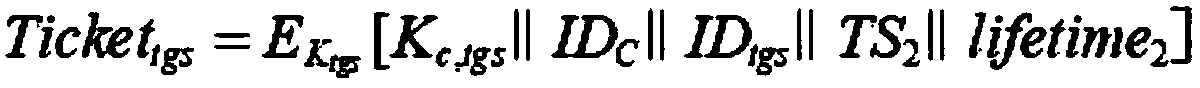Patents
Literature
65 results about "Kerberos" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
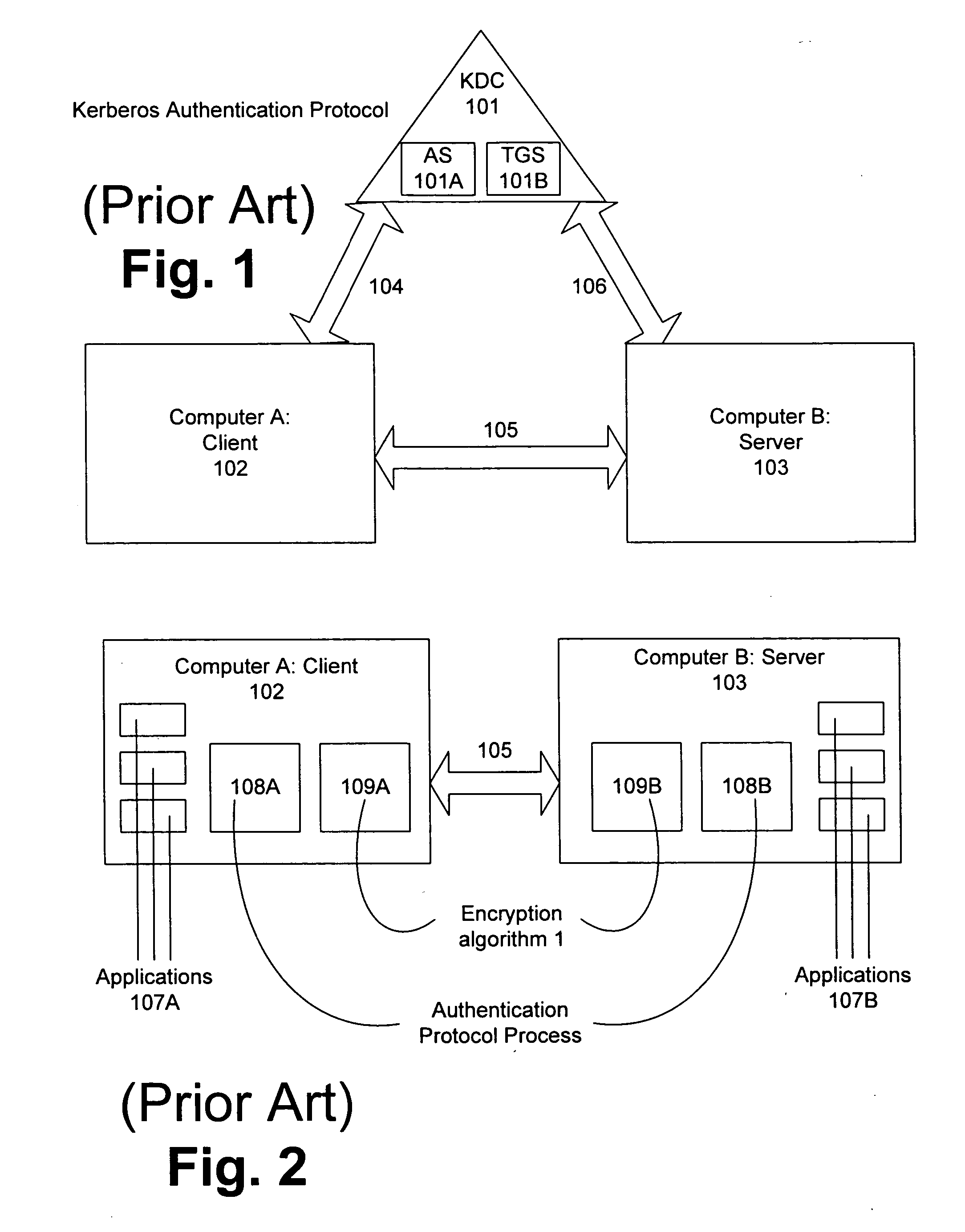
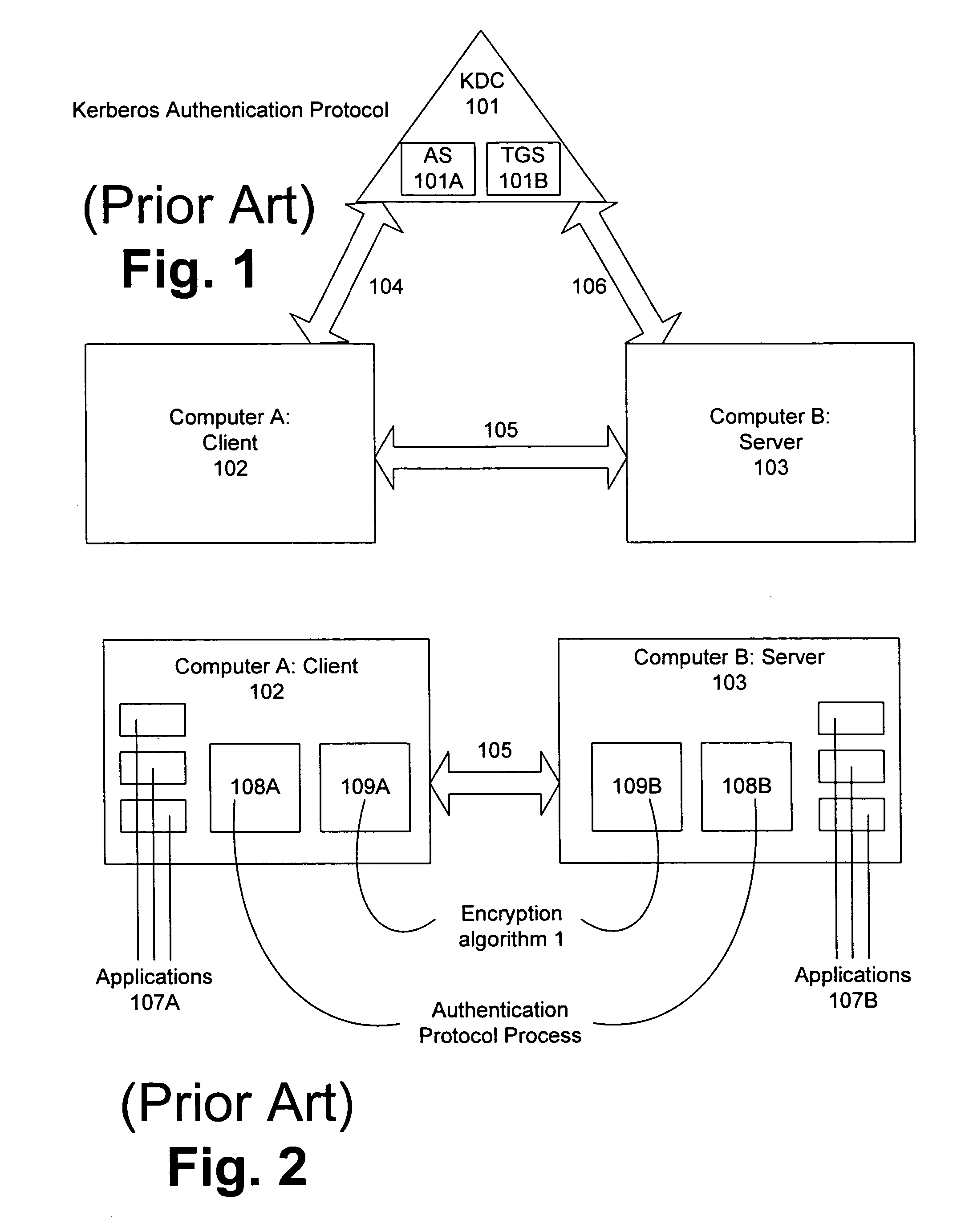
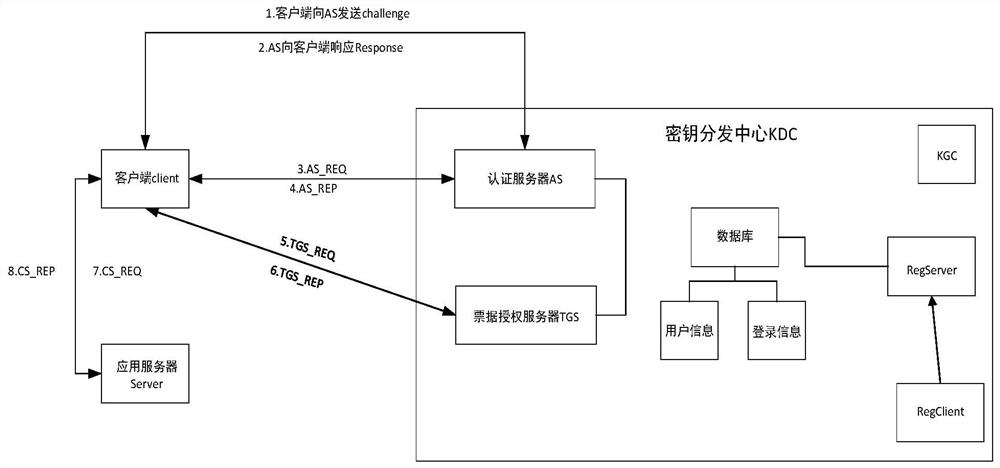
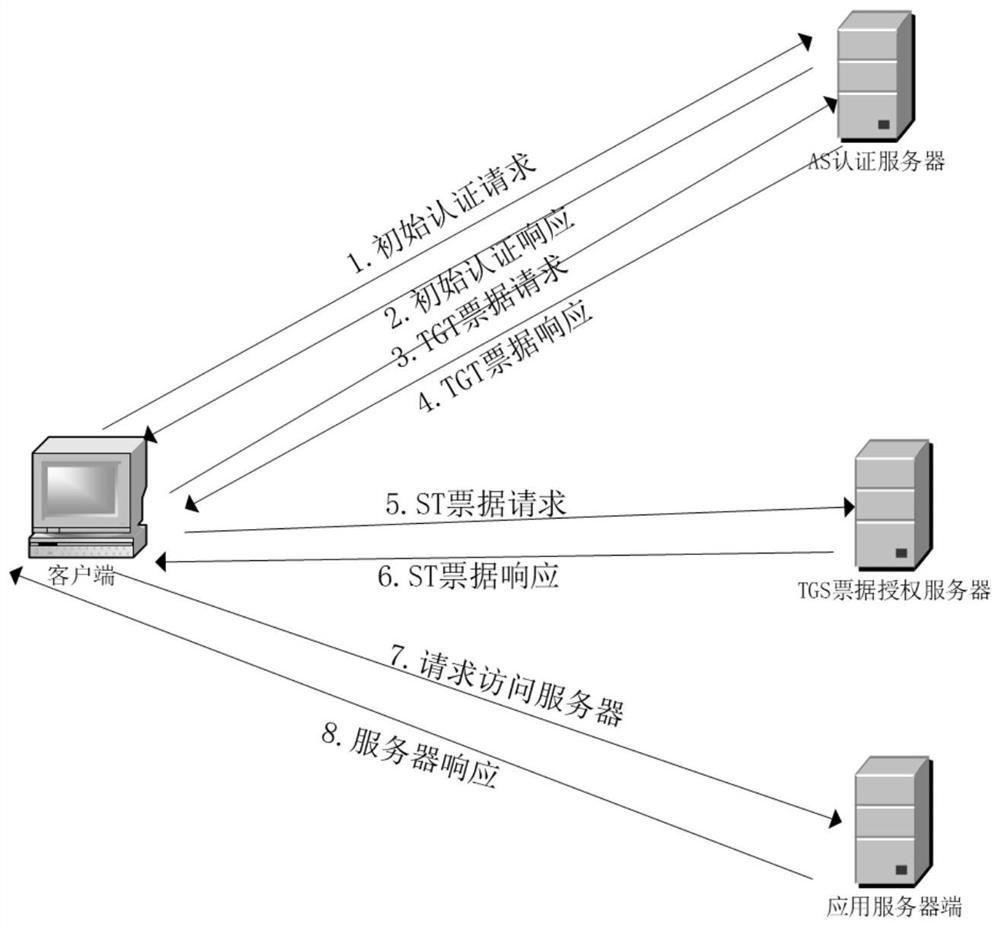
Kerberos (/ˈkɜːrbərɒs/) is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. The protocol was named after the character Kerberos (or Cerberus) from Greek mythology, the ferocious three-headed guard dog of Hades. Its designers aimed it primarily at a client–server model and it provides mutual authentication—both the user and the server verify each other's identity. Kerberos protocol messages are protected against eavesdropping and replay attacks.
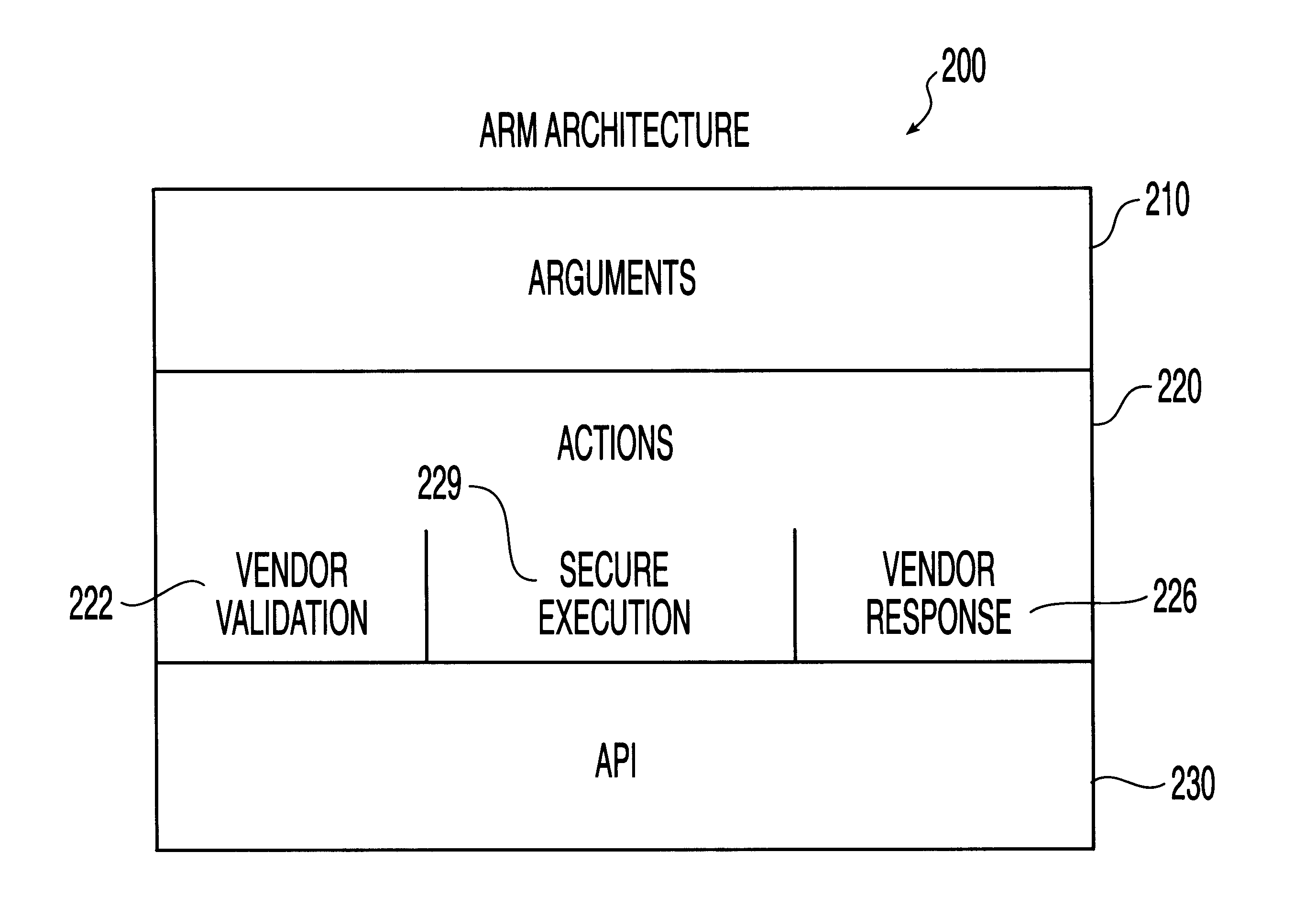
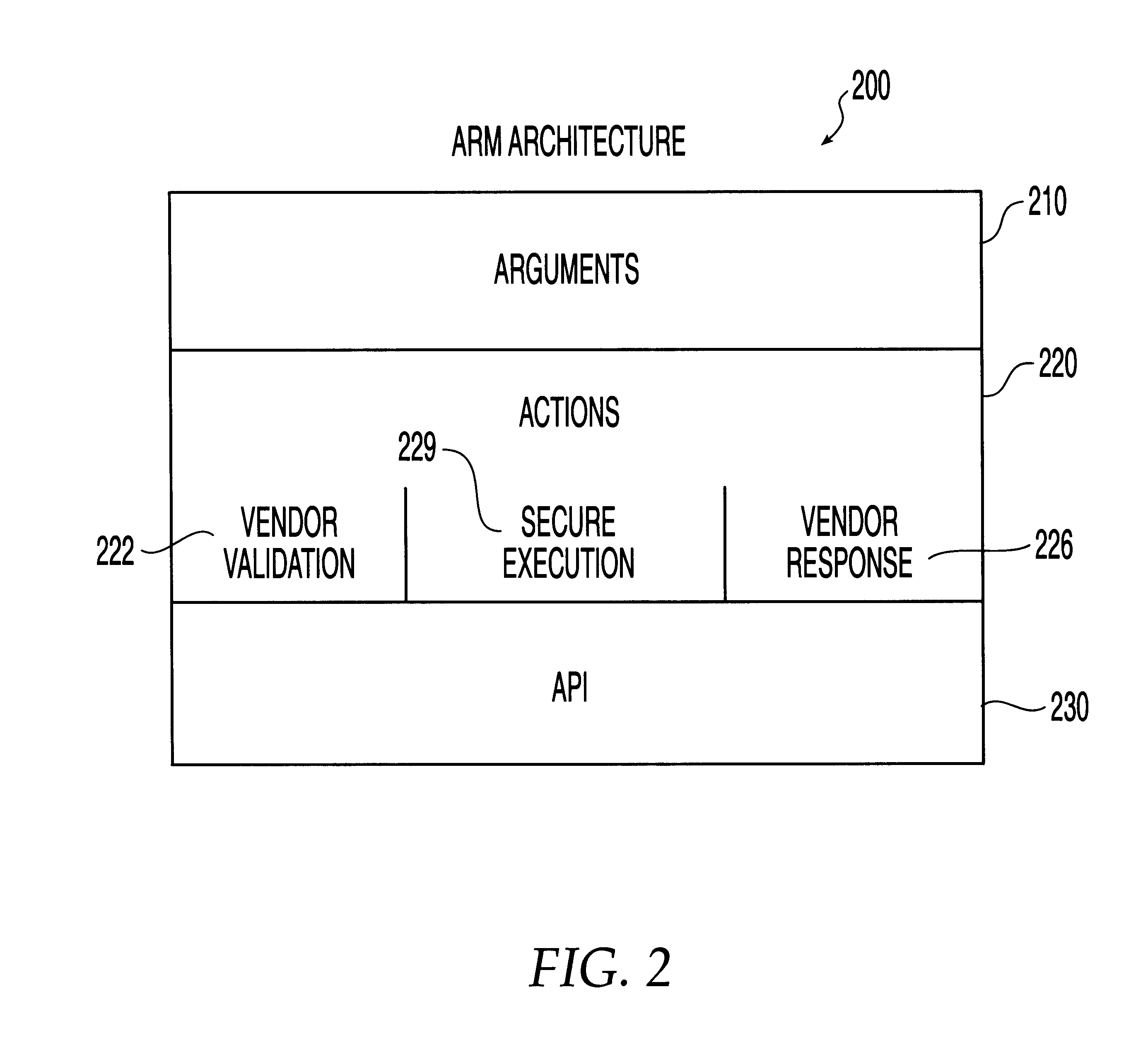
System, method and computer program product for automatic response to computer system misuse using active response modules
InactiveUS6275942B1Rapid responseMemory loss protectionDigital data processing detailsSoftware engineeringSecurity level
A system, method and computer program product for automatic response to computer system misuse using active response modules (ARMs). ARMs are tools that allow static intrusion detection system applications the ability to dynamically increase security levels by allowing real-time responses to detected instances of computer misuse. Several classes of ARMs exist which allow them to interface with several types of network elements found within a computing environment (e.g., firewalls, web servers, Kerberos severs, certificate authorities, etc.). The ARMs, once defined, are deployed in a "plug and play" manner into an existing intrusion detection system within a computing environment. A user (e.g., system administrator) may then configure the ARMs by linking them to specific computer misuses. Upon receipt of an instance of the computer misuse from the intrusion detection system, each ARM linked to the misuse collects pertinent data from the intrusion detection system and invokes a response specified by the ARM class and the collected pertinent data.
