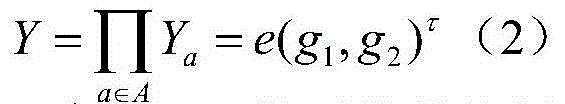Patents
Literature
135 results about "Key distribution center" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
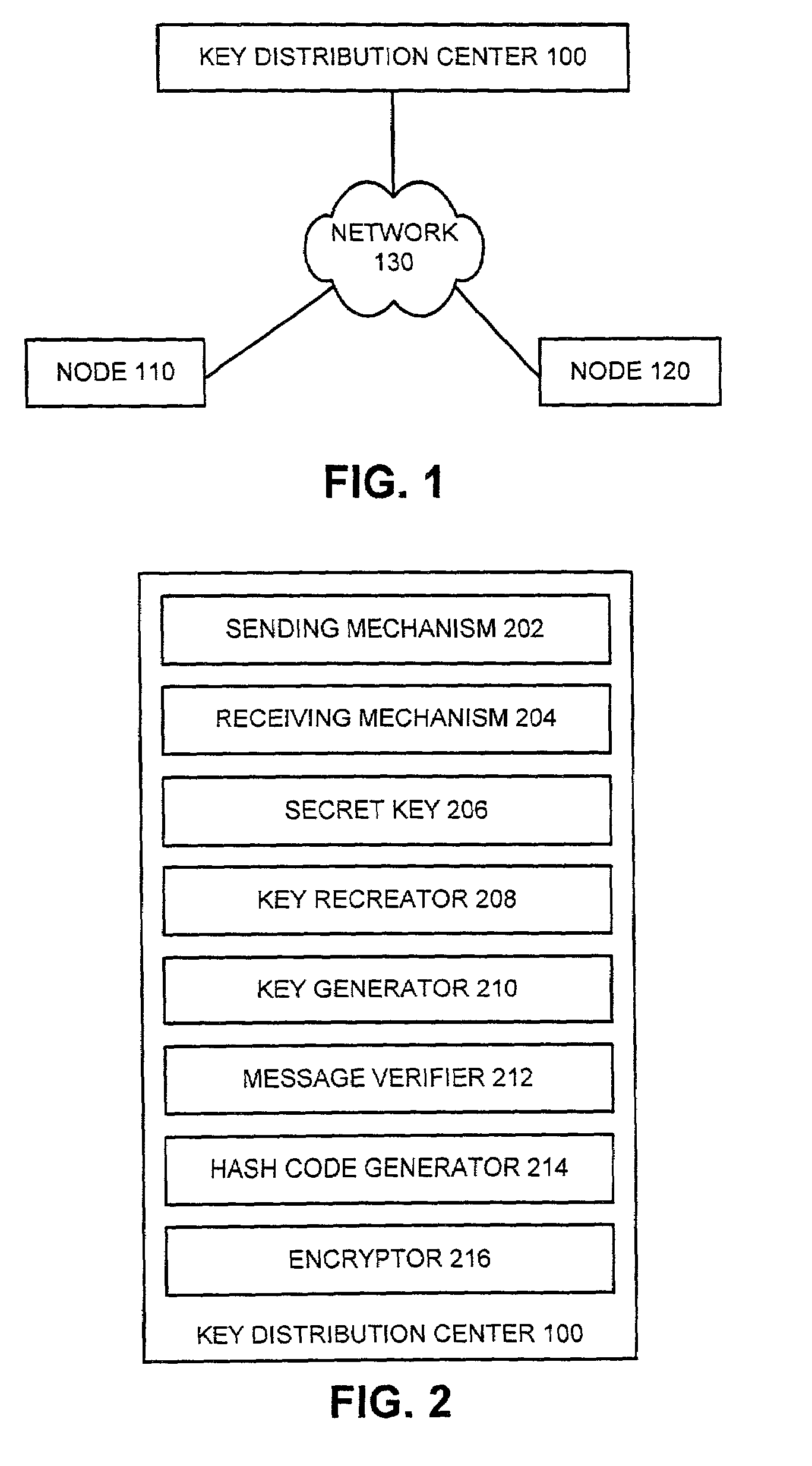
In cryptography, a key distribution center (KDC) is part of a cryptosystem intended to reduce the risks inherent in exchanging keys. KDCs often operate in systems within which some users may have permission to use certain services at some times and not at others.
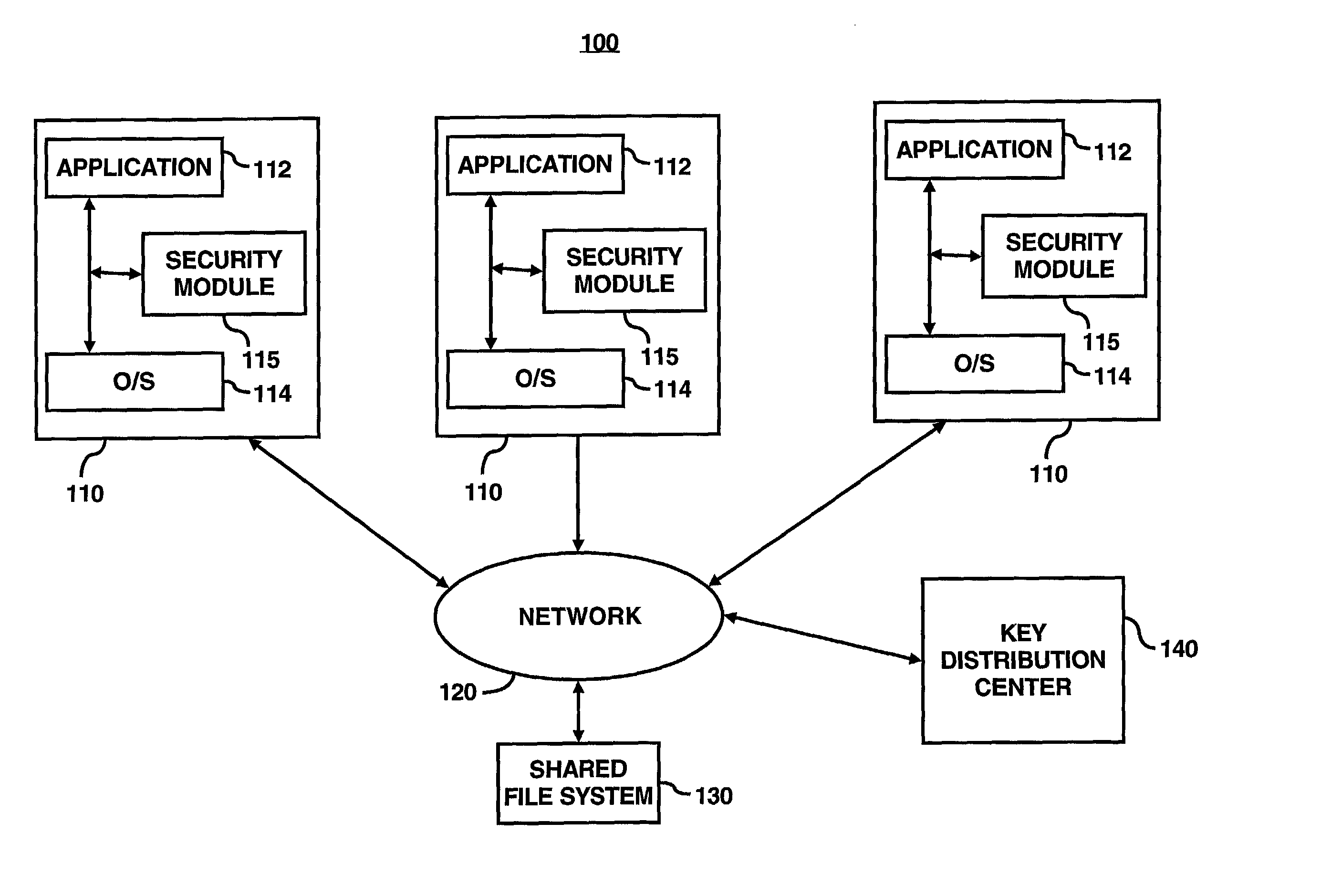
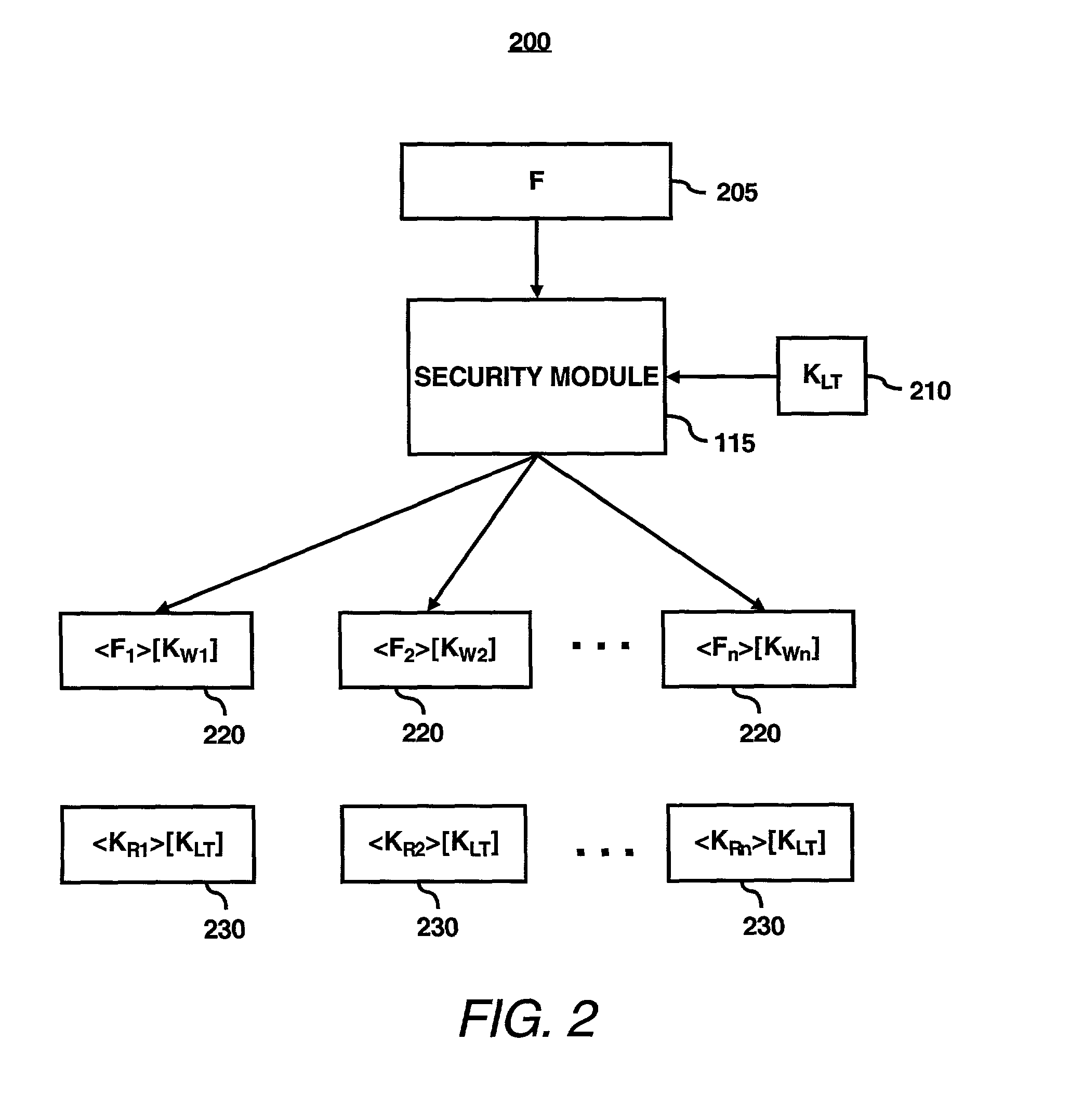
System for ensuring data privacy and user differentiation in a distributed file system
ActiveUS20030081790A1Key distribution for secure communicationComputer security arrangementsDistributed File SystemFile system
In accordance with an embodiment of the present invention, a security module may be configured to provide an owner the capability to differentiate between users. In particular, the security module may be configured to generate an asymmetric read / write key pair for respectively decrypting / encrypting data for storage on a disk. The owner of the file may distribute the read key of the asymmetric key pair to a group of users that the owner has assigned read-permission for the encrypted data, i.e., a group that has read-only access. Moreover, the owner of the file may distribute the write key of the asymmetric pair to another group of users that the owner has assigned write-permission for the encrypted data, i.e., users in the write-permission group may modify the data. Alternatively, the security module may be configured to throw away the write key and not allow further re-use of the key. The security modules may also be configured to encrypt the read key for with a further key for additional protection while stored. The security module may be also configured to generate a first set of read / write key pairs for fragments of a file. Each file fragment is encrypted with a different write key from the set of read / write key pairs. The respective read keys may then be encrypted with a second long-lived key pair chosen by the owner of the file. The security module may then configured to store the encrypted file fragment and the associated encrypted read key in a storage area of a shared computer system accessible to the users of the shared computer system. The security module may also be configured to provide distribution of the required keys-either the read / write keys for direct use, or the long-lived keys for indirect use-either by means of the data owners themselves, or through use of a key distribution center.
Owner:MATSUSHITA KOTOBUKI ELECTRONICS IND LTD +1
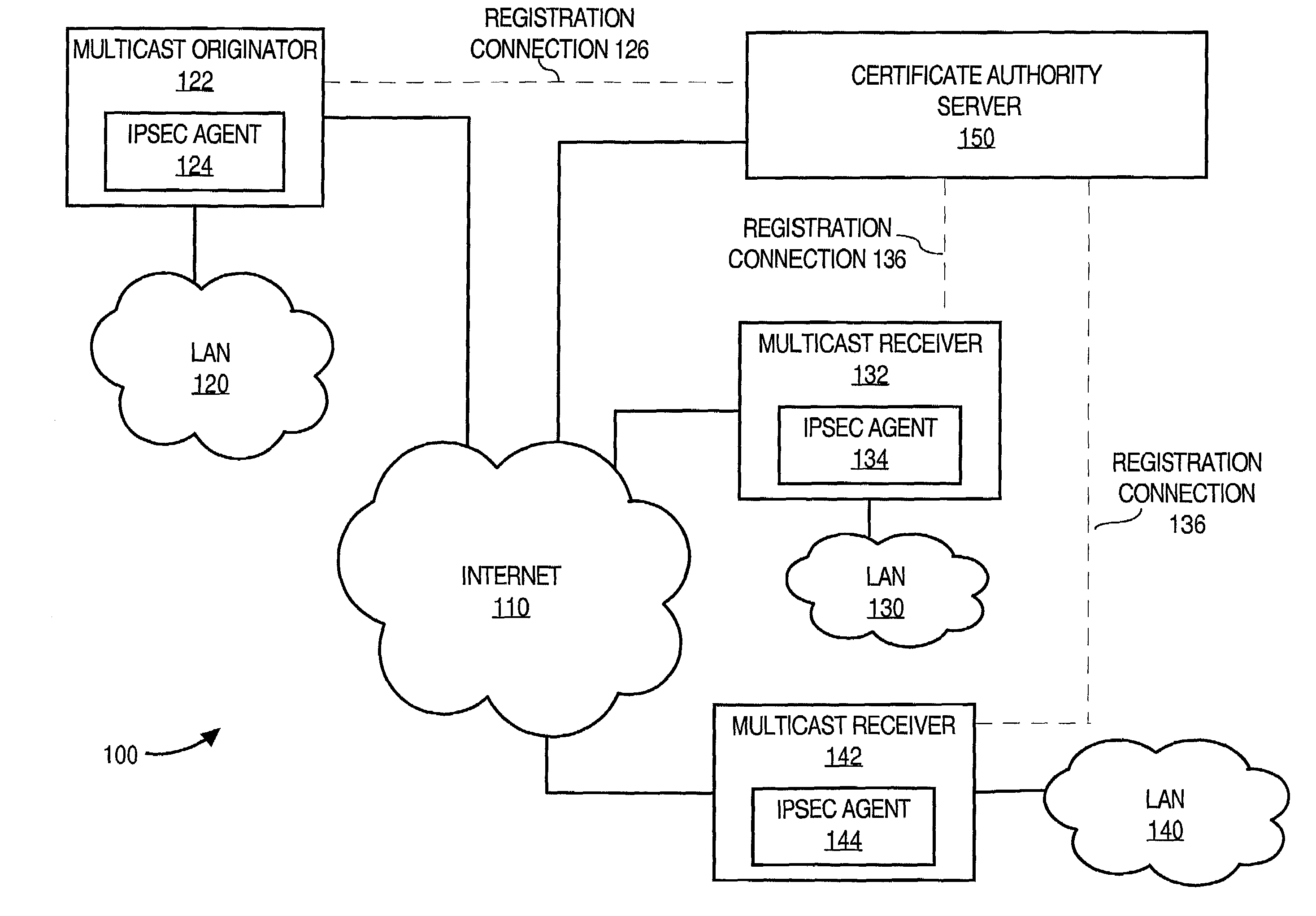
Facilitating secure communications among multicast nodes in a telecommunications network
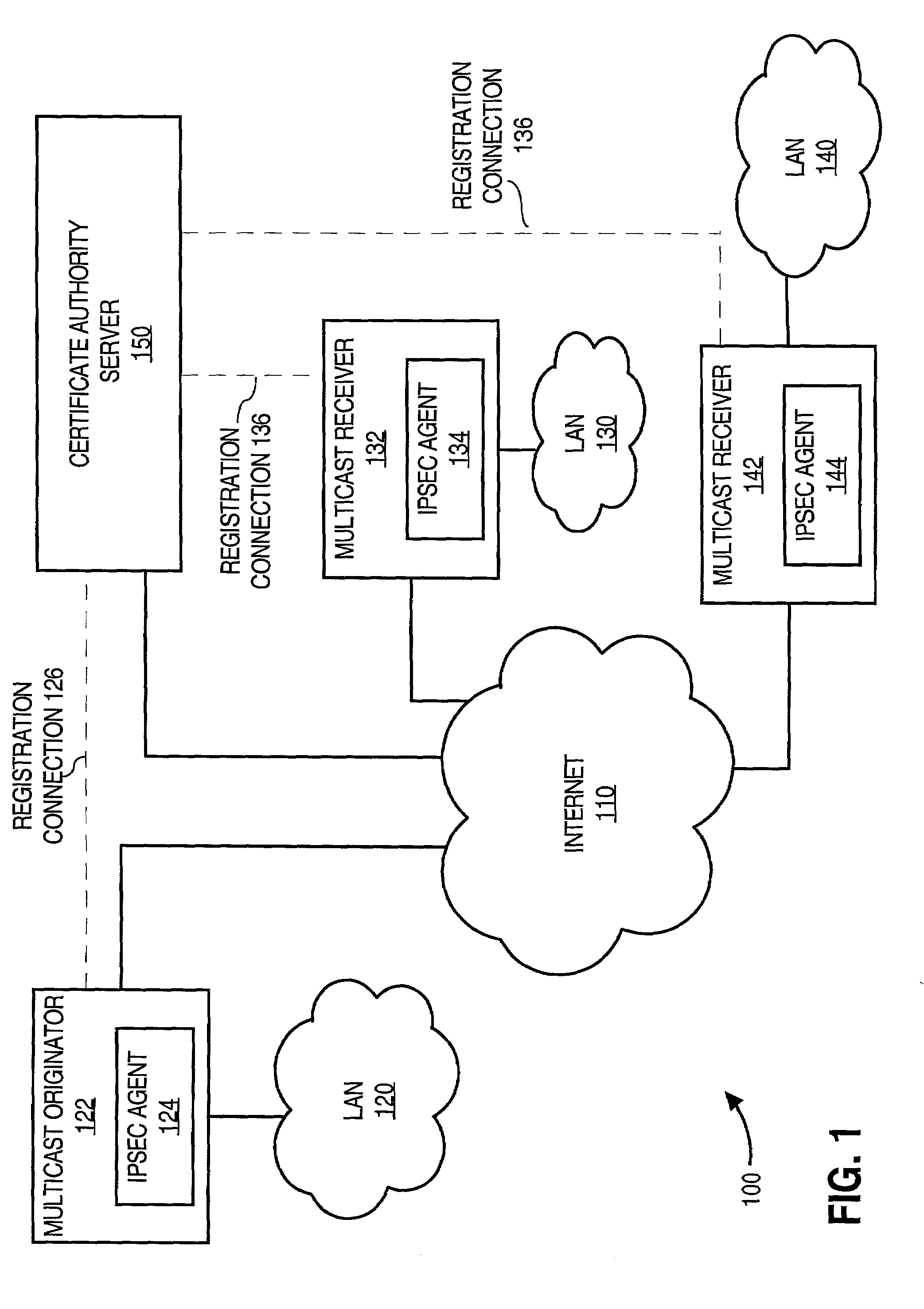
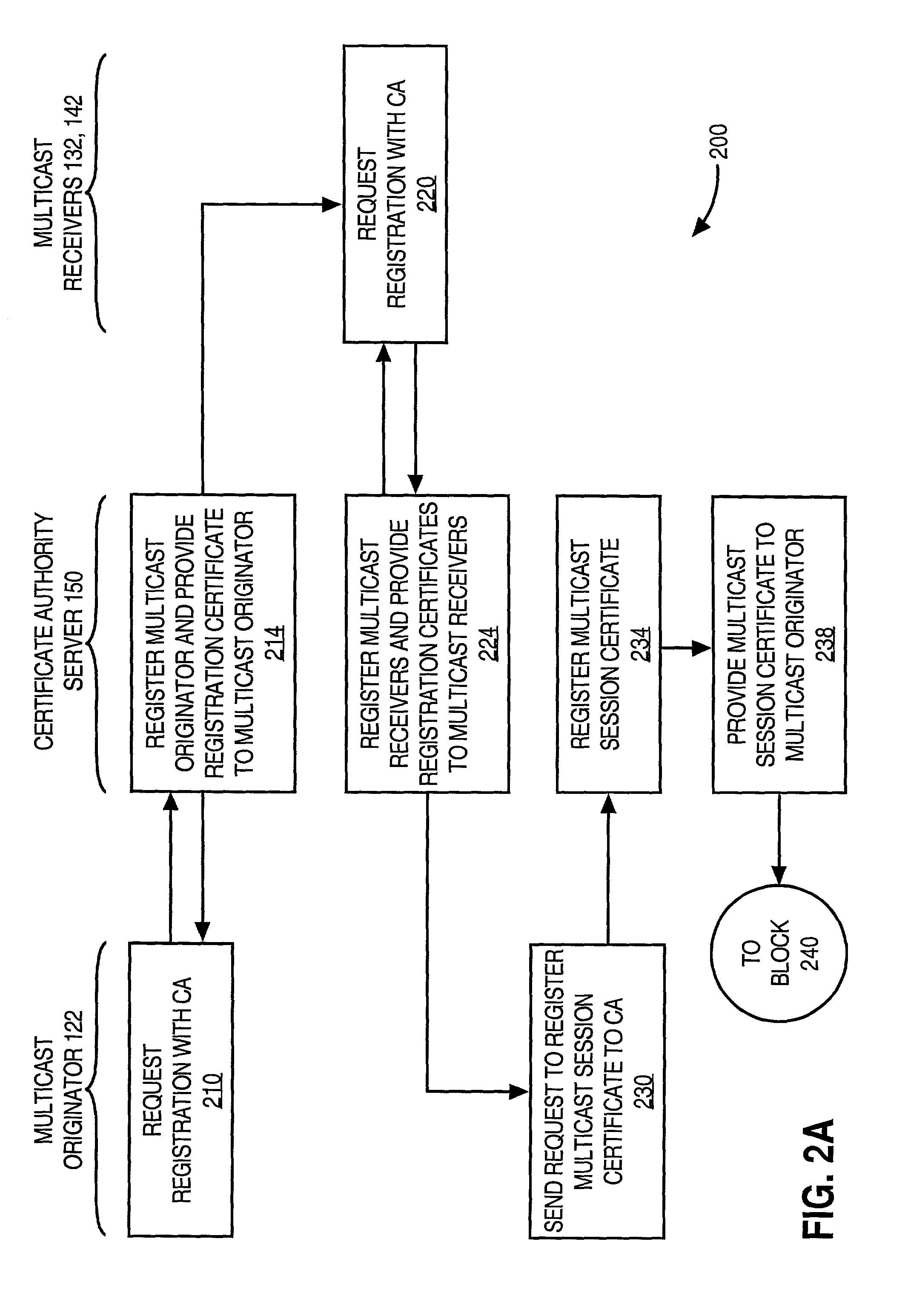
An approach for facilitating secure communications among multicast nodes in a telecommunications network is disclosed. A source node sends an encryption key and an identifier to an authoritative node that stores the encryption key and associates the identifier with the encryption key. The source node encrypts data using the encryption key and sends the encrypted data with the identifier in a multicast. The multicast destination nodes retrieve the encryption key from the authoritative node based on the identifier and then decrypt the multicast. A list of administrative nodes, a list of authorized nodes, and an expiration time may be used to manage the encryption key. The authoritative node may be a certificate authority or key distribution center, and the source node may encrypt the multicast using the Internet security protocol (IPsec) or secure socket layer (SSL). Thus, communications among multicast nodes may be efficiently secured in a scalable manner.
Owner:CISCO TECH INC
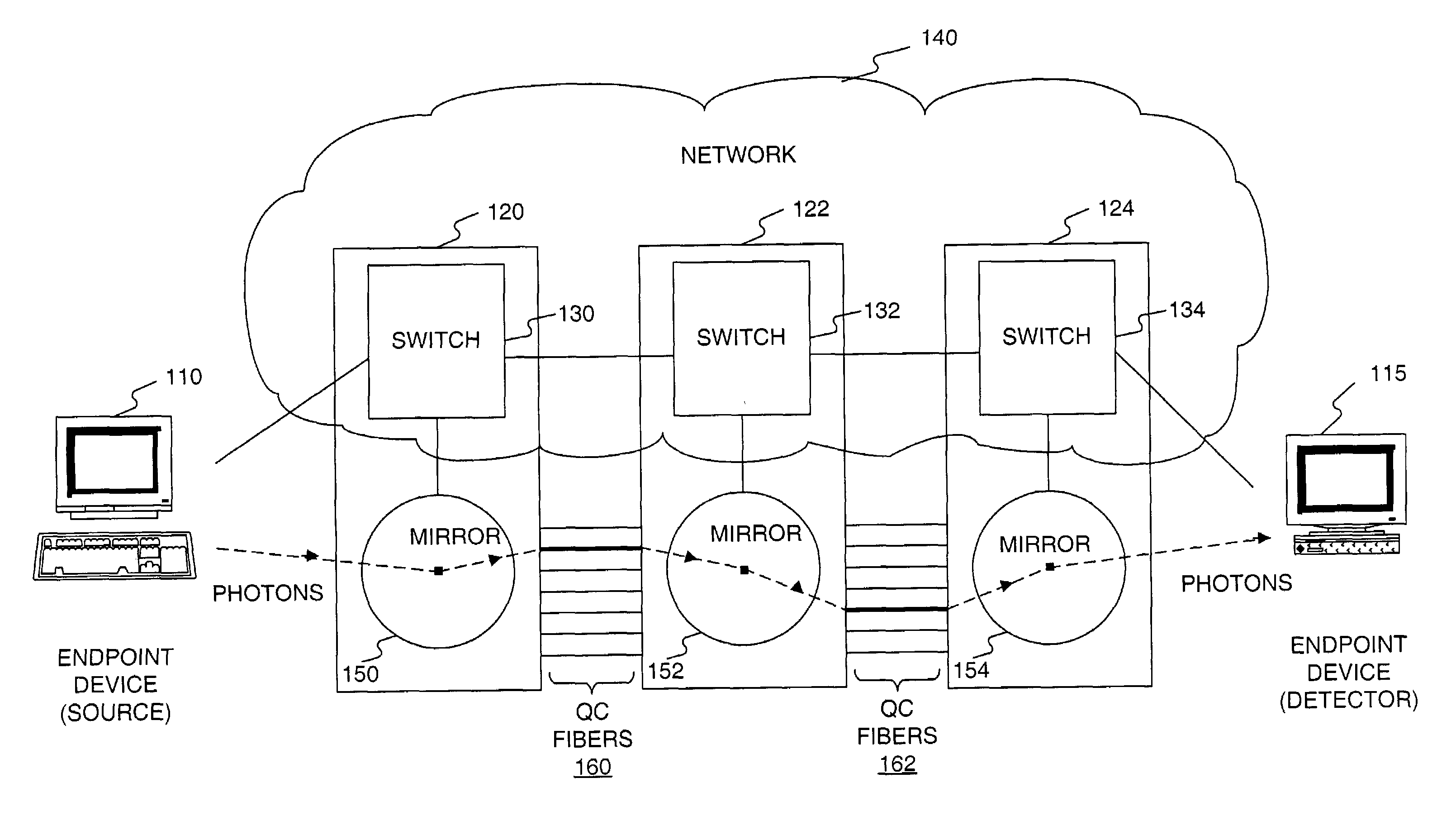
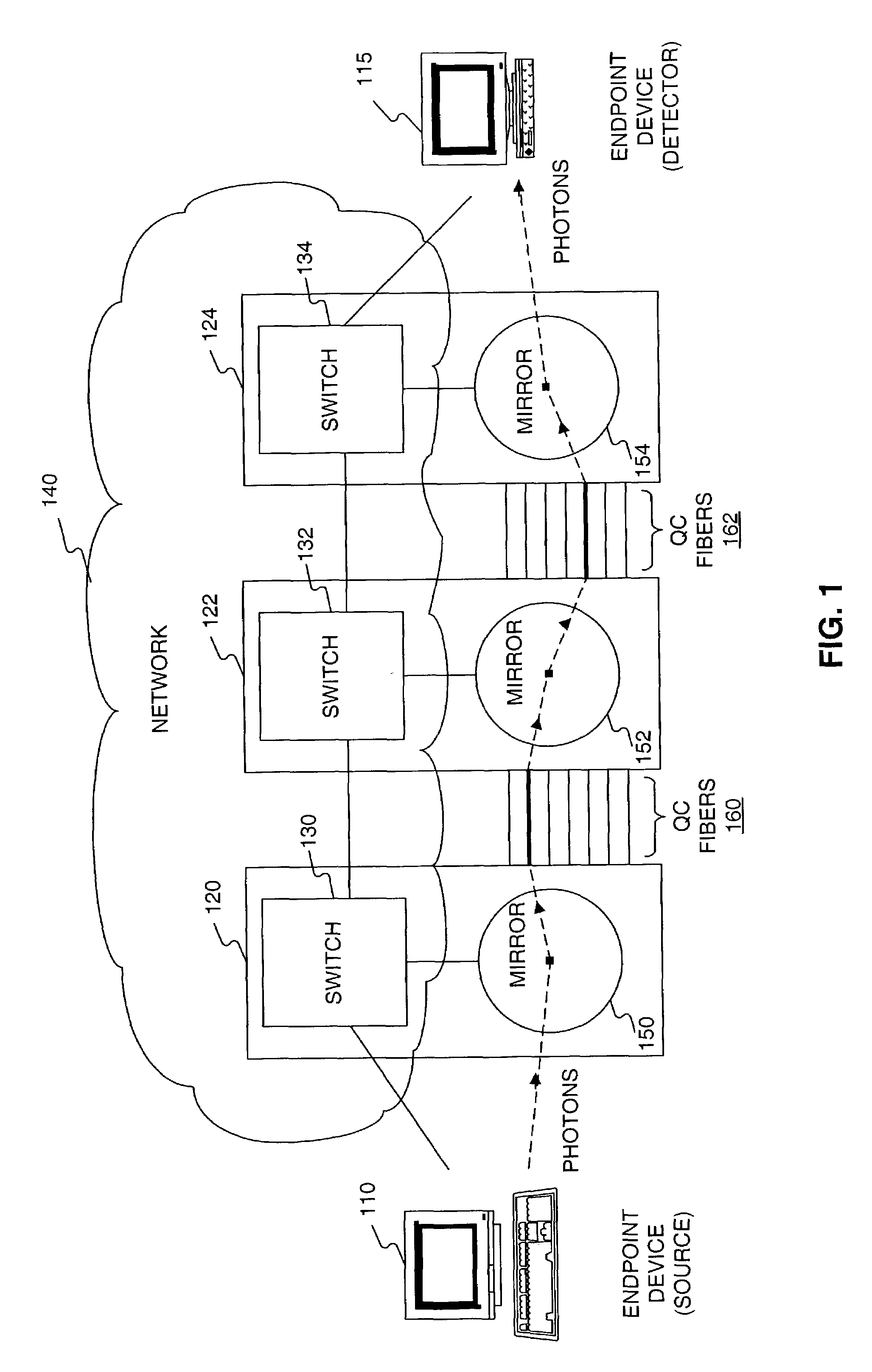
Key distribution center for quantum cryptographic key distribution networks
InactiveUS7457416B1Key distribution for secure communicationUser identity/authority verificationSecure communicationUser device
Methods and systems are provided for distributing key information by securely transmitting light information in a network along a path comprised of a plurality of network devices and by using a key distribution center (KDC) connected with the network. Three or more user devices connected with the network are specified as constituting a secure communication group. Each user device sets up an end-to-end path to the KDC by configuring at least one of the network devices to direct light information along the path. Thereafter, a user key is established between each user device and the KDC, by sending light information using randomly selected quantum bases through the path. The KDC determines a shared secret key, and notifies each user device of the shared secret key by sending the result of a calculation based on the shared secret key and each user key through the network.
