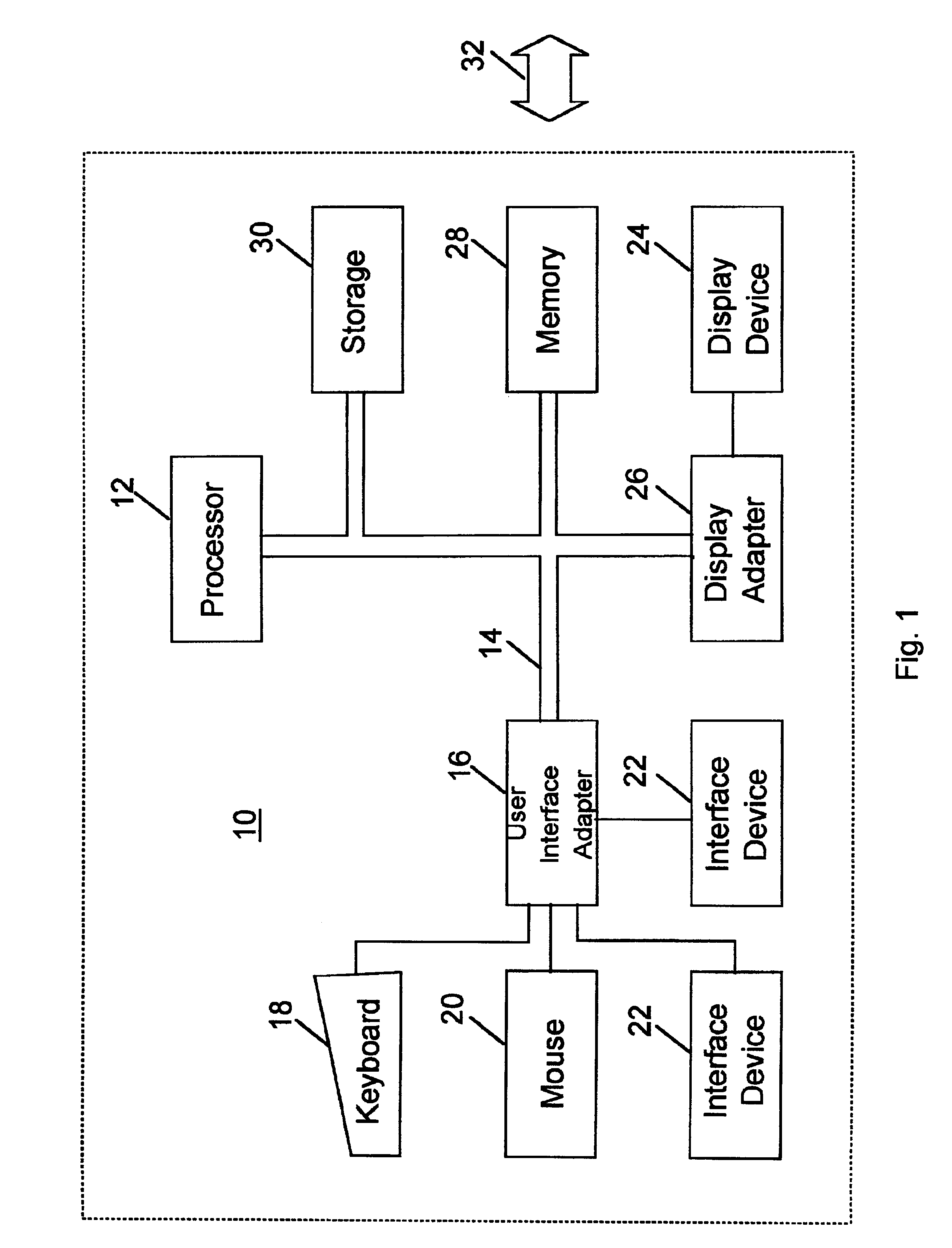
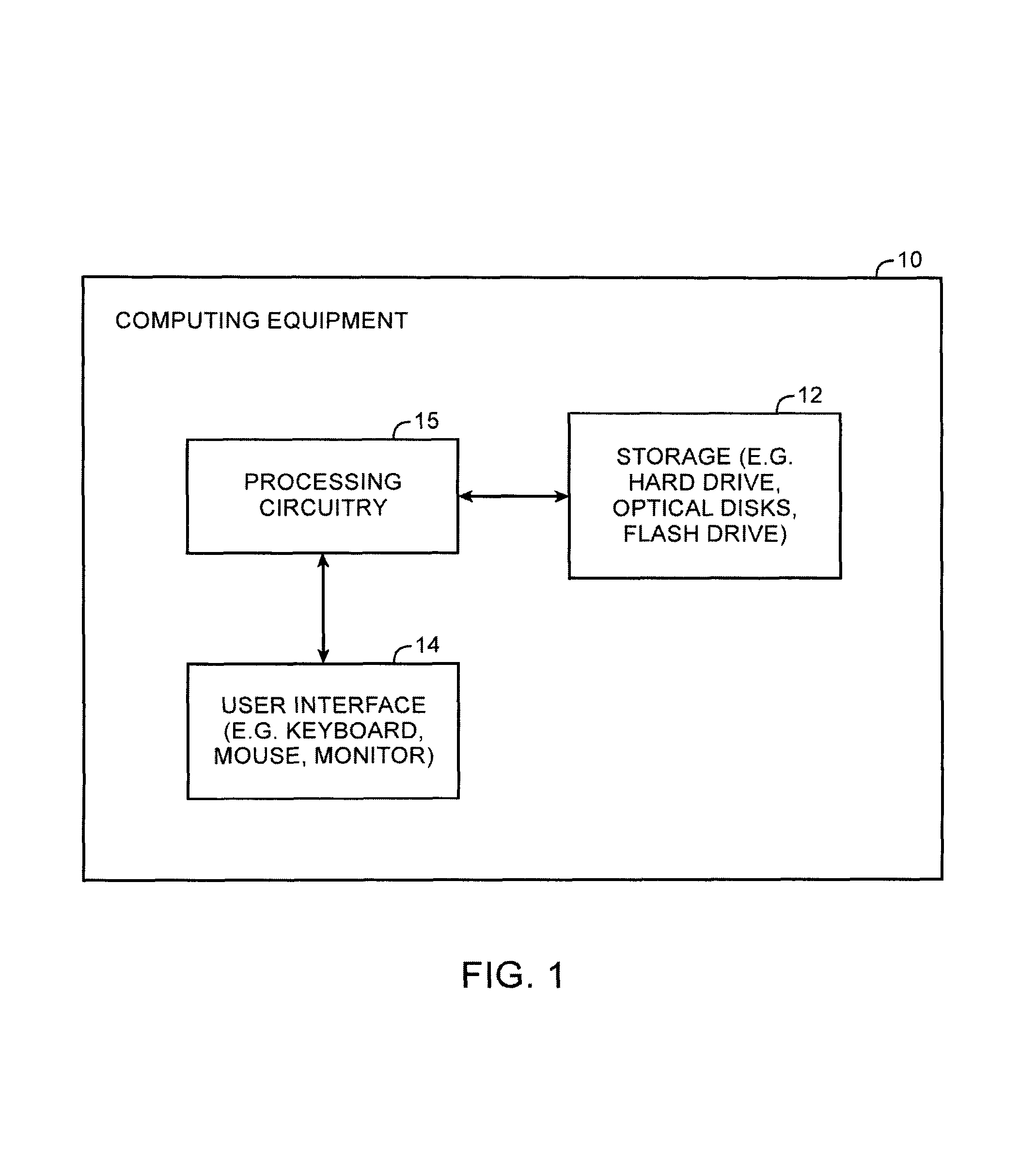
Patents
Literature
212 results about "Key recovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Recovery Key is a combination of numbers and letters that is attributed to your account after you register your account.
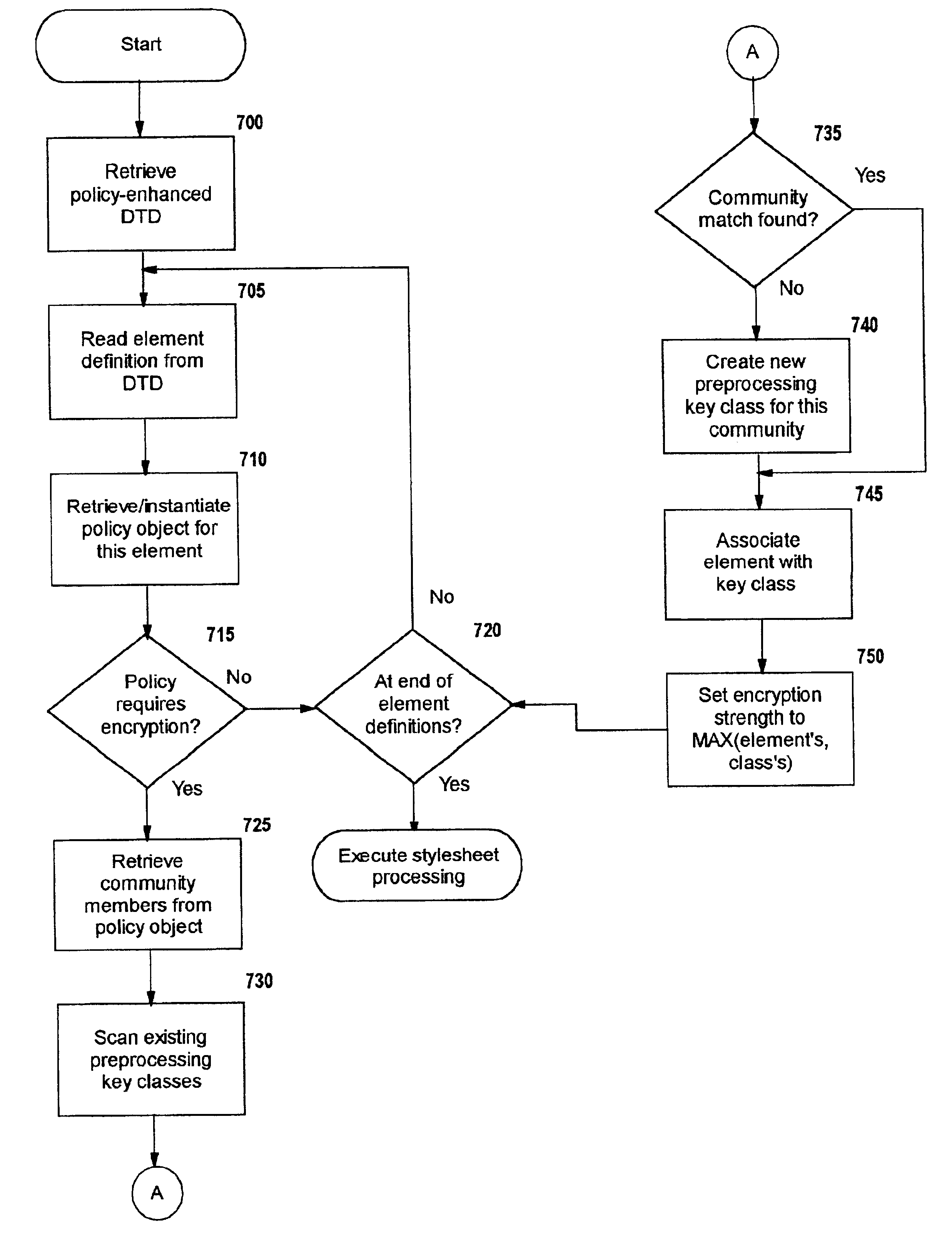
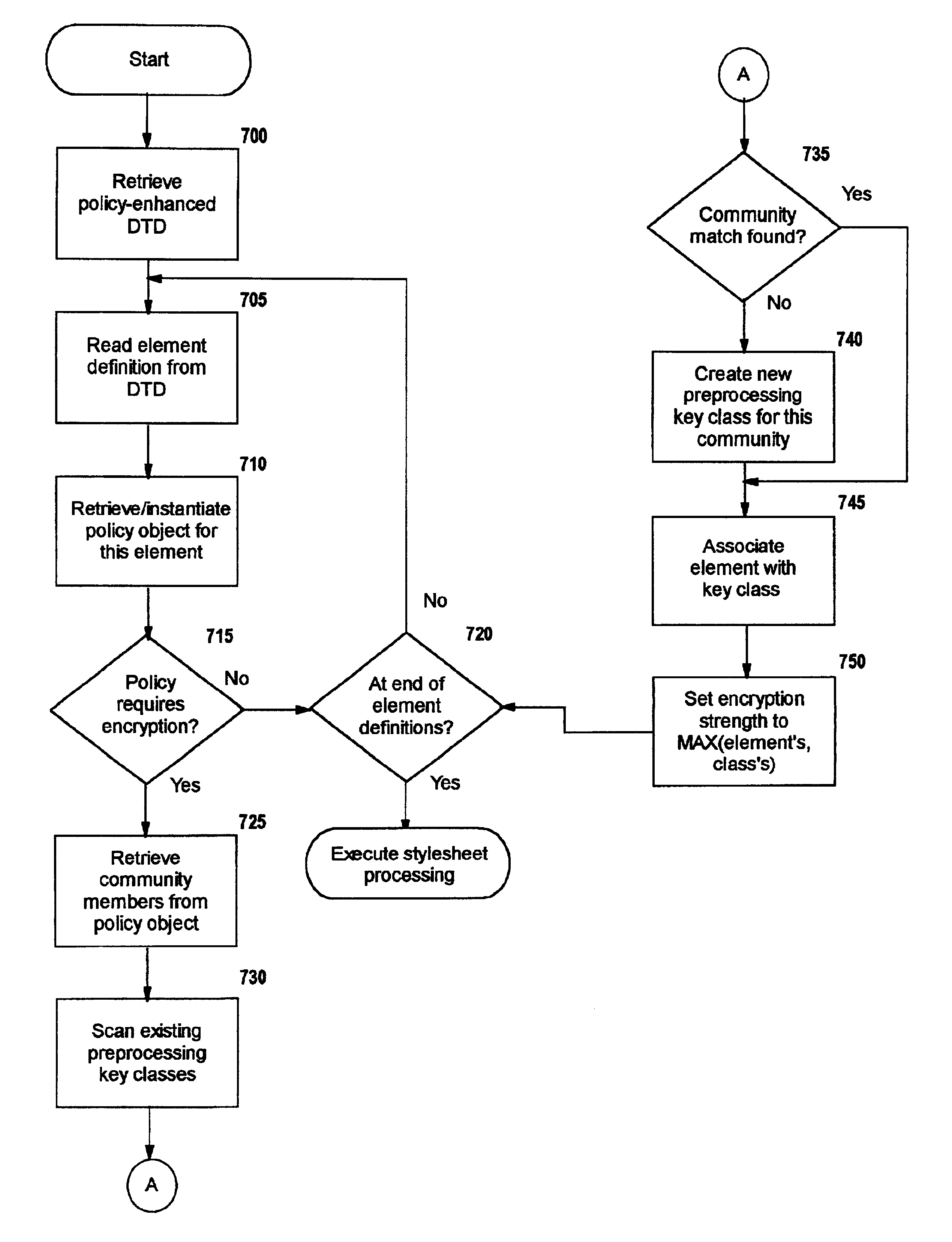
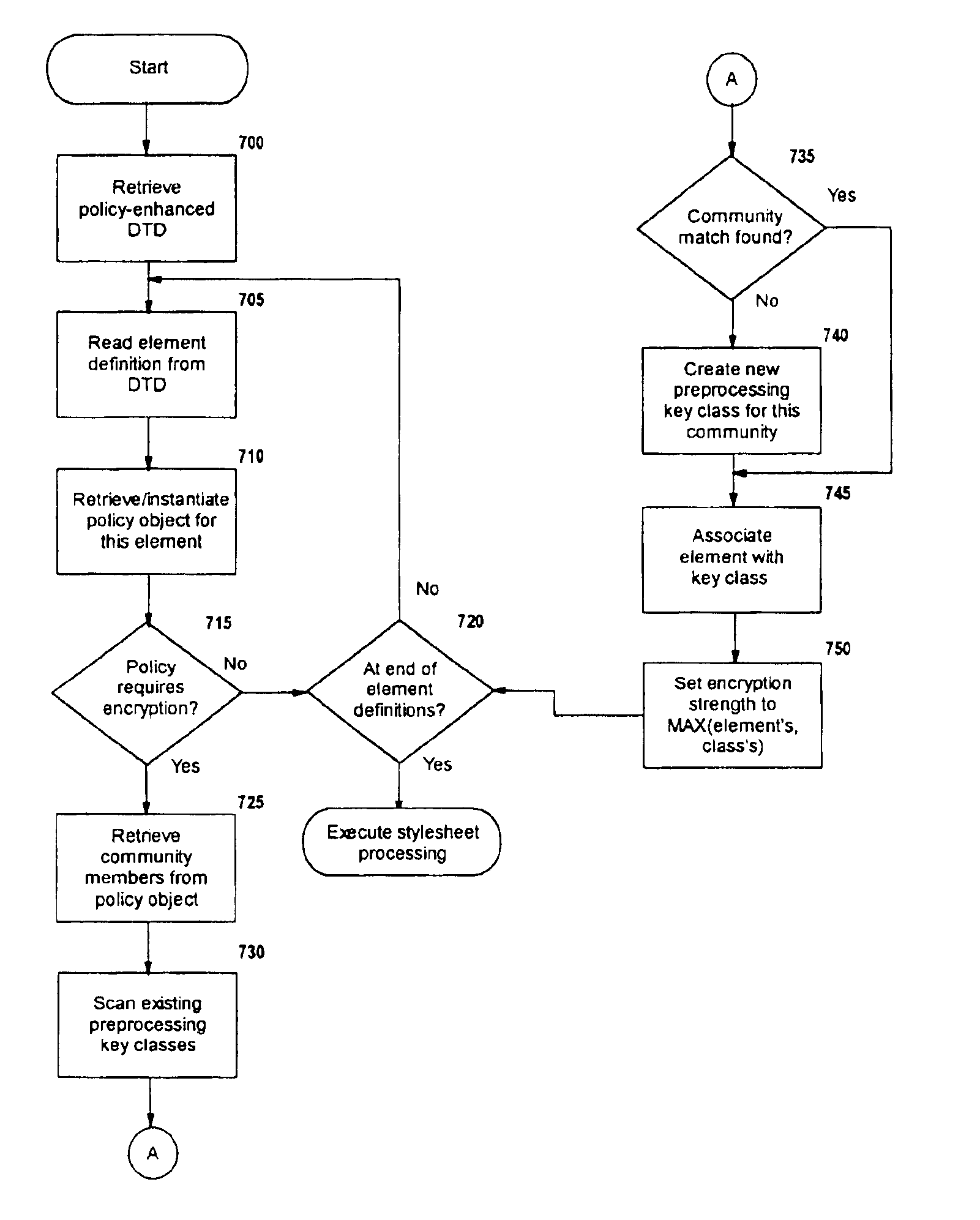
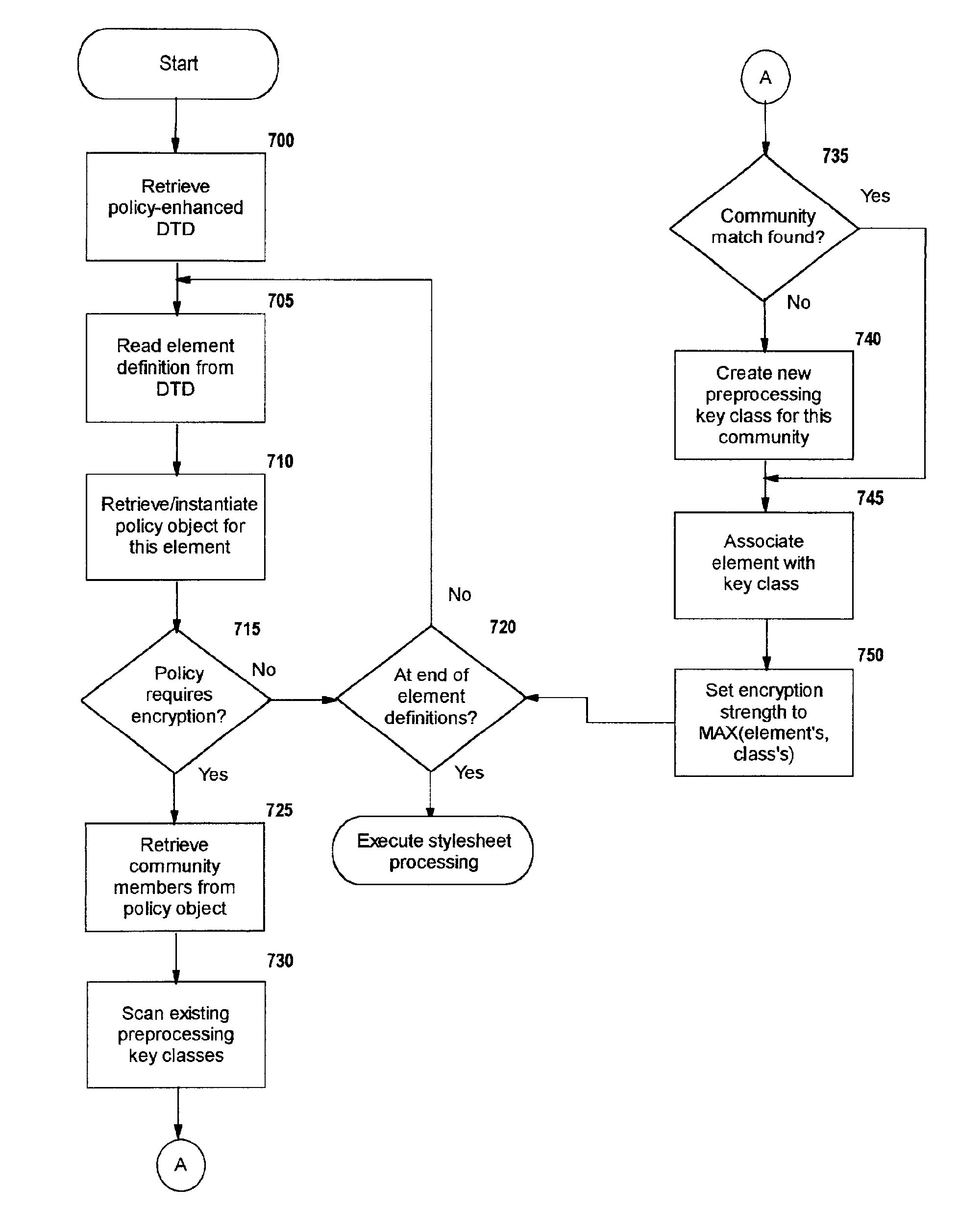
Selective data encryption using style sheet processing
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
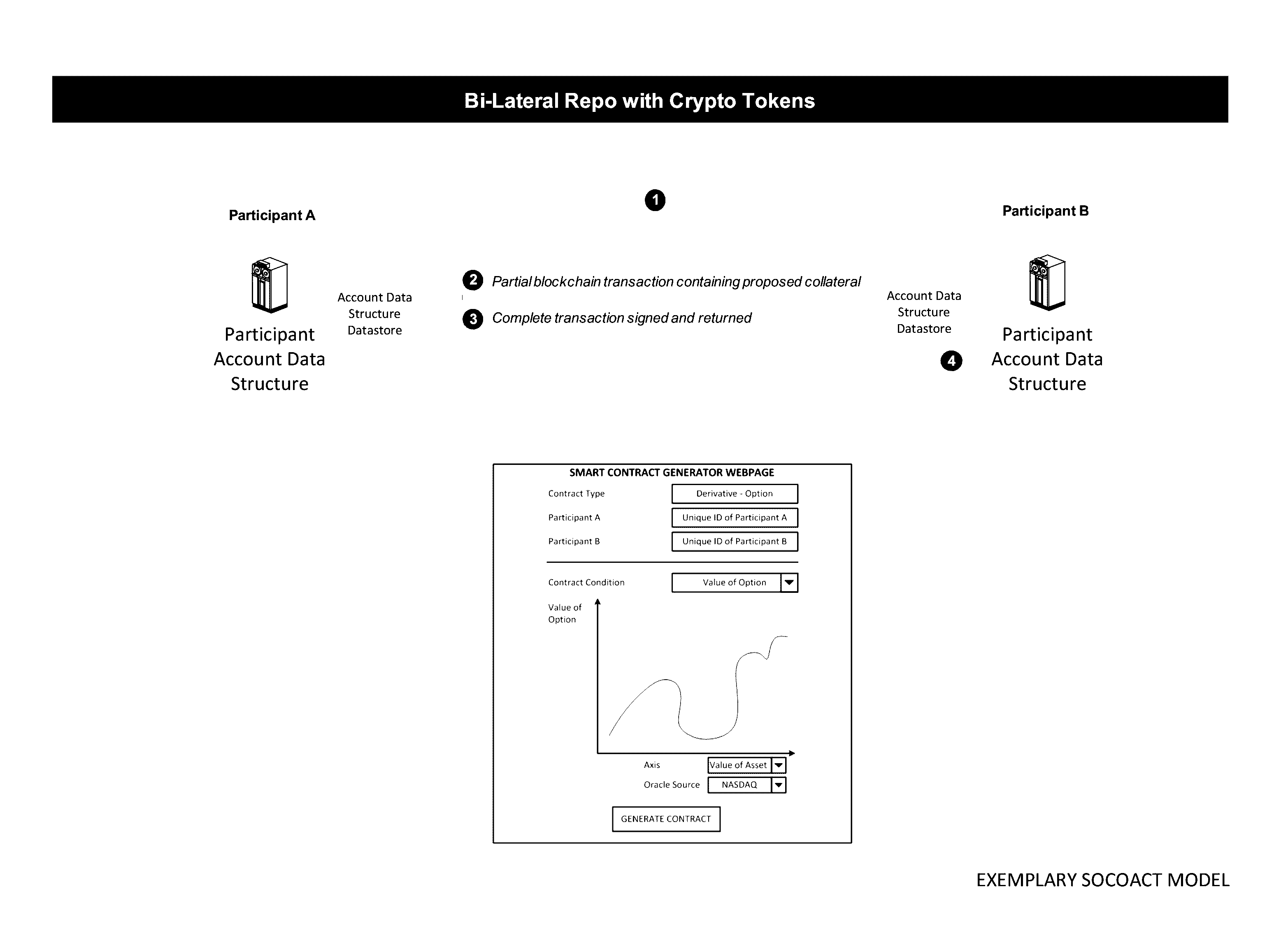
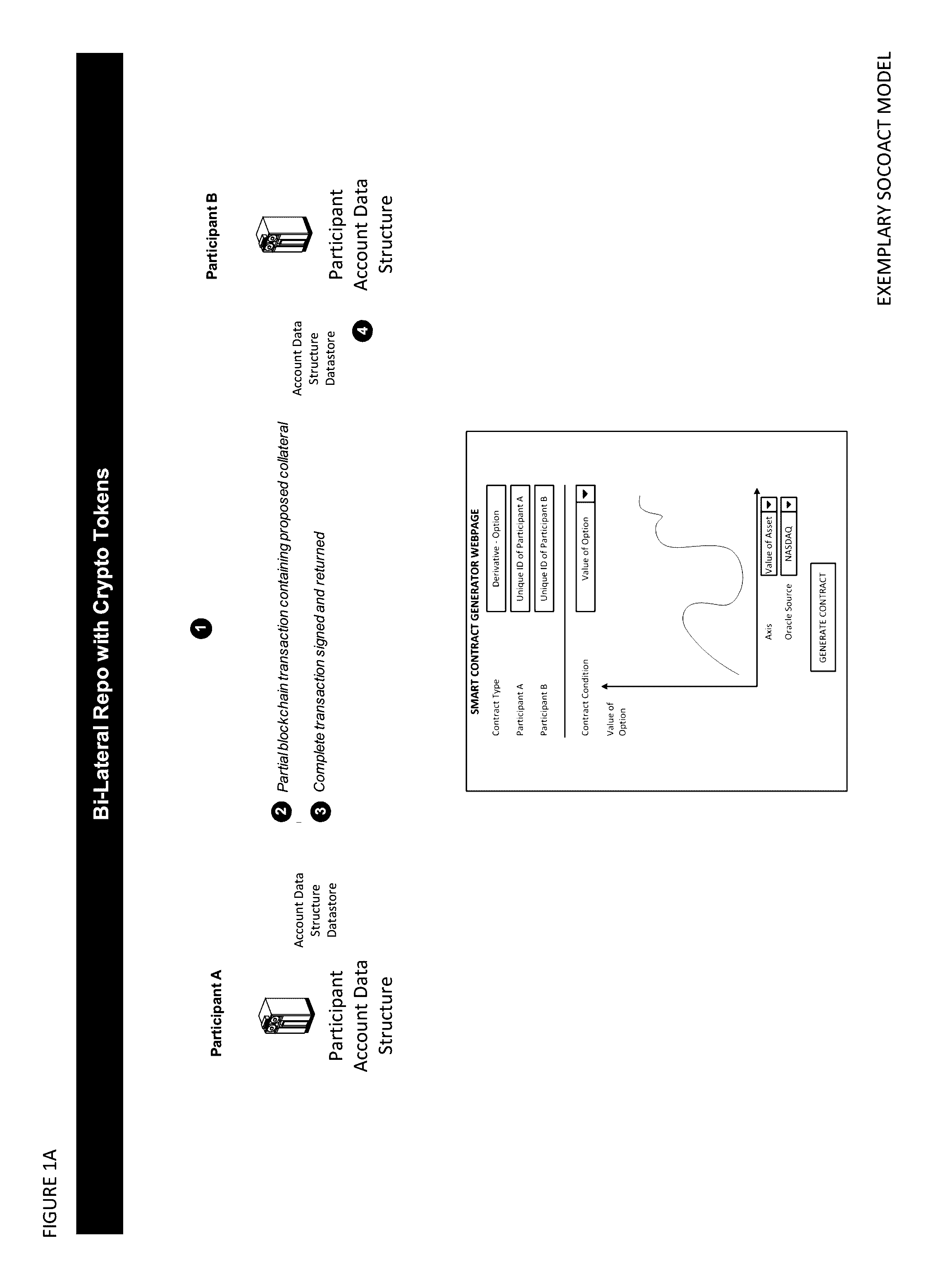
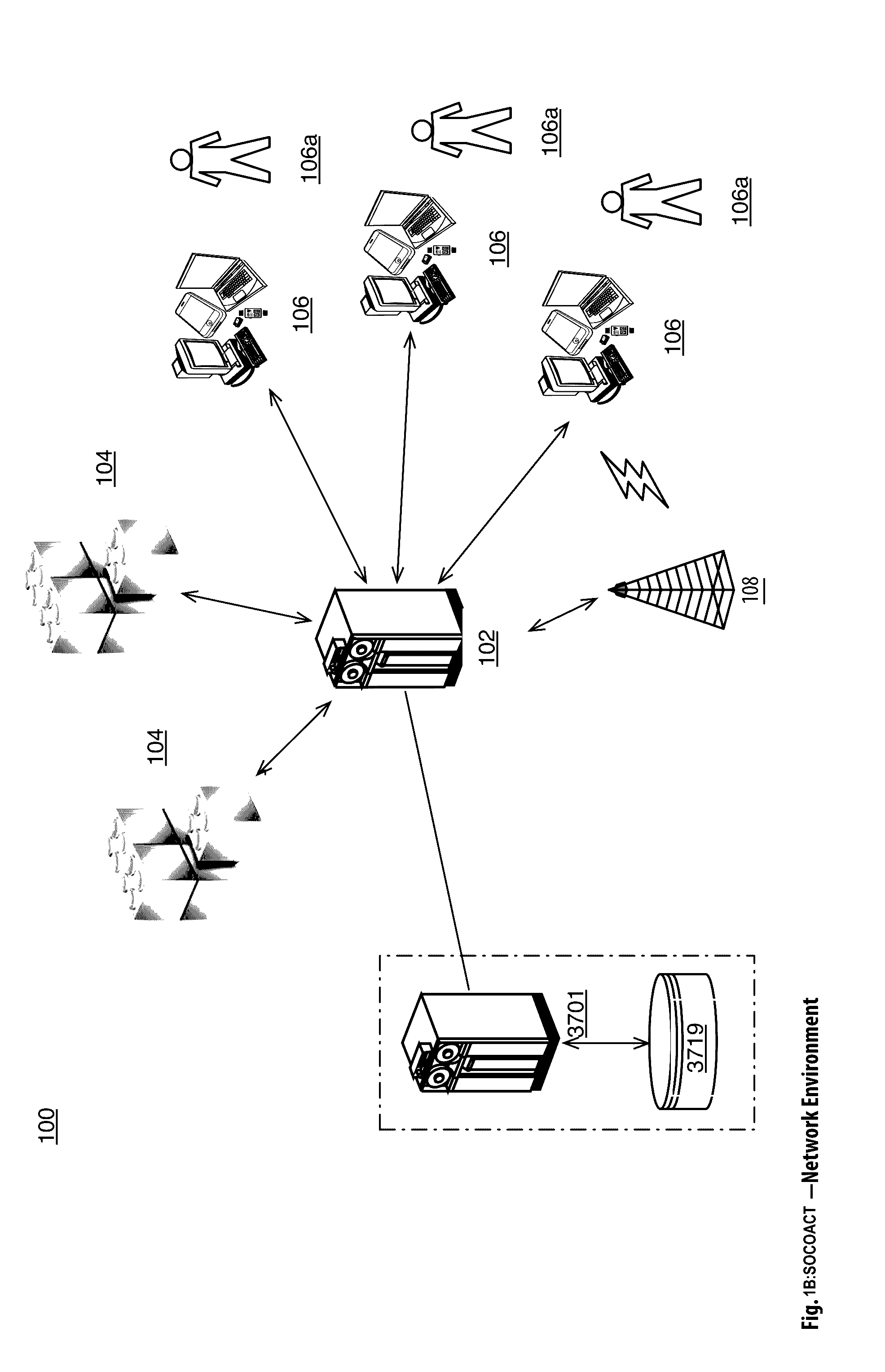
Crypto Key Recovery and Social Aggregating, Fractionally Efficient Transfer Guidance, Conditional Triggered Transaction, Datastructures, Apparatuses, Methods and Systems
InactiveUS20170048209A1Multiple keys/algorithms usageCryptography processingData structureKey recovery
The Crypto Key Recovery and Social Aggregating, Fractionally Efficient Transfer Guidance, Conditional Triggered Transaction, Datastructures, Apparatuses, Methods and Systems (“SOCOACT”) transforms MKADSD generation request, trigger event message inputs via SOCOACT components into transaction confirmation, recovery notification outputs. A multiple key account data structure datastore (MKADSD) generation request may be obtained from a user. A set of crypto public keys for a MKADSD may be determined. The MKADSD may be instantiated in a socially aggregated blockchain datastructure using the determined set of crypto public keys. A crypto recovery private key may be associate with the MKADSD and trigger event recovery settings for the MKADSD may be set. A trigger event message associated with the MKADSD may be obtained and recovery settings associated with a trigger event may be determined. The crypto recovery private key may be retrieved and a recovery action may be facilitated.
