Patents
Literature
187 results about "Client certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
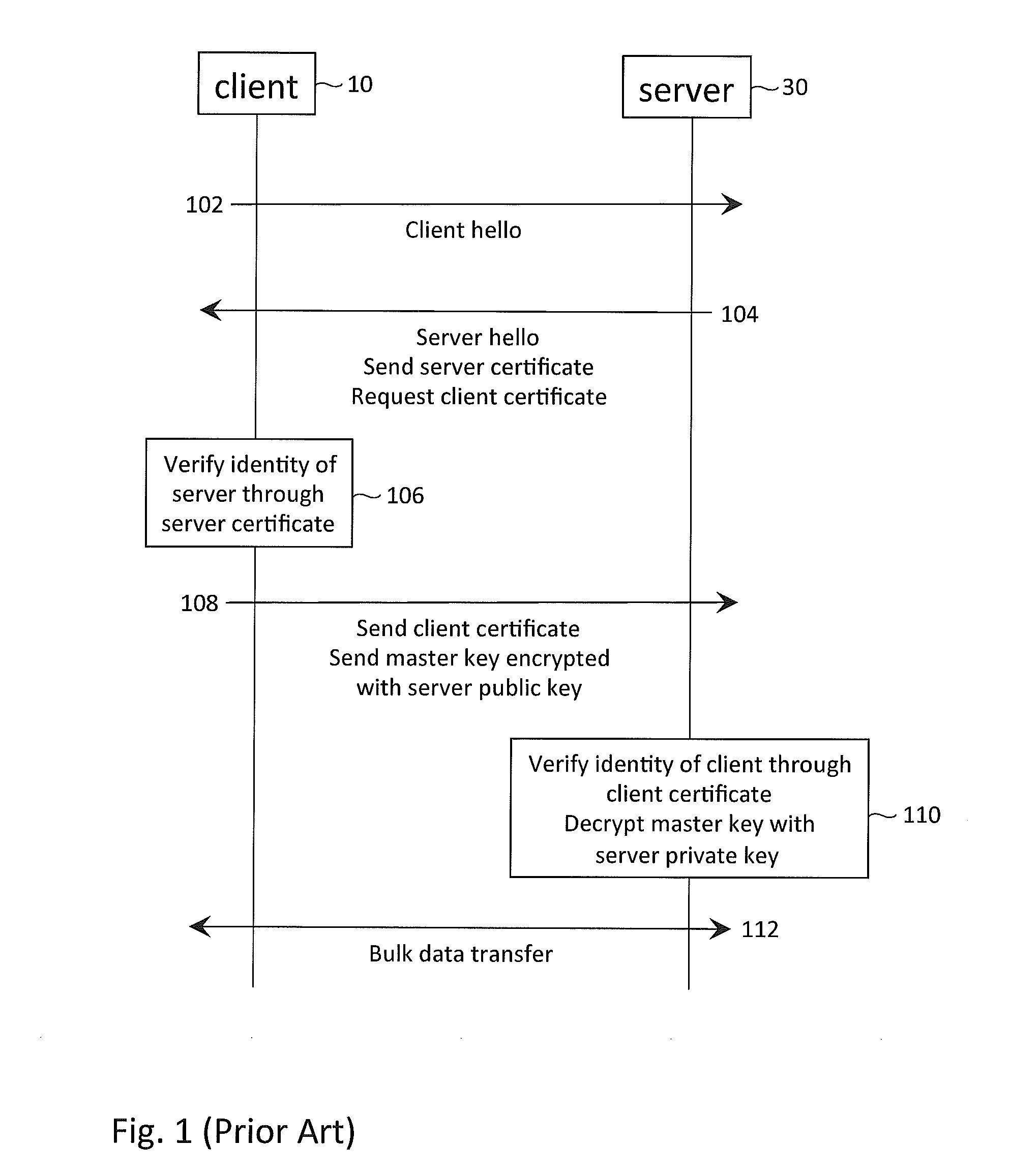
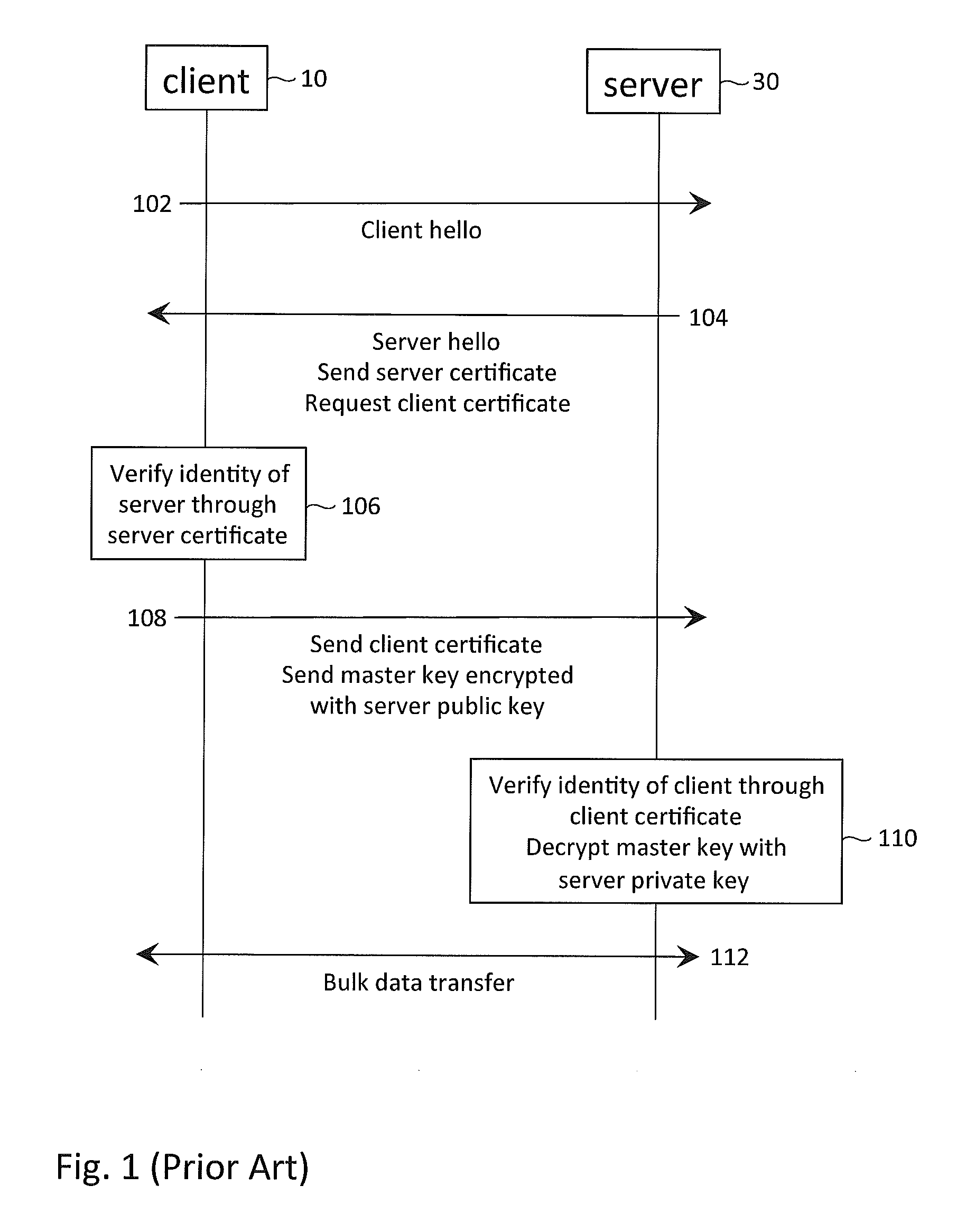
In cryptography, a client certificate is a type of digital certificate that is used by client systems to make authenticated requests to a remote server. Client certificates play a key role in many mutual authentication designs, providing strong assurances of a requester's identity.
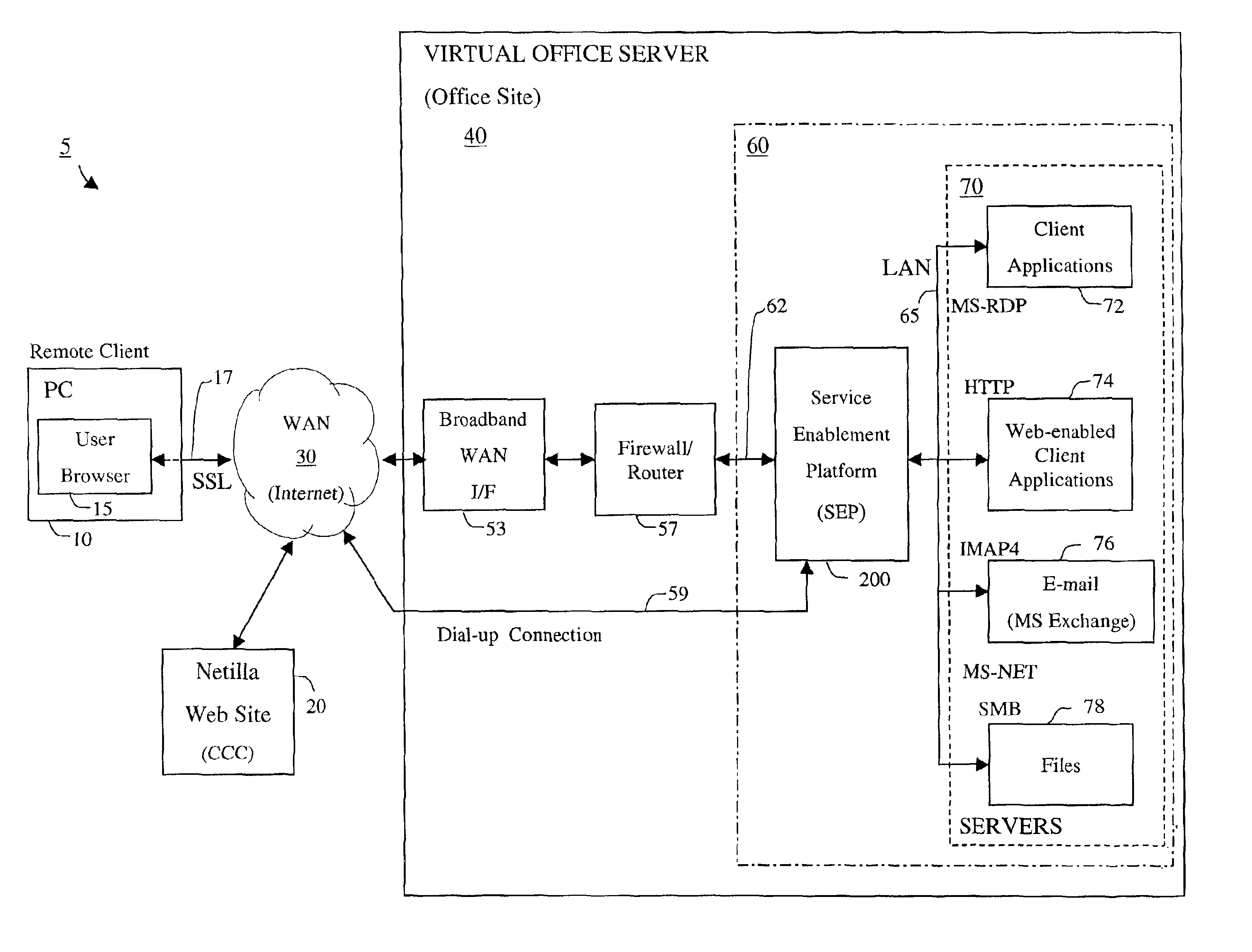
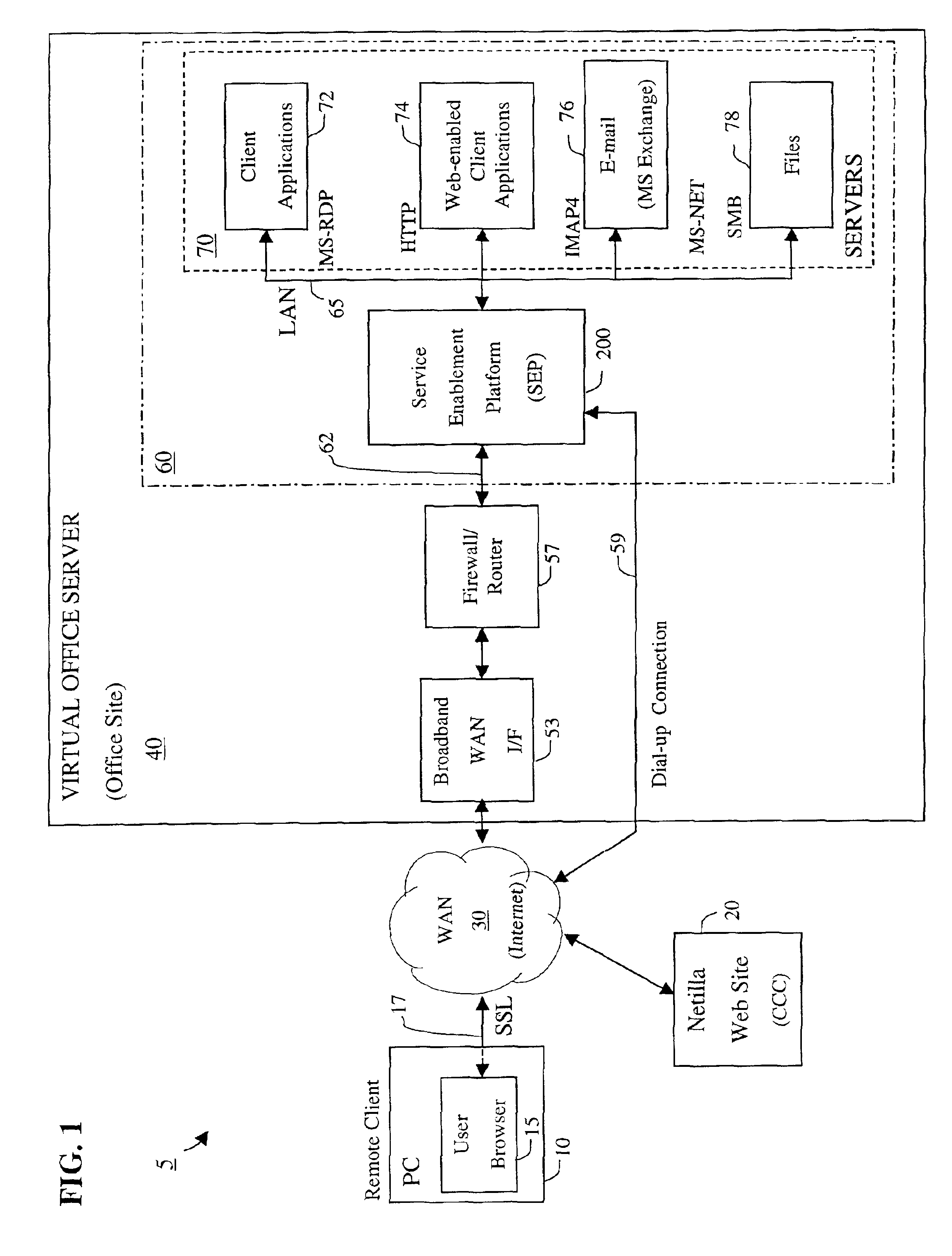
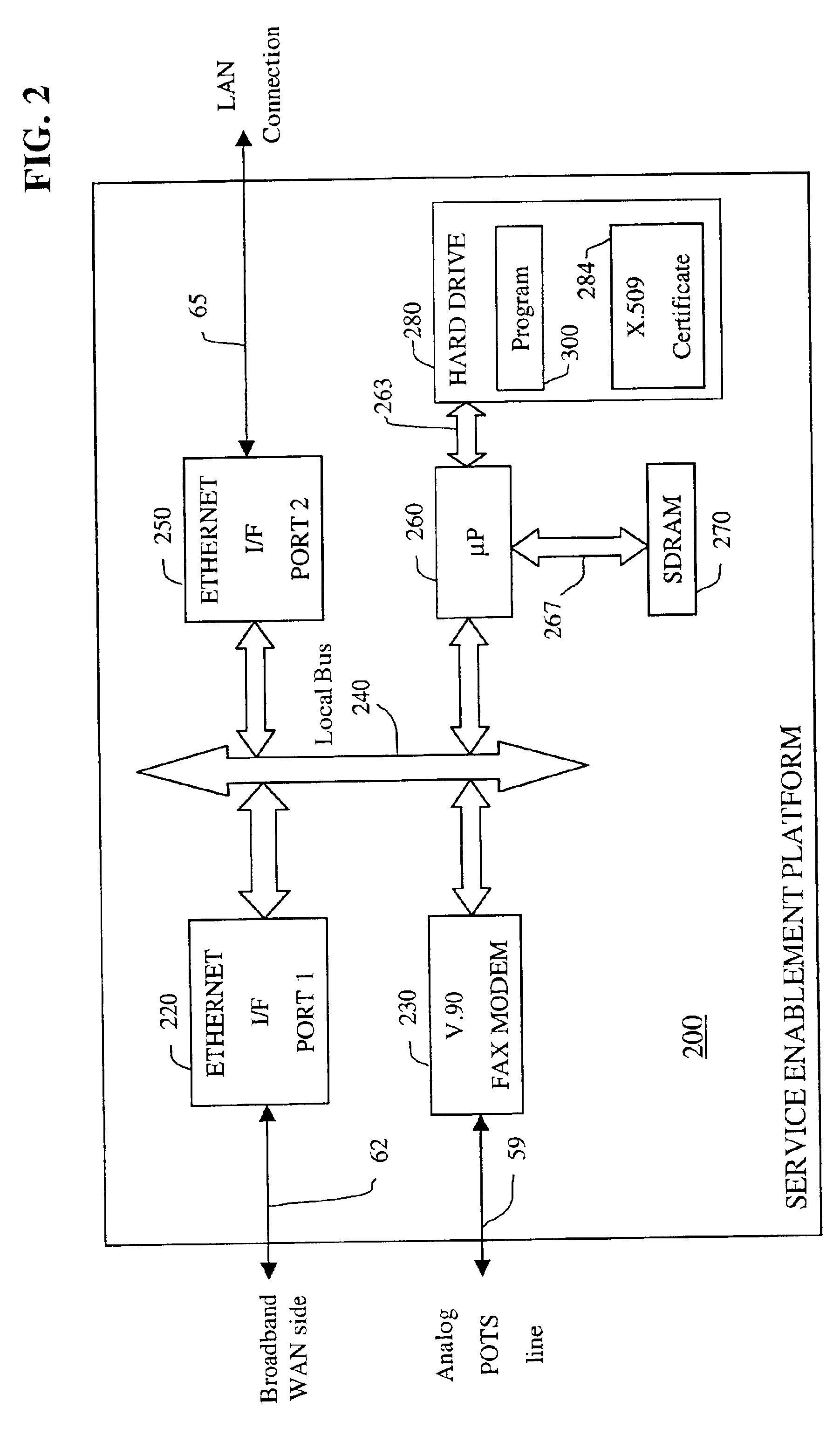
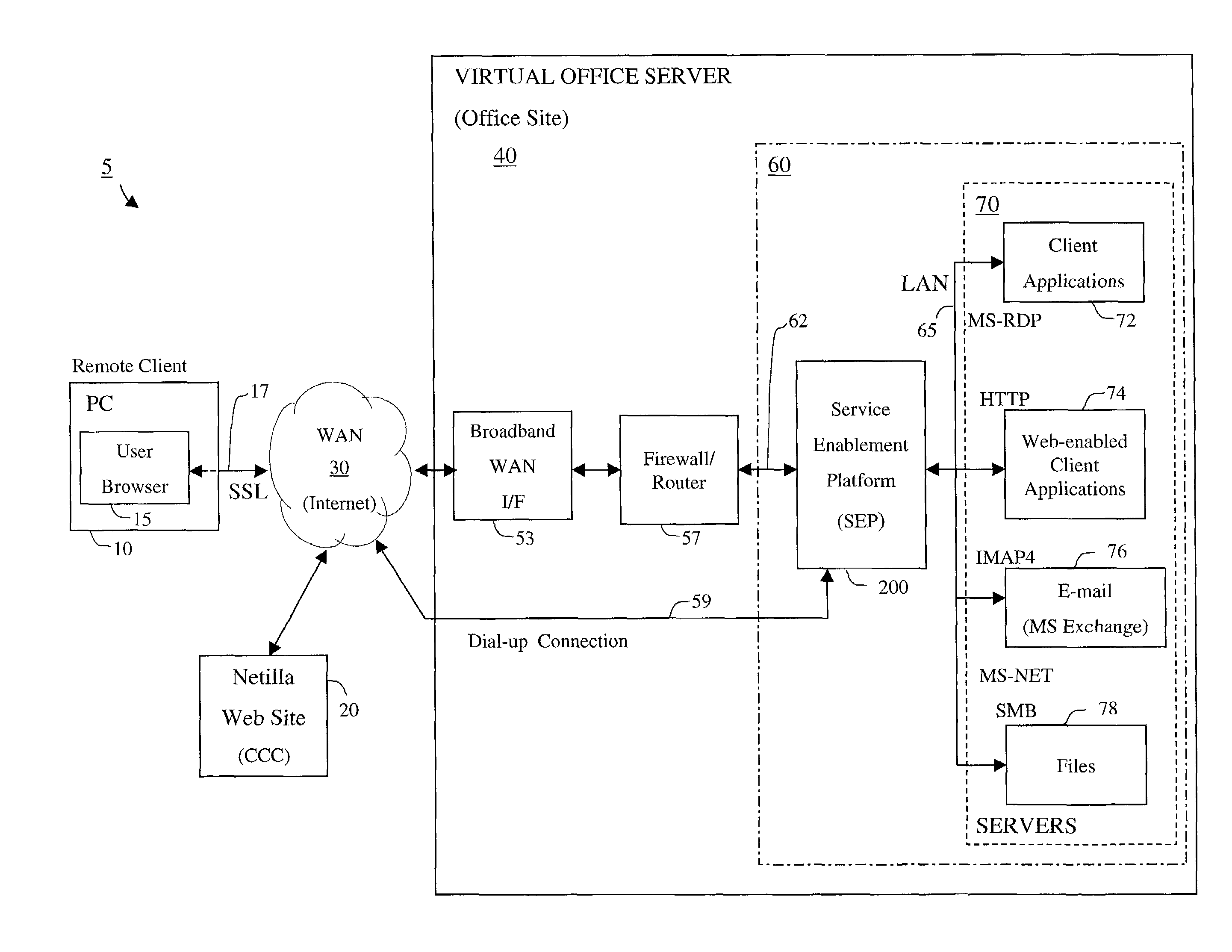
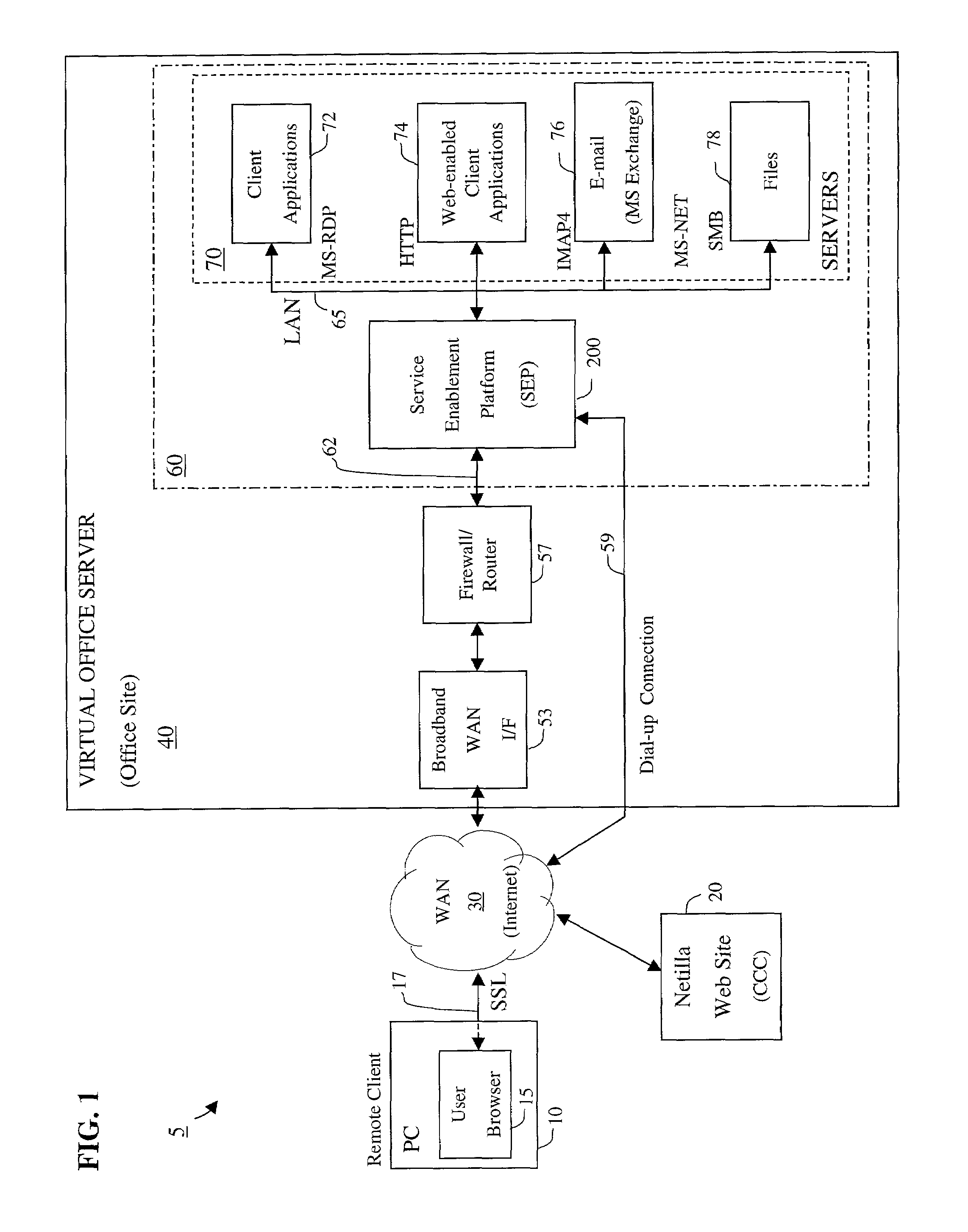
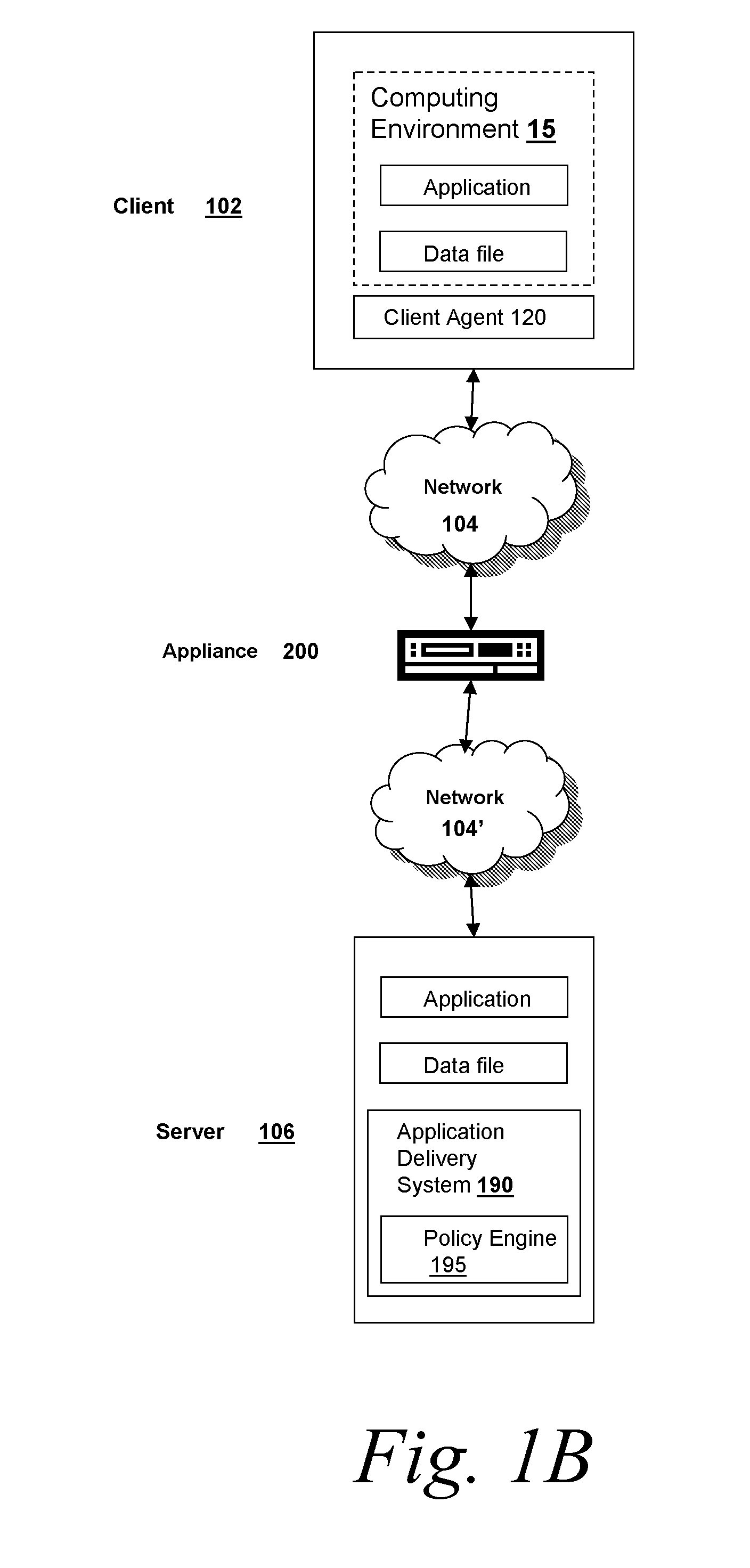
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6920502B2Readily and easily accommodateExpanding processing and storage capacityMultiple digital computer combinationsProgram controlCA protocolNetwork connection
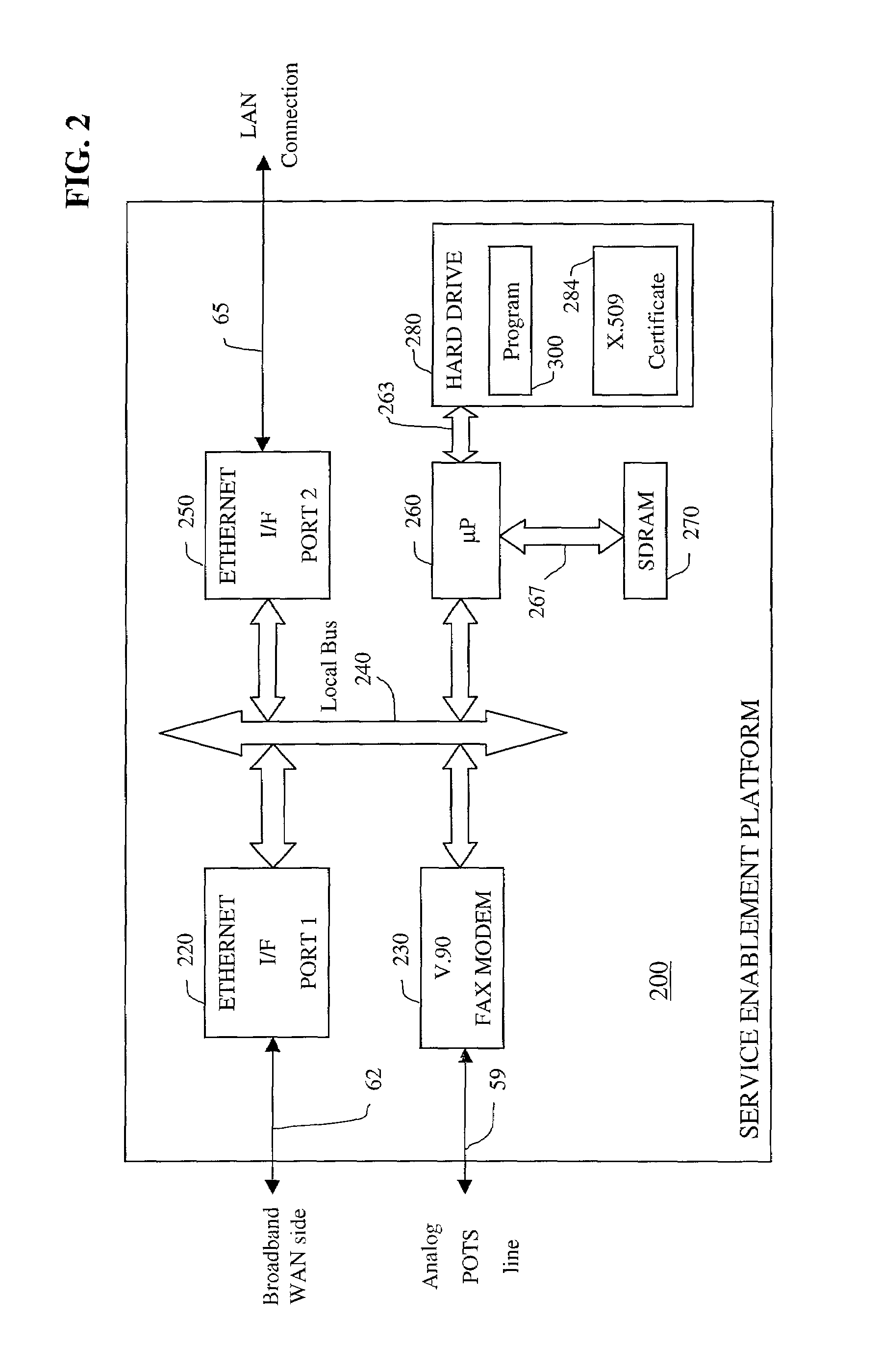
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6981041B2Expanding processing and storage capacityEasy to scaleMultiple digital computer combinationsData switching networksCA protocolNetwork connection
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
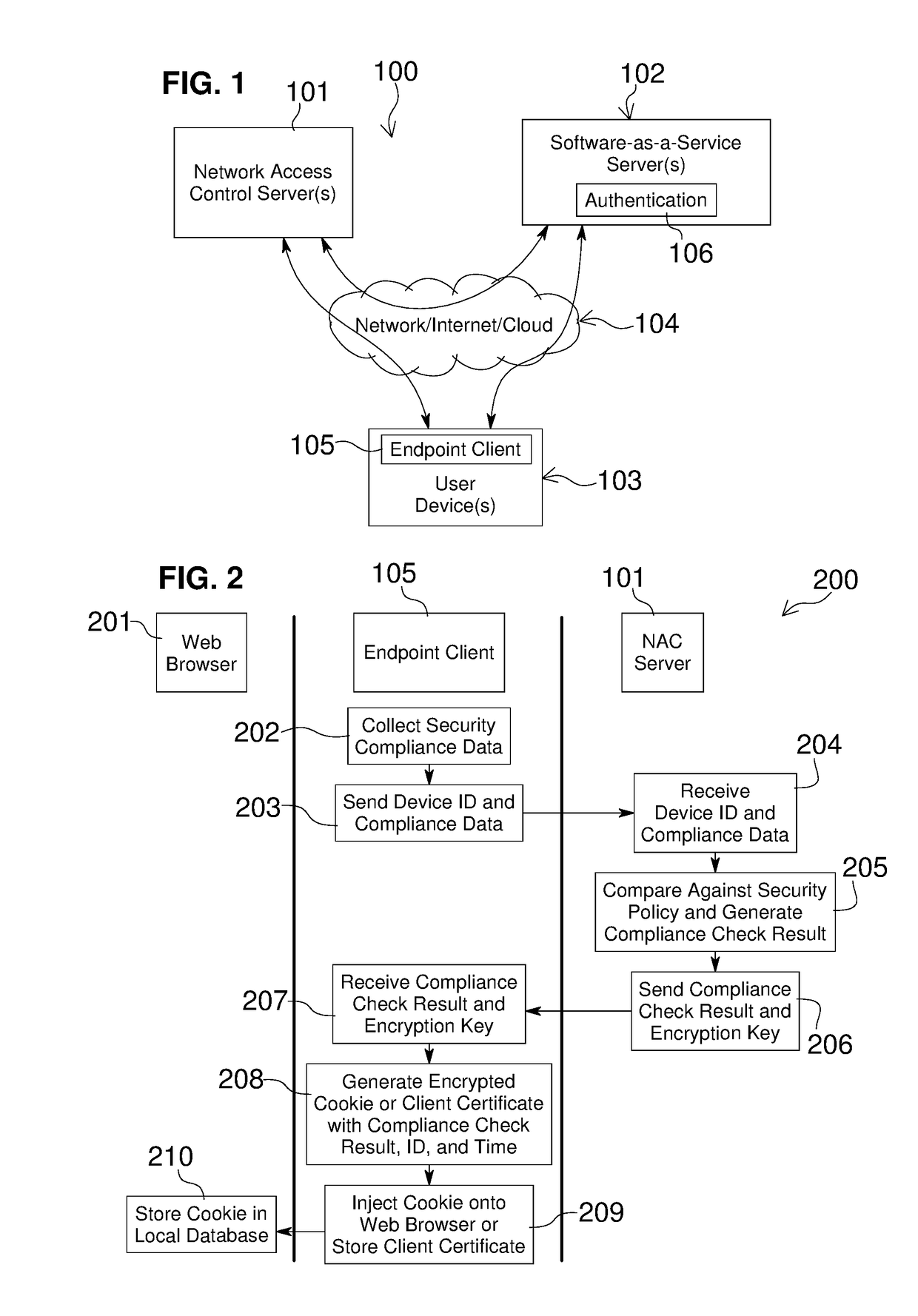
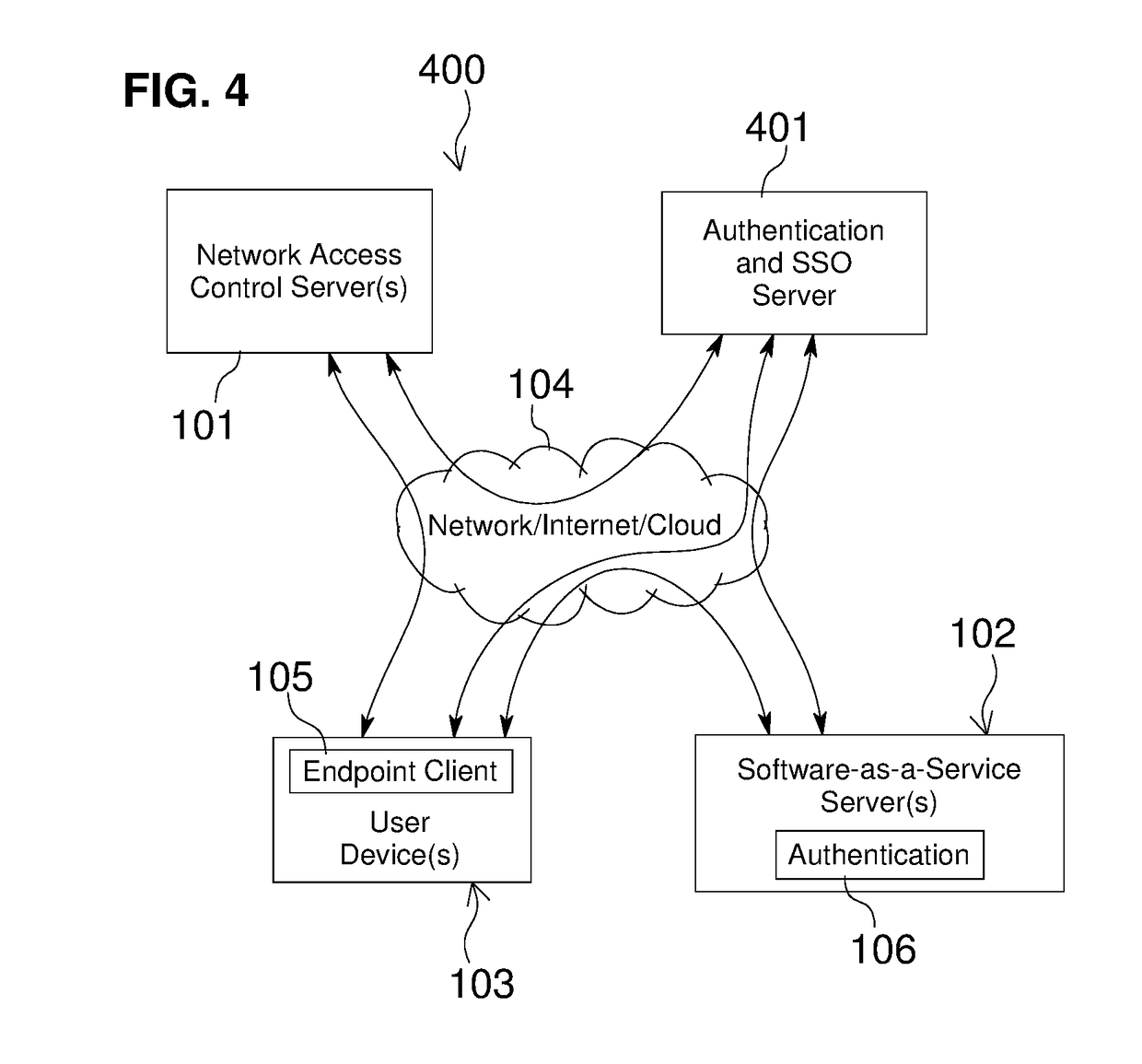
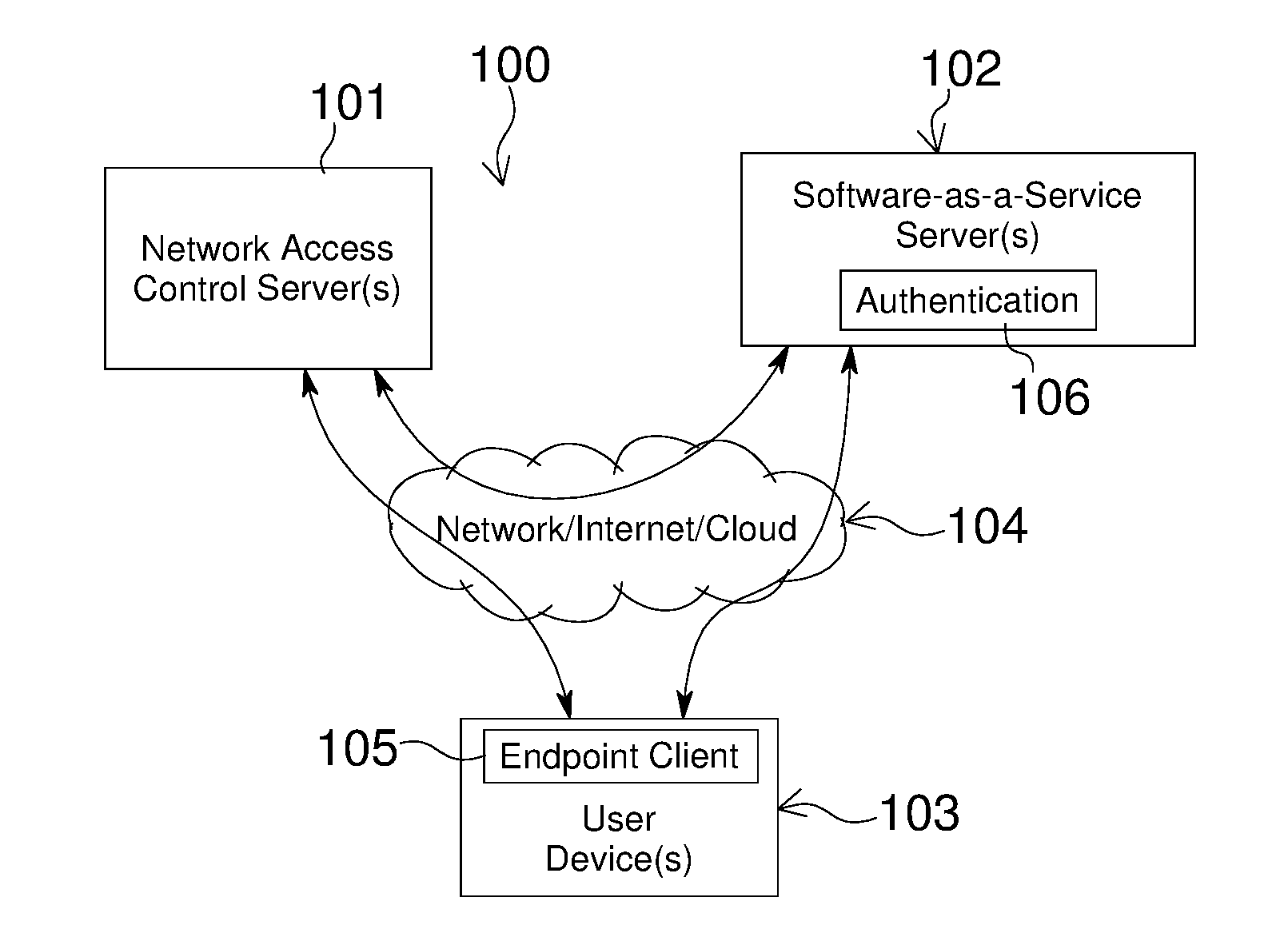
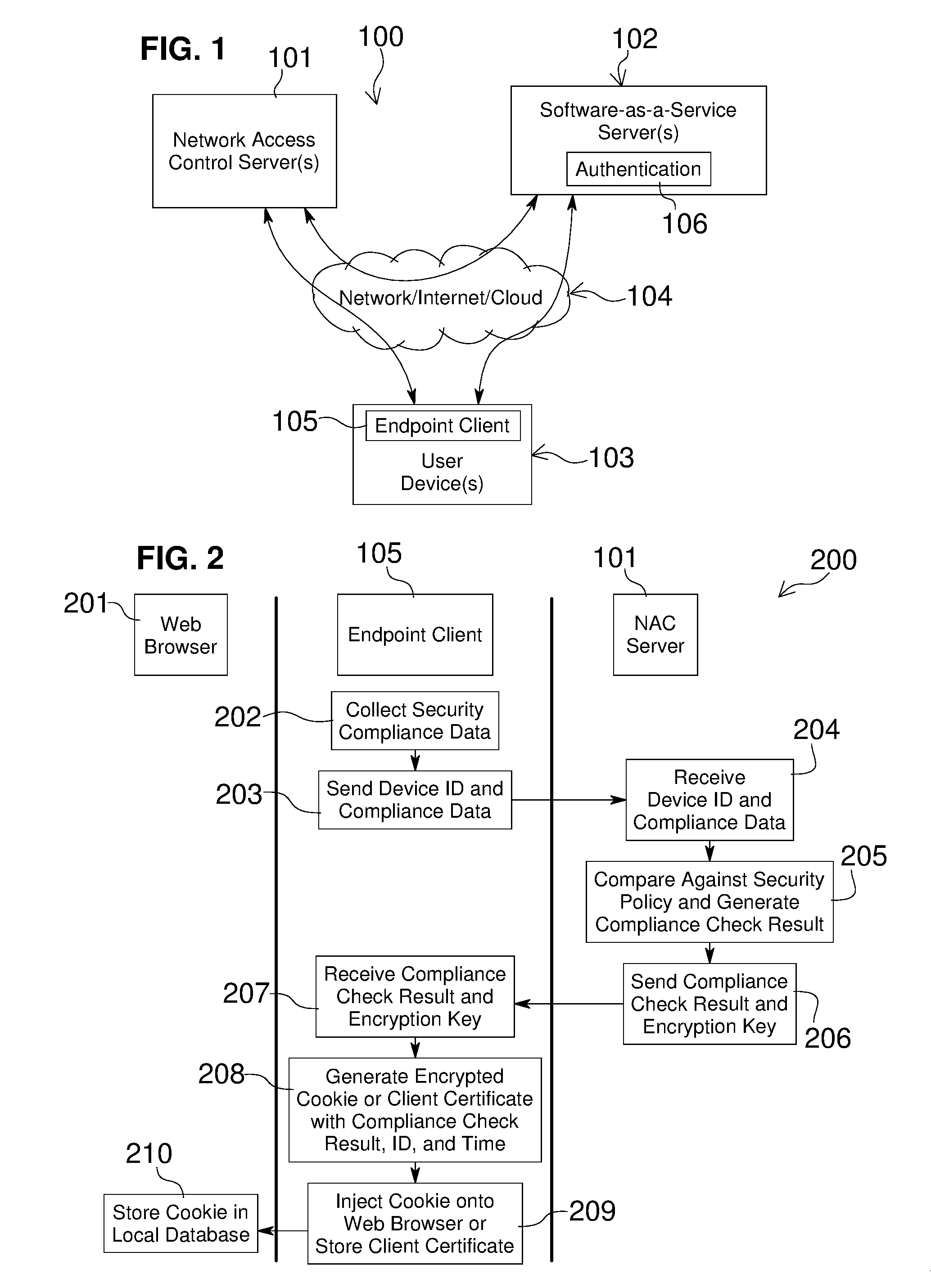
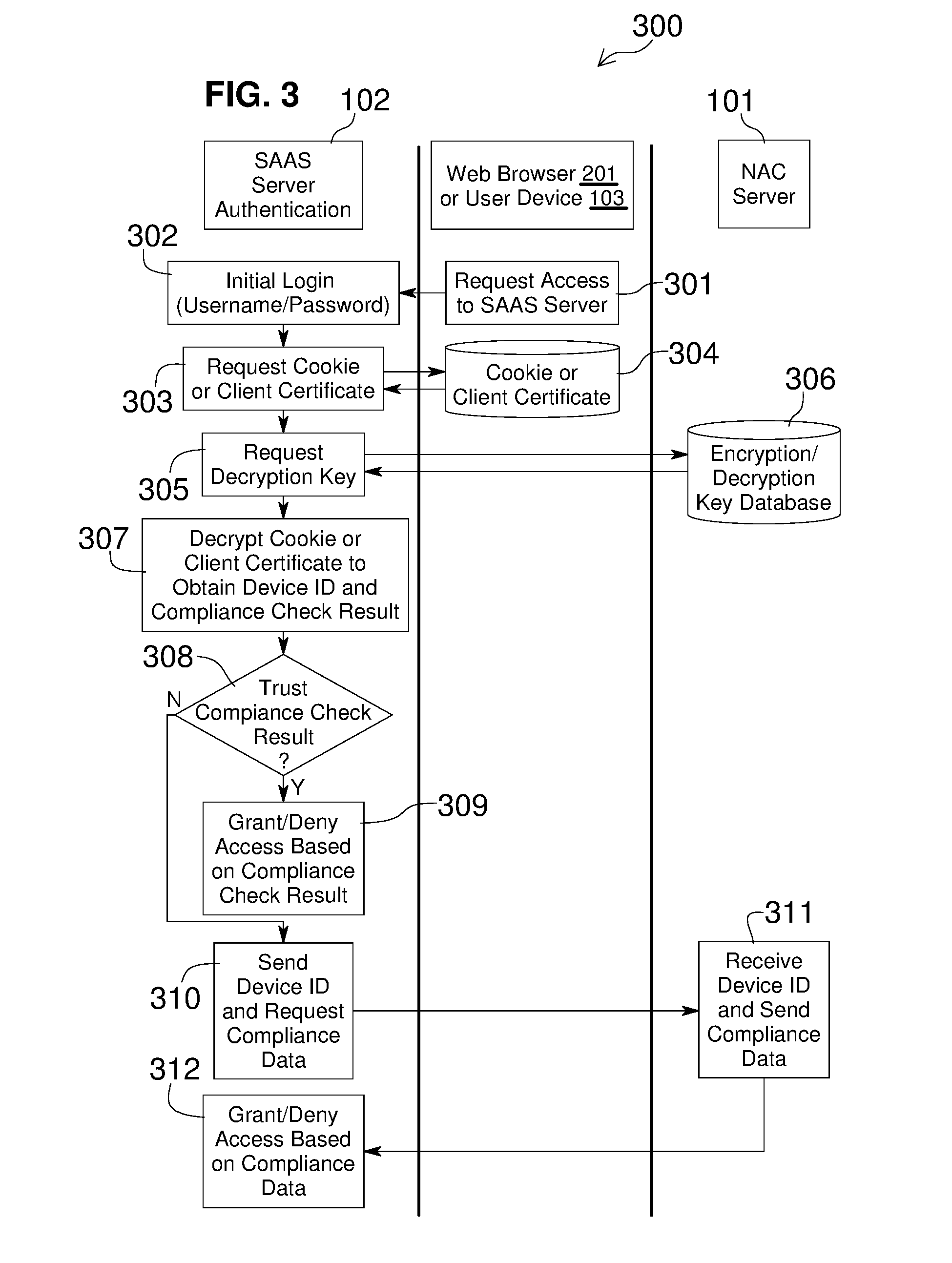
Network Access Control with Compliance Policy Check
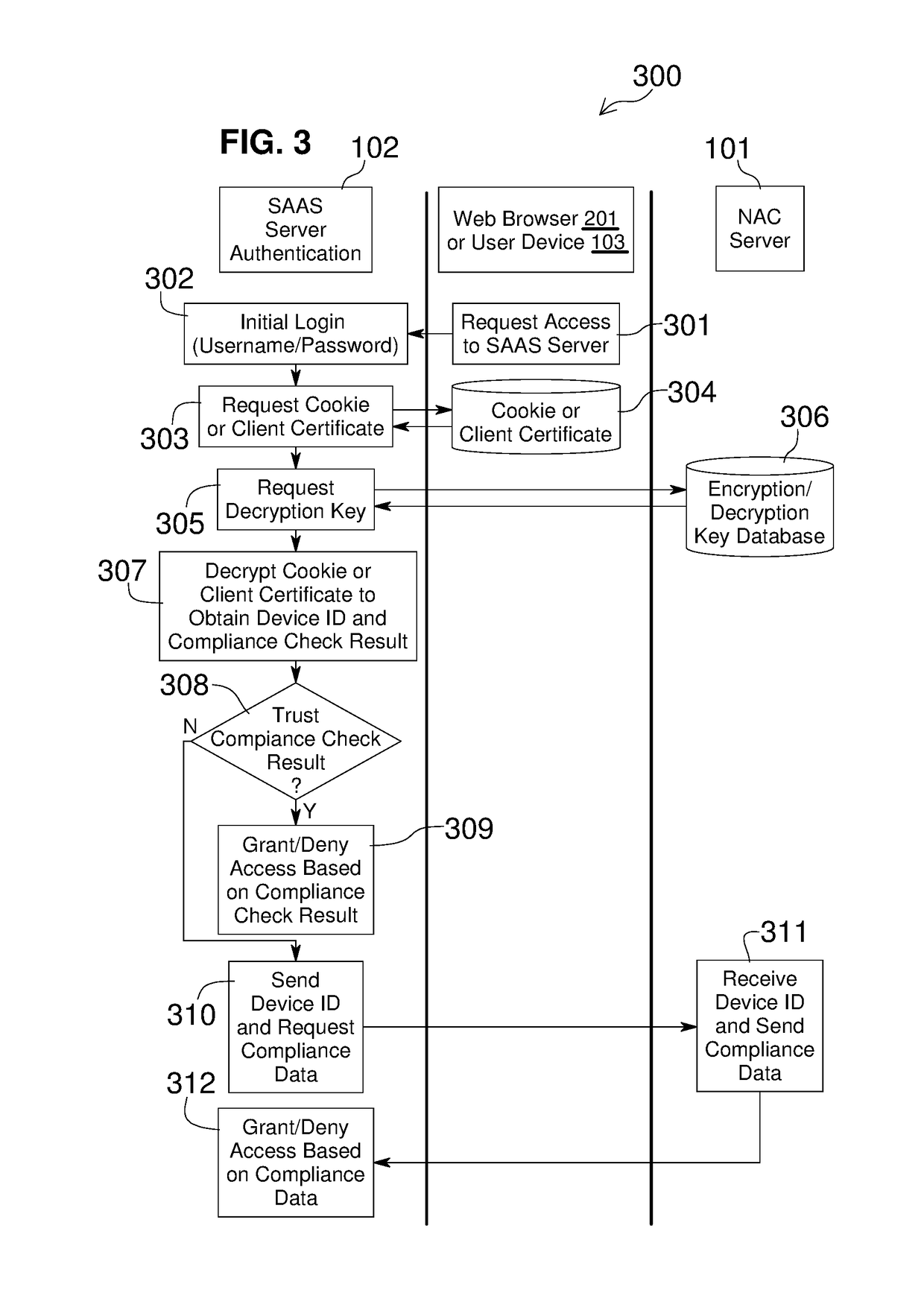
Embodiments of the present invention include methods involving an authentication application, a client application, or a combination of a network access control server with the authentication application and the client application. The client application collects compliance data regarding the user device and communicates the compliance data to the network access control server. The network access control server generates a compliance check result based on whether the compliance data indicates that the user device is compliant with a security policy for the software-as-a-service server. The authentication application grants access by the user device when the compliance check result is positive; and the authentication application denies access by the user device when the compliance check result is negative. In some embodiments, the compliance check result or a user device identifier is stored in a web browser cookie or a client certificate on the user device.
Owner:OPSWAT INC
Networked digital video recording system with copy protection and random access playback
ActiveUS7231516B1Effective positioningHigh rateTelevision system detailsData resettingDigital videoDigital recording
In a multimedia recording and playback network for receiving from a content server a service package of multimedia content, the network including a media server in communication with the content server, a method of securely transmitting a master encryption key from the content server to the media server, including the steps downloading a service package certificate from the content server to the media server, authenticating, in the media server, the received service package certificate, the content server providing to the media server a key server certificate, a public key of the content server, and a client certificate request, the media server authenticating the key server certificate, providing to the content server, upon authentication of the key server certificate by the media server, a client certificate including a challenge signature, and a public key of the media server, the content server authenticating the client certificate including the challenge signature received from the media server, the media server requesting the master encryption key from the content server, and the content server responding by transmitting the master encryption key to media server.
