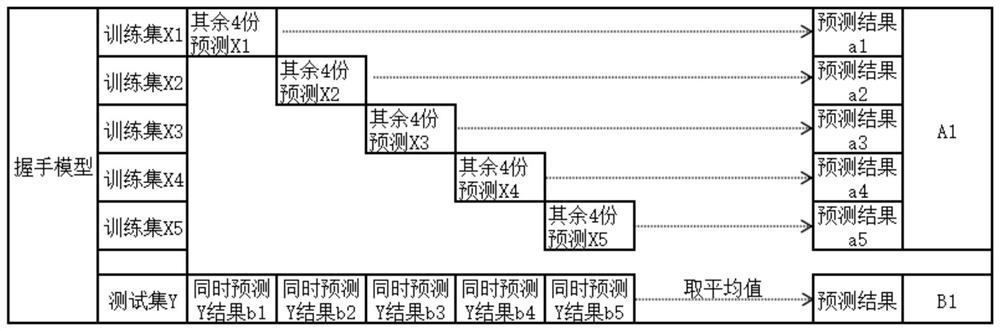
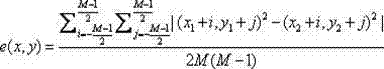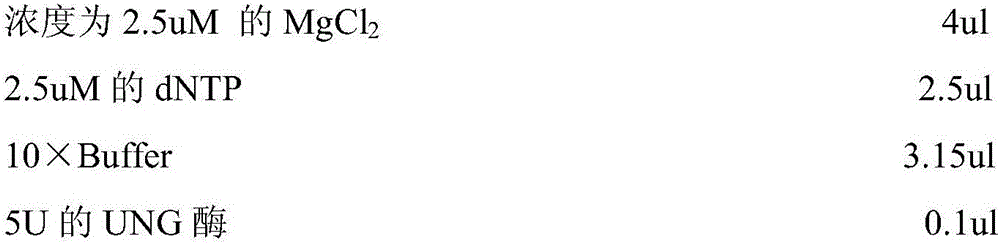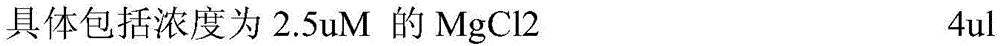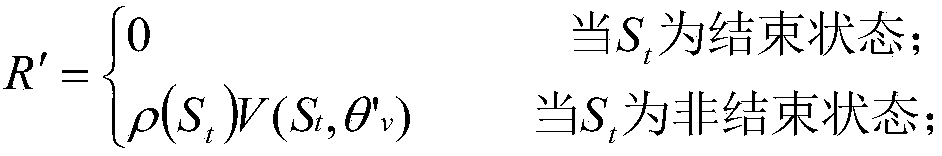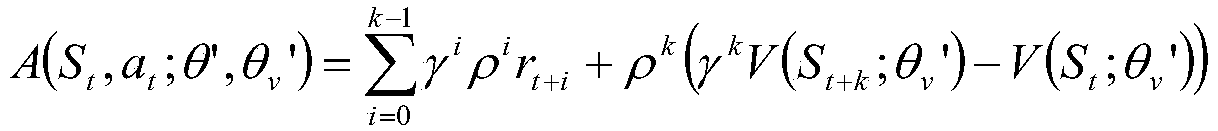Patents
Literature
69results about How to "Solve the high false positive rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
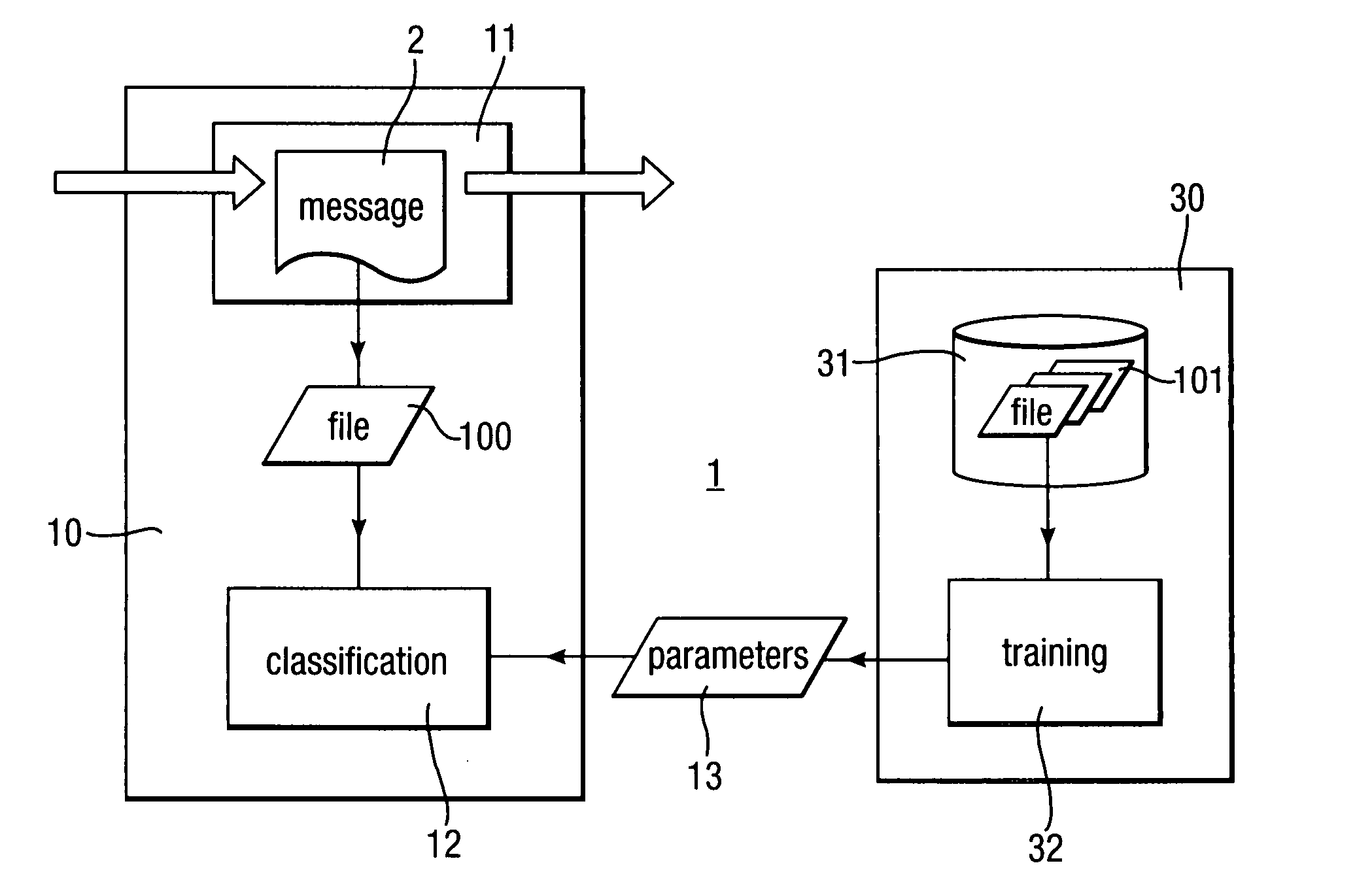
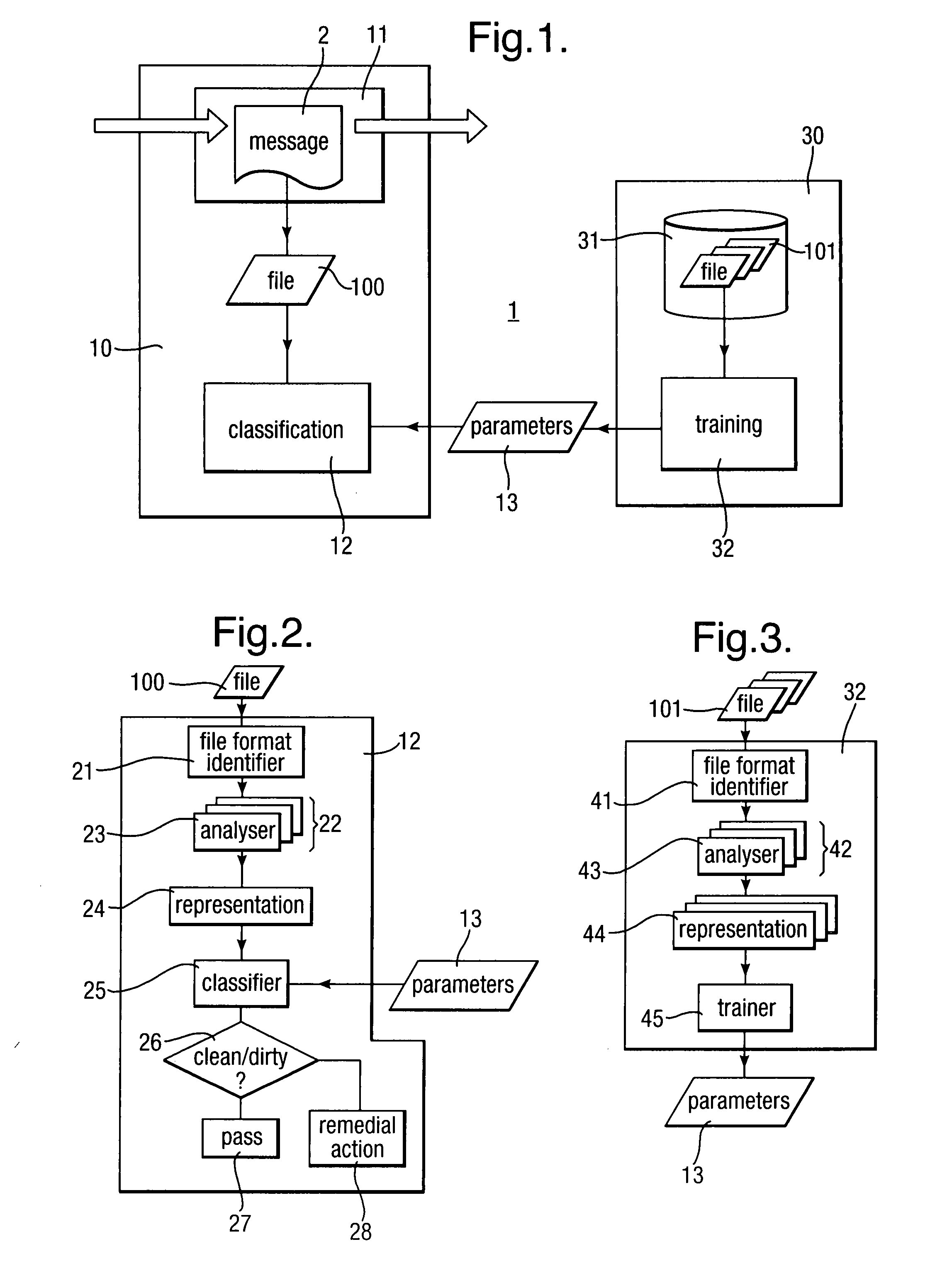
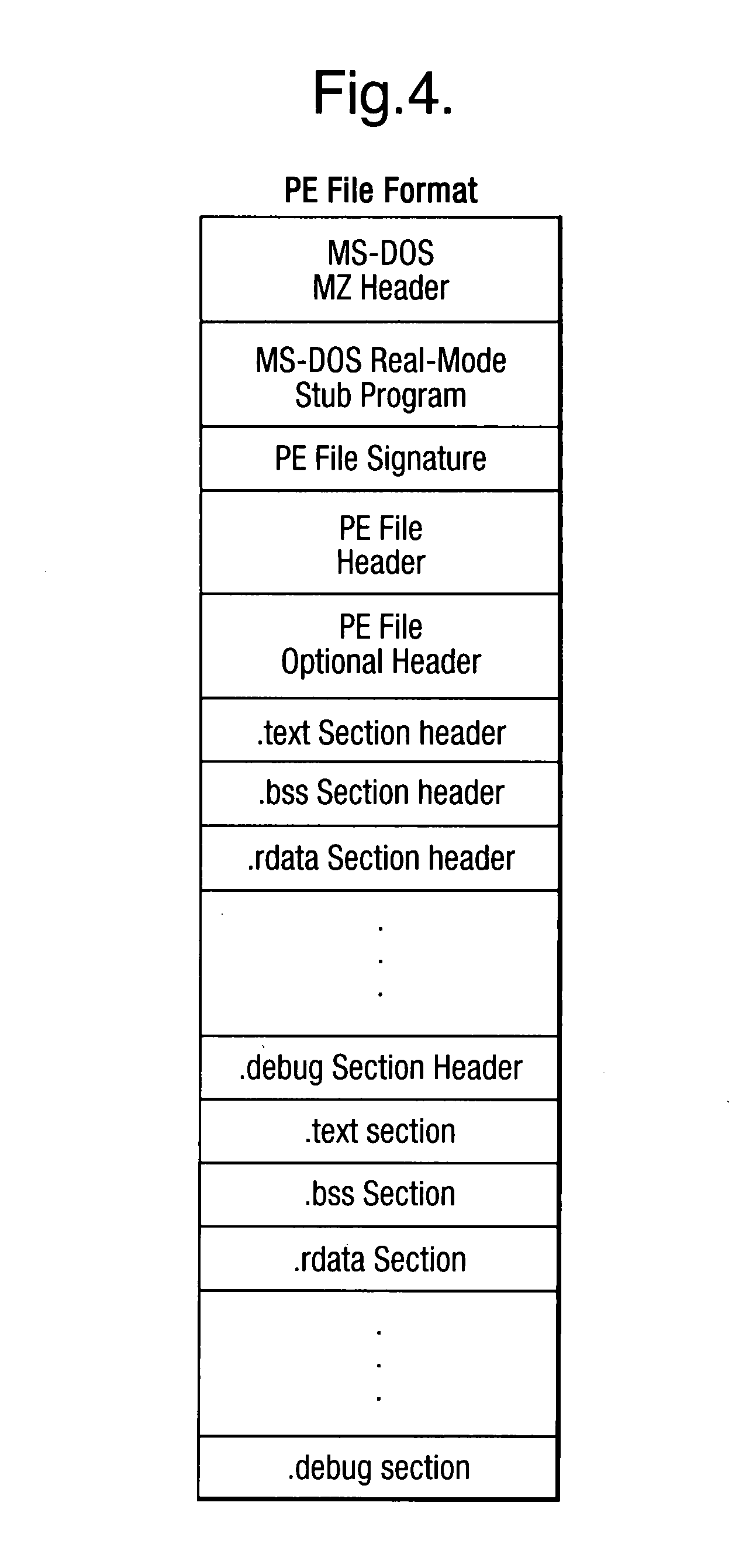
Heuristic detection of malicious code
InactiveUS20090013405A1Avoid the needImprove the detection rateMemory loss protectionUnauthorized memory use protectionData fieldMalware
Scanning of computer files for malware uses a classifying technique to classify an input file as a clean file or a dirty file. The parameters of the classifying technique are derived to train the classification on a corpus of reference files including clean files known to be free of malware and dirty files known to contain malware. The classification is performed using a representation of the files in a feature space defined by a set of predetermined features for respective file formats, the features being a predetermined value or range of values for one or more data fields of given meanings. The representation of a file is derived by determining the file format, parsing the file on the basis of the structure of data fields in the determined file format to identify the data fields and their meaning, and determining, on the basis of the identified data fields, which of the set of predetermined features are present.
Owner:SYMANTEC CORP
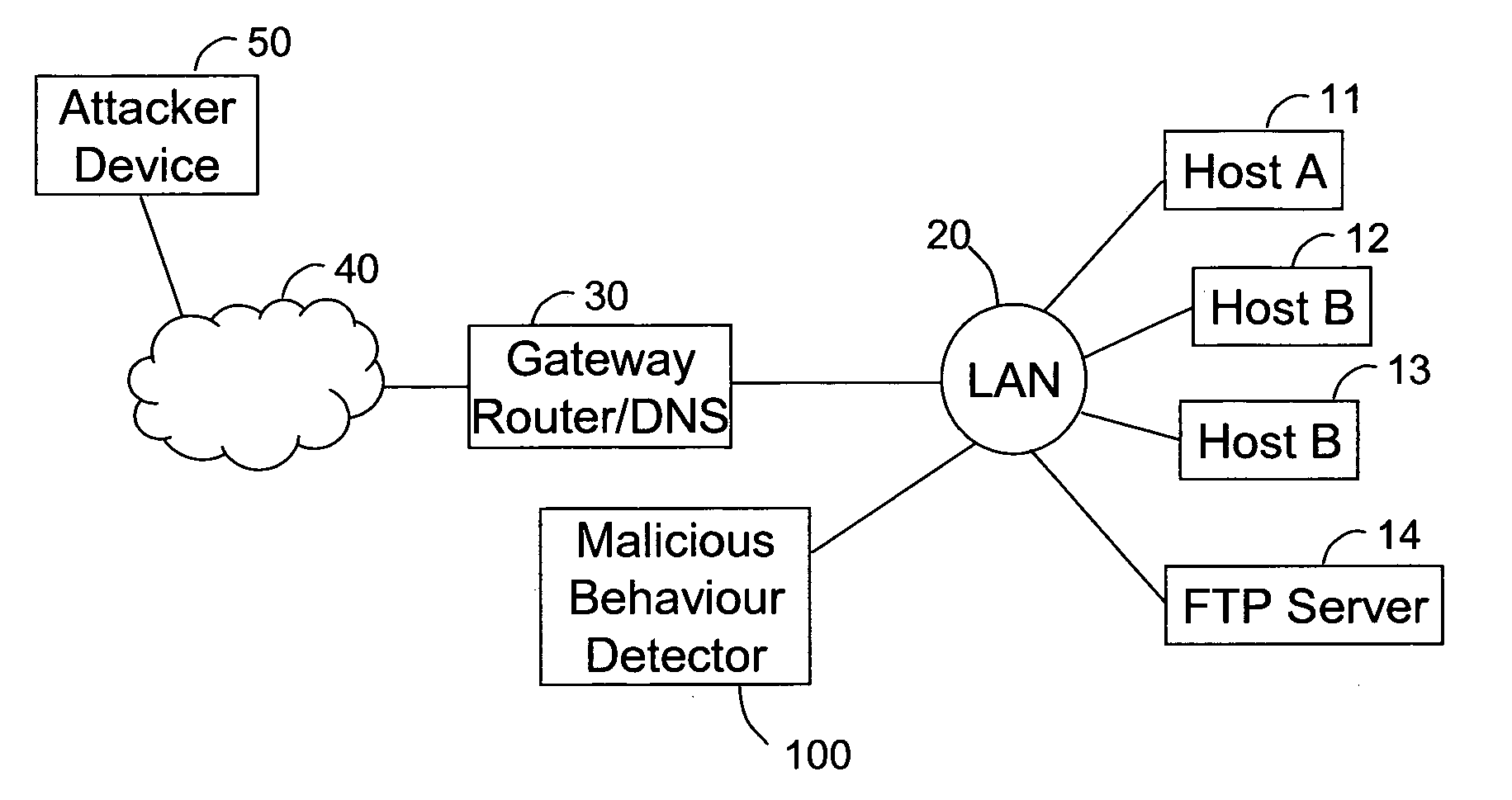
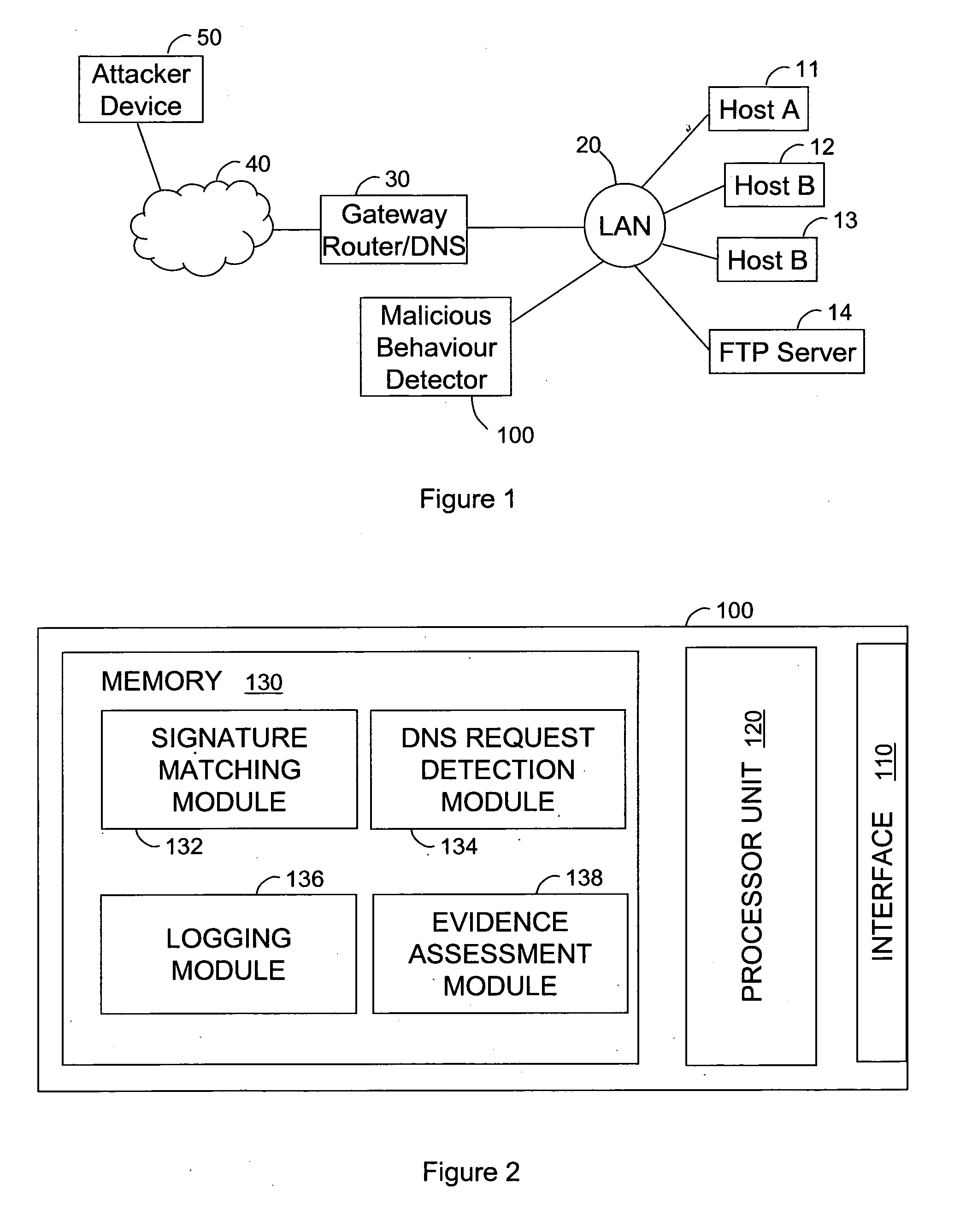
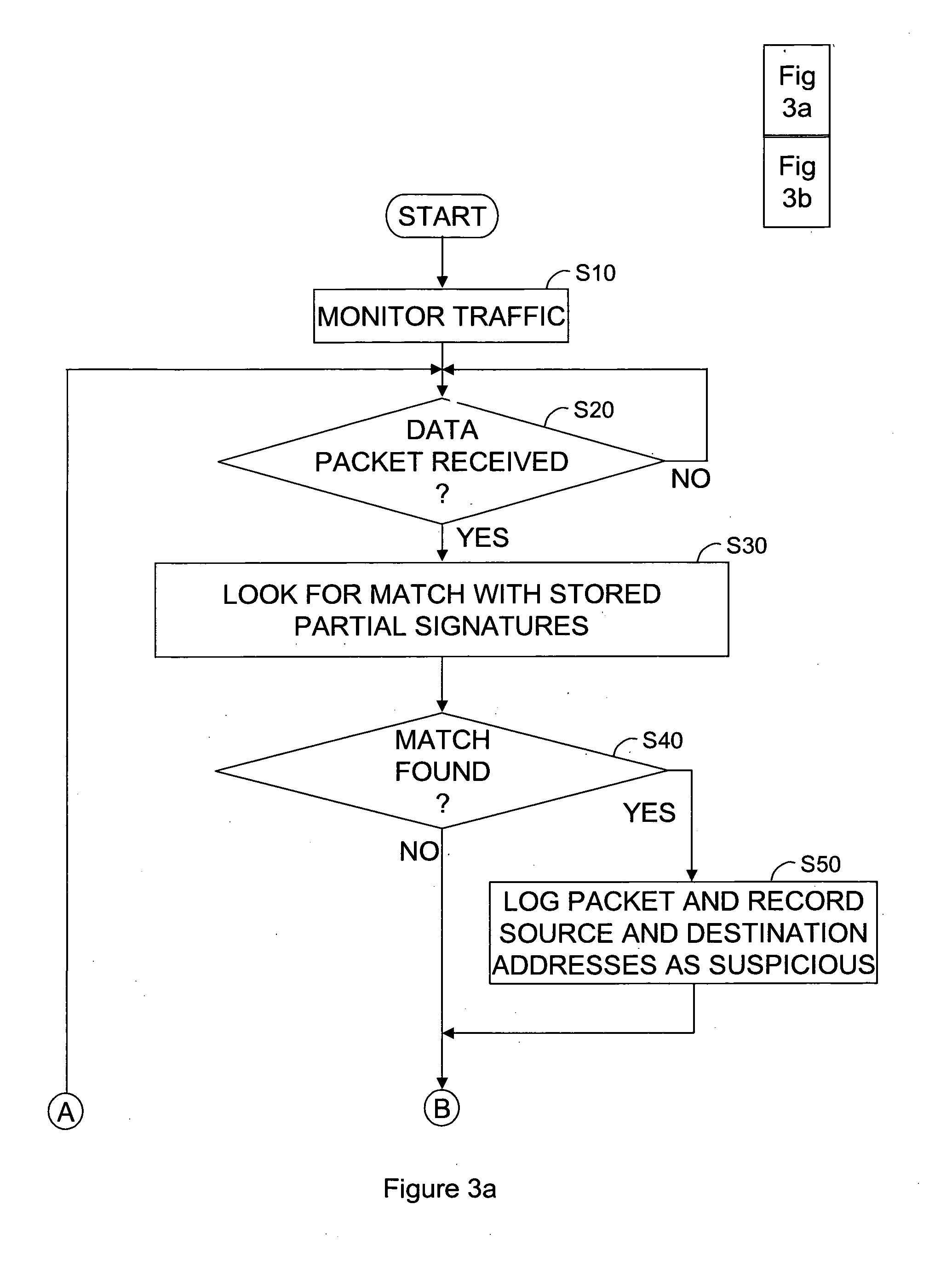
Detecting malicious behaviour on a computer network
ActiveUS20110302656A1Increase opportunitiesReduce riskMemory loss protectionError detection/correctionDomain nameNetwork packet
A malicious behaviour detector (100) for detecting malicious behaviour on a network, comprises a processor unit (120) and associated system memory (130) containing computer program code. The computer program code provides a signature matching module (132) to perform malicious partial signature detection by reading the contents of packets of data passing through the network to look for partial signatures associated with malicious programs; a Domain Name Service, DNS, request and / or response detection module (134) to monitor the requests made by hosts connected to the network and / or responses thereto; and an evidence assessment module (138) to analyse the results of the partial signature detection and the DNS monitoring make a determination of the suspected presence of malicious behaviour on the network based upon the analysis of the results of both the partial signature detection and the DNS monitoring.
