Patents
Literature
131295 results about "Software engineering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Software engineering is the systematic application of engineering approaches to the development of software.
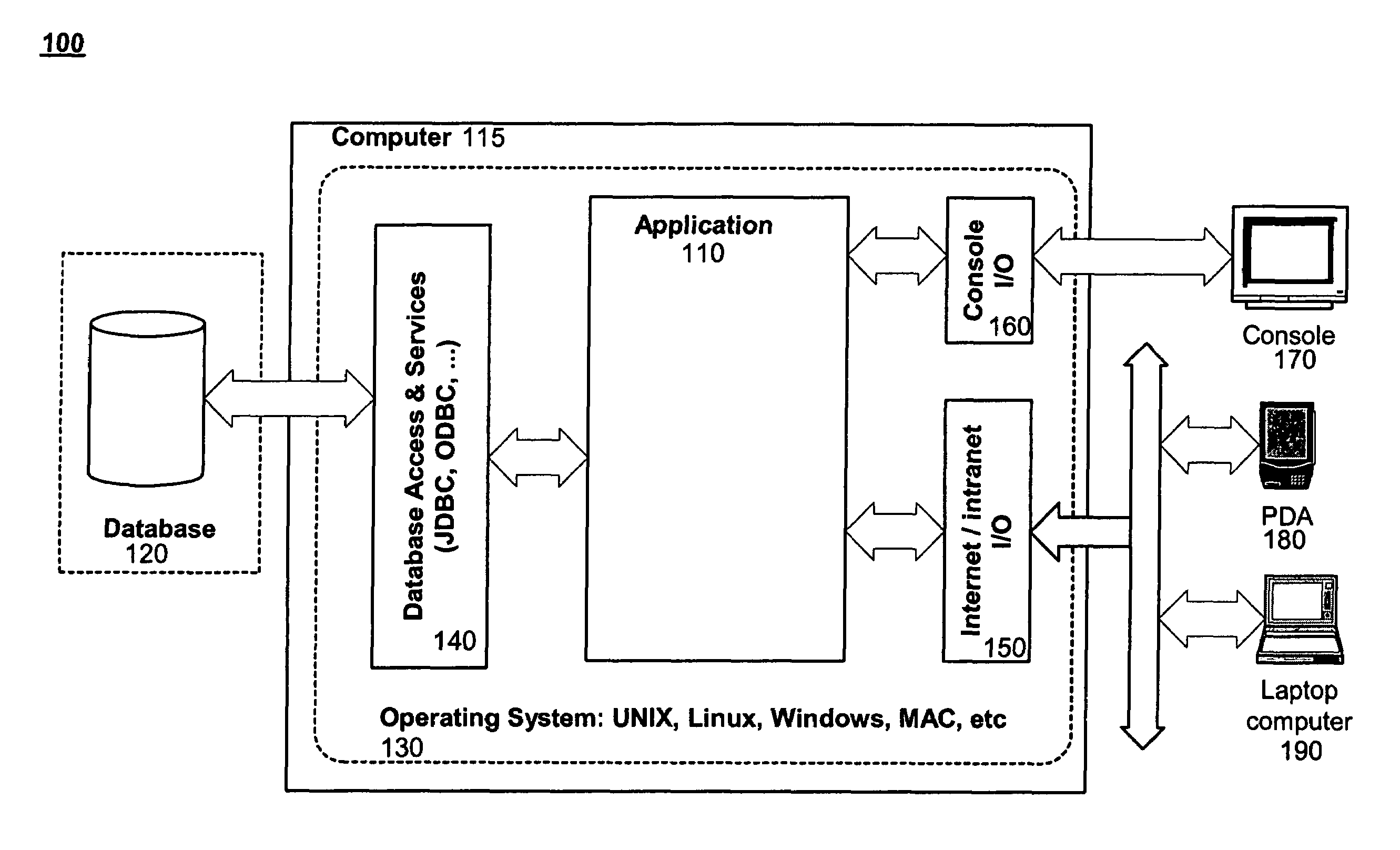
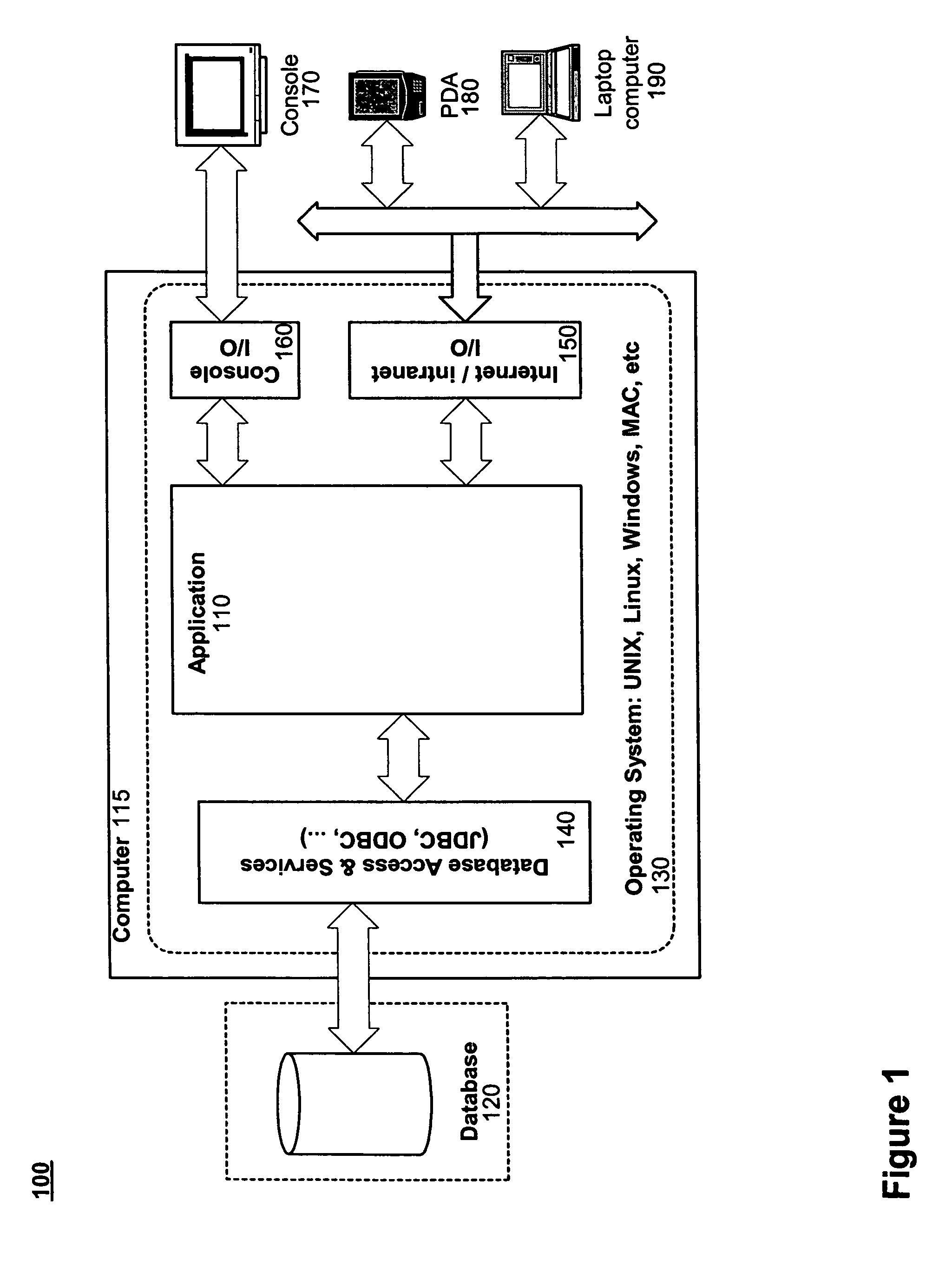
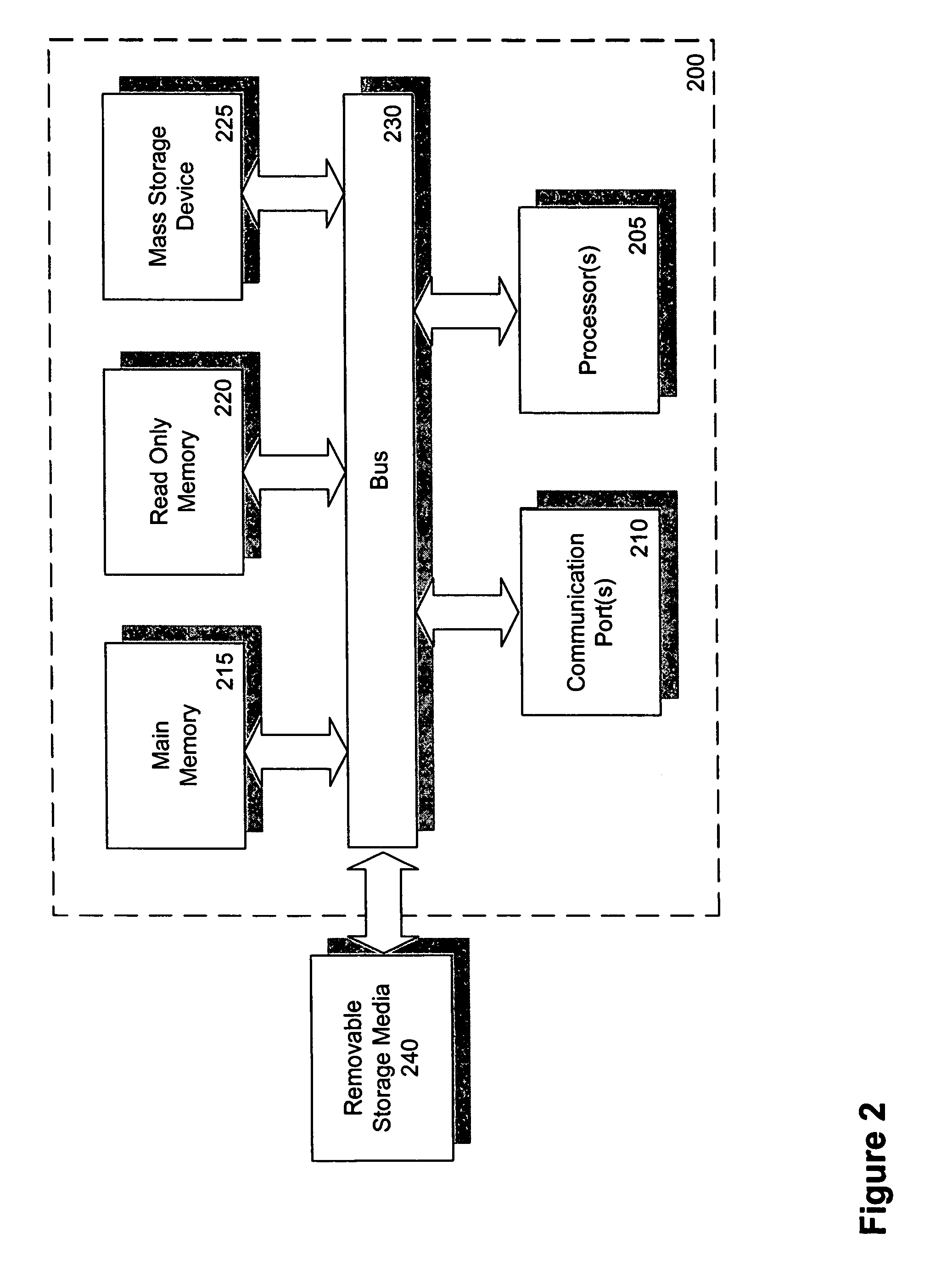
Software framework that facilitates design and implementation of database applications
InactiveUS7412455B2Facilitates efficient design and implementationData processing applicationsDigital data information retrievalSoftware engineeringDatabase application
An intelligent framework is provided that is disposed between a high-level language environment and a database system environment. According to one embodiment, the framework programmatically receives information regarding definitions of data structures of objects participating in a software application and information regarding relationships among the objects. Based upon the particular request from the high-level language environment and upon the definitions and relationships, the framework programmatically and dynamically generates appropriate statements associated with the database system environment that accomplish the request. For example, the framework may issue statements to define the structure of a database, access information from the database, and / or manipulate information within the database.
Owner:RPX CORP
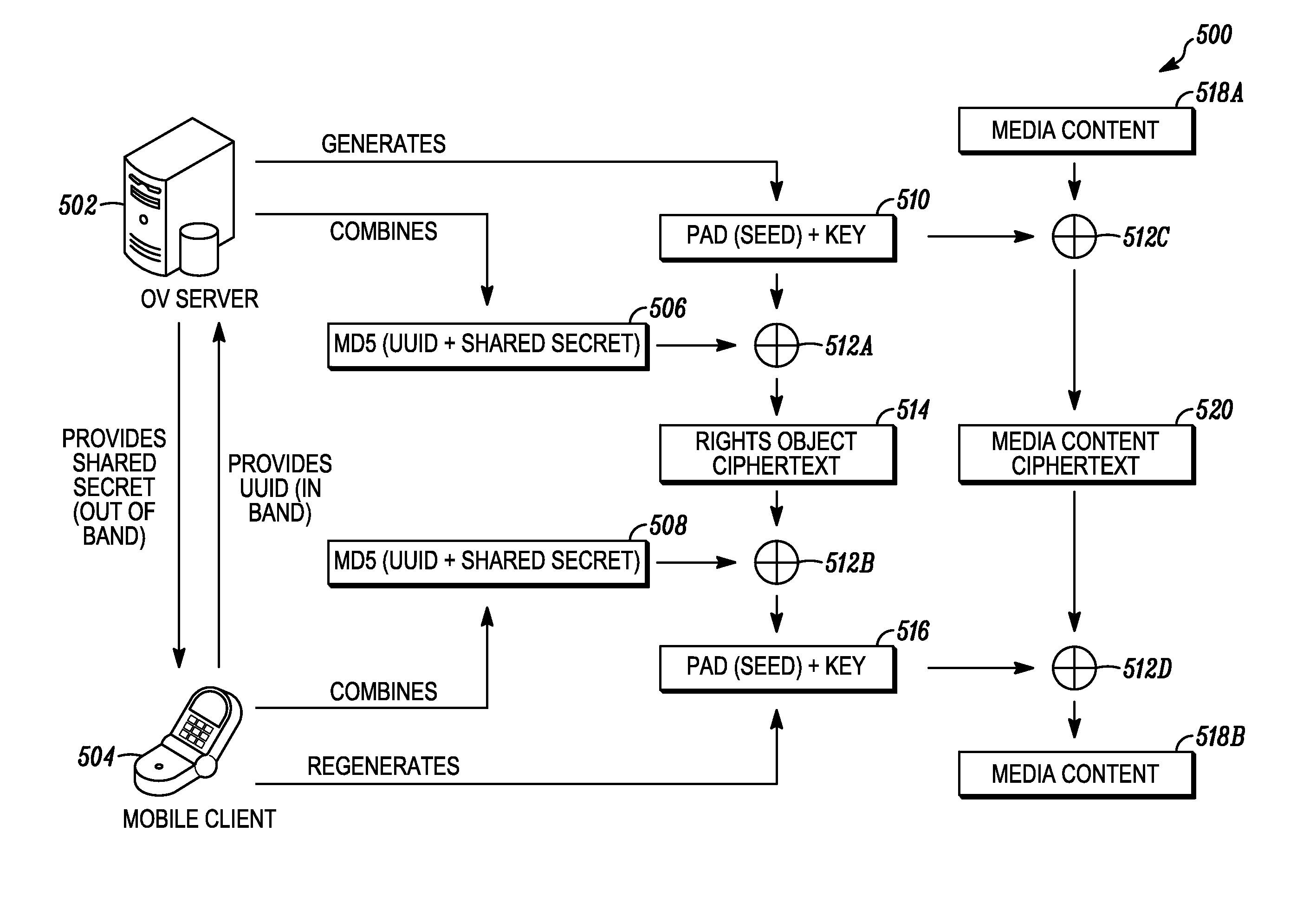
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
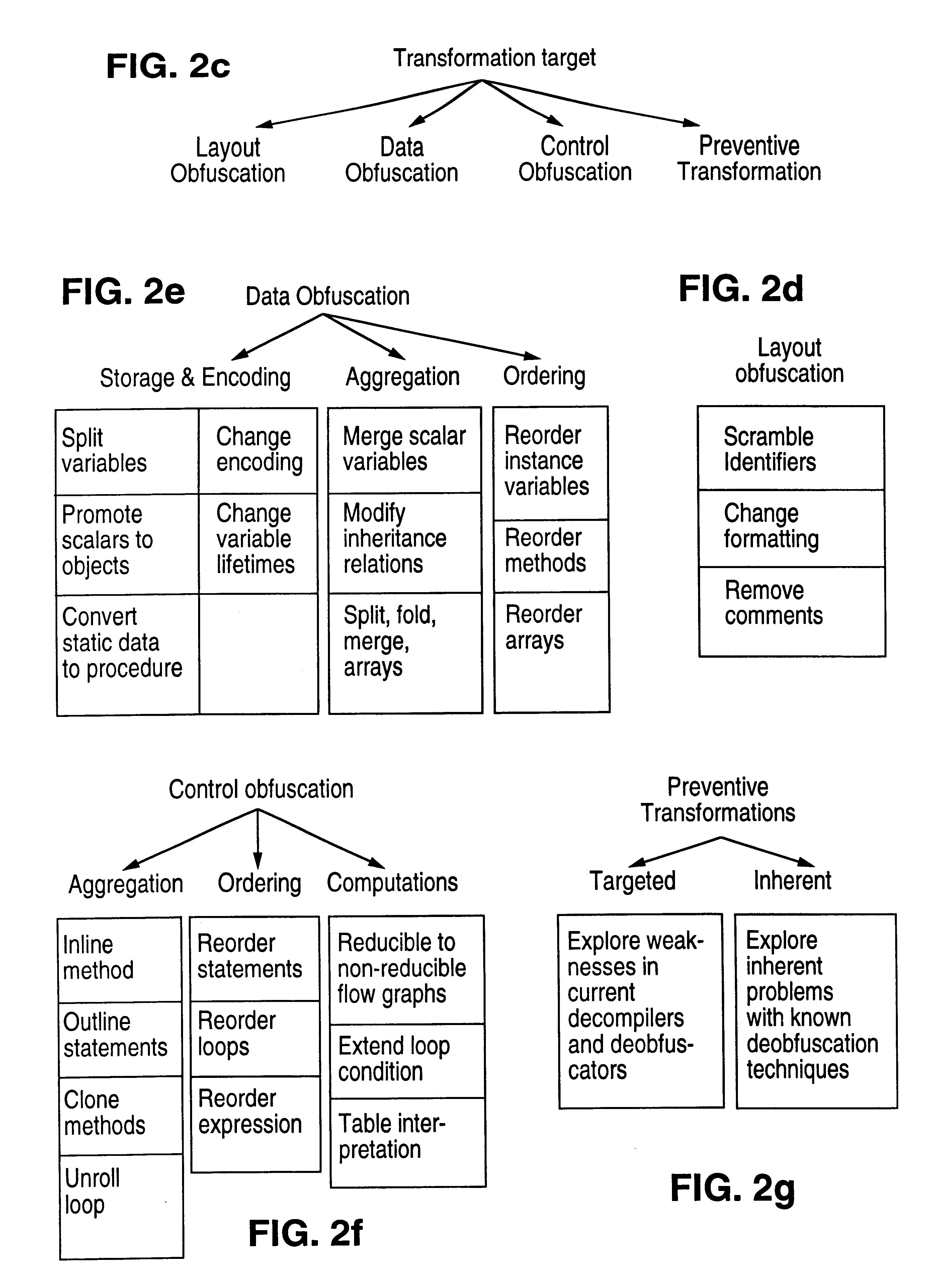
Obfuscation techniques for enhancing software security
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
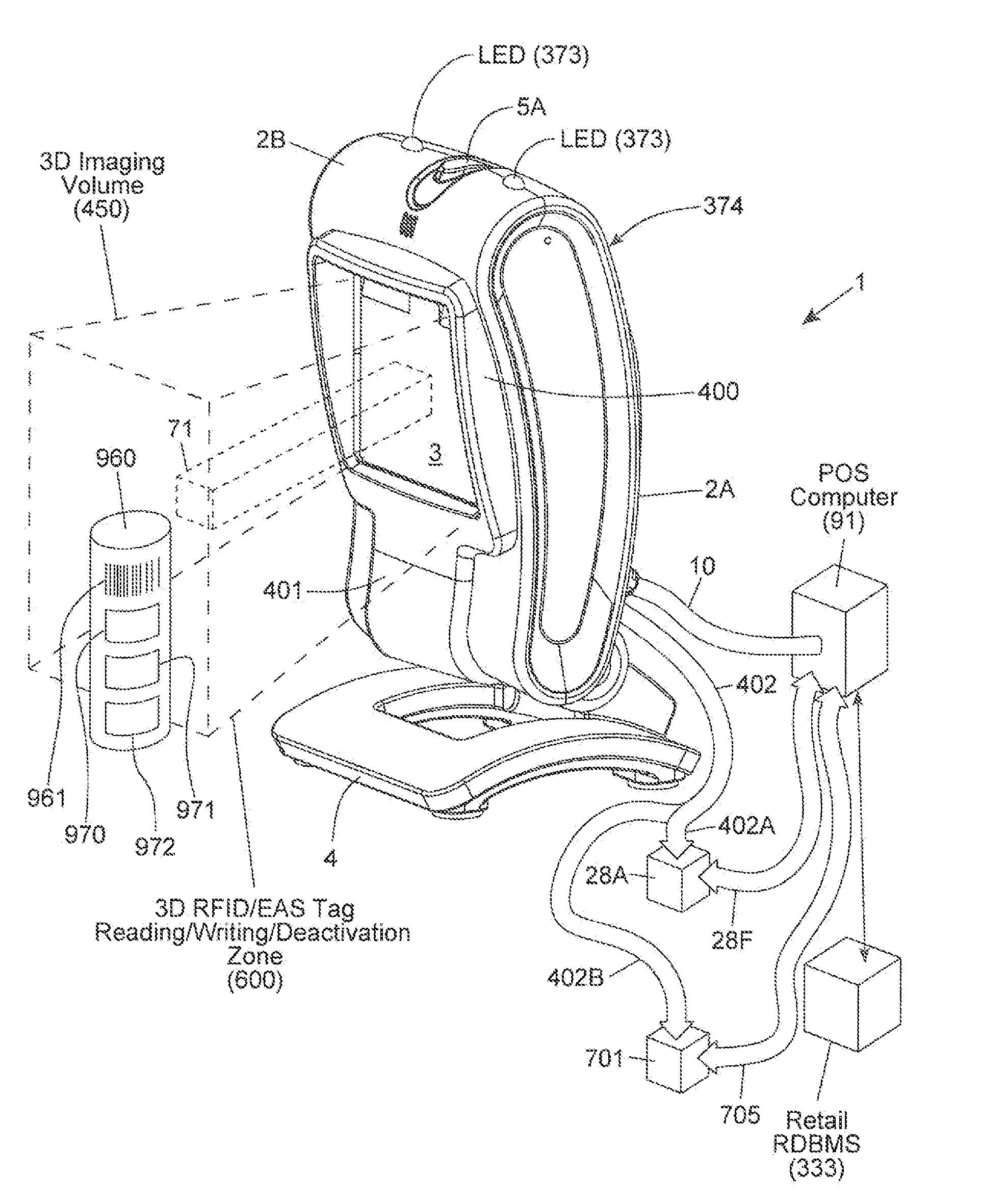
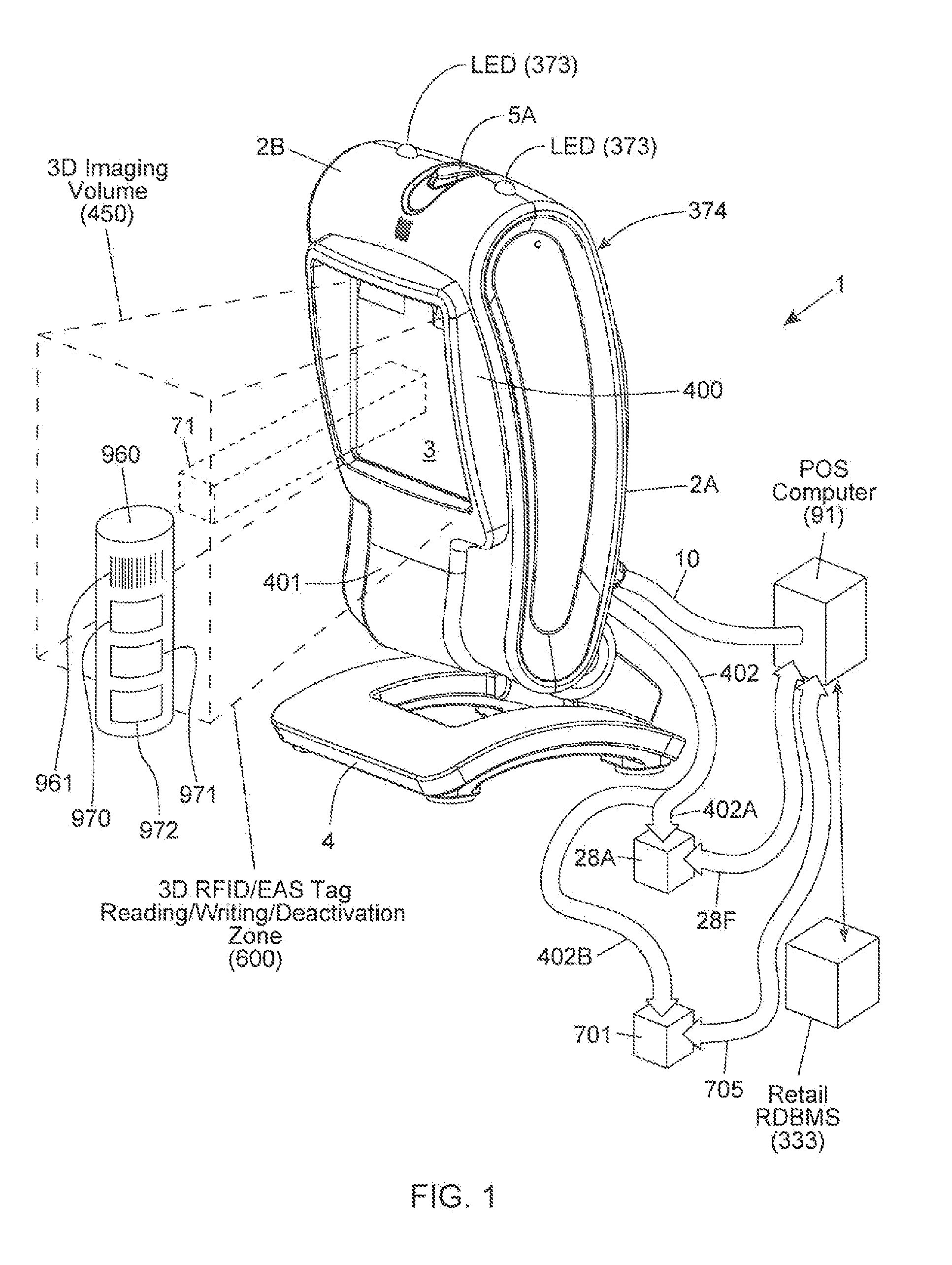
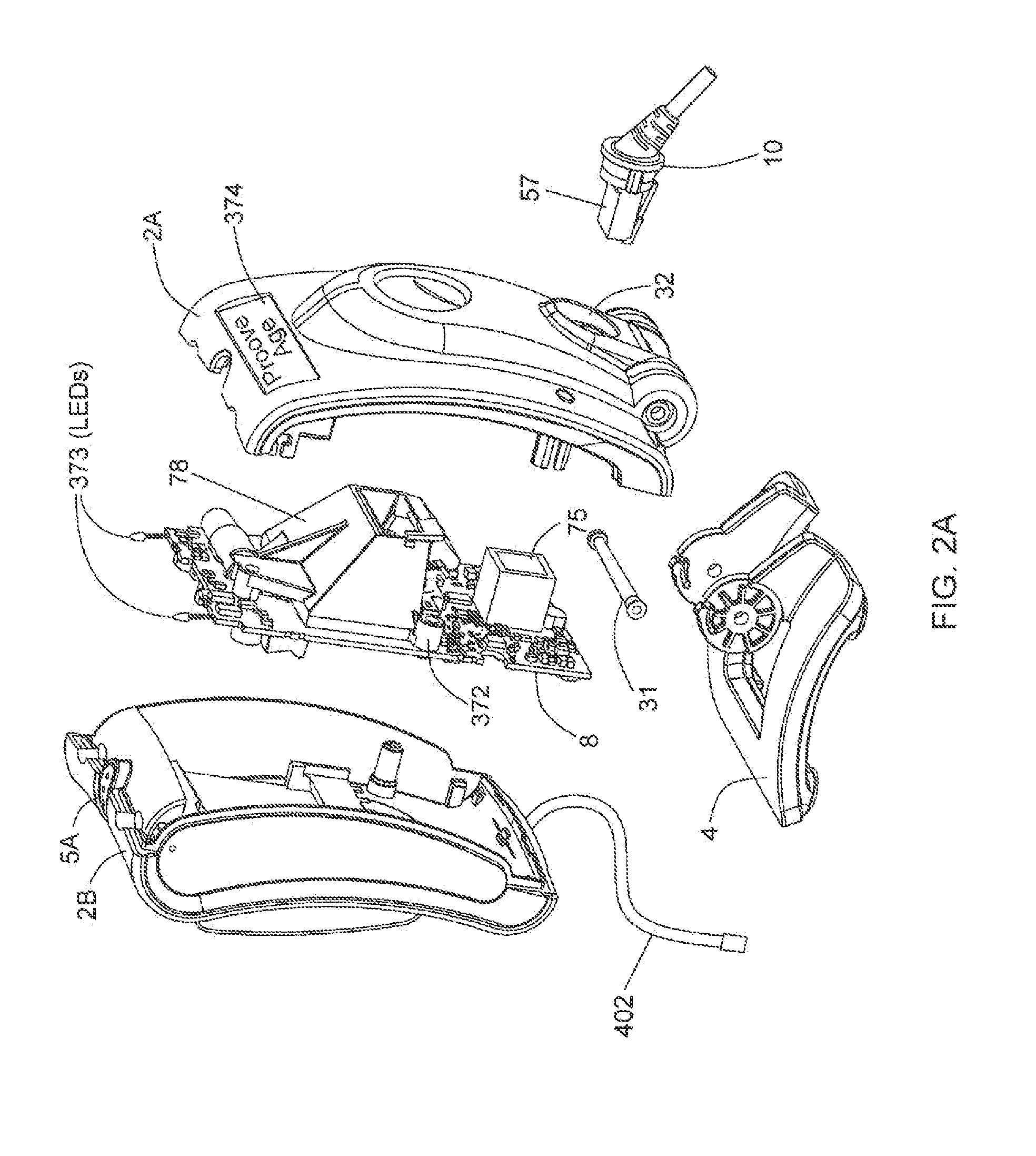
Method of and system for uniquely responding to code data captured from products so as to alert the product handler to carry out exception handling procedures
InactiveUS20120203647A1Avoid disadvantagesEffectively reliably informCash registersPayment architectureLogistics managementSoftware engineering
A code reading system capable of signaling exception handling procedures for products being handled in a work environment, such as, for example, consumer product being purchased in a retail store or a product or package being sorted by a logistics company. The system includes a system housing containing one or more one or more signal sources for generating distinctive visual and / or audible exception handling signals for special classes of products identified in the environment. Such special products may include: EAS tagged products requiring EAS tag deactivation: alcohol and tobacco products requiring proof of age; controlled products requiring additional customer tracking; age restricted products requiring identification; product purchases requiring personnel to show up and approve or assist in a product transaction; and the like.