Owner:GOOGLE TECH HLDG LLC
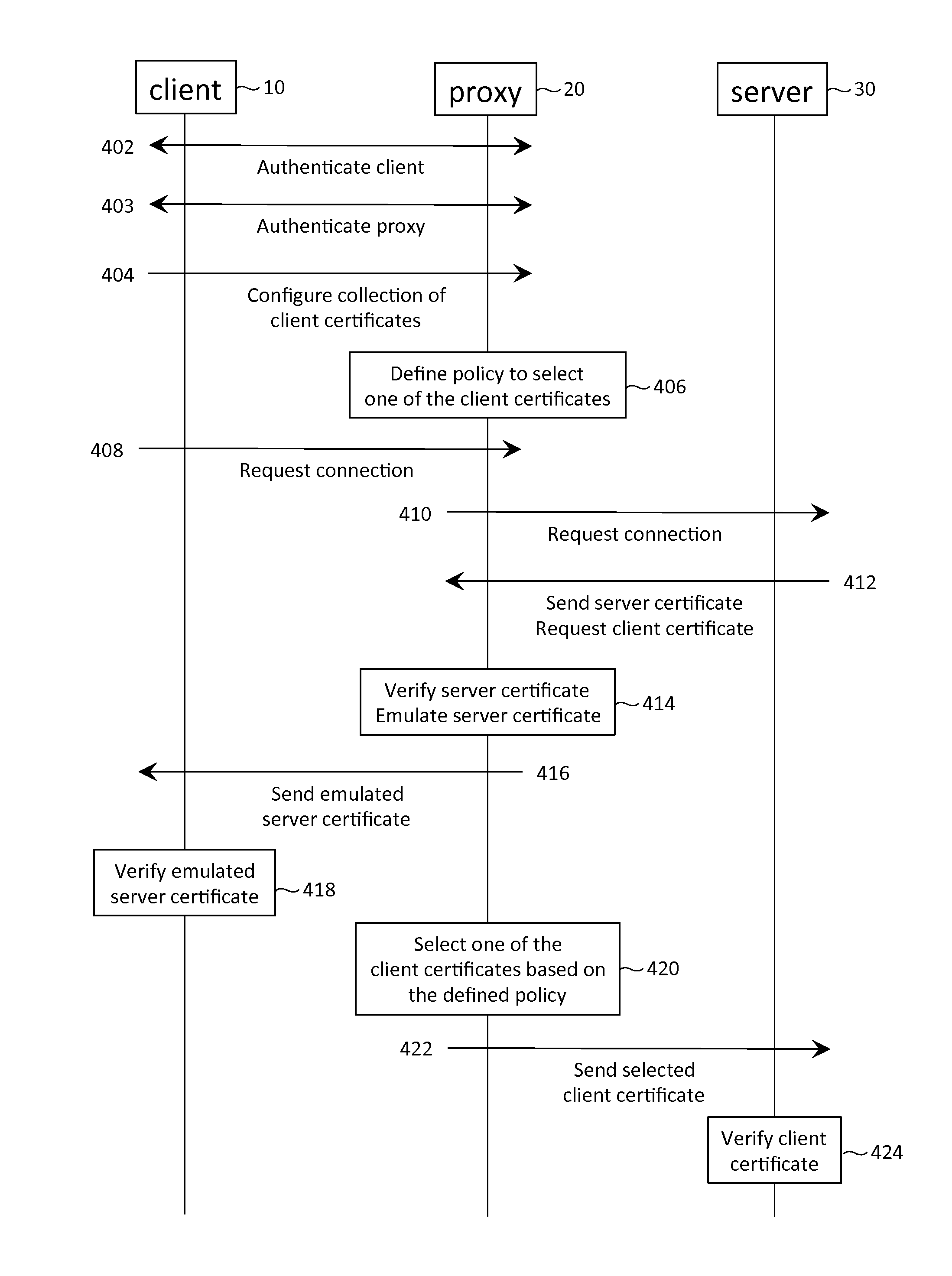
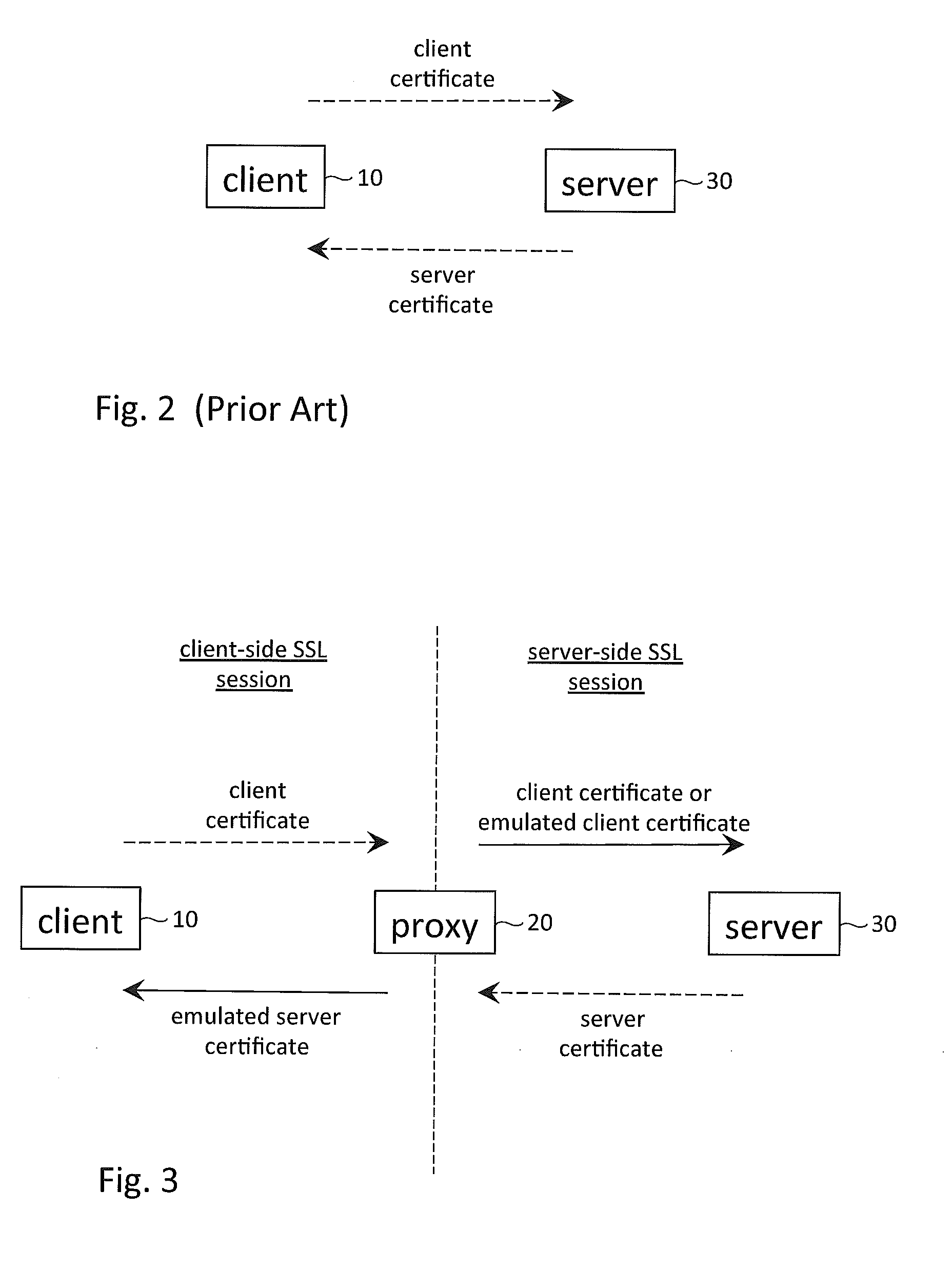
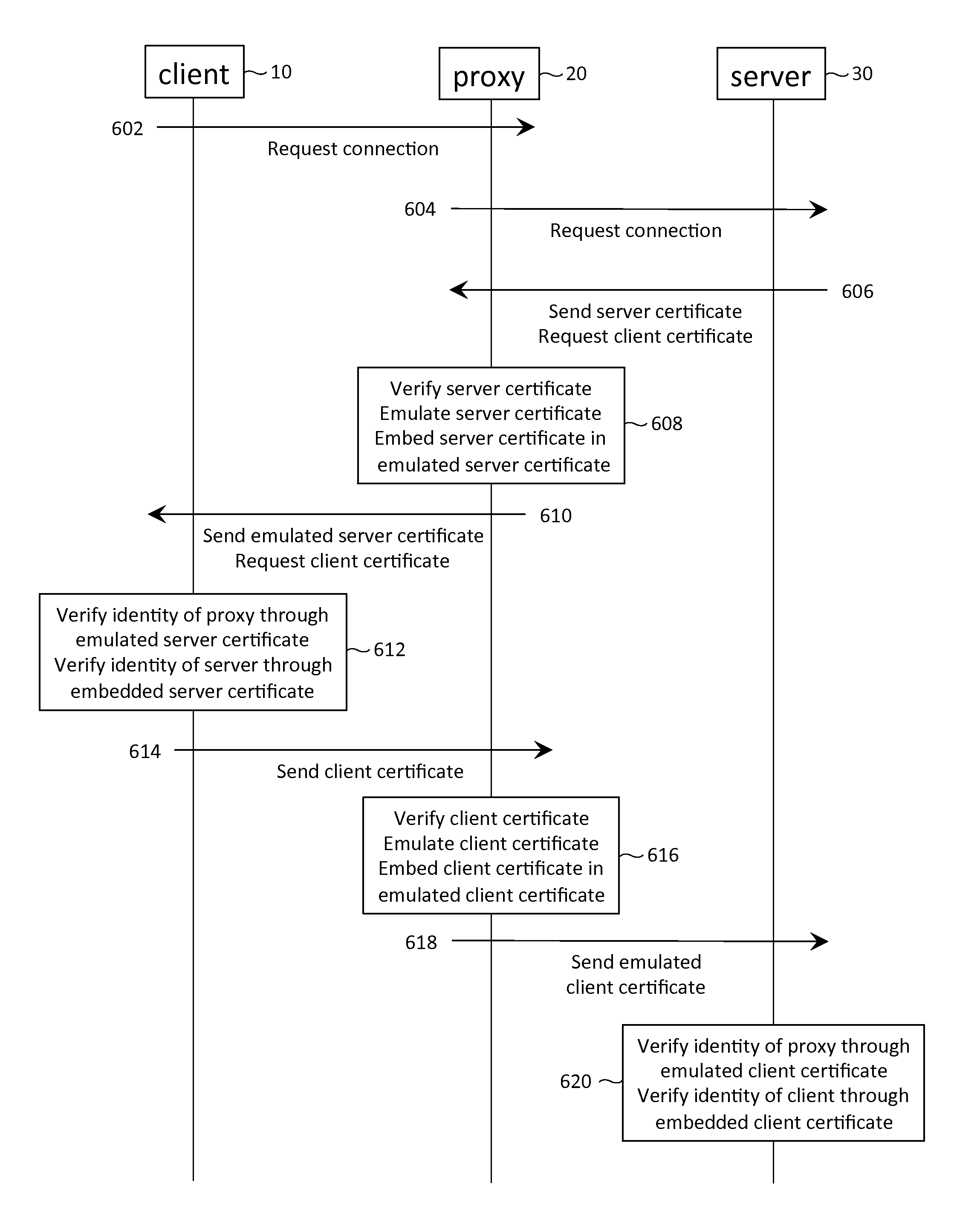
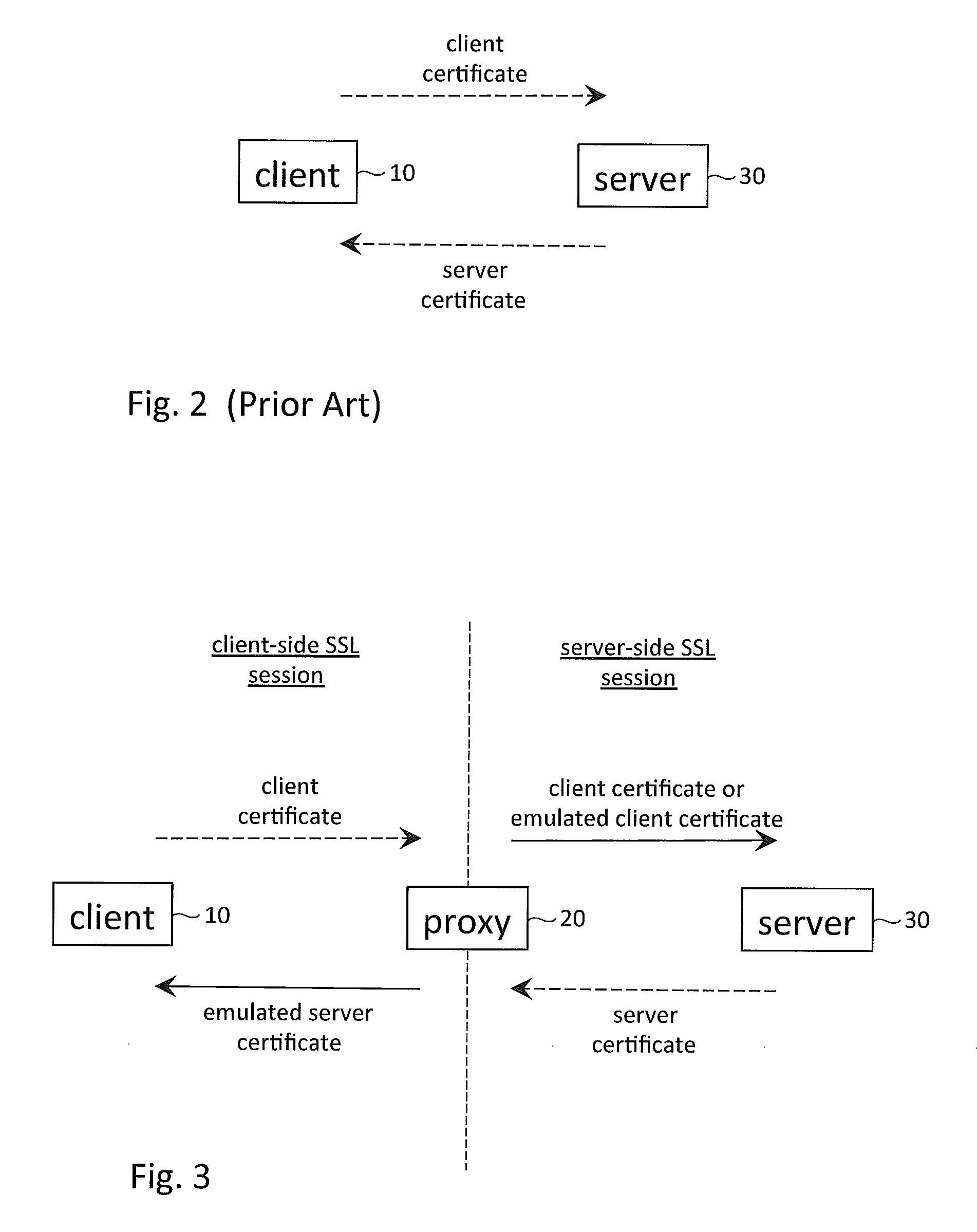
Exchange of digital certificates in a client-proxy-server network configuration
Various techniques are described to authenticate the identity of a proxy in a client-proxy-server configuration. The configuration may have a client-side and a server-side SSL session. In the server-side session, if the proxy has access to the private keys of the client, the proxy may select a client certificate from a collection of client certificates and send the selected certificate to the server to satisfy a client authentication request of the server. If the proxy does not have access to the private keys, the proxy may instead send an emulated client certificate to the server. Further, the client certificate received from the client may be embedded within the emulated client certificate so as to allow the server to directly authenticate the client, in addition to the proxy. An emulated client certificate chain may be formed instead of an emulated client certificate. Similar techniques may be applied to the client-side session.
Owner:CA TECH INC
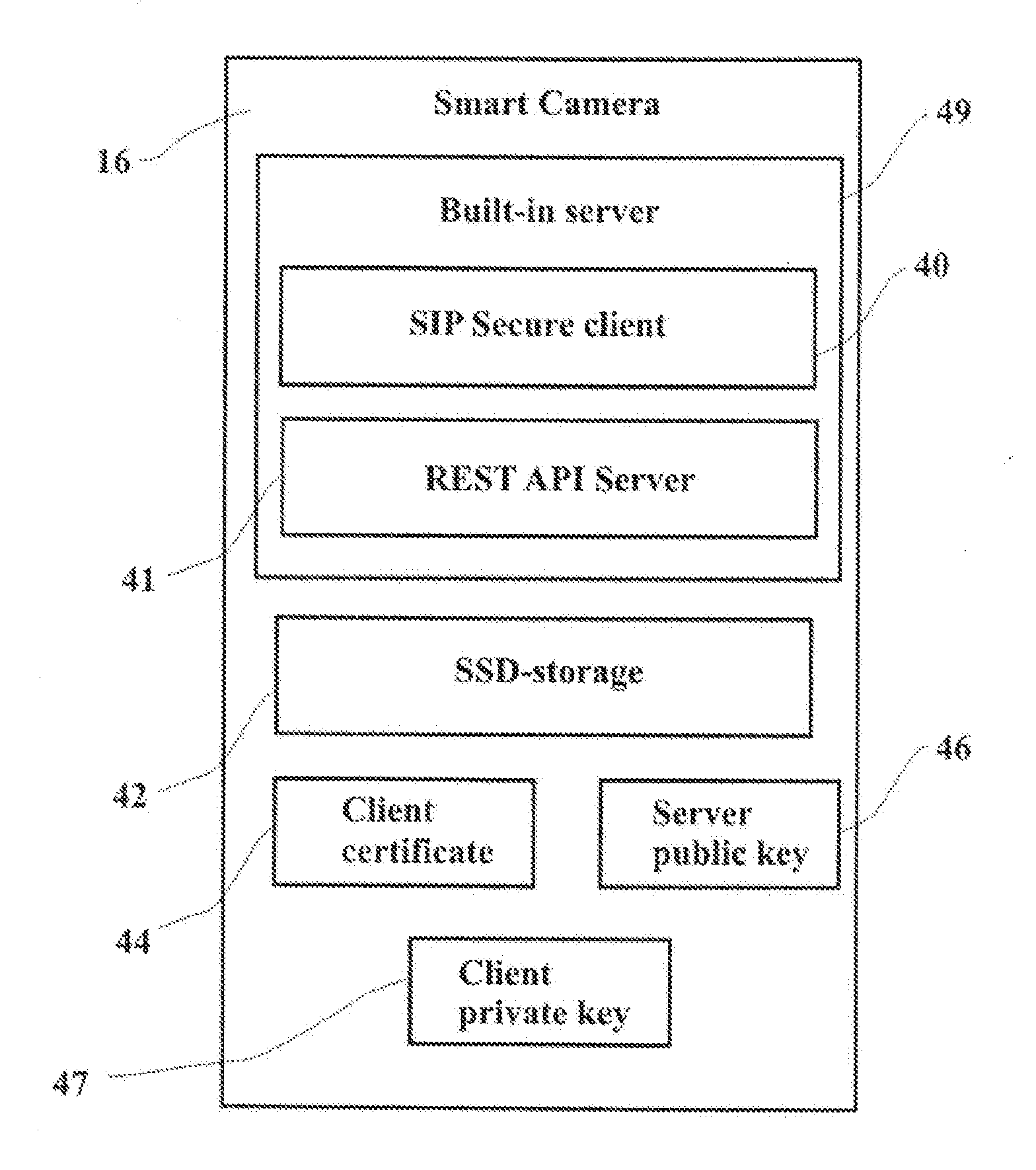
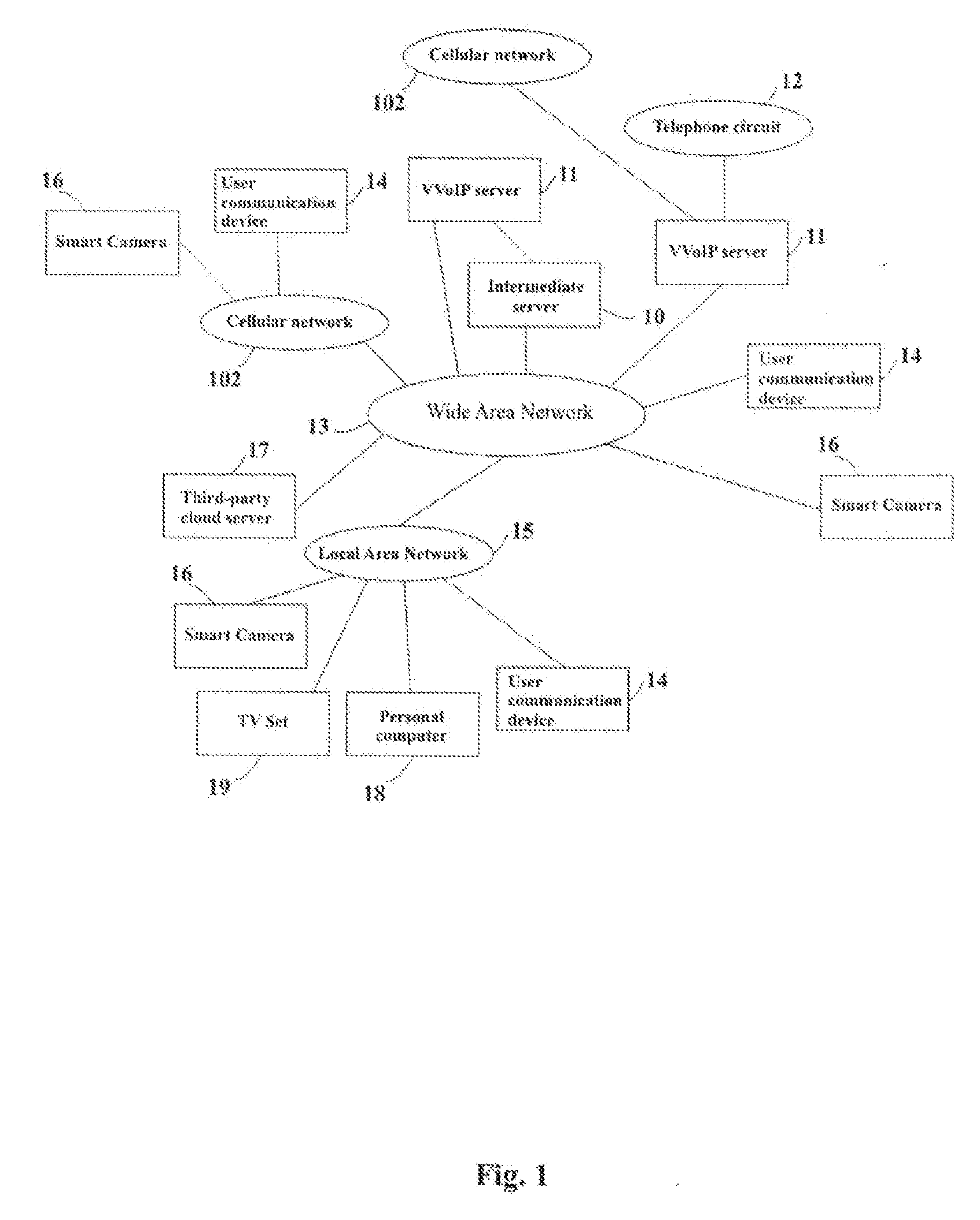
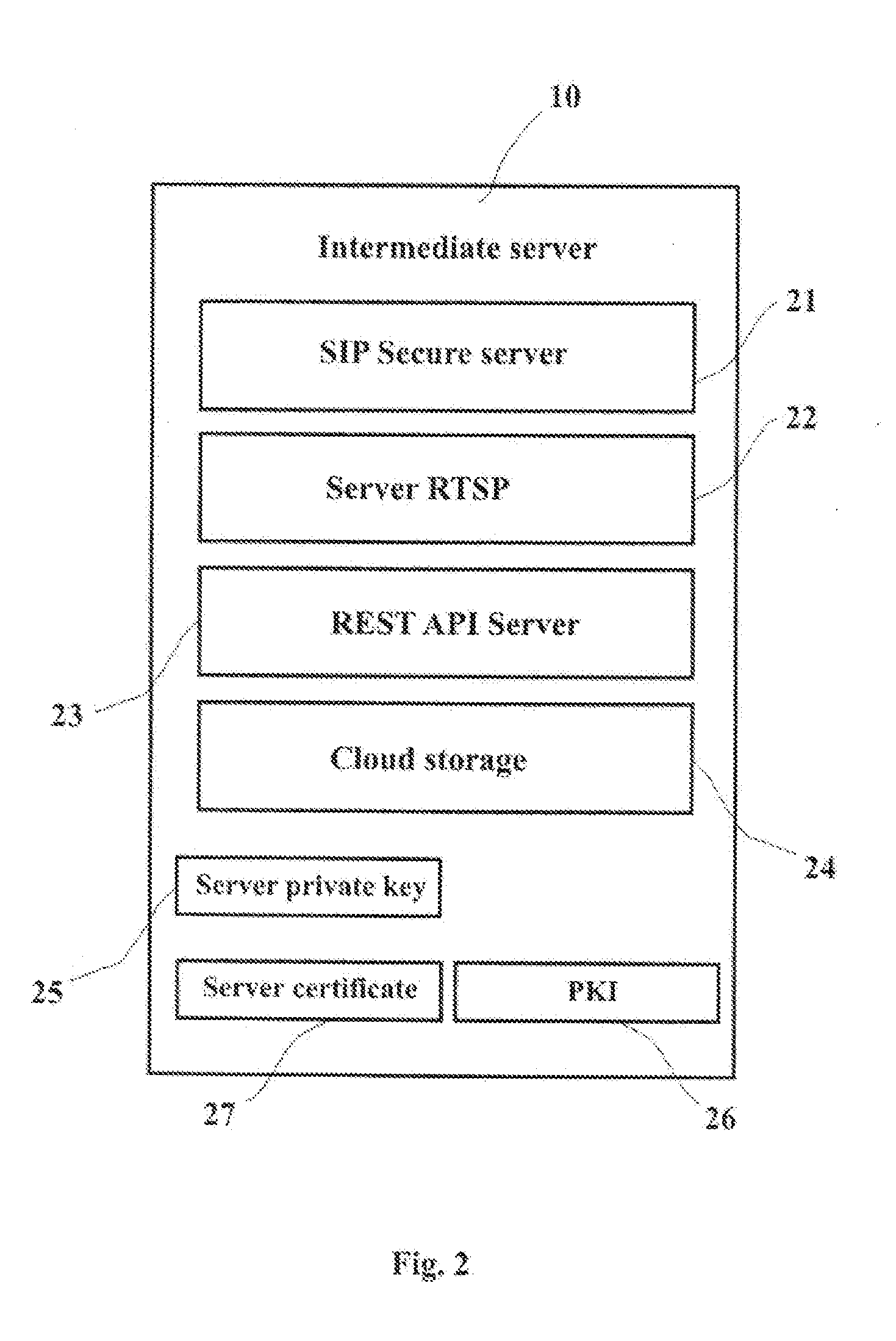
Systems for Securing Control and Data Transfer of Smart Camera
InactiveUS20150222601A1Digital data processing detailsMultiple digital computer combinationsCloud storageData transmission
A system of secure control of a smart camera and transfer a media content from and to smart camera by a user communication device and an intermediate server, comprising: a smart camera, intermediate server and user communication device, which are connected to WAN. The intermediate server includes a SIPS-server, REST API Server, cloud storage, Public Key Infrastructure, private key and server certificate. The smart camera includes a built-in server, a SSD-storage, a client certificate, client private key and an intermediate server public key. The built-in server includes a SIPS-client and REST API Server and the user communication device includes a SIPS-client, a REST Client and a public key of said intermediate server. The smart camera and said user communication devices are connected to common local area networks (LAN) with communicating to wide area network (WAN) or cellular networks.
Owner:BRANTO
Method and appliance for authenticating, by an appliance, a client to access a virtual private network connection, based on an attribute of a client-side certificate
ActiveUS20080072311A1Computer security arrangementsMultiple digital computer combinationsPrivate networkClient-side
In a method and appliance for authenticating, by an appliance, a client to access a virtual network connection, based on an attribute of a client-side certificate, a client authentication certificate is requested from a client. A value of at least one field in the client authentication certificate received from the client is identified. One of a plurality of types of access is assigned responsive to an application of a policy to the identified value of the at least one field, each of the plurality of access types associated with at least one connection characteristic.
