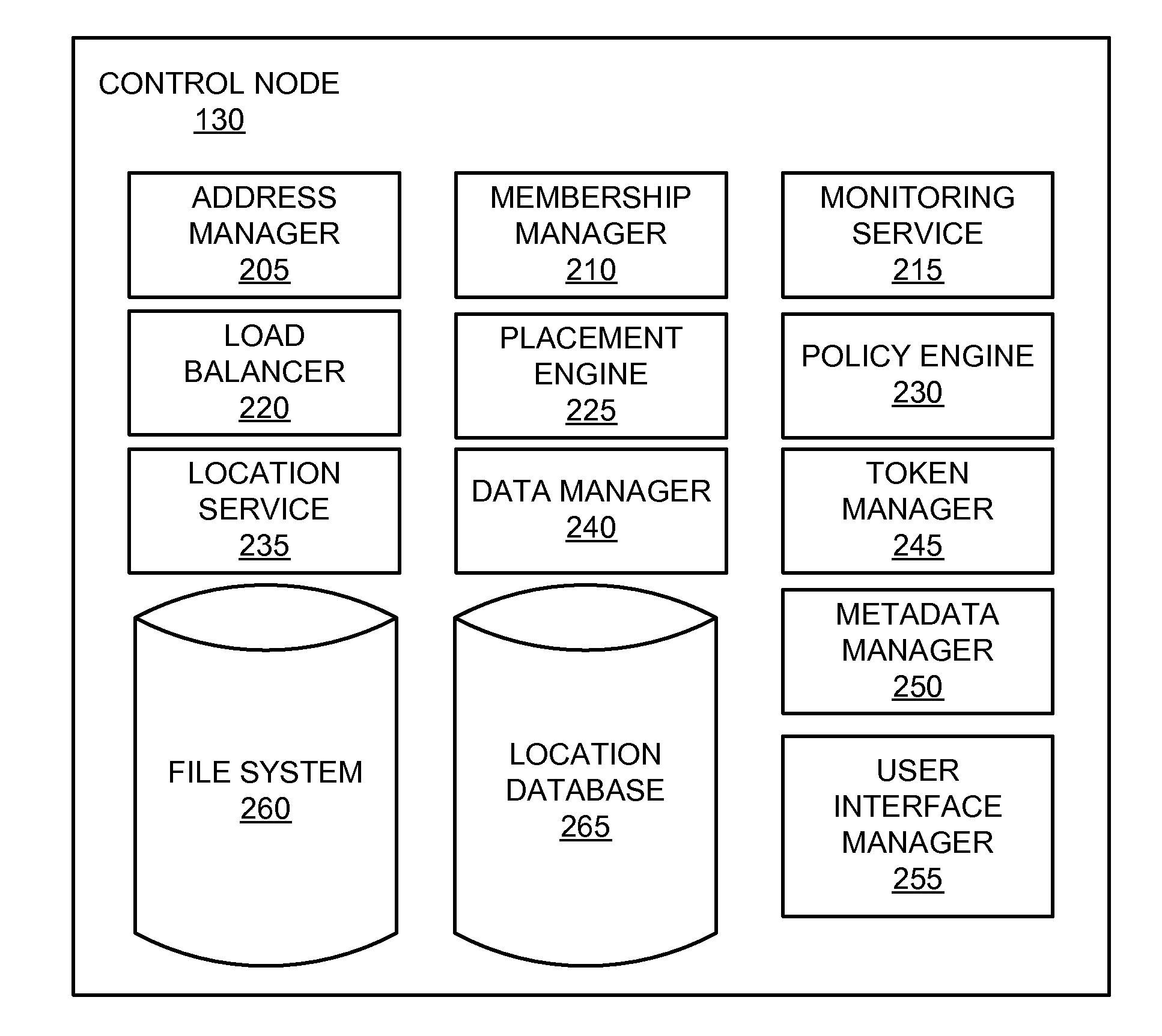
Patents
Literature
461 results about "File copying" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In digital file management, file copying is the creation of a new file which has the same content as an existing file. Computer operating systems include file copying methods to users, with operating systems with graphical user interfaces (GUIs) often providing copy-and-paste or drag-and-drop methods of file copying. Operating systems may have specialized file copying APIs are usually able to tell the server to perform the copying locally, without sending file contents over the network, thus greatly improving performance.
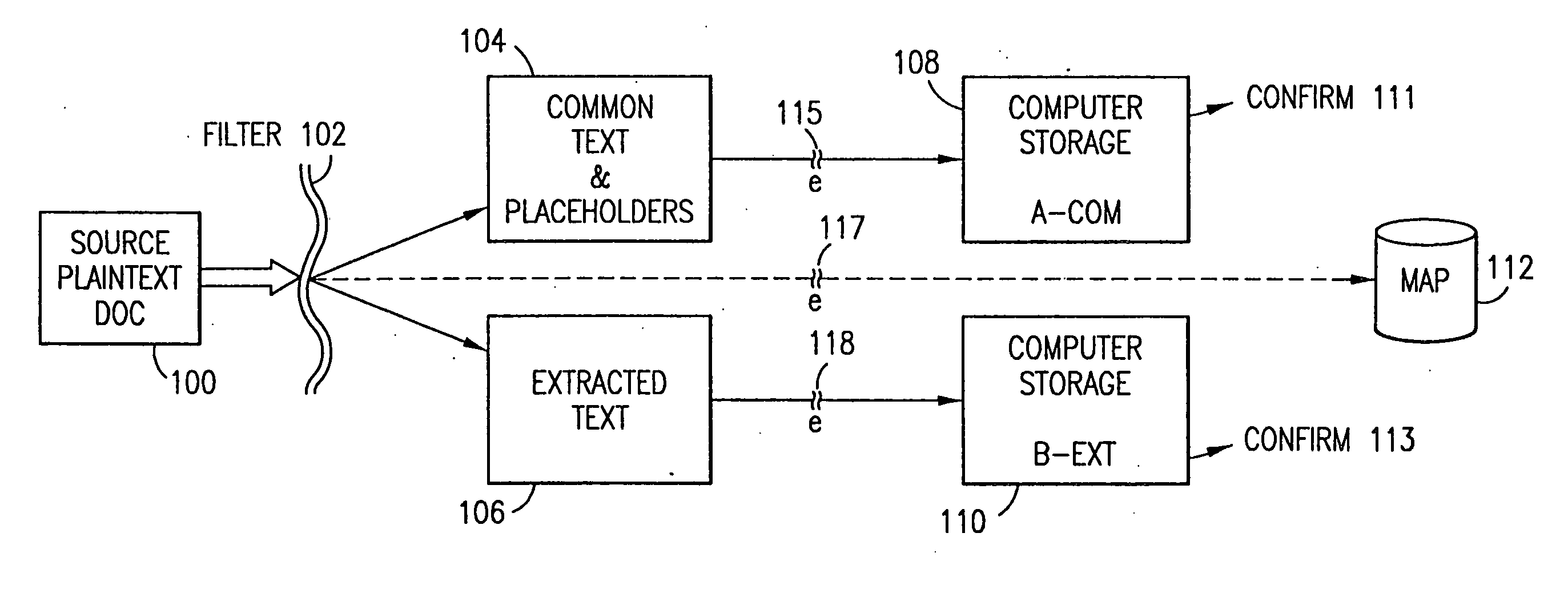
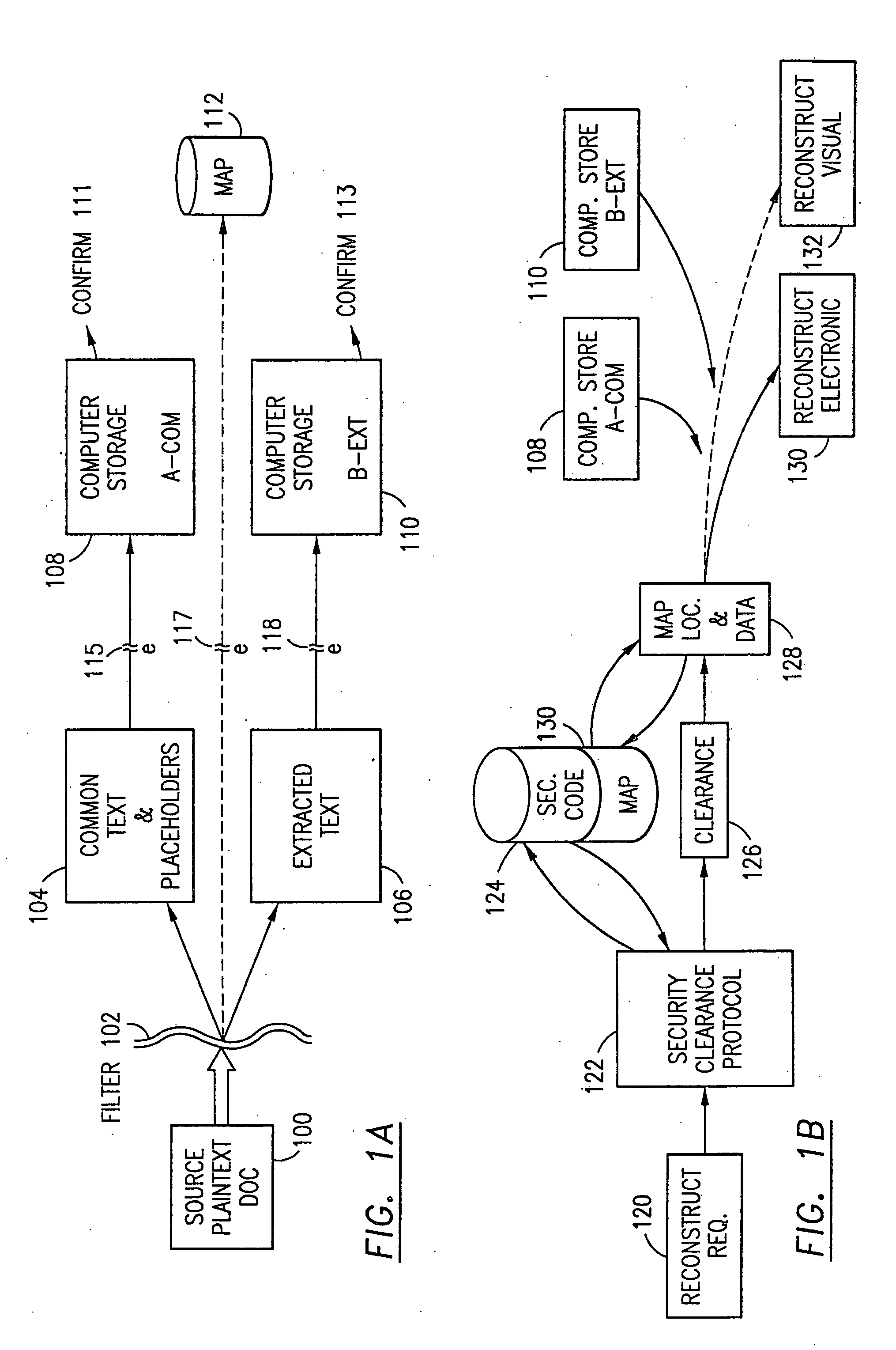
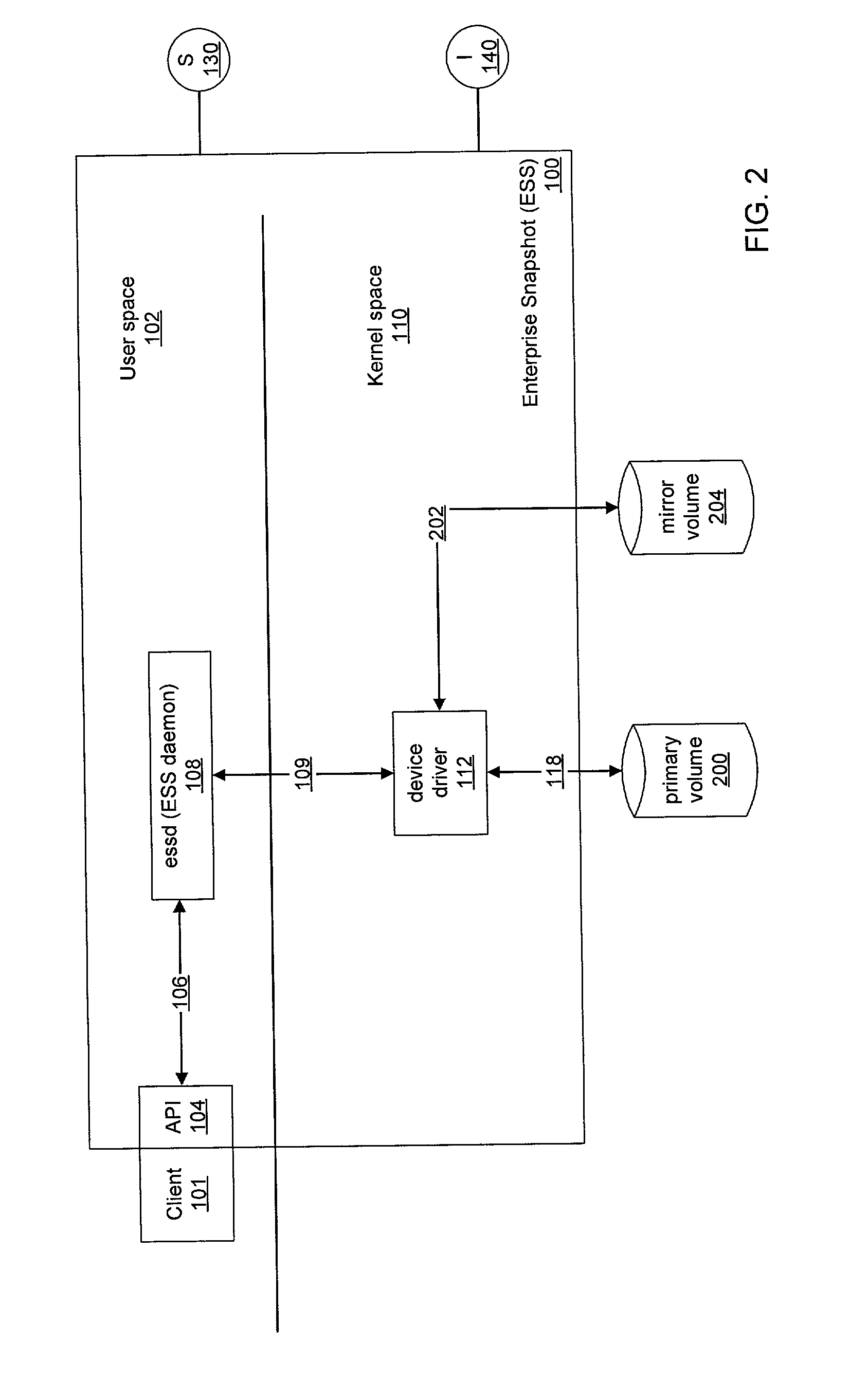
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
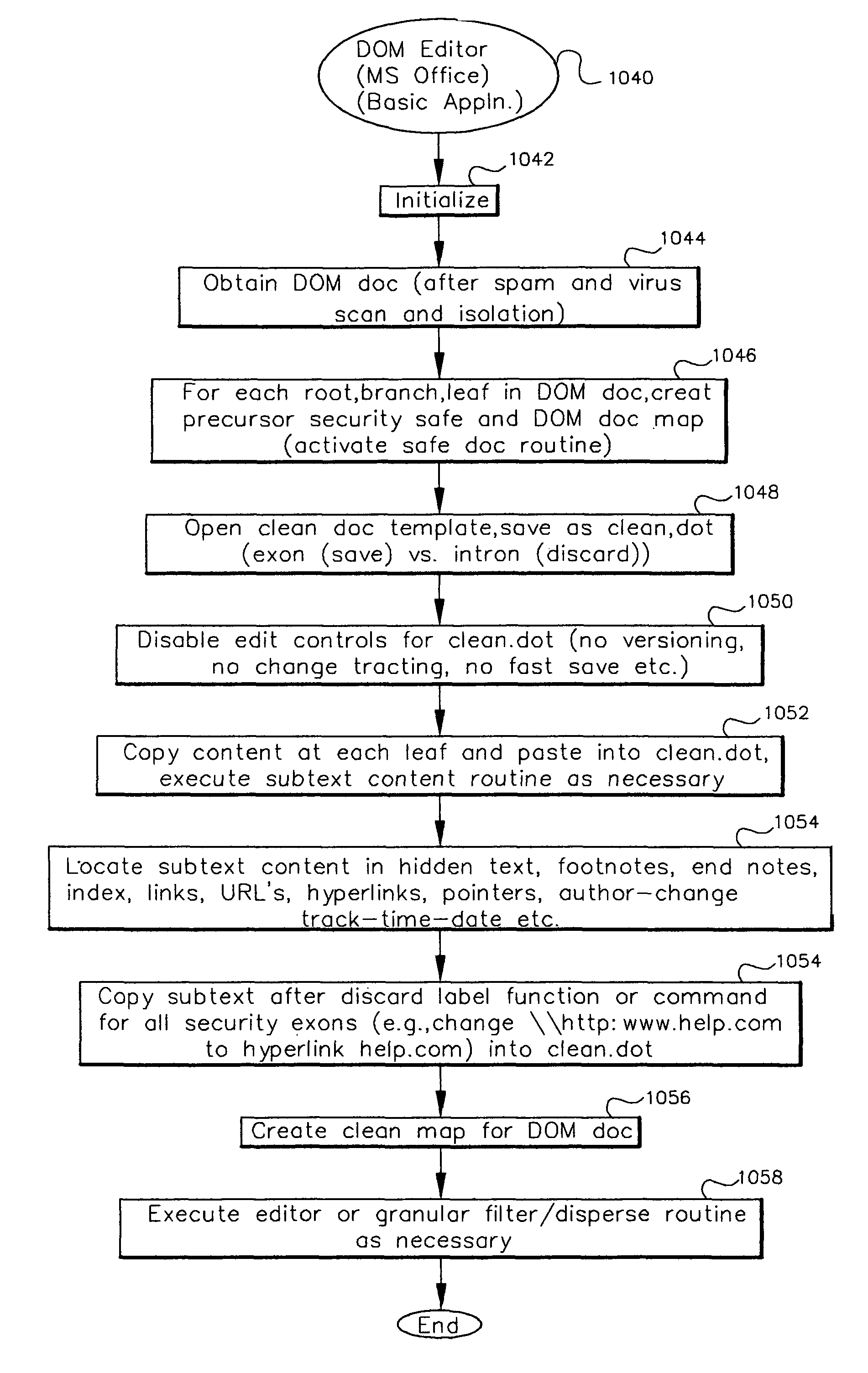
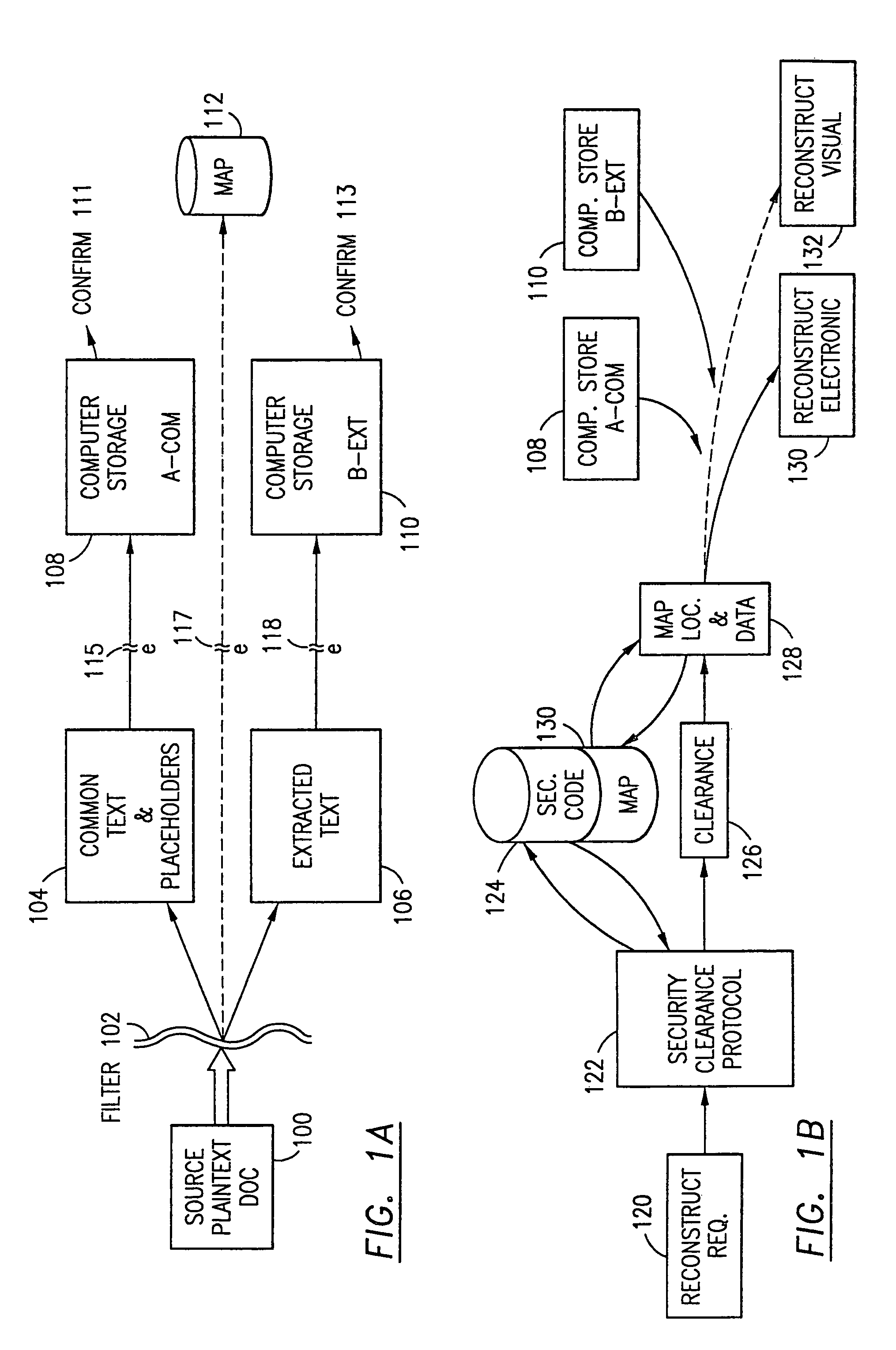
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
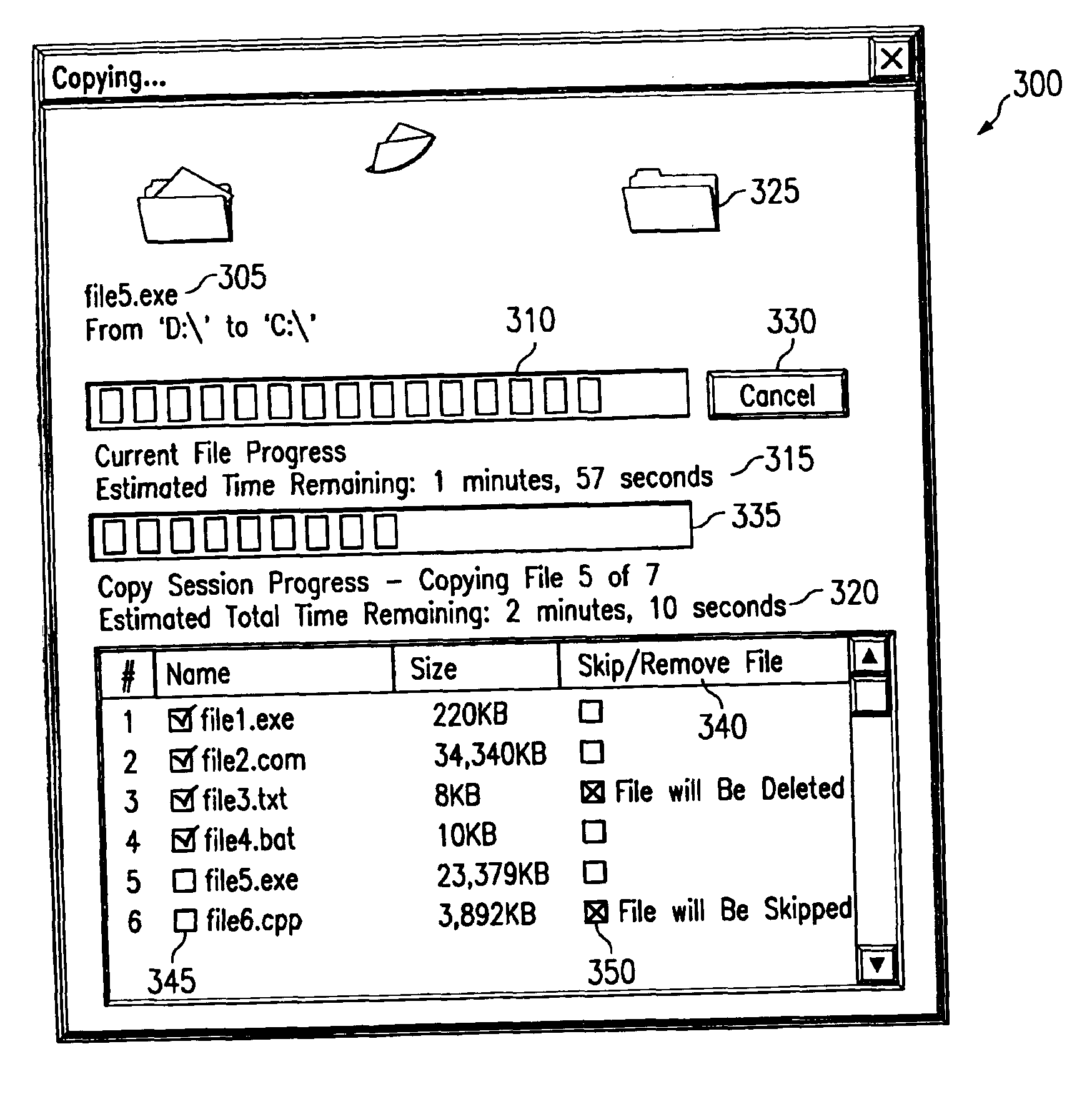
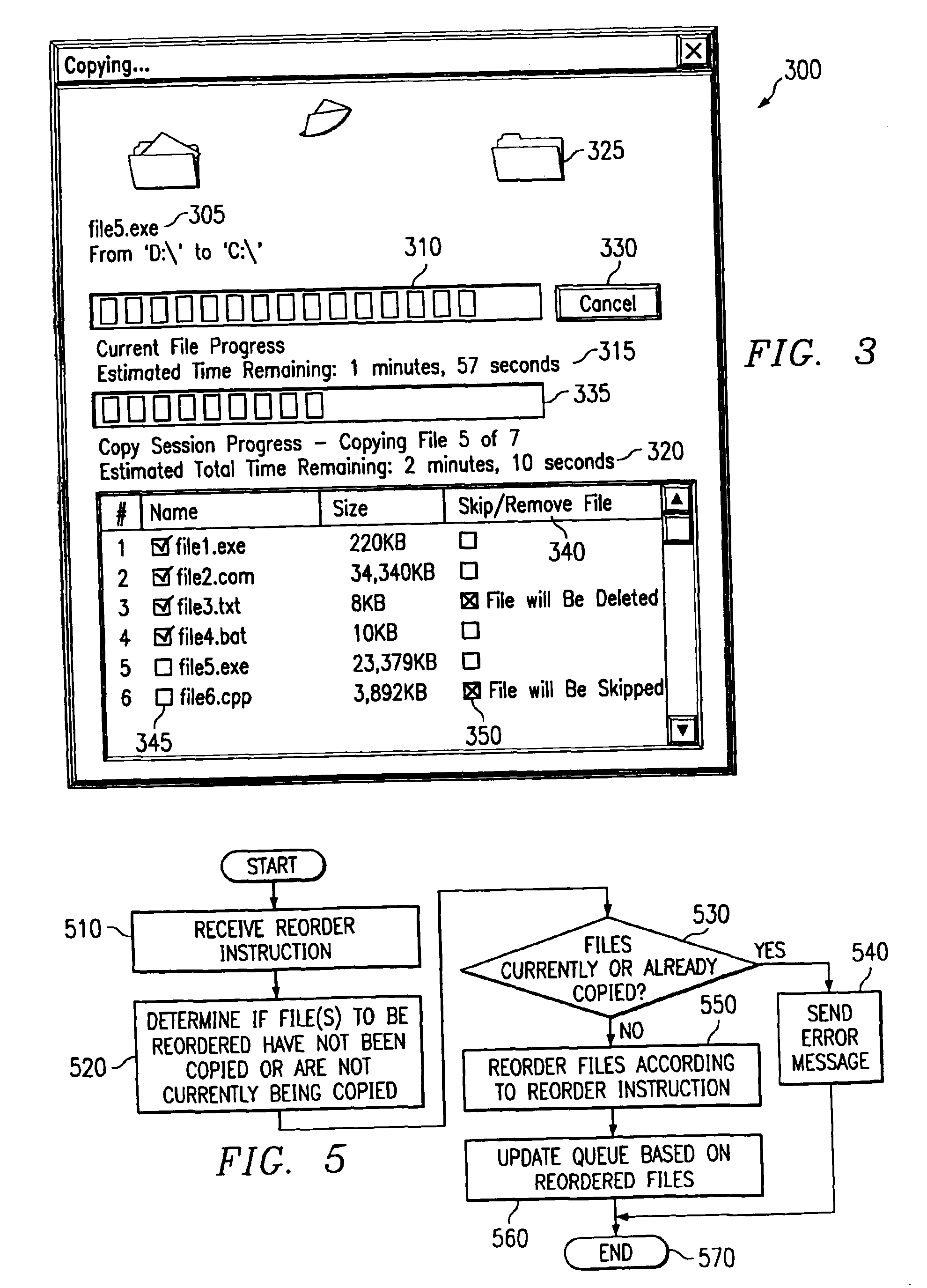
Copy/move graphical user interface apparatus and method
InactiveUS6874130B1Digital computer detailsSpecial data processing applicationsGraphicsGraphical user interface
A copy / move graphical user interface apparatus and method. The apparatus displays a graphical user interface informing a user of a current status of a copy / move operation. The graphical user interface includes progress bars indicating the progress of a current file copy / move operation as well as the overall copy / move operation. The graphic user interface further includes estimated times of completion and a listing of files that are in a copy / move queue. Additionally, the graphical user interface allows a user to modify the order in which files are copied / moved and to skip or delete files in the copy / move queue.
