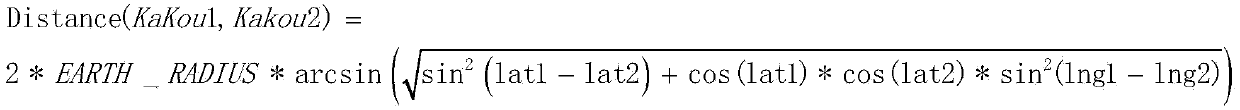Patents
Literature
328results about How to "Efficient query" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
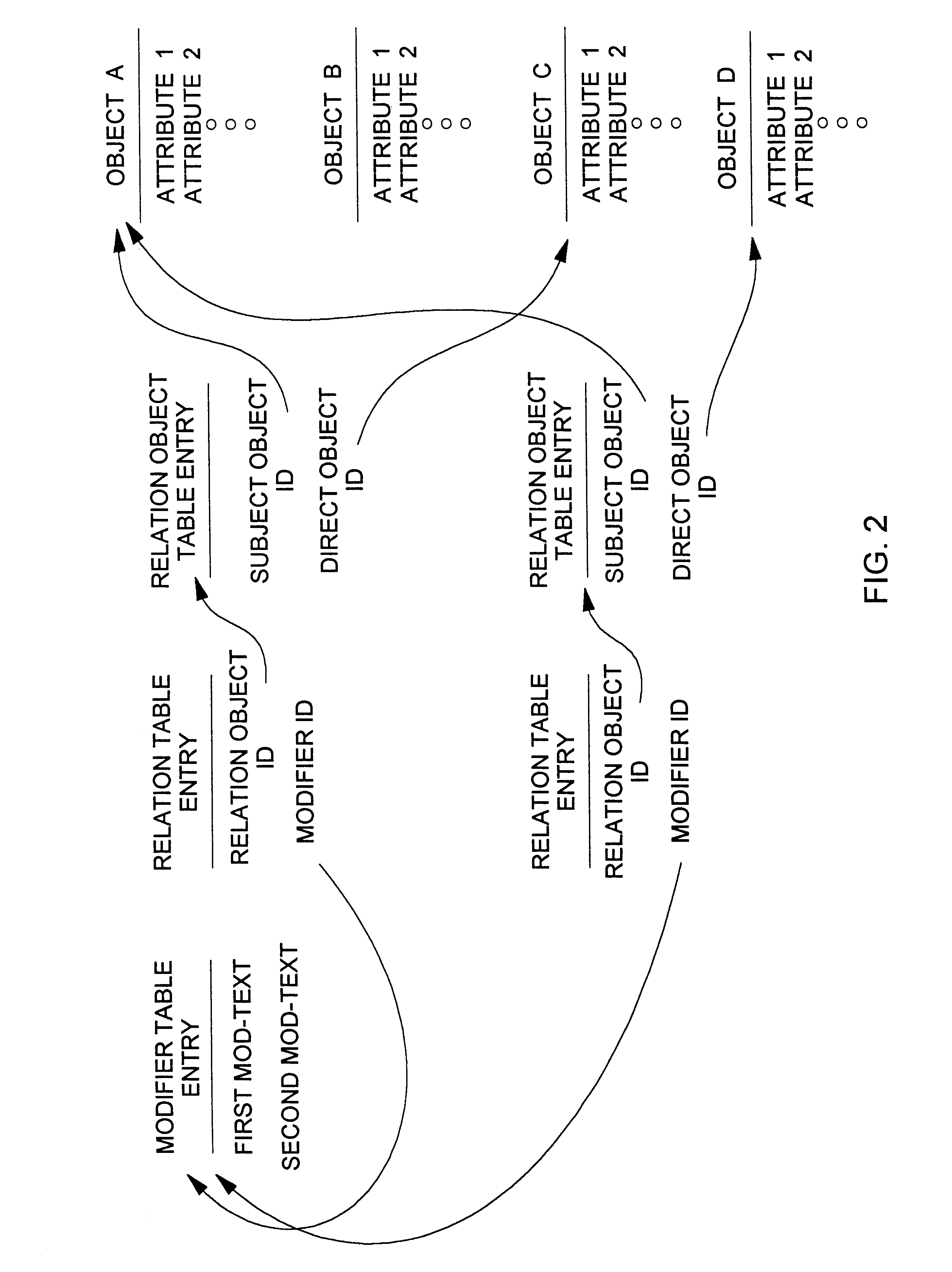
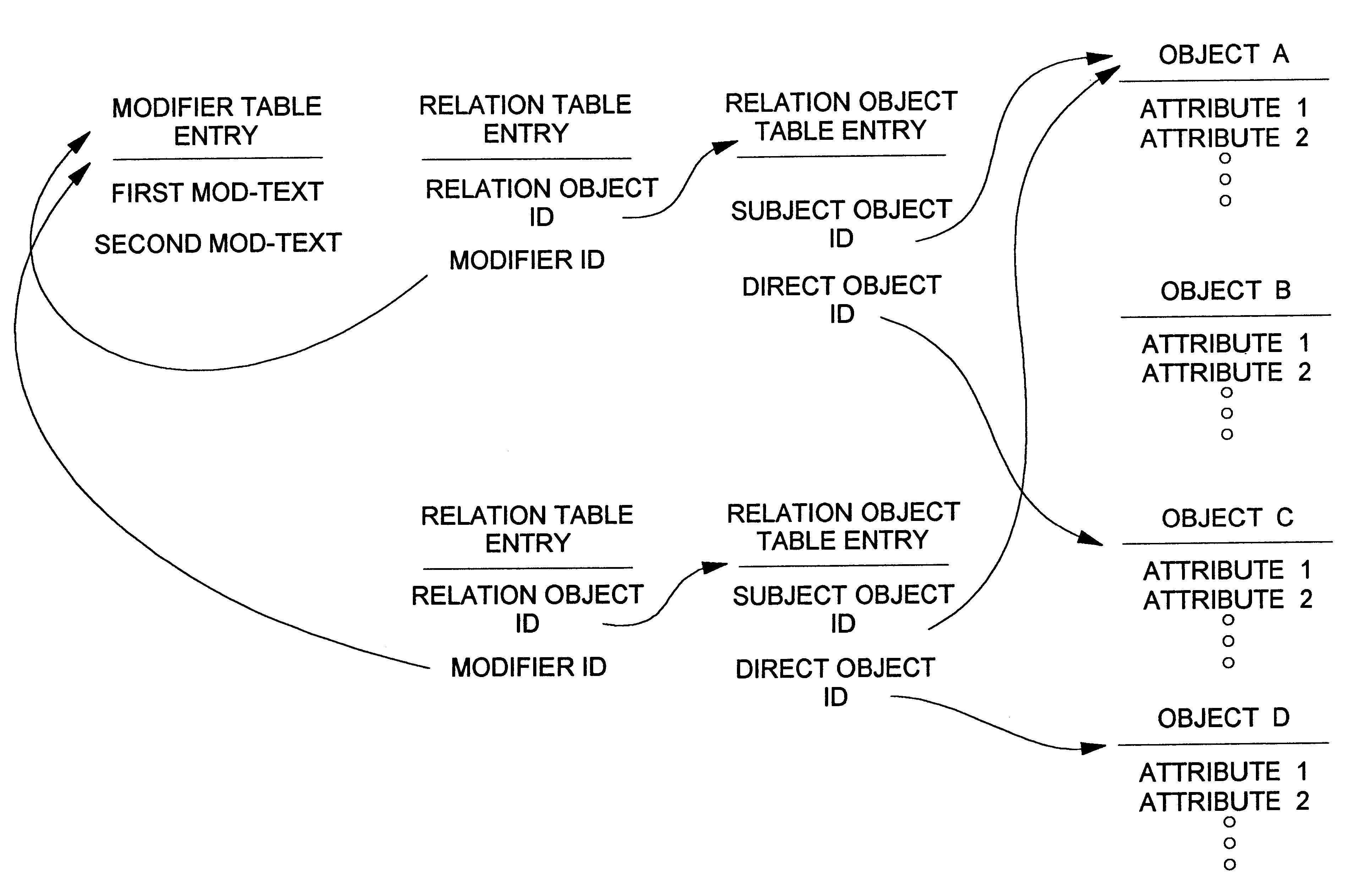
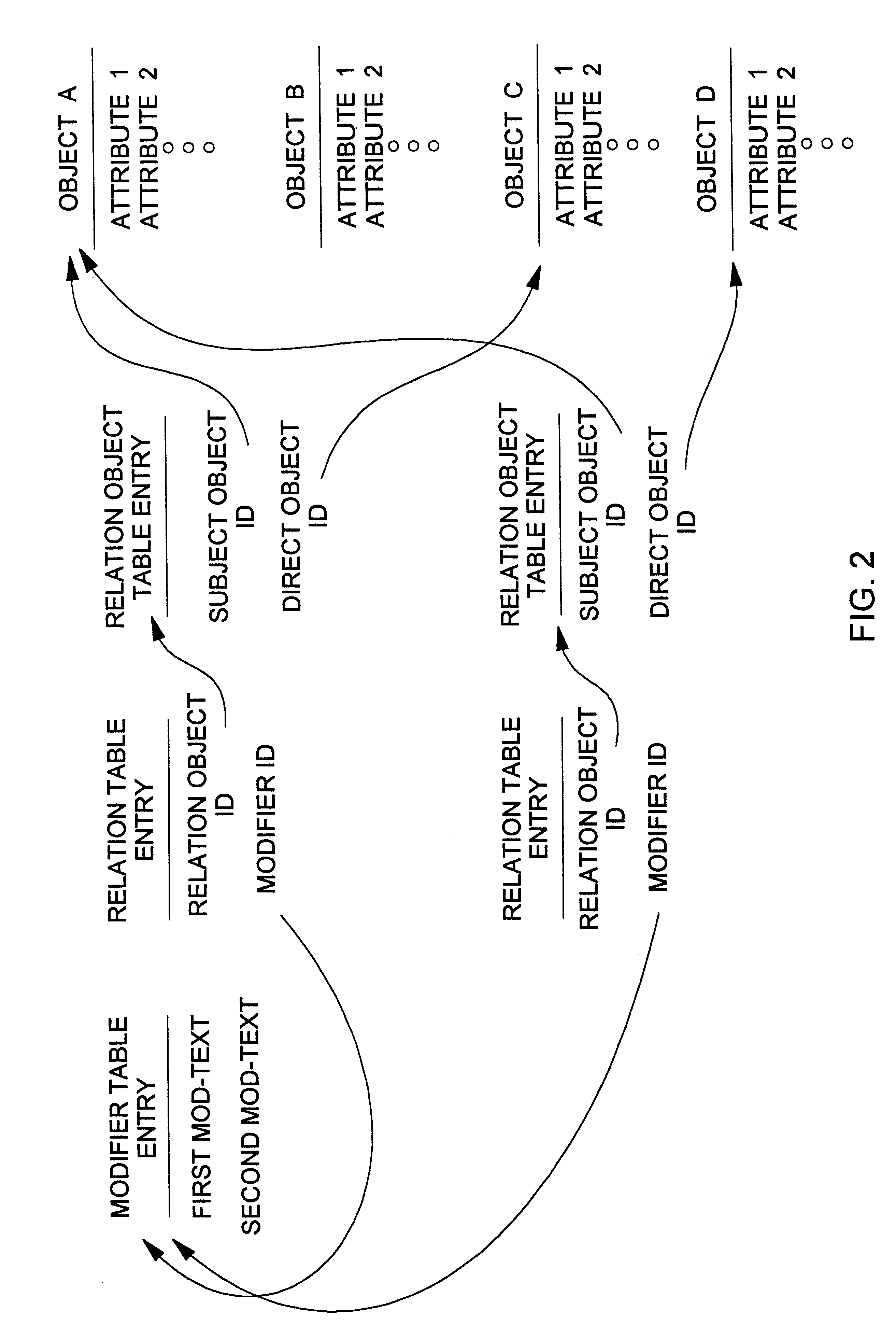
Database query handler supporting querying of textual annotations of relations between data objects
InactiveUS6618732B1EffectivelySave storage spaceData processing applicationsDigital data processing detailsDatabase queryCustomer relationship management
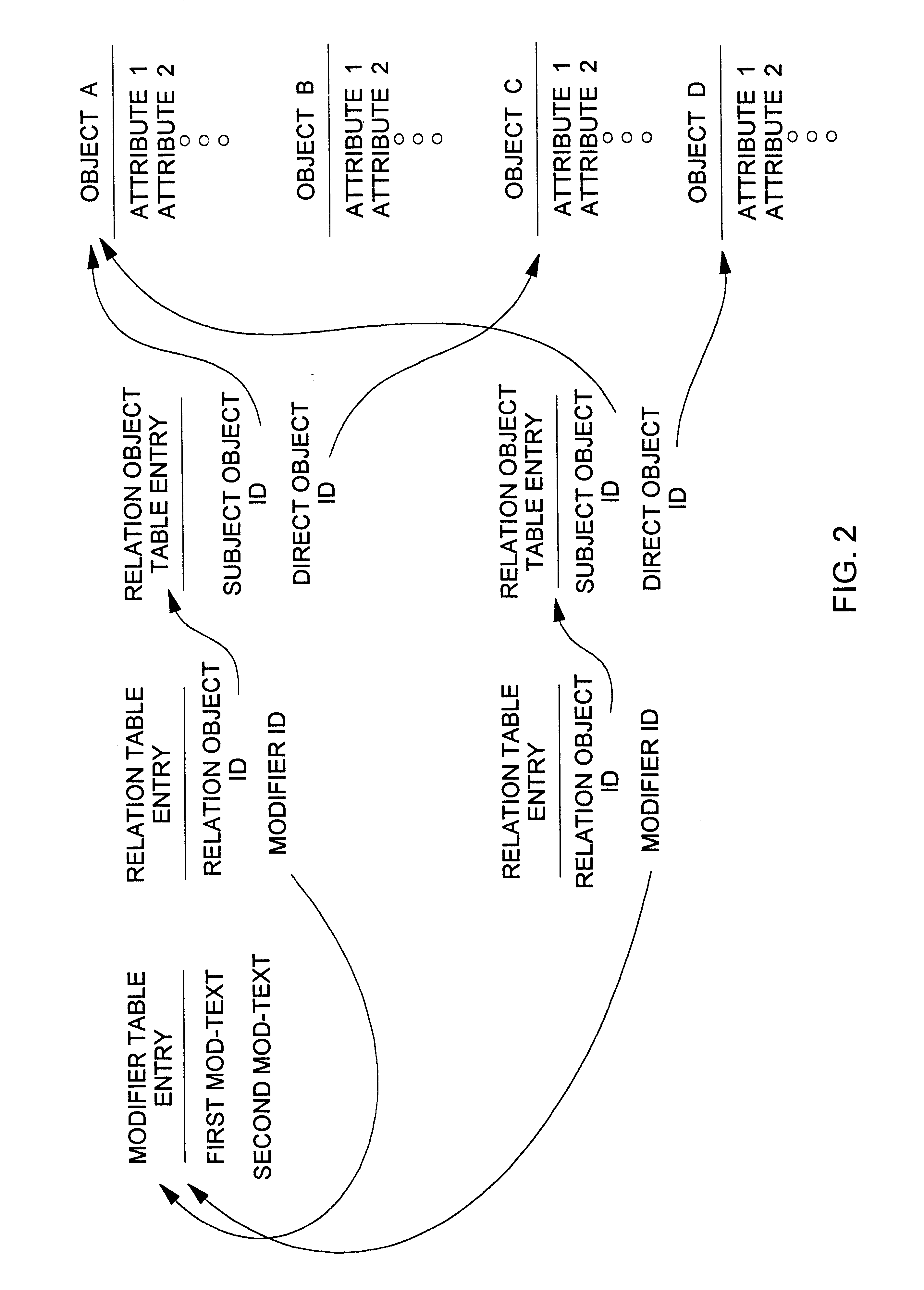
An improved command handler (and database system utilizing the improved command handler) interfaces to a datastore storing item data for a plurality of items and bi-directional modifier data, corresponding to a relation between at least one first item and at least one second item, that represents first text characterizing semantics of a relationship of the at least one first item to the at least one second item, and represents second text characterizing semantics of a relationship of the at least one second item to the at least one first item. The command handler operates, in response to receiving a first-type query command that specifies at least one given item, to access the datastore to identify i) at least one related item that is related to the given item, and identify ii) either the first text or the second text characterizing semantics of the relation between the given item and the at least one related item. The command hander returns i) data corresponding to the at least one related item; and ii) data corresponding to the identified first text and or second text characterizing semantics of the relation between the given item and the at least one related item. Preferably, the data returned in response to the first-type query command identifies the at least one related item. and identifies the first text or second text characterizing semantics of the relation between the given item and the at least one related item. In addition, the command handler preferably supports additional commands that retrieve from the datastore information related to specified objects, object types, and relations.The command handler (and database system) of the present invention may be used in a wide assortment of software applications, including enterprise applications (such as e-business applications, supply chain management applications, customer relationship management applications, decision support applications), the file system in operating systems, web browsers, e-mail applications and personal information management applications. Importantly, the command handler (and database system) provides an efficient mechanism to query the organization of the data elements (and the relationships therebetween) stored and accessed in such software applications, in a manner that efficient and readily adaptable to client-server database systems or other distributed database systems.
Owner:REVELINK
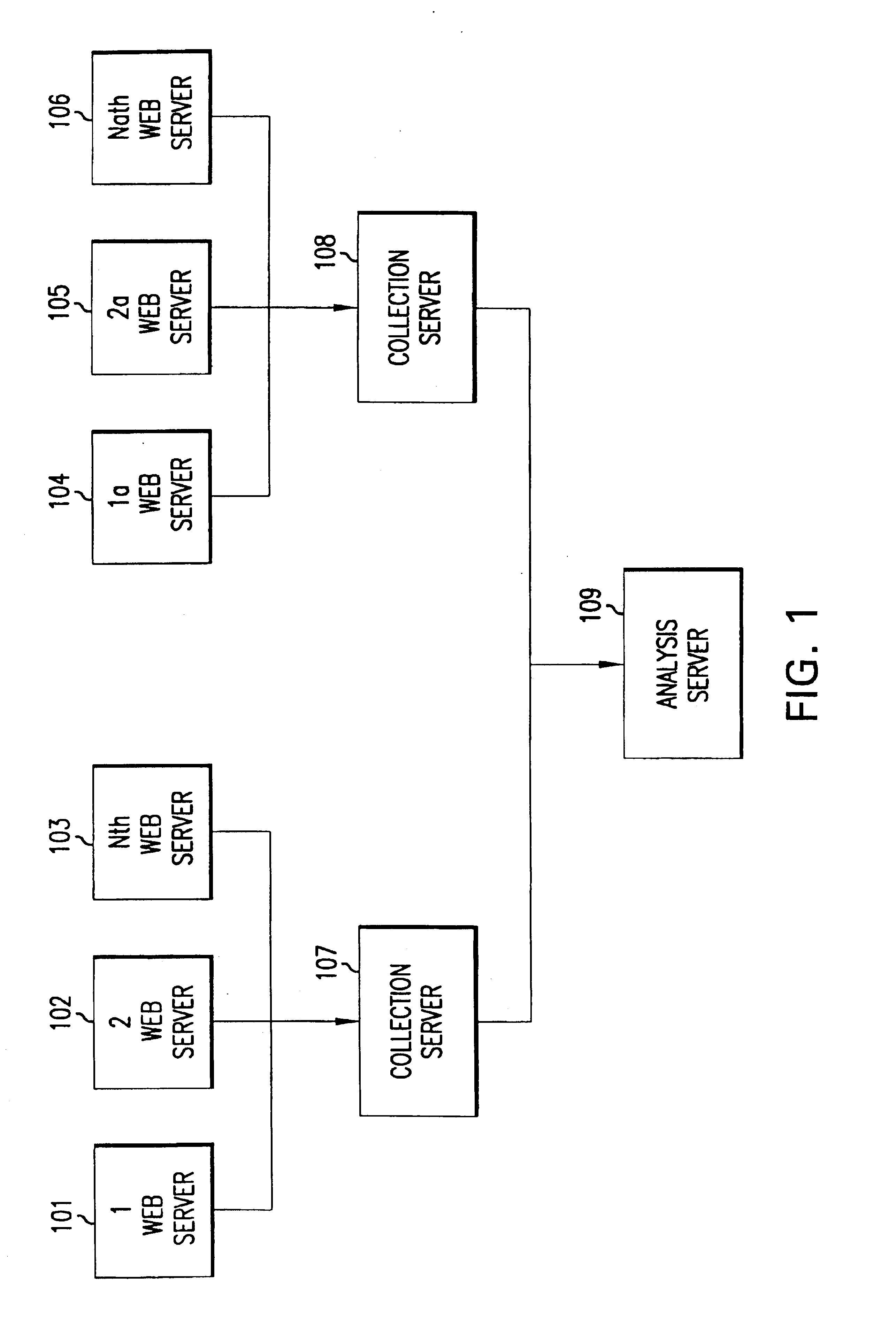
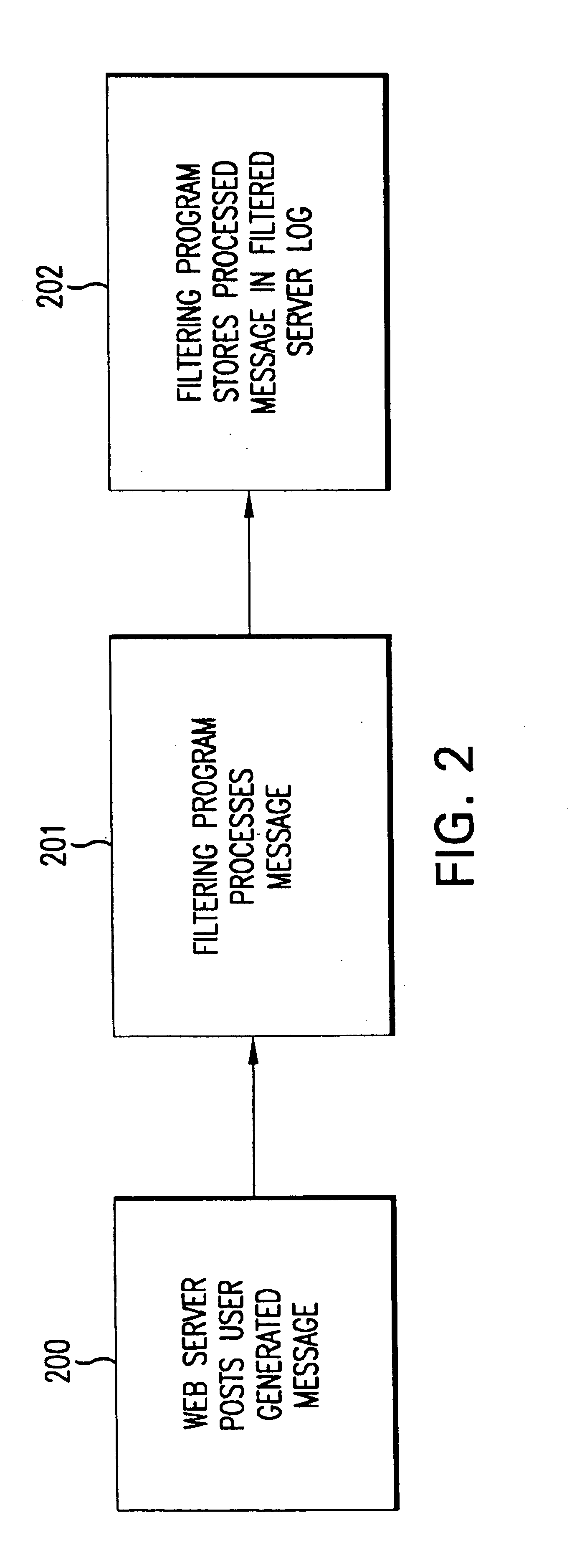
System for collecting, analyzing, and reporting high volume multi-web server usage
InactiveUS6789115B1Minimize data handledEfficient queryData processing applicationsDigital computer detailsServer logRelational database
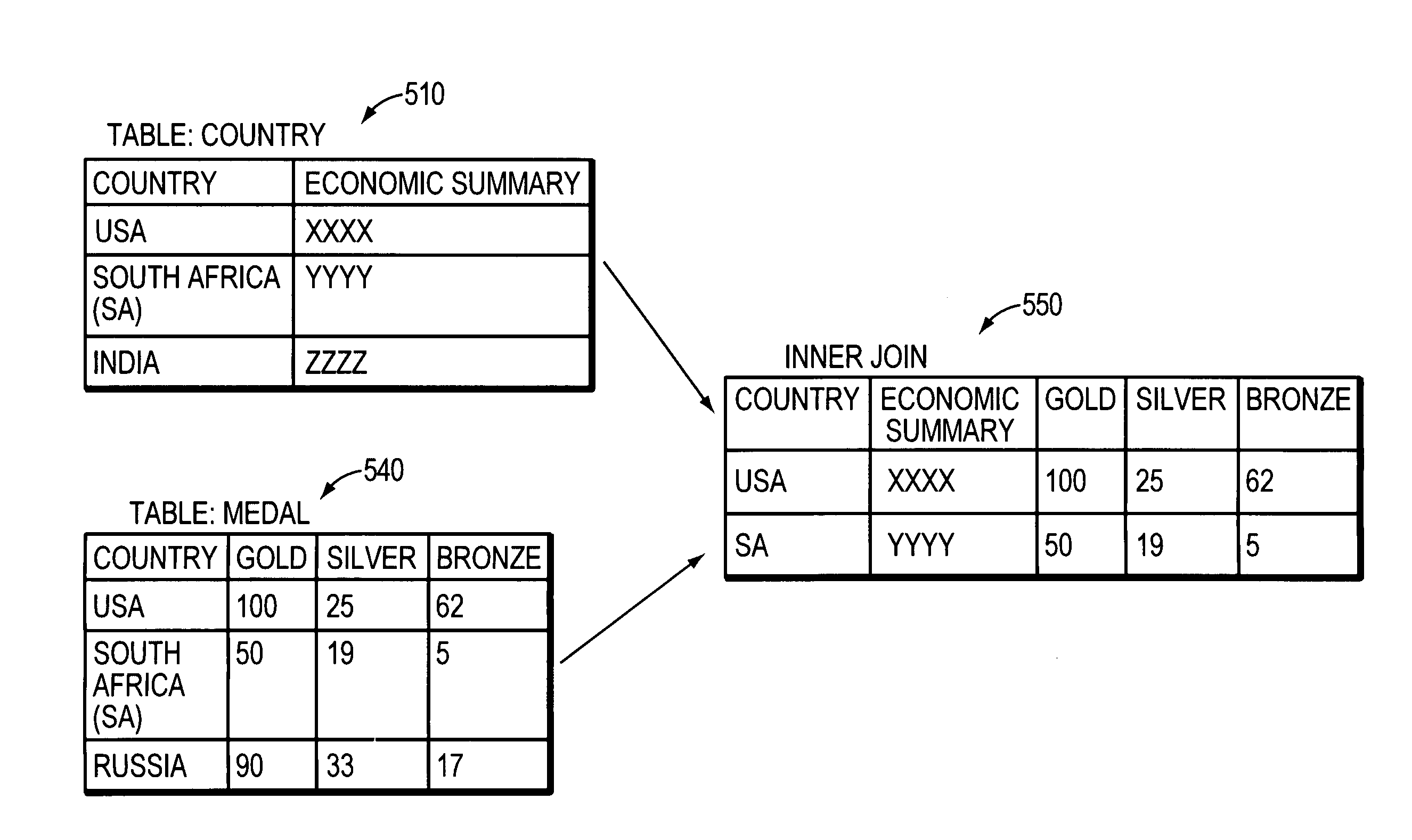
A system for capturing, analyzing, storing and reporting system-users' usage of multiple internet and / or intranet web servers. At each web server in the system, the actions by the system-user create a server log that is processed by the system on a continuous basis. The processing at the server may include, by way of illustration, filtering the logs of about 75 percent of the data and decrypting a system-user's cookie. On a periodic basis, one or more collection servers in the system copy the processed log files from each web server on the system, zip the files, and transfer the files to an analysis server. After the collection is complete, an analysis server processes the data and stores it in a relational database that supports various user specified daily, monthly and quarterly reports of the usage data.