Owner:FMR CORP
Selective data encryption using style sheet processing for decryption by a key recovery agent
InactiveUS6941459B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH
Selective data encryption using style sheet processing for decryption by a group clerk
InactiveUS6961849B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g., an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Methods and apparatus for recovering keys
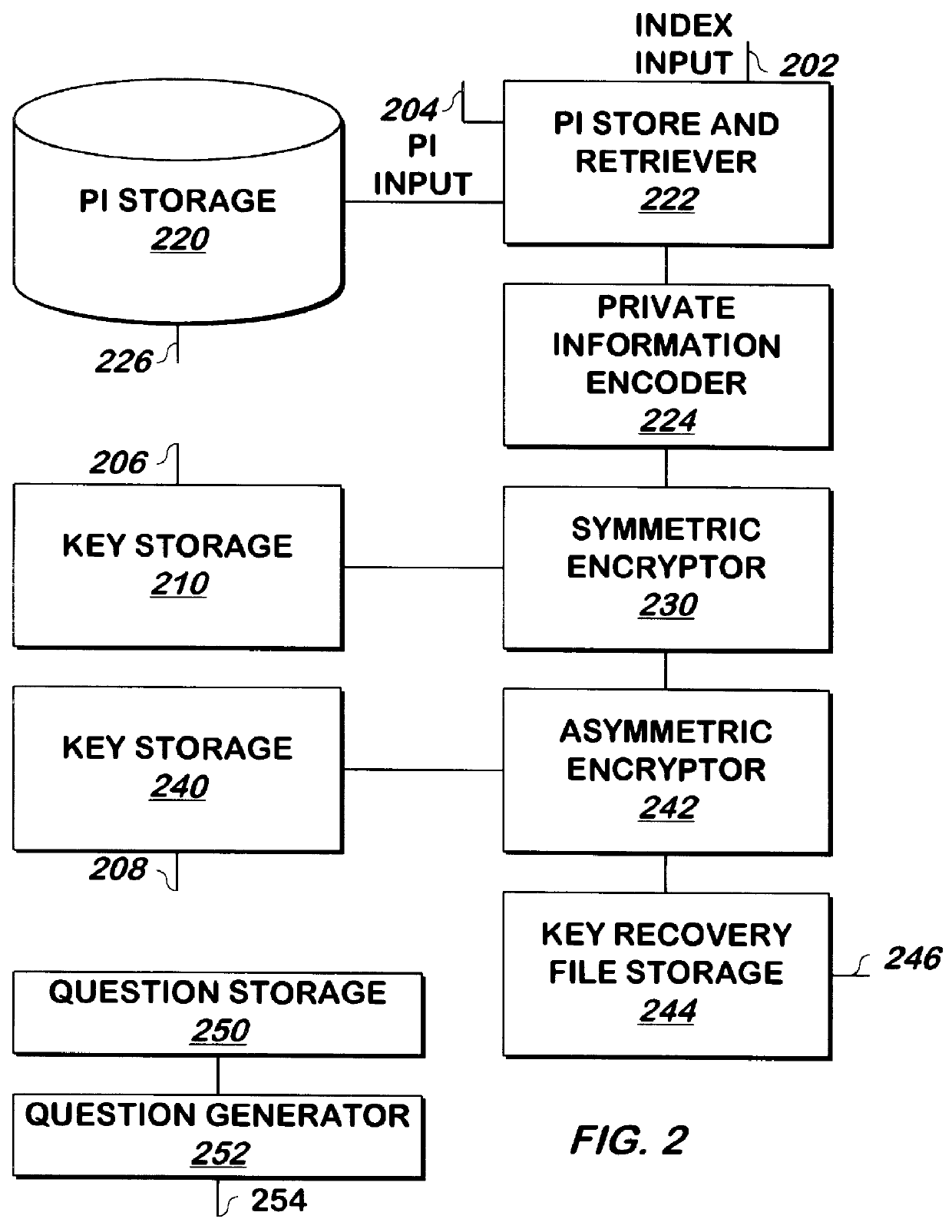
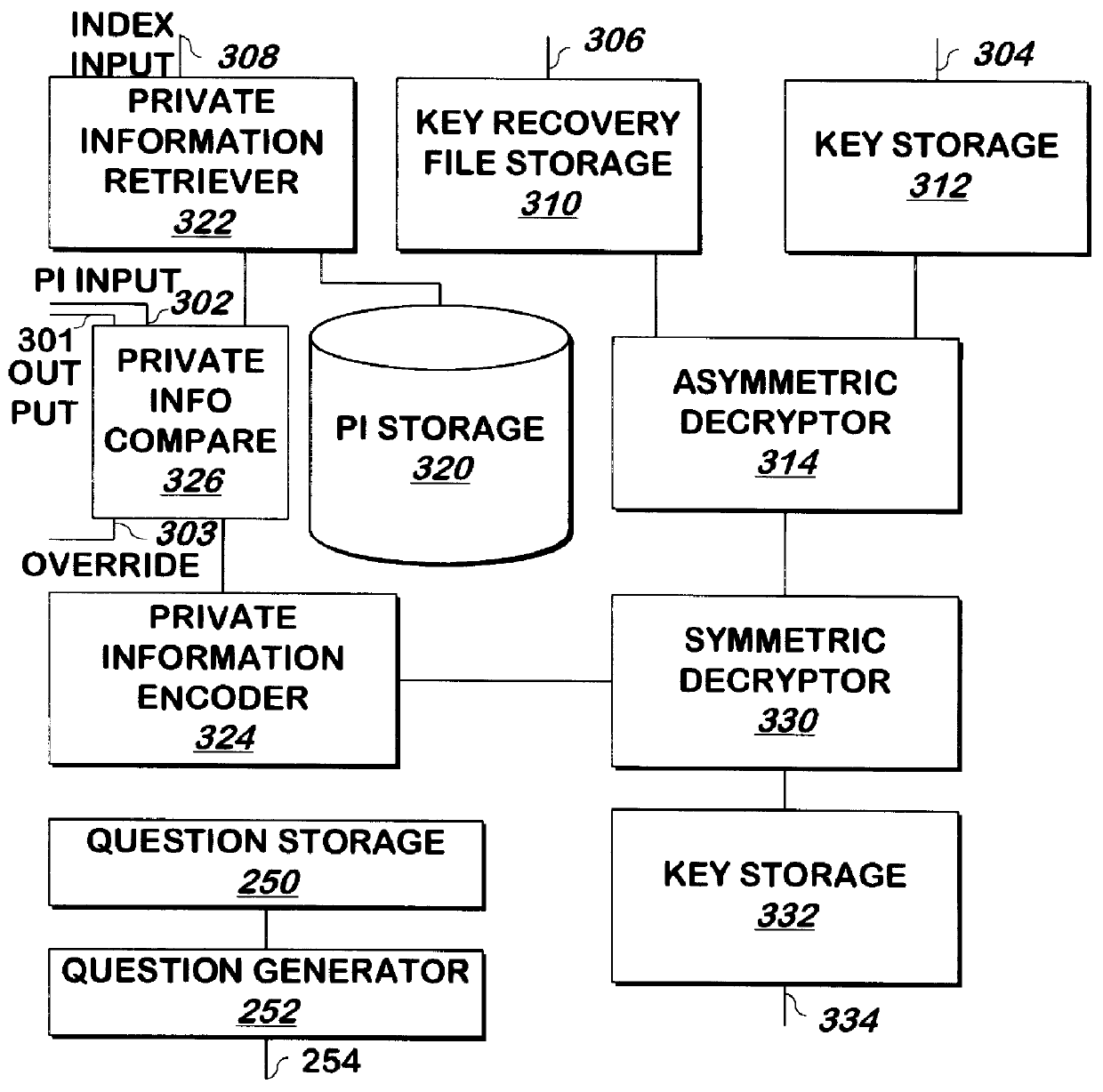
A key such as a private key or key password of a private key is encrypted for storage, and may be decrypted if the private key becomes lost or unavailable. The key is encrypted by encoding, for example, by hashing, private information such as mother's maiden name and social security number, and the result is used as a key to encrypt the private key using DES or another symmetric encryption technique. The encrypted key is again encrypted, for example using asymmetric encryption, using the public key of a trusted party such as the certificate authority that generated the private key. The result may be stored as a key recovery file by the principal of the private key or another party. To decrypt the key recovery file, the private key corresponding to the public key used to encrypt the key recovery file is used to decrypt the key recovery file, for example by asymmetric decryption. The result is symmetrically decrypted using a key obtained by encoding, for example, by hashing, the private information in the same manner as was used to encrypt the key. The result of this decryption is the key.
Owner:ORACLE INT CORP
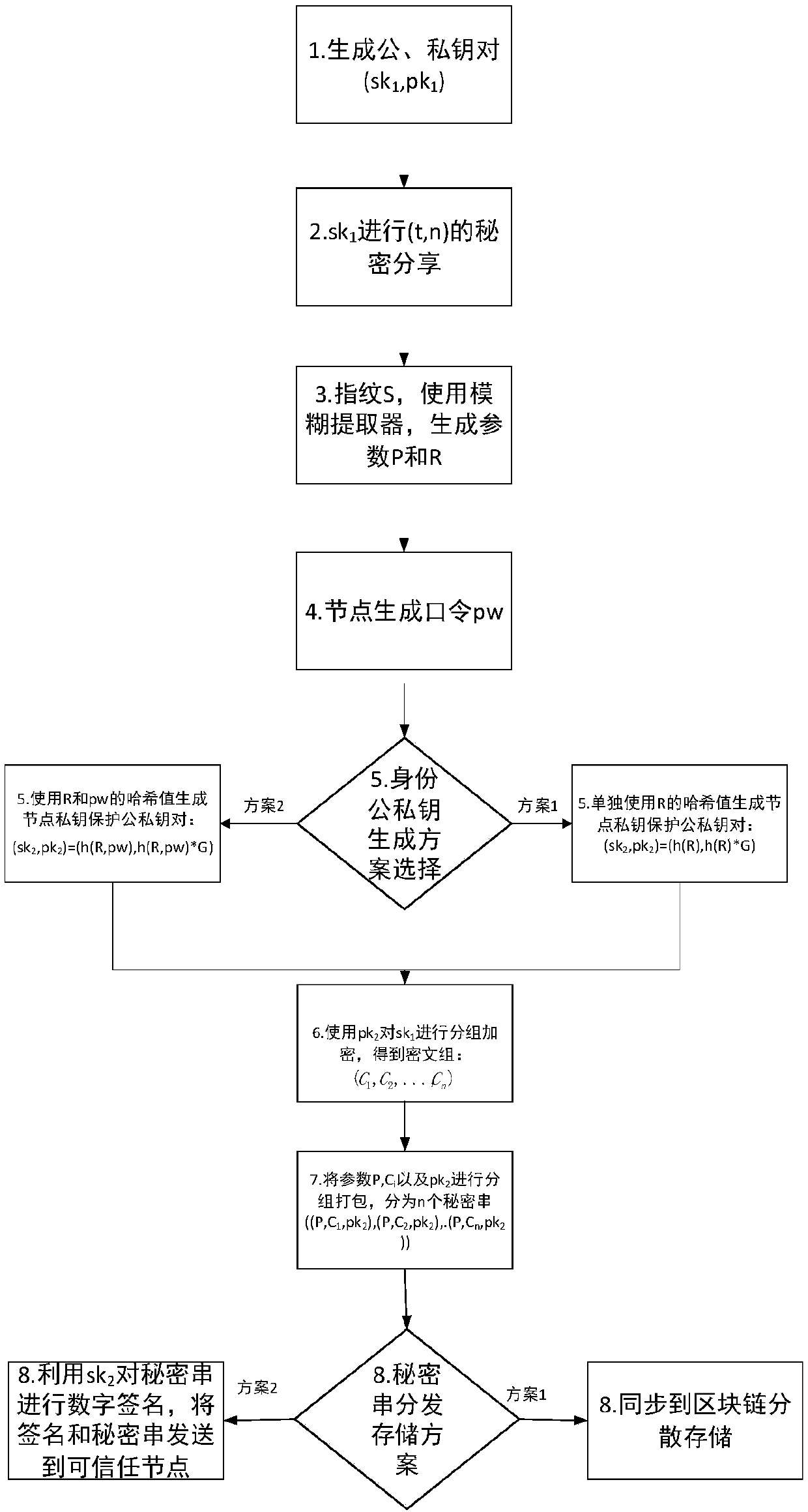
Block chain key trusteeship and recovery method and device based on secrecy sharing technology
InactiveCN107623569ASafekeepingSafe recoveryKey distribution for secure communicationRecovery methodRestoration method
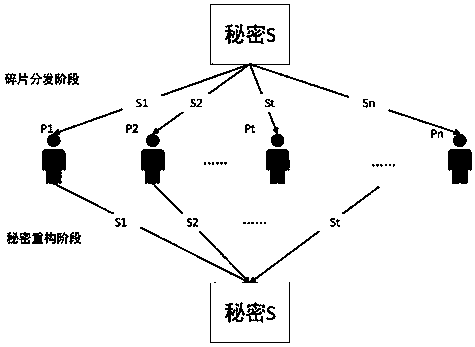
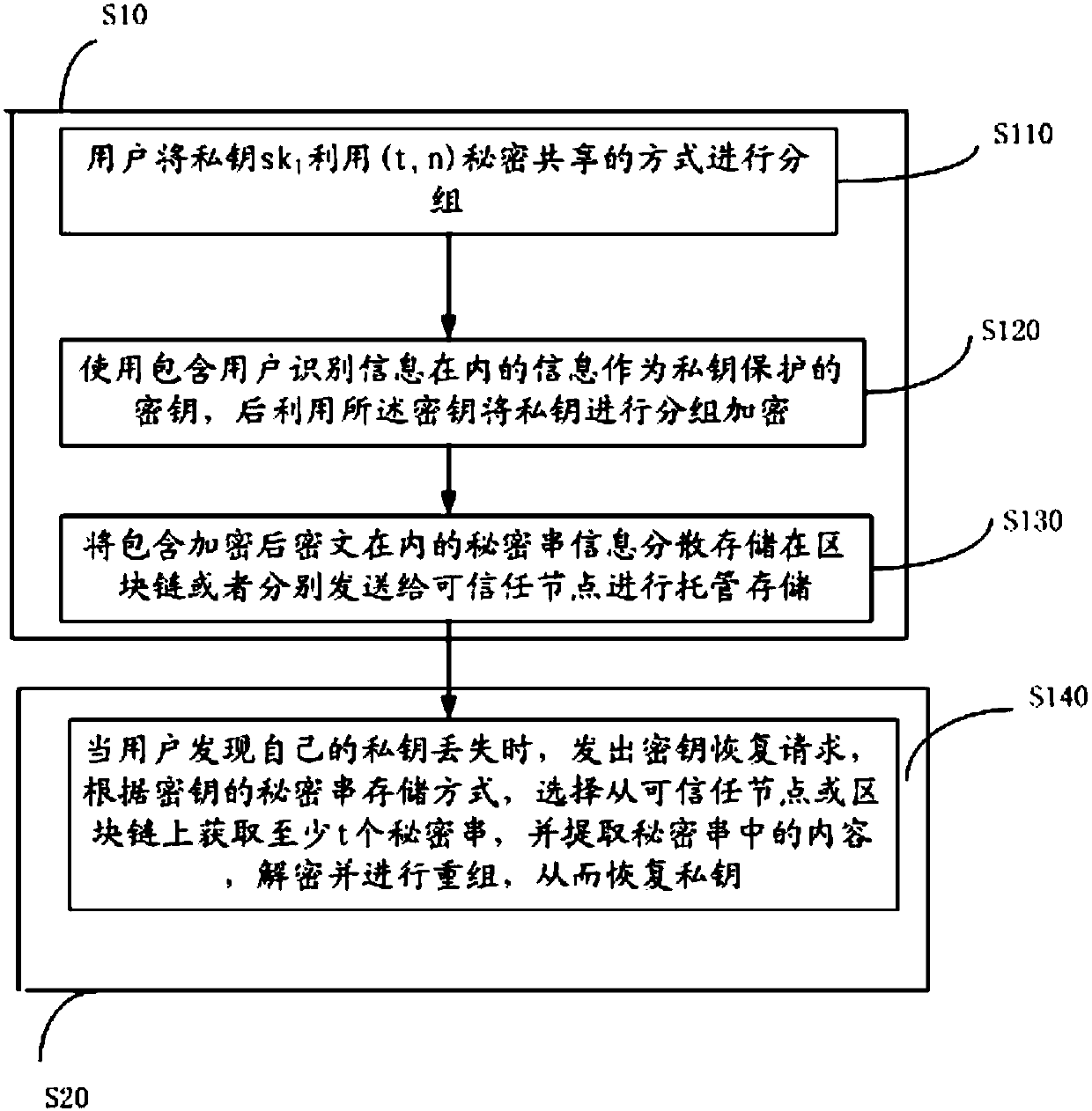
The invention discloses a block chain key trusteeship and recovery method and device based on a secrecy sharing technology. The method comprises the steps that A1, a user groups a private key sk1 in a(t, n) secrecy sharing mode, wherein the n is the number of fragments of shared secrecies obtained by splitting the private key, the t is the minimum number of the fragments for recovery of the private key, and the t is greater than or equal to 2 and is smaller than or equal to the n; A2, information containing user identification information is taken as a private key protection key, and then grouping encryption is carried out on the private key through utilization of the key; and A3, secrecy string information containing encrypted ciphertexts is dispersely stored to a block chain or is sentto trusted nodes for trusteeship and storage, when the user discovers that own private key is lost, a key recovery request is generated, at least t secrecy strings are obtained from the trusted nodesor the block chain in a secrecy string storage mode of the key, and the content in the secrecy strings is extracted, decrypted and recombined, so the private key is recovered. According to the methodand the device, the secrecy sharing technology is applied to a block chain scene for the first time, thereby solving the private key trusteeship and recovery security problem.
Owner:JUZIX TECH SHENZHEN CO LTD
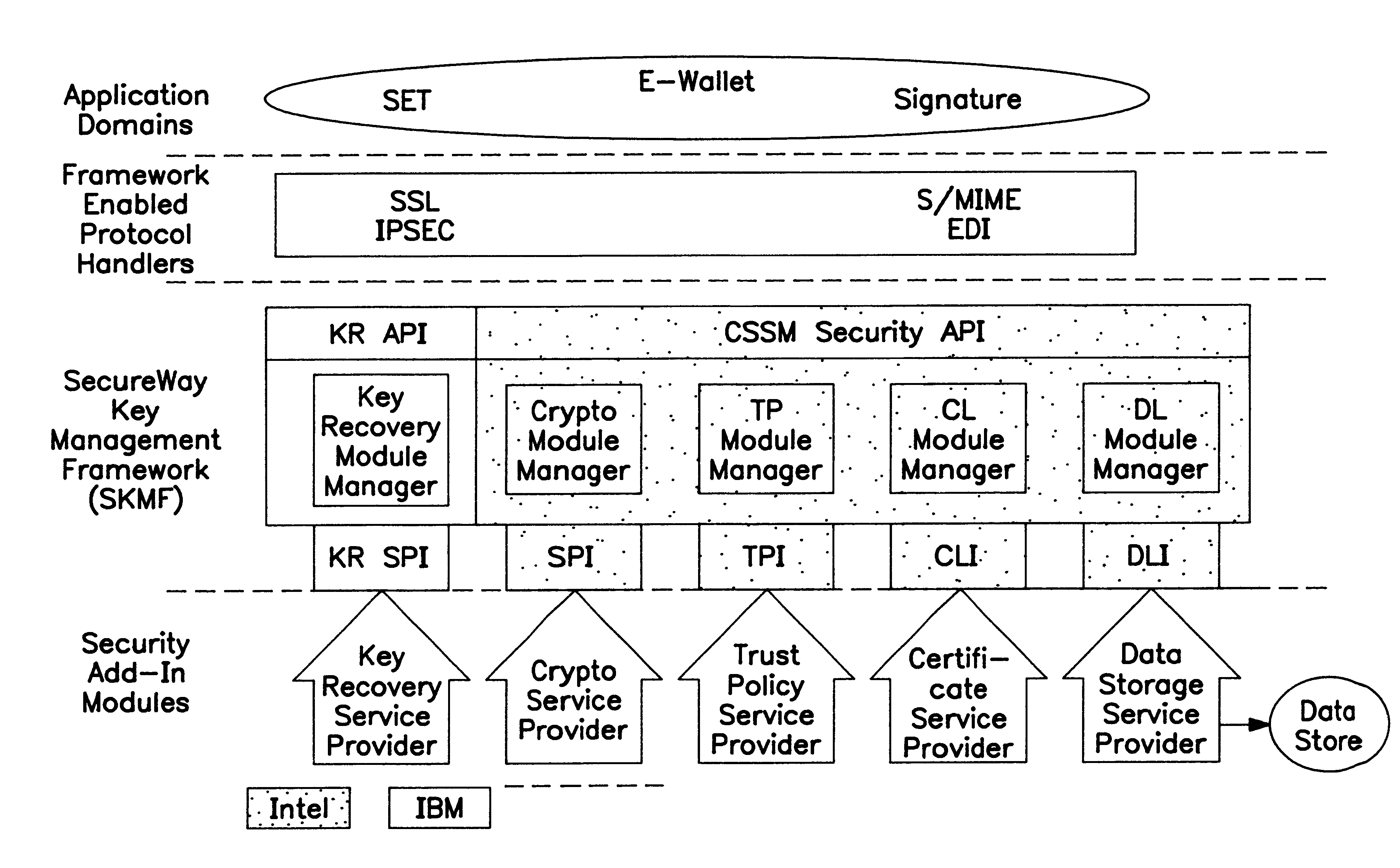
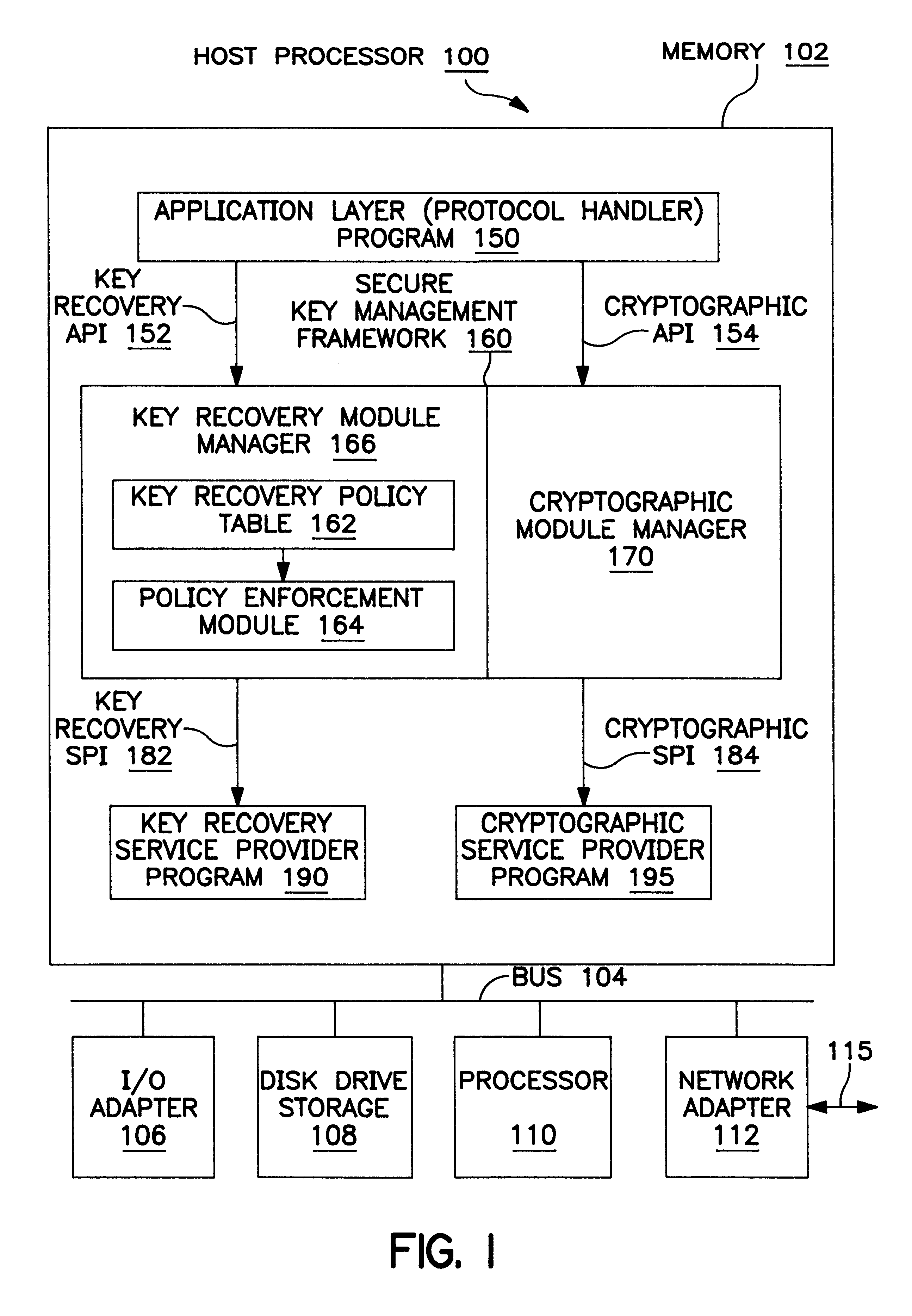
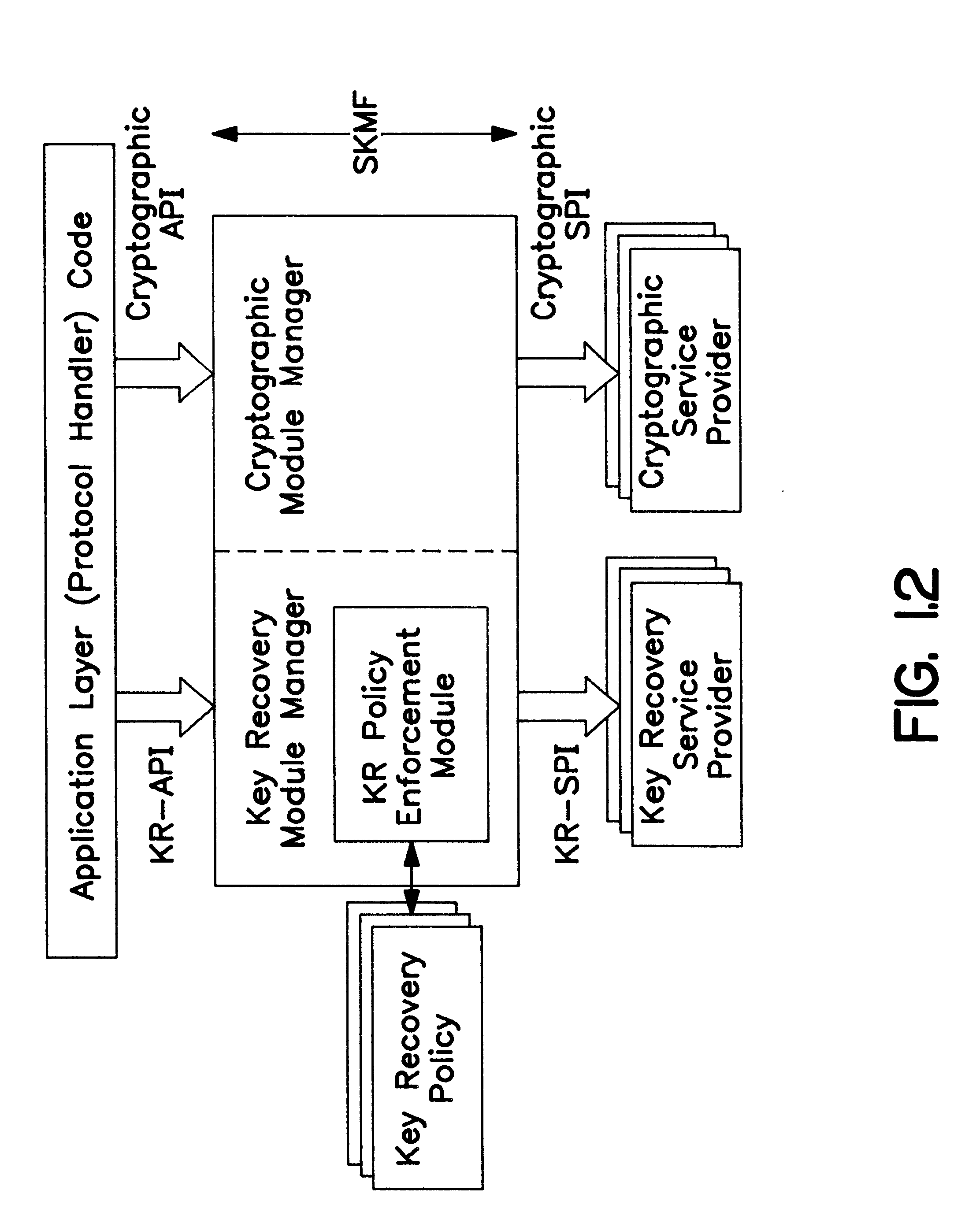
Framework-based cryptographic key recovery system
InactiveUS6335972B1Key distribution for secure communicationUser identity/authority verificationProtocol ApplicationKey management
A Secure Key Management Framework (SKMF) defines an infrastructure for a complete set of cryptographic services augmented with key recovery enablement. There are three major layers-the application layer invokes the SKMF layer, while the SKMF layer invokes the service provider (SP) layer. The application layer code invokes the cryptographic API and key-recovery API supported by the SKMF. Multiple key recovery mechanisms and cryptographic mechanisms can be implemented as service providers that log-in underneath the framework using the well-defined service provider interfaces provided by the framework. The SKMF implements the supported ATP calls by making appropriate invocations of the service provider modules using the SPIs.