Owner:IBM CORP
Video distribution system using disk load balancing by file copying
ActiveUS6925499B1Short response timeImprove load balancingMultiple digital computer combinationsTwo-way working systemsDistribution systemFile copying
Owner:INFOVALUE COMPUTING
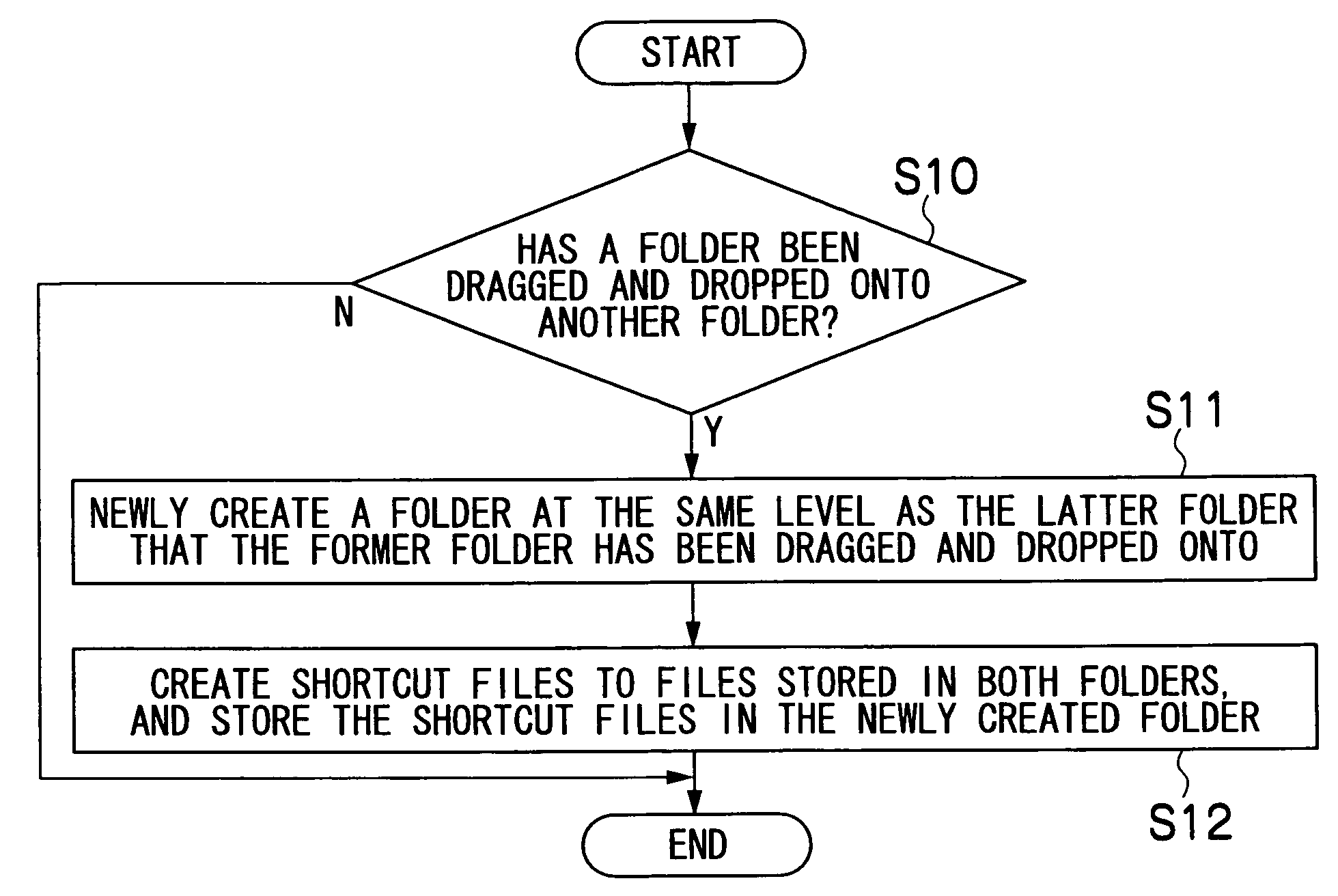
File management program
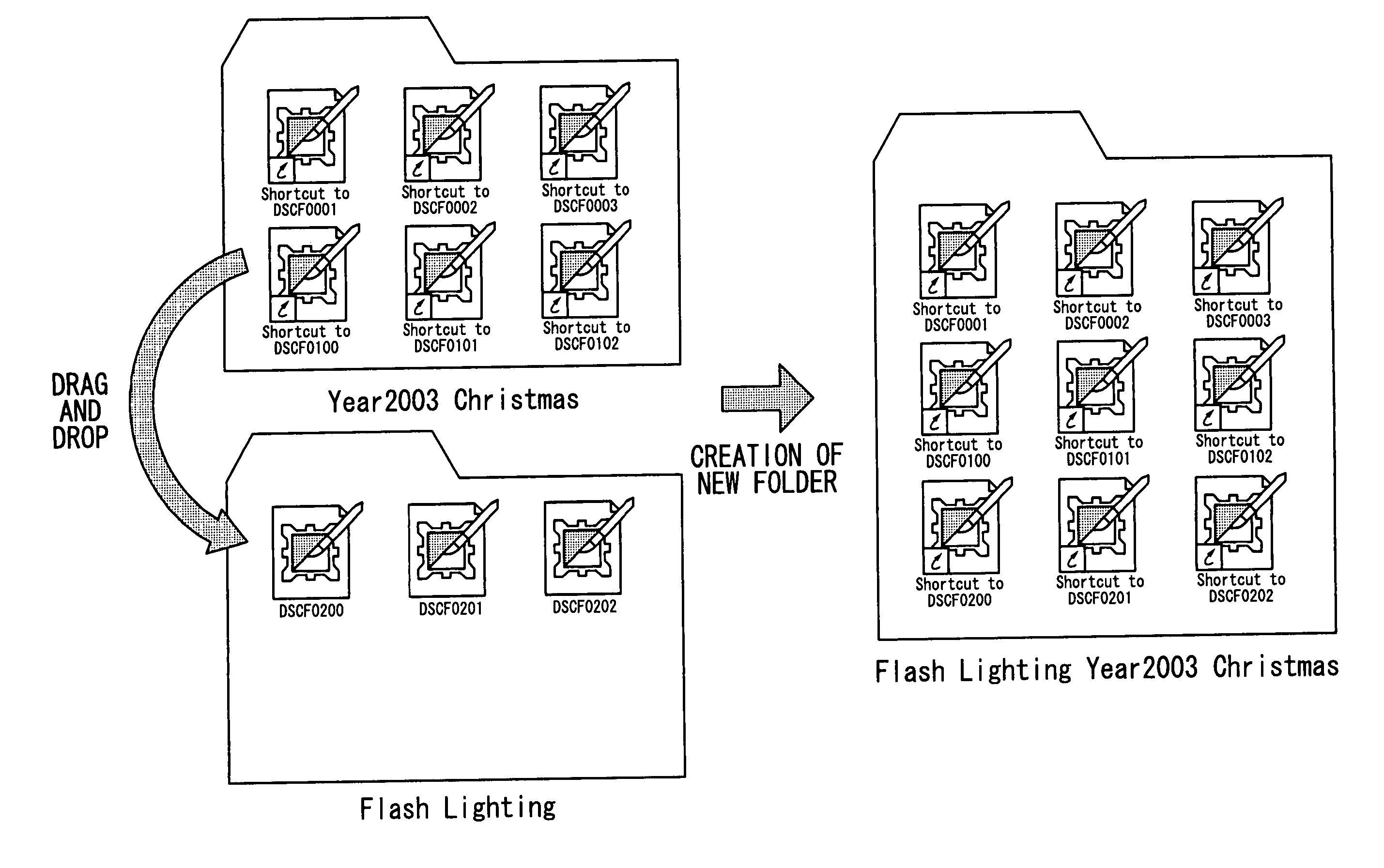
InactiveUS20050177796A1Simplified managementEasy to manageTelevision system detailsColor television detailsDrag and dropComputer science
The computer readable medium has embodied thereon a file management program for processing by a computer, the file management program comprising: a first code segment for, when an icon of a first folder displayed on a display apparatus is dragged and dropped onto another icon of a second folder displayed on the display apparatus, creating a third folder at the same level as the second folder; and a second code segment for copying a file stored in the first folder and a file stored in the second folder into the third folder.
Owner:FUJIFILM CORP
Rule driven automation of file placement, replication, and migration
InactiveUS20070022129A1Digital data information retrievalData processing applicationsDriving automationFile copying
Owner:PARASCALE
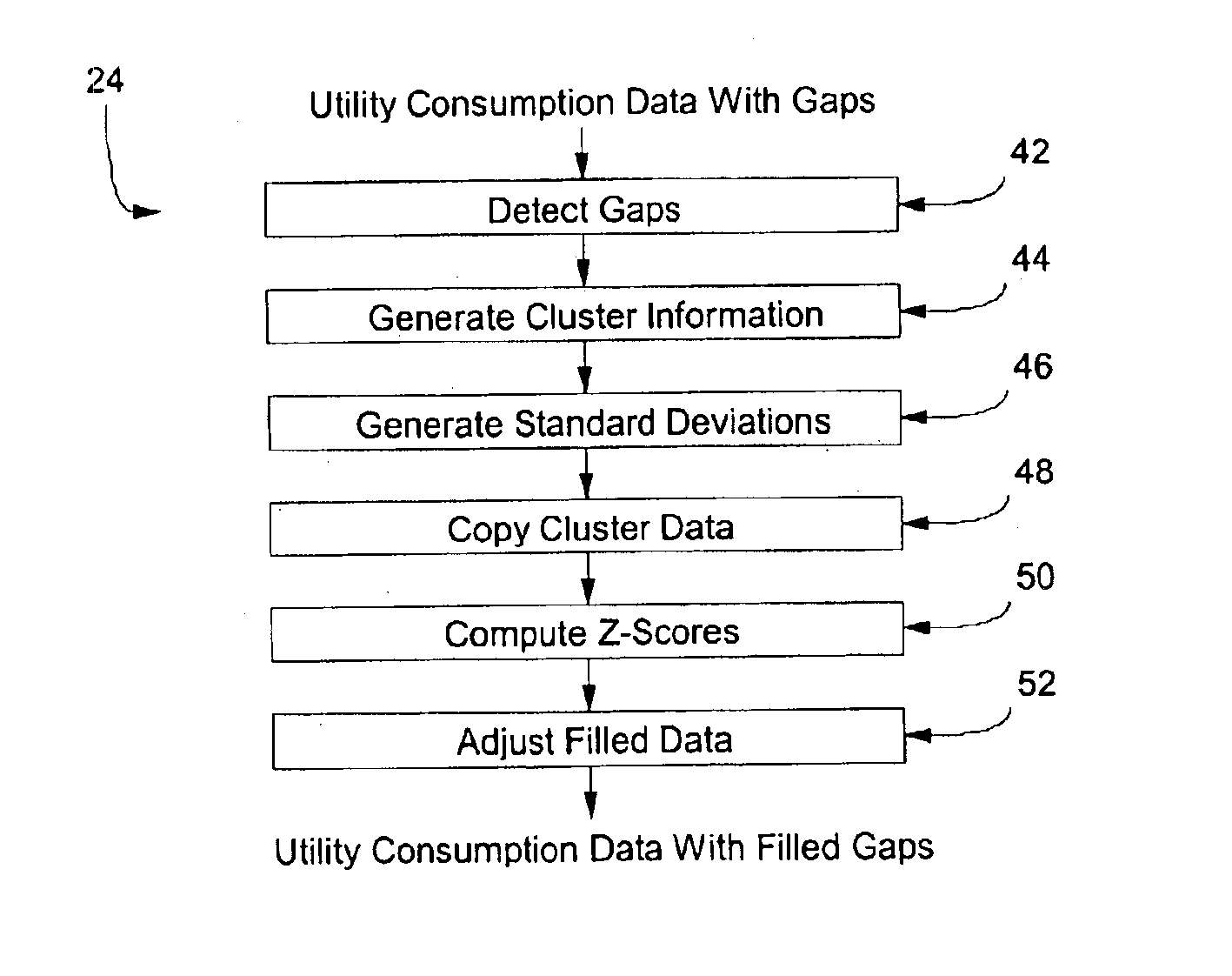
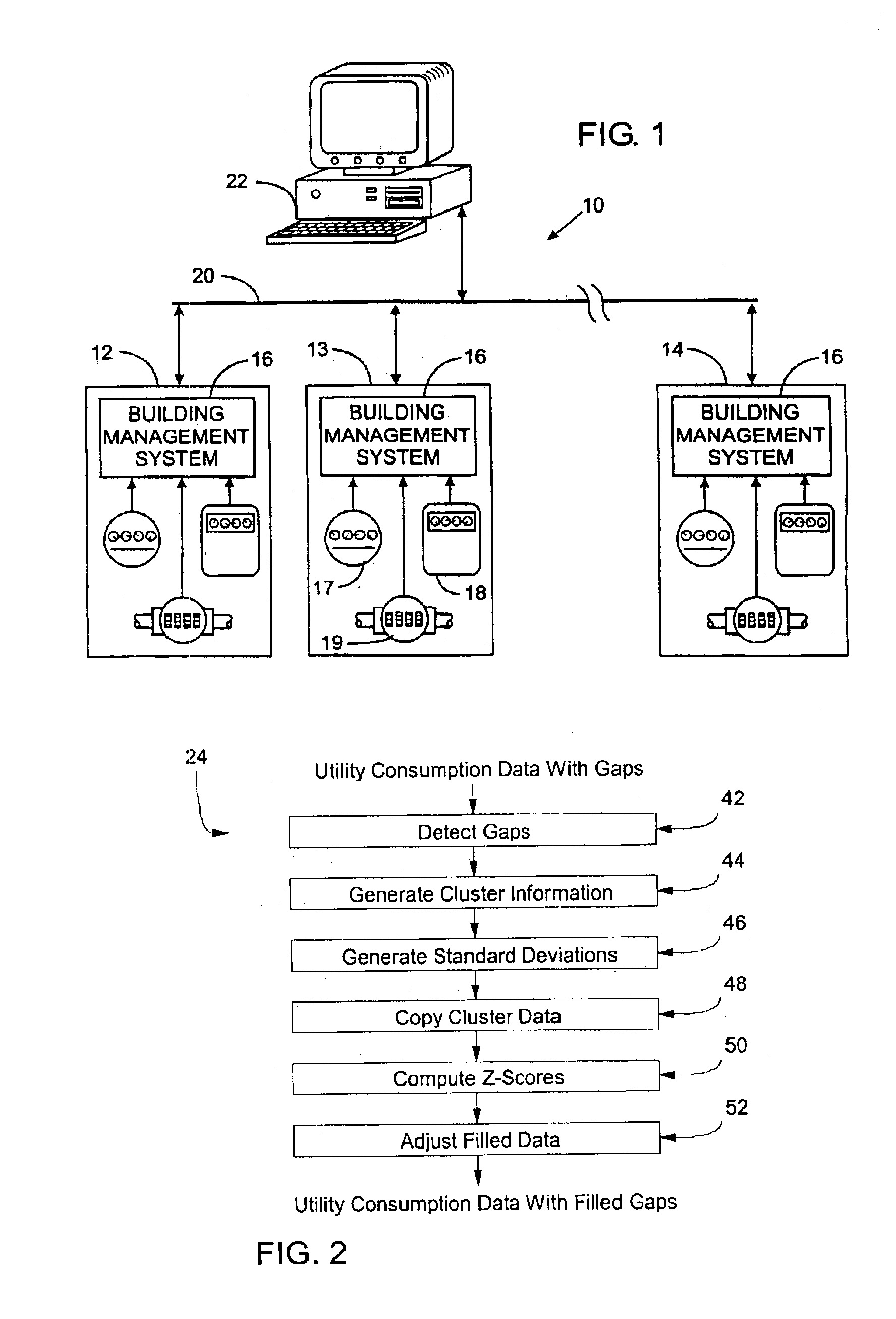
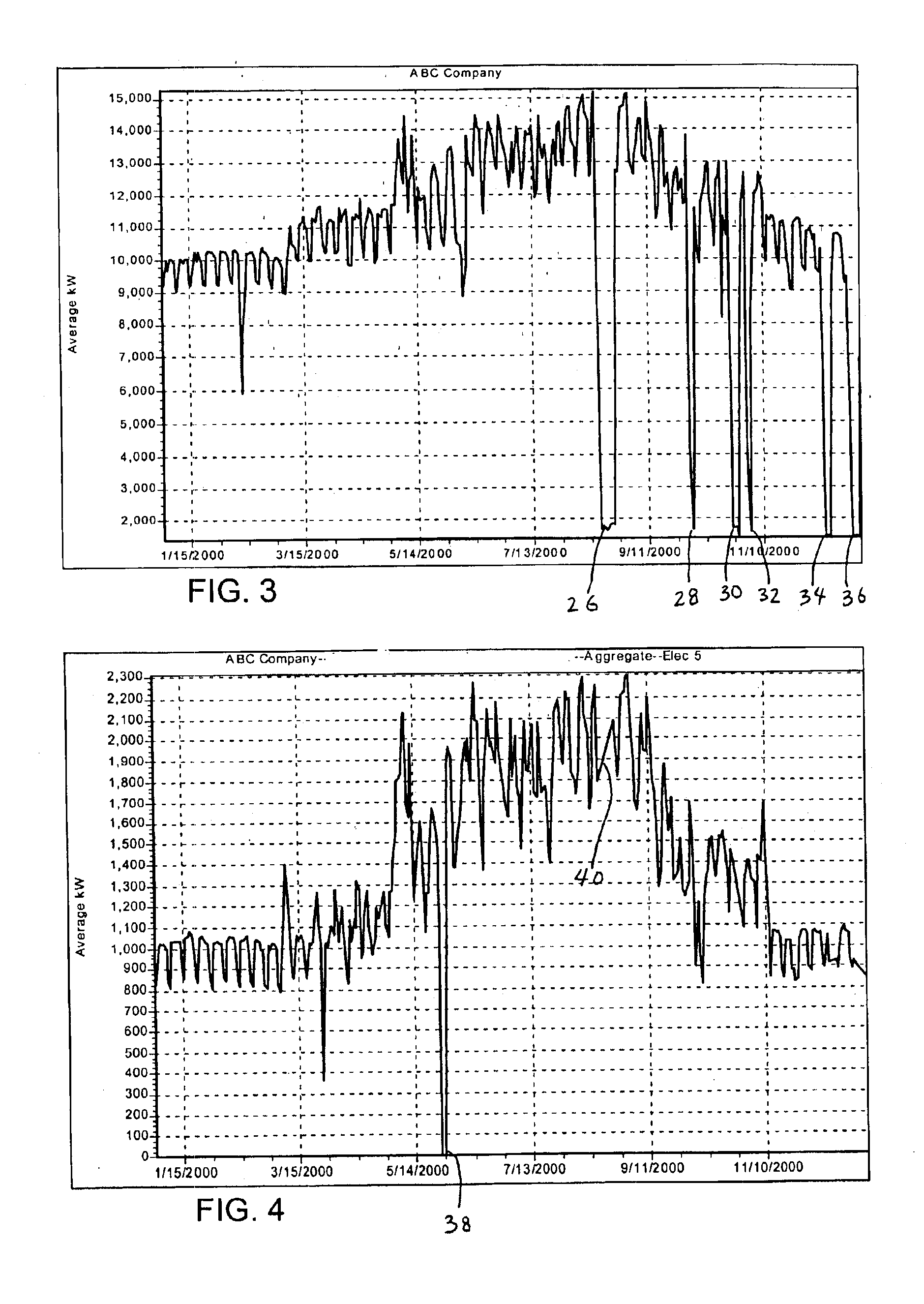
System and method for filling gaps of missing data using source specified data
InactiveUS6862540B1Accurate calculationElectric signal transmission systemsTemperatue controlMissing dataData filling
A method and apparatus are provided for filling a gap of missing data using source specified data. The method includes analyzing a first set of data representative of utility consumption for a plurality of days to determine clusters of days of the week having similar utility consumption. The method further includes generating an individual profile of utility consumption for each cluster, and copying data from at least one individual profile into the gap to form a second set of data without any gaps. A system for filling a gap of missing data using source specified data includes a microprocessor programmed to copy data from at least one individual profile into the gap, and to adjust the copied data up or down to account for local trend information adjacent to the gap.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
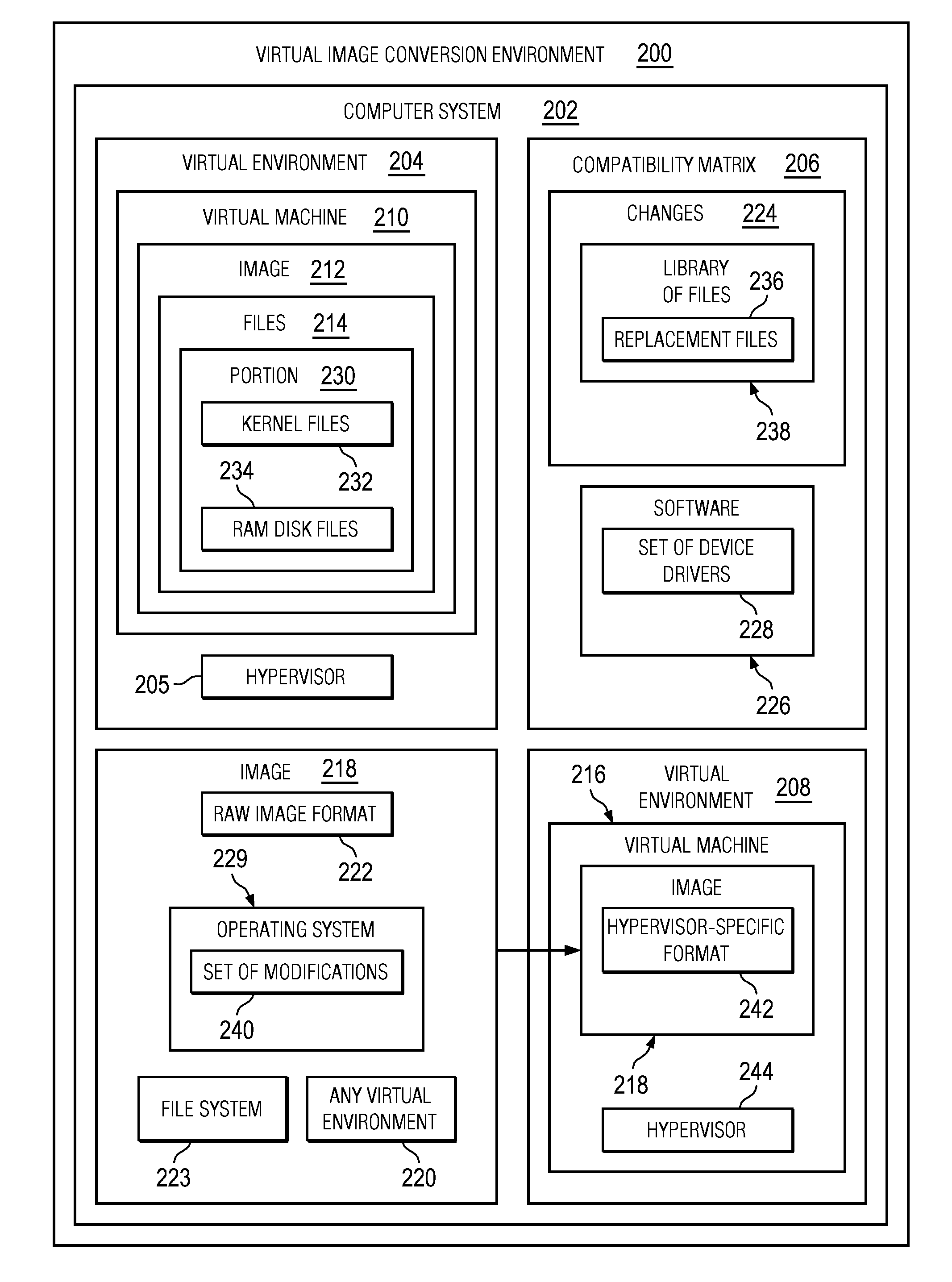
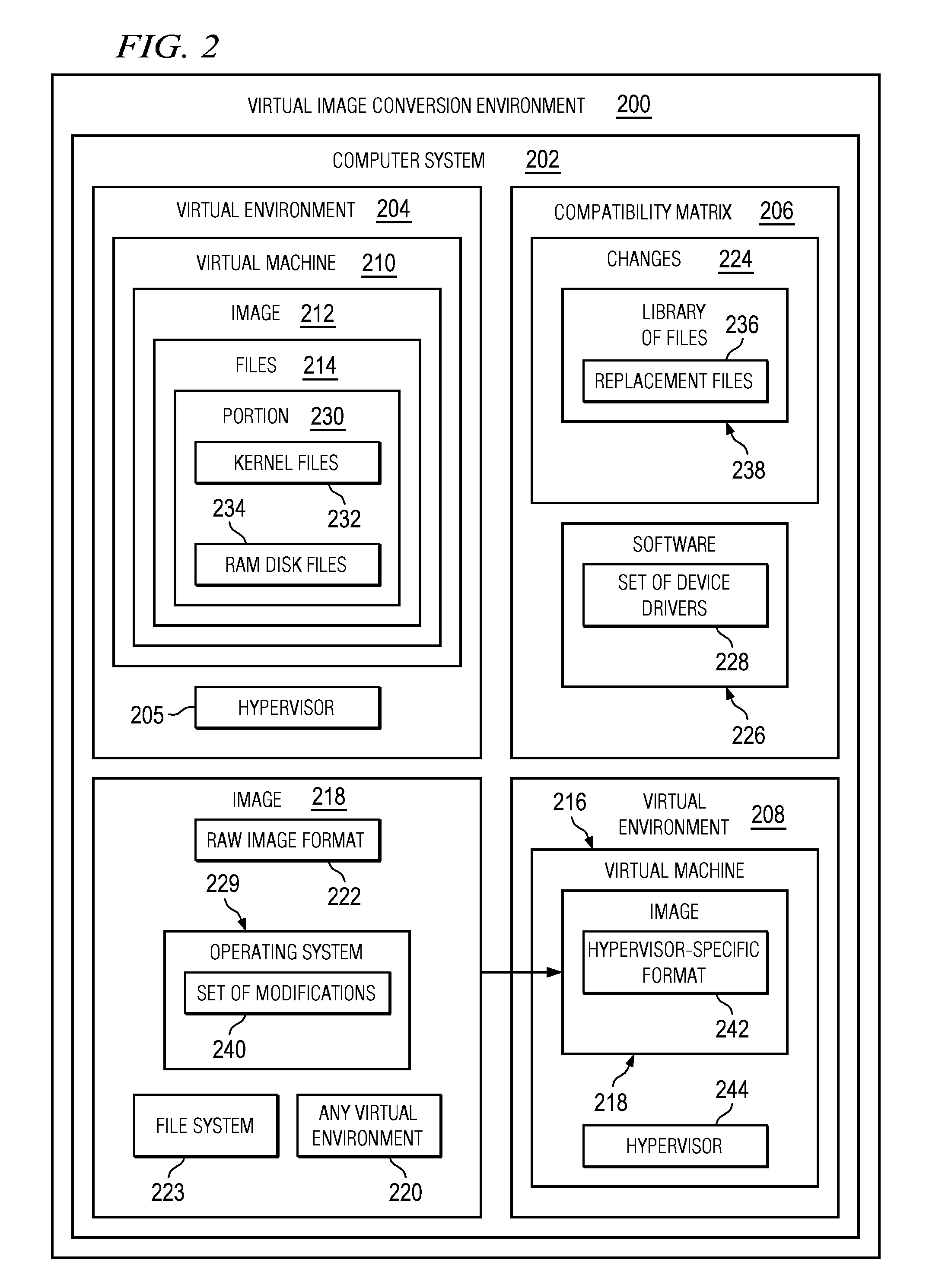
Converting Images in Virtual Environments
The different illustrative embodiments provide a method, computer program product, and apparatus for converting a first image for a virtual machine formatted for a first virtual environment. A second image is created, wherein the second image is non-specific to any virtual environment. A determination is made whether a portion of files to be copied from the first virtual image to the second virtual image should be replaced using a compatibility matrix, wherein the compatibility matrix identifies changes between the first virtual environment and a second virtual environment. A replacement for the portion of the files is copied to the second image using the compatibility matrix responsive to a determination that the portion of the files in the set of files should be replaced. The file is copied to the second image responsive to an absence of a determination that the each file in the set of files should be replaced.