Owner:METROLOGIC INSTR
Multi-object fetch component
InactiveUS6529948B1Digital data processing detailsMultiprogramming arrangementsBusiness objectSoftware engineering
A system, method, and article of manufacture are provided for retrieving multiple business objects across a network in one access operation. A business object and a plurality of remaining objects are provided on a persistent store. Upon receiving a request for the business object, it is established which of the remaining objects are related to the business object. The related objects and the business object are retrieved from the persistent store in one operation and it is determined how the retrieved related objects relate to the business object and each other. A graph of relationships of the business and related objects is instantiated in memory.
Owner:ACCENTURE GLOBAL SERVICES LTD
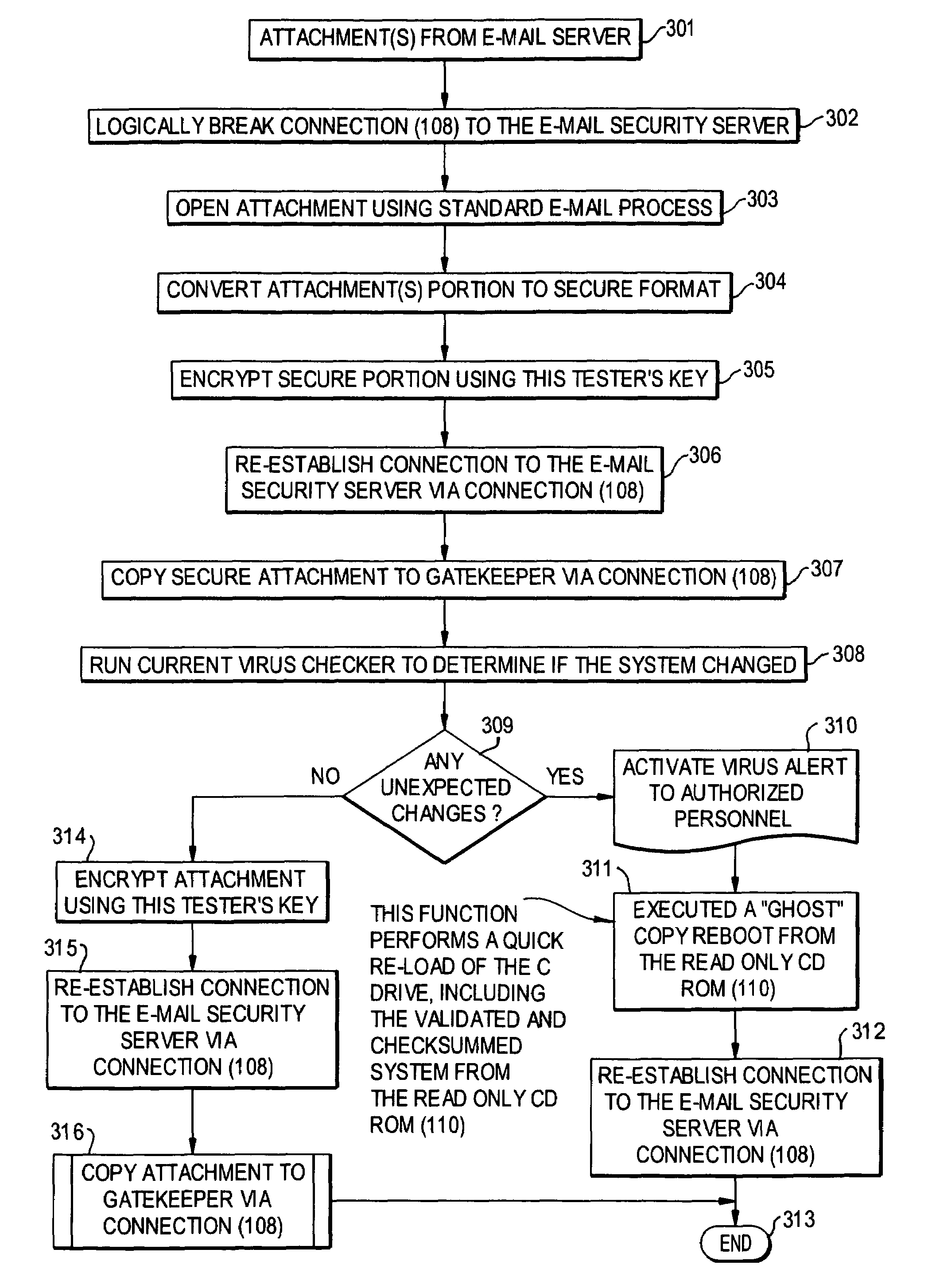
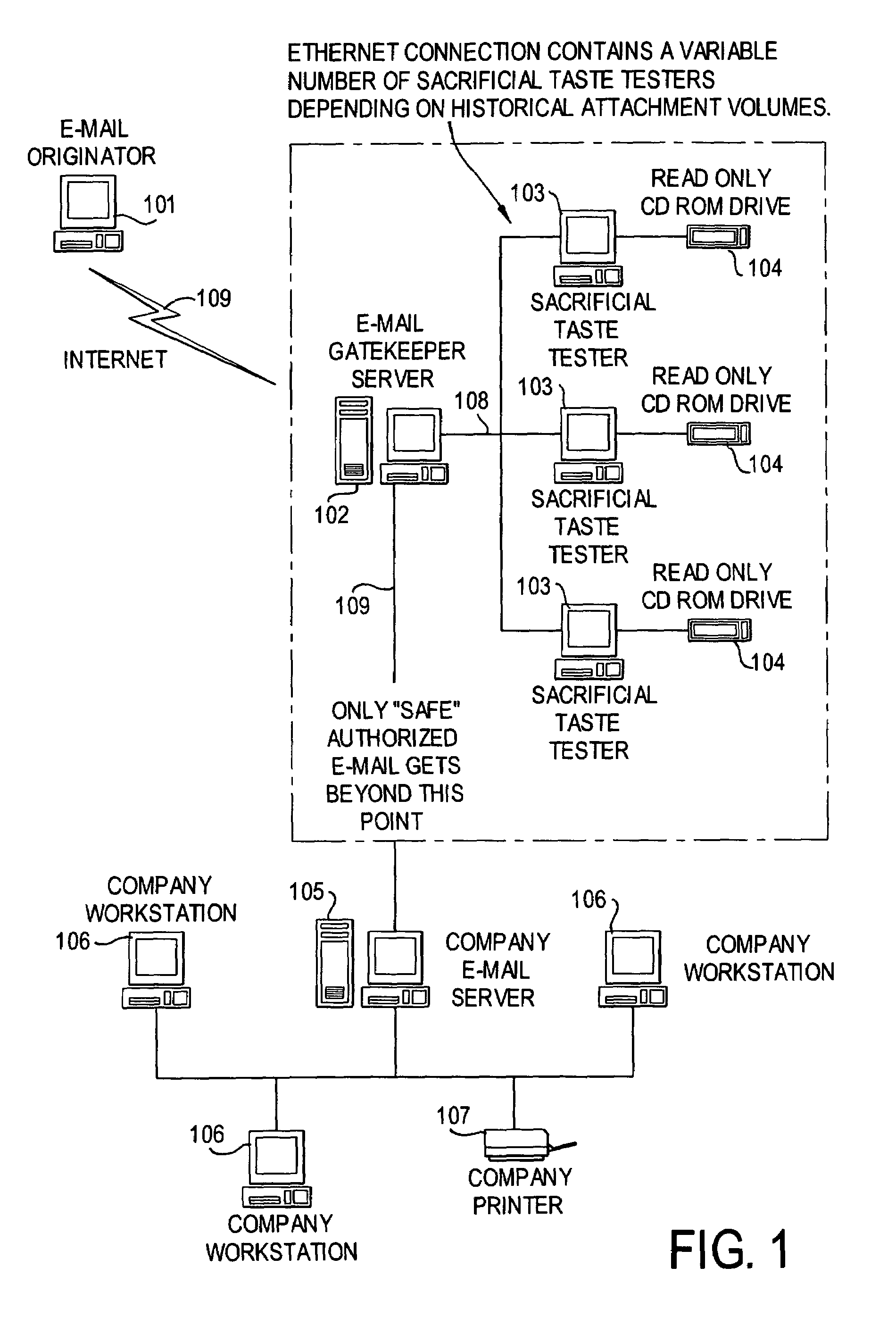
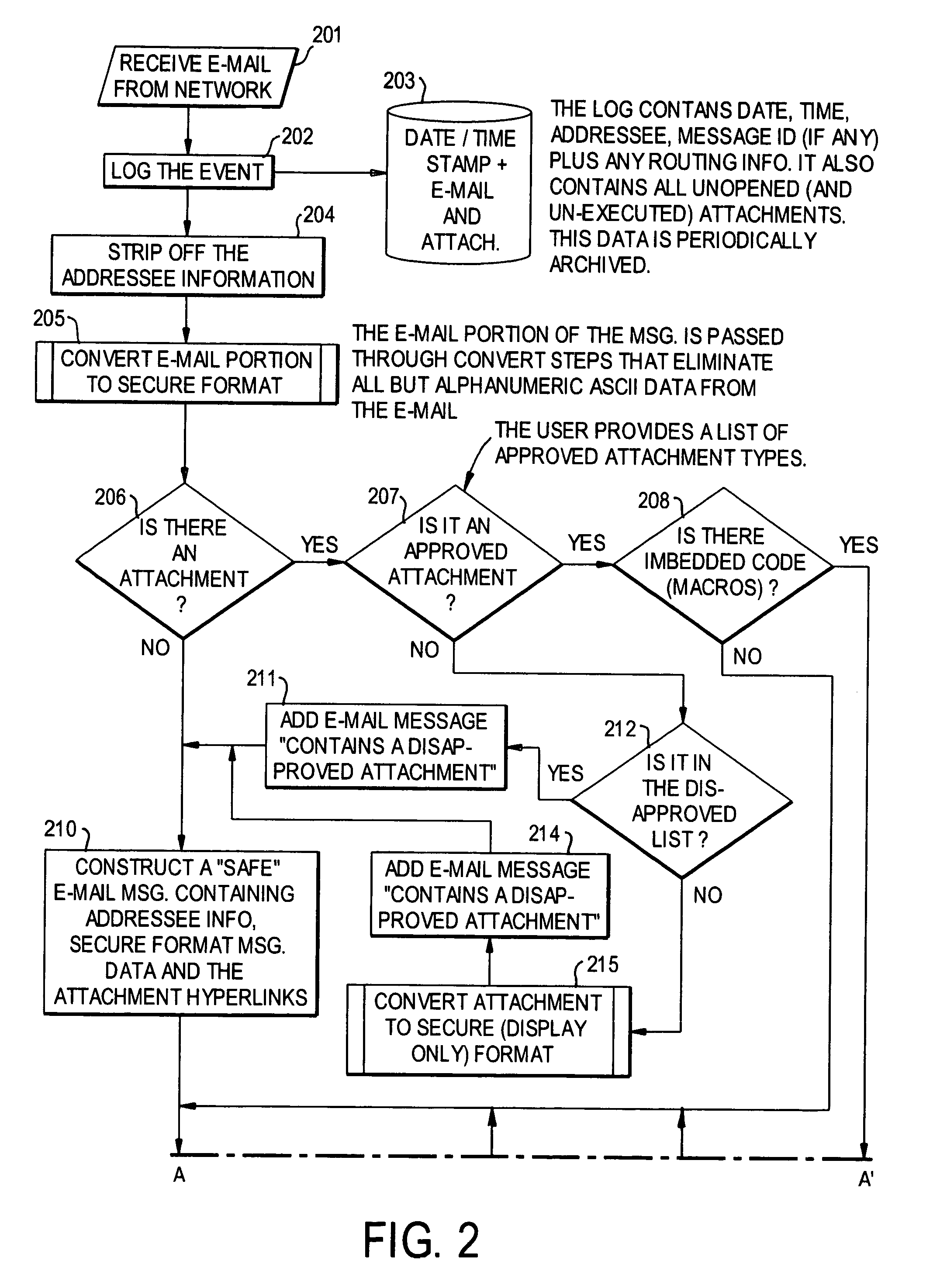
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
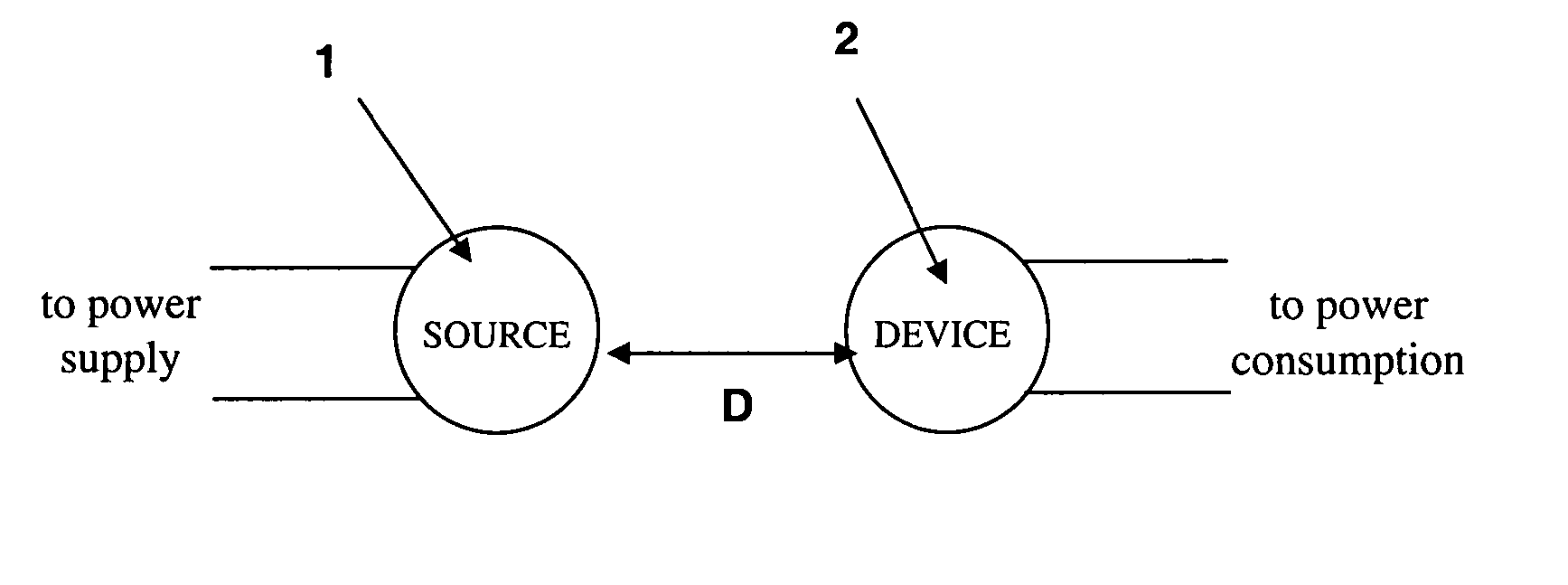
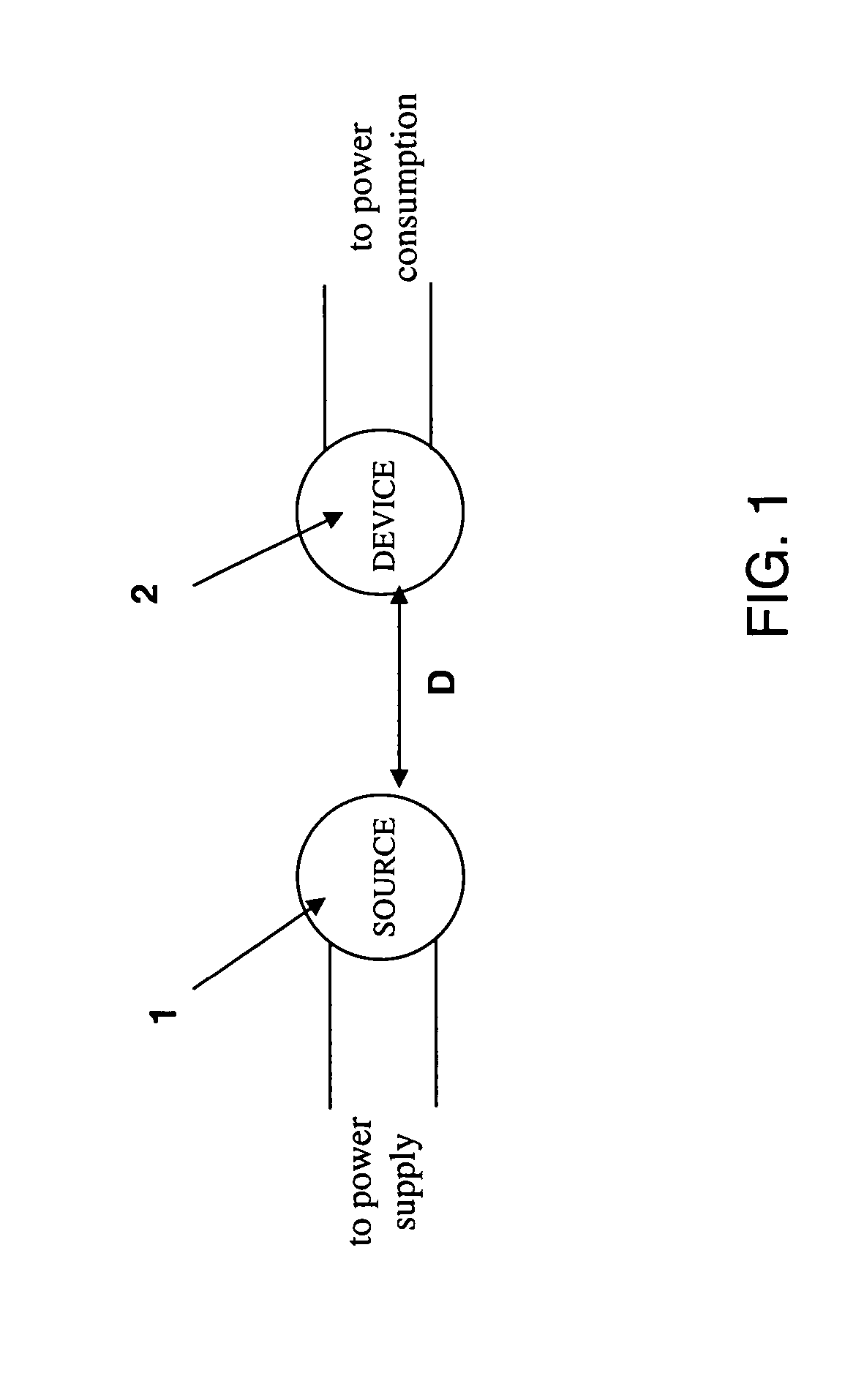
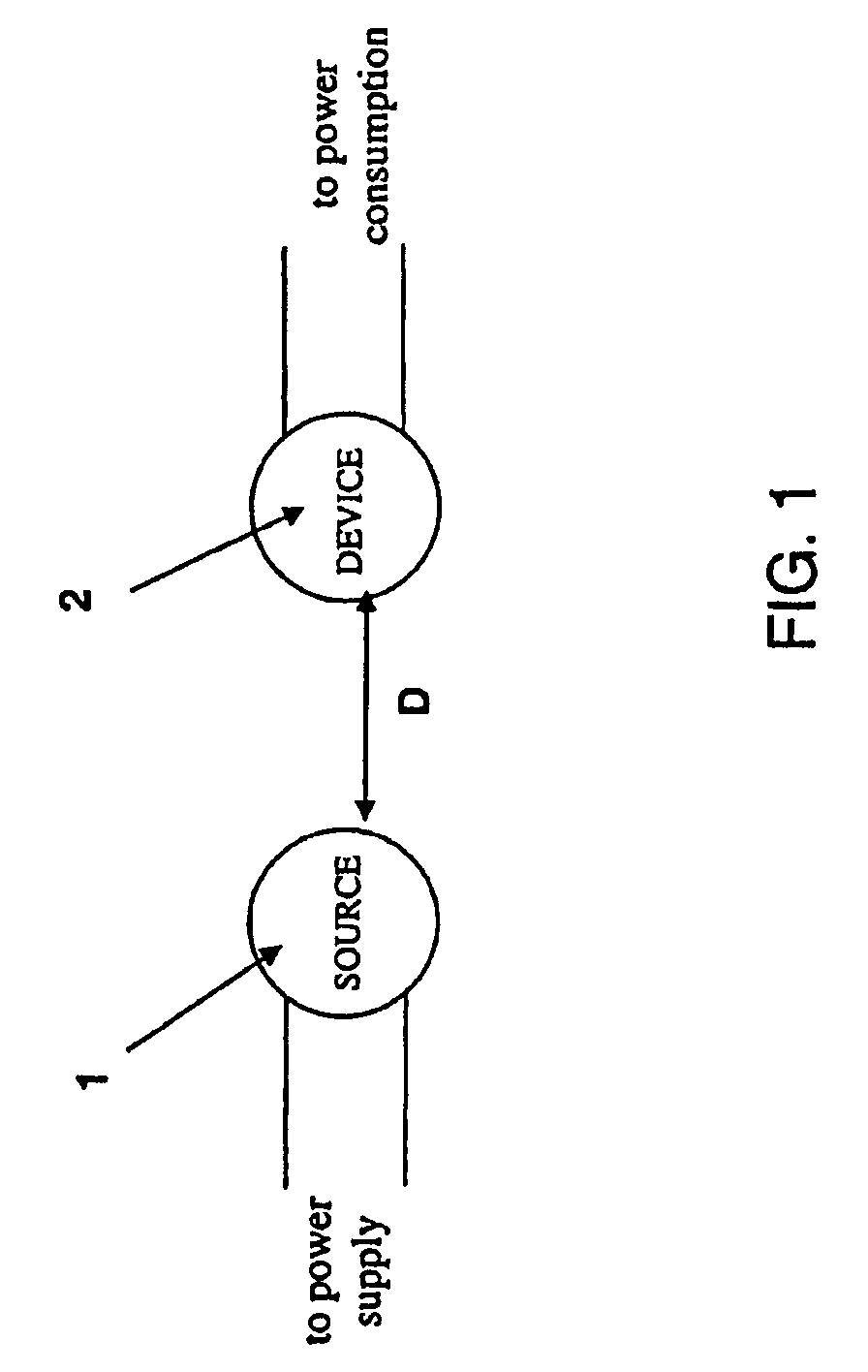
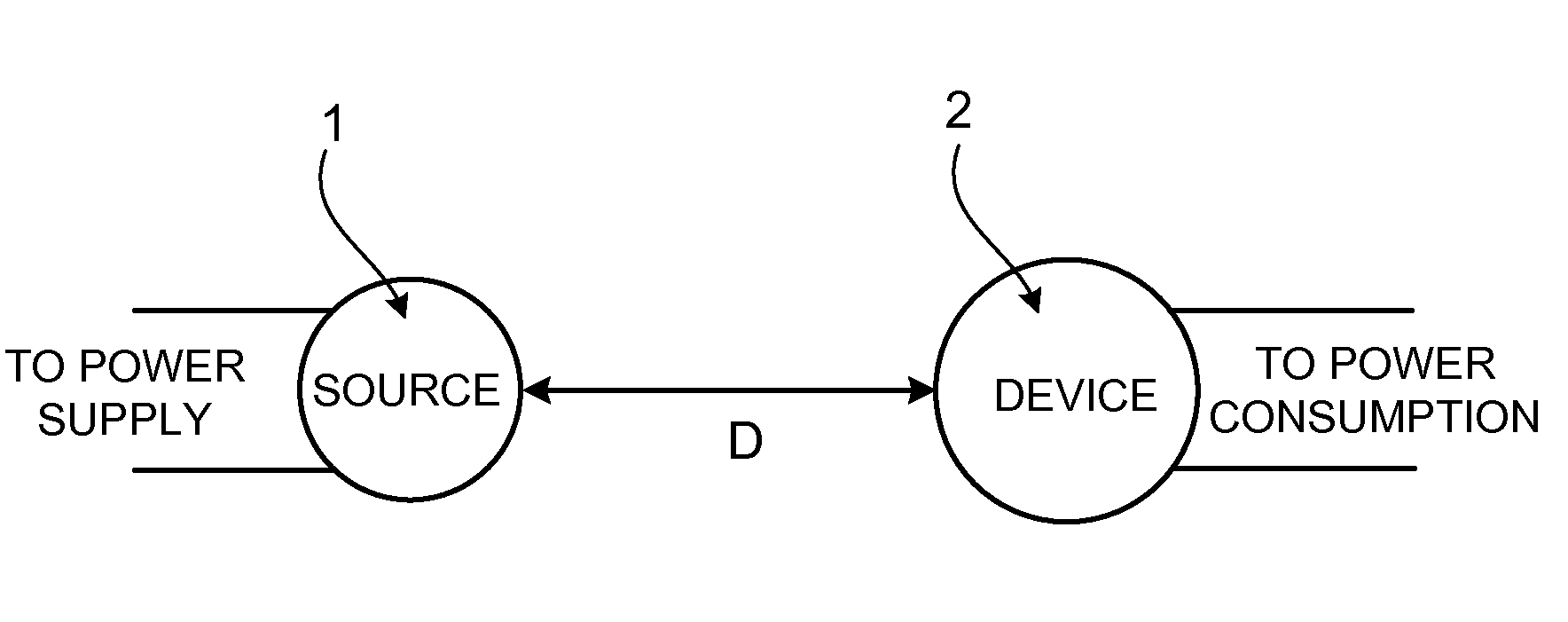
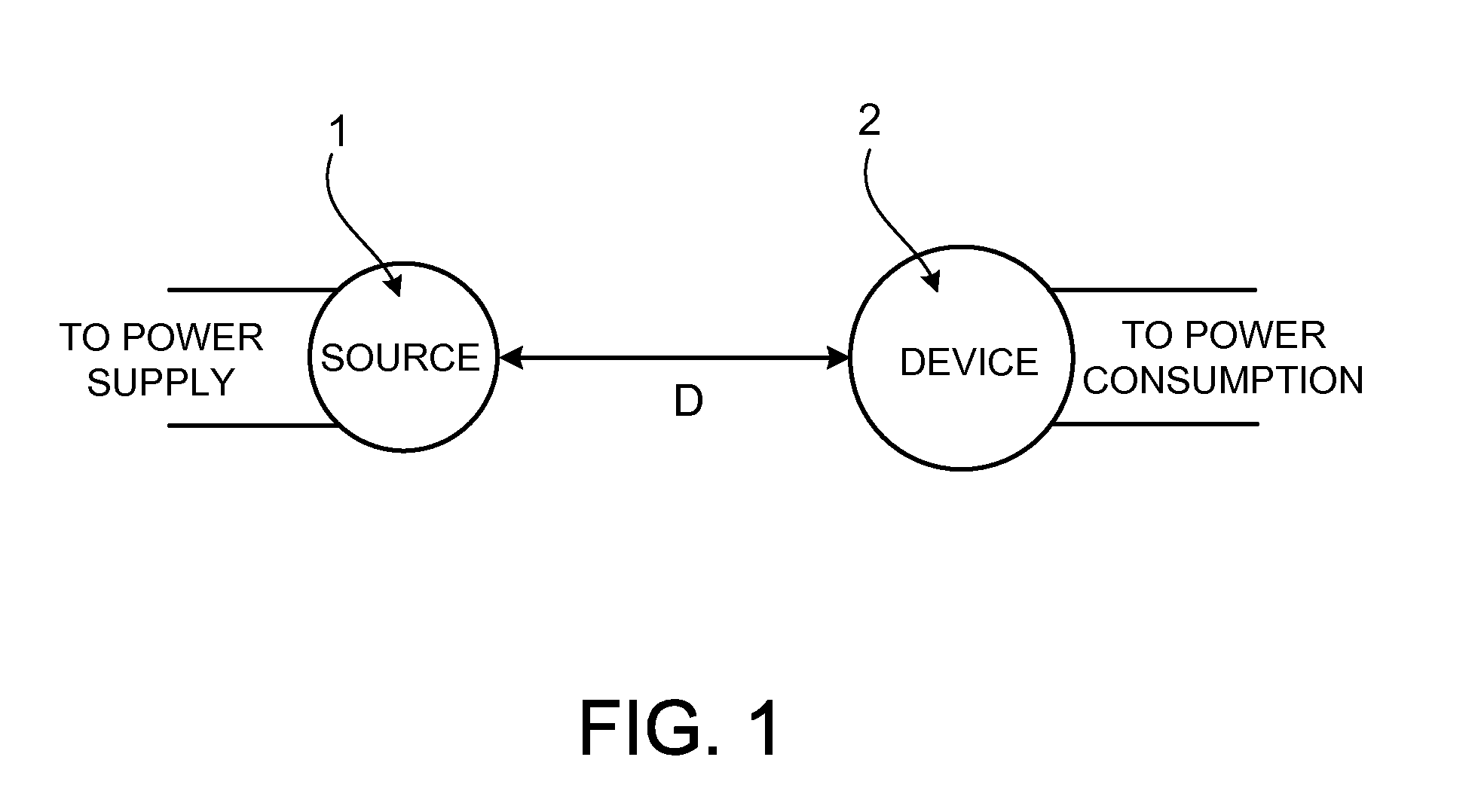
Wireless non-radiative energy transfer
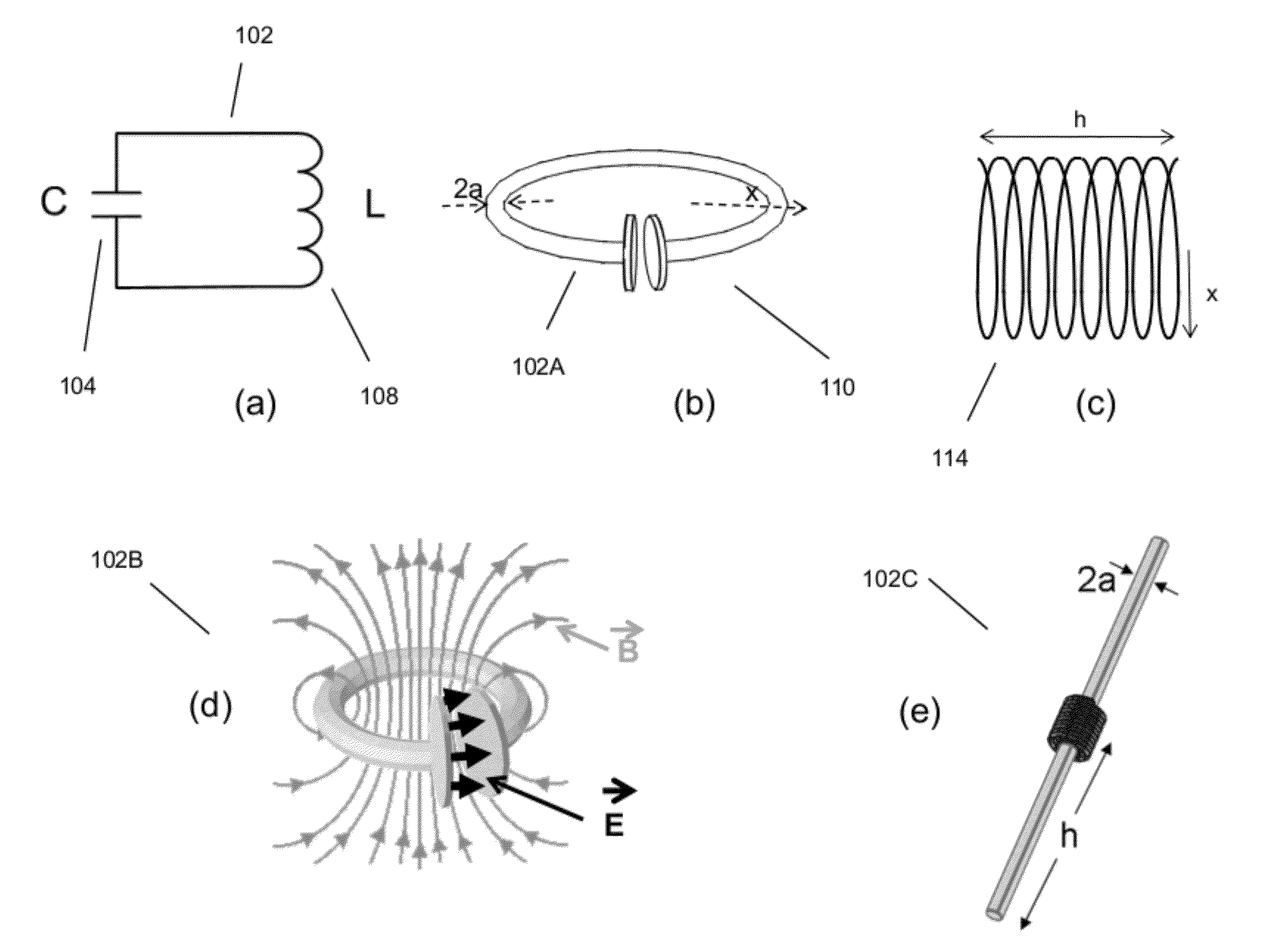
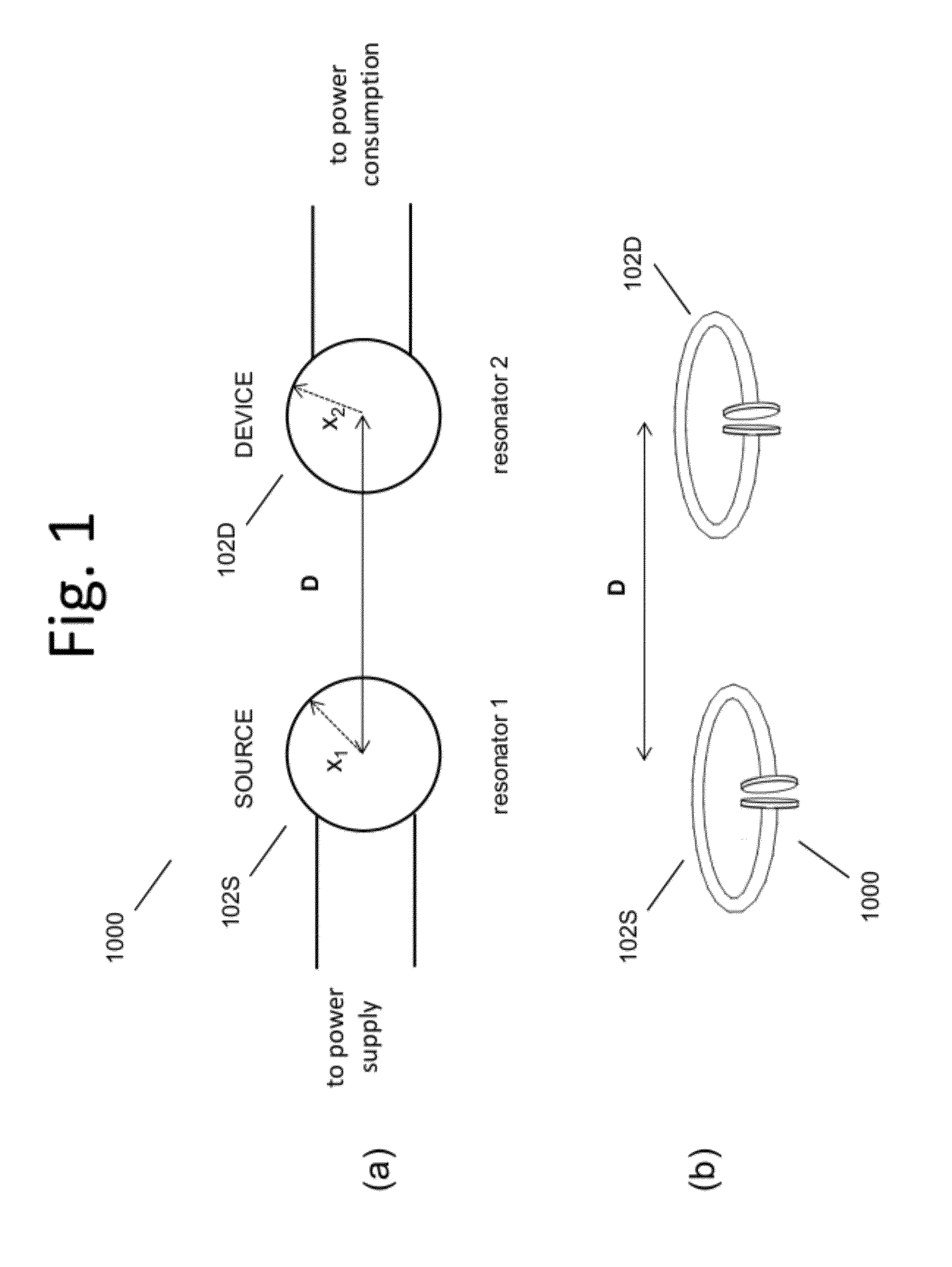
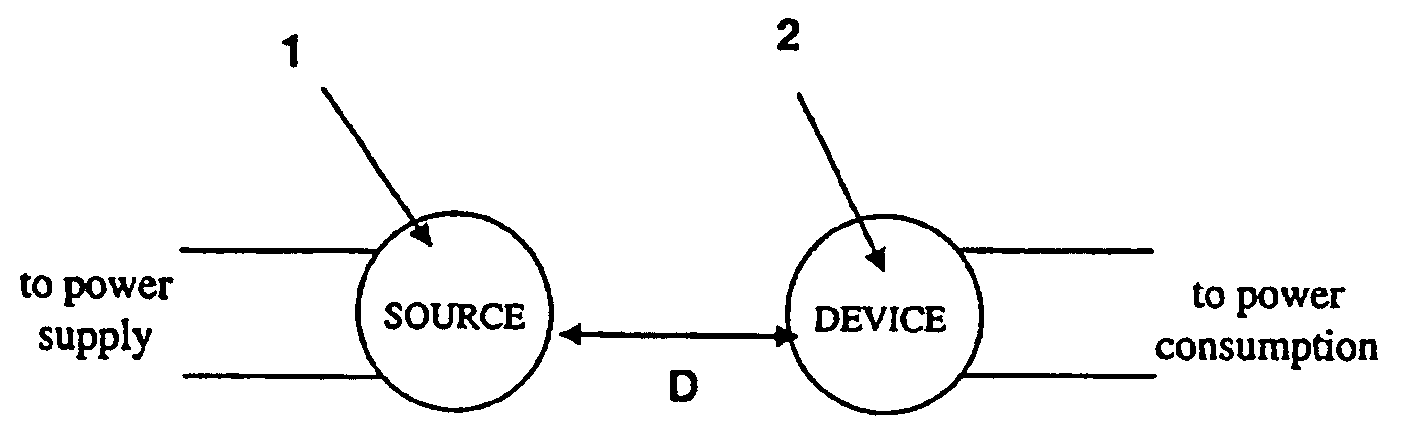
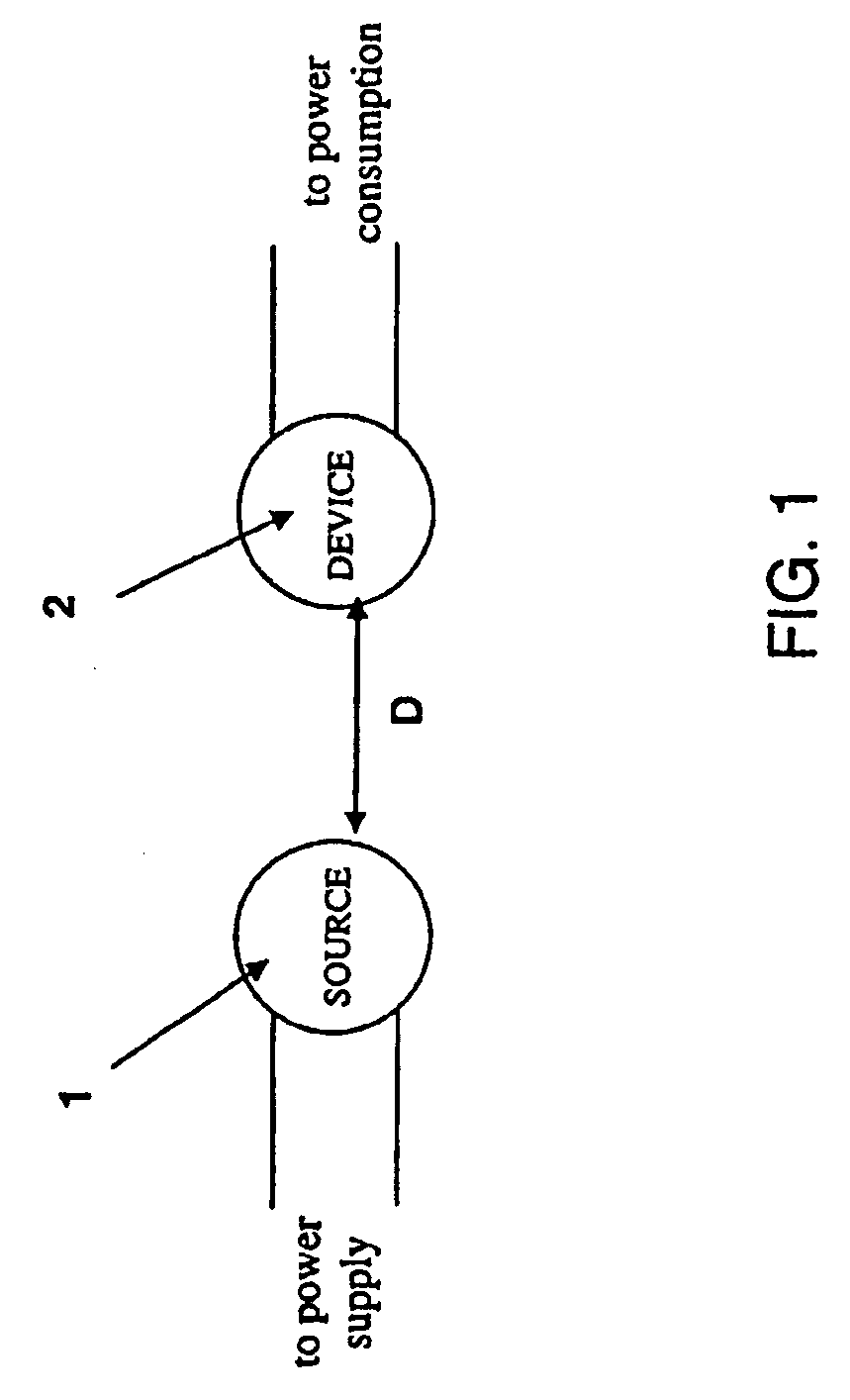
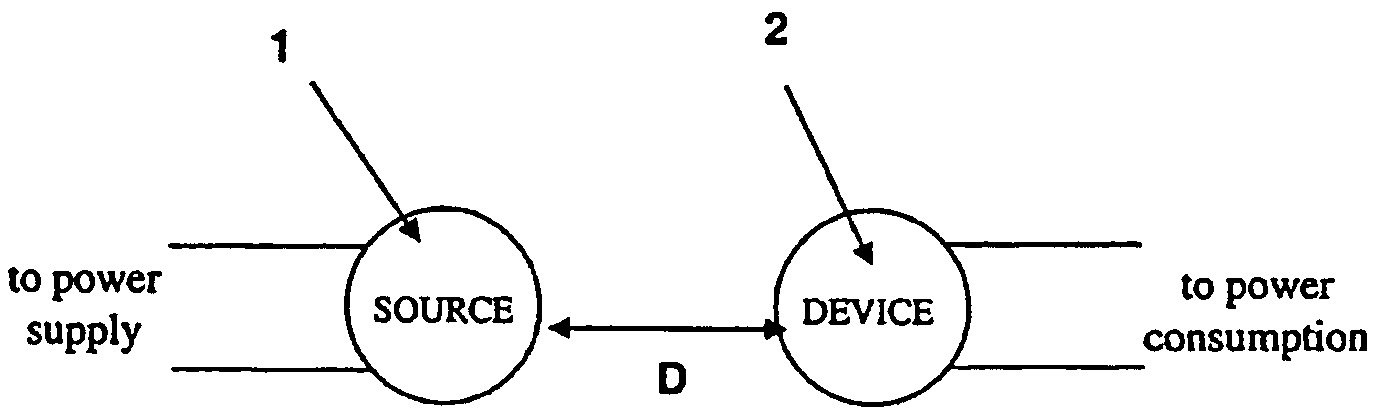
