Patents
Literature
6293results about How to "Prevent theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
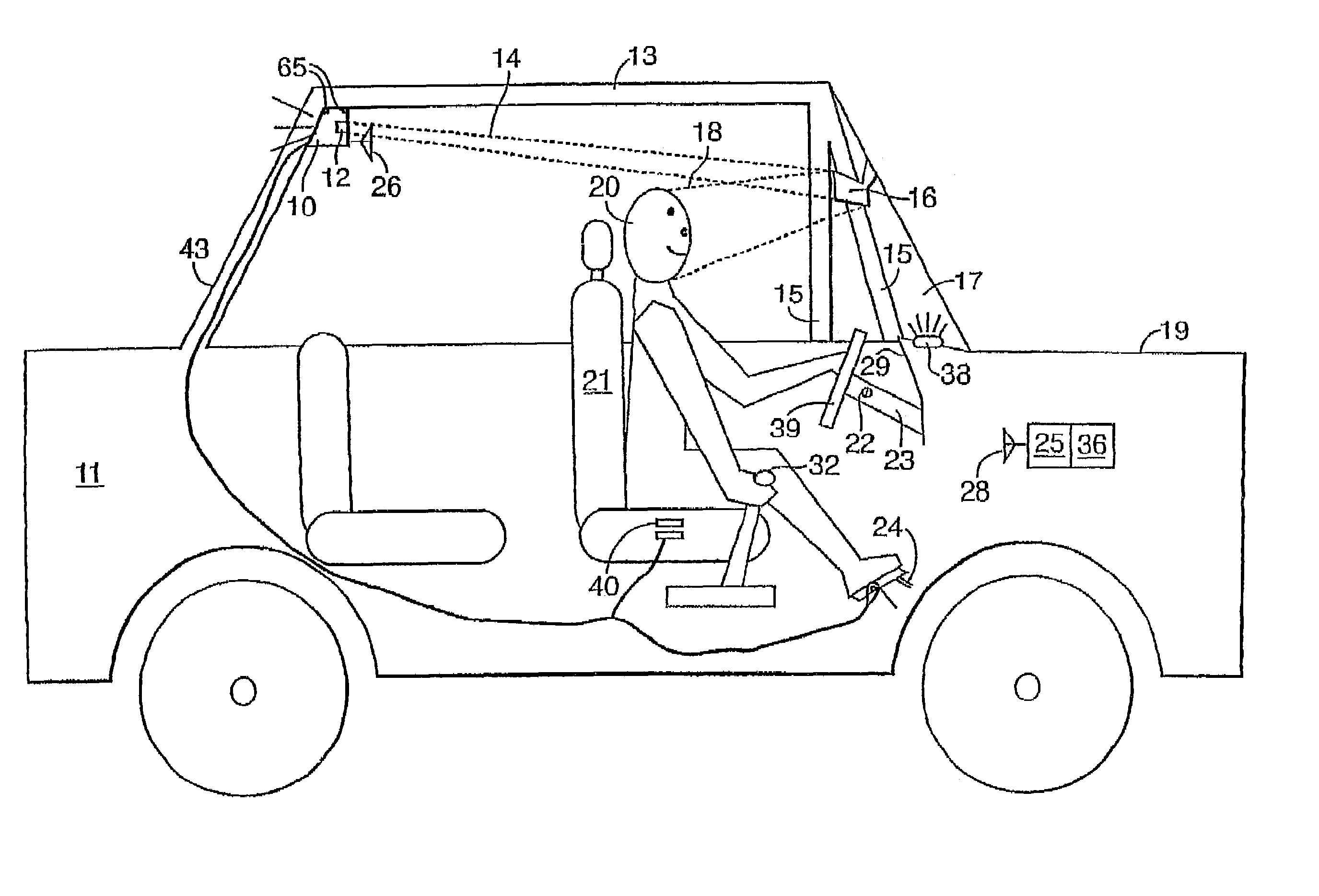
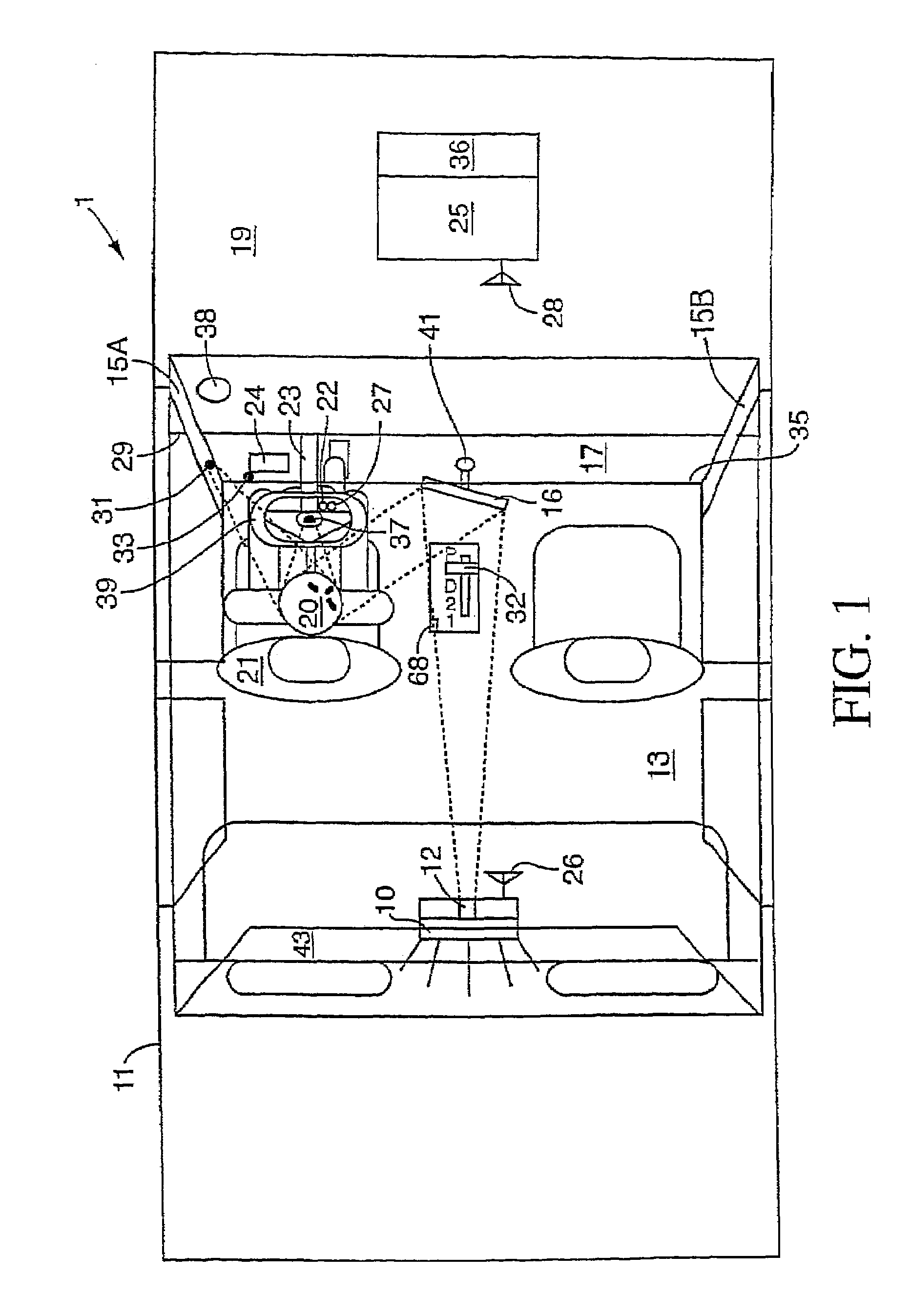
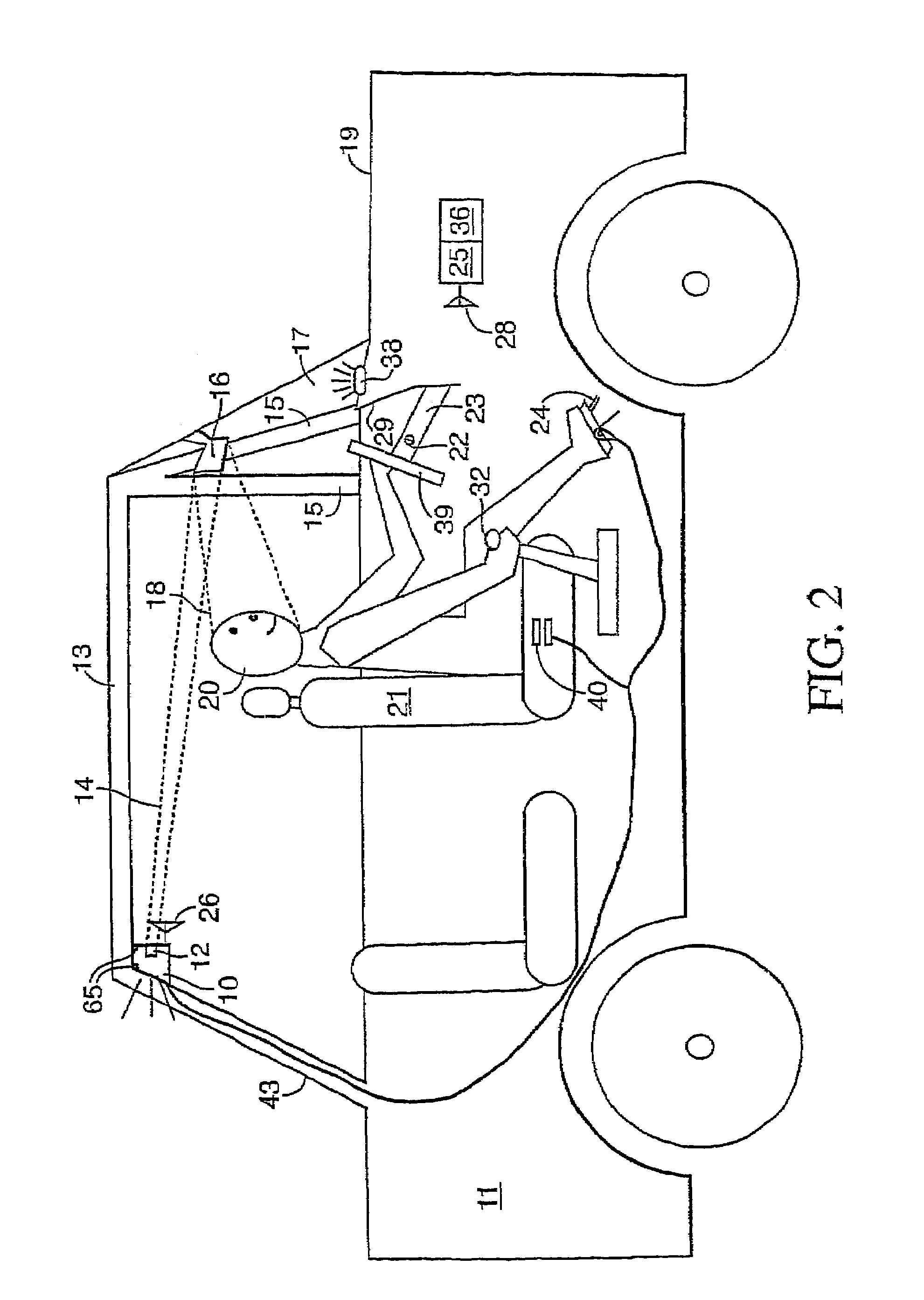
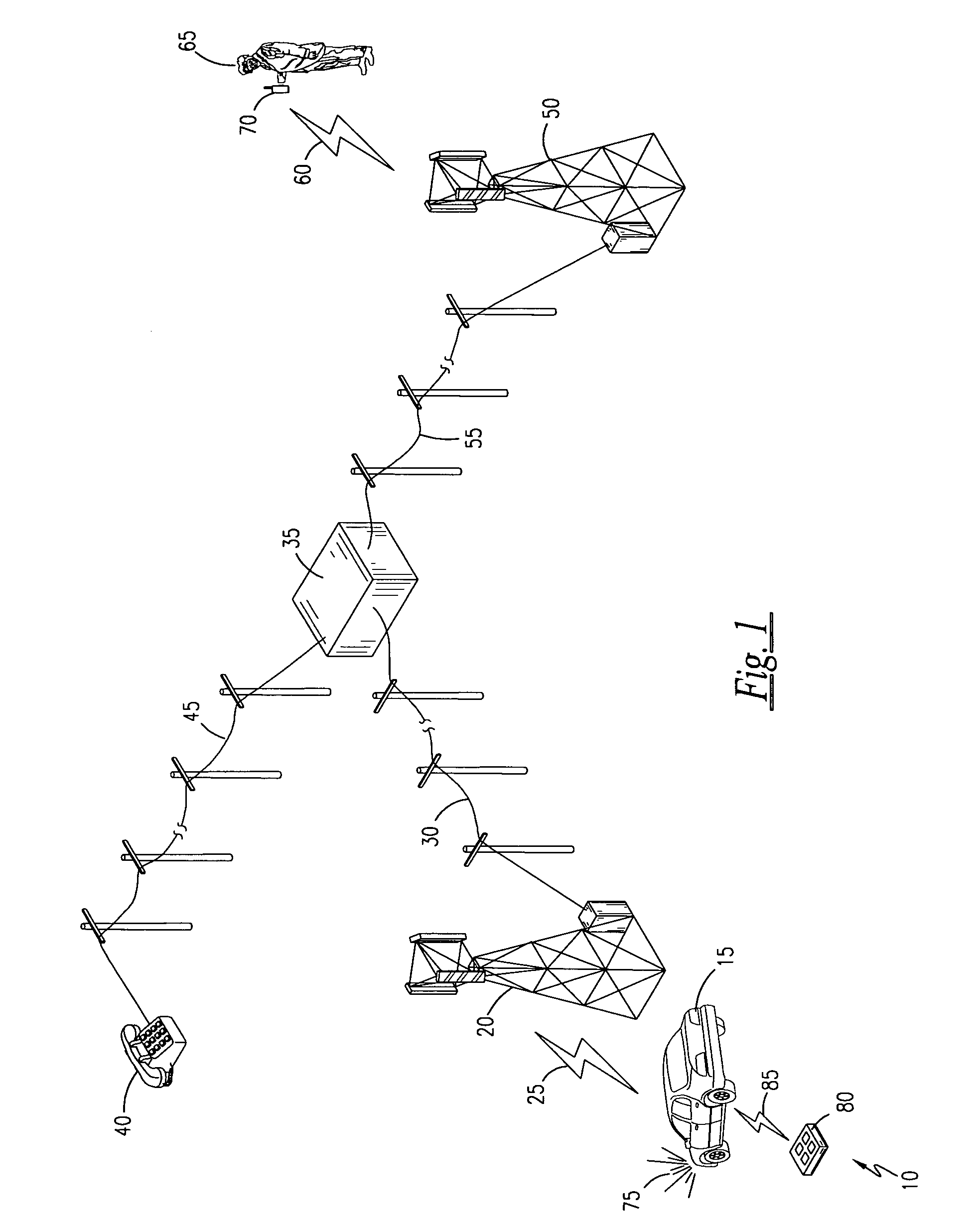
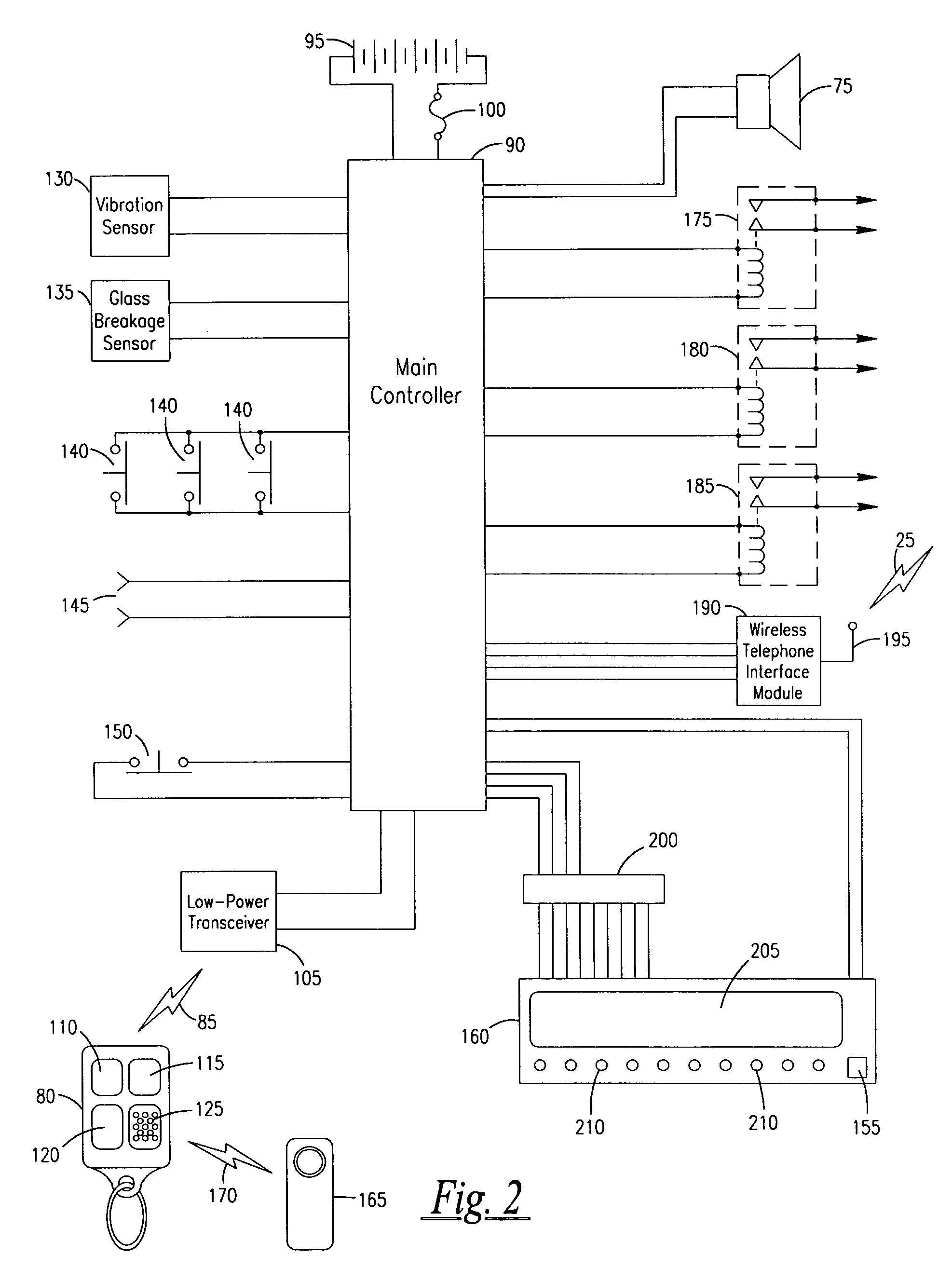
Acceleration-based theft detection system for portable electronic devices
InactiveUS20050190059A1Prevent theftElectric signalling detailsBurglar alarm by hand-portable articles removalGraphical user interfaceEngineering
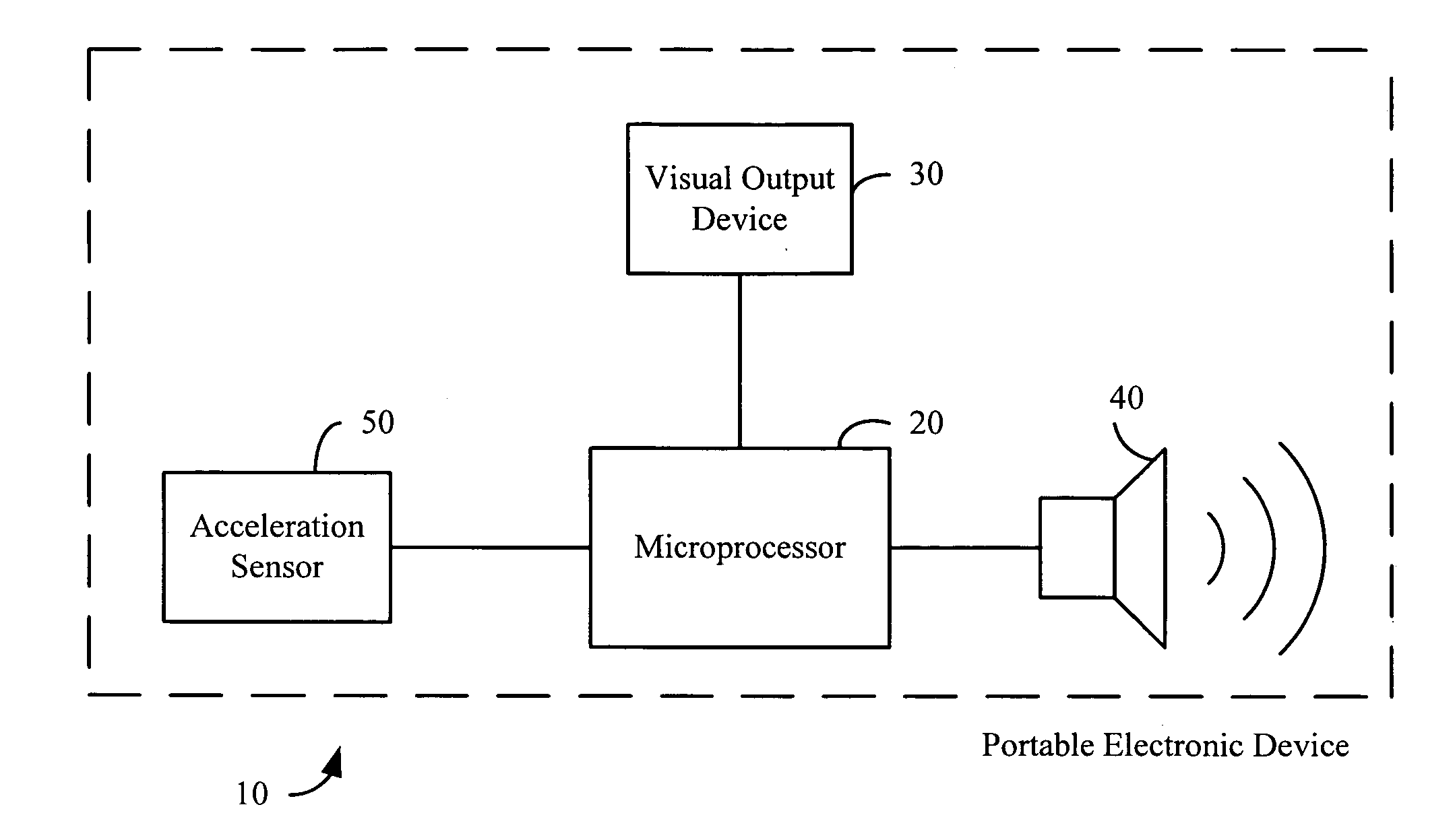
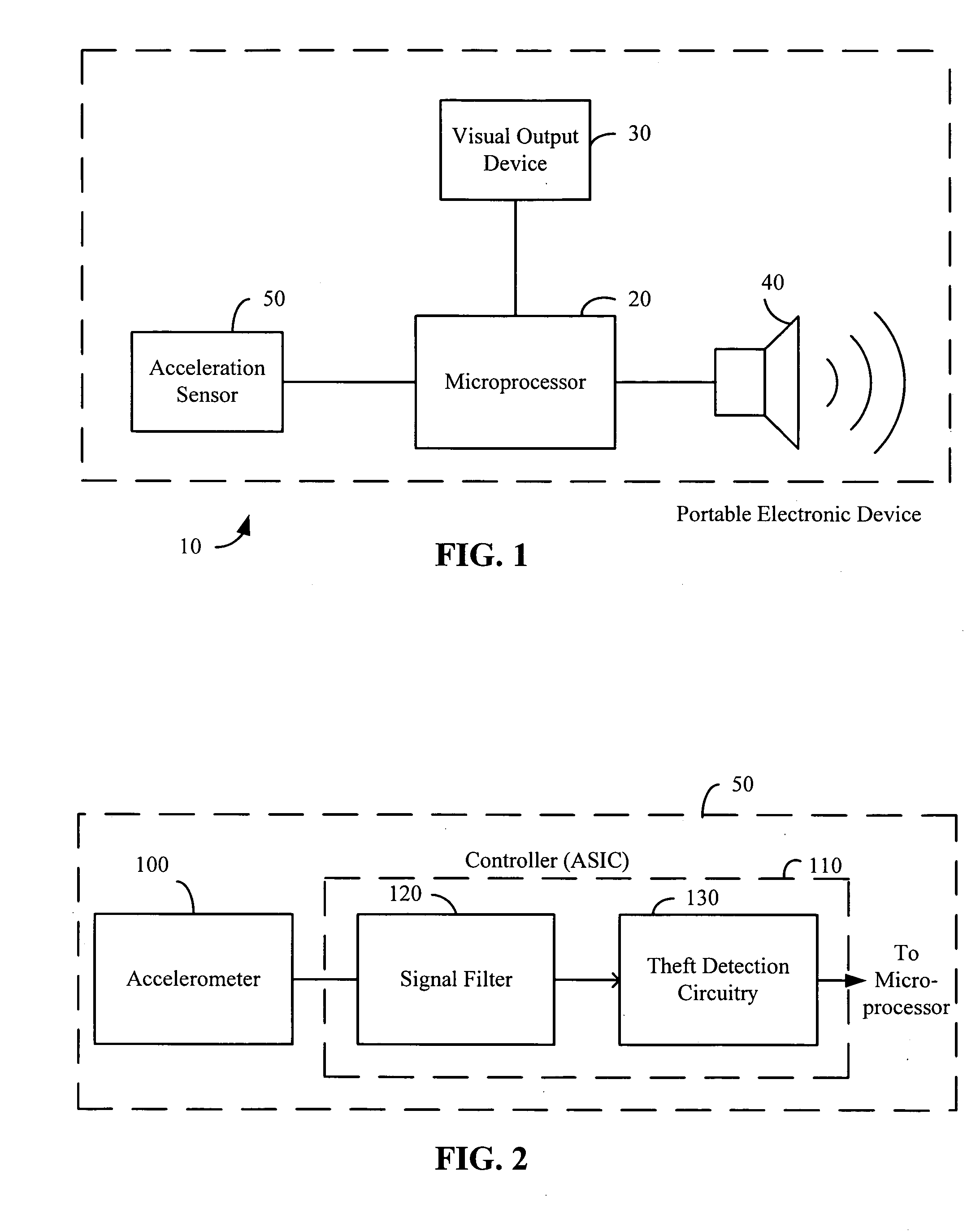
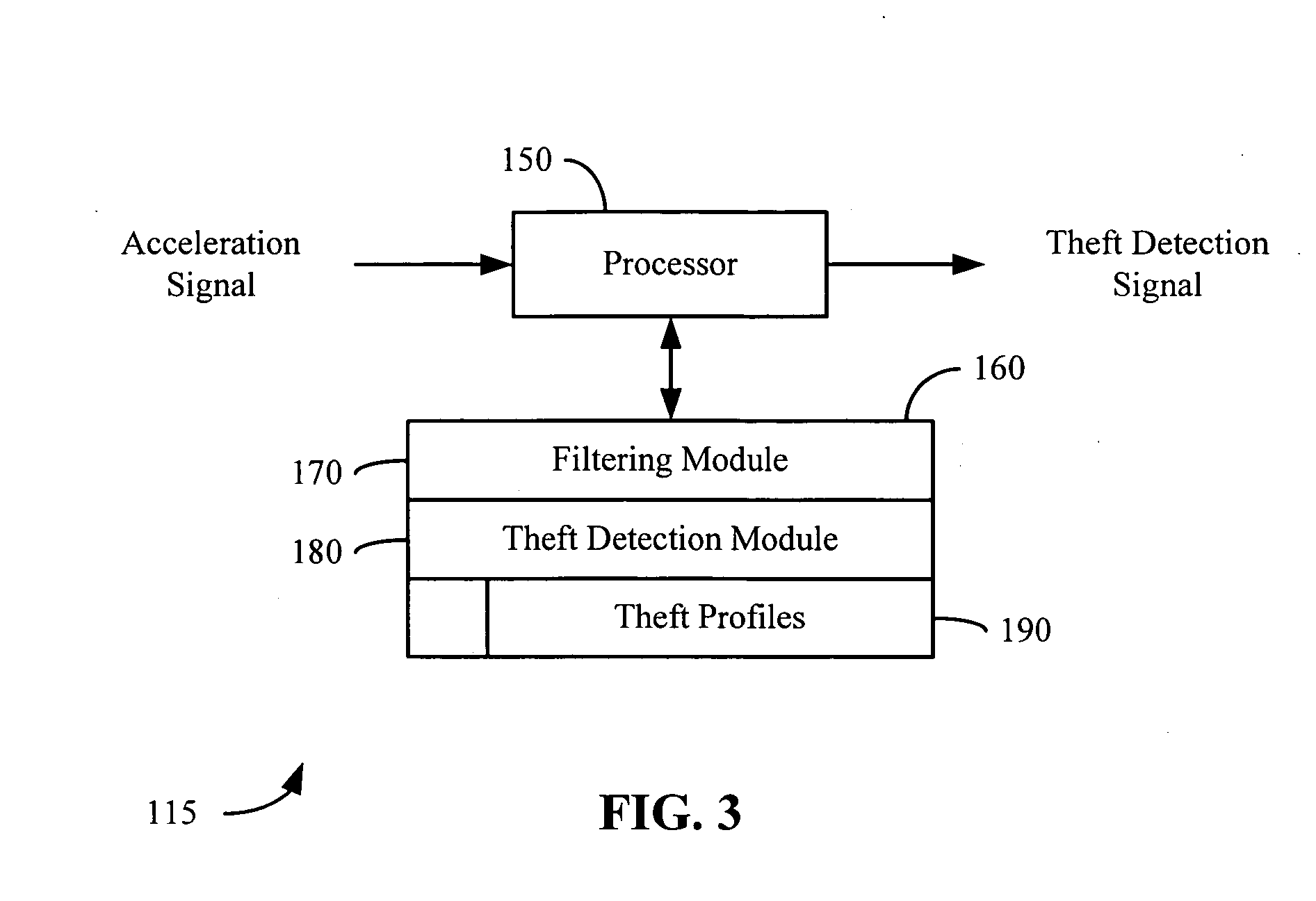
A theft prevention system for protecting portable electronic devices is disclosed. An acceleration sensor detects the acceleration of a portable electronic device, and a controller analyzes this acceleration to determine whether a theft condition is present. If so, an alarm can be initiated. The theft prevention system can include a filter for attenuating irrelevant acceleration frequencies and isolating those representative of theft, and comparison hardware / software for determining whether the detected acceleration matches a known acceleration profile characteristic of theft. Various parameters of the theft prevention system can also be set by a user through mechanisms such as a graphical user interface.