Owner:IBM CORP
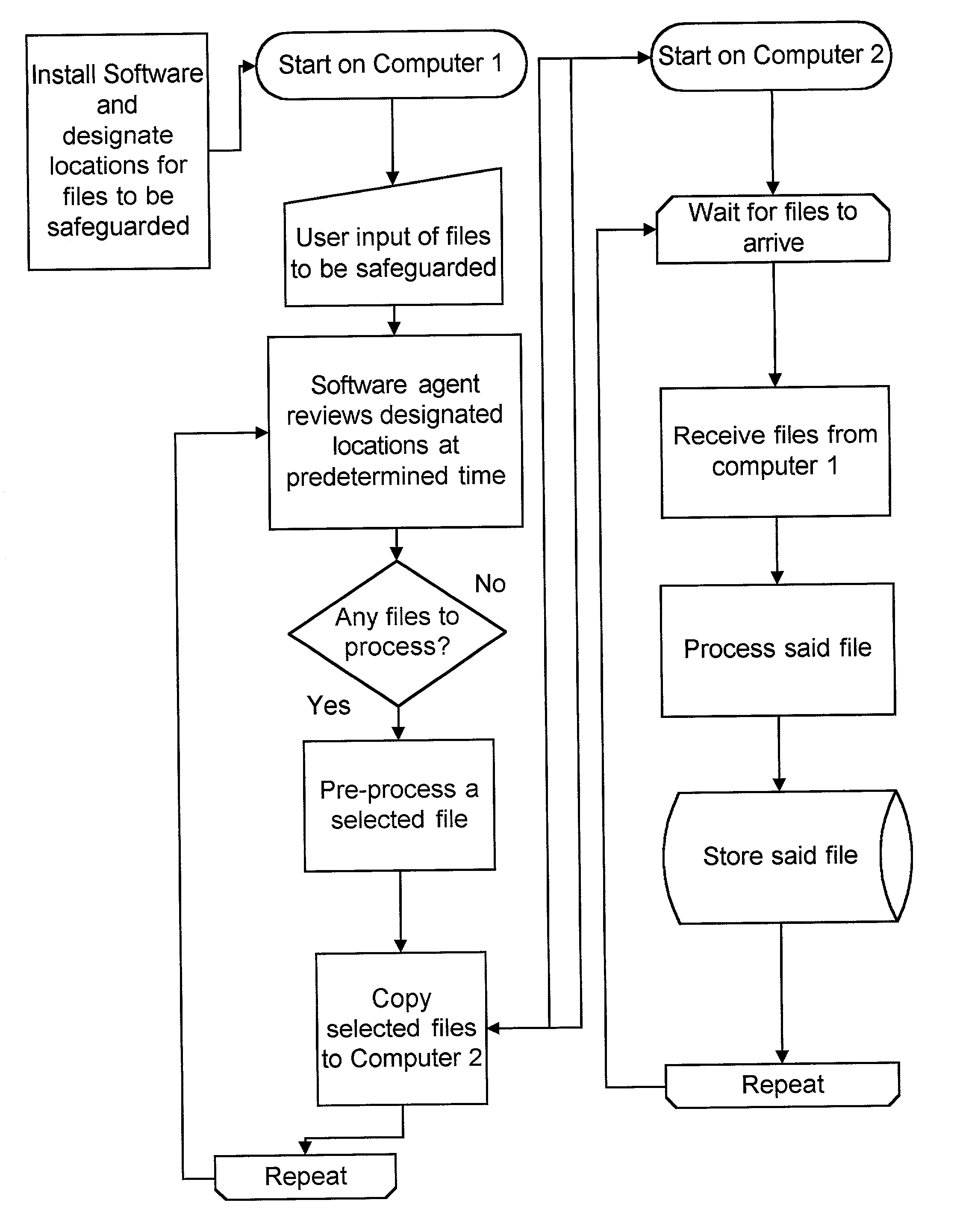
Method and apparatus for safeguarding files
ActiveUS7174332B2Minimal interventionData processing applicationsUser identity/authority verificationSelection criterionRestricted access
A computer implemented method for safeguarding files, comprising the steps of designating a location on a first computer for storage of files to be safeguarded, selecting certain of the files to be safeguarded from the location based upon predetermined selection criteria, copying the selected files to be safeguarded to a second computer, deleting the selected files from the first computer, processing the selected files to be safeguarded on the second computer, and storing the selected files to be safeguarded in a restricted access database. In a second embodiment, the file is copied to a second computer, but not deleted from the first computer, in addition to all other steps of the method. The invention also includes an apparatus for carrying out the methods of the invention.
Owner:IP COM I
Data security system and method with editor
ActiveUS8176563B2Digital data processing detailsTelephonic communicationDocument preparationDocument Object Model
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
Device and method for eliminating file duplication in a distributed storage system
InactiveUS20120191675A1Efficient managementInhibit swellingDigital data information retrievalProgram control using stored programsFile copyingOperating system
The present invention relates to an apparatus and method for eliminating duplication of a file in a distributed storage system. The apparatus and method for eliminating duplication of a file in a distributed storage system according to the present invention calculates a hash value of each chunk for an active file; calculates a secondary hash value by adding the hash values calculated for respective chunks; examines duplication of the file using the hash value of each chunk and the secondary hash value; and eliminates a duplicated file depending on a result of the examination.
Owner:PSPACE
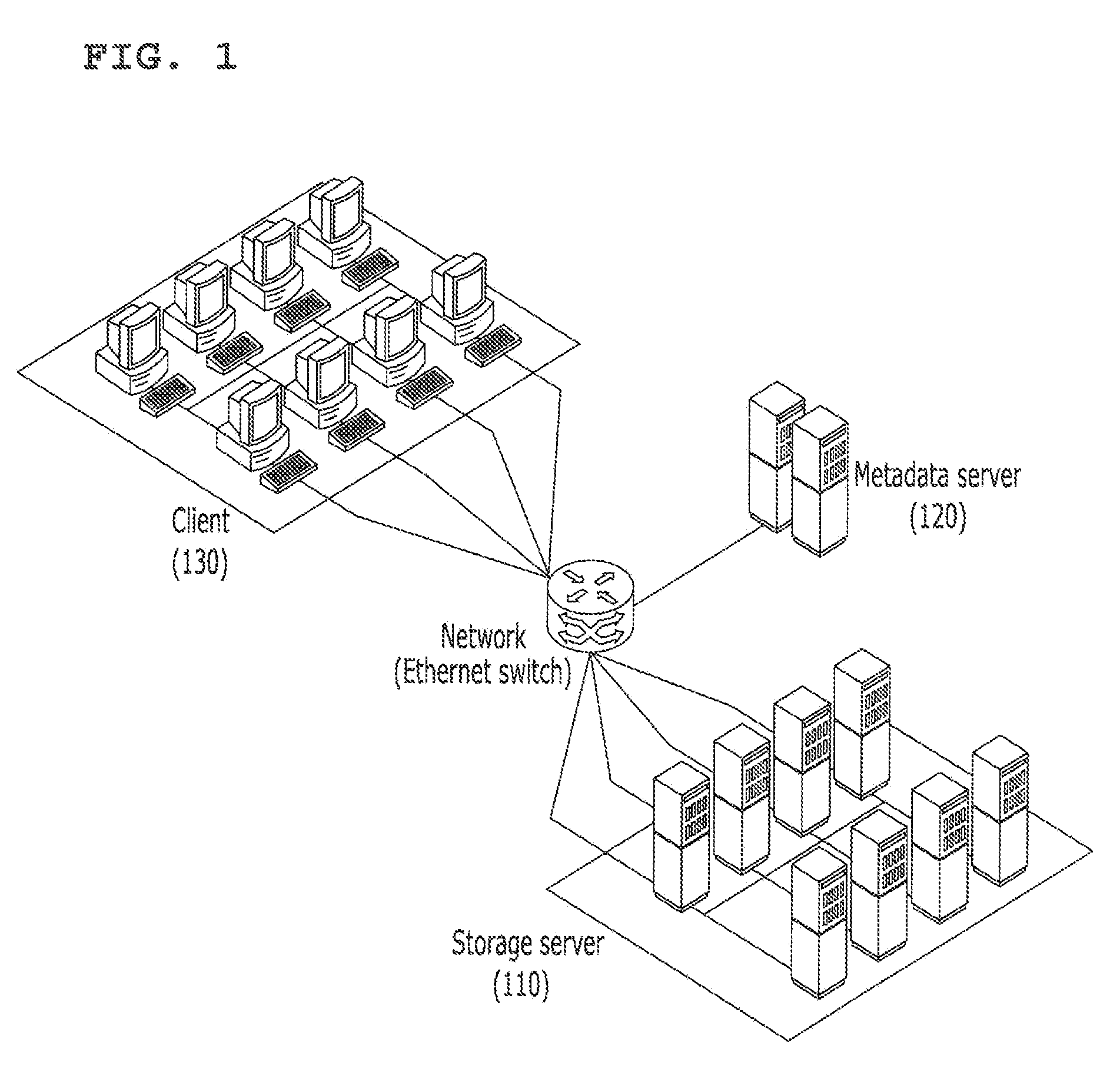
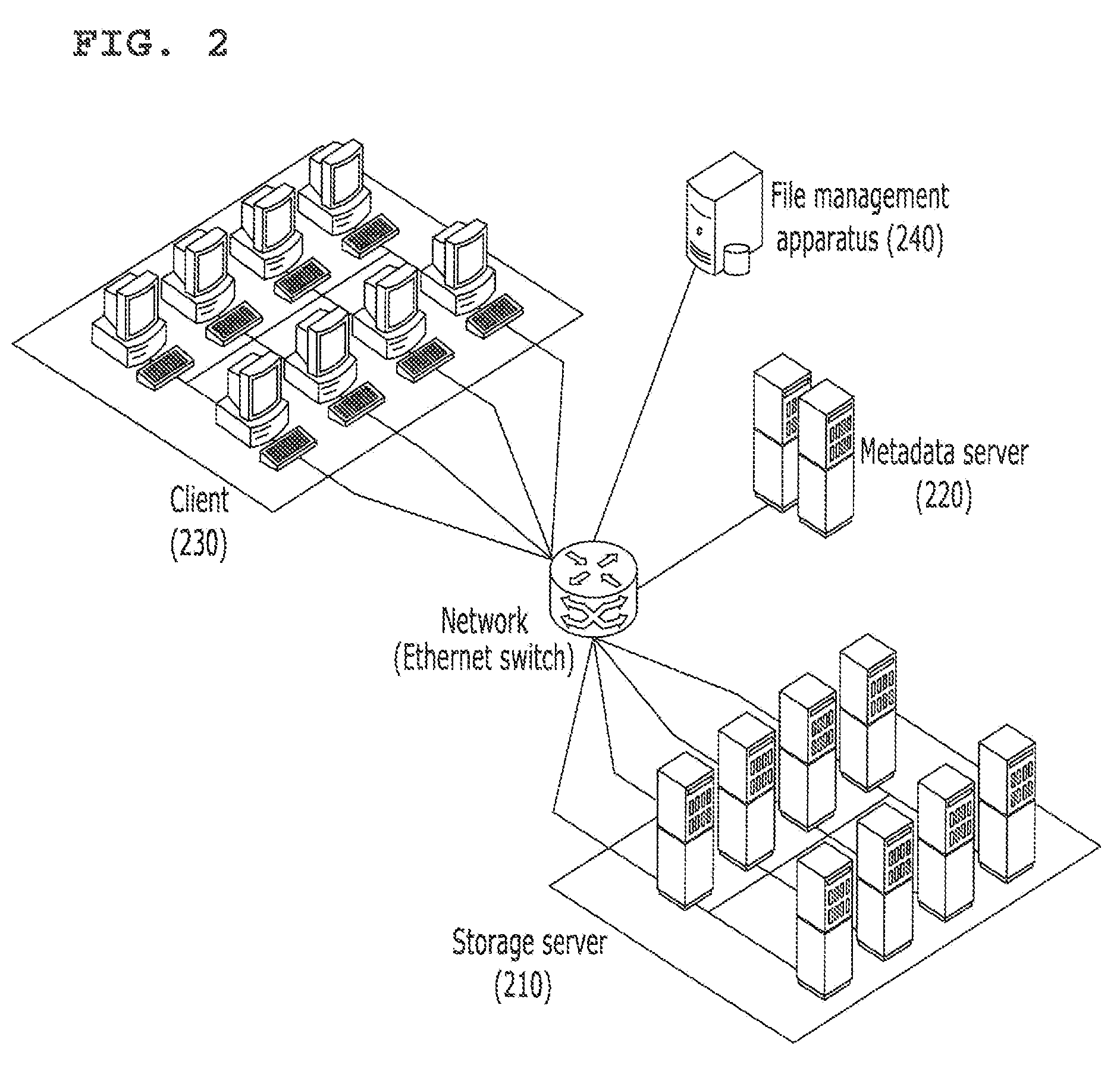
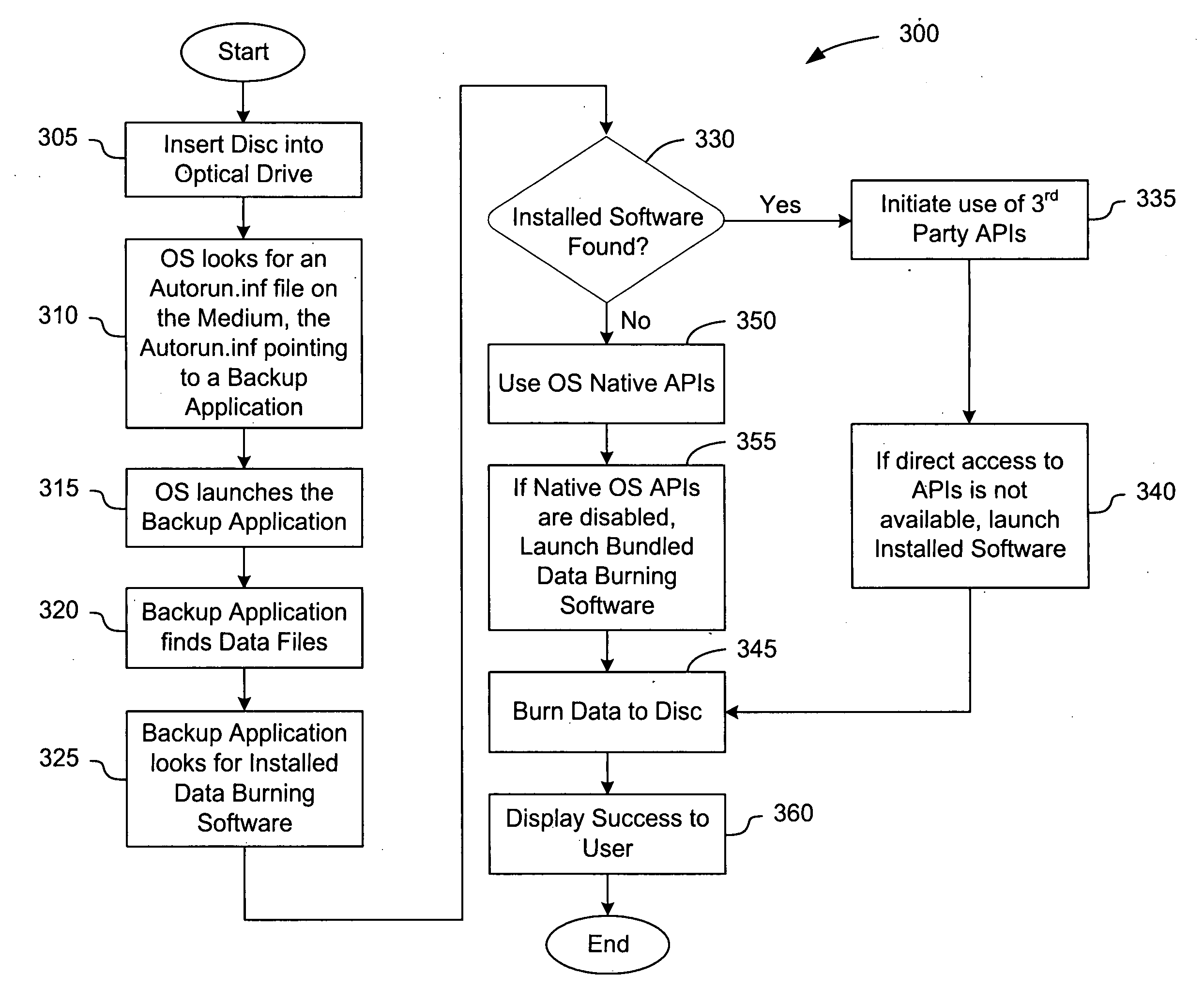
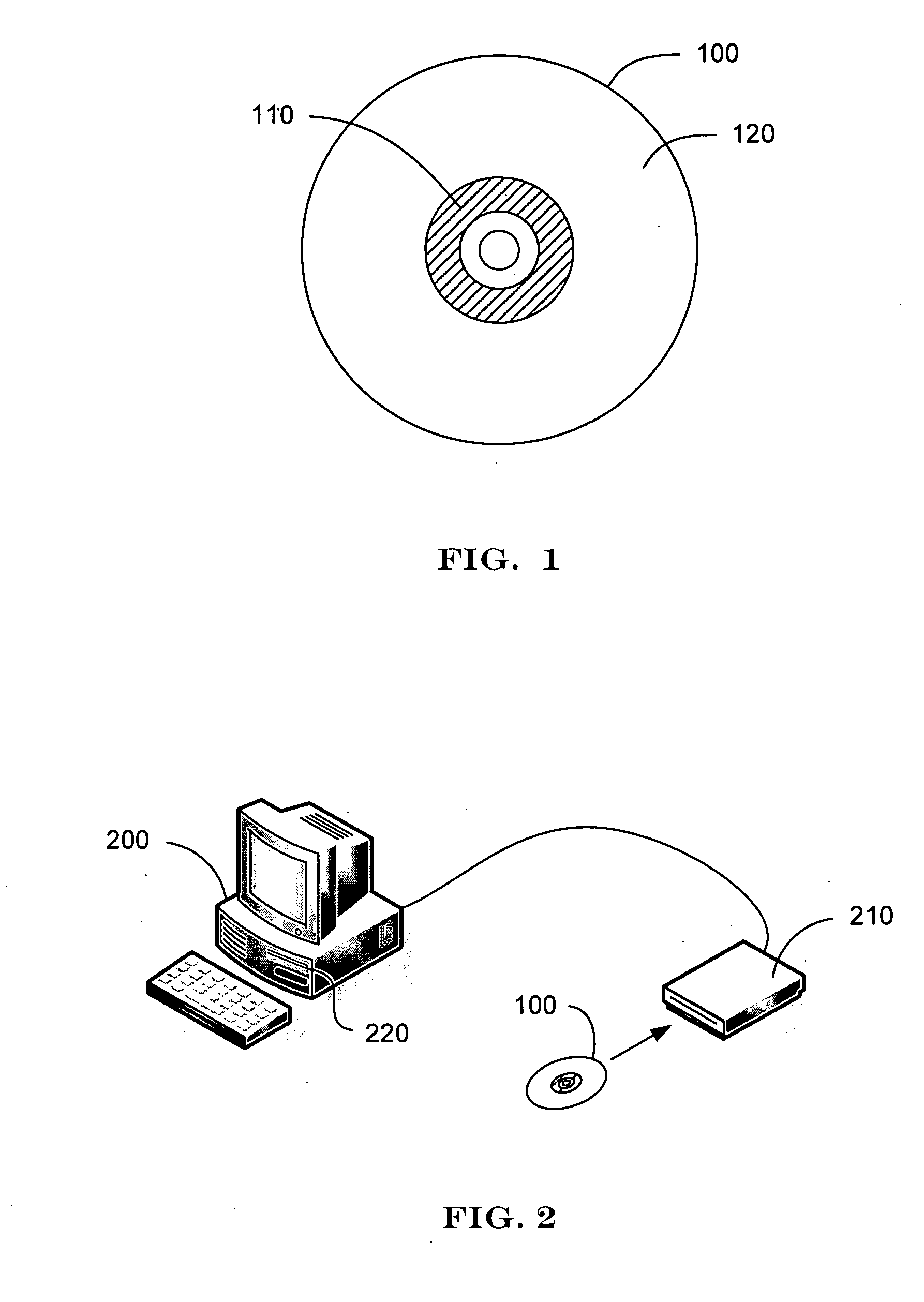
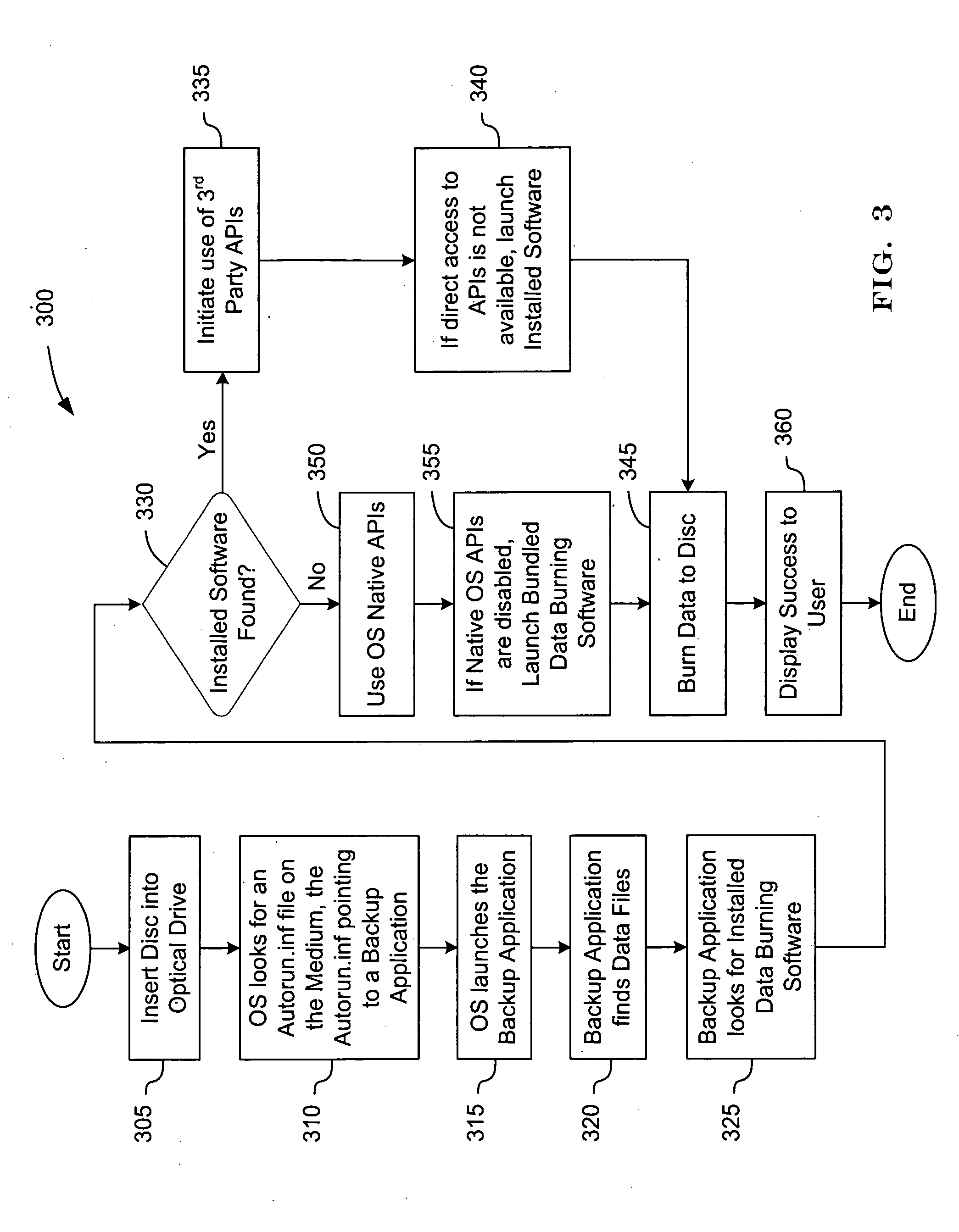
Optical disc initiated data backup
InactiveUS20080028008A1Error detection/correctionSpecial data processing applicationsOperational systemStorage area network
An optical disc comprising computer-readable instructions is provided. The computer-readable instructions include a backup application. When the optical disc is inserted into an optical drive of a data source, such as a personal computer, the operating system of the data source automatically launches the backup application. The backup application is configured to find files on the data source that satisfy search criteria, which can be predefined or user-selected. The backup application copies those files to a networked storage such as a storage area network or a server of a commercial service provider.