The electromagnetic energy transfer device includes a first resonator structure receiving energy from an external power supply. The first resonator structure has a first Q-factor. A second resonator structure is positioned distal from the first resonator structure, and supplies useful working power to an external load. The second resonator structure has a second Q-factor. The distance between the two resonators can be larger than the characteristic size of each resonator. Non-radiative energy transfer between the first resonator structure and the second resonator structure is mediated through coupling of their resonant-field evanescent tails.
Owner:MASSACHUSETTS INST OF TECH
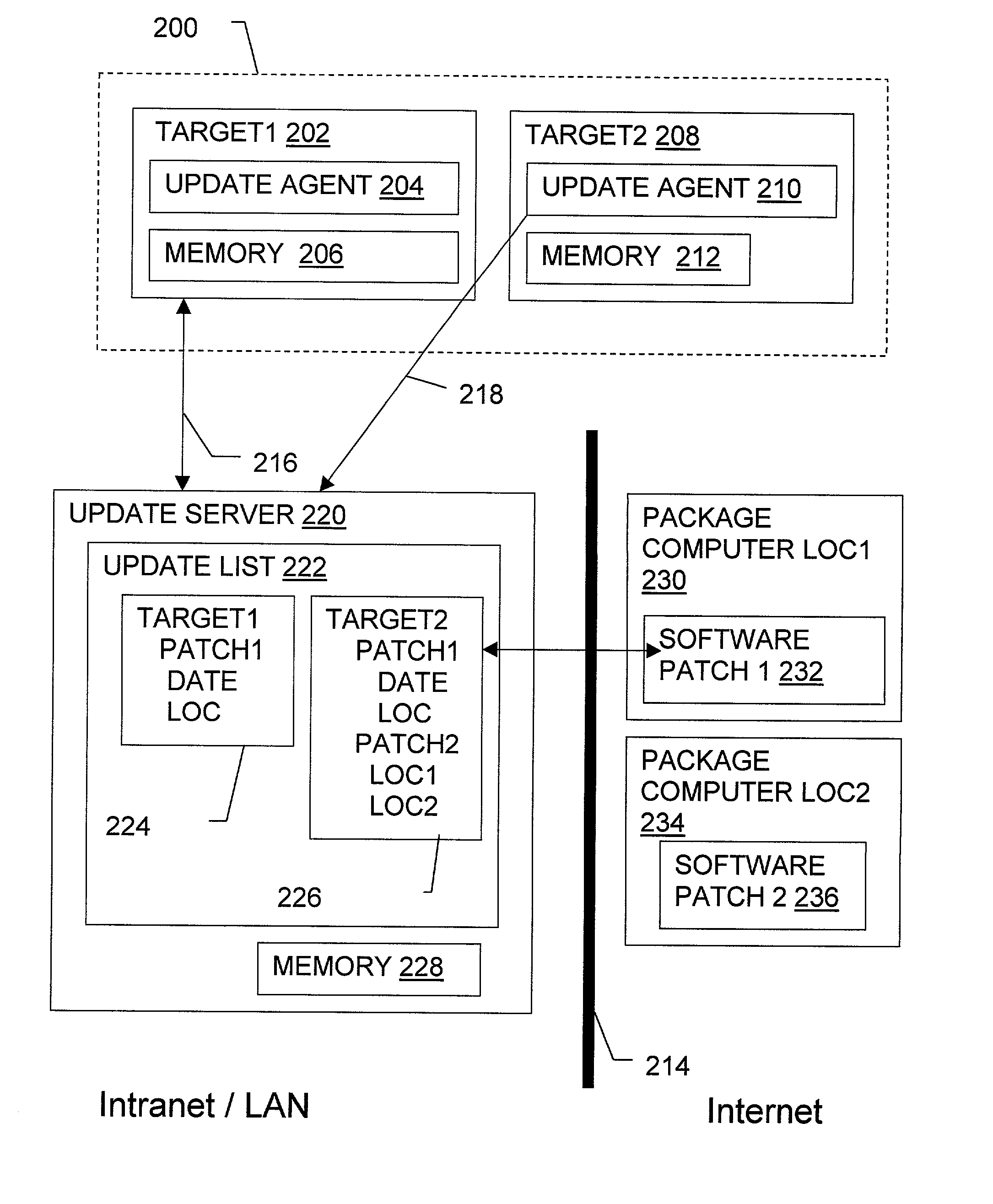
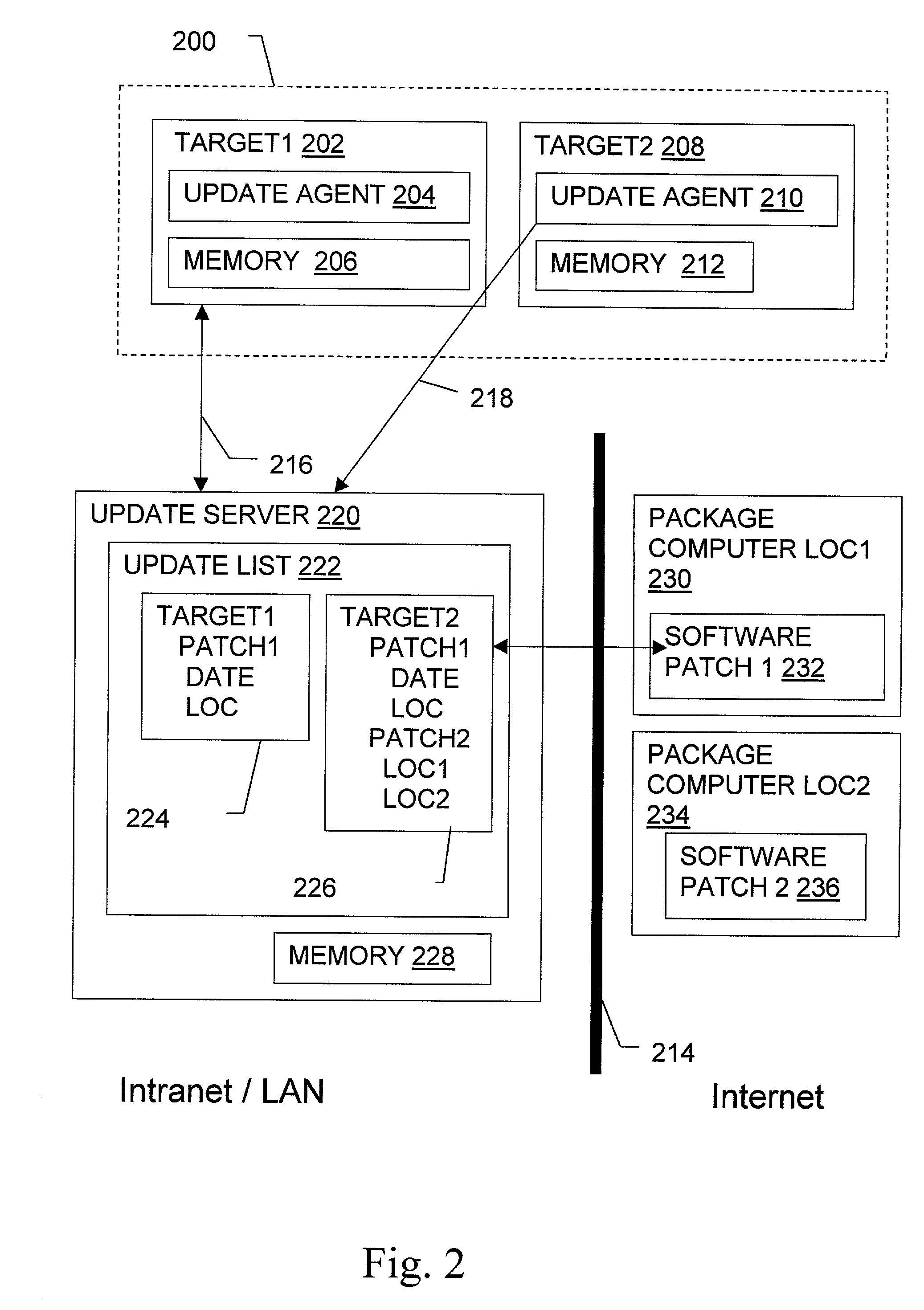
Non-invasive automatic offsite patch fingerprinting and updating system and method
InactiveUS20020100036A1Error detection/correctionDigital computer detailsSoftware updateNon invasive
Methods, systems, and configured storage media are provided for discovering software updates, discovering if a given computer can use the software update, and then updating the computers with the software as needed automatically across a network without storing the updates on an intermediate machine within the network. Furthermore, when a failure is detected, the rollout is stopped and the software can be automatically removed from those computers that already were updated. The software update can be stored originally at an address that is inaccessible through the network firewall by intermediately uploading the software update to an update computer which is not a part of the network but has access through the firewall, which is then used to distribute the update.
