Public key infrastructure system based on block chain, and certificate management method thereof
A technology of public key infrastructure and certificate management, applied in the field of public key infrastructure system and its certificate management, it can solve the problems of complicated client certificate verification process, insecure public key infrastructure, and high communication overhead, so as to avoid CA single Point failure, high safety, and the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
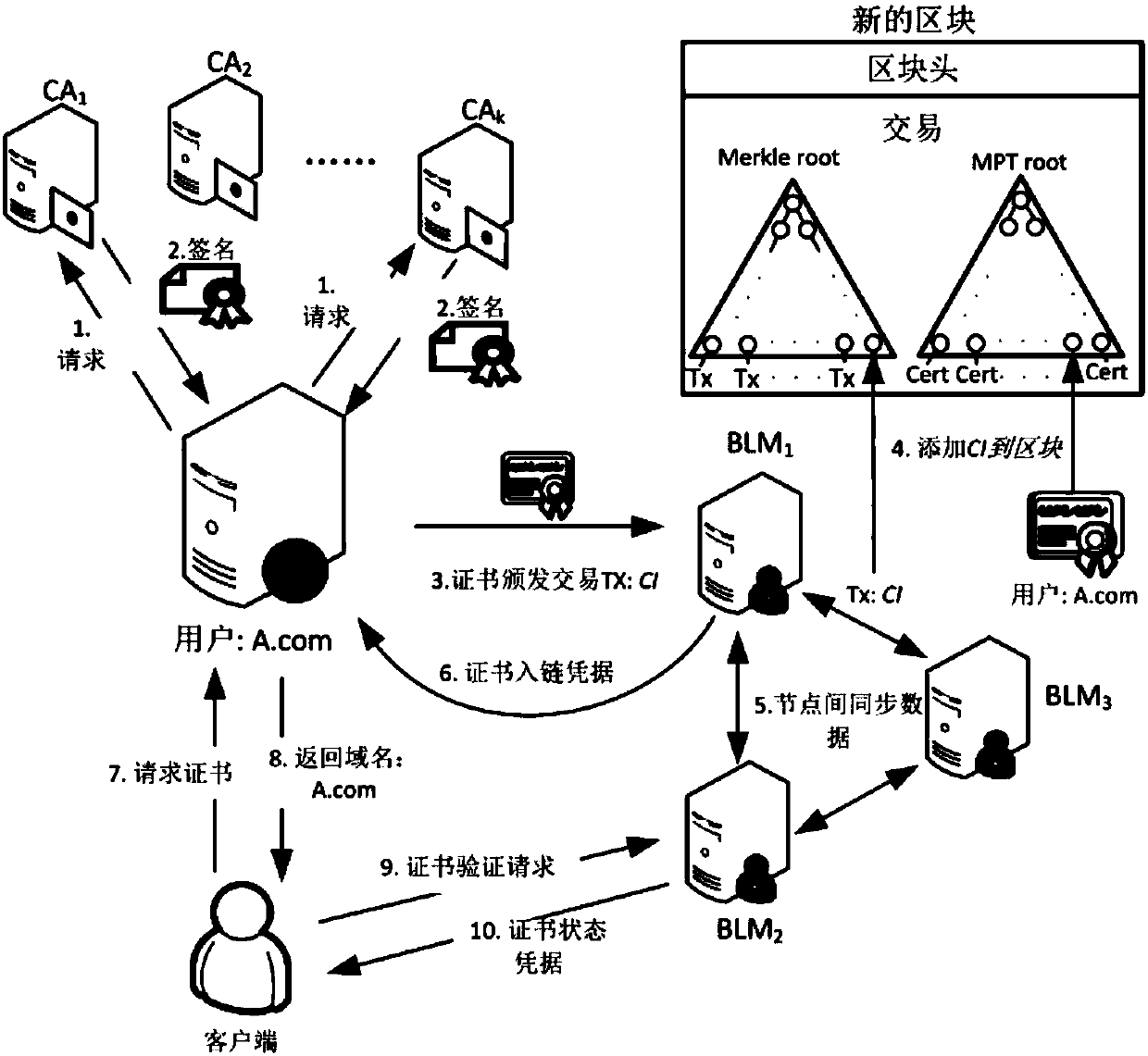
[0070] The blockchain-based public key infrastructure system includes user u (User), several CAs, several blockchain maintainers BLM, blockchain, and Client. Several CAs including CA 1 、CA 2 、CA 3 …CA i …CA n , CA i Generate its public-private key pair for CA i public key, for CA i private key and publish its public key on its website (or other secure location) so that user u verifies the CA i public key of
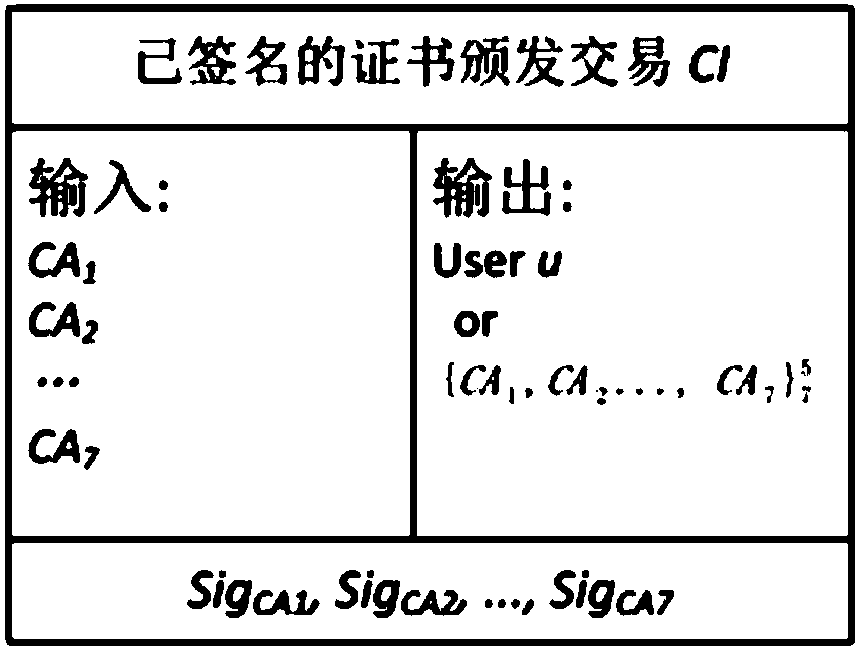
[0071] User u sends a signature request to k CAs, 3≤t≤k≤n, k and t are preset parameters of the blockchain-based public key infrastructure system, k is used for certificate issuance and renewal, and t is used for certificate Revocation, t is any t of k CAs. Larger k and t mean higher security. k CAs verify the