Owner:APPLE INC
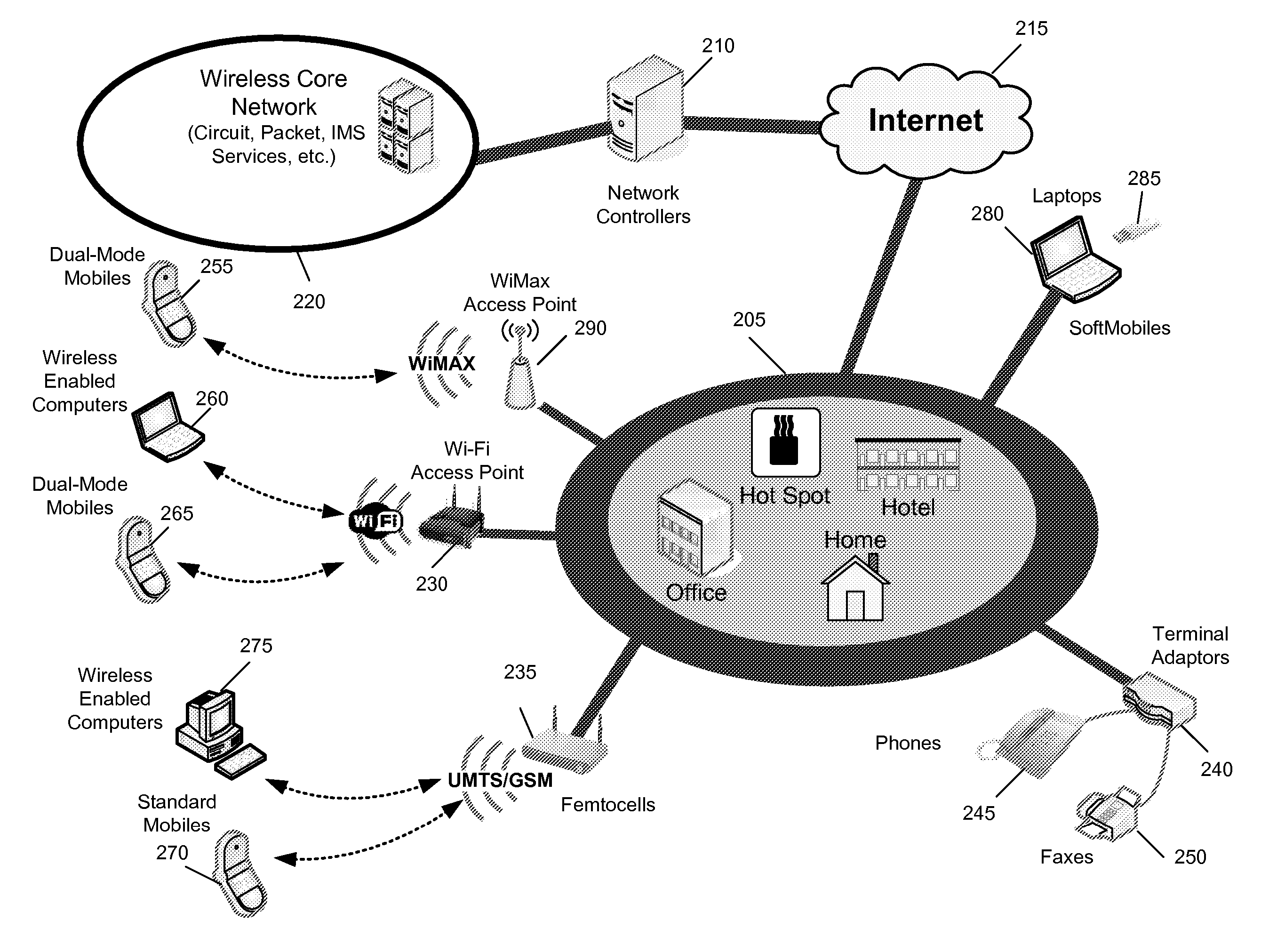
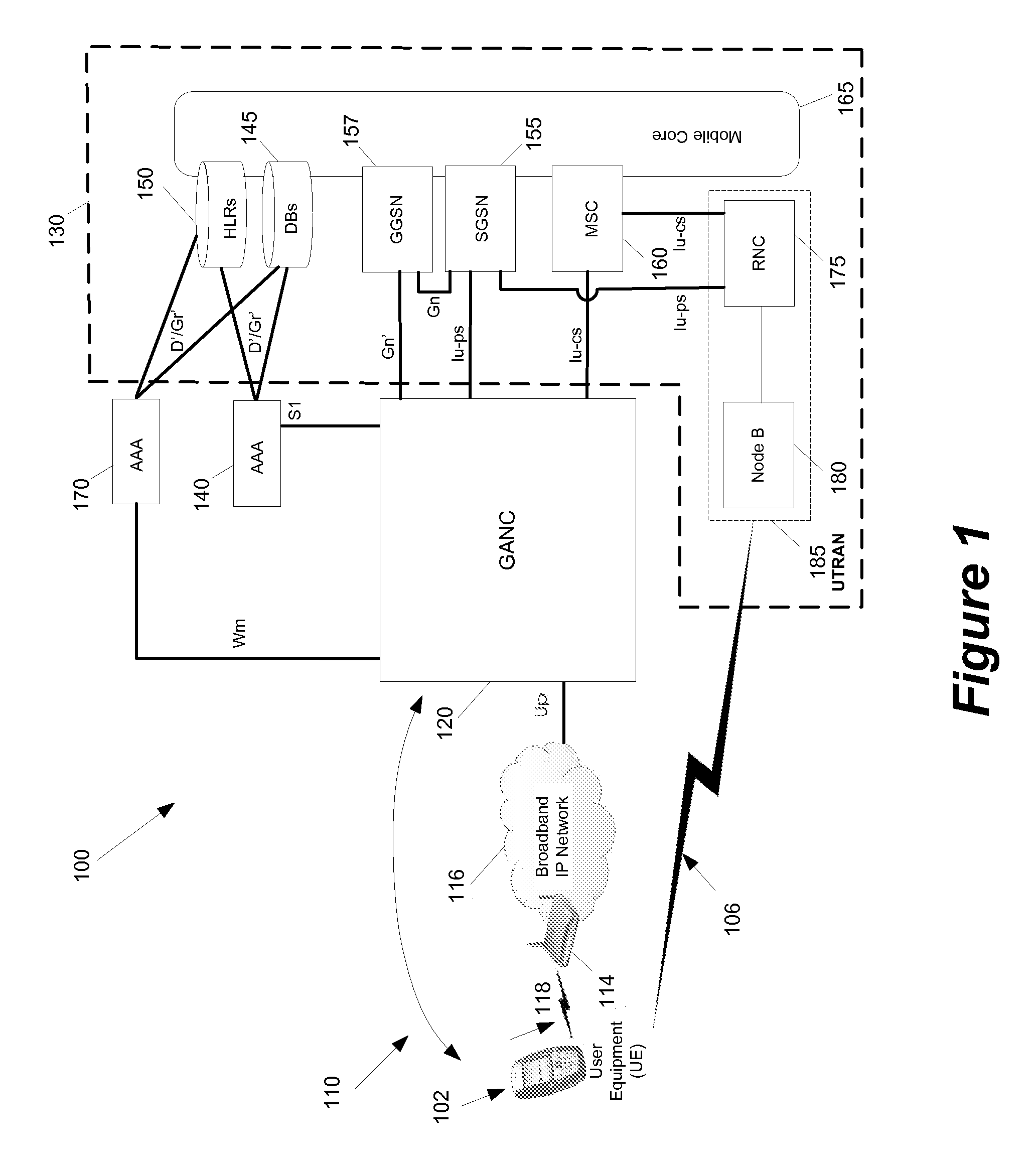
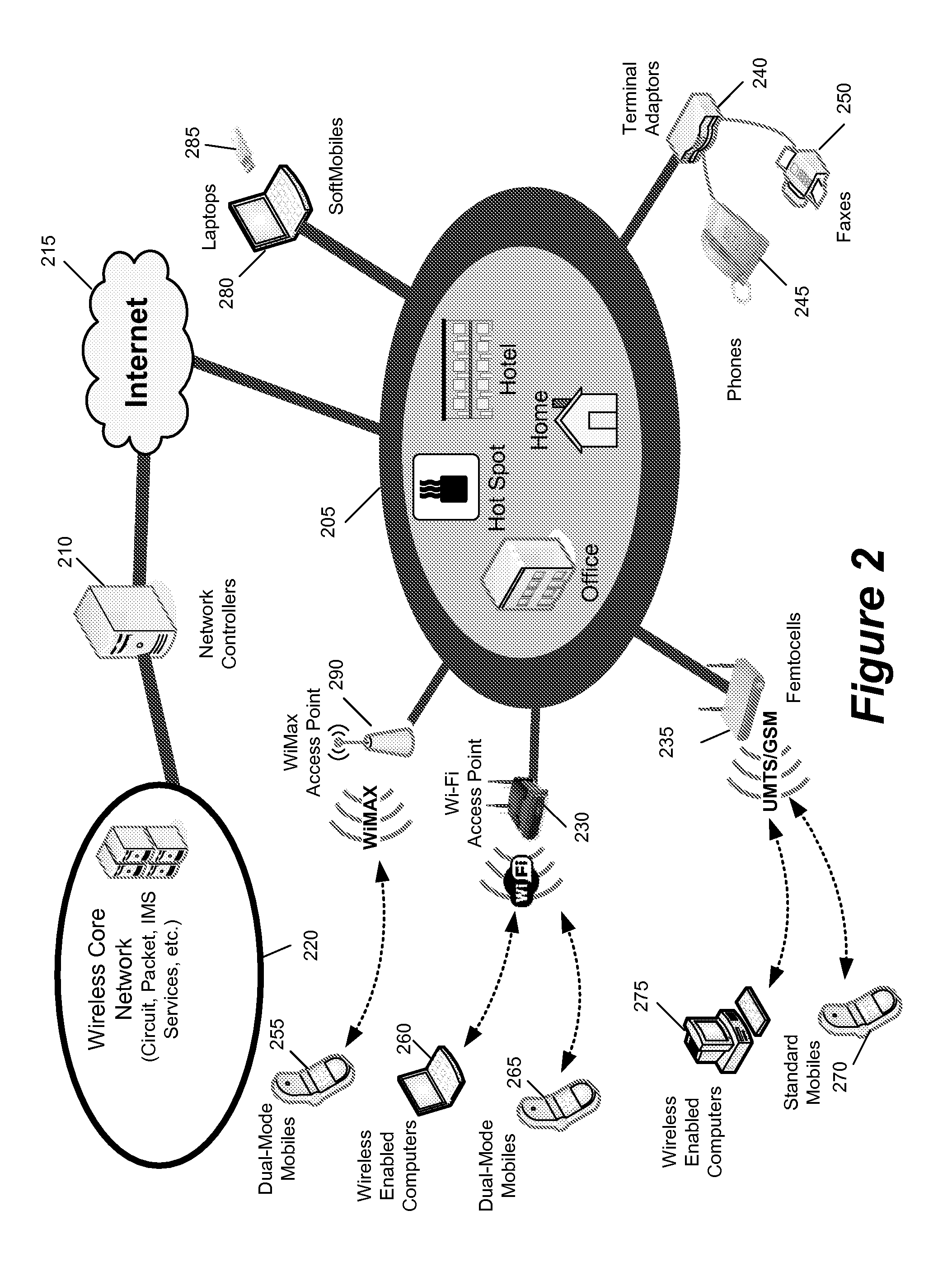
Method and apparatus for discovery
InactiveUS20080076419A1Prevent theftAssess restrictionNetwork topologiesCommunications systemNetwork control
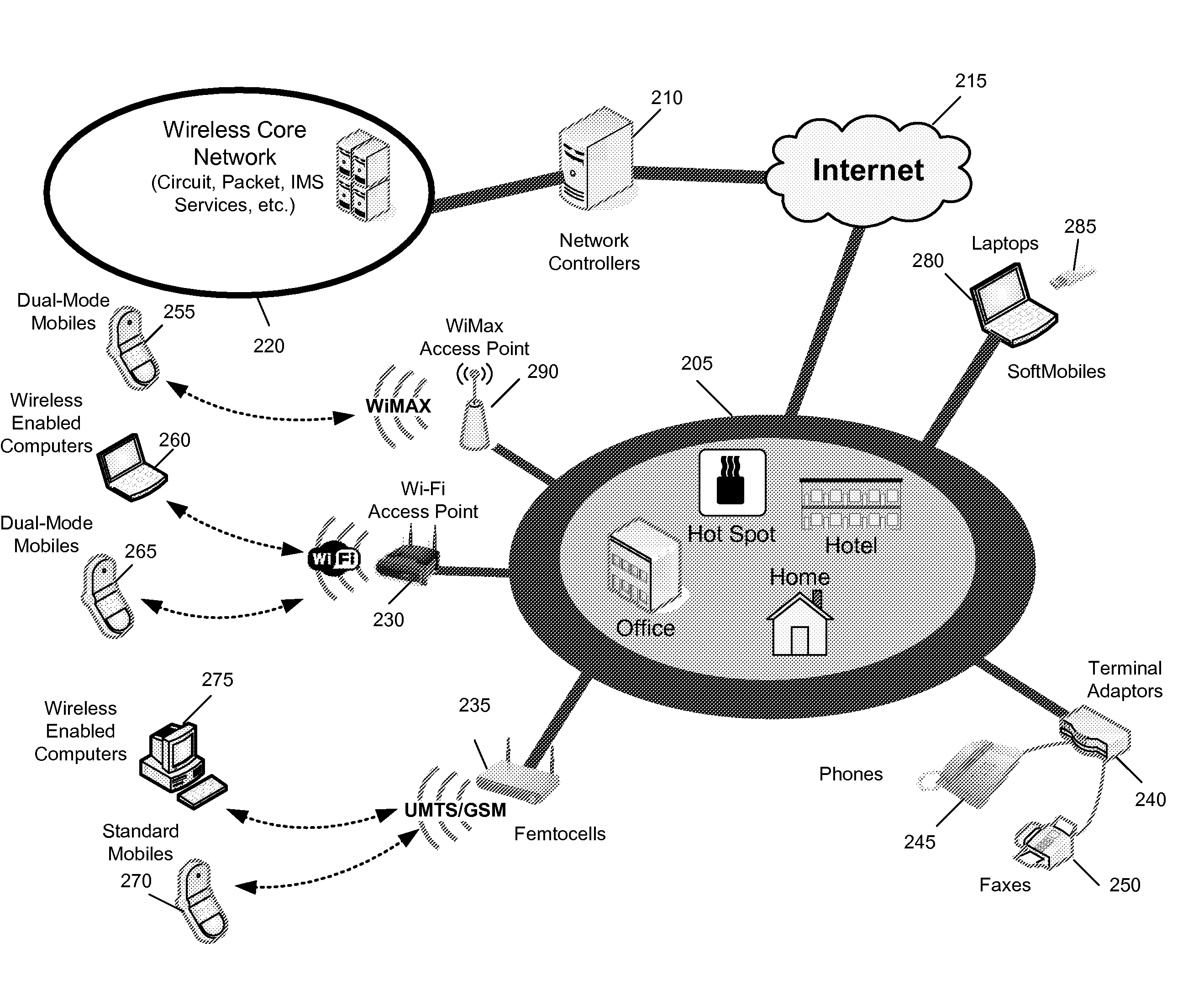
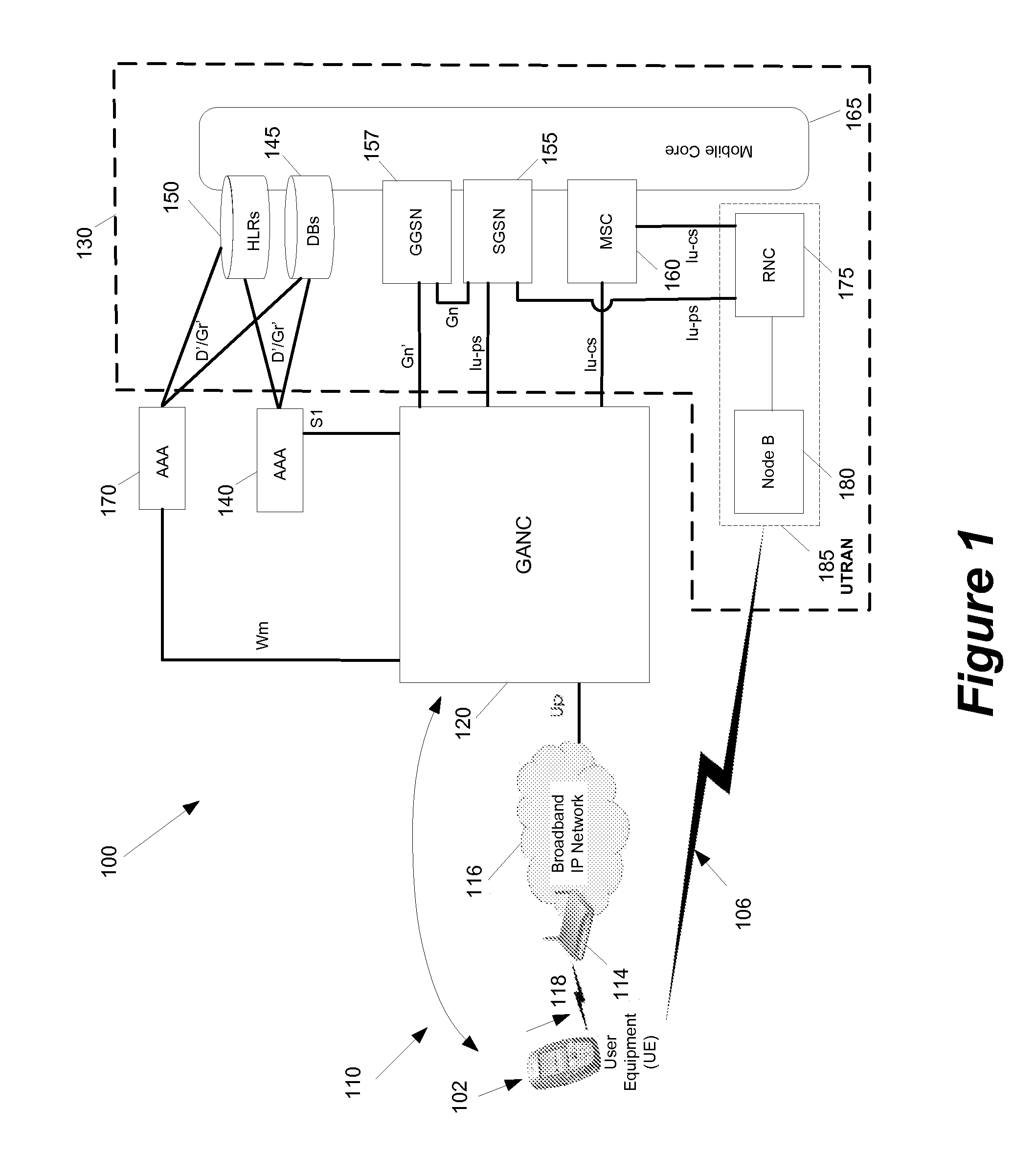
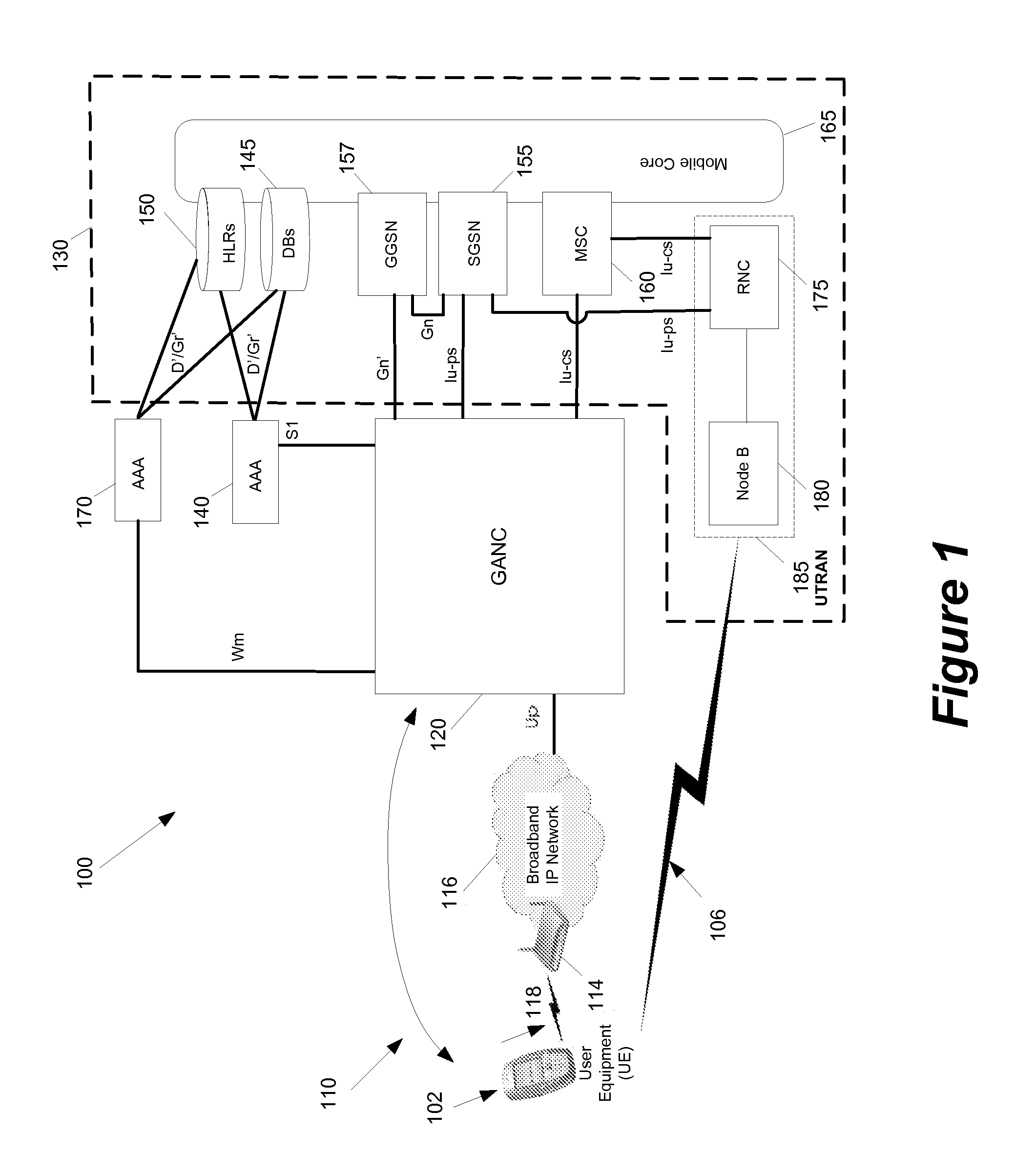
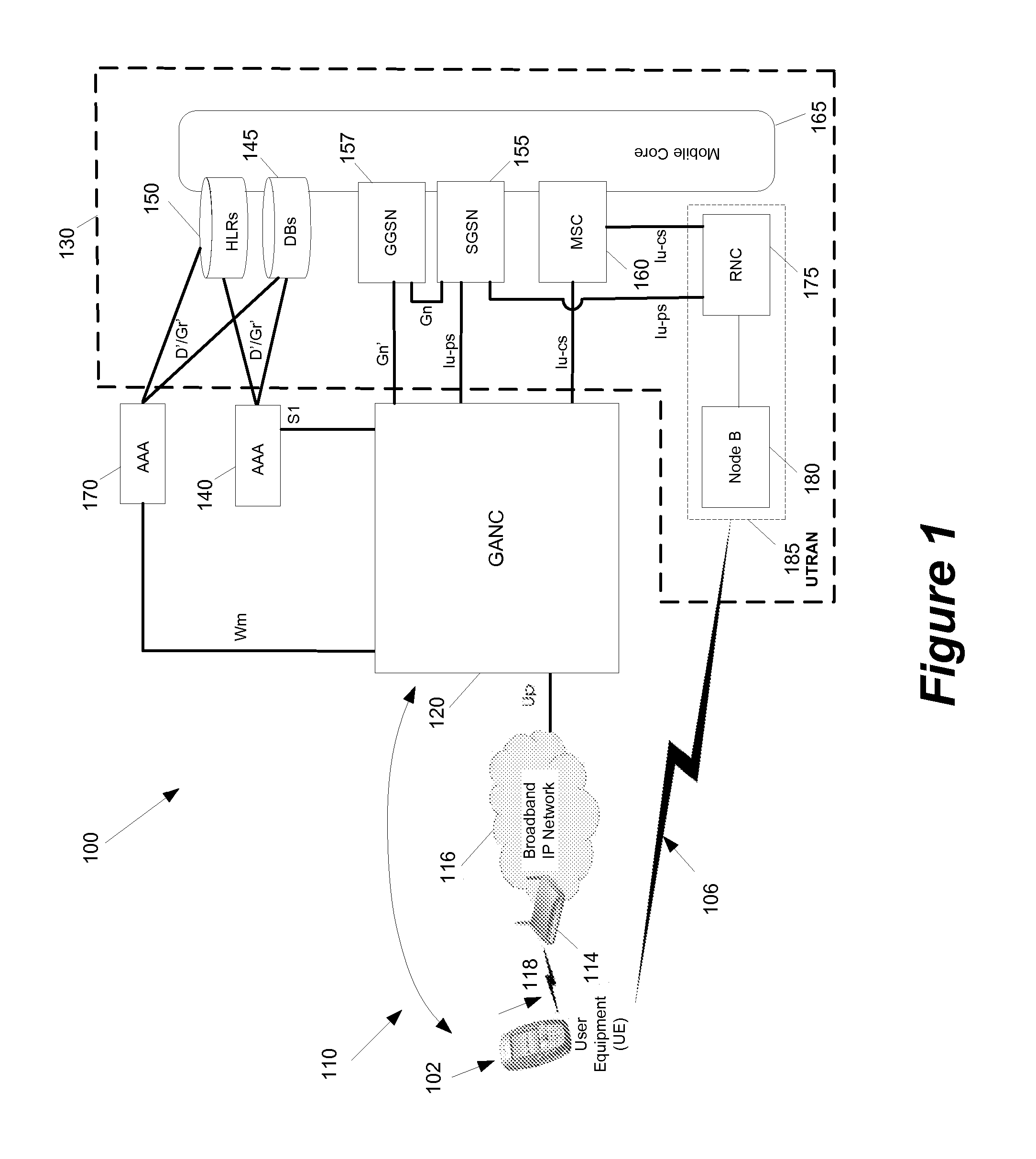
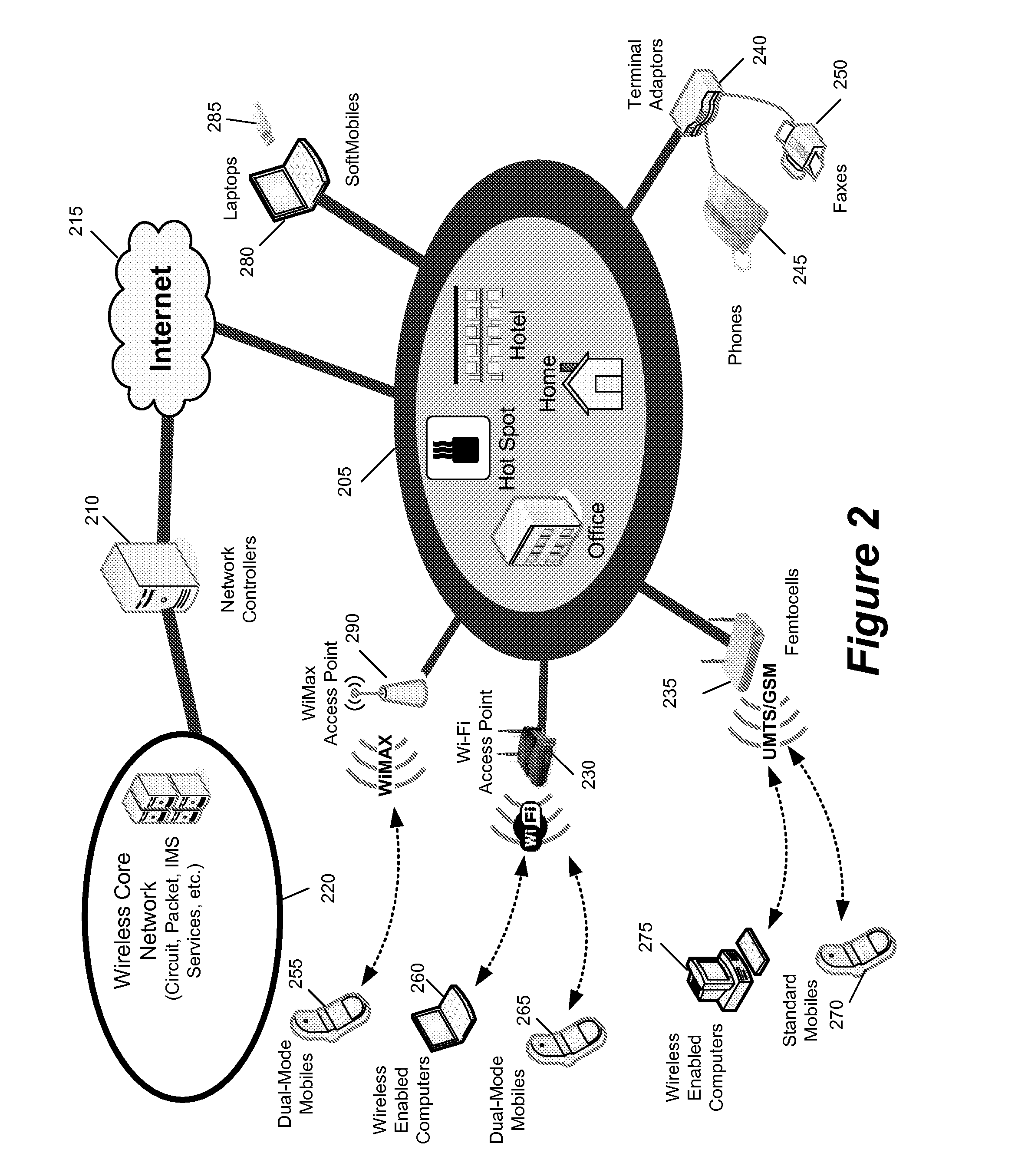
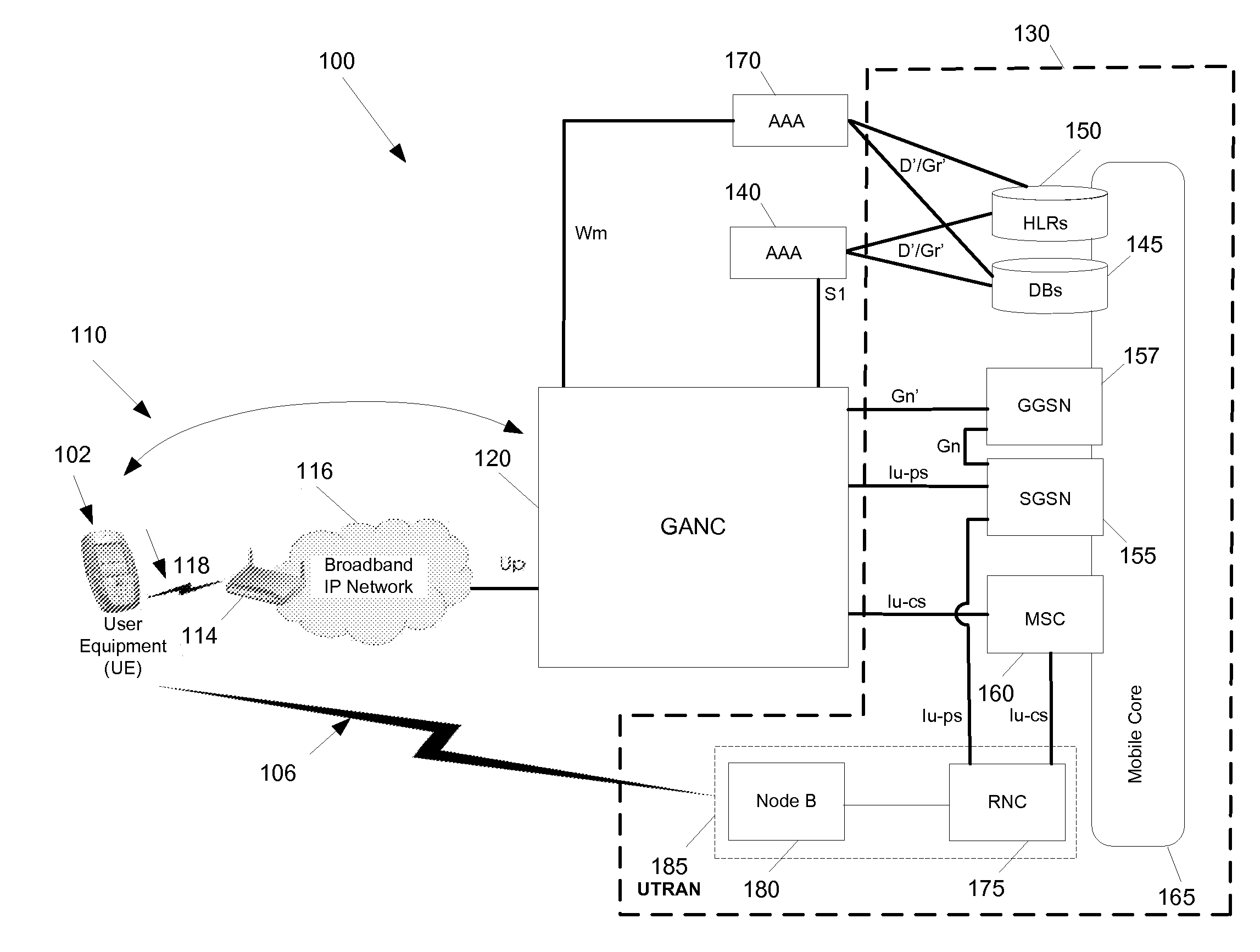
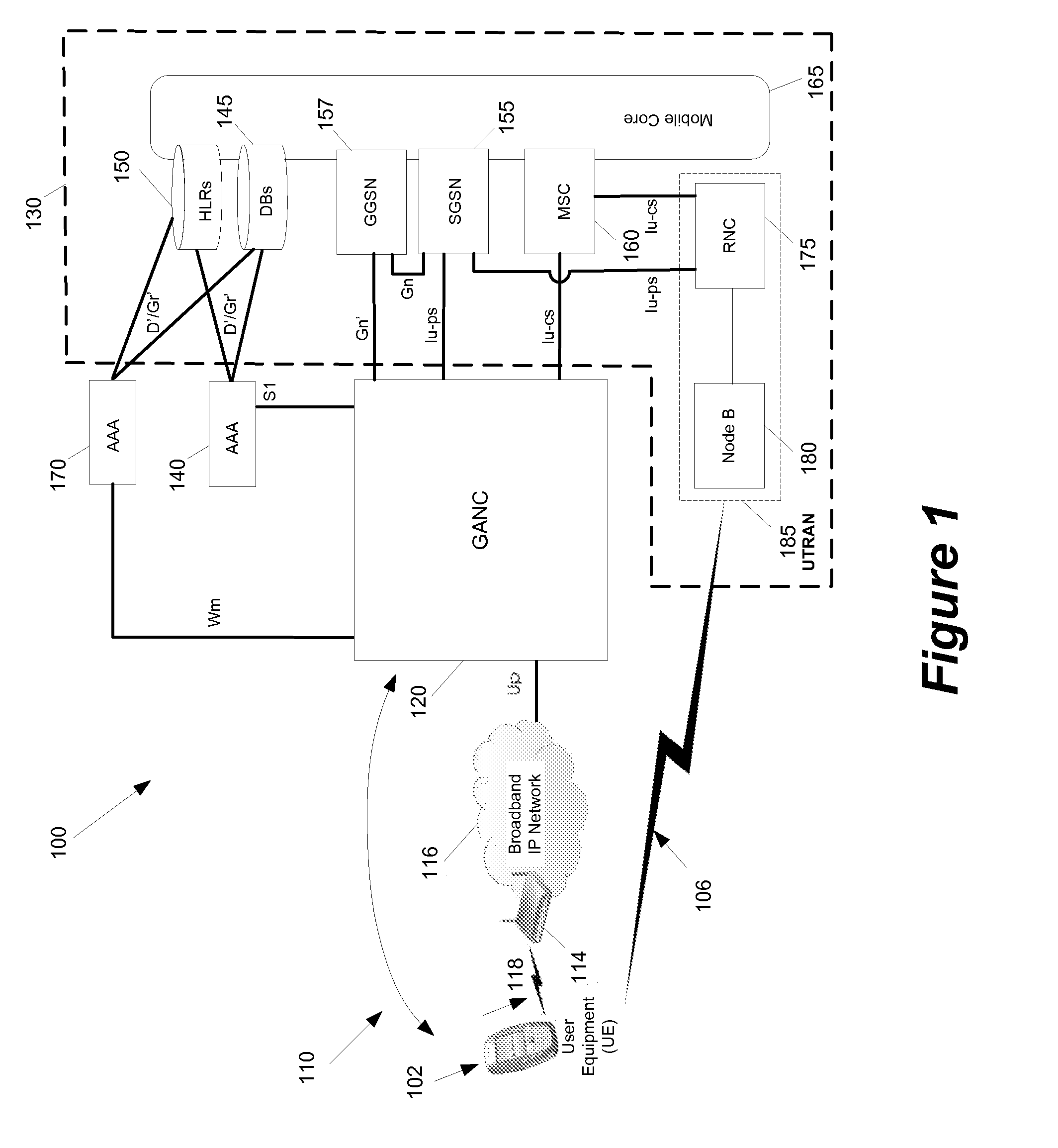
Some embodiments are implemented in a communication system that includes a first wireless communication system and a second wireless communication system that includes a Femtocell access point (FAP) and a network controller that can communicatively couple the FAP to the first wireless communication system. In some embodiments, the network controller can communicatively couple to the first wireless communication system through a UTRAN Iu interface. Some embodiments provide a method for performing discovery. The method sends a discovery request message that includes a licensed wireless cell information to a provisioning network controller. The method receives a discovery accept message at the FAP. The discovery accept message includes identification of a default network controller determined based on the cell information. The discovery accept message is sent by the provisioning network controller when the provisioning network controller determines that the provisioning network controller can accept the discovery request message.
