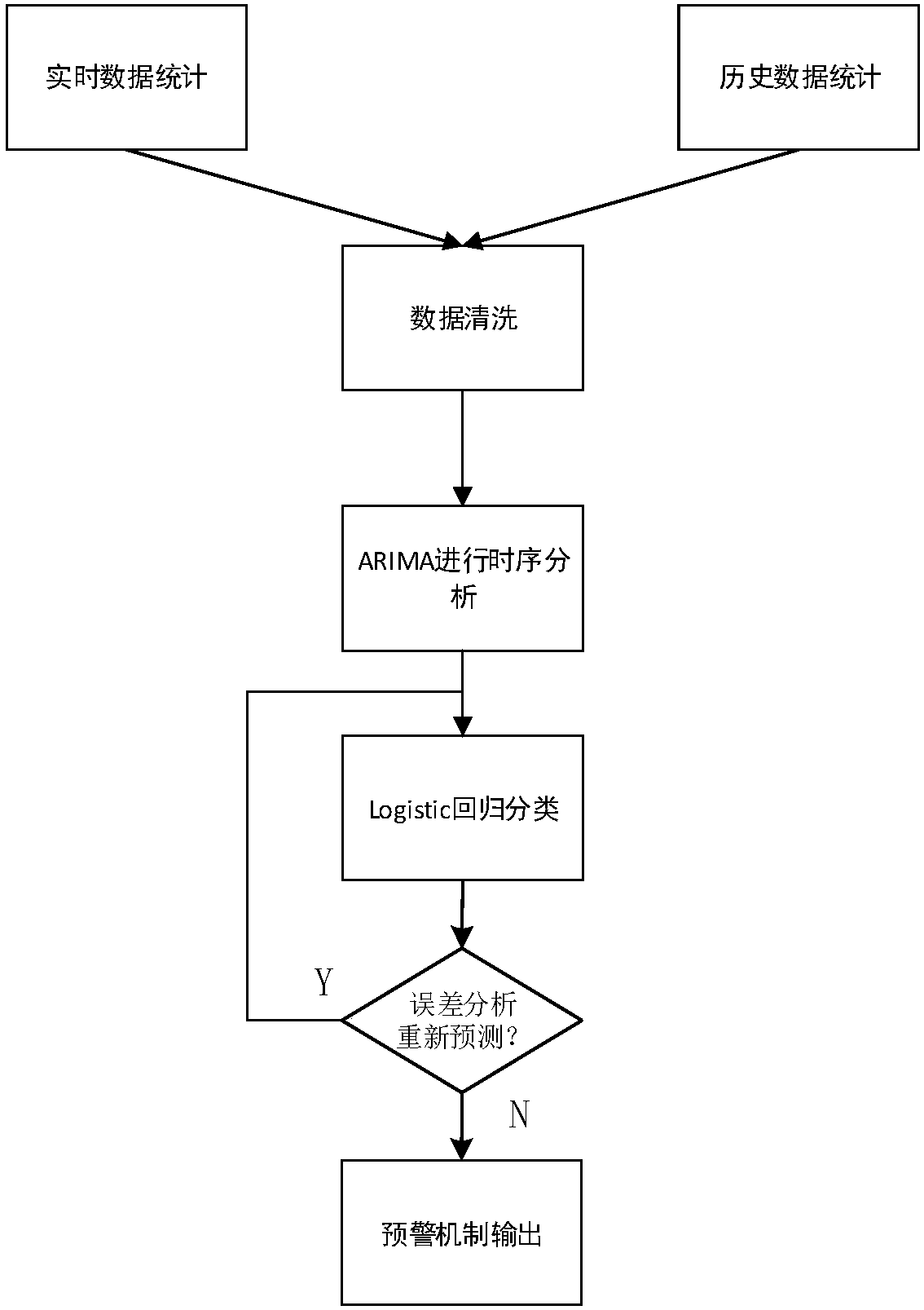
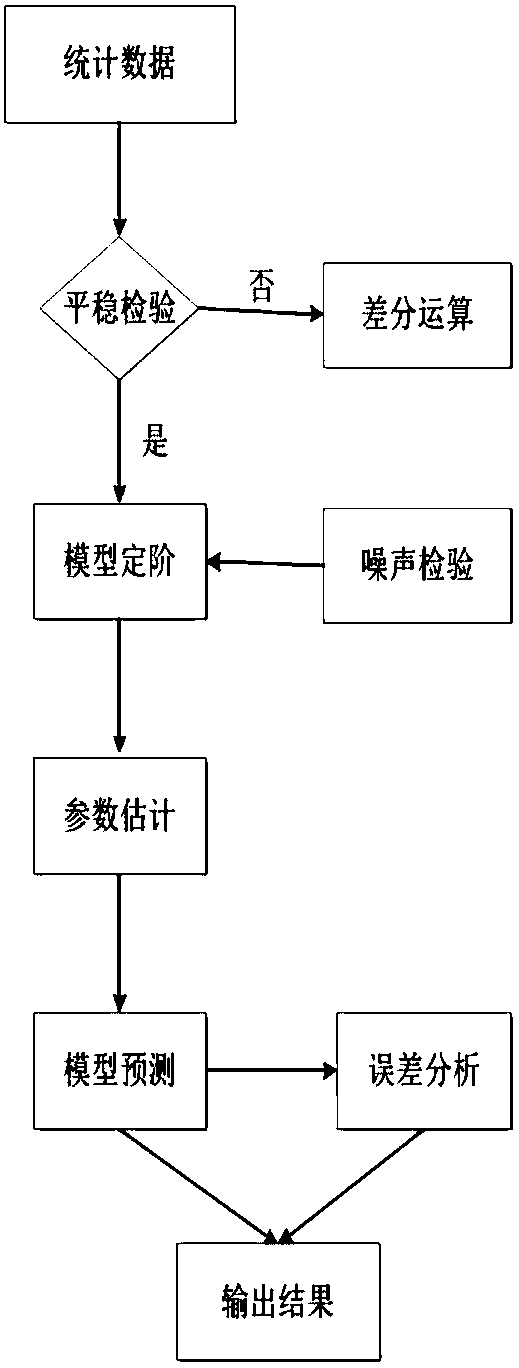
Time sequence classification early warning method for storage device
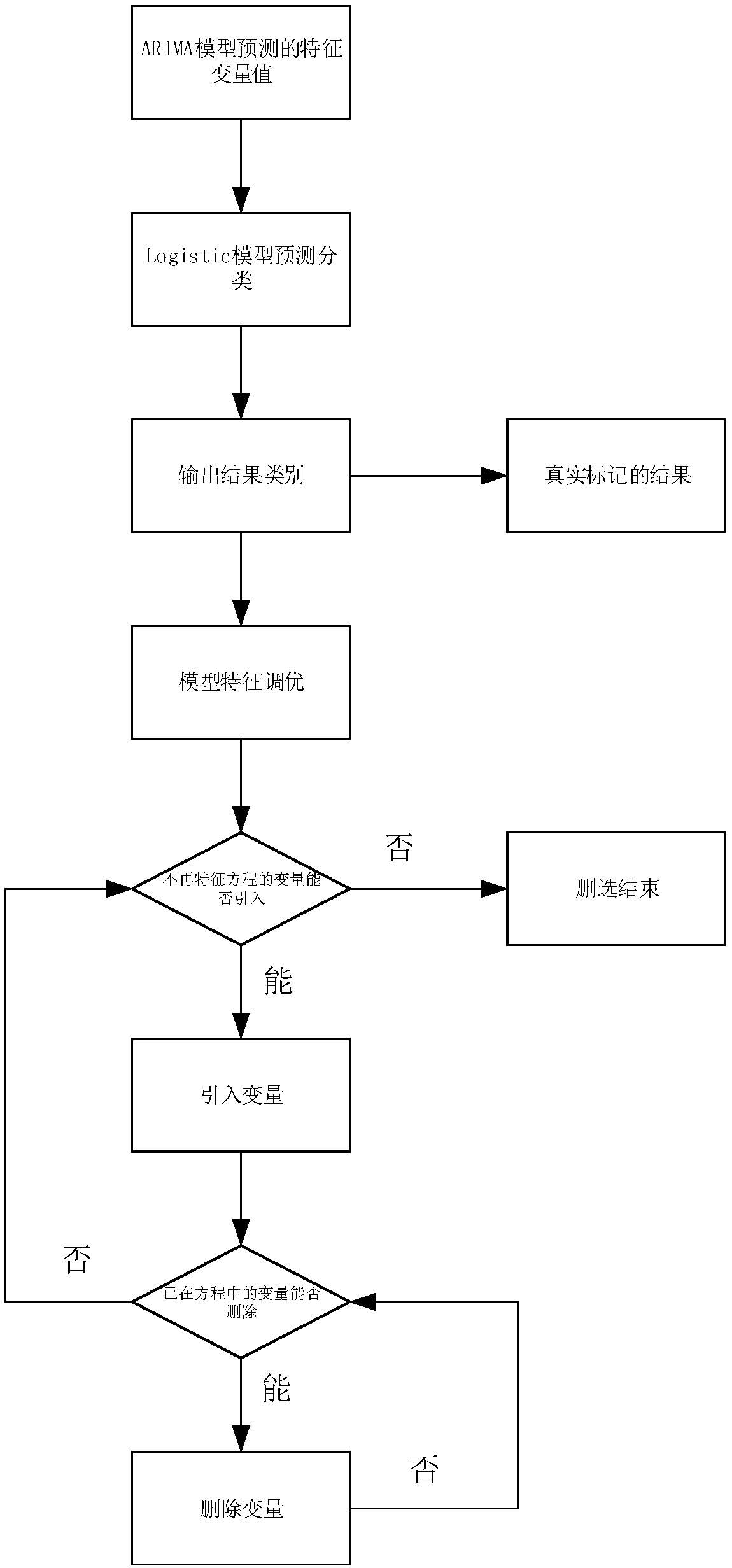
InactiveCN108052528AMitigating the effects of errorsEasy to optimizeCharacter and pattern recognitionSpecial data processing applicationsHysteresisEffective solution
The invention discloses a time sequence classification early warning method for a storage device. The method comprises the steps of collecting storage device parameters in real time; cleaning data; performing ARIMA time sequence analysis; and performing logistic regression analysis and early warning mechanism output. Under the background of a big data environment, time sequence prediction analysisis performed by adopting an ARIMA model according to historical data and hard disk SMART information obtained by statistics; the correlation between a SMART eigenvalue and a fault rate of the storagedevice is analyzed; and an eigenvalue more suitable for a Logistic model is selected out to perform classification prediction. A machine learning method is adopted for predicting the fault rate of the storage device, so that the problems of classification singleness and low early warning intensity in final prediction of the storage device are solved, the defects of hysteresis, low accuracy, pooractual early warning effect and difficult application to the big data environment for a disk early warning mechanism in the prior art are overcome, the occurrence probability of each early warning intensity can be predicted, and an effective solution is provided for real-time operation maintenance and monitoring in a data center environment.
Owner:HUAZHONG UNIV OF SCI & TECH
WebShell detection method and system
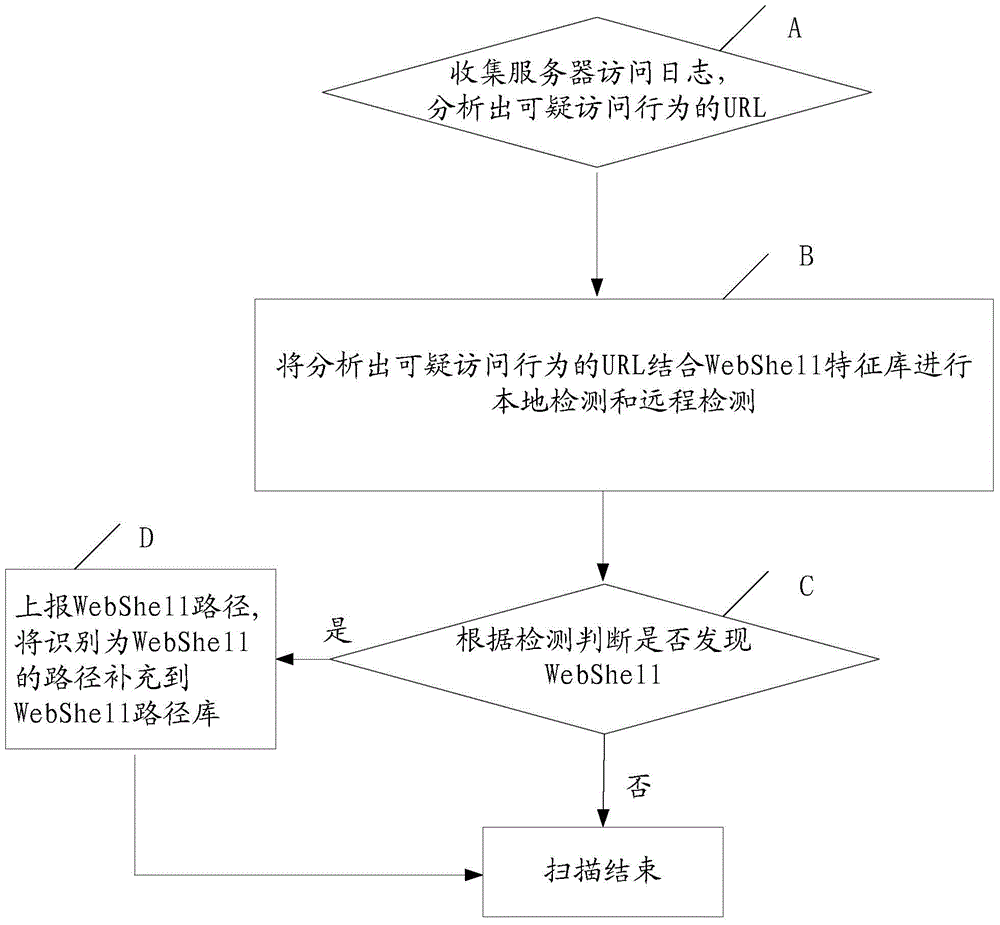
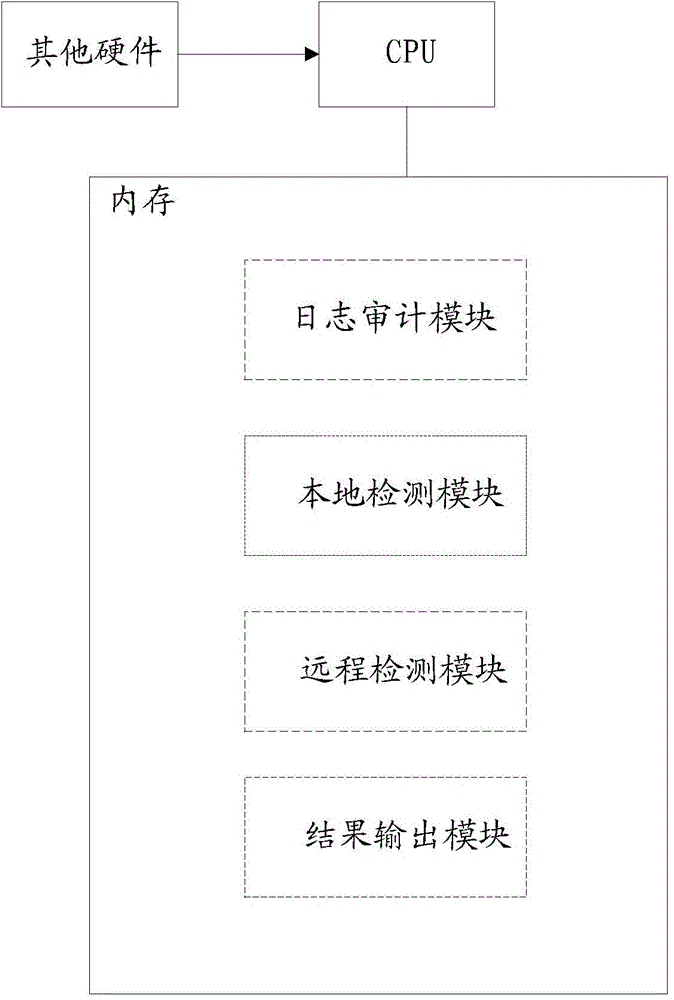
ActiveCN104468477AImprove accuracyImprove the detection rateTransmissionWeb applicationUniform resource locator
The invention provides a WebShell detection method and system. The system comprises a log auditing module, a local detection module, a remote detection module and a result output module. The system executes the following processing flow: A, collecting a server access log, and analyzing a URL (Uniform Resource Locator) with suspicious access behaviors; B, performing local detection and remote detection on the analyzed URL with suspicious access behaviors in combination with a WebShell feature library; C, and performing judgment according to the detection, reporting a WebShell path if WebShell is found, and meanwhile adding the path identified as WebShell into a WebShell path library. Through adoption of the method and the system, the detection rate and detection efficiency of WebShell detection in network Web application are increased, and the missing report rate and false report rate are lowered.