Owner:STORAGE APPLIANCE CORP
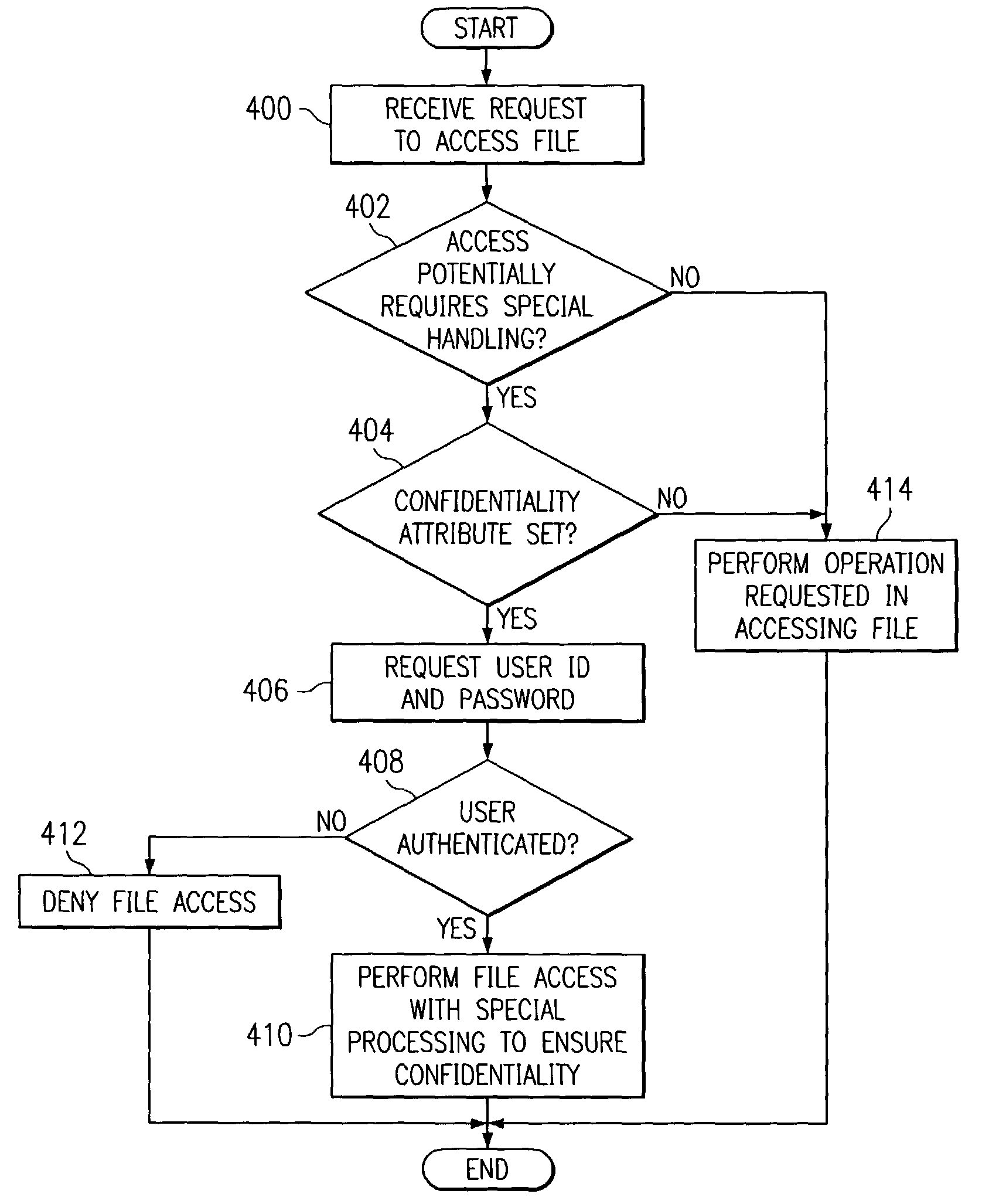
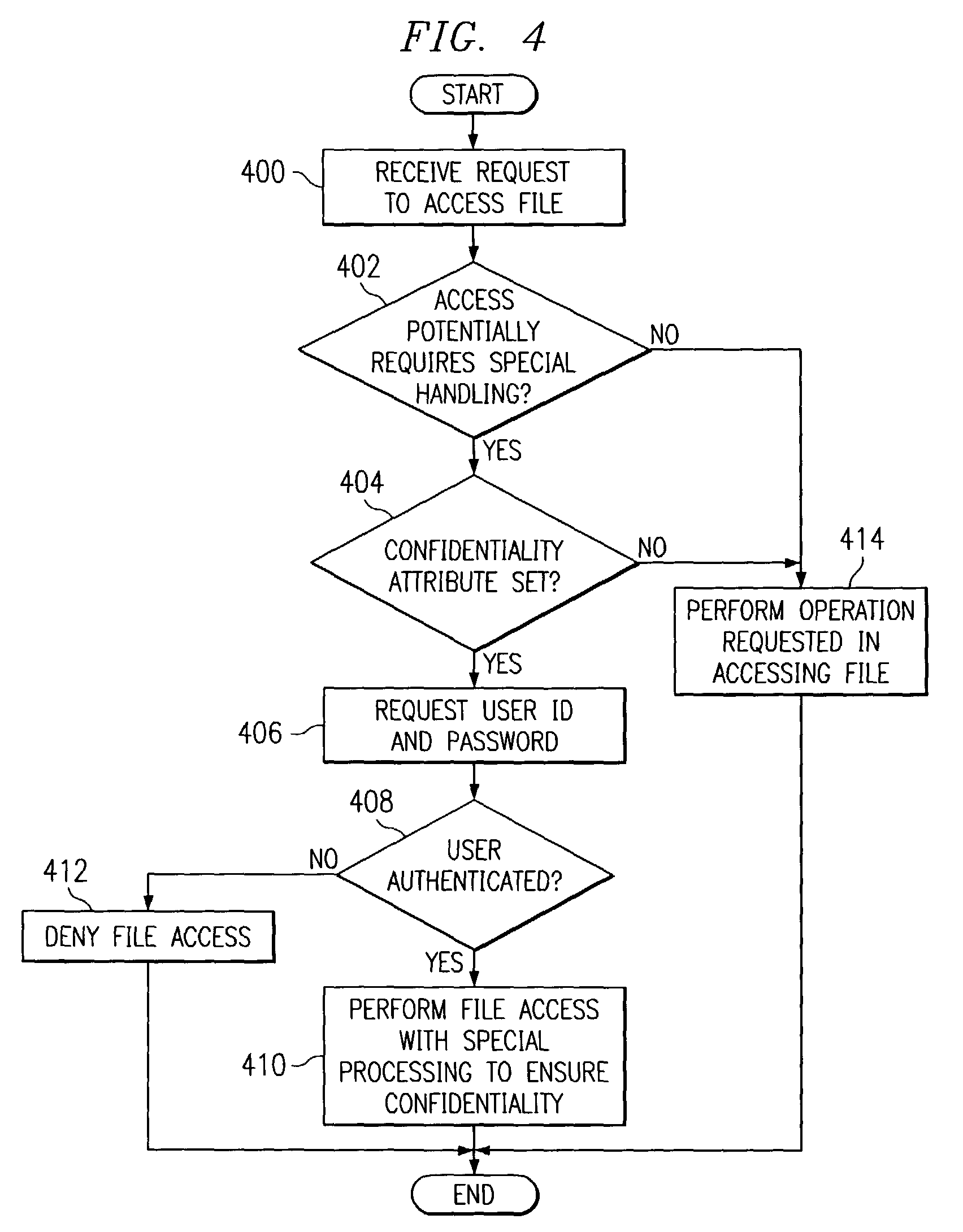
Method and apparatus for handling files containing confidential or sensitive information
InactiveUS7519984B2Digital data processing detailsUnauthorized memory use protectionData processing systemOperational system
A method, apparatus, and computer instructions for managing files in a data processing system. An attribute for a file is specified as having a special designation. The file with the attribute having the special designation is processed, by the operating system, in a different manner from other files when performing operations, such as, for example, copying the file to a removable media, printing the file, or sending the file over a network.
Owner:IBM CORP
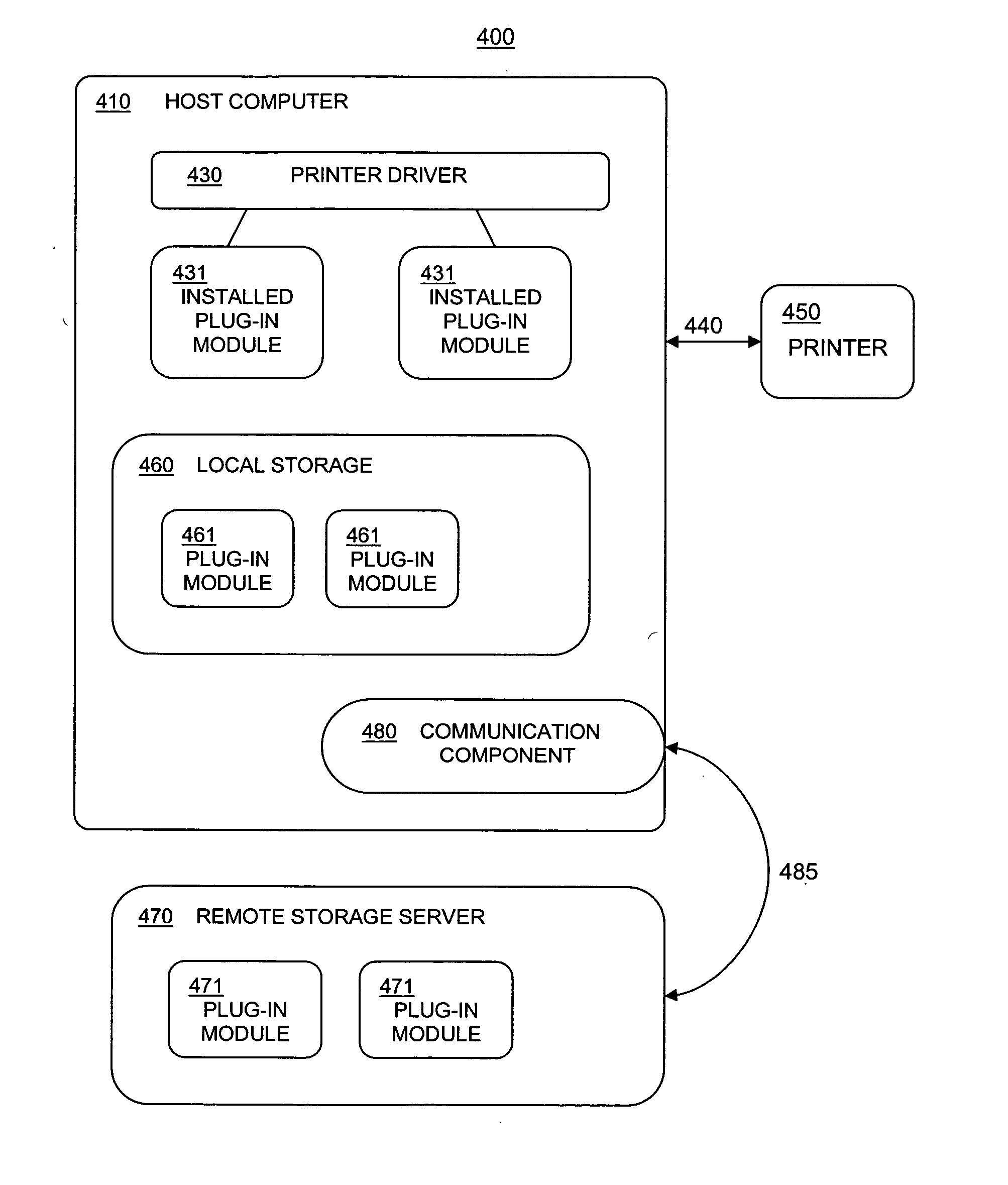
Printer driver plug-in module management system
InactiveUS20050157321A1Digital computer detailsProgram loading/initiatingFeature setServer replication
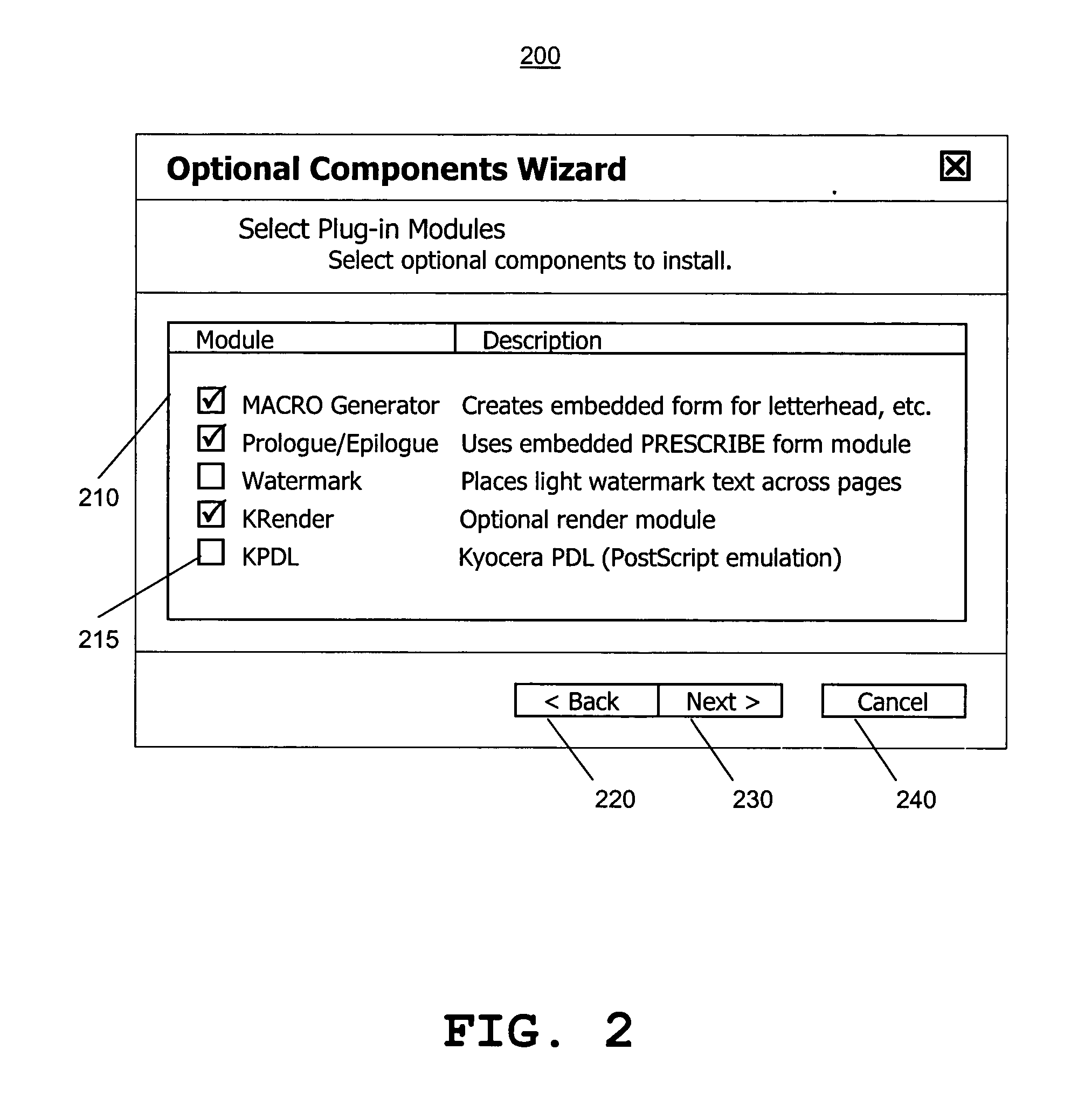
A method for dynamically augmenting printer drivers, by providing a GUI for selecting plug-in modules, and dynamically adding the selected plug-in modules. Addition and deletion of plug-in modules do not require uninstallation and reinstallation of the currently installed printer driver. Plug-in modules implement optional or model-specific functionalities, including feature sets, Page Description Languages (PDLs), and Renders. Settings for plug-in modules are stored in heap-allocated private devmode structures, which may be deallocated when plug-in modules are removed. Methods include copying DLL files to a printer system folder, checking compatibility of the plug-in DLL files, adding registry entries, plug-in module installing itself, adding GUI tabs, and downloading plug-in modules stored at a remote storage over the network. In an embodiment, registry entries are checked for any plug-in modules, and the corresponding DLL files are copied from a server to a client.
Owner:KYOCERA TECH DEV
File management program
InactiveUS7636898B2Simplified managementEasy to manageTelevision system detailsColor television detailsDrag and dropFile copying
The computer readable medium has embodied thereon a file management program for processing by a computer, the file management program comprising: a first code segment for, when an icon of a first folder displayed on a display apparatus is dragged and dropped onto another icon of a second folder displayed on the display apparatus, creating a third folder at the same level as the second folder; and a second code segment for copying a file stored in the first folder and a file stored in the second folder into the third folder.
Owner:FUJIFILM CORP
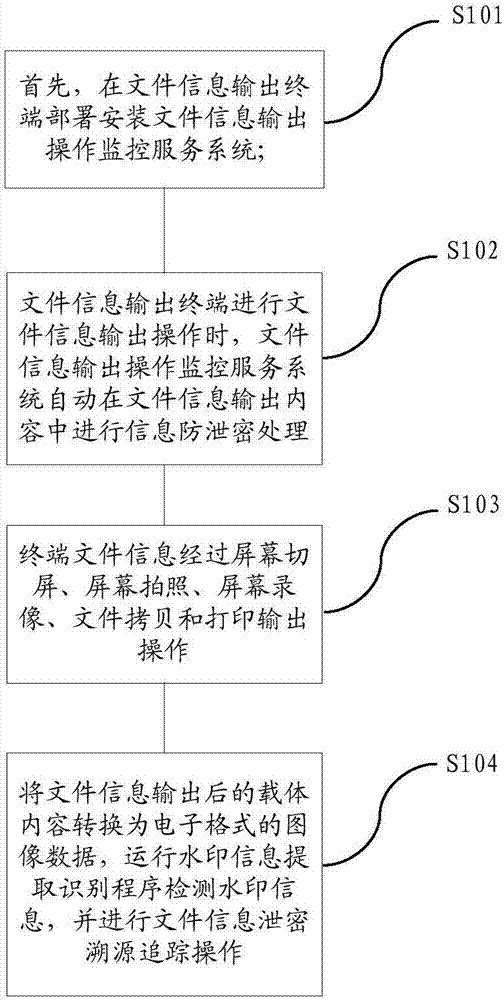
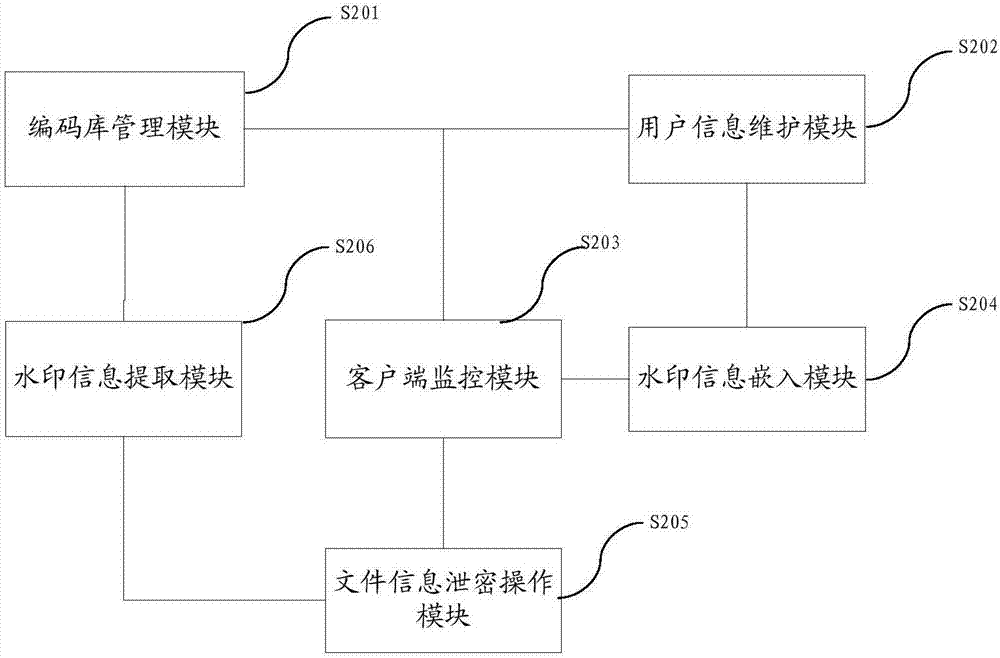
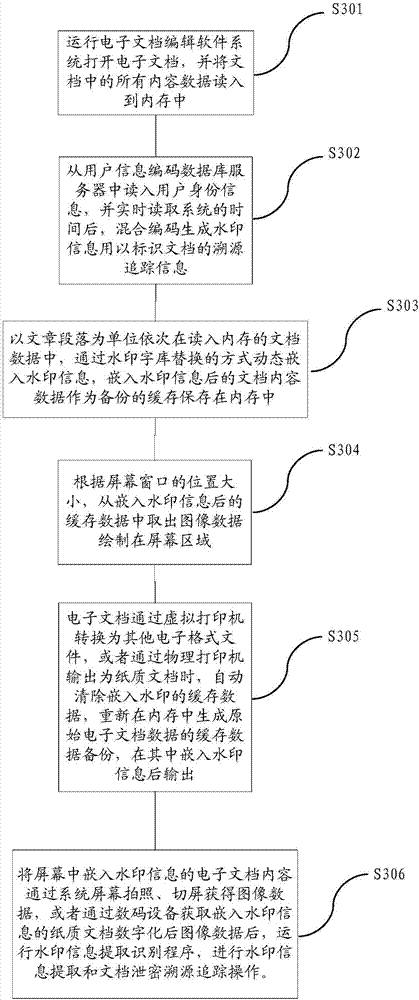
File information output anti-leakage and tracing method and system
ActiveCN107423629AImprove visual effectsDoes not affect normal readingText processingDigital data protectionMonitoring systemComputer terminal
The invention relates to a file information output anti-leakage and tracing method and system. The method comprises the steps of deploying a file information output operation monitoring service system in a file information output terminal; when the file information output terminal performs file information output operation, automatically performing information anti-leakage processing in file information output contents by the file information output operation monitoring system, wherein the anti-leakage processing includes the addition of invisible watermark information; performing one or more of screen switching, screen shooting, screen video recording, file copying and printout operations on file information of the file information output terminal; and converting carrier contents after file information output into image data in an electronic format, running a watermark information extraction identification program to detect the watermark information, and performing file information leakage tracing operation. According to the method and the system, the technical difficult problem of tracing after leakage of screen shooting and printout modes of the file information output terminal can be solved on the premise of not influencing the visual effect of right reading of users.