Owner:BANK OF AMERICA CORP
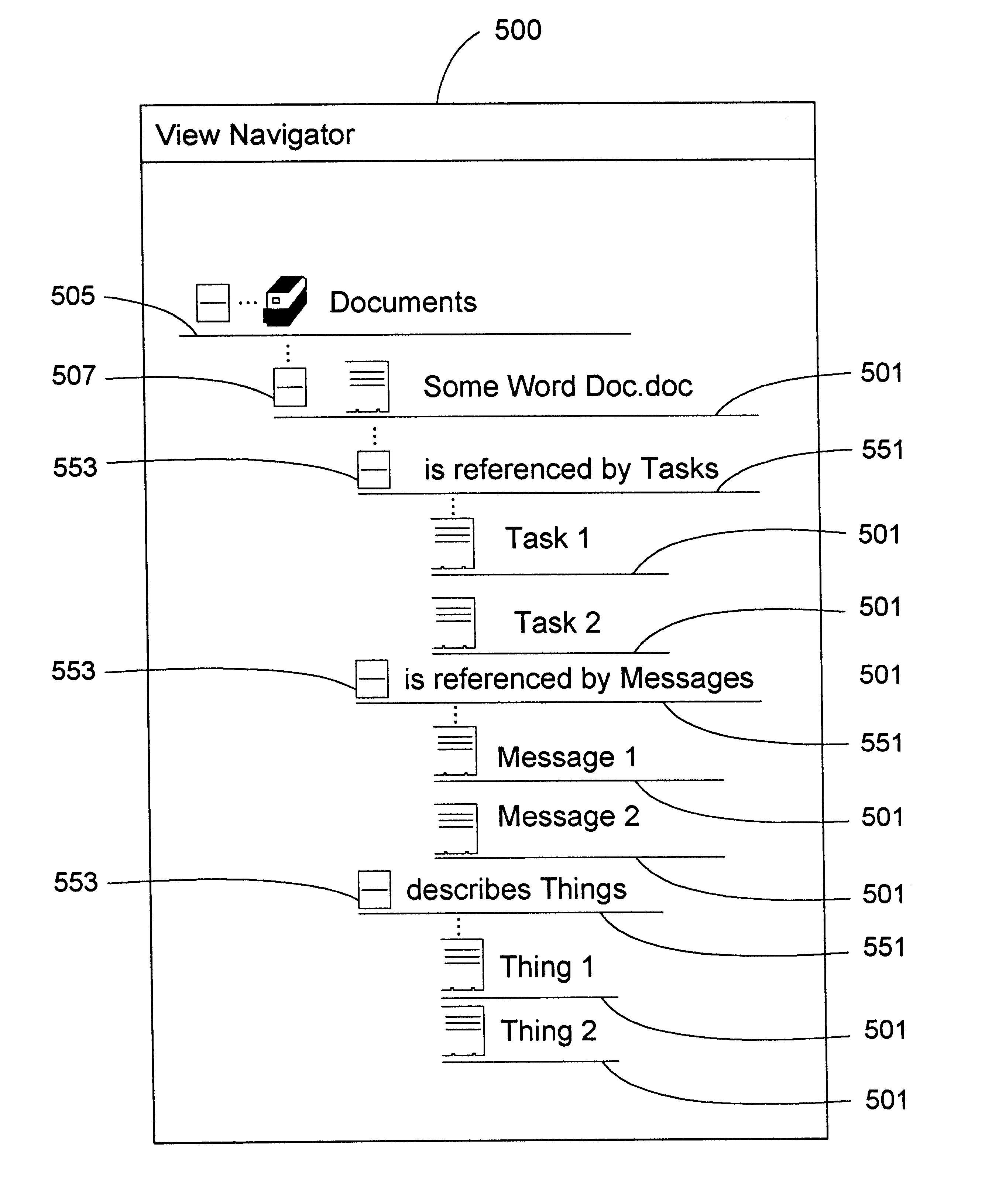
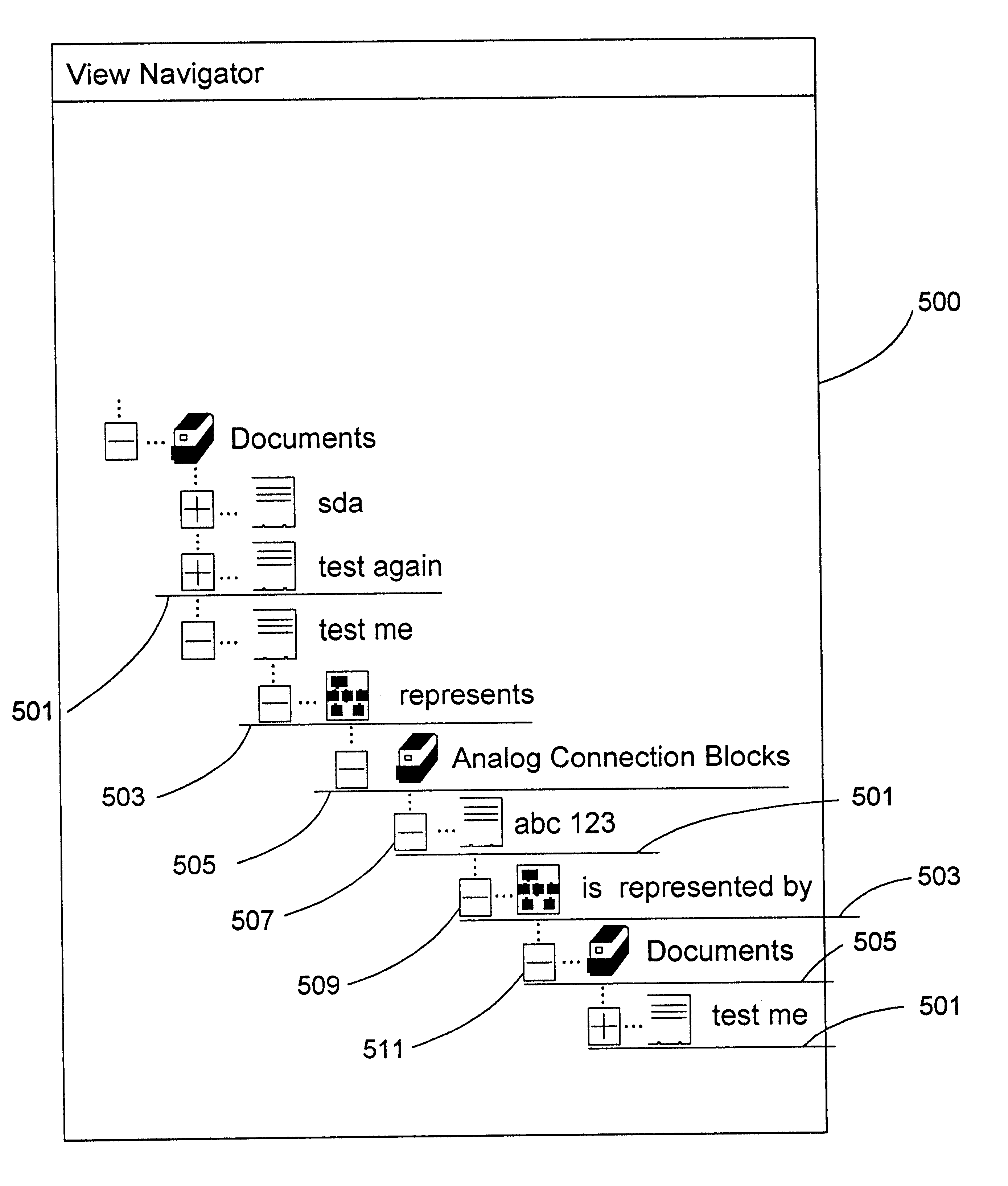
View navigation for creation, update and querying of data objects and textual annotations of relations between data objects
InactiveUS6618733B1EffectivelySave storage spaceData processing applicationsDigital data processing detailsCustomer relationship managementOperational system
A method (and corresponding database system) for displaying in a view window information characterizing semantics of relations between objects. For each given relation between at least one subject object and at least one direct object, bi-directional modifier data is stored that represents first text characterizing semantics of a relationship of the at least one first object to the at least one second object, and represents second text characterizing semantics of a relationship of the at least one second object to the at least one first object. In response to predetermined user input associated with an object node displayed in the view window, a set of relations whose at least one subject object or at least one direct object is associated with the object node is identified. For at least one relation in the set of relations, the view window is updated to include a second node comprising a graphical representation of: the first text of the given relation in the event that the given object is a subject object in the given relation, or the second text of the given relation in the event that the given object is a direct object in the given relation. The second node may be a relation node associated with a given relation, or a mixed node associated with a relation-type pair. In response to predetermined input with a second node, the second node may be expanded to identify and display one or more object nodes (identifying direct object(s) of relations derived from expansion of a subject object associated therewith or identifying subject object(s) of relations derived from expansion of a direct object associated therewith). Preferably, this expansion routine is recursive in nature.The method (and database system) of the present invention may be used in a wide assortment of software applications, including enterprise applications (such as e-business applications, supply chain management applications, customer relationship management applications, decision support applications), the file system in operating systems, web browsers, e-mail applications and personal information management applications. Importantly, the method (and database system) provides an easy, user friendly and efficient mechanism to define, view and query the organization of the data elements (and the relationships therebetween) stored and accessed in such software applications, in a manner that conveys the real-world meaning of such relationships.
Owner:REVELINK
Querying joined data within a search engine index
ActiveUS20100005054A1Efficient queryEfficient retrievalDigital data information retrievalDigital data processing detailsQuery stringDocument preparation
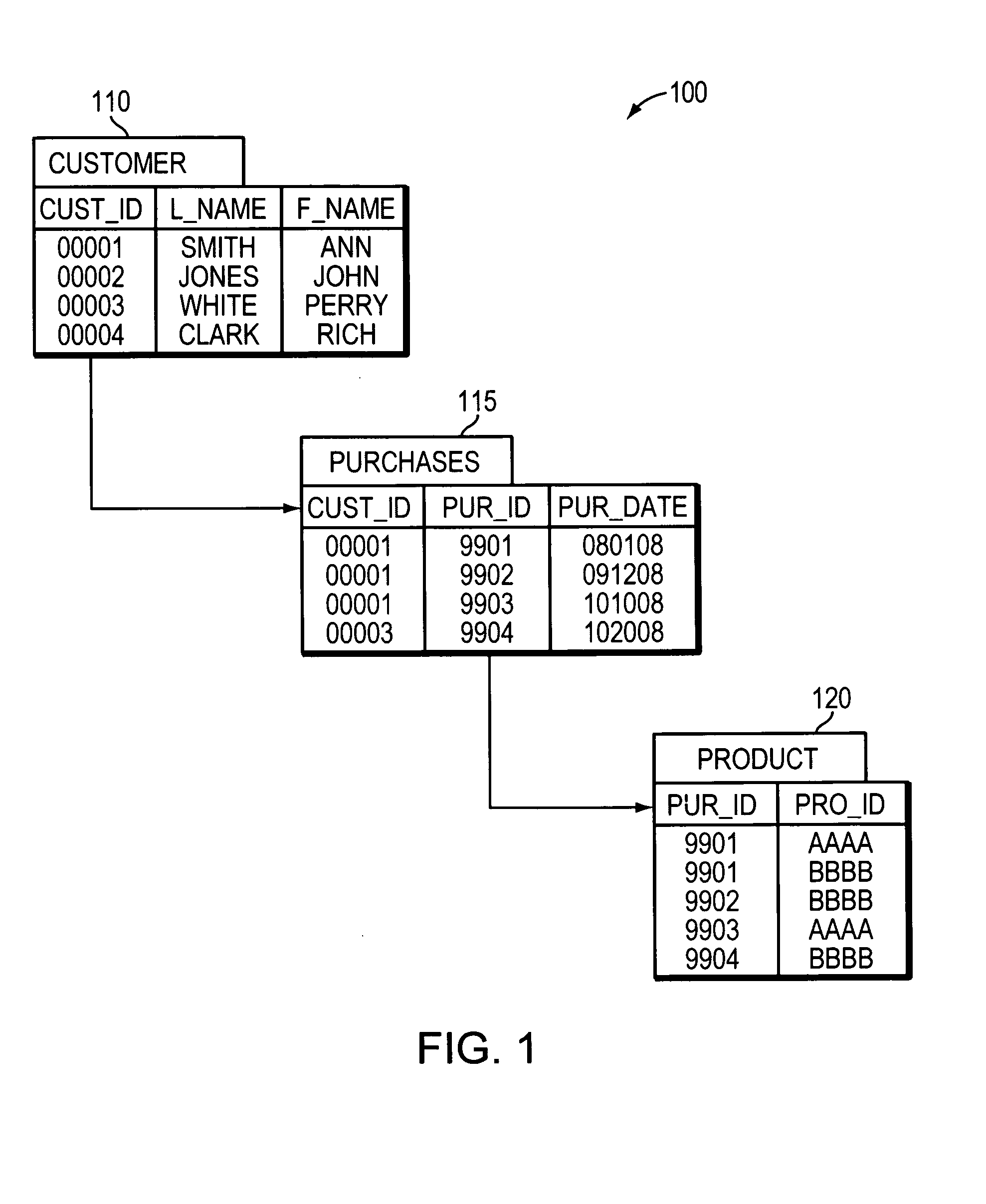
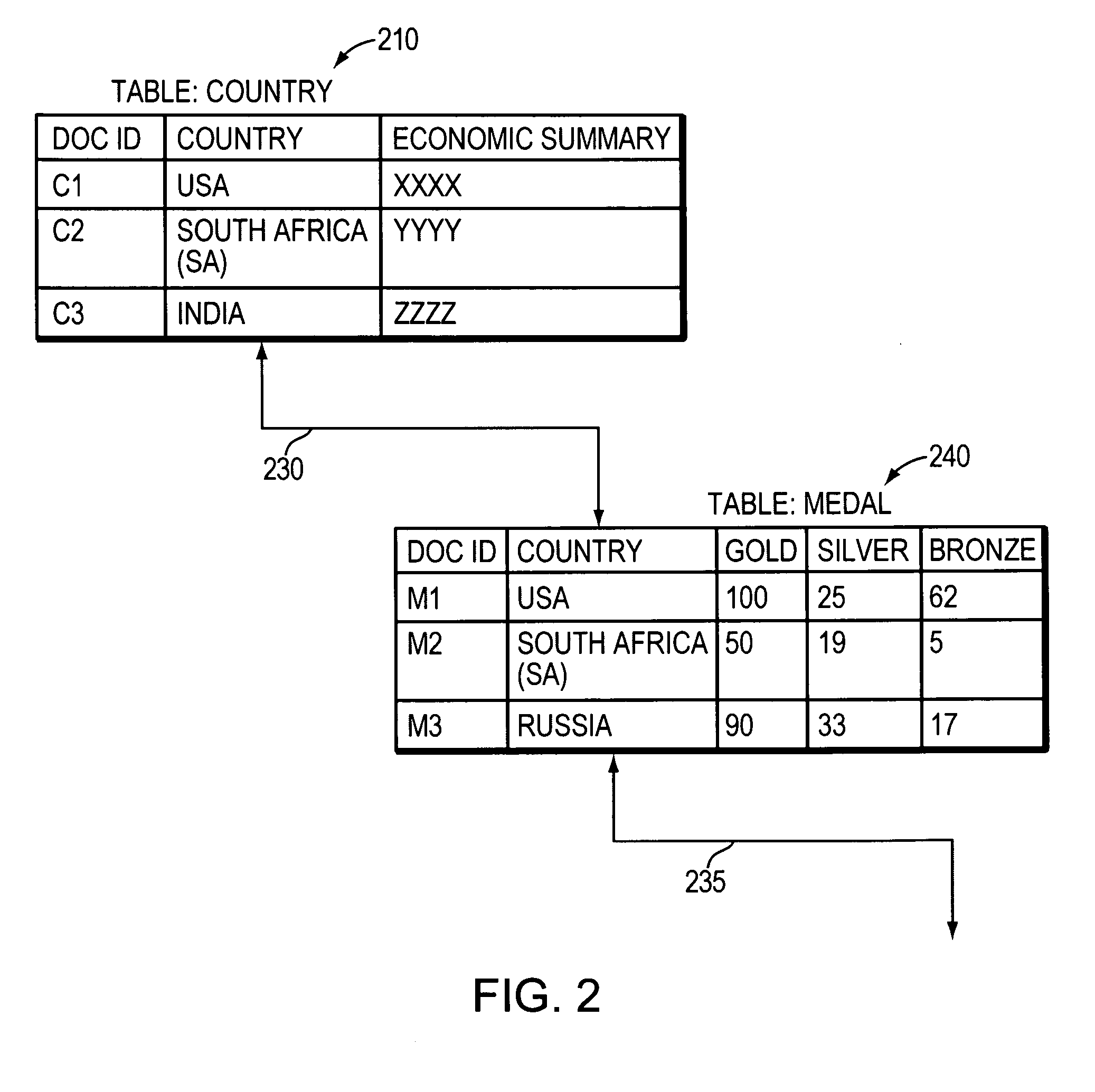
Techniques and systems for indexing and retrieving data and documents stored in a record-based database management system (RDBMS) utilize a search engine interface. Search-engine indices are created from tables in the RDBMS and data from the tables is used to create “documents” for each record. Queries that require data from multiple tables may be parsed into a primary query and a set of one or more secondary queries. Join mappings and documents are created for the necessary tables. Documents matching the query string are retrieved using the search-engine indices and join mappings.
Owner:SERVICENOW INC
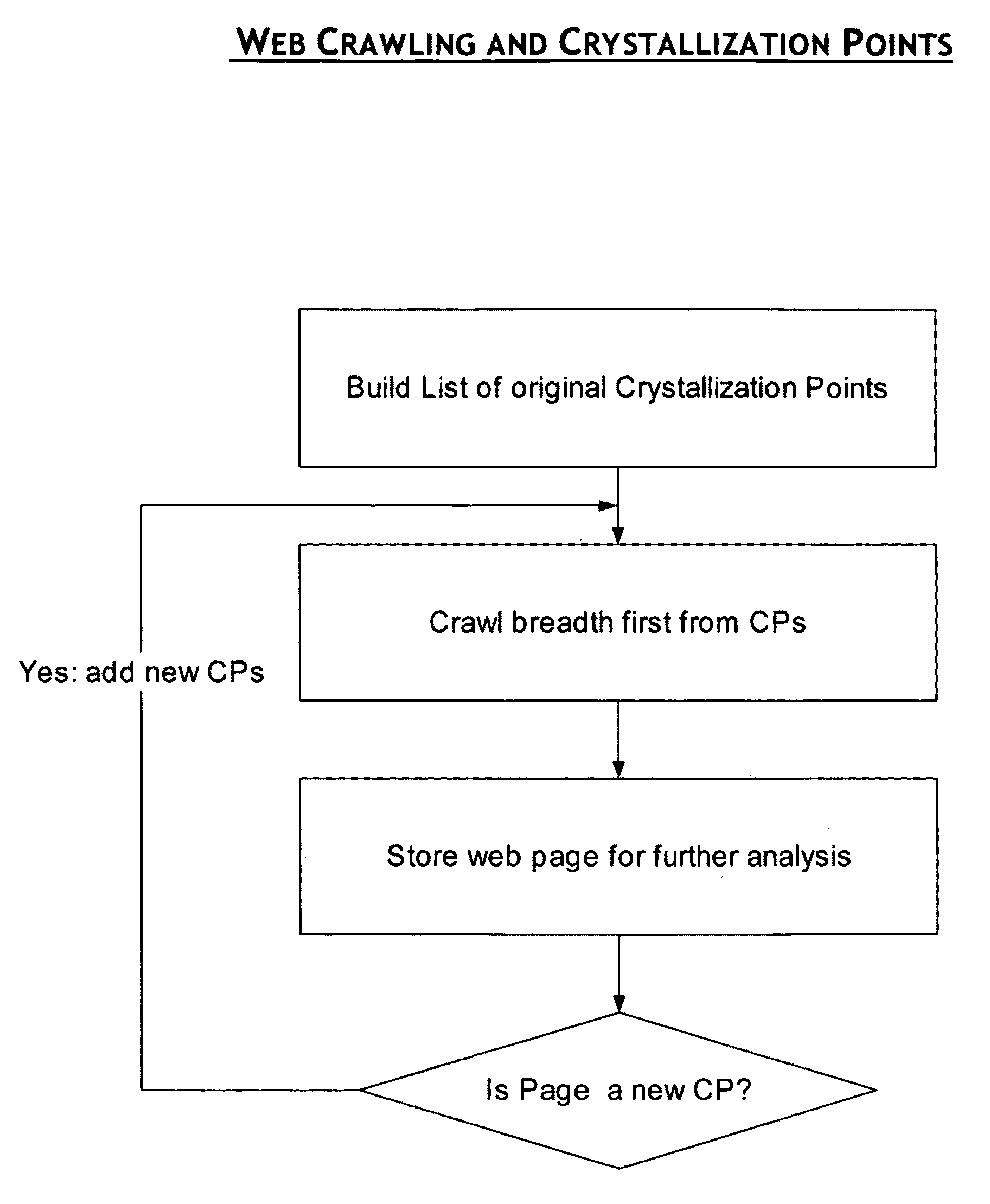
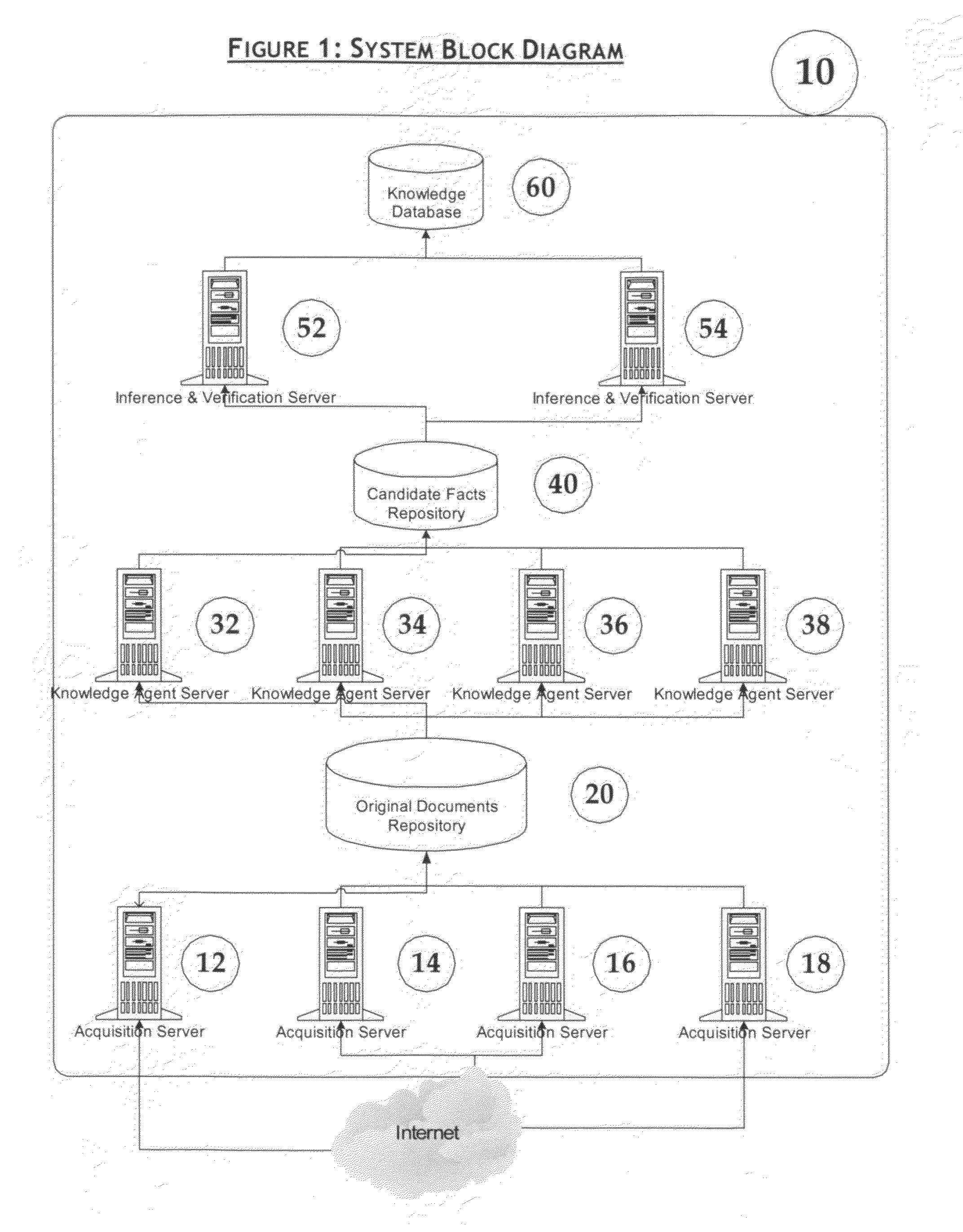
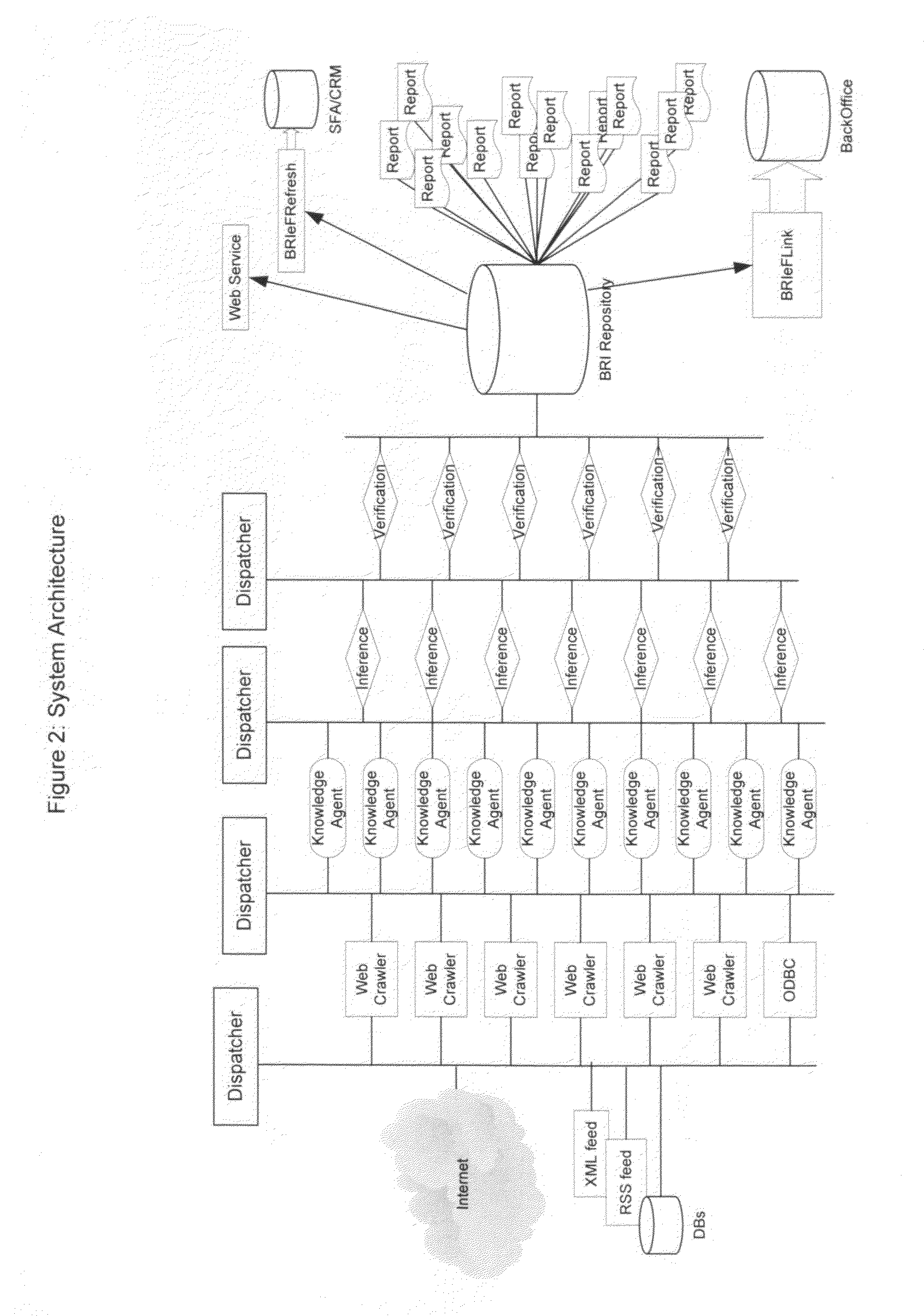
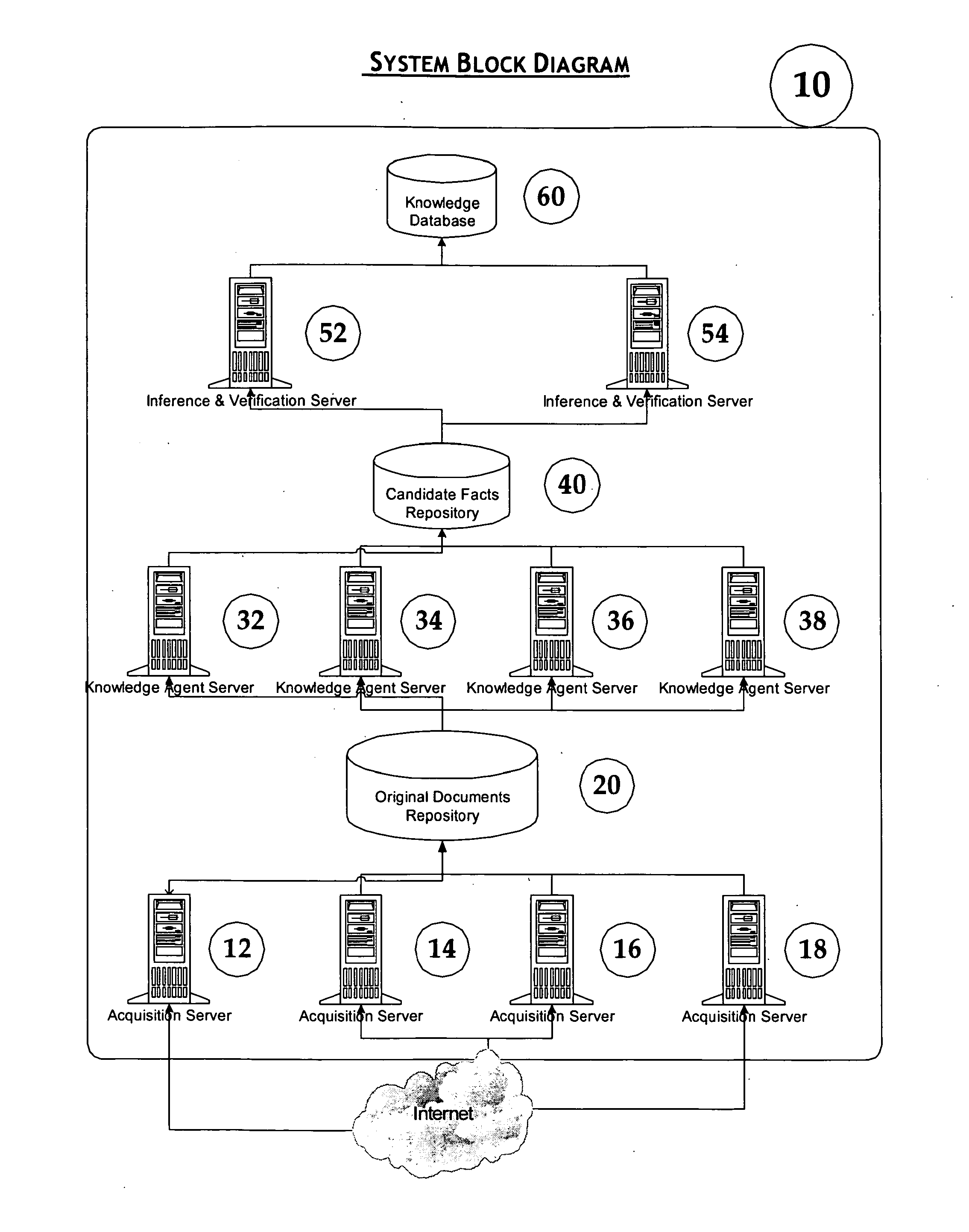
System and method for facts extraction and domain knowledge repository creation from unstructured and semi-structured documents
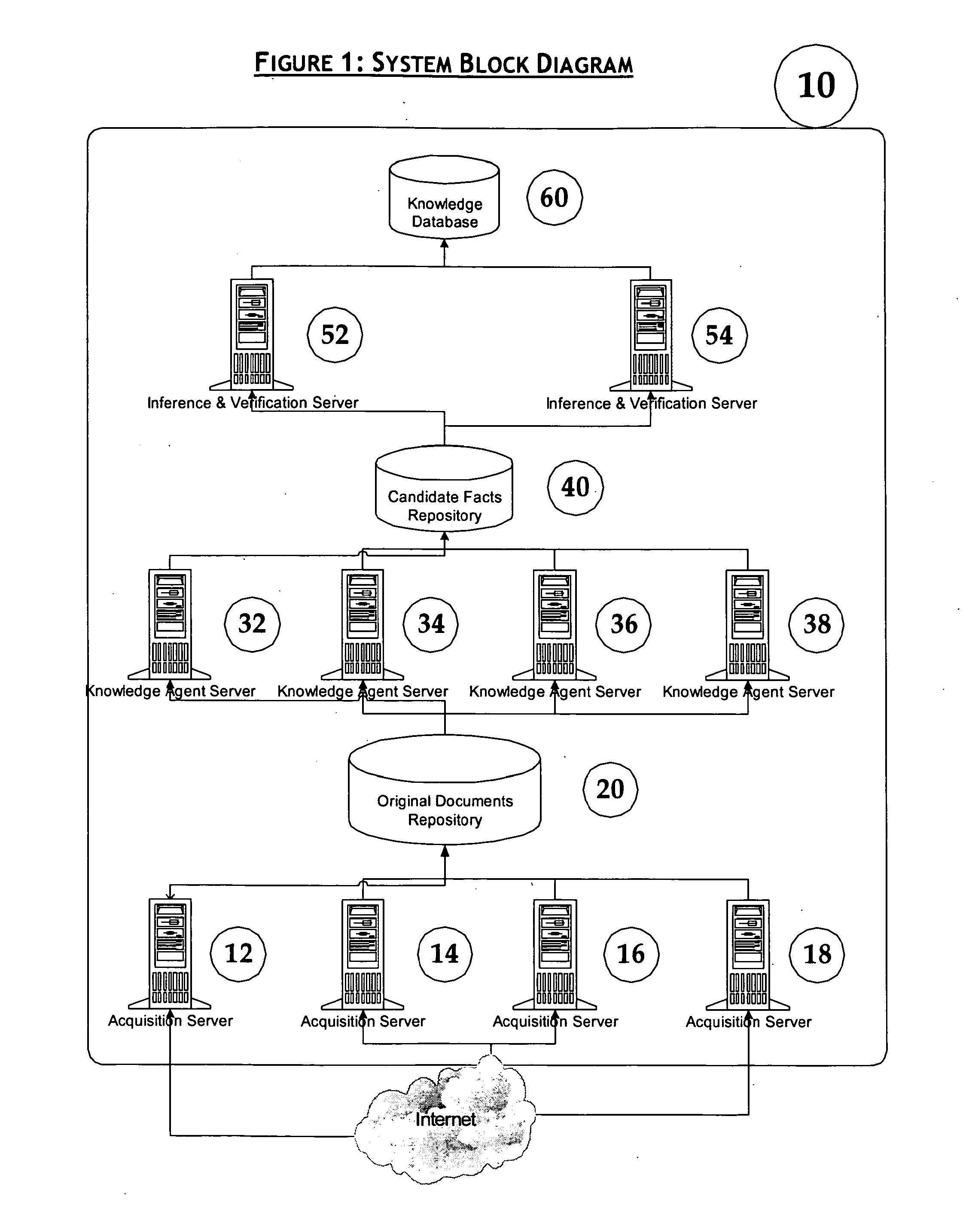
ActiveUS7454430B1Efficiently findEfficiently extract factDigital data information retrievalDigital data processing detailsDomain nameTemporal information
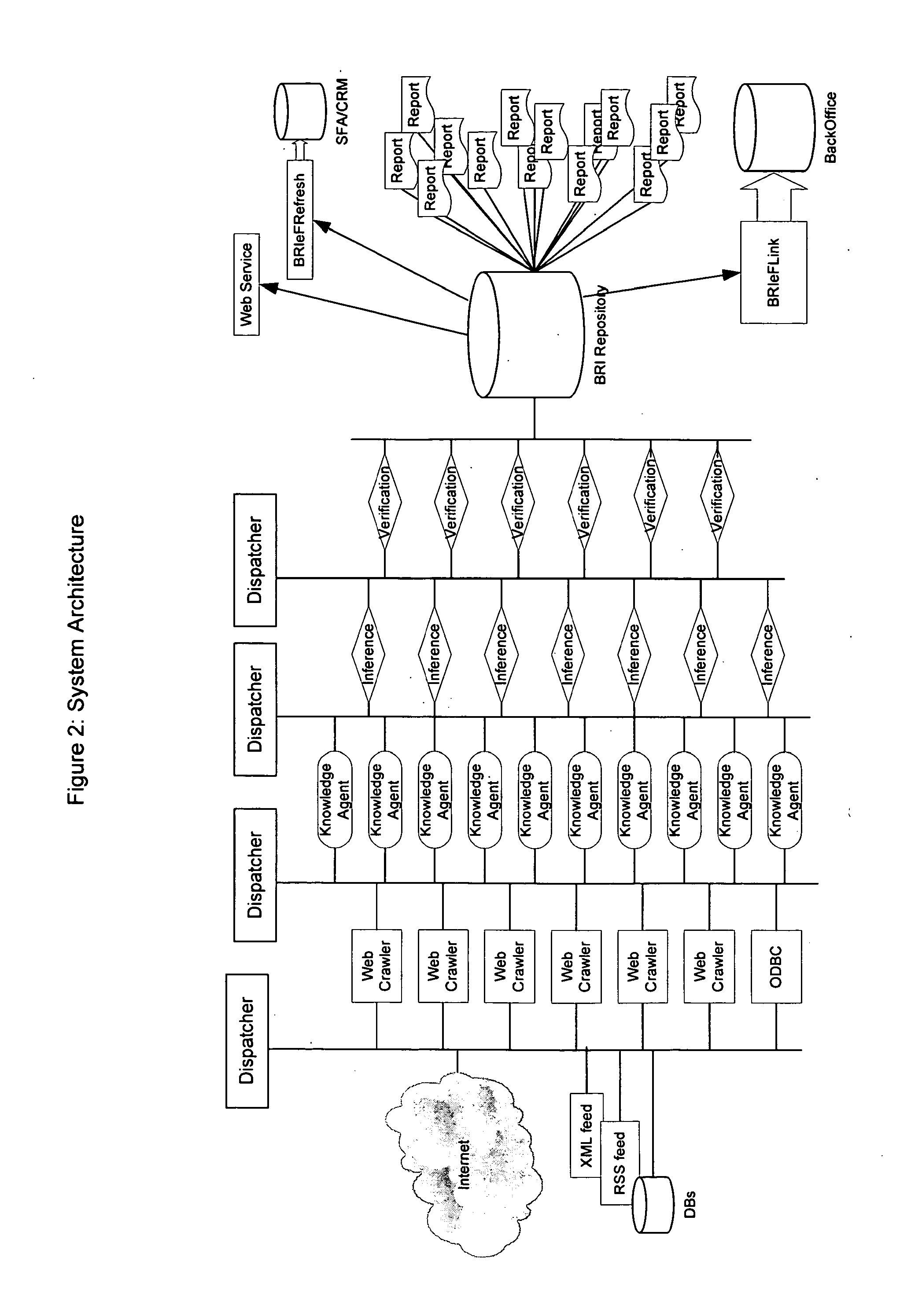
Provided are methods and systems that extract facts of unstructured documents and build an oracle for various domains. The present invention addresses the problem of efficient finding and extraction of facts about a particular subject domain from semi-structured and unstructured documents, makes inferences of new facts from the extracted facts and the ways of verification of the facts, thus becoming a source of knowledge about the domain to be effectively queried. The methods and systems can also extract temporal information from unstructured and semi-structured documents, and can find and extract dynamically generated documents from Deep or Dynamic Web.