Owner:IBM CORP
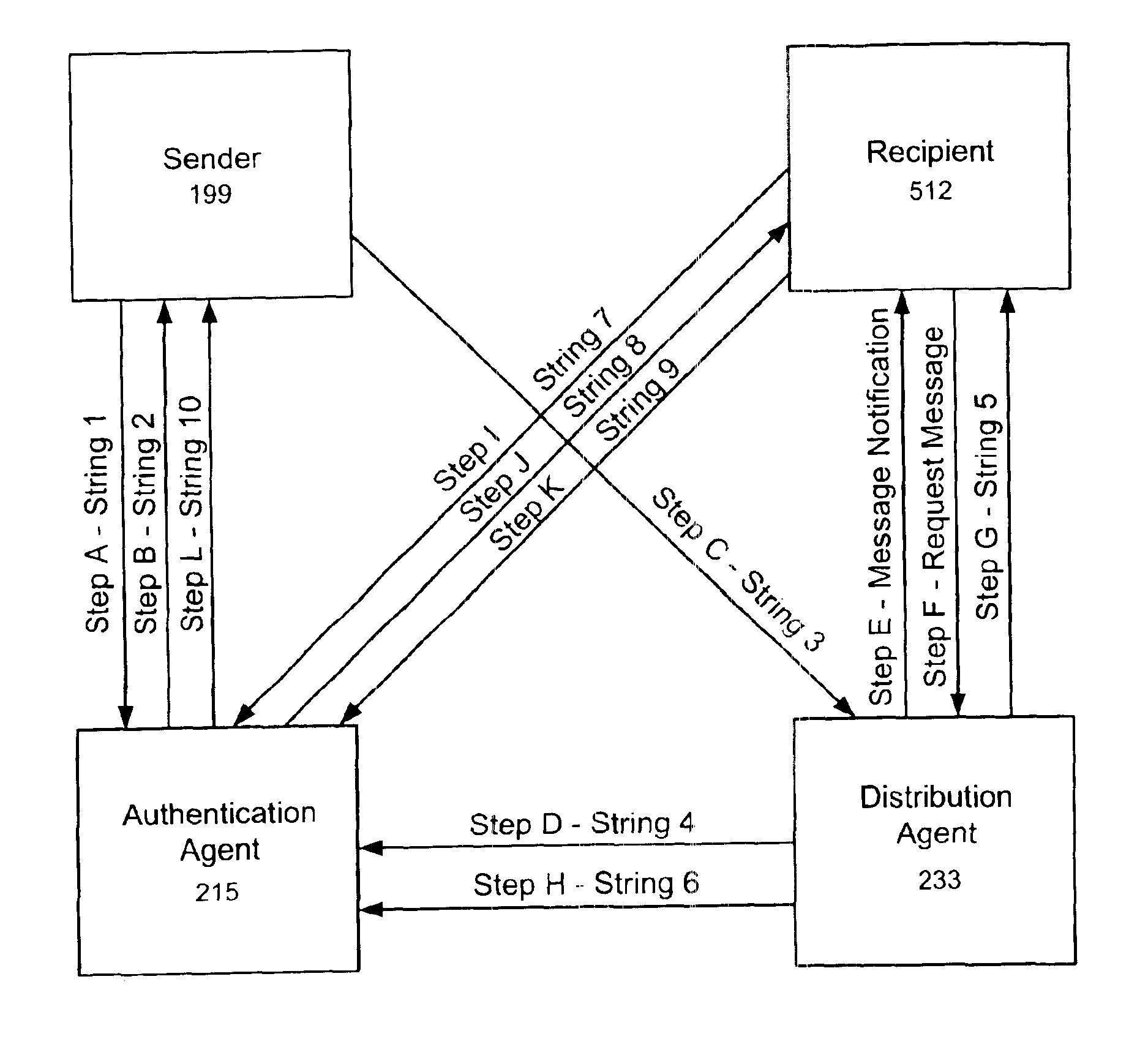
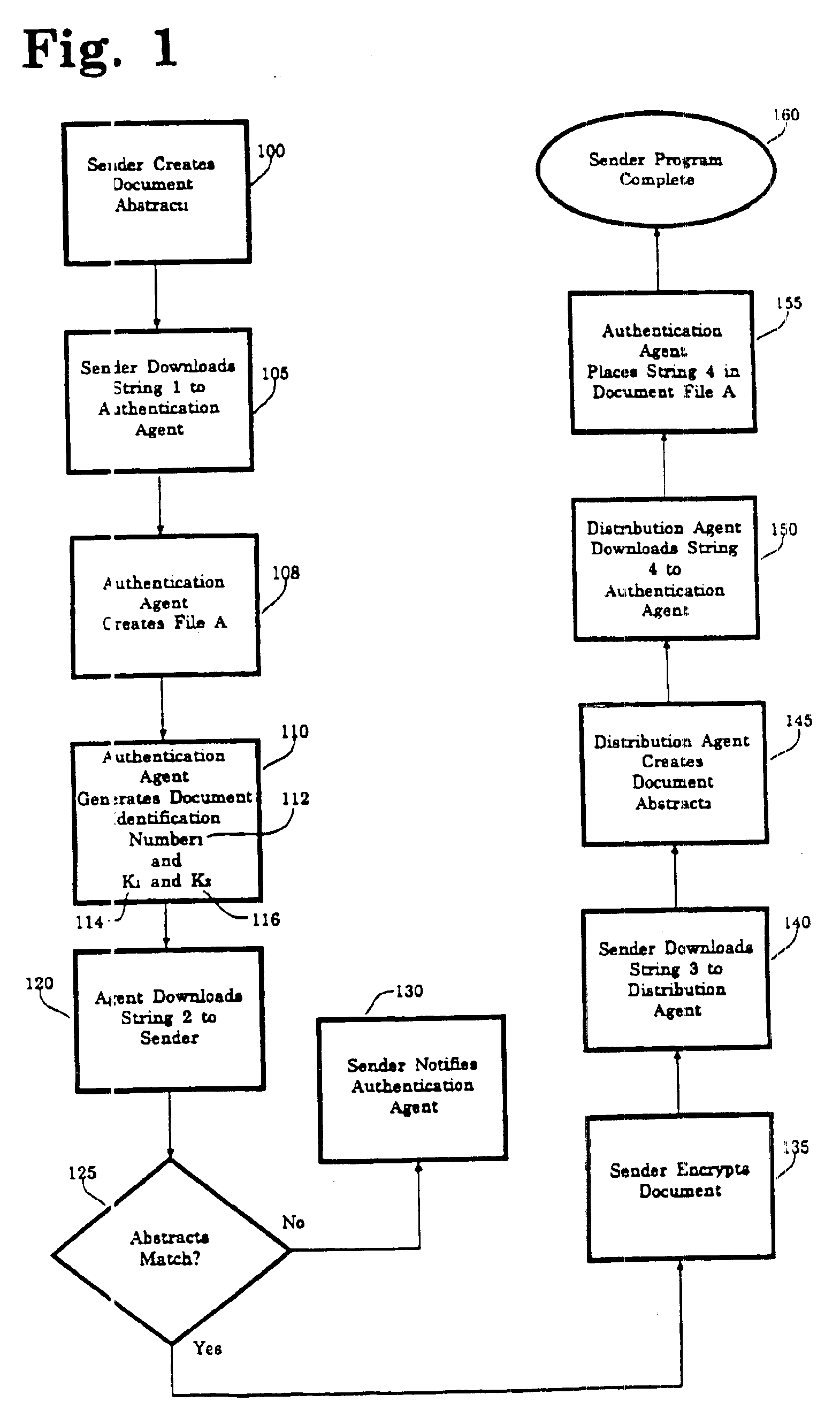
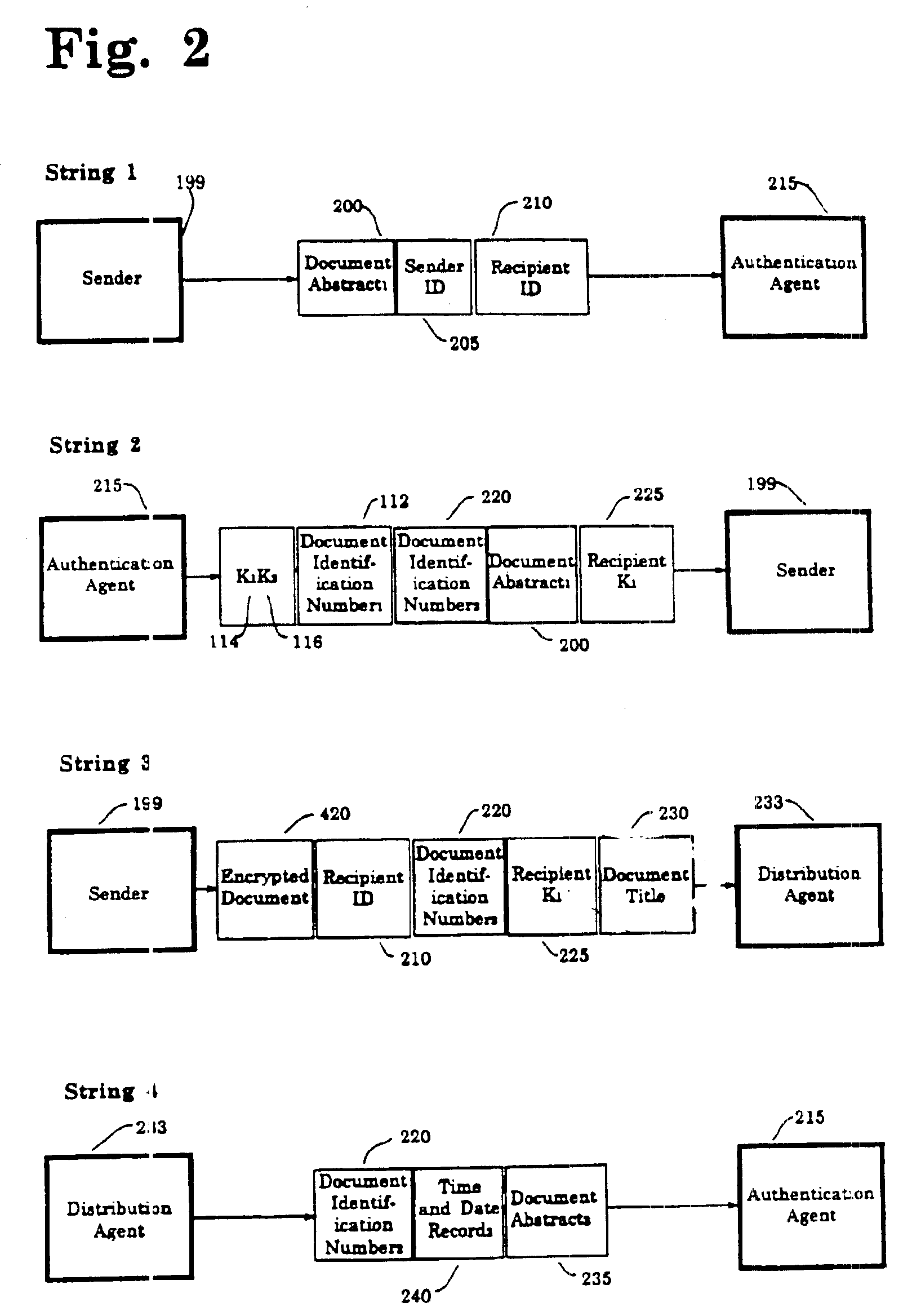
Method for authenticating electronic documents
InactiveUS6963971B1Improve privacyImprove user securityKey distribution for secure communicationUser identity/authority verificationThird partyElectronic document
A secure method for sending registered, authenticated electronic documents. The invention validates sender and recipient identities, provides for non-repudiation of authenticated documents by sender and recipient, provides an evidence trail, and protects the integrity of the document. The invention is constructed so that a sender can be supplied with proof that the intended recipient received and opened an authenticated document. A neutral third party acts as a document registration agent, and witness to the transmission and receipt of the authenticated document. In the event of a dispute between sender and recipient, the third party can provide an irrefutable record of the contents of the document and of the history of the transmission and receipt of the document Because the third party never has possession of the electronic document, the method provides maximum privacy for sender and recipient. The method is readily adaptable to both key recovery and key escrow.
Owner:BUSH GEORGE +4
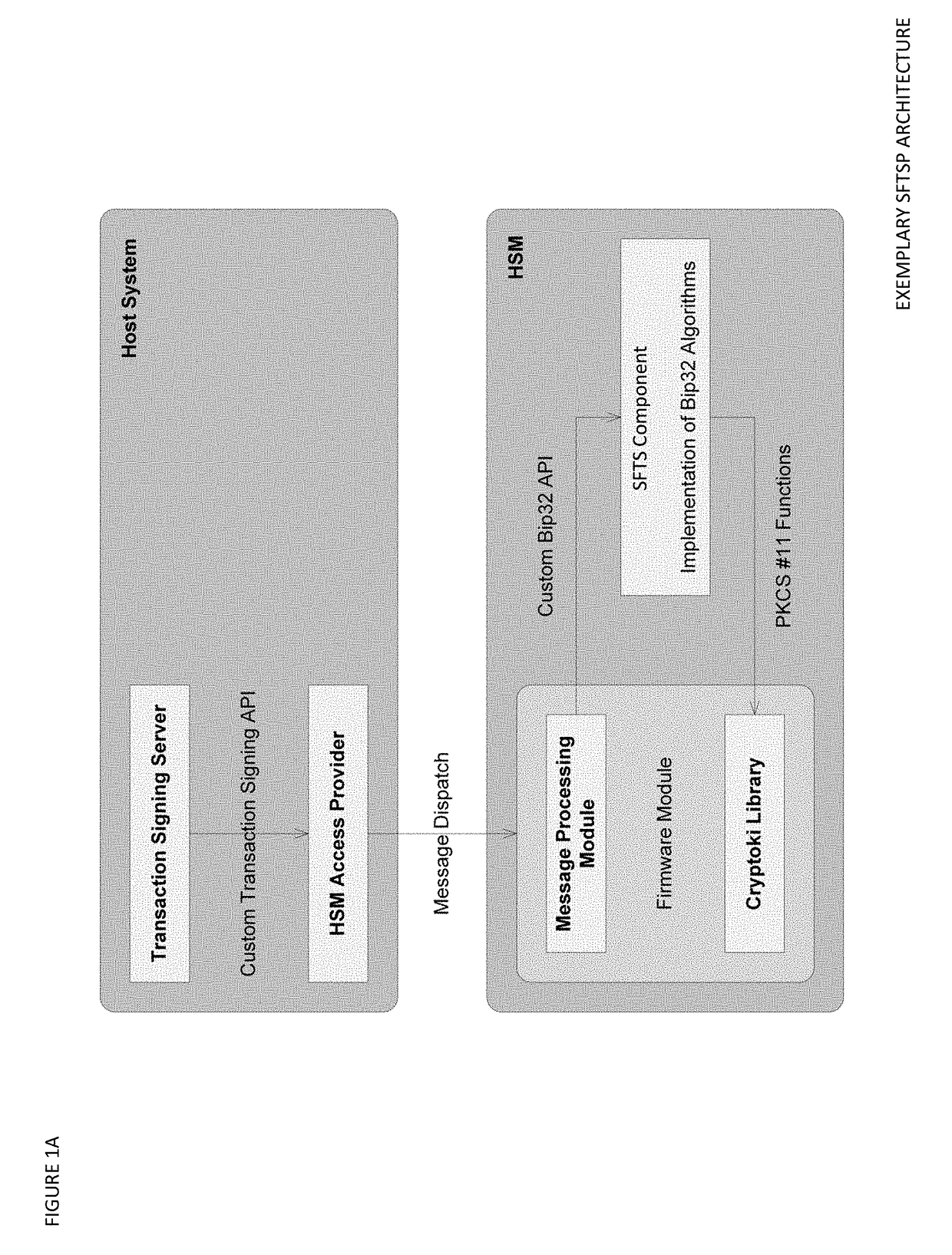
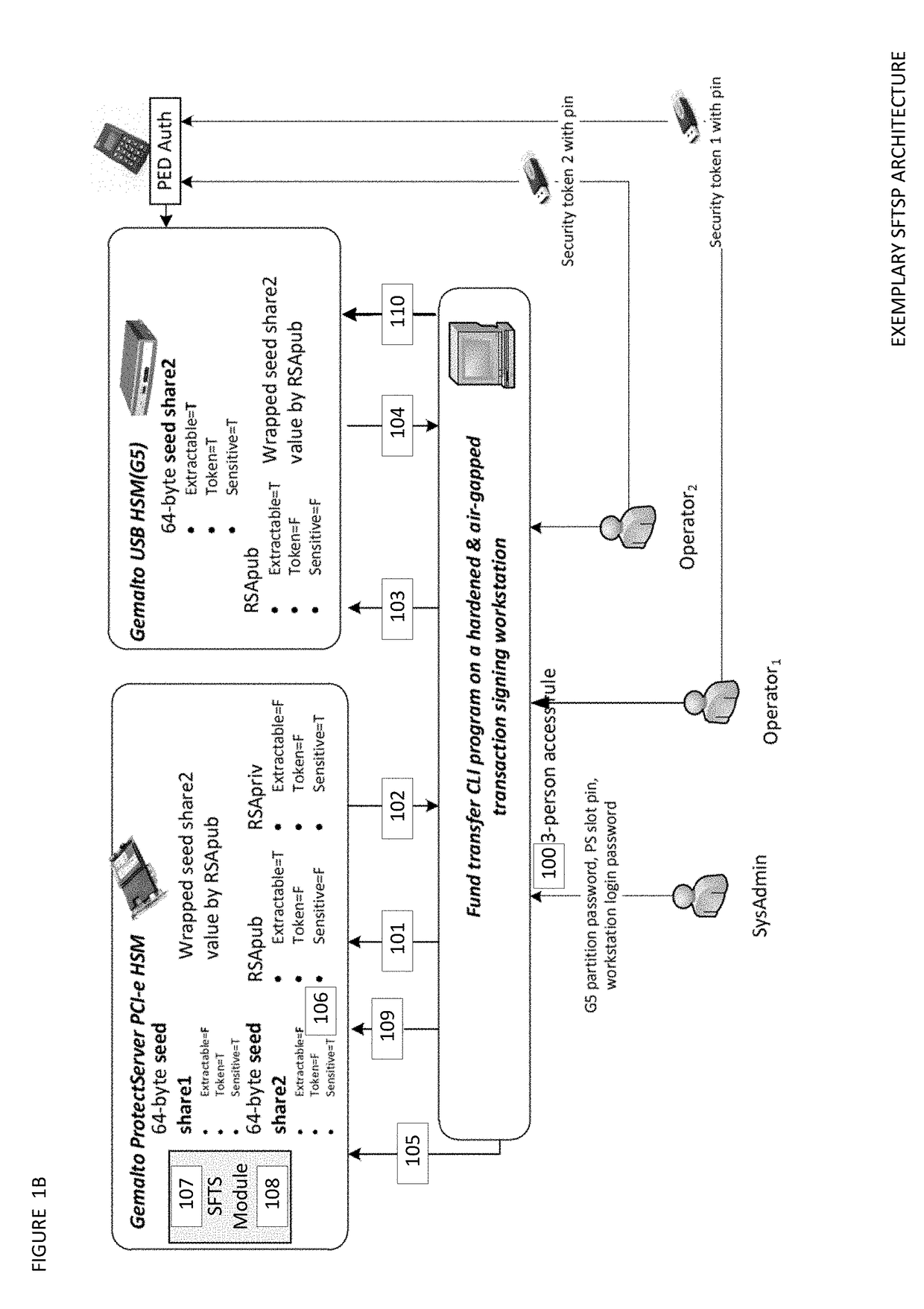
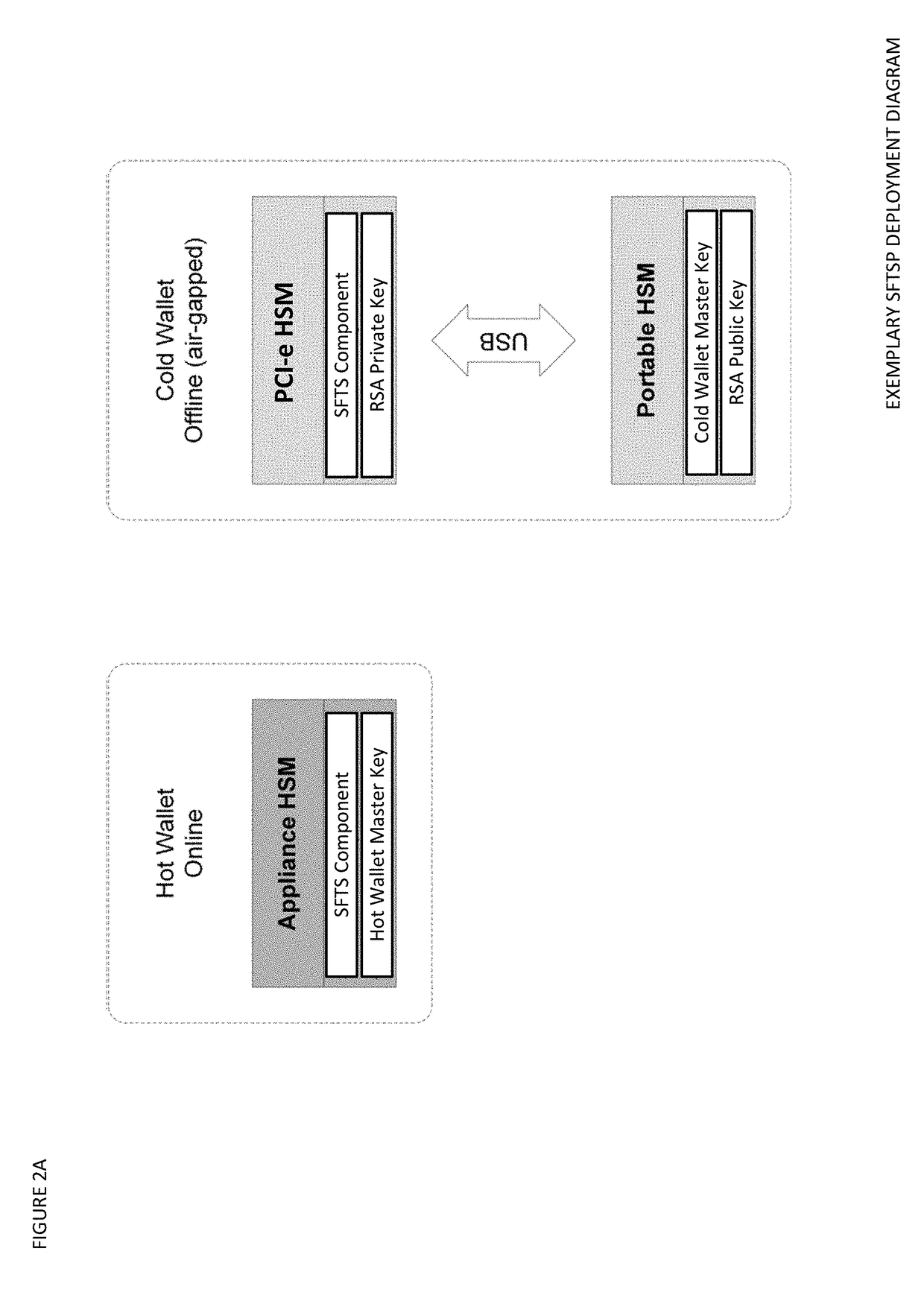
Seed splitting and firmware extension for secure cryptocurrency key backup, restore, and transaction signing platform apparatuses, methods and systems
ActiveUS20180367316A1Improve network efficiencyProlong lifeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMaster keyKey sharing
The Seed Splitting and Firmware Extension for Secure Cryptocurrency Key Backup, Restore, and Transaction Signing Platform Apparatuses, Methods and Systems (“SFTSP”) transforms transaction signing request, key backup request, key recovery request inputs via SFTSP components into transaction signing response, key backup response, key recovery response outputs. A transaction signing request message for a transaction is received by a first HSM and includes an encrypted second master key share from a second HSM whose access is controlled by M-of-N authentication policy. The encrypted second master key share is decrypted. A first master key share is retrieved. A master private key is recovered from the master key shares. A transaction hash and a keychain path is determined. A signing private key for the keychain path is generated using the recovered master private key. The transaction hash is signed using the signing private key, and the generated signature is returned.
Owner:FMR CORP
Method and system for realizing block chain private key protection based on key segmentation
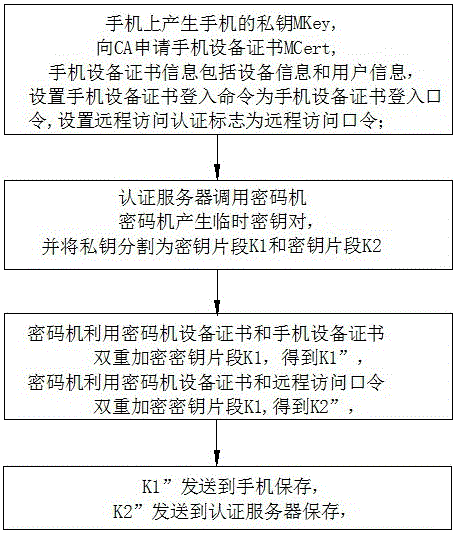
ActiveCN106548345AImprove securityAvoid Permission RisksKey distribution for secure communicationPayment protocolsPasswordStructure of Management Information
The invention discloses a method and a system for realizing block chain private key protection based on key segmentation, and aims to solve a technical problem that a private key of a block chain is lack of security and cannot be retrieved. The method for realizing block chain private key protection based on key segmentation comprises that hard encryption for a block chain private key supporting mobile phone equipment certificate authentication and password authentication is realized by taking a mobile phone as a terminal carrier and using a cipher machine and an authentication server of the cloud; and the block chain private key is segmented by using a threshold algorithm, and multi-party participating key backup and key recovery / retrieval is realized. The method comprises (1) a registration procedure, (2) a private key utilization procedure, (3) a private key backup procedure, and (4) a private key recovery / retrieval procedure. The system structurally comprises a cipher machine and an authentication server of the cloud and a mobile phone acting as the terminal carrier. The method and the system disclosed by the invention can realize safe storage, safe utilization, multi-party participating backup and multi-party participating retrieval of the block chain private key.
