Patents
Literature
3545 results about "Security controls" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security controls are safeguards or countermeasures to avoid, detect, counteract, or minimize security risks to physical property, information, computer systems, or other assets.
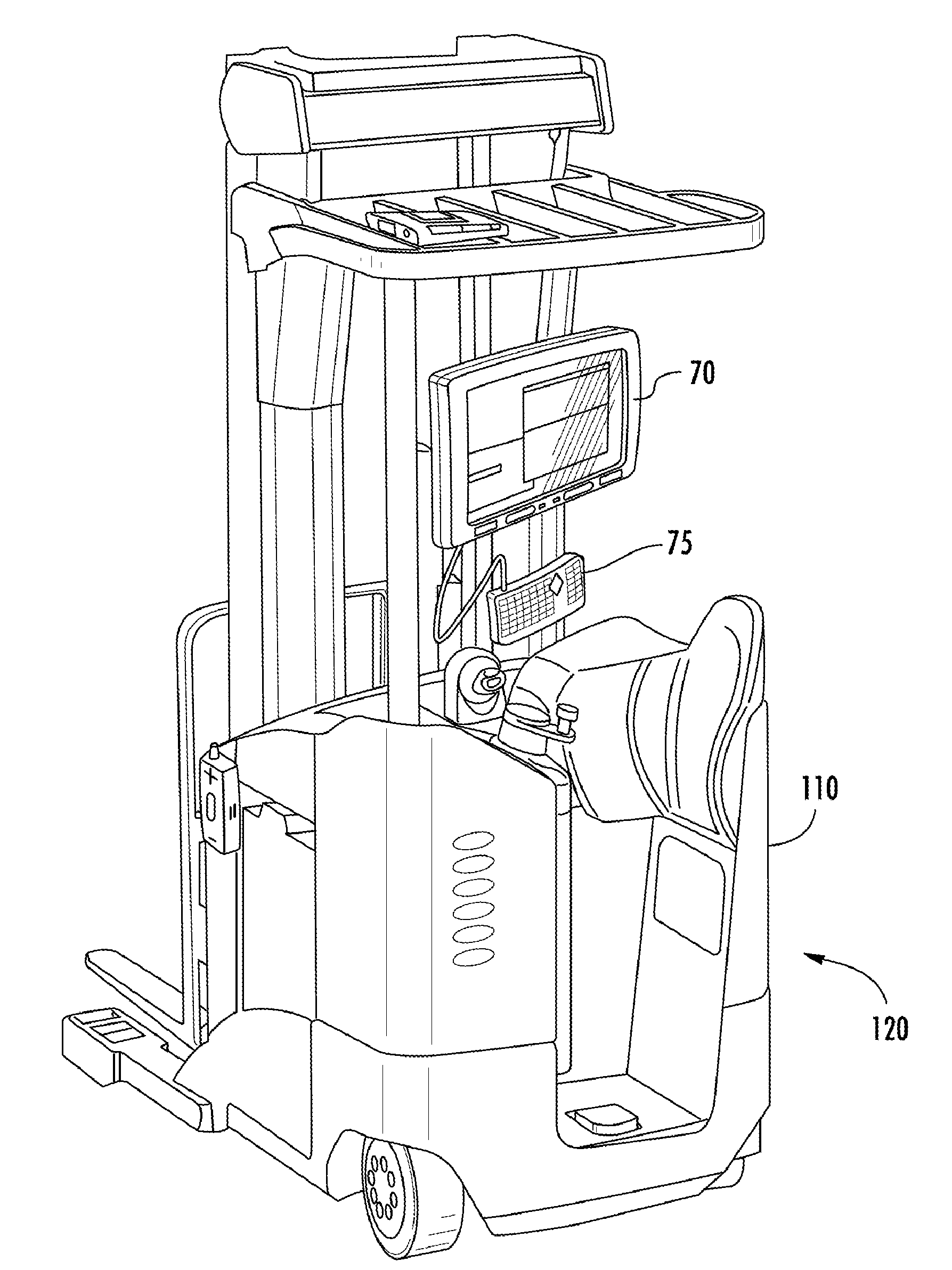
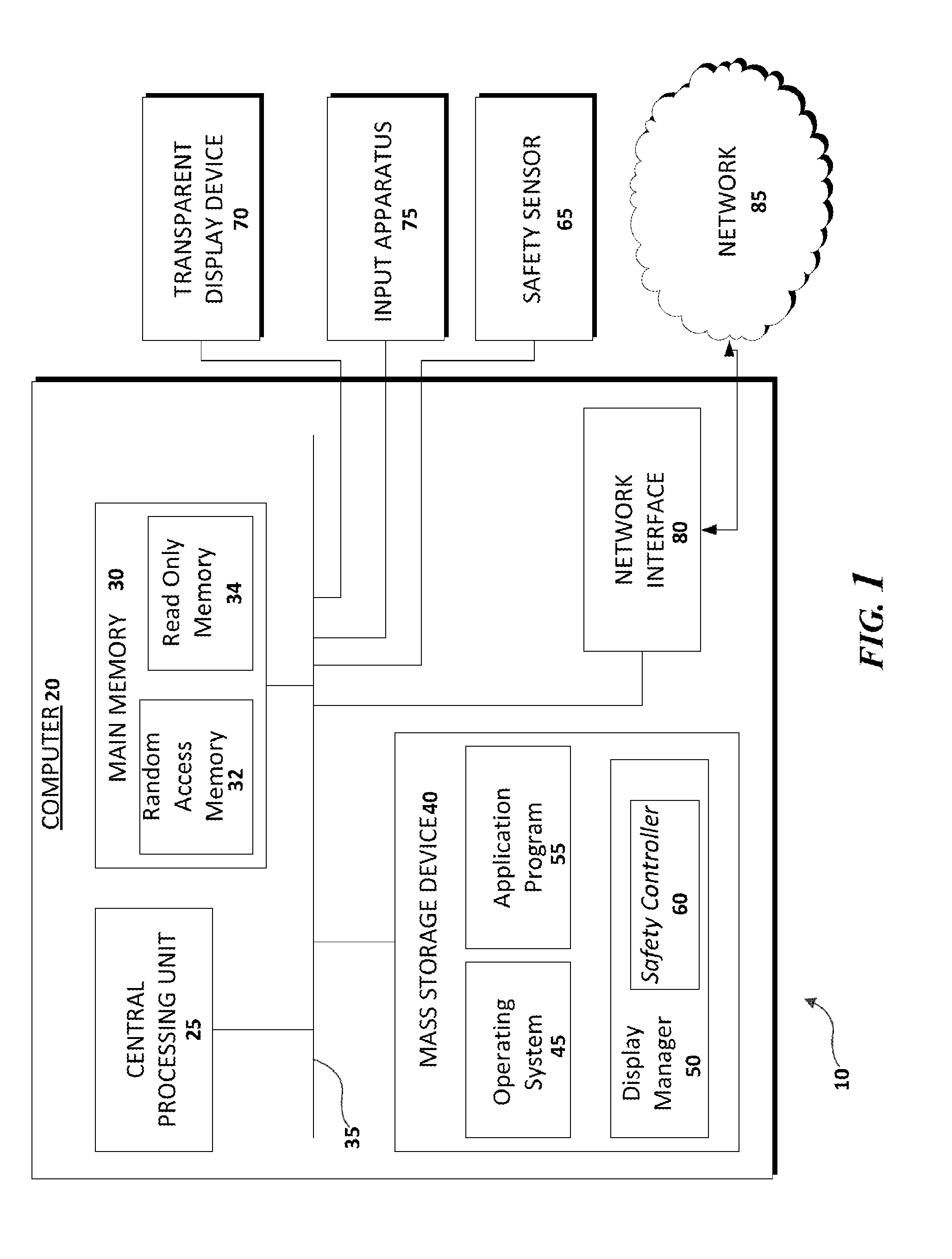
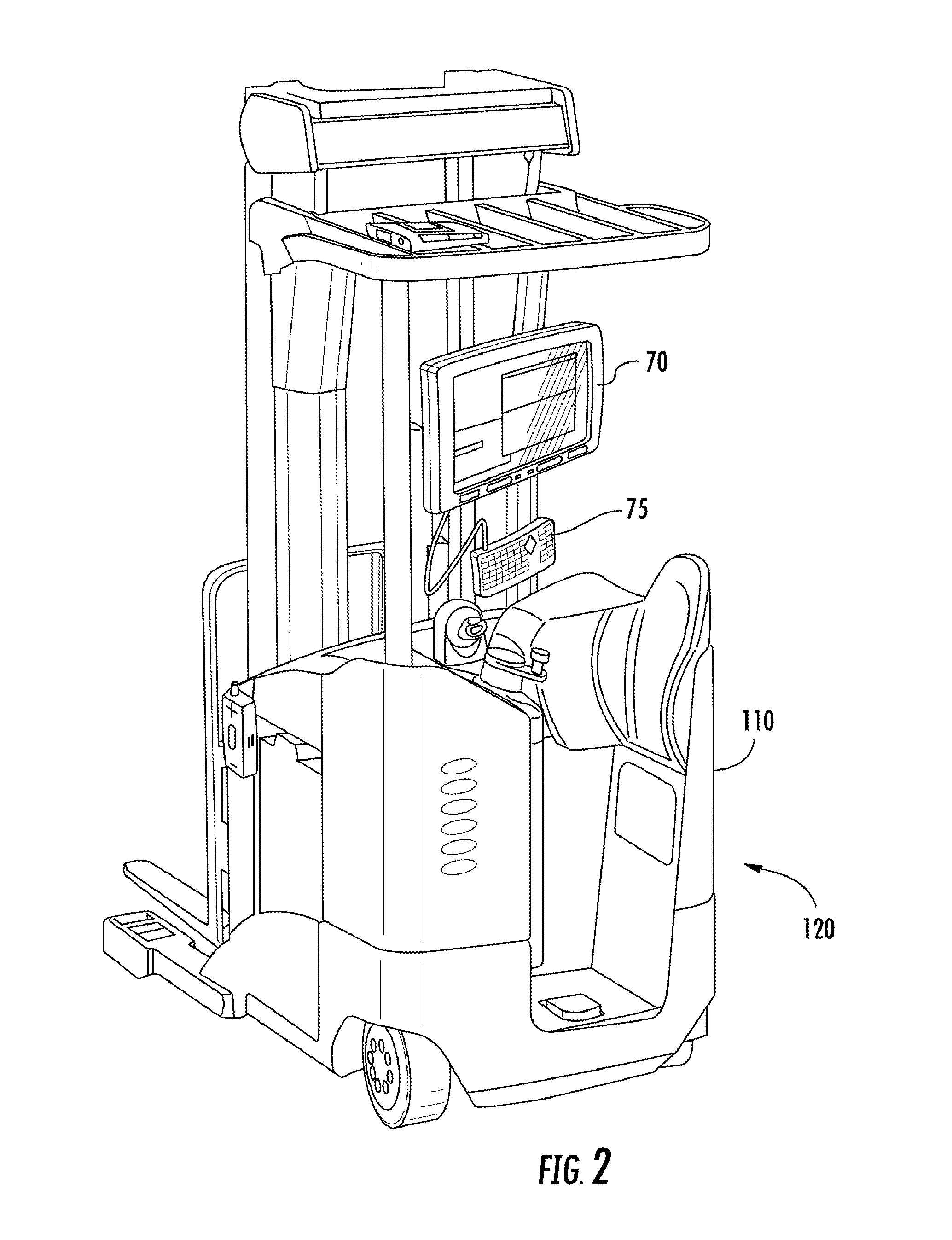
Vehicle computer system with transparent display
ActiveUS20140114530A1Good operating visionImprove visibilityRoad vehicles traffic controlDigital data processing detailsComputerized systemEngineering
The invention relates to a vehicle computer system. The vehicle computer system gathers data from a safety sensor to determine whether the proper safety conditions are present for the vehicle operator to interact with the vehicle computer system. A safety controller receives safety condition data gathered from the safety sensor and instructs the display manager to disable the display of information to the vehicle operator during unsafe operating conditions. The vehicle computer system advantageously employs a transparent display screen to provide greater field of vision of the vehicle operator than could be provided by a traditional display screen.