Owner:RAYTHEON BBN TECH CORP
Internet protocol telephony security architecture
InactiveUS20050027985A1Communication securitySpecial service provision for substationKey distribution for secure communicationMultiple encryptionSecure communication
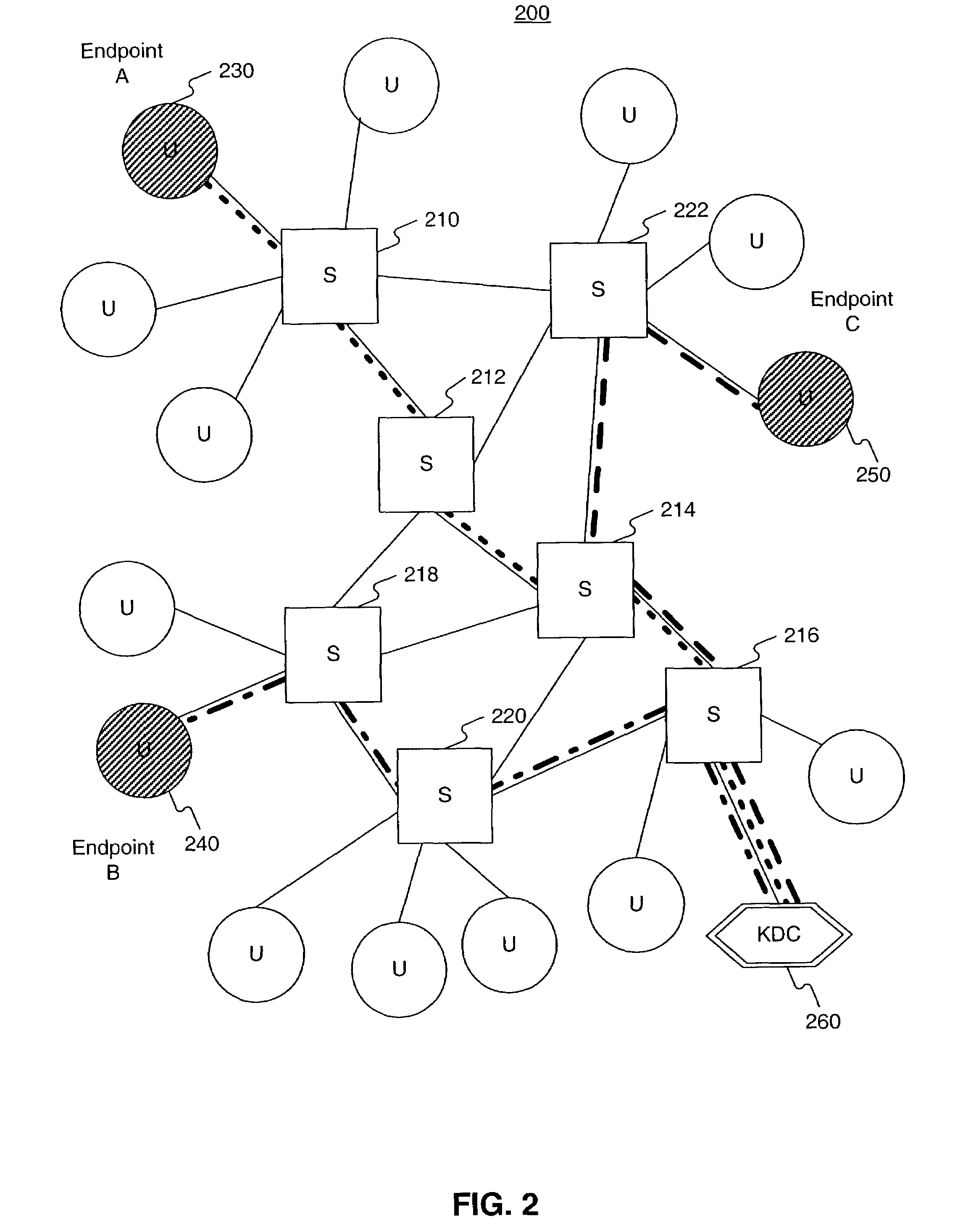
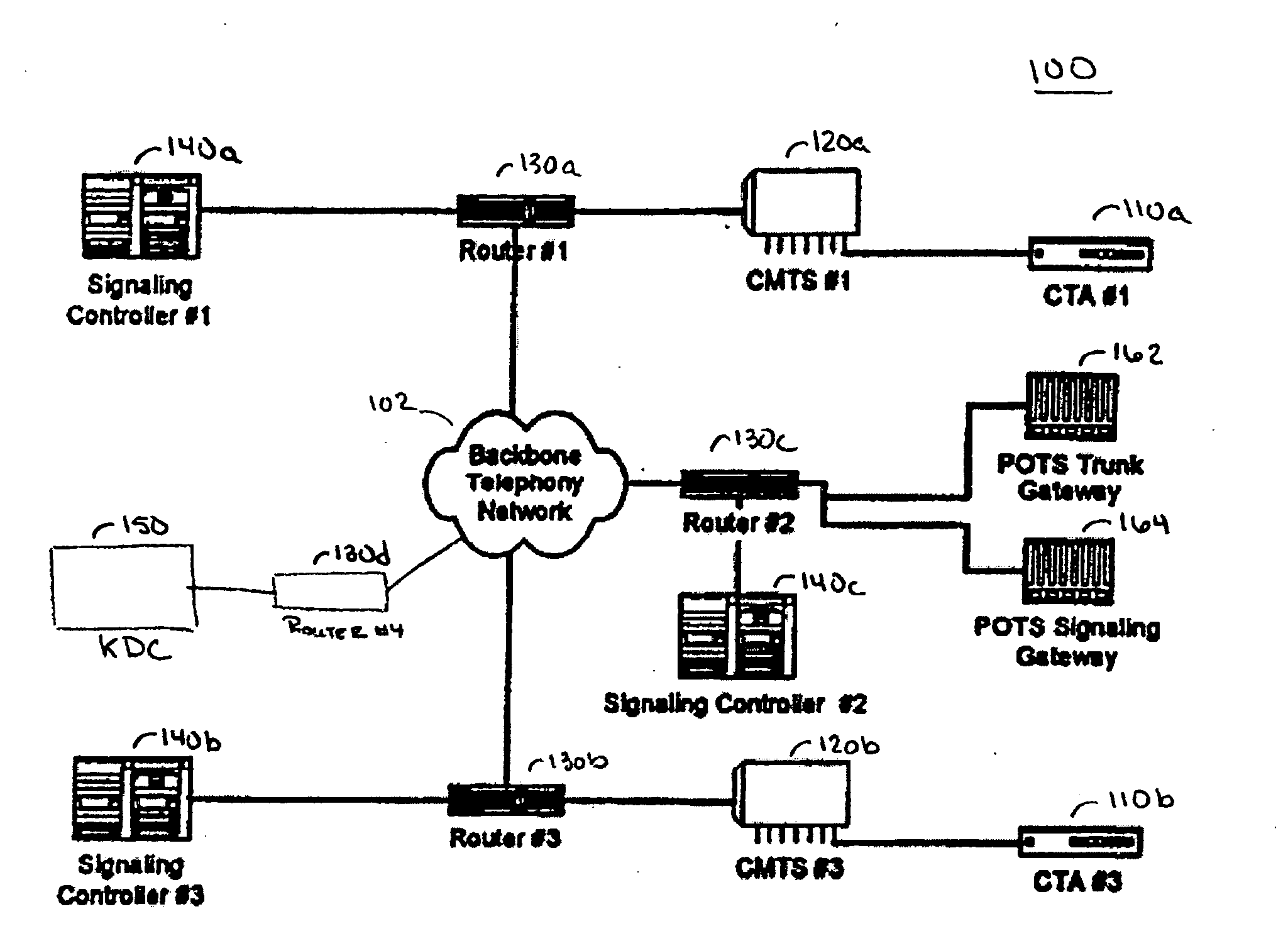
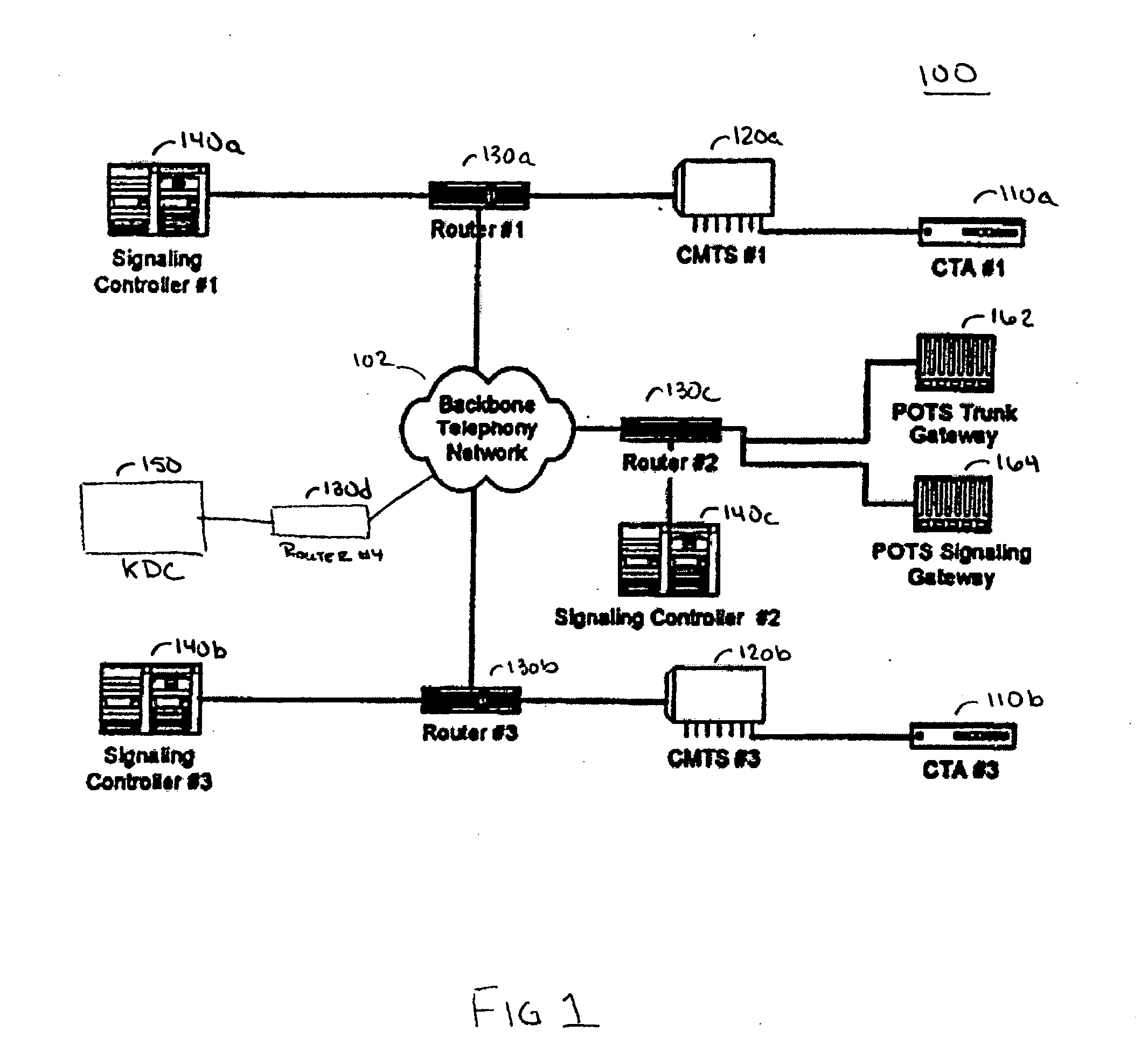
A secure Internet Protocol (IP) telephony system, apparatus, and methods are disclosed. Communications over an IP telephony system can be secured by securing communications to and from a Cable Telephony Adapter (CTA). The system can include one or more CTAs, network servers, servers configured as signaling controllers, key distribution centers (KDC), and can include gateways that couple the IP telephony system to a Public Switched Telephone Network (PSTN). Each CTA can be configured as secure hardware and can be configured with multiple encryption keys that are used to communicate signaling or bearer channel communications. The KDC can be configured to periodically distribute symmetric encryption keys to secure communications between devices that have been provisioned to operate in the system and signaling controllers. The secure devices, such as the CTA, can communicate with other secure devices by establishing signaling and bearer channels that are encrypted with session specific symmetric keys derived from a symmetric key distributed by a signaling controller.
Owner:GOOGLE TECH HLDG LLC
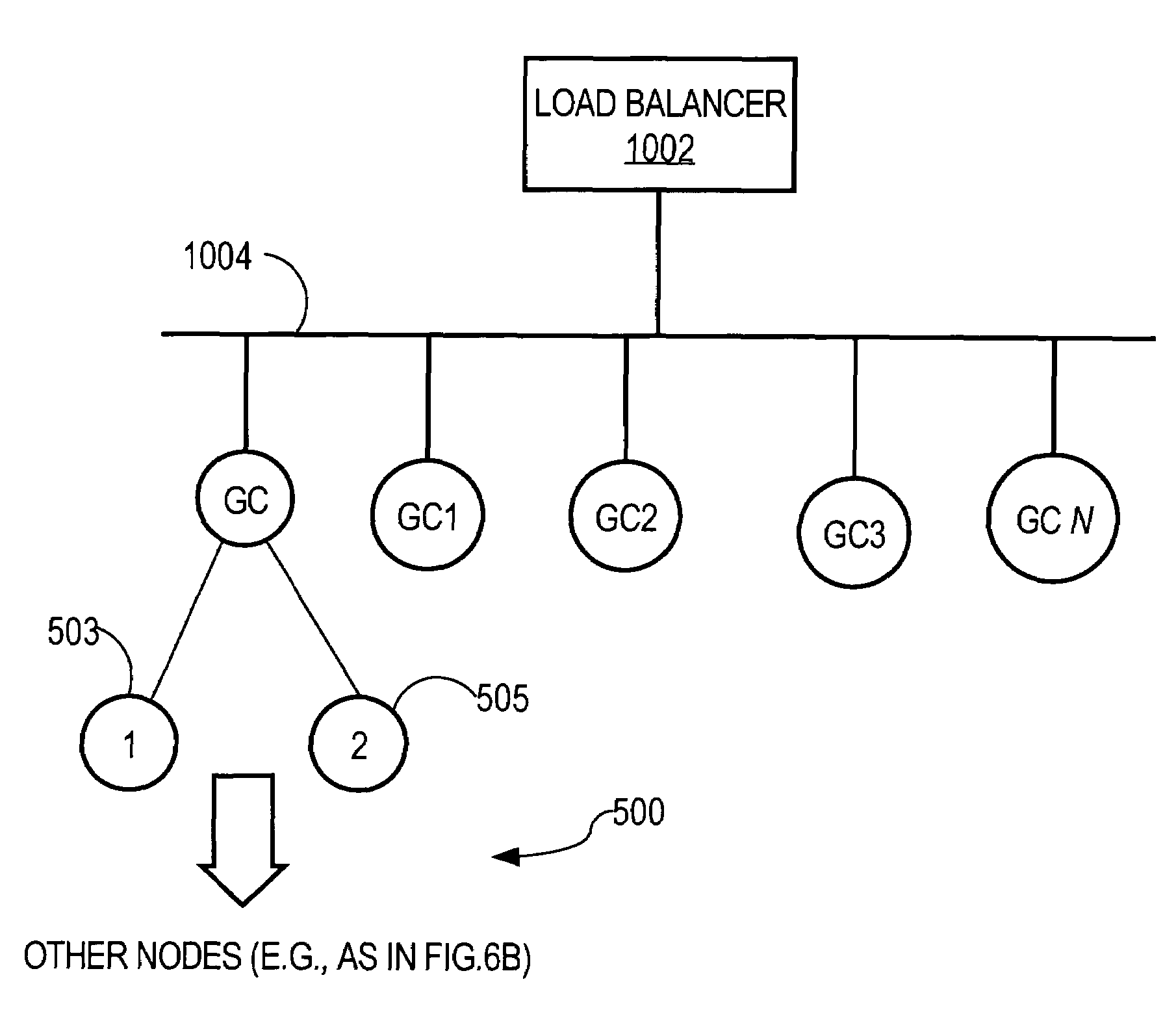
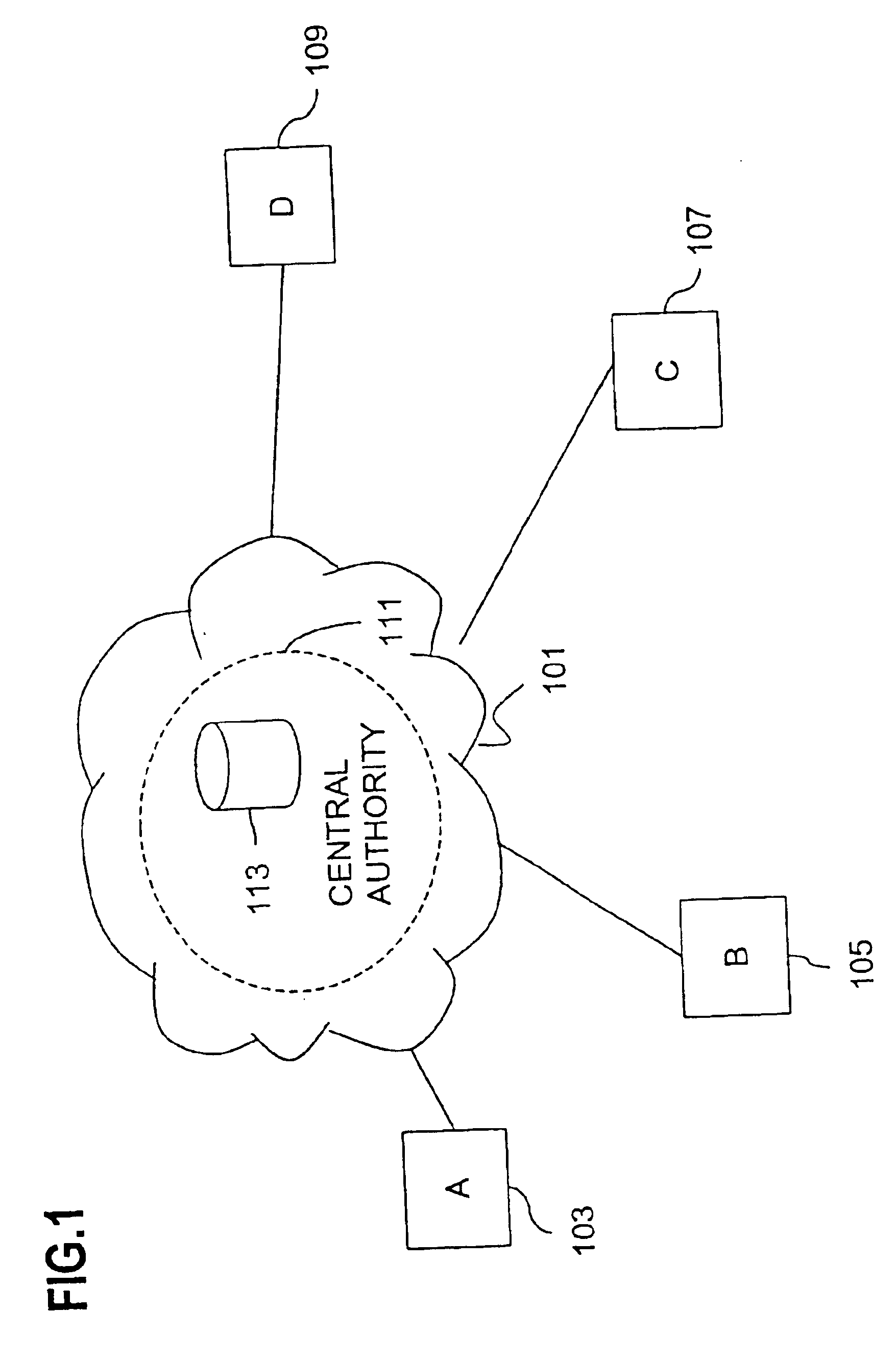
Method for overcoming the single point of failure of the central group controller in a binary tree group key exchange approach
InactiveUS7260716B1Improve scalabilityLess attentionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkStructure of Management Information
An approach for managing addition or deletion of nodes in a multicast or broadcast group, which avoids introducing a single point of failure at a group controller, certificate authority, or key distribution center, is disclosed. A central group controller utilizes a binary tree structure to generate and distribute session keys for the establishment of a secure multicast group among multiple user nodes. The central group controller is replicated in a plurality of other group controllers, interconnected in a network having a secure communication channel and connected to a load balancer. The secure communication channel is established using a public key exchange protocol. The load balancer distributes incoming join / leave requests to a master group controller. The master group controller processes the join or leave, generates a new group session key, and distributes the new group session key to all other group controller replicas. Each group controller is successively designated as master group controller in real time when a former master group controller crashes or relinquishes its master authority.
Owner:CISCO TECH INC
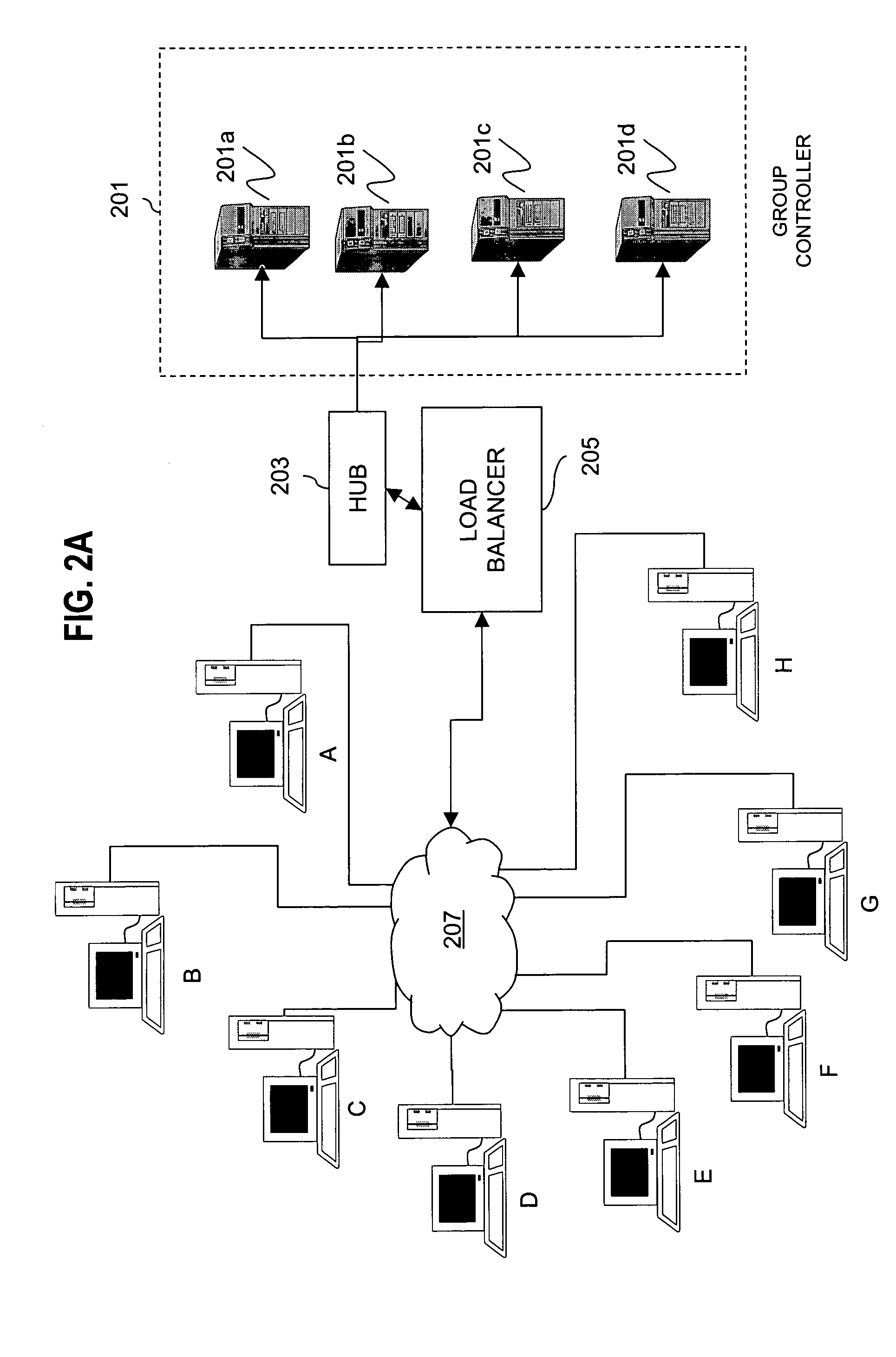
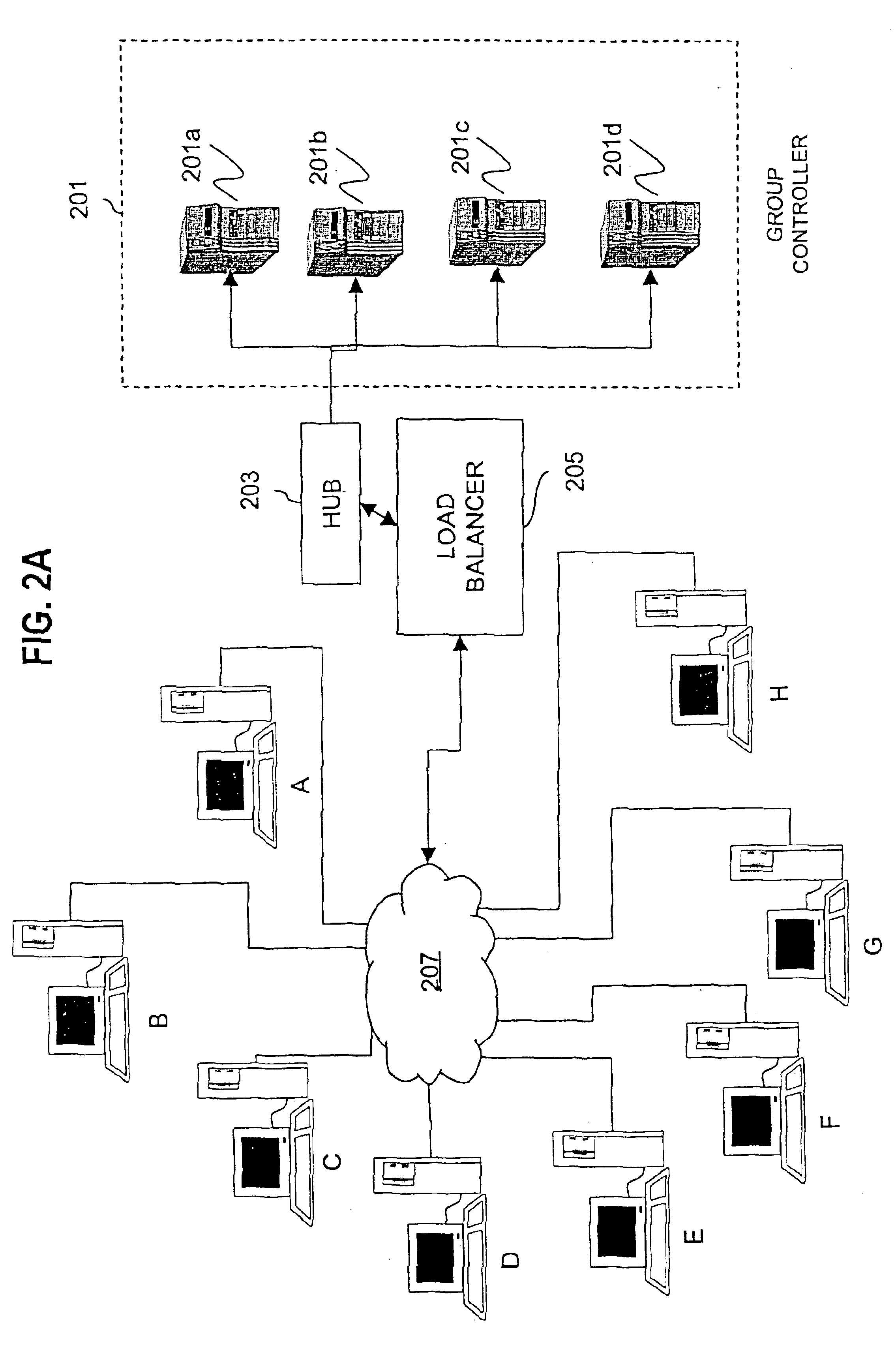
Method and apparatus for distributing and updating group controllers over a wide area network using a tree structure
InactiveUS6901510B1Reduces the workload on the group controllerSpecial service provision for substationKey distribution for secure communicationBinary treeWide area network
Apparatus and computer-readable media are disclosed for establishing secure multicast communication among multiple multicast proxy service nodes of domains of a replicated directory service that spans a wide area network. Domains are organized in a logical tree. Each domain has a logical tree that organizes the multicast proxy service nodes, a group manager at the root node, a multicast key distribution center, multicast service agent, directory service agent and key distribution center. Multicast proxy service nodes store a group session key and a private key. Replication of the directory performs key distribution. A multicast group member joins or leaves the group by publishing message. The local key distribution center and multicast service agent obtain the publisher's identity from a local directory service agent. Based on the identity, a secure channel is established with the directory service agent in the group member's domain. Keys of the binary tree branch that contains the joining or leaving node are updated, and an updated group session key and a new private key are received.