Owner:HEAT SOFTWARE USA
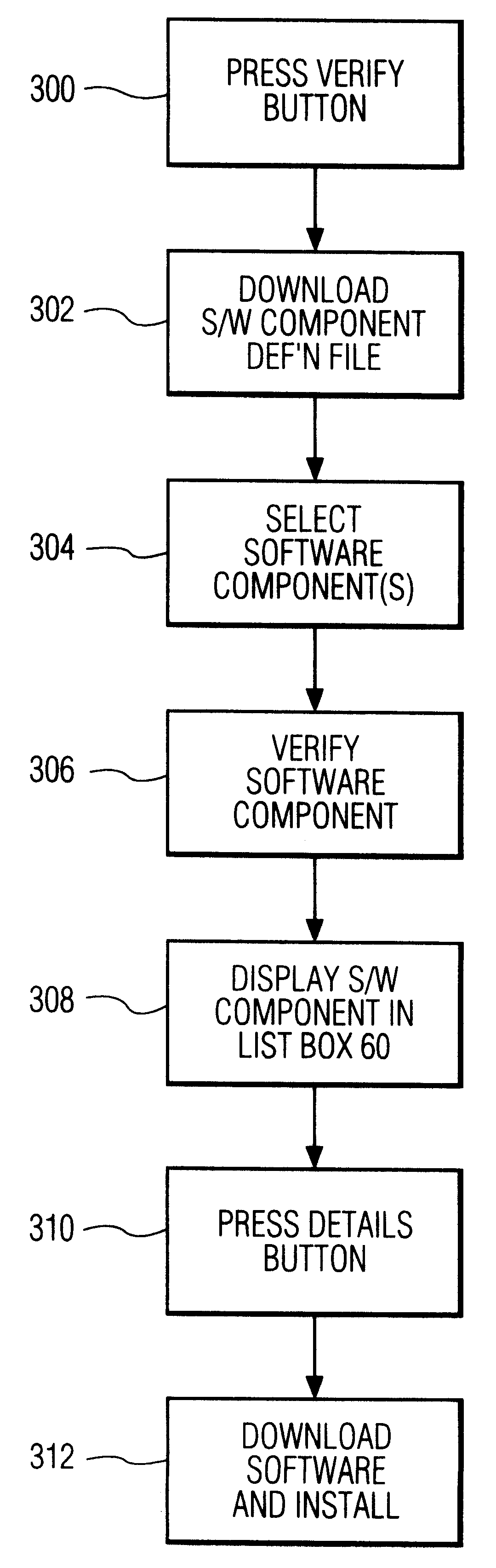
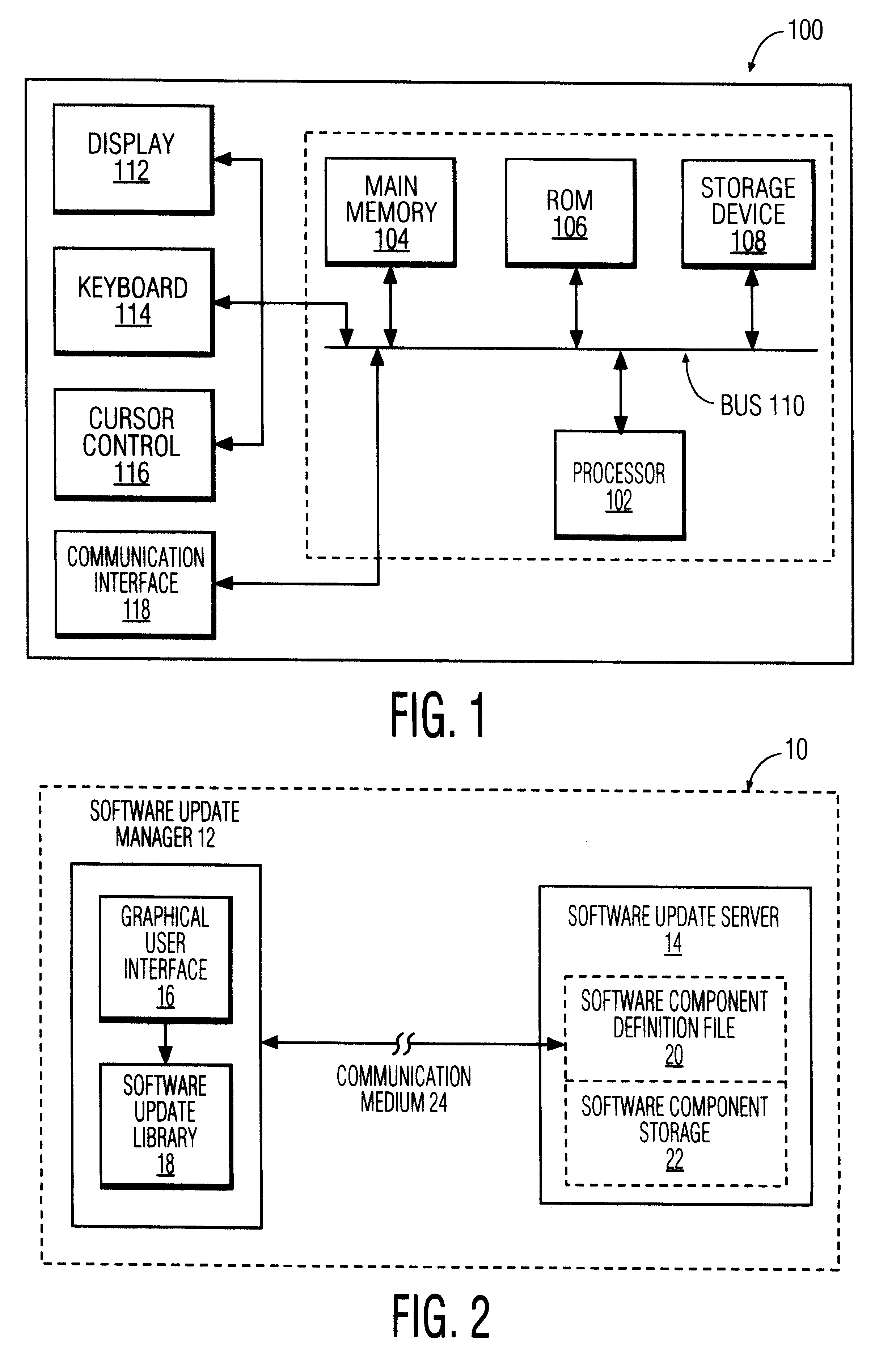
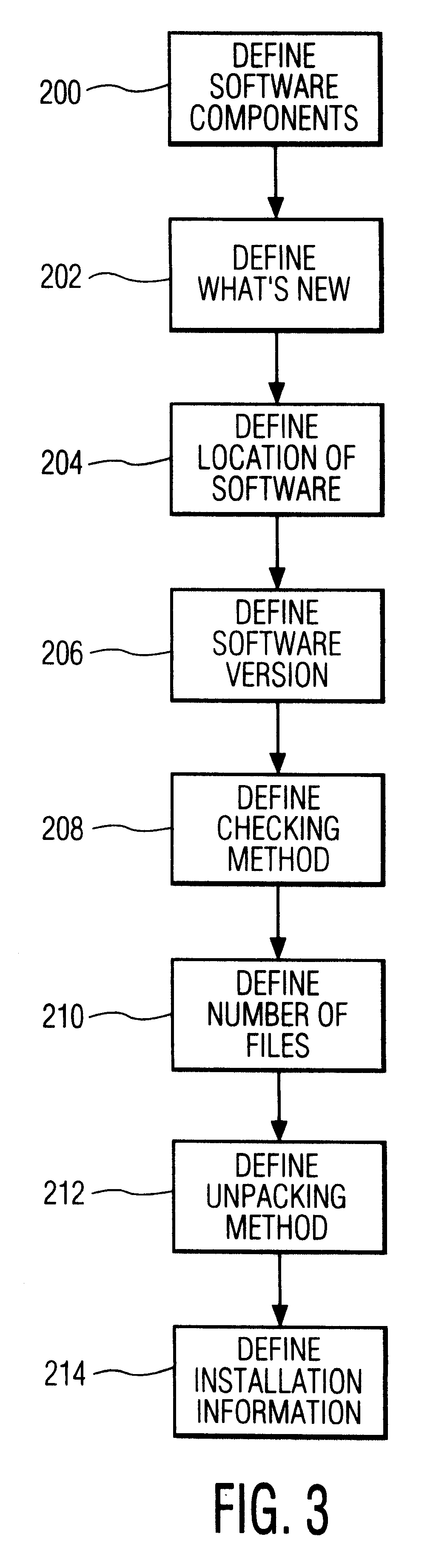
Software update manager
A method and apparatus for checking / updating existing software on a user's computer utilizes a graphical user interface (GUI). The GUI enables the user, without knowing what software exists on the computer, to download a text file from a remote server and check whether the software on the remote server is contained on the user's computer. The user can also download and automatically install a new or updated program via the GUI.
Owner:PHILIPS ELECTRONICS NORTH AMERICA
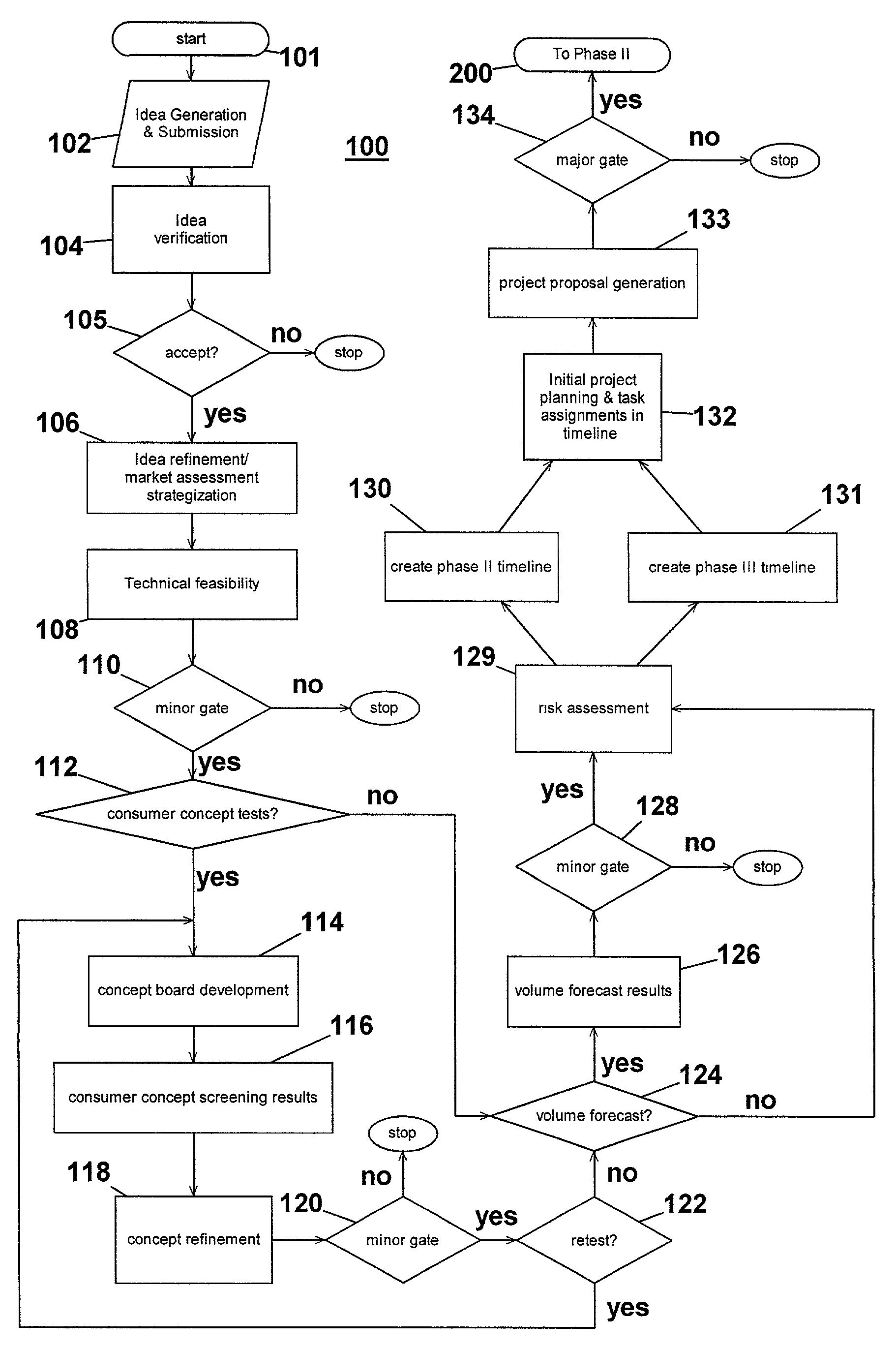
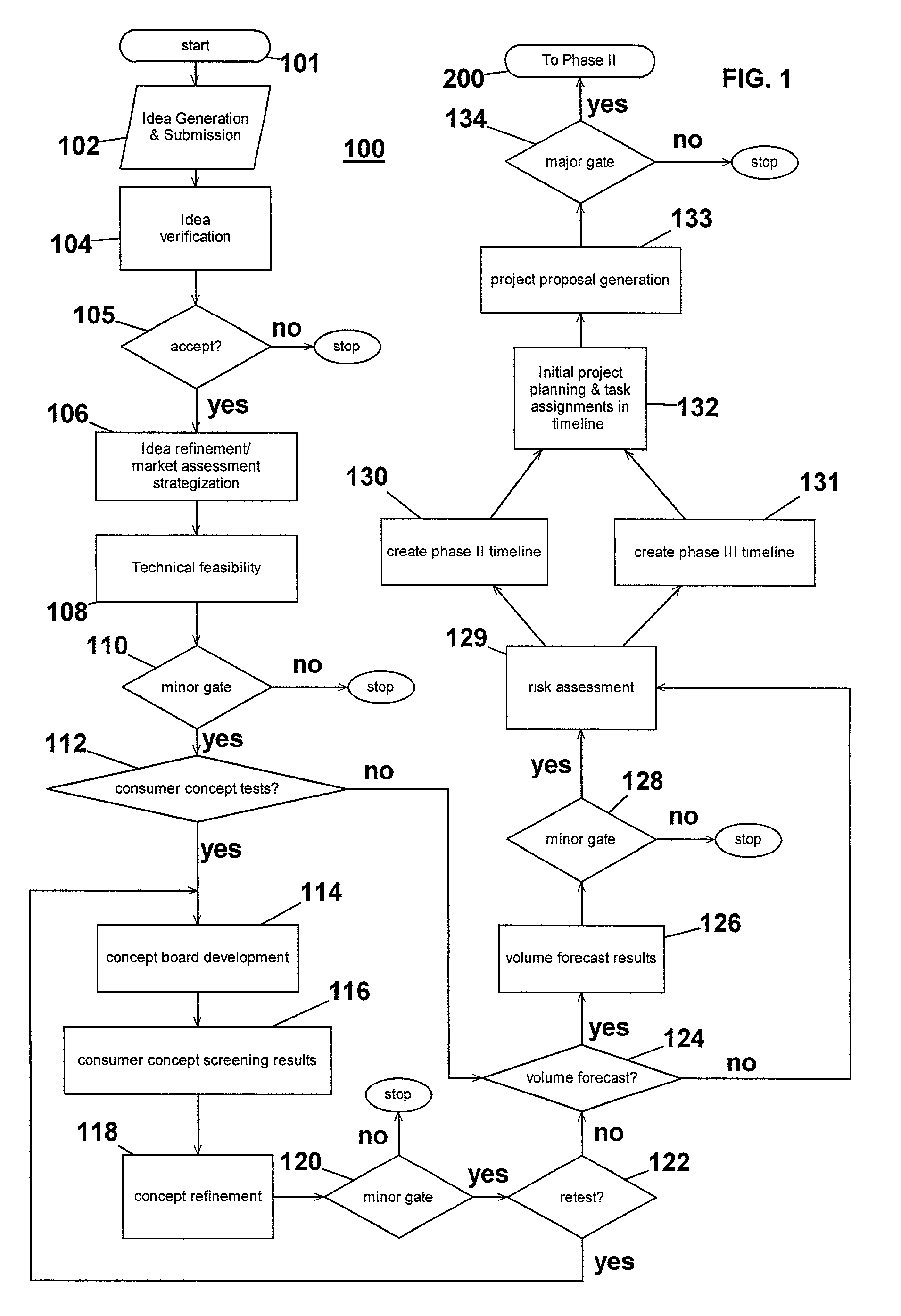
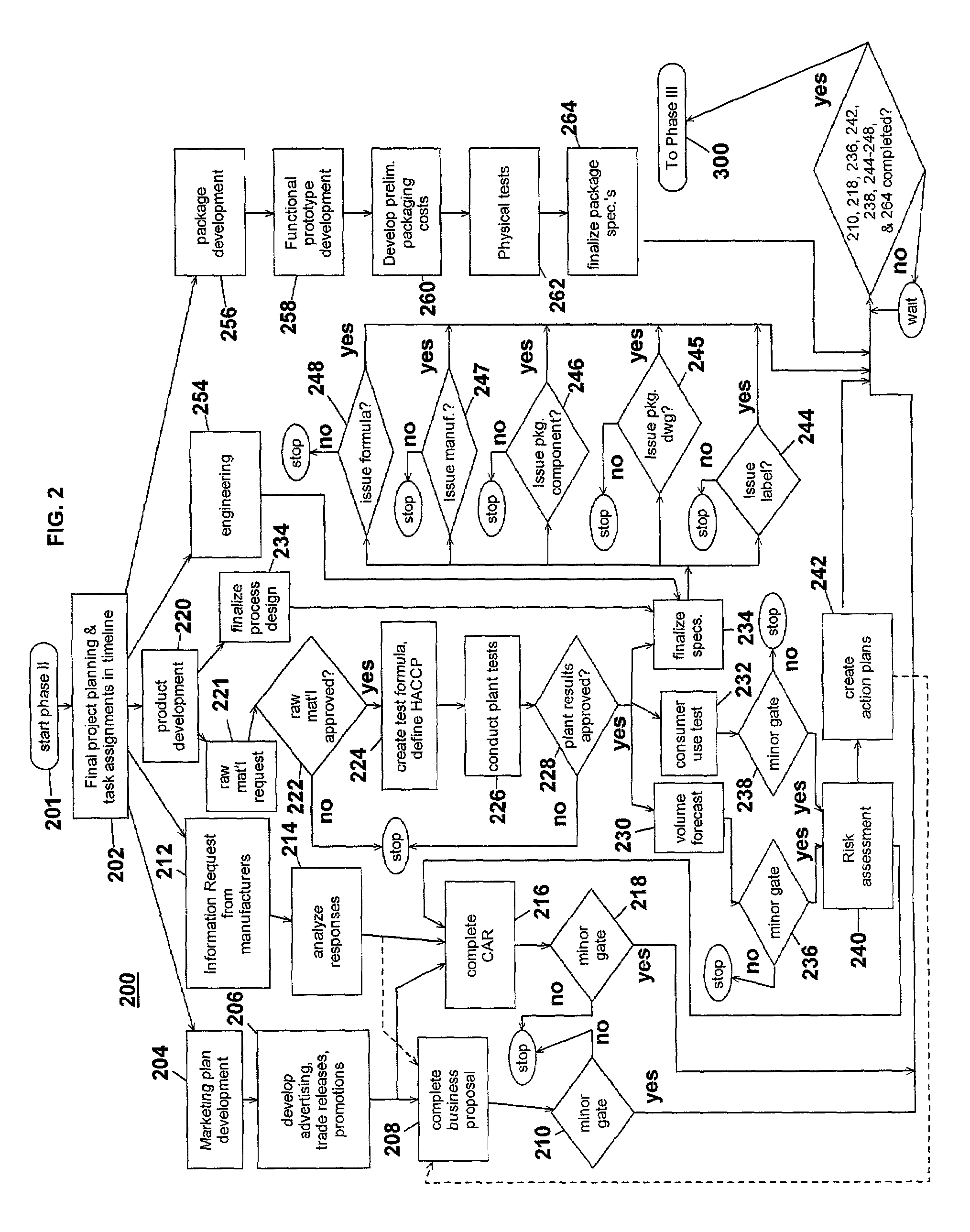
Computer-implemented system and method for project development
InactiveUS7051036B2Avoid repetitionPractical and convenientDigital data processing detailsResourcesProject proposalComputer science
The present invention generally relates to an inventive automated system, and method for its use, including a computer having a computer program defining three development phases including project proposal development, business proposition development, and implementation for market introduction. The project proposal development phase includes a unique idea verification feature by automated reference to an internal knowledge repository and database. The computer is coupled for intercommunication to a plurality of stations or clients from which respective authorized users each have a browser-based interface with the computer.
Owner:KRAFT FOODS GRP BRANDS LLC
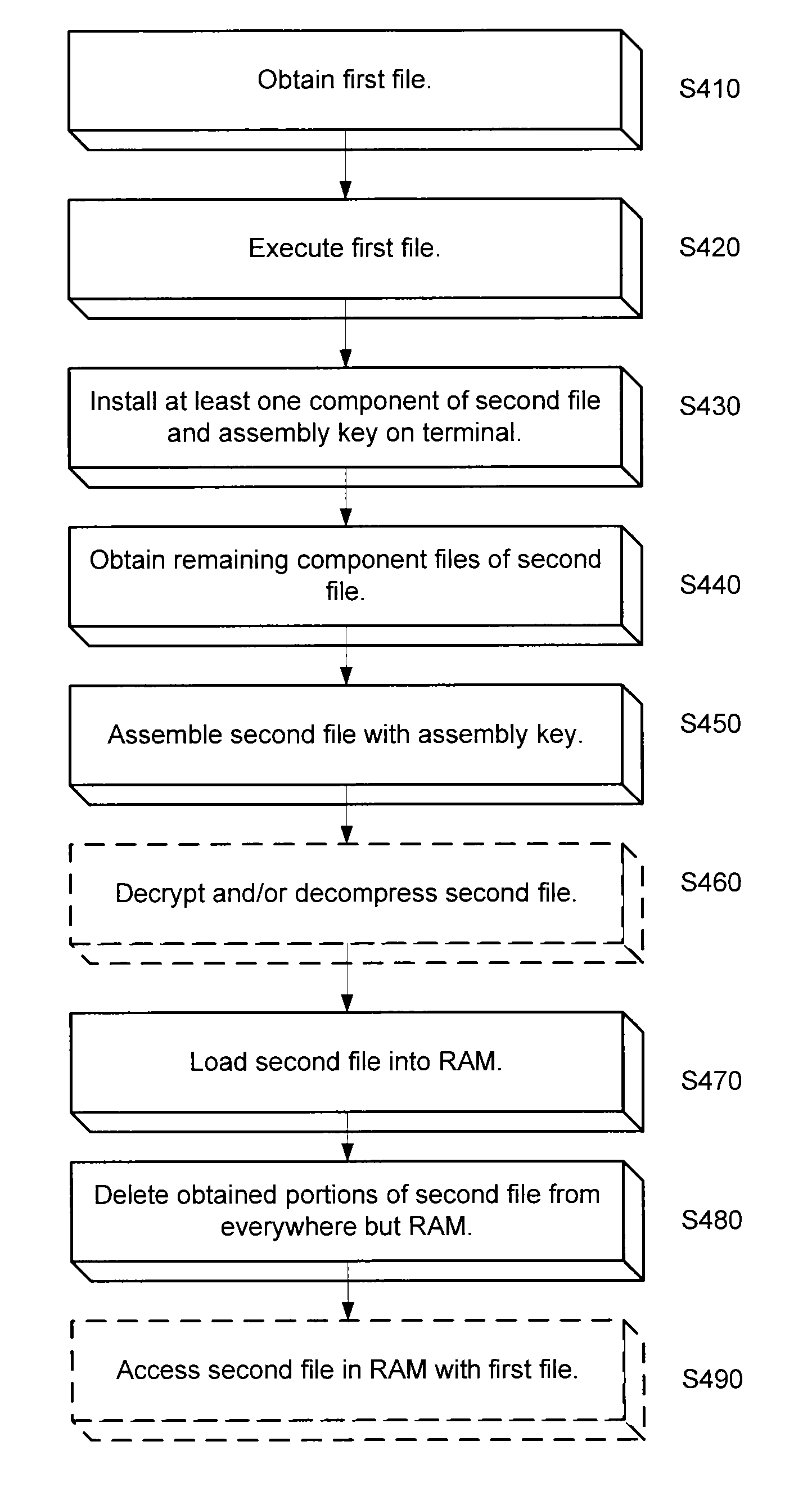
System and method for securing sensitive data
ActiveUS20140344943A1Digital data processing detailsUser identity/authority verificationSoftware engineeringOperating system
An approach is provided for securing data in a technical environment. In one embodiment, a processor obtains a first file, which when executed installs a first portion of a second file and an assembly key to assemble the second file. The processor executes this first file and then obtains the second portion of the second file. The processor assembles the second file using the first portion, the second portion, and the assembly key.
Owner:HAND HELD PRODS
Tunable wireless energy transfer for in-vehicle applications
ActiveUS20120112532A1Efficient deliveryEfficient energy transferMultiple-port networksCharging stationsEnergy transferIn vehicle
A mobile wireless receiver for use with a first electromagnetic resonator coupled to a power supply includes a load associated with an electrically powered system that is disposed interior to a vehicle, and a second electromagnetic resonator configured to be coupled to the load and moveable relative to the first electromagnetic resonator, wherein the second electromagnetic resonator is configured to be wirelessly coupled to the first electromagnetic resonator to provide resonant, non-radiative wireless power to the second electromagnetic resonator from the first electromagnetic resonator; and wherein the second electromagnetic resonator is configured to be tunable during system operation so as to at least one of tune the power provided to the second electromagnetic resonator and tune the power delivered to the load.
Owner:WITRICITY CORP
Extensible information system
InactiveUS20020184401A1Determining correlationEasy to determineDatabase management systemsInterprogram communicationInformation systemApplication software
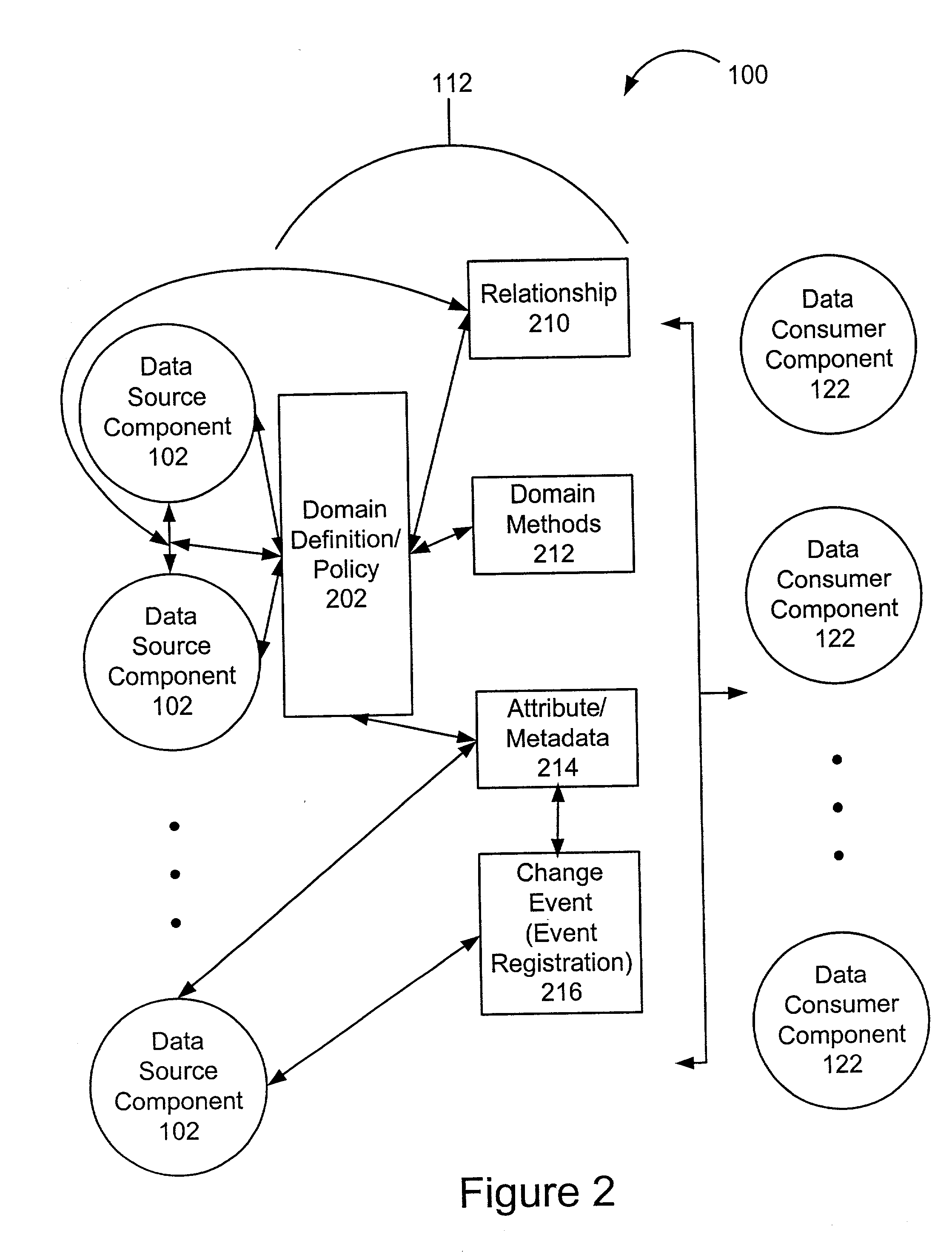
A framework enables data source components to be developed independently of data consumer components. A mediation layer, typically implemented as a group of APIs (application programming interface), handles and defines the mediation and interface between the source and data components. The framework, called XIS (extensible information system), is especially suited for development of information-handling systems and applications. Data source components and data consumer components are typically designed to communicate with each other via several interfaces. Domain, relationship, attribute / metadata, and change event interfaces are defined within the mediation layer. Other interfaces may also be defined. Data source components that are written for non-XIS aware environments or frameworks may still be used with XIS by "wrapping" such source components with code to conform to the interface requirements. Java objects are examples of data source components. Data consumer components thus are able to use or consume various source components regardless of the data types and the data source. Thus, once a data consumer component is developed within the XIS framework, any data source components within the XIS framework may be consumed by a data consumer component.
Owner:POLEXIS
System and method for automated configuration of hosting resources
ActiveUS8352608B1Facilitate efficient deploymentMaximize useDigital computer detailsProgram controlAuto-configurationFile system
Some embodiments provide a method for automated configuration of a set of resources for hosting a virtual machine at a particular node in a hosting system. The hosting system includes several nodes for hosting several virtual machines. The method, at a first virtual machine operating using a first set of resources of the particular node, receives a configuration for a second virtual machine to be hosted on a second set of resources of the particular node. The method, from the first virtual machine, accesses the second set of resources to partition a file system for storing the second virtual machine. The method modifies the file system to configure the second virtual machine as specified by the configuration.
