Patents
Literature
79 results about "Object handling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Objection handling is when a prospect presents a concern about the product/service a salesperson is selling, and the salesperson responds in a way that alleviates those concerns and allows the deal to move forward. Objections are generally around price, product fit, competitors, and good old-fashioned brush offs.
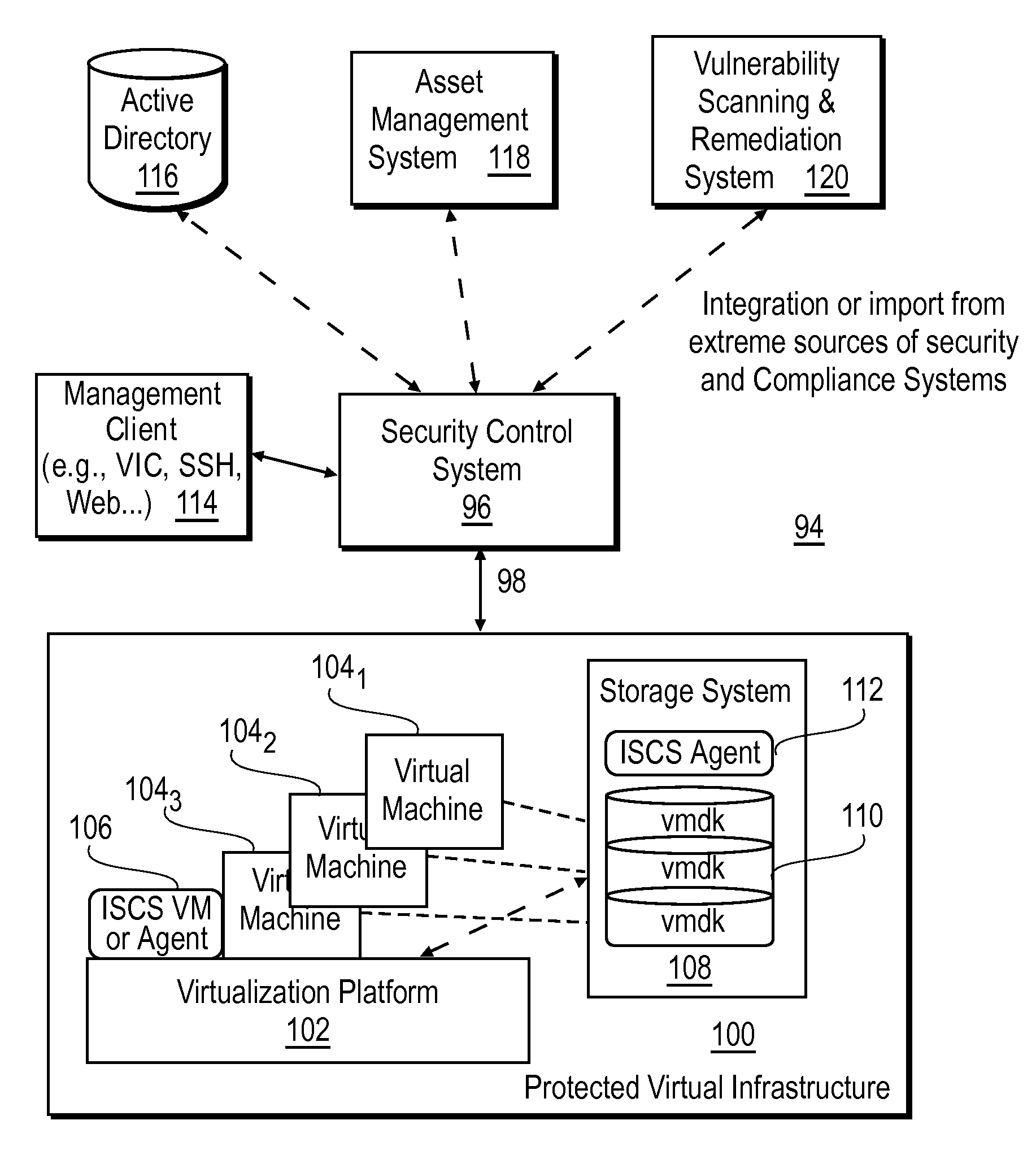
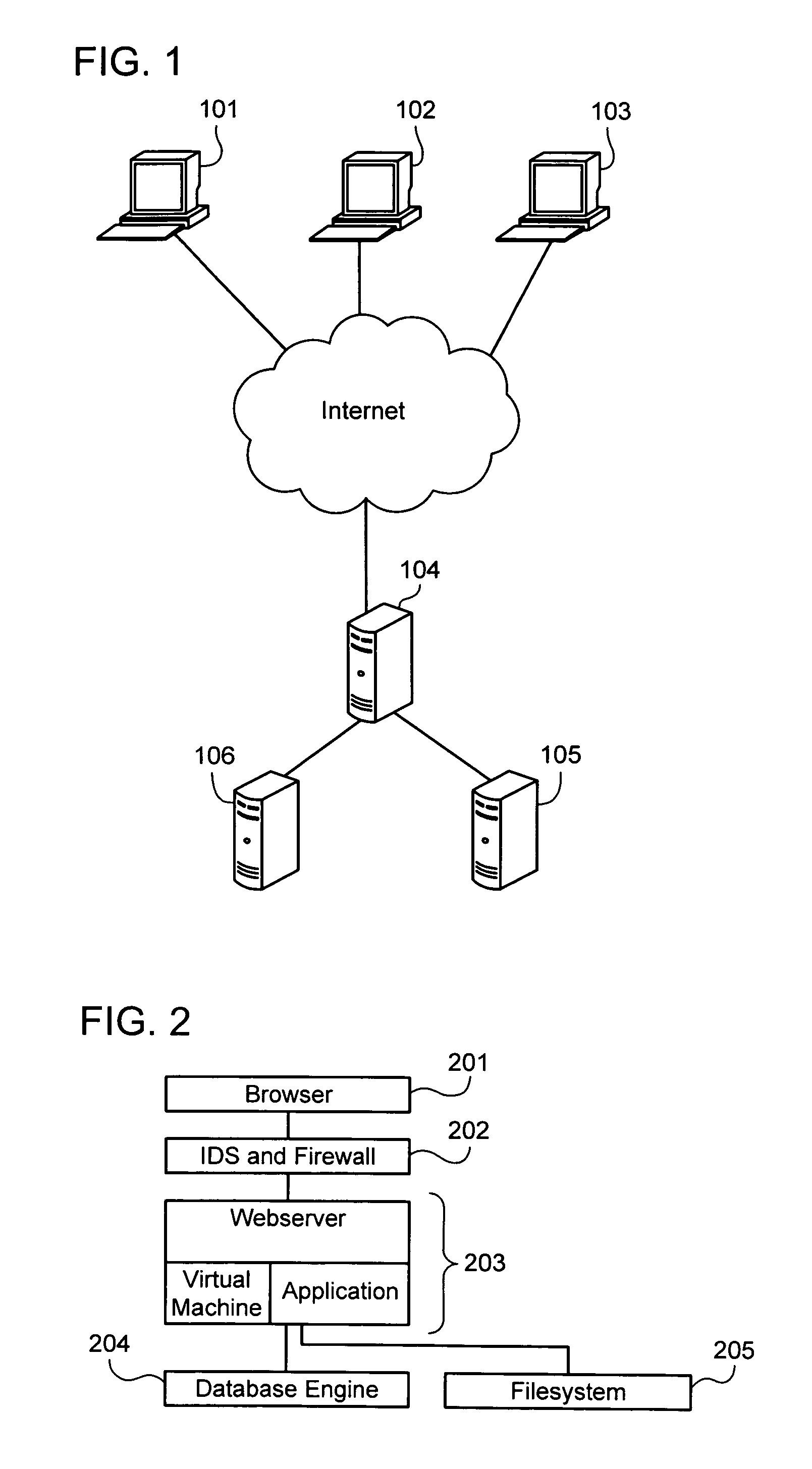
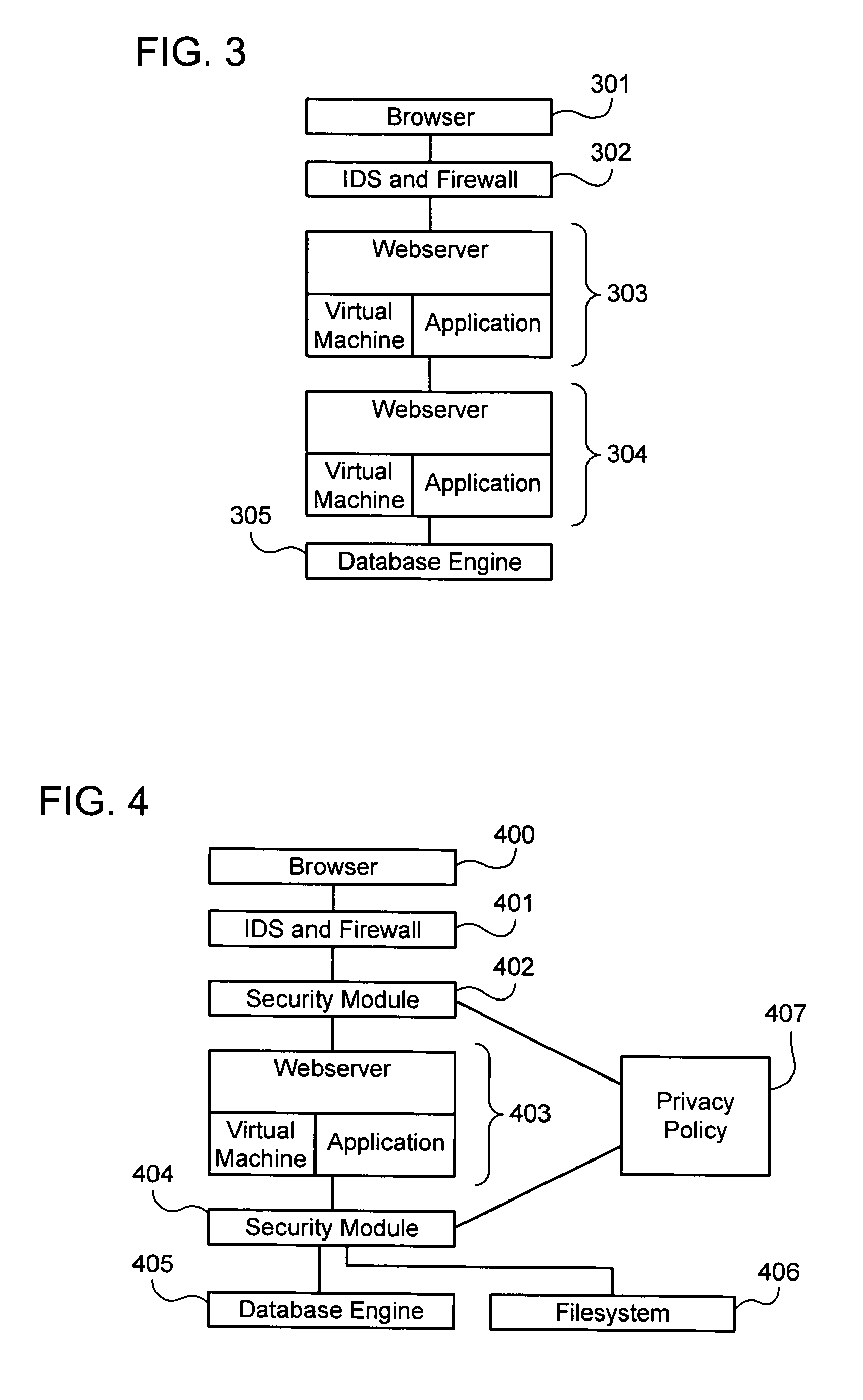
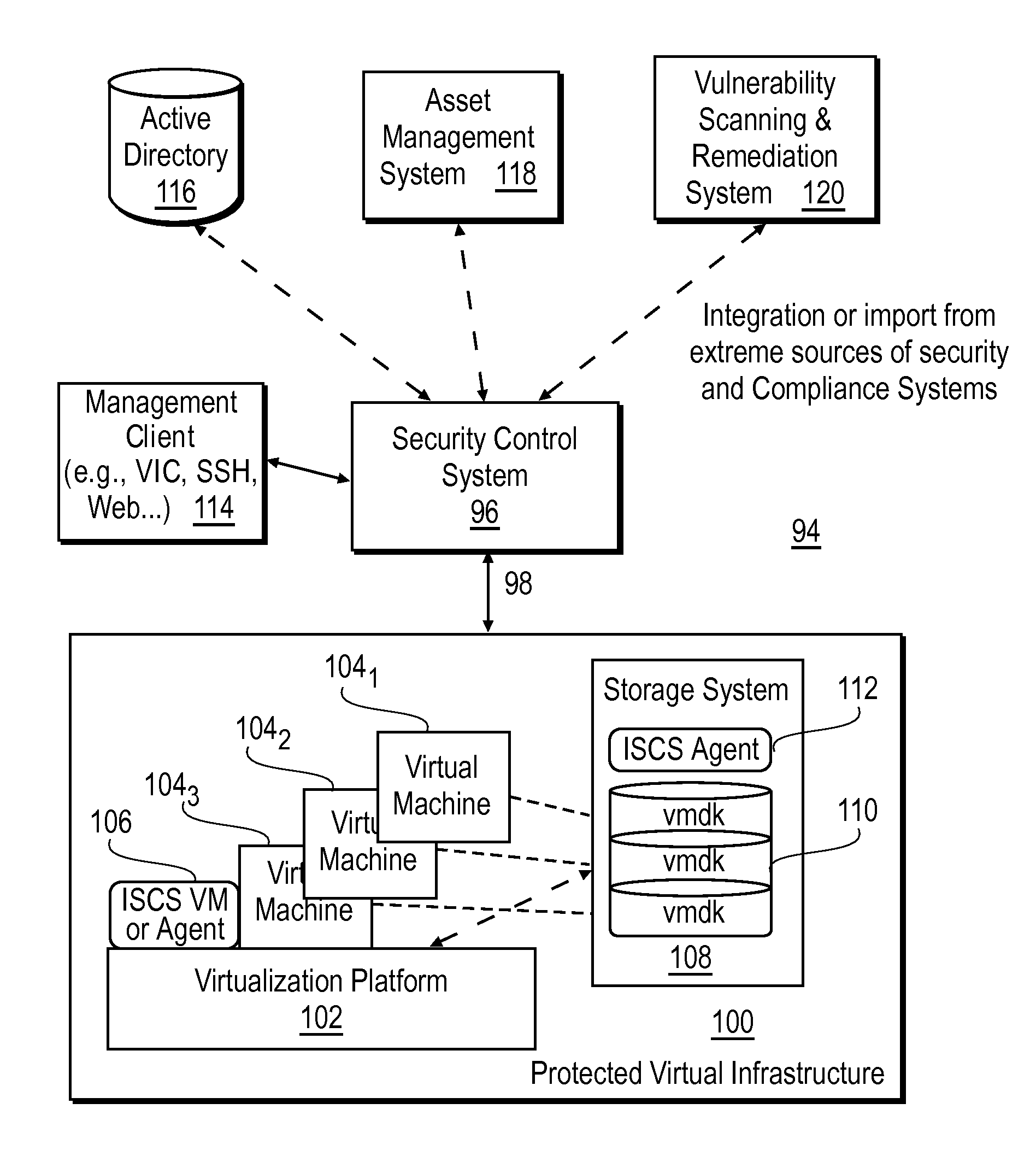
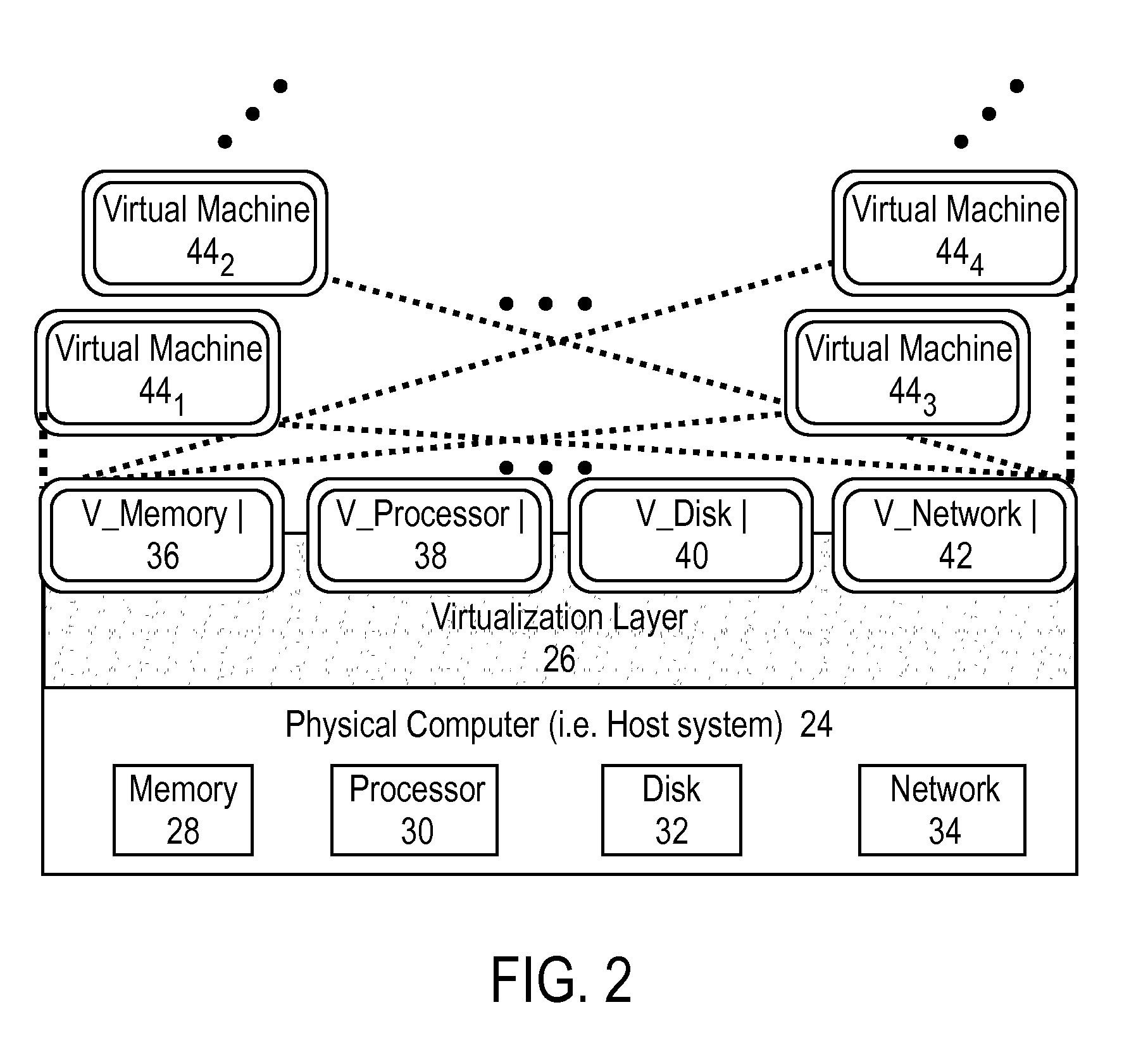
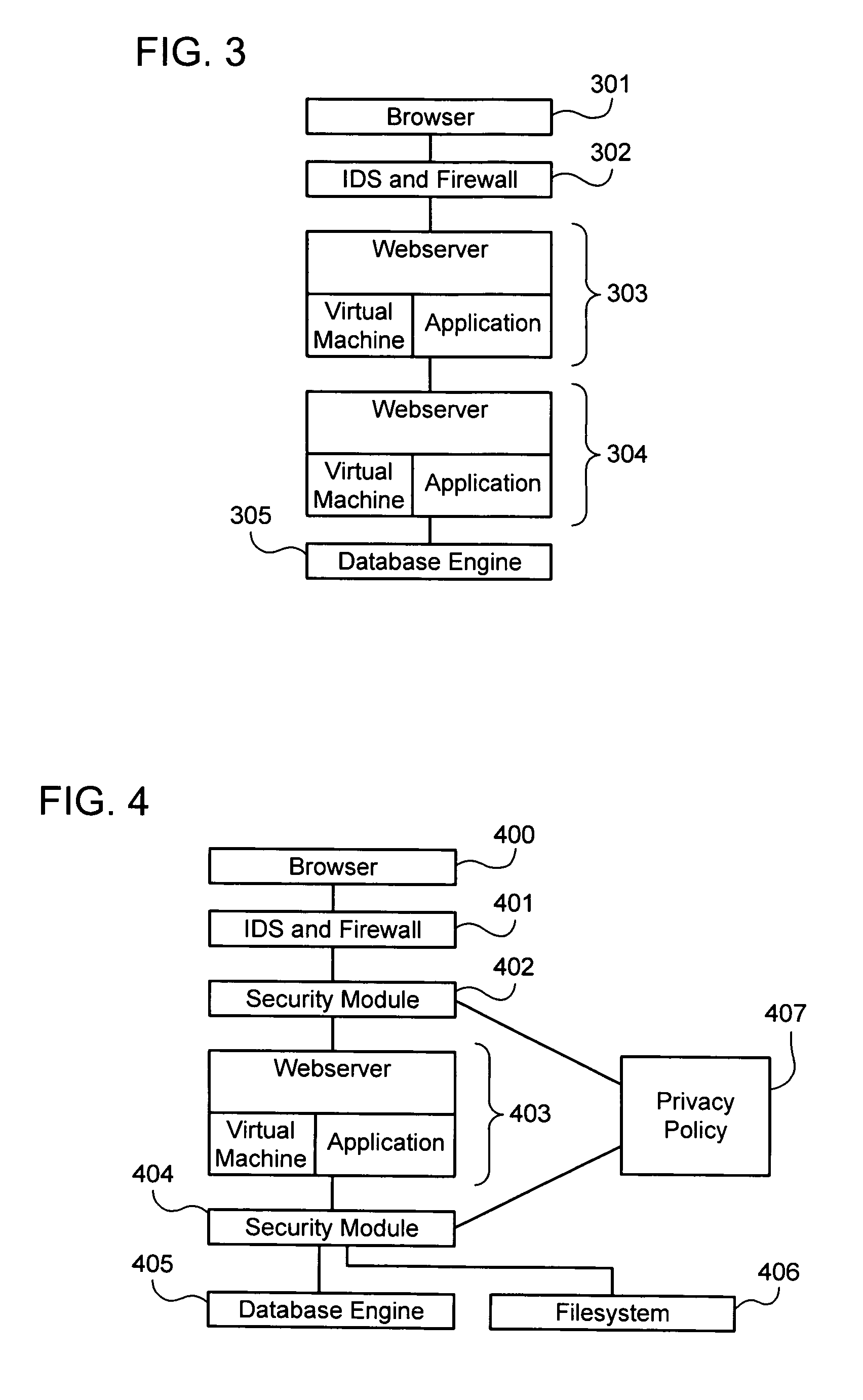
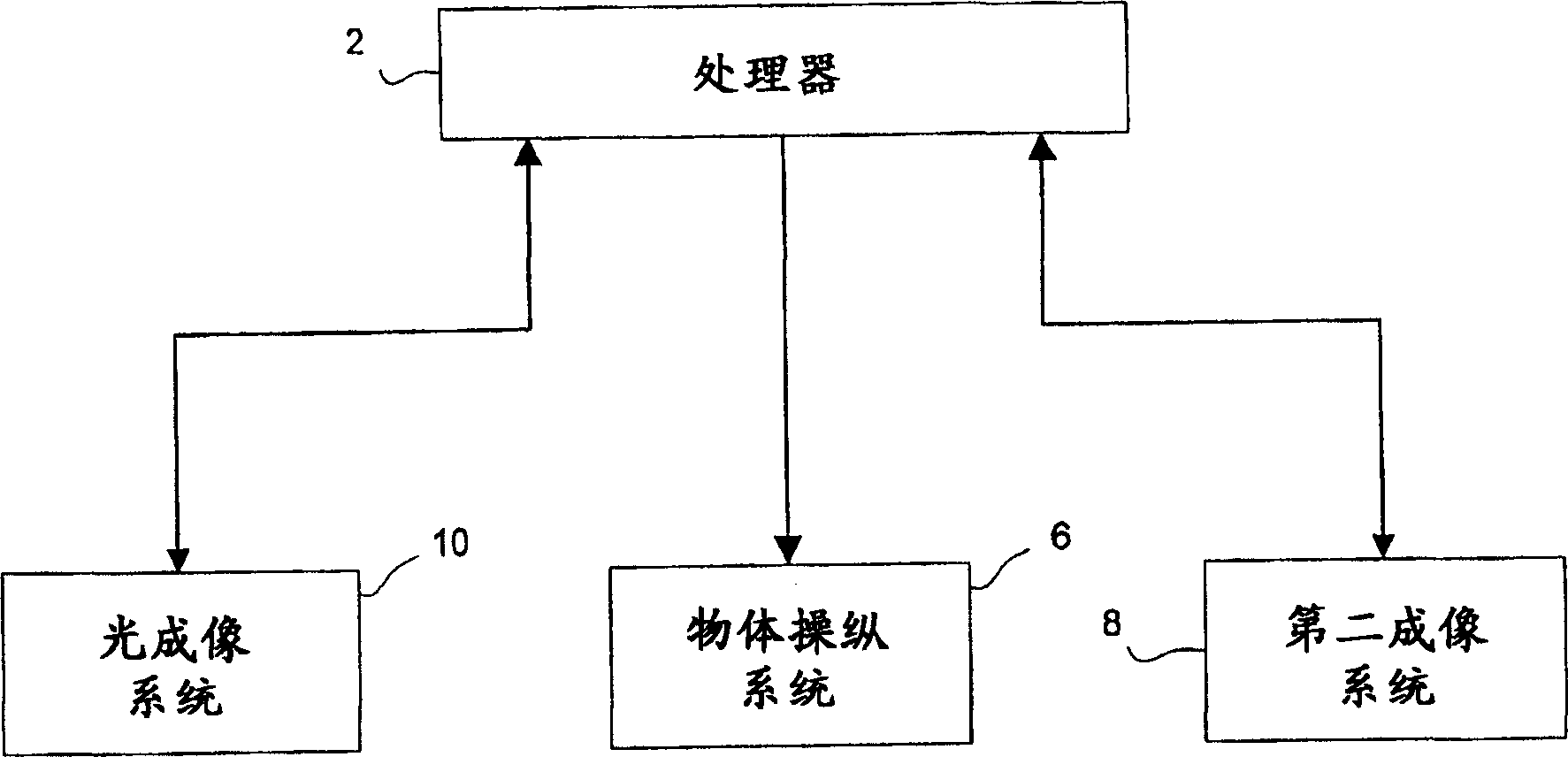
Intelligent security control system for virtualized ecosystems
ActiveUS20100169948A1Digital data processing detailsPublic key for secure communicationObject handlingVirtualization
Resources of a virtualized ecosystem are intelligently secured by defining and analyzing object handling security control information for one or more logical resources in the virtualized ecosystem and deriving therefrom object properties for each of the logical resources involved in the execution of a virtual machine in any given context within the virtualized ecosystem.
Owner:HYTRUST
Relational database extenders for handling complex data types
InactiveUS6047291AData processing applicationsDigital data processing detailsObject handlingRelational database
This invention is directed to relational extenders for a computer-based relational database. Each relational extender includes at least one column, in a first, business table containing a user defined application database, dedicated to object handles for defining the complex data type of an object; a second, attribute, table containing at least one column defining a unique characteristic associated with the one object and one column dedicated to containing the object handle; and a third, metadata, table containing at least one column defining a common characteristic associated with all objects defined within the business table and one column dedicated to containing the object handles and at least one column dedicated to containing a reference to object data associated with the object. The relational extender further includes a fourth table containing a reference to each object handle column defined in the first table, and a fifth table containing the names of the second and third tables for each object defined in the first table.
Owner:IBM CORP
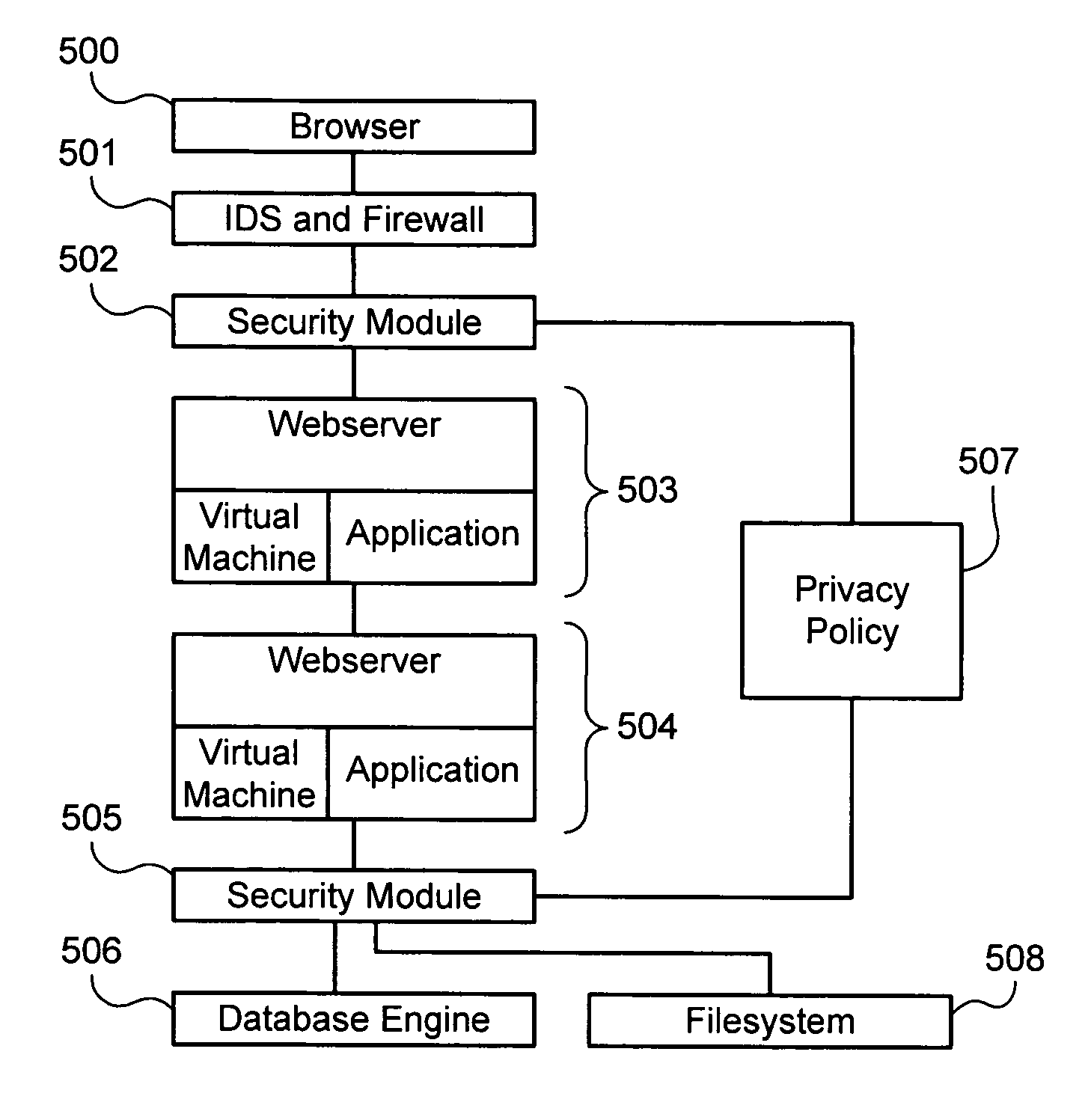
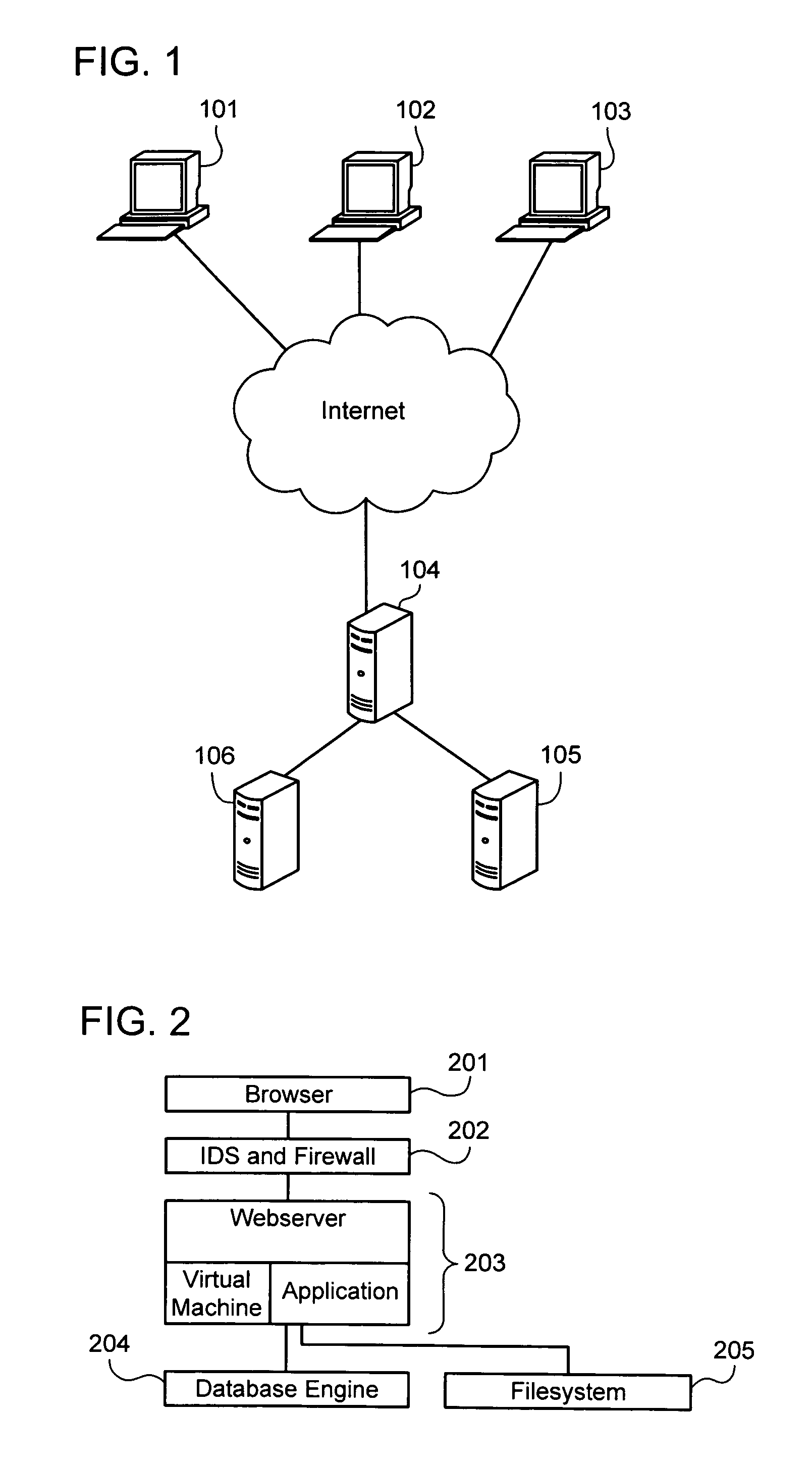
Establishing and enforcing security and privacy policies in web-based applications
ActiveUS20060143688A1Enhances security and privacyIncrease flexibilityMemory loss protectionUnauthorized memory use protectionObject handlingWeb application
Method, system, and computer code for implementing security and privacy policy in a web application having an execution environment in which a representation of each object handled by the execution environment accommodates data and an associated tag. An inbound tagging rule is established for tagging inbound objects according to a respective source of each of the inbound objects. A tag is assigned to an object being operated on by the execution environment based on the inbound tagging rule. A security / privacy rule is established for performing security / privacy actions on outbound objects according to a respective tag of each of the outbound objects. A security / privacy action is performed on the object being operated on by the execution environment based on the security / privacy rule.
