Patents
Literature
125620 results about "Database" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
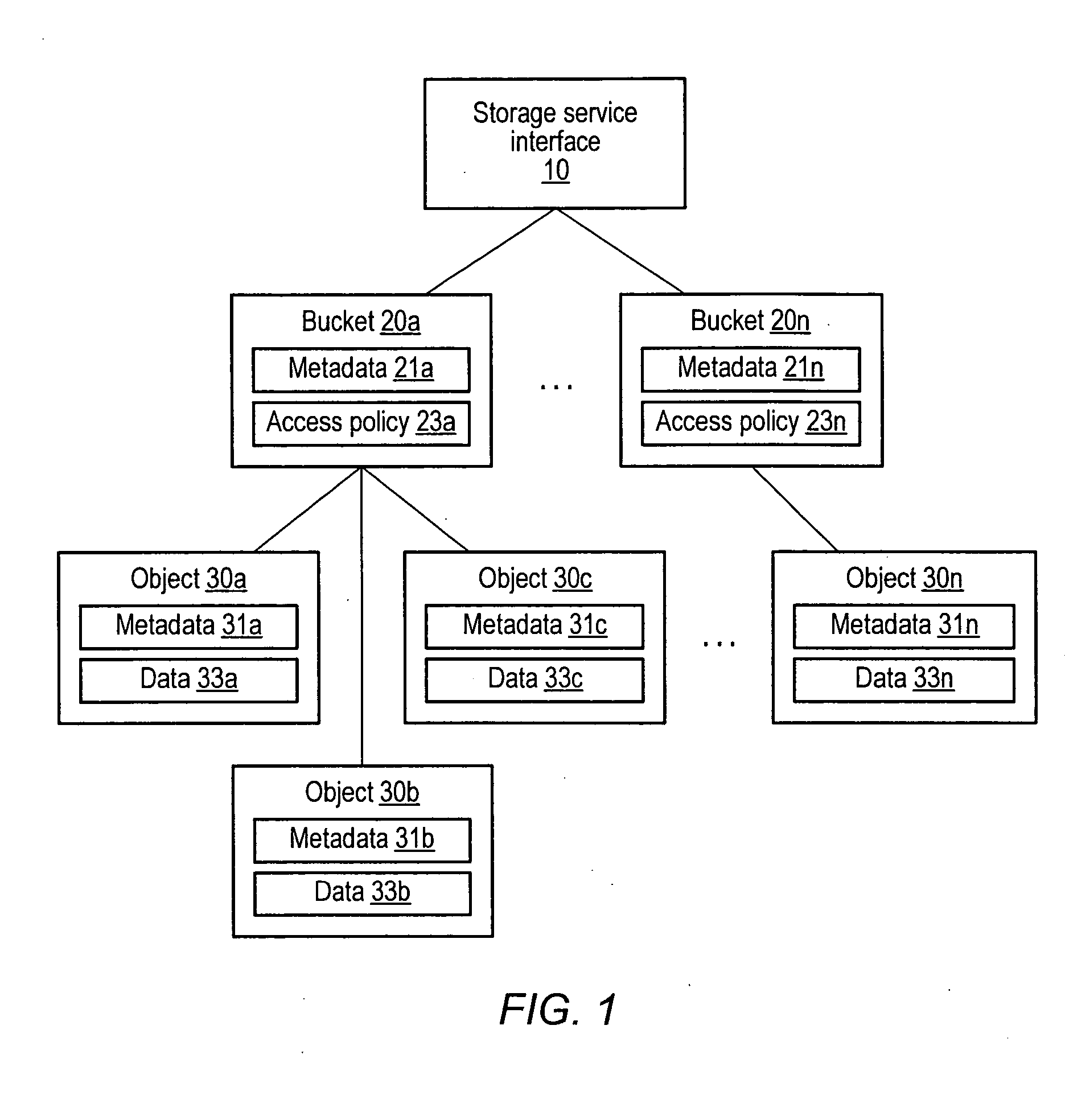
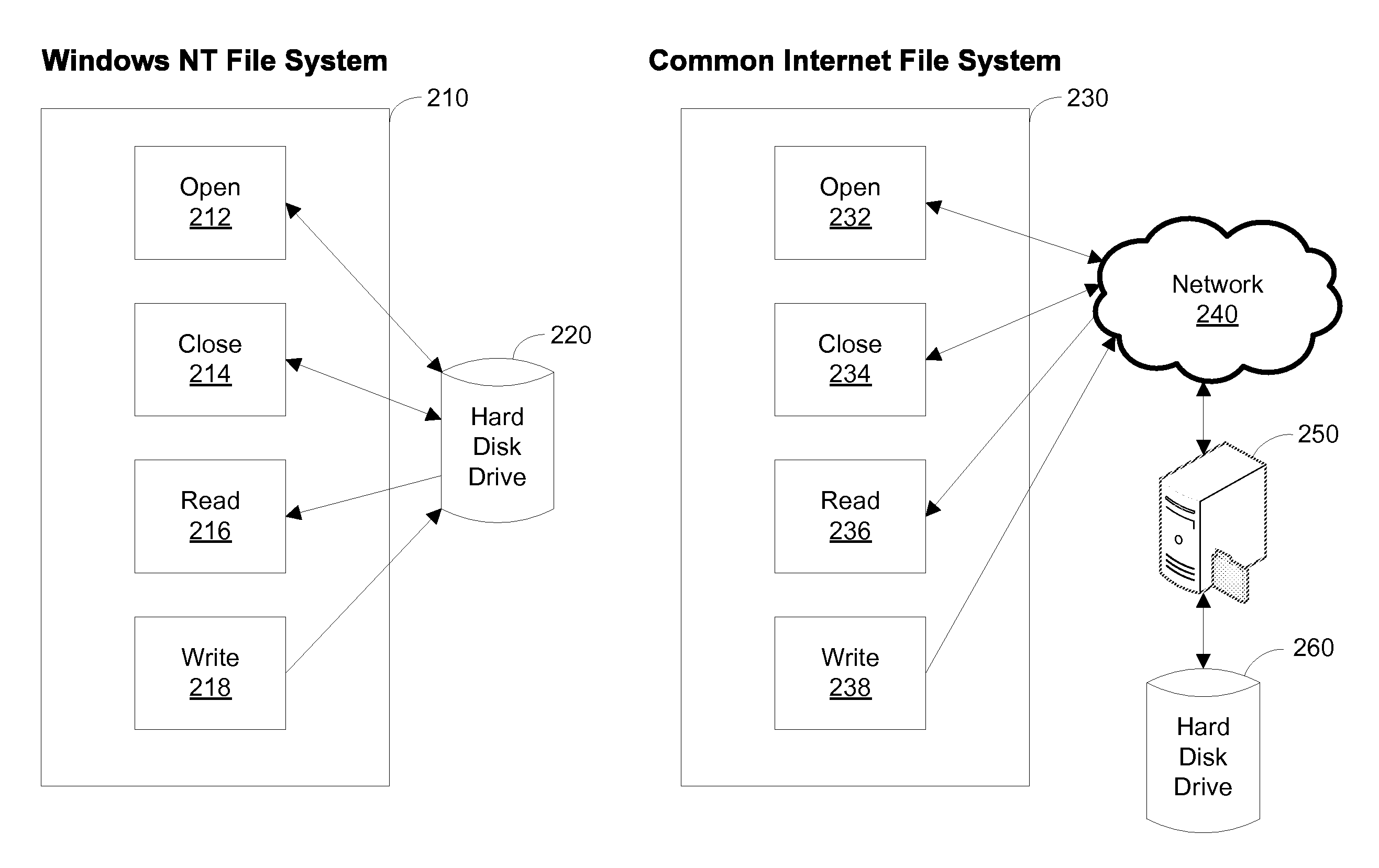
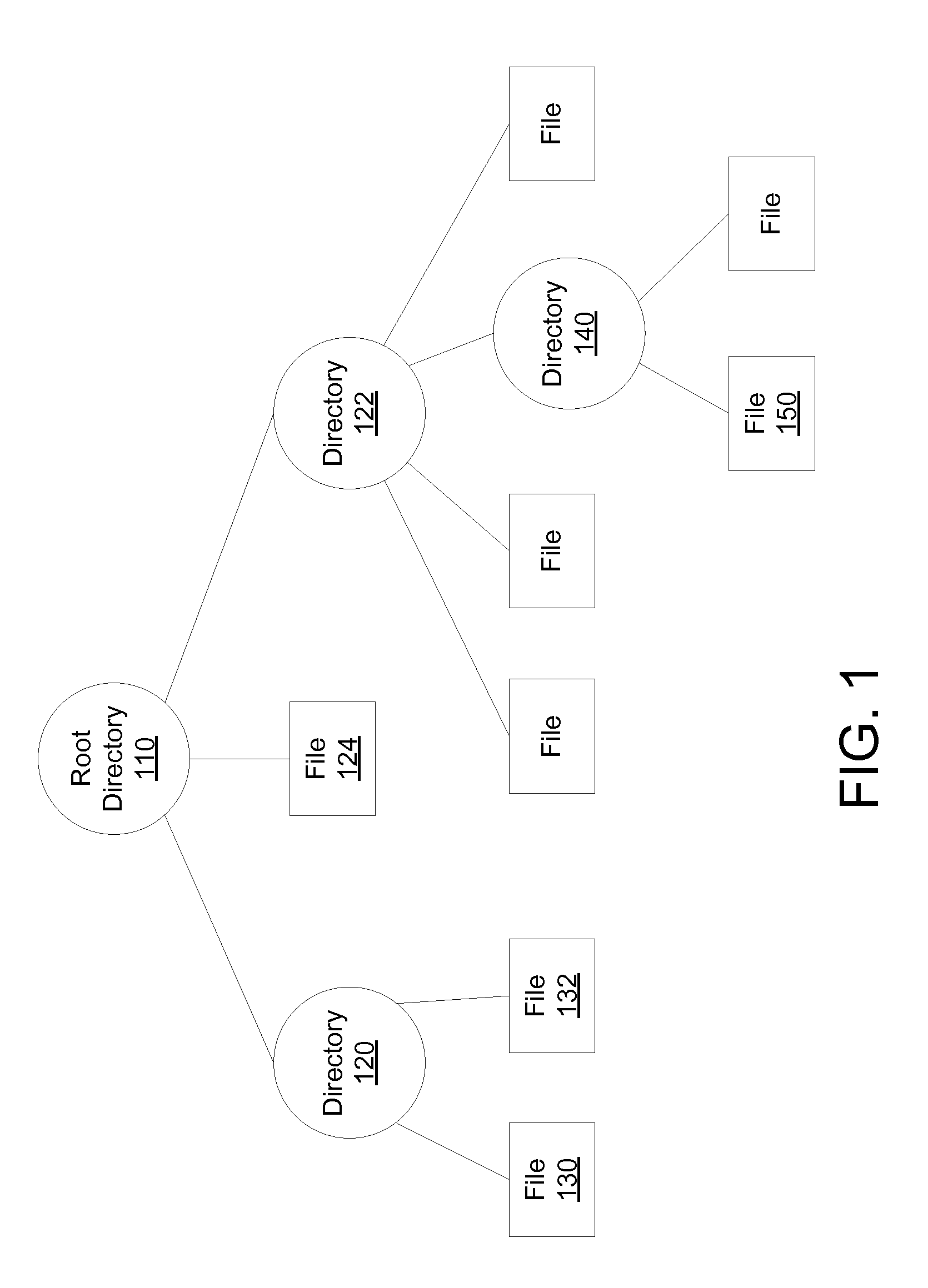
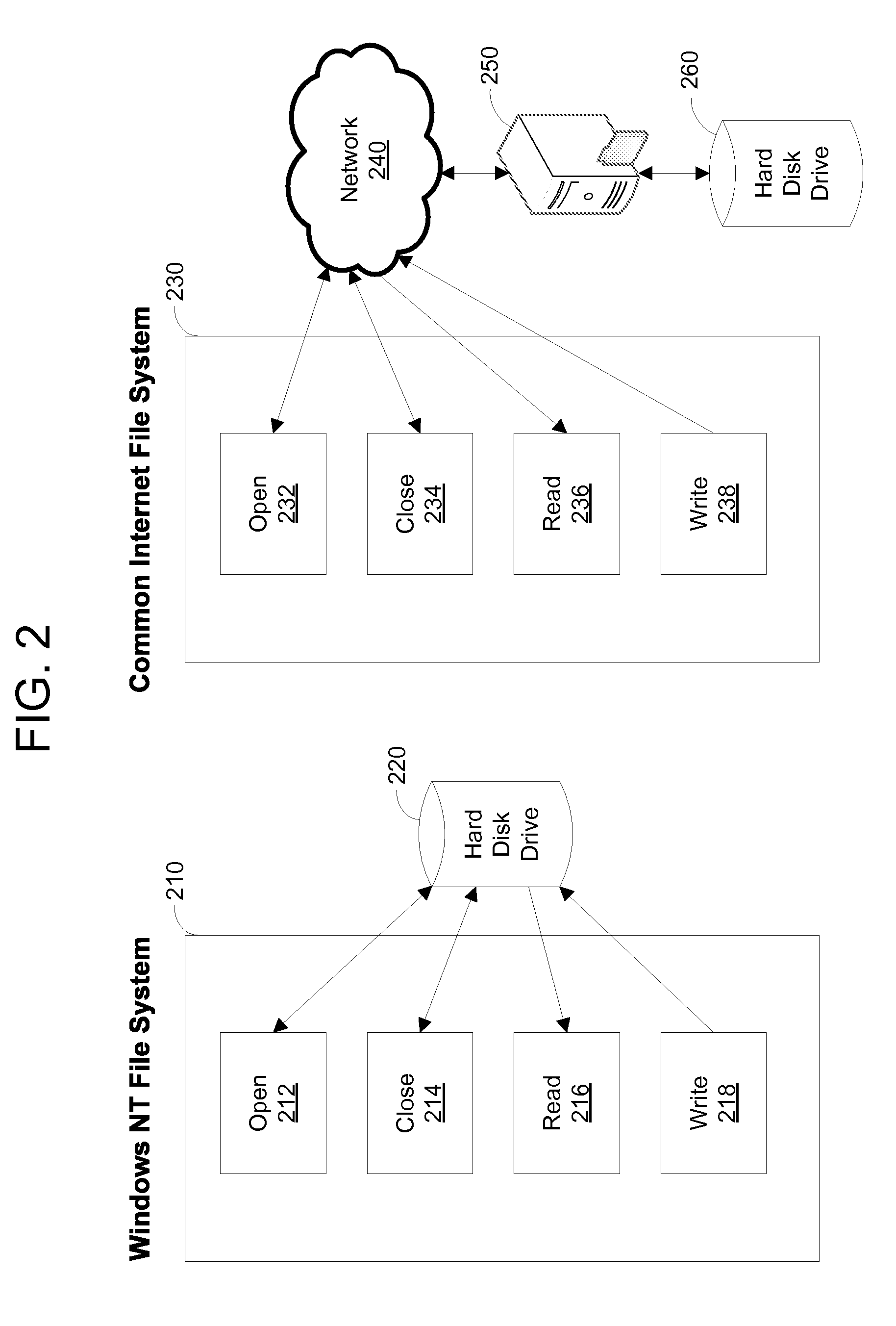
A database is an organized collection of data, generally stored and accessed electronically from a computer system. Where databases are more complex they are often developed using formal design and modeling techniques.
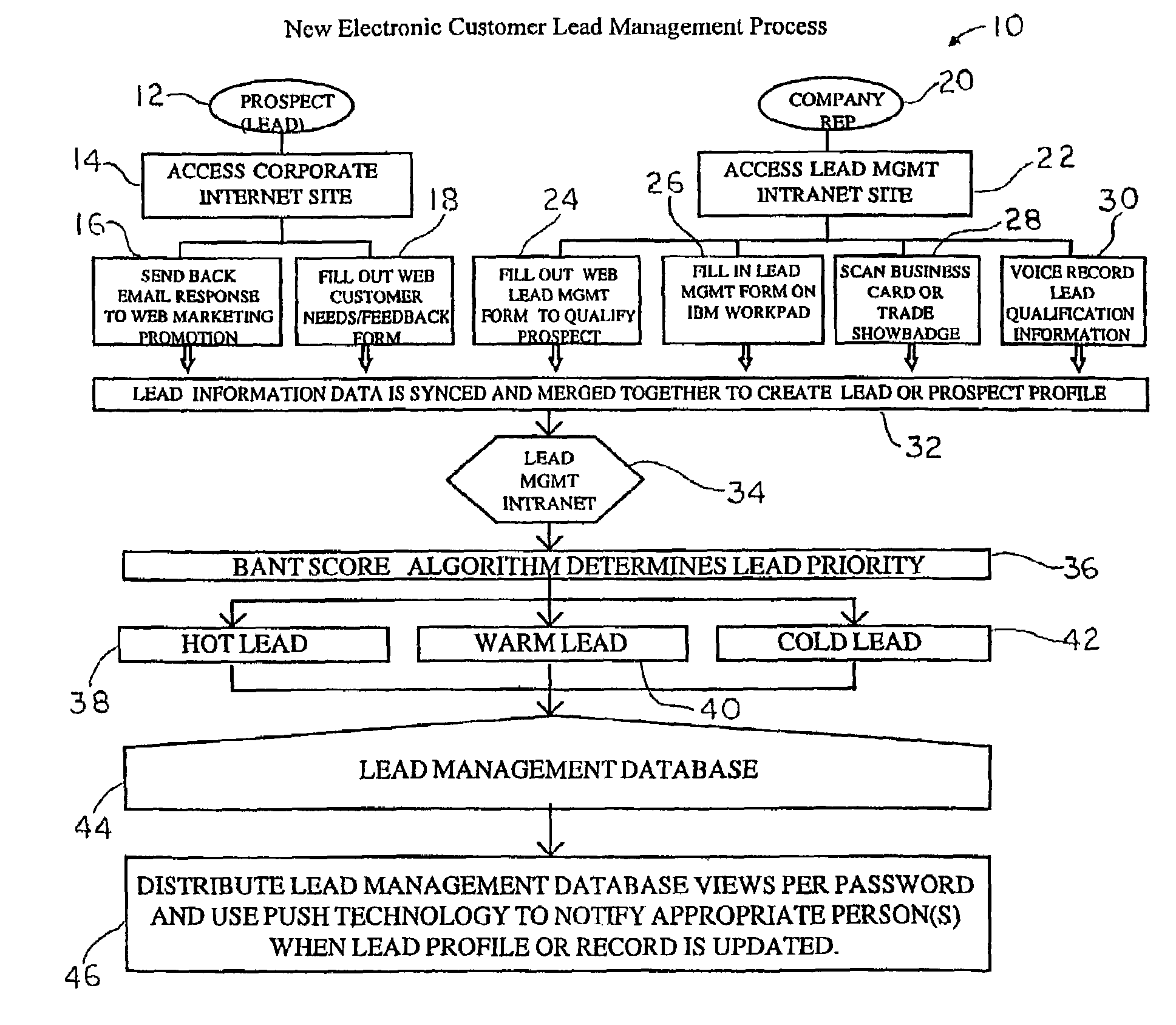
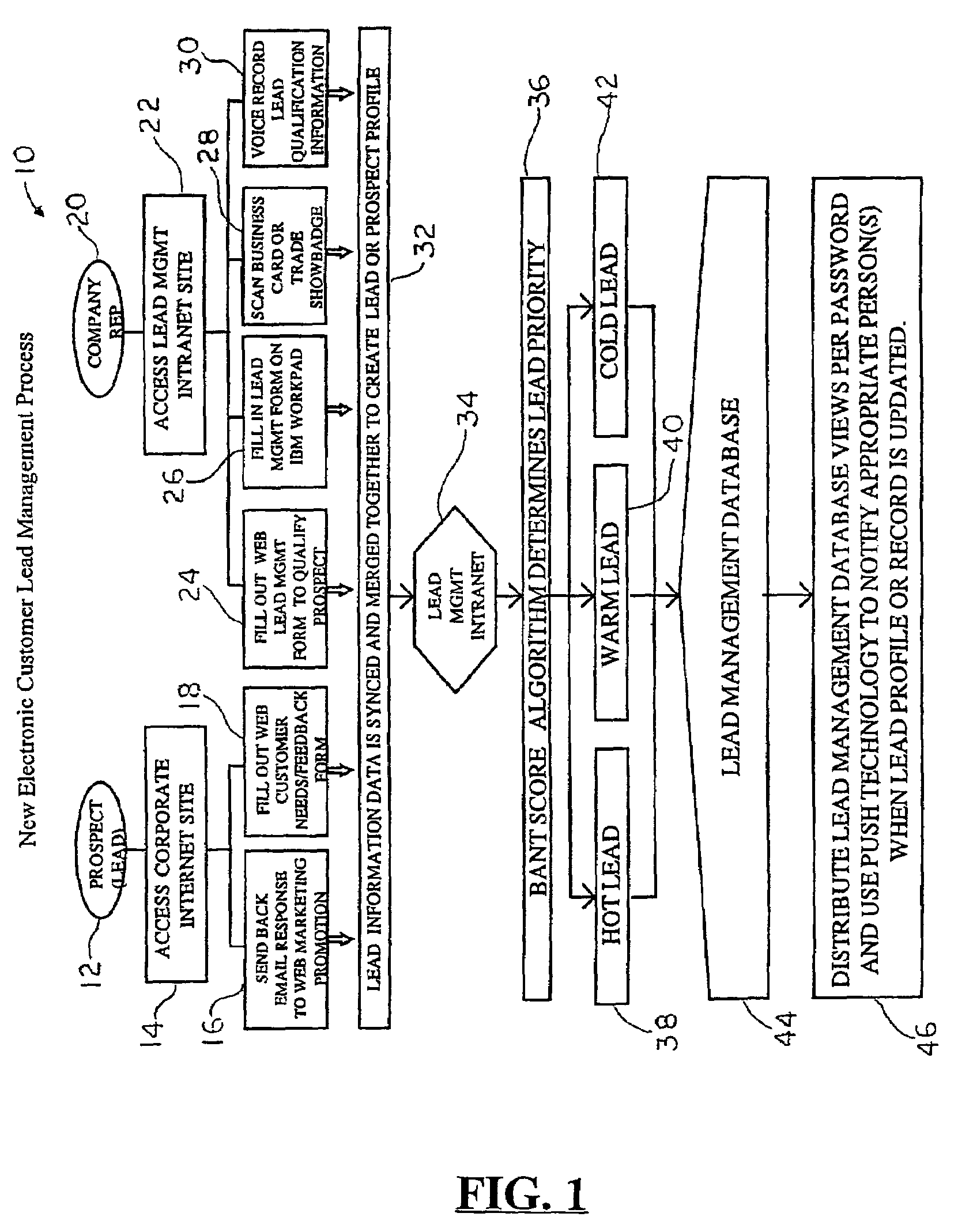
System and method for generating, capturing, and managing customer lead information over a computer network
A customer lead management system that relates to a system and method for collecting and organizing customer-marketing data, which is then made available to business representatives to assess. Specifically, using a computer network, and data on a potential customer's Budget, Authority, Needs, Timeframe, and other related customer data is collected. While this data is being collected, the customer lead management system stores the customer lead data in real-time instantly, automatically ranking the viability of the customer lead on the interest level of the customer lead and other variable criteria used in the web-based algorithm calculation, and automatically electronically notifies the appropriate company and / or company representative about the customer lead. The resulting customer lead profile record is located in a web server database, and can be accessed and undated in real-time by a portable computer or electronic device that has been web-enabled. The customer lead data is then capable of being accessed via a computer network by various companies that have goods / services that satisfy the needs and requirements of the customer lead. A company representative can be automatically notified when a customer lead profile has been updated.