Owner:KINETO WIRELESS
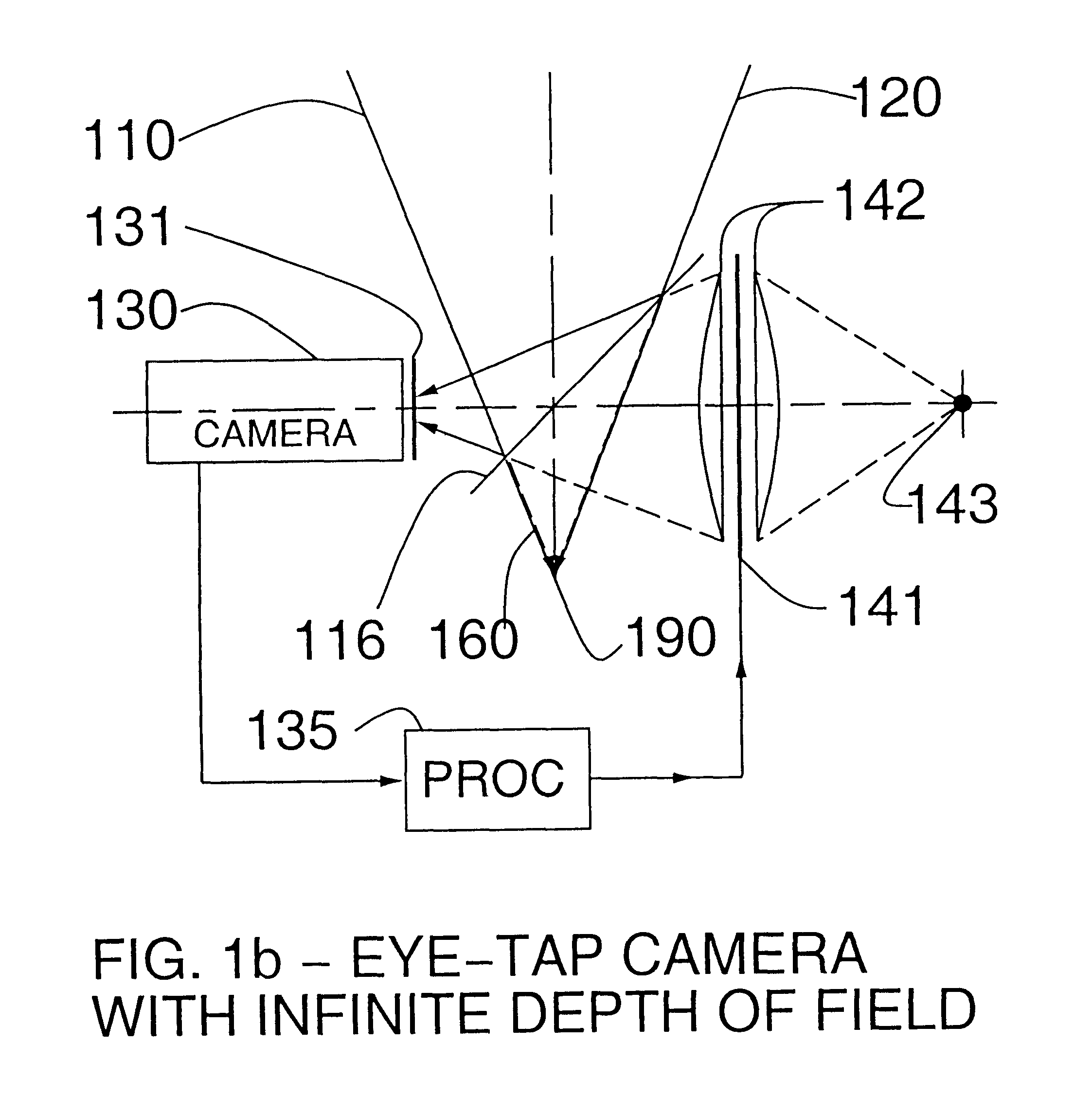
Eye-tap for electronic newsgathering, documentary video, photojournalism, and personal safety
InactiveUS6614408B1Augment and diminishEasy to catchTelevision system detailsCathode-ray tube indicatorsCommunications mediaComputer science
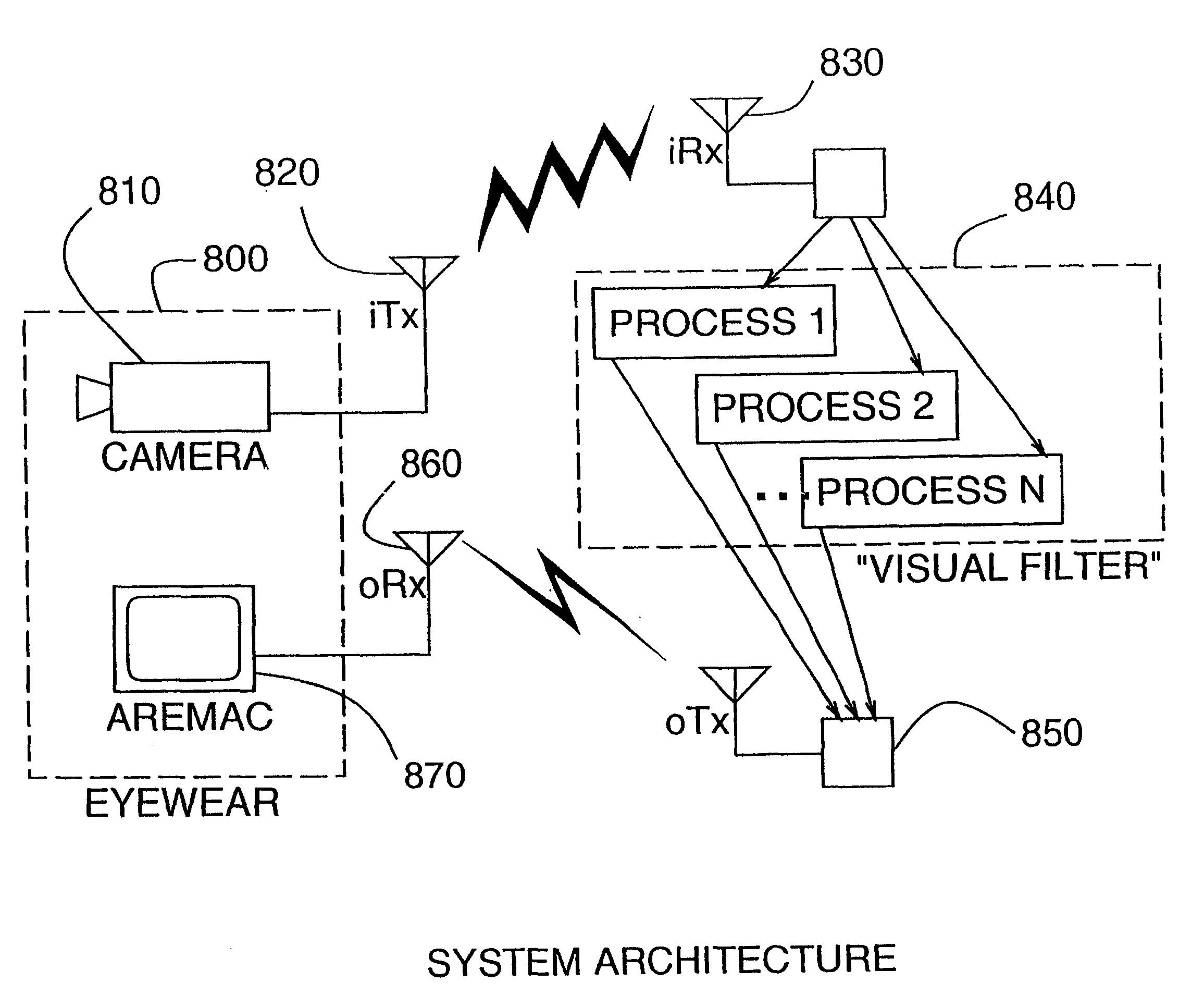
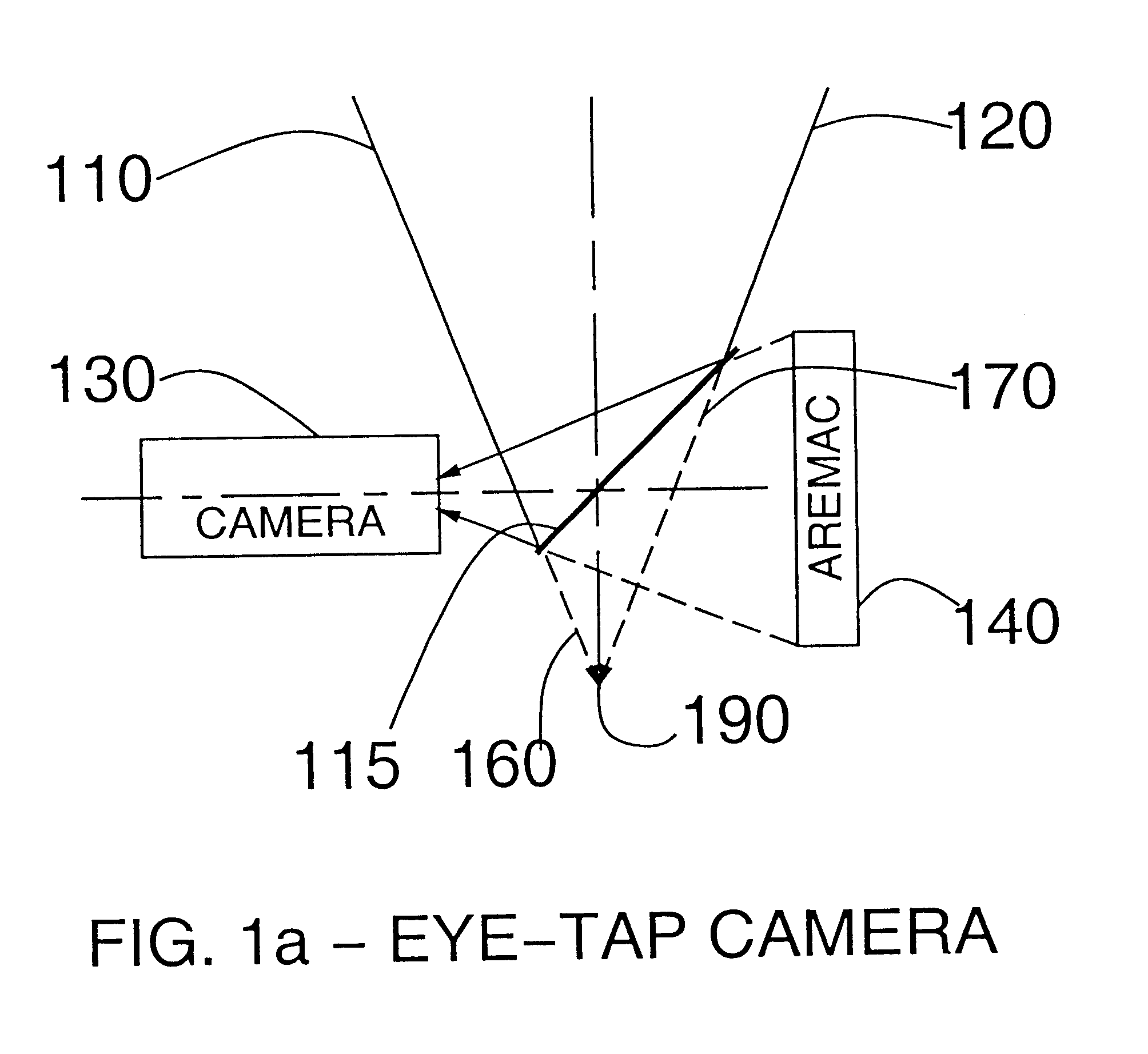
A novel system for a new kind of electronic news gathering and videography is described. In particular, a camera that captures light passing through the center of a lens of an eye of the user is described. Such an electronic newsgathering system allows the eye itself to, in effect, function as a camera. In wearable embodiments of the invention, a journalist wearing the apparatus becomes, after adaptation, an entity that seeks, without conscious thought or effort, an optimal point of vantage and camera orientation. Moreover, the journalist can easily become part of a human intelligence network, and draw upon the intellectual resources and technical photographic skills of a large community. Because of the journalist's ability to constantly see the world through the apparatus of the invention, which may also function as an image enhancement device, the apparatus behaves as a true extension of the journalist's mind and body, giving rise to a new genre of documentary video. In this way, it functions as a seamless communications medium that uses a reality-based user-interface.
Owner:MANN W STEPHEN G
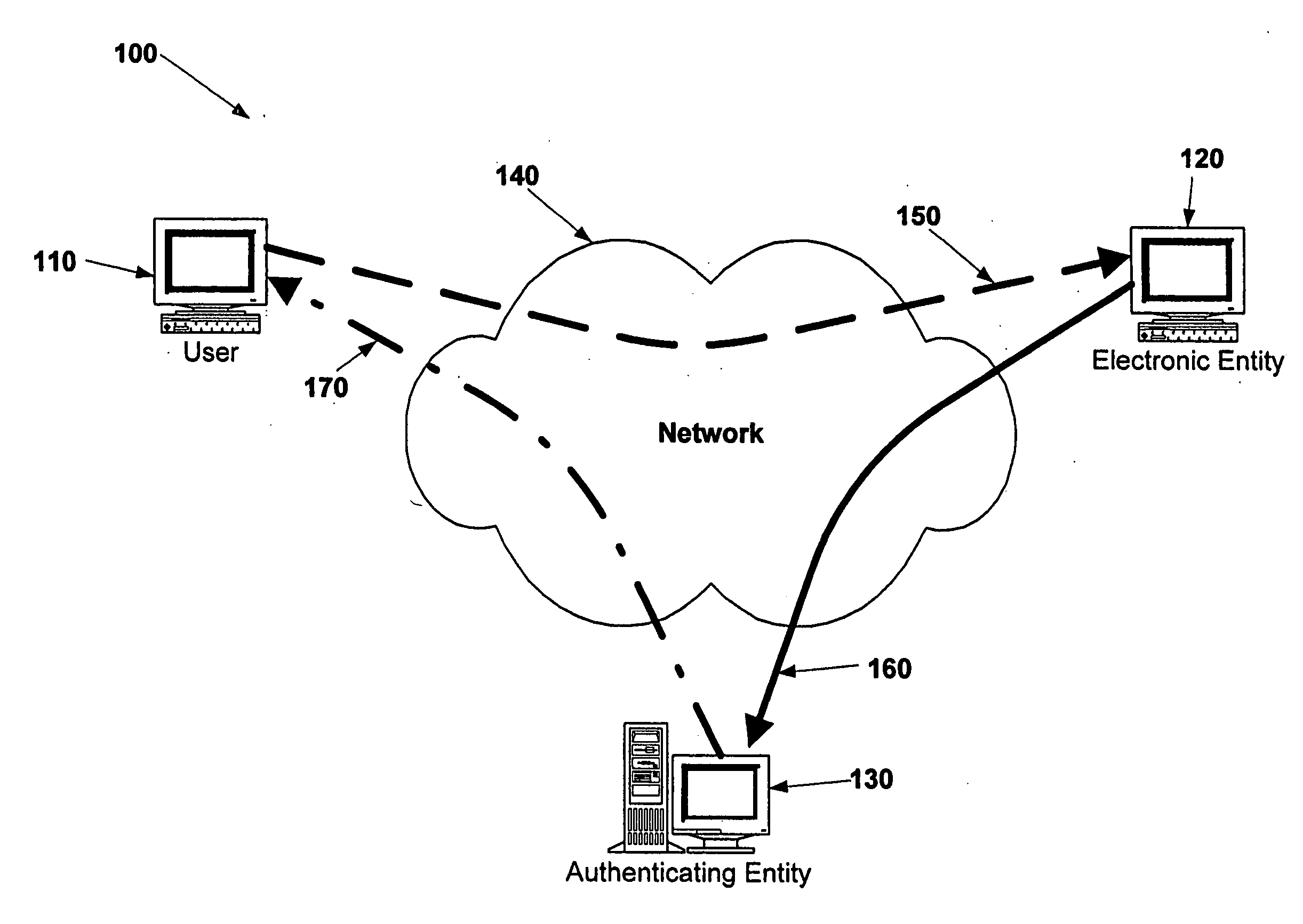
Electronic verification systems
ActiveUS20060200855A1Verify authenticityPrevent account hijacking and frustrate fraudulent electronic transactionsDigital data processing detailsUser identity/authority verificationObject basedThe Internet
A verification system which can be used over electronic networks, such as the Internet, to help prevent phishing, electronic identity theft, and similar illicit activities, by verifying the authenticity of electronic entities (for example, websites). Users and electronic entities register with an authenticating entity. The authenticating entity shares an encryption method with registered electronic entities and establishes a secret code for each registered electronic entity. The secret code is combined with other information and encrypted before being transmitted over the network to ensure that the secret code cannot be compromised. Also disclosed are systems for virtual token devices, which provided object-based authentication without a physical device. Also disclosed are dynamic media credentials, which display nearly-unique behavior, previously specified and known to a user, to assist in verifying the authenticity of the presenter.
Owner:SYCCURE INC
Authentication method, authentication system, in-vehicle device, and authentication apparatus
InactiveUS20100241857A1Prevent unauthorized accessSimple wayKey distribution for secure communicationAnti-theft devicesIn vehicleTerminal equipment
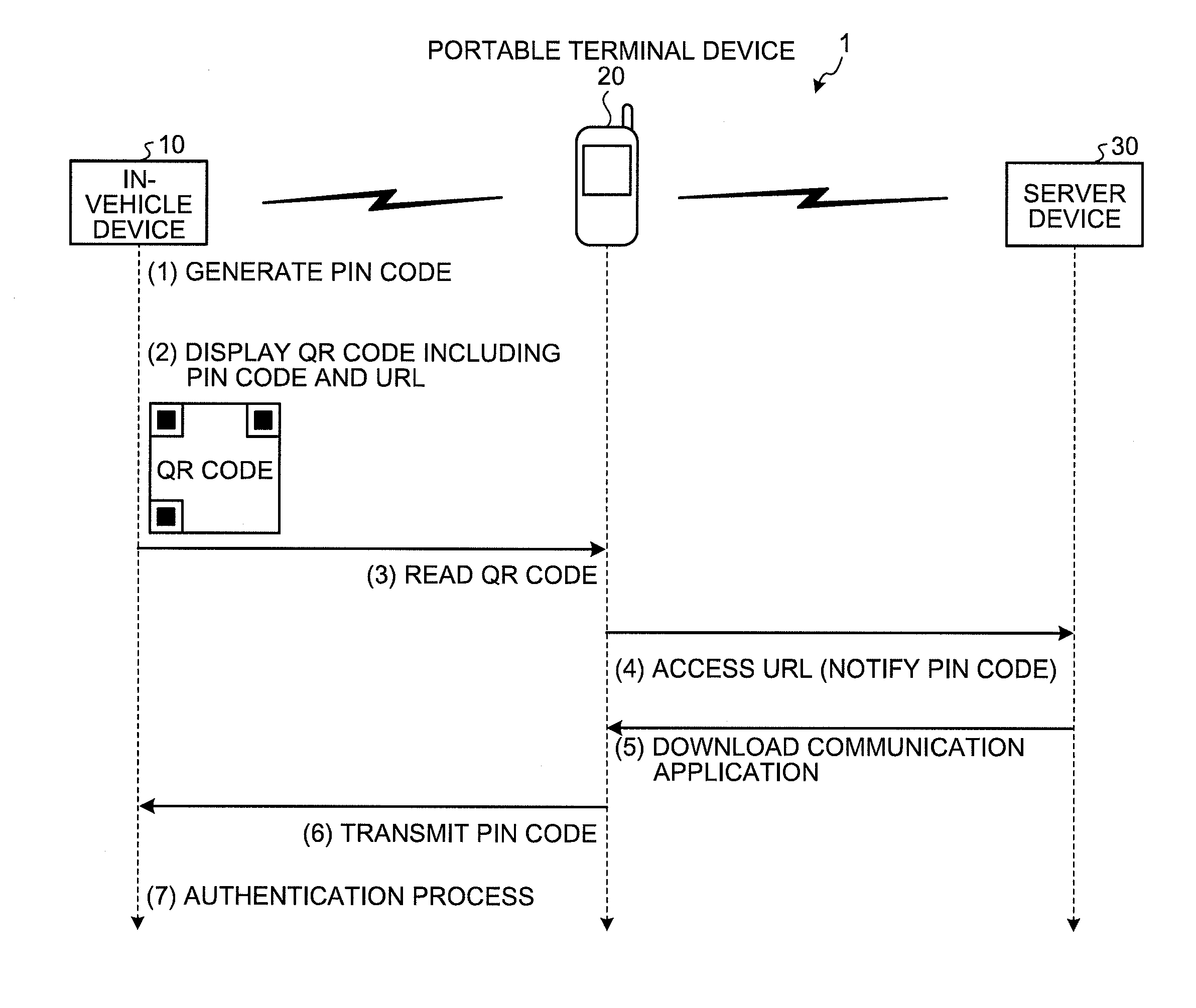
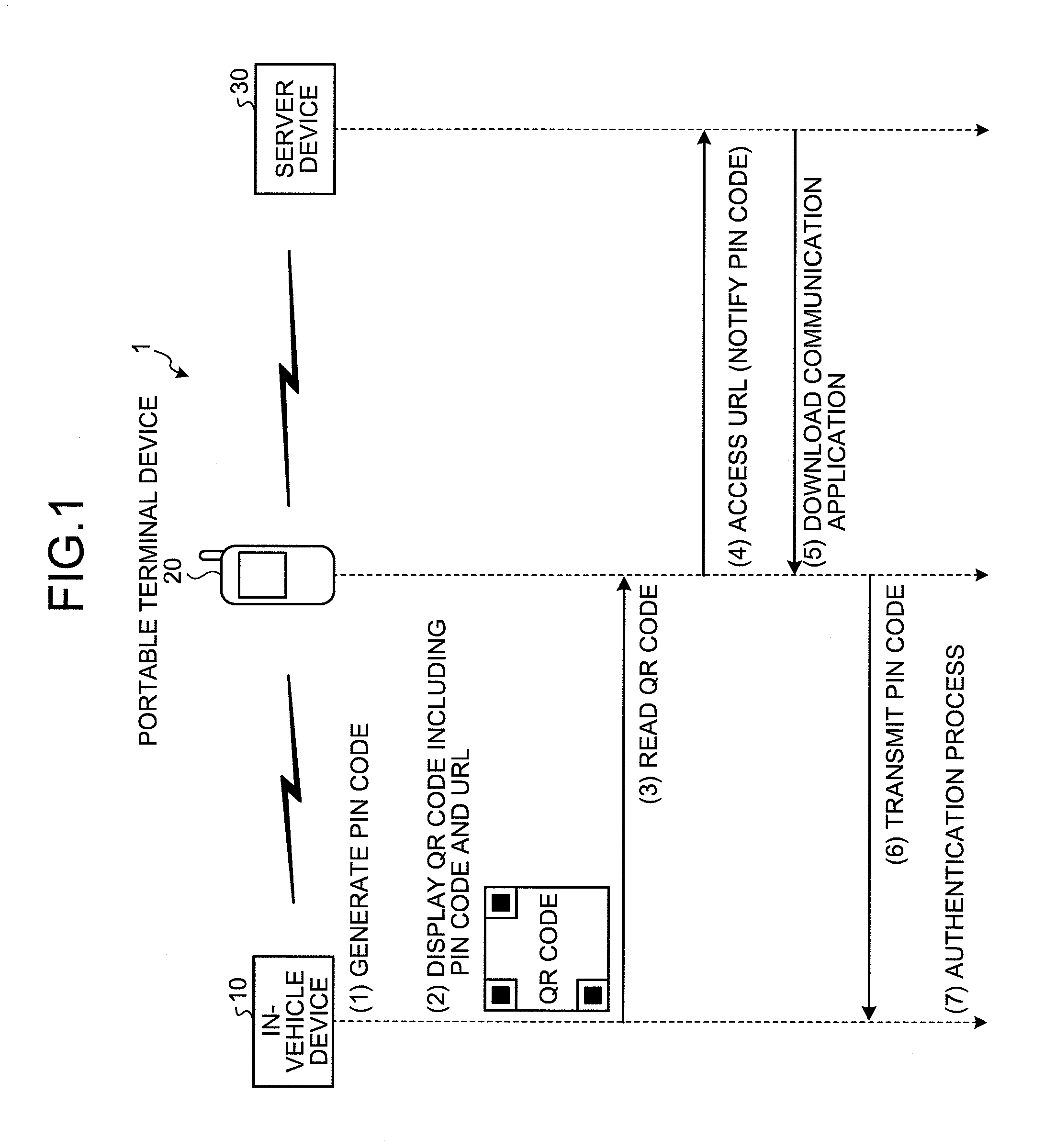
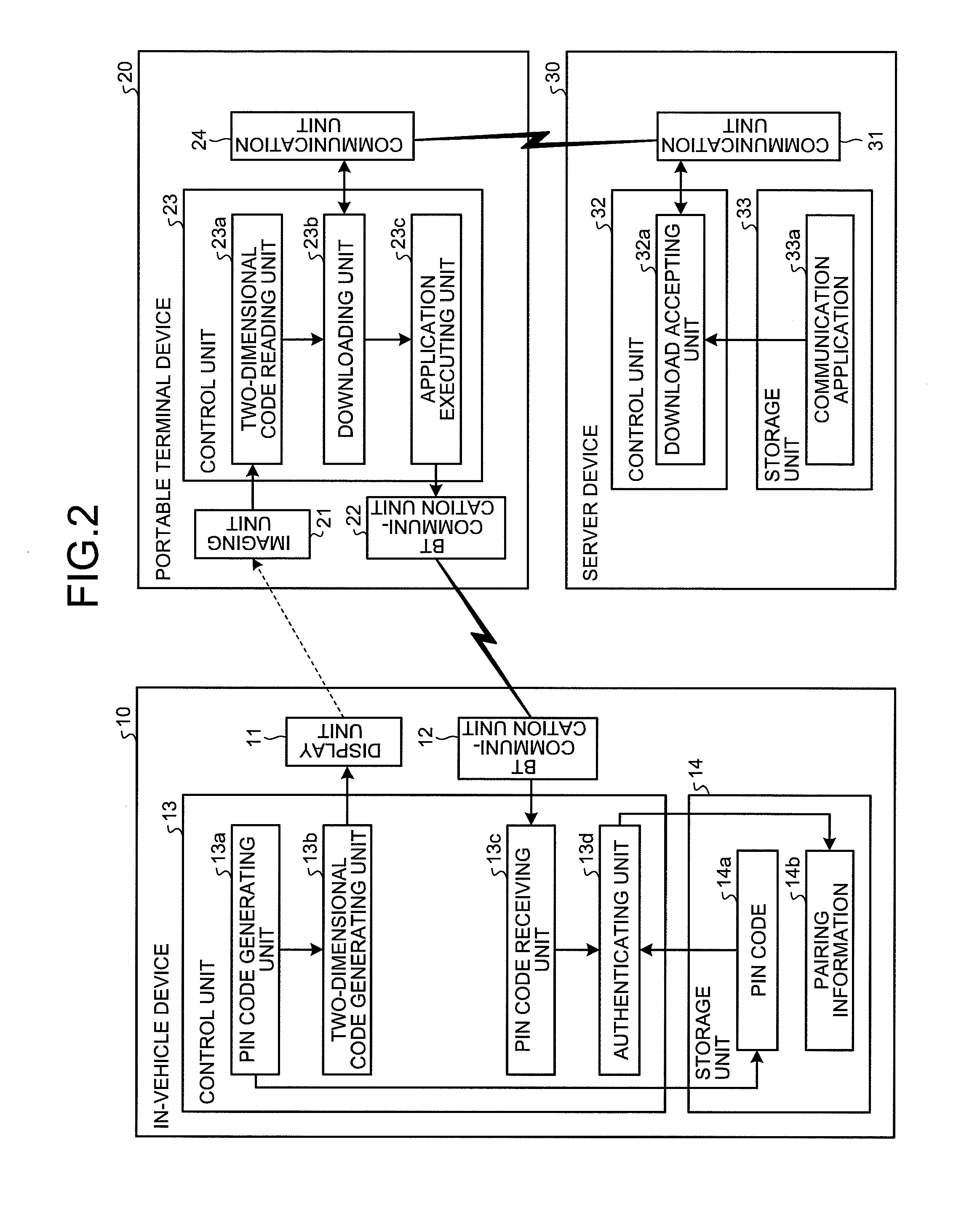
An authentication system is configured such that: an in-vehicle device generates an authentication key, and displays on a display unit, a two-dimensional code including the generated authentication key and a URL indicating a predetermined WEB page on a network; and a portable terminal device acquires the authentication key and the URL from the two-dimensional code by reading the two-dimensional code via an imaging unit, downloads a communication program for communicating with the in-vehicle device from the WEB page indicated by the URL, and transmits the authentication key to the in-vehicle device by causing the downloaded communication program to operate.
