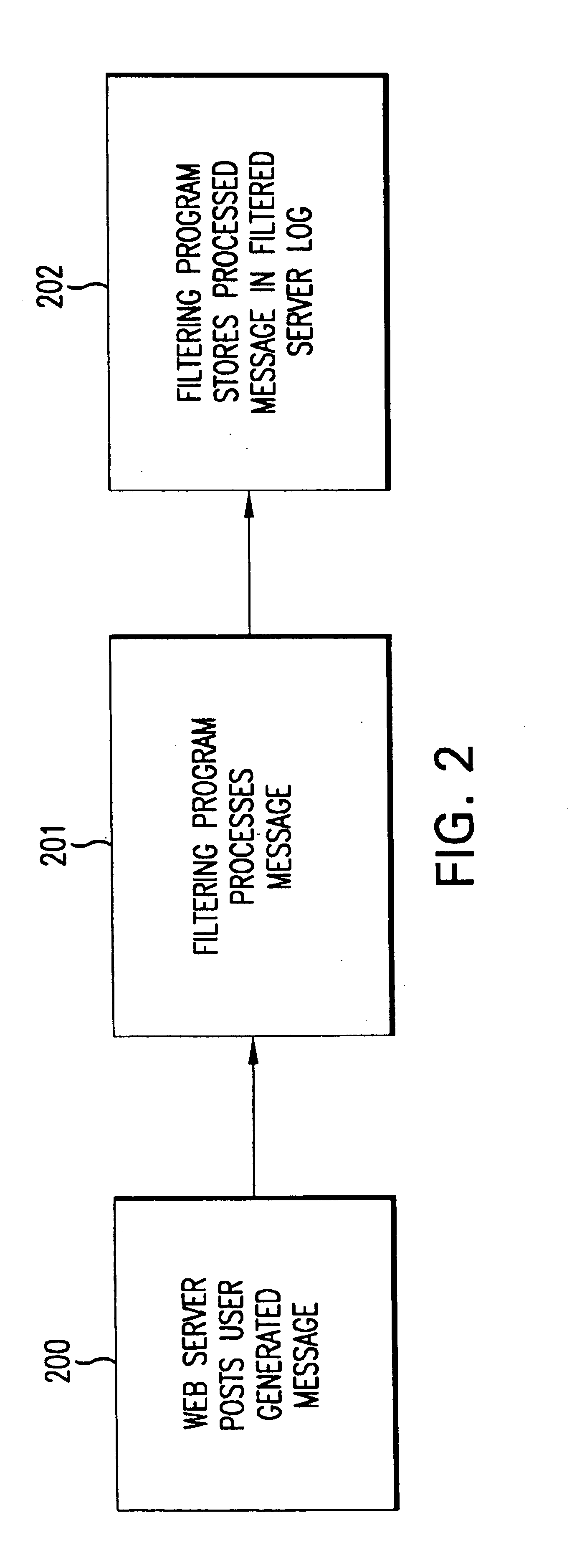
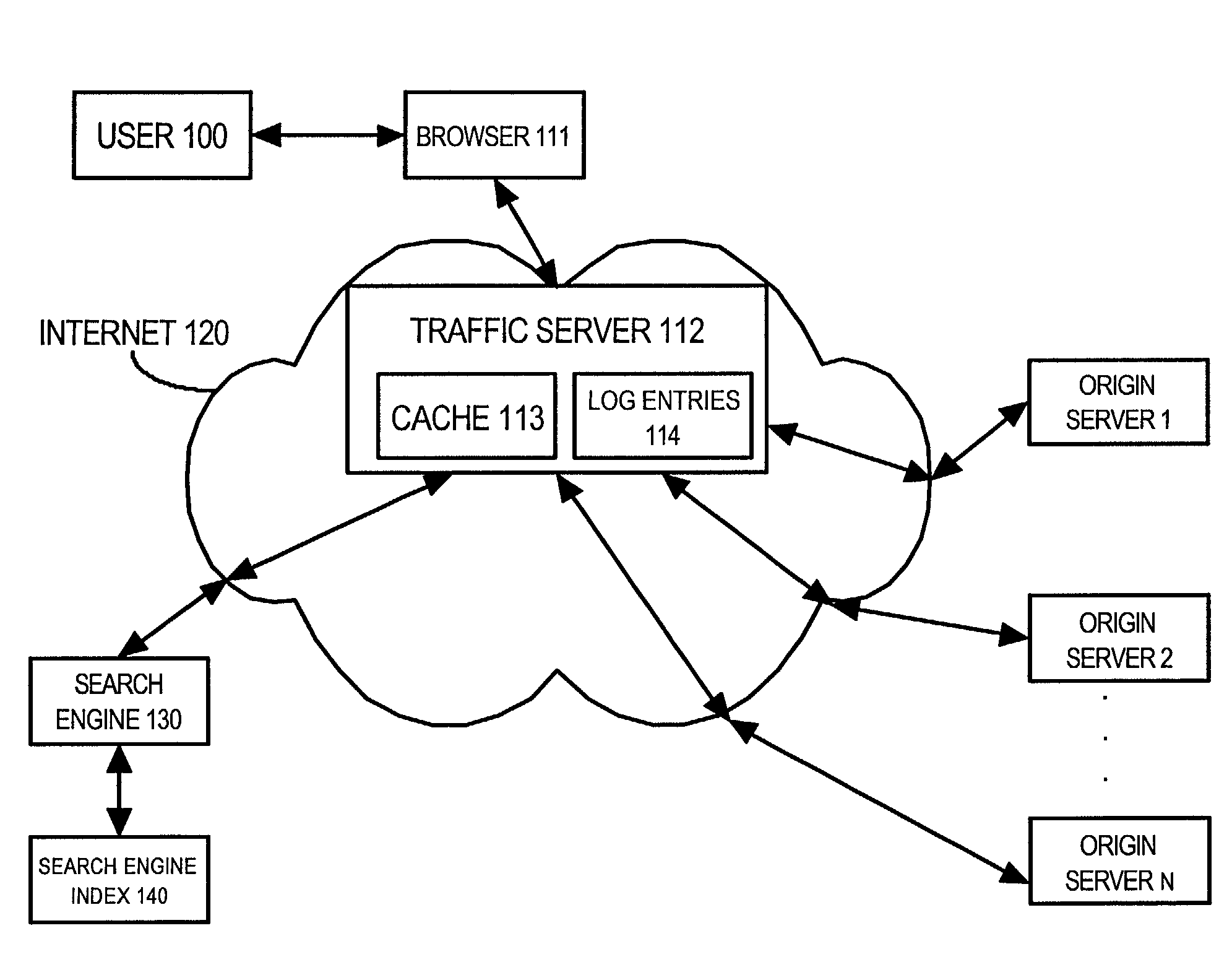
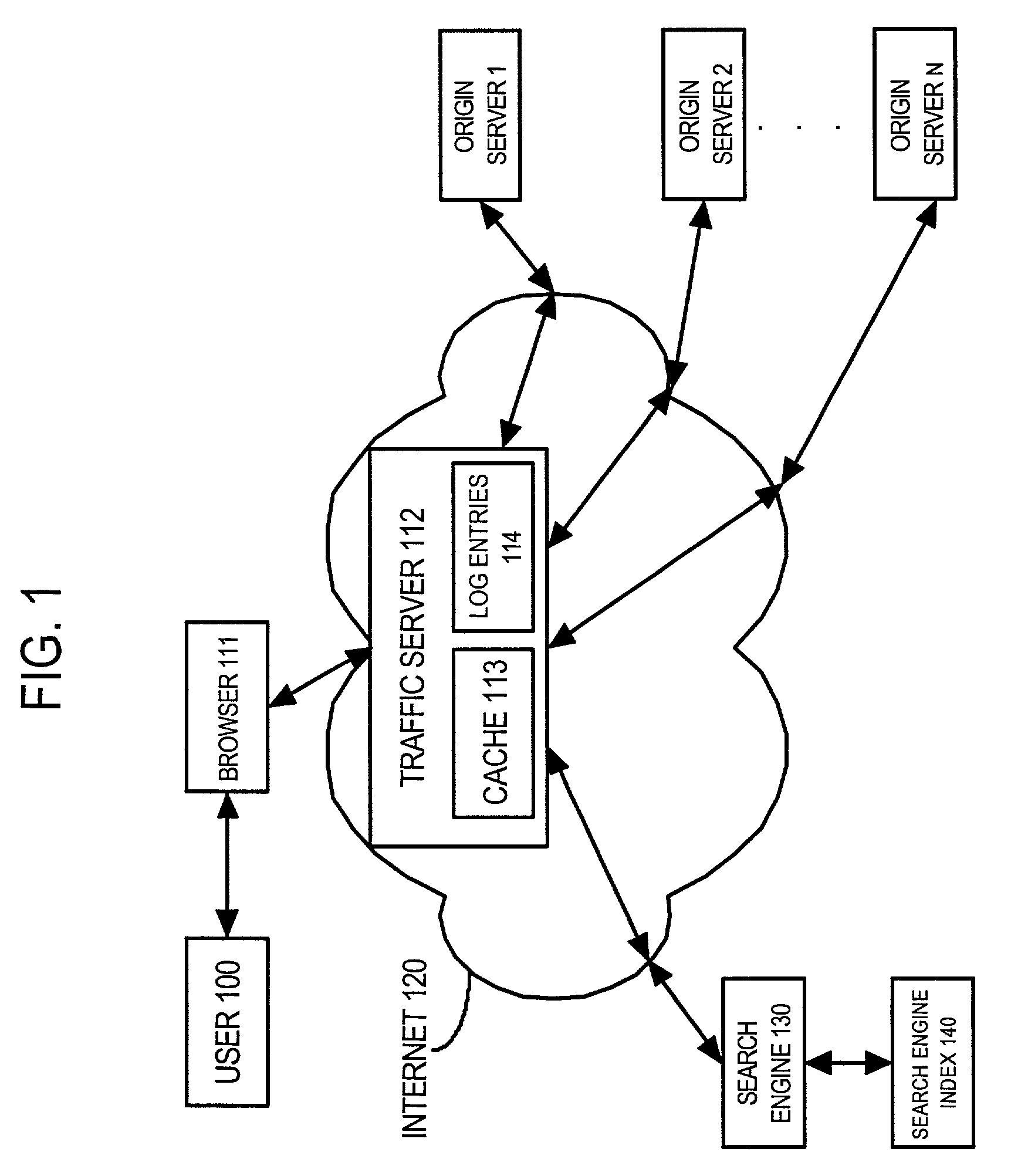
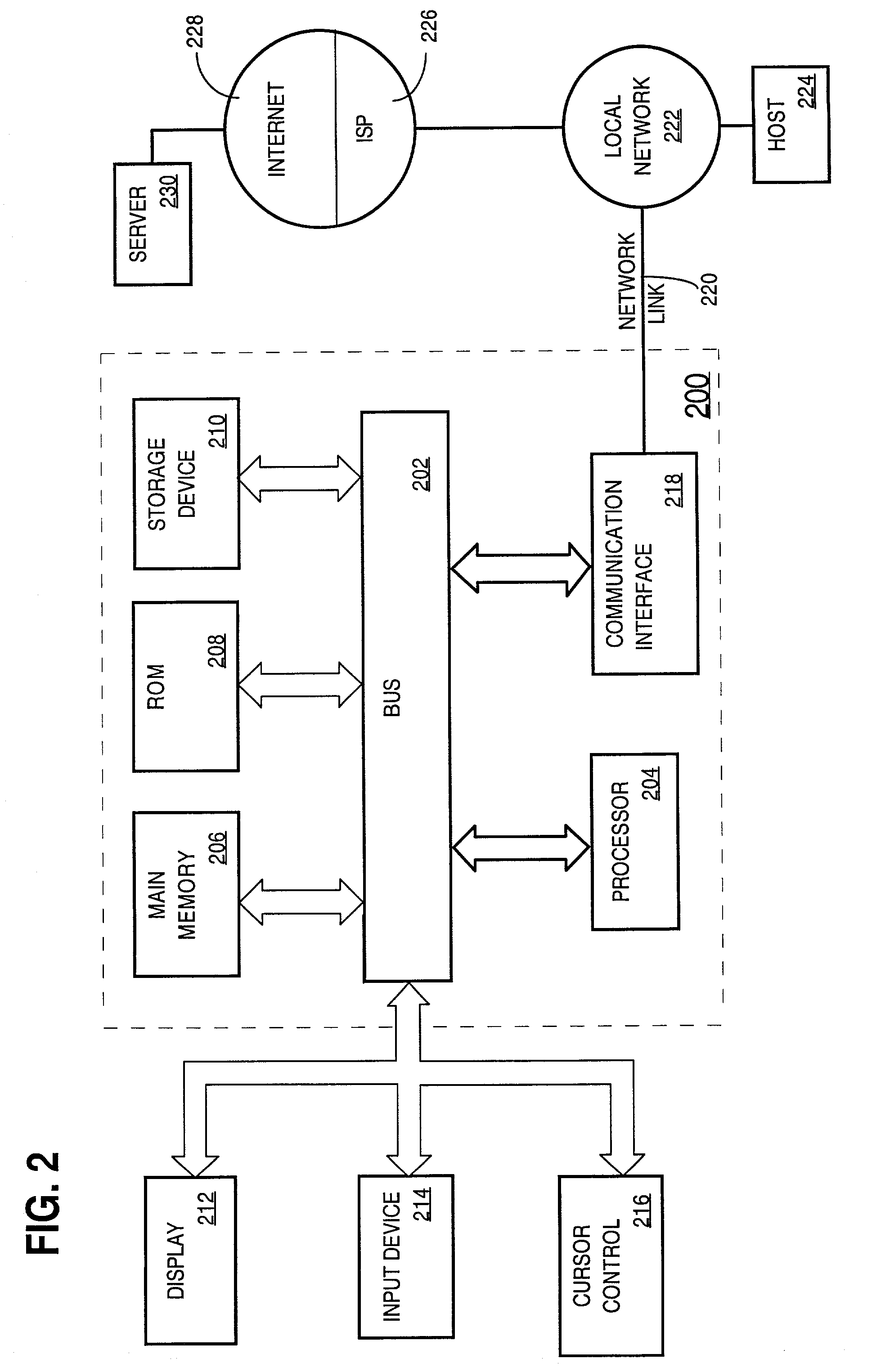
Patents
Literature
2533 results about "Logfile" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
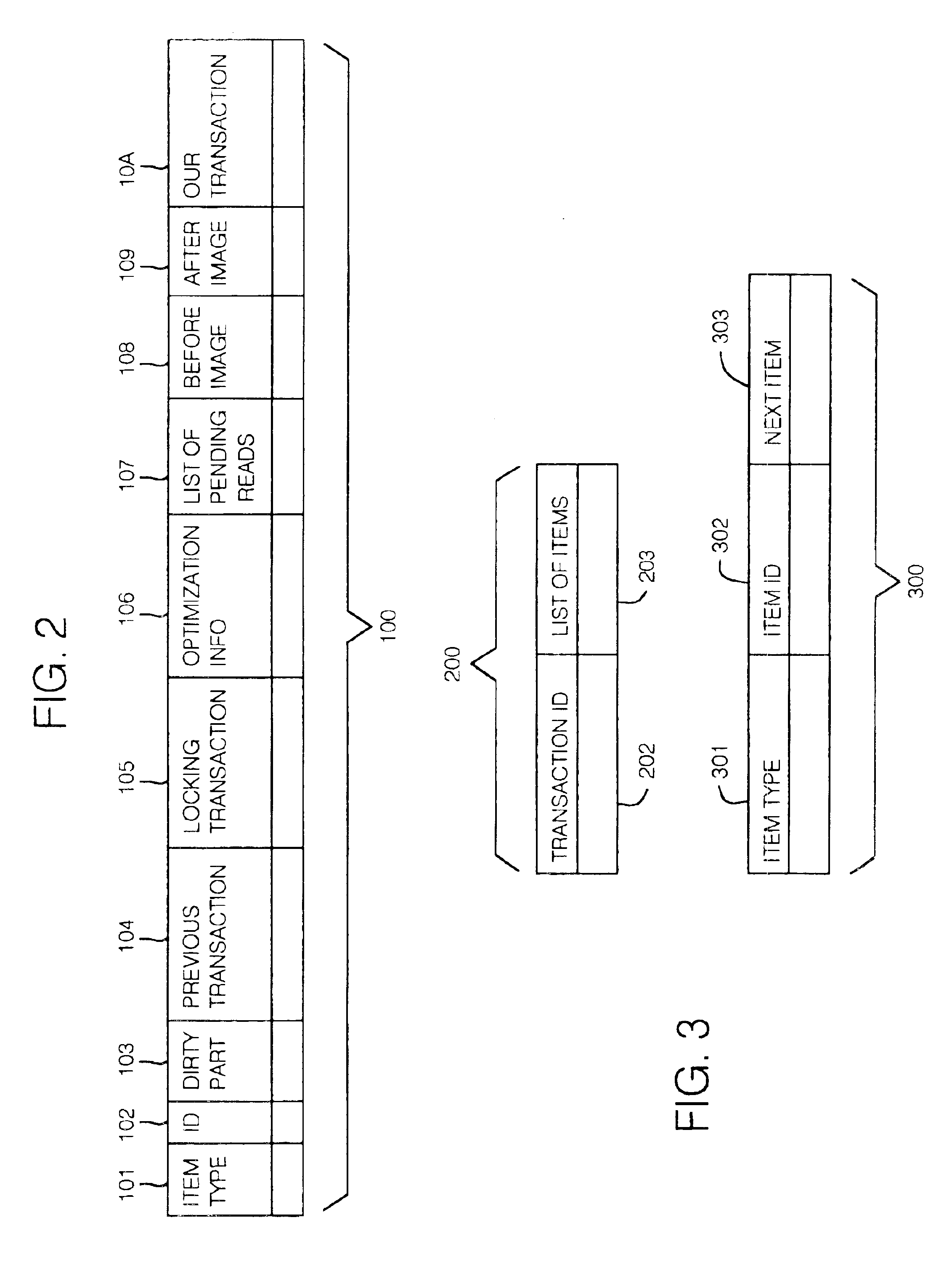
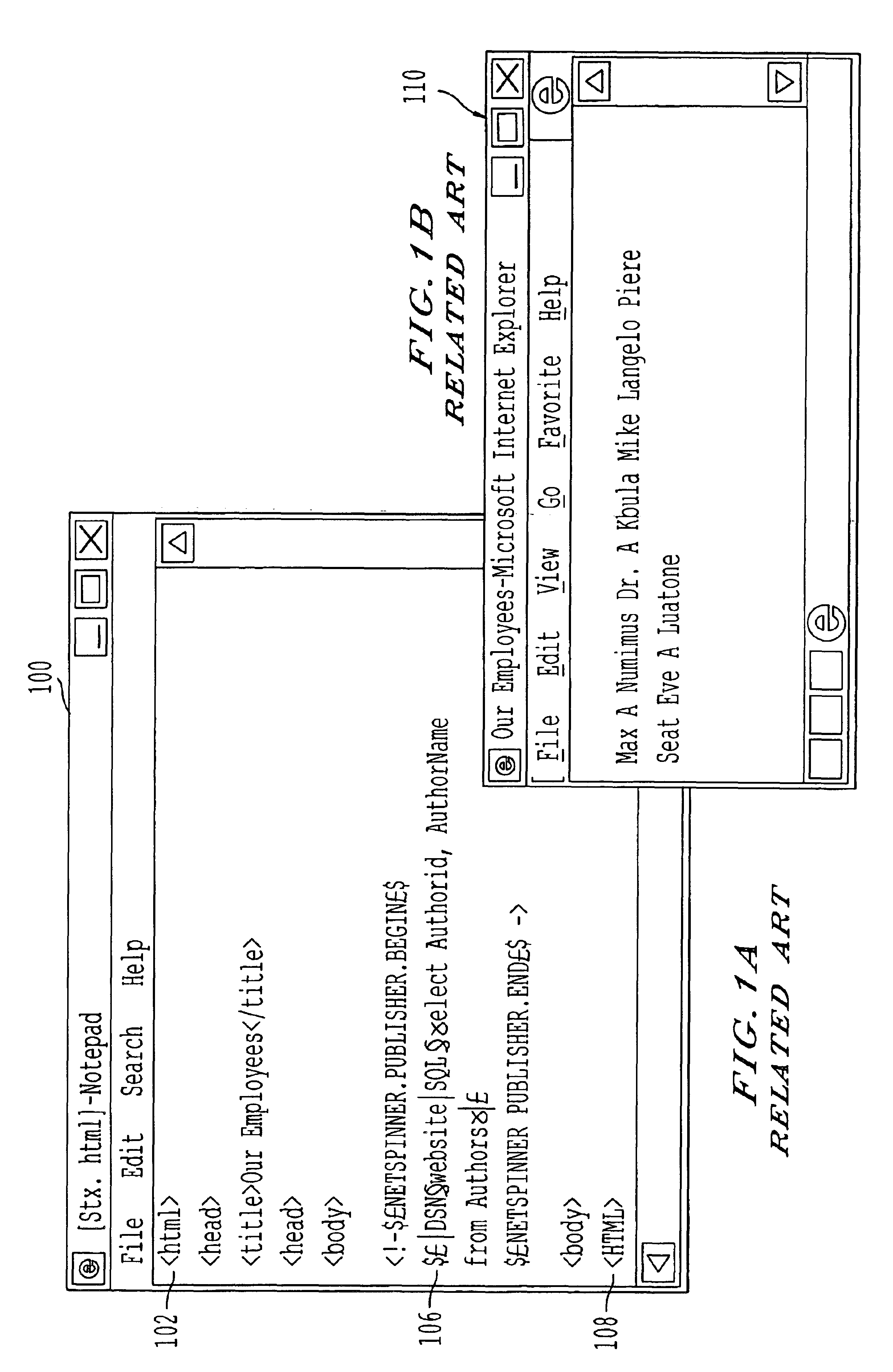
In computing, a log file is a file that records either events that occur in an operating system or other software runs, or messages between different users of a communication software. Logging (Computer) is the act of keeping a log. In the simplest case, messages are written to a single log file.
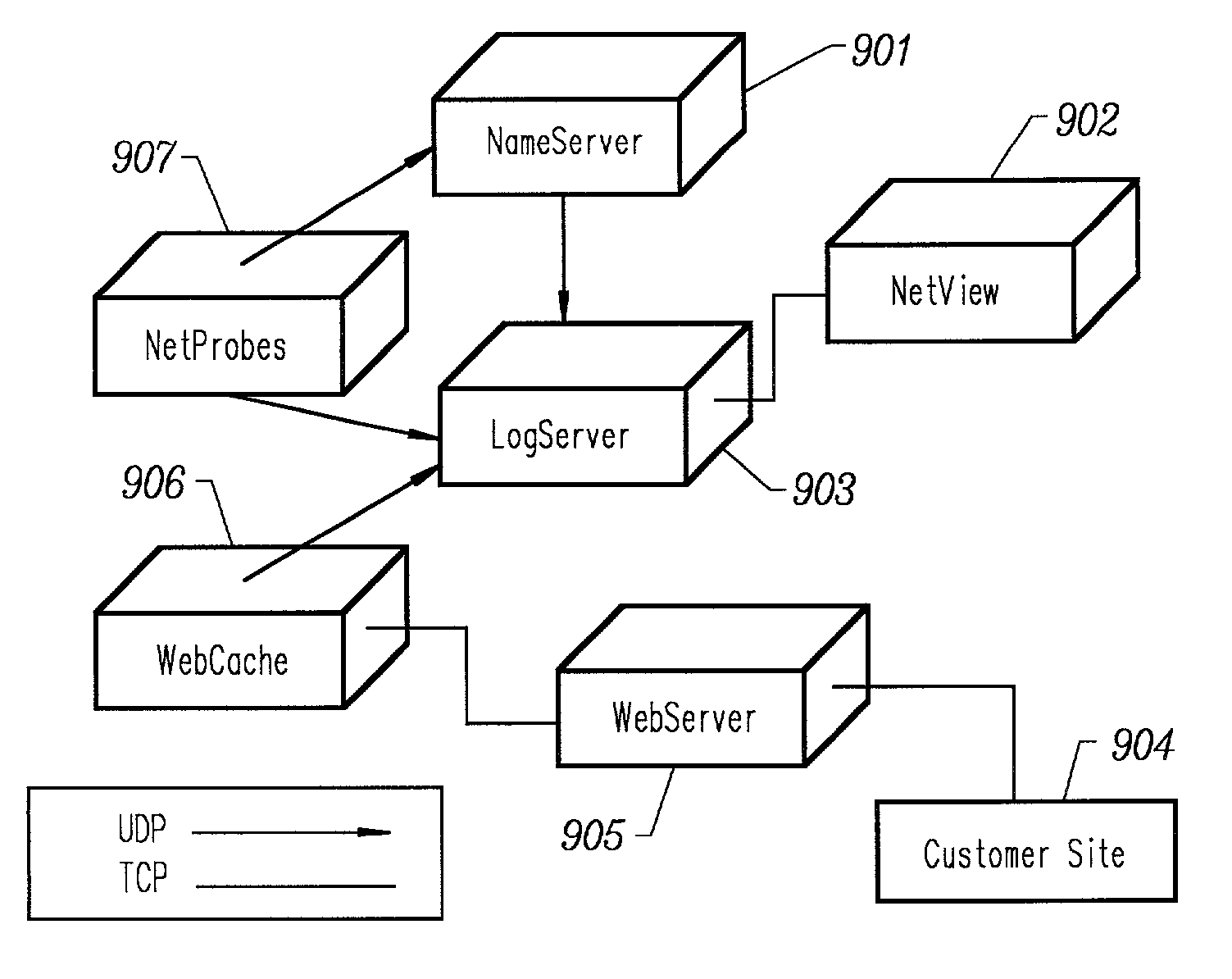
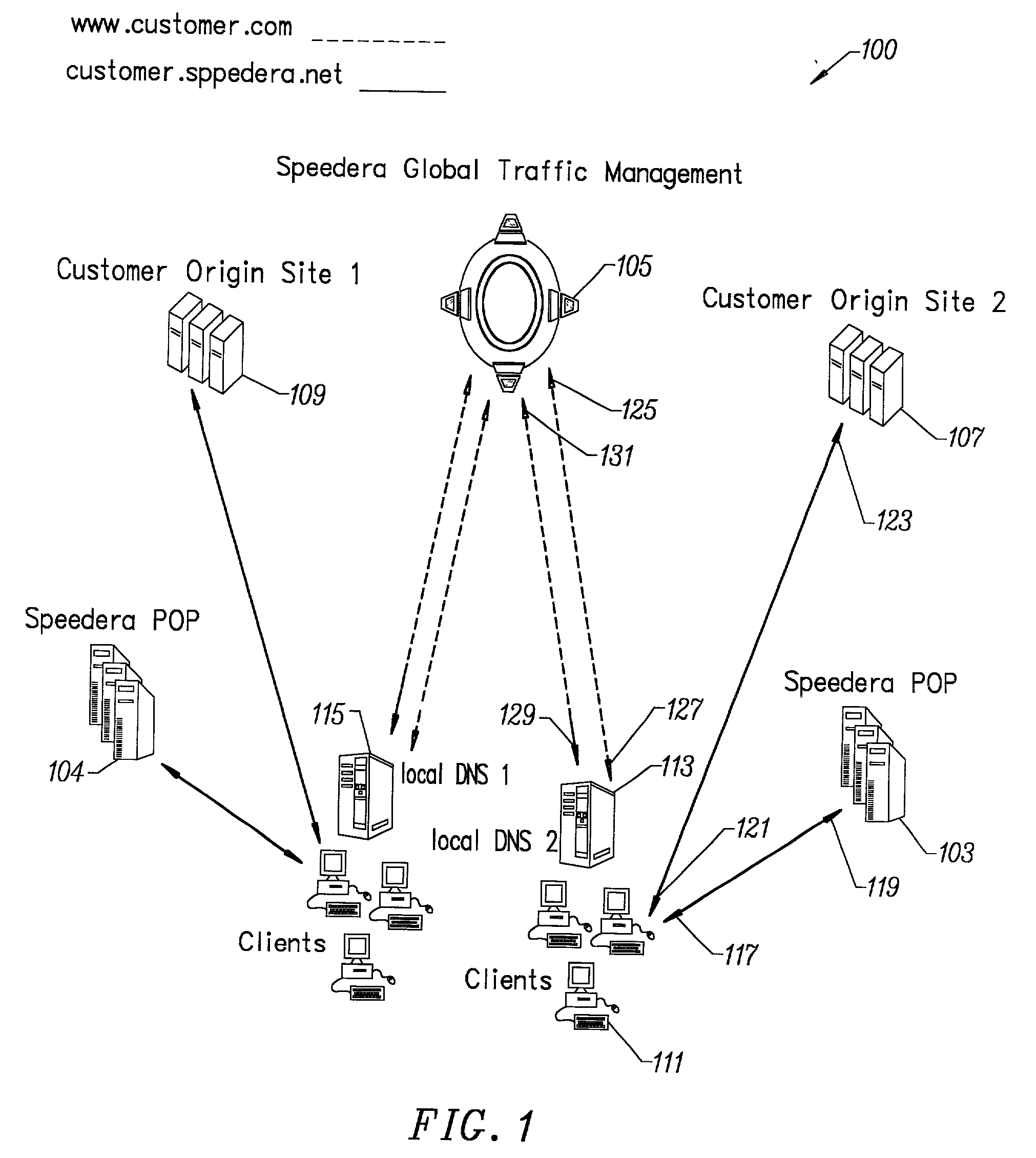
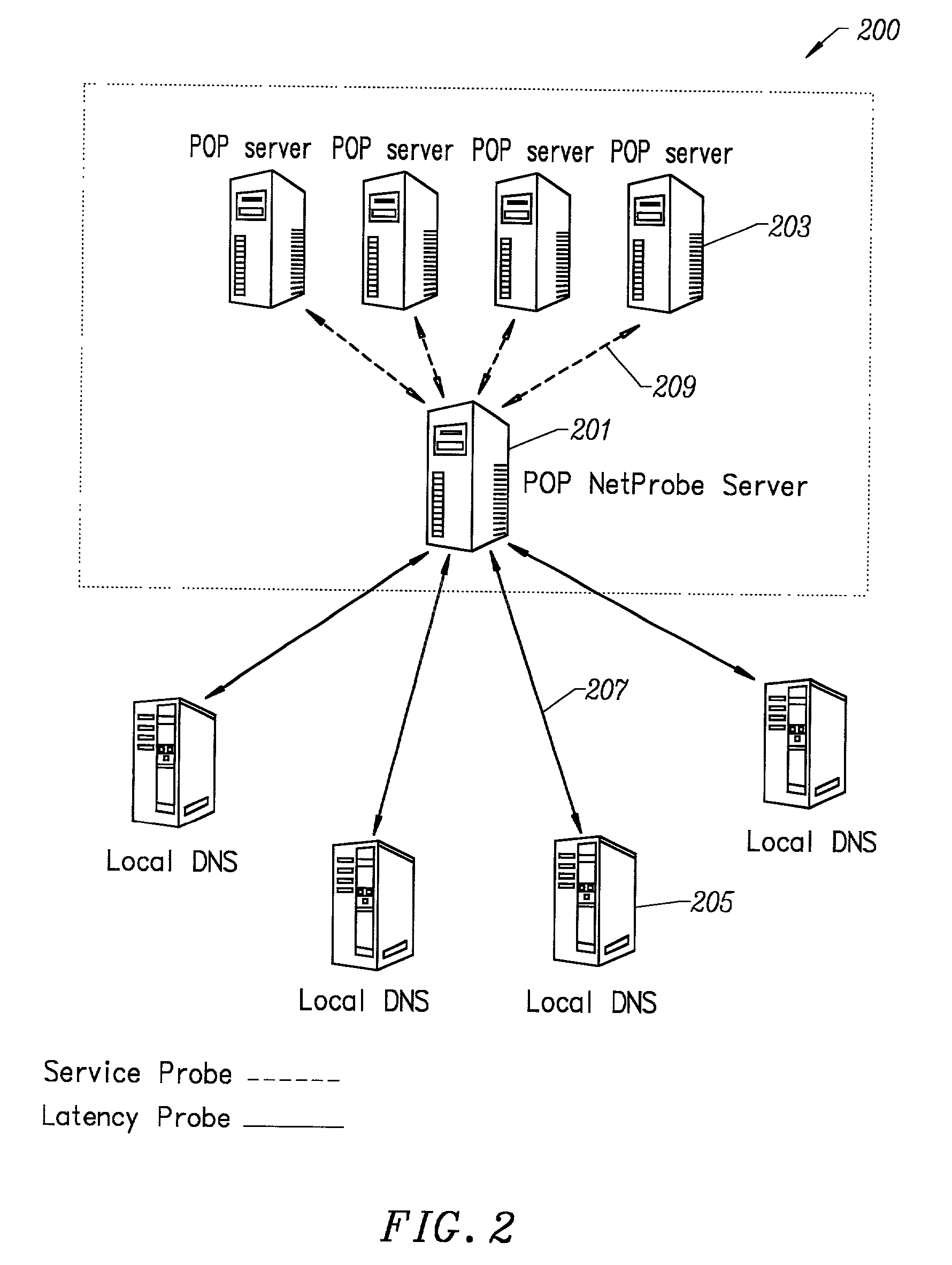
Content delivery and global traffic management network system
InactiveUS20020052942A1Meet cutting requirementsReduce trafficMetering/charging/biilling arrangementsError preventionWeb serviceCache server
Owner:AKAMAI TECH INC
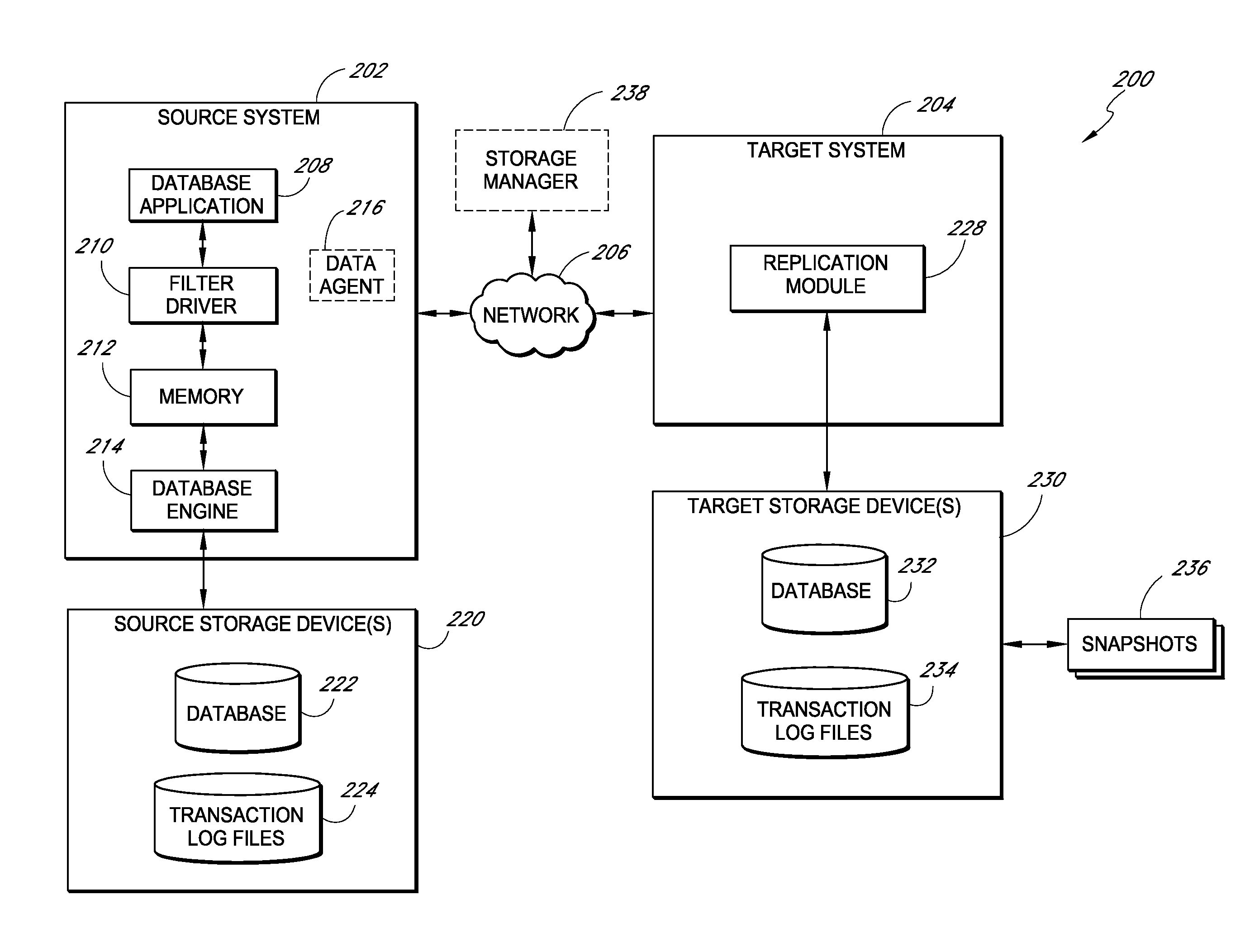
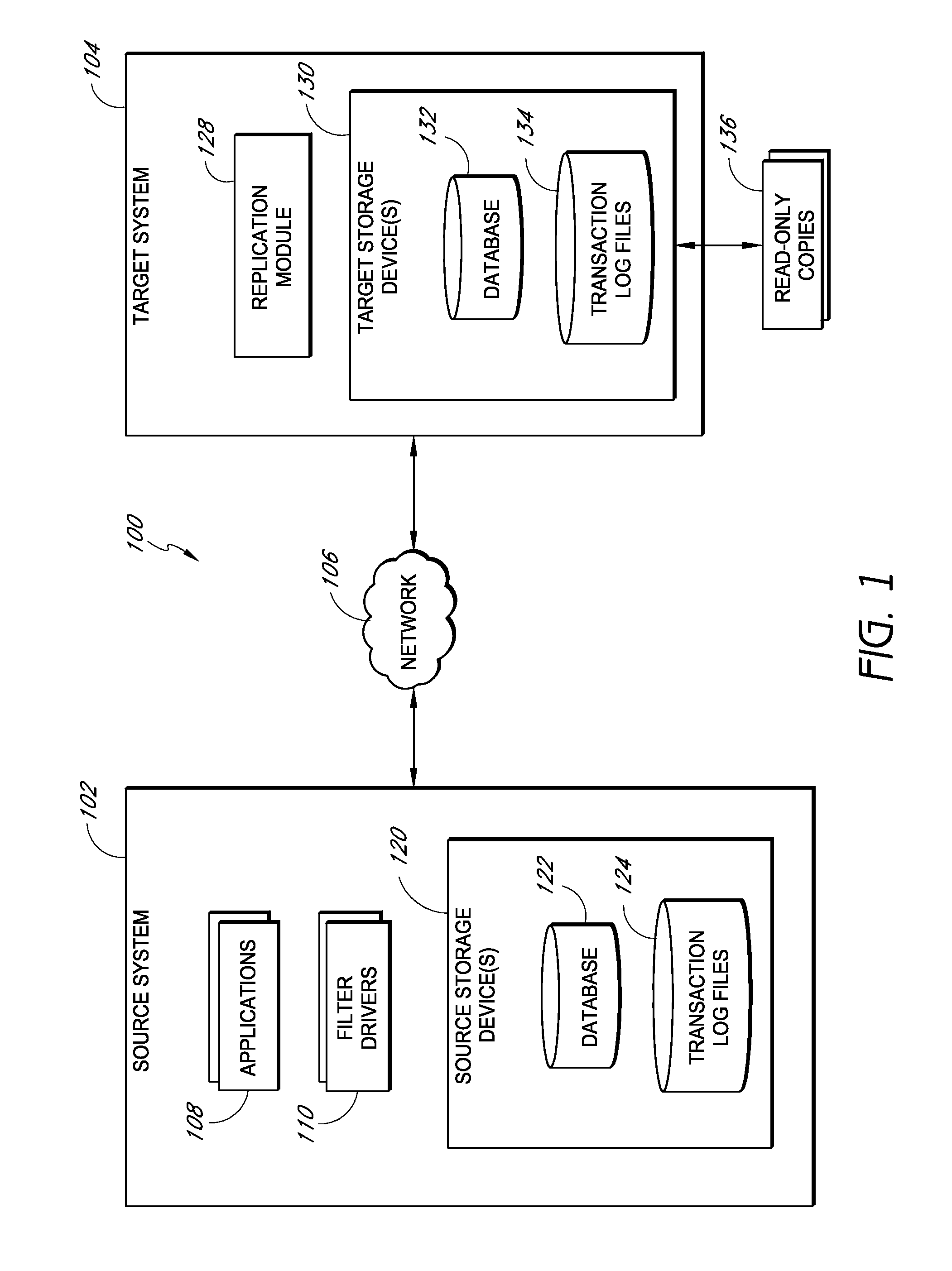
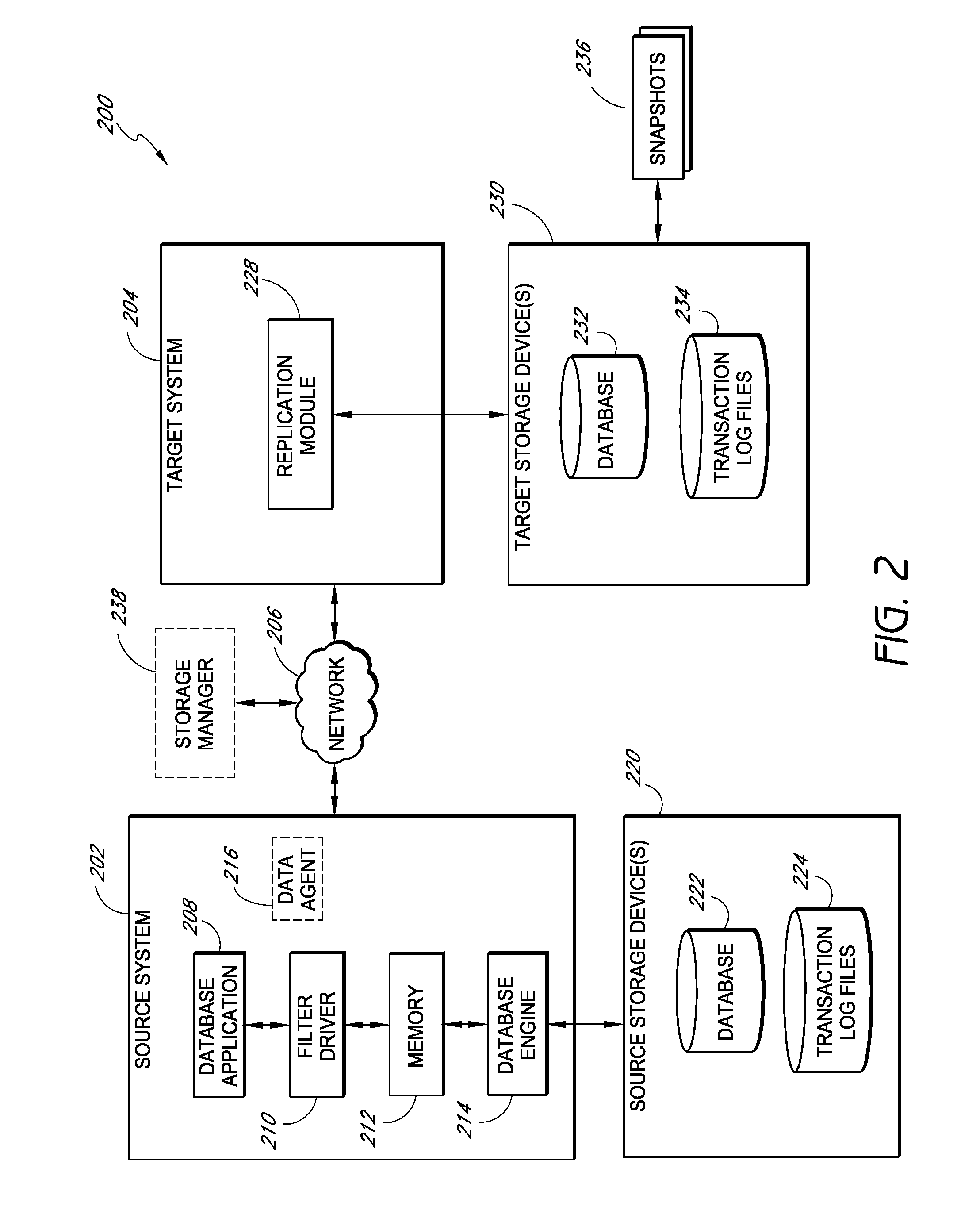
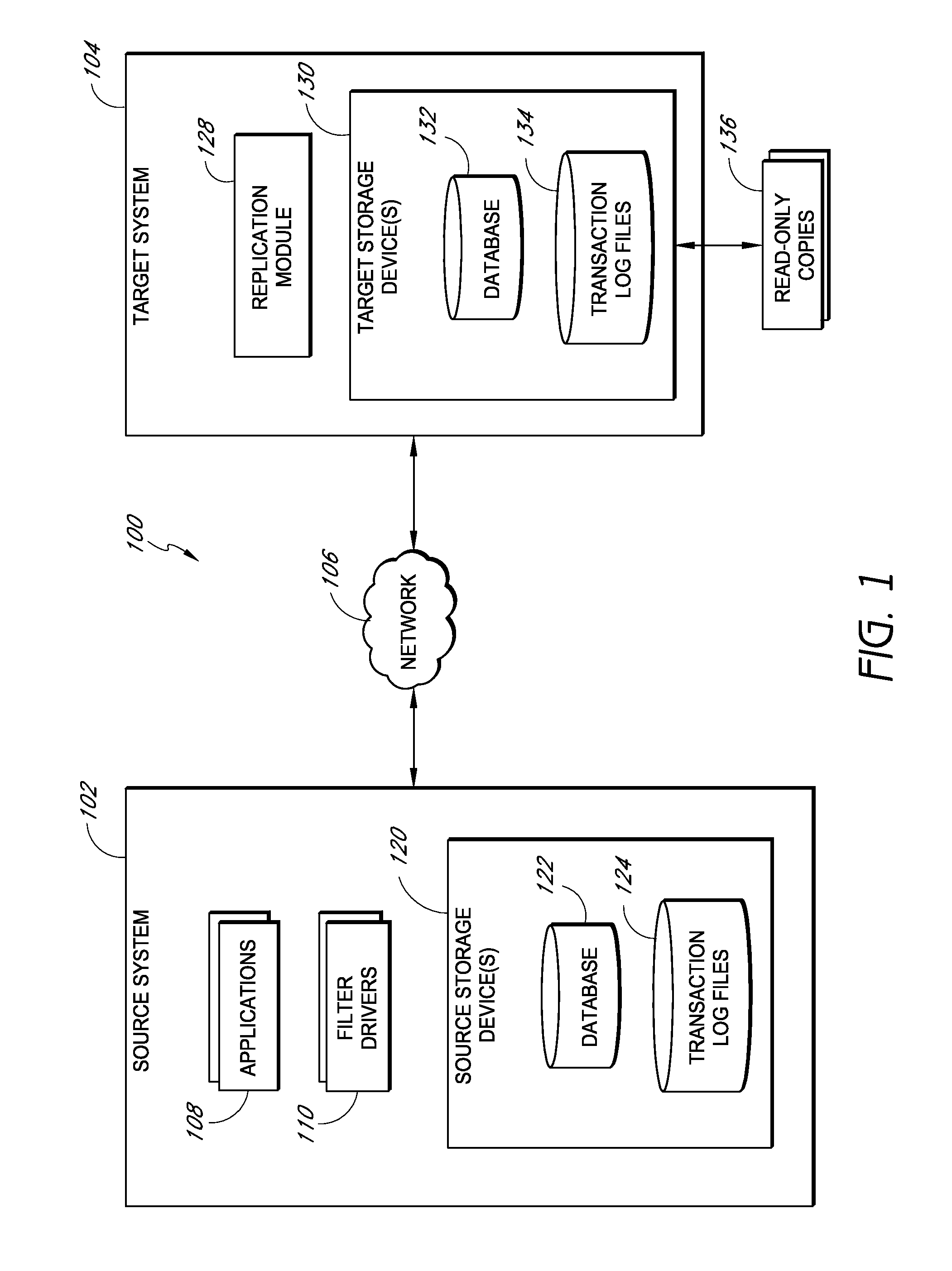
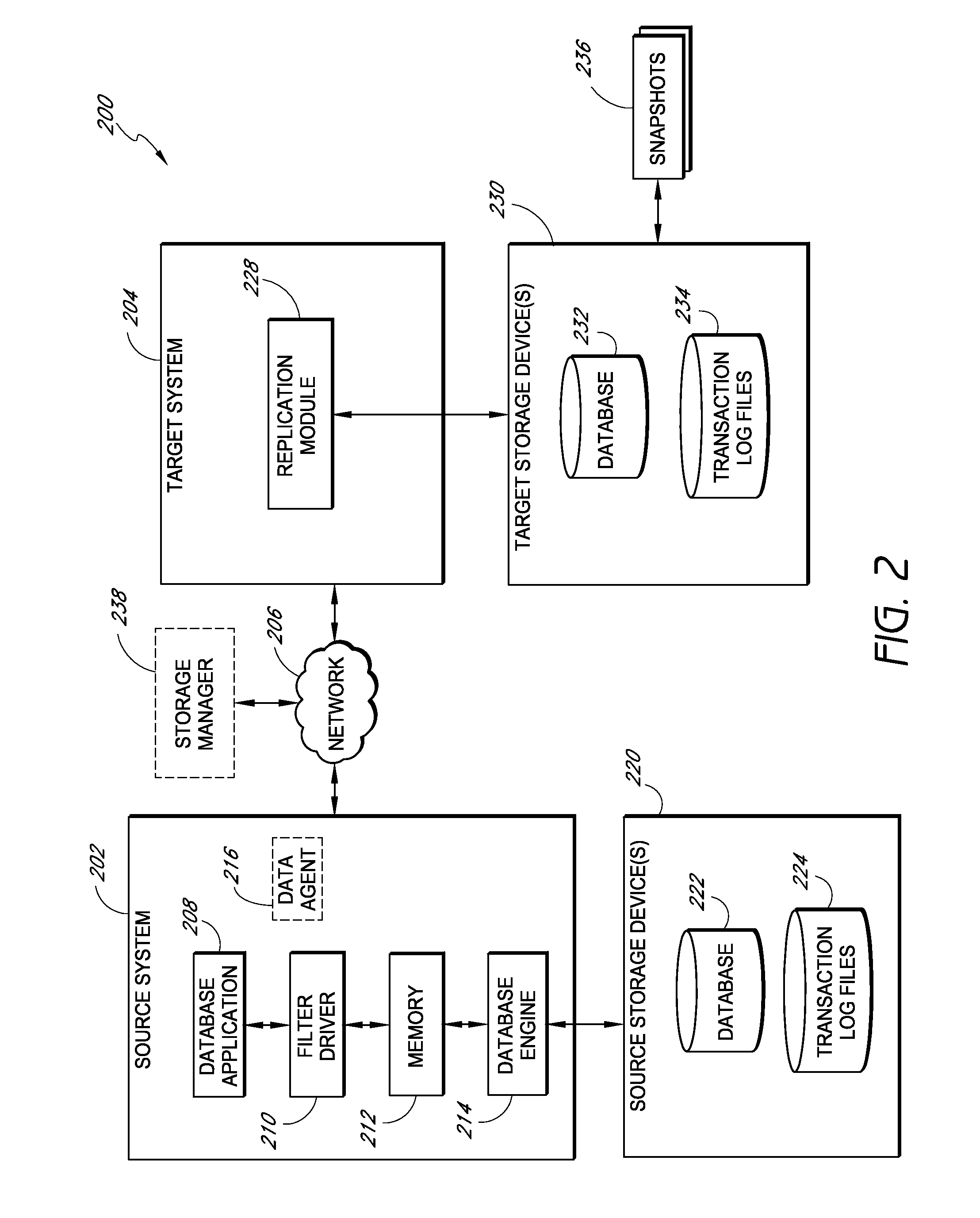
Systems and methods for managing replicated database data
ActiveUS20100145909A1Reduce memory requirementsImprove performanceError detection/correctionDigital data processing detailsDatabase applicationApplication software
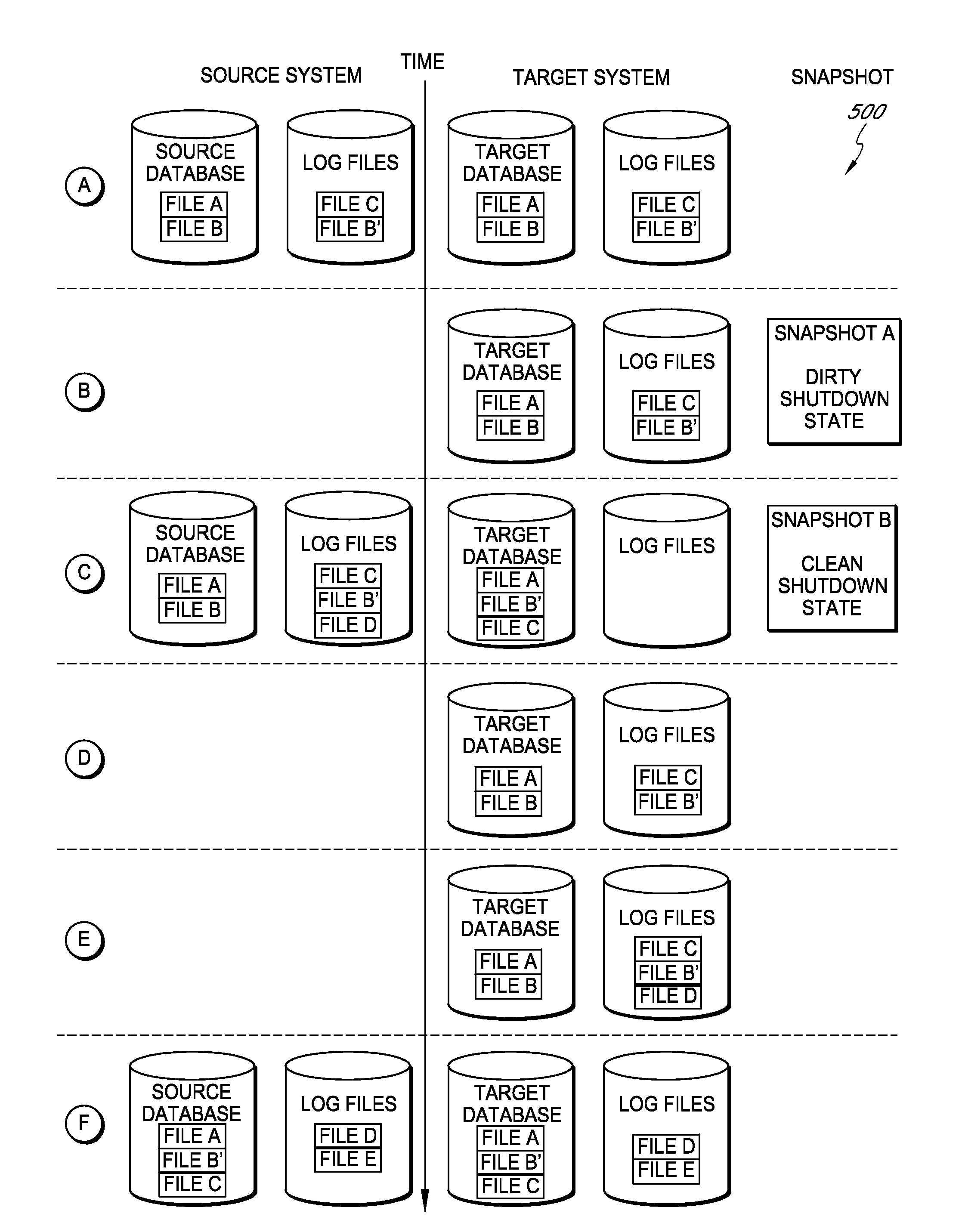
Systems and methods for replicating database data and generating read-only copies of the replicated data in a clean shutdown state. For example, systems can include a tracking module (e.g., a filter driver) that monitors transactions from a database application to a source storage device to generate log entries having at least one marker indicating a known good state of the application. The systems further include a computer coupled to a target storage device comprising a database and log files. The computer processes the transactions, based on the log entries, to replicate data to the target storage device; performs a first snapshot on data stored in the database and log files; replays into the database data stored in the log files; performs another snapshot on the database; and reverts the database back to a state in which the database existed at the time of the first snapshot.
Owner:COMMVAULT SYST INC
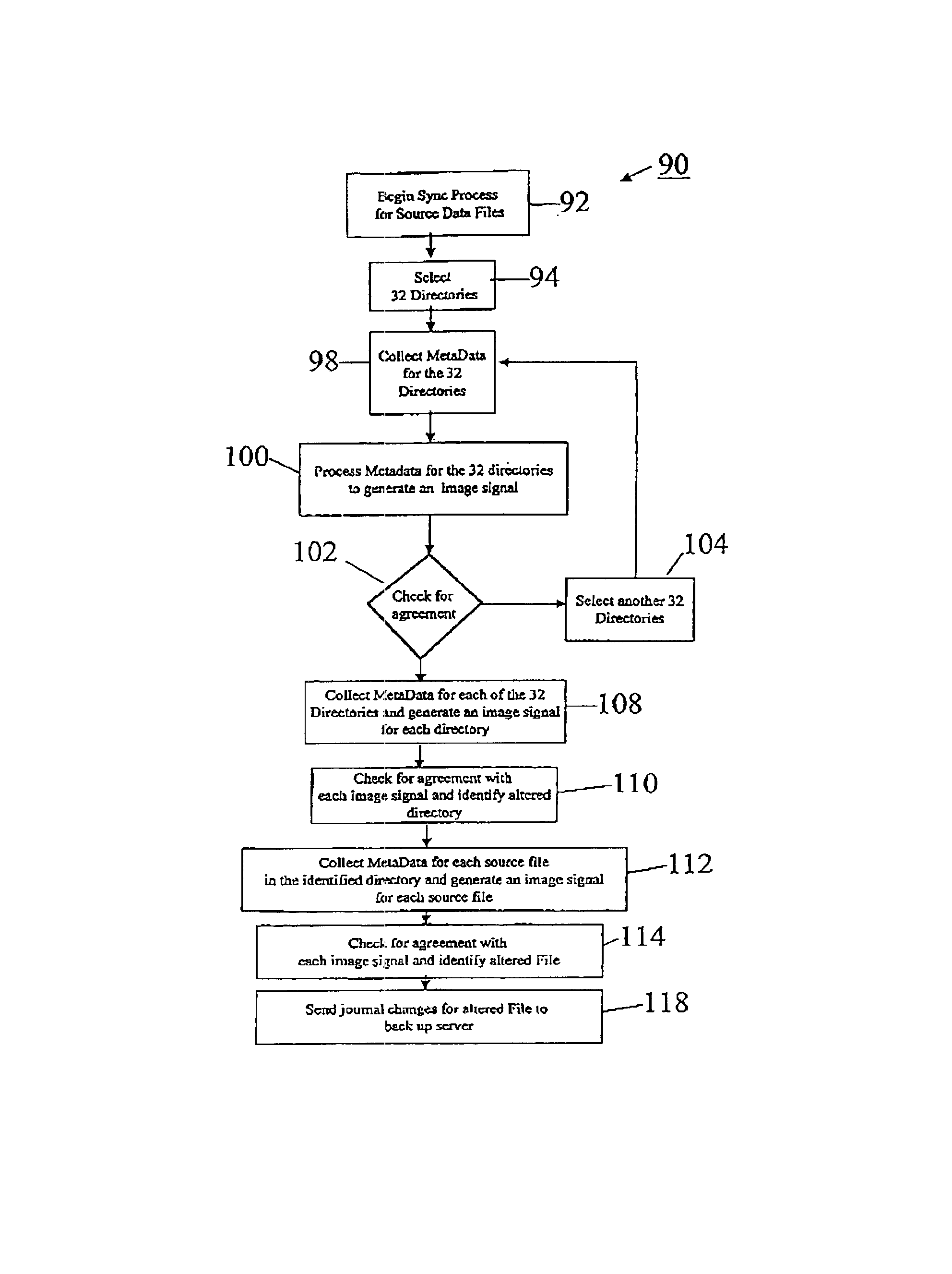
Systems and methods for backing up data files
