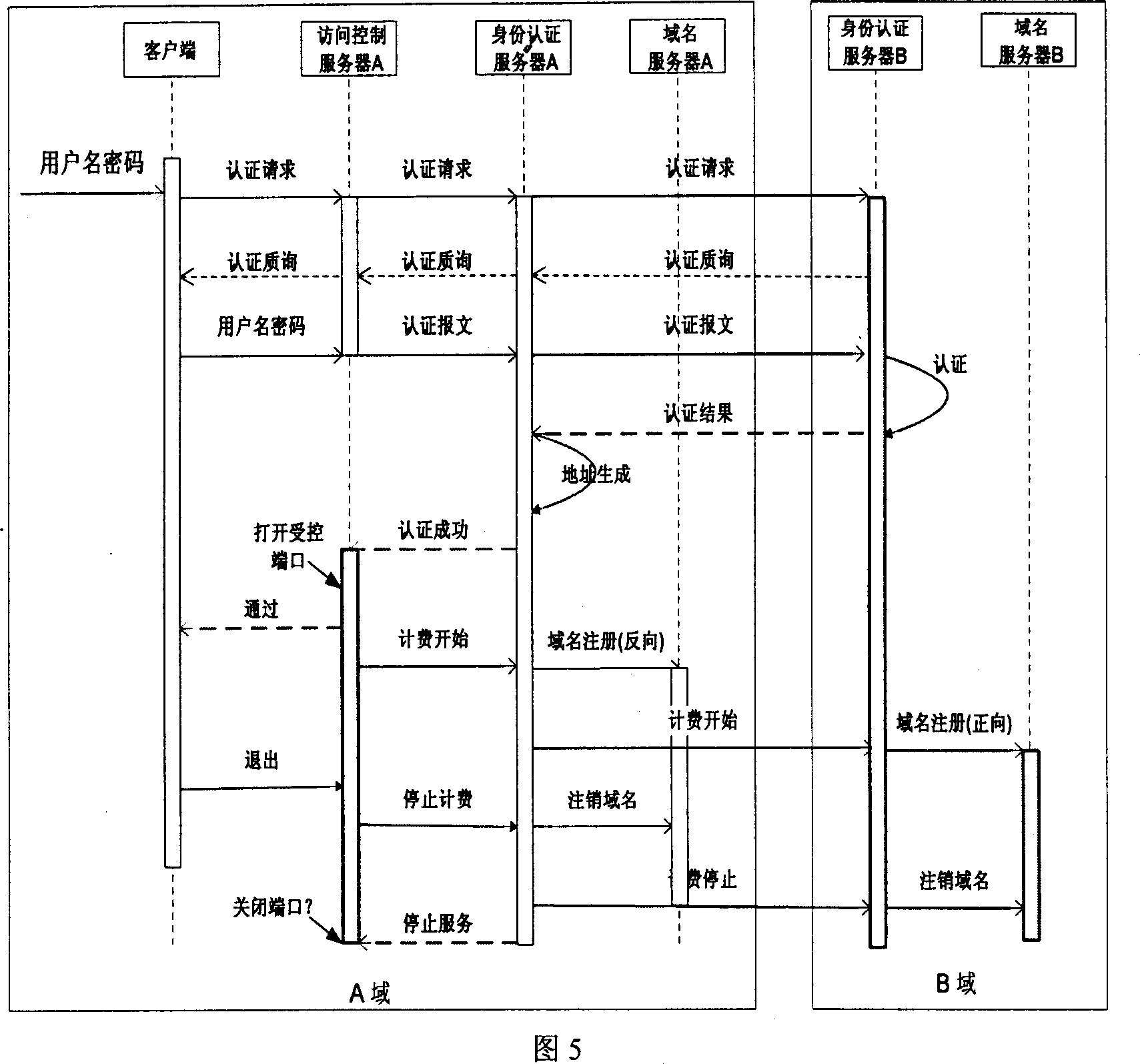
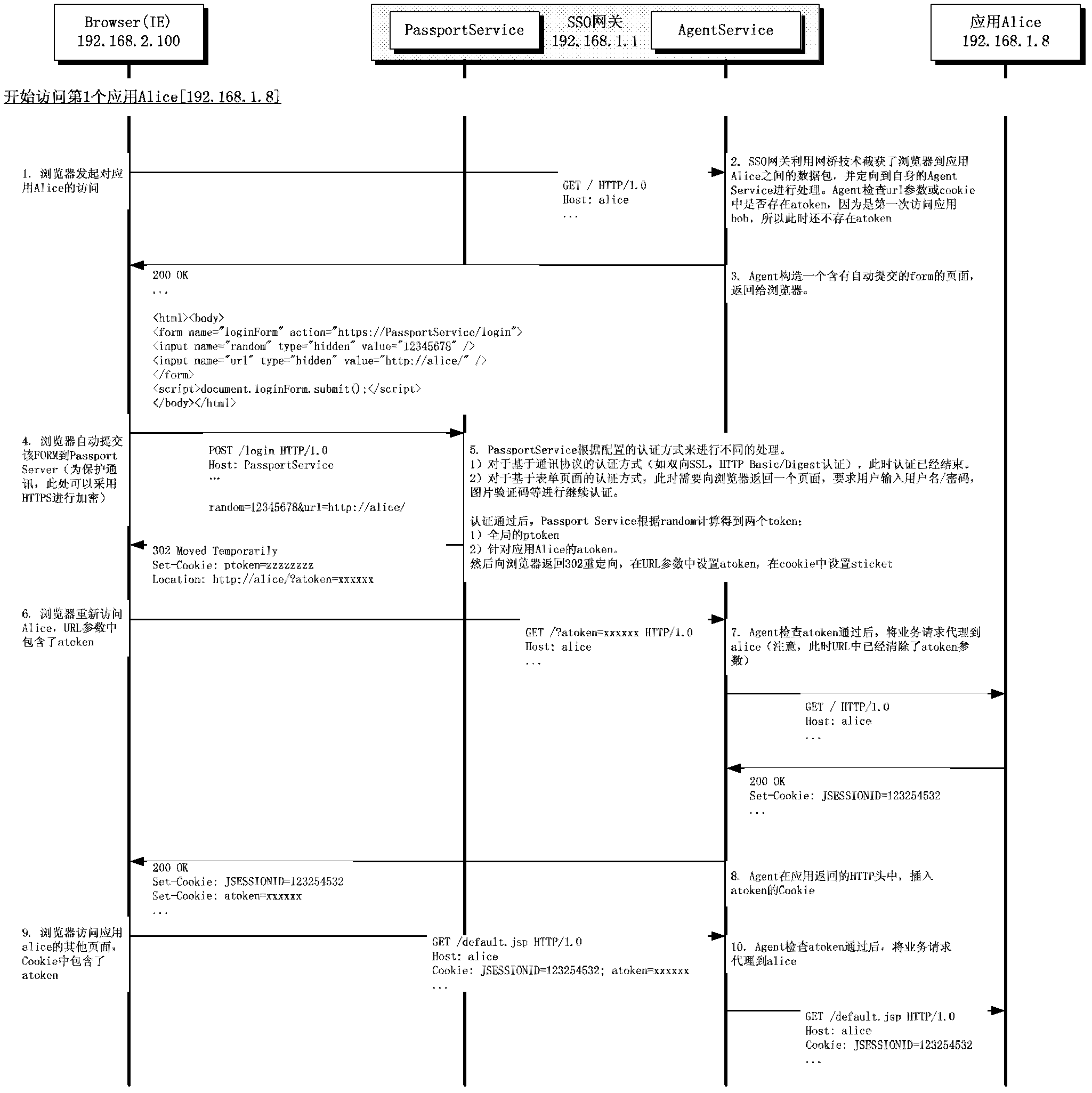
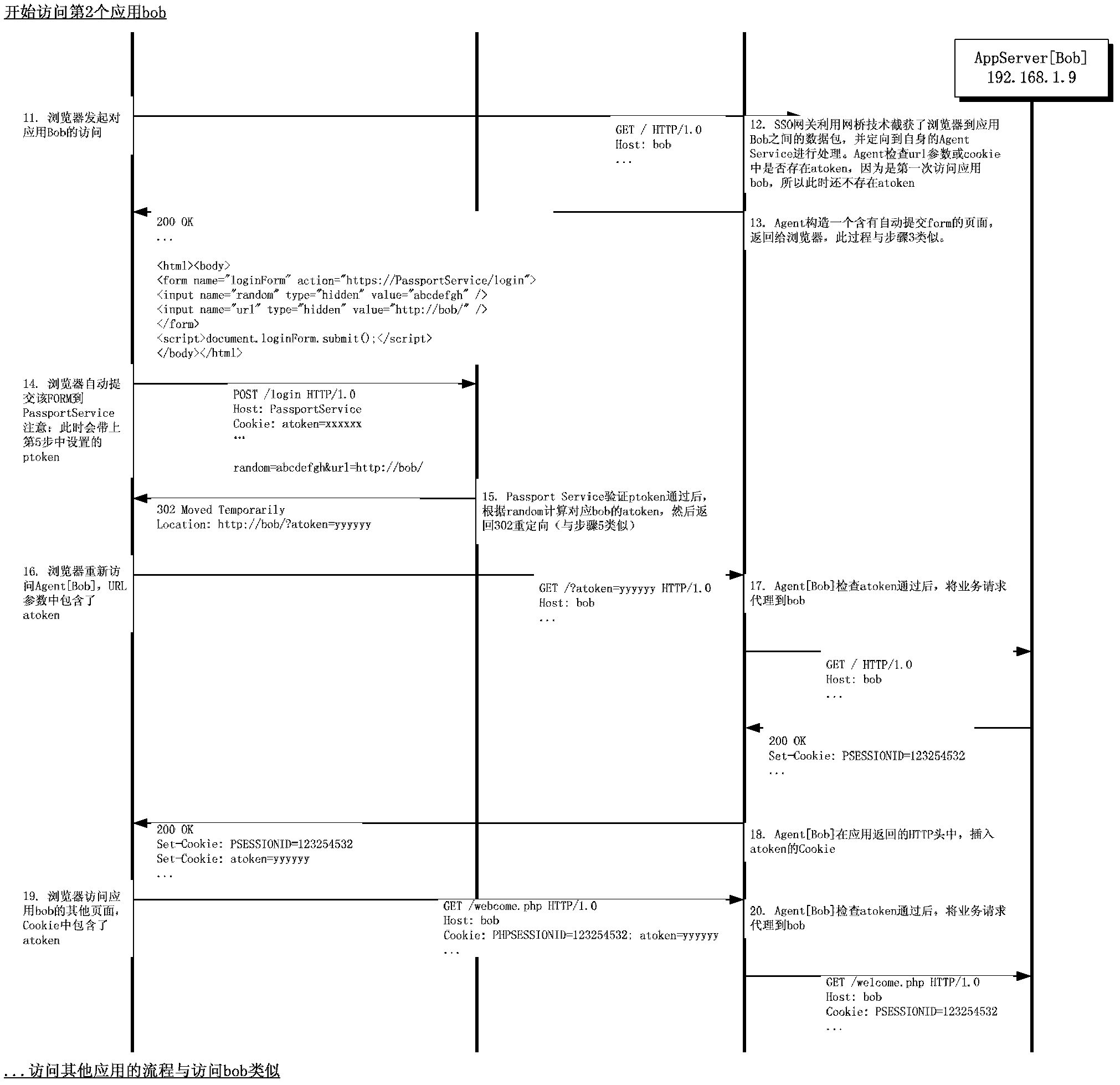
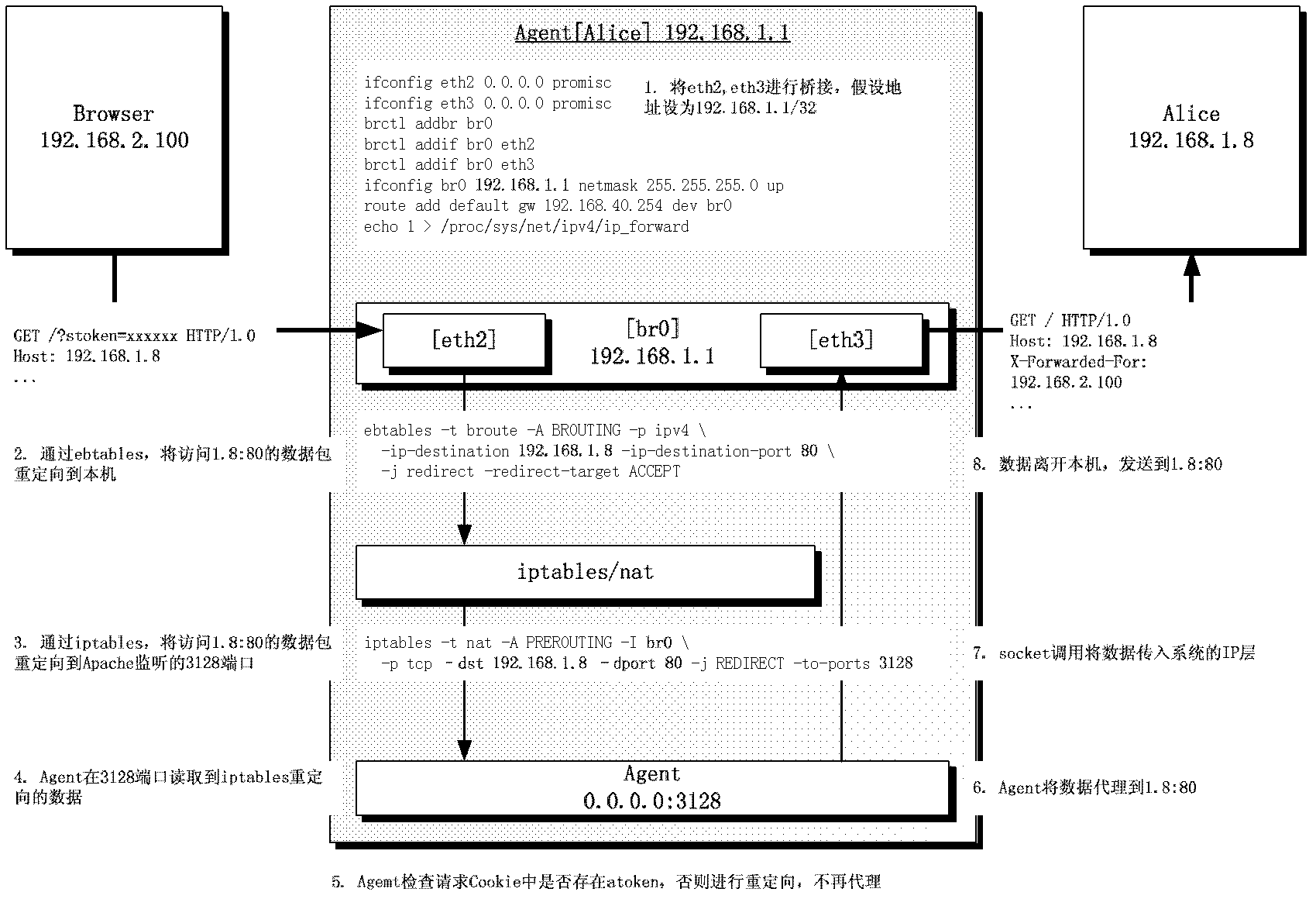
Patents
Literature
51results about How to "Implement single sign-on" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Single sign-on integrated method for Form identity authentication in single login system
InactiveCN102624737AImplement single sign-onEasy to implementUser identity/authority verificationWeb applicationWeb service
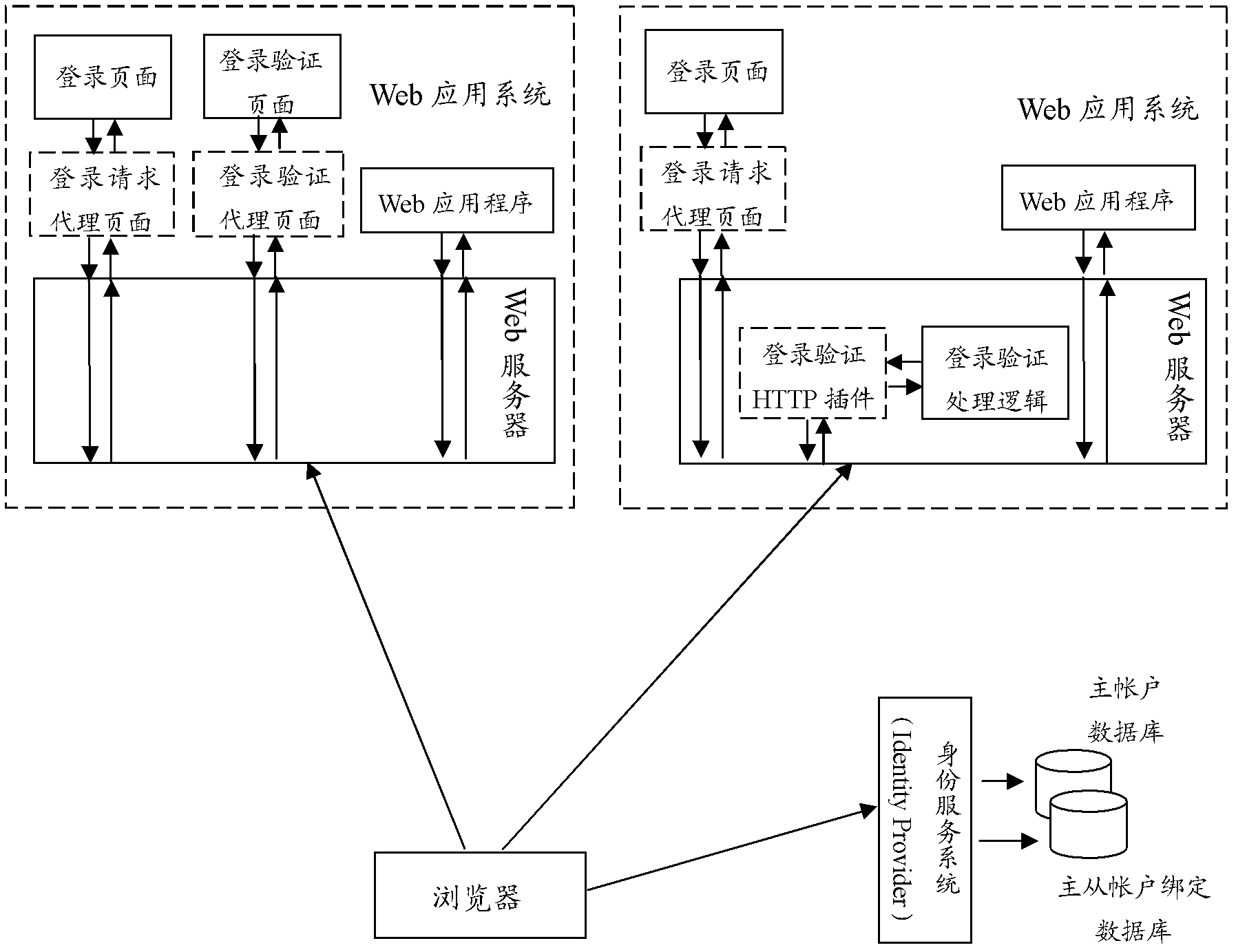
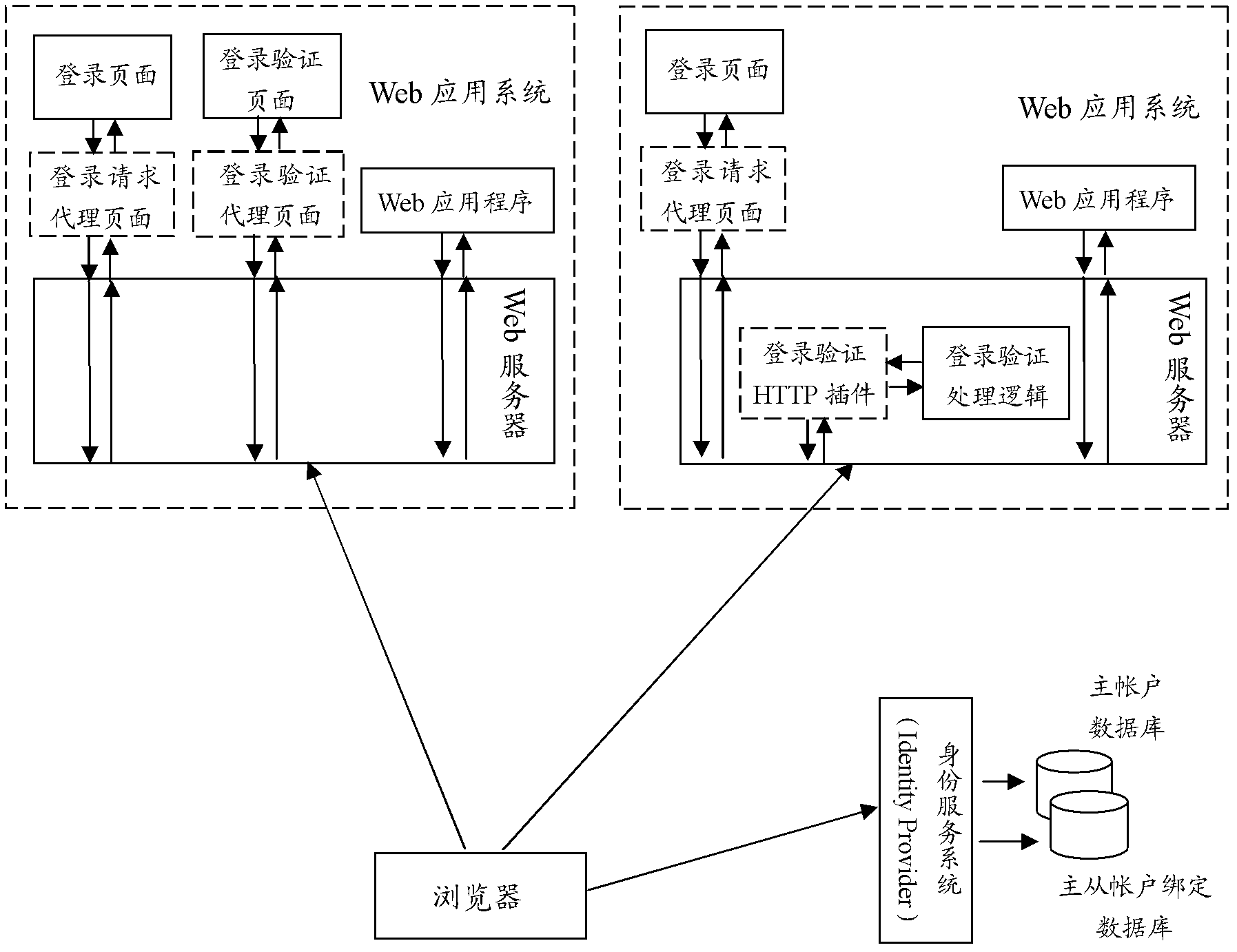
The invention relates to a single sign-on integrated method for Form identity authentication in a single sign-on system. The single sign-on system comprises a Web application program, a Web server, a login request proxy page, a login authentication proxy page, a login authentication HTTP (hypertext transfer protocol) plug-in, a browser, an identity service system, a master account database and a master-slave account binding database. The method includes that the login request proxy page receives and acquires an HTTP request of the login page to guide a user not logging in to log in the identity service system; the identity service system submits a security token authenticating identity of the user to an account name and a password authentication URL (uniform resource locator) of the Web application system to be accessed by the user through the browser after performing the identity authentication of the user; the login authentication proxy page or the HTTP plug-in completes the security token authentication and adds the local account name and password of the Web application system to the HTTP request after receiving or intercepting the HTTP request submitted to the account name and the password authentication URL, so that the user can log in the Web application system.