Owner:BRITISH TELECOMM PLC
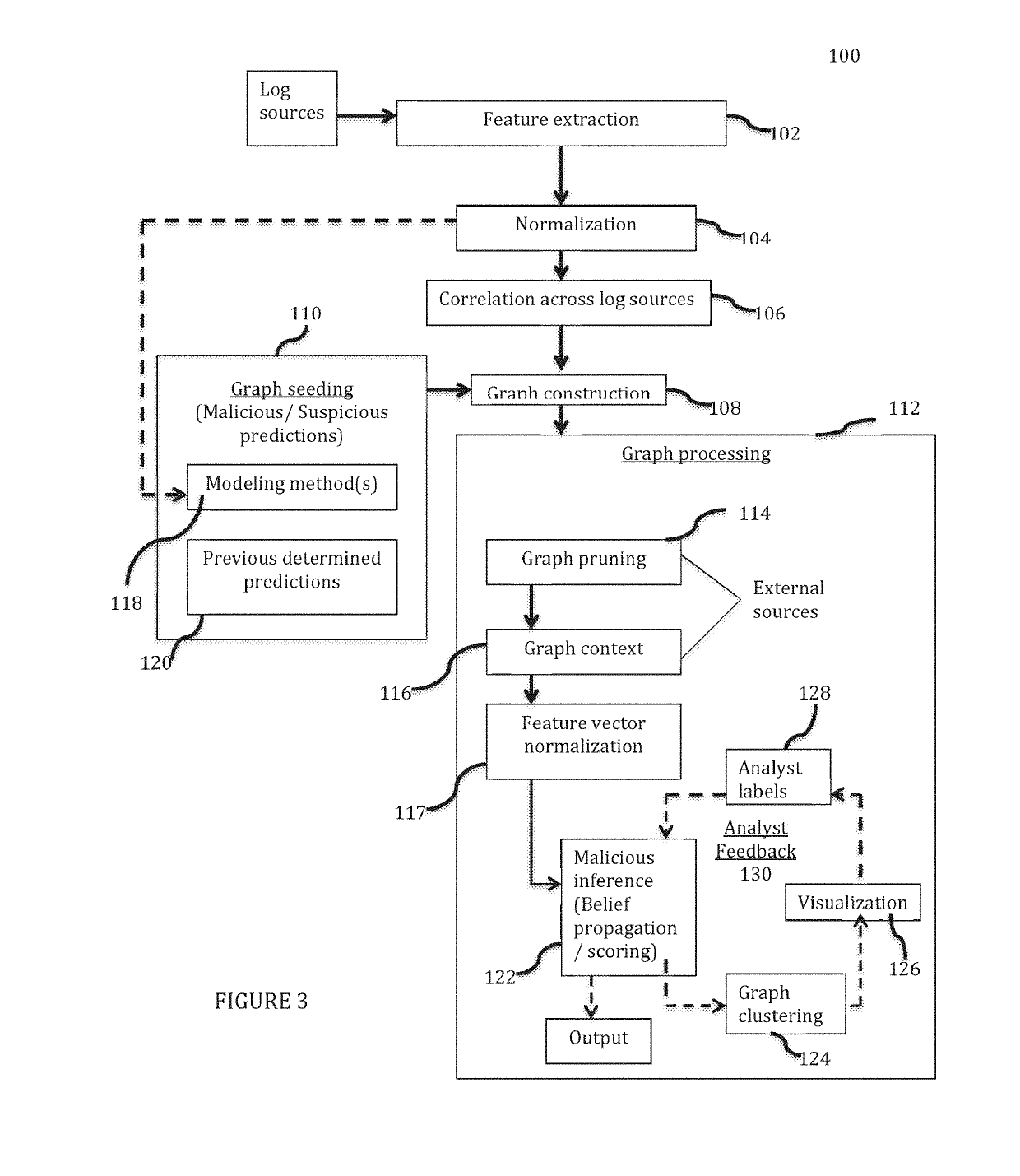
Method and system for employing graph analysis for detecting malicious activity in time evolving networks
ActiveUS20190132344A1Demonstrate scalabilityDemonstrate effectivenessComputer security arrangementsProbabilistic networksGraph inferenceClassification methods
Disclosed is a method and system for detecting malicious entities and malicious behavior in a time evolving network via a graph framework by modeling activity in a network graph representing associations between entities. The system utilizes classification methods to give score predictions indicative of a degree of suspected maliciousness, and presents a unified graph inference method for surfacing previously undetected malicious entities that utilizes both the structure and behavioral features to detect malicious entities.
Owner:CORELIGHT INC
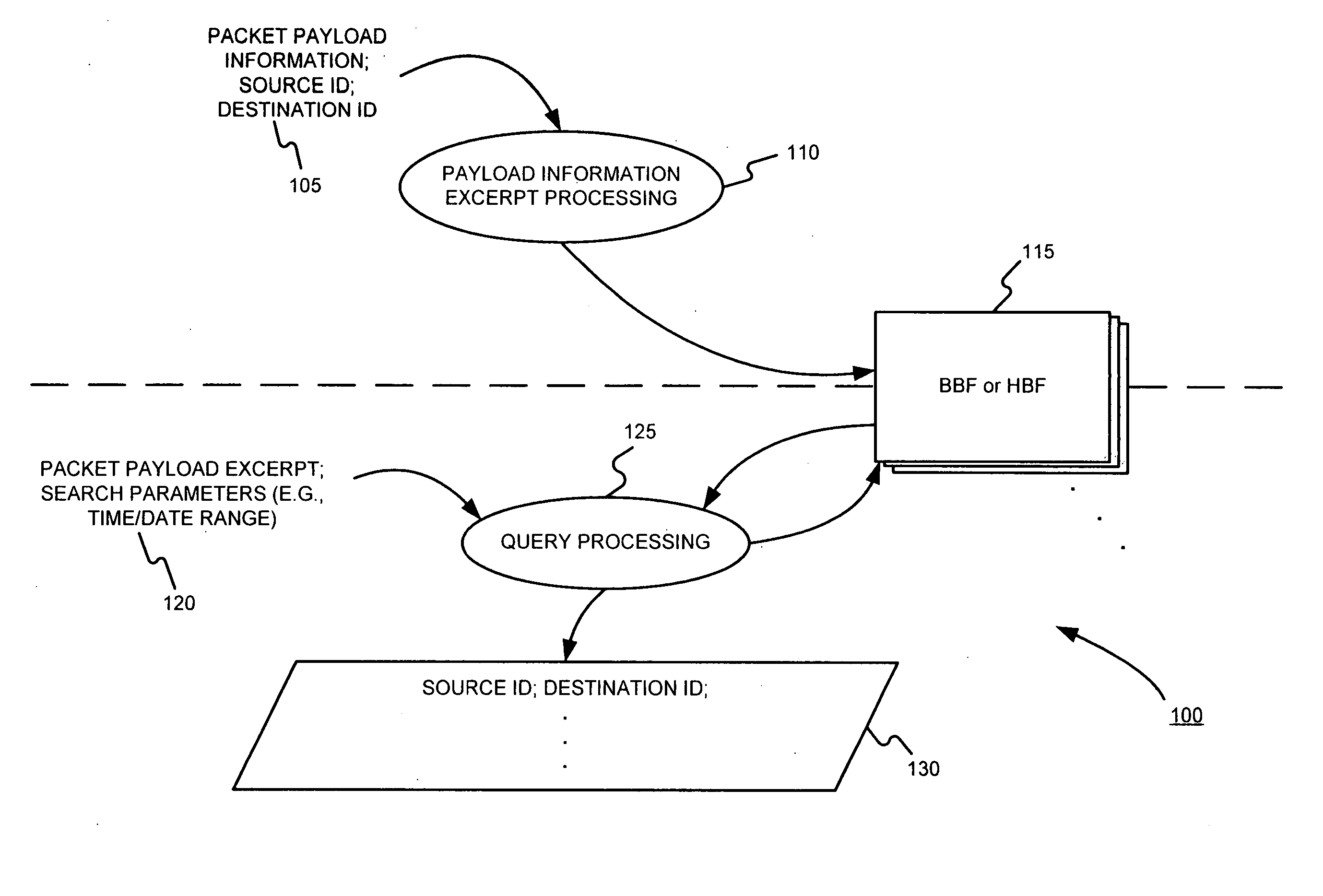
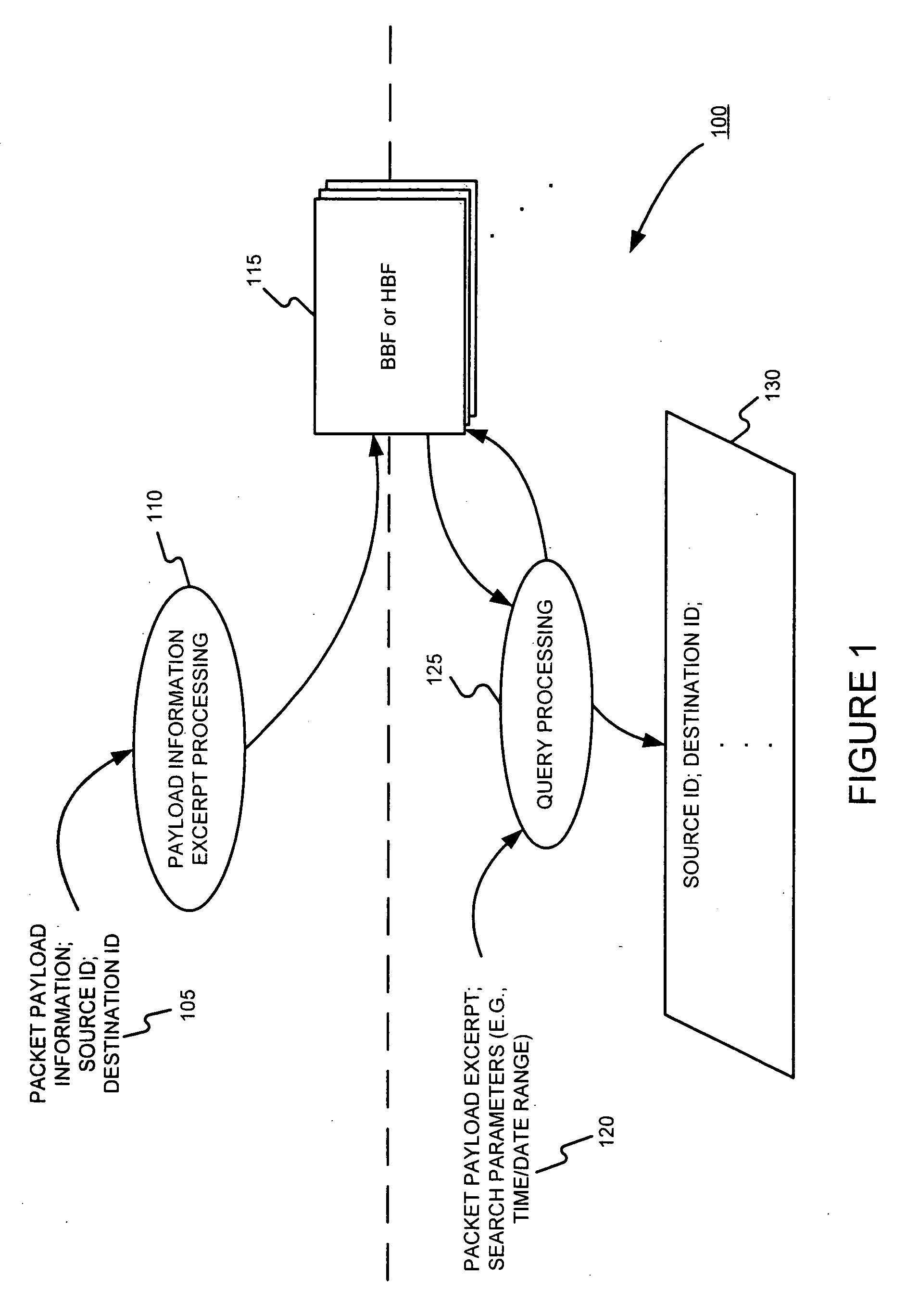
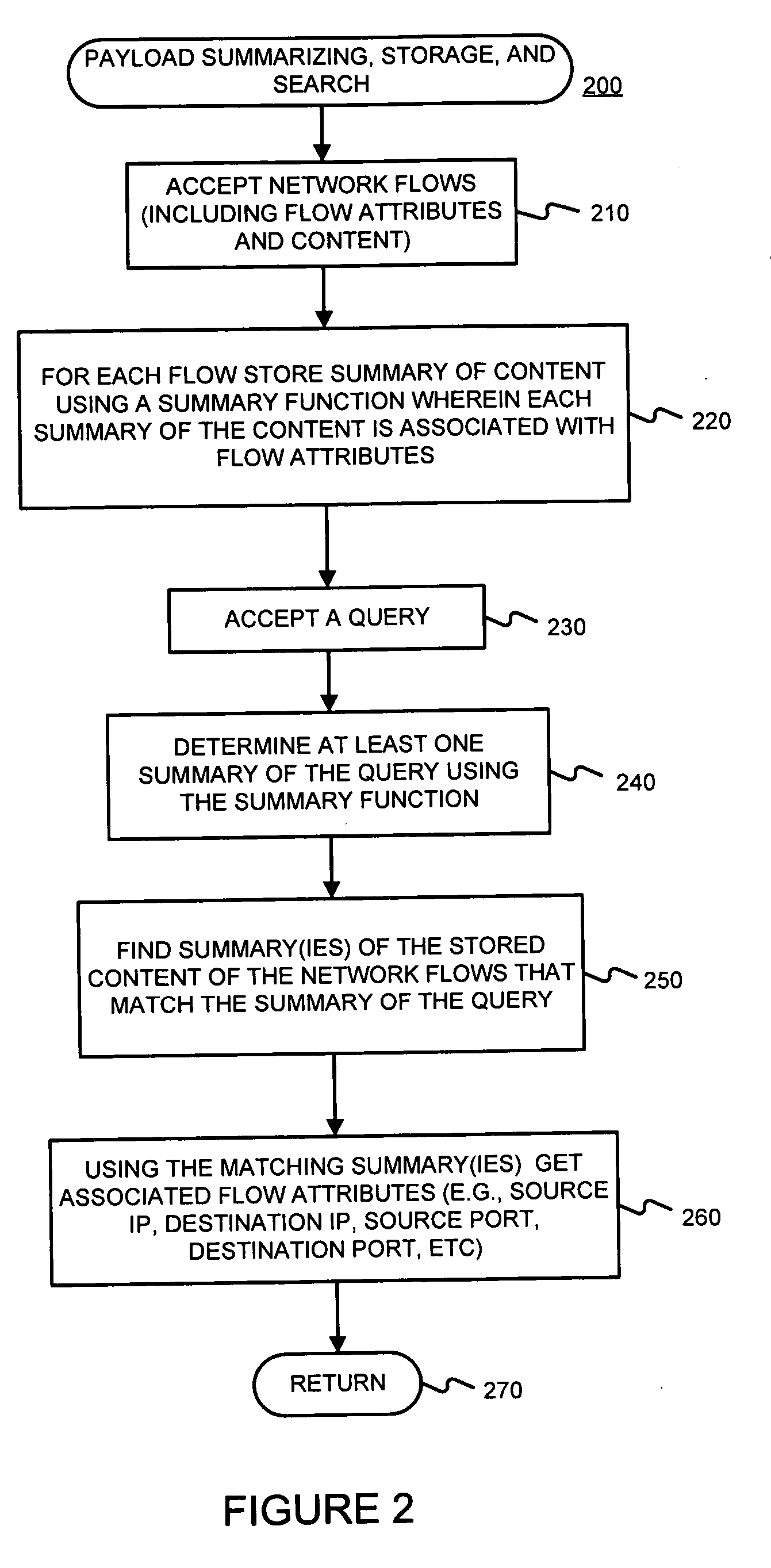
Facilitating storage and querying of payload attribution information
InactiveUS20060072582A1Solve the high false positive rateImprove accuracyError preventionFrequency-division multiplex detailsComputer hardwareBloom filter
A hierarchical data structure of digested payload information (e.g., information within a payload, or information spanning two or more payloads) allows a payload excerpt to be attributed to earlier network flow information. These compact data structures permit data storage reduction, while permitting efficient query processing with a low level of false positives. One example of such a compact data structure is a hierarchical Bloom filter. Different layers of the hierarchy may correspond to different block sizes.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
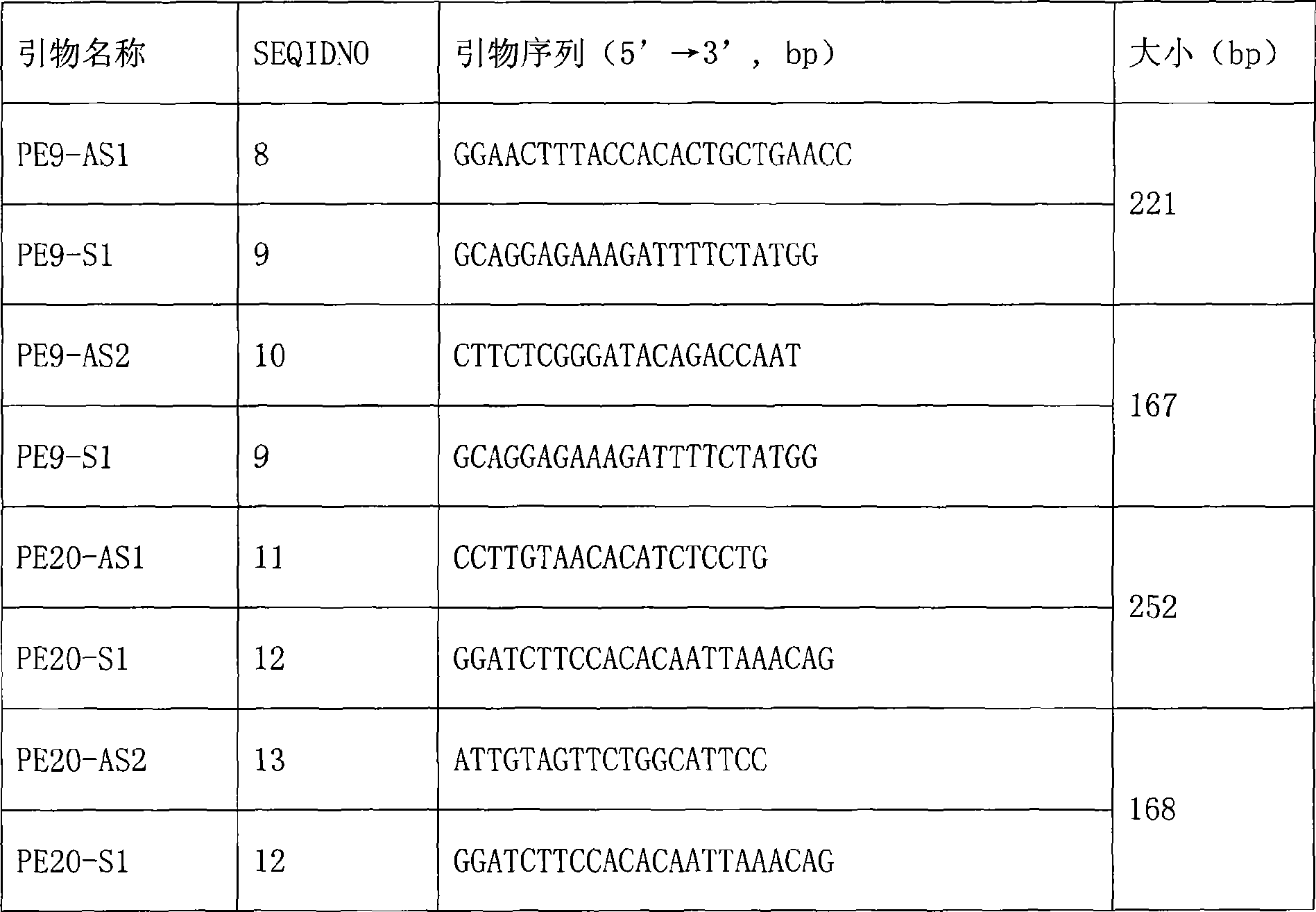
PIK3CA gene mutation detection probe, detection liquid phase chip and detection method thereof
ActiveCN101445832AImprove throughputUniform reaction conditionsMicrobiological testing/measurementDNA/RNA fragmentationPIK3CA Gene MutationBioinformatics
The invention discloses a PIK3CA gene mutation site detection probe, a detection liquid phase chip and a detection method thereof. The PIK3CA gene mutation detection liquid phase chip mainly comprises a microball covered with a probe and a primer for amplifying a target sequence carrying a 9th exon and / or a 20th exon. The PIK3CA gene mutation detection liquid phase chip and the detection method can help simultaneously detect the sites with relatively higher frequency of the PIK3CA gene mutation, and can separately detect the 9th exon and the 20th exon or detect the 9th exon and the 20th exon at the same time, and the detection has uniform reaction condition, good specificity of detection results, high sensitivity, good accuracy up to 90% and short detection time.
Owner:广州益善医学检验所有限公司
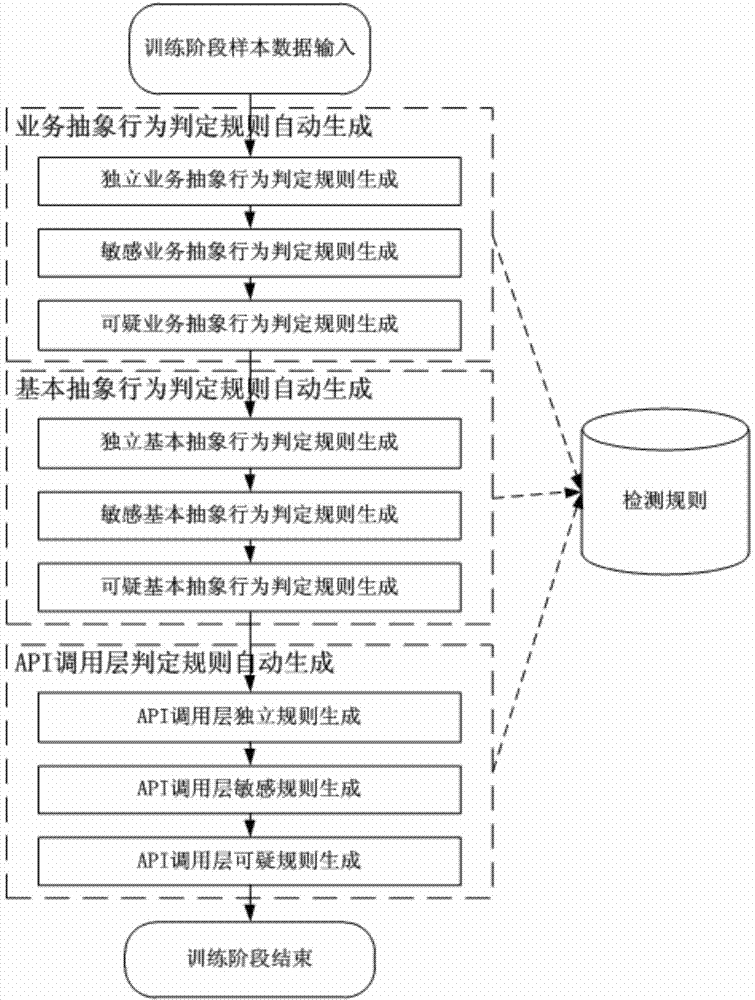
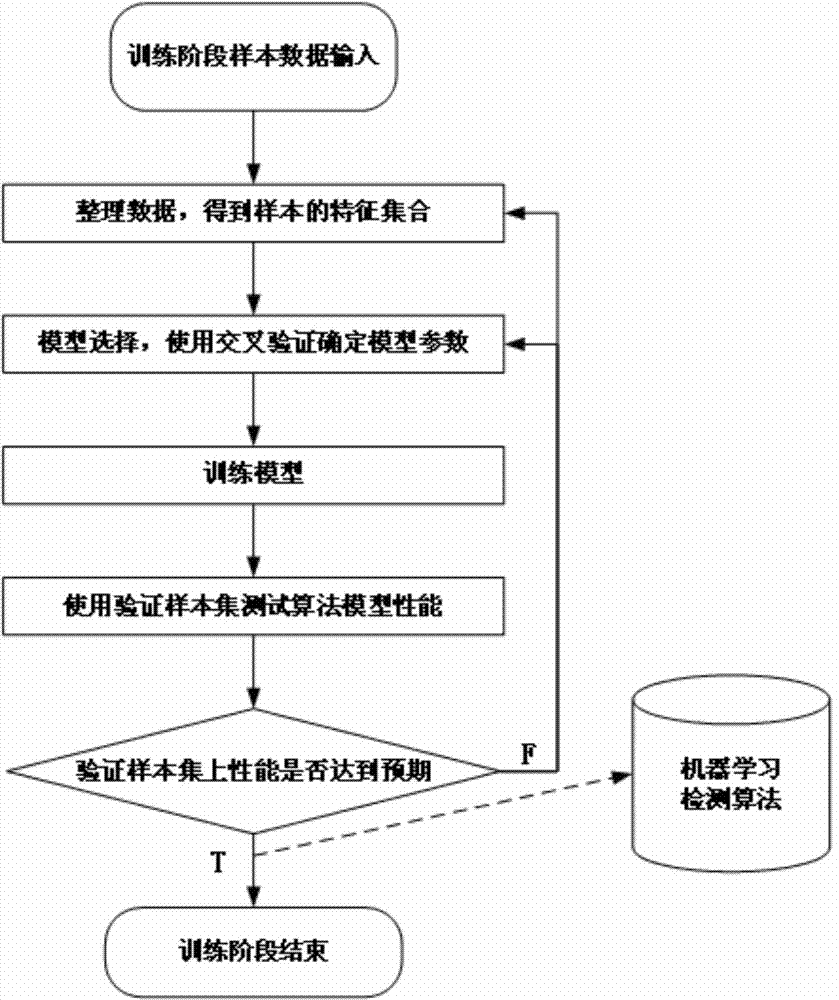
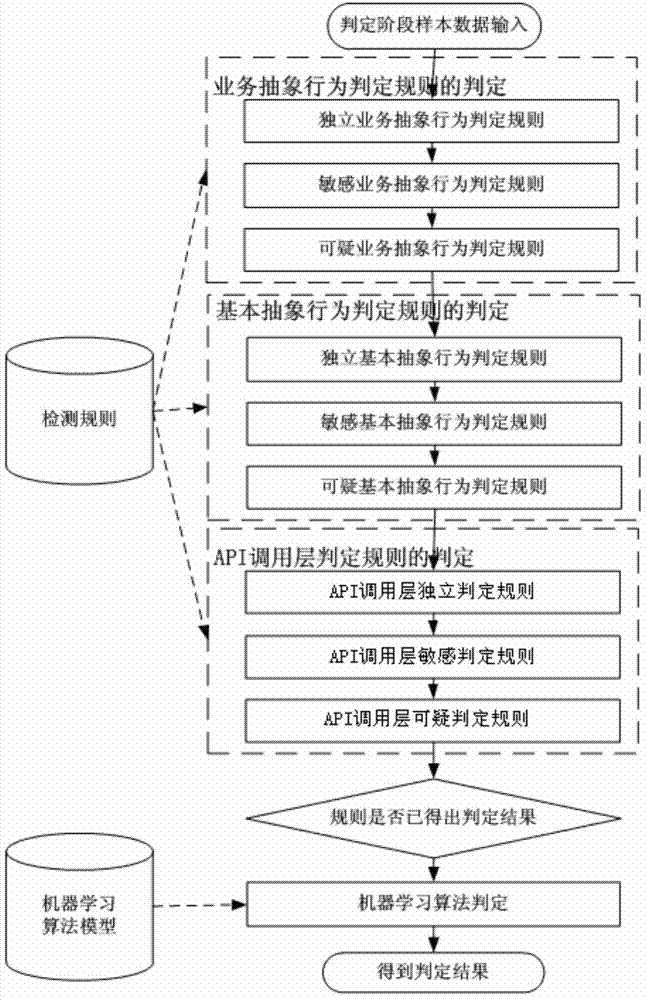
Decision model used for detecting malicious programs and detecting method of malicious programs
ActiveCN103927483AAvoid high manpower consumptionImprove accuracyPlatform integrity maintainanceFalse detectionProgram behavior
The invention relates to a decision model used for detecting malicious programs and a detecting method of the malicious programs. The detecting method includes rule generation and machine learning algorithm training, the rule generation is characterized in that a training sample set composed of a 'malicious program' sample set and a 'non-malicious program' sample set is generated into a decision rule set in an API (application programming interface) calling layer, a basic abstraction layer and a business abstraction layer; the decision rule set includes an API calling layer decision rule, a basic abstraction layer decision rule and a business abstraction layer decision rule; the machine learning algorithm training is characterized in that an OCSVM algorithm training model is utilized to obtain an OCSVM algorithm model. The malicious program related detecting method is characterized in that the programs to be detected are subjected to decision by the aid of the related decision model. According to the technical scheme, multilevel and systematic features are achieved, false detection can be effectively controlled in the steps, and feasibility of application of the malicious program behavior detection in actual computer security is improved.