Owner:FORTRA LLC
Intelligent security control system for virtualized ecosystems
ActiveUS8336079B2Digital data processing detailsDigital computer detailsVirtualizationObject handling
Resources of a virtualized ecosystem are intelligently secured by defining and analyzing object handling security control information for one or more logical resources in the virtualized ecosystem and deriving therefrom object properties for each of the logical resources involved in the execution of a virtual machine in any given context within the virtualized ecosystem.
Owner:HYTRUST
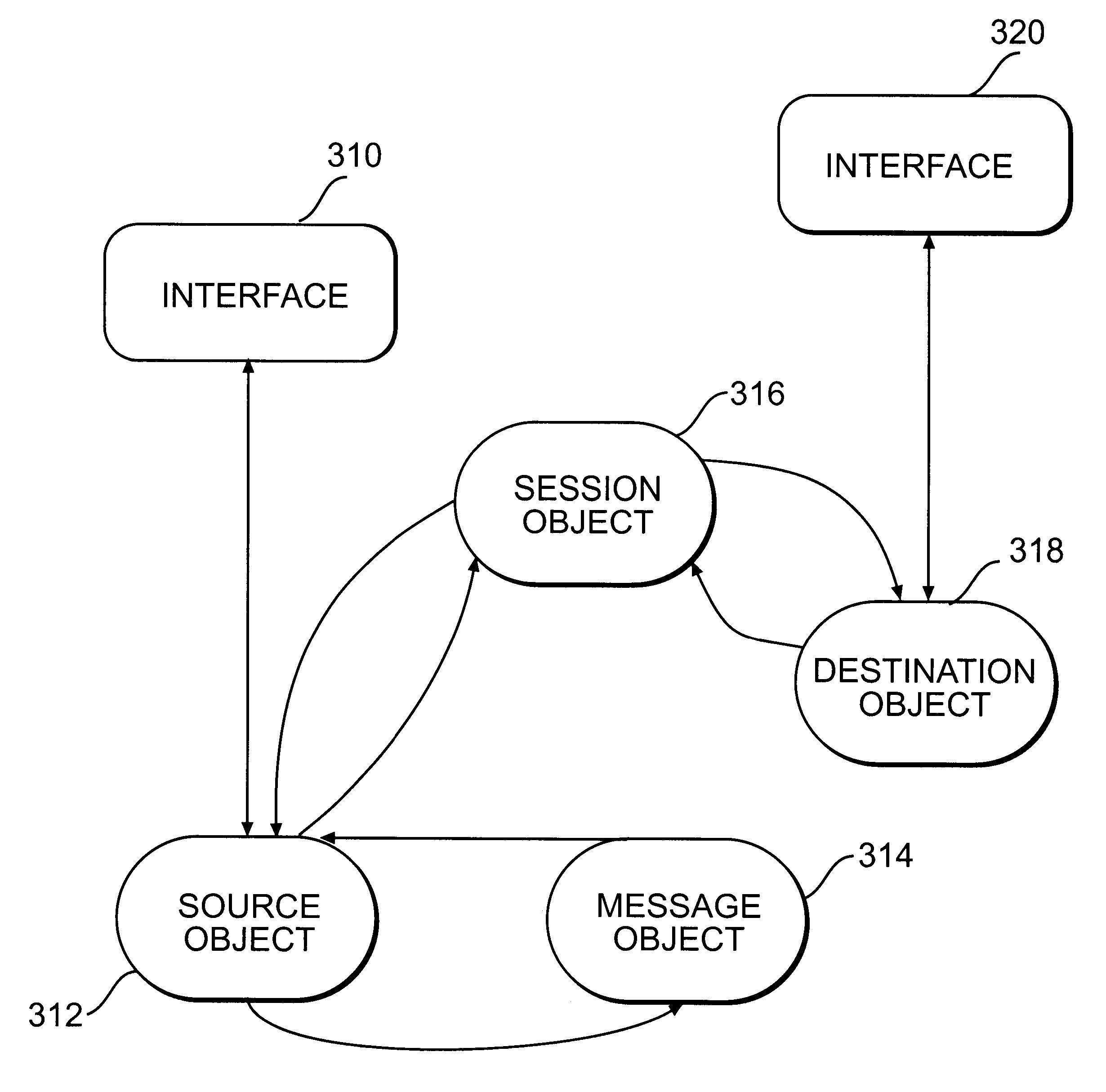
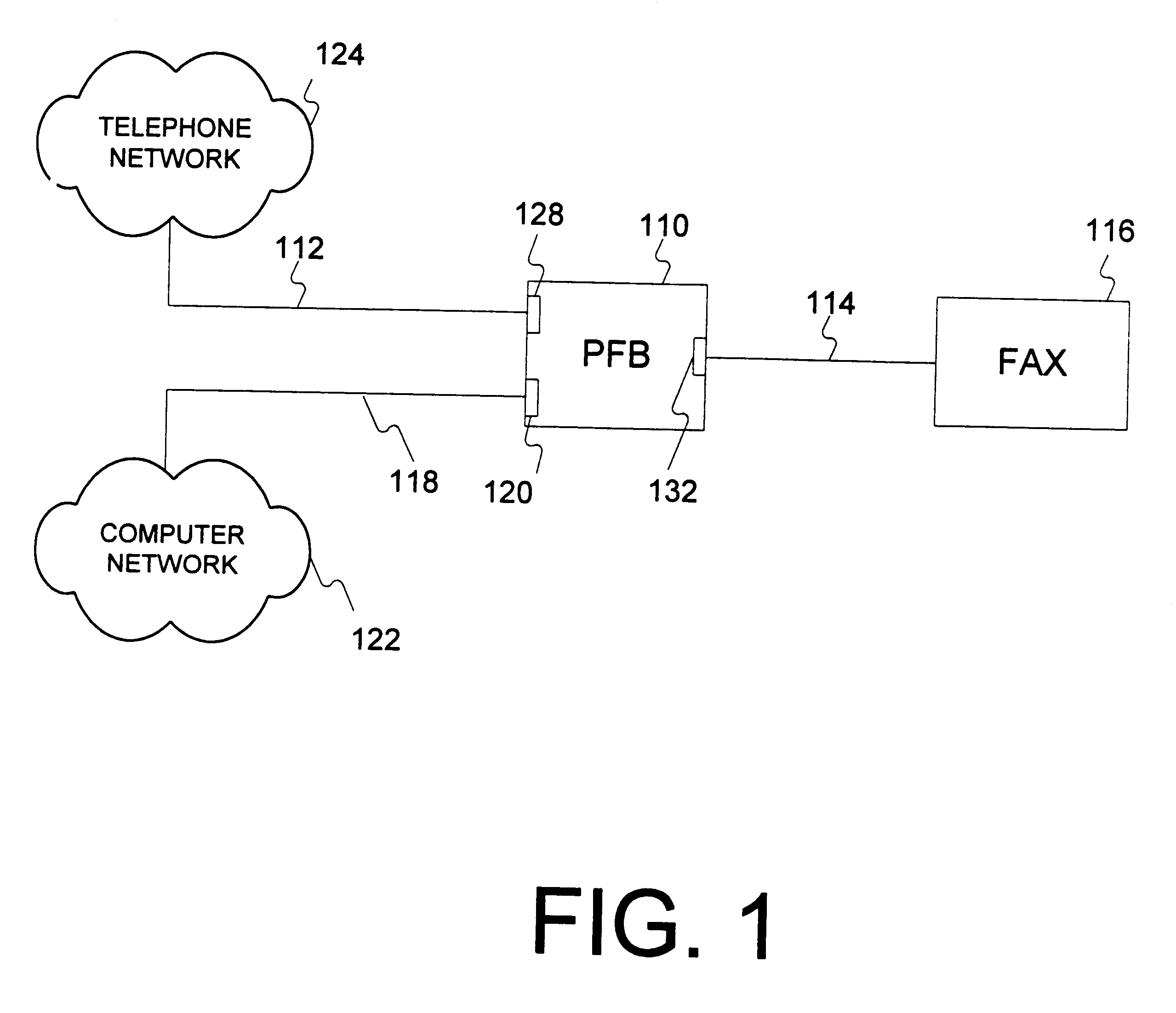
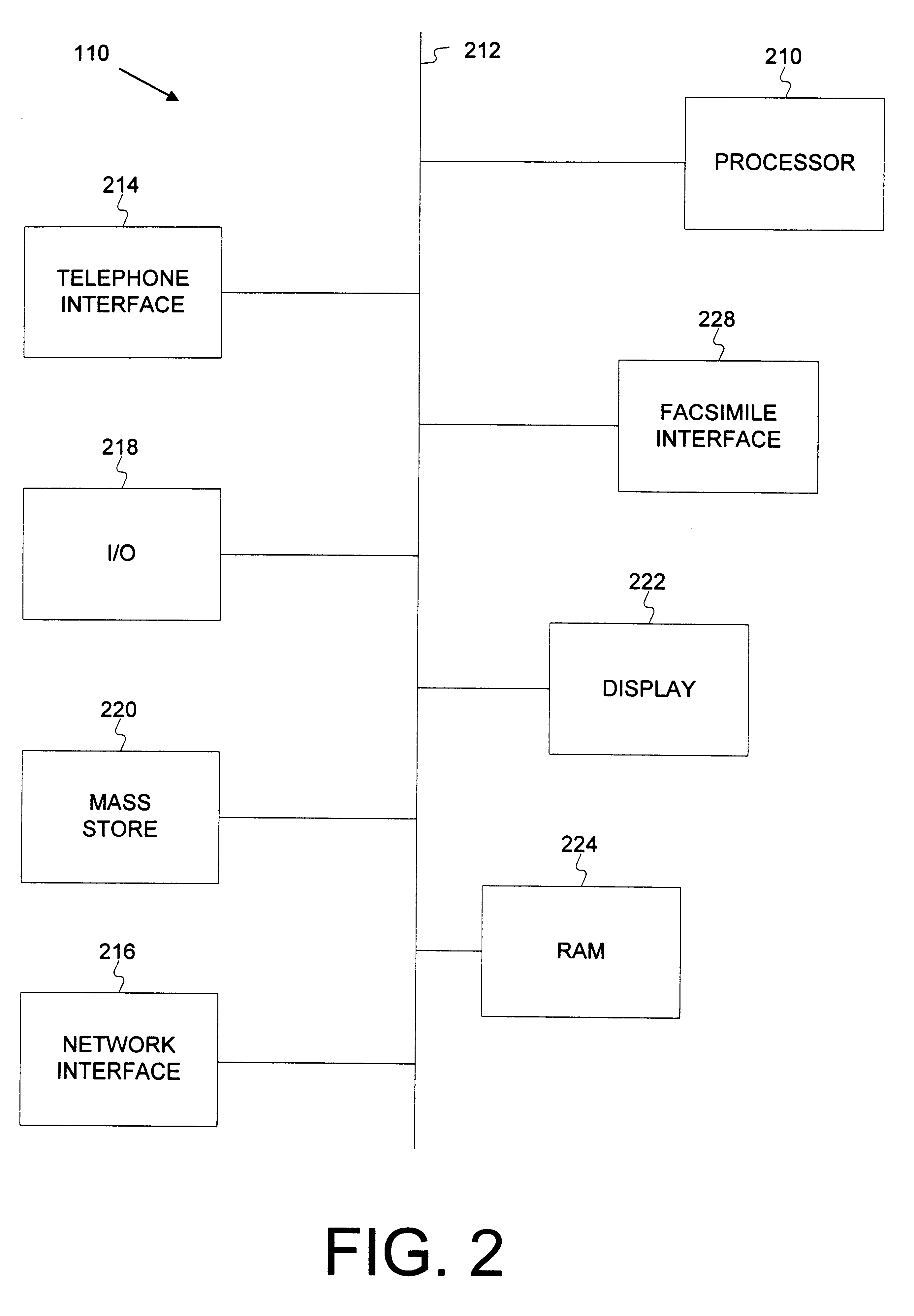
Apparatus and method for reception and transmission of information using different protocols
A Protocol Fax Box (PFB) receives information, determines destinations for the information, and converts the information protocol and data, if necessary, for transmission to the destinations. The PFB has plural interfaces from which it receives and sends data. Upon receiving information on one of its interfaces, the PFB creates a set of objects for handling the transfer of the information from the incoming interface to an outgoing, or destination, interface. A source object handles the incoming communication, a session object handles destination determination, and a destination object handles protocol conversion from the source interface to the destination interface. The session object also logs information regarding each session. The PFB may use a client server model to download information as needed from a network, or have processing be performed on the network.
Owner:BROCADE COMMUNICATIONS SYSTEMS
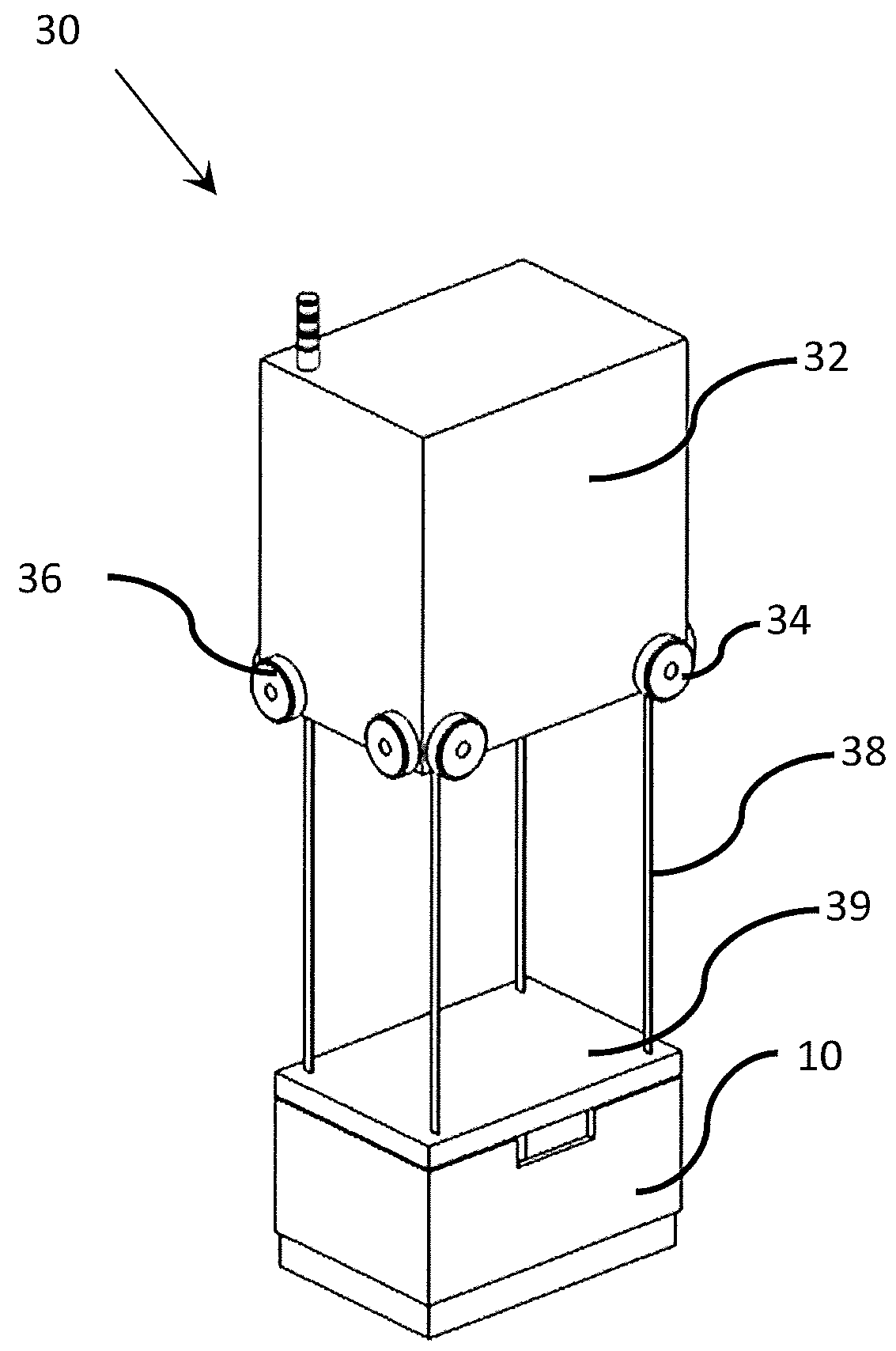
Methods and apparatus for storing and serving streaming media data
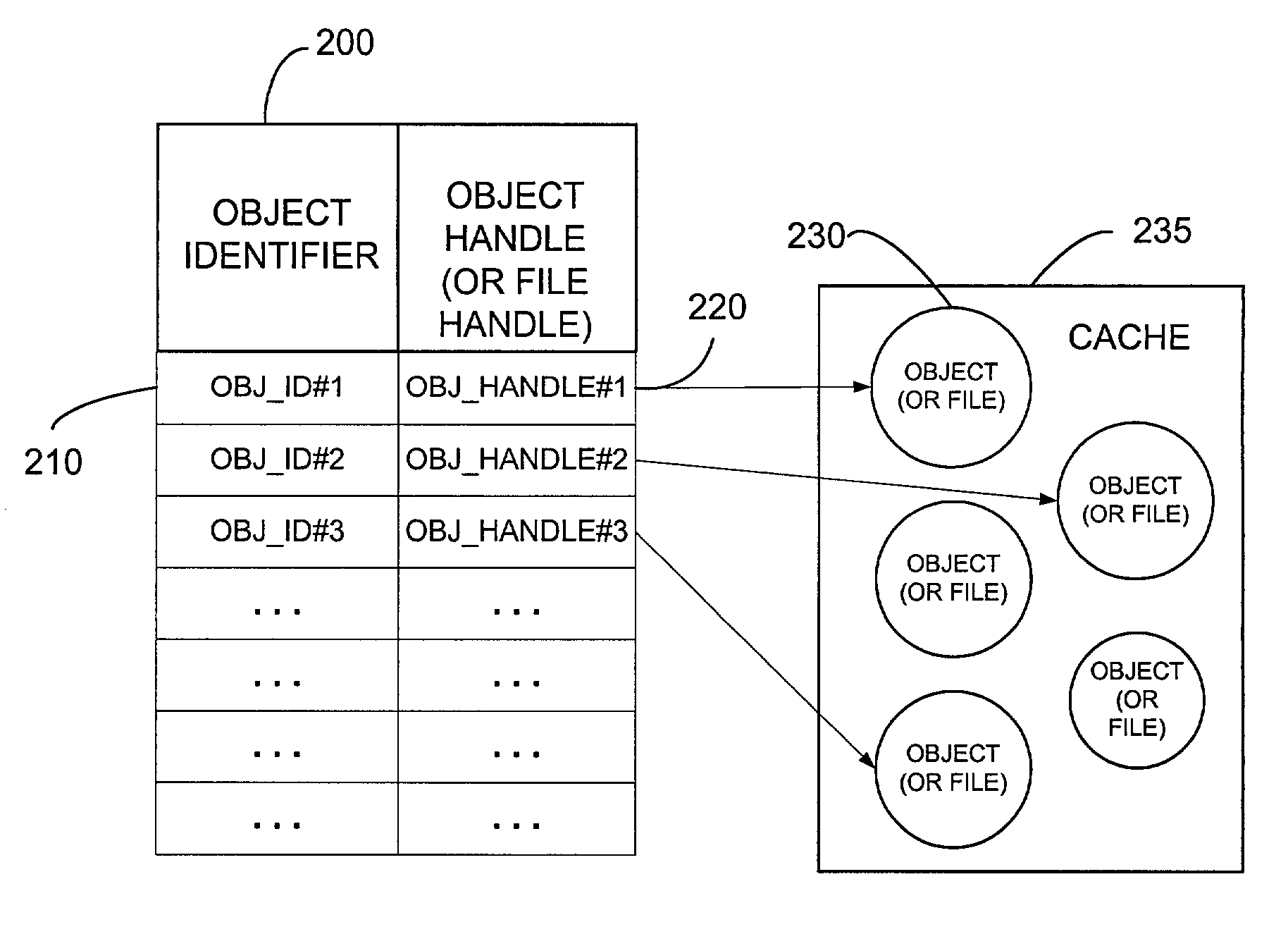
A method for storing streaming media data in a cache memory includes receiving the streaming media data from a streaming media server, the streaming media data comprising a series of packets of media data, the packets of media data including header data and payload data, separating the header data from payload data, storing a portion of the header data in a session data object in the cache memory, and storing the payload data in a first plurality of data objects in the cache memory, wherein each data object of the first plurality of data objects is directly addressable in the cache memory via an associated object handle, and wherein each data object of the first plurality of data objects stores a portion of the payload data.
Owner:NETWORK APPLIANCE INC
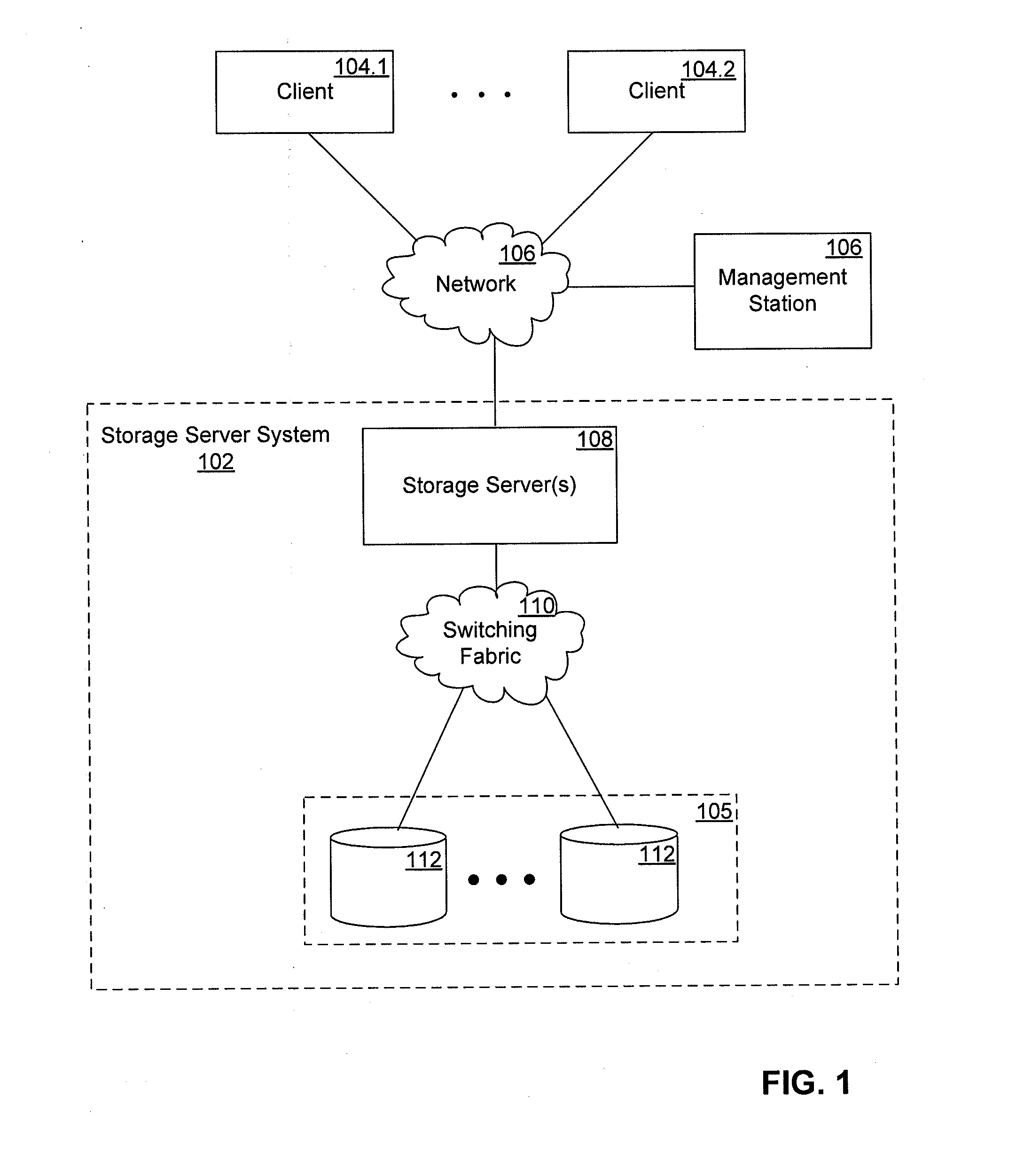
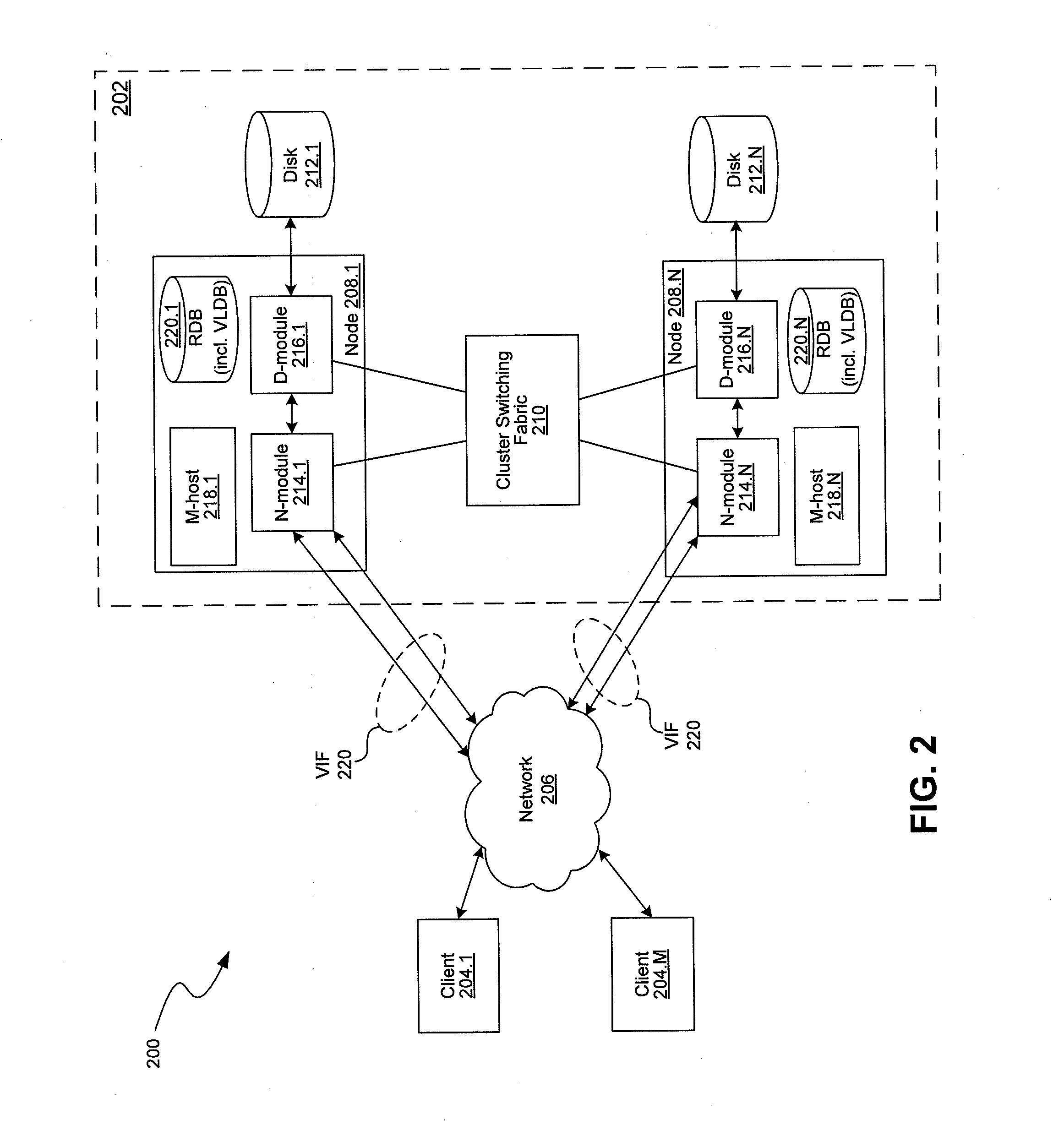
Methods and systems for providing a unified namespace for multiple network protocols
InactiveUS20110137966A1Easy data migrationEasy to navigateTransmissionSpecial data processing applicationsObject handlingObject store
A network storage server system includes a presentation layer that presents multiple namespaces over the same data stored in an object store, allowing users to simultaneously access data over multiple protocols. The system supports object location independence of the stored data objects by introducing a layer of indirection between directory entries and storage locations of stored data objects. In one embodiment, the directory entry of a data object points to a redirector file that includes an object locator (e.g., an object handle or a global object ID) of the data object. The directory entries of data objects are stored in a directory namespace (e.g., NAS path namespace). In another embodiment, a global object ID of the data object is directly encoded within the directory entry of the data object.
Owner:NETWORK APPLIANCE INC
Computer program product for database relational extenders
InactiveUS6078925AEasy accessFast and efficient mechanismData processing applicationsDigital data processing detailsObject handlingData integrity
This invention is directed to relational extenders for a computer-based relational database. Each relational extender includes at least one column, in a first, business, table containing a user defined application database, dedicated to object handles for defining the complex data type of an object; a second, attribute, table containing at least one column defining a unique characteristic associated with the one object and one column dedicated to containing the object handle; and a third, metadata, table containing at least one column defining a common characteristic associated with all objects defined within the business table and one column dedicated to containing the object handle and at least one column dedicated to containing a reference to object data associated with the object. The relational extender further includes a fourth table containing a reference to each object handle column defined in the first table, a fifth table containing the names of the second and third tables for each object defined in the first table, a sixth table containing a reference to each object handle removed from the first table and including one column dedicated to containing a reference to the location of the object data associated with the removed object handle, and a seventh table having at least one column which describes a property of the data type of each object defined in the first table. The relational extender further includes an eighth table as a temporary holding table for the second table, and a ninth table as a temporary holding table for the third table. Both the eighth and ninth tables are used in conjunction with the extender triggers to ensure data integrity.