Owner:GLENBROOK NETWORKS INC
System and method for automatic building of business contacts temporal social network using corporate emails and internet
InactiveUS20140195449A1Effectively queryEfficiently find and extract factData processing applicationsKnowledge representationSocial webElectronic mail
Provided are system and methods for automatically generating a temporal social network. A method includes extracting a plurality of emails from an email server and extracting pre-facts from the plurality of emails. The method further includes navigating the Internet and extracting pre-facts from the Internet that are related to the pre-facts extracted from the plurality of emails and facts already stored in a temporal social network database. The method further includes determining pre-facts that can be declared facts and storing the facts in the temporal social network database.
Owner:GLENBROOK NETWORKS
System and method for optimizing queries with aggregates and collection conversions
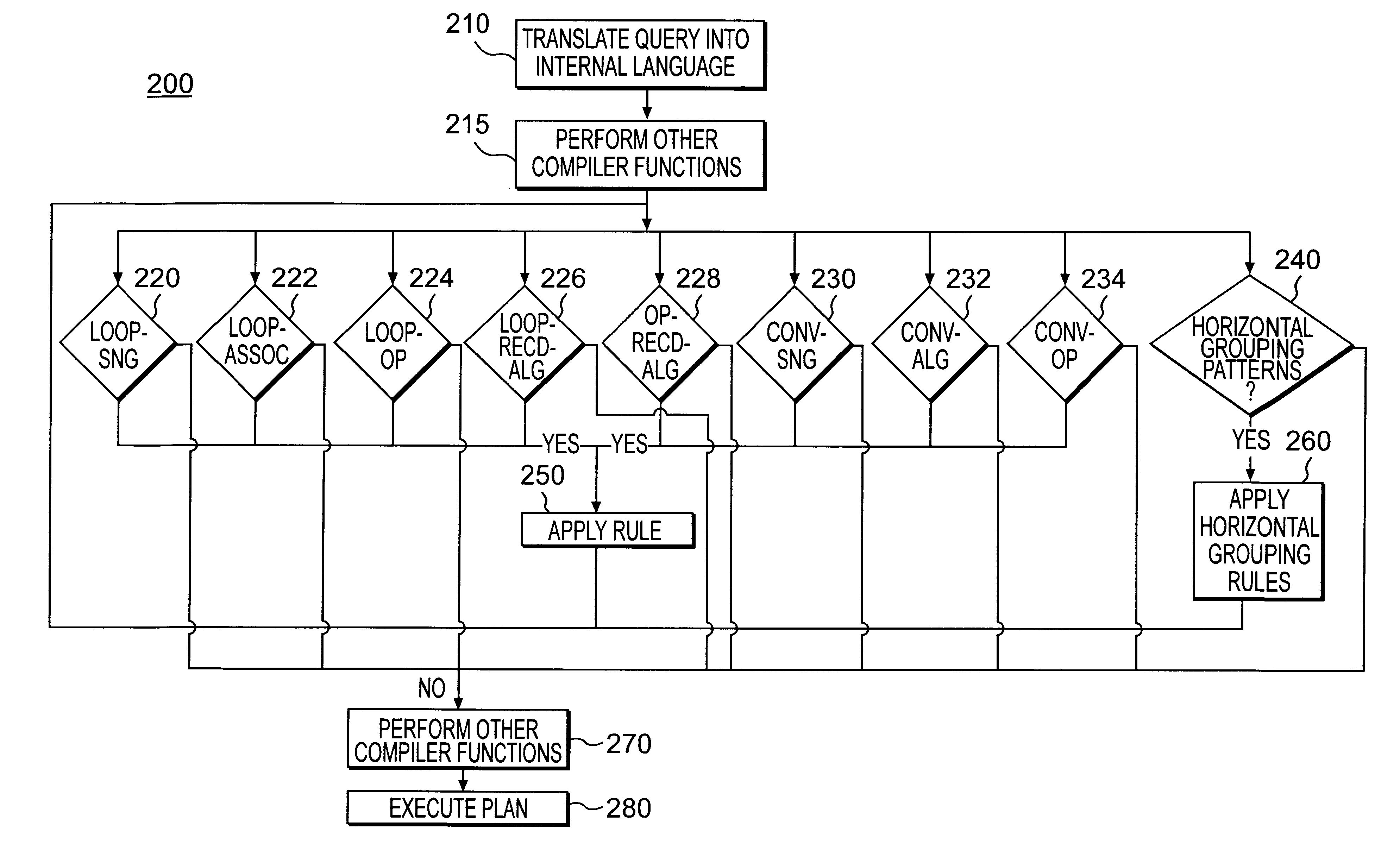
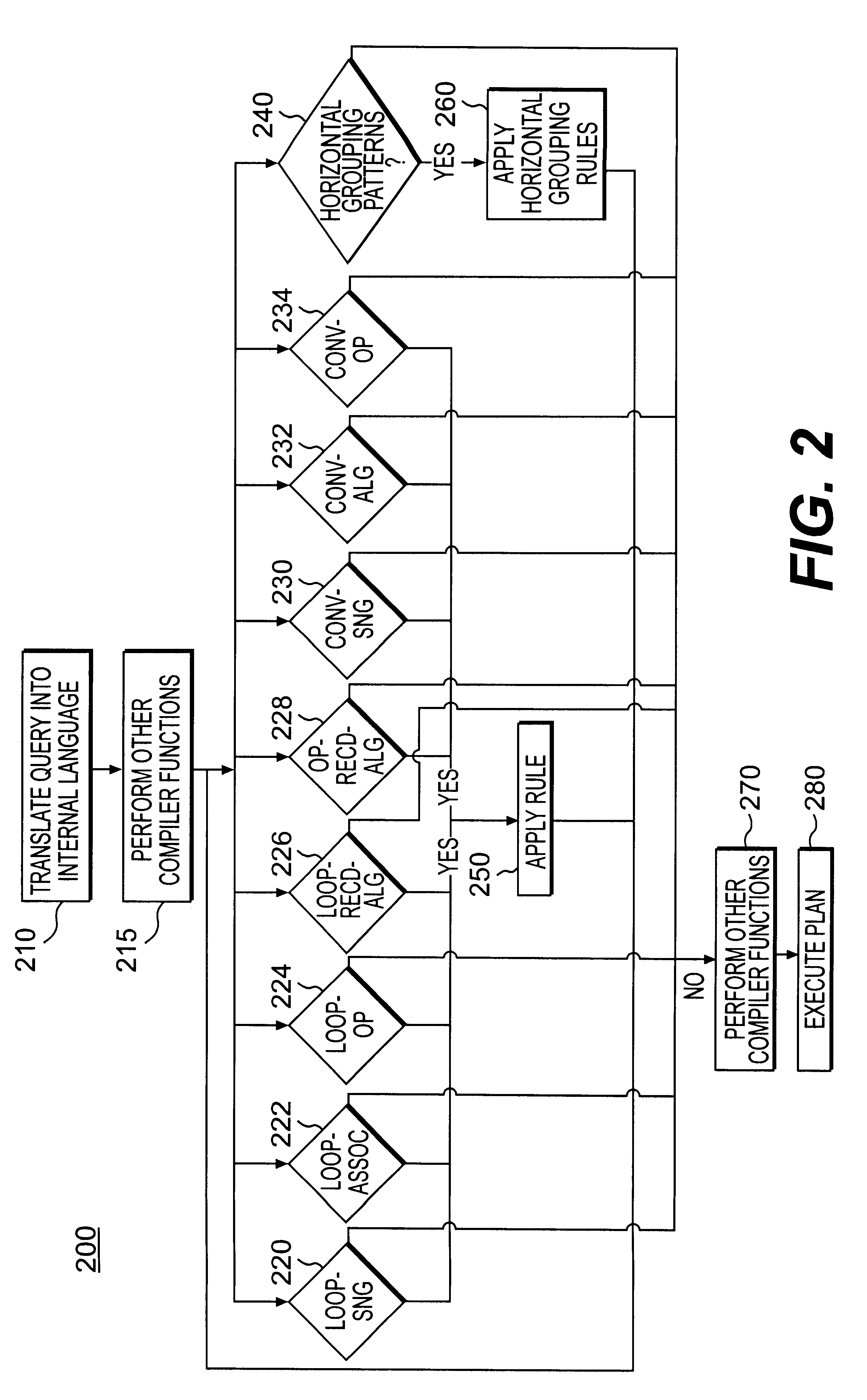
InactiveUS6240406B1Efficient queryData processing applicationsDigital data information retrievalExecution planData mining
Systems and methods for optimizing database queries involving aggregates identify instantiations of rules in an internal language representation of the original query, and then applies the rules to those instantiations to form an optimized query execution plan.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
System and apparatus to manage data using a peer-to-peer network and the blockchain
ActiveUS20190158594A1Low costStrong incentiveKey distribution for secure communicationStructured data retrievalClient-sideDistributed servers
A method of answering a data request directed to a network of distributed servers includes receiving the data request from a client at a server. The method further includes extracting identifying information of requested data in the data request, using the server. The method further includes obtaining location information of the requested data indicating which of the distributed servers is storing the requested data, by comparing the identifying information to a distributed ledger. The method further includes sending the requested data from the server to the client.
Owner:SHADMON MOSHE +3
Decentralized public key management method and system based on trusted network
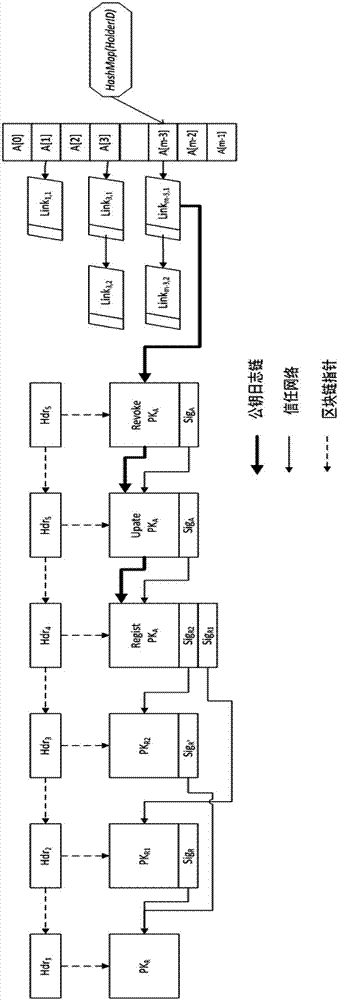
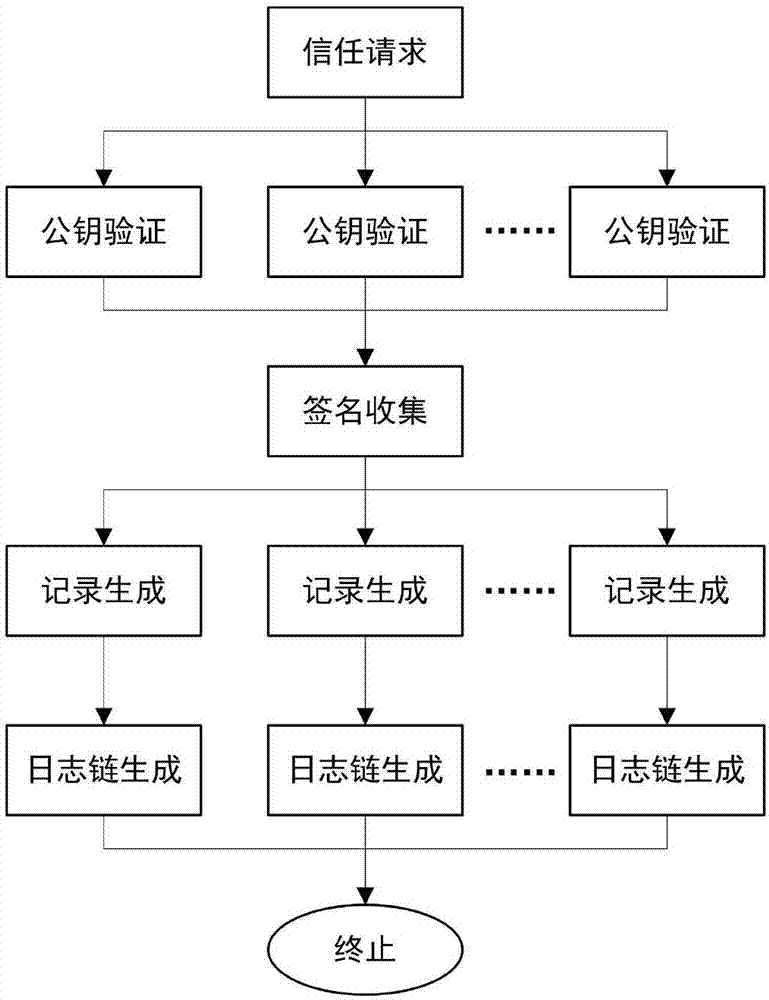
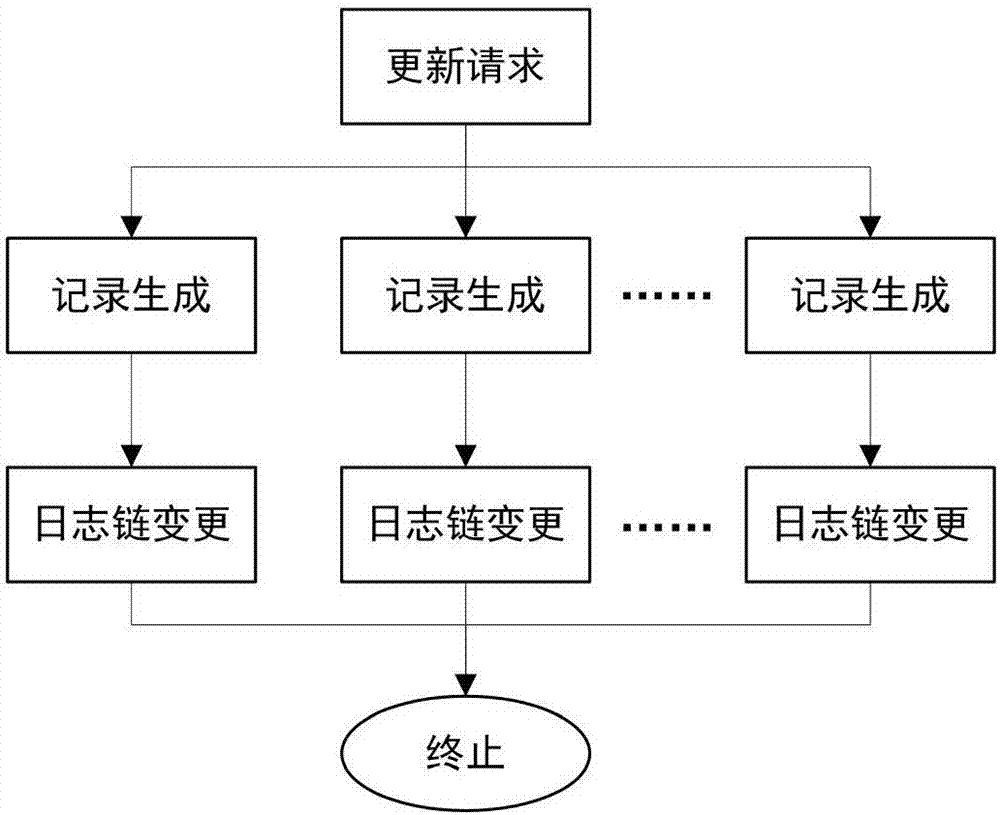
ActiveCN107070644AEfficient verificationEfficient queryKey distribution for secure communicationStructure of Management InformationUser identifier
The invention mainly belongs to the technical field of information security, and specifically relates to a novel decentralized public key management method and a trusted model. The method is constructed on distributed data network platforms such as a block chain and P2P (Peer to Peer) in order to ensure that all nodes in the platforms can participate in maintenance of whole-life-cycle management of public keys of users, and the changes of the public keys of the users in various states in a life cycle are recorded in a bill form. Through the method, public keys passing verification can be recorded and added into a consistent public key storage structure of a platform to be saved; a public key log chain is generated for all public key records of the same user according to a time sequence, and an authentication chain and a trusted network are formed on the basis of a referrer signature; and efficient search of the public keys can be realized on the basis of user identifiers. Through adoption of the method, the public keys of the users can be issued and acquired conveniently and accurately, and the effectiveness, correctness, consistency and non-fraudulence of acquired public keys are ensured. The method can be taken as an infrastructure supporting authentication, encryption, integrity and accountability services.