Owner:西安电子科技大学重庆集成电路创新研究院
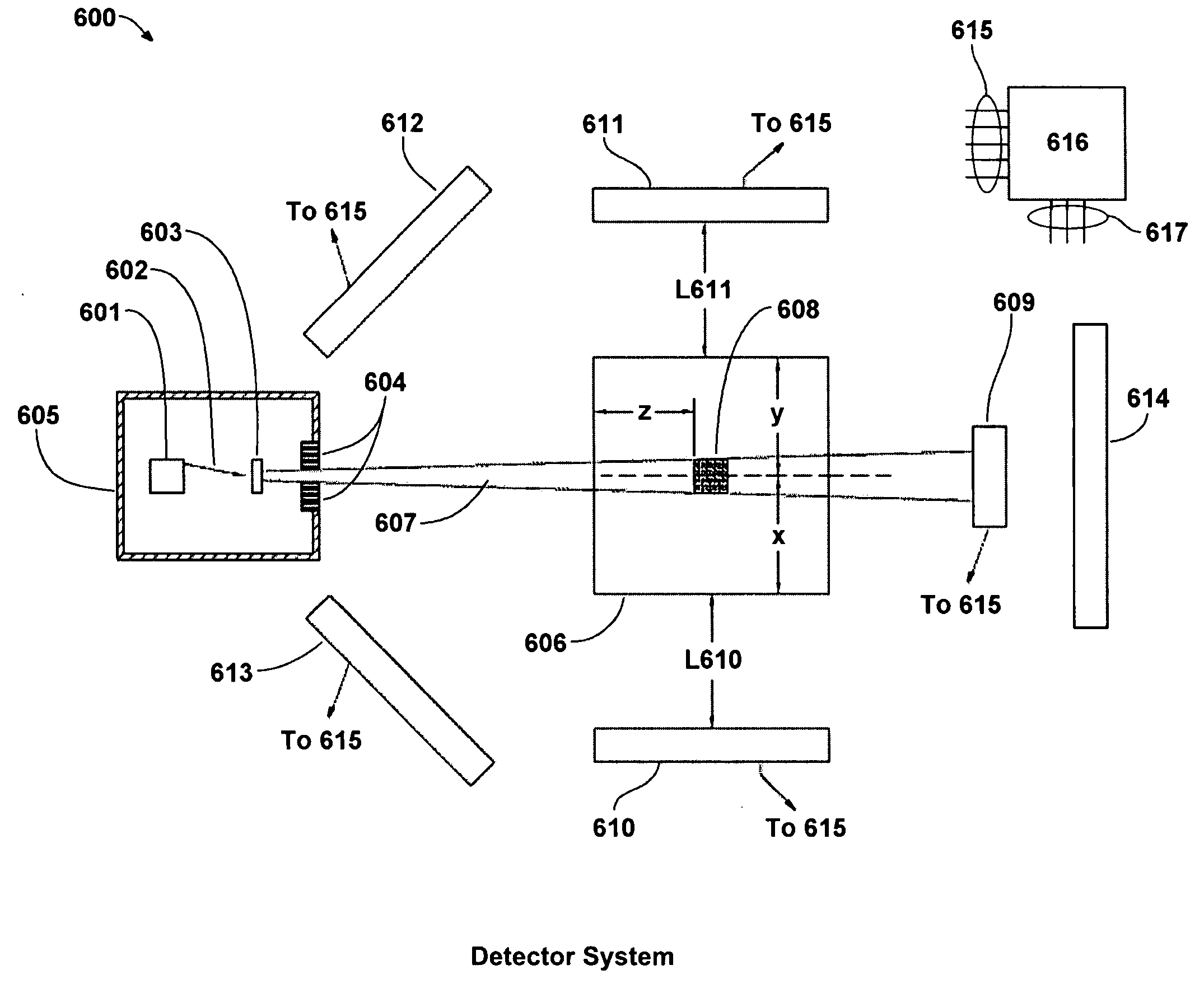
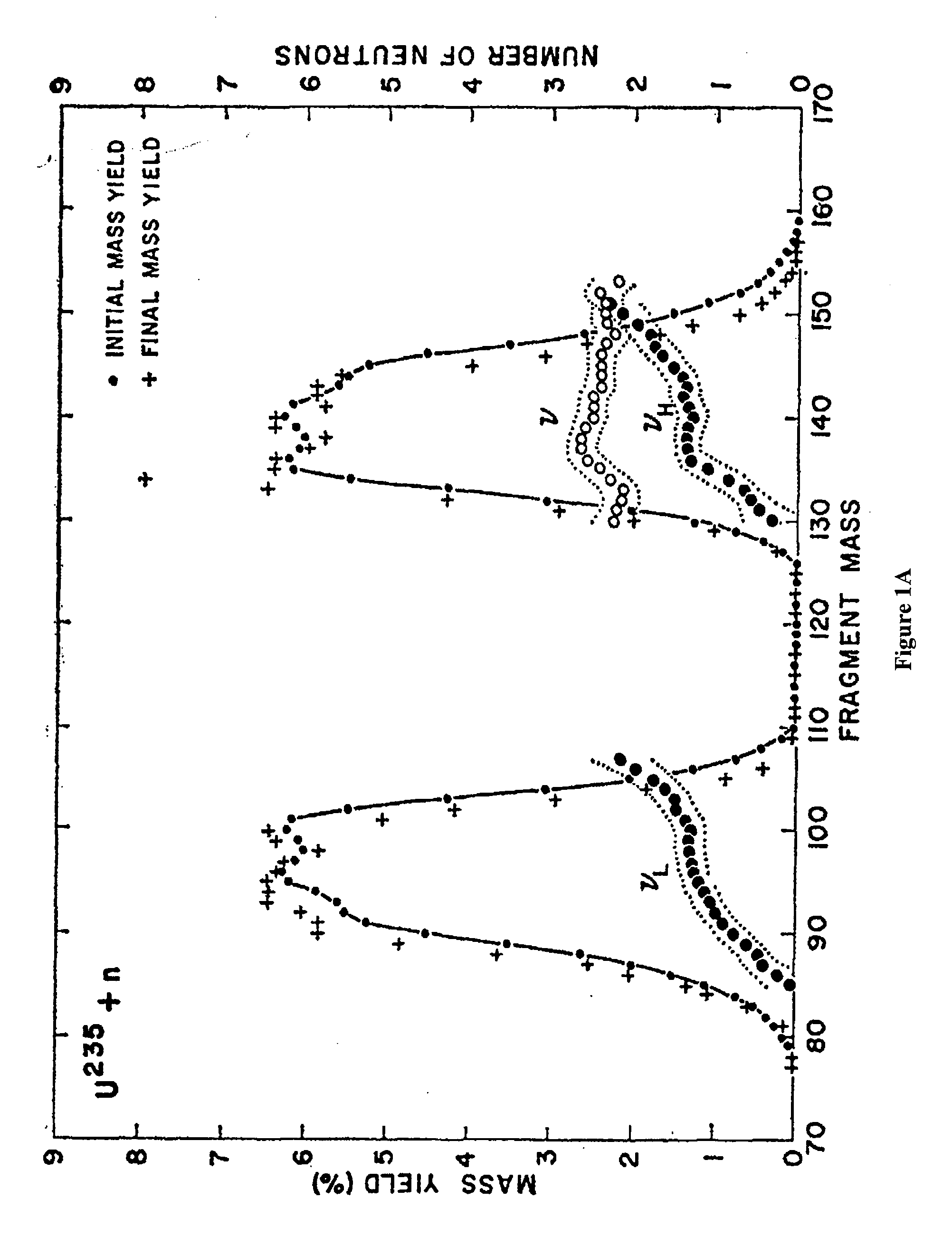
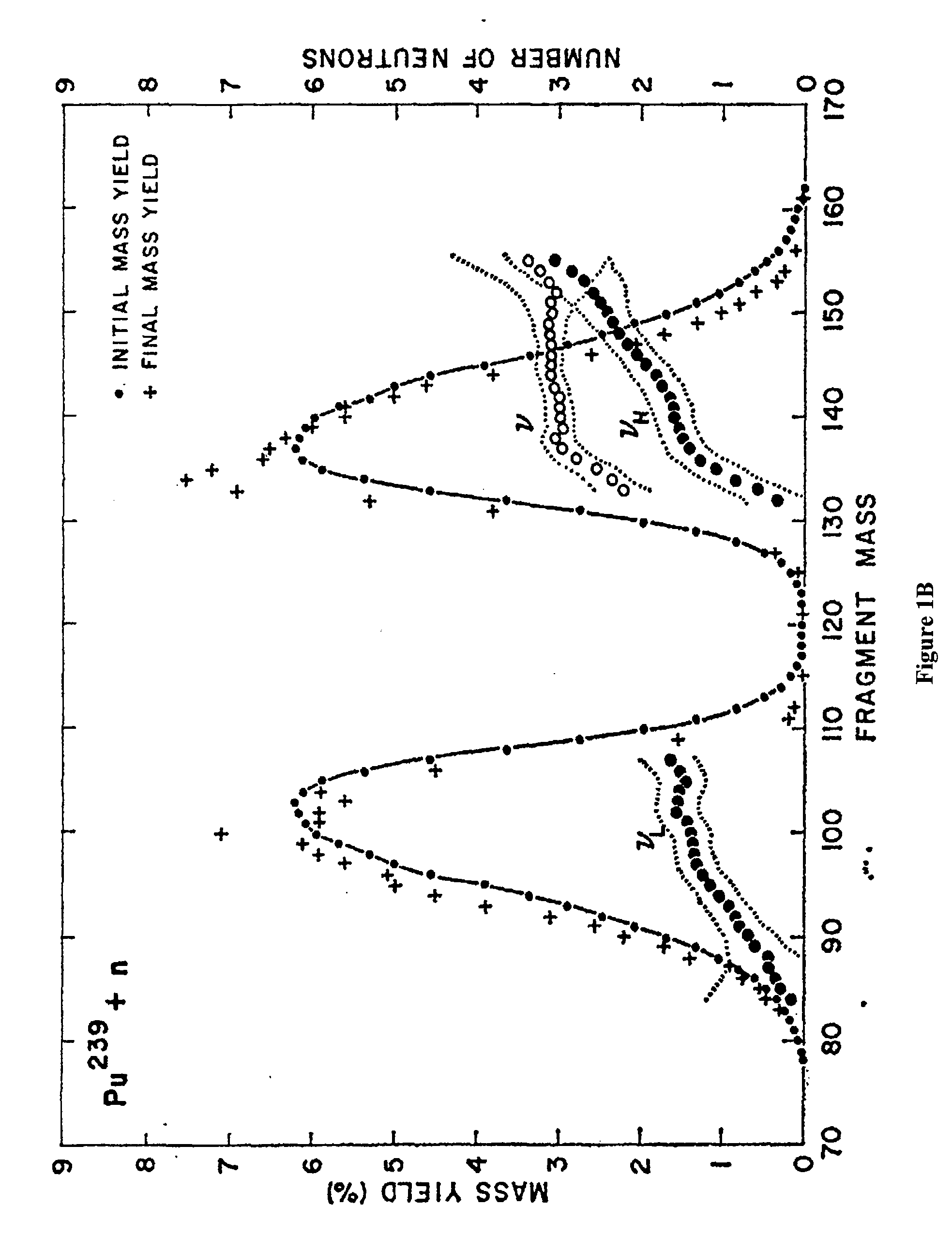
Non-intrusive method to identify presence of nuclear materials using energetic prompt neutrons from photon-induced fission
InactiveUS20090074128A1Improve detection rateSolve the high false positive rateConversion outside reactor/acceleratorsNeutron radiation measurementBeam energySmall fragment
Methods and systems for non-intrusively detecting the existence of fissile materials in a container via the measurement of energetic prompt neutrons are disclosed. The methods and systems use the unique nature of the prompt neutron energy spectrum from photo-fission arising from the emission of neutrons from almost fully accelerated fragments to unambiguously identify fissile material. The angular distribution of the prompt neutrons from photo-fission and the energy distribution correlated to neutron angle relative to the photon beam are used to distinguish odd-even from even-even nuclei undergoing photo-fission. The independence of the neutron yield curve (yield as a function of electron beam energy or photon energy) on neutron energy also is also used to distinguish photo-fission from other processes such as (γ, n). Different beam geometries are used to detect localized samples of fissile material and also fissile materials dispersed as small fragments or thin sheets over broad regions. These signals from photo-fission are unique and allow the detection of any material in the actinide region of the nuclear periodic table.
Owner:PASSPORT SYSTEMS INC
Patch security detecting method and system for software update
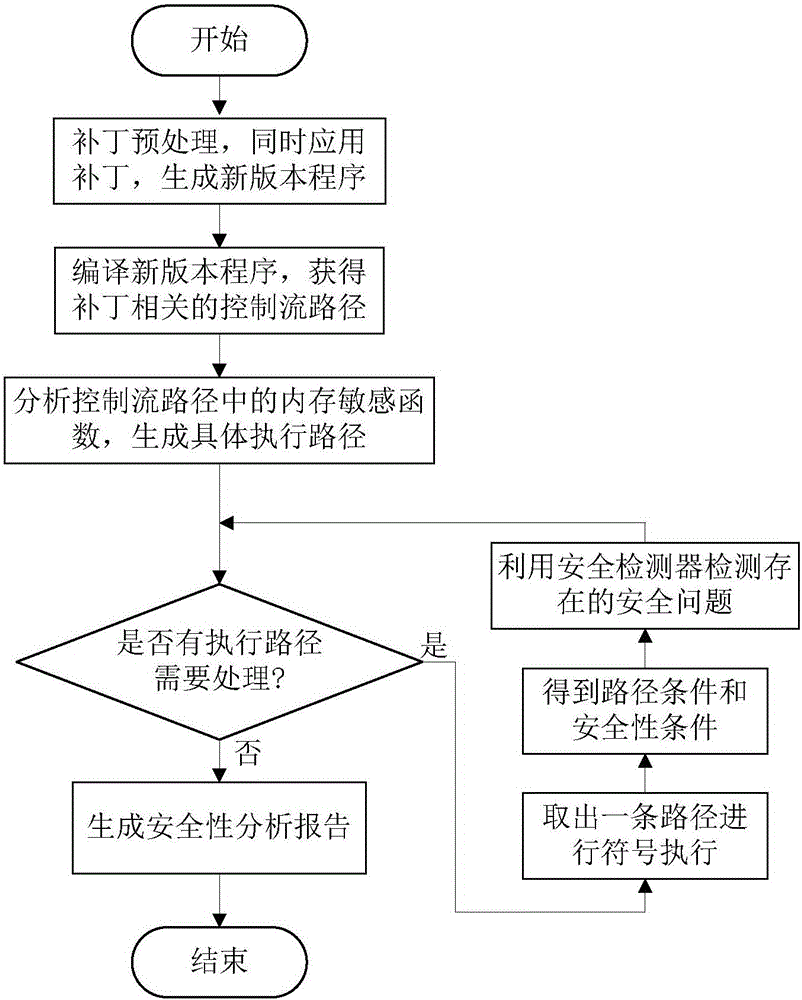
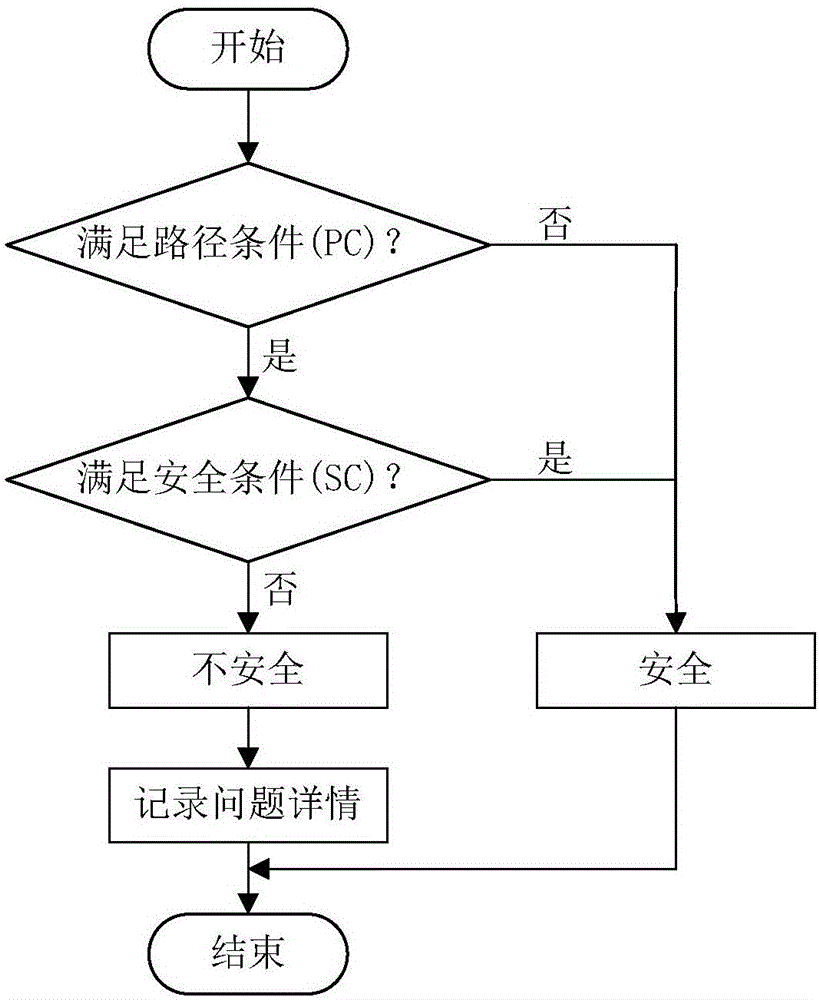
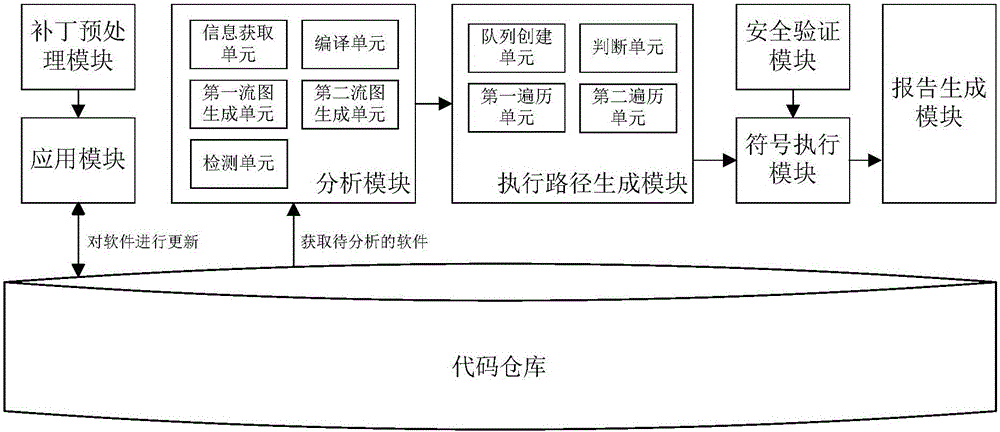
ActiveCN105787367AIncrease coverageReduce false alarm ratePlatform integrity maintainanceSoftware updatePath condition
The invention discloses a patch security detecting method and system for software update.The method comprises the steps that by means of conducting preprocessing on patches, intermediate code analysis is conducted to obtain basic blocks affected by the patches, memory sensitive functions and variables thereof are obtained by means of the basic blocks affected by the patches, and a main execution path is constructed by starting from the memory sensitive functions; in the process of conducting symbolic execution on the path, the specific path condition is determined, and when the specific memory sensitive function is reached, the path condition at this time is combined with a corresponding security detector to judge whether a software update security problem exists or not.The patch security detecting method and system for the software update focus on detecting the security of different parts, relative to an older version, of the new version after software is updated, the problems that in an existing patch security detection scheme, the false positive rate and false negative rate are high, the efficiency is low due to duplicate detection, and overdependence on test set effectiveness exists are solved, the detection efficiency is significantly improved, and the accuracy of patch security detection is further improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for extracting and differentiating human body heat source features of infrared pyroelectricity wavelet packet energy
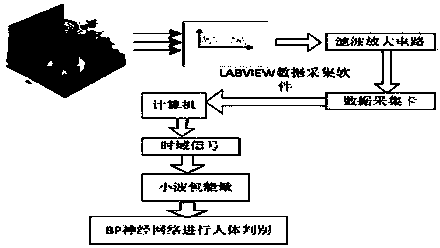
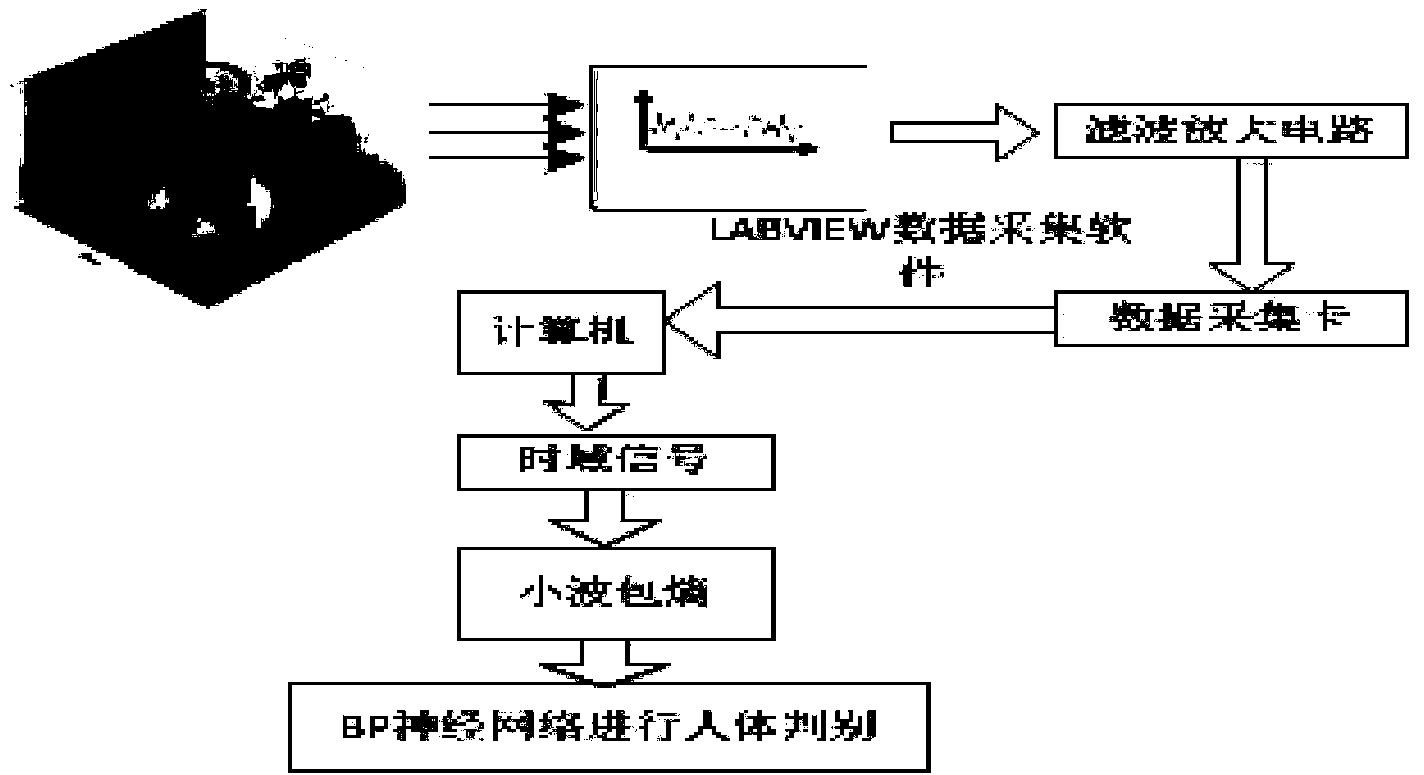
InactiveCN103728028ASolve the comfortSolve the problem of energy savingPyrometry using electric radation detectorsCircular discHuman body
The invention belongs to the technical field of human body differentiation and provides a method for extracting and differentiating human body heat source features of infrared pyroelectricity wavelet packet energy. According to the method, the purposes of detection within a 360-degree large-scale range and with a long distance and detection of a static infrared heat source are achieved and the problems that the comfort and the energy-saving performance in an intelligent air conditioner conflict and the false alarm rate in a safety supervision system is high are effectively solved. Thus, according to the technical scheme, the method for extracting and differentiating the human body heat source features of infrared pyroelectricity wavelet packet energy comprises the following steps that a single pyroelectricity infrared detector is driven by a stepping motor to rotate at a constant speed, so that detection of a static object at the long distance and within 360-degree large-scale range is achieved; the detection range is within a disc, wavelet packet analysis is conducted on a collected sample of the human body heat source and a collected sample of a non-human-body heat source, wavelet packet energy serves as a feature of a signal, 5-folding-time cross validation is conducted through a BP neural network, and therefore the human body heat source and the non-human-body heat source are differentiated. The method for extracting and differentiating the human body heat source features of infrared pyroelectricity wavelet packet energy is mainly applied to occasions of the human body differentiation technology.
