Kerberos security enhancement method based on Intel SGX
A security, safe zone technology, applied in the field of information security, can solve problems such as system security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
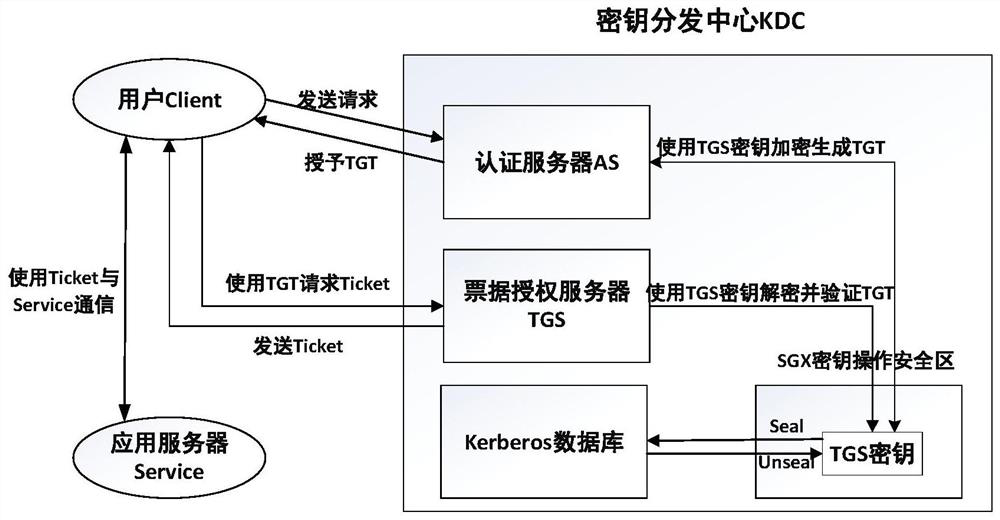
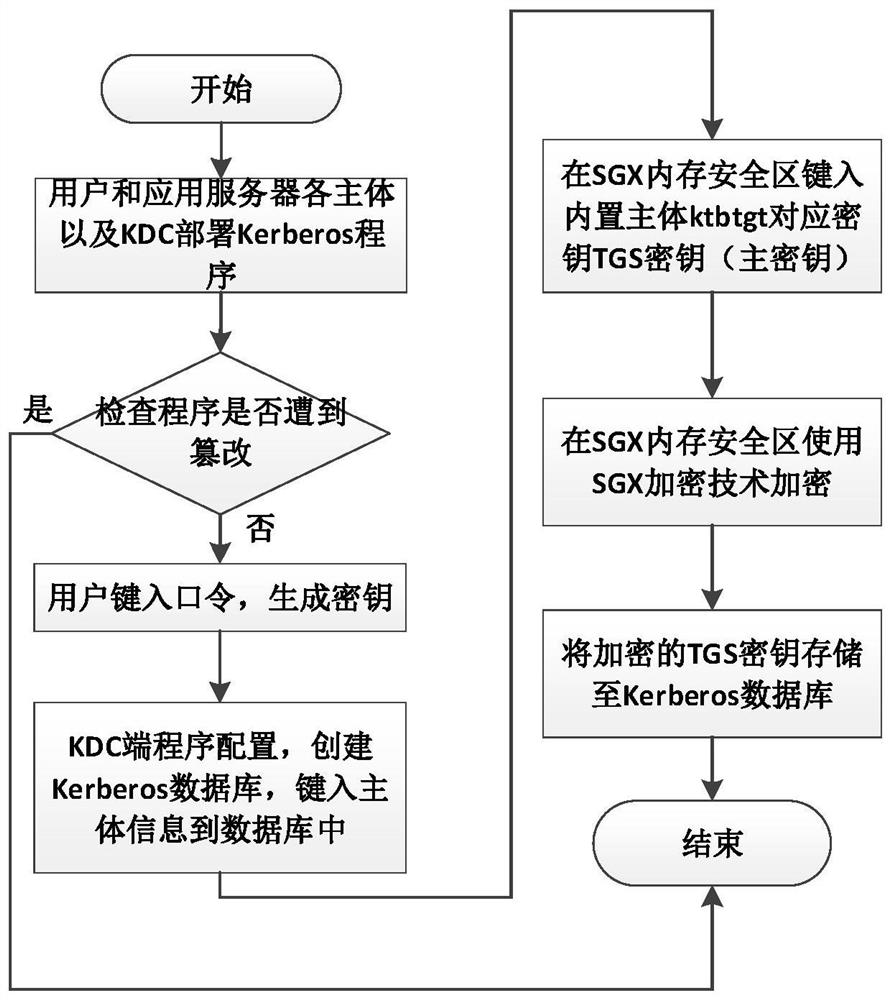
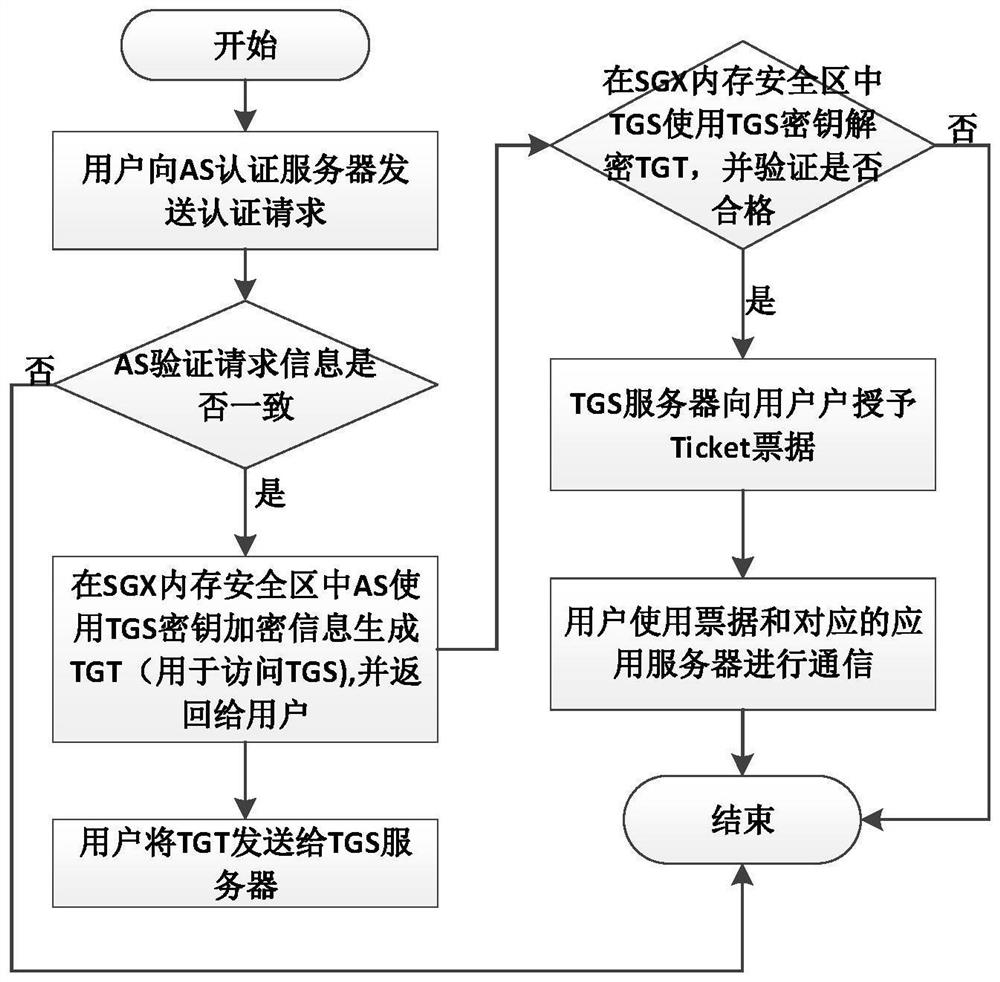
[0053] The purpose of the present invention is to provide a Kerberos security enhancement method and system based on Intel SGX, the overall framework of this scheme is as follows figure 1 As shown, the main flow chart is as figure 2 , image 3 shown. The invention mainly includes three modules: a security initialization module, a key-protected authentication service module, and a key security encapsulation module.
[0054] 1. The security initialization module is mainly to complete the deployment of the user and the main body of the application server and the Kerberos program of the KDC, and complete the relevant configuration. The main steps are as follows:
[0055] (1-1): The user and the application server deploy the Kerberos program, and check whether the program has been tampered with after the deployment is complete.
[0056] (1-2) The user configures the program, enters the user password and generates a user key for Kerberos authentication.
[0057] (1-3): The adm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com