Owner:MCAFEE LLC +1
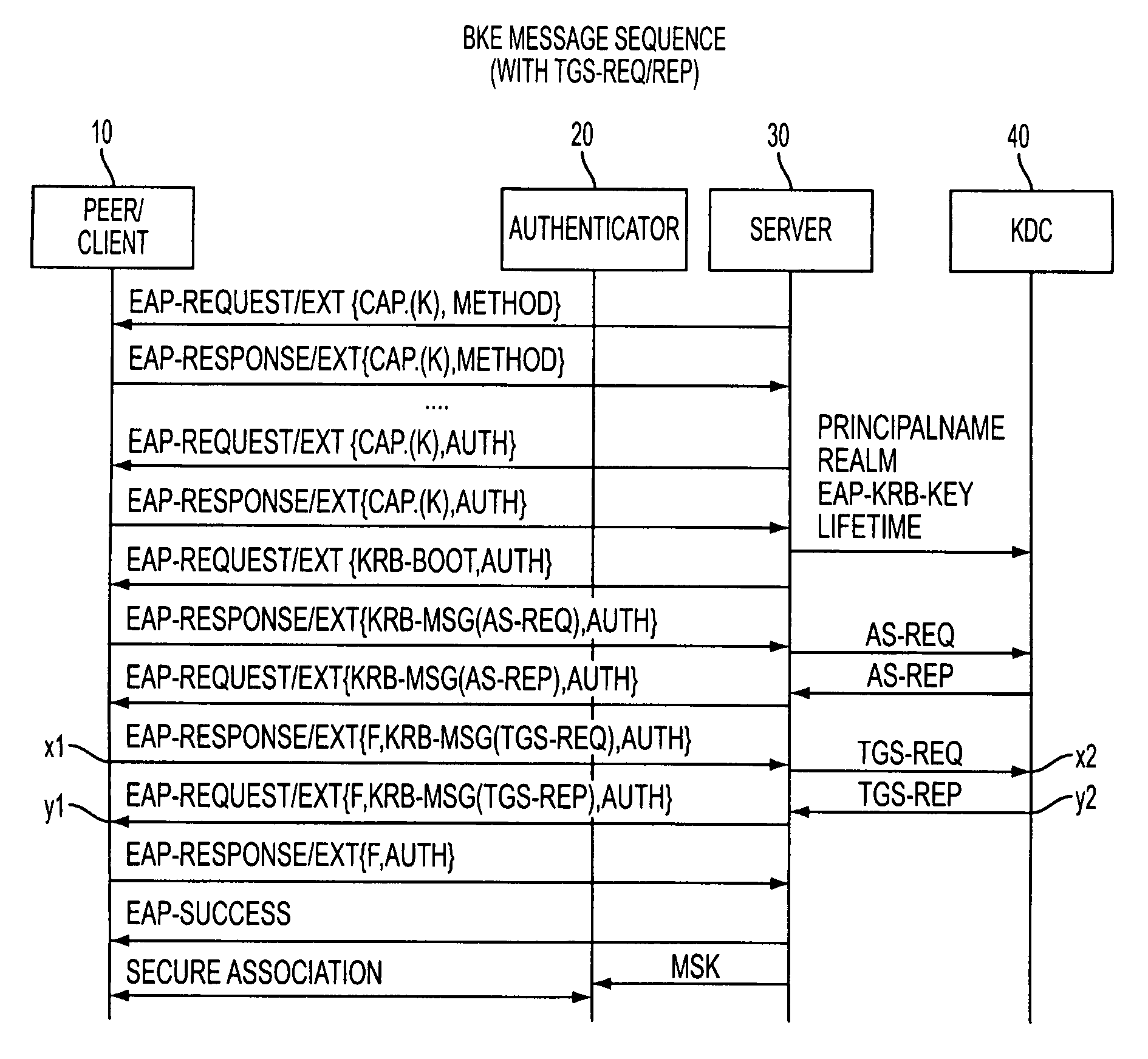
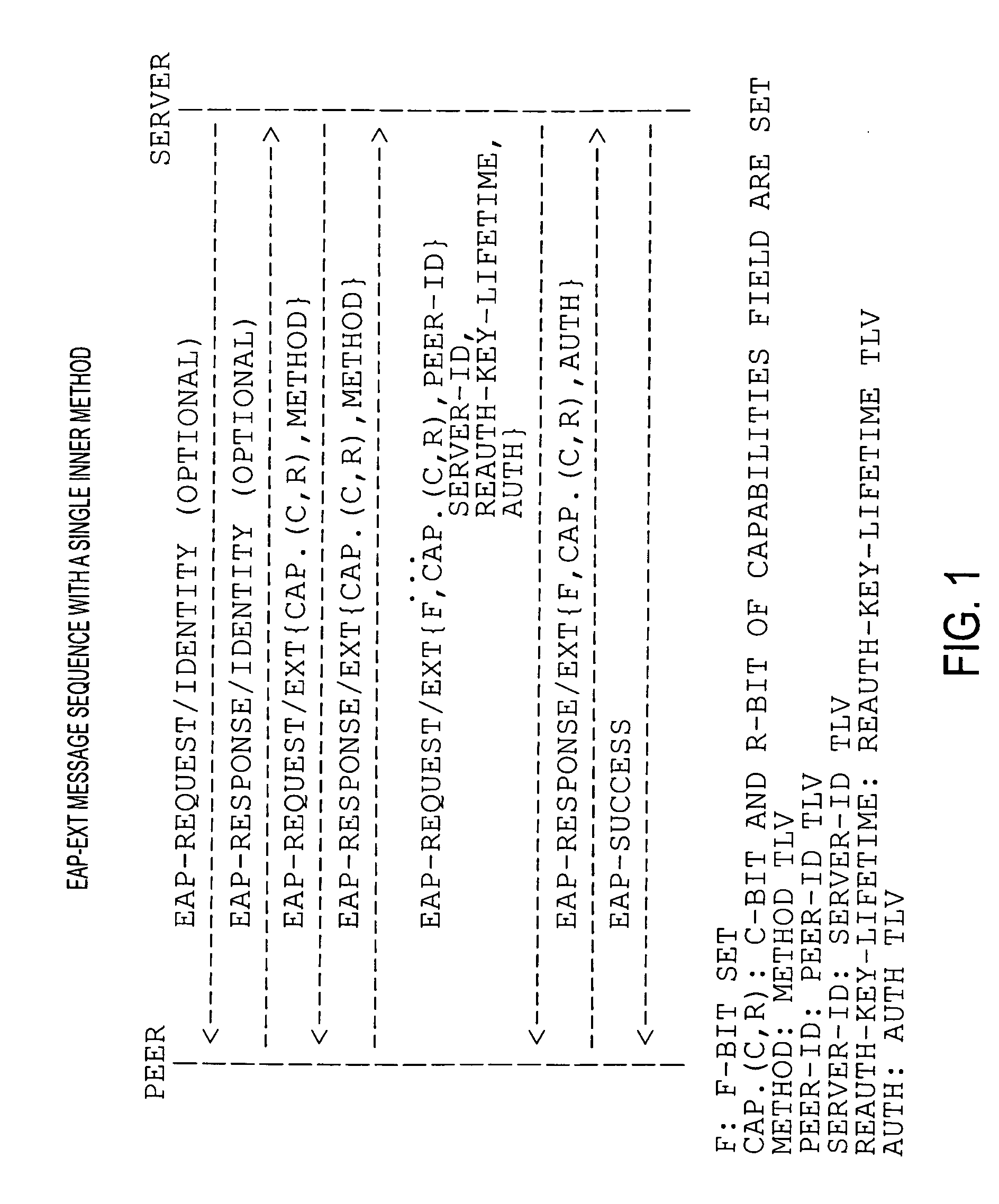
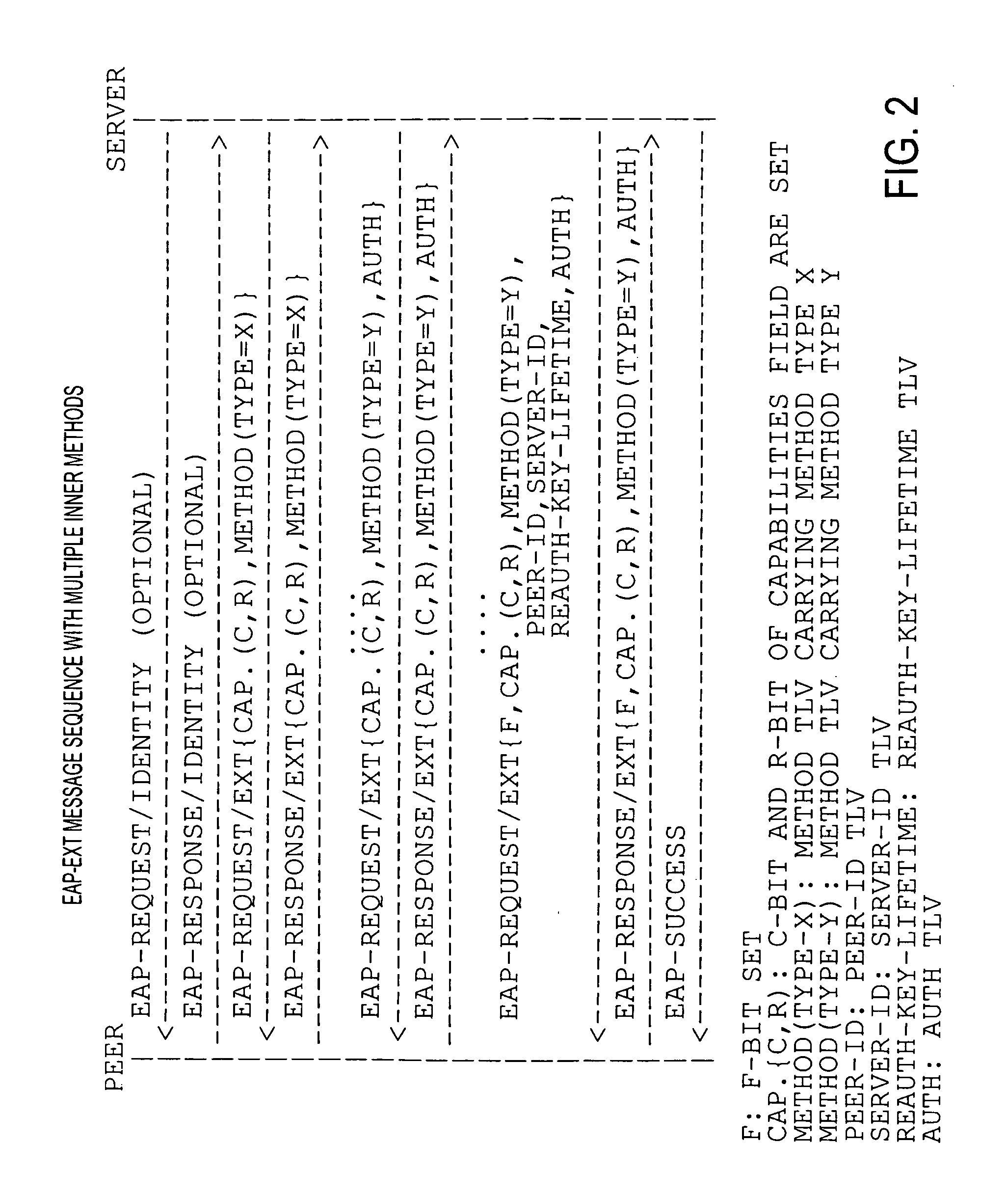
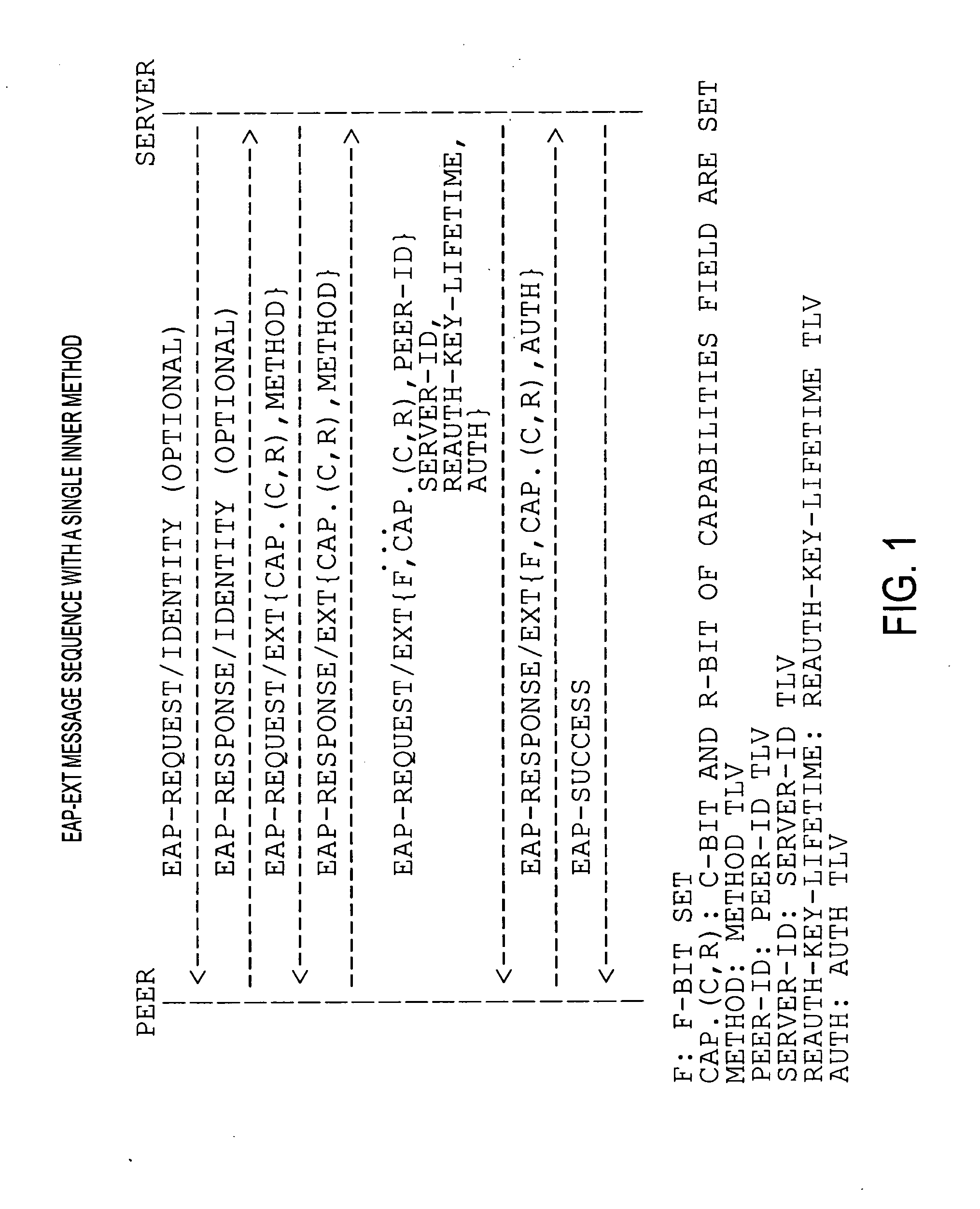
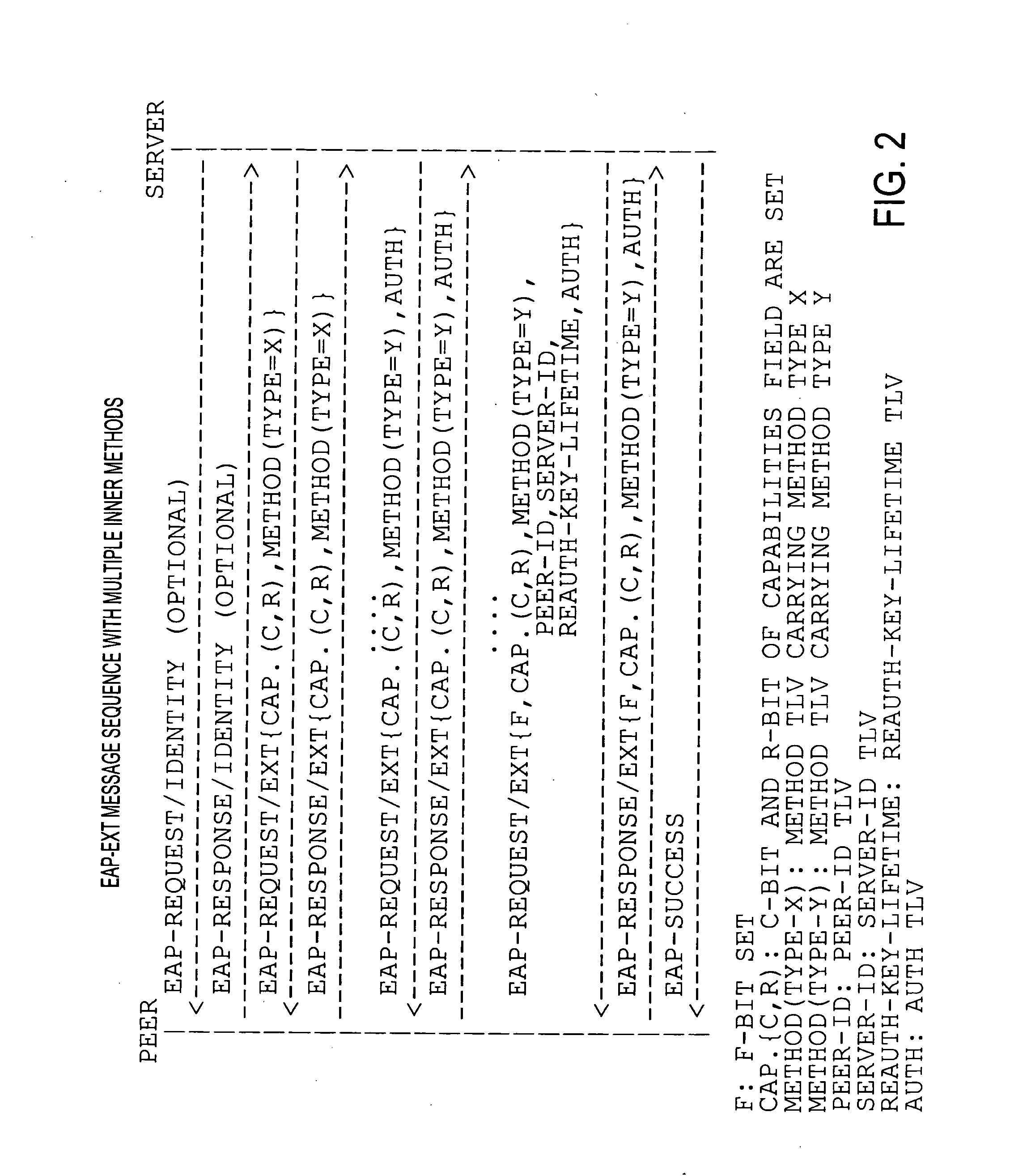
Bootstrapping Kerberos from EAP (BKE)
InactiveUS20080178277A1Improve performanceDigital data processing detailsComputer security arrangementsProtocol for Carrying Authentication for Network AccessSession key
The preferred embodiments involve a mechanism to bootstrap Kerberos from EAP in which EAP is used for initial network access authentication and Kerberos is used for provisioning session keys to multiple different protocols. The preferred embodiments make use of an EAP extension method (EAP-EXT) to realize the mechanism.
Owner:TELCORDIA TECHNOLOGIES INC
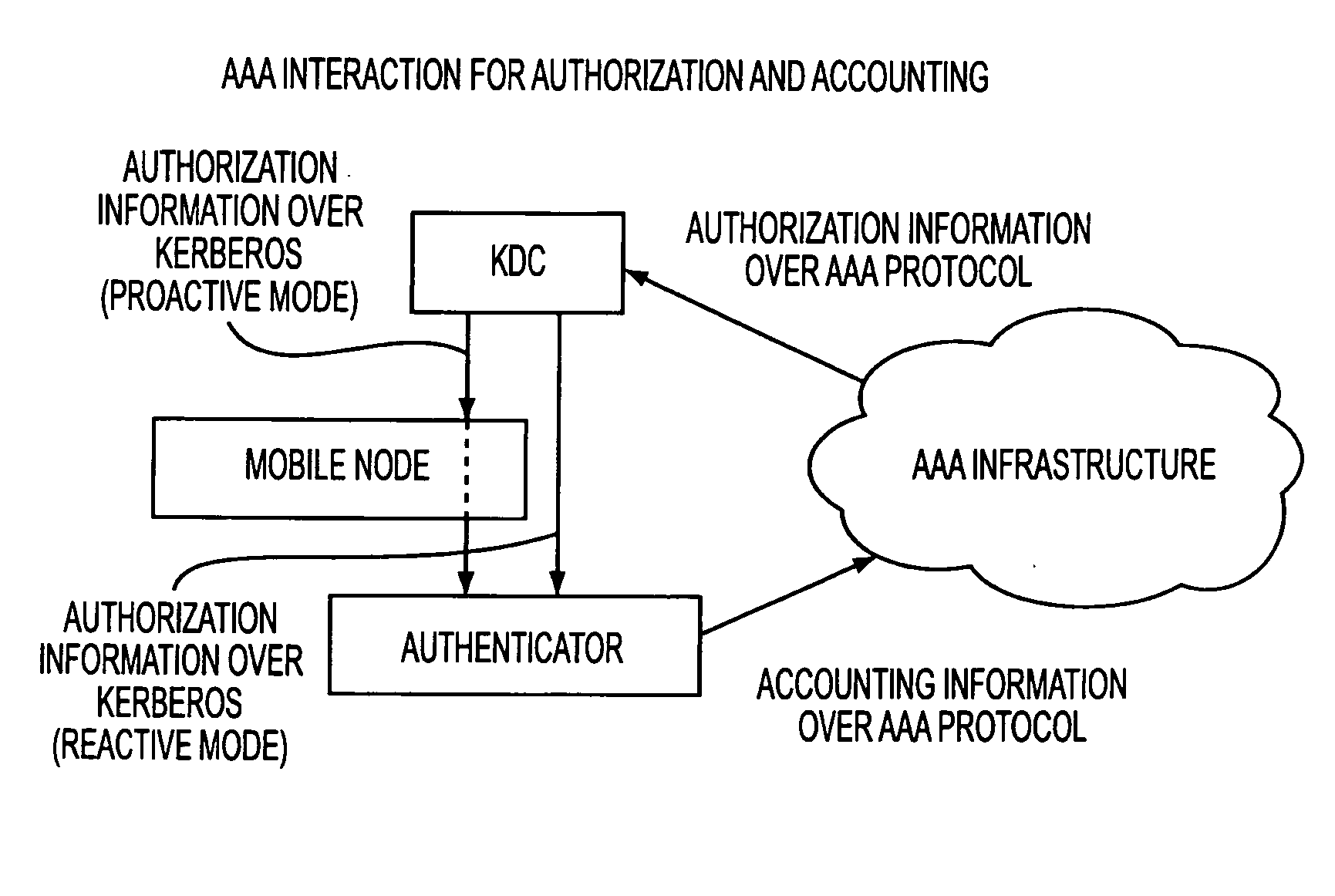
Kerberized handover keying
ActiveUS20080175393A1Key distribution for secure communicationDigital data processing detailsRe keyingProtocol for Carrying Authentication for Network Access
A media-independent handover key management architecture is disclosed that uses Kerberos for secure key distribution among a server, an authenticator, and a mobile node. In the preferred embodiments, signaling for key distribution is based on re-keying and is decoupled from re-authentication that requires EAP (Extensible Authentication Protocol) and AAA (Authentication, Authorization and Accounting) signaling similar to initial network access authentication. In this framework, the mobile node is able to obtain master session keys required for dynamically establishing the security associations with a set of authenticators without communicating with them before handover. By separating re-key operation from re-authentication, the proposed architecture is more optimized for a proactive mode of operation. It can also be optimized for reactive mode of operation by reversing the key distribution roles between the mobile node and the target access node.
Owner:TELCORDIA TECHNOLOGIES INC +1
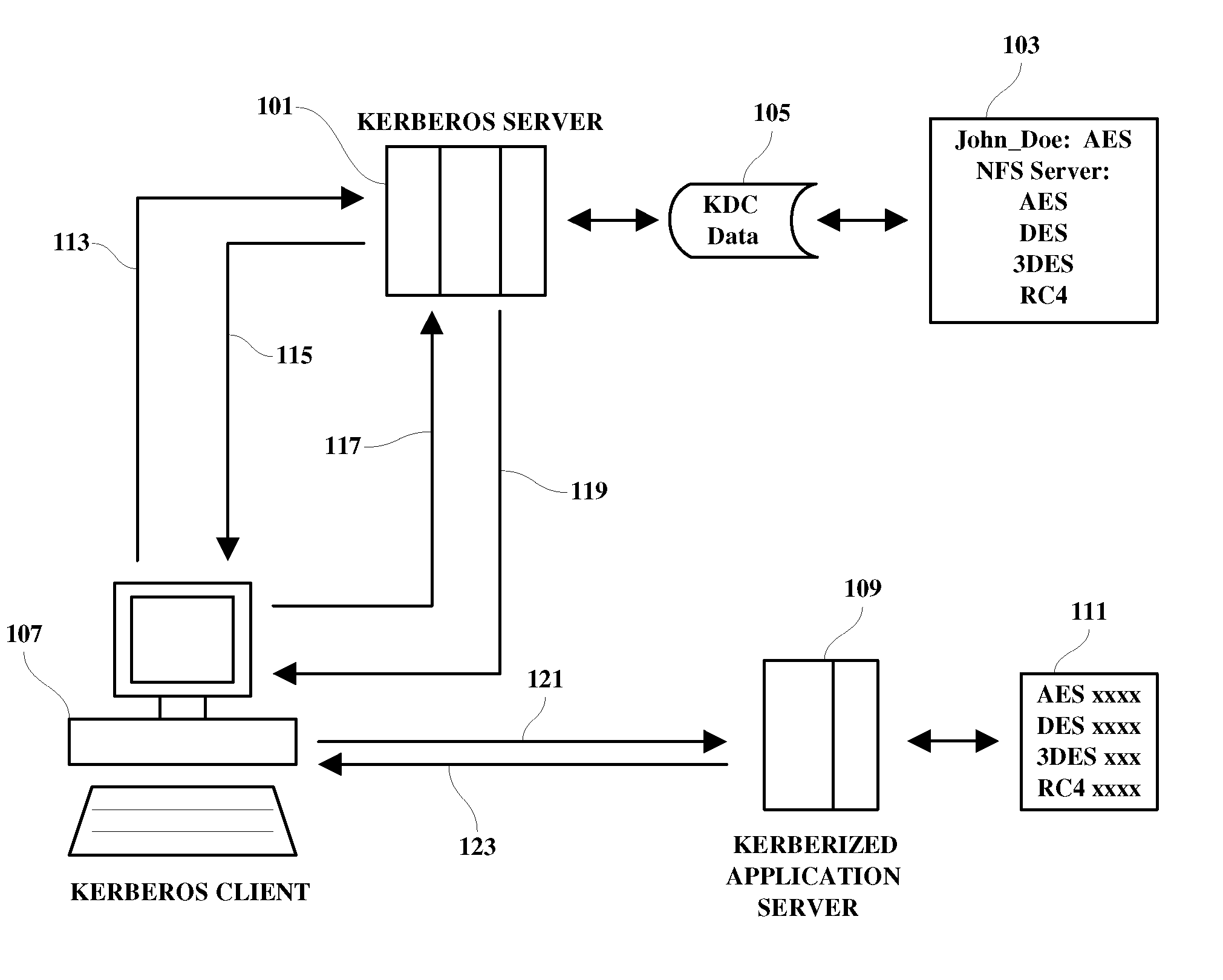
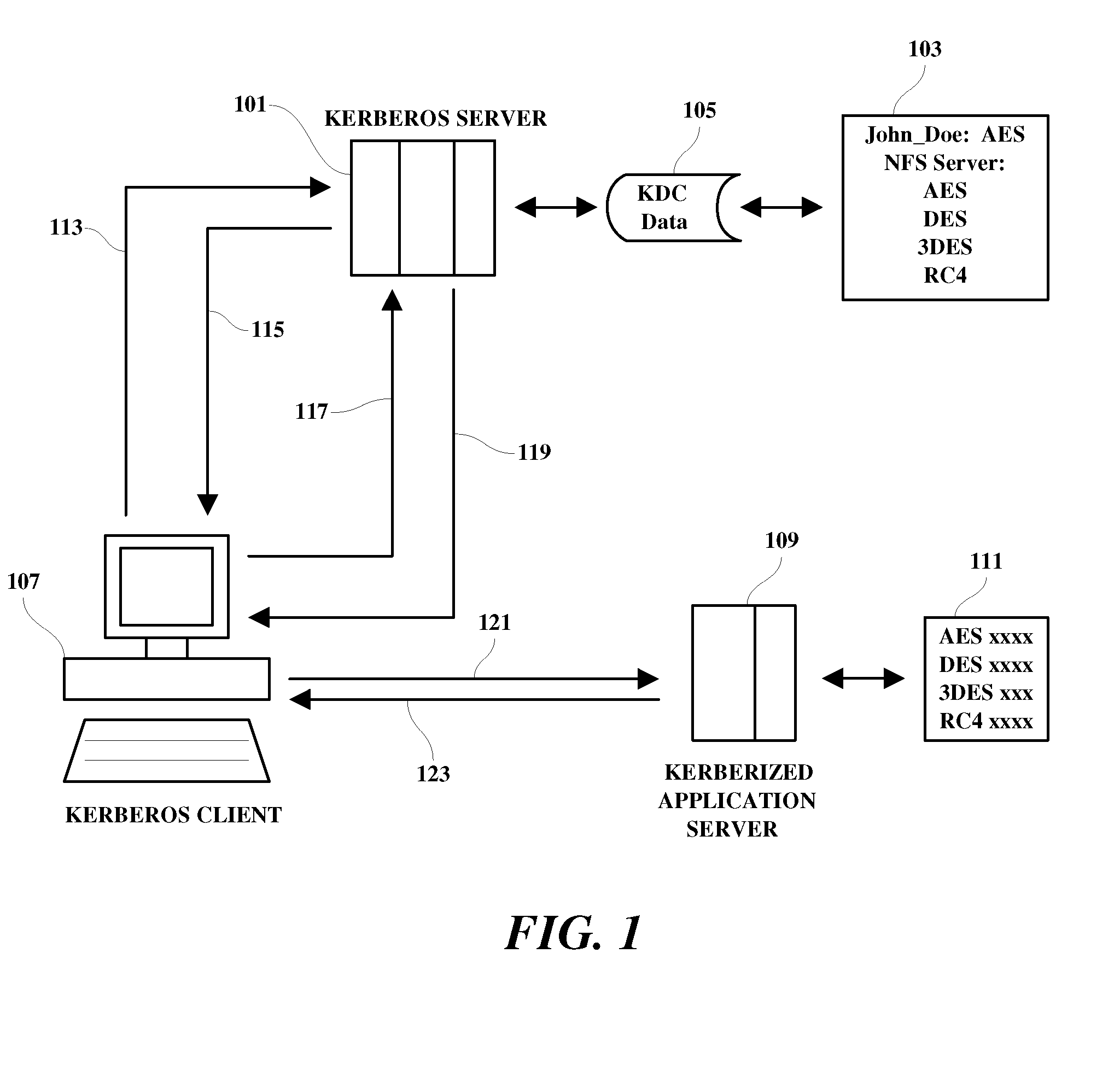
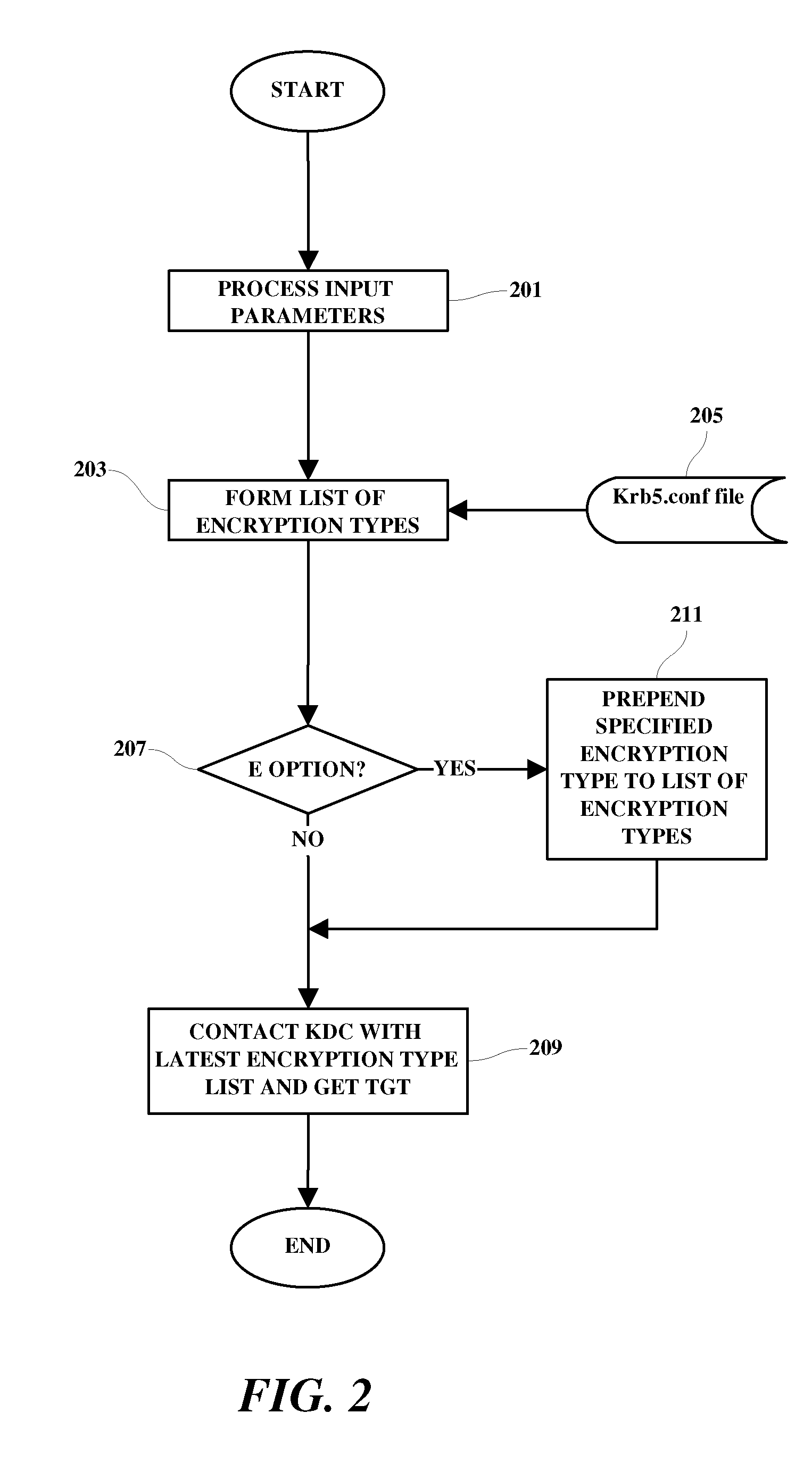
Tunable encryption system
InactiveUS20100095127A1Communication securityUser identity/authority verificationSecure communicationApplication server
A method, programmed medium and system are provided for enabling a user to choose a user-preferred encryption type from among a plurality of encryption types listed in a user's Kerberos configuration file. During the ticket granting process in a Kerberos system, a user is requested to select a preferred encryption type to be used in the Kerberos communication from among encryption types contained in the user's Kerberos configuration file. The user-selected encryption type is then implemented for use in encrypting a session ticket (as well as generating the session key of user requested encryption type) for use by the user machine in communicating securely with an Kerberized application server when being communicated by that particular user. Thus, the system allows different users to simultaneously communicate with the same Kerberized application server using a supported encryption type of the user's own choice.