Owner:北京信任度科技有限公司
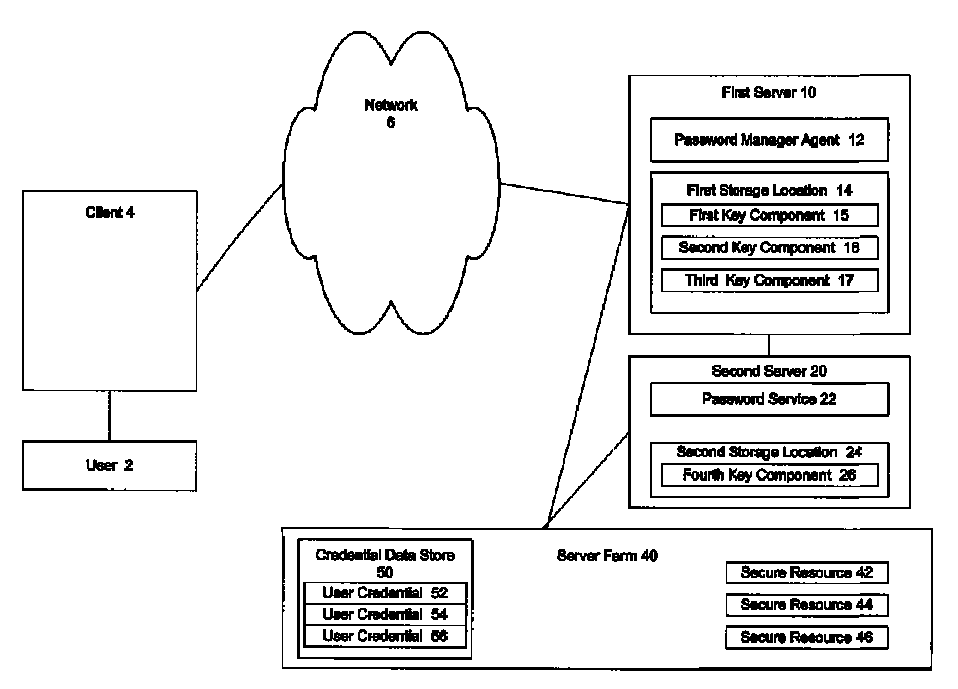
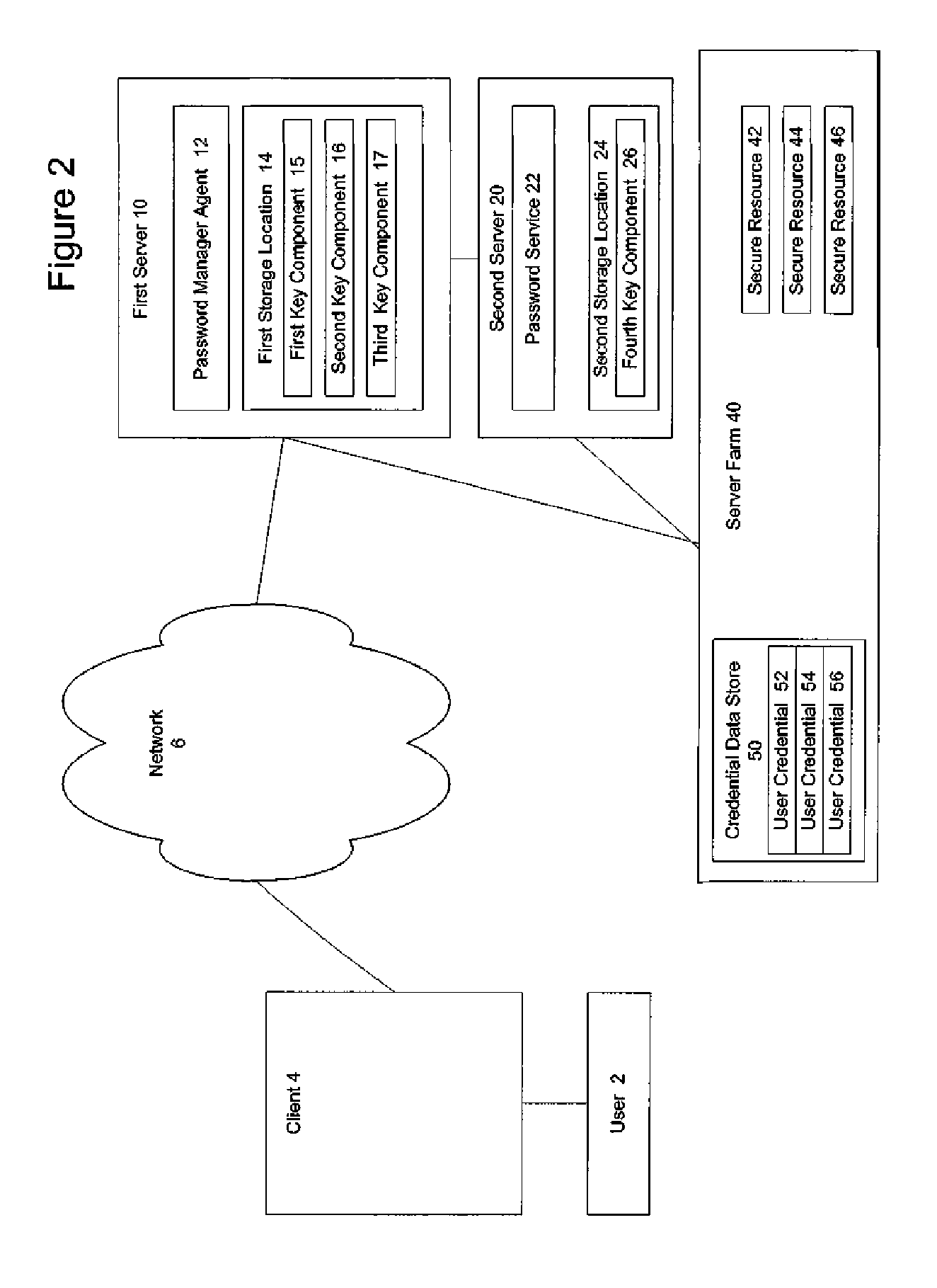
System and method for key recovery
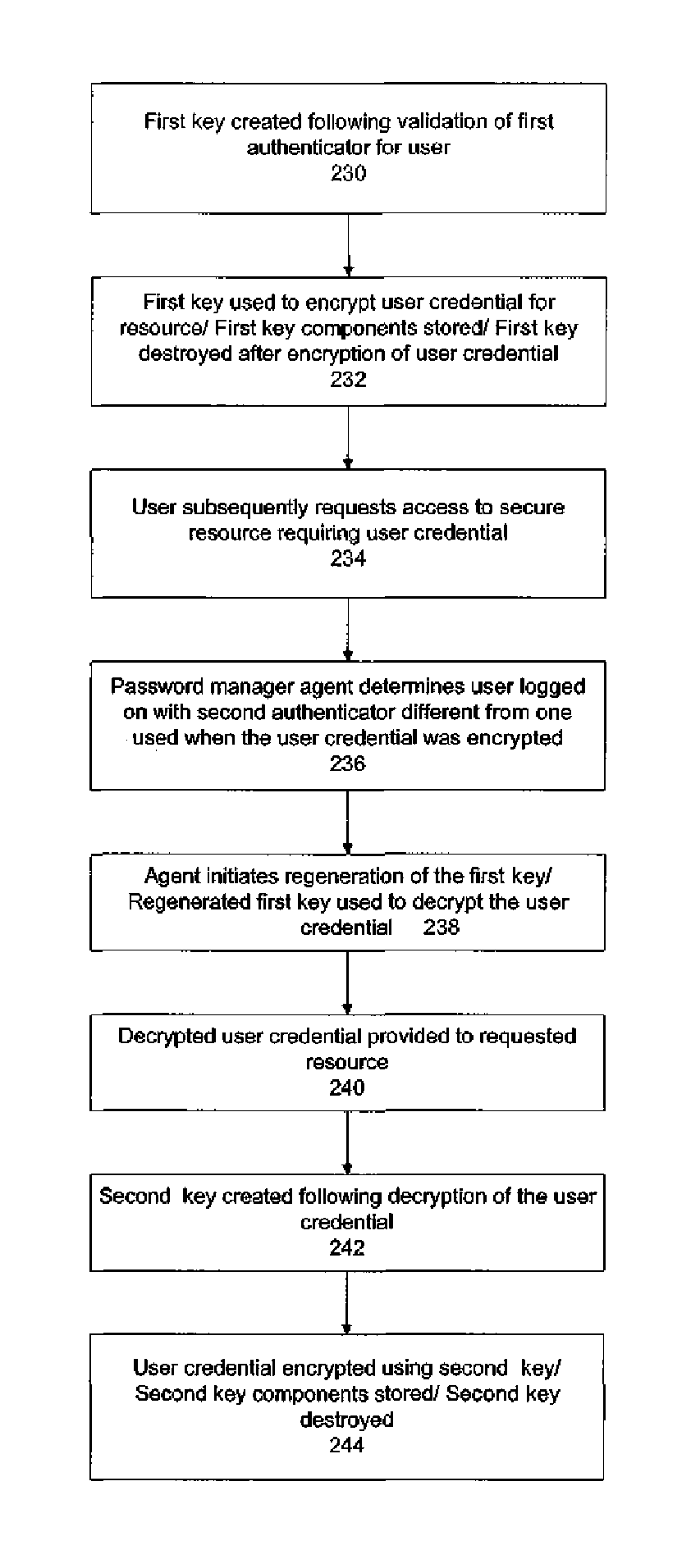
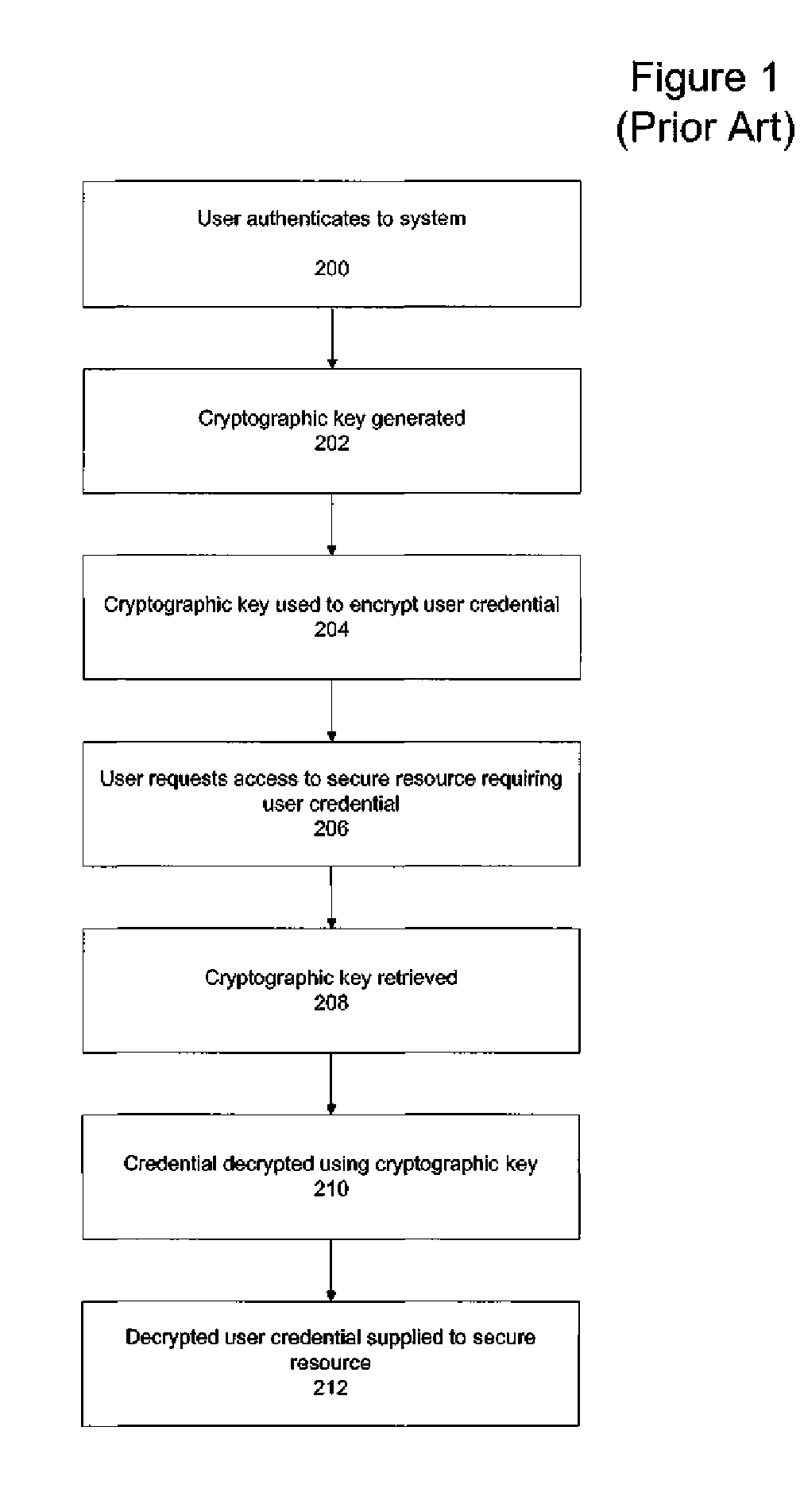
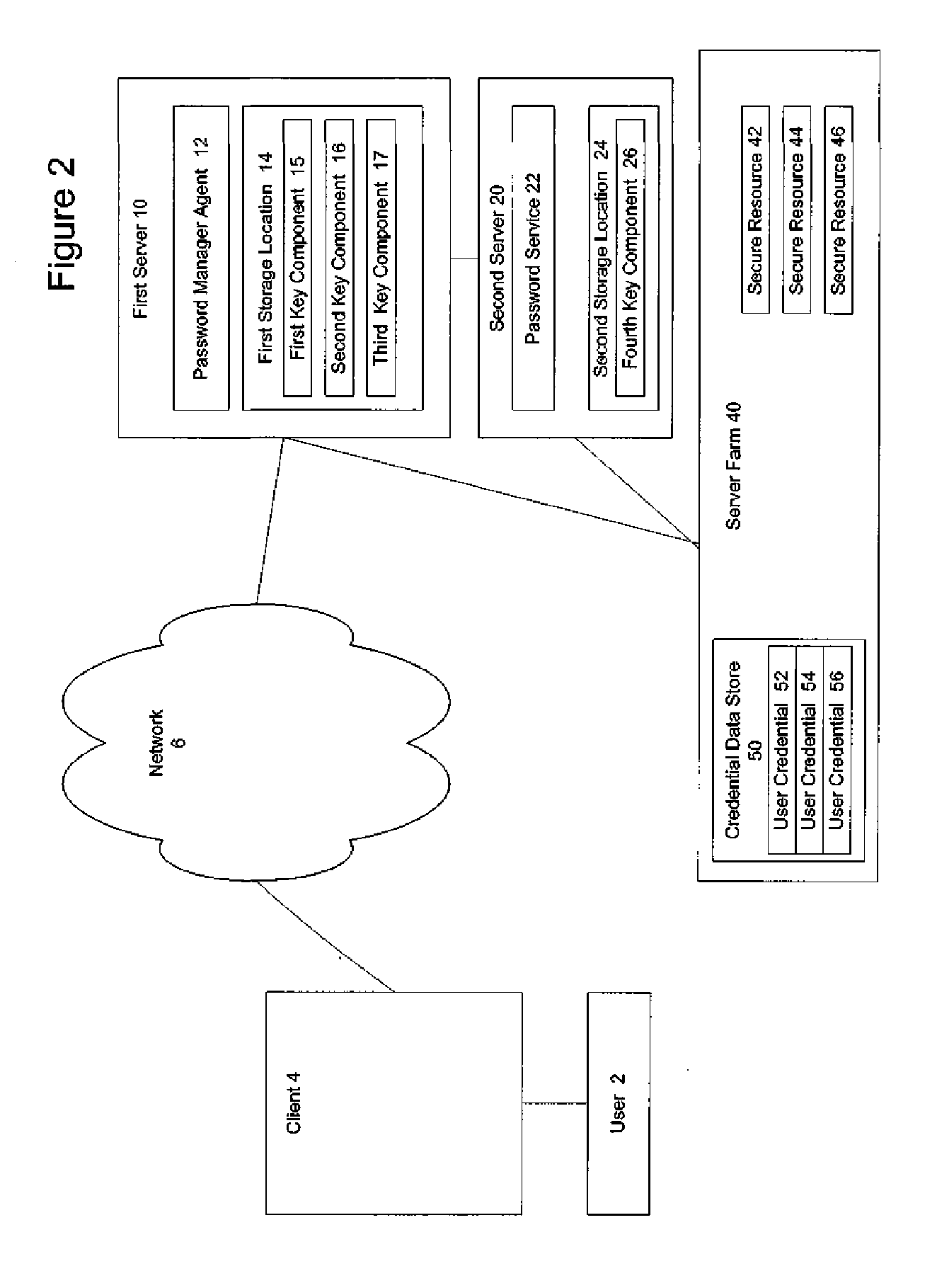
ActiveUS20060242415A1Key distribution for secure communicationDigital data processing detailsPassword managerKey recovery
A secure mechanism for transparent key recovery for a user who has changed authentication information is disclosed. A password manager agent intercepts requests by a user to access secure resources that require user credentials. Upon detecting changed authentication information for the user, the password manager agent automatically regenerates the components of a cryptographic key associated with the user that was previously used to encrypt user credentials for the user and then destroyed. After regeneration of the original cryptographic key, the password manager agent uses the key to decrypt the user credentials necessary for the requested application. The regenerated key is then destroyed and the user credentials are re-encrypted by the password manager agent using a new cryptographic key associated with the user made up of multiple components. Following the re-encryption of the user credentials, the components used to assemble the new key are securely stored in multiple locations and the new key is destroyed.
Owner:CITRIX SYST INC
Key agreement system, shared-key generation apparatus, and shared-key recovery apparatus
ActiveUS20040165726A1Hinders derivationKey distribution for secure communicationPublic key for secure communicationContent distributionHash function
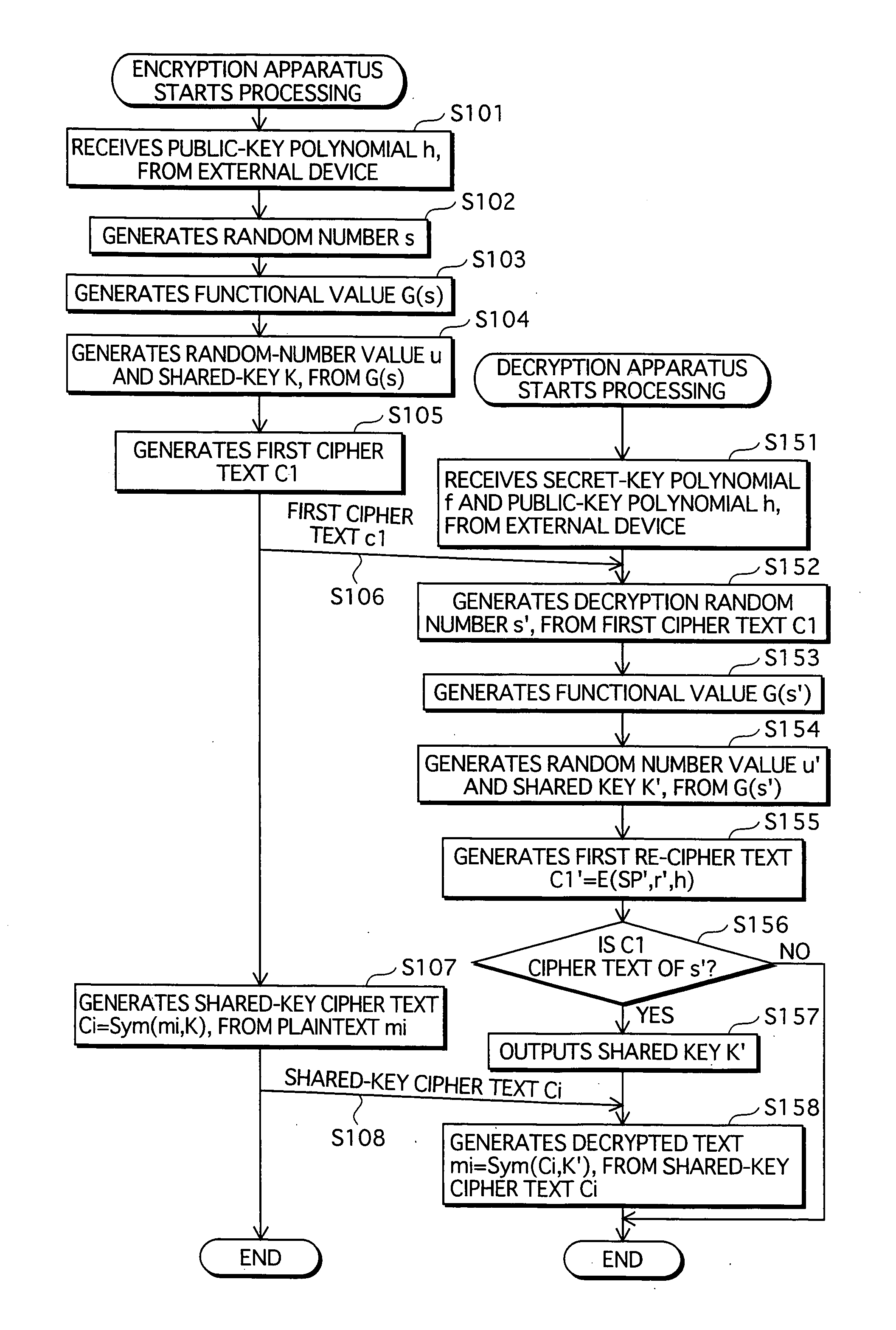
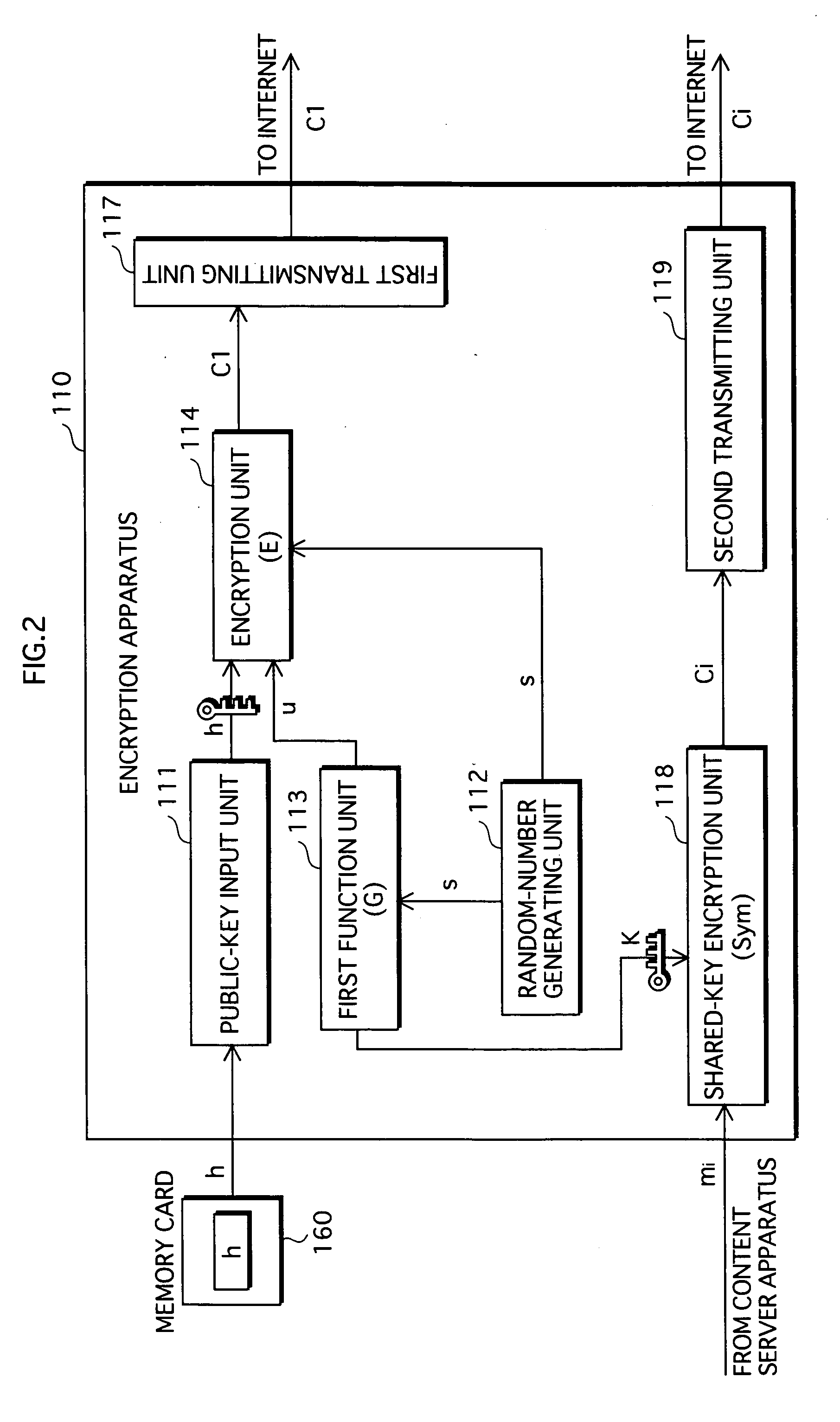
Provided is a content distribution system that prevents different keys to be derived between an encryption apparatus and a decryption apparatus. A random-number generating unit 112d, in an encryption apparatus 110d, generates a random number s, and a first function unit 113d generates a functional value G(s) of the random number s, and generates a verification value a and a shared key K from the functional value G(s). An encryption unit 114d generates a first cipher text c1 of the verification value a using a public-key polynomial h, and a second function unit 115d generates a functional value H(a,c1) of the verification value a and the first cipher text c1, and a random-number mask unit 116d generates a second cipher text c2=s xor H(a,c1). A decryption unit 123d, in a decryption apparatus 120d, decrypts the first cipher text c1 using a secret-key polynomial f, to generate a decryption verification value a'. A third function unit 124d generates a functional value H(a',c1) of the decryption verification value a' and the first cipher text c1, and a random-number mask removal unit 125d generates a decryption random number s'=c2 xor H(a',c1). A fourth function unit 126d generates a hash functional value G(s') of the decryption random number s', and generates a verification value a'' and a shared key K' from the functional value G(s') A comparison unit 127d outputs the shared key K' if the decryption verification value a' is equal to the verification value a''.
Owner:SAMARIA CO LTD
Encryption apparatus, cryptographic communication system, key recovery system, and storage medium
InactiveUS6842523B1Avoid concentrationImprove securityKey distribution for secure communicationUser identity/authority verificationCommunications systemS/KEY
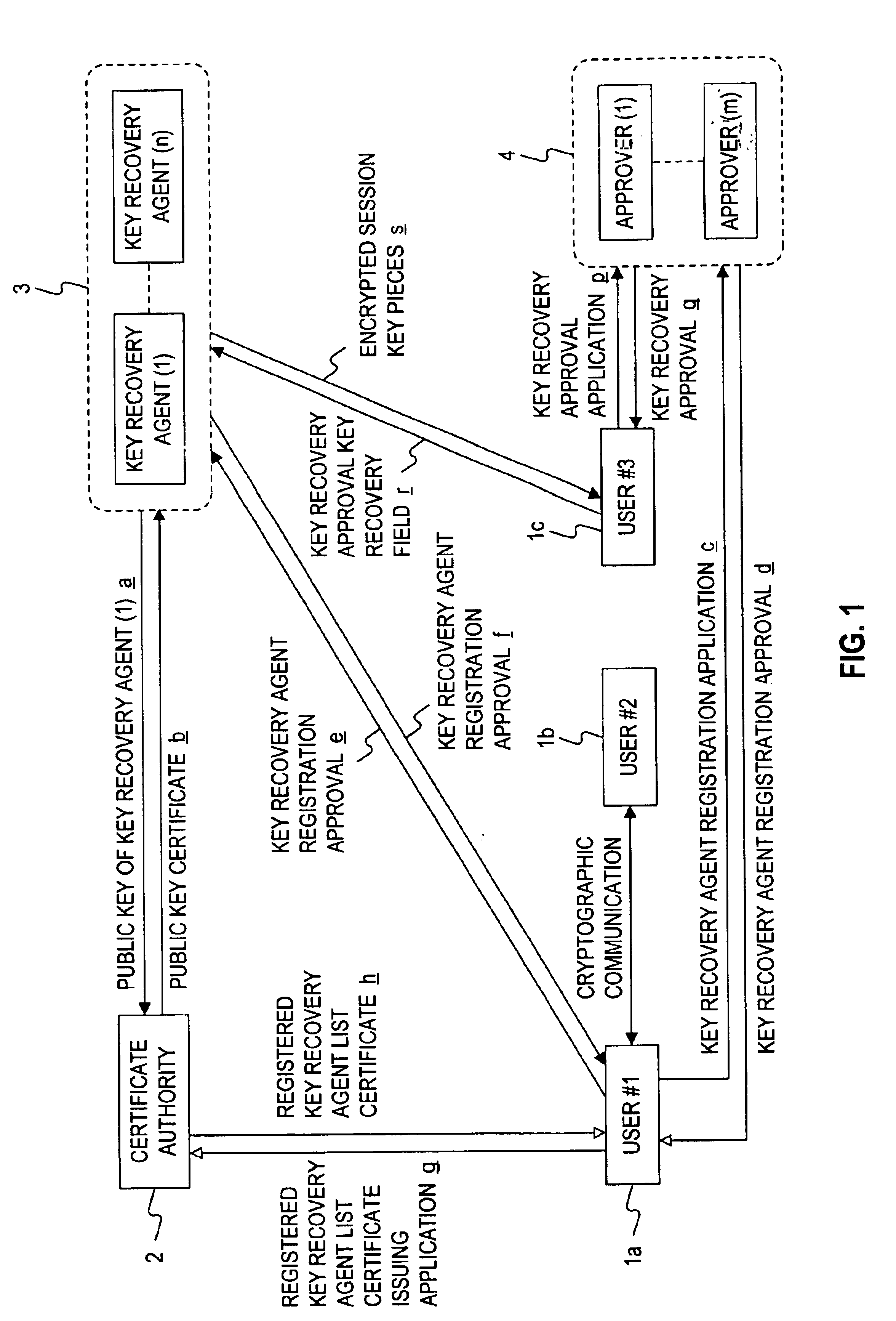
In an encryption apparatus for encrypting a data body to contain an encrypted data body in transmission data and transmitting the transmission data to a receiver, the transmission data includes sender's key recovery data obtained by encrypting recovery information for recovering a key for decrypting the encrypted data body to allow a key recovery agent registered by a sender to decrypt the recovery information, and receiver's key recovery data obtained by encrypting the recovery information for recovering the key for decrypting the encrypted data body to allow a key recovery agent registered by a receiver to decrypt the recovery information.
Owner:KK TOSHIBA
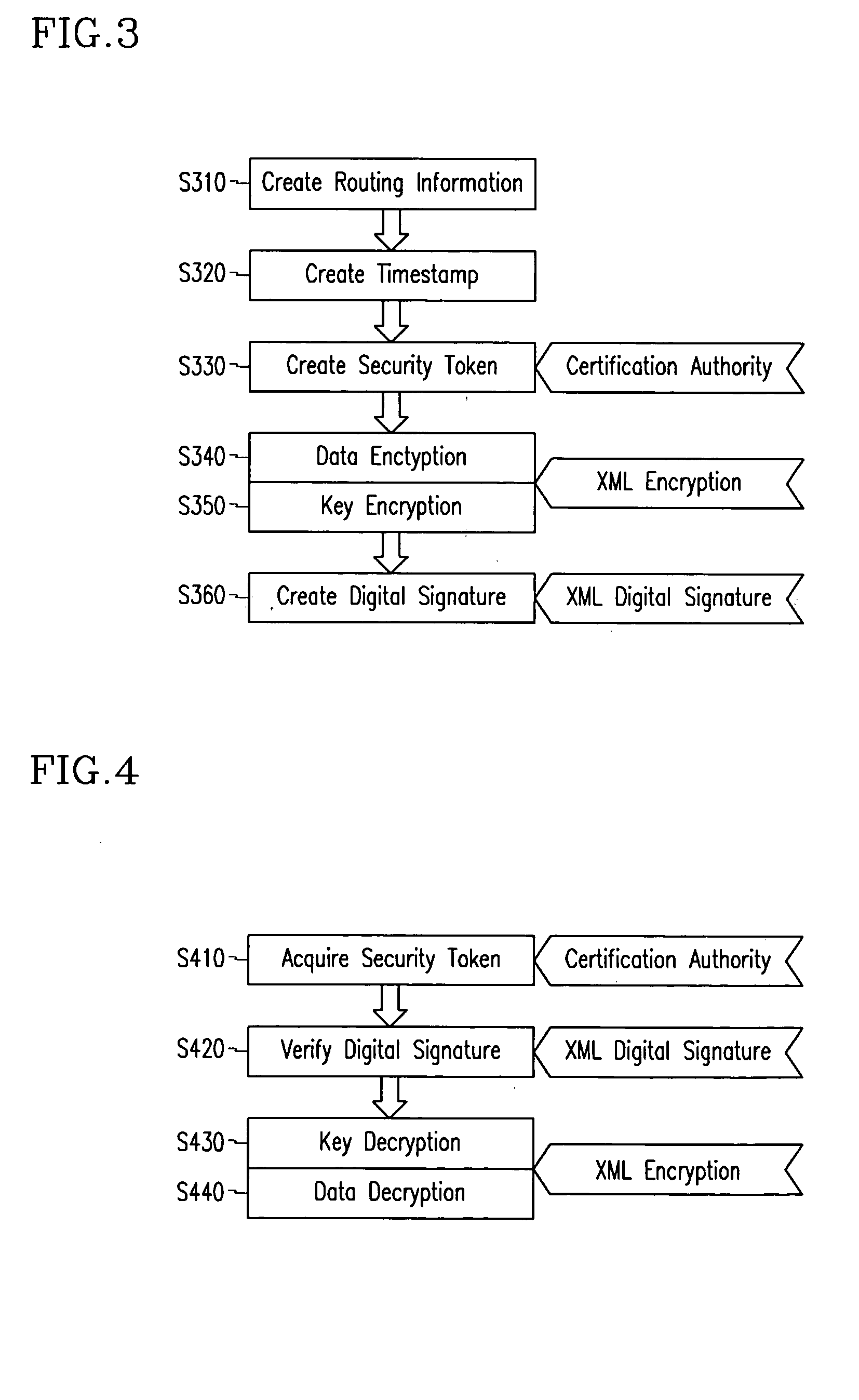
Method for creating and verifying simple object access protocol message in web service security using signature encryption
InactiveUS20050081039A1Restoring dataKey distribution for secure communicationData taking preventionSimple objectKey recovery
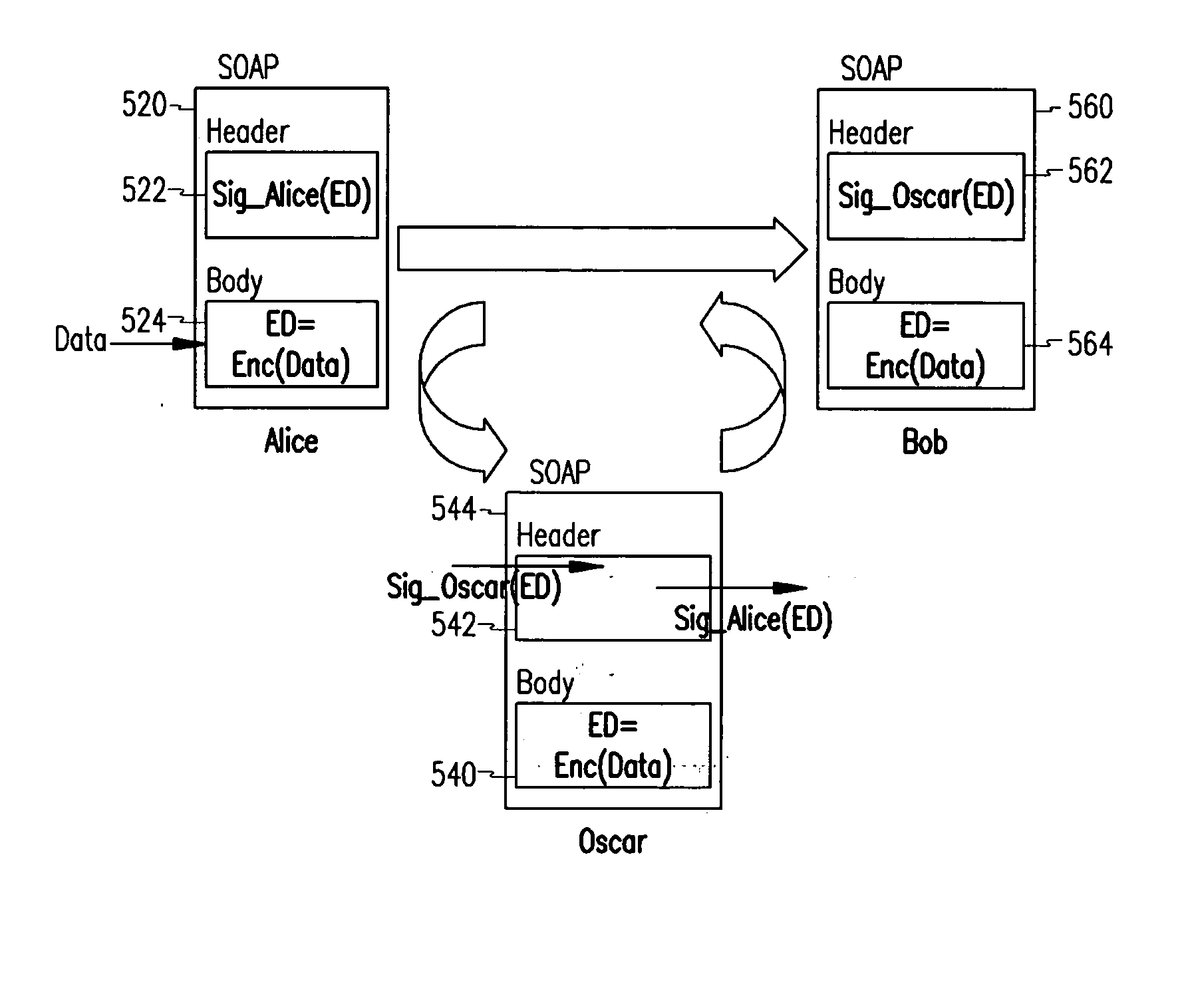
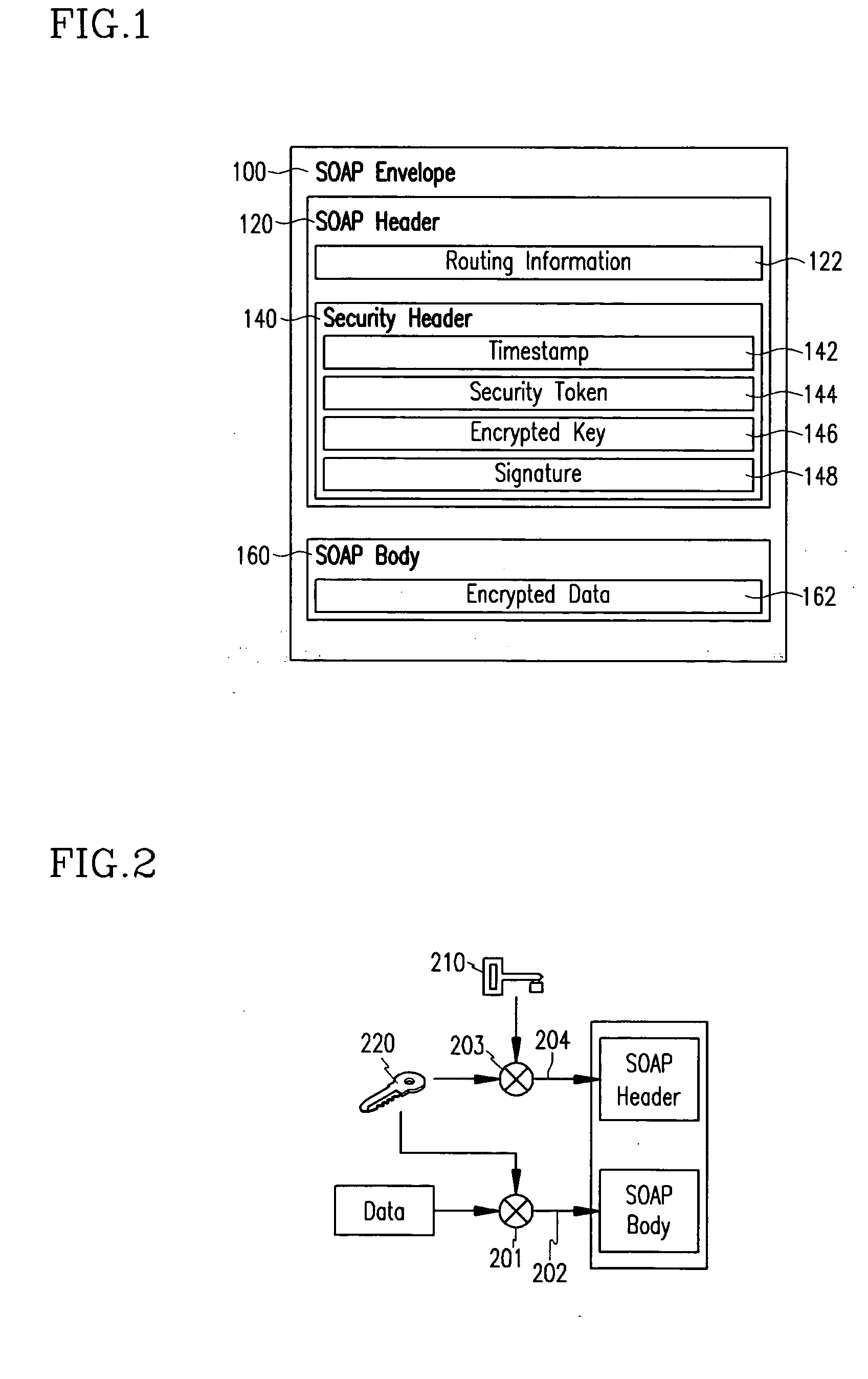
Disclosed is a method for creating and verifying SOAP messages in web service security using signature encryption. The SOAP message sender encrypts a signature used for SOAP message security with a secret key for encrypting data to be contained in the SOAP body. The encrypted signature is inserted in the security header of the SOAP header and sent to the recipient. The SOAP message recipient decrypts the encrypted key with his / her private key and restores the secret key. The restored secret key is used to decrypt the encrypted signature in the security header of the SOAP header, and the decrypted signature is used to verify the SOAP message.