Owner:CXT SYST INC
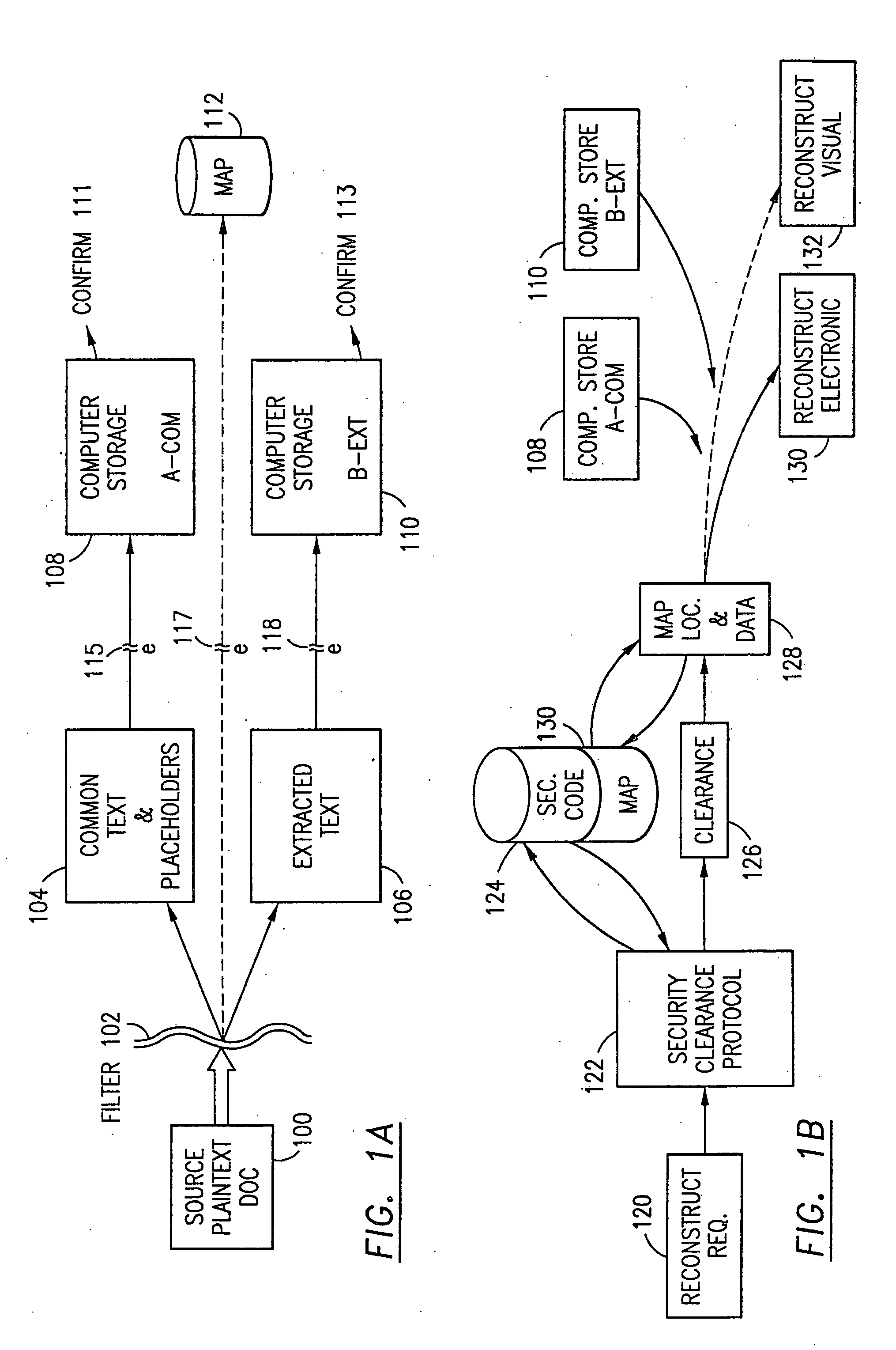
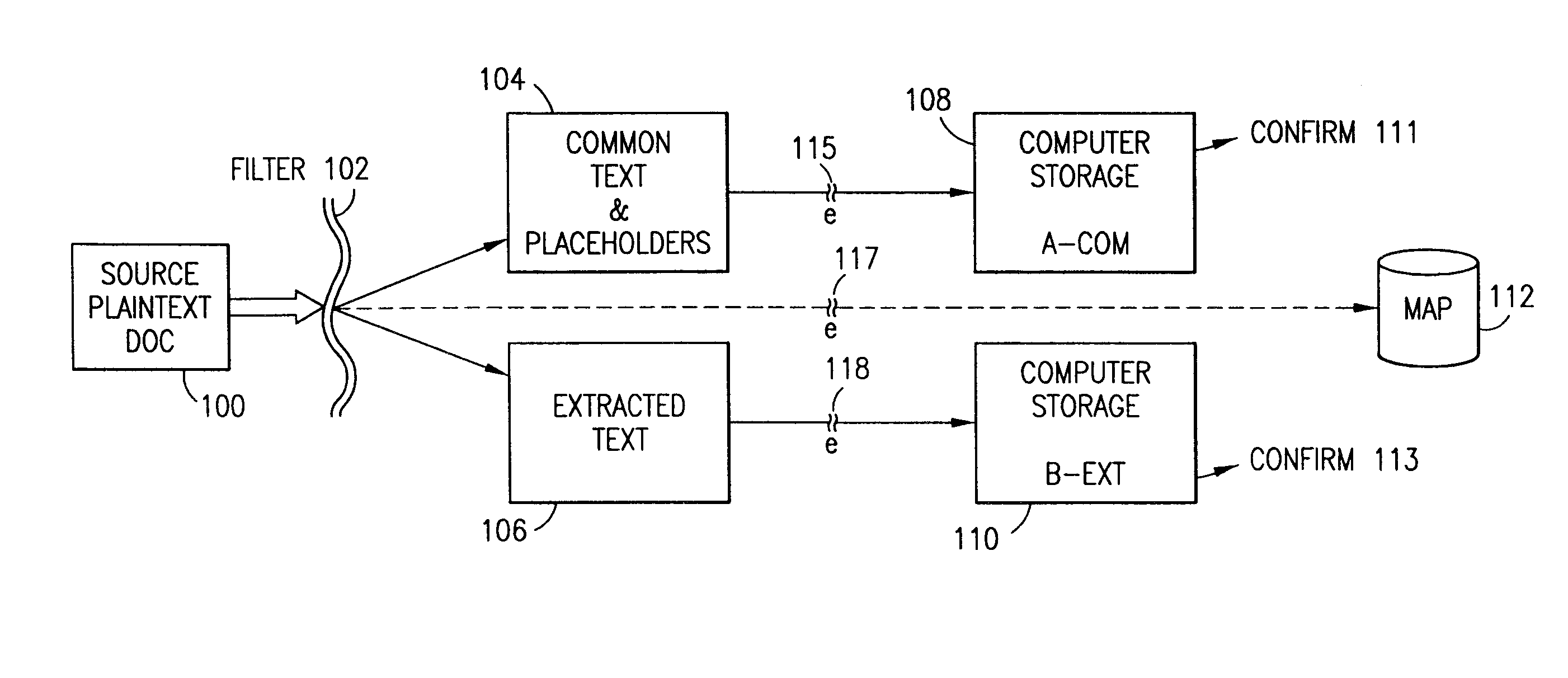
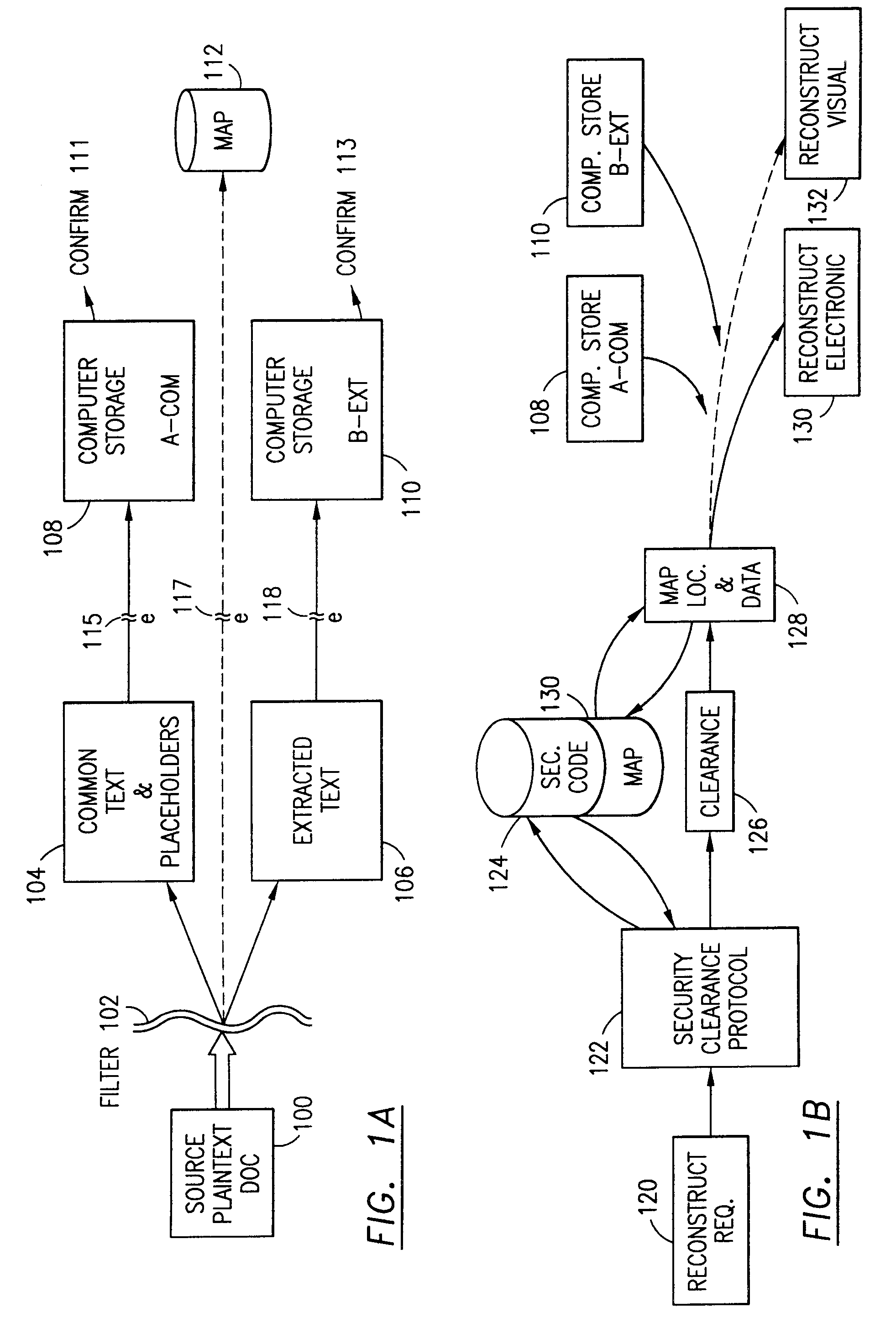
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
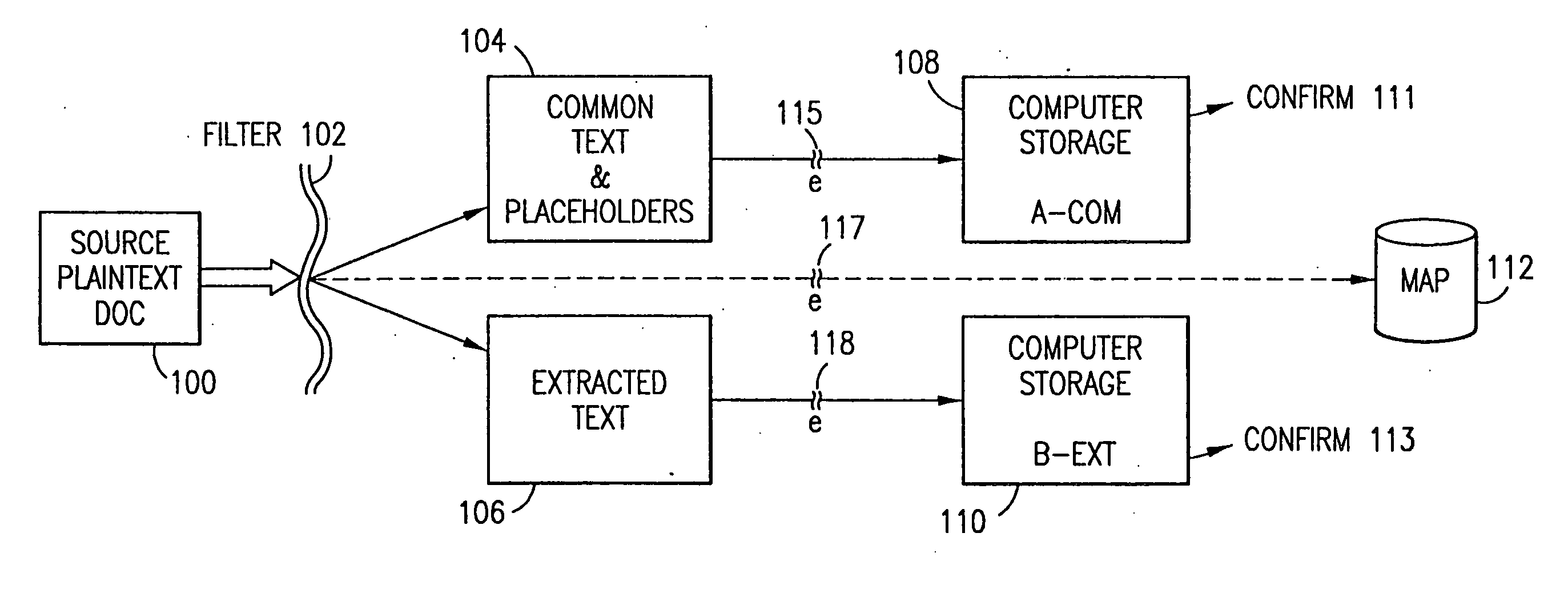
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
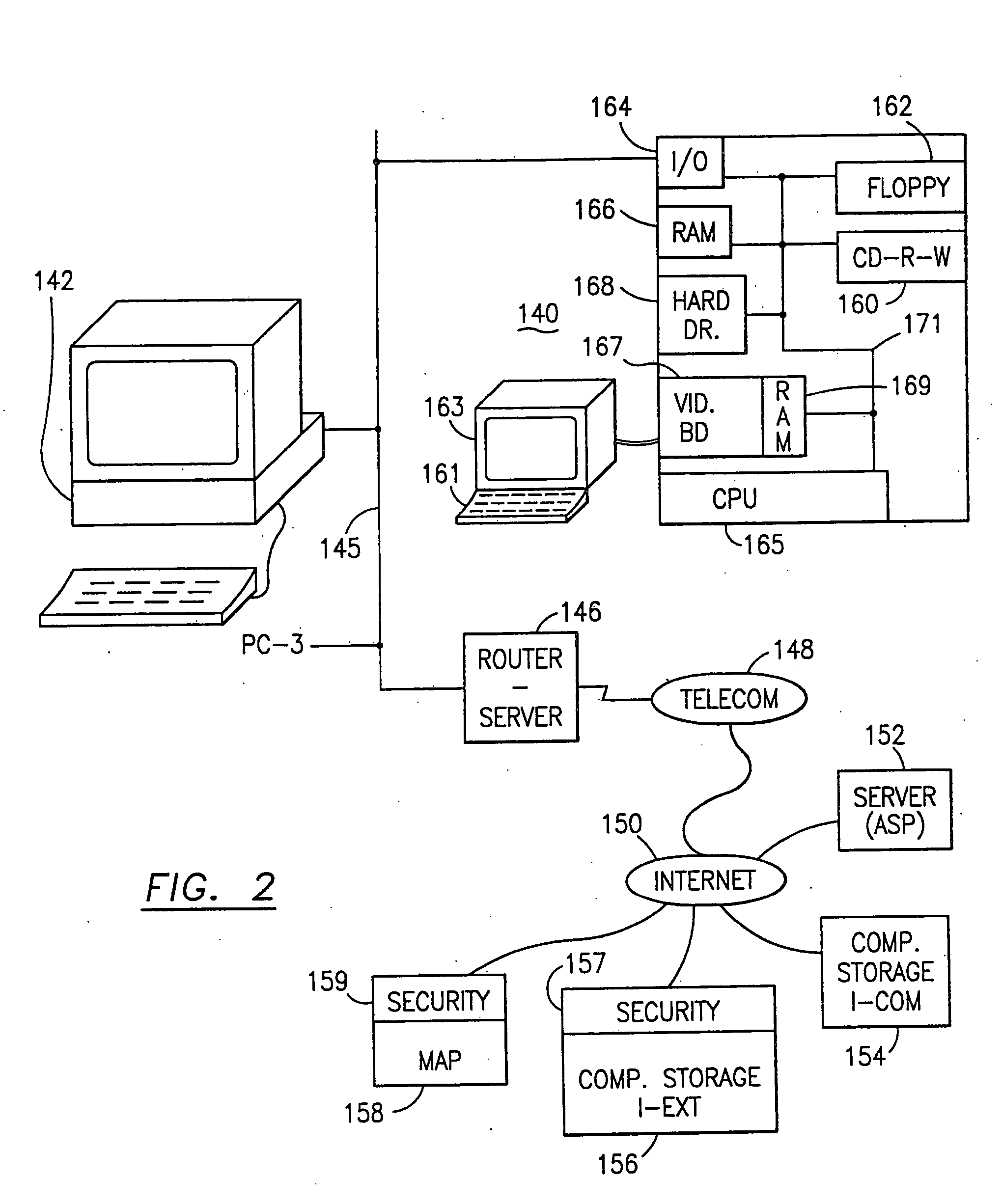
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
Managing user information on an e-commerce system
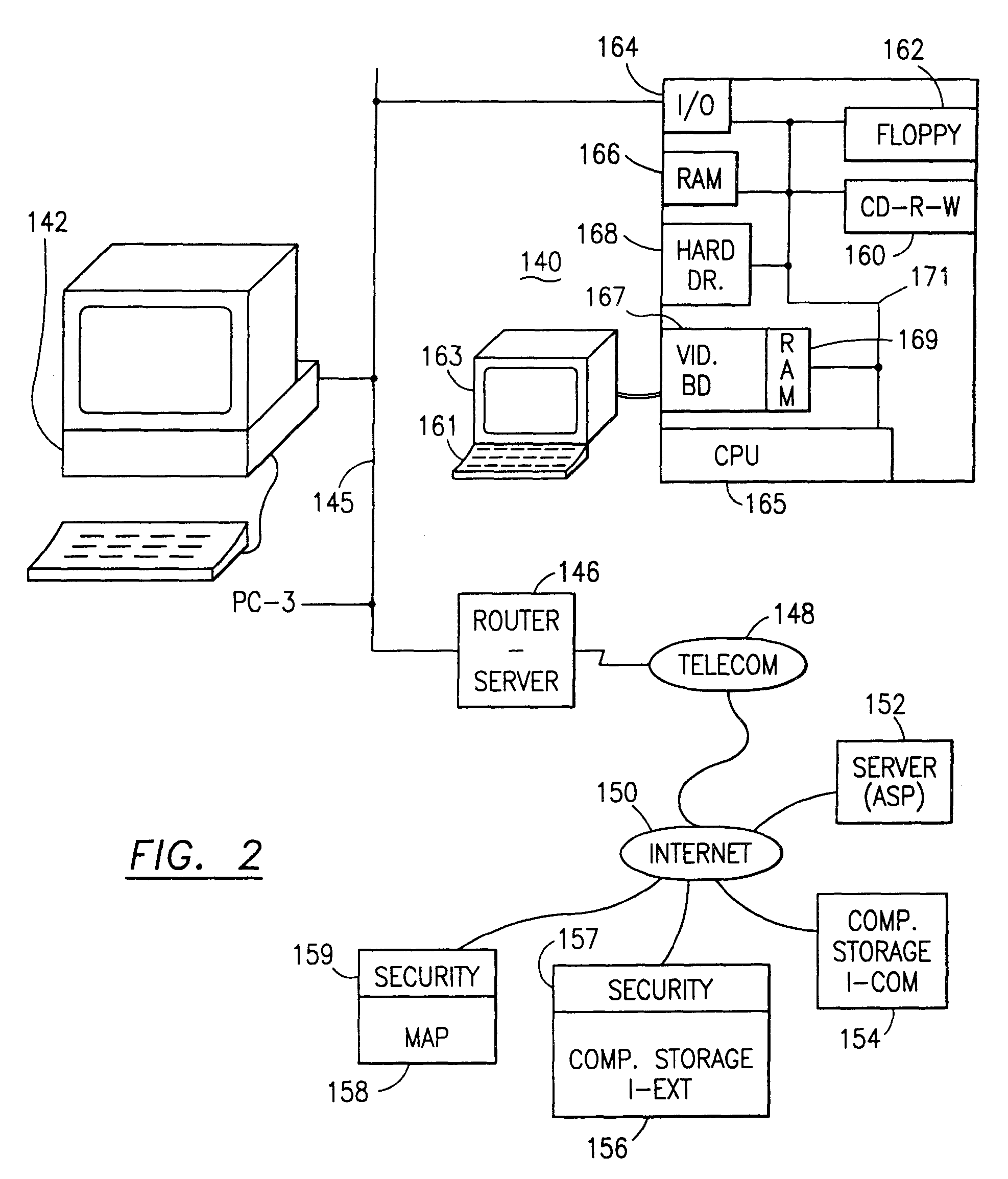
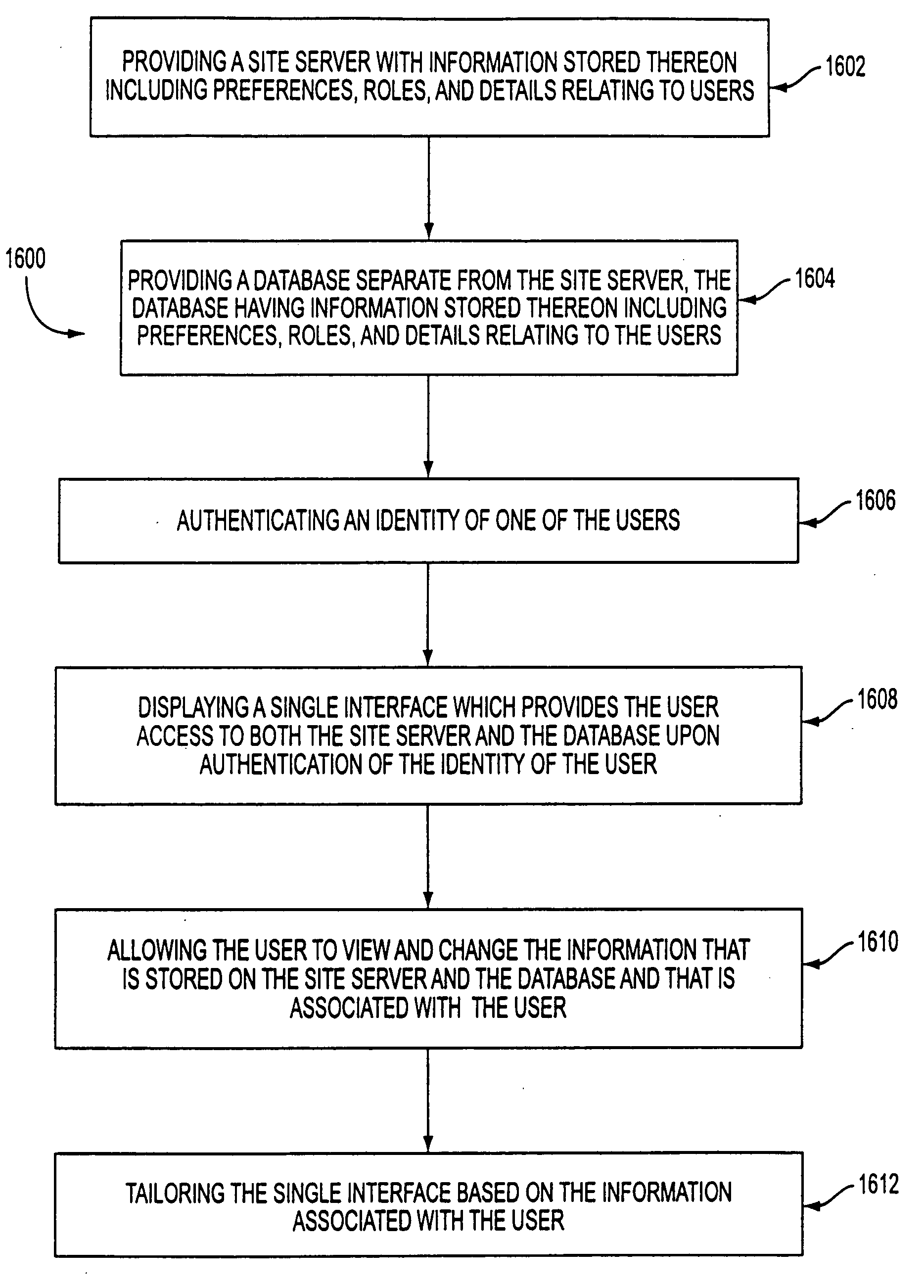
The present invention provides for the management of user information of both site server and regular web site users. A site server is provided with information stored thereon including preferences, roles, and details related to users. A database separate from the site server is also provided. The database has information stored thereon including preferences, roles, and details relating to the users. An identity of one of the users is authenticated. A single interface is displayed which provides the user access to both the site server and the database upon authentication of the identity of the user. The user is allowed to view and change the information that is stored on the site server and the database and that is associated with the user. The single interface is tailored based on the information associated with the user.
Owner:ACCENTURE GLOBAL SERVICES LTD
Metadata management system for an information dispersed storage system
ActiveUS20070079083A1Less usableImprove privacyComputer security arrangementsMemory systemsInformation dispersalMetadata management
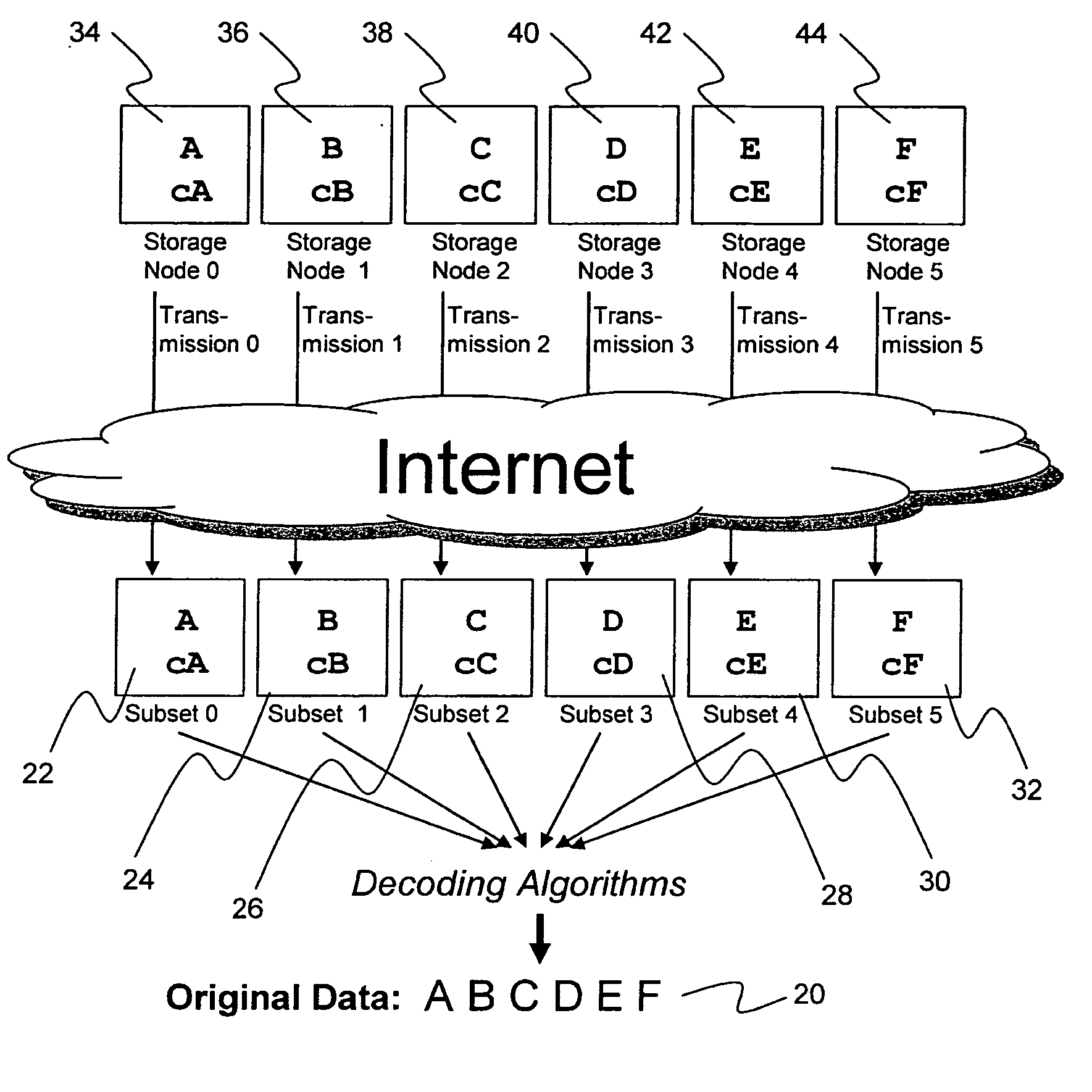
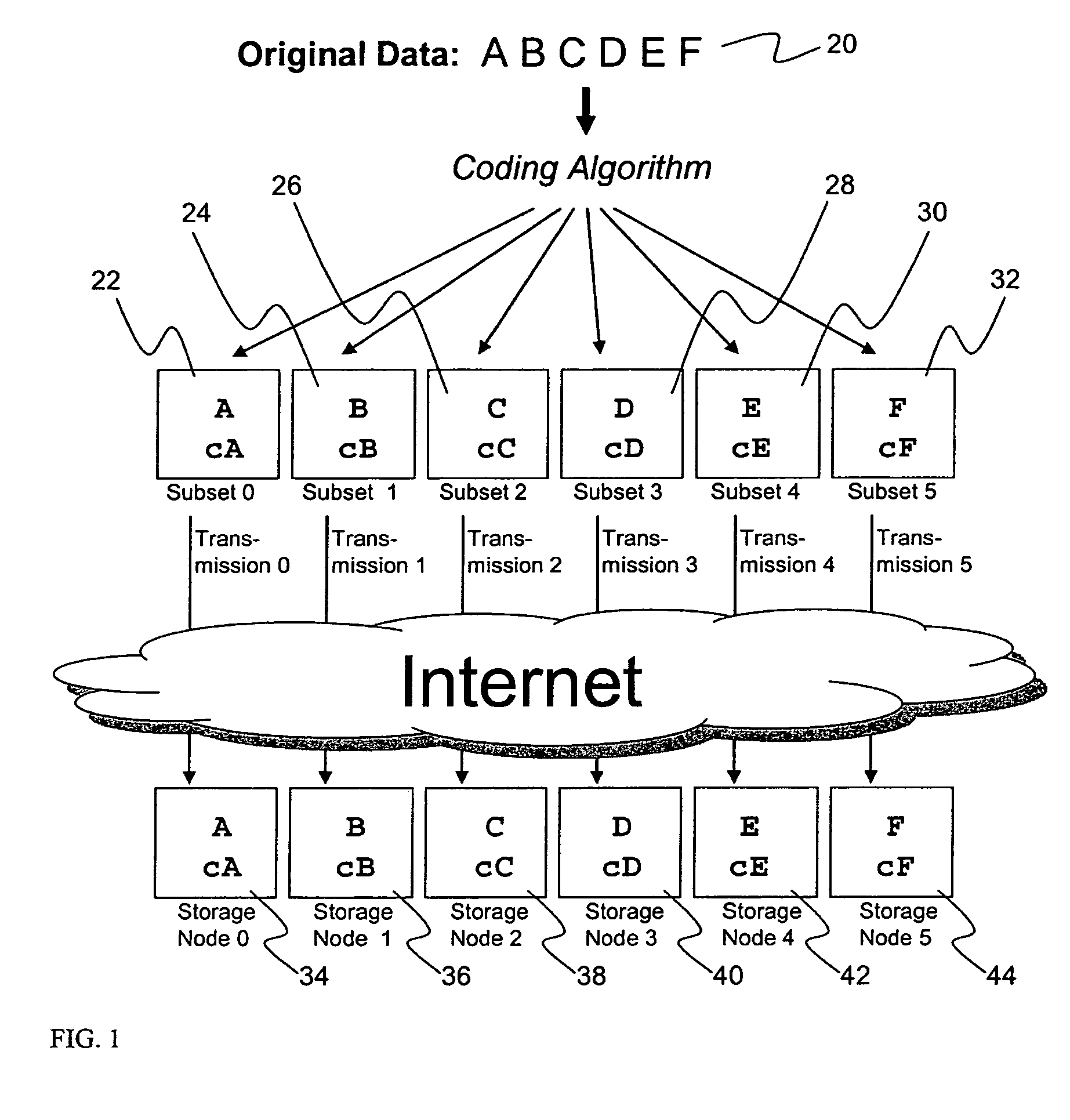
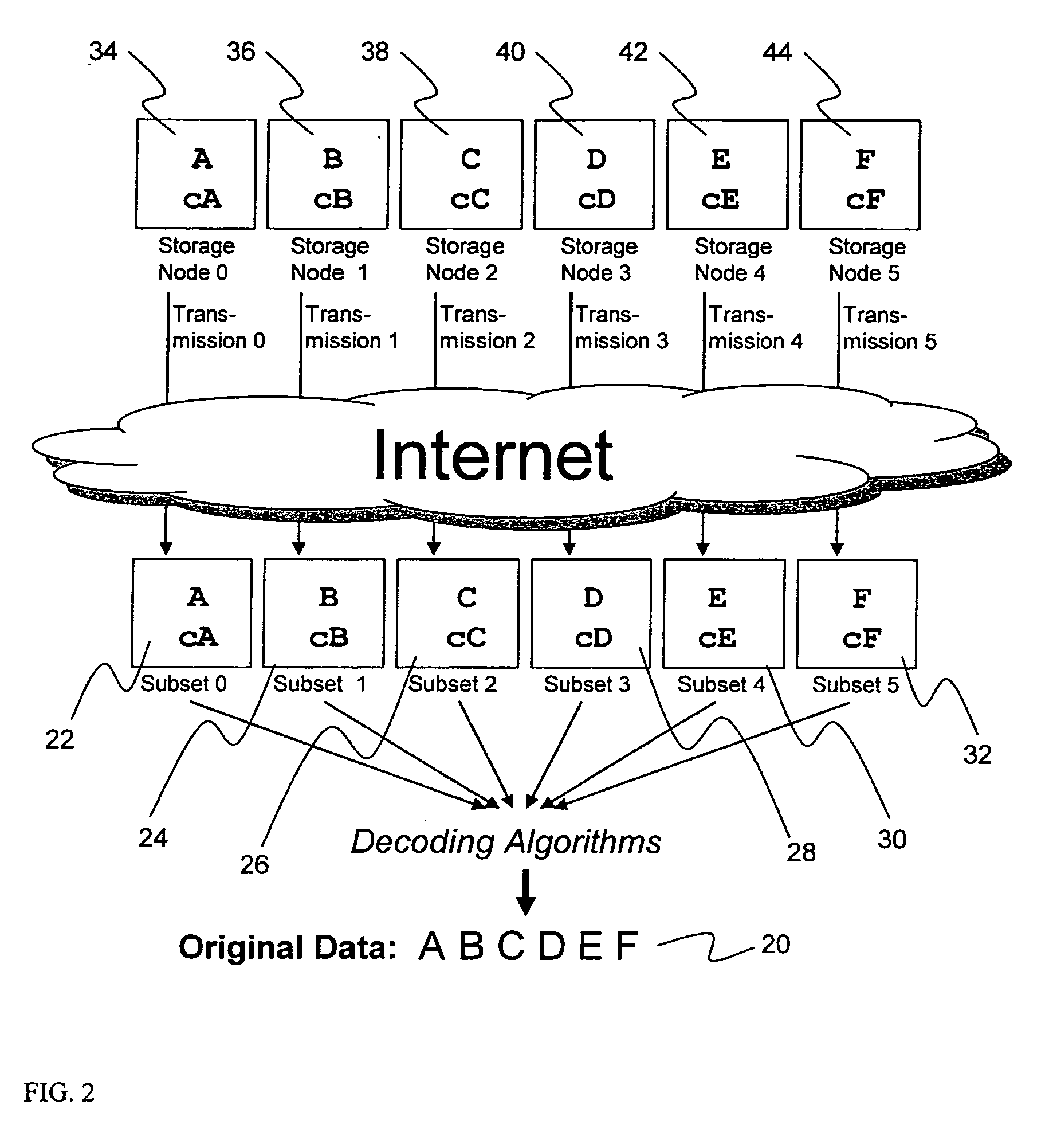
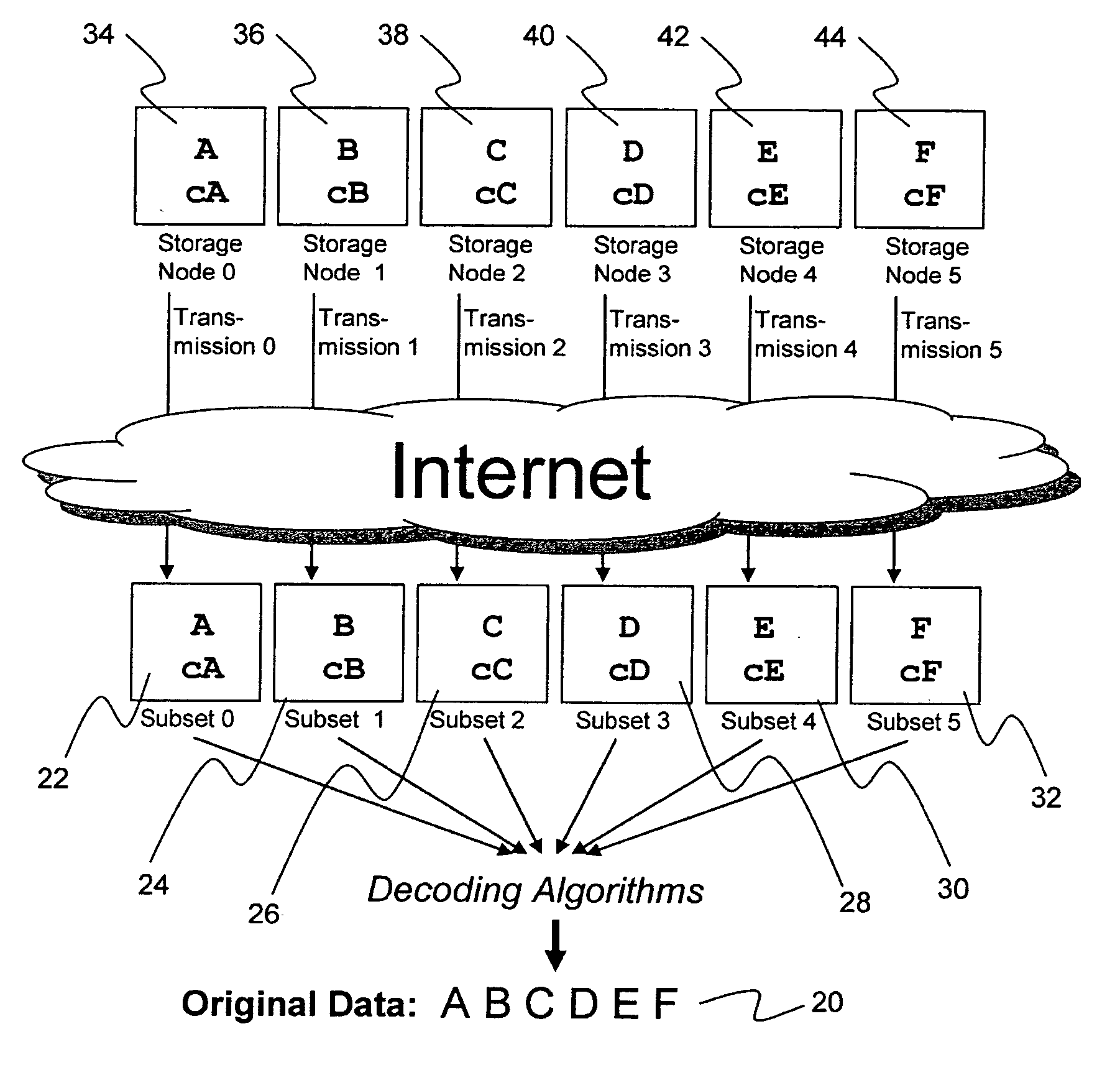
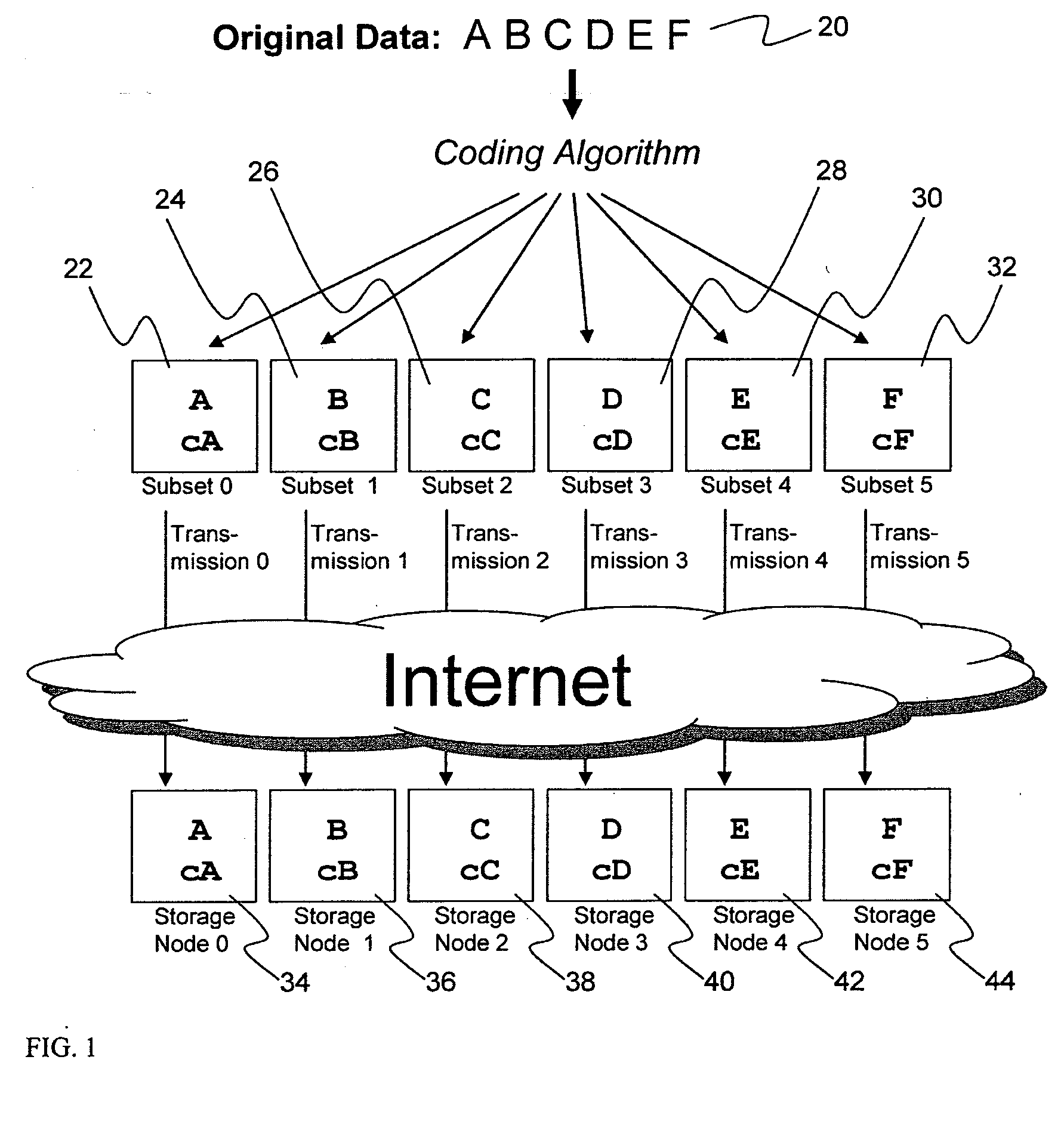
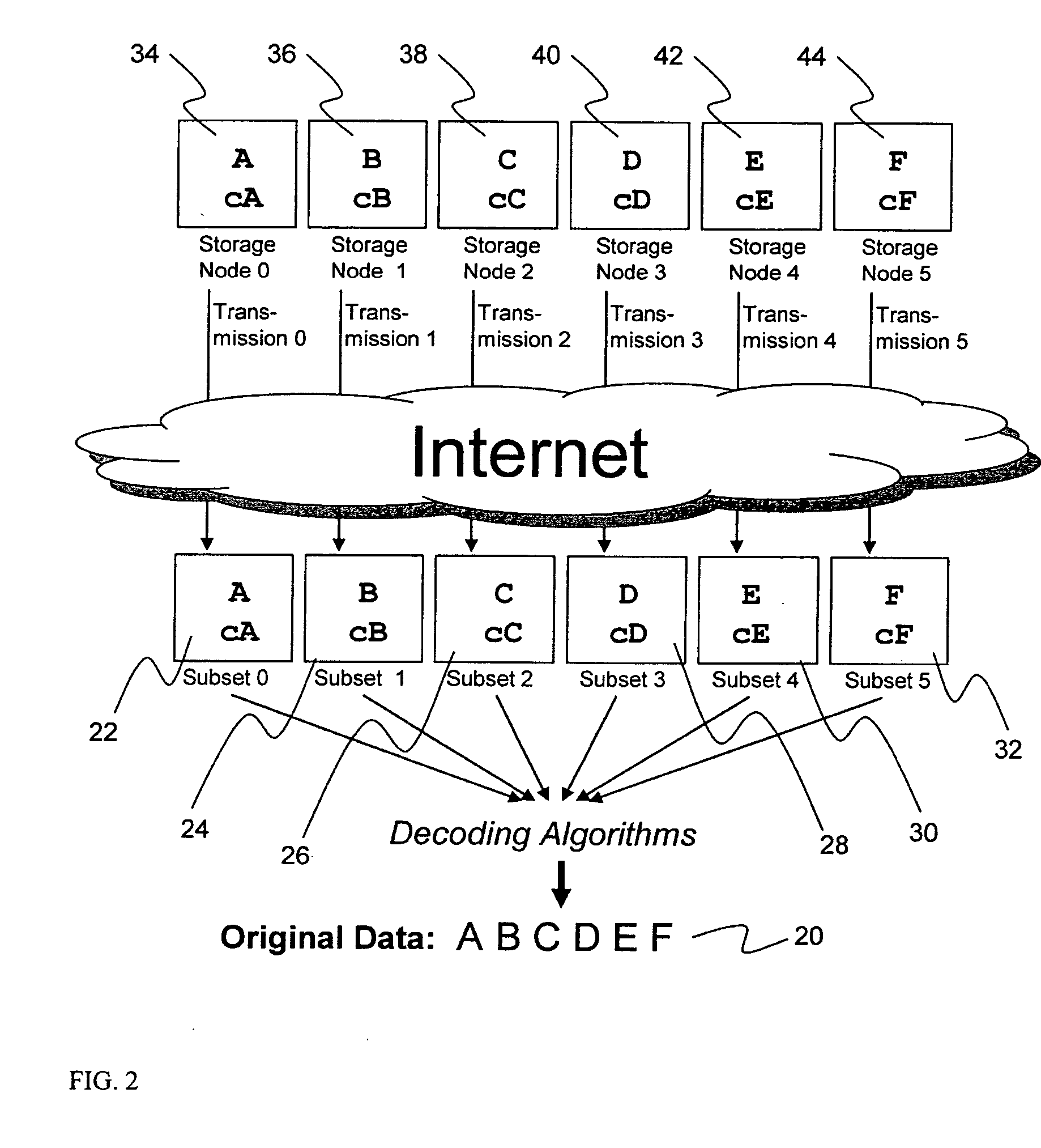
Briefly, the present invention relates to an information dispersal sytem in which original data to be stored is separated into a number of data “slices” in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate storage devices as a way of increasing privacy and security. In accordance with an important aspect of the invention, a metadata management system stores and indexes user files across all of the storage nodes. A number of applications run on the servers supporting these storage nodes and are responsible for controlling the metadata. Metadata is the information about the data, the data slices or data subsets and the way in which these data subsets are dispersed among different storage nodes running over the network. As used herein, metadata includes data source names, their size, last modification date, authentication information etc. This information is required to keep track of dispersed data subsets among all the nodes in the system. Every time new data subsets are stored and old ones are removed from the storage nodes, the metadata is updated. In accordance with an important aspect of the invention, the metadata management system stores metadata for dispersed data where: The dispersed data is in several pieces. The metadata is in a separate dataspace from the dispersed data. Accordingly, the metadata management system is able to manage the metadata in a manner that is computationally efficient relative to known systems in order to enable broad use of the invention using the types of computers generally used by businesses, consumers and other organizations currently.