Owner:杭州迪普信息技术有限公司
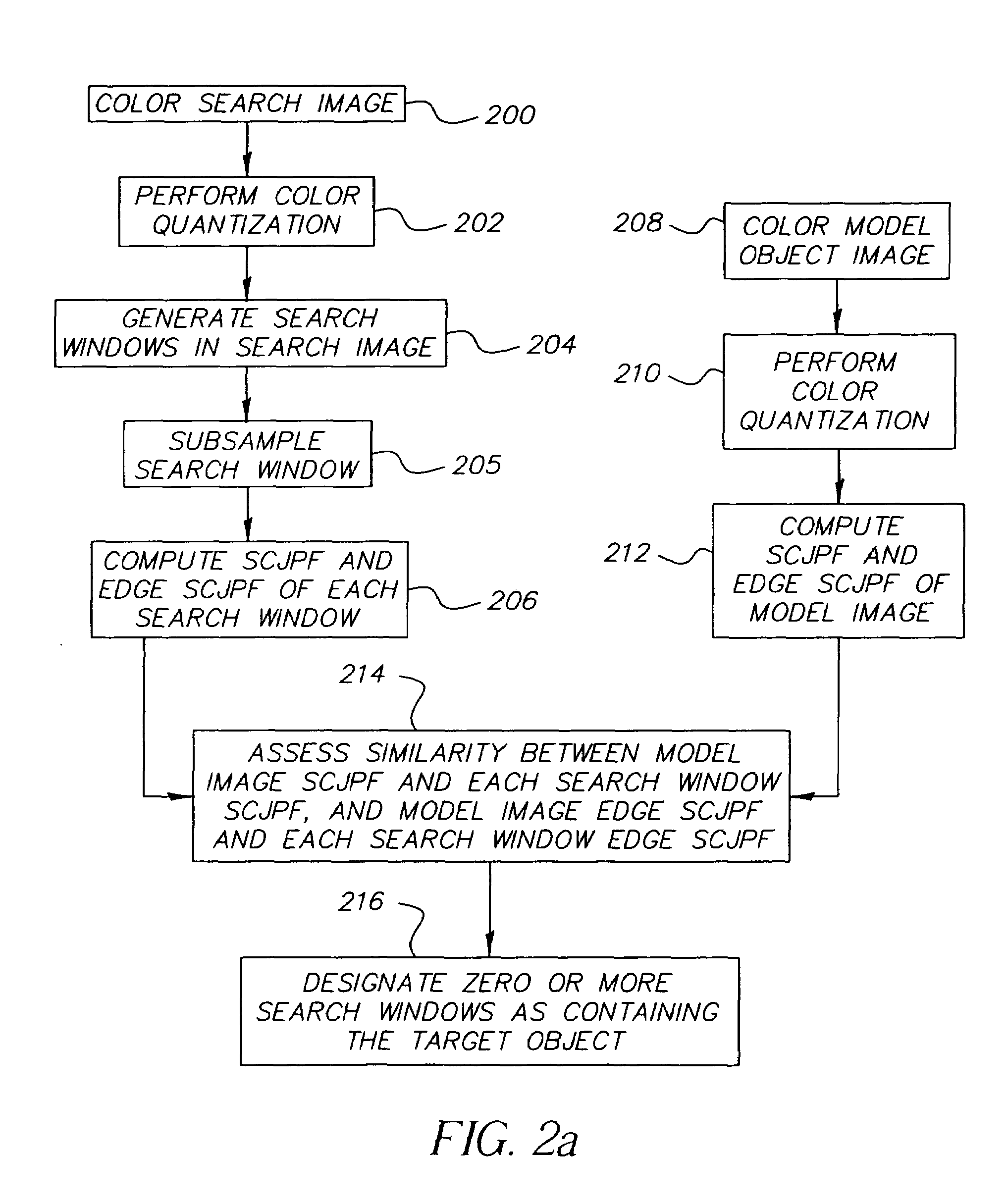
Method for detecting color objects in digital images
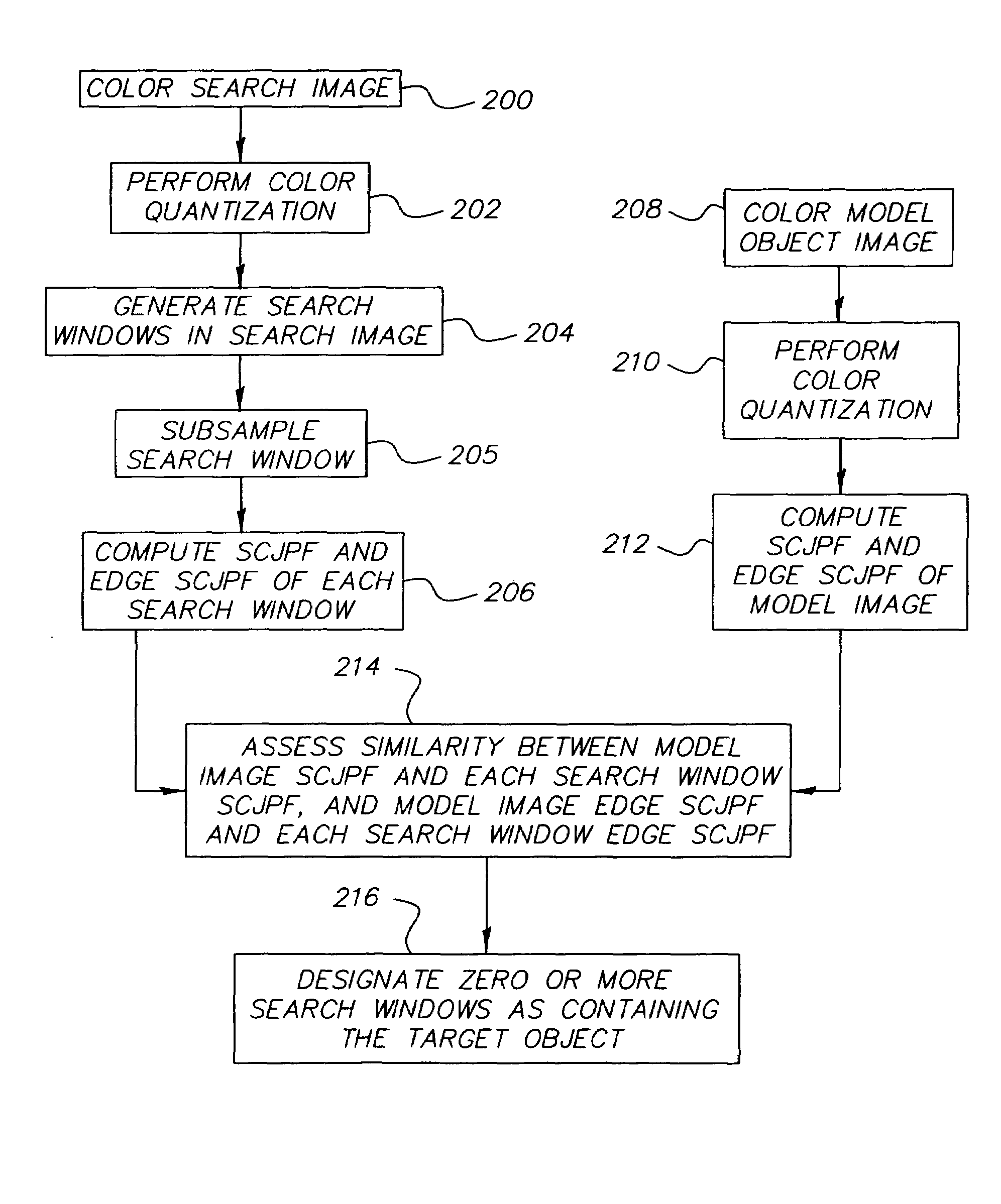
InactiveUS7263220B2Improve the detection rateLower detection rateImage analysisCharacter and pattern recognitionCo-occurrenceDigital image
A method for detecting an object in a digital image including the steps of performing color quantization on a model image including the object and on a search image that potentially includes the object, generating a plurality of search windows, computing spatial-color joint probability functions of each model and search image, where the color co-occurrence edge histogram is chosen to be the spatial-color joint probability function, assessing the similarity of each search image to the model, and designating search windows as containing the target object.
Owner:MONUMENT PEAK VENTURES LLC
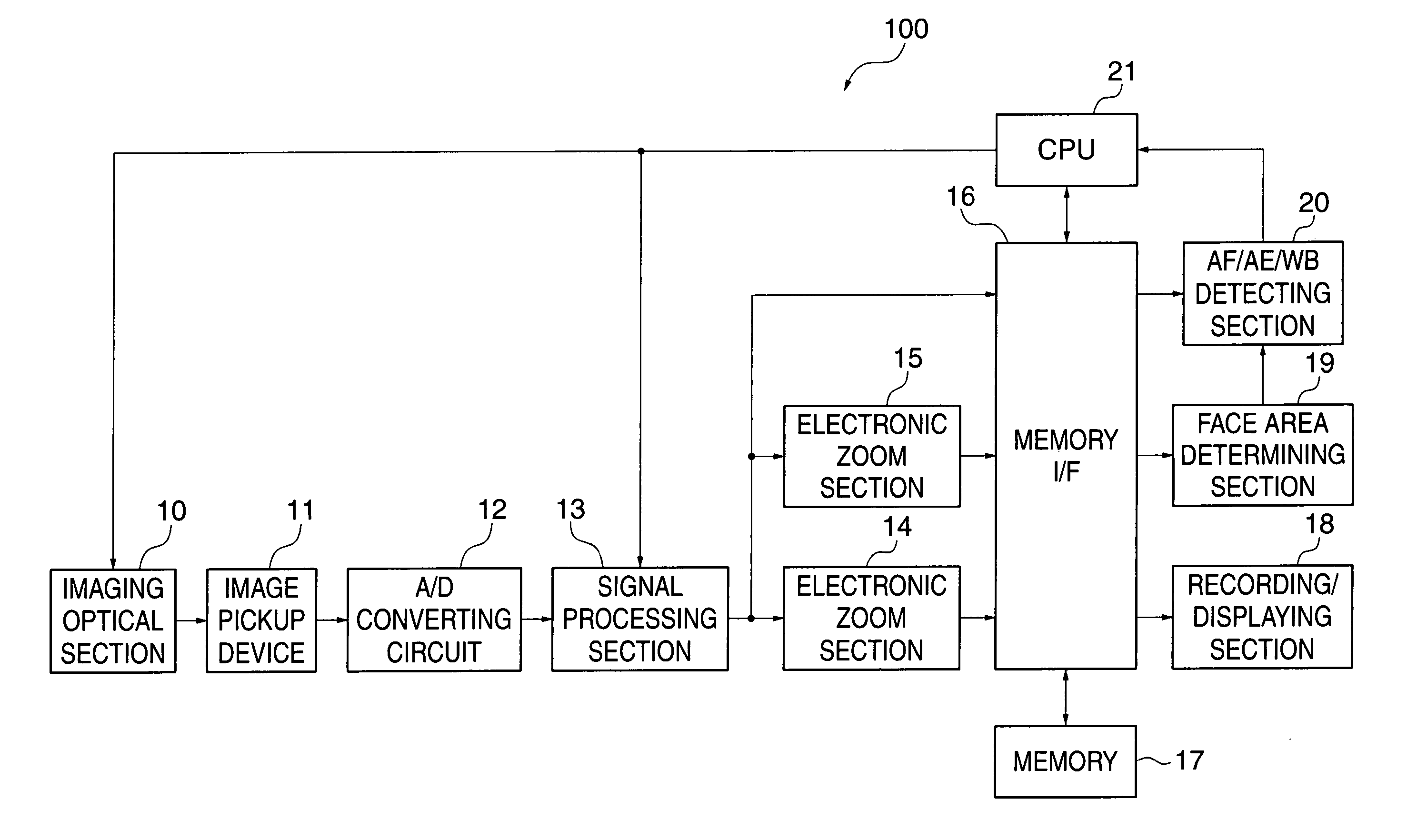
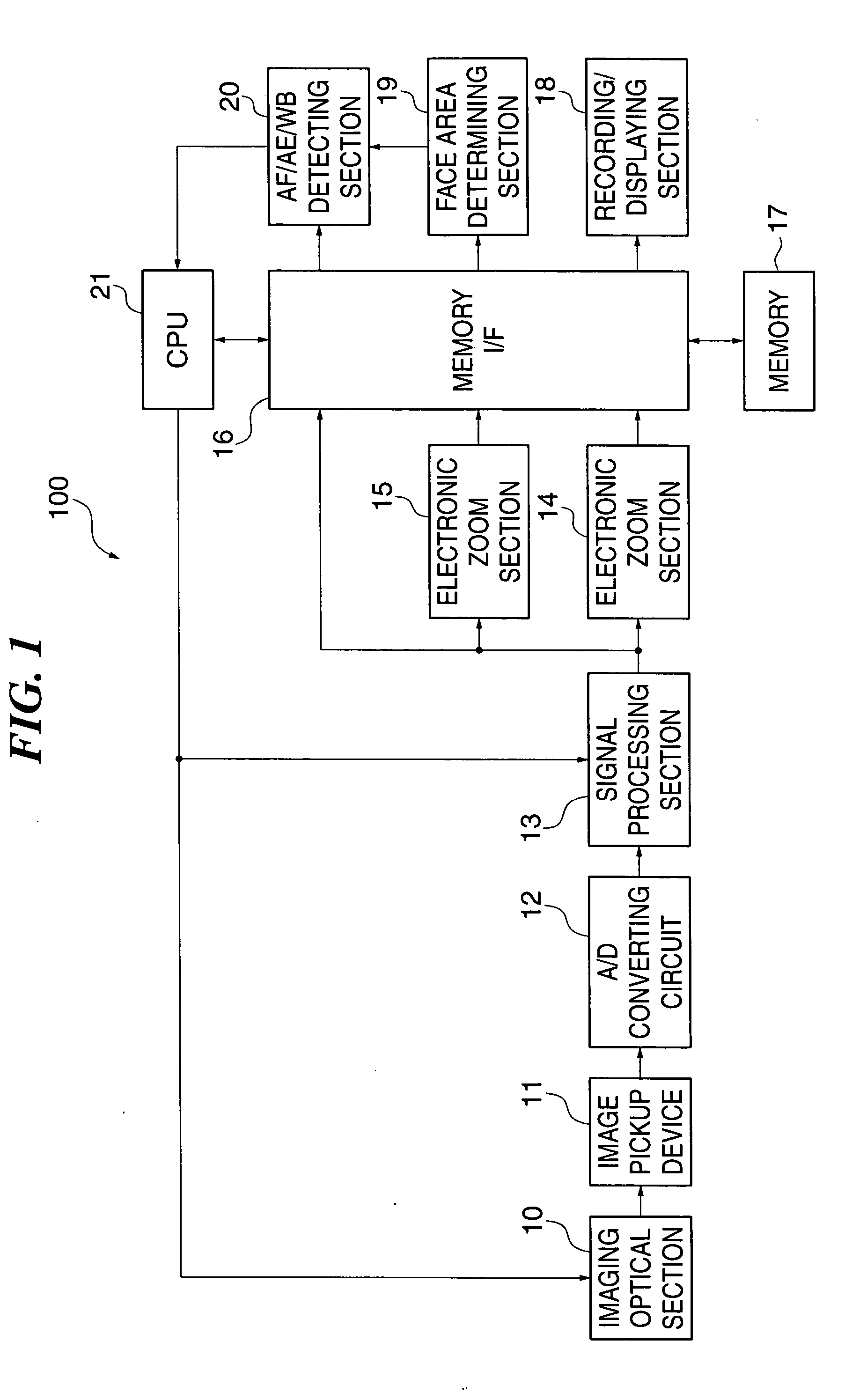
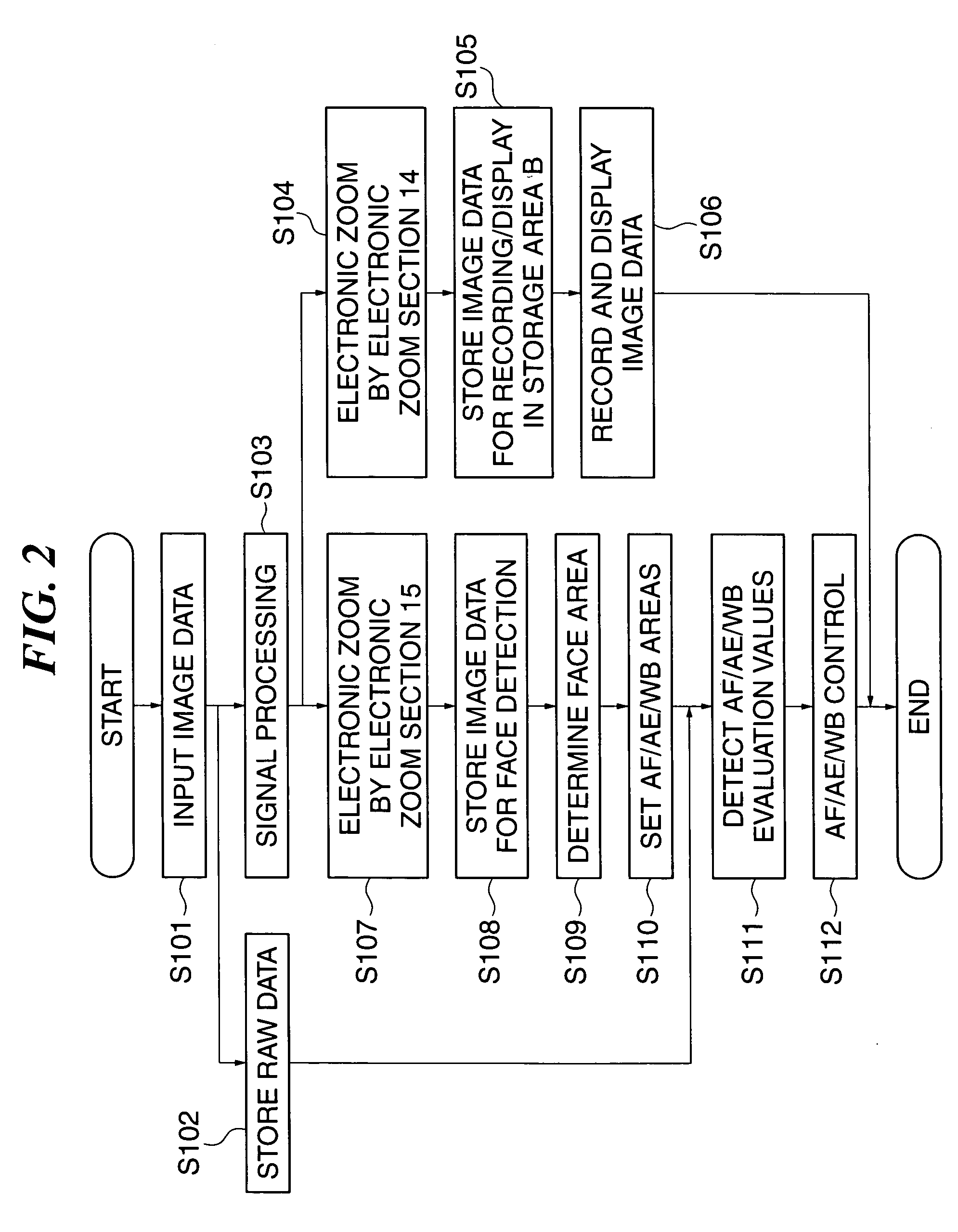
Image pickup apparatus, method of controlling the apparatus, and program for implementing the method, and storage medium storing the program
InactiveUS20050270399A1Improve the detection rateAccurate areaTelevision system detailsColor television detailsAnalog signalDigital image
An image pickup apparatus which increases the rate at which a person's face is detected in electronic zoom and accurately focuses on a person's face area and provides exposure / white balance control. An A / D converting unit converts an analog signal obtained from an image pickup device into a digital image signal. A signal processing unit performs signal processing on the digital image signal as image data. A display unit displays a zoom area in the image data magnified / reduced to a desired angle of view. A face detecting unit detects a person's face area from image data of a face detecting area narrower than the whole area of the image data and wider than the zoom area to acquire information on the person's face area.