Owner:WUHAN UNIV OF TECH +1
Domainname-based unified identification mark and authentication method
InactiveCN1937499AGood scalabilityAvoid visitingUser identity/authority verificationData switching by path configurationVerification systemMAC address
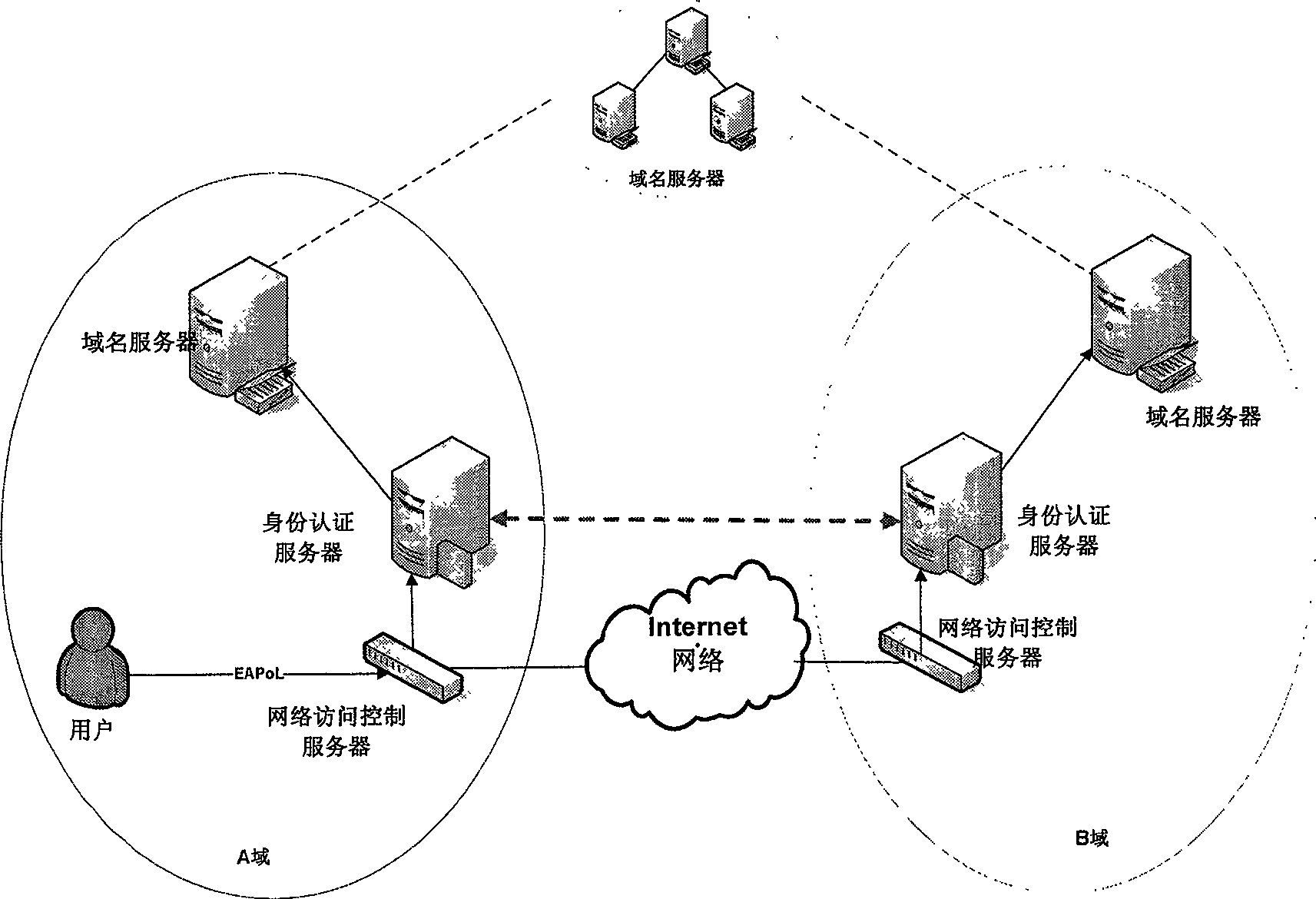
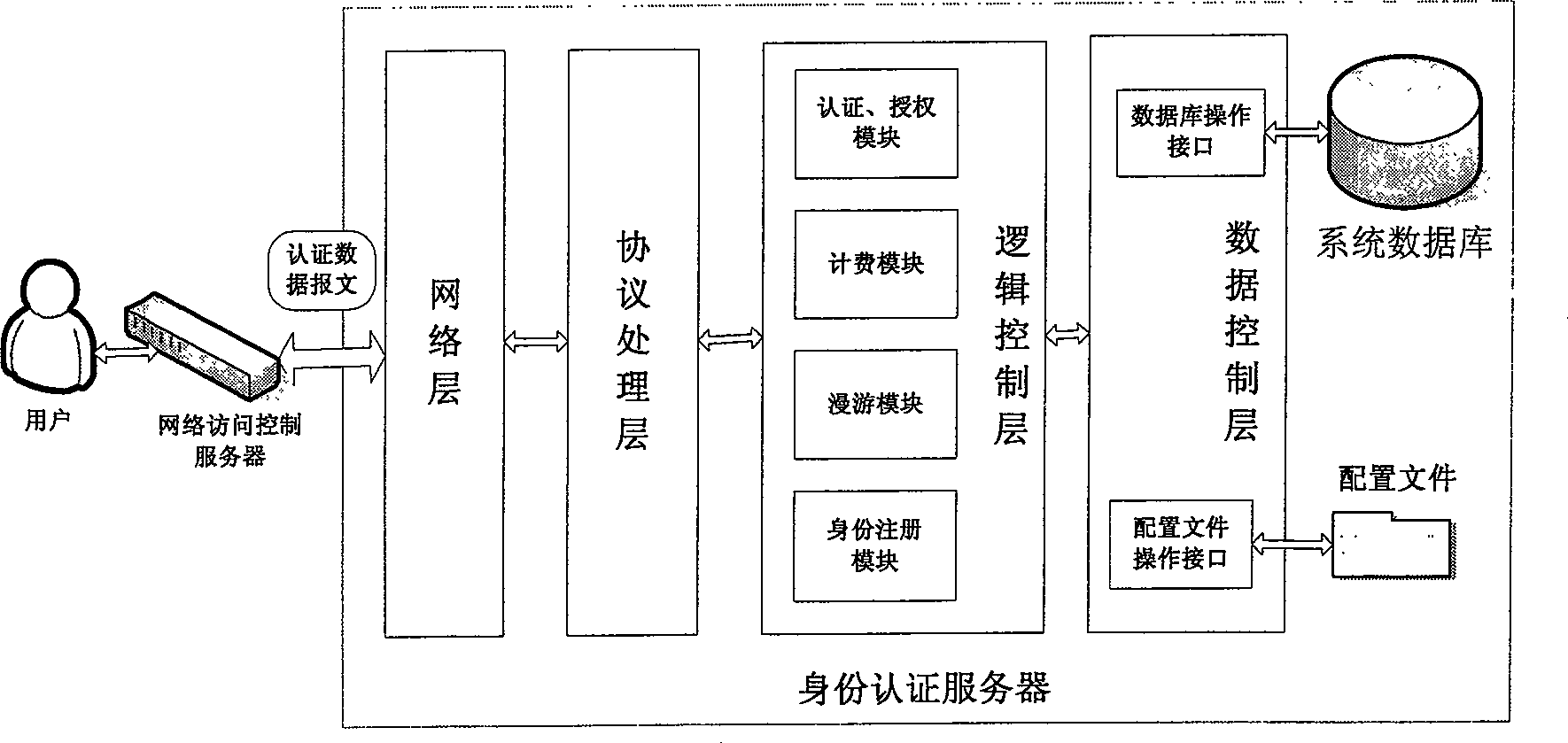
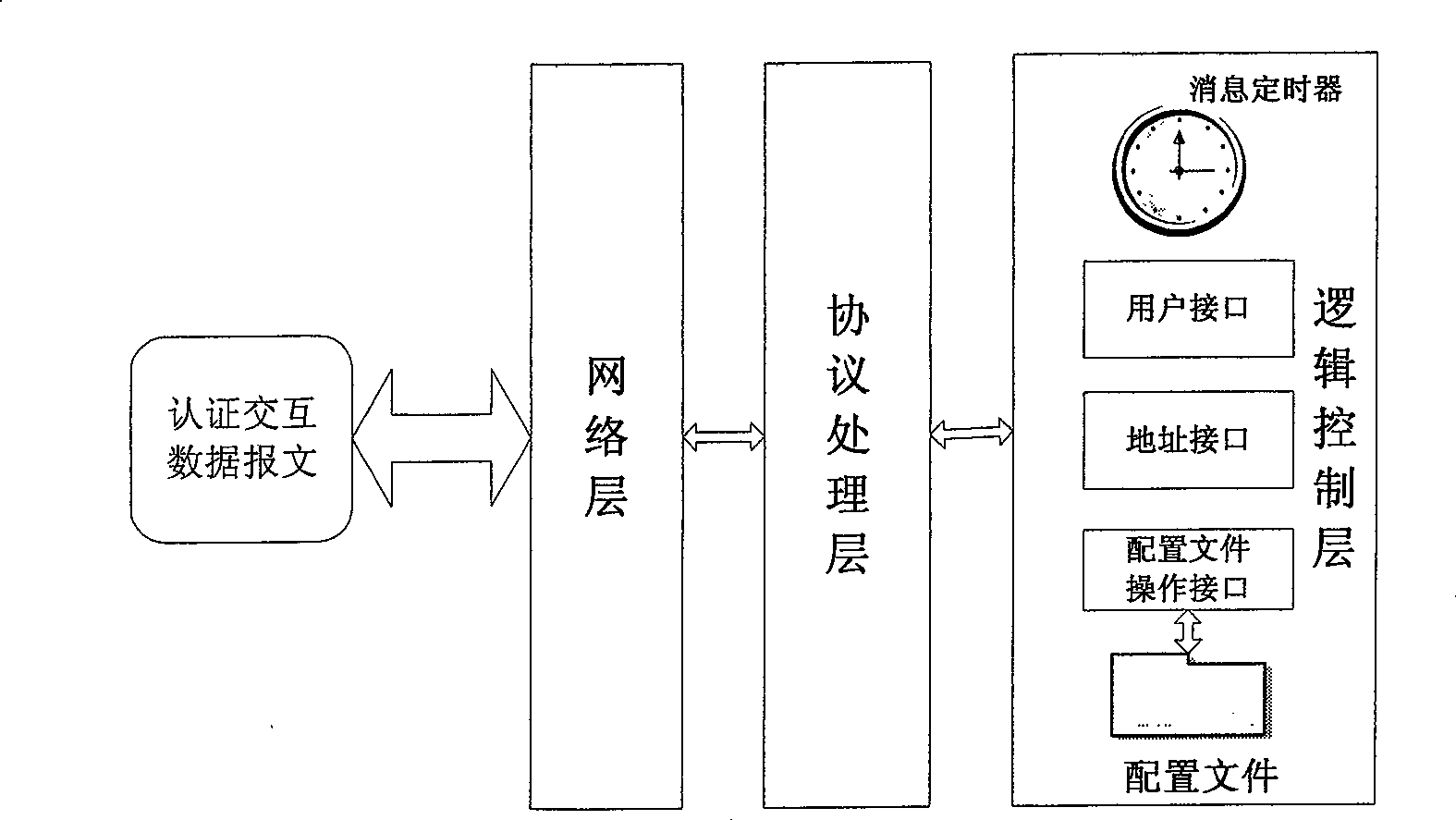
This invention utilizes the good architecture design presented by the latest Internet protocol IPv6, combines with safety domain name (DN) service, extends the existed ID verification system functions, realizes the bounding relation between the user ID and recent real IPv6 address to offer a reliable security service for the upper application. In the user management domain, there are a net access control server (NACS), an ID authentication server (IDAS) and a DN server. NACS recognizes the registered user via a 3-element group consisted of user computer source MAC address, the source IPv6 address and the port. IDAS authenticates the user ID recognition and defines related accessing priority. DN server establishes the positive-negative direction relations between user private DN and IPv6 address. This invention provides more effective ID authentication means and possesses a great extendable function to meet the requirement of the future Internet application development.
Owner:TSINGHUA UNIV
WEB single sign-on method completely transparent to user and application
InactiveCN103188295ANo need to change network deploymentNo need to change access habitsTransmissionWeb applicationNetwork packet
The invention discloses a WEB single sign-on method completely transparent to a user and an application. The method comprises the following steps that: 1, an HTTP (Hyper Text Transport Protocol) data packet between the user (a browser) and the WEB application is intercepted by a transparent bridge technology, 2, the user is redirected to an SSO (Single Sign-on) server by a page redirection technology during first access, 3, after SSO service is certified, the browser is redirected back to the WEB application and a security Token is set, and 4, when the browser accesses the application again, an SSO gateway inspects the security Token, and the access is passed if the security Token is valid. According to the WEB single sign-on method, the single sign-on of the WEB application can be achieved under the conditions that a client or plugin is not required to be installed and the application is not required to be modified, and a top-level domain can be crossed.
Owner:KOAL SOFTWARE CO LTD
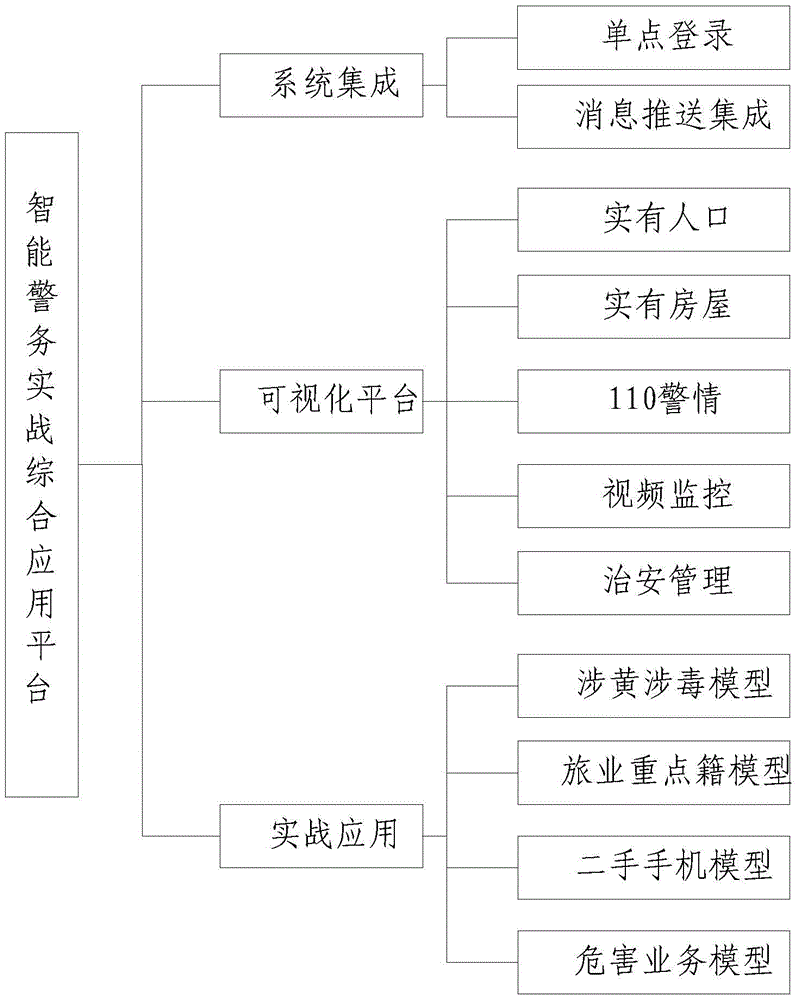
Intelligent police actual combat comprehensive application platform
InactiveCN105574657AImprove the efficiency of driver developmentAchieve integrationResourcesInformatizationData warehouse
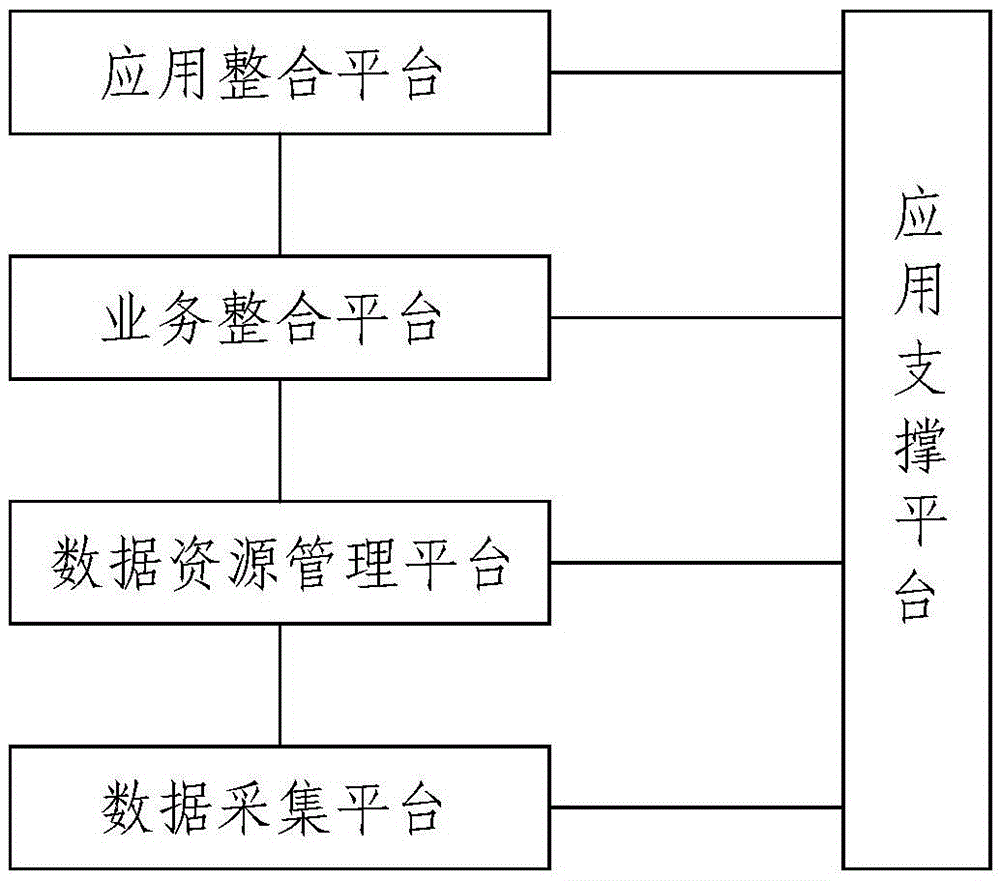
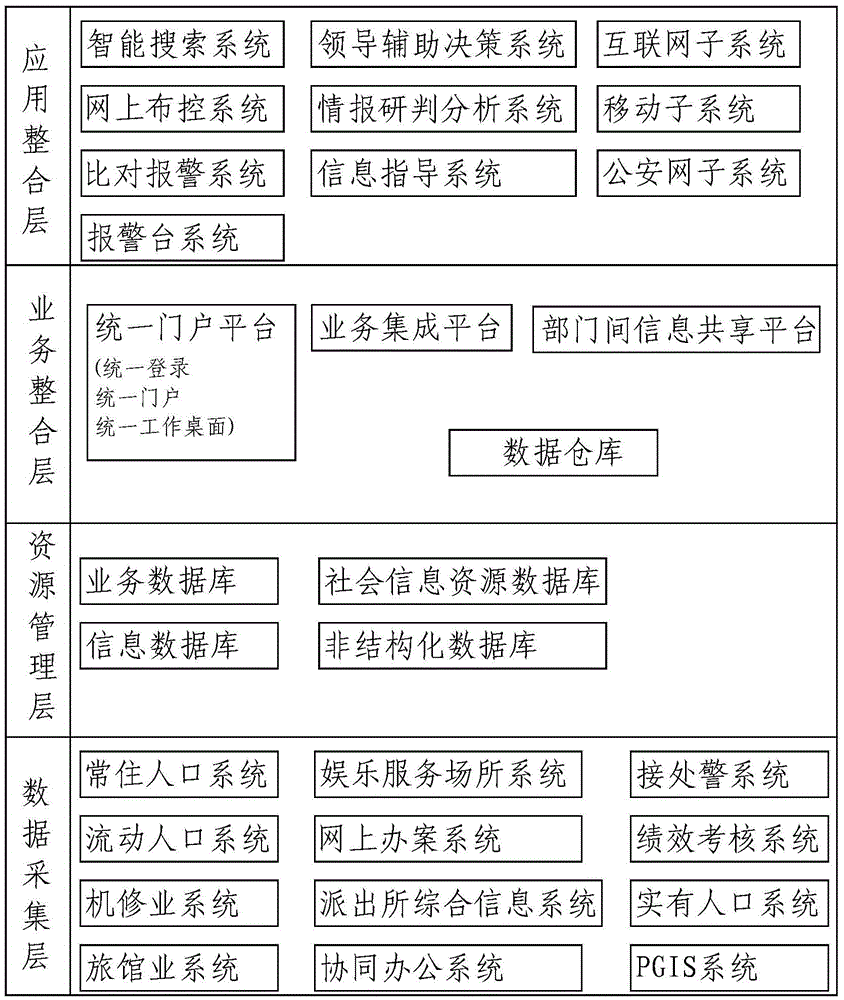
The invention discloses an intelligent police actual combat comprehensive application platform. The intelligent police actual combat comprehensive application platform comprises a data acquisition platform, a data resource management platform, a business integration platform and an application integration platform, wherein the data acquisition platform is used for acquiring public security basic data of various application business information systems of public security; the data resource management platform is used for storing the acquired various business data and establishing a comprehensive database of public security data, social aspect information, governments and other department information; the business integration platform is used for integrating various information of the data resource management platform and establishing a data warehouse to realize system level and business module level integration, unified login, unified portal and unified business handling functions, business integration of the business systems and business collaboration and data multiplexing of the business systems; and the application integration platform is used for establishing a unified application platform integrating functions of public security intelligence information comprehensive application, intelligence studying and judging comprehensive analysis and police geographic information basis application. The intelligent police actual combat comprehensive application platform can promote public security informatization application to be popularized and deepened, thereby comprehensively improving the overall application level.