identity of user u, sign them separately, and give feedback to user u; user u merges the signature into the certificate issuance transaction CI, and finally obtains the signed certificate issuance transaction CI_signed, and sends it to the blockc...
Embodiment 2
[0077] The certificate management method of the blockchain-based public key infrastructure system described in Embodiment 1, such as figure 1 shown, including the following steps:
[0078] (1) Send request: user u generates its public-private key pair (PK u ,SK u ); the domain name is A.com; several CAs include CA 1 、CA 2 、CA 3 …CA i …CA n , from which user u selects 7 CAs as its certificate authority, including CA 1 ,CA 2 ,...,CA 7 ;
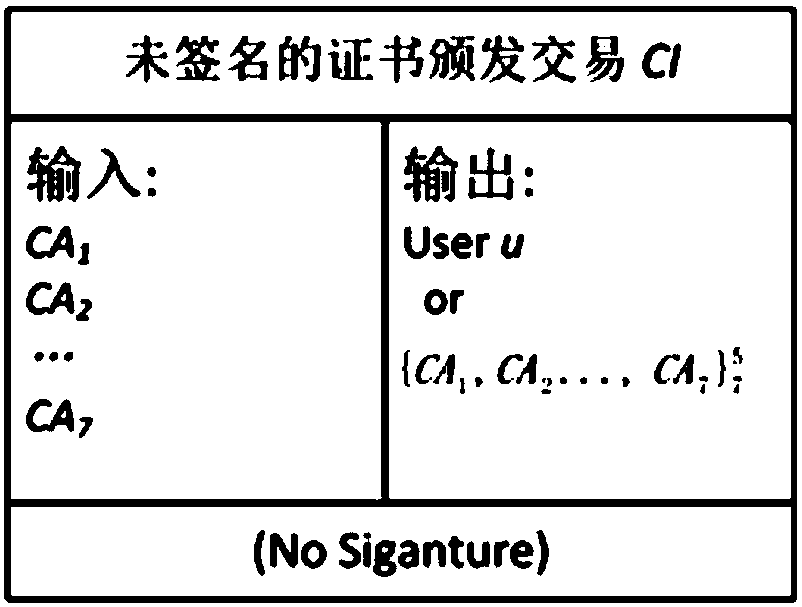
[0079] User u creates transaction CI: Such as figure 2 As shown, TX_ID refers to the identification of the current transaction CI, NULL refers to the identification of the preceding transaction CI (the reason why it is set to NULL is because this transaction is a certificate issuance transaction), and 20190809 indicates that the certificate expires on August 9, 2019 day (including August 9, 2019); Indicates the threshold mechanism, that is, 5 of the 7 CAs can revoke the certificate;
[0080] User u sends transaction CI and u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com