Owner:TIANJIN UNIV
Human body heat source feature extracting and distinguishing method based on infrared pyroelectric information
InactiveCN103729626ASolve the comfortSolve the problem of energy savingBiological neural network modelsCharacter and pattern recognitionElectricityFeature extraction
The invention belongs to the technical field of human body distinguishing and discloses a human body heat source feature extracting and distinguishing method based on infrared pyroelectric information. The method aims to achieve 360-degree wide-range and remote detection and detection of static infrared heat sources and effectively solves the problems of confliction between comfort and energy saving of an intelligent air-conditioner and high false alarm rate of a safety supervision system. According to the technical scheme, the method comprises the steps that a stepping motor is adopted to drive a single pyroelectric infrared detector to rotate at a uniform speed, and then remote, 360-degree wide-range and static object detection is achieved; the detection range is a disk shape, wavelet packet analysis is conducted on collected human body heat source samples and non-human-body heat source samples, a signal wavelet entropy is taken as the features of the signal, 5-fold cross-validation is conducted by means of the BP neural network, and then human body heat resources are distinguished from non-human-body heat resources. The method is mainly applied to human body distinguishing.
Owner:TIANJIN UNIV
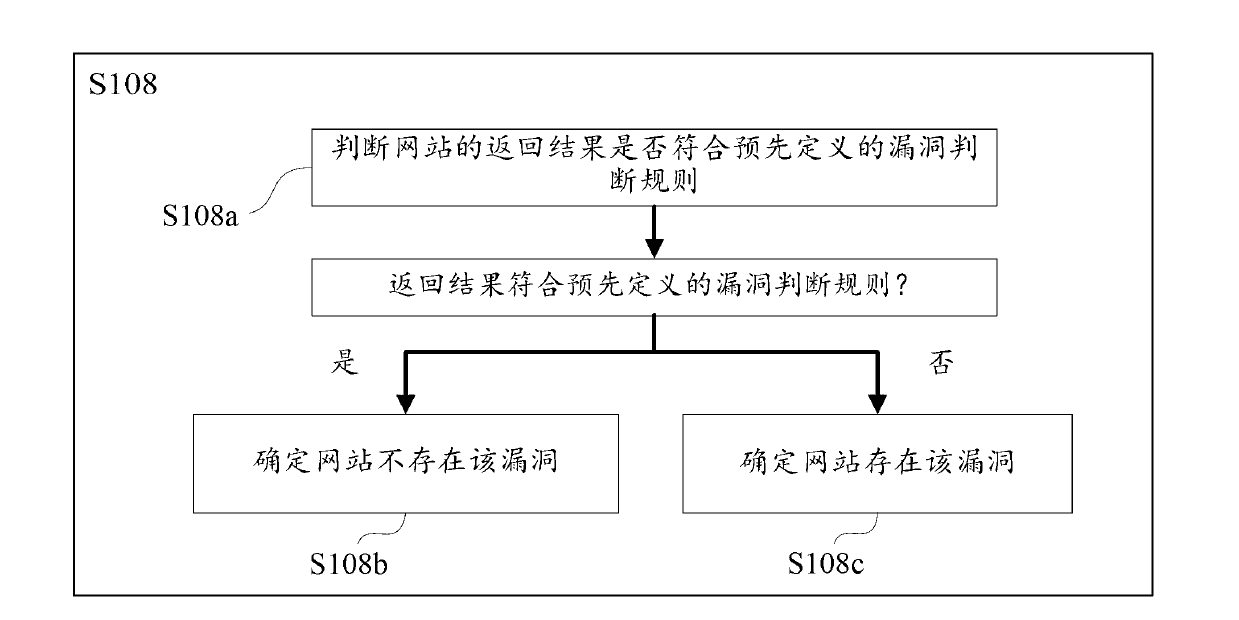
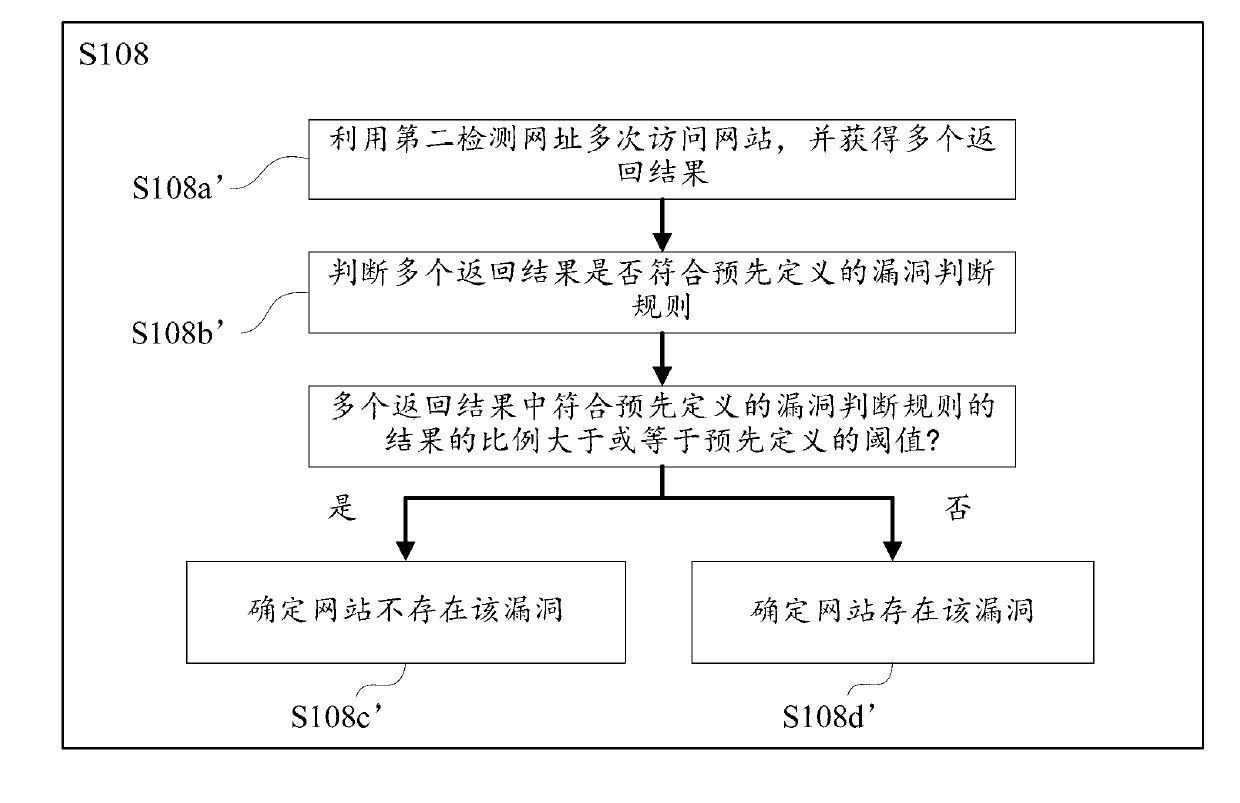
Website security detection method, website security detection equipment and website security detection system
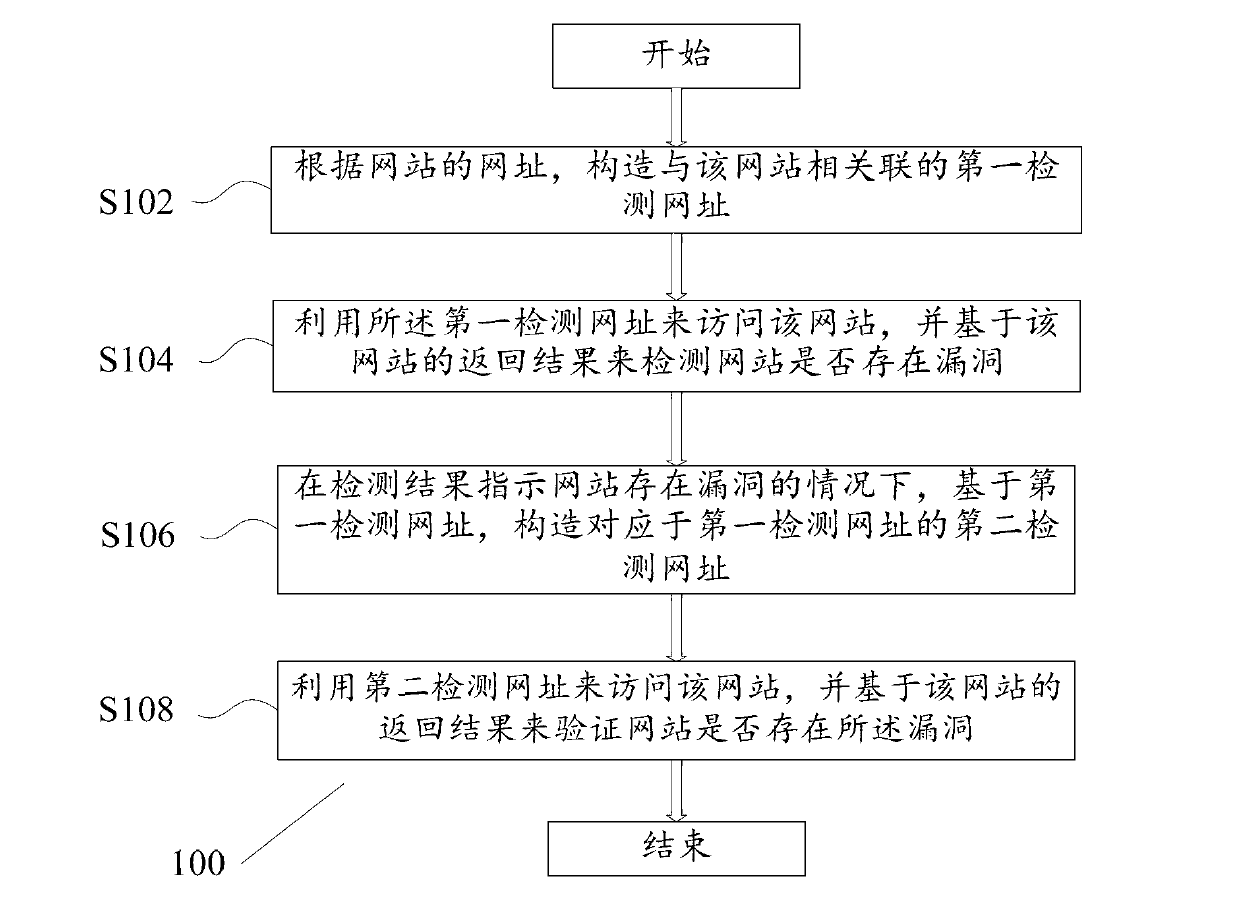
ActiveCN103001946AQuality improvementImprove efficiencyData switching networksInternet privacyVulnerability
The invention discloses a website security detection method, website security detection equipment and a website security detection system. The method includes the steps: according to a web address of a website, constructing a first detection web address relevant to the website; accessing to the website by the aid of the first detection web address, and detecting whether the website has vulnerabilities or not on the basis of return results of the website; under the circumstance that the detection results indicate that the website has the vulnerabilities, constructing a second detection web address corresponding to the first detection web address based on the first detection web address; and accessing to the website by the aid of the second detection web address, and verifying whether the website has the vulnerabilities or not on the basis of the return results of the website.
Owner:QI-ANXIN LEGENDSEC INFORMATION TECH (BEIJING) INC +1
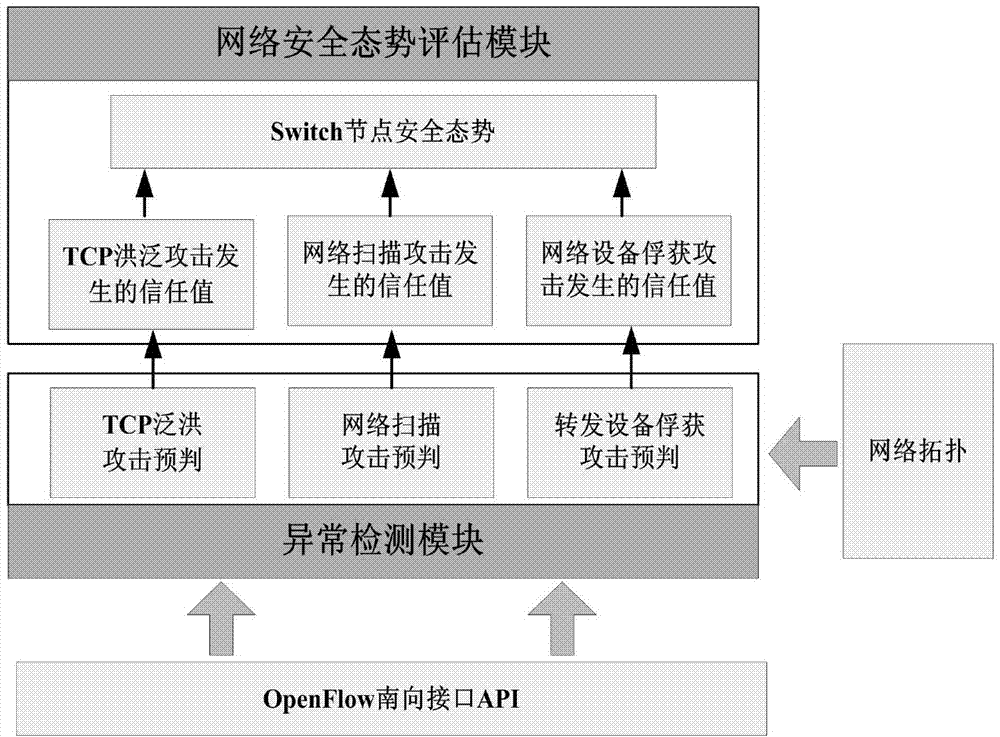
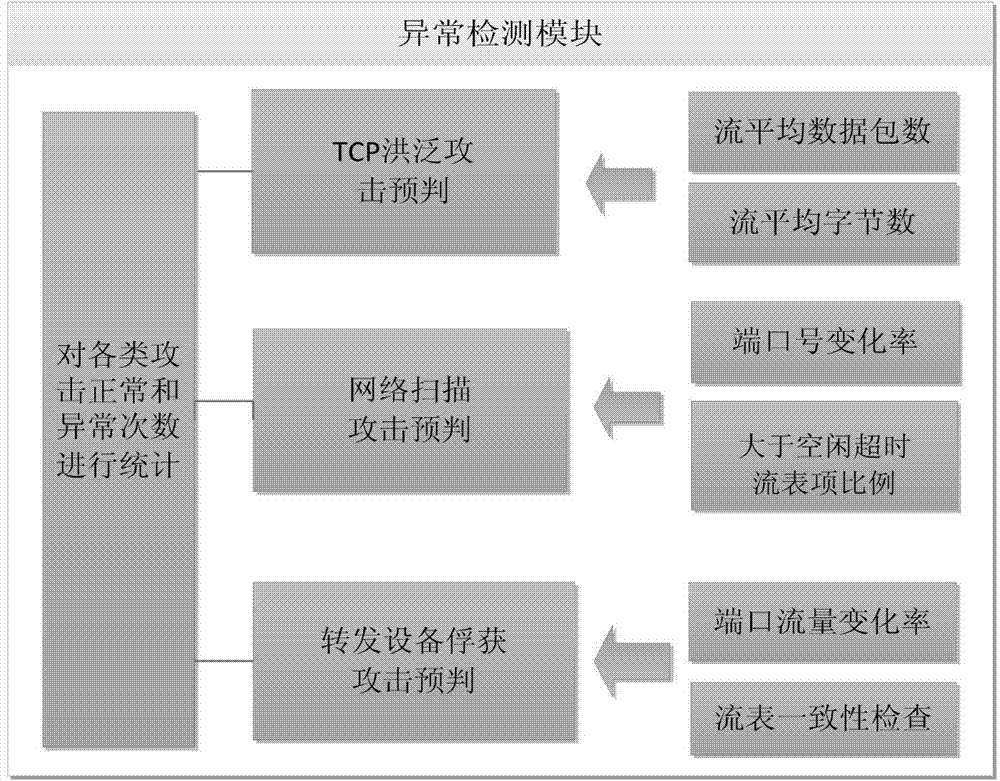
Software defined network security situation assessment method
ActiveCN104506385ASolve the high false positive rateReduce the number of hopsData switching networksSecurity frameworkSafety status
The invention discloses a software defined network security situation assessment method. The advantages of SDN (software defined network) control and direct and quick information collection are combined, an open SDN security situation assessment framework is provided on account of three kinds of attacks of an SDN forwarding surface, the security framework closely fits a framework of an SDN controller, an anomaly detection module extracts characteristic indexes according to the SDN and various attack characteristics, an SVM (support vector machine) classification algorithm is selected for identification, and attack pre-judgment is given. A security situation assessment module performs quantitative assessment on network security situations according to information collected by the anomaly detection module, and attack sensitivity and noise resistance of an assessment system are regulated through setting of a threshold value. Different weights are allocated to different attacks based on an AHP (analytic hierarchy process) so as to fit out a comprehensive security situation of the network. The method is flexible and simple, attach behaviors can be detected accurately, the quantitative assessment of the security situations of the network is given, and monitoring and assessment of the security status of the SDN forwarding surface are realized with lower cost.
Owner:XIDIAN UNIV
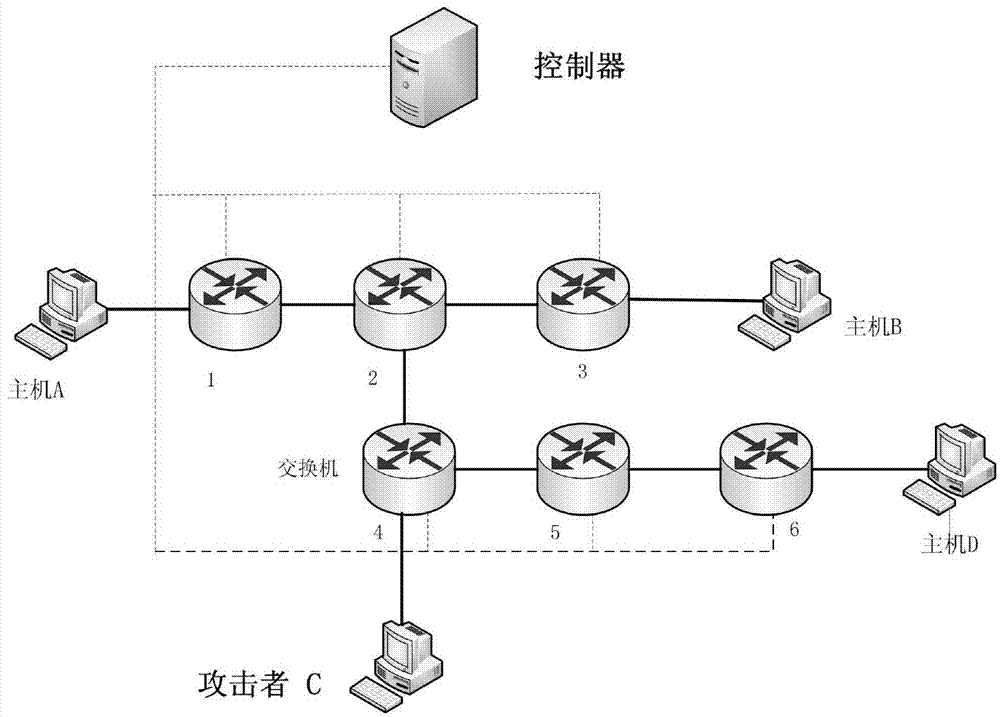
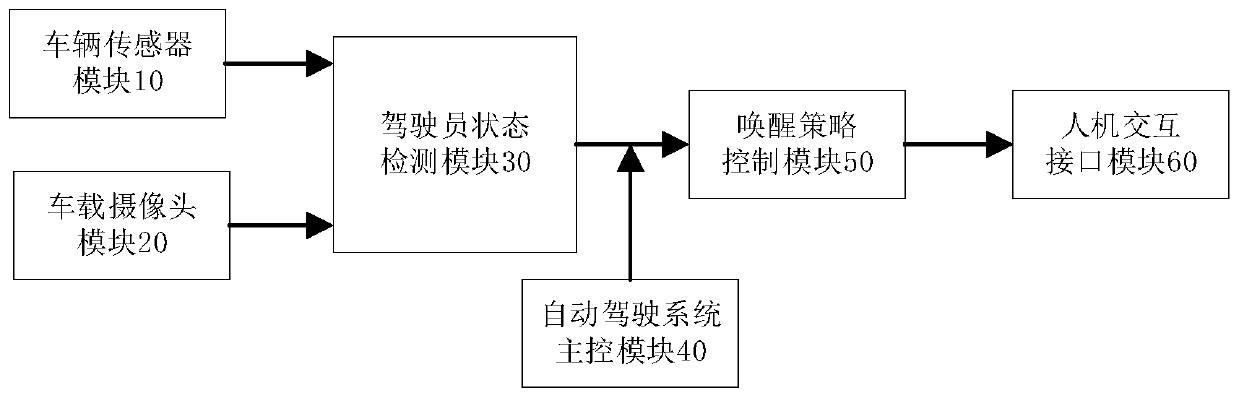
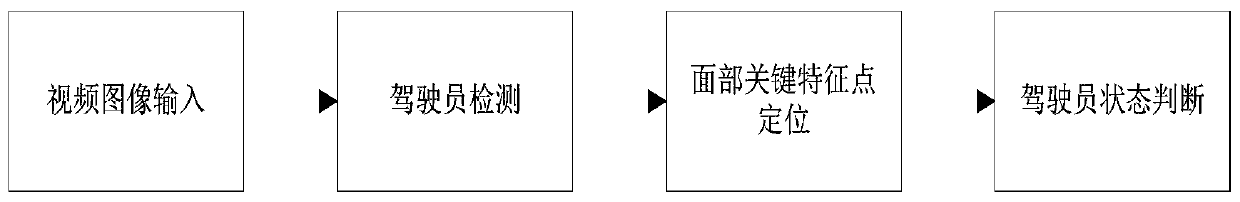
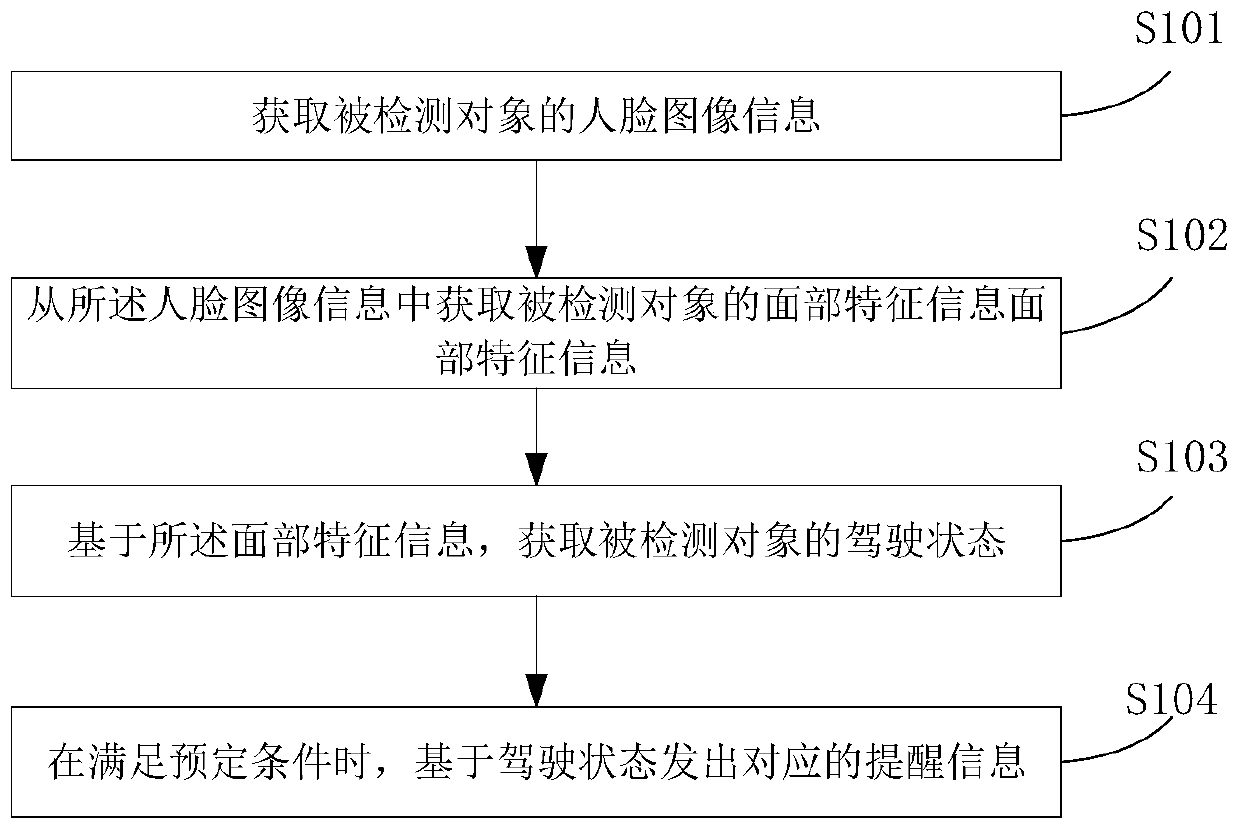
Driving reminder method, driving state detection method and computing device
PendingCN110582437ASolve the high false positive rateEnsure safe takeoverCharacter and pattern recognitionControl devicesTime rangeDriver/operator
The application discloses a driving reminder method, a driving state detection method and a computing device. The driving reminder method includes: obtaining face image information of the detected object; obtaining at least one facial feature information of the detected object from the face image information; judging the driving state of the detected object according to the facial feature information; When the predetermined condition is met, corresponding reminder information is issued based on the driving state. The method proposed in the embodiment of the present invention can solve the problem of high false alarm rate in the existing driver state detection system, and ensure that the driver has the ability to safely take over the vehicle within a specified time range.