Owner:PURE STORAGE
Digital data storage system
ActiveUS20070079081A1Less usableImprove privacyComputer security arrangementsMemory systemsOriginal dataSmall data
An efficient method for breaking source data into smaller data subsets and storing those subsets along with coded information about some of the other data subsets on different storage nodes such that the original data can be recreated from a portion of those data subsets in an efficient manner.
Owner:PURE STORAGE
Fixed content distributed data storage using permutation ring encoding
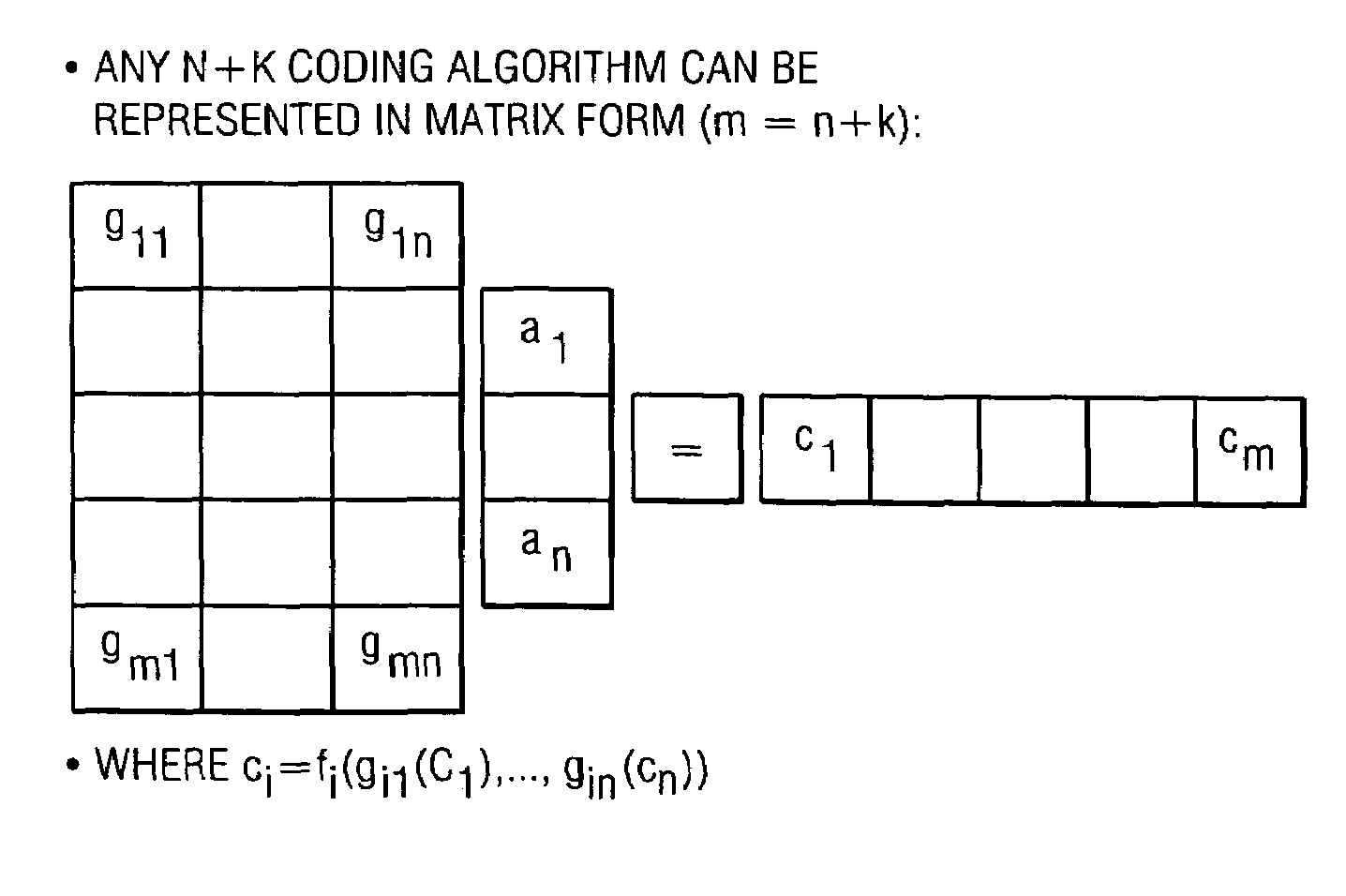
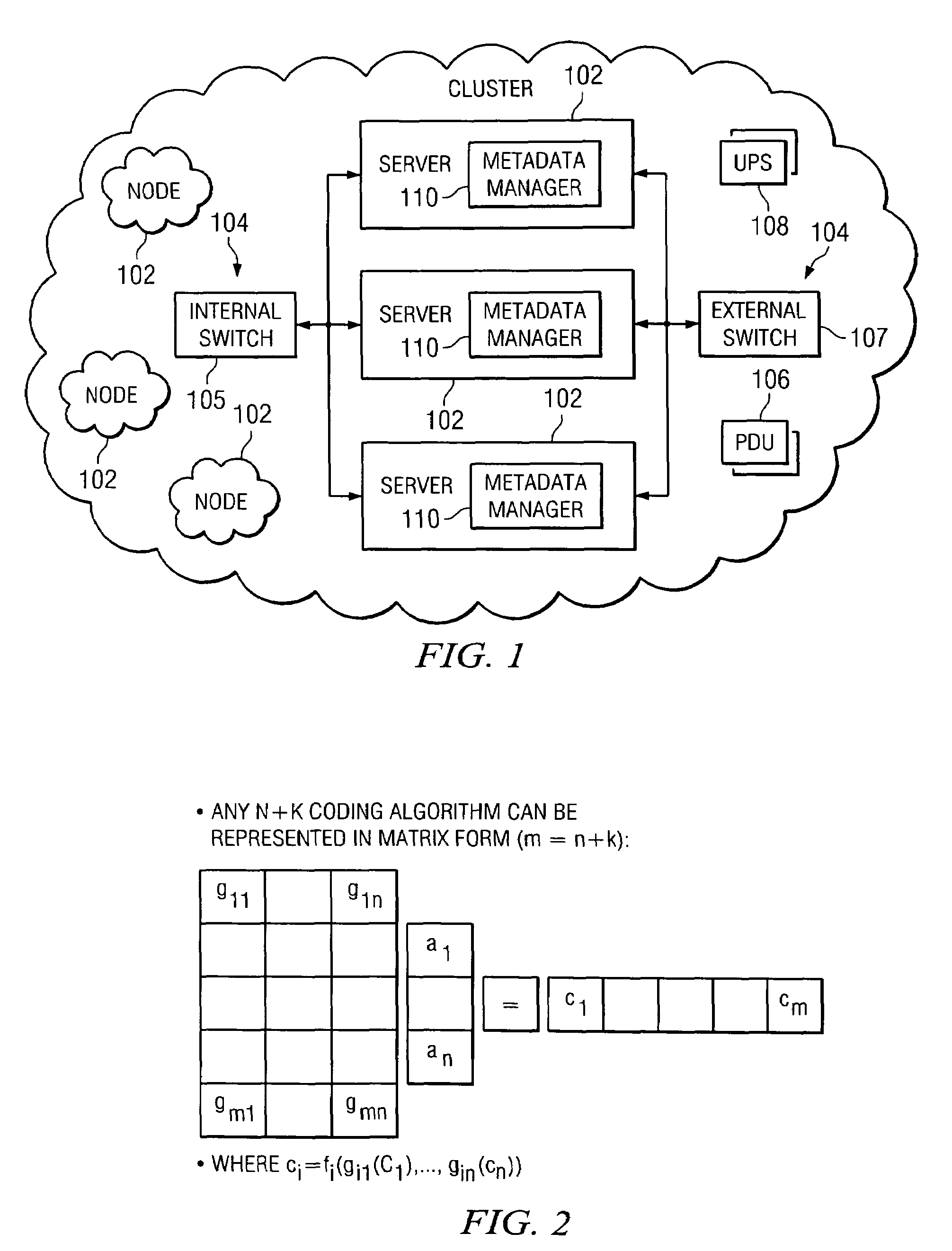
InactiveUS7240236B2Highly available and reliable and persistent storageError correction/detection using multiple parity bitsCode conversionCoding blockDatabase
A file protection scheme for fixed content in a distributed data archive uses computations that leverage permutation operators of a cyclic code. In an illustrative embodiment, an N+K coding technique is described for use to protect data that is being distributed in a redundant array of independent nodes (RAIN). The data itself may be of any type, and it may also include system metadata. According to the invention, the data to be distributed is encoded by a dispersal operation that uses a group of permutation ring operators. In a preferred embodiment, the dispersal operation is carried out using a matrix of the form [IN<sub2>—< / sub2>C] where IN is an n×n identity sub-matrix and C is a k×n sub-matrix of code blocks. The identity sub-matrix is used to preserve the data blocks intact. The sub-matrix C preferably comprises a set of permutation ring operators that are used to generate the code blocks. The operators are preferably superpositions that are selected from a group ring of a permutation group with base ring Z2.
Owner:HITACHI VANTARA CORP
Apparatus and method for dynamically selecting componentized executable instructions at run time
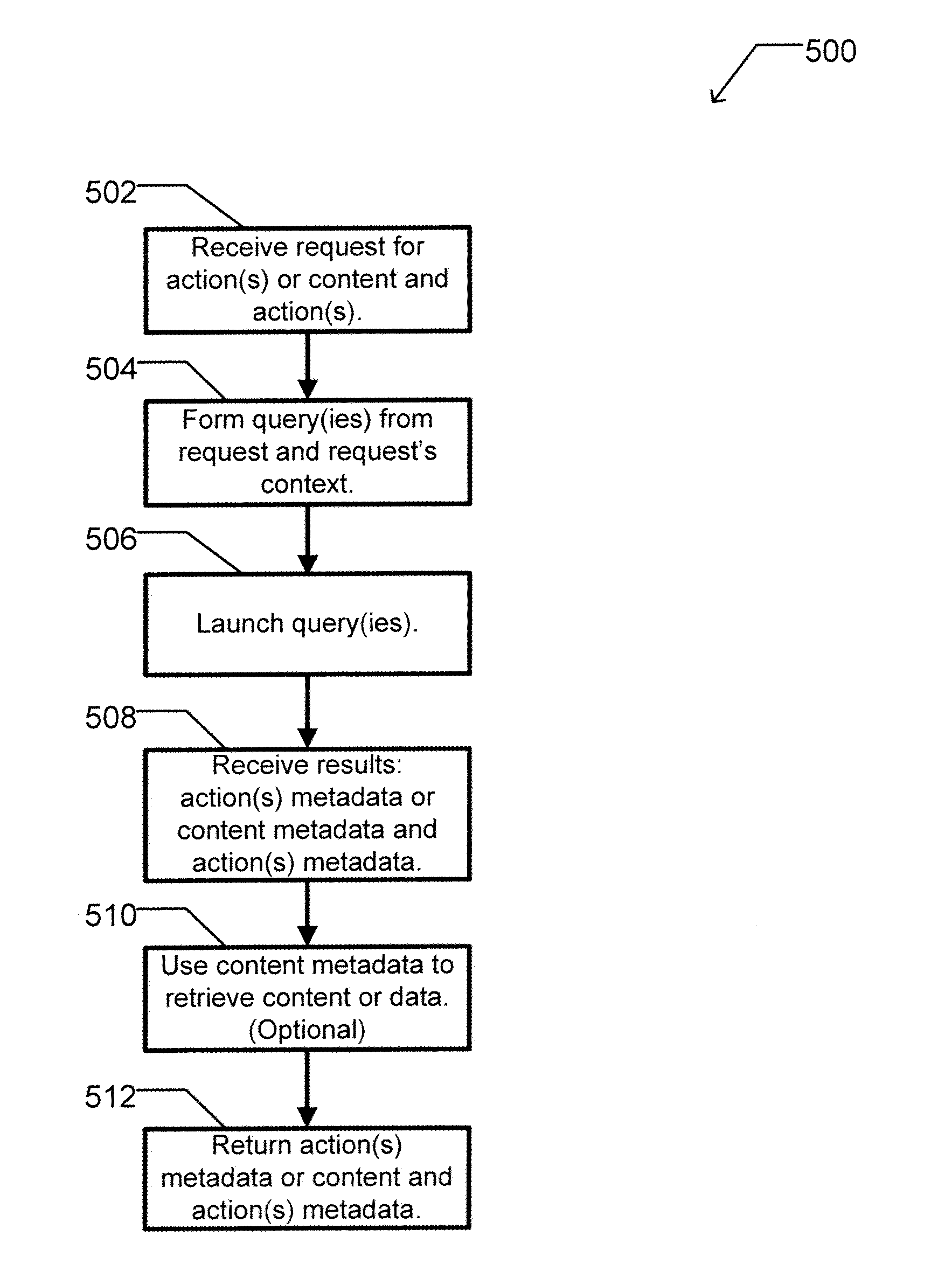
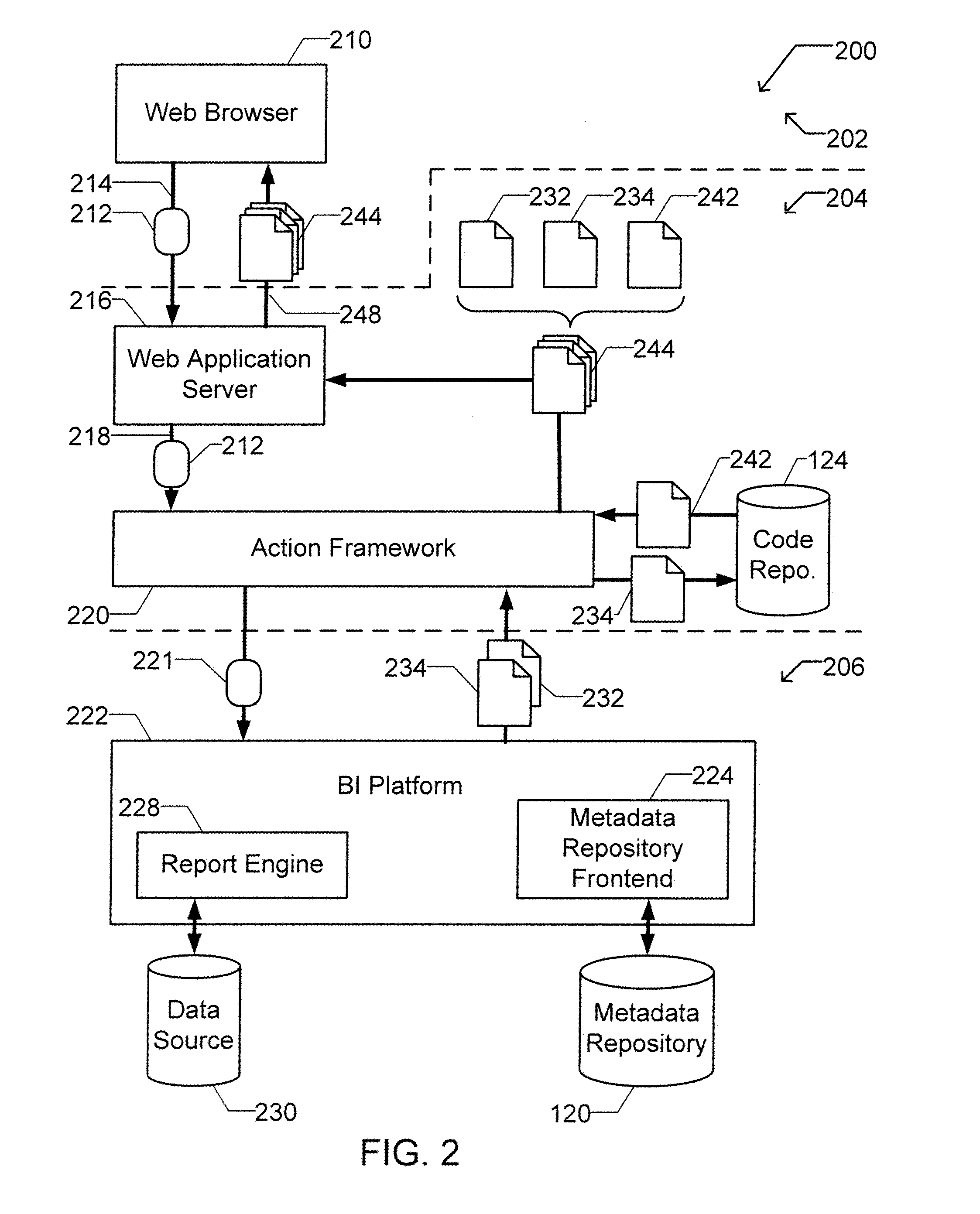
A computer readable storage medium includes executable instructions to receive a request for an action. An action context is received where the action context includes an application requesting the action. A set of metadata is searched for metadata corresponding to the action, where the search is limited by the action context. Selected metadata for the action is inserted into a collection. The selected metadata is a result of searching the set of metadata. The selected metadata includes a reference to the set of executable instructions that implements the action and a description of the action. The collection is then returned.
Owner:BUSINESS OBJECTS SOFTWARE
Content delivery network (CDN) content server request handling mechanism with metadata framework support
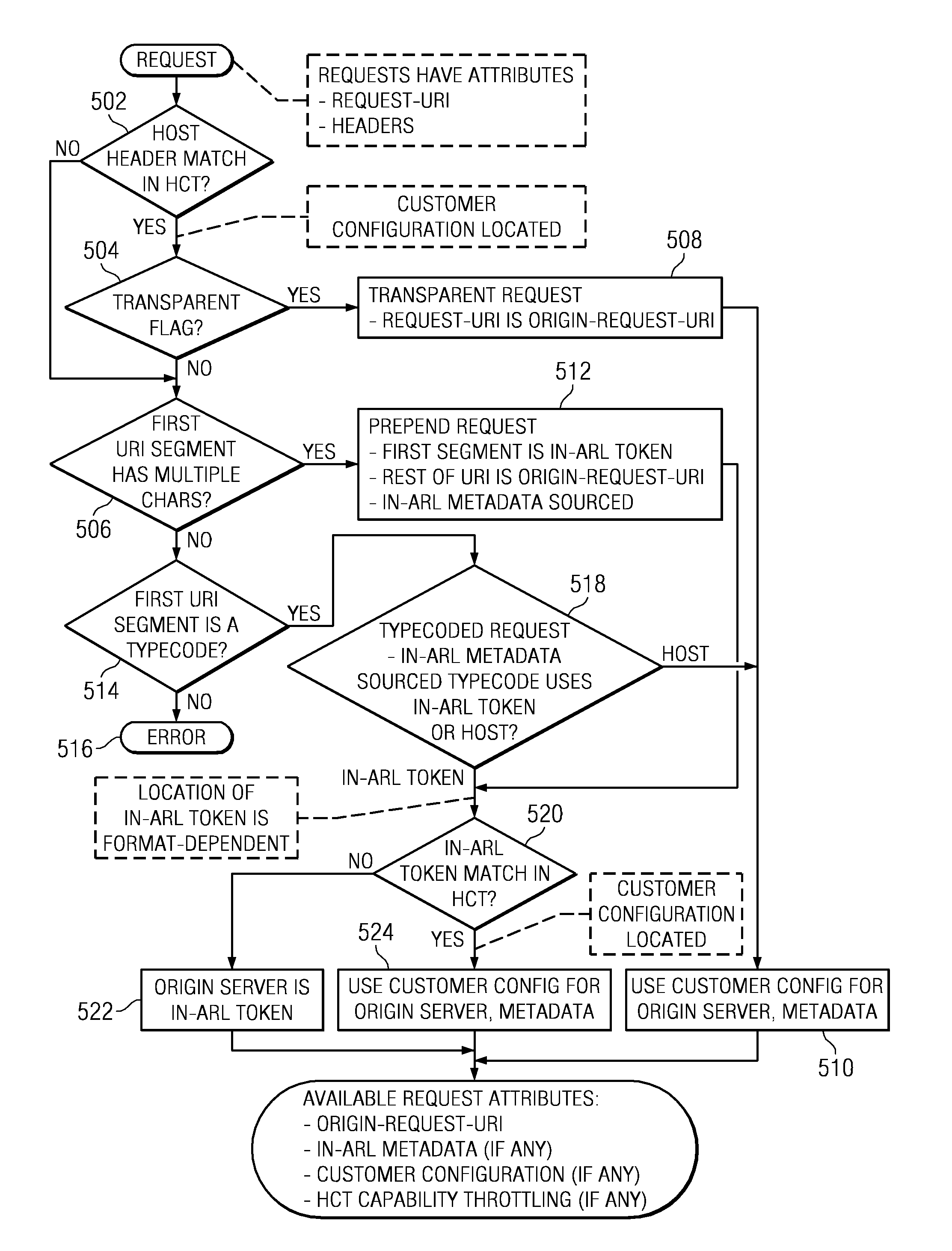
To serve content through a content delivery network (CDN), the CDN must have some information about the identity, characteristics and state of its target objects. Such additional information is provided in the form of object metadata, which according to the invention can be located in the request string itself, in the response headers from the origin server, in a metadata configuration file distributed to CDN servers, or in a per-customer metadata configuration file. CDN content servers execute a request identification and parsing process to locate object metadata and to handle the request in accordance therewith. Where different types of metadata exist for a particular object, metadata in a configuration file is overridden by metadata in a response header or request string, with metadata in the request string taking precedence.