Owner:FUJITSU GENERAL LTD
Method and apparatus for securing a wireless air interface
InactiveUS20080076392A1Prevent theftUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemAir interface
Some embodiments are implemented in a communication system that includes a first wireless communication system and a second wireless communication system that includes a Femtocell access point (FAP) and a network controller that can communicatively couple the FAP to the first wireless communication system. In some embodiments, the network controller can communicatively couple to the first wireless communication system through a UTRAN Iu interface. Some embodiments provide a method of securing a wireless air interface. The method receives a security mode command that includes a set of security keys and a set of security algorithms at the FAP from the network controller. The method determines the integrity of a set of messages that are exchanged between the FAP and a user equipment that is communicatively coupled to the FAP through an air interface.
Owner:KINETO WIRELESS
Method and apparatus for securing communication between an access point and a network controller
ActiveUS20080076393A1Prevent theftUnauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure communicationCommunications system
Some embodiments are implemented in a communication system that includes a first wireless communication system and a second wireless communication system that includes a Femtocell access point (FAP) and a network controller that can communicatively couple the FAP to the first wireless communication system. In some embodiments, the network controller can communicatively couple to the first wireless communication system through a UTRAN Iu interface. In some embodiments, the FAP can communicatively couple to a user equipment using a short-range licensed wireless frequency. Some embodiments provide method of securing communication between the FAP and the network controller. The method establishes a secure tunnel between the FAP and the network controller. The method communicatively couples the FAP and several user equipments (UEs) to the network controller by using the secure tunnel. The UEs are communicatively coupled to the FAP through an air interface.
Owner:RIBBON COMM OPERATING CO INC
Method and system for preventing and detecting identity theft
ActiveUS20070244807A1Preventing and detecting identity theftStop in trackFinanceCredit cardData provider
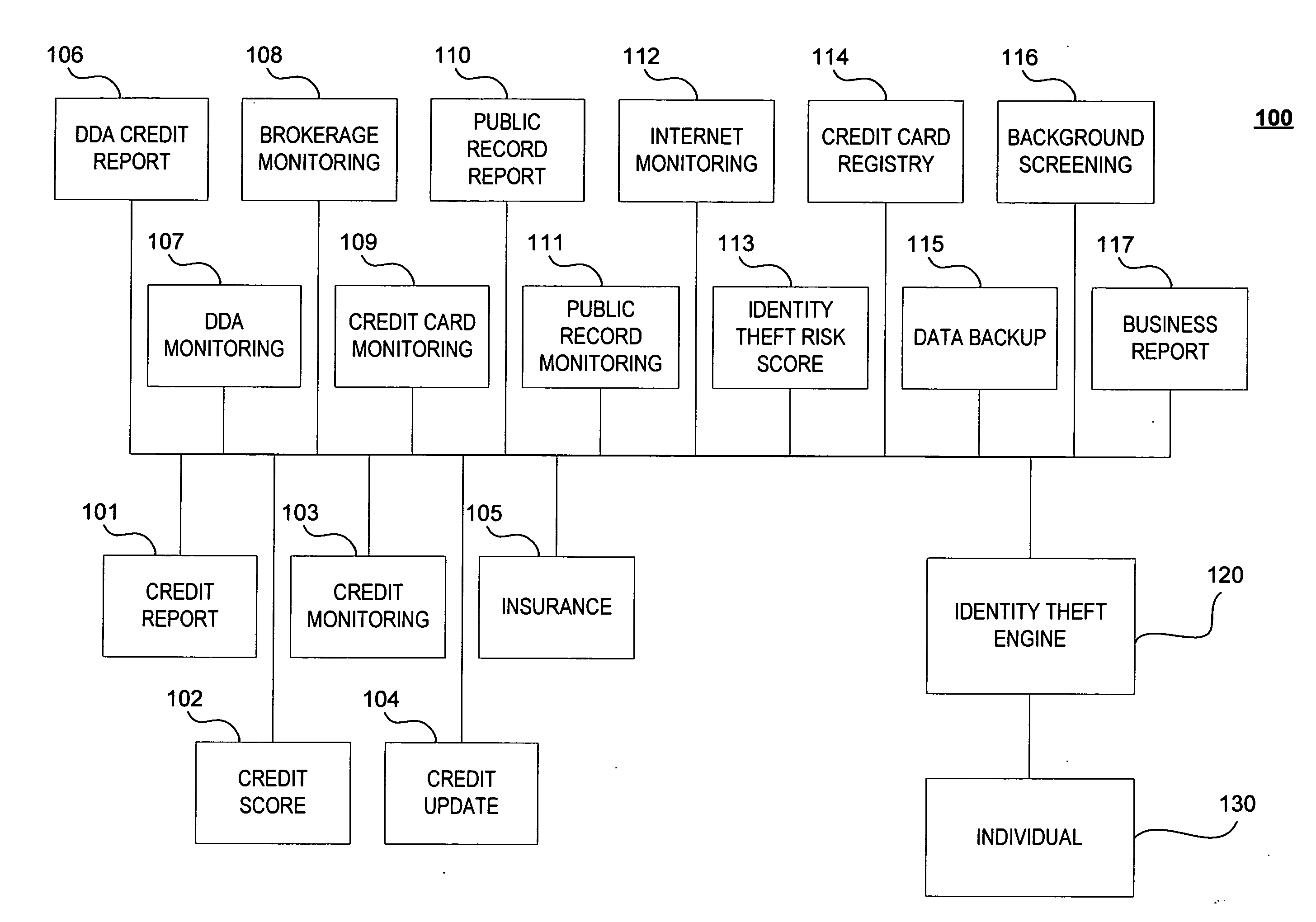
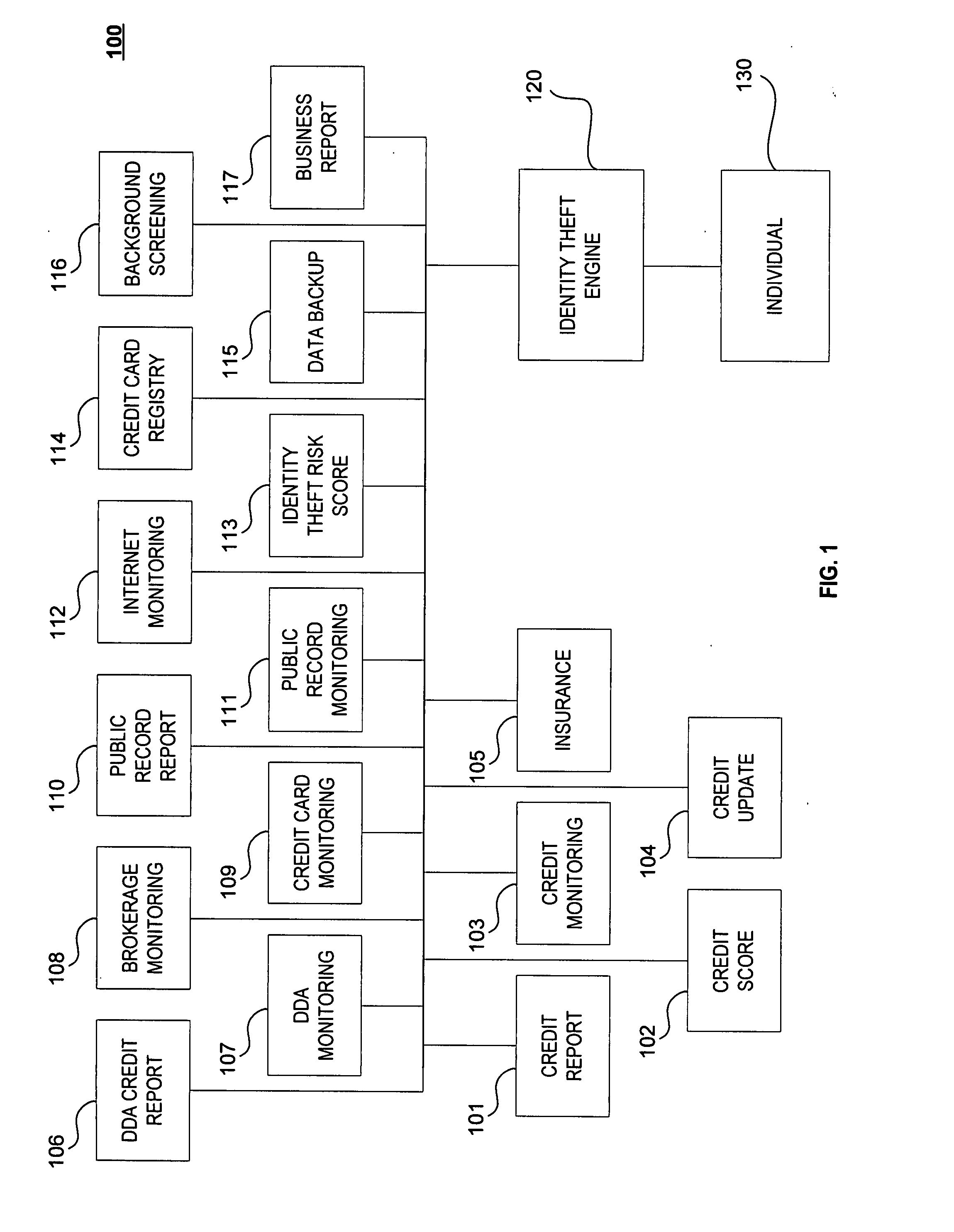
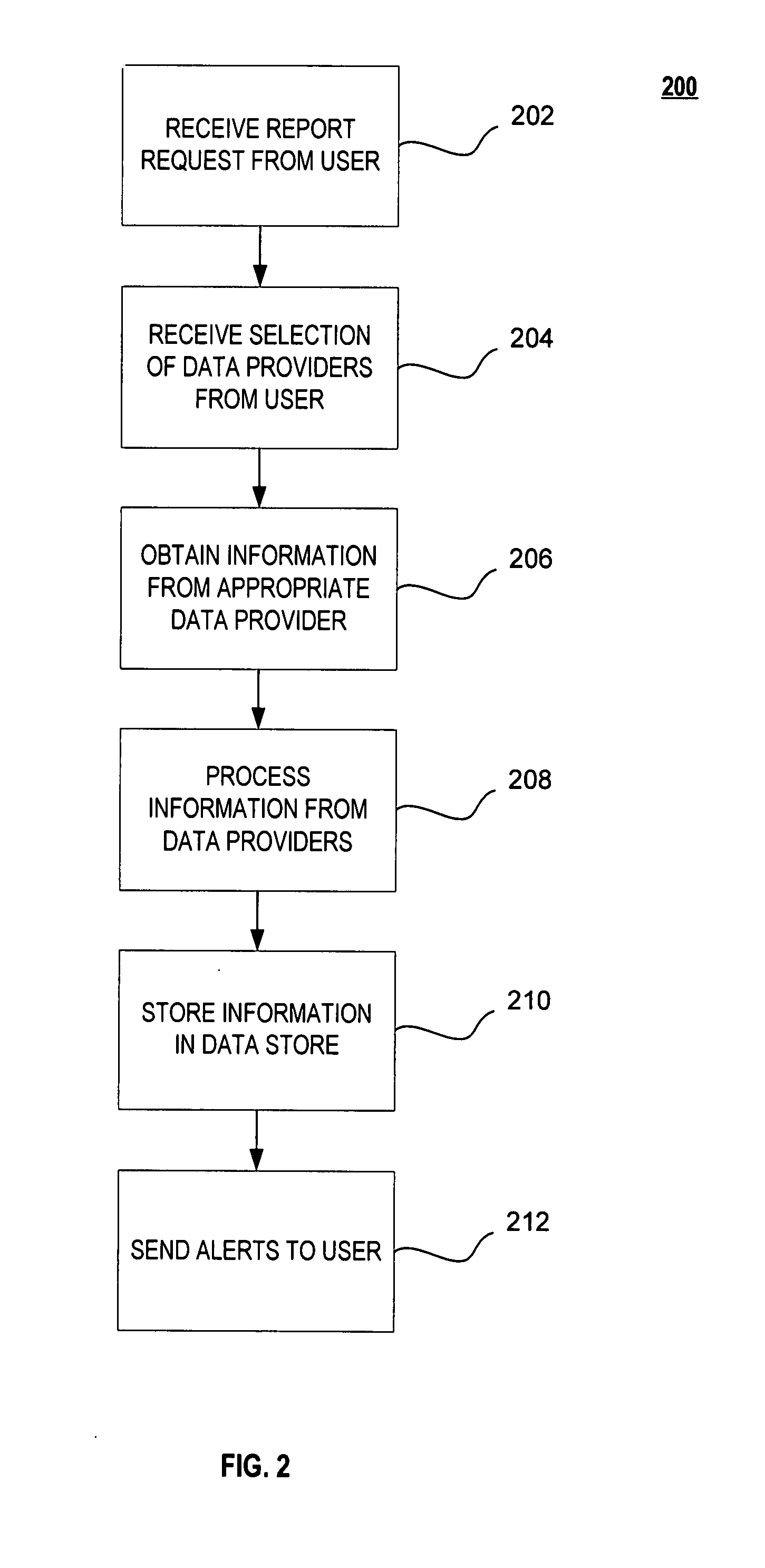
A system, method and computer program product for receiving information relating to a financial account of an individual from at least one first data provider; receiving information relating to at least one of an identity theft expense reimbursement insurance policy of the individual, a public information relating to the individual, an identity theft risk score of the individual, a credit card registry of the individual, a backup data relating to the individual, a background information of the individual, and a business report relating to the individual, from at least one second data provider; and preparing a report relating to the individual's identity theft based on the information.
Owner:AURA SUB LLC +1
Golf data recorder with integrated missing club reminder and theft prevention system
InactiveUS20090233735A1Inexpensive and simple electronicsWithout slowing down gameBall sportsSatellite radio beaconingSemi automaticEngineering
Apparatuses, methods and systems relating to at least one or more of golf club reminding and golf data collecting and recording. In one embodiment an apparatus on a golf club includes an integrated reminder and a stroke cancellation system and is semi-automatic in that the recording of the stroke is directly in response to changing the state (e.g. activating) of a switch which indicates that the golfer has pressed a button on the golf club. The pressing of the button indicates that the golfer will or has taken a stroke with the golf club and that the stroke is to be recorded, with the location of the stroke and an identifier of the club (e.g. 9 iron). The system may also be equipped with a missing club reminder and theft prevention function that notifies the golfer is a golf club has been left behind or if a club or golf bag has been removed without authorization.
Owner:LEI CO LTD
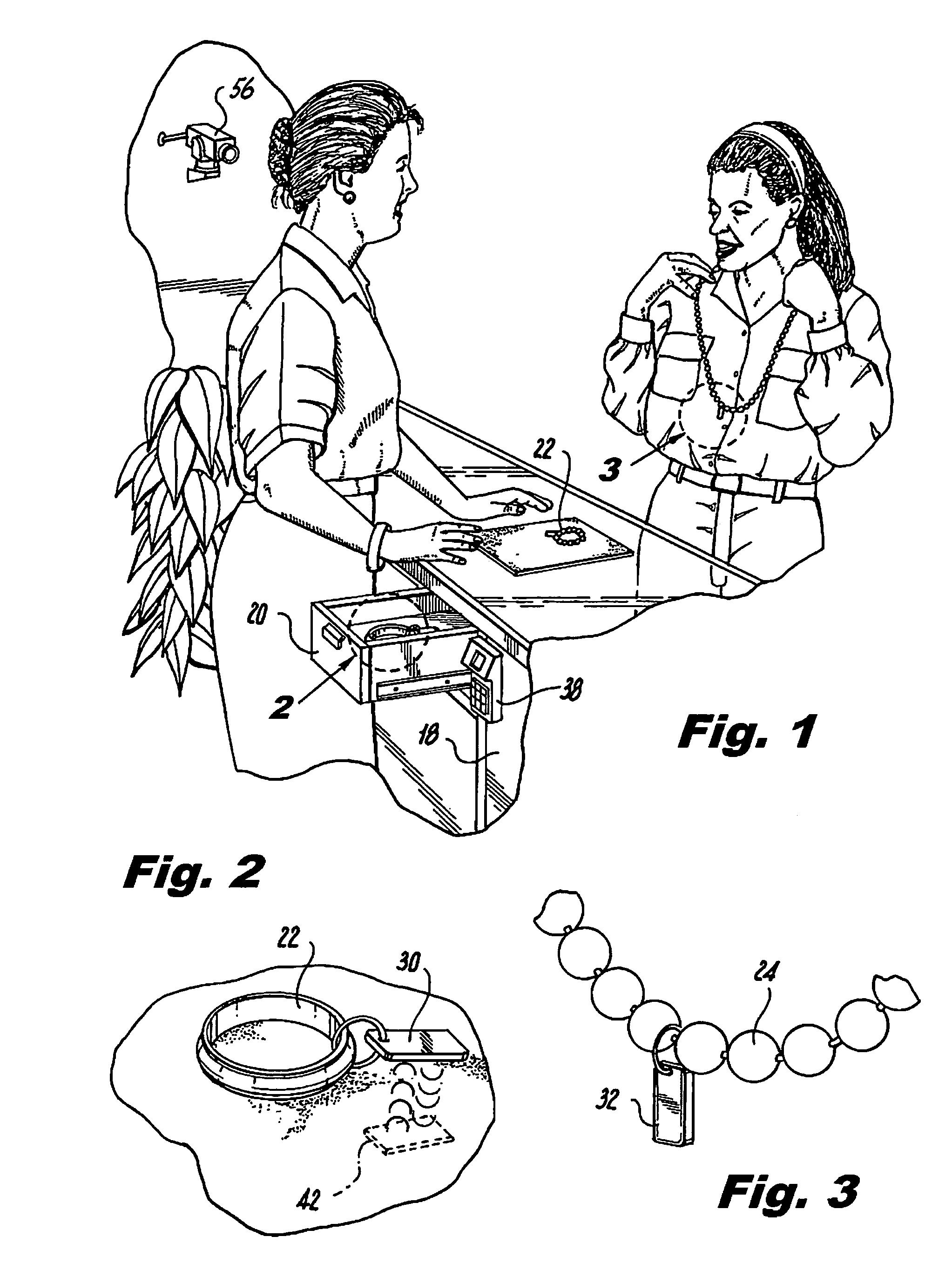
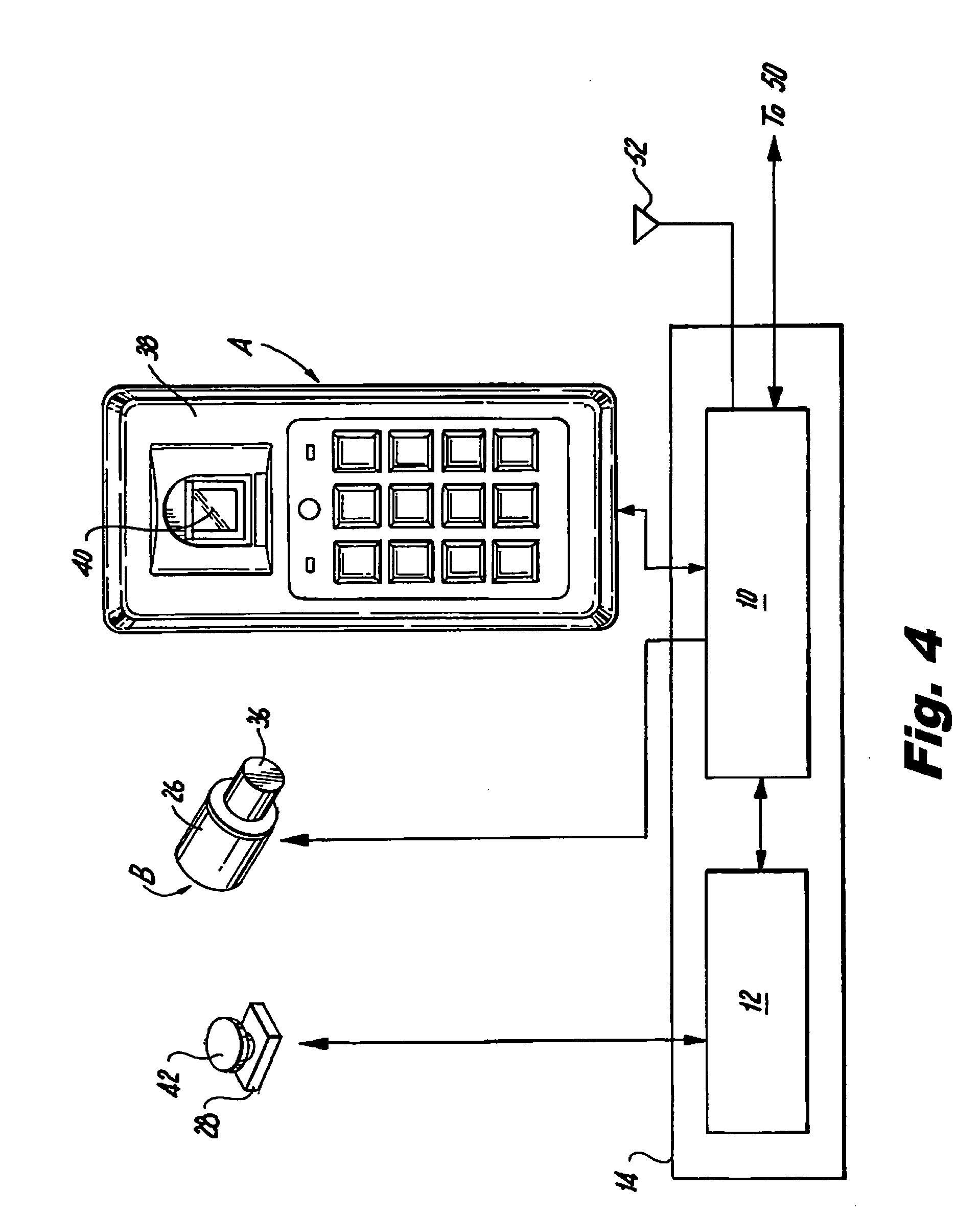
System for preventing theft of articles from an enclosure
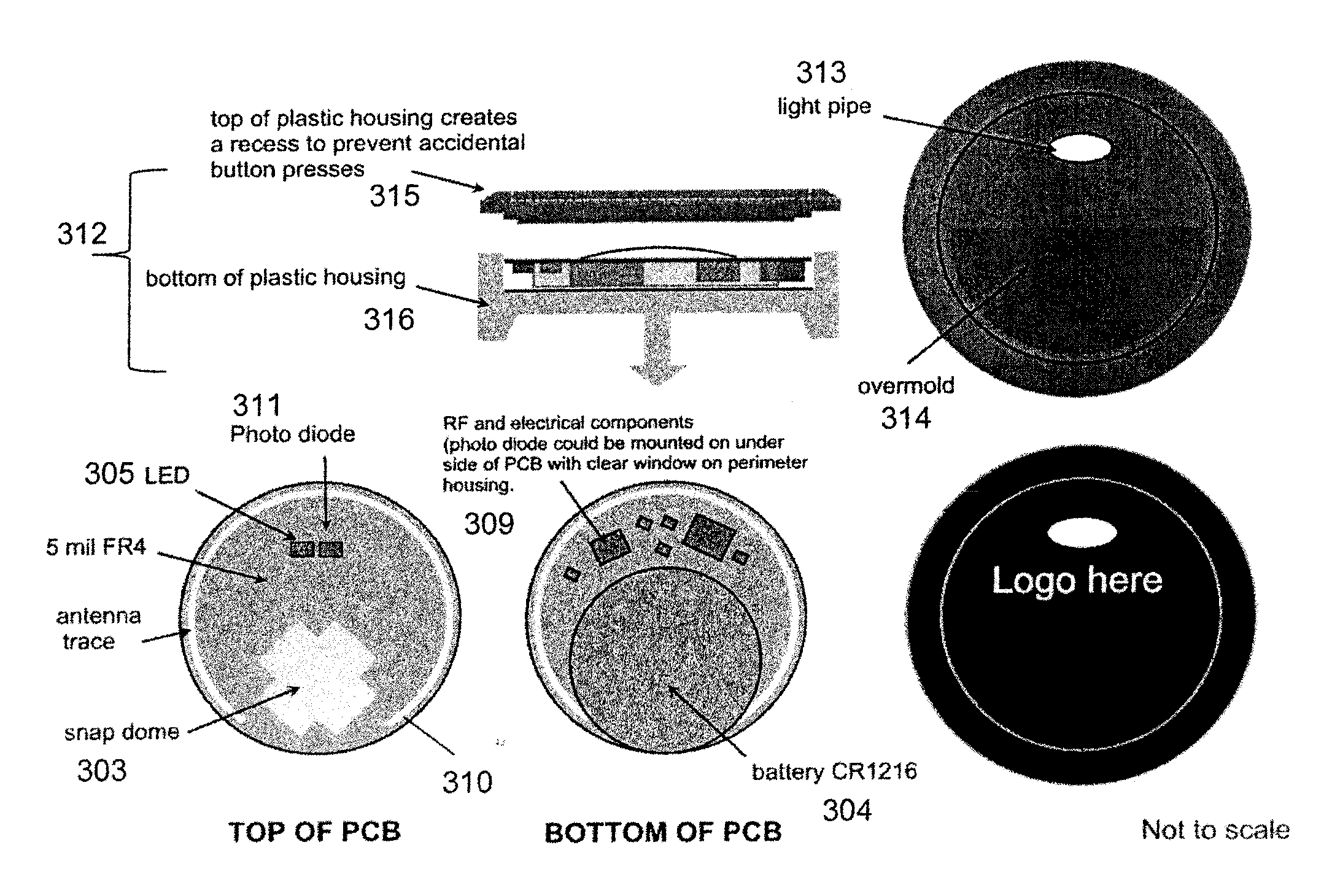
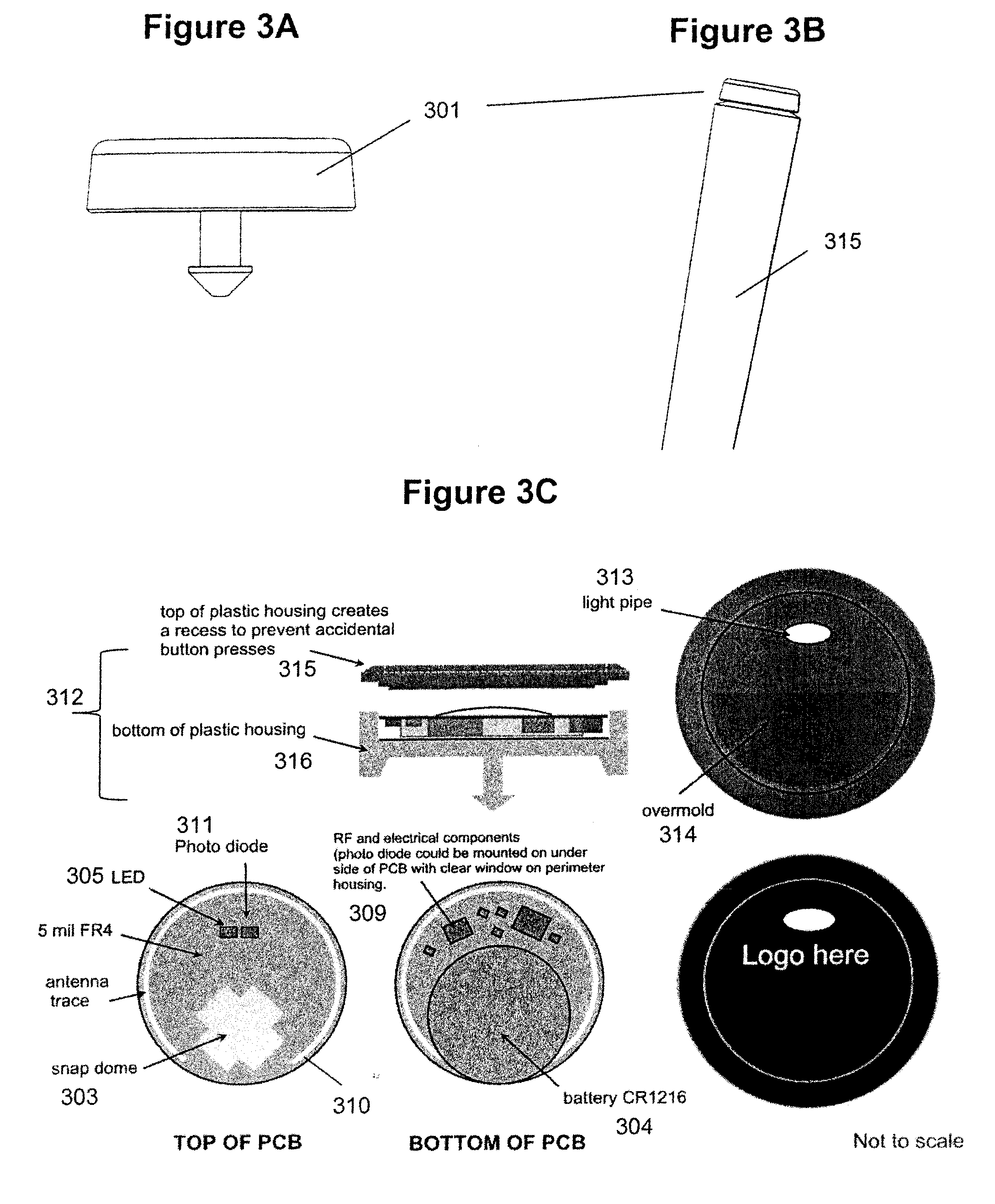
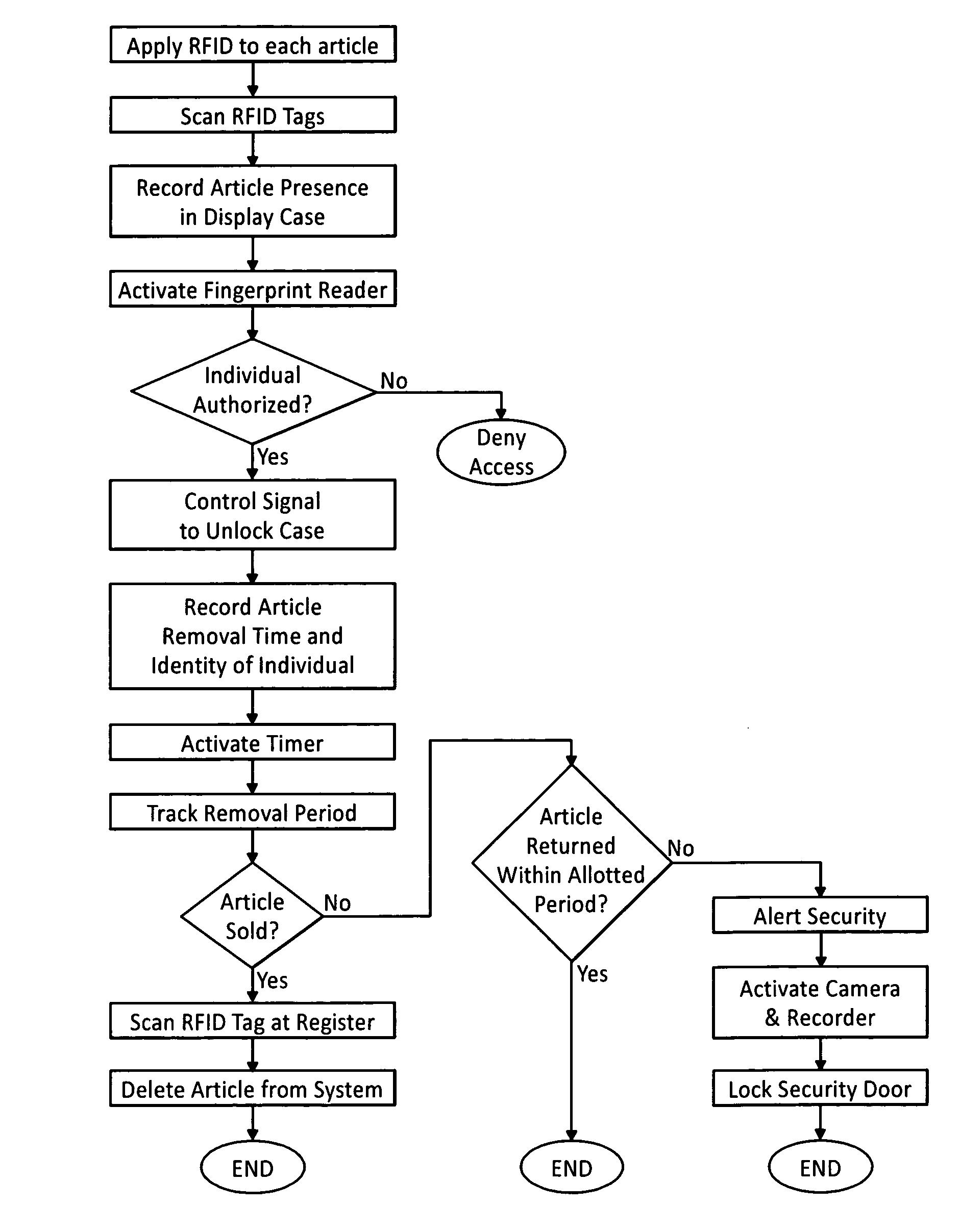
InactiveUS20090224875A1Prevent theftElectric signal transmission systemsImage analysisEngineeringClosed-circuit television camera
The security system prevents theft of articles from an enclosure having a lockable access opening. Using RFID technology, a transponder periodically scans the enclosed display area to interrogate RFID tags associated with each of the articles within the enclosure. Access to the enclosure is controlled by an electronically activated retrofit lock associated with the access opening. Biometric technology is used to identify an individual attempting to access the enclosure and to determine whether the identified individual is authorized to access the enclosure. If the individual is authorized, the identity of the authorized individual, the identity of an article removed from the enclosure, and the time that the article was removed from the enclosure are recorded. A POS / inventory control system notes the sale of the removed article. A security alert signal is generated if the removed article is not sold or returned to the enclosure within a given time period after the article was removed from the enclosure. Images of the area proximate the enclosure may be captured by a closed circuit video camera and stored.