Owner:李晓妮
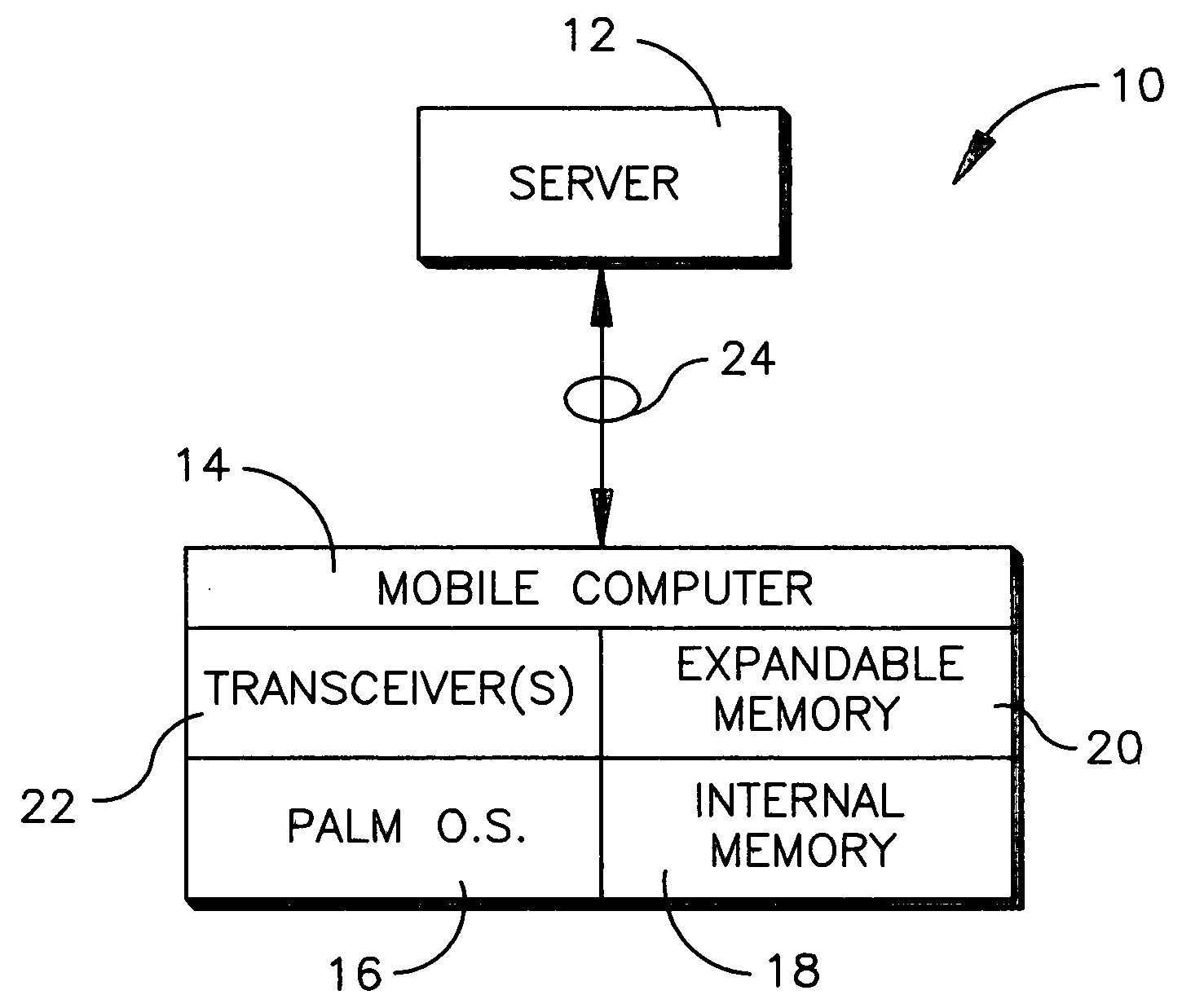
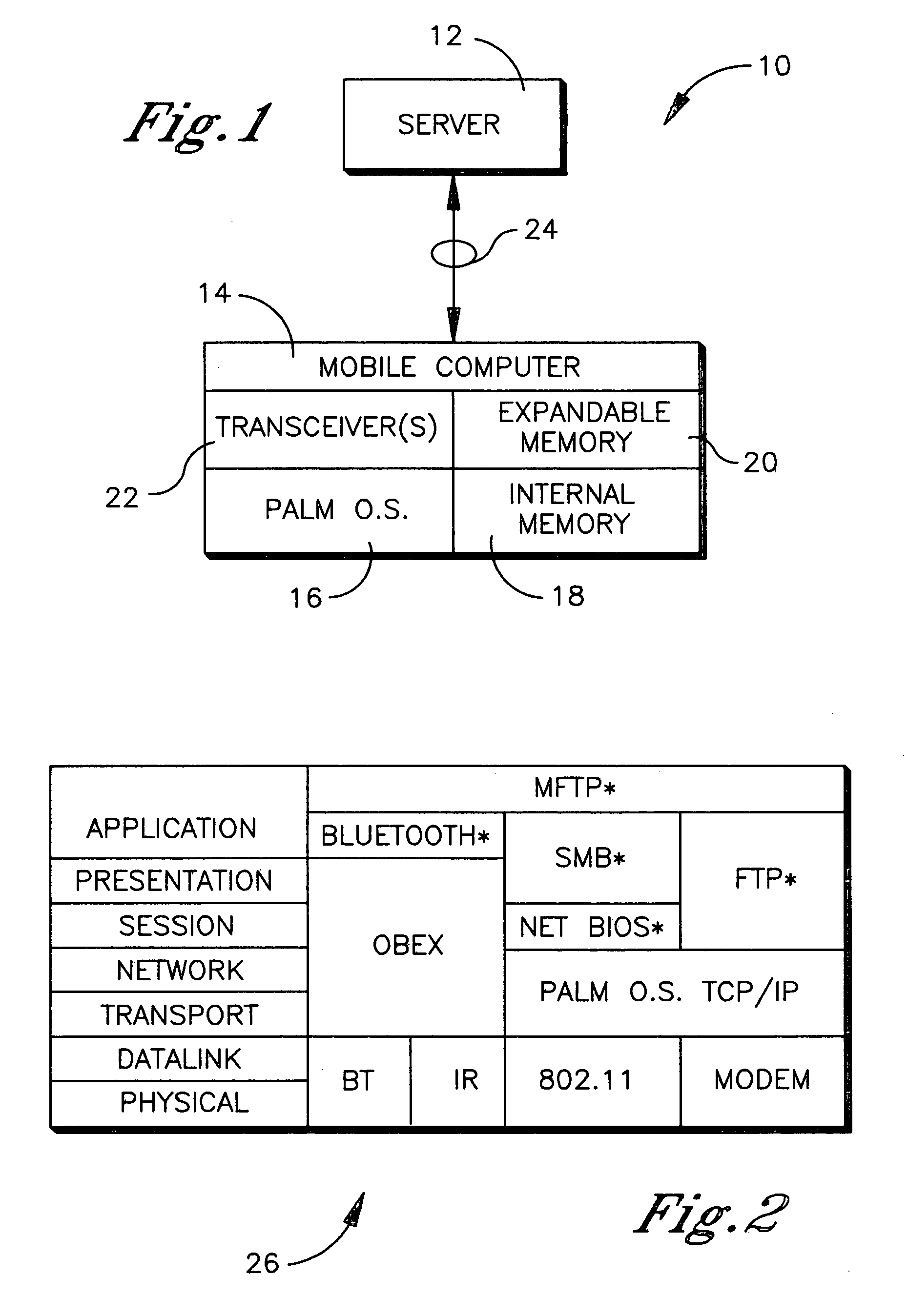
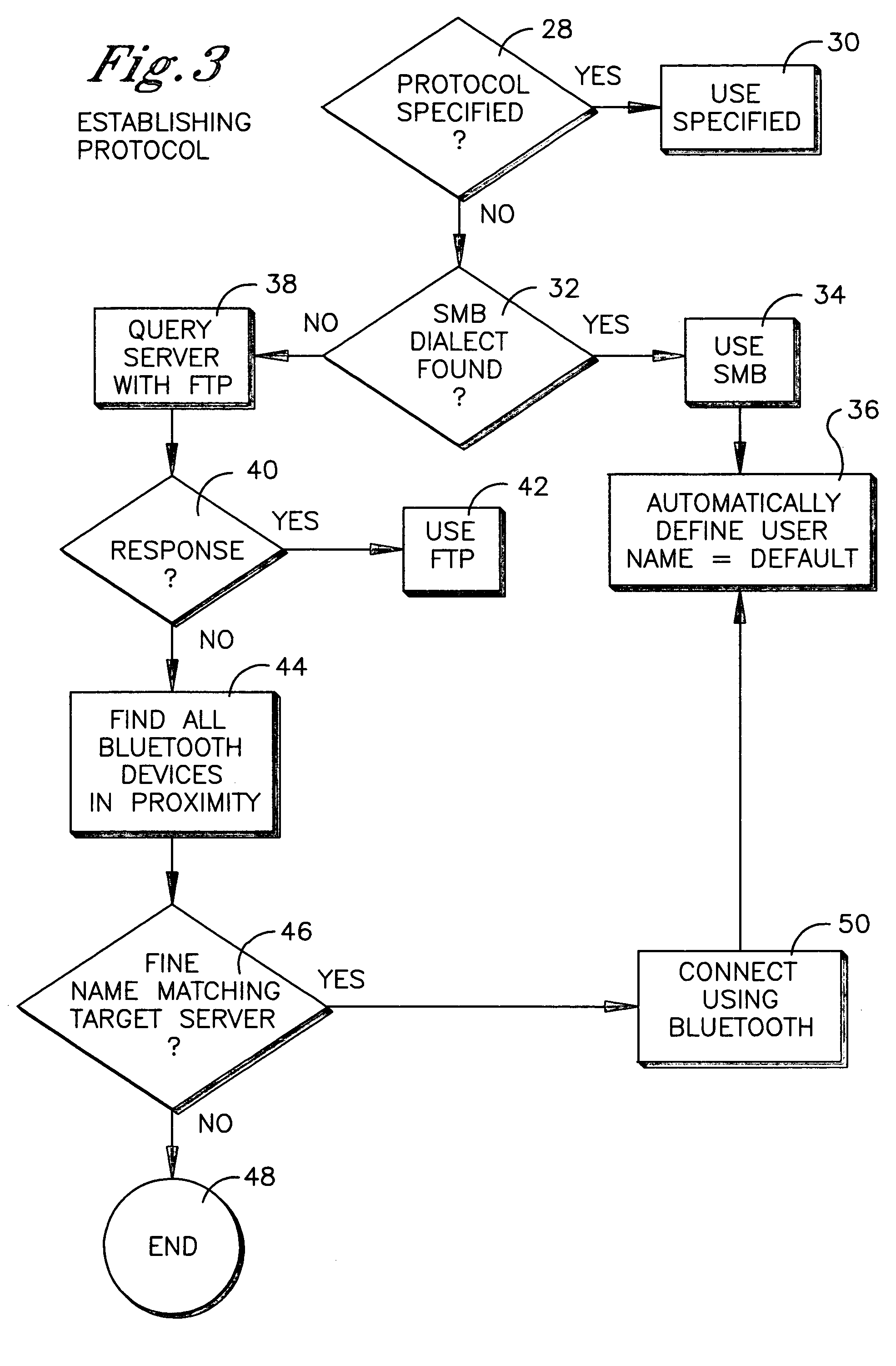
File transfer protocol for mobile computer
InactiveUS20050102537A1Digital data processing detailsPicture reproducers using cathode ray tubesInternal memoryBluetooth
A method is disclosed for communicating using a device having a Palm OS. SMB is preferentially used to communicate with a node, and if use of SMB is not possible, FTP is used, and if use of FTP is not possible, Bluetooth is used. If FTP or Bluetooth is selected as the protocol, file sharing between the device and node that entails a read or write is executed by temporarily copying a file to an internal Palm OS memory of the device, performing the read or write on the file, and then copying the file back to the node to overwrite a previous version of the file at the node. For non-Palm OS file transfer to the internal memory, the file is wrapped in a Palm OS stream in the internal memory for executing reads or writes. For file transfer to an expansion Palm OS memory card, byte-to-byte copying of the file is executed using the FAT of the expansion memory, with the file being transferred through an internal Palm OS memory of the device.
Owner:SONY CORP +1
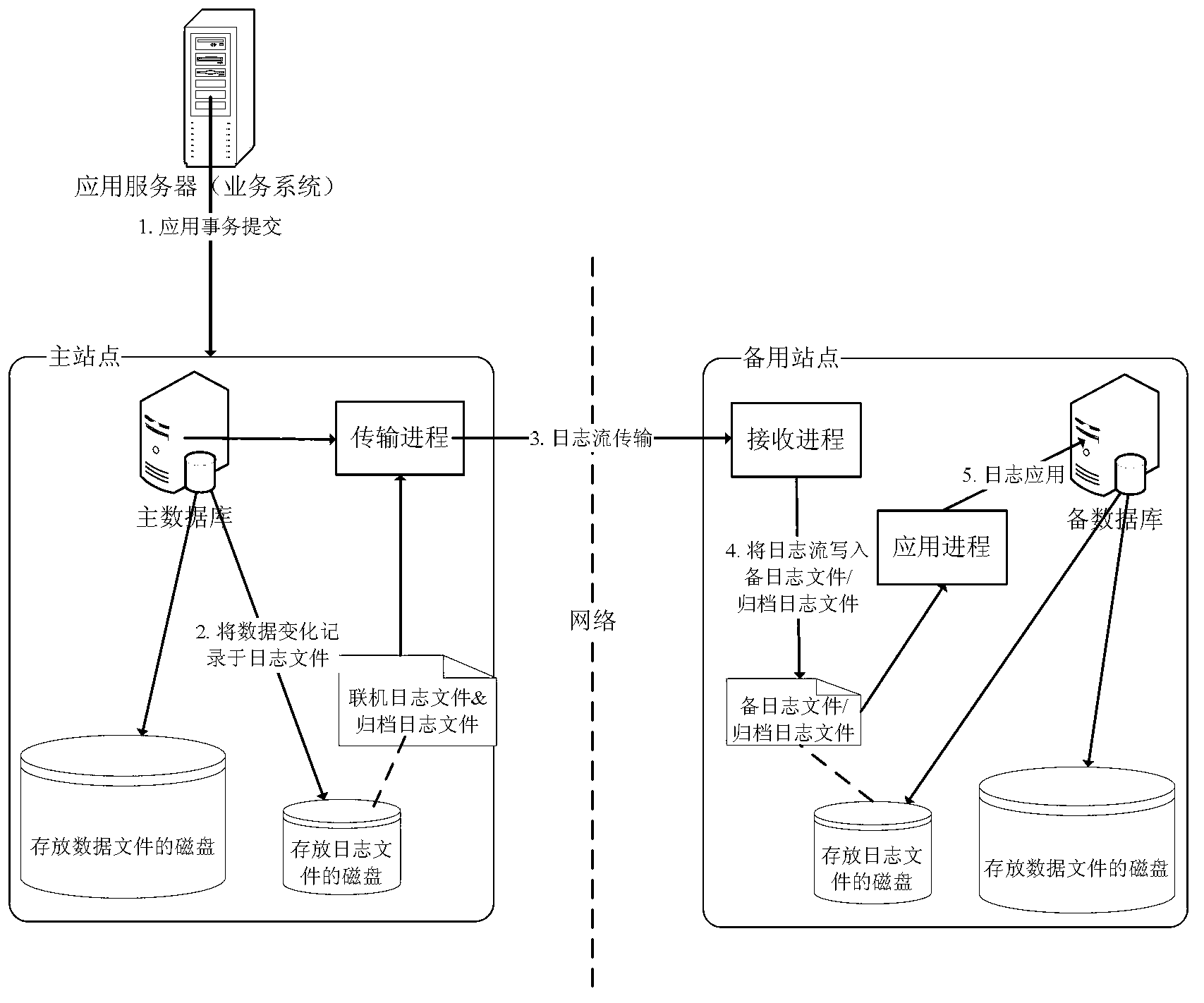
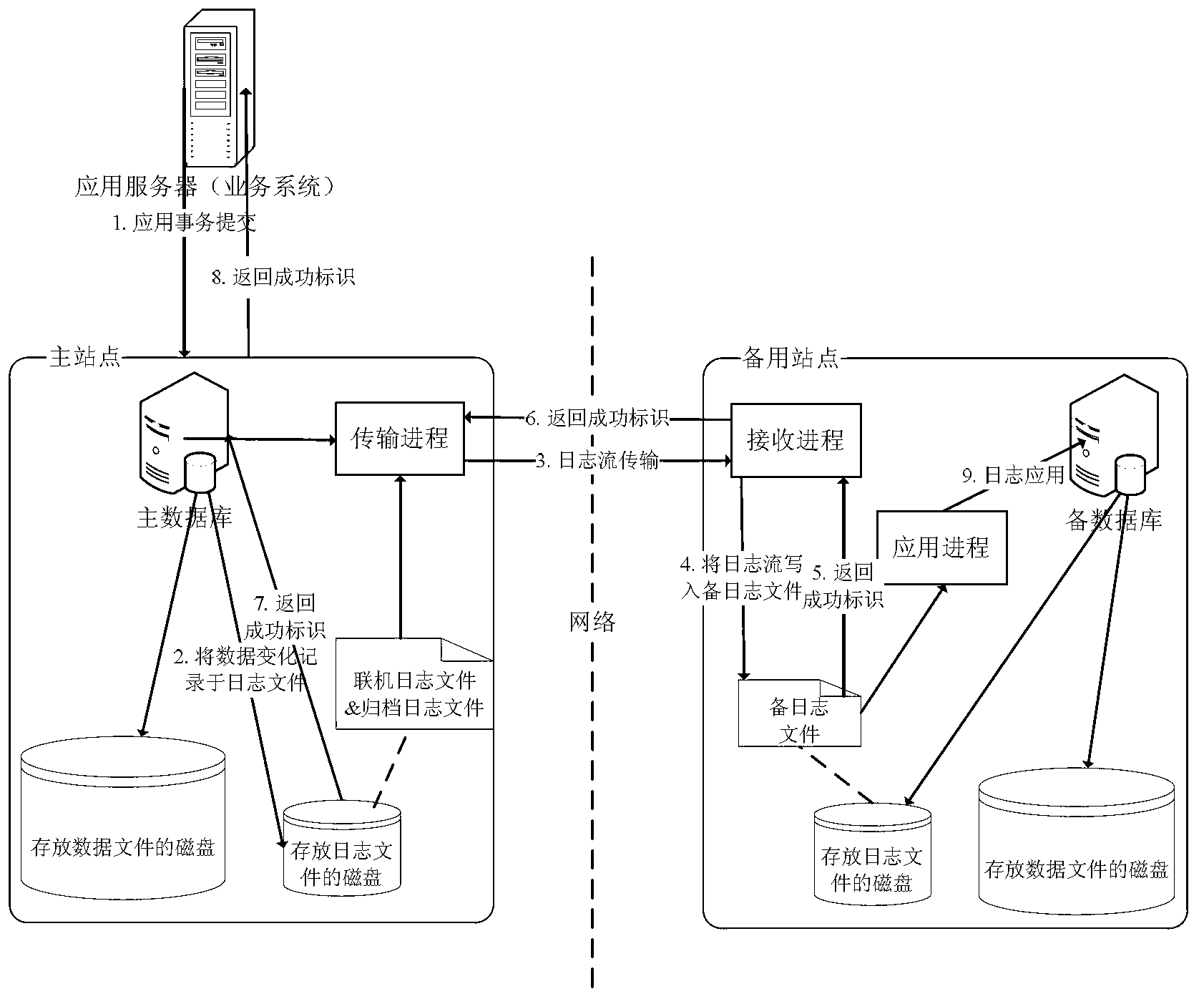
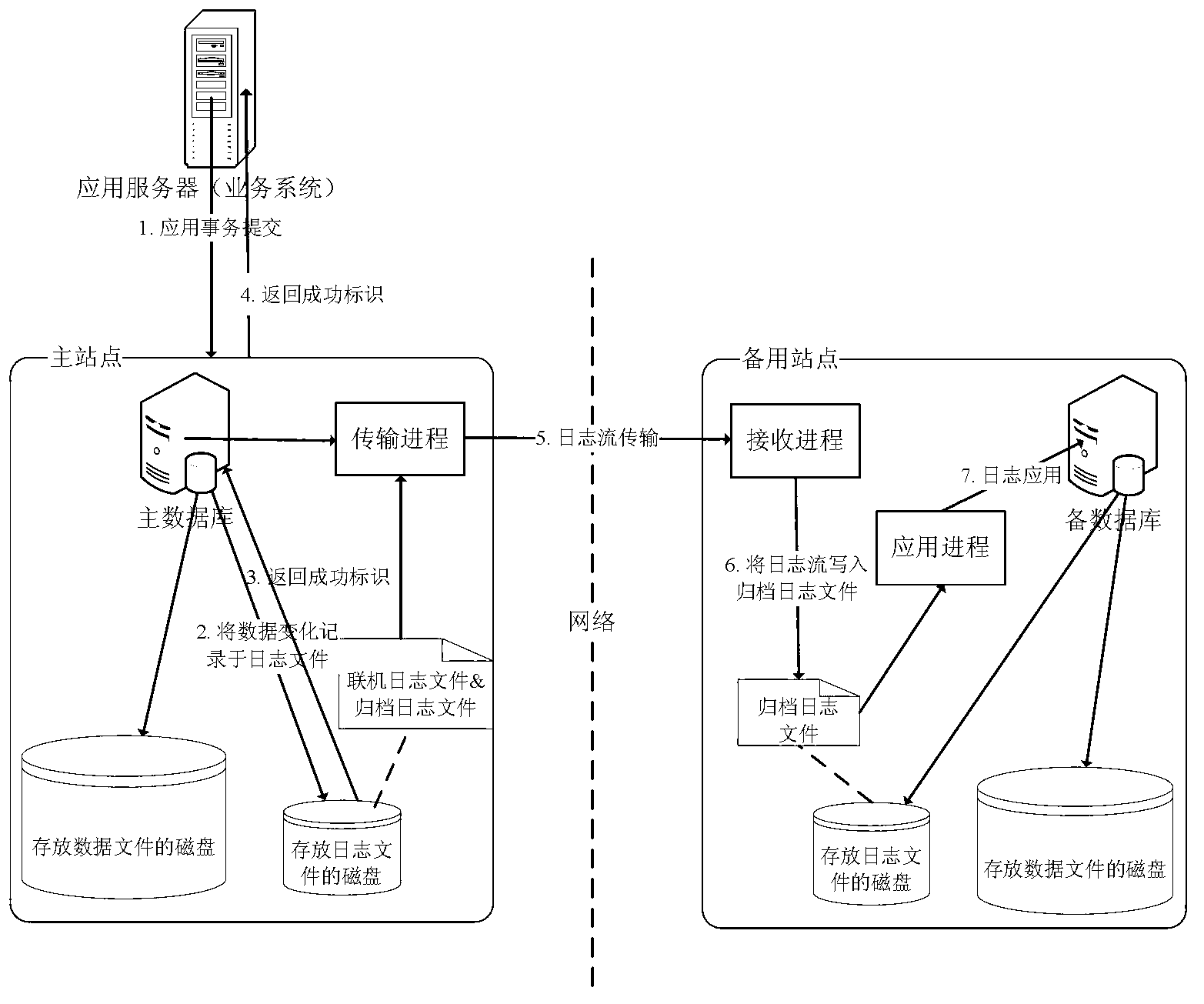
Data disaster backup control system and data recovery method
ActiveCN103226502ALittle impact on performanceMake sure to loseRedundant operation error correctionLogfileFile copying
The invention discloses a data disaster backup control system which comprises a data loss identifying device, a main and standby switching executing device, an archive log file application device, a log disc switching device and an online log file application device, wherein the data loss identifying device is in charge of inquiring a data state of a standby database to check whether data loss exists and calling the main and standby switching executing device if the data loss does not exist; the main and standby switching executing device is used for starting the standby database and confirming that the state of the standby database is available; the archive log file application device is in charge of applying an archive log file in a log file disc and an archive log file in a log file copying disc to the standby database; the log disc switching device is in charge of deleting the log file disc from a server in which the standby database is set, controlling a control disc controller to add the log file copying disc to the server in which the standby database is set and enabling the standby database to access the log files in the disc; and the online log file application device is called by a control engine device and is in charge of applying an online log file from the log file copying disc to the standby database.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
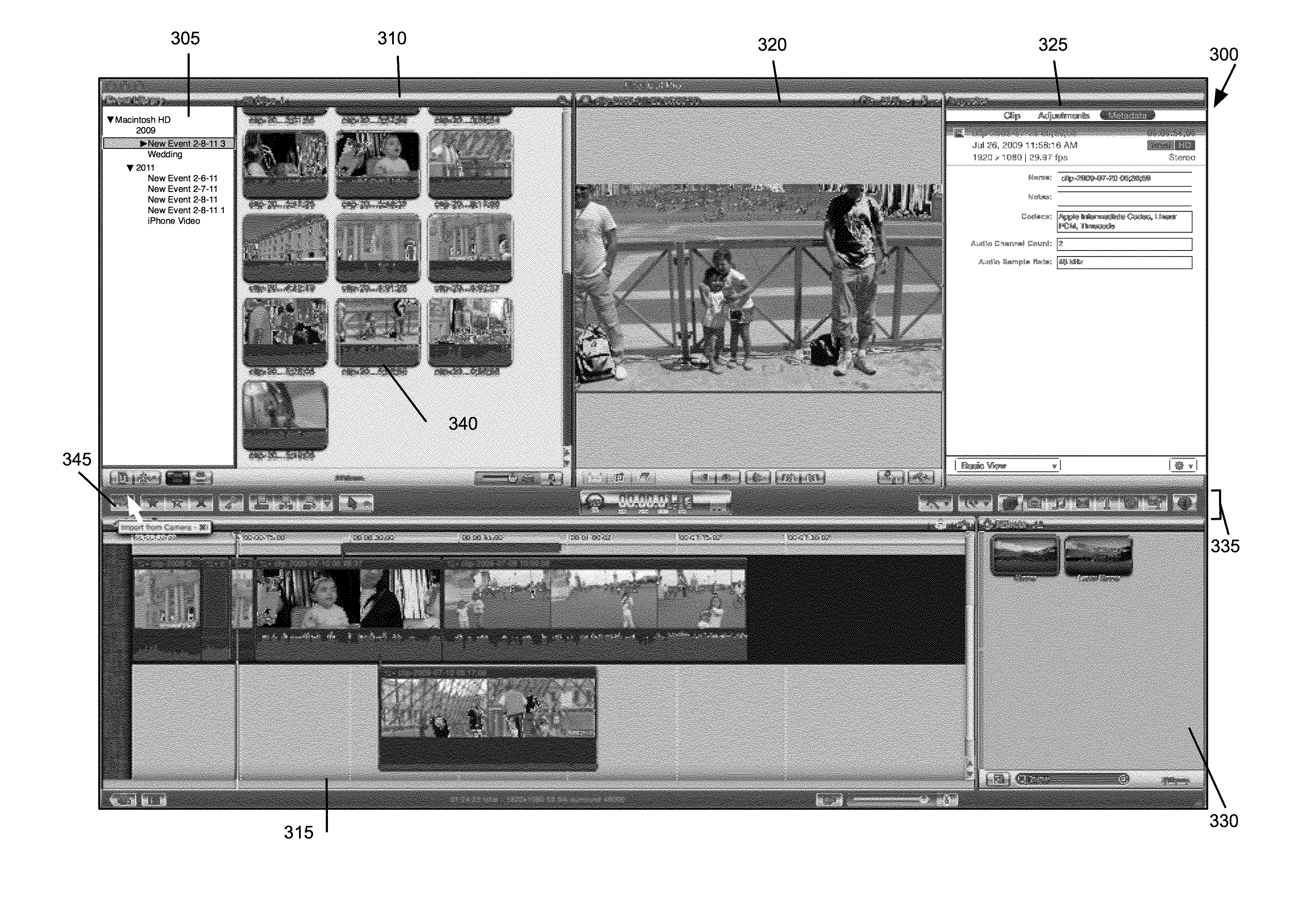
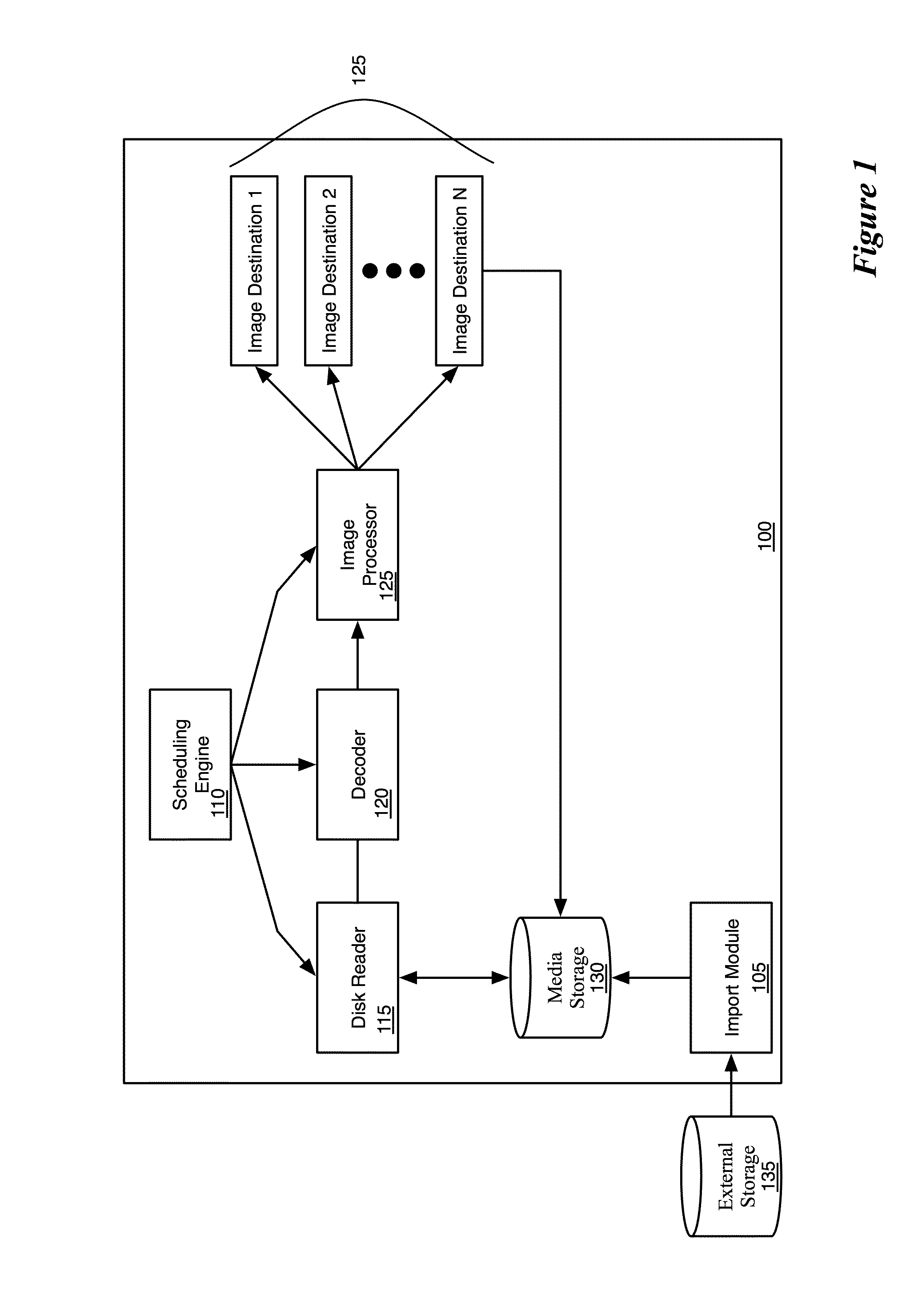
Efficient Media Import
ActiveUS20120207449A1Minimize the numberPrevents duplicative disk readsTelevision system detailsGeometric image transformationComputer graphics (images)Application software
Some embodiments provide a media-editing application. The application receives a command to import a media file into the media-editing application. The media file includes a sequence of video images. The application copies the media file to a storage location associated with the media-editing application. The method performs several analysis and transcode operations on the media file in parallel. In some embodiments, the application identifies a video image on which to the operations. The application schedules a single set of image preparation operations for the video image to generate one or more sets of image data for the operations. The method sends the image data to the different operations. A same set of image data is sent to at least two of the operations.