Owner:SHANDONG XINWANGGE INFORMATION TECH
Single sign-on method and device
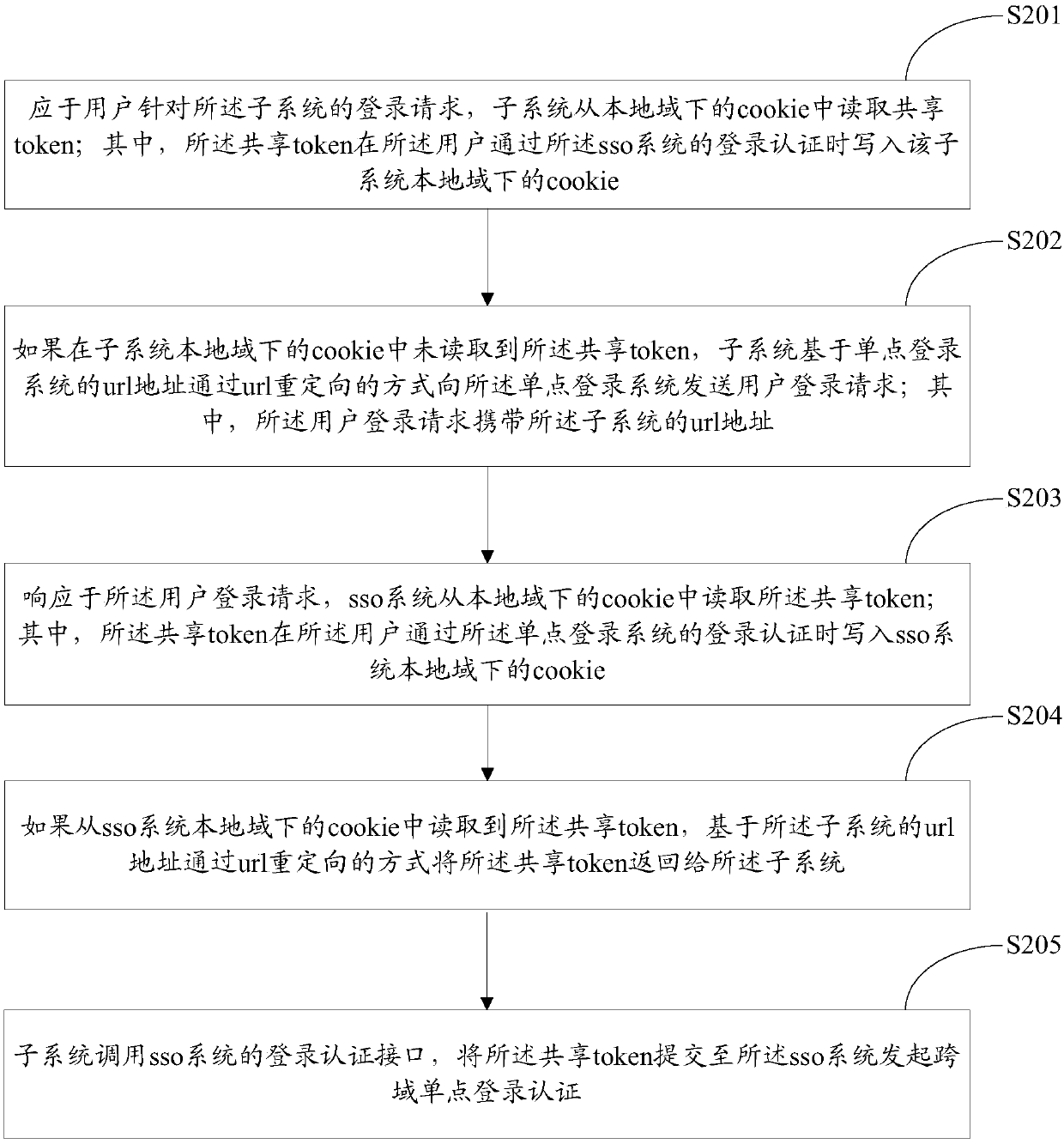
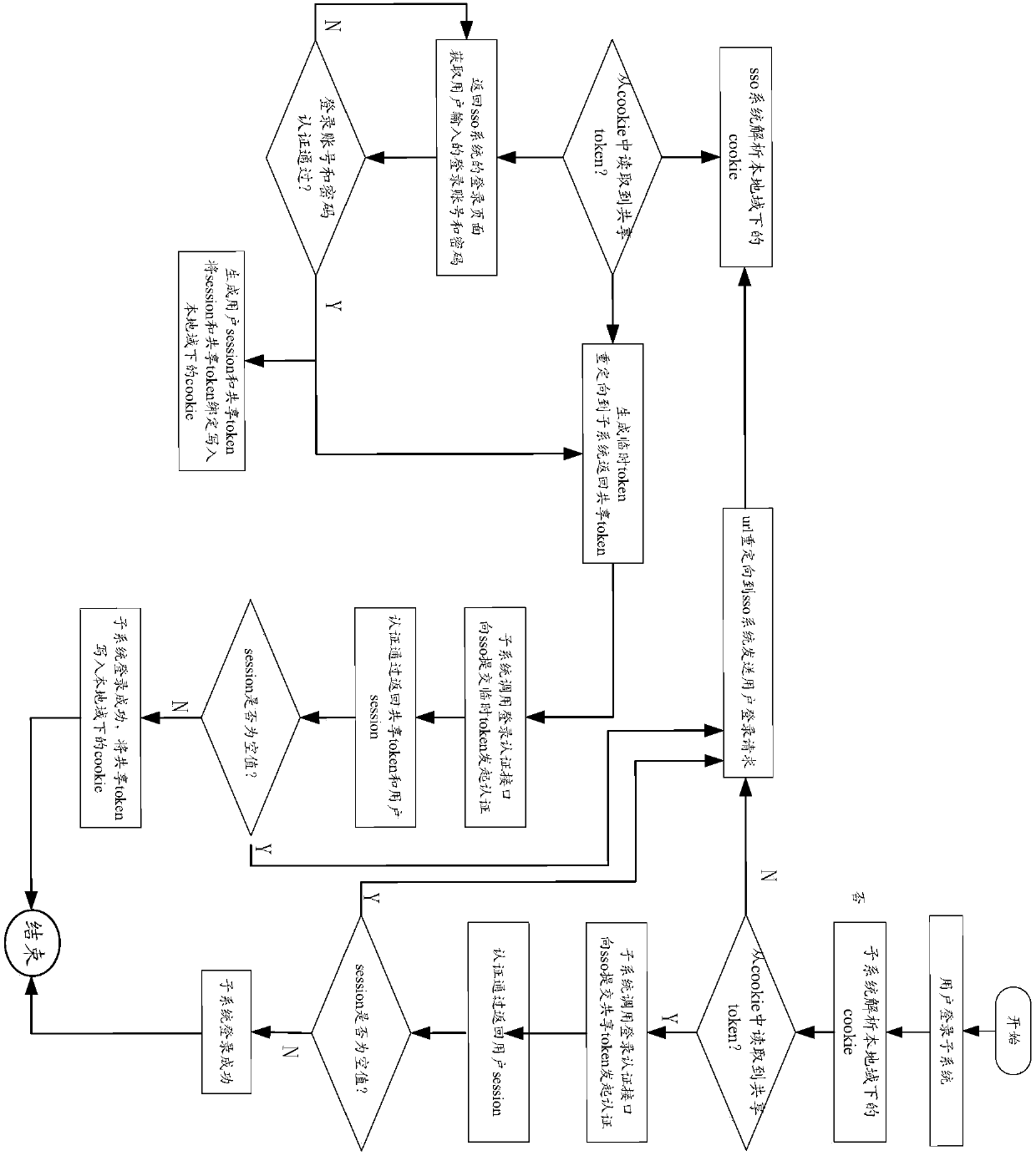
ActiveCN107948167AOvercome the problem of not being able to achieve cross-domain loginImplement single sign-onTransmissionInternet privacyURL redirection
The invention provides a single sign-on method. The method comprises the following steps: in response to a login request of a user for a subsystem, reading a shared token by the subsystem from a cookie under the local domain; respectively writing the shared token into the cookie under the local domain of the subsystem and a cookie under the local domain of an sso system when the user passes the login authentication of the sso system; if the shared token is not read in the cookie under the local domain of the subsystem, then sending the user login request to a single sign-on system by the subsystem based on a url address of the single sign-on system through a url redirection way, wherein the user login request carries the url address of the subsystem; reading the shared token by the sso system from the cookie under the local domain; if the shared token is read from the cookie under the local domain of the sso system, then returning the shared token to the subsystem based on the url address of the subsystem through the redirection way; and calling a login authentication interface of the sso system by the subsystem, and submitting the shared token to the sso system and initiating cross-domain single sign-on authentication.
Owner:ZHEJIANG NUMBER CHAIN TECH CO LTD
Secure web page tag library system supported by multiple strategies
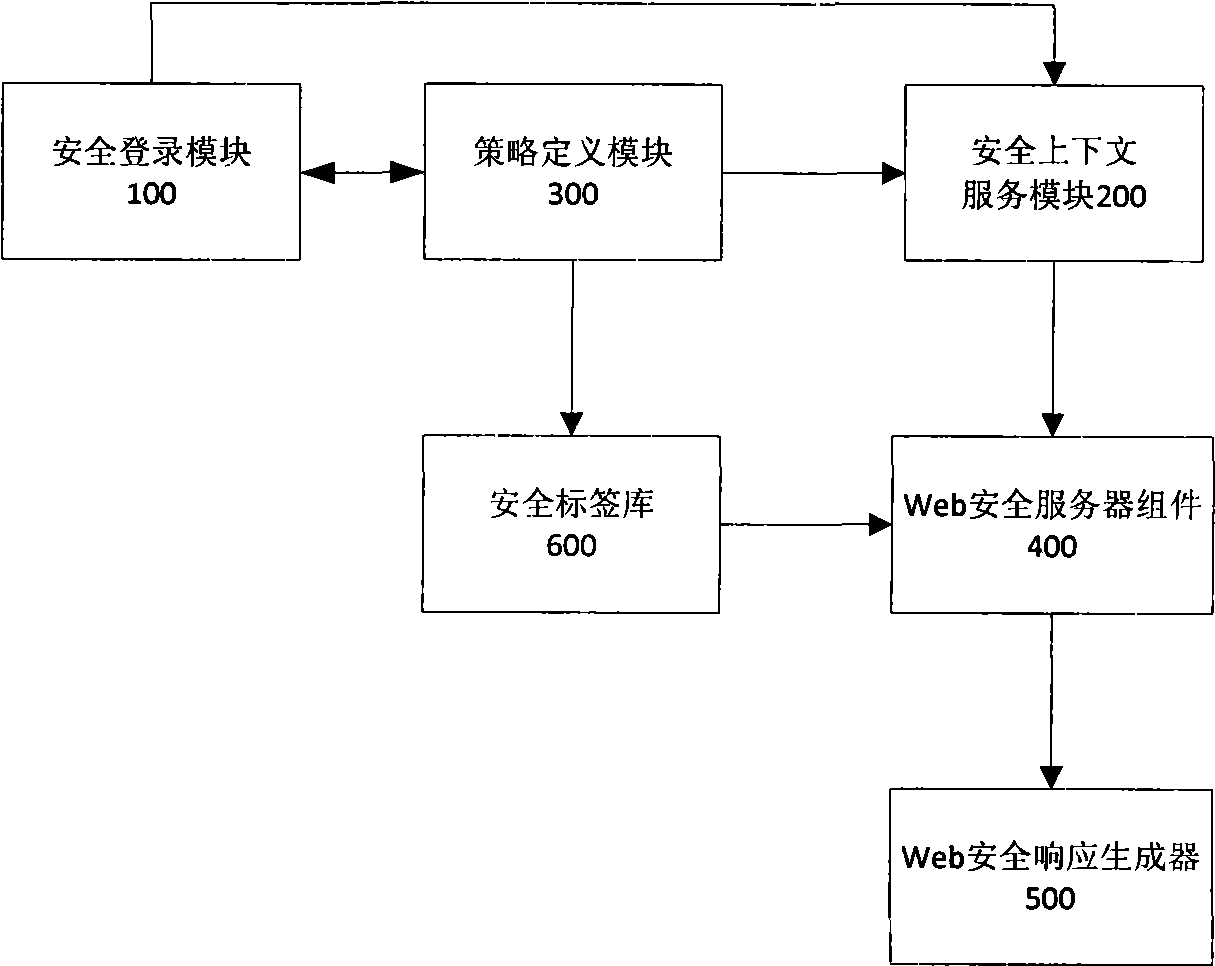
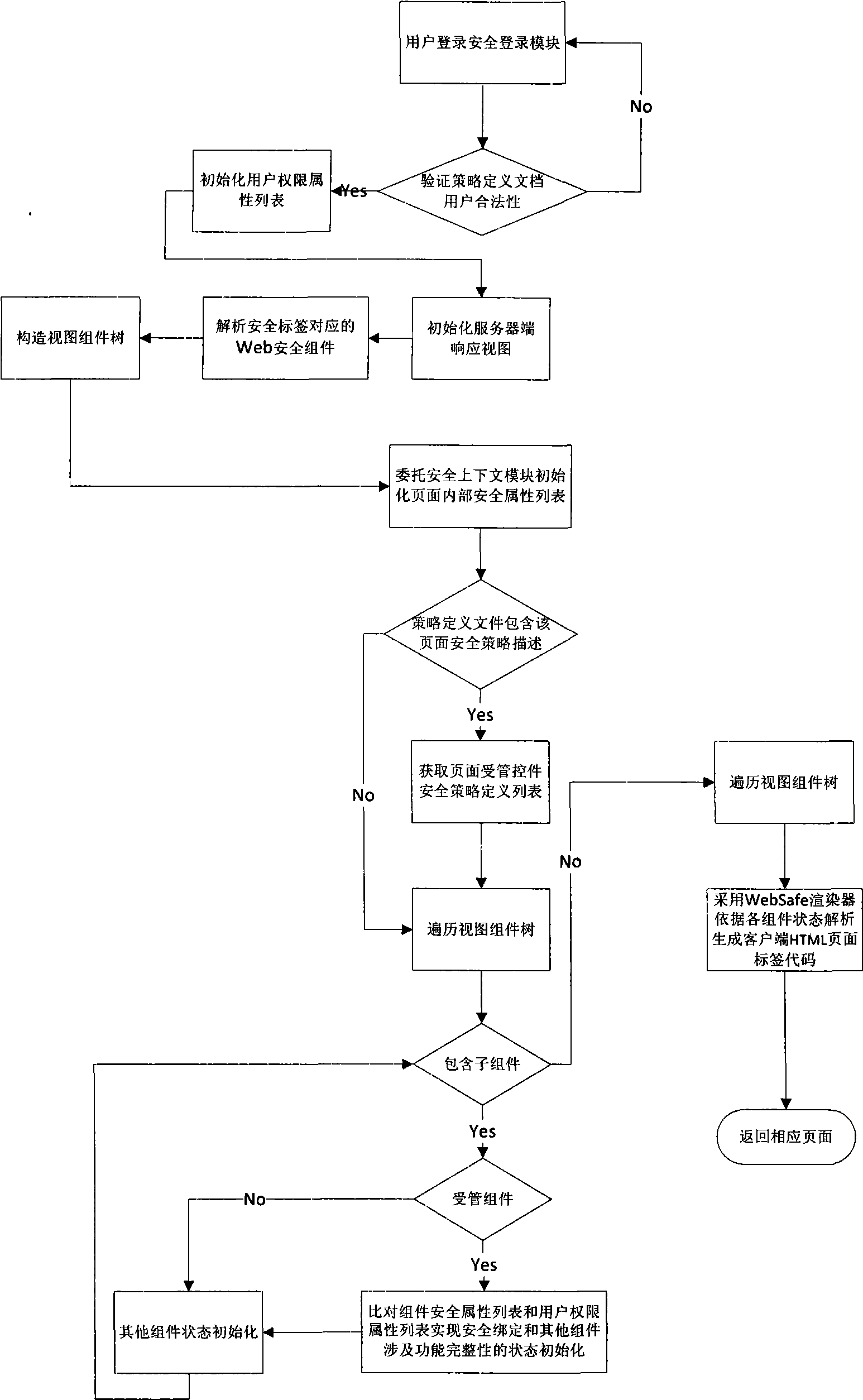
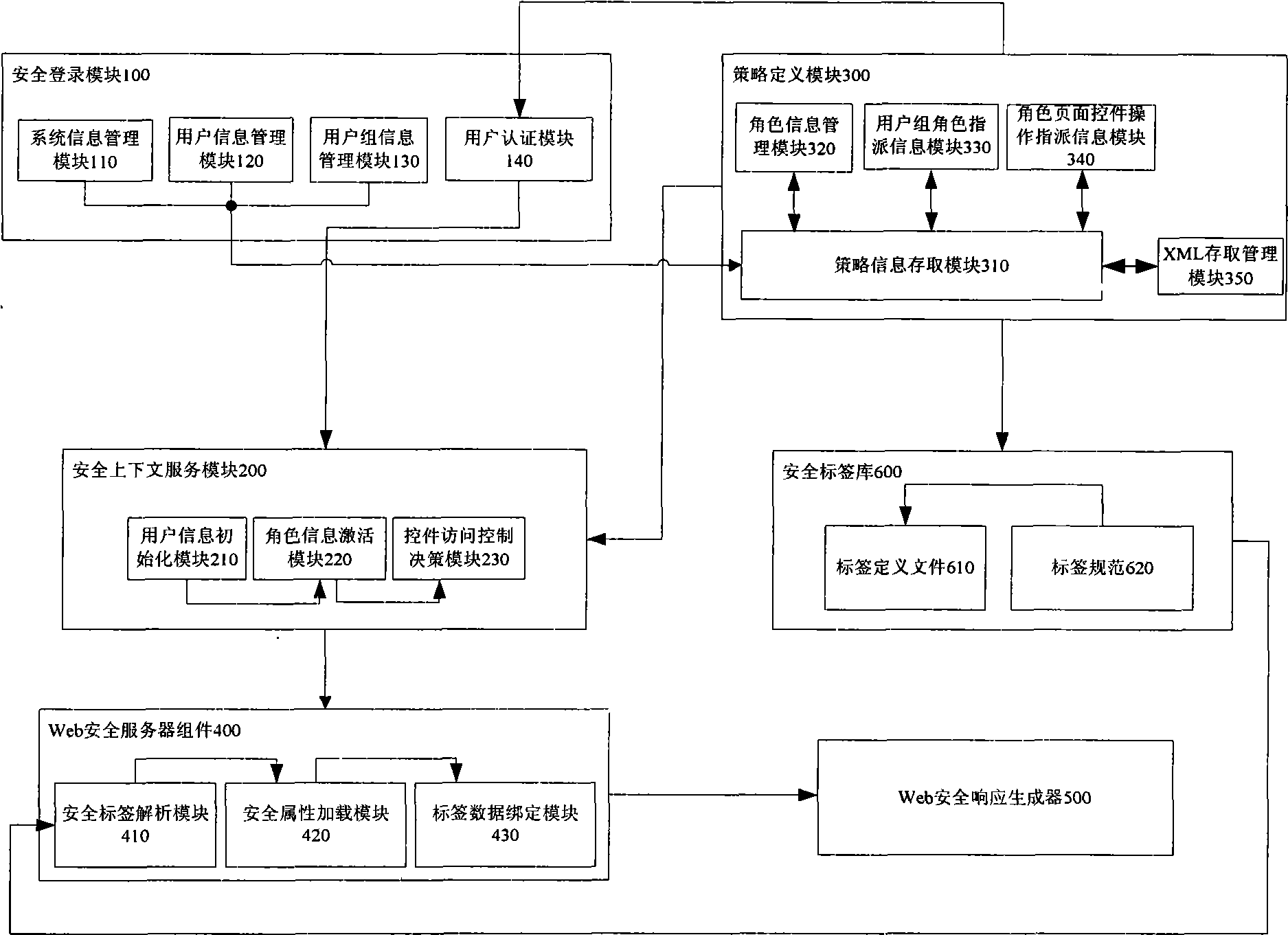
InactiveCN101546261AFlexible useImplement access control needsSpecial data processing applicationsSpecific program execution arrangementsWeb applicationDocumentation
A secure Java Web application page tag library system supported by multiple strategies comprises a secure logging module, a secure context service module, a strategy definition file, a Web secure server subassembly, a Web security responding generator, a secure tag library and a responding page. The secure Java Web application page tag library system can provide various page tags controlled by secure access on a Web page and basically contains expression forms of all page tags in a JSP tag library, thereby providing a set of high-efficiency integral page developing tag library with a secure access control function for developers. The secure Java Web application page tag library supported by multiple strategies can not only accomplish a basic page HTML control component display function but also display visible and available resources of a user according to the own authority of the user after being installed, and the developers need not carrying out extra coding work.
Owner:HUAZHONG UNIV OF SCI & TECH
APP real name authentication secure login system and method based on mobile phone IMSI
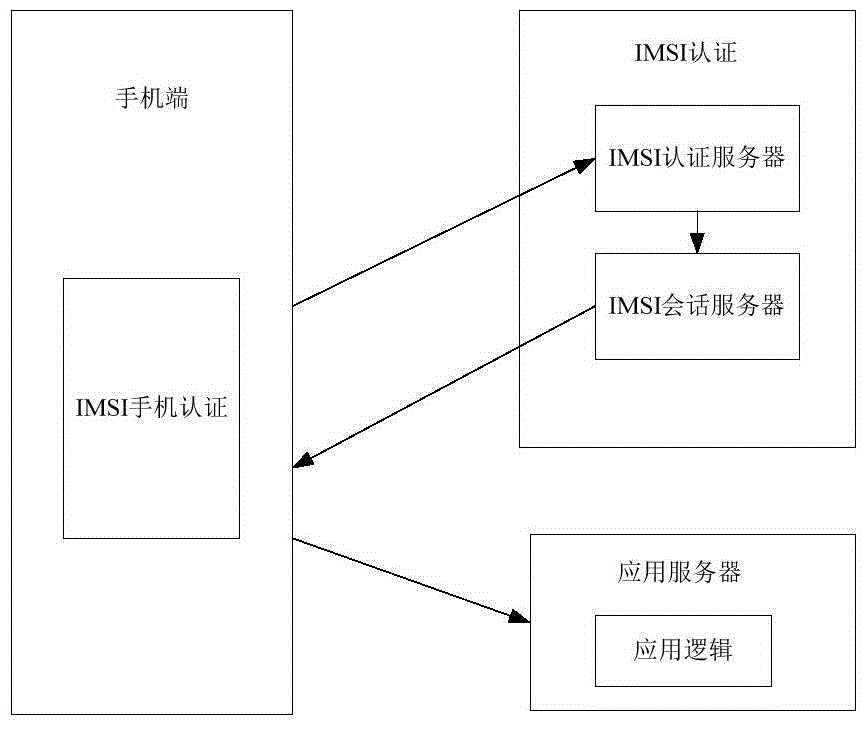
ActiveCN105791262AReduce development costsImplement single sign-onTransmissionSecurity arrangementThird partyAuthentication server
The invention discloses an APP real name authentication secure login system based on a mobile phone IMSI. The system comprises an IMSI authentication APP development SDK, an IMSI authentication server and an IMSI session server. Wherein, the IMSI authentication APP development SDK is provided for a third party APP development manufacturer by an IMSI authentication system, and a third party APP uses the SDK in a development process. The IMSI authentication server receives an authentication login request initiated by the third party APP and returns an authentication result. The IMSI session server registers an authentication login record of the third party APP and manages and records online information of a user APP. In addition, the invention further discloses an APP real name authentication secure login method based on the mobile phone IMSI. By adopting the system and the method disclosed by the invention, the APP application experience of the user is perfected, the login procedure is simplified, the development complexity of the login authentication part of the third party APP manufacturer is reduced, and the development time is shortened.