Owner:ELECTRONICS & TELECOMM RES INST
Key management and recovery method for encrypted digital certificate
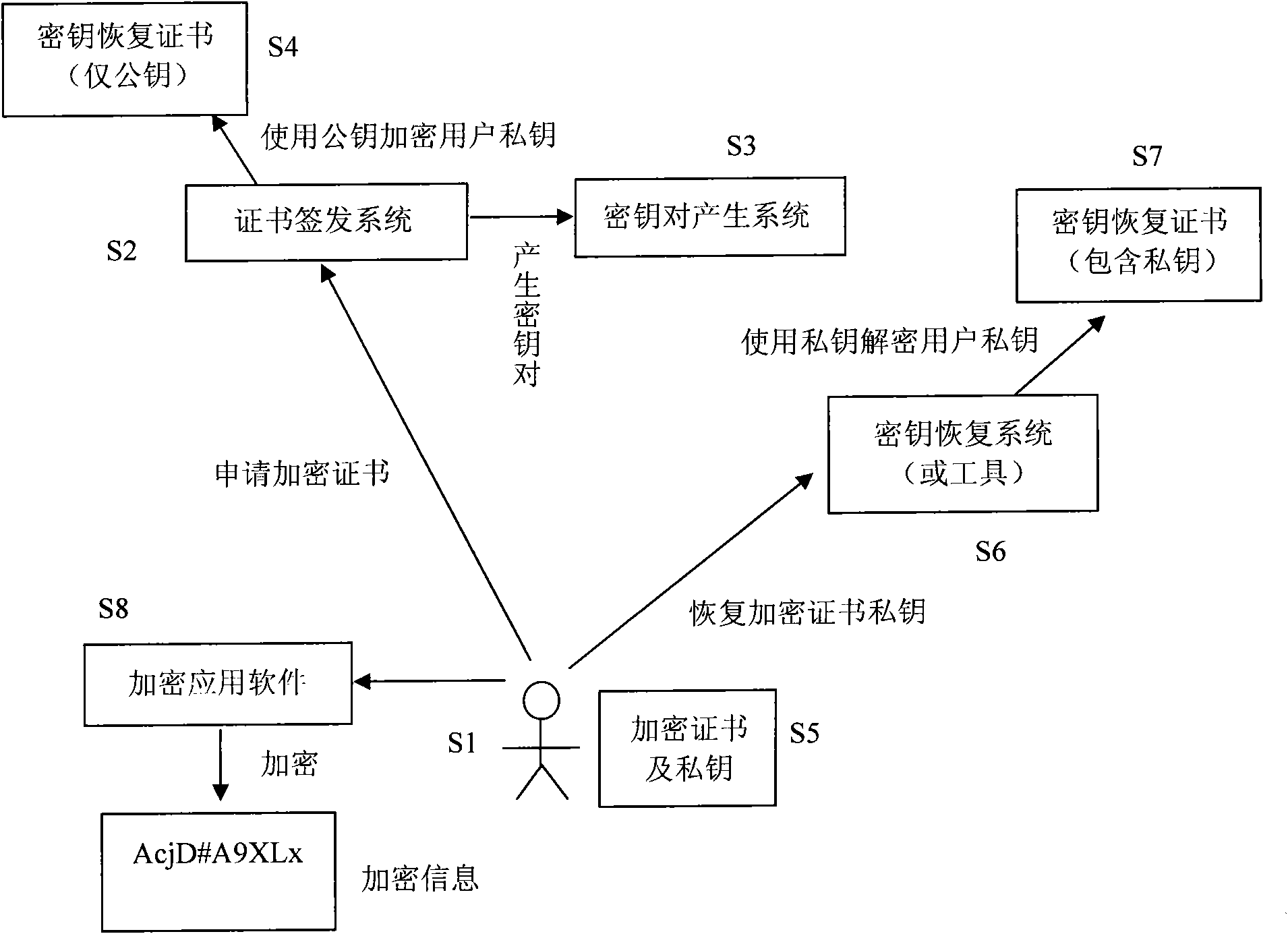
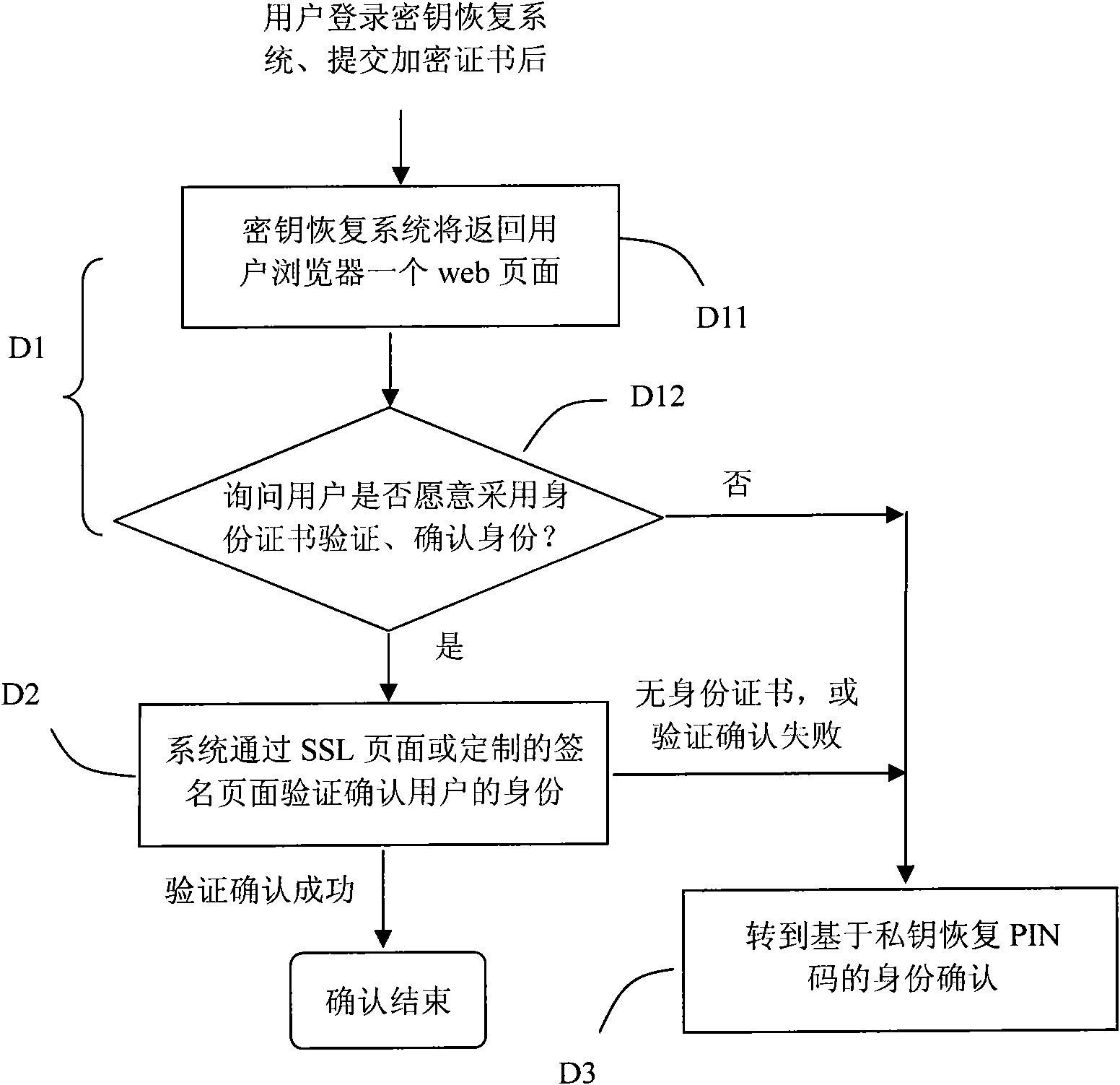
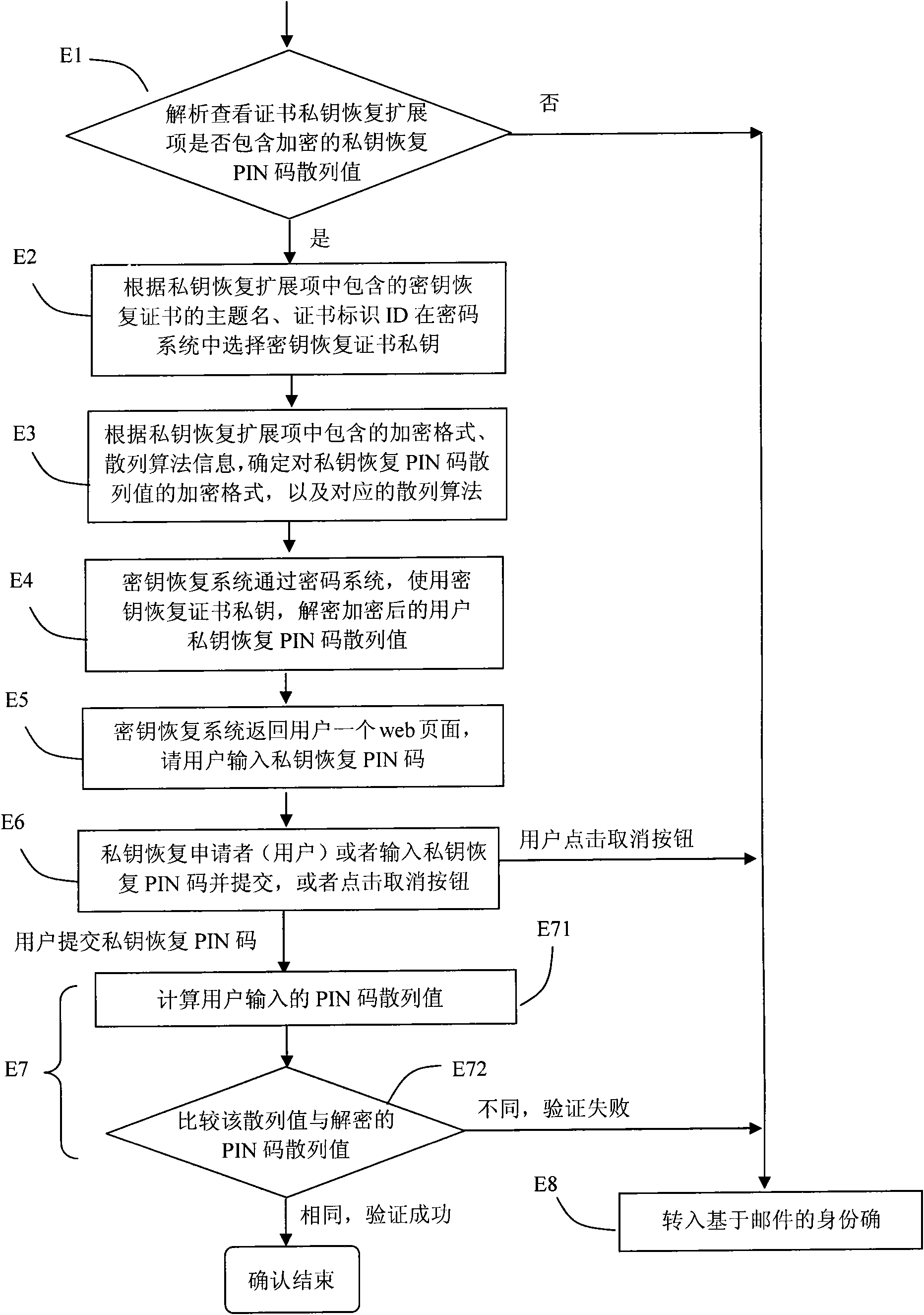
InactiveCN101567780AAvoid Storage Security IssuesAvoid System Performance IssuesKey distribution for secure communicationRecovery methodOnline and offline
The invention relates to a key management and recovery method for an encrypted digital certificate. When a certificate issuing system based on the method issues an encrypted certificate of a user, a specific certificate public key recovered by a key is used for encrypting a private key of the user and then the private key encrypted is put into a newly defined private key recovery extension item in the certificate; when the encrypted private key of the user is damaged or lost, a key recovering system or tool can recover the private key of the encrypted certificate of the user by using a corresponding certificate private key for recovering the certificate and safely send the private key of the encrypted certificate to the user according to necessary private key recovering strategies after necessary user ID confirmation is finished. On the basis of the method, the private key of the user can be recovered in both online and offline manners. Compared with the commonly adopted key management and recovery method for an encrypted digital certificate currently, the invention does not require a special system to collectively store the private of the encrypted certificate of the user, which greatly lowers the complexity of key management and recovery system and causes the private key recovery to become easy, simple and flexible.
Owner:WUHAN UNIV OF TECH +1
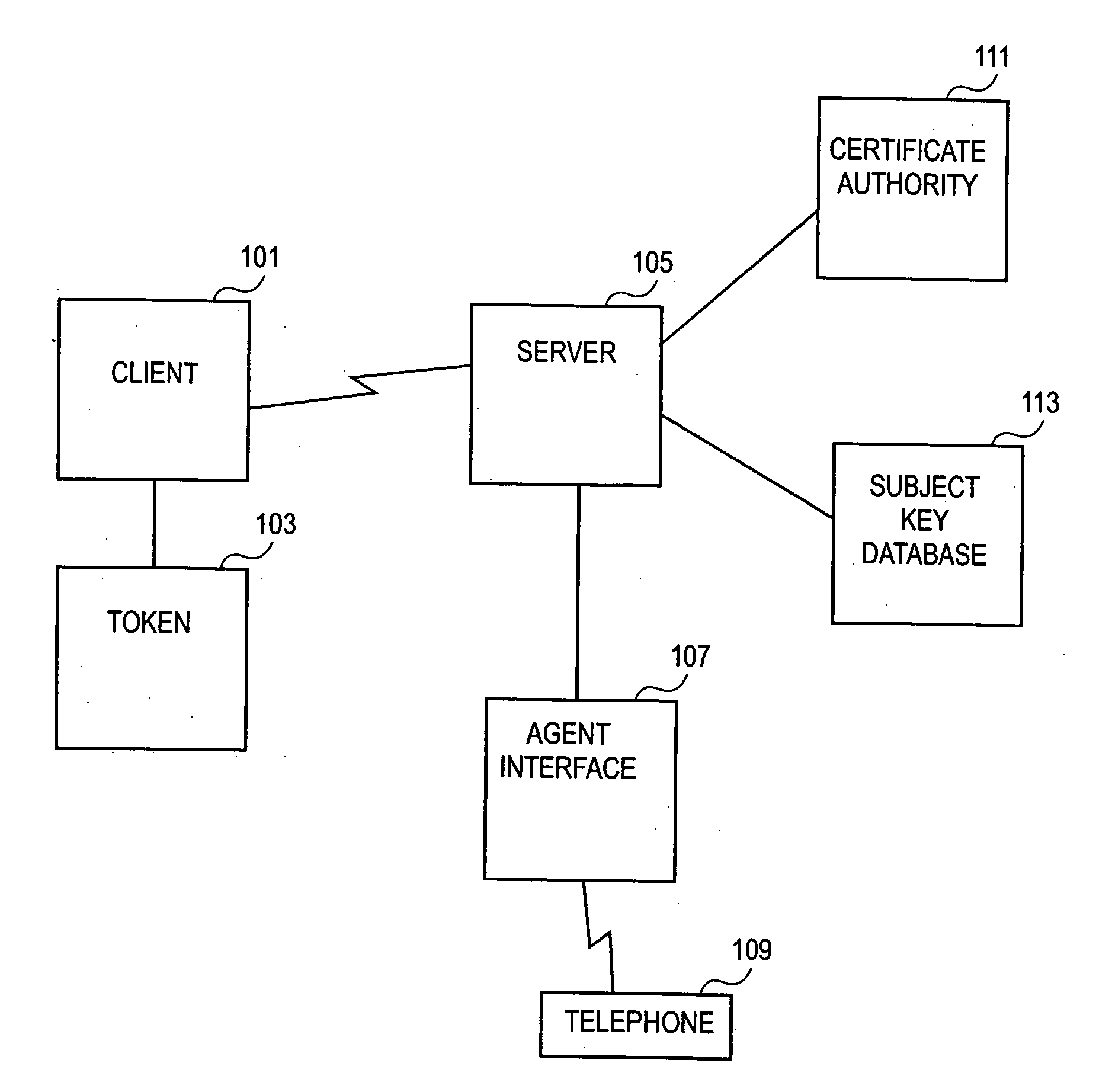
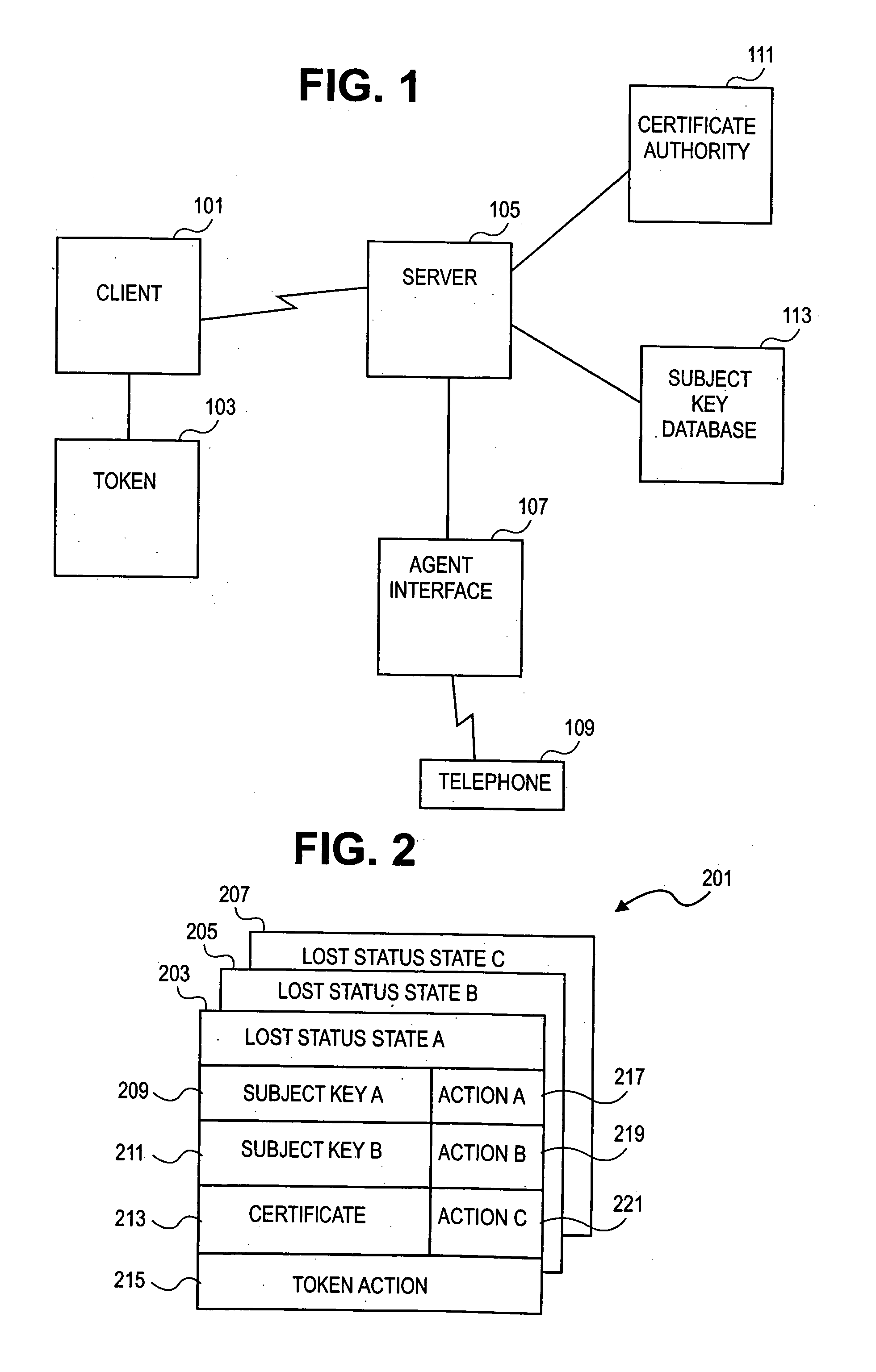
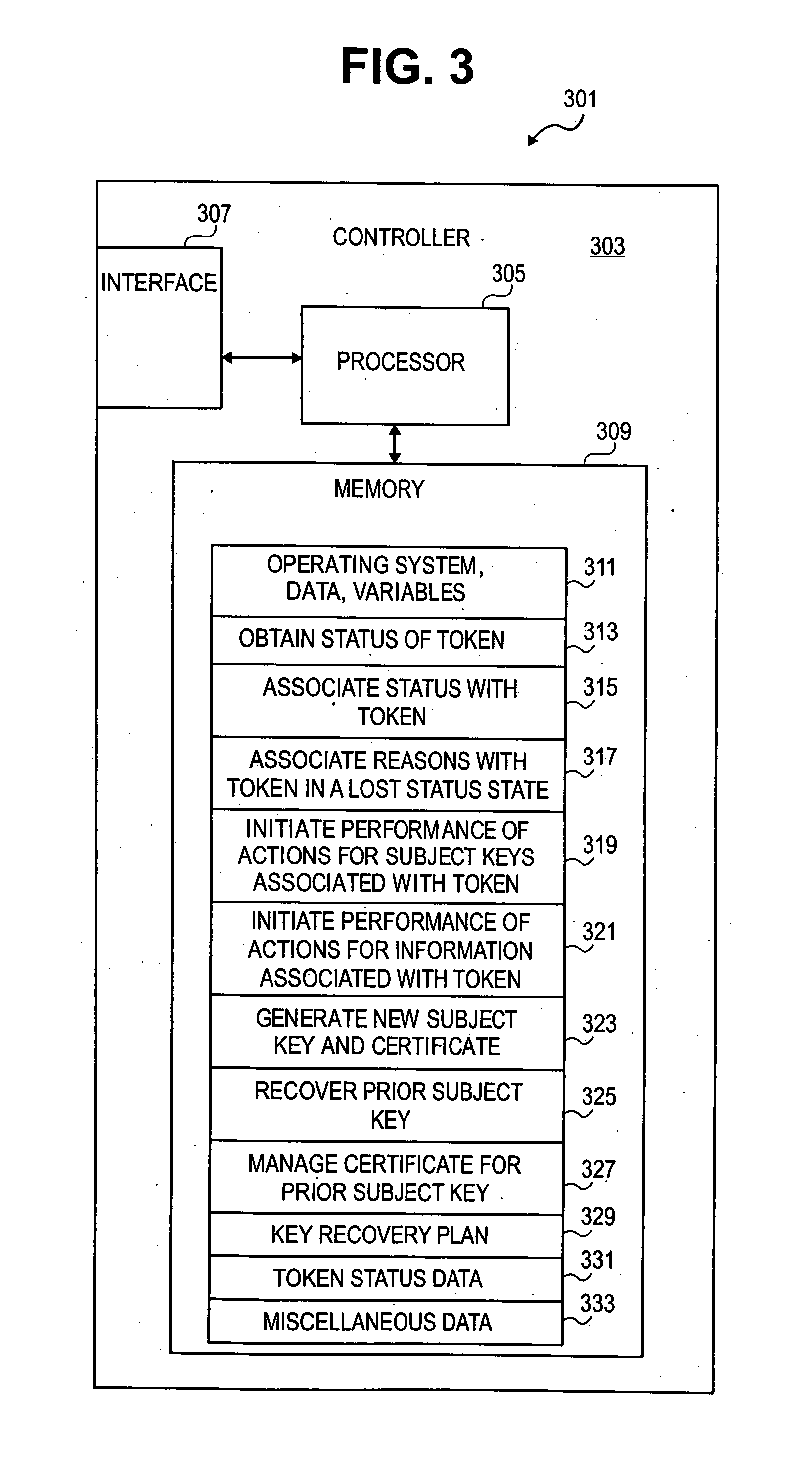
Methods and system for a key recovery plan
ActiveUS20080022086A1Key distribution for secure communicationPublic key for secure communicationUnique identifierKey recovery
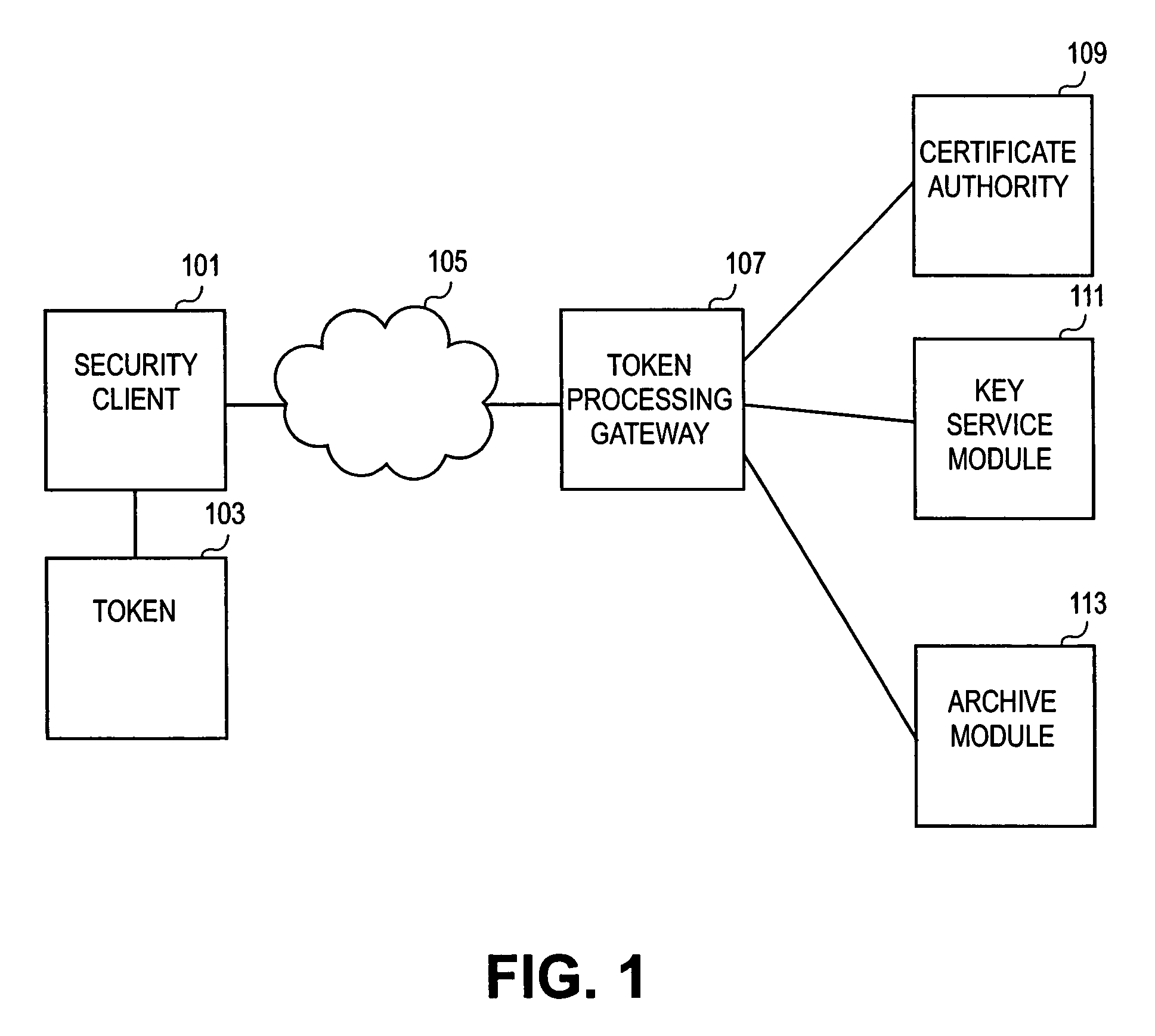
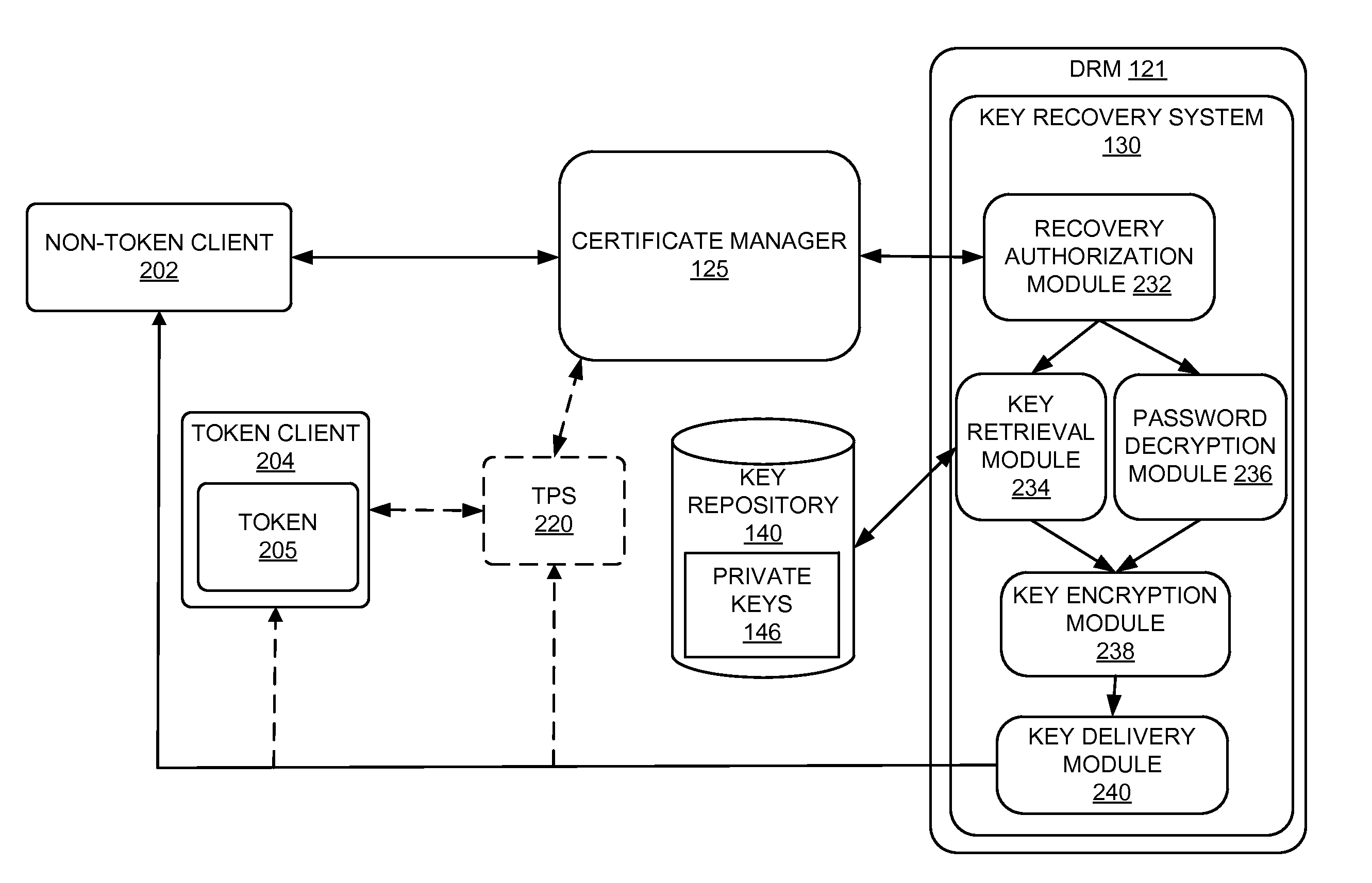
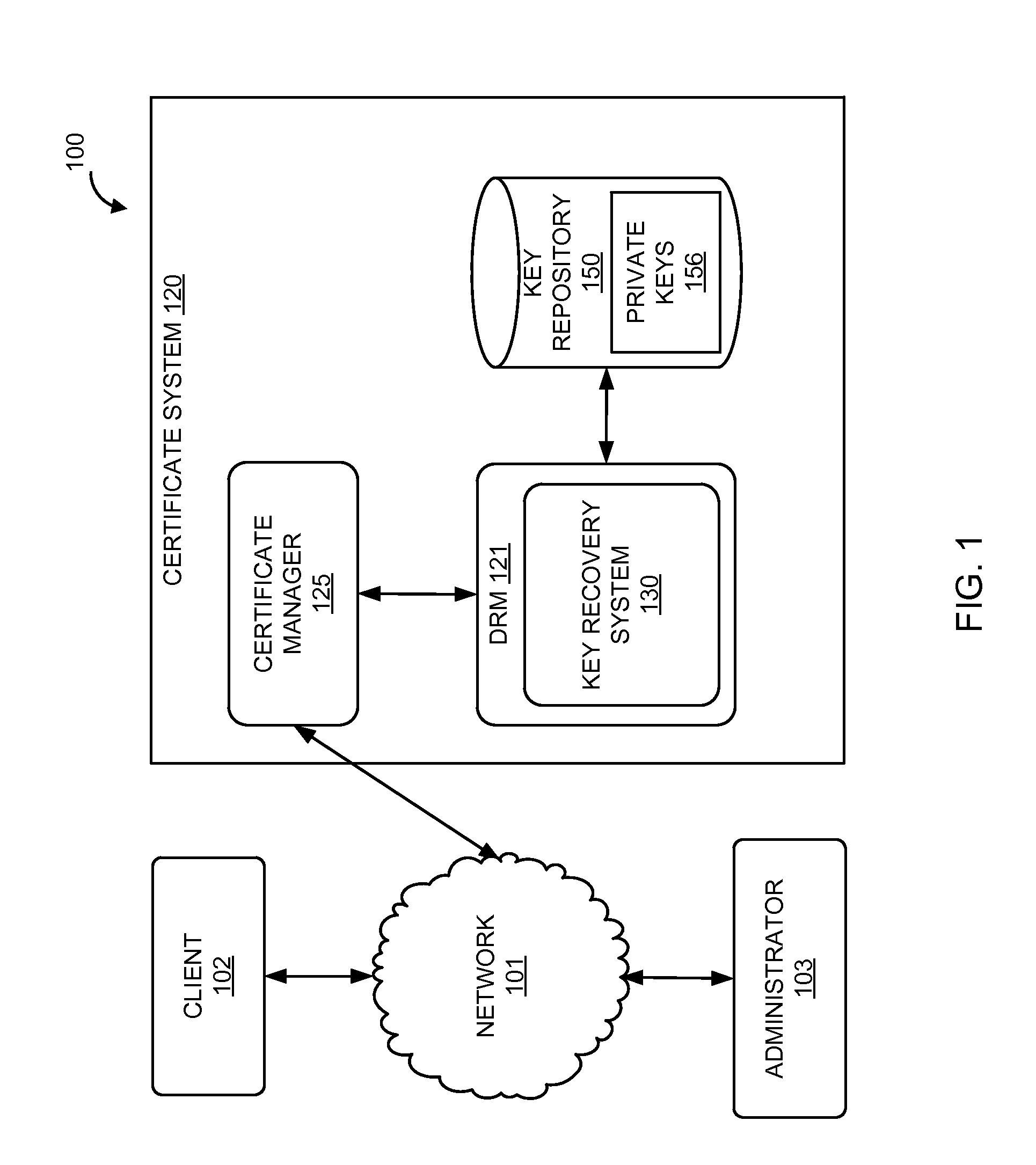
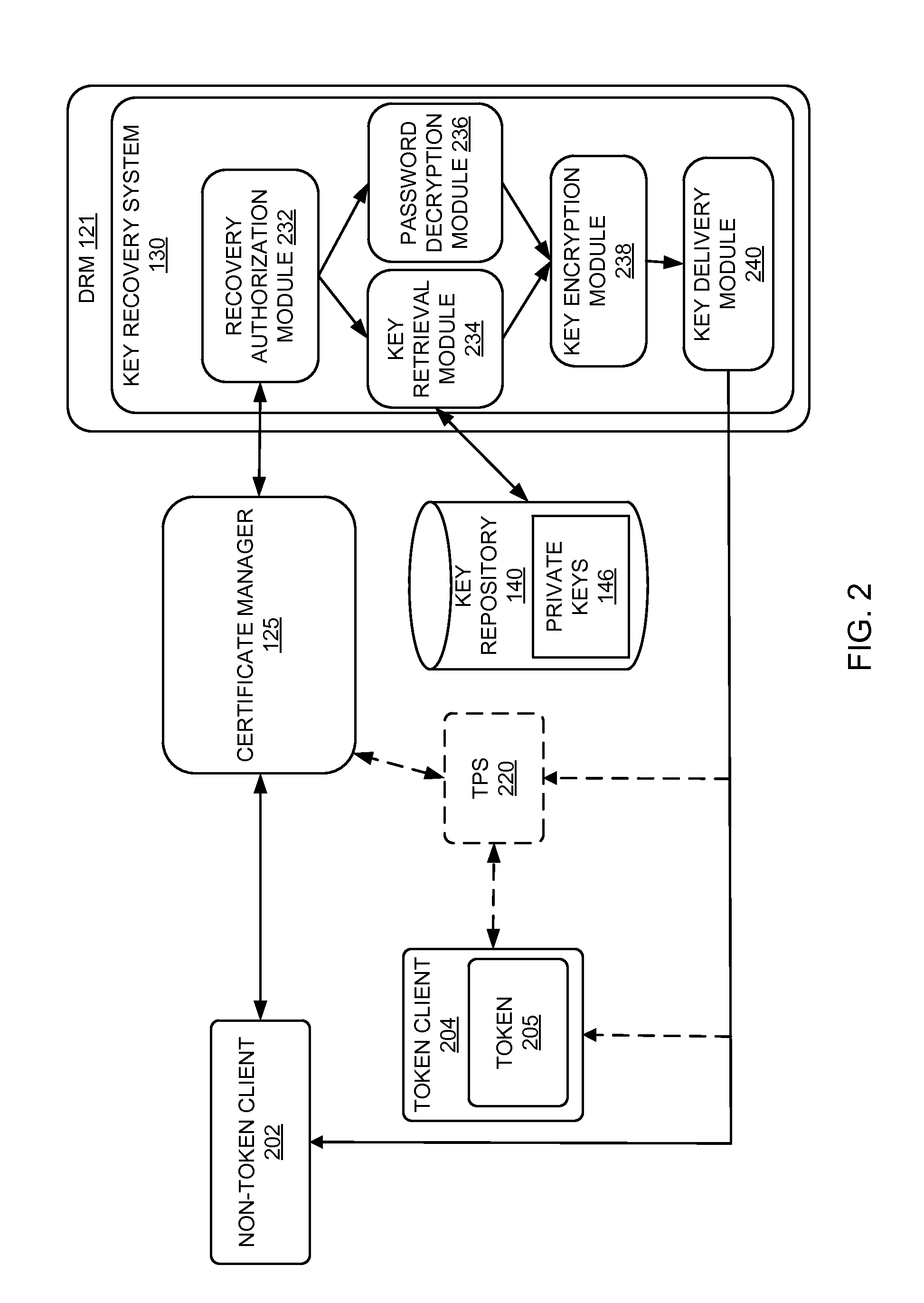
Methods, systems and computer readable mediums are provided for recovering subject keys and / or certificates for a token. A unique identifier associated with the token is obtained. The token is associated with subject keys and with a first status of statuses, the statuses including a lost status state and an other status state. In response to the token being in the lost status state, a key recovery plan is determined to recover at least one of the subject keys and the certificates associated with the token.
Owner:RED HAT
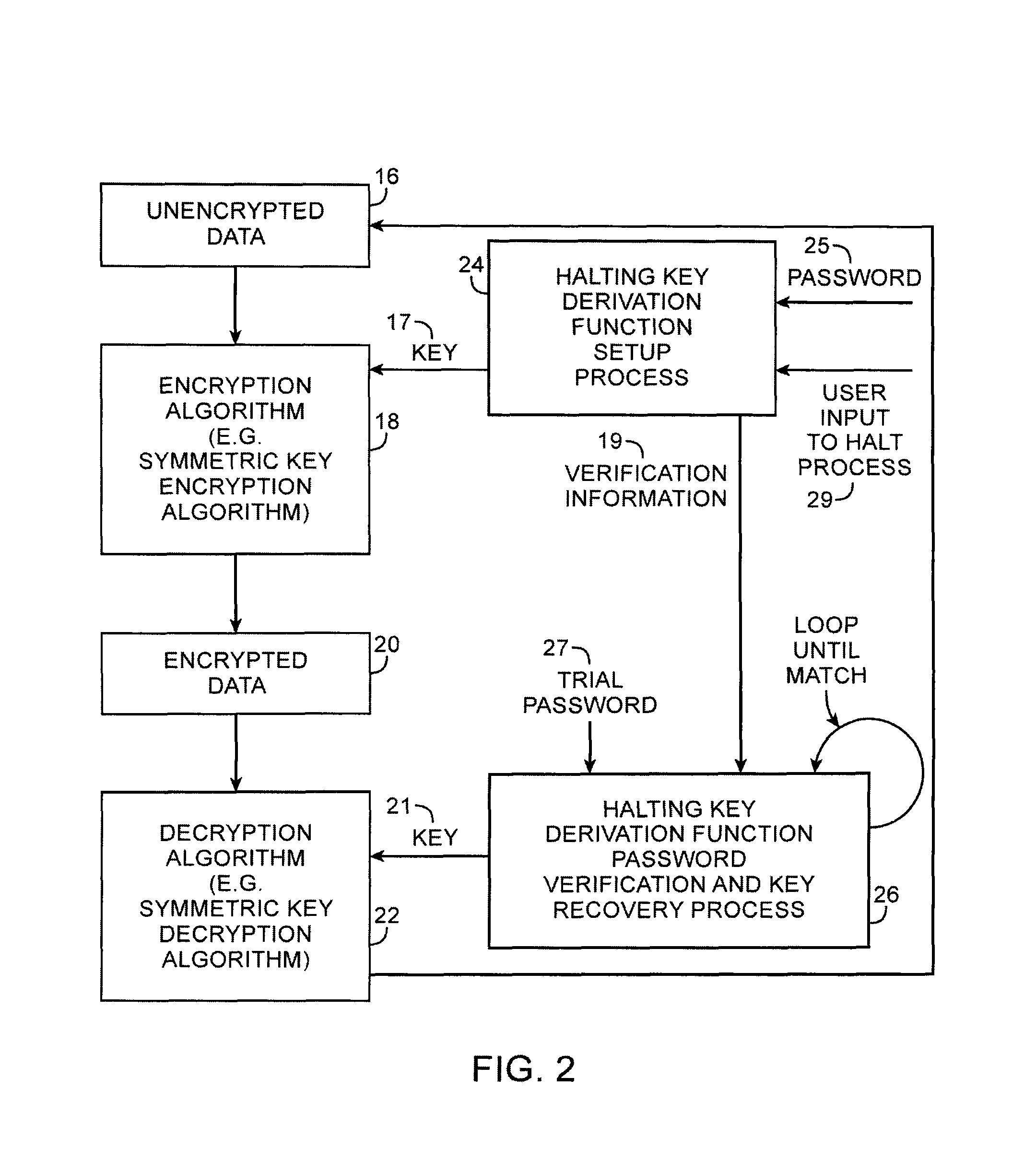
Cryptographic system with halting key derivation function capabilities
ActiveUS8254571B1Key distribution for secure communicationDigital data processing detailsUser inputPassword