Owner:AKAMAI TECH INC
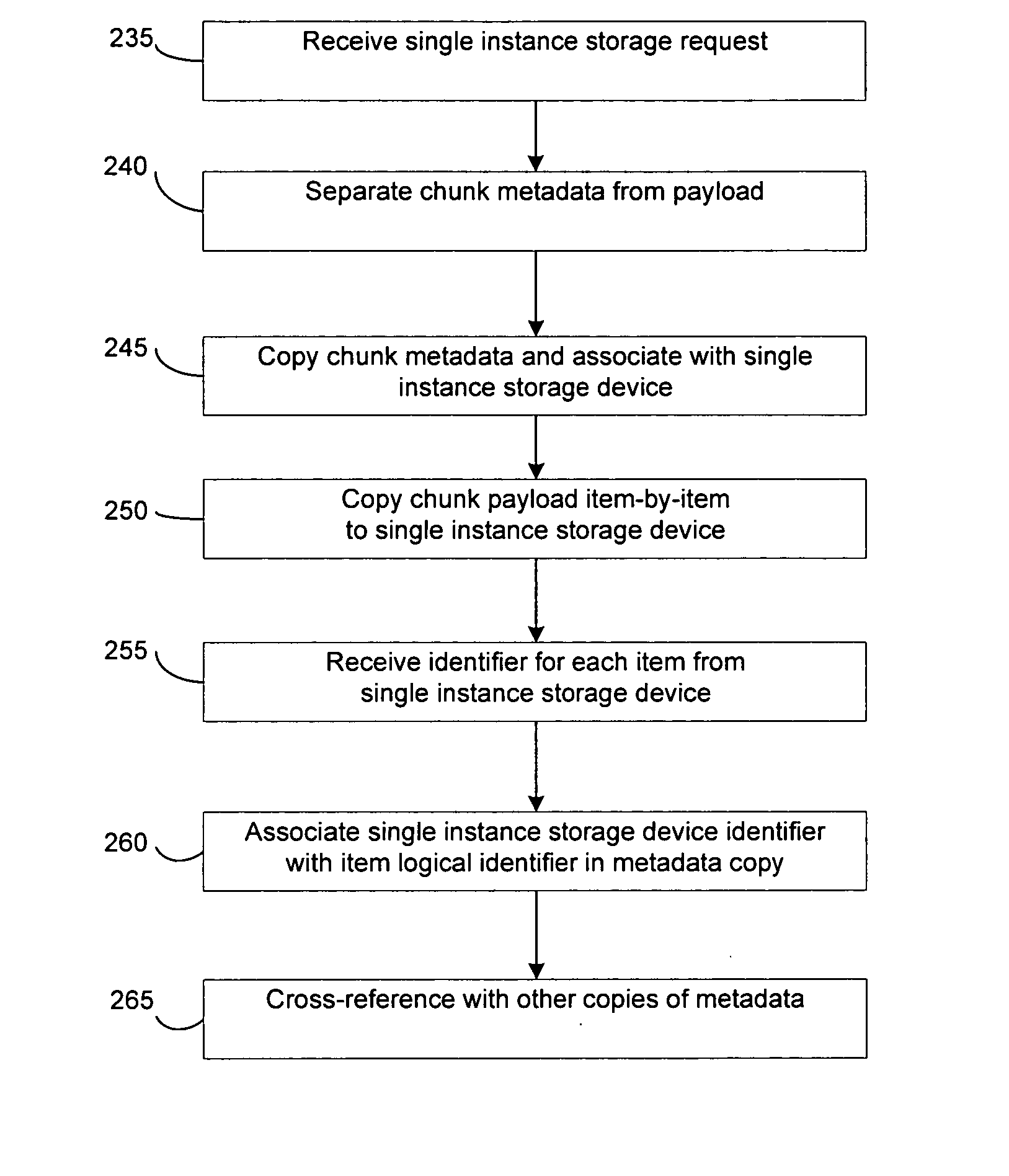
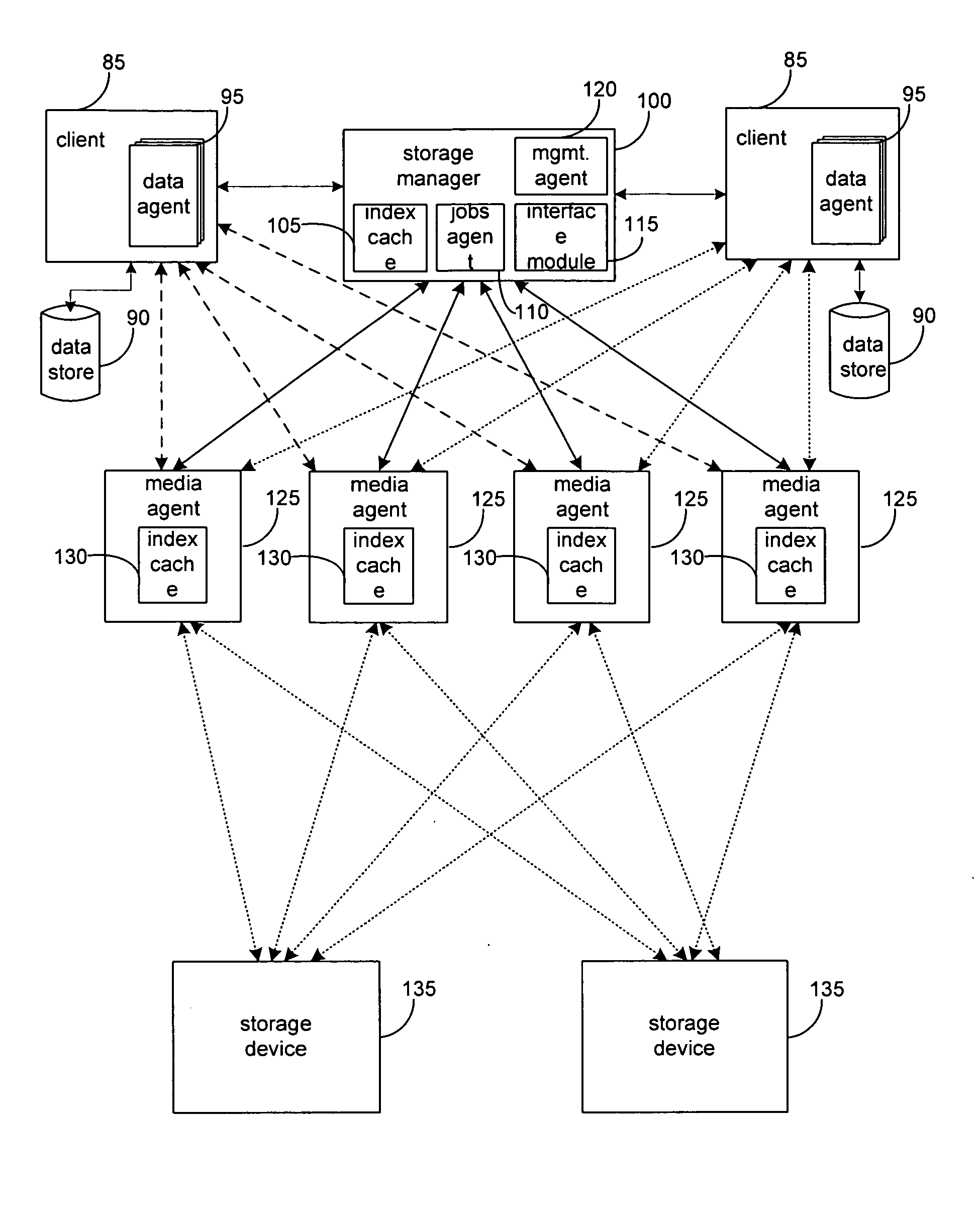
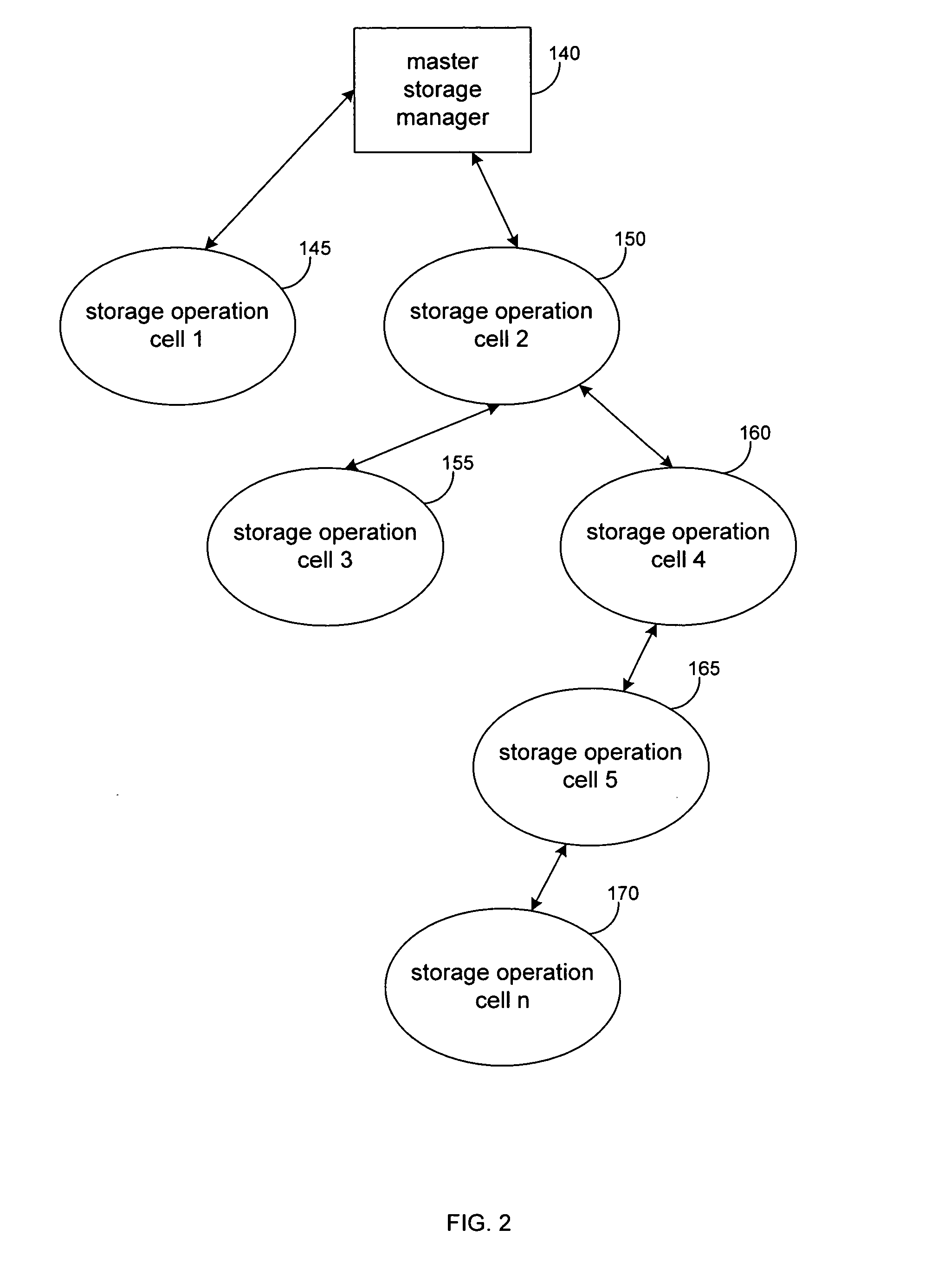
System and method to support single instance storage operations
Systems and methods for single instance storage operations are provided. Systems constructed in accordance with the principals of the present invention may process data containing a payload and associated metadata. Often, chunks of data are copied to traditional archive storage wherein some or all of the chunk, including the payload and associated metadata are copied to the physical archive storage medium. In some embodiments, chunks of data are designated for storage in single instance storage devices. The system may remove the encapsulation from the chunk and may copy the chunk payload to a single instance storage device. The single instance storage device may return a signature or other identifier for items copied from the chunk payload. The metadata associated with the chunk may be maintained in separate storage and may track the association between the logical identifiers and the signatures for the individual items of the chunk payload which may be generated by the single instance storage device.
Owner:COMMVAULT SYST INC
Transactional services
InactiveUS20070198432A1High level of throughputHigh level of efficiencyCryptography processingComputer security arrangementsTransaction serviceDatabase
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
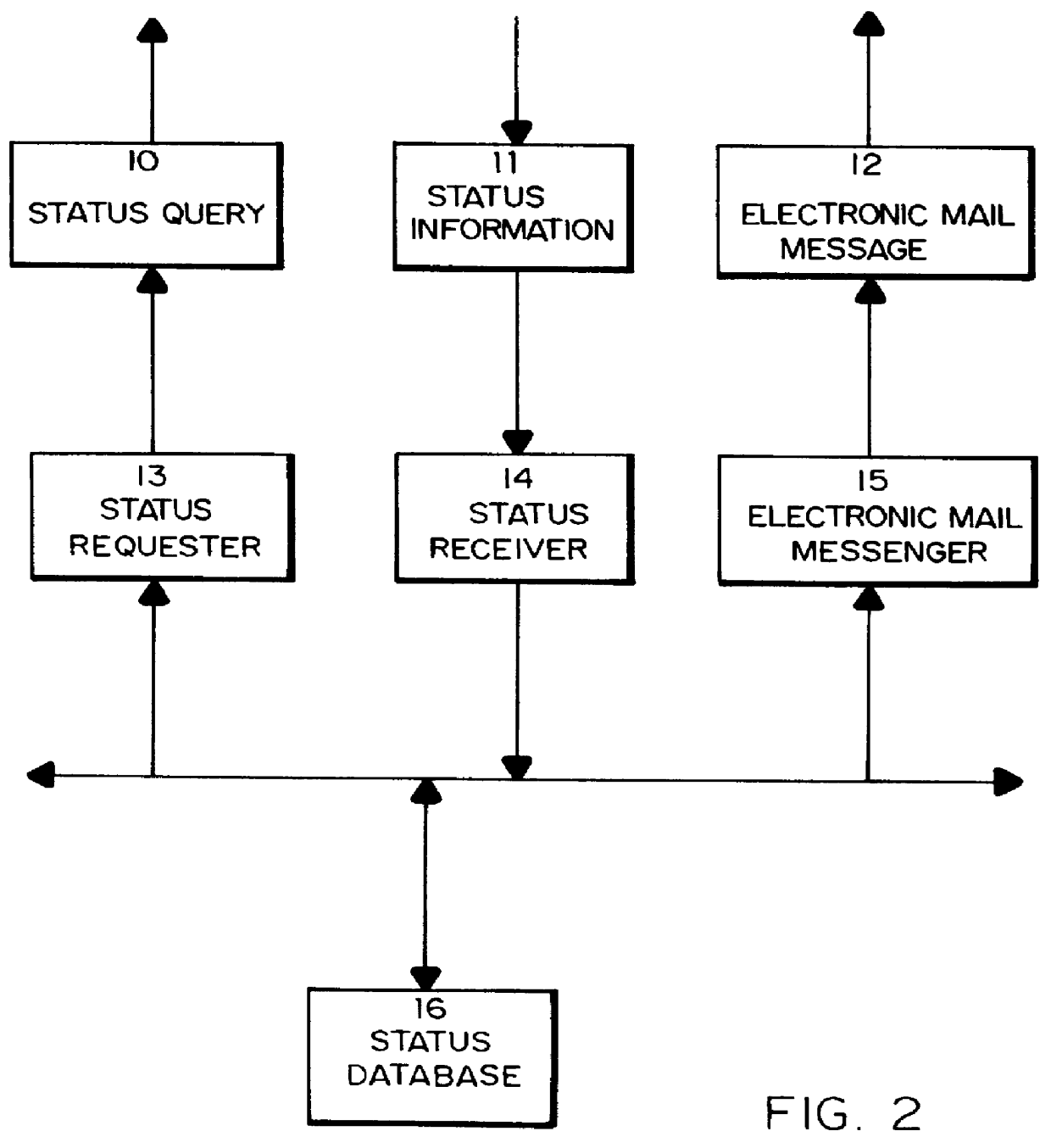
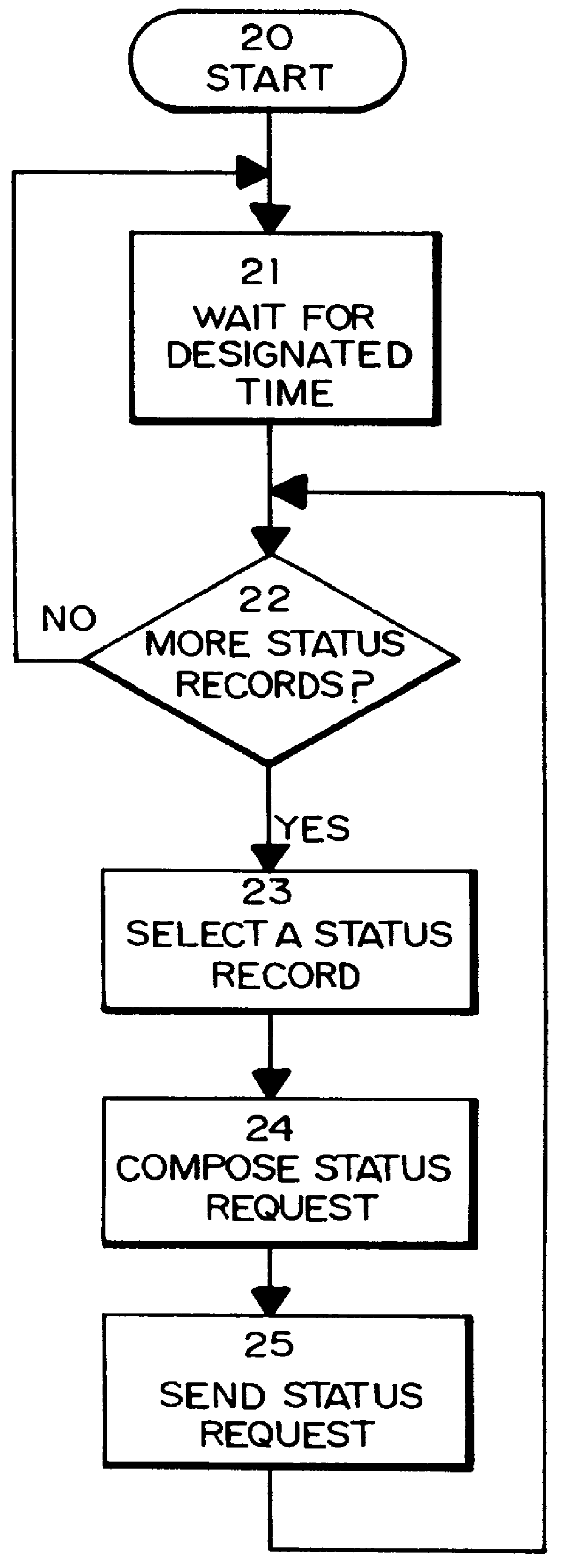
Method for supplying automatic status updates using electronic mail
A method is disclosed for automatically updating the status of customers' orders and shipments via electronic mail without using a human attendant to create and send the electronic mail messages. Preferably implemented in software, the updating method allows a large set of customers to be periodically updated over a computer or communications network via electronic mail. The method utilizes a database for maintaining order and shipping status and other relevant information.
Owner:EBAY INC
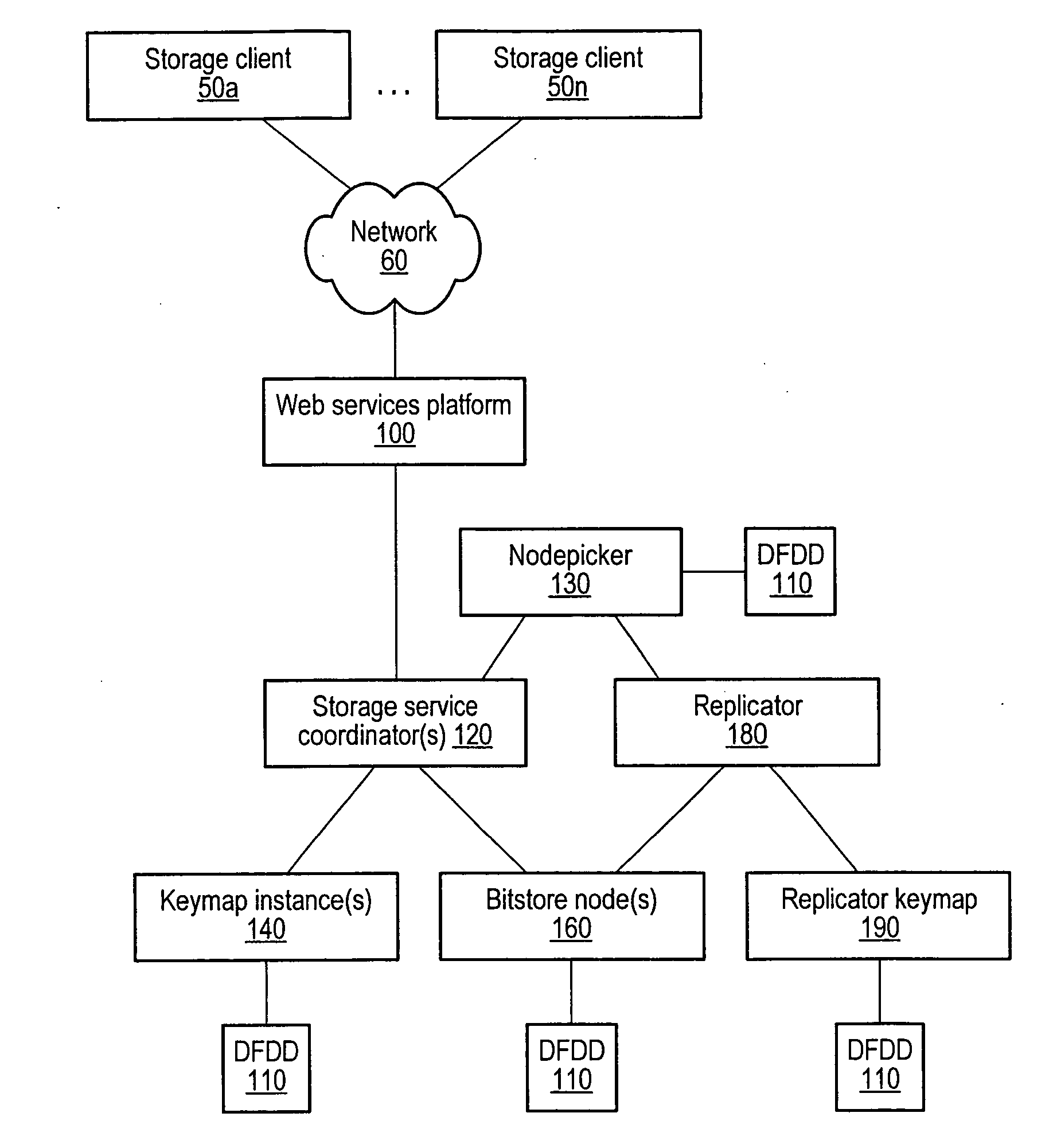
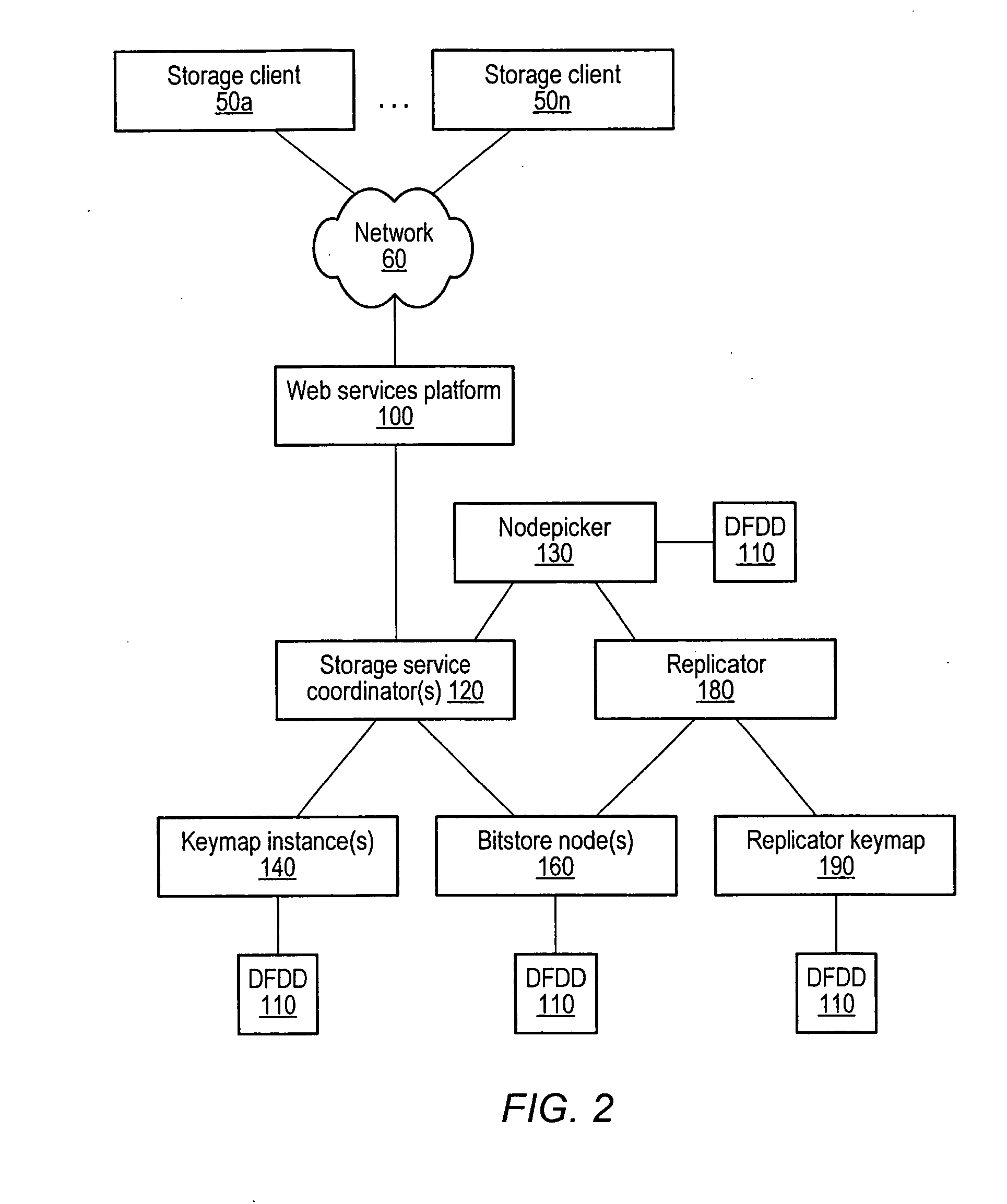
Distributed storage system with web services client interface
ActiveUS20070156842A1Digital data information retrievalMultiple digital computer combinationsWeb serviceClient-side
A distributed, web-services based storage system. A system may include a web services interface configured to receive, according to a web services protocol, a given client request for access to a given data object, the request including a key value corresponding to the object. The system may also include storage nodes configured to store replicas of the objects, where each replica is accessible via a respective unique locator value, and a keymap instance configured to store a respective keymap entry for each object. For the given object, the respective keymap entry includes the key value and each locator value corresponding to replicas of the object. A coordinator may receive the given client request from the web services interface, responsively access the keymap instance to identify locator values corresponding to the key value and, for a particular locator value, retrieve a corresponding replica from a corresponding storage node.