InactiveUS6847984B1Provide integrityReduce demandData processing applicationsError detection/correctionBaseline dataData file
The invention provides systems and methods for continuous back up of data stored on a computer network. To this end the systems of the invention include a synchronization process that replicates selected source data files data stored on the network and to create a corresponding set of replicated data files, called the target data files, that are stored on a back up server. This synchronization process builds a baseline data structure of target data files. In parallel to this synchronization process, the system includes a dynamic replication process that includes a plurality of agents, each of which monitors a portion of the source data files to detect and capture, at the byte-level, changes to the source data files. Each agent may record the changes to a respective journal file, and as the dynamic replication process detects that the journal files contain data, the journal files are transferred or copied to the back up server so that the captured changes can be written to the appropriate ones of the target data files.
Owner:KEEPITSAFE INC
System and methods for semiautomatic generation and tuning of natural language interaction applications
ActiveUS20140019116A1Natural language translationSemantic analysisIdentifying problemsSemi automatic
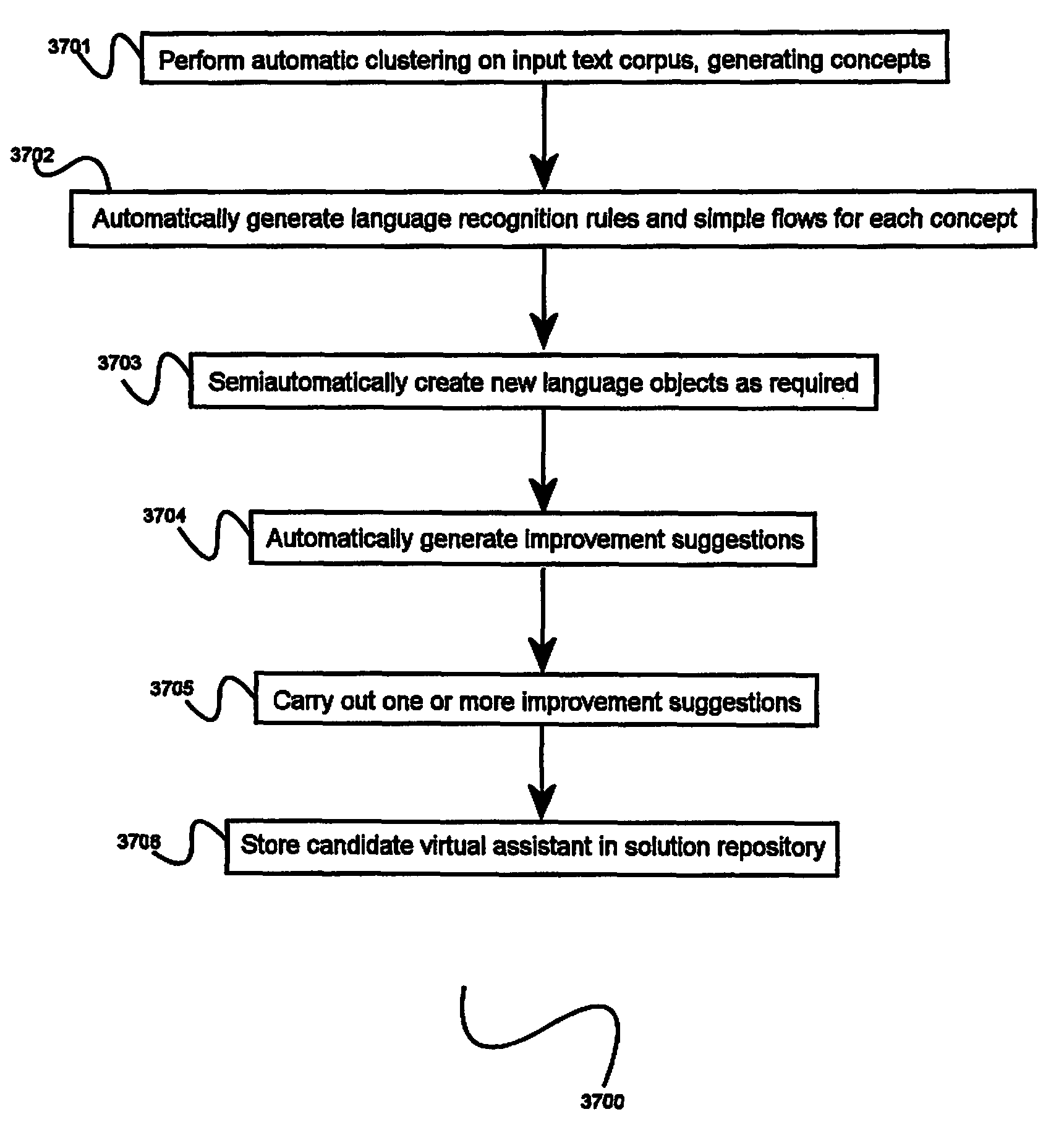
A system for supervised automatic code generation and tuning for natural language interaction applications, comprising a build environment comprising a developer user interface, automated coding tools, automated testing tools, and automated optimization tools, and an analytics framework software module. Text samples are imported into the build environment and automated clustering is performed to assign them to a plurality of input groups, each input group comprising a plurality of semantically related inputs. Language recognition rules are generated by automated coding tools. Automated testing tools carry out automated testing of language recognition rules and generate recommendations for tuning language recognition rules. The analytics framework performs analysis of interaction log files to identify problems in a candidate natural language interaction application. Optimizations to the candidate natural language interaction application are carried out and an optimized natural language interaction application is deployed into production and stored in the solution data repository.