Owner:CISCO TECH INC
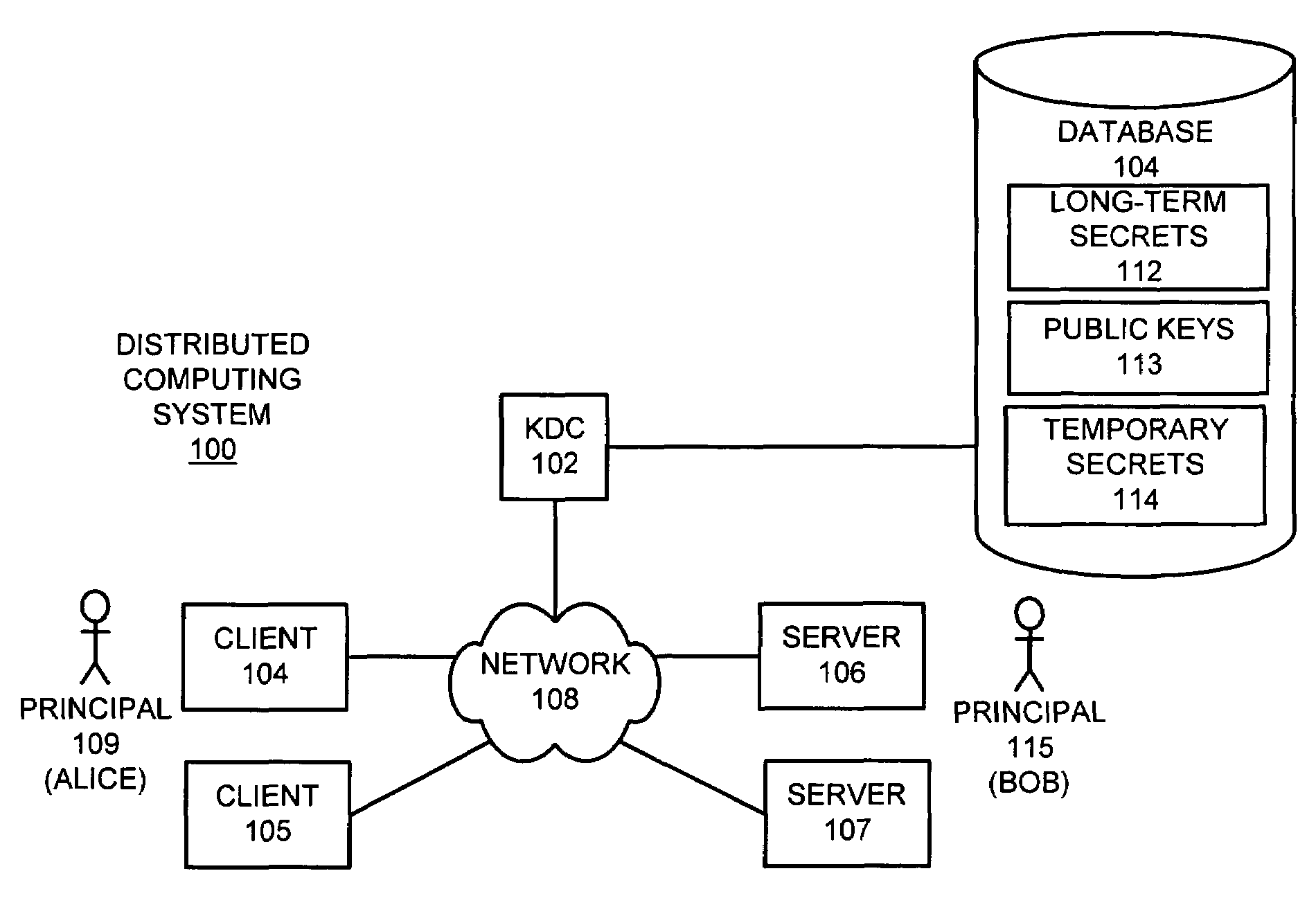
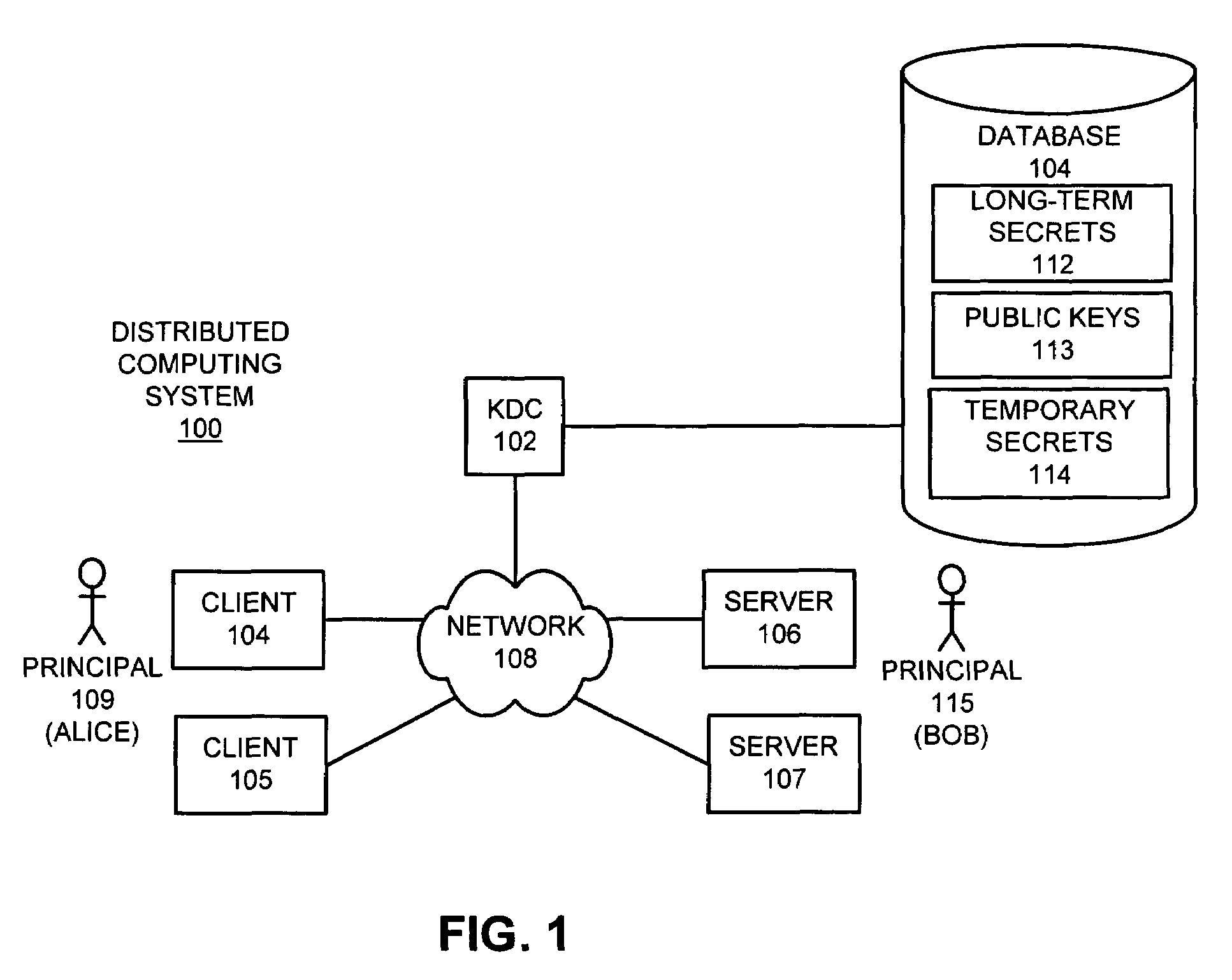
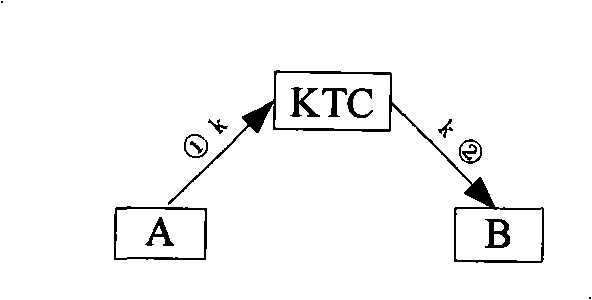
Method and apparatus for providing a key distribution center without storing long-term server secrets
InactiveUS7395549B1Facilitates secure communicationFacilitate communicationKey distribution for secure communicationDigital data processing detailsSecure communicationClient-side
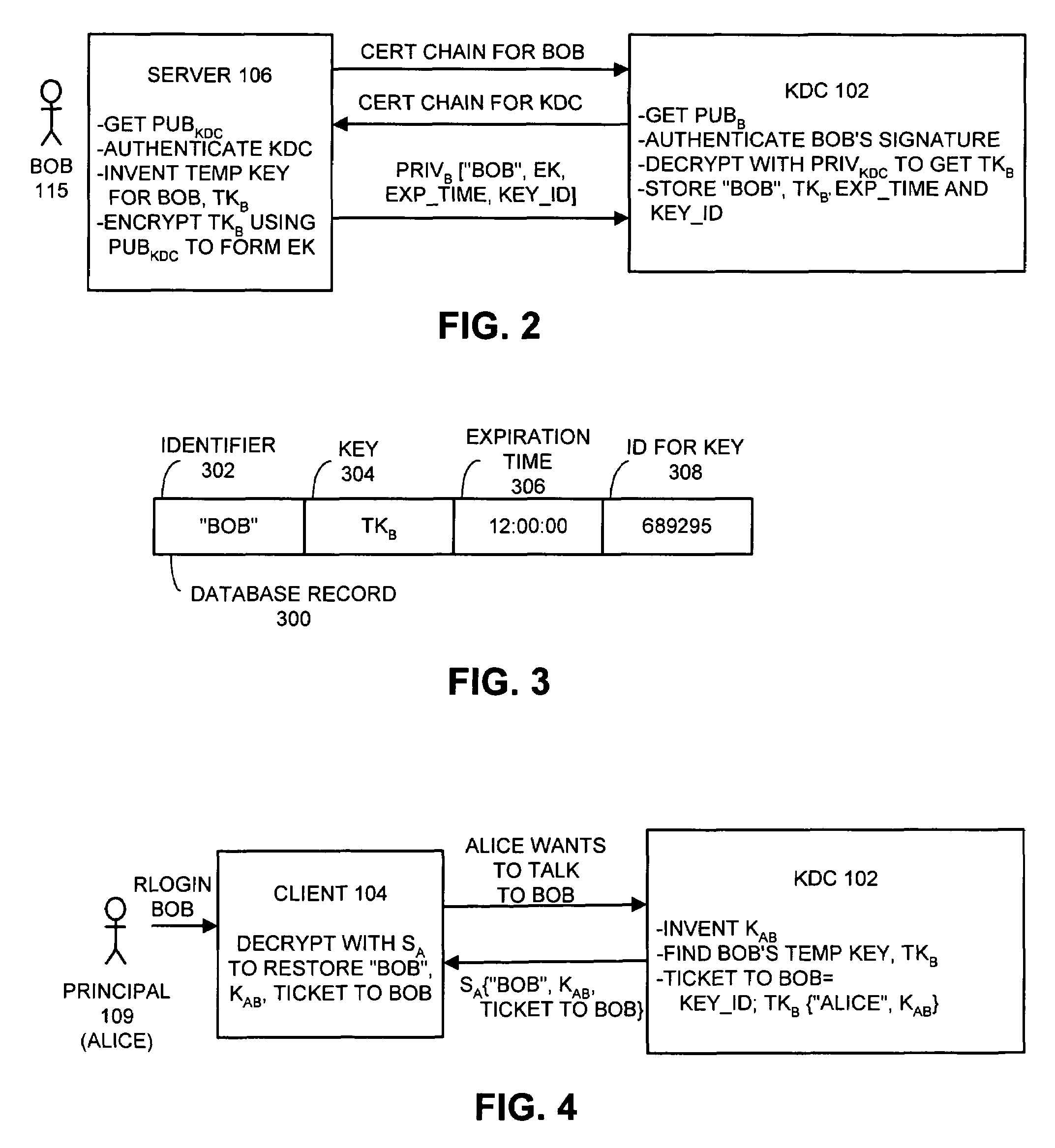
One embodiment of the present invention provides a system for operating a key distribution center (KDC) that provides keys to facilitate secure communications between clients and servers across a computer network, wherein the system operates without having to store long-term server secrets. The system operates by receiving a communication from a server at the KDC. This communication includes an identifier for the server, as well as a temporary secret key to be used in communications between a client and the server for a limited time period. In response the communication, the system attempts to authenticate the server. If the server is successfully authenticated, the system stores the temporary secret key at the KDC, so that the temporary secret key can be subsequently used to facilitate communications with the server. Upon subsequently receiving a request at the KDC from a client that desires to communicate with the server, the system produces a session key to be used in communications between the client and server, and then creates a ticket to the server by encrypting an identifier for the client and the session key with the temporary secret key for the server. Next, the system assembles a message that includes the identifier for the server, the session key and the ticket to the server, and sends the message to the client in a secure manner. The system subsequently allows the client to forward the ticket to the server in order to initiate communications between the client and the server.
Owner:ORACLE INT CORP
Method and apparatus providing secure multicast group communication
InactiveUS7434046B1Eliminating single point of failureReduce in quantityKey distribution for secure communicationMultiple keys/algorithms usageComputer networkGroup session
An approach for establishing secure multicast communication among multiple members that participate in a multicast group is disclosed. In one feature, multiple multicast proxy service nodes (MPSNs) are defined and control when members join or leave the multicast group. The MPSNs are logically represented by a first binary tree in which each node of the first binary tree is associated with a domain of a directory service and one or more of the MPSNs. A second binary tree is created that has leaf nodes representing each member. The second binary tree is stored in a domain of the directory service with a root node that represents one or more of the MPSNs. The members can each establish multicast communication and serve as a key distribution center. When a member joins the multicast group, a new group session key is determined by replicating a branch of the second binary tree.
Owner:CISCO TECH INC
Information processing system and method
InactiveUS7346170B2Secure transmissionReduce data sizeKey distribution for secure communicationUser identity/authority verificationInformation processingTheoretical computer science
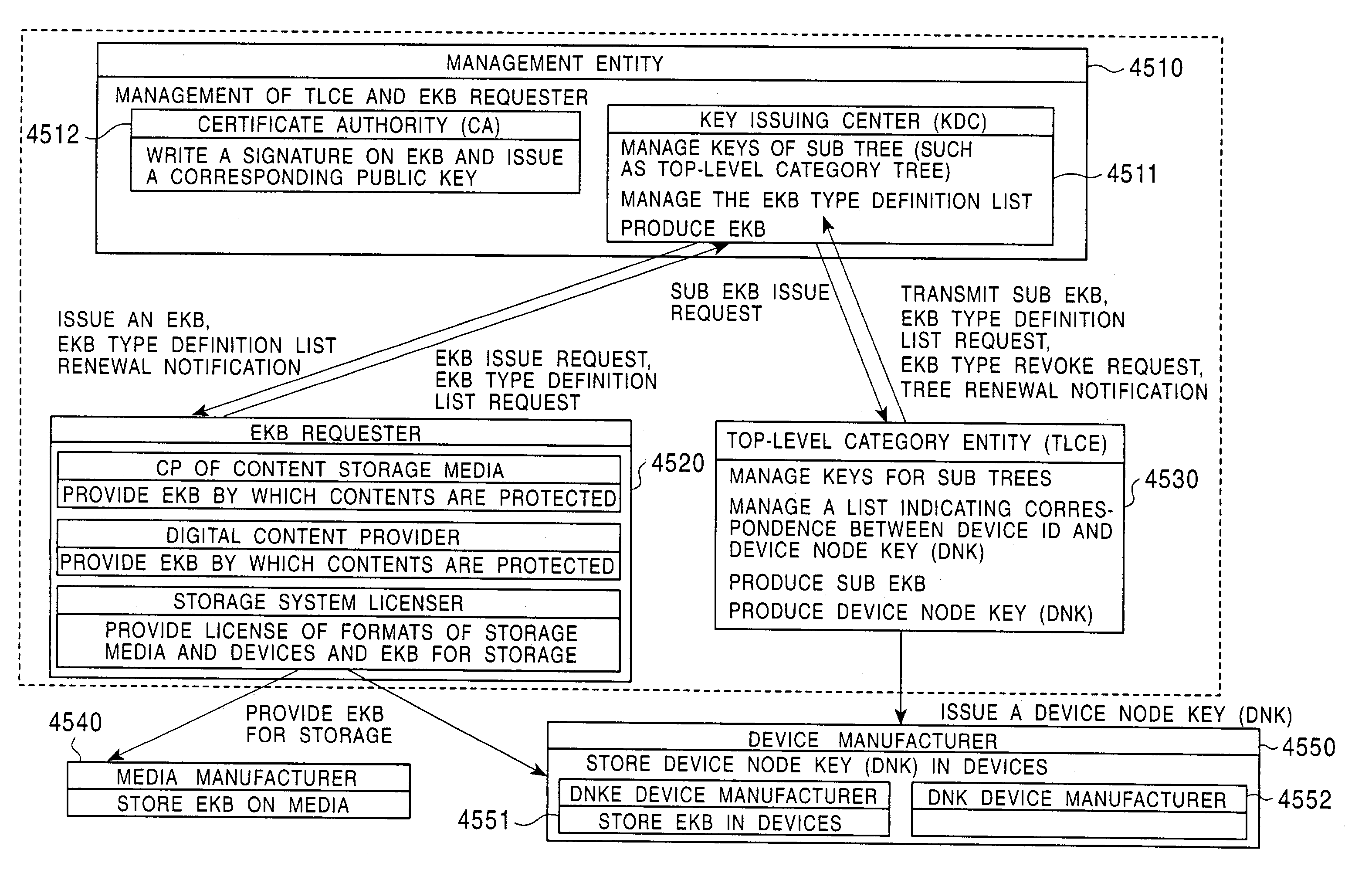
An information processing system and method are disclosed in which information processing is performed using an enabling key block (EKB) in association with a tree structure including category subtrees. A key tree is produced, which include subtrees that are grouped in accordance with categories and are managed by category entities. The EKB includes data produced by selecting a path in the key tree and encrypting a higher-level key in the selected path using a lower-level key in the selected path. The EKB is then provided to a device. A requester, which requests production of the EKB, may produce a root key or may request a key distribution center (KDC) to produce a root key. If the (KDC) produces the EKB, it may also request a category entity to produce a sub-EKB.
Owner:SONY CORP
Method and apparatus for cryptographic key establishment using an identity based symmetric keying technique
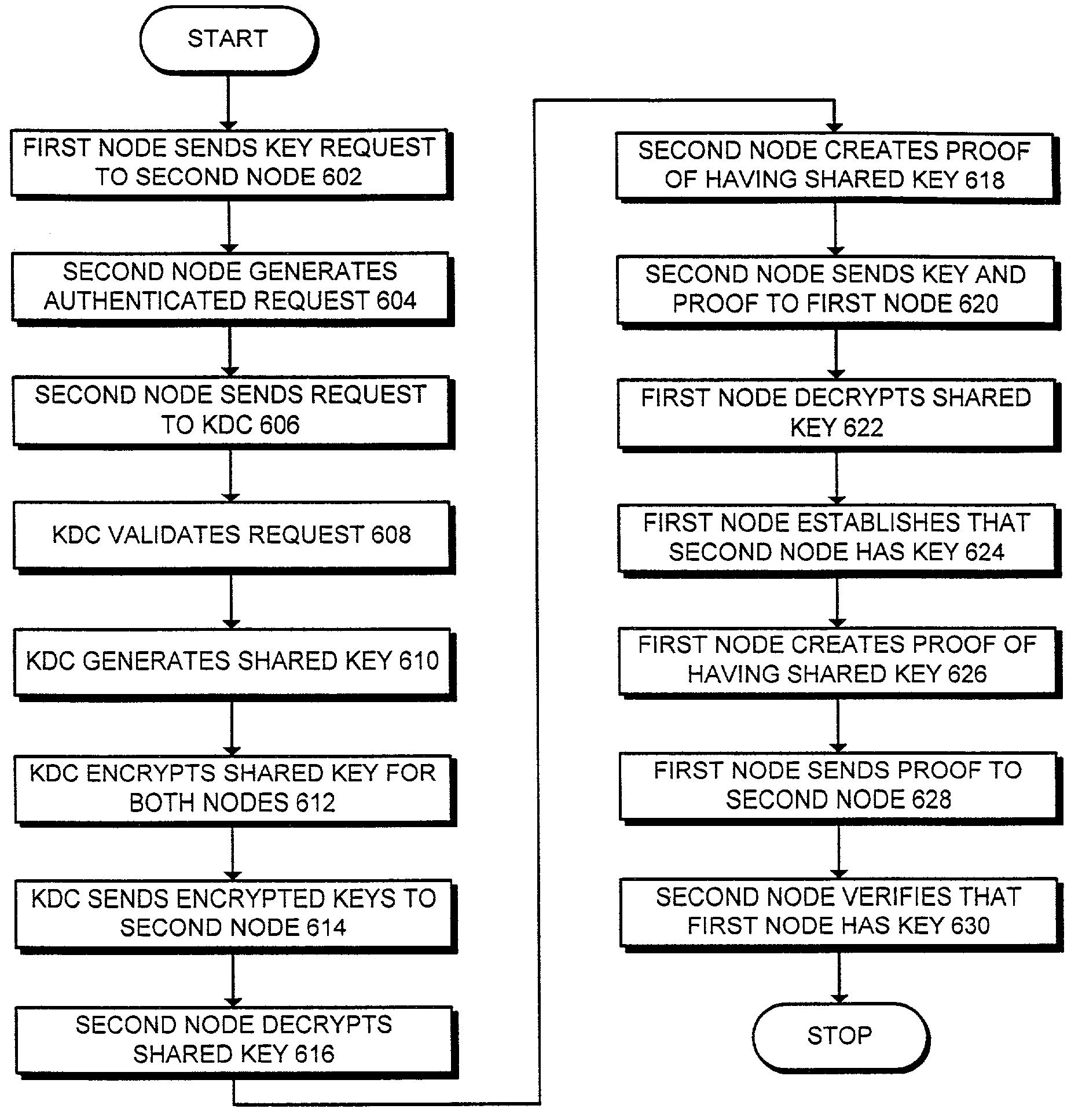
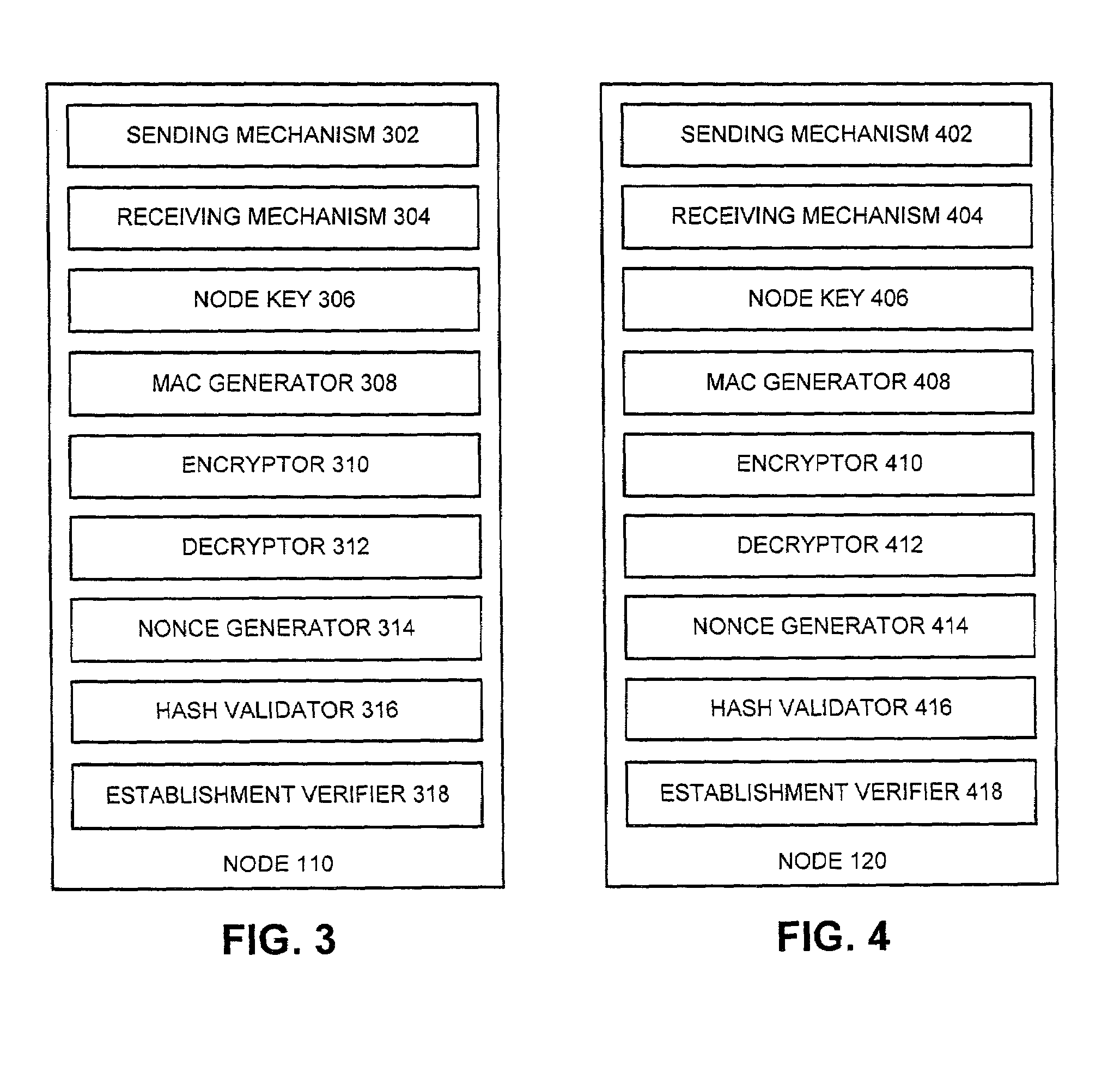
One embodiment of the present invention provides a system for establishing a shared cryptographic key between participating nodes in a network. The system operates by sending a first message from the first node to the second node requesting establishment of a shared key. The second node sends a second message containing identifiers and a message authentication code to a key distribution center (KDC). The authentication code is generated using a second node key belonging to the second node. The KDC recreates the previously created second node key using the second node identifier and a secret key known only to the key distribution center. The KDC then verifies the message authentication code using the second node key. If the message authentication code is verified, the KDC creates a shared key for the nodes to use while communicating with each other. The KDC securely communicates this shared key to the participating nodes
Owner:MCAFEE LLC
Enhanced encryption method and system for ultra secure applications
InactiveUS7831049B1Improve securityIncrease ratingsError detection/correctionData resettingSpatial light modulatorAlgorithm
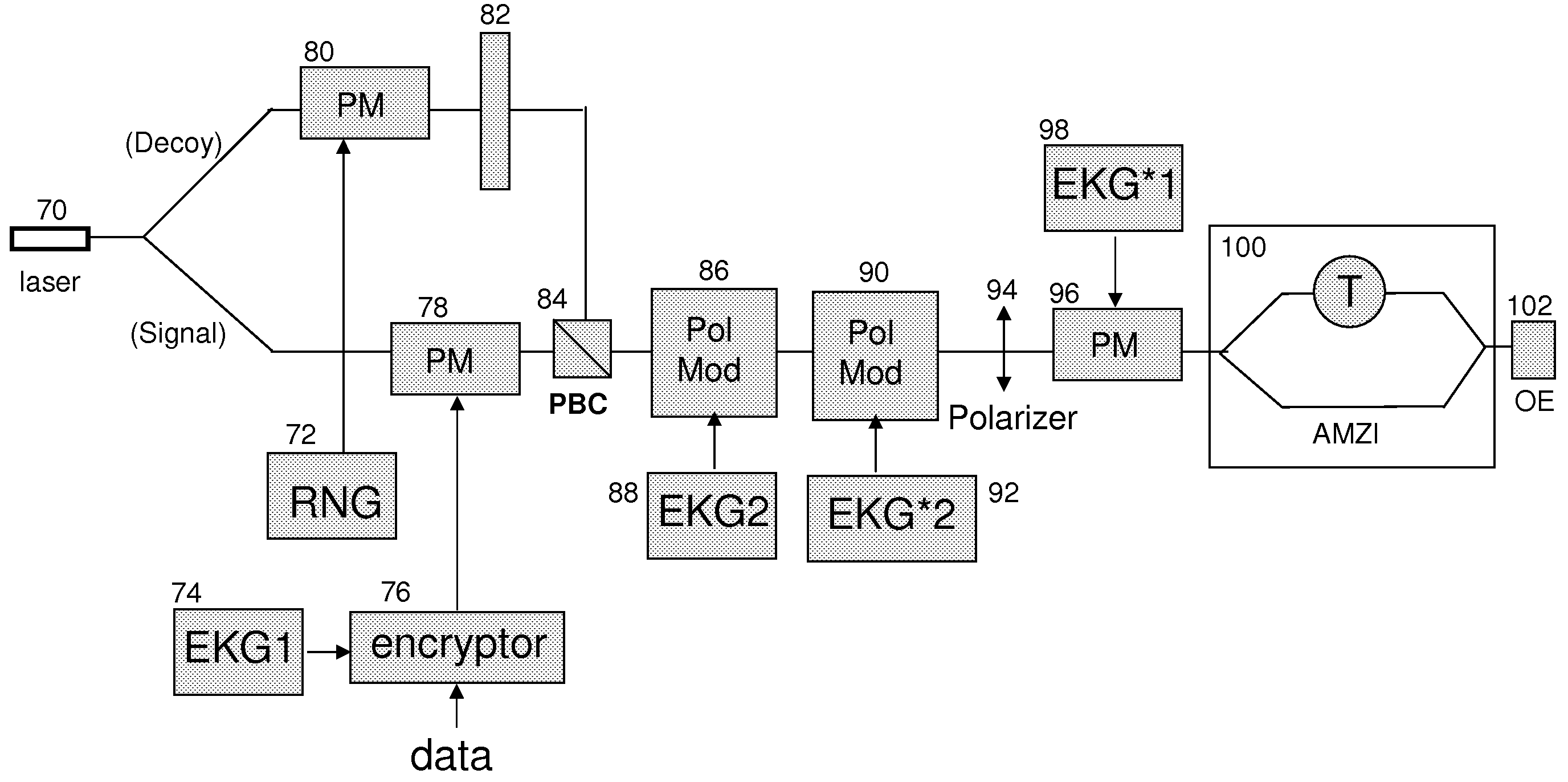
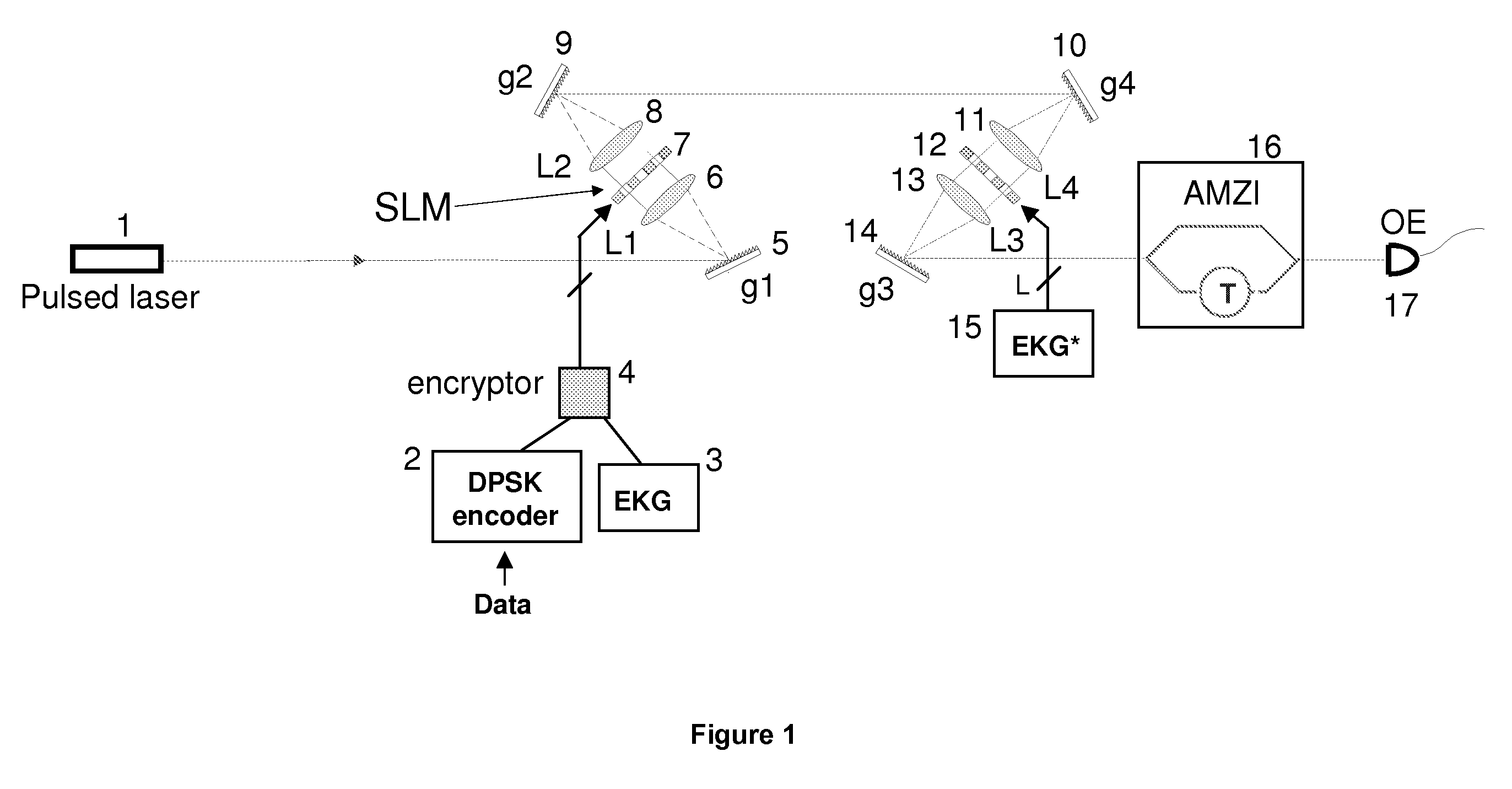
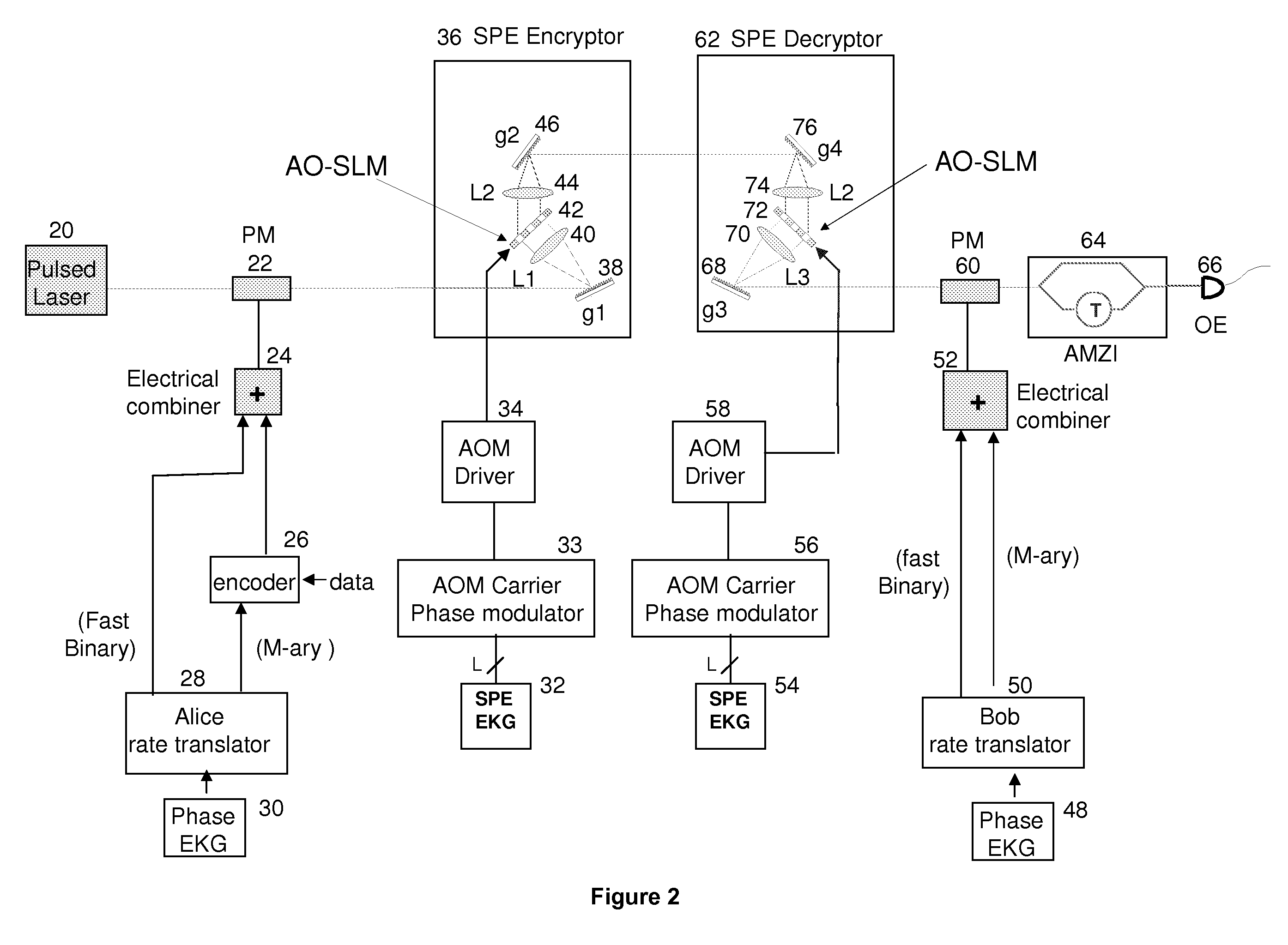
Techniques to bolster the security of an AlphaEta cryptosystem using spectral phase encoding. In one aspect, a spatial light modulator (SLM) is used to change the spectral code (spectral phase) of each optical bit in response to the output of an extended key generator based on a cryptographic algorithm. In other aspects, additional time and polarization modulations are used to maintain high security levels as well as good performance levels. Such methods are combined with traditional key generation methods such as key-distribution centers or one-way mathematical algorithms to bolster the security of traditional key generation as well.