Owner:GUANGDONG ESHORE TECH
Cross-domain single-point registration system and method facing system integration
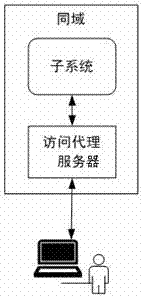
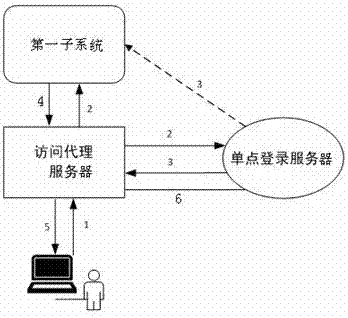
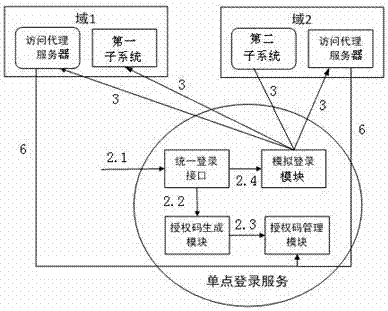
ActiveCN106936853AImplement single sign-onSupport free loginTransmissionSystem integrationProxy server
The invention discloses a cross-domain single-point registration system and method facing system integration. The system comprises a terminal, access proxy servers and a single-point registration server. Each access proxy server is disposed in front of a subsystem, positioned in the same top level domain with the subsystem, and used to process and forward all requests to the subsystem in full authority; and the single-point registration server comprises a unified registration interface, an authorization code generation module, an authorization code management module and a simulated registration module. Under the condition that codes of the system are not invaded and system setting is not changed, cross-domain cross-development-platform single-point registration is realized, and the system is suitable for a high concurrent scene and supports a registration-free condition. When a user access the subsystem, the corresponding access proxy server redirects a request to a unified registration interface, and a unique authorization code is generated after that the user succeeds in registration. A simulated registration manner is used to send the authorization code and registration information to the subsystem. The user can use the authorization code to access the system or other systems directly needless of registration again.
Owner:HOHAI UNIV +1
Cross-domain single login system applied to TV station
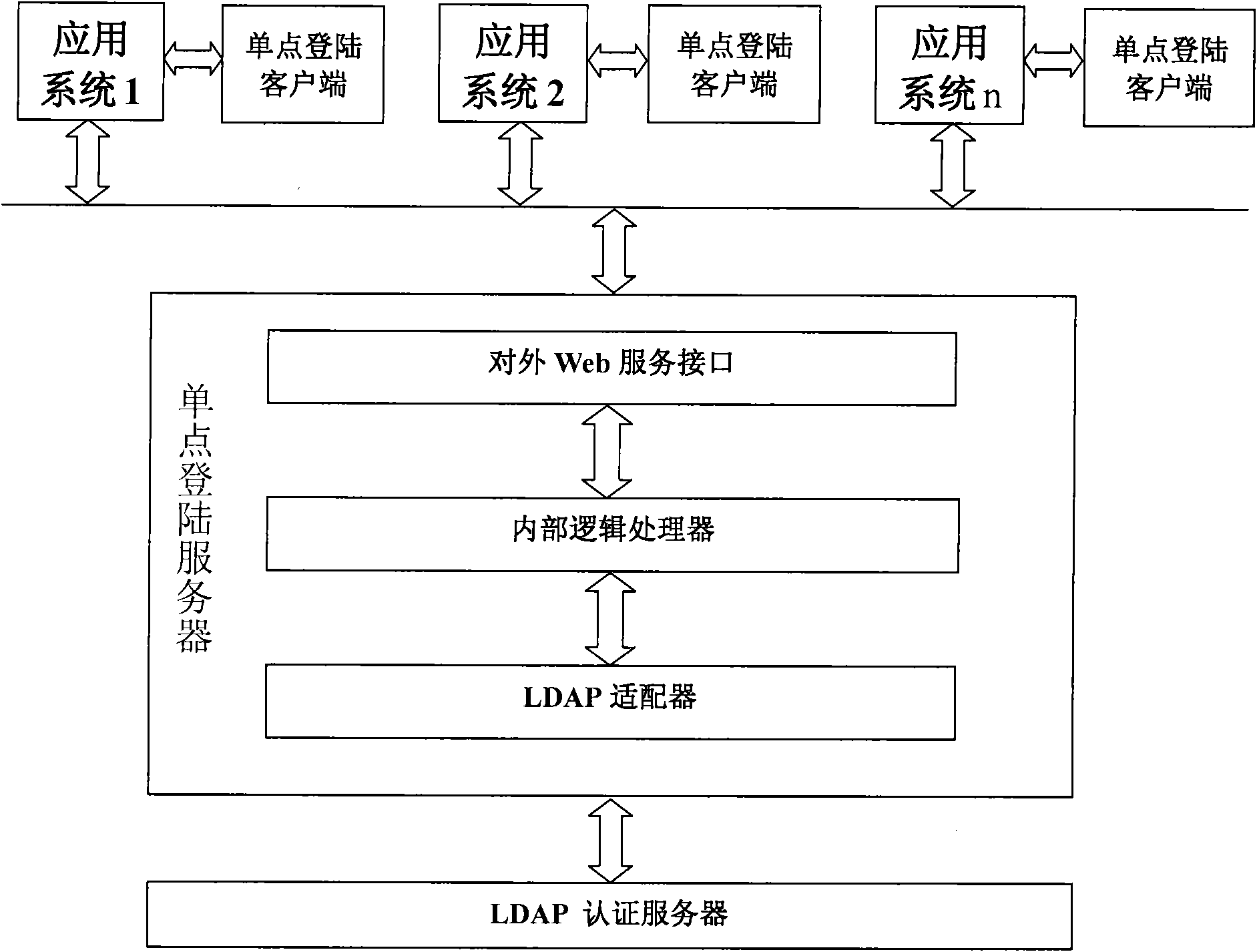
InactiveCN101605031AImplement single sign-onTelevision system detailsUser identity/authority verificationClient-sideA domain
The invention discloses a single login system, in particular a cross-domain single login system applied to a TV station. The prior single login system can not cross a domain and singly log in among a plurality of browsers simultaneously. The system comprises a lightweight directory access protocol (LDAP) authentication server, a single login server and a single login user terminal, wherein the LDAP authentication server is used for storing the organization structure information and the user information of application systems and authenticating the user information; the single login server submits authentication information or other operation requests to the LDAP authentication server and obtains an authentication result or an operation result from the LDAP authentication server, and the single login user terminal is used for transferring a conversation token among the application systems. The system can realize the single login of all the application systems in different domains in the TV station, and the application systems can be of a B / S or C / S structure.
Owner:CHINA DIGITAL VIDEO BEIJING
Digital certificate and multilevel field based unified identification management and authentication method
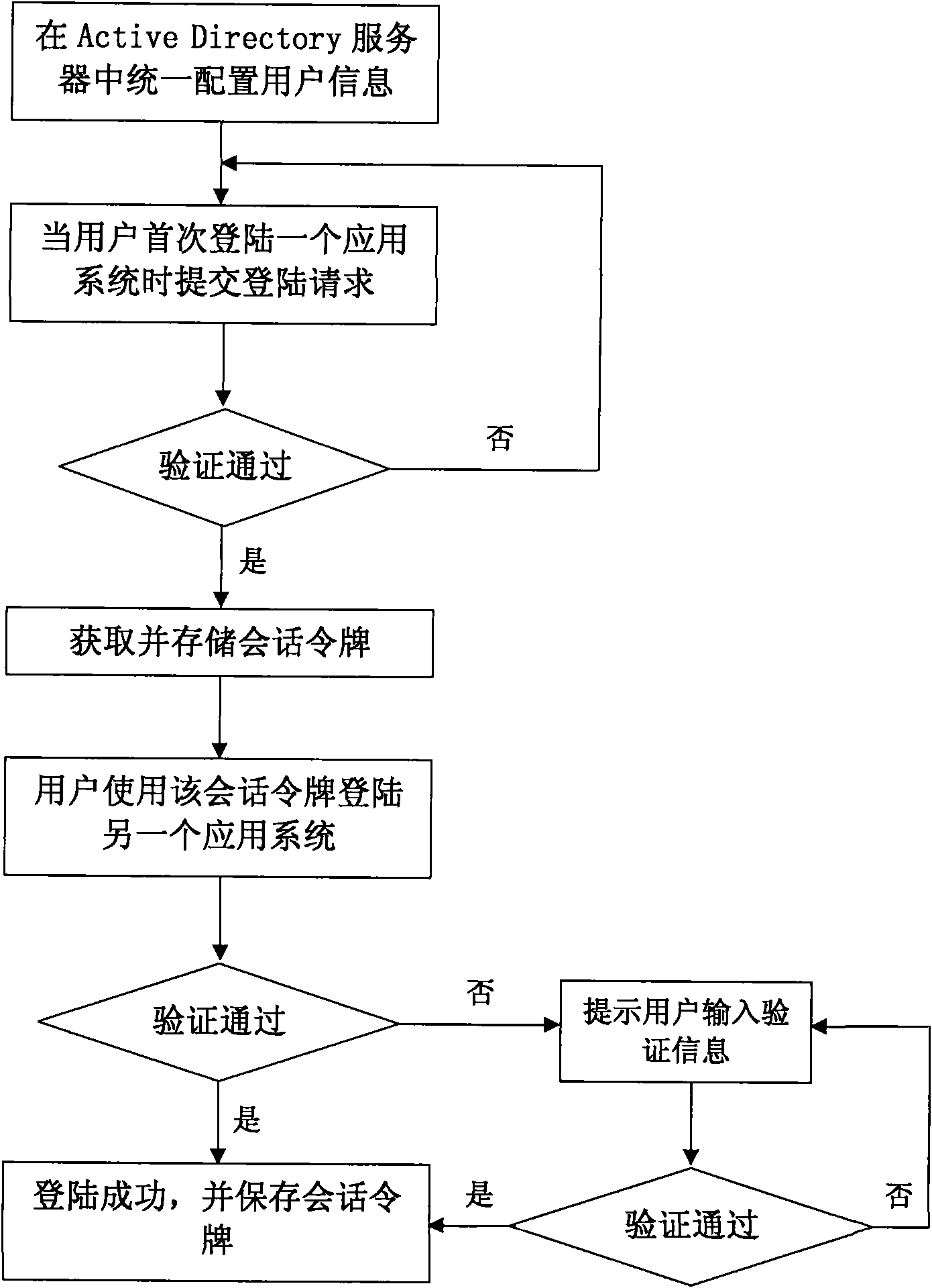
InactiveCN101179387AImplement single sign-onImprove development efficiencyUser identity/authority verificationData switching networksMultilevel modelData information
The invention discloses a unified identification management and authentication method based on digital certificates and multi-leveled domains. At first, user identification is maintained. User identification information is synchronized with the human resource system. User data information management is then completed by means of manual maintenance. User identification information is synchronized to the domain. By the standard LDAP agreement, user identification information is synchronized to the corresponding AD sub-domain according to the unit the information belongs to. Then user authentication is realized. The user can logon in two ways. First, when the computer of the user logons onto the AD domain, all the business systems can be visited without inputting the user name and password. Second, all the business systems can be visited after the user has input the user name and password for once. The invention avoids the possibility that user information does not agree or is not in time. Besides, single sign-on among all the business systems is realized, thus avoiding logon for twice or multiple times. Then technical and developing cost to realize single sign-on is reduced.
Owner:JIANGSU ELECTRIC POWER CO
Single sign on method, application client side, browser, terminal and server
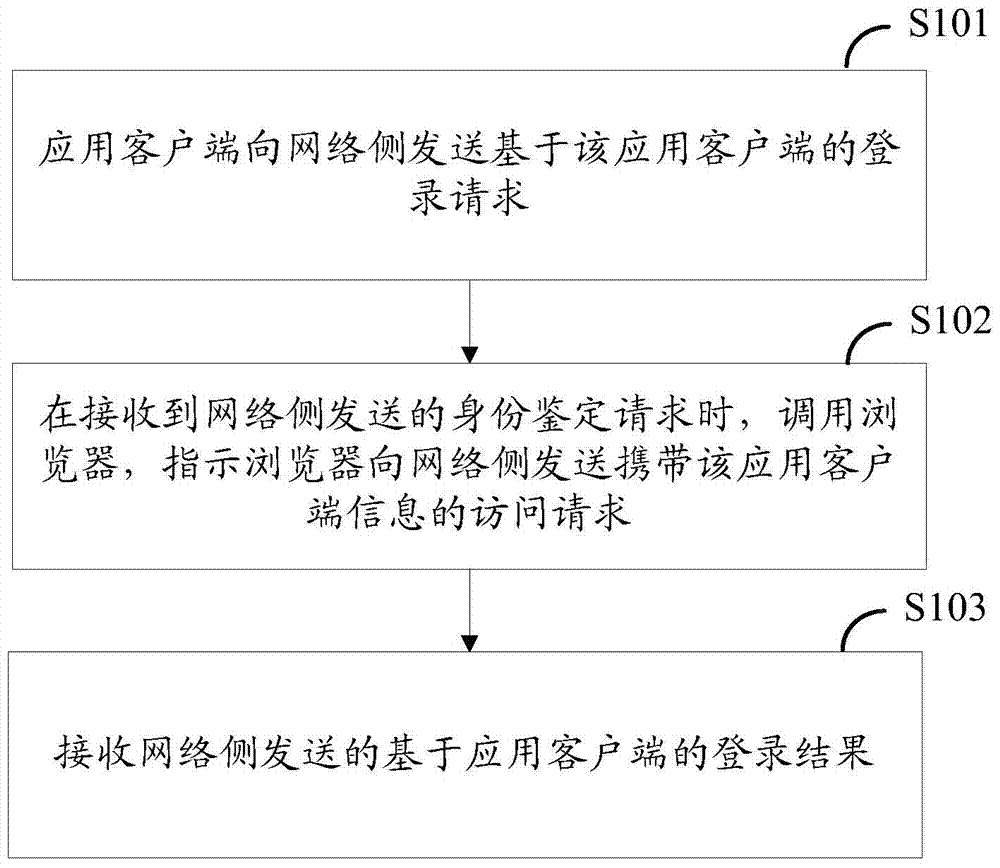
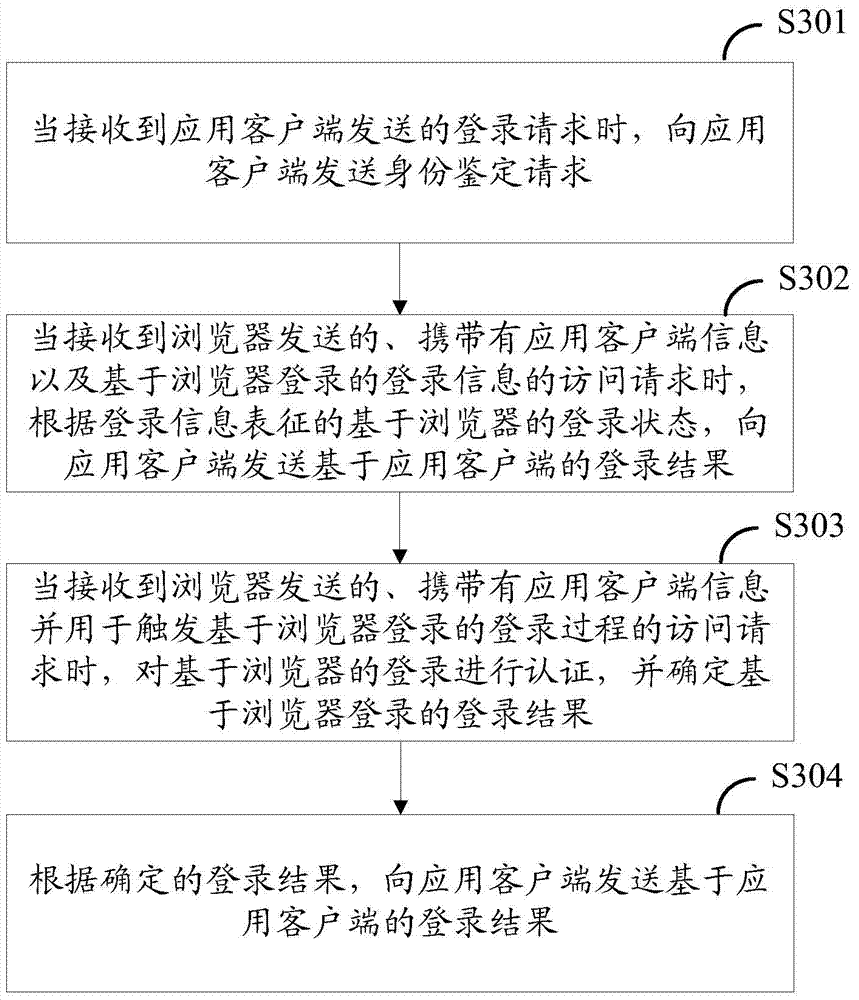
ActiveCN104753855ASave resourcesImplement single sign-onUser identity/authority verificationDigital data authenticationComputer terminalApplication software
Embodiments of the invention provide a single sign on method, an application client side, a browser, a terminal and a server. The application client side sends a login request based on the application client side to a network side; when receiving a personal identification request sent from the network side, the application client side invokes the browser and gives an indication that the browser sends an access request with application client side information to the network side, wherein when a user logs in successfully through the browser, the access request also carries login information; if the user fails to login, the access request is used for triggering a login process through the browser so as to obtain a login result based on the browser; and a login result based on the application client side determined by the network side according to the login information or the login result is received. The problem that single sign on of Webs and application programs costs a lot of system resources is solved. The invention relates to the technical field of mobile communication.
Owner:CHINA MOBILE COMM GRP CO LTD
Data center middleware system
InactiveCN104866316AAchieve integrationImplement single sign-onSpecific program execution arrangementsSpecial data processing applicationsData synchronizationData warehouse
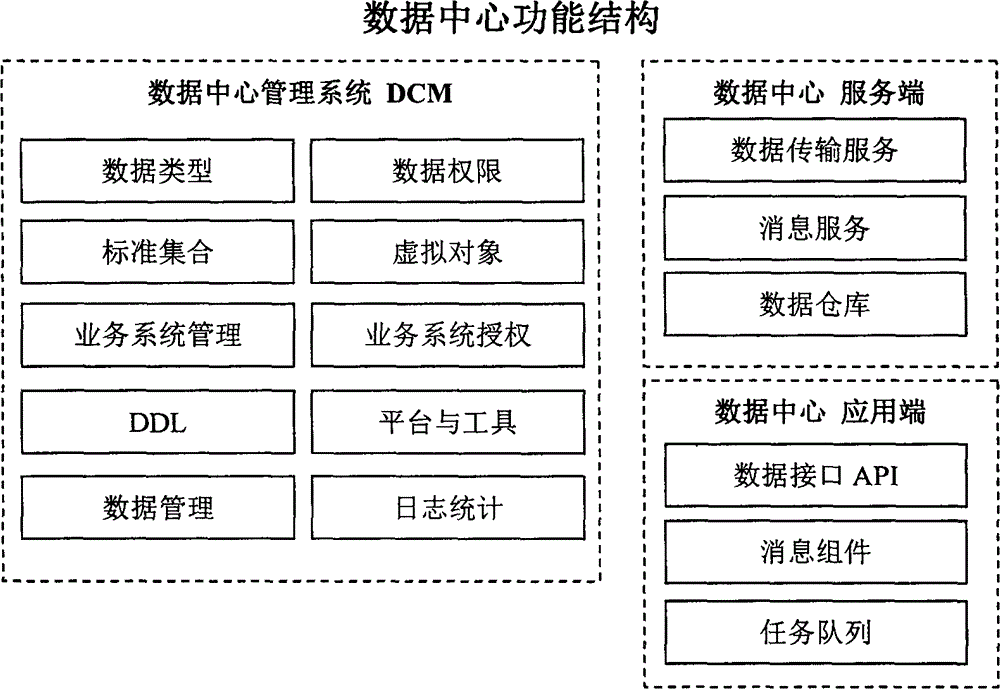
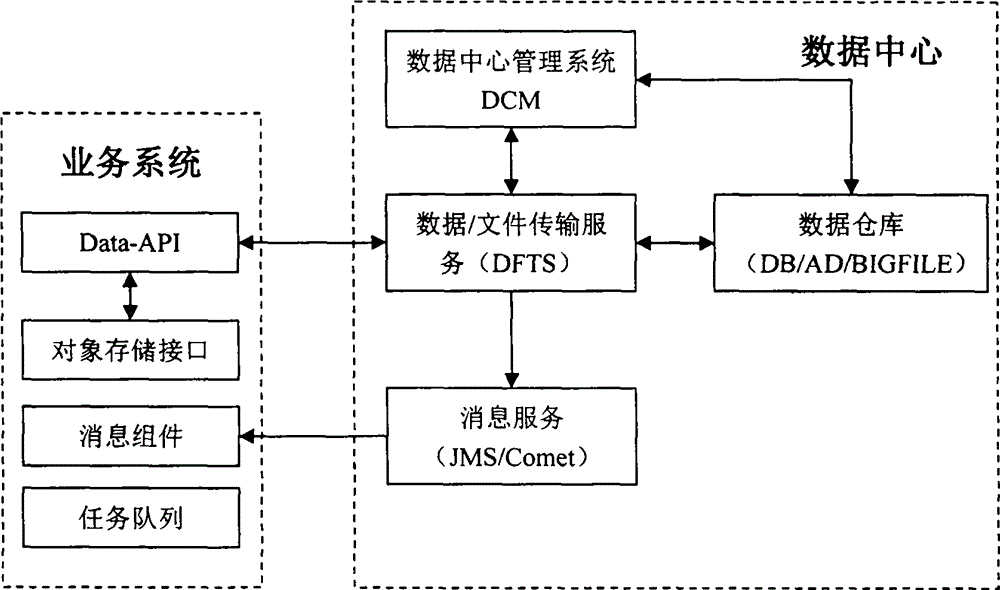
The present invention discloses a data center middleware system. According to the data center middleware system, definition of data and registration management of applications are provided, and data is analyzed and defined in a manner of virtual objects; the applications connected to a data center are registered, and data objects associated with each of the applications and read-write permission of the data objects are determined; describing is carried out on definition of the data objects and setting of the applications by creating a data center describing file language (DDL), a describing file based on an XML (X Exrensible Markup Language) format is formed, different development languages can generate localized development components suitable for calling aiming at the file, and the generated development components comprise a data center client service, data object definition and data manipulation API (Application Program Interface). According to the data center middleware system disclosed by the present invention, the uniform data center can be created in a B / S (Brower / Server) mode, data synchronization and uniform identity authentication services can be provided for each of application systems, and a uniform data warehouse can be created by various types of persistent data storage systems.
Owner:雷虹
Authentication and access method and authentication system
InactiveCN103023921AHigh overall integrationHighly integratedTransmissionAuthentication systemSingle point
The invention discloses an authentication and access method. The authentication and access method includes logging on a first server through a user name, generating an authentication mark related to time of logging on the first server after passing authentication, writing the user name and the authentication mark into a database of the first server and databases of one or a plurality of second servers connected with the first server, starting access modules configured at the second servers to read authentication marks from the databases of the second servers according to the user name if the second servers are accessed by the first server according to the user name, comparing the read authentication marks with the authentication mark read from the database of the first server, and being allowed to continue to access the second servers if comparison result is consistent. The invention further provides a corresponding authentication system. By the method and the system, single-point logging on between the two types of servers is achieved, and accordingly integrated authentication efficiency of the authentication system is improved on the whole.