Owner:UNIV OF SCI & TECH BEIJING
Block chain fragment storage and query method based on erasure codes
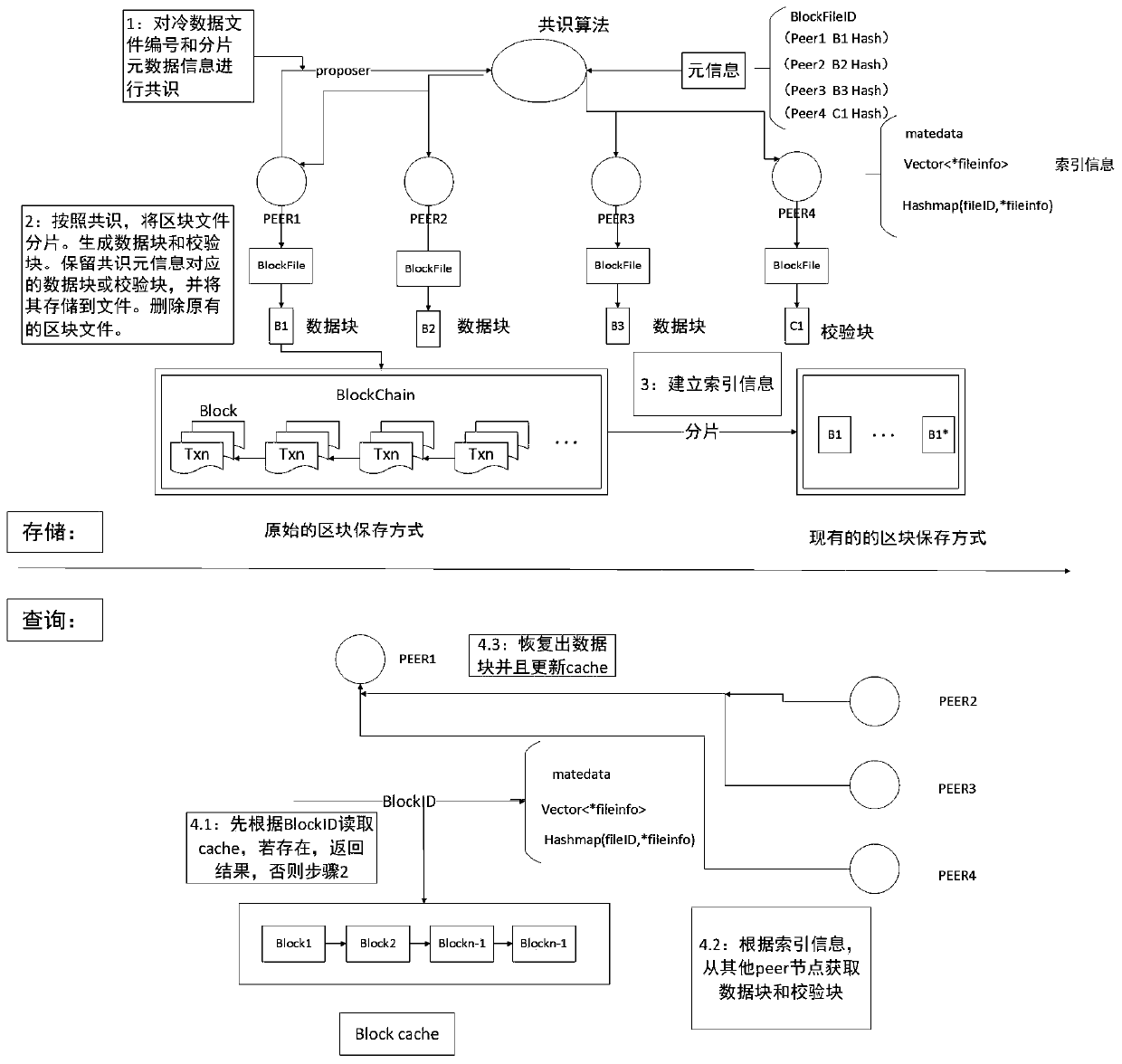
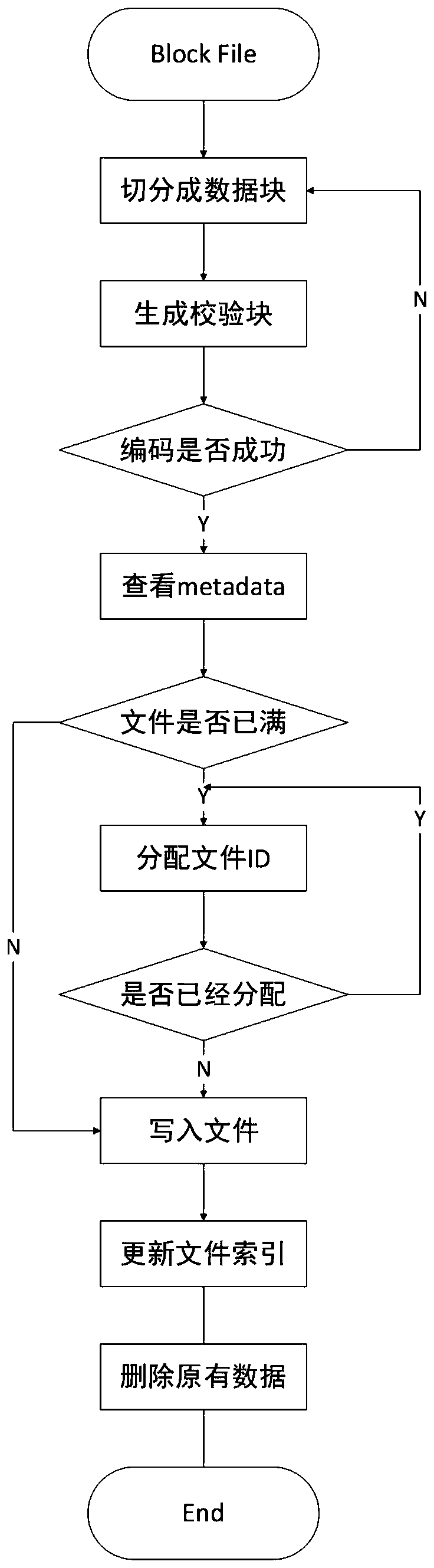
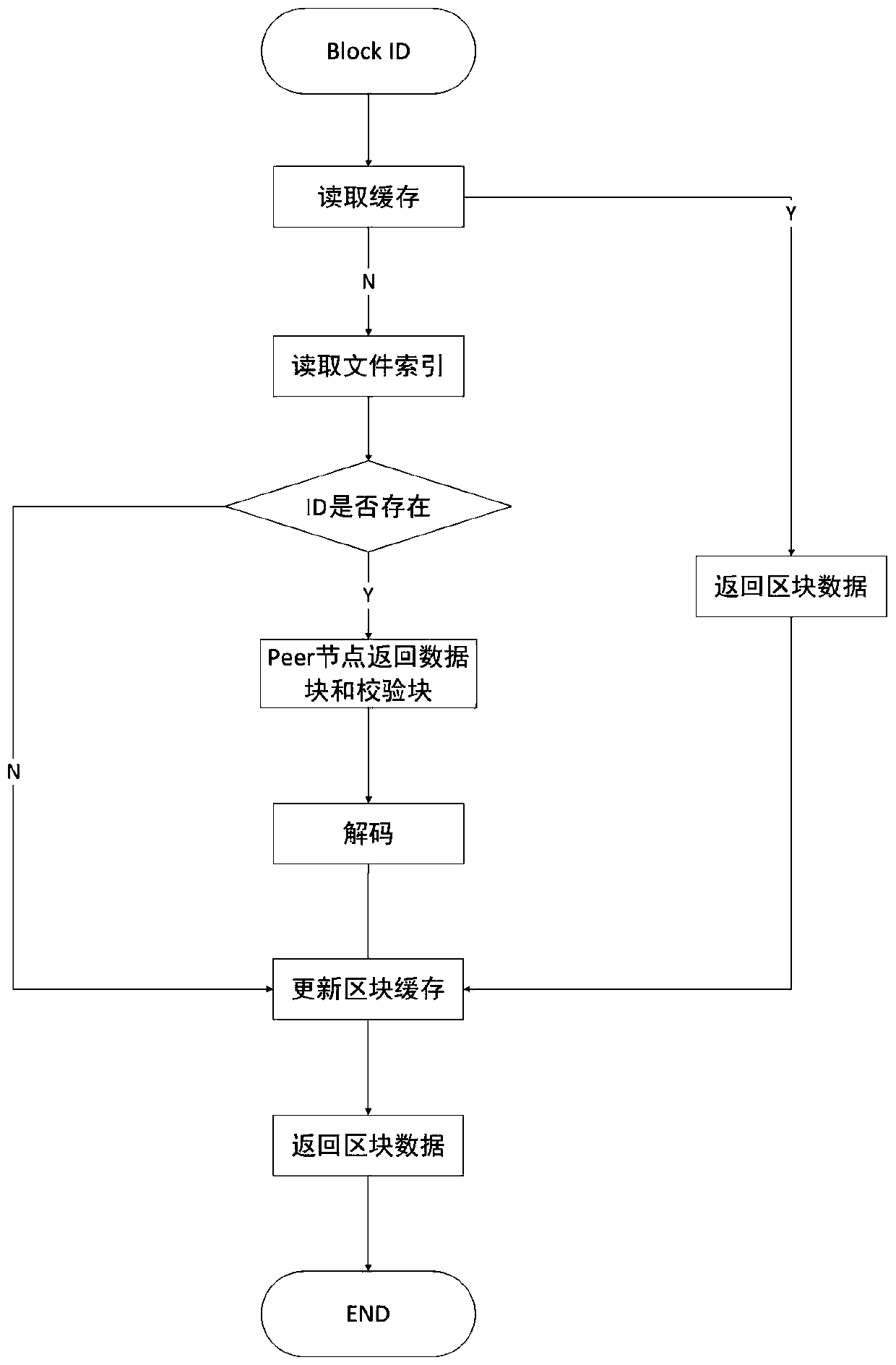
ActiveCN109871366AQuick searchEfficient queryFile access structuresSpecial data processing applicationsByzantine fault toleranceErasure code
The invention discloses a block chain fragment storage and query method based on erasure codes. When the block storage reaches a certain threshold, a block is sliced and stored. The method comprises the following steps that firstly, the meta-information of the block file fragments is consented, after the consensus is achieved, the erasure codes are utilized to fragment the block files within thethreshold value into the data blocks and the check blocks, and each node stores one part of the data blocks and the check blocks, so that the storage cost is reduced, and meanwhile, the data fault tolerance under the Bayer fault tolerance is also realized. Besides, when the block files are fragmented, the corresponding index is established, and the corresponding data block or check block can be queried from each node by utilizing the index, so that the block data can be queried efficiently under the condition that the storage space is saved.
Owner:EAST CHINA NORMAL UNIV
Network discovery
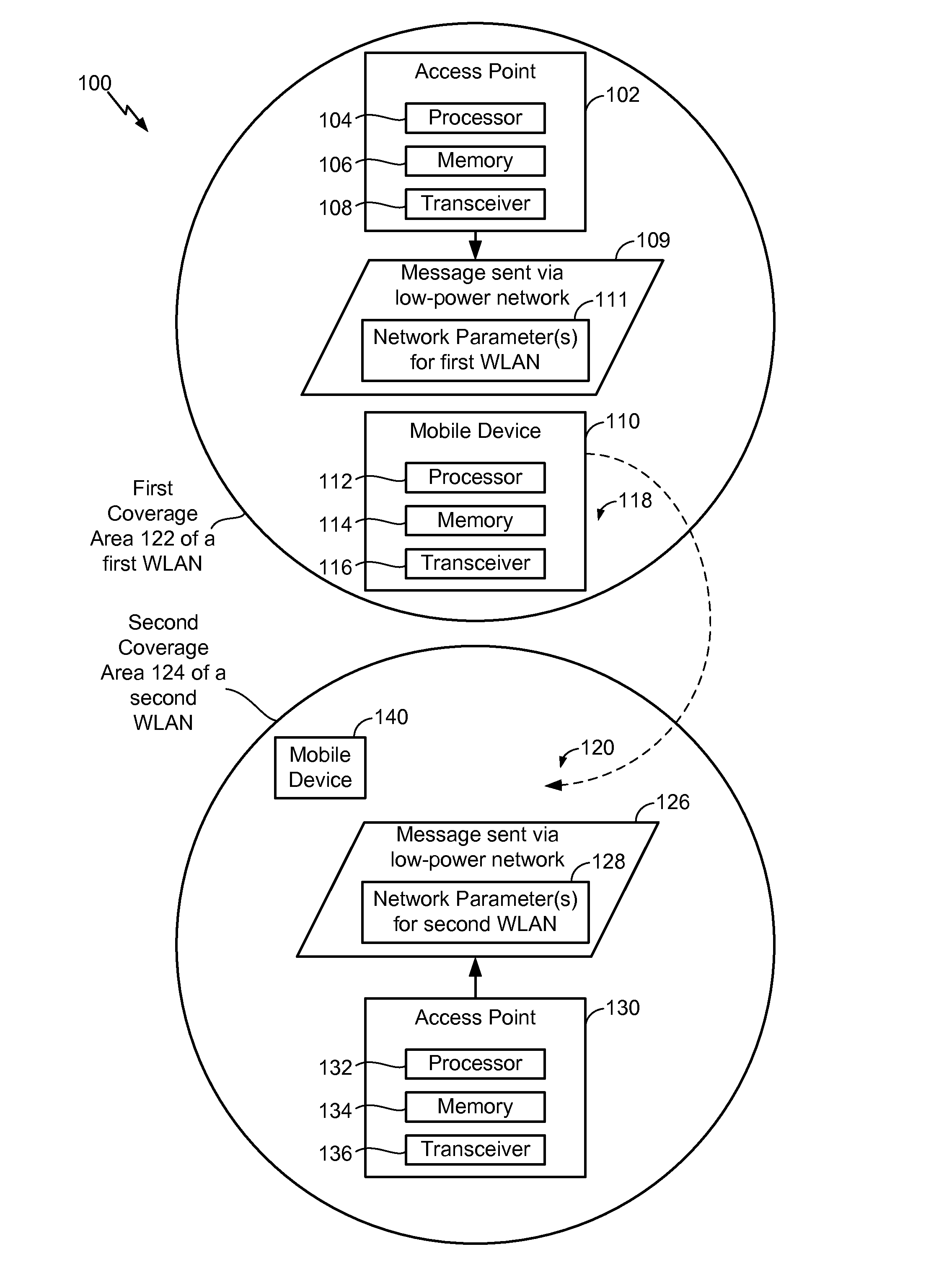
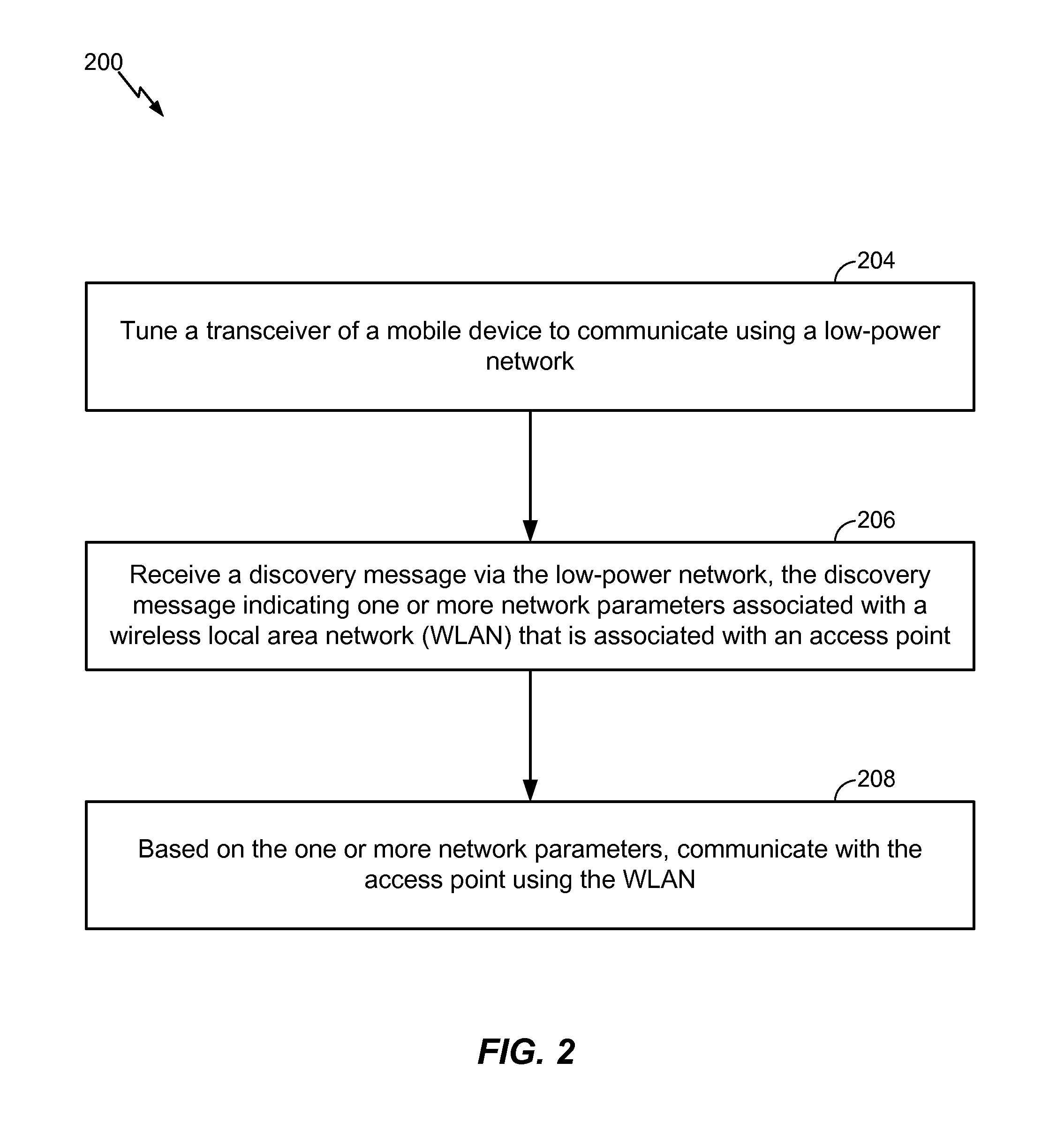
ActiveUS20160127996A1Reduce in quantityEfficient queryPower managementTransmission systemsTransceiverMobile device
A method of operation of a mobile device includes tuning a transceiver of the mobile device to communicate using a low-power (e.g., NAN) network and receiving a discovery message via the low-power (e.g., NAN) network. The discovery message indicates one or more network parameters associated with a wireless local area network (WLAN) that is associated with an access point. The method further includes communicating with the access point using the WLAN based on the one or more network parameters.
Owner:QUALCOMM INC
System and method for an interactive shopping news and price information service
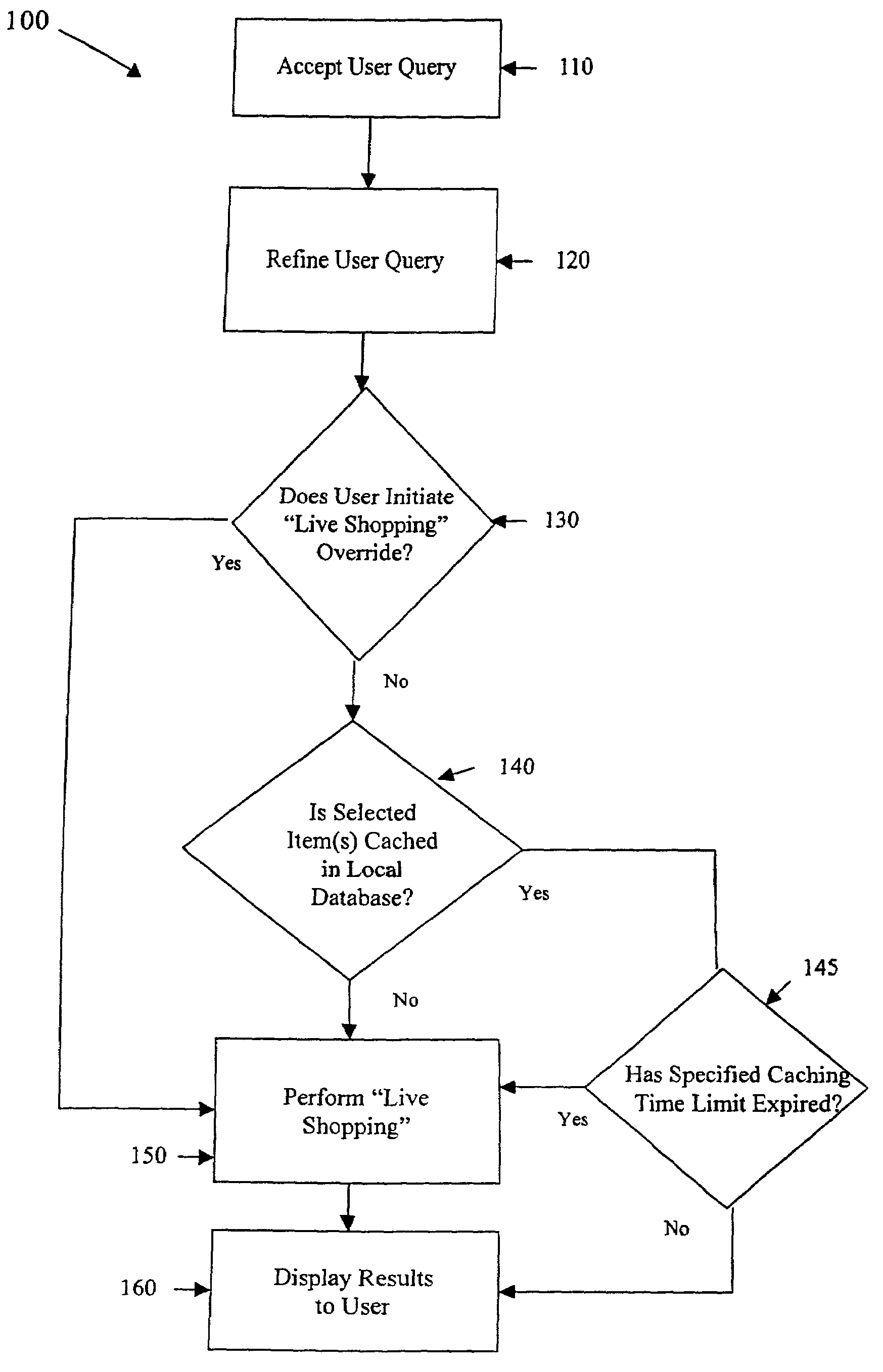
ActiveUS7177818B2Efficient queryPreserving Internet bandwidth.Web data indexingCustomer communicationsThe InternetE-commerce
A system and associated method for assisting a user to efficiently query for product information and promotional information available from electronic commerce websites over the Internet includes a sub-server for searching the electronic commerce websites, a controlling server, and a local database. The method involves determining whether product information related to a user query is cached in a local database and if the requested information is not cached, searching the electronic commerce websites for the requested information.
Owner:ANDERSON MERCHANDISERS
Object data model for a framework for creation, update and view navigation of data objects and textual annotations of relations between data objects
InactiveUS6609132B1EffectivelySave storage spaceData processing applicationsObject oriented databasesUser inputBusiness enterprise
A method and system for displaying information characterizing the semantics of relations between objects. For each given relation between at least one subject object and at least one direct object, bi-directional modifier data is stored in a separate table and characterizes the semantics of a relationship between objects of different type. A bi-directional modifier is stored in distinct tables and comprises arbitrary text strings defined by user input. Test is linked to a relation between at two different object types and represents text. The present invention may be used in a wide assortment of software applications, including enterprise applications.
Owner:REVELINK
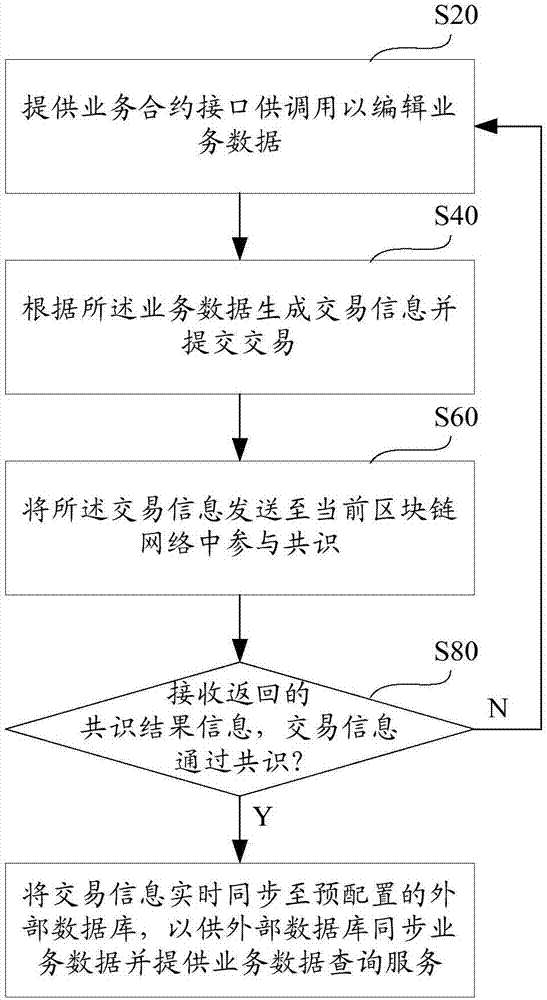
Business data synchronization method and system based on block chain and database system
InactiveCN106874393AEfficient queryGuaranteed experienceFinanceSpecial data processing applicationsData synchronizationBusiness data
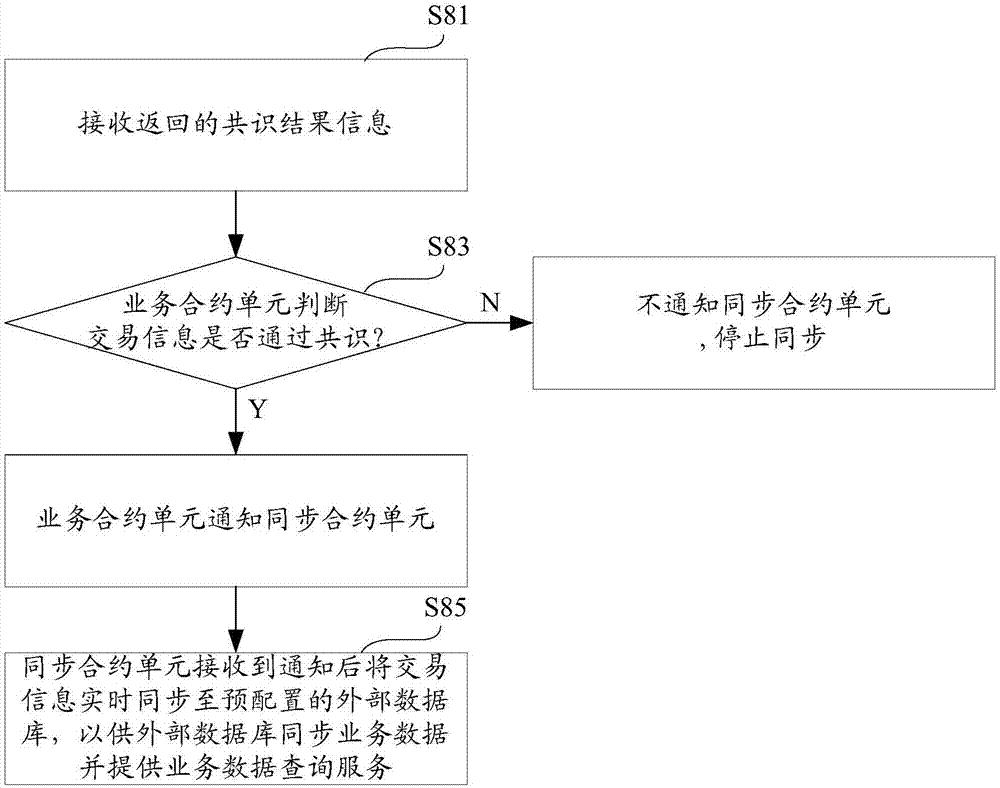
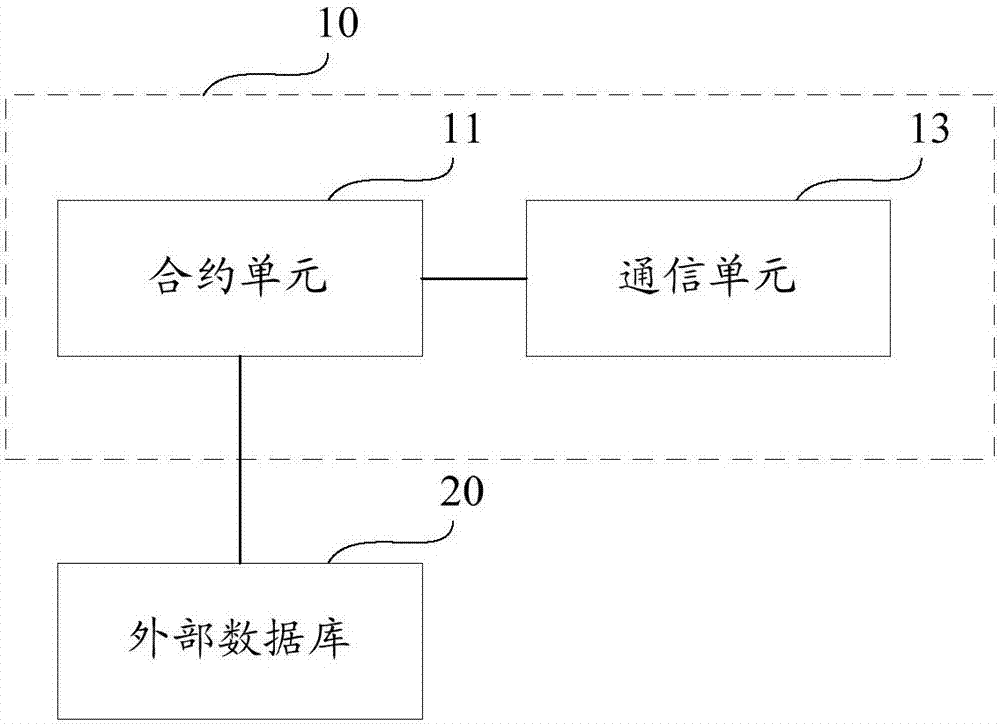
The invention provides a business data synchronization method and a business data synchronization system based on a block chain and a database system. The method comprises the following steps: providing a business contract interface for calling, so as to edit business data; generating transaction information according to the business data and submitting a transaction; sending the transaction information to a current block chain network and participating in agreement processing; receiving returned agreement result information; and if the transaction information reaches an agreement, synchronizing the transaction information to a pre-configured external database in real time, so as to synchronize the business data by the external database and provide a business data inquiry service. According to the business data synchronization method and system, the business data is synchronized to the external database and the inquiry service is provided by the external database to realize efficient inquiry of the business data in the block chain, so that user experience is guaranteed.