Owner:AMAZON TECH INC
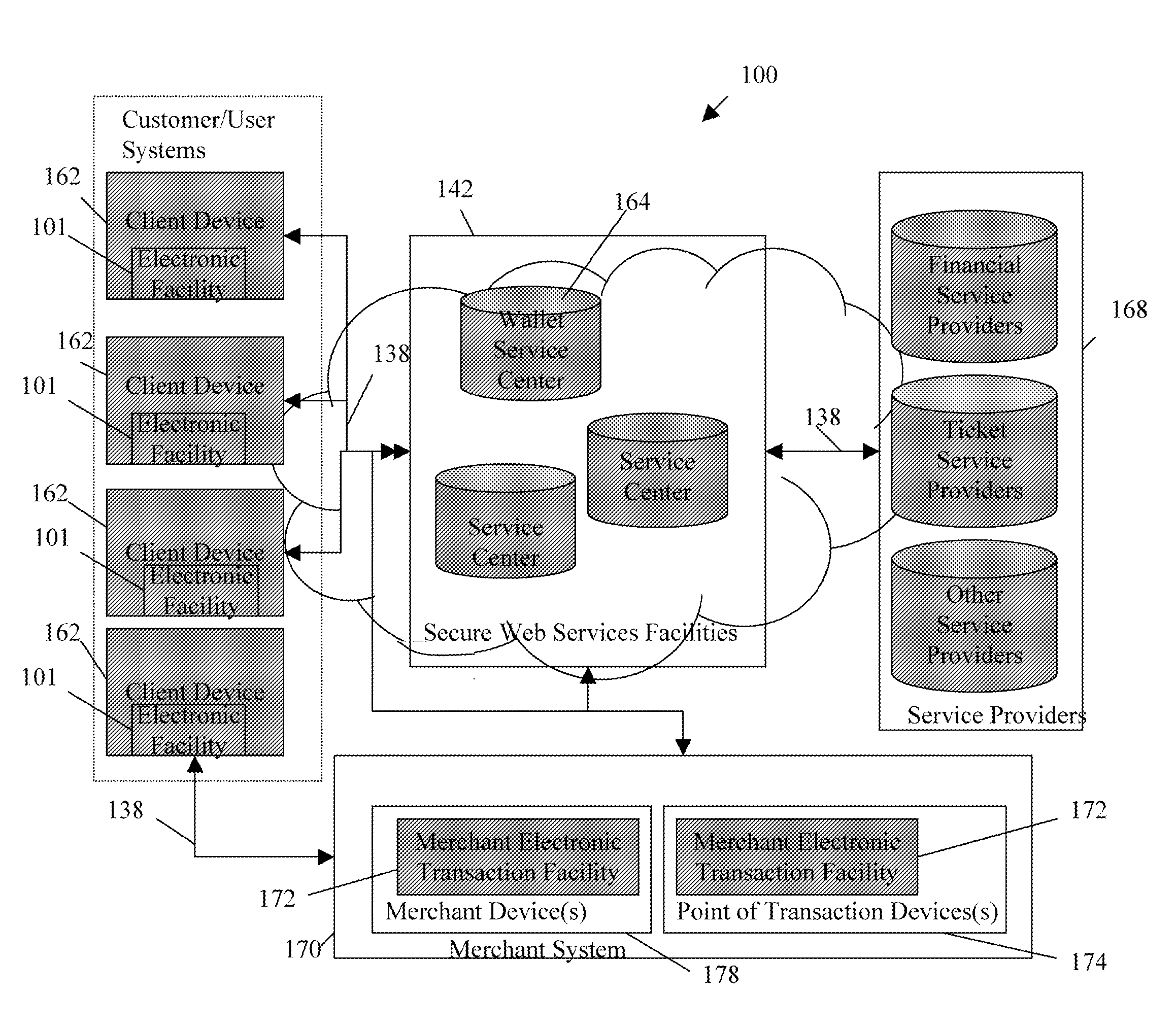
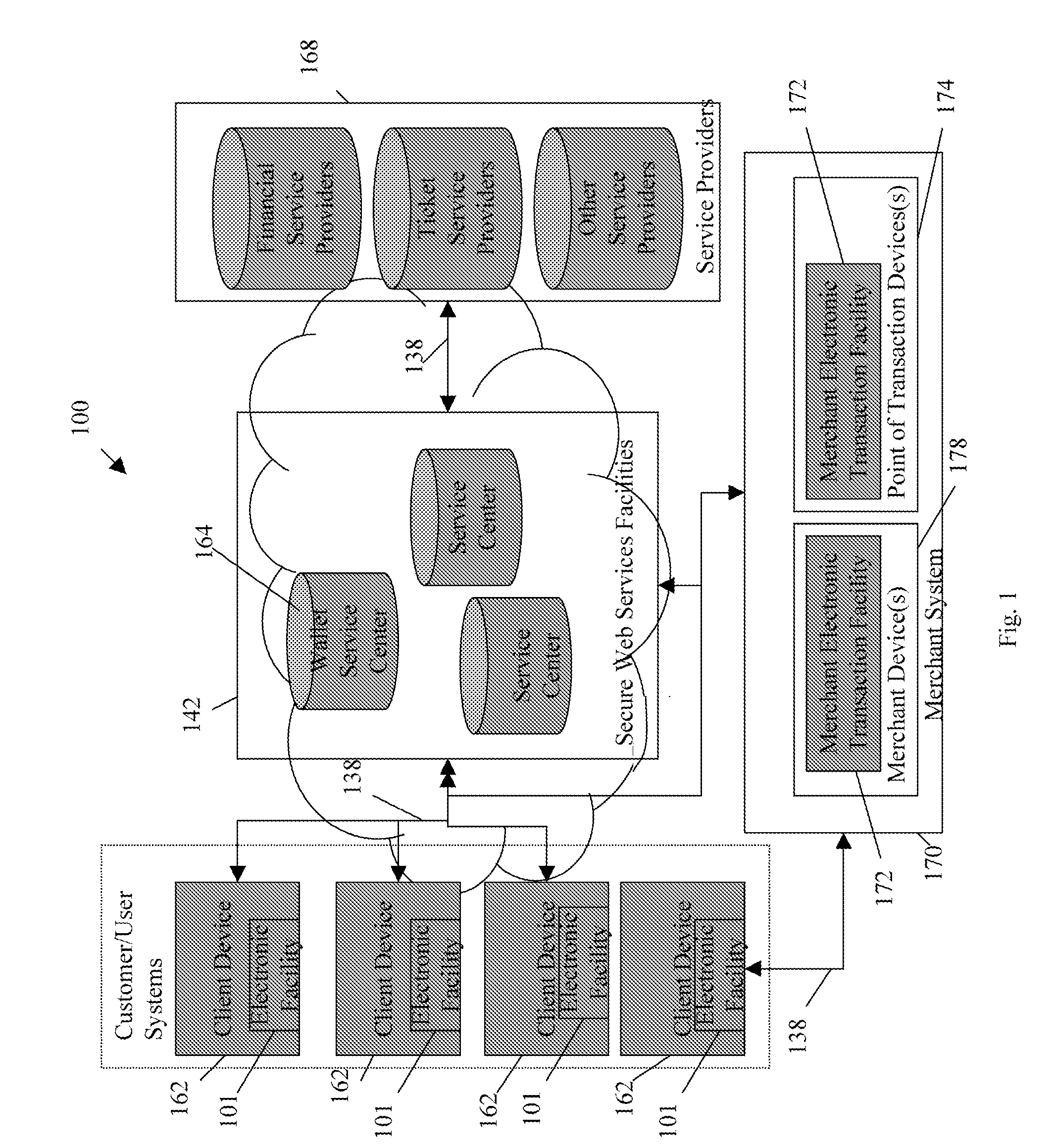
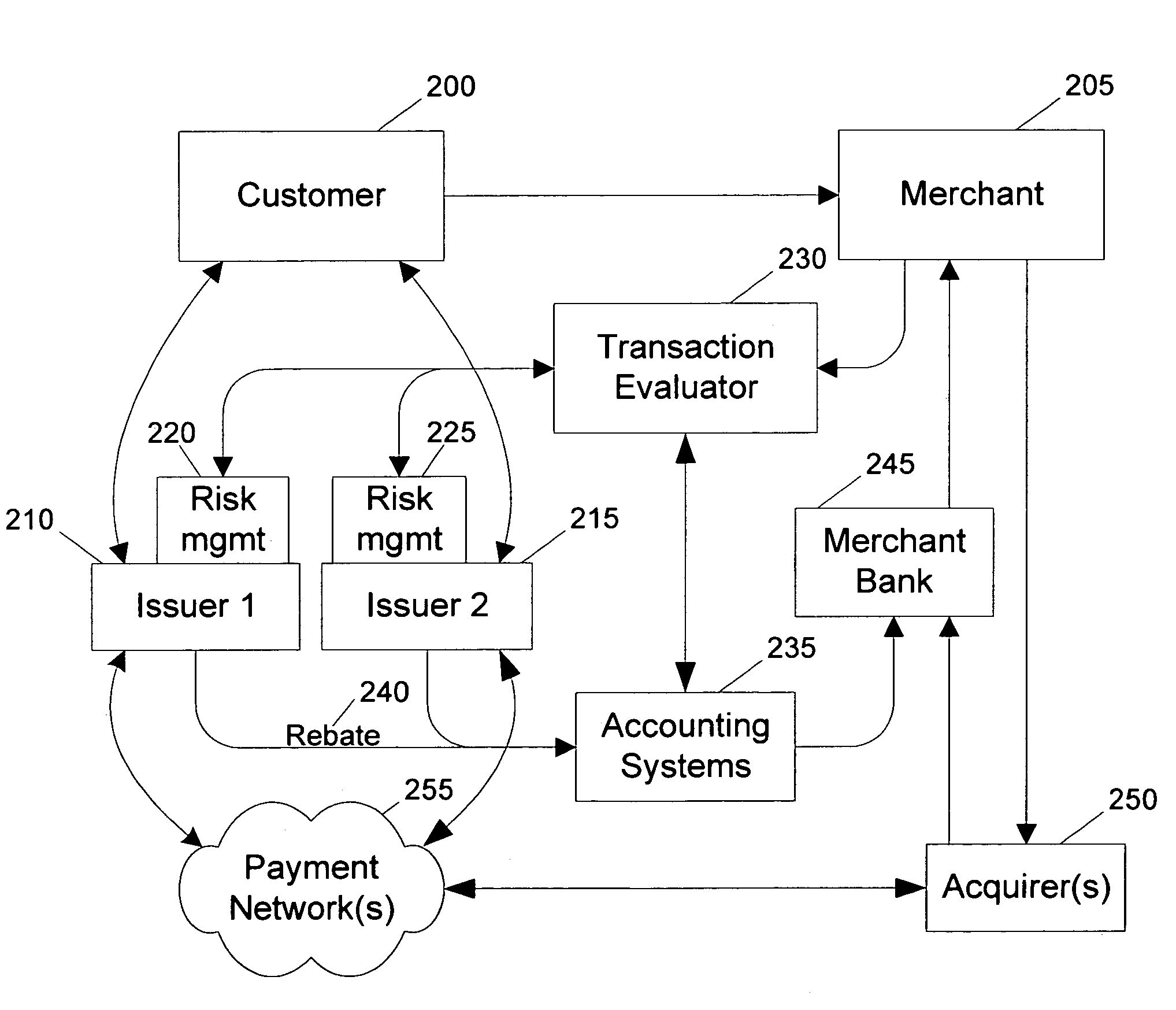
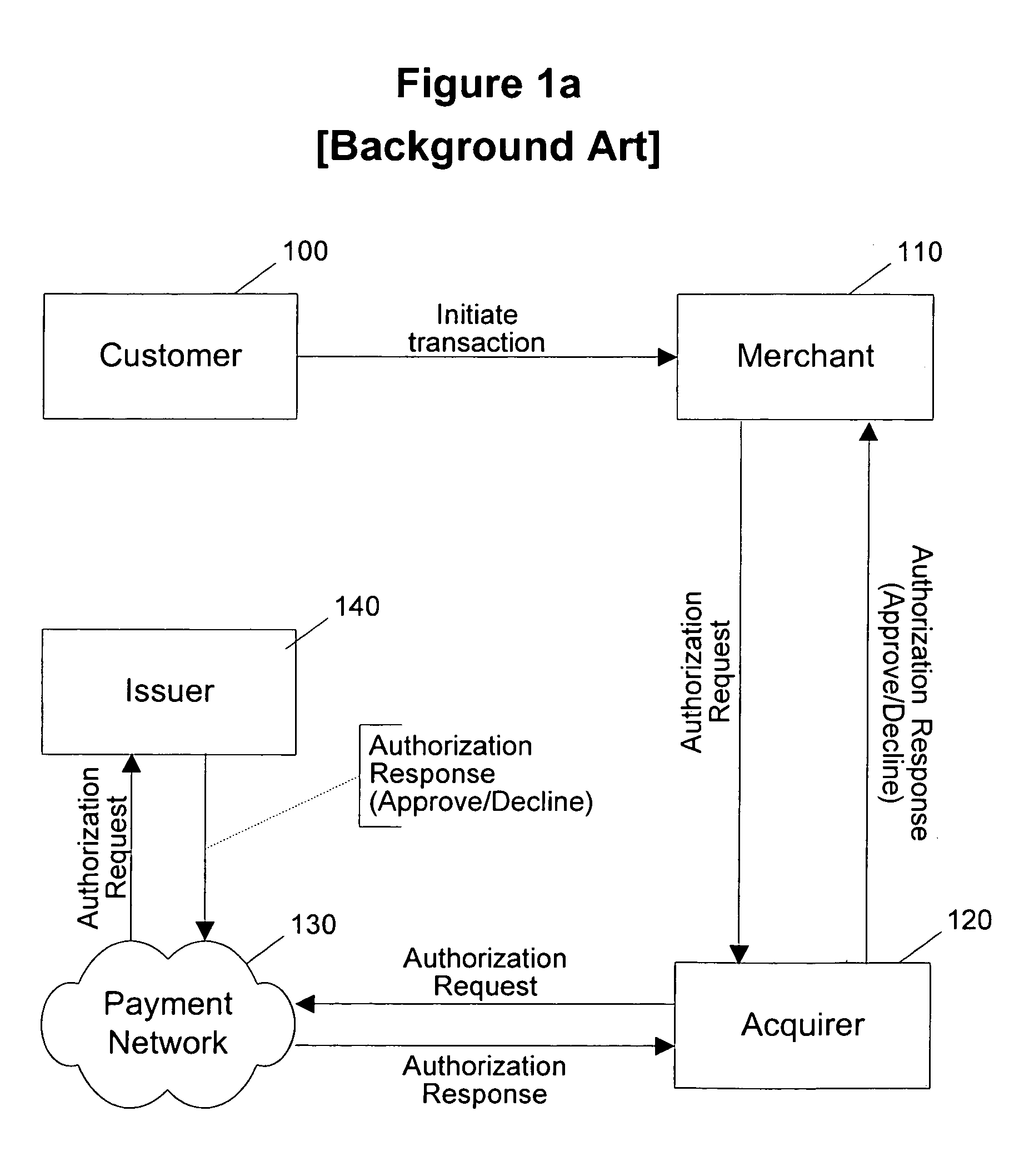
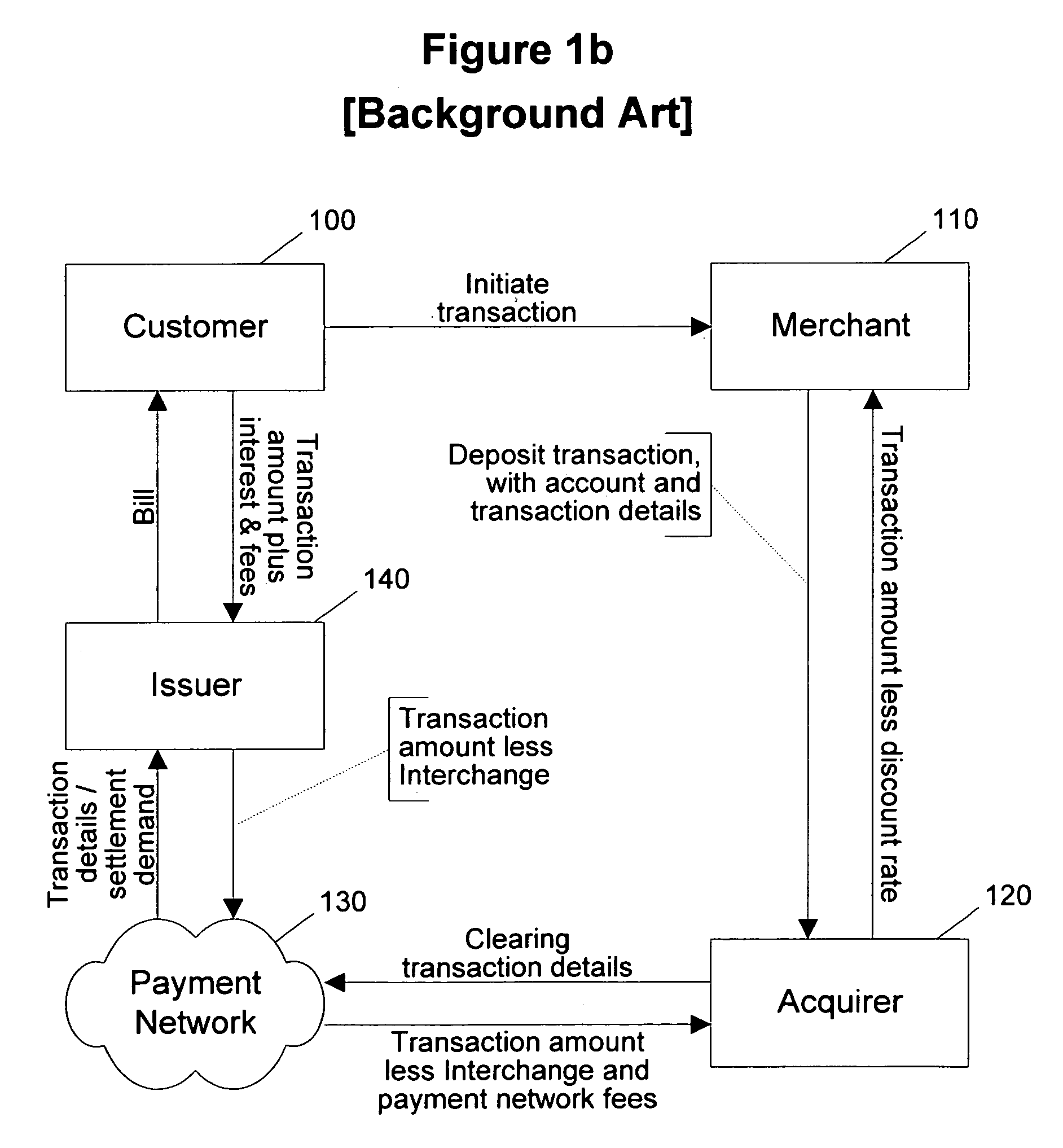
Routing methods and systems for increasing payment transaction volume and profitability
InactiveUS6999943B1More transactionEfficient routingFinancePayment architecturePayment transactionBenefit analysis
Customers often have access to multiple payment methods for any given transaction. In one embodiment of the invention, a merchant obtains information regarding multiple payment methods from a customer, and sends said information to a transaction evaluator. Via computer networks, the transaction evaluator sends information about the transaction to the issuers of one or more of the payment methods. The issuers perform a cost / benefit analysis of the transactions and respond with a description of the terms under which they are willing to process the transaction. Based on the issuer response, the transaction evaluator selects one of the payment methods. By enabling participating issuers to select favorable transactions and avoid unprofitable ones, the invention can thus improve issuer profitability by directing profitable transactions to participating issuers while directing unprofitable transactions away from participating issuers or to alternate transaction methods that are more profitable or less costly.
Owner:DOUBLECREDIT CORP
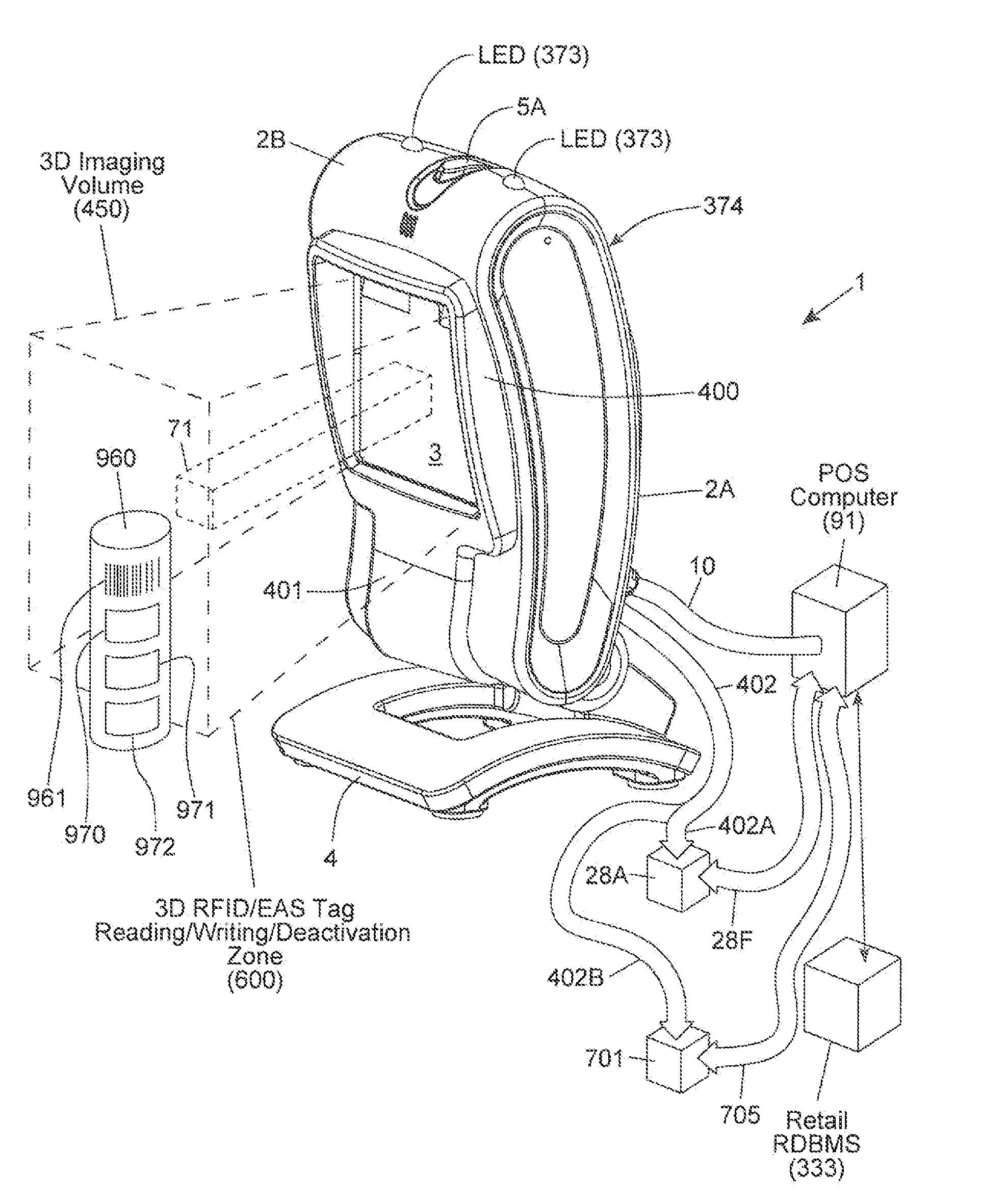
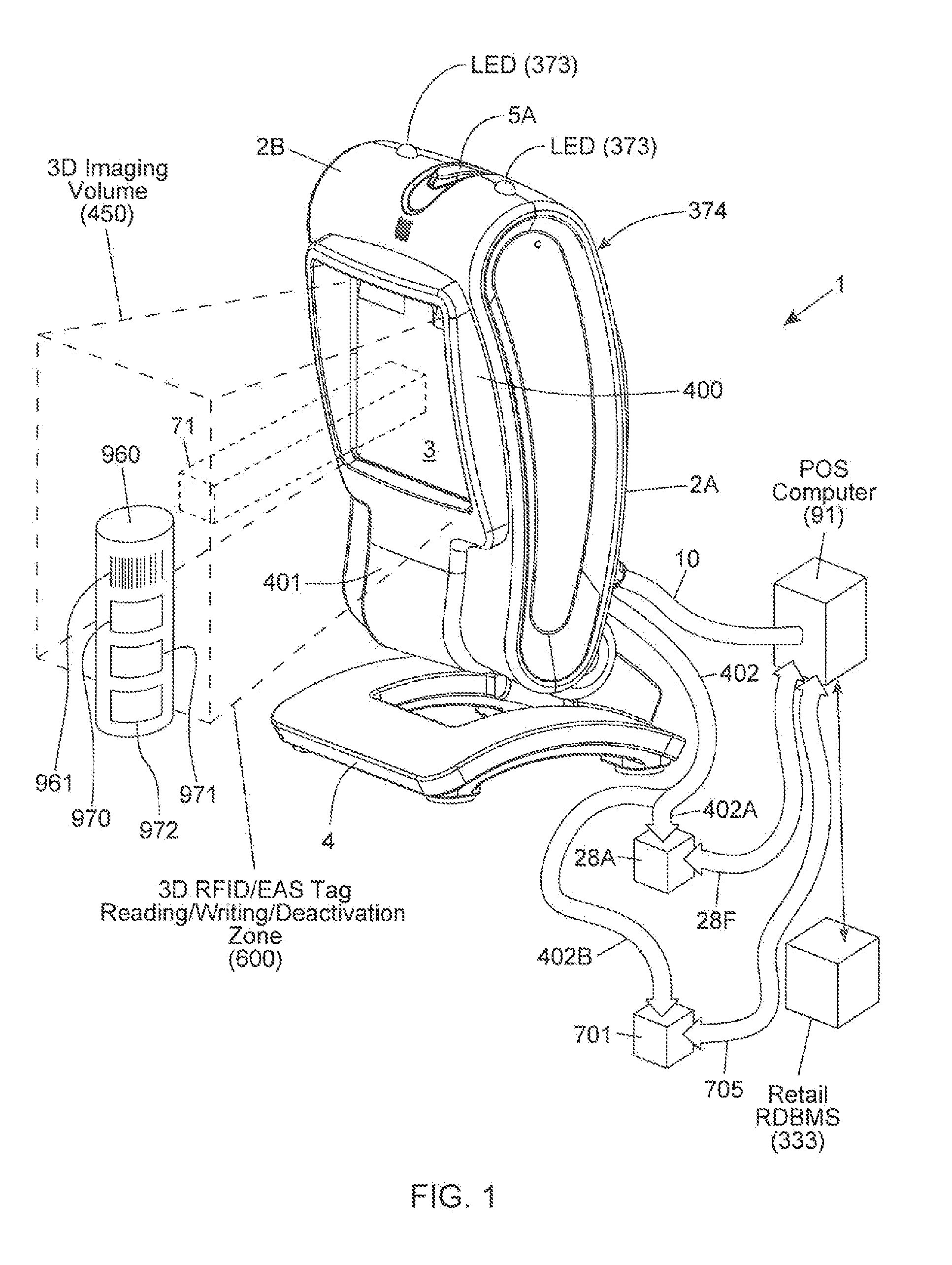
Method of and system for uniquely responding to code data captured from products so as to alert the product handler to carry out exception handling procedures
InactiveUS20120203647A1Avoid disadvantagesEffectively reliably informCash registersPayment architectureLogistics managementSoftware engineering
A code reading system capable of signaling exception handling procedures for products being handled in a work environment, such as, for example, consumer product being purchased in a retail store or a product or package being sorted by a logistics company. The system includes a system housing containing one or more one or more signal sources for generating distinctive visual and / or audible exception handling signals for special classes of products identified in the environment. Such special products may include: EAS tagged products requiring EAS tag deactivation: alcohol and tobacco products requiring proof of age; controlled products requiring additional customer tracking; age restricted products requiring identification; product purchases requiring personnel to show up and approve or assist in a product transaction; and the like.
Owner:METROLOGIC INSTR
Method and System for the Creating, Managing, and Delivery of Enhanced Feed Formatted Content
InactiveUS20080126476A1Multiple digital computer combinationsOffice automationCharacteristic responseWorld Wide Web
The invention provides a method, system, and computer usable medium including a program for sponsoring customizing feed content. The method includes associating a user with a profile group based on characteristic response data; receiving at least one keyword from the user; determining whether feed formatted content contains the keyword; associating a sponsorship with the feed formatted content based on the keyword and the associated profile group; and providing the feed formatted content with associated sponsorship to the user based on the determination.
Owner:DIZPERSION
Package source verification
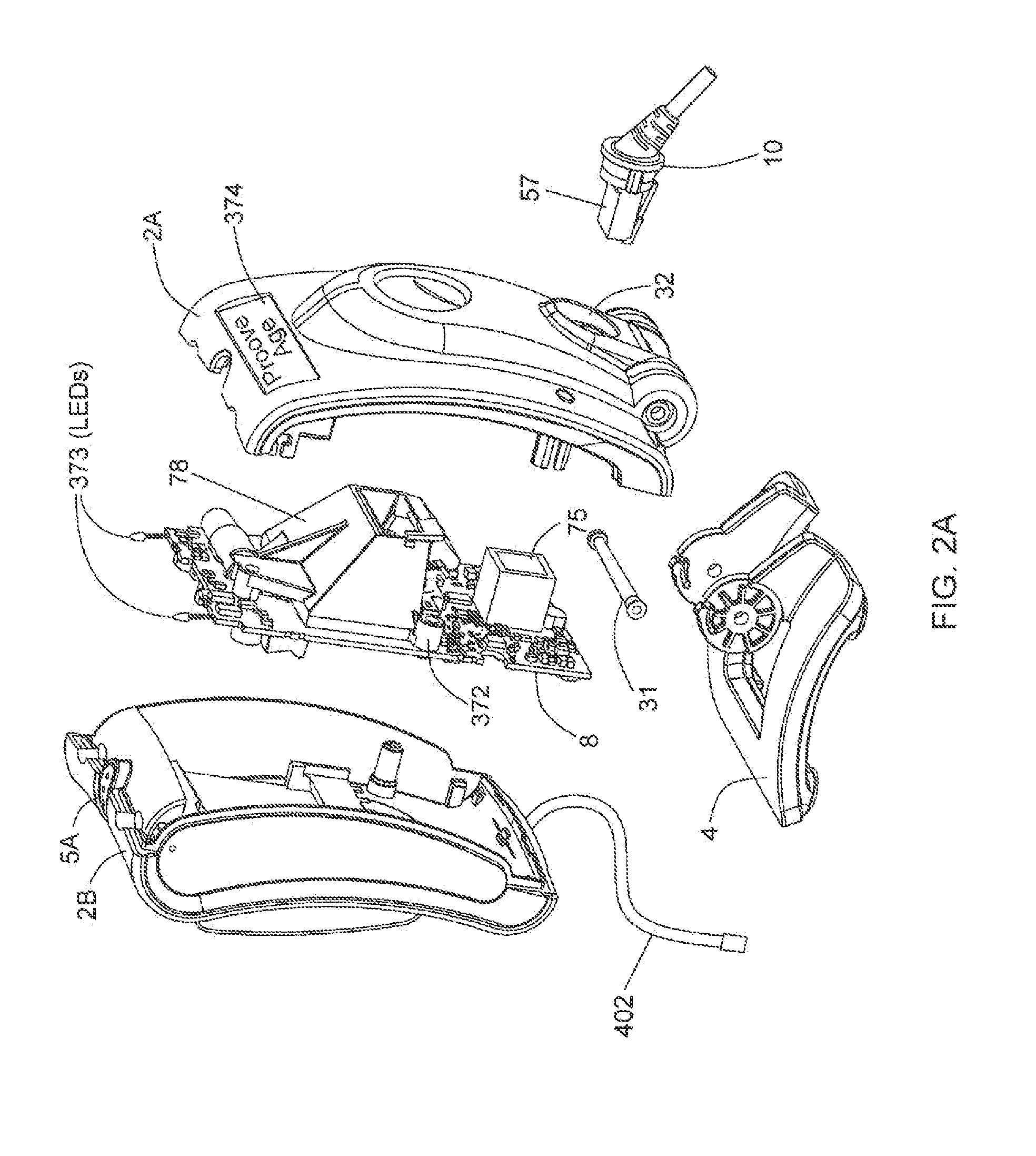
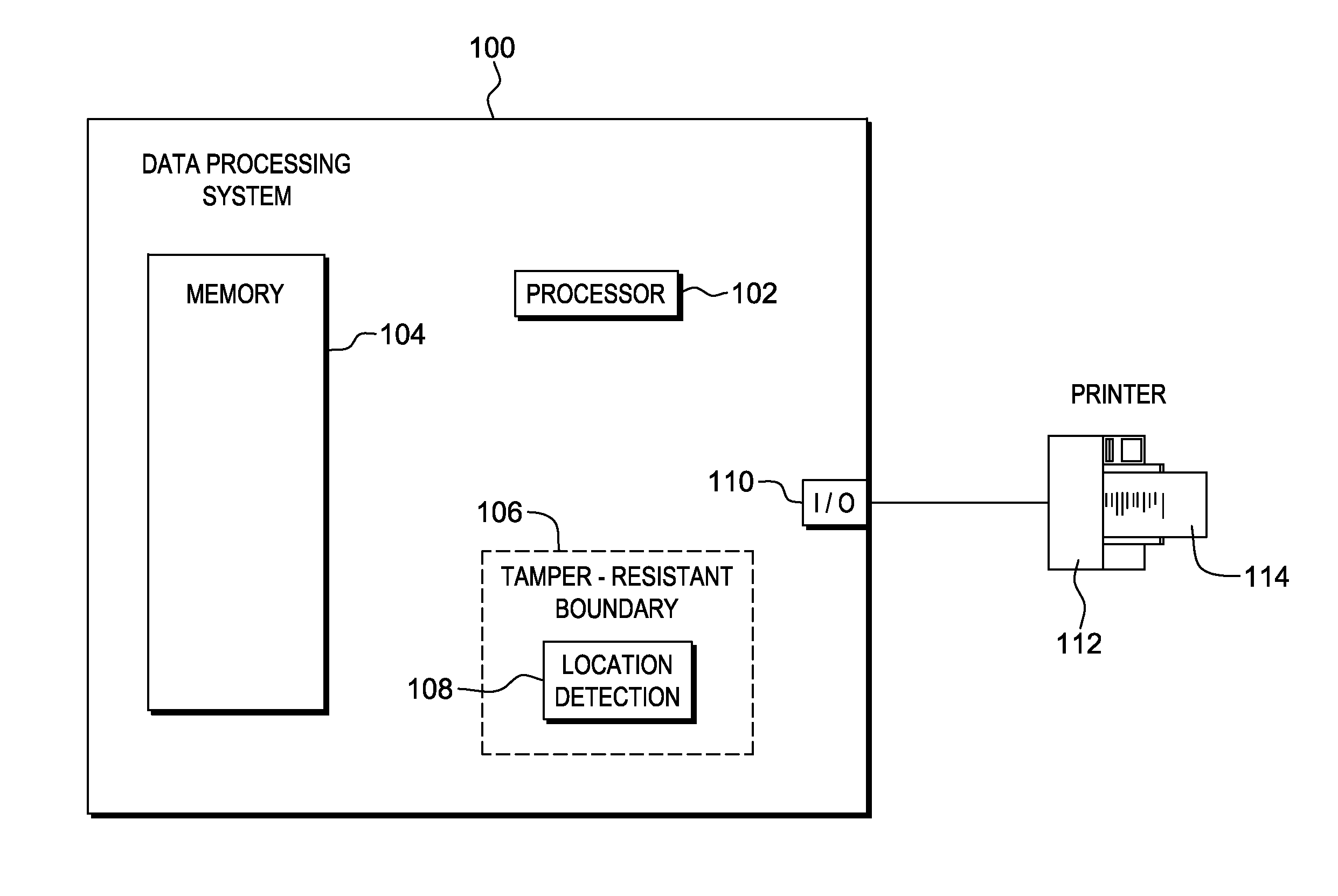
InactiveUS20140074746A1Convenient verificationOvercomes shortcomingCommerceLogisticsData terminalTamper resistance
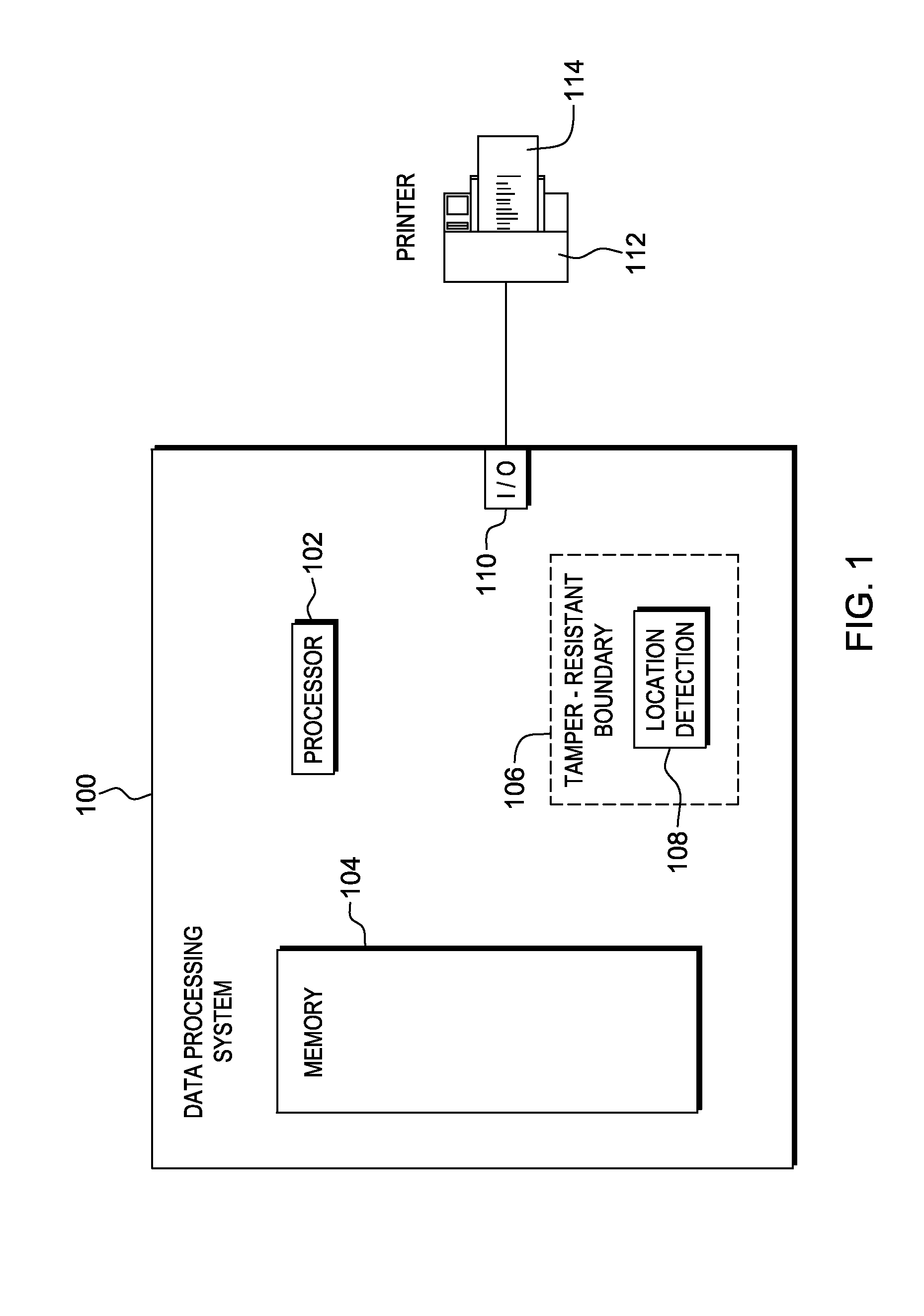
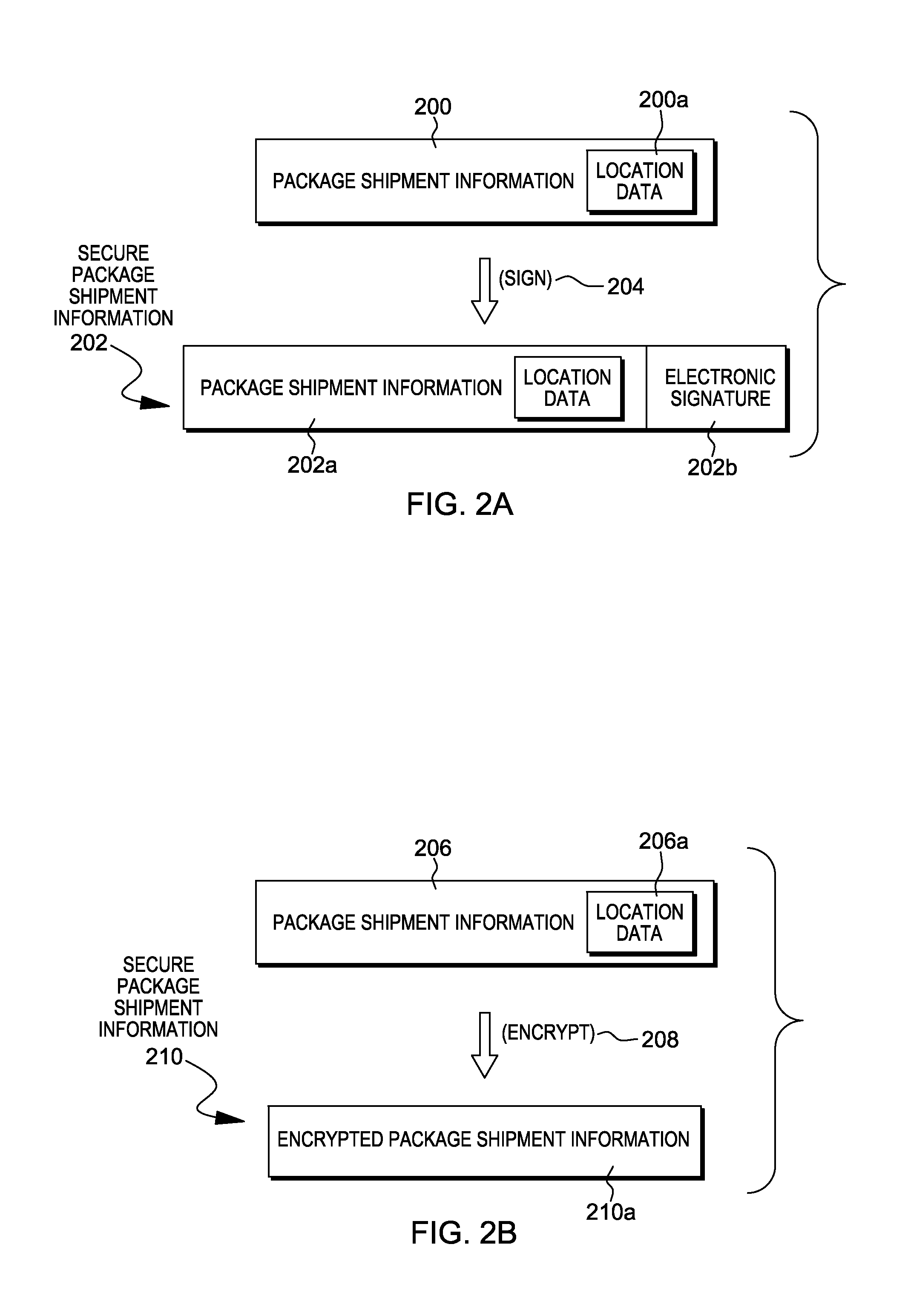
Verification of a source of a package is facilitated. A data terminal certified by an authority obtains location data from a location detection component. The location data indicates a source location from which the package is to be shipped, and is detected by the location detection component at the source location. Secure package shipment information, including the location data, is provided with the package to securely convey the detected source location to facilitate verifying the source of the package. The data terminal can be a portable data terminal certified by the authority and have a tamper-proof boundary behind which resides the location detection component and one or more keys for securing the package shipment information. Upon tampering with the tamper-resistant boundary, the certification of the portable data terminal can be nullified.