Owner:IBM CORP
Using one-time passwords with single sign-on authentication
ActiveUS7540022B2Digital data processing detailsMultiple digital computer combinationsOne-time passwordProxy server
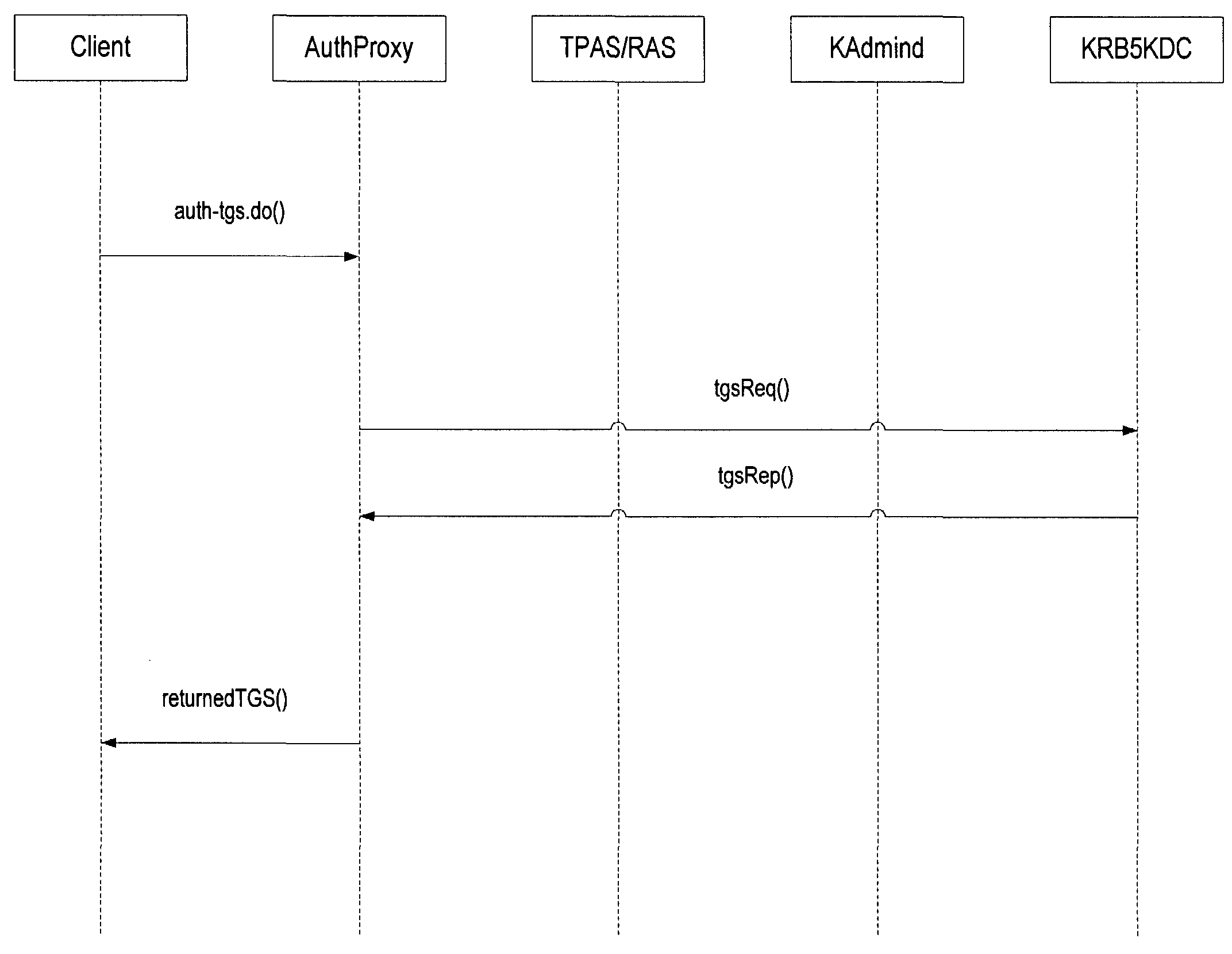
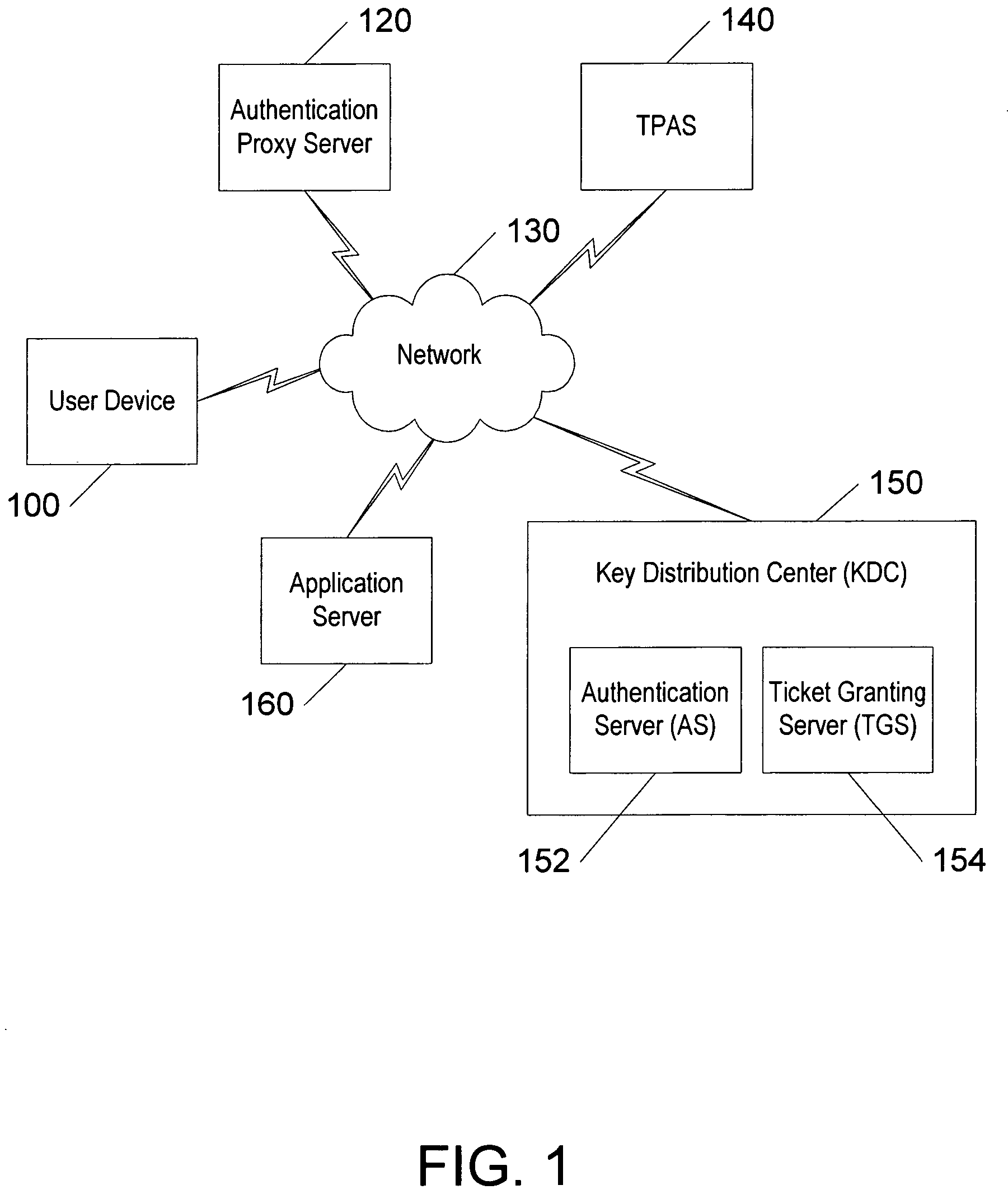
A method, computer program product, authentication proxy server, and system for enabling a user to use a one-time password in conjunction with single sign-on authentication and external authentication, such as provided by the Kerberos protocol, are provided.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Scheme for sub-realms within an authentication protocol
ActiveUS20060224891A1Reduce security risksUser identity/authority verificationMultiple digital computer combinationsVirtual fieldPassword
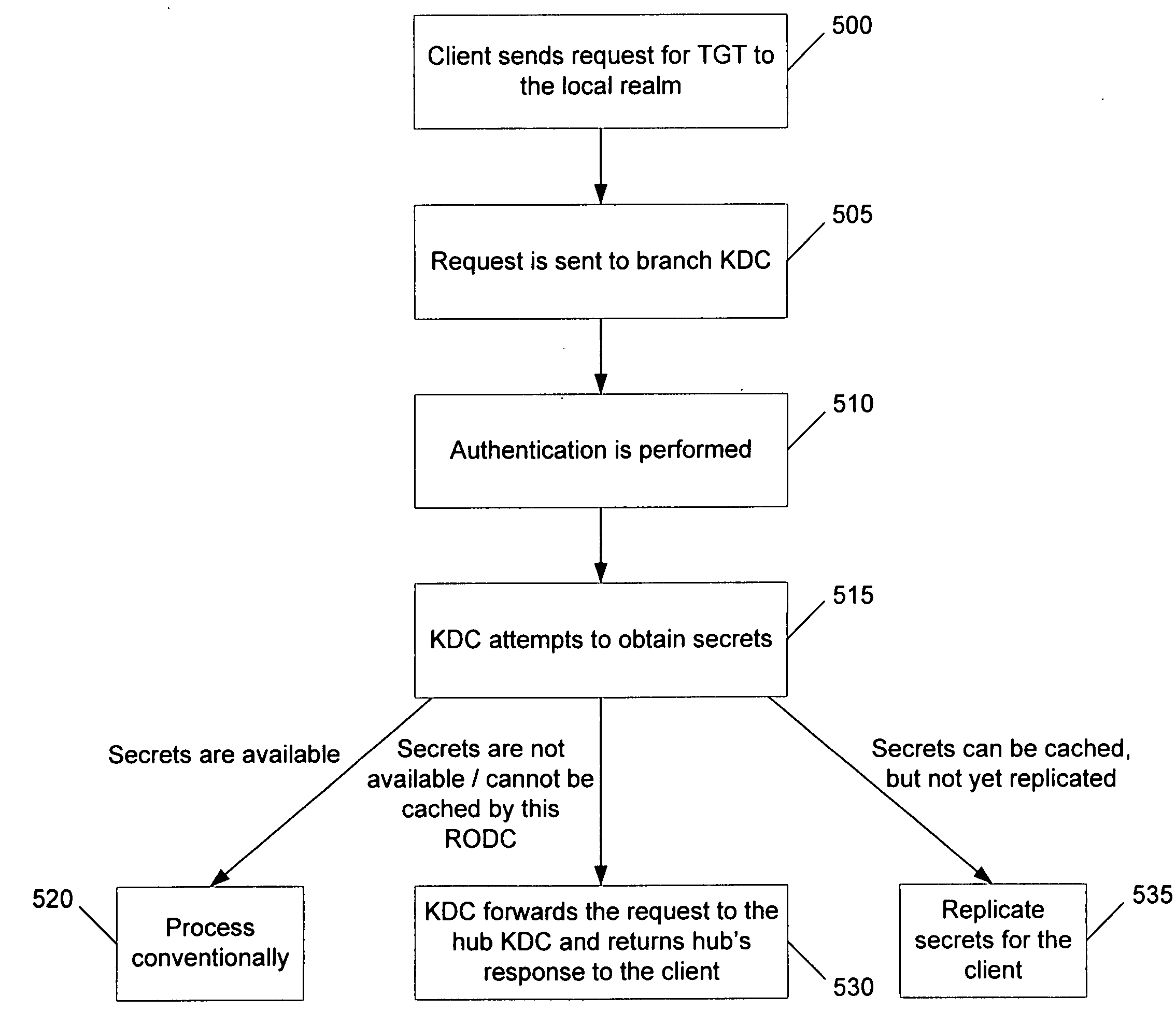
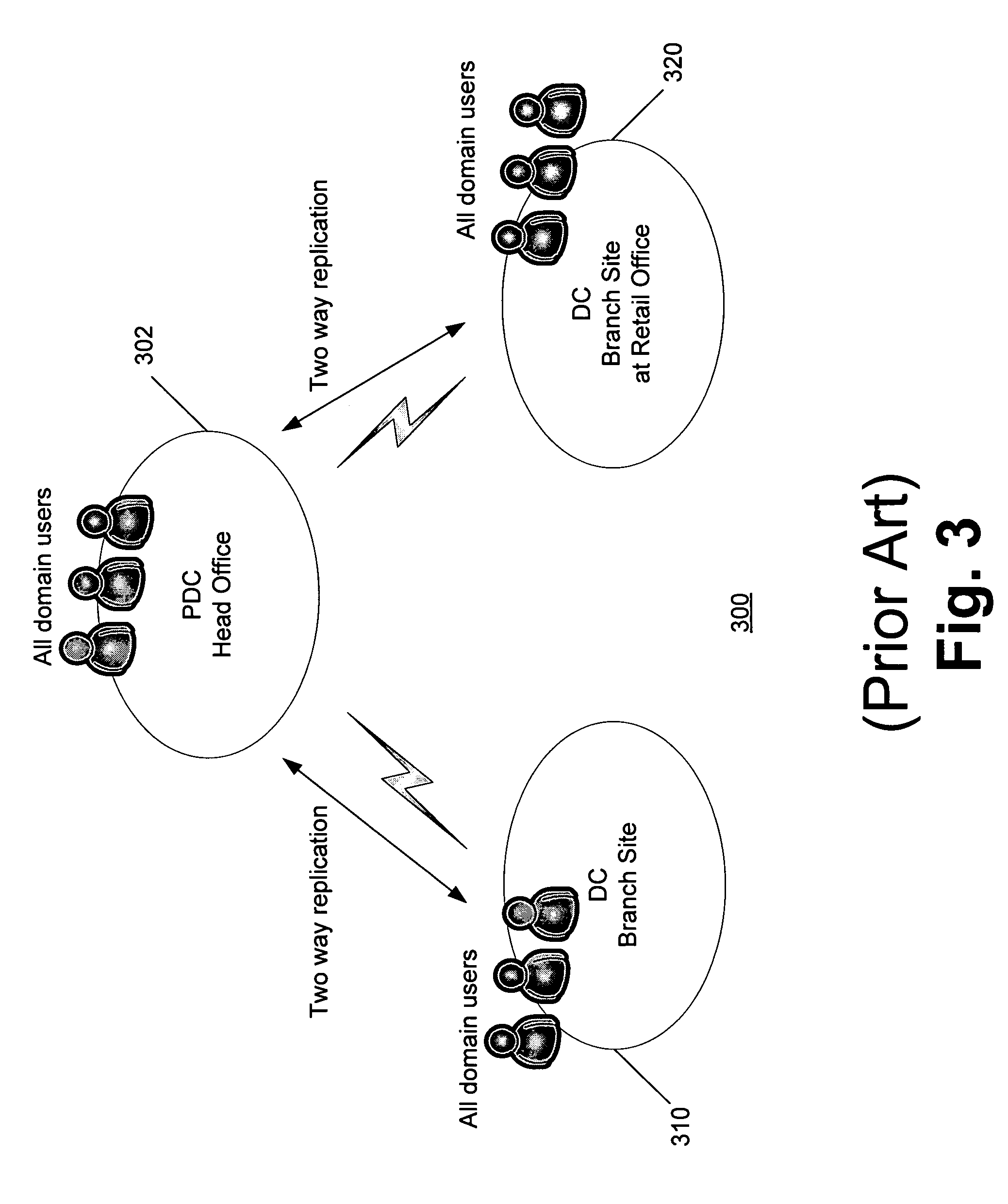
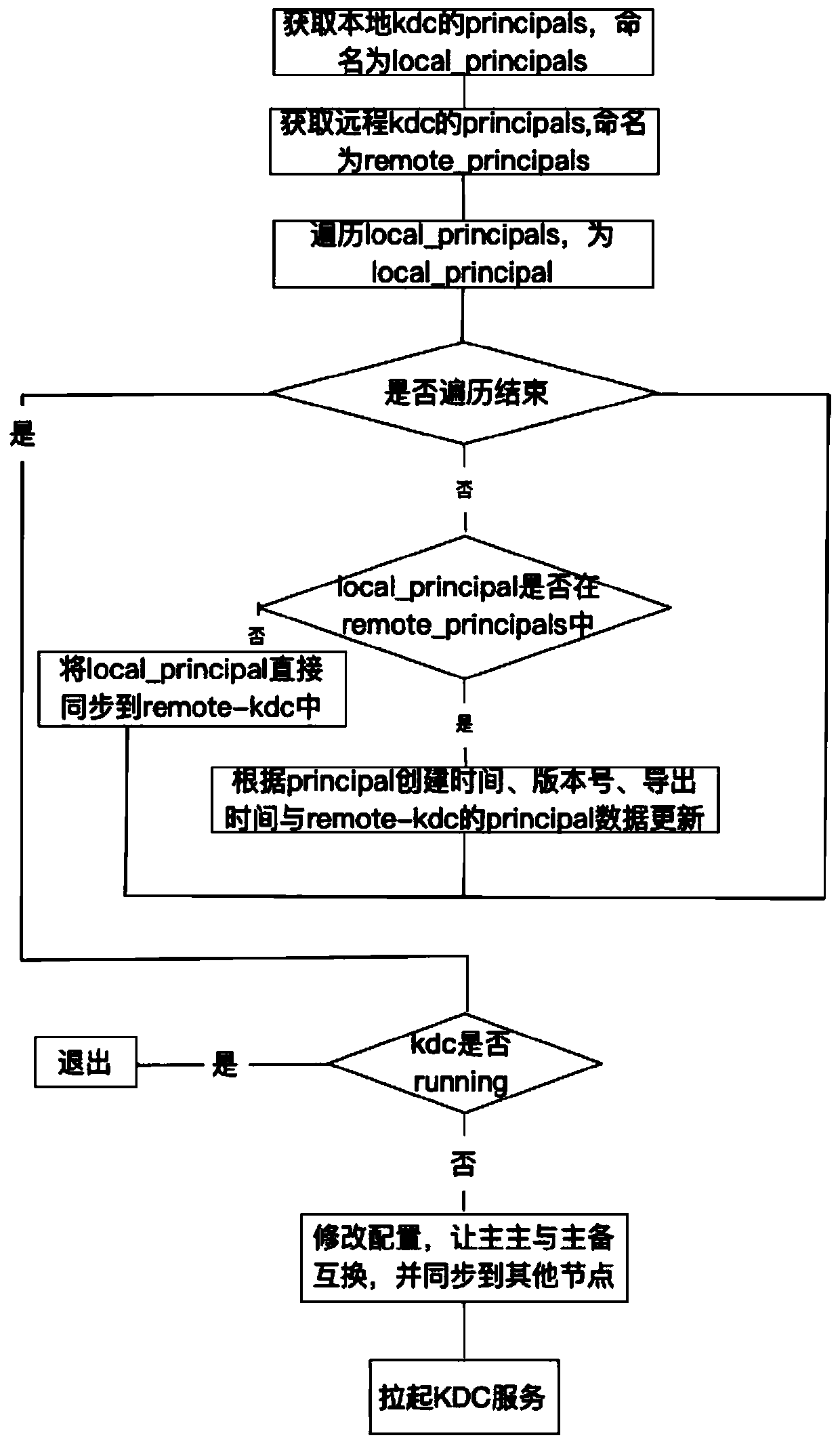
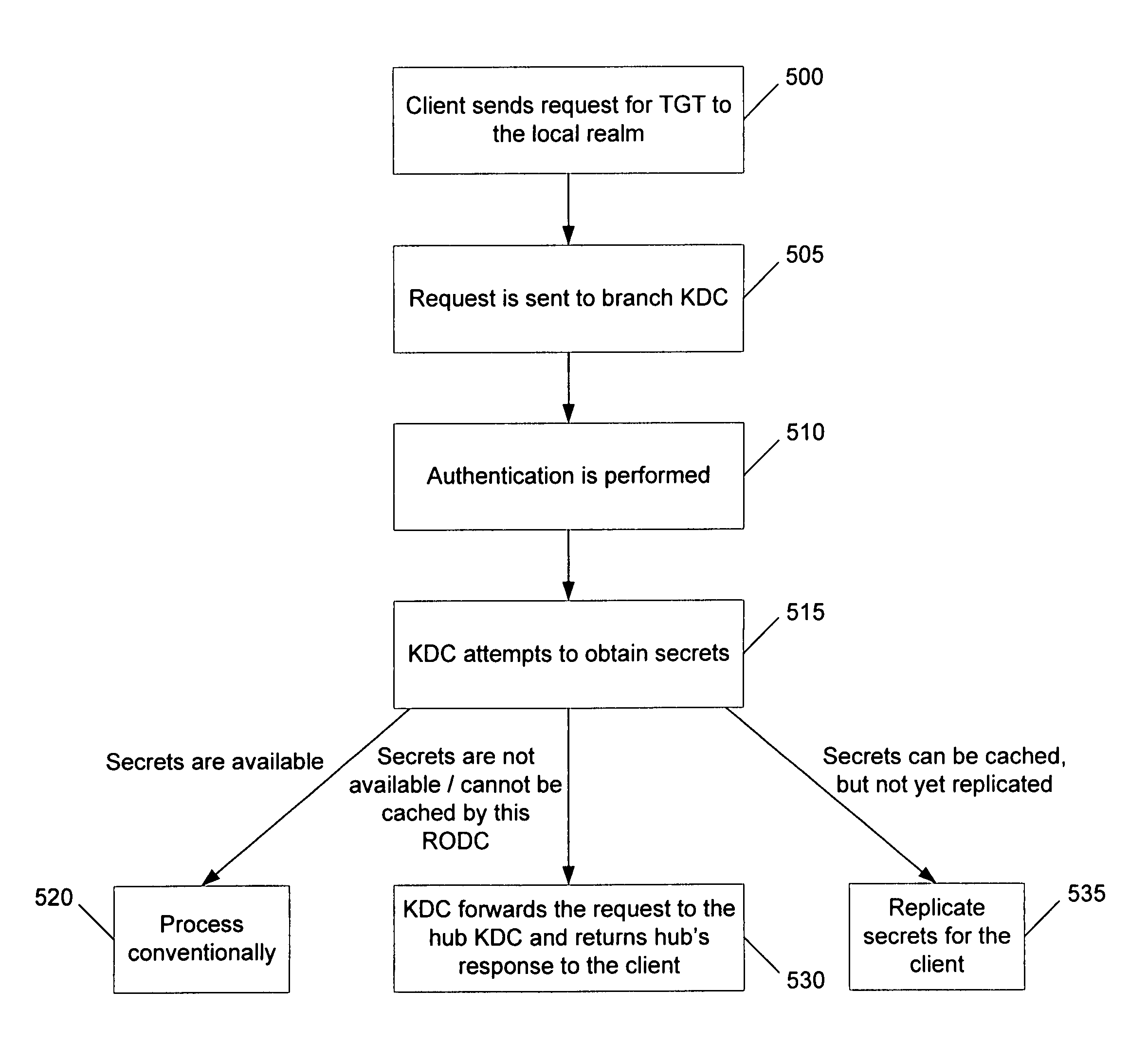
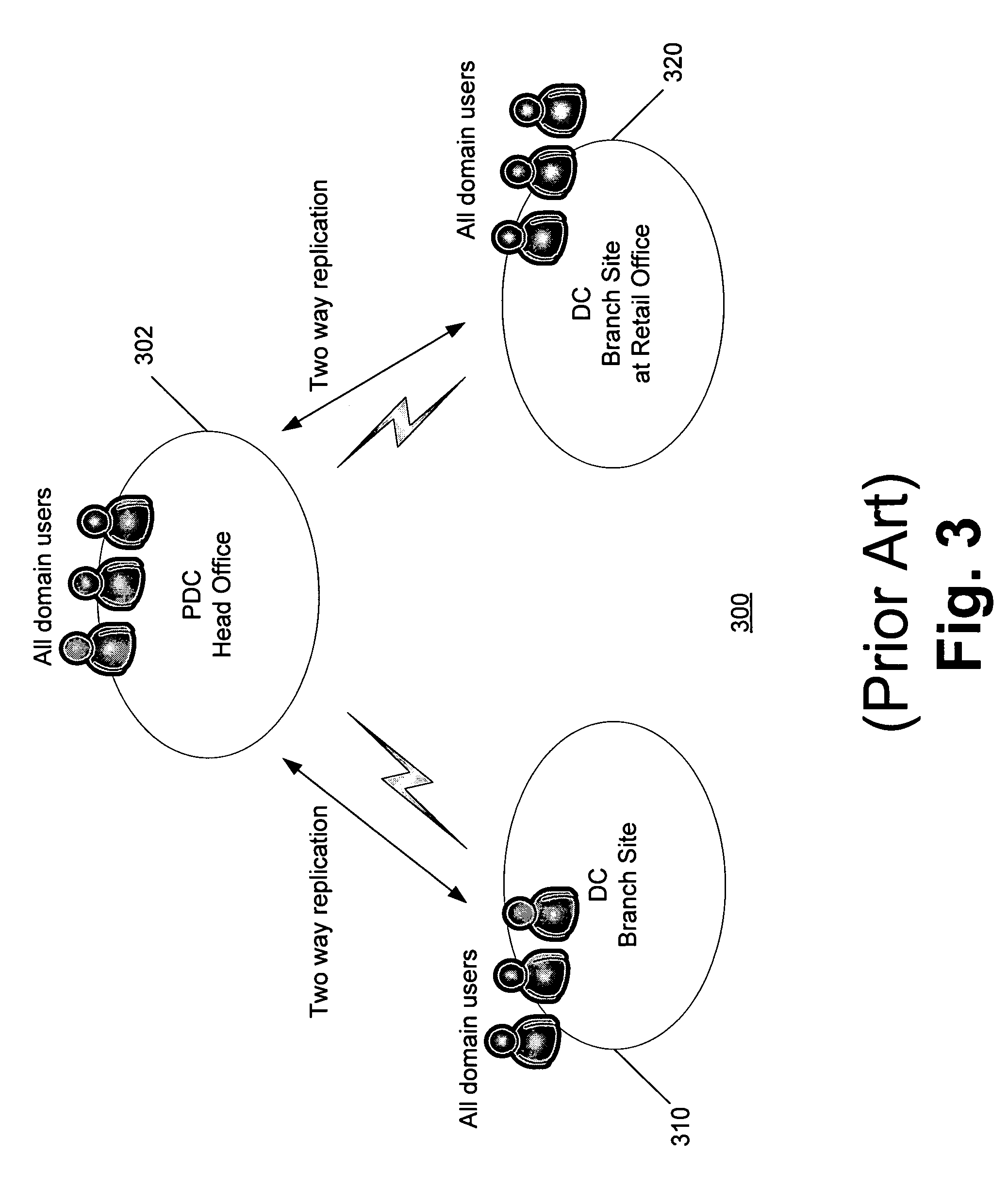
Branch domain controllers (DCs) contain read only replicas of the data in a normal domain DC. This includes information about the groups a user belongs to so it can be used to determine authorization information. Password information, however, is desirably replicated to the branch DCs only for users and services (including machines) designated for that particular branch. Moreover, all write operations are desirably handled by hub DCs, the primary domain controller (PDC), or other DCs trusted by the corporate office. Rapid authentication and authorization in branch offices is supported using Kerberos sub-realms in which each branch office operates as a virtual realm. The Kerberos protocol employs different key version numbers to distinguish between the virtual realms of the head and branch key distribution centers (KDCs). Accounts may be named krbtgt_<ID> where <ID> is carried in the kvno field of the ticket granting ticket (TGT) to indicate to the hub KDC which krbtgt′ key was used to encrypt the TGT.