Owner:UISEE SHANGHAI AUTOMOTIVE TECH LTD
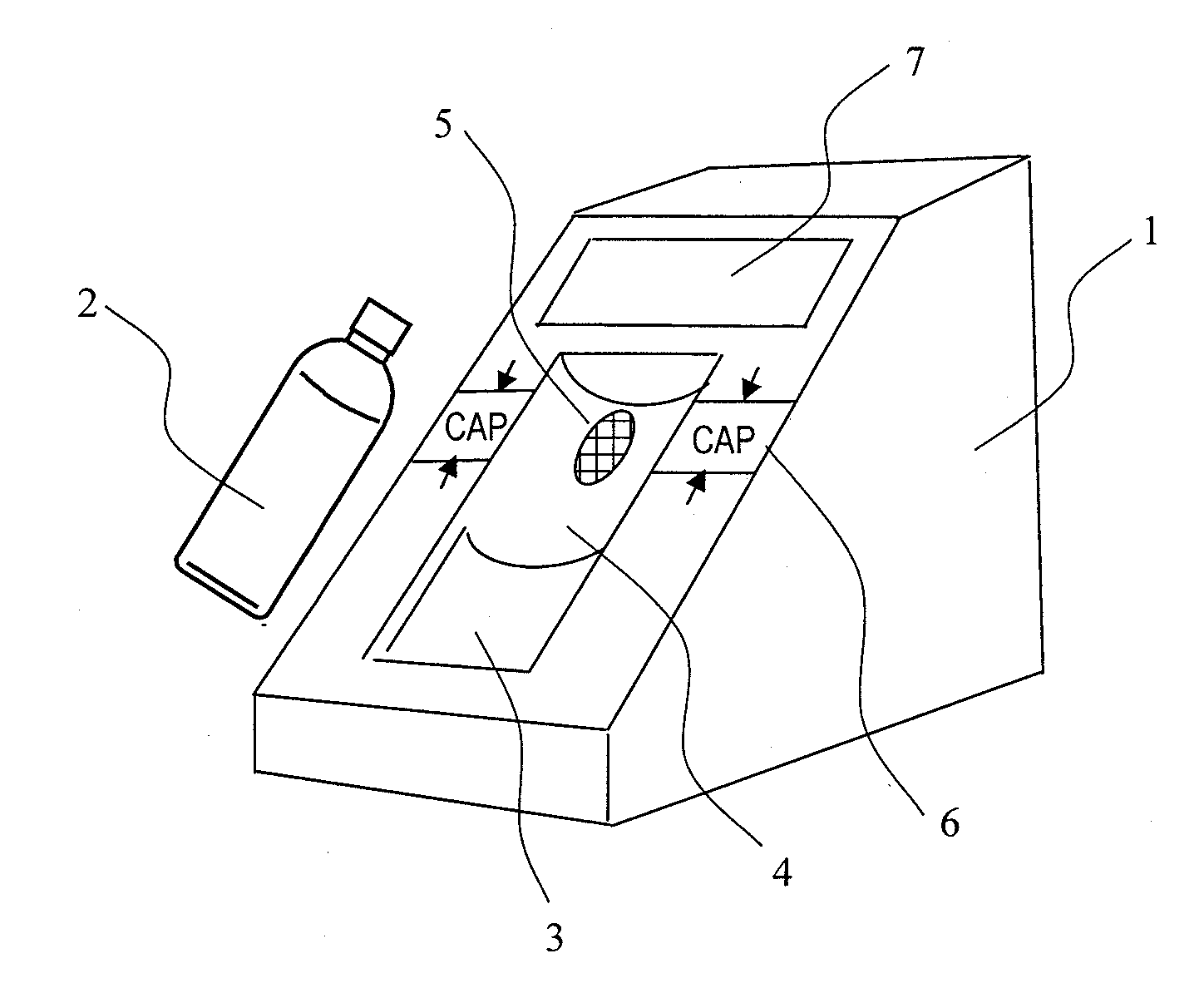
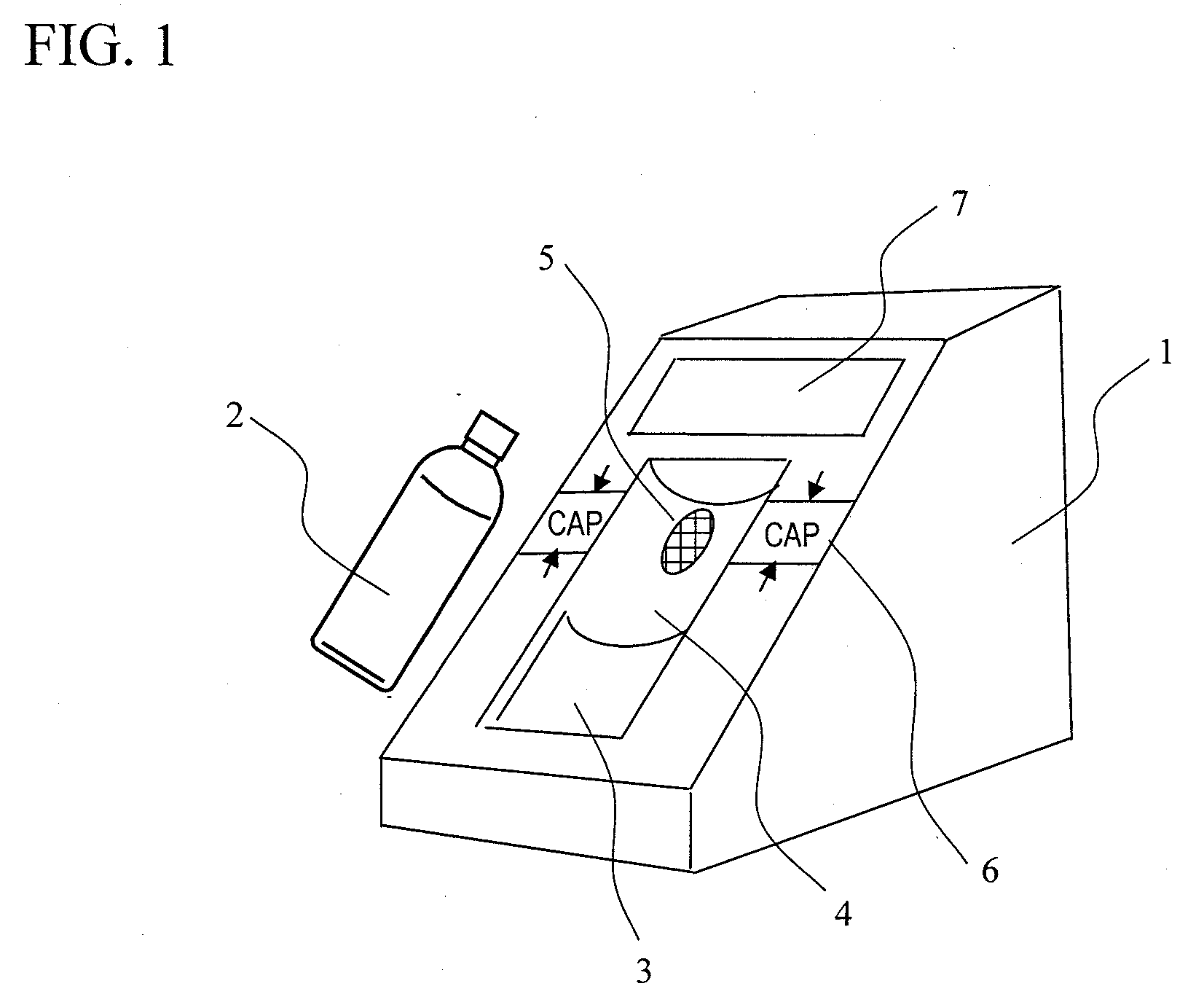
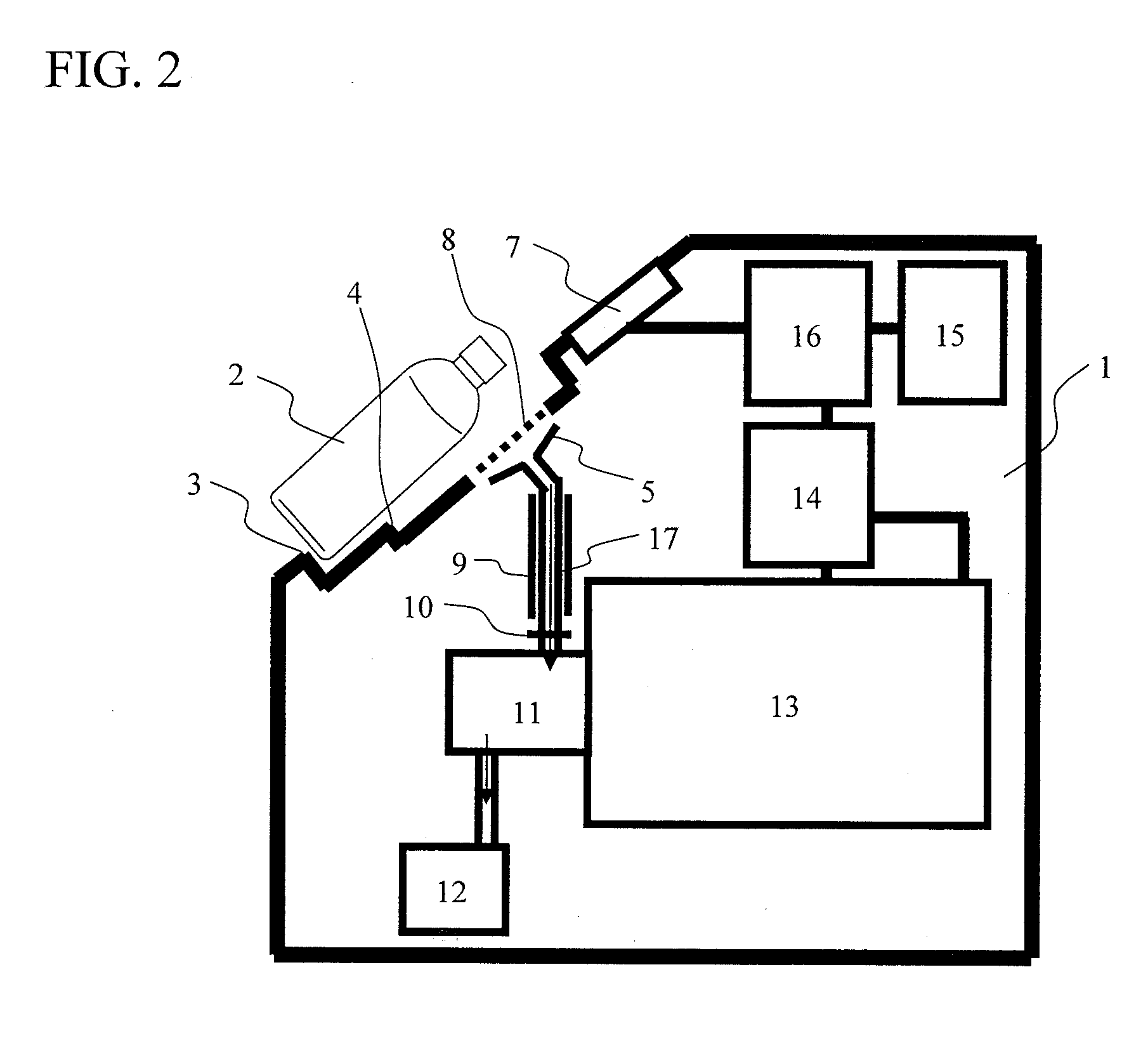
Dangerous substance detection system
InactiveUS20110093214A1High-precision detectionQuick checkFuel testingIsotope separationProduct gasBottle
A method of quickly detecting a handmade explosive in a bottle with a low erroneous alarm frequency is provided. A sample gas generated from a bottle placed on a bottle placement space is sucked-in, and ions of the sample gas are generated by an ion source and subjected to mass analysis. The presence / absence of a mass spectrum derived from the handmade explosive is determined from an obtained mass spectrum, and the result thereof is displayed on a monitor, thereby quickly detecting the handmade explosive in the bottle or the handmade explosive adhering to the surface of the bottle at a low erroneous alarm frequency.
Owner:HITACHI LTD
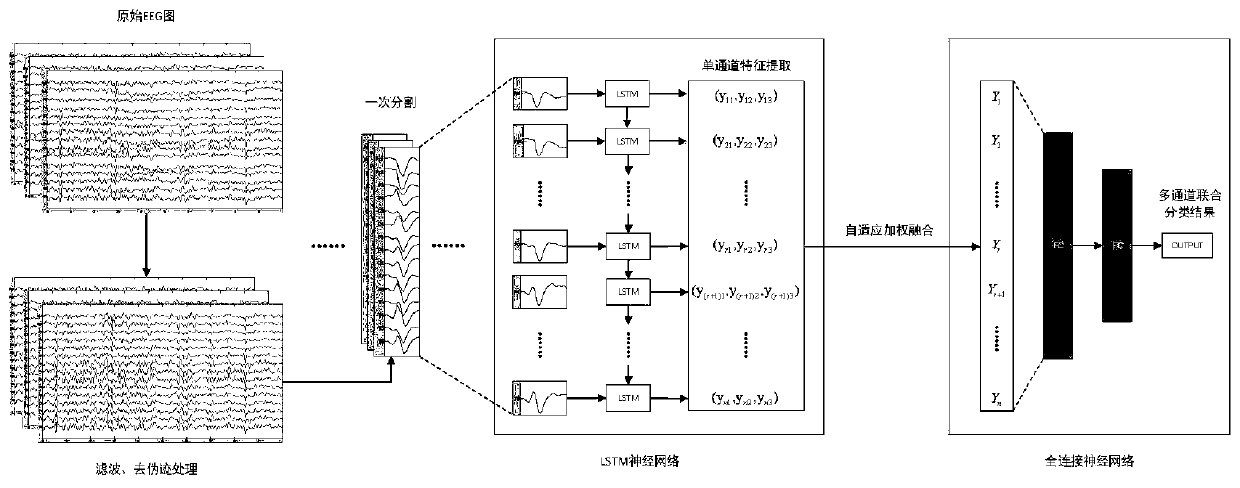
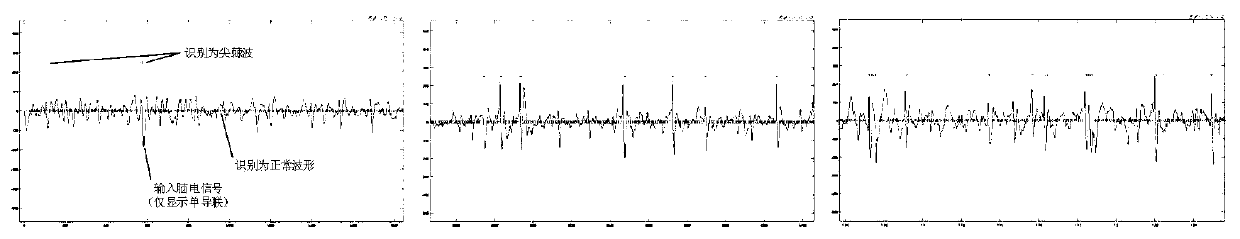
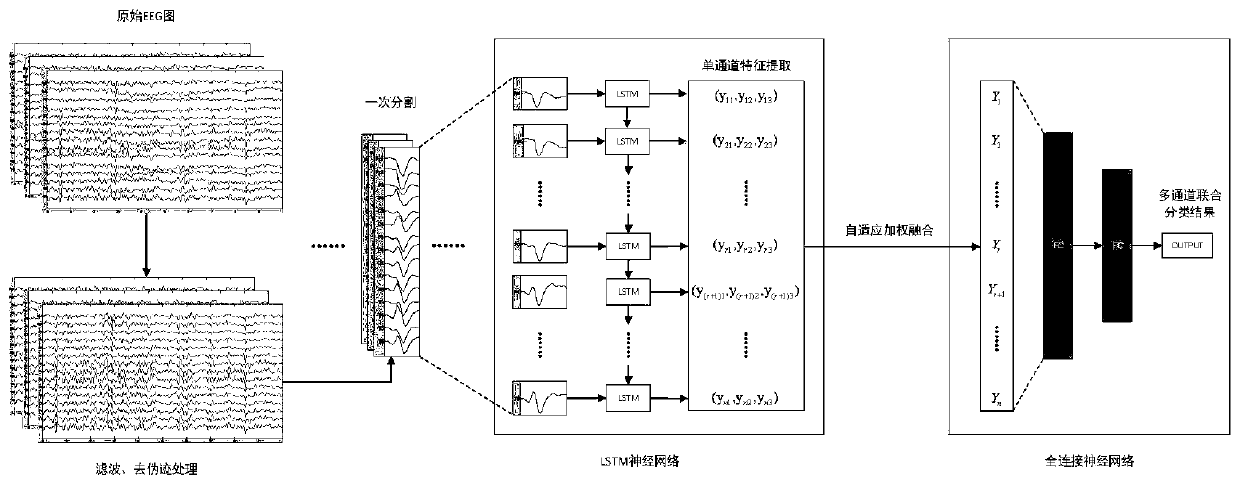
Combined detection method of electroencephalogram epilepsy sharp and spike wave discharge based on long short term memory network (LSTM) multi-channels
ActiveCN111150393AAccurate detectionImprove the efficiency of clinical diagnosisDiagnostic recording/measuringSensorsTime domainAlgorithm
The present invention discloses a combined detection method of electroencephalogram epilepsy sharp and spike wave discharge based on long short term memory network (LSTM) multi-channels. The combineddetection method comprises the following steps: step 1, filtering input original multi-lead electroencephalogram and eliminating artifacts caused by physiological activities of electrocatdiogram, chewing and swallowing; segmenting processed signals in time domain firstly according to characteristics of target waveform duration characteristics and transforming the signals into a recognition form ofthe subsequent steps; step 2, conducting feature extraction of data of each channel in the segmented signals through the long short term memory network and conducting feature fusion through an adaptive weighted fusion algorithm; and step 3, using results obtained by the feature fusion to classify multi-channel signal fragments through fully connected neural network and finally obtaining classification results of the entire signal at different periods, so as to achieve a purpose of sharp and spike wave discharge detection. The combined detection method can realize a sharp and spike detection effect with higher precision and stronger anti-interference ability under multi-channel signal input.
Owner:HANGZHOU DIANZI UNIV
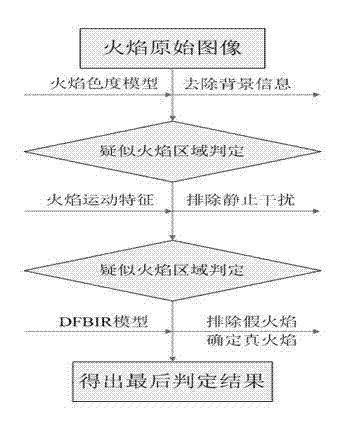
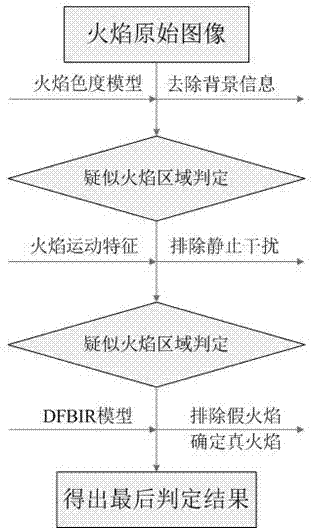
Method applied to recognition of flame image generated by gas combustion associated in oil drilling
ActiveCN102646191AAccurate identificationSolve the high false positive rateCharacter and pattern recognitionCombustionImaging processing
The invention discloses a method applied to recognition of a flame image generated by gas combustion associated in oil drilling, relating to the field of image processing technologies. According to the color characteristic and the motion characteristic of the flame image, and by combination with discrete fractal Brownian random field, the flame of gas combustion associated in oil drilling is recognized. The method disclosed by the invention can be applied to monitoring the flame of gas combustion gas combustion associated in onshore oil drilling platforms and offshore oil drilling platforms, and also can be used for monitoring the whole safety of the oil drilling platform by combination with an oil-well monitoring system.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Binary program bug detection method based on function difference
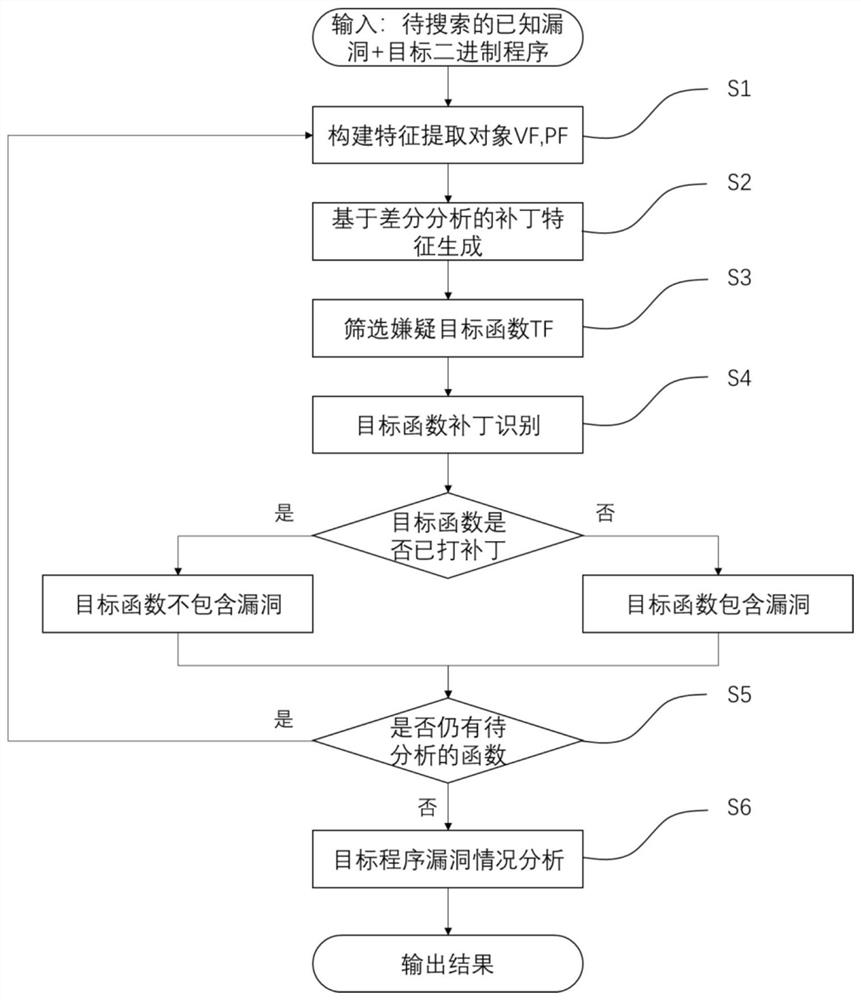
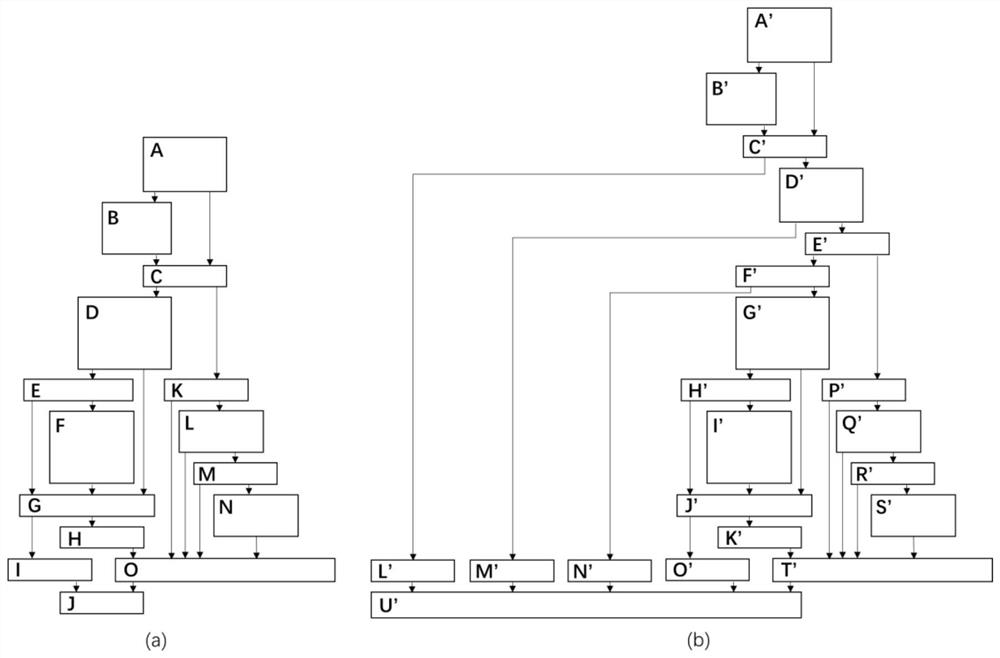
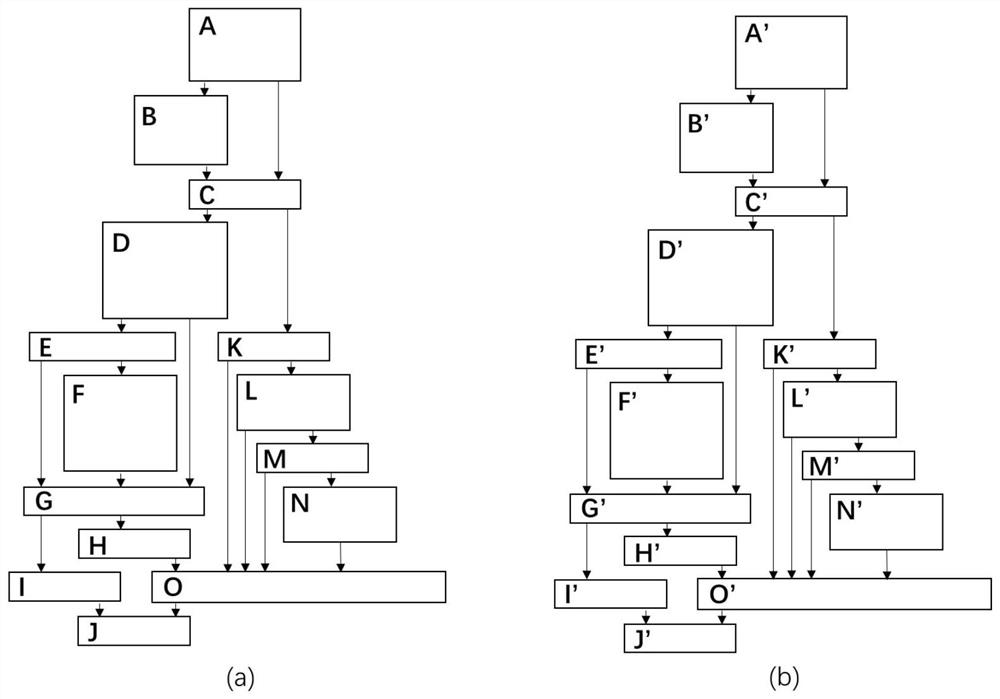
ActiveCN111914260ASolve the high false positive rateImprove detection accuracySoftware testing/debuggingPlatform integrity maintainanceAlgorithmDifferential analysis
The invention discloses a binary program bug detection method based on function difference. The method comprises the following steps of: extracting patch features for a known bug function, performingfeature matching in a suspected target function, identifying whether a corresponding patch is made in the suspected target function or not, and judging whether a known bug is contained or not. The method comprises the following steps: firstly, determining a bug related function, collecting a binary code containing the bug function and a repaired function, and disassembling the binary code; secondly, determining the change between two versions of the same function by using a differential analysis technology, and generating patch features; and finally, screening out a suspected target function from a target program, positioning and representing a local key area in the suspected target function, performing feature matching through similarity calculation to detect whether the target function contains vulnerabilities, and completing vulnerability detection of the target program accordingly. The method aims at quickly and accurately detecting whether a target program contains a bug or not after a to-be-searched known bug is given, and the problem that an existing bug detection method based on function matching is high in false alarm rate is solved.