Owner:HAND HELD PRODS
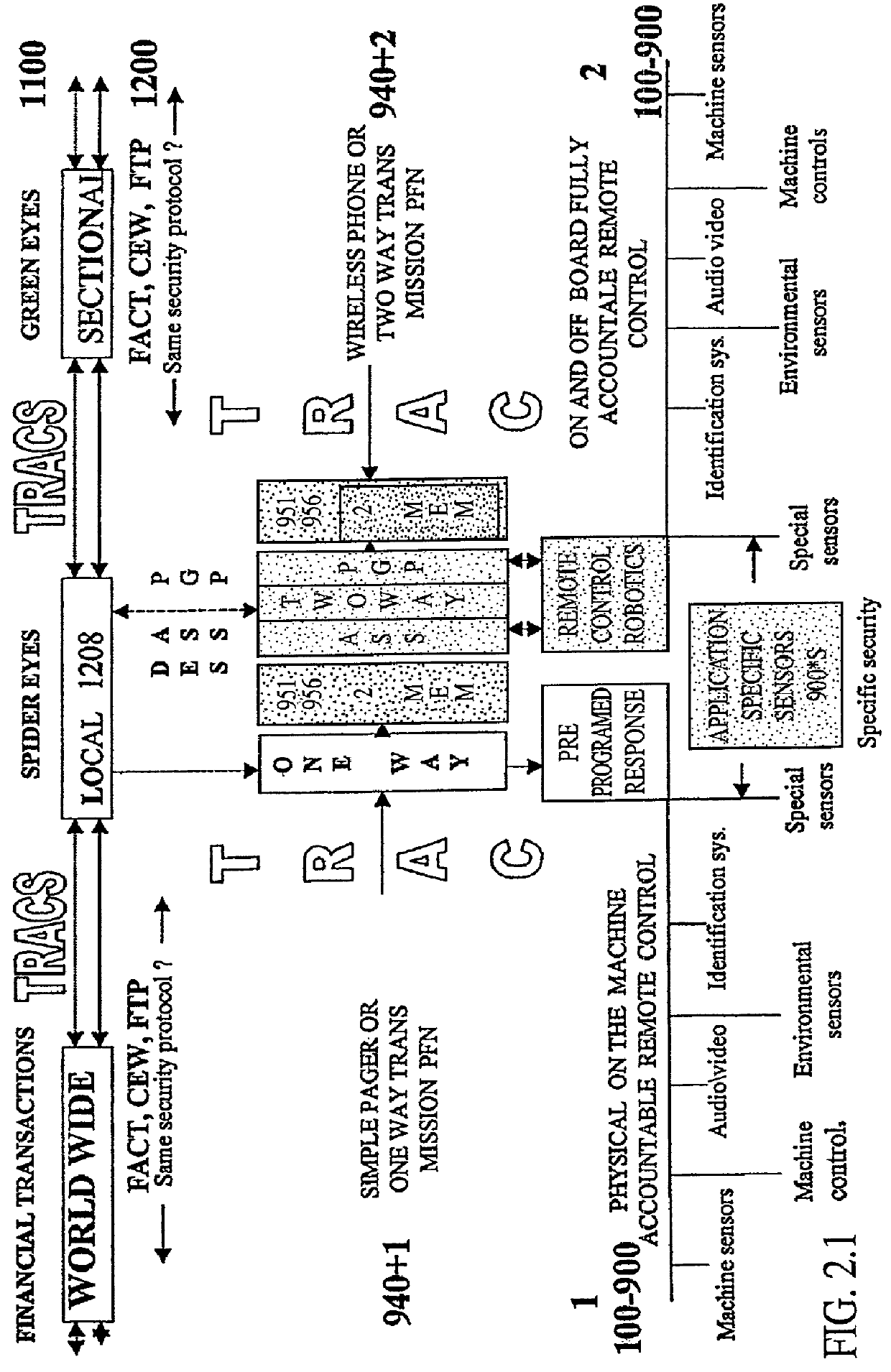
Electrically controlled automated devices to control equipment and machinery with remote control and accountability worldwide
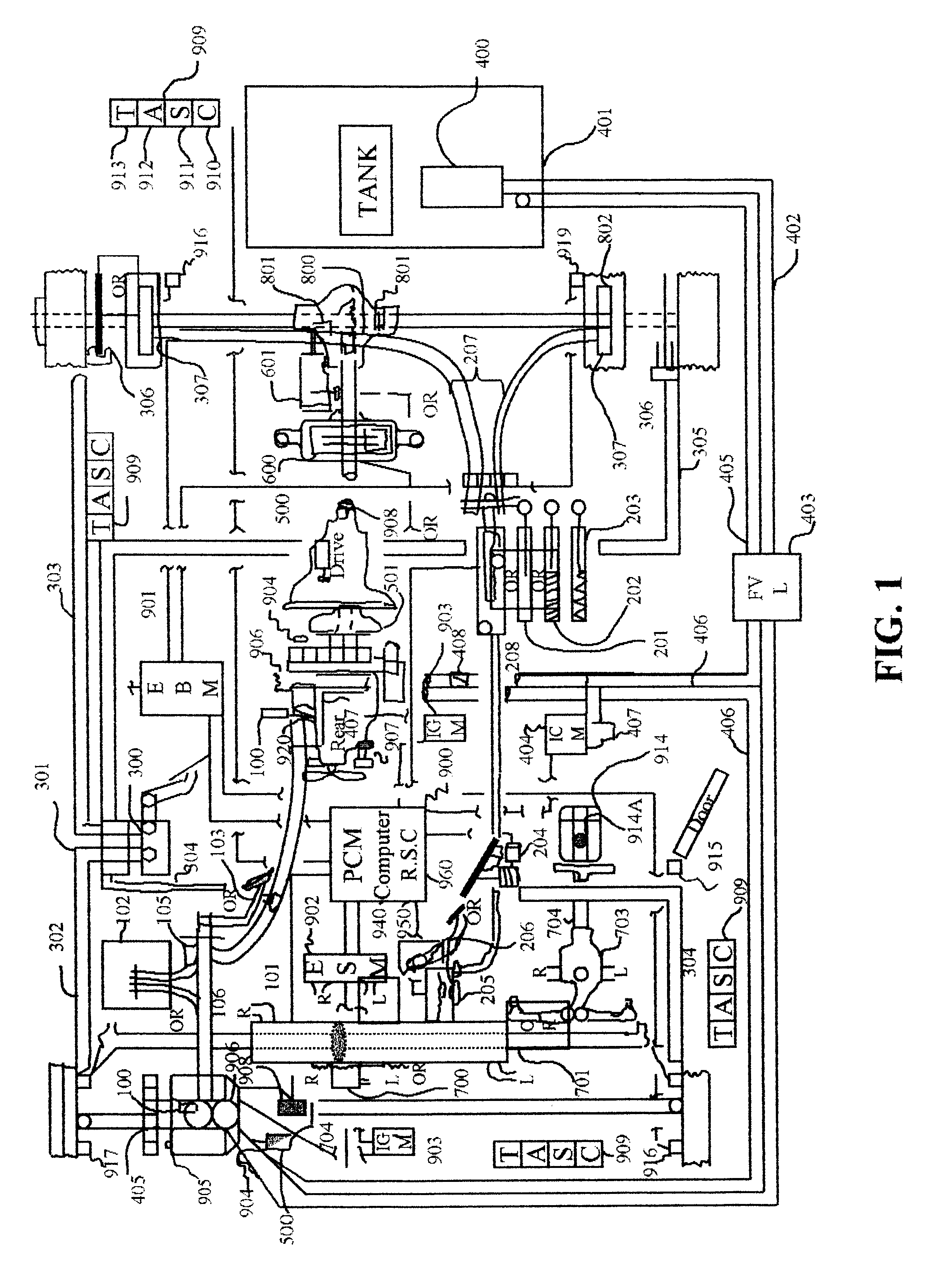
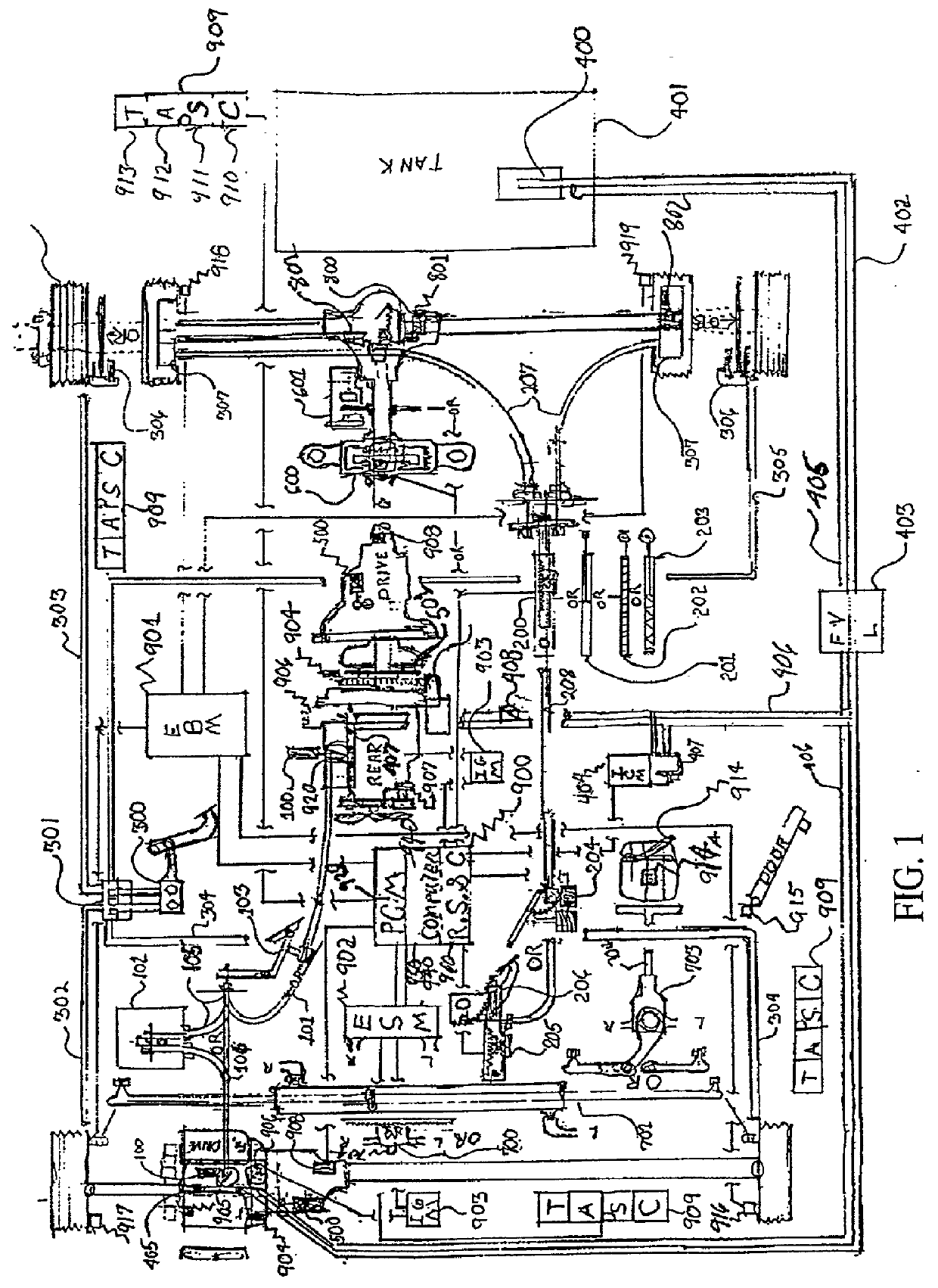
This application describes completely in many unique ways and detail all the devices to reduce a vehicle's speed and / or reduce a machines RPMs and / or stop any piece of equipment's as well as guide it if mobile through automated controls. First to slow it down, and guide it and / or control it if necessary (i.e., other pieces of equipment). Secondly it discusses how to stop any piece of equipment completely. And thirdly, the invention secures it in a safe stationary position either entirely or any number of specific moving parts. Many of these systems are initially here described to slow, reduce speed, steer, stop and / or secure equipment functions. However, they also can be used to increase a piece of equipment's functions. In other words their variations are completely capable to serve any remote or automated controls on a vehicle in the future to provide full robotics systems, e.g., for automated transportation systems, automated manufacturing, etc., either through individually isolated remote control systems and / or interfaced with other off-board systems through communication links, gateway computers, computer networks and the world wide web for inexpensive long distance monitoring and remote control. The invention focuses on the automobile industry but as has always been maintained throughout all these applications these devices and systems are designed to control every piece of equipment. The invention includes various accountable protocols and commercial developments to control speed, brake and steering for an automobile shut down to be performed through automation to a safe controlled secured deactivated state to be considered as a basis for a standard in aggressive vehicle remote control and / or to control and guide a vehicle and / or piece of equipment through many different automated systems.
Owner:KLINE & WALKER
Electrically controlled automated devices to operate, slow, guide, stop and secure, equipment and machinery for the purpose of controlling their unsafe, unattended, unauthorized, unlawful hazardous and/or legal use, with remote control and accountability worldwide
InactiveUS20010056544A1The degree of freedom becomes largerElectrical controlVehicle fittingsRobotic systemsRobotics
This application describes completely in many unique ways and detail all the devices to reduce a vehicle's speed and / or reduce a machines RPM's and / or stop any piece of equipment's as well as guide it if mobile through automated controls. First to slow it down, and guide it and / or control it if necessary (i.e., other pieces of equipment). Secondly it discusses how to stop any piece of equipment completely. And thirdly, the invention secures it in a safe stationary position either entirely or any number of specific moving parts. Many of these systems are initially here described to slow, reduce speed, steer, stop and / or secure equipment functions. However, they also can be used to increase a piece of equipment's functions. In other words their variations are completely capable to serve any remote or automated controls on a vehicle in the future to provide full robotics systems, e.g., for automated transportation systems, automated manufacturing, etc., either through individually isolated remote control systems and / or interfaced with other off-board systems through communication links, gateway computers, computer networks and the world wide web for inexpensive long distance monitoring and remote control. The invention focuses on the automobile industry but as has always been maintained throughout all these applications these devices and systems are designed to control every piece of equipment. The invention includes various accountable protocols and commercial developments to control speed, brake and steering for an automobile shut down to be performed through automation to a safe controlled secured deactivated state to be considered as a basis for a standard in aggressive vehicle remote control and / or to control and guide a vehicle and / or piece of equipment through many different automated systems.