Owner:INT BUSINESS MASCH CORP
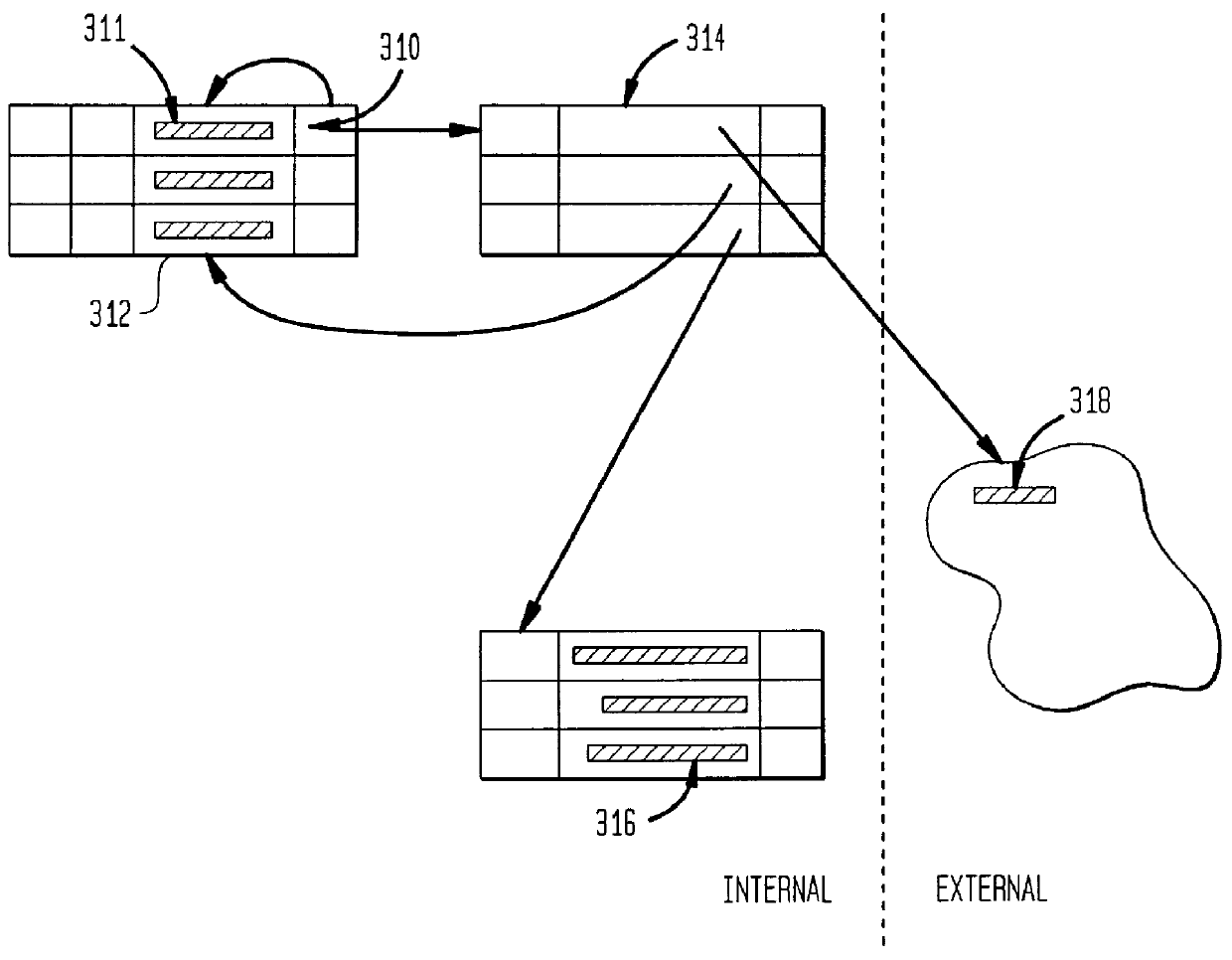
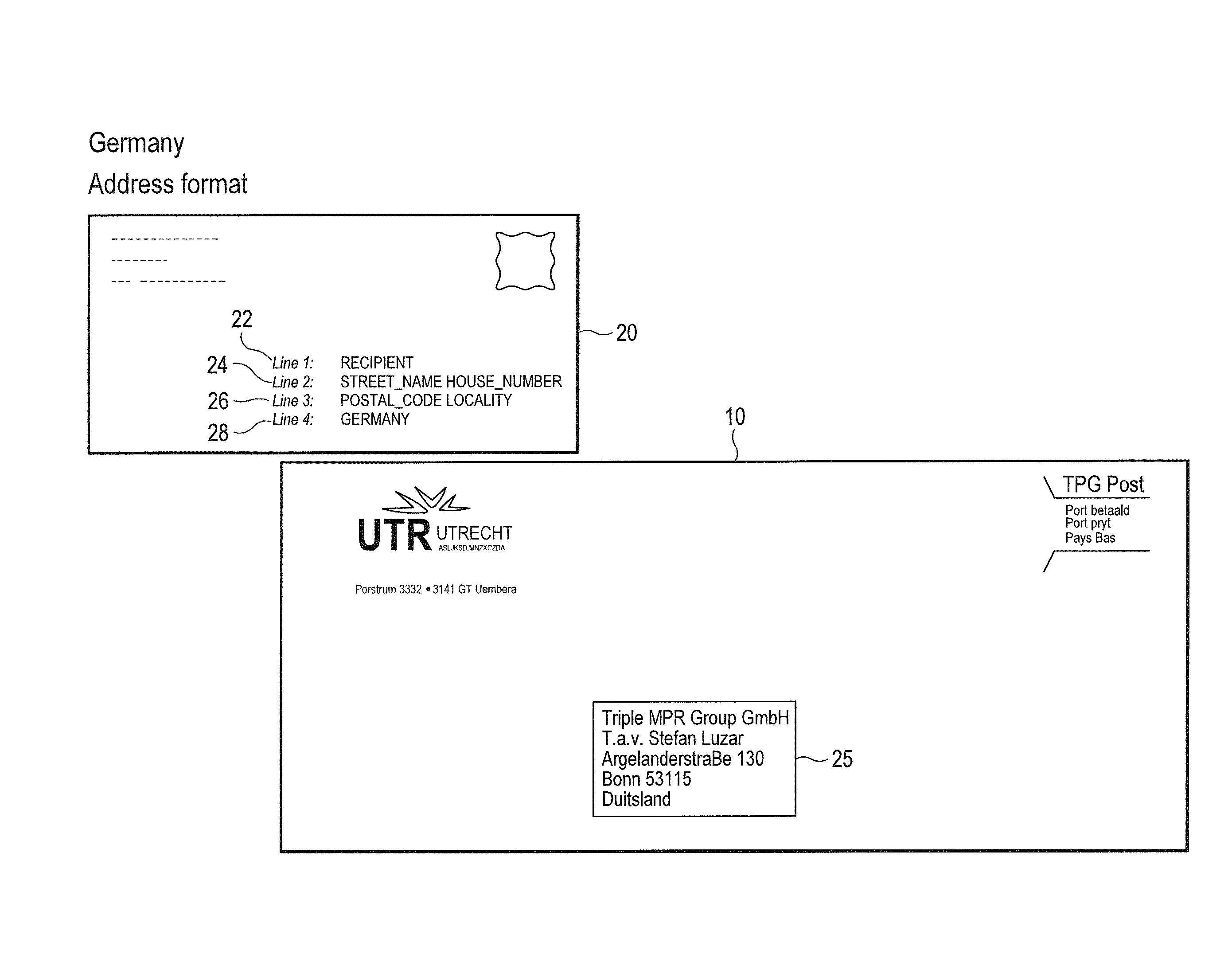
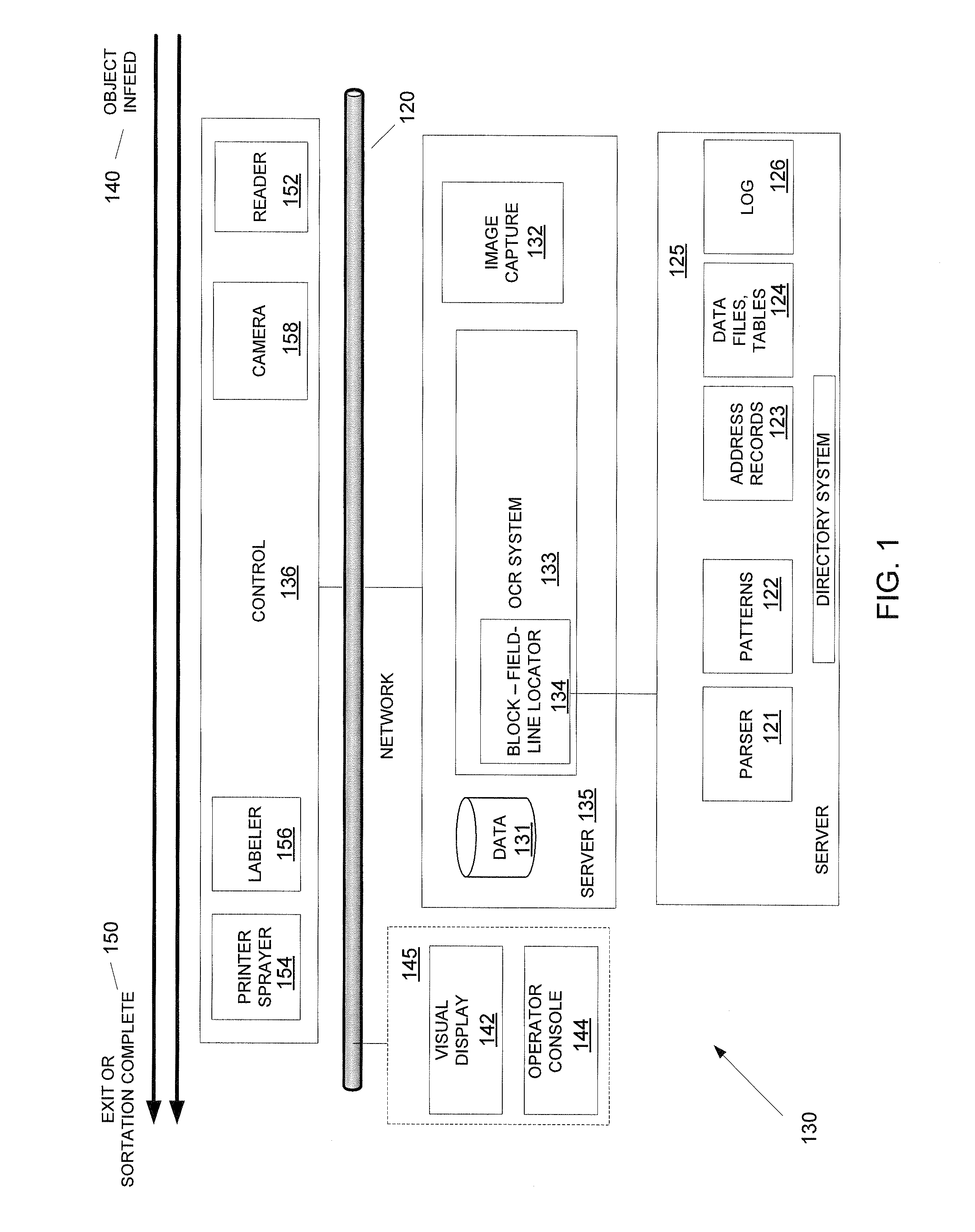
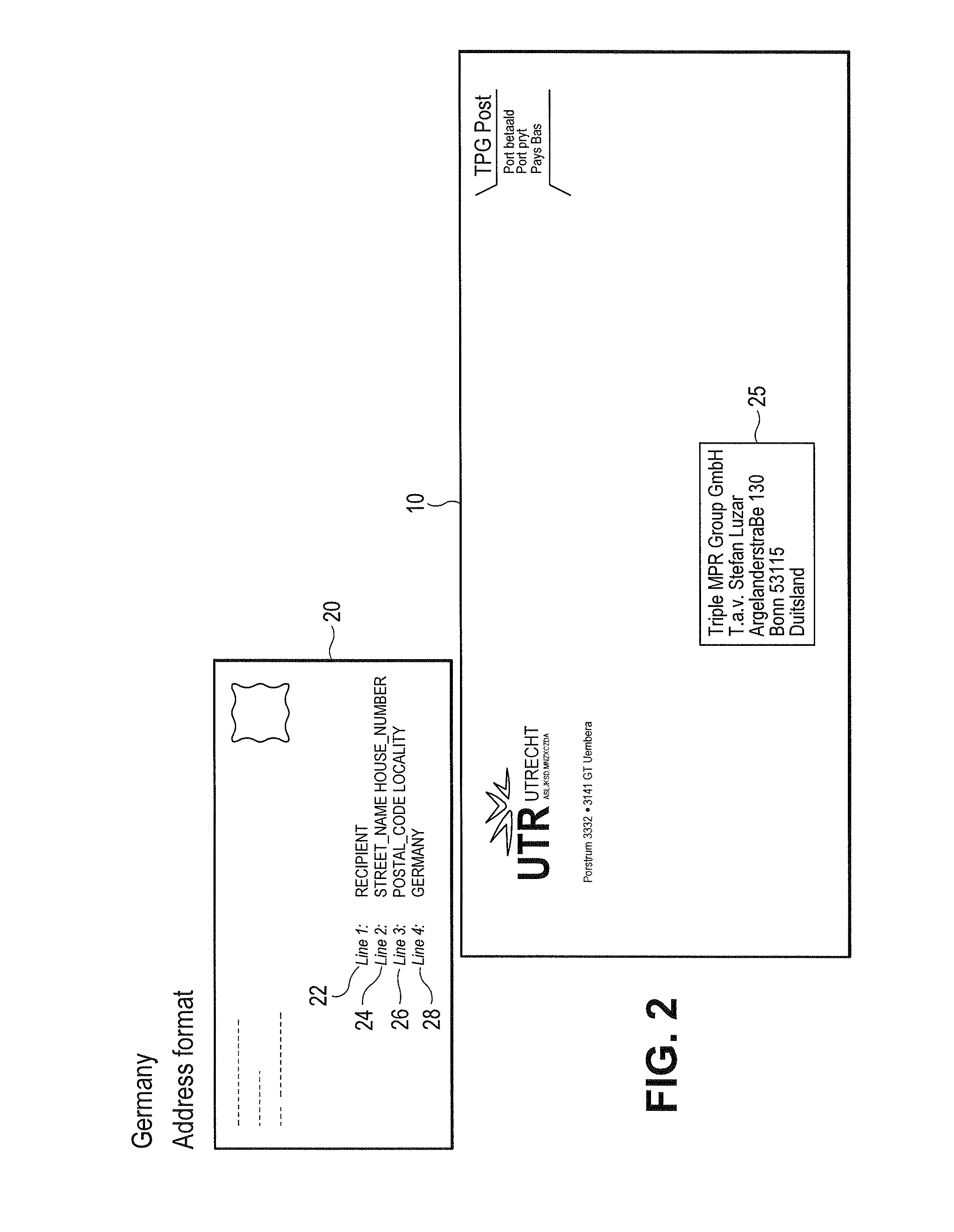
Defined data patterns for object handling
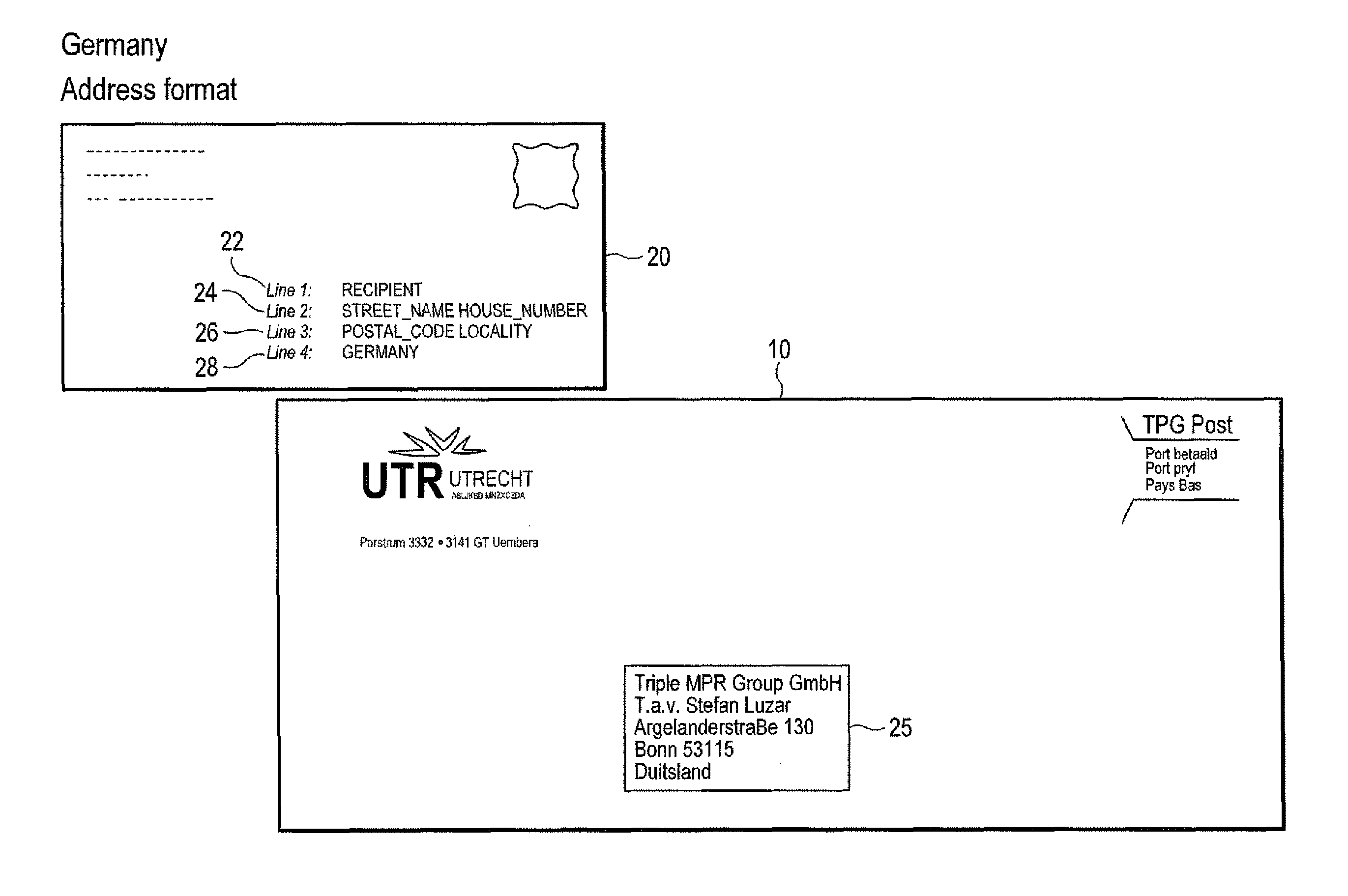
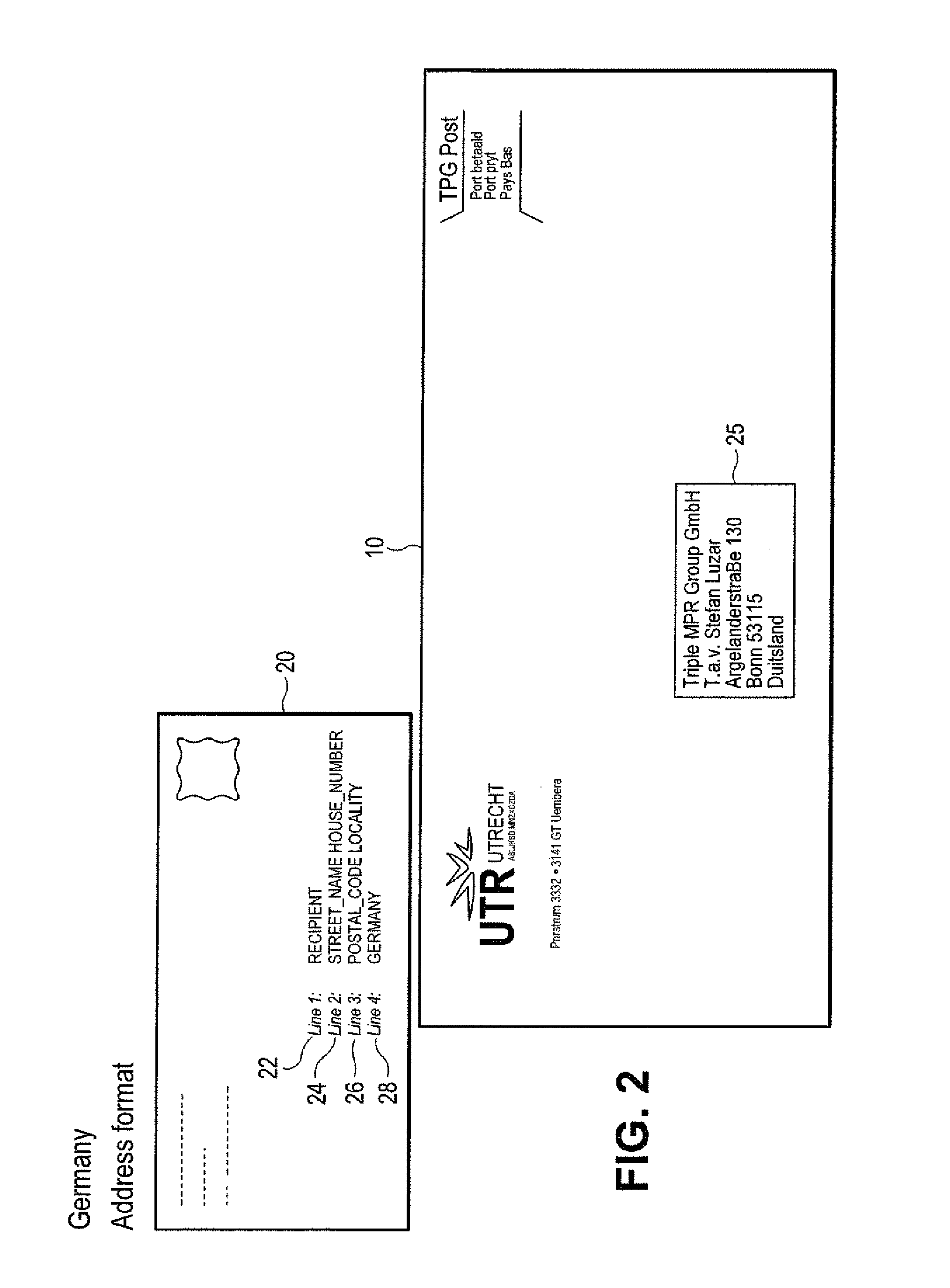
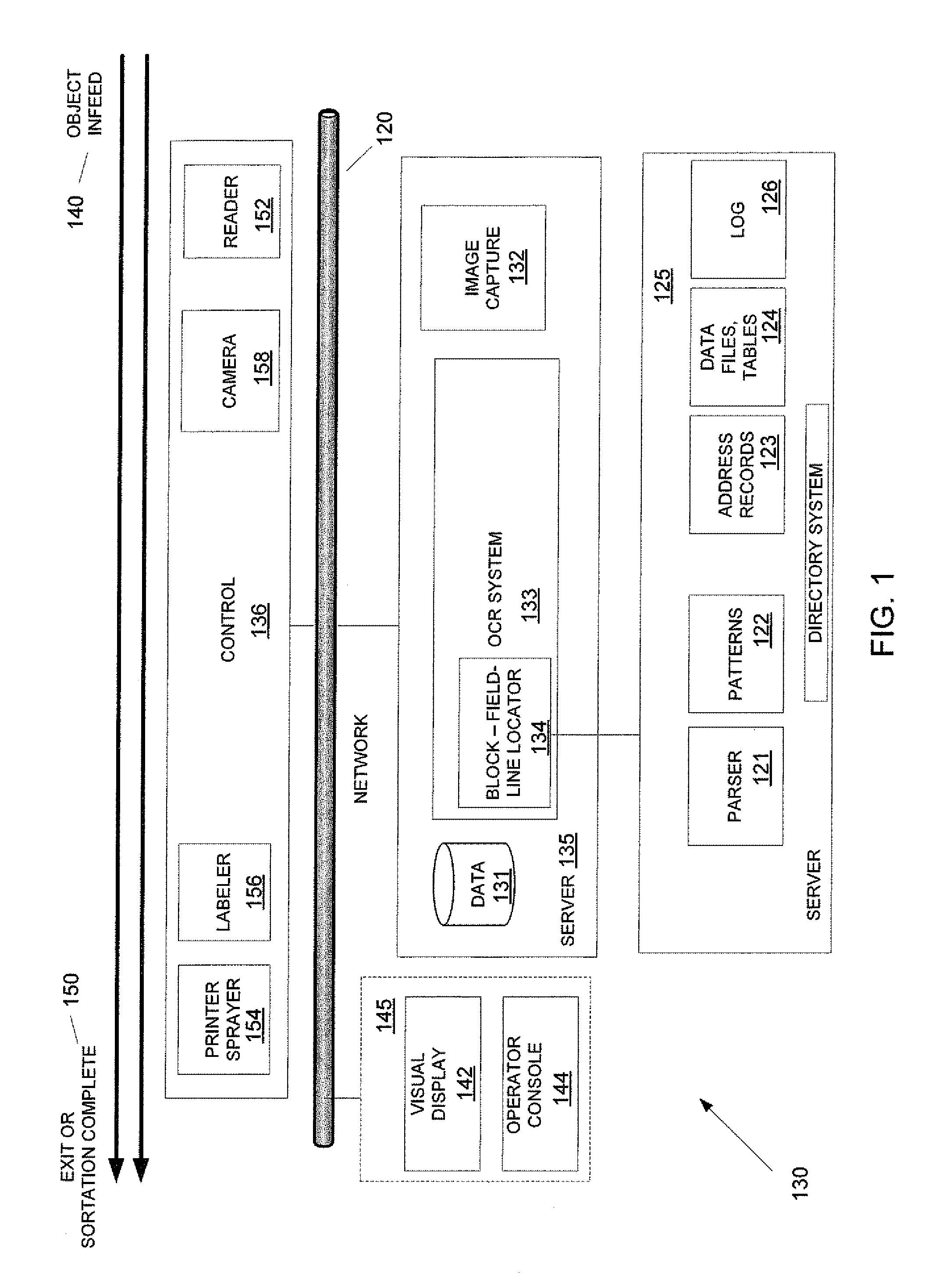
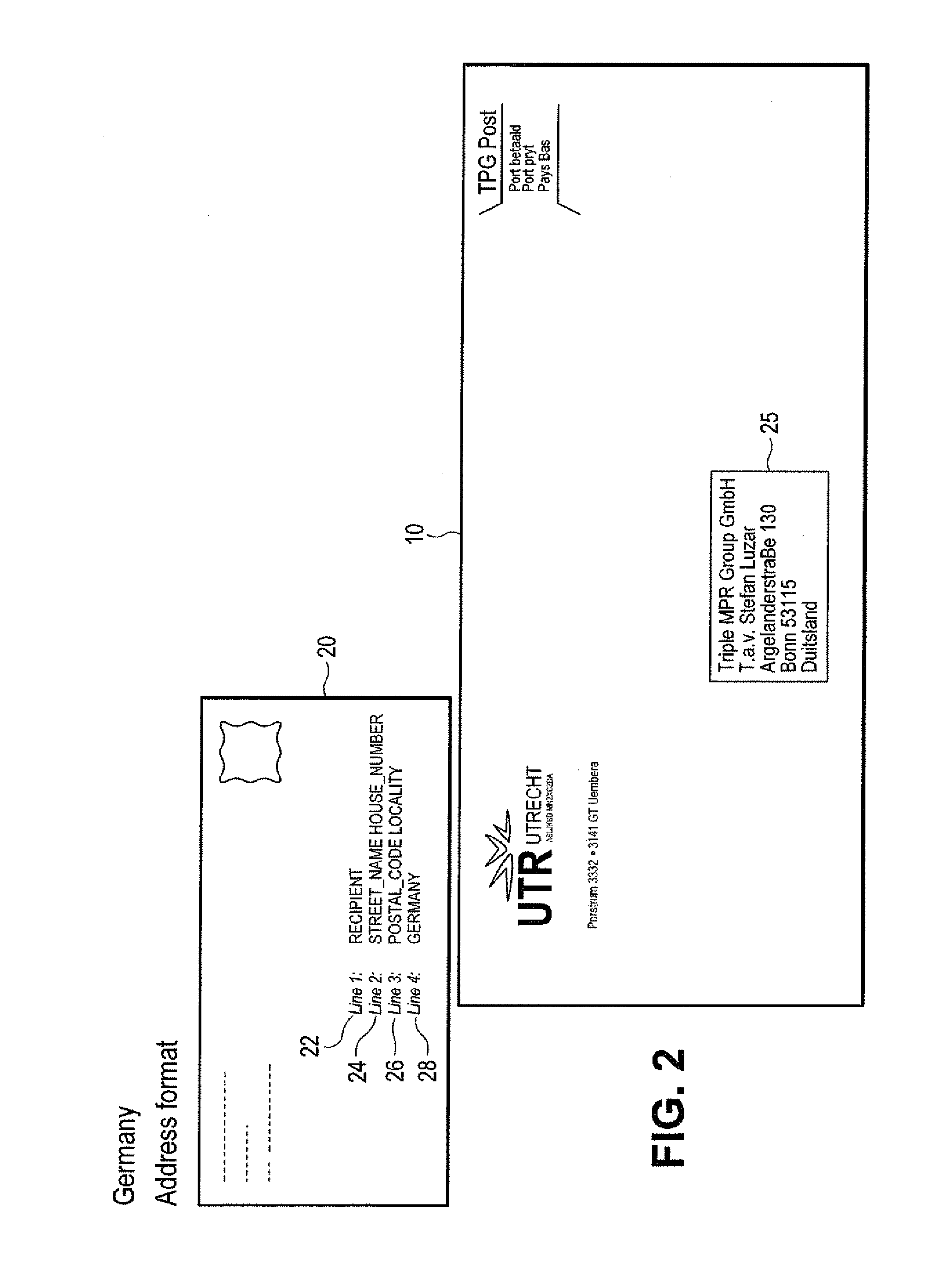
ActiveUS8526743B1Lower Level RequirementsMaximizing numberTelevision system detailsCharacter recognitionPattern recognitionObject handling
A method of defining data patterns for object handling includes obtaining an image of an input data area, processing the image to obtain image data, and comparing the image data with a pattern, wherein the pattern identifies spatial information of corresponding pattern fields of the pattern. The method further includes determining a confidence level of the comparison of the image data according to a success in matching the image data with the pattern fields, comparing the confidence level with a confidence threshold associated with the pattern, and selecting the pattern. A pattern output associated with the selected pattern is identified, wherein the pattern output corresponds to a canonical return format, and the pattern output is applied to the image data.
Owner:MATTHEWS INT CORP
Defined data patterns for object handling
ActiveUS9058543B2Lower Level RequirementsMaximizing numberTelevision system detailsColor television detailsPattern recognitionObject handling
A method of defining data patterns for object handling includes obtaining an image of an input data area, processing the image to obtain image data, and comparing the image data with a pattern, wherein the pattern identifies spatial information of corresponding pattern fields of the pattern. The method further includes determining a confidence level of the comparison of the image data according to a success in matching the image data with the pattern fields, comparing the confidence level with a confidence threshold associated with the pattern, and selecting the pattern. A pattern output associated with the selected pattern is identified, wherein the pattern output corresponds to a canonical return format, and the pattern output is applied to the image data.
Owner:RAF SOFTWARE TECH INC
Defined data patterns for object handling
ActiveUS20140184843A1Lower Level RequirementsMaximizing numberTelevision system detailsColor television detailsPattern recognitionObject handling
A method of defining data patterns for object handling includes obtaining an image of an input data area, processing the image to obtain image data, and comparing the image data with a pattern, wherein the pattern identifies spatial information of corresponding pattern fields of the pattern. The method further includes determining a confidence level of the comparison of the image data according to a success in matching the image data with the pattern fields, comparing the confidence level with a confidence threshold associated with the pattern, and selecting the pattern. A pattern output associated with the selected pattern is identified, wherein the pattern output corresponds to a canonical return format, and the pattern output is applied to the image data.
Owner:RAF SOFTWARE TECH INC
Object storage, handling, and retrieving system and method
ActiveUS20180162639A1Reduce the impactReduce impactConveyorsStorage devicesProduction lineEngineering
An object handling and retrieving system and method are described. A storage system is described suitable for storing multiple product lines in an automated warehouse environment. The storage system includes a plurality of load handling devices disposed above a frame and independently moveable to access different stacks. The load handling device can retrieve and transport a target container to a sequencing and temporary storage portion having a sorting frame for taking delivery of the target container and moving it to an output port of the sorting frame.