Owner:BEIJING ZHONGXIANG BIT TECH
Space-time coding method, space-time index and query method and device
ActiveCN109992636AEfficient organizationEfficient managementGeographical information databasesSensing dataLongitude
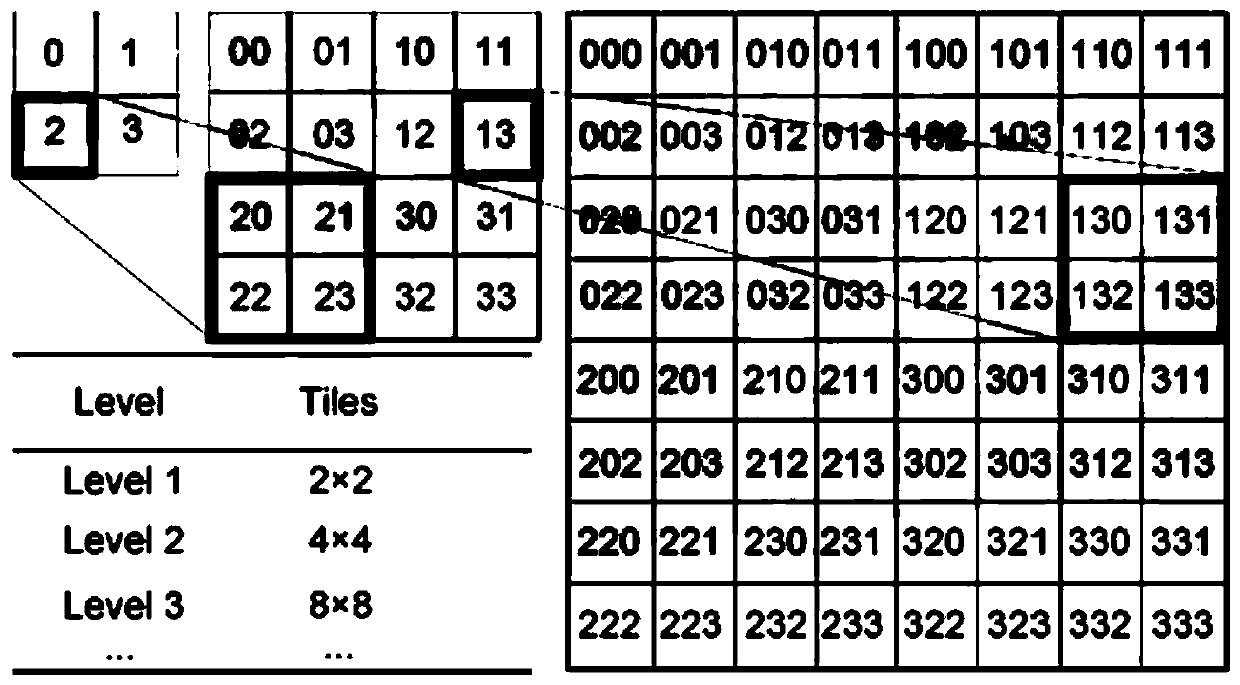
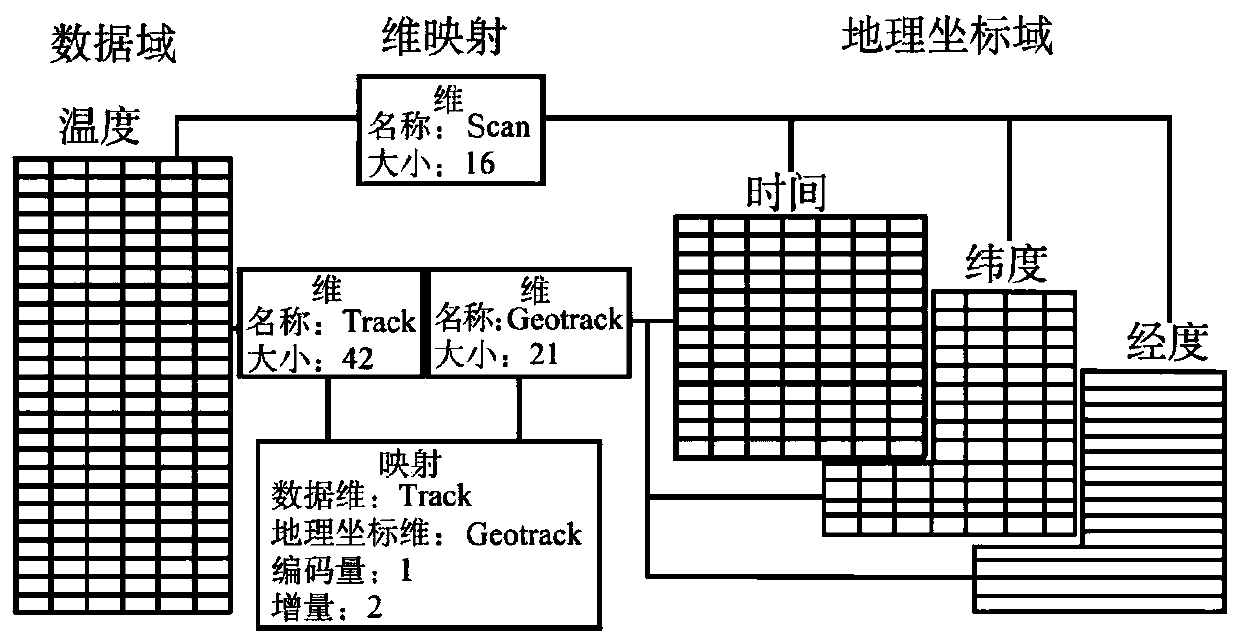
One or more embodiments of the invention disclose a space-time coding method, a space-time index and a query method and device, which are used for realizing efficient organization, management and query of mass multi-source remote sensing data. The method comprises the following steps: dividing a latitude and longitude space of the earth according to a specified division mode to obtain a pluralityof grids; wherein the corresponding mesh numbers in the longitude direction and the latitude direction are the same; wherein the specified subdivision mode comprises specified subdivision hierarchies;carrying out integer coding on the coordinate information corresponding to each grid to obtain a first coded value corresponding to each grid; and establishing the grid and an association relationship between the first coding value corresponding to each grid and the remote sensing image data. According to the technical scheme, global multi-scale grid integer coding can be used for achieving position association with multi-source remote sensing data, and space-time indexing and query of the multi-source remote sensing data are achieved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
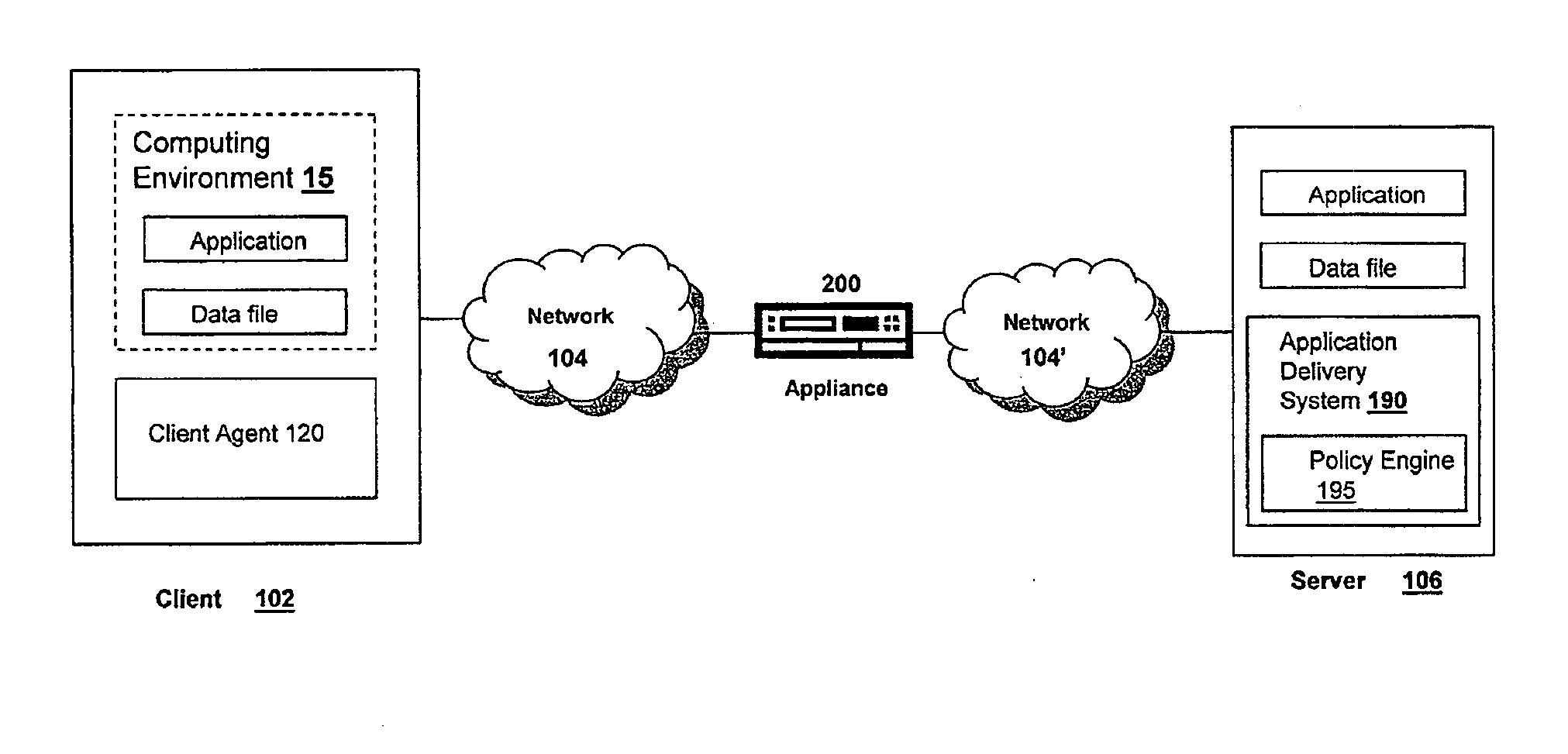
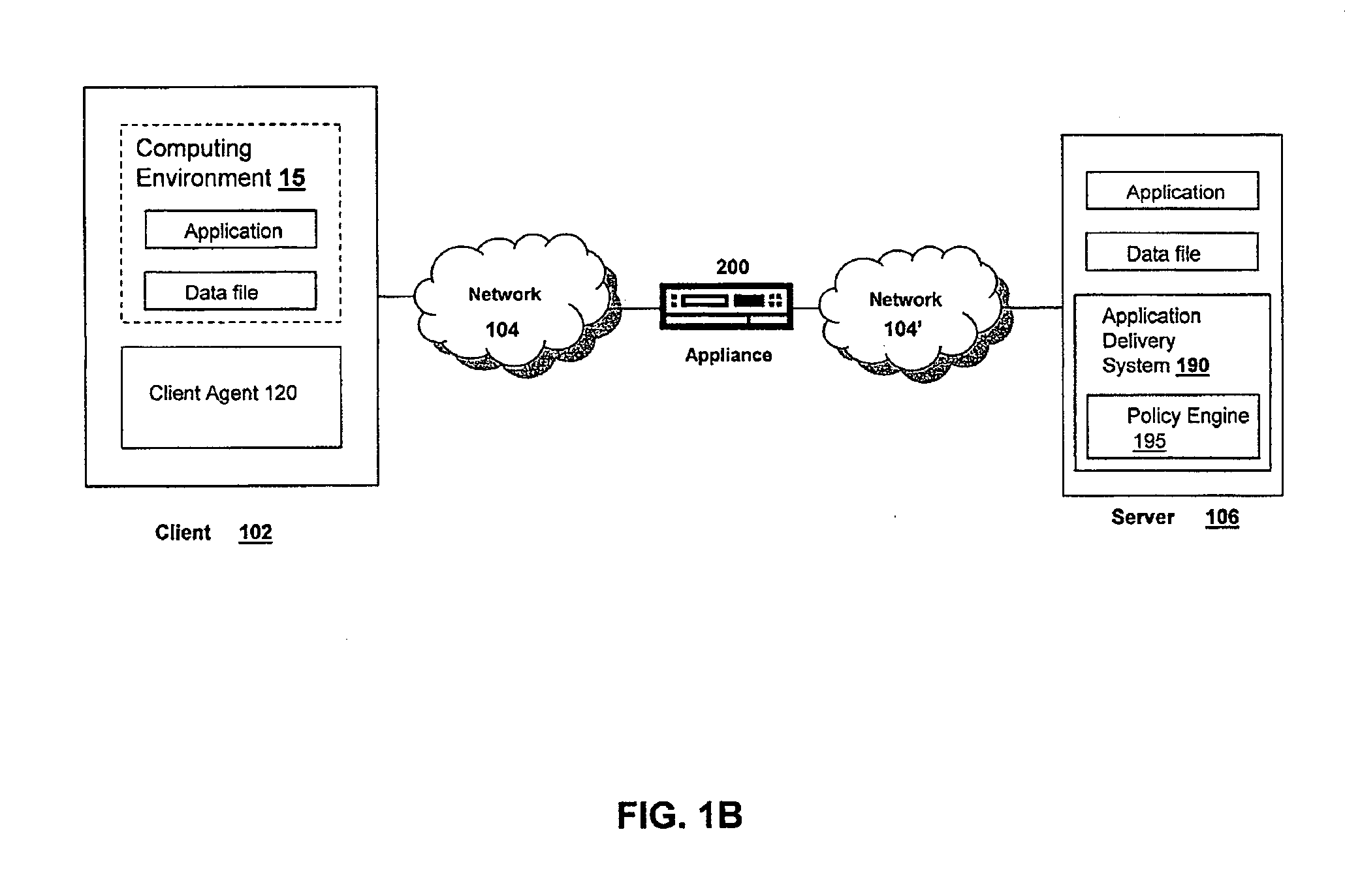
Systems and Methods of Providing An Intranet Internet Protocol Address to a Client on a Virtual Private Network
ActiveUS20080046994A1Efficiently assigningEfficient managementDigital data processing detailsAnalogue secracy/subscription systemsClient agentWebID
The intranet IP address management solution of the appliance and / or client described herein provides an environment for efficiently assigning, managing and querying virtual private network addresses, referred to as intranet IP (IIP) addresses of virtual private network users, such as a multitude of SSL VPN users on an enterprise network. The appliance provides techniques and policies for assigning previously assigned virtual private network addresses of a user to subsequent sessions of the user as the user logs in multiple times or roams between access points. This technique is referred to IIP stickiness as the appliance attempts to provide the same IIP address to a roaming VPN user. The appliance also provides a configurable user domain naming policy so that one can ping or query the virtual private network address of a user by an easily referenceable host name identifying the user. The appliance and / or client agent also provide techniques to allow applications to seamlessly and transparently communicate on the virtual private network using the virtual private network address of the user or client on the private network.
Owner:CITRIX SYST INC
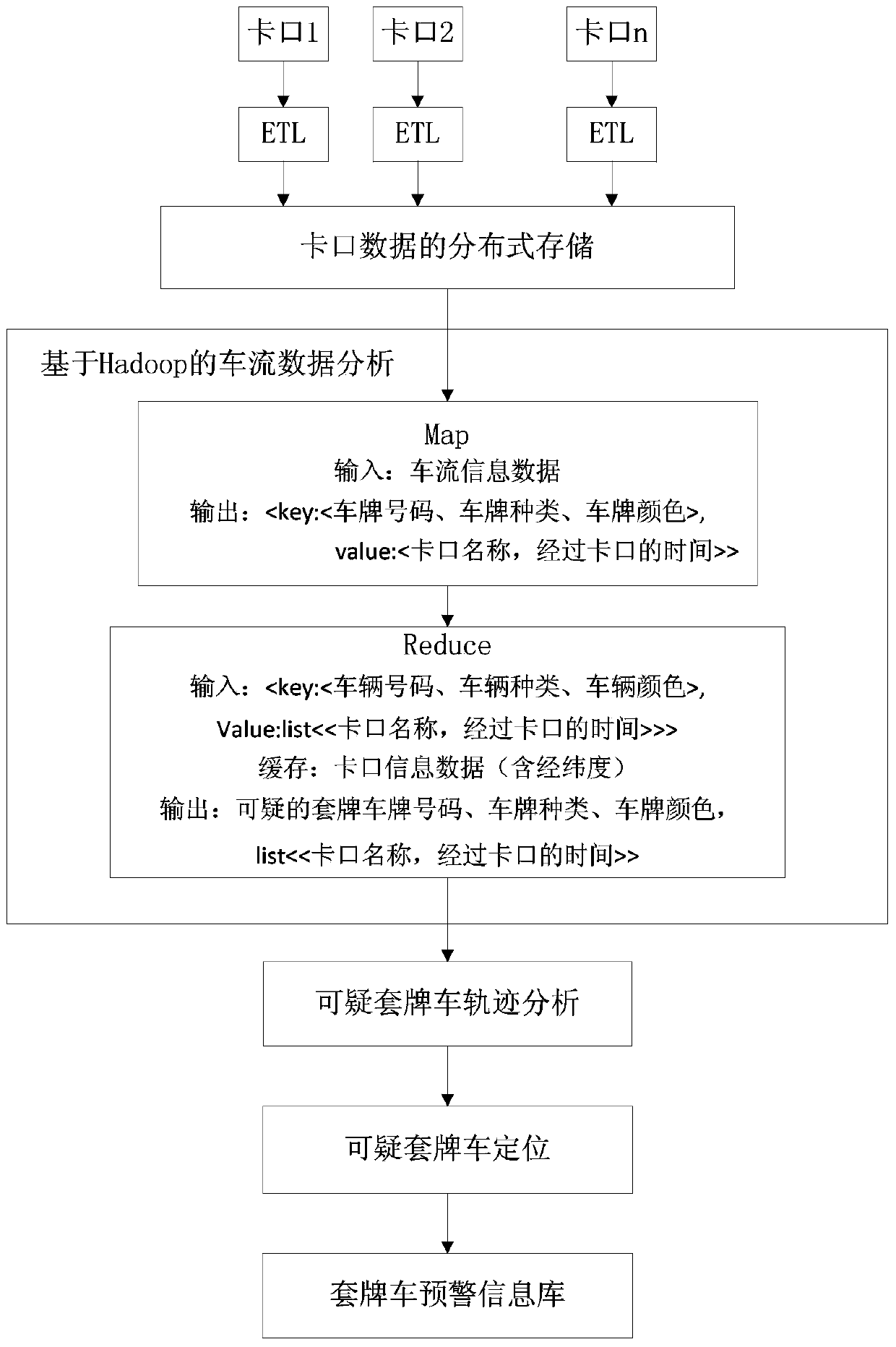
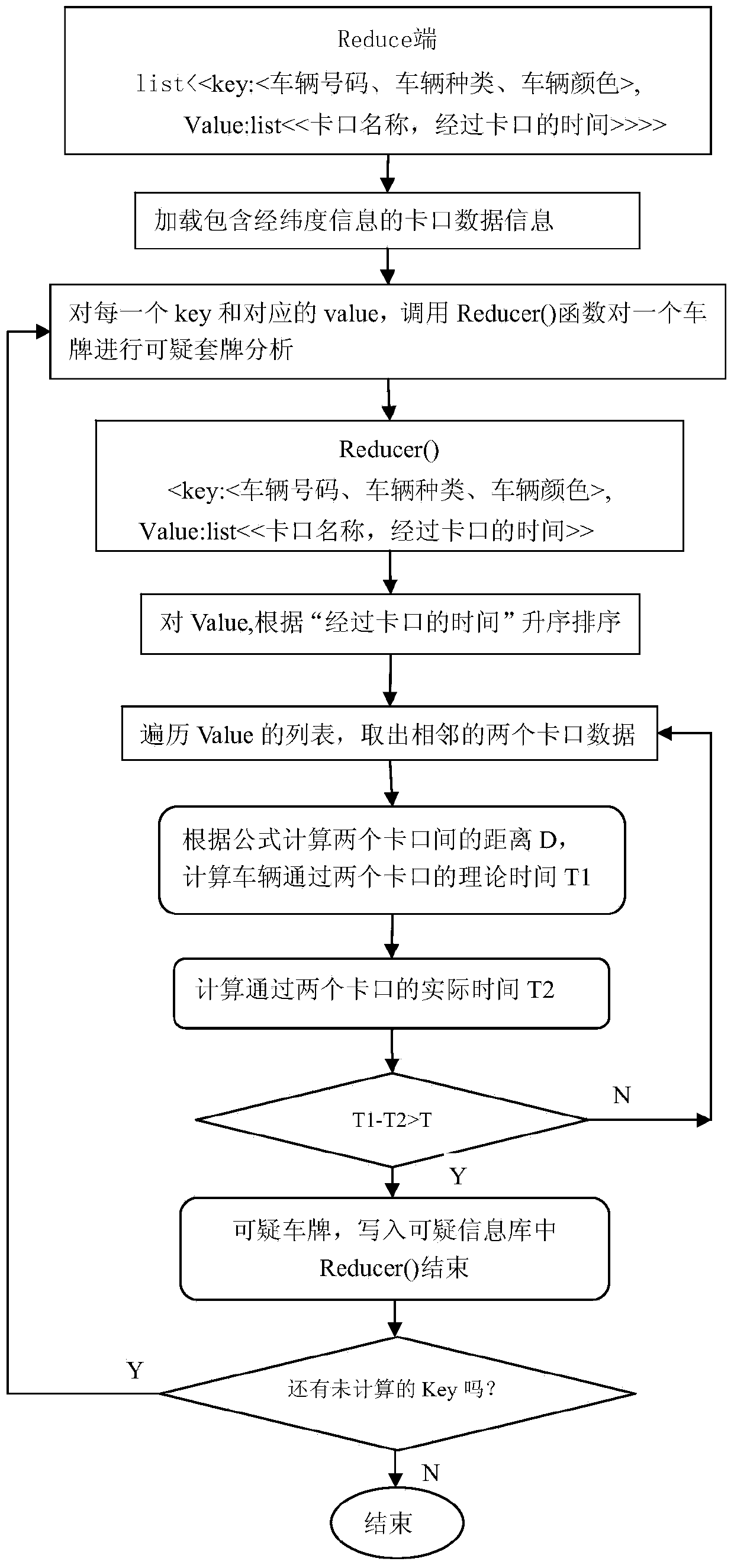
Fake-licensed car recognition method and system based on Hadoop
ActiveCN104200669AEfficient queryEfficient analysisRoad vehicles traffic controlSpecial data processing applicationsTrack analysisData processing
The invention discloses a fake-licensed car recognition method and system based on Hadoop. The method includes the following steps sequentially: preprocessing and collecting information of vehicles and collected by intelligent bayonet systems and adopting an HBase distributed database to store vehicle flow data; utilizing the Hadoop distributed frame to conduct modeling and analysis on the vehicle flow data and the bayonet data, utilizing a Map-Reducer programming frame to achieve suspicious fake-licensed car recognition, conducting traveling track analysis on suspicious fake-licensed cars and building a fake-licensed car early warning information base. According to the method and the system, a distributed technology is adopted, the problem in the prior art that the fake-licensed cars cannot be recognized effectively due to large data processing quantity is solved, data above the TB level can be effectively processed, the fake-licensed cars can be found accurately, and the method and system provides a basis for the traffic management department to investigate the fake-licensed cars.
Owner:SOUTH CHINA UNIV OF TECH +1
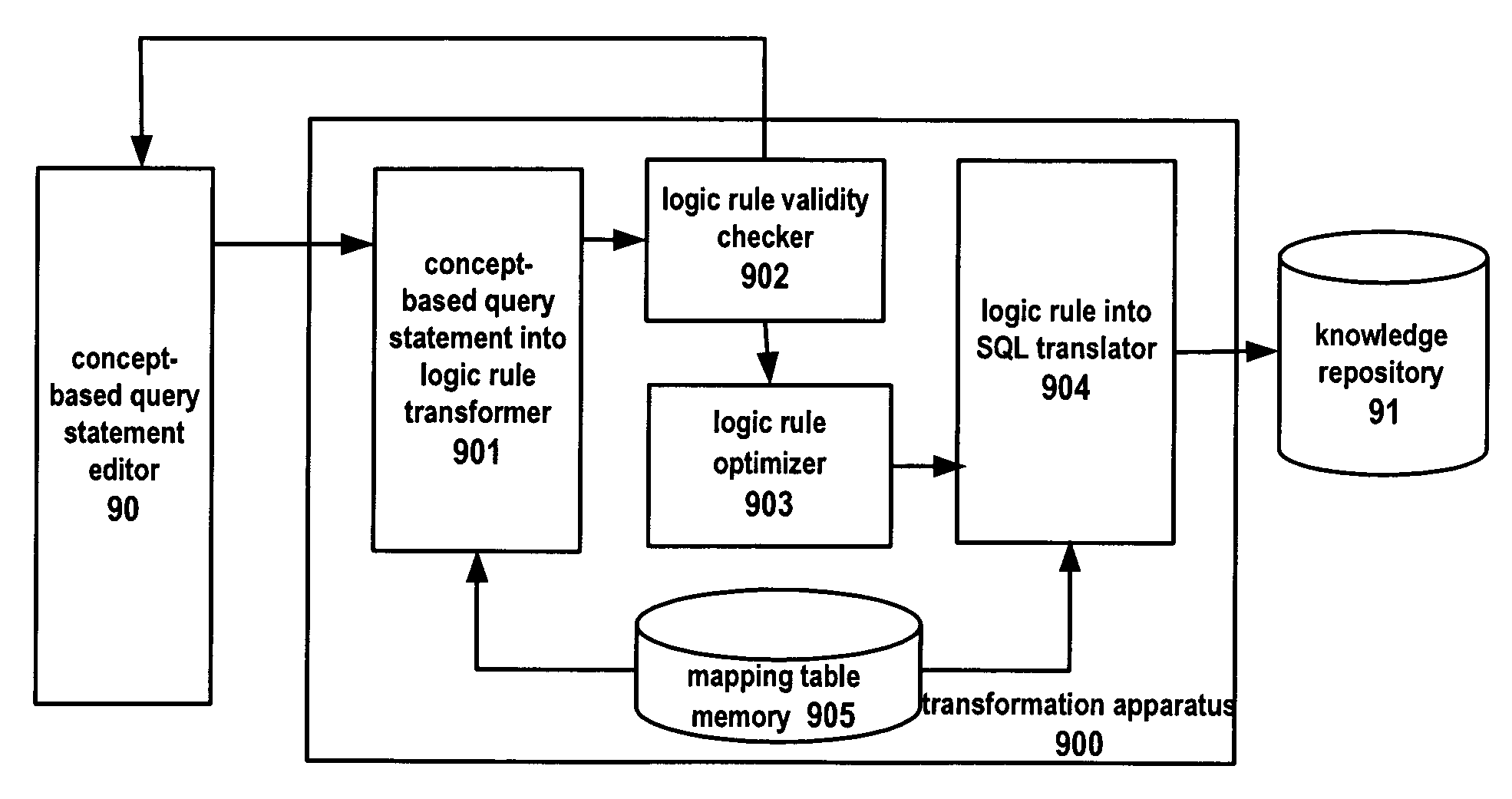
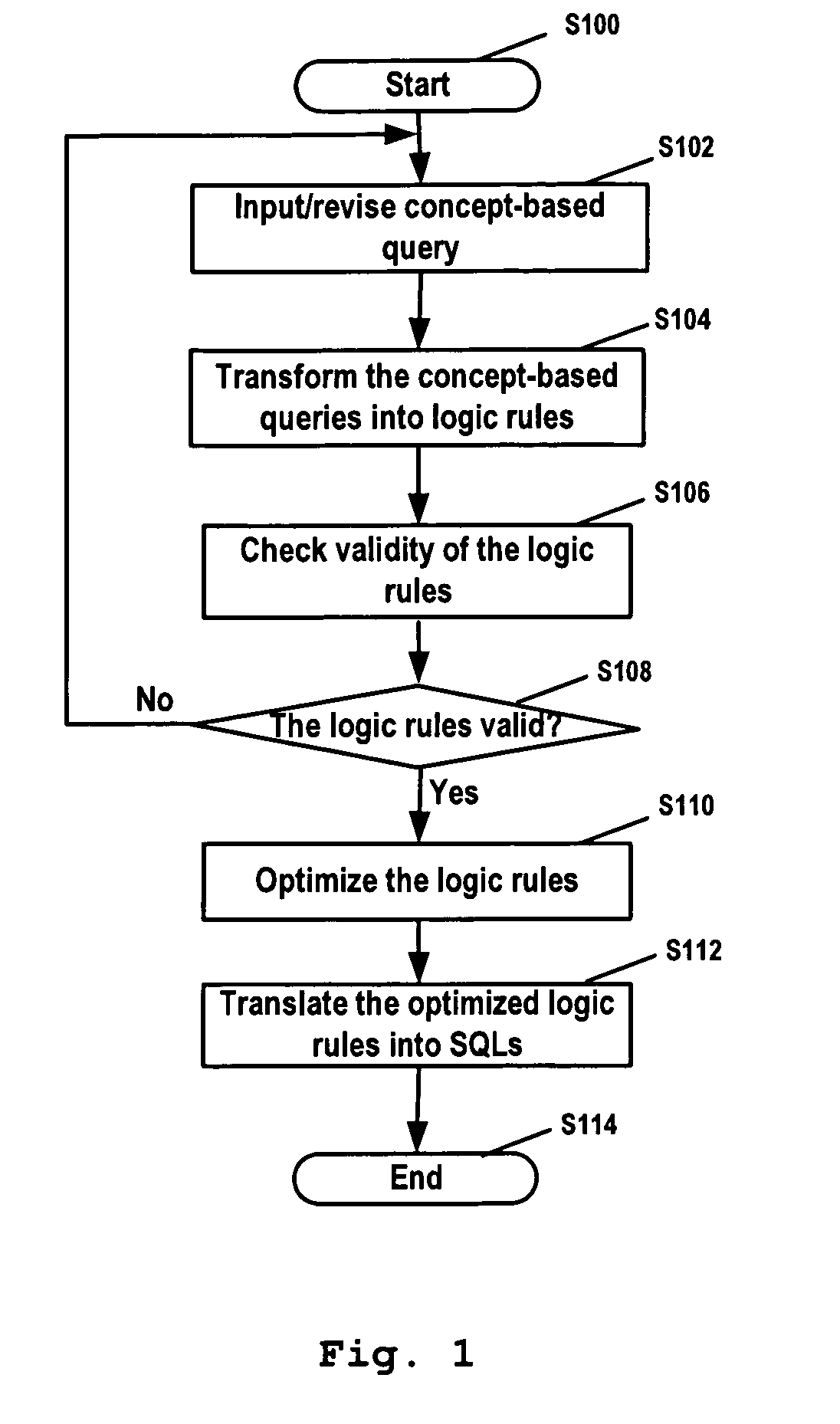
Database query language transformation method, transformation apparatus and database query system
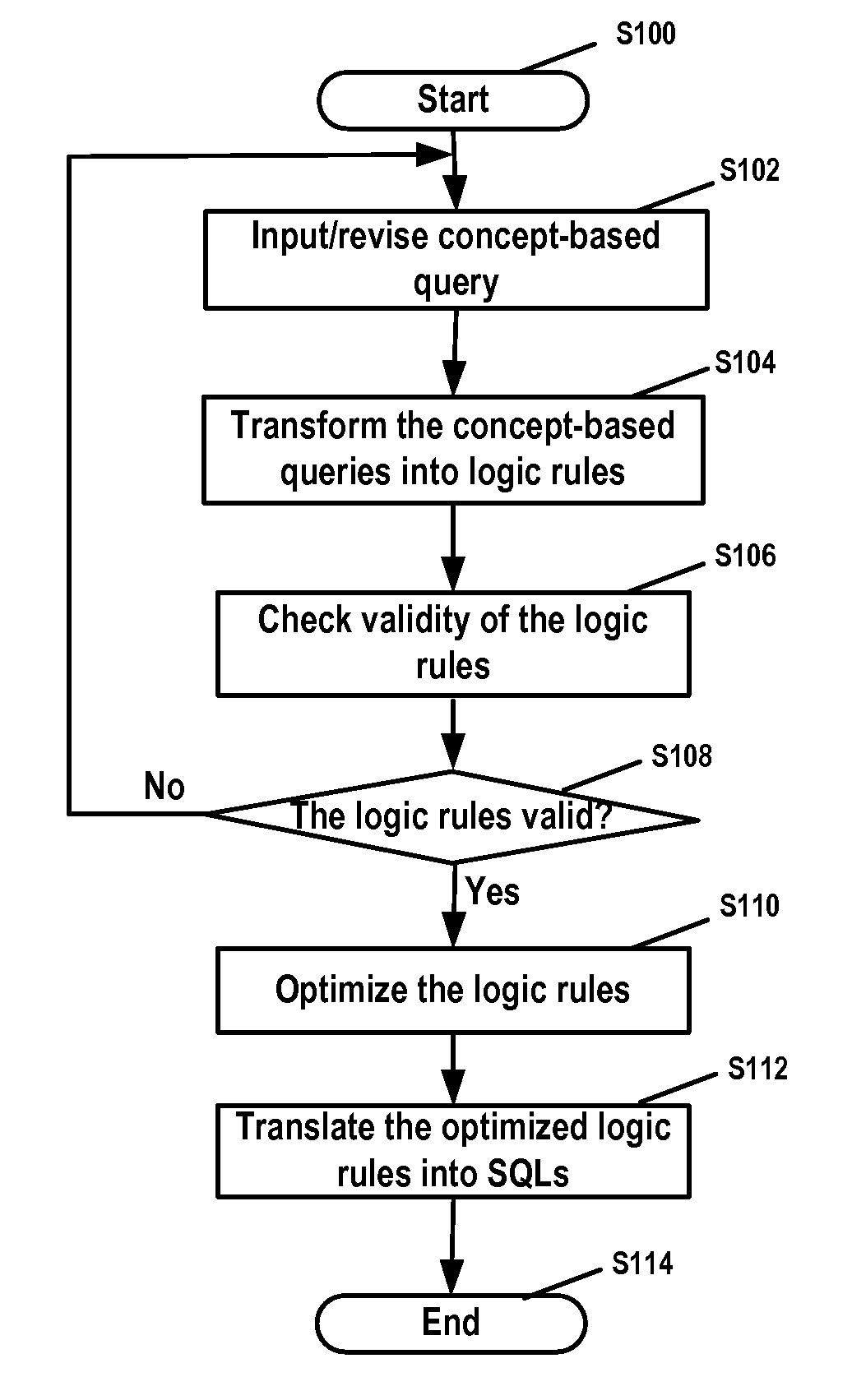
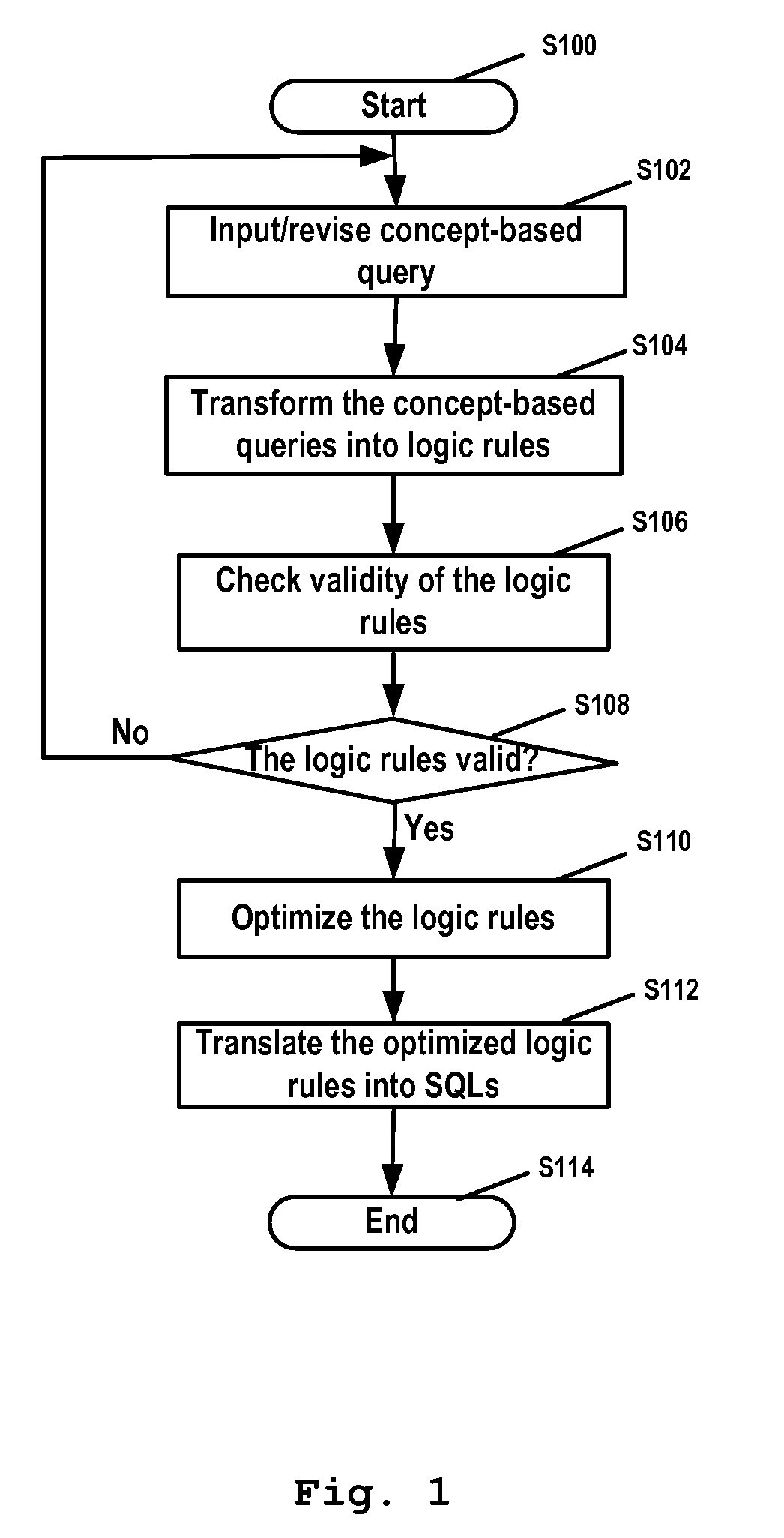
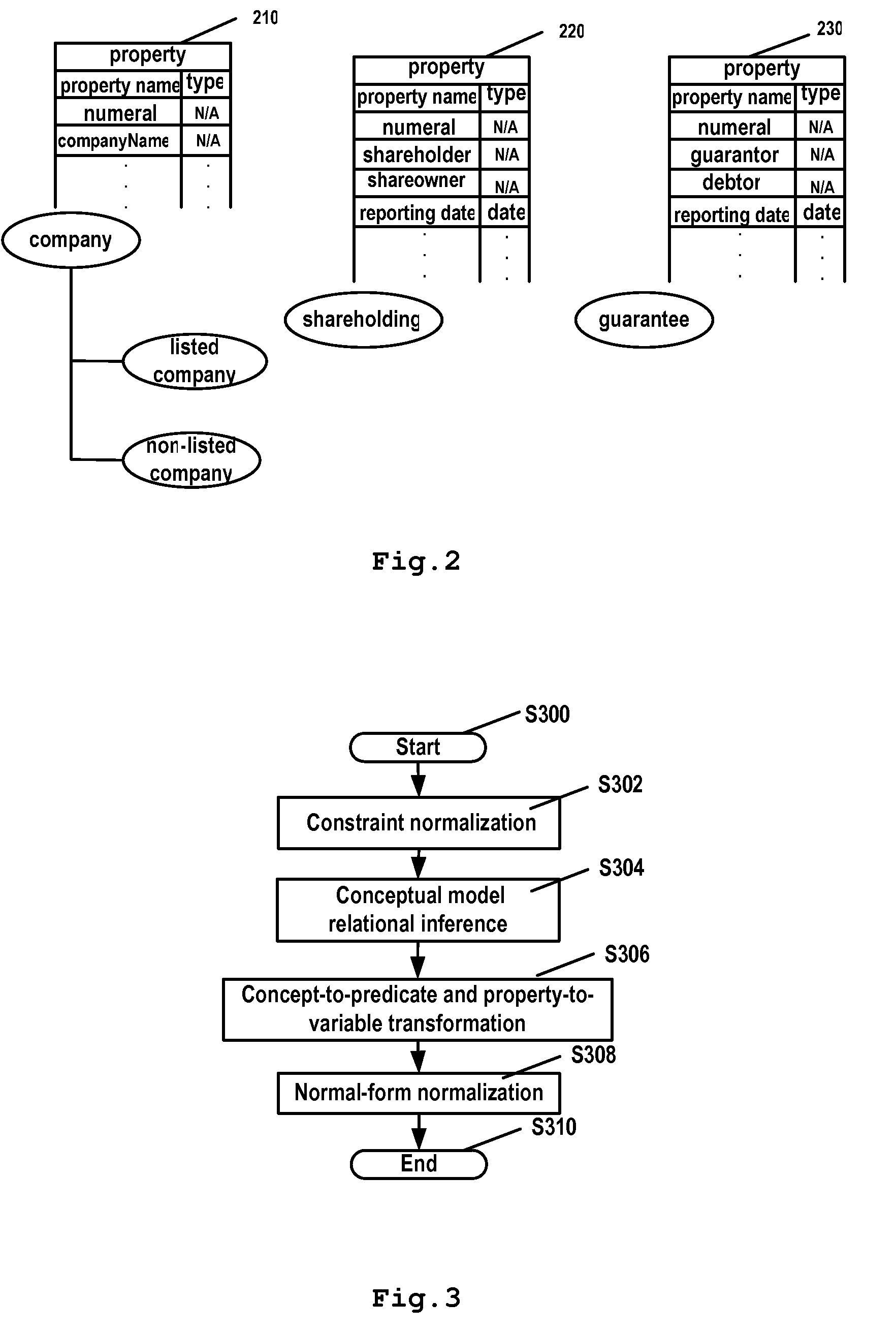
ActiveUS20090094216A1Efficient queryExpressed in concept-based query languageData processing applicationsDigital data information retrievalRelational databaseQuery statement