Owner:KLINE & WALKER
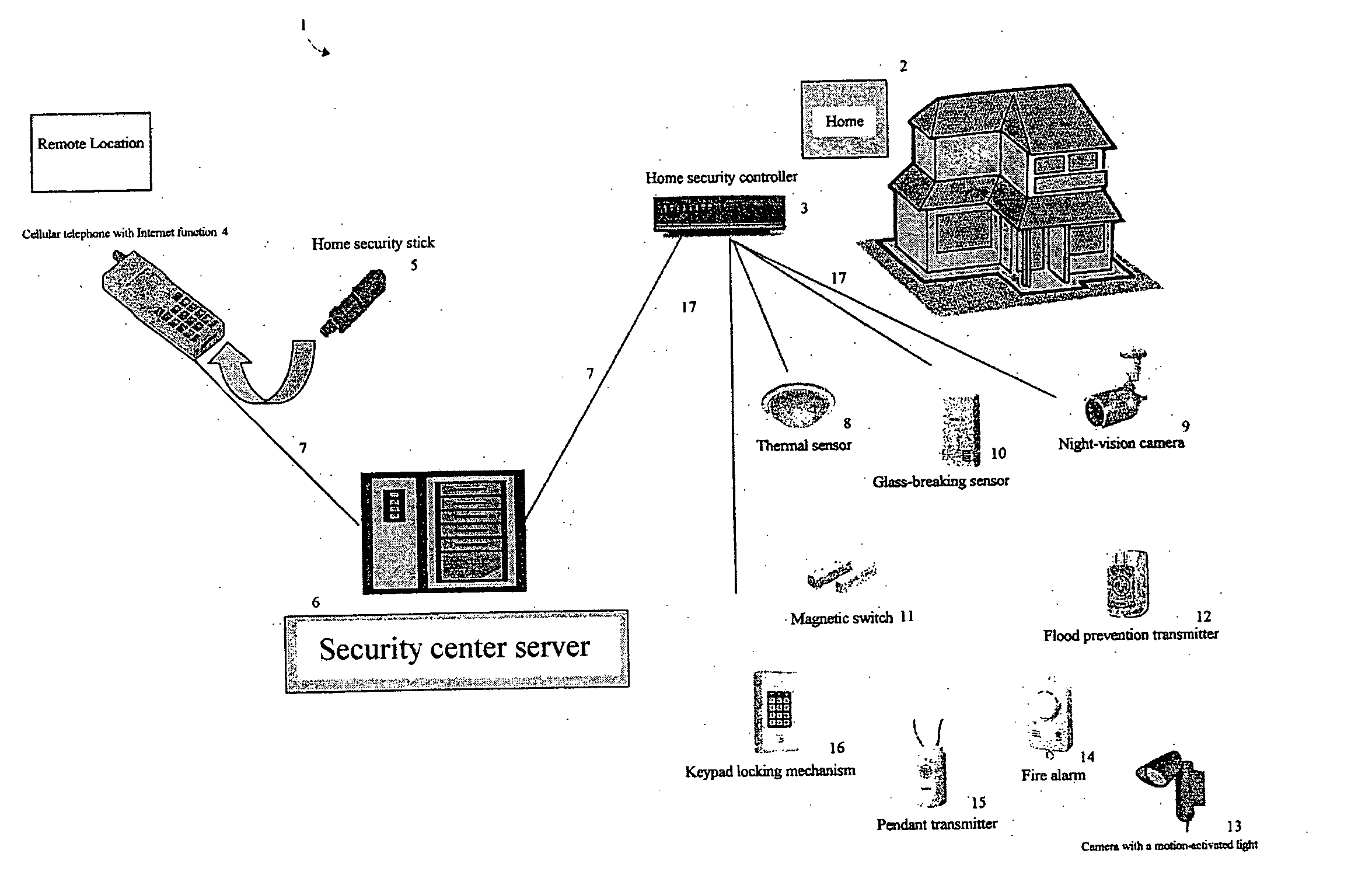
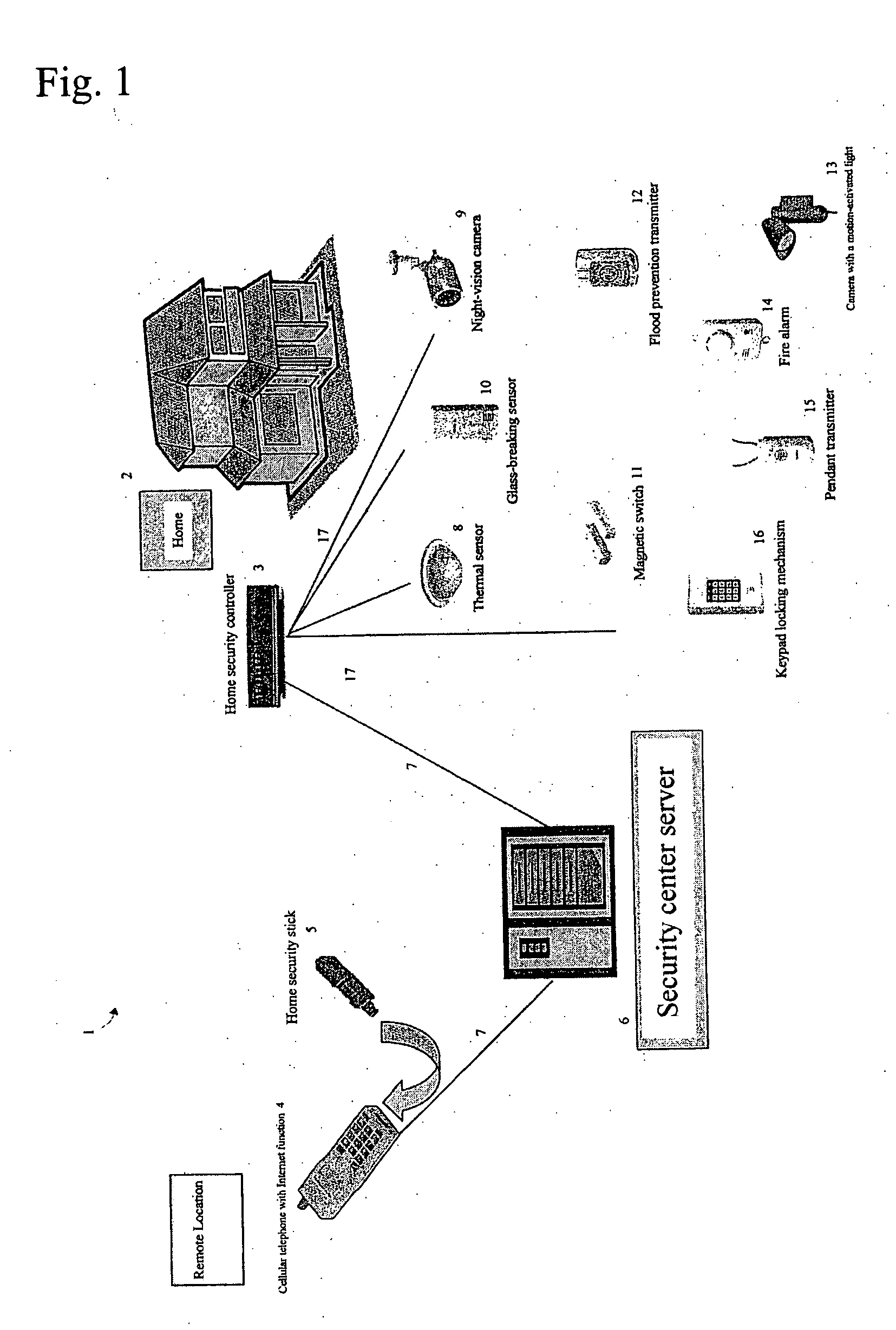
Home security system
InactiveUS20060022816A1Prevent intrusionEasy to operateElectric signal transmission systemsImage analysisRemote controlEngineering
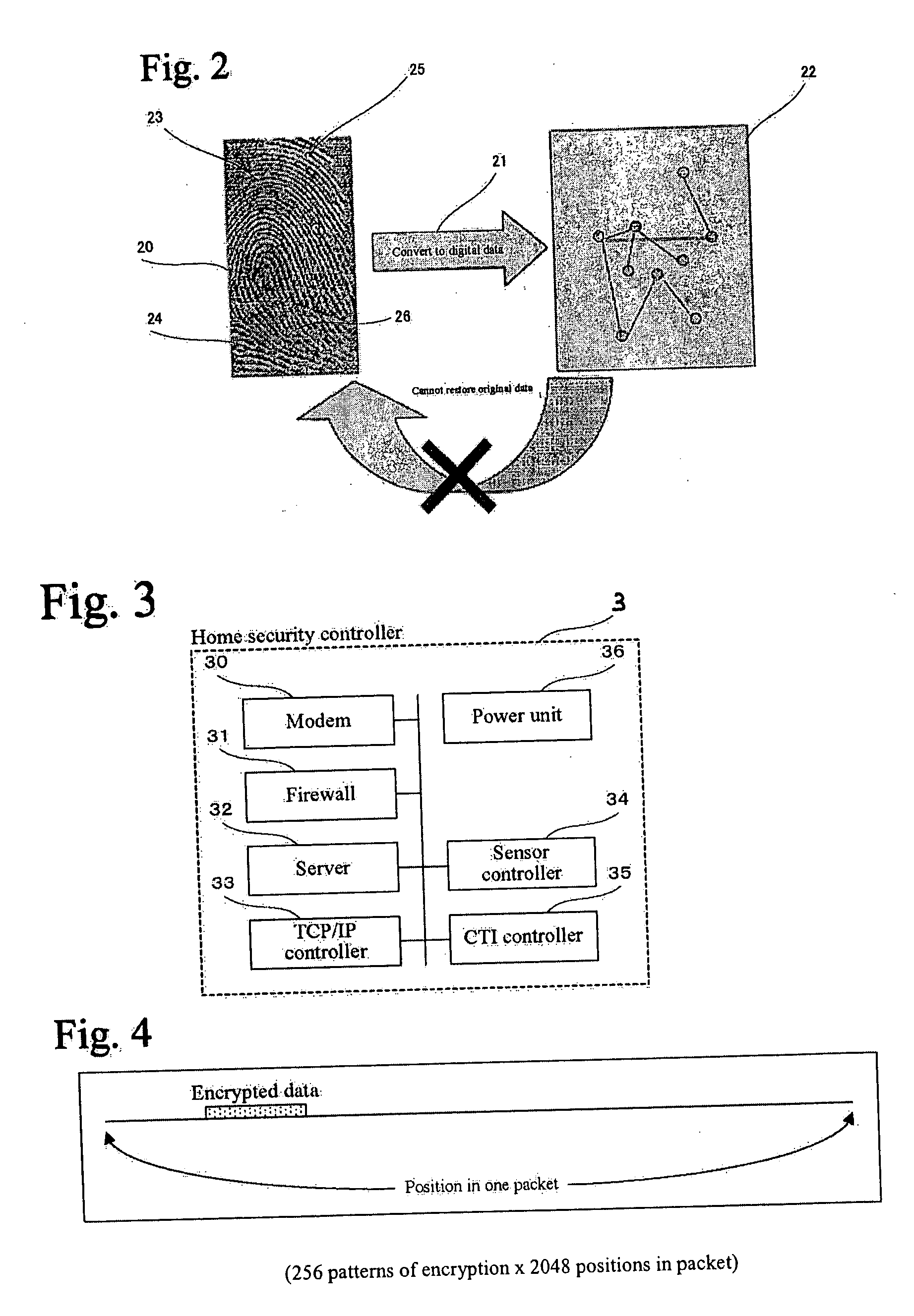
The present invention provides a home security system that includes a home security controller for collecting monitor data from various crime prevention and disaster prevention sensors installed in a home via a home network and notifying the portable terminal when a state of emergency occurs. The home security controller also enables devices in the home to be operated through remote control signals via an external network. The home security system further includes a portable terminal capable of connecting to the external network and having fingerprint data inputting means mounted on the body of the portable terminal for inputting fingerprints used for authentication. The fingerprint data inputting means has an assigned ID number. The home security system further includes a security center server having fingerprint authenticating means for receiving fingerprint data from the portable terminal via the external network and authenticating the fingerprint data through comparisons with registered fingerprint data. The fingerprint authenticating means completes authentication by checking the assigned ID number of the fingerprint data inputting means and matching the received fingerprint data with fingerprint data registered in association with the ID number. The security center server allows a connection between the portable terminal and the home security controller and controls bi-directional communications between the two after the security center server has completed authentication, enabling the portable terminal to receive monitor data from and transmit remote control signals to the home security controller via the external network.
Owner:AMERICAN TECH GRP JAPAN
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS20130104236A1Reduce analysisLower control priorityMemory loss protectionError detection/correctionApplication softwareBusiness process
Real time security, integrity, and reliability postures of operational (OT), information (IT), and security (ST) systems, as well as slower changing security and operational blueprint, policies, processes, and rules governing the enterprise security and business risk management process, dynamically evolve and adapt to domain, context, and situational awareness, as well as the controls implemented across the operational and information systems that are controlled. Embodiments of the invention are systematized and pervasively applied across interconnected, interdependent, and diverse operational, information, and security systems to mitigate system-wide business risk, to improve efficiency and effectiveness of business processes and to enhance security control which conventional perimeter, network, or host based control and protection schemes cannot successfully perform.