Owner:MICROSOFT TECH LICENSING LLC
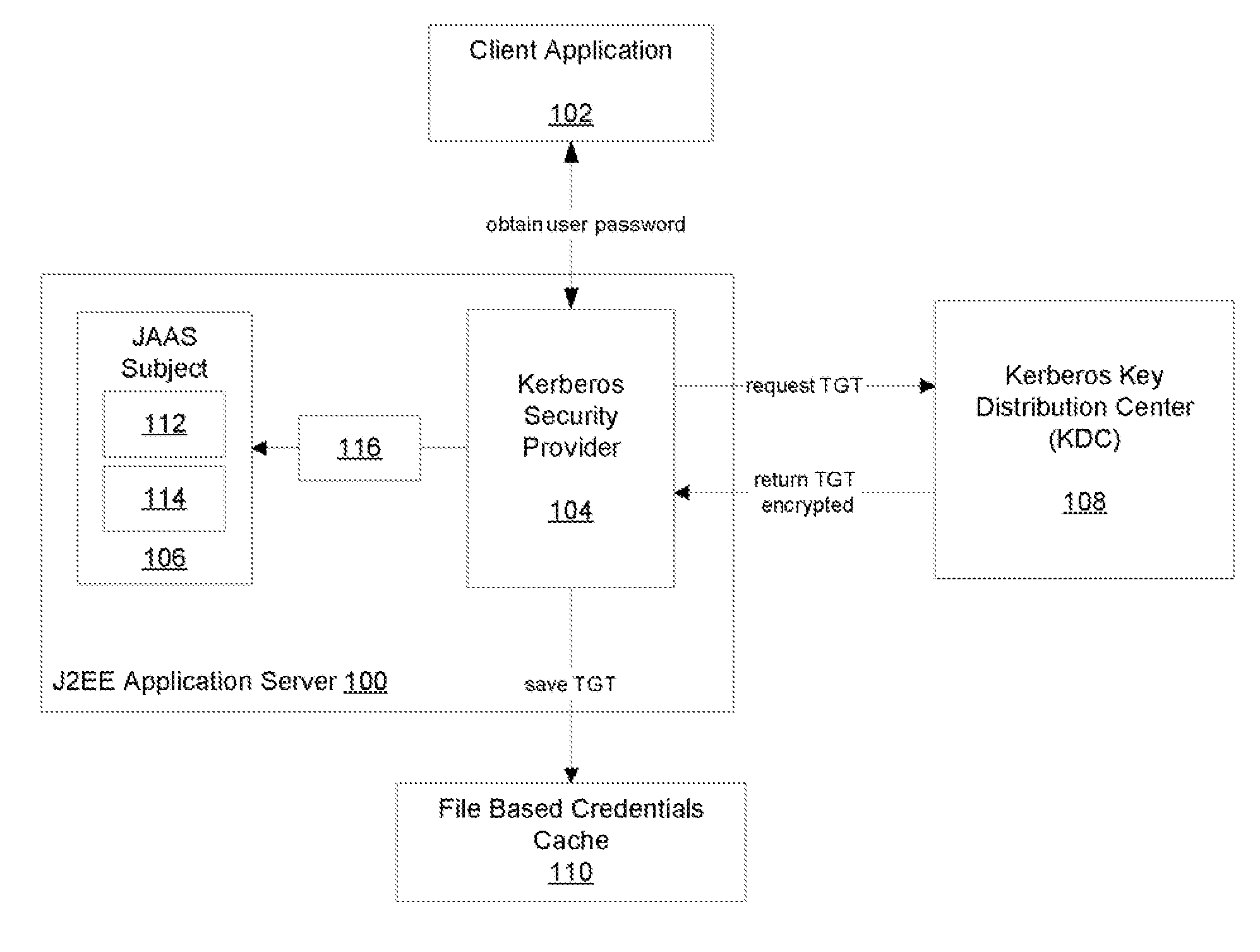
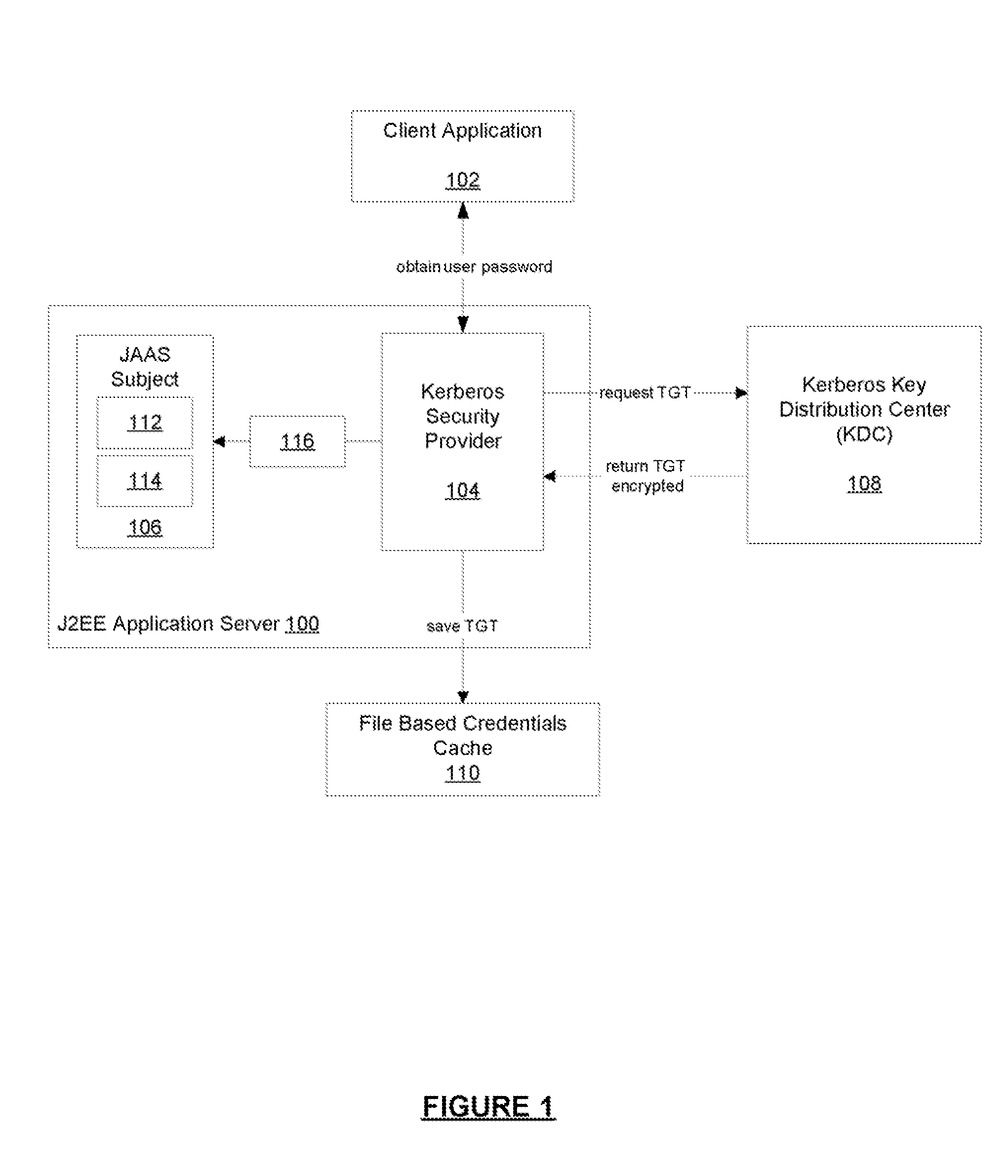
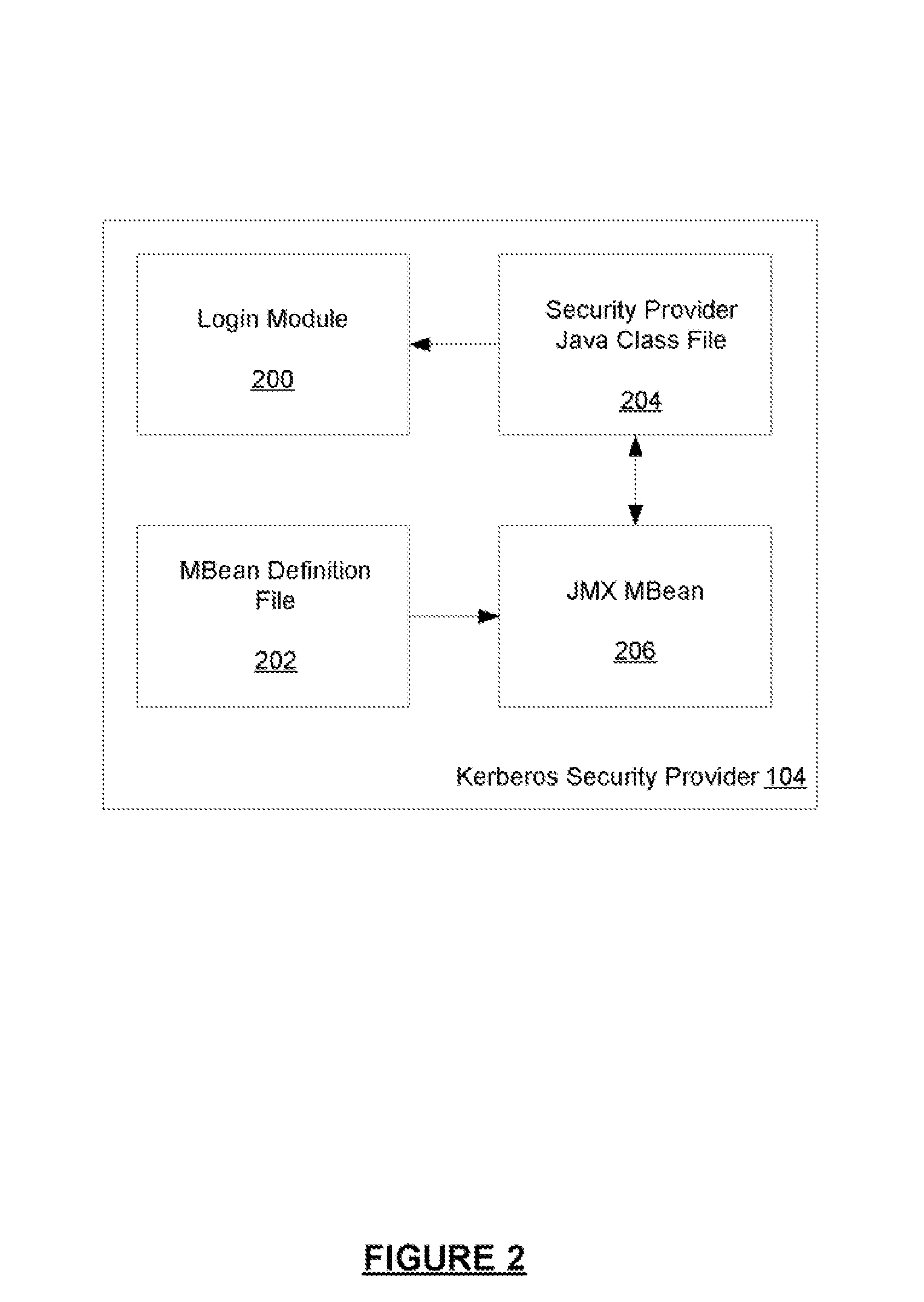
Kerberos Protocol Security Provider for a Java Based Application Server
InactiveUS20080083026A1Digital data processing detailsUser identity/authority verificationApplication serverPassword
A security provider is presented that integrates a Java based application server with Kerberos security protocol. The security provider includes a login module, a JMX MBean, an MBean definition file and a security provider java class. The JMX MBeans can contain various options that contain configuration information for the login module. The login module is responsible for authenticating the users by obtaining the user name and password, creating encryption keys, sending requests to the Kerberos key distribution center and receiving a ticket granting ticket encrypted with the user's password. The login module can then create an authenticated principal and add it to the subject associated with the user. The ticket granting ticket can also be added to the subject's private credentials. The security provider also supports the persistence of Kerberos credentials into a file based credentials cache.
Owner:ORACLE INT CORP
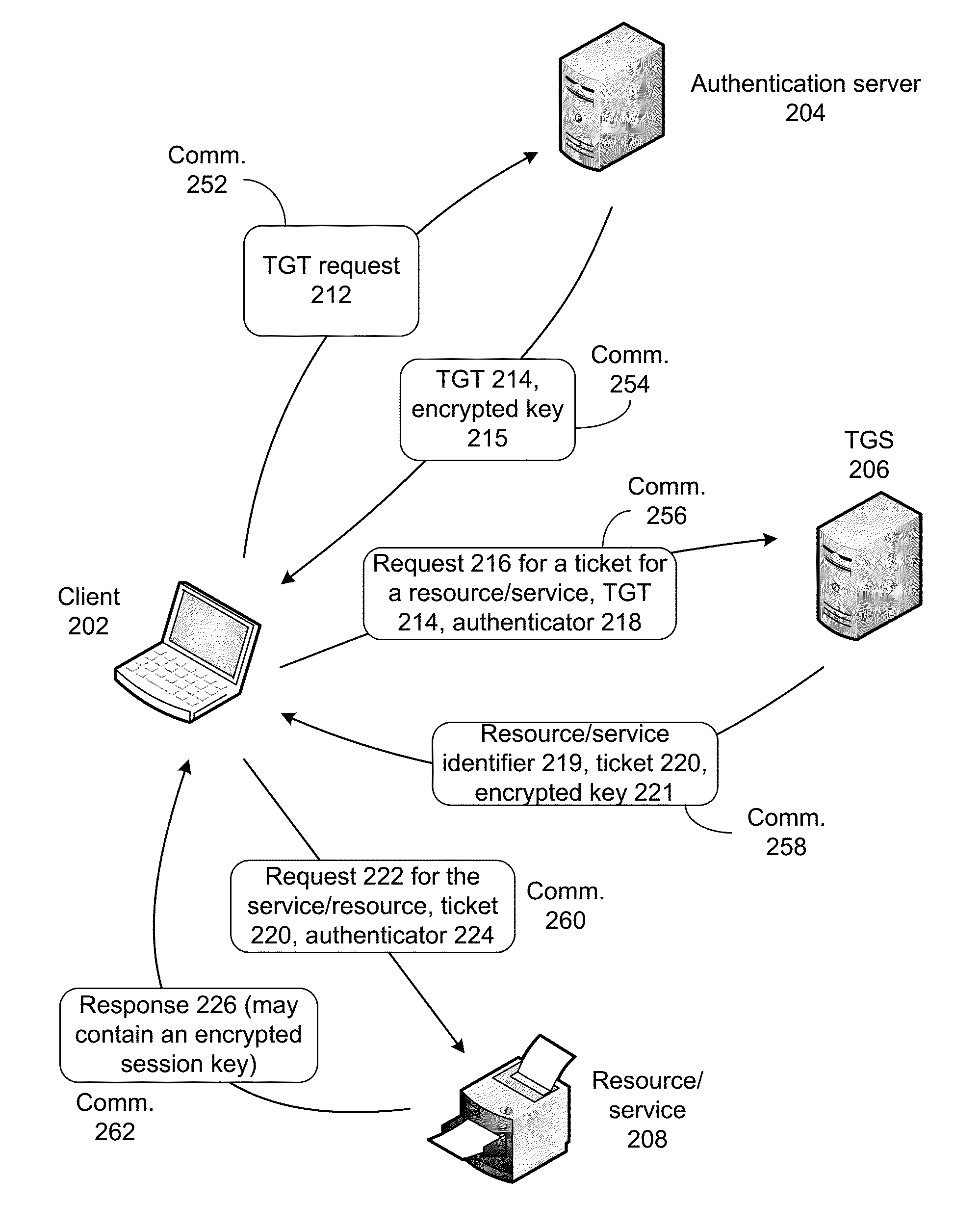
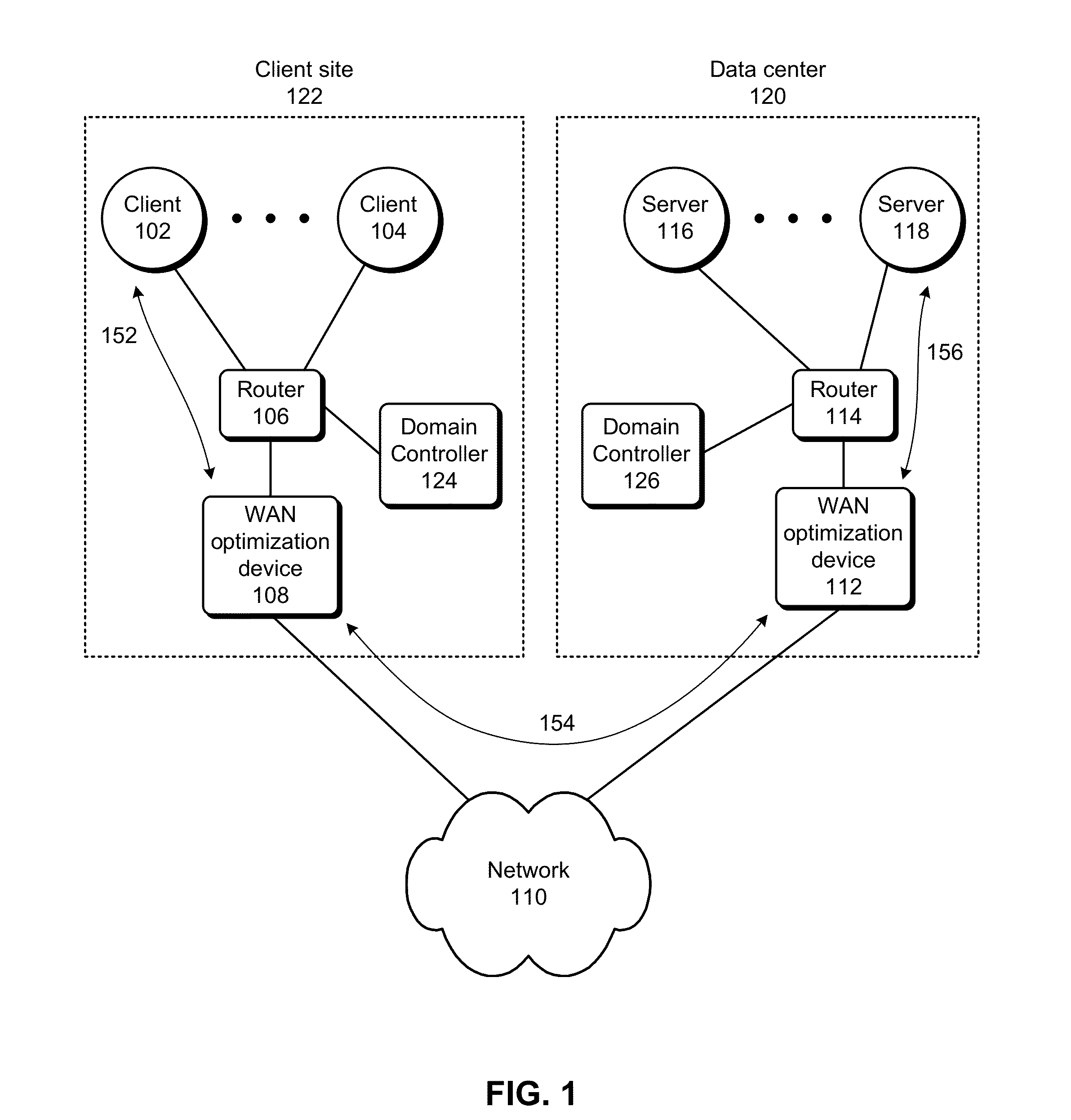
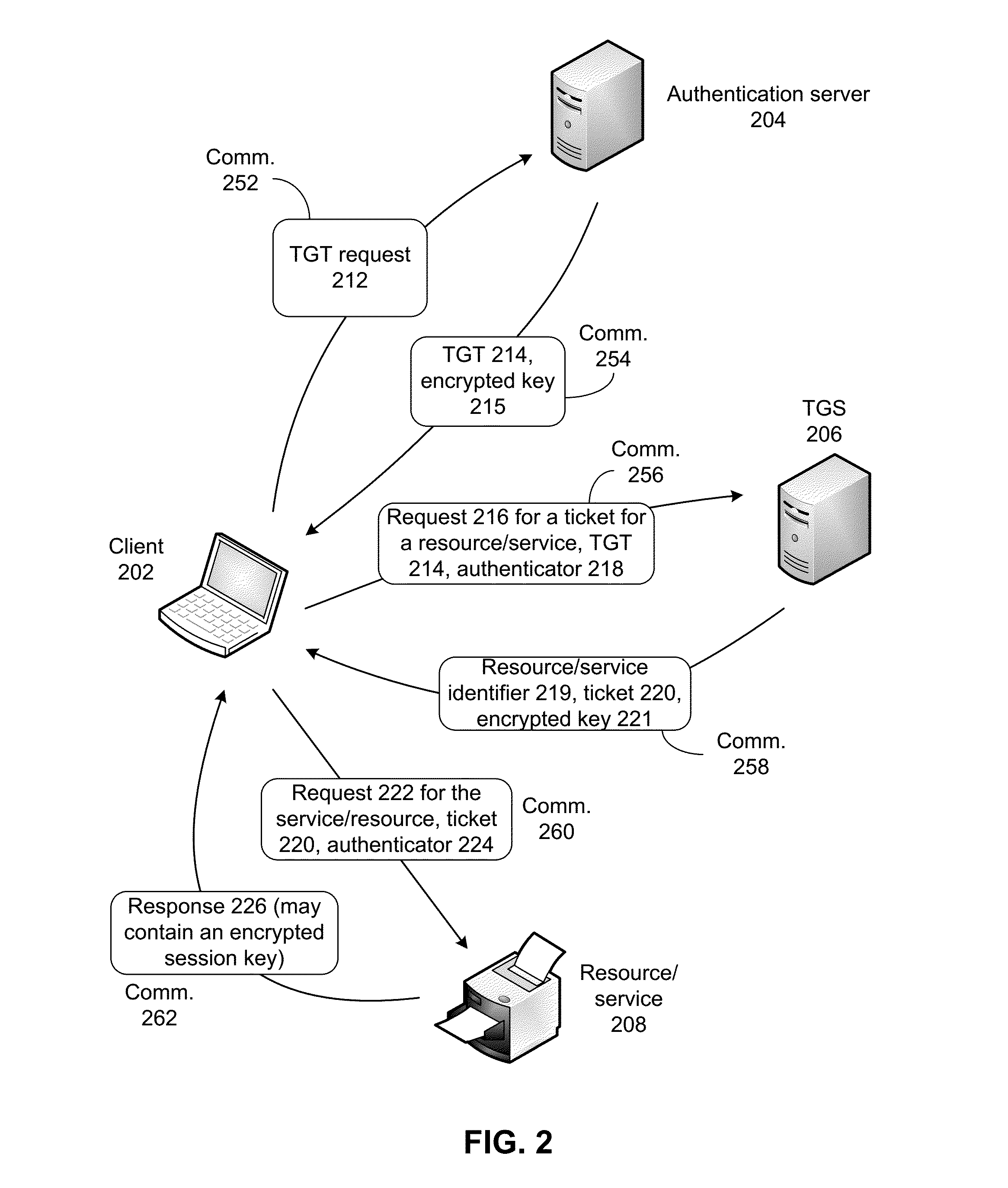
Optimizing secure communications
Systems and techniques are described for optimizing secure communications. A client can use an authentication protocol, e.g., Kerberos, to authenticate with the server. Specifically, the client can obtain a service ticket from a ticket granting server, and then use the service ticket to authenticate with the server. The server can respond by providing an encrypted session key. The session key can then be used by the client and server to securely communicate with each other. A wide area network (WAN) optimization device described in this disclosure is capable of obtaining the session key without decrypting the service ticket. Specifically, the WAN optimization device can use information other than the service ticket to obtain the session key.
Owner:RIVERBED TECH LLC
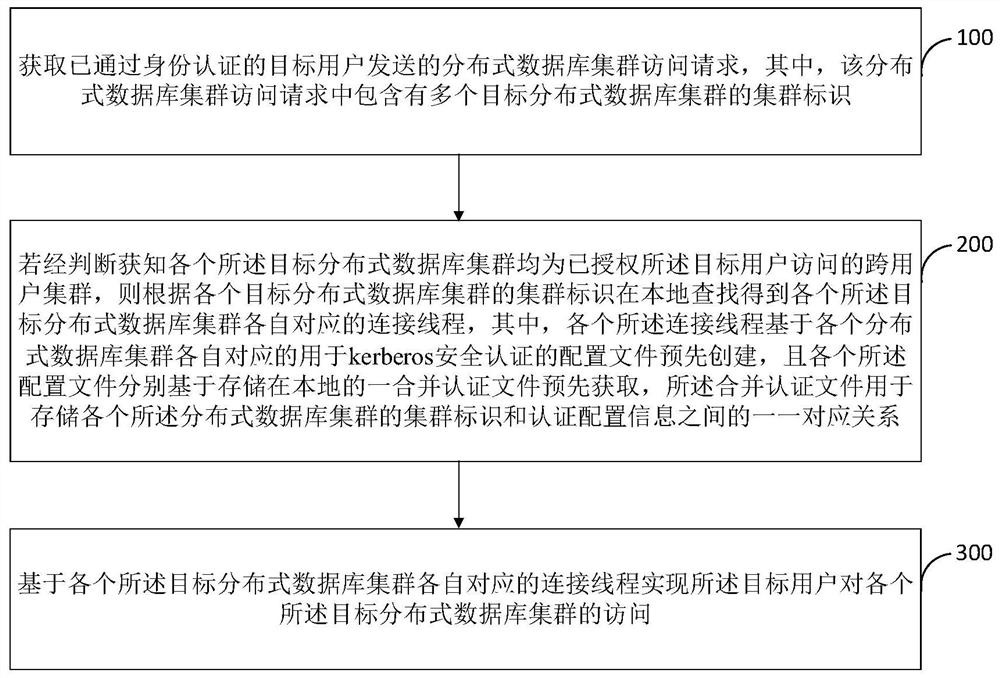
Distributed database cluster access method and intermediate service layer
PendingCN111737741AImprove reliabilityReduce maintenance costsDatabase management systemsDatabase distribution/replicationParallel computingEngineering
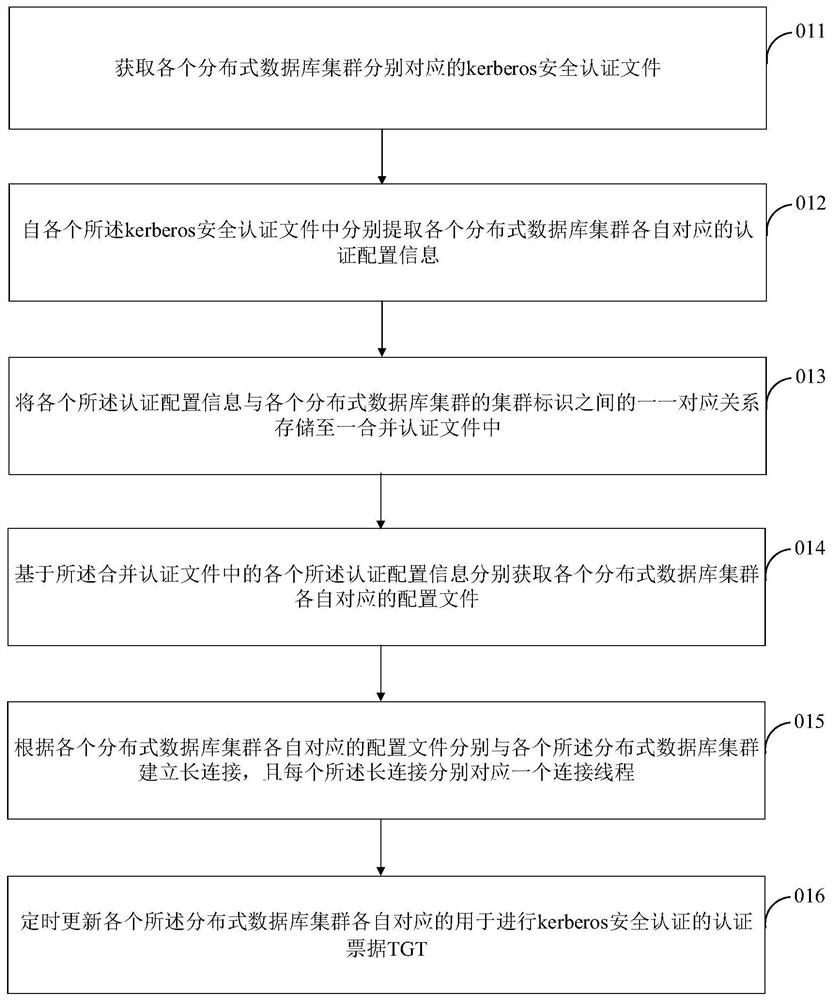
The embodiment of the invention provides a distributed database cluster access method and an intermediate service layer. The method comprises the following steps: locally searching according to the cluster identifier of each target distributed database cluster to obtain a connecting thread corresponding to each target distributed database cluster, wherein each connecting thread is created based oneach configuration file for kerberos security authentication, each configuration file is acquired based on a local combined authentication file, and the combined authentication file is used for storing a one-to-one correspondence relationship between each cluster identifier and authentication configuration information; and realizing access of the target user to each target distributed database cluster based on the connection thread. According to the application, a user can access a plurality of distributed database clusters at the same time, so the cross-cluster access effectiveness and reliability of the user for the plurality of distributed database clusters at the same time can be improved while the cross-cluster access safety and timeliness of the user for the distributed database clusters are effectively improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
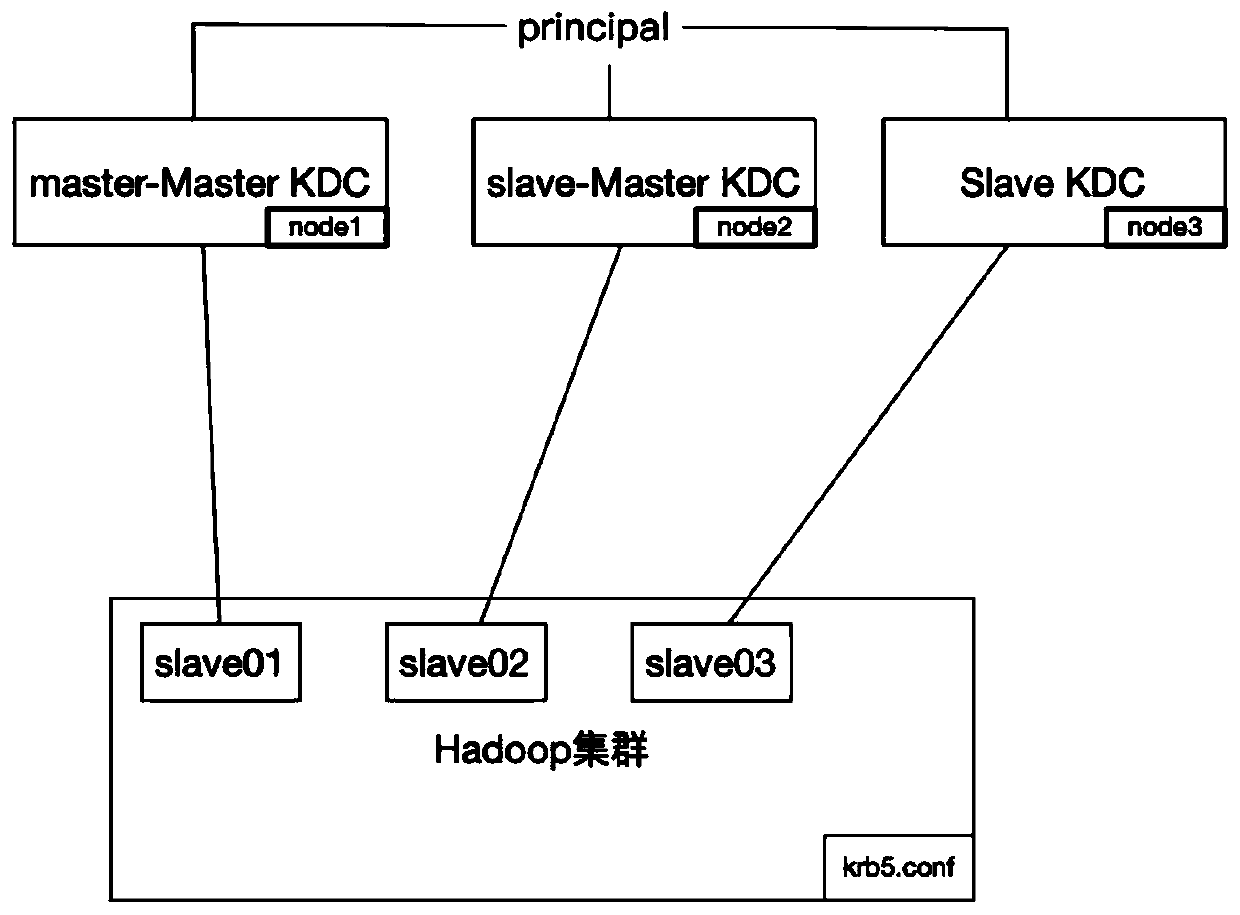
High-availability authentication method for hadoop cluster kerberos
ActiveCN111597536AHigh availability requirementsGuaranteed stabilityDigital data authenticationRedundant operation error correctionAuthentication serverDistributed computing
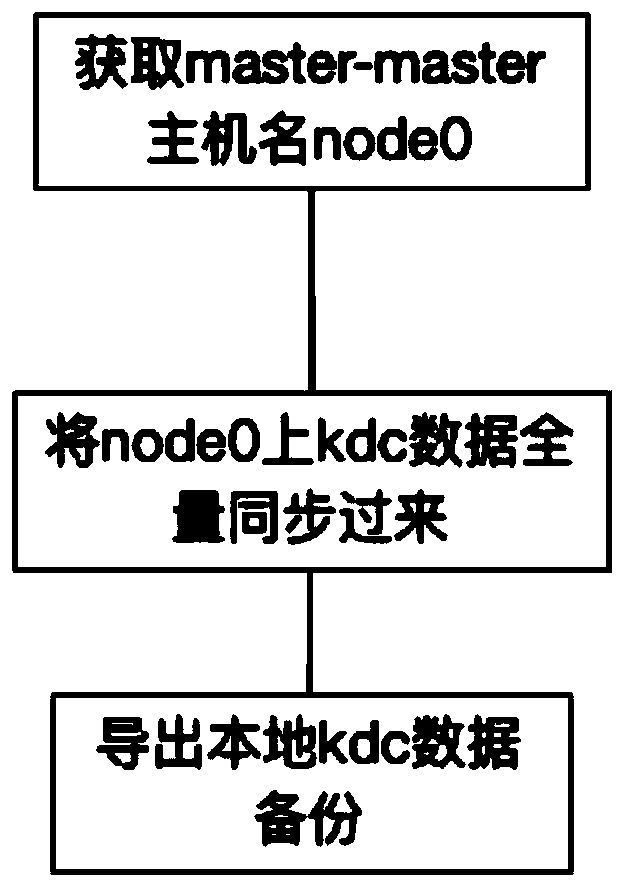
The invention discloses a high-availability authentication method for a hadoop cluster kerberos. The high-availability authentication method comprises the following steps: deploying a plurality of kerberos servers in different Linux servers; calling the shell script at regular time by the Linux timer to synchronize and back up the data of the plurality of kernel servers; when the kernel authentication is started by the Hadoop, configuring all the kdc server addresses used in kdc parameter configuration of krb5. Conf; and in the hadoop cluster, adjusting the kerberos authentication priority sequence by adjusting the kdc parameter sequence by the node, so that the kernel server realizes multiple backups. When the hadoop performs kernel authentication, the adjustment can be performed according to the configuration of the authentication server, and in a large-scale cluster, the time delay caused by authentication can be reduced; and meanwhile, the load of a kernel server single server is reduced, and the stability of kernel authentication of the cluster is guaranteed.