Owner:ARTIFICIAL SOLUTIONS
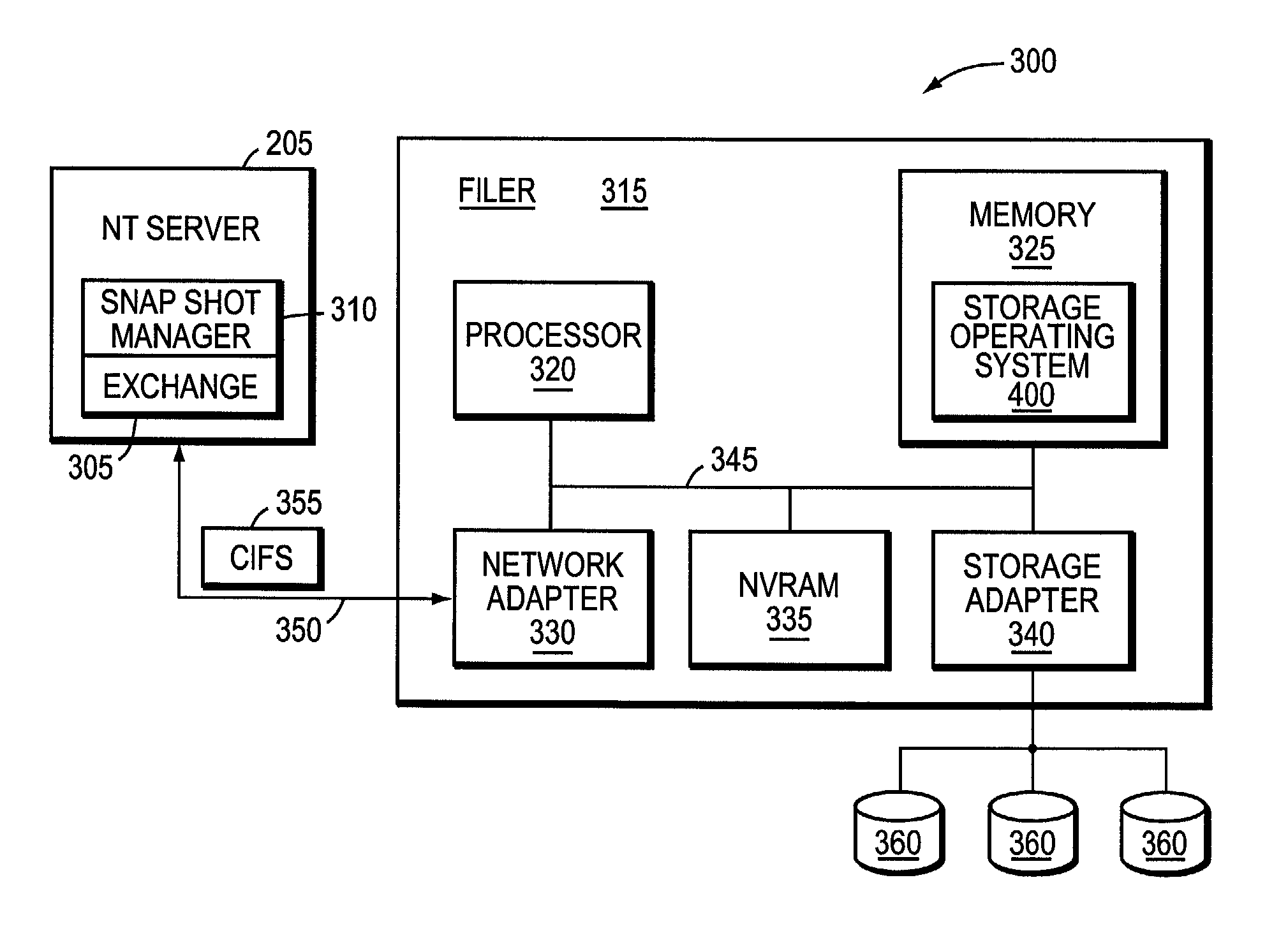
System and method for creating a point-in-time restoration of a database file
InactiveUS7373364B1Overcome disadvantagesAvoid data lossData processing applicationsError detection/correctionFile systemDatabase file
The present invention provides a method for generating a point-in-time restoration of database files and associated log files by utilizing a snapshot feature of the file system storing the files. At regular intervals, snapshots, which produce read-only copies of the files, are taken along with backups of the associated log files. To restore to a given point-in-time, the snapshot and stored log files are transferred to the active file system. In a second embodiment, all log files associated with snapshots taken after the selected snapshot are also restored.
Owner:NETWORK APPLIANCE INC
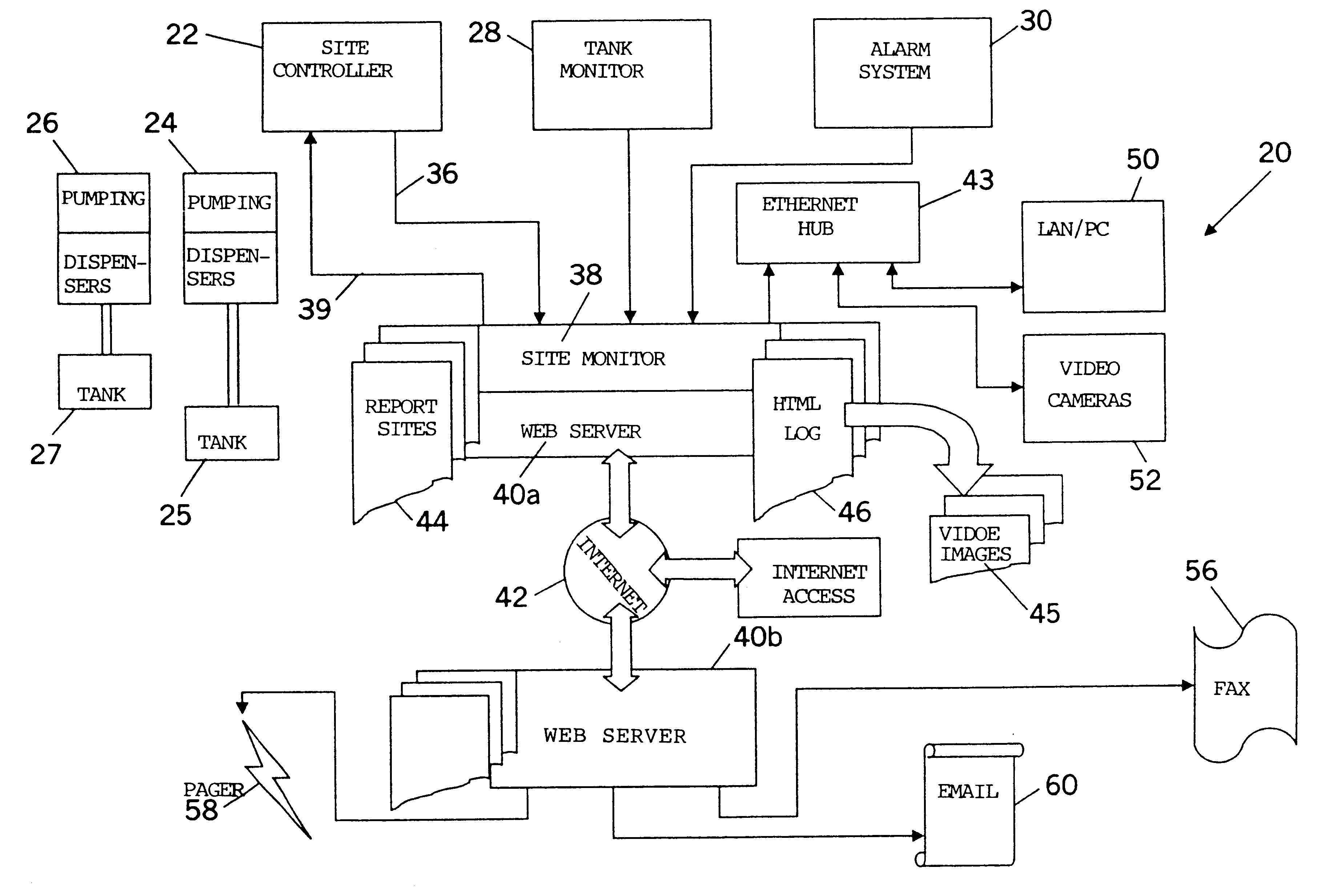
Method and apparatus for site management
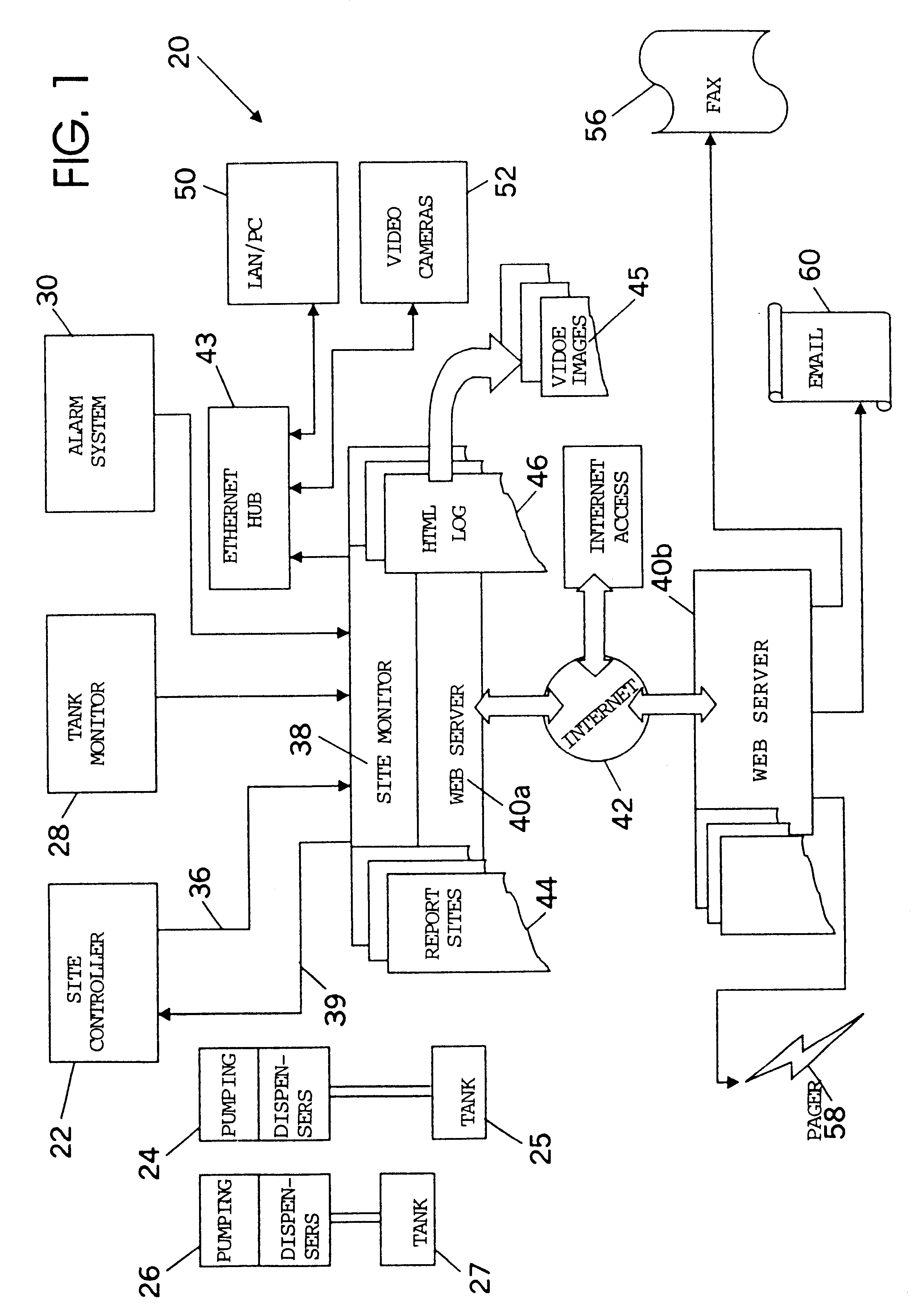
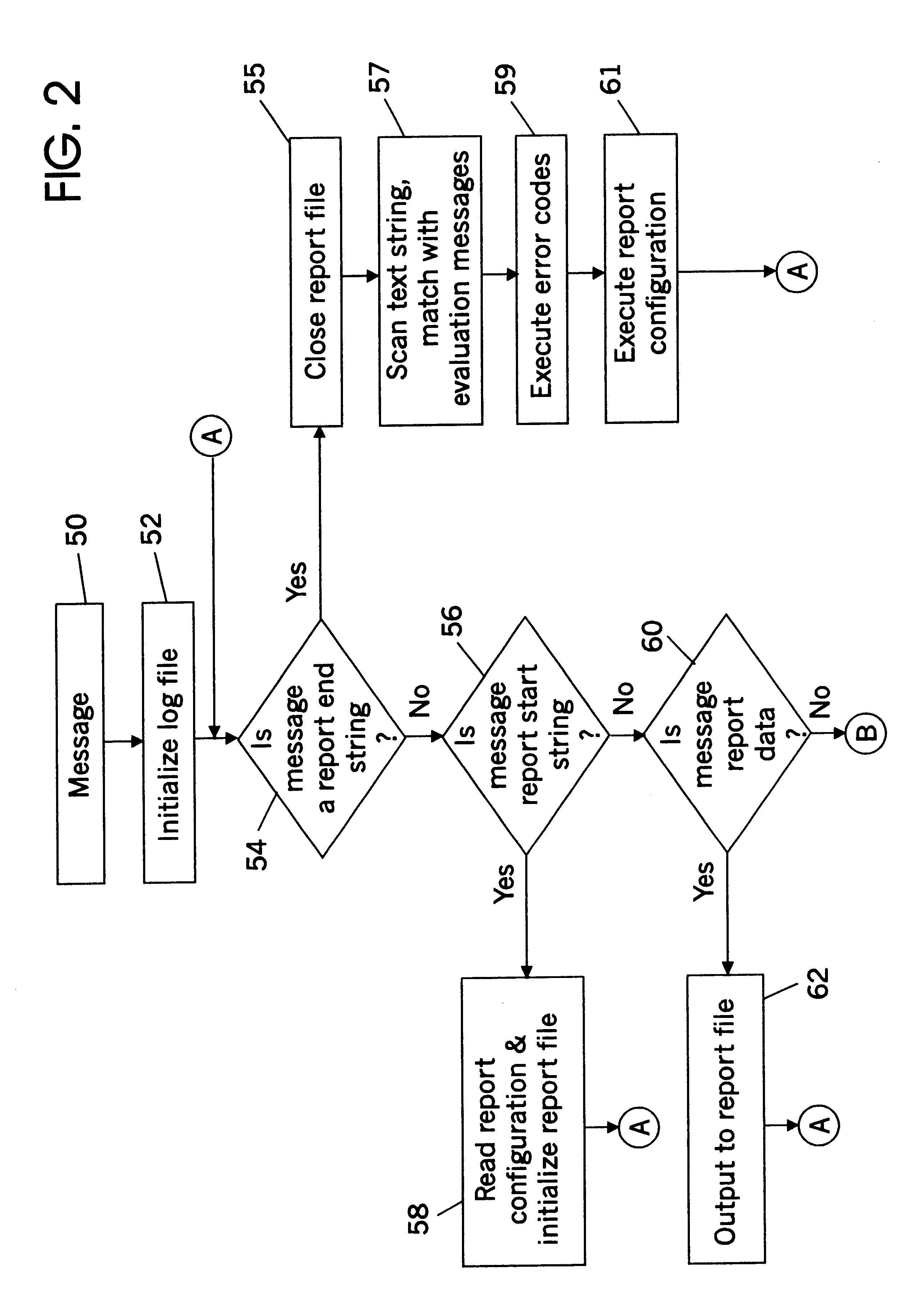
A method and apparatus for monitoring and maintenance of unattended robot liquid storage and dispensing sites, including a site controller and site monitor. The site monitor continuously appends text strings received from the site controller to HTML text log files and HTLM text report files and simultaneously compares the stored text strings representing site events to be monitored with evaluation messages. Each evaluation message is linked to an alert code, which in response to an evaluation message text string match initiates a particular set of responses, including sending notice of site failures and other remote site information to a home office via fax, pager and / or email. The site monitor also collects the information gathered from the site controller, the tank monitor, alarm system and any other site devices and stores the information in a one or more HTML text files, which information then takes the form of a web page with hypertext links to images related to the stored information.
Owner:RAWLS & WINSTEAD
Sharing live data with a non cooperative DBMS
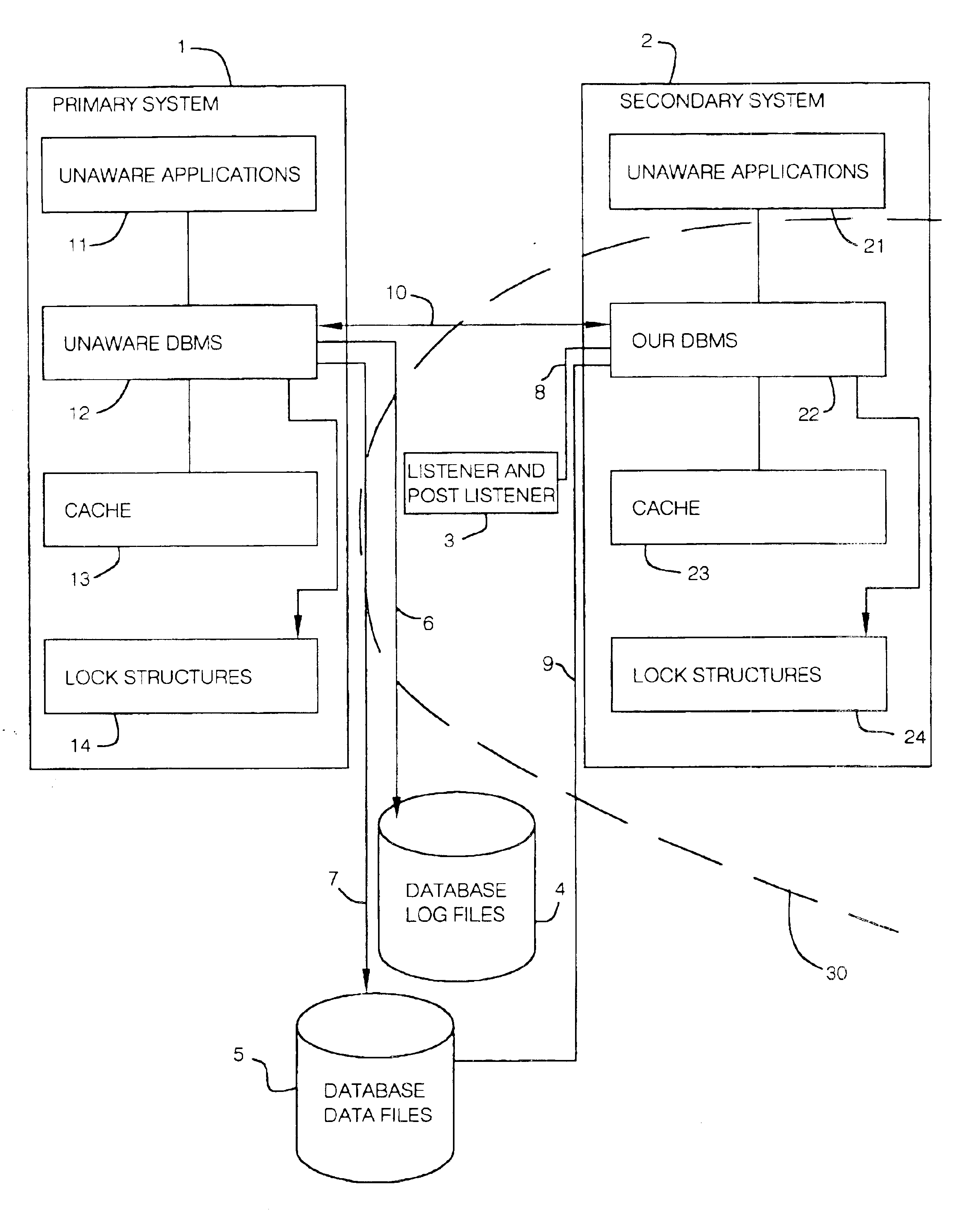
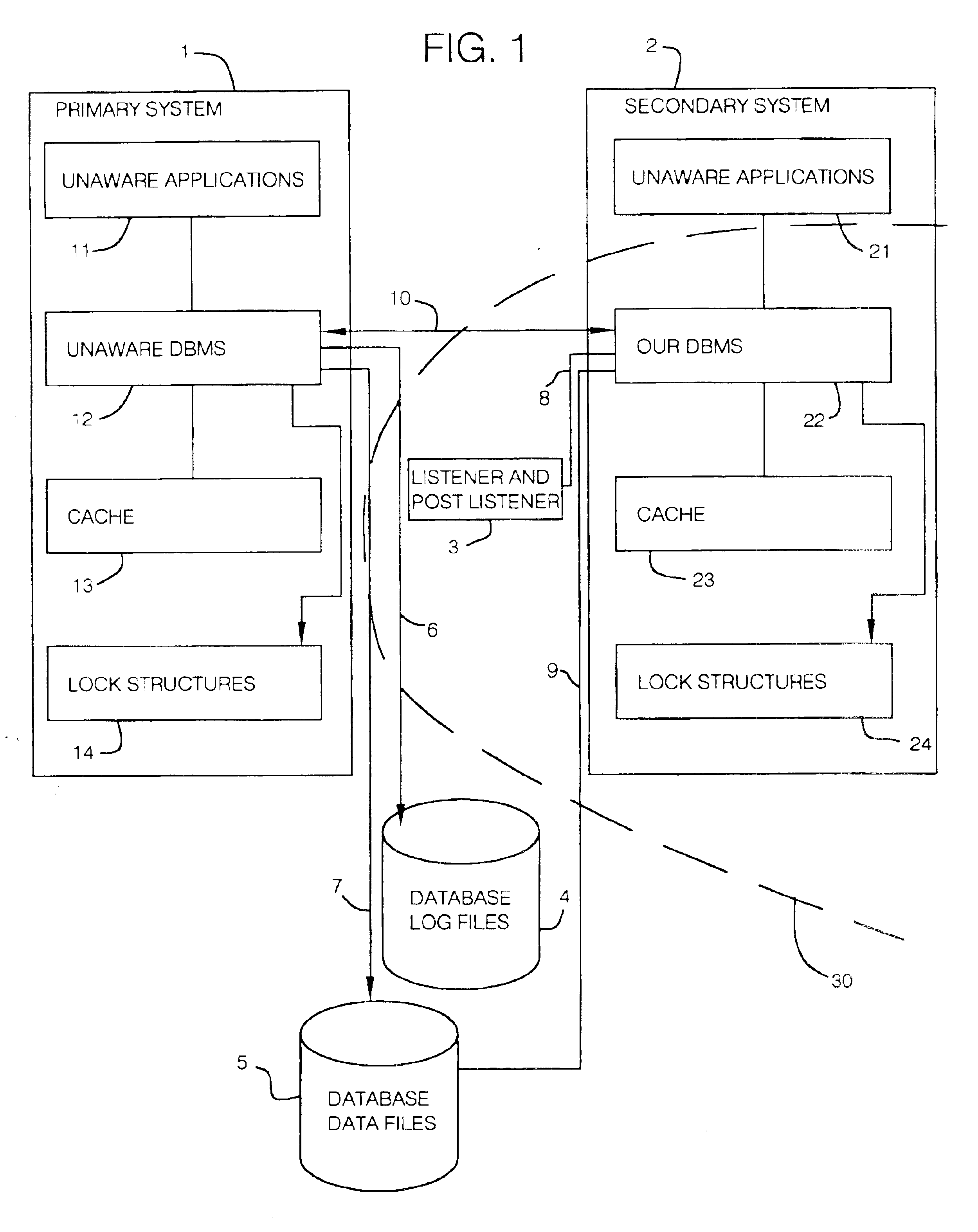
InactiveUS6879981B2Interrupting their activitySolve insufficient capacityData processing applicationsDigital data information retrievalReal-time dataLocking mechanism
Owner:DATACLOUD TECH LLC
System and methods for semiautomatic generation and tuning of natural language interaction applications
ActiveUS20130268260A1Natural language translationSemantic analysisIdentifying problemsApplication software
A system for supervised automatic code generation and tuning for natural language interaction applications, comprising a build environment comprising a developer user interface, automated coding tools, automated testing tools, and automated optimization tools, and an analytics framework software module. Text samples are imported into the build environment and automated clustering is performed to assign them to a plurality of input groups, each input group comprising a plurality of semantically related inputs. Language recognition rules are generated by automated coding tools. Automated testing tools carry out automated testing of language recognition rules and generate recommendations for tuning language recognition rules. The analytics framework performs analysis of interaction log files to identify problems in a candidate natural language interaction application. Optimizations to the candidate natural language interaction application are carried out and an optimized natural language interaction application is deployed into production and stored in the solution data repository.