Owner:ALBEADO
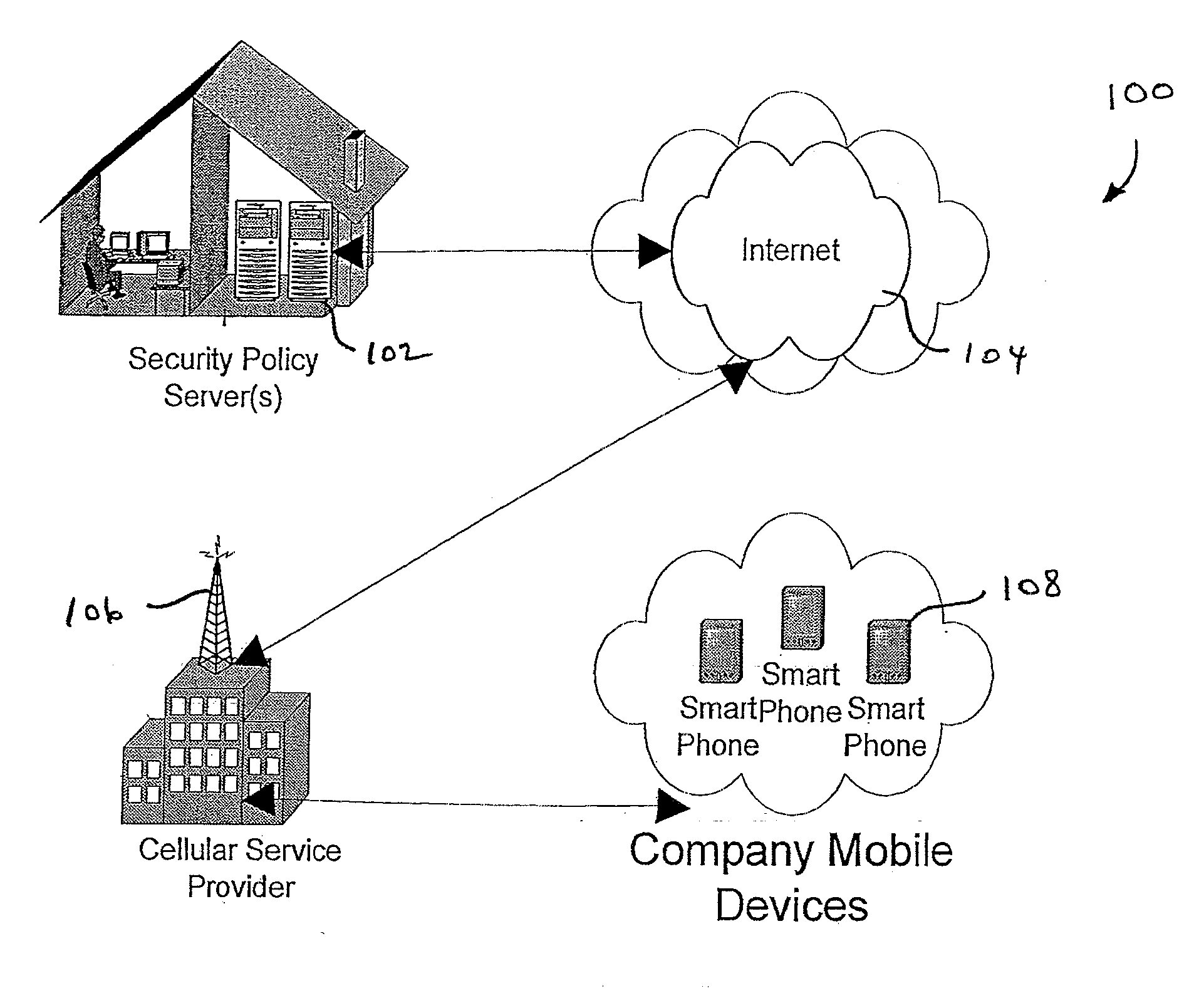
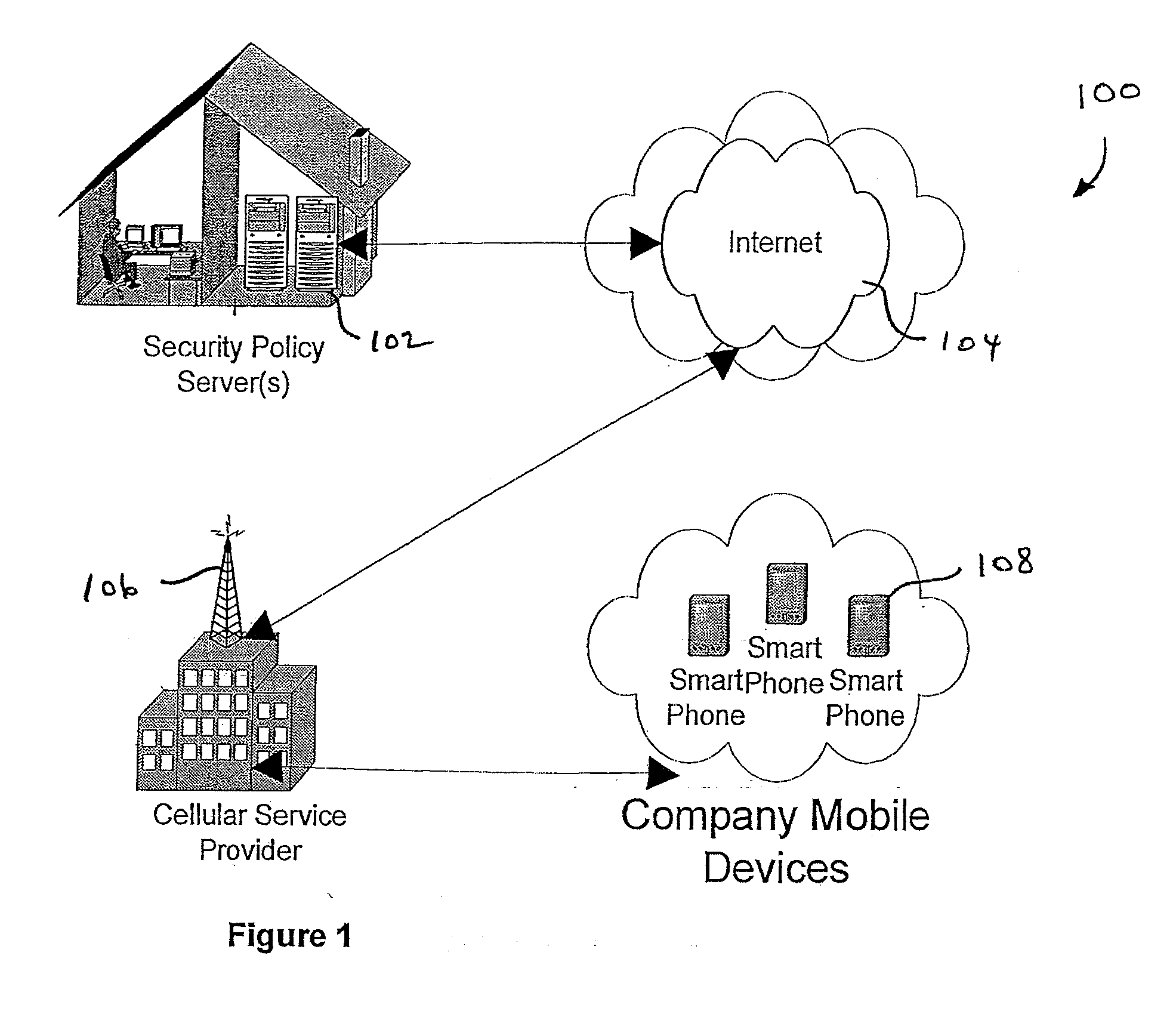
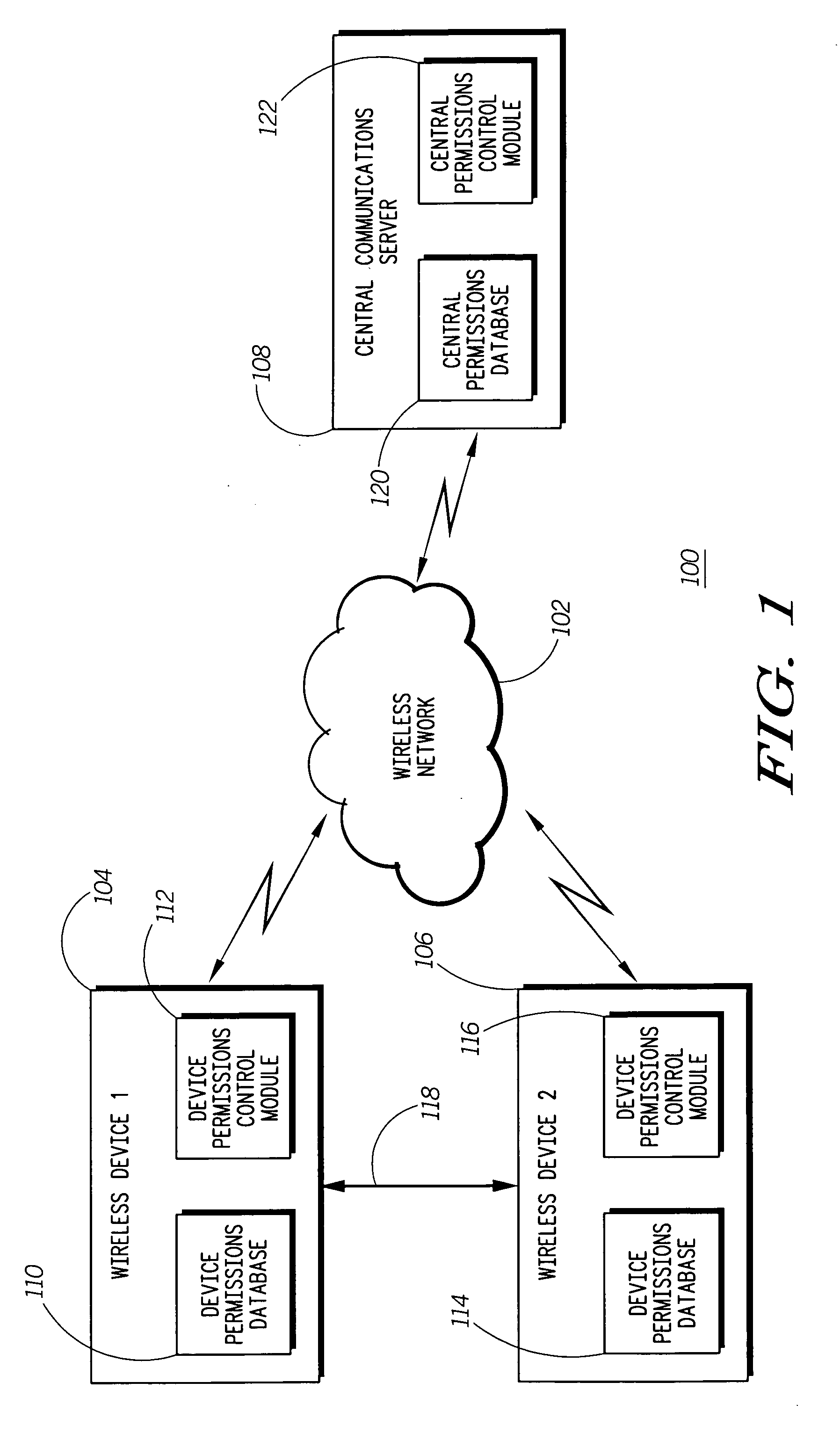
Centralized Dynamic Security Control for a Mobile Device Network
InactiveUS20070266422A1Well formedSecurity arrangementSpecial data processing applicationsTimerSecurity system
An security system for an enterprise network and data automates the revision, deployment, enforcement, auditing and control of security policies on mobile devices connected to said enterprise network, through automated communication between a security policy server and the mobile device. Control of the security system is centralized through administrative control of security policies stored on the security policy server. Automation of deployment of security policies to mobile devices occurs through transparent background communication and transfer of updated policies either triggered by a change in a security policy within the central repository of security policies or upon the expiration of a certain time period during which no policies were downloaded to the mobile device. When the mobile device is not in compliance with a security policy, a software security agent operating thereon limits access to said enterprise network and enterprise data. To aid in preventing the overwhelming of the enterprise network and the security policy server as a result of to many synchronization communications coming from too many mobile devices, a randomized timer is set by the software security agent upon receipt by the mobile device of a synchronization command from the security policy server.