Owner:OCADO INNOVATION
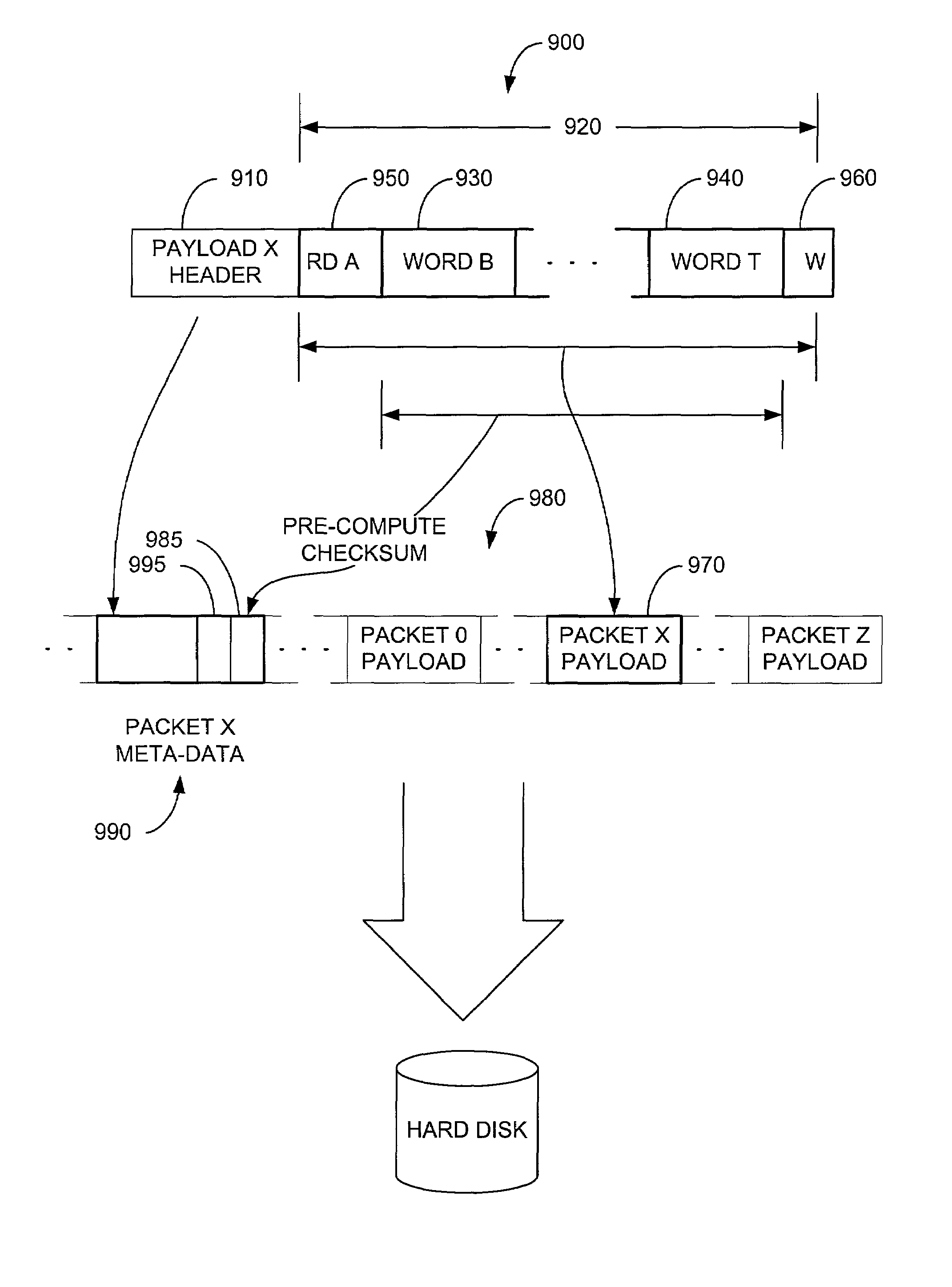
Methods and apparatus for precomputing checksums for streaming media
ActiveUS7386627B1Efficiently streamedEfficient retrievalCode conversionMultiple digital computer combinationsObject handlingChecksum
A method for storing streaming media data packets in a cache includes receiving a first streaming media data packet from a streaming media server, the first streaming media data packet comprising first header data and first payload data, pre-determining a first payload checksum in response to at least a portion of the first payload data, storing at least a portion of the first header data and the first payload checksum as first packet meta data in a first data object in the cache memory, and storing the first payload data in the first data object in the cache memory, wherein the first data object is directly addressable in the cache memory via an associated object handle.
Owner:NETWORK APPLLANCE
Methods and systems for applications to interact with hardware
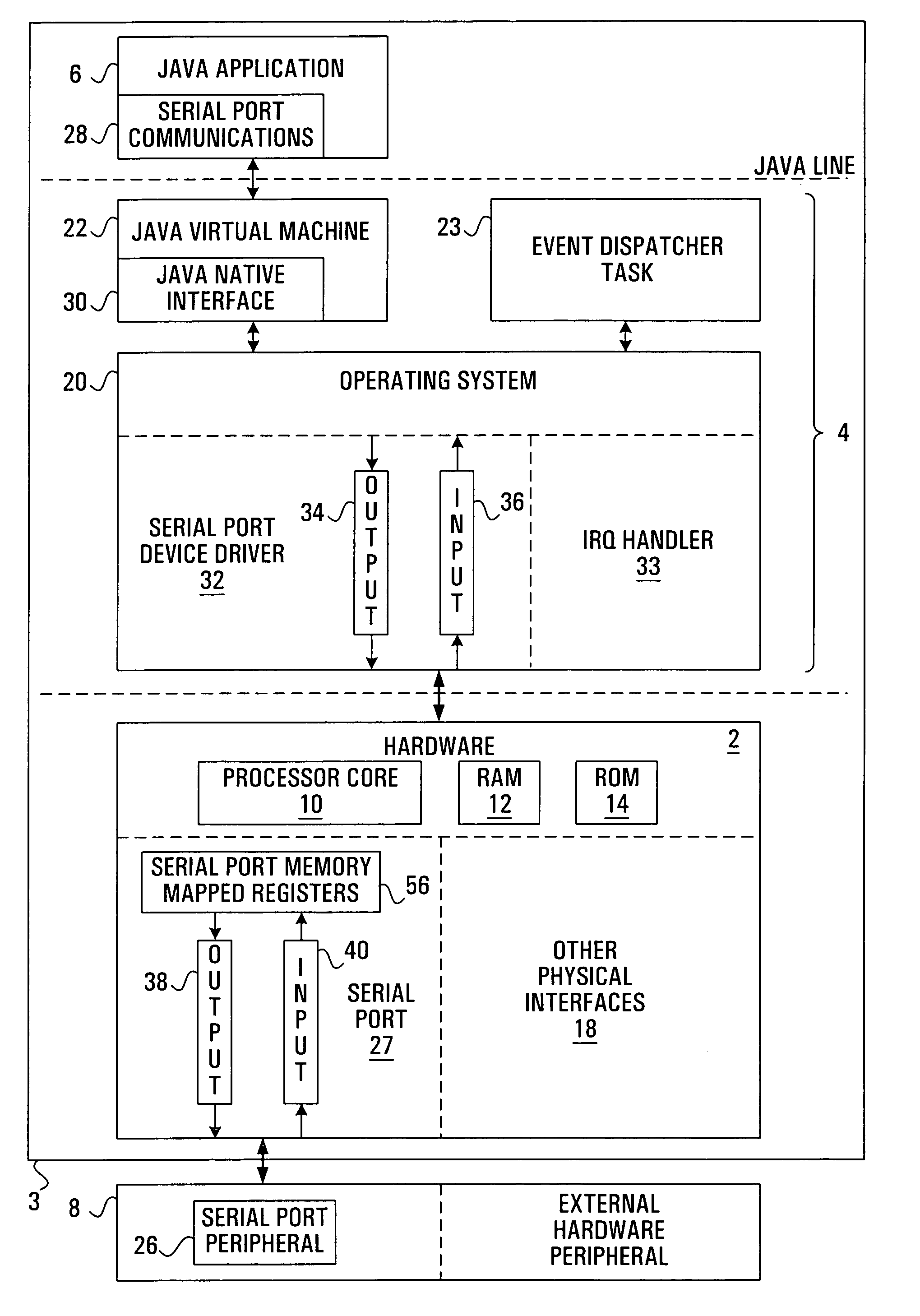
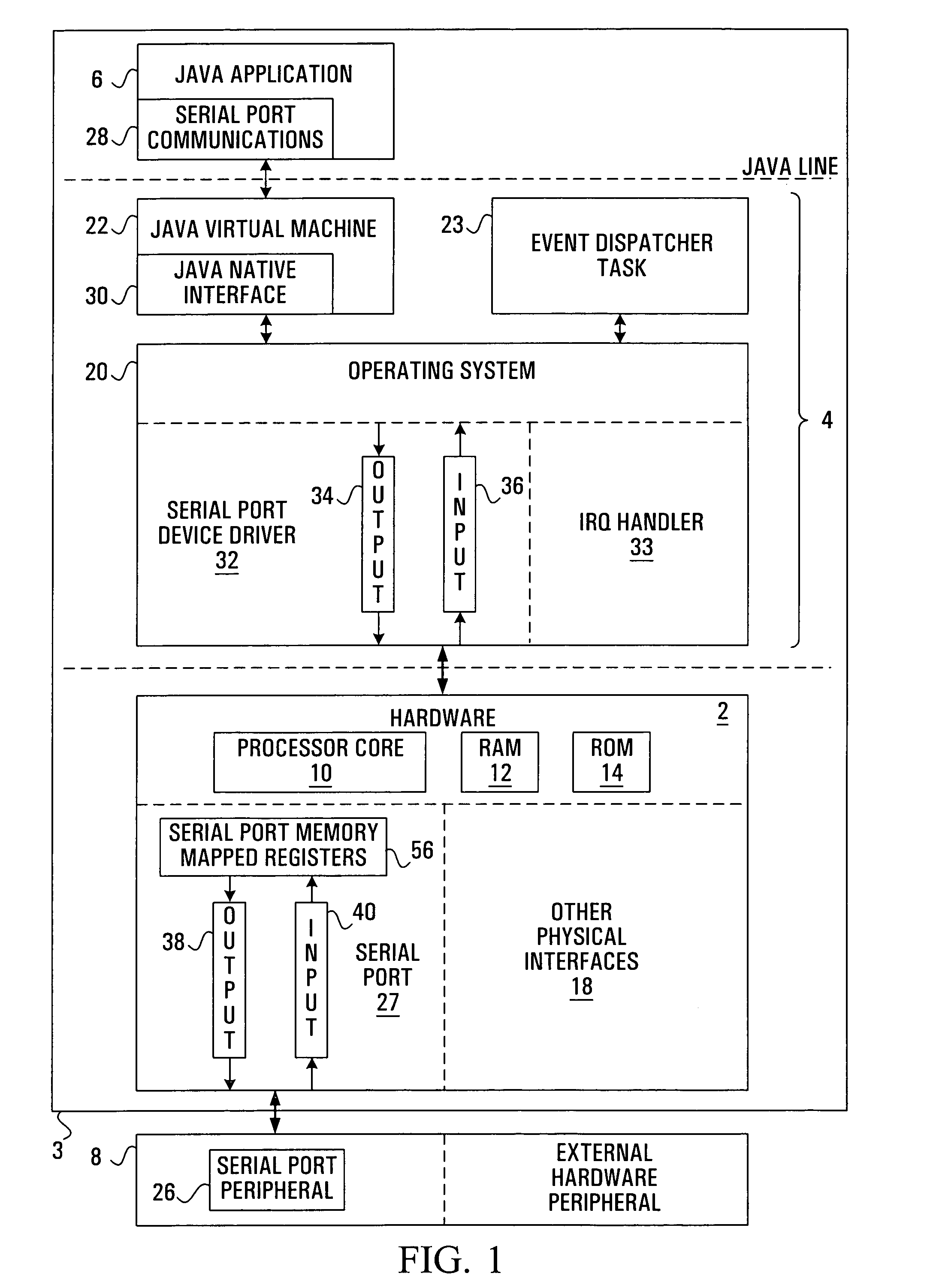
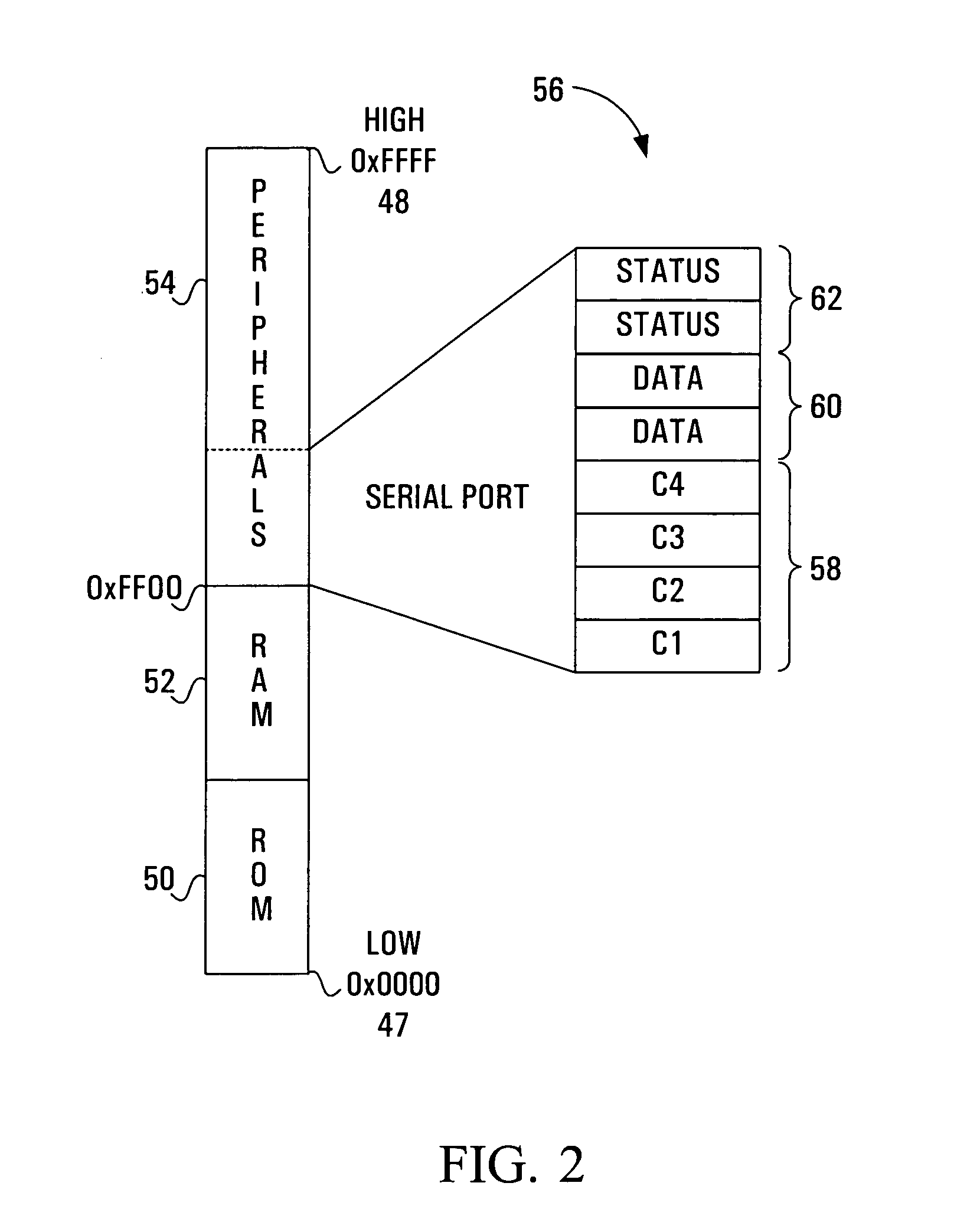
InactiveUS7159223B1Promote rapid developmentFast integrationMemory architecture accessing/allocationMemory adressing/allocation/relocationObject handlingMemory address
A method of providing Java application layer access to hardware peripheral memory mapped registers is provided together with a processor adapted to implement such a method. A fixed memory address space for a hardware peripheral's memory mapped registers is identified, and a Java object is constructed having elements which occupy this fixed memory address space. This allows a Java application to be provided with access to the hardware peripheral's memory mapped registers directly through the Java object. A new Java class is defined having base address and length parameters and in some cases also having a type parameter. This is used in constructing the Java object. When a Java object has an object descriptor which is effectively an object header and a pointer to where the object data is located, constructing the Java object may be done by creating an object descriptor, and then creating an object handle for the Java object which points to the object descriptor. Alternatively, a level of indirection may be removed, and the object handle created to point directly to the object created so as to exist in memory mapped register space.
Owner:ZW
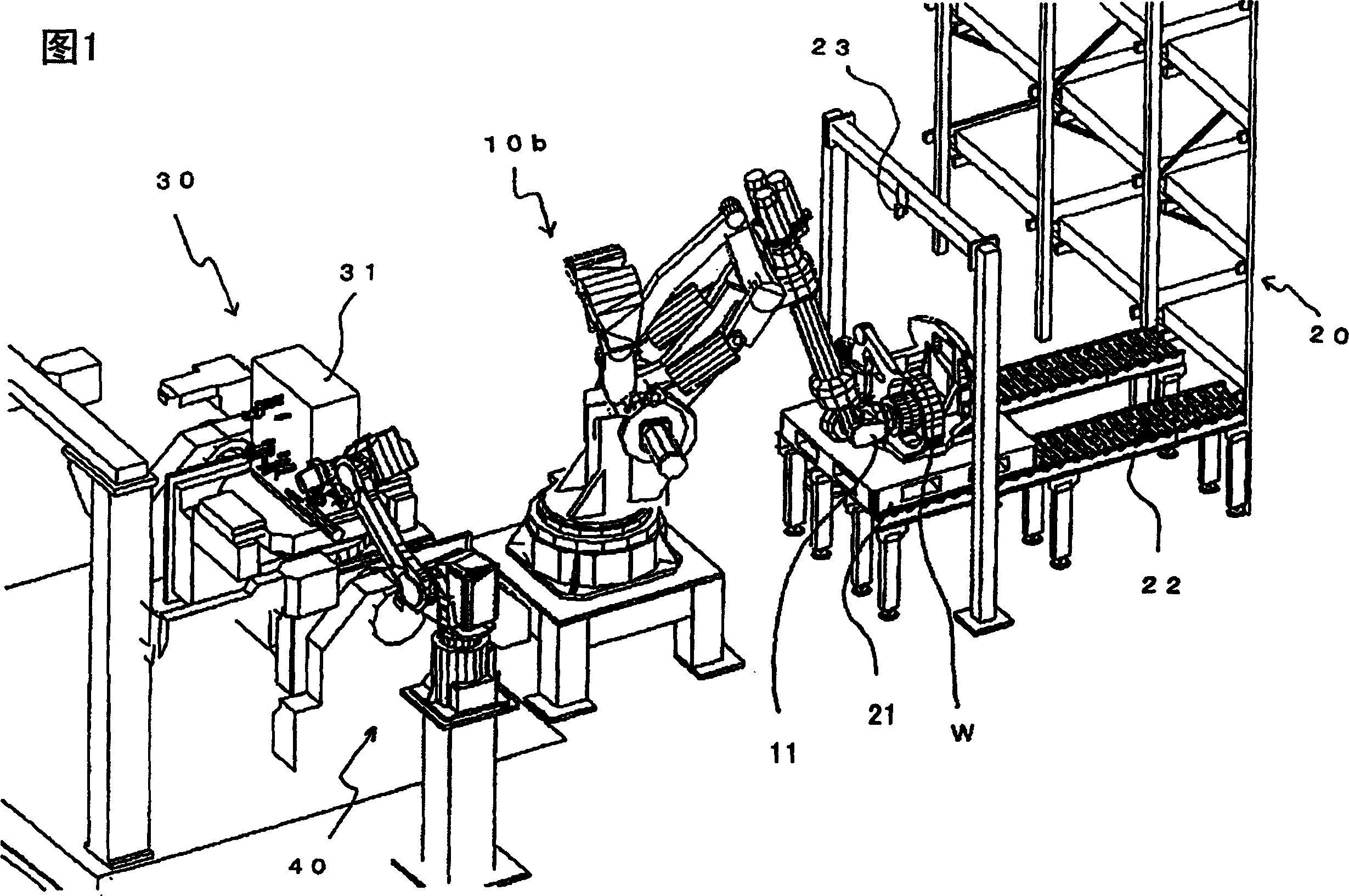
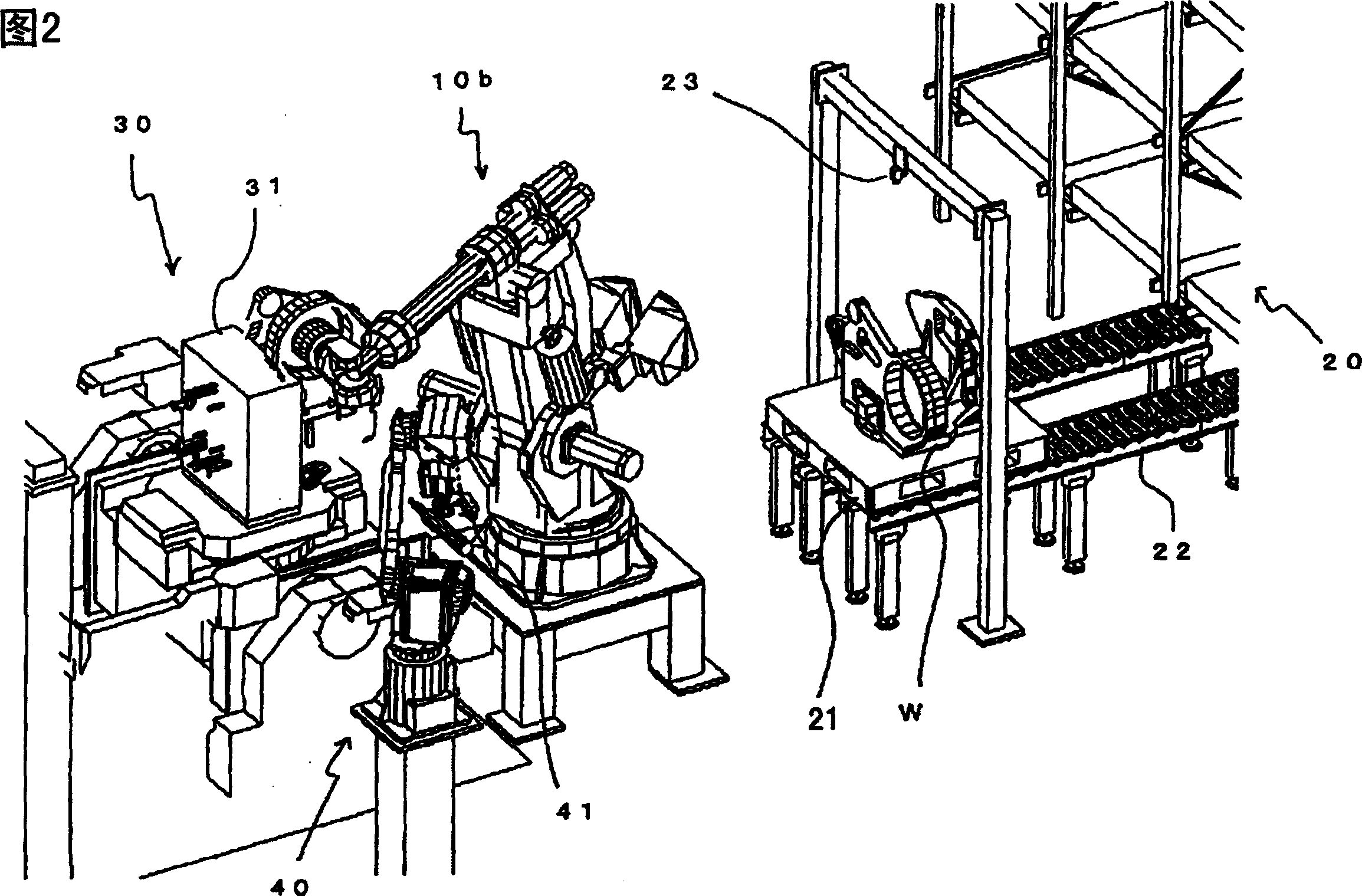
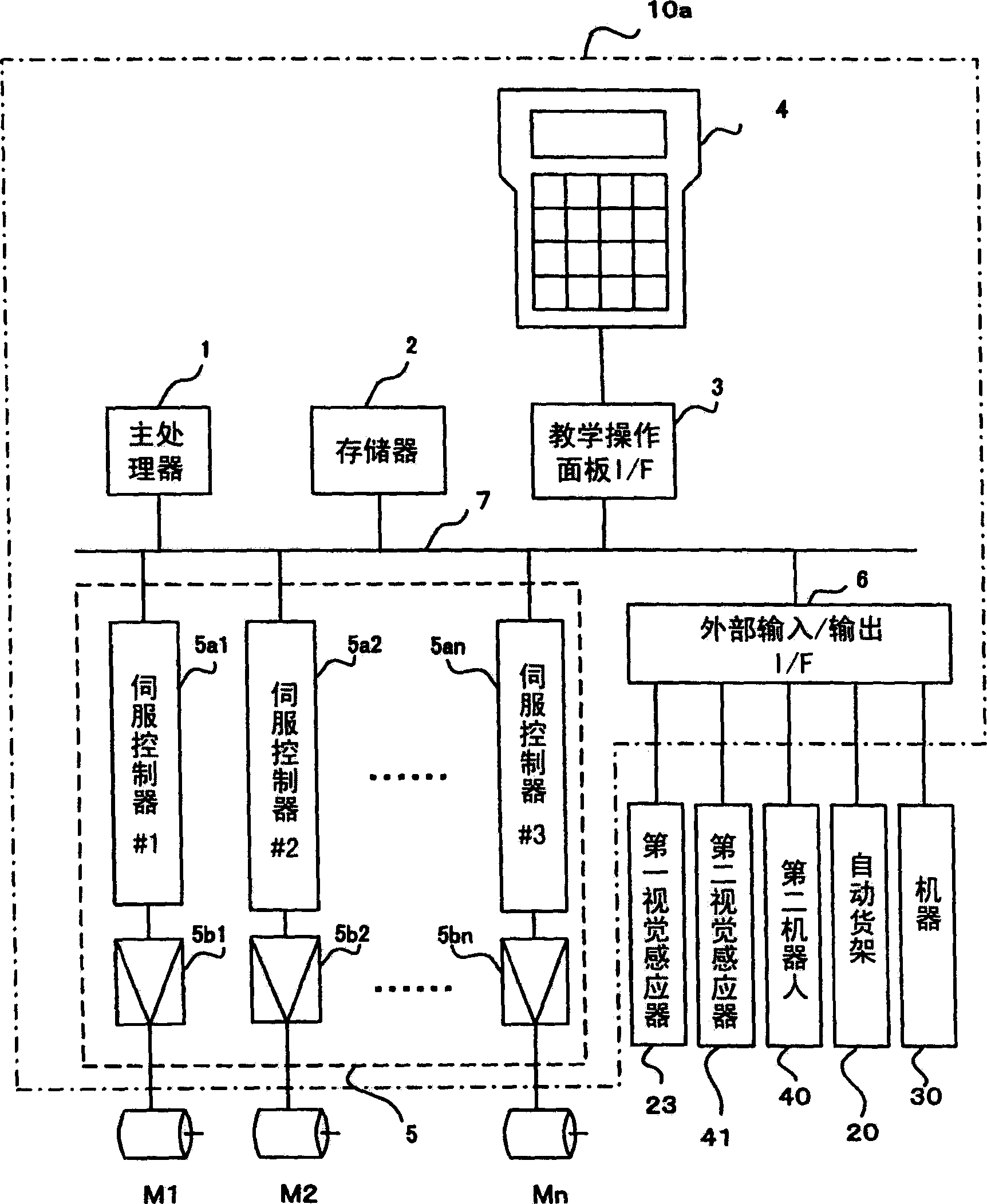
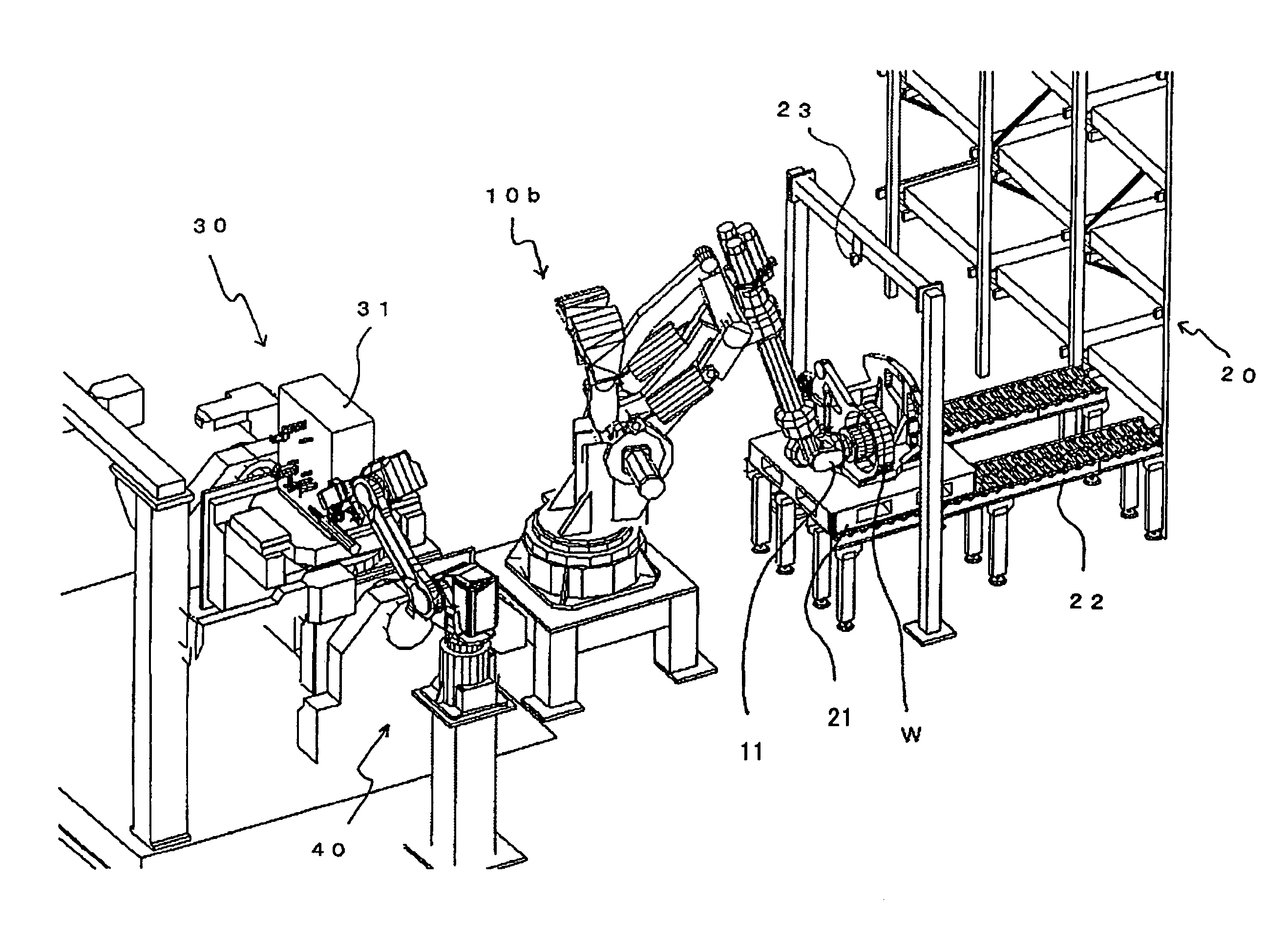
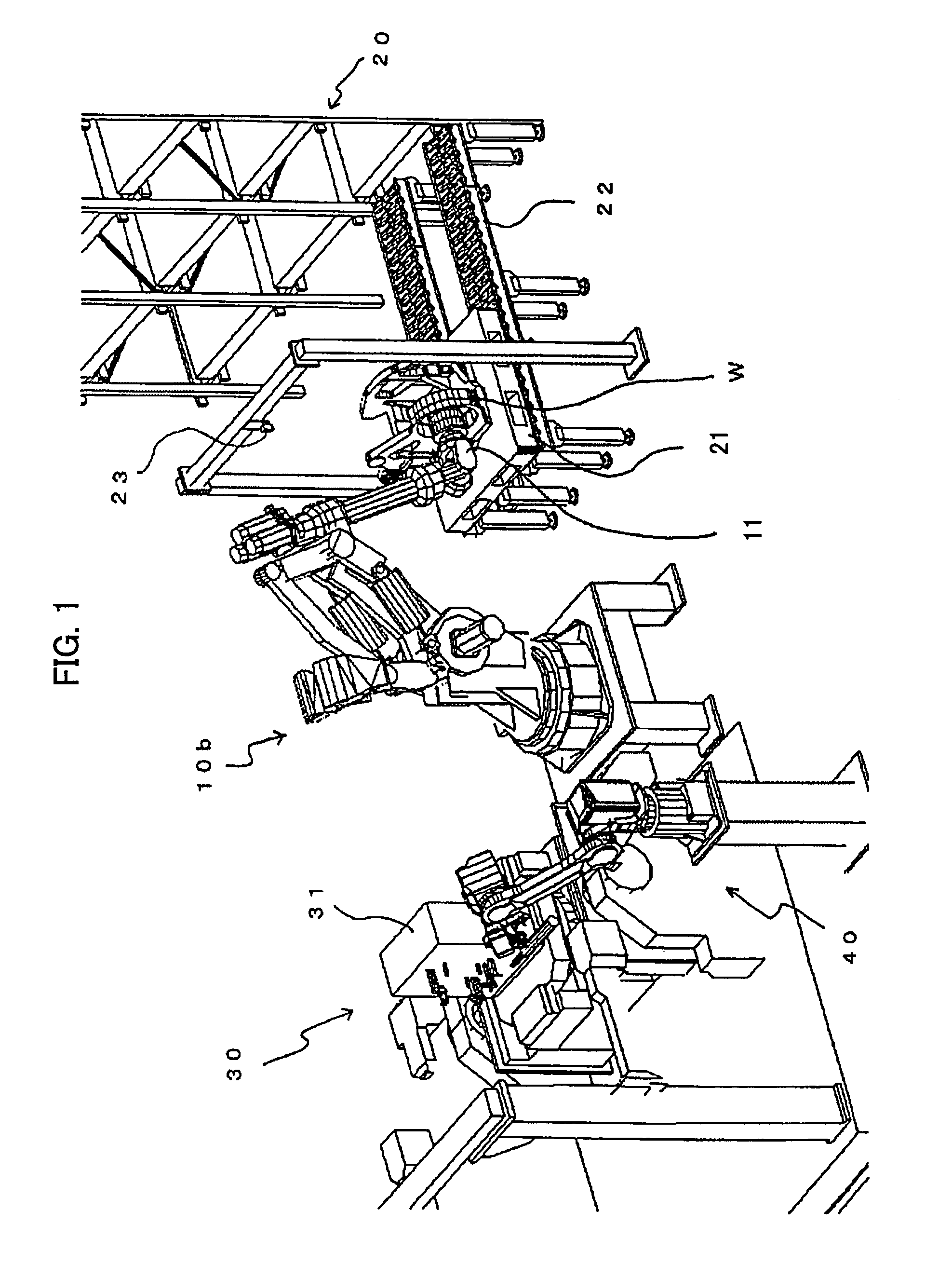
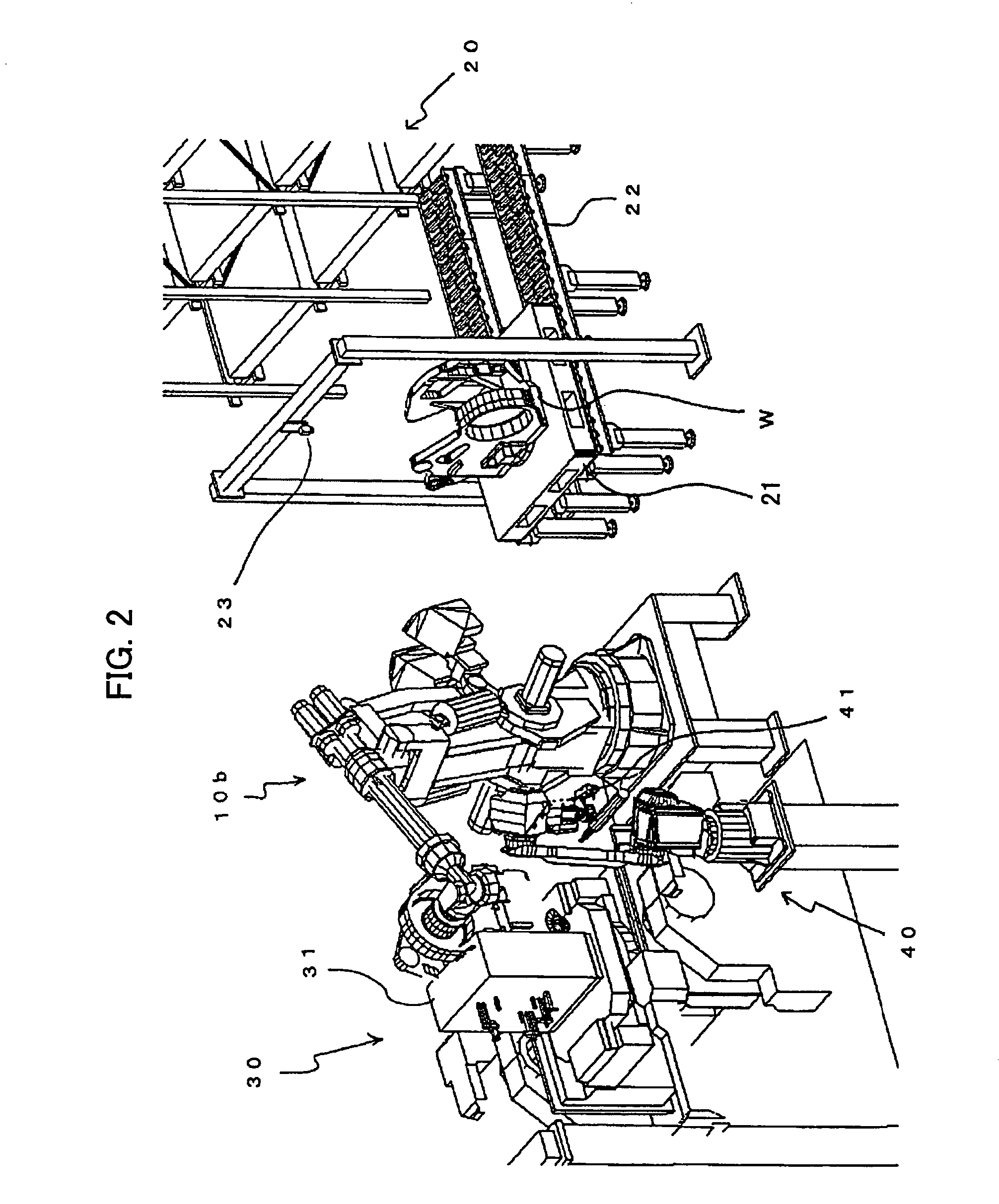
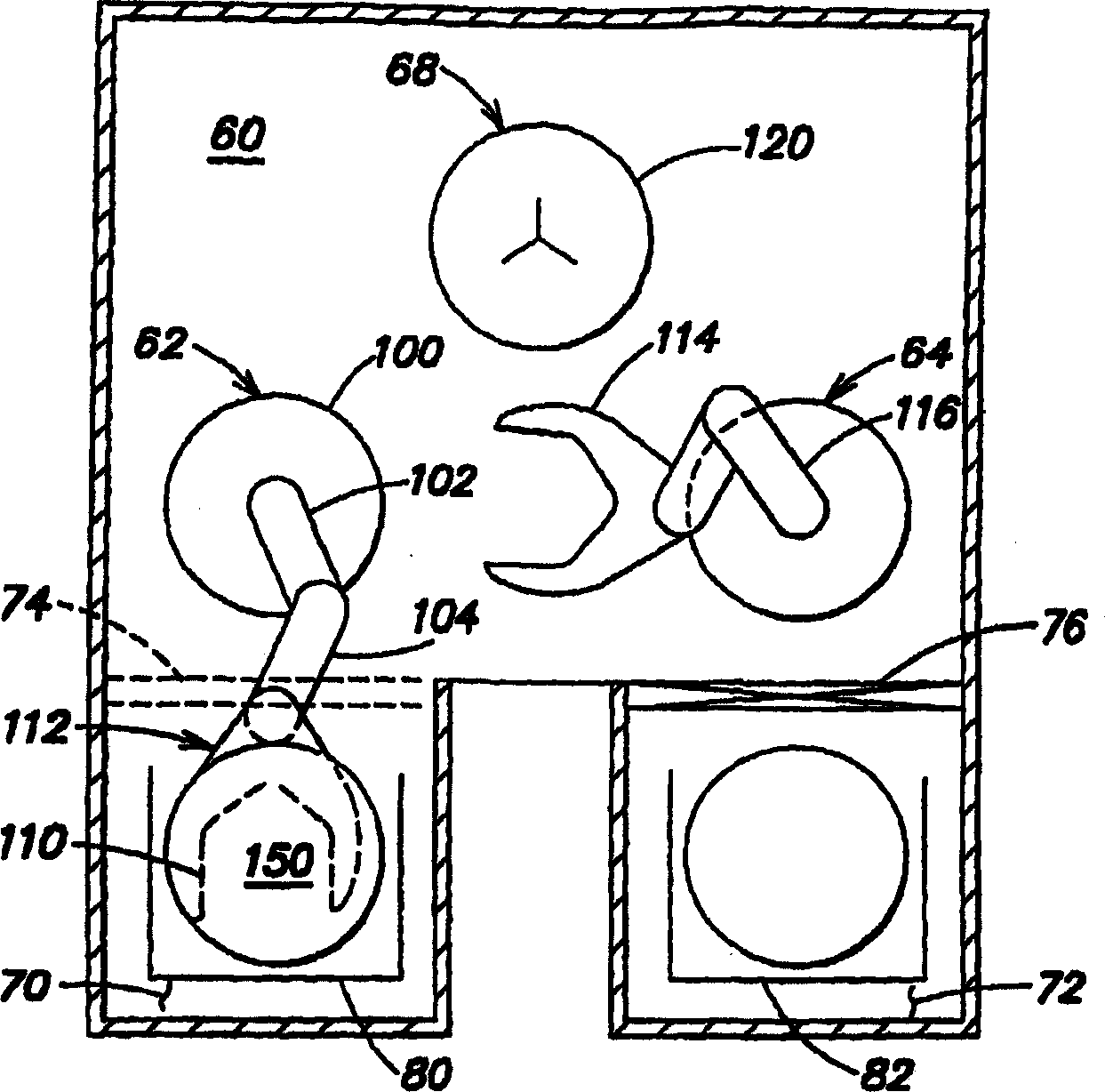
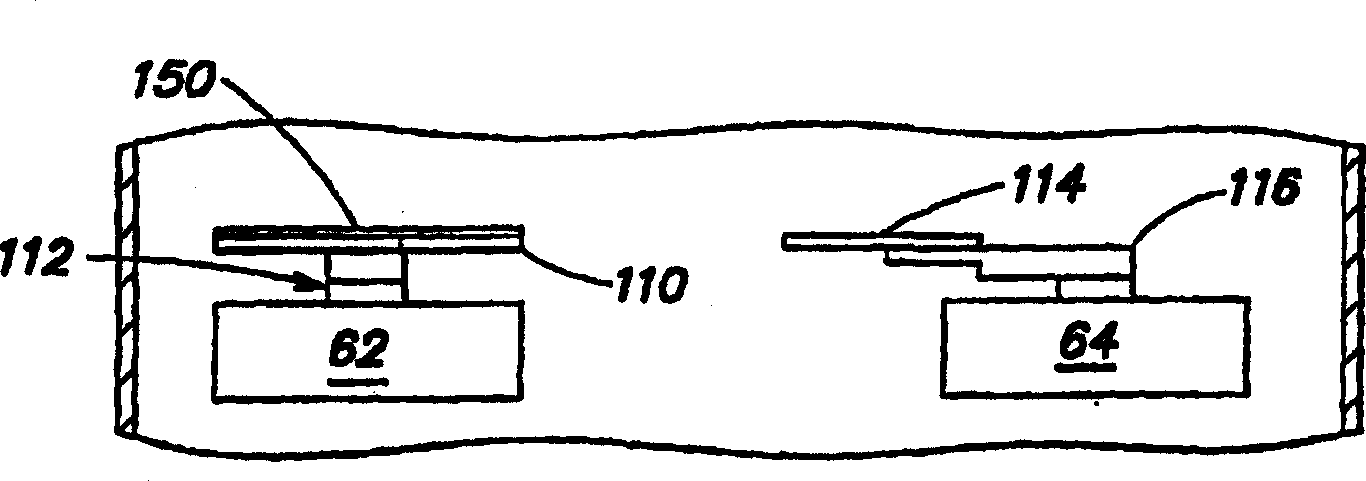
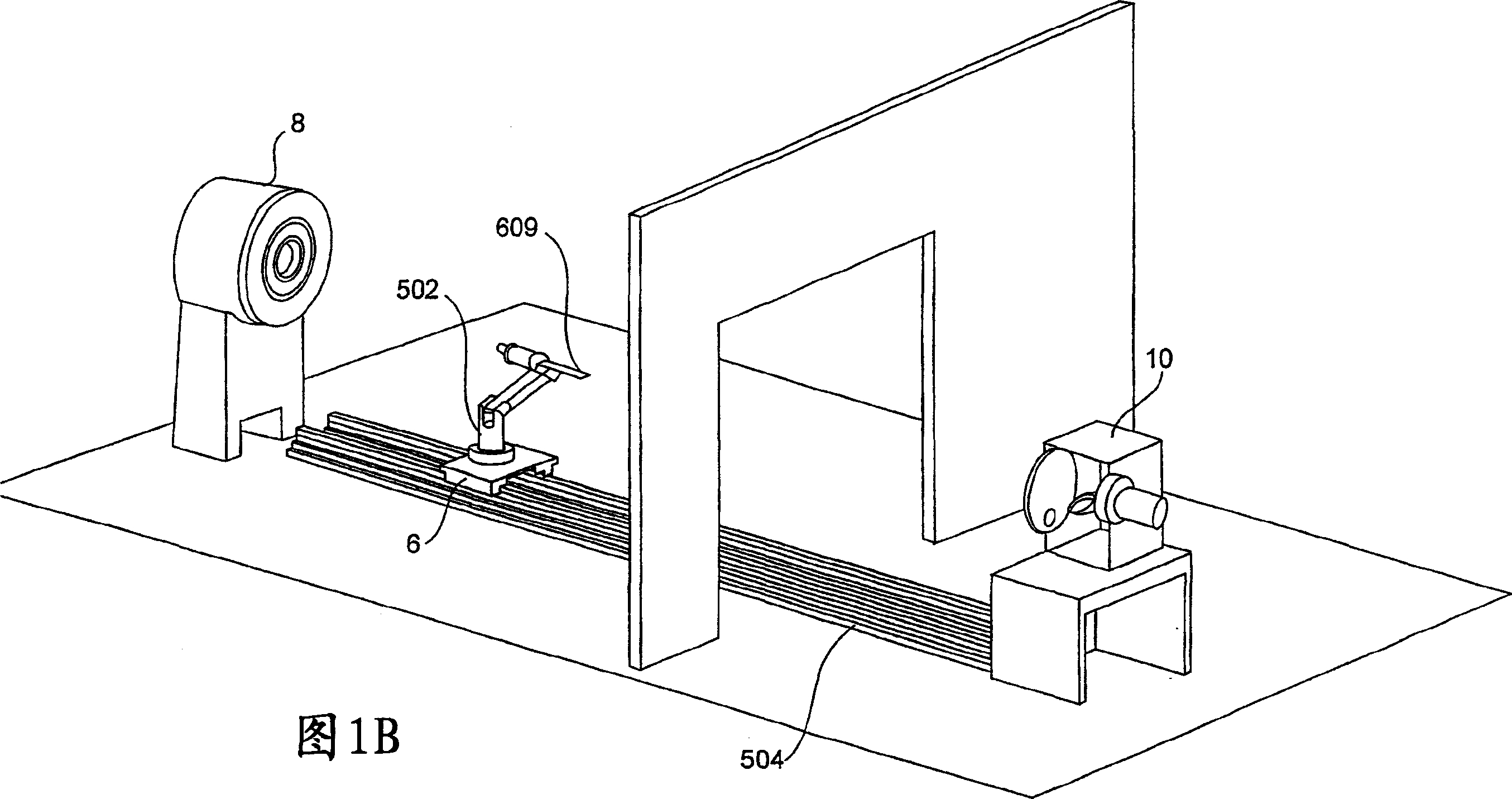
Articles transfer device
An object handling apparatus capable of securely holding an object and precisely transferring the held object from a first place to a second place without need of a specific jig for positioning the object on a pallet. A position of an object supplied to the first place is detected by a first visual sensor to obtain a compensation amount for compensating a position displacement of the supplied object. The object is held by a robot hand having position / orientation compensated using the compensation amount and position / orientation of the object held by the robot hand relative to the robot hand is detected by a second visual sensor. A displacement of the position / orientation of the object held by the robot hand from a reference position / orientation is compensated based on the detected position / orientation of the object on the robot hand, so that the object held by the robot hand is precisely moved to have a predetermined position / orientation to be transferred to the second place. The robot hand may be a servo hand having fingers driven by one or more servomotors so that position and force of the fingers in holding the object is controlled.