Owner:CHINA CONSTRUCTION BANK
Electric power operation and maintenance security defending system
InactiveCN103685242AImplement single sign-onBlock illegal operationsResourcesTransmissionProtective systemSystem safety
The invention relates to the technical field of electric power system security, in particular to an electric power operation and maintenance security defending system. Internal operation and maintenance staff or external technicians access a server through a client. The electric power operation and maintenance security defending system comprises an operation and maintenance management module which is disposed between the client and the server. The account password information of the server is stored in the operation and maintenance management module which is used for creating an operation and maintenance account and setting authority for the client. The electric power operation and maintenance security defending system has the advantages that single sign-on of an application system requiring electric power operation and maintenance can be achieved, the identity logging in the system can be identified and certified, access and operation can be authorized, operation process can be monitored, violation operation can be stopped, and the whole system is safe and reliable.
Owner:STATE GRID CORP OF CHINA +1
Method and device for achieving single sign on of applications in terminal
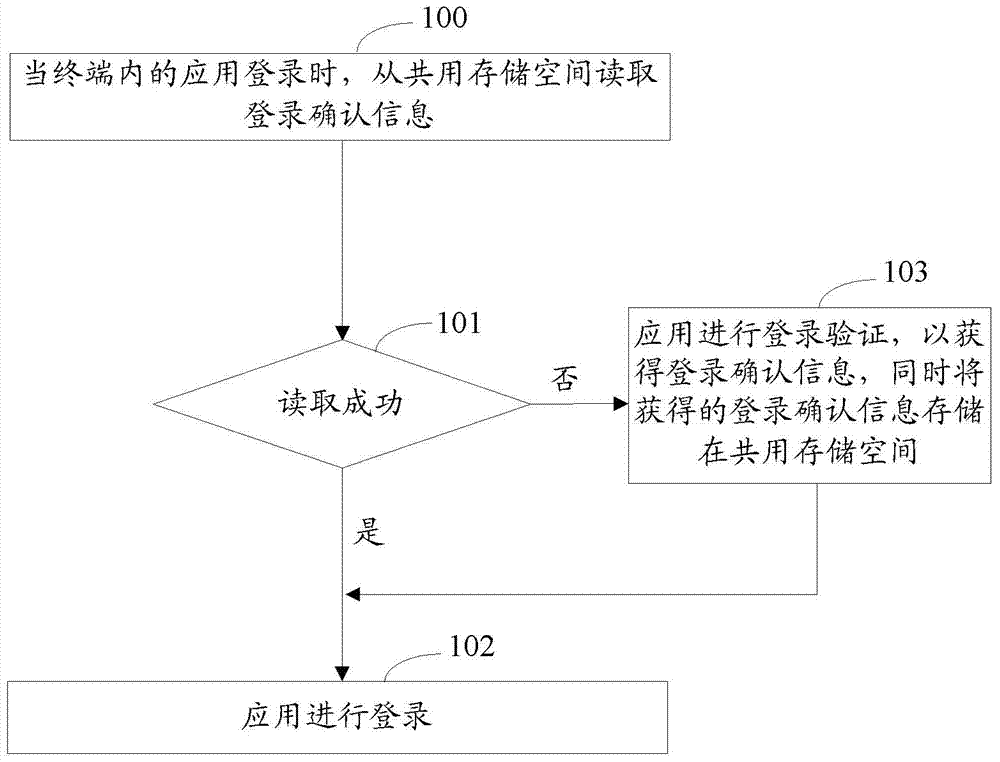
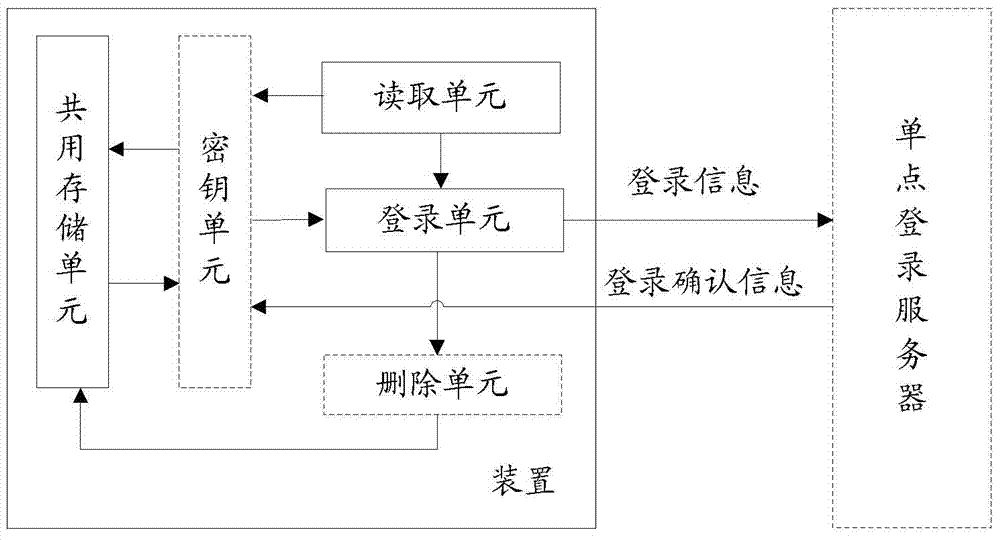
InactiveCN103618612AEasy to implementImplement single sign-onUser identity/authority verificationComputer terminalEmbedded system
The embodiment of the invention discloses a method and device for achieving single sign on of applications in a terminal. The same logging information is set for all the applications in the terminal. The method further includes the steps that when the applications in the terminal log on, logging confirmation messages are read from a sharing storage space; if the logging confirmation messages exist in the sharing storage space, the logging confirmation messages are directly read for logging; if the logging confirmation messages do not exist in the sharing storage space, logging certification is carried out on the applications to obtain the logging confirmation messages and to log on, and meanwhile the obtained logging confirmation messages are stored in the sharing storage space. The embodiment of the invention further discloses a device corresponding to the method. According to the method and device, the same logging information is set for all the applications in the terminal, when the applications log on, the applications read in the logging confirmation messages in the sharing storage space and log on, and therefore single sign on of the applications in the terminal is achieved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
JWT-based authorization method capable of being manually revoked
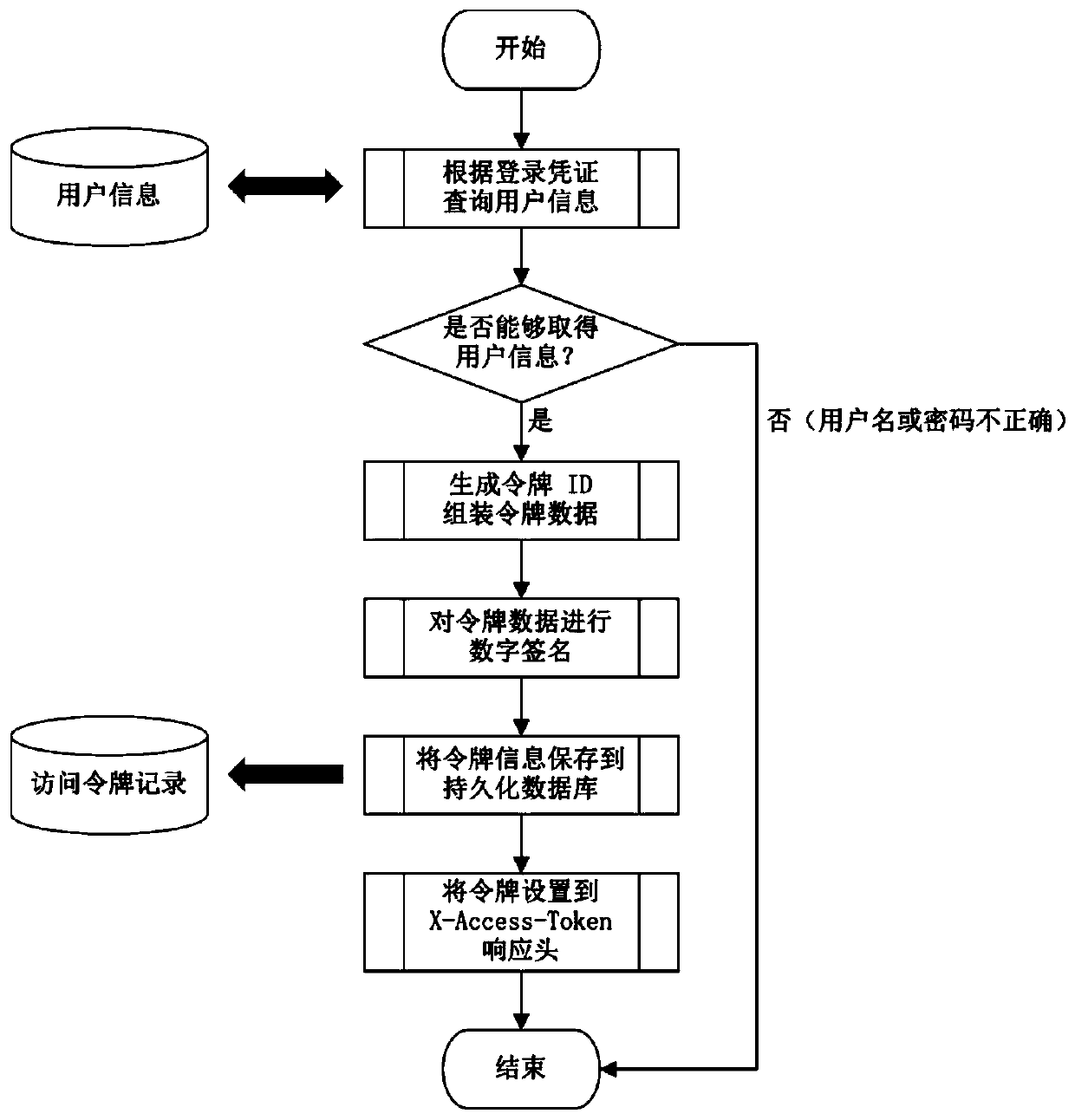
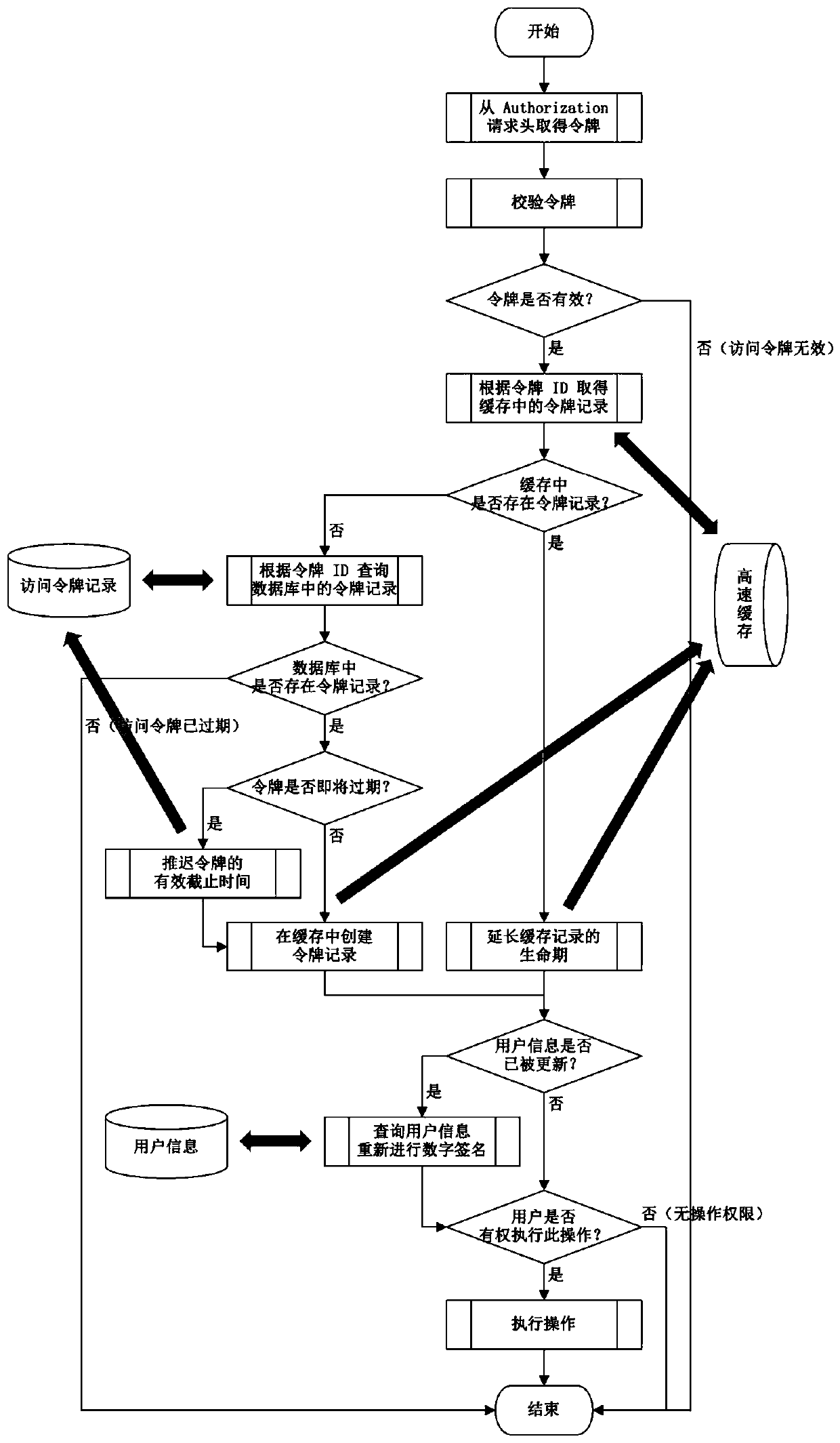
InactiveCN110855672APrevent theftReduce consumptionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signatureEngineering
The invention relates to application of a network authorization technology, in particular to a JWT-based authorization method capable of being manually revoked, which is an efficient, recyclable and instantly-updated authorization mechanism based on an access token. The method comprises a program used for providing login certificate verification and a server access token verification process; theprogram for providing the login certificate verification comprises the following steps: 1a, querying user information according to the login certificate; 2a, judging whether the user information can be obtained or not, and generating token ID assembly token data if the user information can be obtained; 3a, performing digital signature on the token data in the 2a; 4a, storing the token informationin a persistent database, and creating an access token record; 5a, setting the token to an X-Access-Token response header, and ending the authentication; 6a, judging whether the user information can be obtained or not in the 2a, and if the user information cannot be obtained, directly ending the authentication.
Owner:无锡家校邦网络科技有限公司
Management information system reuse, isolated independence and fused synergy
InactiveCN106548298AAddress planning management needsRealize multiplexingNatural language data processingDigital data authenticationManagement information baseWeb page
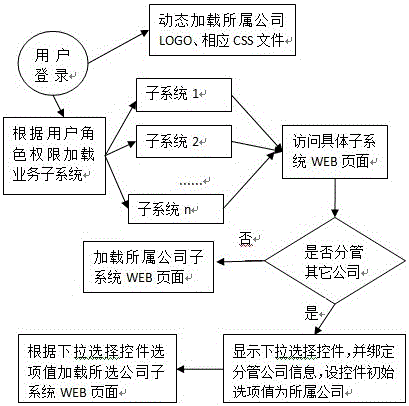
The invention provides a management information system reuse, isolated independence and fused synergy method. The method comprises the following steps: performing organization tree management, and adding, modifying or deleting enterprise group department information, company information and company department information; adding, modifying or deleting company or organization information and department information in employee information, and dynamically adding, modifying or deleting branch company information; loading the LOGO and style of the company or organization of a user based on the company information of the user; and for each WEB page with a data adding or deleting operation command in each business subsystem, adding a company dropdown selection control to the page, and binding branch company information, wherein load and resources loaded on the WEB page are all from a branch company selected in the dropdown selection control. Reuse, isolated independence and fused synergy of a management information system are realized. Single sign-on of the system in enterprises and between different companies is realized. The data is unified. Information isolated islands are eliminated.
Owner:HEFEI HANTENG INFORMATION TECH CO LTD
Domainname-based unified identification mark and authentication method
InactiveCN100539501CAvoid visitingSupport roamingUser identity/authority verificationData switching by path configurationDomain nameExtensibility
The invention belongs to the field of Internet user identity identification and authentication, and is characterized in that it utilizes the good system structure design proposed by the next-generation Internet protocol IPv6, and expands the functions of the existing identity authentication system by combining with the secure domain name service to realize user identity and authentication. The current binding relationship of real IPv6 addresses provides more reliable security services for upper-layer applications. In the user management domain, there are: network access control server: through the triplet composed of the source MAC address of the user computer, the source IPv6 address and the port <mac,ipv6,port>To identify the registered user; identity authentication server: authenticate the user identity and set the corresponding access rights; the domain name server establishes the positive and negative correspondence between the user's personal domain name and IPv6 address. The present invention can provide multiple effective identity authentication means for the application of the Internet in the future, has good scalability and can adapt to the requirements brought by the application development of the Internet in the future.< / mac,ipv6,port>
Owner:TSINGHUA UNIV
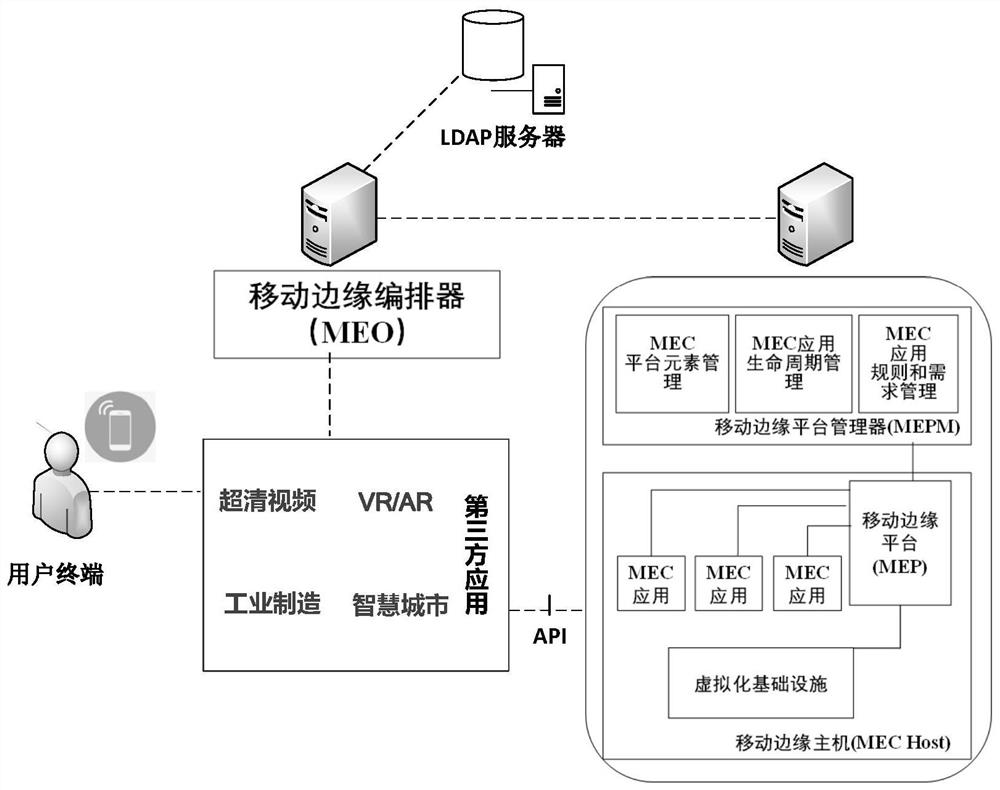
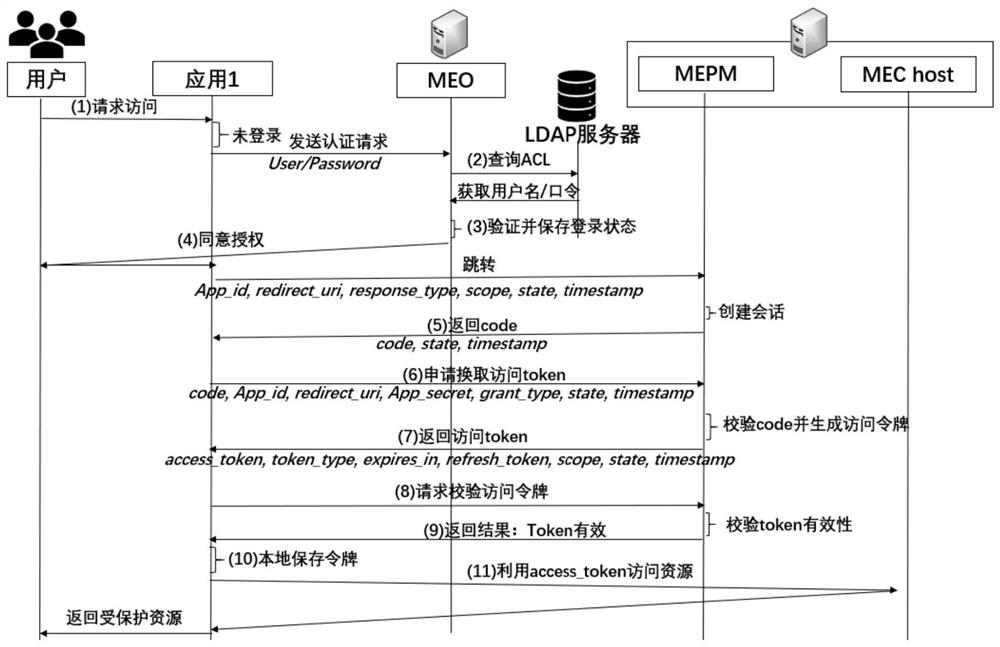
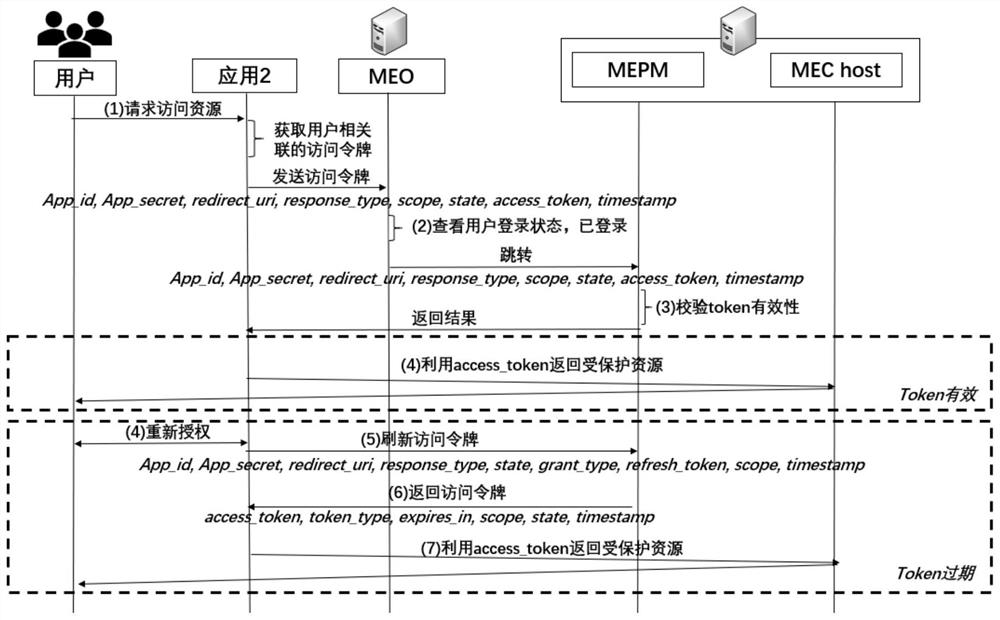
Single sign-on mechanism oriented to MEC environment and based on OAuth2.0
ActiveCN112822675AEnsure safetyImplement single sign-onDigital data authenticationTransmissionThird partyEdge computing
With the rapid development of a 5G network, traditional cloud computing cannot meet the requirements of edge devices in the aspects of computational analysis, resource processing and the like. Therefore, a multi-access edge computing (MEC) (Multi-Access Edge Computing) is provided. The MEC technology has the characteristic of openness, and is convenient for various service operators to develop and deploy third-party applications based on user service requirements. However, this also causes the resource data stored in the environment to be inevitably subjected to some security and privacy threats. Therefore, in order to ensure the security of the privacy data in the MEC, the invention provides a single sign-on mechanism based on OAuth2.0 and oriented to the MEC environment. The mechanism (1) realizes user identity authentication and authorization oriented to the MEC environment, and ensures the security of resource data in the MEC by verifying the authenticity of user identity information and authorizing the identity access authority; and (2) unified authentication is realized, the repeated registration process of the user is effectively reduced, the user experience is improved, and the management cost of a service operator on account information is reduced at the same time.