Owner:SQUARE 1 BANK
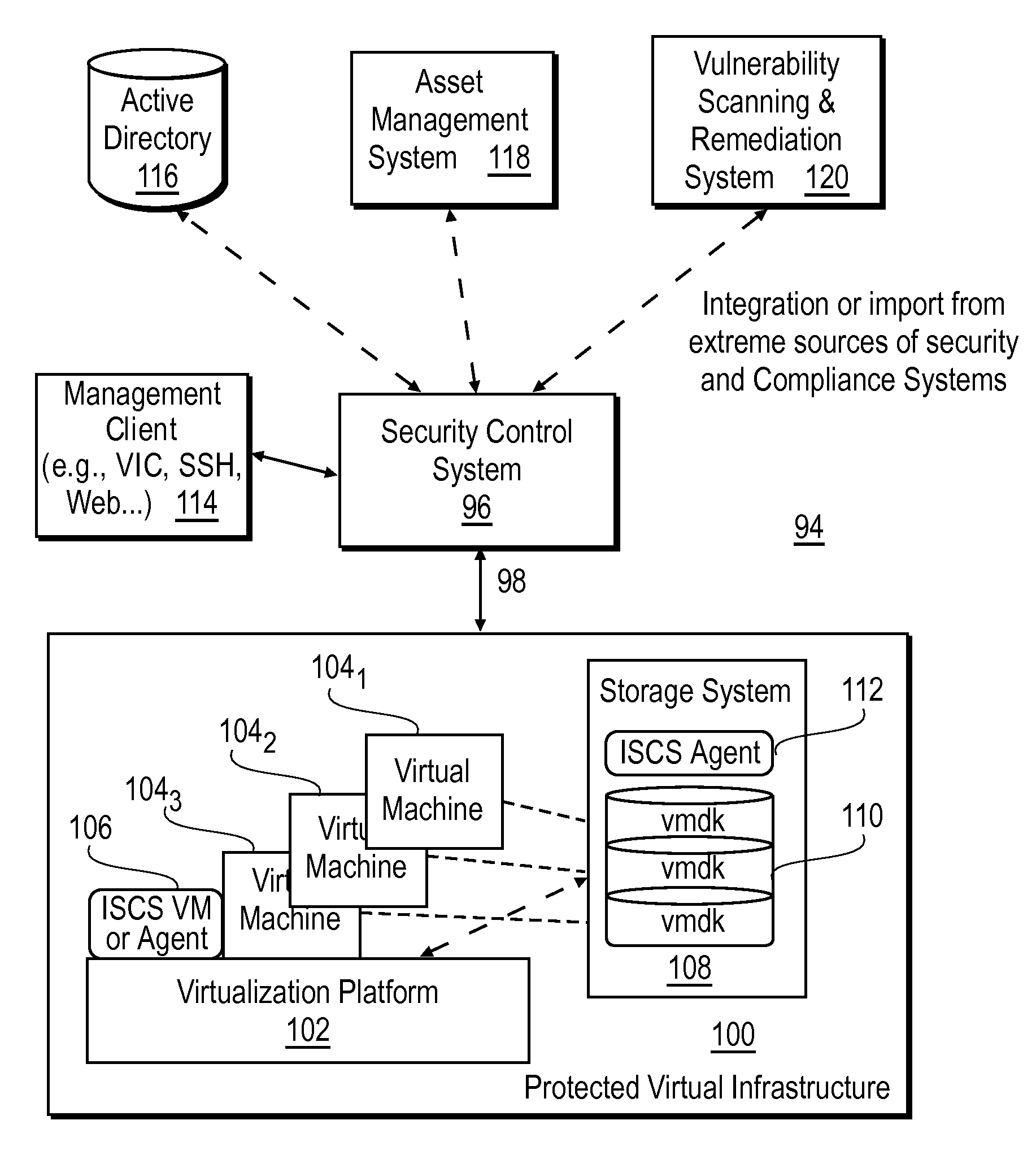
Intelligent security control system for virtualized ecosystems
ActiveUS20100169948A1Digital data processing detailsPublic key for secure communicationObject handlingVirtualization
Resources of a virtualized ecosystem are intelligently secured by defining and analyzing object handling security control information for one or more logical resources in the virtualized ecosystem and deriving therefrom object properties for each of the logical resources involved in the execution of a virtual machine in any given context within the virtualized ecosystem.
Owner:HYTRUST
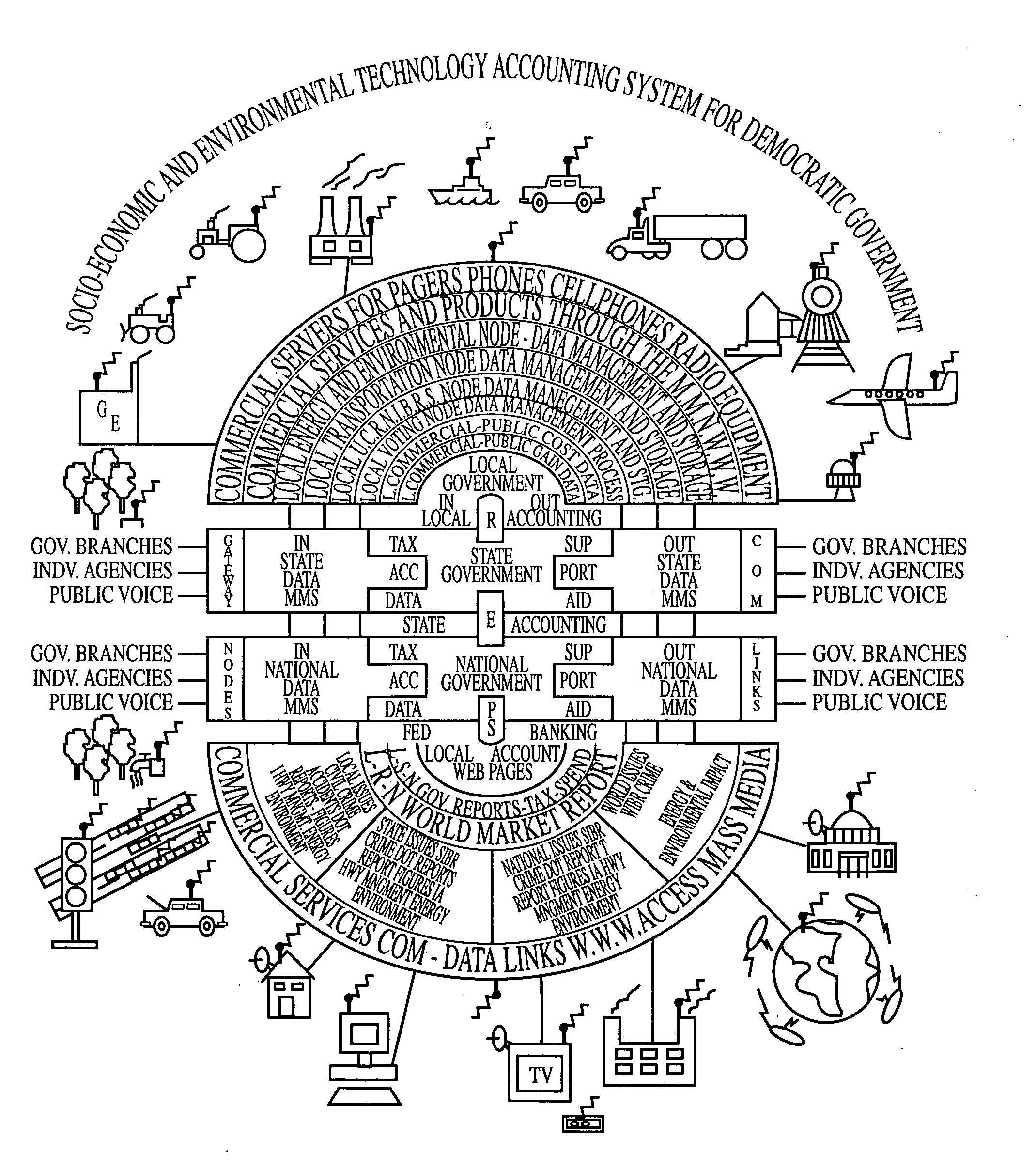
Automated accounting system that values, controls, records and bills the uses of equipment/vehicles for society
InactiveUS20060287783A1Fairly and accurately monitor and control the impact of equipment use on the world's environment andVehicle testingTelemetry/telecontrol selection arrangementsSecure communicationEnvironment effect
This invention addresses environmental social and commercial uses and includes a monitoring system which is a network of on, in, out and off-board devices working together with people through software and interfaces to provide services and make accountable humanity's machines and their actions through safe secure communication. Control devices are used to provide accountability for their socio-economic and environmental impact. Along with these systems networked together, additional devices and variations needed to complete these operations nationally and world wide are also provided. Unique ways interface a network of separate devices or IC circuits to create an interactive secure control system or center that can be remotely controlled. A control device for society to fairly and accurately monitor and control the impact of equipment use on the world environment, and a nation's infrastructure while developing commercial companies to fulfill these needs and services for the equipment and the people who own and operate them for today and into the future are also provided. A set of secure devices and systems are also included to analyze society and machine interaction.
Owner:KLINE & WALKER
Security Compliance Methodology and Tool
An apparatus is provided for evaluating risk to an organization. The apparatus includes a plurality of governmental rules directed to protecting shareholders, a plurality of security domains of the organization wherein each security domain is associated with a different asset of the organization and a request for an information risk assessment within at least one of the plurality of security domains of the organization formed under the plurality of governmental rules from a set of initializing inputs. The apparatus further includes a information risk assessment plan formed from the request for the information risk assessment, a set of information assessment templates and test cases formed from the information risk assessment plan, a set of information risk assessment tests conducted on the IT system using the assessment templates and test cases, a set of test results generated by the risk assessment tests, one or more security control gaps identified by the assessment responses and one or more gap remediation plans formed from the identified security gaps.
Owner:DENOVO ANDREW +1
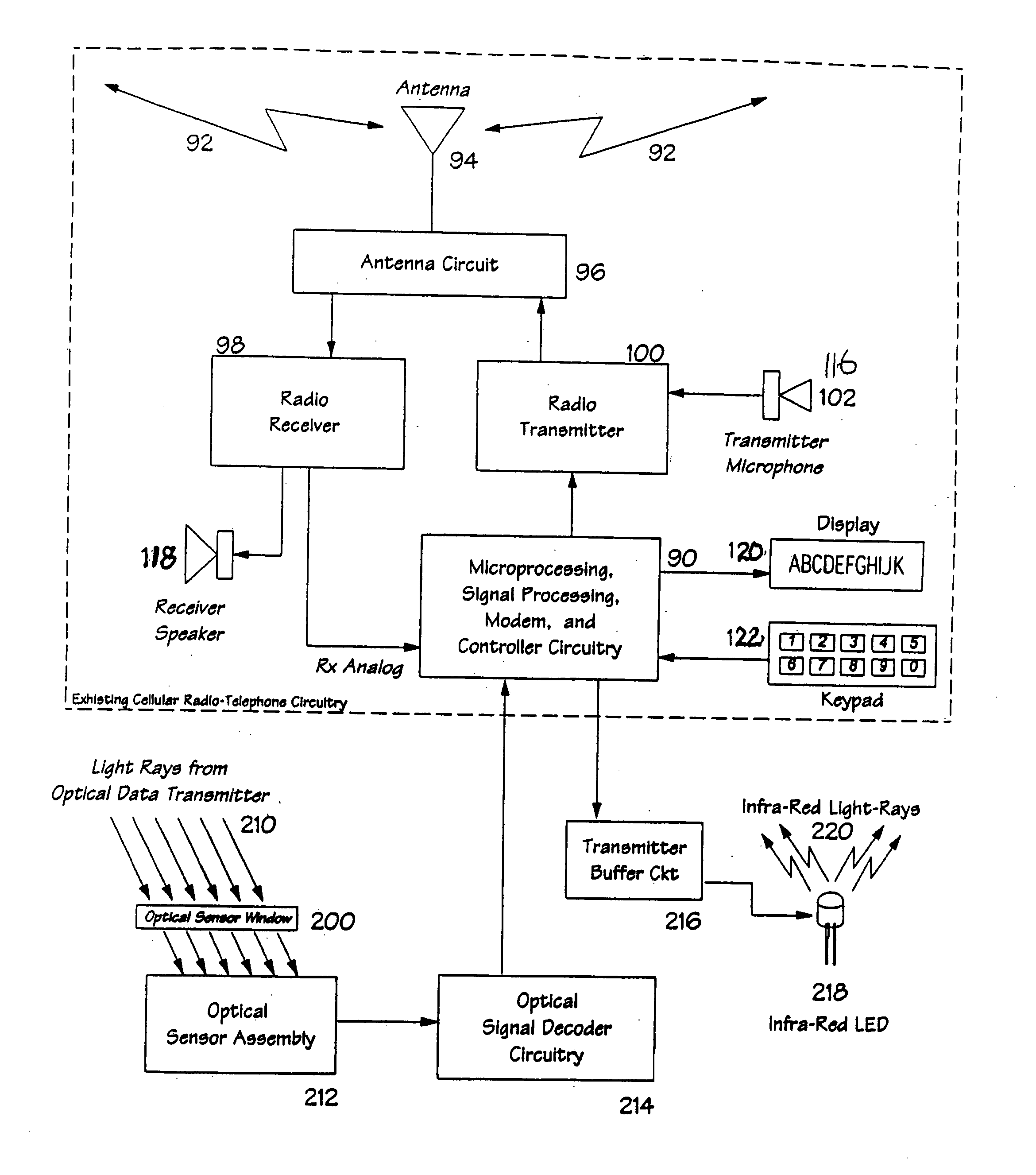
Method and apparatus for the zonal transmission of data using building lighting fixtures
InactiveUS20050169643A1Facilitate great top-securityFacilitate great privacy communicationBreech mechanismsElectric light circuit arrangementCommunications systemEffect light
This invention relates to the zonal transmission of data by optical means through the modulation of light from common building light fixtures, including the light output of fluorescent, mercury vapor, and other arc or discharge lamps and fixtures; a system for the reuse of radio frequencies by smart radios, and the accurate locating and tracking of objects or persons as they move through a building; by means of creating a communications system which exploits the existing infrastructure of a building to facilitate the transmission of relatively secure control and communications data via creation of a multiplicity of area-limited interference-free communication zones. The system facilitates the transmission of wide-area as well as zonal-specific data. The system facilitates the creation of a database that contains present location and history location and movement data of persons and objects as they move through a building.