Owner:APPLE INC
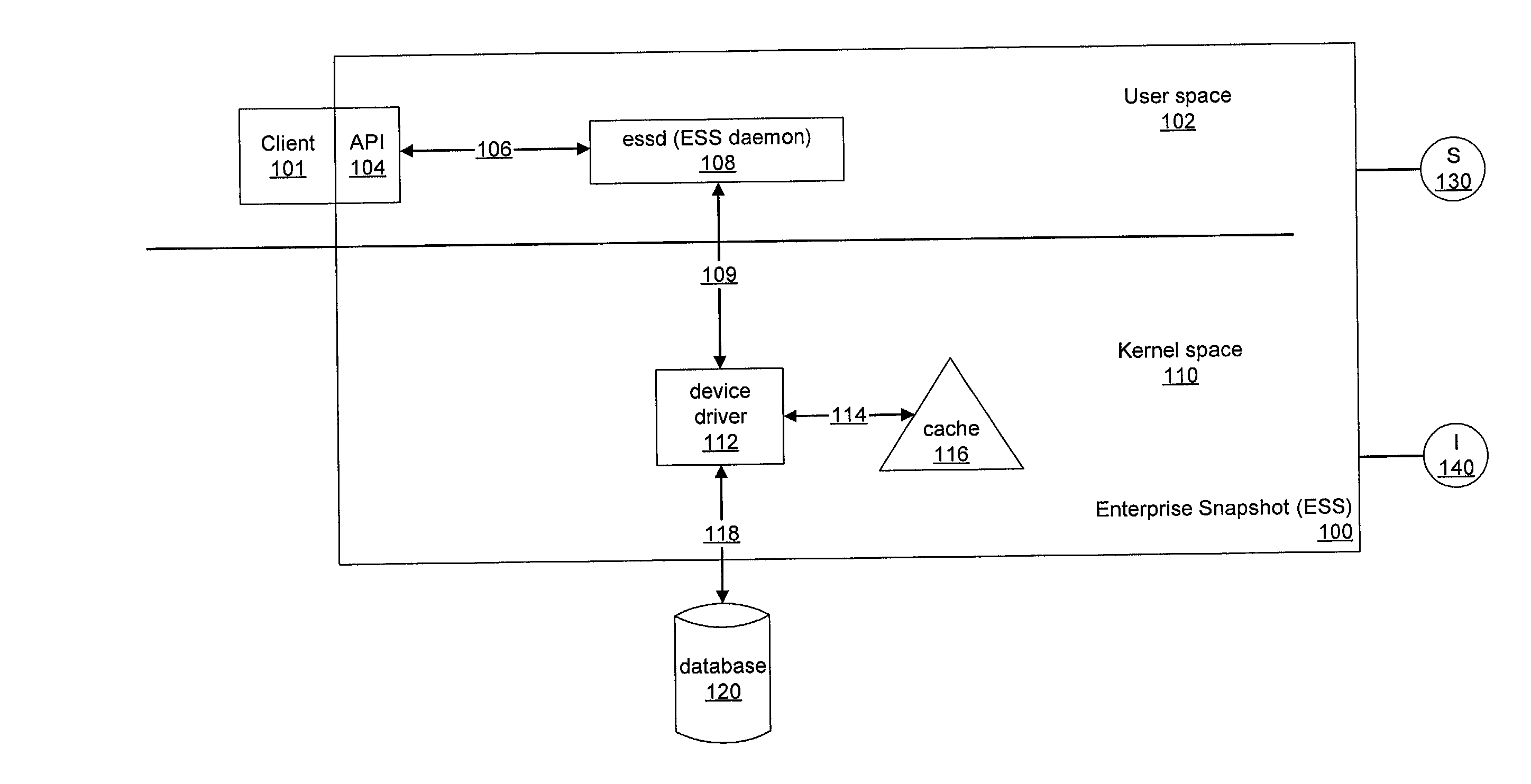
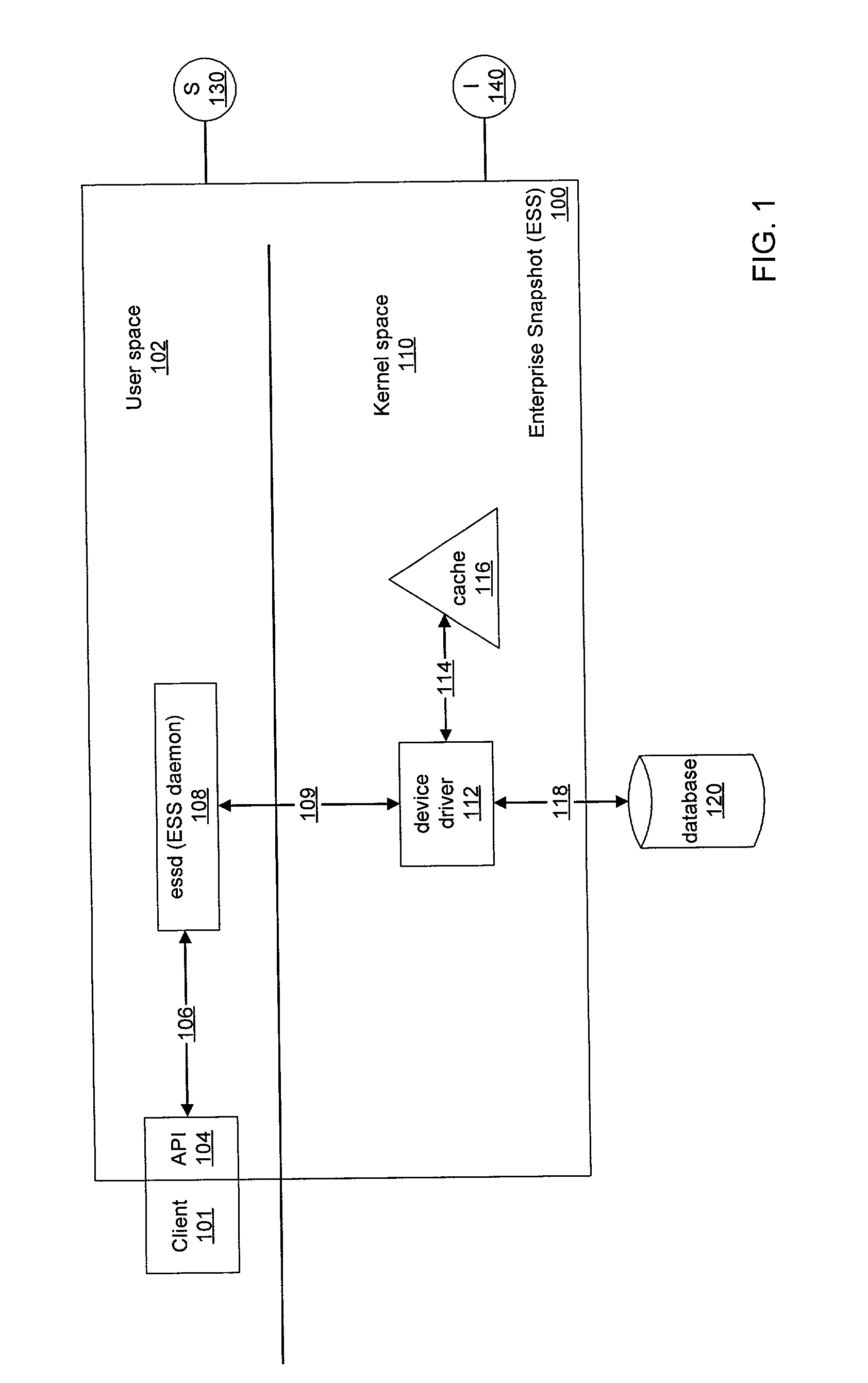
System and method for creating online snapshots
InactiveUS20030093443A1Redundant operation error correctionMemory systemsDatabase fileImproved method
An improved method and system for creating online snapshots. Files (e.g., database files) are registered with a snapshot software component technology by a backup software utility. A methodology (e.g., software or hardware based) to backup each file is determined. For the software methodology, captured reads for updated data receive data returned from the cache; captured reads for non-updated data receive data returned from the registered file; a pre-image of an appropriate data block of the registered file for captured writes is saved to a cache if the data block has no previously saved pre-image. The backup is consistent with the state of each registered file at the point in time of the start of the snapshot software component technology. Non-updated data is copied from the registered file to a backup device; a pre-image version of updated data is copied to the backup device.
Owner:BMC SOFTWARE
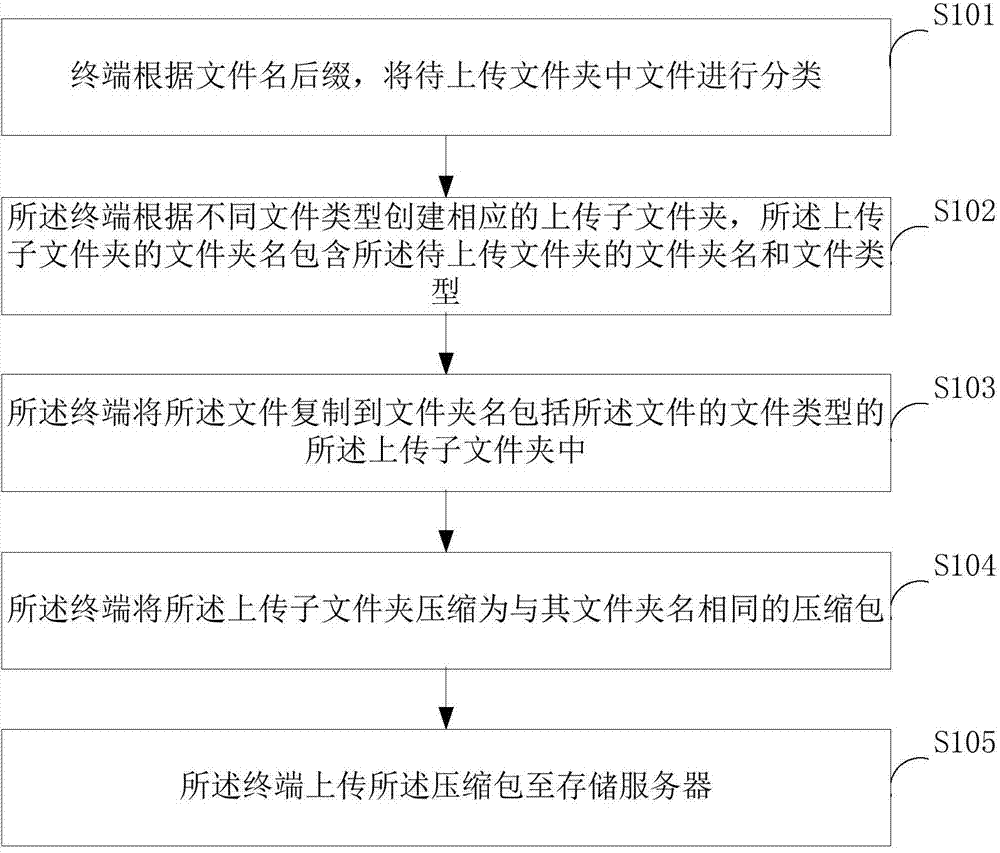
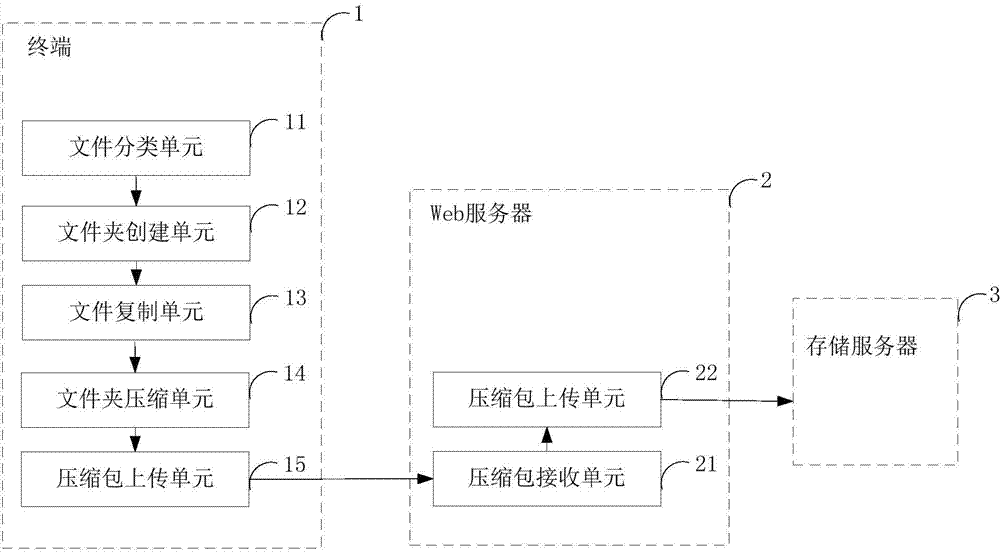
Method and system for uploading files in classifying and batching mode
ActiveCN103677673AReduce cumbersomeReduce misinformationInput/output to record carriersFilename extensionData transmission
The invention is suitable for the technical field of computer data transmission and provides a method and system for uploading files in a classifying and batching mode. The method comprises the steps that a terminal classifies the files in folders to be uploaded according to filename extensions, corresponding uploading subfolders are set up according to different file types, folder names of the uploading subfolders comprise the folder names and the file types of the folders to be uploaded, the files are copied to the uploading subfolders with the folder names comprising the file types of the files, the uploading subfolders are compressed into packages with names the same as the folder names of the uploading subfolders, and the packages are uploaded into storage servers. According to the method and the system, the files of a plurality of types are classified and uploaded to the different storage servers, the defect that the file batch uploading function is operated for many times due to difference of the file types is overcome, error and leakage of uploading are reduced, and the work efficiency is improved.
Owner:TCL CORPORATION
Data processing system for instrumental analysis, server and data processing method
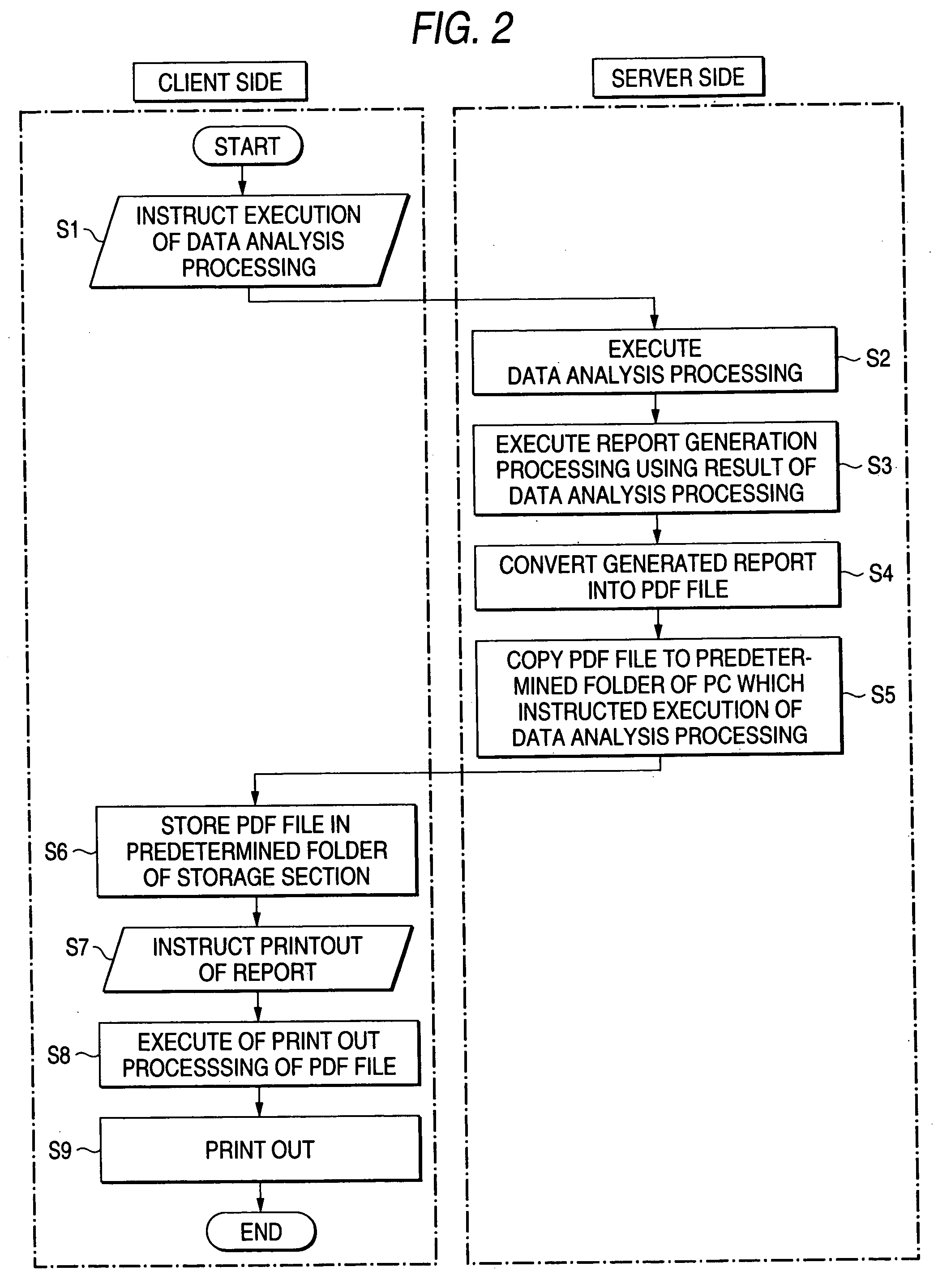
InactiveUS20050240586A1Reduce loadSignificant burdenSpecial data processing applicationsDigital output to print unitsProcessing InstructionComputer printing
A server receiving instruction of data analysis processing executes the analysis processing, generates a report using the processing result, and then converts the report document into a PDF file and copies the file into a predetermined folder of a PC of the processing instruction source. When an operator instructs print out with a PC at hand, a report of a PDF format is printed out by a function of a printer driver installed in the PC. Thus, the server does not participate in print out processing at all, load is not imposed on the server, and also there is no need for the server to have a printer driver for a printer connected to each of the PCs.
Owner:SHIMADZU CORP
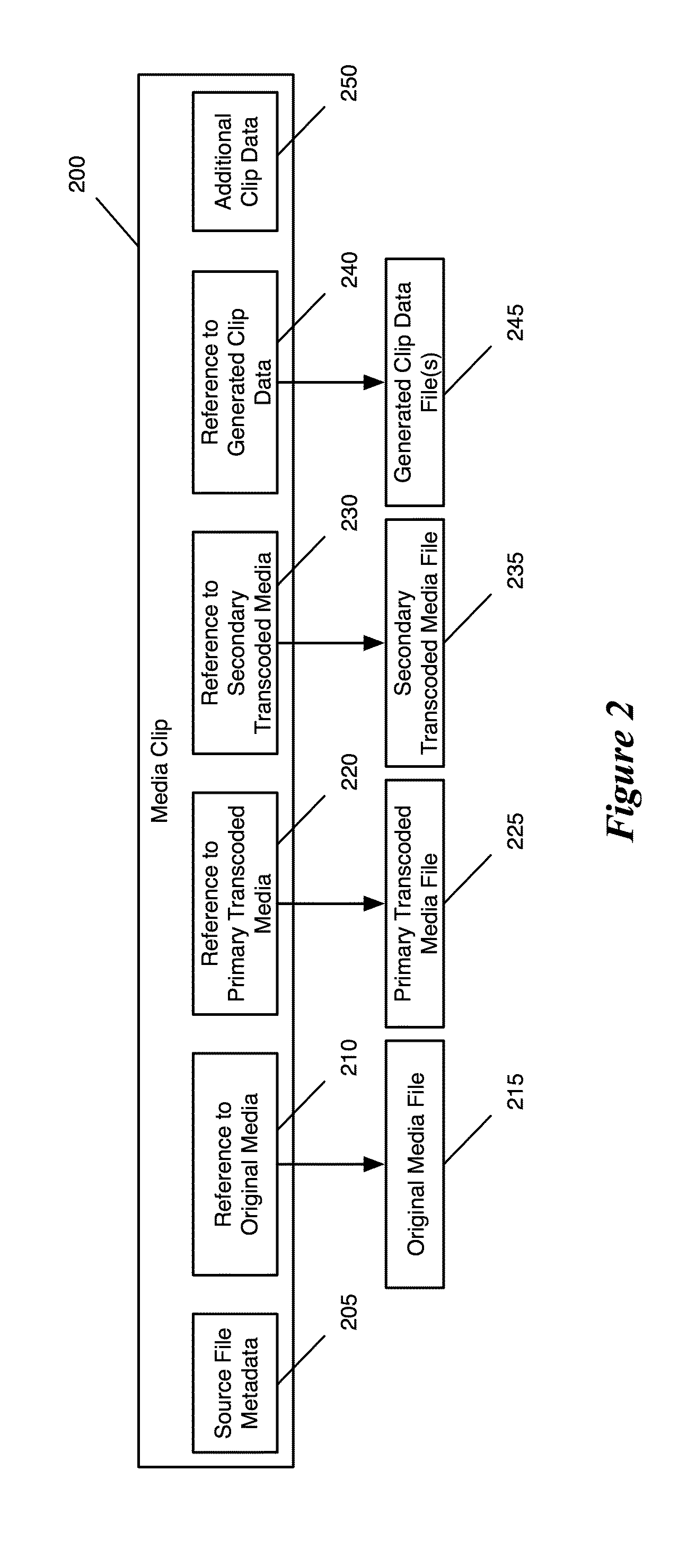
System and method for client mastered replication of local files
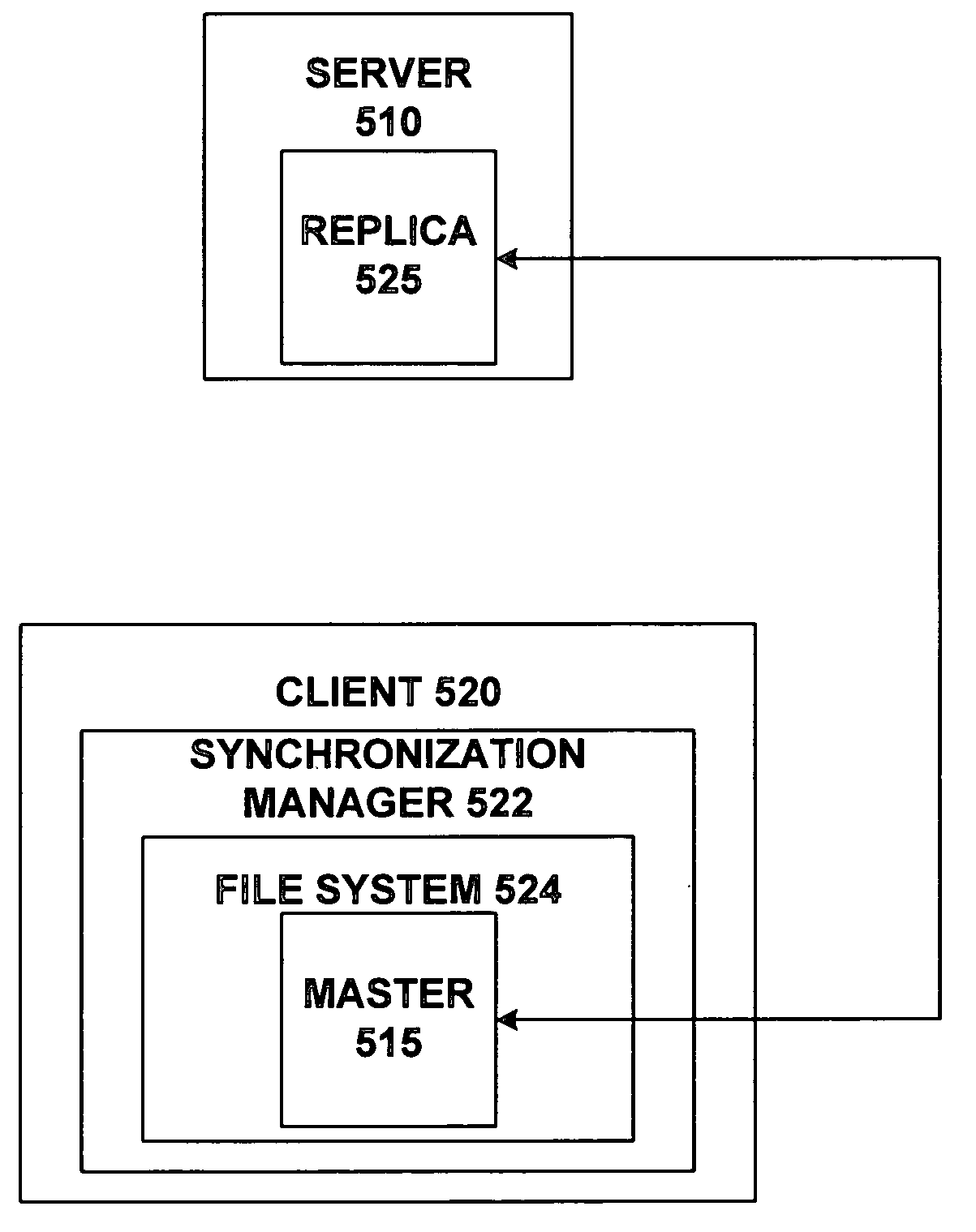
ActiveUS20050114412A1Data processing applicationsDigital data information retrievalClient-sideFile copying
A master file may be created and stored on a client computing device. Changes to the master file may be made locally at the client computing device. The master file may be selected for replication using an associated replication property. Changes to the master file may be replicated to a connected computing device such as a server. Changes to a replica of the master file may be made at the connected computing device. If they do not conflict with local changes the to master file, changes to the replica may be replicated back to the master file.