Owner:BEIJING JIAOTONG UNIV
Terminal, server and login method during application access
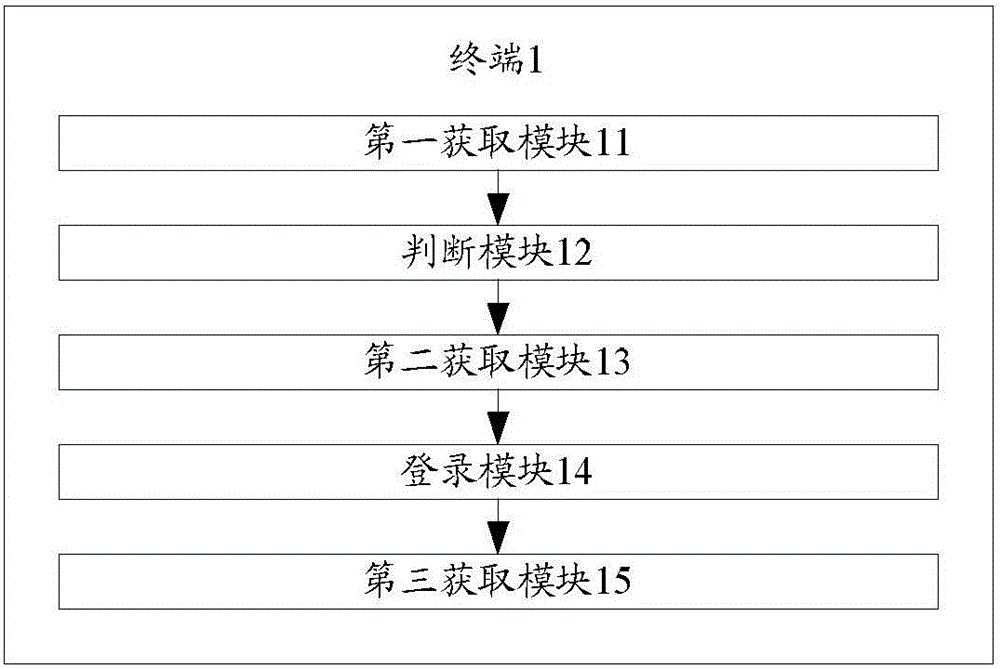
InactiveCN106790122AAvoid repeated login operationsImprove experienceSubstation equipmentTransmissionDatabaseCurrent user
The invention discloses a terminal, a server and a login method during application access. The terminal comprises a first acquisition module, a judgment module, a second acquisition module and a login module, wherein the first acquisition module acquires an access request of a terminal application; the judgment module judges whether a current user logins a preset account center according to the access request; when the current user is judged to login in the account center, the second acquisition module acquires temporary authority of the terminal application; the login module exchanges the temporary authority for formal authority to access the terminal application. With the adoption of the scheme, single sign-on between the account center and the application self-established by a terminal manufacturer is realized, repeated login operation of the user can be avoided, the login efficiency and user experience are improved, single sign-on is performed by exchanging the issued temporary authority for the formal authority, the login safety is improved, and the user experience is further improved.
Owner:NUBIA TECHNOLOGY CO LTD
Network customer service and pass management system based on doctor on-line interaction
InactiveCN102306247AEfficient integrationImprove experienceSpecial data processing applicationsManagement systemDatabase
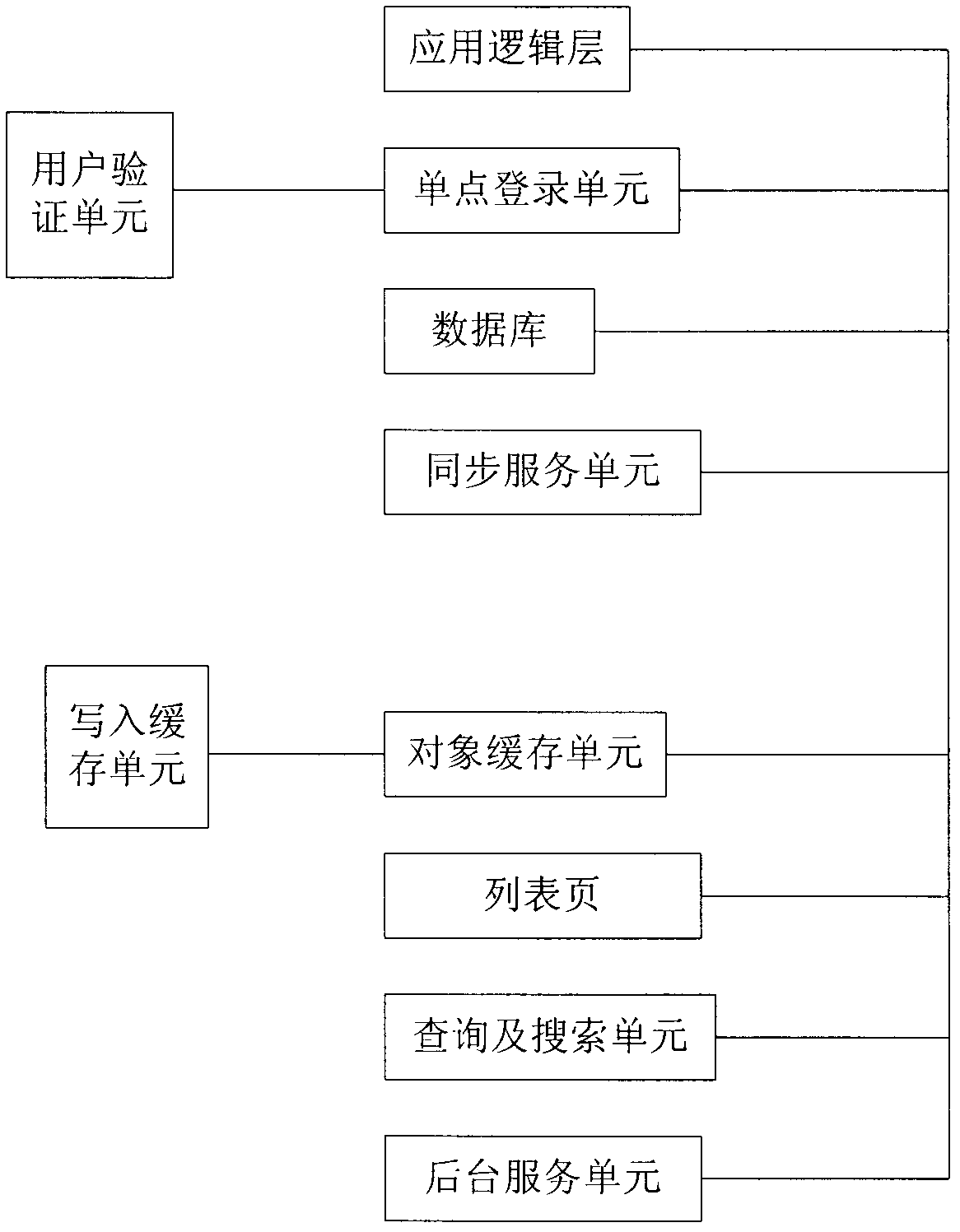
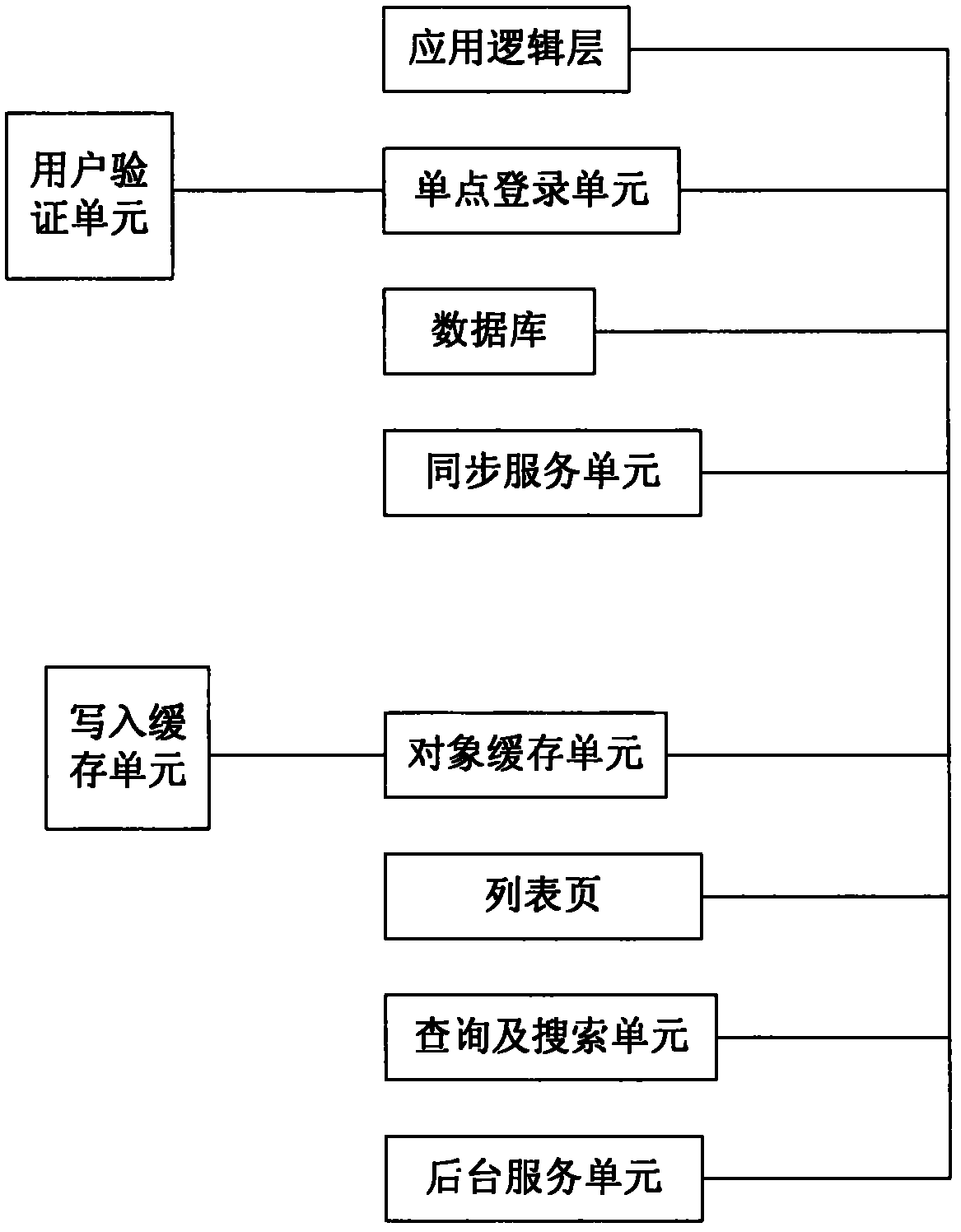
The invention discloses a network customer service and pass management system based on doctor on-line interaction. The system comprises an application logic layer, a single sign-on unit, an object cache unit, a database, a background service unit, a synchronous service unit, a list item and a query and search unit which are mutually connected. The system can more effectively integrate the user resources of a platform, provides more convenient and professional service, can greatly improve the user experience, is favorable for establishing good use public praise, and contributes to wider popularization.
Owner:GUANGZHOU QISHENG INFORMATION TECH
Method for accessing application, user equipment, login server and storage medium
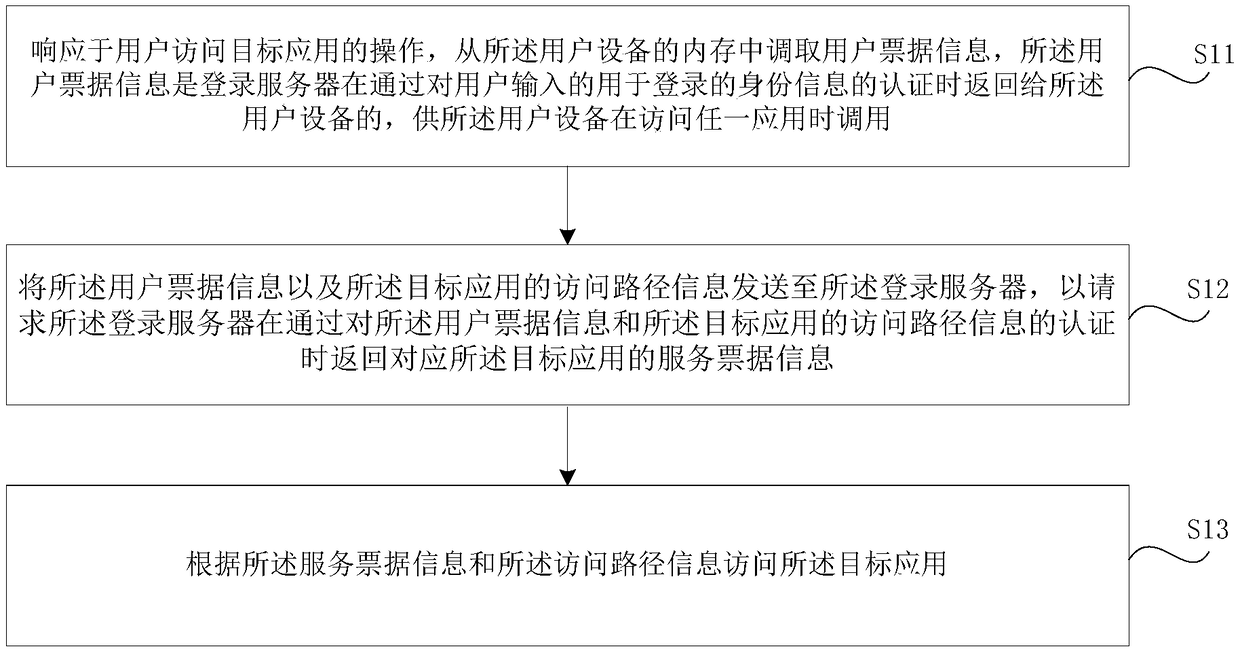
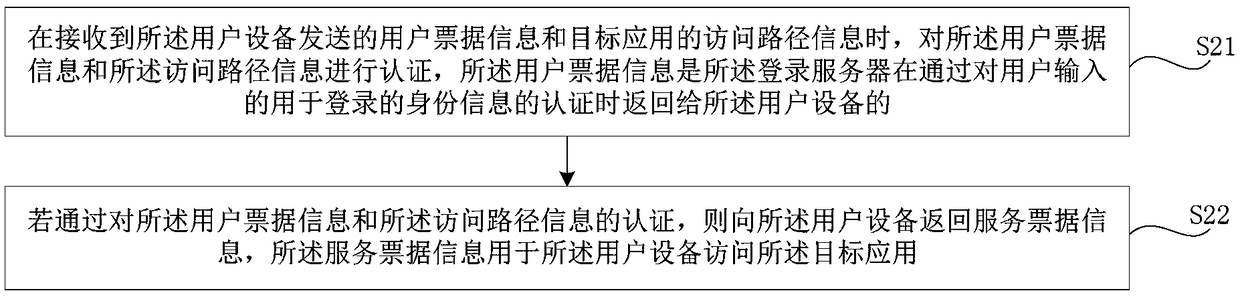
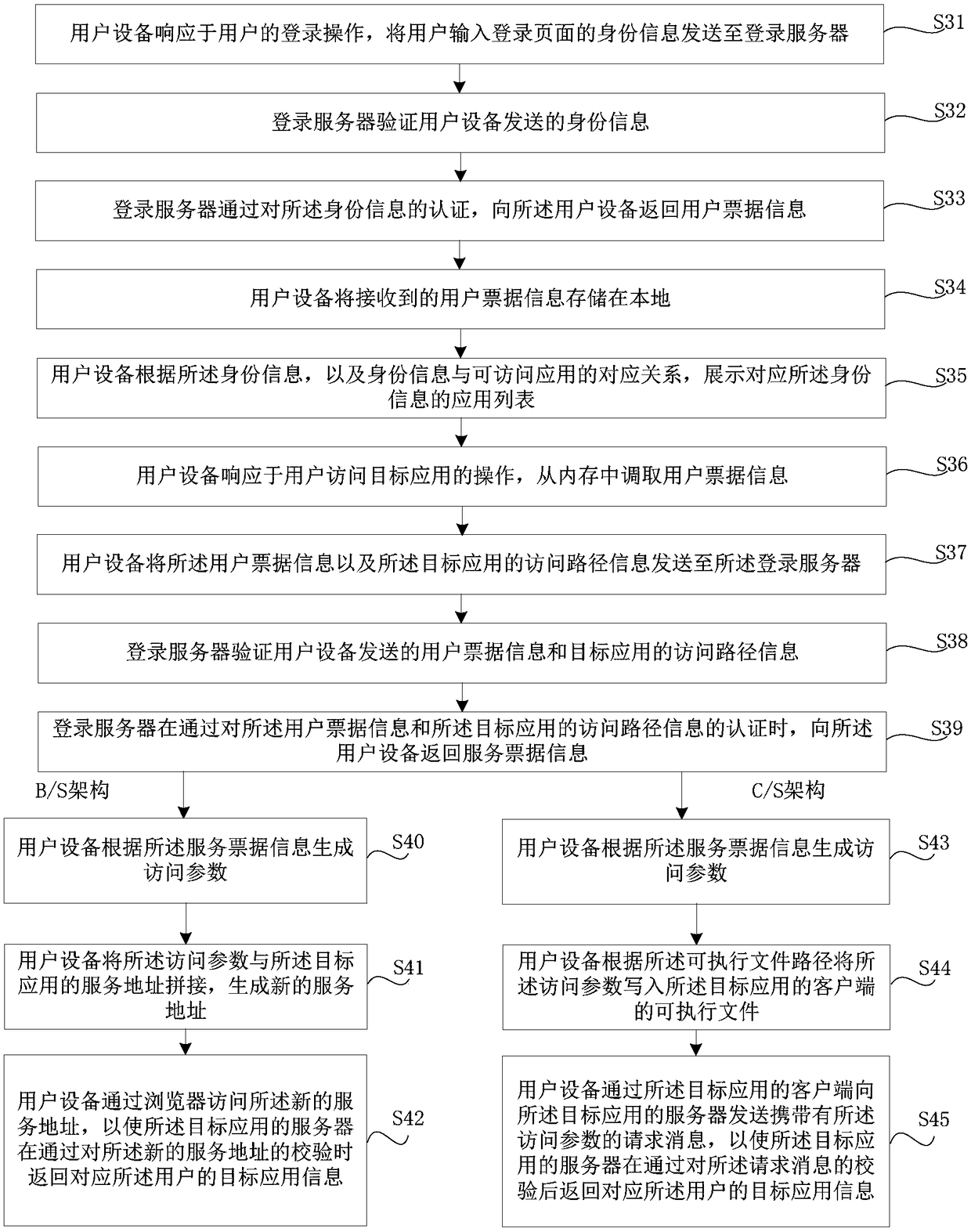
InactiveCN109462600AImplement single sign-onEasy to implementTransmissionInformation accessUser input
The purpose of the invention is to provide a method for accessing an application, user equipment, a login server, and a storage medium, in order to solve the problem that a single sign on implementation effect in related art is poor. The method is applied to the user equipment, and the method comprises the following steps: calling user ticket information from a memory of the user equipment in response to an operation of a user to access a target application, wherein the user ticket information is input by the login server to the user equipment when the authentication of the identity information input by the user for login is passed to be called by the user equipment when accessing any application; sending the user ticket information and the access path information of the target applicationto the login server so as to request the login server to return service ticket information corresponding to the target application when the authentication of the user ticket information and the access path information of the target application is passed; and accessing the target application according to the service ticket information and the access path Information.