Owner:XI AN JIAOTONG UNIV
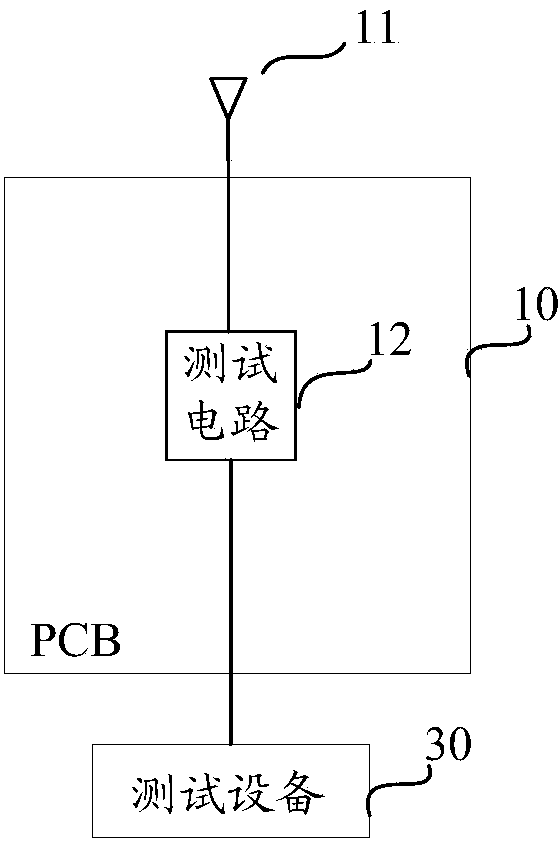
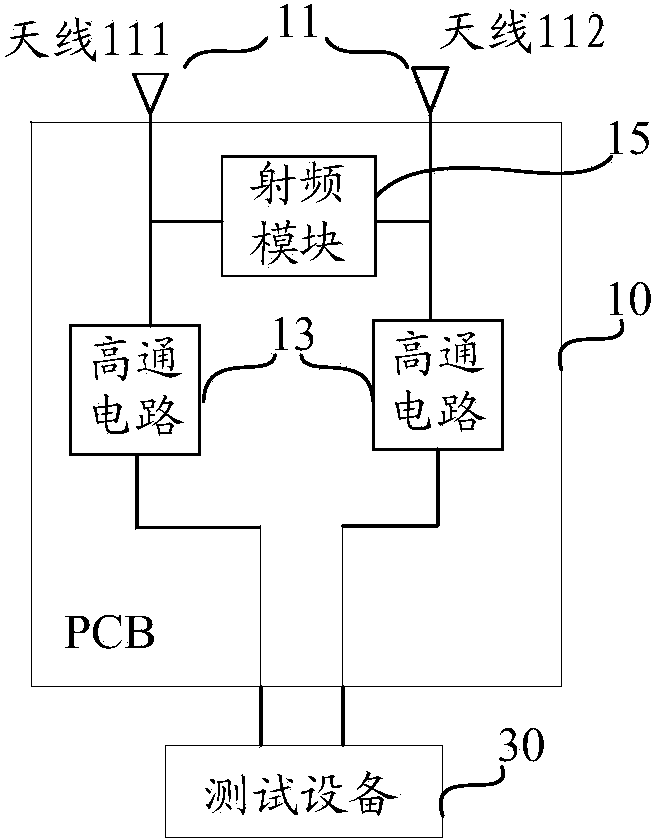
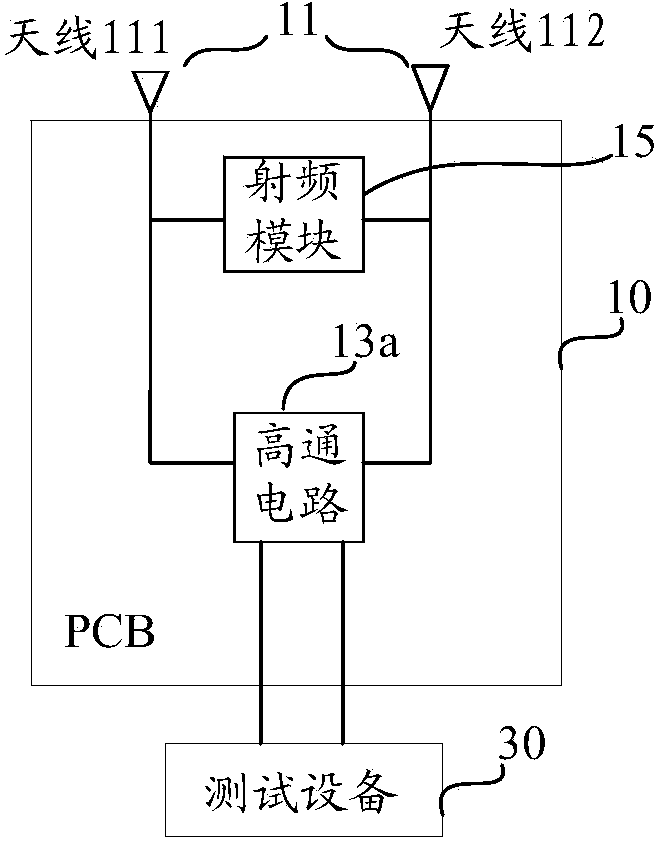
Antenna test method and system and wireless terminal
ActiveCN103728502ASolve the high false positive rateReduce the probability of false positivesTransmitters monitoringResistance/reactance/impedenceElectricityTest error rate
The invention provides an antenna test method and system and a wireless terminal, and relates to the field of antennae. The antenna test method and system and the wireless terminal can reduce the test error rate. The method is applied to the wireless terminal. The wireless terminal comprises an antenna and a test circuit, wherein the antenna is electrically connected with one end of the test circuit, and test equipment outside the wireless terminal is electrically connected with the other end of the test circuit. The method comprises the steps that the test circuit receives test signals sent by the test equipment and transmits the test signals to the antenna, and the test circuit receives reflected signals which are reflected by the antenna and correspond to the test signals and transmits the reflected signals to the test equipment so that the test equipment can determine parameters of the antenna according to the reflected signals. The antenna test method and system and the wireless terminal are applied to the antenna test technology.
Owner:HONOR DEVICE CO LTD
VOCs gas leakage detection method and system based on optical gas imaging
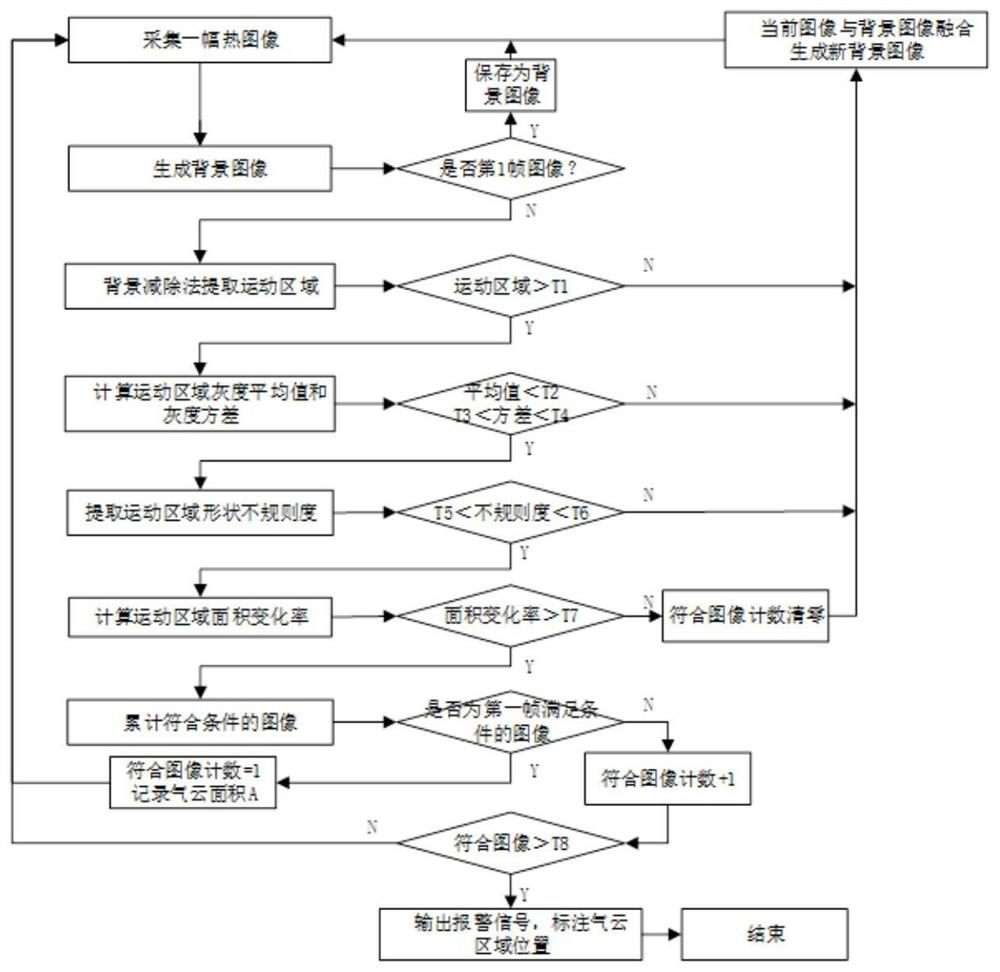
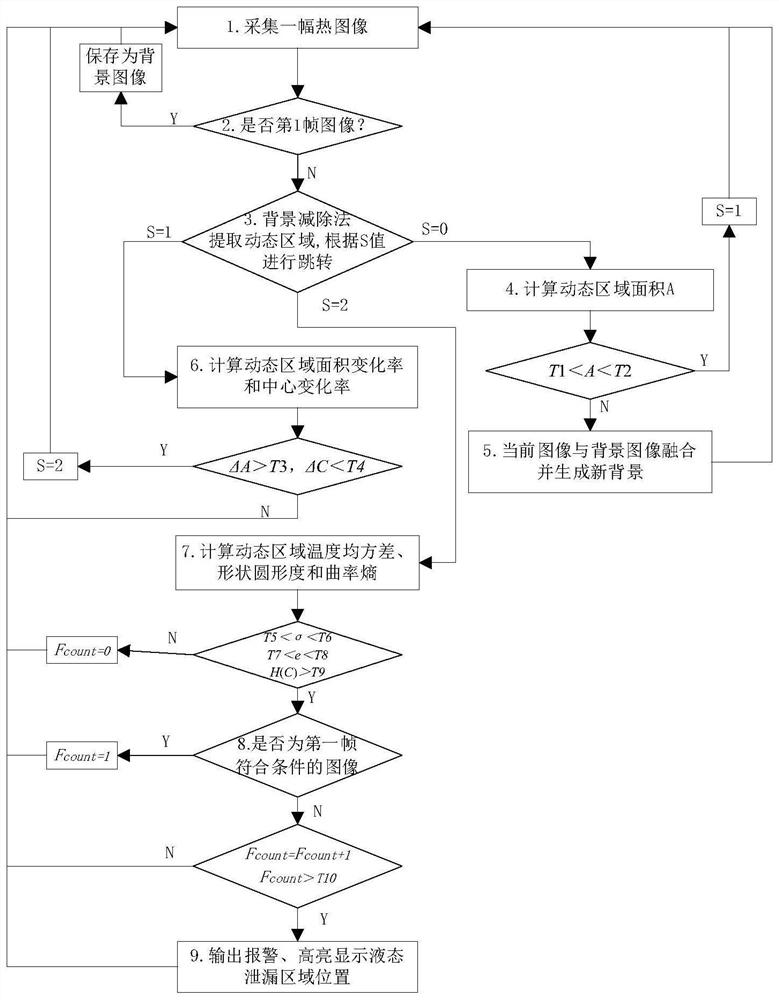
ActiveCN112781791ARealize traceabilityEasy to detectImage enhancementImage analysisGas leakBackground image
The invention relates to a VOCs gas leakage detection method and system based on optical gas imaging. The system is characterized in that the system comprises: an image collection module which is used for obtaining a frame of infrared image of a to-be-detected region, wherein if the frame of infrared image is a first frame of infrared image, the frame of infrared image is used as a background image; a background subtraction module used for extracting a dynamic change area of the current frame of infrared image; a parameter calculation module used for calculating parameters of the dynamic change area meeting the dynamic area detection conditions; a gas leakage judgment module used for judging whether gas leakage occurs or not when the calculated parameters of the infrared image meet the detection conditions; an alarm module used for outputting an alarm signal when gas leakage occurs and marking the extracted dynamic change area; and an image fusion module used for fusing the current frame of infrared image with the original background image to generate a new background image when the calculated parameters of the infrared image do not meet the detection conditions. The method and the system can be widely applied to the field of volatile organic compound leakage detection.
Owner:咏峰(大连)科技有限公司
Encrypted traffic identification method and device and equipment
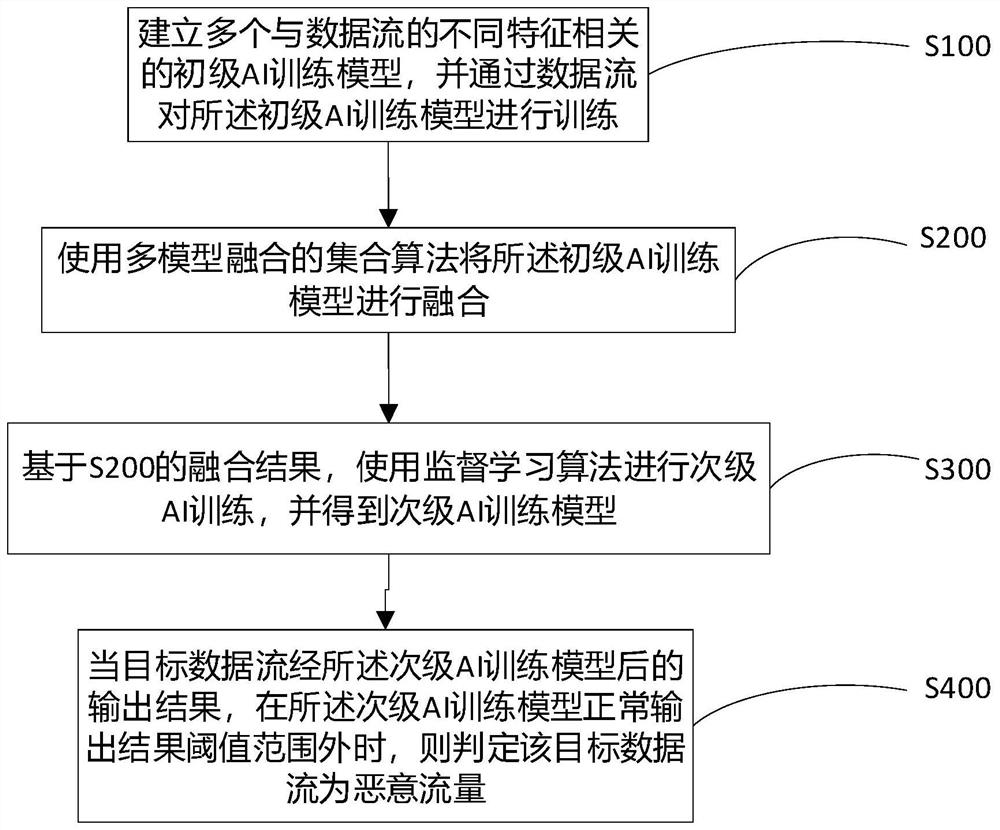
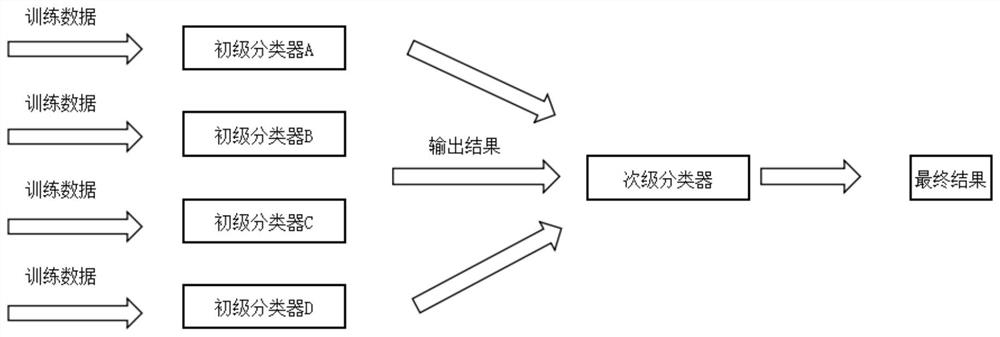
PendingCN113469366AReduce computing pressureSolve the high false positive rateKernel methodsTransmissionData streamAlgorithm
The invention discloses an encrypted traffic identification method and device and equipment, an AI model is used to identify encrypted traffic, and the training process of the AI model comprises the following steps: S100, establishing a plurality of primary AI training models related to different features of a data stream, and training the primary AI training models through the data stream; S200, fusing the primary AI training models by using a multi-model fusion set algorithm; S300, performing secondary AI training by using a supervised learning algorithm based on a fusion result of S200, and obtaining a secondary AI training model; and S400, when an output result obtained after target data flow flows through the secondary AI training model is out of a threshold range of a normal output result of the secondary AI training model, determining that the target data flow is malicious flow. The encrypted traffic is detected by using a multi-dimensional and multi-model method, and the problems of high false alarm rate and poor interpretability caused by dependence on a single AI model are well solved.
Owner:北京观成科技有限公司
Secondary dialing method based on wireless access system and wireless access equipment
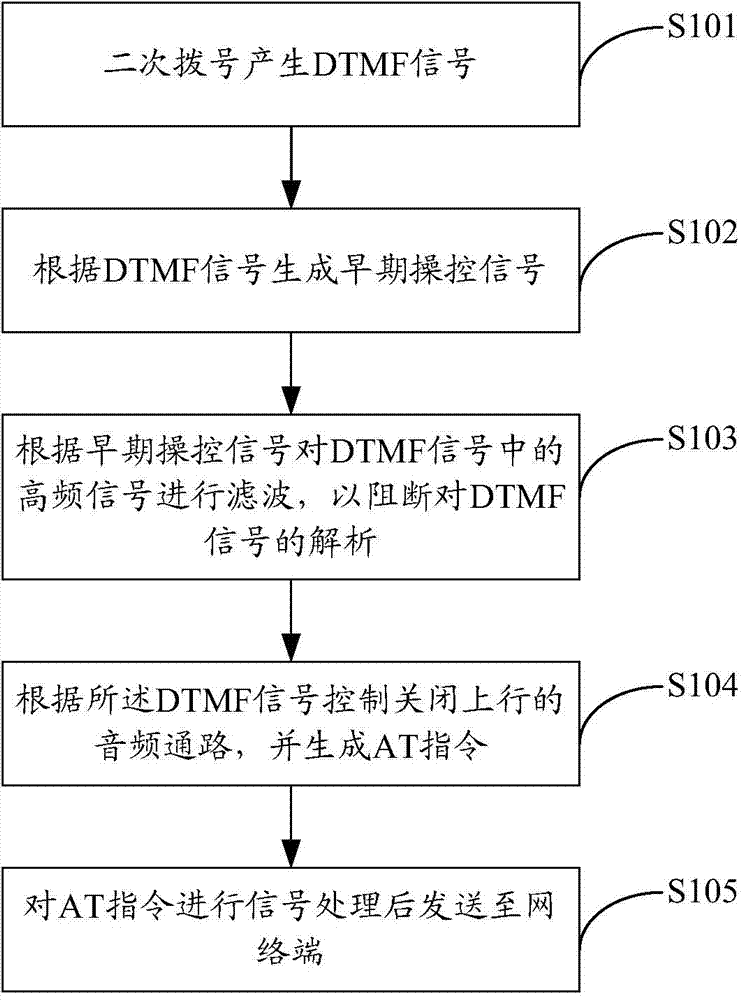
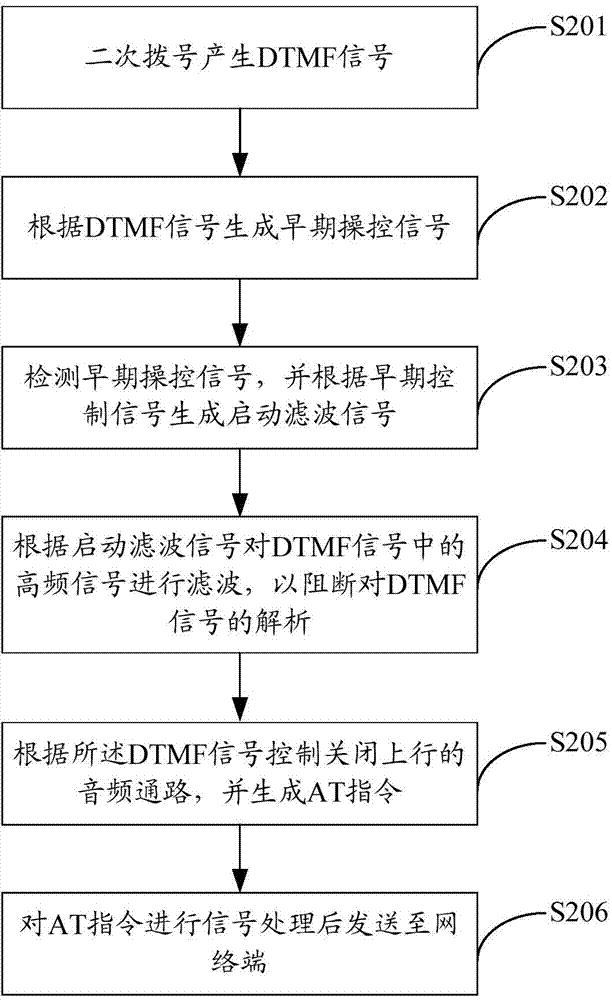
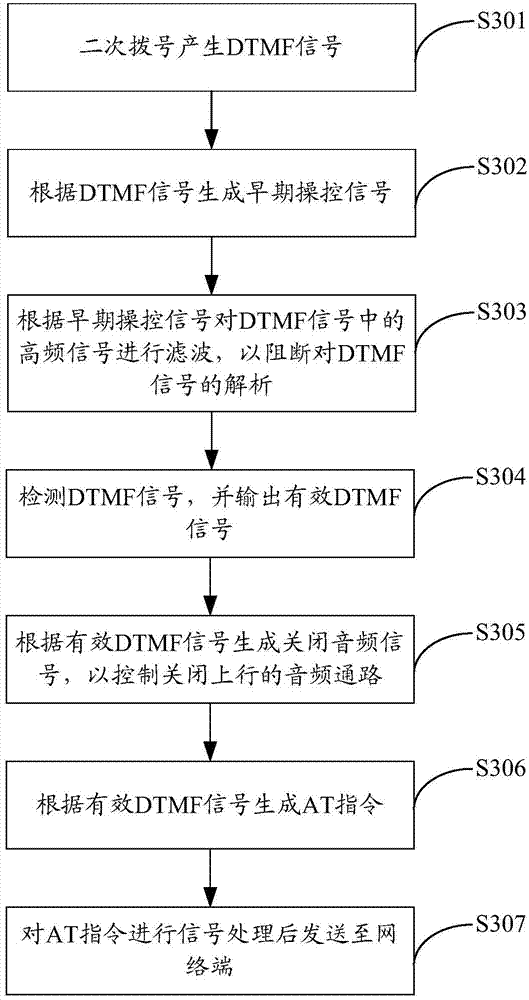
ActiveCN104735811ASolution success rateSolve the high false positive rateConnection managementCommmunication supplementary servicesCommunication unitControl signal
The invention is applicable to the field of communication and provides a secondary dialing method based on a wireless access system and wireless access equipment. The method comprises the steps that DTMF signals are produced through secondary dialing; early-stage control signals are generated according to the DTMF signals; high-frequency signals in the DTMF signals are filtered according to the early-stage control signals so that resolution of the DTMF signals can be blocked; an uplink audio frequency channel is controlled and closed according to the DTMF signals, and an AT instruction is generated; the AT instruction is subjected to signal processing and then transmitted to a network end. According to the secondary dialing method based on the wireless access system, a digital filter in the uplink audio frequency channel in a wireless communication unit is used for finishing blocking the DTMF signals of the uplink audio frequency channel so that a receiving terminal of an opposite side can not recognize the DTMF signals transmitted to the receiving terminal through the audio frequency channel, and the problems that the wireless access equipment is low in success rate, high in false alarm rate and prone to being disturbed by wireless radio frequency in the secondary dialing process are solved thoroughly; the method has the advantages of being economical, practical, simple and effective.