Owner:VERSATILE SYST
Inventory control system
InactiveUS20050040123A1Increase inventoryPrevent theftRacksService system furnitureRelevant informationControl system
The present invention relates to an inventory control system where the most updated number of products displayed on a display space is electronically determined and communicated to a computer for remote users, and electronically displayed along with other relevant information about the products.
Owner:ALI ALA
Method and apparatus for preventing theft of service in a communication system
ActiveUS7995994B2Prevent theftUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemNetwork control
A method of preventing theft of service in a communication system that includes a first wireless communication system and a second wireless communication system that includes a Femtocell access point (FAP) and a network controller that can communicatively couple the FAP to the first wireless communication system. The method creates an authorized session that includes a session identify for a first user equipment (UE). The UE is recognized by the first communication as an authorized UE to use the FAP. The method rejects a request by the FAP to register a second UE when the identity of the second UE does not match any identity in the set of first UE identities. The rejected request includes the session identity of the authorized session and the identity of the second UE. The second UE is not recognized by the first communication system as an authorized UE to use the FAP.
Owner:RIBBON COMM OPERATING CO INC
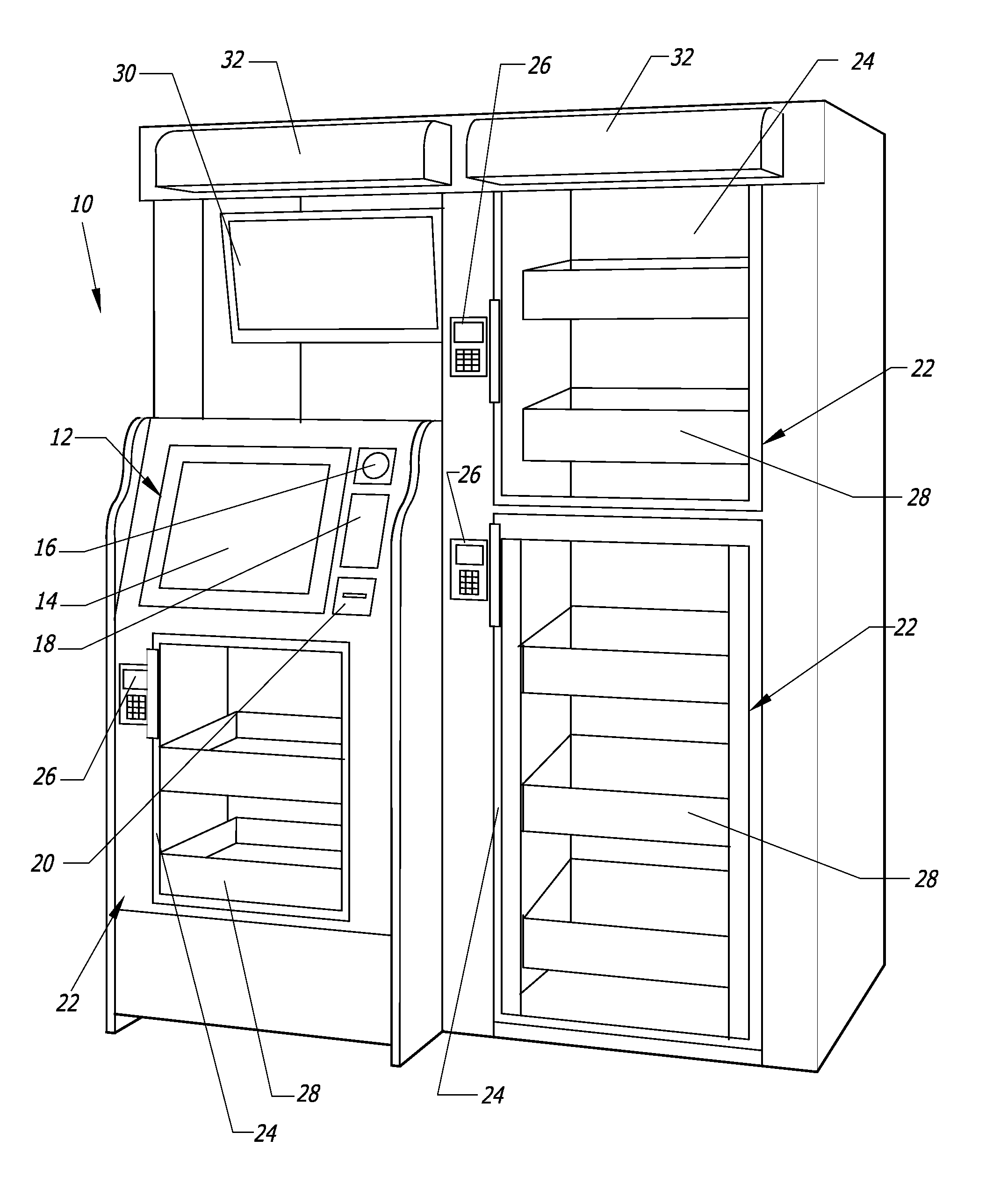
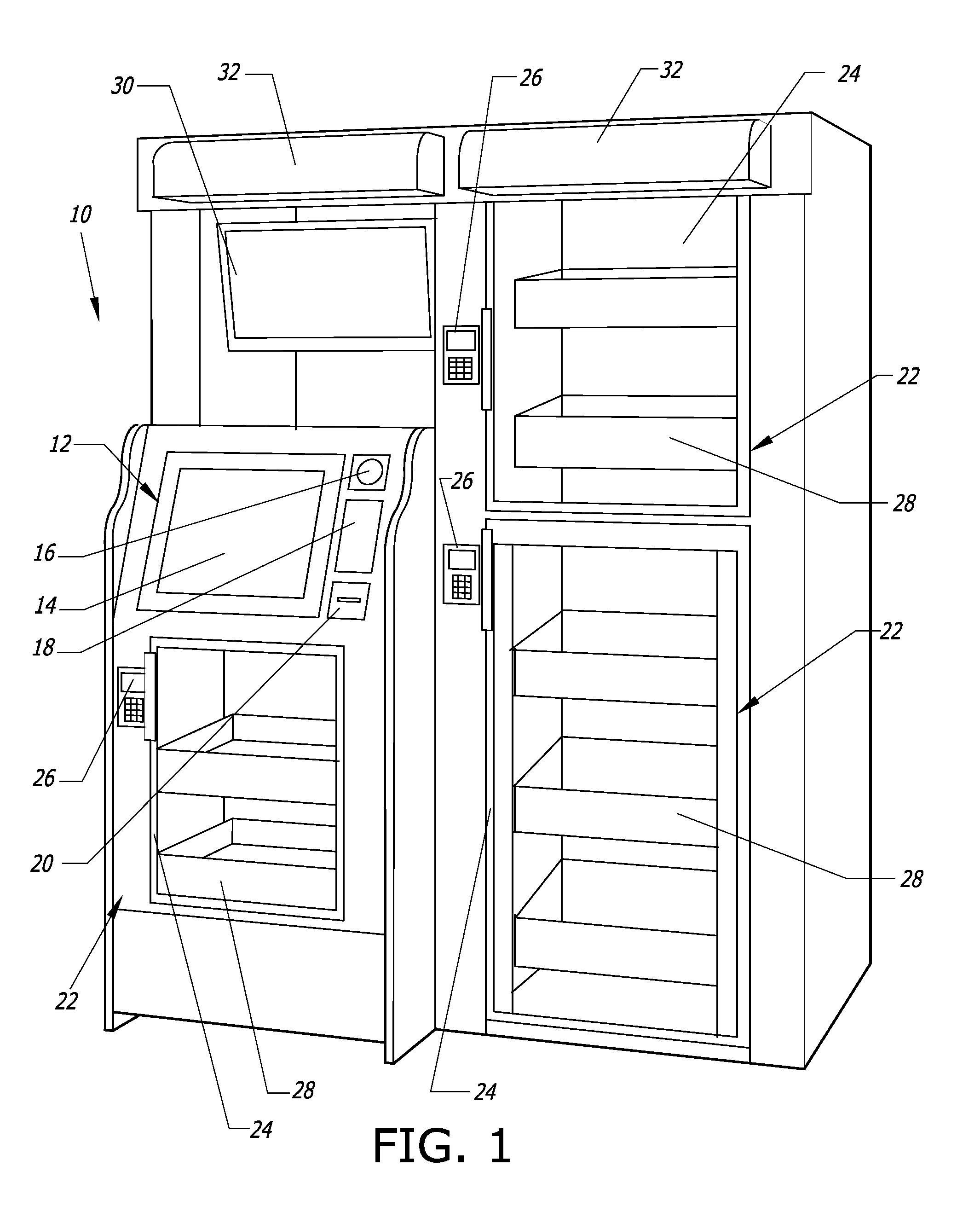
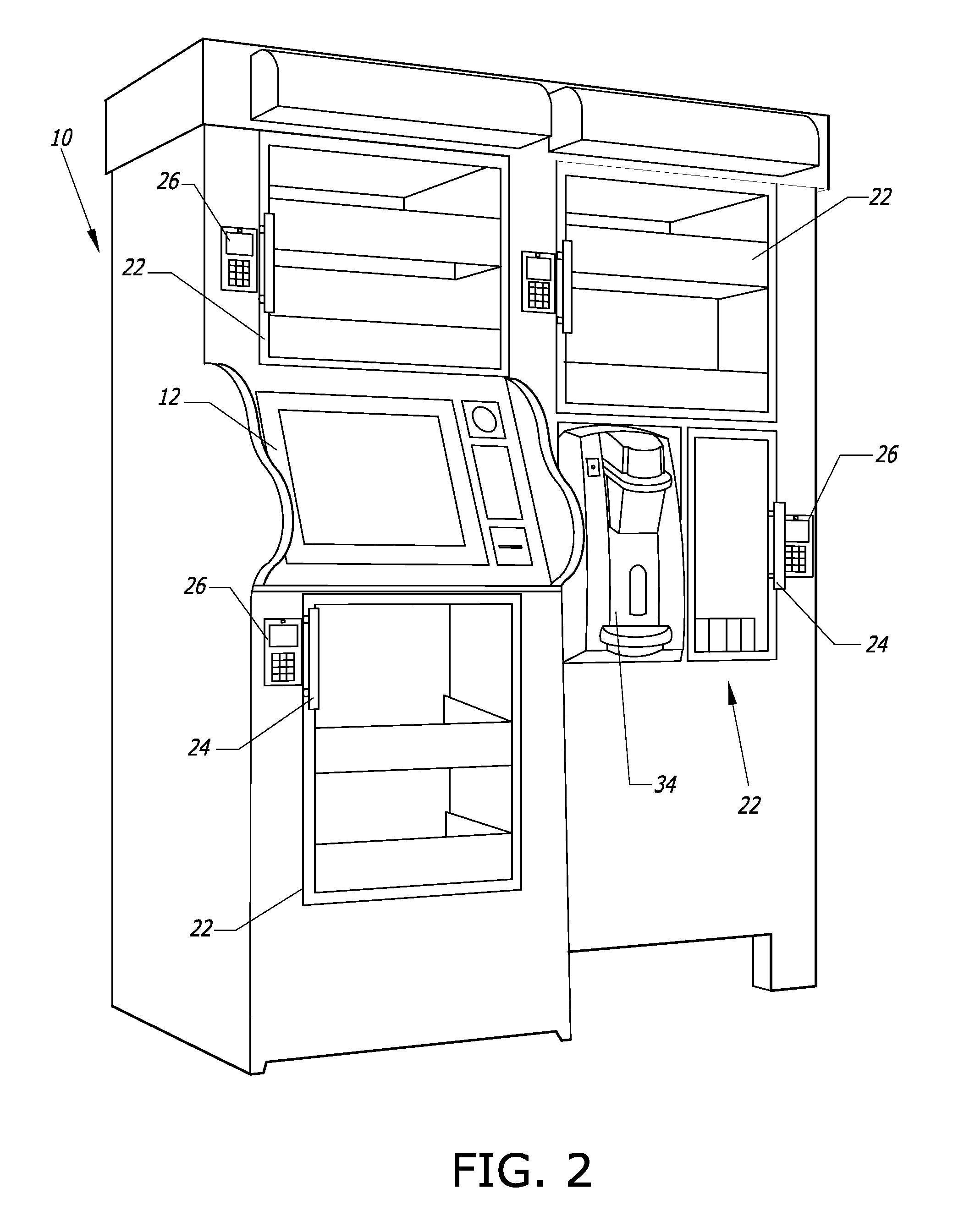
Computer-controlled, unattended, automated checkout store outlet and related method
ActiveUS20140316916A1Provide securityPrevent theftHand manipulated computer devicesCoin-freed apparatus detailsEngineeringSensor system
A computer-controlled, automated checkout store outlet comprises at least one bay. A normally locked door is associated with each bay, and provides access to items within the bay by customers approved by a computer of the automated store outlet. At least one tray is disposed within at least one bay, and adapted to hold items to be stocked by the bay. A sensor system is configured to detect the removal of an item from the bay and identify the removed item, such as when a customer is removing the item for purchase.
Owner:HAY RONNY
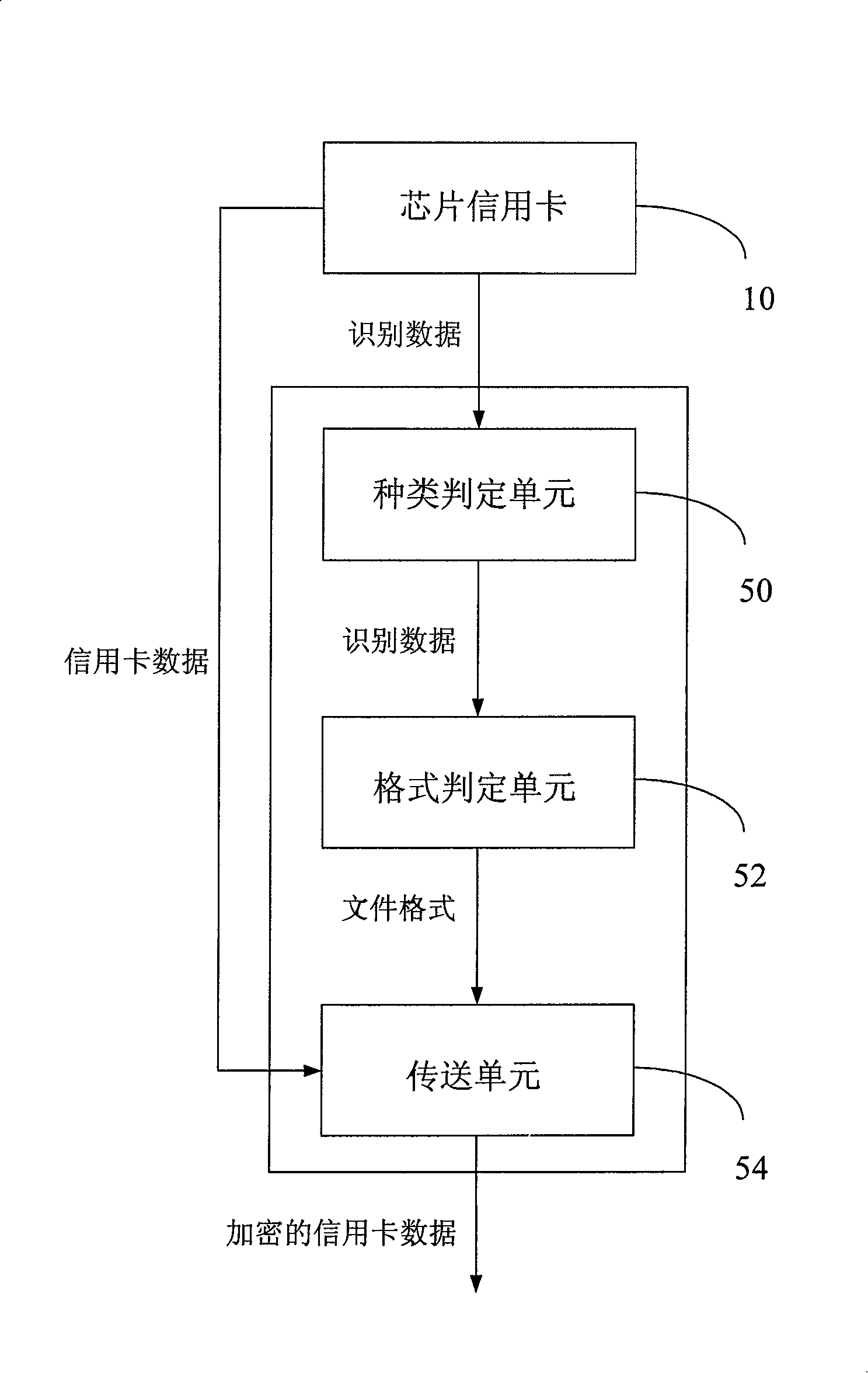
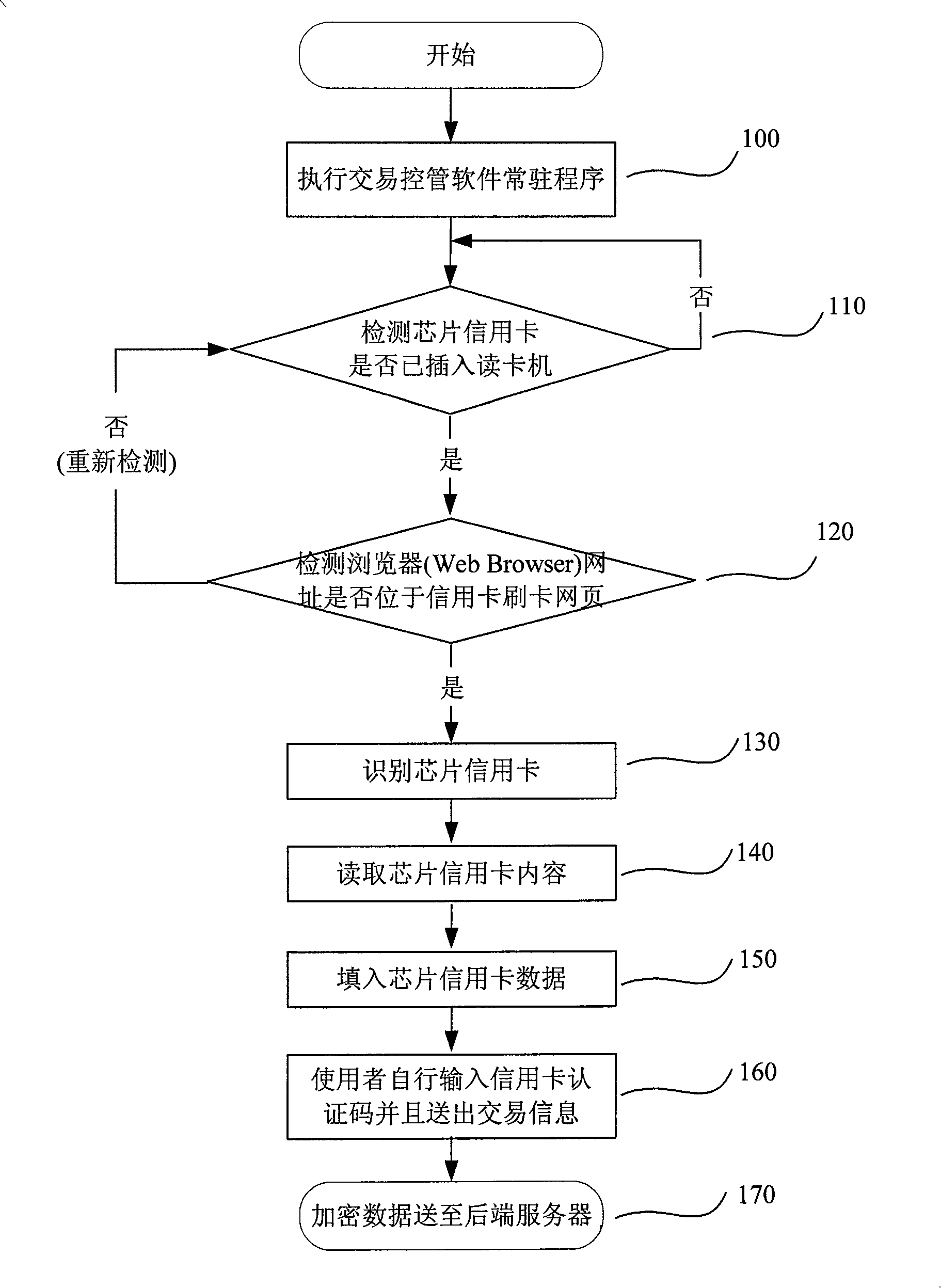
Chip credit card network transaction system and method
The invention provides a network exchanging system and a method of chip credit card, when the chip credit card is inserted into a card reader, the card reader transfers a control signal to a computer, after a controlling and managing module for exchanging executed on the computer detects the control signal transferred from the card reader, the identification data on the chip credit card can be read through the card reader so as to identify the type of the chip credit card, after the database is compared, a card number, an expiry date and a data required for the network exchanging can be acquired from the chip credit card, the controlling and managing module for exchanging can be automatically filled into a credit card data column on the exchanging web page by an encrypting method so as to complete the exchanging operation of the credit card. User does not have to type the card number and other confidential data on the exchanging web page to avoid a Trojan program from recording such as keyboard recording and image recording as well as to prevent the credit card data from leaking.
Owner:INFOTHINK TECH
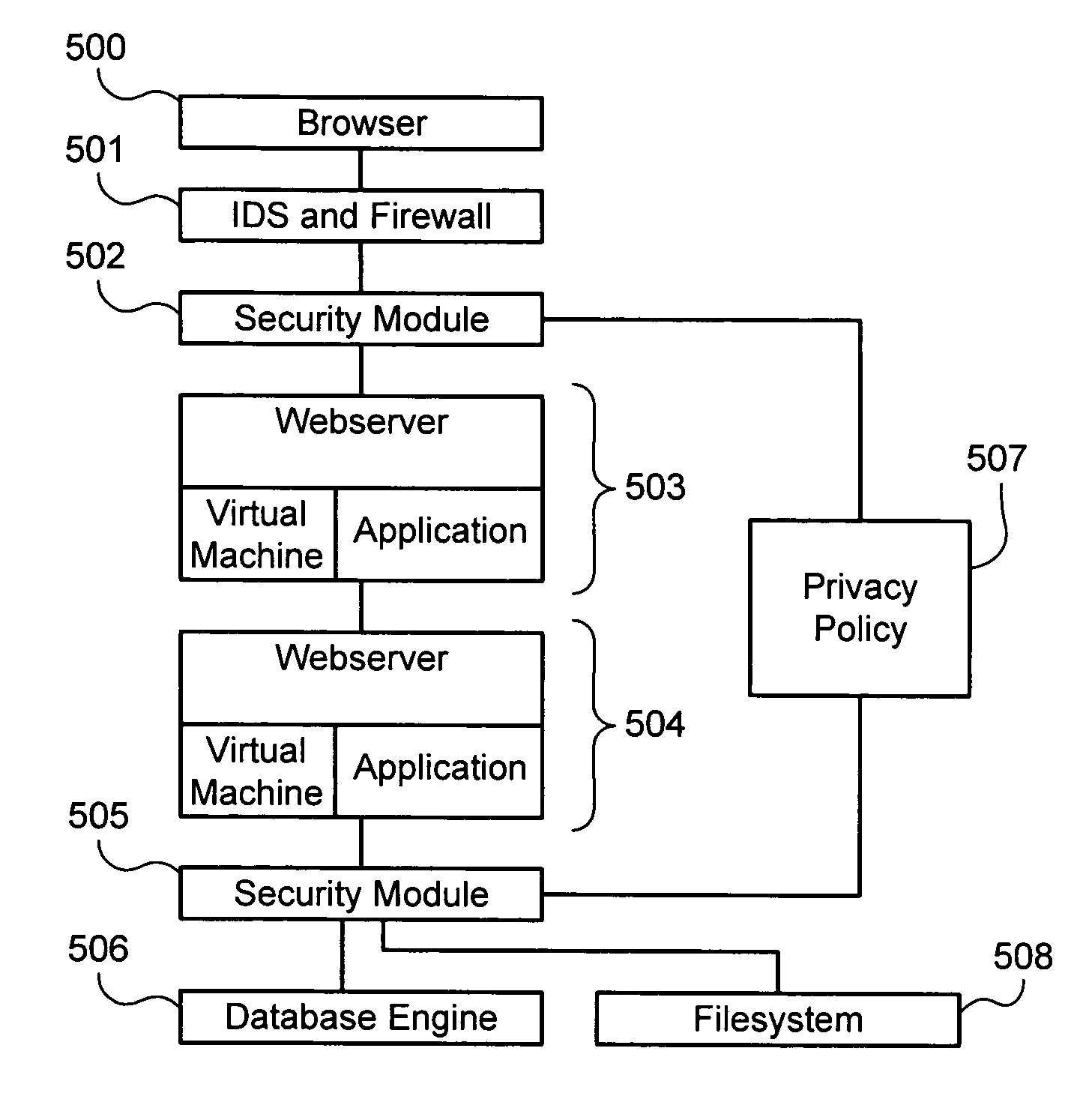
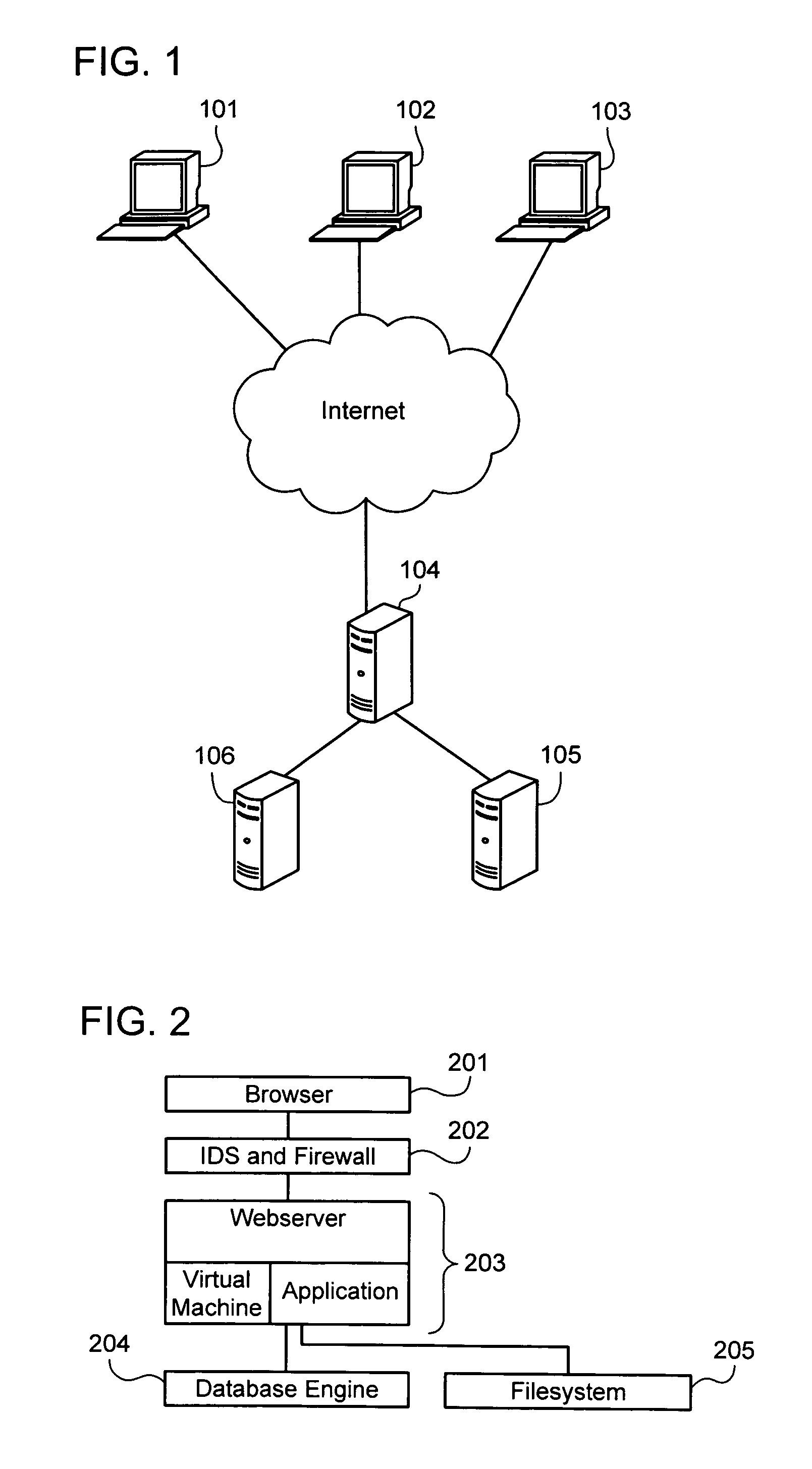
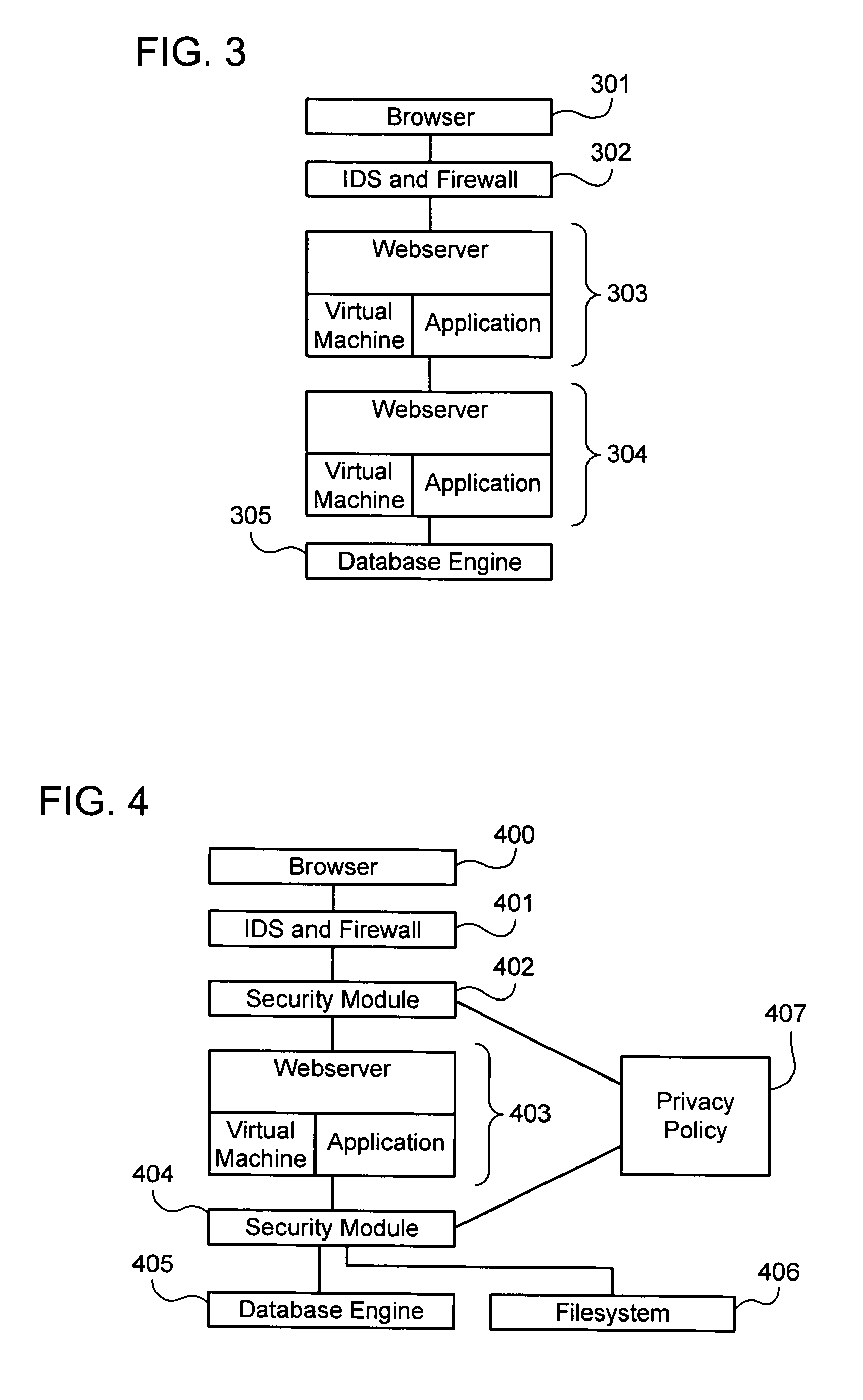
Establishing and enforcing security and privacy policies in web-based applications
ActiveUS20060143688A1Enhances security and privacyIncrease flexibilityMemory loss protectionUnauthorized memory use protectionObject handlingWeb application
Method, system, and computer code for implementing security and privacy policy in a web application having an execution environment in which a representation of each object handled by the execution environment accommodates data and an associated tag. An inbound tagging rule is established for tagging inbound objects according to a respective source of each of the inbound objects. A tag is assigned to an object being operated on by the execution environment based on the inbound tagging rule. A security / privacy rule is established for performing security / privacy actions on outbound objects according to a respective tag of each of the outbound objects. A security / privacy action is performed on the object being operated on by the execution environment based on the security / privacy rule.