Owner:ARTIFICIAL SOLUTIONS
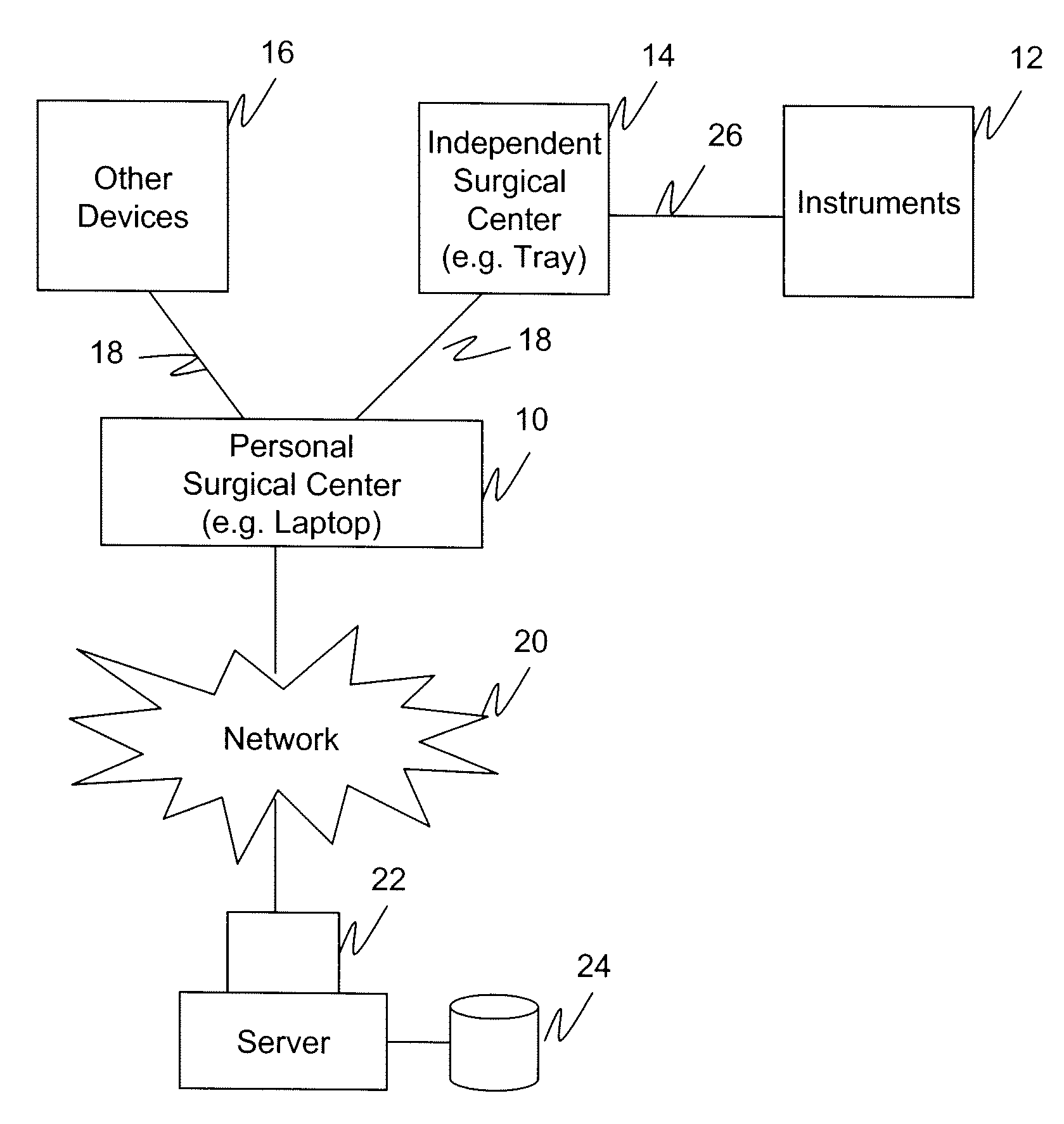
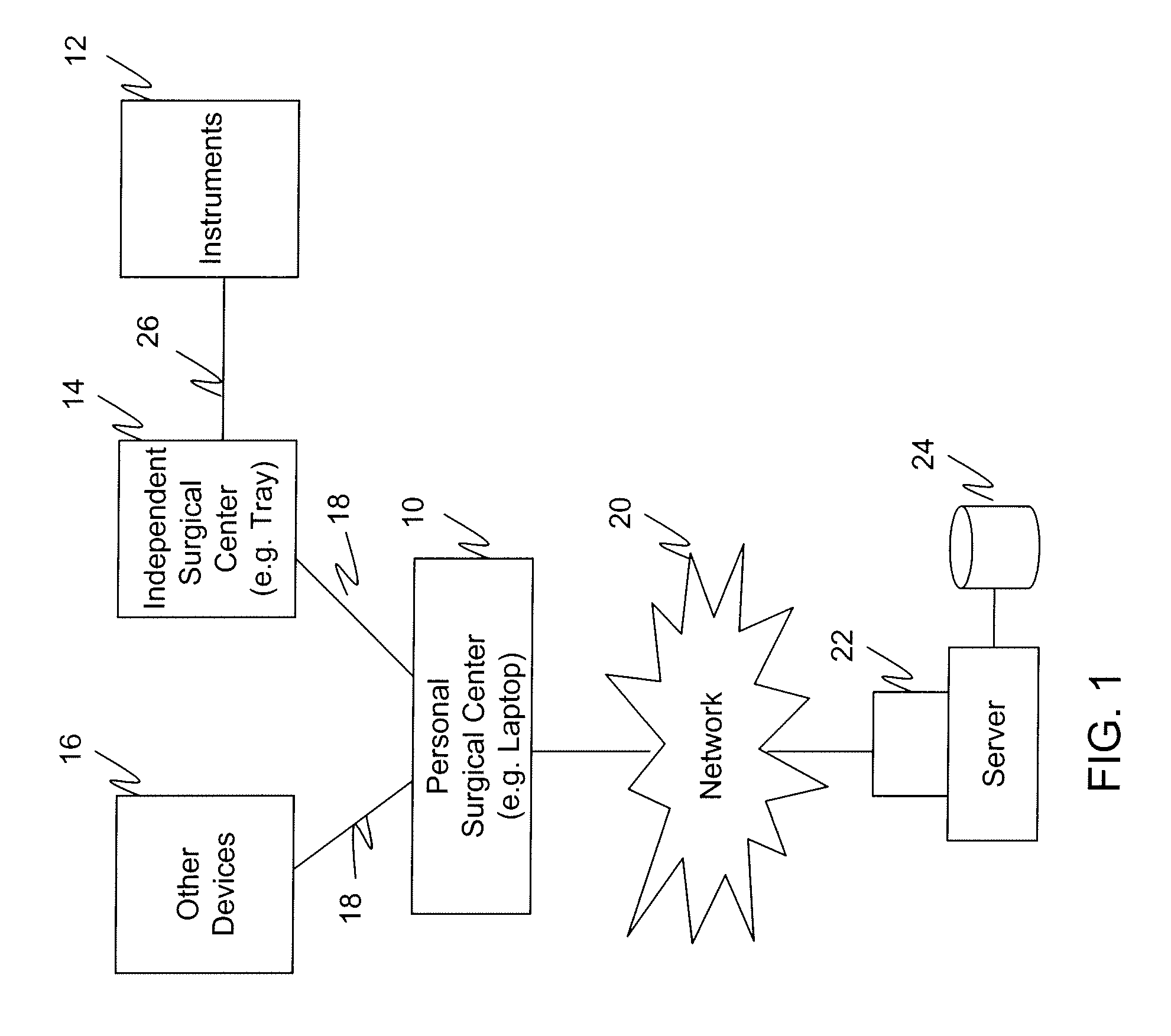
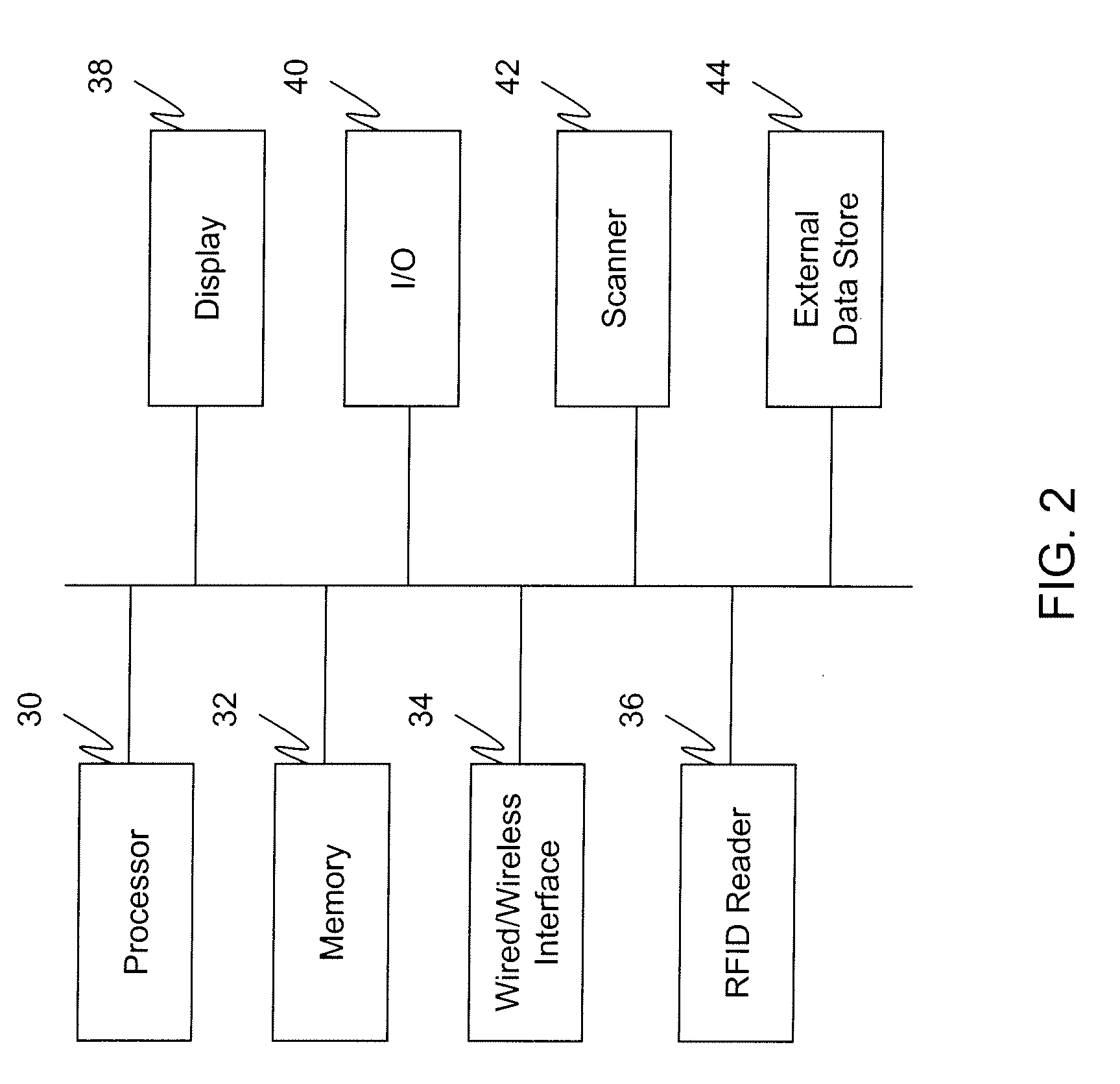
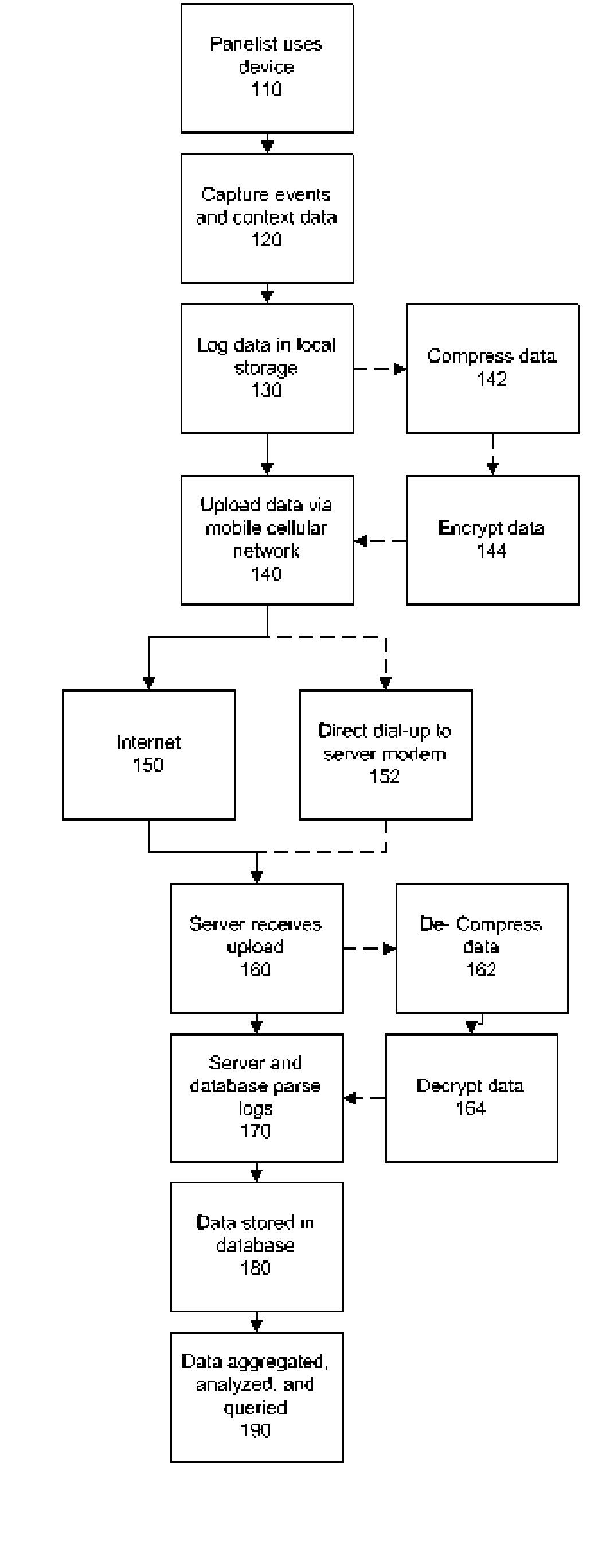
Personal Surgical Center
InactiveUS20080281301A1Small and no footprintOperating room spaceSurgical drapesOffice automationHand heldGeneral purpose computer
A personal surgical center embodied as a general purpose computer (e.g. laptop) with wireless technology for monitoring the operation of an independent surgical center and / or handheld instruments. The computer tracks procedures in the operating room and instruments used during those procedures, and accounts for billing, supply management, and payment options. The monitoring of the instruments used during the surgery is conducted by the personal surgical center while actual control of the settings of those instruments is via the independent surgical center or via controls included in the instruments themselves. The monitored information is stored in a log file which is then transmitted to a hospital server for generating reports, inventory control, billing, and the like. Other information generated during the procedure (e.g. doctor notes) is also stored in the log file. The personal surgical center may also access the hospital server or local data storage device for retrieving a surgeon's specific surgery parameters, obtaining patient files, and the like.
Owner:DOHENY EYE INST
System and method to track wireless device and communications usage
InactiveUS20050213511A1Short timeLow costError preventionTransmission systemsCommunications systemSignal quality
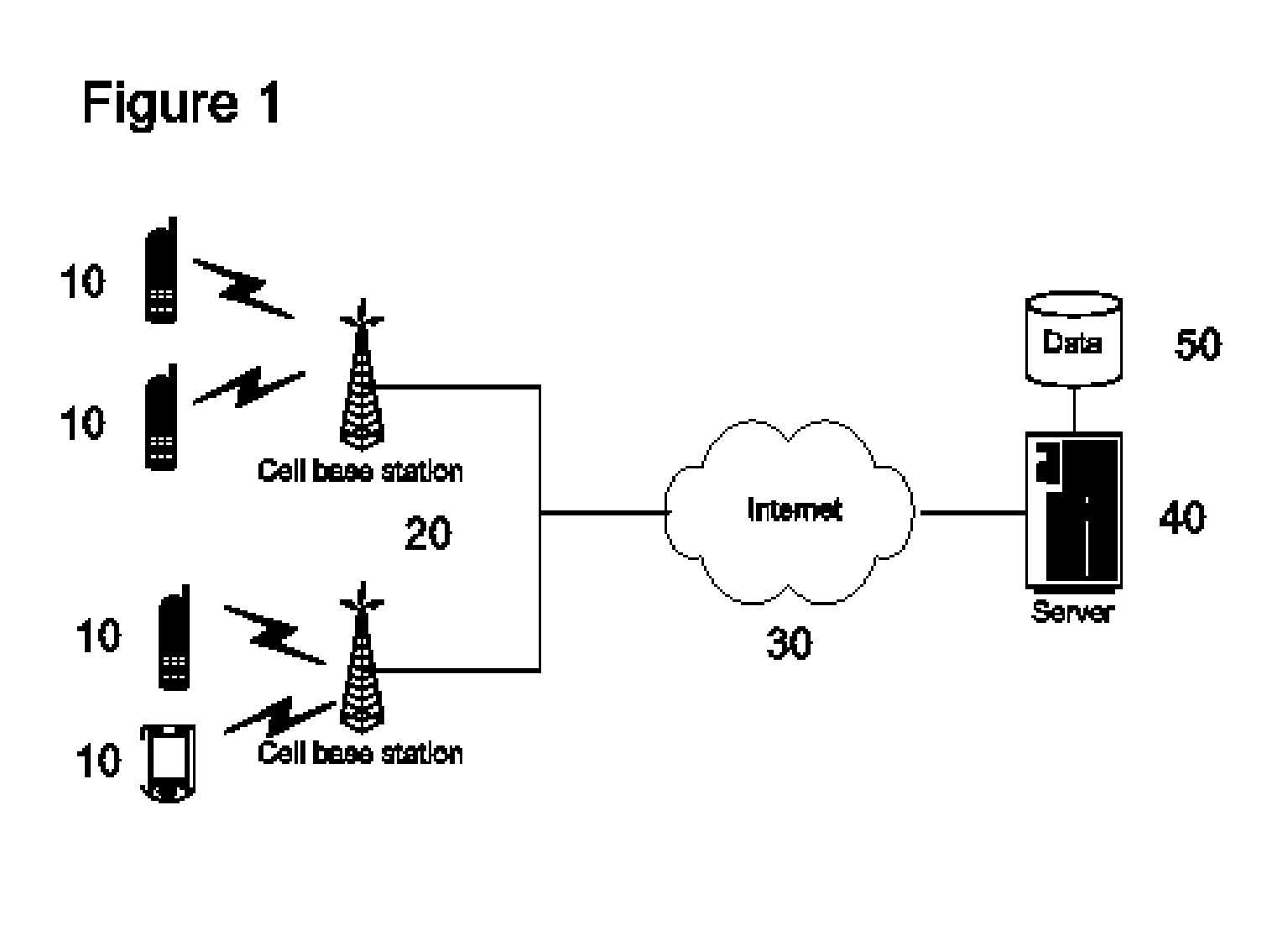
A system and method for gathering and reporting user and device activity data from wireless communication devices through a log file. The log file stores entries related to user events including the use of communications and applications, as well as access to local and remote media resource files. The log file entries may include parameters critical to mobile device operation such as location, signal quality, and battery power. The data gathering system comprises a plurality of wireless communications devices, each of which sends the log files through an available wireless communications system to a central facility for processing and aggregation into a database. Stored data is analyzed to generate, display, and marketing information that may include historical trends and projections of future consumer preferences and activities.
Owner:MERLIN MOBILE MEDIA
Diagnostics And Monitoring Services In A Mobile Network For A Mobile Device
InactiveUS20070207800A1Radio/inductive link selection arrangementsData switching networksPagerMobile electronics
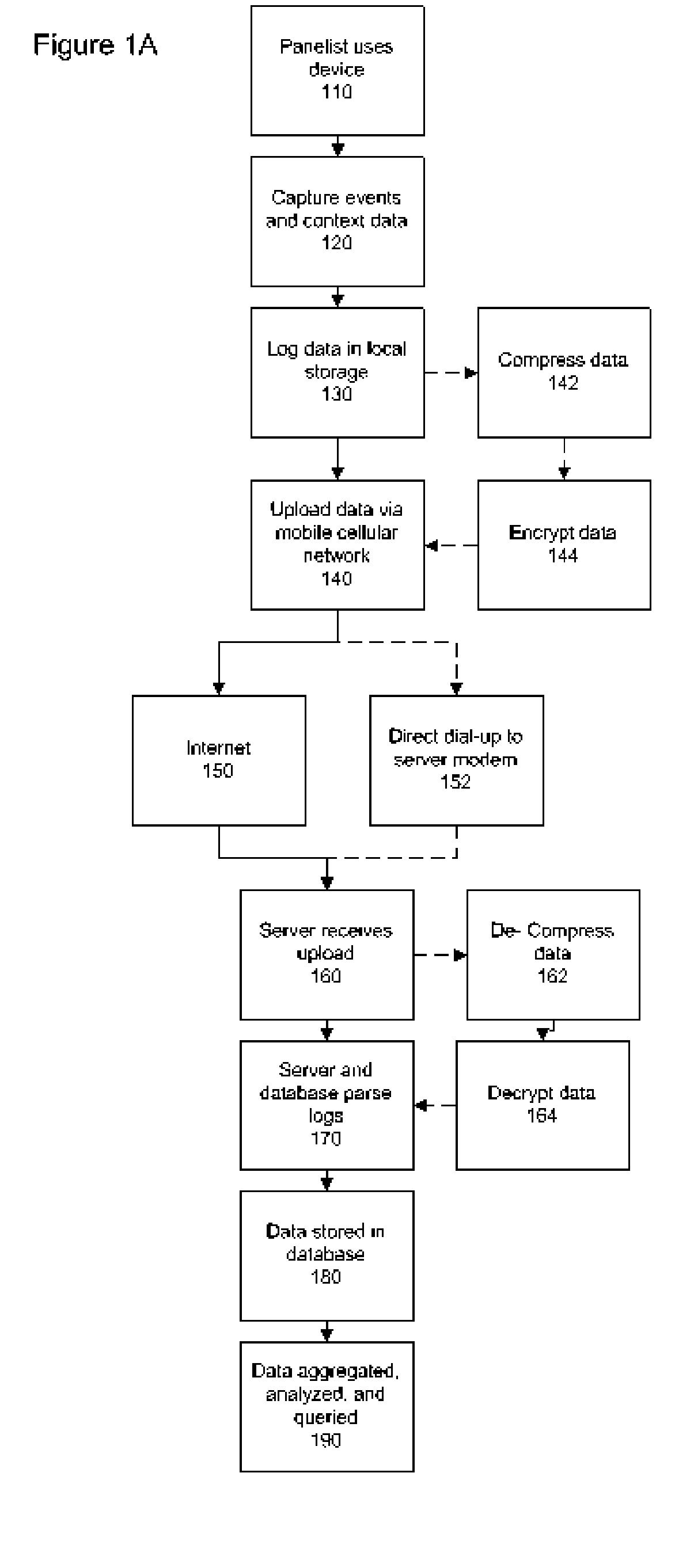
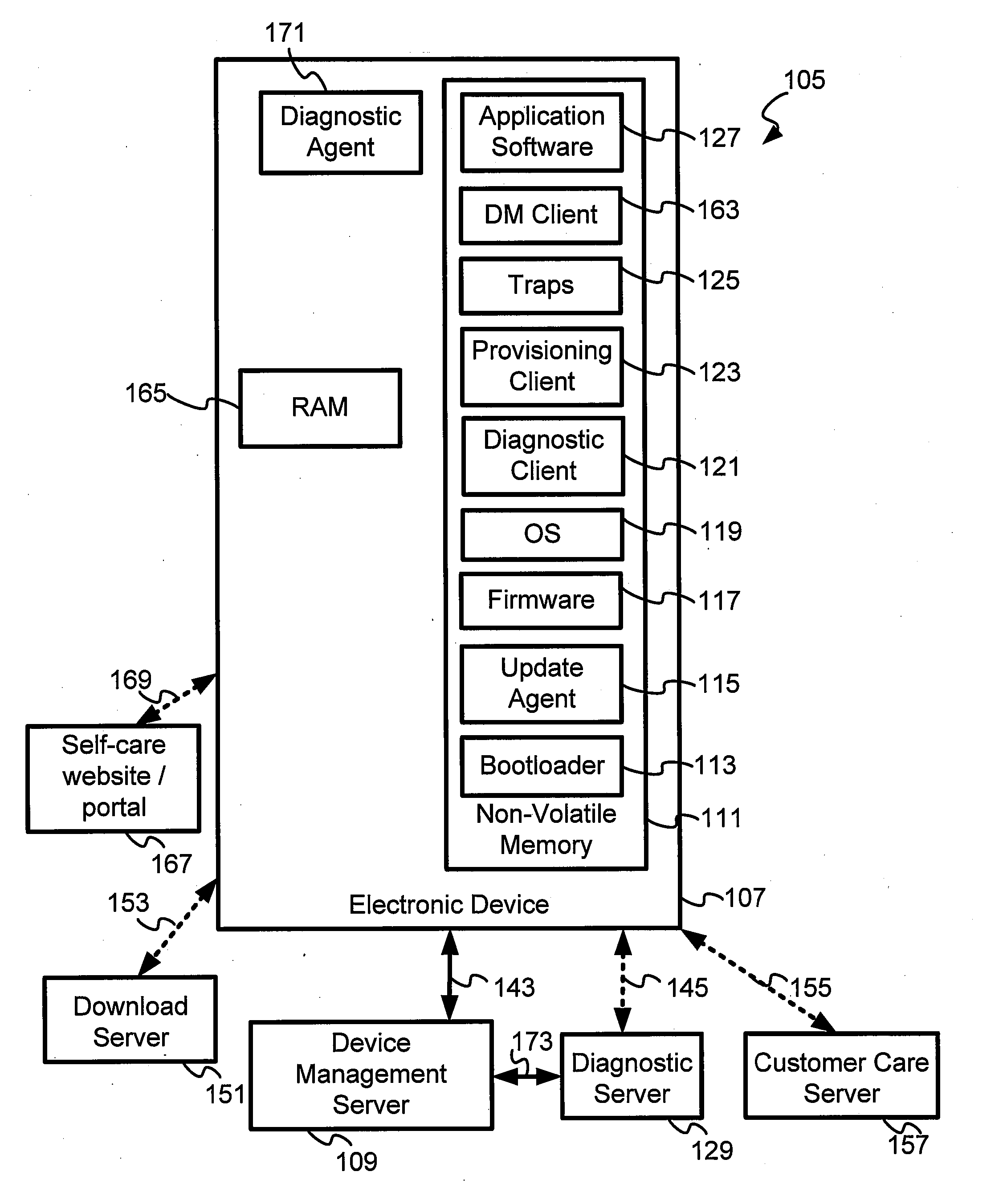
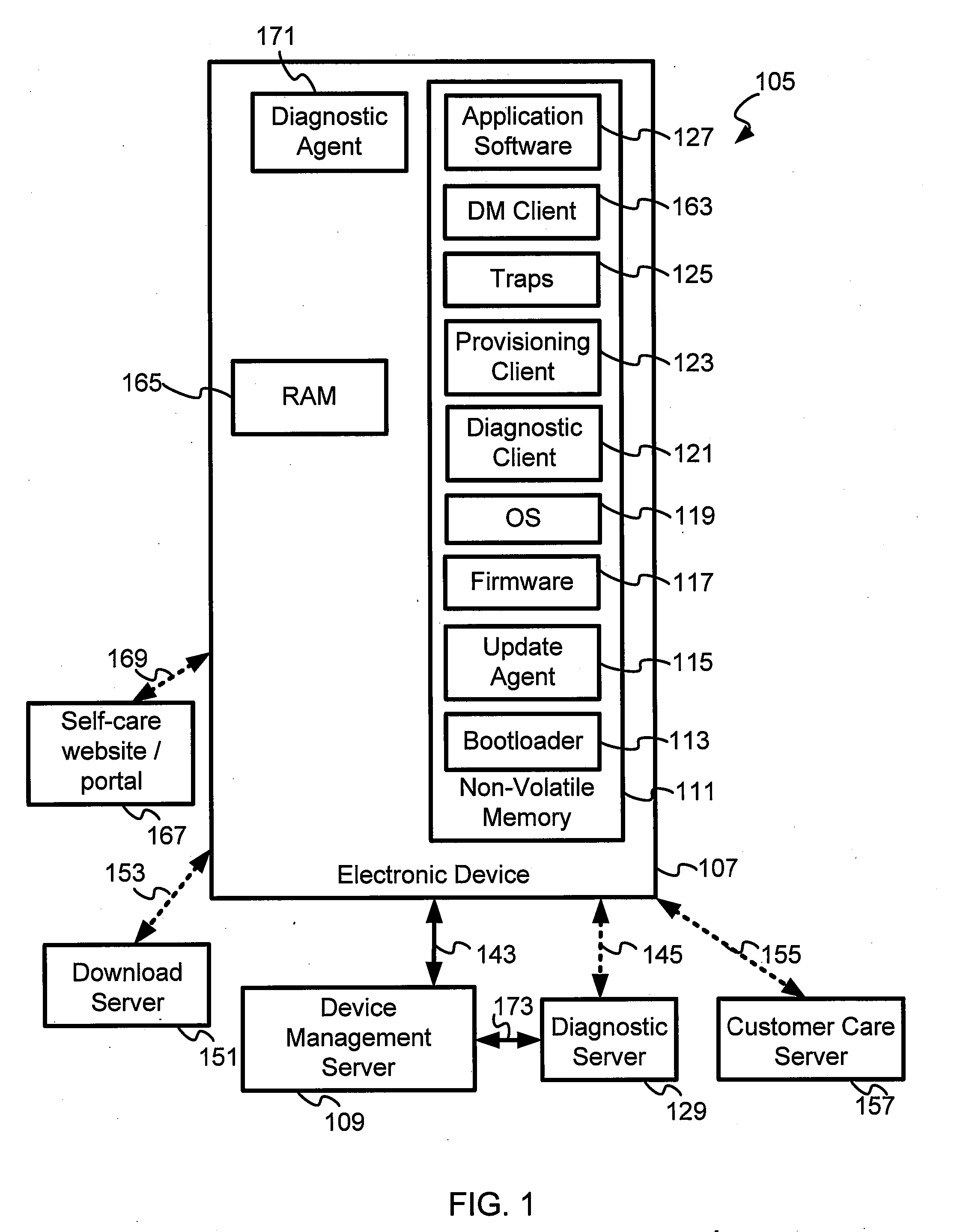
The present invention makes it possible to obtain debug- and other diagnostic information from mobile electronic devices in a system operator network. A Log Management object provides support for logging diagnostic data. A log file is employed to collect information on various device features for which tracing or debugging is turned on in a mobile electronic device such as, for example, a mobile handset, cellular phone, a personal digital assistant, a pager and a personal computer. It is also used to selectively collect information on specific events that are monitored, device specific data being collected, and network performance data, among other items. The diagnostic agent in the mobile device is a client side application that may run on the mobile device when required, or continuously as a monitoring application, and which manages and collects tracing information wirelessly to a server using a cellular data network. A diagnostic client may also be downloaded and executed to collect diagnostic data from applications, for example. Traps may also be set and data collected from them. The Log file may be retrieved from the server side in pull or push mode.