Owner:CHONGQING UNIV OF EDUCATION
Scheme for sub-realms within an authentication protocol
ActiveUS7571311B2Reduce security risksUser identity/authority verificationMultiple digital computer combinationsVirtual fieldPassword
Branch domain controllers (DCs) contain read only replicas of the data in a normal domain DC. This includes information about the groups a user belongs to so it can be used to determine authorization information. Password information, however, is desirably replicated to the branch DCs only for users and services (including machines) designated for that particular branch. Moreover, all write operations are desirably handled by hub DCs, the primary domain controller (PDC), or other DCs trusted by the corporate office. Rapid authentication and authorization in branch offices is supported using Kerberos sub-realms in which each branch office operates as a virtual realm. The Kerberos protocol employs different key version numbers to distinguish between the virtual realms of the head and branch key distribution centers (KDCs). Accounts may be named krbtgt_<ID> where <ID> is carried in the kvno field of the ticket granting ticket (TGT) to indicate to the hub KDC which krbtgt′ key was used to encrypt the TGT.
Owner:MICROSOFT TECH LICENSING LLC
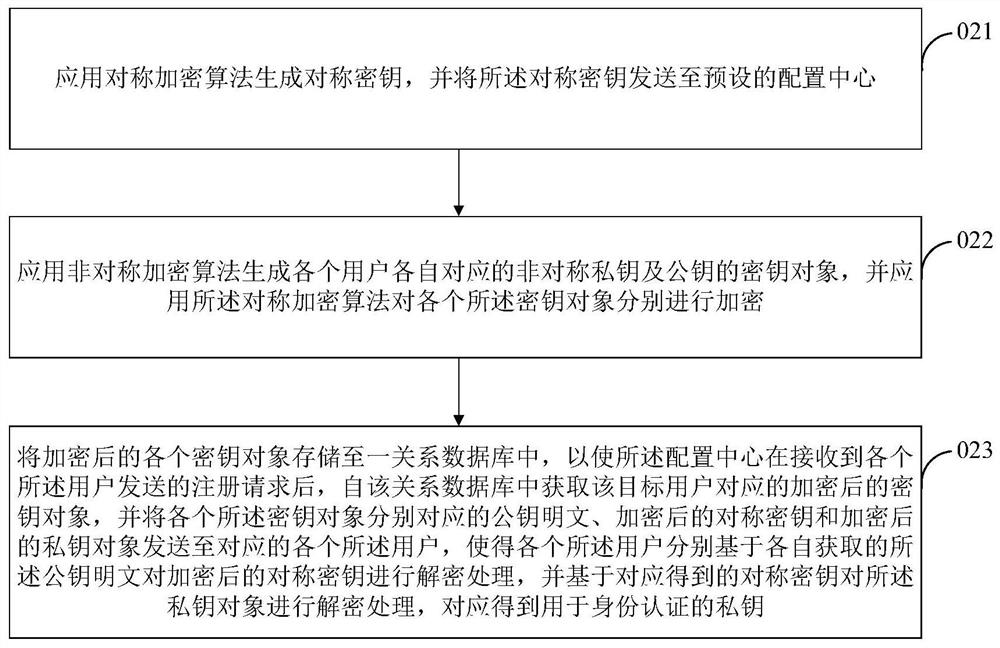
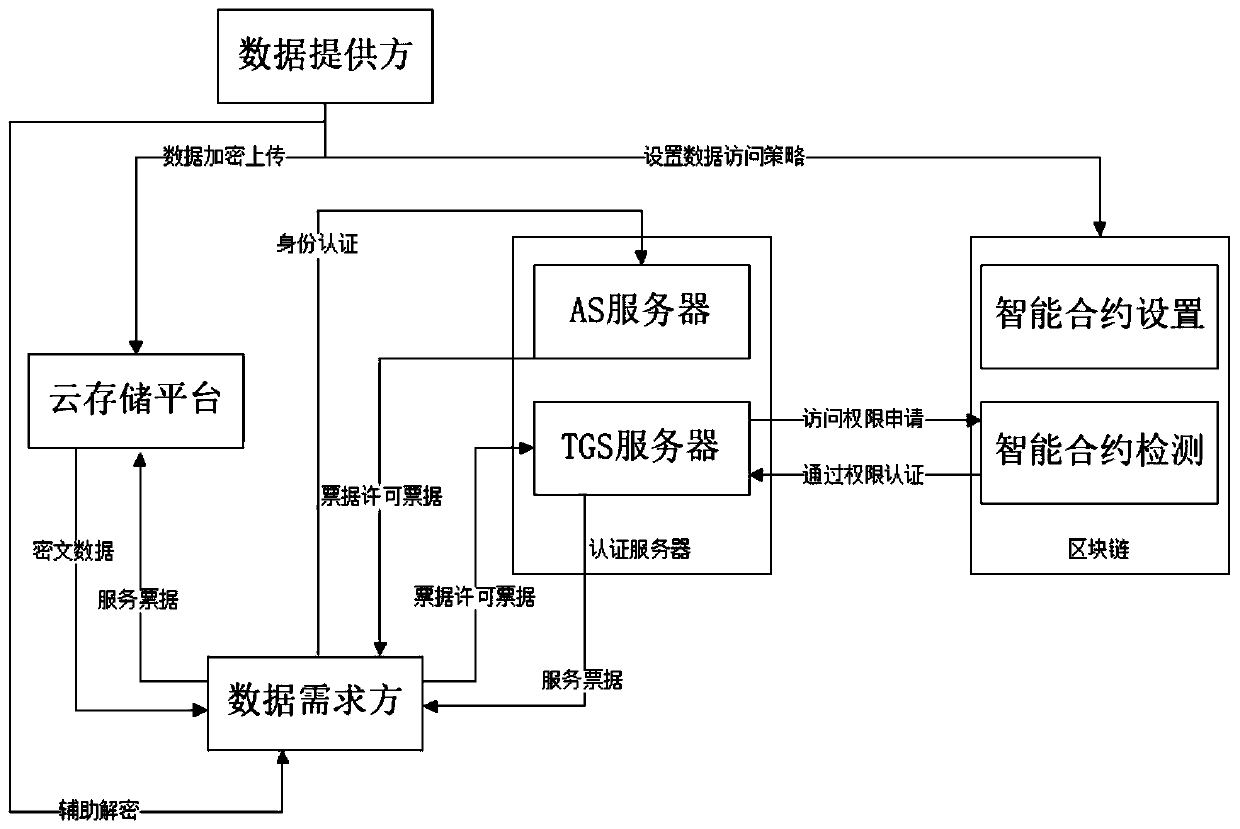
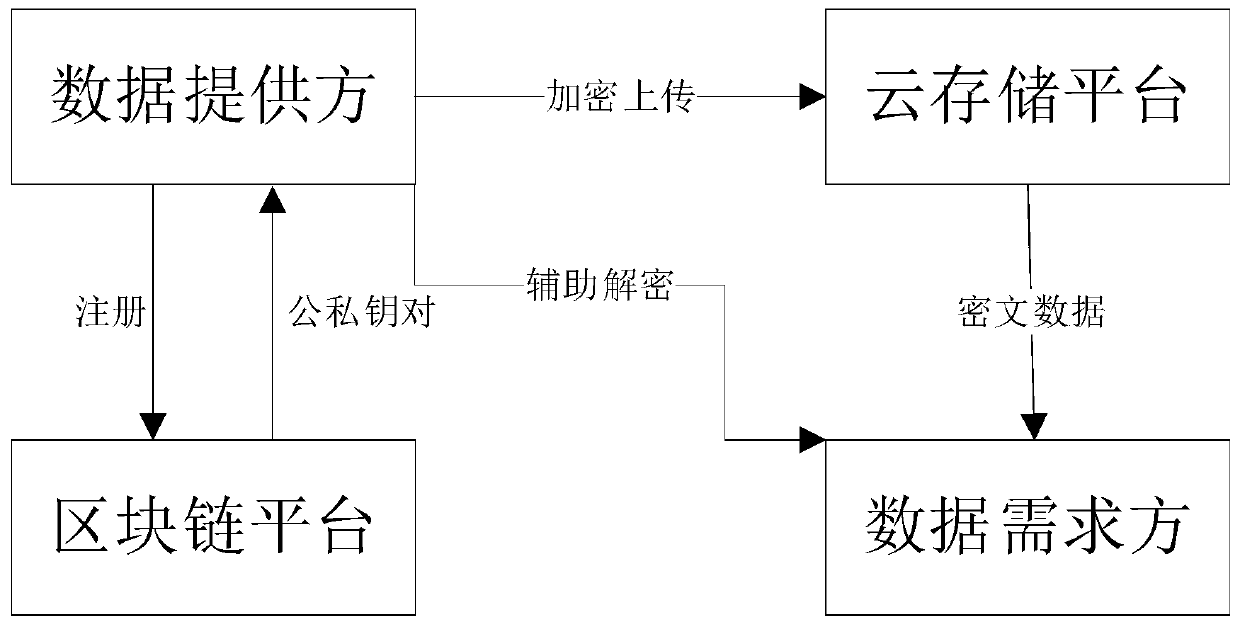
Data security sharing system and method integrating Kerberos authentication server and block chain
ActiveCN111324881AImprove securityNo data leakageFinanceDigital data protectionCommunications securityTerminal server
The invention relates to a data security sharing system and method integrating a Kerberos authentication server and a block chain. The data security sharing system comprises a data providing terminal,a data demand terminal, an AS server, a TGS server, the block chain and a cloud storage platform. Wherein the data providing terminal is connected with the cloud storage platform and the block chain,the data demand terminal is connected with the cloud storage platform, the AS server and the TGS server, and the TGS server is connected with the block chain. According to the method, data privacy security and communication security are ensured by using symmetric encryption and asymmetric encryption algorithms, and multiple parties participate in authority management by using the decentralizationcharacteristic of the blockchain, so that the problem of data security access which cannot be provided by a traditional data sharing method can be solved. According to the method, the management right and the verification right of the data are separately realized, so that the burden of the blockchain network is reduced, the throughput is large, and the expandability and the robustness are relatively good.
Owner:铭数科技(青岛)有限公司
Advanced detection of identity-based attacks to assure identity fidelity in information technology environments
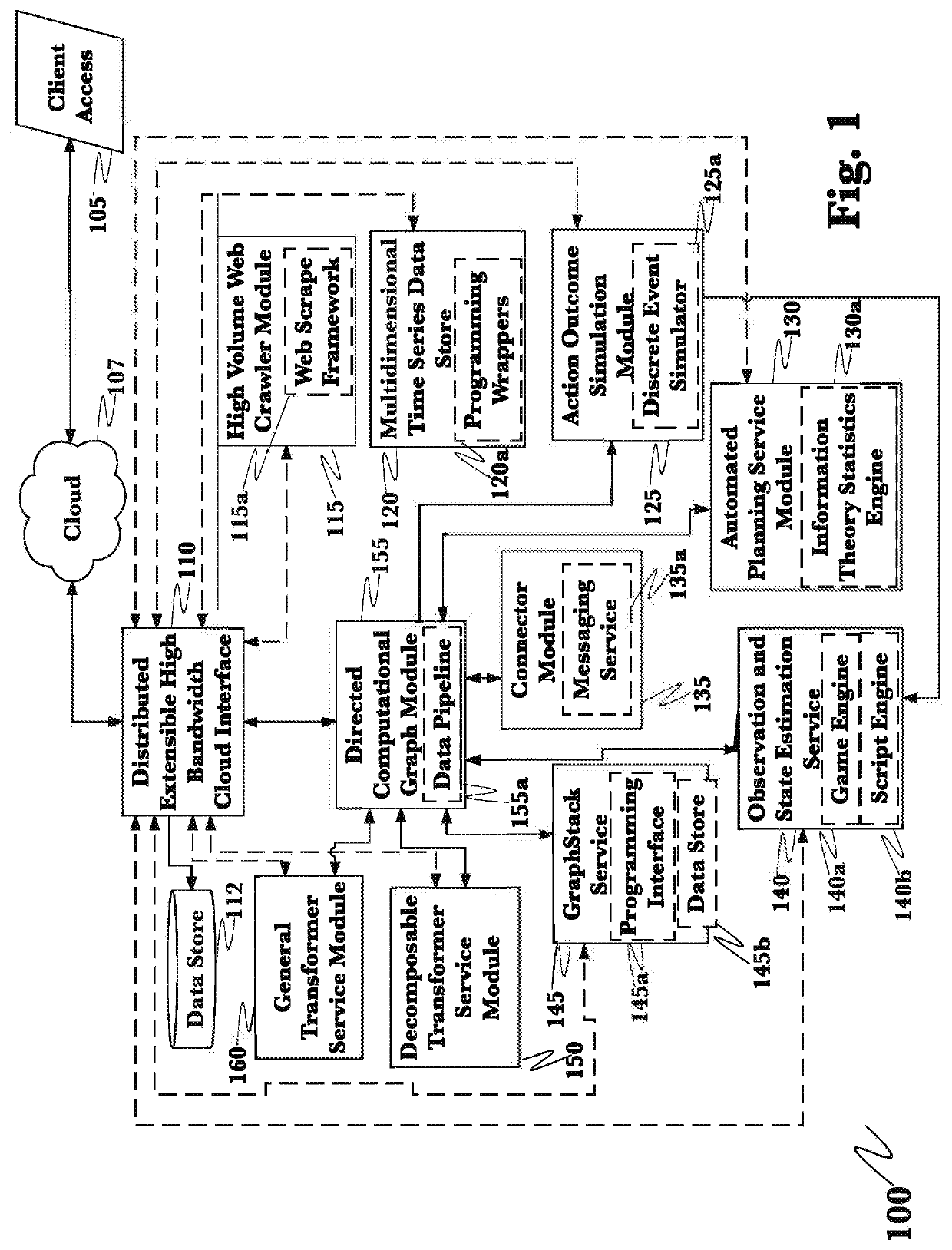
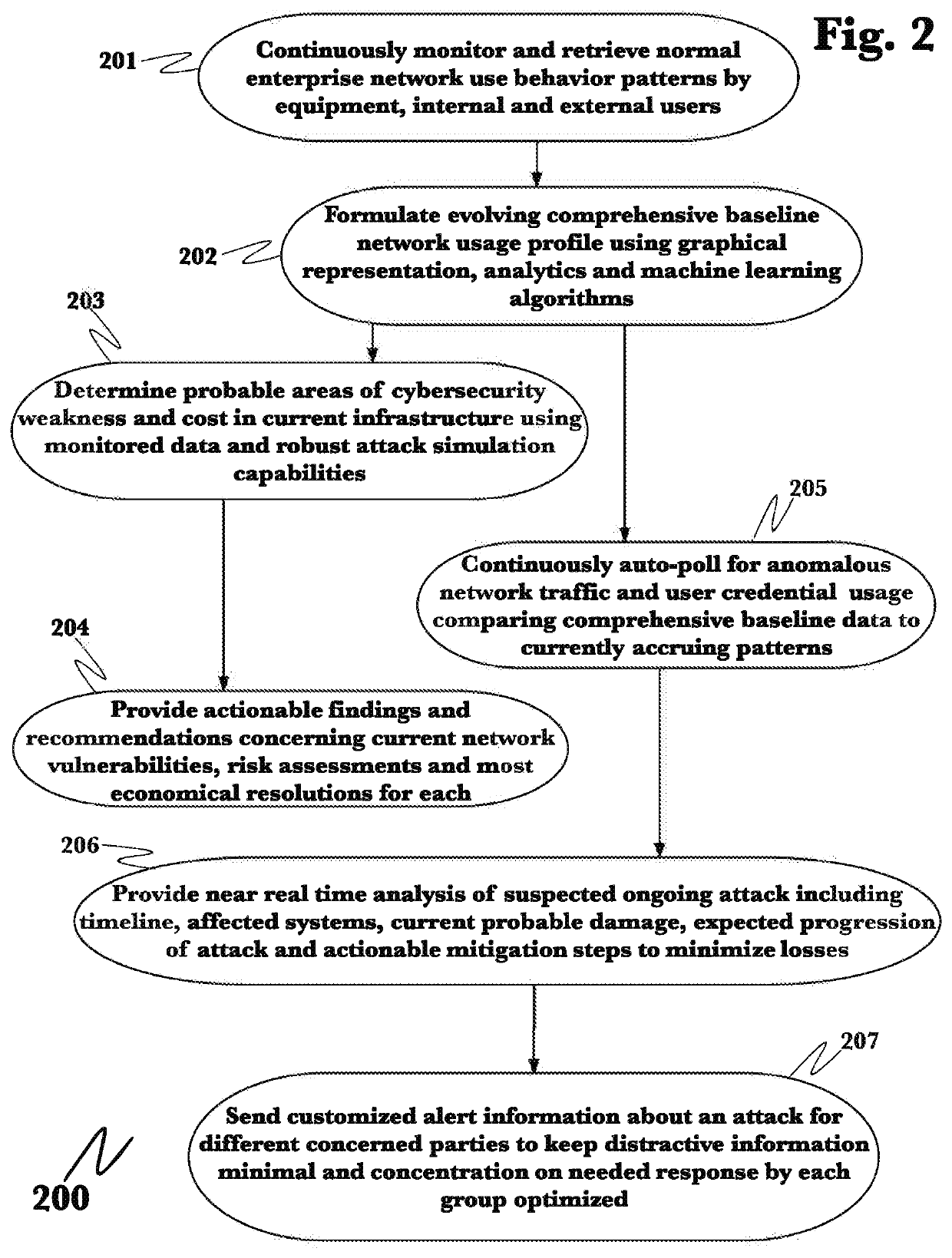
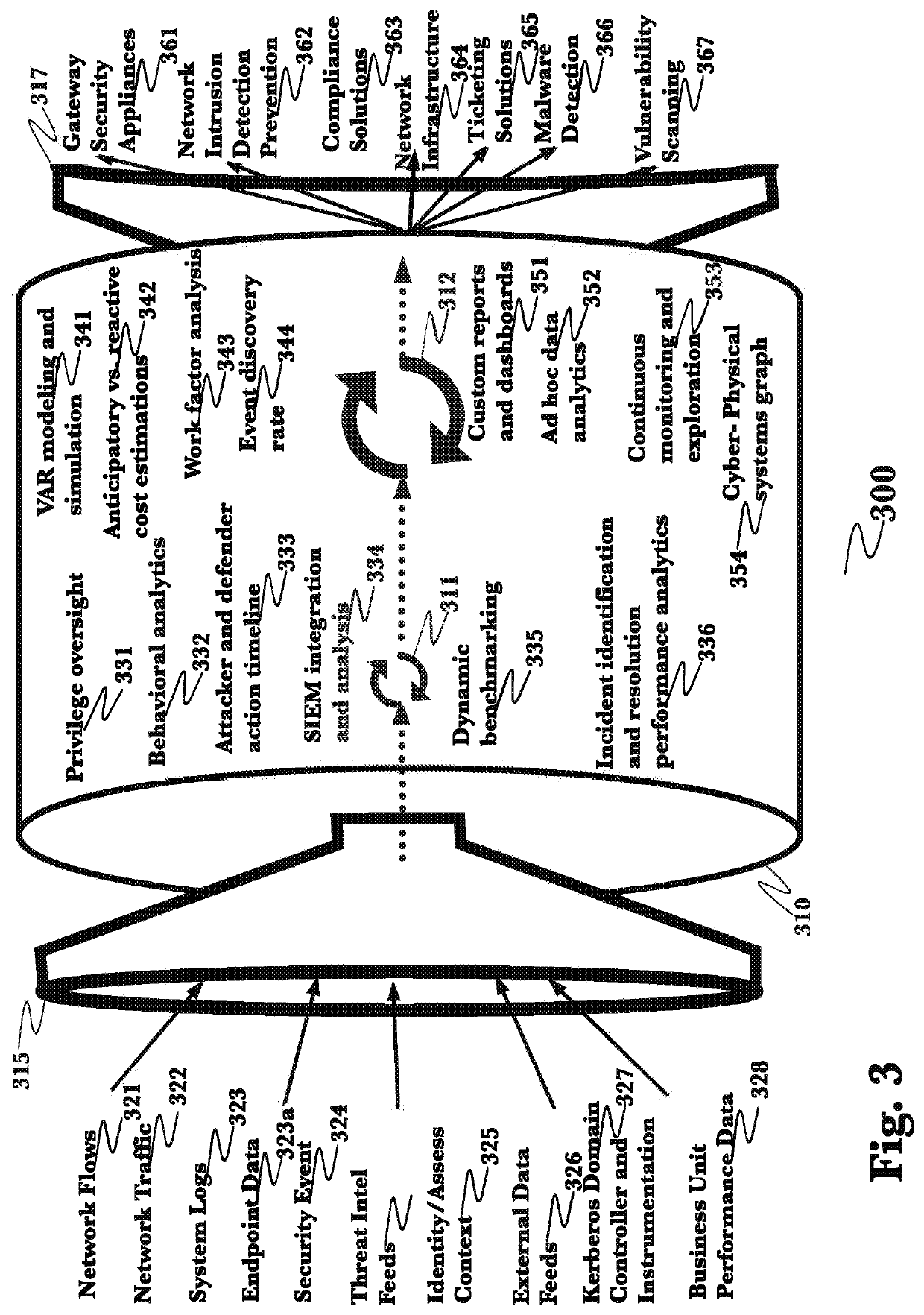
A system and method for the detection and mitigation of Kerberos golden ticket, silver ticket, and related identity-based cyberattacks by passively monitoring and analyzing Kerberos and authentication operations within the network. The system and method provide real-time detections of identity attacks using time-series data and data pipelines, and by transforming the stateless Kerberos protocol into stateful protocol. A packet capturing agent is deployed on the network where captured time-series Kerberos and related event and log information is processed in distributed computational graph (DCG) stages where declarative rules determine if an attack is being carried out and what type of attack it is.
Owner:QOMPLX LLC
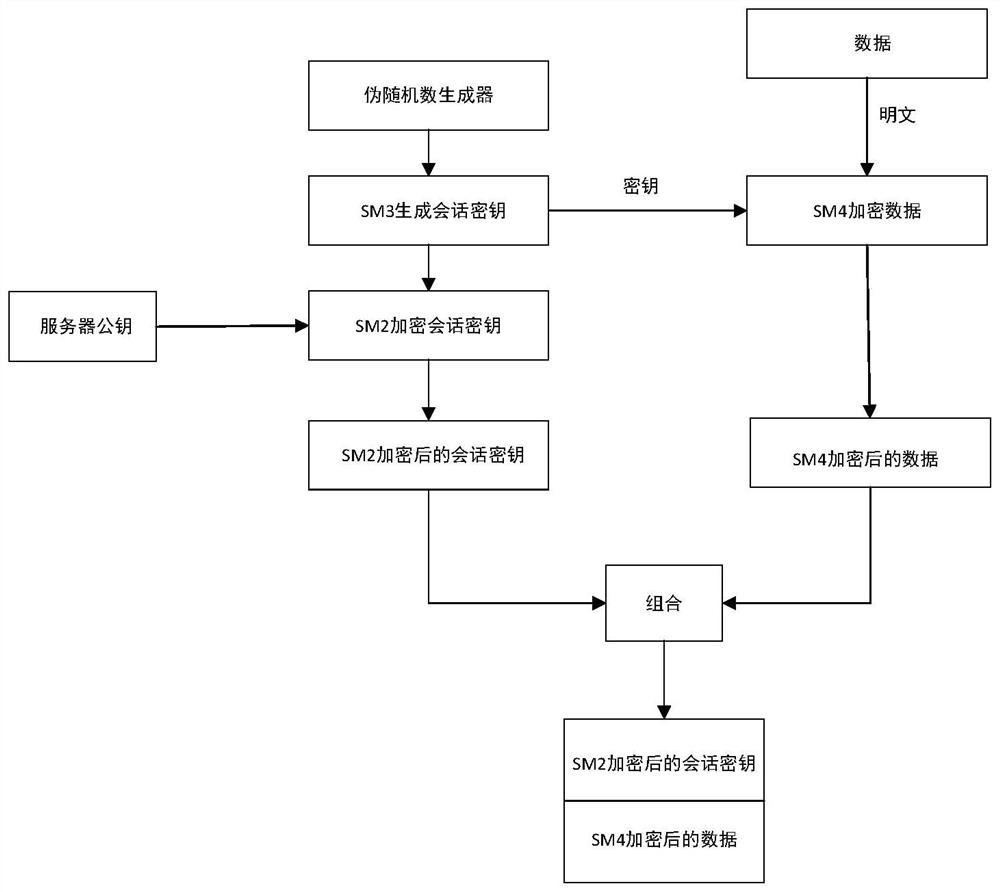
Kerberos identity authentication protocol improvement method based on national cryptographic algorithm
InactiveCN113612797AImprove securityImprove efficiencyKey distribution for secure communicationMultiple keys/algorithms usageAlgorithmEngineering
The invention discloses a Kerberos identity authentication protocol improvement method based on a national cryptographic algorithm, a traditional Kerberos protocol is improved by using session key dynamics and a hybrid cryptosystem based on the national cryptographic algorithm, and the improved Kerberos protocol comprises a registration process and an authentication process; wherein the authentication process comprises three stages: mutual authentication between the client and the AS; the client communicates with the TGS; the client communicates with the application server; a dynamic key is used as a shared key between the client and the AS, and encryption and decryption are carried out by adopting a hybrid cryptosystem based on a national cryptographic algorithm in an authentication process. According to the method, rainbow table attacks, blasting attacks and counterfeit user attacks caused by weak passwords can be effectively resisted, and replay attacks, man-in-the-middle attacks and the like caused by time synchronization can be effectively resisted, so that the security and the efficiency of a Kerberos identity authentication protocol are improved.