The present invention provides a method for transforming a concept-based query into SQL query statements, comprising the steps of: transforming inputted concept-based queries into logic rules; checking validity of the logic rules; optimizing the valid logic rules; and translating the logic rules into SQL query statements in accordance with the optimization result. The present invention further provides corresponding transformation engine, database query system and computer program product. The present invention facilitates people to use more descriptive query language to query data stored in relational database. Furthermore, the present invention can automatically generate the correct and efficient SQL query statements so that people's efforts to deal with complex data model are saved significantly.
Owner:IBM CORP
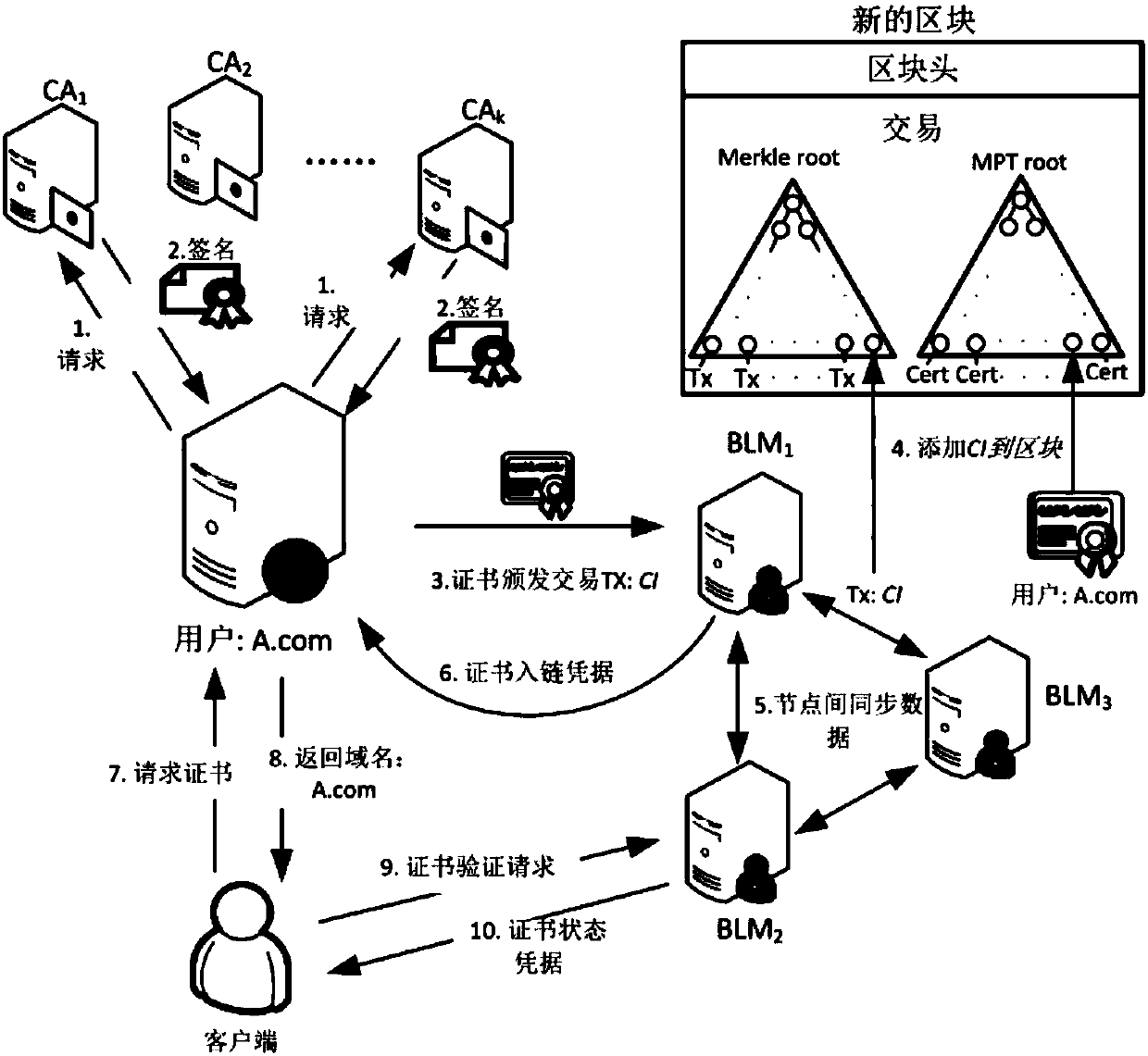
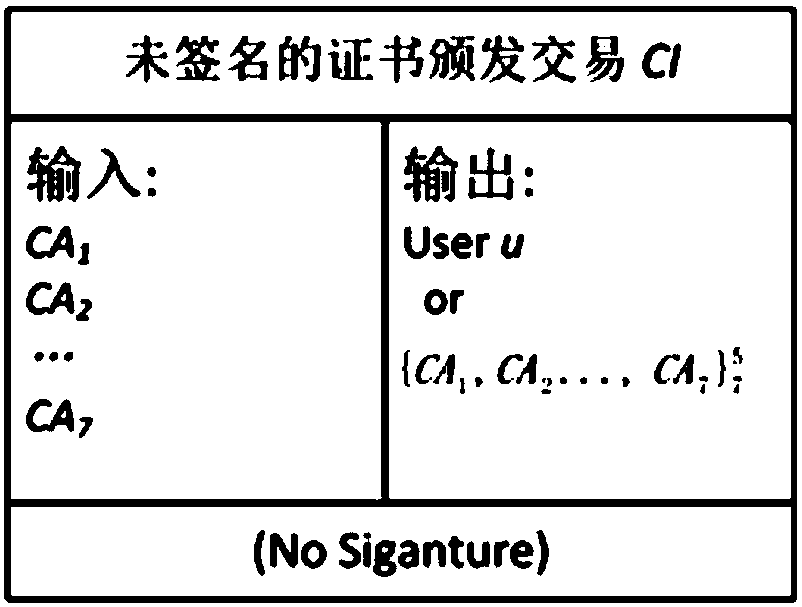
Public key infrastructure system based on block chain, and certificate management method thereof
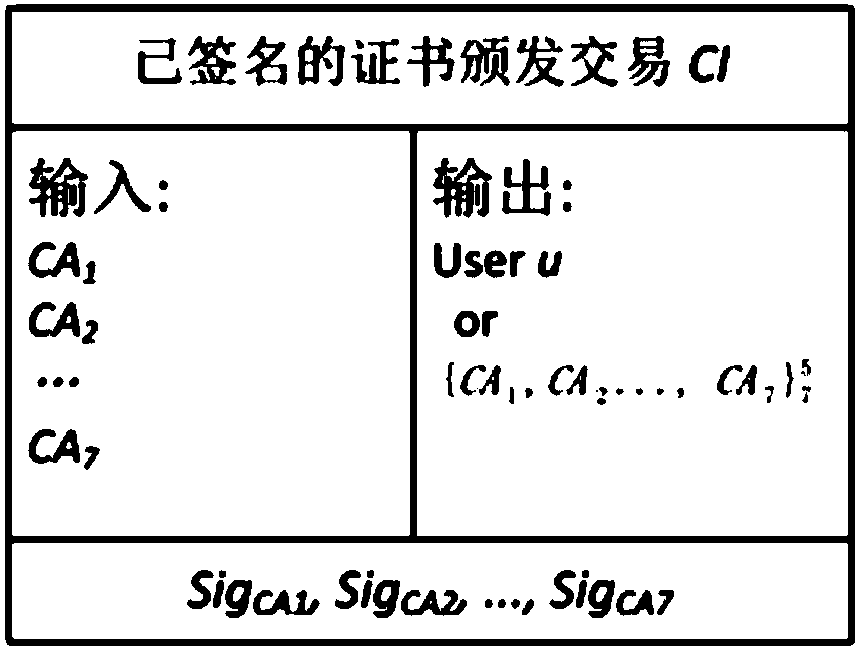
ActiveCN107769925ASafe and efficient managementImprove efficiencyUser identity/authority verificationDomain nameE infrastructure
The invention relates to a public key infrastructure system based on a block chain, and a certificate management method thereof. The public key infrastructure system comprises a user u, a plurality ofCAs, a plurality of block chain maintainers BLM, a block chain and a client, the user u sends a signature request to the plurality of CAs, the plurality of CAs separately perform signature and feed back the same to the user u; the user u merges the signatures in a singed certificate issue affair and sends the same to the block chain maintainers BLM; the block chain maintainers BLM verify and store the signatures in candidate blocks of the block chain, and send proves of existence of the singed certificate issue affair CI-signed to the user u; and the client requests a certificate from the user u, the user u replies the domain name and the block chain maintainers BLM, and the client sends a query and verification request to the block chain maintainers BLM to query the state of the certificate and make response. By adoption of the public key infrastructure system, simple, convenient and efficient management of the certificates are achieved, and the problem of single point fault of CA can be avoided.
Owner:SHANDONG UNIV
Database query language transformation method, transformation apparatus and database query system
InactiveUS20070299836A1Save effortHigh expressionData processing applicationsDigital data information retrievalRelational databaseQuery statement
The present invention provides a method for transforming a concept-based query into SQL query statements, comprising the steps of: transforming inputted concept-based queries into logic rules; checking validity of the logic rules; optimizing the valid logic rules; and translating the logic rules into SQL query statements in accordance with the optimization result. The present invention further provides corresponding transformation engine, database query system and computer program product. The present invention facilitates people to use more descriptive query language to query data stored in relational database. Furthermore, the present invention can automatically generate the correct and efficient SQL query statements so that people's efforts to deal with complex data model are saved significantly.
Owner:IBM CORP
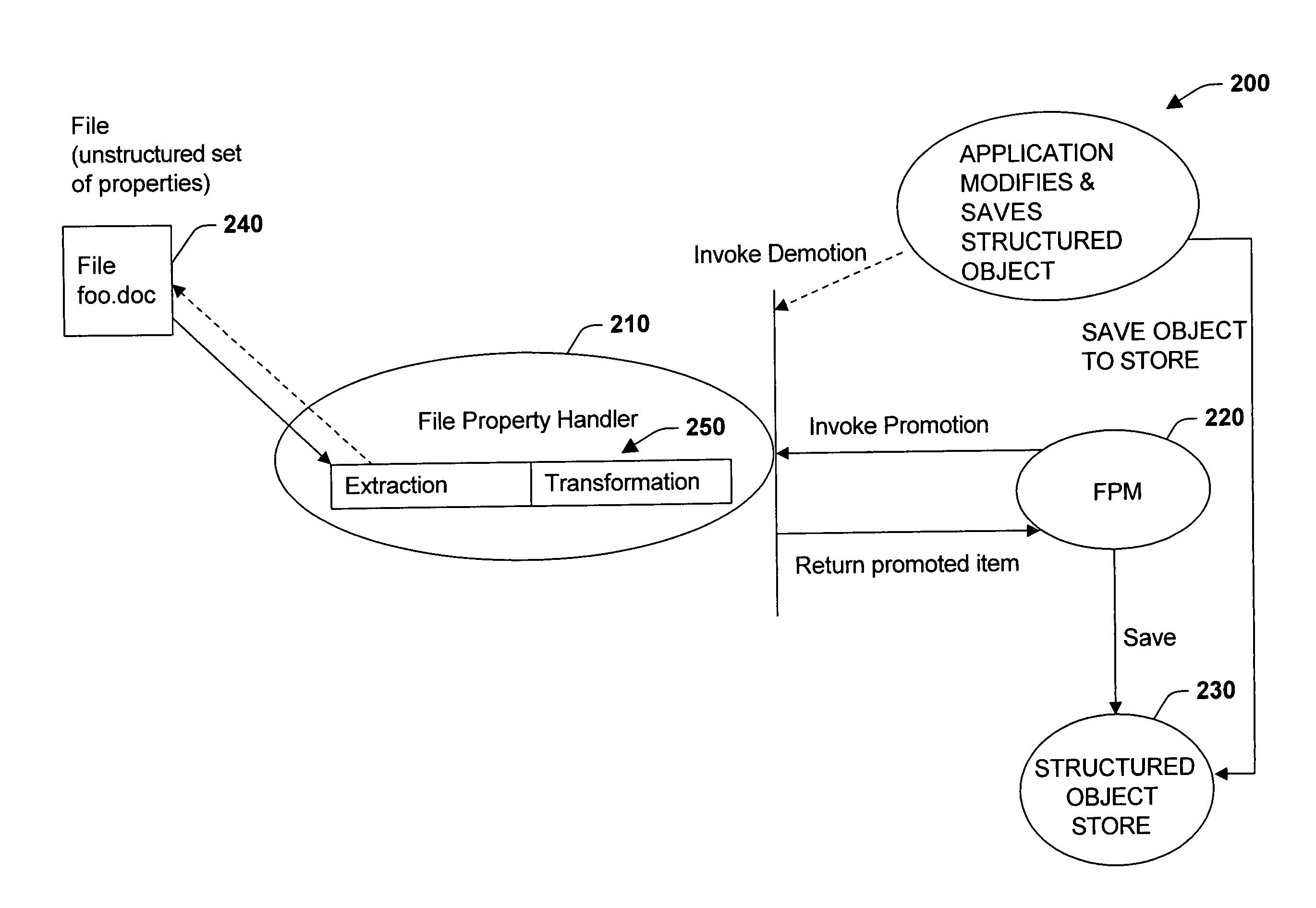
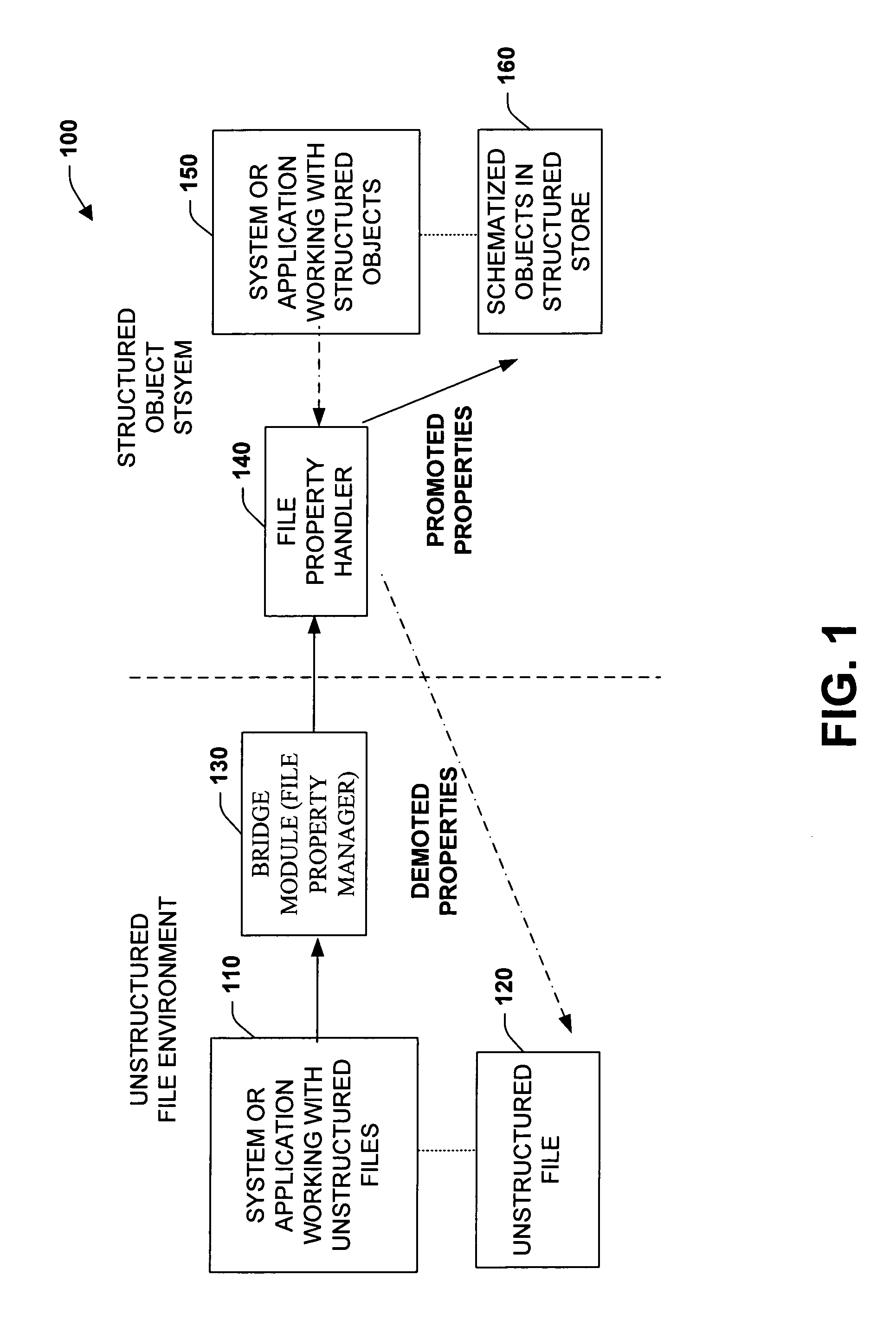
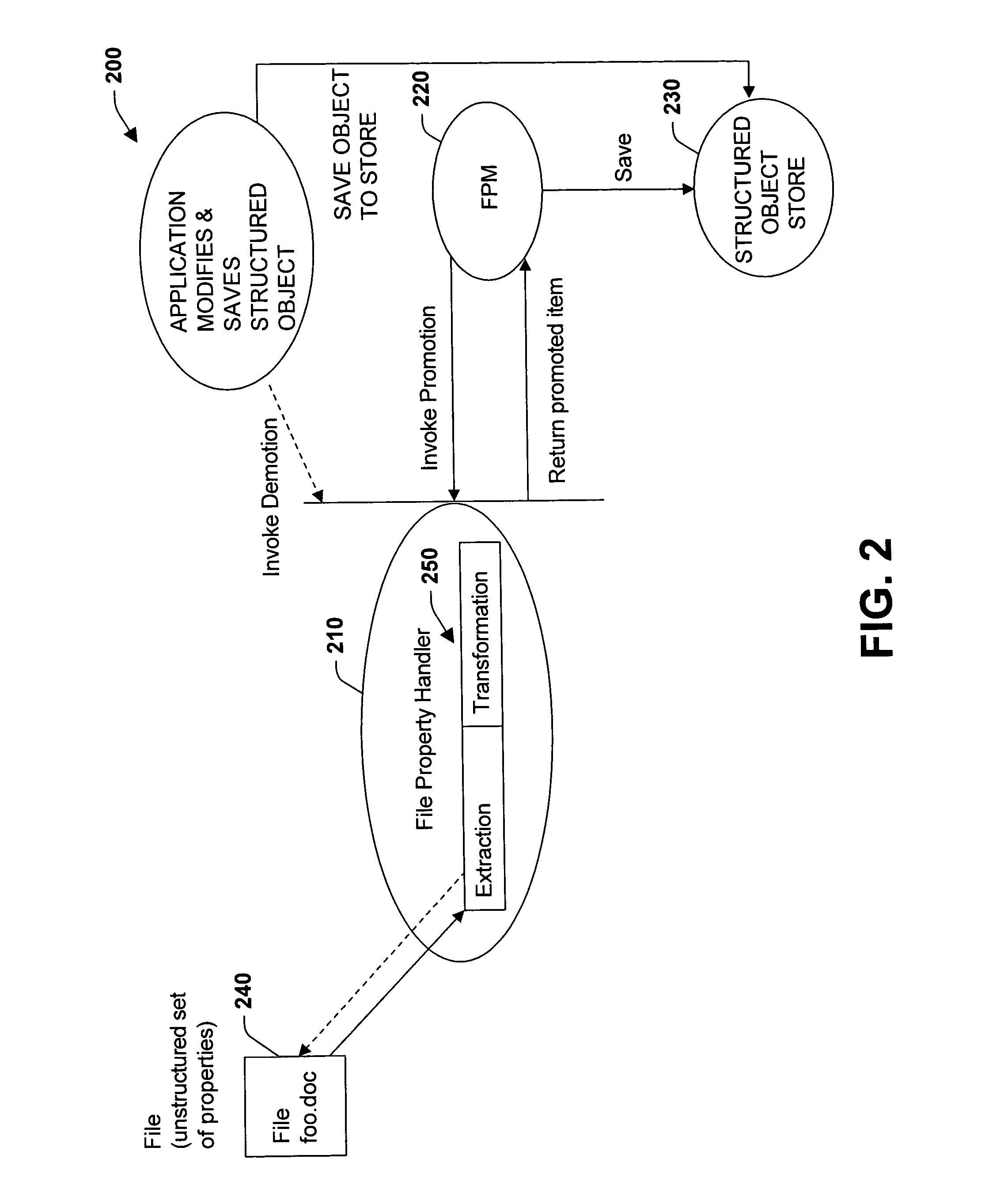
Promotion and demotion techniques to facilitate file property management between object systems
ActiveUS7155444B2Facilitate file manipulationAchieve consistencyAcutation objectsData processing applicationsComputer compatibilityObject store
The present invention relates to a system and methodology to facilitate interoperability and compatibility between disparate data systems. In one aspect, a file transformation system is provided having at least one file associated with one or more unstructured properties. A file property handler manipulates the unstructured properties in accordance with one or more structured properties associated with a structured object store environment. If an unstructured file is to be operated in the context of a structured object store environment, a promotion operation is performed to update unstructured properties in the file with structured properties suitable for operation in the structured object store environment. If a promoted item were to be manipulated in the structured object store environment, a demotion operation or reverse transformation is performed to update properties in the file.