Owner:MICROSOFT TECH LICENSING LLC
System and Method for Managing Content of Rich Media
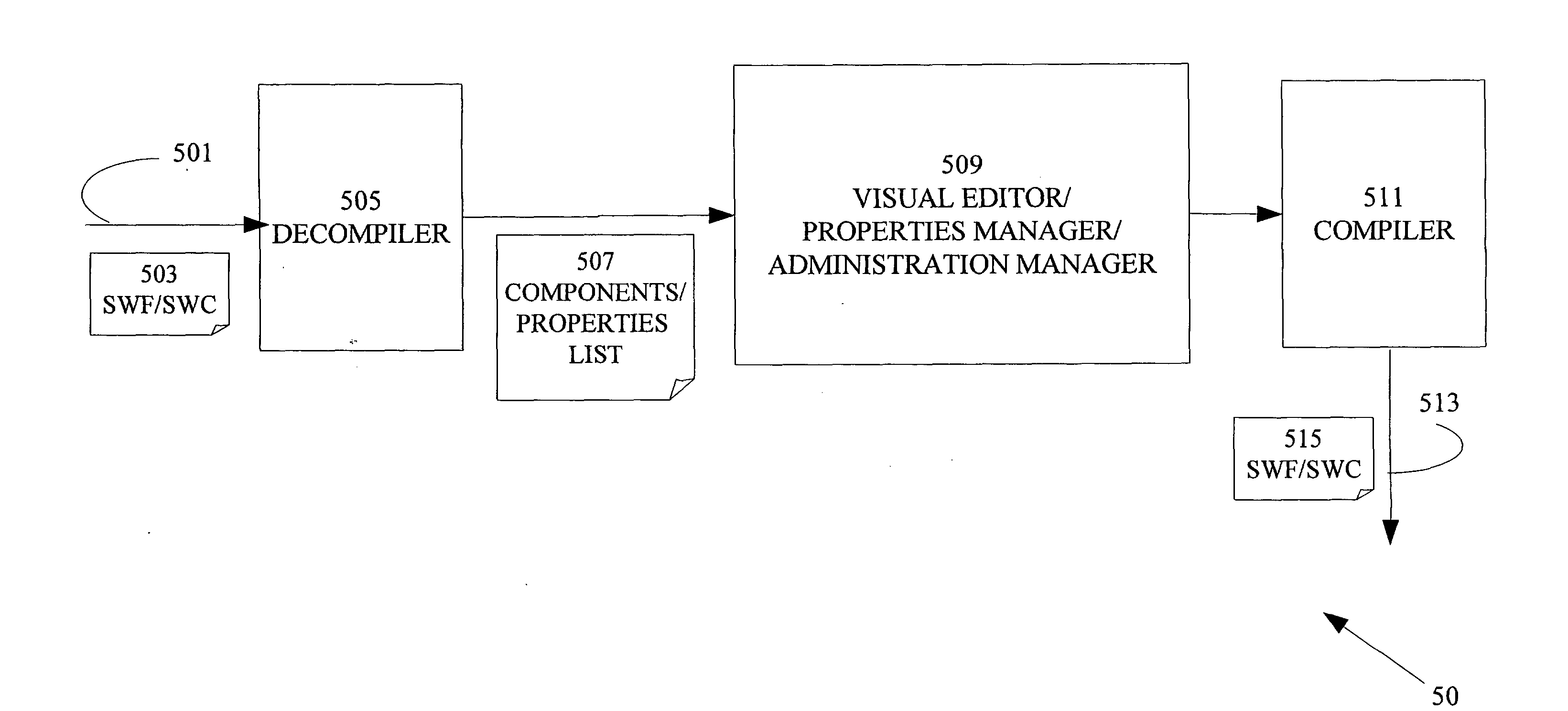
InactiveUS20080215968A1Decompilation/disassemblyNatural language data processingReal time displayFile copying
A method for editing rich media content in a computerized device. The rich media content is stored in a static or binary file. The binary file is copied into storage operatively attached to the computerized device and decompiled and component s of the rich media content are extracted, (FIGS. 5&6). Properties of the components of the rich media content are presented and the properties are edited, (FIGS. 5&6). Preferably, during editing the modified rich media content is displayed in real time. An edited file including modified rich media content is stored preferably in lieu of the original binary file:
Owner:DYNAMIC FLASH
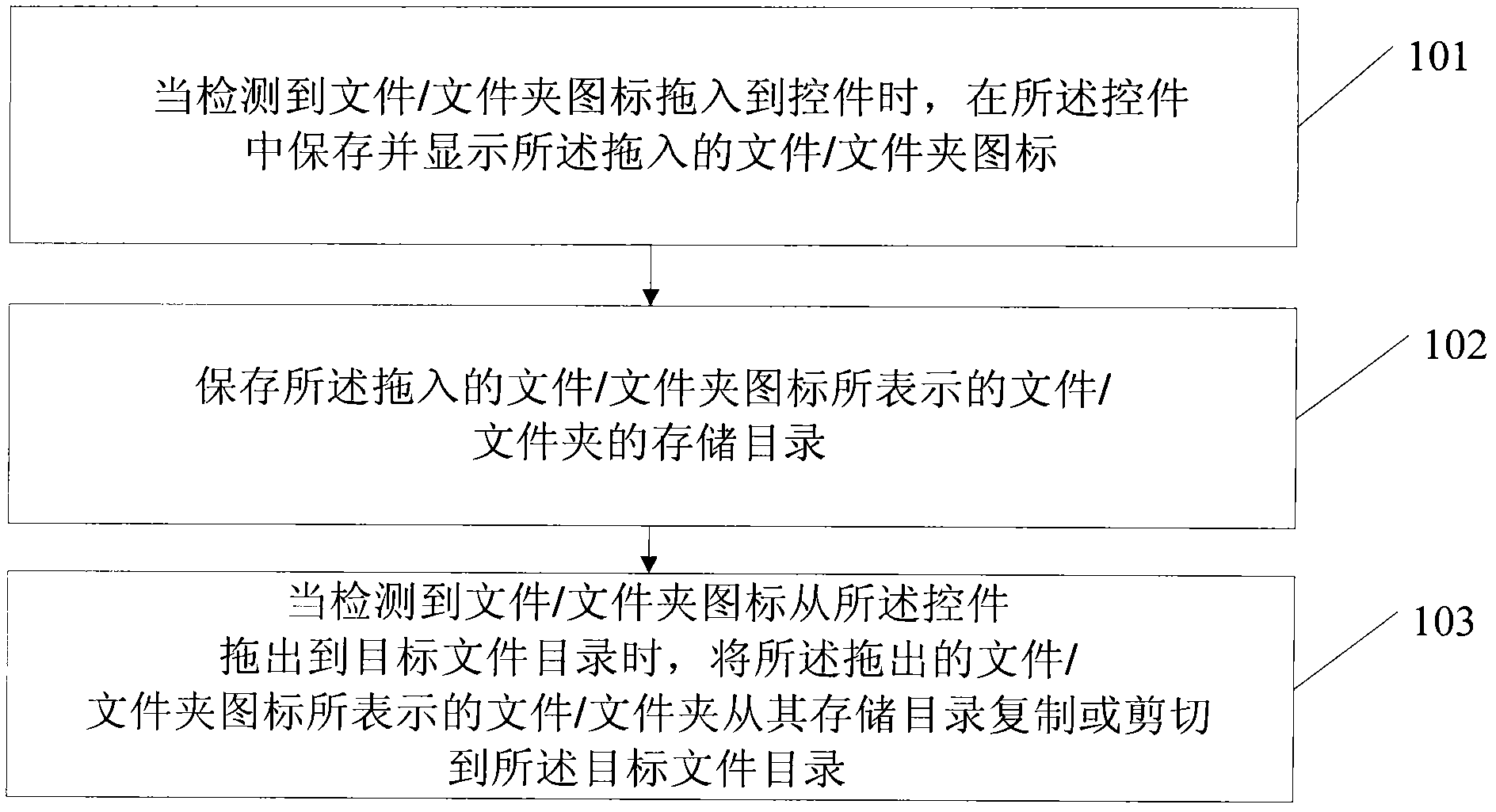
File copying method and terminal
ActiveCN101937310AAchieve replicationImprove replication efficiencySubstation equipmentInput/output processes for data processingComputer terminalFile copying
The invention discloses a file copying method and a terminal, and relates to the technical field of electronic products. The method for copying a file is simple and efficient to operate. The method comprises the following steps of: when a file / folder icon is pulled into a control is detected, storing and displaying the pulled file / folder icon in the control; storing the storage catalog of a file / folder expressed by the pulled file / folder icon; and when the file / folder icon is pulled out to a target file catalog from the control is detected, copying or cutting the file / folder expressed by the pulled file / folder icon to the target file catalog from the storage catalog. The embodiment of the invention is mainly applied in the file copying process, and can conveniently and quickly realize copy of the file when the terminal does not support a functional combined key.
Owner:SHENZHEN TRANSSION HLDG CO LTD
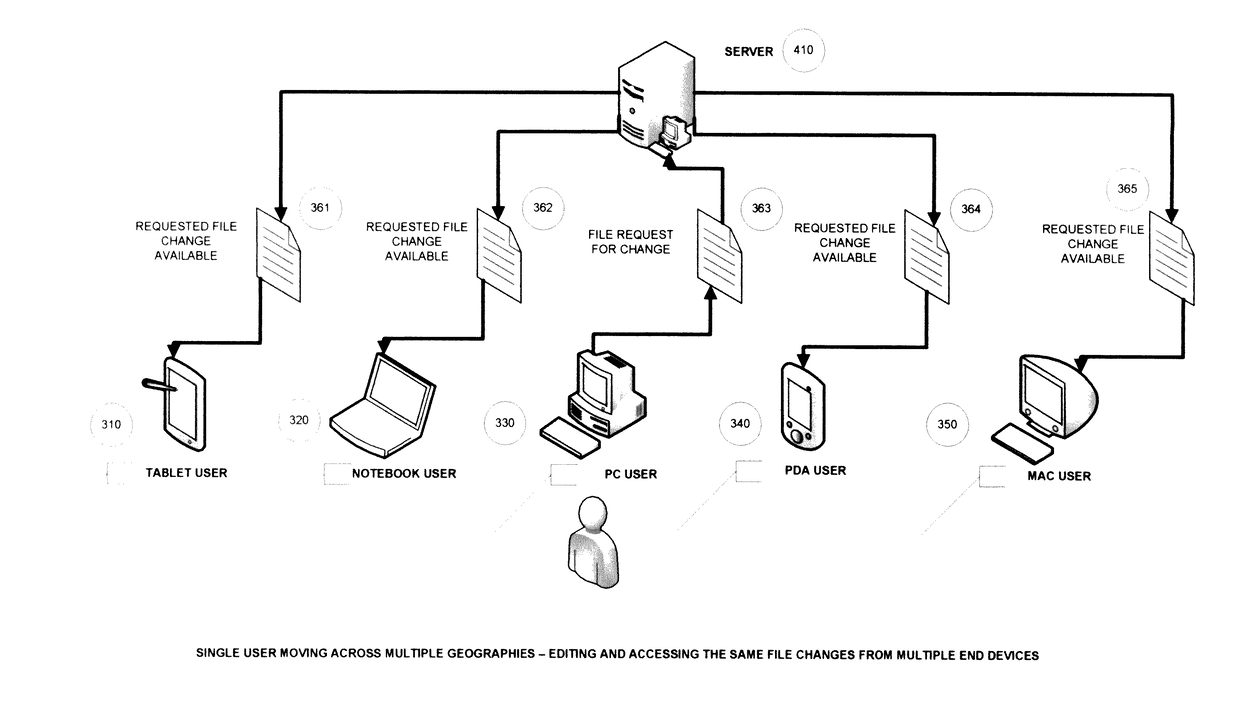
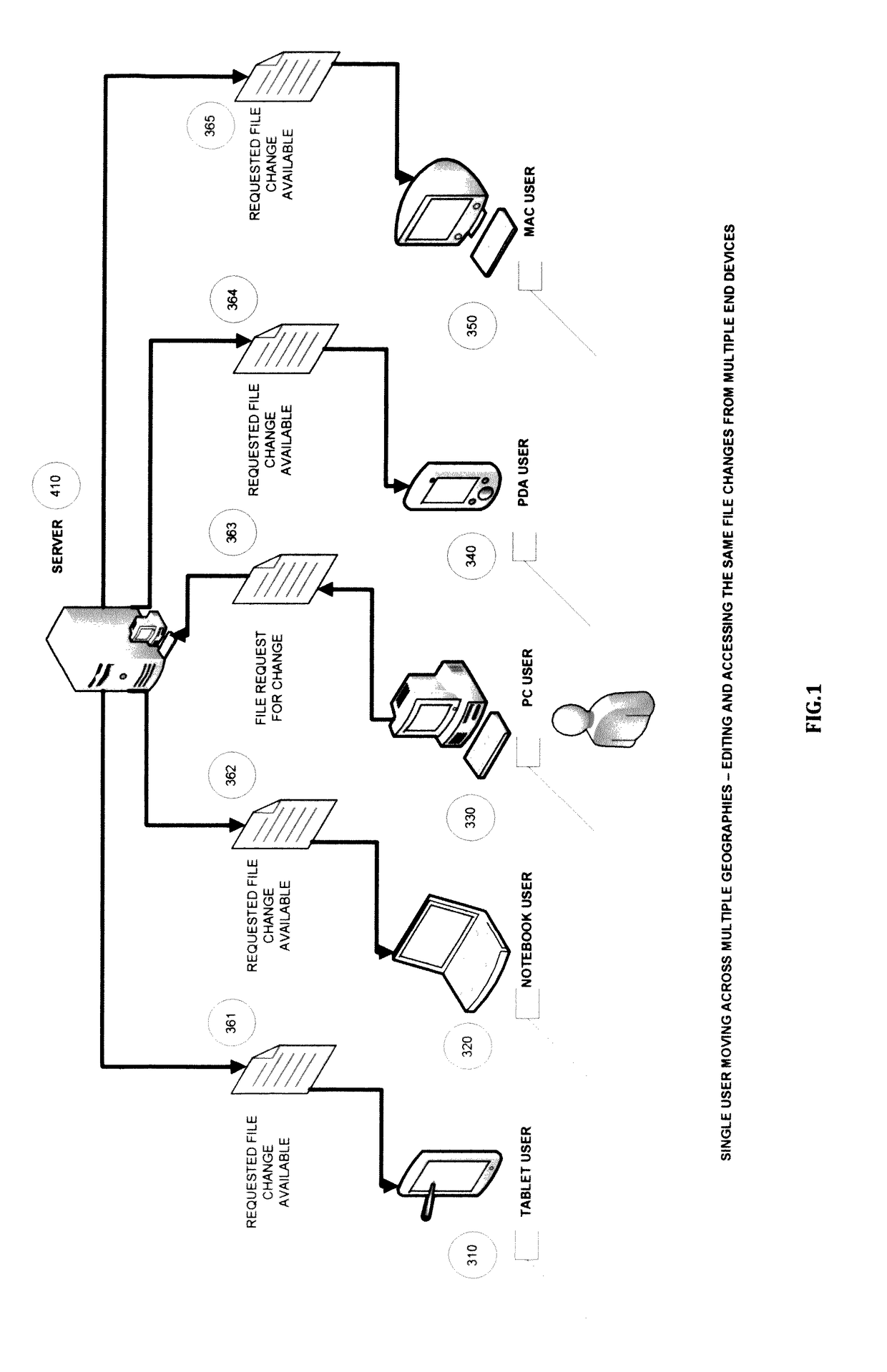
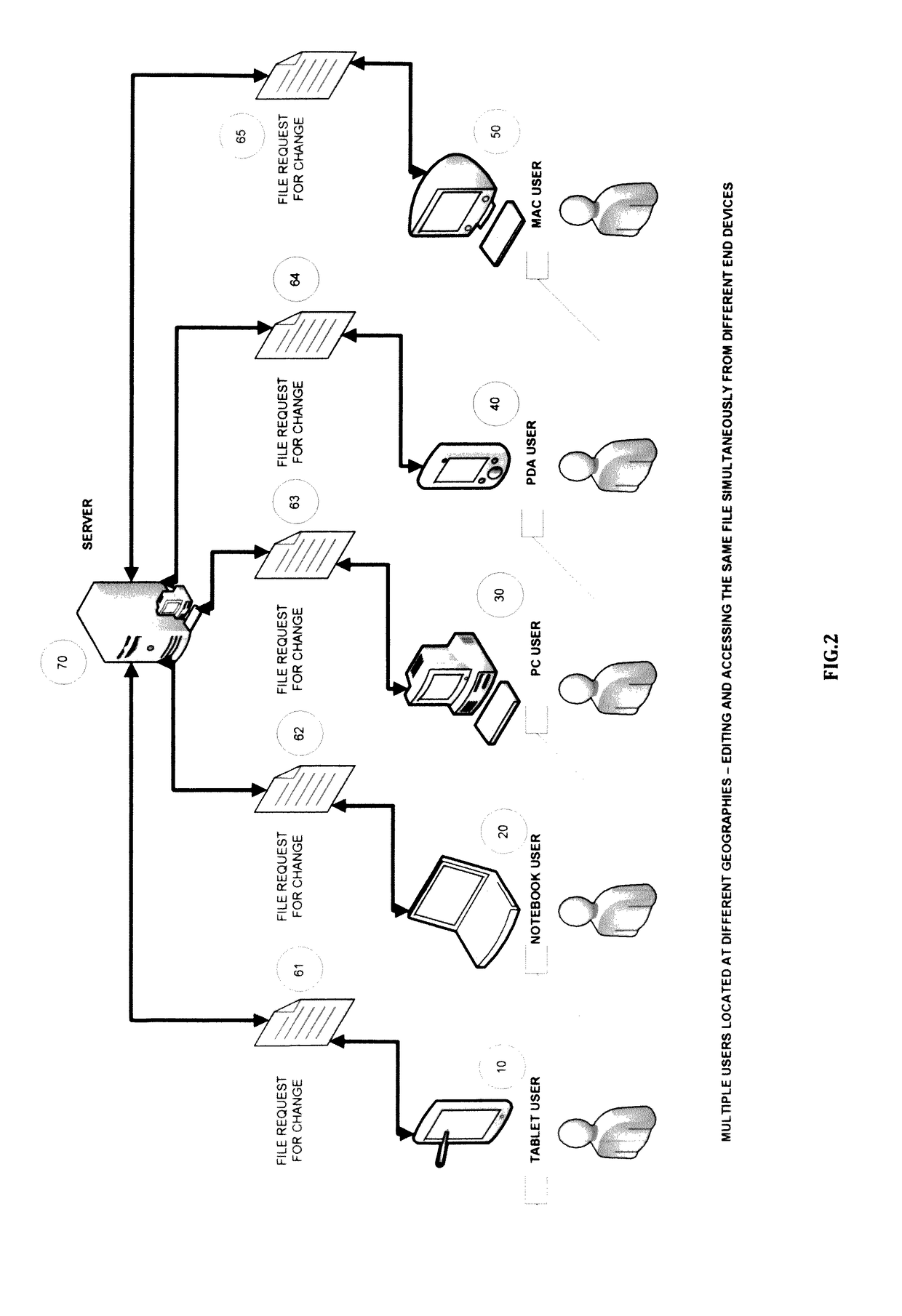
System and methods for detecting precise file system events from a large number and assortment of automatically-generated file system events during user operations
InactiveUS20170075920A1Digital data information retrievalSpecial data processing applicationsFile systemGeolocation
System and methods for precise detection of file system events for user operations during file sharing and synchronization across different end user devices and geographical locations. Corresponding to a user operation, a multitude of file system events is automatically generated. For different types of user operations (e.g. ‘File Create’, ‘File Rename’ et al.) involving different types of files (e.g. Microsoft PowerPoint, Microsoft Word, PDF et al.), an assortment of file system events are automatically generated. A profiler that detects the exact file system events for corresponding user operations is designed. Methods for identifying and matching the detected file system events to corresponding user operations are developed. Through those developed methods, further methods are developed for large-sized file sharing (e.g. large file copy) between multiple end users and resolving conflicts in simultaneous file change requests.
Owner:NETCRYPT PTY LTD
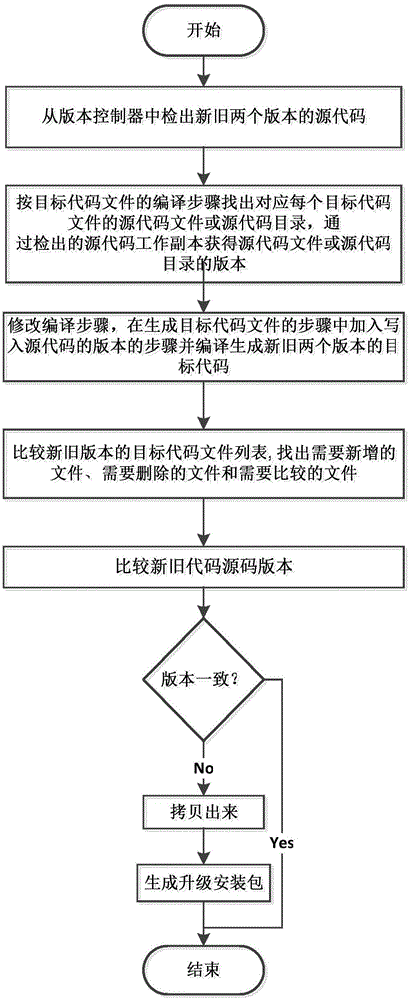
Manufacturing method of program upgrade and installation package
ActiveCN103955363ANo mistakesDoes not cause an errorProgram loading/initiatingObject codeSoftware engineering
The invention relates to the technical field of software upgrade, in particular to a manufacturing method of a program upgrade and installation package. The method comprises the following steps: firstly comparing new and old source code versions; if a new version exists, further comparing code files of the new and old versions; setting a newly-increased file in the new version as a newly-increased file, and recording a redundant file list in the old version as a to-be-deleted file; when the new and old versions are not consistent, setting an object code file of the corresponding new version as a to-be-replaced file; manufacturing the files and / or file record list into the installation package; performing file copying, replacement and delete operations. The manufacturing method for generating a program increment upgrade and installation package, provided by the invention, is simple and effective and is especially applicable to upgrading and installing large programs.
Owner:G CLOUD TECH
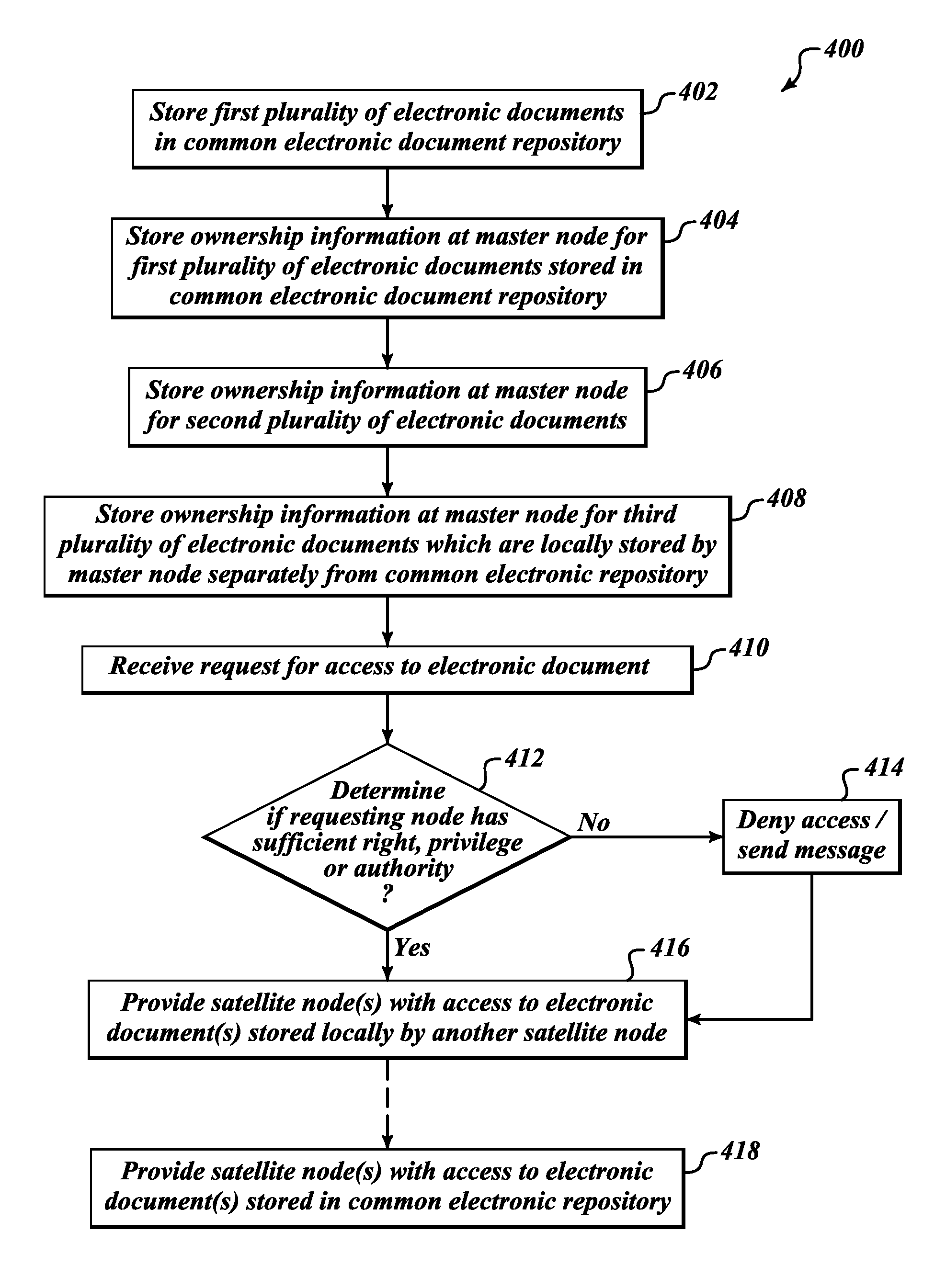
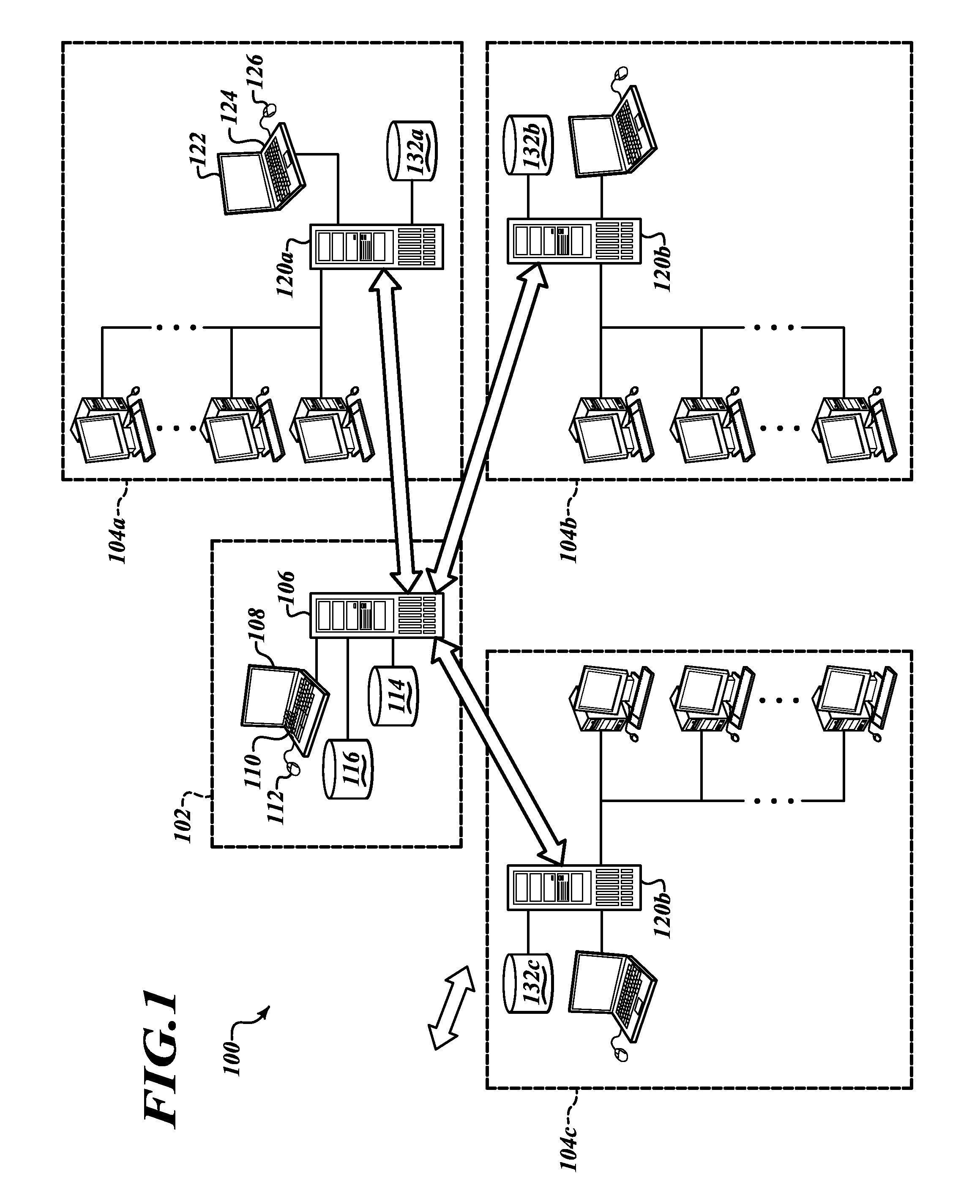
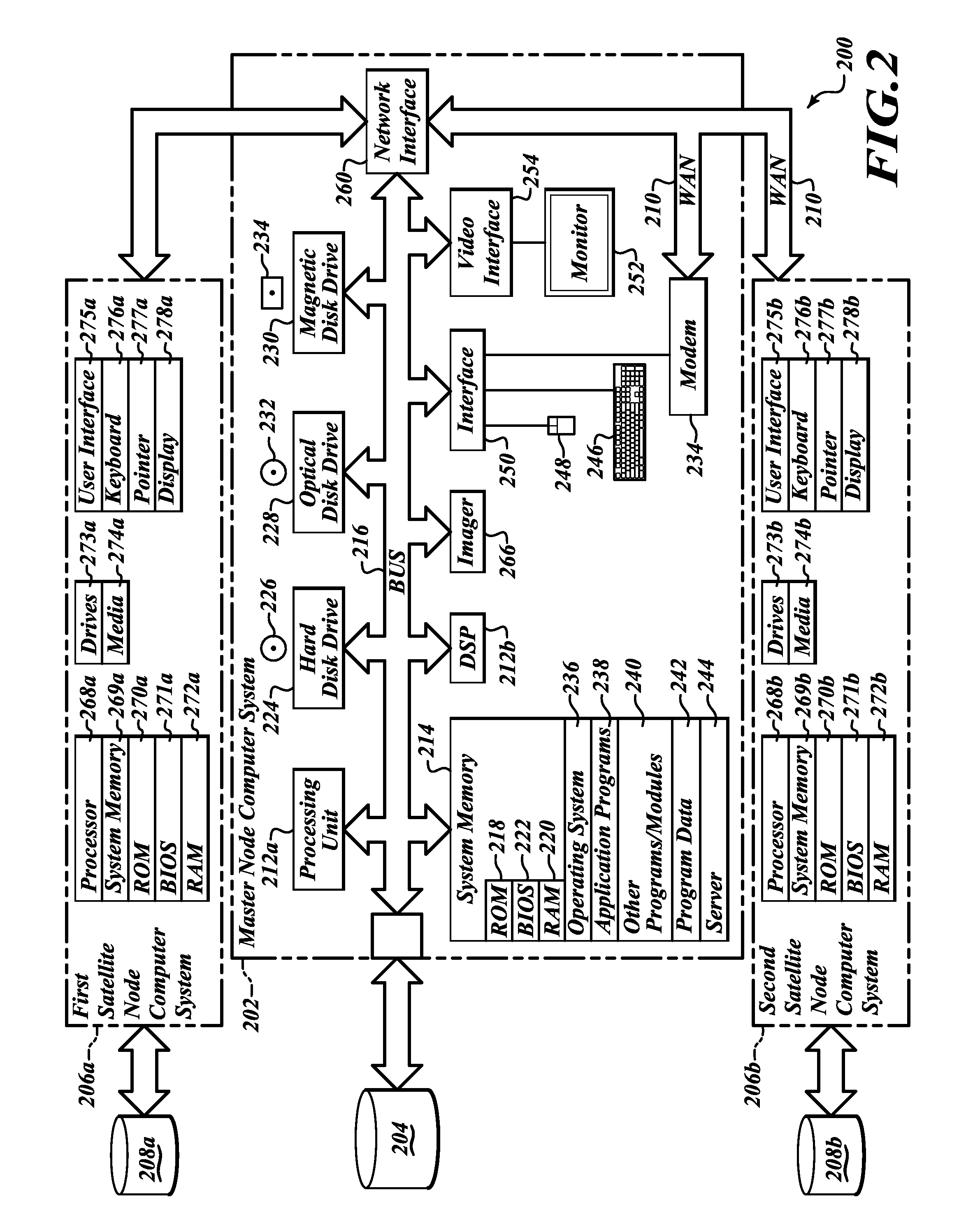
Apparatus, method and article to manage electronic or digital documents in networked environment
ActiveUS20110153560A1Digital data processing detailsDigital computer detailsElectronic documentDocumentation procedure
Systems and methods of electronic or digital document management allow satellite offices, sites or facilities to replicate some documents in a shared or common electronic document repository, while storing other documents only locally, while allowing document management functions seamlessly across an enterprise independent of whether the electronic or digital documents or files are replicated to a shared or common repository, for instance a central electronic or digital document repository.