Owner:CANON KK
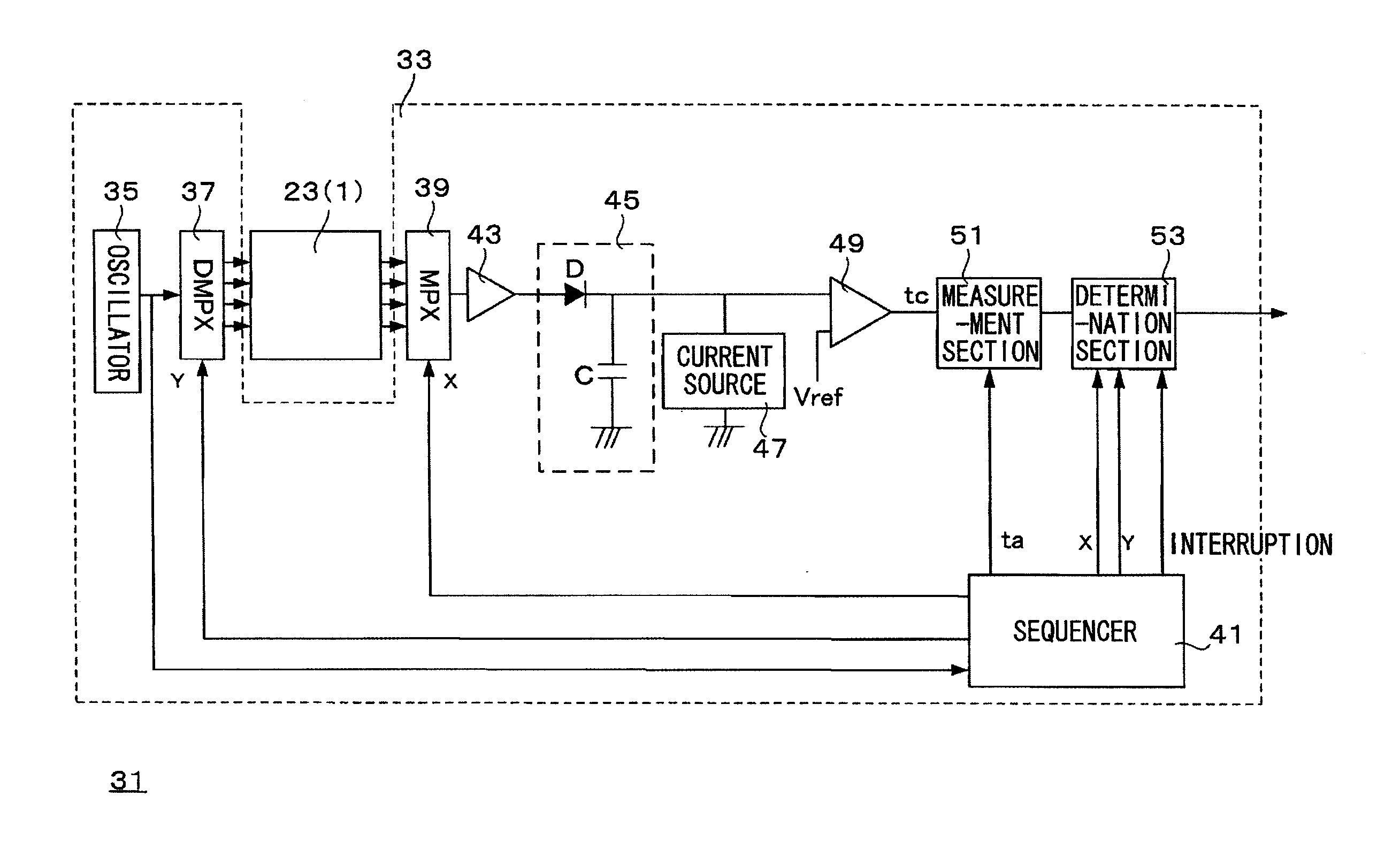
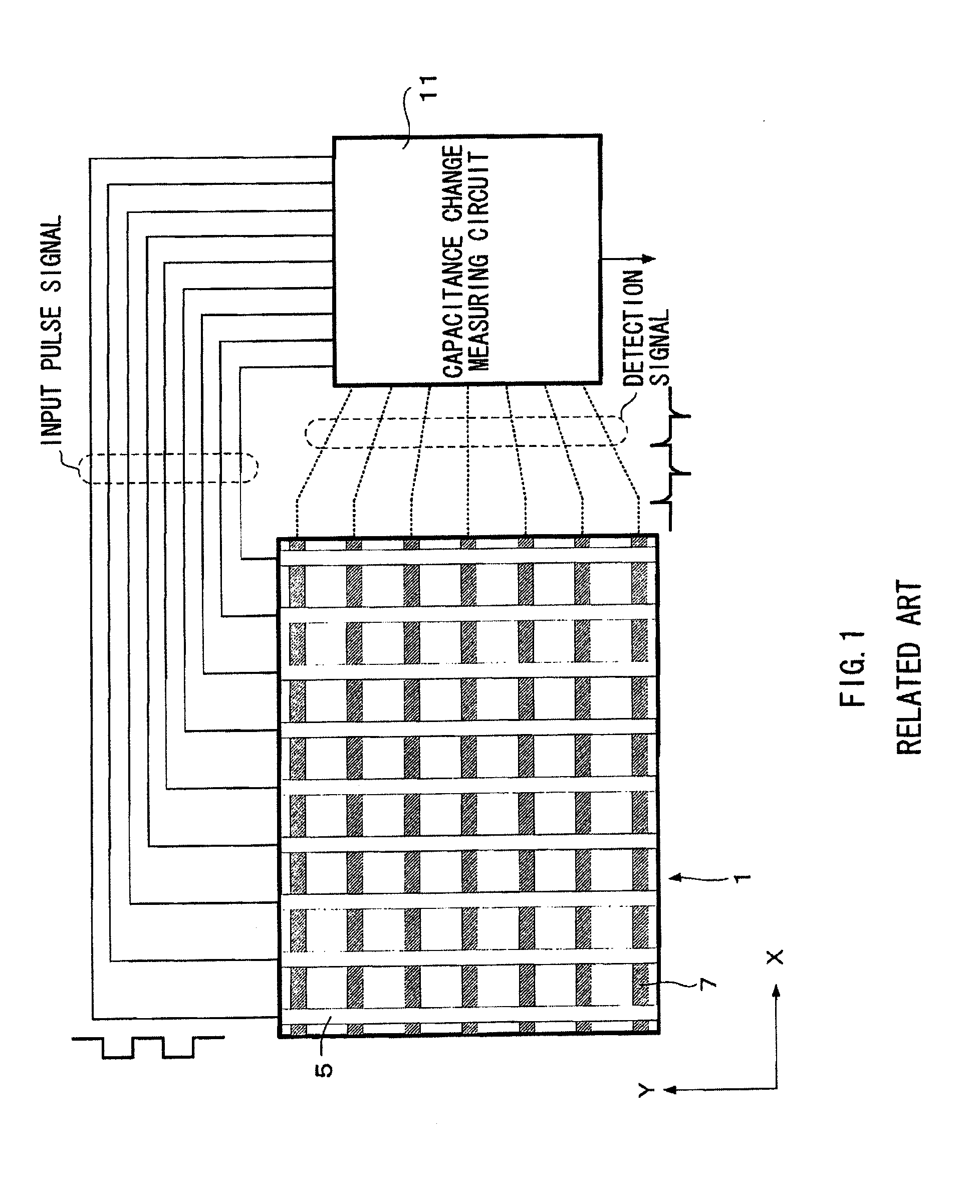
Capacitance change measuring circuit of capacitive sensor device, capacitive sensor module, method of measuring capacitance change of capacitive sensor device, and electronic device
InactiveUS20100066391A1Easy to detectShort timeResistance/reactance/impedenceCharacter and pattern recognitionPeak valueCapacitance transducer
Scanning rate in a capacitance change measuring circuit for a capacitive sensor device is enhanced. The circuit includes: an electrode drive section line-sequentially applying an input pulse signal to a plurality of columns of first electrode patterns in the capacitive sensor device; a peak hold circuit storing a peak level of a detection signal extracted from each column of second electrode patterns into a capacitive element as a corresponding potential; a current source initializing the potential in the capacitive element within one period of the input pulse signal; a comparator comparing the potential in the capacitive element with a reference value; and determination sections each determining whether or not an input operation using a human body or the like is executed, based on a timing information and a reference timing information, the timing information representing a timing when the potential held in the capacitive element crosses the reference value.
Owner:SONY CORP
Distributed Optical Fibre Sensor
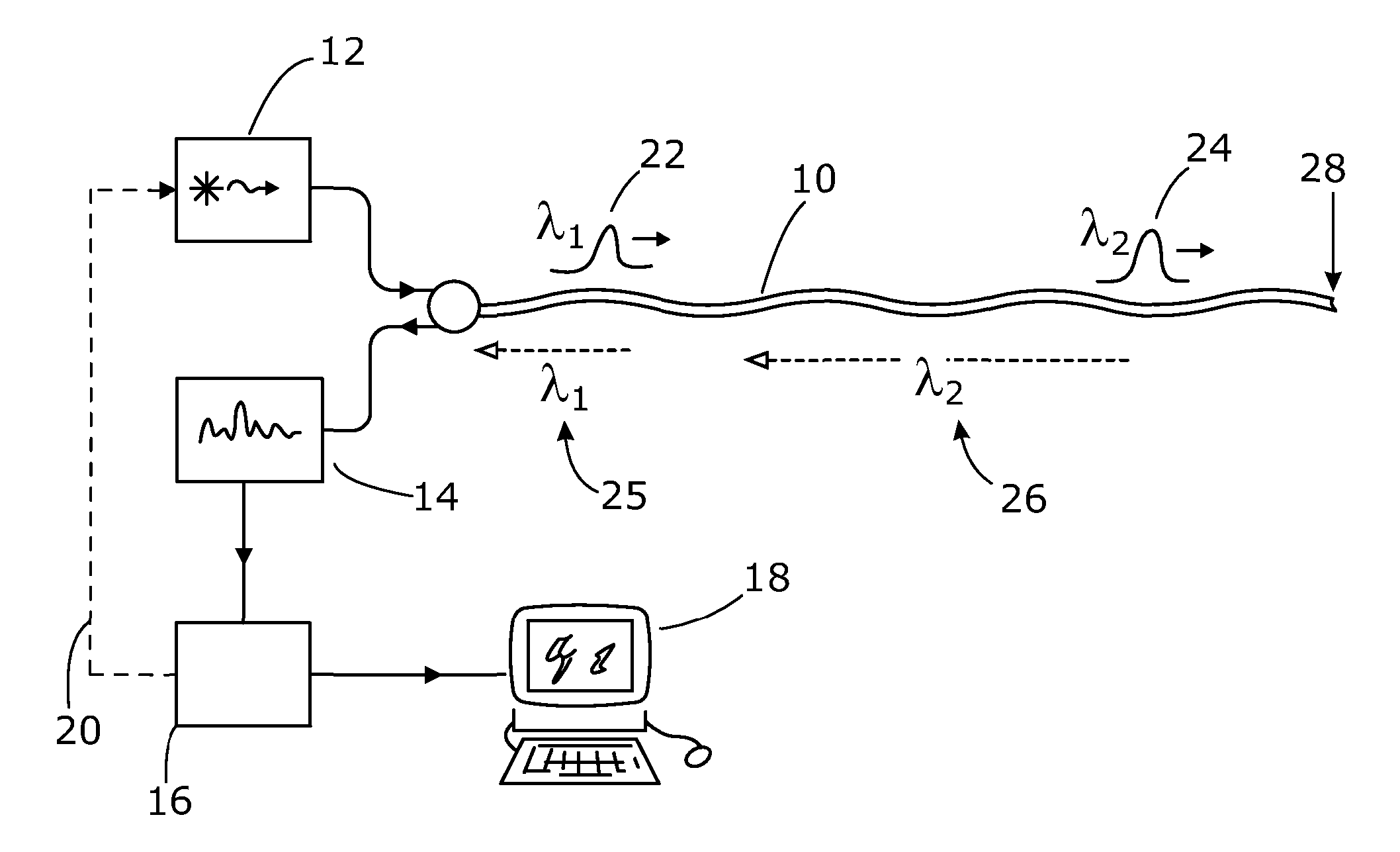
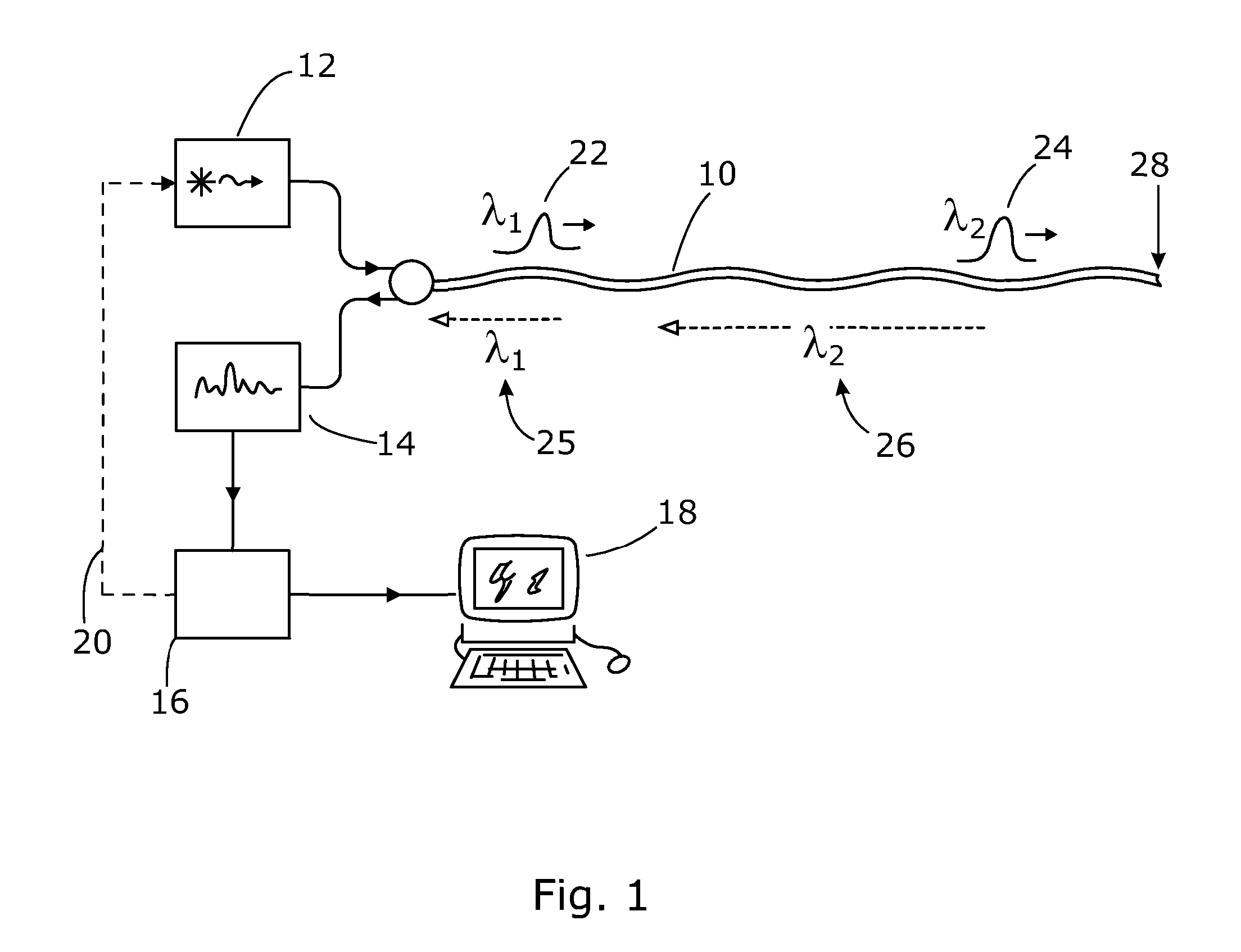
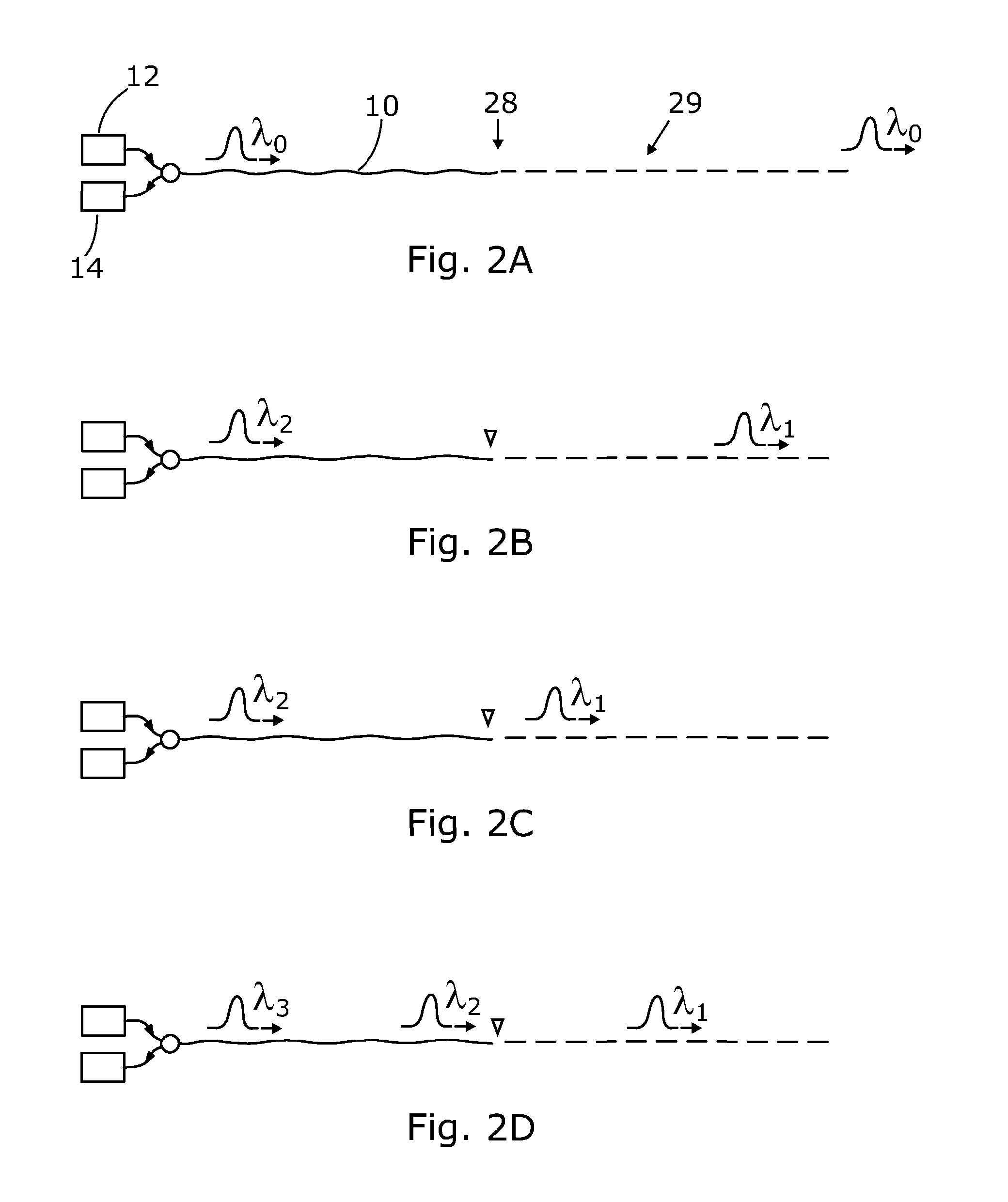
ActiveUS20130222811A1Improve the detection rateImprove dynamic rangeSubsonic/sonic/ultrasonic wave measurementFluid pressure measurementRelative phaseLength wave
There is described a distributed optical fibre sensor for detecting one or more physical parameters indicative of an environmental influence on a sensor optical fibre, as a function of position along the sensor fibre. The sensor uses probe light pulses of different wavelengths. At least some of the probe light pulses may also be of different pulse lengths. The relative phase bias between interferometric signals in backscattered probe light of different wavelength pulses may also be controlled.