Owner:GOOGLE LLC
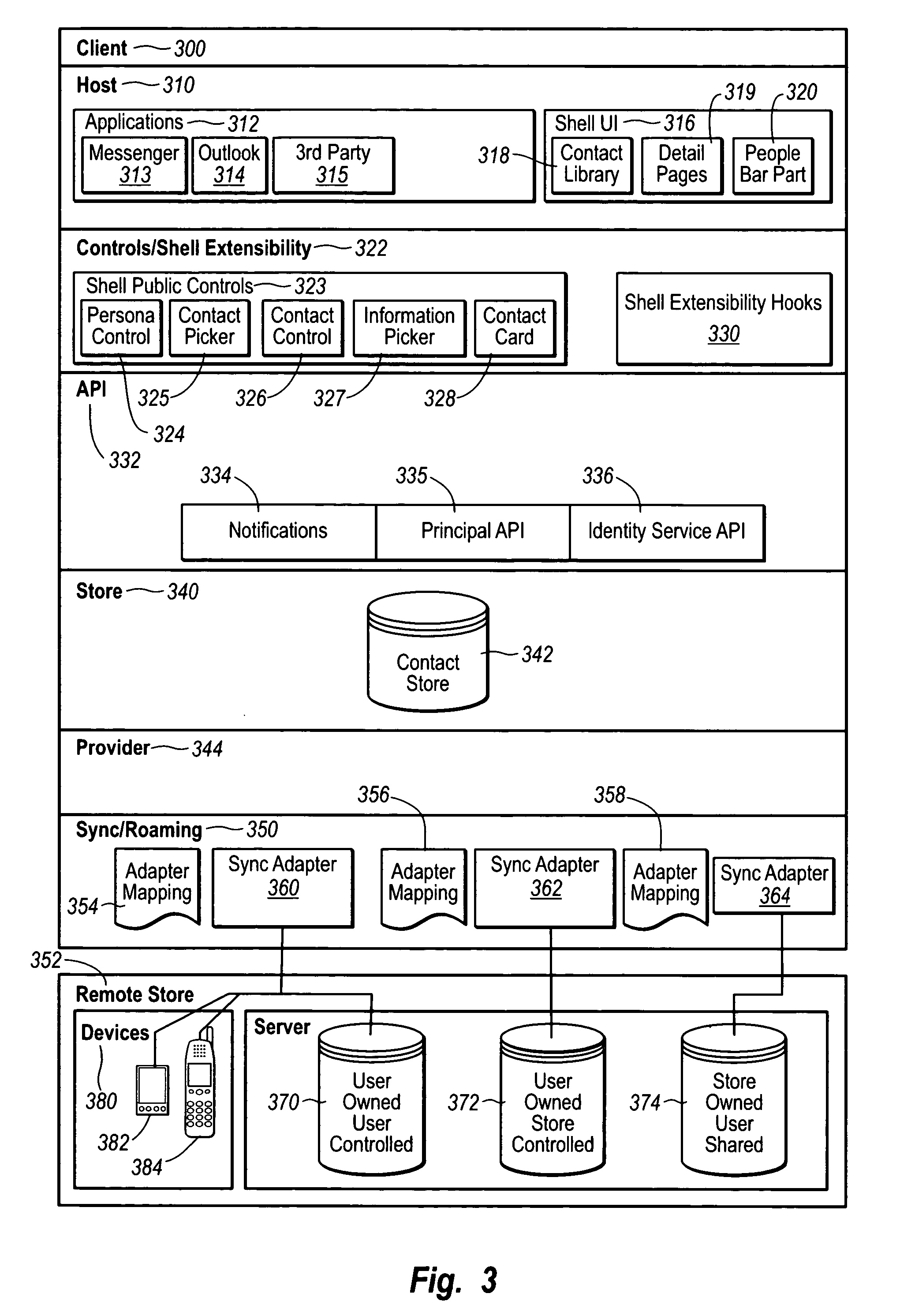
Contact management
InactiveUS20050091272A1Effective synchronizationCentralized storageDigital data processing detailsSubstation equipmentSoftware engineeringMechanical engineering
Owner:MICROSOFT TECH LICENSING LLC
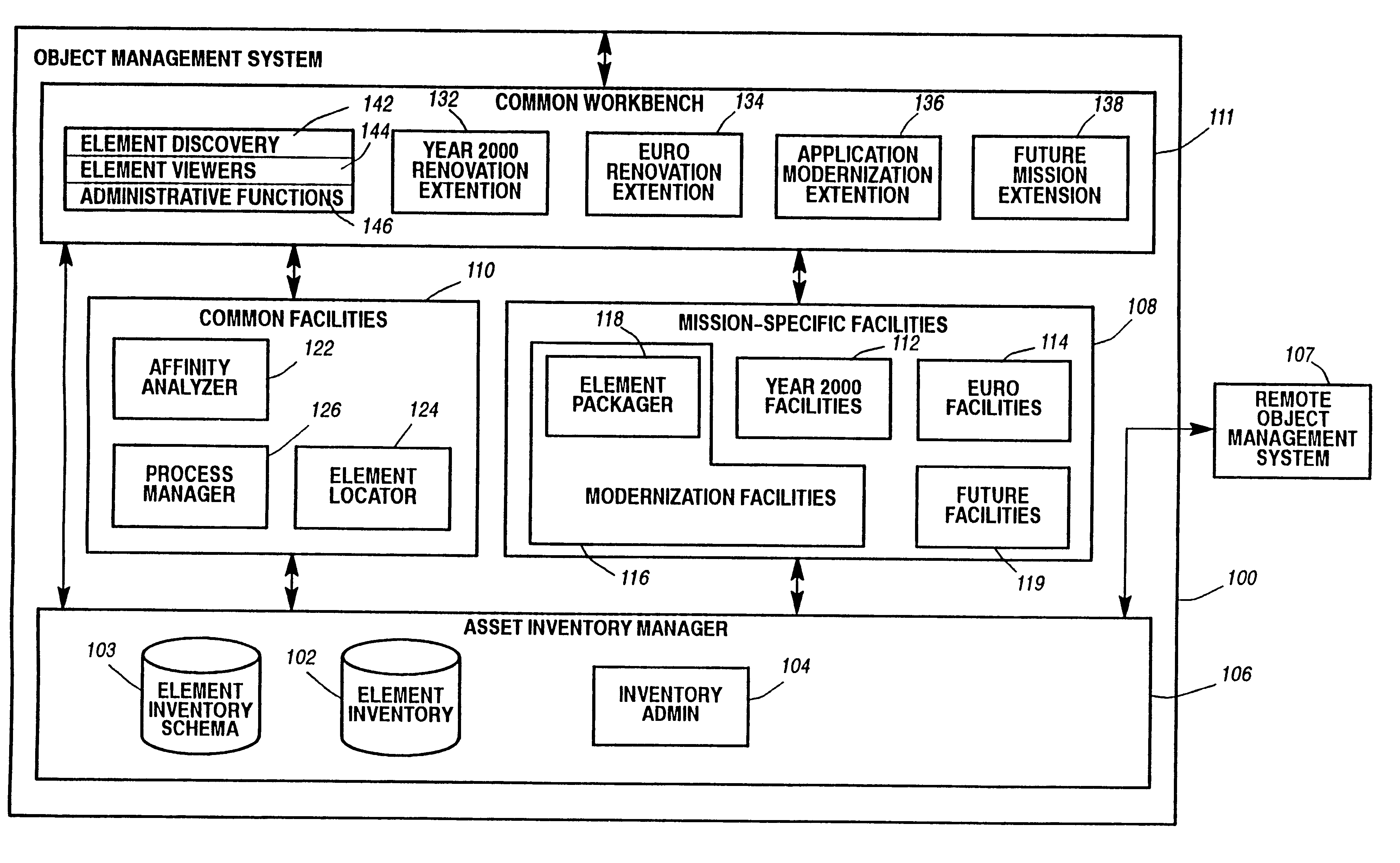
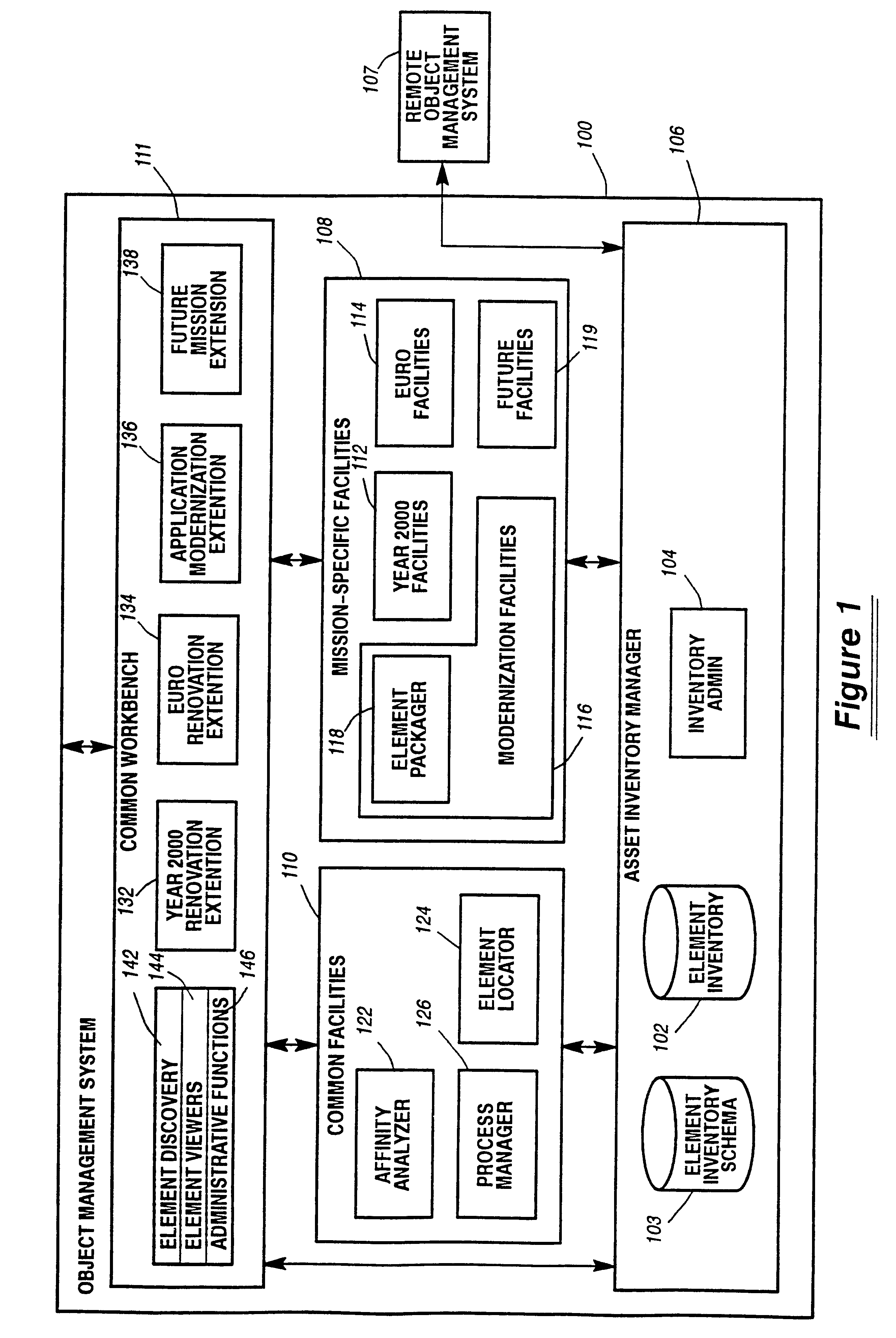
System and method for defining and managing reusable groups software constructs within an object management system
InactiveUS6427230B1Sure easyEasy to understandSoftware reuseSpecific program execution arrangementsManagement systemSoftware
A system for maintaining an object repository within an object management system where the objects are software constructs and the system provides a set of tools for creating packages of the objects that can be reused as well as monitored as they are changed or recombined. The packages themselves become new objects for the repository to store. The set of relationships within a package is also stored as are any relationships between any of the objects within the object management system object repository.
Owner:UNISYS CORP
Wireless non-radiative energy transfer
ActiveUS20090195333A1Near-field transmissionElectromagnetic wave systemEnergy transferSoftware engineering
The electromagnetic energy transfer device includes a first resonator structure receiving energy from an external power supply. The first resonator structure has a first Q-factor. A second resonator structure is positioned distal from the first resonator structure, and supplies useful working power to an external load. The second resonator structure has a second Q-factor. The distance between the two resonators can be larger than the characteristic size of each resonator. Non-radiative energy transfer between the first resonator structure and the second resonator structure is mediated through coupling of their resonant-field evanescent tails.
Owner:MASSACHUSETTS INST OF TECH
Wireless non-radiative energy transfer
The electromagnetic energy transfer device includes a first resonator structure receiving energy from an external power supply. The first resonator structure has a first Q-factor. A second resonator structure is positioned distal from the first resonator structure, and supplies useful working power to an external load. The second resonator structure has a second Q-factor. The distance between the two resonators can be larger than the characteristic size of each resonator. Non-radiative energy transfer between the first resonator structure and the second resonator structure is mediated through coupling of their resonant-field evanescent tails.
Owner:MASSACHUSETTS INST OF TECH
Wireless non-radiative energy transfer
The electromagnetic energy transfer device includes a first resonator structure receiving energy from an external power supply. The first resonator structure has a first Q-factor. A second resonator structure is positioned distal from the first resonator structure, and supplies useful working power to an external load. The second resonator structure has a second Q-factor. The distance between the two resonators can be larger than the characteristic size of each resonator. Non-radiative energy transfer between the first resonator structure and the second resonator structure is mediated through coupling of their resonant-field evanescent tails.
Owner:MASSACHUSETTS INST OF TECH
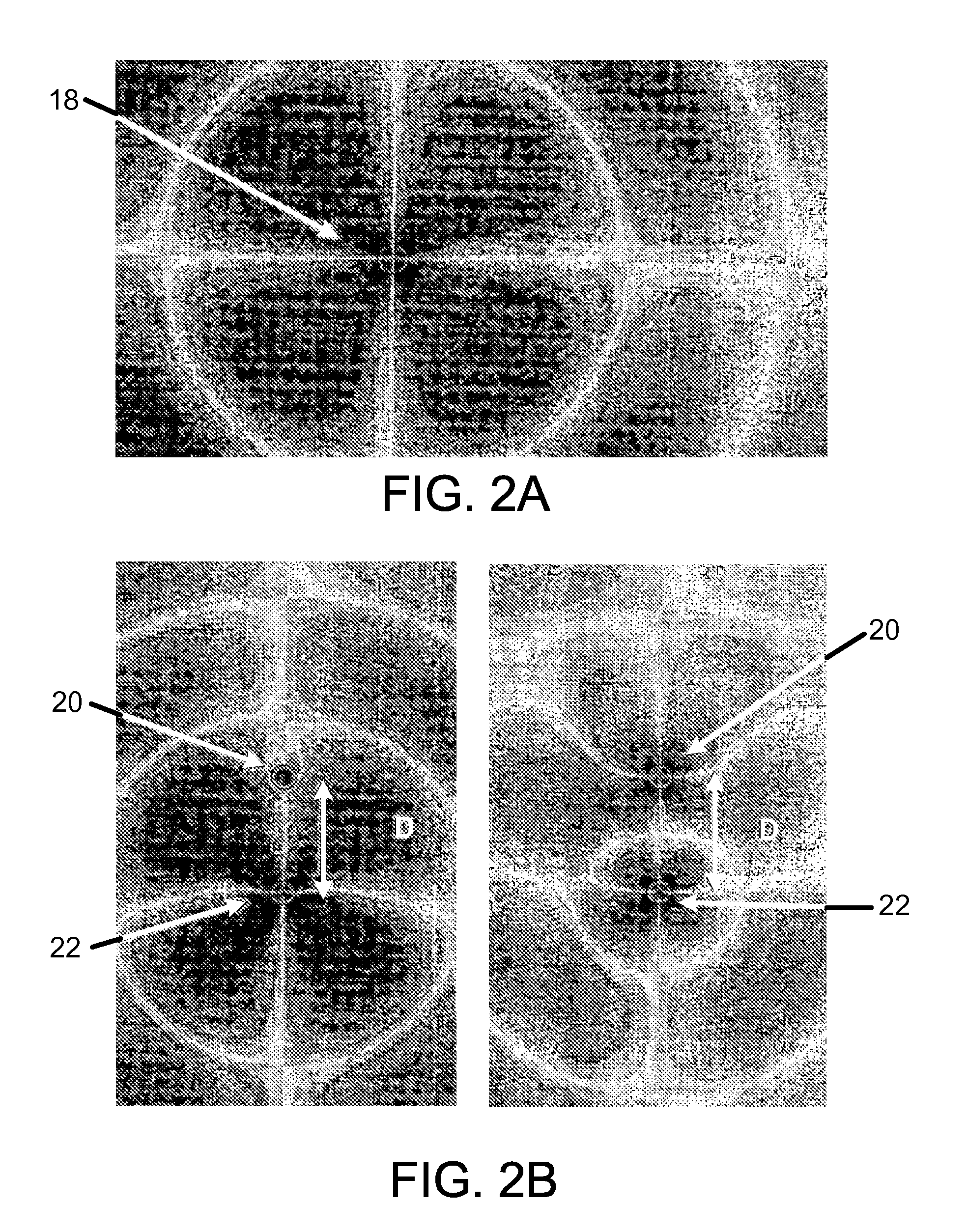
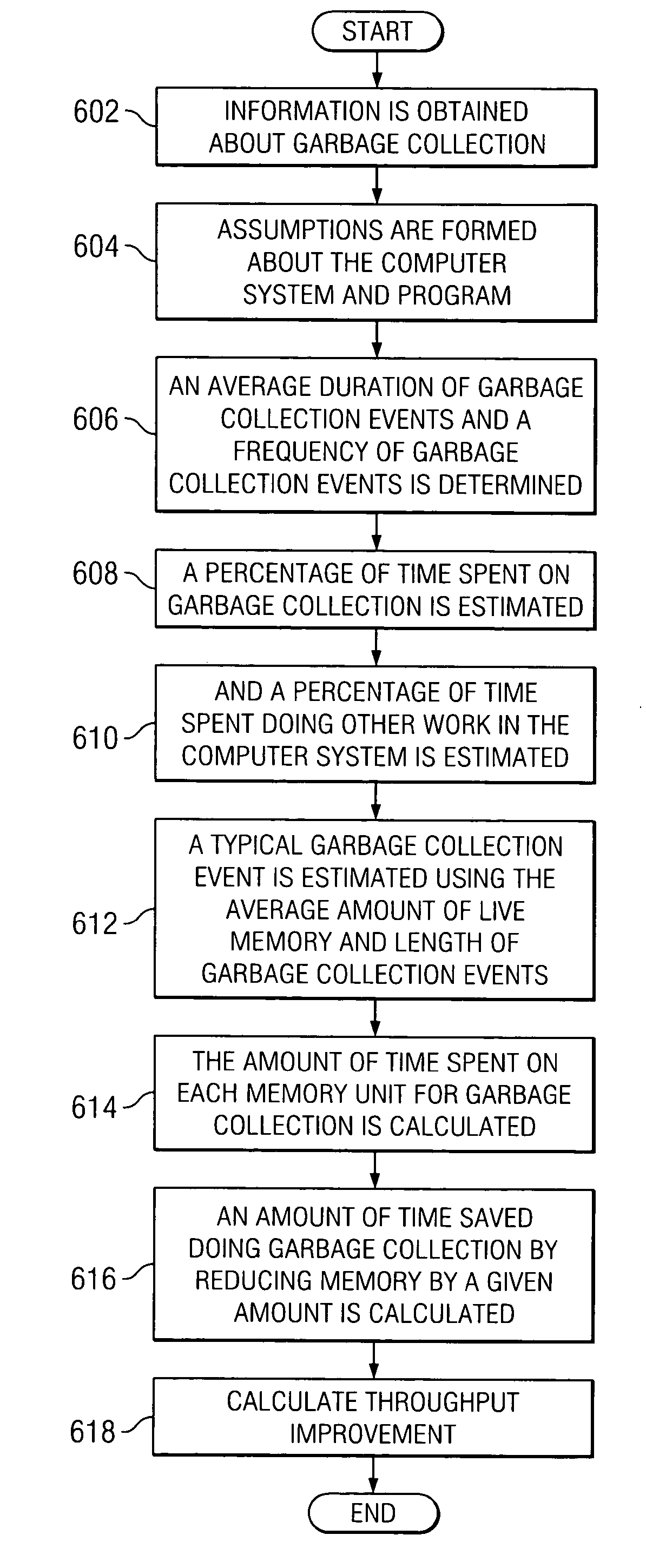
Method for determining a close approximate benefit of reducing memory footprint of a Java application
InactiveUS20050160416A1Improve performanceData processing applicationsSoftware engineeringMemory footprintParallel computing
Changes in performance in a Java program are deduced from information related to garbage collection events of the program. Assumptions are made about the system, the application and garbage collection, and changes in performance that will result from modifying the program are deduced.
Owner:IBM CORP
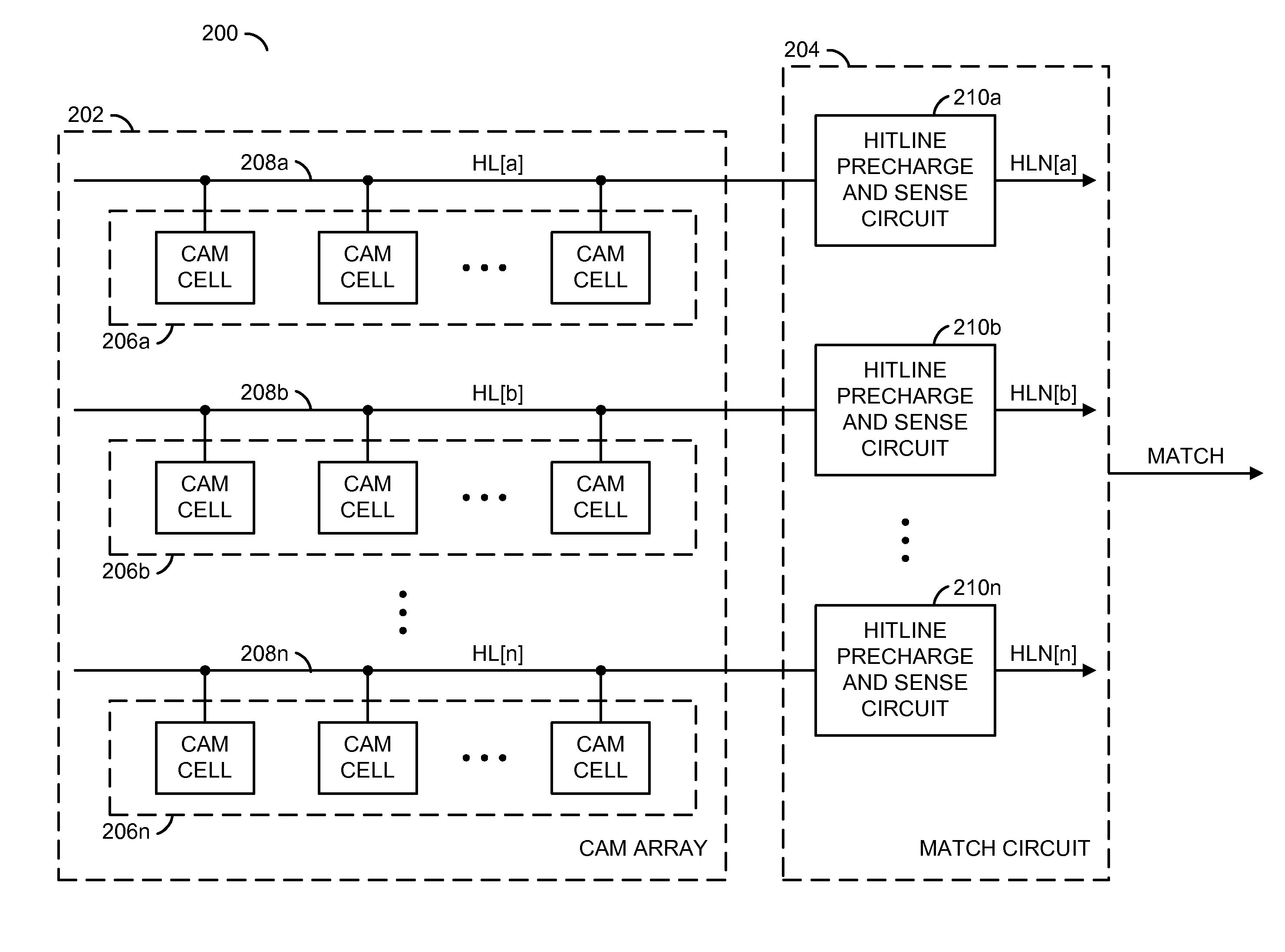
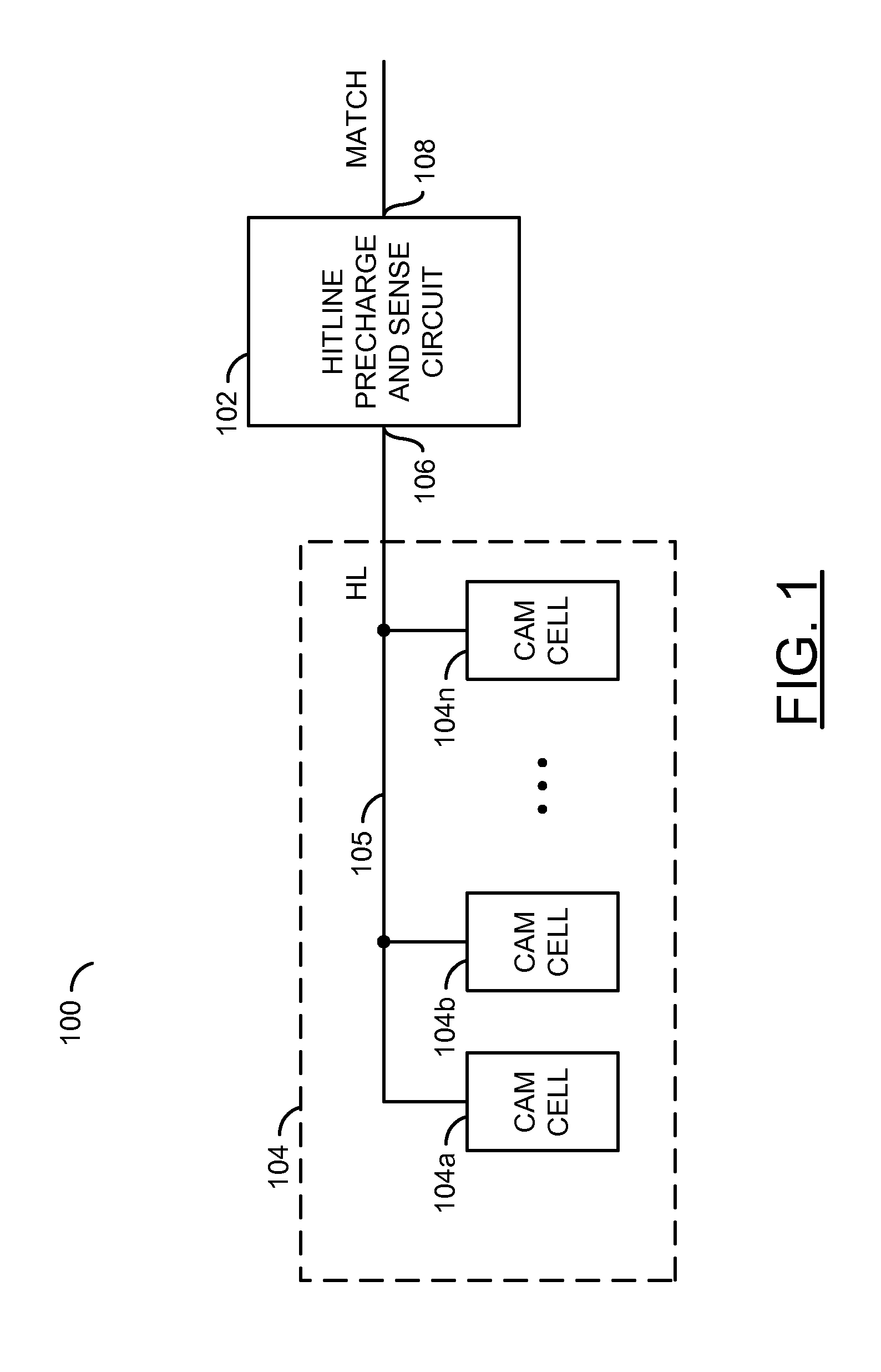
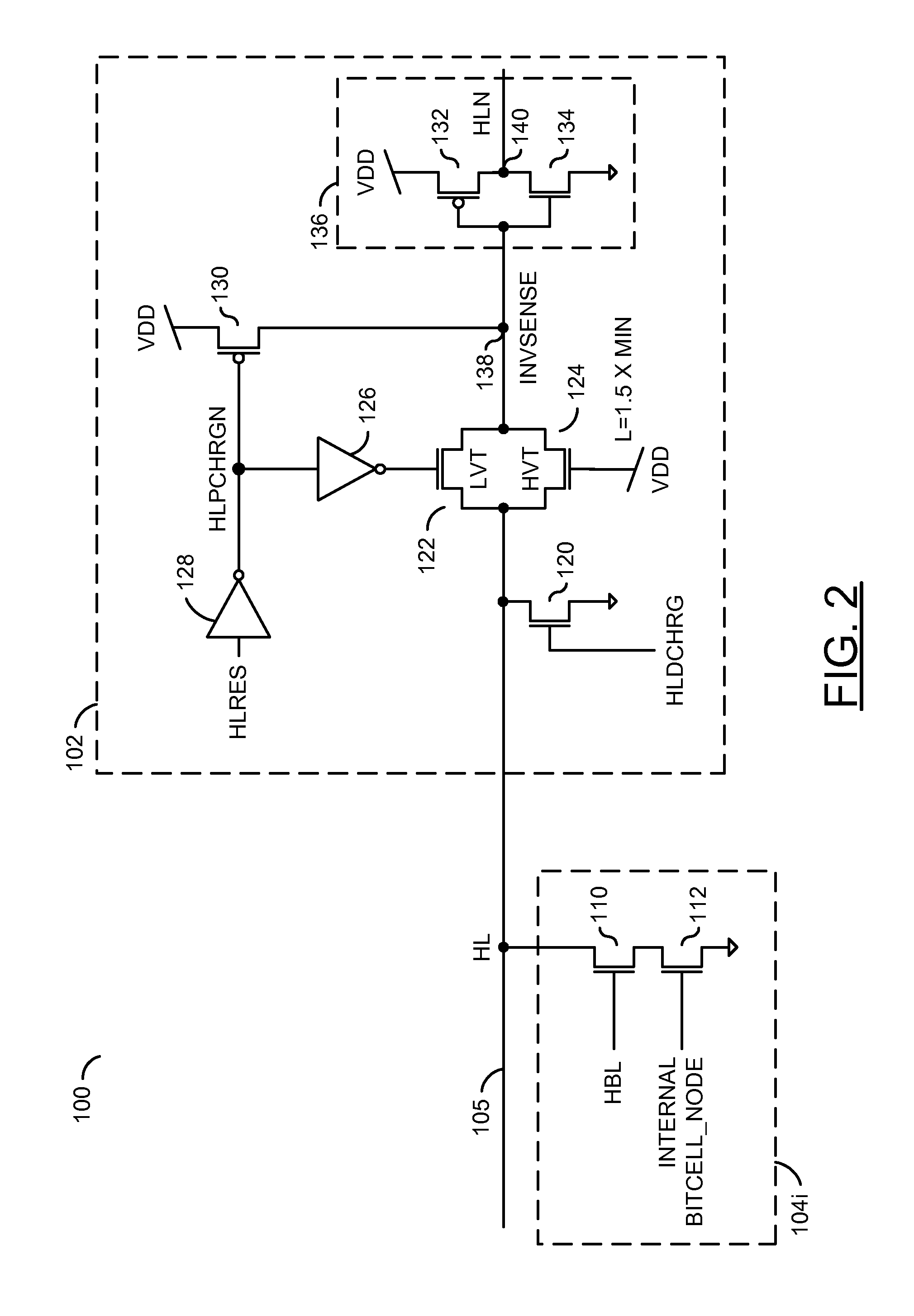
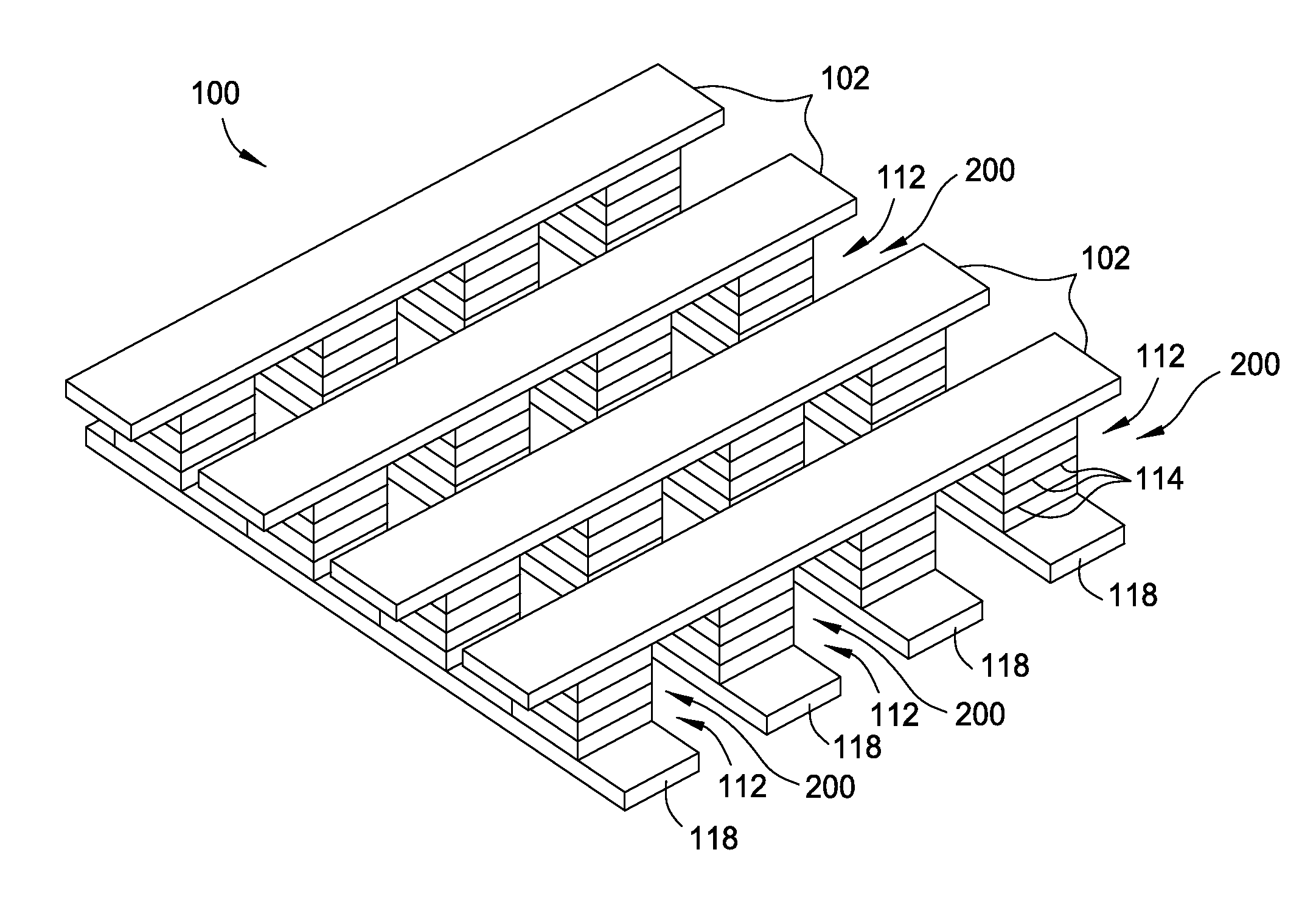
Low power content addressable memory hitline precharge and sensing circuit
An apparatus and a method of operating the apparatus. The apparatus includes a driver circuit and a memory circuit. The driver circuit may be configured to precharge a hitline in response to a predetermined voltage level and a control signal and sense a result of a compare operation based upon a hitline signal on the hitline. The driver circuit generally precharges the hitline to a voltage level lower than the predetermined voltage level and senses the result of the compare operation using the full predetermined voltage level. The memory circuit may be configured to perform the compare operation using the hitline.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Nonvolatile memory device using a varistor as a current limiter element
ActiveUS20130214232A1Reduce voltageTotal current dropSolid-state devicesSemiconductor/solid-state device manufacturingSoftware engineeringMusic player
Embodiments of the invention include a method of forming a nonvolatile memory device that contains a resistive switching memory element that has improved device switching performance and lifetime, due to the addition of a current limiting component disposed therein. The electrical properties of the current limiting component are configured to lower the current flow through the variable resistance layer during the logic state programming steps by adding a fixed series resistance in the resistive switching memory element of the nonvolatile memory device. In some embodiments, the current limiting component comprises a varistor that is a current limiting material disposed within a resistive switching memory element in a nonvolatile resistive switching memory device. Typically, resistive switching memory elements may be formed as part of a high-capacity nonvolatile memory integrated circuit, which can be used in various electronic devices, such as digital cameras, mobile telephones, handheld computers, and music players.