Owner:MICROSOFT TECH LICENSING LLC
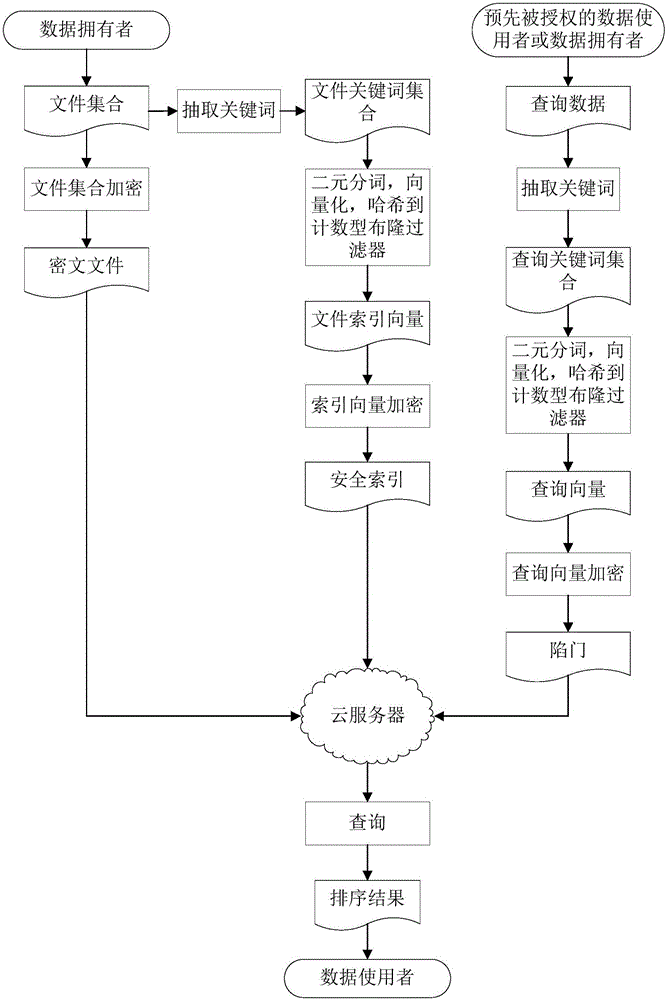
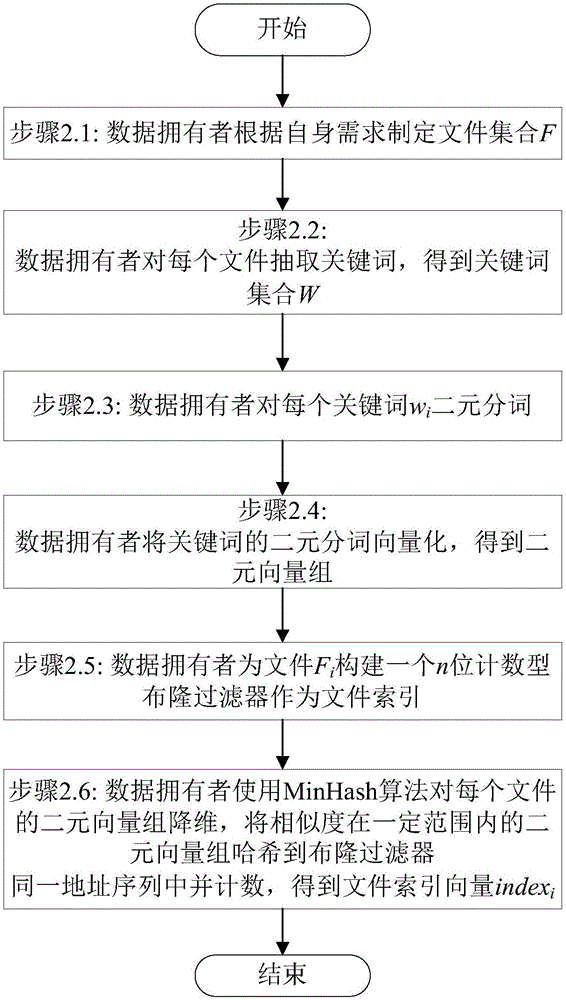
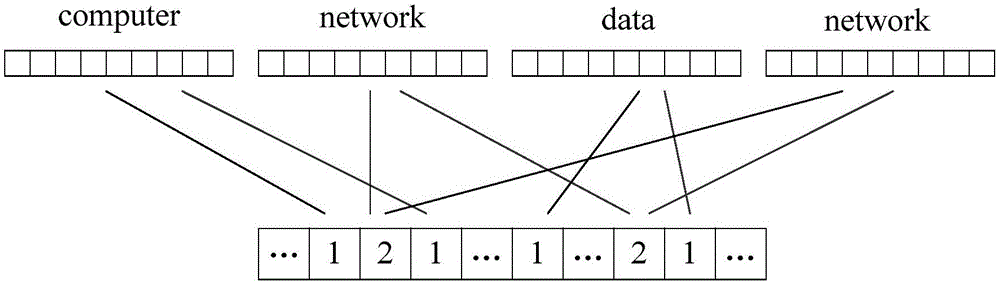
Fuzzy multi-keyword retrieval method of encrypted data in cloud environment
ActiveCN106326360AAchieve retrievalImprove securityDatabase queryingTransmissionDimensionality reductionCiphertext
The invention discloses a fuzzy multi-keyword retrieval method of encrypted data in cloud environment. A file is subjected to set encryption by a data owner to generate a ciphertext file; keywords are extracted from each file; the keywords are subjected to binary segmentation and vectorization to obtain a binary vector group; the binary vector group is subjected to dimensionality reduction and is then inserted into a counting type bloom filter to generate index vectors; each index vector is encrypted to obtain a security index; the ciphertext file and the security indexes are sent to a cloud server; a pre-authorized data user or the data owner extracts the keywords from query data; binary segmentation and vectorization are performed to generate a query vector; encryption is performed to obtain a trap door; the trap door is sent to the cloud server; the cloud server obtains a certain number of files with the highest relevancy degree through query according to the trap door and the security index; after sorting, the files are returned to the data owner. The large data volume of ciphertext multi-keyword retrieval is supported; compared with the prior art, the method has the advantages that the index building and query processes are more efficient; the sorting result is more accurate; the data privacy is effectively protected.
Owner:WUHAN UNIV OF SCI & TECH
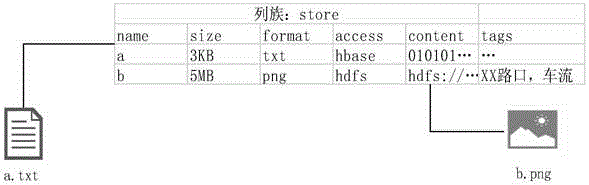
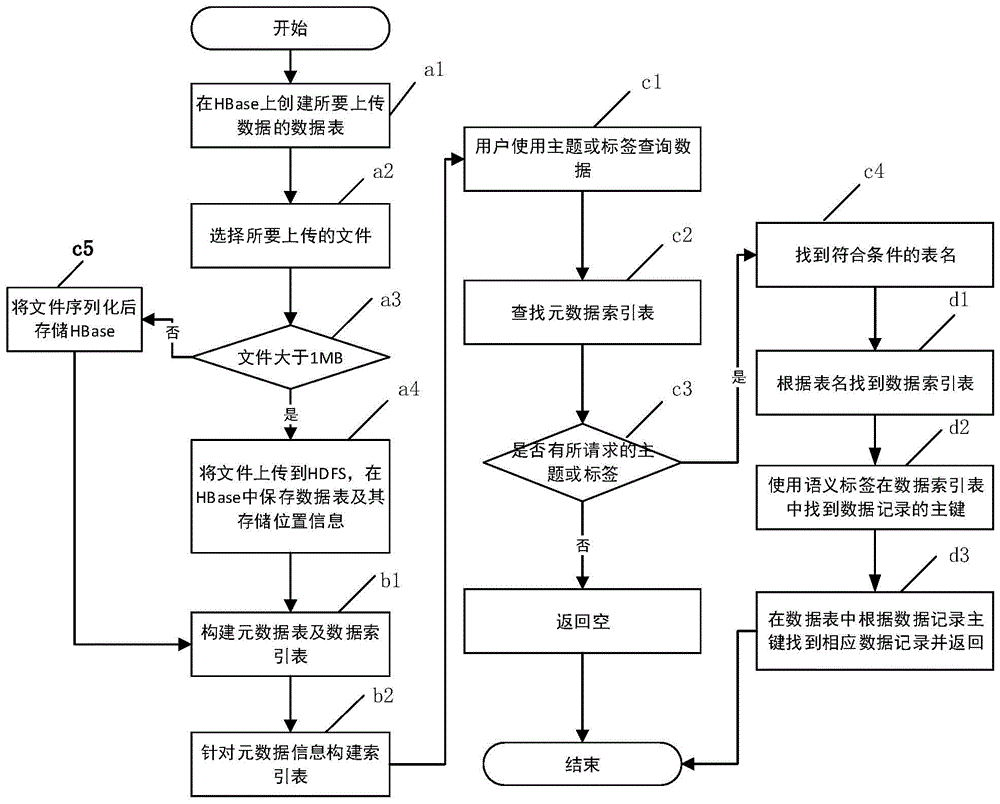
Resource management method for massive unstructured data
InactiveCN105677826AEffective organizationEfficient managementSpecial data processing applicationsData needsResource management
The invention provides a resource management method for massive unstructured data. The method includes the steps that a, the storage mode of the massive unstructured data is determined according to the size of a file of the massive unstructured data, and the file is stored on an HDFS or in an HBase; b, metadata information of the data is stored in the HBase, and query speed is increased by building index tables of metadata according to themes, tags and other information of the metadata; c, when the metadata is queried, the index tables of the metadata can be searched for according to the themes or the tags of the metadata needing to be searched for, and a data table is fast positioned; d, when unstructured data records are queried, the data index table corresponding to the data table needs to be found according to the naming rule of the data index tables, semantic tags of the data are queried in the data index table, recording main keys of the data needing to be searched for are found, and the data is fast positioned in the data table according to the main keys. By means of the resource management method, the massive unstructured data can be effectively organized and managed, and fast and efficient query can be performed.
Owner:ENC DATA SERVICE CO LTD
Data storage system and method and data analysis system and method
ActiveCN105718515AOrderly storageQuick storageSpecial data processing applicationsData acquisitionData needs
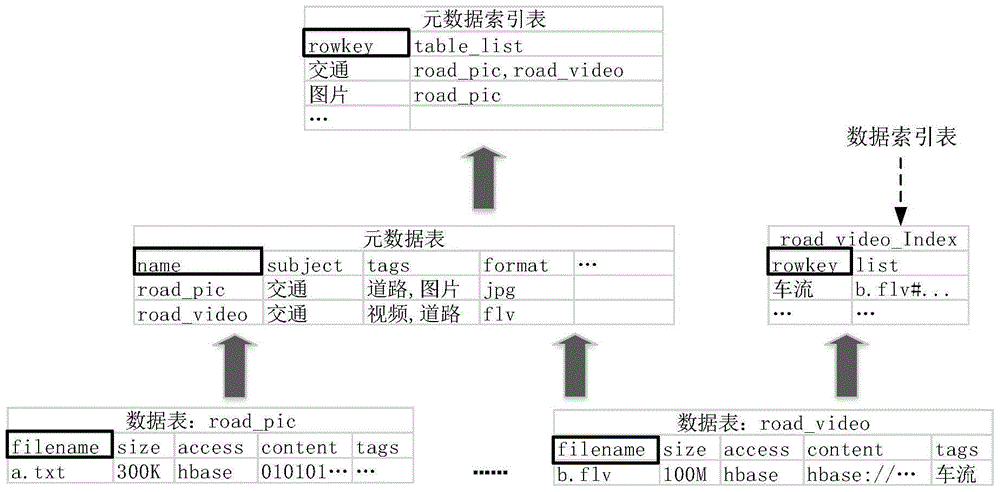
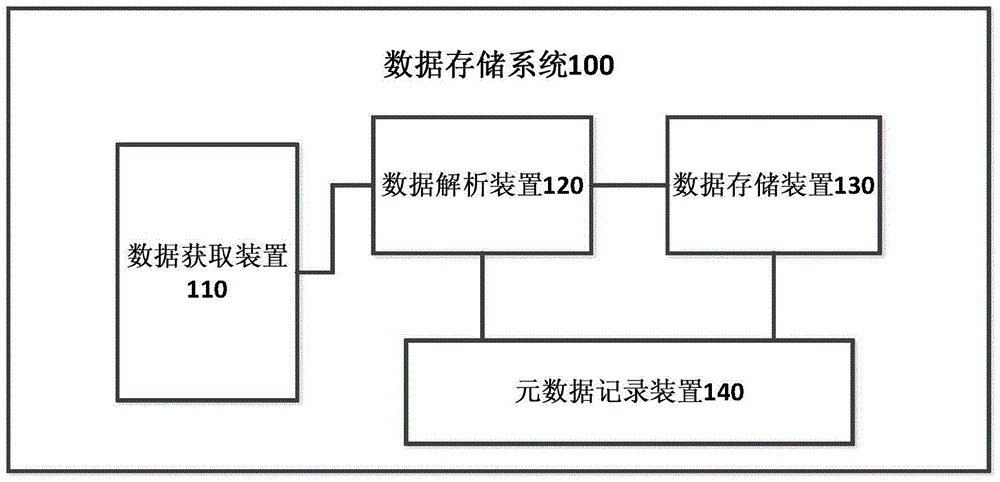
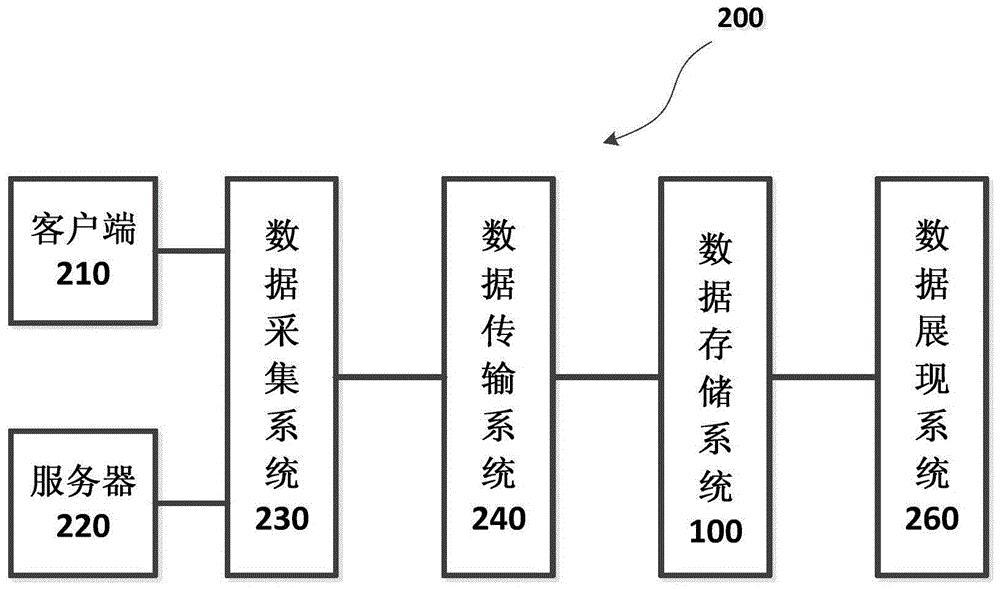
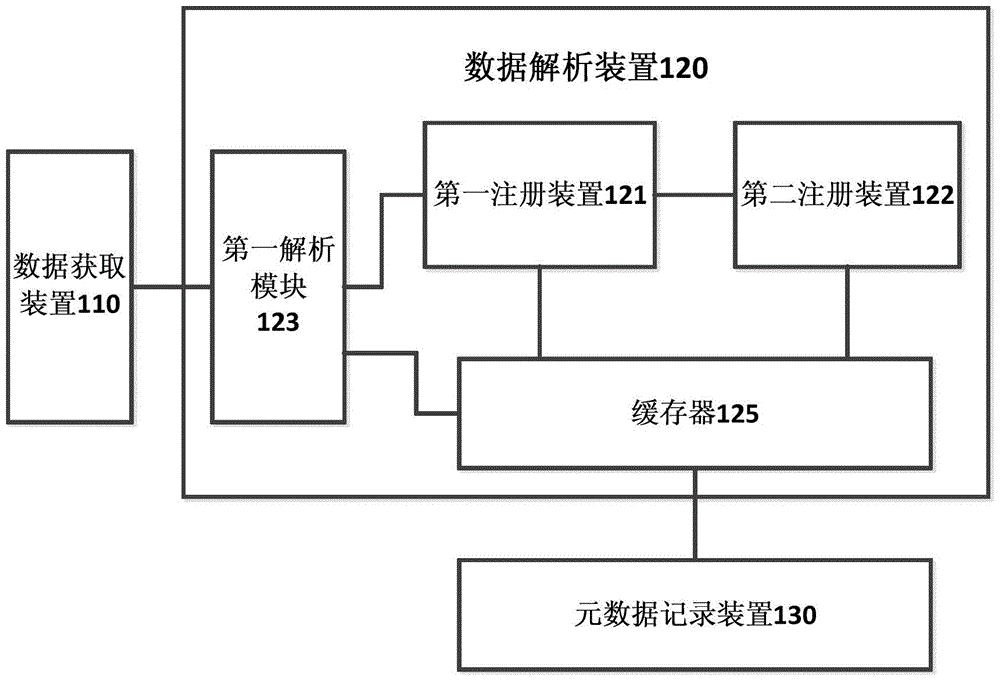
The invention provides a data storage system, which comprises a data acquisition device, a data analysis device, a metadata recording device and a data storage device, wherein the data acquisition device is suitable to acquire data which needs to be stored; the data analysis device is suitable to analyze the data which needs to be stored to obtain the characteristic of the data which needs to be stored and determine a storage position, wherein the data which needs to be stored is acquired by the data acquisition device; the metadata recording device is suitable to record the metadata information of the data which needs to be stored, wherein the metadata information comprises the characteristics and the storage position of the data which needs to be stored; and the data storage device is suitable for storing the data analyzed by the data analysis device into a corresponding storage device on the basis of the metadata information recorded by the metadata recording device. In addition, the invention also provides a data storage method and a data analysis system and method. Data storage can be flexibly and orderly realized especially under a situation that a great quantity of data needs to be stored.
Owner:SENSOR NETWORKS TECH BEIJING CO LTD
Entity recognition
ActiveUS20110320186A1Reduce overheadLow costDigital data information retrievalNatural language data processingNamed-entity recognitionDocument preparation
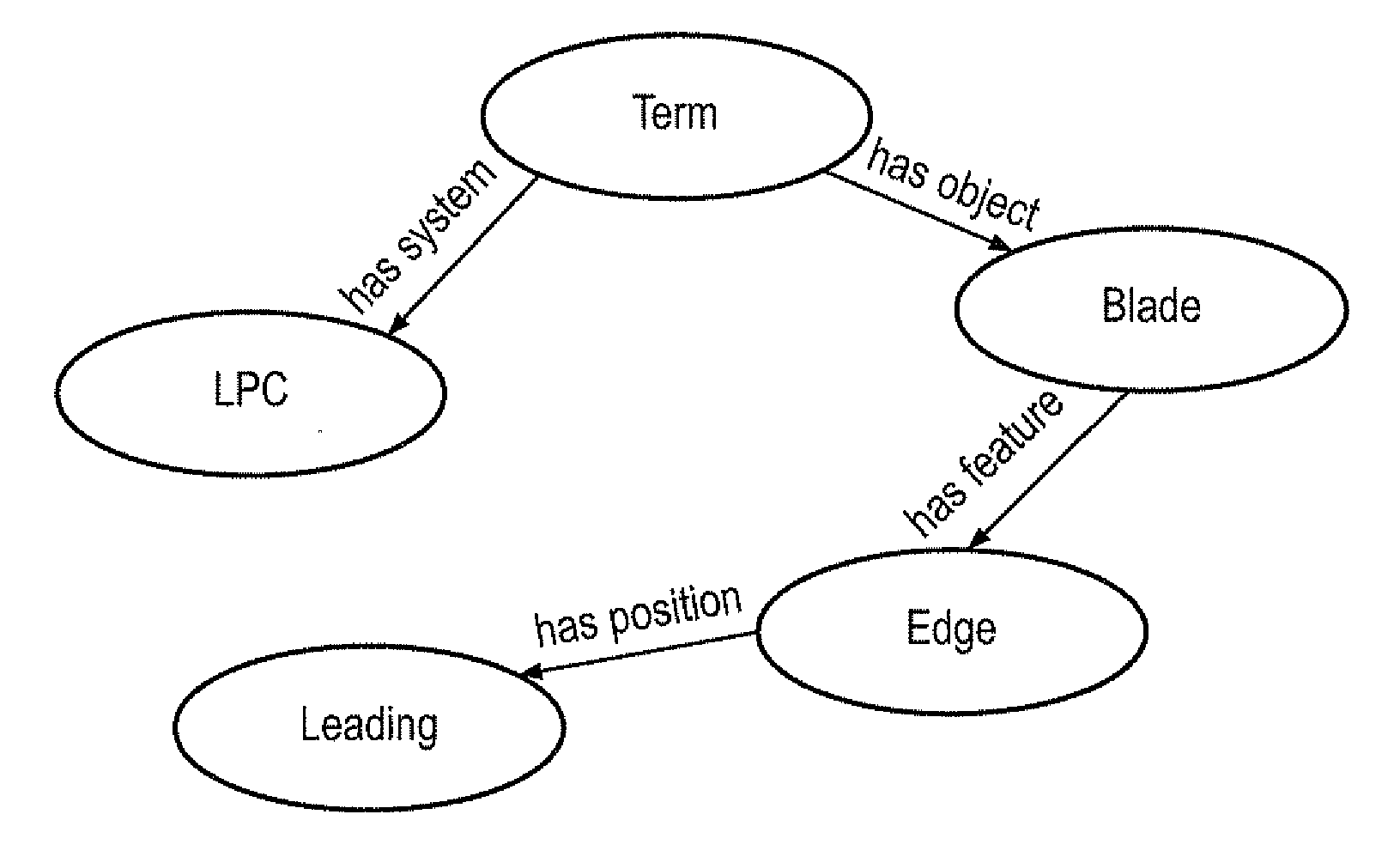
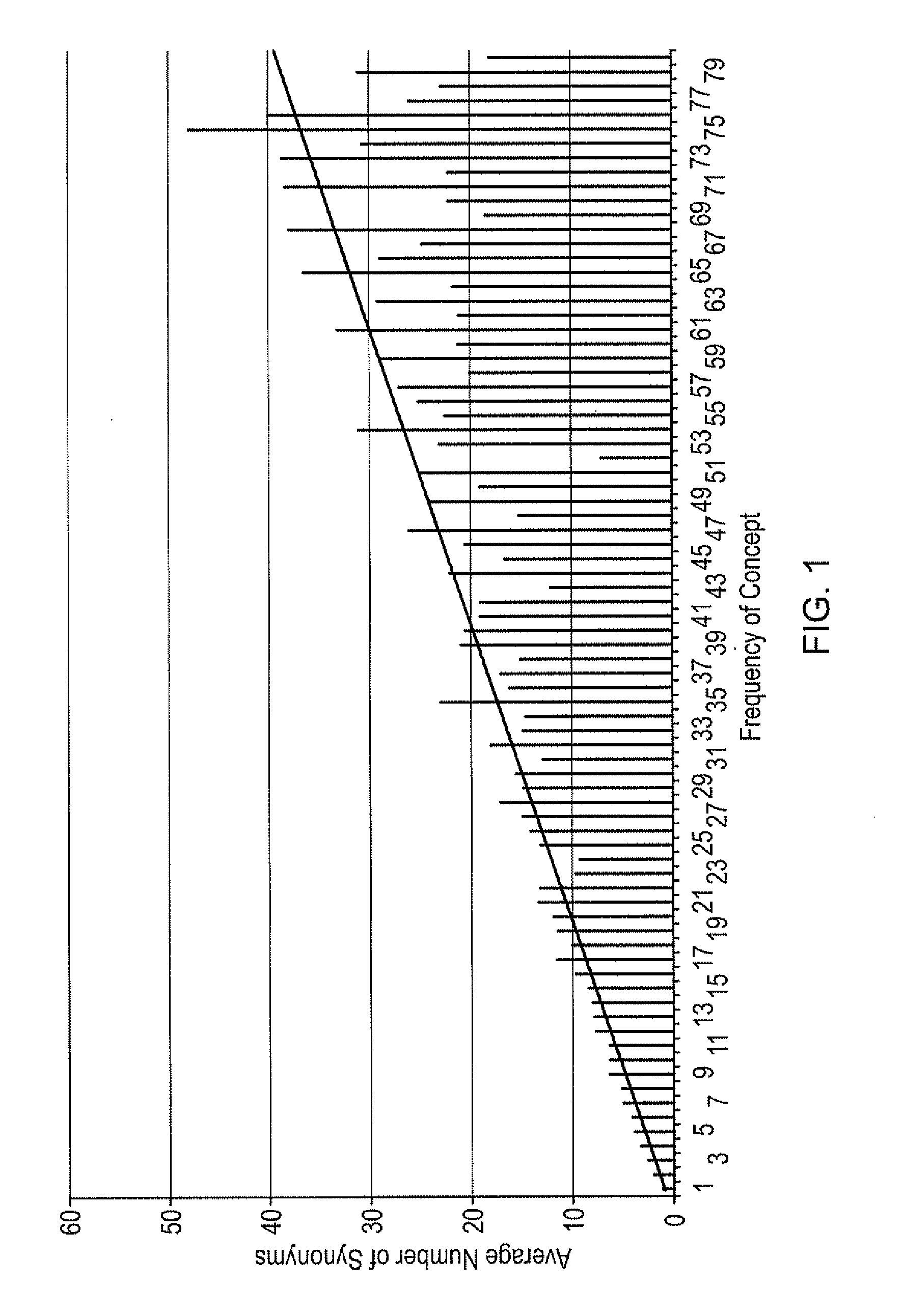
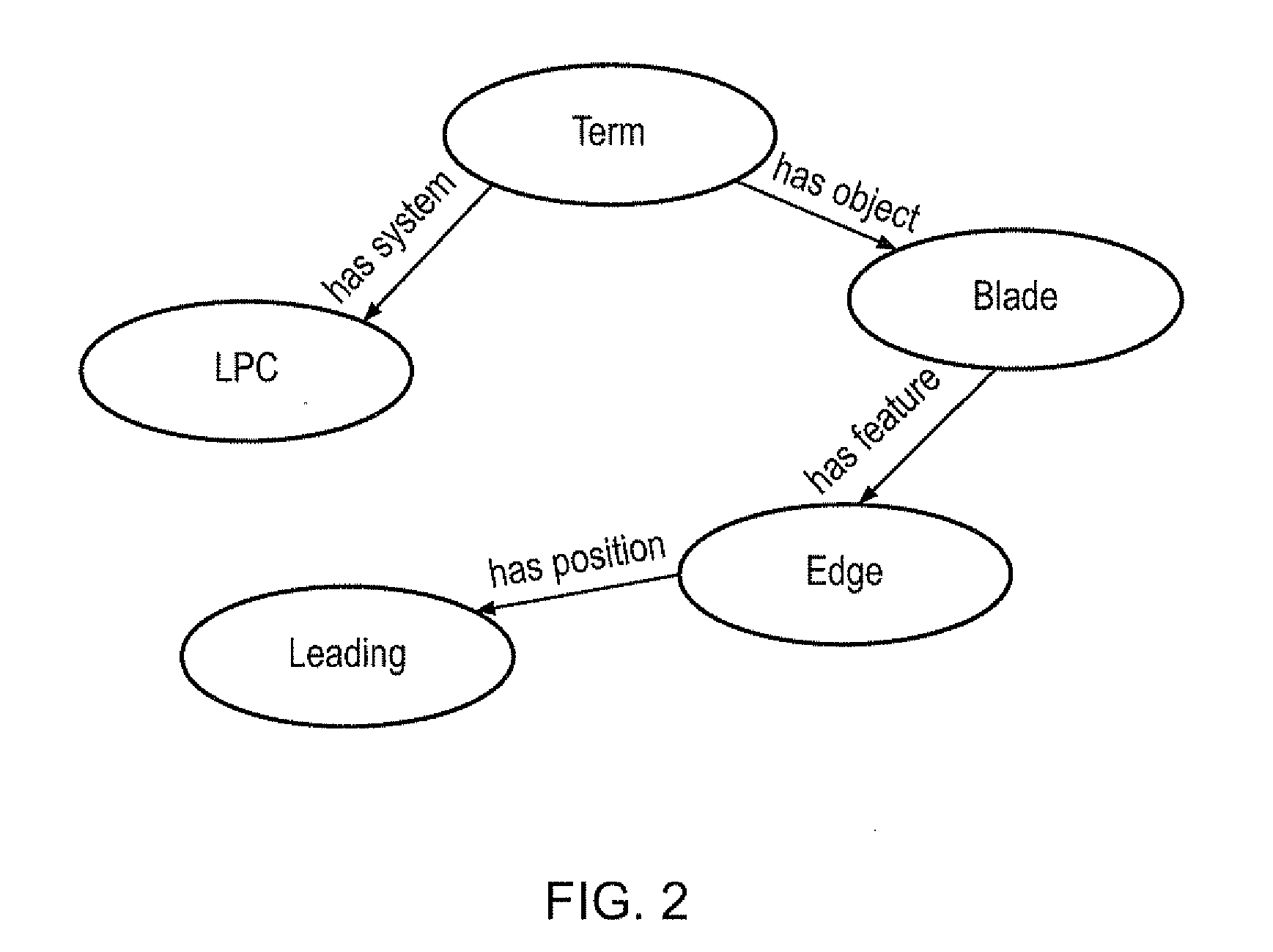
The invention relates to a method of querying technical domains that recognises the concepts represented by strings of characters, rather than merely comparing strings. It can be used to compute conceptual similarity between terms. The method employs string distance metrics and a cyclic progression of lexical processing to recognise constituent term concepts that are then combined to form full-term concepts by means of a grammar. Terms can be extracted and identified as being conceptually similar (or dissimilar) to other terms even if they have never previously been encountered.A key advantage is the ability to extract terms from documents based on the combination of a limited number of sub-concepts. This avoids the need for the prior identification of all possible terms that current methods require. A second key advantage is the ability to introduce or remove concepts and synonyms individually without the need to alter terms which the concept or synonym constitutes.