Owner:NUCRYPT
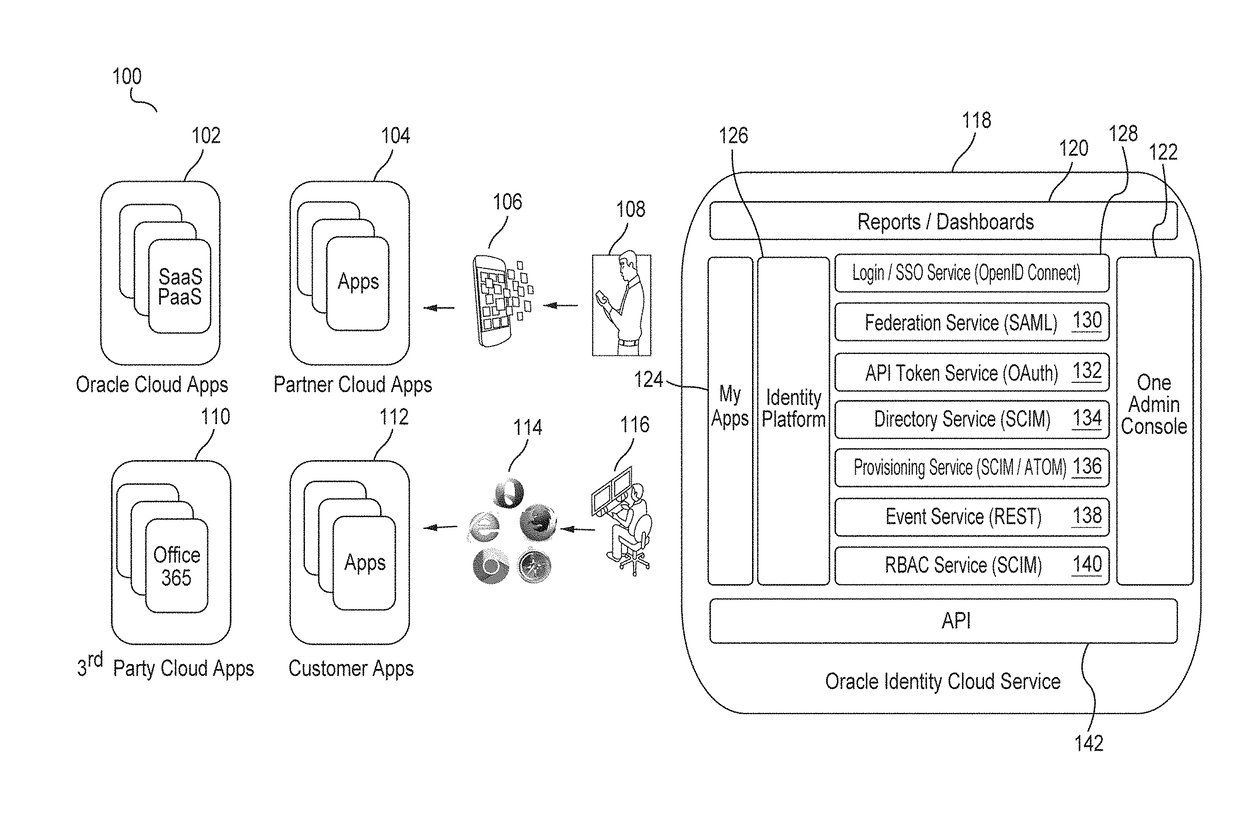
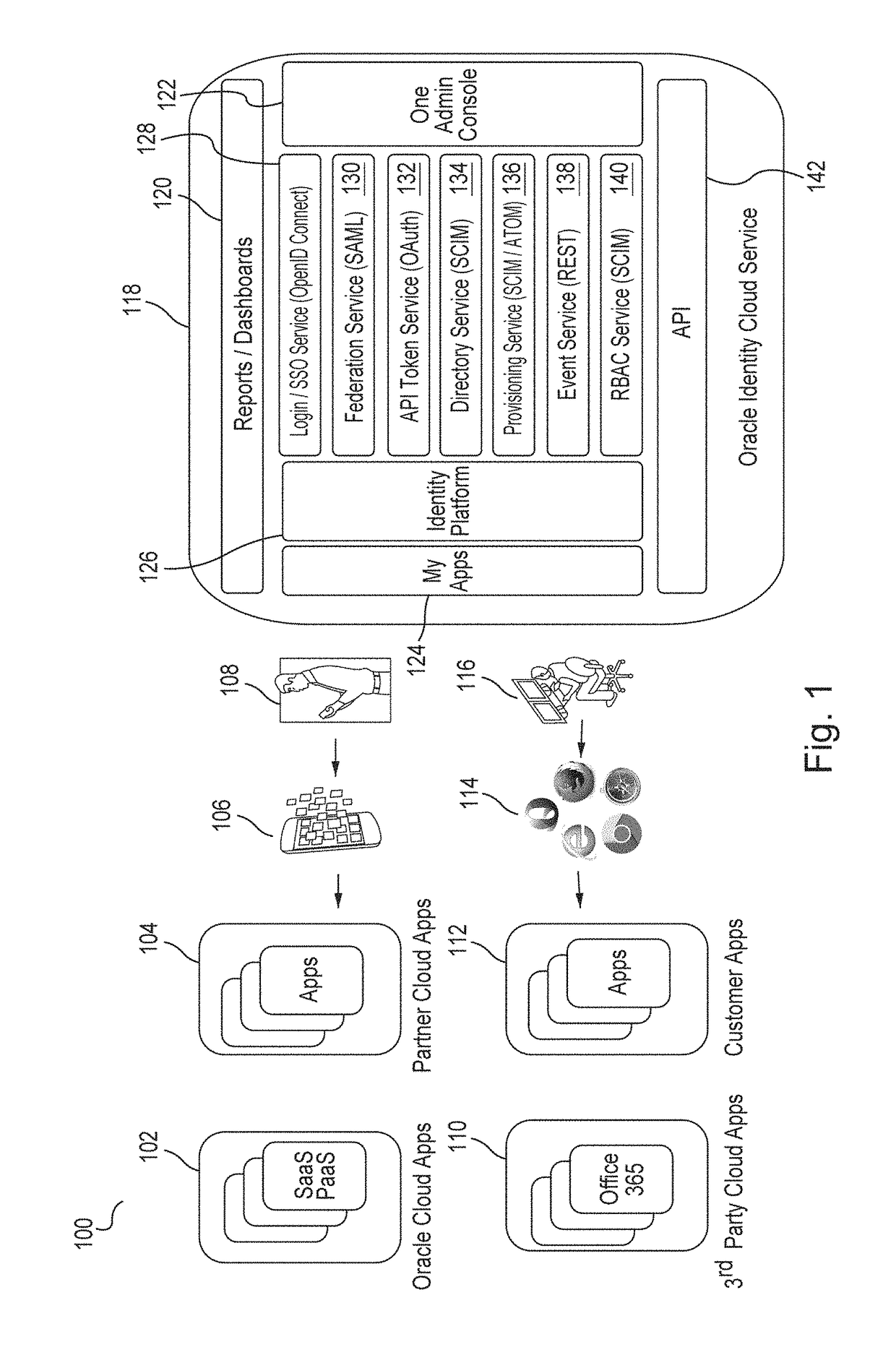
User authentication using kerberos with identity cloud service
ActiveUS20180337914A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesPassword policyPassword
Embodiments authenticate a user in response to receiving from a Kerberos key distribution center (“KDC”) a request to authenticate the user that includes a user identification (“ID”). Embodiments retrieve a user record corresponding to the user ID, the user record including a principal key. Embodiments decrypt the principal key using a tenant-specific encryption key and encrypt the decrypted principal key using a Kerberos master key to generate an encrypted principal key. Embodiments retrieve a password policy corresponding to the user ID. Based on the retrieved password policies, embodiments construct password state attributes and return to the KDC the encrypted principal key, the password policy and the password state attributes.
Owner:ORACLE INT CORP
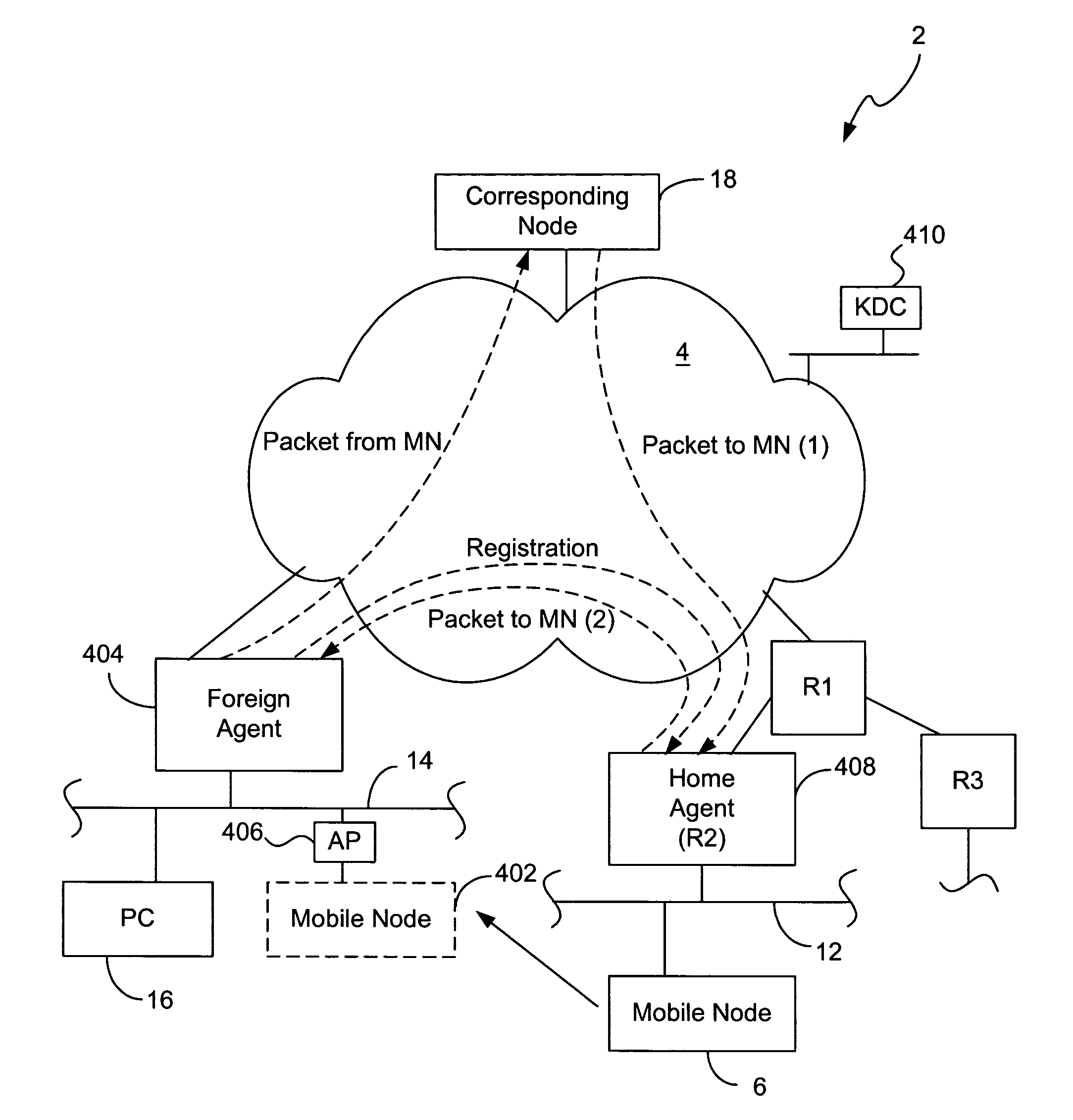
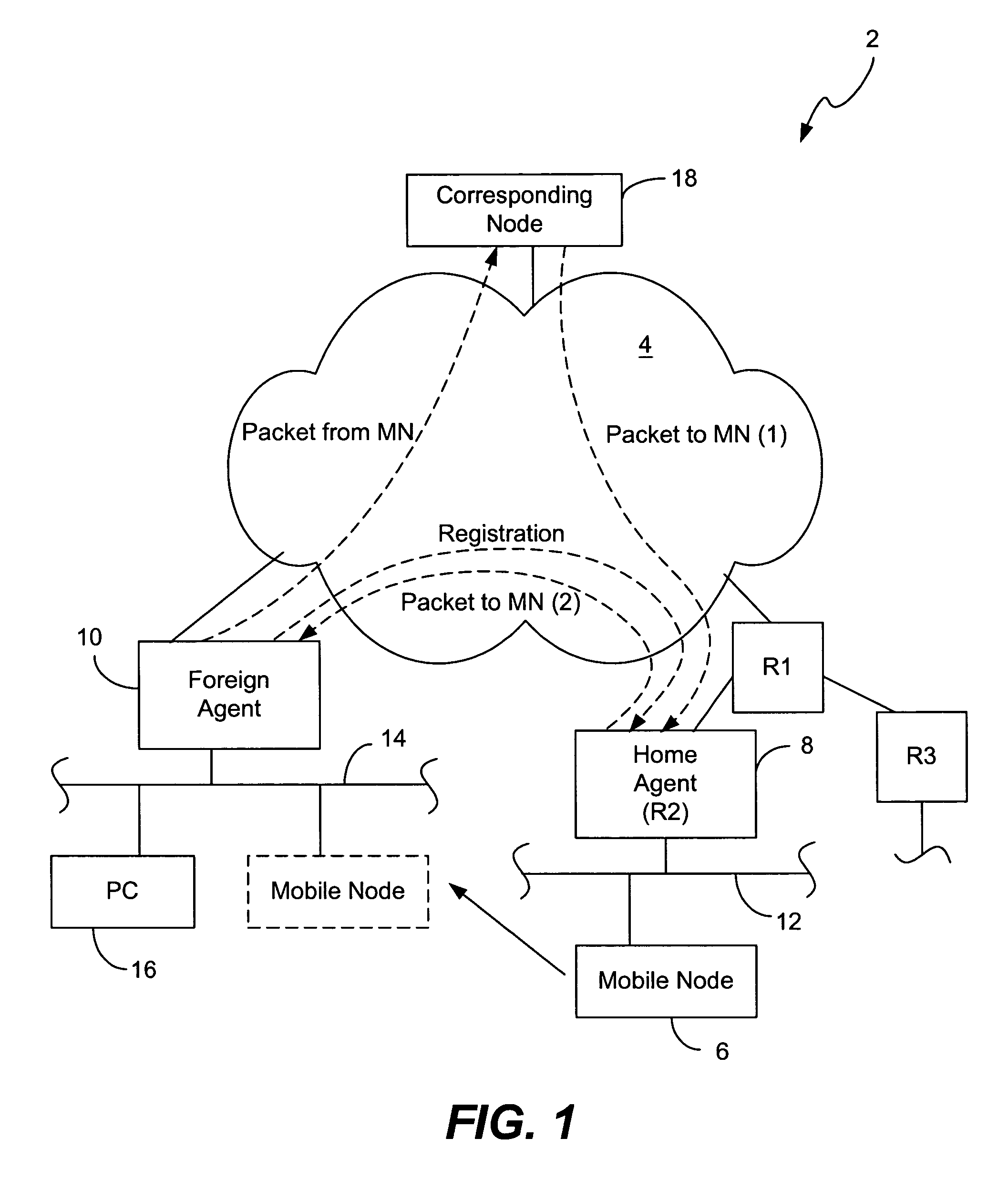
Methods and apparatus for authenticating mobility entities using kerberos
InactiveUS7870389B1Unauthorised/fraudulent call preventionMultiple keys/algorithms usageComputer networkKey distribution center
Methods and apparatus for generating and transmitting dynamically generated session keys are disclosed. A key distribution center generates a session key between the key distribution center and a first mobility entity (e.g., an access point). Once the session key between the key distribution center and the access point is transmitted to the access point, the access point retrieves a shared session key between the access point and a Mobile Node from the key distribution center, which is then transmitted to the Mobile Node, enabling the Mobile Node to connect to the network. Similarly, either the Mobile Node or its Home Agent retrieves a session key between the key distribution center and the access point from the key distribution center, enabling a shared session key between the Home Agent and the Mobile Node to be obtained from the key distribution center. The Mobile Node (or Home Agent) then transmits the shared session key to the Home Agent (or Mobile Node). Once the shared session key is obtained by both the Home Agent and the Mobile Node, the shared session key is used to authenticate registration messages (e.g., including registration request and reply packets). In this manner, dynamically generated session keys may be used to securely transmit registration messages in a Mobile IP environment.
Owner:CISCO TECH INC
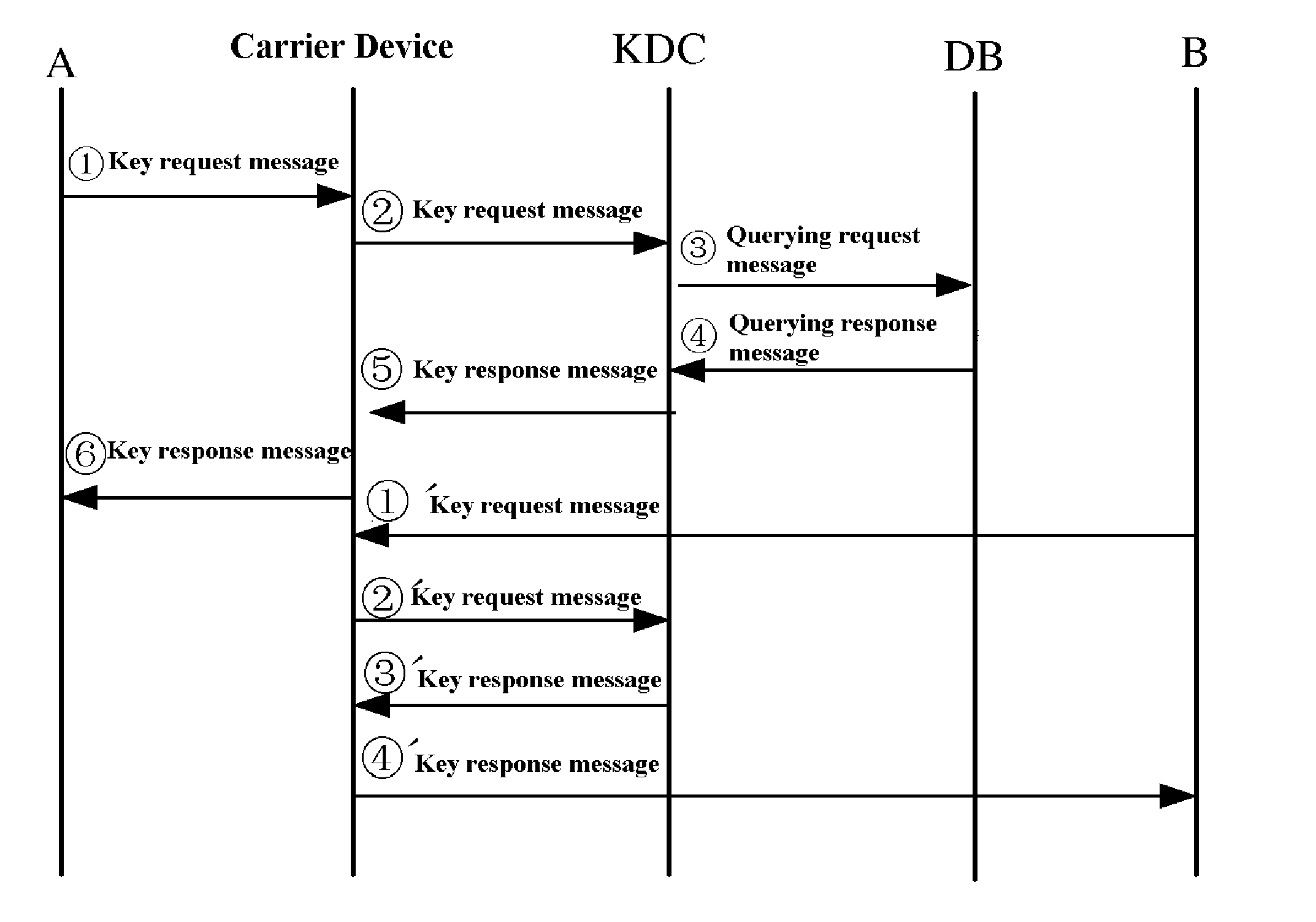
Key distributing method, public key of key distribution centre online updating method and device
InactiveUS20110103589A1Reduces key management complexitySecure distributionKey distribution for secure communicationTrusted third partyKey distribution center
A key distributing method, a public key of key distribution centre online updating method, a key distribution centre, a communication entity and a key management system. The system includes: communication entities, a carrying device, a key distribution centre and a database, wherein the carrying device carries or transports the information during the key distributing course and the public key online updating course, the database stores whether each communication entity registered secret service; the database connects with the key distribution centre, the key distribution centre connects with the carrying device, and the carrying device connects with each communication entity. Using the cipher technology of public key, a key distribution system is provided based on principle of three-element peer authentication (TePA). The system safely distributes the communication key to each pair entities to enable keys have PFS attribute, reduces the key management complexity of the system, and realizes online updating of the public key of the trusted third party i.e. key distribution centre.