Owner:VERTAFORE
Method and system for incremental backup of virtual machine data based on Qcow2 snapshots
InactiveCN103699459AIncremental backup implementationReduce consumptionSoftware simulation/interpretation/emulationRedundant operation error correctionVirtualizationUser environment
The invention discloses a method and a system for incremental backup of virtual machine data based on Qcow2 snapshots. The method includes the following steps: creating a virtual machine on the basis of a first image file in a qcow2 format, and installing user environment and data; copying the first image file in the qcow2 format into a second image file of the qcow2 format; creating a first snapshot of the first image file of the qcow2 format; operating the virtual machine, and updating the first image file of the qcow2 format; suspending operation of the virtual machine, and creating a second snapshot of the qcow2 format; restoring the operation of the virtual machine; analyzing the first snapshot of the qcow2 format and the second snapshot of the qcow2 format, and combining a difference part between the two snapshots with the second image file of the qcow2 format. Therefore, incremental backup of the data of the virtual machine in the cloud computing virtualization field is realized, and time for data backup and consumption of network bandwidth are reduced substantially.
Owner:OPZOON TECH
Method for installing software
InactiveUS20050193265A1Overcomes drawbackError detection/correctionProgram loading/initiatingComputer hardwareFile copying
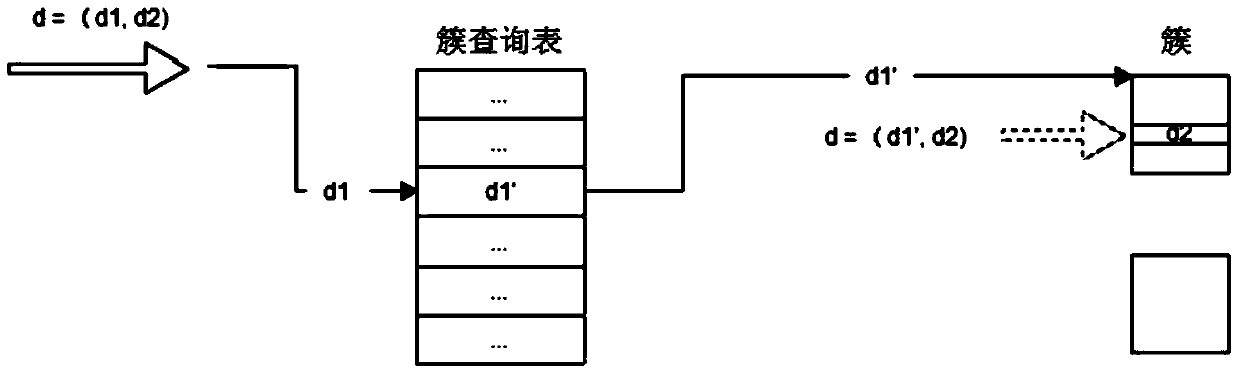
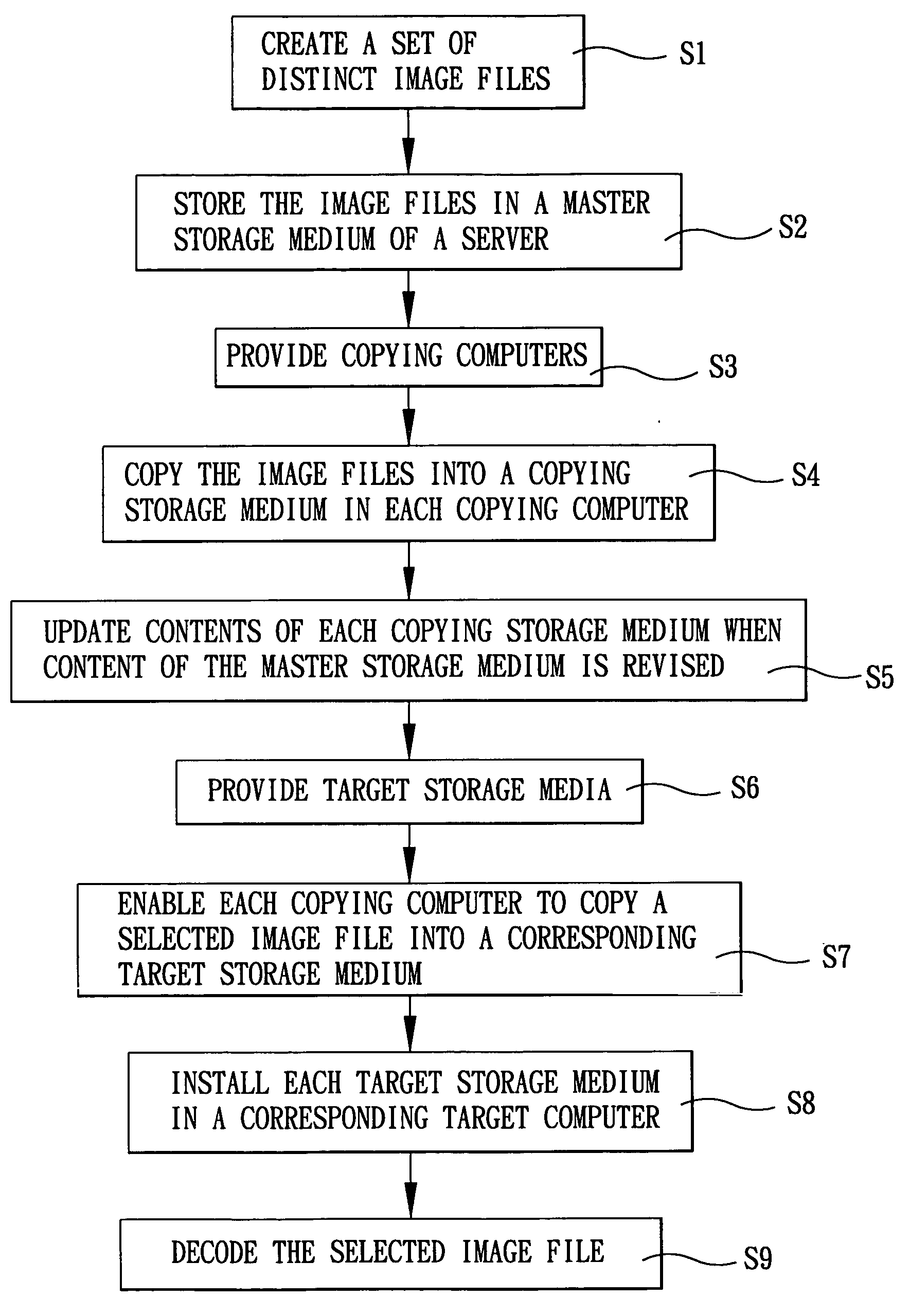
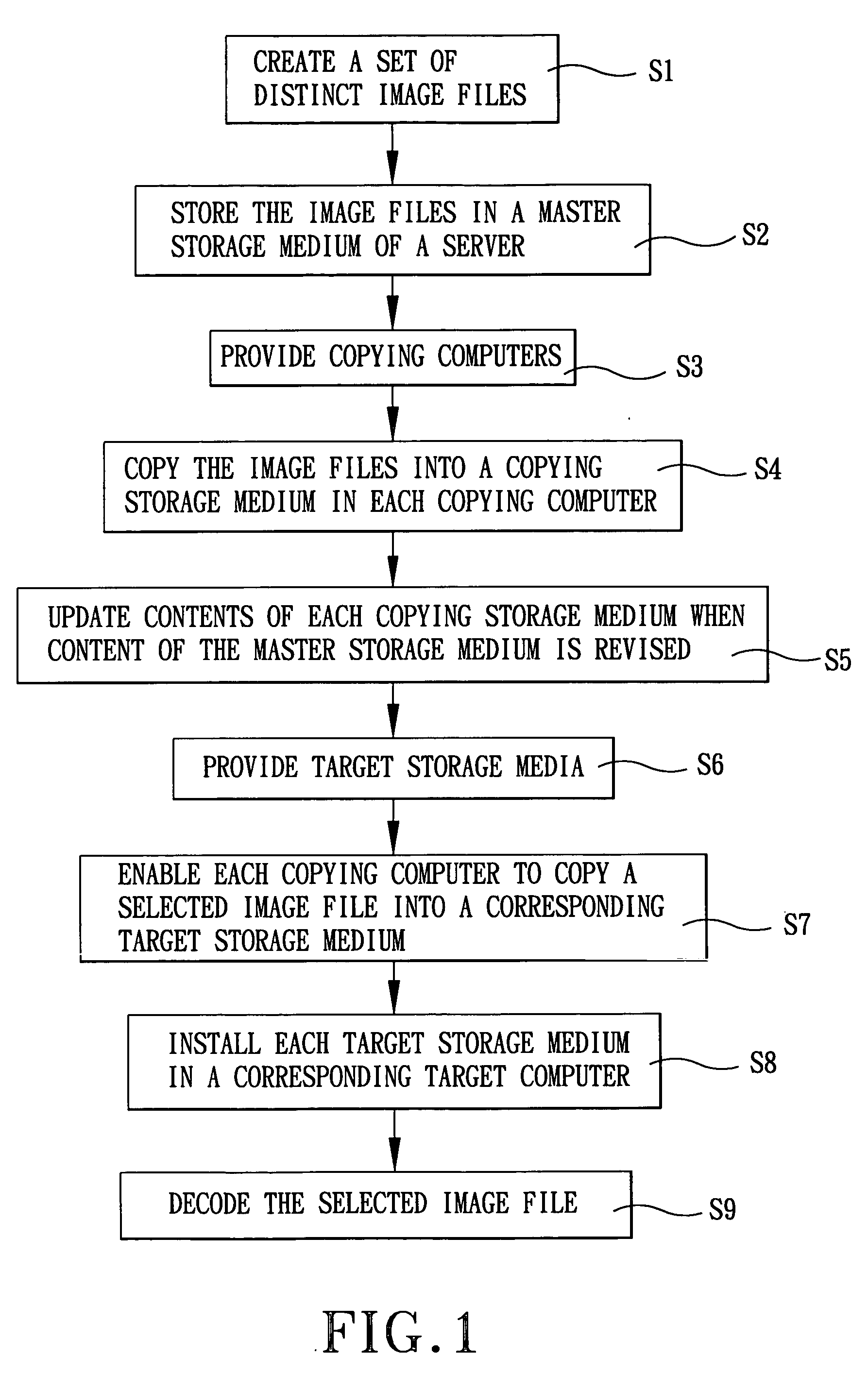
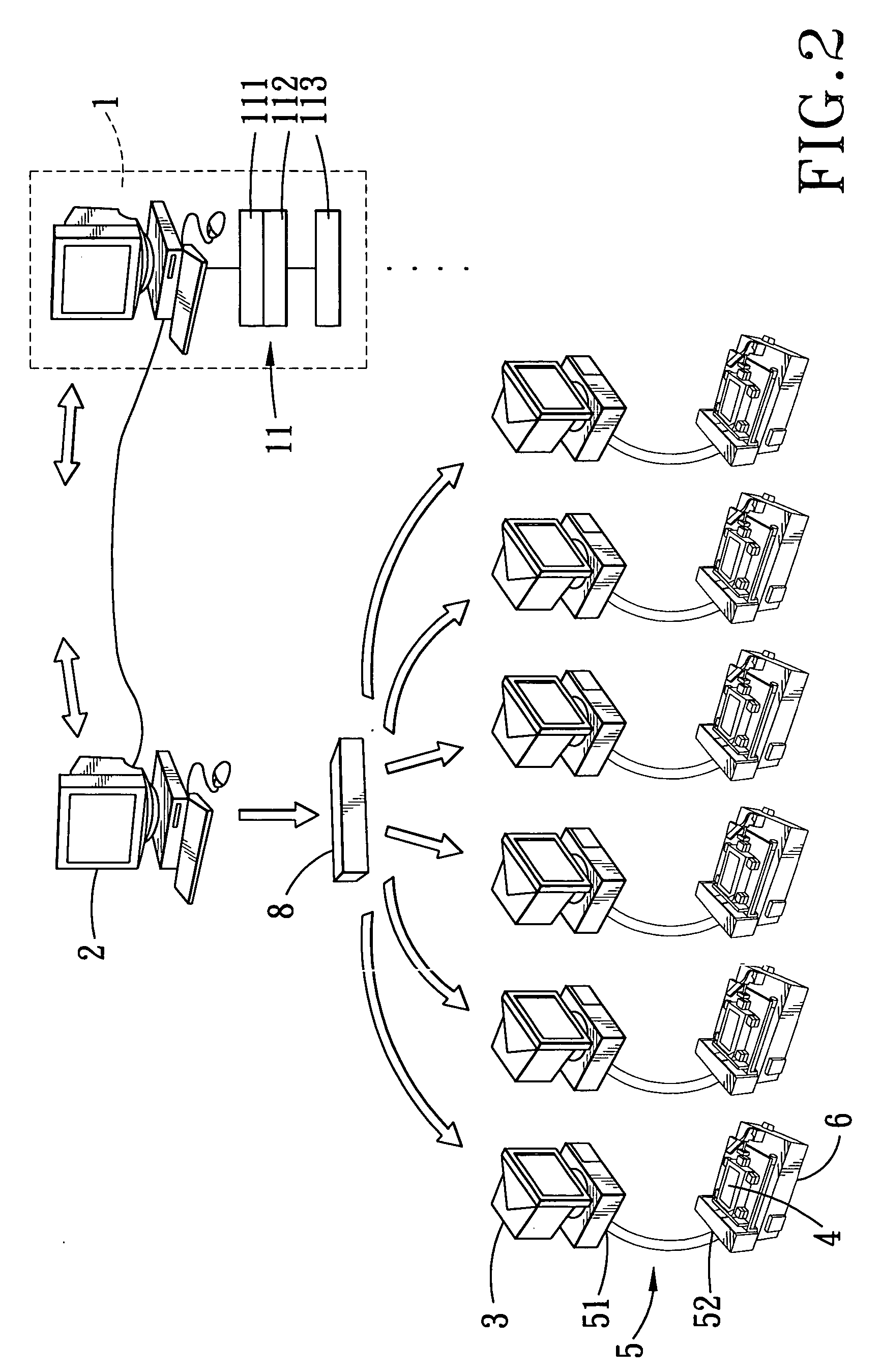
In a method for installing software, distinct image files, each of which corresponds to a software bundle resident in a reference storage medium of a reference computer that was built according to a specified hardware and software configuration, stored in a master storage medium of a server that is coupled to the reference computers via a communications network are copied into copying storage media installed in copying computers. Each copying computer is configured to copy a selected image file in the copying storage medium that is installed therein into a corresponding target storage medium, which is coupled externally thereto via a connector unit. The selected image file corresponds to hardware configuration of a target computer and having a desired software configuration.
Owner:SYNNEX TECH INT CORP
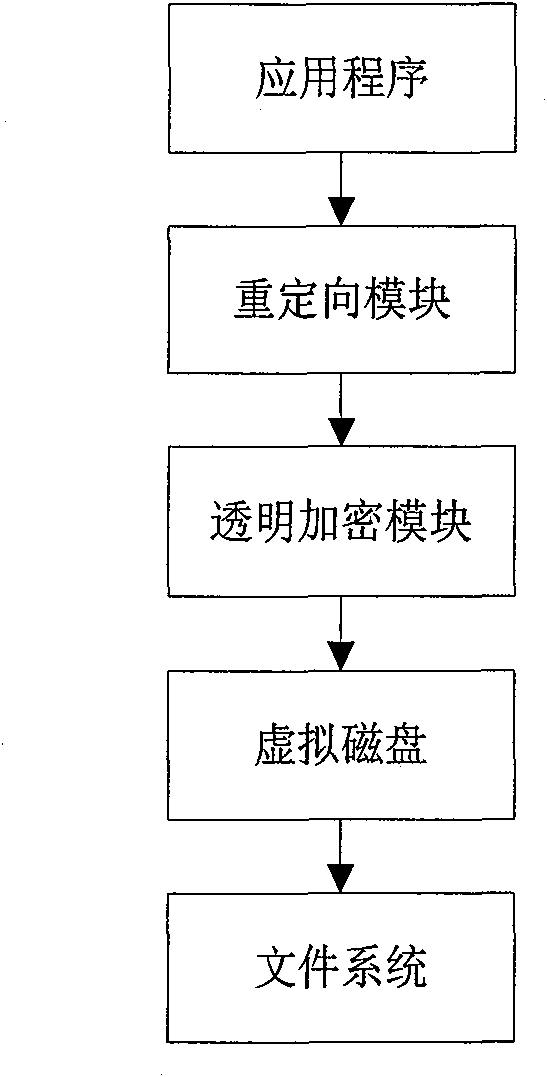
Method for encrypting files by adopting encryption sandbox
InactiveCN101847184AWill not cause leaksSolve the leakage problemDigital data protectionPlatform integrity maintainanceComputer hardwareFile copying
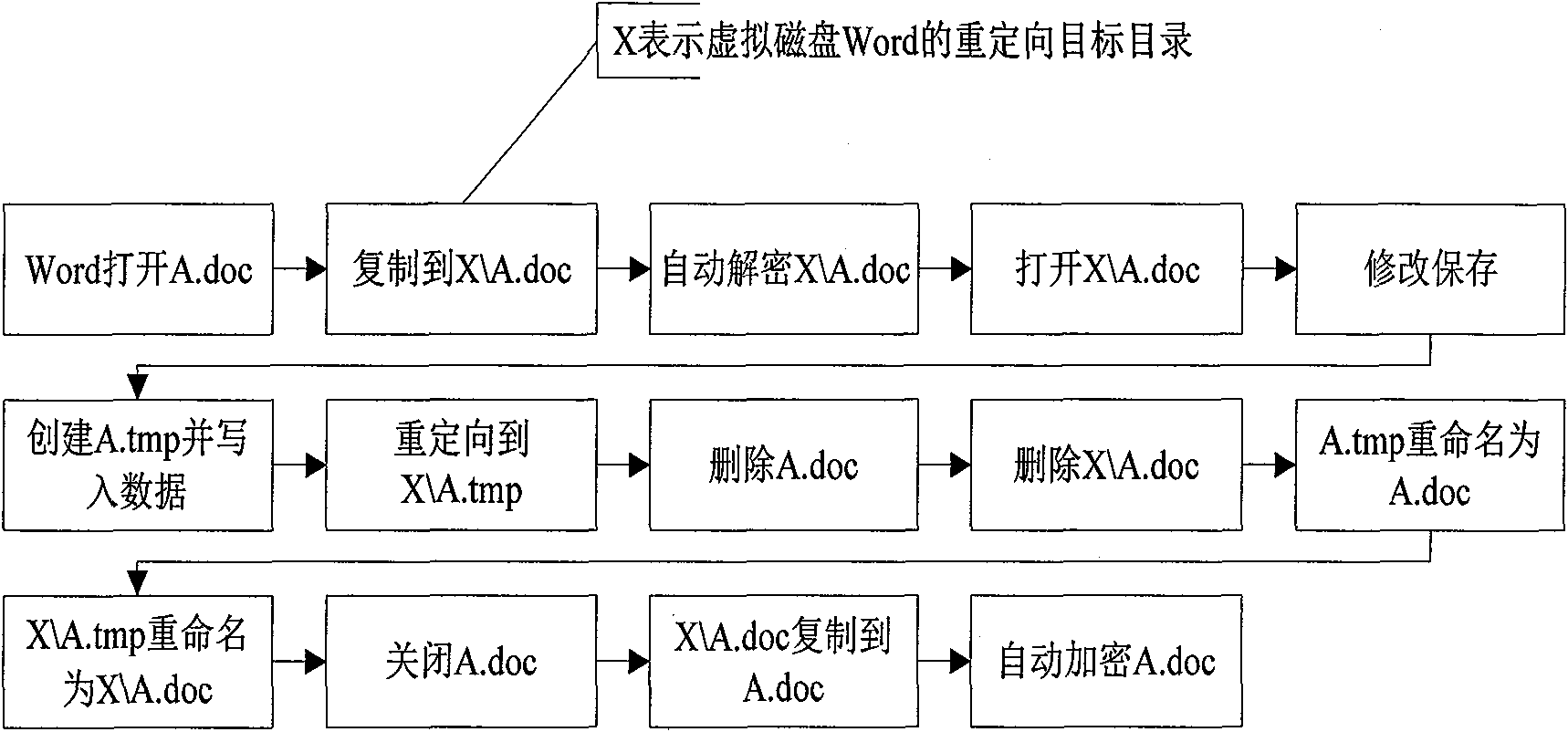
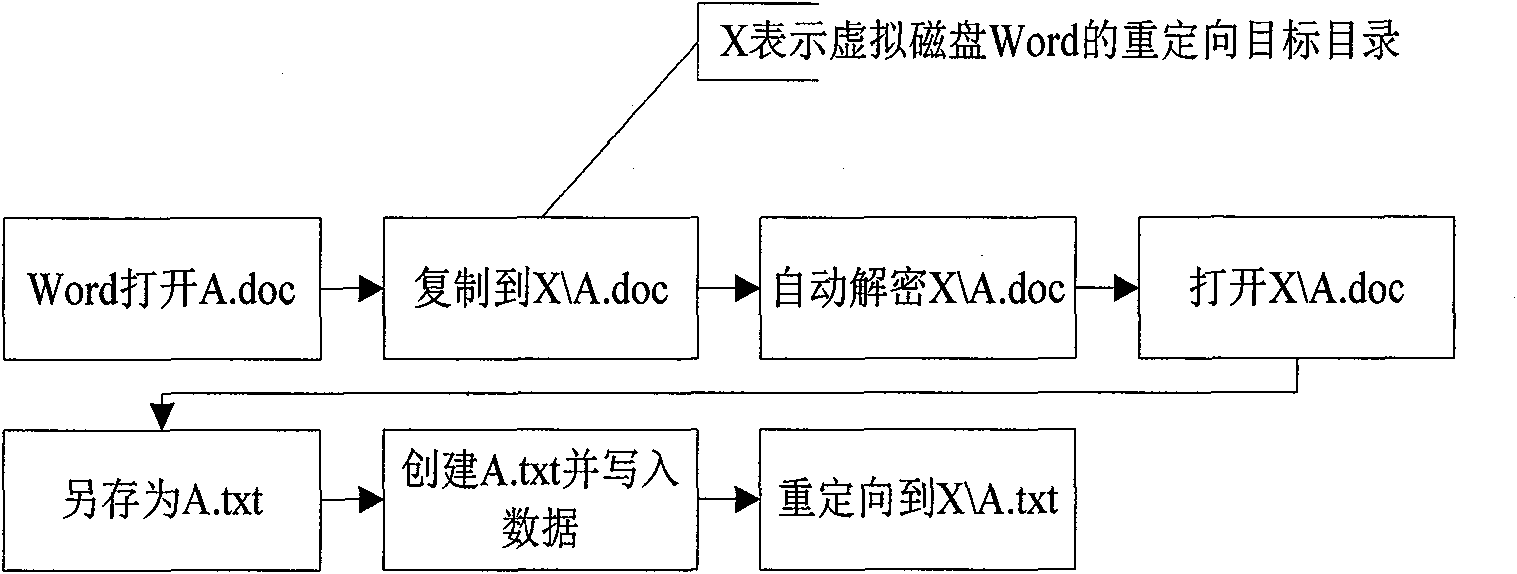
The invention discloses a method for encrypting files by adopting an encryption sandbox, which borrows ideas from the sandbox principle. When opened, a filed is copied and reoriented to a virtual disk, and all editing operations are performed in the virtual disk; when closed (or every once in a while), the file is encrypted and copied and covers the original file to achieve the effect of encryption. All files stored in the virtual disk are temporary files which can be deleted, but the deletion can not influence a system, which is just like a sandbox. With the method, the stability of encryption and decryption can be improved and the policy setting can be simplified.
Owner:深圳市虹安信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com