Owner:FORTRA LLC
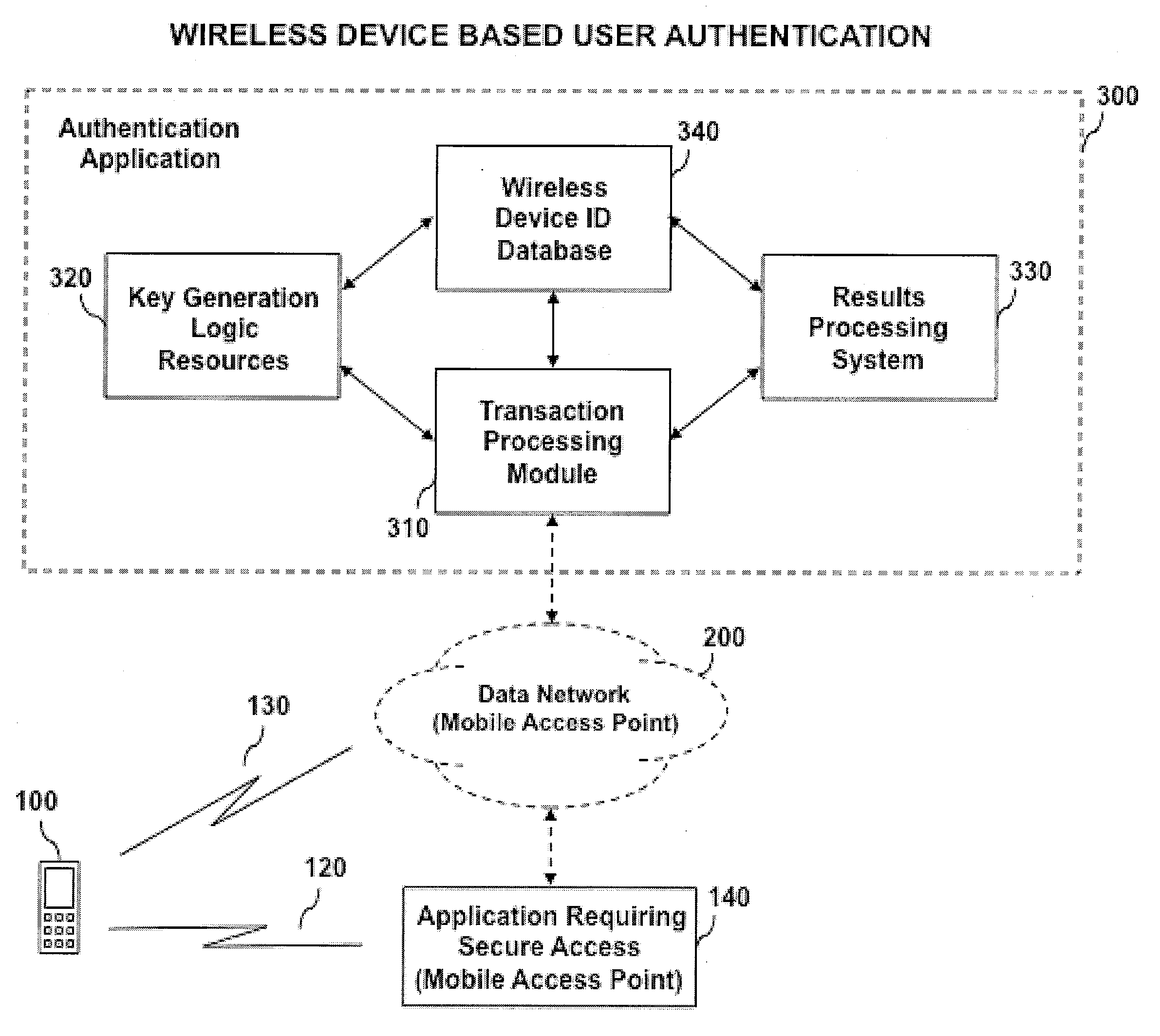
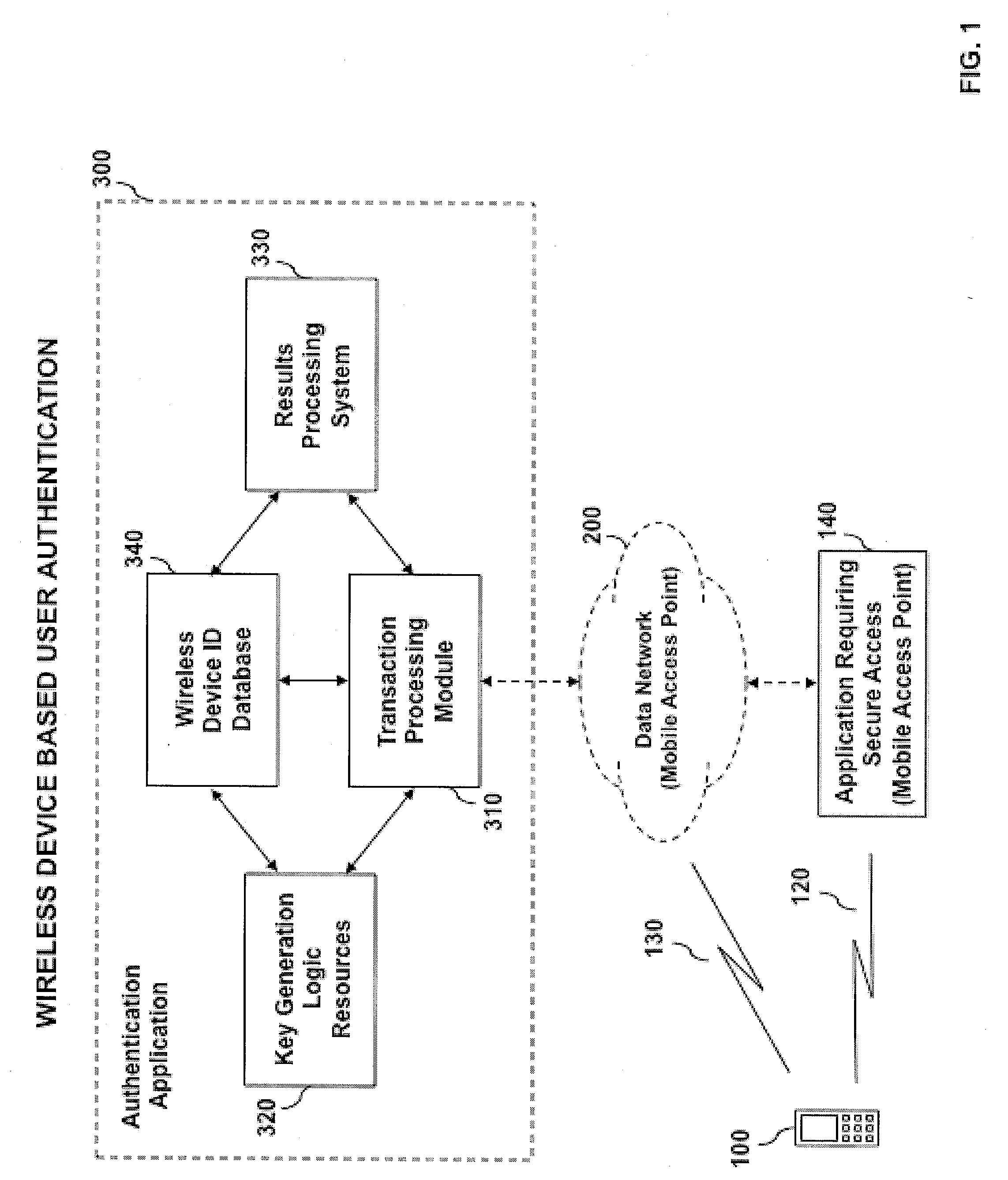
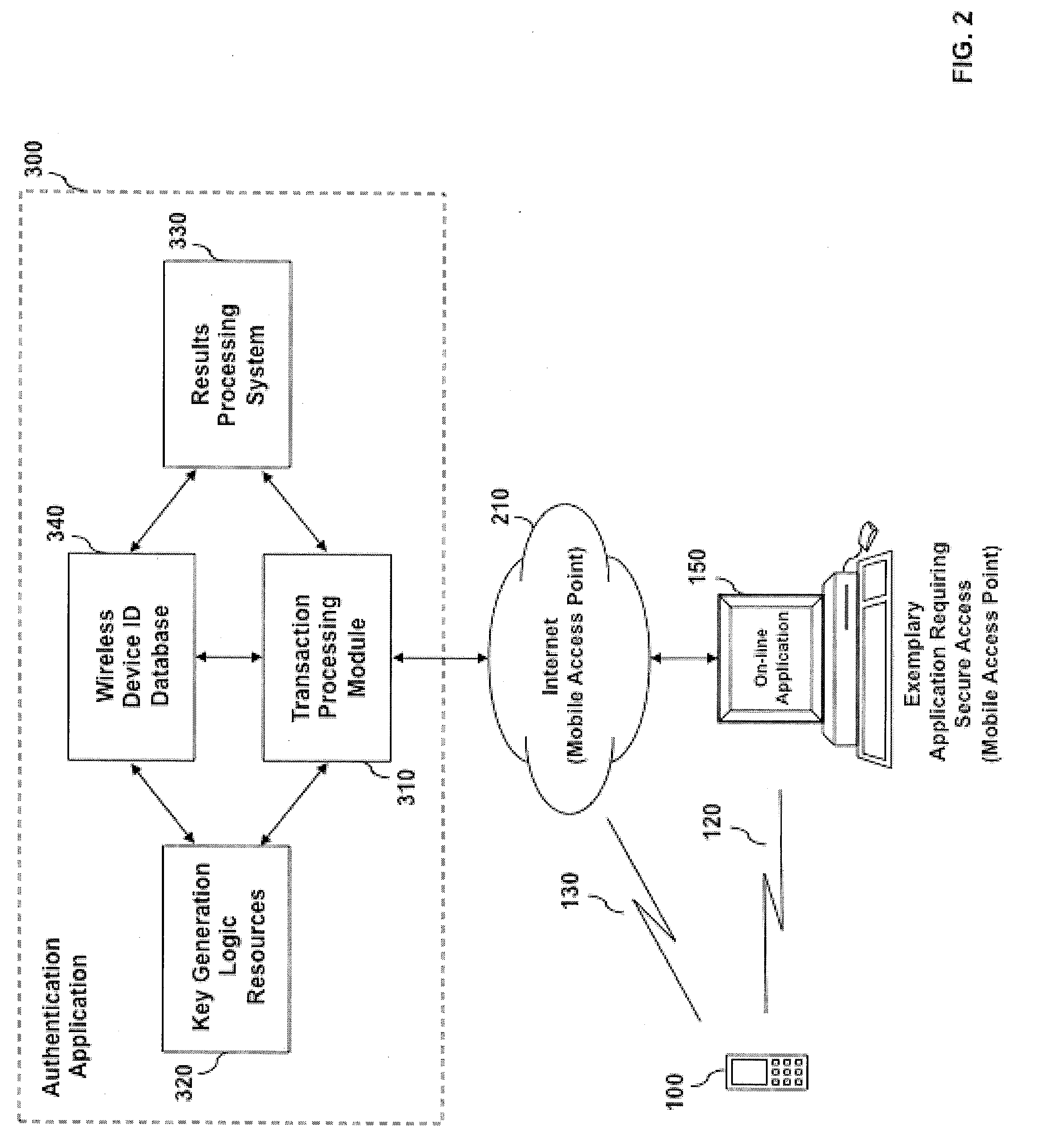
System and method for wireless device based user authentication
ActiveUS20090204815A1Preventing identify theftPrevent theftUser identity/authority verificationNetwork topologiesWi-FiUnique identifier
An automated system and method for authenticating entities or individuals attempting to access a computer application, network, system or device using a wireless device is provided. The system employs one or more short-range wireless interfaces (e.g. BLUETOOTH or Wi-Fi) or long-range wireless interfaces (e.g. cellular or WiMAX) to detect the presence or location of the wireless device and it's proximity to the secure system to be accessed. The wireless device incorporates a unique identifier and secure authentication key information associated with the user of the wireless device. An authentication result is generated and may be used for a variety of applications. The application may process the result and determine the degree of access for which the entity or individual is allowed.
Owner:VISA INT SERVICE ASSOC
Data security
InactiveUS20060277413A1Reduce theftPrevent theftUnauthorized memory use protectionHardware monitoringComputer hardwareData field
Data Security methods, computer programs, and systems for encrypting and decrypting data, process sharing, and redundancy. The invention provides techniques for encryption including the encryption of a structured data file where each smallest unit of the data file (e.g., a field in a database record) is encrypted separately. The invention also provides techniques for decrypting such an encrypted data file. Requested fields of data are decrypted, stored in temporary memory, and displayed to the user or used to complete a task. Once the display is over or the task is completed, the decrypted data in temporary memory is deleted. The invention also provides techniques for real time process sharing and redundancy that utilize system characteristics to determine the apportionment of processes.
Owner:DREWS DENNIS T
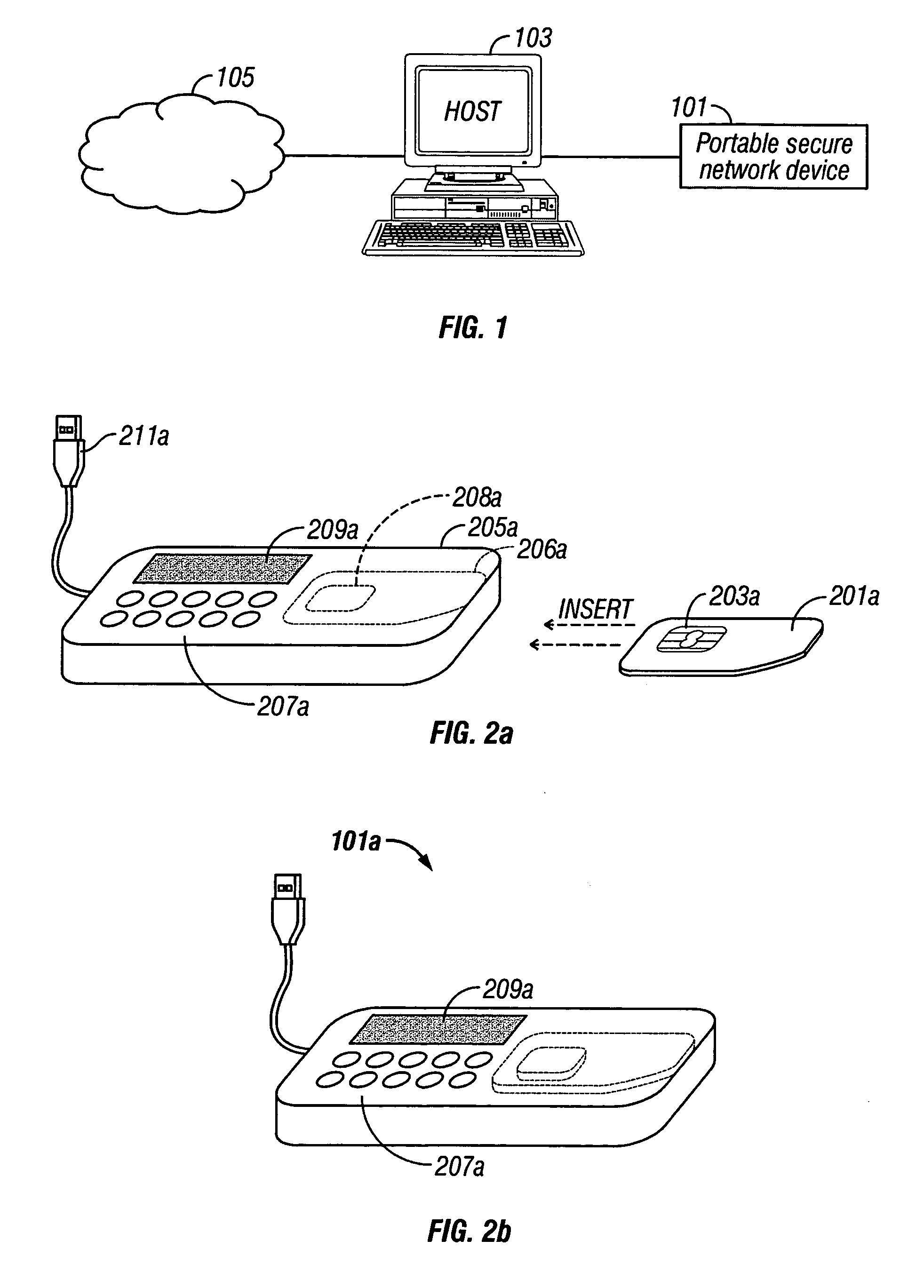
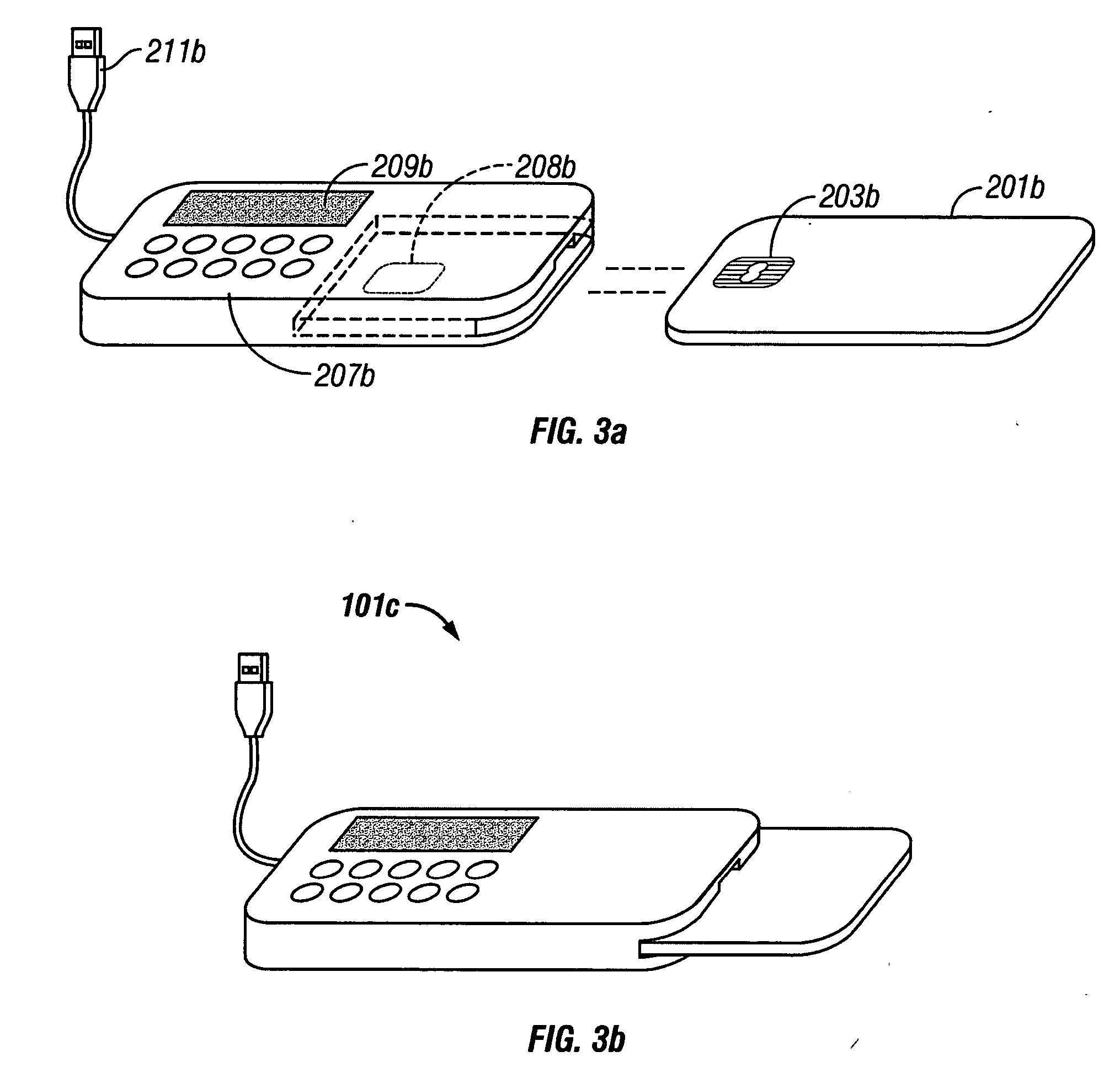
System and method for secure online transactions using portable secure network devices
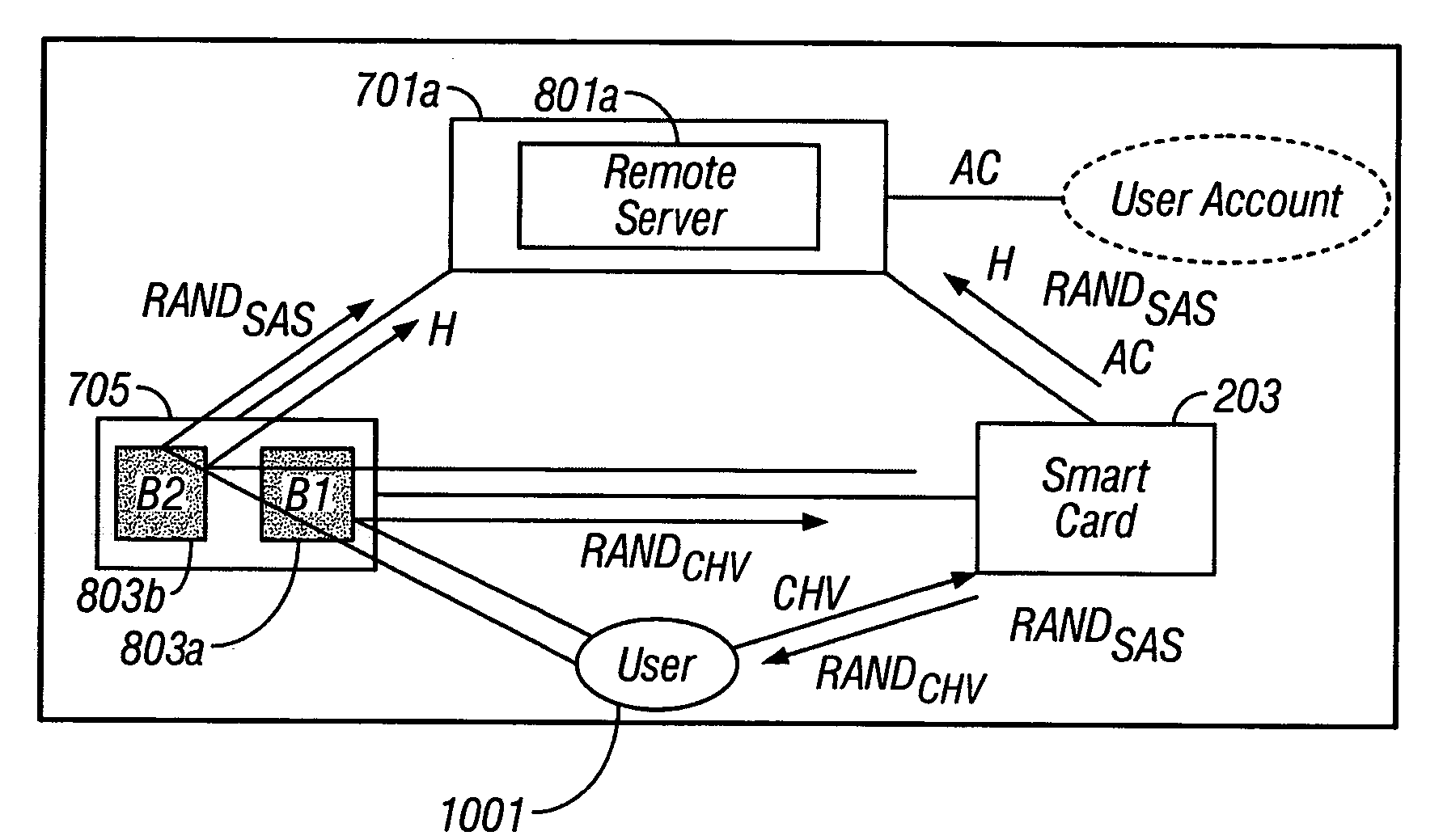
InactiveUS20060294023A1Prevent online identity theftPrevent theftPayment architectureDigital data authenticationIdentity theftSmart card
A portable secure network device and method to operate such a device to provide secure login, secure online transactions, and to prevent online identity theft. An embodiment of the invention may be constructed by inserting a network smart card into a card reader, wherein either the card reader or the card itself has an output device and input device wherein the processor is programmed to execute according to instructions to cause the microprocessor: to produce a shared association secret; to display the shared association secret on the output device; and to transmit the shared association secret to the remote server; thereby ensuring that a user observing the output device and the remote server computer both possess the shared association secret.