Owner:CHINA IWNCOMM
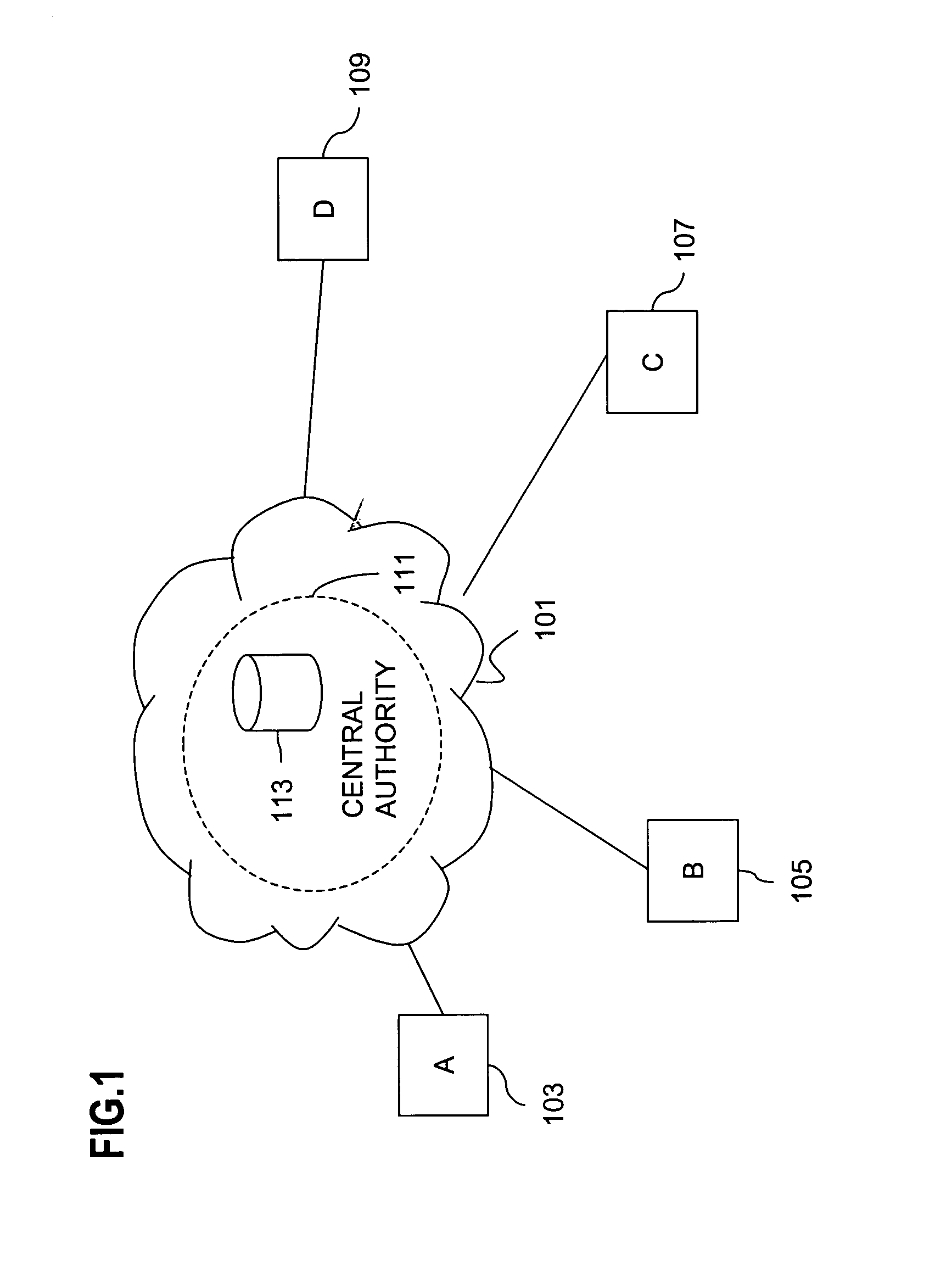
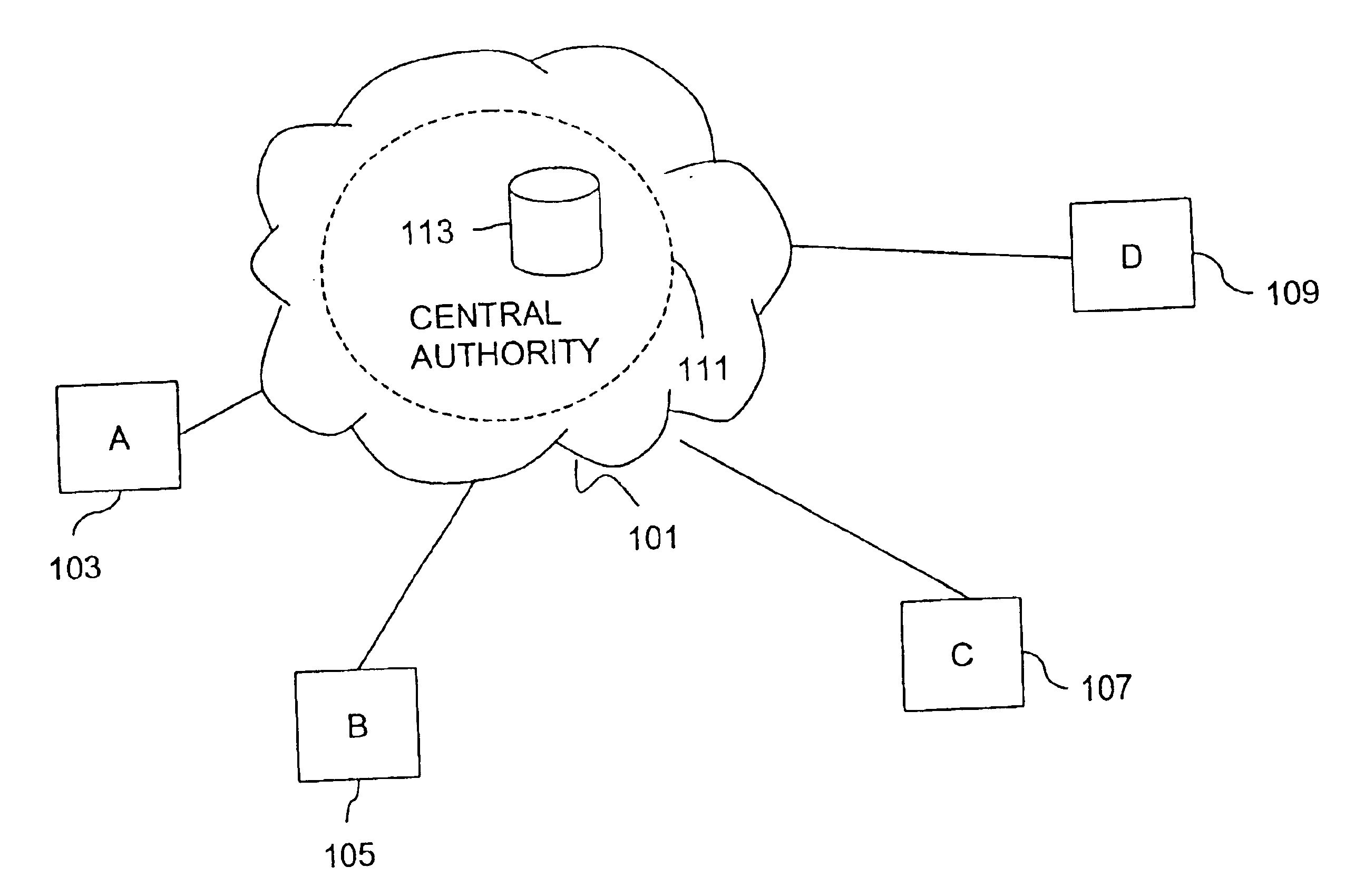
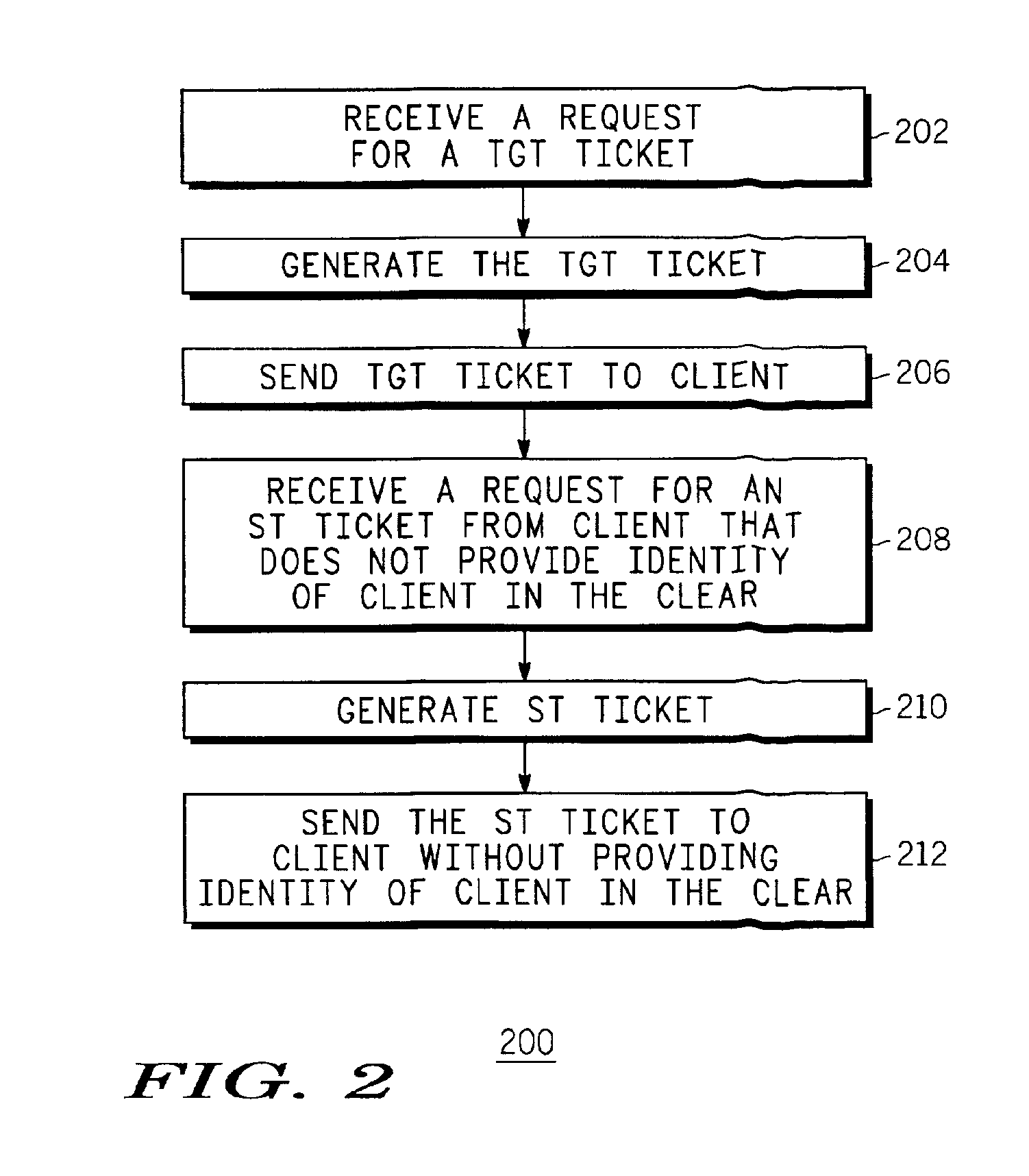
Method and system for providing client privacy when requesting content from a public server
InactiveUS6993652B2Key distribution for secure communicationDigital data processing detailsPlaintextApplication server
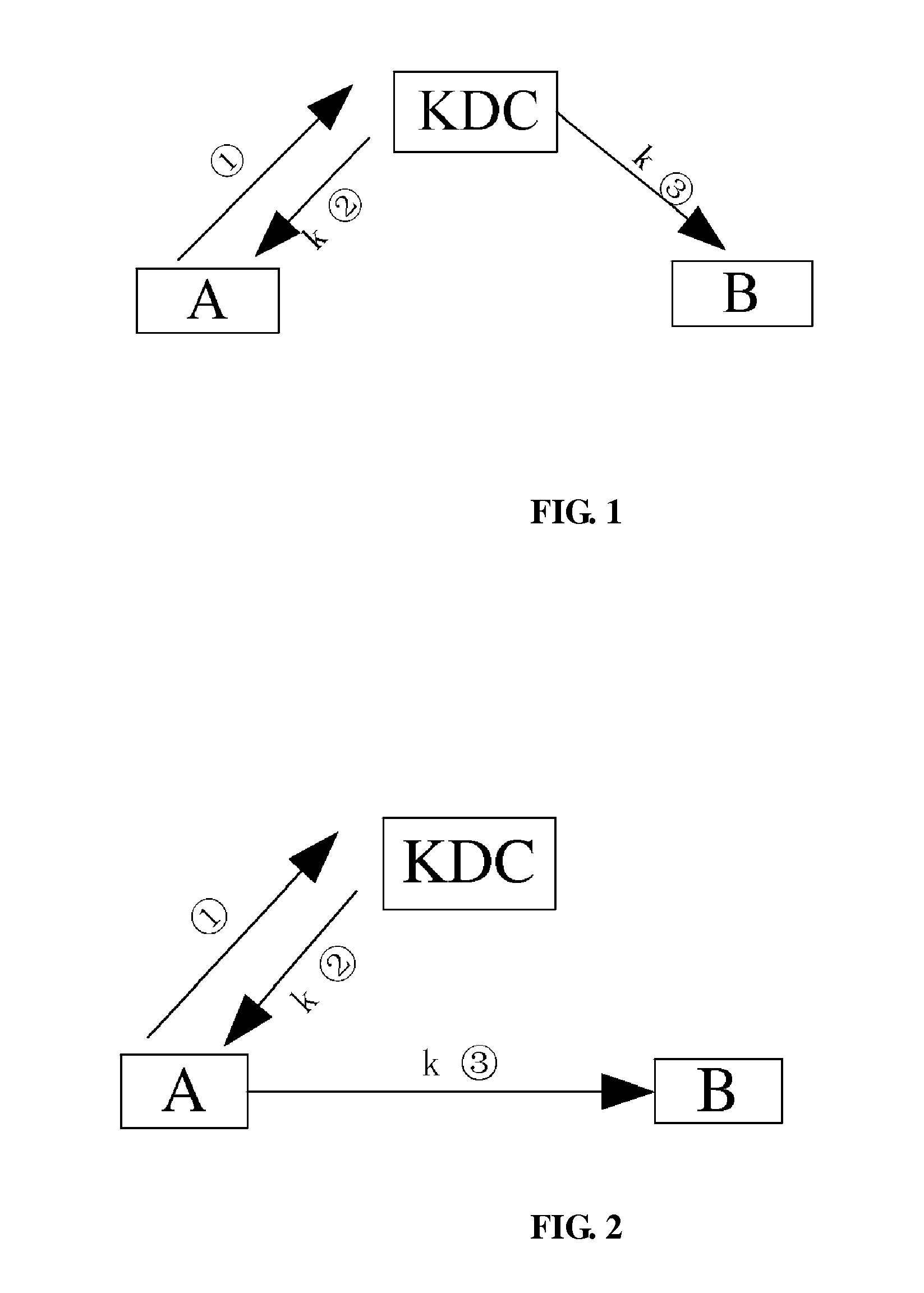
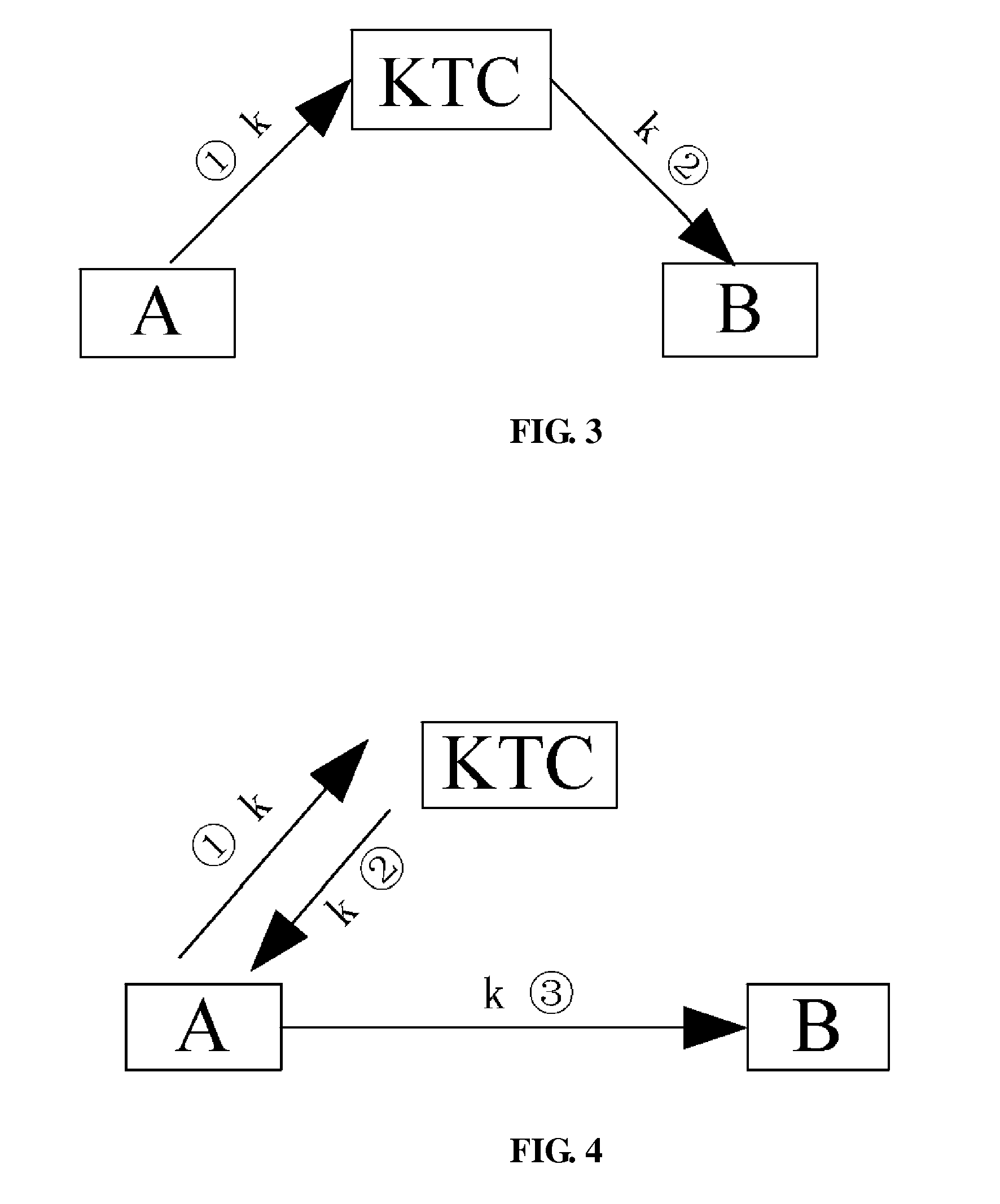
Method and system for providing client privacy on the Internet when the client requests content from a public application server. The method is well-suited to key management protocols that utilize the concept of tickets. The client name or identity is encrypted in all key management messages where the client is requesting a ticket for a specific application server. The key management messages are between the client and a key distribution center (KDC) and between the client and the specific application server. The KDC does not provide the client name or identity in the clear in such messages. This prevents the client's identity from being linked with the content provided by the specific application server, which results in improved user privacy.
Owner:GOOGLE TECH HLDG LLC
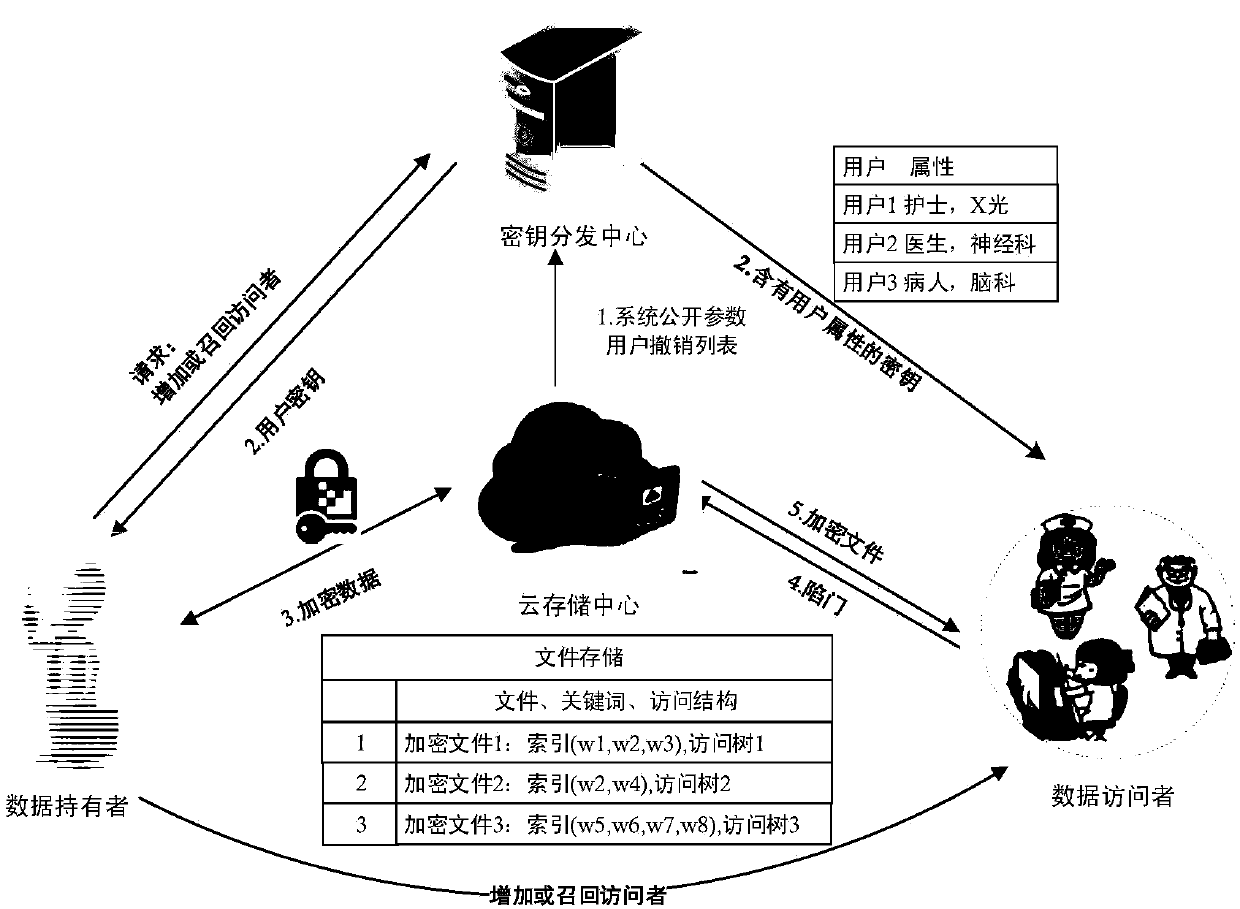
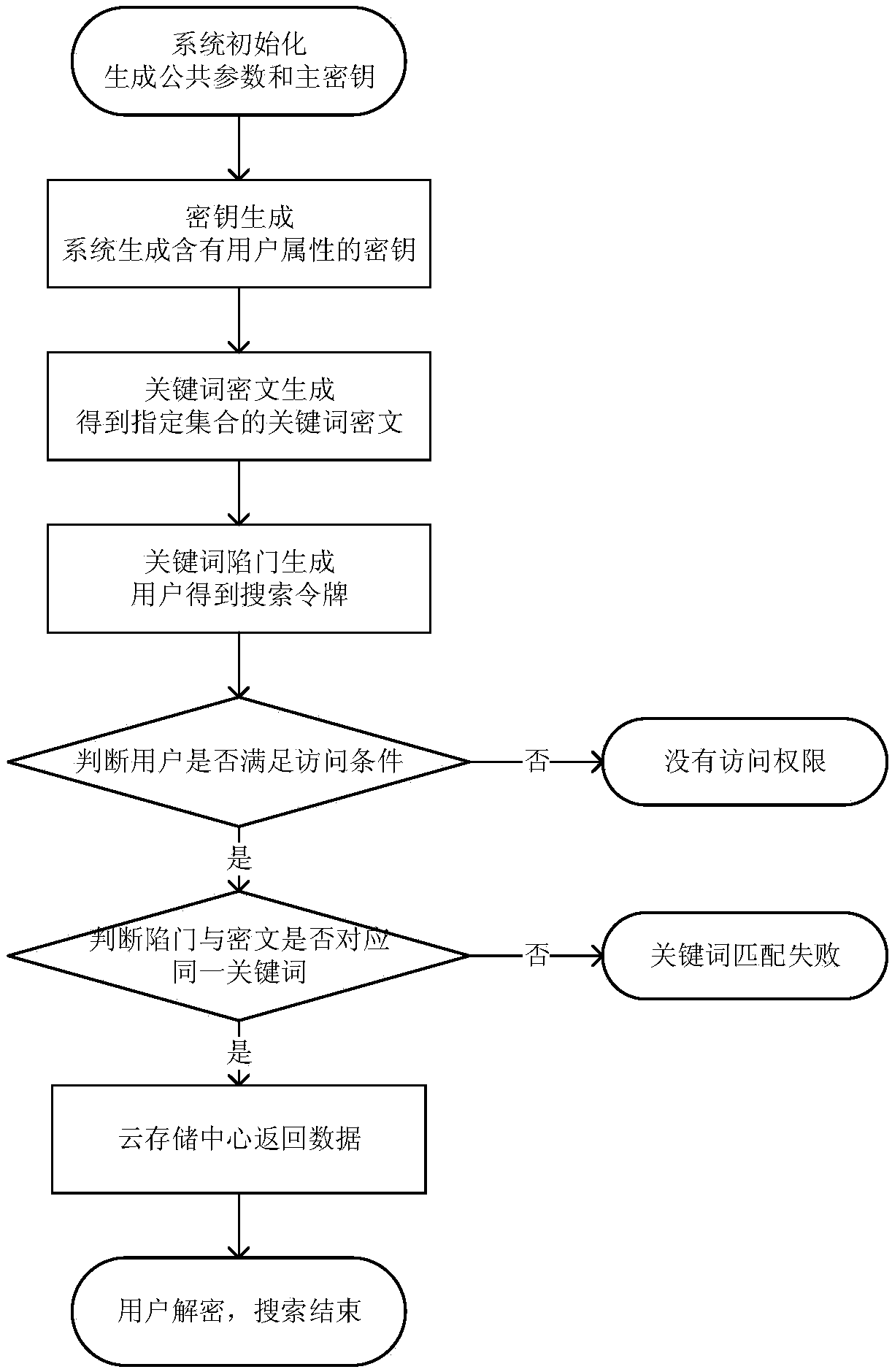
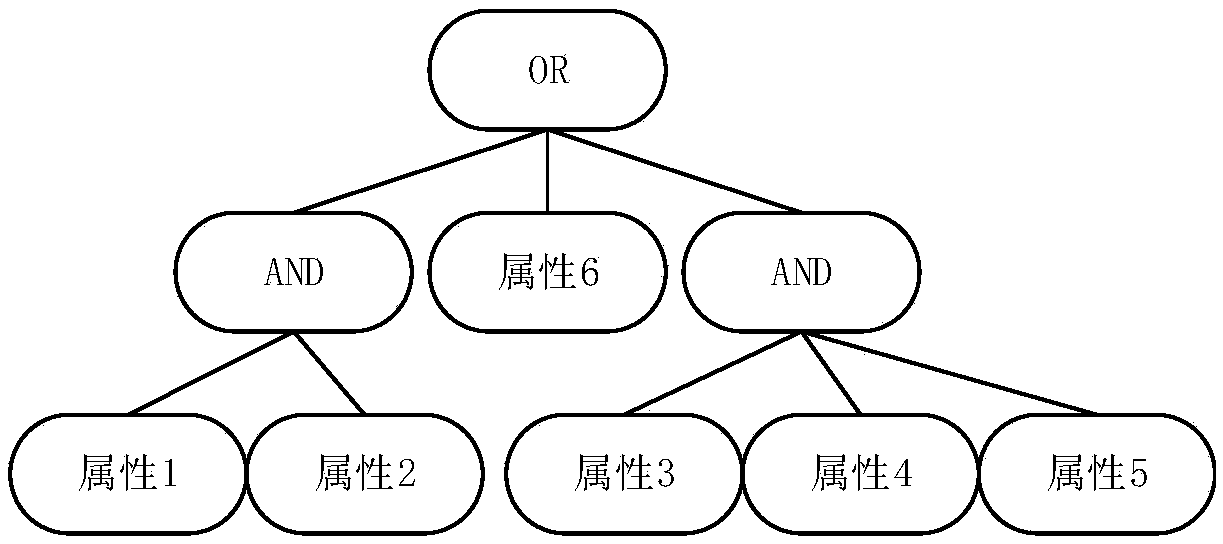
Attribute-based searchable encrypted electronic medical record system and encryption method
InactiveCN107634829AReduce computing requirementsReduce computational complexityKey distribution for secure communicationSpecial data processing applicationsMedical recordCiphertext
The invention discloses an attribute-based searchable encrypted electronic medical record system and an encryption method. The system comprises a key distribution center and a cloud storage center, wherein the key distribution center generates public parameters and a master key to initialize the system; the key distribution center generates and distributes keys containing user attributes to users;a data owner sets an access strategy before uploading medical record data, encrypts the data, and then uploads the data to the cloud storage center; a data visitor generates a trap door according tokeywords and the keys, and provides a query request to the cloud storage center; and after receiving the query request, the cloud storage center determines to return corresponding encrypted data to the data visitor according to the trap door and keyword ciphertexts. According to the scheme of the invention, the difficulty of key management in a multi-user environment can be reduced, data users canbe supported to accurately query the keywords of the ciphertexts, guessing attacks of the keywords can be resisted, and the leakage of privacy data can be effectively prevented.
Owner:NANJING UNIV OF SCI & TECH
Method for distributing key using public key cryptographic technique and on-line updating of the public key
ActiveCN101286842ASupport online update functionEnable secure distributionKey distribution for secure communicationPublic key for secure communicationTrusted third partyKey distribution center
The invention relates to a method for the distribution of an encryption key and the online innovation of a public key, which comprises the steps that: (1) a first entity produces a temporary public and private key pair; (2) a communication conversation encryption key exists between the first entity and a second entity; (3) an encryption key distribution center locally stored is utilized to carry out the signature verification of the public key; (4) the second entity produces a temporary public and private key pair; (5) a encryption key response message is formed and returned to the second entity; (6) the encryption key distribution center locally stored is utilized to carry out the signature verification of the public key; (7) the communication conversation encryption key is utilized by the first entity and the second entity to serve as a conversation encryption key to carry out secret communication. The method proposes a method that safely distributes communication encryption key to each pair of entity, causes the encryption key to have PFS property and lowers the complexity of the encryption key management of the system, and also supports the online innovation function of a public key of the encryption key distribution center which is the trusted third party.
Owner:CHINA IWNCOMM
Method for distributing key
ActiveCN101282211AEnable secure distributionRealize dynamic updateKey distribution for secure communicationPublic key for secure communicationCommunications systemNetworked system
The present invention relates to a key distribution method which comprises the following steps: 1) respectively generating a pair of temporary public / private key pair by a first entity and a second entity which requires communication; and 2) through the public / private key pairs respectively generated by the first entity and the second entity, applying to a key distribution center to obtain a communication conversation key. The invention is based on a ternary equal identification (TePA) and adopts a public key cryptographic technique for distributing key to the entity which needs communication through the key distribution center KDC. The safe distribution and dynamic upgrading of the communication key are realized. A perfect forward security PFS is furthermore provided. The method settles the problems of considerable keys managed in the key distribution center, long storing period of the key by the user and no forward security of the communication key in the traditional method. The invention can be applied for the mobile communication network system and other communication system.
Owner:CHINA IWNCOMM
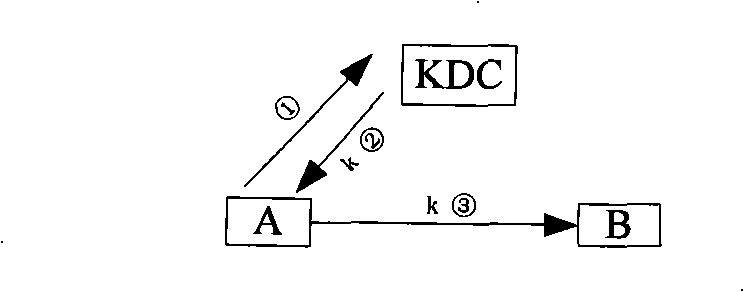
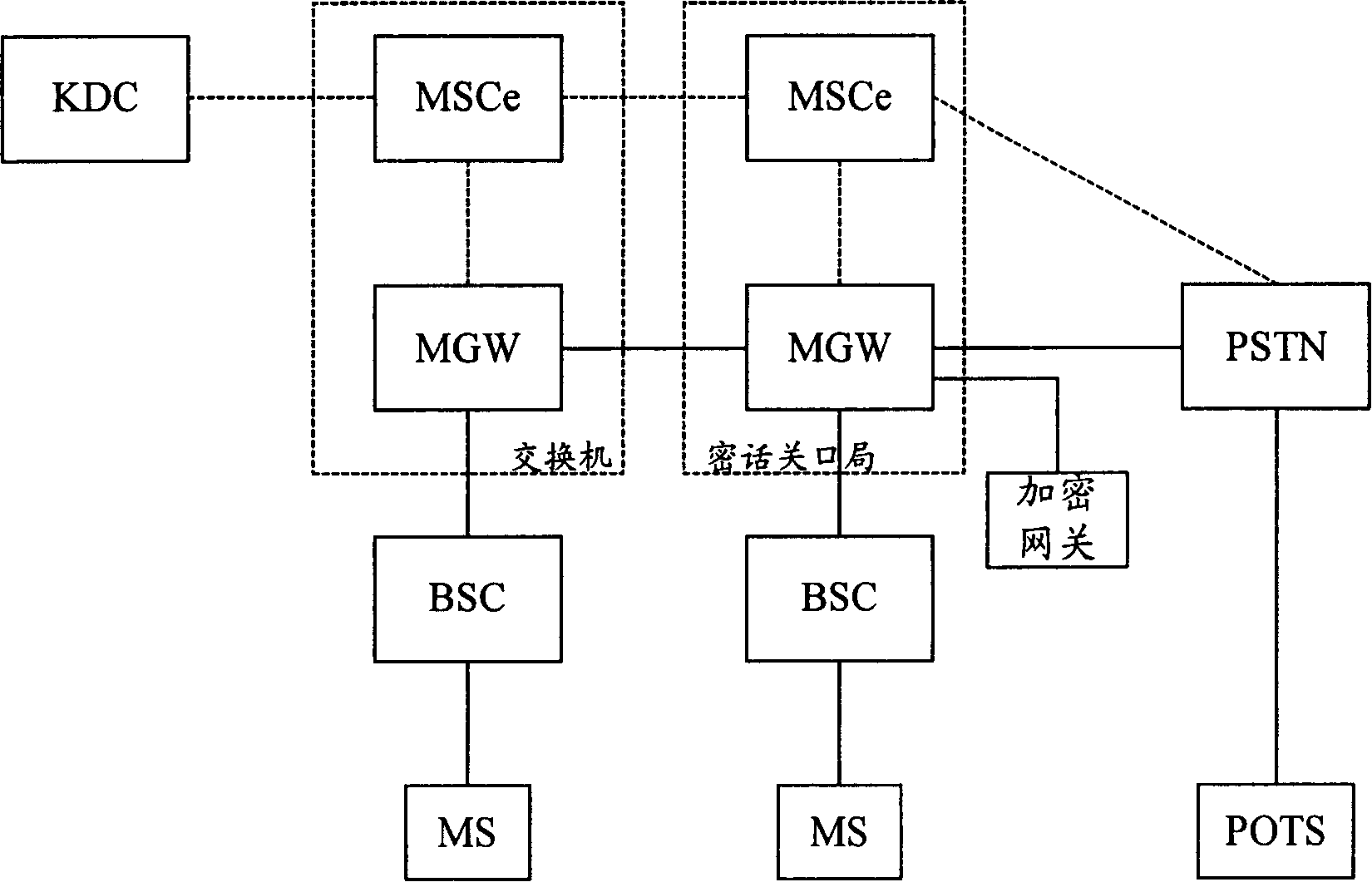
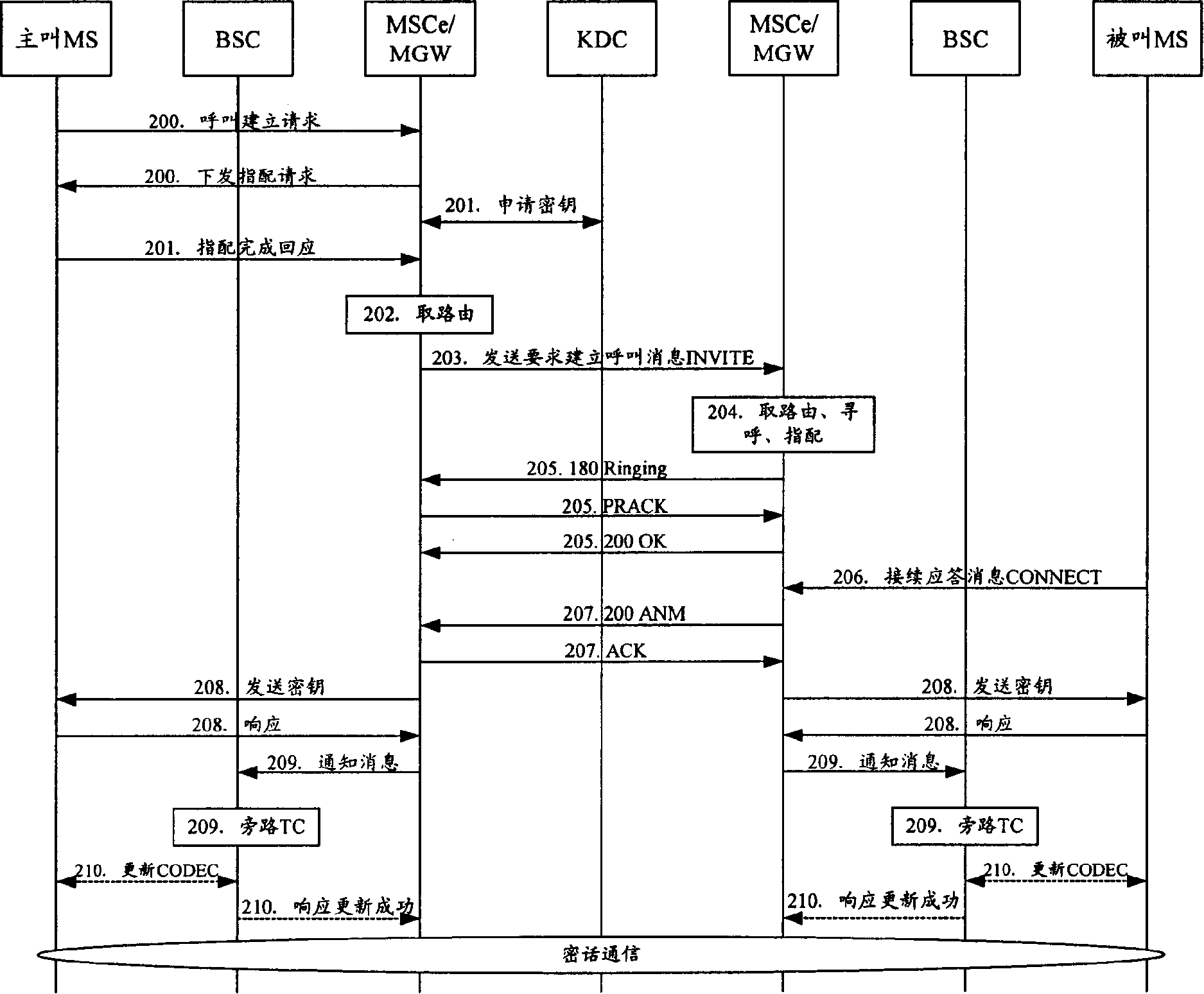
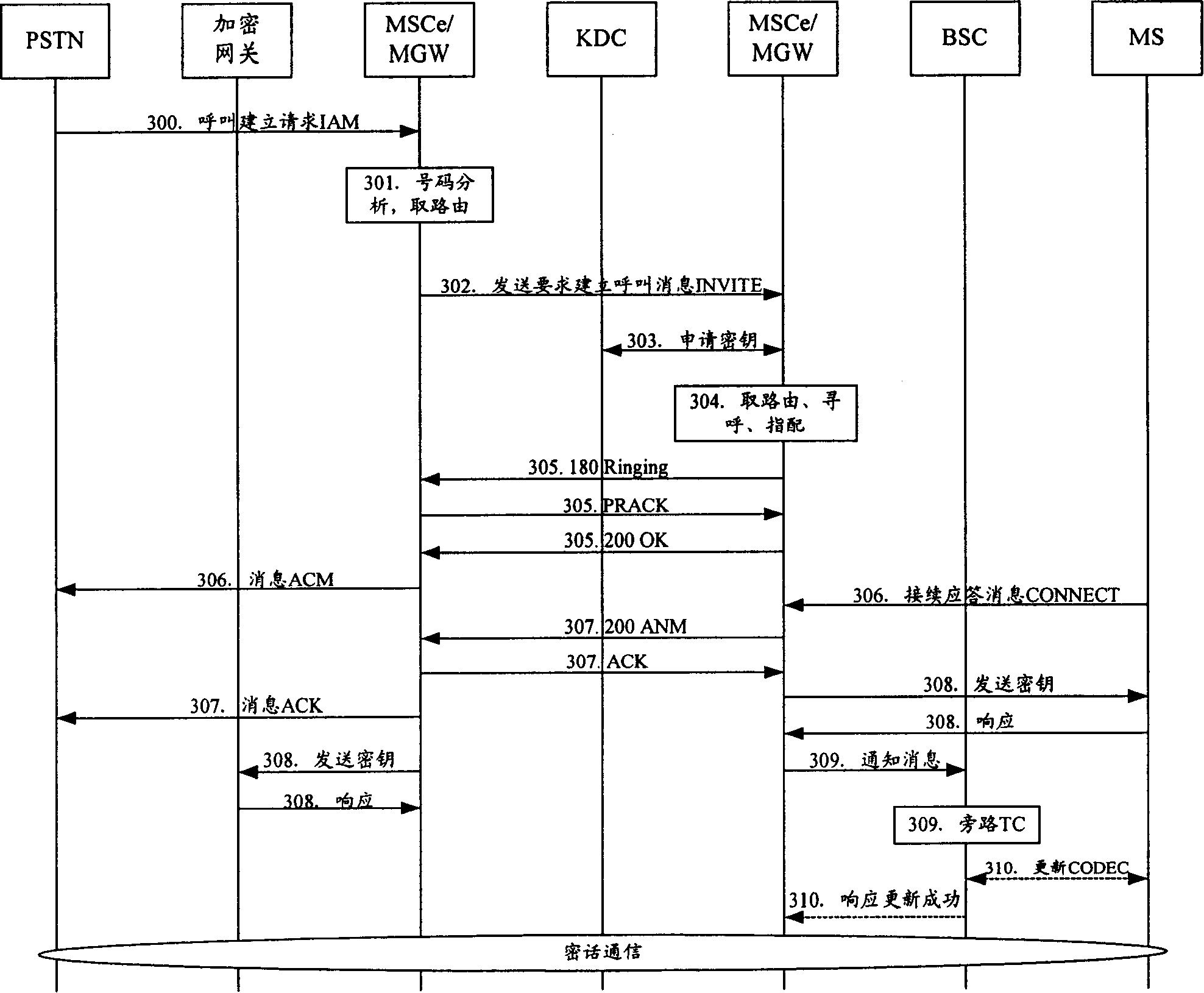
Method for end-to-end enciphoring voice telecommunication
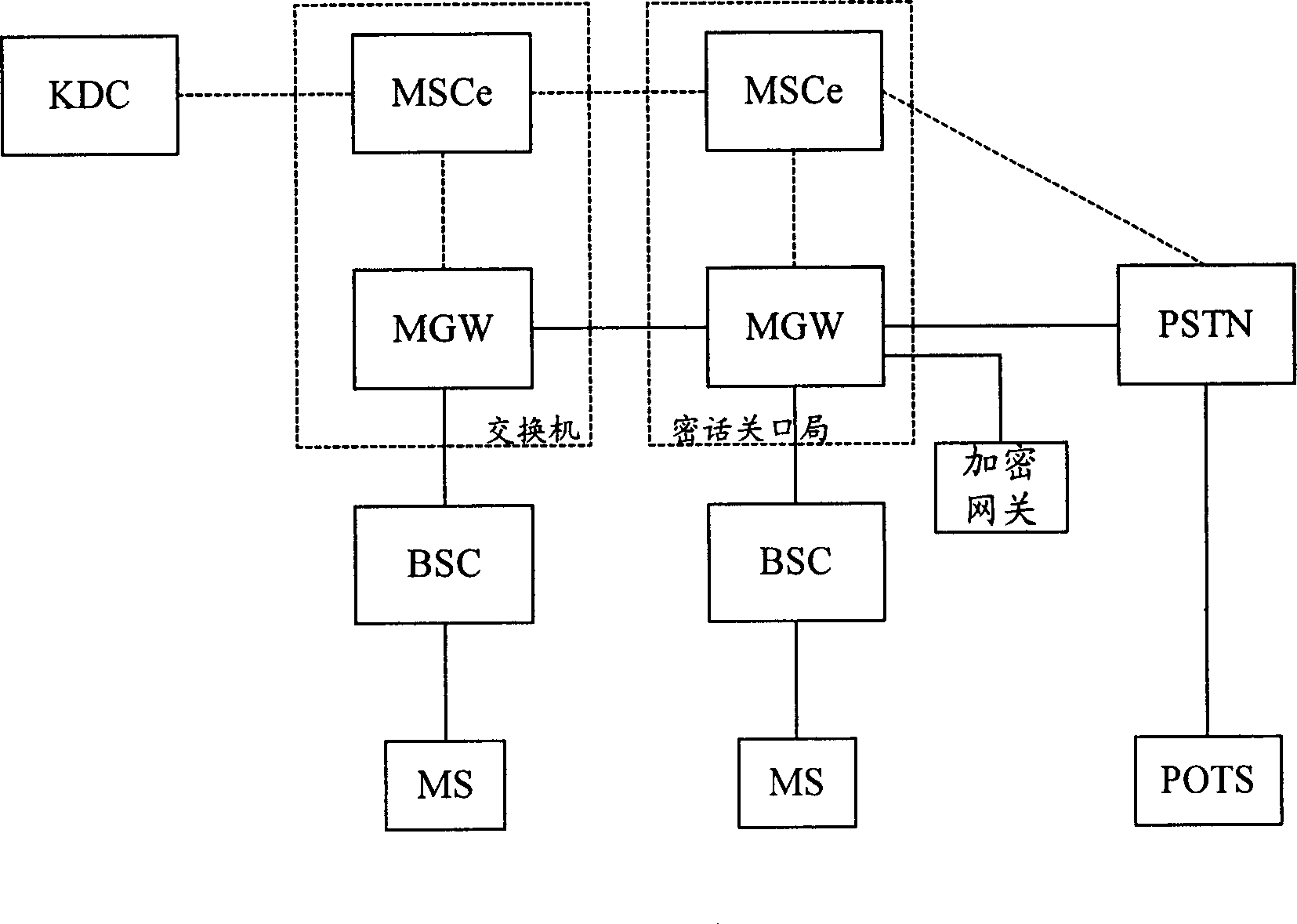
InactiveCN1816213AImprove scalabilityRealize safe and reliableSynchronising transmission/receiving encryption devicesRadio/inductive link selection arrangementsEnd-to-end encryptionExtensibility
The method includes steps: after receiving request for building encrypted call from calling terminal, switchboard sends request for applying encryption key to key distribution center (KDC); receiving the request, and passing through authentication of encrypting qualification, KDC generates calling and called encryption keys, which are returned back to switchboard; switchboard sends the calling and called encryption keys to calling party and called party respectively, and switchboard the mobile terminal locates on informs converter TC in bypass speech encoding format of base station controller; using the received encryption keys, the calling terminal and called terminal carry out encrypted speech communication. Based on network control being as center, the invention realizes point-to-point encrypted speech communication. Powerful function on network side provides advantages are: safety, reliable, flexible and enhanced extensibility.