Owner:VIAVI SOLUTIONS INC
Detection kit for antigens of novel coronavirus (SARS-CoV-2)
InactiveCN111303254AThe test result is accurateHigh sensitivitySsRNA viruses positive-senseVirus peptidesAntigen testingColloidal au
The invention relates to the technical field of biology, and specifically provides a detection kit for a detection kit for antigens of a novel coronavirus (SARS-CoV-2). According to the detection kitprovided by the invention, the antigens of the SARS-CoV-2 are detected by virtue of a colloidal gold double antibody sandwich method, and two monoclonal antibodies and colloidal gold are mixed for labeling, so that a detection result of the antigens of the SARS-CoV-2 is accurate and high in sensitivity, and meanwhile, the detection rate can be remarkably increased. According to the detection kit,a blank in immunological detection of the SARS-CoV-2 is filled up, and field detection can be realized without a detection instrument, so that the time and the labor are saved, and operation is flexible.
Owner:北京新创生物工程有限公司
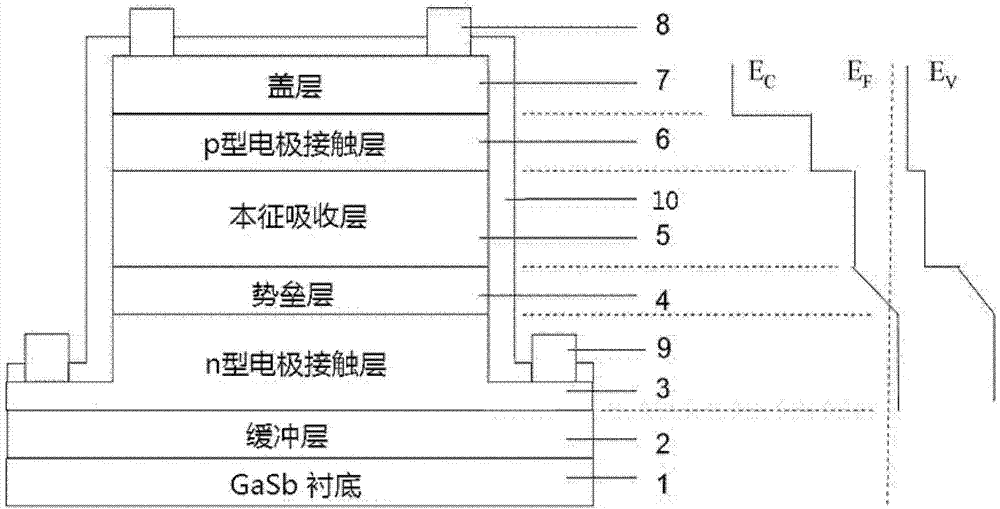
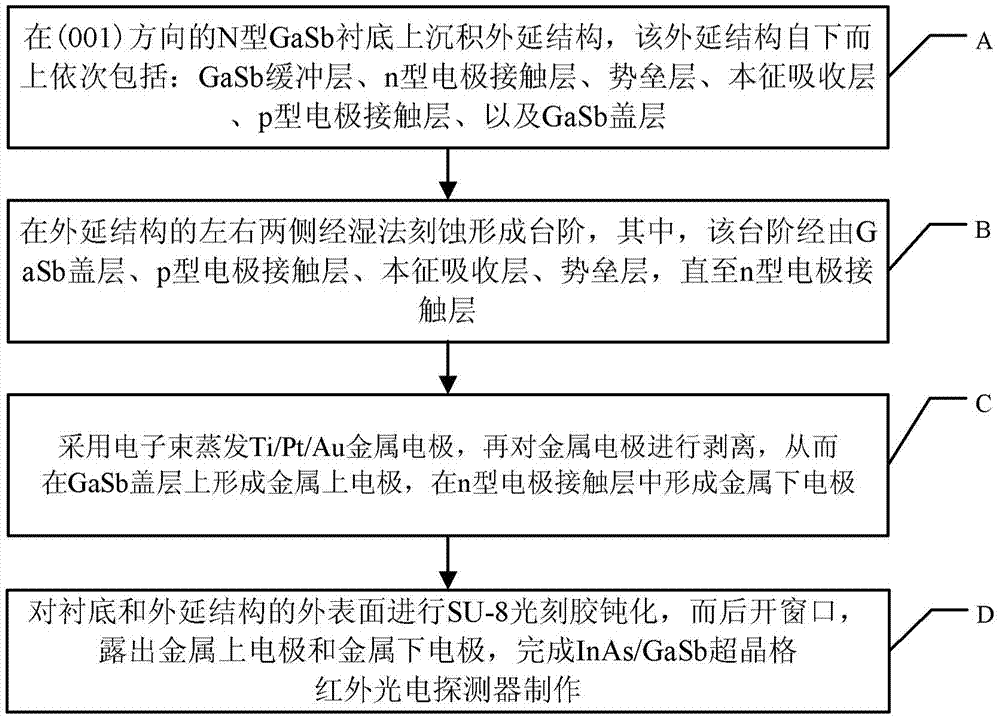
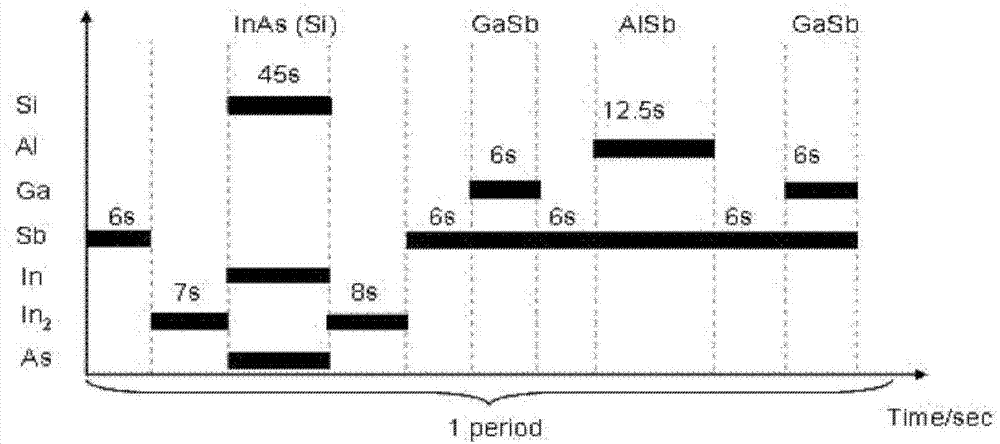
InAs/GaSb superlattice infrared photoelectric detector and manufacturing method thereof
ActiveCN103887360AImprove performanceSuppression-recombination dark currentFinal product manufactureSemiconductor devicesPhotovoltaic detectorsElectrode Contact
The invention provides an InAs / GaSb superlattice infrared photoelectric detector and a manufacturing method thereof. The InAs / GaSb superlattice infrared photoelectric detector comprises a substrate, an epitaxy structure deposited on the substrate, an upper metal electrode formed above steps, a lower metal electrode formed under the steps and a passivation layer, wherein the epitaxy structure comprises an n-type doping buffer layer, an n-type electrode contact layer, a barrier layer, an intrinsic absorption layer, a p-type electrode contact layer and a cover layer, the steps are formed on two sides of the epitaxy structure through etching, the intrinsic absorption layer is composed of a plurality of periodical InAs / InSb / GaSb / InSb superlattice structures. In the InAs / GaSb superlattice infrared photoelectric detector, InSb is respectively inserted into two interfaces of each superlattice period of the intrinsic absorption layer to form strained superlattices, the stress between the superlattices and the substrate is effectively balanced, the material growing quality is improved, and accordingly the photoelectric performance of the detector is improved.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
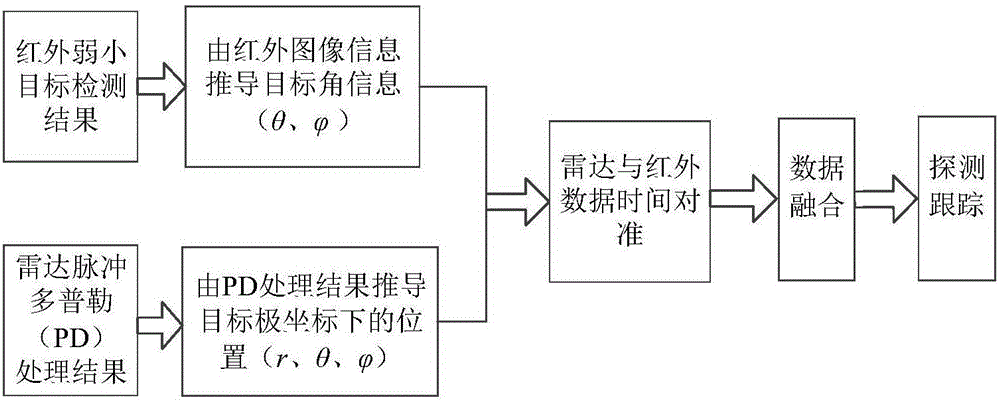
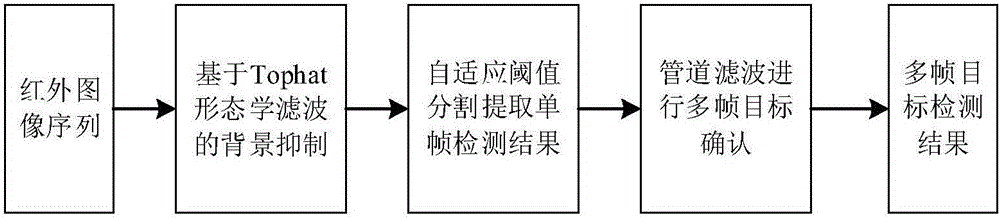
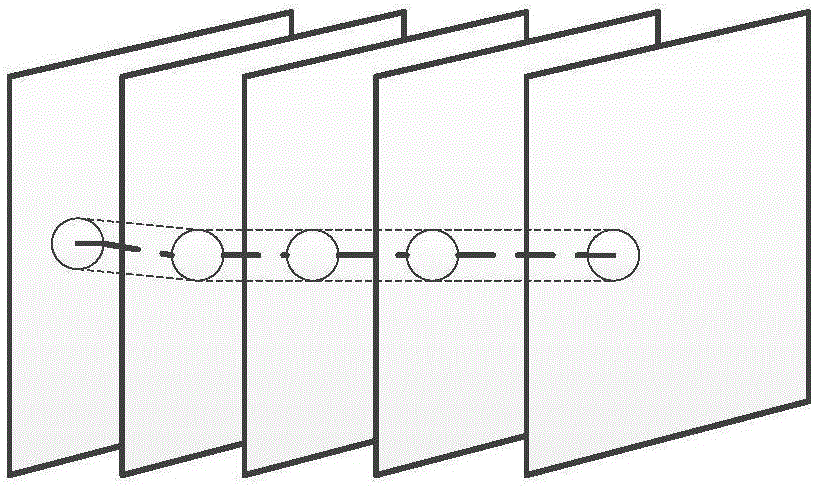
In-orbit moving target detecting method with space-based radar and infrared data fusion
InactiveCN106204629AAvoid moving out of the pipelineImprove performanceImage enhancementImage analysisRadar detectionTrack algorithm
The invention discloses an in-orbit moving target detecting method with space-based radar and infrared data fusion. The method includes the steps that when an infrared detecting system is used for detection, background suppression is carried out on each frame in an infrared image sequence by adopting a filtering method based on the morphology, self-adaptive threshold segmentation is carried out on images obtained after background suppression, a single frame detection result is extracted, a multi-frame target is determined through a tracking algorithm, and whether the detection result is a real target or not is judged to obtain the detection result of the multi-frame target; during radar detection, pulse doppler (PD) is adopted for processing. After time calibration and space calibration are carried out on the obtained infrared and radar target information, data fusion is carried out on the information by adopting a measurement fusion method, and track prediction is carried out on fused data to obtain the estimated position of the target.