Owner:AXALTO INC
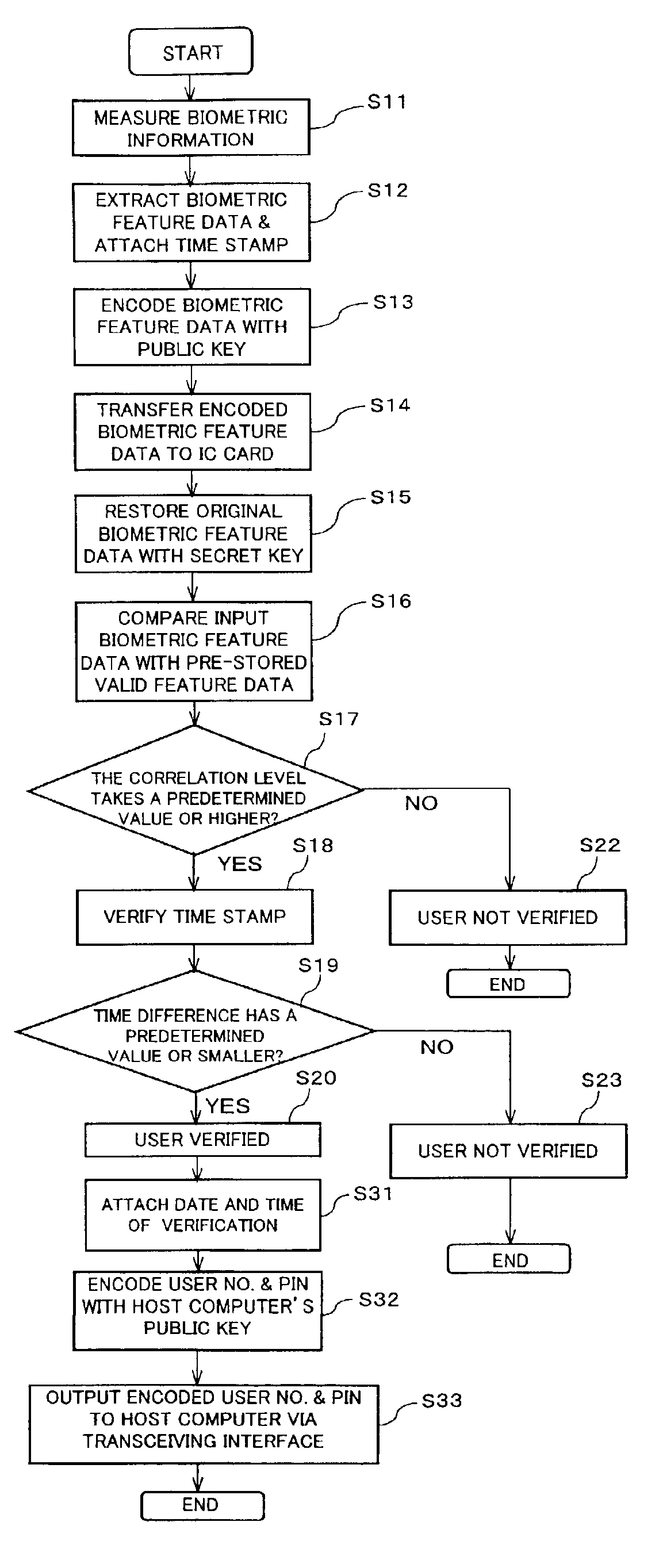
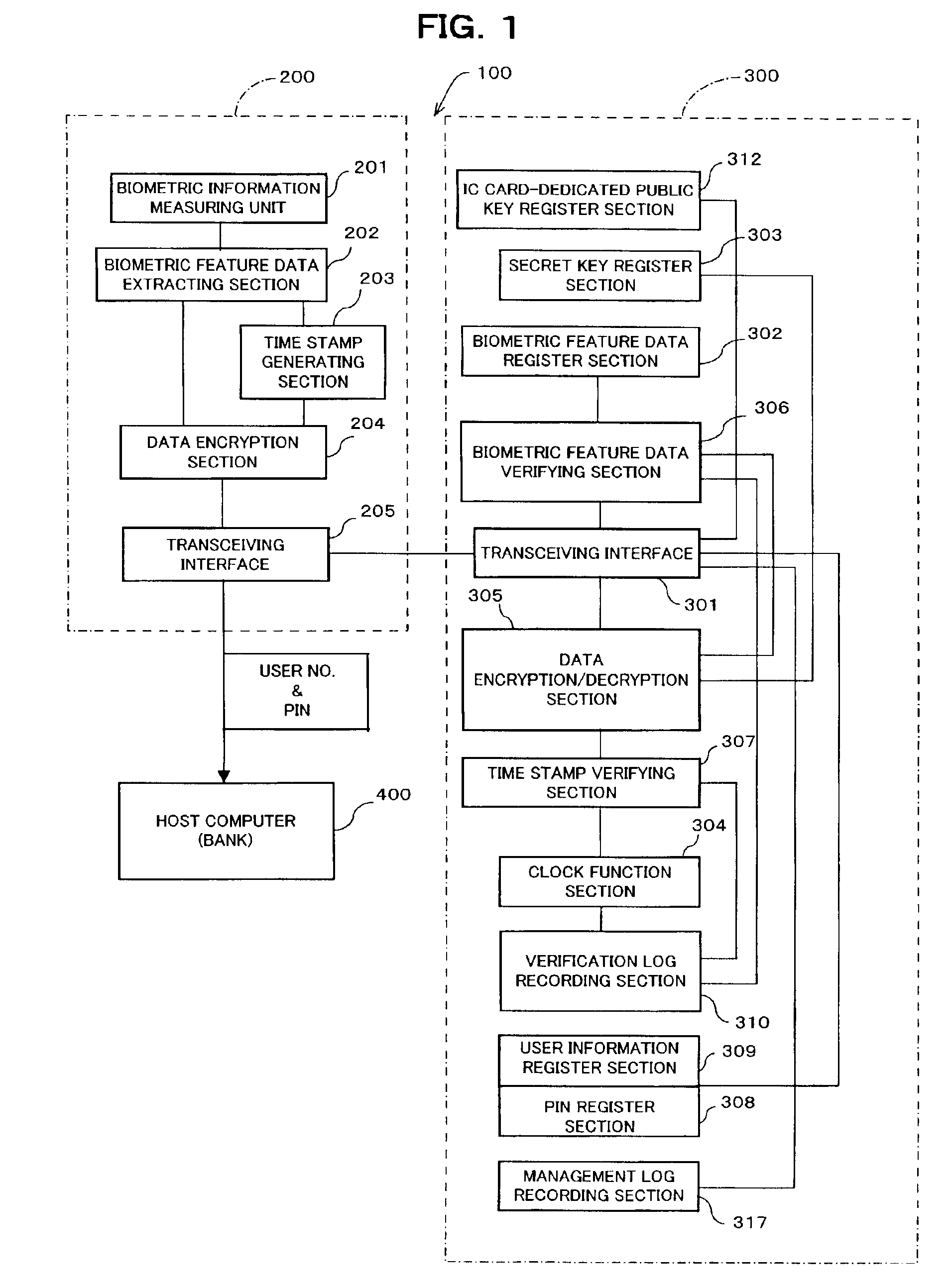
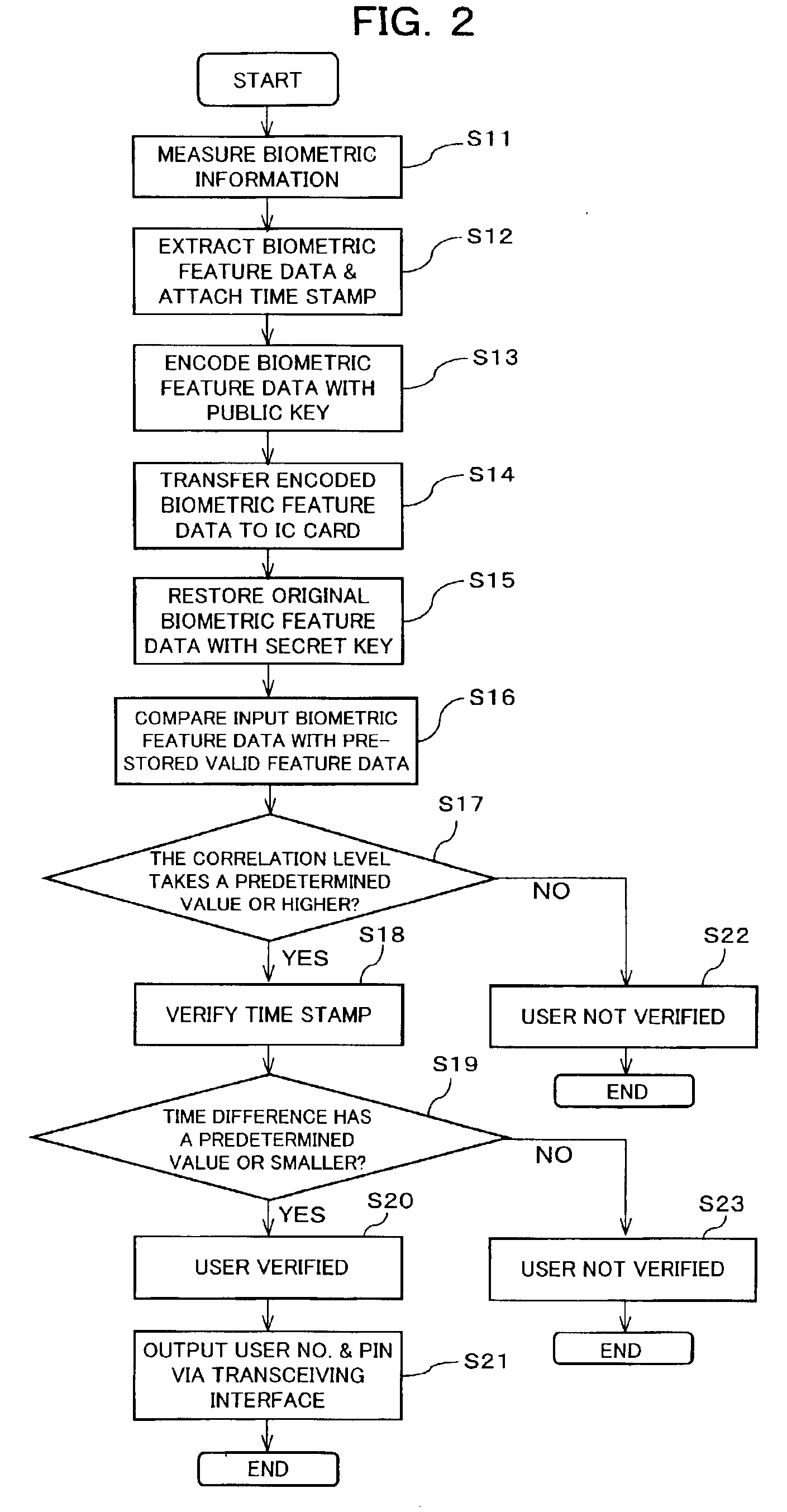
User verification system, and portable electronic device with user verification function utilizing biometric information
InactiveUS6957339B2Risk minimizationPrevent leakageDigital data processing detailsUser identity/authority verificationUser verificationComputer hardware
In a system (e.g., debit card) where a PIN is entered as verification, the PIN and biometric information, which is free of being stolen or faked, are combined to realize secure user verification. The leakage and the theft of a PIN is reliably prevented, thereby realizing a high security ability. To-be-verified biometric feature data is transmitted from first transceiving interface (205) of data processing device (200) to portable electronic device (300). Biometric feature data verifying section (306) of portable electronic device (300) compares the to-be-verified biometric feature data, which has been received by second transceiving interface (301), with valid biometric feature data. If a predetermined matching condition between the to-be-verified biometric feature data and the valid biometric feature data is satisfied, a PIN stored in portable electronic device (300) is transmitted from second transceiving interface (301) to management device (400) via first transceiving interface (205) of data processing device (200).
Owner:FUJITSU LTD
Method and apparatus for determining rove-out
ActiveUS20080076411A1Prevent theftError preventionTransmission systemsCommunications systemNetwork control
Some embodiments are implemented in a communication system that includes a first wireless communication system that includes a Femtocell access point (FAP) and a network controller that can communicatively couple the FAP to a second wireless communication system. In some embodiments, the network controller can communicatively couple to the second wireless communication system through a UTRAN Iu interface. In some embodiments, the FAP can communicatively couple to a user equipment using a short-range licensed wireless frequency. Some embodiments provide method that determines whether a user equipment (UE) has roved-out of the first wireless communication system. The method receives a periodic message at the FAP from the UE. When the FAP fails to receive a pre-determined number of the periodic messages, the method sends a deregister message to the network controller over a unique connection dedicated to the UE and releases the dedicated connection.
Owner:RIBBON COMM OPERATING CO INC
Facial-recognition vehicle security system
InactiveUS7602947B1Prevent theftEasily defeatedAnti-theft devicesCharacter and pattern recognitionDriver/operatorControl signal
A movable-vehicle security system includes a facial-recognition system including a scanner such as a television or infrared camera directed at the face of a person in the driver's seat, which system produces output control signals that are applied to enable or disable operation of the vehicle, with or without a key or other supplemental security system. In a particular embodiment, the system includes a camera mounted on the “third taillight” assembly (which is preferably mounted below the roof and inside the rear window), directed at the rear-view mirror, and coupled to a facial-recognition computer, which in turn is coupled (with appropriate security precautions) to an enabling element for the vehicle, such as a starter motor. In a further embodiment, the system can be coupled to various elements of the motive system to create an auto-starting car.
Owner:LEMELSON JEROME H +1
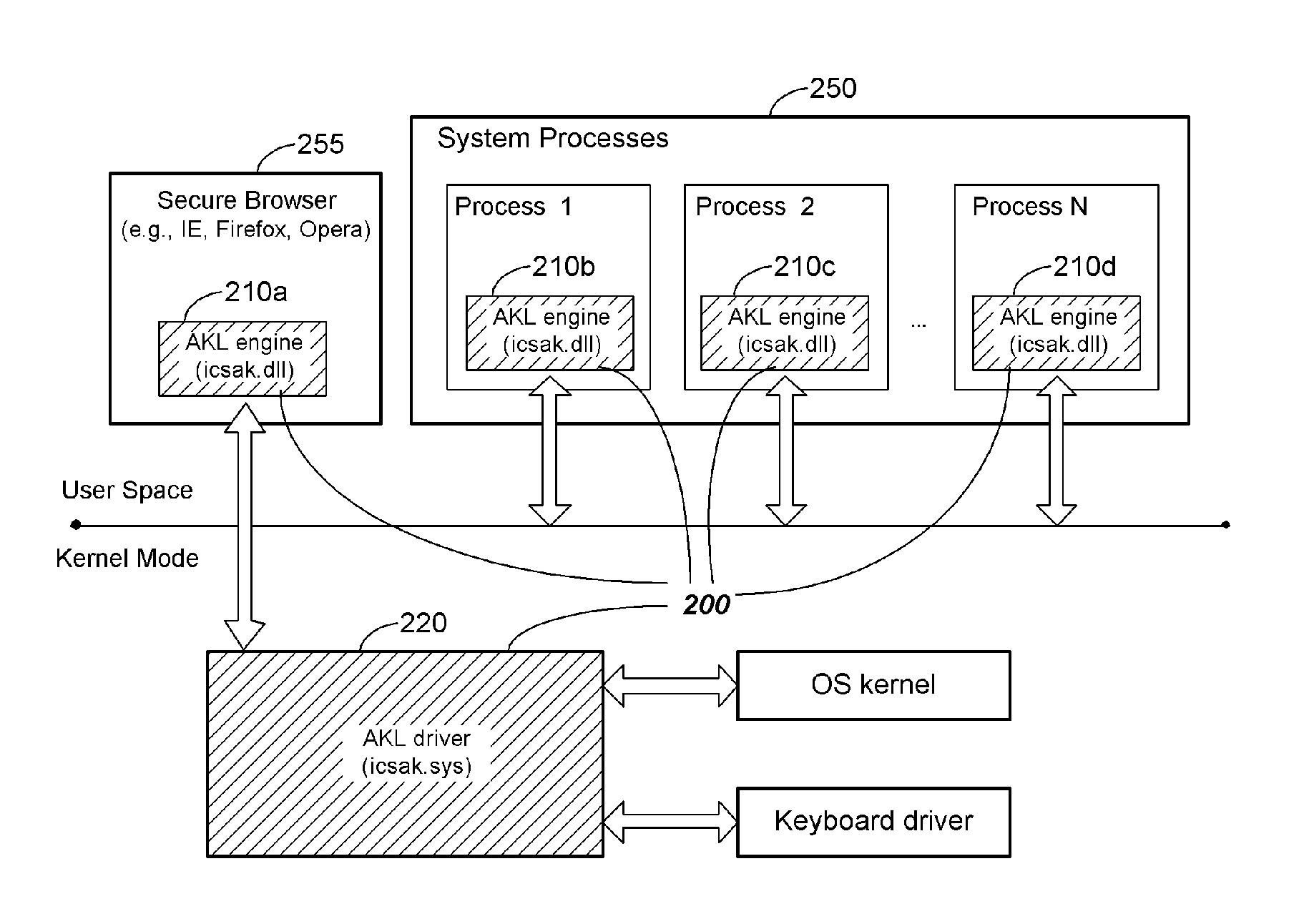
System and Methodology Protecting Against Key Logger Spyware
InactiveUS20070240212A1Prevent theftMemory loss protectionError detection/correctionUser inputVulnerability
System and methodology protecting against key logger software (spyware) is described. In one embodiment, for example, a method is described for protecting a computer system from security breaches that include unauthorized logging of user input, the method comprises steps of: specifying a particular application to be protected from unauthorized logging of user input; identifying additional system processes that may serve as a source of unauthorized logging of user input; injecting into the particular application and each identified system process an engine capable of detecting and blocking attempts at unauthorized logging of user input; and upon detection of an attempt at unauthorized logging of user input, blocking the attempt so that user input for the particular application remains protected from unauthorized logging.
Owner:CHECK POINT SOFTWARE TECH INC
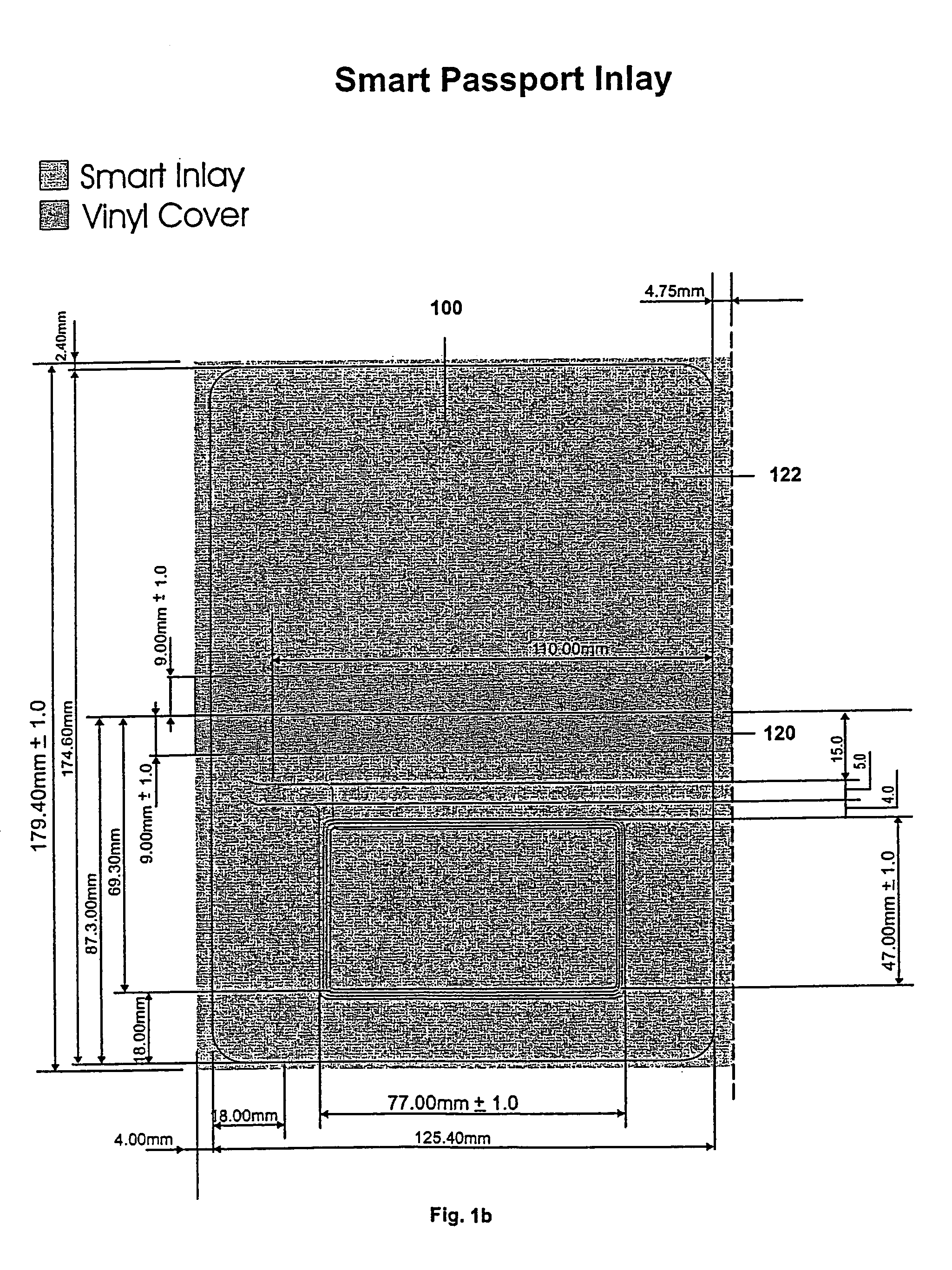
Smart identification document
InactiveUS7243840B2Prevent theftRecord carriers used with machinesSpecial data processing applicationsEmbedded systemOperating system
A smart electronic personal identification document, including a smart identification module and an automated anti-skimming element. The smart identification module includes a contactless chip module and an antenna. The smart identification module is operative to store and exchange personal identification information contactlessly with an external reader. The automated anti-skimming element is configured for preventing unauthorized theft of the information.
Owner:SUPERCOM +1
Method and Apparatus for Establishing Transport Channels for a Femtocell
ActiveUS20080261596A1Prevent theftNetwork topologiesTelephonic communicationCommunications systemResource management
Some embodiments are implemented in a communication system that includes a first wireless communication system and a second wireless communication system that includes a Femtocell access point (FAP) and a network controller that can communicatively couple the FAP to the first wireless communication system. In some embodiments, the network controller can communicatively couple to the first wireless communication system through a UTRAN Iu interface. Some embodiments provide a resource management method that determines that a user equipment (UE) has roved in a region serviced by the FAP. The FAP includes a generic access resource control (GA-RC) protocol sub-layer. The method creates a separate GA-RC state dedicated to the UE in the GA-RC protocol sub-layer. The method also sets the GA-RC state dedicated to the UE to a deregistered state to indicate that the UE is not registered to use the services of the second wireless communication system.
Owner:RIBBON COMM OPERATING CO INC
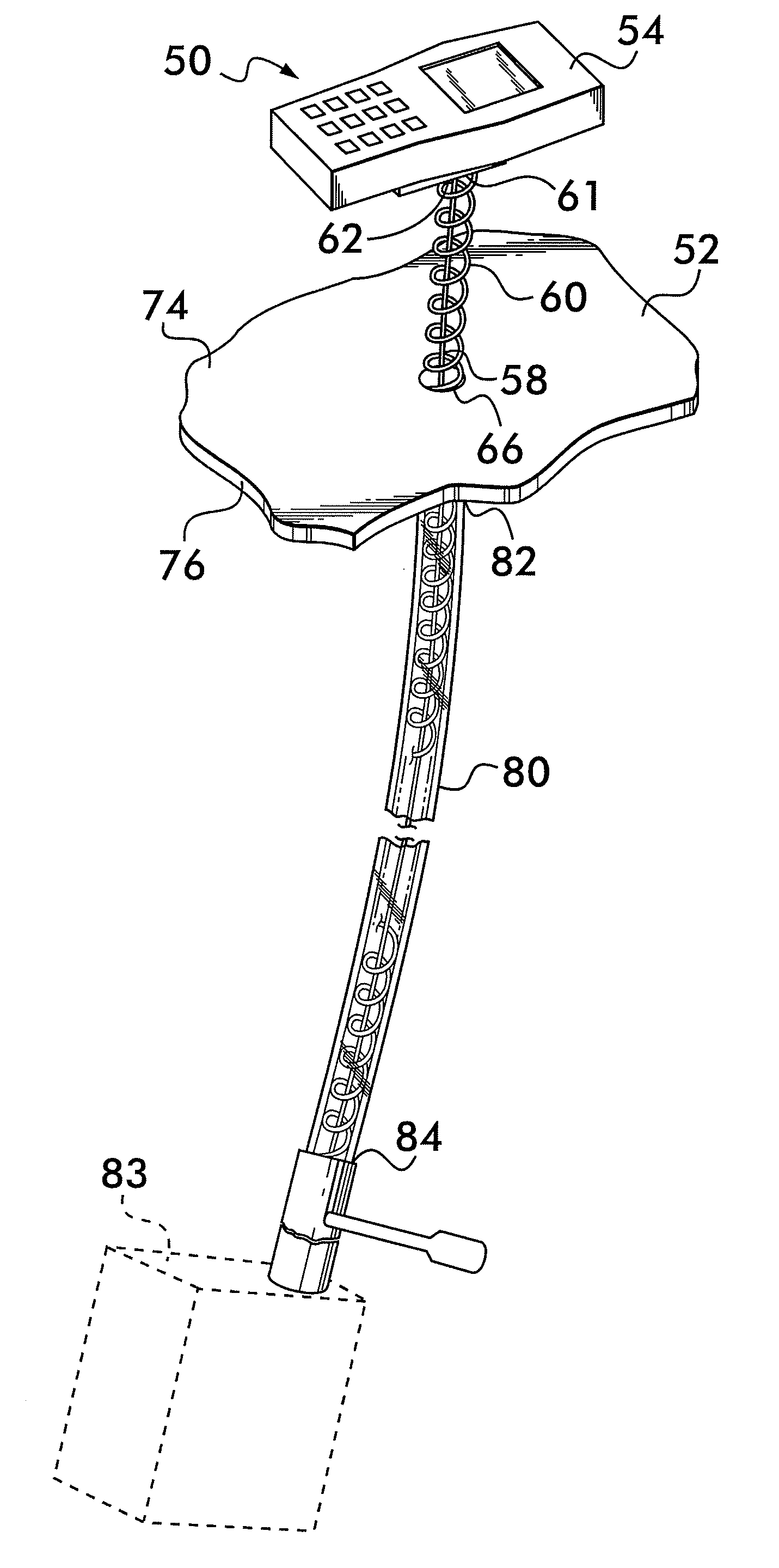
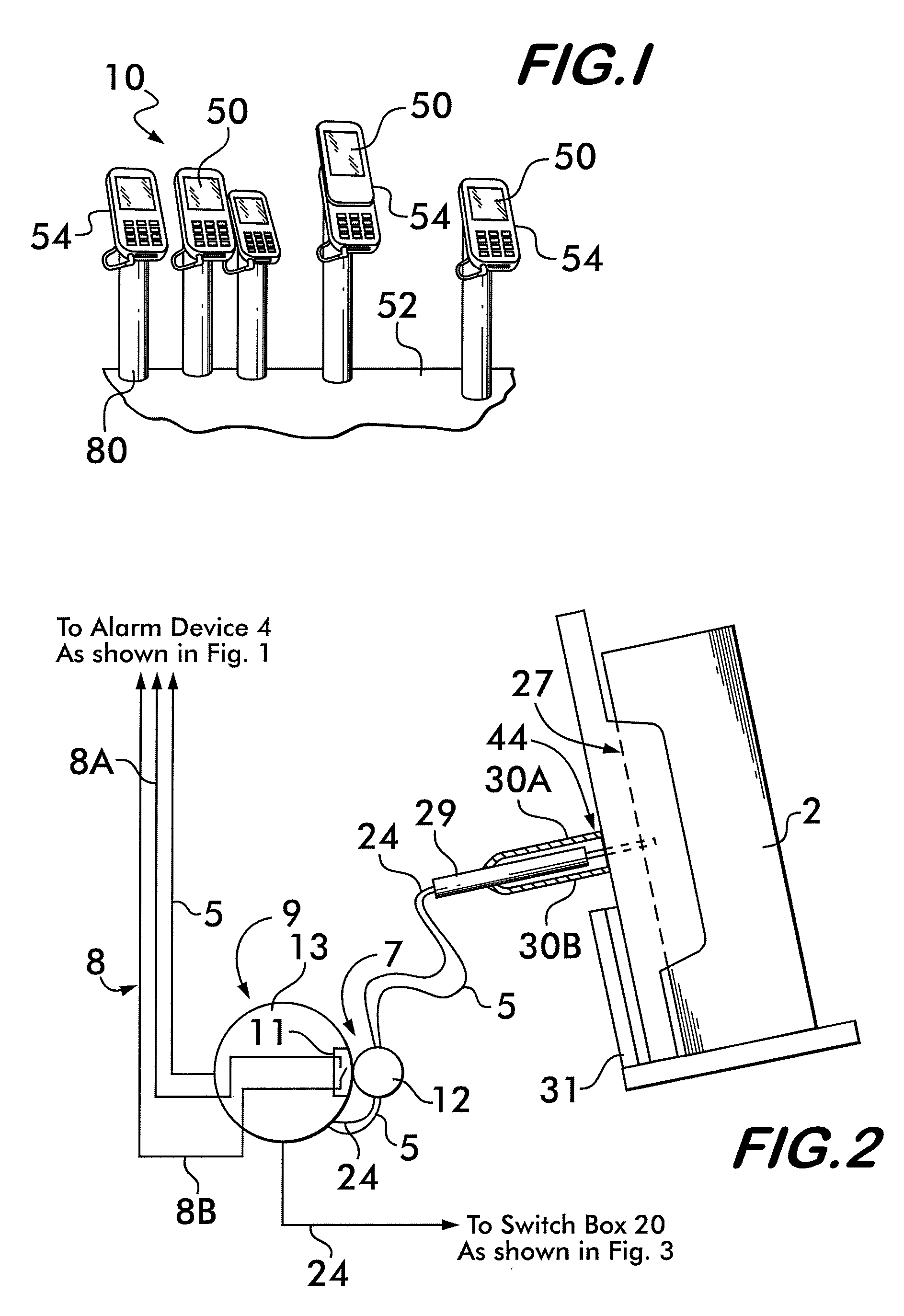
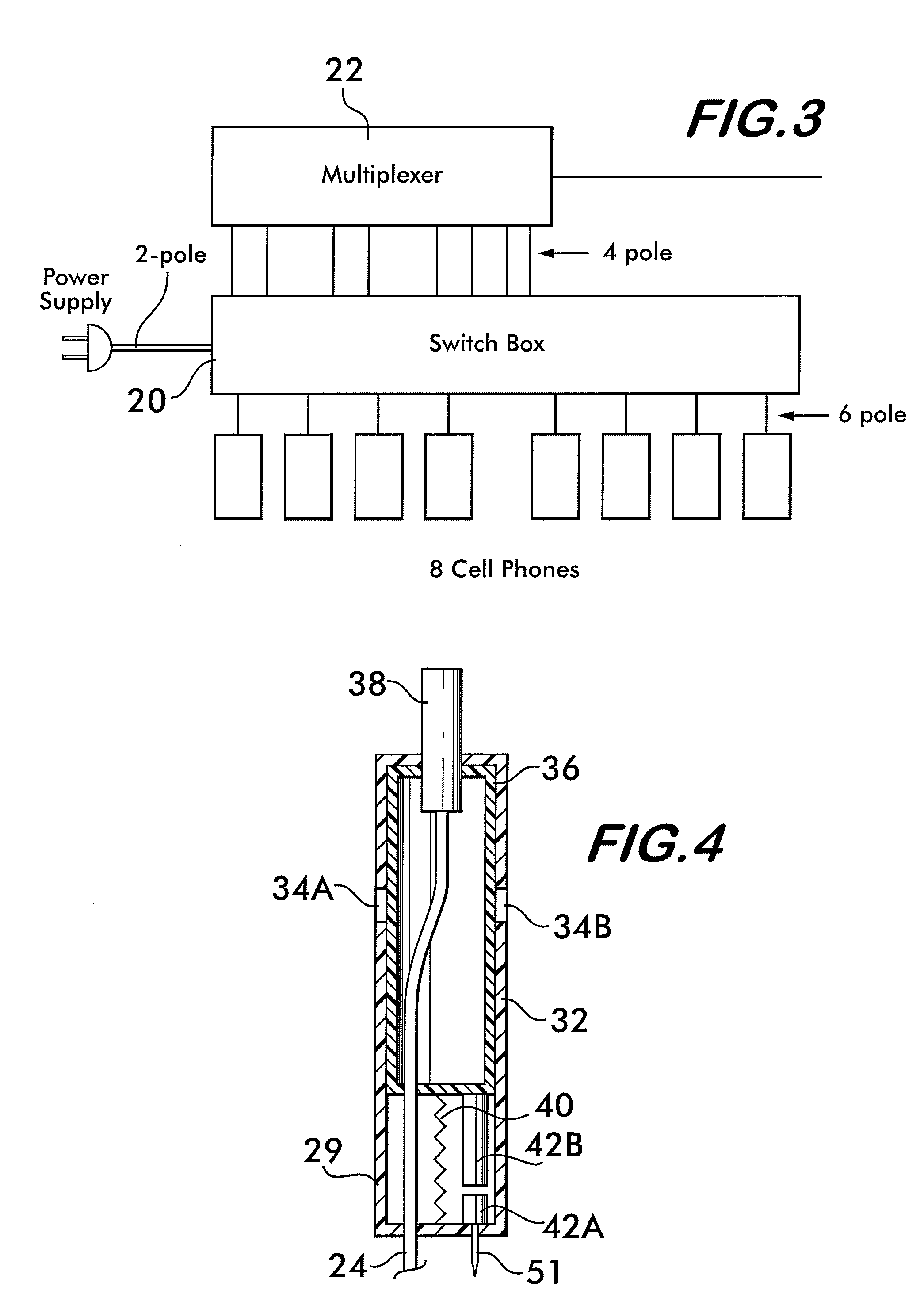
Coiled cable display device
A system for displaying an item includes a display shelf having an aperture through it and a thin tether having a first end and a second end that extends through the aperture. The first end of the tether is secured to a mount above a top side of said display shelf and the second end of said tether is secured adjacent to a bottom side of the displays shelf. The first end of the tether has a mount for connection of tether to the item, above the shelf. The system further includes a coiled cable coiled around the tether extending through the aperture. The coiled cable provides an electrical path to the item. The coiled cable has a first end and a second end. The first end is secured adjacent to the mount and the second end securely terminates below the bottom unexposed side of said display shelf.