Owner:TRIONES TECH
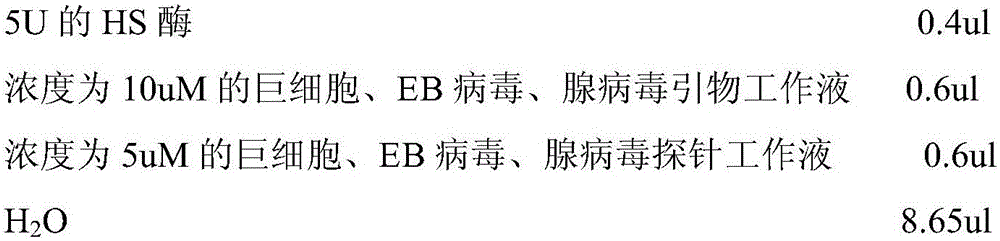
Primer-probe assembly for detecting cytomegalovirus, EB (epstein-barr) virus and adenovirus
InactiveCN106191308AAvoid pollutionHigh degree of automationMicrobiological testing/measurementMicroorganism based processesFluorescenceRespiratory infection
The invention relates to primers and probes for detection of various respiratory viruses and provides a primer-probe assembly for detecting cytomegalovirus, EB (epstein-barr) virus and adenovirus. Sequences of a probe and a primer pair for detecting the cytomegalovirus, the EB virus and the adenovirus are as shown in SEQ ID NO:1-9. The invention further provides a kit for simultaneous detection of the cytomegalovirus, the EB virus and the adenovirus. By combination of multiplex PCR (polymerase chain reaction) and Taqman fluorescent probe technique, simultaneous detection of various pathogens possibly causing acute respiratory infection can be realized in one-time detection, and quickness in diagnosis and treatment guide is realized. In addition, shortening of operation time and reduction of raw material consumption are realized, and high sensitivity and specificity, effectiveness in solving of PCR pollution, high automation degree and the like are achieved.
Owner:ZHEJIANG UNIV
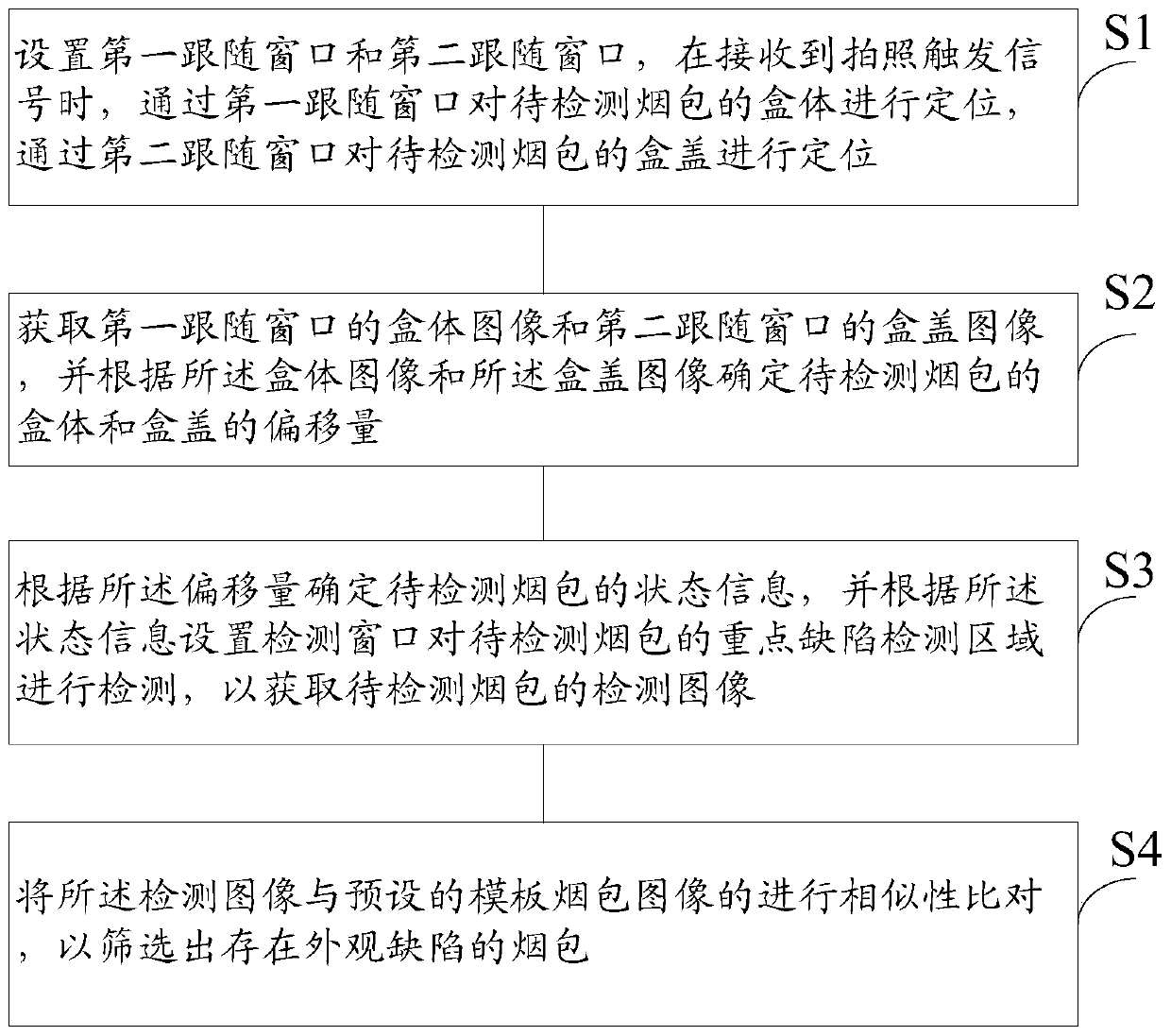
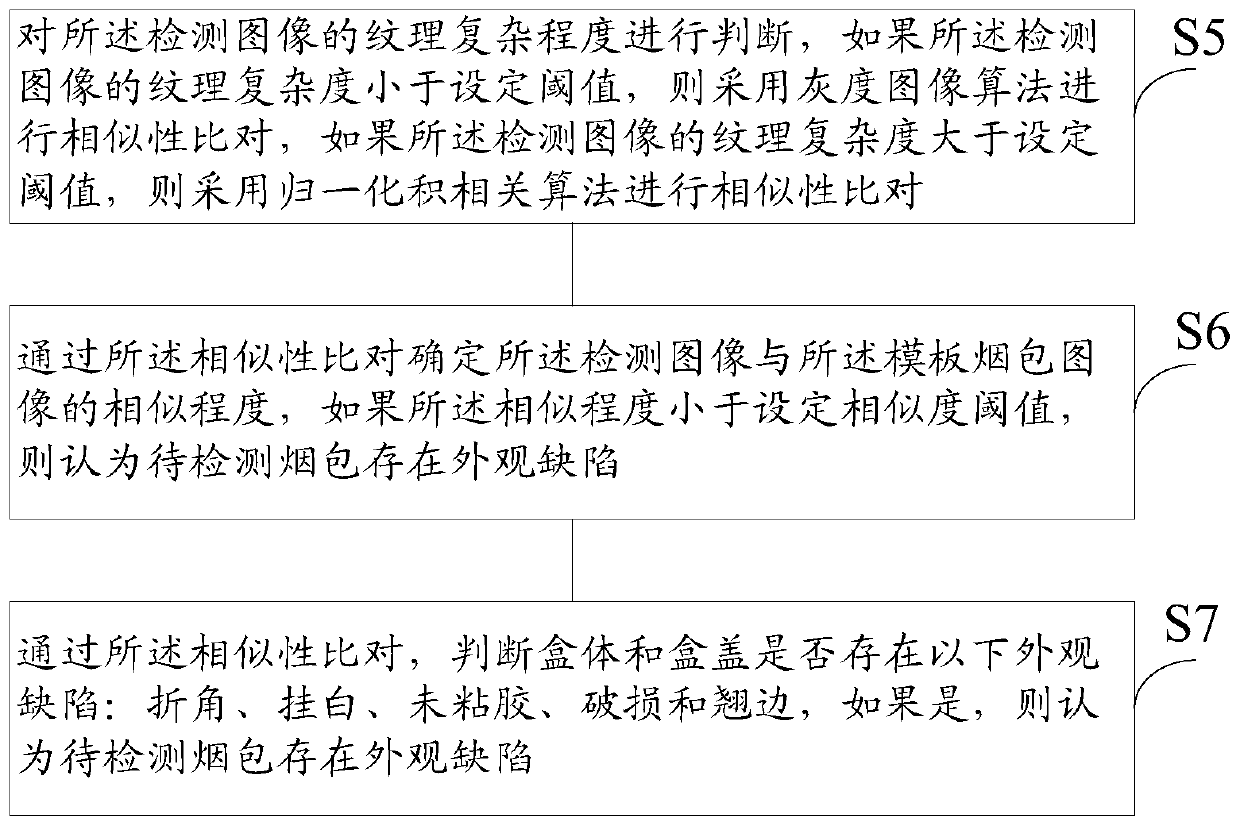
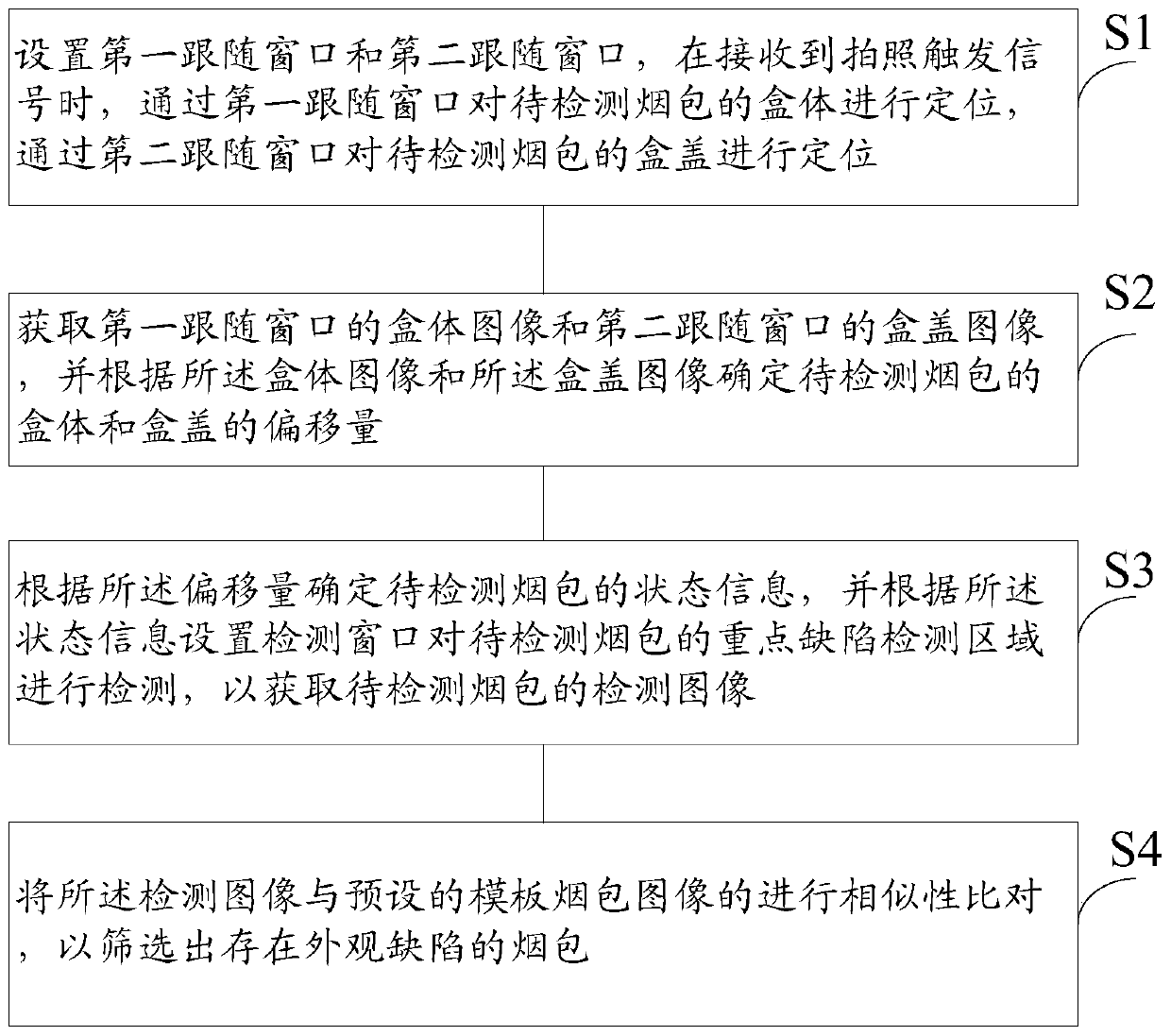
Cigarette package appearance defect detection method and system
ActiveCN109911280ASolve the accuracy problemSolve the high false positive ratePackaging cigarettePackaging cigarsBody imagesFalse detection
The invention provides a cigarette package appearance defect detection method and system. The method comprises the steps that a first following window and a second following window are arranged, whena photographing triggering signal is received, a box body of a to-be-detected cigarette package is positioned through the first following window, and a box cover of the to-be-detected cigarette package is positioned through the second following window; a box body image of the first following window and a box cover image of the second following window are acquired, and the offset of the box body and the box cover of the to-be-detected cigarette package is determined; state information of the to-be-detected cigarette package is determined according to the offset, a detection window is set according to the state information to detect a key defect detection area of the to-be-detected cigarette package, and then a detection image of the to-be-detected cigarette package is acquired; and similarity comparison is conducted on the detection image and a preset template cigarette package image to screen out the cigarette package with the appearance defect. According to the cigarette package appearance defect detection method and system, the intelligence of cigarette package appearance quality detection can be improved, and the false detection rate of cigarette package appearance defect detection is decreased.
Owner:HONGYUN HONGHE TOBACCO (GRP) CO LTD
Liquid medium leakage automatic detection method and system based on thermal imaging
ActiveCN112733646ARealize automatic identificationRealize the alarmCharacter and pattern recognitionAlarmsLiquid mediumEngineering
The invention relates to a liquid medium leakage automatic detection method and system based on thermal imaging. The system is characterized by comprising an image collection module which is used for obtaining a frame of thermal image of a to-be-detected region, and enabling the frame of thermal image to serve as a background image if the frame of thermal image is a first frame of infrared image; the background subtraction module is used for extracting a dynamic change region of the current frame of thermal image by adopting a background subtraction method; the processing stage setting module is used for setting a processing stage; the parameter calculation module is used for calculating parameters of the thermal image; the gas leakage judgment module is used for judging whether liquid medium leakage occurs in the to-be-detected area or not when the calculated parameters of the thermal image meet preset detection conditions; the alarm module is used for outputting an alarm signal when liquid medium leakage occurs in the to-be-detected area, and marking an extracted dynamic change area in the corresponding frame of thermal image; the hazardous chemical substance leakage detection system and the hazardous chemical substance leakage detection method can be widely applied to the field of hazardous chemical substance leakage detection.
Owner:咏峰(大连)科技有限公司
Magnet polarity detection equipment
ActiveCN112354879ASolve labor intensitySolve the high false positive rateMagnetic property measurementsSortingControl systemMagnetic poles
The invention discloses magnet polarity detection equipment. The equipment comprises a feeding platform, a Hall detection platform, a stock bin platform, a manipulator and a control system; a Hall sensor for detecting the magnet polarity is arranged on the Hall detection platform; the manipulator is used for grabbing a to-be-detected product from the feeding platform, placing the to-be-detected product on the Hall detection platform, and grabbing the qualified product and placing the same on the stock bin platform after the to-be-detected product placed on the Hall detection platform is detected to be qualified; and the control system is used for controlling the manipulator to act, receiving an induction signal output by the Hall sensor after detection, judging the magnetic pole mounting direction of a magnet in the to-be-detected product according to the induction signal, and determining the to-be-detected product with the correct mounting direction as the qualified product. Accordingto the magnet polarity detection equipment, the polarity of the magnet arranged in the to-be-detected product can be automatically detected, and whether the magnetic pole of the magnet is reversely mounted in the to-be-detected product or not can be automatically recognized.
Owner:GEER TECH CO LTD
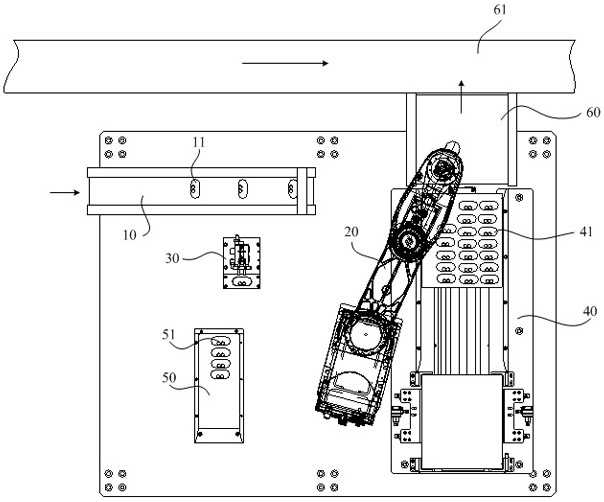
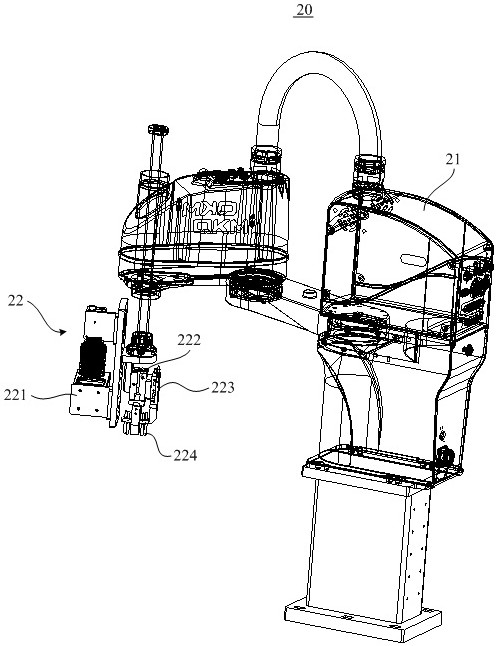
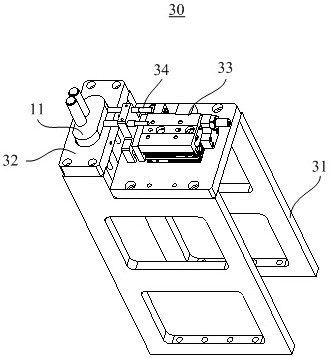
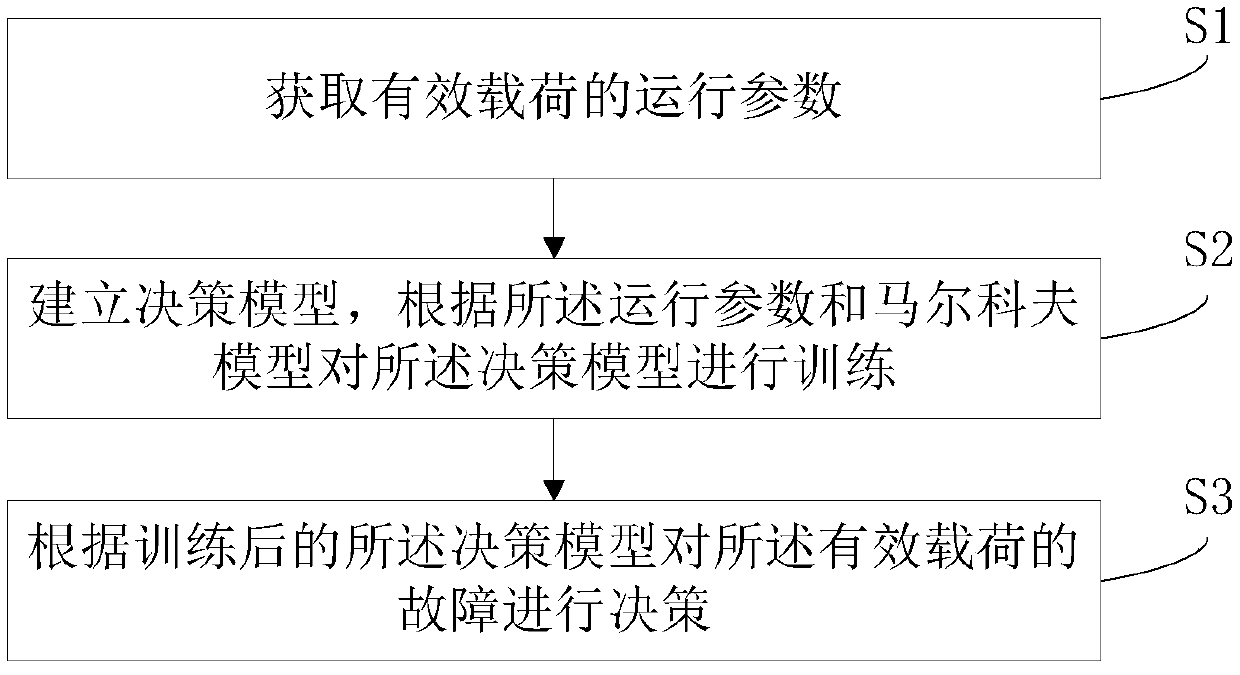
Fault decision-making method for effective load
ActiveCN109583751ASolve the associativity problemSolve the high false positive rateNeural architecturesResourcesFalse detectionInference
The invention discloses a fault decision-making method for a payload, and relates to the field of spacecrafts. The method comprises the steps that operation parameters of a payload are acquired; Establishing a decision-making model, and training the decision-making model according to the operation parameters and the Markov model, the decision-making model being a deep enhanced network model; And making a decision on the fault of the effective load according to the trained decision model. The invention provides a fault decision-making method, the depth enhancement network model is trained through the operation parameters and the Markov model; and fault diagnosis, Inference and decision are combined, According to the method, the complete cycle process from fault discovery to fault decision making of the spacecraft effective load is achieved, the problem that under the influence of multiple factors, the complex jump parameter relevance and the false detection rate are high is solved, probability fuzzy diagnosis and dynamic updating of the context logic relation are achieved, and the accuracy and timeliness of fault diagnosis and decision making are improved.
