Binary program bug detection method based on function difference
A binary program and vulnerability detection technology, applied in error detection/correction, electrical digital data processing, software testing/debugging, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] In order to make the purpose, features and advantages of the present invention more obvious and understandable, the implementation of the present invention will be described in detail below in conjunction with the accompanying drawings and examples.
[0047] Taking the known vulnerability CVE-2014-0160 as an example, the binary program of the class library OpenSSL1.0.1e is used as the target binary program to be detected to detect this vulnerability.
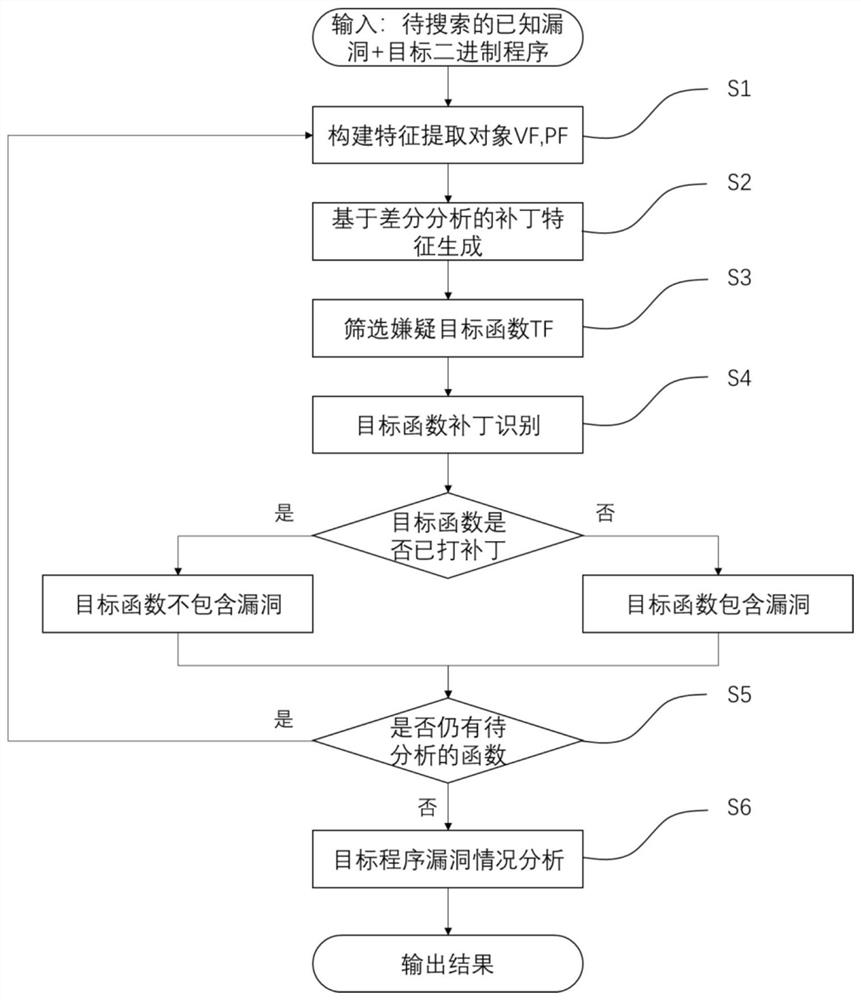
[0048] Such as figure 1 As shown, a binary program vulnerability detection method based on function difference includes the following steps:
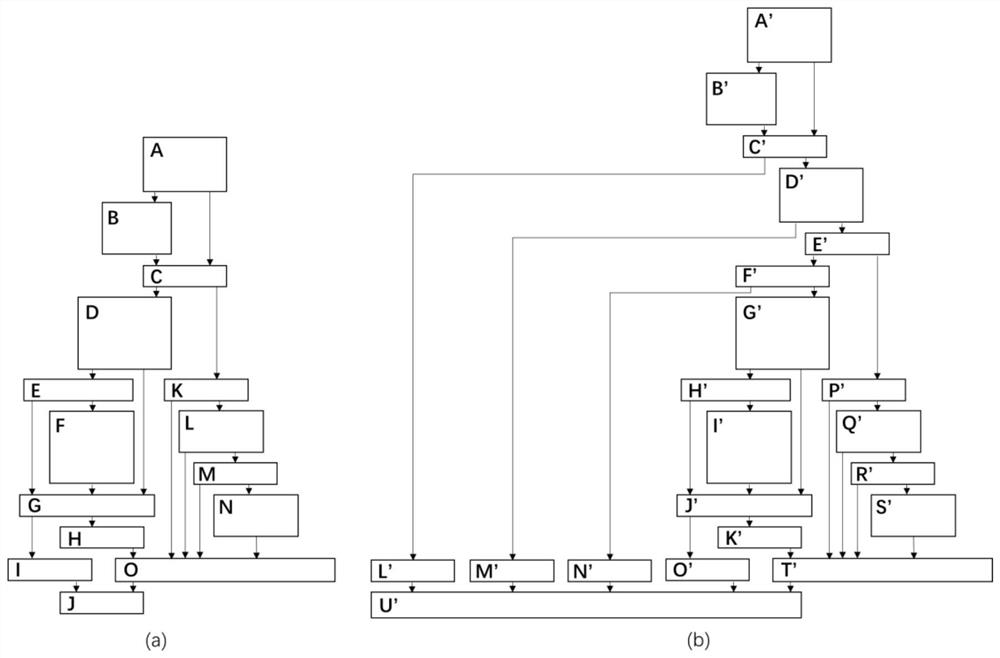
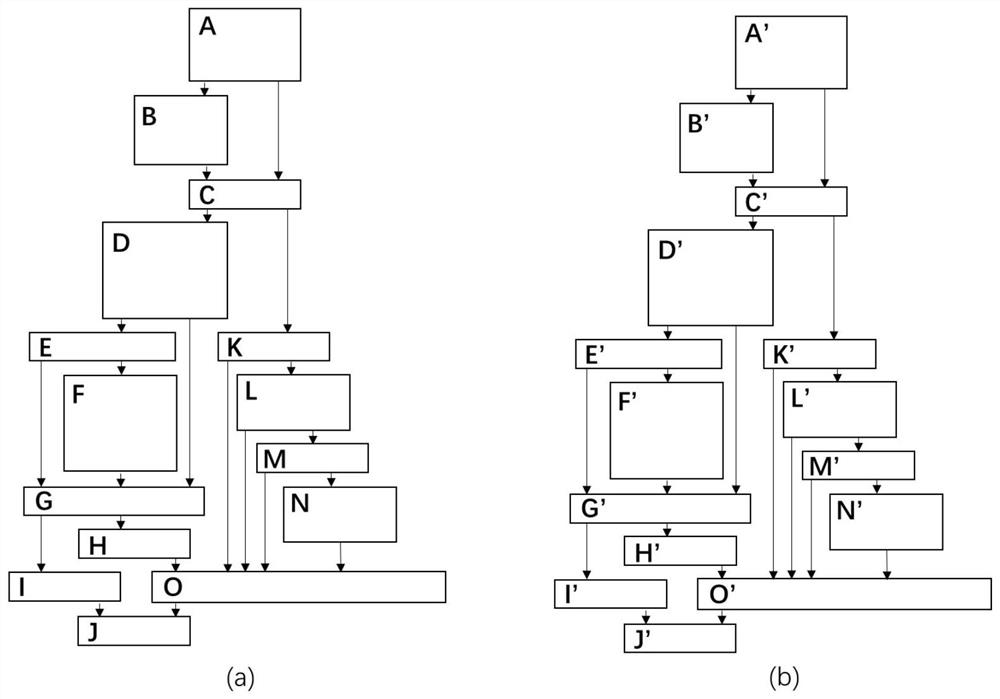
[0049] Step S1: According to the patch and other relevant information, determine that the functions related to the known vulnerability CVE-2014-0160 are dtls1_process_heartbeat(), tls1_process_heartbeat(), first select dtls1_process_heartbeat() for analysis; collect the last vulnerability version function, namely OpenSSL1.0.1 The binary code of the function dtls1_process_heartbeat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com