Owner:HAND HELD PRODS
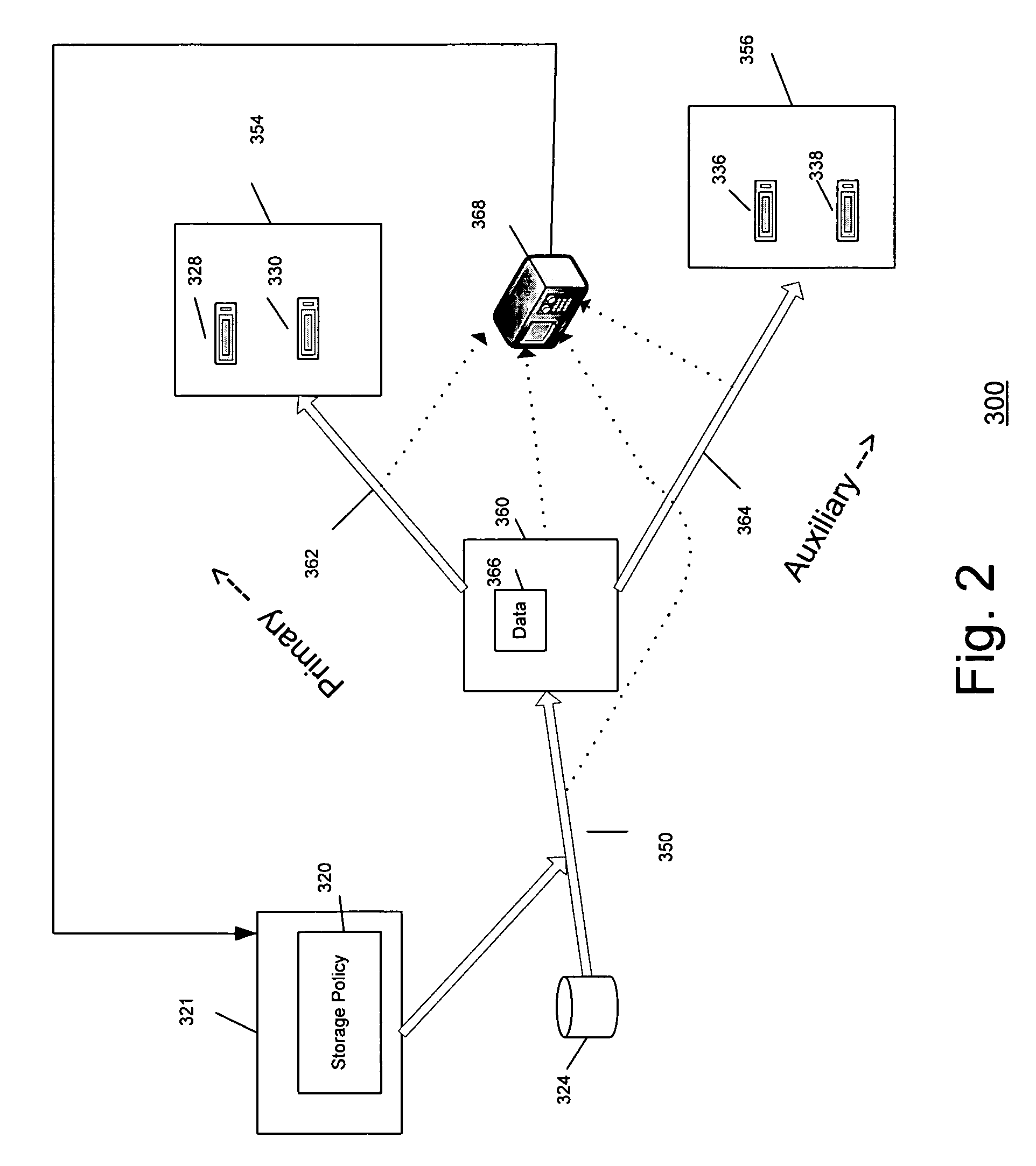
System and method for performing auxiliary storage operations
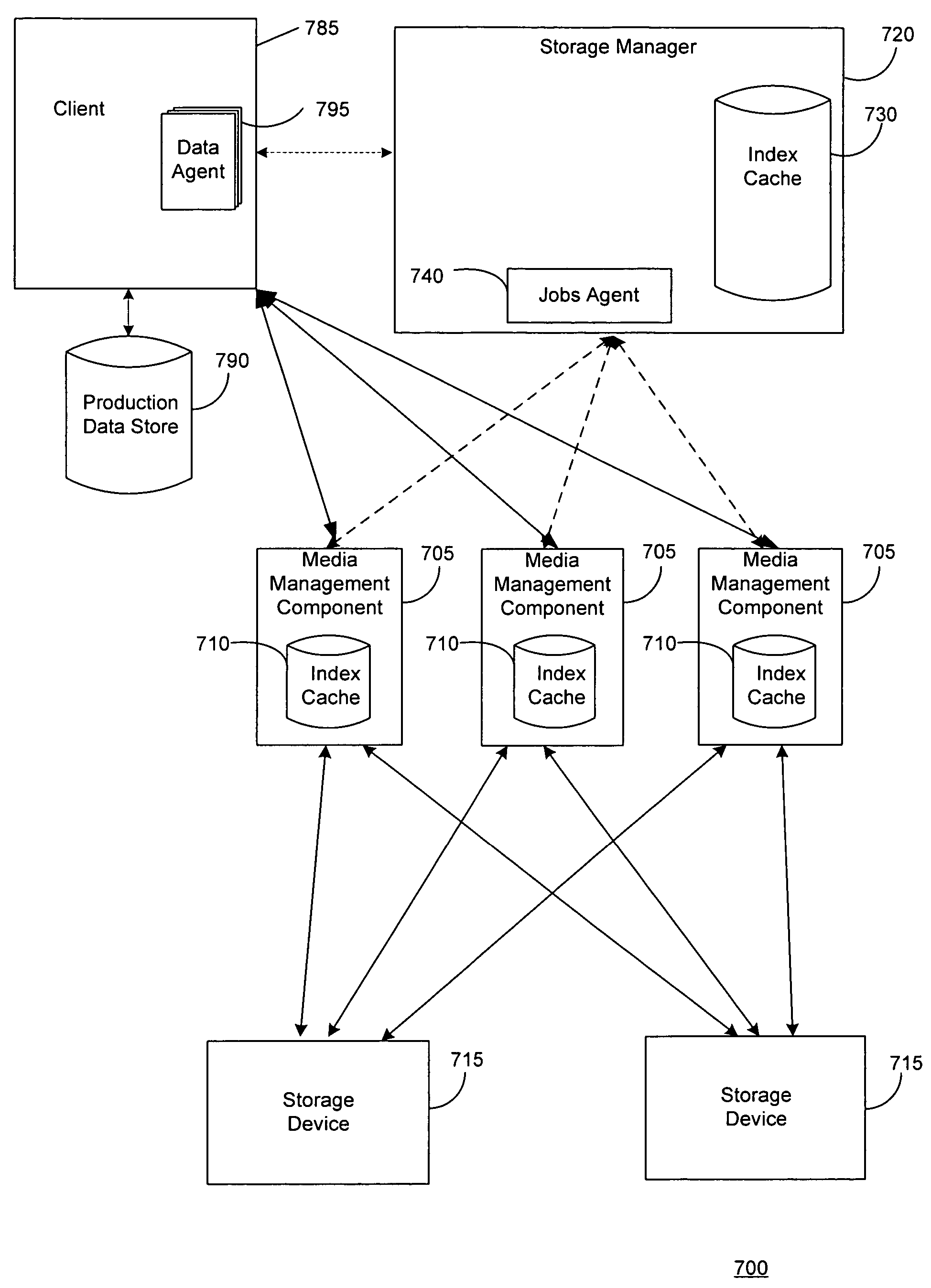
Systems and methods for protecting data in a tiered storage system are provided. The storage system comprises a management server, a media management component connected to the management server, a plurality of storage media connected to the media management component, and a data source connected to the media management component. Source data is copied from a source to a buffer to produce intermediate data. The intermediate data is copied to both a first and second medium to produce a primary and auxiliary copy, respectively. An auxiliary copy may be made from another auxiliary copy. An auxiliary copy may also be made from a primary copy right before the primary copy is pruned.
Owner:COMMVAULT SYST INC
Peer-to-Peer Redundant File Server System and Methods
InactiveUS20090271412A1Digital data information retrievalMultiple digital computer combinationsHash functionFile system
Peer-to-peer redundant file server system and methods include clients that determine a target storage provider to contact for a particular storage transaction based on a pathname provided by the filesystem and a predetermined scheme such as a hash function applied to a portion of the pathname. Servers use the same scheme to determine where to store relevant file information so that the clients can locate the file information. The target storage provider may store the file itself and / or may store metadata that identifies one or more other storage providers where the file is stored. A file may be replicated in multiple storage providers, and the metadata may include a list of storage providers from which the clients can select (e.g., randomly) in order to access the file.
Owner:OVERLAND STORAGE
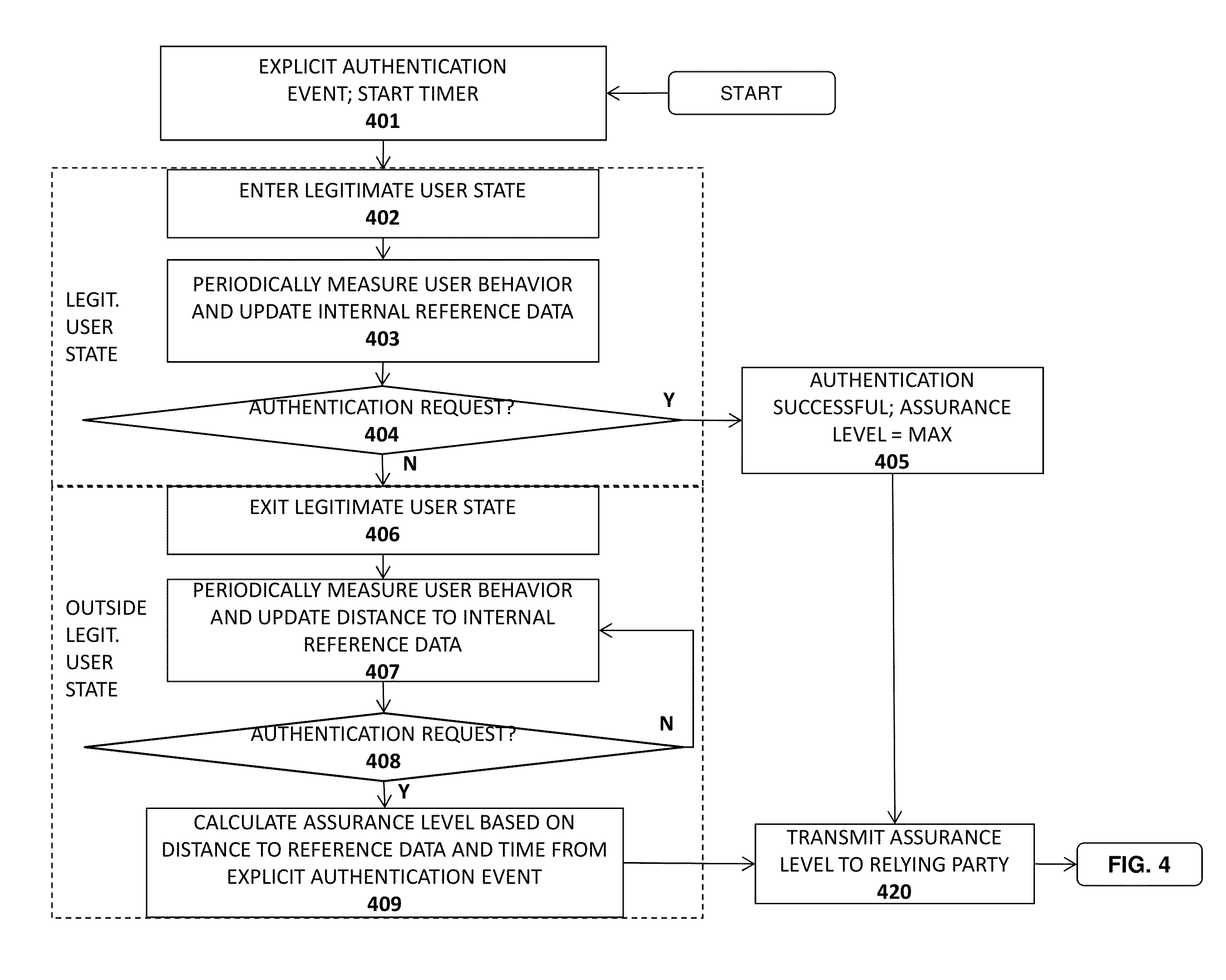
Advanced authentication techniques and applications
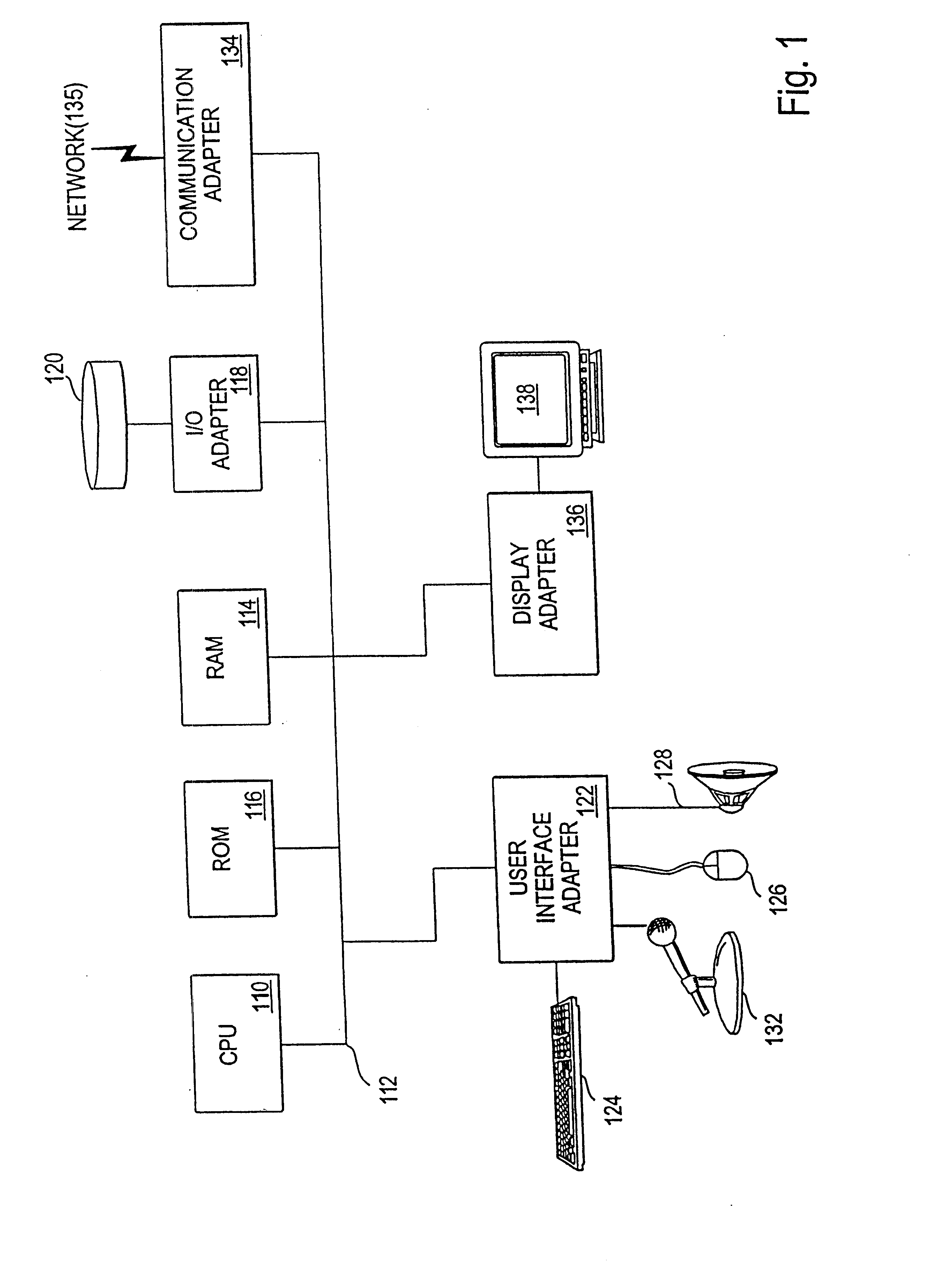
ActiveUS20140289833A1Digital data processing detailsMultiple digital computer combinationsEngineeringDatabase
A system, apparatus, method, and machine readable medium are described for performing advanced authentication techniques and associated applications. For example, one embodiment of a method comprises: receiving a policy identifying a set of acceptable authentication capabilities; determining a set of client authentication capabilities; and filtering the set of acceptable authentication capabilities based on the determined set of client authentication capabilities to arrive at a filtered set of one or more authentication capabilities for authenticating a user of the client.
Owner:NOK NOK LABS
Self-described stream in a communication services patterns environment
InactiveUS6477580B1Interprogram communicationMultiple digital computer combinationsCommunications systemDatabase
A system, method, and article of manufacture are described for providing a self-describing stream-based communication system. Messages are sent which include data between a sending system and a receiving system. Meta-data is attached to the messages being sent between the sending system and the receiving system. The data of the messages sent from the sending system to the receiving system is translated based on the meta-data. The meta-data includes first and second sections. The first section identifies a type of object associated with the data and a number of attribute descriptors in the data. The second section includes a series of the attribute descriptors defining elements of the data.
Owner:ACCENTURE GLOBAL SERVICES LTD
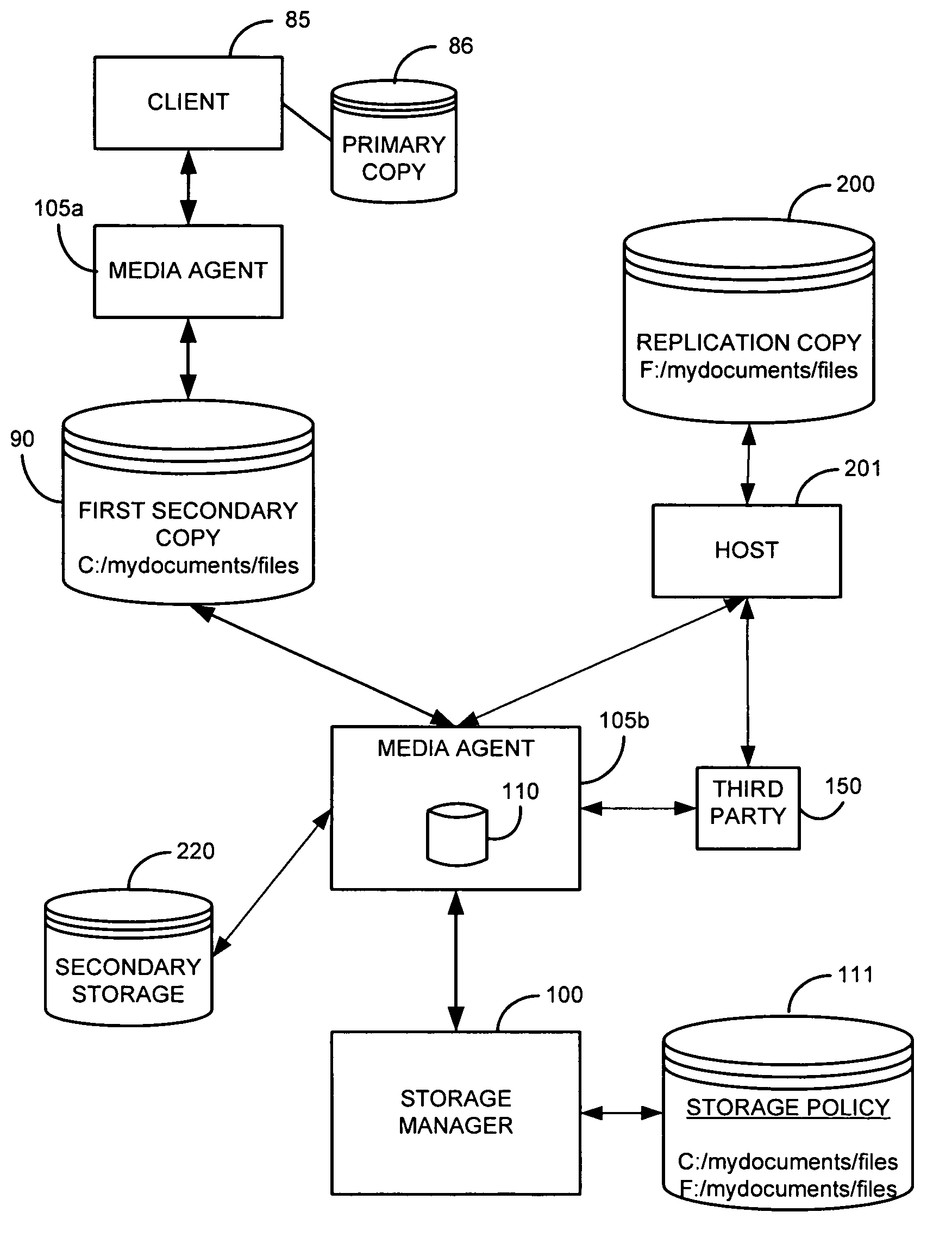
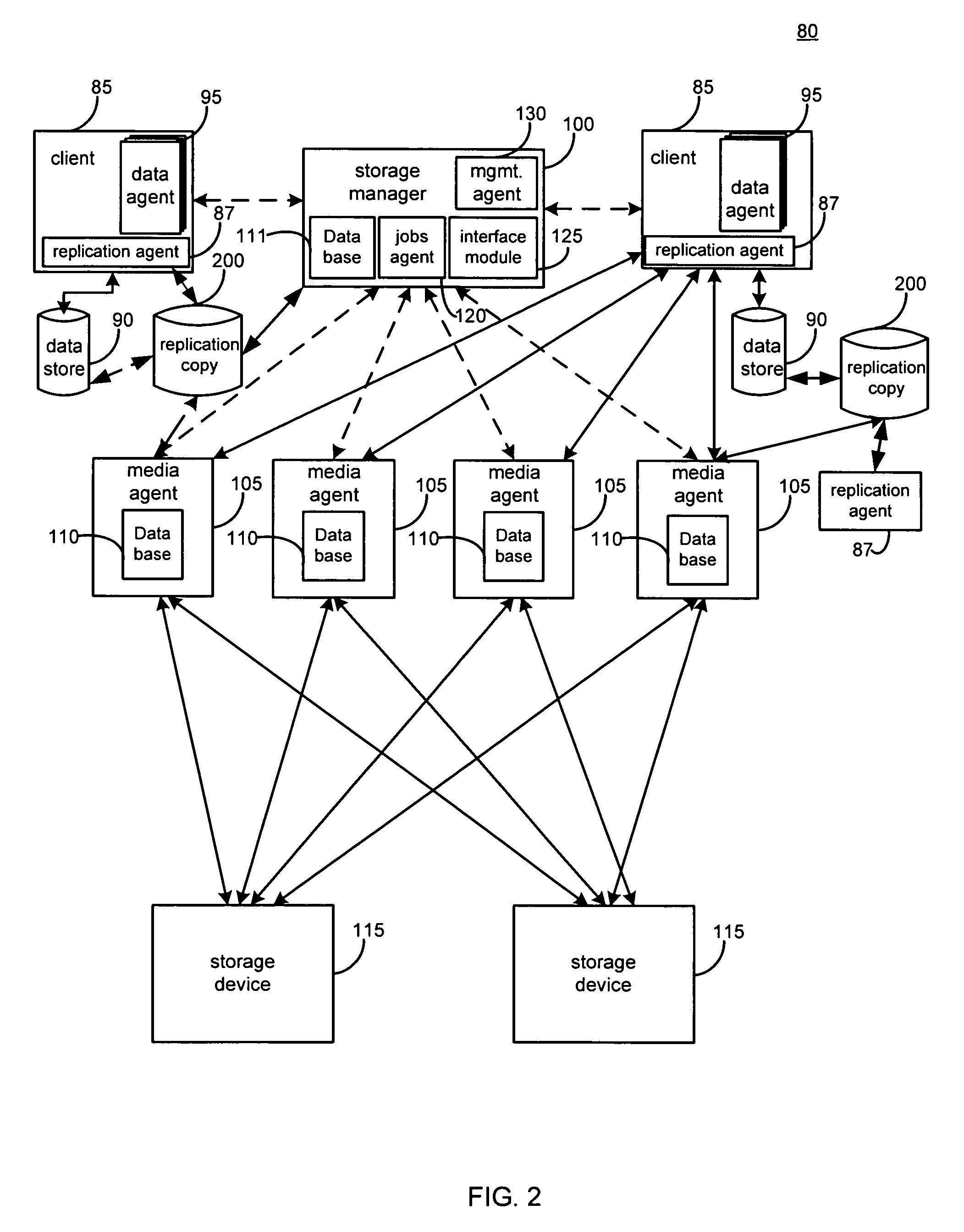
System and method for performing replication copy storage operations
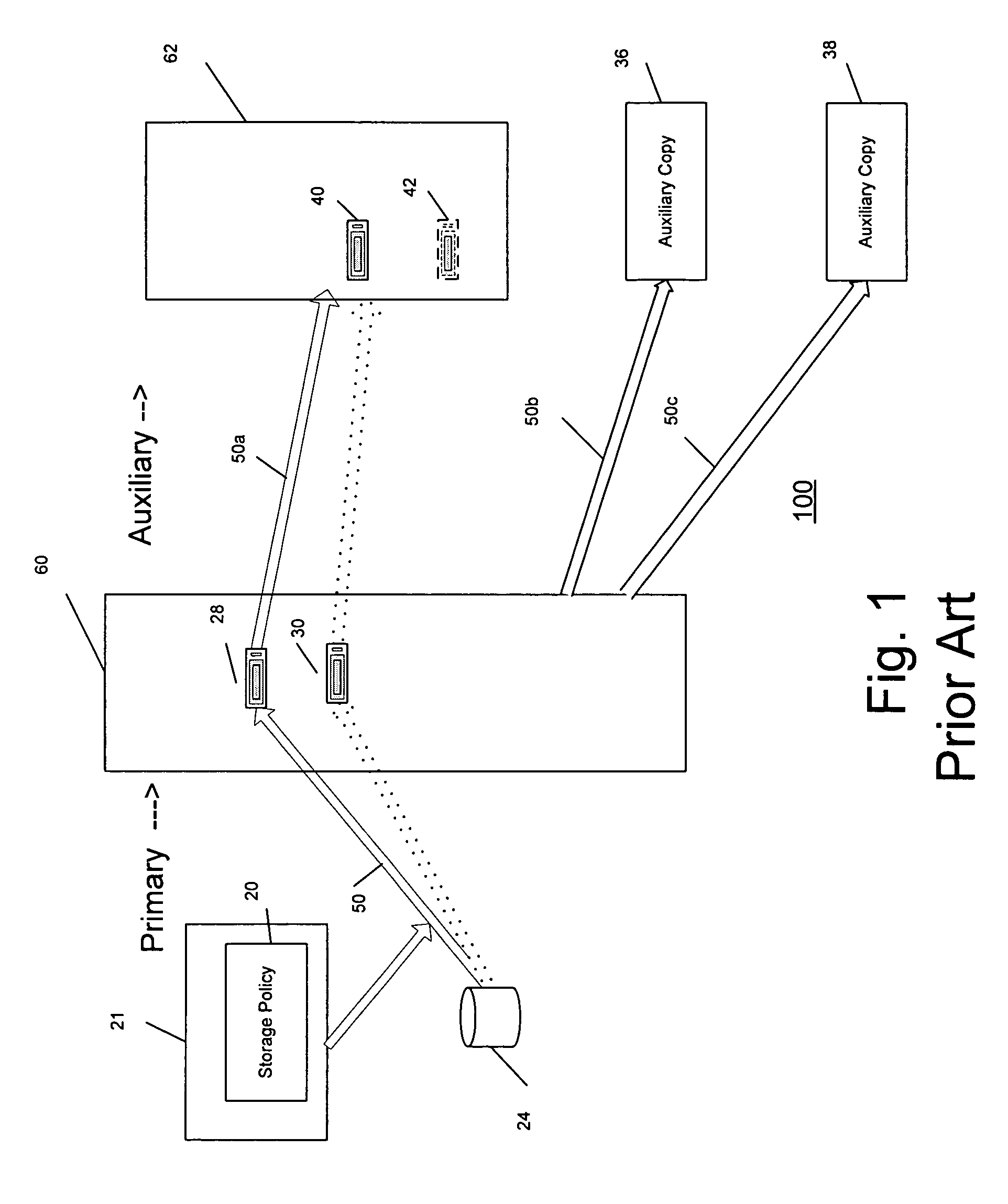
InactiveUS7606844B2Data processing applicationsDatabase distribution/replicationThird partyEngineering
A system and method are provided for performing storage operations relating to a first secondary copy of electronic data. A storage policy or storage preferences may dictate that a replication copy should be used in storage operations performed to a particular client, sub-client, data, media or other item. Based on the storage policy, when a new client, sub-client, data, media or other item is received, a media agent determines whether there is a replication copy of the item. In the absence of a replication copy, one may be created. The replication copy may be provided by a third party application, or created by the client or a storage management system component. Information regarding the replication copy and its corresponding first secondary copy may be stored in a database. To optimize use of system resources, storage operations relating to the first secondary copy may be performed using the replication copy instead of the first secondary copy.
Owner:COMMVAULT SYST INC
Graphical user interface for 3-dimensional view of a data collection based on an attribute of the data
A three-dimensional (3D) view of a data collection based on an attribute is disclosed. A timeline is provided for displaying files and folders. The timeline may include a focal group that displays detailed information about its contents to the user. Remaining items on the timeline are displayed in less detail and may be positioned to appear further away from the user. A histogram may be provided as part of the view to allow the user to more easily navigate the timeline to find a desired file or folder.