Owner:HUAWEI TECH CO LTD
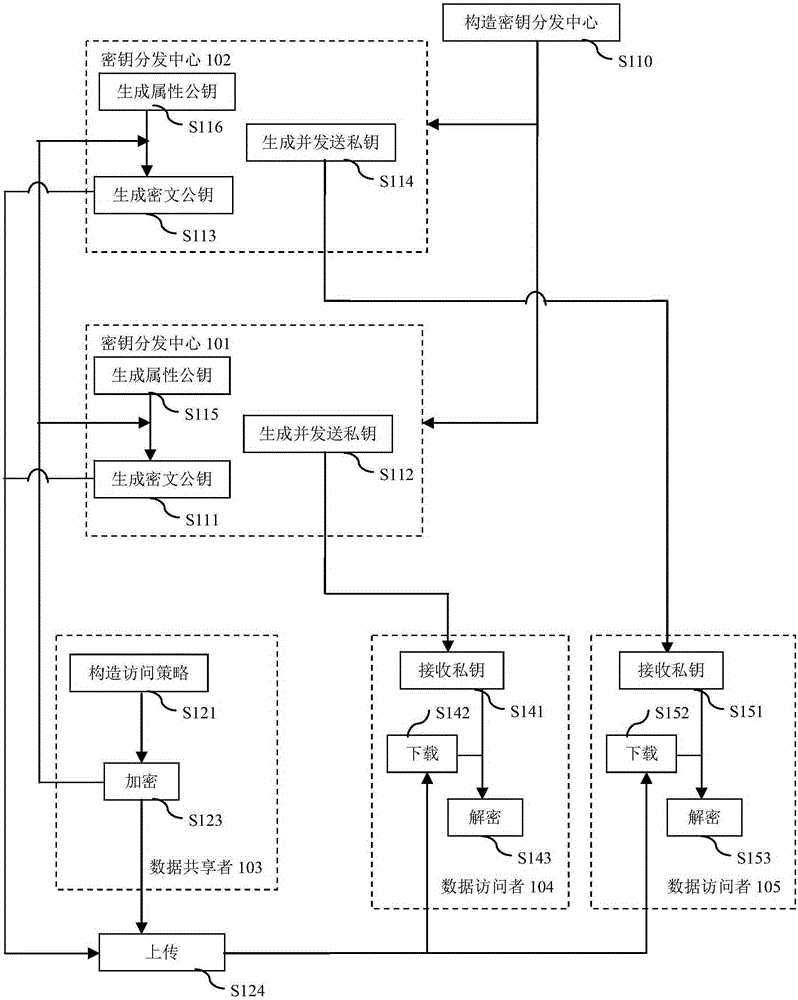
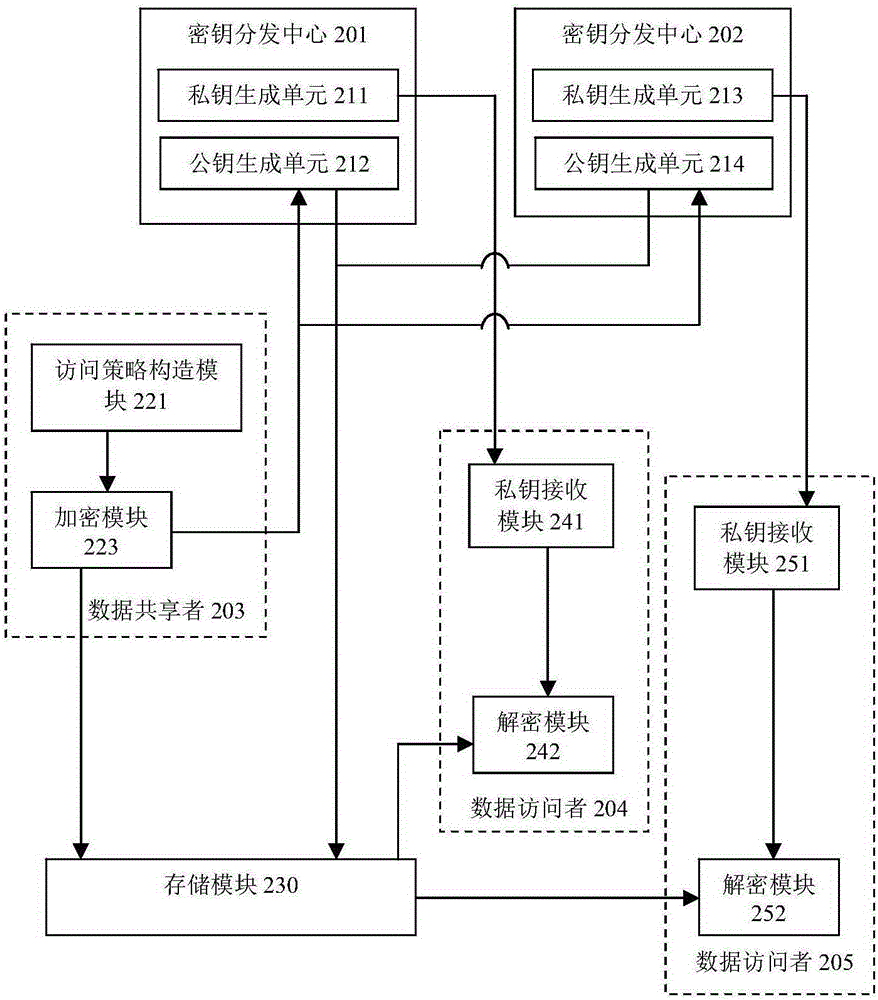
Data sharing system
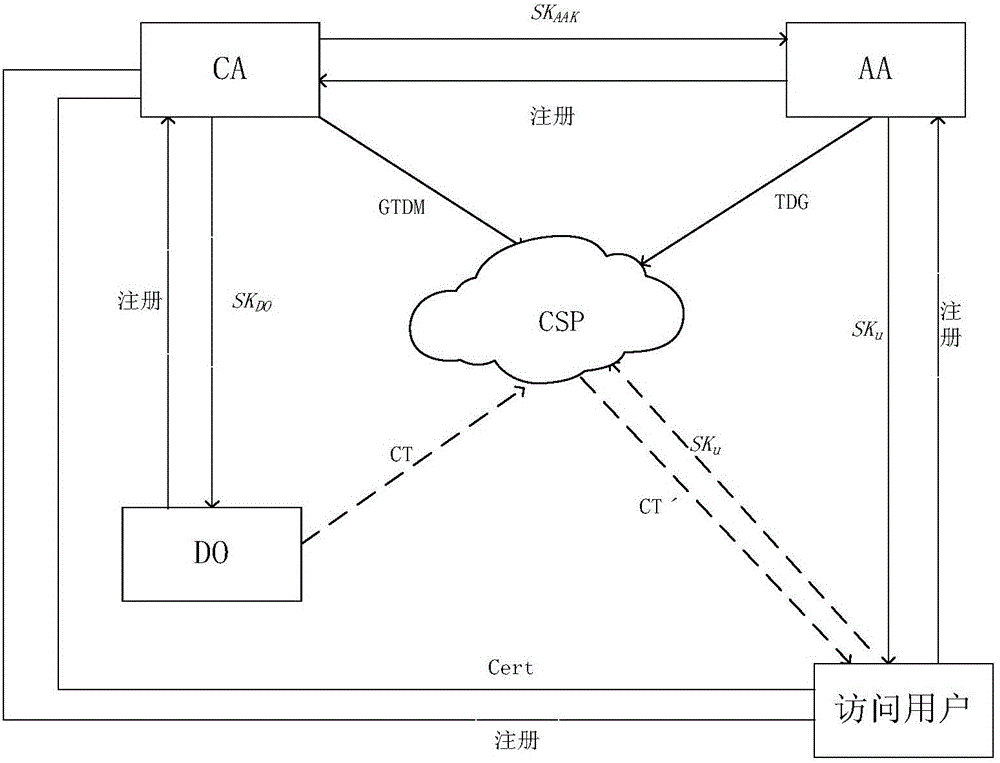
The invention discloses a data sharing method and system. The method comprises the following steps that: a plurality of secret key distribution center is constructed by using a unified common parameter; on the basis of the common parameter, each secret key distribution center generates an attribute public key corresponding to an attribute of a user; a corresponding secret key is generated based on a user attribute of a data visitor; a data sharer constructs an access strategy according to an access limit demand of shared data; encryption is carried out on the shared data by using an encryption secret key to generate a ciphertext; on the basis of the access strategy and the corresponding attribute public key, the encryption secret key is encrypted to generate a ciphertext public key; and the ciphertext is decrypted according to the ciphertext public key and a private key of the data visitor meeting the access strategy. Compared with the prior art, the safety performance of the system can be substantially improved with the method; and on the premise that safety is not reduced, the computational work of the method can be substantially reduced.
Owner:CHINA STANDARD SOFTWARE
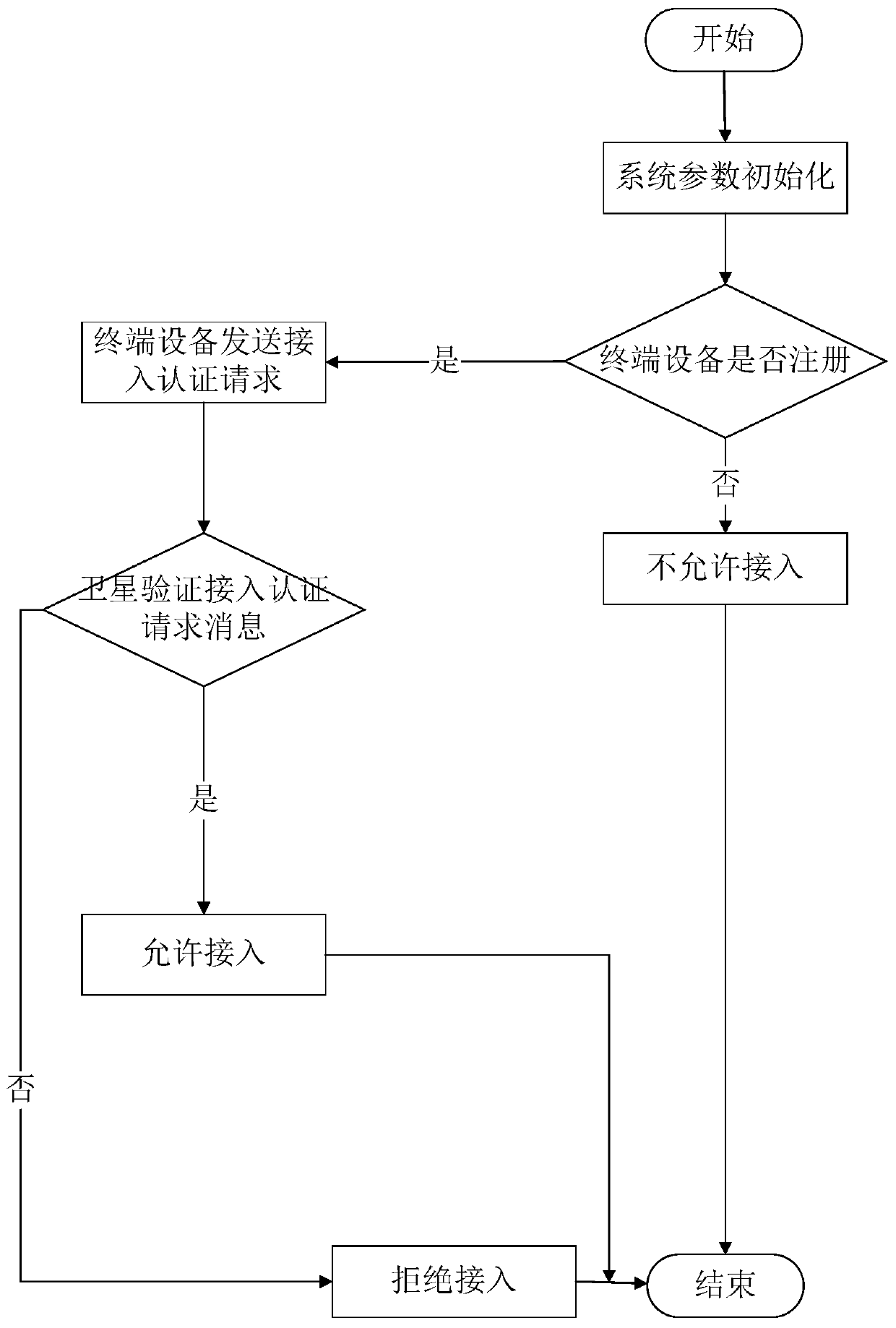
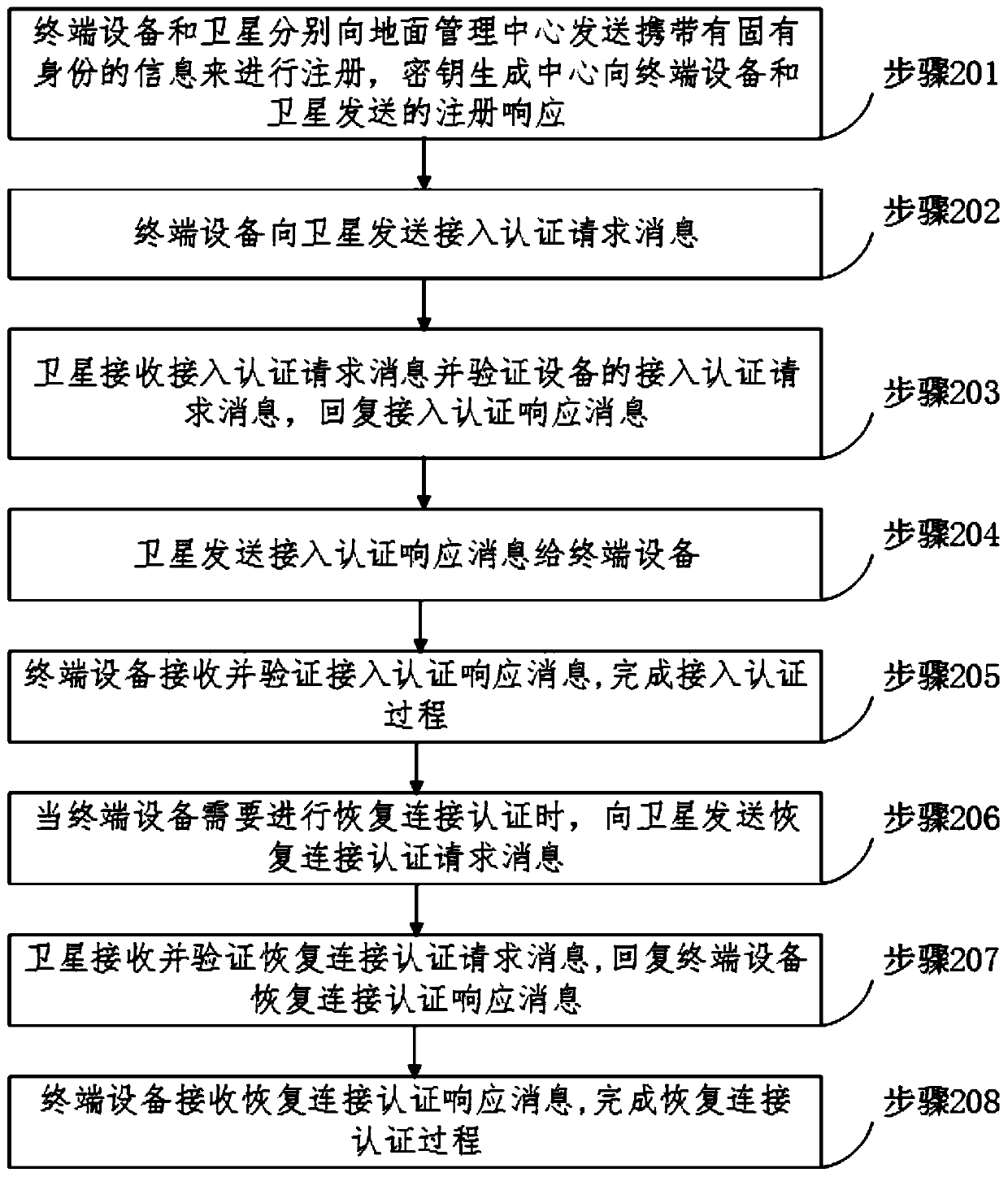
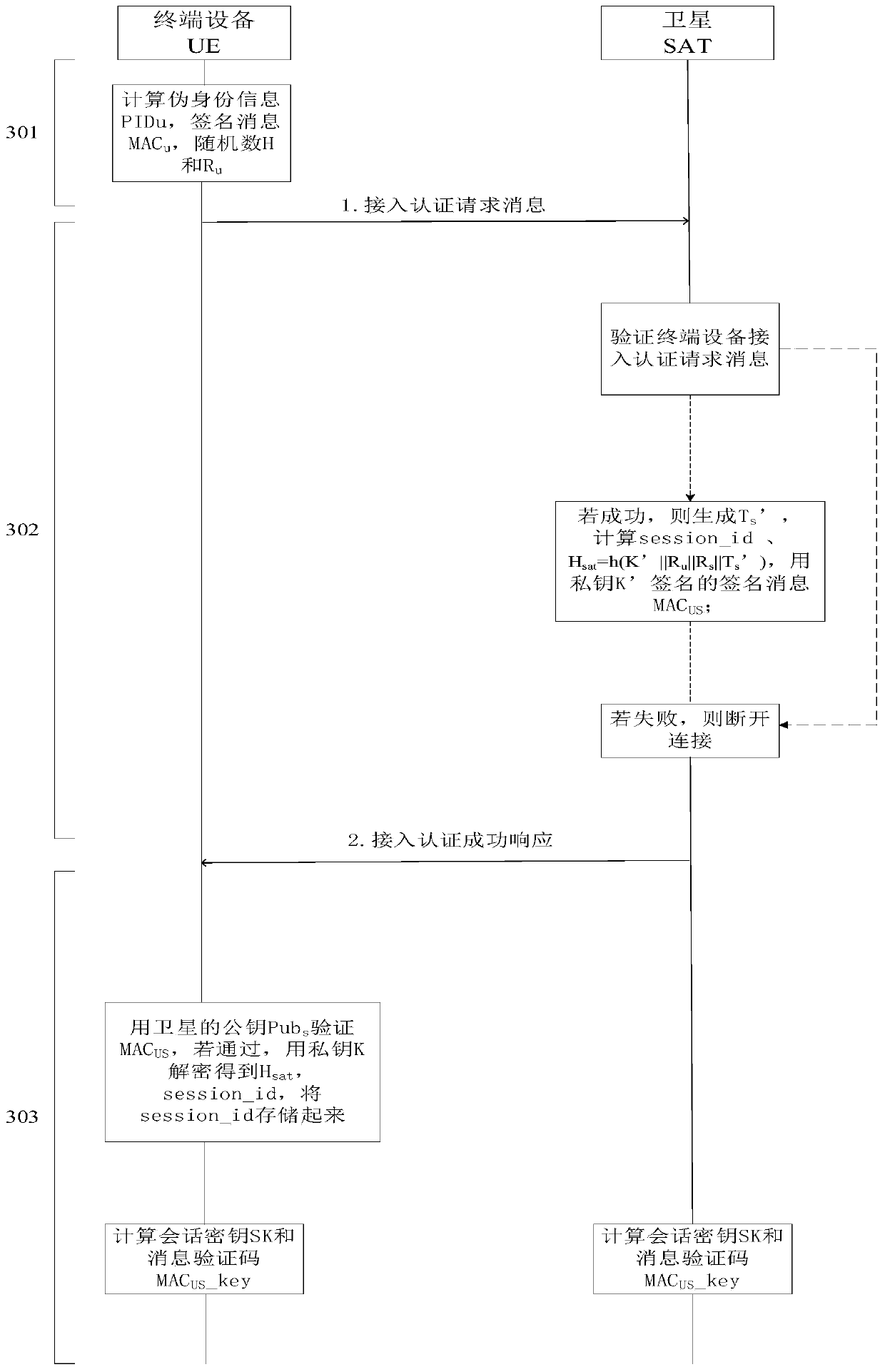
Space-ground integrated network anonymous access authentication method based on identity encryption system
ActiveCN111314056APrivacy protectionReduce overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacyTerminal equipment
The invention discloses a space-ground integrated network anonymous access authentication method based on an identity encryption system. Belonging to the field of information network security, according to the method, offline registration is carried out on a key distribution center by terminal equipment and a satellite respectively; the terminal device sends an access authentication request to thesatellite, the satellite receives an access authentication request and an identity authentication message of the terminal equipment, after verifying the legality of the terminal equipment, replying aterminal equipment access authentication response message; completing access authentication procedures, the terminal device sends a connection recovery authentication request to the satellite, according to the method, the terminal equipment does not need to be re-authenticated, the connection recovery authentication process is completed, the legality of the terminal equipment can be effectively verified, multiple access authentication mode selections are provided for users with different security requirements, the privacy security of the terminal equipment is ensured, and the complexity of access authentication is greatly reduced.
Owner:四川九强通信科技有限公司
Attribute-based encryption access control system of cloud storage digit library, and access control method thereof
ActiveCN105681355AAchieve integrationSolve the repeatabilityTransmissionStorage securitySecure authentication
The invention discloses an attribute-based encryption access control system of a cloud storage digit library, and an access control method thereof. The access control system comprises five entities: an authority center, a key distribution center, a cloud server, an uploading center, and an access user. The access control method comprise the steps of: system initialization, uploading center encryption and accessing a digit library. In the access control system, the uploading center uploads book data in categories according to corresponding attributes of books, so that the system realizes data integration, and effectively solves the problems of digital resource repeated construction and low sharing degree; in the access control method, the attribute-based encryption technology is introduced, which guarantees data storage security on one hand, and realizes user access control on the other hand. Accordingly, the method realizes user safety certificate and fine grit access control.