Owner:XIDIAN UNIV
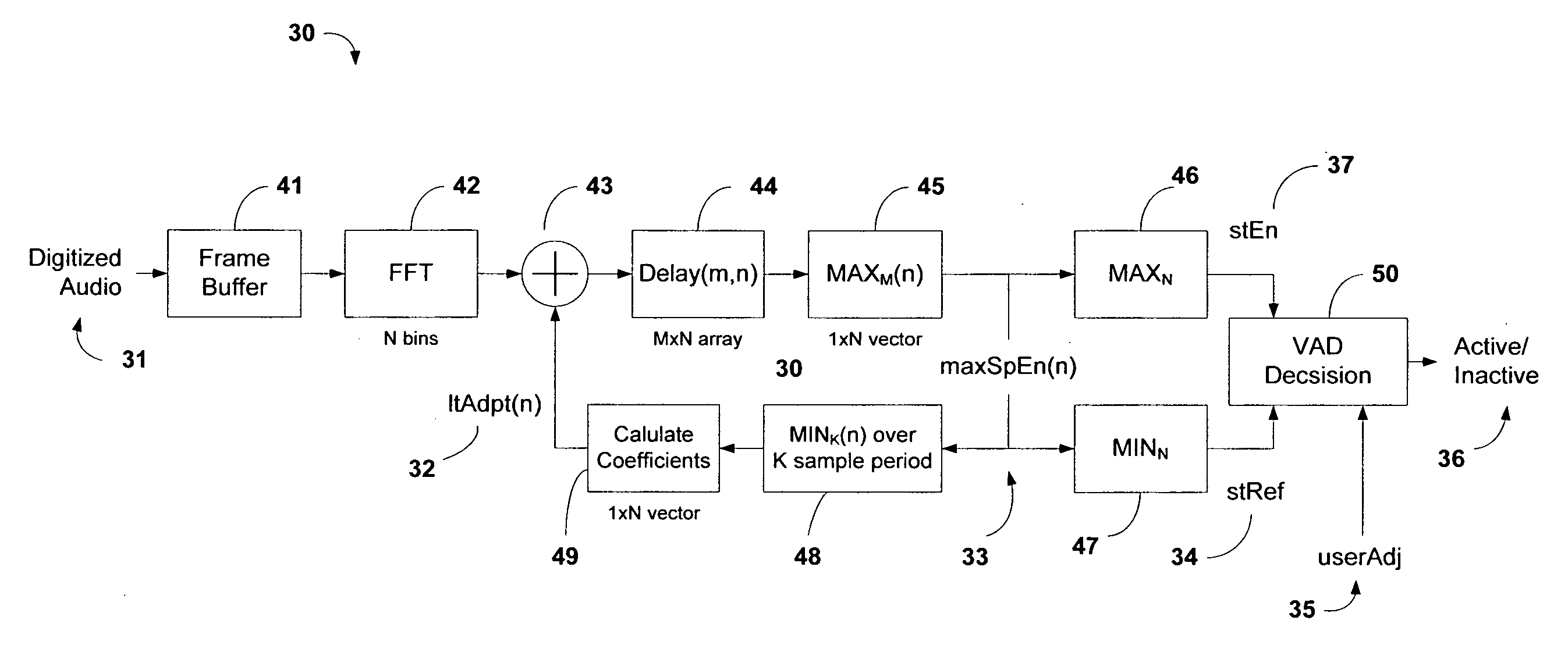
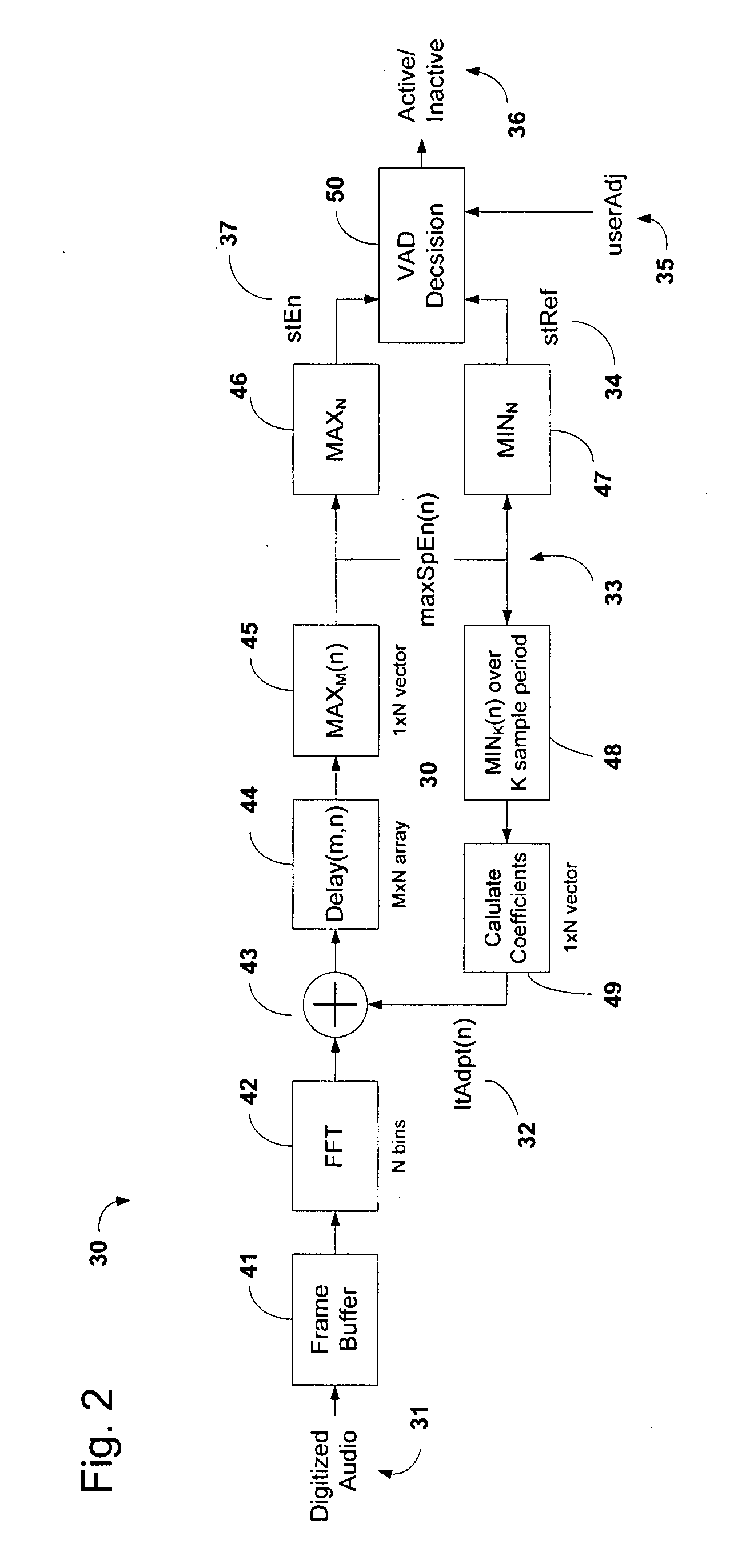
System and method of voice activity detection in noisy environments
InactiveUS20080249771A1Improve the detection rateImprove detection rateSpeech recognitionTraining periodHarmonic
An efficient voice activity detection method and system suitable for real-time operation in low SNR (signal-to-noise) environments corrupted by non-Gaussian non-stationary background noise. The method utilizes rank order statistics to generate a binary voice detection output based on deviations between a short-term energy magnitude signal and a short-term noise reference signal. The method does not require voice-free training periods to track the background noise nor is it susceptible to rapid changes in overall noise level making it very robust. In addition a long-term adaptation mechanism is applied to reject harmonic or tonal interference.
Owner:AVIDYNE CORPORATION
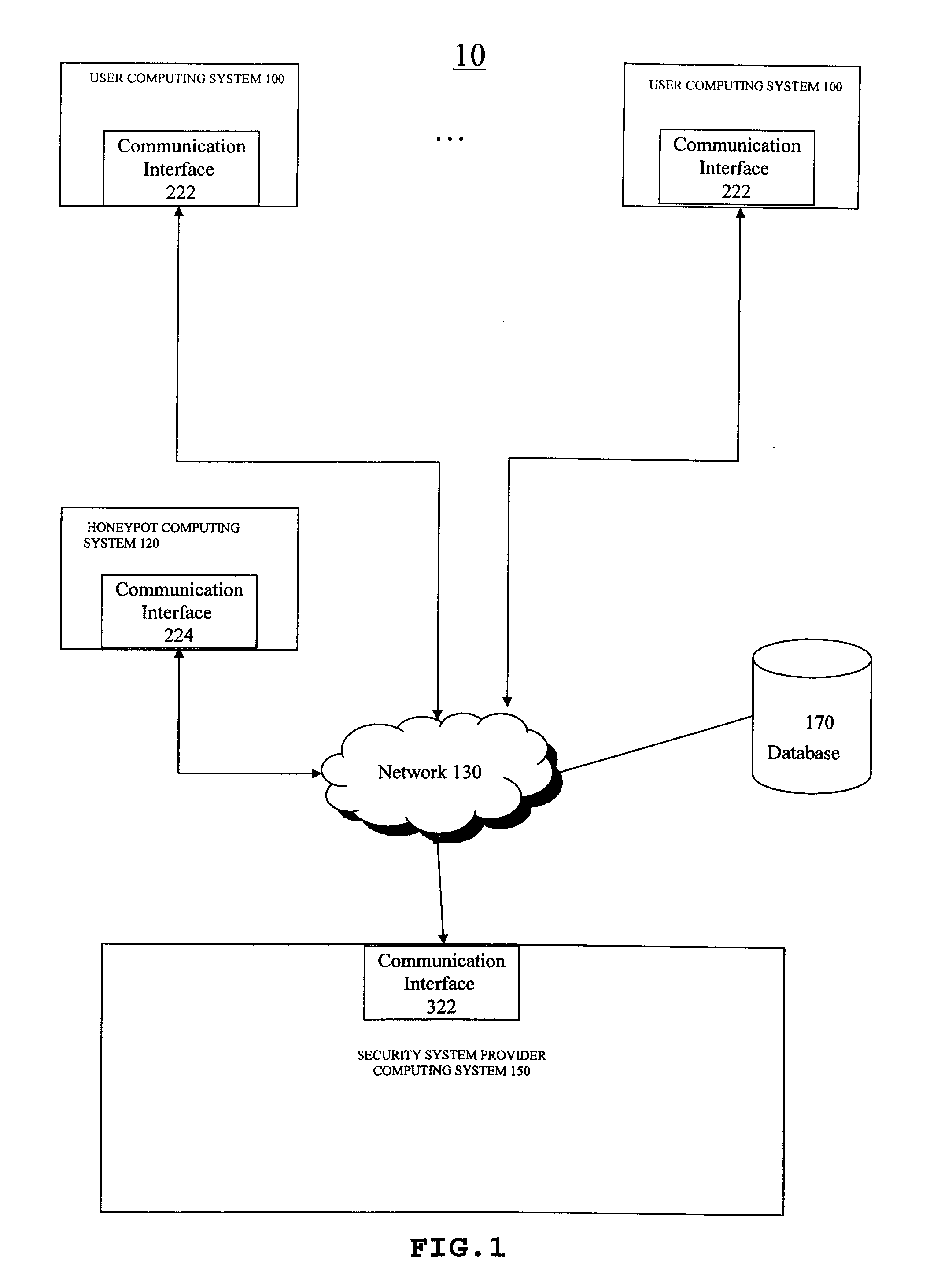
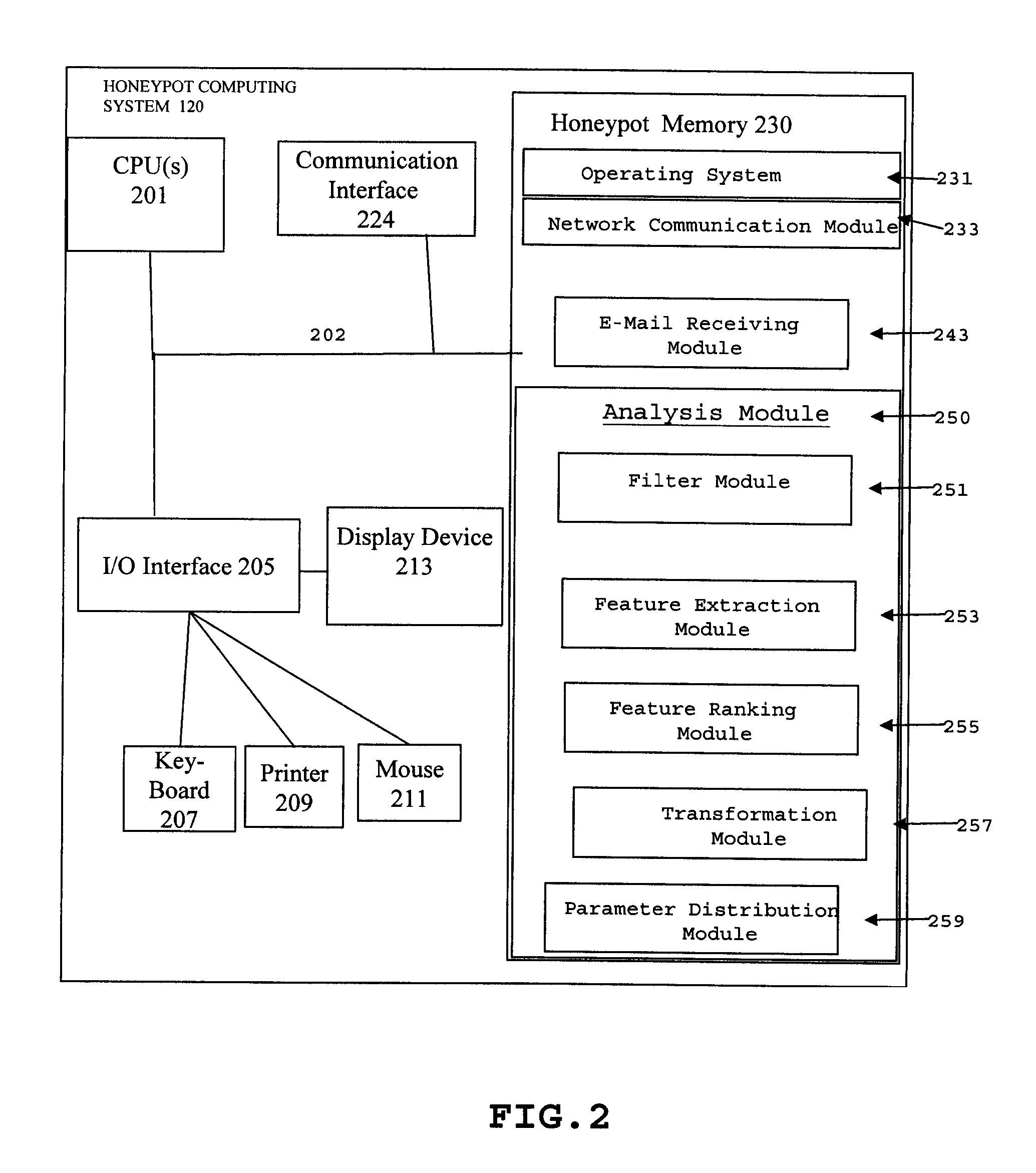
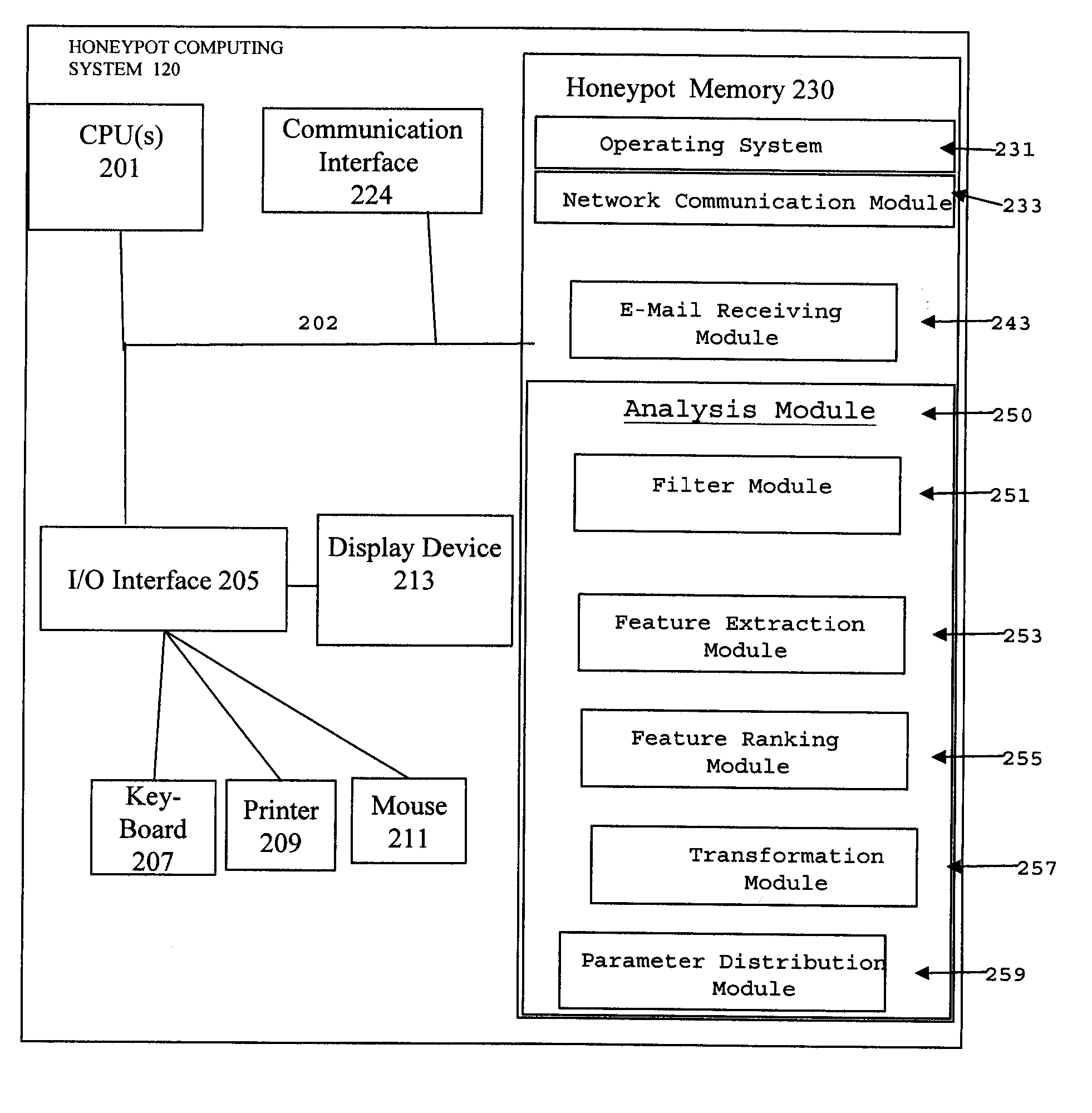
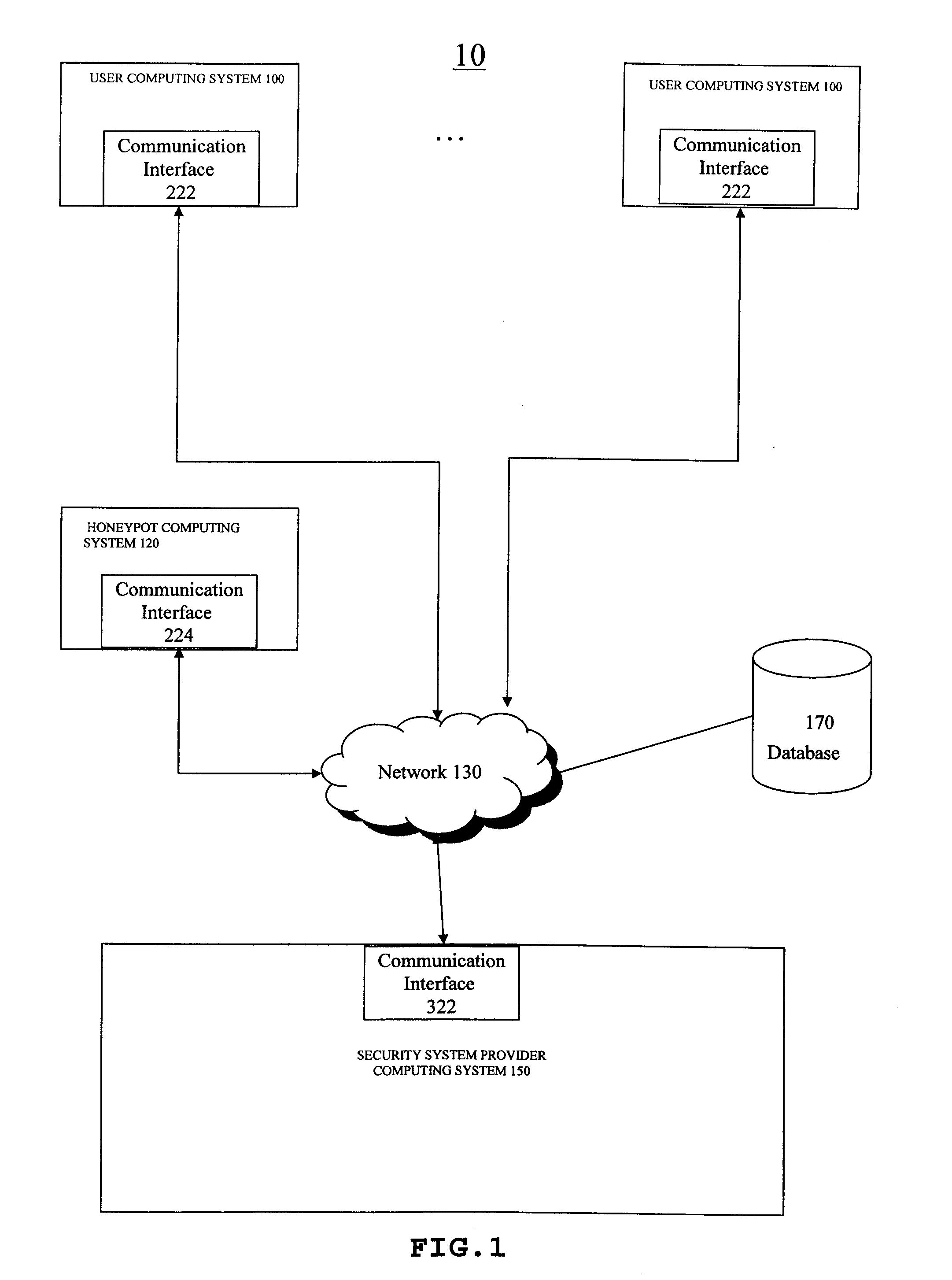
Method and system for using spam e-mail honeypots to identify potential malware containing e-mails
ActiveUS8549642B2Improve the detection rateMemory loss protectionError detection/correctionDecoyInternet privacy
A method and apparatus for employing honeypot systems to identify potential malware containing messages whereby a decoy system to receive illegitimate e-mails is established. E-mails sent to the spam e-mail honeypot decoy are initially scanned / filtered and e-mails that are not considered possible malware containing e-mails are filtered out while the remaining e-mails sent to the spam e-mail honeypot decoy are identified as potential malware containing e-mails. One or more features, and / or feature values, of the identified e-mails are then identified, extracted and ranked. Once a given feature, and / or feature value, occurs more than a burst threshold number of times, the status of the given feature, and / or feature value, is transformed to that of suspicious e-mail parameter.