Owner:FANUC LTD
Establishing and enforcing security and privacy policies in web-based applications
ActiveUS7831995B2Enhances security and privacyIncrease flexibilityMemory loss protectionUnauthorized memory use protectionObject handlingWeb application
Method, system, and computer code for implementing security and privacy policy in a web application having an execution environment in which a representation of each object handled by the execution environment accommodates data and an associated tag. An inbound tagging rule is established for tagging inbound objects according to a respective source of each of the inbound objects. A tag is assigned to an object being operated on by the execution environment based on the inbound tagging rule. A security / privacy rule is established for performing security / privacy actions on outbound objects according to a respective tag of each of the outbound objects. A security / privacy action is performed on the object being operated on by the execution environment based on the security / privacy rule.
Owner:FORTRA LLC
Object handling apparatus
InactiveUS7244093B2Securely holdAccurate transferProgramme controlProgramme-controlled manipulatorObject handlingRobot hand
An object handling apparatus capable of securely holding an object and precisely transferring the held object from a first place to a second place without need of a specific jig for positioning the object on a pallet. A position of an object supplied to the first place is detected by a first visual sensor to obtain a compensation amount for compensating a position displacement of the supplied object. The object is held by a robot hand having position / orientation compensated using the compensation amount and position / orientation of the object held by the robot hand relative to the robot hand is detected by a second visual sensor. A displacement of the position / orientation of the object held by the robot hand from a reference position / orientation is compensated based on the detected position / orientation of the object on the robot hand, so that the object held by the robot hand is precisely moved to have a predetermined position / orientation to be transferred to the second place. The robot hand may be a servo hand having fingers driven by one or more servomotors so that position and force of the fingers in holding the object is controlled.
Owner:FANUC LTD
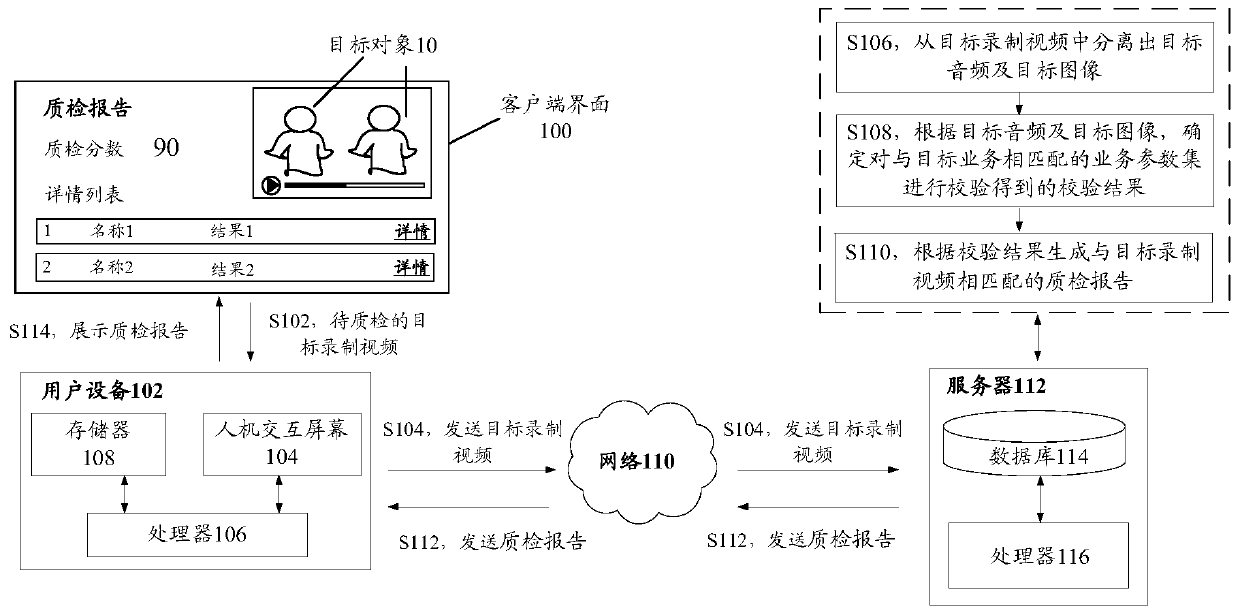
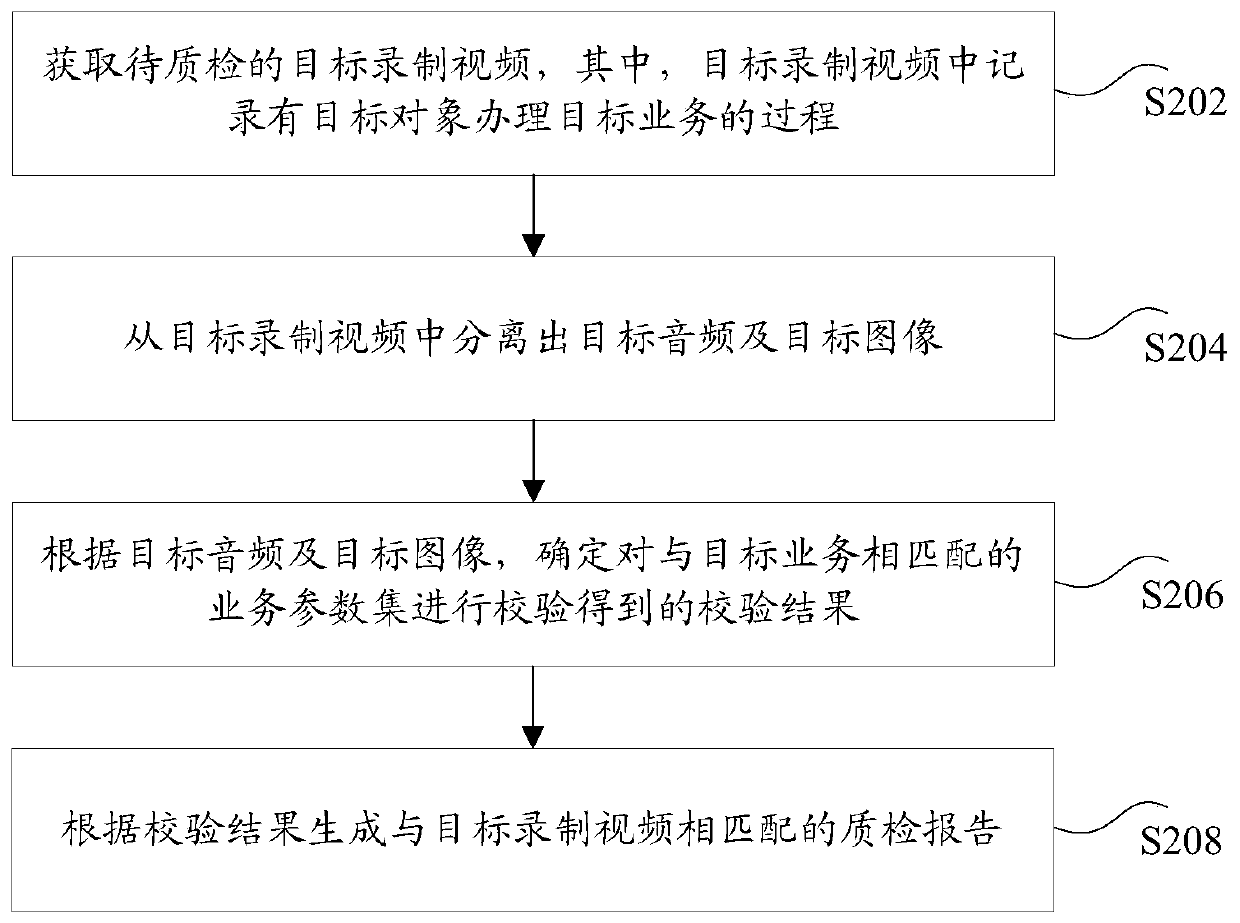
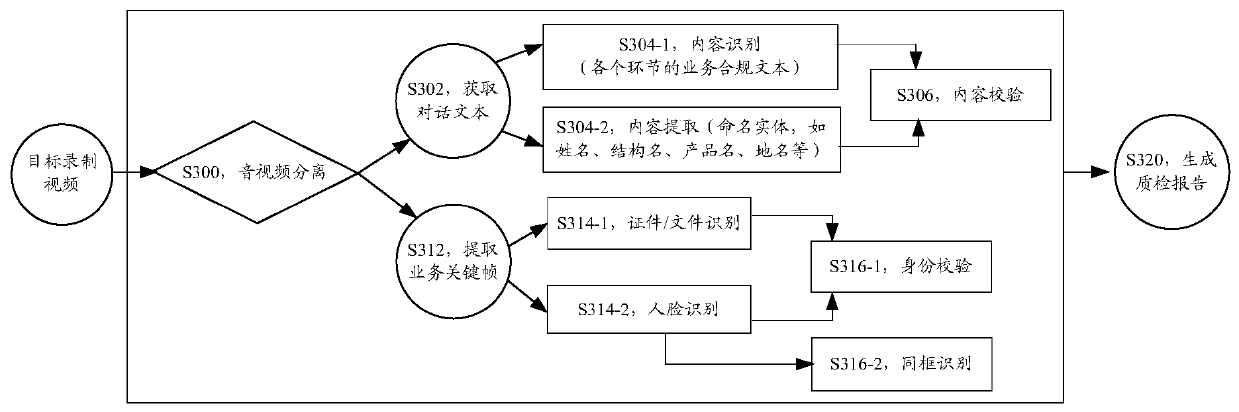
Service quality inspection method and device, storage medium and electronic device
PendingCN110147726AImprove accuracyOvercoming the problem of lower accuracySemantic analysisCharacter and pattern recognitionComputer hardwareObject handling
The embodiment of the invention discloses a service quality inspection method and device, a storage medium and an electronic device. The service quality inspection method comprises the steps: acquiring a target recorded video to be subjected to quality inspection, wherein the process that a target object handles a target service is recorded in the target recorded video; separating a target audio and a target image from the target recorded video; determining a verification result obtained by verifying the service parameter set matching the target service according to the target audio and the target image; and generating a quality inspection report matching the target recorded video according to the verification result. The service quality inspection method can solve the technical problem that the quality inspection result is not accurate enough due to the fact that the service quality inspection content is single.