Owner:JINLING INST OF TECH
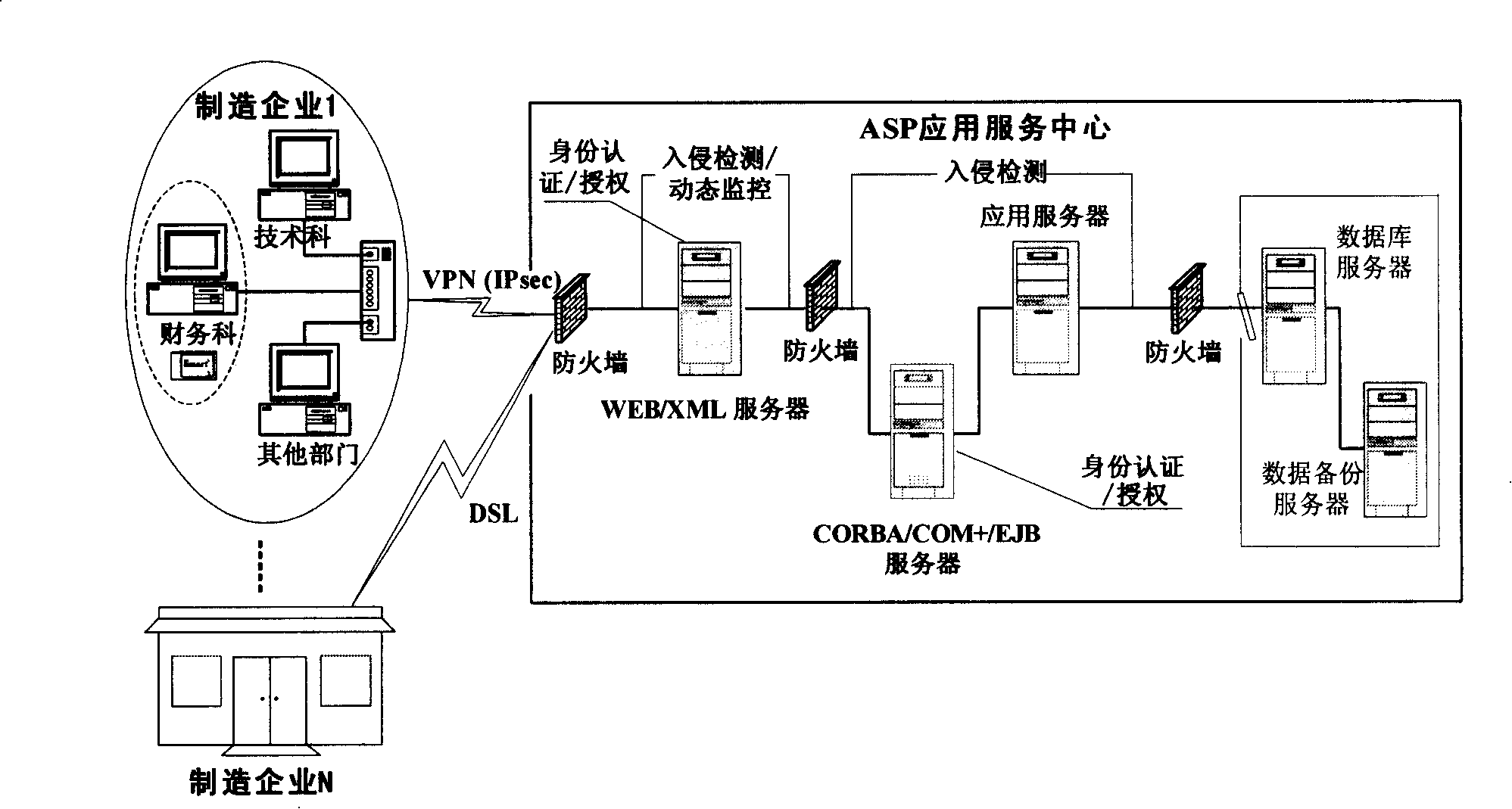
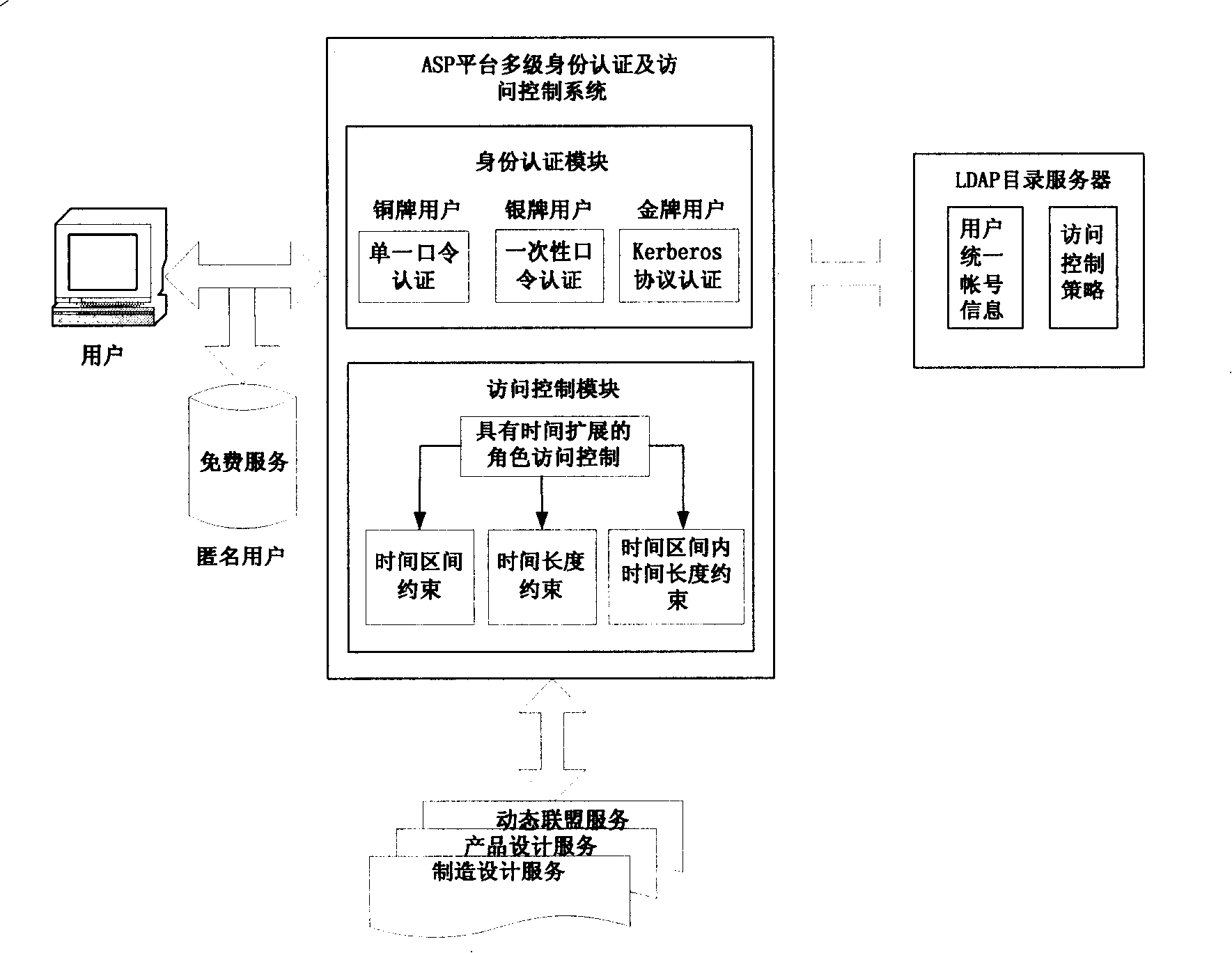
Networking fabrication safety integrating system based on ASP mode
InactiveCN101232373AEnsure permissionsAvoid Session Time SituationsUser identity/authority verificationWeight coefficientConfidentiality
An ASP-based network manufacturing safety integrated system provides a complete set of network safety protection system to ensure the rights, the data confidentiality and the integrity of a legitimate user. To the multi-user access, the authentication of a user is realized by a system by using a single sign-on mode; the single password authentication, the one-time password authentication and the Kerberos protocol authentication are respectively adopted to carry out the ID authentication to the users of the different levels; a time-constrained access control module is adopted to protect the access rights of the legitimate user. The AHP level analysis method is adopted to calculate the distribution time of the conversation in the time constraint which affects a plurality of conversations. A safety administrator develops s different evaluating indicators according to the characteristics of the system, uses the AHP algorithm to obtain the weight coefficient of each conversation and carries out the time distribution according to the weight coefficient of the conversation which is obtained by the calculation. The algorithm avoids the situation of even distribution of each conversation time, which is in line with the practical needs.
Owner:TONGJI UNIV
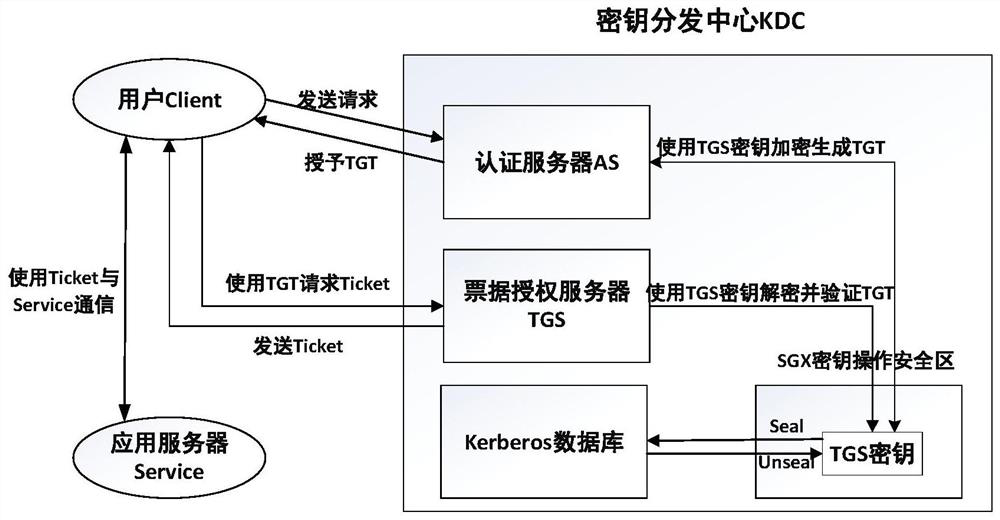
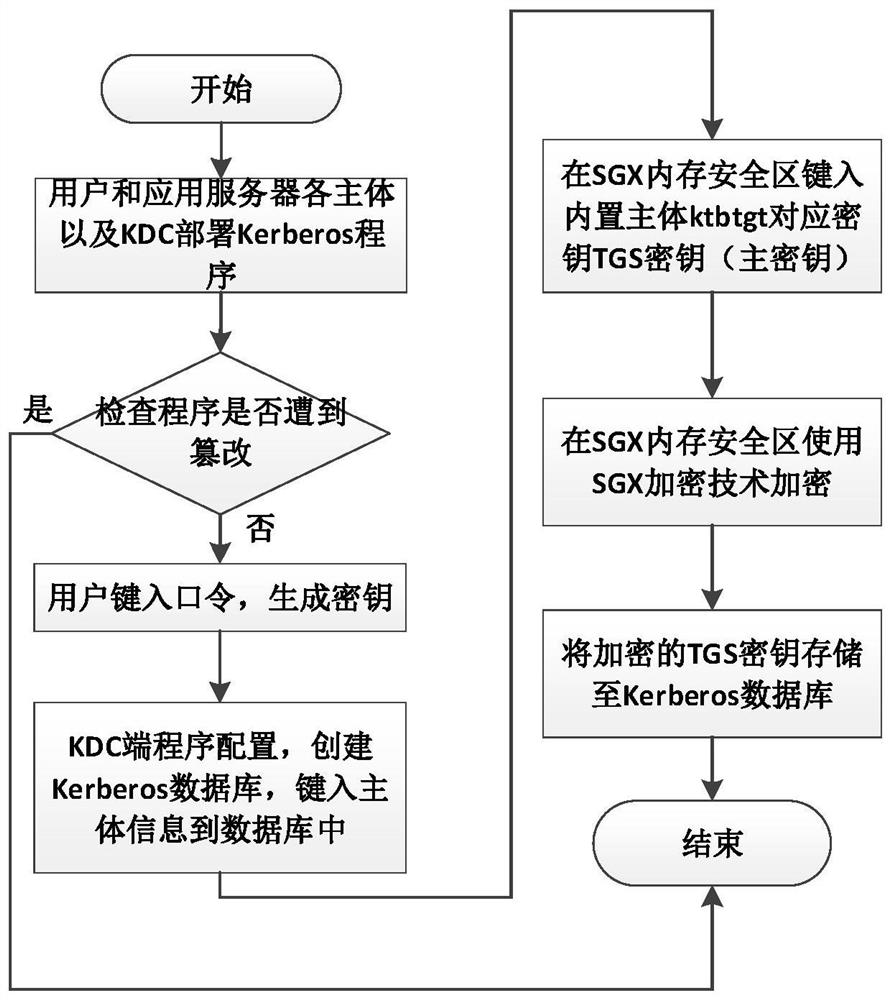
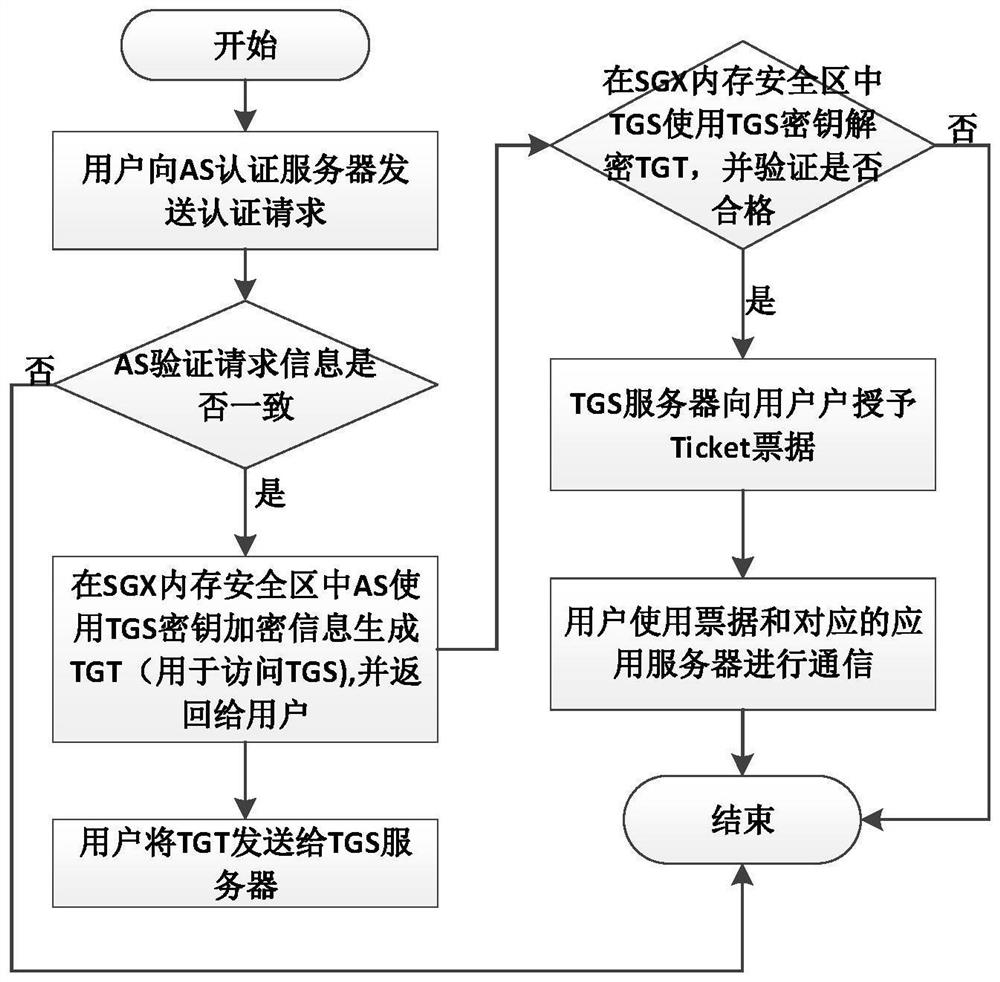
Kerberos security enhancement method based on Intel SGX
PendingCN113037477AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMaster keyKey storage
The invention discloses a Kerberos security enhancement method based on Intel SGX. The method comprises the following steps: (1) security initialization of a Kerberos authentication system; (2) security execution of the authentication service of the KDC key distribution center. (3) secure storage of the key after the authentication service is ended. By introducing Intel SGX hardware and a trusted spatial mechanism of SGX, a safe KDC key distribution center master key storage and use environment in the Kerberos identity authentication system is constructed. The method comprises three modules: a key security initialization module; a key security operation module; and a secret key security storage module. The main key is a long-term key only held by the KDC and is used for encrypting authentication information, so that a secure execution environment is needed, the method can ensure the storage and operation security, and ensures that the bill information cannot be decrypted even if an attacker eavesdrops the information, thereby ensuring the transmission and verification security of the bill.
Owner:BEIJING UNIV OF TECH
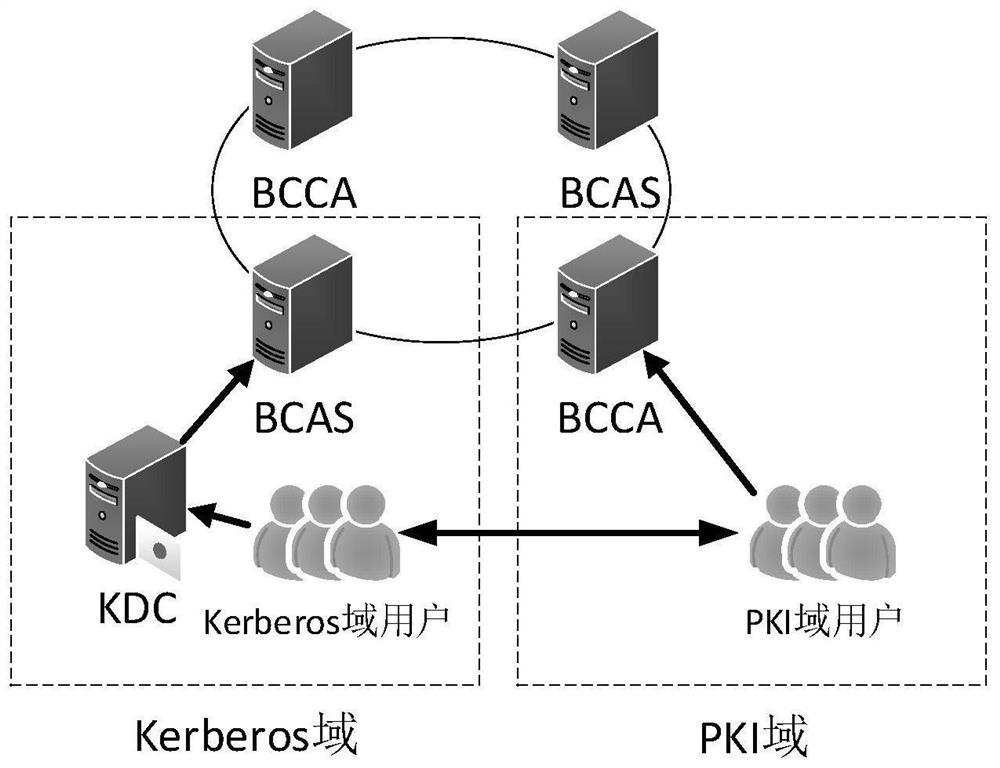
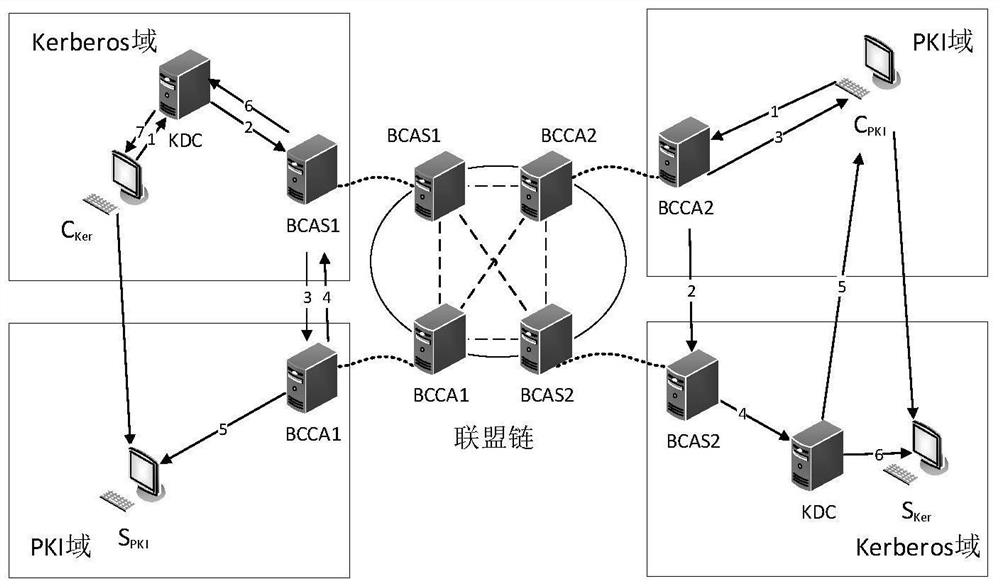
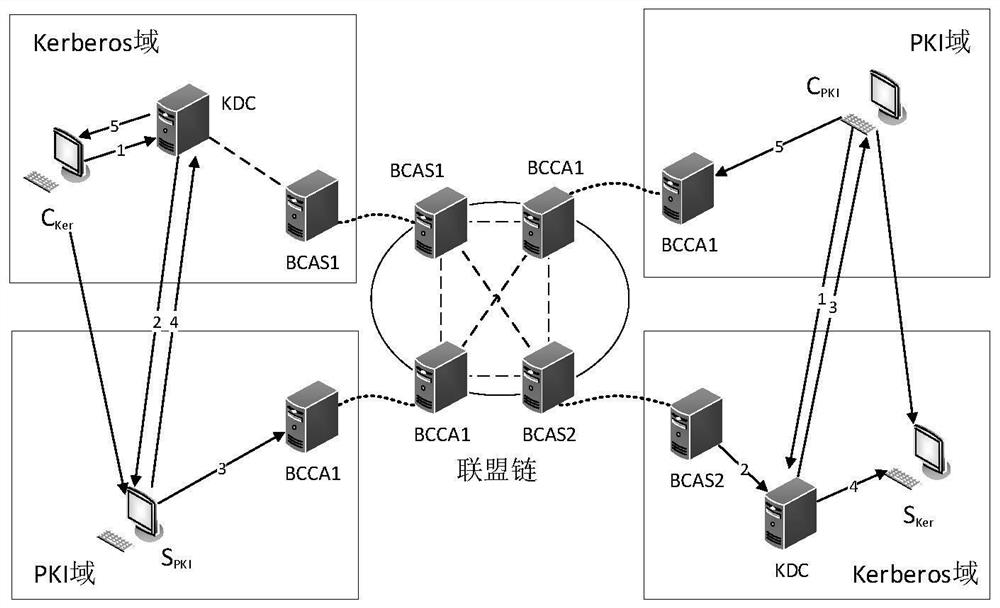
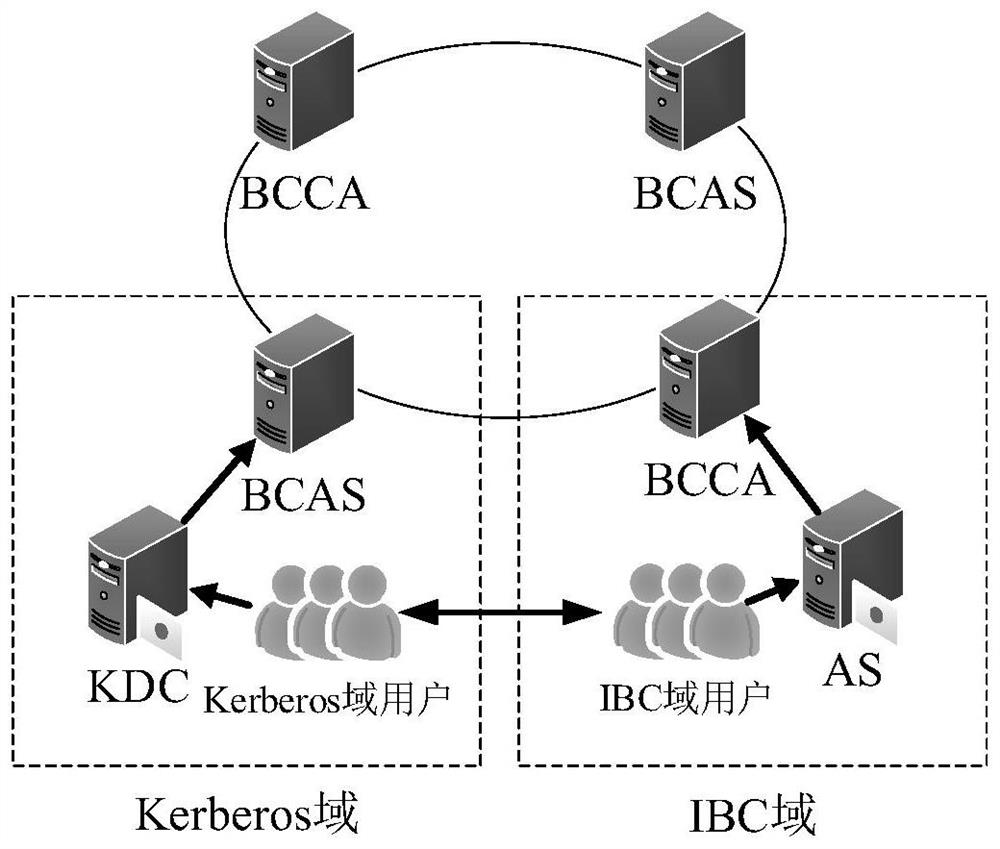
Cross-domain authentication method between Kerberos and PKI safety domains based on alliance chain
PendingCN114036472ASolve complexityFix security issuesDatabase distribution/replicationDigital data protectionSecurity domainInter-domain
The invention relates to a cross-domain authentication method between Kerberos and PKI safety domains of an alliance chain, and belongs to the technical field of computer safety. The method comprises the steps of constructing a Kerberos and PKI inter-domain identity authentication model based on an alliance chain, performing primary cross-domain identity authentication from a Kerberos safety domain to a PKI safety domain, performing primary cross-domain identity authentication from the PKI safety domain to the Kerberos safety domain, and performing cross-domain re-identity authentication from the Kerberos safety domain to the PKI safety domain. According to the method, the block chain model is used as a basis, a consensus mechanism of an alliance chain is adopted, and the entity authentication method between the PKI domain and the Kerberos domain is provided, so that cross-domain authentication certificates can be reliably stored in different safety domains in a tamper-proof manner, and cross-domain identity authentication is realized while safety and reliability are ensured.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
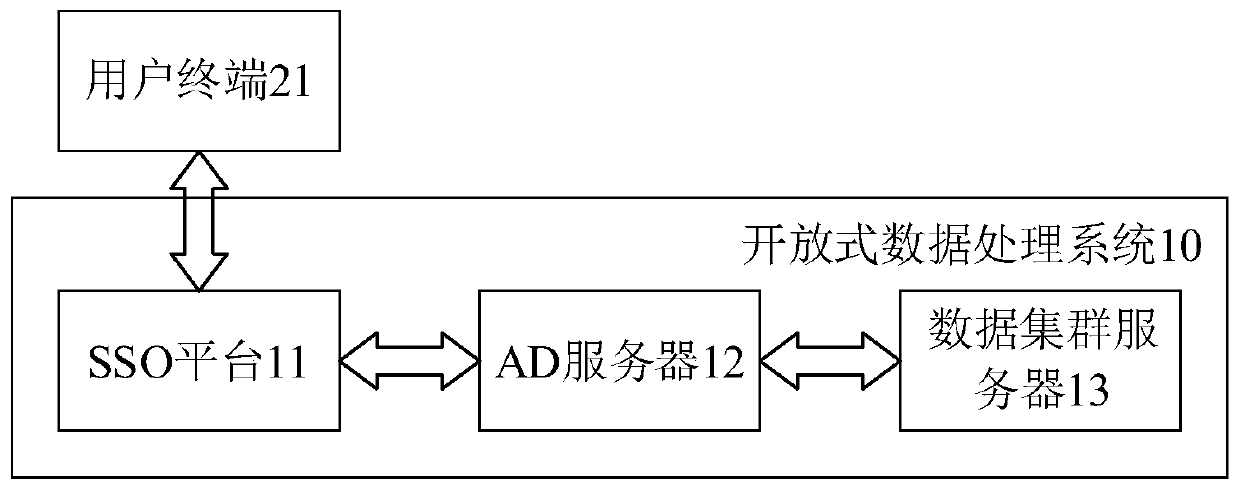
Open type data processing system, open type data system and data processing method
ActiveCN111125674AEnsure safetyImprove securityDigital data authenticationData processing systemData system
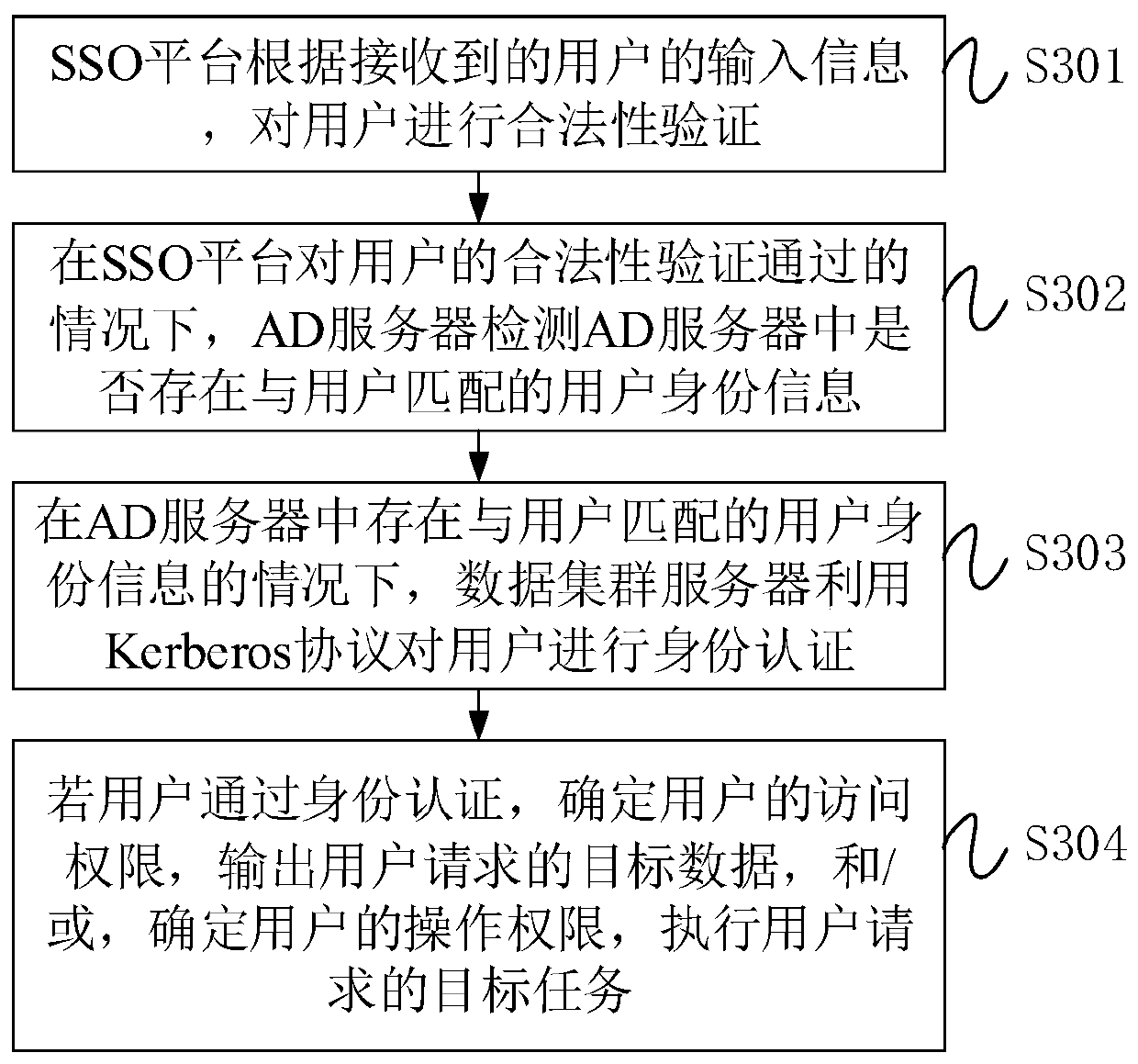
The invention provides an open type data processing system, an open type data system and a data processing method, and relates to the field of data processing. The open type data processing system comprises: an SSO platform used for carrying out legality verification on a user according to received input information of the user; an AD server which is used for detecting whether user identity information matched with the user exists in the AD server or not under the condition that the SSO platform verifies the legality of the user successfully; a data cluster server which is used for using a Kerberos protocol to carry out identity authentication on a user when the AD server has the user identity information matched with the user; determining the access permission of the user if the user passes the identity authentication, outputting target data requested by the user, and / or, determining the operation permission of the user, executing a target task requested by the user, the target data being matched with the access permission of the user, and the target task being matched with the operation permission of the user. By means of the technical scheme, the safety of the open type data processing system can be improved.