Owner:KK TOSHIBA +1
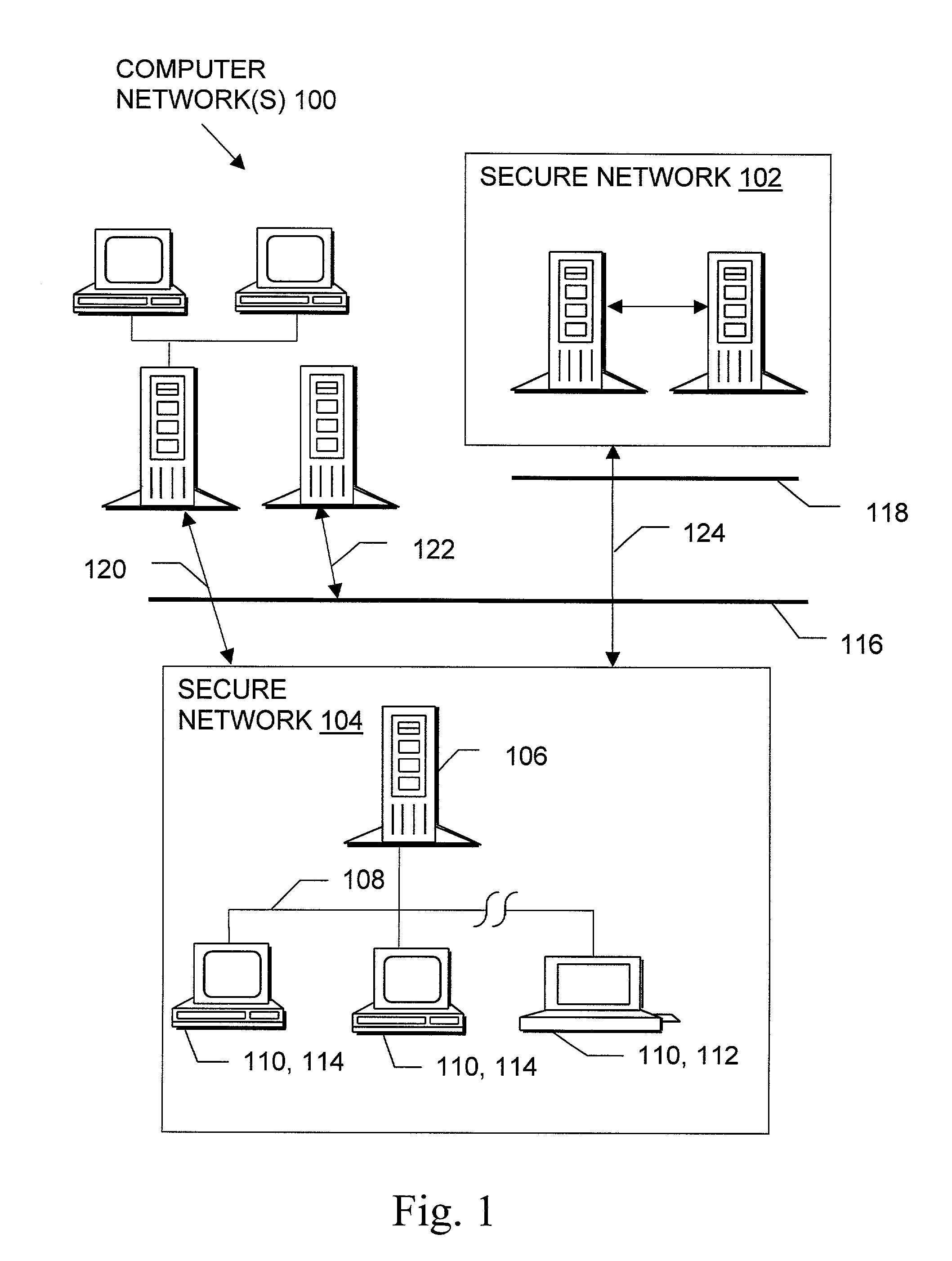
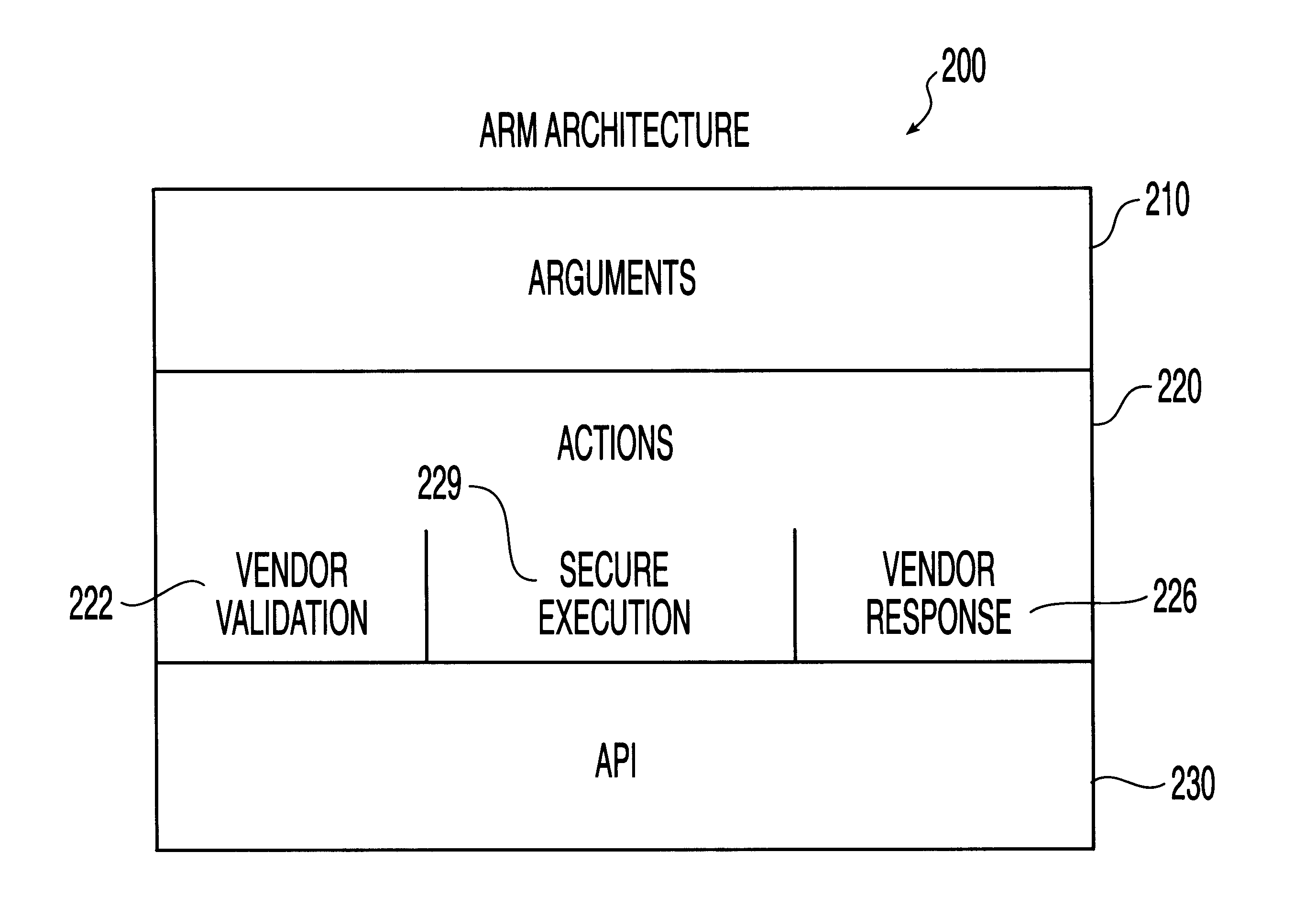
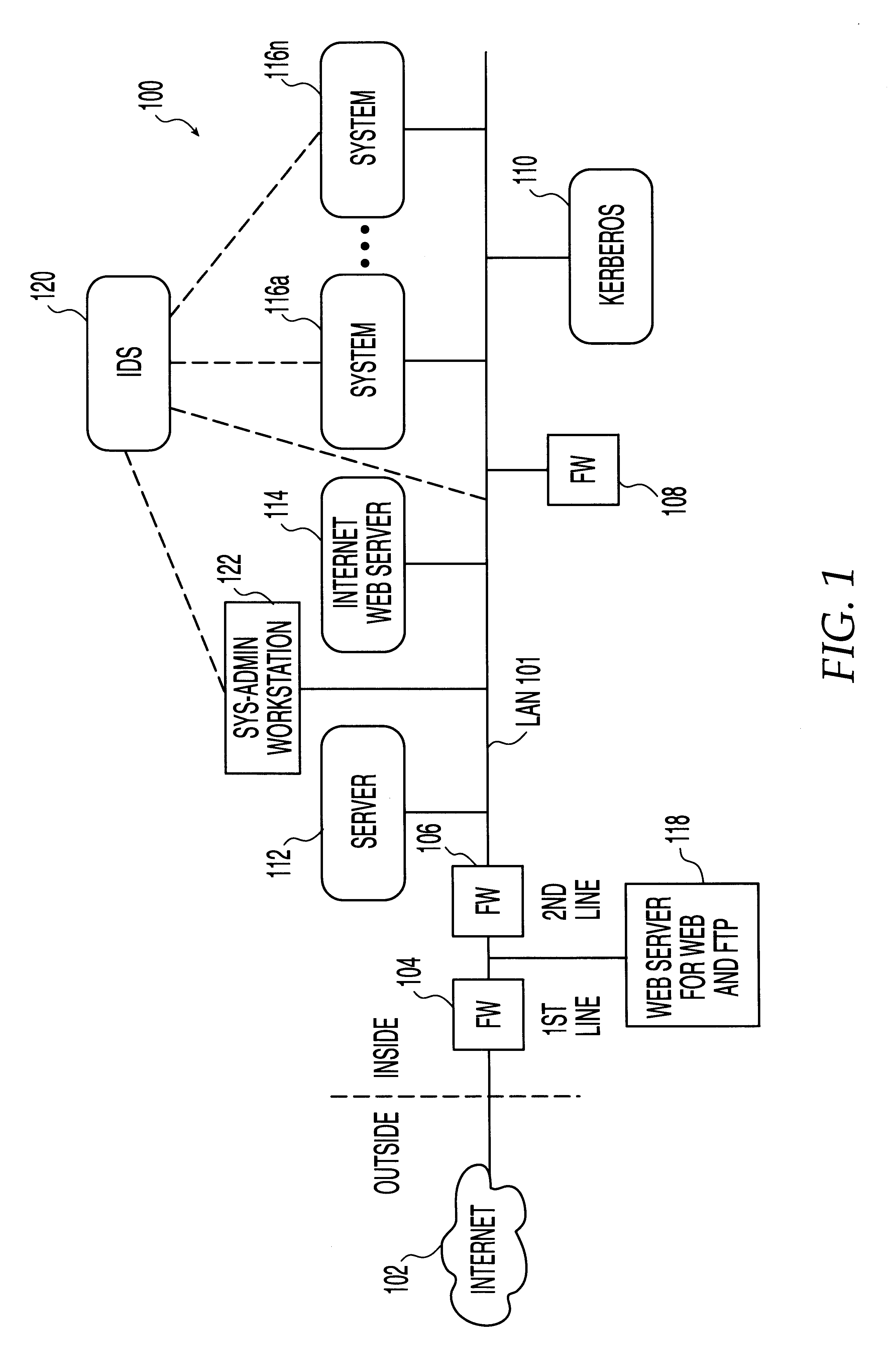
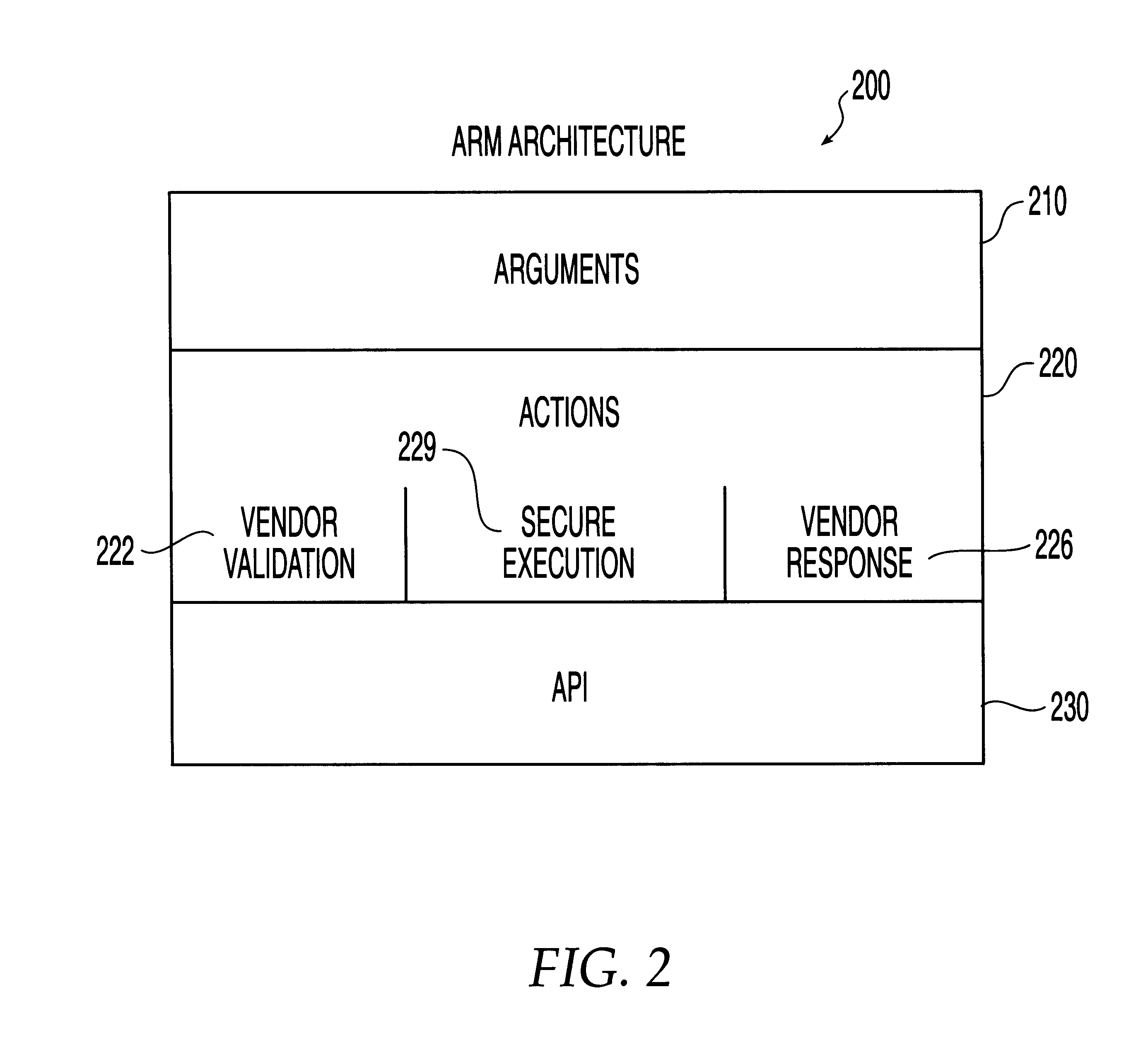
System, method and computer program product for automatic response to computer system misuse using active response modules
InactiveUS6275942B1Rapid responseMemory loss protectionDigital data processing detailsSoftware engineeringSecurity level
A system, method and computer program product for automatic response to computer system misuse using active response modules (ARMs). ARMs are tools that allow static intrusion detection system applications the ability to dynamically increase security levels by allowing real-time responses to detected instances of computer misuse. Several classes of ARMs exist which allow them to interface with several types of network elements found within a computing environment (e.g., firewalls, web servers, Kerberos severs, certificate authorities, etc.). The ARMs, once defined, are deployed in a "plug and play" manner into an existing intrusion detection system within a computing environment. A user (e.g., system administrator) may then configure the ARMs by linking them to specific computer misuses. Upon receipt of an instance of the computer misuse from the intrusion detection system, each ARM linked to the misuse collects pertinent data from the intrusion detection system and invokes a response specified by the ARM class and the collected pertinent data.
Owner:MCAFEE LLC +1
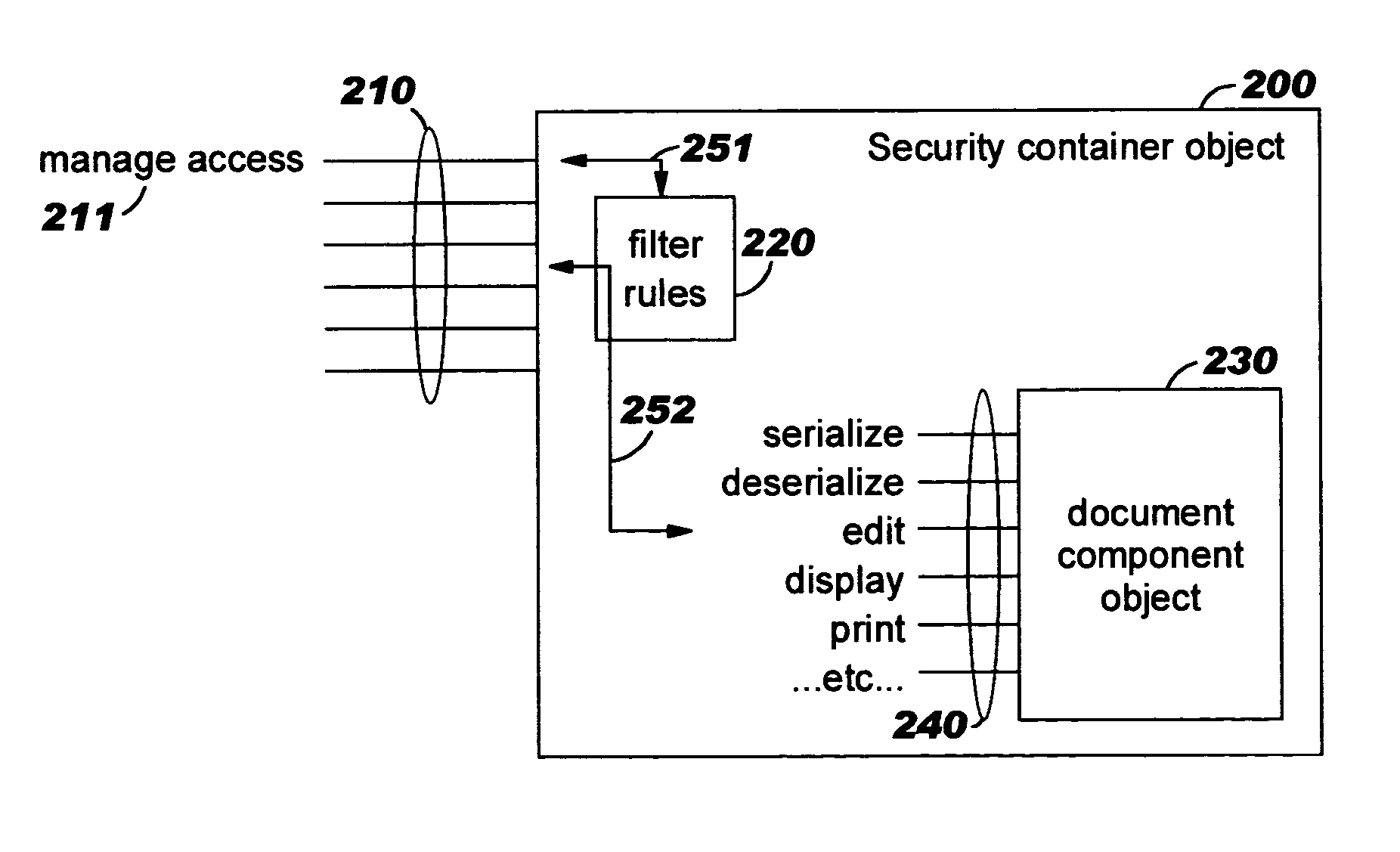
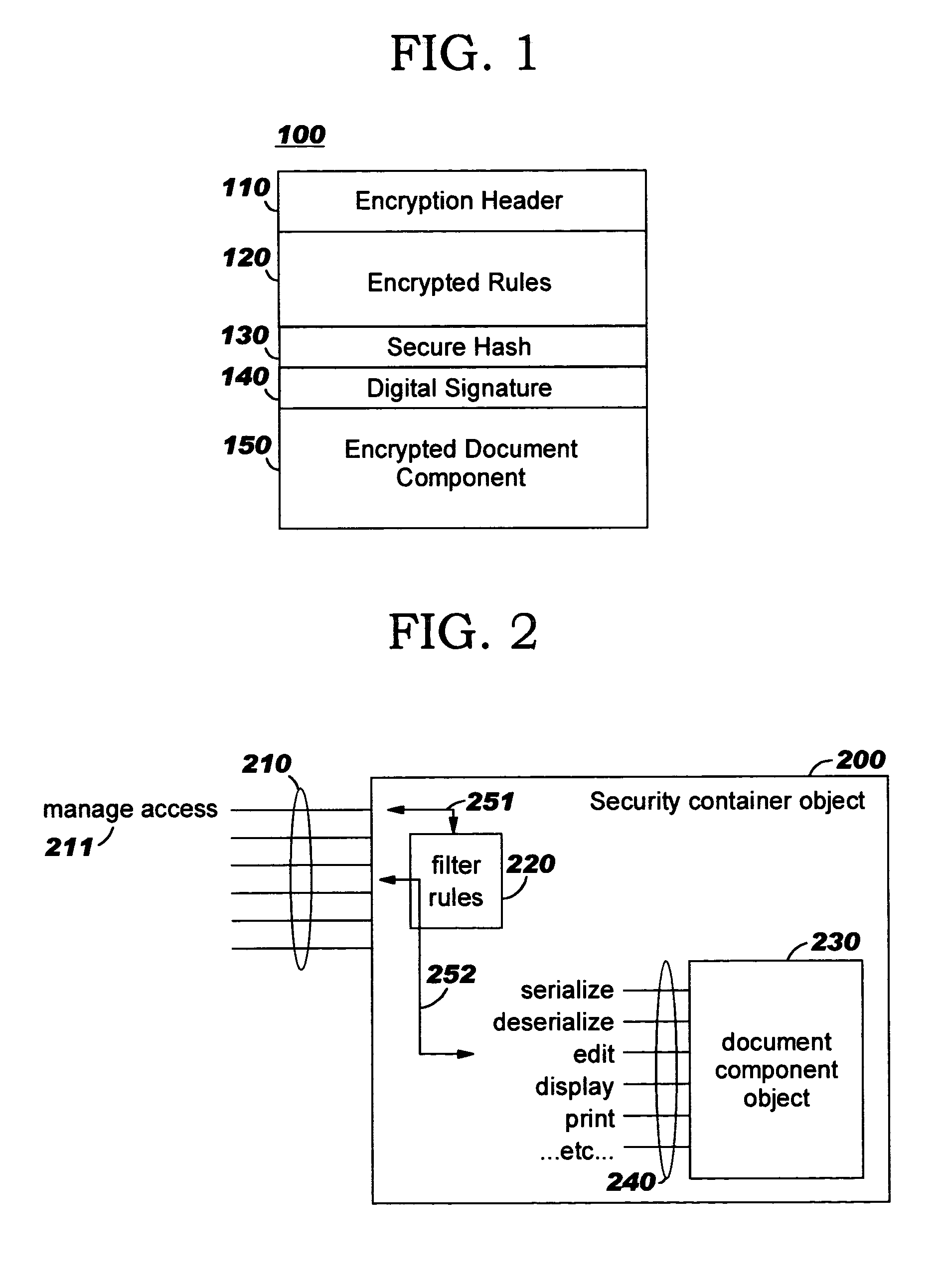
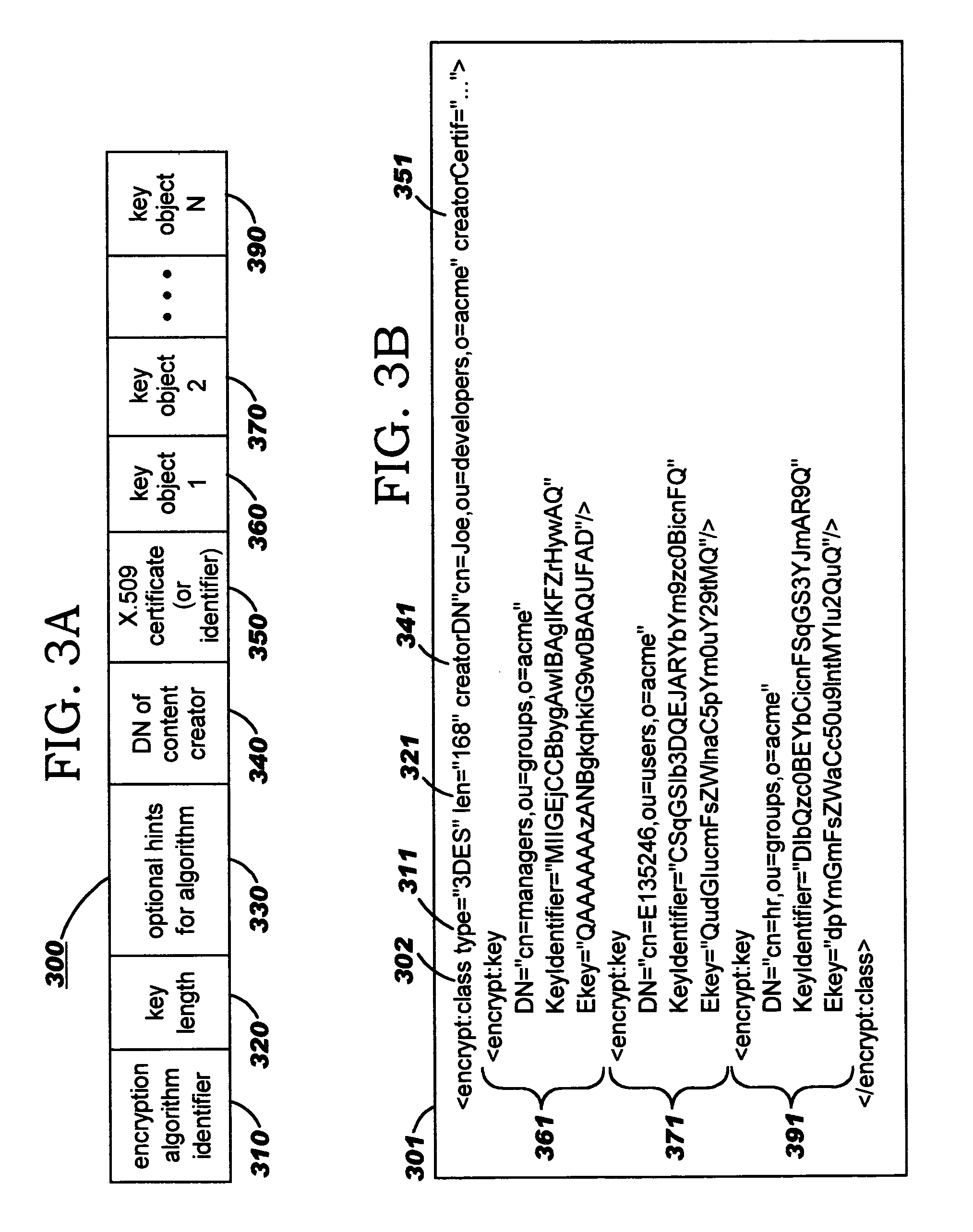
Security containers for document components
ActiveUS20050039034A1Easy to useSafe storageKey distribution for secure communicationUser identity/authority verificationSoftware engineeringPaper document
Methods, systems, computer program products, and methods of doing business whereby document components are secured or controlled using “security containers” which encapsulate the components (and other component metadata). A “security container” encapsulates the component (i.e., content) that is to be controlled within a higher-level construct such as a compound document. The security container also contains rules for interacting with the encapsulated component, and one or more encryption keys usable for decrypting the component and rules for authorized requesters.