Owner:QUALCOMM INC
Method, system, and program for logging statements to monitor execution of a program
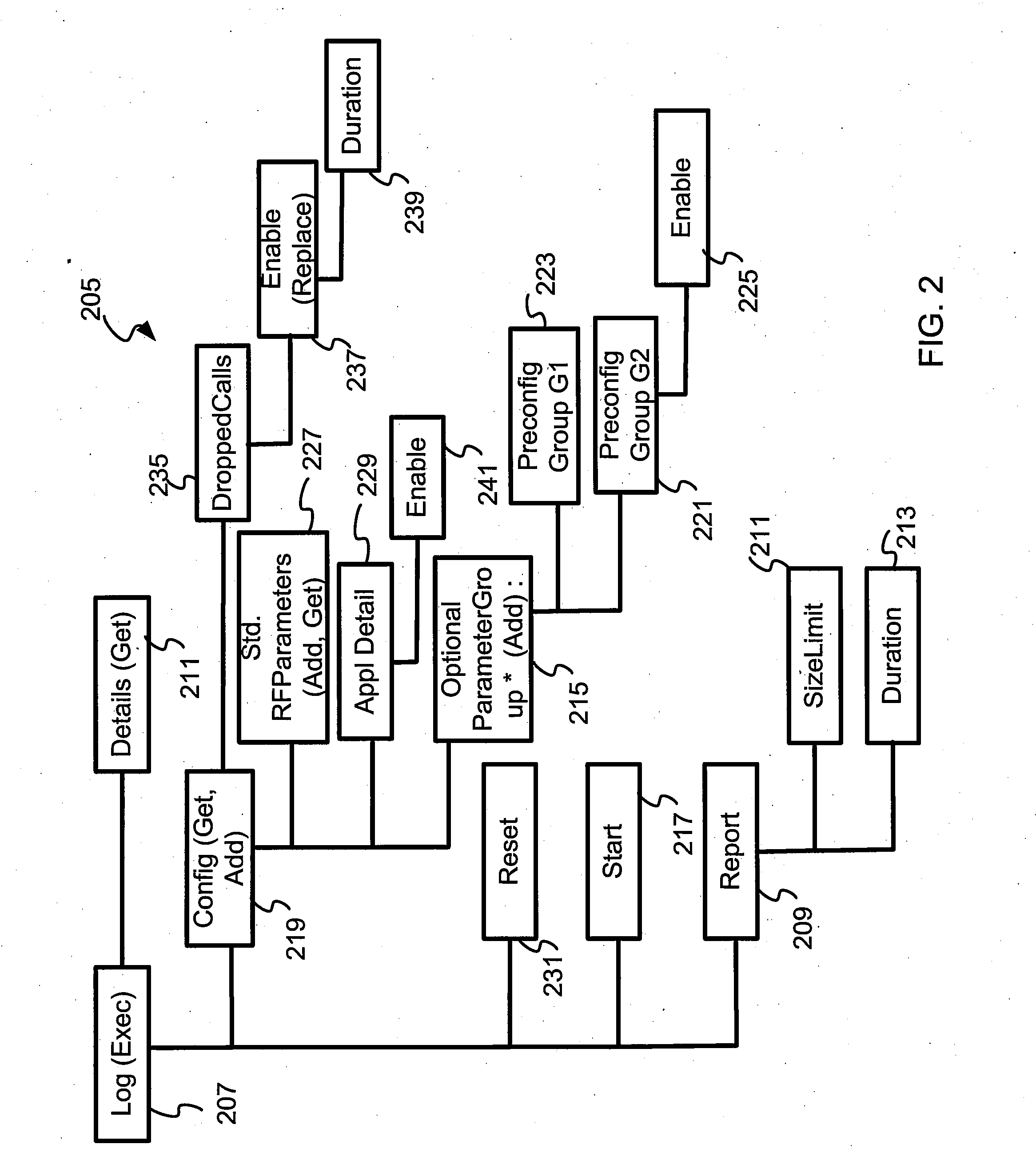
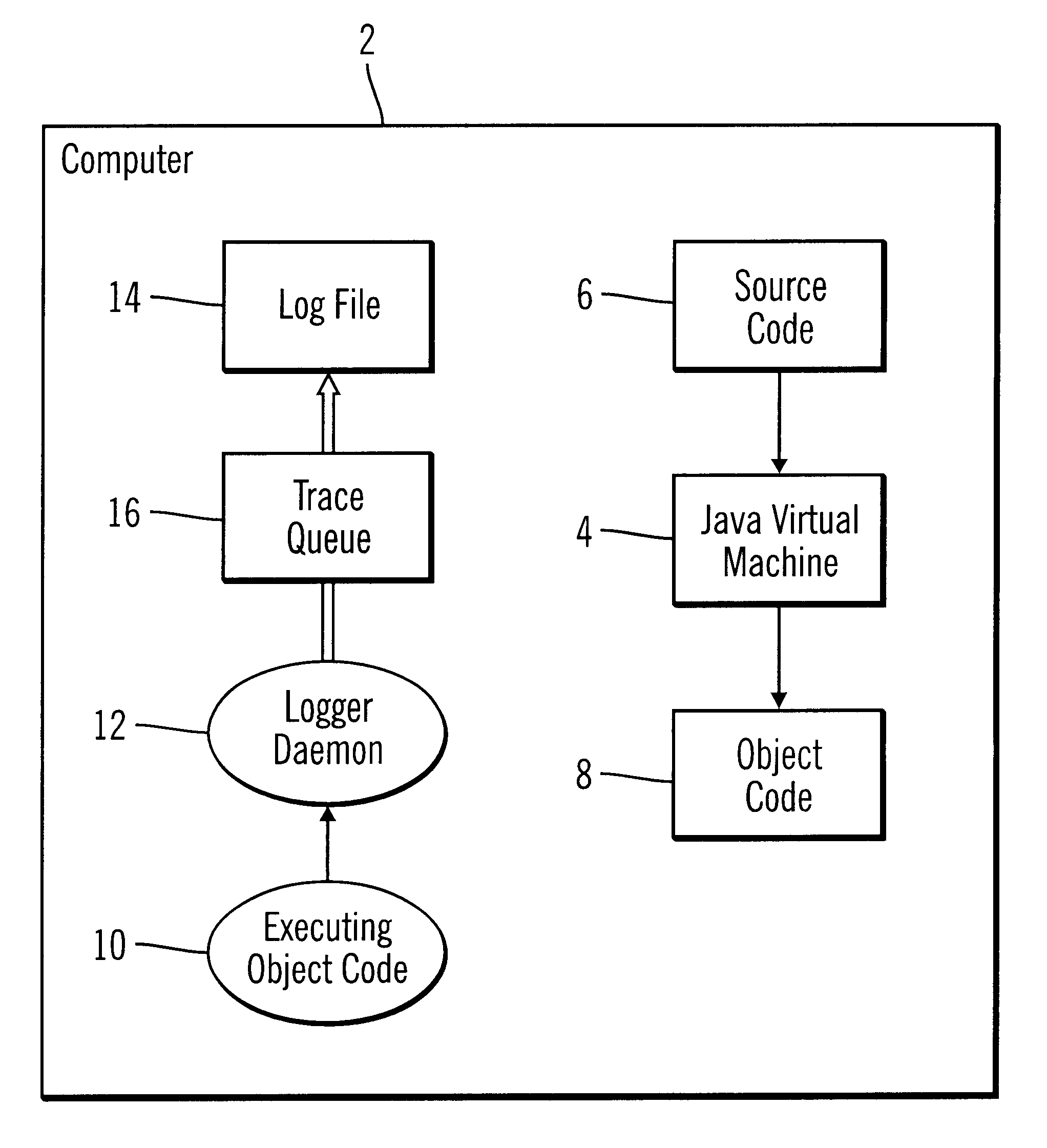
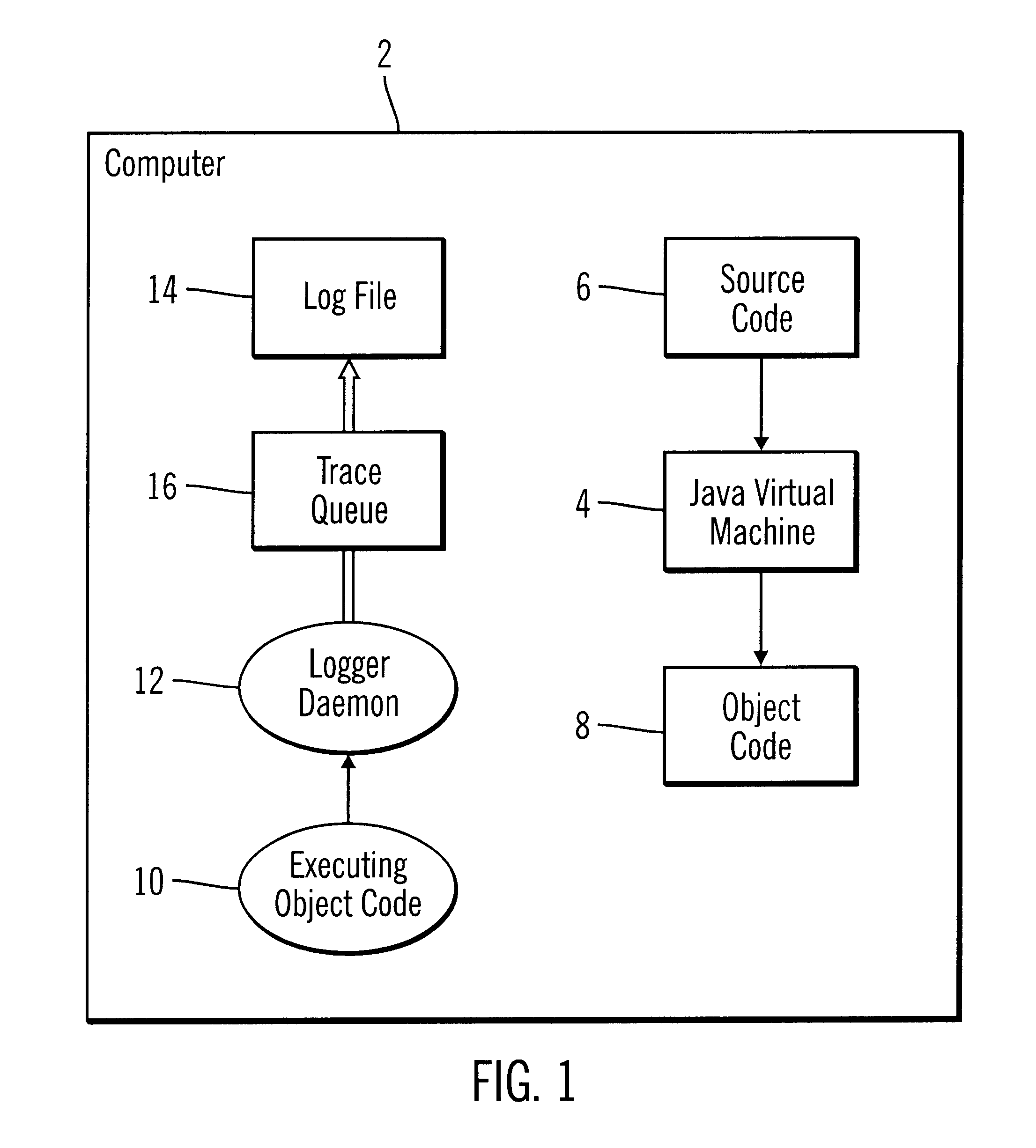
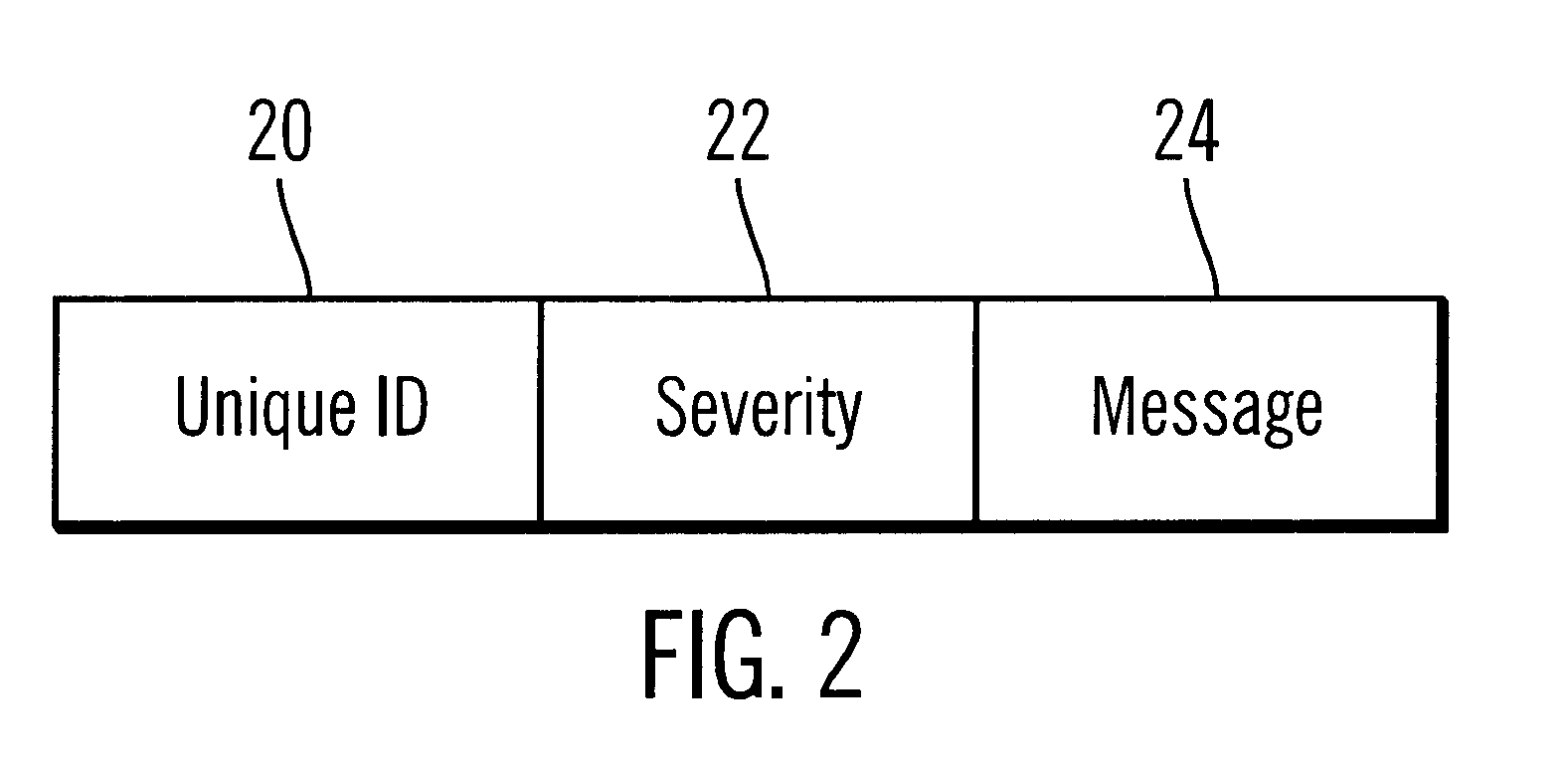
InactiveUS6539501B1Shorten the timeImprove space utilizationHardware monitoringSoftware testing/debuggingProgramming languageLogfile
Disclosed is a system, method, and program for generating trace statements to a log file. A log method in a program, such as a Java program, including an identifier parameter is processed. The program includes multiple instances of the log method to trace the execution of the program during debugging operations. A determination is made as to whether a variable indicates that log methods called with the identifier parameter should be processed. The class and method from which the log method was called is determined if the variable indicates that log methods called with the identifier parameter should be processed. Information on the identifier parameter and determined class and method are written to the log file.
Owner:IBM CORP
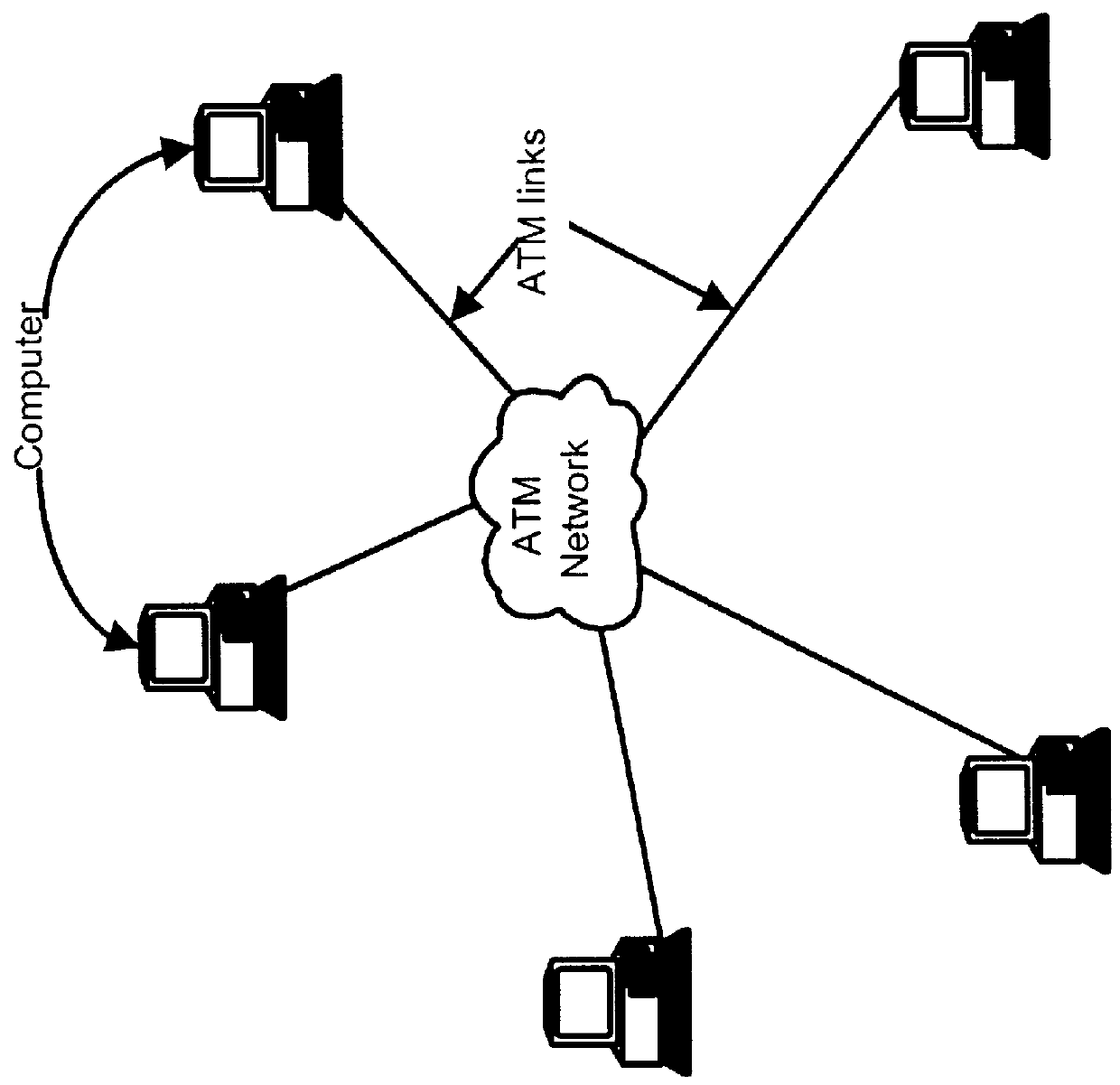
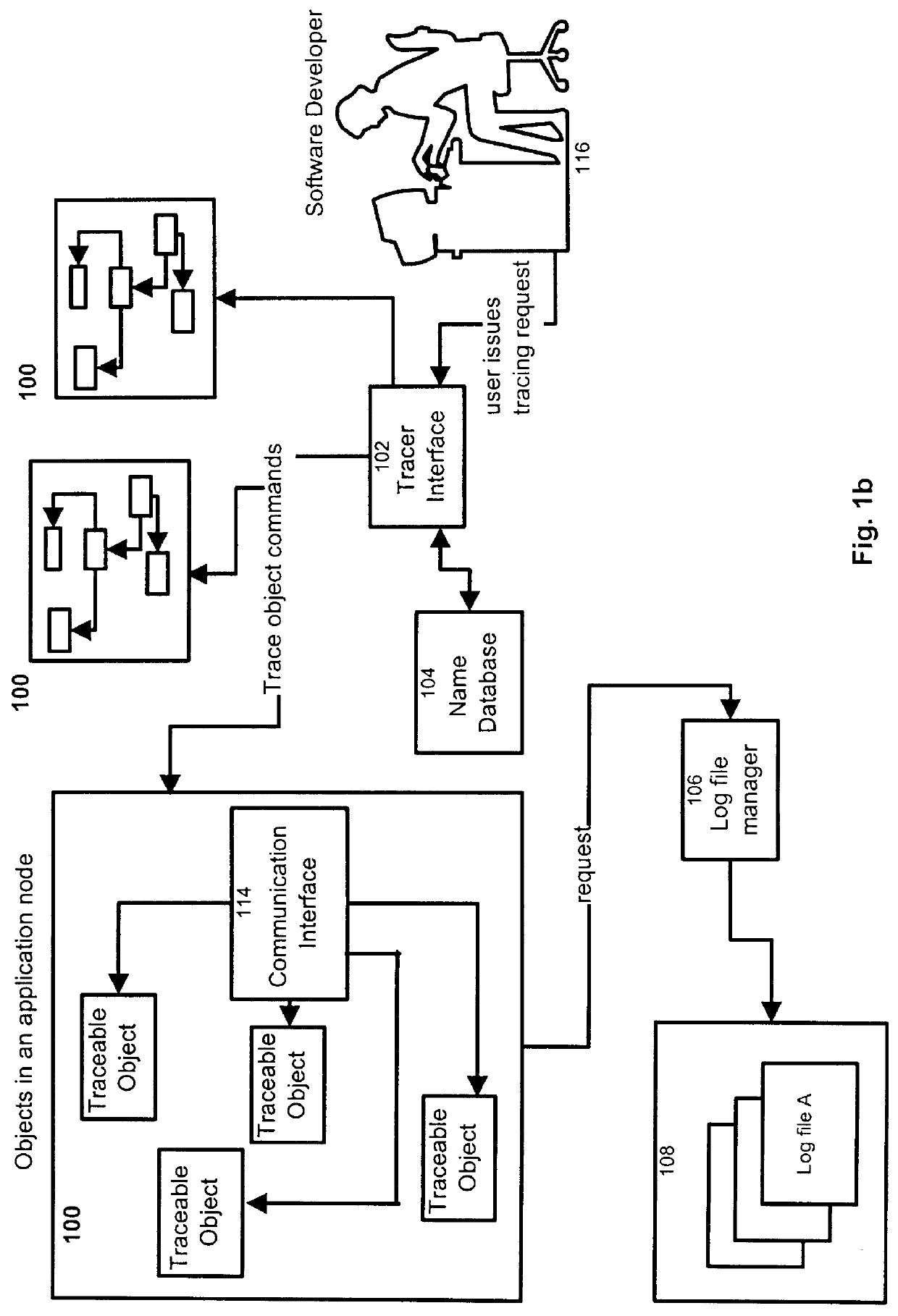
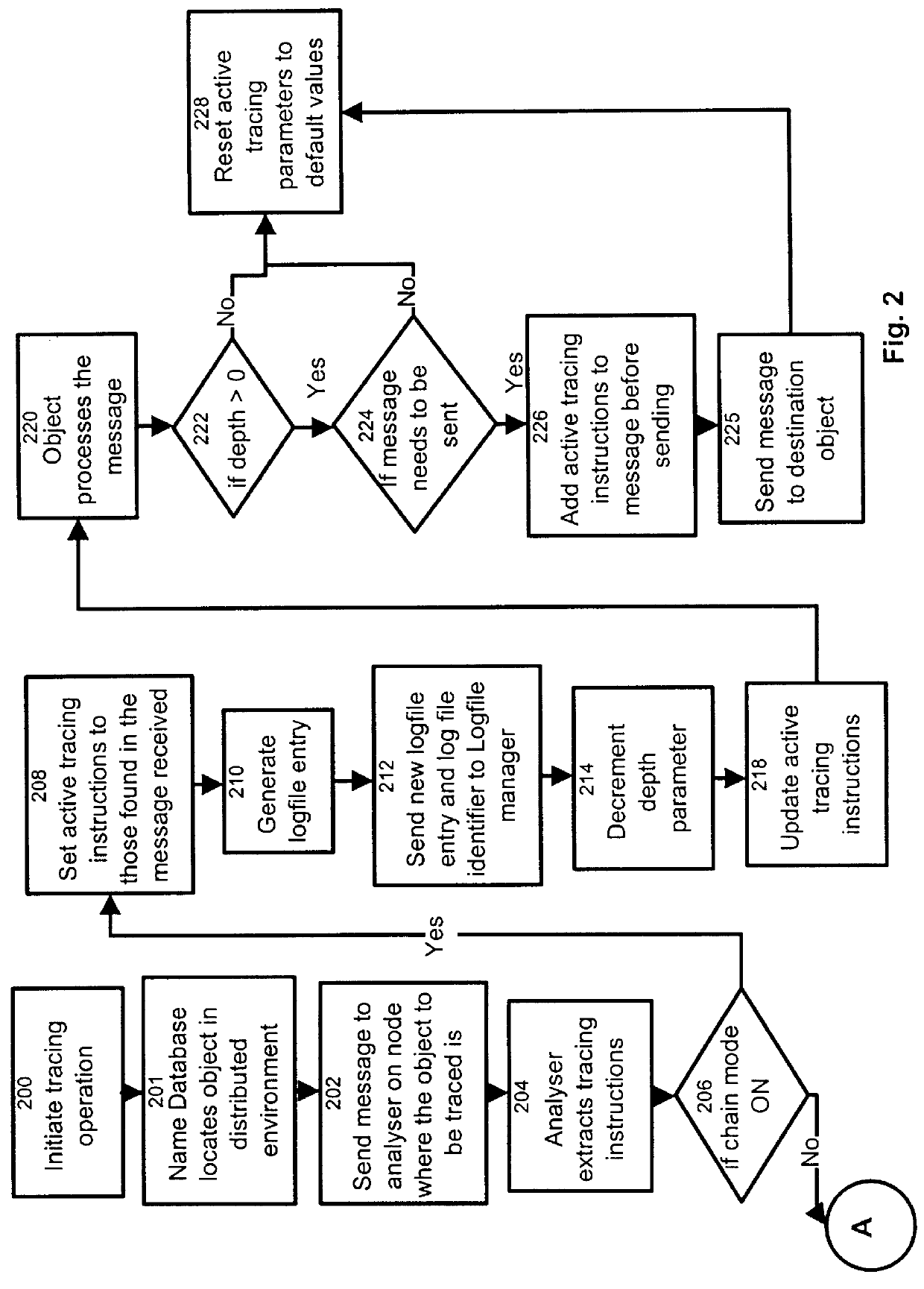
Process and apparatus for tracing software entities in a distributed system
InactiveUS6083281AHardware monitoringSoftware testing/debuggingControl flowDistributed Computing Environment
The invention relates to a process and apparatus for tracing software entities, more particularly a tracing tool providing tracing capabilities to entities in an application. The object-tracing tool provides software components to allow tracing the execution of an application. Tracing software entities is important for software developers to permit the quick localization of errors and hence facilitate the debugging process. It is also useful for the software user who wishes to view the control flow and perhaps add some modifications to the software. Traditionally, software-tracing tools have been confined to single node systems where all the components of an application run on a single machine. The novel tracing tool presented in this application provides a method and an apparatus for tracing software entities in a distributed computing environment. This is done by using a network management entity to keep track of the location of the entities in the system and by using a library of modules that can be inherited to provide tracing capabilities. It also uses a log file to allow the program developer or user to examine the flow, the occurrence of events during a trace and the values of designated attributes. The invention also provides a computer readable storage medium containing a program element to direct a processor of a computer to implement the software tracing process.
Owner:RPX CLEARINGHOUSE
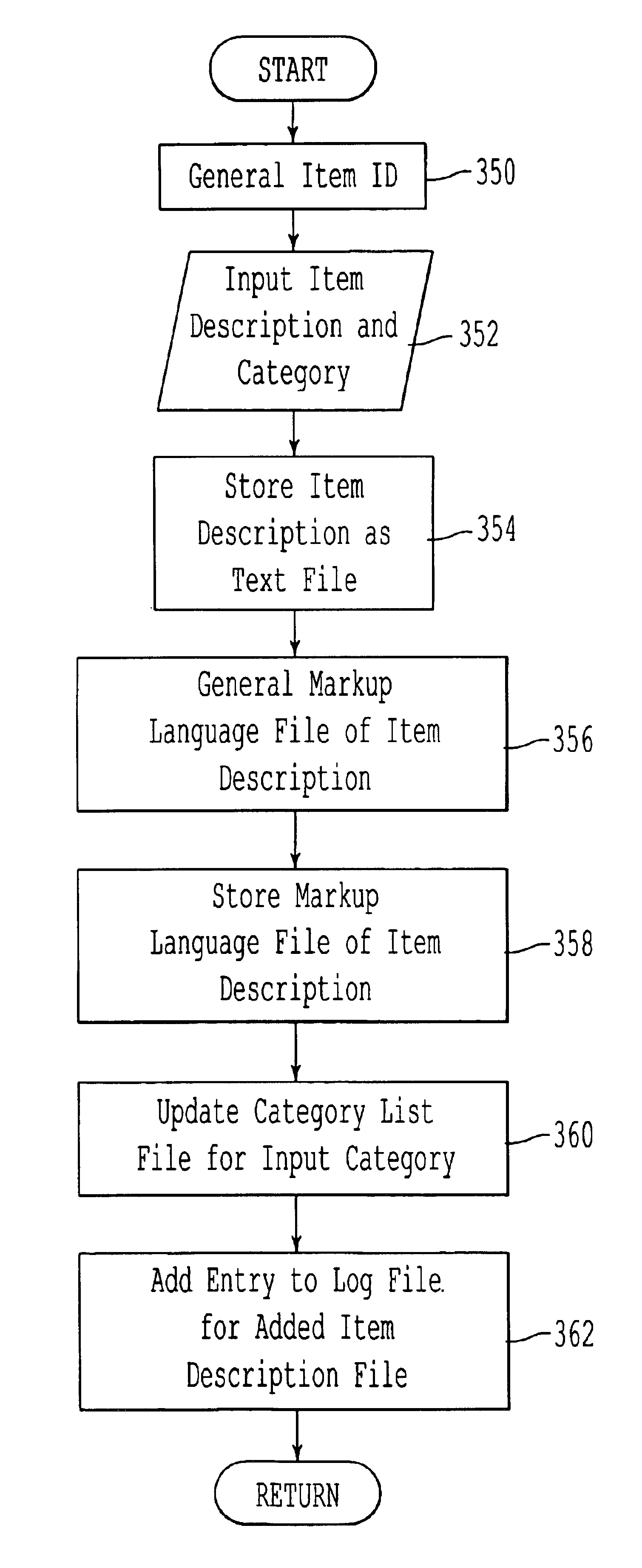
Creating web pages category list prior to the list being served to a browser
InactiveUS7039860B1Simplifies setup and maintenanceData processing applicationsDigital data processing detailsDocumentation procedureDocument preparation
A method, system and computer program product for revising and publishing electronic documents. Two sets of electronic documents are generated and maintained on first and second computers. One set is stored on a first computer, for example, as static web pages at a company site. Another set is stored on a second computer at a non-local site such as, for example, an Internet server where the electronic documents are accessible to clients. Any modifications in the set of electronic documents at the local or company site are logged in a log file, and the set of electronic documents at the non-local site is modified accordingly so as to produce what appears to the client as a “dynamic” set of web pages. The revision and publication occurs through generation on the first computer of at least one category list document containing an item identifier, an item category, and descriptive data with hyperlinks to underlying detailed description electronic document files. The category list documents group items together which belong in a given category. The category list and the underlying detailed description electronic document files are saved in a format for accessing from a general viewer program such as, for example, a web browser. The detailed description data may also stored as text based records in, for example, a file of text records or a database of text records at the local site.
Owner:P P P CAPITAL ONE +1
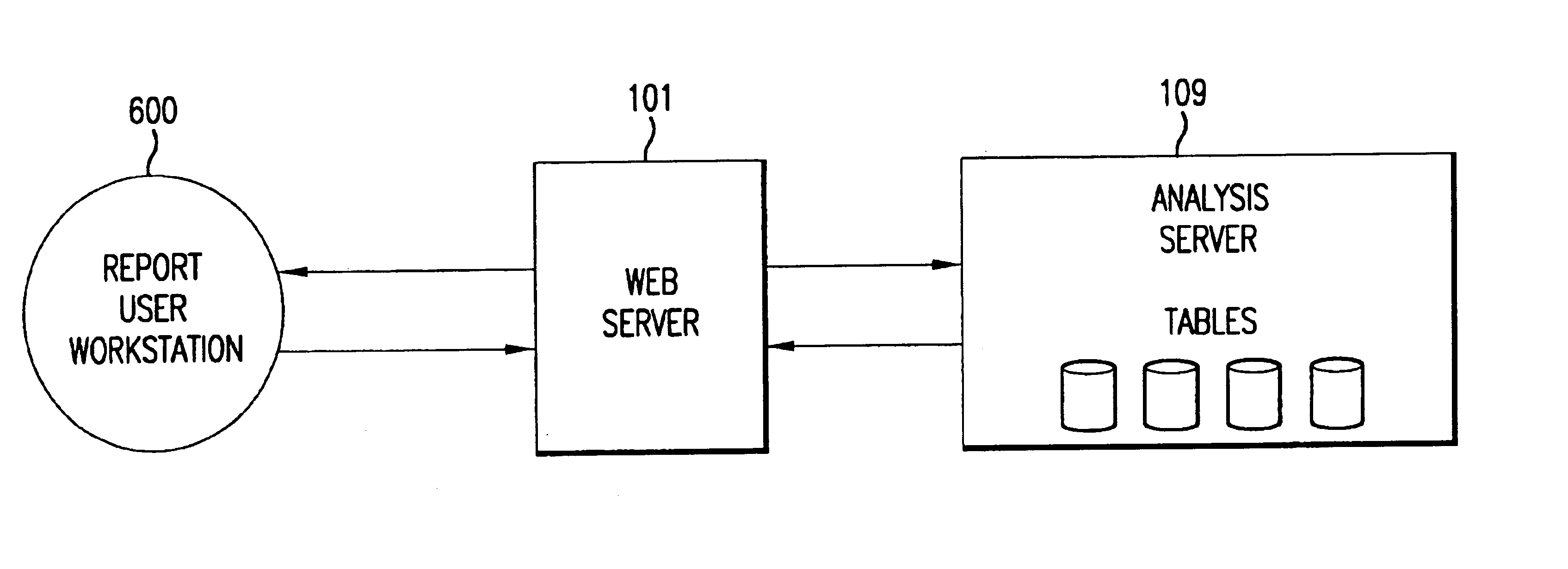
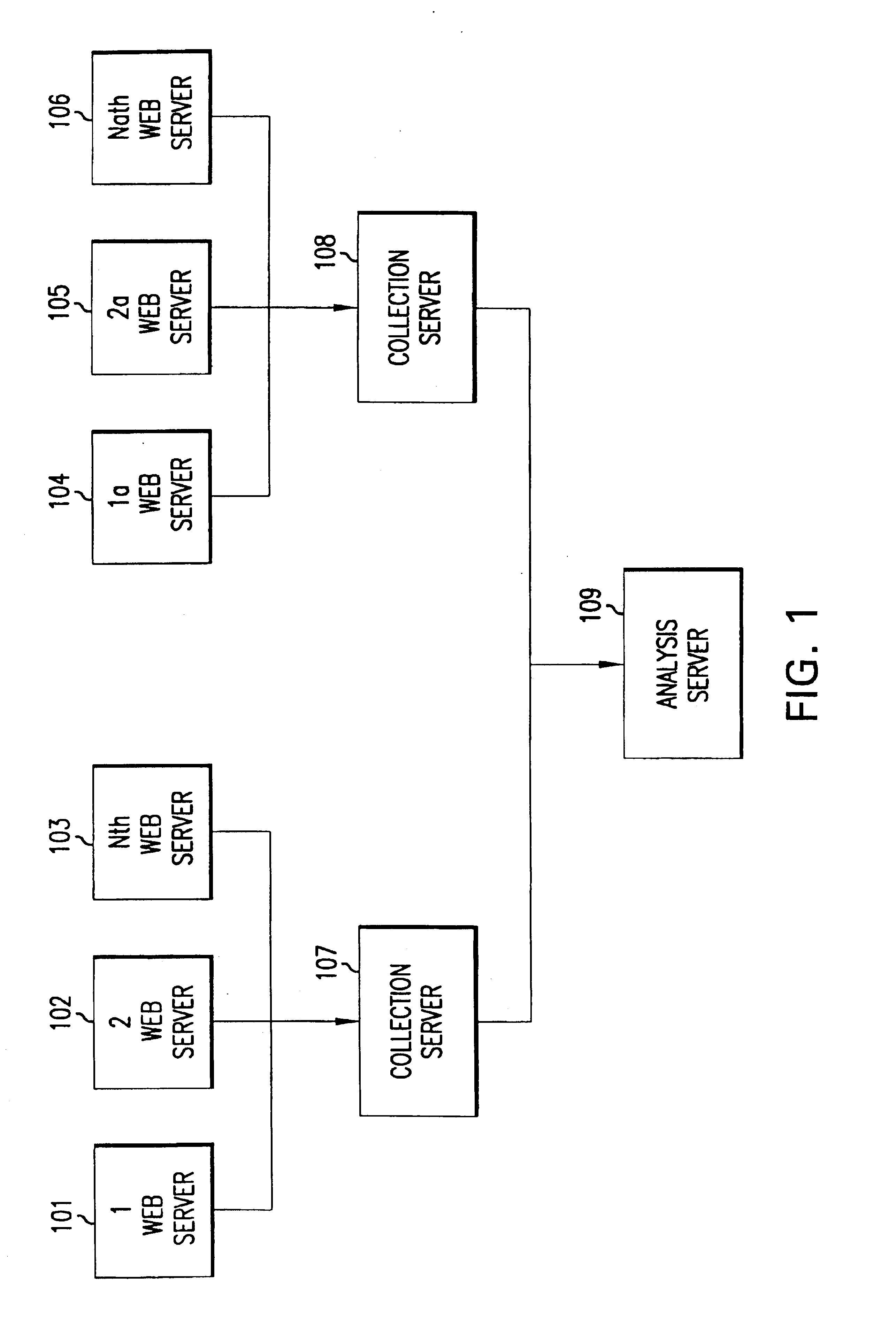
System for collecting, analyzing, and reporting high volume multi-web server usage
InactiveUS6789115B1Minimize data handledEfficient queryData processing applicationsDigital computer detailsServer logRelational database
A system for capturing, analyzing, storing and reporting system-users' usage of multiple internet and / or intranet web servers. At each web server in the system, the actions by the system-user create a server log that is processed by the system on a continuous basis. The processing at the server may include, by way of illustration, filtering the logs of about 75 percent of the data and decrypting a system-user's cookie. On a periodic basis, one or more collection servers in the system copy the processed log files from each web server on the system, zip the files, and transfer the files to an analysis server. After the collection is complete, an analysis server processes the data and stores it in a relational database that supports various user specified daily, monthly and quarterly reports of the usage data.