Owner:CHINA UNIONPAY
Spark task submitting method and device and server
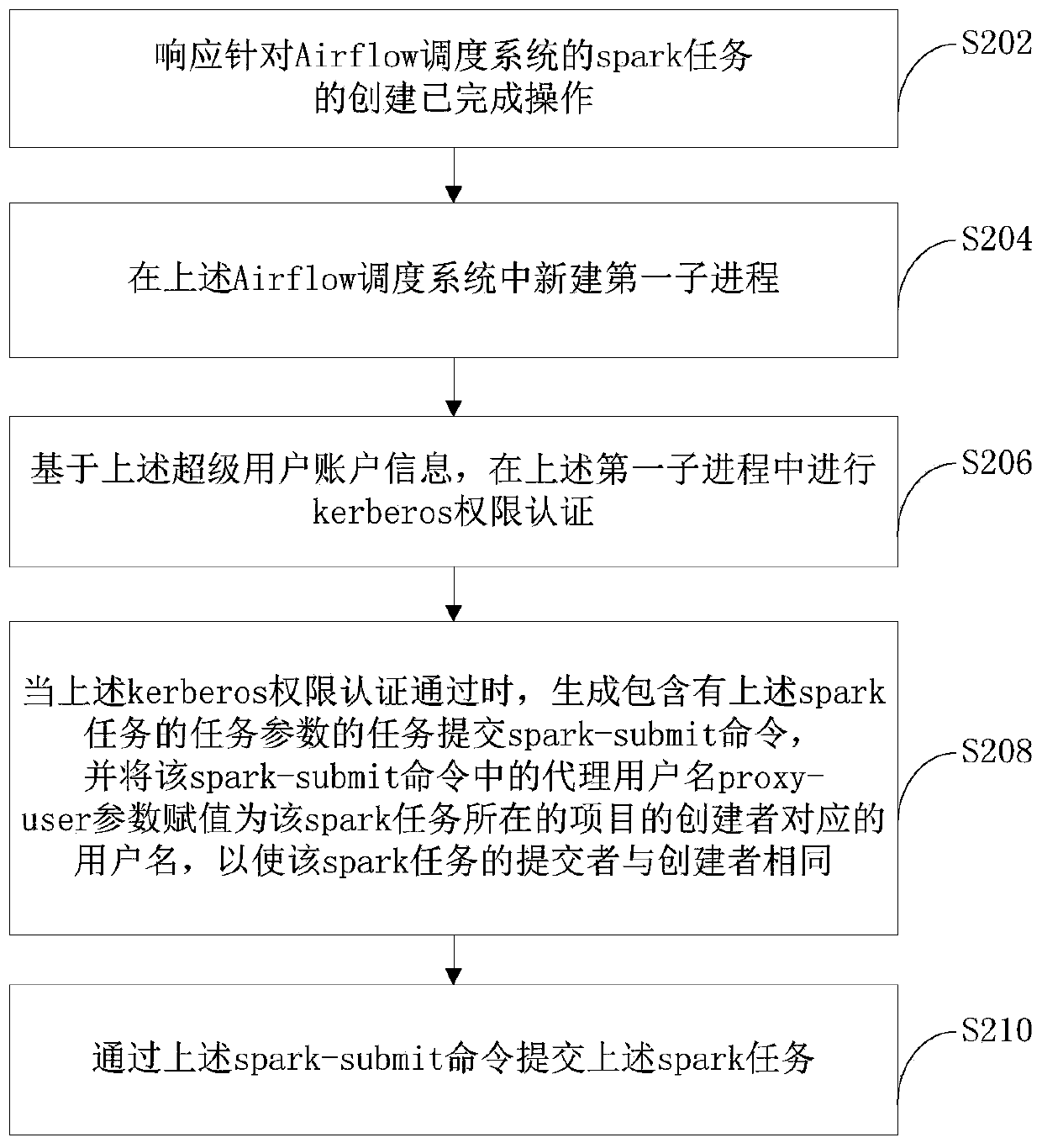
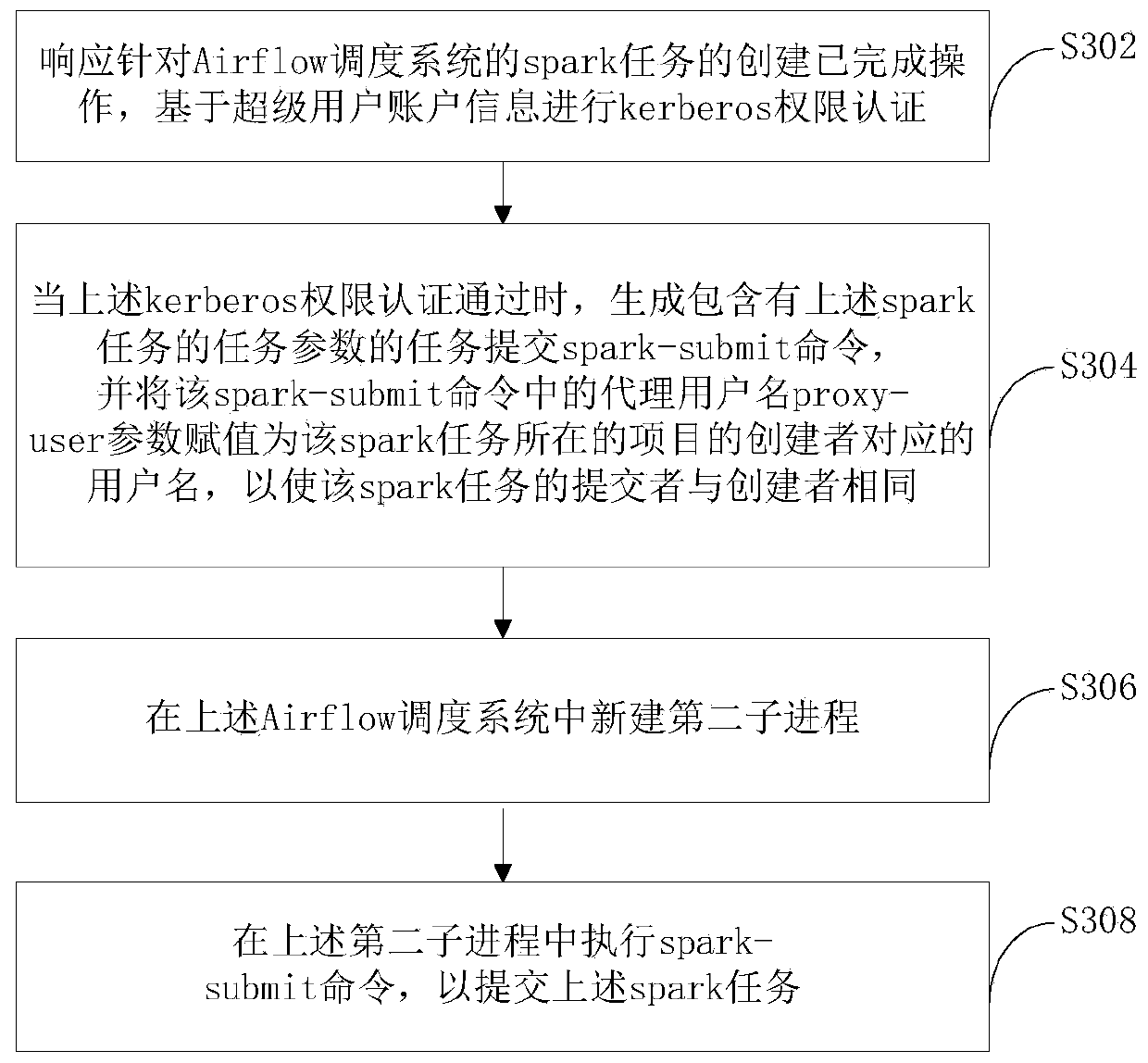
ActiveCN110889108AImprove authentication efficiencyReduce usageDigital data protectionDigital data authenticationSoftware engineeringData system
The invention provides a spark task submitting method, a spark task submitting device and a server. The method comprises the following steps: responding to the creation completion operation of the spark task, if the kerberos authority authentication based on the super user is passed, generating a spark-submit command containing task parameters of the spark task, and assigning an agent user name ofthe spark-sub command as a user name corresponding to a creator of a project where the spark task is located; and submitting a spark task through the spark-submit command. According to the method, kerberos permission authentication is automatically carried out while the spark task is submitted, so that the authentication efficiency is improved; the proxy user name in the spark-submit is assignedas the user name corresponding to the creator, so that the creator and the submitter of the spark task are ensured to be the same user, the user identity information is prevented from being used by other users, and the security of a big data system is ensured.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Concurrent access method and device for plurality of KERBEROS clusters
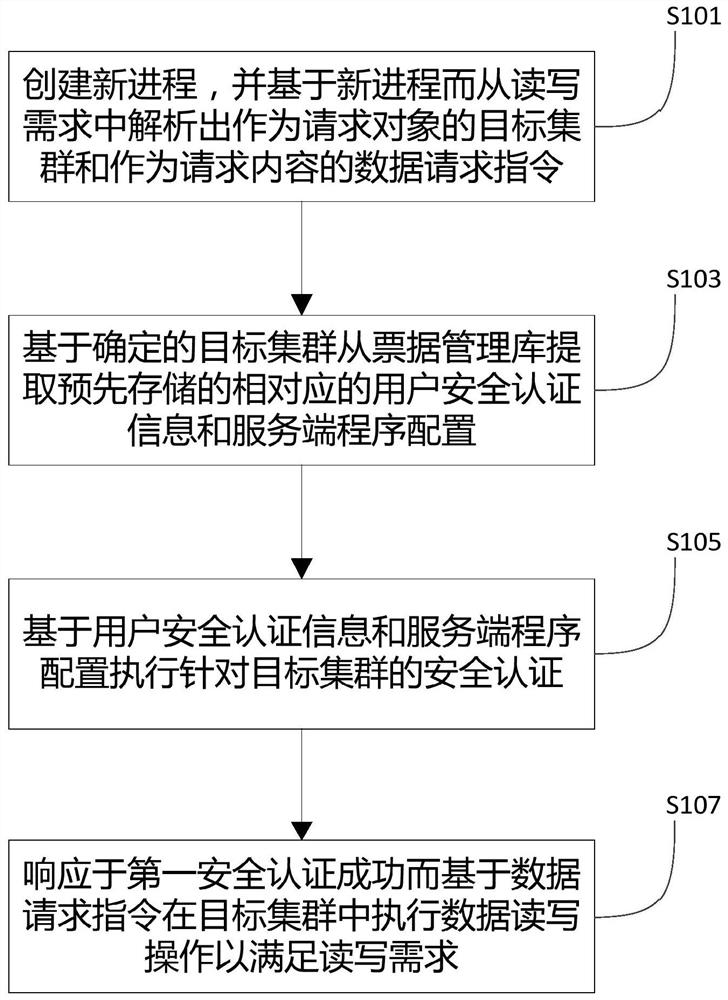
ActiveCN112134707AIncrease flexibilityEnsure data securityUser identity/authority verificationAccess methodTheoretical computer science
The invention discloses a concurrent access method and device for multiple KERBEROS clusters, and the method comprises the steps: building a new process, and analyzing a target cluster serving as a request object and a data request instruction serving as request content from a read-write demand based on the new process; extracting pre-stored corresponding user security authentication information and server program configuration from a bill management library based on the determined target cluster; executing security authentication for the target cluster based on the user security authentication information and the server program configuration; in response to successful security authentication, executing a data read-write operation in the target cluster based on the data request instructionto meet a read-write demand. According to the invention, a plurality of KERBEROS clusters can be authenticated and accessed concurrently, and the flexibility of cluster access is improved while the data security is ensured.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
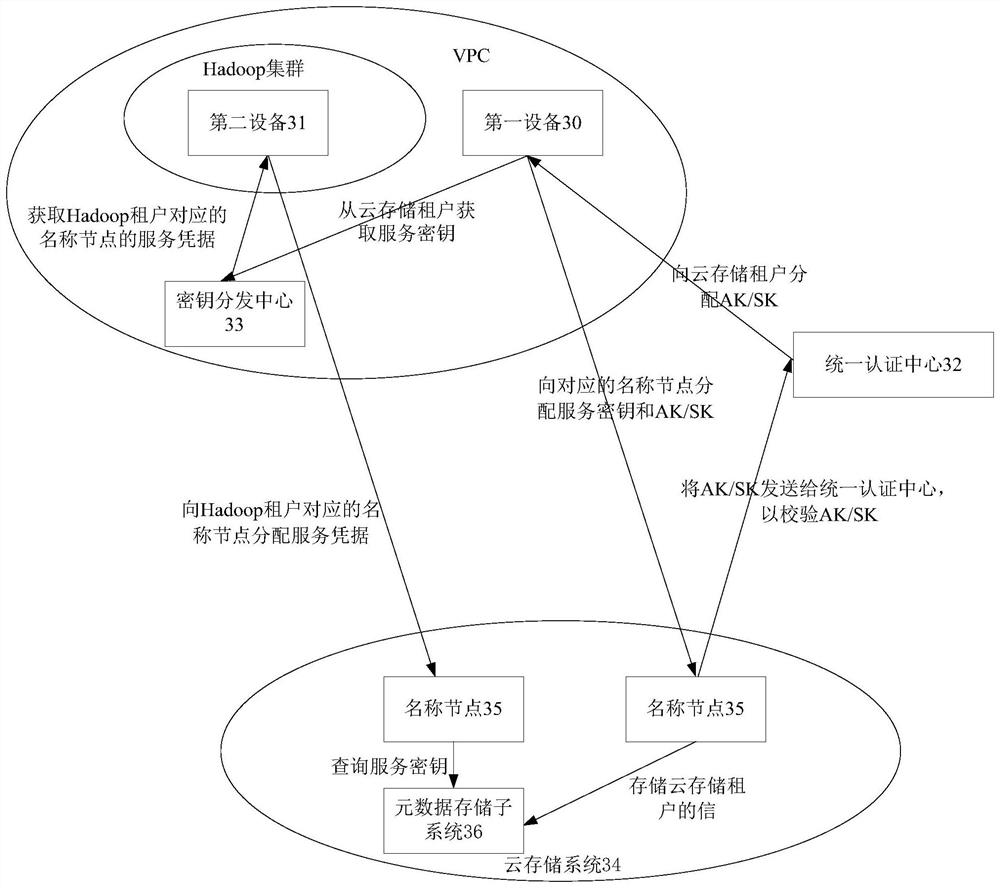
Multi-tenant authentication system and method of Hadoop cluster based on cloud storage
The invention provides a multi-tenant authentication system and method of a Hadoop cluster based on cloud storage. The cloud storage system authenticates the cloud storage tenant based on a unified authentication mode, and the first device can configure the service key into the cloud storage system only when the cloud storage tenant passes the authentication. And the key distribution center allocates a service credential to the name node corresponding to the Hadoop tenant. And the second device corresponding to the target Hadoop tenant sends a service credential to the cloud storage system. And the cloud storage system analyzes the service credential according to the service key to obtain information of the target Hadoop tenant, and authenticates the target Hadoop tenant according to the information of the target Hadoop tenant. The multi-tenant authentication system is combined with a unified authentication mode and a Kerberos authentication mode, so that the multi-tenant authentication system can be suitable for multi-tenant authentication of a Hadoop cluster.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
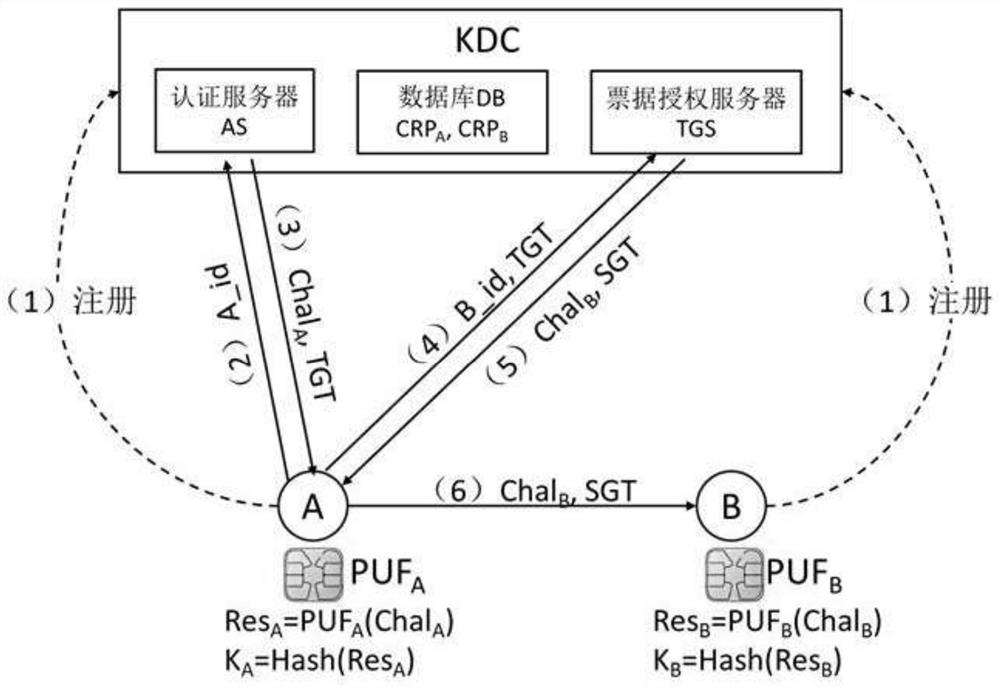
Kerberos authentication system and based on physical unclonable function
ActiveCN111682936ARealize secure transmissionPrevent leakageKey distribution for secure communicationUser identity/authority verificationAttackEngineering
The invention discloses a Kerberos authentication system and method based on a physical unclonable function, and the system comprises equipment A, equipment B, and a key distribution center (KDC), wherein the key distribution center KDC comprises an authentication server (AS), a ticket granting server (TGS), and a database (DB). The method comprises the following steps: registering equipment A andequipment B in the KDC; the equipment A requests a ticket granting ticket (TGT) from the AS; the equipment A obtains the TGT; the equipment A requests a service granting ticket from the TGS; the equipment A obtains a service granting ticket (SGT); and the equipment A requests a communication service from the equipment B. According to the method, key leakage caused by physical attacks such as invasion, semi-invasion and side channel attacks of attackers can be prevented, meanwhile, the problems of high public key calculation complexity, low speed and excessive communication bandwidth occupation are solved, and the method is suitable for resource-limited network application.
Owner:JINLING INST OF TECH
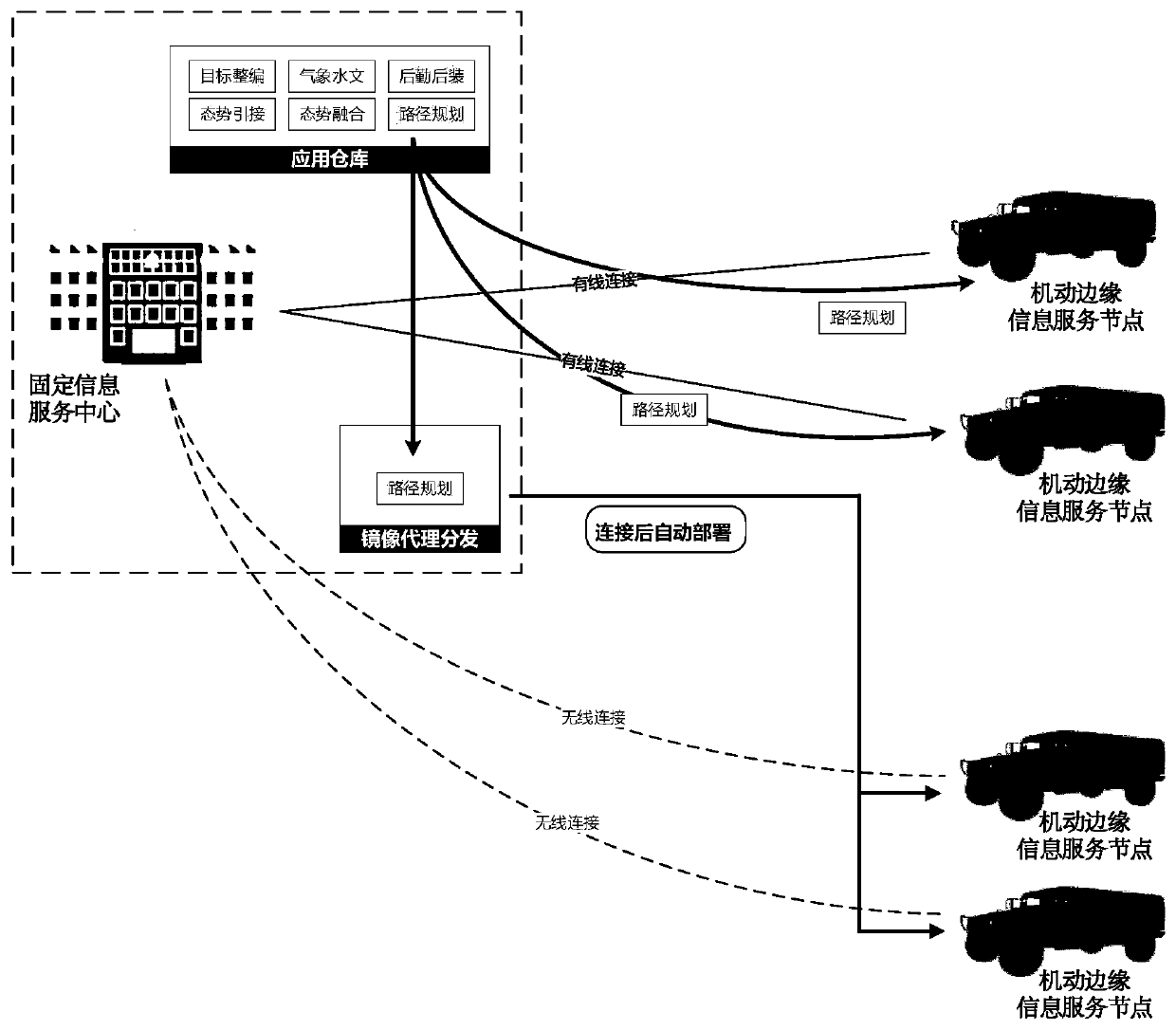
Machine-fixed multi-node integrated authorization management method
The invention relates to a machine-fixed multi-node integrated authorization management method. The method comprises the following steps: (a) networking a fixed information service center and a plurality of maneuvering edge information service nodes; (b) performing identity authentication between the fixed information service center and the plurality of maneuvering edge information service nodes based on an identity authentication model improved by a Kerberos protocol; and (c) performing cross-node data transmission between the fixed information service center or / and the plurality of maneuvering edge information service nodes. Identity authentication between the fixed information service center and the plurality of maneuvering edge information service nodes is carried out by adopting an improved identity authentication model based on a Kerberos protocol so as to be used for cross-node data transmission, so that the security of identity authentication authorization is greatly improved.