Owner:SYMANTEC CORP
Method and system for using spam e-mail honeypots to identify potential malware containing e-mails
ActiveUS20110179487A1Improve the detection rateMemory loss protectionError detection/correctionDecoyInternet privacy
A method and apparatus for employing honeypot systems to identify potential malware containing messages whereby a decoy system to receive illegitimate e-mails is established. E-mails sent to the spam e-mail honeypot decoy are initially scanned / filtered and e-mails that are not considered possible malware containing e-mails are filtered out while the remaining e-mails sent to the spam e-mail honeypot decoy are identified as potential malware containing e-mails. One or more features, and / or feature values, of the identified e-mails are then identified, extracted and ranked. Once a given feature, and / or feature value, occurs more than a burst threshold number of times, the status of the given feature, and / or feature value, is transformed to that of suspicious e-mail parameter.
Owner:SYMANTEC CORP
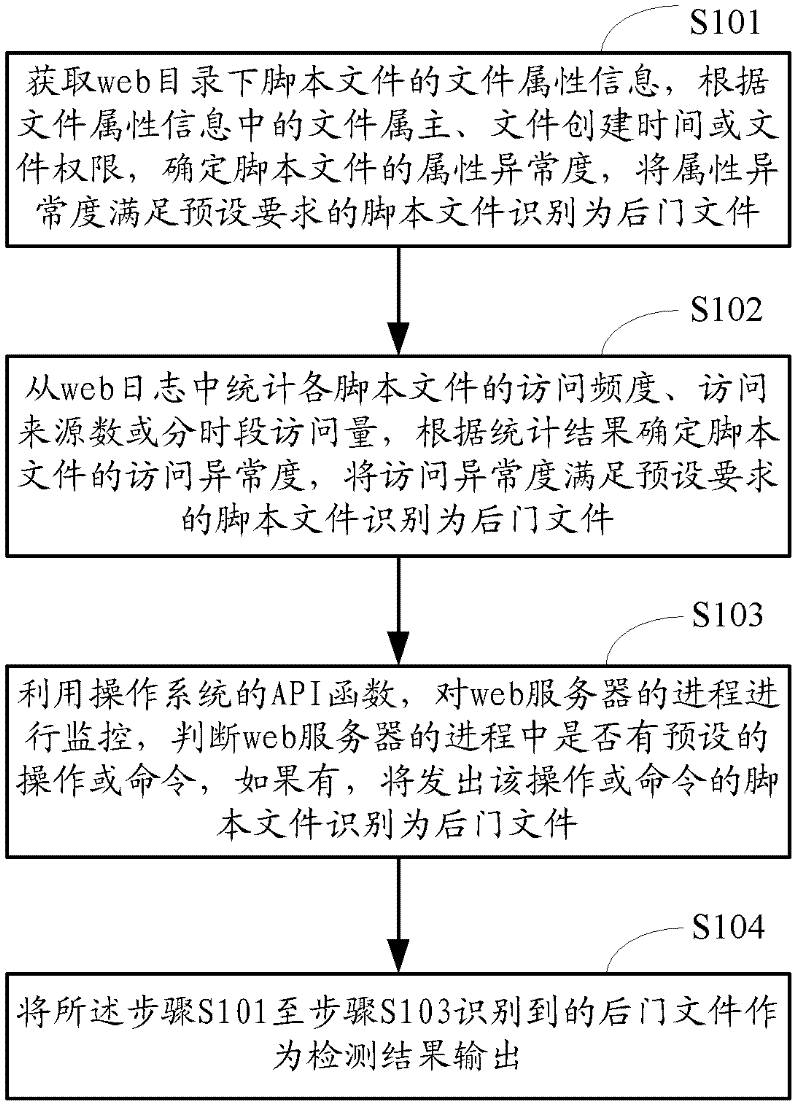
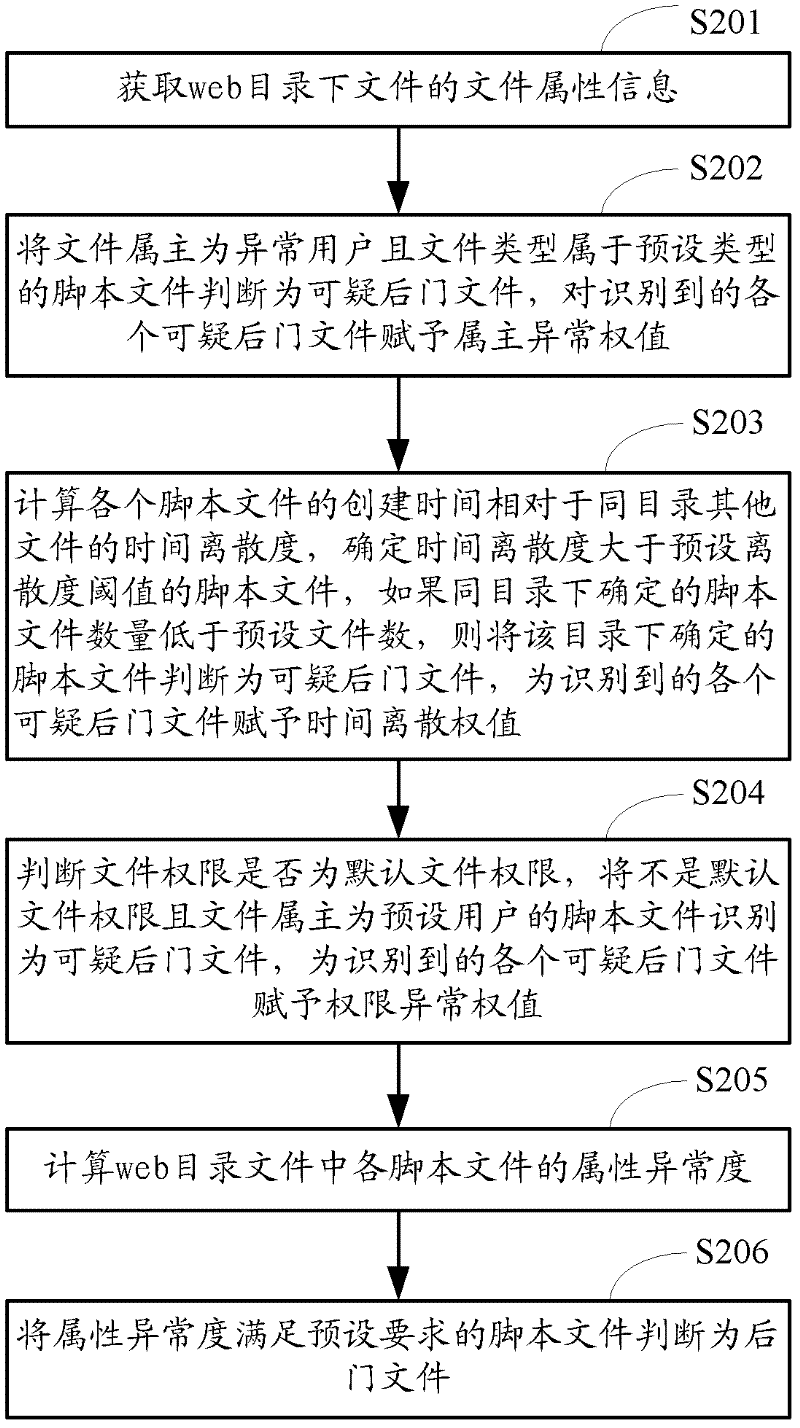
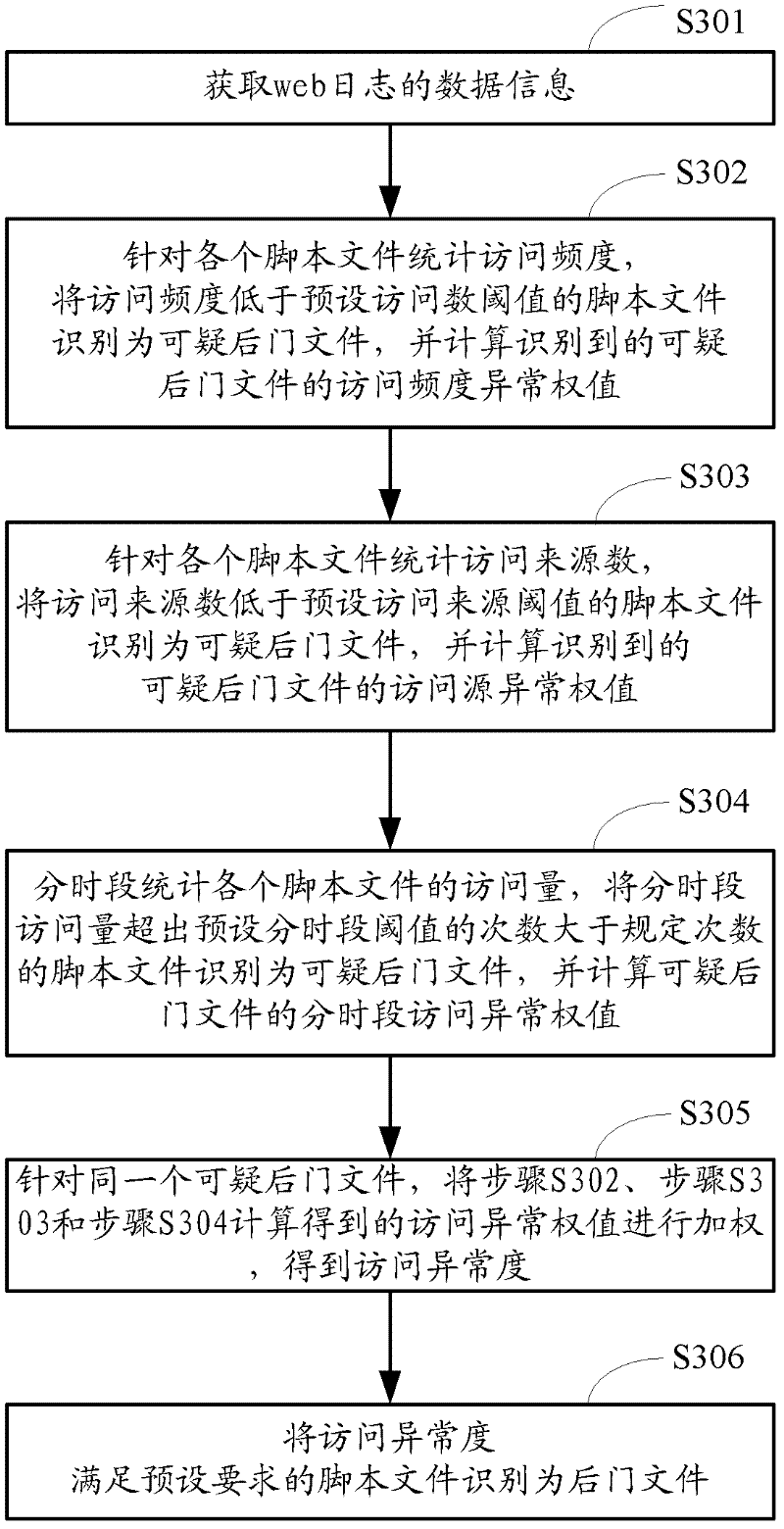
Web back door detection method and device based on behavioral characteristics
ActiveCN102647421AEfficient detectionImprove the detection rateTransmissionOperational systemWeb service
The invention provides a web back door detection method and device based on behavioral characteristics. The method comprises the following steps of: step S1_1, obtaining file attribute information of a script file under a web catalogue; determining an attribute abnormality of the script file according to file establishing time, a file owner or a file authority limit in the file attribute information; and identifying the script file with the attribute abnormality which meets pre-set requirements into a back door file; step S1_2, counting an accessing frequency, accessing source quantity or different-time accessing amount of each script file from a web log and determining an accessing abnormality; and identifying the script file with the accessing abnormality which meets pre-set requirements as the back door file; and step S1_3, utilizing an operating system to monitor a progress of a web server; judging whether a pre-set operation or order exists; and if so, identifying the script file which sends out the operation or the order as the back door file. The web back door detection method and device based on the behavioral characteristics can effectively detect an encrypted and deformed wed back door based on a detection manner of the behavioral characteristics, so that the relevance ratio and the detection efficiency are improved and the misinformation rate is reduced.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Generic shellcode detection
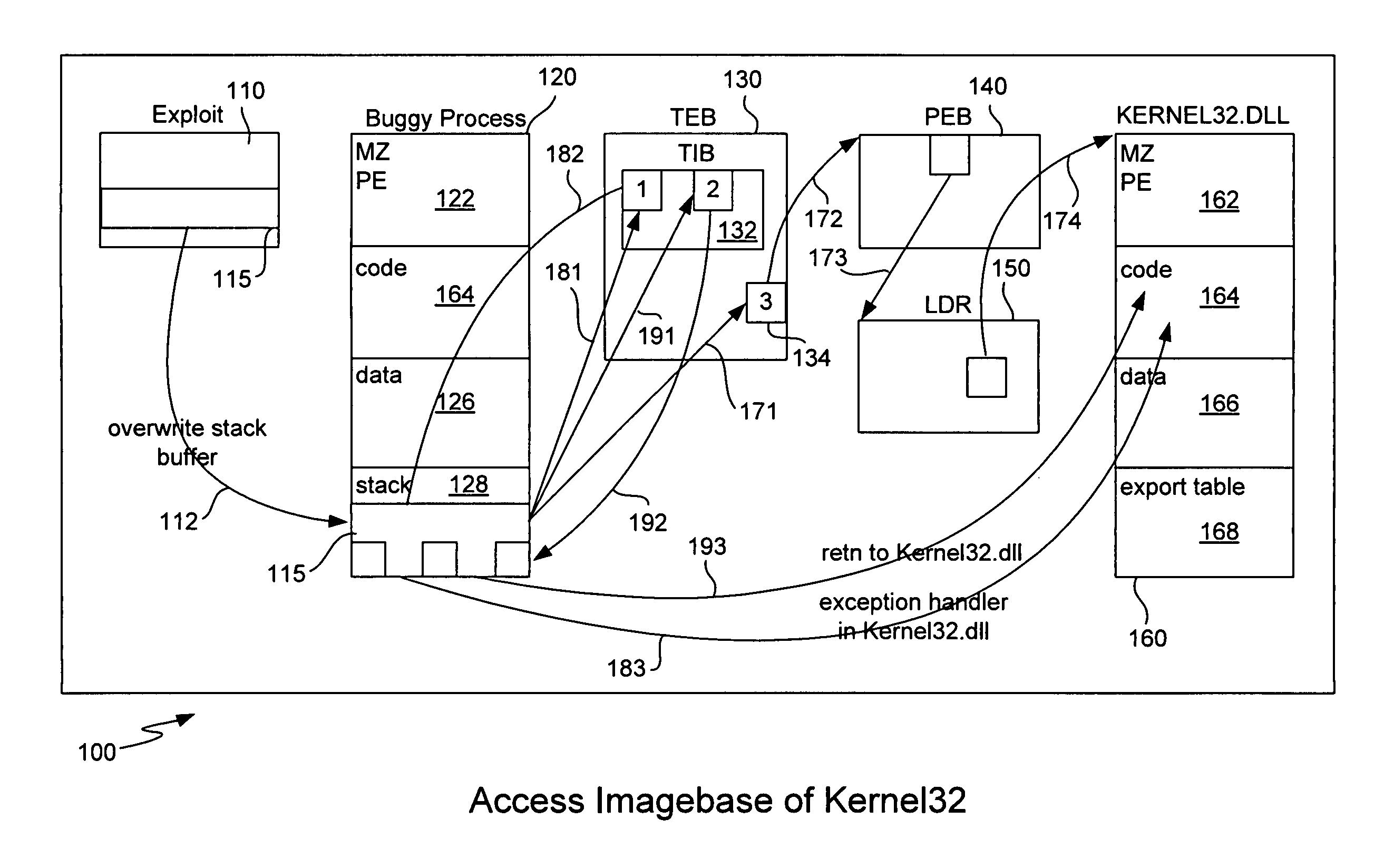
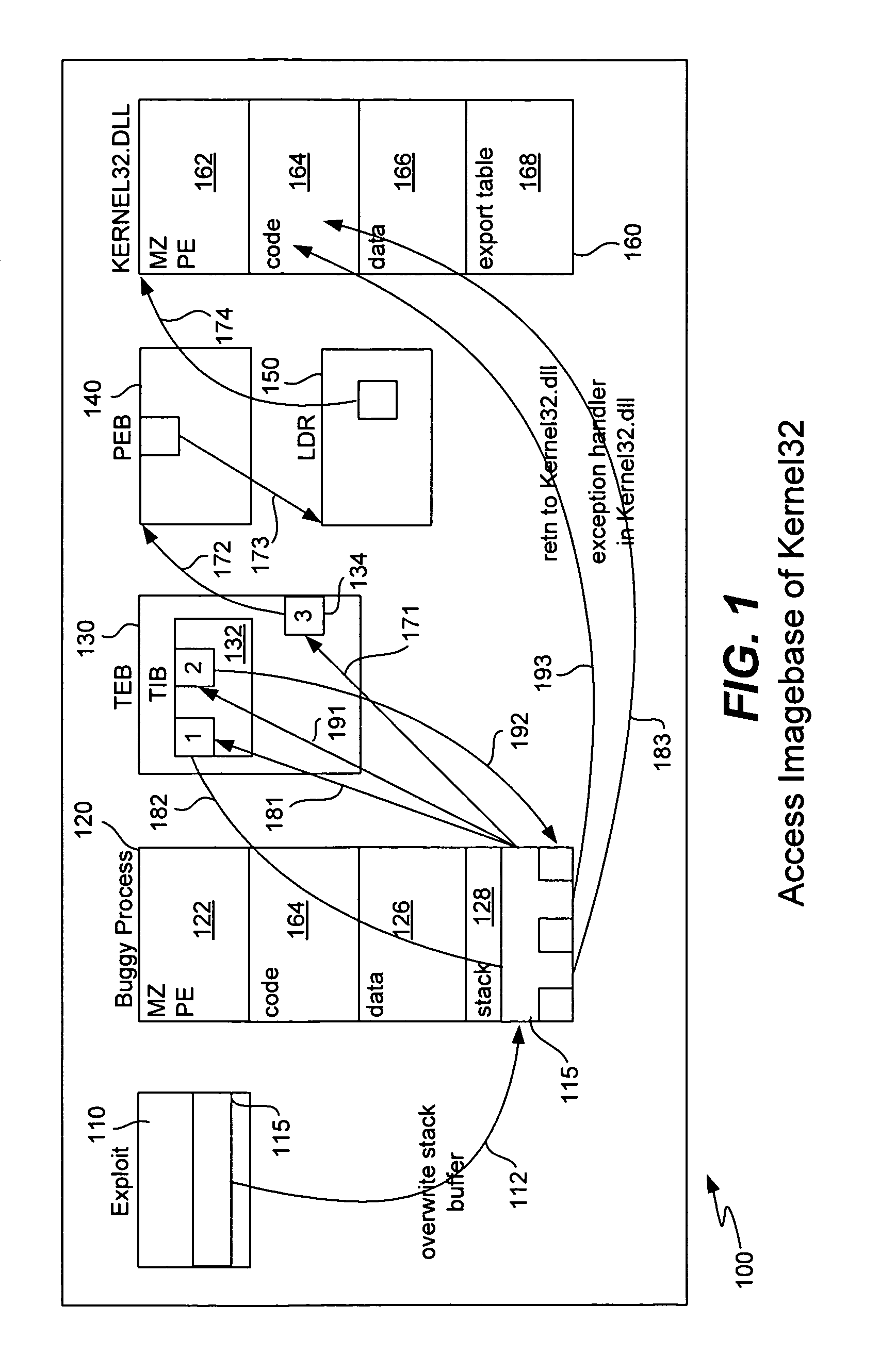
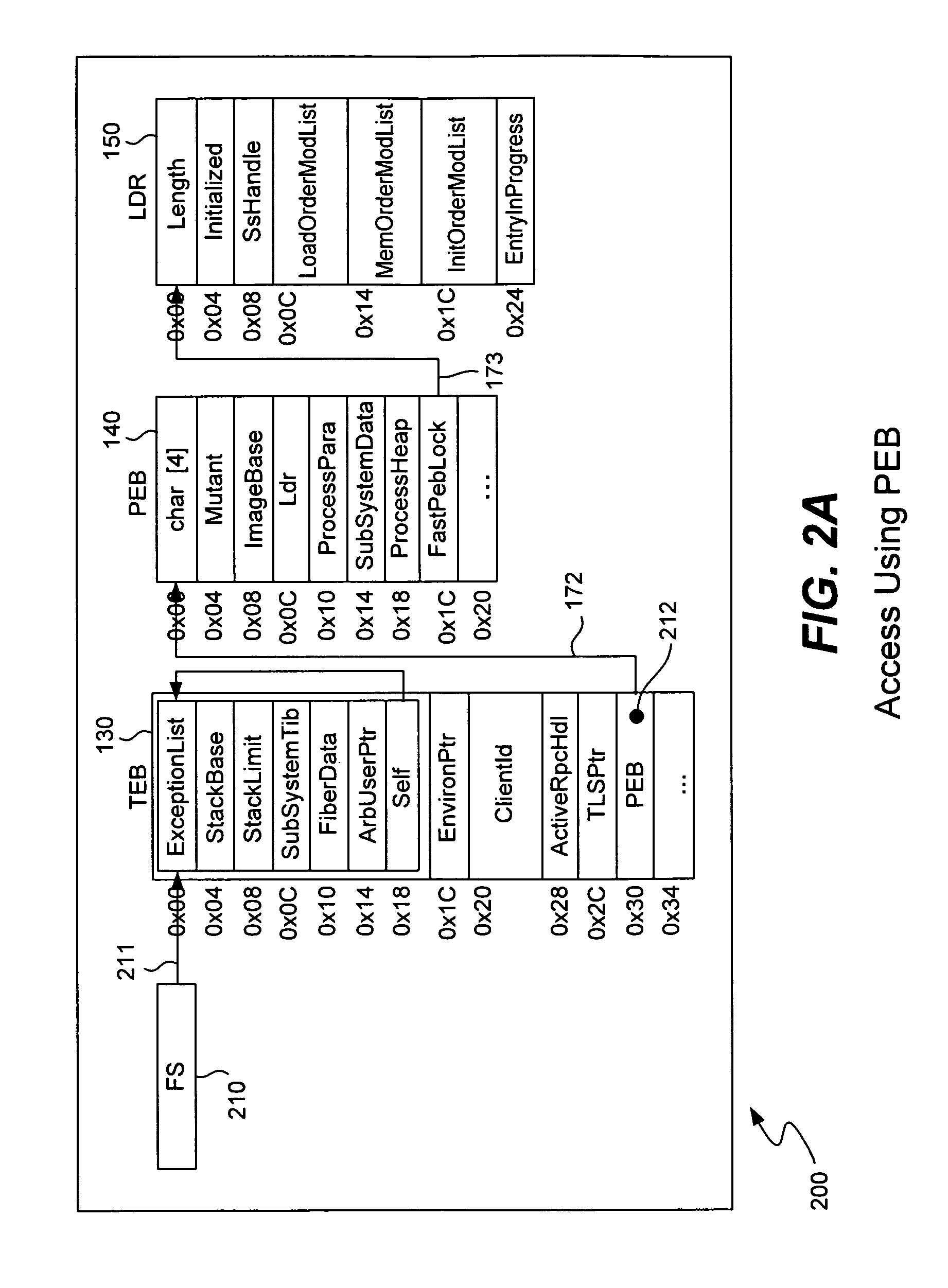
ActiveUS8307432B1Quick analysisImprove the detection rateMemory loss protectionError detection/correctionBuffer overflowShellcode