Owner:CITRIX SYST INC
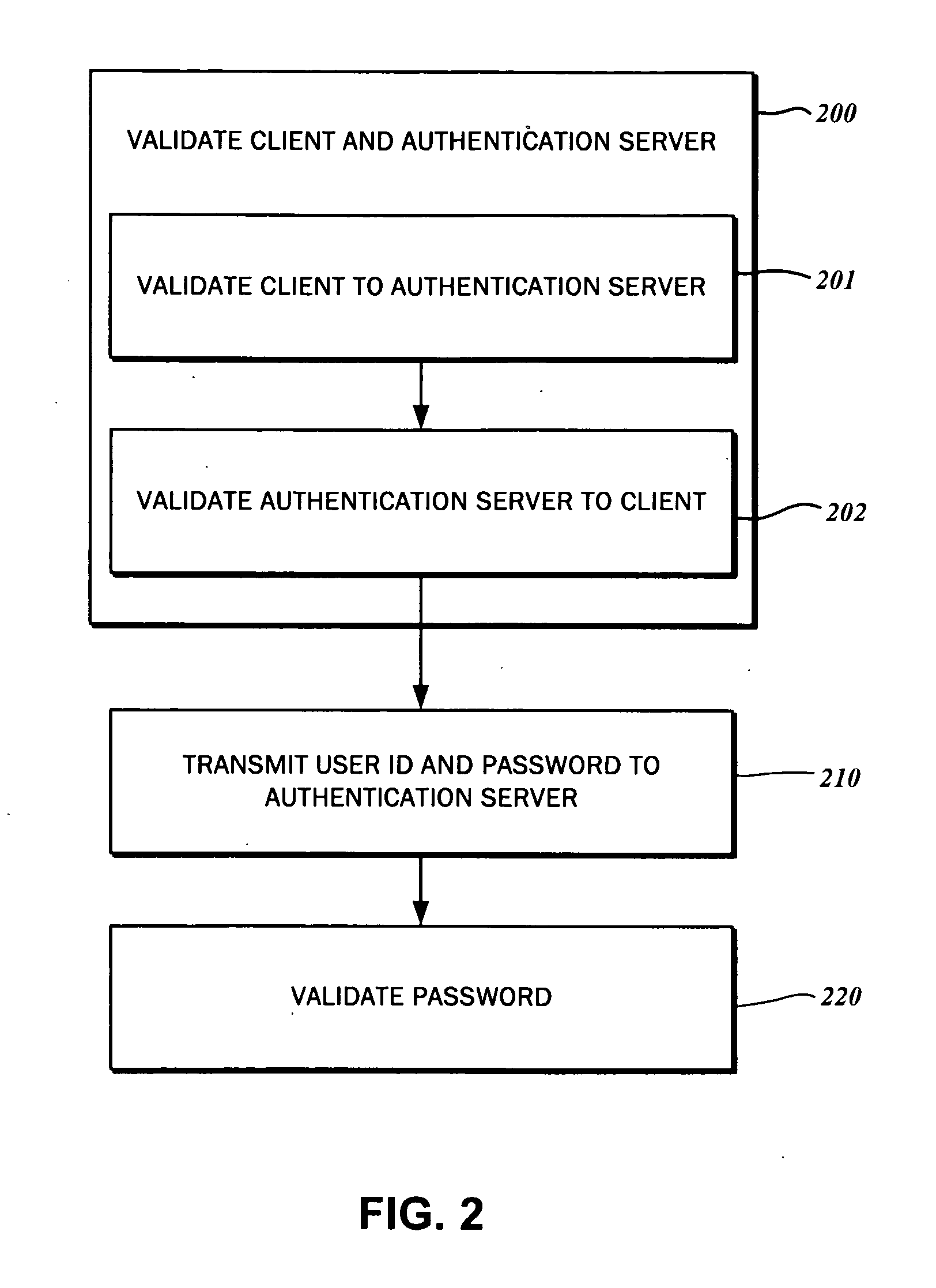
Method and system for secure online transactions with message-level validation
InactiveUS20100217975A1User identity/authority verificationComputer security arrangementsPasswordClient-side
A method and system for authenticating a client and a server is disclosed. In one contemplated embodiment, the client has a client certificate and the server have a server certificate. The client is validated to an authentication module based upon a certificate request identifier generated thereby, a secure data link certificate, and an authentication module Uniform Resource Locator. The authentication module is validated to the client based upon the client certificate and the certificate request identifier. A password associated with a user identifier that is encrypted with a private client key and signed with a public server key is transmitted to the authentication module. The password is then validated.
Owner:SECUREAUTH CORP
Policy bound key creation and re-wrap service
ActiveUS20120297200A1Timely controlReduce usageUnauthorized memory use protectionHardware monitoringClient-sideElectronic mail
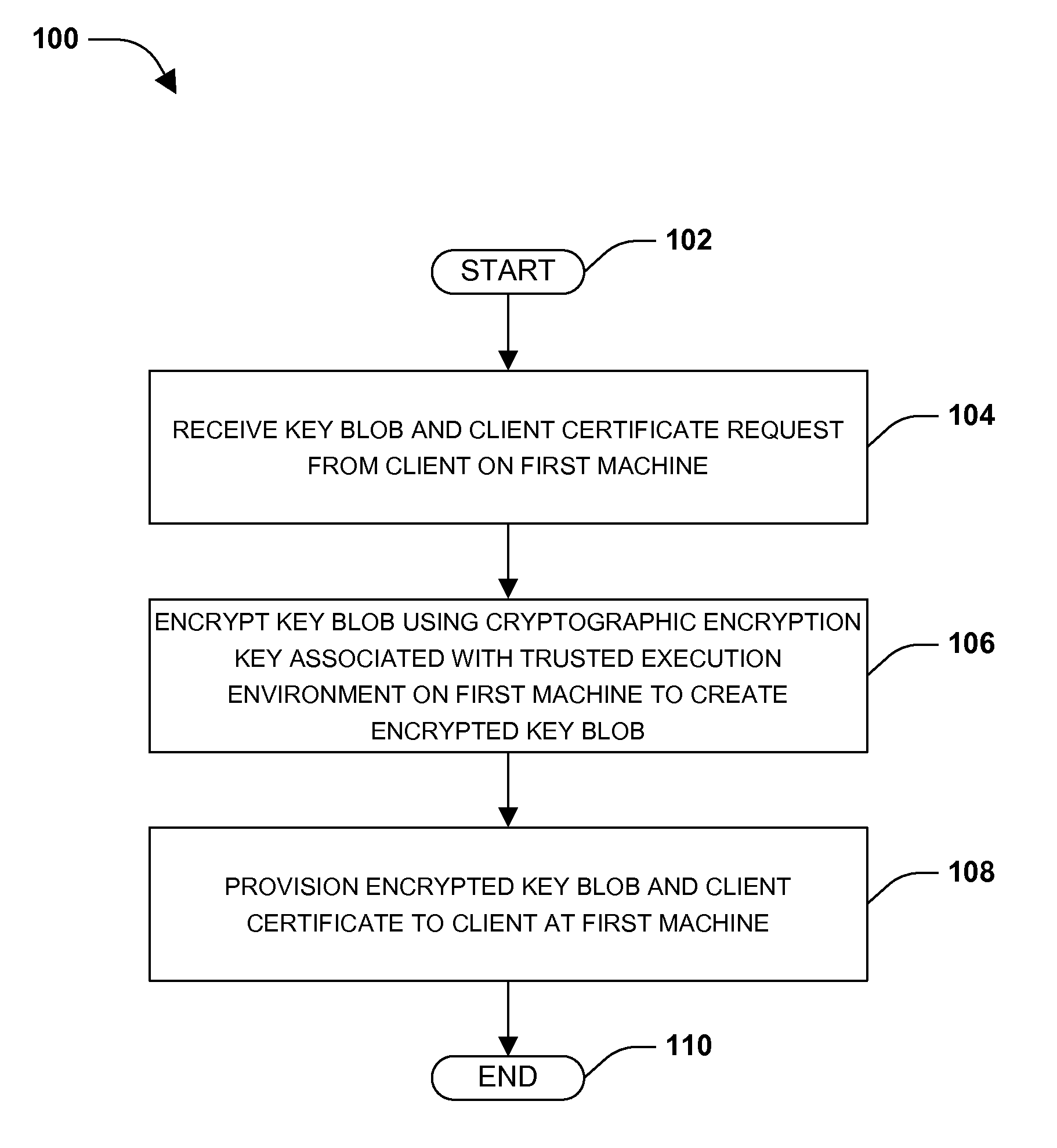
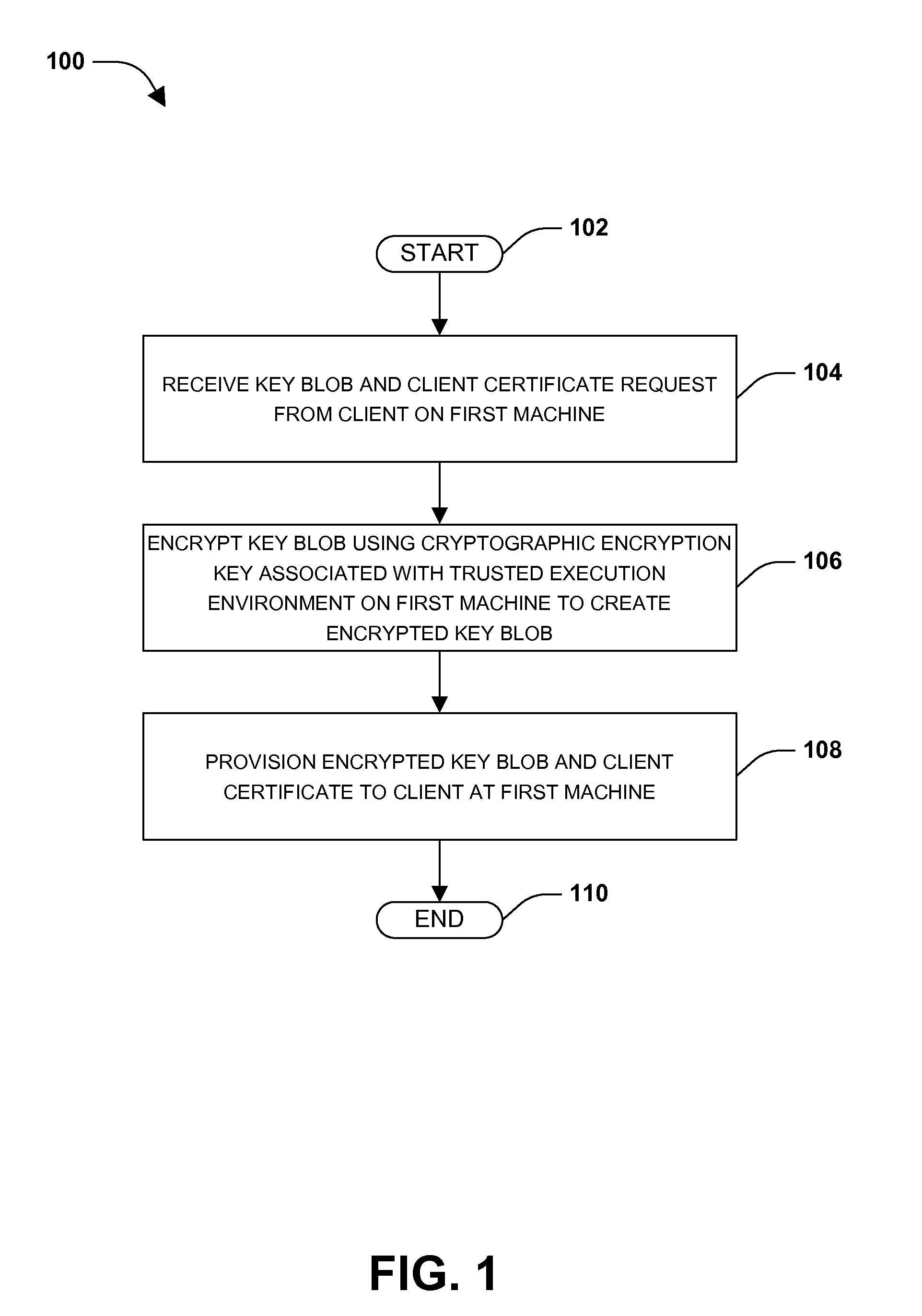
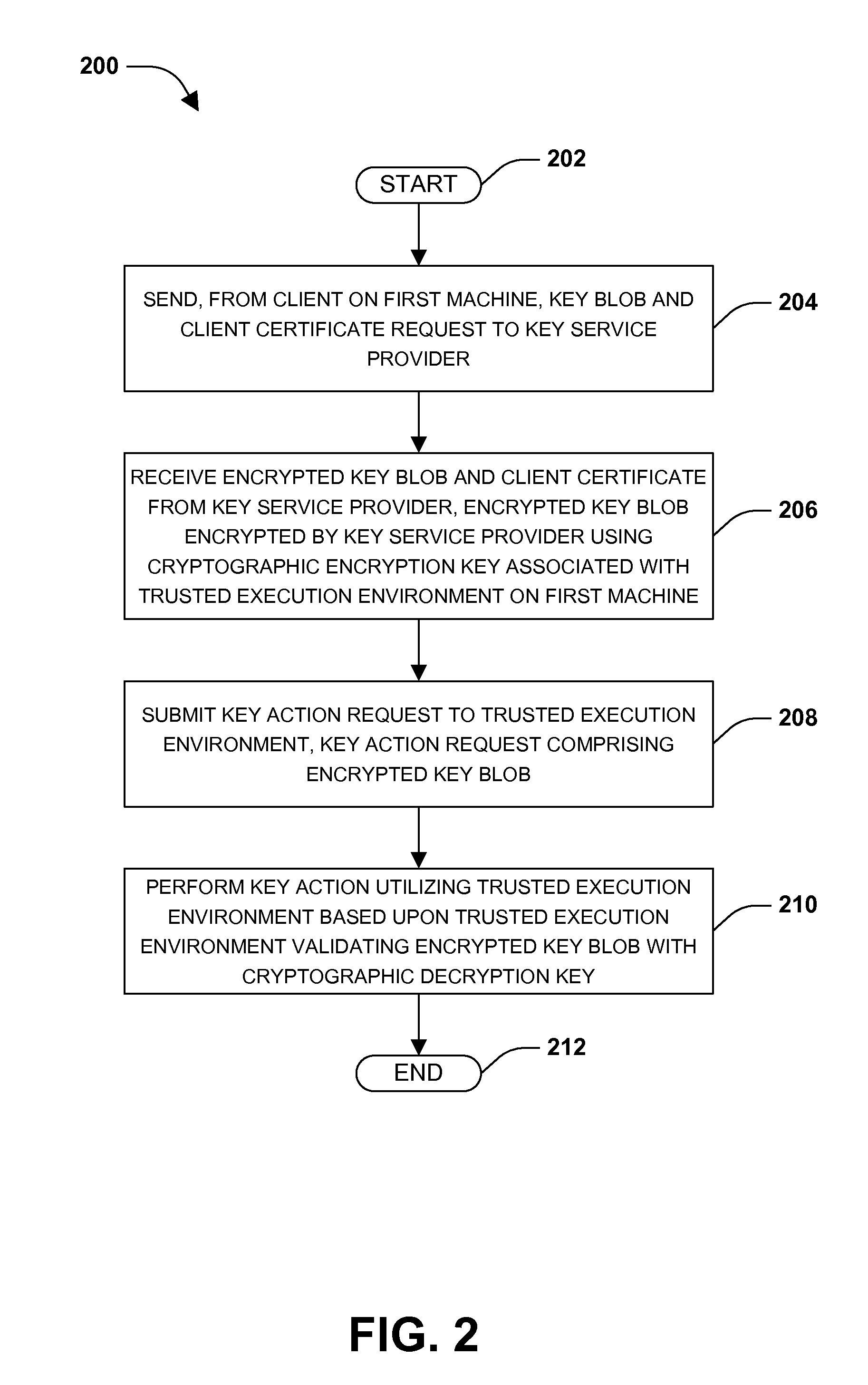
One or more techniques and / or systems are provided for provisioning encrypted key blobs and client certificates. That is, a trusted execution environment on a first machine may provide a key service provider with a cryptographic encryption key. The key service provider may encrypt a key blob using the cryptographic encryption key and / or wrap the encrypted key blob with one or more policies, such as a platform policy. The key service provider may provision the encrypted key blob to a client on the first machine. The client may submit the encrypted key blob to the trusted execution environment for validation so that the client may perform key actions, such as sign an email or encrypt data. Because the key blob may be specific to a particular trusted execution environment and / or machine, the key service provider may re-wrap the key blob if the client “roams” to a second machine.
Owner:MICROSOFT TECH LICENSING LLC
System and method for secured network access
A method and system for secured network access is provided in accordance with the present invention. The method begins with receiving a login request from a client on a router. Thereafter, a certificate transfer instruction for the router to an authentication appliance is generated where the client lacks a copy of a client certificate. The client is authenticated with a challenge-response sequence, the response to which is deliverable through an out-of-band communications channel. Upon authentication, the client certificate and the client private key are transmitted to the client, which are used to authenticate the client to the network.
Owner:MULTIFACTOR CORP
System and method for secured network access utilizing a client .net software component
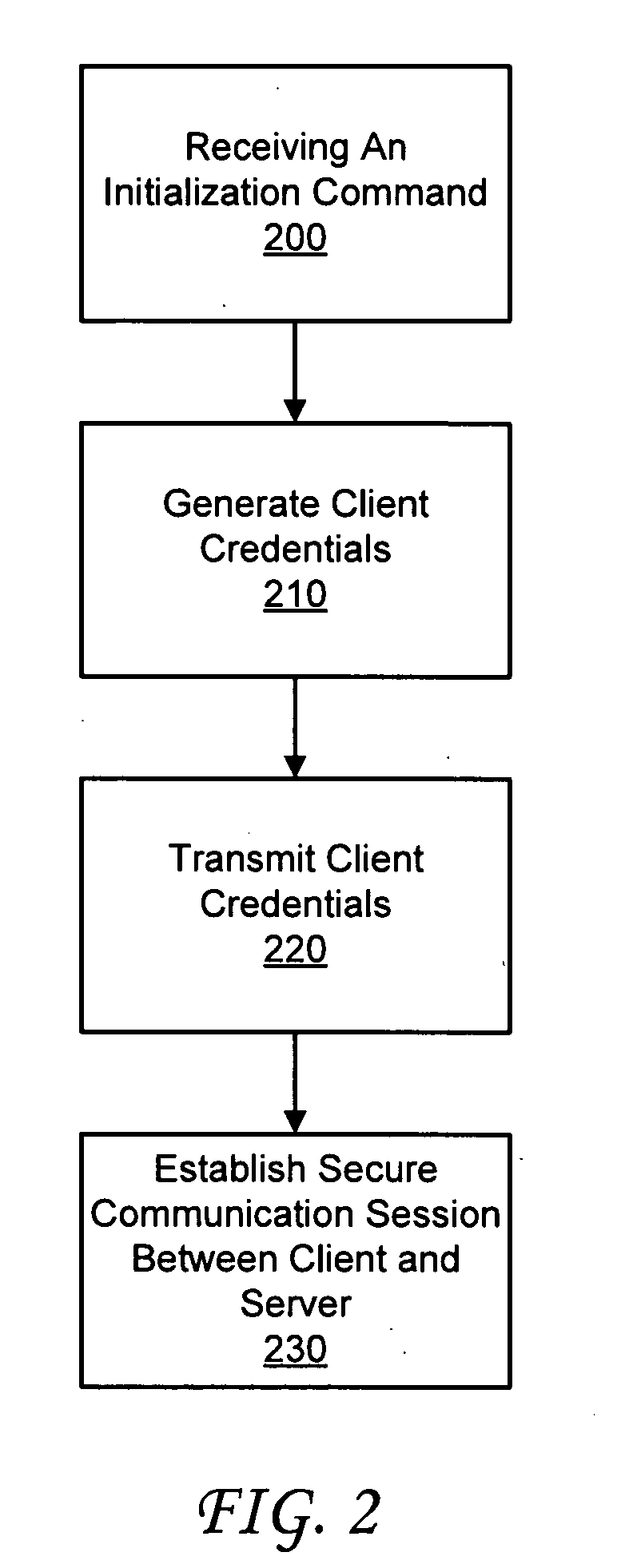
InactiveUS20090307486A1Accurate informationUser identity/authority verificationOperational systemWeb browser
A method for self-service authentication of a client and a server. The method includes the server receiving an initialization command from the client. The initialization command may be transmitted to the server via a client web browser over an unsecured data transfer link. The method continues with requesting authentication information from the client. In response to receiving the authentication information from the client, the server transmits a client software component to the client. The client software component utilizes a client-side library installed on the operating system of the client to generate the various client credentials described above. Thereafter, the certificate signing request may be transmitted to a certificate server for signing the certificate signing request. The signed certificate signing request is then received by the client via the client web browser. The client utilizes the information associated with the signed certificate signing request with the client-side library installed on the client to generate a client certificate.
Owner:MULTIFACTOR CORP
Method and appliance for authenticating, by an appliance, a client to access a virtual private network connection, based on an attribute of a client-side certificate
ActiveUS8413229B2Computer security arrangementsMultiple digital computer combinationsPrivate networkVia device
In a method and appliance for authenticating, by an appliance, a client to access a virtual network connection, based on an attribute of a client-side certificate, a client authentication certificate is requested from a client. A value of at least one field in the client authentication certificate received from the client is identified. One of a plurality of types of access is assigned responsive to an application of a policy to the identified value of the at least one field, each of the plurality of access types associated with at least one connection characteristic.
Owner:CITRIX SYST INC
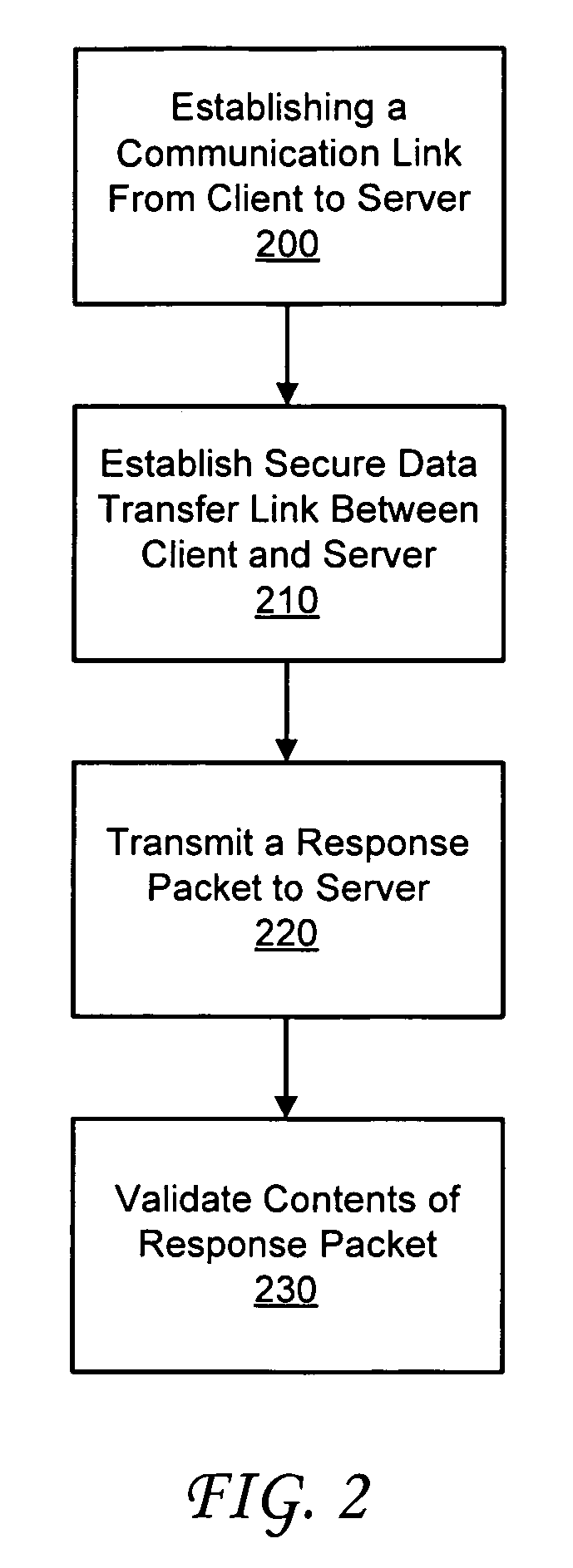
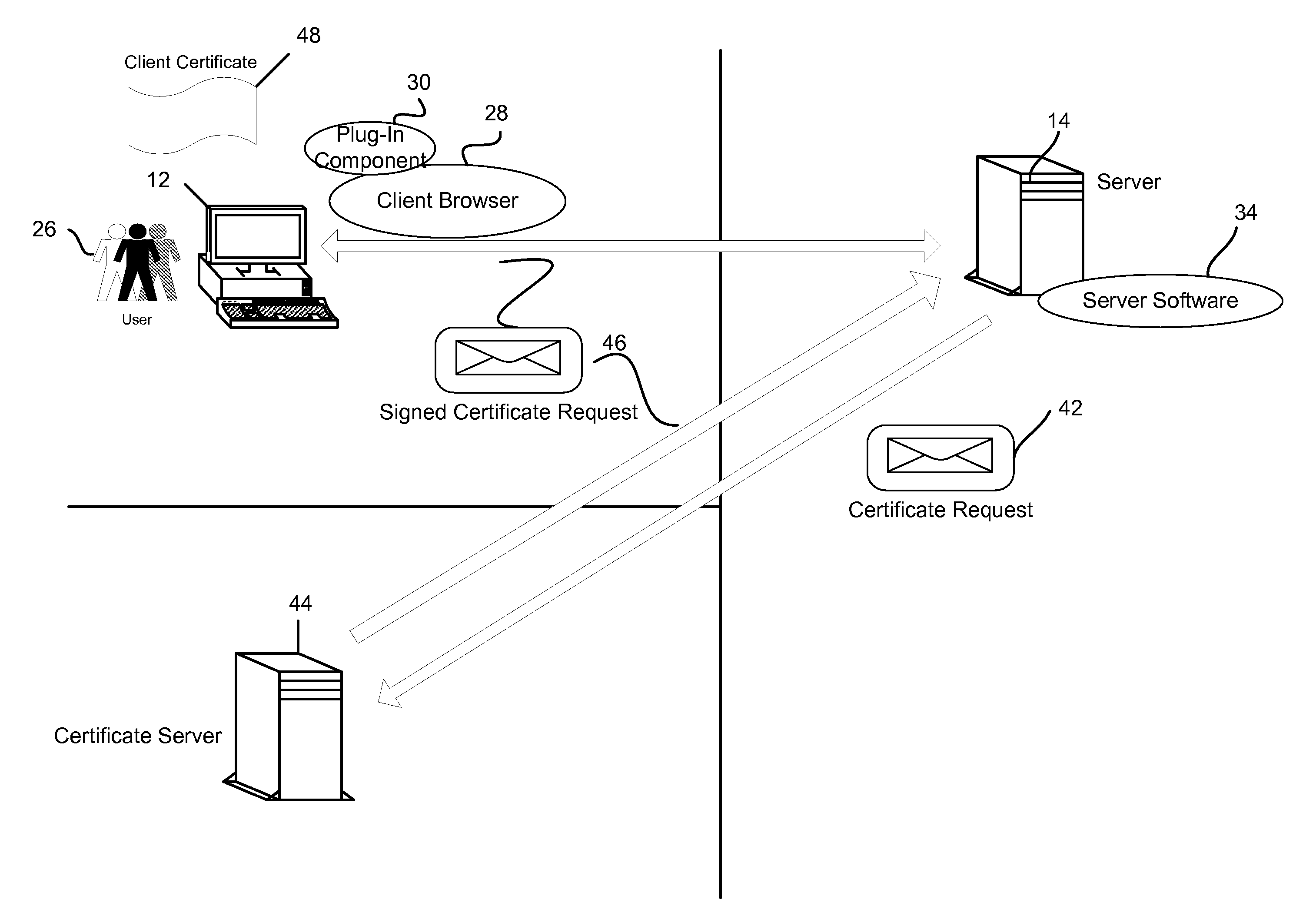
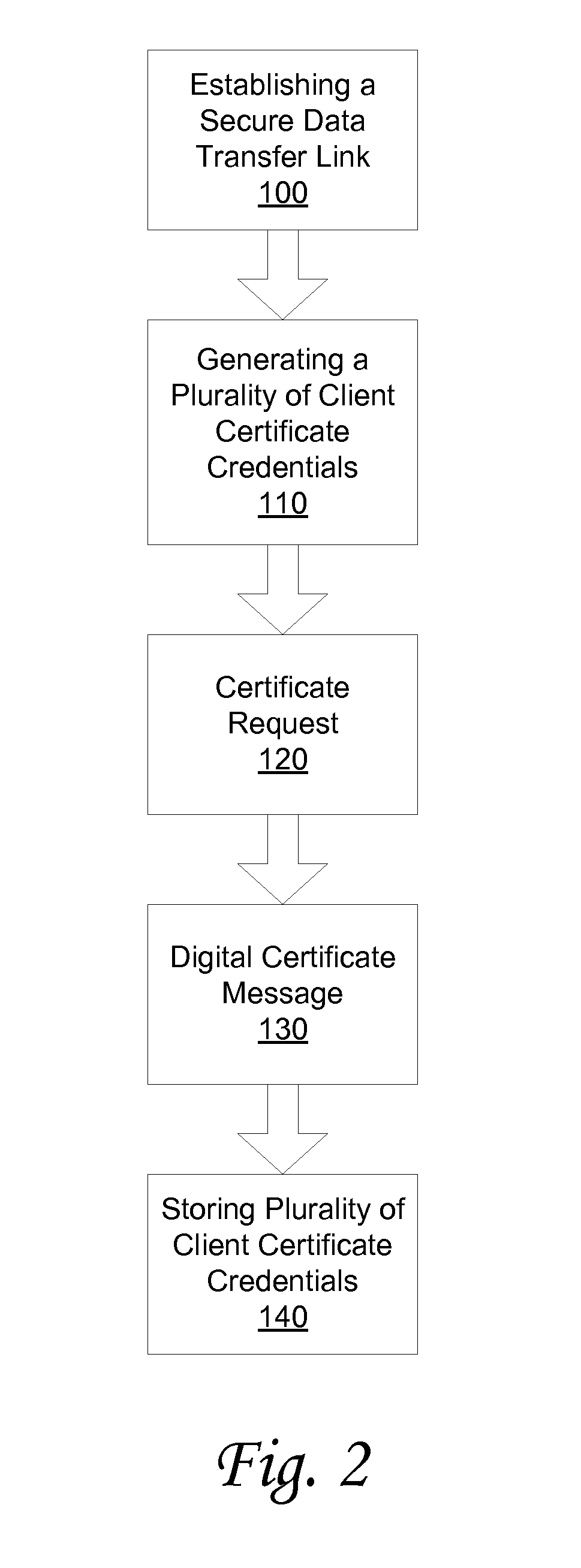
System and method for storing client-side certificate credentials
InactiveUS20090240936A1Digital data authenticationSecuring communicationWeb browserDigital signature
A method and system is provided for storing a plurality of client certificate credentials via a client web browser into one or more keystore file(s). The client web browser is used to establish the secure data transfer link between the client and the server. The client web browser includes a plug-in software component. The plug-in software component is configured to generate the keystore file and a key pair. The method may continue with generating a certificate request on the client. The certificate request generated is then transmitted to a certificate server. The certificate server is configured to digitally sign the certificate request generated. The method continues with the client receiving a signed certificate request. The signed certificate request is received by the client via the client web browser. The method may conclude by storing the plurality of client certificate credentials associated with the signed certificate request in one or more keystore file(s).