Owner:TENPAY PAID TECH
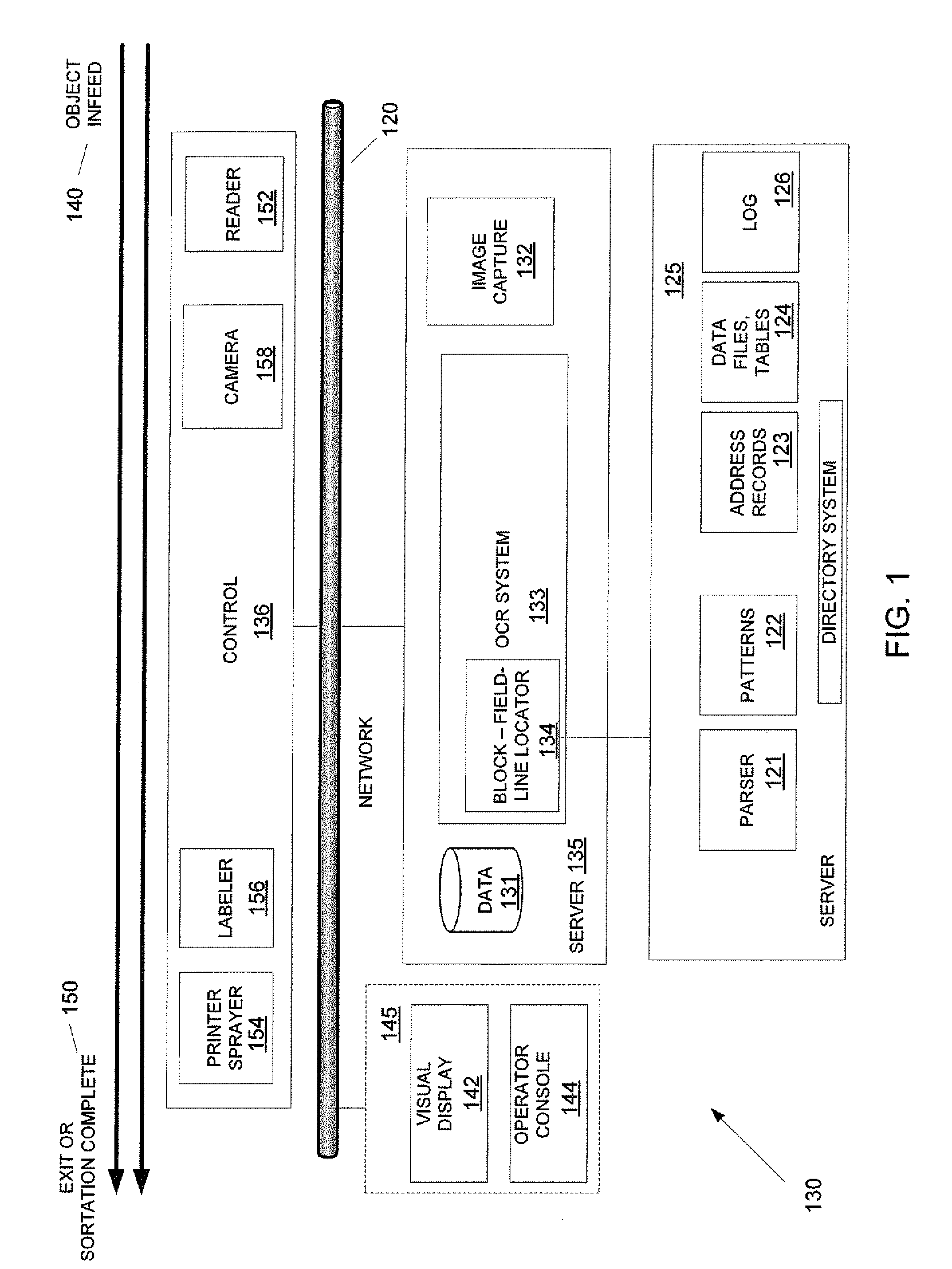
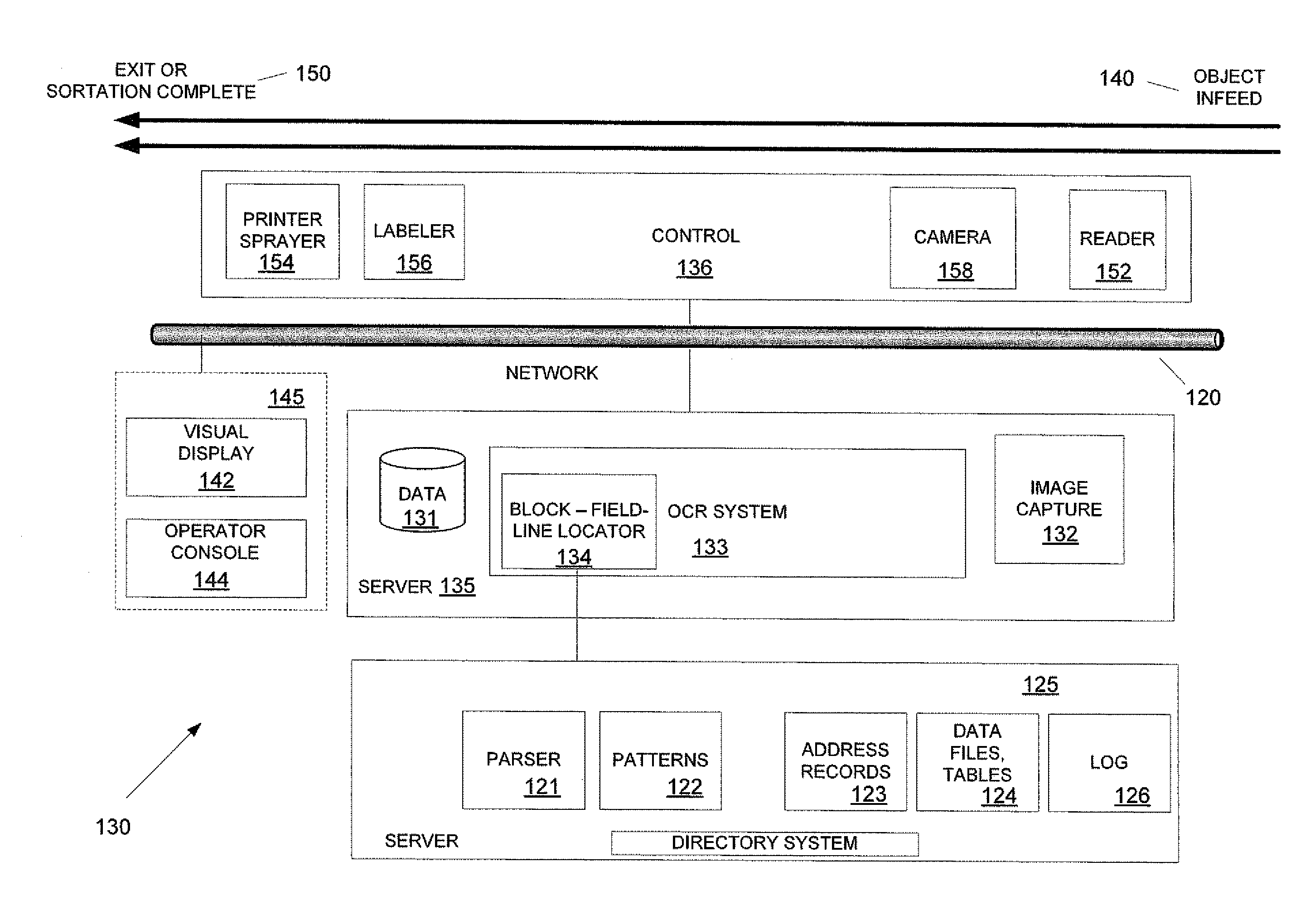
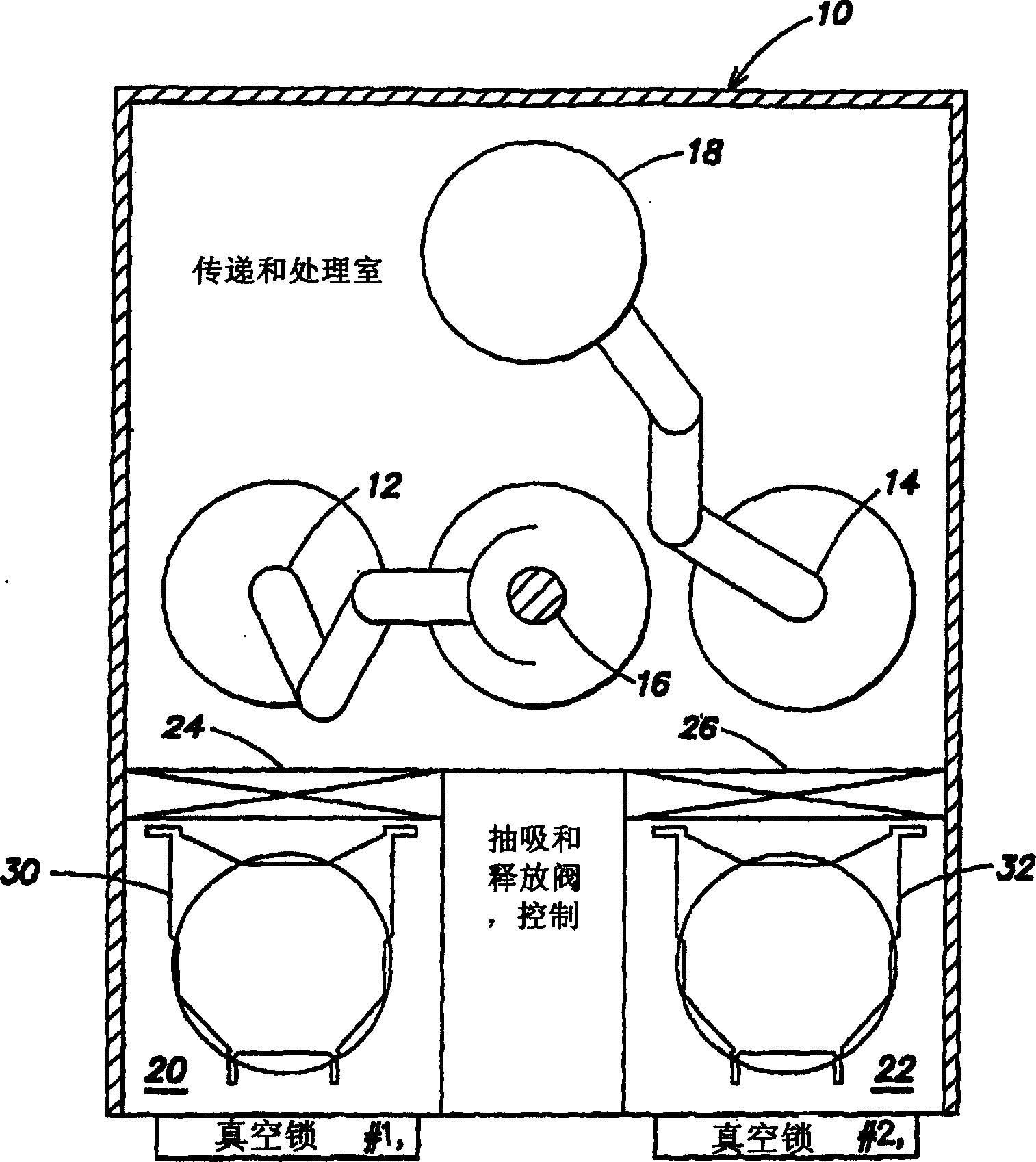
Methods and apparatus for high speed object handling
InactiveCN1765004ADigital data processing detailsSemiconductor/solid-state device manufacturingObject handlingRotational error
Methods and apparatus for high speed workpiece handling are provided. A method for workpiece handling includes: utilizing a first robot to remove a workpiece from a first magazine; transferring the workpiece from the first robot directly to a second robot without transferring the workpiece to a transfer station; utilizing the A second robot places the workpiece on a workpiece holder at a processing station; and transfers the workpiece from the workpiece holder to the first cassette with the first robot after processing. The end effectors of the first and second robots may each have a plurality of vertical positions for efficient workpiece handling. The displacement and rotation errors of the workpiece can be sensed and corrected without using a transfer station. The method and apparatus are useful for handling semiconductor wafers.
Owner:VARIAN SEMICON EQUIP ASSOC INC
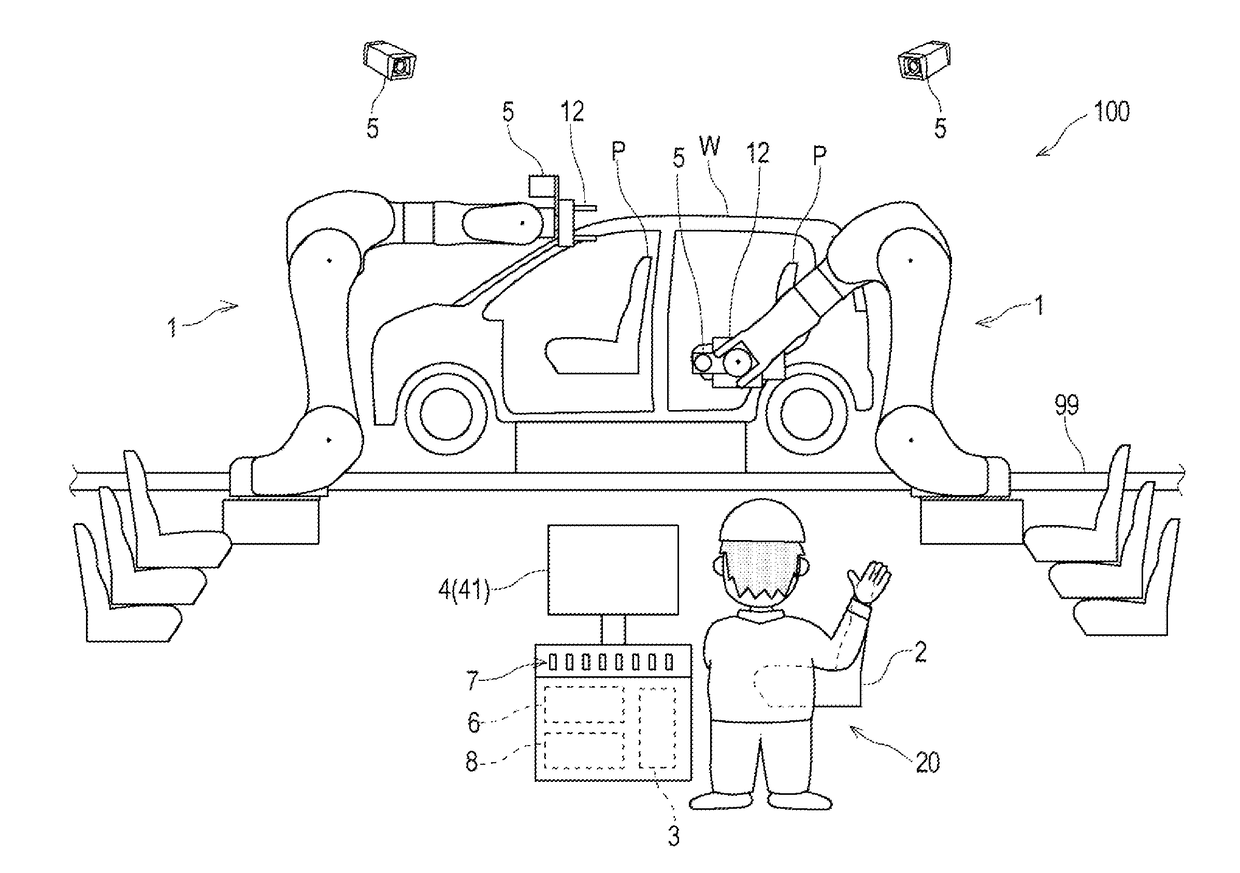
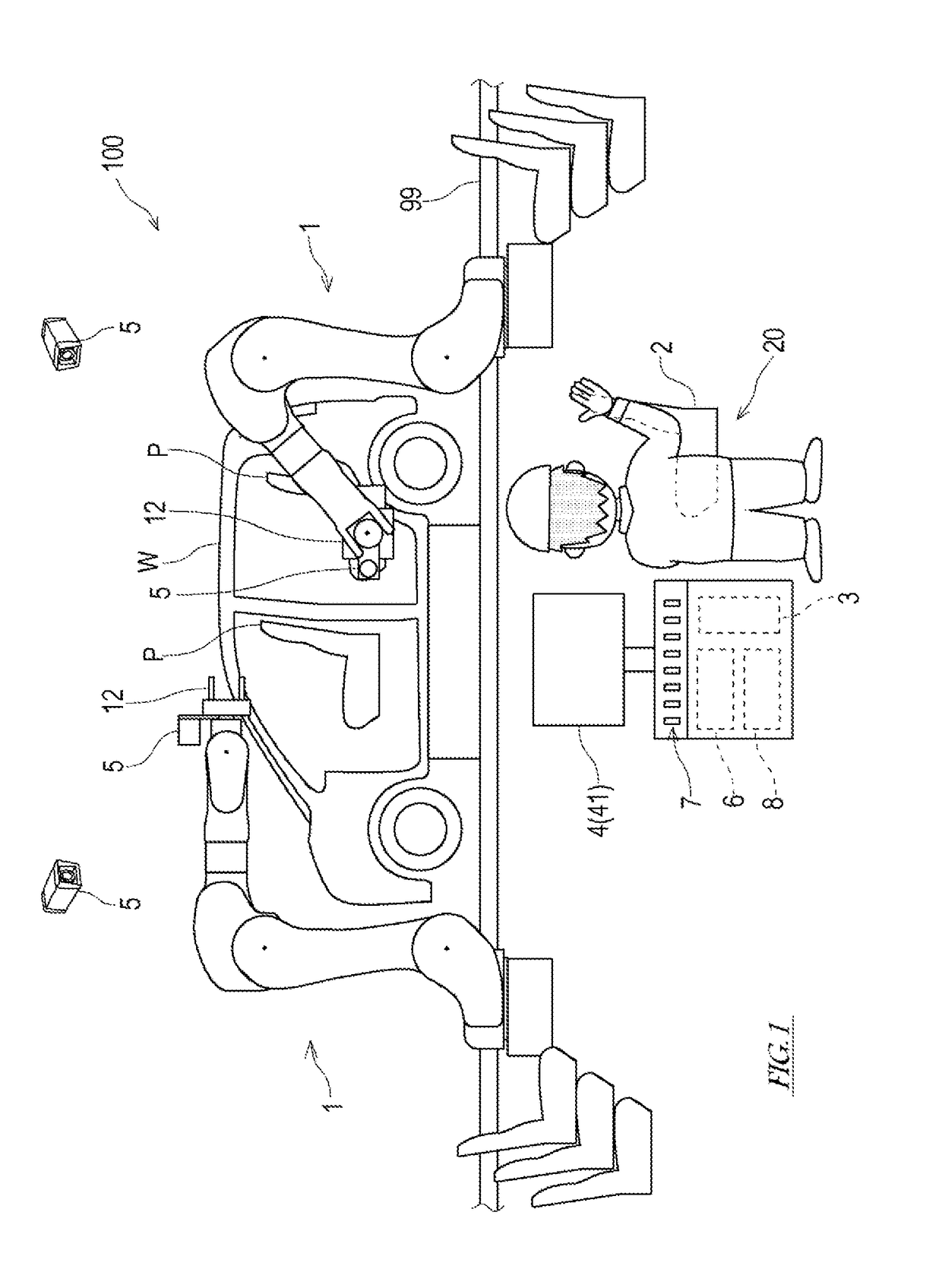
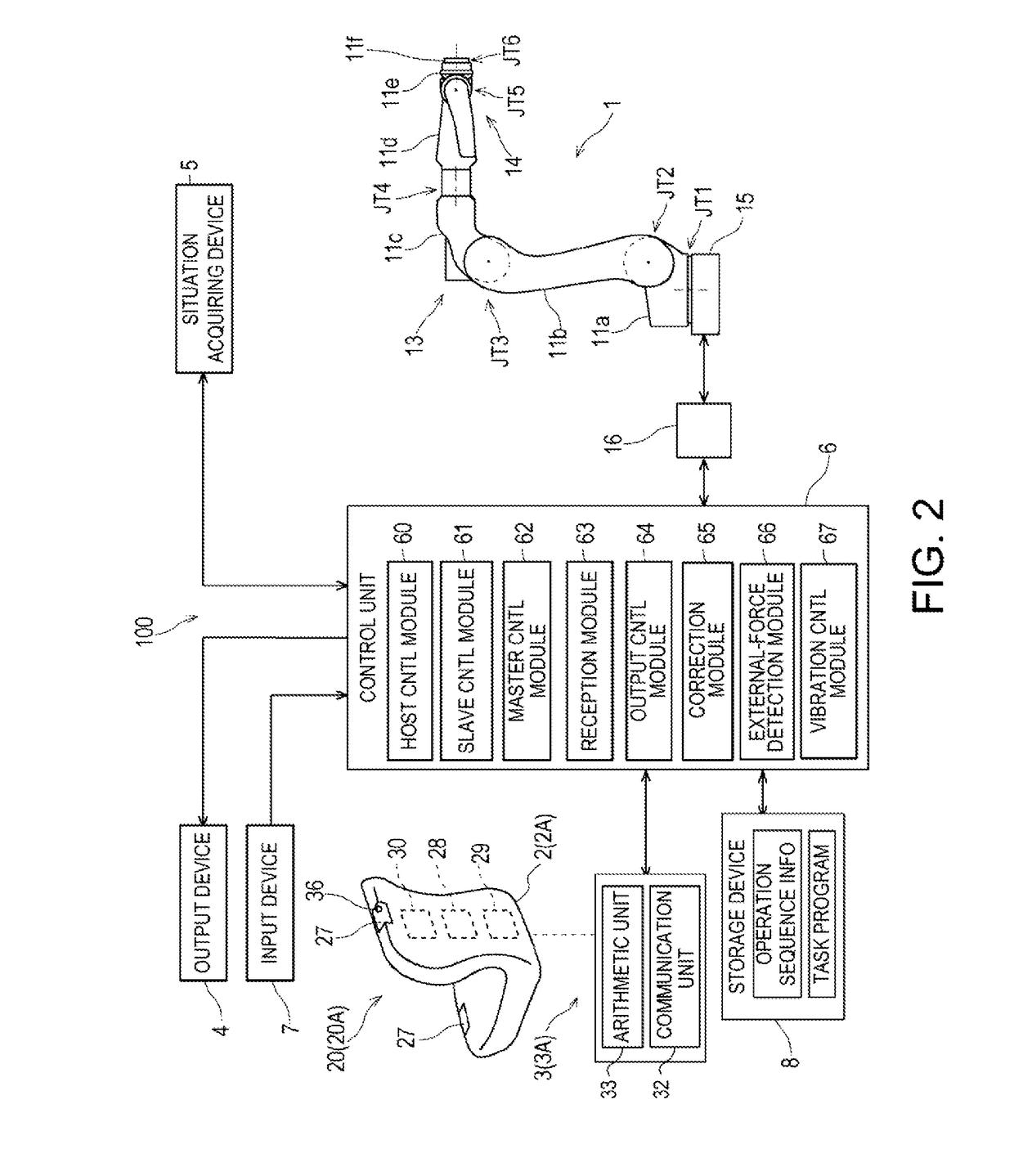
Remote control robot system
ActiveUS20180243897A1Programme controlProgramme-controlled manipulatorObject handlingRobotic systems
A remote control robot system includes a slave arm, a master main body imitating the shape of an object handled by the slave arm, a manipulation receiving device configured to receive manipulation of an operator based on the position and posture of the master main body, and a control device configured to control operation of the slave arm based on the manipulation received by the manipulation receiving device so that behavior of the object corresponds to behavior of the master main body.
Owner:KAWASAKI HEAVY IND LTD
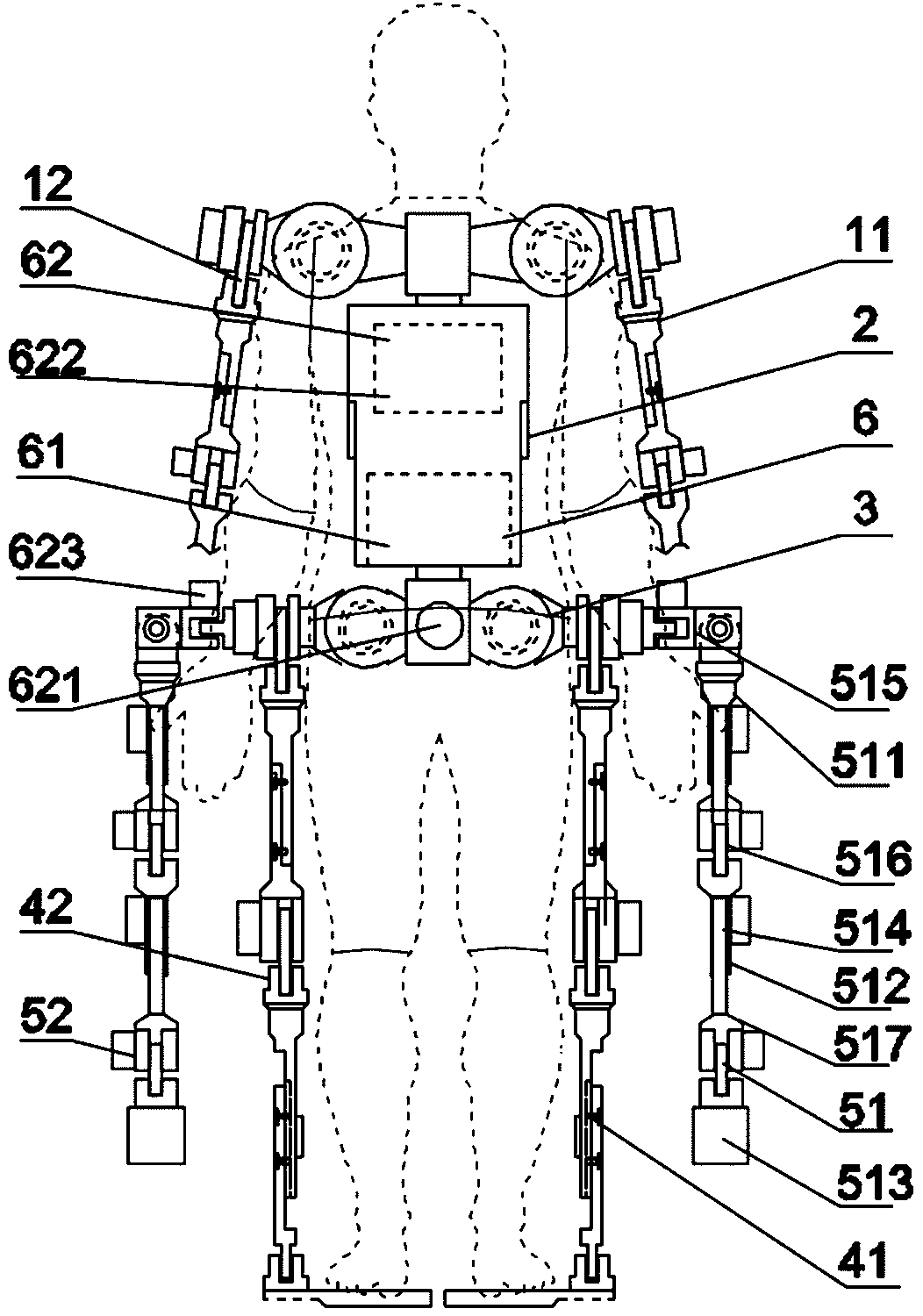
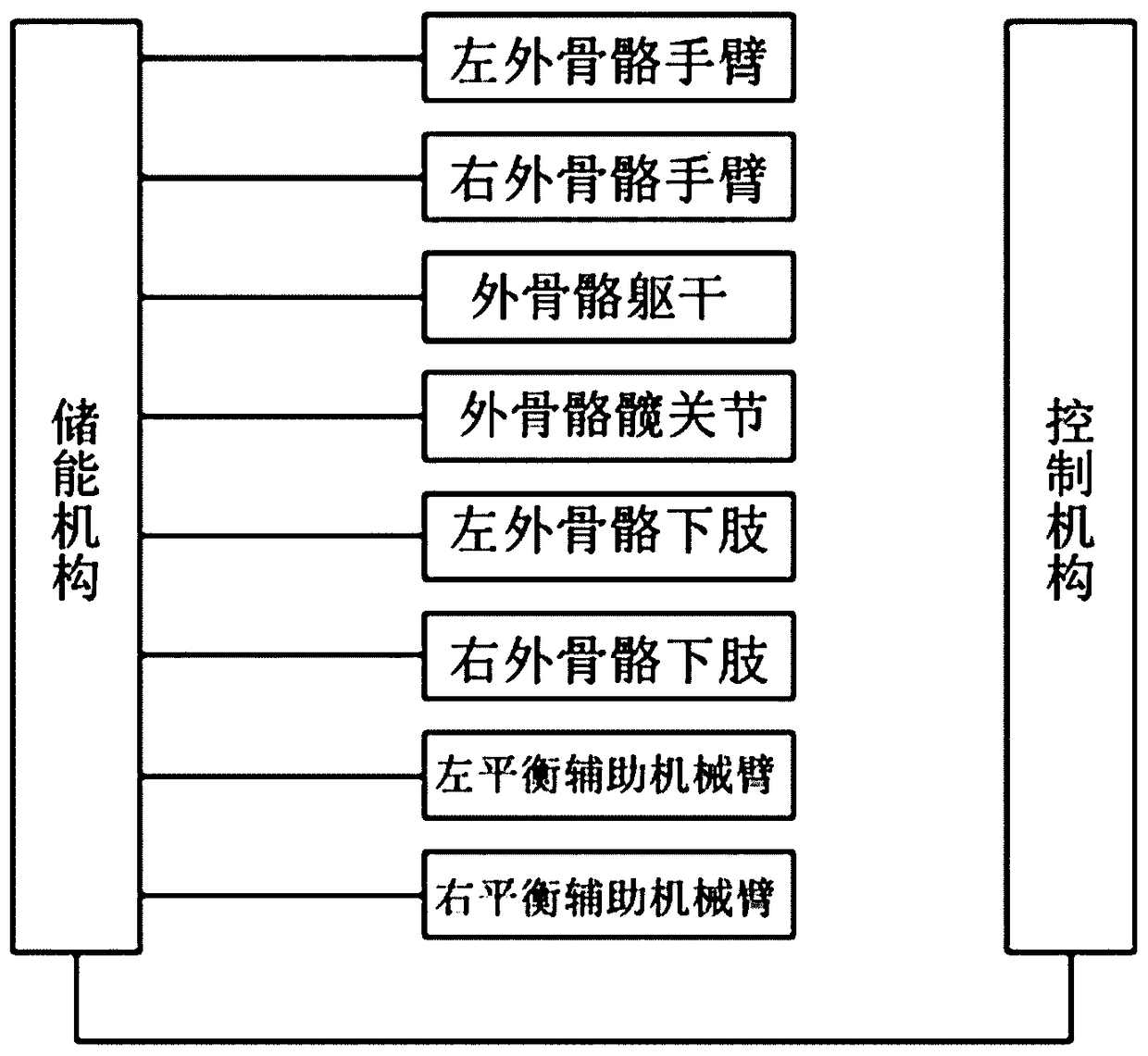
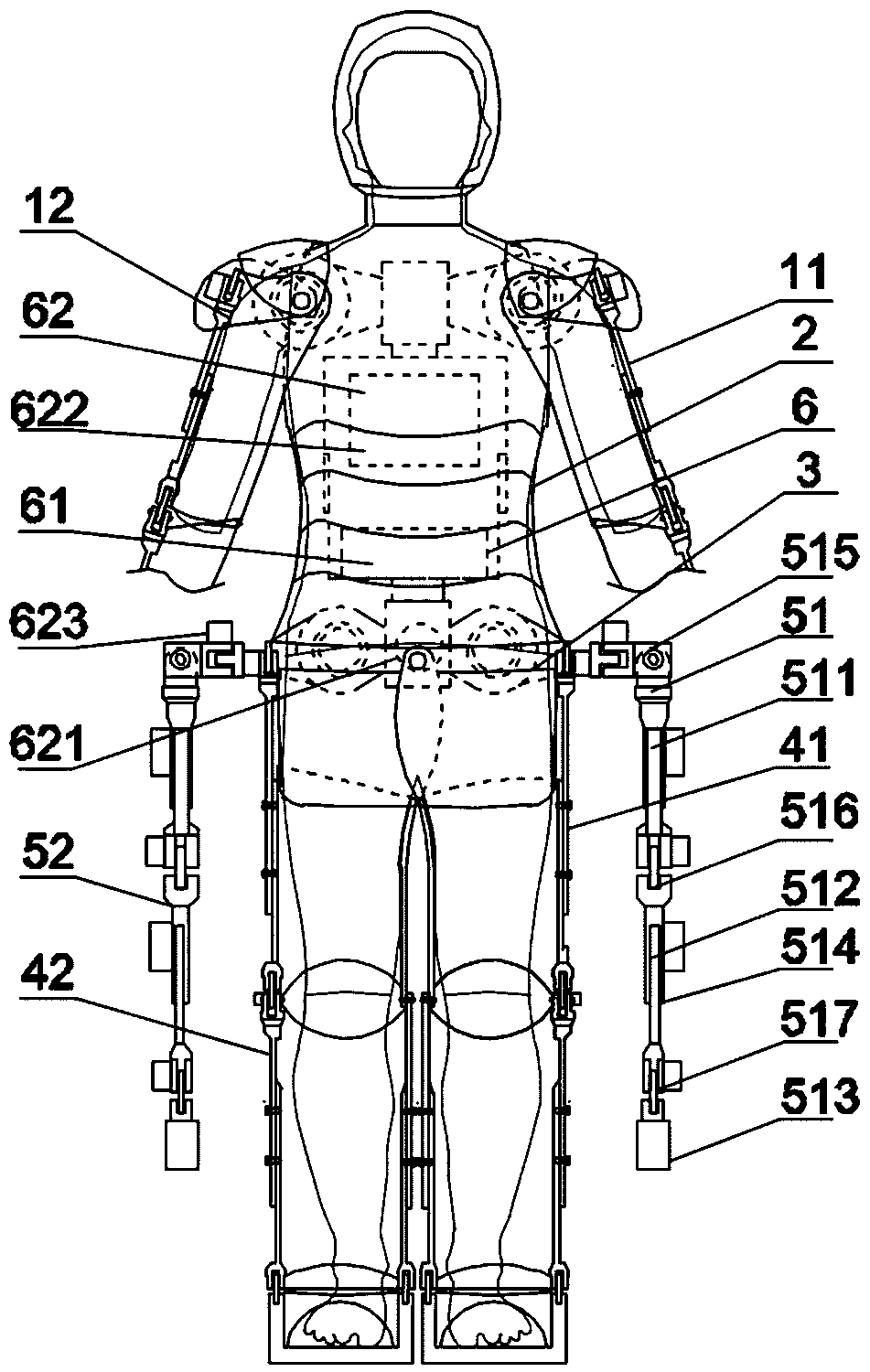
Multi-functional auxiliary arm self-balancing mechanical exoskeleton
ActiveCN109176463AProtection securityAvoid impact damageProgramme-controlled manipulatorAgainst vector-borne diseasesObject handlingElectricity
A multi-functional auxiliary arm self-balancing mechanical exoskeleton comprises a left exoskeleton arm and a right exoskeleton arm, wherein the left exoskeleton arm and the right exoskeleton arm areconnected with an exoskeleton trunk; and an exoskeleton hip joint is connected with a left exoskeleton lower limb and a right exoskeleton lower limb. The multi-functional auxiliary arm self-balancingmechanical exoskeleton is characterized by further comprising a left balancing auxiliary mechanism arm, a right balancing auxiliary mechanism arm and an electric self-control system, wherein the leftbalancing auxiliary mechanism arm and the right balancing auxiliary mechanism arm are connected with the exoskeleton hip joint; and the electric self-control system is electrically connected with theleft exoskeleton arm, the right exoskeleton arm, the exoskeleton trunk, the exoskeleton hip joint, the exoskeleton lower limb, the right exoskeleton lower limb, the left balancing auxiliary mechanismarm and the right balancing auxiliary mechanism arm. The multi-functional auxiliary arm self-balancing mechanical exoskeleton provided by the invention is simple in structure, high in applicability and high in safety; the multi-functional auxiliary arm self-balancing mechanical exoskeleton is applicable to not only tilting prevention, falling prevention and balance keeping for the medical rehabilitation of old people or patients but also the auxiliary handling of heavy objects; and accordingly, the heavy object handling weight can be improved.