Owner:BANK OF AMERICA CORP
Using network traffic logs for search enhancement
ActiveUS7398271B1Handy search resultsImprove the level ofData processing applicationsWeb data indexingTraffic capacityLink weight
A method and apparatus for using network traffic logs for search enhancement is disclosed. According to one embodiment, network usage is tracked by generating log files. These log files among other things indicate the frequency web pages are referenced and modified. These log files or information from these log files can then be used to improve document ranking, improve web crawling, determine tiers in a multi-tiered index, determine where to insert a document in a multi-tiered index, determine link weights, and update a search engine index.
Owner:R2 SOLUTIONS
Method and apparatus for implementing a service-level agreement
InactiveUS7058704B1Precise processingMultiplex system selection arrangementsSpecial service provision for substationWeb siteService-level agreement
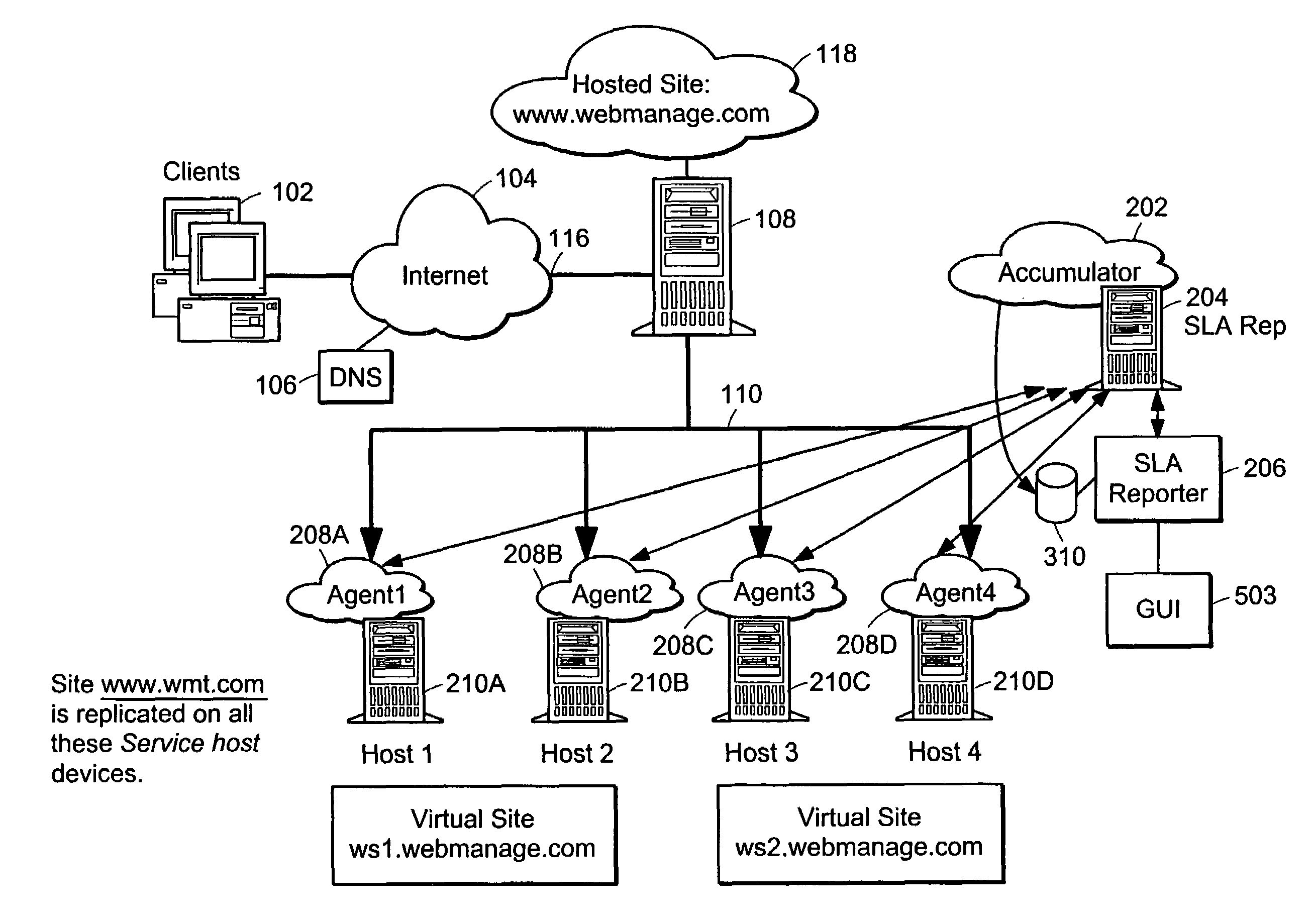
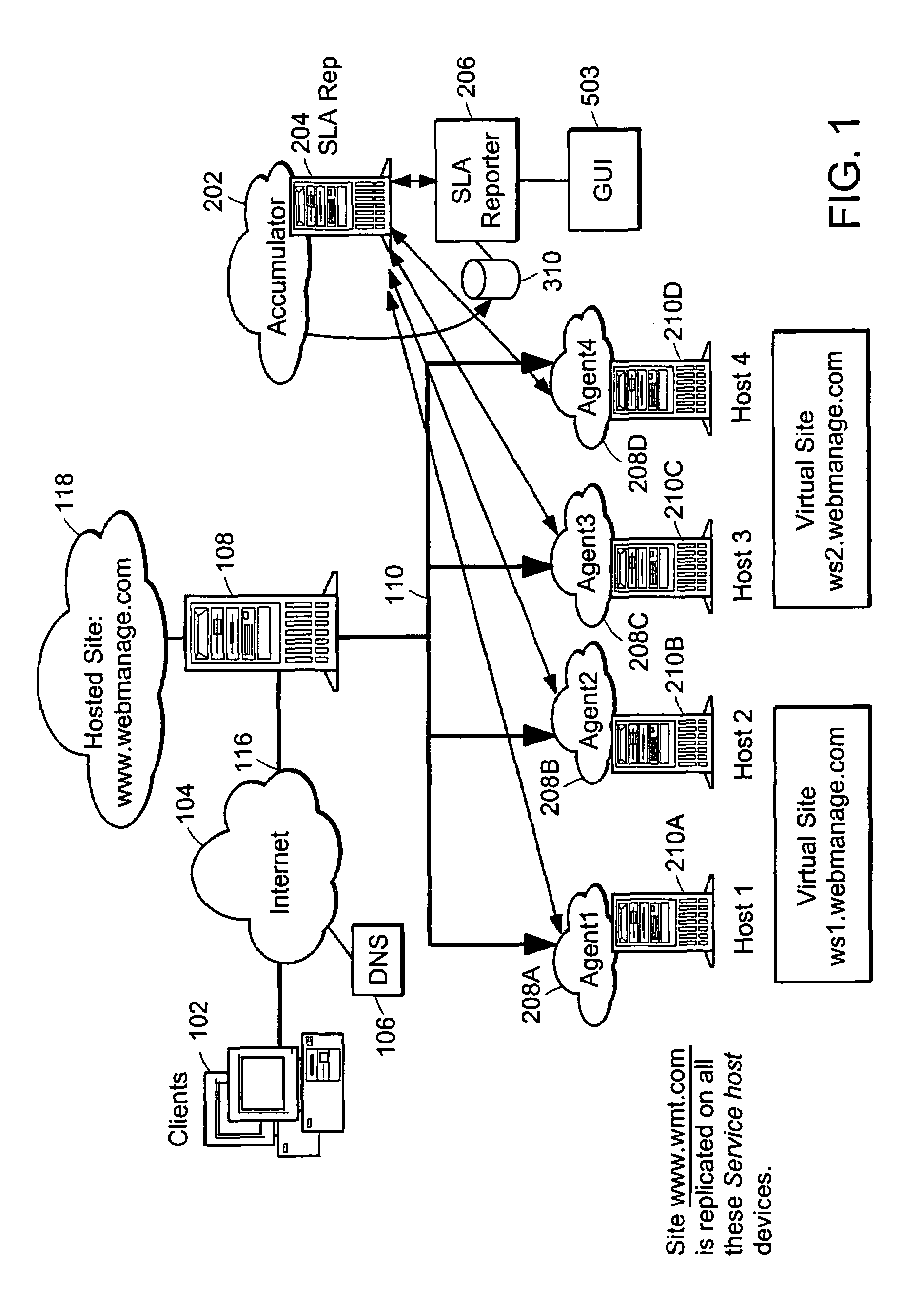
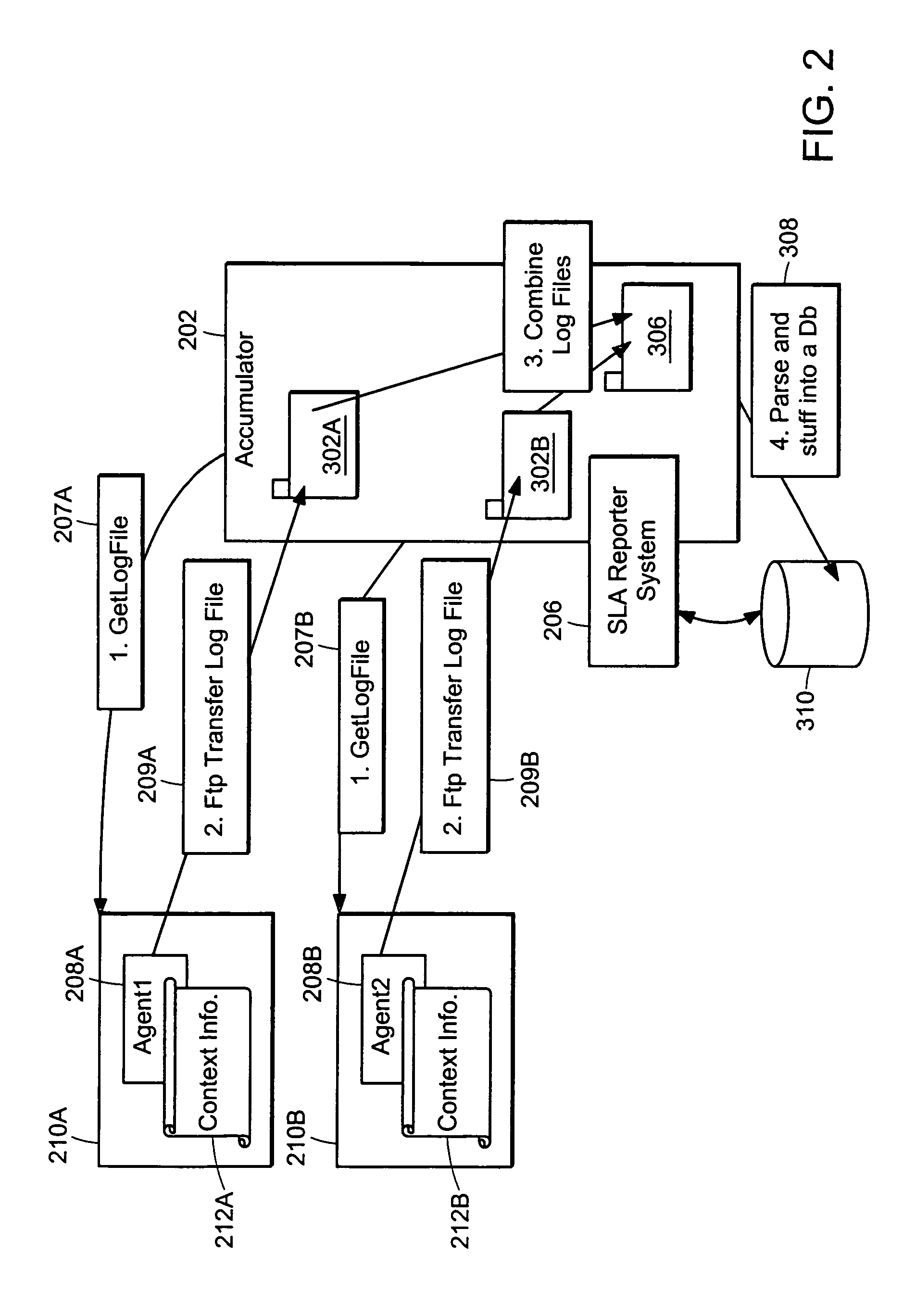
A method and apparatus is provided for generating, collecting, and manipulating useful information for validating or defining SLAs of web servers on a network. Web servers comprising a web farm on the network are adapted for logging detailed runtime information regarding user transactions and performance parameters. An Accumulator device interacts with intelligent agents to collect and combine their log files, process the combined file and post information into a database. An operator enters committed performance parameters into an SLA Reporter system according to classes of users, classes of web sites being hosted on the web servers, classes of URLs, transaction, content and file type. When compared with the database, processing of SLA reports indicate how well the parameters of the SLAs are being met for users, web sites, classes, URL's and transactions, or other measurable elements. By generating, collecting, combining and processing in this manner, application-specific performance can be quickly and automatically evaluated with respect to parameters related to user satisfaction and detailed signals can be issued for cases in which remedial steps should be undertaken.
Owner:NETWORK APPLIANCE INC
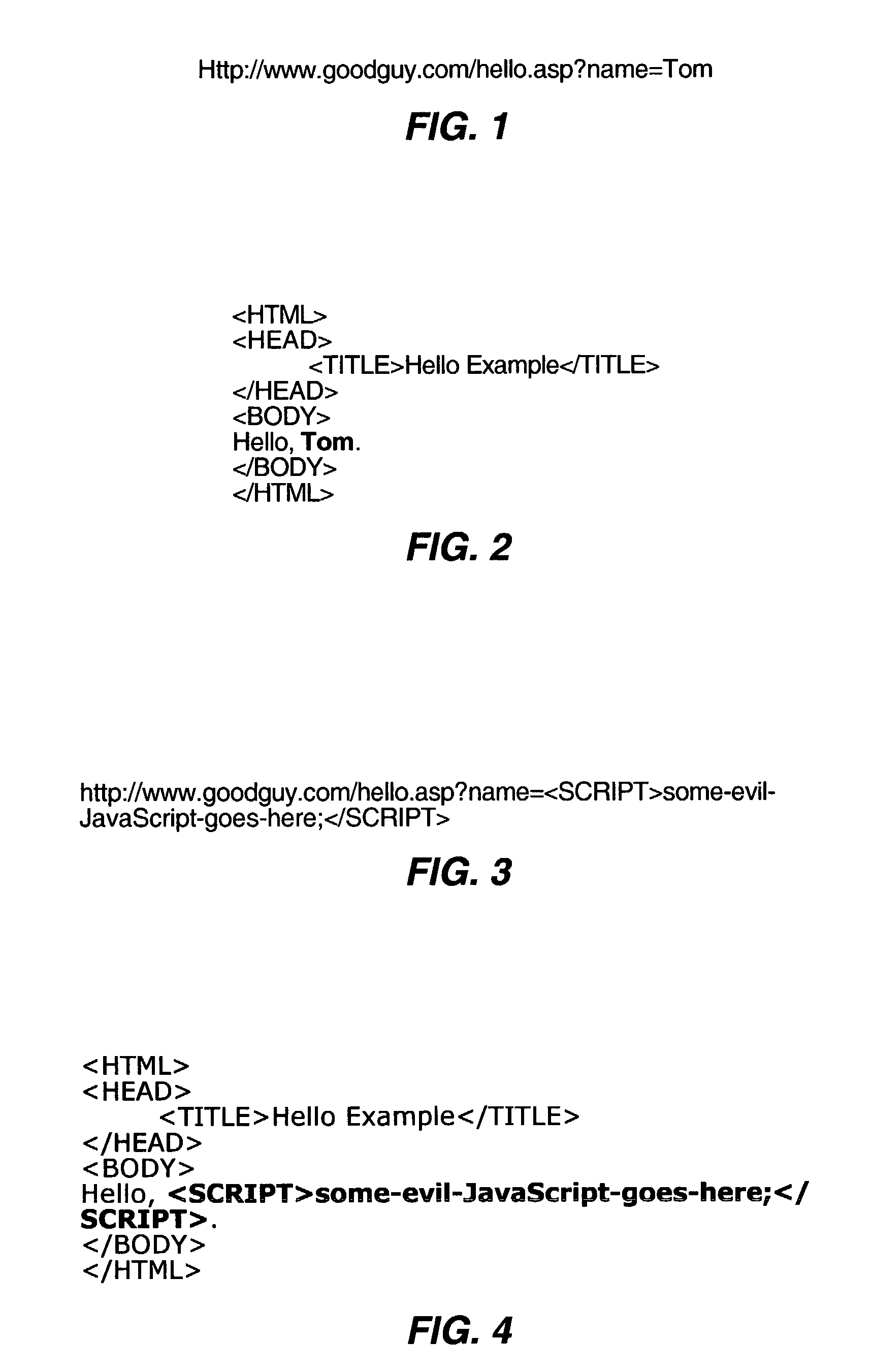
Automated detection of cross site scripting vulnerabilities
An automated method and system for testing a web site for vulnerability to a cross site scripting (XSS) attack are disclosed. The automated tool injects a tracer value into both GET and POST form data, and monitors the resultant HTML to determine whether the tracer value is returned to the local machine by the server to which it was sent. If the tracer value is returned, the automated tool attempts to exploit the web site by injecting a non-malicious script as part of an input value for some form data, based on the location in the returned HTML in which the returned tracer value was found. If the exploit is successful, as indicated by the non-malicious script, the automated tool logs the exploit to a log file that a user can review at a later time, e.g., to assist in debugging the web site.
Owner:MICROSOFT TECH LICENSING LLC
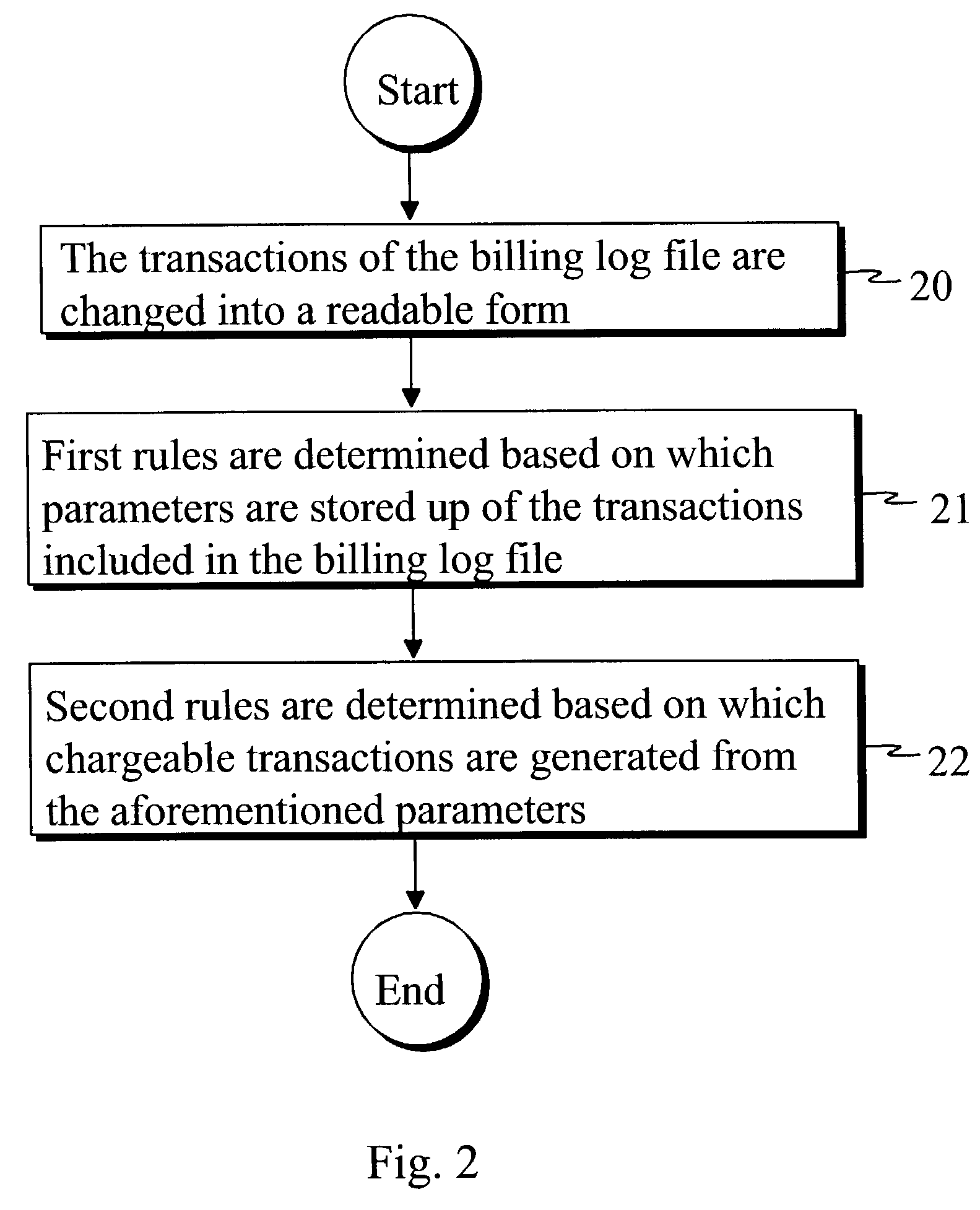
Transaction-based service billing in a telecommunication system
ActiveUS20040002324A1Alleviate, the drawbacks and deficienciesAccurately reportMetering/charging/biilling arrangementsAccounting/billing servicesTelecommunications networkTerminal equipment
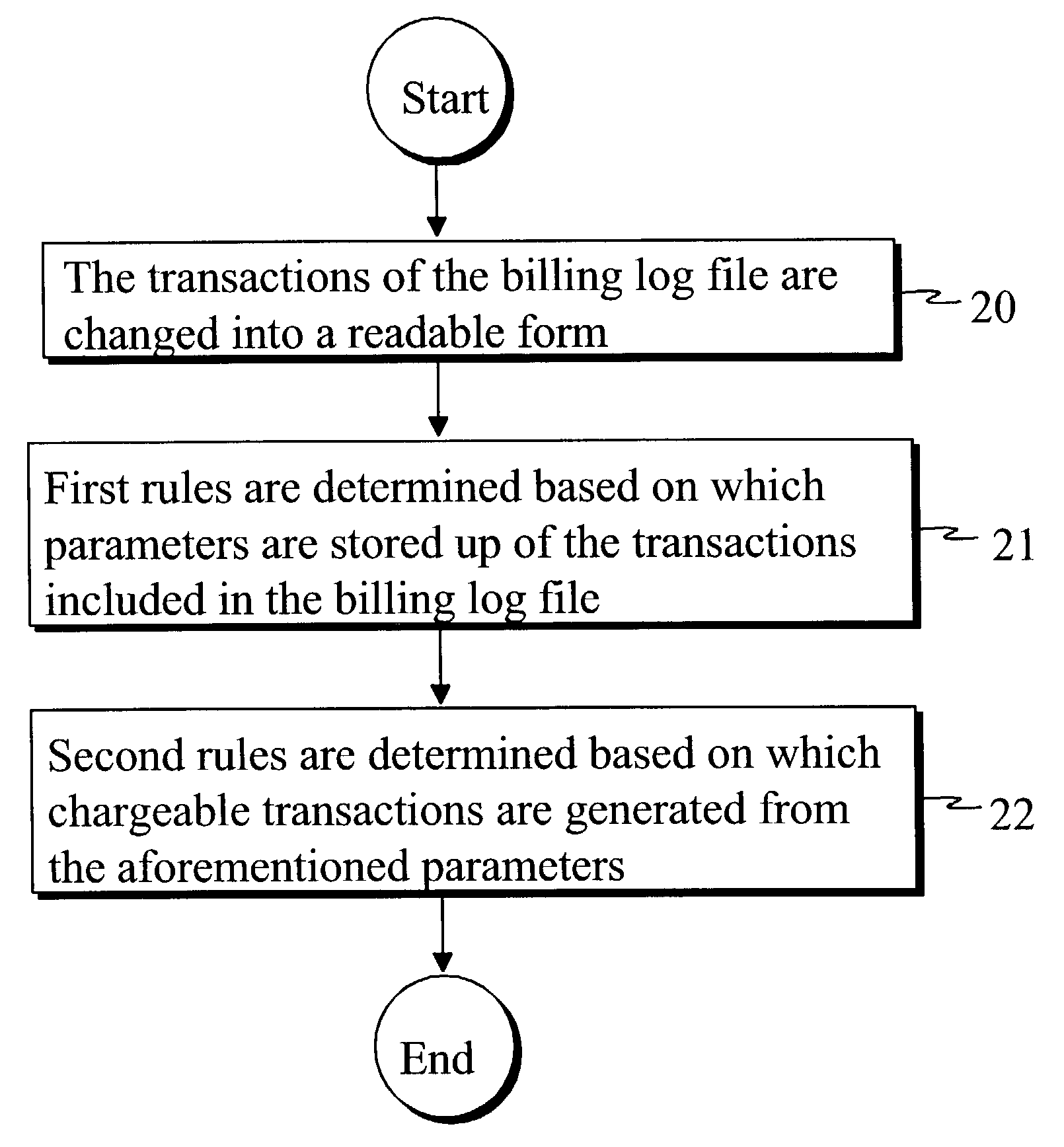
A WAP Charging Gateway, and a method and system, for arranging transaction-based billing for WAP services in a telecommunication system that includes a telecommunication network, a terminal device connected to the telecommunication network and used for accessing WAP services, a WAP Gateway connected to the telecommunication network, a content provider of WAP services connected to the WAP Gateway, a billing log file, a transaction manager for recording transactions associated with billable services and generated from different WAP protocol levels in the billing log file, and reading devices for reading the billing log file. Transactions associated with billable services, generated from different WAP protocol levels, are written to the billing log file and are read from the billing log file (LOG). The transactions in the billing log file are converted into a readable form. First rules are applied to the converted transactions to generate and store predefined transaction parameters, and second rules are then applied to the stored transaction parameters for generating chargeable transactions therefrom.