Owner:SECUREAUTH CORP
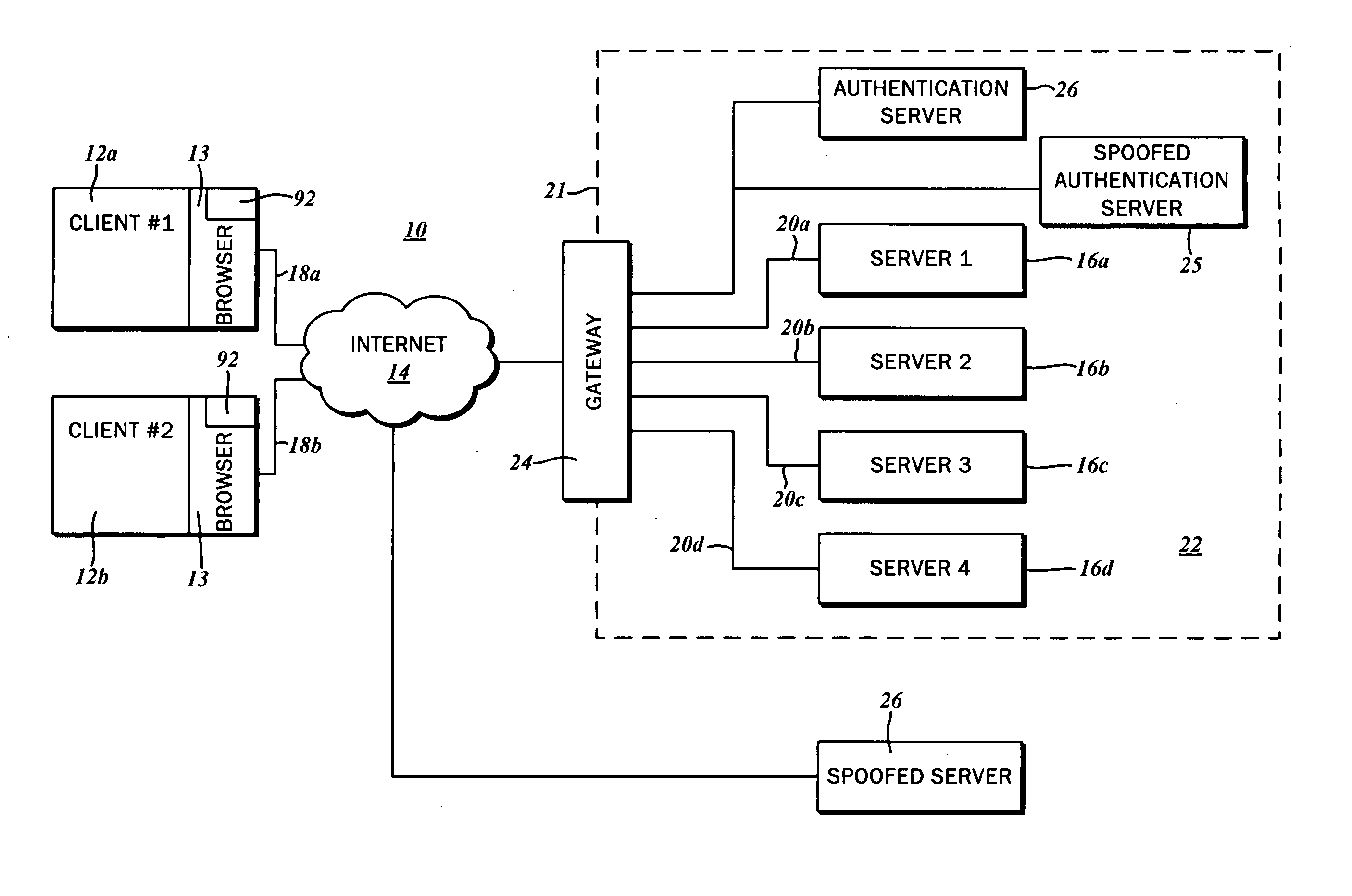
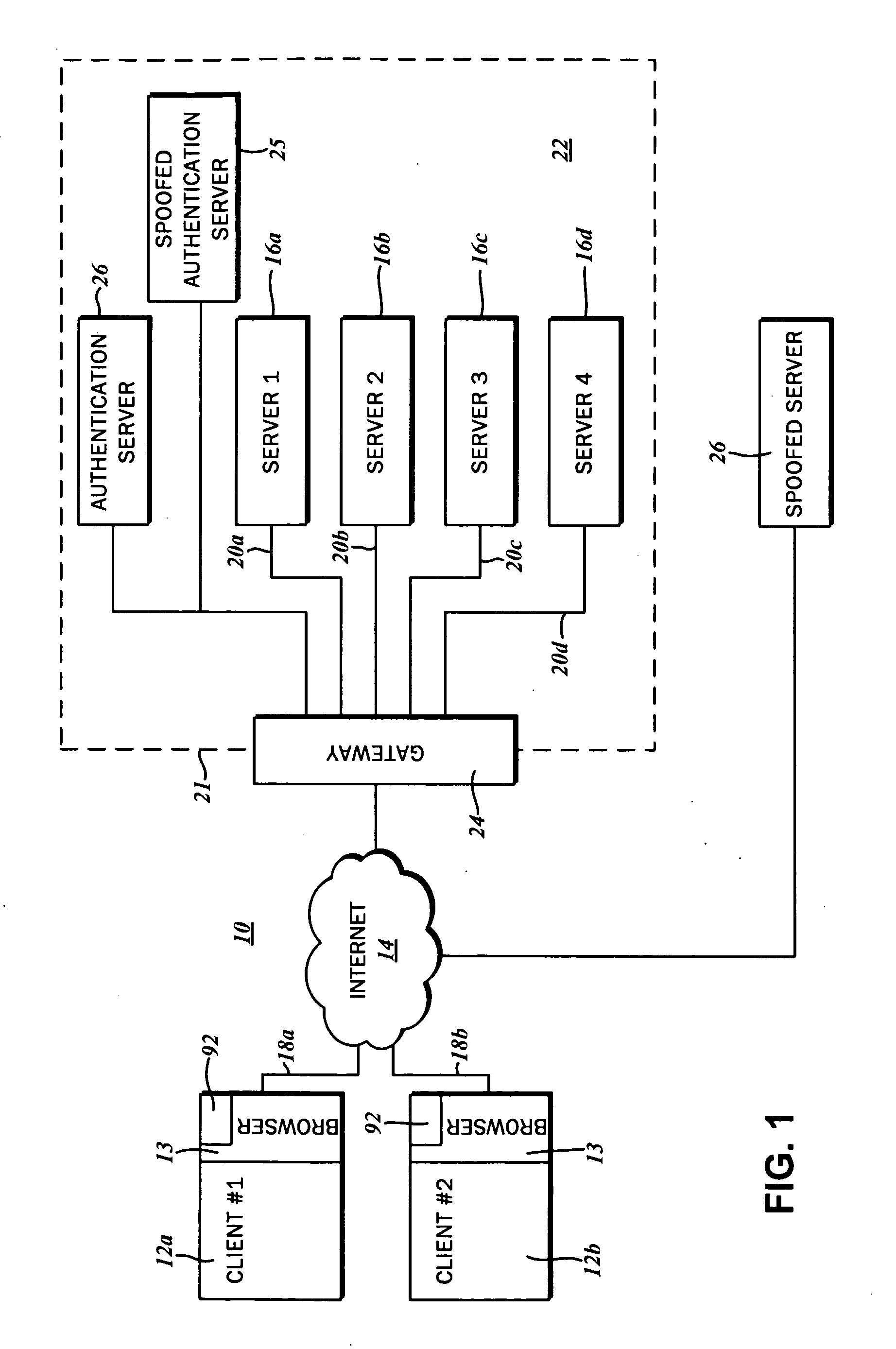
Anonymous Spoof resistant authentication and enrollment methods
InactiveUS20060143695A1Digital data processing detailsUser identity/authority verificationTelecommunications linkCommunication link
Methods for creating and authenticating a message sent from a client over a communication link to a server comprising the steps of creating a message at client containing client identification data adding to said message a first anti-spoof data element computed as a function of a key derived from a shared secret and communication link attribute data, sending said message from client to server over communication link, verifying at server said anti-spoof data element by computing a verification function of anti-spoof element data, server link attribute data and server key computed from said shared secret related to client. These methods are also used for enrolling clients to an authentication system employing authenticated anonymous client certificates.
Owner:GRYNBERG AMIRAM
System and method for authenticating a client to a server via an ipsec VPN and facilitating a secure migration to ssl VPN remote access
InactiveUS20090025080A1Multiple digital computer combinationsProgram controlSecure communicationPrivate network
Authenticating a client to a server accessible through an Internet Protocol Security (IPSec) Virtual Private Network (VPN) appliance. The IPSec VPN appliance and an SSL VPN appliance are configured to receive an initialization command from the client. The SSL VPN appliance is in communication with an authentication appliance for authenticating the client to the server. In response to the initialization command, the authentication appliance generates a client key pair including a client private key and a client public key. The authentication appliance generates a client certificate and a client IPSec profile. The authentication appliance transmits the client key pair, the client certificate and the client IPSec profile to the client. A secure communication session between the client and the server is established. The secure communication session is established through the IPSec VPN appliance. Upon receipt of the IPSec profile, the communication session between the client and the server is encrypted.
Owner:SECUREAUTH CORP
Method and apparatus for subscription sharing
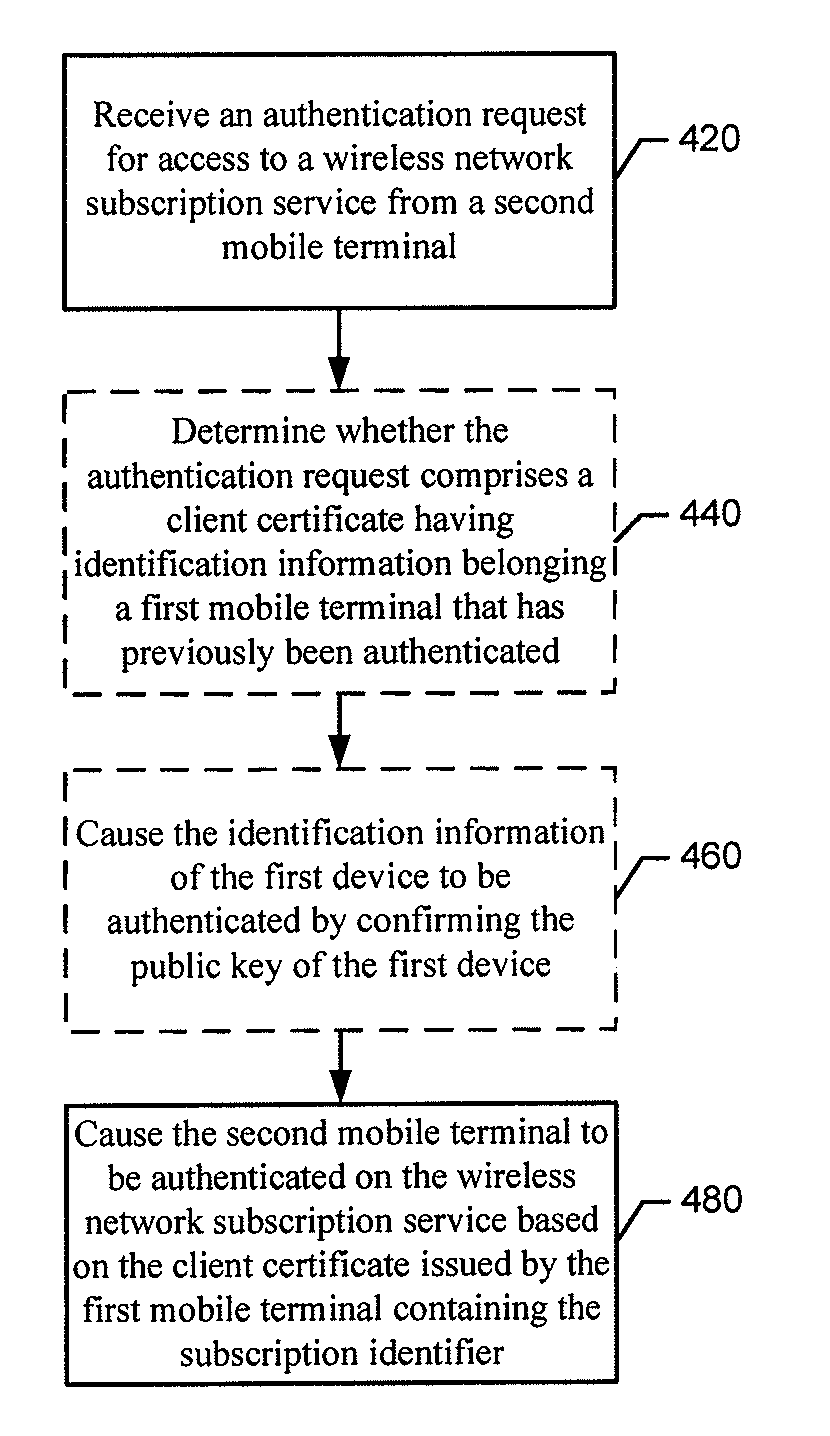
InactiveUS20130247161A1Digital data processing detailsUser identity/authority verificationClient-sideClient certificate
A method, apparatus and computer program product are provided for enabling multiple mobile terminals to access a subscription service. The method may further include causing a client certificate to be issued to the first mobile terminal as a result of the certificate enrollment procedure. In some example embodiments, the client certificate comprises a subscription identifier and a flag indicating whether the client certificate is to be sharable with a second mobile terminal. The method may further include causing a certificate enrollment procedure to be initiated by a second mobile terminal with the first mobile terminal in an instance in which the first mobile terminal possesses one or more credentials that are configured to be shared with another mobile terminal. The method may further include the second mobile terminal receiving at least one credential in the form of a client certificate from the first mobile terminal.
Owner:NOKIA TECHNOLOGLES OY
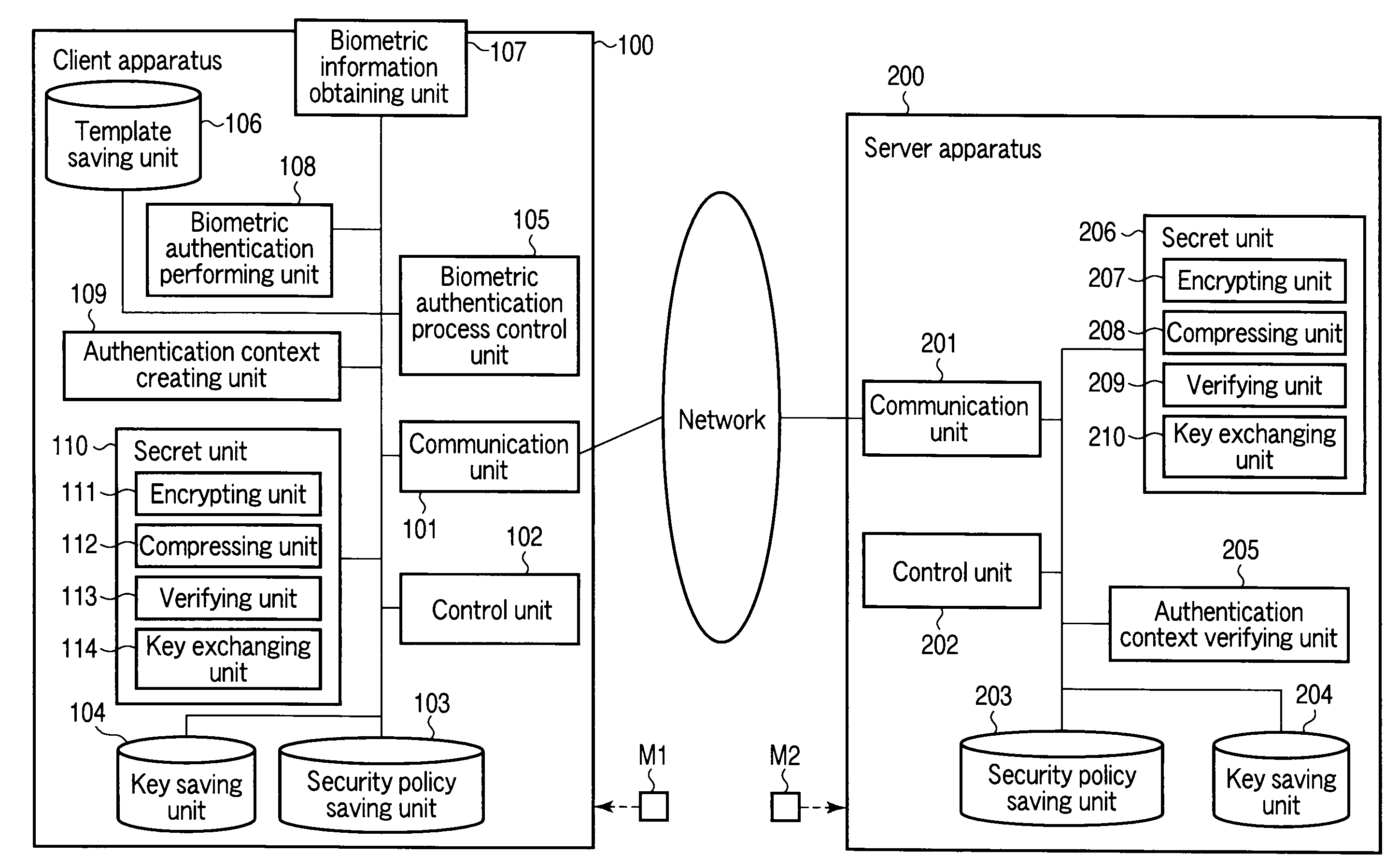
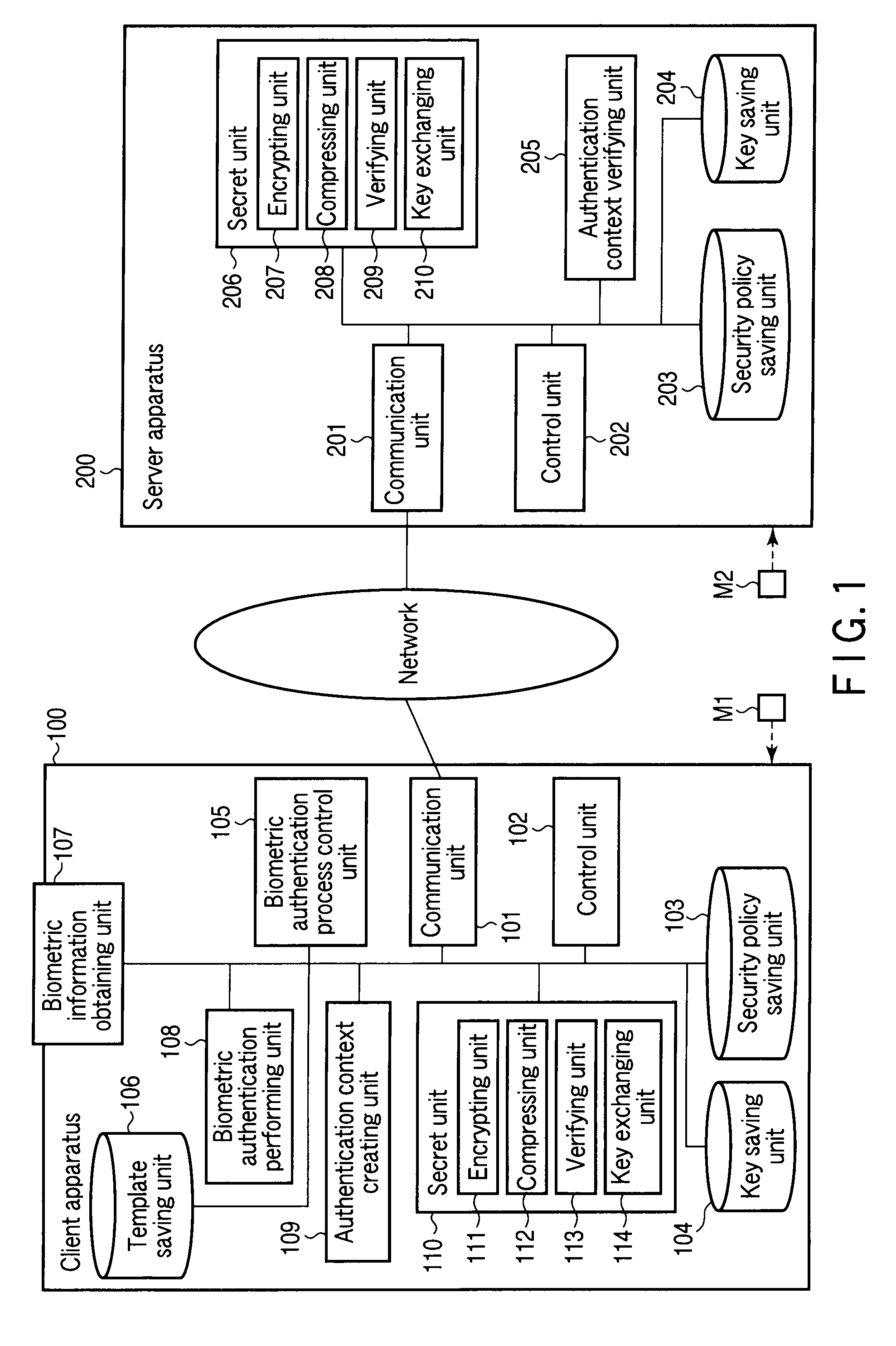
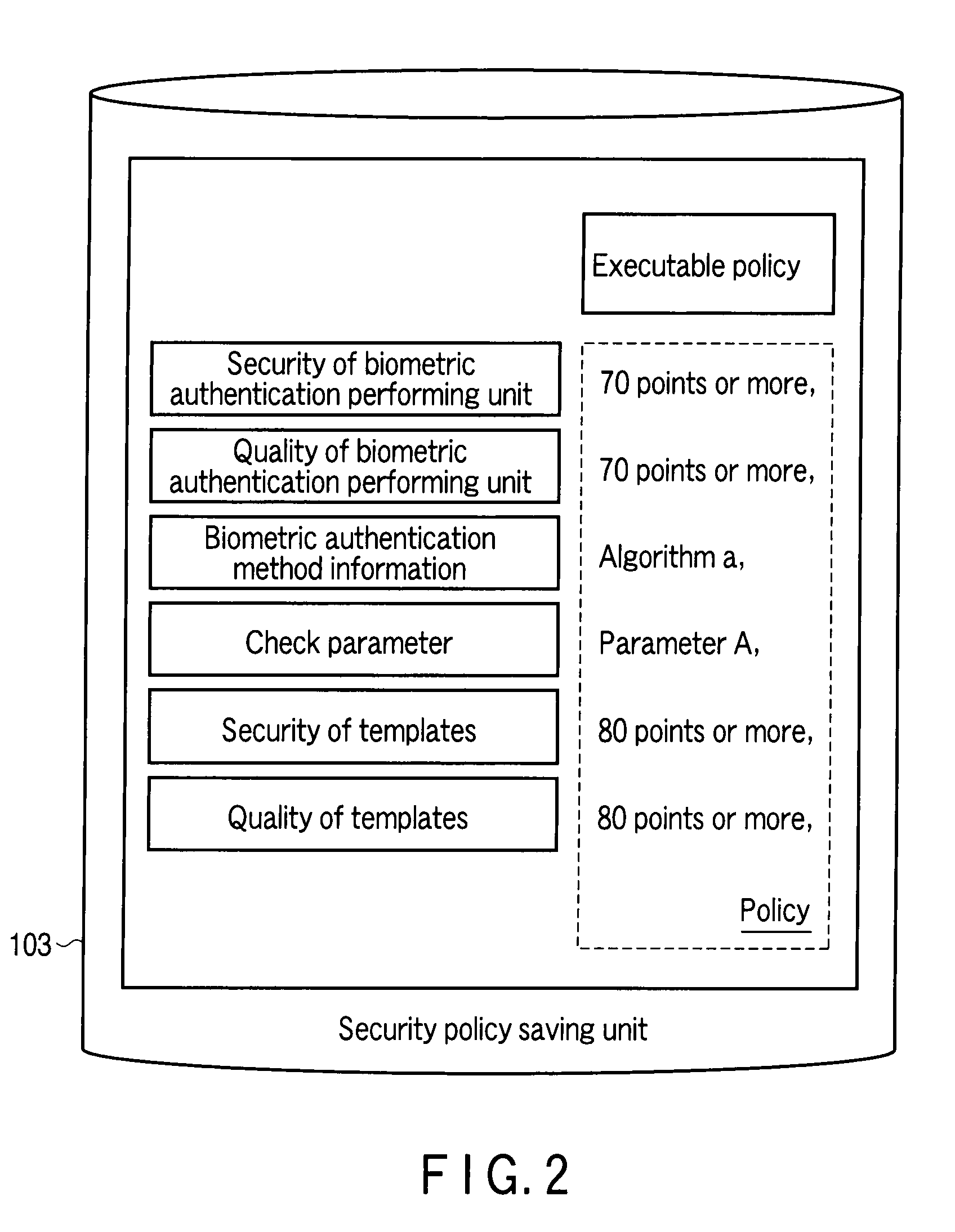
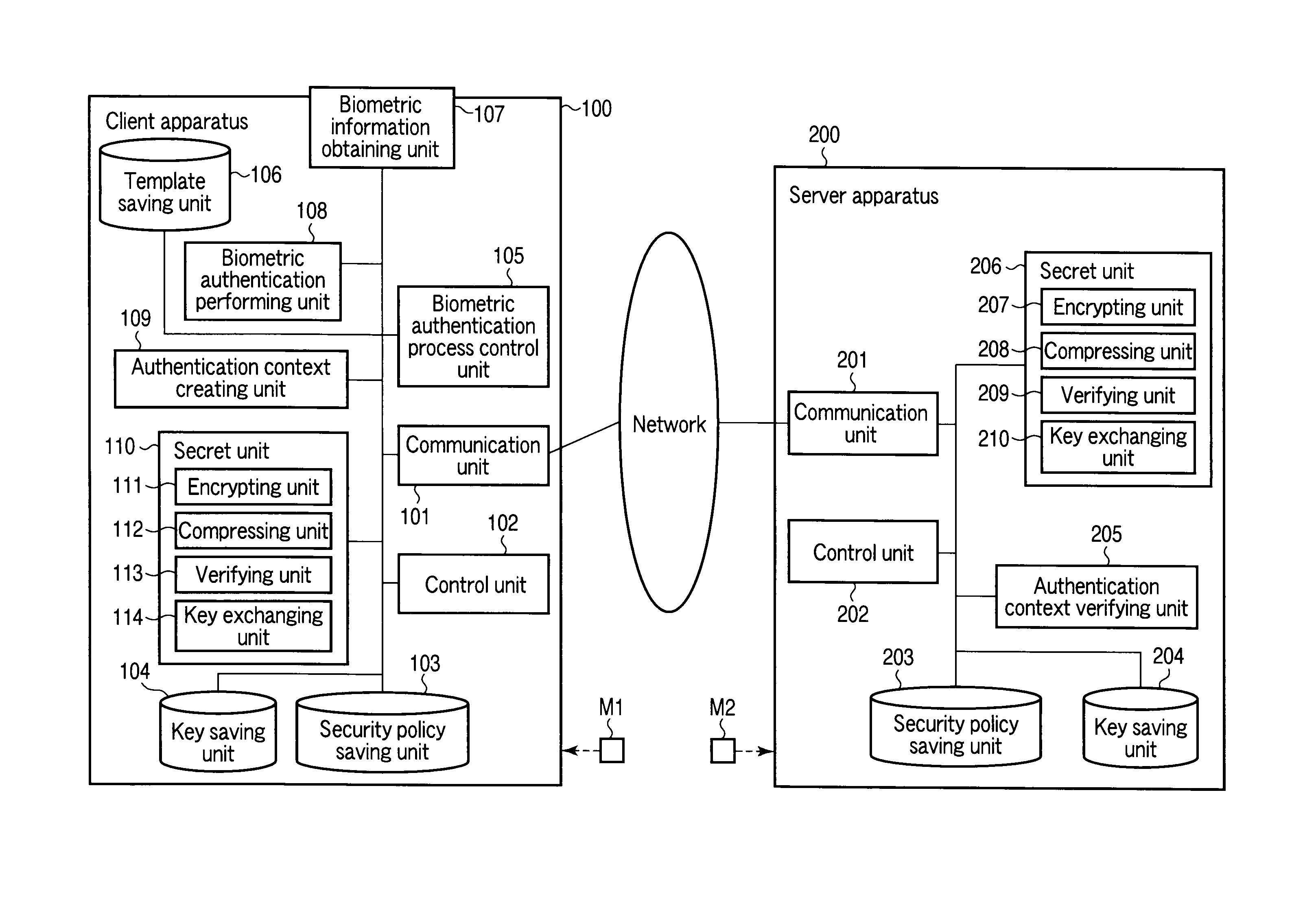
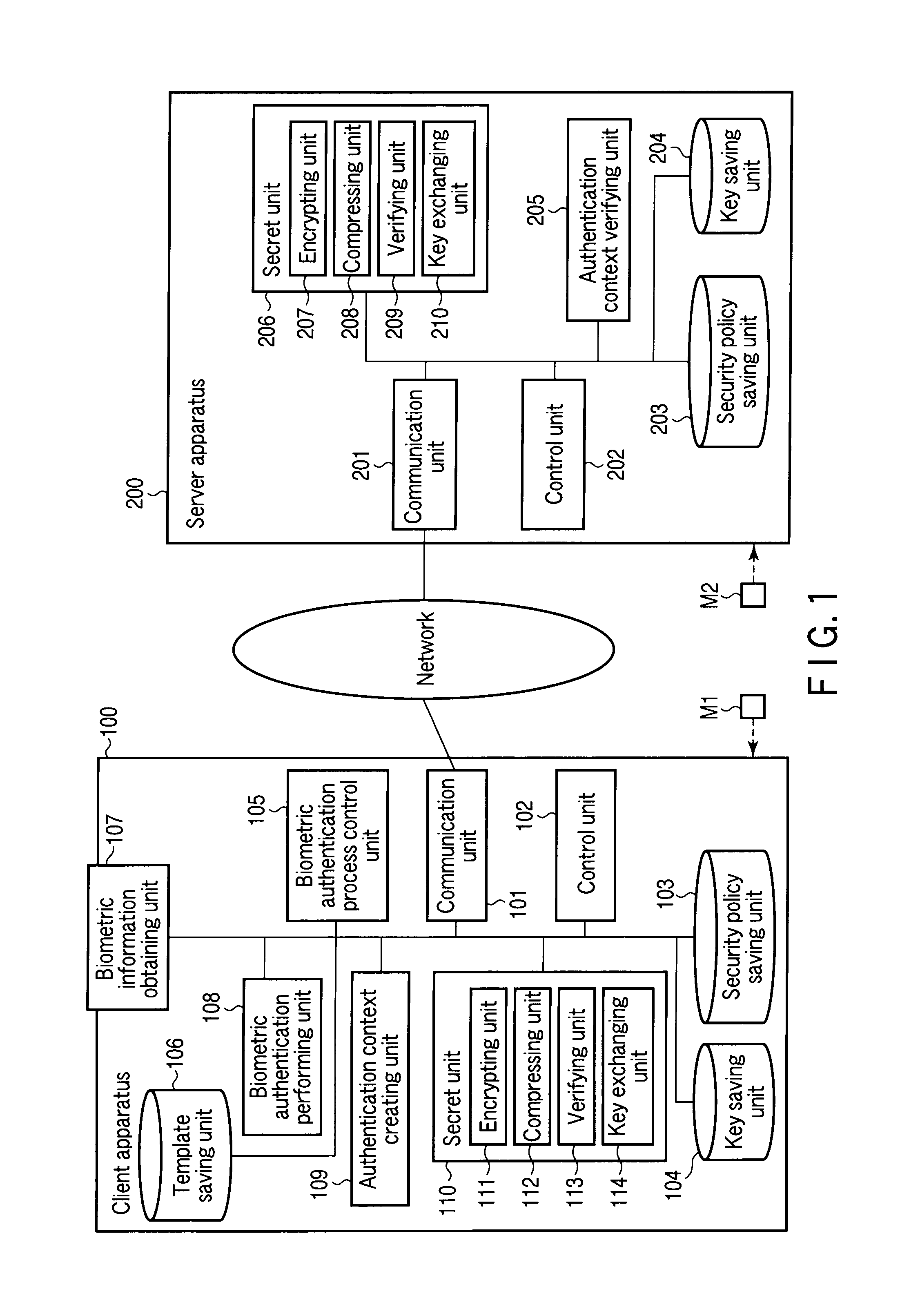
Client apparatus, server apparatus, and program
ActiveUS20100191967A1Reduce the number of processesReduce in quantityUser identity/authority verificationDigital data authenticationProtocol processingClient-side
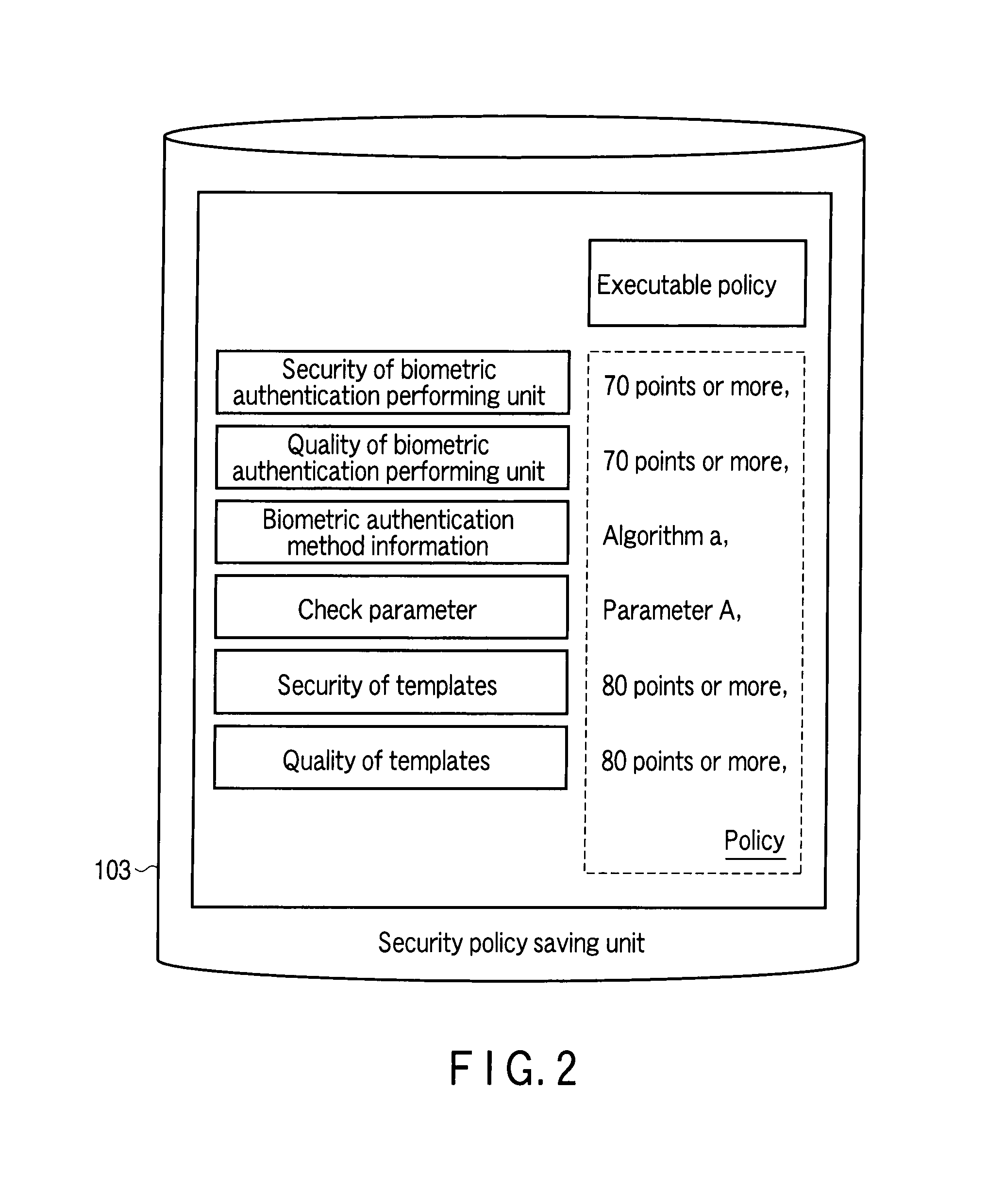
A client apparatus receives a message including a random number from a server apparatus during the handshake of agreement process, creates a biometric negotiation message including the biometric authentication method information and sends the biometric negotiation message to the server apparatus. Then, the client apparatus executes a biometric authentication based on biometric authentication method information notified from the server apparatus and encrypts the random number based on the private key. In addition, the client apparatus generates an authenticator from a result of the biometric authentication, the biometric authentication method information, the encrypted random number, and the client certificate, and sends to the server apparatus an authentication context including these. The server apparatus verifies the authentication context and establishes a secure session in one handshake.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
Remote access to resouces
ActiveUS20070088834A1Simple meansMultiple digital computer combinationsTransmissionClient agentPublic network
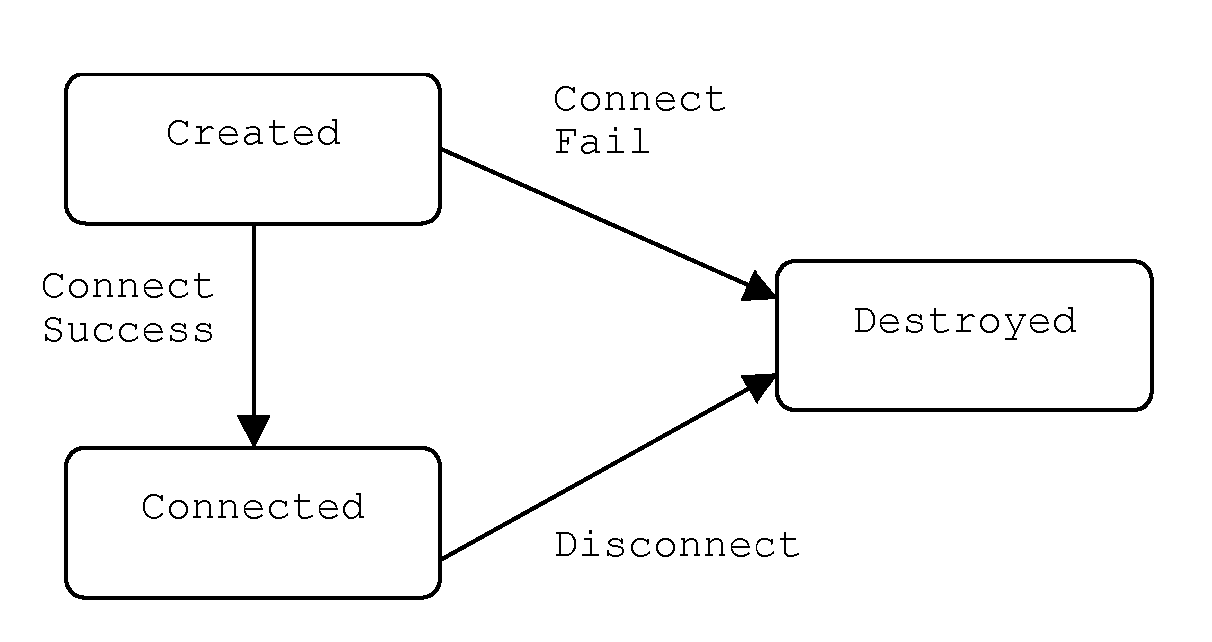