Owner:CHECKPOINT SYST INC
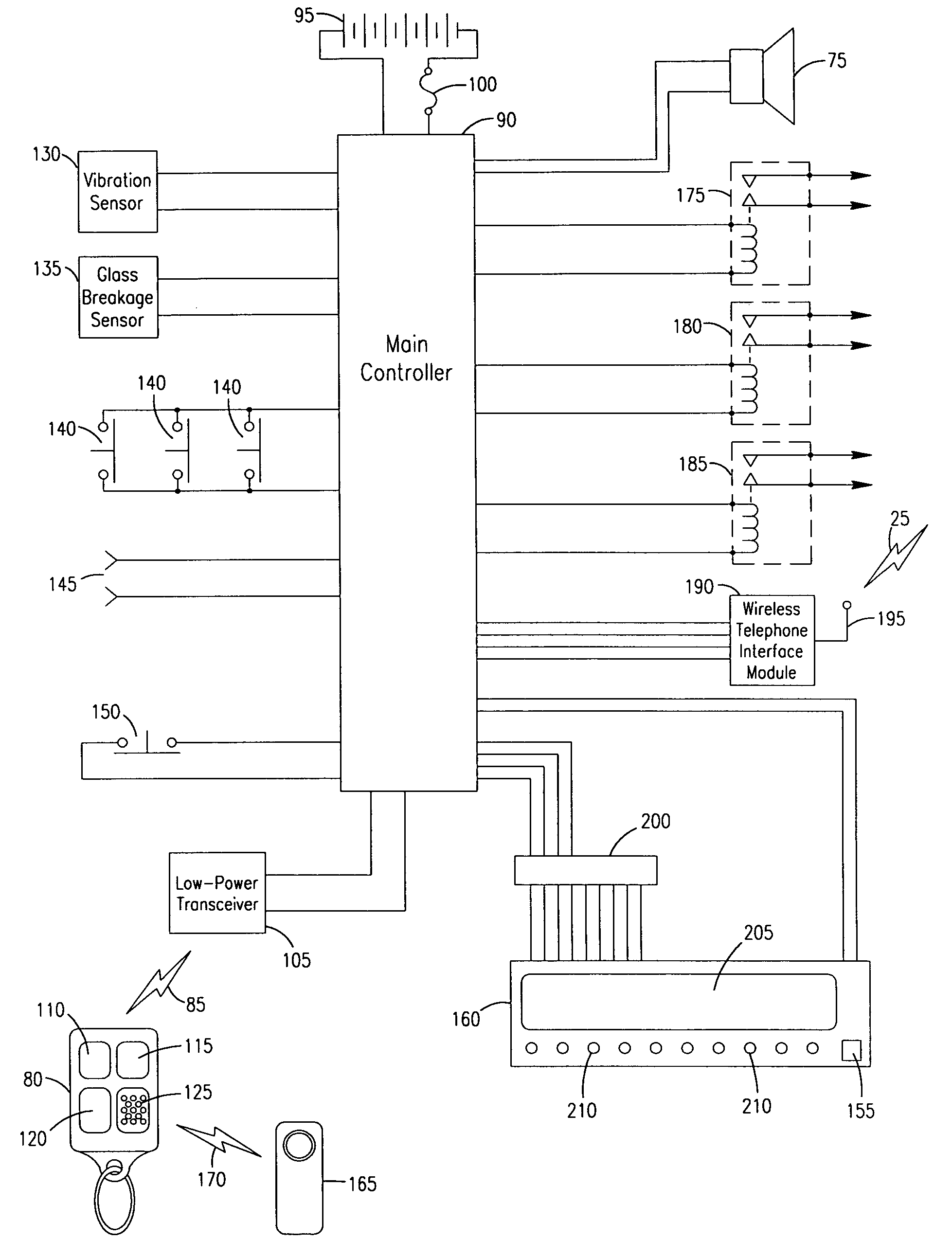
Car alarm with automatic dialer
InactiveUS6956467B1Discourages vehicle theftPrevent theftAnti-theft devicesOptical signallingPagerCar alarm
A car alarm is providing including an annunciator for providing an alarm signal from a car alarm system and n automatic dialer that provides automatic dialing capabilities to a wireless phone or pager upon initiation of said annunciator.
Owner:MERCADO JR ADELINO
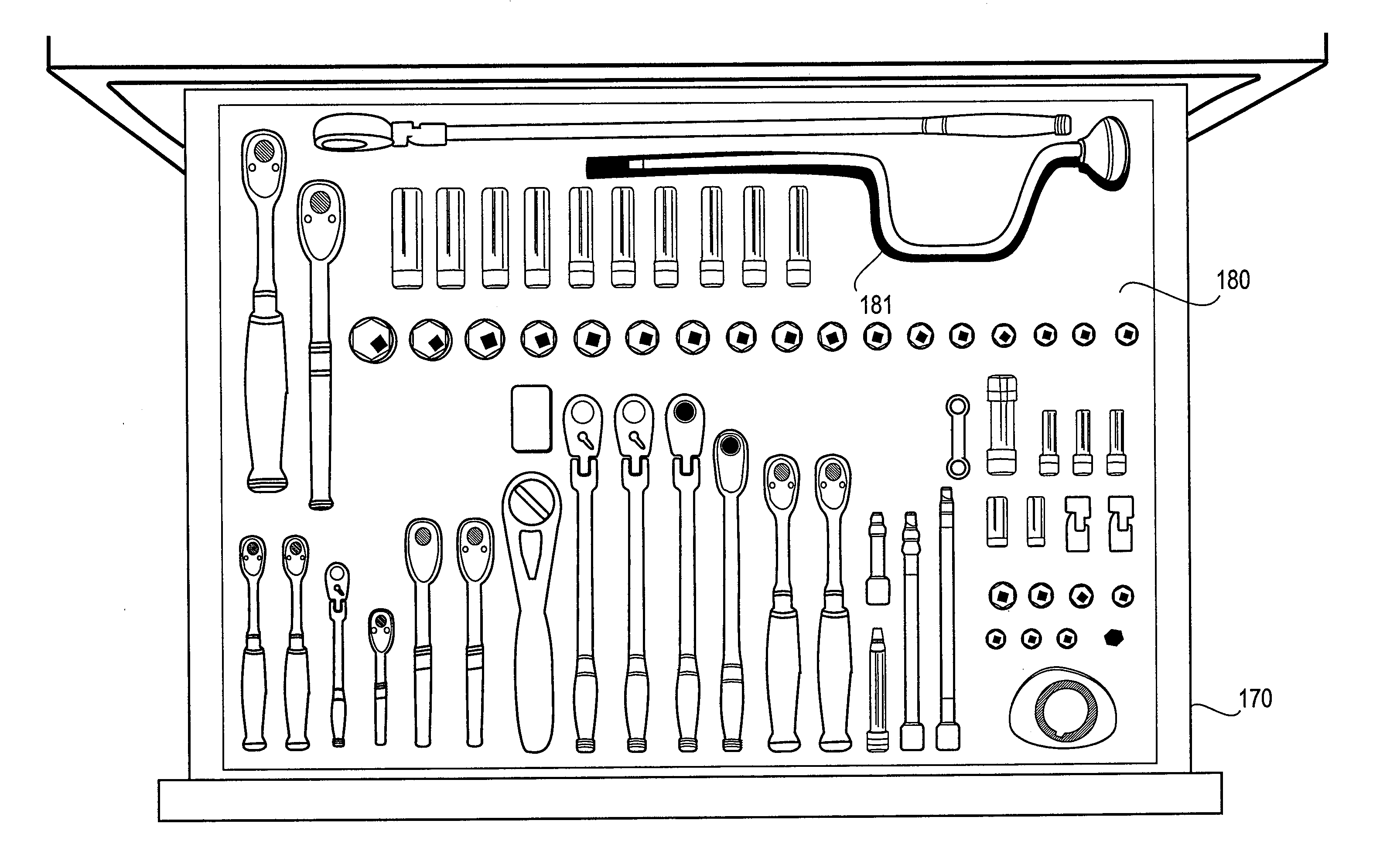
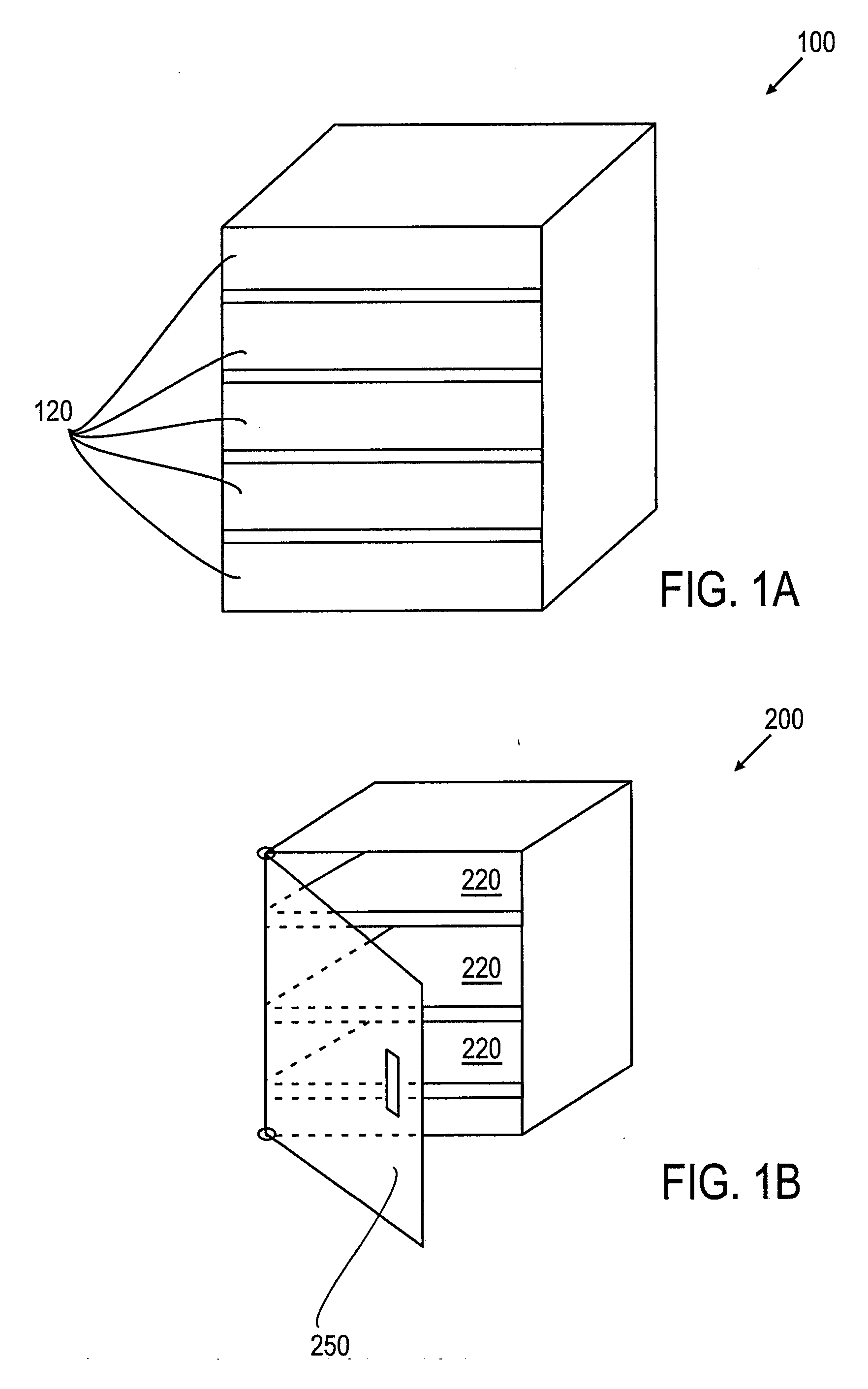
Image-based inventory control system using advanced image recognition
ActiveUS20100046791A1Minimize and eliminate of misplacementMinimize and eliminate of and theftImage enhancementImage analysisObject basedControl system
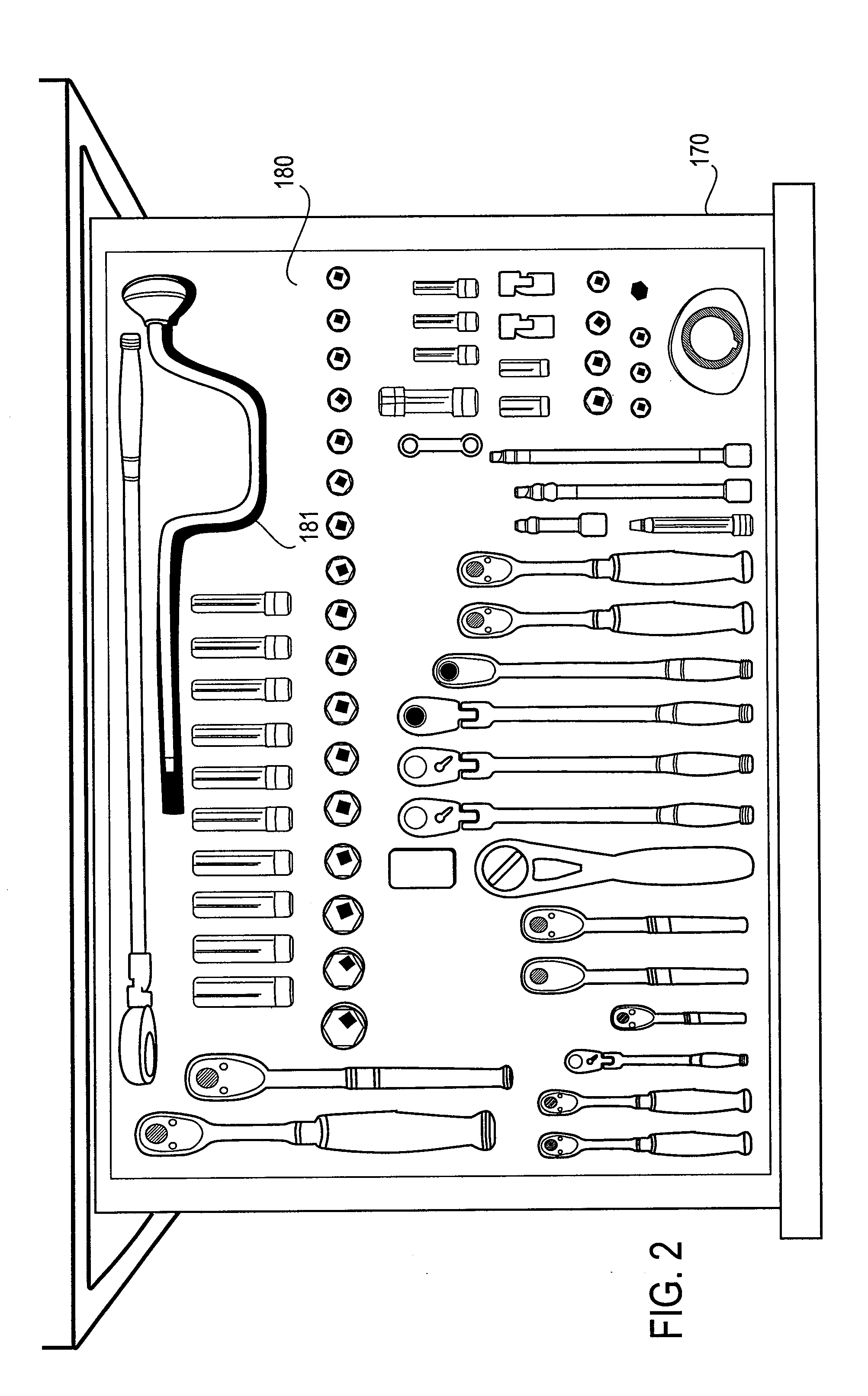
Systems for monitoring an inventory condition of objects based on captured images are described. An exemplary system includes at least one storage drawer, each storage drawer including a plurality of storage locations for storing objects; and a data storage device storing reference data for each storage drawer. The reference data includes, for each region of interest corresponding to each respective storage drawer, at least one of a reference image signature representing attributes of the region of interest when a stored object is present, and a reference image signature representing attributes of the region of interest when the stored object is not present. A data processor of the system is configured to derive an image signature representing attributes of a region of interest corresponding to a drawer using a captured image of the drawer; and determine an inventory condition of the drawer according to the stored reference data corresponding to the region of interest and the derived image signature representing attributes of the captured image of the region of interest.
Owner:SNAP ON INC
Dispensing system
Owner:WESTROCK SHARED SERVICES LLC
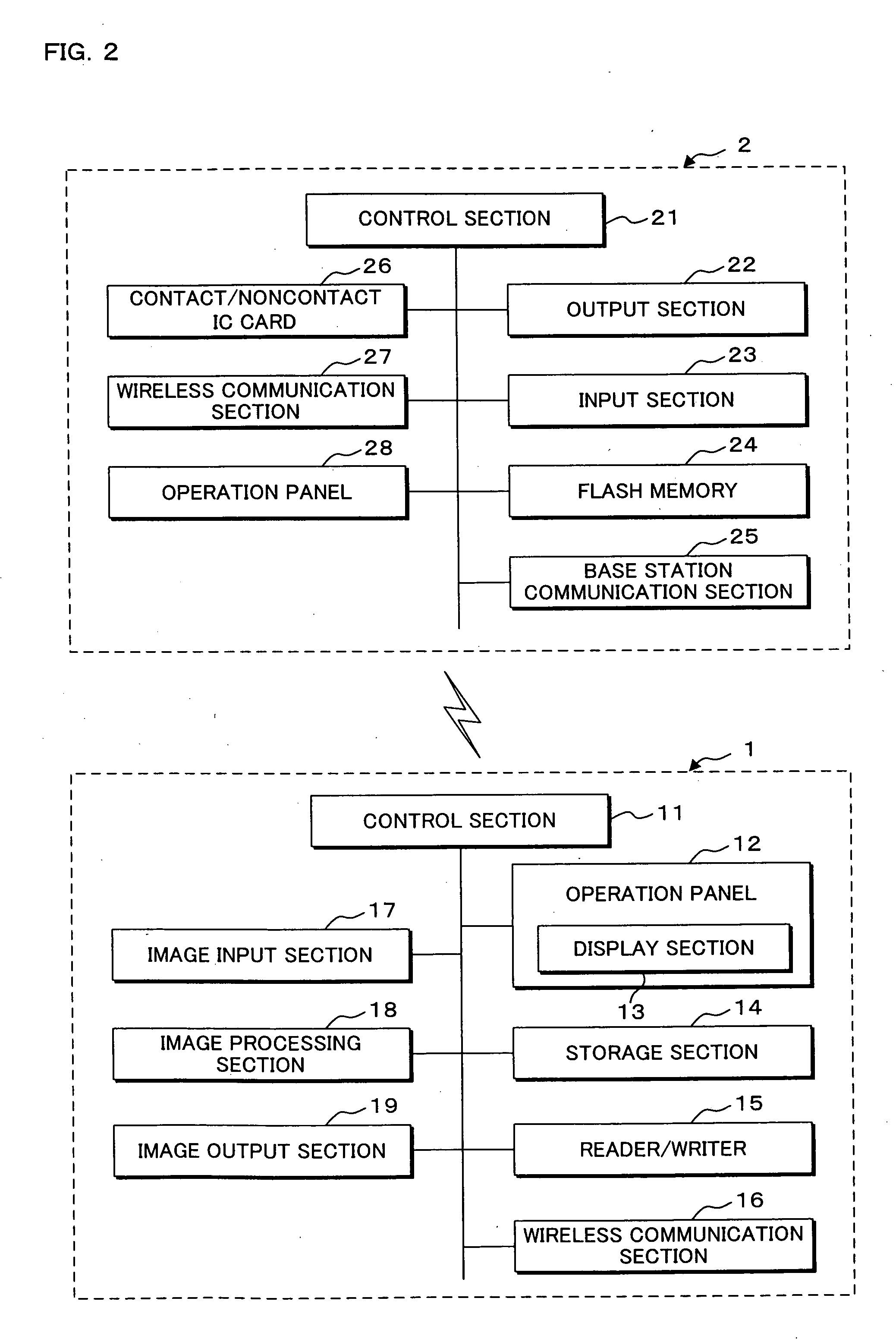
Communication system, information processing system, image formation system, image forming apparatus, mobile information terminal device and information processing device
InactiveUS20100225962A1Prevent leakageEstablishment of connectionConnection managementSubstation equipmentInformation processingCommunications system
After a digital multi-function peripheral establishes a connection with a mobile phone once, it rejects connection establishment requests made to a wireless communication section by other devices. Moreover, after a connection is established with a mobile phone once, the digital multi-function peripheral stops sending of the address of the wireless communication section through a reader / writer. After completing the sending / receiving of data, the digital multi-function peripheral and the mobile phone delete the addresses of their partner devices stored in them, respectively, for use in sending / receiving data.
Owner:SHARP KK
Biometric identification and security system associated with cash register
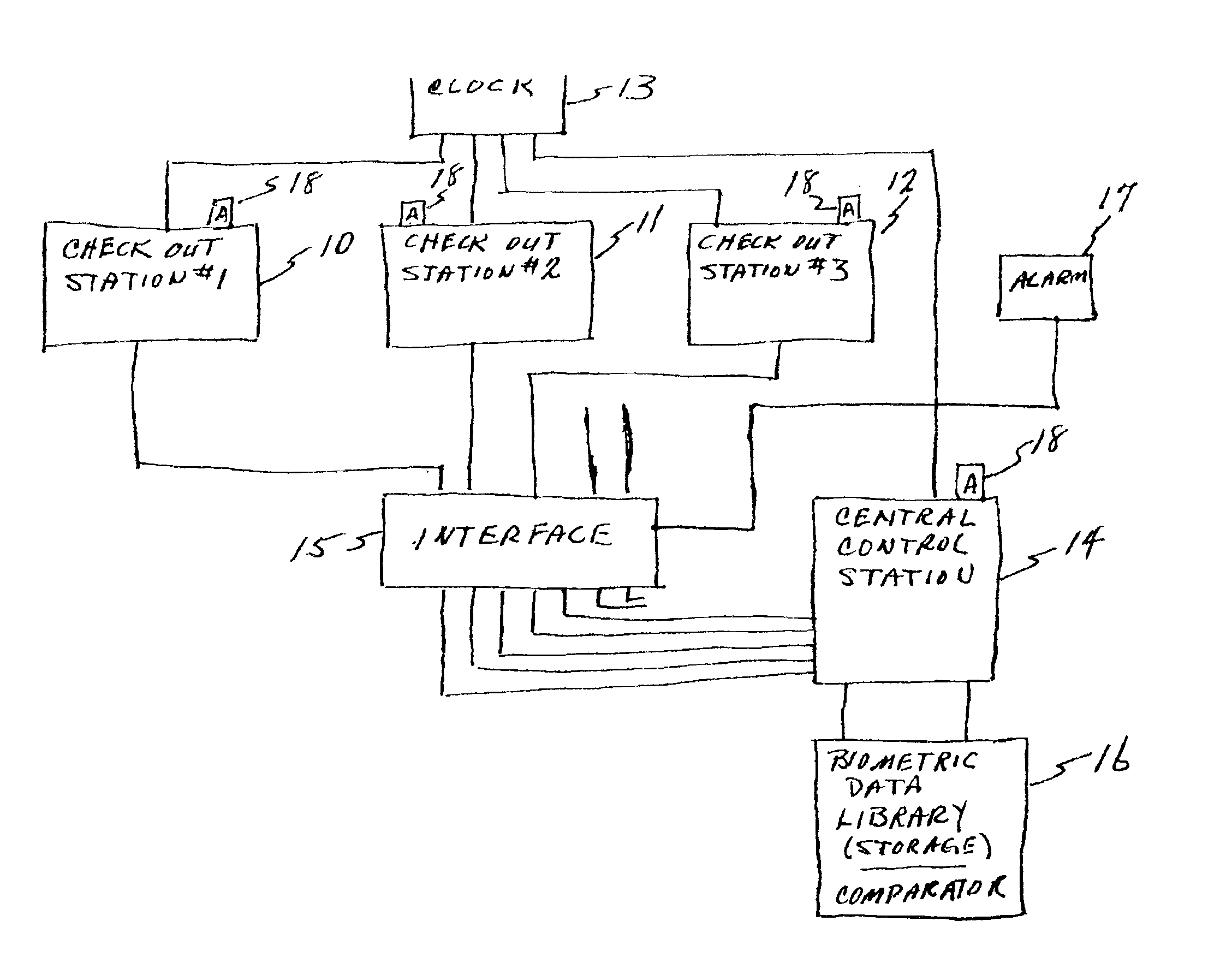
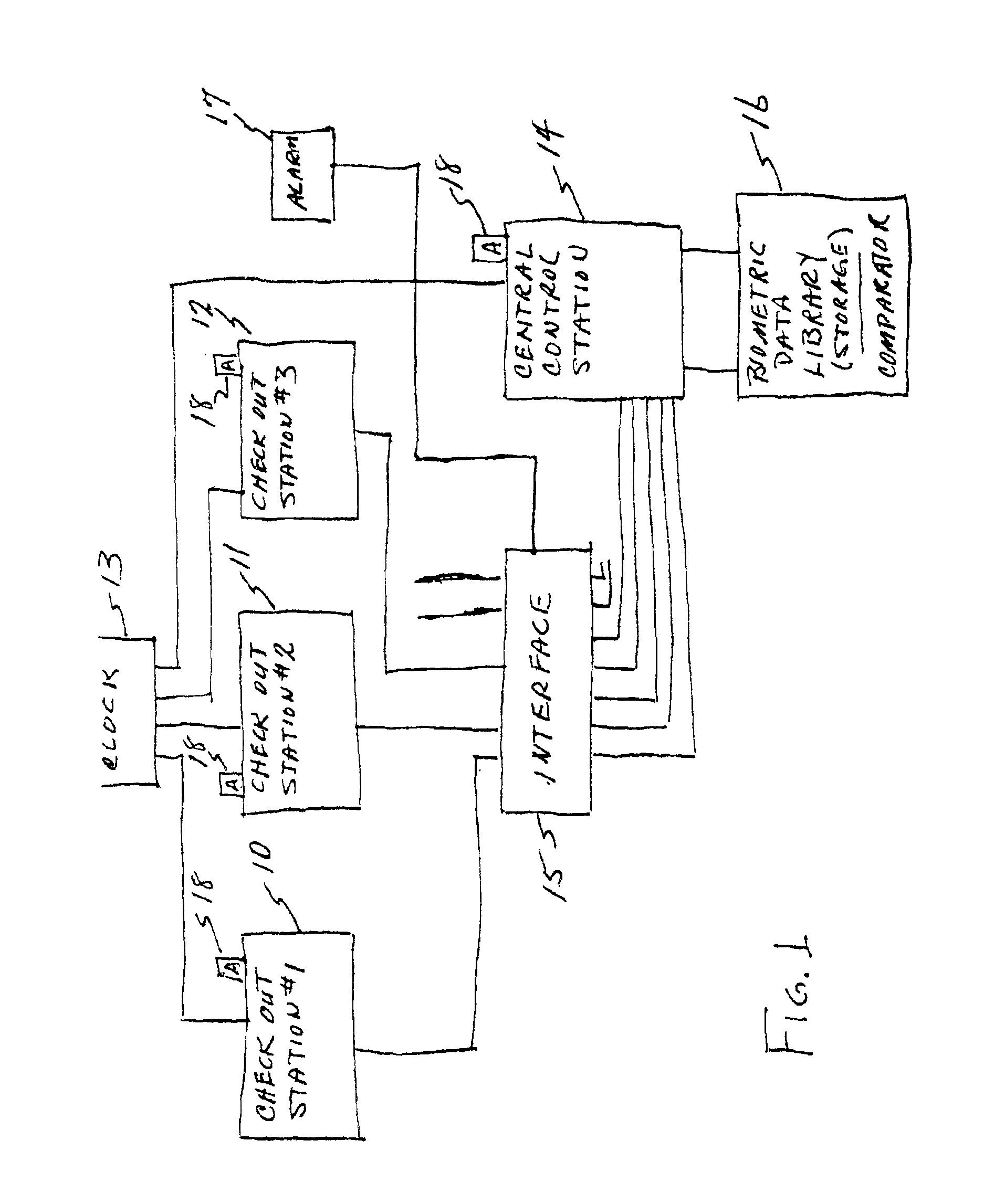
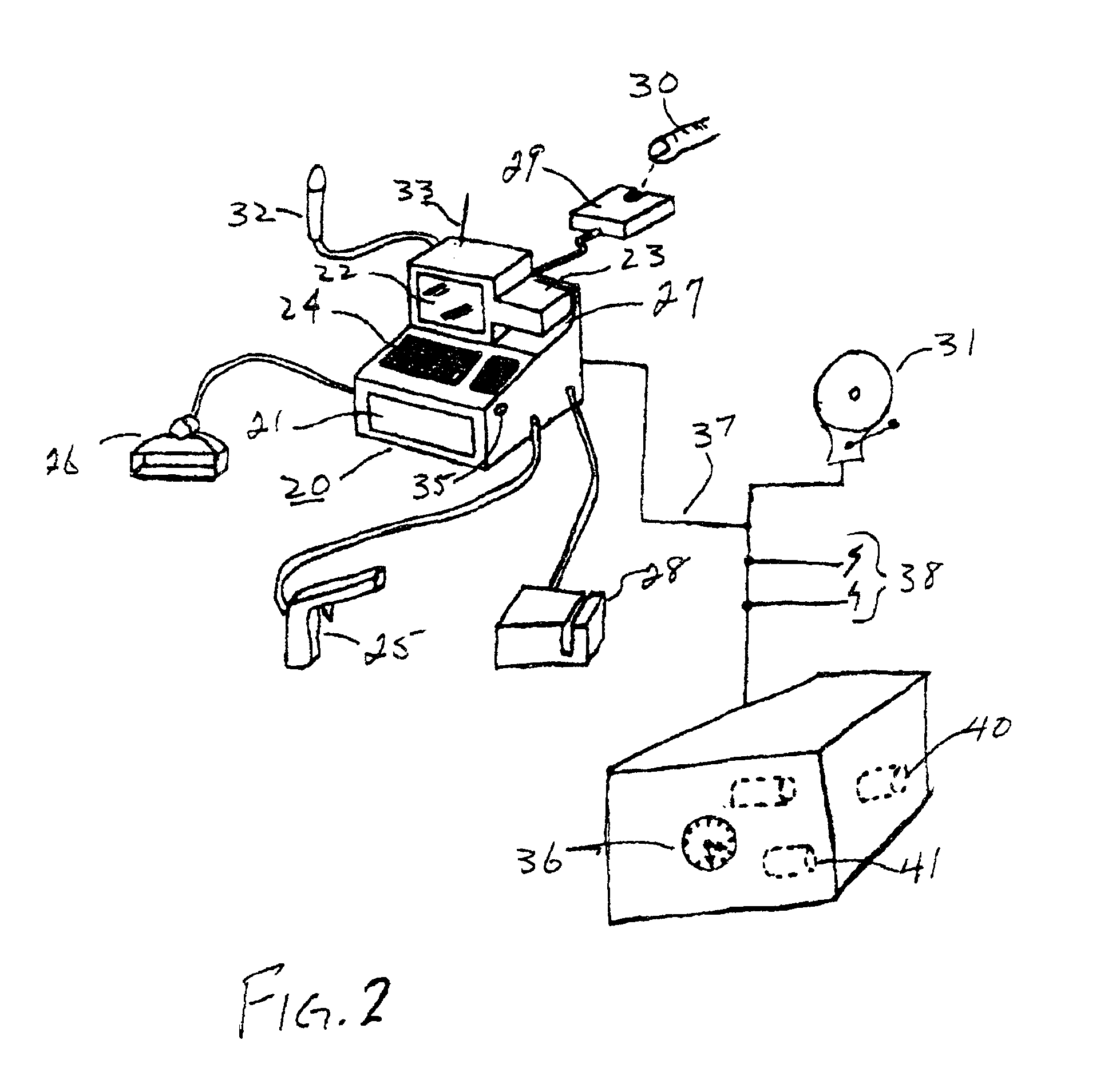
InactiveUS6883709B2Prevent theftReduce stepsCredit registering devices actuationCo-operative working arrangementsBiometric dataCheque
A wholesale and / or retail check out station system includes a biometric finger print reader and storage for reading and storing biometric data of employees having access to the cash registers of the check out stations in the system. Authorization to use a cash register in the system is programmed into the microprocessor in the system, limiting use of a cash register to authorized employees. Employees are identified by finger print using biometric technology. Limitations of use is extended to access to operate particular cash register(s); handling returned merchandise at a cash register; refunds on returned purchases require authorization of the manager and the cashier; cashing checks at a cash register, where the limitation includes only cashing of employer drawn payroll checks of employees; and, clearing errors made in tabulations at a cash register. Unauthorized persons attempting to gain access to cash registers to which they are not authorized serves to activate an alarm.
Owner:FAMOUS HORSE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com