Detecting buffer-overflow exploits scans generically for shellcode without using virus signatures and maintains close to a zero false-positive rate. Shellcode is detected generically without determining specifically which buffer-overflow exploit is being used. Protection is offered against unknown buffer-overflow exploits. A file is scanned to determine if a vulnerable buffer in that file includes suspect code that has characteristics of shellcode. Next, it is determined if the suspect code contains a routine to find the imagebase of Kernel32.dll using any of the techniques of PEB, TOS or SEH (process environment block, top of stack or structured exception handling). It is next determined if the suspect code contains a routine to search for APIs in the export table of kernel32.dll. Techniques for analyzing the suspect code include static analysis and executing the code in an emulator. A high sensitivity setting determines that shellcode is present when any of the techniques of PEB, TOS or SEH are found.
Owner:TREND MICRO INC
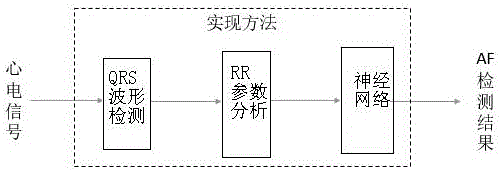
Method for realizing automatic recognition of atrial fibrillation on mini dynamic electrocardiogram monitoring equipment
InactiveCN106073755AImprove the detection rateEasy to useDiagnostic recording/measuringSensorsEcg signalHuman body
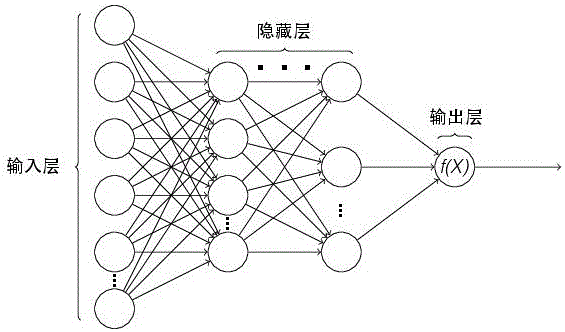
The invention discloses a method for realizing automatic recognition of atrial fibrillation on mini dynamic electrocardiogram monitoring equipment. The method includes: calling an MIT-BIH arrhythmia database, an MIT-BIH normal sinus rhythm database and a long-time atrial fibrillation database as training samples, and introducing an artificial neural network for learning training; setting a weight value for each layer of the artificial neural network, and inputting the training data samples to repeatedly and iteratively correct the weight value of each layer until training errors are less than a certain specified value, through the means, a weight value matrix capable of judging occurrence of atrial fibrillation can be found; utilizing the weight value matrix, and adding the same into an original artificial neural network to build a new artificial neural network; using collected electrocardiosignals of a target human body, processing the electrocardiosignals of the human body, acquiring a target human body feature vector X, and performing prediction operation according to the target human body feature vector X and the new artificial neural network.
Owner:成都信汇聚源科技有限公司
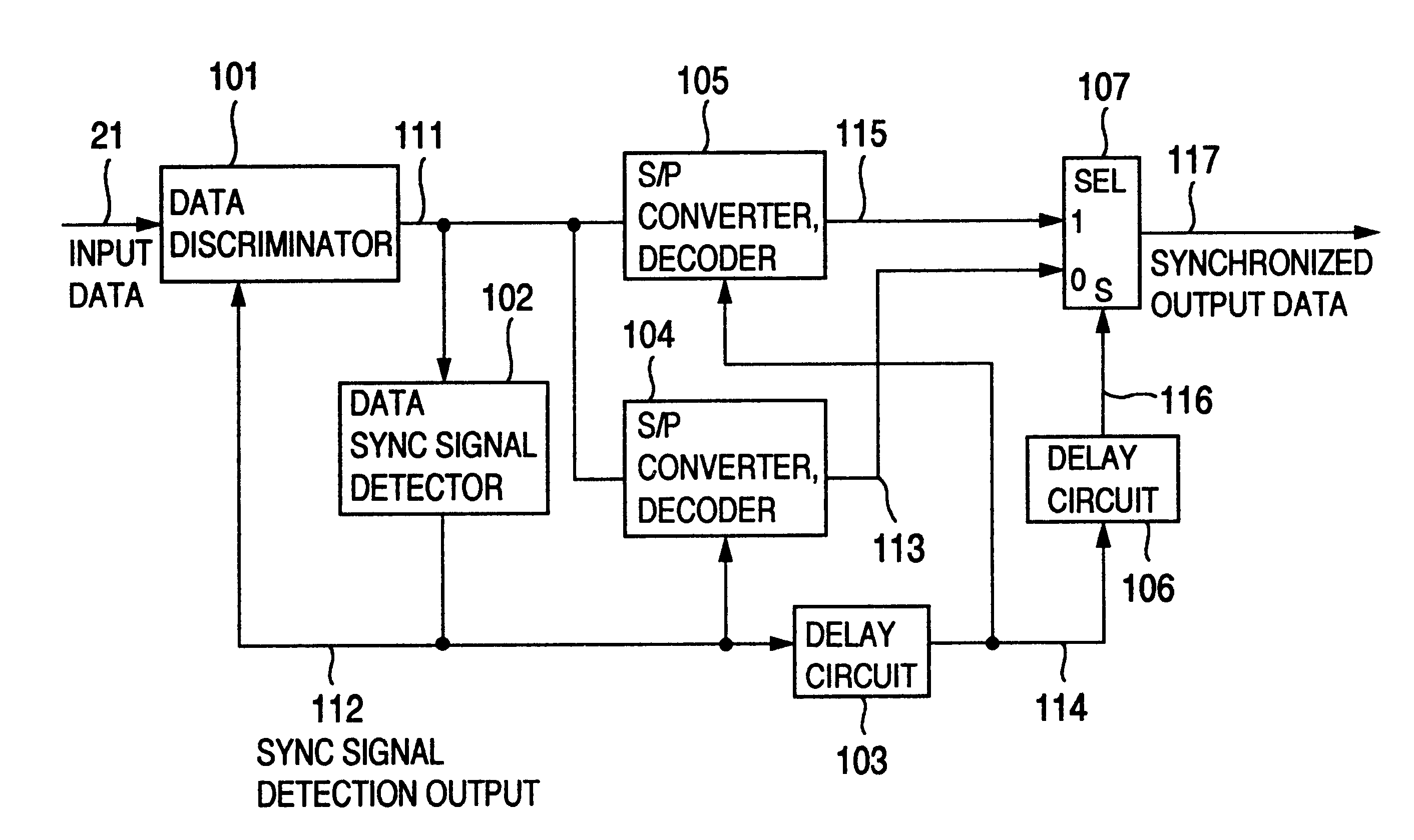
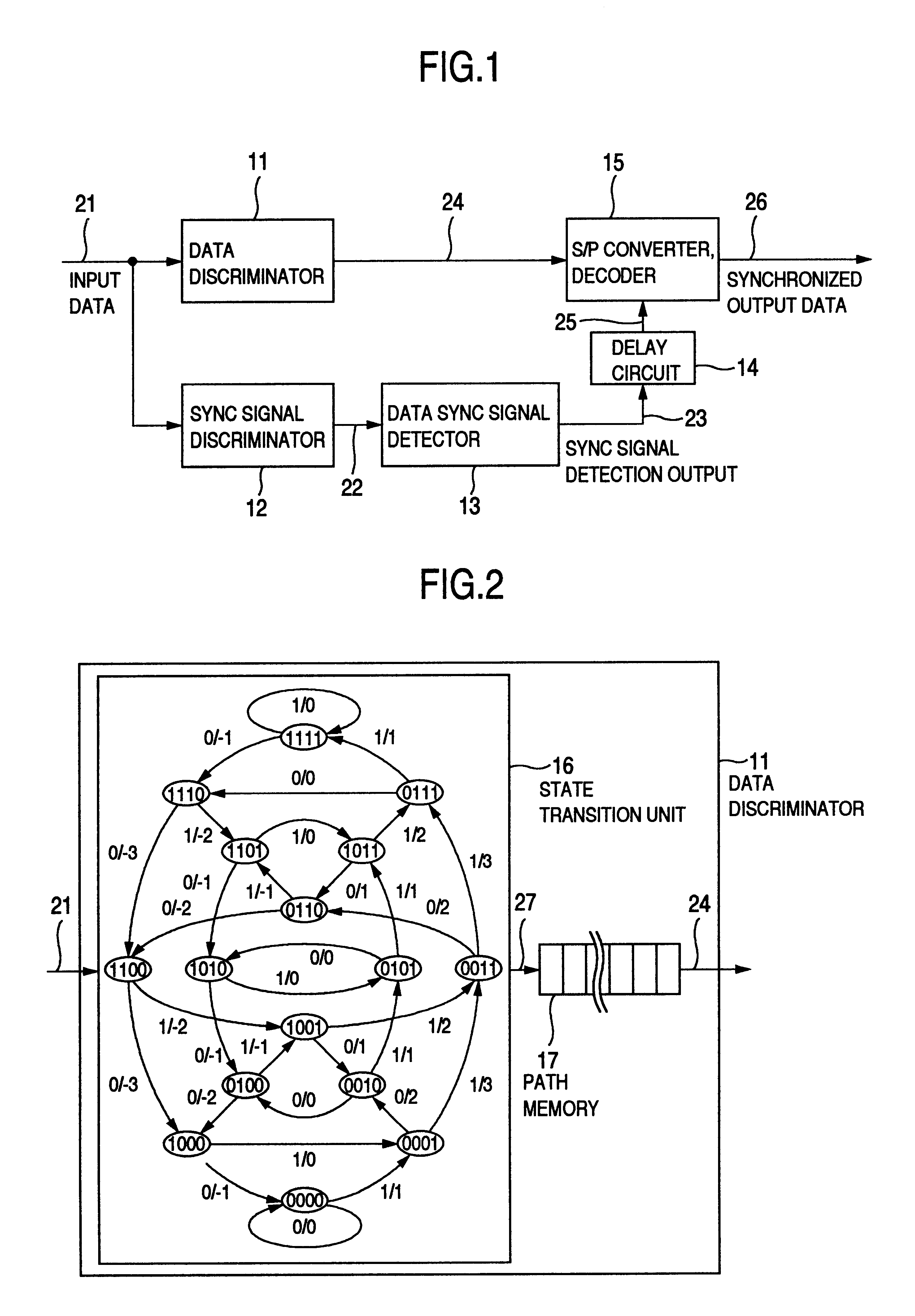
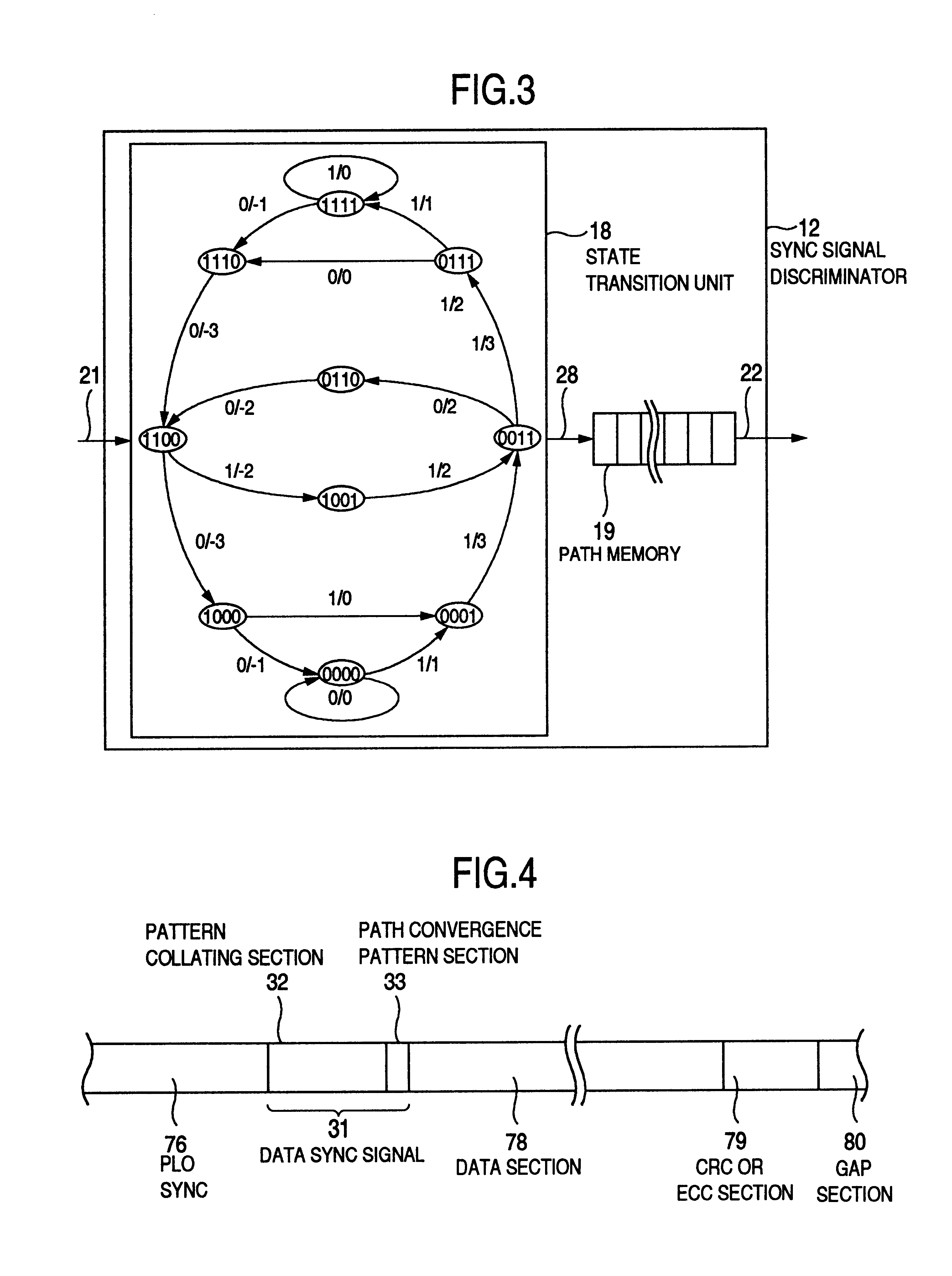
Data synchronizing signal detector, signal processing device using the detector, information recording and reproducing apparatus having the detector and the device, data synchronizing signal detecting method, and information recording medium for using in the method
InactiveUS6791777B2Improve accuracyImprove the detection rateModification of read/write signalsSynchronisation information channelsDiscriminatorData synchronization