Owner:INTELLECTUAL VENTURES I LLC
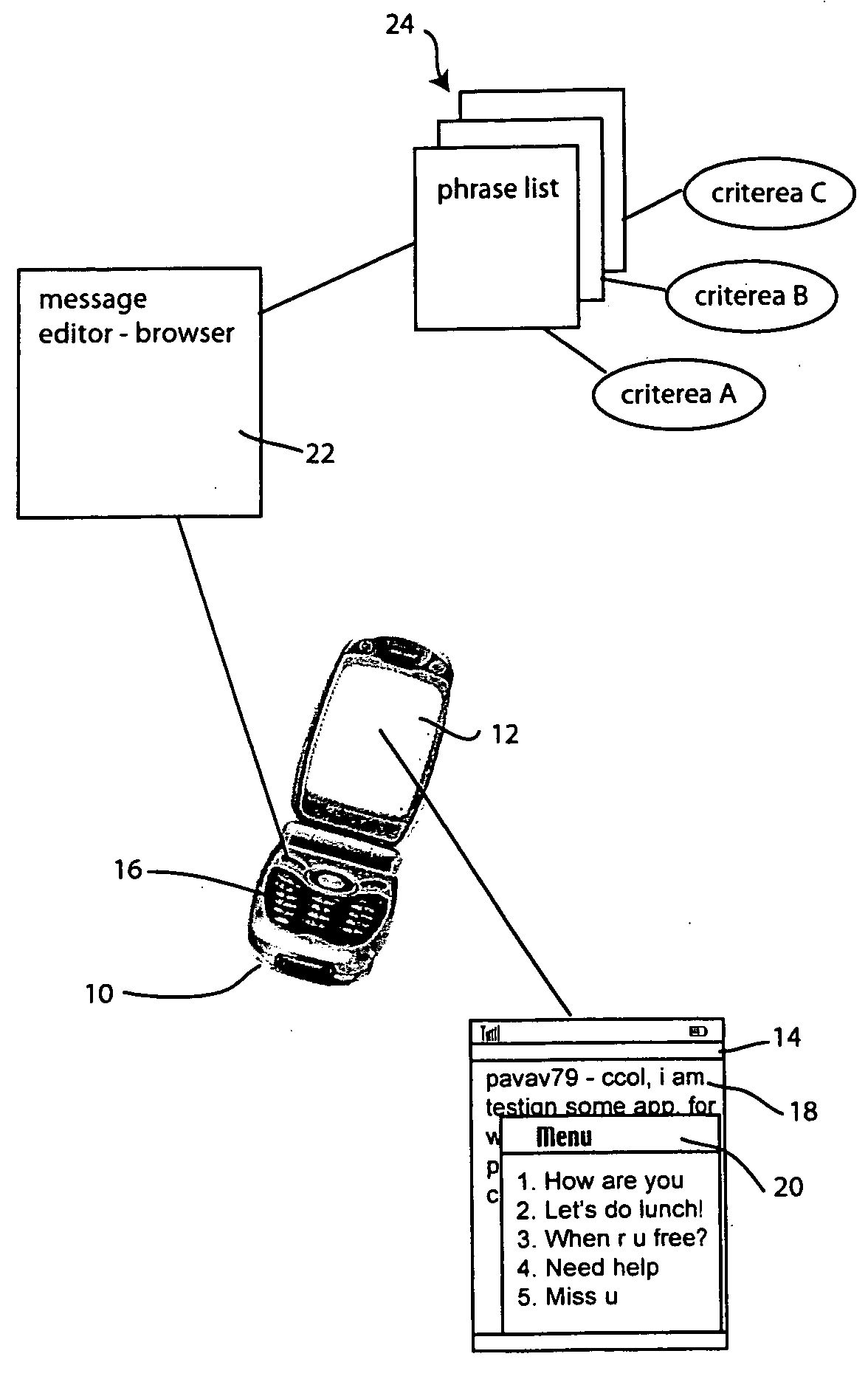
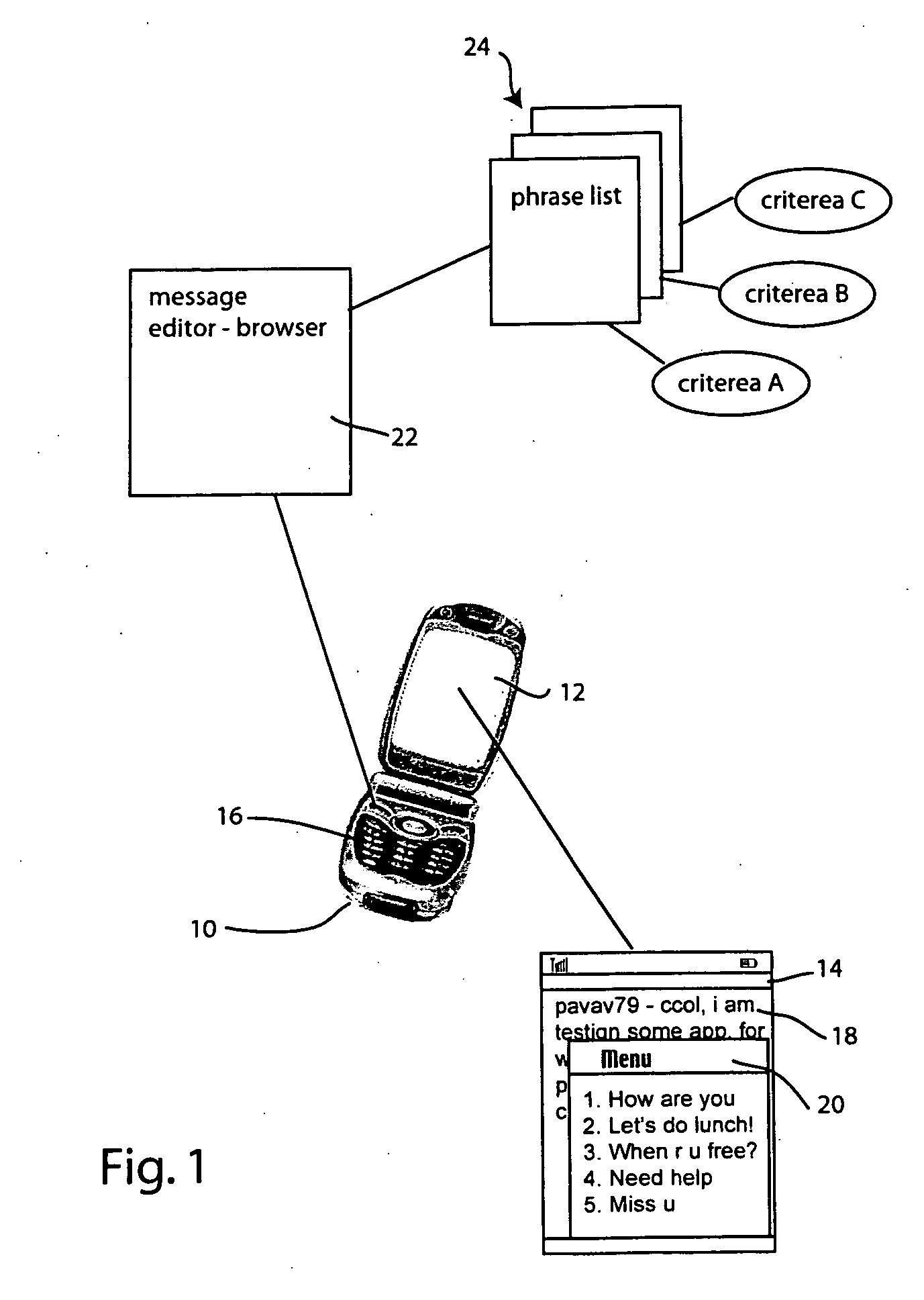
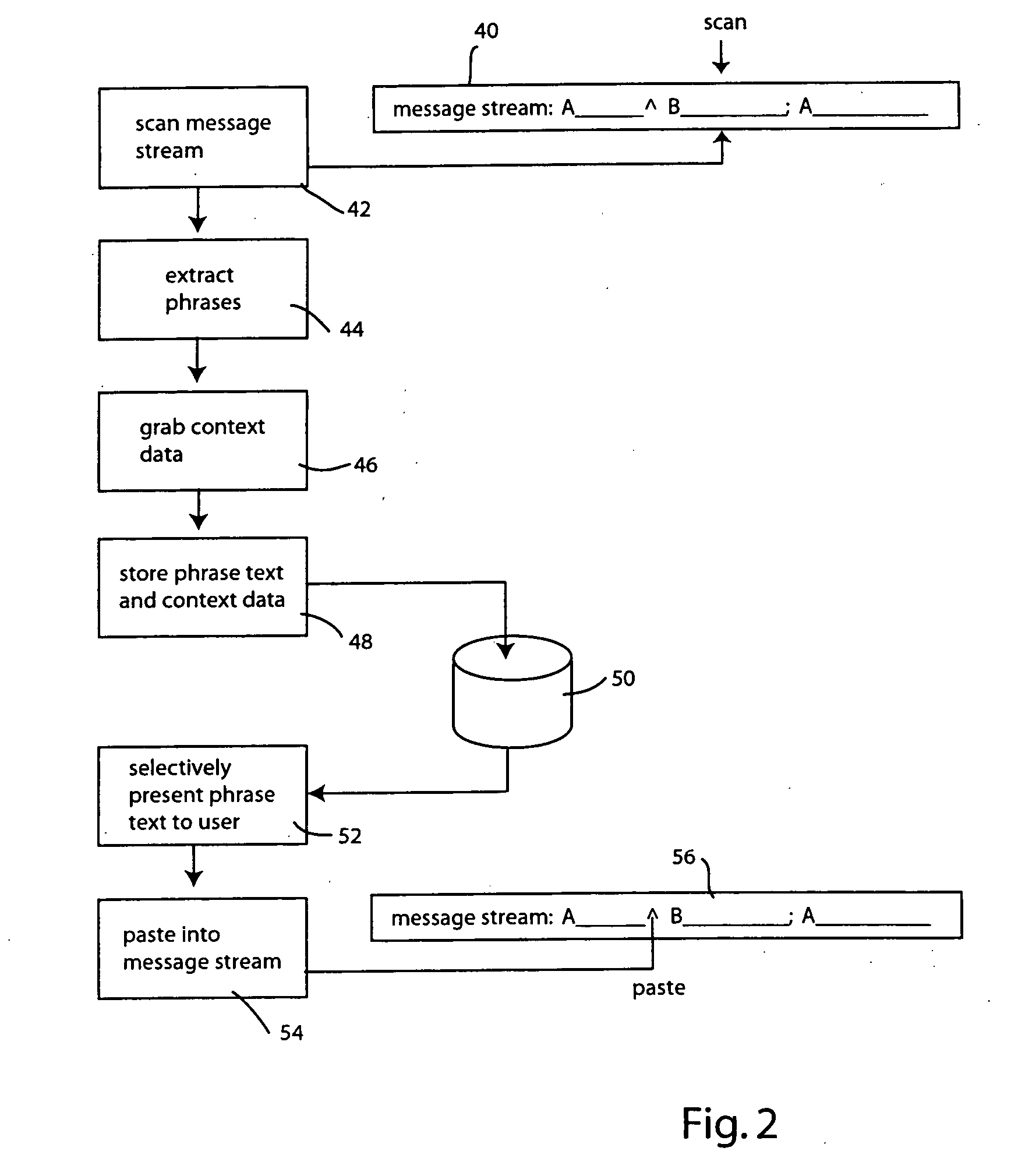
Method for creating and using phrase history for accelerating instant messaging input on mobile devices
Rapid instant messaging input is enabled through a system that displays frequently used or useful message phrases in a pop-up window from which the user may select a desired phrase to be inserted into the message stream. The system allows multiple phrase lists to be utilized and individual phrase messages are tagged with context information, allowing them to be selectively retrieved to provide only the most useful messages for a given context or scenario. The system automatically generates phrase lists by scanning the message stream data within instant messaging log files and the scanned information is then processed to select phrases for inclusion in the phrase list based on predefined heuristics.
Owner:PANASONIC CORP
Creating frequent application-consistent backups efficiently
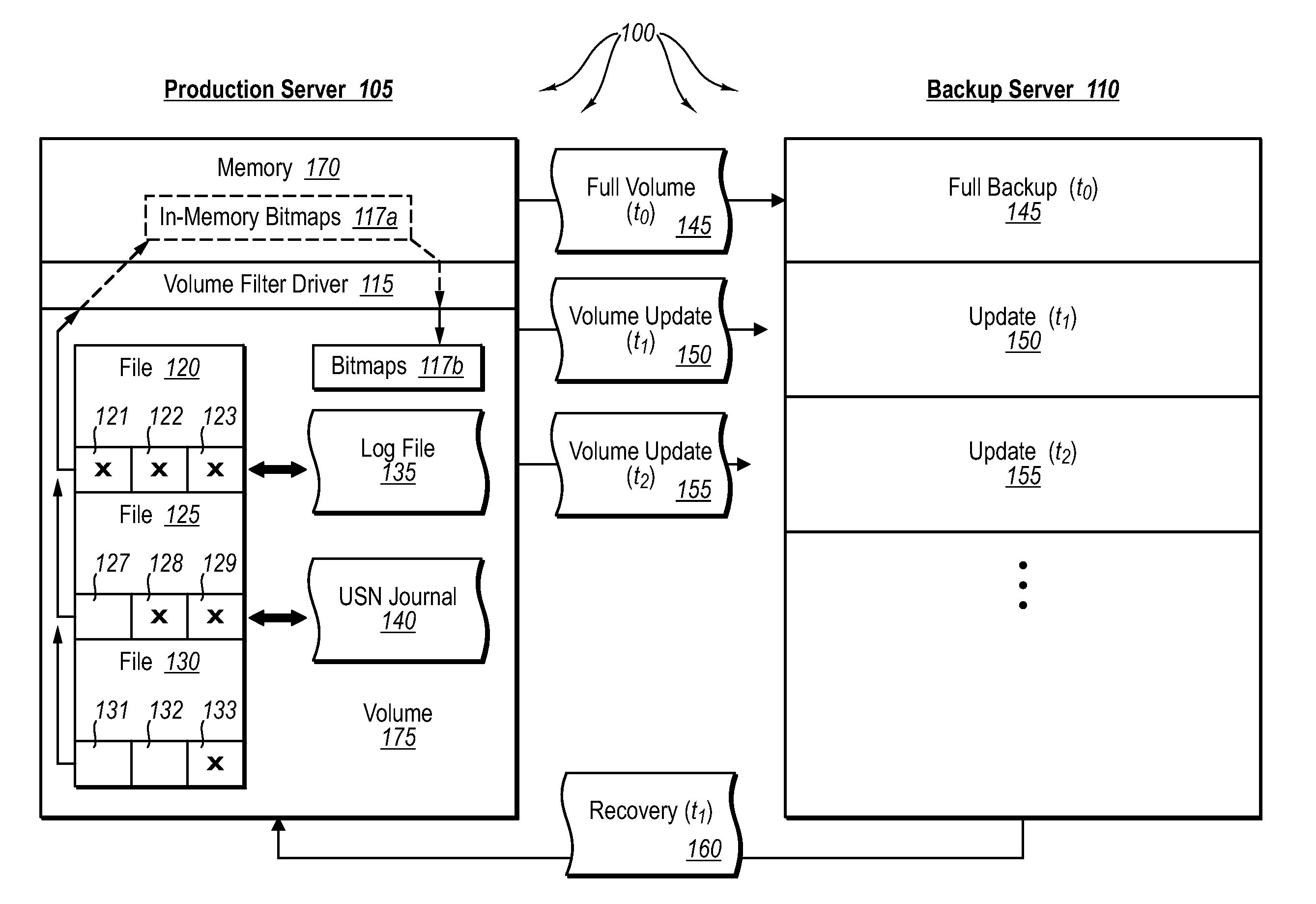
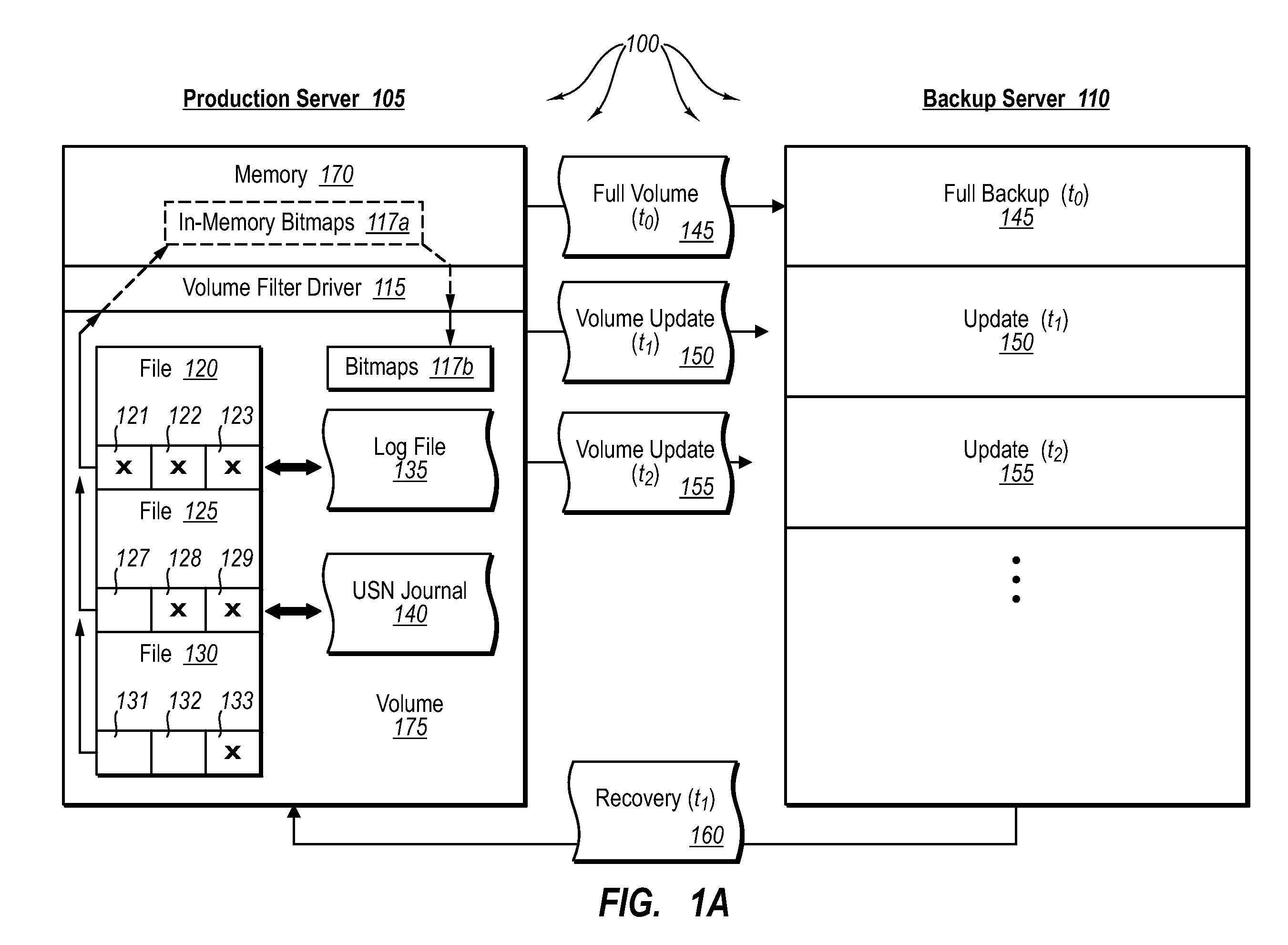
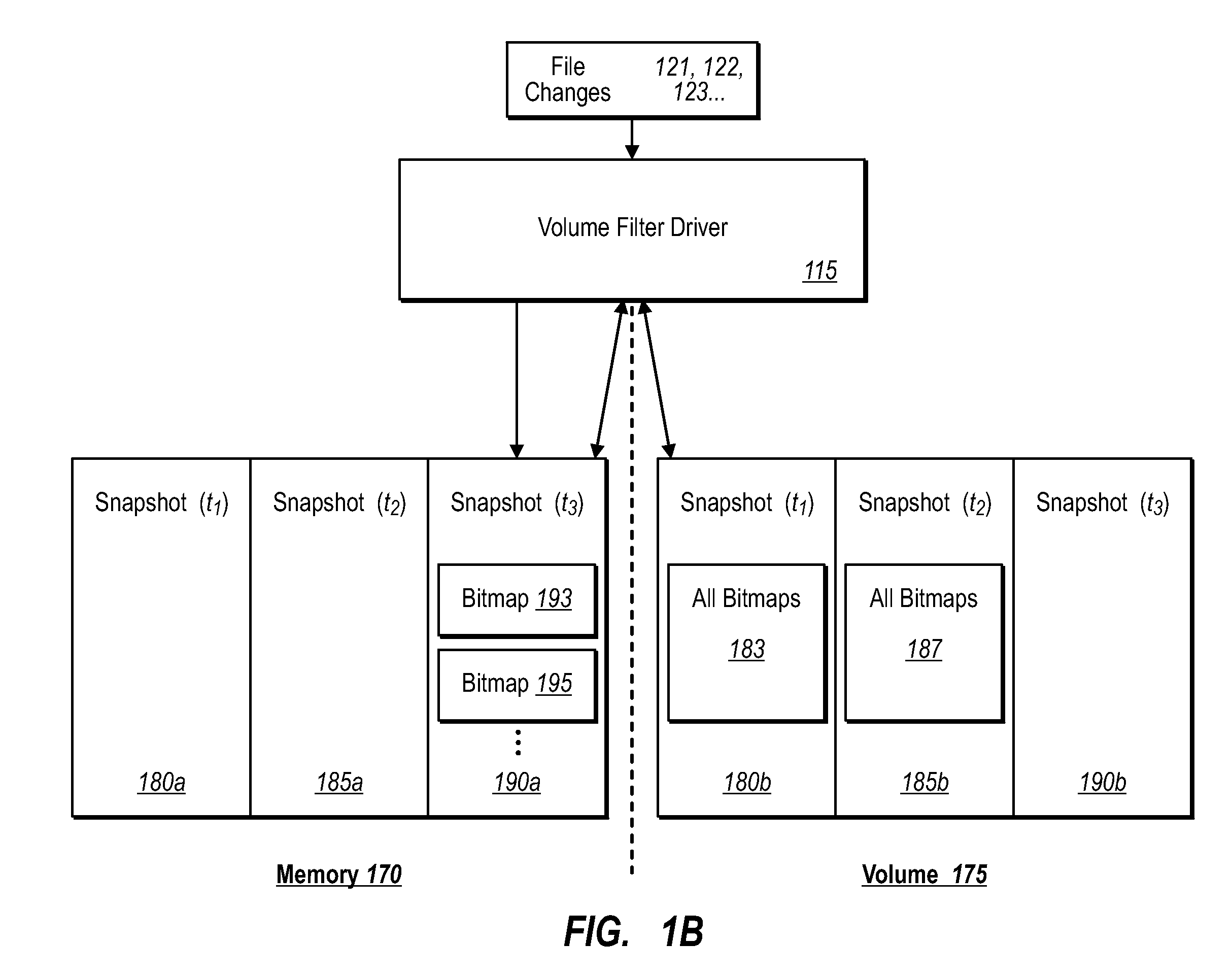
ActiveUS20070276885A1Save resourcesProduction serverData processing applicationsMemory loss protectionApplication softwareBitmap
Data can be protected at a production server in a virtually continuous fashion, without necessarily imposing severe constraints on the source application(s). For example, a production server can create an application-consistent backup of one or more volumes, the backups corresponding to a first instance in time. A volume filter driver can monitor data changes in each volume using an in-memory bitmap, while a log file and / or update sequence number journal can keep track of which files have been added to or updated. The volume updates are also consistent for an instance (later) in time. At the next replication cycle, such as every few minutes (however configured), the volume filter driver passes each in-memory bitmap to the physical disk on the production server. The production server then sends the updates to the backup server, which thus stores application-consistent backups for the volume for multiple instances of time.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for managing replicated database data
ActiveUS8204859B2Reduce memory requirementsImprove performanceDigital data processing detailsError detection/correctionDatabase applicationApplication software
Systems and methods for replicating database data and generating read-only copies of the replicated data in a clean shutdown state. For example, systems can include a tracking module (e.g., a filter driver) that monitors transactions from a database application to a source storage device to generate log entries having at least one marker indicating a known good state of the application. The systems further include a computer coupled to a target storage device comprising a database and log files. The computer processes the transactions, based on the log entries, to replicate data to the target storage device; performs a first snapshot on data stored in the database and log files; replays into the database data stored in the log files; performs another snapshot on the database; and reverts the database back to a state in which the database existed at the time of the first snapshot.
Owner:COMMVAULT SYST INC
Element management system with dynamic database updates based on parsed snooping
InactiveUS7185075B1Easy accessSpecial service for subscribersDigital computer detailsElement management systemBackground process
A new approach to maintaining concurrency in a network element management database. A background process constantly monitors the channels which carry network element configuration commands, and automatically parses any messages which carry information about the status of network elements. The information derived from parsing these messages is then used for a dynamic update of the database of network element attributes. This means that the database is completely current on the very latest status changes, and operators do not have to cross-check log files to see if their data is current. Instead, a simple database query retrieves fully current information.
Owner:FUJITSU LTD
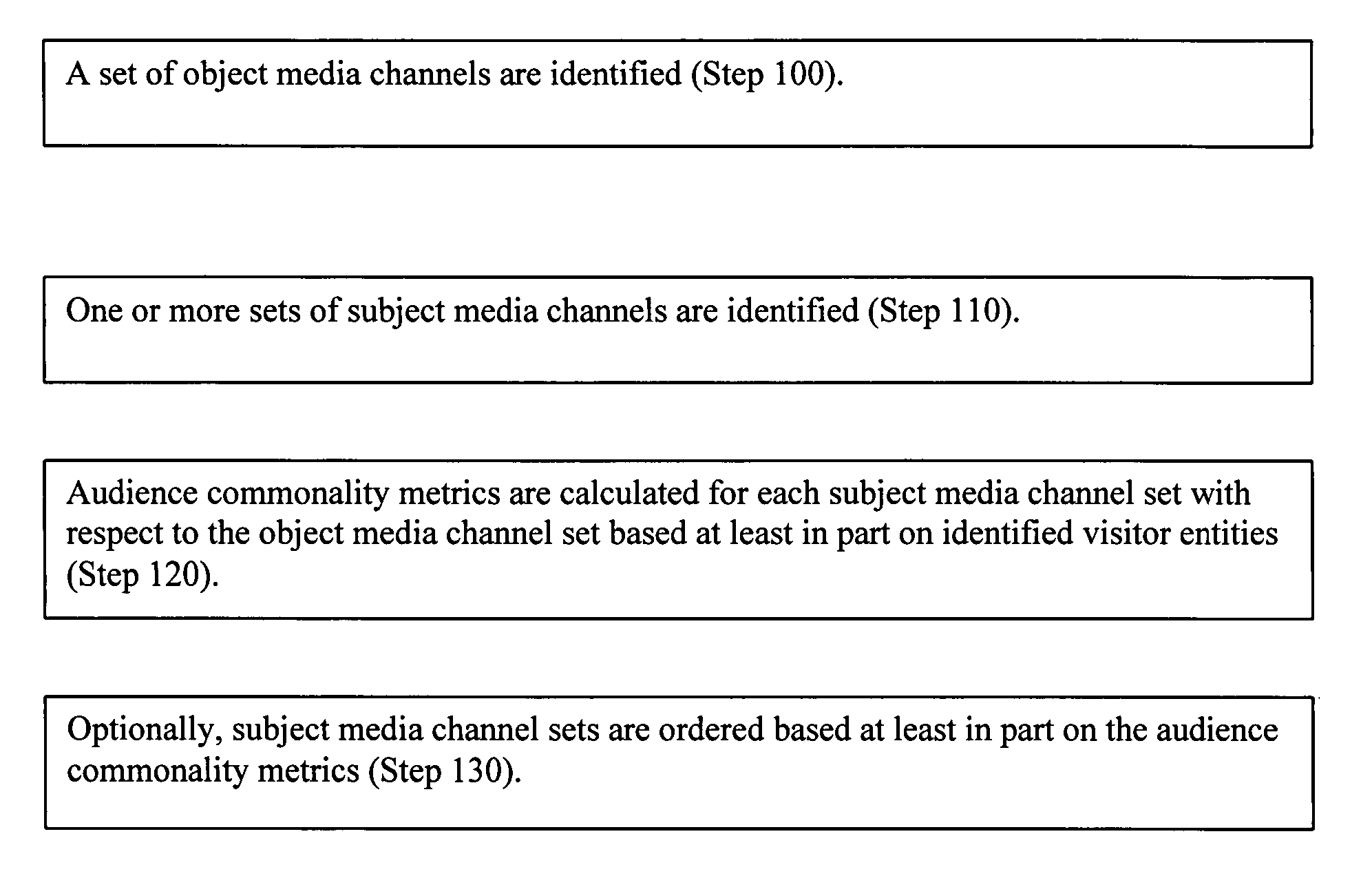
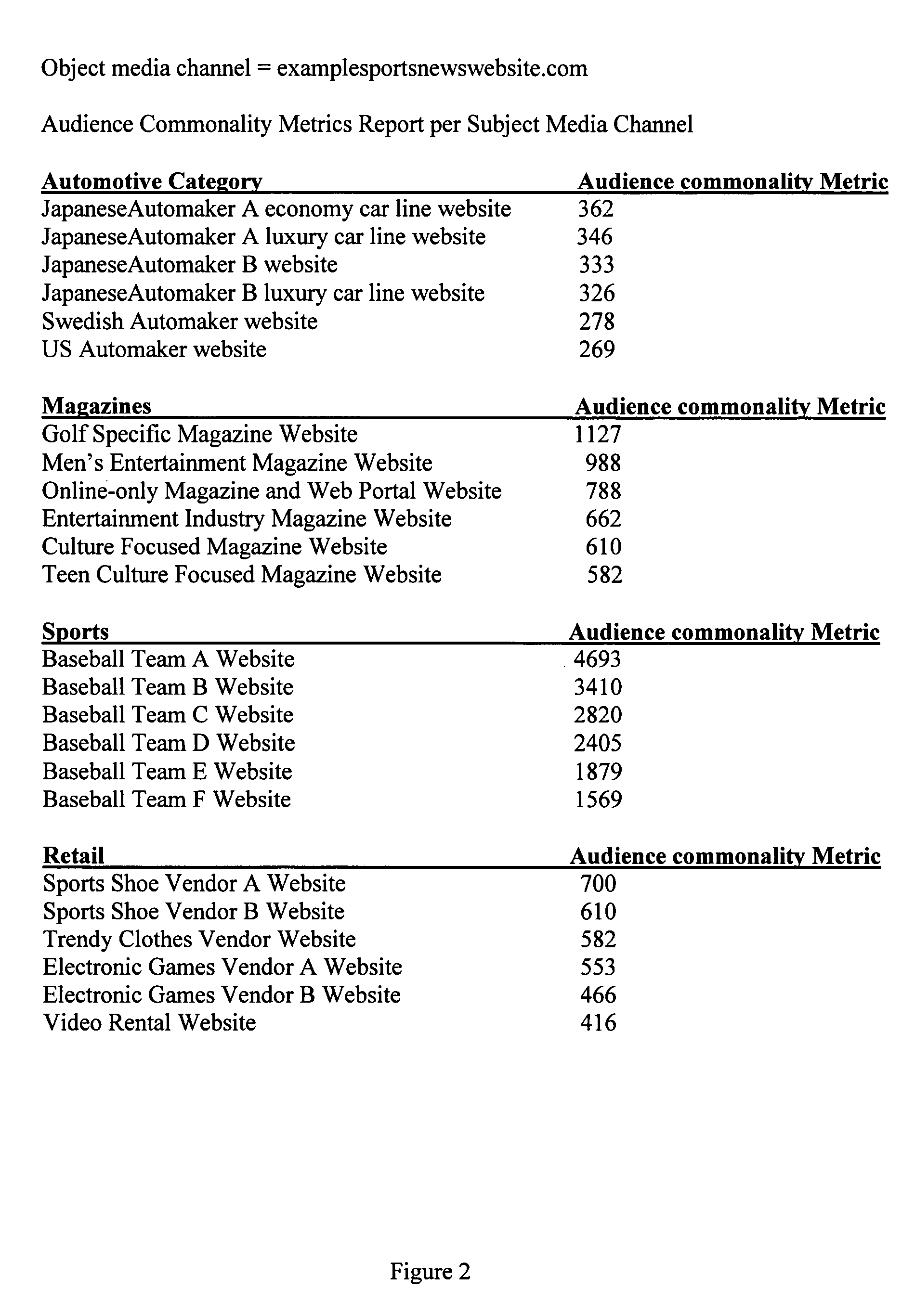
Audience commonality and measurement
InactiveUS20080086741A1Analogue secracy/subscription systemsBroadcast information monitoringNetwork activityClient agent
Audience commonality metrics for characterizing the relationship between networked media channels based on audience overlap of identified visitor entities and their related media consumption histories. Audience commonality metrics may be scalars or multi-dimensional metrics and may take into account and / or be used in conjunction with data related to on- or off-network media channels, on- or off-network activities, sociographics and / or demographics. The current invention may be used in the design of networked advertising campaigns, identification of new or unusual market segments and / or valuation of media buys. A system according to the current invention comprises access to a configuration, an input for receiving audience commonality data, an audience commonality metrics engine and an output for providing calculated audience commonality metrics. Data related to identified visitor entities may be received, determined and / or inferred from resources such as a cookie, log file, sniffer, firewall, proxy server, client agent, tracking pixel and / or tool
Owner:QUANTCAST CORP
System and method for creating pathfiles for use to predict patterns of web surfaces
InactiveUS6055572AEfficiently uses its free bandwidthReduce demandDigital data information retrievalMultiple digital computer combinationsControl systemServer allocation
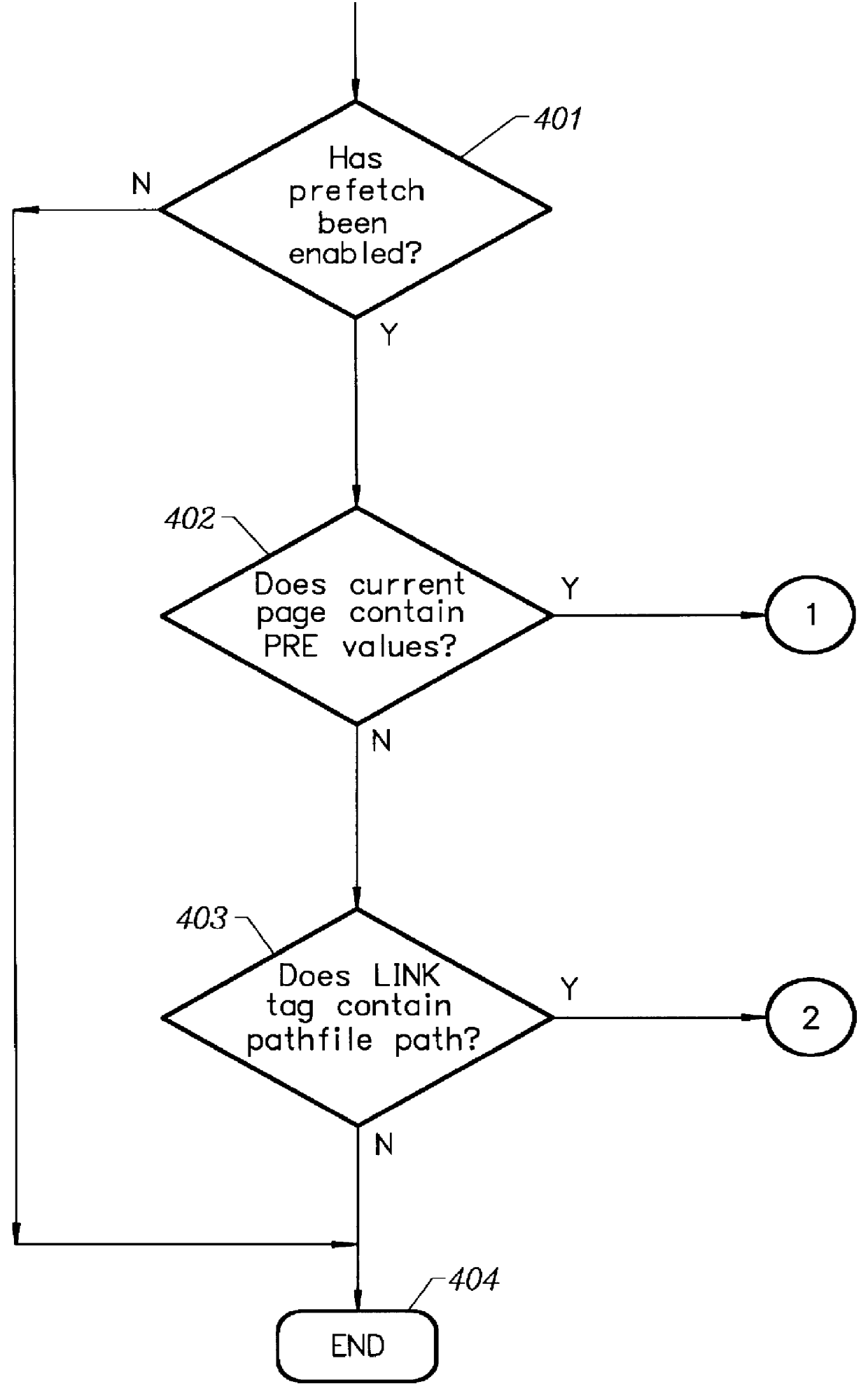
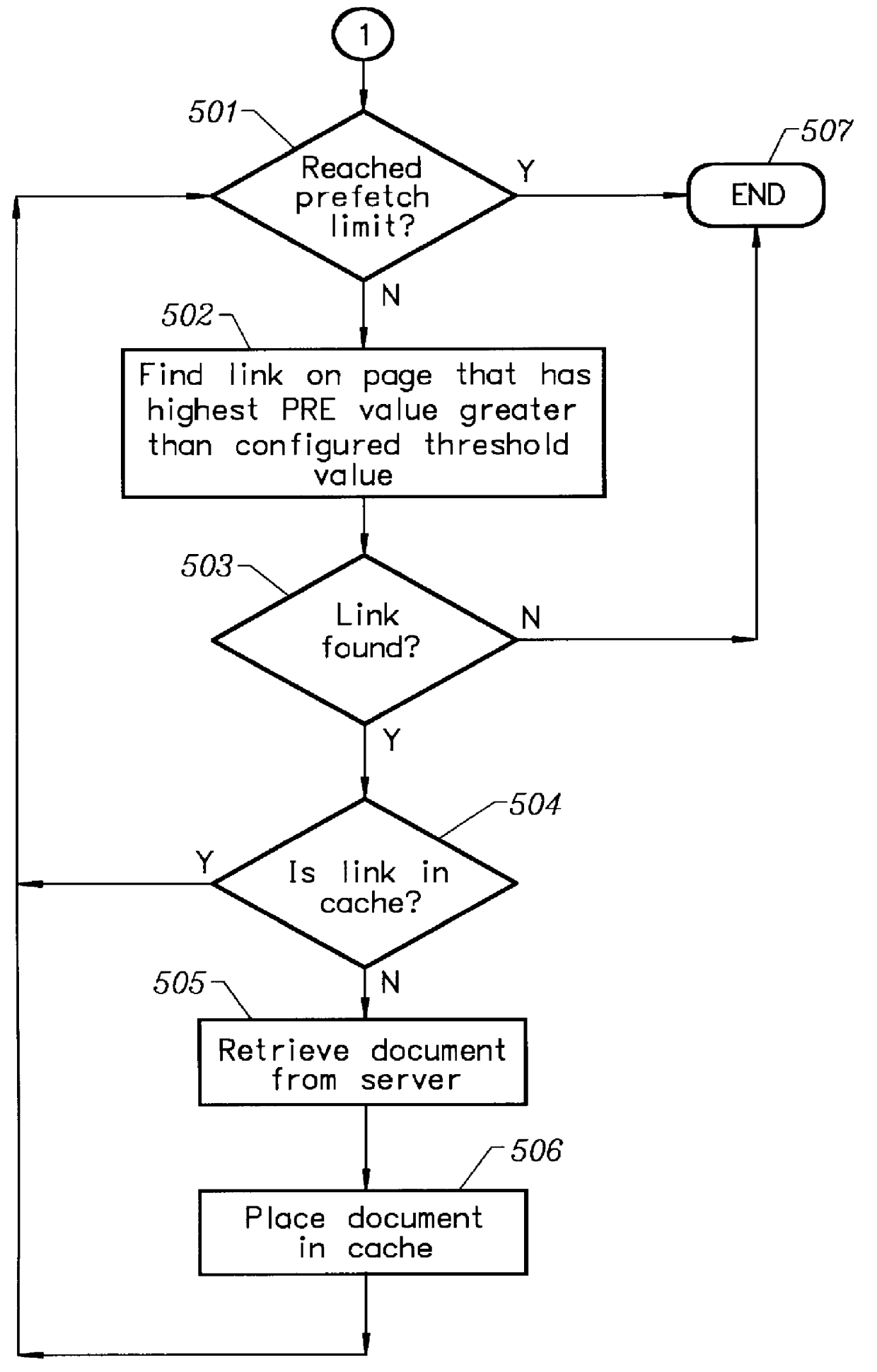
A prefetching and control system for a computer network environment. The user configures the client's prefetch parameters which are: enabling / disabling prefetching, prefetch threshold value, and the maximum number of documents to prefetch. A prefetch value or weight is contained in the Hypertext Markup Language (HTML) page or prefetch file, called a pathfile, for each link. The HTML page contains the prefetch values for each of its links, while pathfile contains the weights for every link on the HTML page associated with the Universal Resource Locator (URL). The client compares the prefetch or weight values of each link with its threshold value to decide if the link should be prefetched and placed in the local cache as long as the maximum number of documents to prefetch is not exceeded. Pathfiles reside on the server and are created by the server or web administrator / author. The server automatically creates the pathfiles from its log files which are filtered to retain all of the valid document requests and average paths are derived from the filtered results. Weights are assigned to each path in the URL by the server and inserted into the pathfile along with the associated paths. If no log files exist on the server, then the web administrator / author may manually enter in the weights for each path.