Owner:中科边缘智慧信息科技(苏州)有限公司
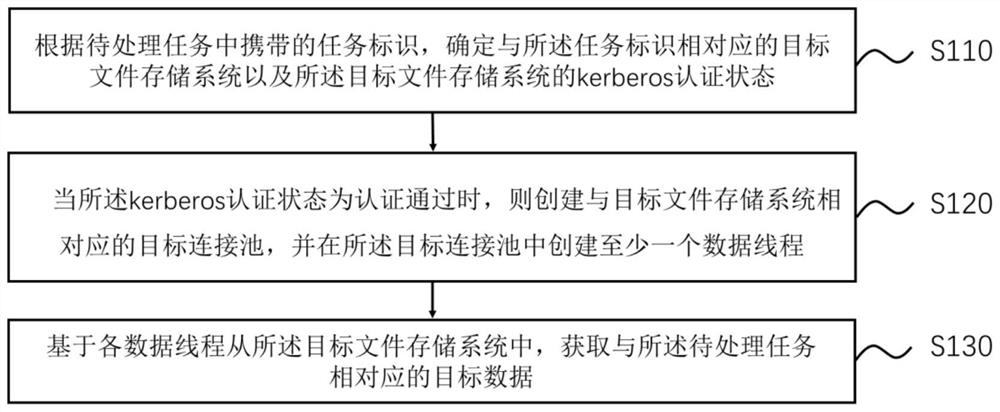
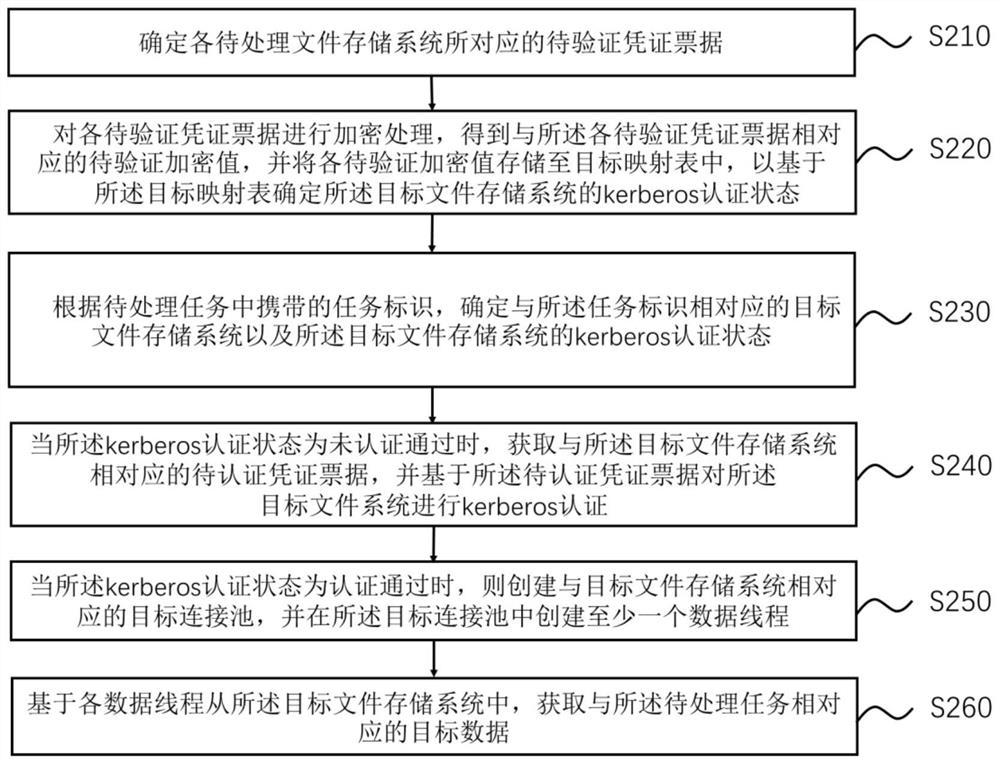
Data processing method and device and electronic equipment
PendingCN114547592ALow efficiencyHigh performance consumptionDigital data protectionDigital data authenticationComputer hardwareConnection pool
The invention discloses a data processing method and device and electronic equipment, and the method comprises the steps: determining a target file storage system corresponding to a task identifier and a kerberos authentication state of the target file storage system according to the task identifier carried in a to-be-processed task; when the Kerberos authentication state is that authentication is passed, creating a target connection pool corresponding to a target file storage system, and creating at least one data thread in the target connection pool; and obtaining target data corresponding to the to-be-processed task from the target file storage system based on each data thread. The problem of low efficiency in the data transmission process is solved, and the effect of greatly reducing the consumption performance in the data transmission is achieved.
Owner:EVERSEC BEIJING TECH
Multi-lease user method of industrial production data real-time processing platform system
InactiveCN112291244AEnsure safetySolve potential safety hazardsTransmissionDistributed File SystemFile system
The invention discloses a multi-lease user method for an industrial production data real-time processing platform system, and the method comprises the steps: 1, unifying an identity authentication service; 2, enabling the multi-lease user to create mapping with the system user; 3, performing Zeppelin login authentication module modification; 4, automatically authenticating the task; managing the user by using a unified identity authentication service and controlling the resource range of the account; creating a plurality of user accounts, enabling each user account to correspond to one group,and controlling the authority through a user file system and a distributed file system; changing the Zeppelin login authentication module to call a unified identity authentication service; and submitting the task to a cluster to realize Kerberos automatic authentication. Unified identity authentication service is adopted, multi-lease user isolation is achieved, cluster data safety is guaranteed, seamless connection between an industrial production data real-time processing platform system and a big data system platform is achieved, and user login authentication and platform service authentication authorization are completed.
Owner:CHANGZHOU MICROINTELLIGENCE CO LTD
A method for simultaneously supporting multiple kerberos authentications in a single jvm process
ActiveCN112540830BAchieve accessEfficient Kerberos authenticationSoftware simulation/interpretation/emulationTicketSoftware engineering
The present invention relates to a method for simultaneously supporting multiple Kerberos authentications in a single JVM process, the steps are as follows: to multiple Hadoop clusters that use Kerberos authentication, perform the following operations one by one; step 2.1, select a Hadoop cluster; step 2.2, set Kerberos Authentication environment variables and parameters; step 2.3, initiate a Kerberos authentication request, generate a ticket and return; step 2.4, select the next Hadoop cluster, repeat steps 2.2 and 2.3 until multiple Hadoop clusters have performed Kerberos authentication operations. In the present invention, in a JVM process (single JVM process), two or more Kerberos authentications can be used (supported) at the same time, so that software services in multiple Kerberos domains can be accessed simultaneously in a single JVM process, and more than two The data interaction of Kerberos authentication software services is enabled, providing efficient and convenient Kerberos authentication.
Owner:广州华资软件技术有限公司
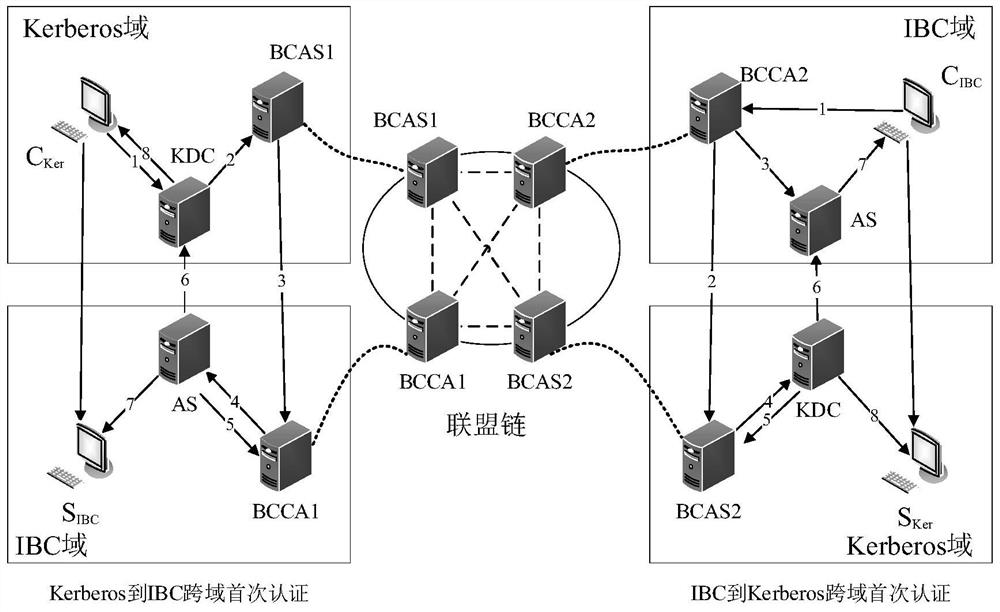
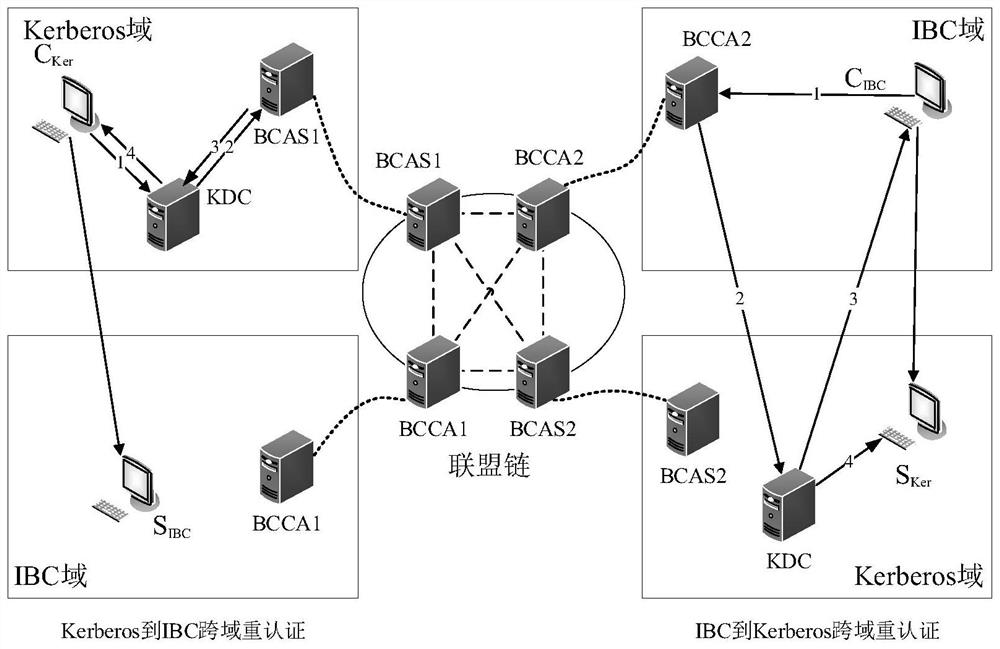
Cross-domain authentication method between Kerberos and IBC security domains based on alliance chain
ActiveCN114884698ASolve complexitySolve technical problems such as certification information management difficultiesUser identity/authority verificationManufacturing computing systemsSecurity domainEngineering
The invention relates to a cross-domain authentication method between Kerberos and IBC security domains based on an alliance chain, and the method comprises the steps: firstly authenticating the identity information of a target domain entity through a protocol when an entity node in a security domain initiates a cross-domain authentication request, then enabling the identity information of the entity to generate a cross-domain certificate, and storing the cross-domain certificate on a block chain; the authentication information cannot be tampered on the block chain and is confirmed by a plurality of cross-domain nodes according to a consensus protocol, so that decentralization of entity authentication information storage is realized; when an entity node in a security domain requests to authenticate an entity node which has been subjected to cross-domain authentication, in order to improve authentication efficiency, a cross-domain certificate can be directly sent to a target entity node, and the target entity node can complete re-authentication service of an entity identity after the validity of the target entity node is verified by a block chain. The technical problems that a cross-domain authentication centralization model between the Kerberos and the IBC is complex, authentication information management is difficult and the like are solved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
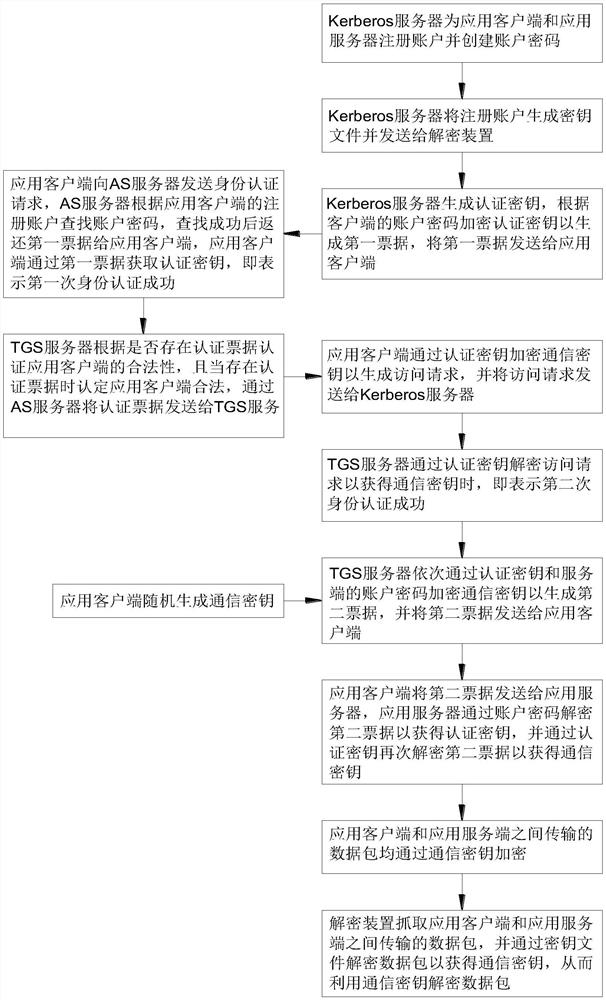
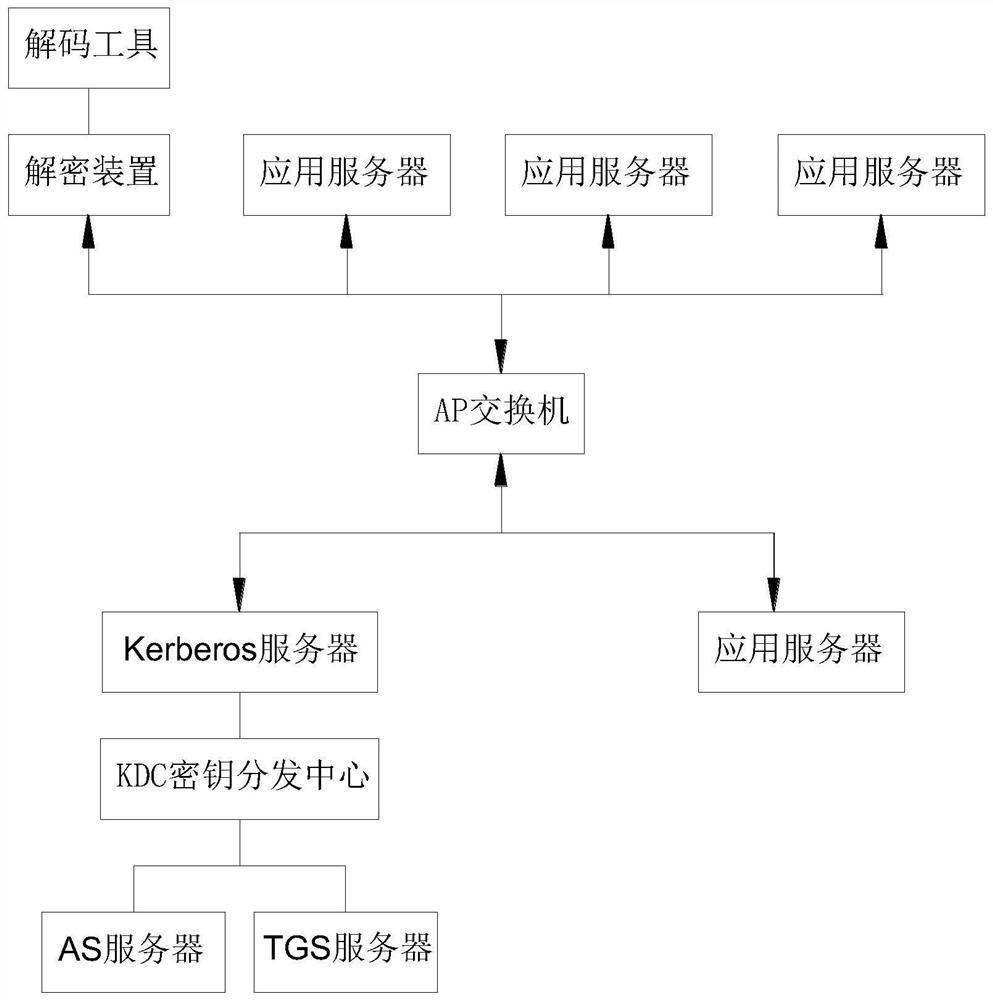
Data analysis method used in Kerberos encryption environment
PendingCN112035820AImprove communication securityImprove securityDigital data protectionDigital data authenticationKey serverApplication server
The invention provides a data analysis method used in a Kerberos encryption environment, and relates to the field of Kerberos encryption and decryption. A data analysis method used in a Kerberos encryption environment comprises the following specific steps: a Kerberos server registers an account for an application client and creates a client password, and the Kerberos server registers an account for the application server and creates a server password; the Kerberos server generates a key file according to the client password and the server password and sends the key file to the decryption device; the application client generates a communication key; the Kerberos server generates an authentication key, and encrypts the authentication key through a client password to generate a first bill. According to the invention, the problem that the communication content between the client and the server cannot be supervised in a Kerberos authentication environment is solved.
Owner:北京中安星云软件技术有限公司
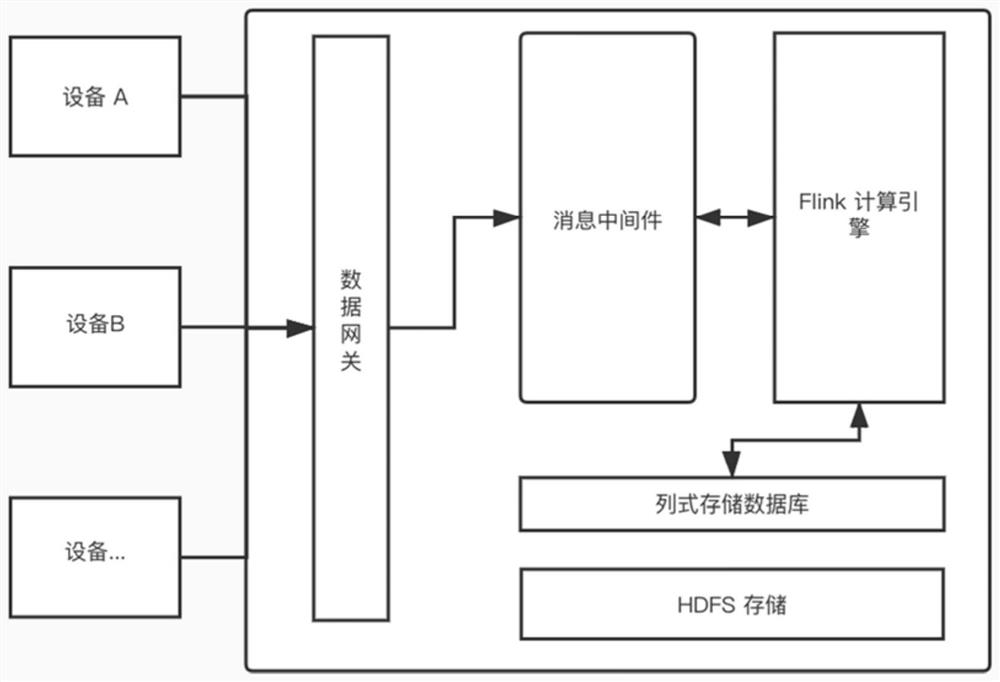
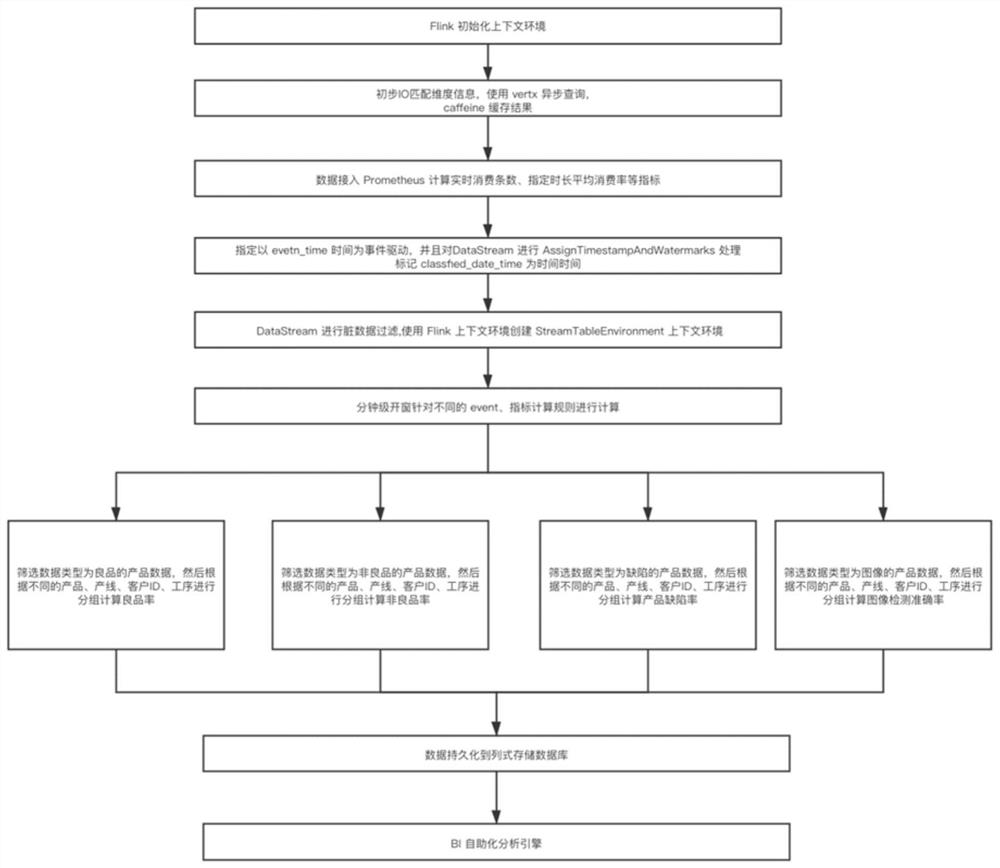
Streaming computing method and system supporting industrial data
ActiveCN111935226ASolve data collection adaptation problemsProvide quicklyTransmissionSpecial data processing applicationsBit arrayData acquisition
The invention provides a streaming processing calculation method and system for industrial data. The method comprises the steps: carrying out the data collection of equipment, obtaining a bit array generated by the equipment, recognizing an equipment field, converting the equipment field into a JSON character string, and transmitting the JSON character string to message-oriented middleware in realtime; analyzing the data information of the message-oriented middleware by using an Flink computing engine, and carrying out asynchronous matching on corresponding dimension information; performing windowing calculation on the data information according to different dimensions, writing a first calculation result into an analysis layer of the message-oriented middleware, performing index calculation, and packaging and storing a second calculation result into a column-type storage database. Data calculation is achieved through a big data flow calculation engine Flink, data storage is completedthrough a big data distributed file storage system Hadoop, and data access is safe through a kerberos network authorization protocol; the problems of data timeliness calculation, automatic analysis report and data storage safety of a current industrial enterprise are solved.
Owner:上海微亿智造科技有限公司
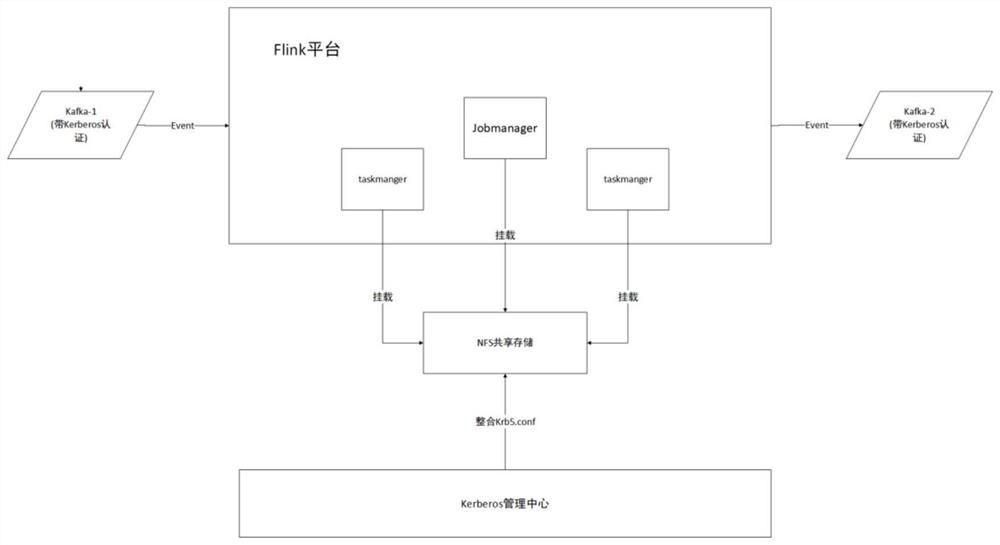
Implementation method of dynamic connection of Flink and Kerberos authentication components
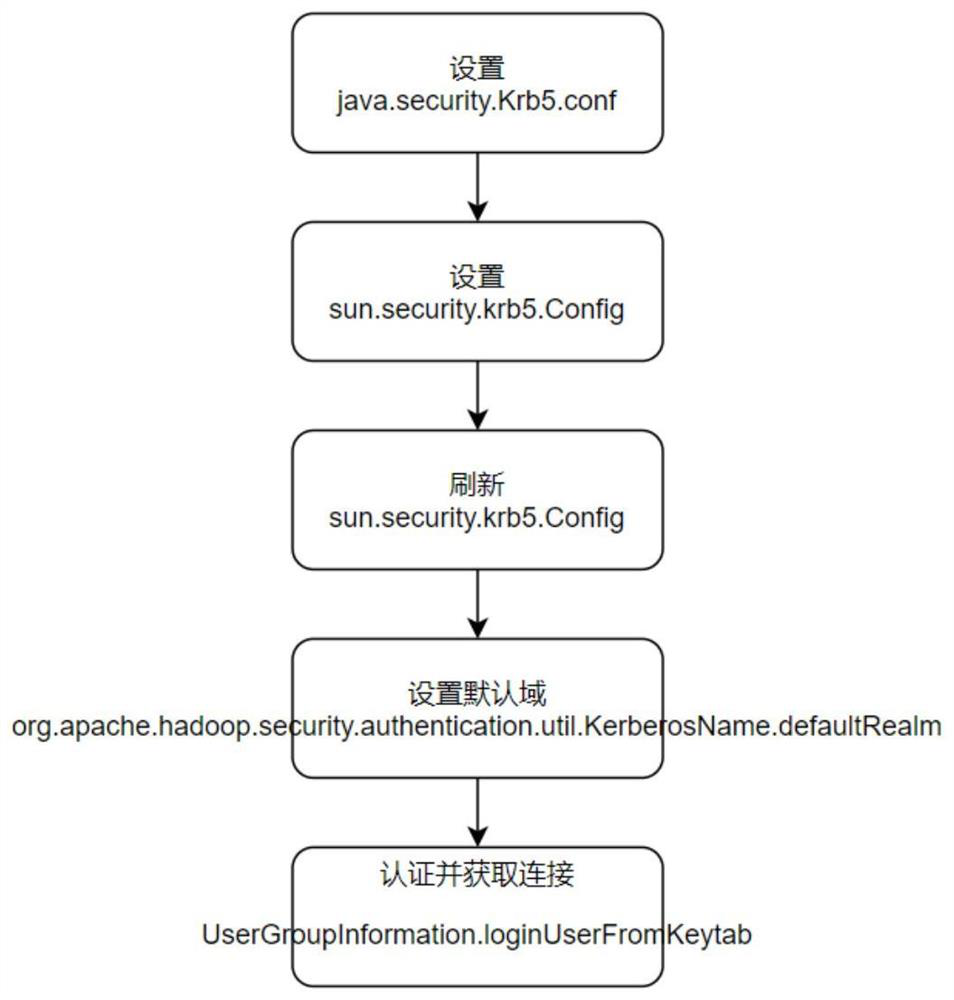
PendingCN113377454ASimplify usage complexitySolve problems such as restarting the clusterProgram loading/initiatingStorage managementDirectory
The invention relates to the field of computing, and particularly provides an implementation method of dynamic connection of Flink and Kerberos authentication components, which comprises the following steps of: S1, preparing an Flink cluster and a plurality of sets of different Kerberos authentication components; S2, mounting NFS shared storage; S3, dynamically integrating Kerberos authentication files by a Kerberos management center, and storing the Kerberos authentication files in a shared storage directory; S4, changing the flink-conf.yaml configuration file of the Flink cluster; S5, in a Job related code of the Flink, refreshing Krb5.conf related configuration in real time; and S6, operating the Job of the Flink so that the Flink cluster is successfully connected with the plurality of sets of Kerberos authentication components. Compared with the prior art, the method has the advantages that the problems that conflicts occur when Flink is connected with a plurality of different Kerberos authentication components, a cluster needs to be restarted when the Kerberos authentication components are changed and the like are solved.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com