Owner:XIDIAN UNIV
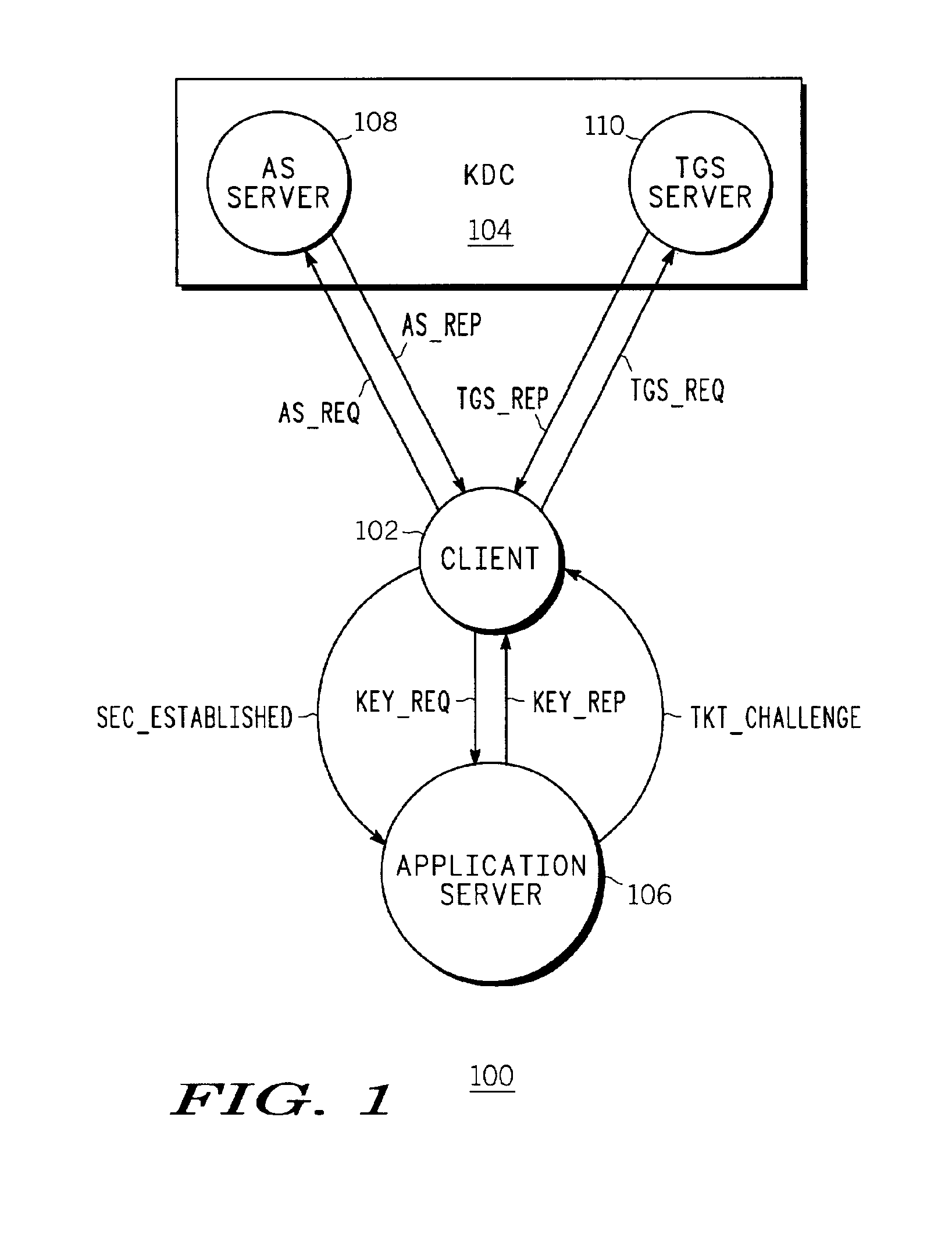
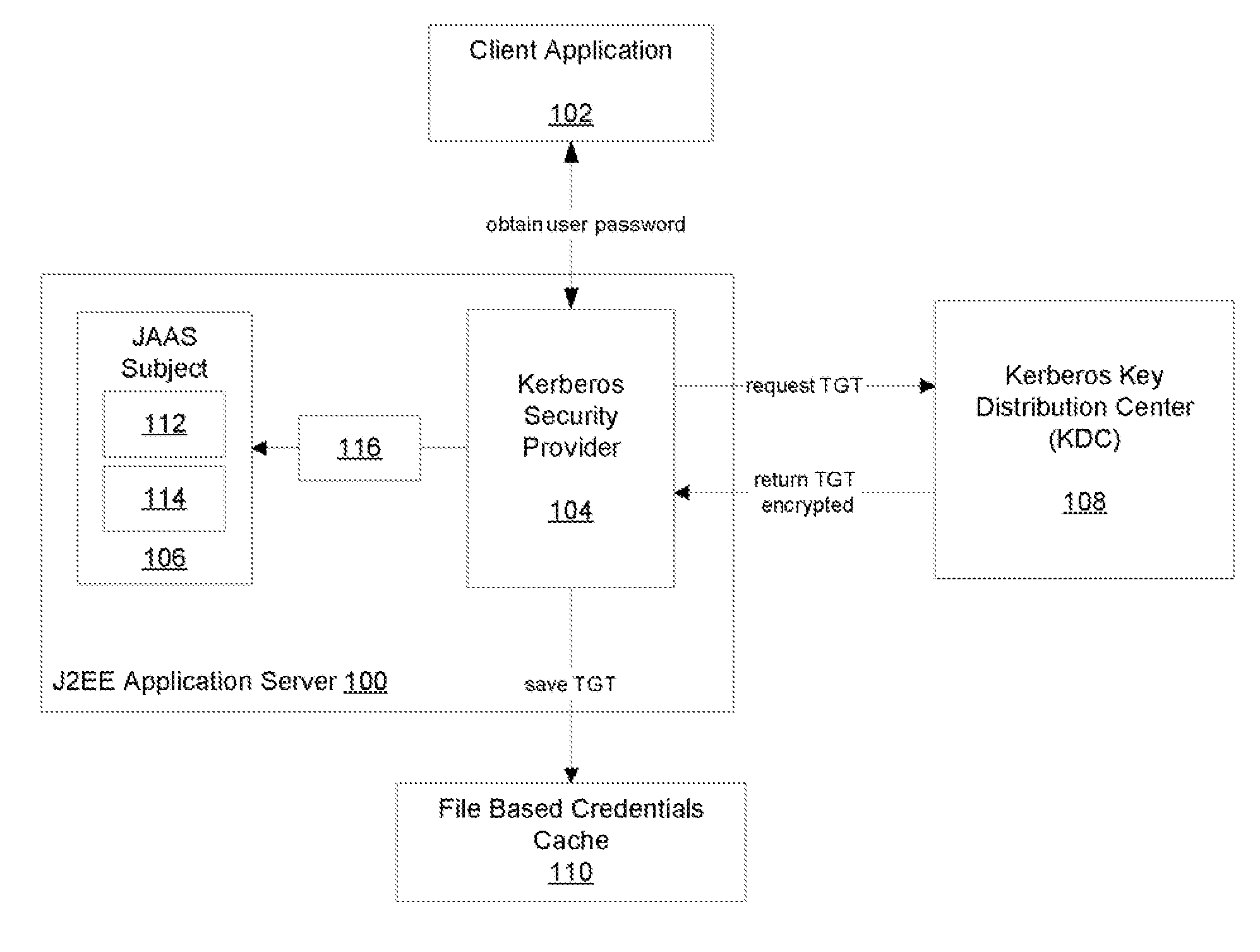
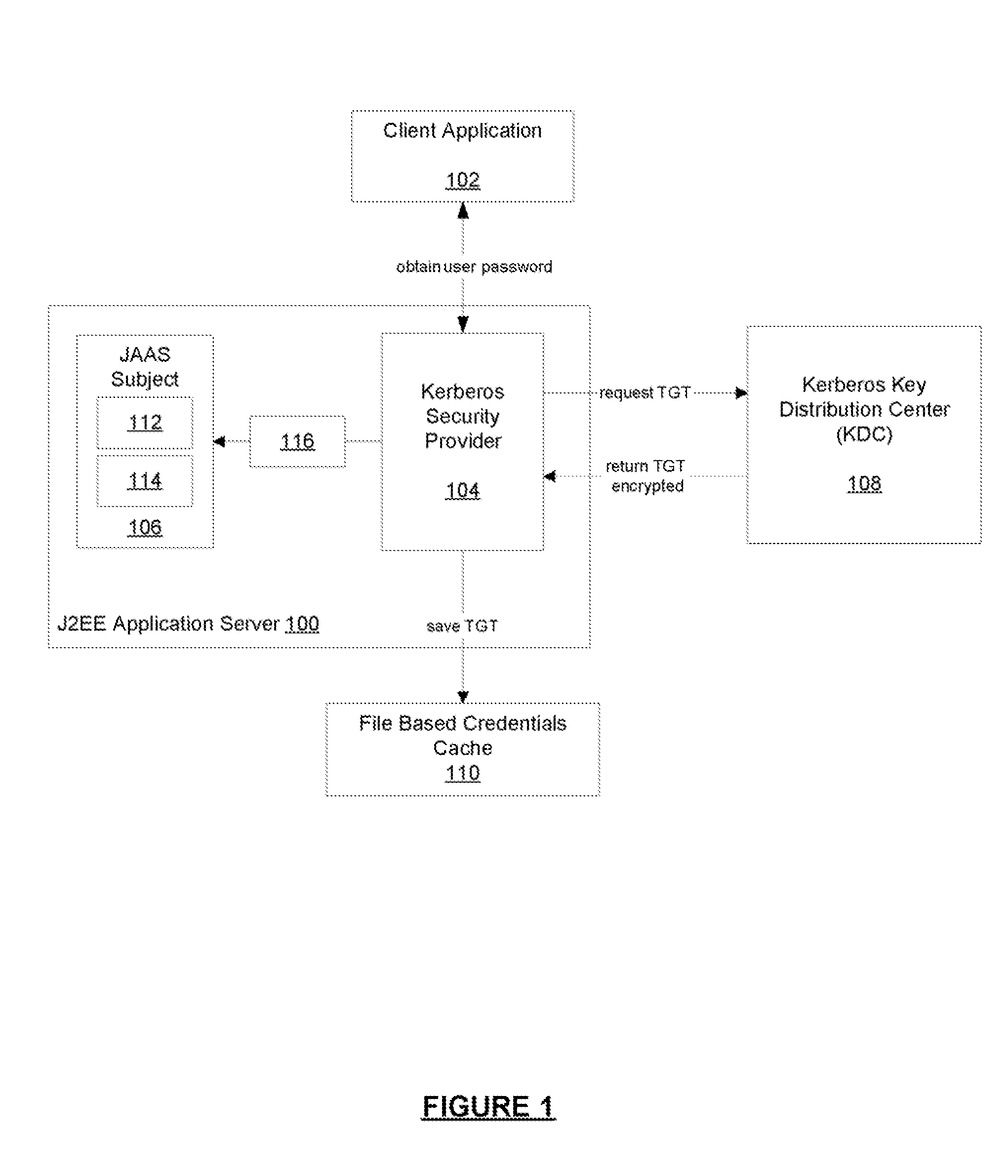
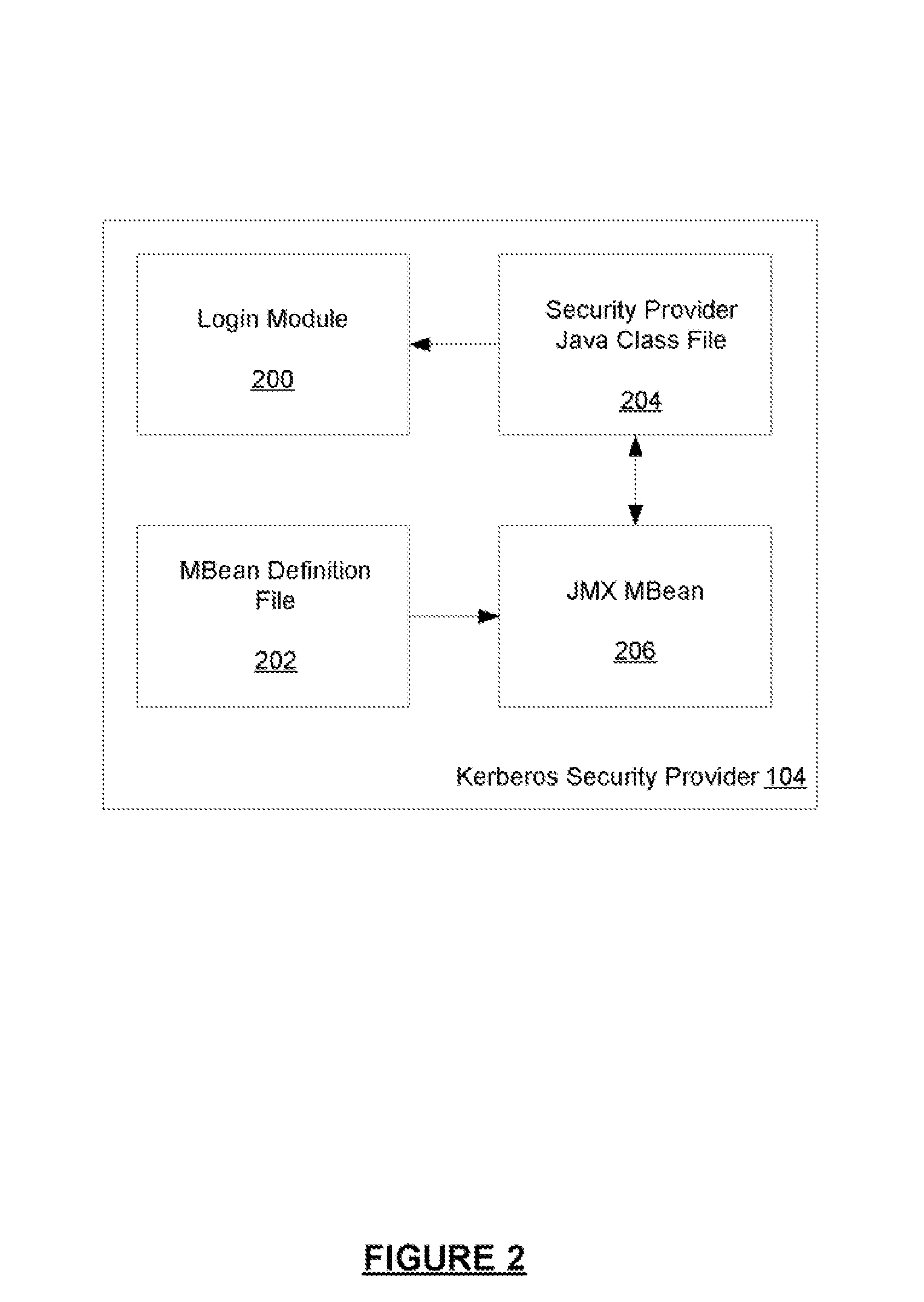
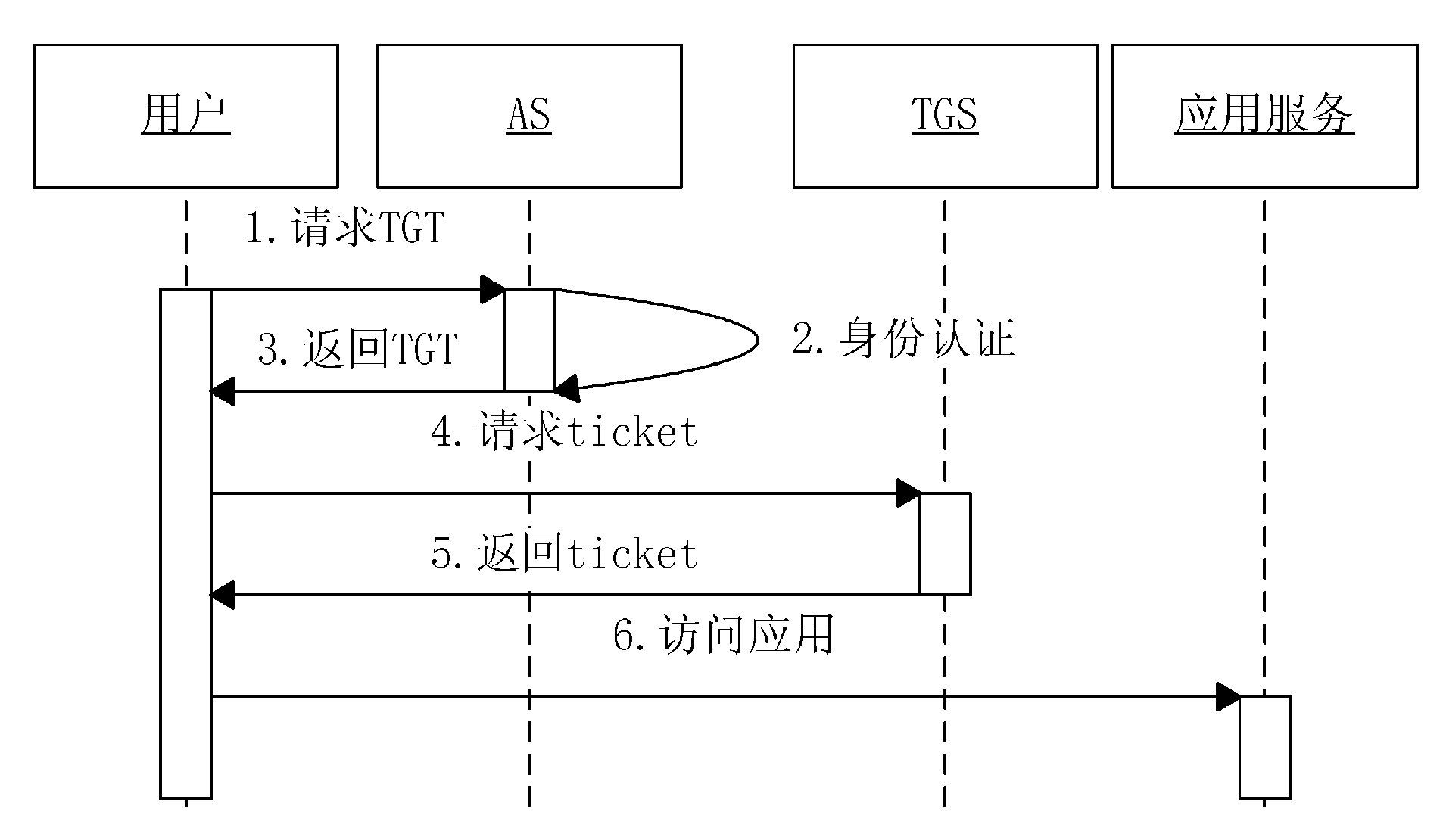
Kerberos Protocol Security Provider for a Java Based Application Server
InactiveUS20080083026A1Digital data processing detailsUser identity/authority verificationApplication serverPassword
A security provider is presented that integrates a Java based application server with Kerberos security protocol. The security provider includes a login module, a JMX MBean, an MBean definition file and a security provider java class. The JMX MBeans can contain various options that contain configuration information for the login module. The login module is responsible for authenticating the users by obtaining the user name and password, creating encryption keys, sending requests to the Kerberos key distribution center and receiving a ticket granting ticket encrypted with the user's password. The login module can then create an authenticated principal and add it to the subject associated with the user. The ticket granting ticket can also be added to the subject's private credentials. The security provider also supports the persistence of Kerberos credentials into a file based credentials cache.
Owner:ORACLE INT CORP
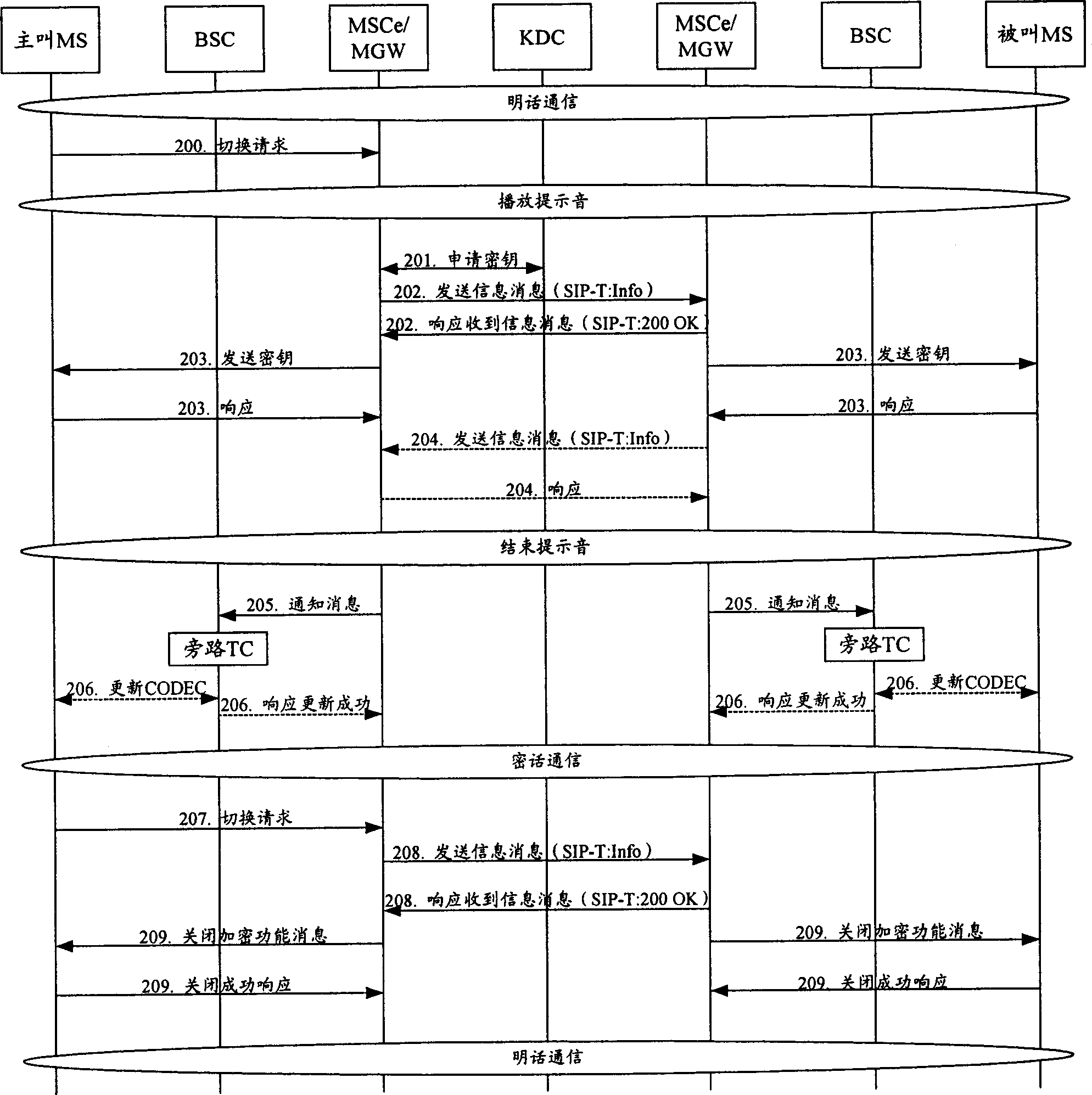
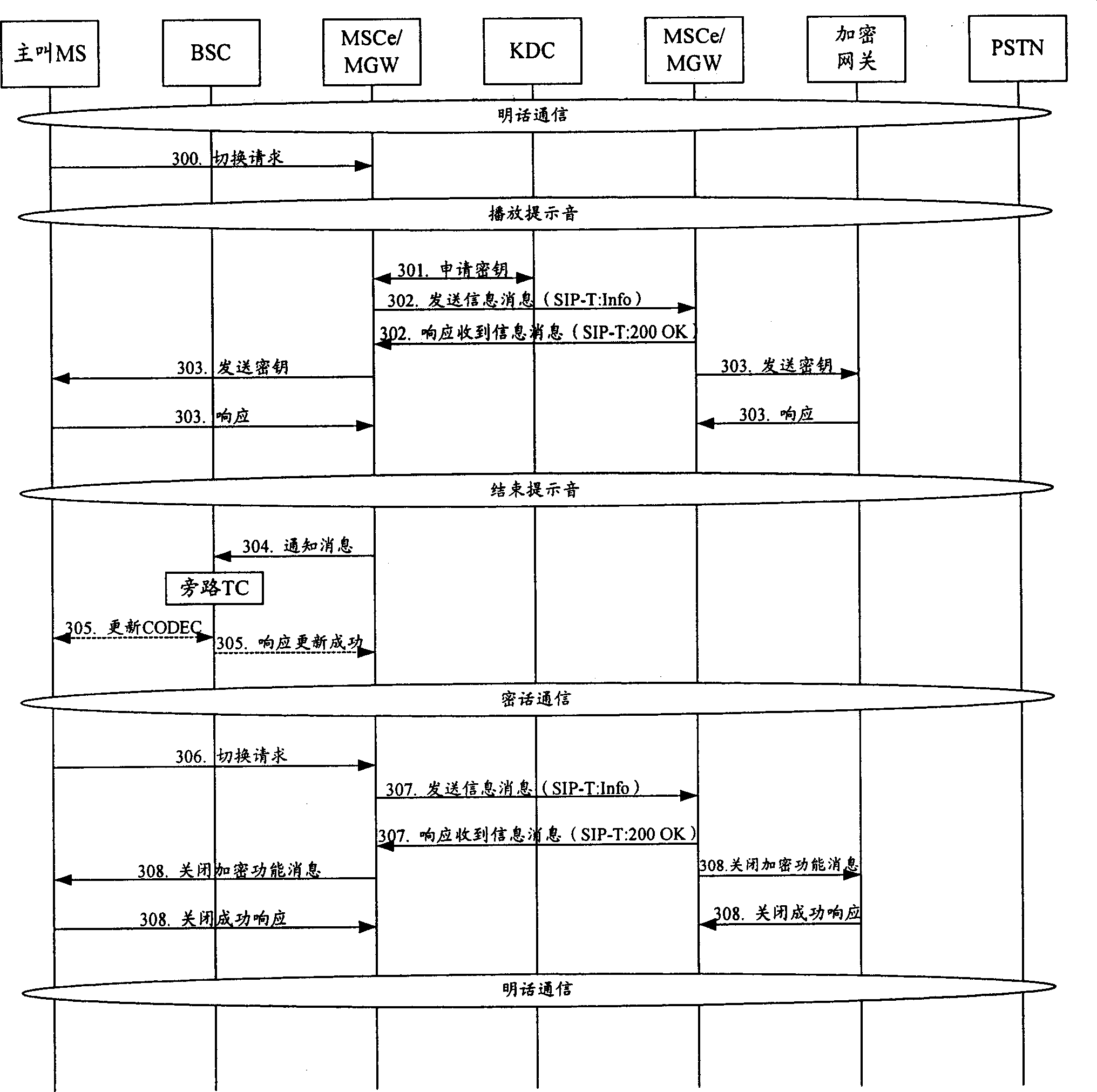
Method for realizing switch-over between open call/secrete call in end-to-end voice telecommunication
ActiveCN1816172ATo achieve mutual switchingGuaranteed confidentialityKey distribution for secure communicationRadio/inductive link selection arrangementsSoft switchingSwitched current
The disclosed method is applicable to soft switching system composed of switchboard, cipher key distribution center, controller of base station, public telephone switching network, and encrypted gateway when a call is built for both calling party and called party, and normal communication is carried out. The method also includes following steps: receiving switching request, switchboard determines current communication mode; if the current mode is plain mode, then switchboard at the party, who initiates switching request, applies to cipher key distribution center for cipher key, and switches plain mode to cipher mode; if the current mode is cipher mode, then switchboard at the party, who initiates switching request, sends message for closing cipher mode to another party, and switches current mode to plain mode, and closes cue tone. Plain mode and cipher mode can be switched by initiating switching request by calling party without interrupting normal communication in the invention.
Owner:HUAWEI TECH CO LTD
Secure kerberized access of encrypted file system
ActiveCN102668503AComputer security arrangementsSpecial data processing applicationsCryptographic protocolClient-side
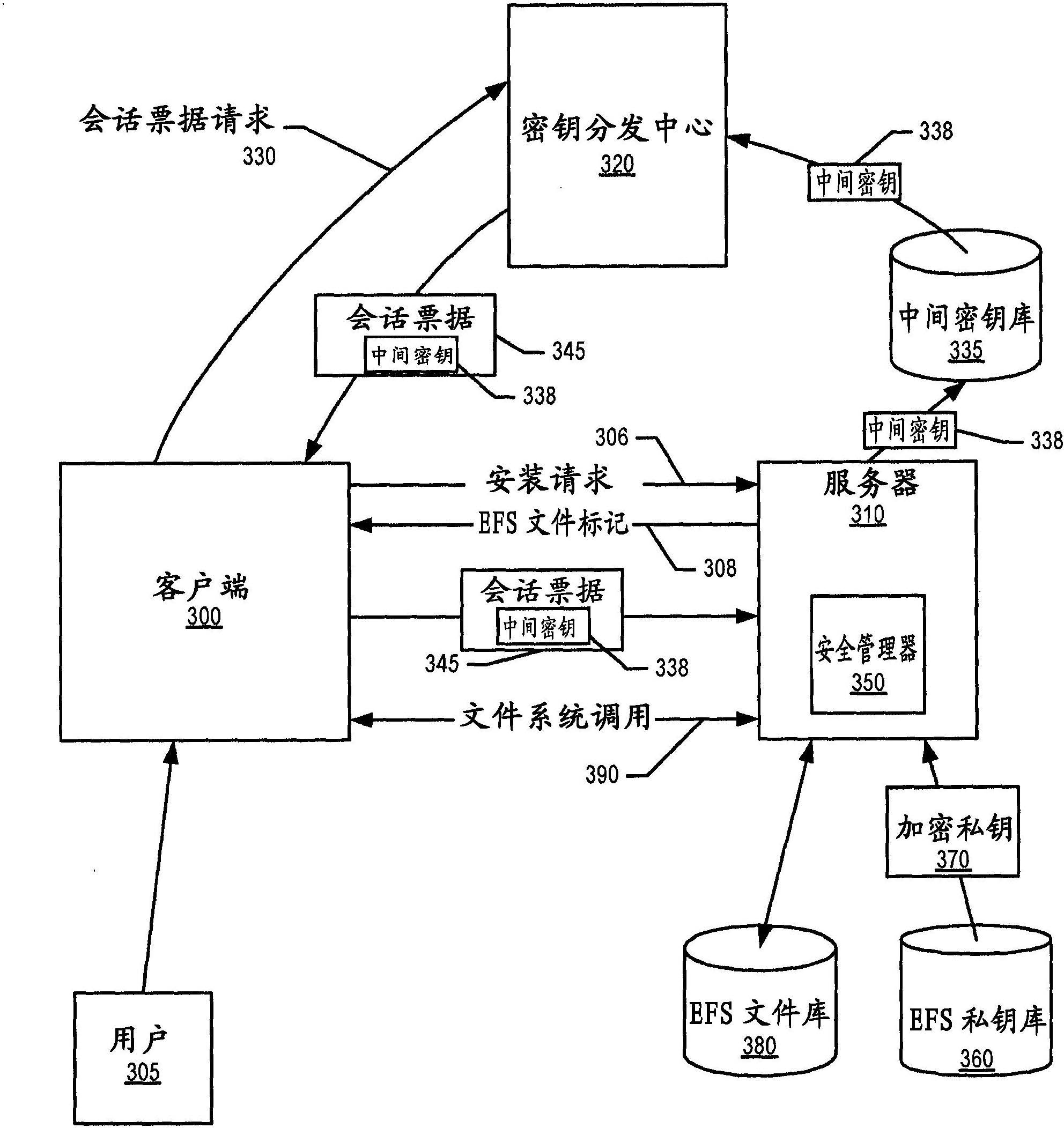
A file server receives a request from a client to mount an encrypted file system. The file server informs the client that the requested file system is encrypted and, in turn, receives a session ticket from the client that includes a security protocol mounting selection. The file server decrypts the client's user's encrypted private key, and then decrypts the requested encrypted file system using the private key. In turn, the file server sends the decrypted file system to the client over a secure channel, which is based upon the security protocol mounting selection. In one embodiment, a key distribution center server receives a request from the client for the client's user to access the encrypted file system at the file server. The key distribution center server retrieves an intermediate key; includes the intermediate key in a session ticket; and sends the session ticket to the client.
Owner:INT BUSINESS MASCH CORP
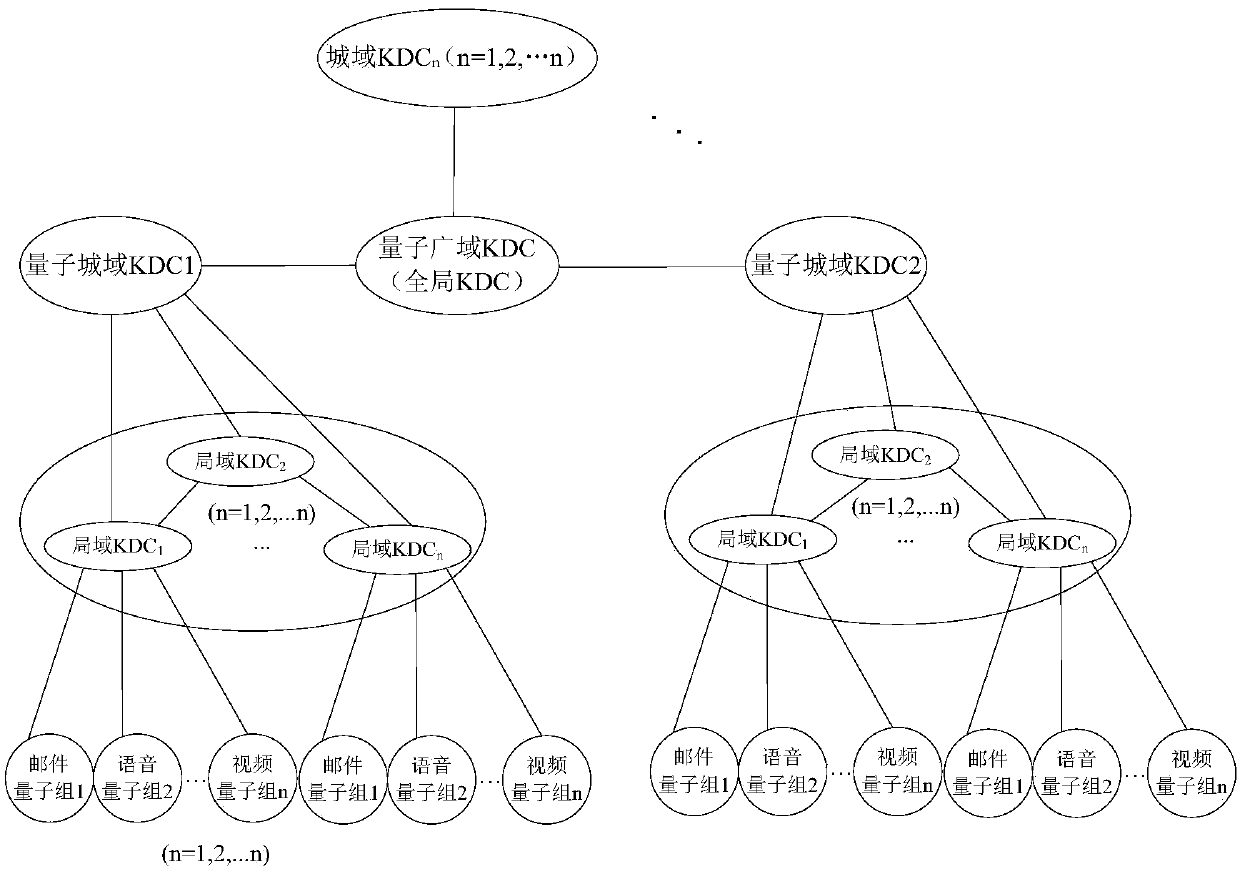
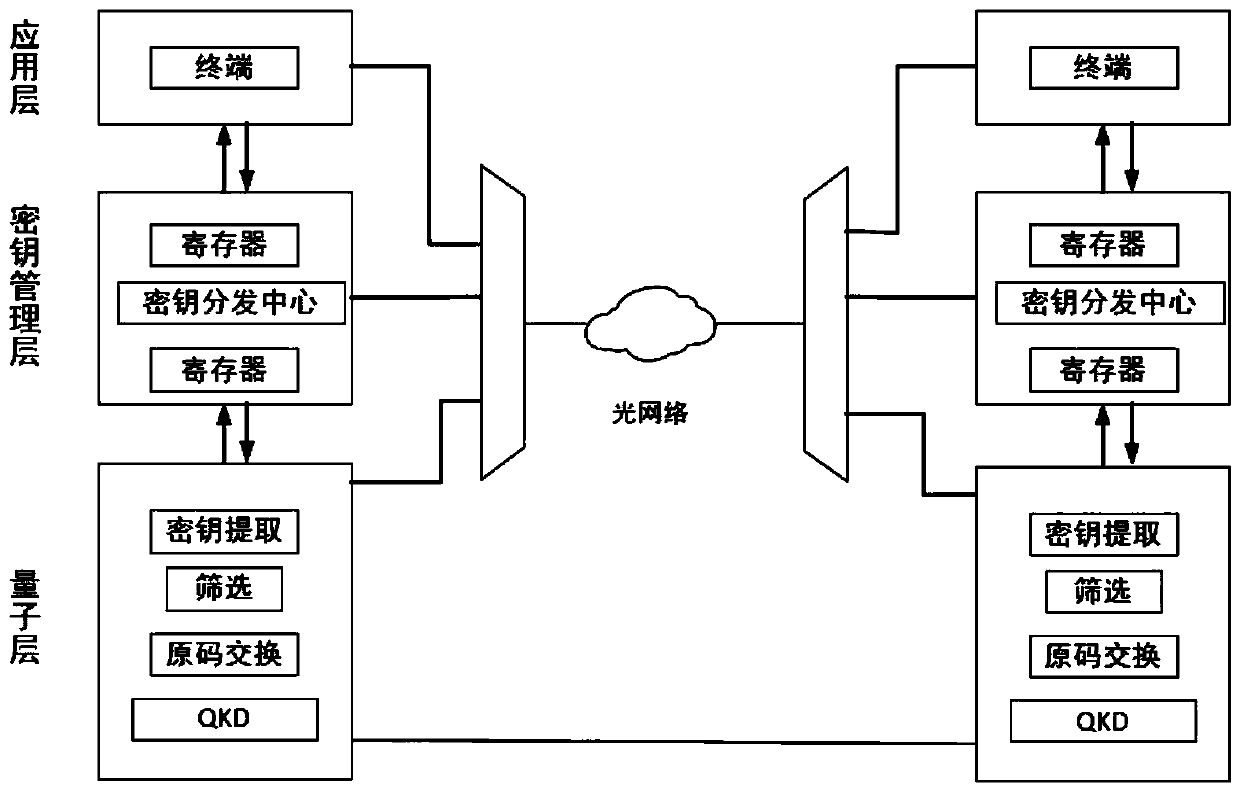
Quantum and classical integrated communication network system and key distribution method thereof
ActiveCN109660337AClear functionalityConducive to industry standardizatioKey distribution for secure communicationWavelength-division multiplex systemsNetworked systemModularity
The invention provides a quantum and classical integrated communication network system and a key distribution method thereof. The system adopts a three-layer mechanism, from the quantum key generationof a quantum layer to the storage and forwarding of a key management layer, and terminal application of an application layer, the functionality of each layer is clear, and the more appropriate QKD can be selected according to the application layer quantum group terminal, the communication distance, the key rate and like requirements; an engineering modularization system is more flexible and convenient to facilitate the industry standardization and the large-scale market application; the key distribution method provided by the invention adopts a dynamic distribution technology, namely, the request-distribution online distribution technology, a session mechanism is established according to a request and key distribution center of the terminal, and the key distribution can be efficiently accomplished in real time.