Owner:MICROSOFT TECH LICENSING LLC
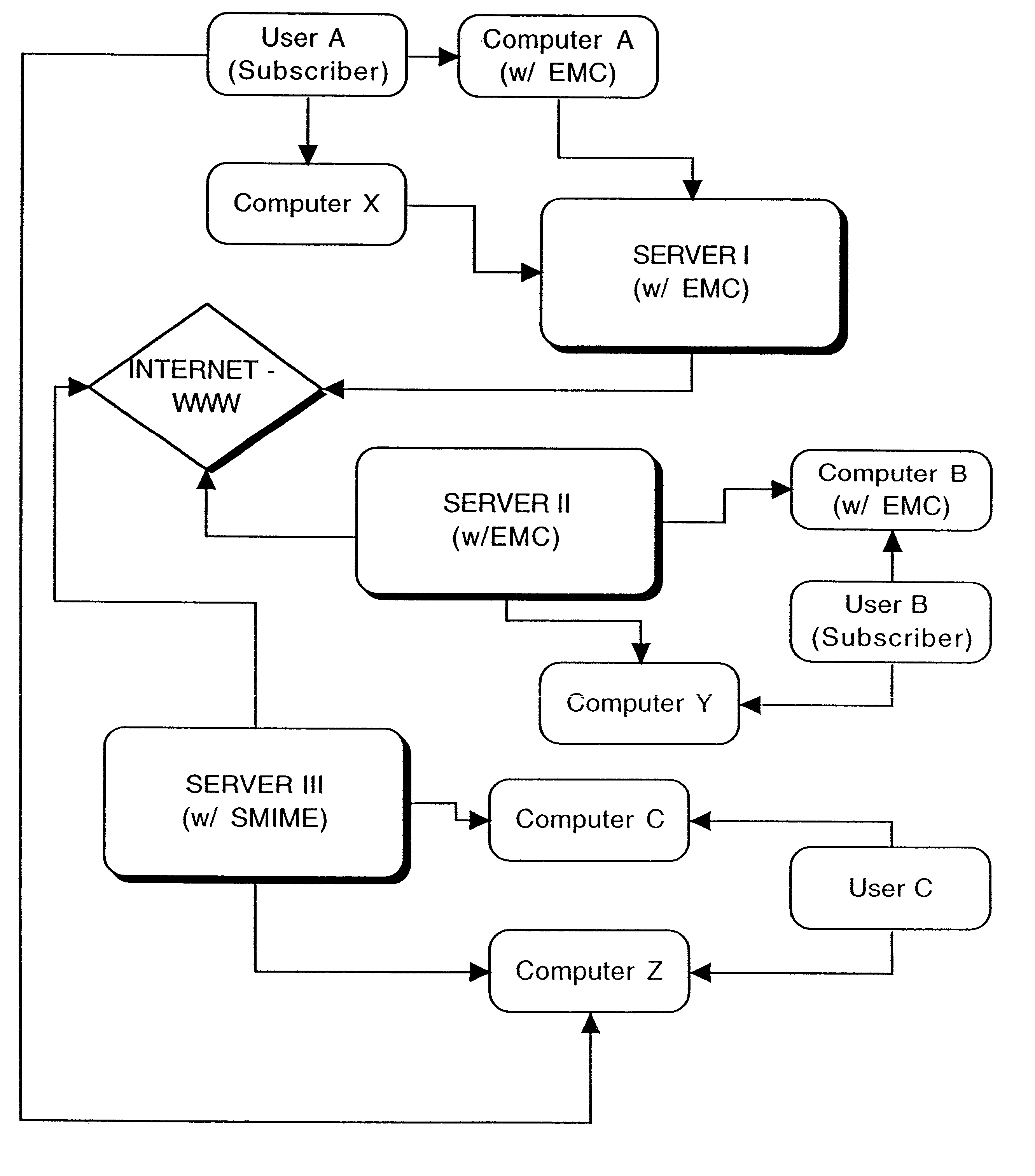
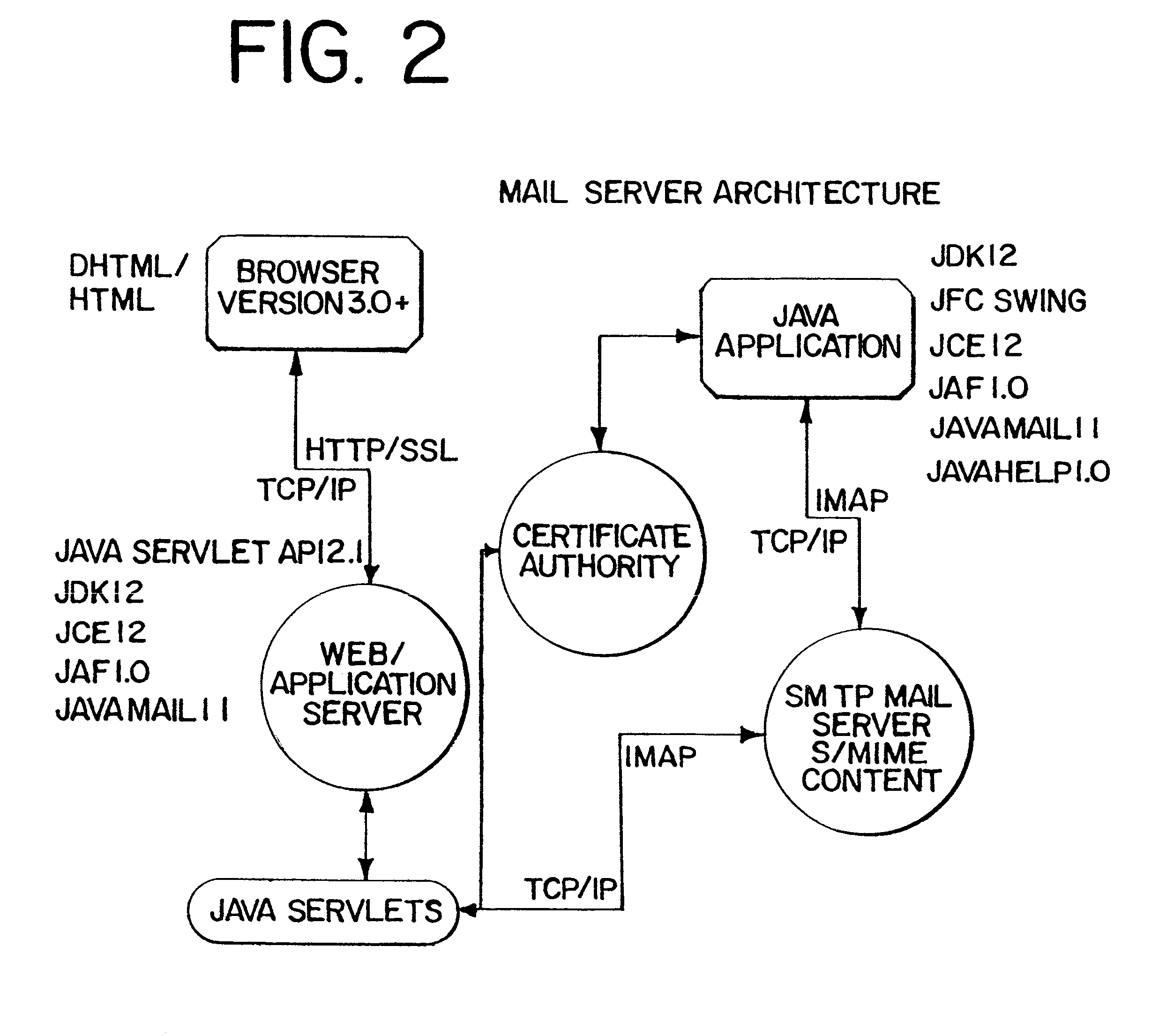
Interoperable full-featured web-based and client-side e-mail system
InactiveUS6356937B1More secure log-inMultiple digital computer combinationsOffice automationApplication softwareProprietary software
A full-featured e-mail system is used in both Internet-based and client-side (personal computer) forms. In each form, either basic e-mail service is provided to system subscribers or a secure, premium service with authentication, concealment, integrity, and non-repudiation functions for electronic messaging services is provided. In either form and at either level of service, subscribers can work off-line on their own computers with proprietary software loaded or, alternatively, on-line on any computer with an Internet connection. The system is interoperable, to preserve security, with all S / MIME compliant software applications, even for those users not subscribing to a service implementing the disclosed system. Digital certificates can be provided as a security service of the disclosed system, rather than requiring a second source with separate verification procedures. As additional optional features, the subscriber can control compression of outgoing attachment files, rather than having that function absent or operate in some automatic way. Decompression of such file attachments when received occurs automatically for subscribers, without having to invoke a different program or system. Interactive help features, book hierarchy uniformity for messages, accounts, certificates, virus warnings, and dual naming capability are also provided and available to subscribers in both the Web-based and the client-side application forms disclosed herein, and in both basic and premium service levels.
Owner:MEC MANAGEMENT LLC
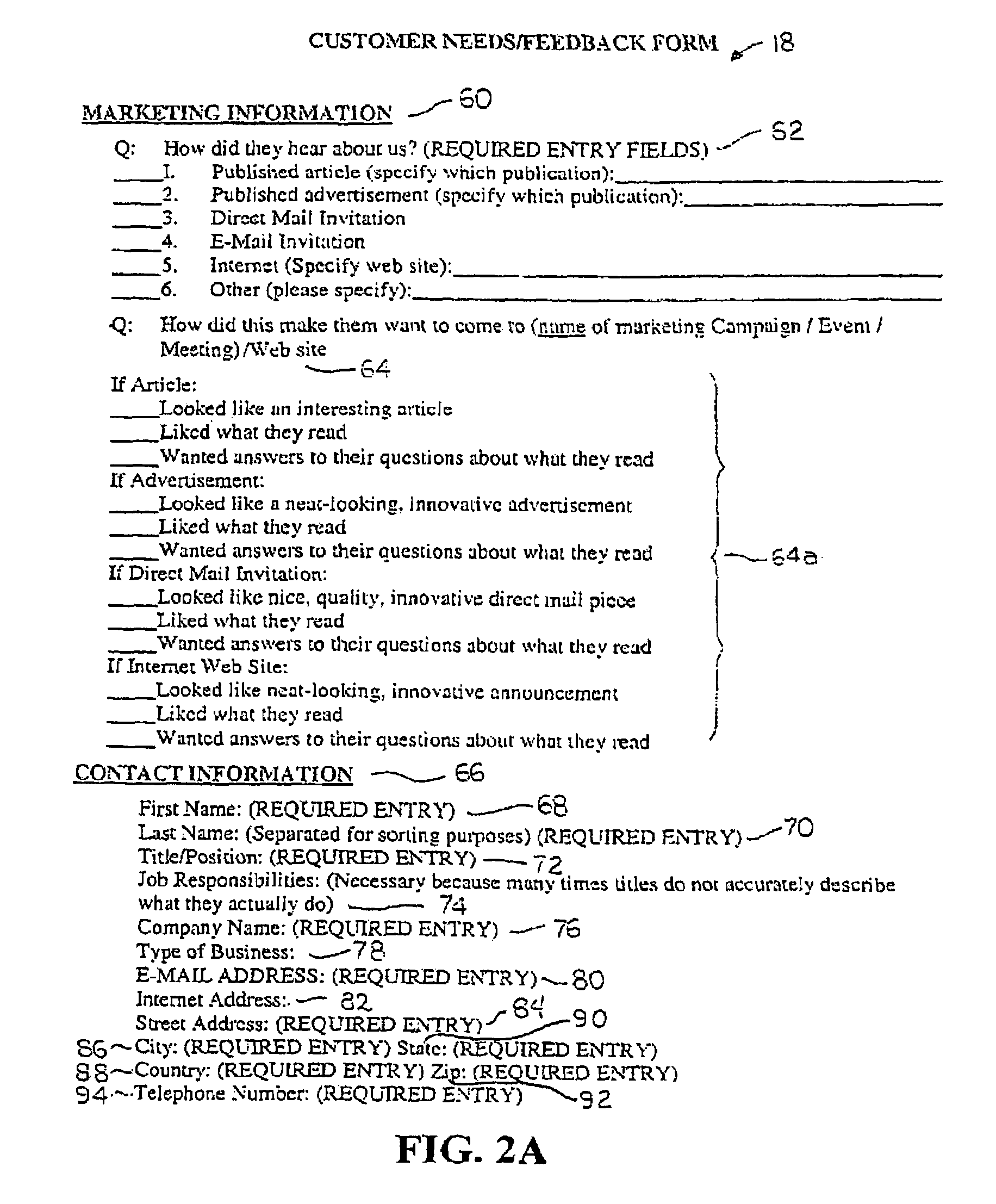
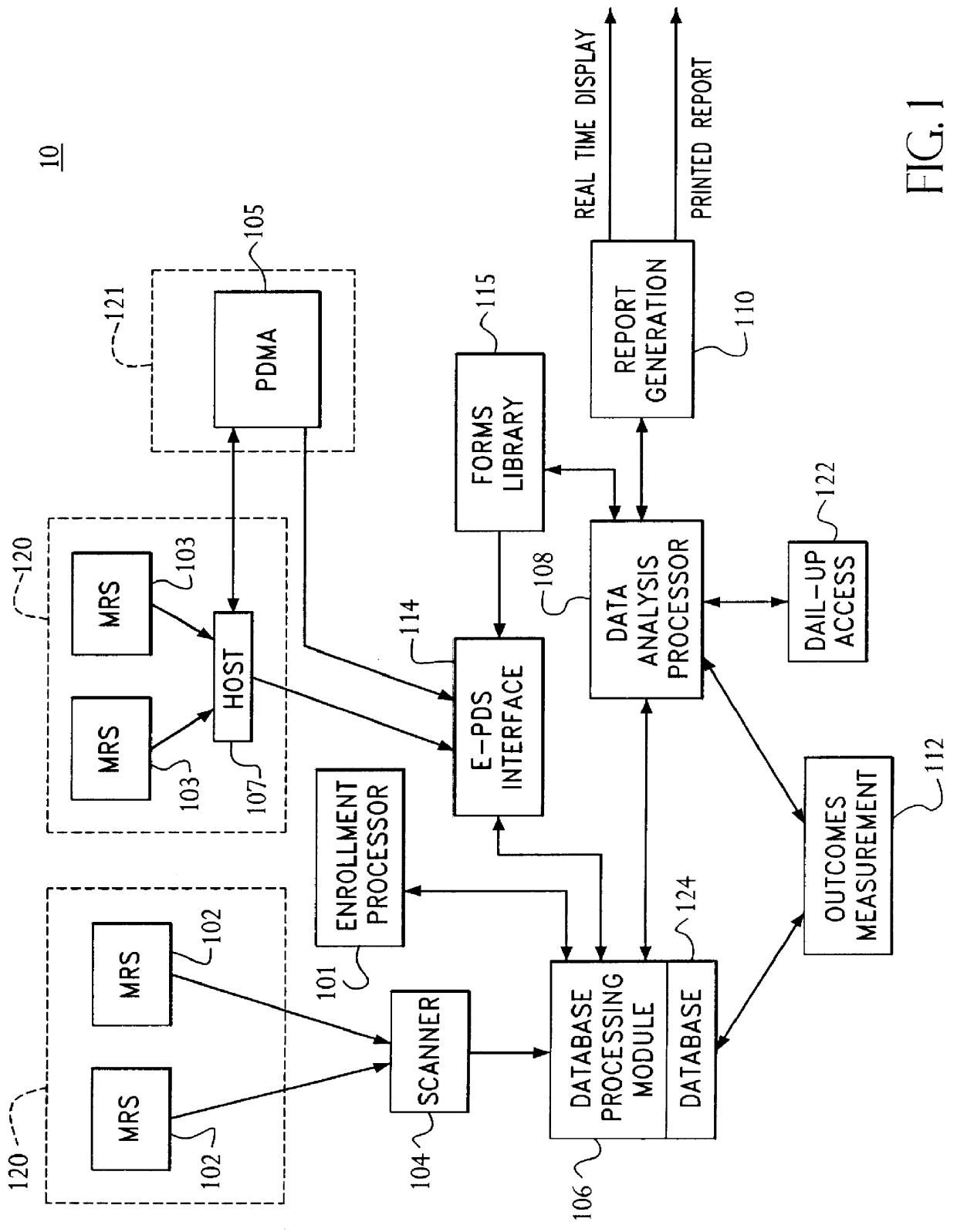
System for and method of collecting and populating a database with physician/patient data for processing to improve practice quality and healthcare delivery
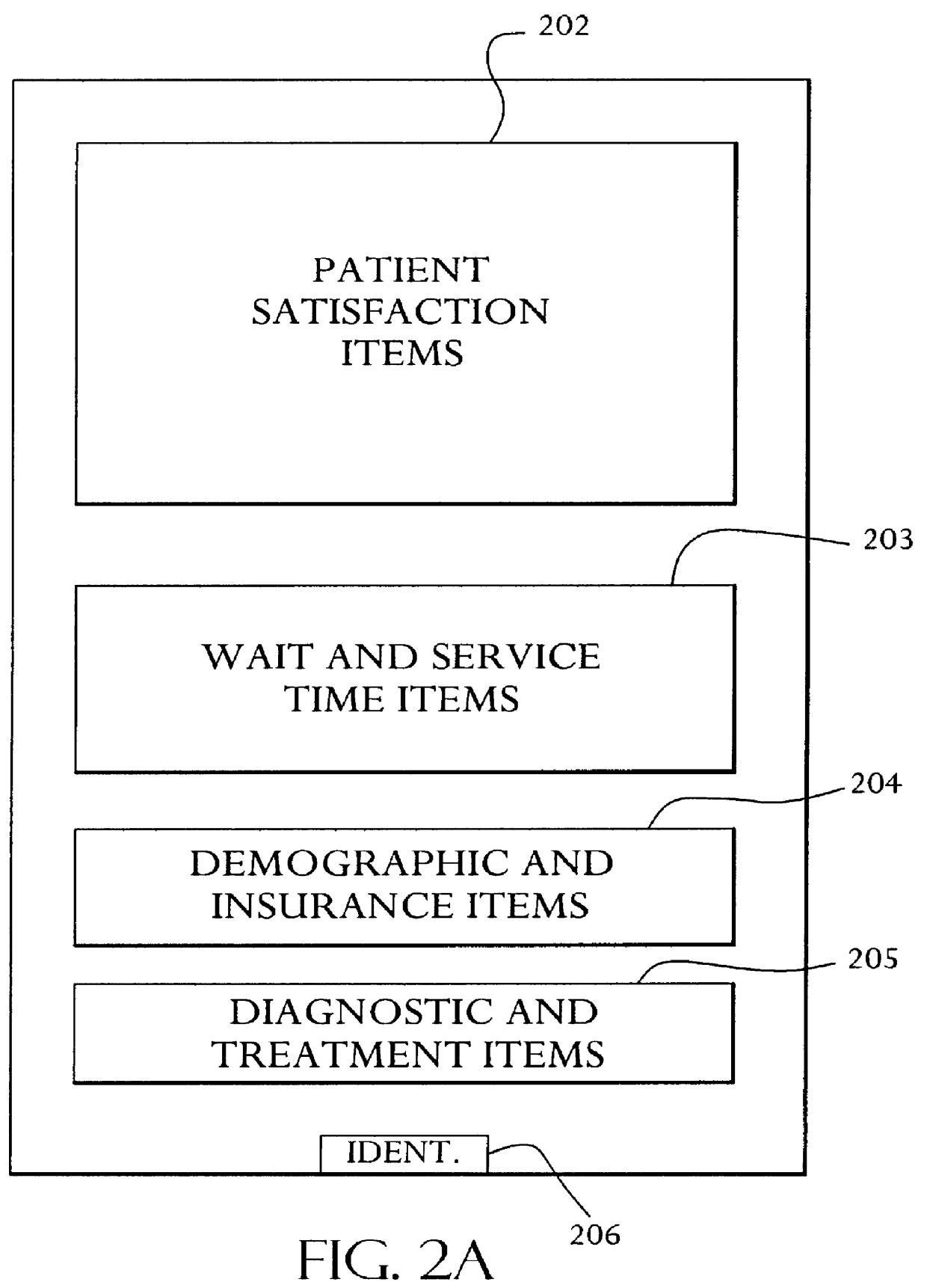
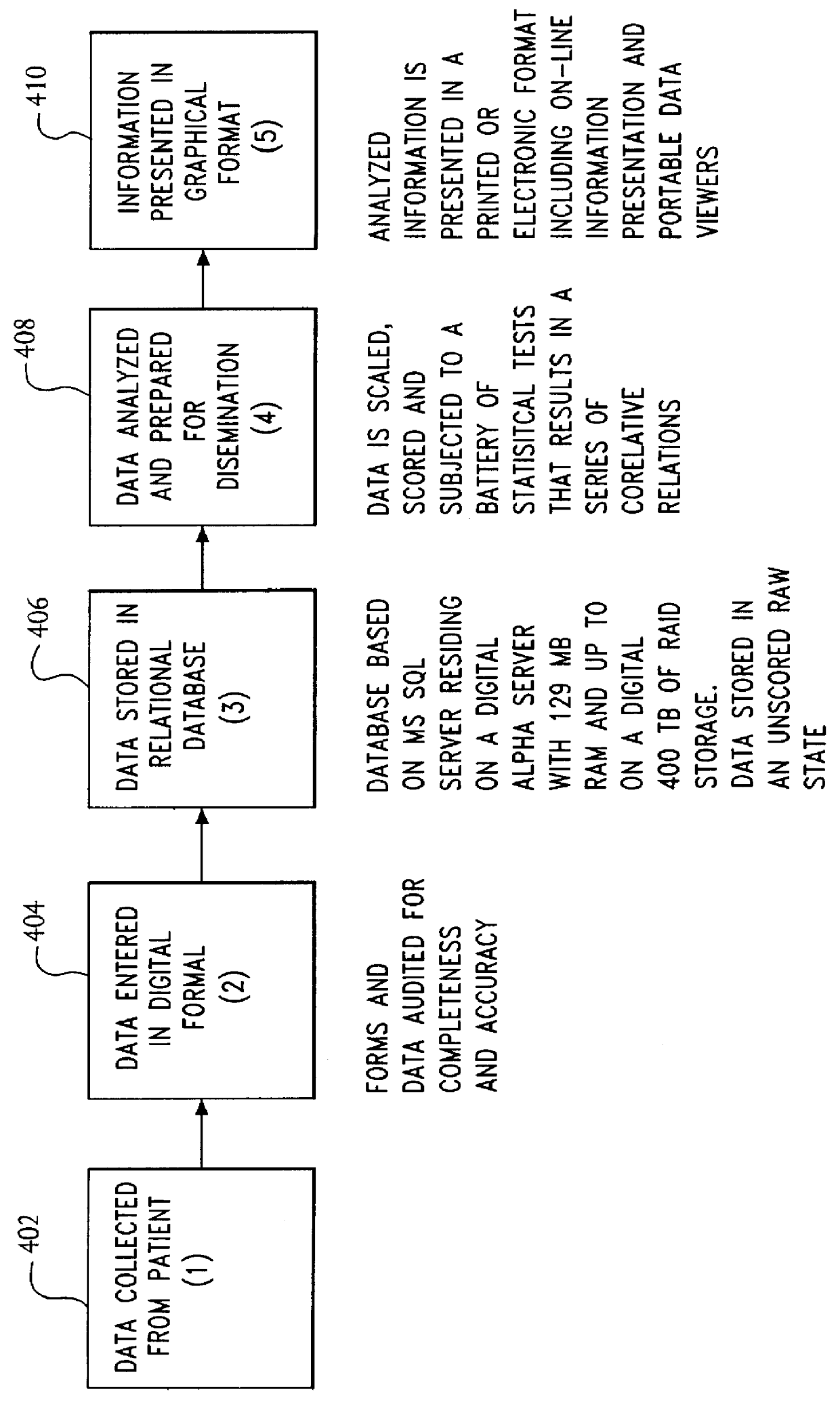
A system and method relates to the field of building and administrating a patient management and health care management database containing data relevant to the clinical care of patients, to the management of the practices to which the patients belong, and to outcomes of that health care and practice management. The disclosed system encompasses (i) designing and administering paper and pen and hand held computer survey instruments; (ii) administering and collecting completed surveys (iii) building and managing a database of information collected from the surveys; (iv) analyzing data collected from the surveys; (v) and providing clinical practices with summary information. Summary information may be used to improve patient care, health outcomes, and the management of physician practices.
Owner:PULSEGROUP
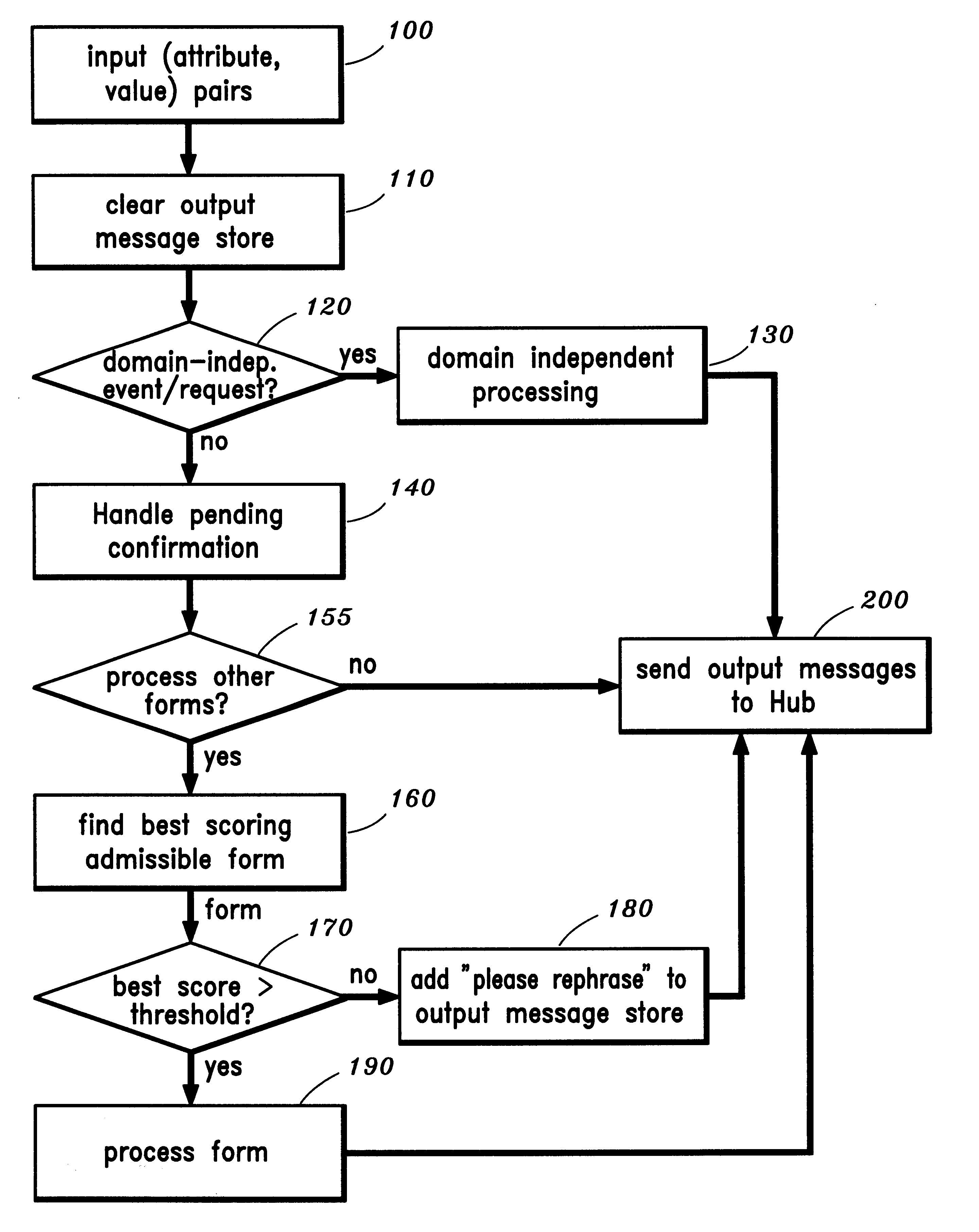
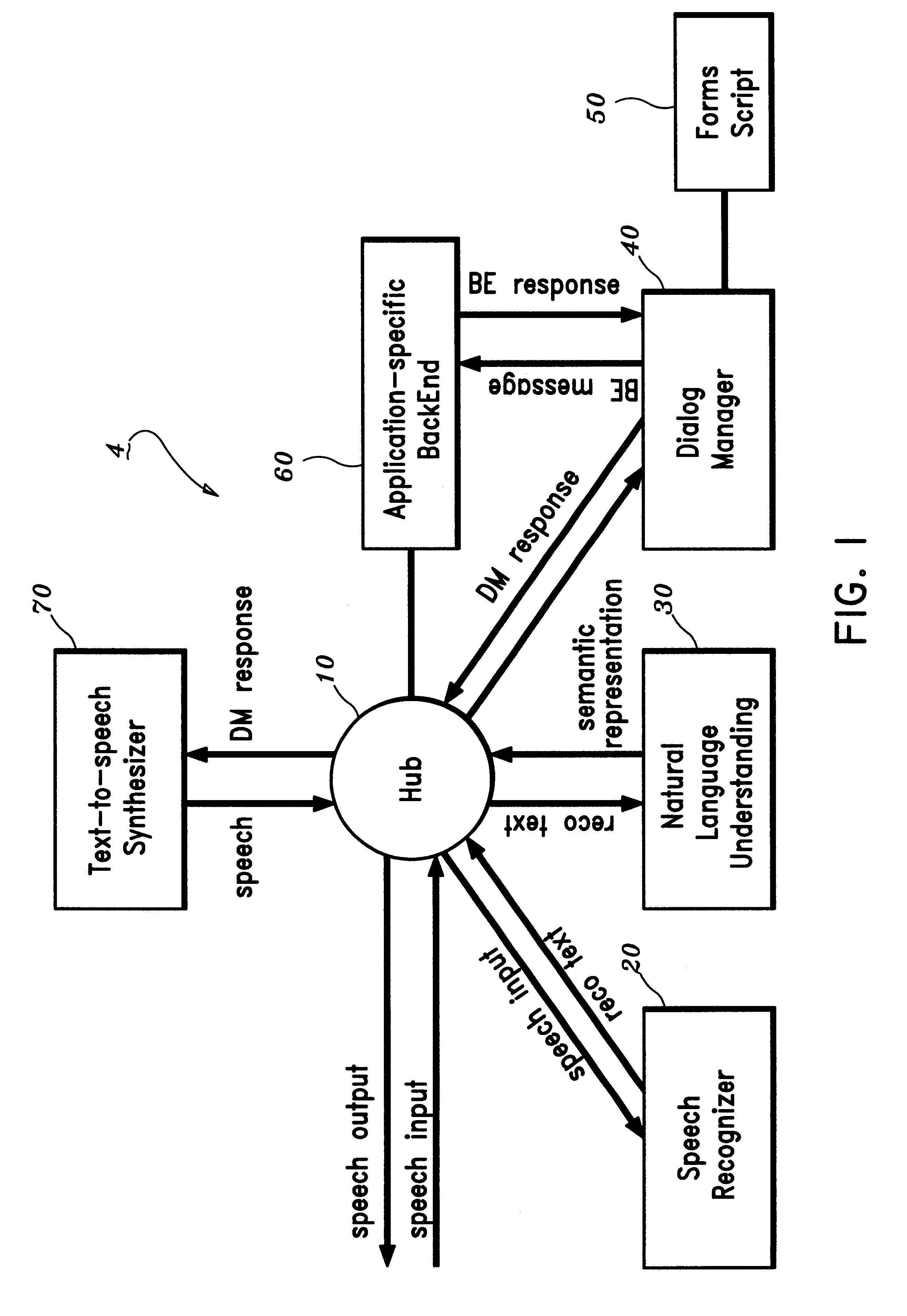
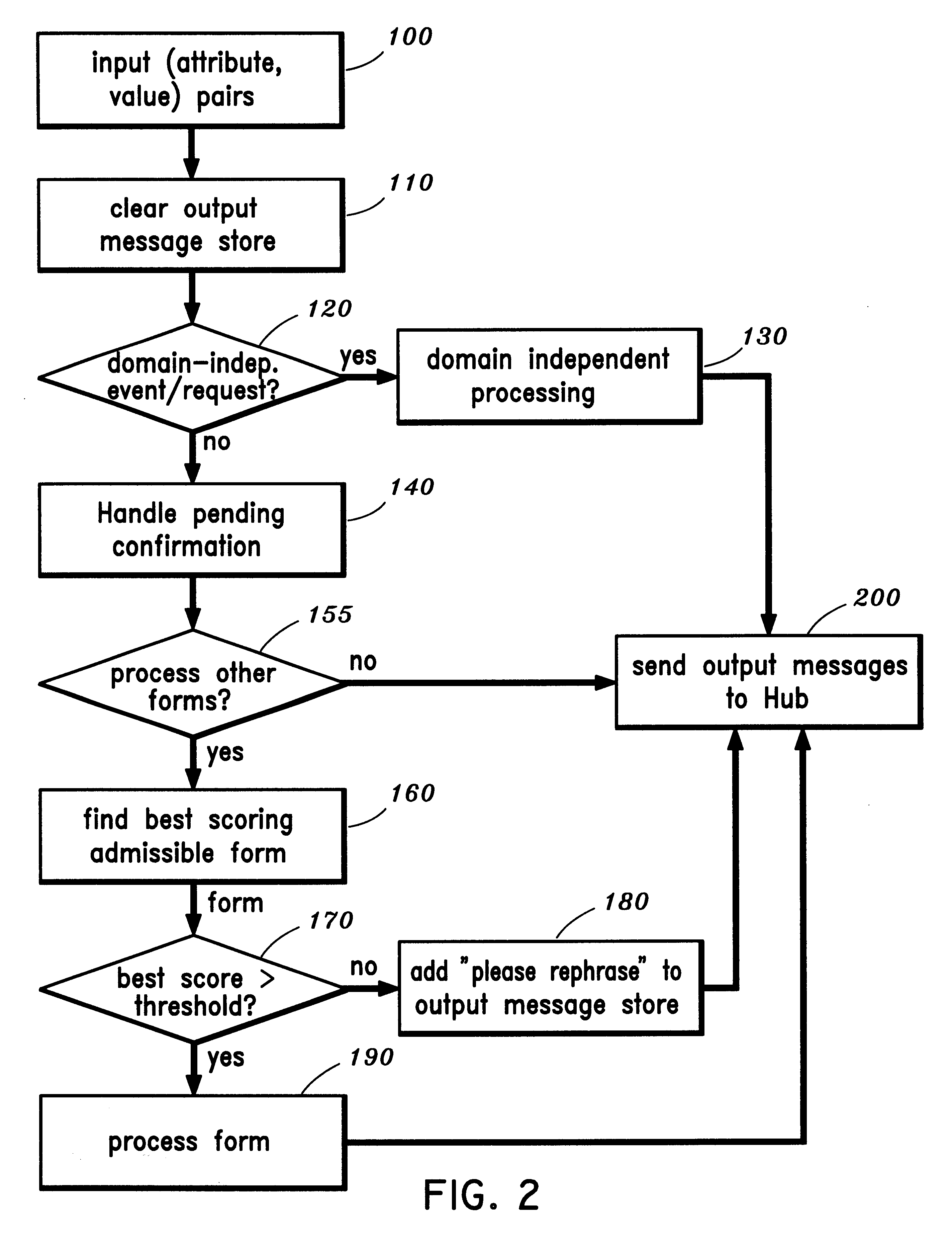
Natural language task-oriented dialog manager and method
A system for conversant interaction includes a recognizer for receiving and processing input information and outputting a recognized representation of the input information. A dialog manager is coupled to the recognizer for receiving the recognized representation of the input information, the dialog manager having task-oriented forms for associating user input information therewith, the dialog manager being capable of selecting an applicable form from the task-oriented forms responsive to the input information by scoring the forms relative to each other. A synthesizer is employed for converting a response generated by the dialog manager to output the response. A program storage device and method are also provided.