Owner:ROLLS ROYCE PLC
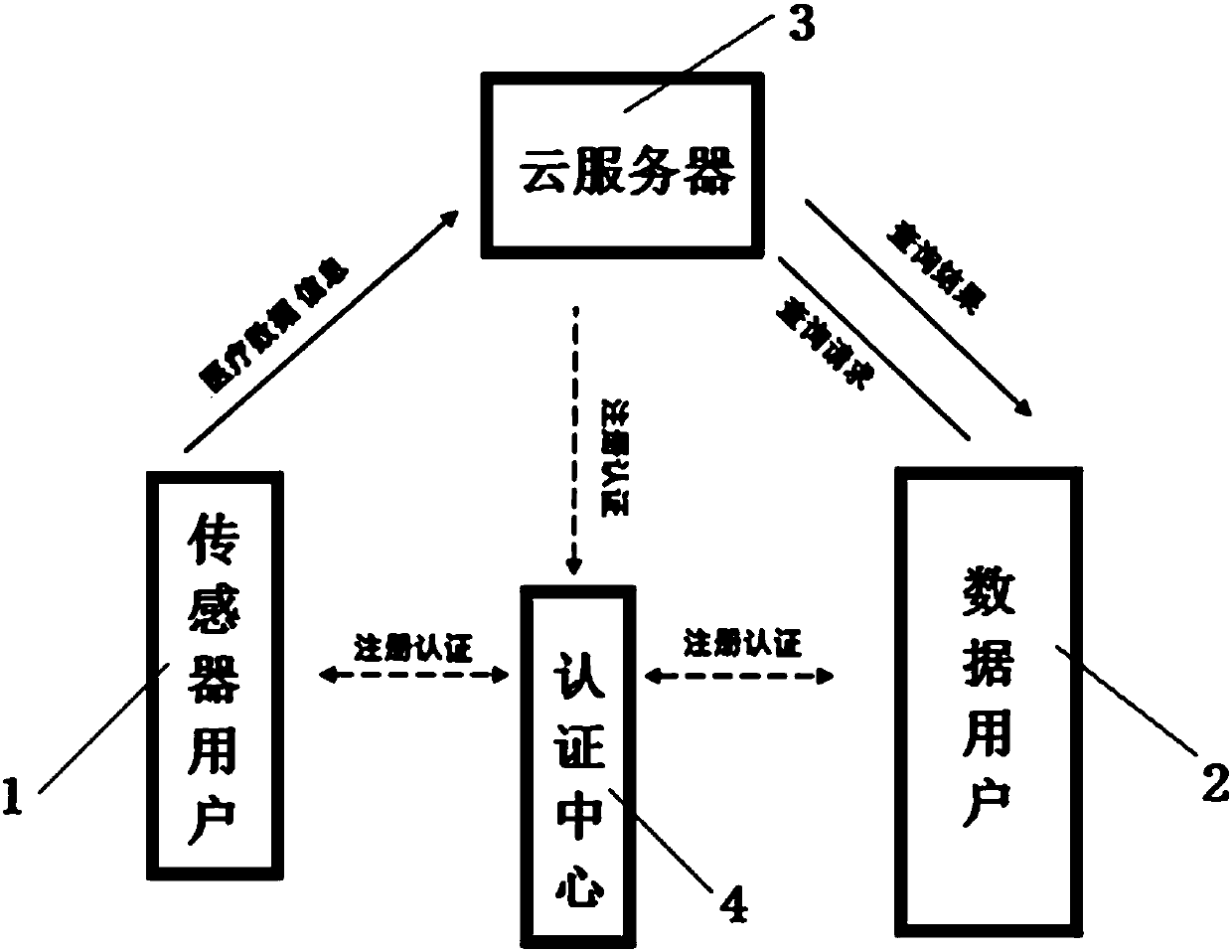
Cloud medical data monitoring system and monitoring method with efficient privacy protection function
ActiveCN106650205AProtect personal privacyEfficient queryTelemedicineSpecial data processing applicationsCiphertextData information
The invention discloses a cloud medical data monitoring system with an efficient privacy protection function, and a cloud medical data monitoring method with the efficient privacy protection function. The monitoring system comprises a sensor user used for providing medical data information, a data user used for querying the medical data information, a cloud server used for receiving a query request of the data user and sending the medical data information of the sensor user to the data user, and an authentication center used for performing registration authentication on the sensor user, the data user and the cloud server, wherein the sensor user encrypts the medical data information through encoding and uploads the encrypted medical data information to the cloud server; the cloud server directly performs query and vital sign situation analysis on a ciphertext without decrypting data; and the data user decrypts the ciphertext through a secret key and reads a query result. The monitoring method comprises five stages of system establishment, user registration, data acquisition, query request generation and query result returning. According to the system and the method, a ciphertext data query function is realized through encoding, and reliability and high efficiency are achieved.
Owner:XIDIAN UNIV
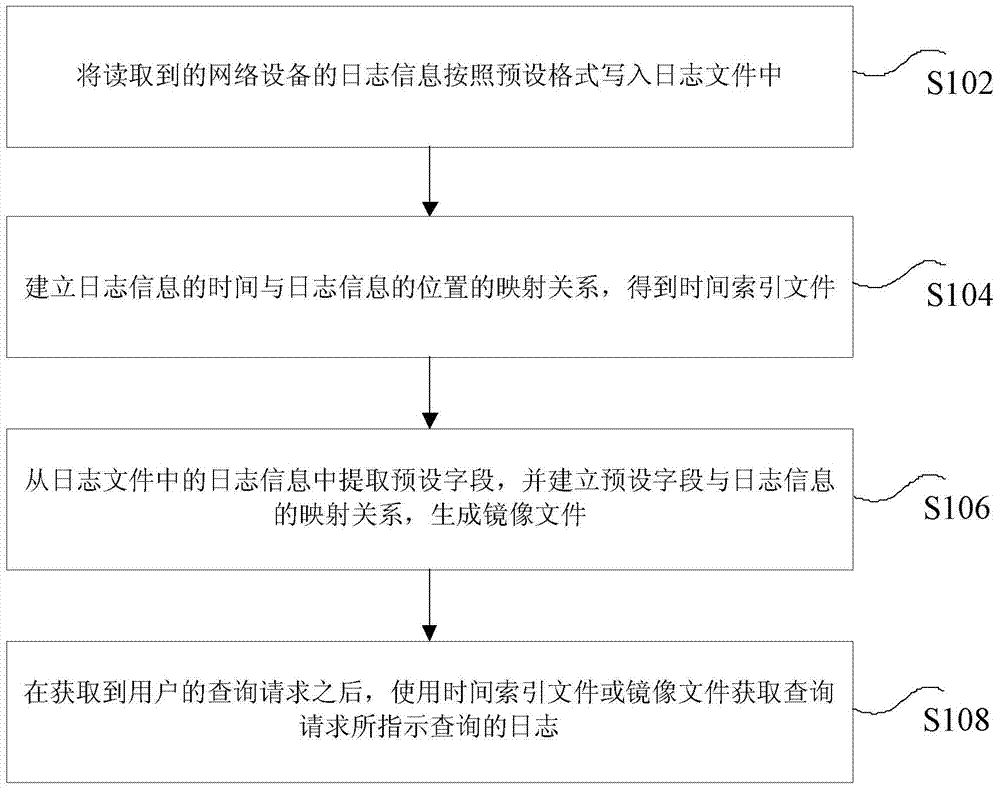
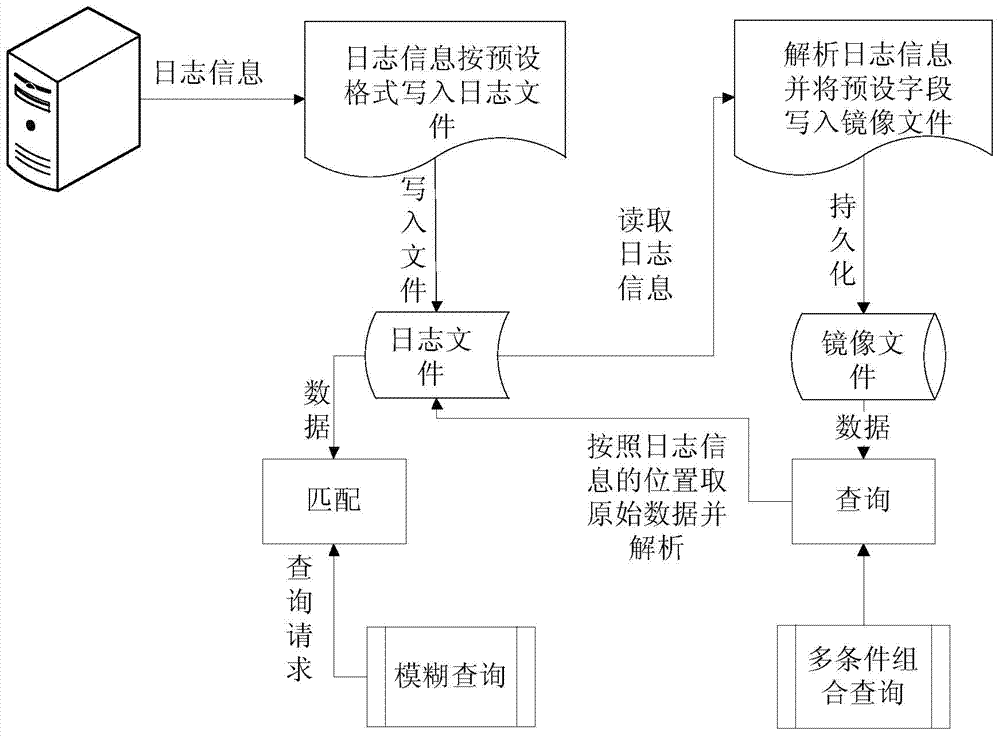
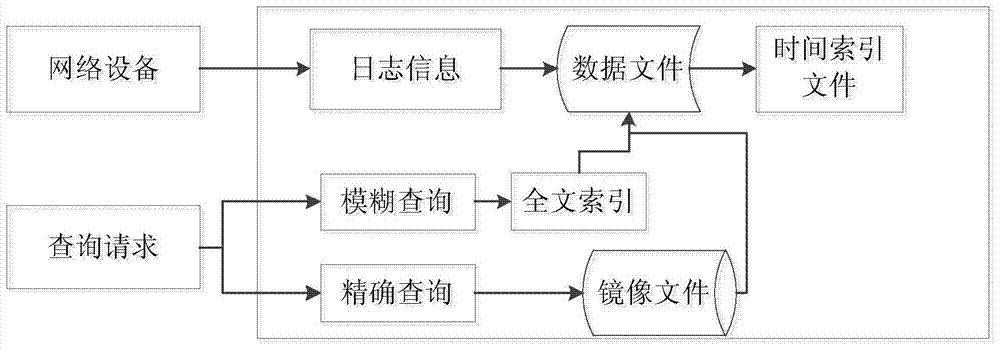
Log data processing method and device
ActiveCN104281672AEfficient storageImprove collection effectWeb data indexingSpecial data processing applicationsRelational databaseTime index
The invention discloses a log data processing method and device. The method includes: writing read log information of a network device into a log file according to a preset format; establishing a mapping relation between the time of the log information and the position of the log information to obtain a time index file; extracting preset fields from the log information of the log file, and establishing a mapping relation between the preset fields and the log information to generate an image file; after a user's search request is acquired, using the time index file or the image file to acquire logs indicated for search by the search request. The time index file and the image file are stored in a database. By the use of the log data processing method and device, the problem that the prior art is low in efficiency of storing the mass log data using the relational database and low in efficiency of searching the log data is solved; quick efficient storage of the log information is achieved, and the log information can be searched fast.
Owner:QI-ANXIN LEGENDSEC INFORMATION TECH (BEIJING) INC
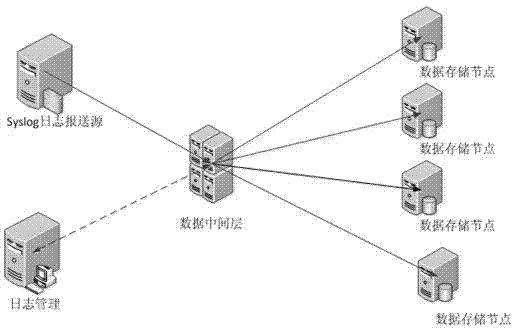
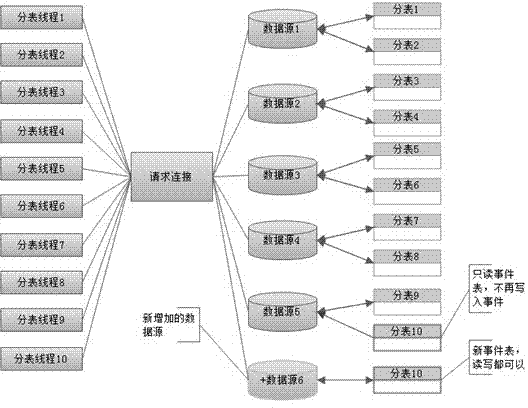
Distributed device log collection method
ActiveCN104778188AImprove storage speedIncrease storage capacityTransmissionSpecial data processing applicationsData connectionDatabase index
The invention discloses a distributed device log collection method. According to the method, an integrated data intermediate layer is built through a distributed log processing framework in a mediator mode, integrated data intermediate management service is formed, the data intermediate management service collects device logs, the logs are stored on each distributed storage point in a distributed way, in addition, data collection is carried out, and if the distributed storage points need to be increased, the goal is achieved by adopting a distributed storage point dynamic expansion mechanism. The distributed device log collection method has the advantages that the integrated data intermediate layer is built by adopting the mediator mode, the logs are subjected to collection and formatting processing in a unified way, and the distributed storage points are uniformly managed and dispatched in a centralized way; the sub table structure is adopted, the multithreading processing advantages are better realized, a particular sub table indexing mechanism is built, and forms a super-volume data grading indexing system together with MariaDb database indexes of each data storage point, meanwhile, the performance advantage of a distributed server is utilized, and the storage and query performance of log data is greatly improved.
Owner:GUIZHOU POWER GRID INFORMATION & TELECOMM
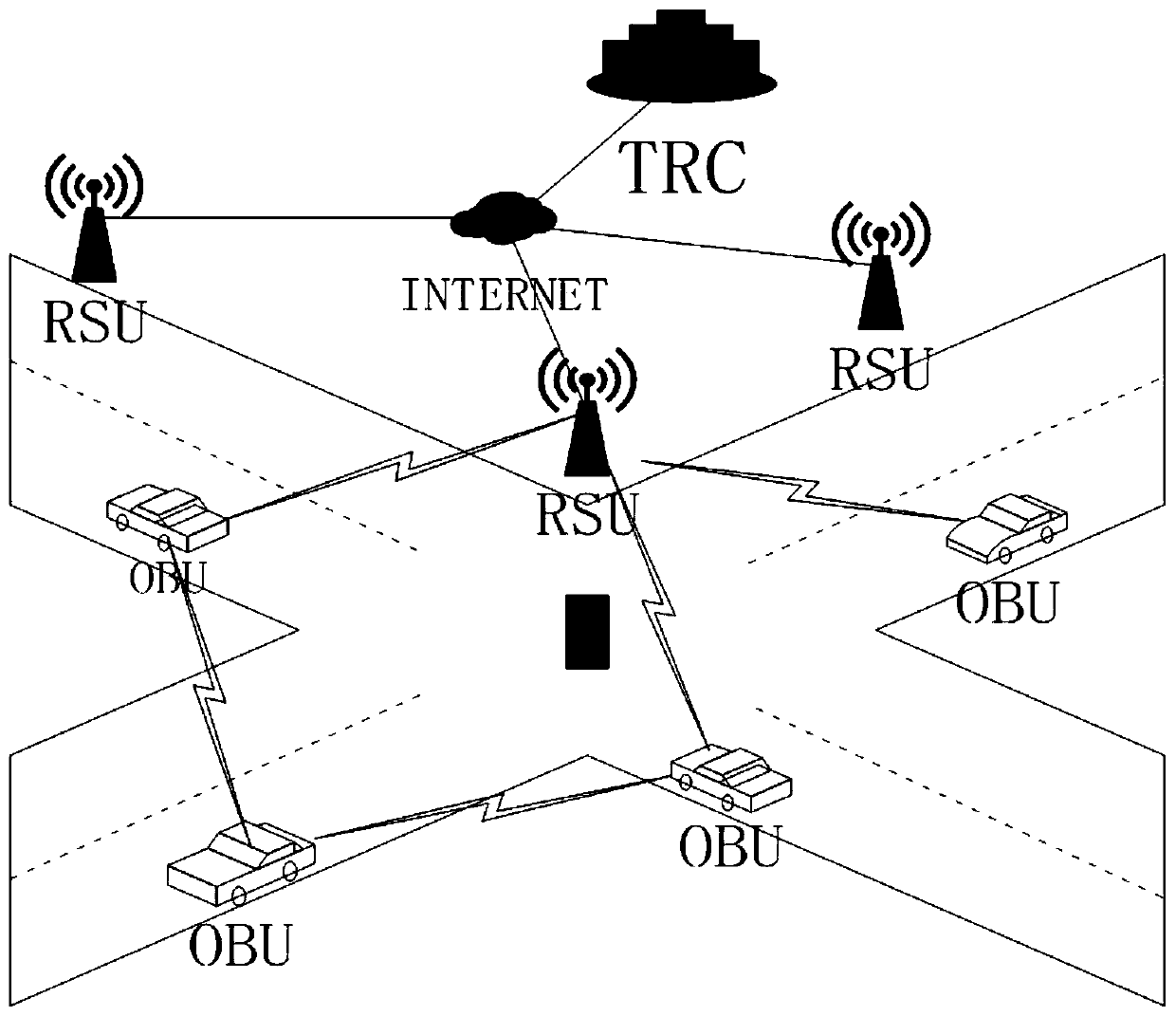
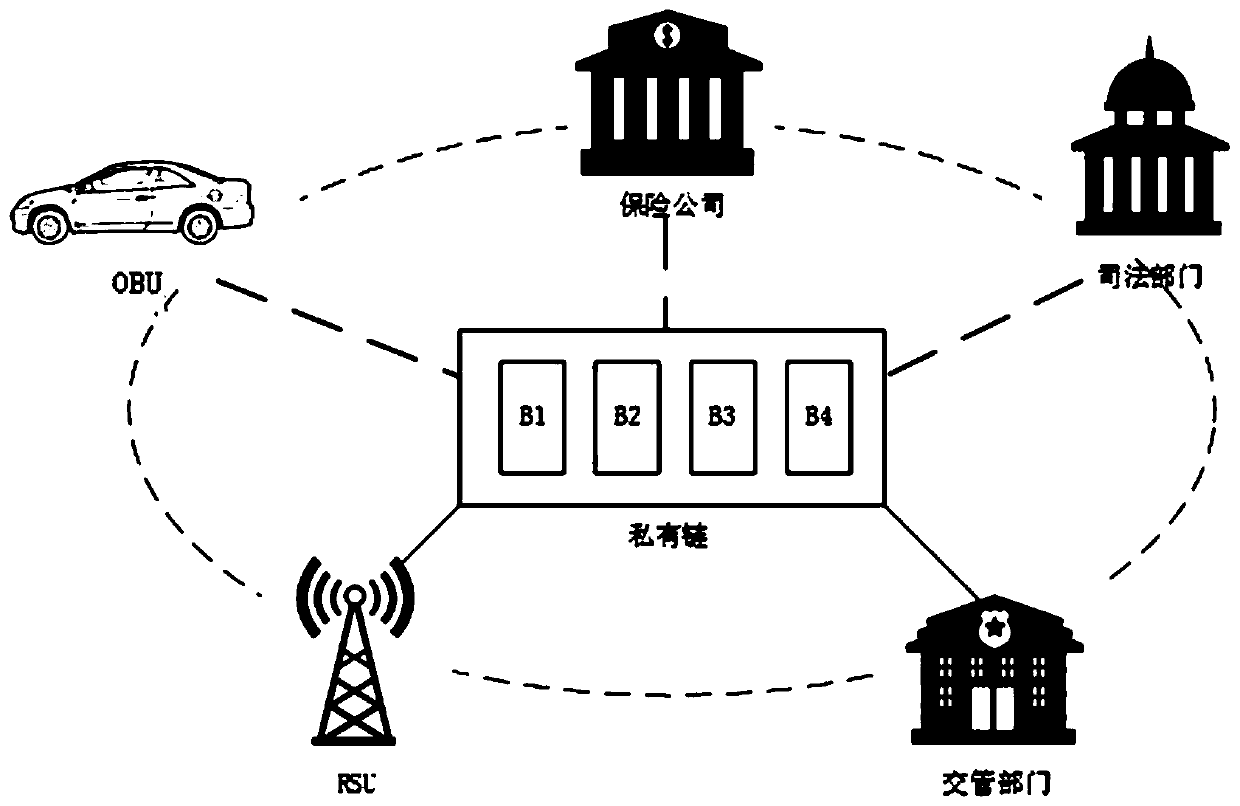
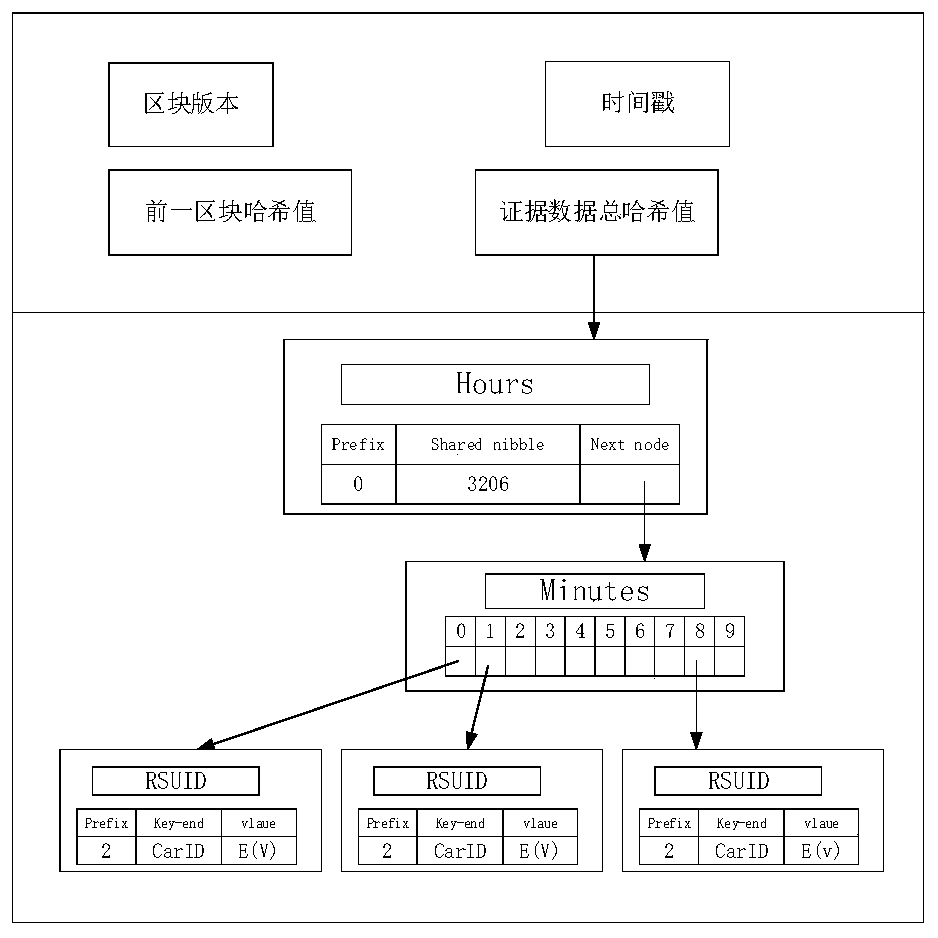
Electronic evidence obtaining device and method based on block chain in Internet-of-Vehicles environment
ActiveCN111464980AProtection against the risk of tamperingImprove access efficiencyData processing applicationsParticular environment based servicesComputer networkTraffic crash
The invention provides an electronic evidence obtaining device and method based on a block chain in an Internet-of-Vehicles environment. The method comprises the following steps of S10, offline registration, S20, vehicle online identity registration, S30, real-time evidence storage and S40, query and evidence obtaining. According to the electronic evidence obtaining device and method based on theblock chain in the Internet-of-Vehicles environment, the block chain technology is used for traffic accident electronic evidence obtaining, the integrity, non-repudiation and permanence of evidence are guaranteed through the characteristics of block chain distributed data storage and the like, many problems of traditional traffic accident evidence obtaining are solved, and the evidence obtaining efficiency is high.
Owner:NANTONG UNIVERSITY
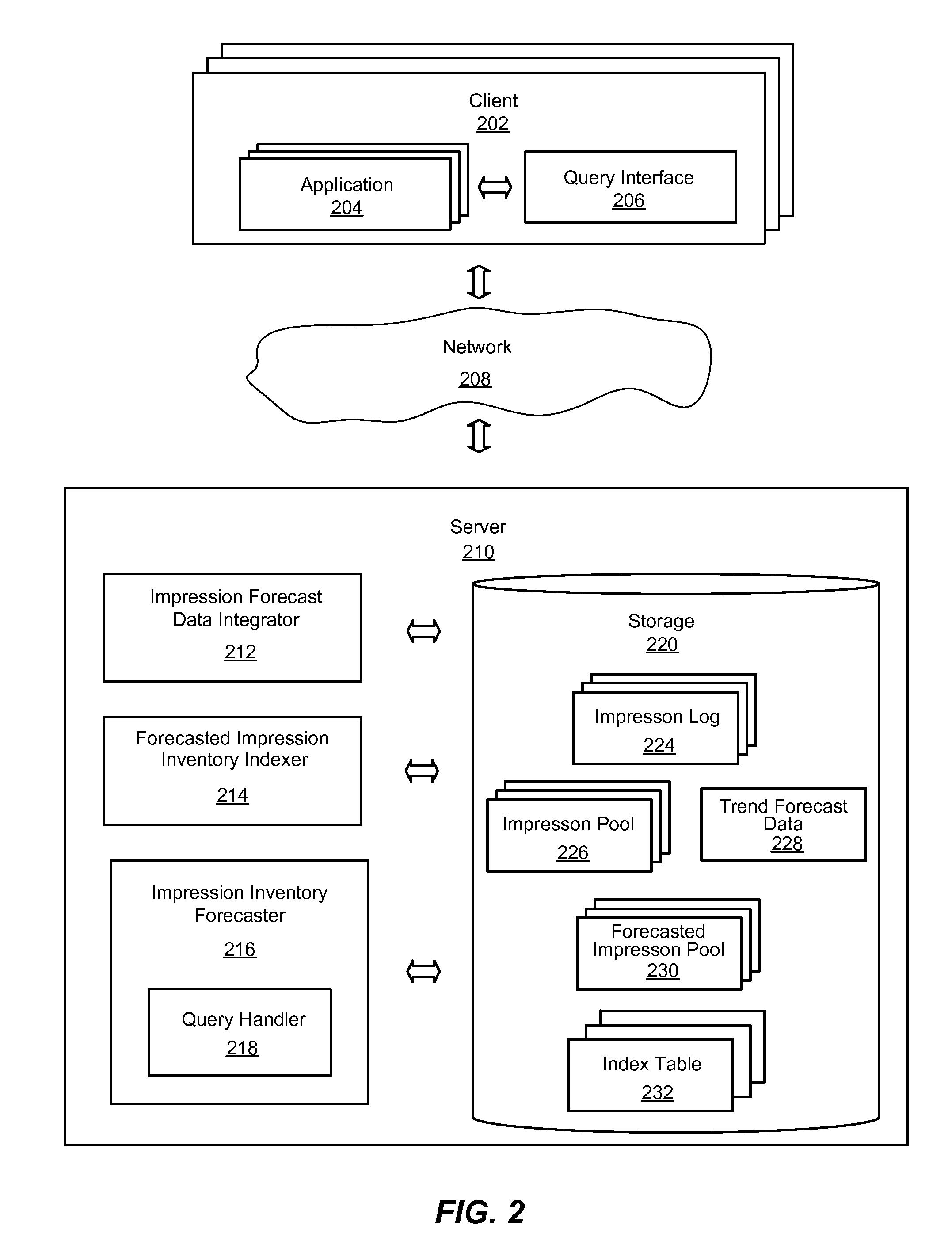
System and method for forecasting an inventory of online advertisement impressions for targeting impression attributes
An improved system and method for forecasting an inventory of online advertisement impressions for targeting profiles of attributes is provided. An index of advertisement impressions on display advertising properties may be built for a targeting profile of attributes from forecasted impression pools. Impression pools of advertisements sharing the same attributes and trend forecast data for web pages and advertisement placements on the web pages may be integrated to generate the forecasted impression pools. An index of several index tables may be generated from forecasted impression pools. A query may be submitted to obtain an inventory forecast of advertisement impressions for targeting profiles of attributes and the index may be searched to match forecasted impression pools for the targeted profile of attributes. Then the inventory forecast of advertisement impressions on display advertising properties may be returned as query results for the targeting profile of attributes.
Owner:R2 SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com