Owner:NEUSOFT CORP
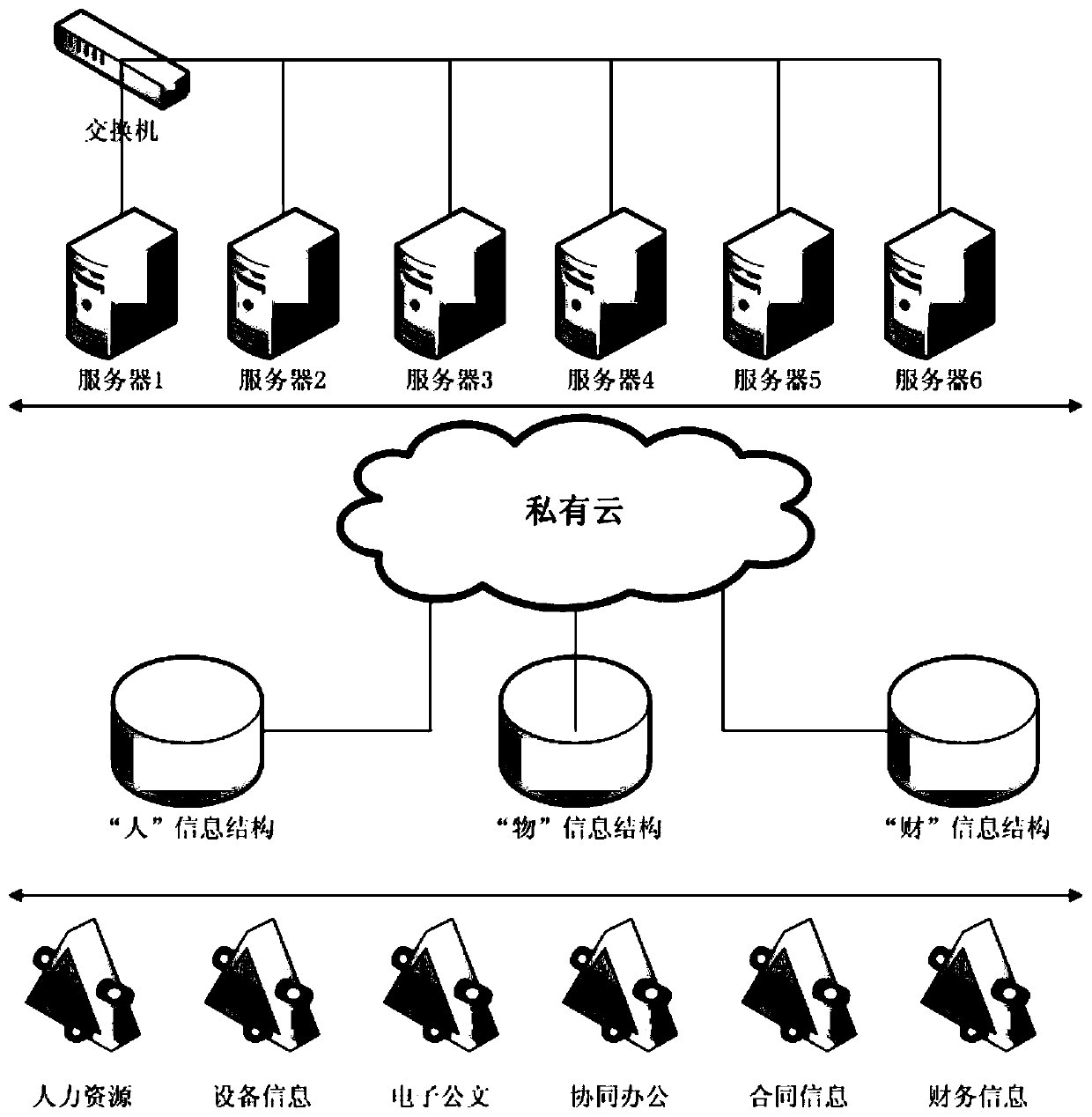
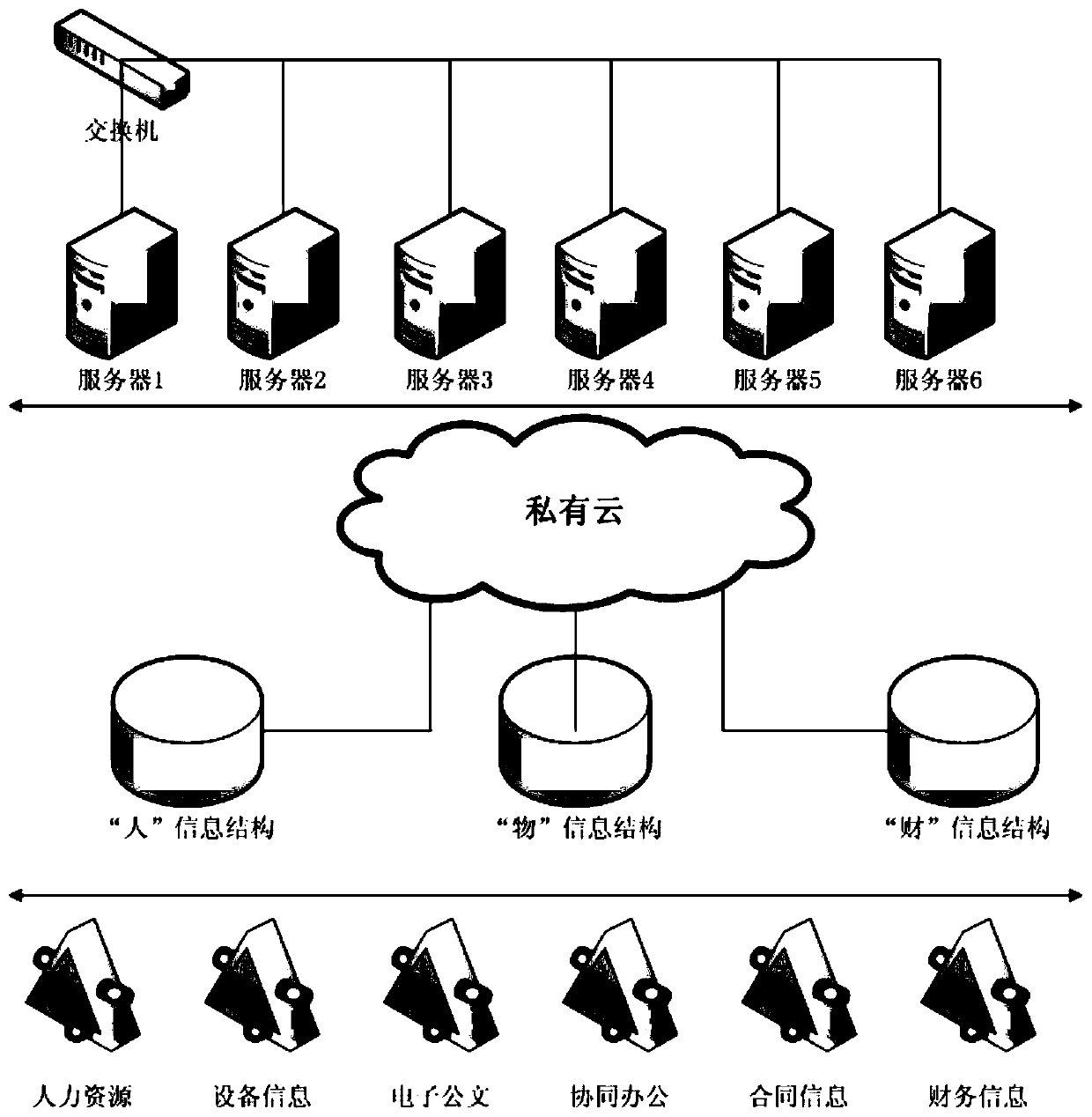
Enterprise management informatization system construction method based on private cloud
InactiveCN110009295AImprove performanceEasy to stretchResource allocationFinanceInformatizationResource utilization
The invention discloses an enterprise management informatization system construction method based on private cloud, which comprises the following steps of: establishing an enterprise informatization basic resource hardware system by adopting a private cloud technology, and providing an informatization resource platform for the interior; establishing a personnel basic database to realize user information multiplexing and single sign-on; classifying and summarizing information of various assets, equipment, materials, products and buildings of the enterprise, and establishing a unified asset information platform; establishing an enterprise-based financial account information database according to the enterprise financial statement and the subject information; and according to the establishedpersonnel basic database, asset information platform and financial account information database, constructing a basic data framework of enterprise resource elements, establishing various information management platforms, and realizing system construction based on a unified data standard in enterprise information management. According to the invention, the resource configuration level is improved,the system resource utilization rate is optimized, the downtime caused by a single-node fault is avoided, and the problems of hardware aging and fault transfer of the system are fundamentally solved.
Owner:BC P INC CHINA NAT PETROLEUM CORP +1
Multi-terminal fusion territorial resource mobile government affair system based on heterogeneous network
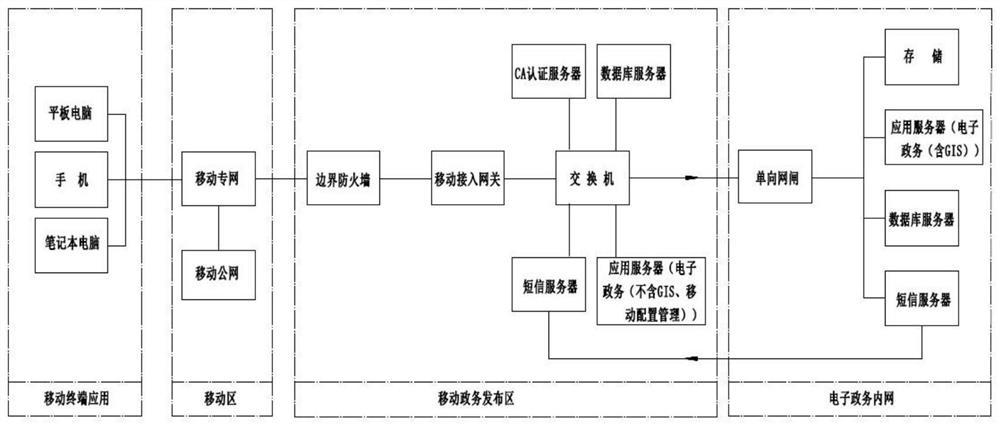
PendingCN112437031AAchieve Consistency and CompletenessRealize seamless dockingOffice automationMessaging/mailboxes/announcementsApplication serverMobile end
The invention discloses a multi-terminal fusion territorial resource mobile government affair system based on a heterogeneous network, which mainly relates to the technical field of government affairsystems and comprises an overall architecture module and a security design module, wherein the overall architecture module comprises a mobile office unit, a mobile terminal application, a mobile database, a mobile application server, mobile application software and a mobile configuration management workstation, and the security design module comprises a terminal access security unit, a storage security unit, a transmission security unit, an operation security unit and a mechanism security unit. According to the invention, the unified territorial resource mobile government affair platform of the mobile terminal and the PC terminal is applied as a whole, seamless connection between a territorial resource bureau mobile office application and a government affair system application is realized,and integrated application of the business approval system at the mobile terminal and the PC terminal is realized; and based on a mobile wireless network, high collaborative application with an e-government affair system is realized, and dual expansion and extension of territorial office and government affair application in time and space are completed.
Owner:金田产业发展(山东)集团有限公司
Split terminal single sign-on combined authentication method and system
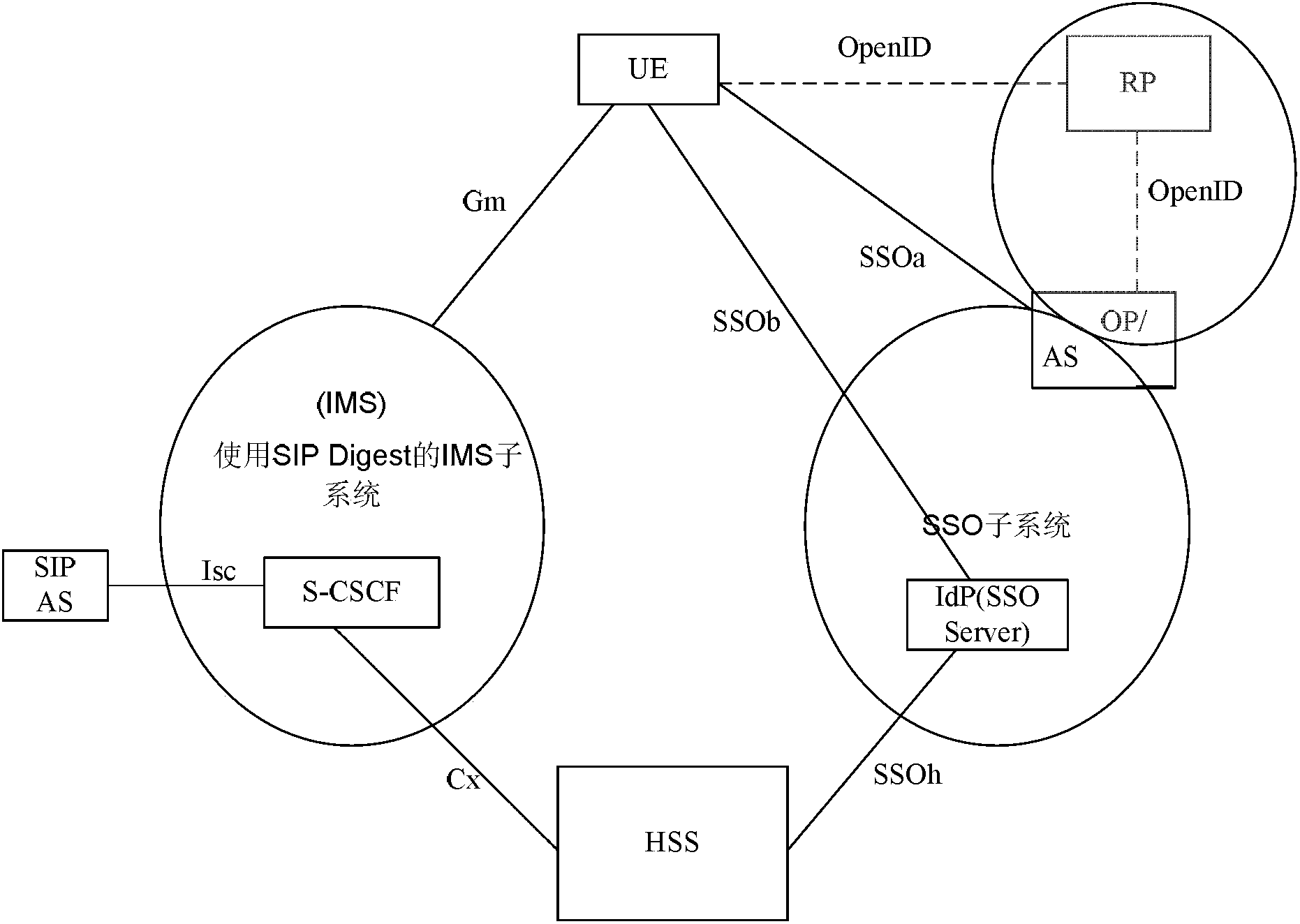
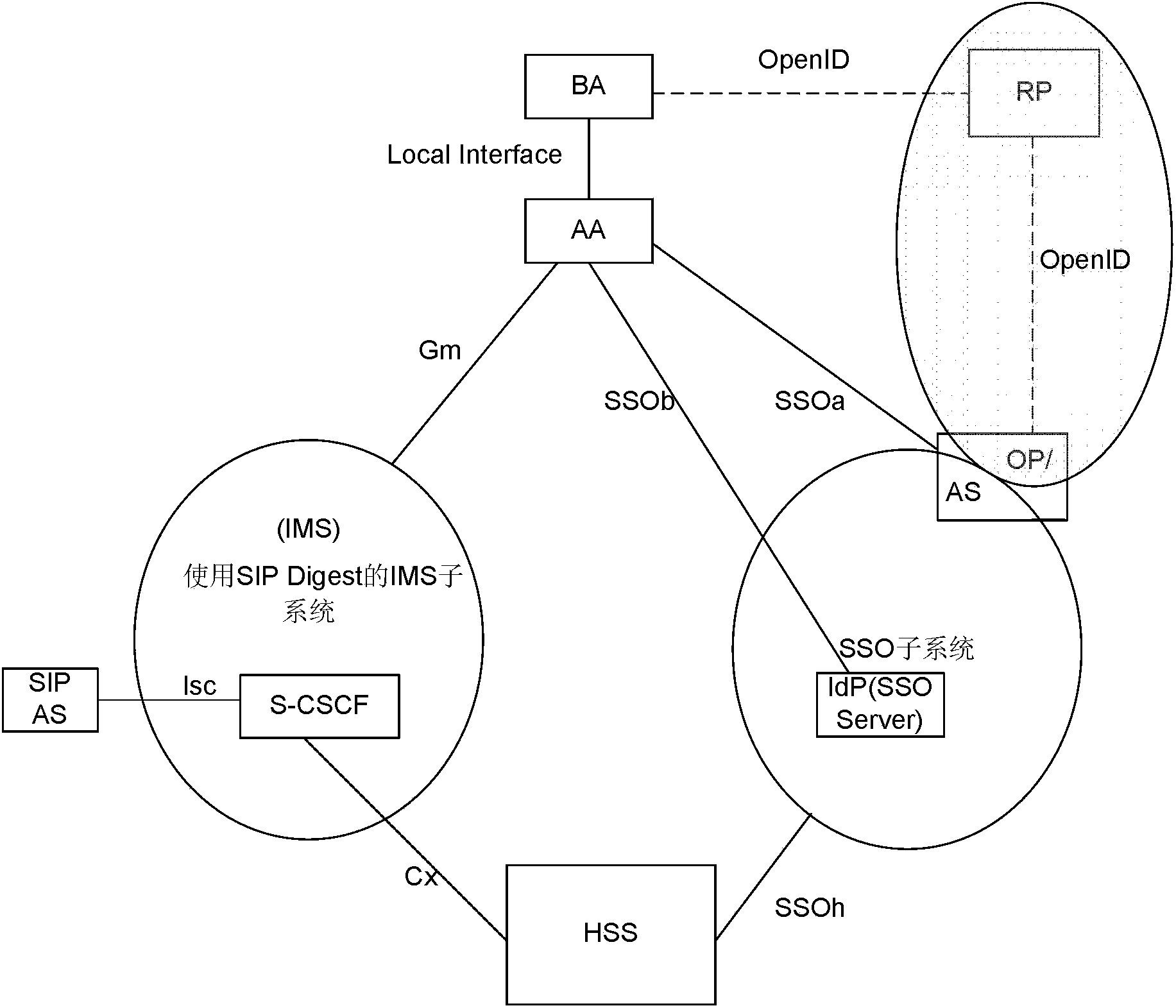
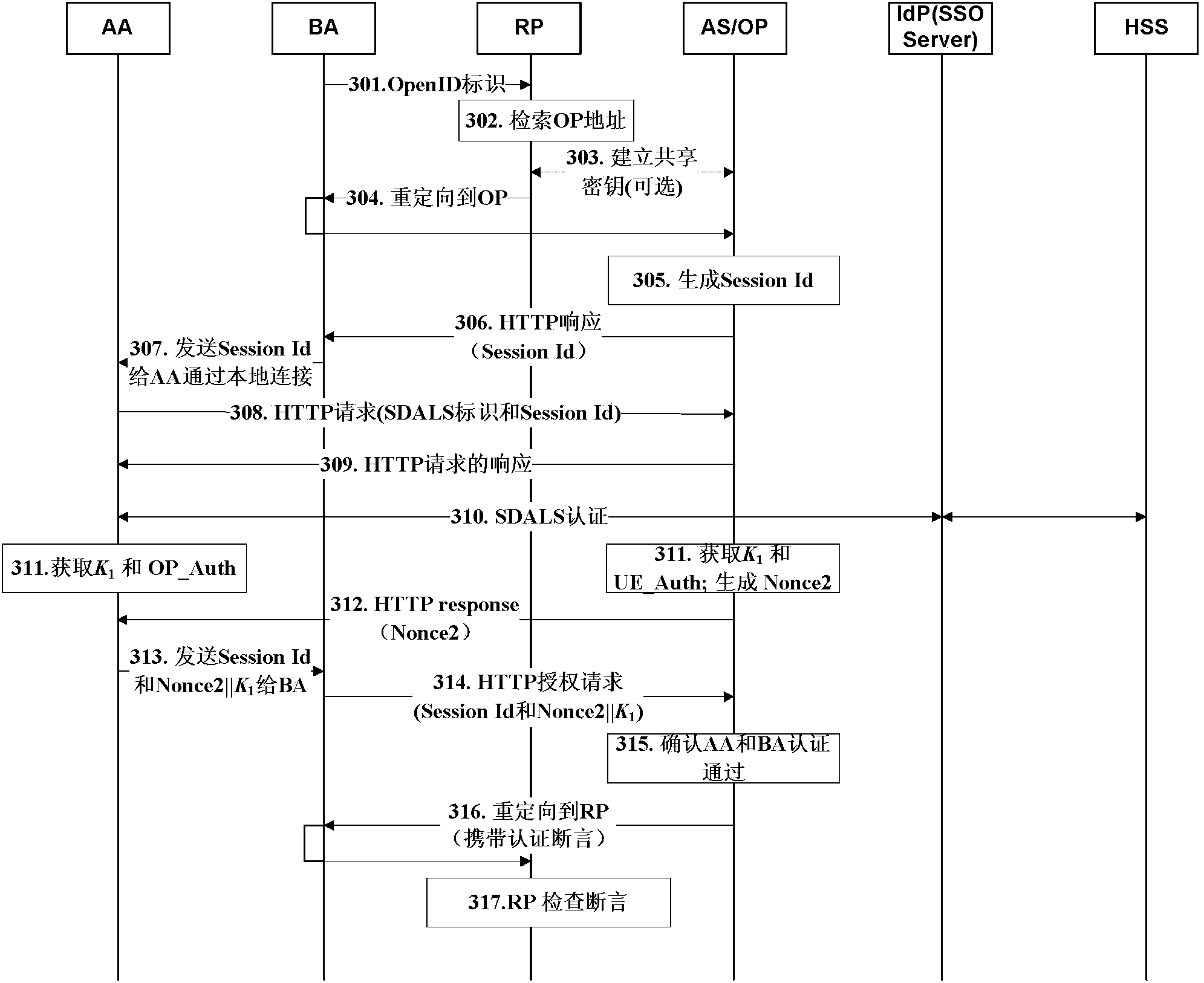
The invention discloses a split terminal single sign-on combined authentication method and system. The method comprises the steps that a BA in an OpenID is redirected to an OP by an RP, and the OP generates a Session Id and pushes the Session Id to the BA; communication is carried out between an AA and the OP according to the Session Id acquired by the AA, the OP instructs the AA to carry out SDALS authentication, and after authentication is carried out between the AA and an IdPDALS, the OP generates a random number Nonce2 and sends the random number Nonce2 to the AA according to an acquired session key K1 between the OP and the AA and an authentication result of the AA; the AA sends the Session Id, the acquired session key K1 and the received random number Nonce2 to the BA; OpenID authentication is carried out on the OP and the RP by the BA according to the Session Id, the session key K1 and the random number Nonce2. According to the split terminal single sign-on combined authentication method and system, single sign-on is achieved based on a split terminal under the condition that a GBA is not arranged, and then various WEB services can be available.
Owner:ZTE CORP
Method and device for using software resource remotely without password
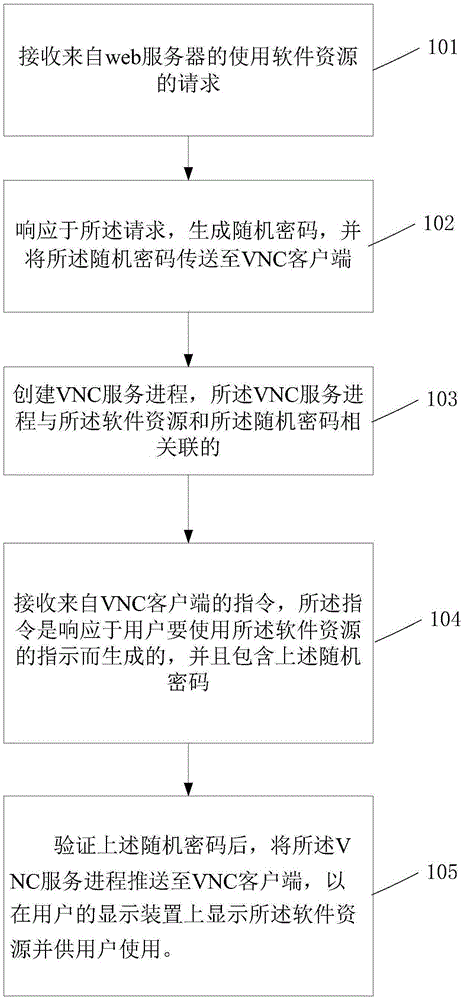
InactiveCN106570352AImplement single sign-onRealize remote interactionDigital data authenticationProgram/content distribution protectionPasswordWeb service
The invention relates to a method and device for using a software resource remotely without a password, and the method comprises the steps: receiving a request for using the software resource from a web server; responding to the request, generating a random password, and transmitting the random password to a VNC client; building a VNC service process, wherein the VNC service process is correlated with the software resource and the random password; receiving an instruction from the VNC client, wherein the instruction is generated through response to the request of a user for using the software resource, and comprises the random password; verifying the random password, and pushing the VNC service process to the VNC client, so as to display the software resource on a display device of the user so that the user uses the software resource.