Owner:NUANCE COMM INC
Method of buying or selling items and a user interface to facilitate the same
InactiveUS20060069635A1Easy to useFast and efficient and intuitive and user friendlySpecial service provision for substationFinanceMarket placeFinancial transaction
A method of buying or selling items having at least one market and its associated processes are disclosed. The method includes the steps of, under control of a client system, displaying information identifying at least one item and a bid and / or ask price for the item in the market; and specifying transaction conditions based on a user directed position of a moveable icon, where the transaction conditions are related to the buying or selling of the identified item in the active market. Then, in response to an action of the user sending a user transaction request at the transaction conditions displayed at the time of said action, facilitating financial transactions for the user in accordance with the transaction conditions to complete the transaction. In this manner, the item may be bought or sold by the user at the transaction conditions specified. A user interface to facilitate this method is also disclosed. A quantity recommendation system to facilitate the quantity decision of a financial transaction is further disclosed.
Owner:RAM PRANIL
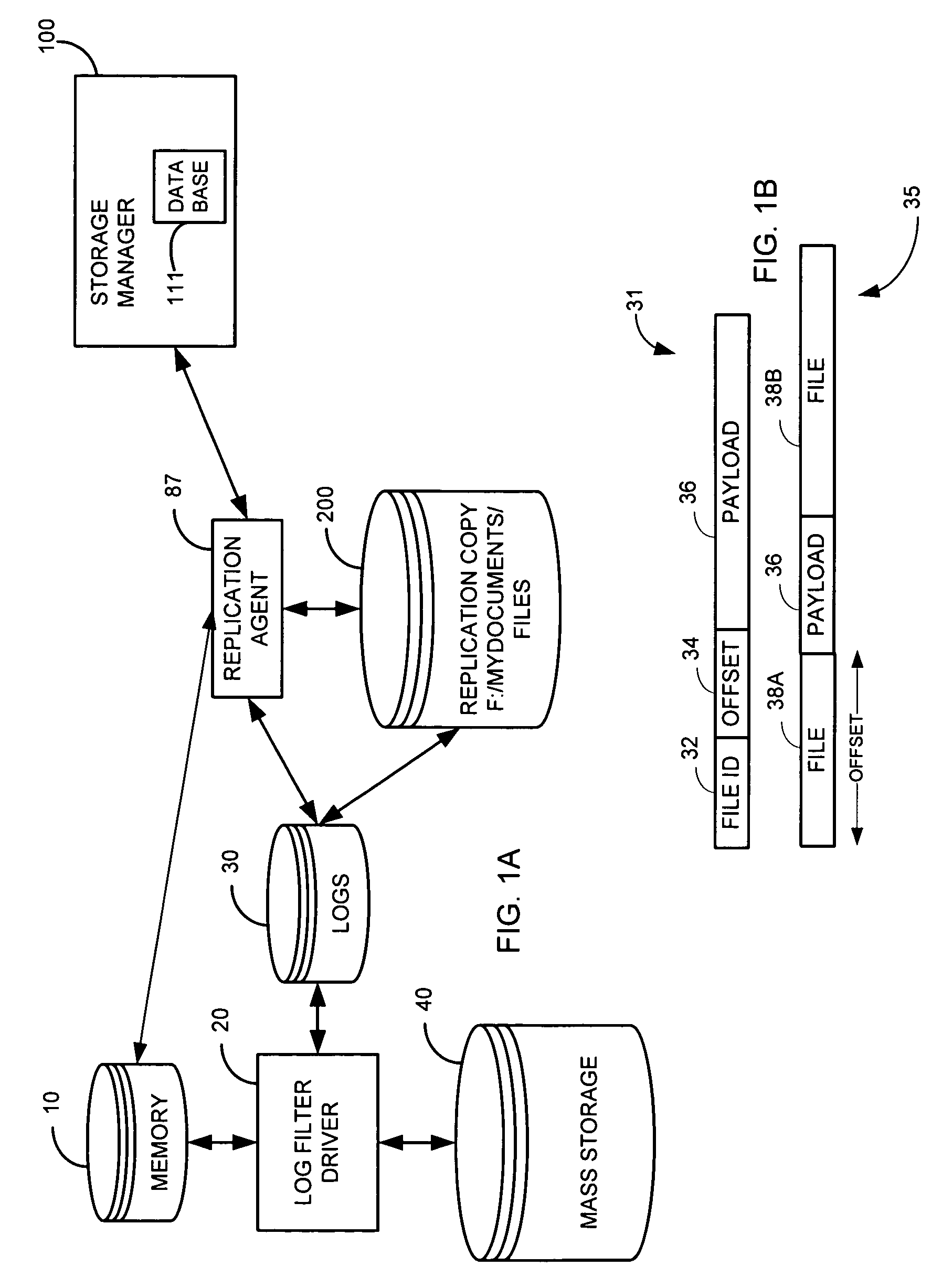
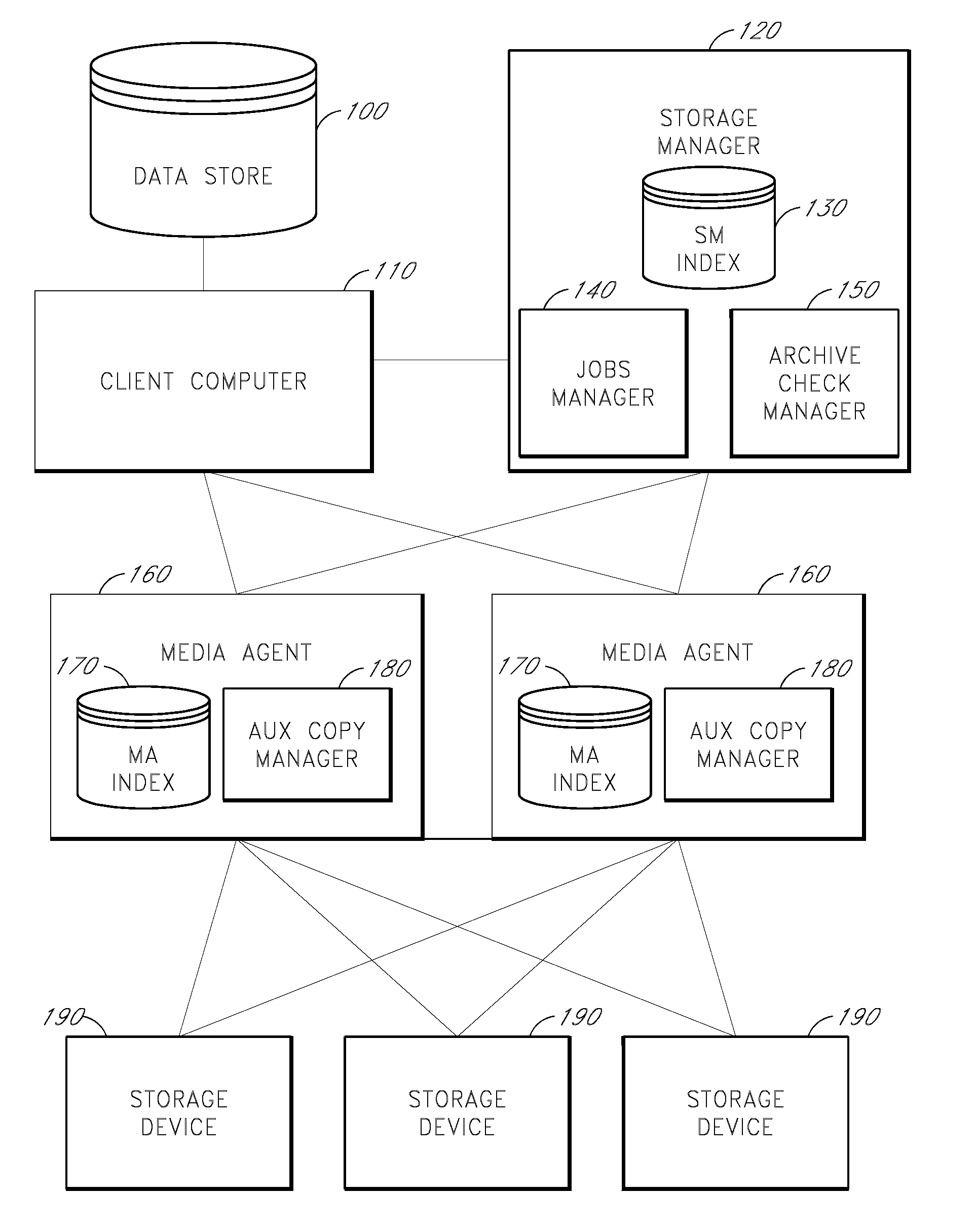
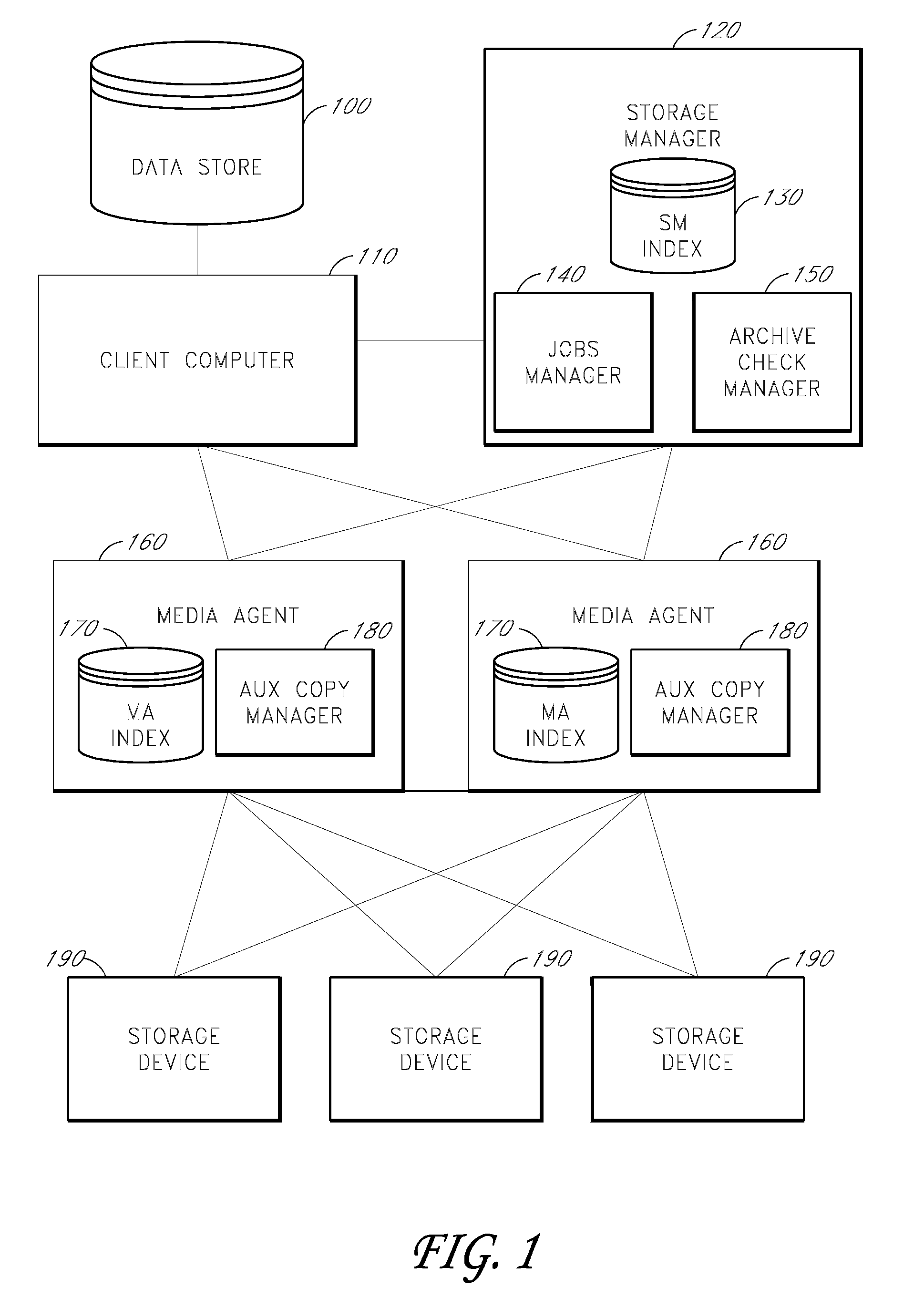
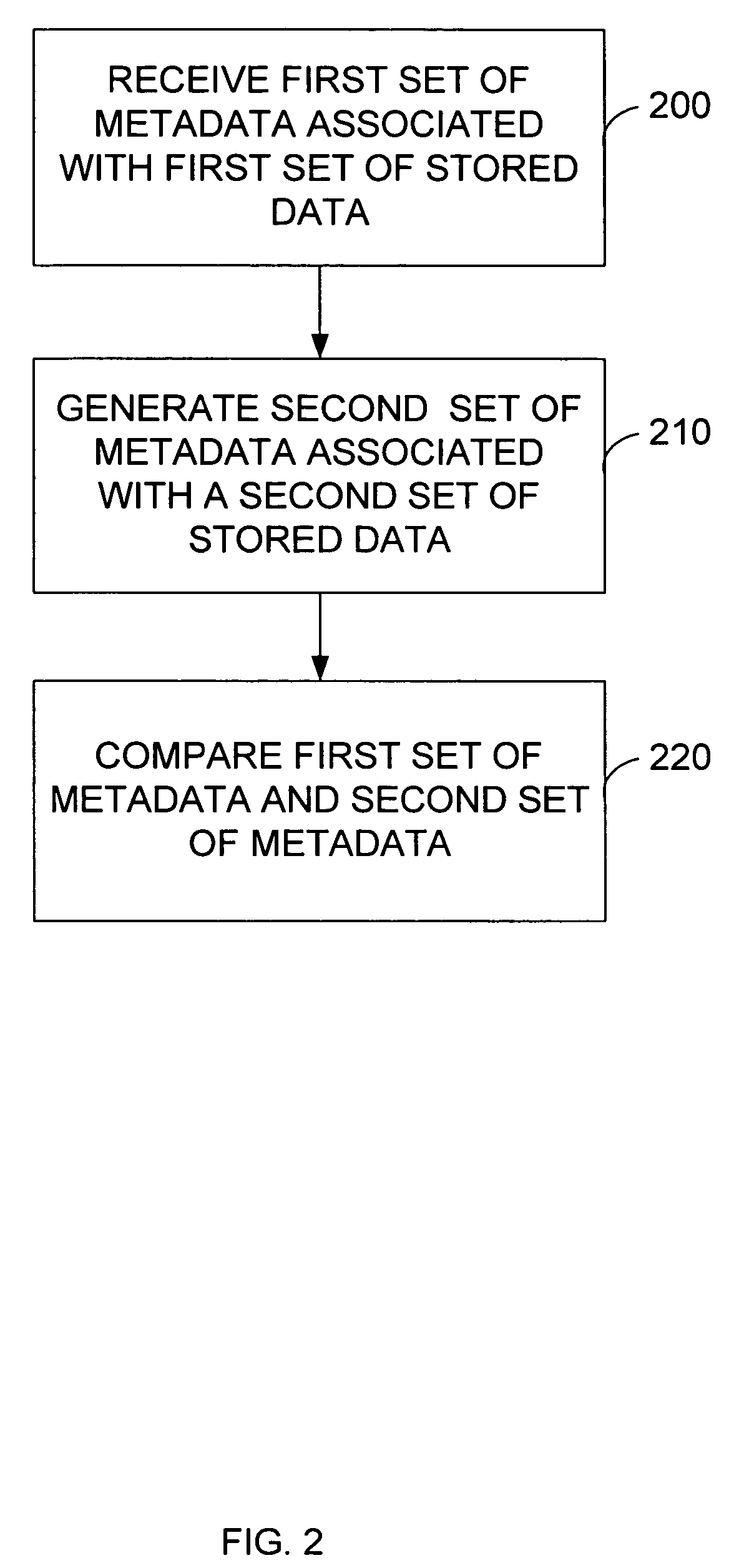
System and method for stored data archive verification
Methods and systems are described for verifying stored data by receiving a first set of metadata associated with a first set of stored data, generating a second set of metadata associated with a second set of stored data which is associated with the first set of stored data, and comparing the first set of metadata and second set of metadata. Alternatively, the storage system can also generate a first set of metadata associated with a first set of stored data, generate a second set of stored data which is a copy of the first set of stored data, generate a second set of metadata associated with the second set of stored data, and compare the first set of metadata and the second set of metadata.
Owner:COMMVAULT SYST INC
Method and apparatus to dynamically create a customized user interface based on a document type definition
InactiveUS20020152244A1Natural language data processingSpecial data processing applicationsInformation processingSERCOS interface
A method on an information processing unit performing steps for creating a user interface (UI) to assemble a document that conforms to a particular document type definition. The method hides the specific syntax of document type definitions such as DTDs and schemas from the user. The method begins with a selection from a user for a document type or an existing document. Once the document type is selected or determined from the existing document the document type definitions are retrieved. The document type definitions include one or more elements. The method parses the elements which are subsequently mapped to one or more interface controls such as icons, pull-down menus, buttons, selection boxes, progress indicators, on-off checkmarks, scroll bars, windows, window edges for resizing the window, toggle buttons, forms, and UI widgets. UI can be GUIs or interactive voice response systems. A UI editor is presented by assembling the one or more interface controls without presenting specific document type definition syntax to a user. The UI editor permits the user to create and edit the content objects that are associated with the interface controls. The content objects are aggregated in an XML compatible format and ready to be checked in for further processing. The method permits specific UI interfaces to be created for specific publishing environments and at the same time permit the creation of reusable content objects.
Owner:IBM CORP
Computer-based method and apparatus for controlling, monitoring, recording and reporting telephone access
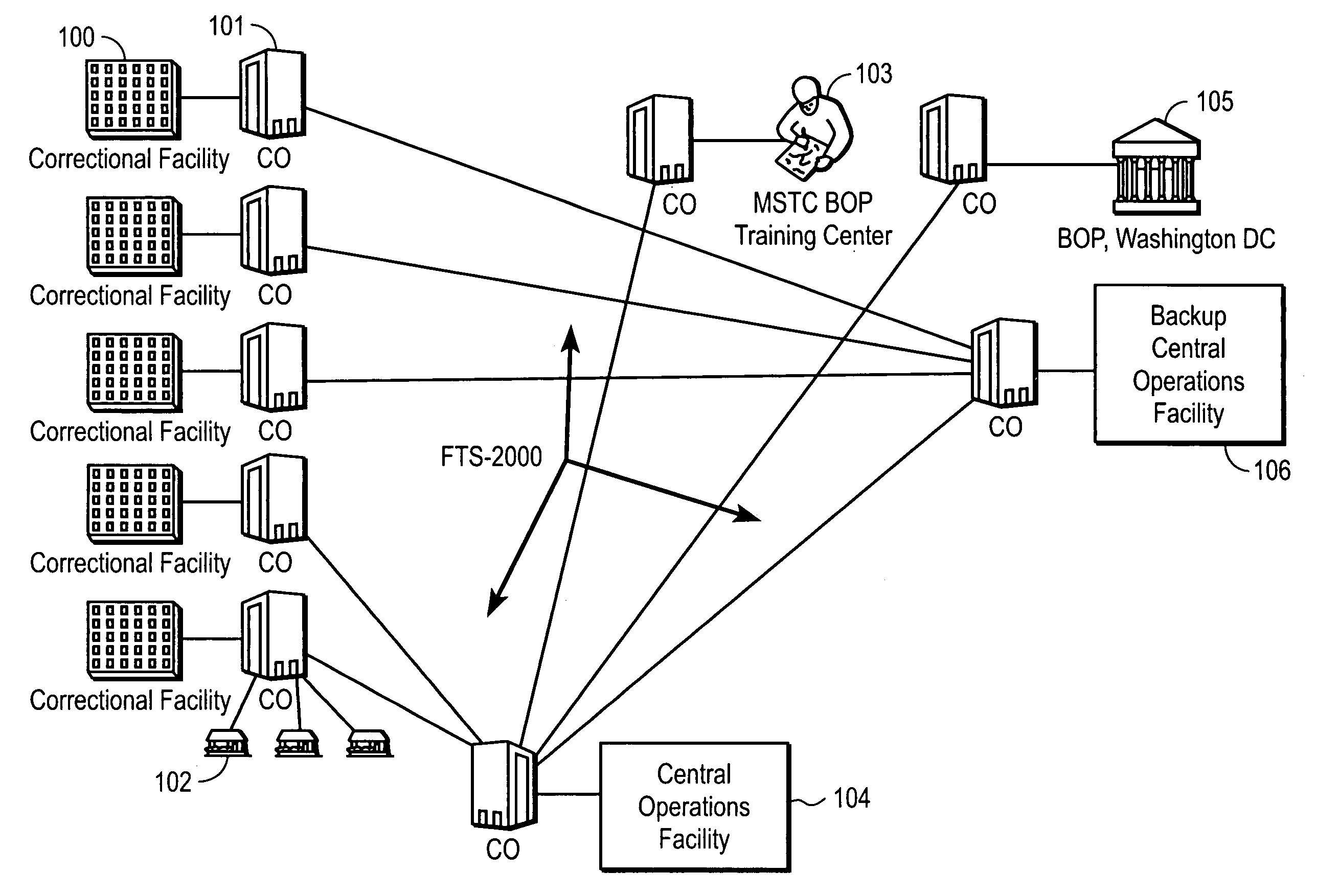
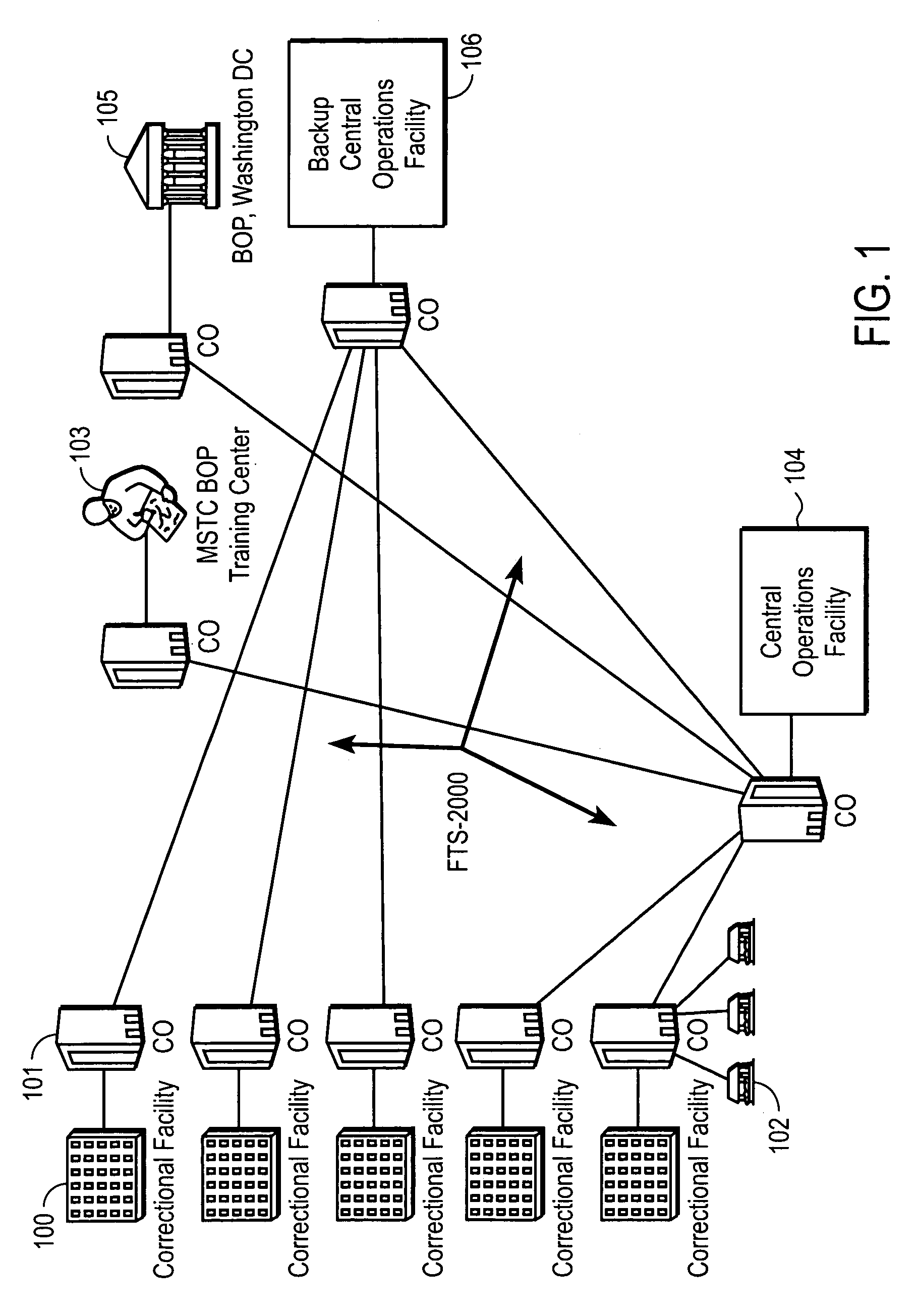
InactiveUS7106843B1Improve securityLow costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsManagement unitCentralized management
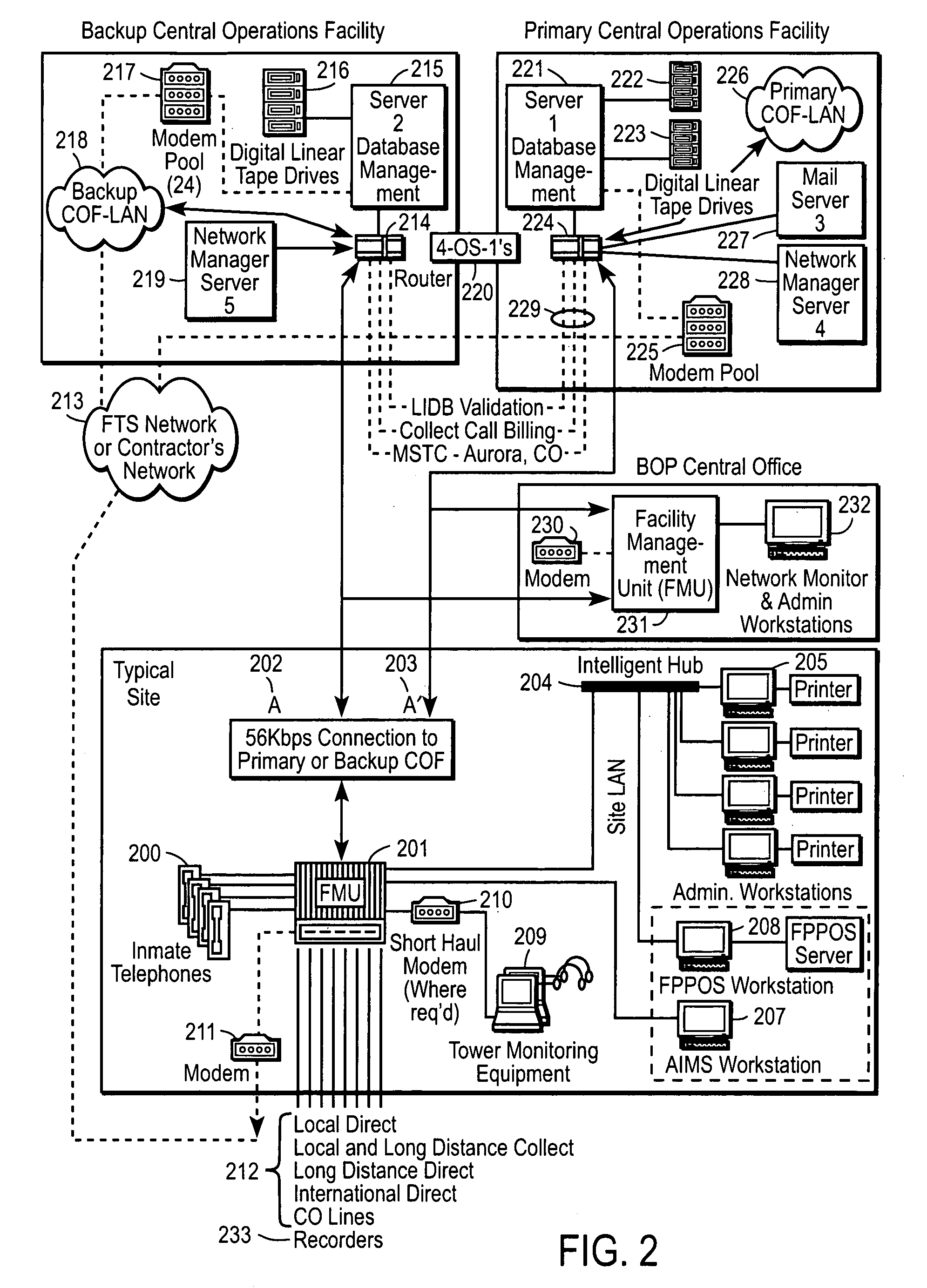
A method and apparatus for managing institutional telephone activity utilizing a computer-based telephony management unit to connect institutional telephones with outside telephone lines. The unit provides institutional users with fully automated, direct dial and collect calling privileges for local, long distance, and international calls. The unit contains a database for storing the calling privileges and restrictions of institutional users, for recording calling transactions made by the users, and for managing user monetary accounts. The unit can record up to 400 hours of conversation in a digital format. The unit provides various administrative capabilities, including user account management, audit trails, transaction reports, centralized management and report capabilities, and detection of fraudulent calling.
Owner:AMERICAN CAPITAL FINANCIAL SERVICES +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com