Owner:CONVERGENCE WIRELESS A CALIFORNIA CORP
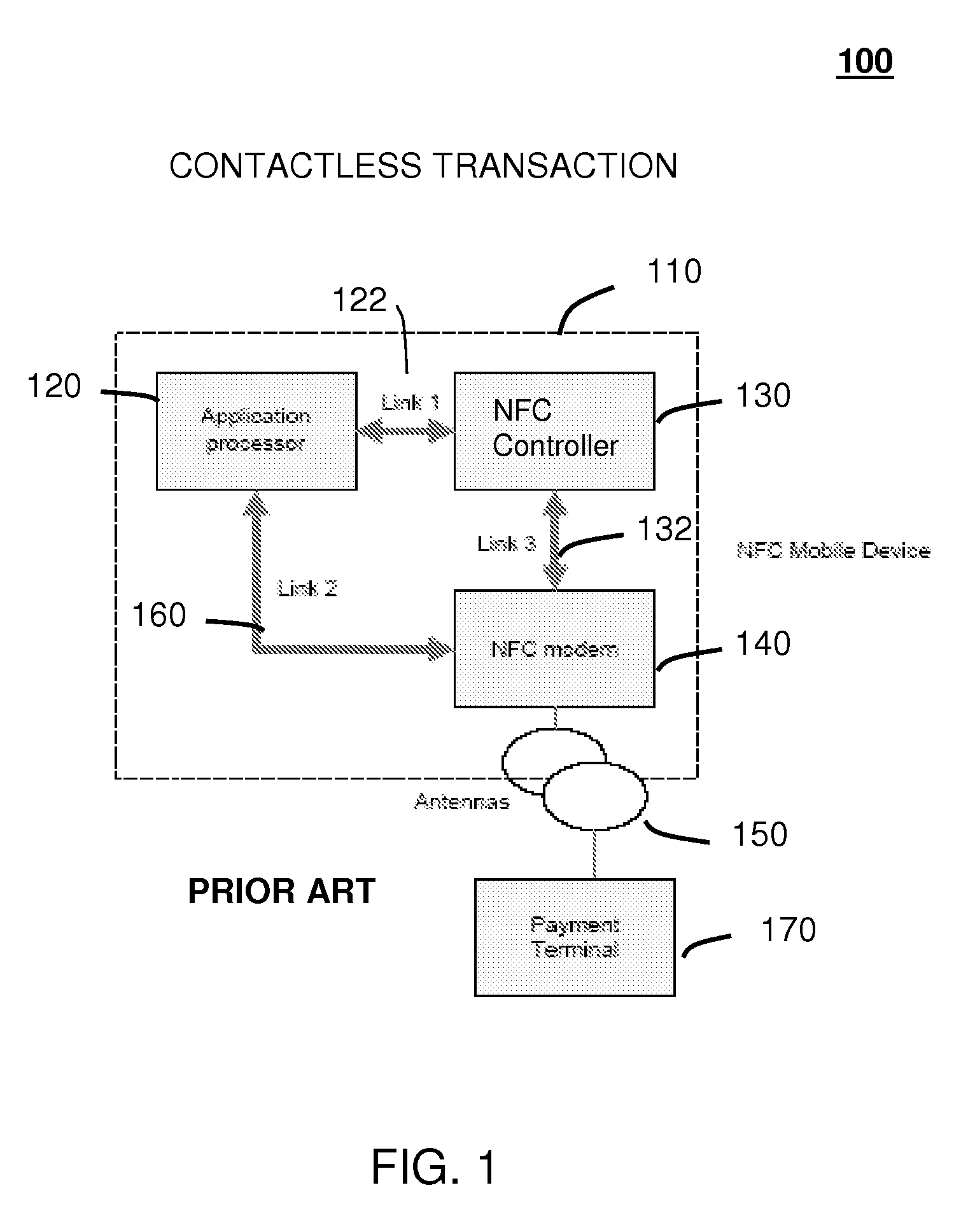
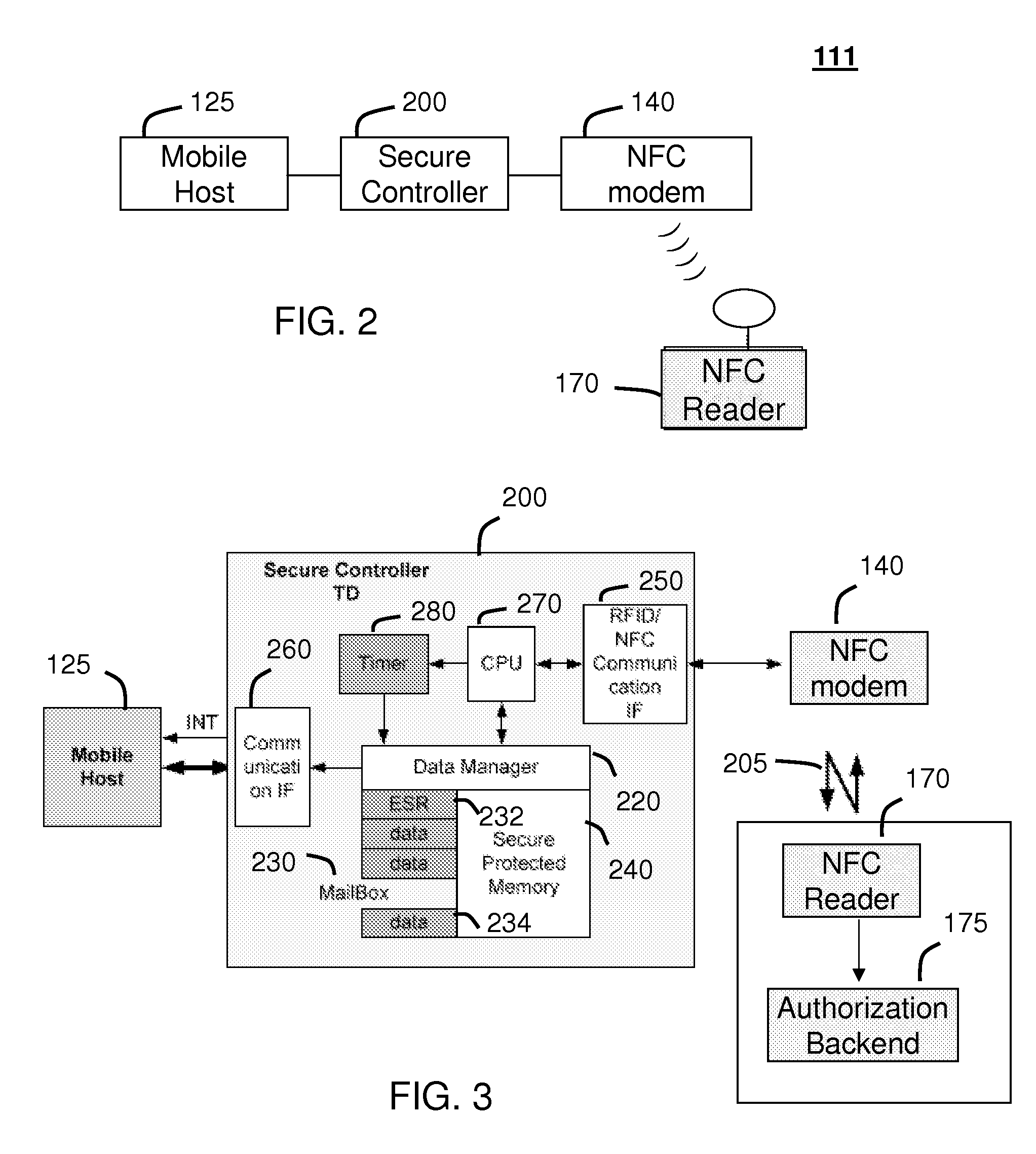
Method and system for monitoring secure applet events during contactless rfid/nfc communication
InactiveUS20080162312A1Reliable monitoringFinanceNetwork topologiesModem deviceApplication programming interface
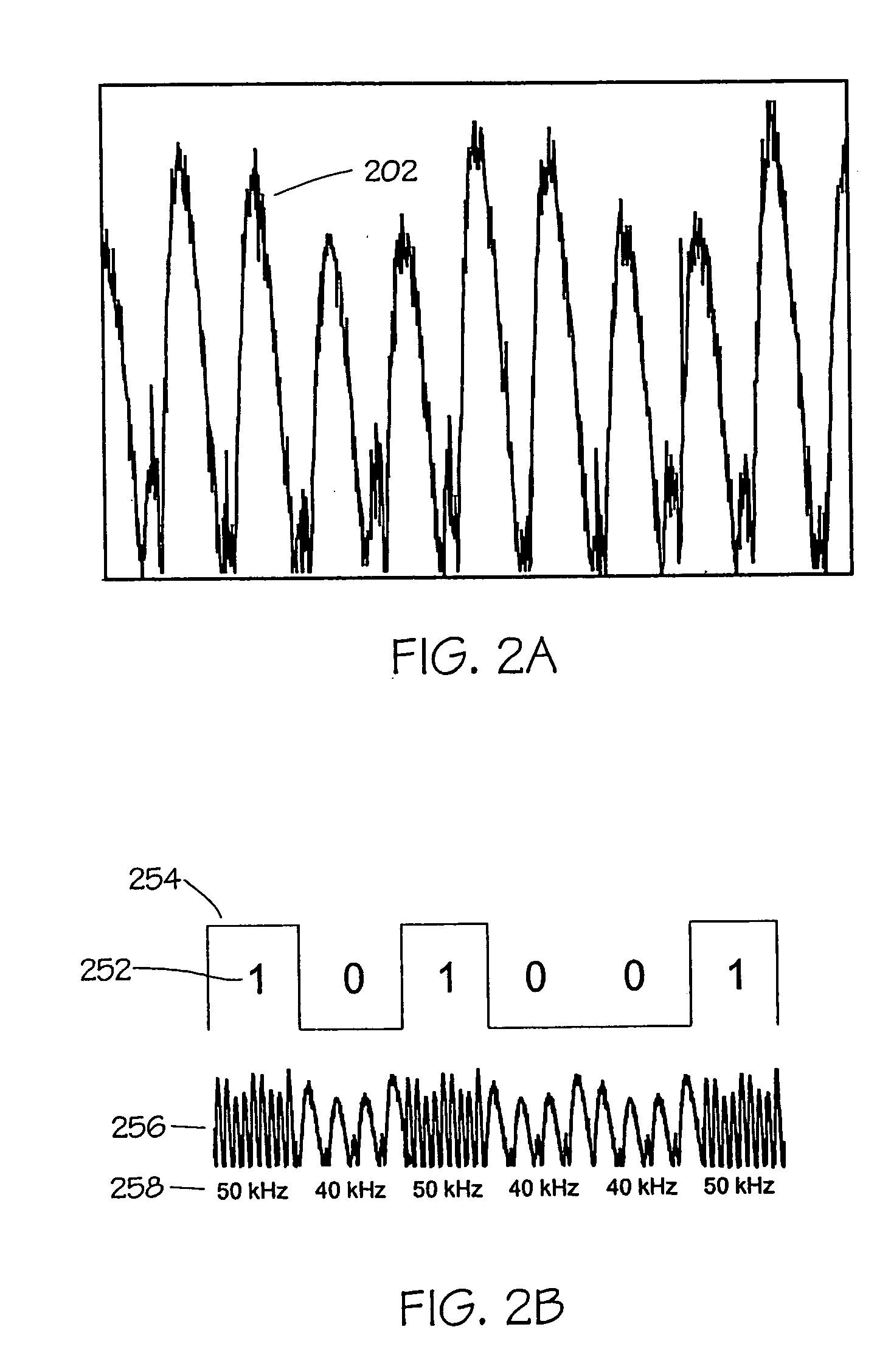
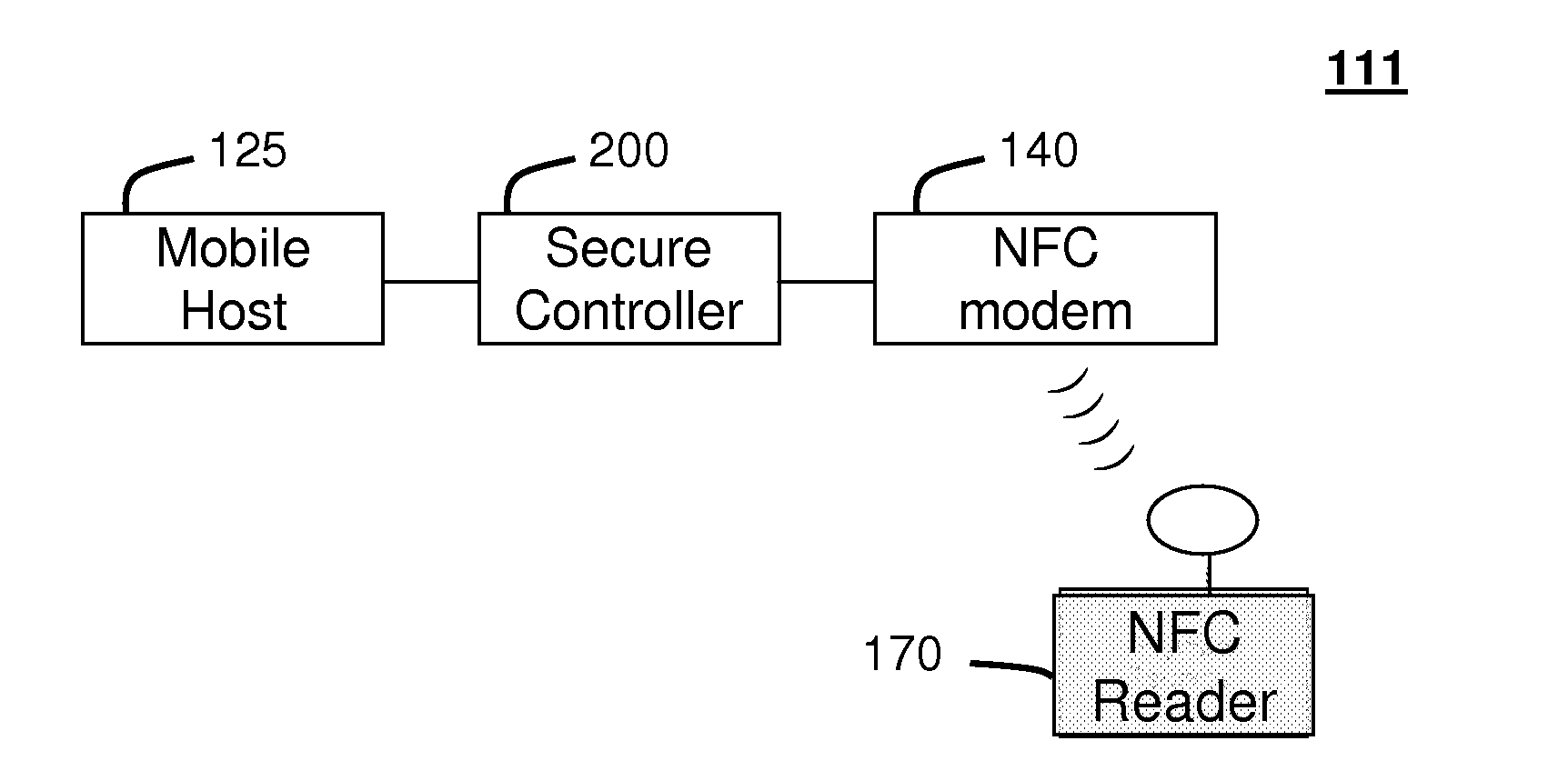
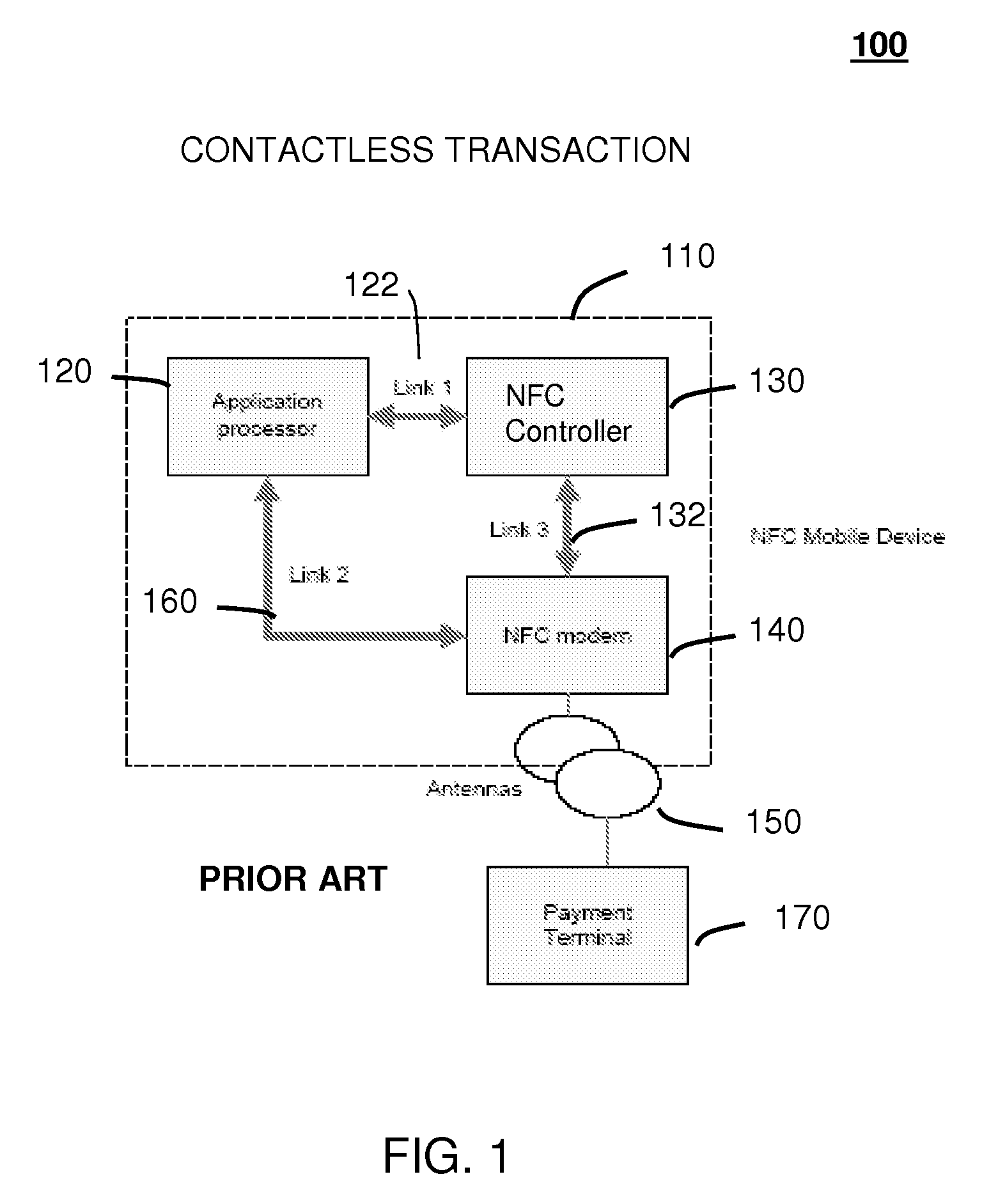
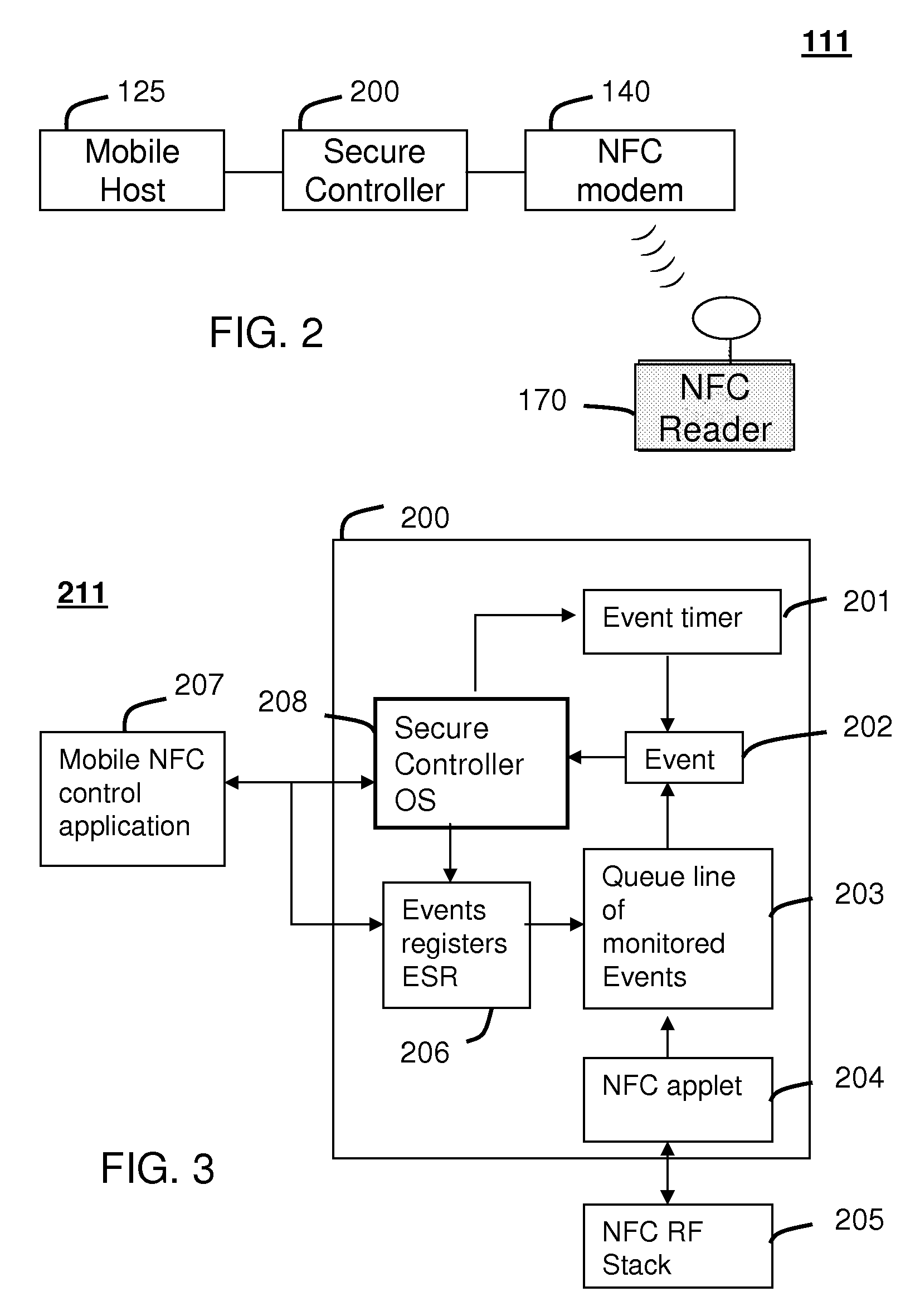
A system (211) and method (400) for reliable monitoring of secure applet events is provided. The system can include a Near Field Communication (NFC) modem (140) for communicating transaction events, a secure controller (200) for monitoring state transitions caused by the transaction events, and a mobile host (125) for receiving event notifications of the state transitions via an Applications Programming Interface. An NFC reader can send a Transaction Acknowledgement TACK (403) to the NFC modem to confirm a receipt of data associated with an applet event. An INFO message (405) can be included with the TACK for informing a user of secure contactless transaction status through a user interface (190) of the mobile host.