The invention provides systems and methods for securely transmitting data between a roaming computer and a managed network service over a shared public network. A secure connection is created between the roaming computer and a server computer that hosts or acts as a secure gateway to the managed network service. The connection is set up and established by a client agent installed on the roaming computer and a connection component of the managed service on the server computer. The client agent and the connection component of the managed service operate, on an initial request from the roaming computer to the managed service to negotiate the secure connection using certificate-based client authentication. The client certificate preferably includes user-specific attributes that can be extracted by the connection component and made available to the managed service to apply processing rules specific to the user.
Owner:CISCO TECH INC
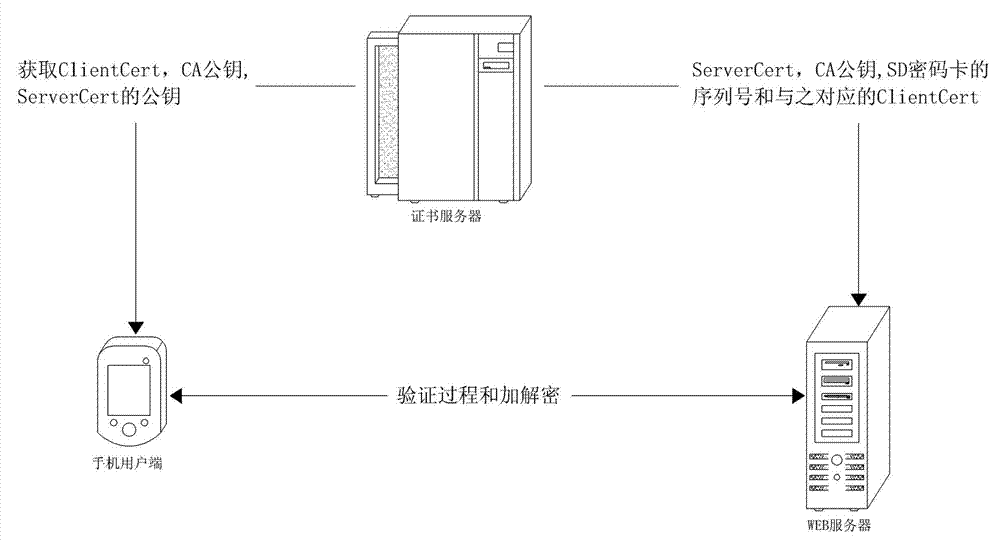
Secure digital (SD)-password-card-based Internet of things healthcare service system and secure communication method thereof
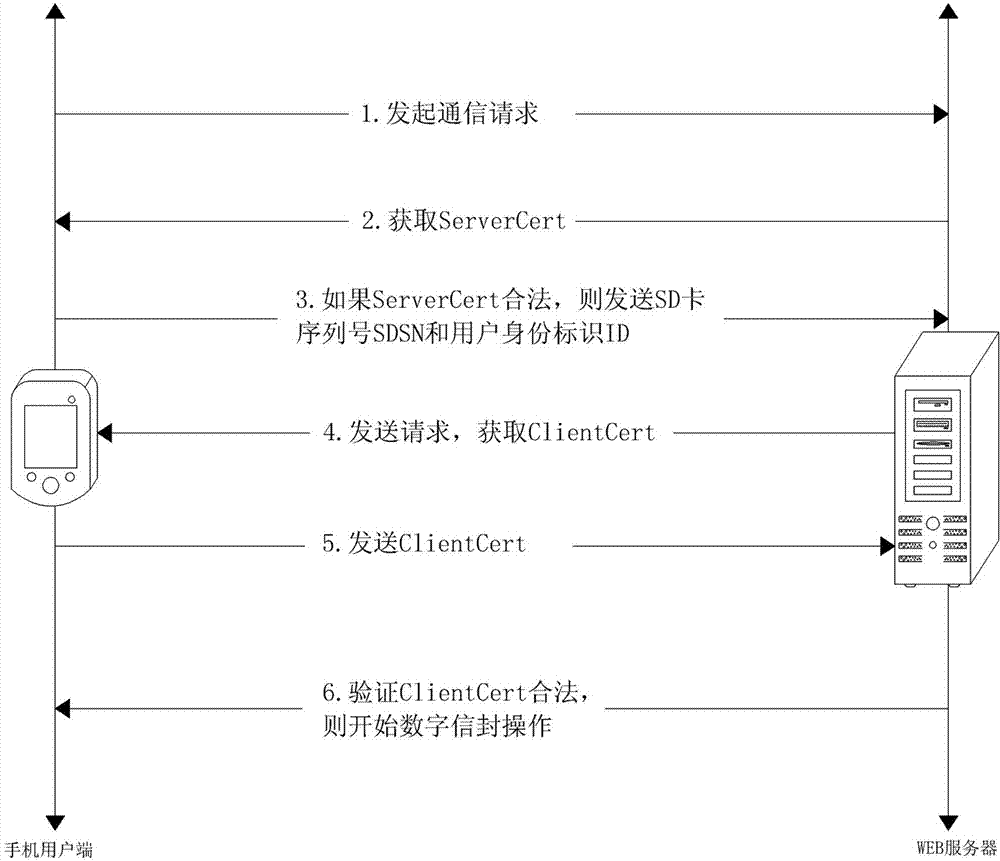
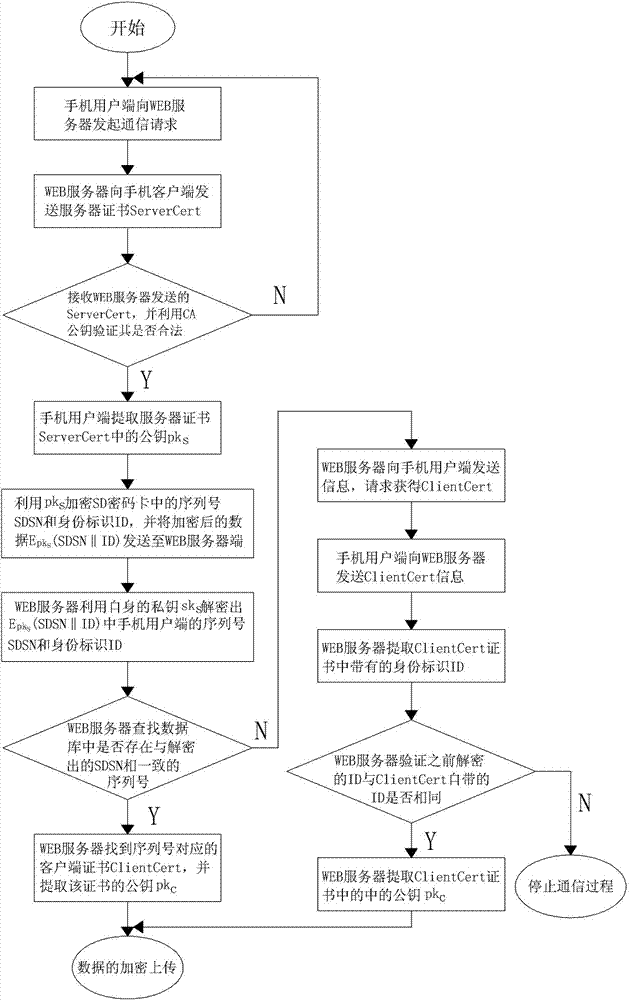
ActiveCN102882847AEnsure safetyImprove securityData processing applicationsUser identity/authority verificationWeb serviceMedical treatment
The invention discloses a secure digital (SD)-password-card-based Internet of things healthcare service system. The system comprises a server, a WEB server, a sensor and a client; and an SD password card stores a client certificate, a certificate authority (CA) public key and a public pks. The invention also discloses a secure communication method of the system. According to the method, an identity authentication process comprises the following steps of: (a), initiating a request; (c), verifying whether ServerCert is legal; (d), encrypting and transmitting data; and (e), decrypting a secure digital serial number (SDSN) and an identity (ID); and (f) acquiring a public key pkc. And an uploading process comprises the following steps of: 1), generating a random number K; 2), signing the K; 3), encrypting the K; 5), verifying a signature; and 6), decrypting the K, wherein the K is used as a communication key. By the system and the method, the security of medical information is ensured, and the advantages of high speed, high security and convenience in management of a symmetrical encryption algorithm are realized, so that health data can be prevented from being stolen, destroyed, modified and unauthorizedly used.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Client apparatus, server apparatus, and program using entity authentication and biometric authentication
ActiveUS8732461B2Reduce the number of processesReduce in quantityKey distribution for secure communicationDigital data processing detailsProtocol processingClient-side
A client apparatus receives a message including a random number from a server apparatus during the handshake of agreement process, creates a biometric negotiation message including the biometric authentication method information and sends the biometric negotiation message to the server apparatus. Then, the client apparatus executes a biometric authentication based on biometric authentication method information notified from the server apparatus and encrypts the random number based on the private key. In addition, the client apparatus generates an authenticator from a result of the biometric authentication, the biometric authentication method information, the encrypted random number, and the client certificate, and sends to the server apparatus an authentication context including these. The server apparatus verifies the authentication context and establishes a secure session in one handshake.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
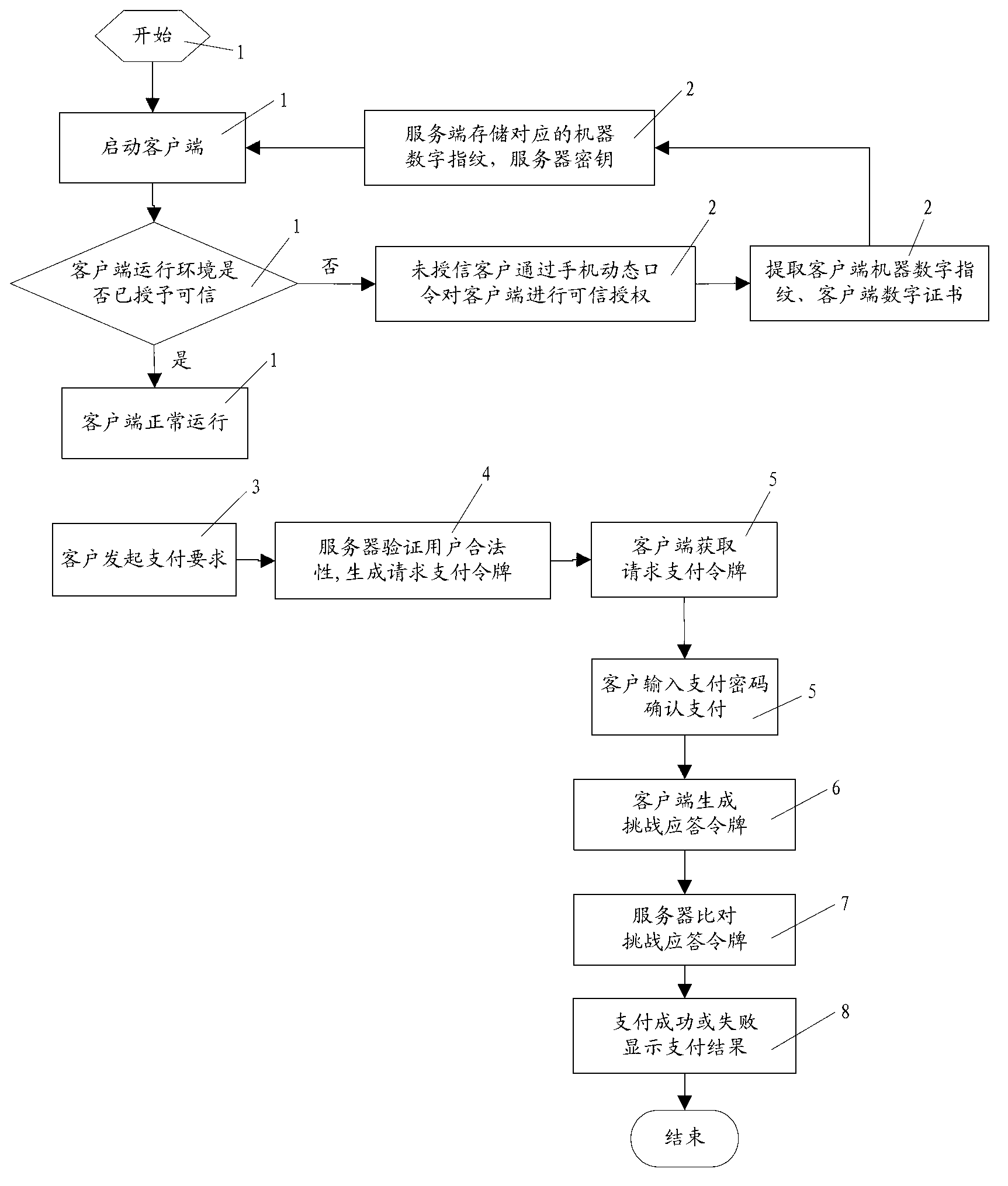
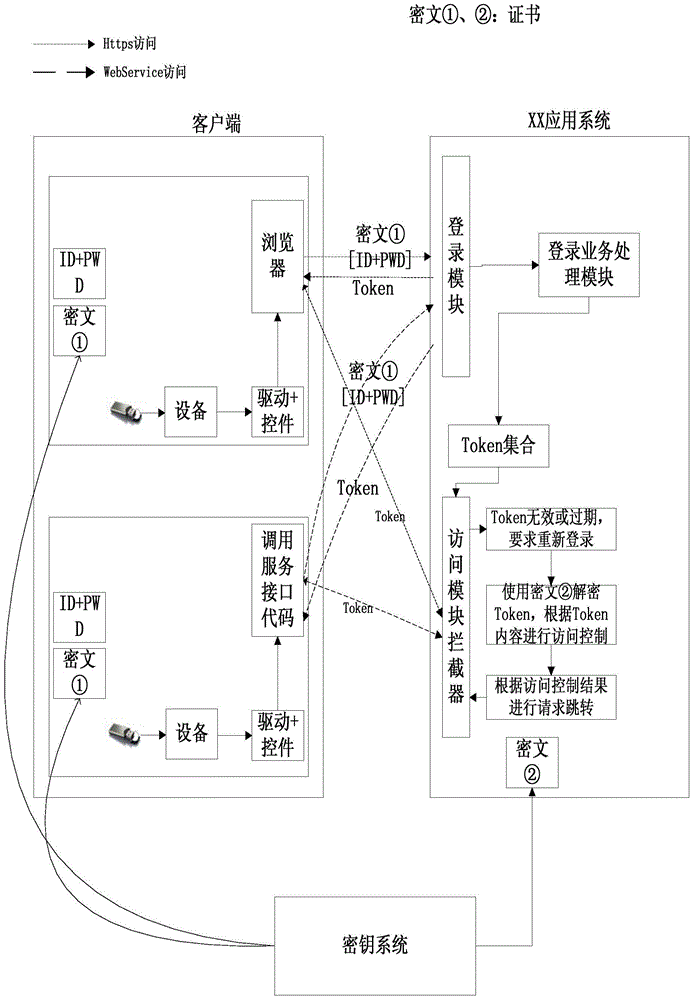
Safety payment authentication method based on software client
InactiveCN103020825AImprove convenienceCost controlTransmissionProtocol authorisationPaymentPayment order
The invention provides a safety payment authentication method based on a software client. The method includes that credible authorization is performed on the operating environment of the client, namely, machine digital fingerprints of the environment of the client are extracted, an original secret order and a client digital certificate are generated accordingly, and the client submits the original secret order to an authentication server which authenticates the identity of the submitter to generate a corresponding server key; during payment, the client requires payment authentication; the authentication server generates a 'challenge' random number after verifying the user validity, adds the random number into payment information, generates a request payment token through a reversible encryption algorithm, and sends the token to the client; the client decrypts the request payment token after receiving and displays the payment information, and the user confirms the payment information and inputs a payment code; and the like. According to the safety payment authentication method, the challenge-response payment authentication mode is improved, and the problems of limitation on popularization caused by the usbkey hardware medium transmission cost and safety systemic bugs are solved.