A data discriminating unit includes a data discriminator and a sync signal discriminator. A data sync signal is detected for the bit string discriminated from the output of the sync signal discriminator, and the data is demodulated for the bit string discriminated from the output of the data discriminator, thereby optimizing the signal to a form suitable for discrimination and detection of the data sync signal and demodulation for data reproduction. As a result, the detection performance of the data sync signal can be improved while maintaining the data discrimination performance. A Viterbi decoder is used for discrimination by the data discriminator and the sync signal discriminator for the optimization thereby to optimize the number of states, the number of paths for state transition and the path memory length. A signal having no continuous inversions of the recording data is used as the data sync signal.
Owner:HITACHI GLOBAL STORAGE TECH JAPAN LTD +1
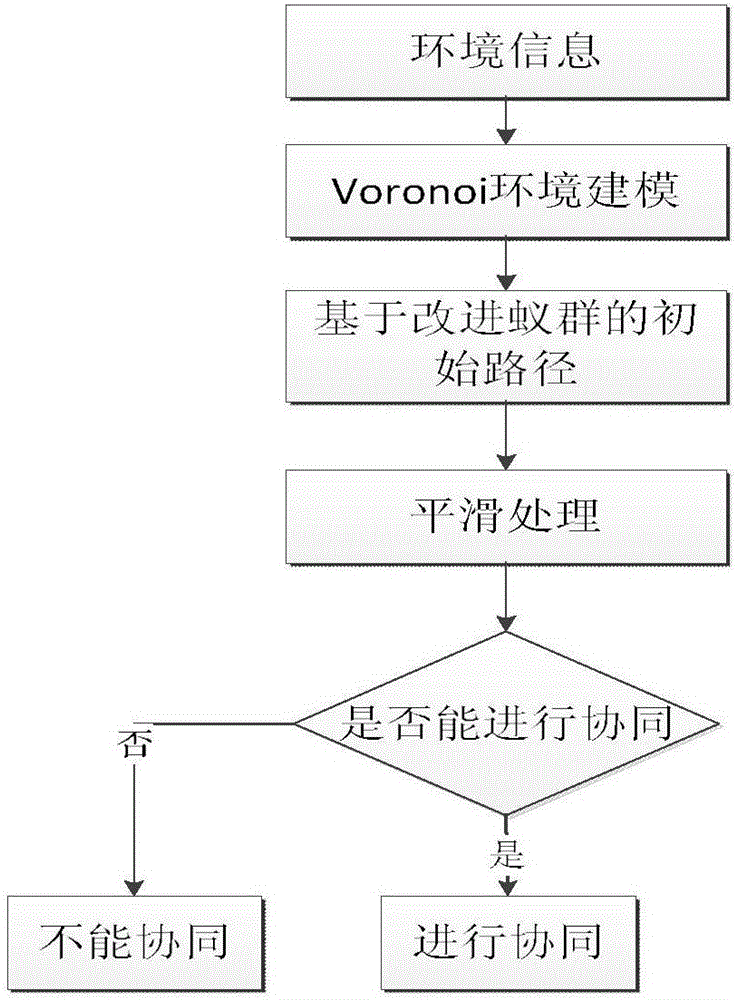
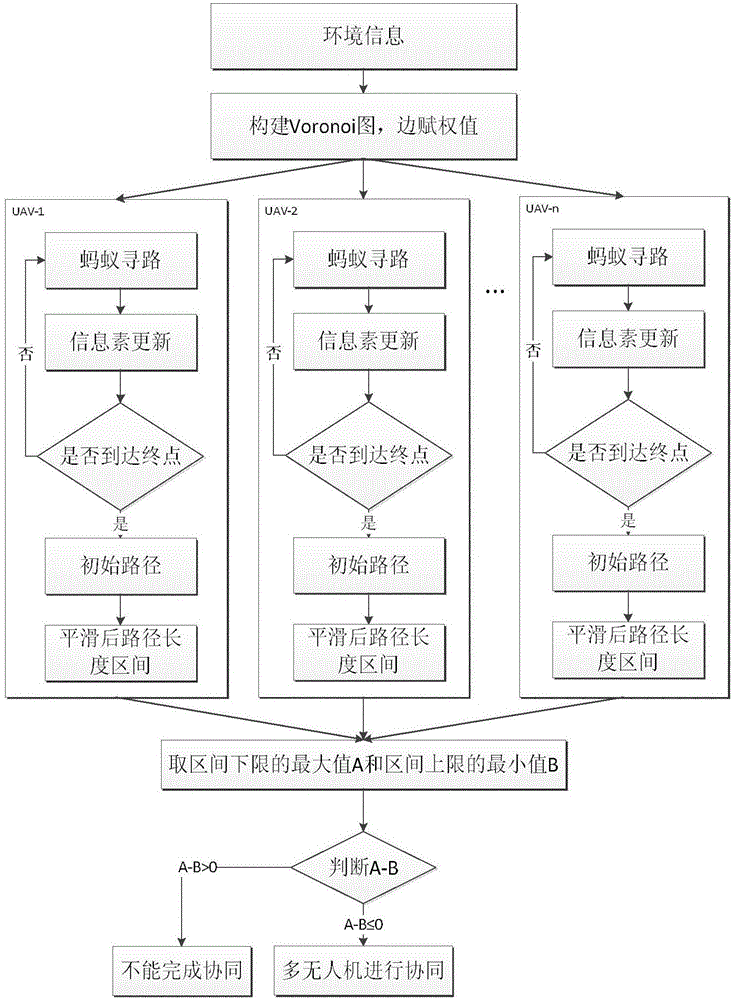
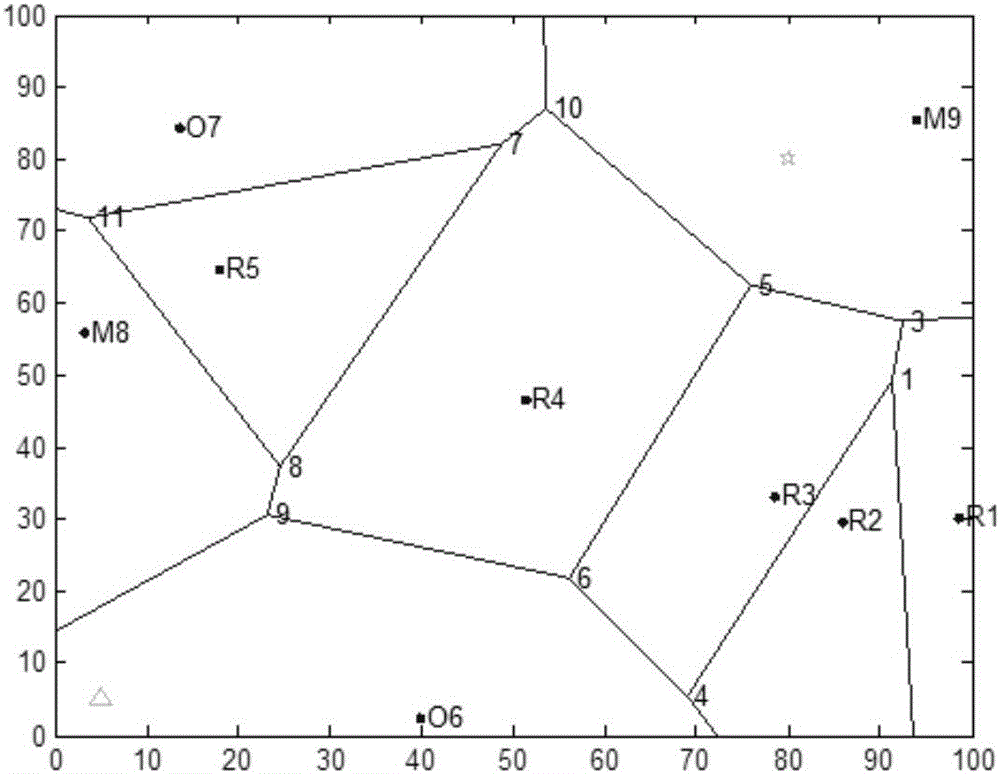
Multi-UAV(Unmanned Aerial Vehicle) cooperation path planning method based on ant colony algorithm
ActiveCN106705970AAvoid prematureFast convergenceNavigational calculation instrumentsBuilt environmentAnt colony
The invention discloses a multi-UAV (Unmanned Aerial Vehicle) cooperation path planning method based on an ant colony algorithm. The method comprises the following steps of (1) analyzing a UAV flight environment, and building environment modeling based on a Voronoi diagram; (2) calculating consideration of an edge in the environment modeling based on the Voronoi diagram; (3) utilizing the ant colony algorithm to plan an initial path for a UAV; (4) smoothing the initial path of each UAV to judge whether cooperation is achieved or not, and carrying out corresponding operation according to the results. According to the multi-UAV cooperation path planning method based on the ant colony algorithm provided by the invention, multiple different kinds of unmanned aerial vehicles are mutually cooperated, intelligently and autonomously adapt to complicated and changeable war environment factors, and dynamically adjust self-strategies so as to cooperatively accomplish the combat mission.
Owner:CHINESE AERONAUTICAL RADIO ELECTRONICS RES INST
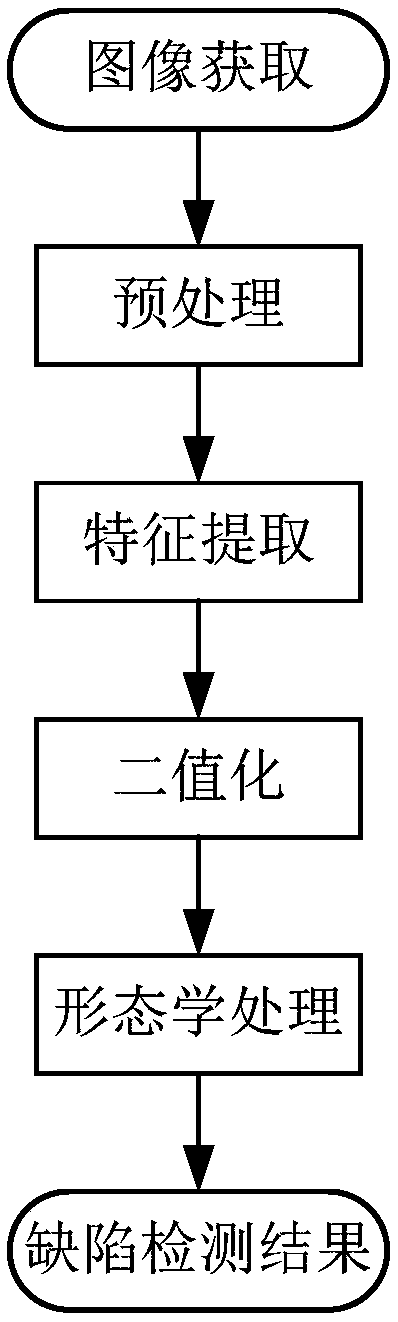
Surface defect detection method and device and electronic device
ActiveCN110619618AImprove the detection rateRaise the possibilityImage enhancementImage analysisSample imageNetwork model
The embodiment of the invention provides a surface defect detection method and device and an electronic device, and the method comprises the steps: obtaining a to-be-detected image; inputting an image to be detected into a deep learning network model obtained through pre-training, obtaining a defect-free reconstructed image corresponding to the image to be detected, and the deep learning networkmodel being a deep learning network model obtained through pre-training based on a sample training set containing multiple defect-free training sample images; subtracting the reconstructed image fromthe to-be-detected image to obtain a difference image; and in the difference image, determining that a surface defect exists in a corresponding region in the to-be-detected image if a region of whichthe difference is greater than a preset difference exists. Through the scheme, the detection rate of the surface defects can be improved.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com