A halting key derivation function is provided. A setup process scrambles a user-supplied password and a random string in a loop. When the loop is halted by user input, the setup process may generate verification information and a cryptographic key. The key may be used to encrypt data. During a subsequent password verification and key recovery process, the verification information is retrieved, a user-supplied trial password obtained, and both are used together to recover the key using a loop computation. During the loop, the verification process repeatedly tests the results produced by the looping scrambling function against the verification information. In case of match, the trial password is correct and a cryptographic key matching the key produced by the setup process may be generated and used for data decryption. As long as there is no match, the loop may continue indefinitely until interrupted exogenously, such as by user input.
Owner:MICRO FOCUS LLC
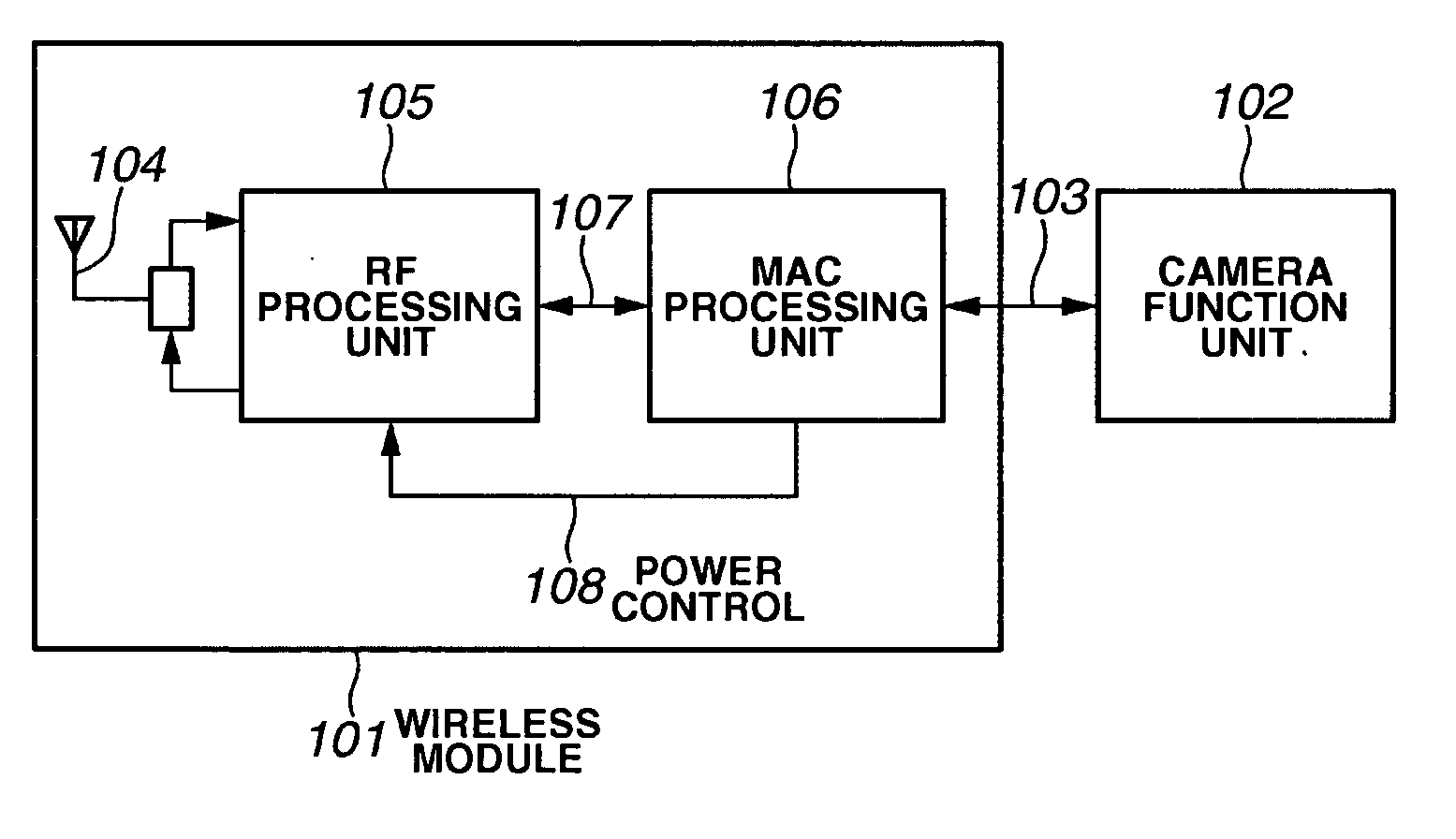
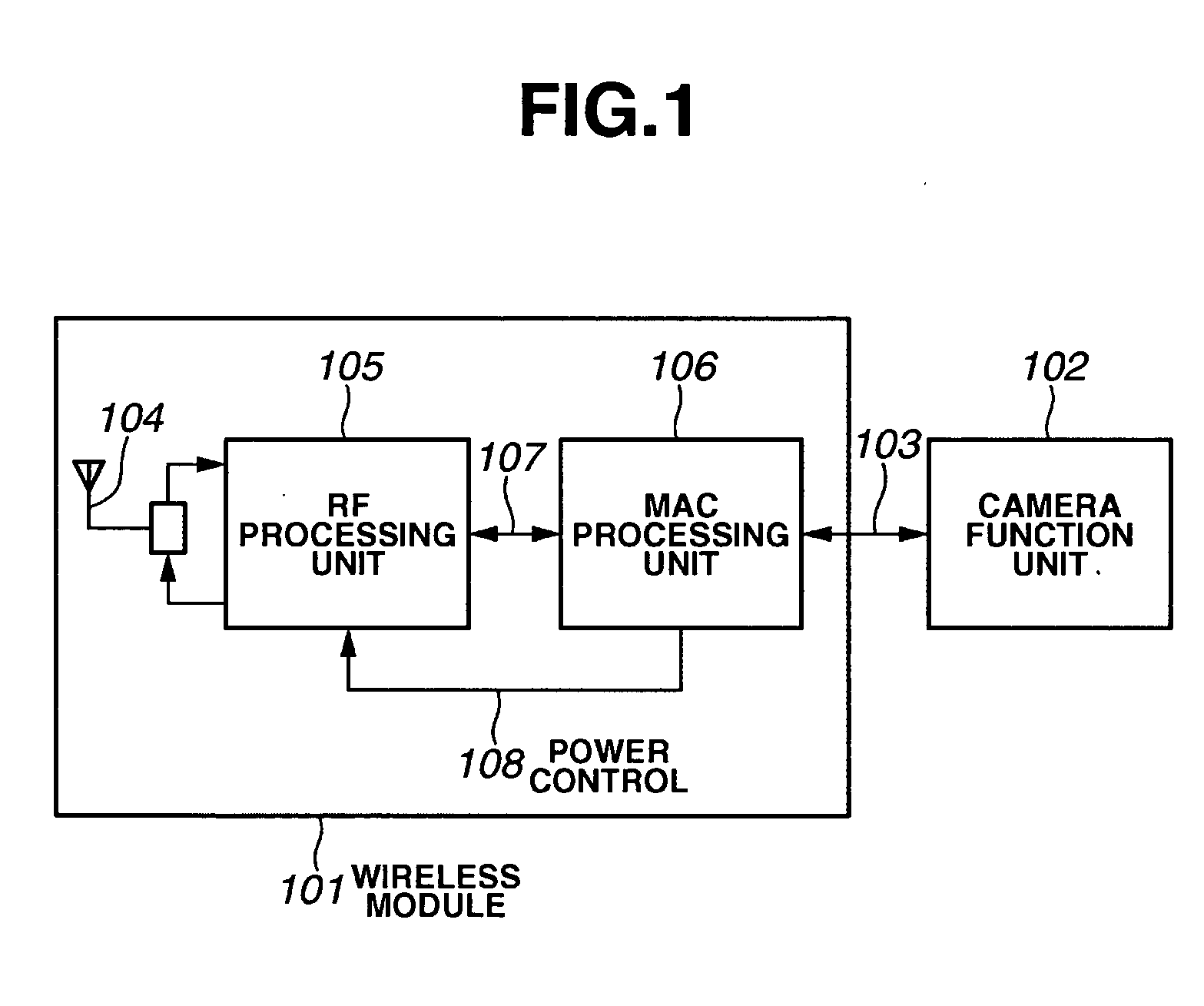
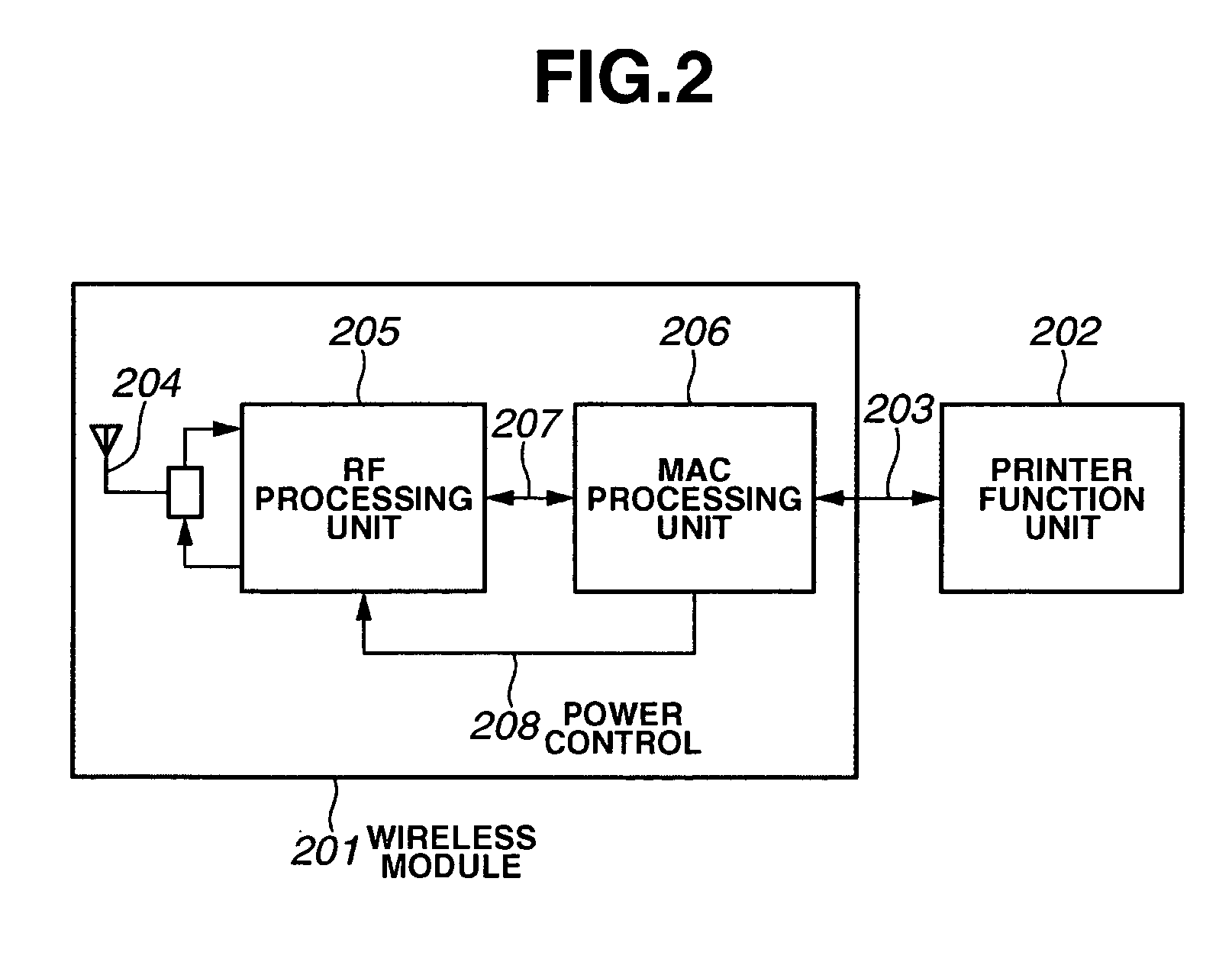
Communication apparatus having power-saving communication function, and communication method
InactiveUS20070173296A1Power managementUser identity/authority verificationIp addressComputer science
A communication apparatus which starts communication using a power-saving function changes, with its communication counterpart, a key for a confidential mode and performs power-saving communication. When terminating the power-saving function, the communication apparatus returns, with its communication counterpart, the key for the confidential mode to the original one. Then, after returning the key for the confidential mode to the original one, the communication apparatus performs an IP address reassignment process.
Owner:CANON KK
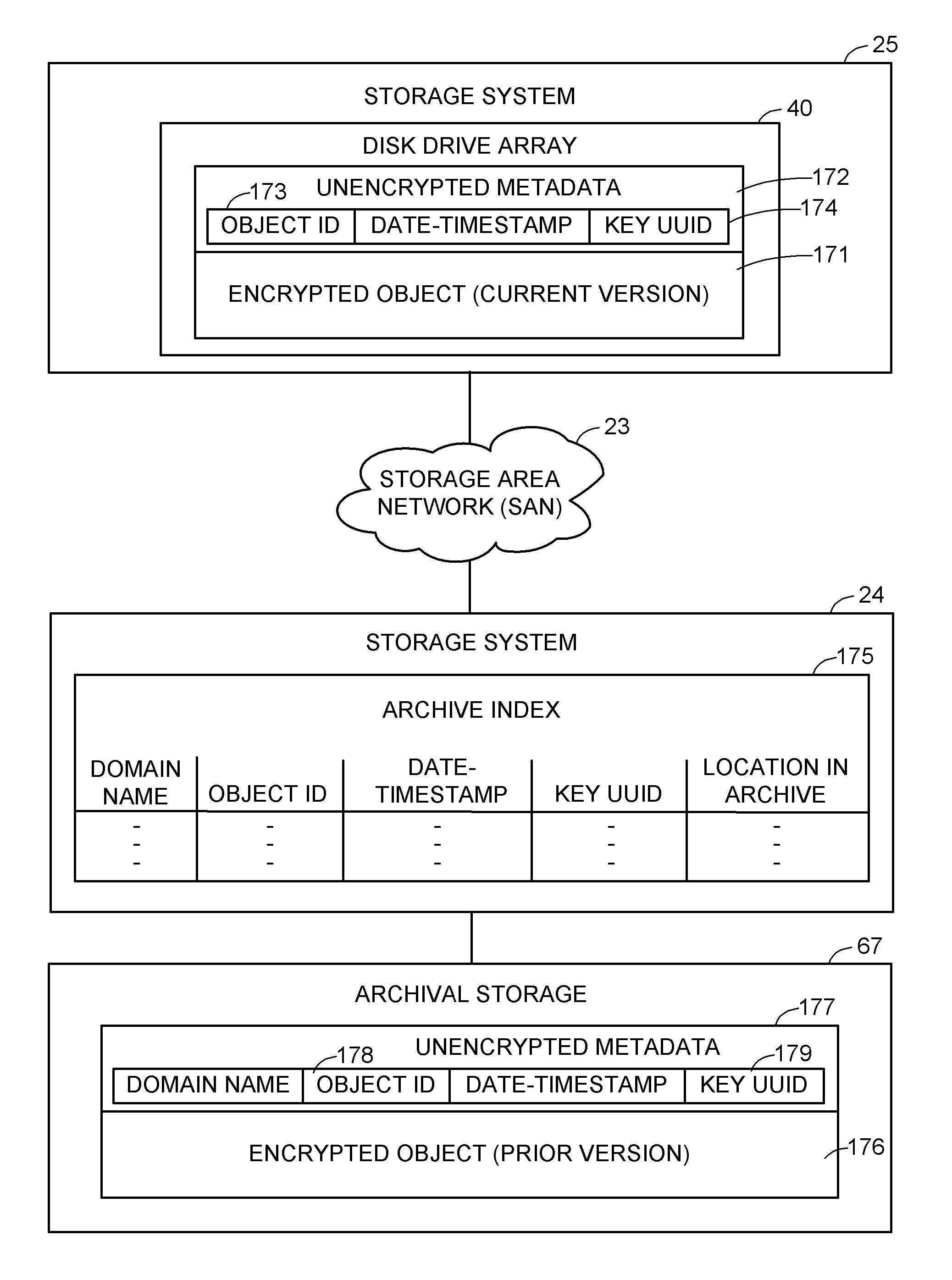
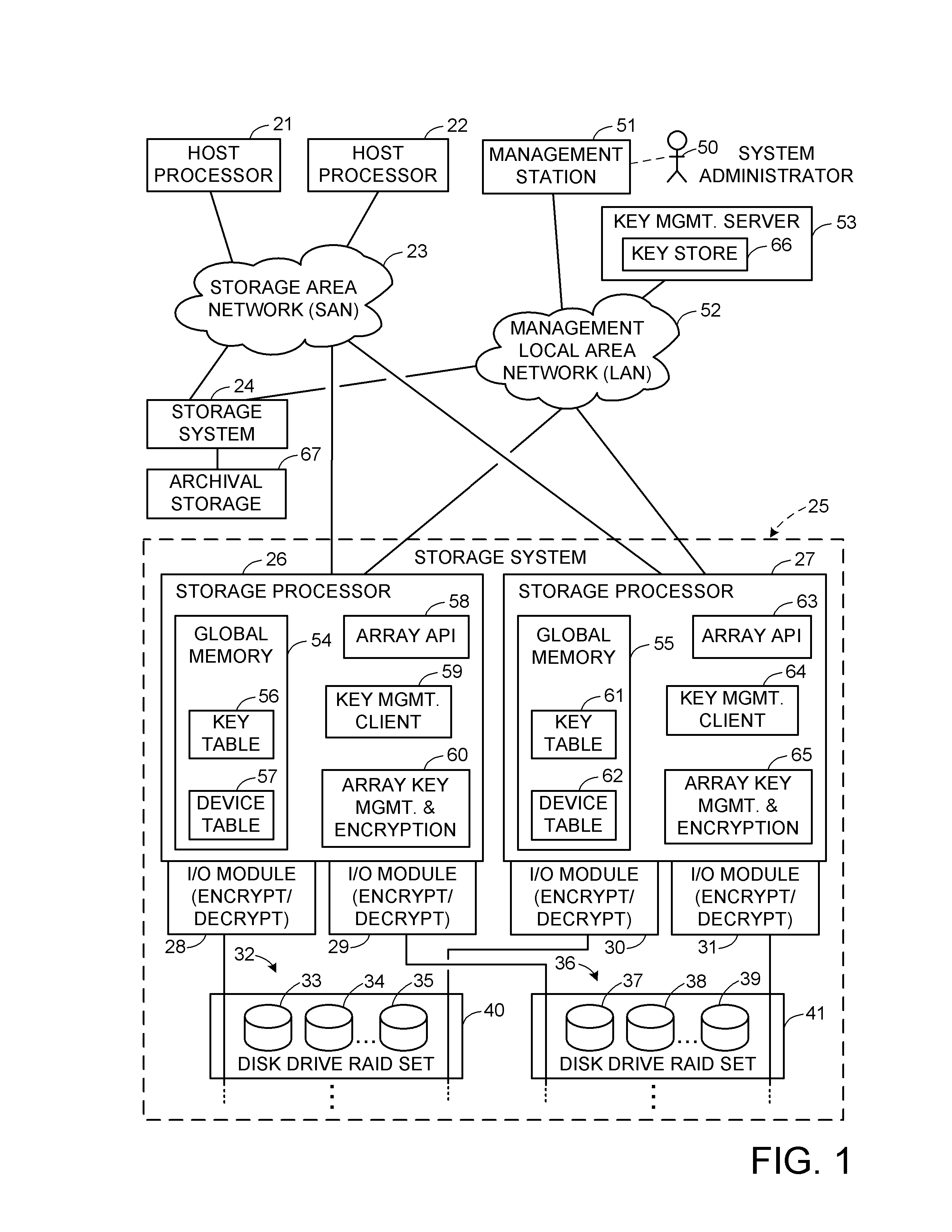
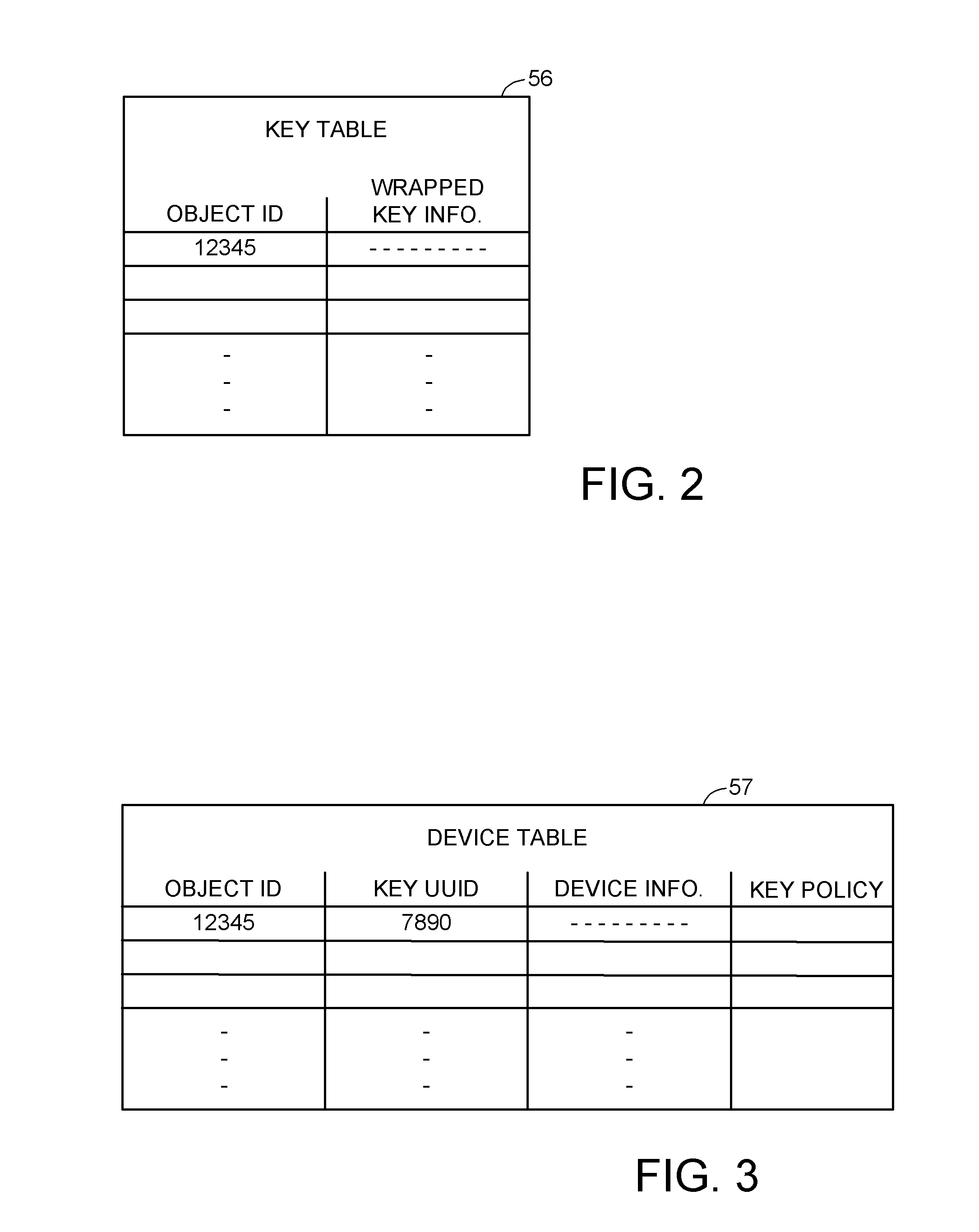
Encryption key recovery in the event of storage management failure
ActiveUS8588425B1Key distribution for secure communicationUser identity/authority verificationData processing systemOccurrence data
A data processing system stores encrypted data. Object identifiers are assigned to storage objects, and data encryption keys are assigned to the storage objects. When performing an operation upon a storage object, data encryption key failure may occur due to a corrupt or incorrect key. In this case, a copy of the data encryption key is fetched from a key server. It is possible for the association of the object identifiers with the data encryption keys to become lost or confused, so that the key server may fail to provide the correct key for a specified object identifier. Therefore, an absolute key identifier that is unique across the key server namespace also is stored in association with the object identifier in the storage system and in the key store of the key server, and the absolute key identifier is used as a failsafe for recovery of encrypted data.