Owner:长沙紫宸科技开发有限公司
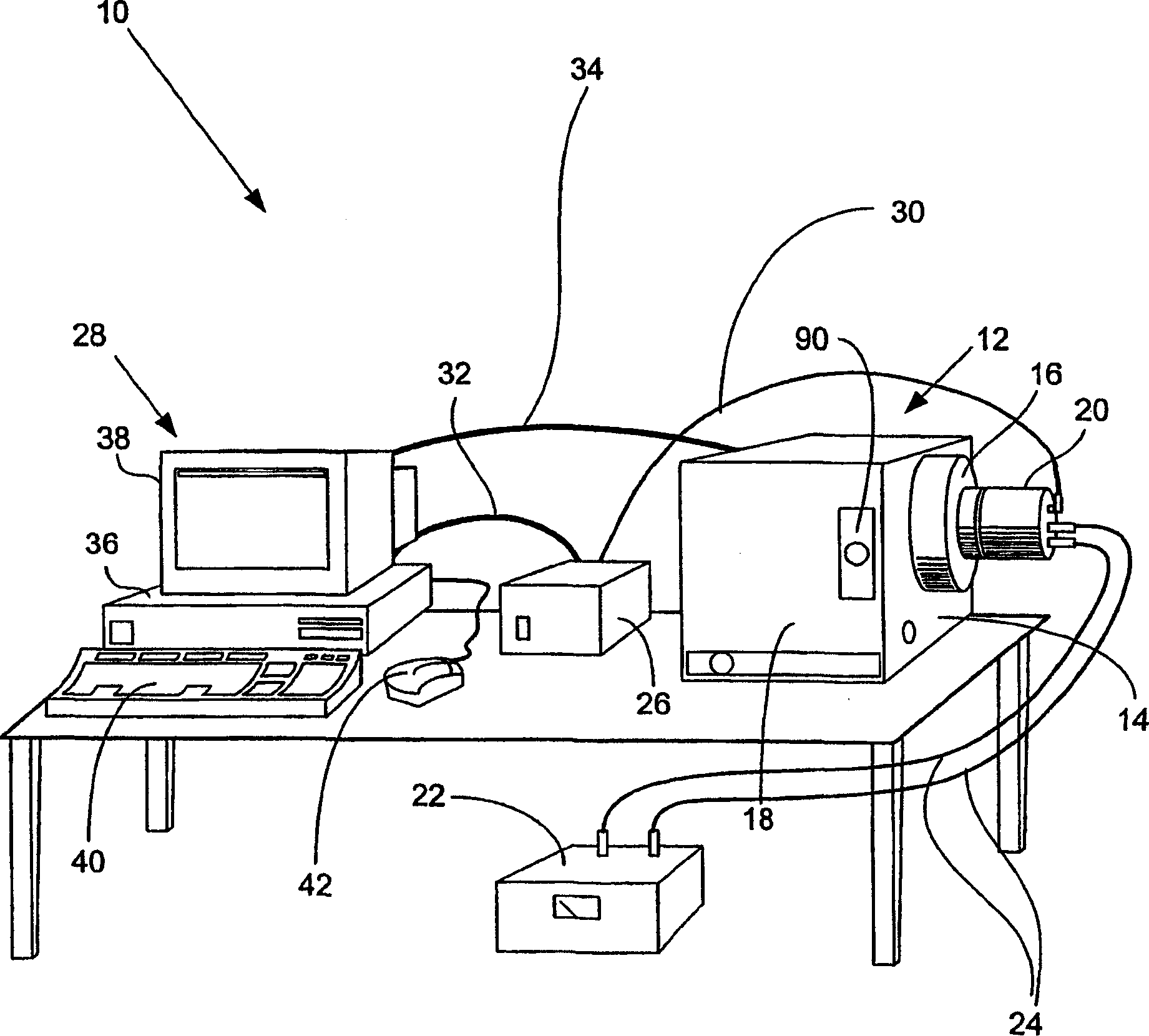
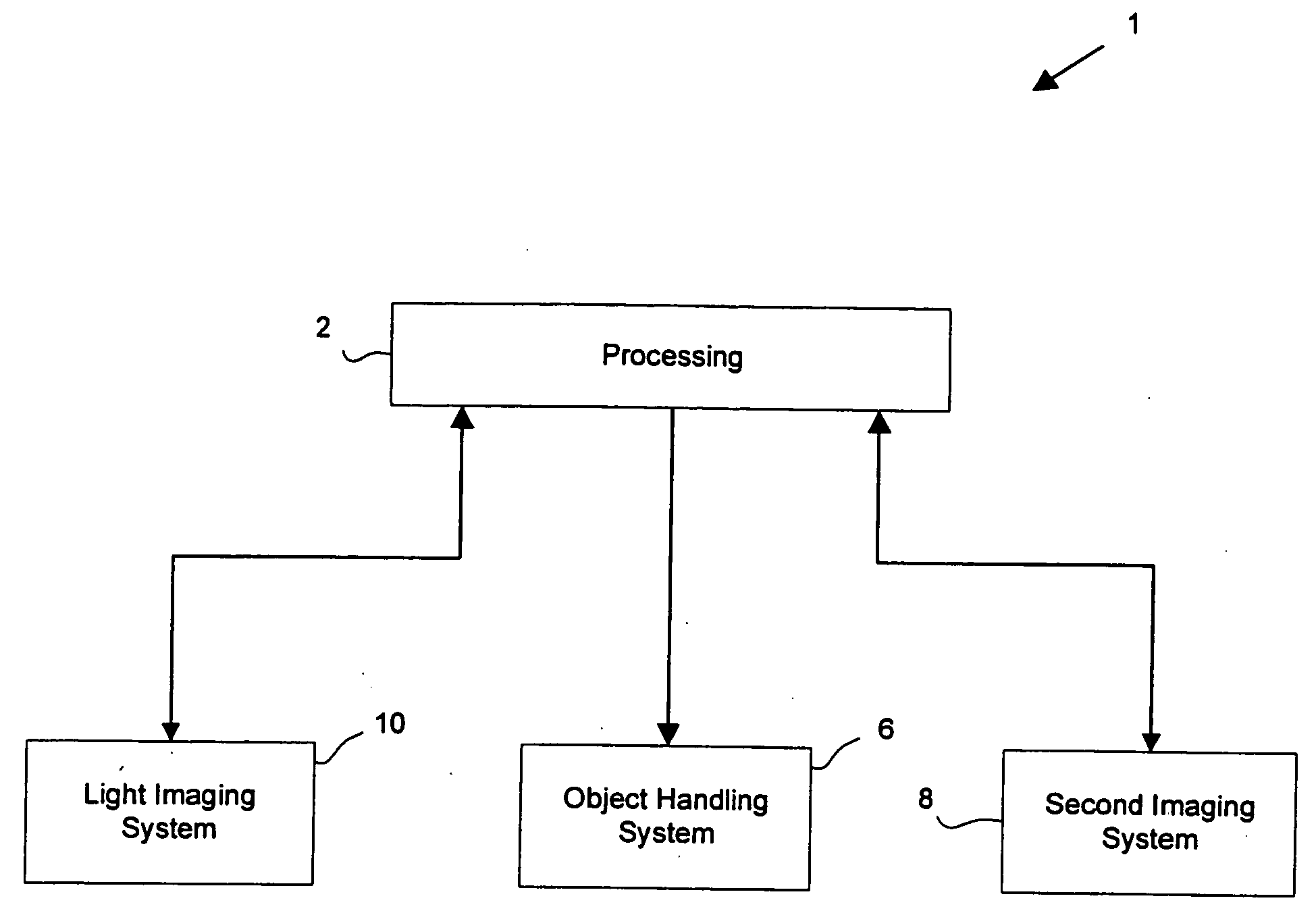
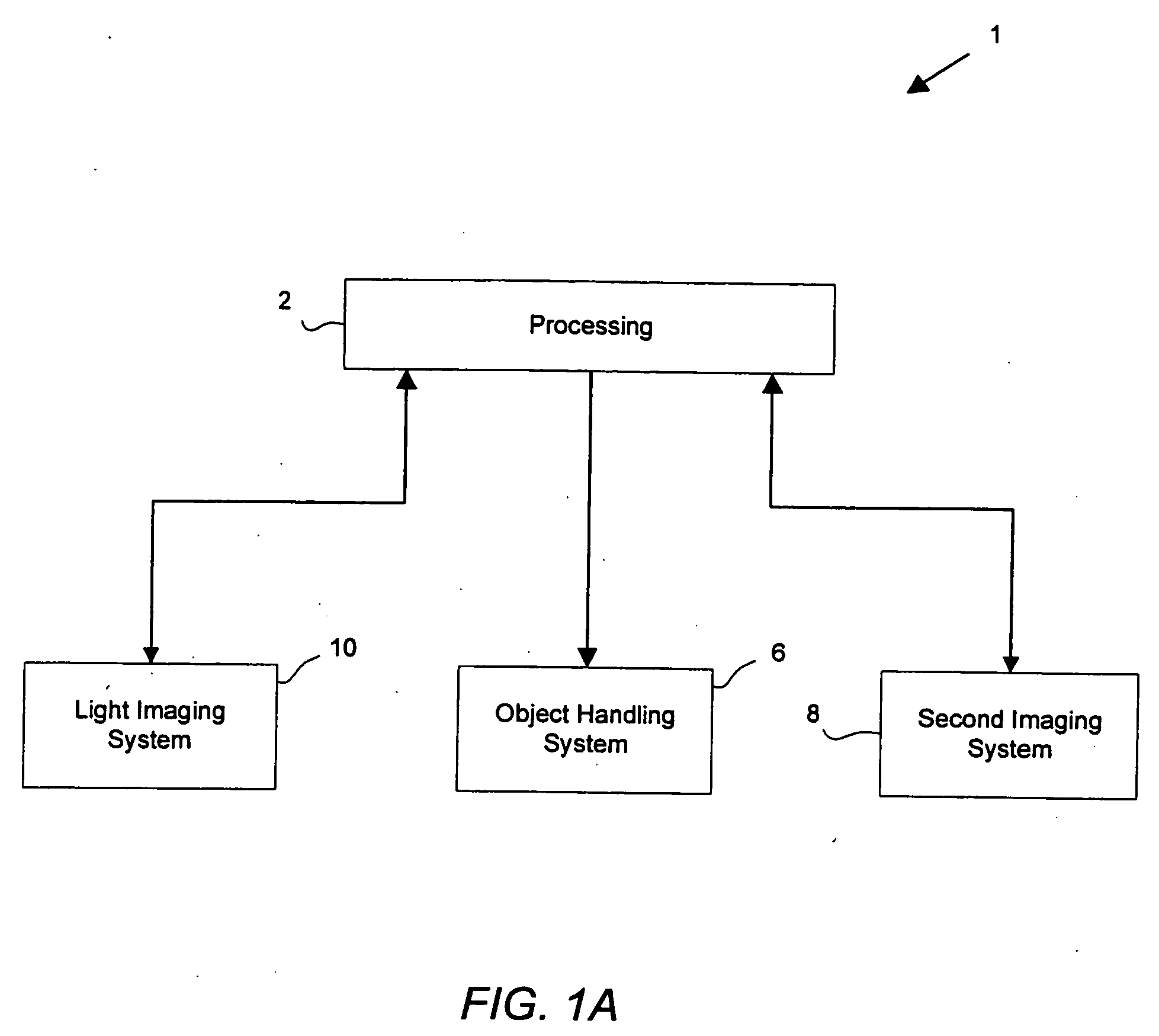
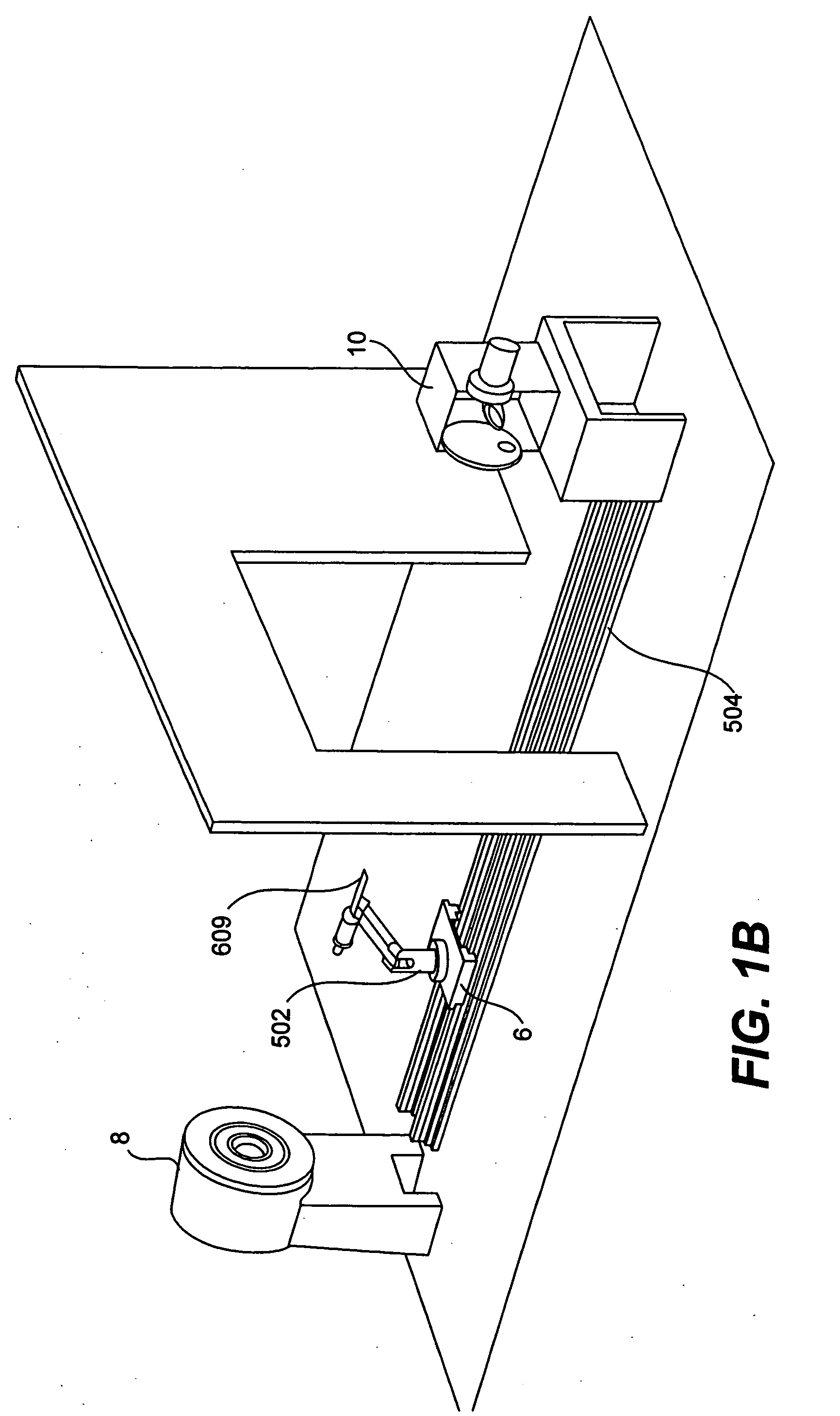
Multi-mode internal imaging
The invention described herein provides systems and methods for multi-modal imaging with light and a second form of imaging. Light imaging involves the capture of low intensity light from a light-emitting object. A camera obtains a two-dimensional spatial distribution of the light emitted from the surface of the subject. Software operated by a computer in communication with the camera may then convert two-dimensional spatial distribution data from one or more images into a three-dimensional spatial representation. The second imaging mode may include any imaging technique that compliments light imaging. Examples include magnetic resonance imaging (MRI) and computer topography (CT). An object handling system moves the object to be imaged between the light imaging system and the second imaging system, and is configured to interface with each system.
Owner:色诺根公司
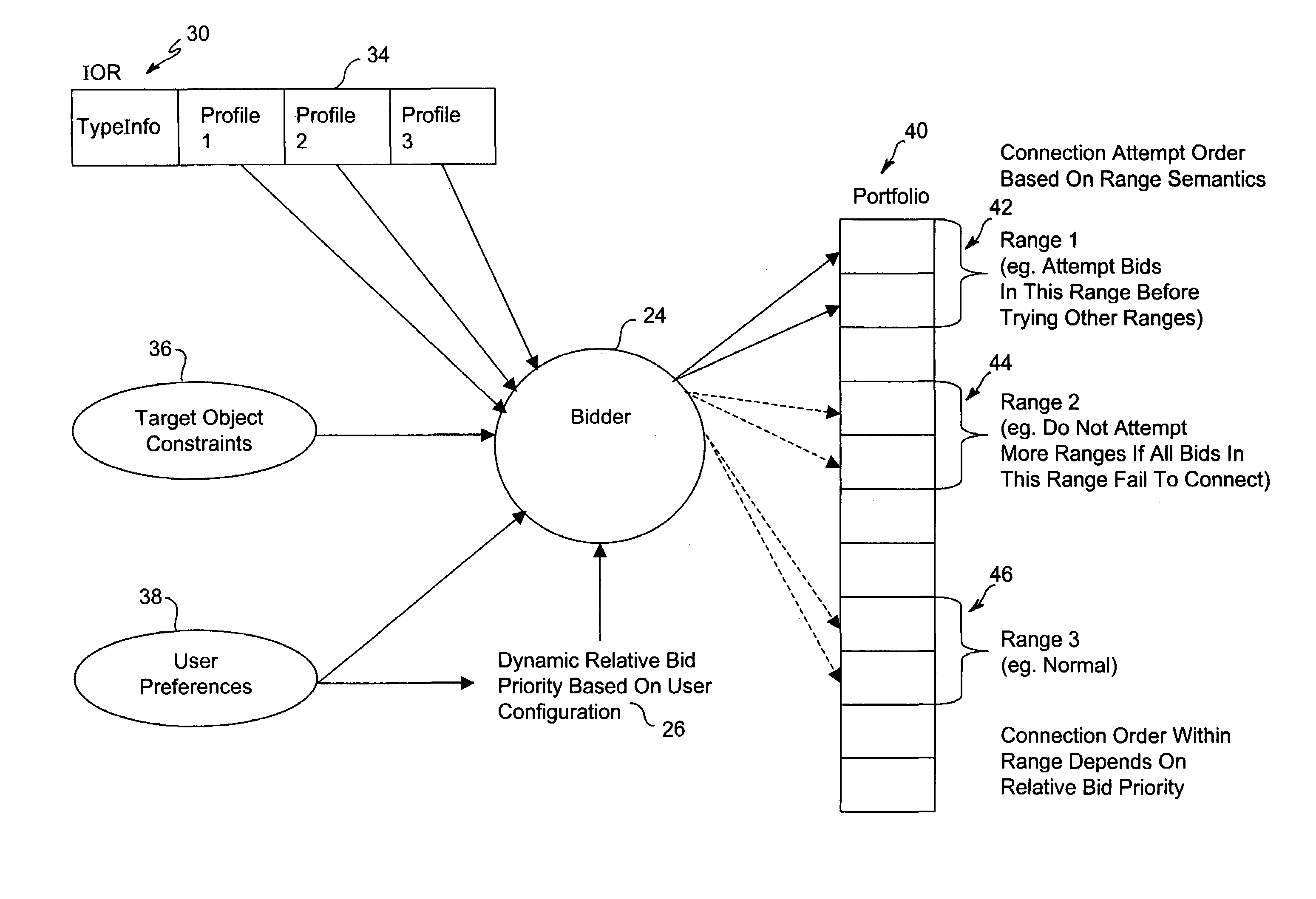
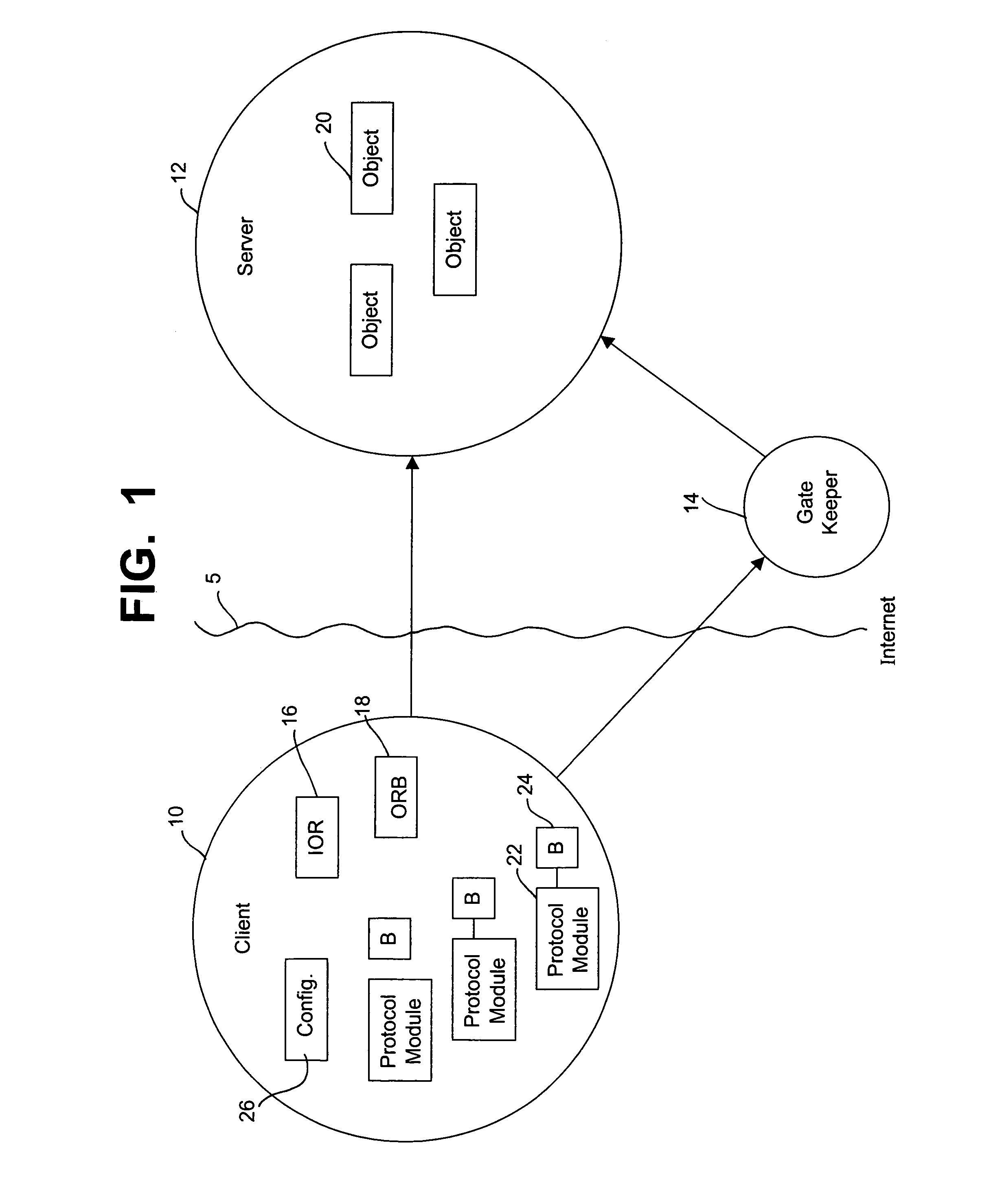
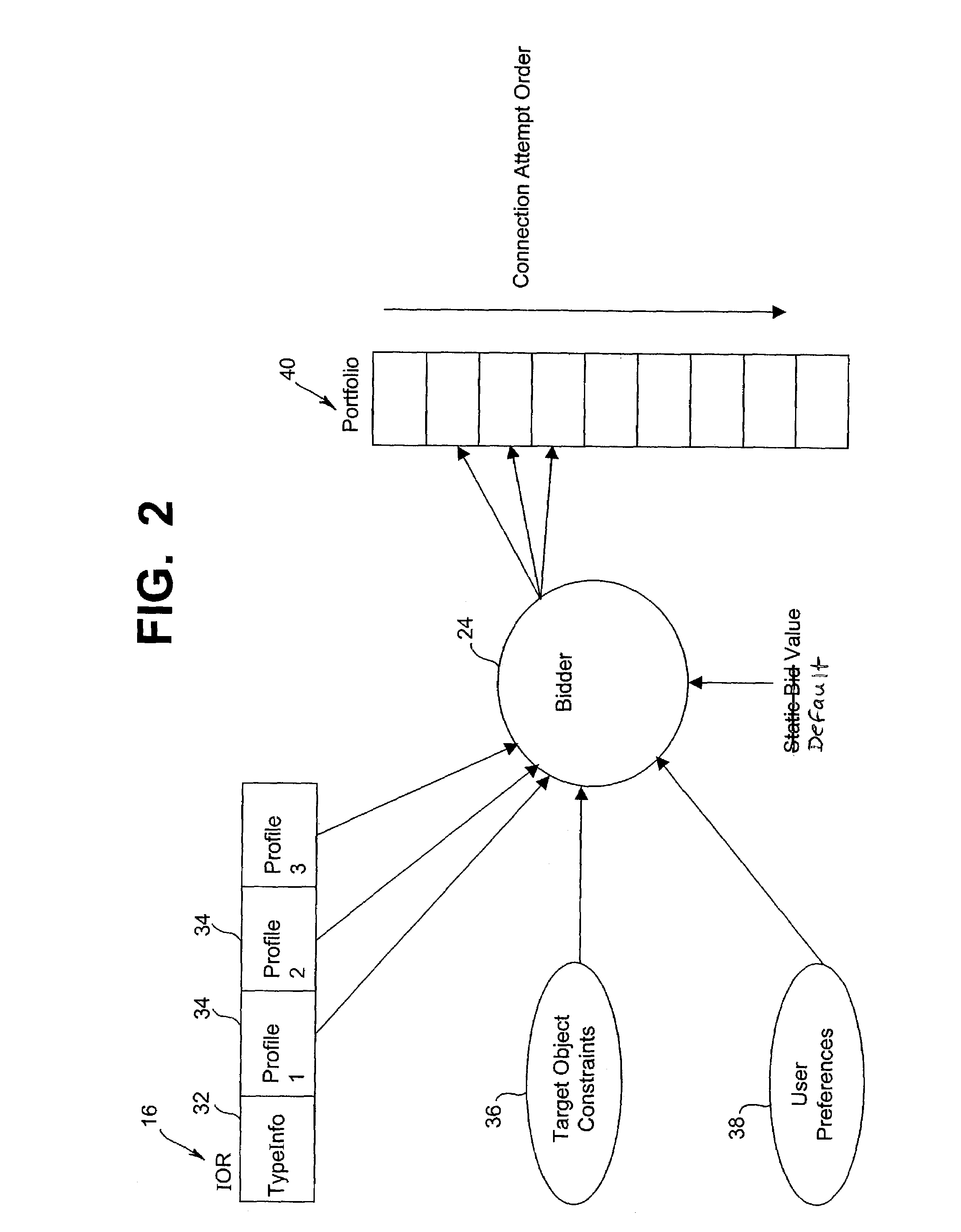
Method and system for dynamic protocol selection among object-handled specified protocols
InactiveUS7194544B2EfficiencyMultiple digital computer combinationsElectric digital data processingObject handlingDistributed computing
The bidding method for selecting a protocol involves generating a bid for each protocol and ranking the bids in a prescribed order such that the order of the bids reflects the order of preference among the protocols. Thereafter, the most preferred protocol is executed or processes to establish the intended communication. If for some reason the more preferred protocol is unsuccessful, the next best protocol according to the order of the bids is processed. The bids are generated according to system / user set configuration and target object constraints. Bids fall into ranges of bid values where each range indicates a certain priority and associated rules.
Owner:BORLAND
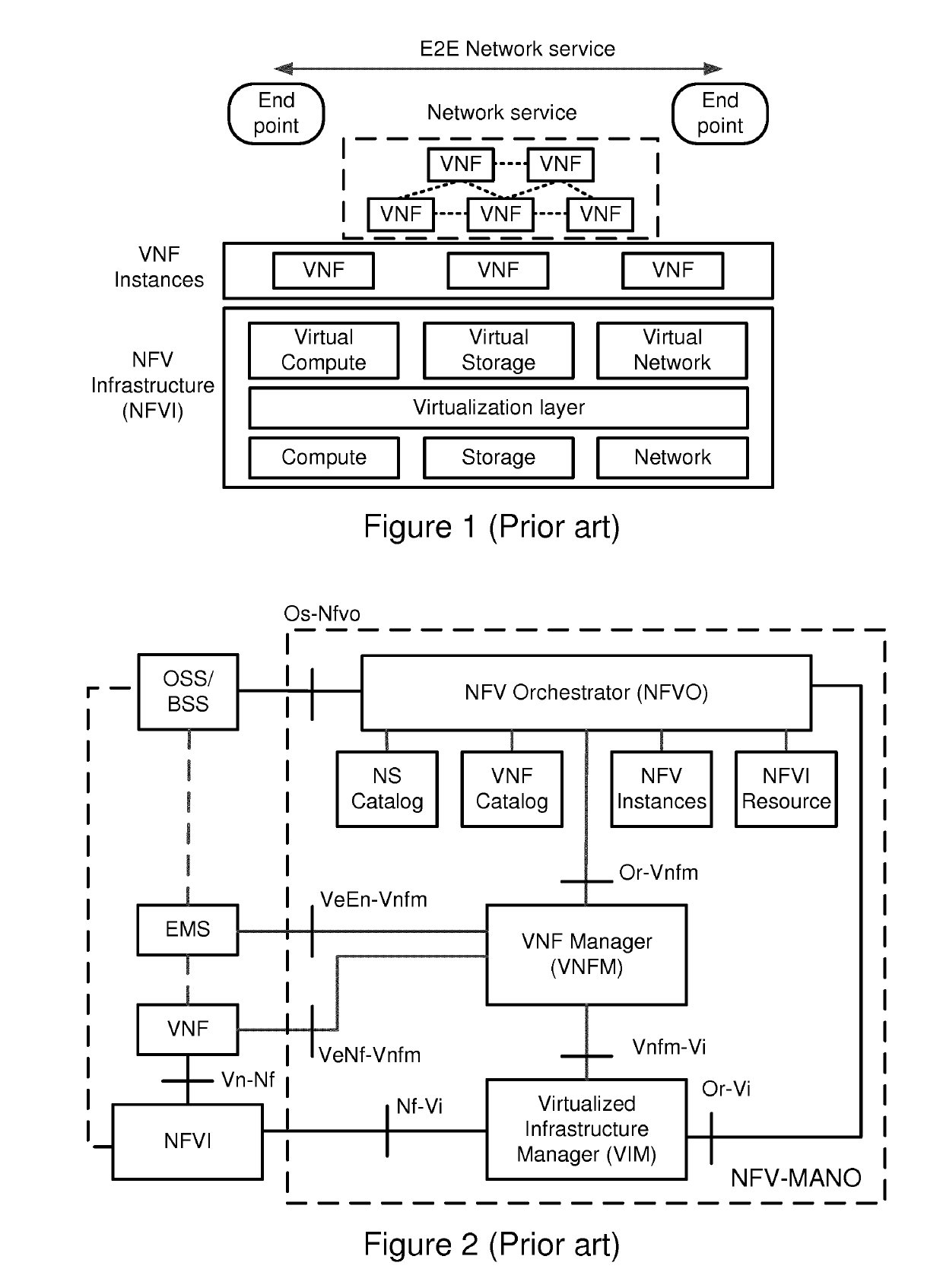
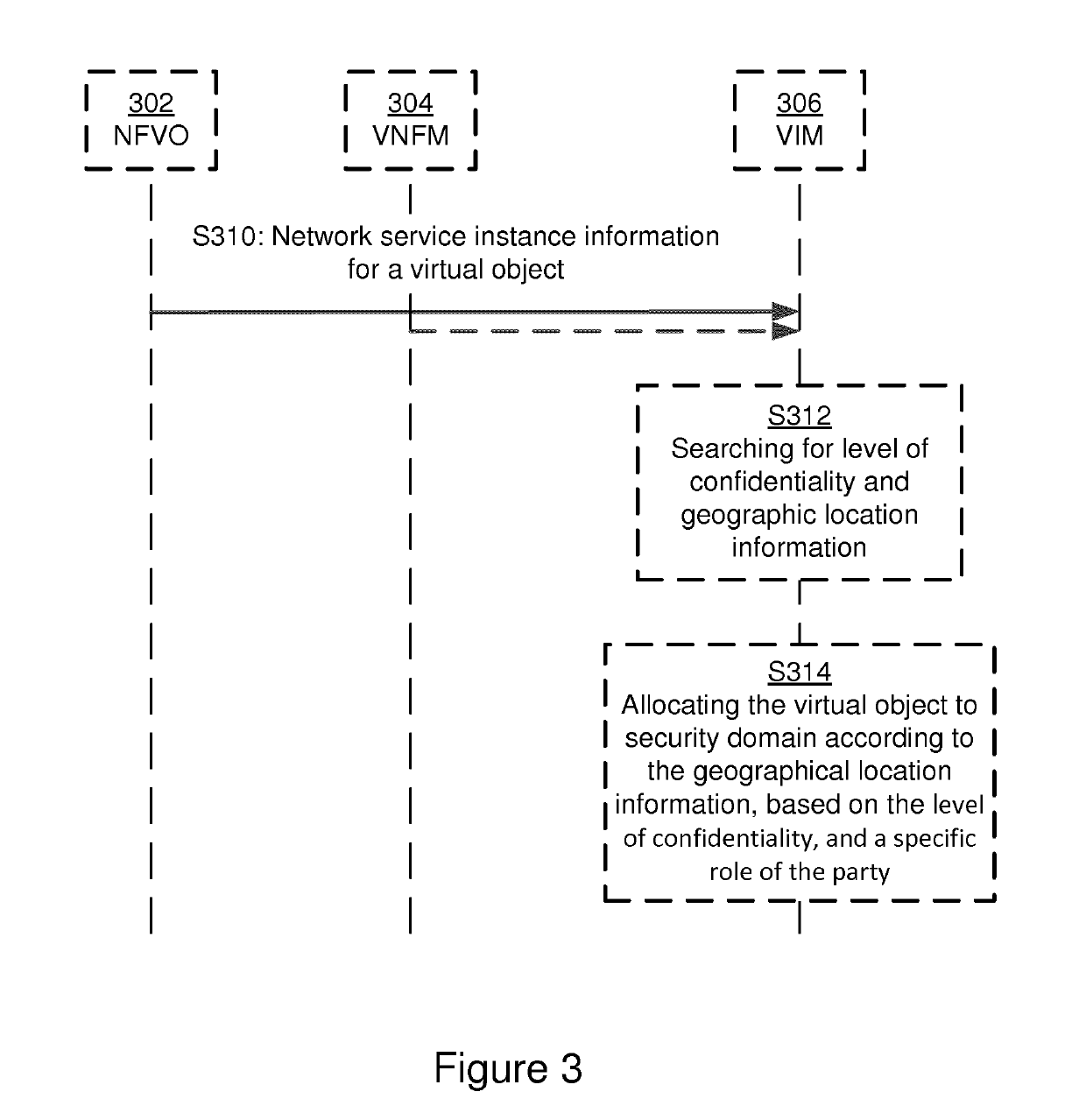
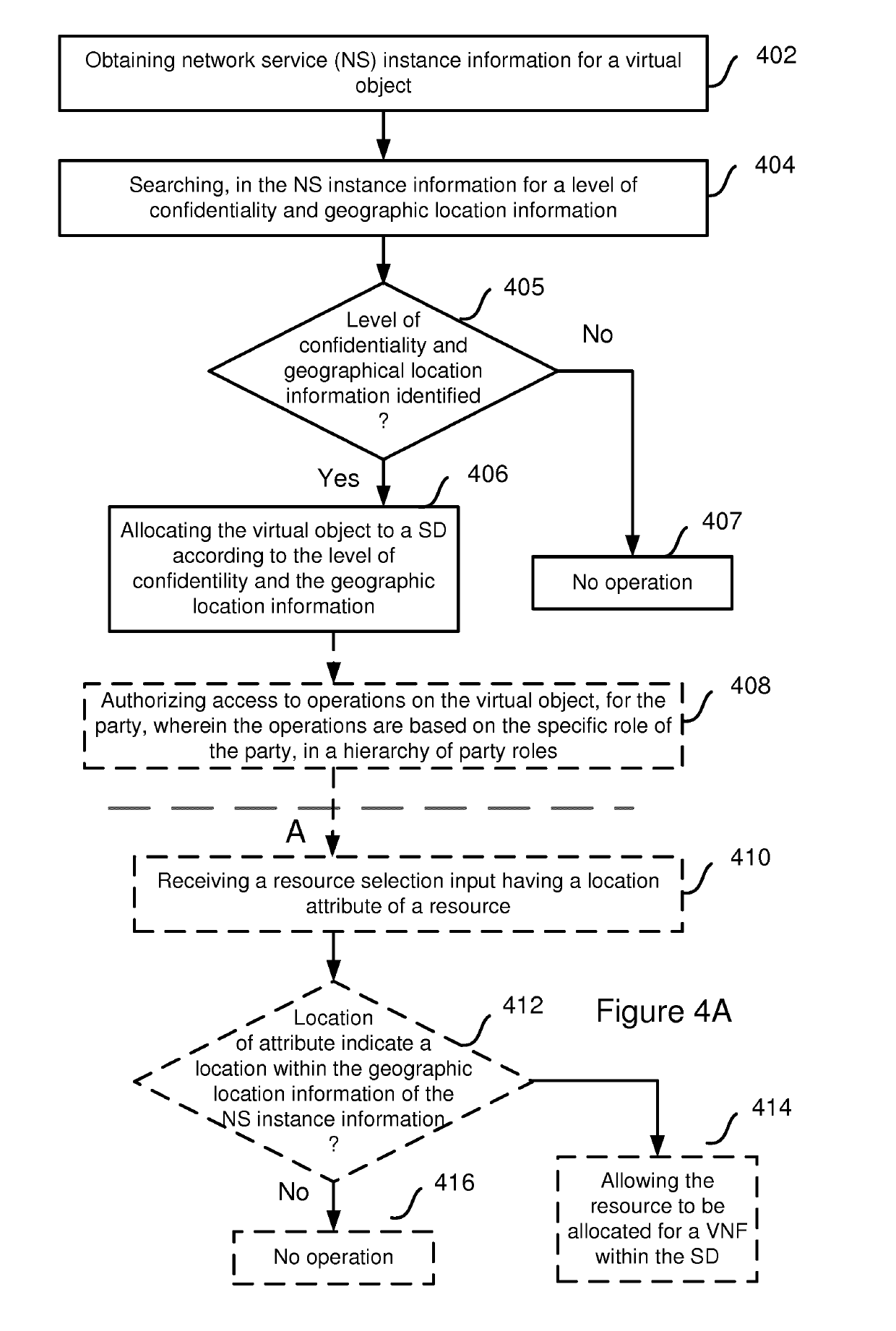
Method and arrangement for configuring a secure domain in a network functions virtualization infrastructure
ActiveUS20190132330A1Extract safeResource allocationPlatform integrity maintainanceVirtualizationObject handling
It is disclosed a method, an arrangement and a computer program for configuring a secure domain, SD, in a network functions virtualization infrastructure. The SD comprises virtual objects handling privileged information. NS instance information of a virtual object is obtained based on input from a party associated with the SD. The NS instance information is searched for a level of confidentiality and a geographic location information. When having identified the level of confidentiality and the geographic location information, the virtual object is allocated to the SD according to the geographic location information, based on the level of confidentiality and a specific role of the party. It is an advantage that access to a SD is allowed or granted based on the specific role of the party.