Owner:CHINA PETROLEUM & CHEM CORP +1
Tourism big data cloud platform and user authority management method thereof
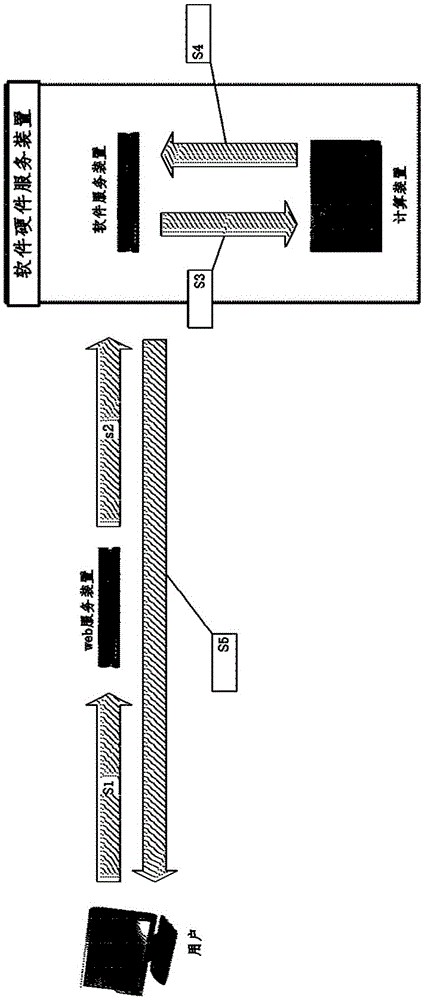
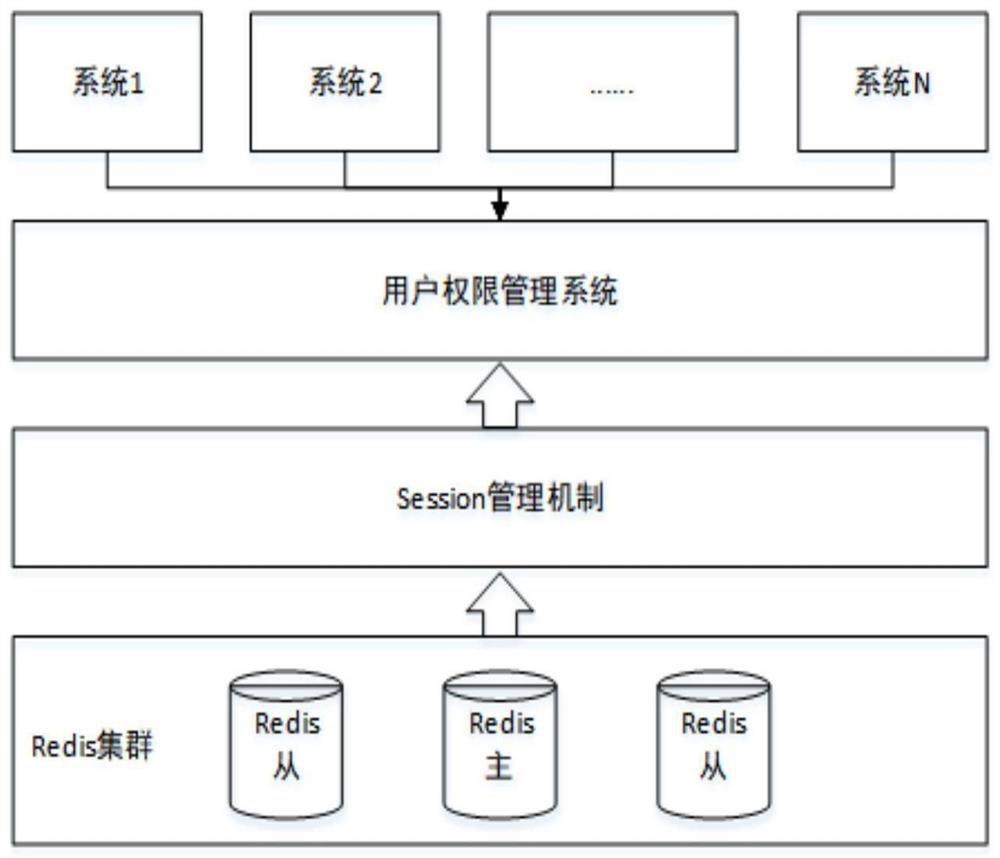
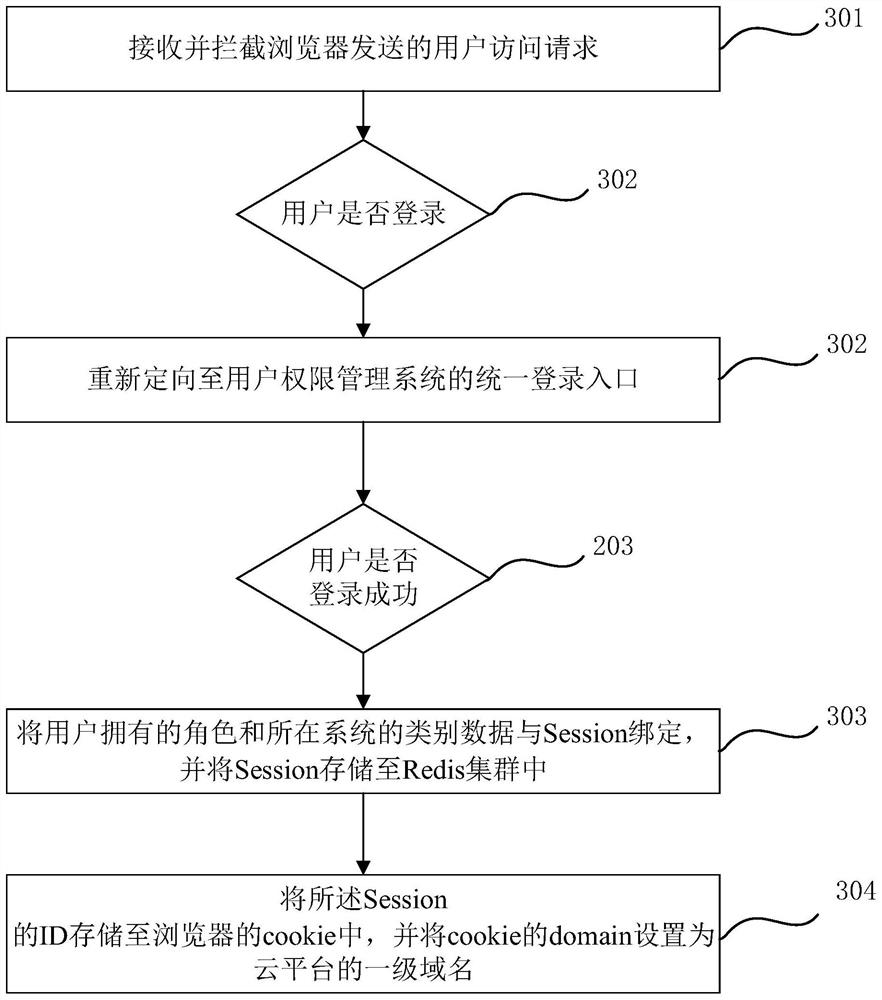
PendingCN112100590AImplement single sign-onData processing applicationsDigital data protectionDomain nameUser Privilege
The invention belongs to the technical field of computers, and particularly relates to a tourism big data cloud platform and a user authority management method thereof.The method comprises the steps:receiving and intercepting a user access request sent by a browser, determining whether a user logs in or not, and if not, redirecting the user to a unified login entrance of a user authority management system; determining whether the user logs in successfully or not, if so, binding a role owned by the user and the category data of the system where the user is located with Session, and storing theSession in a Redis cluster; and storing the ID of the Session in the cookie of a browser, and setting the domain of the cookie as a first-level domain name of the cloud platform. According to the embodiment of the invention, single sign-on of a user among a plurality of application systems of the tourism big data cloud platform is realized.
Owner:上饶市中科院云计算中心大数据研究院
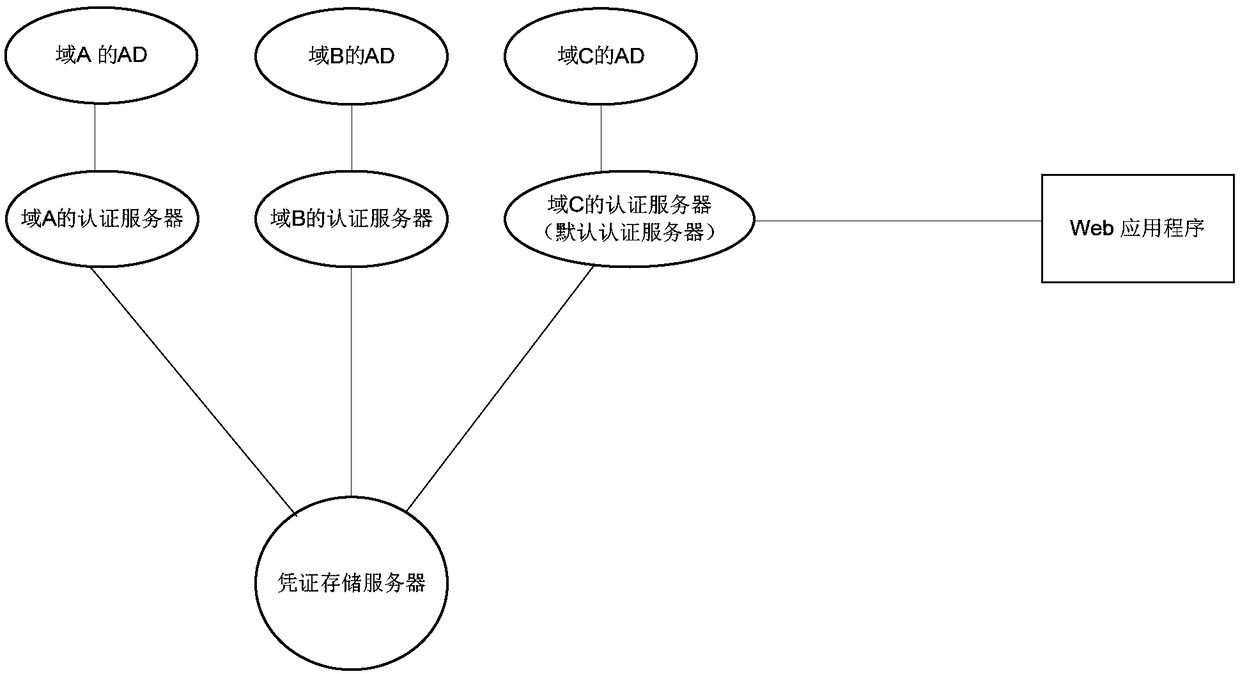
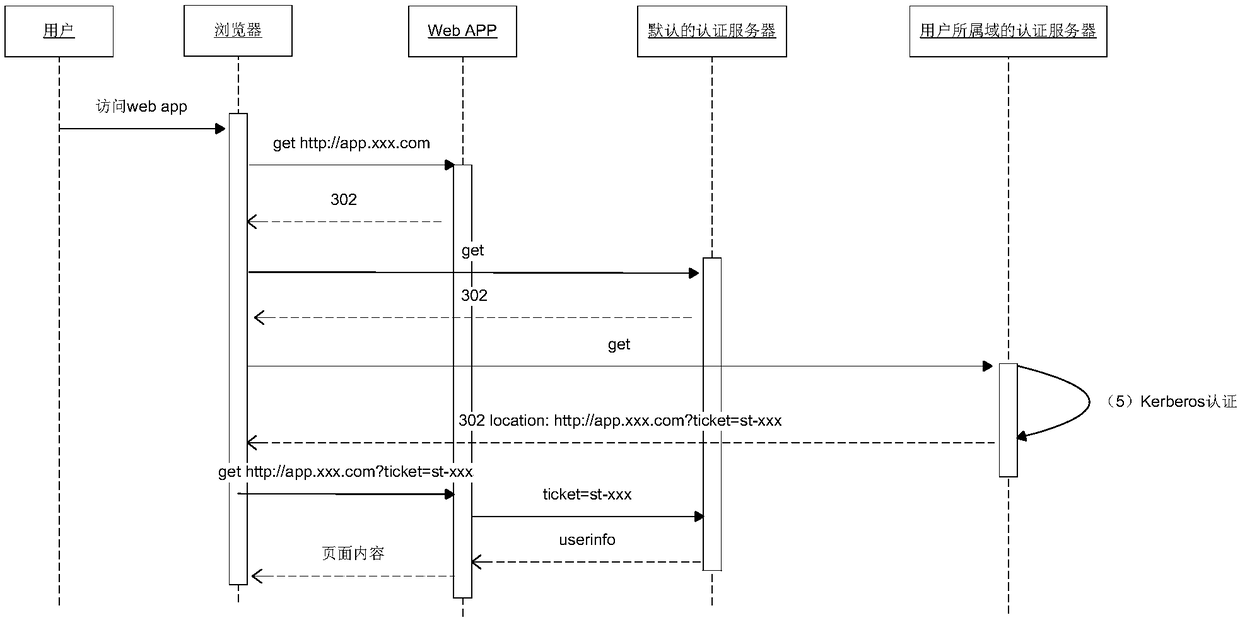
Method for implementing single sign on in multi-domain environment
The invention discloses a method for implementing single sign on in a multi-domain environment. In the multi-domain environment, each domain is configured with a Kerberos authentication server, the authentication servers share a credential, and the authentication server of one domain is set as a default authentication server. According to the method, a group policy is set on a domain controller, ascript is executed when a user logs in the domain, and the domain information to which the user belongs is added to a User-Agent identifier of the browser. The default authentication server can redirect users to the authentication server of the belonging domain based on the domain information in this field for Kerberos authentication. By adoption of the method disclosed by the invention, the problem of single sign on of the user in the multi-domain environment is effectively solved, and the user in the domain can access all application systems just by inputting once password during the startup. As the domain authentication servers share the credential, no additional burden is brought to a Web application program, the Web application program only needs to interact with the default authentication server, and just like the single domain environment, the existence of the multi-domain environment does not need to be concerned.
Owner:浙江网新恒天软件有限公司
School educational administration management system
InactiveCN109858875AImprove securityStrengthen information constructionDatabase management systemsOffice automationExchange of informationManagement system
The invention discloses a school educational administration management system. The system comprises a database system and an educational administration management system connected with the database system. The database system is used for acquiring data, exchanging the acquired data according to an exchange rule and then storing the data; the educational administration management system is used forreading and managing data stored in the database system, and the data comprises student data, teacher data, classroom data, semester data, grade data, class data, subject data and course information;the educational administration management system comprises a course selection and arrangement system, and the course selection and arrangement system is used for arranging course schedule data according to course data selected by students and data stored in the database system. By arranging the database system, integration of an existing system, a system to be built, application systems of all departments and future development or operation systems of other units and organizations within a proper range is achieved, and high sharing and exchange of information are achieved on the basis of integration.
Owner:成都非络通达科技有限公司
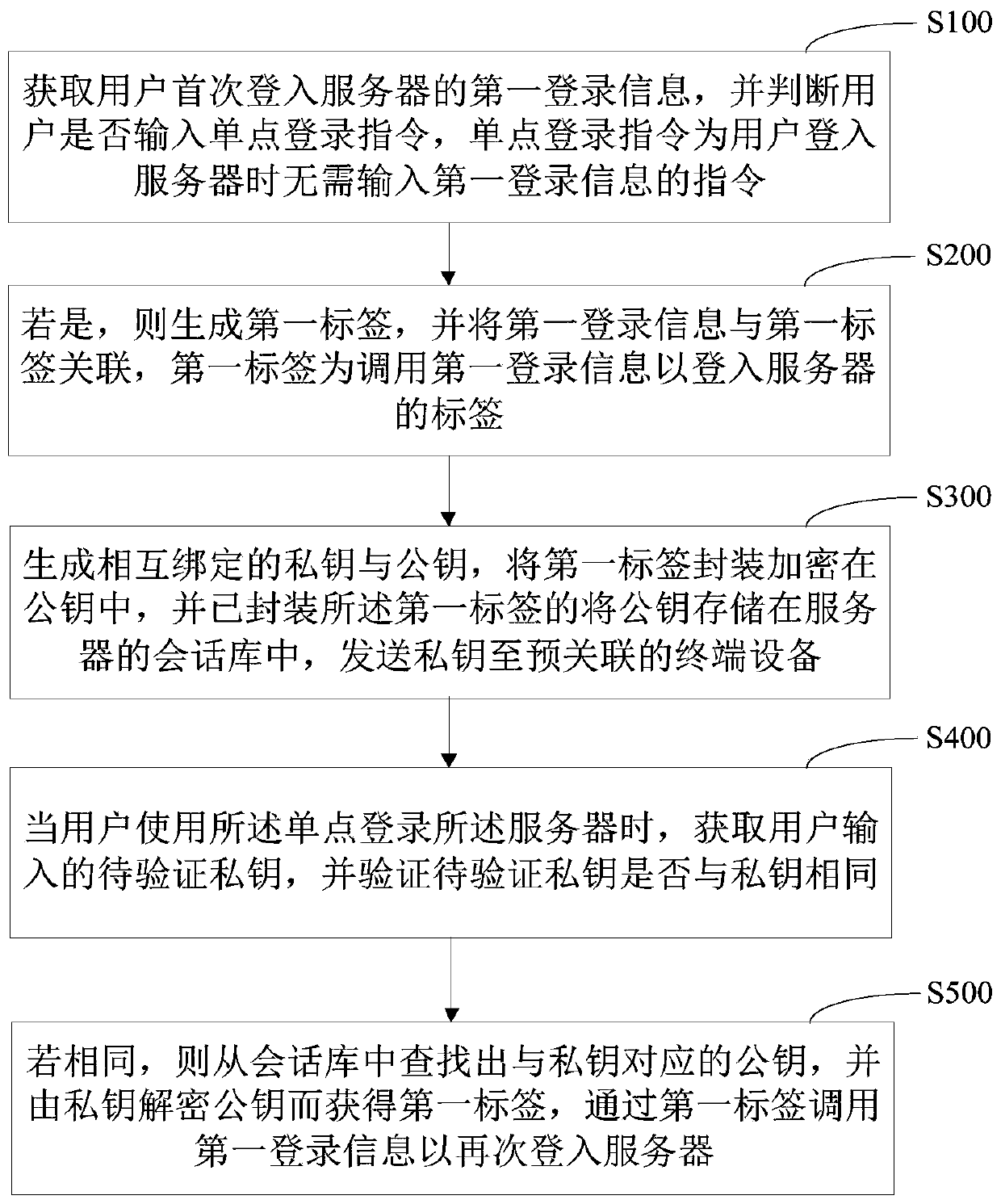
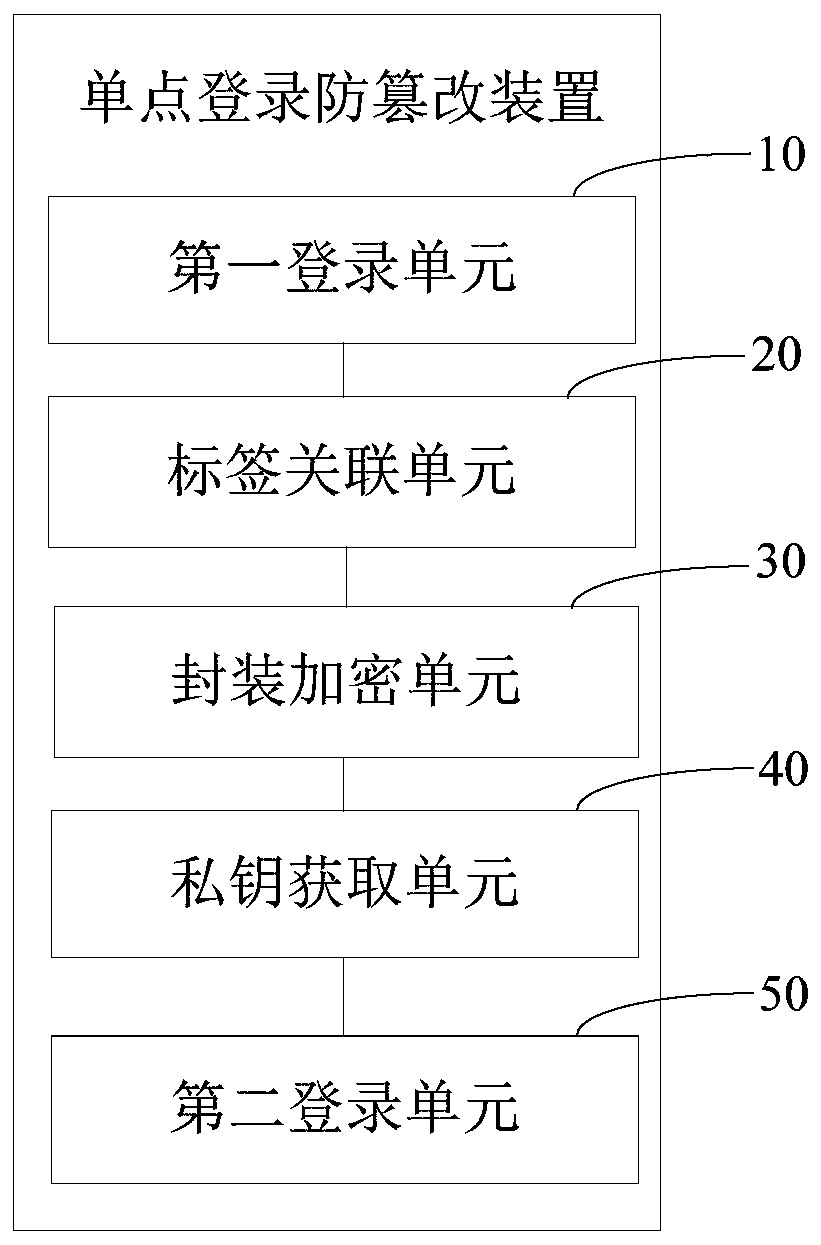
Single sign-on tamper-proofing method and device, computer equipment and storage medium
ActiveCN110266640AImplement single sign-onImplement encryptionTransmissionTamper resistanceTerminal equipment
The invention provides a single sign-on tamper-proofing method and device, computer equipment and a storage medium. The method comprises the following steps: obtaining first login information of a user logging in a server, associating the first login information with a first tag, generating a private key and a public key which are bound with each other, packaging and encrypting the first tag in the public key, and storing the public key in a session library of the server, thereby realizing the encryption of the tag, and preventing an illegal person from inputting the tag into the session library and directly entering the server; sending the private key to a pre-associated terminal device; obtaining a to-be-verified private key input by the user through the terminal equipment; judging whether the to-be-verified private key is the same as a private key or not, if yes, searching whether a public key corresponding to the private key exists in a session library, if yes, decrypting the public key by the private key to obtain a first label, and obtaining first login information corresponding to the first label to log in a server again through the first login information, thereby realizing single sign-on of a user.
Owner:PING AN TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com