Cloud storage integrity detection method for recovering lost secret keys and system applying cloud storage integrity detection method
A technology for integrity detection and cloud storage, applied in the field of cloud storage security, which can solve problems such as computational and communication costs, inability to apply to cloud storage environments, and security issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
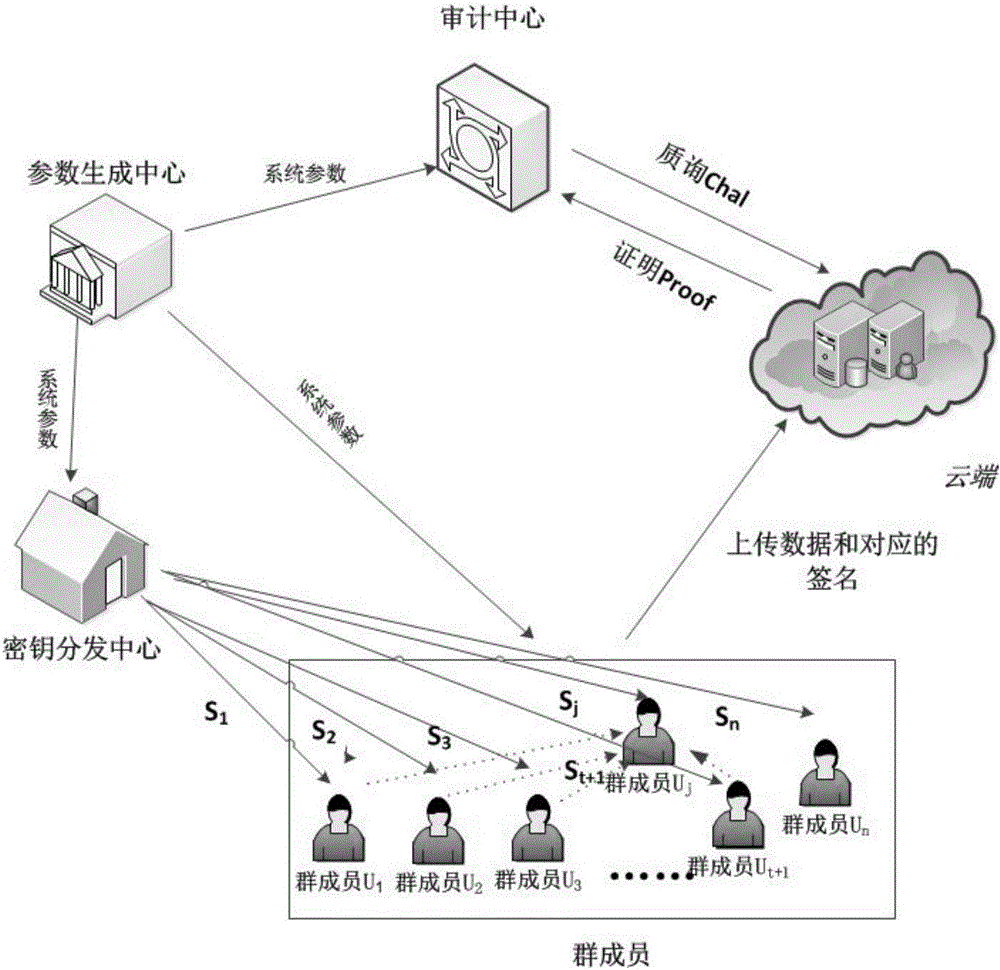
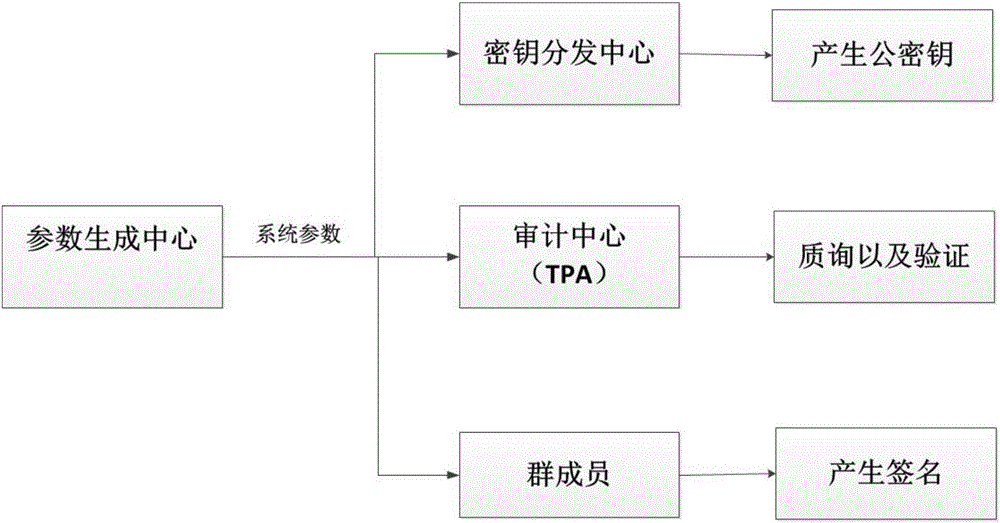
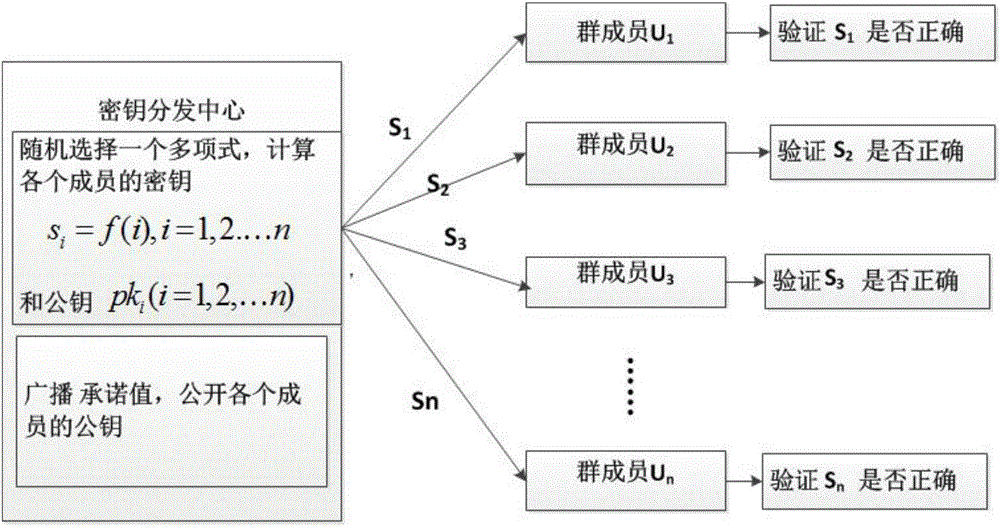
[0055] The following examples are used to describe the implementation of the present invention in detail, so as to fully understand and implement the process of how to apply technical means to solve technical problems and achieve technical effects in the present invention.
[0056] One, the relevant theory applied in the present invention
[0057] (1) Bilinear pairing
[0058] Let G 1 ,G 2 is the multiplicative group of two order prime numbers q, if the mapping satisfy the following properties:
[0059] 1) Bilinear: For ∀ P , Q ∈ G 1 , a , b ∈ Z q * ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com