Owner:META PLATFORMS INC
Gathering enriched web server activity data of cached web content
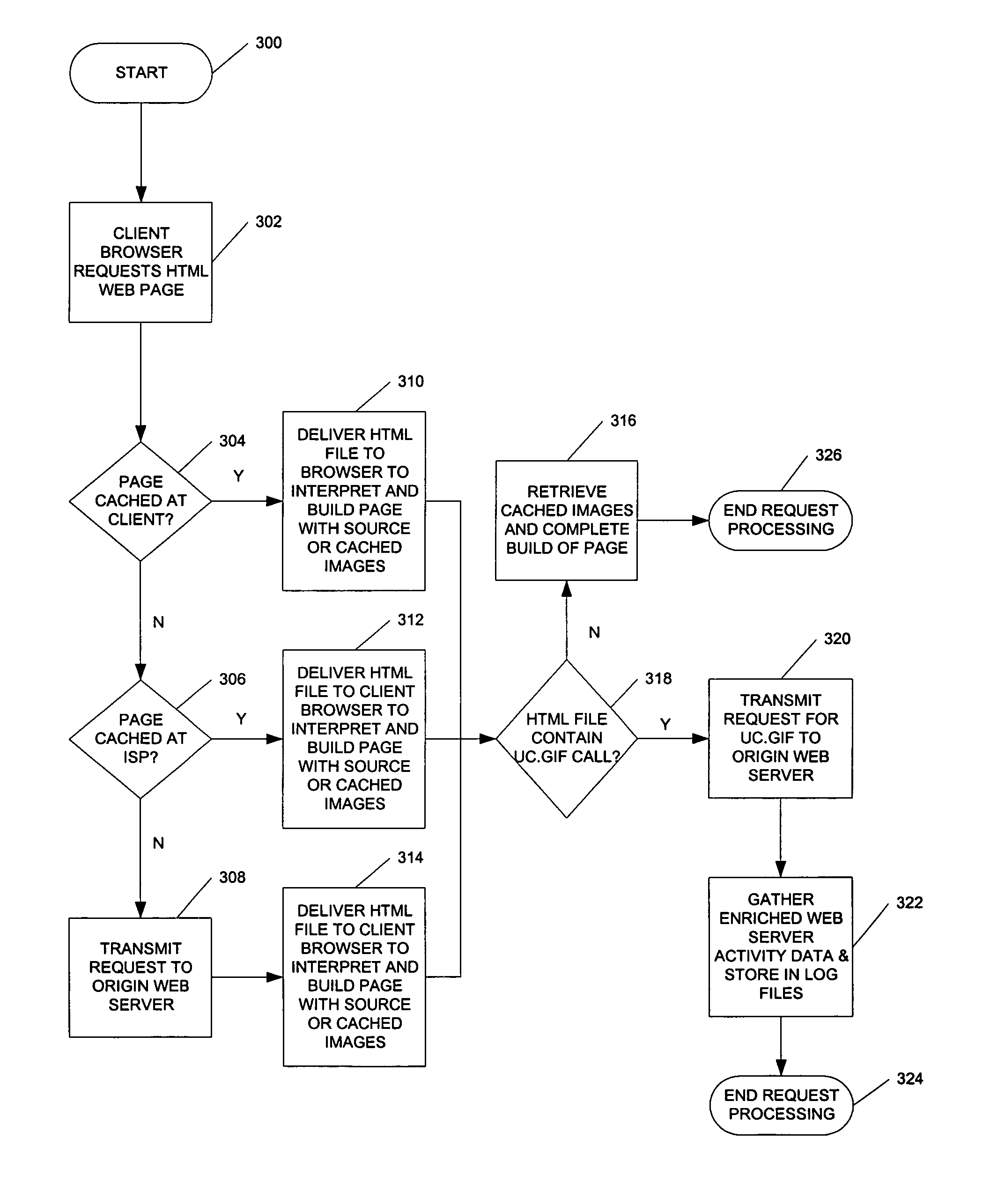
A method and system for gathering enriched web server activity data in a global communications network in which requested information files are cached at a plurality of network devices. With the prevalence of web caching on the Internet, the origin web servers do not serve the majority of requests for web site content. A single pixel clear Graphics Image Format (GIF) request is added to the HyperText Markup Language (HTML) source file for a web page. Appended to the GIF request is a Common Gateway Interface (CGI) string of data that contains enhanced web activity data information, including the number of images (“hits”) that have to be retrieved by a client browser to build the web page, and the referring identifier that resulted in access to the web page. The single pixel clear GIF request is not cacheable and results in the request being transmitted to the origin web server when the client browser interprets the HTML file. The enriched data is stored in log files at the origin web server to accumulate an accurate number of hits on the web page.
Owner:IBM CORP
Data base synchronizing system with at least two host databases and a remote database
InactiveUS6466951B1Data processing applicationsDatabase distribution/replicationDatabaseHost machine
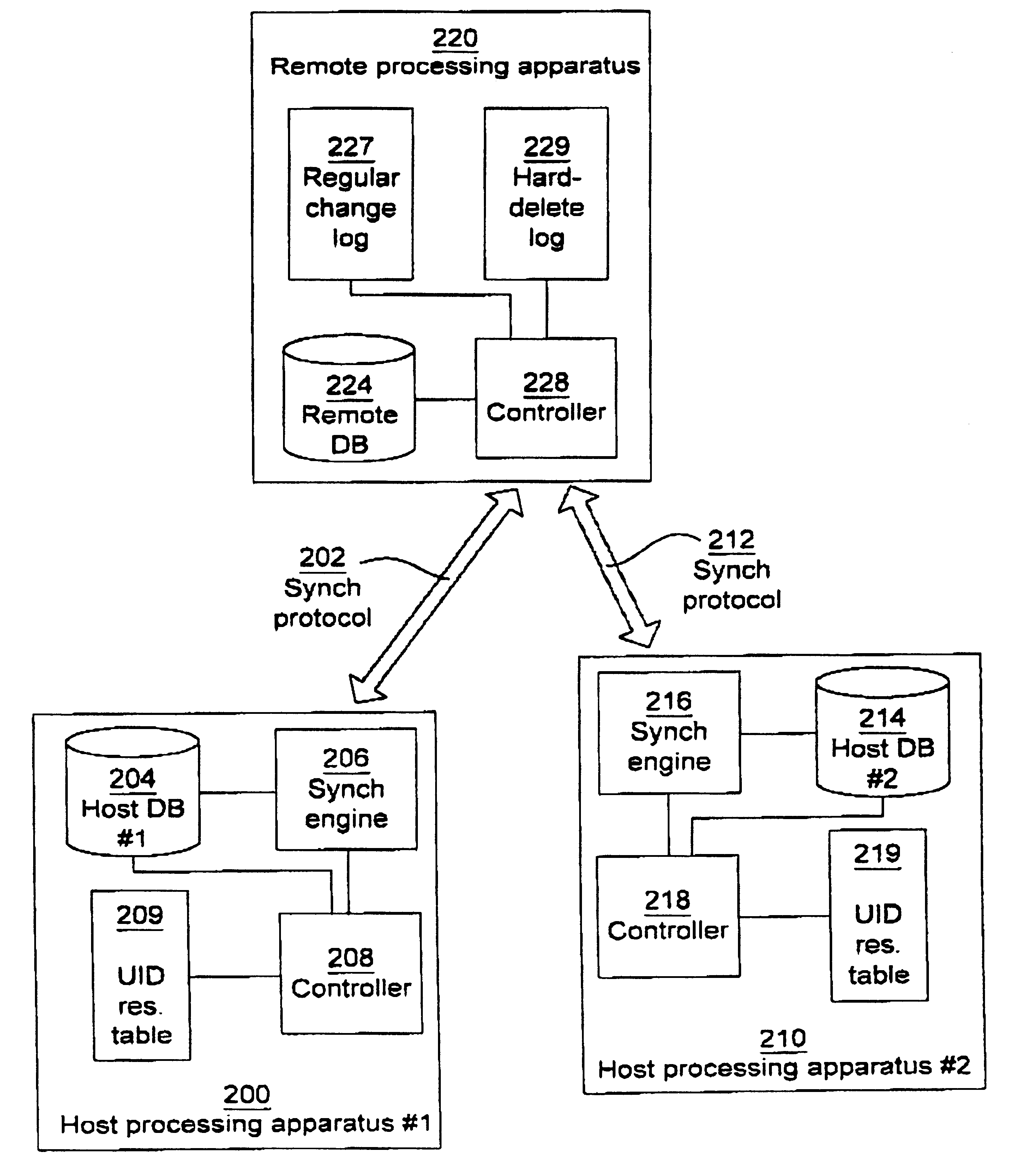
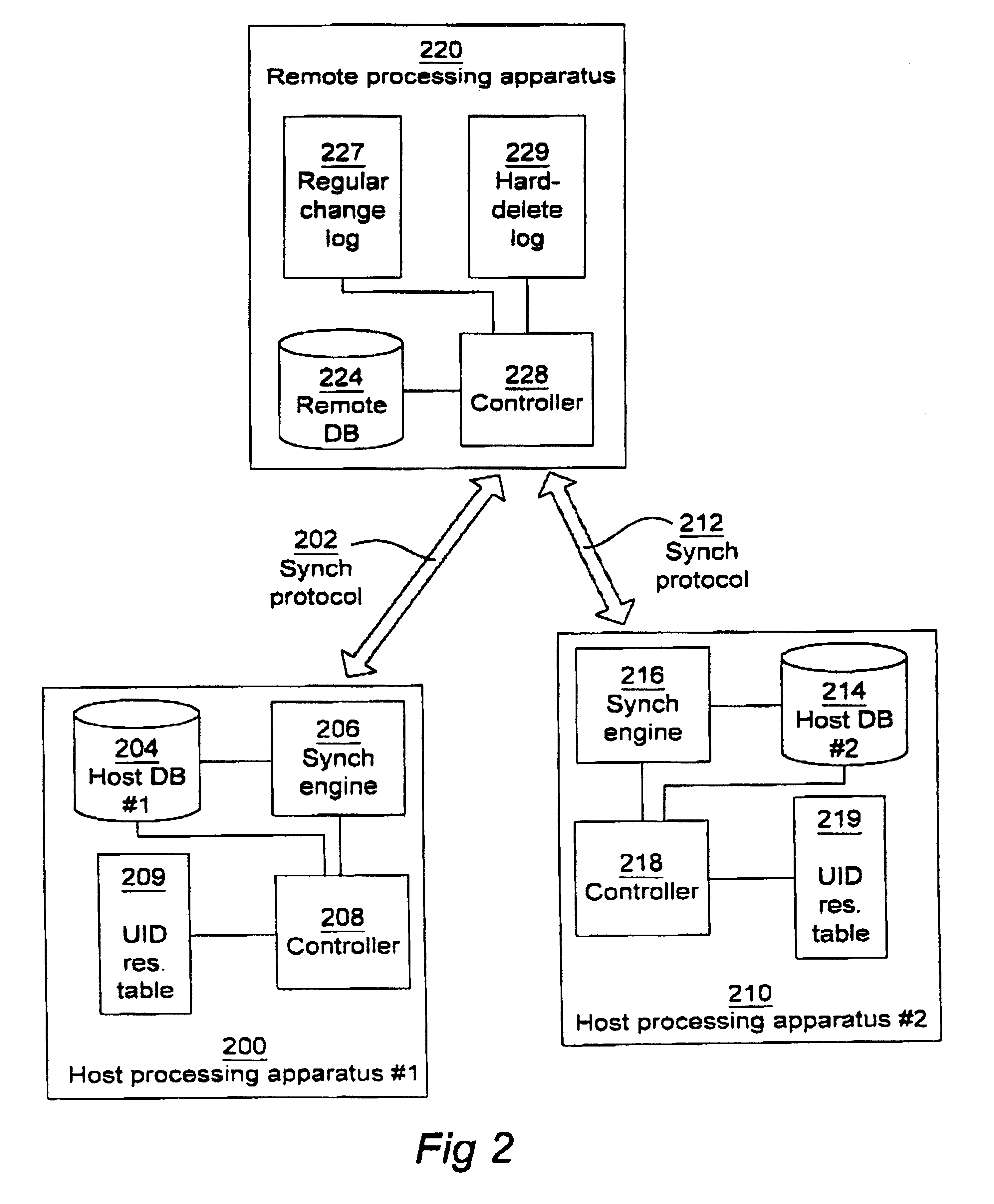
A database system has at least two hose databases (204, 214) in respective host processing apparatuses (200, 210). A remote database (224) is provided in a remote processing apparatus (220). The host databases and the remote database store a plurality of database items. A synchronization engine (206, 216) is provided in each host processing apparatus for synchronizing its host database with the remote database. A first log file (227) contains entries, that represent changes made to the remote database (224), including additions and modifications of items in the remote database as well as deletions of items from the remote database in order to increase its free storage space available for storing new items. A second log file (229) contains entries, that represent deletions from the remote database upon respective deletions in either of the host databases (204, 214). The synchronization engine (206, 216) deletes items in its host database in accordance with the entries in the second log file but not in the first log file.
Owner:OPTIS WIRELESS TECH LLC
Method and apparatus for managing session information
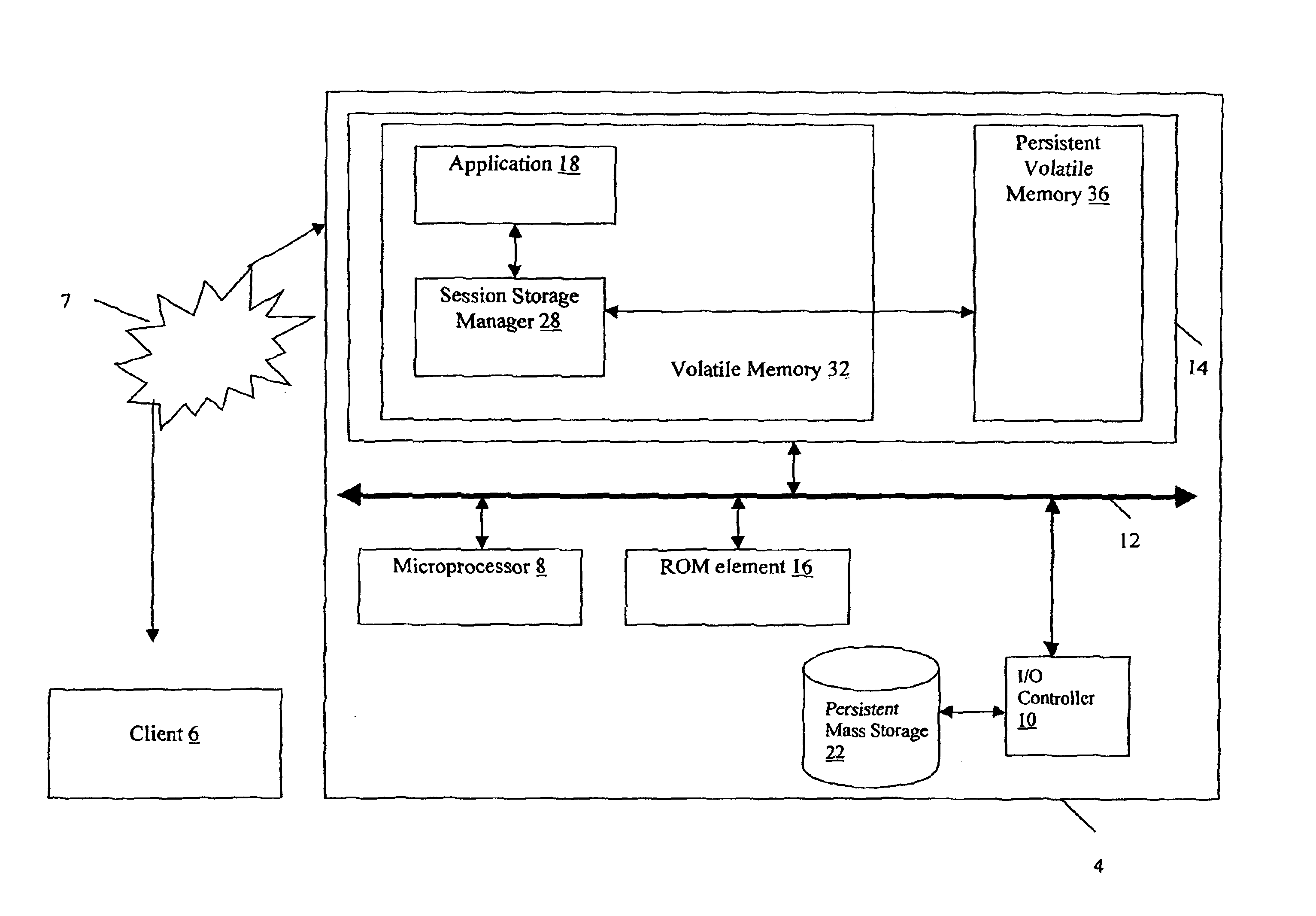
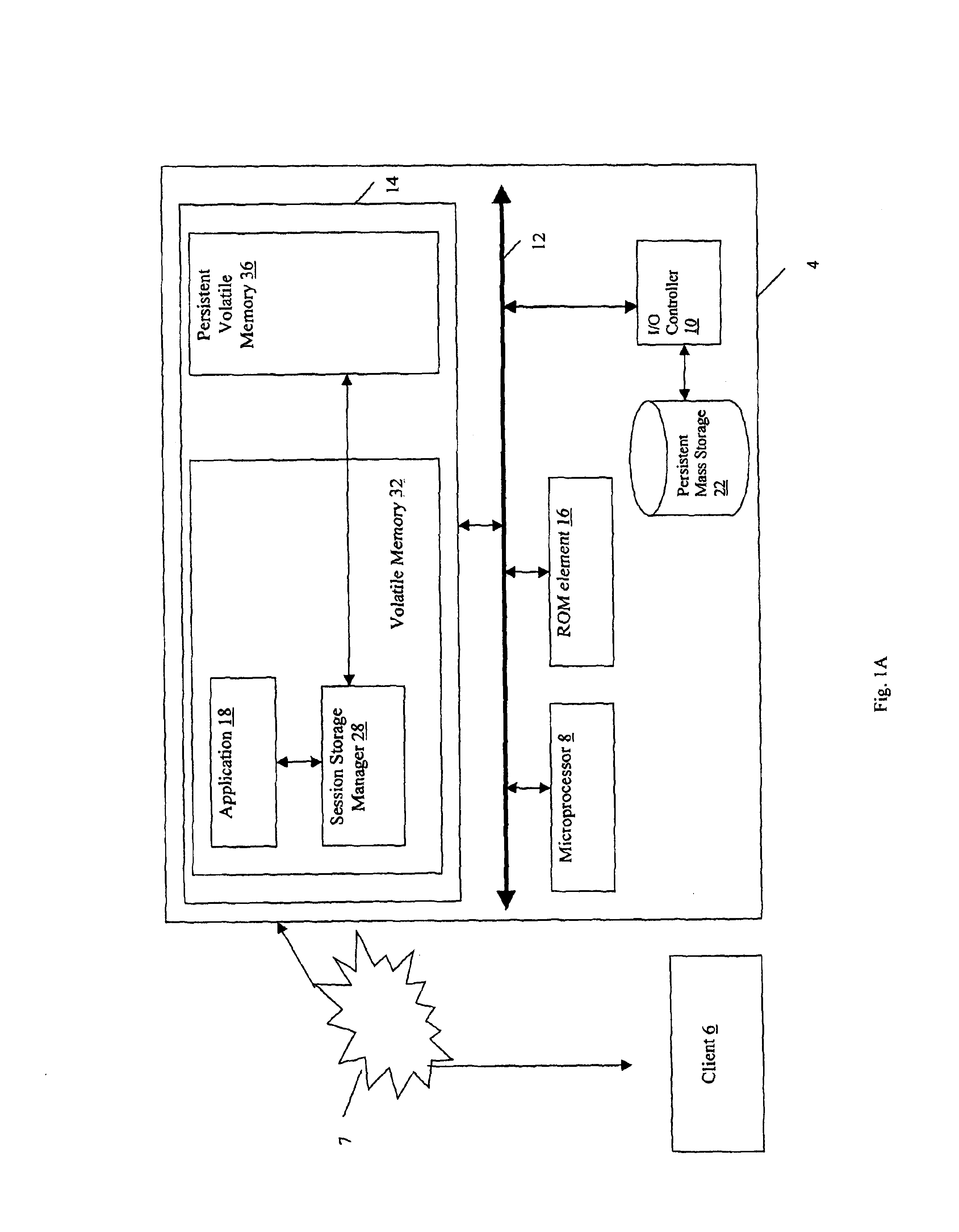
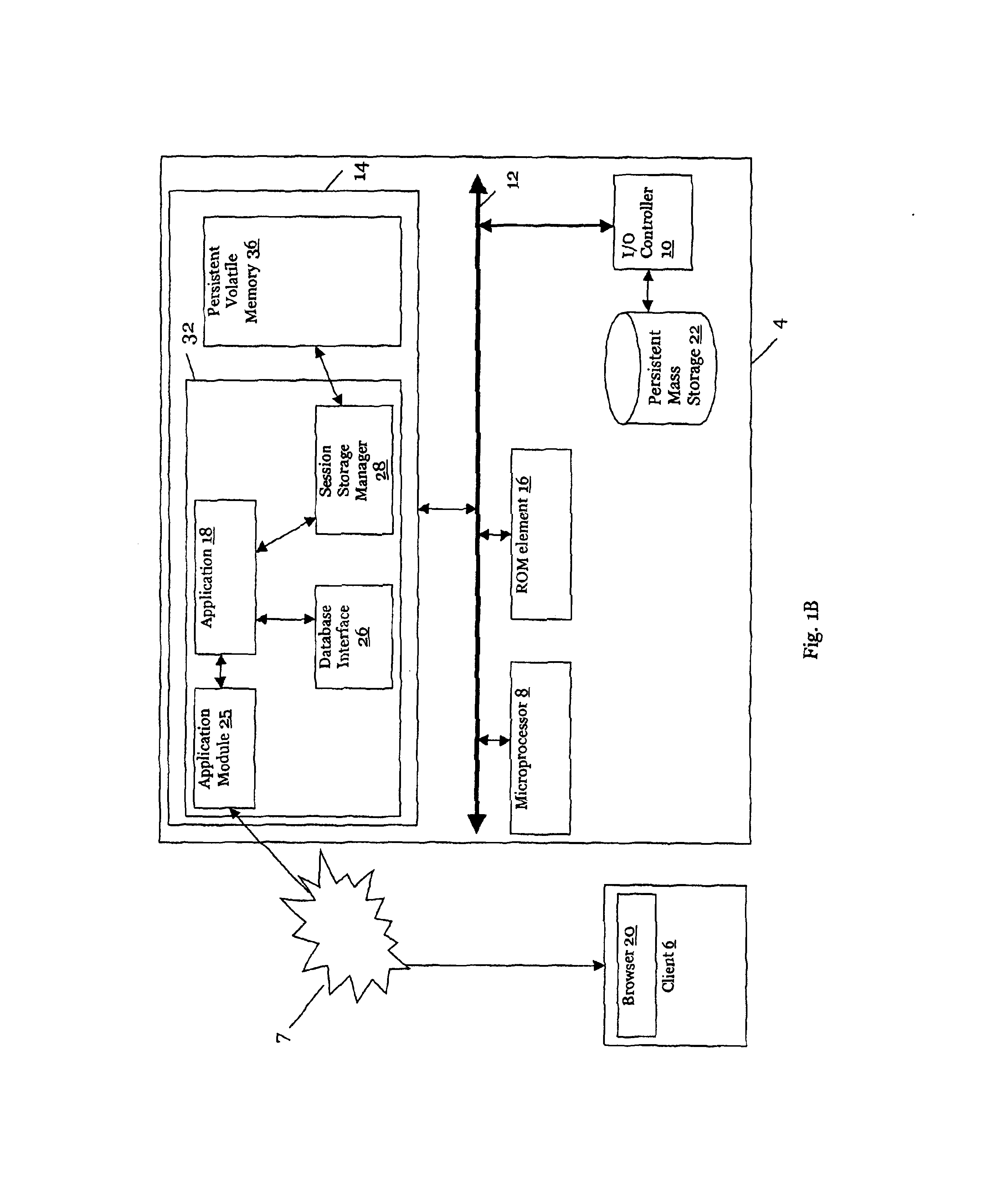
InactiveUS6862689B2Improve performanceError detection/correctionEmergency protective arrangements for automatic disconnectionClient-sideClient machine
A method and apparatus for managing session information. In one embodiment, a communication session is established between a client computer and a server computer. When the client computer and the server computer establish the communication session, the client or the server typically stores information about the communication session, which is referred to as “session information.” The session information is stored in a first log file stored in a persistent volatile memory and in a cache file stored in a volatile memory of the server. The cache file is reconstructed after a server failure by retrieving the session information stored in the first log file.
Owner:STRATUS TECH IRELAND LTD
System and methods for semiautomatic generation and tuning of natural language interaction applications
A system for supervised automatic code generation and tuning for natural language interaction applications, comprising a build environment comprising a developer user interface, automated coding tools, automated testing tools, and automated optimization tools, and an analytics framework software module. Text samples are imported into the build environment and automated clustering is performed to assign them to a plurality of input groups, each input group comprising a plurality of semantically related inputs. Language recognition rules are generated by automated coding tools. Automated testing tools carry out automated testing of language recognition rules and generate recommendations for tuning language recognition rules. The analytics framework performs analysis of interaction log files to identify problems in a candidate natural language interaction application. Optimizations to the candidate natural language interaction application are carried out and an optimized natural language interaction application is deployed into production and stored in the solution data repository.
Owner:ARTIFICIAL SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com