Owner:FUJIAN PAIHUOYUAN SCI & TECH INFORMATION
Cross-trust-domain identity authentication method
ActiveCN104378210AImplement single sign-onSimplify the identity development processUser identity/authority verificationPasswordService provision
Owner:成都卫士通信息安全技术有限公司
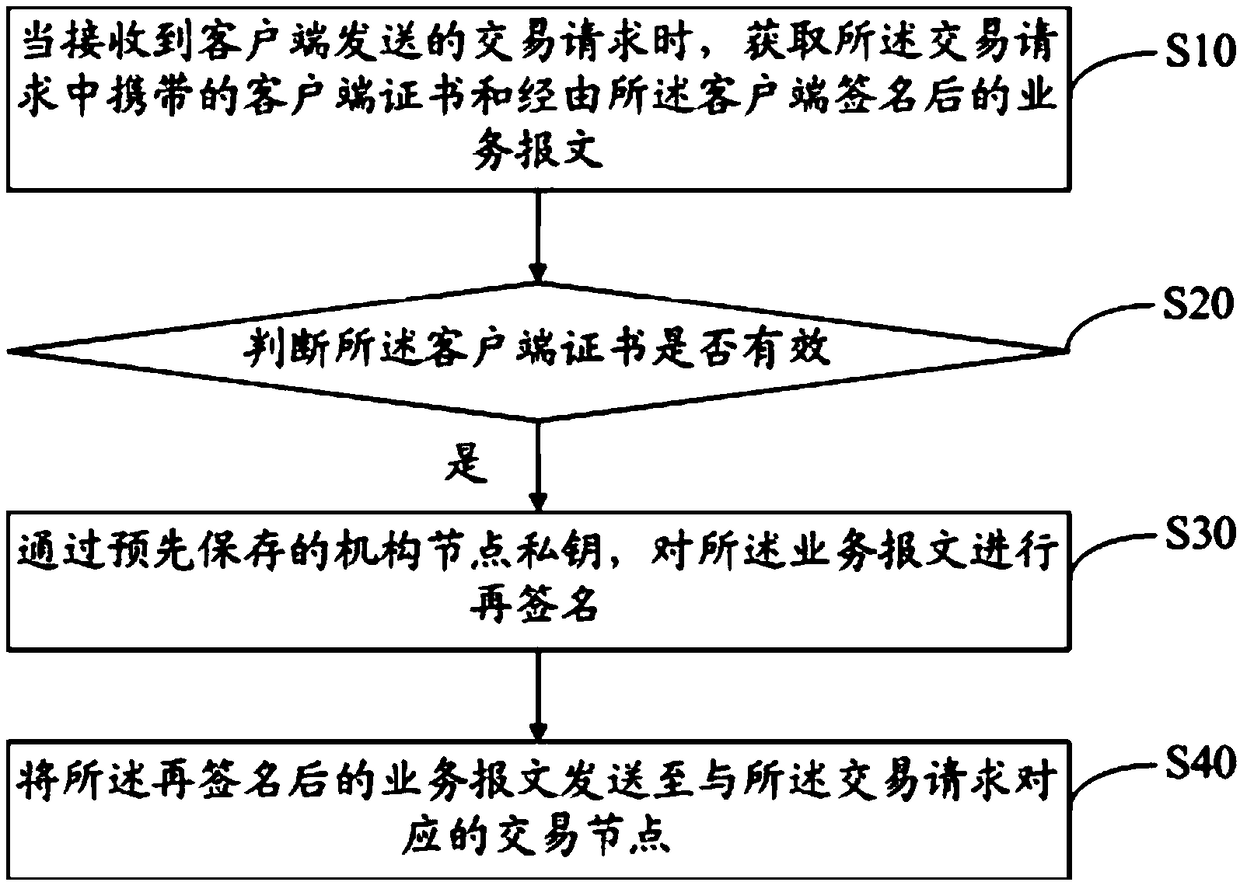
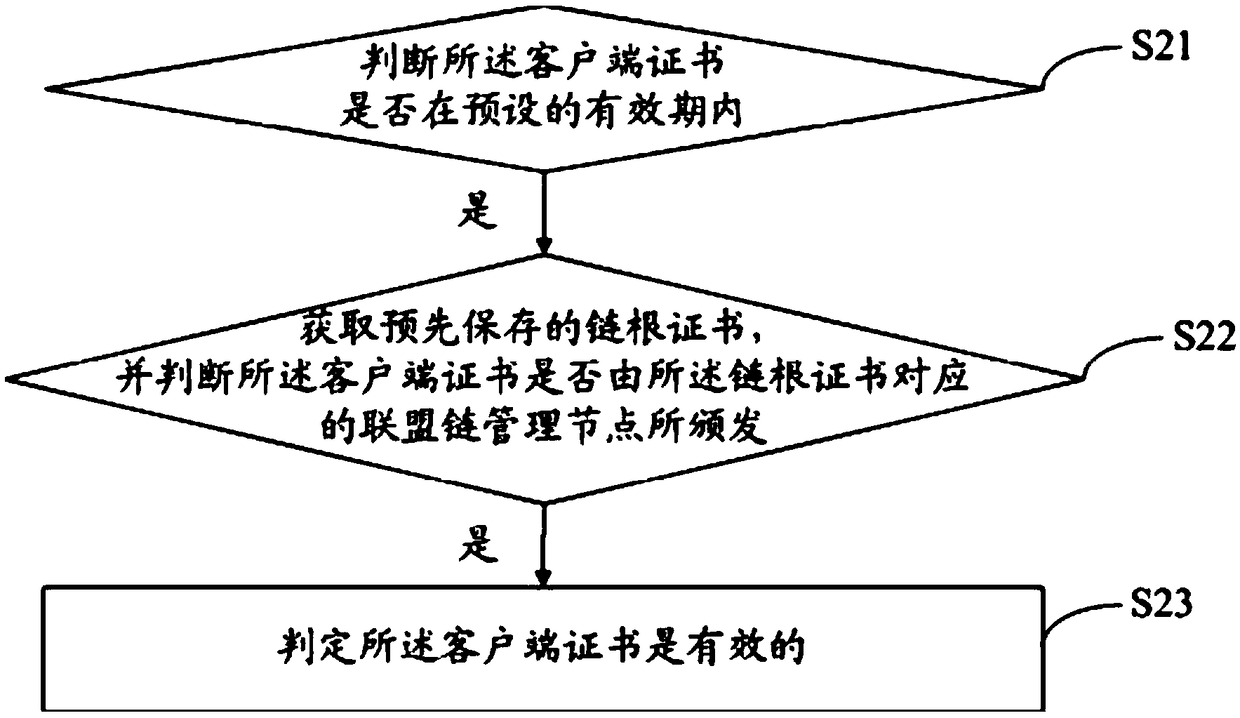
Federation chain transaction method, apparatus, and compute readable storage medium
ActiveCN109067539AGuarantee authenticityEnsure safetyFinanceUser identity/authority verificationFinancial transactionClient-side
The invention discloses a federation chain transaction method. The method comprises the following steps: when receiving a transaction request sent by a client, obtaining a client certificate carried in the transaction request and a service message signed by the client; judging whether the client certificate is valid; When the client certificate is valid, re-signing the service message through thepre-stored private key of the institution node; sending the re-signed service message to a transaction node corresponding to the transaction request. The invention also discloses a federation chain trading device and a computer-readable storage medium. The invention can realize the safe and effective identity authentication of the participants of the alliance chain, thereby ensuring the authenticity and security of the transaction of the alliance chain.
Owner:WEBANK (CHINA)
Network Access Control with Compliance Policy Check
ActiveUS20160197962A1User identity/authority verificationSpecial data processing applicationsUser deviceWeb browser
Embodiments of the present invention include methods involving an authentication application, a client application, or a combination of a network access control server with the authentication application and the client application. The client application collects compliance data regarding the user device and communicates the compliance data to the network access control server. The network access control server generates a compliance check result based on whether the compliance data indicates that the user device is compliant with a security policy for the software-as-a-service server. The authentication application grants access by the user device when the compliance check result is positive; and the authentication application denies access by the user device when the compliance check result is negative. In some embodiments, the compliance check result or a user device identifier is stored in a web browser cookie or a client certificate on the user device.
Owner:OPSWAT
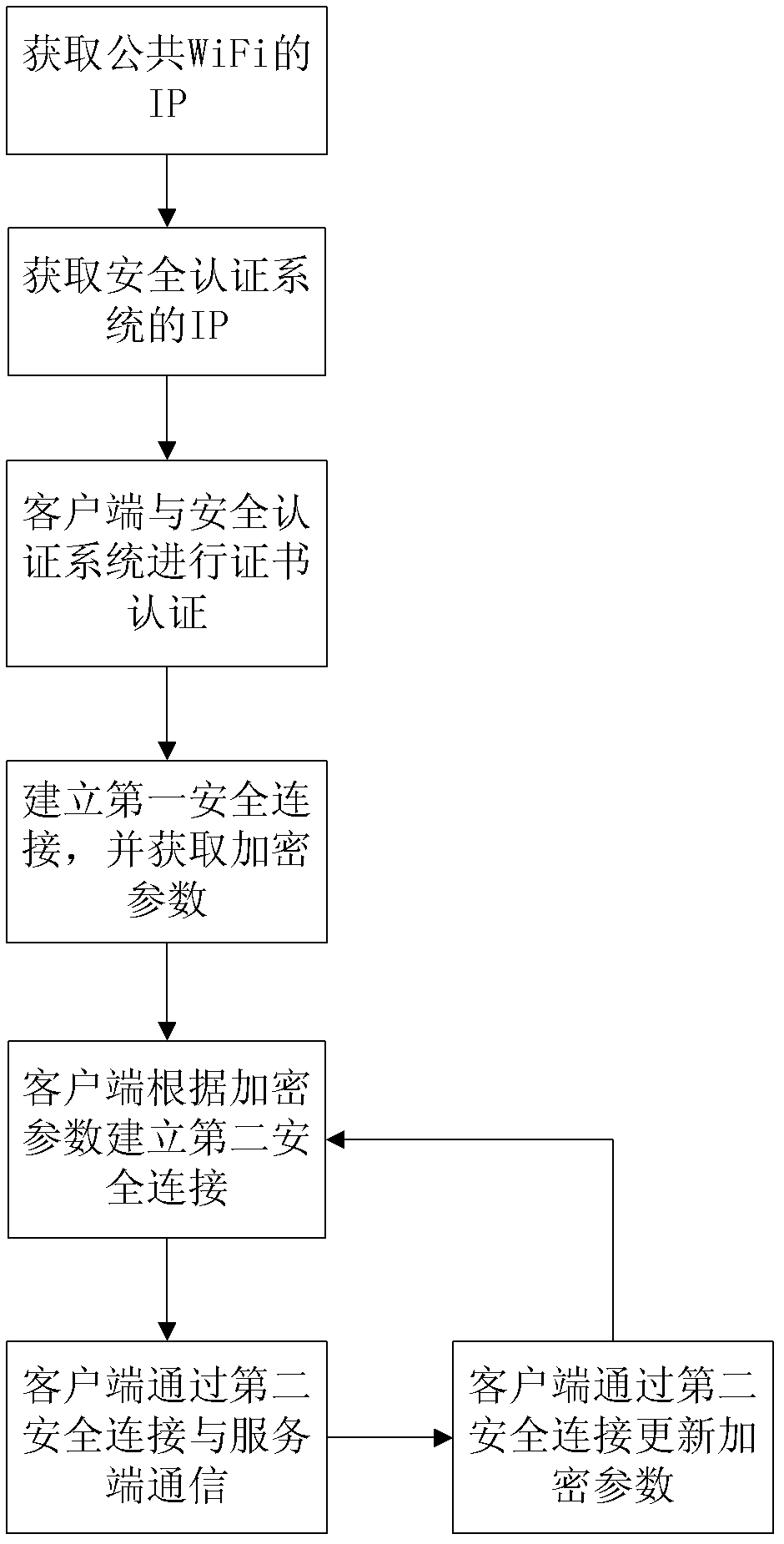
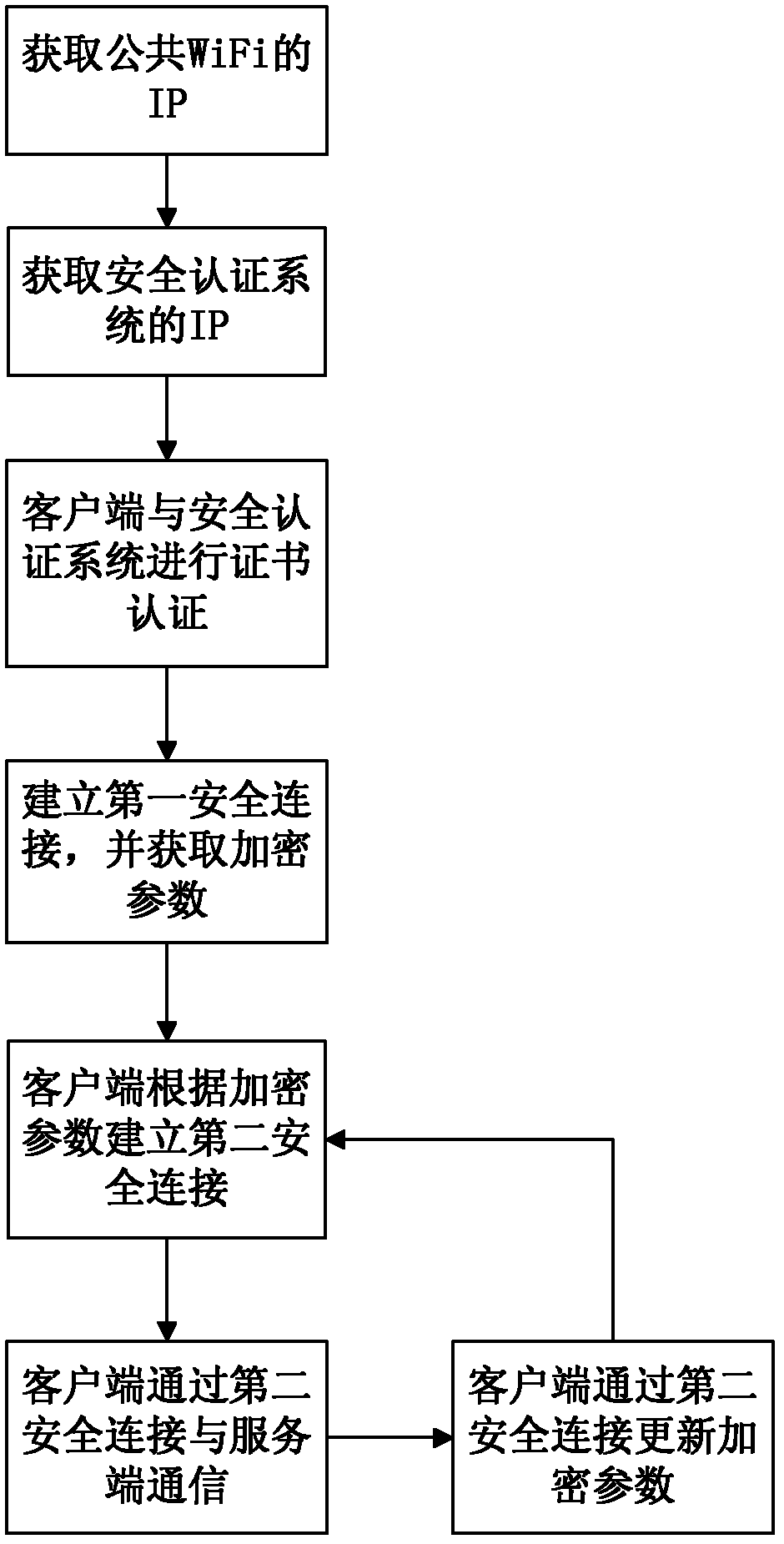
Security authentication method for wireless network
ActiveCN102547695AImplement Live BindingAvoid the possibility of leakageConnection managementSecurity arrangementBrute forceIp address
The invention relates to a security authentication method for a wireless network. A wireless fidelity (WiFi) server and a client are involved, and the security authentication method comprises the following steps that: a, an authentication service program is deployed in the client, and the client is connected to a public open system of the WiFi server to acquire a corresponding internet protocol (IP) address; b, according to the IP address, the client acquires and accesses an IP address of a security authentication system of the WiFi server; c, the WiFi server authenticates a client certificate; d, the client which passes the authentication establishes first security connection with the WiFi server and acquires encryption parameters; e, the client establishes a second security connection with the security authentication system of the WiFi server according to the encryption parameters; and f, the client and the WiFi server communicate and are updated through the second security connection. By the security authentication method, the client and the WiFi server can be connected easily and quickly by using a complex key and a complex encryption way; and meanwhile, the security during connecting can be guaranteed by using a method of updating the key regularly to ensure that brute force-based cracking and possibility of key leakage are avoided.
Owner:成都飞鱼星科技股份有限公司
Apparatuses, method and computer software products for controlling a home terminal
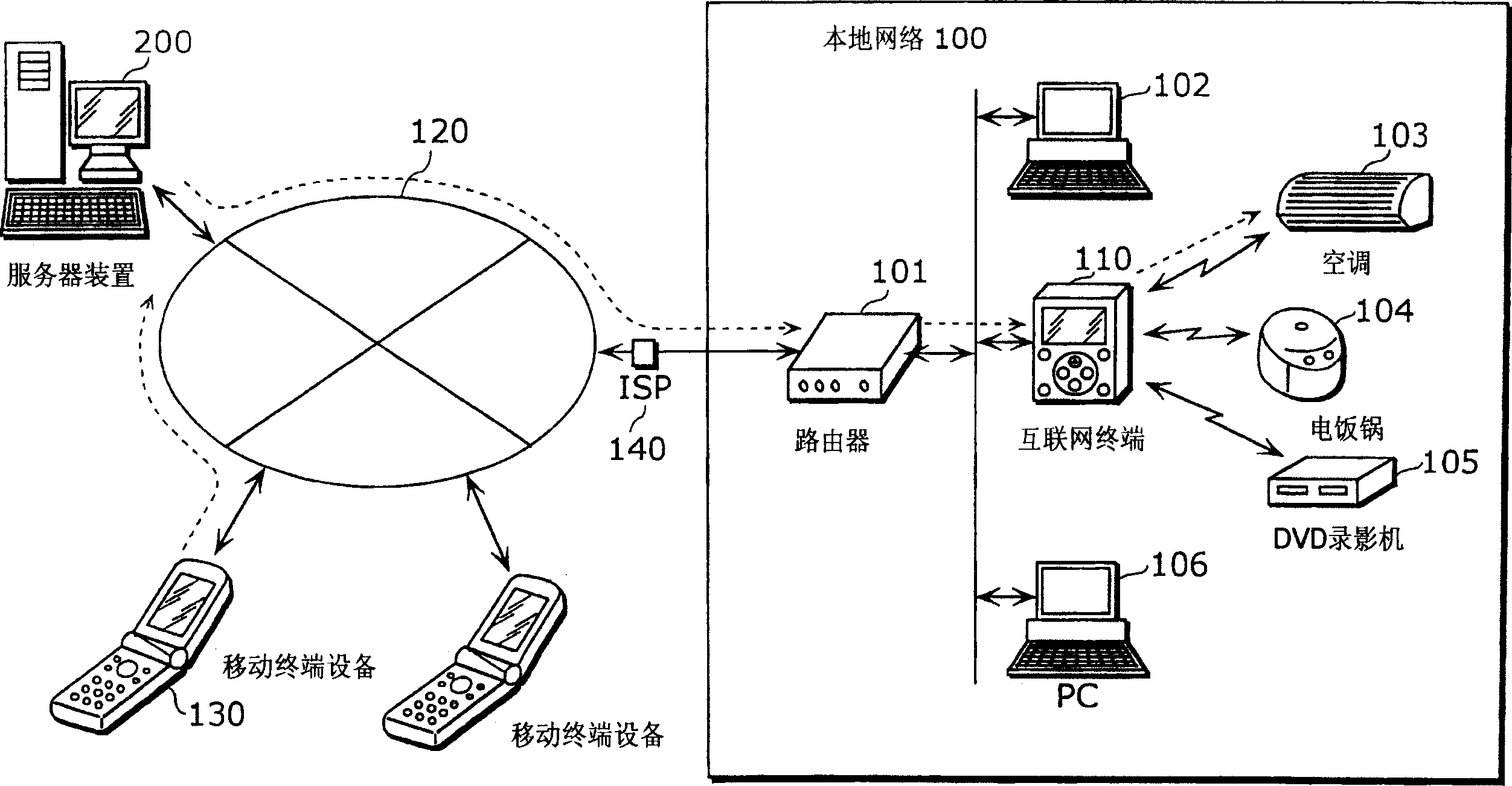
InactiveCN1685689AReduce operating loadAvoid controlNetwork traffic/resource managementWireless network protocolsCommunication unitManagement unit
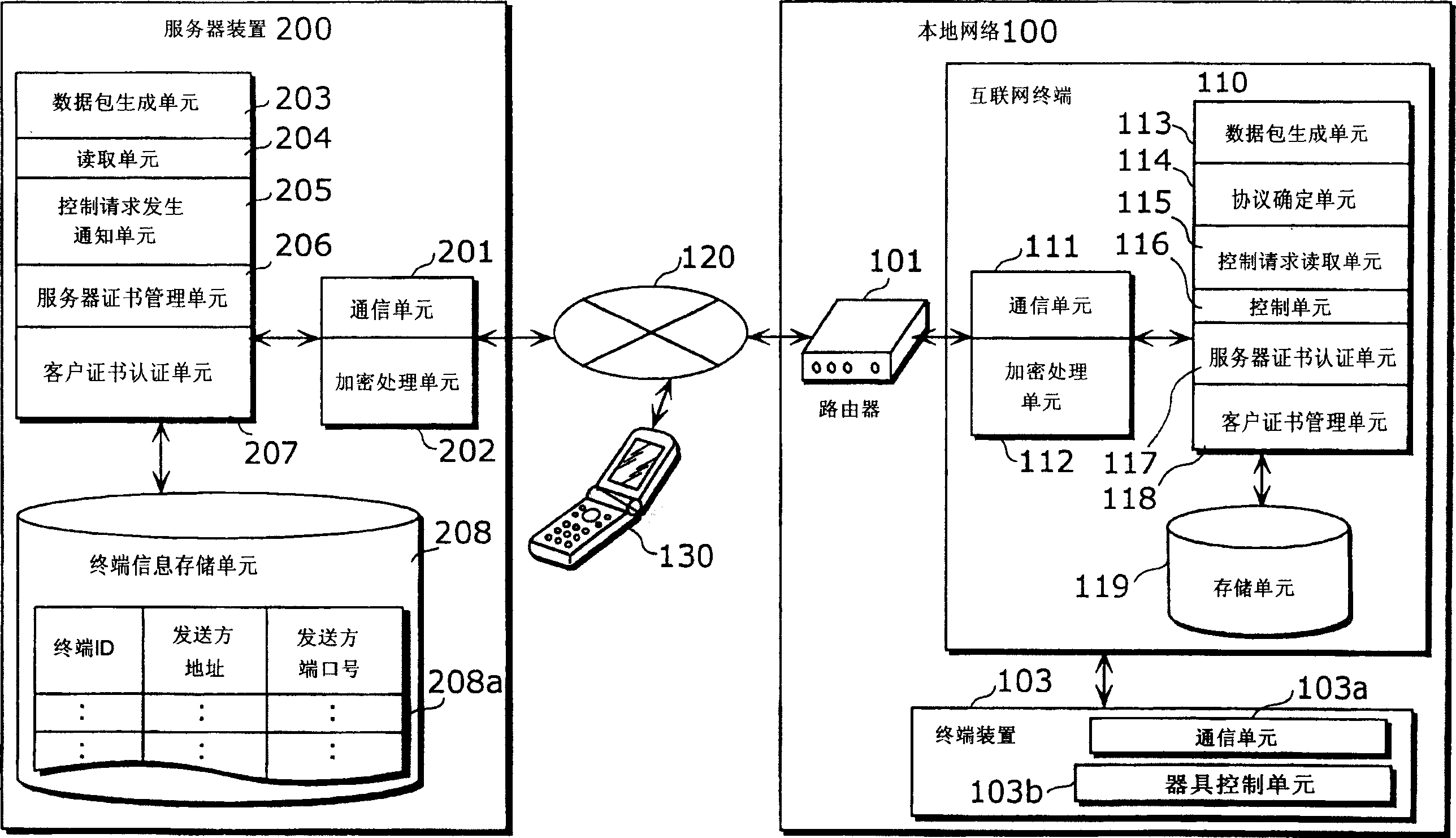
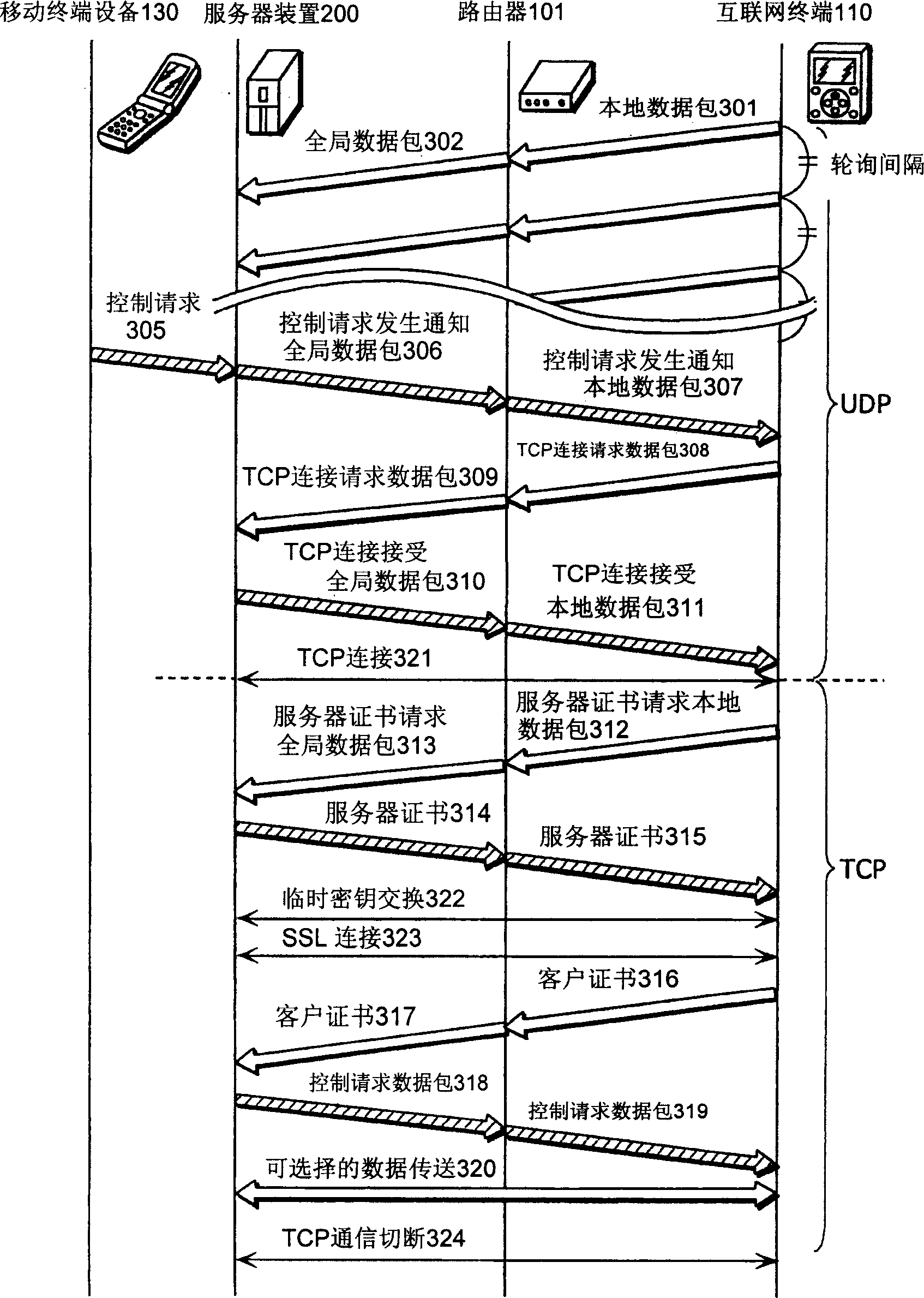
An internet terminal (110), which is a home terminal apparatus, is comprised of: a communication unit (111) for sending and receiving packet data; an encryption unit (112) for encrypting and decrypting packet data; a packet generation unit (113) for generating packet data to be sent to a server apparatus (200); a protocol determination unit (114) for determining a communication protocol to be used between the internet terminal (110) and the server apparatus (200); a control information request unit (115) for reading in packet data and a control request packet that includes a control request; a control unit (116) for receiving control information and controlling the internet terminal (110) or a terminal apparatus (103) accordingly; a server certificate authentication unit (117) for authenticating the validity of a server certificate sent by the server apparatus (200); a client certificate management unit (118) for sending a client certificate to the server apparatus (200); and a storage unit (119) for storing a terminal ID and other information.