Owner:IBM CORP
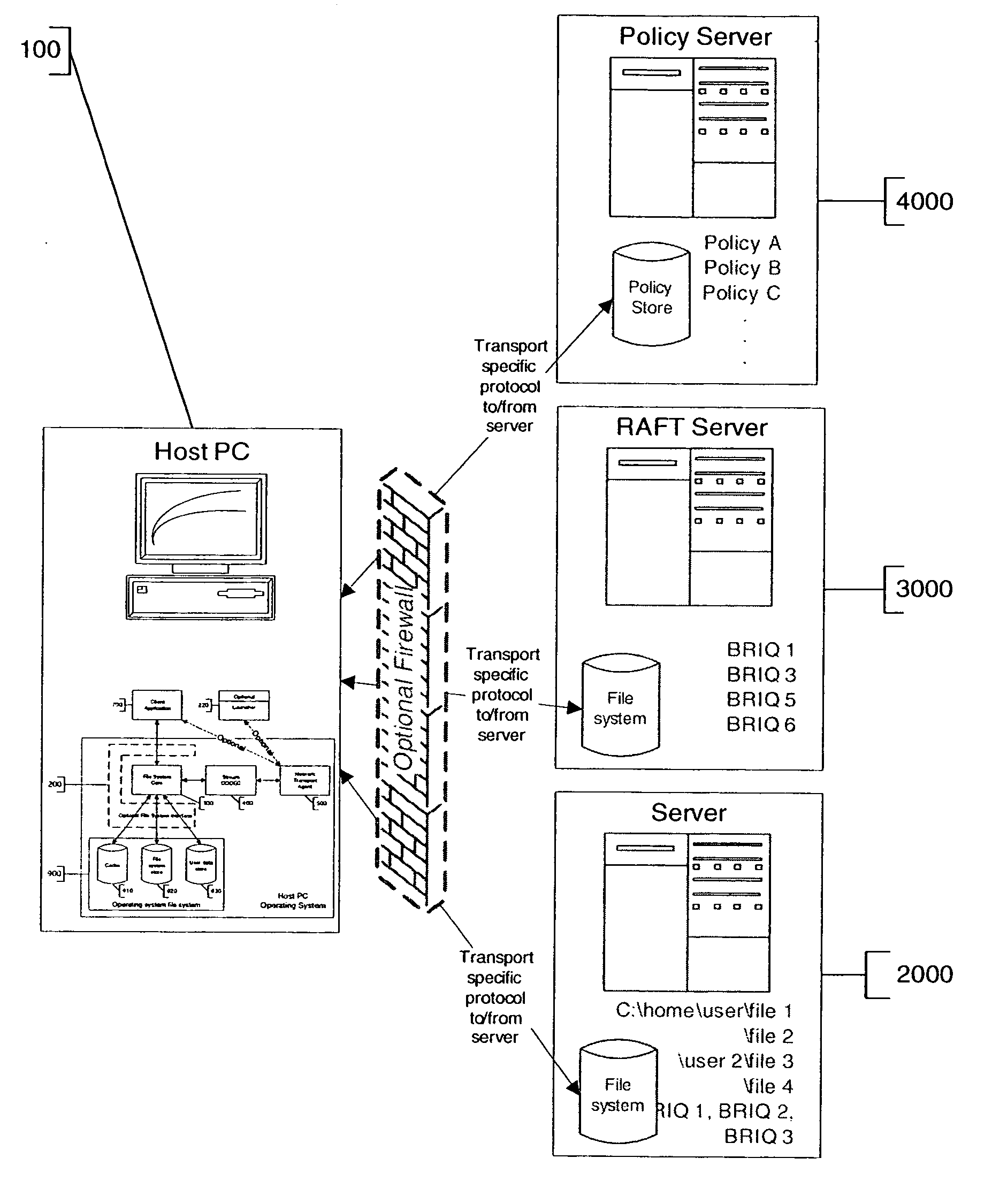
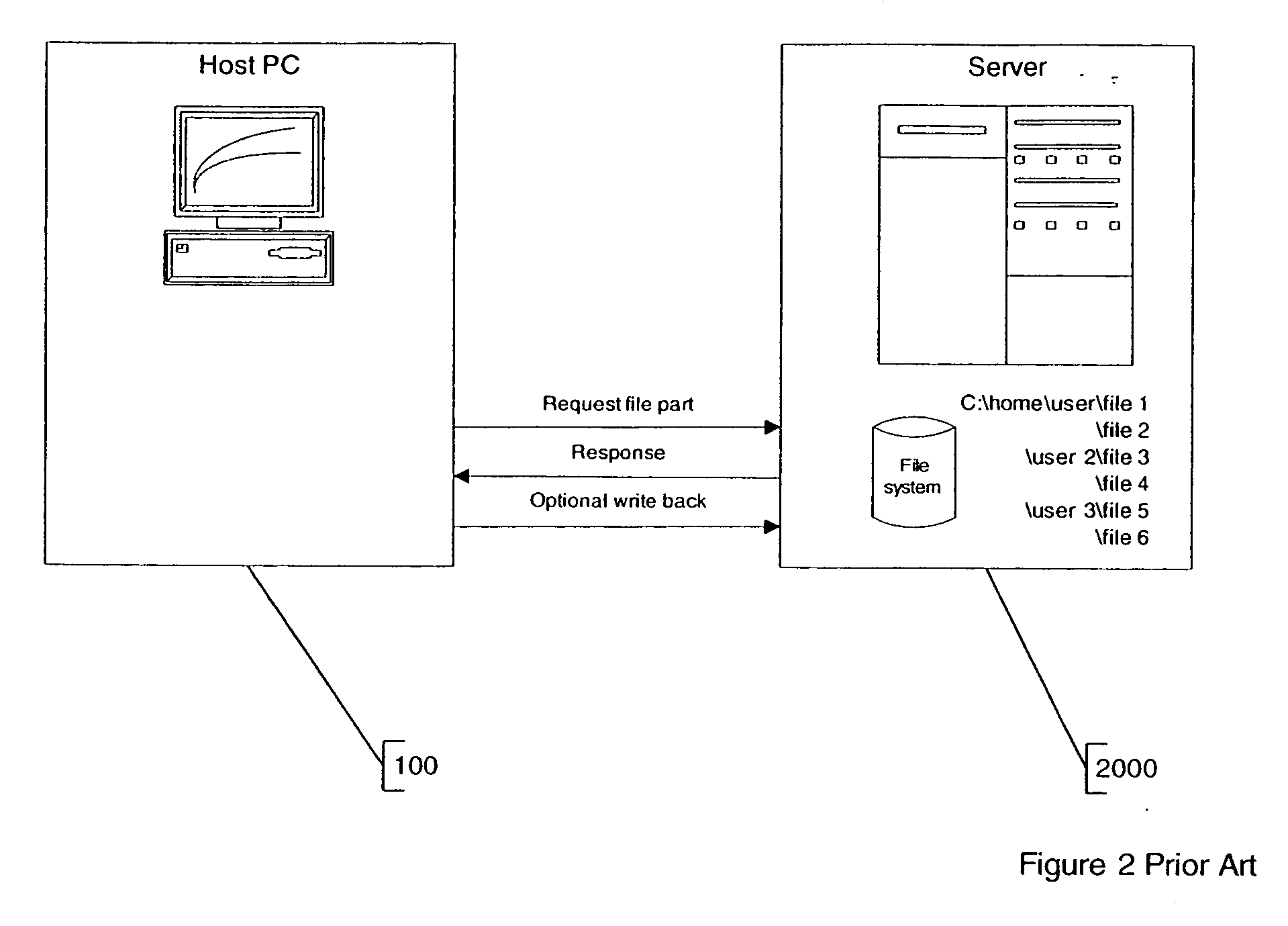
Policy based composite file system and method
InactiveUS20060259949A1Digital data information retrievalSpecial data processing applicationsFile systemConfigfs
A policy configurable file system includes a computer system upon which the policy configurable file system operates, a policy source for providing the configuration policies, and one or more file servers. The computer system includes software for enforcing one or more configuration policies. The policy source is typically either a policy server such that the policy is derived from the policy server, or a policy configurable file system, such that the policy is embedded in the policy configurable file system. The one or more file servers each uses a protocol, wherein the protocols of the one or more file servers are not all the same. In one case, the one or more of the configurable policies are separable from the policy configurable file system. In another case, the one or more configurable policies are downloadable to the computer system.
Owner:MICROSOFT TECH LICENSING LLC
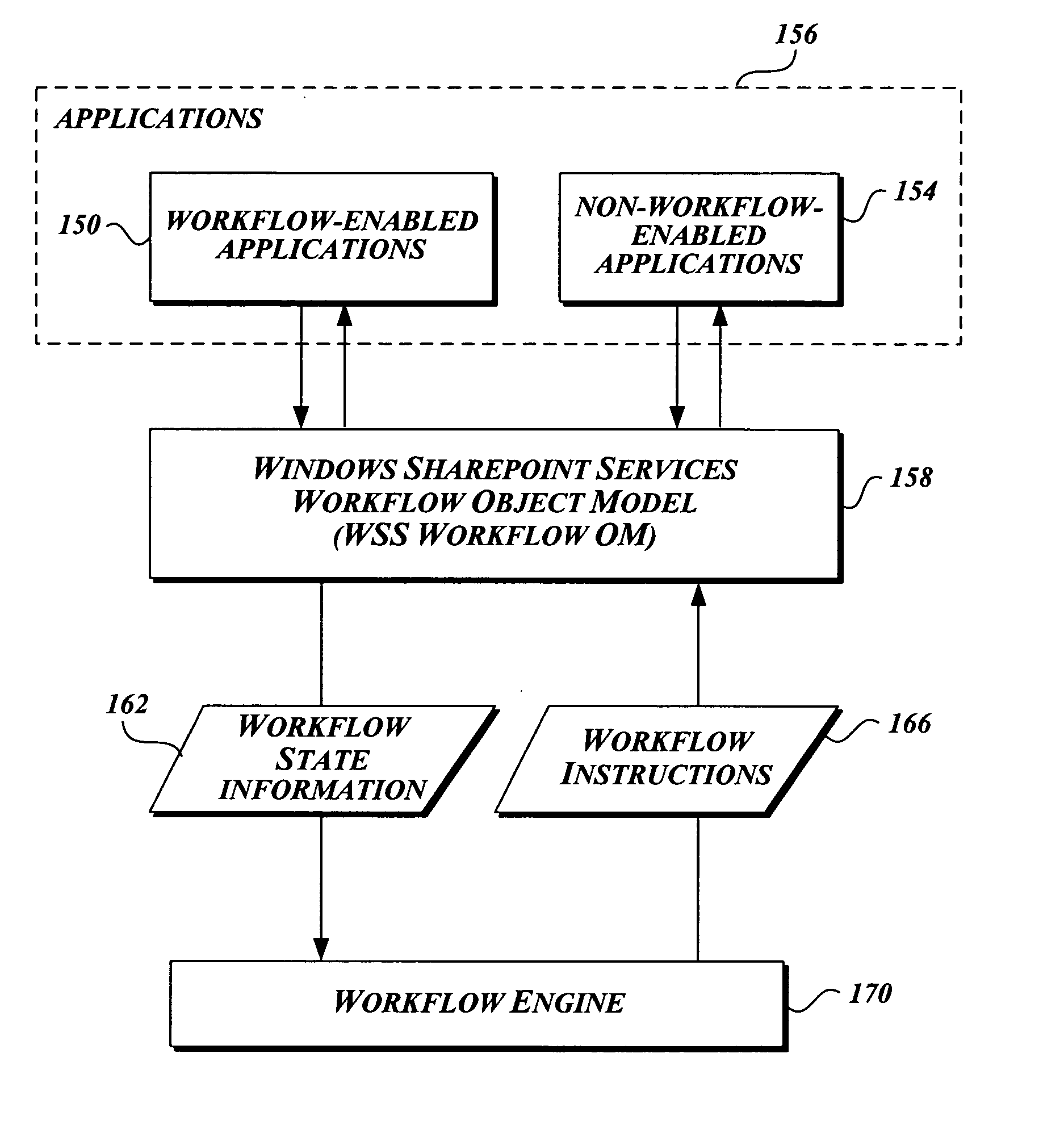
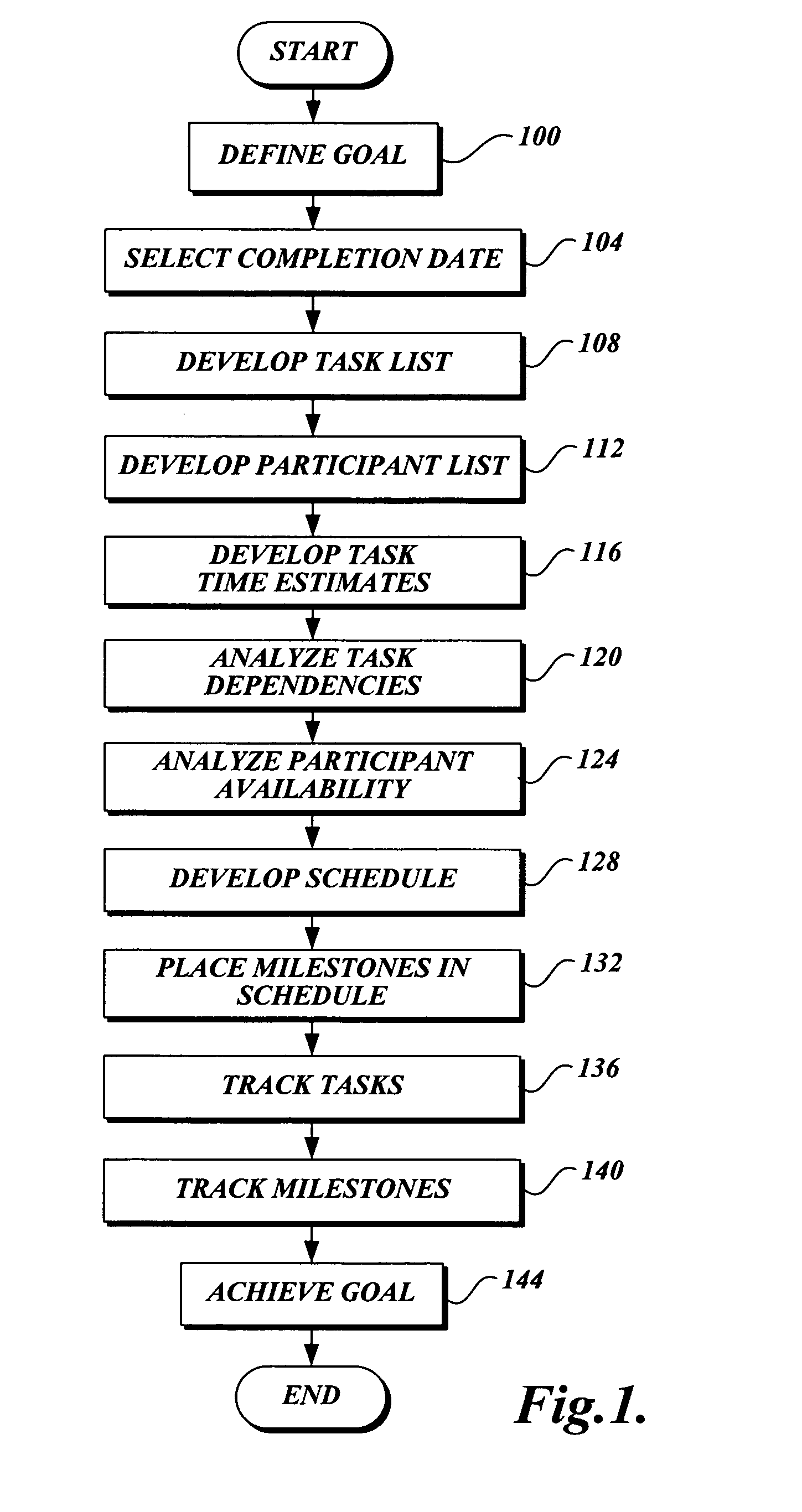
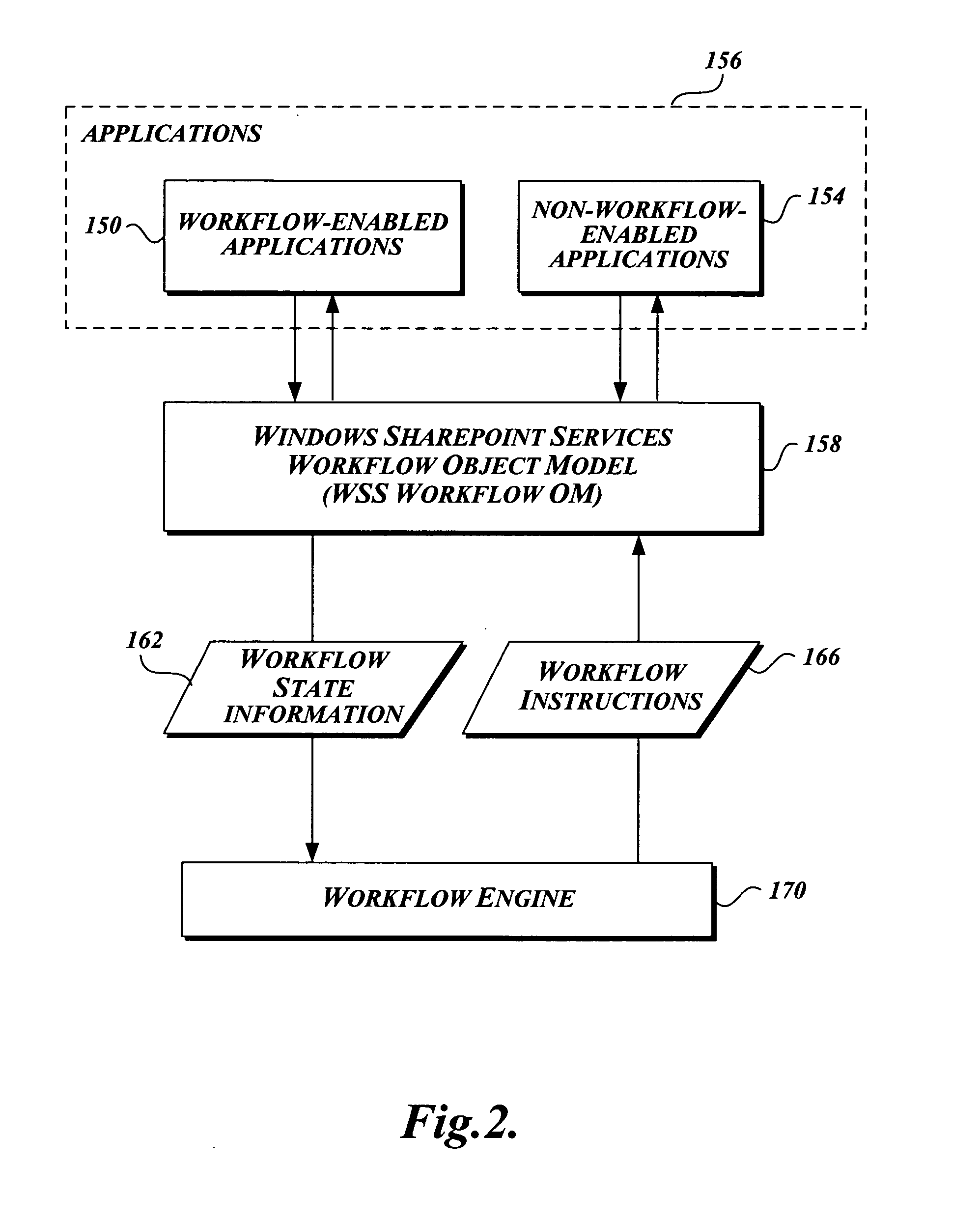
Workflow association in a collaborative application
A method for developing and managing workflows is disclosed. The method enables the development of workflows from workflow templates and / or preprogrammed components; associating a workflow with a schedule; modeling a workflow as a plurality of tasks and a plurality of human-to-human or human-to-computer interaction points; and persistently storing the internal state of a workflow. The method employs computer-implemented forms to control the development, packaging, installation, deployment, enablement, association, instantiation, and termination of workflows.
Owner:MICROSOFT TECH LICENSING LLC
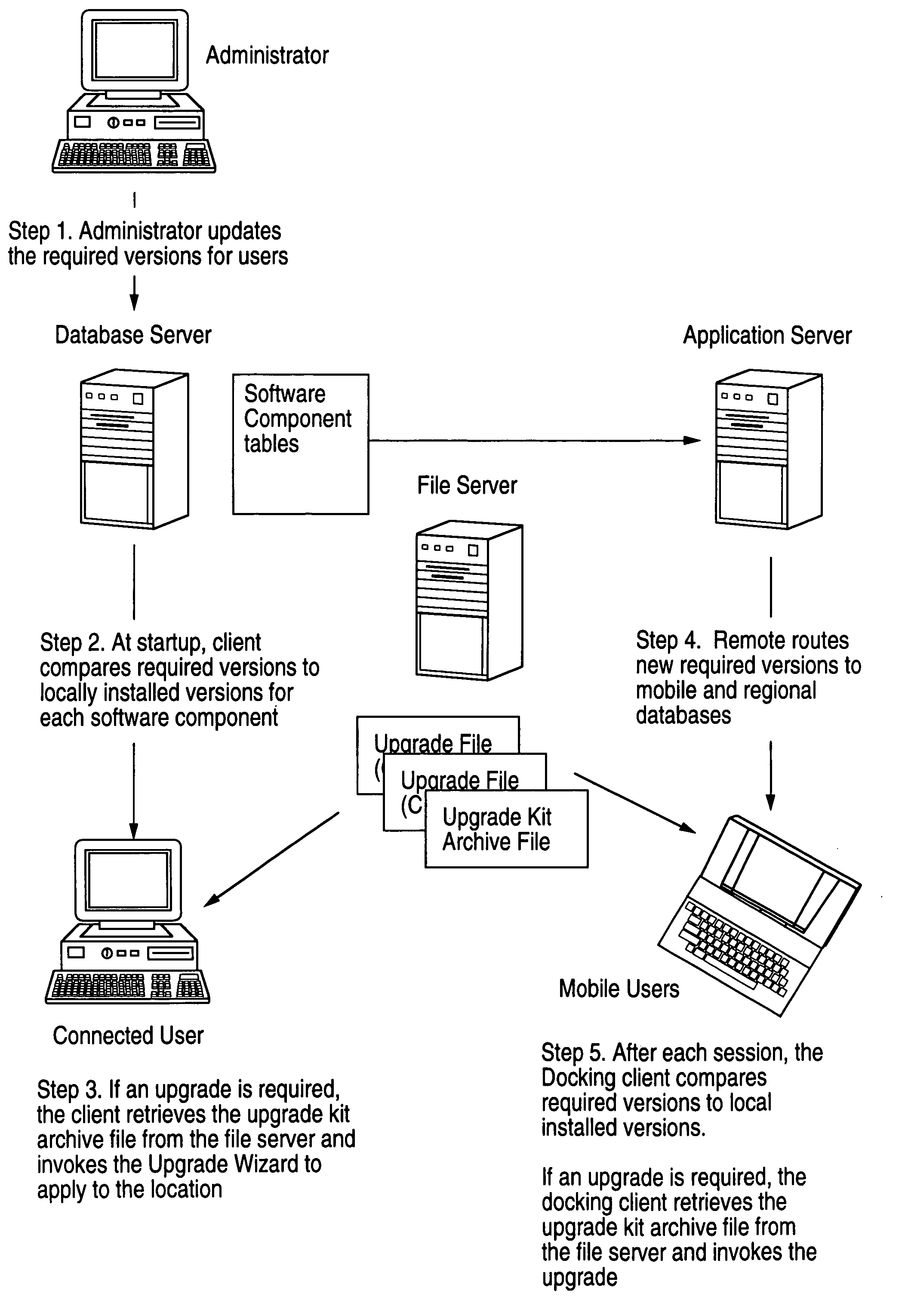
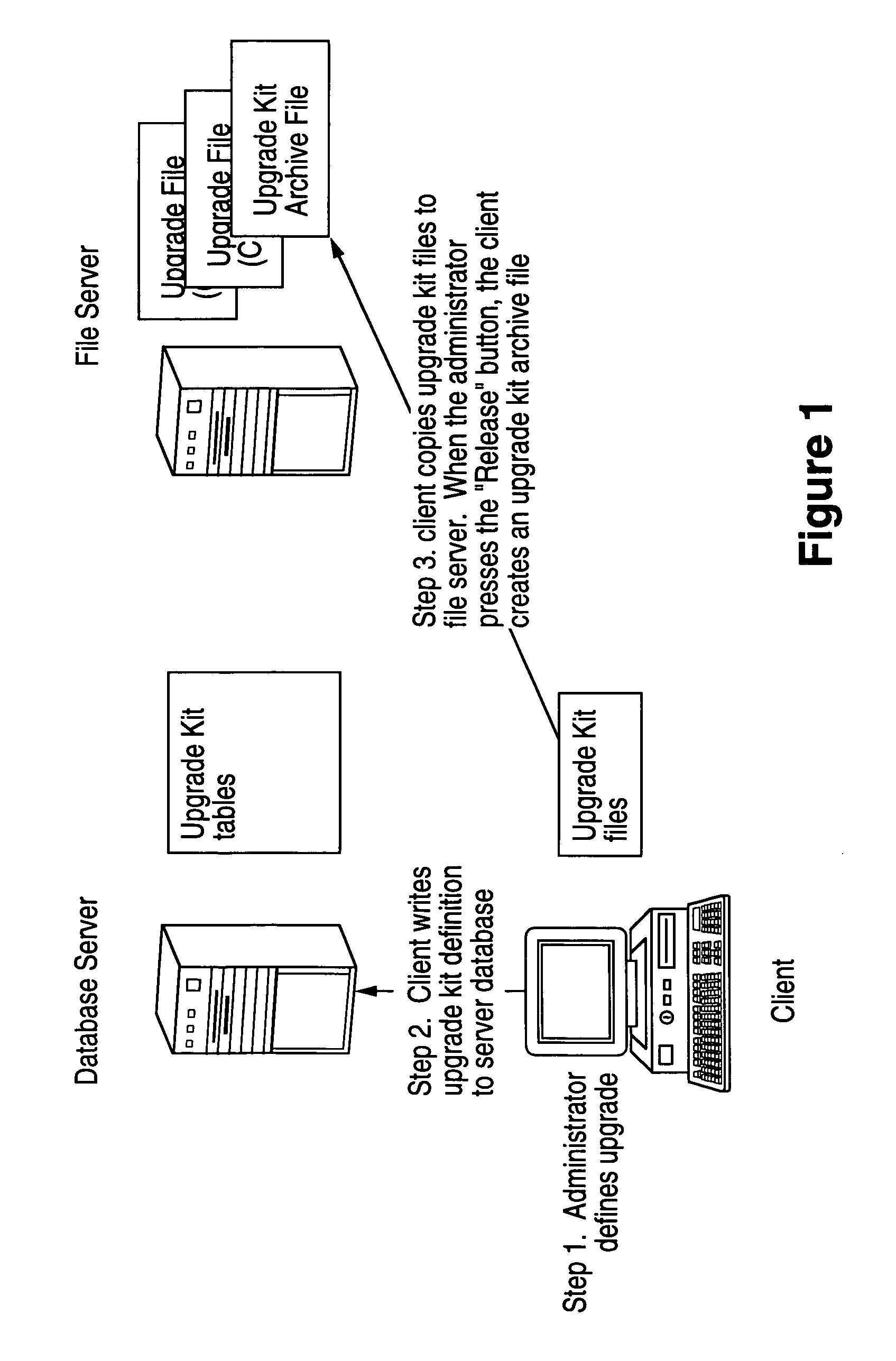
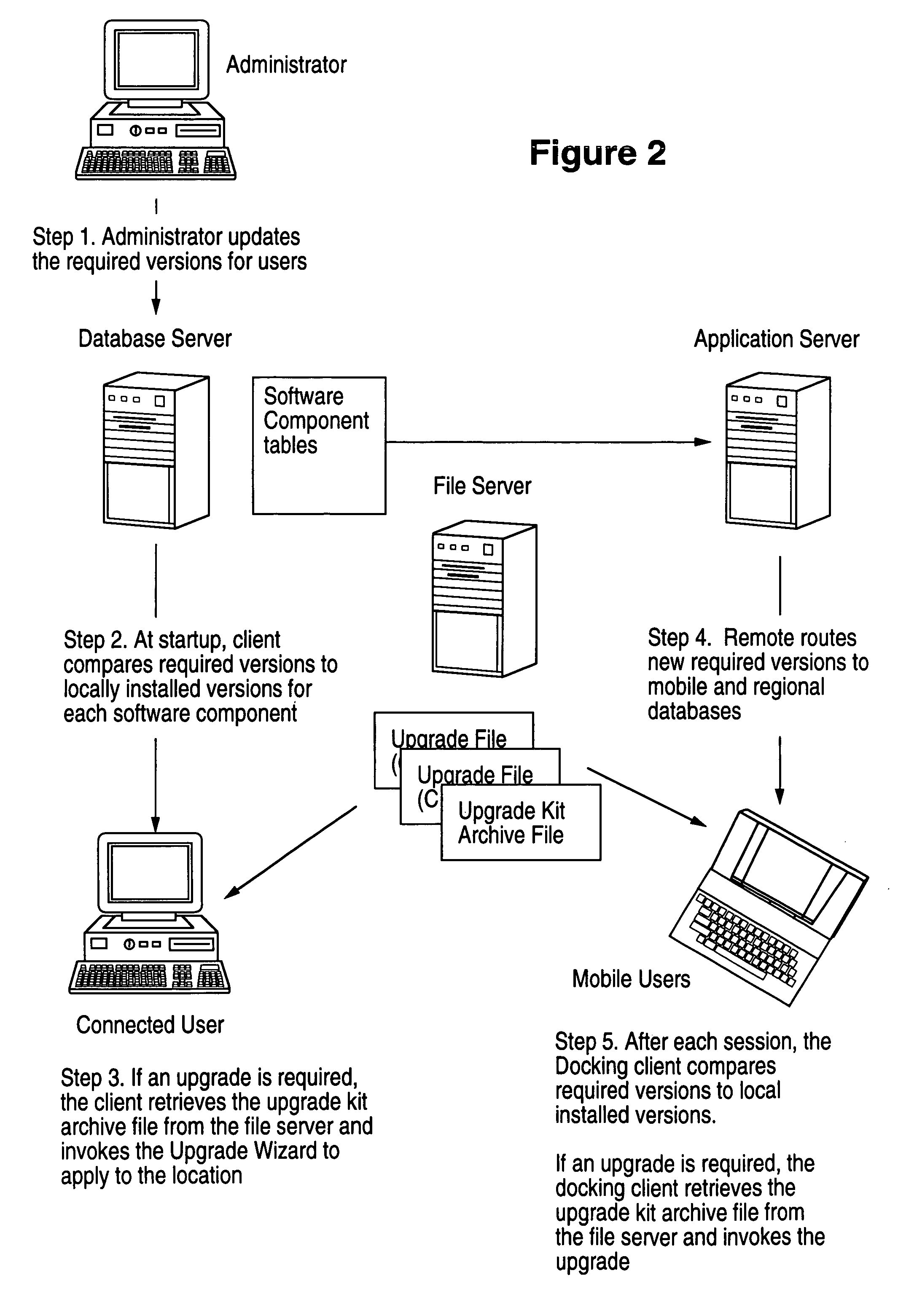
Method, system, apparatus and program product for distribution and instantiation of software upgrades
InactiveUS7080371B1Program loading/initiatingMemory systemsDistributed Computing EnvironmentSoftware engineering
Distributing and instantiating software version upgrades in a distributed computing environment. This includes defining the required versions of software as the contents of a software version upgrade kit. This is written, e.g., as a table of contents or a list, to a database to generate software version upgrade kit tables. These tables are used to generate software version upgrade kits. The kits are then used as a source to download copies of the upgrade kits to clients to be upgraded. This enables upgrading the software on the client.