Owner:EMC IP HLDG CO LLC
Secure Peer-to-Peer Distribution of an Updatable Keyring
ActiveUS20090060201A1Improve balanceKey distribution for secure communicationDigital data protectionPersonalizationUser needs
A distributed peer-to-peer document archive system provides version-control, security, access control, linking among stored documents and remote access to documents usually associated with centralized storage systems while still providing the simplicity, personalization and robustness to network outages associated with personal and peer-to-peer storage systems. A “keyring” is an encrypted repository that allows a user to recover and access a user's entire digital archive with a single master key. After the key is created, it does not need to be updated, and can be stored in a safe, safety-deposit box or other secure location. In the event the user's computer is stolen or destroyed, the user need only install the system on a new machine and import the master key. The system will then use that key to browse nearby servers to find and decrypt all files necessary to recreate the full digital archive in its most recent state.
Owner:RICOH KK
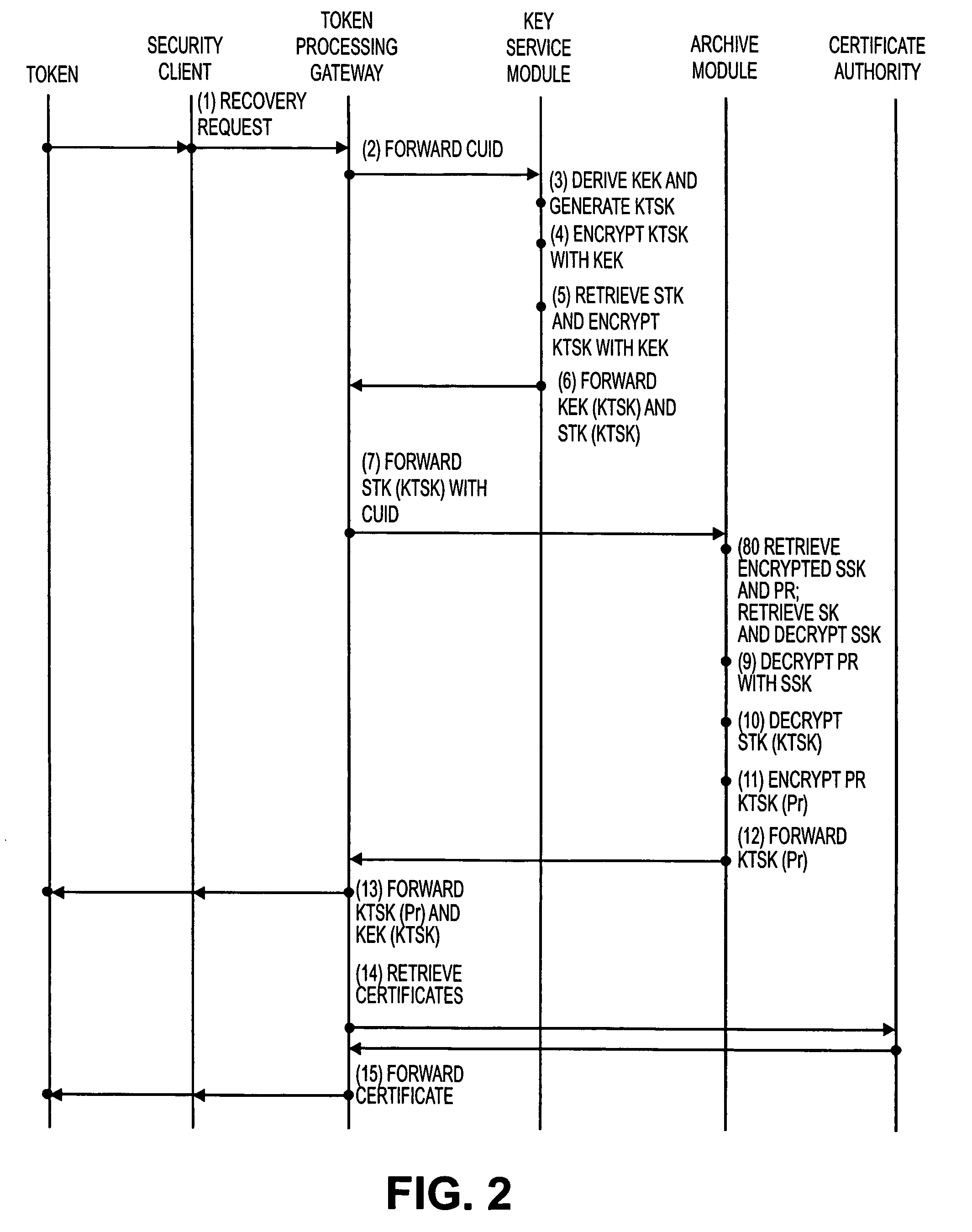
Methods and systems for key recovery for a token
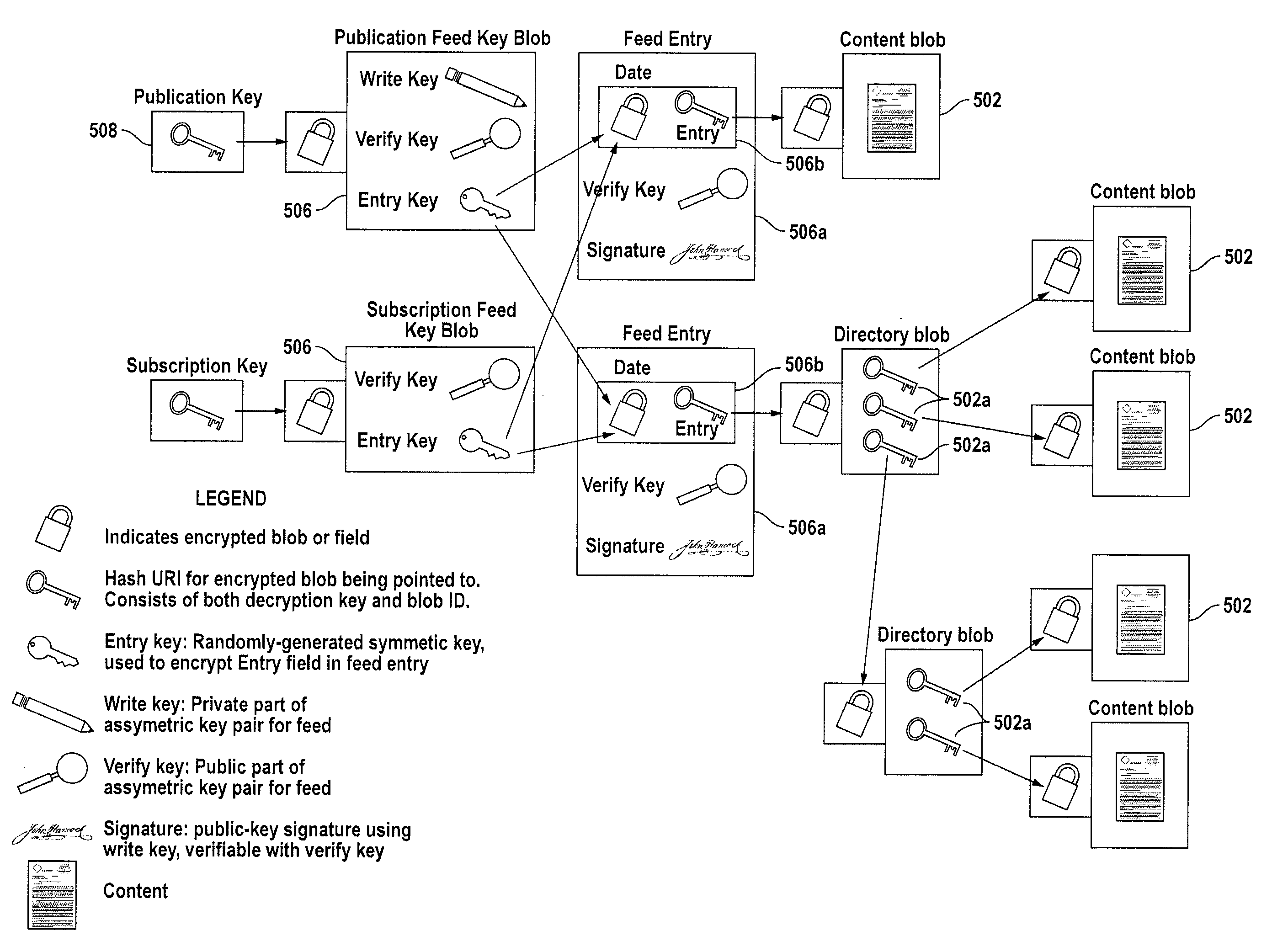
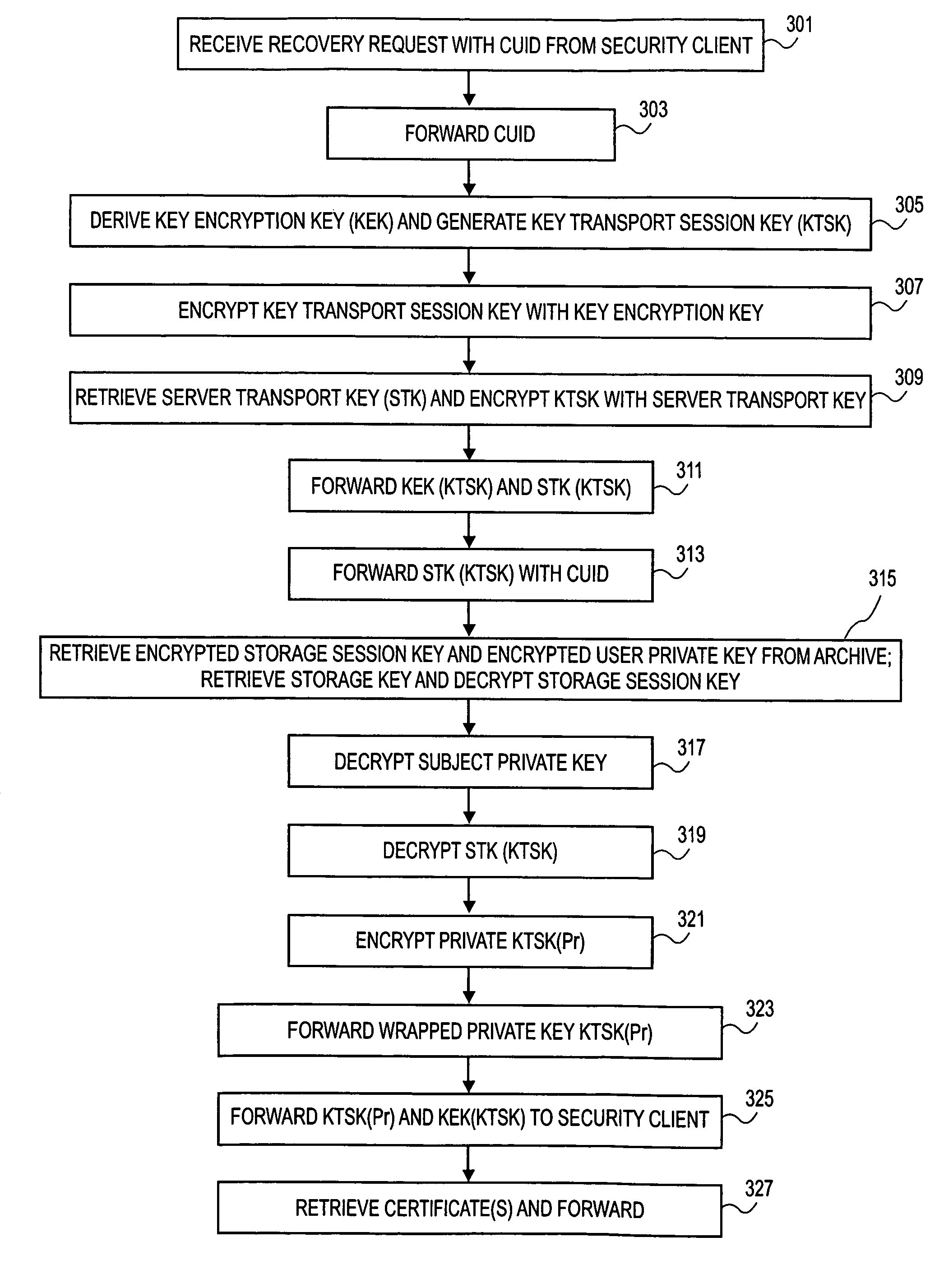
ActiveUS7822209B2Key distribution for secure communicationDigital data processing detailsMaster keySession key
Methods, systems and computer readable mediums are provided for recovering keys. A key transport session key is generated, and a key encryption key is derived based on a server master key and an identification associated with a token. The key transport session key is encrypted with the key encryption key as a first wrapped key transport session key. An encrypted storage session key and an encrypted private key are retrieved from an archive. The encrypted storage session key is decrypted with a server storage key as a storage session key. The encrypted private key is decrypted with the storage session key. The decrypted private key is encrypted with the key transport session key as a wrapped private key. The wrapped private key and the first wrapped key transport session key are forwarded.
Owner:RED HAT
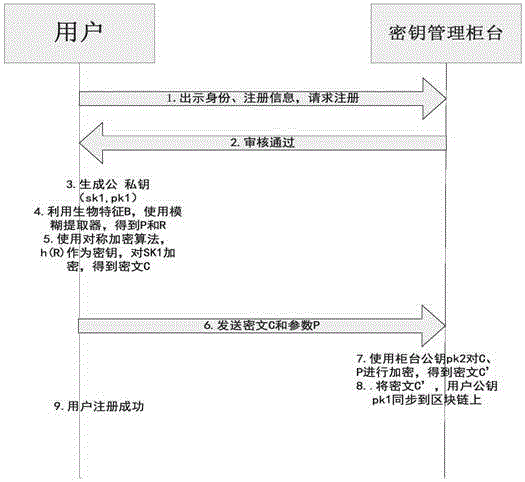
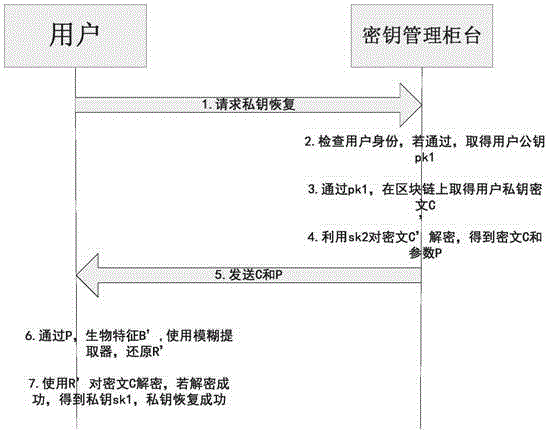
Block chain key keeping and recovery method based on encryption entrustment technology and block chain key keeping and recovery device thereof
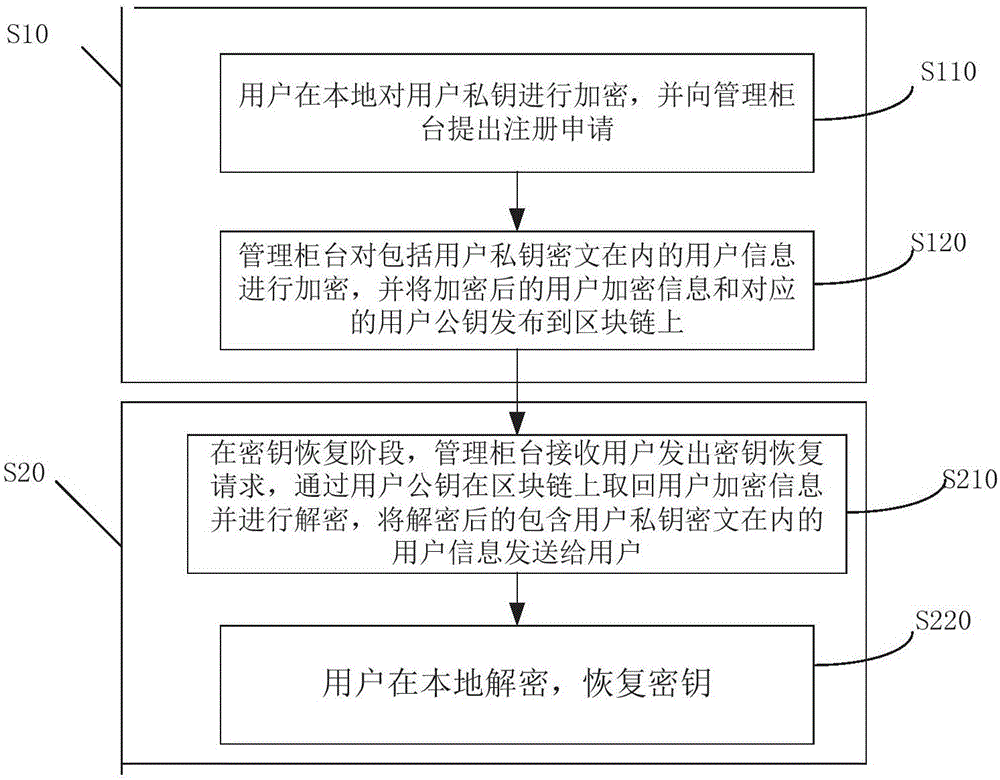
ActiveCN107528688ASafety backupSafe recoveryKey distribution for secure communicationRecovery methodCiphertext
The invention provides a block chain key keeping and recovery method based on the encryption entrustment technology and a block chain key keeping and recovery device thereof. The method comprises the registration phase: the user encrypts a user private key locally and puts forwards application for registration to a management counter, and the management counter encrypts user information including the user private key cipher and publishes the encrypted user encryption information and the corresponding user public key to the block chain; and the key recovery phase: in the key recovery phase, the management counter receives a key recovery request transmitted by the user, retrieves the user encryption information from the block chain through the user public key and decrypts the user encryption information and transmits the decrypted user information including the user private key cipher to the user, and the user performs local decryption to recover the key. The key encryption entrustment technology is introduced and the user is enabled to entrust the encrypted private key to the management counter to be saved, and the management counter does not know the real content of the private key so that backup and recovery of the private key are enabled to be more secure, and the user's rights can be protected.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Backup and recovery method of computer system, device and computer system
ActiveCN102567136ASaving backupSave costsProgram loading/initiatingRedundant operation error correctionInternal memoryRecovery method
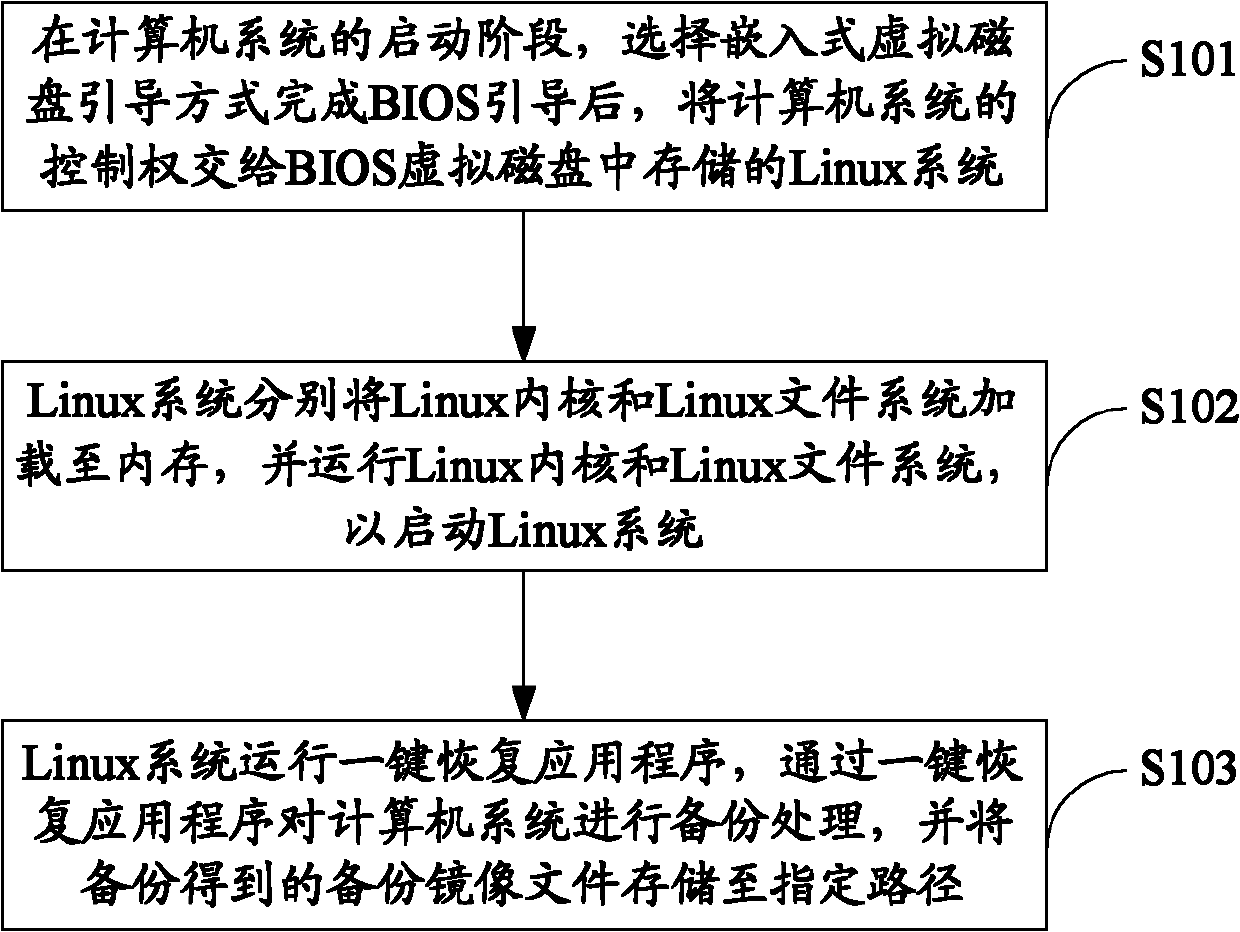
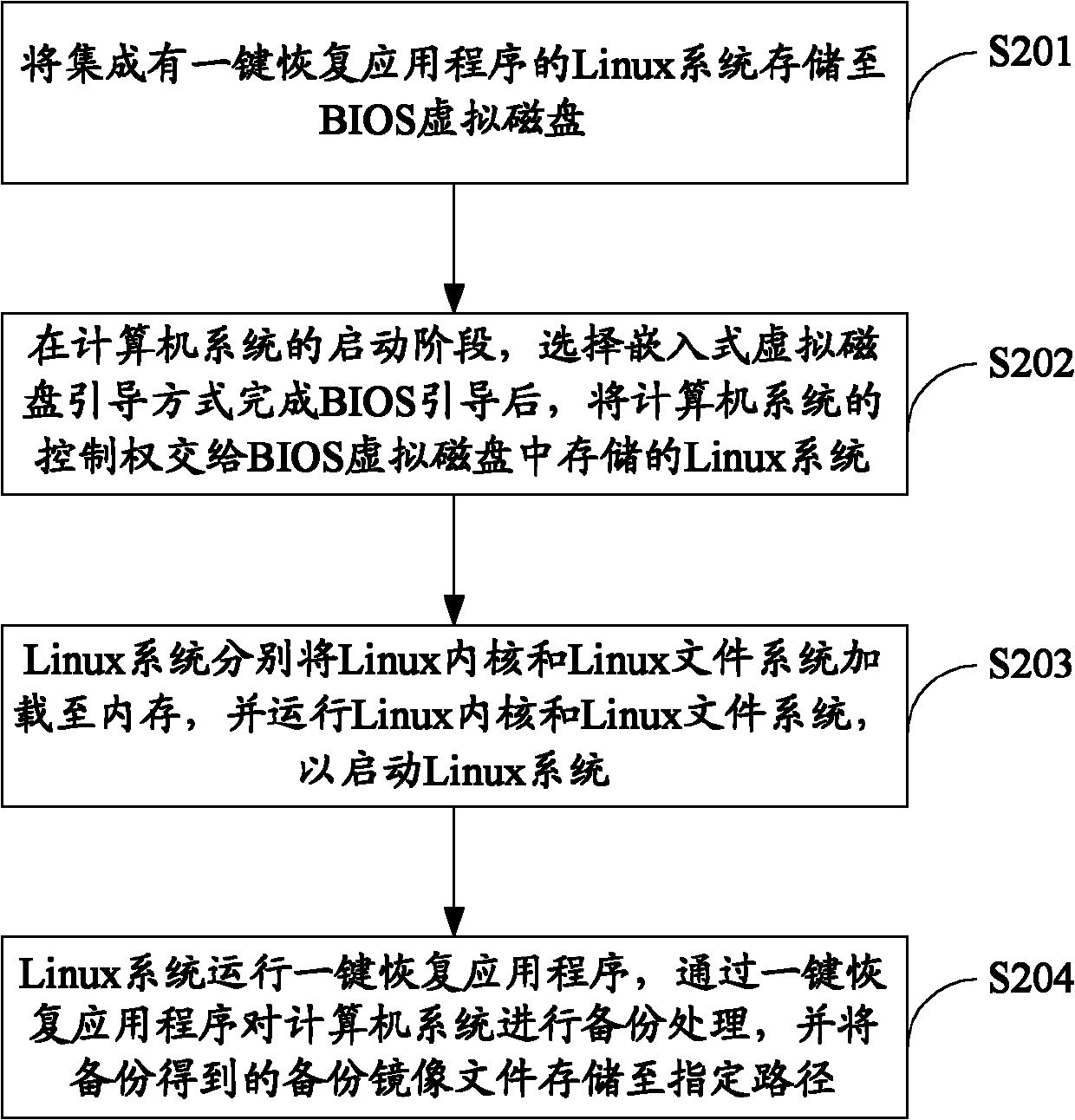
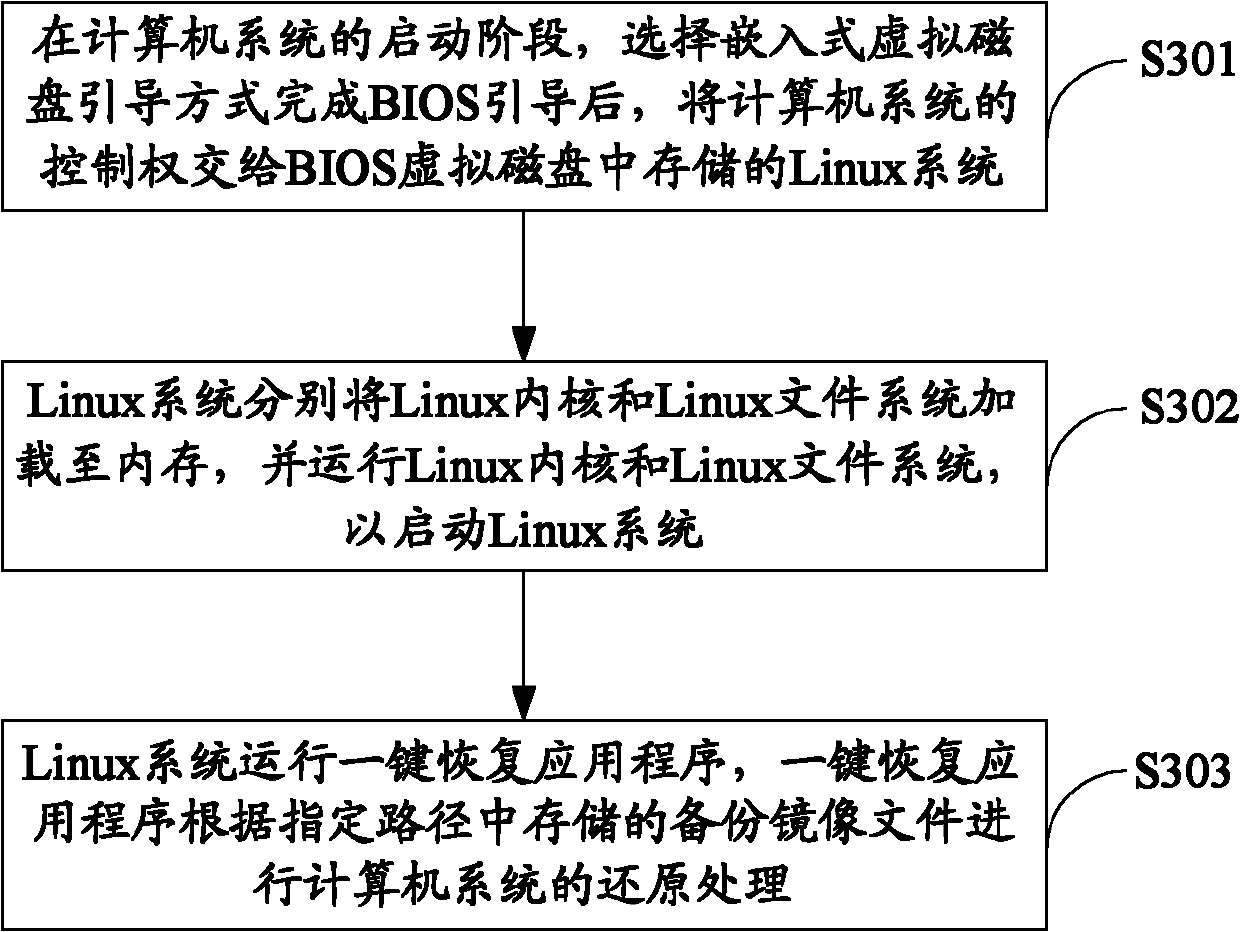
The invention is suitable for the field of computer security, and provides a backup and recovery method of a computer system, a device and the computer system. The backup method comprises the following steps of: at the initiating stage of the computer system, selecting an embedded virtual disk boot mode to finish the BIOS boot, then, handing the control right of the computer system to a Linux system stored in the BIOS virtual disk; respectively loading a Linux kernel and a Linux file system to an internal memory by the Linux system, and running the Linux kernel and the Linux file system to start the Linux system; running a one-key recovery application program by the Linux system, executing backup for the computer system through the one-key recovery application program, and storing a backup image file obtained by executing backup into a specified path. The backup and recovery method provided by the invention has high security and excellent compatibility, and occupies small space of the disk.