Owner:NAT QUANTUM COMM GUANGDONG CO LTD
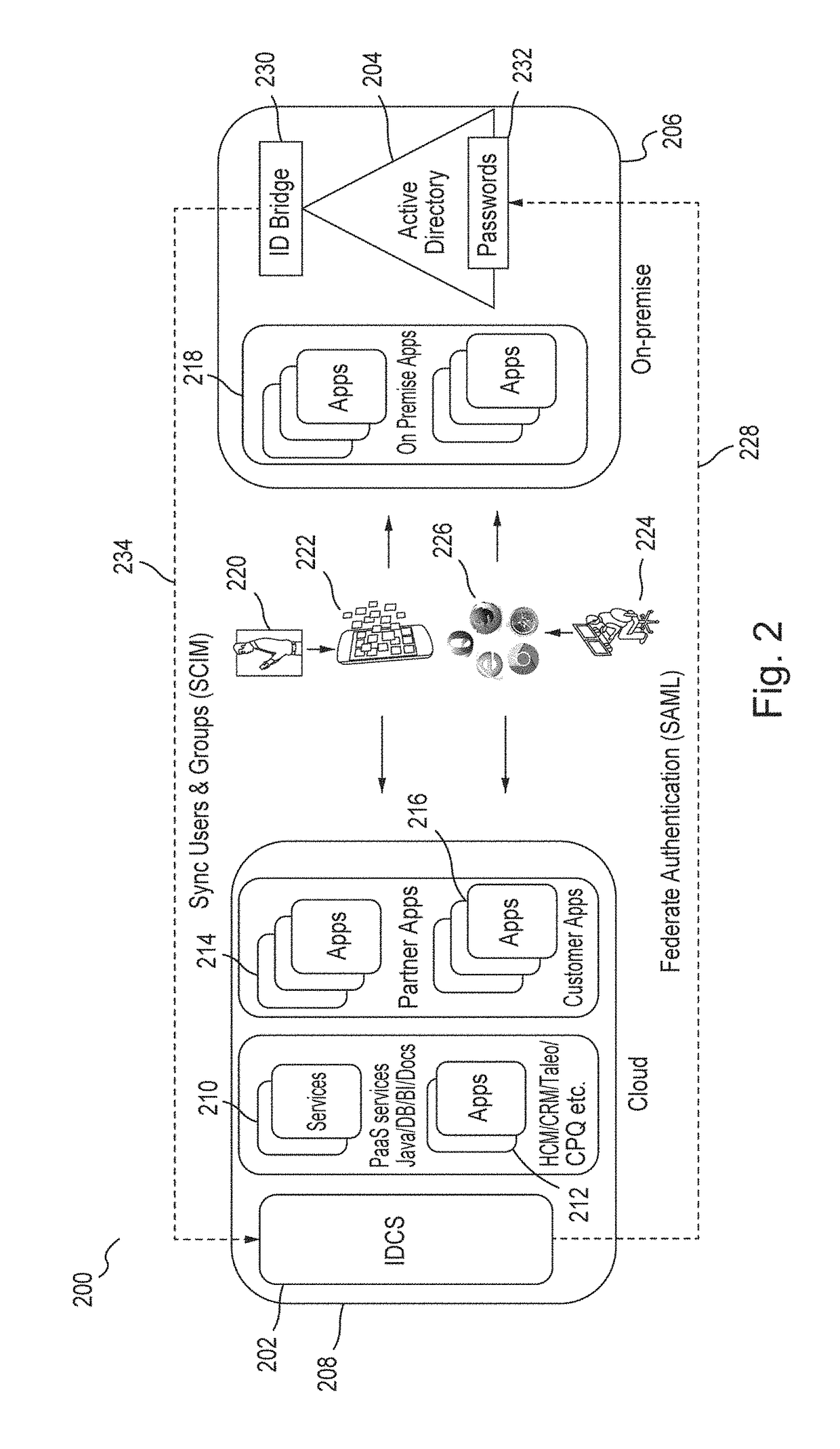
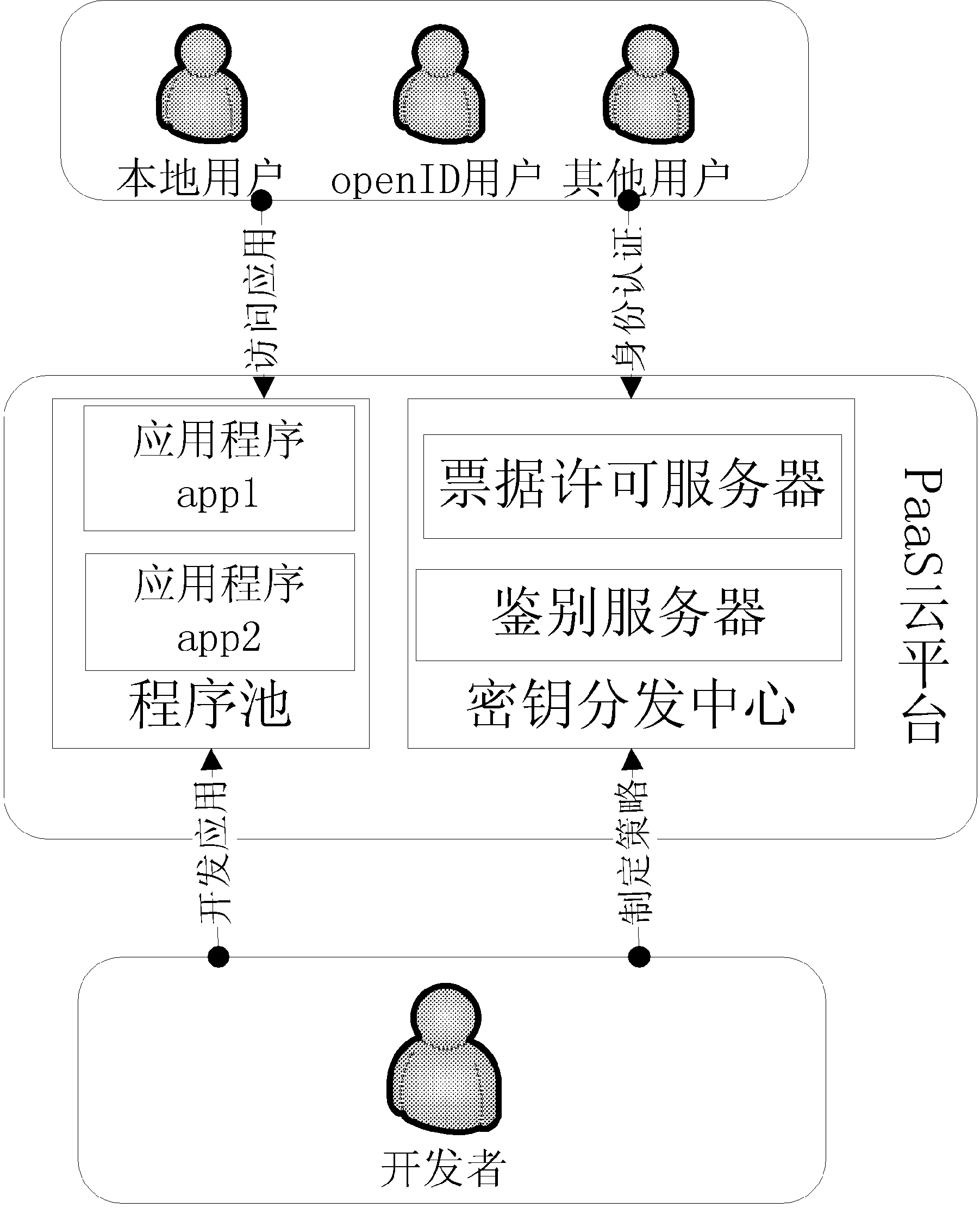
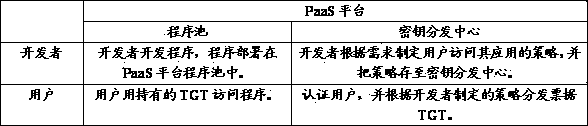
PaaS platform-based identity authentication method and identity authentication apparatus
InactiveCN104113412AImprove scalabilityUser identity/authority verificationDigital data authenticationTicketInternet privacy
The invention discloses an identity authentication apparatus on a PaaS platform. The identity authentication apparatus is used for authenticating the identities of users who are to access applications on the PaaS platform; the identity authentication apparatus includes a key distribution center which is used for authenticating the users according to access strategies made by the developers of the applications, and distributing tickets; the key distribution center includes an authentication server; and the authentication server is configured to receive verification requests from the users, to determine protocols to which the identities of the users belong, to determine the verification modes of the users according to the protocols and transmit first granting tickets to the users after successful verification. The invention also discloses a PaaS platform-based identity authentication method.
Owner:CHINA UNIONPAY
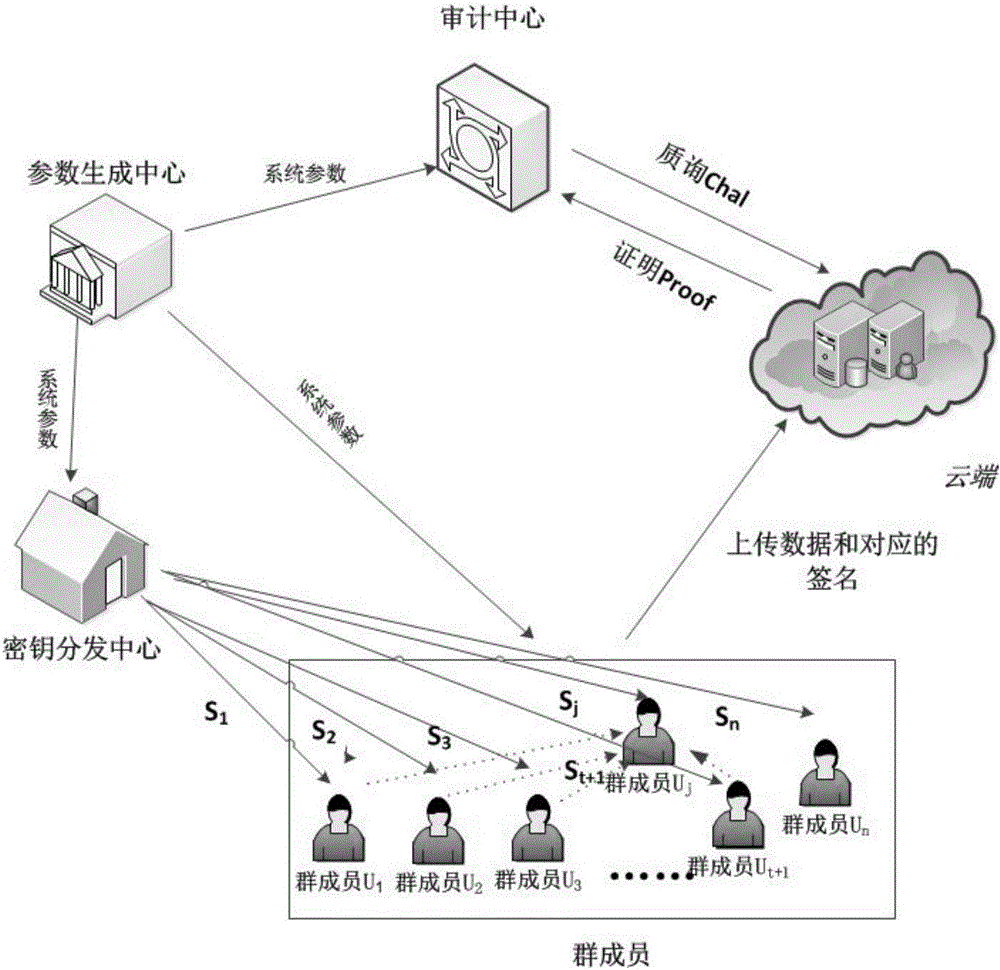
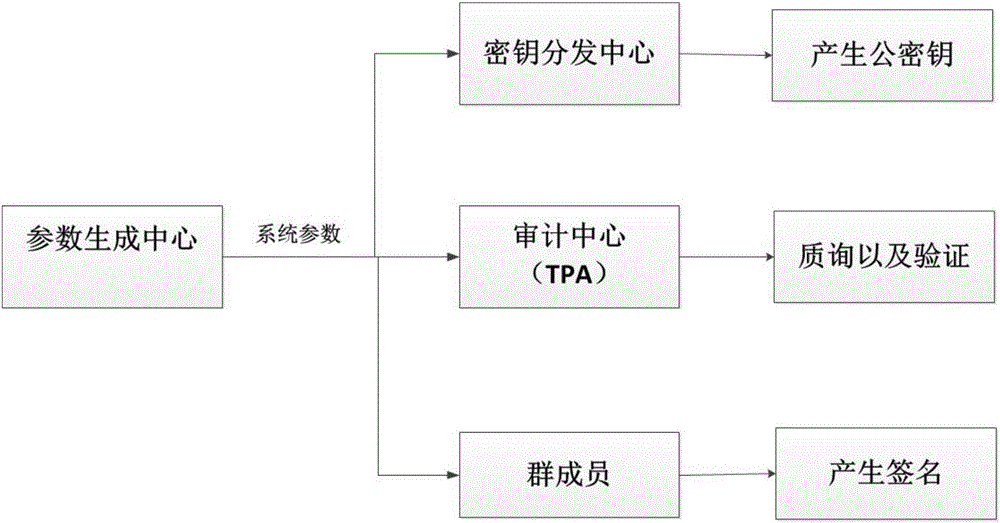
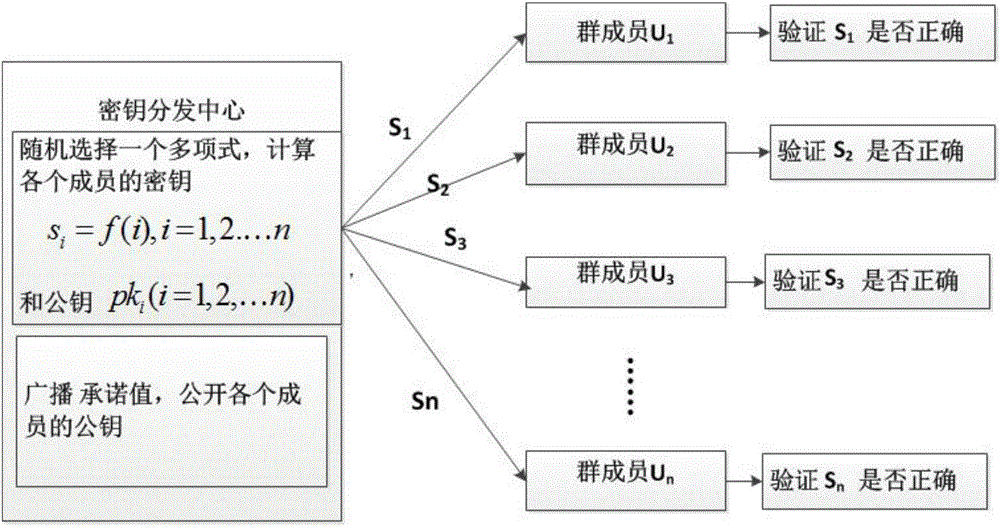
Cloud storage integrity detection method for recovering lost secret keys and system applying cloud storage integrity detection method
ActiveCN104954390AAvoid regeneratingPrevent dishonestyTransmissionCloud storageKey distribution center
The invention provides a cloud storage integrity detection method for recovering lost secret keys, and a system applying the cloud storage integrity detection method. The system comprises a parameter generation center module, a cloud module, a secret key distribution center module, a group member module and an audit center module. Through the adoption of the system, when the secrete keys of members in a group are lost, the conditions that new secrete keys are regenerated and signatures are regenerated for part of data can be avoided; the secrete keys can be verified, namely, each member in the group can verify whether the secrete key sent by a secrete key distribution center is correct or not, and the user of which the secrete key is lost can also verify whether the share, sent by other t+1 members in the group, is correct or not, so as to avoid the condition that the secret key distribution center or the user distributing the share to the user of which the secrete key is lost is dishonest; when the secrete keys are recovered, the secrete keys of the members are blinded, so that all the members do not know the secrete keys of the others. Therefore, the secrete key recovering safety is improved, and a cloud is prevented from being framed by malicious users.
Owner:建投数据科技(山东)有限公司
Authentication method based on public key encryption system
ActiveCN108400867AVerify freshnessDefense against replay attacksKey distribution for secure communicationUser identity/authority verificationImpersonation attackKey distribution center
Owner:中国科学院沈阳计算技术研究所有限公司
Internet of Things terminal card binding, network access authentication and service authentication method and device
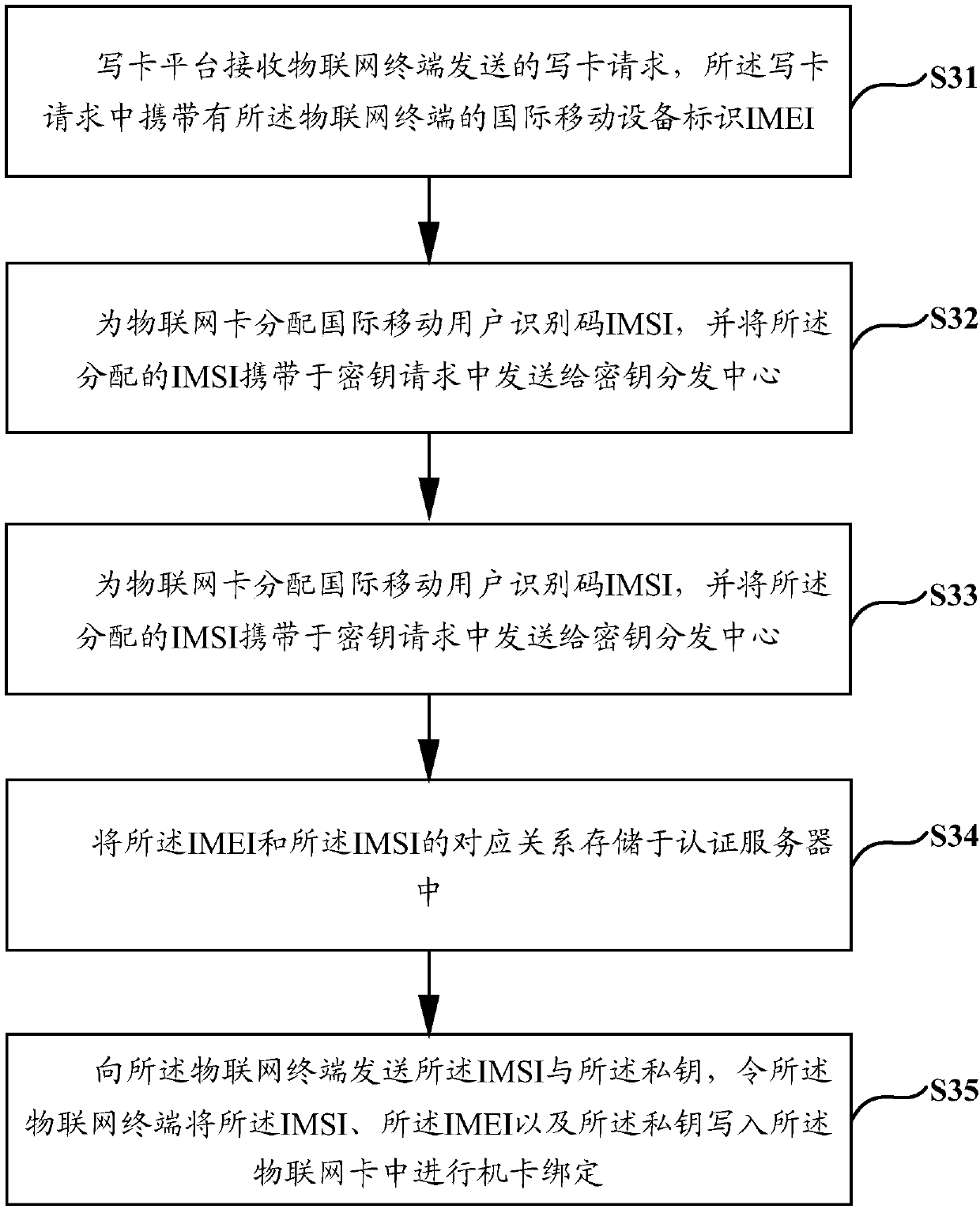
ActiveCN111182521AImprove versatilityReduce transmissionNetwork topologiesSecurity arrangementInternet privacyMobile equipment identifier
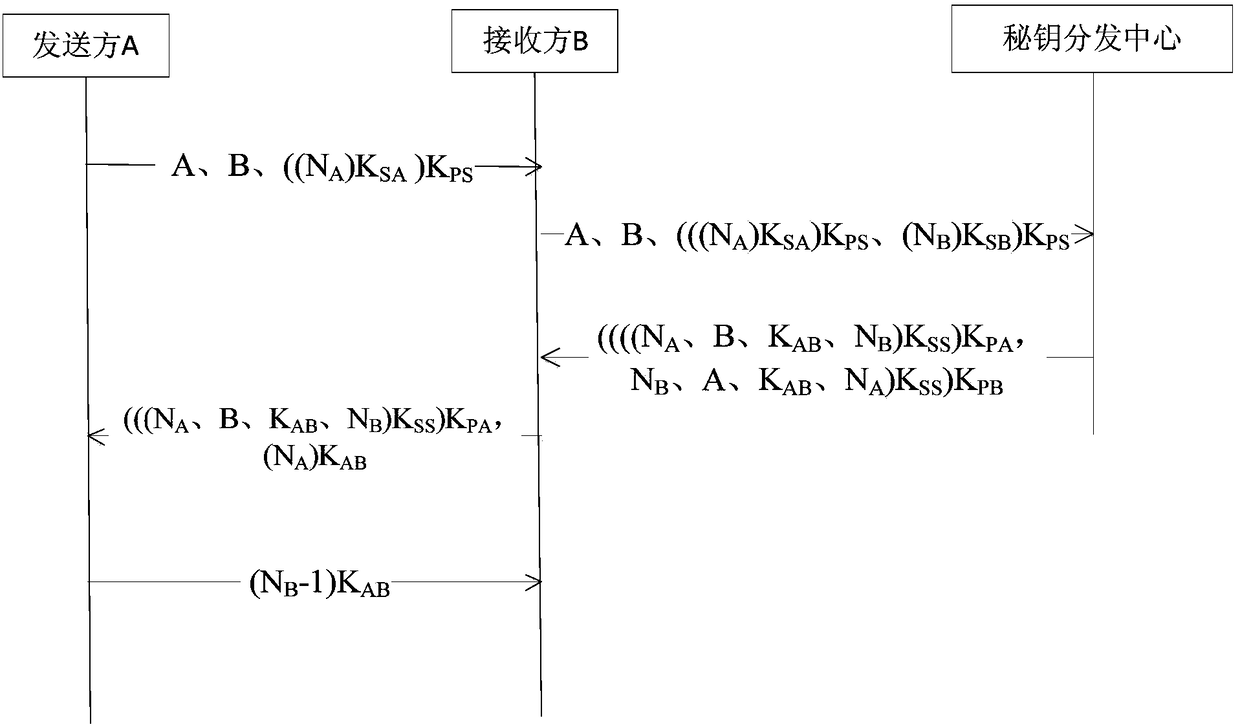
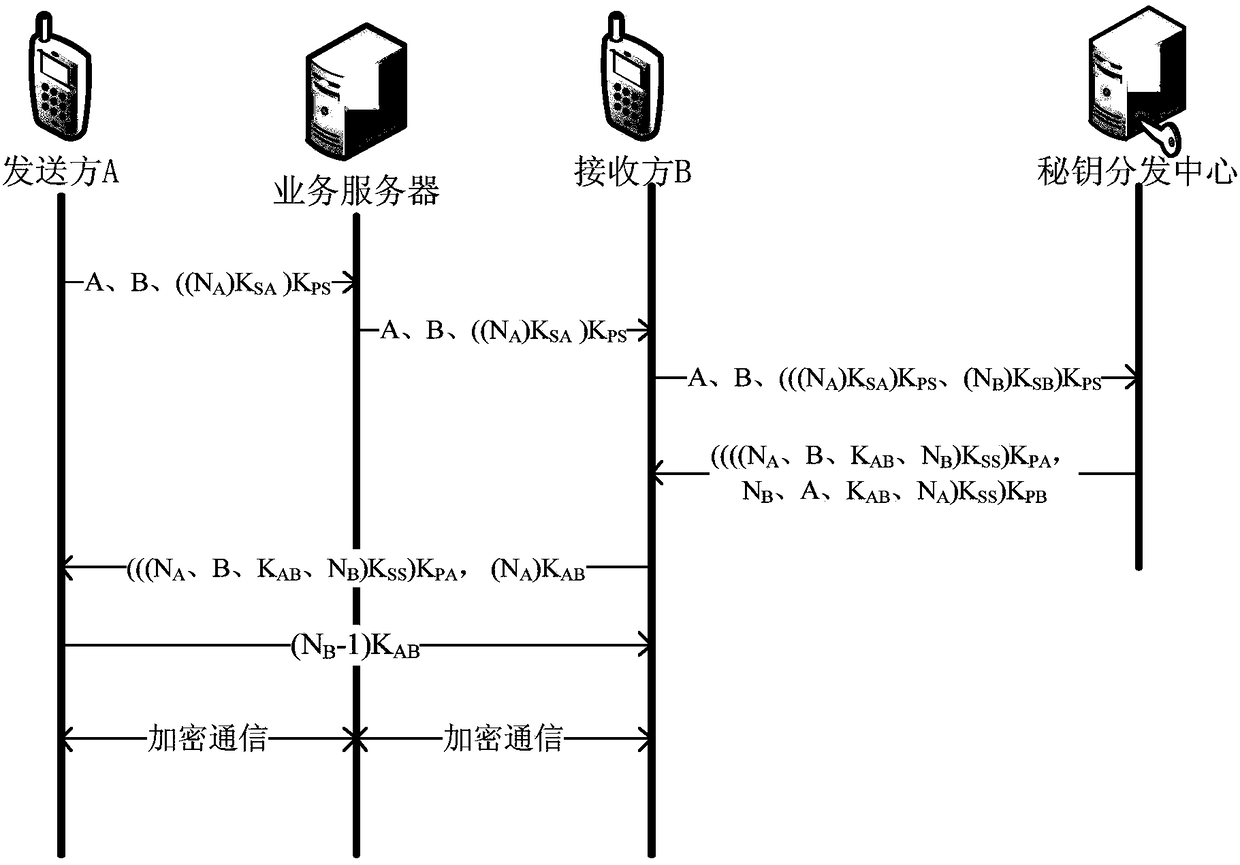
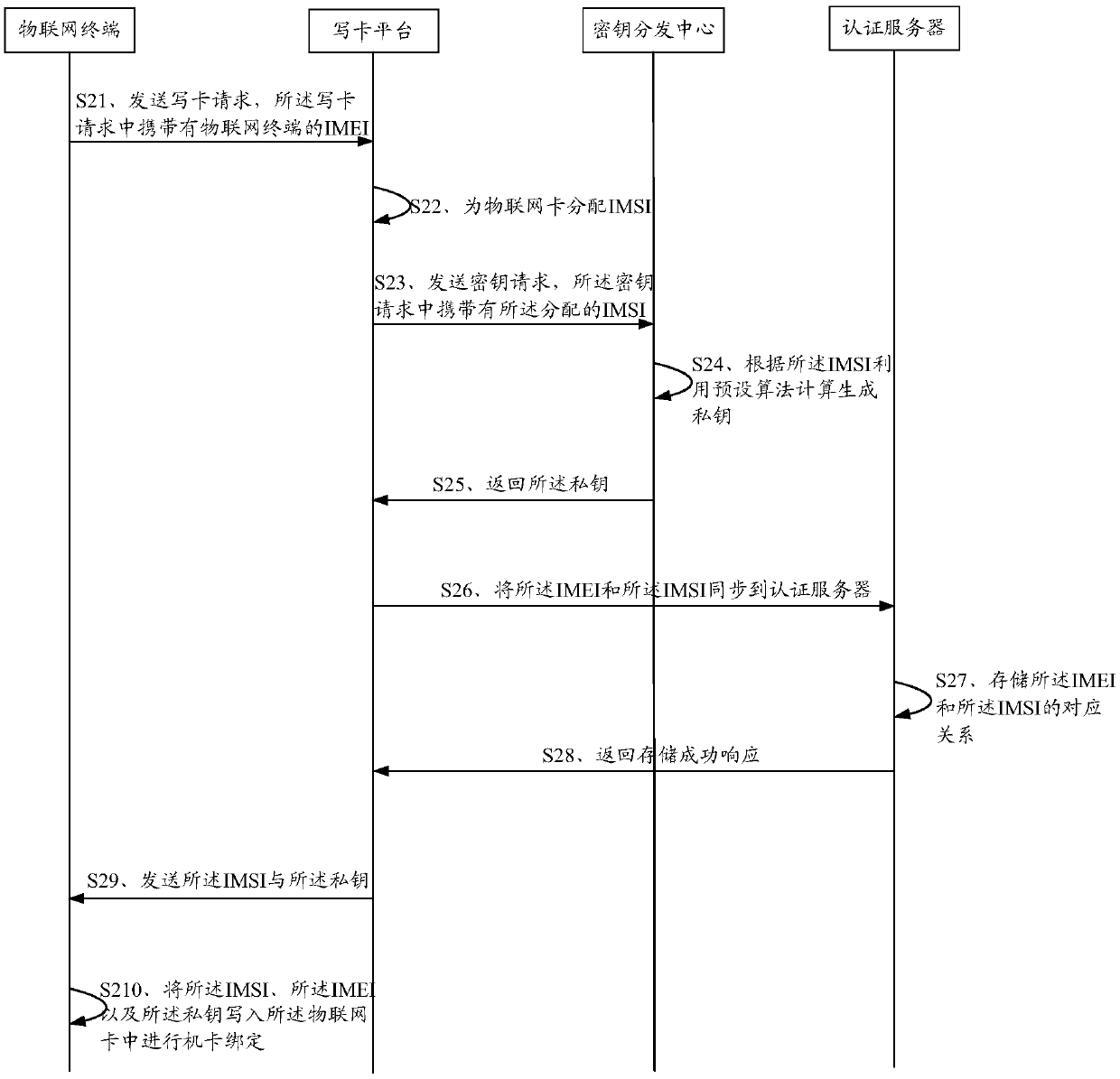
The invention discloses an Internet of Things terminal card binding, network access authentication and service authentication method and device, which are used for solving the problems of a complex authentication process and a high cost of Internet of Things equipment in the prior art. The Internet of Things terminal card binding method comprises the following steps: receiving a card writing request sent by an Internet of Things terminal, wherein the card writing request carries an international mobile equipment identifier (IMEI) of the Internet of Things terminal, distributing the IMSI for the Internet of Things card, carrying the distributed IMSI in a key request, sending the key request to a key distribution center, receiving a private key which is sent by the key distribution center and is calculated and generated by utilizing a preset algorithm according to the IMSI, storing the corresponding relationship between the IMEI and the IMSI in an authentication server, sending the IMSIand the private key to the Internet of Things terminal, and enabling the Internet of Things terminal to write the IMSI, the IMEI and the private key into the Internet of Things card for machine-card binding.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com