Owner:ORACLE INT CORP
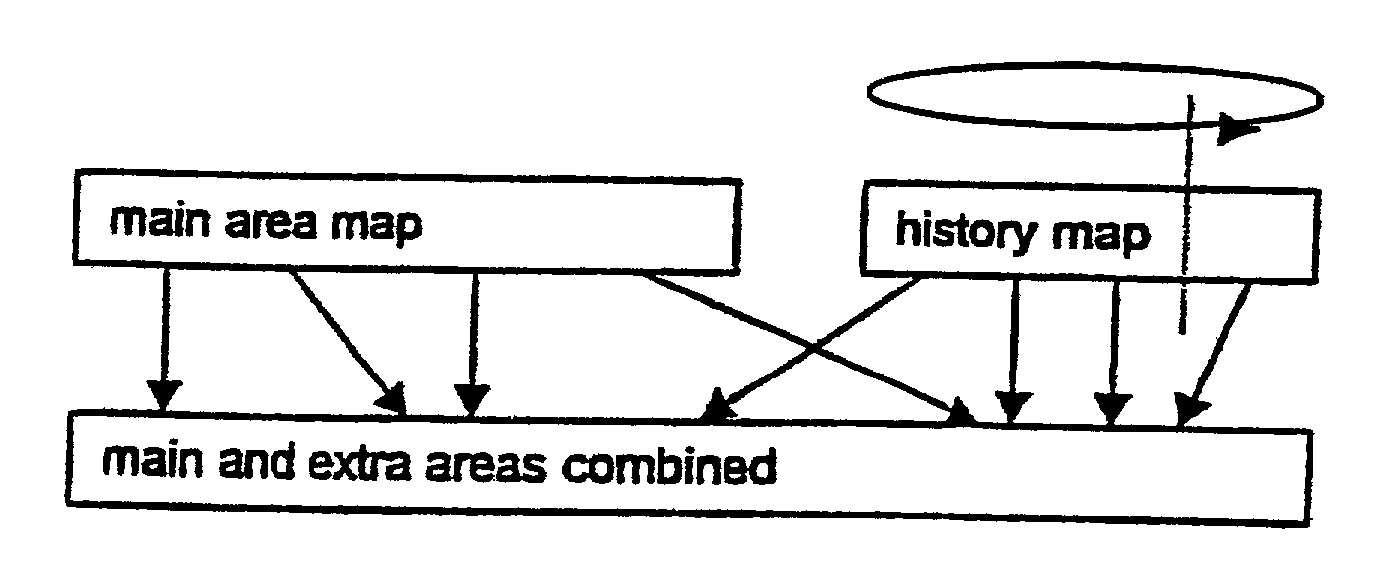
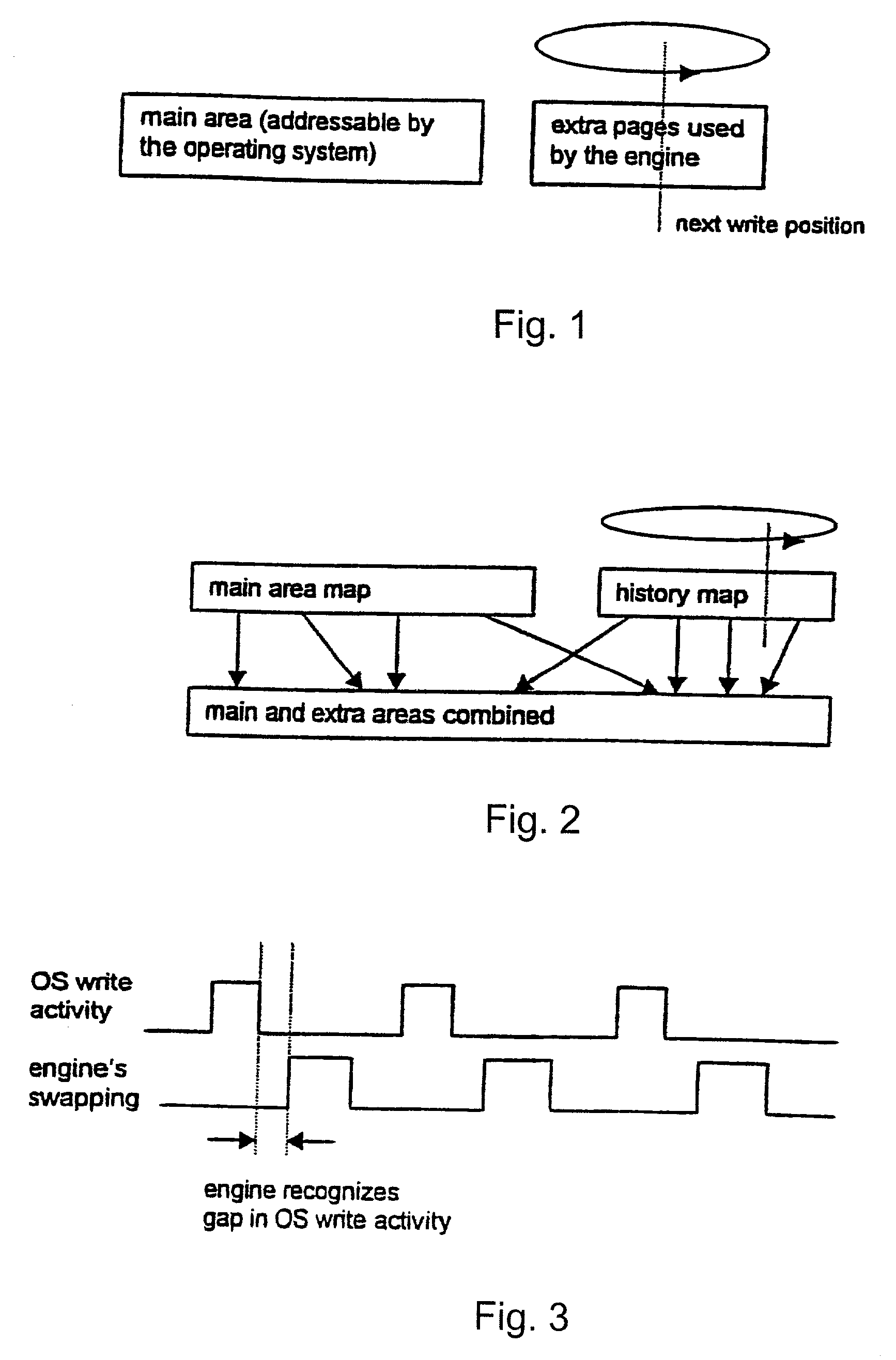
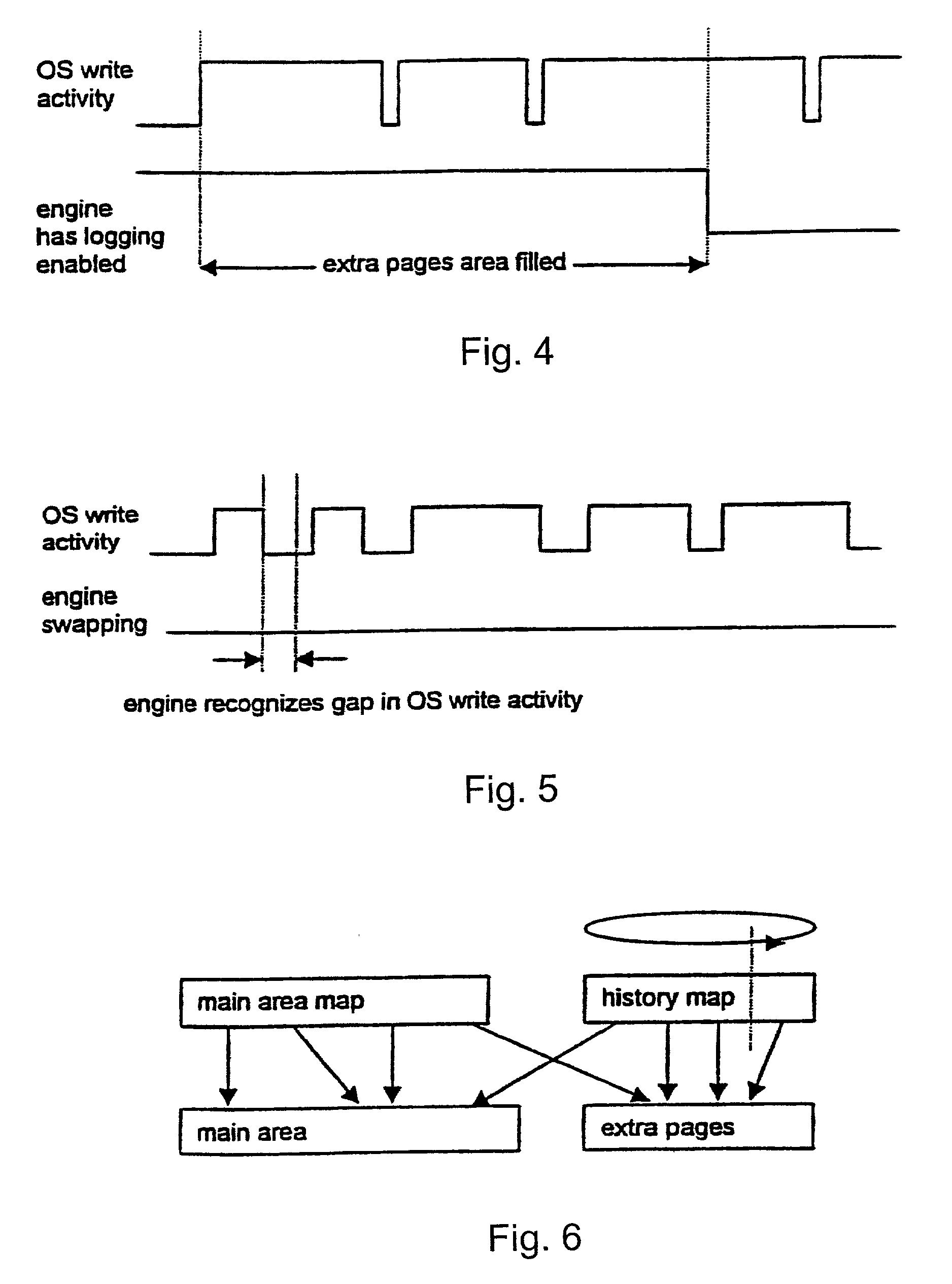
System and method for restoring a computer system after a failure
InactiveUS20020049883A1Memory adressing/allocation/relocationInternal/peripheral component protectionOperational systemOriginal data
A method and apparatus for reverting a disk drive to an earlier point in time is disclosed. Changes made to the drive are saved in a circular history buffer which includes the old data, the time it was replaced by new data, and the original location of the data. The circular history buffer may also be implemented by saving new data elements into new locations and leaving the old data elements in their original locations. References to the new data elements are mapped to the new location. The disk drive is reverted to an earlier point in time by replacing the new data elements with the original data elements retrieved from the history buffer, or in the case of the other embodiment, reads to the disk are mapped to the old data elements stilled stored in their original locations. The method and apparatus may be implemented as part of an operating system, or as a separate program, or in the controller for the disk drive. The method and apparatus are applicable to other forms of data storage as well. Also disclosed are method and apparatus for providing firewall protection to data in a data storage medium of a computer system.
Owner:NORTONLIFELOCK INC
Methods and systems for selecting a method for execution, by a virtual machine, of an application program
ActiveUS20070180450A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideClient machine
A method for selecting a method of execution for an application includes the step of receiving credentials. A plurality of applications available to a client machine is enumerated responsive to the received credentials. A request to execute an enumerated application is received. One of a predetermined number of methods for executing the requested application is selected responsive to a policy, the predetermined number of methods including a method for executing the requested application in a computing environment provided by a virtual machine.
Owner:CITRIX SYST INC
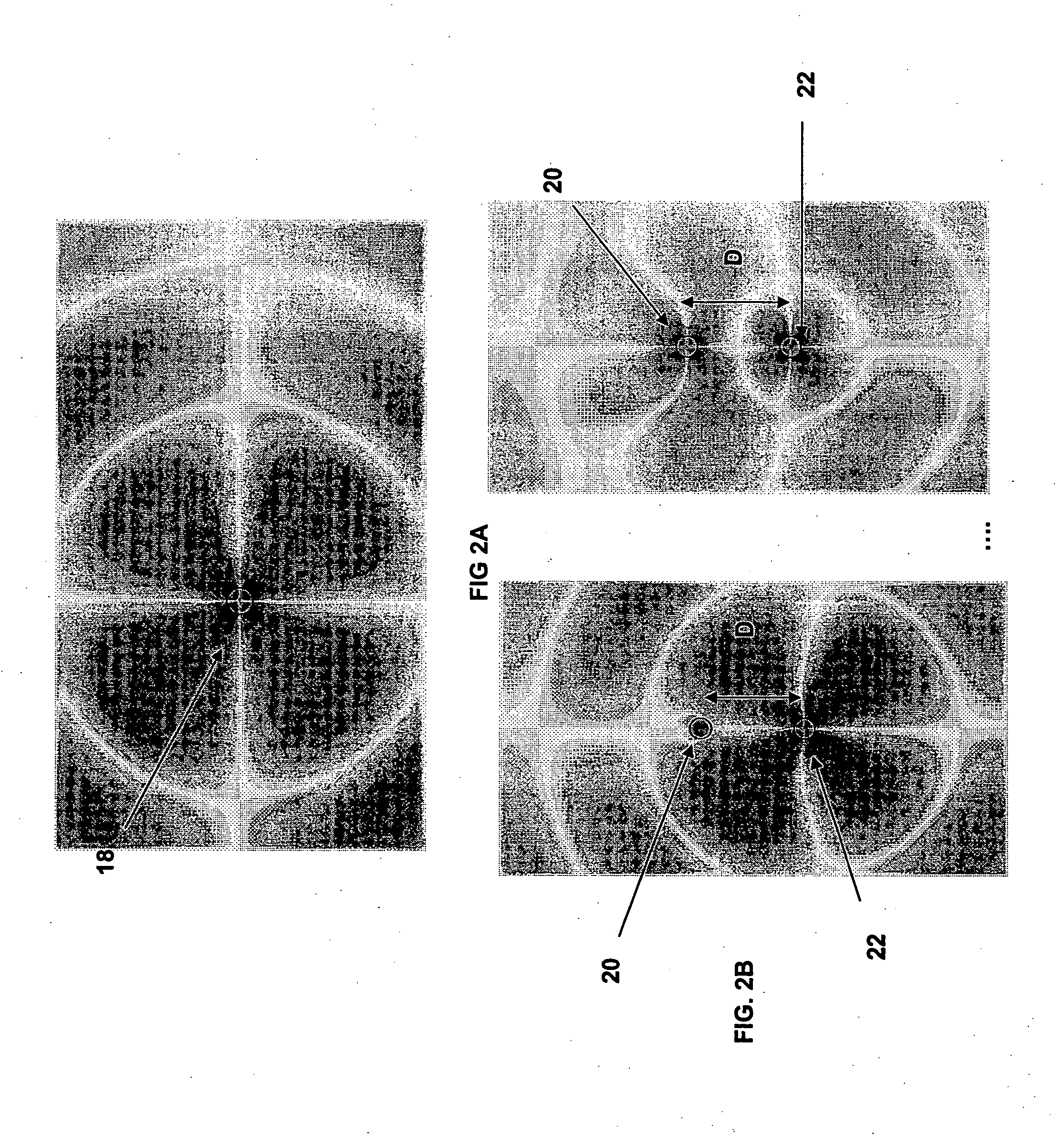
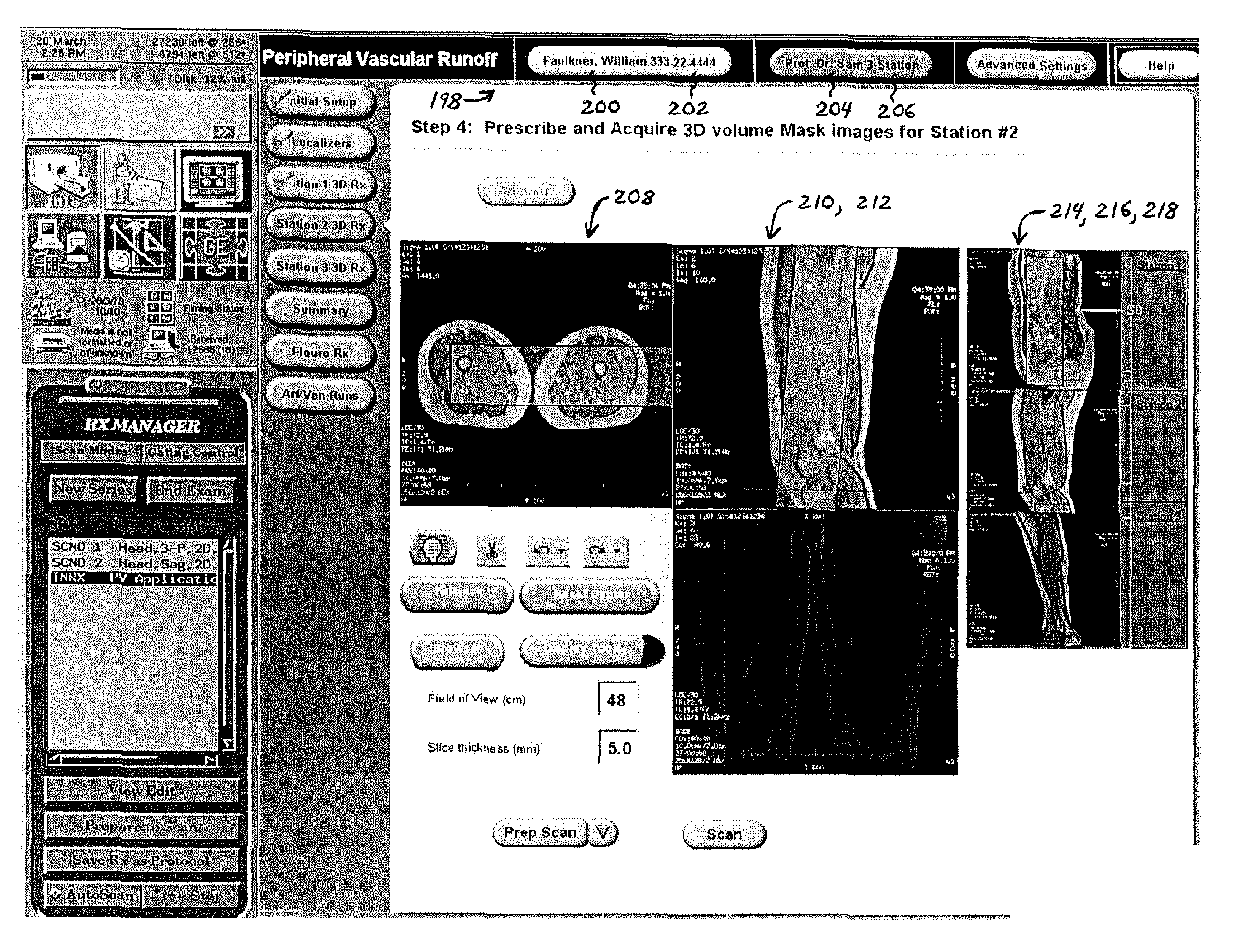
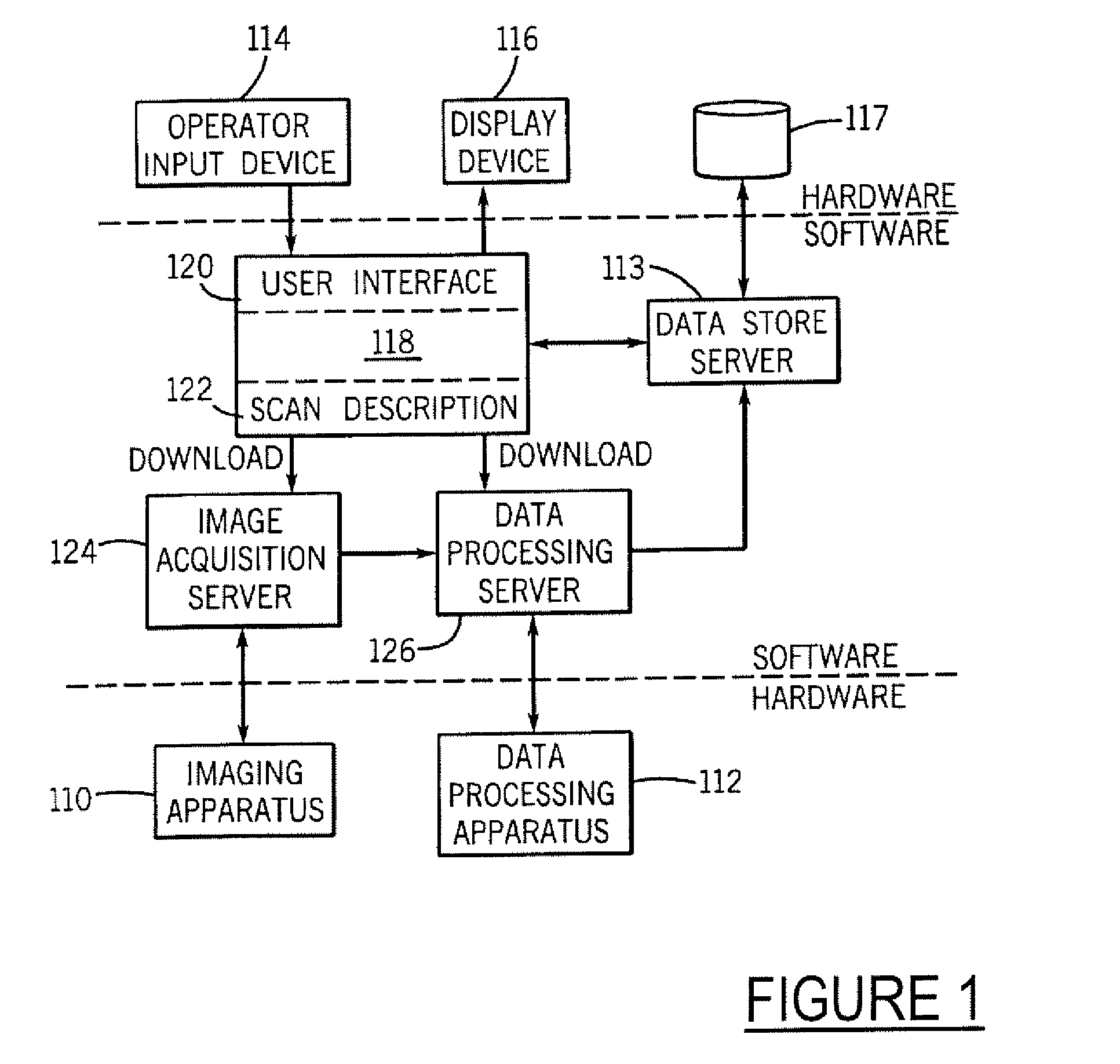
System and method for enabling a software developer to introduce informational attributes for selective inclusion within image headers for medical imaging apparatus applications
InactiveUS20050063575A1Character and pattern recognitionMedical imagesSoftware engineeringSoftware development
A system and method for enabling a developer to introduce informational attributes suitable for selective inclusion within image headers is disclosed herein. The image headers, along with their selectively included informational attributes, are displayable on a monitor screen together with associated digital images produced by an imaging apparatus. The image headers are also selectively storable in a database together with the pixel data of the associated digital images. The system includes an interactive workstation computer system having memory-stored software applications for operating the imaging apparatus, a memory-stored updatable table of defined informational attributes suited for selective inclusion within image headers, an interactive computer for generating software files of image header definitions from the table of defined informational attributes, and a means to transport the software files of image header definitions to the interactive workstation computer system.
Owner:GE MEDICAL SYST GLOBAL TECH CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com