Owner:PANASONIC CORP
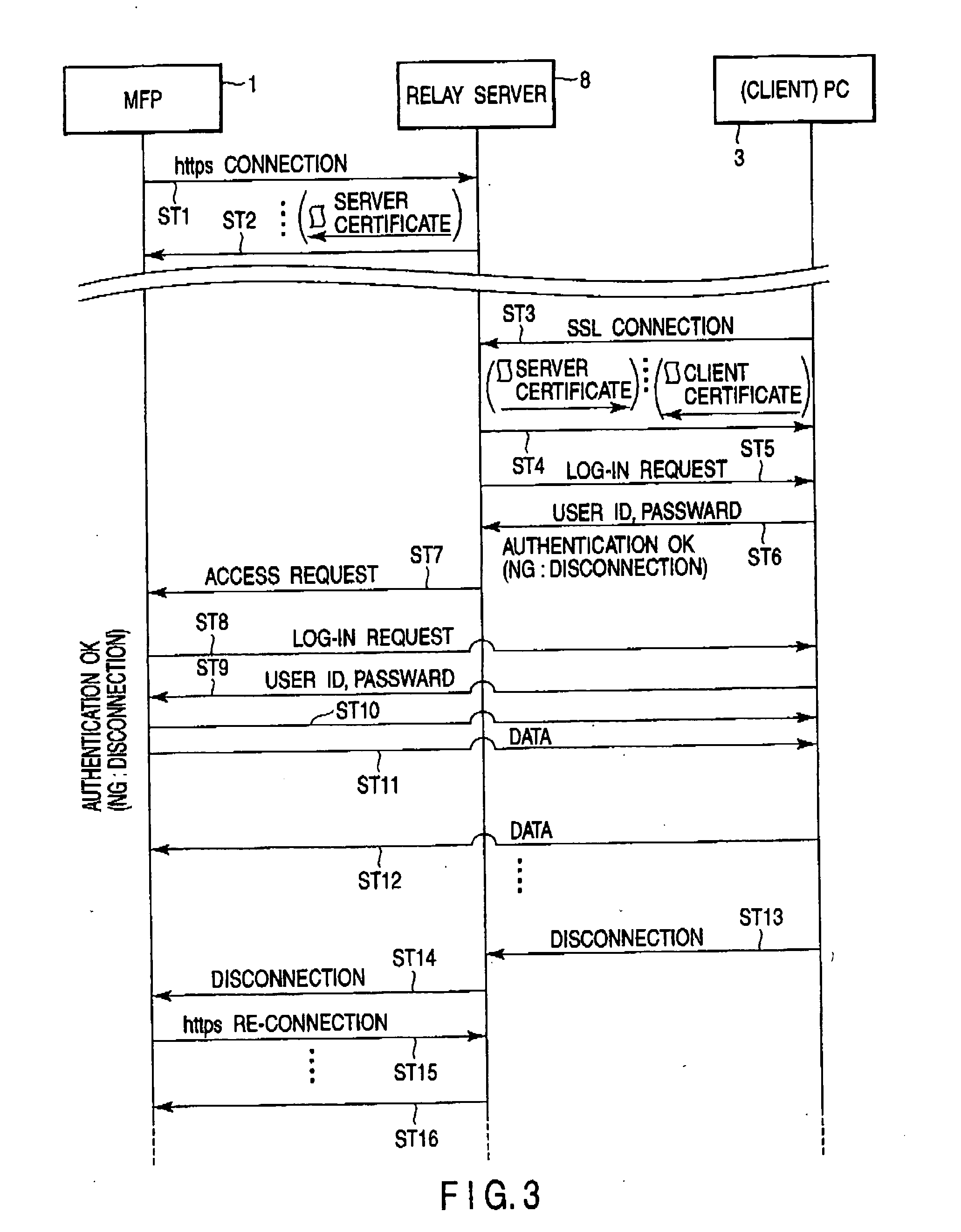
Image forming system and communication method
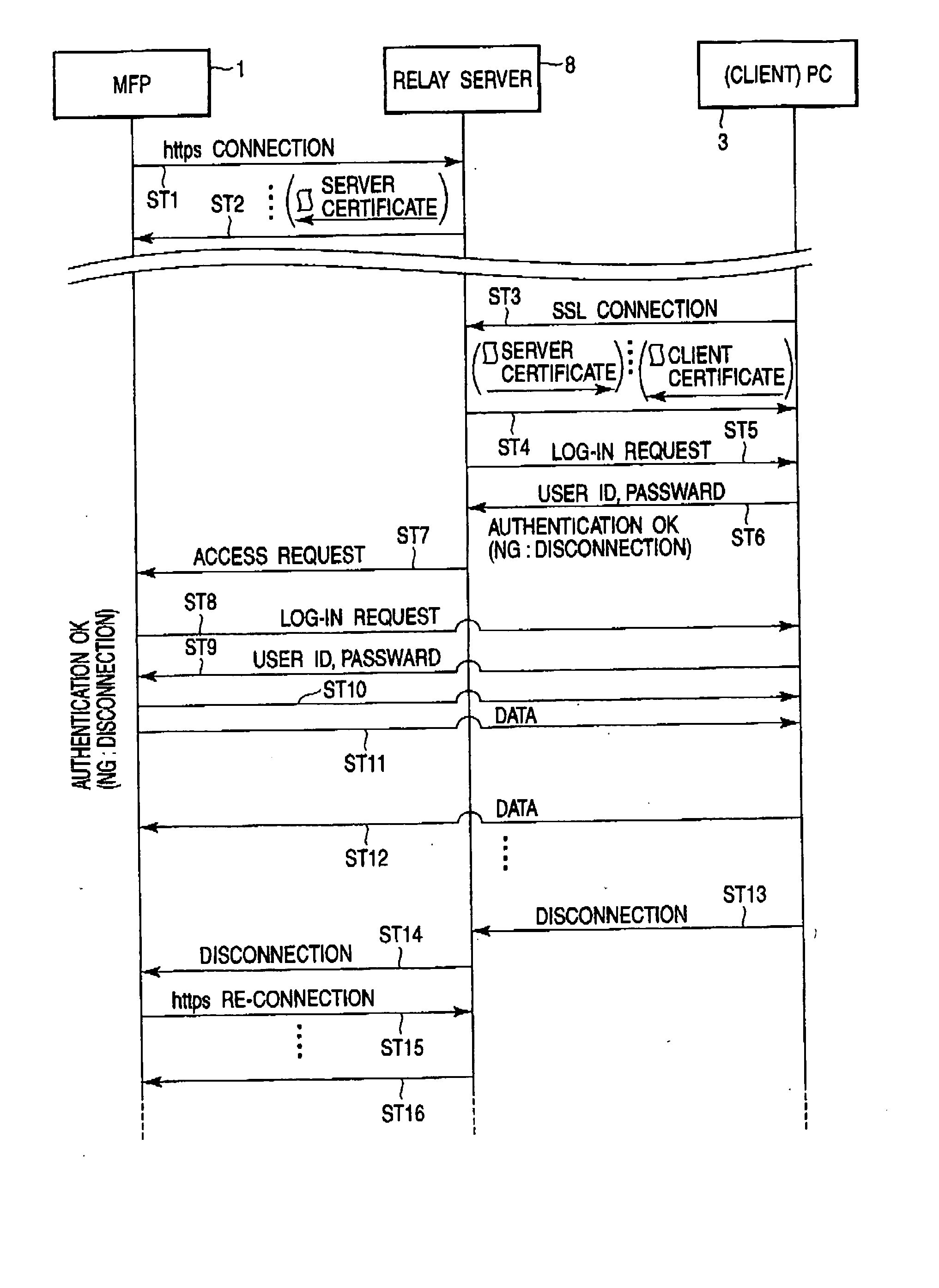
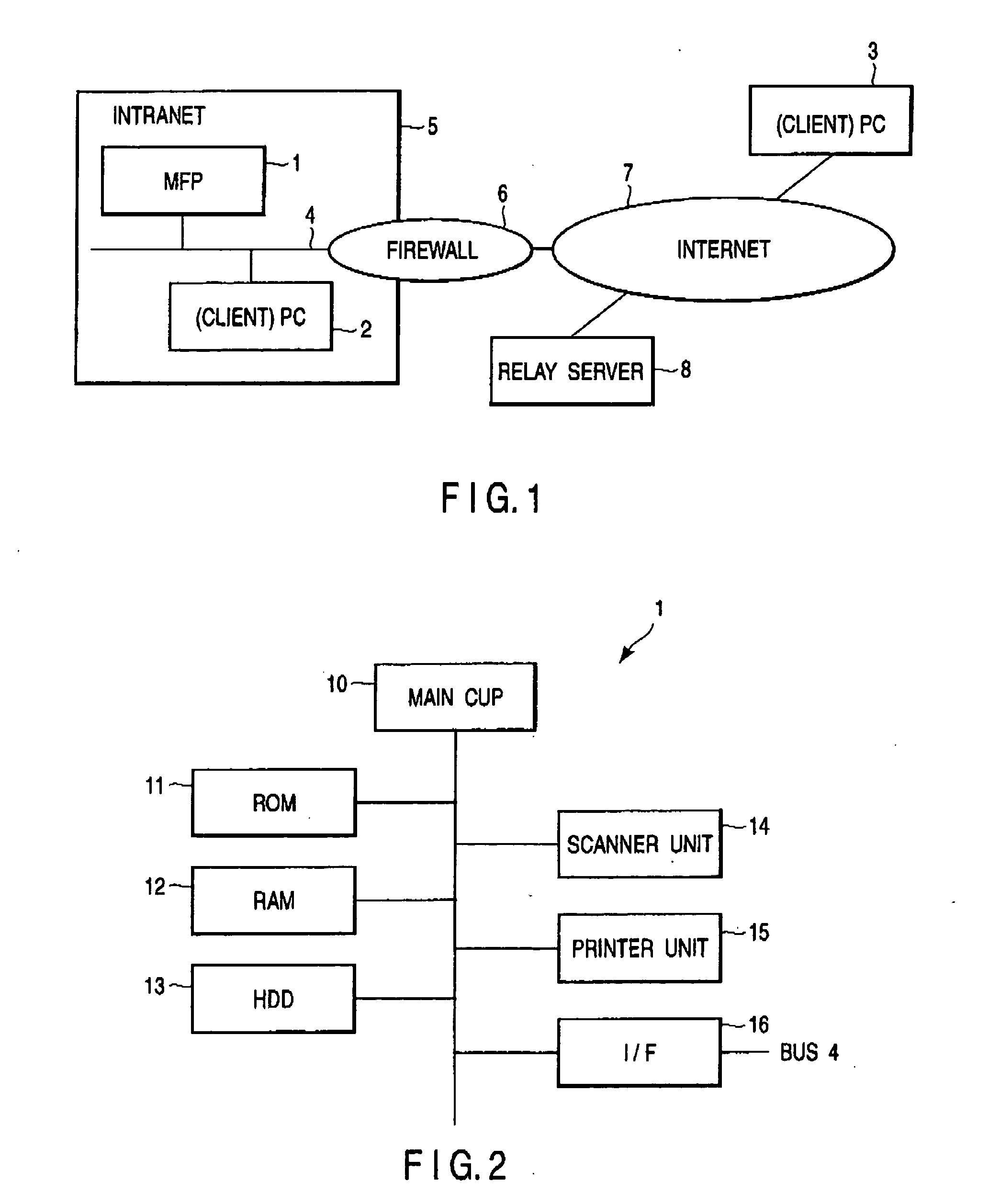
A main CPU of an MFP reads out an IP address or URL of a relay server on the Internet, which is set in an HDD, and connects to the relay server via a firewall using https. The main CPU confirms security of the relay server on the basis of a server certificate. A PC on the Internet accesses the relay server on the Internet, establishes SSL connection, and sends a client certificate. The relay server receives the client certificate from the PC by SSL connection, and sends a server certificate to the PC. If mutual authentication is successfully executed, the PC sends data to the MFP via the relay server and executes such a job as print data transmission, scan data acquisition, or change of setting information.
Owner:KK TOSHIBA +1
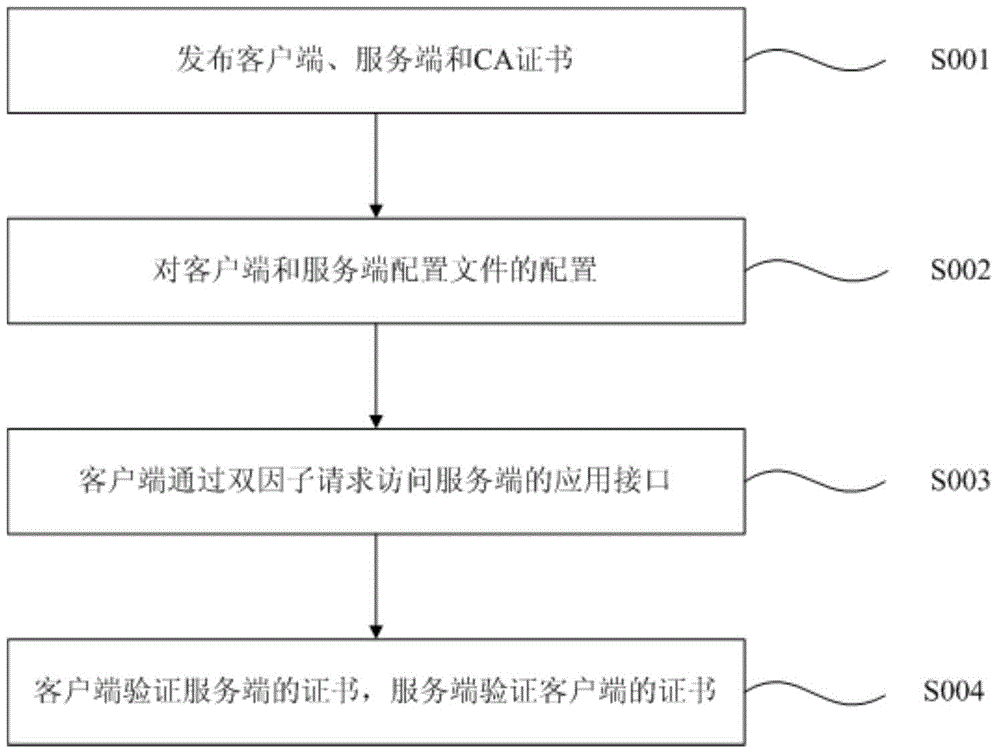
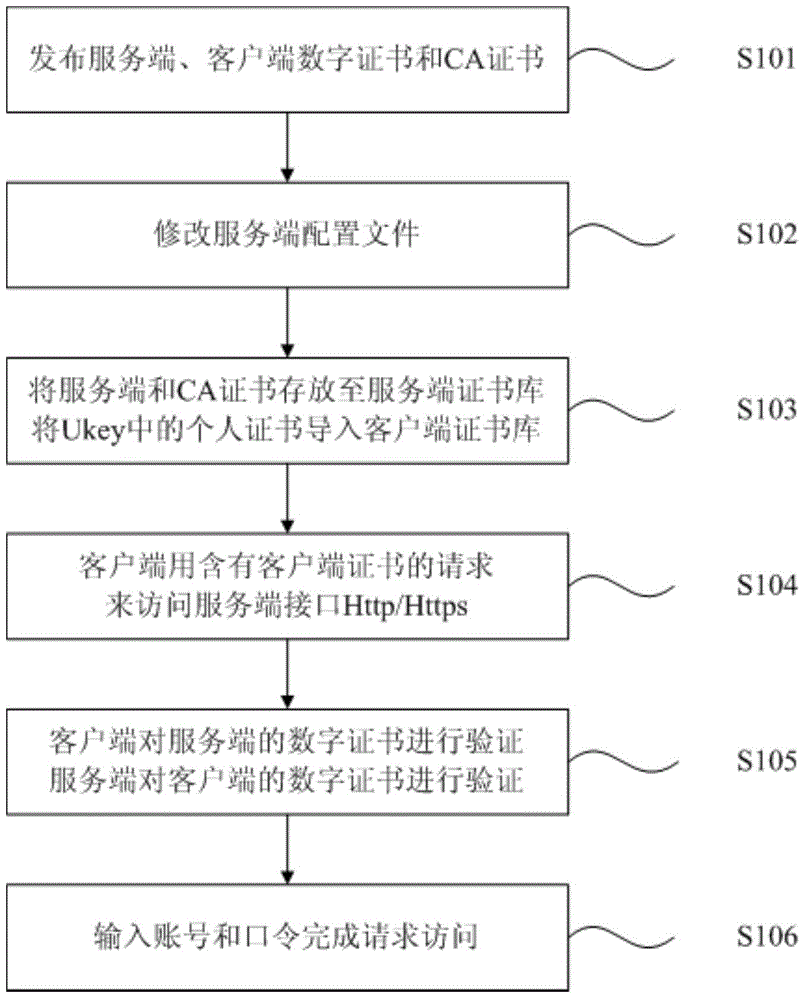
Method and system for double-factor bidirectional authentication
ActiveCN104486343AImprove compatibilitySimple designUser identity/authority verificationClient-sideClient certificate
The invention discloses a method for double-factor bidirectional authentication. The method comprises the following steps: releasing a digital certificate and a CA certificate used for signature during the making of the digital certificate by a secret key system; configuring the configuration files of a client and a server-side so as to support the access of the client to an application interface of the server-side; accessing the application interface of the server-side by the client in a double-factor authentication mode; carrying out first verification on a server-side certificate by the client, carrying out second verification on a client certificate by the server-side, and after passing through of both the first verification and the second verification, allowing the client to access the application interface of the server-side. Besides, the invention discloses a system for double-factor bidirectional authentication, corresponding to the method. The method and the system for double-factor bidirectional authentication have the advantages of higher compatibility, wider application range, simpler design, more efficiency in use, and higher safety in data communication.
Owner:GUANGDONG RAILWAY TECH
Exchange of digital certificates in a client-proxy-server network configuration
Various techniques are described to authenticate the identity of a proxy in a client-proxy-server configuration. The configuration may have a client-side and a server-side SSL session. In the server-side session, if the proxy has access to the private keys of the client, the proxy may select a client certificate from a collection of client certificates and send the selected certificate to the server to satisfy a client authentication request of the server. If the proxy does not have access to the private keys, the proxy may instead send an emulated client certificate to the server. Further, the client certificate received from the client may be embedded within the emulated client certificate so as to allow the server to directly authenticate the client, in addition to the proxy. An emulated client certificate chain may be formed instead of an emulated client certificate. Similar techniques may be applied to the client-side session.
Owner:CA TECH INC
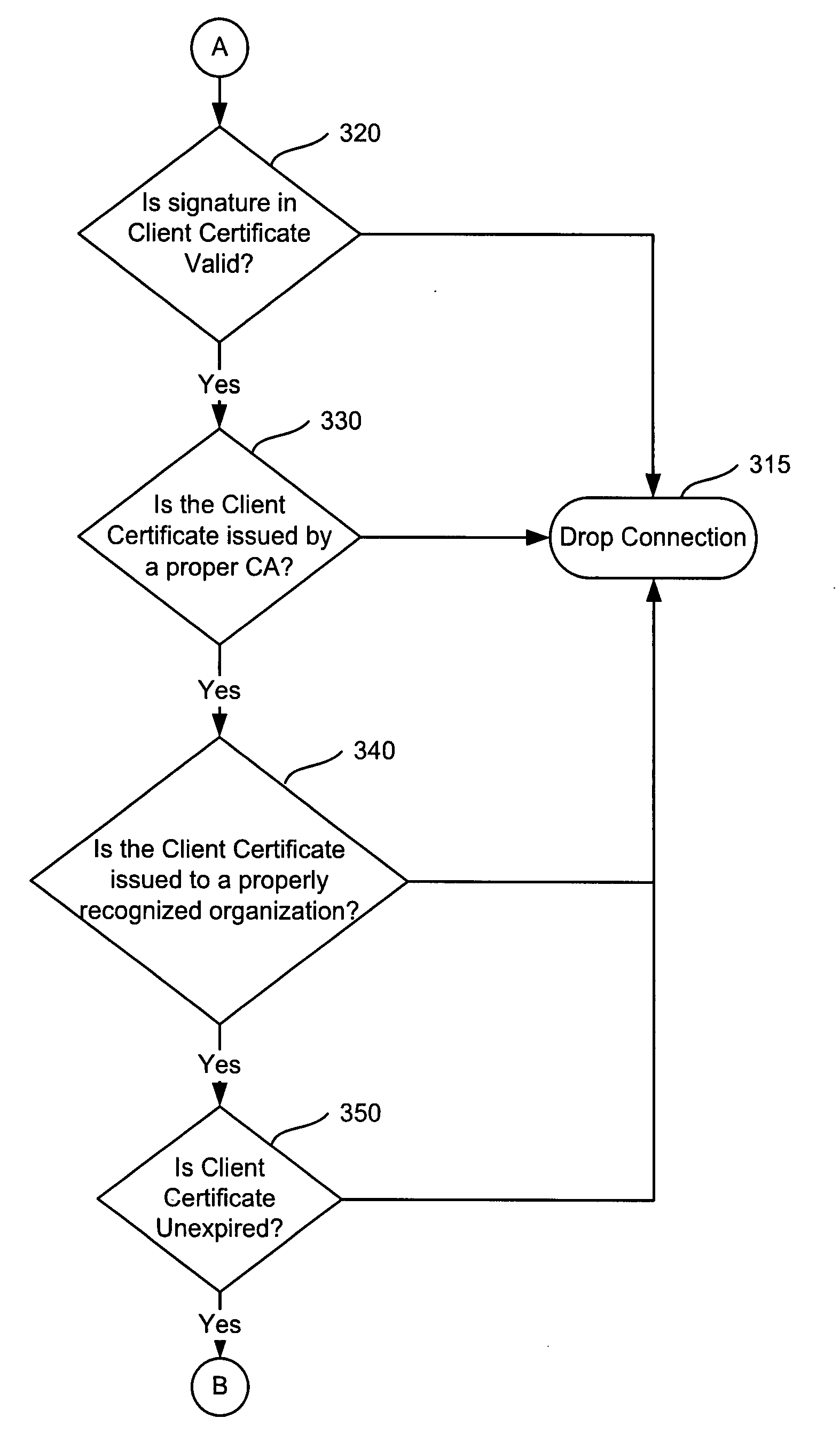
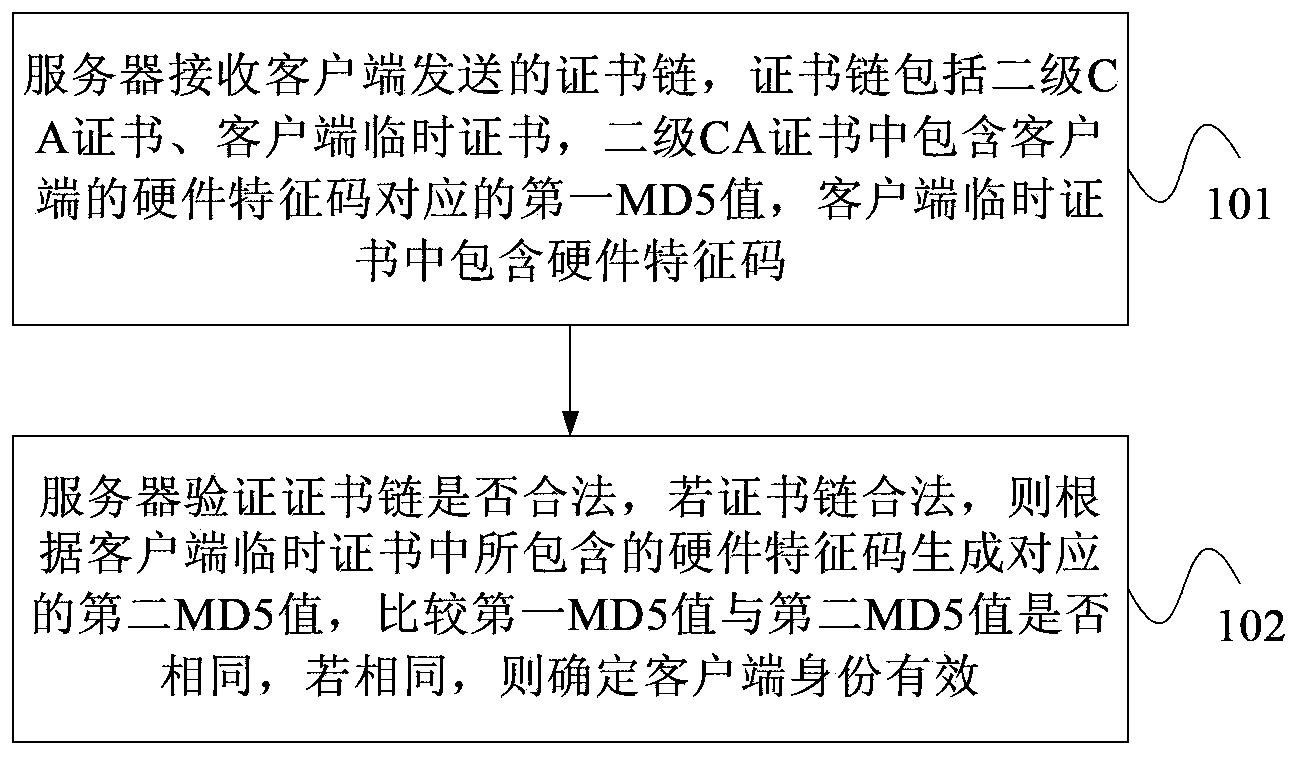
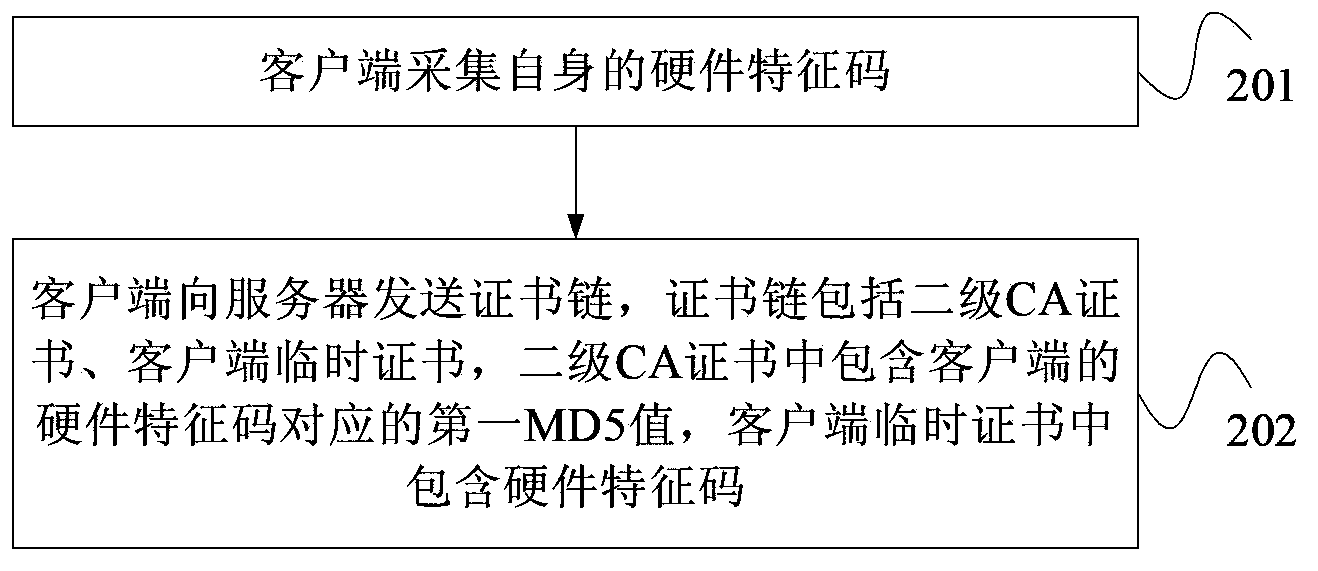
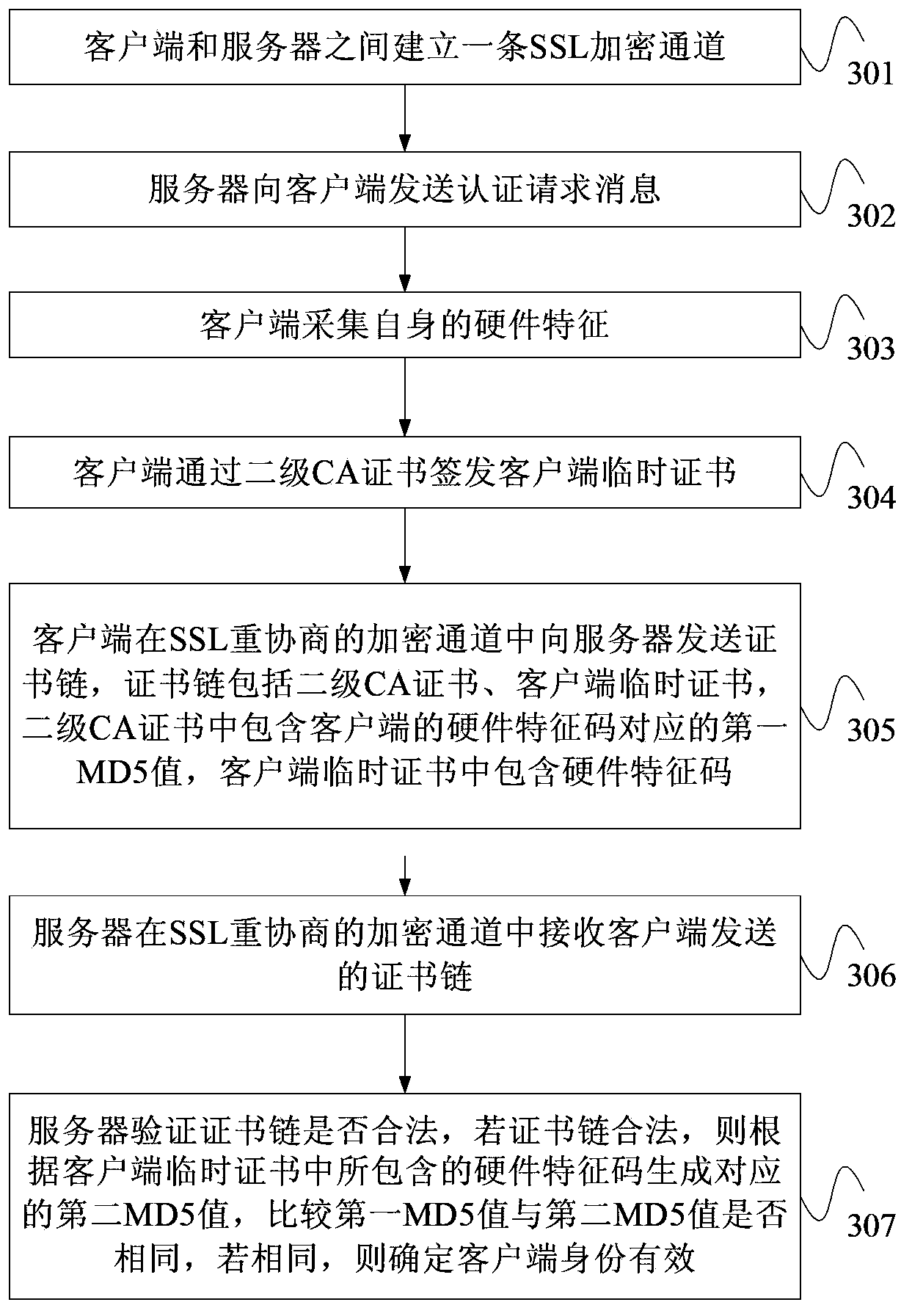
Authentication method for client certificate, server and client
The invention provides an authentication method for a client certificate, a server and a client. The authentication method includes the steps that the server receives a certificate chain sent by the client, the certificate chain comprises a second-level CA certificate and a client temporary certificate, the second-level CA certificate includes a first MD5 value corresponding to a hardware feature code of the client, and the client temporary certificate includes a hardware feature code; the server verifies whether the certificate chain is legal or not, if the certificate chain is legal, a corresponding second MD5 value is generated according to the hardware feature code included in the client temporary certificate, the first MD5 value and the second MD5 value are compared whether to be same or not, and if yes, the situation that the identification of the client is effective is determined. Due to the uniqueness of the MD5 values, if the client temporary certificate is stolen, the second MD5 value is bound to be different from the first MD5 value. Therefore, the client can not be counterfeited, and the situation that in the prior art, a digital certificate is stolen and causes identification mistakes is avoided.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com