Owner:TECH & ENG CENT FOR SPACE UTILIZATION CHINESE ACAD OF SCI
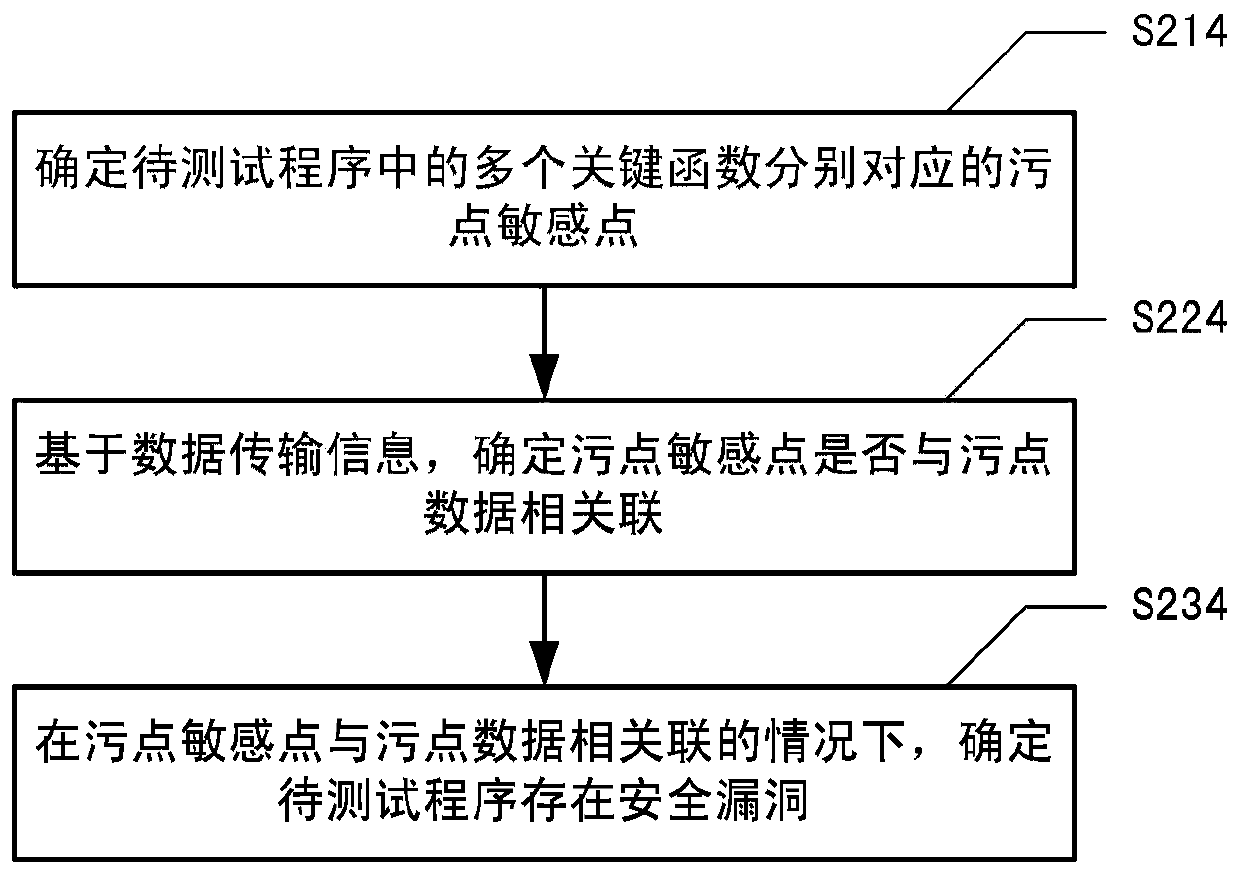
Test method and device, electronic equipment and readable storage medium
PendingCN111427792ASolve the high false positive rateImprove test efficiencySoftware testing/debuggingPlatform integrity maintainanceData streamSoftware engineering
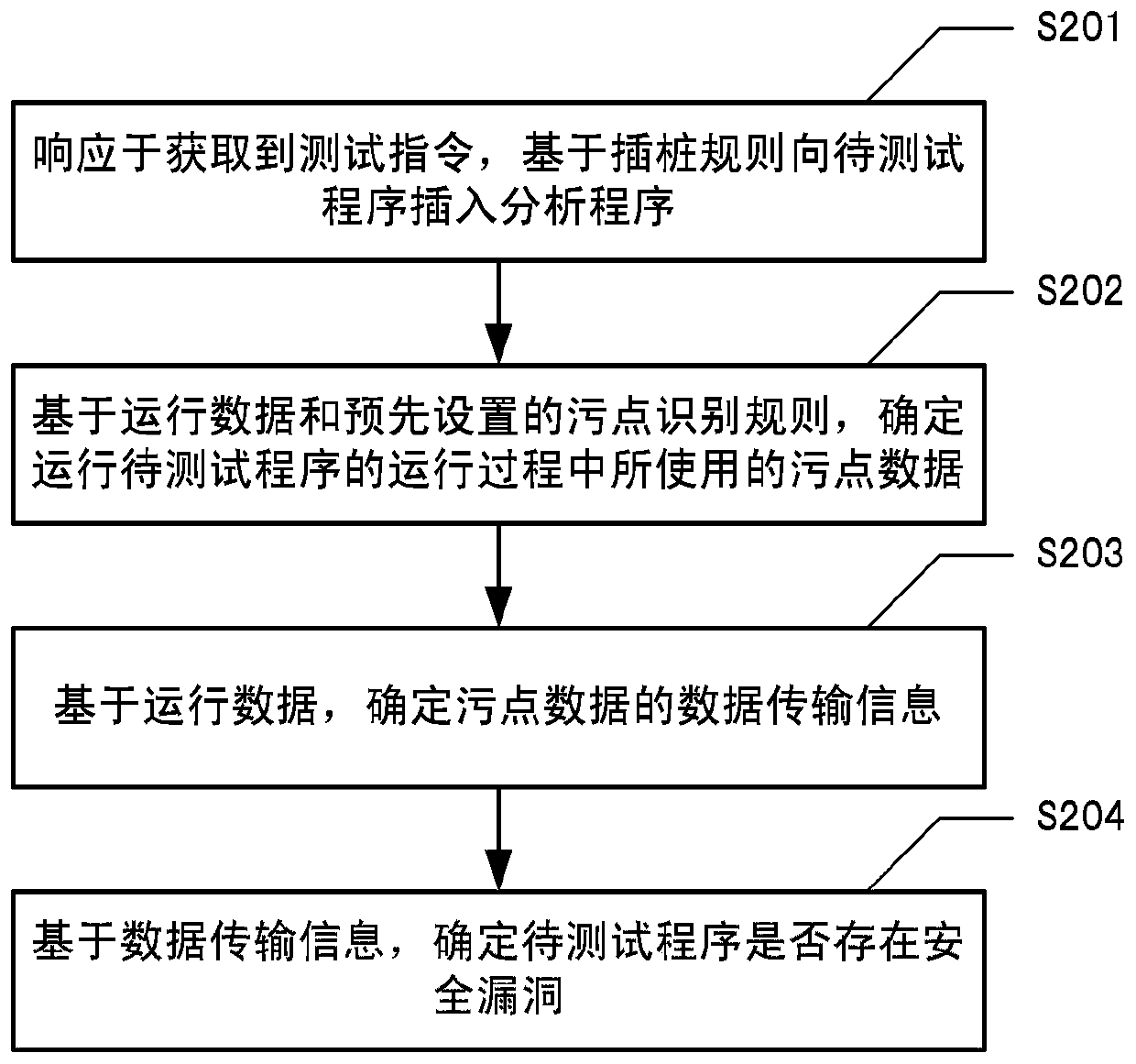
The invention relates to the field of security testing, and provides a testing method, which comprises the steps of inserting an analysis program into a to-be-tested program based on an instrumentation rule in response to an obtained testing instruction, so as to obtain running data generated in a running process of the to-be-tested program through the analysis program; based on the operation dataand a preset stain identification rule, determining stain data used in the operation process of the to-be-tested program; determining data transmission information of the taint data based on the operation data; and determining whether the to-be-tested program has security holes or not based on the data transmission information. The invention further provides a test device, electronic equipment and a computer readable storage medium. According to the method, the IDE plug-in is integrated in the development environment, and the instrumentation technology is used for dynamically tracking the stain data flow direction so as to determine whether the program has potential security vulnerabilities or not.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
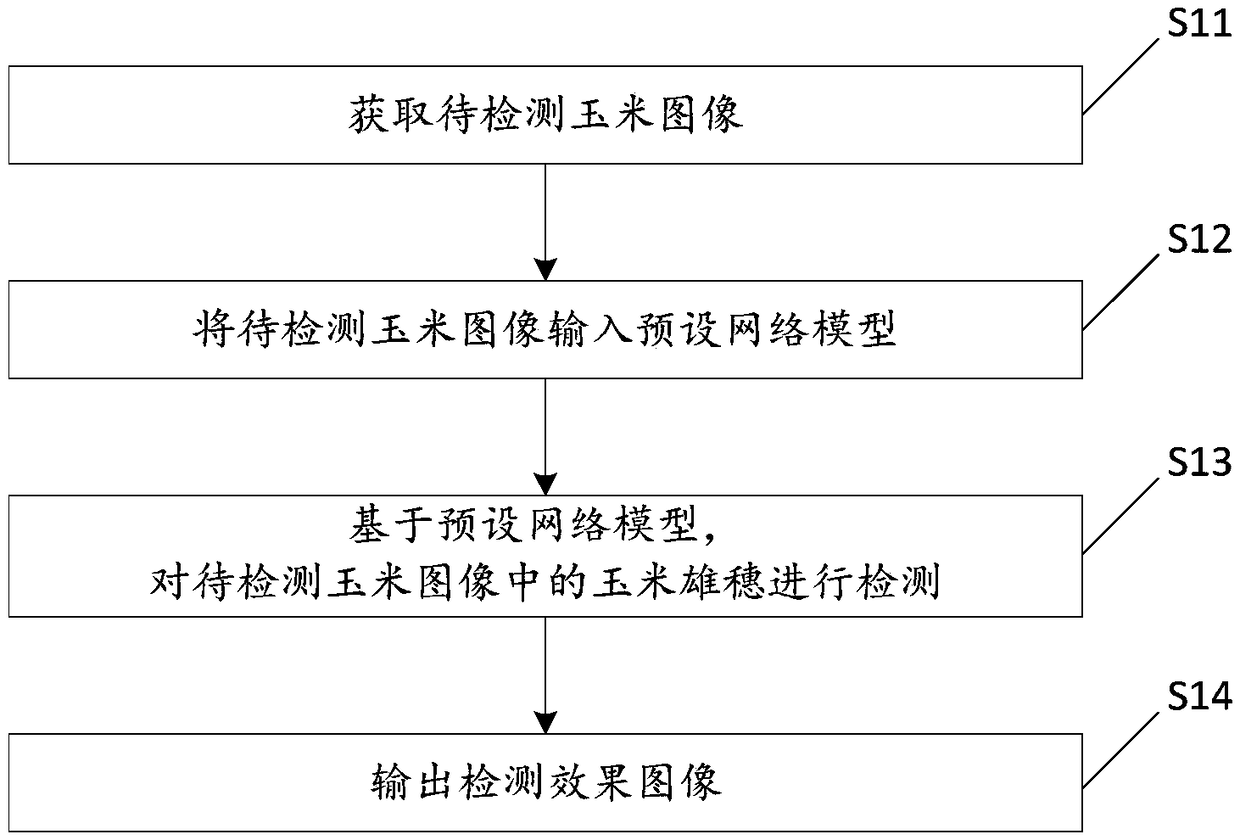
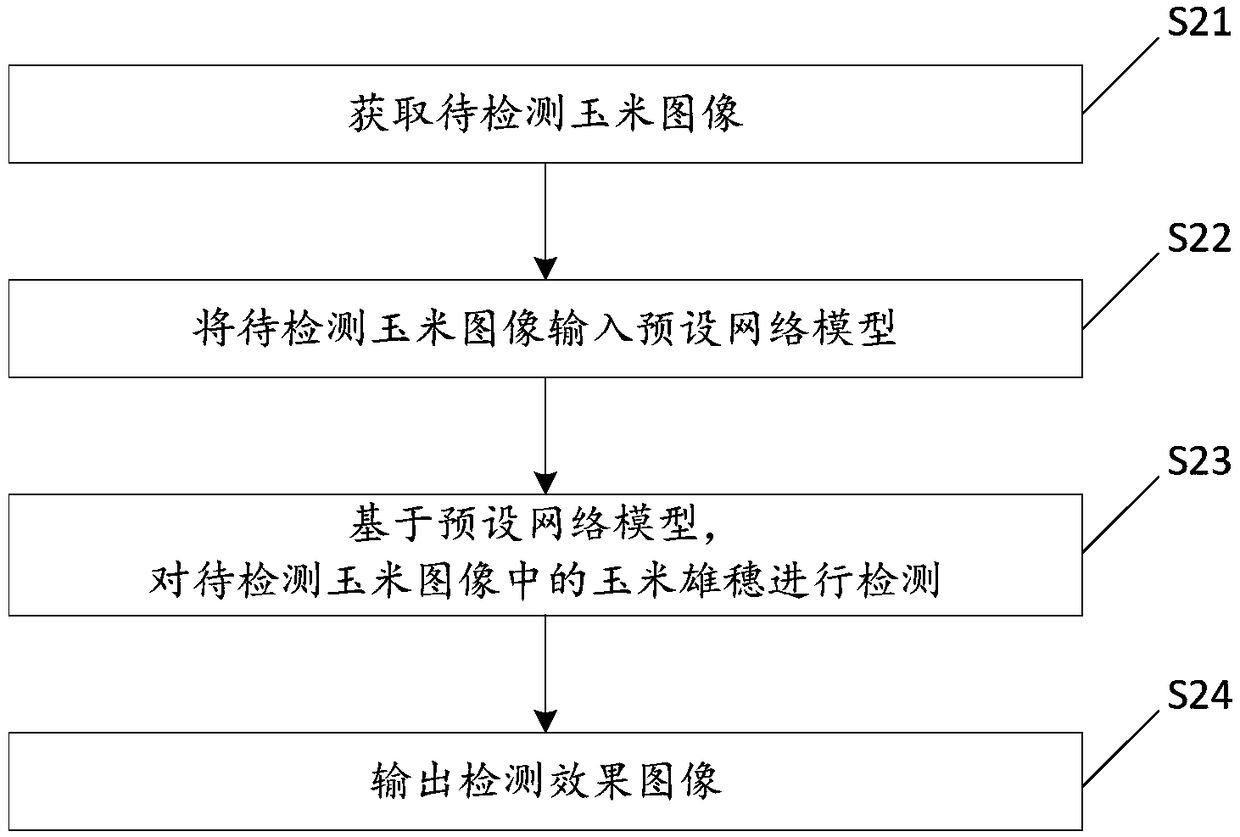
Testing method, device and testing equipment for corn stalk
InactiveCN109472771AReduce false detection rateReduce gapImage enhancementImage analysisSample imageNetwork model
The invention discloses a detection method, a device and a detection device of a corn stalk. The method comprises the following steps: obtaining an image of the corn to be detected; Inputting the cornimage to be detected into a preset network model; Wherein, the preset network model is obtained by using a convolution neural network to train sample images of several corn stalks; The convolution neural network comprises at least one convolution layer, at least one activation layer, at least one pooling layer and at least one full connection layer. Detecting the corn stalk in the corn image to be detected based on the preset network model; Output Detection Effect Image. This method takes the sample image of corn tassels under the farmland as the object, The preset network model based on theimage feature detection of corn stalks is established by using the image features of corn stalks in the sample images. The preset network model can accurately detect the corn stalks in the corn imagesto be detected, which greatly reduces the false detection rate of corn stalks.
Owner:江苏省无线电科学研究所有限公司
Comprehensive perimeter security and protection system and method with infrared thermal image verification
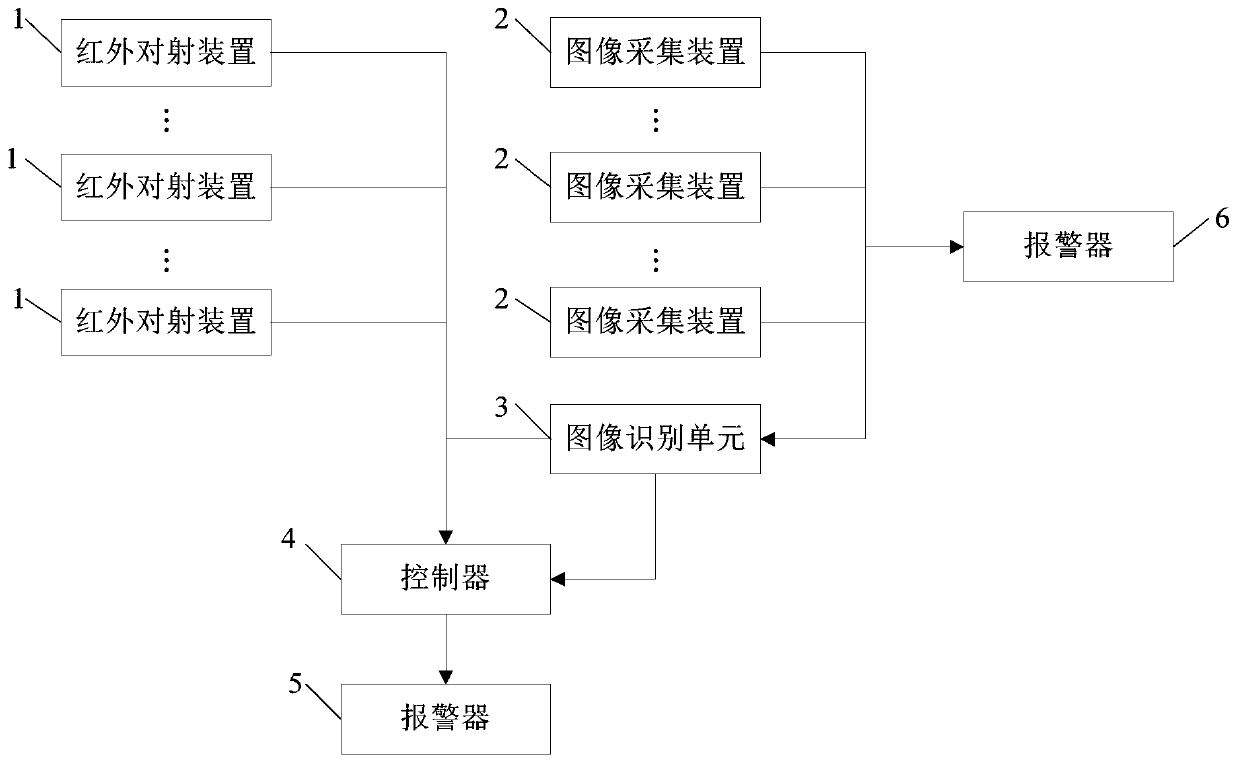
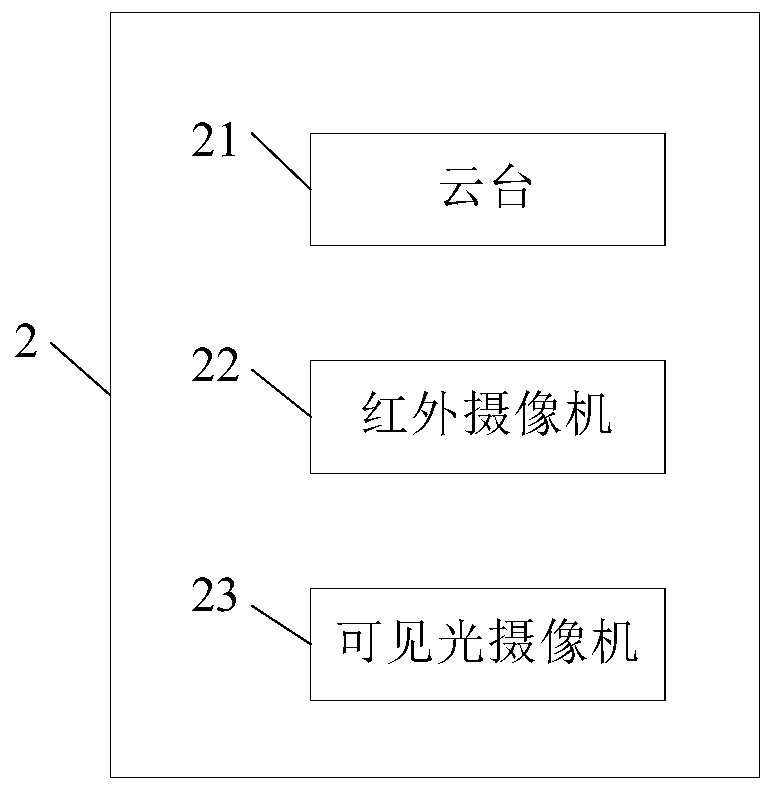
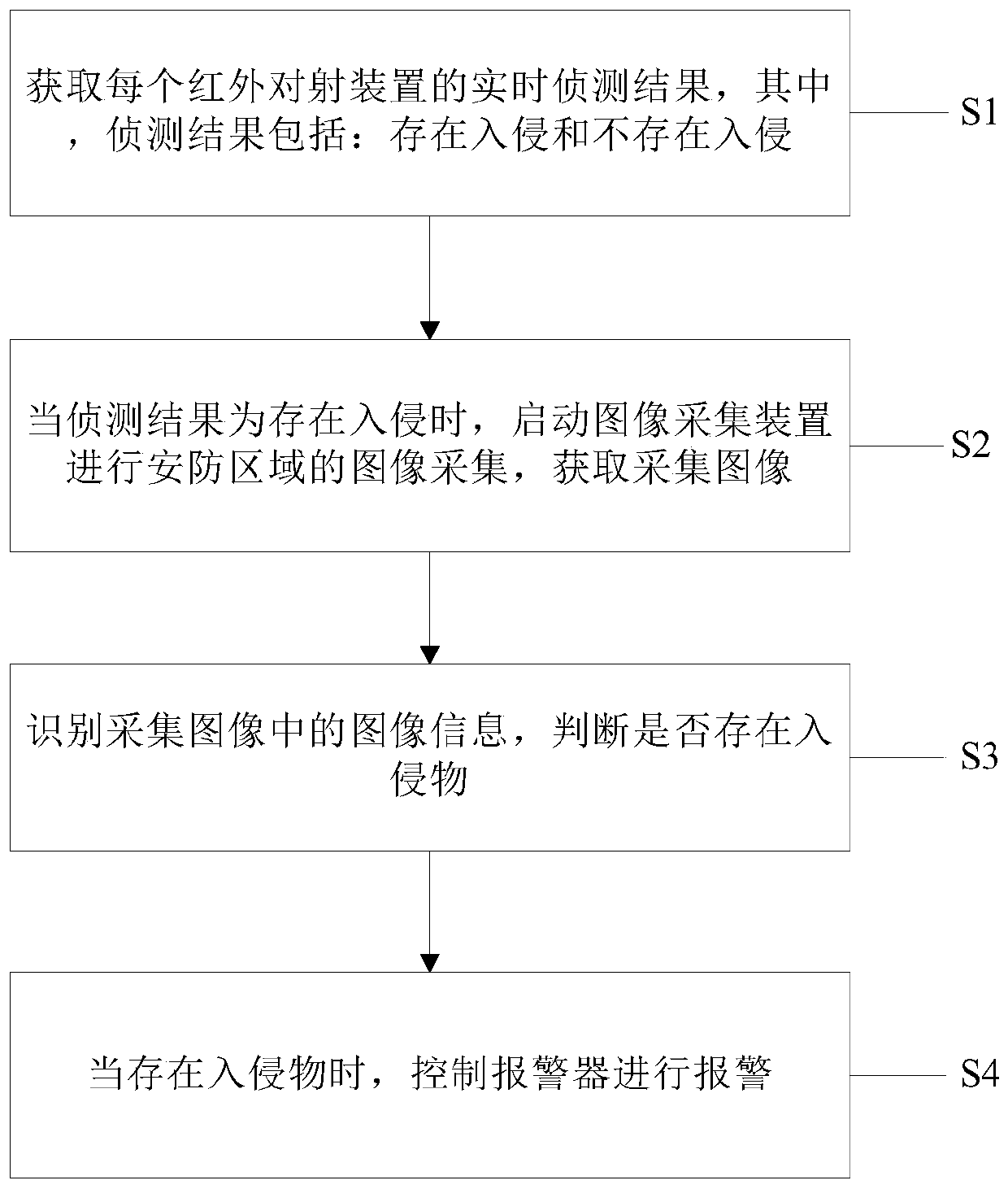
PendingCN111429681ASolve the high false positive rateCannot restrict disclosureBurglar alarm electric actuationBurglar alarm short radiation actuationReal-time computingImage identification
The invention discloses a comprehensive perimeter security and protection system and method with infrared thermal image verification. Compared with an existing security and protection system, the security and protection system in the invention has the advantages that an image acquisition device and an image recognition unit are additionally arranged; an alarm signal of the infrared correlation device is confirmed and verified, a controller controls an alarm to give an alarm only after successful verification is confirmed, and at the moment, the problem that the false alarm rate of the infraredcorrelation device is high due to the influence of fallen leaves or rain and snow and other external environments mentioned in the background technology can be effectively solved. The security and protection method is completed based on the security and protection system and has the advantages of being simple, high in operability, high in alarm accuracy and the like.
Owner:SHENYANG HONGJI ELECTRICAL
Detection method and system for micro bar materials
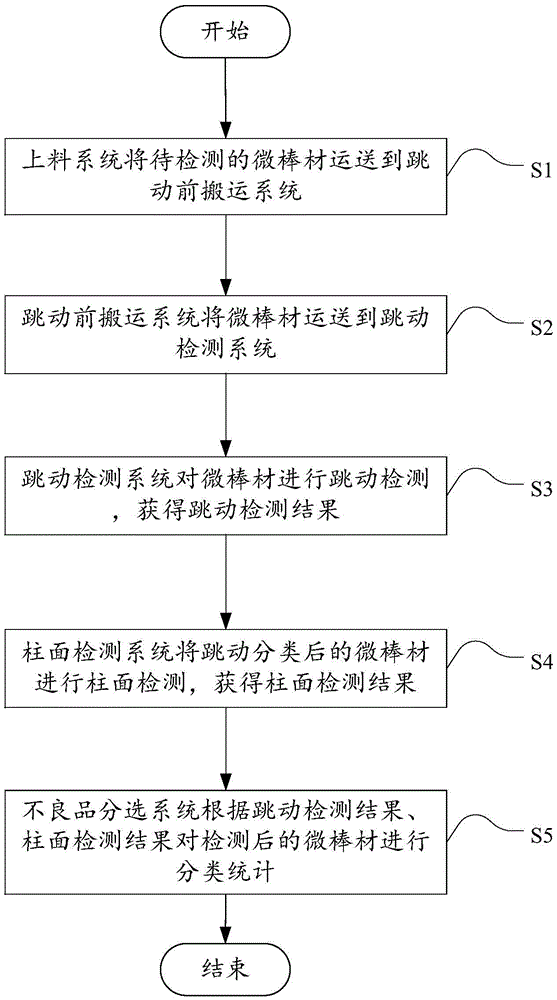
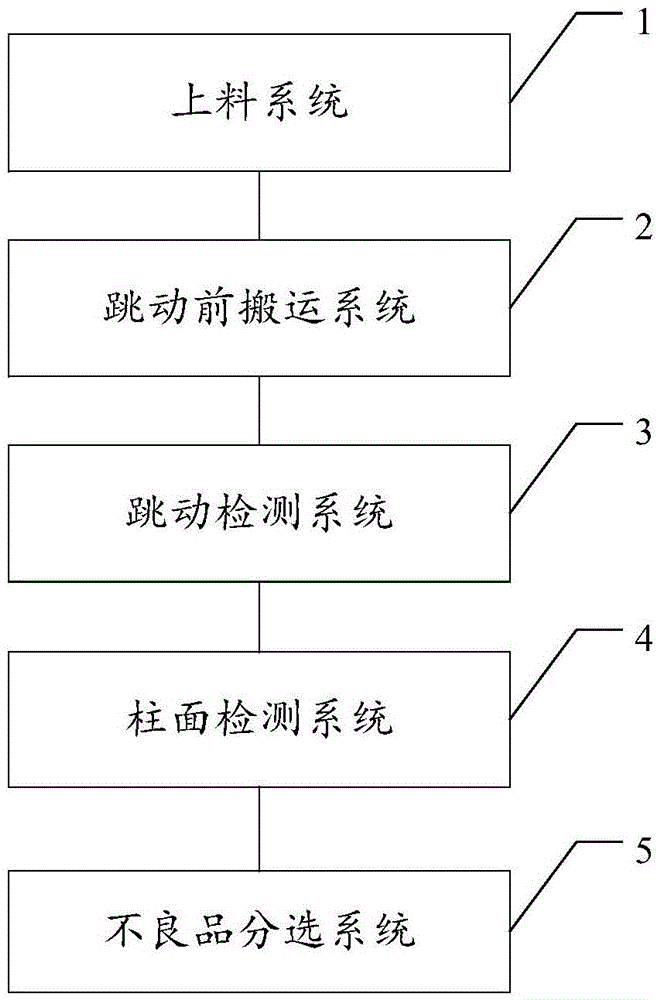
ActiveCN105618387ASolve the problem of not being able to detect surface defects on micro-barsHigh precisionUsing optical meansSortingTest sampleEngineering
The embodiment of the invention discloses a detection method and system for micro bar materials. The method comprises the steps that a feeding system conveys the micro bar materials to be detected to a before-jumping carrying system; the before-jumping carrying system conveys the micro bar materials to a jumping detection system; the jumping detection system carries out jumping detection on the micro bar materials, and a jumping detection result is obtained; a cylindrical detection system carries out cylindrical detection on the micro bar materials obtained after jumping classifying, and a cylindrical detection result is obtained; and a defective-product sorting system carries out classified statistic on the detected micro bar materials according to the jumping detection result and the cylindrical detection result. According to the method and system, precision and repeat reliability of the detection result can be improved; in addition, the detection efficiency can be improved, different kinds of failed test samples can be subject to classified statistic, the problems that in the prior art, when manual detection is adopted, the false drop rate is high, the yield is low, and detection reliability is low are solved, and the problem that in the prior art, surface defective detection cannot be carried out on the micro bar materials can also be solved.
Owner:GUANGDONG INST OF INTELLIGENT MFG +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com