Owner:深圳市研祥智慧科技股份有限公司
System and method for key recovery
ActiveUS7831833B2Key distribution for secure communicationDigital data processing detailsApplication softwareComputer science
A secure mechanism for transparent key recovery for a user who has changed authentication information is disclosed. A password manager agent intercepts requests by a user to access secure resources that require user credentials. Upon detecting changed authentication information for the user, the password manager agent automatically regenerates the components of a cryptographic key associated with the user that was previously used to encrypt user credentials for the user and then destroyed. After regeneration of the original cryptographic key, the password manager agent uses the key to decrypt the user credentials necessary for the requested application. The regenerated key is then destroyed and the user credentials are re-encrypted by the password manager agent using a new cryptographic key associated with the user made up of multiple components. Following the re-encryption of the user credentials, the components used to assemble the new key are securely stored in multiple locations and the new key is destroyed.
Owner:CITRIX SYST INC
Personal Information Management Device, Distributed Key Storage Device, and Personal Information Management System
InactiveUS20070239615A1Recovery is limitedKey distribution for secure communicationData processing applicationsConfidentialityPassword
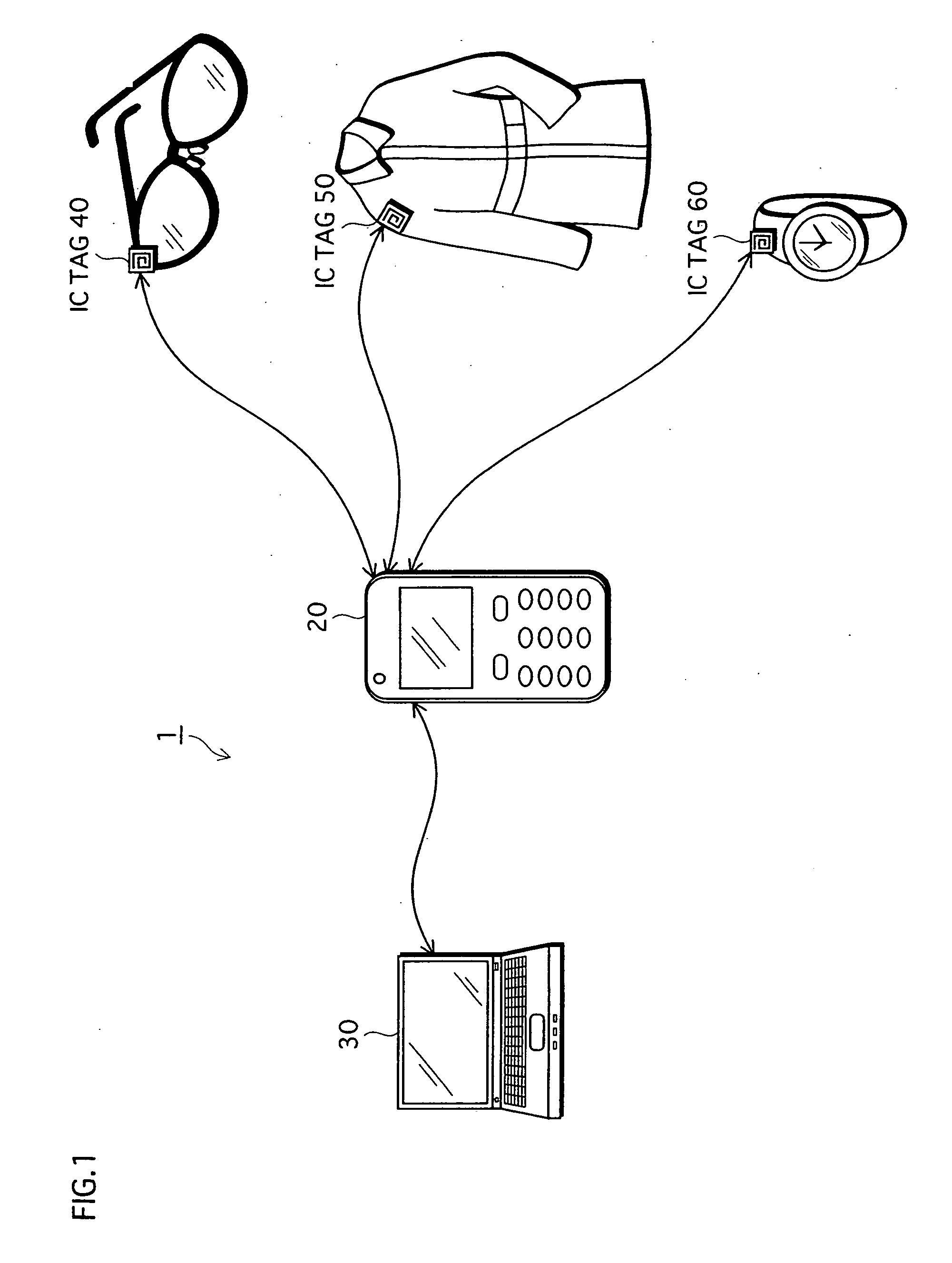
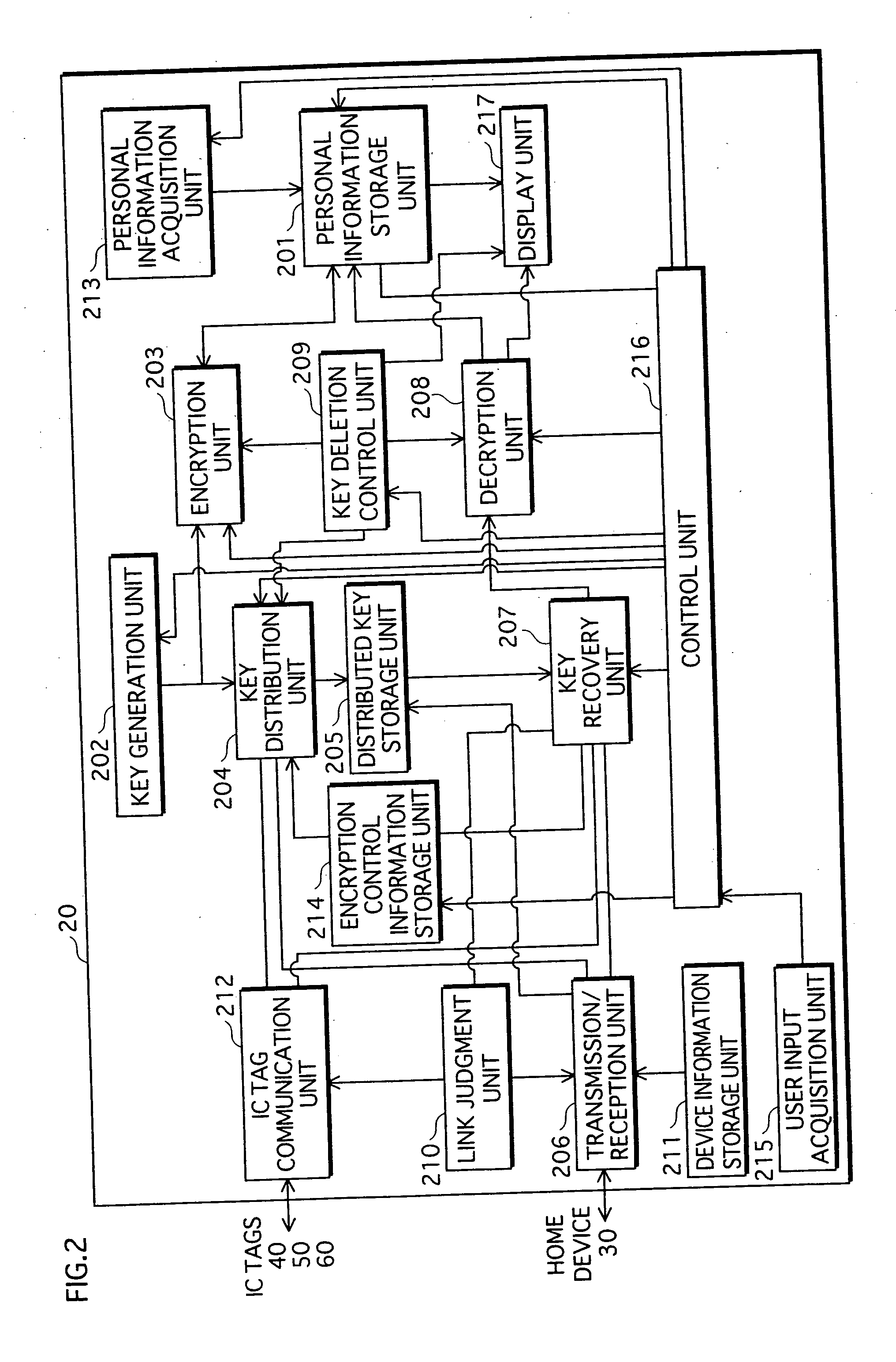
A personal information management device aims to save troubles of inputting passwords and deleting personal information, to prevent others from viewing the personal information, and to maintain confidentiality of the personal information even when a mobile device is lost. Personal information storage unit 201 holds encrypted personal information, key distribution unit 204 distributes a decryption key used for decrypting the encrypted personal information into a first and a second distributed keys based on a secret sharing scheme, distributed key storage unit 205 stores thereon the first distributed key, stores the second distributed key on home device 30, and deletes the decryption key. Upon decryption, link judgment unit 210 judges link establishment. Key recovery unit 207 acquires the second distributed key from home device 30, and recovers the decryption key using the first and the second distributed keys. Decryption unit 208 decrypts the encrypted personal information using the decryption key.
Owner:PANASONIC CORP
Method of transmitting and receiving message using encryption/decryption key
InactiveUS20050141718A1Accurate recoveryKey distribution for secure communicationPublic key for secure communicationEncryption decryptionSession key
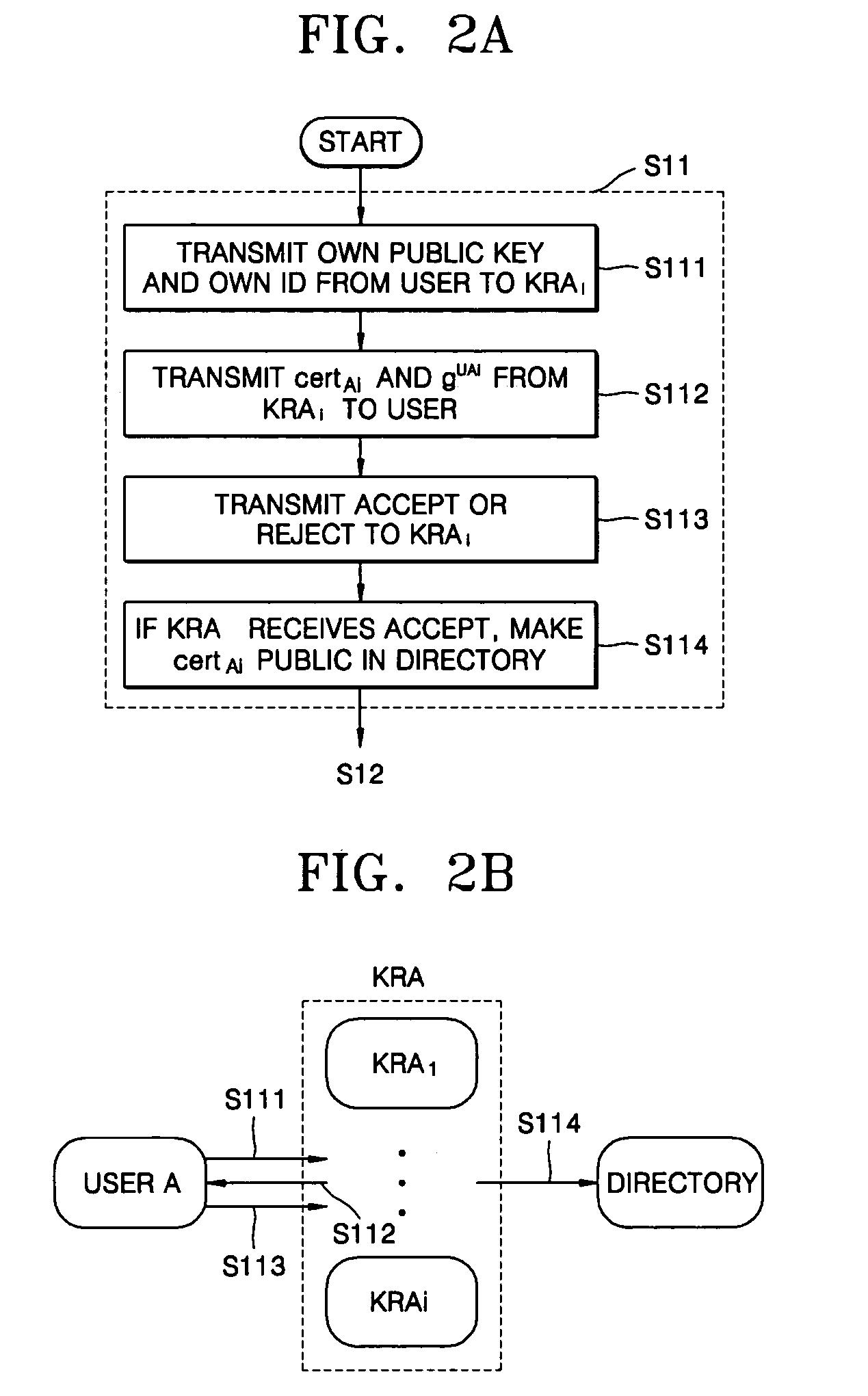
Provided is a method of transmitting and receiving a message using an encryption / decryption key, by which each of a sender and a recipient can generate an encryption / decryption key and recover a key used for encryption / decryption while transmitting and receiving the message using an electronic device. The method includes: (a) a user generating his / her own private key and a public key, registering the public key with a key recovery agent (KRA), and setting shared secret information; and (b) a sender transmitting the recovery information necessary for decryption of the transmission message to a recipient, and the recipient generating a key necessary for the decryption from the recovery information and decrypting the transmission message. The method may further include the recipient requesting recovery of the session key to the KRA.
Owner:ELECTRONICS & TELECOMM RES INST
Key recovery mechanism
Owner:RED HAT
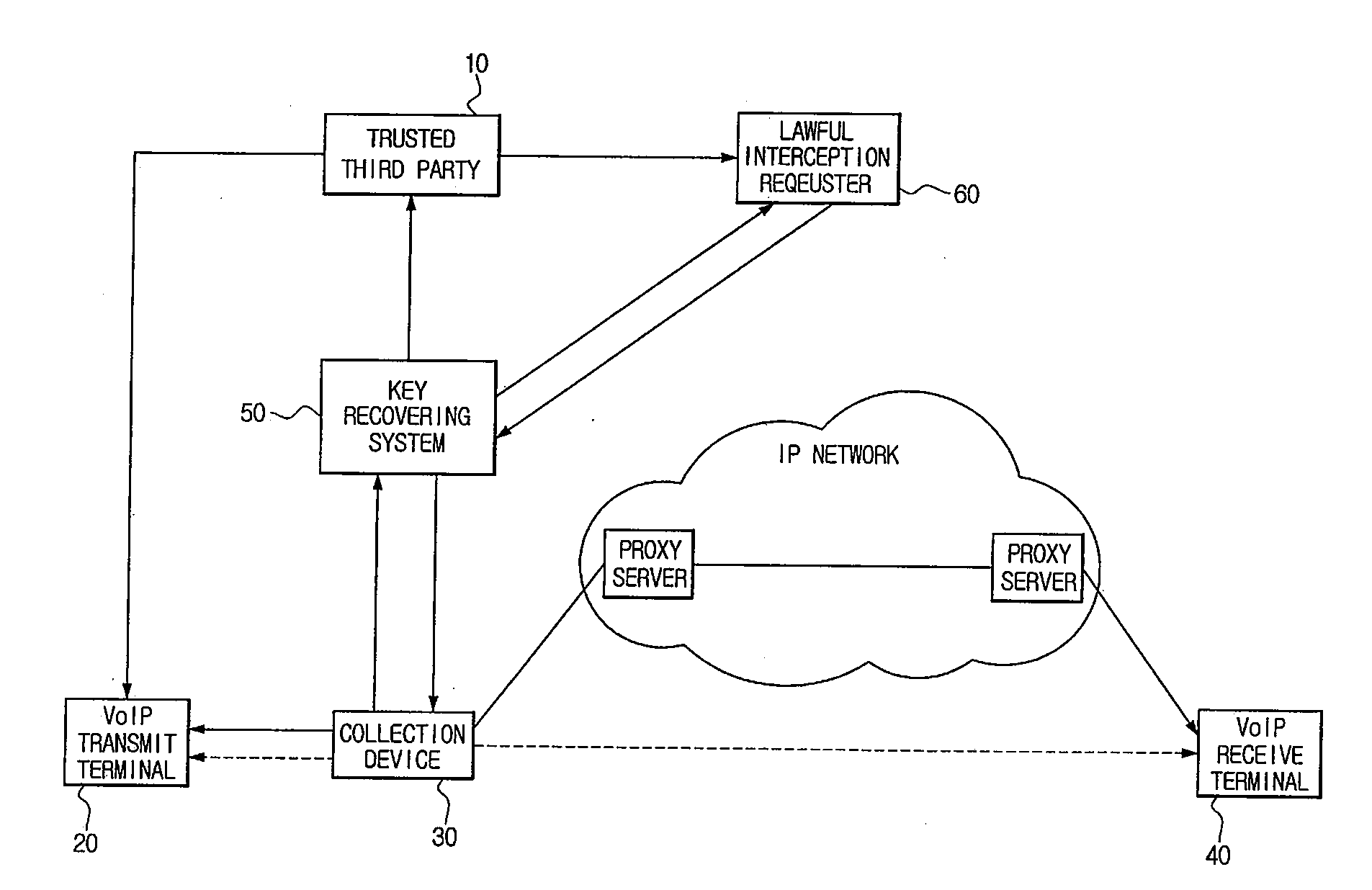
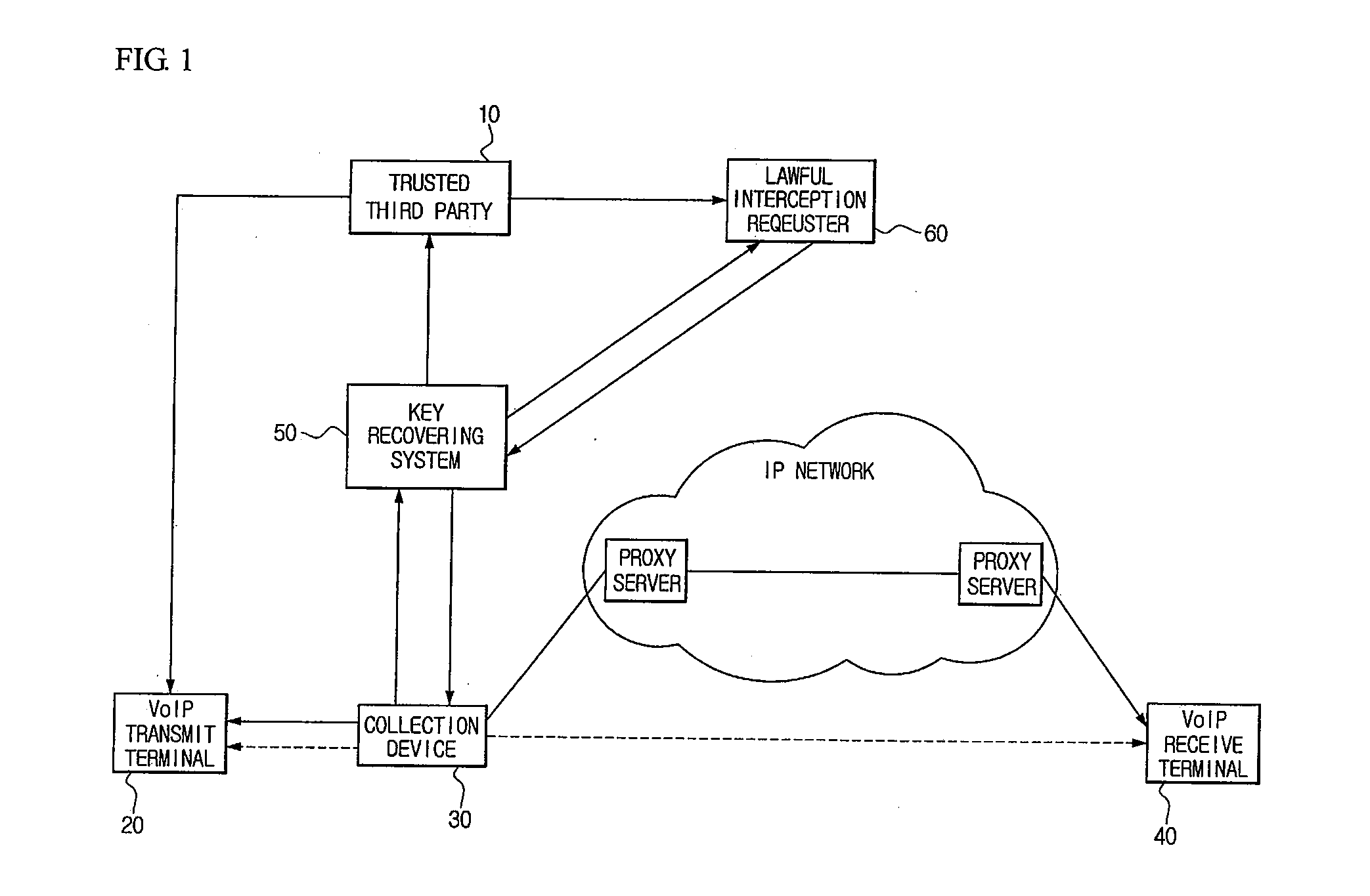
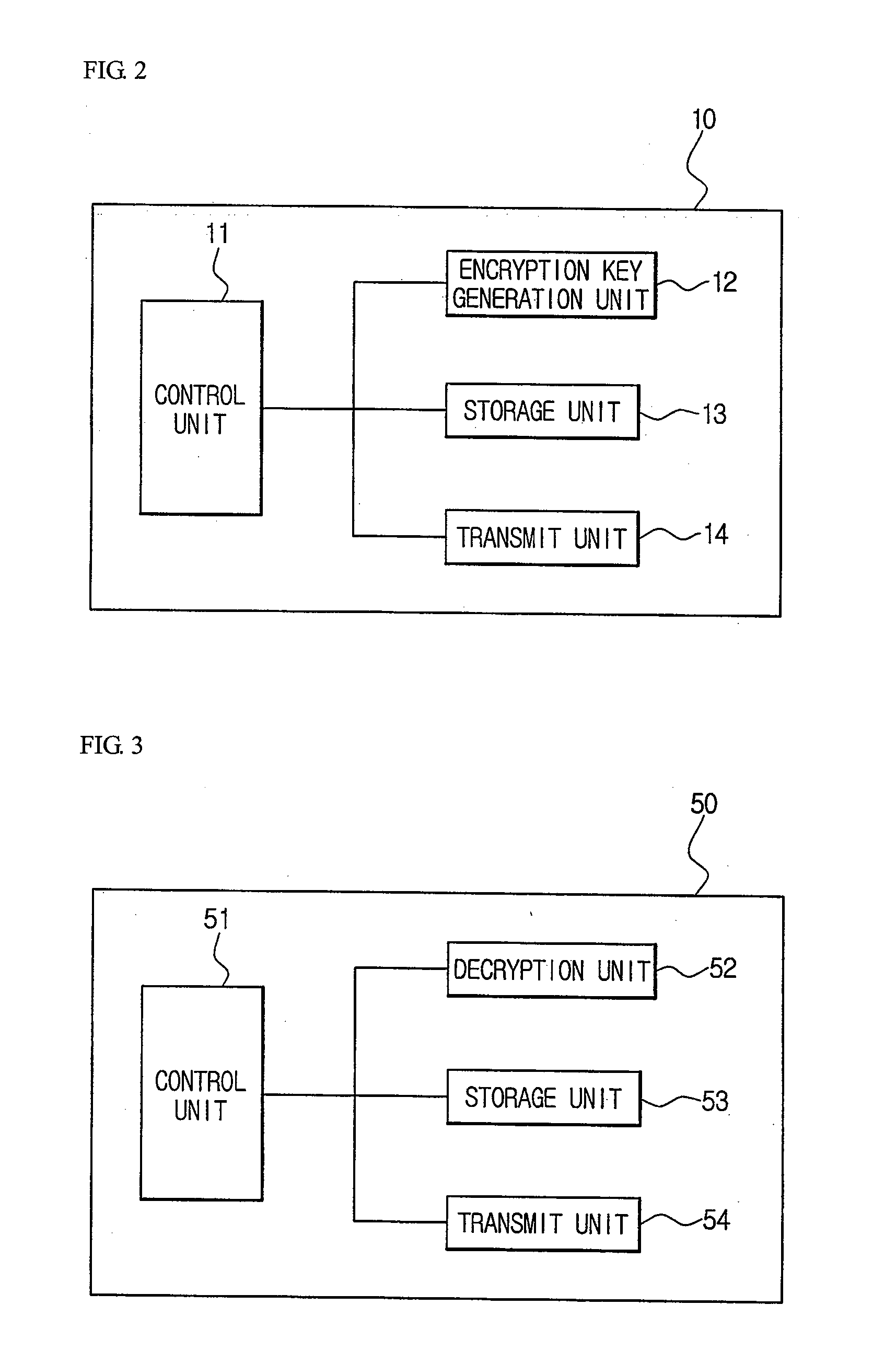
SYSTEM AND METHOD FOR LAWFUL INTERCEPTION USING TRUSTED THIRD PARTIES IN SECURE VoIP COMMUNICATIONS
InactiveUS20100002880A1Perfect forward secrecyKey distribution for secure communicationSecret communicationLawful interceptionMaster key
Disclosed is a system for lawful interception using a trusted third party in secure VoIP communication. A VoIP transmit terminal generates a secure packet using a master key received from a trusted third party and then communicates with a VoIP receive terminal. A collection device having received a lawful interception instruction from a key recovering system collects and transmits the secure packet to the key recovering system. The key recovering system decrypts the secure packet using the master key received from the trusted third party and provides the decrypted secure packet to a lawful interception requester or provides the master key received from the trusted third party and the secure packet to the lawful interception requester. It is possible to provide the perfect lawful interception in the secure VoIP communication environment, and to guarantee a perfect forward secrecy since the master key is changed for each call.
Owner:KOREA INTERNET & SECURITY AGENCY
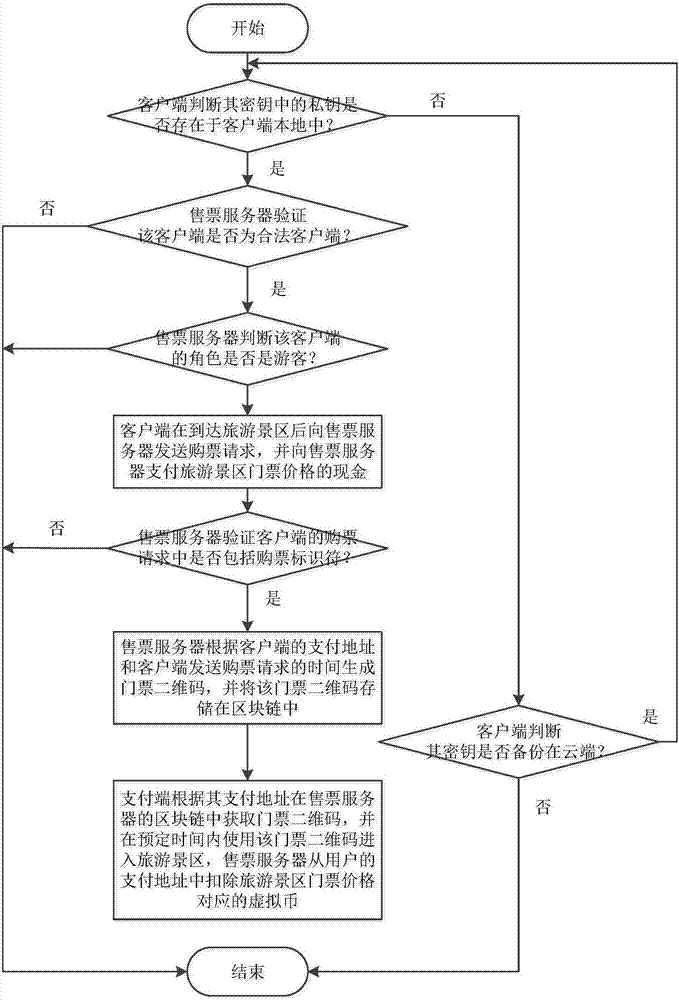
Block-chain-based method and system for selling ticket at tourist attraction
InactiveCN107169826AGuaranteed immediacyGuaranteed privacyBuying/selling/leasing transactionsProtocol authorisationTransaction dataAuthentication
The invention discloses a block-chain-based mechanism for selling a ticket at a trusted tourist attraction. A novel application model based on a block chain is put forward, security of transaction data is guaranteed based on transparent and credible characteristics of the block chain and a zero-confirmation contract mechanism is designed based on the contract characteristic of the block chain, so that a convenient ticket buying service of transaction confirmation after ticket buying for attraction entrance can be provided for the tourist. A credible identity authentication management mechanism is put forward and functions of secret key back up and secret key recovery are designed to guarantee validity of each operation, thereby guaranteeing security of account transaction. And one set of block audit data reading interfaces is provided and thus an auditor can carry out clearing and statistics on transaction data at the tourist attraction conveniently, so that the manual account clearing time and cost can be reduced. The method and system are suitable for the tourist attraction with a trusted transaction need to provide transparent and trusted transaction data and transaction processes and one set of convenient data statistic interfaces for account clearing.
Owner:武汉凤链科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com