Owner:TELEFON AB LM ERICSSON (PUBL)
Multi-mode internal imaging
InactiveUS20060253013A1Ultrasonic/sonic/infrasonic diagnosticsChemiluminescene/bioluminescenceLow intensity lightObject handling
The invention described herein provides systems and methods for multi-modal imaging with light and a second form of imaging. Light imaging involves the capture of low intensity light from a light-emitting object. A camera obtains a two-dimensional spatial distribution of the light emitted from the surface of the subject. Software operated by a computer in communication with the camera may then convert two-dimensional spatial distribution data from one or more images into a three-dimensional spatial representation. The second imaging mode may include any imaging technique that compliments light imaging. Examples include magnetic resonance imaging (MRI) and computer topography (CT). An object handling system moves the object to be imaged between the light imaging system and the second imaging system, and is configured to interface with each system.
Owner:XENOGEN CORP
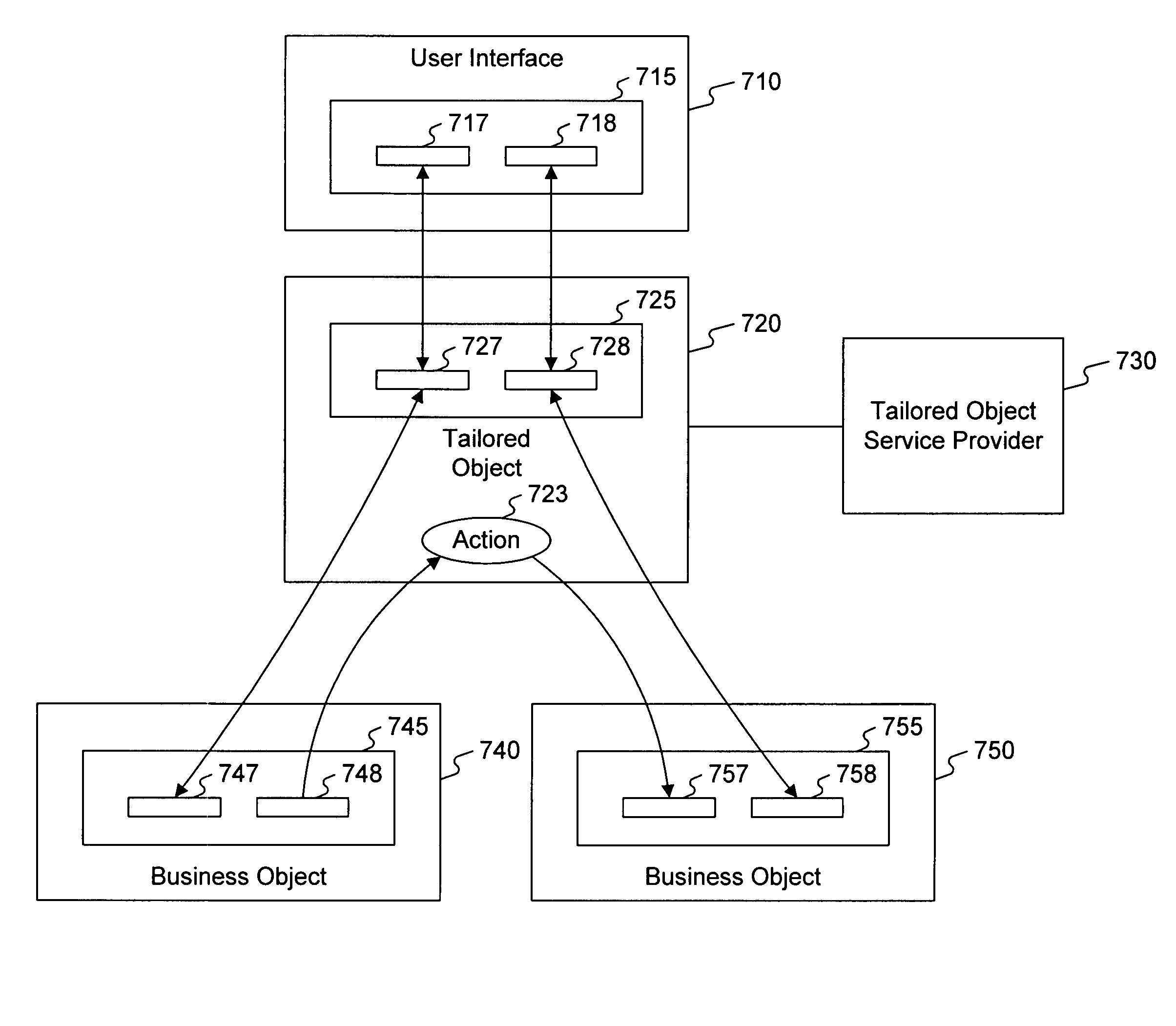
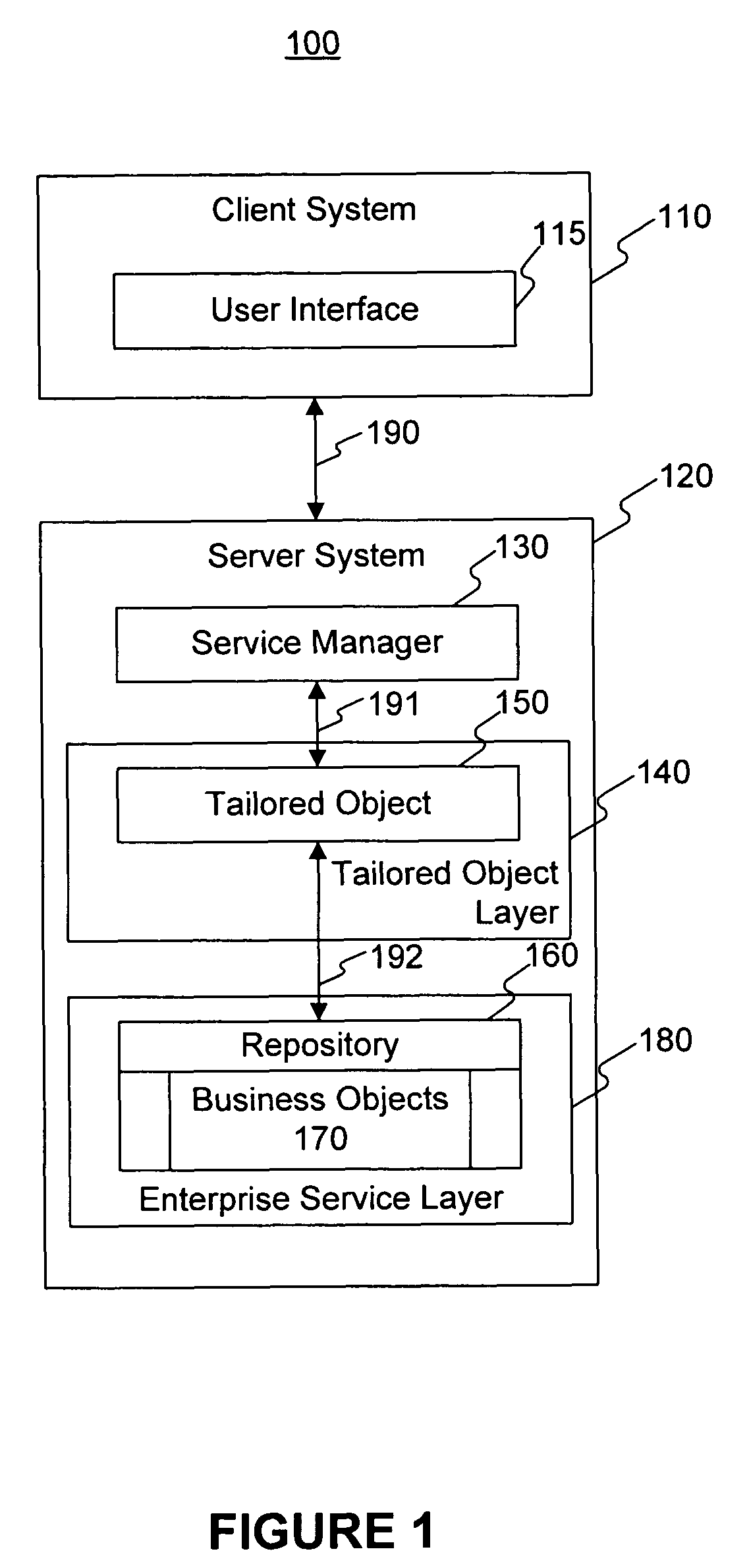
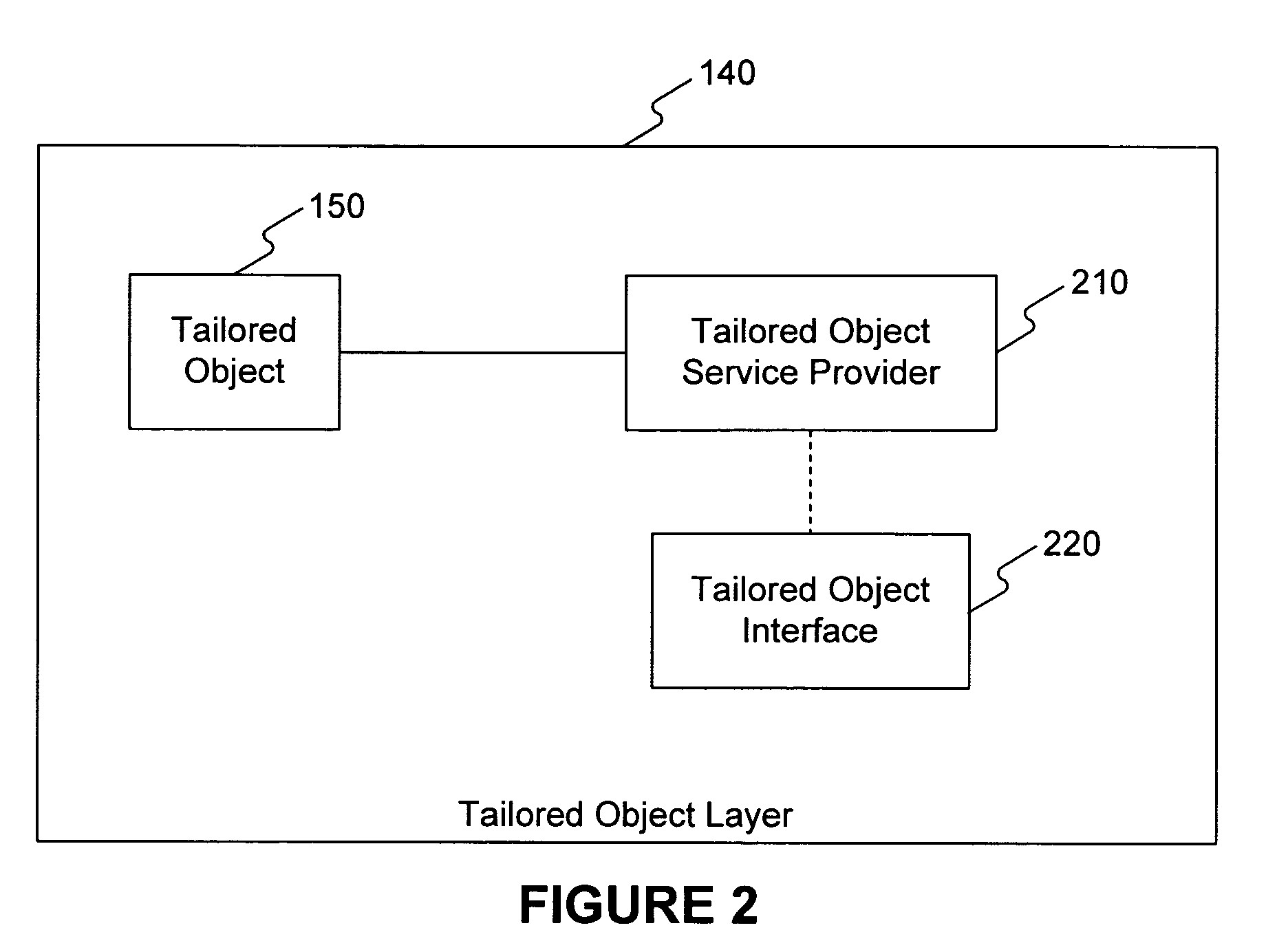
Tailored object
ActiveUS7877695B2Execution for user interfacesInput/output processes for data processingObject handlingUser interface
A system for managing user interface events in user interface of a client system. The system includes a service layer including a business object. The system also includes an intermediate object layer comprising an intermediate object associated with the business object, wherein the intermediate object handles user interface messages raised by the business object and retrieves data from the business object for user interface. The system further includes a service manager that provides the retrieved data from the intermediate object for display on the user interface.
Owner:SAP AG
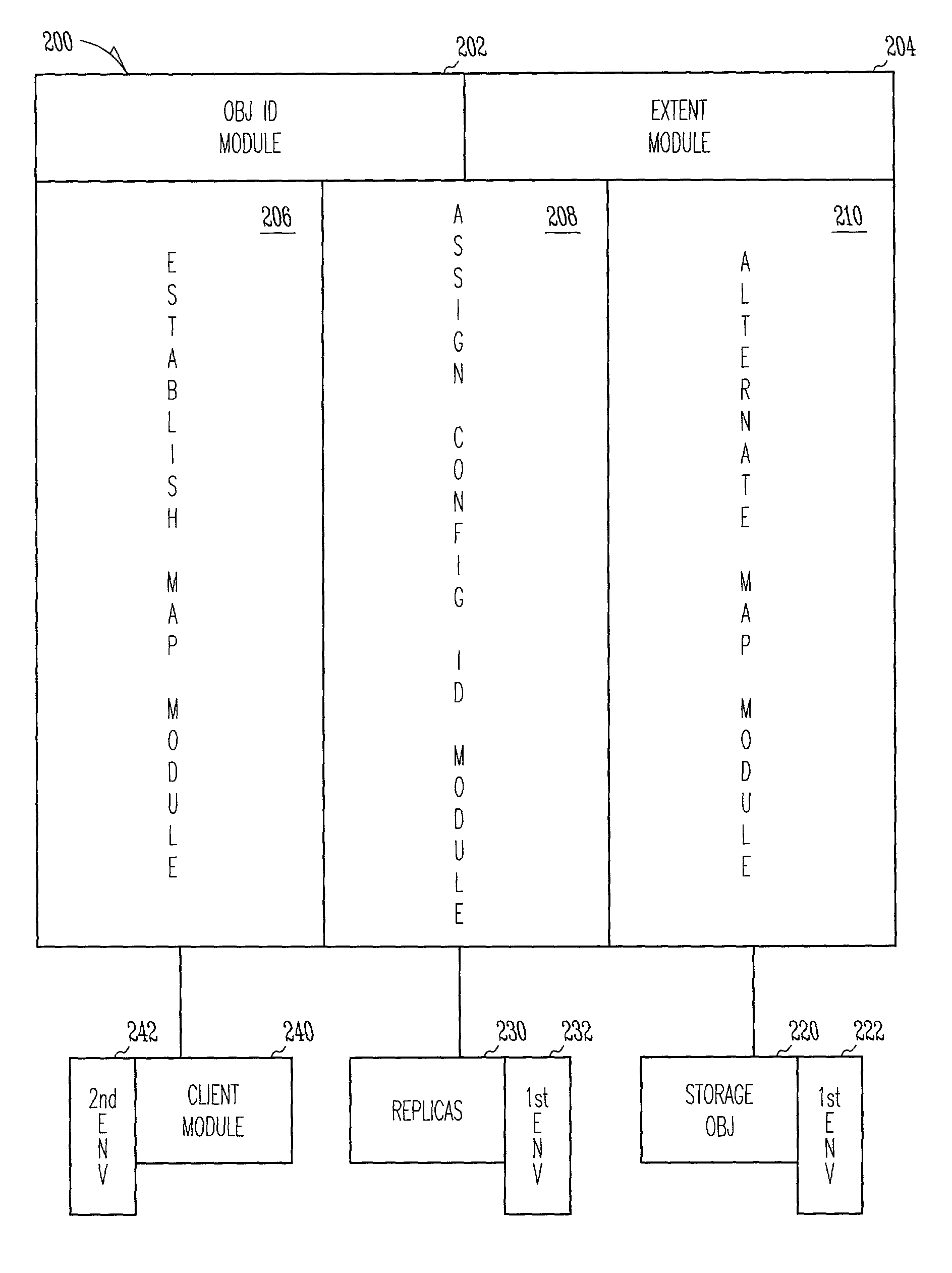
Methods, systems, and apparatus to interface with storage objects
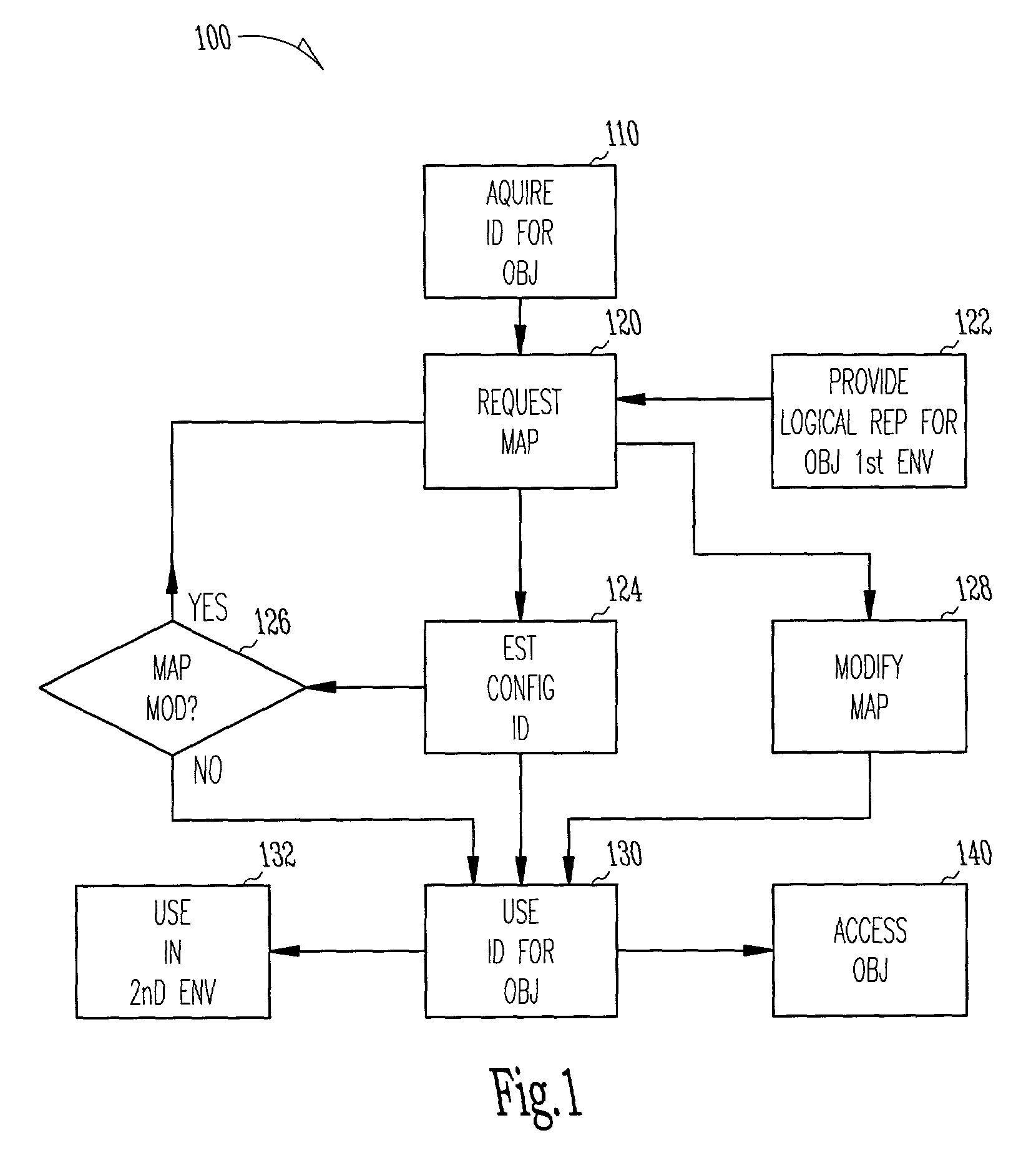
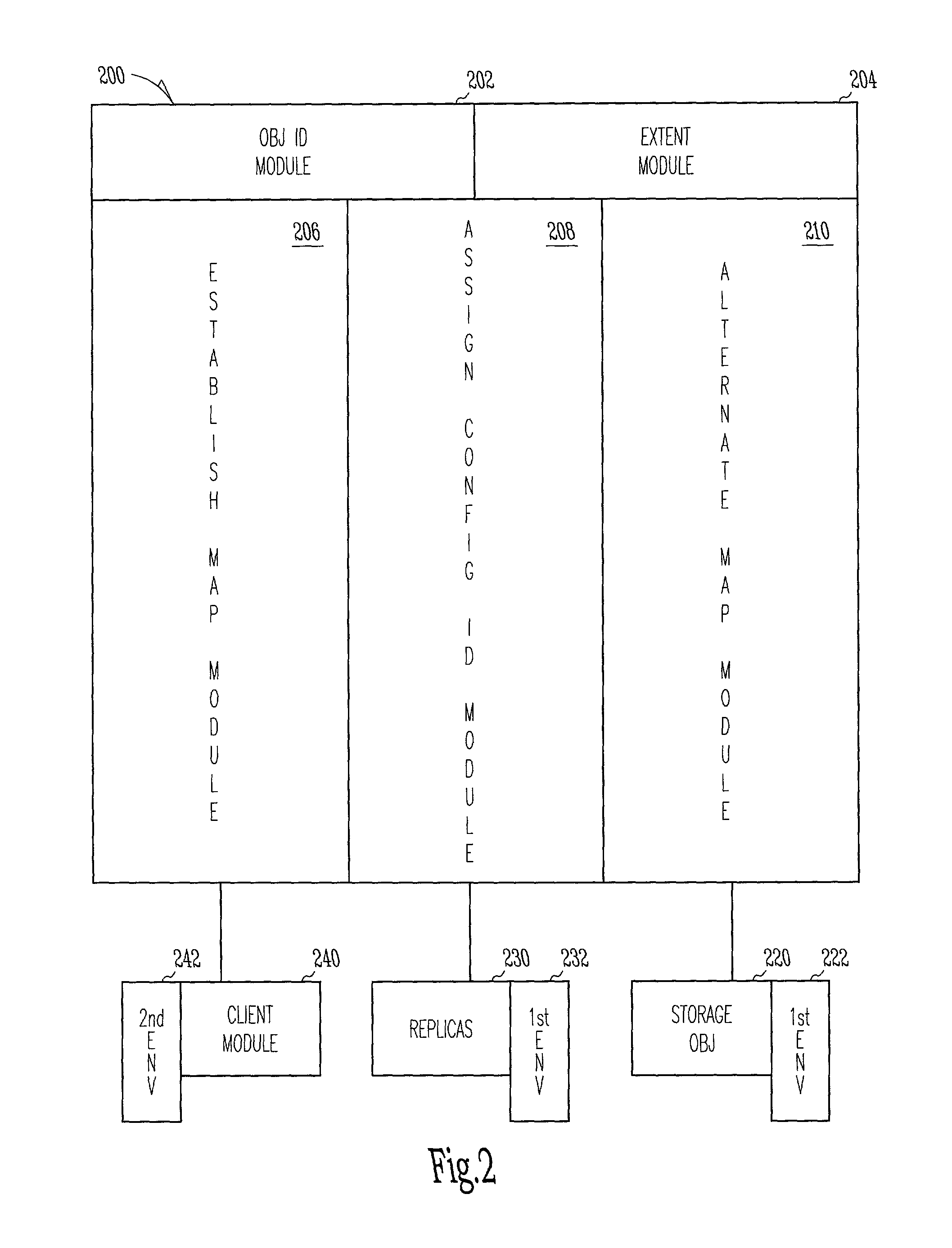
ActiveUS7117505B2Input/output to record carriersData processing applicationsObject handlingClient-side
Methods, systems, and apparatus to interface with storage objects are provided. A storage object handle is provided on request and a storage object is mapped within a first storage environment. Further, a configuration identifier notifies client modules when the storage object's physical locations are altered in the first storage environment. API libraries provide client modules access to use the storage object, even when the client modules reside in a second storage environment.
Owner:SYMANTEC OPERATING CORP
Object storage, handling, and retrieving system and method
ActiveUS10822166B2Reduce impactReduces load handling device congestionConveyorsStorage devicesComputer hardwareObject handling
Owner:OCADO INNOVATION
Method, system and computer-readable media for managing software object handles in a dual threaded environment
ActiveUS20090019079A1Improved object-oriented database management efficiencyFacilitate transparent communicationData processing applicationsProgram controlObject handlingPersistent object
A method and computer-readable media for managing software object handles in a dual threaded or multi-threaded environment are provided. In a first version a software driven computational process drives a first thread, while a garbage collector process drives a second active computational thread within a host computer. The software driven computational process generates persistent software objects that are temporarily stored in a memory of the host. Each handle may include an object identifier of the handle itself, an open / closed flag and a pointer to a unique persistent object. The open / closed flag indicates whether the persistent object associated with a handle shall remain open and accessible for processing or may be selected for closure by the garbage collector process. A plurality of handle wrappers are each associated in a one-to-one correspondence with a unique handle. Each handle wrapper is a software data structure that may include a in-use / not in-use flag and a specific handle or a pointer to a handle.
Owner:OBJECTIVITY
Processing method supporting calling of various safety devices
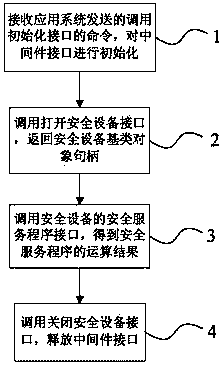
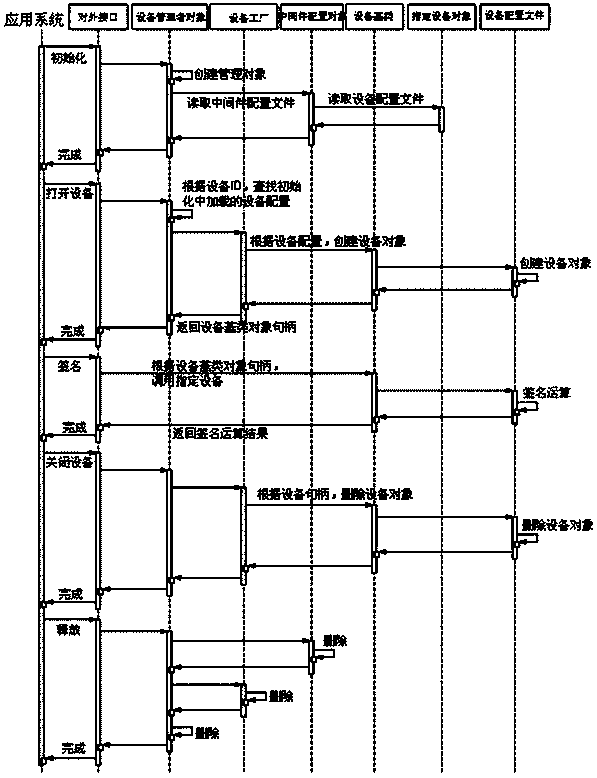
ActiveCN104199680AEasy to useImprove acceleration performanceInternal/peripheral component protectionProgram loading/initiatingObject handlingMiddleware
The invention provides a processing method supporting calling of various safety devices. The method comprises the steps that (1) an instruction of calling an initialization interface is received, and a middleware interface is initialized, wherein the instruction is sent by an application system; (2) safety device interfaces are called to be opened, and a safety device base class object handle is returned; (3) safety service program interfaces of safety devices are called, and safety service program operation results are obtained; (4) the safety device interfaces are called to be closed, and the middleware interface is released. The processing method supporting calling of the various safety devices has the advantages that a user can achieve connection communication between the safety devices and devices provided with application programs without the need of knowing various algorithms or an API, and the user can use the safety devices conveniently.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com