Method and system for realizing block chain private key protection based on key segmentation
A blockchain and key technology, applied in the field of information security, can solve problems such as irretrievability and lack of security of the private key of the blockchain
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
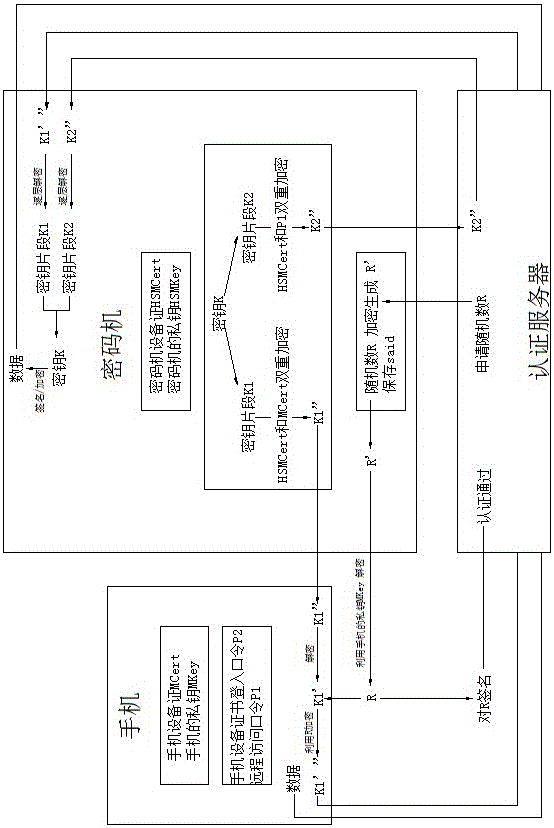
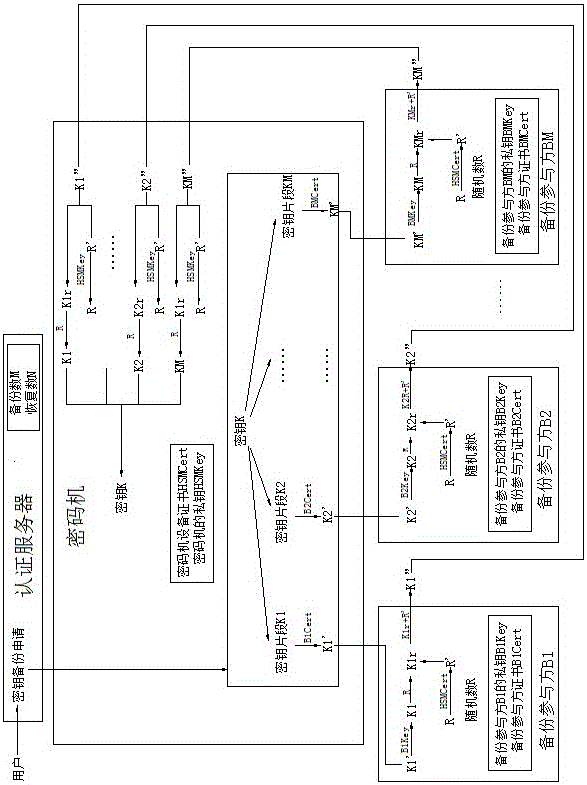
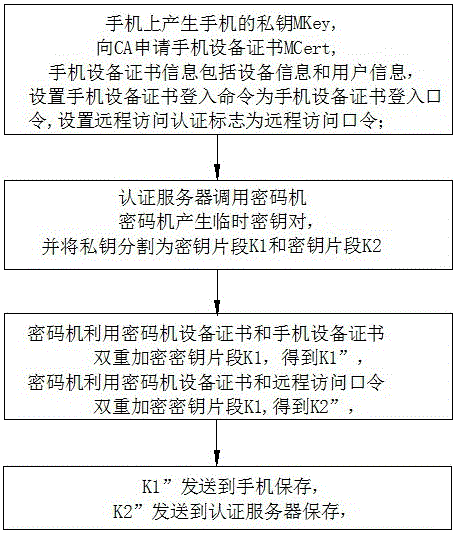
[0098] as attached figure 1 And attached figure 2 As shown, the method for realizing blockchain private key protection based on key splitting in the present invention uses a cloud cipher machine and an authentication server, and uses a mobile phone as a terminal carrier to implement a blockchain private key that supports certificate authentication and password authentication for mobile devices. Hard encryption; use the threshold algorithm to split the private key of the blockchain to achieve multi-party participation in key backup and key recovery / retrieval, including:
[0099] (1) Registration process: After the encryption machine generates a temporary key pair, it divides the private key to generate key fragments, and then double-encrypts the key fragments and outputs them to the mobile phone and the authentication server;
[0100] (2) The process of using the private key: decrypt the key fragment within the validity period of the key synthesis, synthesize the decrypted ke...
Embodiment 2
[0170] as attached Figure 7 , attached Figure 8 And attached Figure 9 As shown, this embodiment is an improvement on the basis of Embodiment 1. The difference between this embodiment and Embodiment 1 is: In this embodiment, the mobile device certificate login command is the mobile device certificate login fingerprint P4, and the remote access authentication flag P3 for biometric authentication. details as follows:
[0171] In step (1.1), the mobile device certificate login command is the mobile device certificate login fingerprint P4, that is, access to the mobile phone is realized by entering the mobile device certificate login fingerprint P4 on the mobile phone; the remote access authentication mark is biometric authentication P3, namely Remote access via biometric authentication P3.
[0172] Correspondingly, in step (1.3), the cipher machine uses the cipher machine device certificate HSMCert and the biometric authentication P3 double encryption key fragment K2 to obt...
Embodiment 3
[0180] as attached Figure 10 , attached Figure 11 And attached Figure 12 As shown, this embodiment is a further improvement on the basis of Embodiment 1. The difference between this embodiment and Embodiment 1 is: In this embodiment, the mobile device certificate login command is the mobile device certificate login password P2 and the mobile device certificate Login fingerprint P4, remote access authentication marks are remote access password P1 and biometric authentication P3. details as follows:
[0181] In step (1.1), the mobile device certificate login command is the mobile device certificate login password P2 and the mobile device certificate login fingerprint P4, you can optionally enter the mobile device certificate login password P2 on the mobile phone or enter the mobile device on the mobile phone The certificate is registered in the fingerprint P4 to realize the access to the mobile phone; the remote access authentication mark is the remote access password P1 and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com