Owner:MOTOROLA MOBILITY LLC
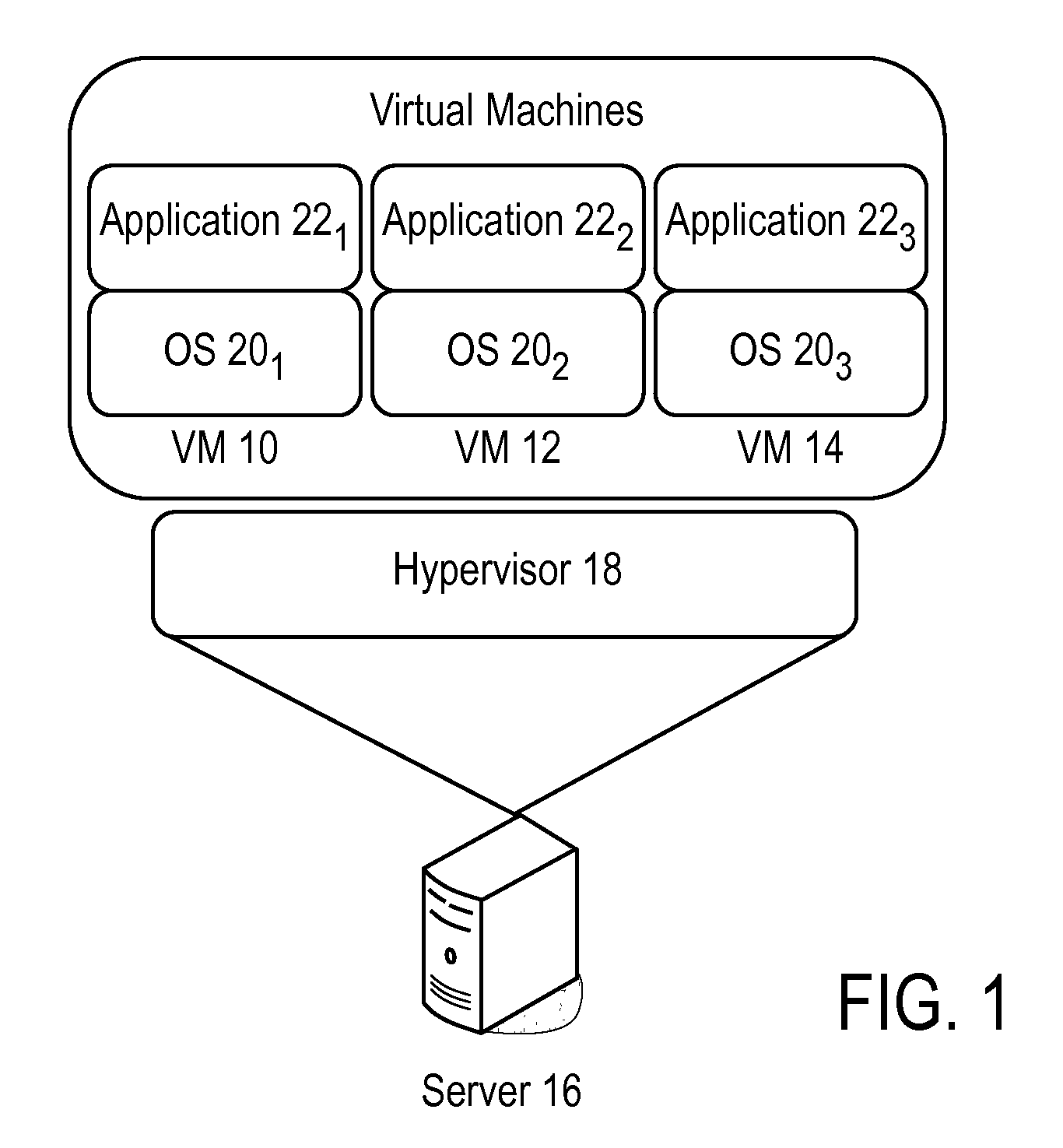
Virtual machine based network carriers
InactiveUS20070079307A1Environment safetyTransmissionSoftware simulation/interpretation/emulationData packData set
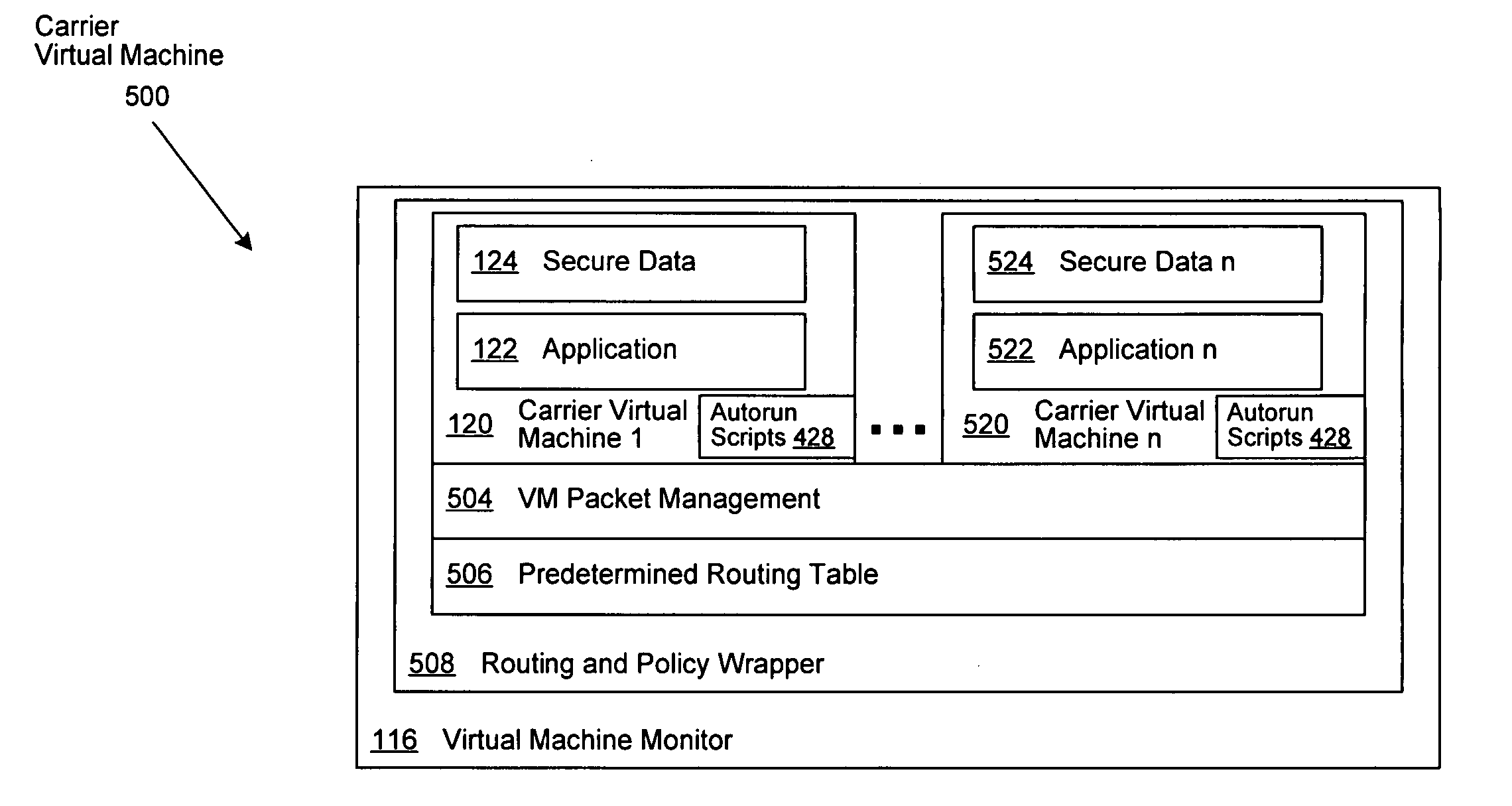
A system and method is disclosed for the secure transfer of data by carrier virtual machines between participating physical hosts through a virtual network (VNET) implemented on one or more internal and / or external networks. The method of the invention can provide additional security controls, comprising parameters that may include, but are not limited to, time-to-live (TTL), access control lists (ACLs), usage policies, directory roles, etc. Additionally, access to one or more of a plurality of carrier virtual machine payloads by security groups, individual access, subdivided individual access, and MIME-like subdivision of a VM-encapsulated payload may be controlled, thereby providing the carrier VM the ability to carry many secured payloads. In addition, VM packets, a group of packets, a single VM, or subpackets within a VM between network endpoints, or at a predetermined intermediary network point, may be quarantined to realize further security. Individual or combinations of these functionalities on carrier virtual machines, and by extension, application and / or one or more sets of secure data may be implemented.
Owner:DELL PROD LP
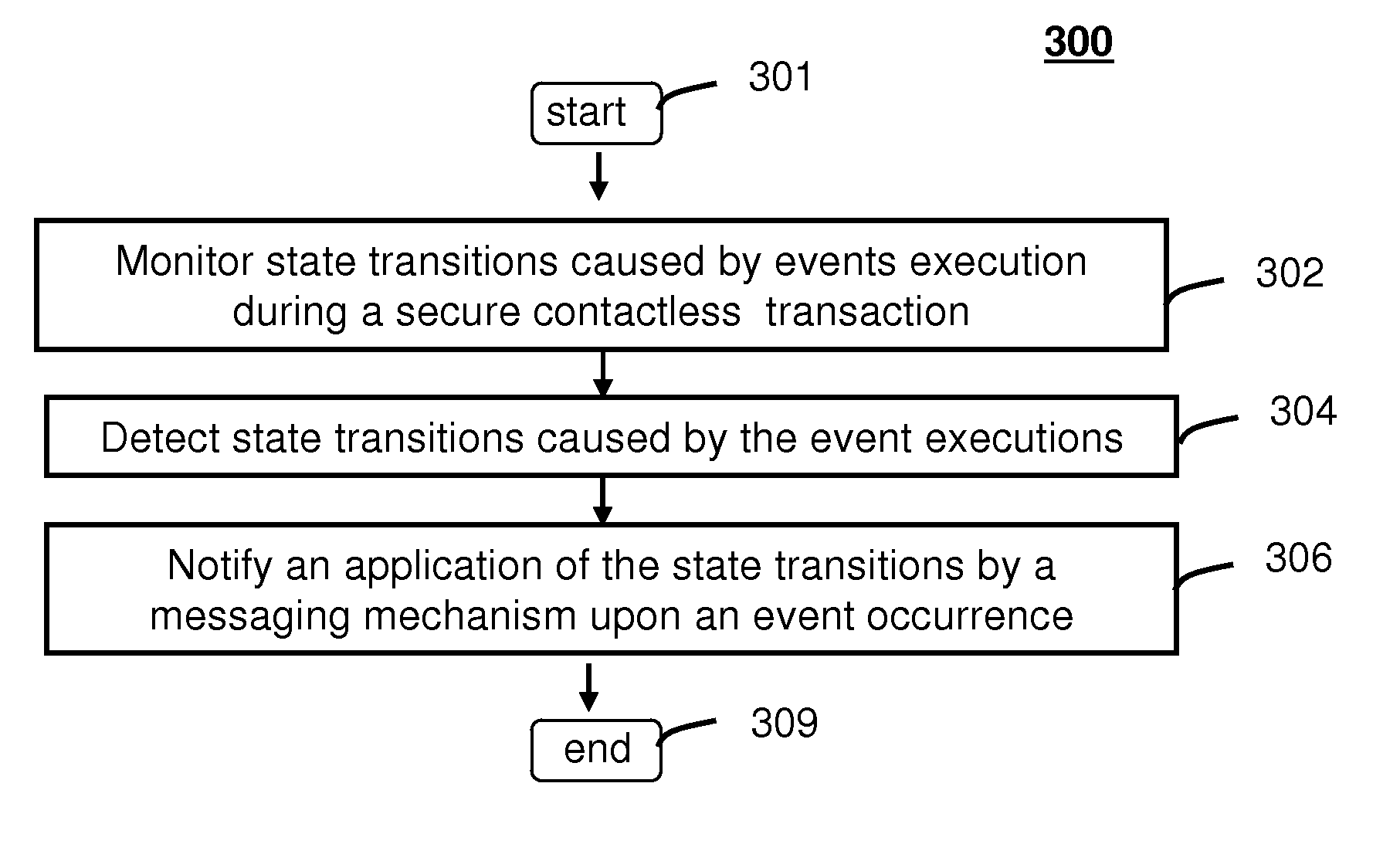
Method and system for monitoring secure application execution events during contactless rfid/nfc communication
ActiveUS20080162361A1Radio transmissionSecuring communicationCommunications securityTechnical communication
A system (211) and method (300) for reliable monitoring of secure application execution events is provided. The system can include a Near Field Communication (NFC) modem (140) for communicating transaction events of a secure contactless transaction (358) with a NFC reader (170), a secure controller (200) for monitoring state transitions caused by the transaction events, and a mobile host communicatively coupled to the secure controller for receiving hardware event notifications of the state transitions. The secure controller can generate message using a hardware interrupt to a mobile host based on secure applet state transition monitoring by setting up the events flag such as a Transaction Completion Flag (TCF) (372) into an Events Status Register (232) to identify a status of a secure contactless transactions
Owner:GOOGLE TECH HLDG LLC
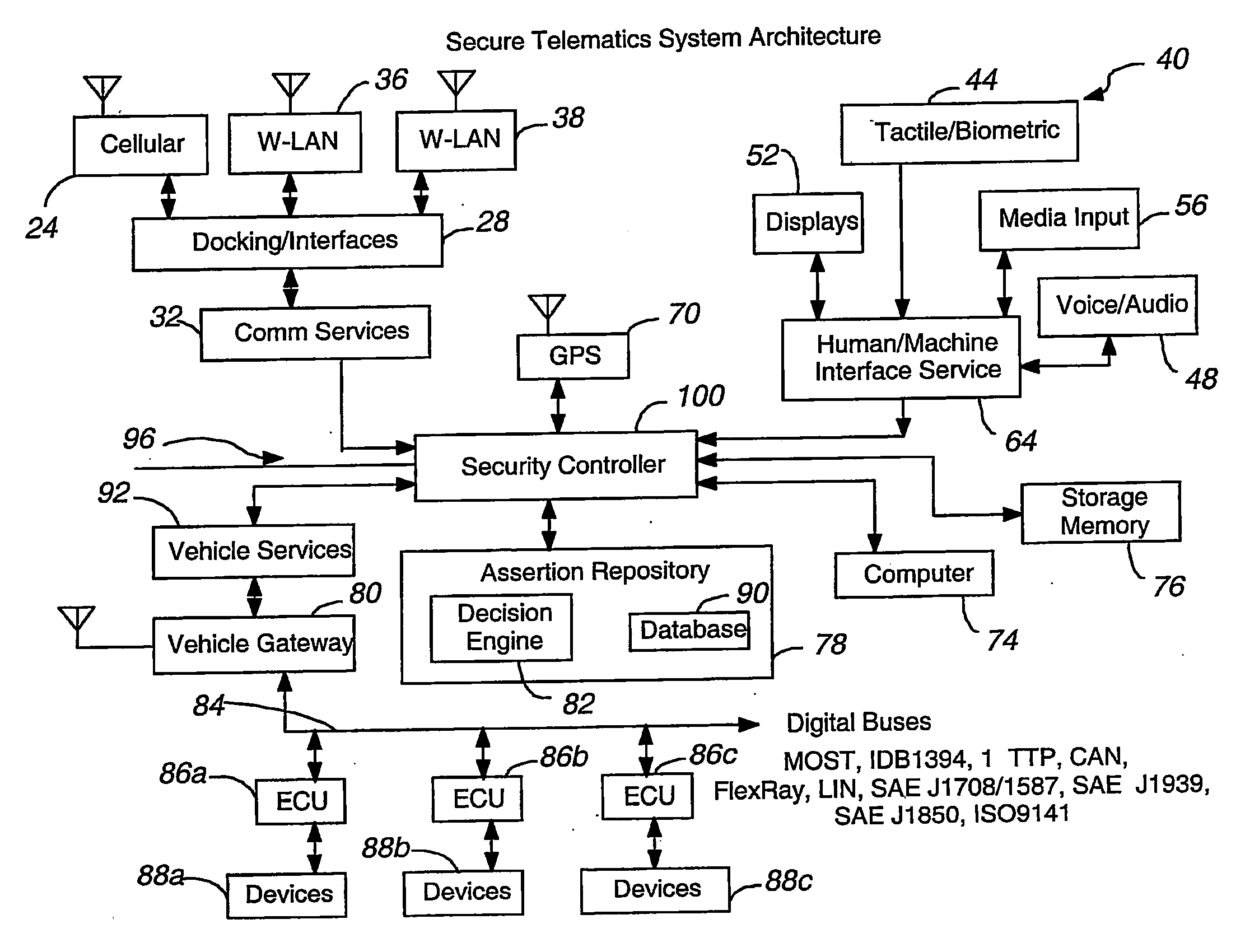
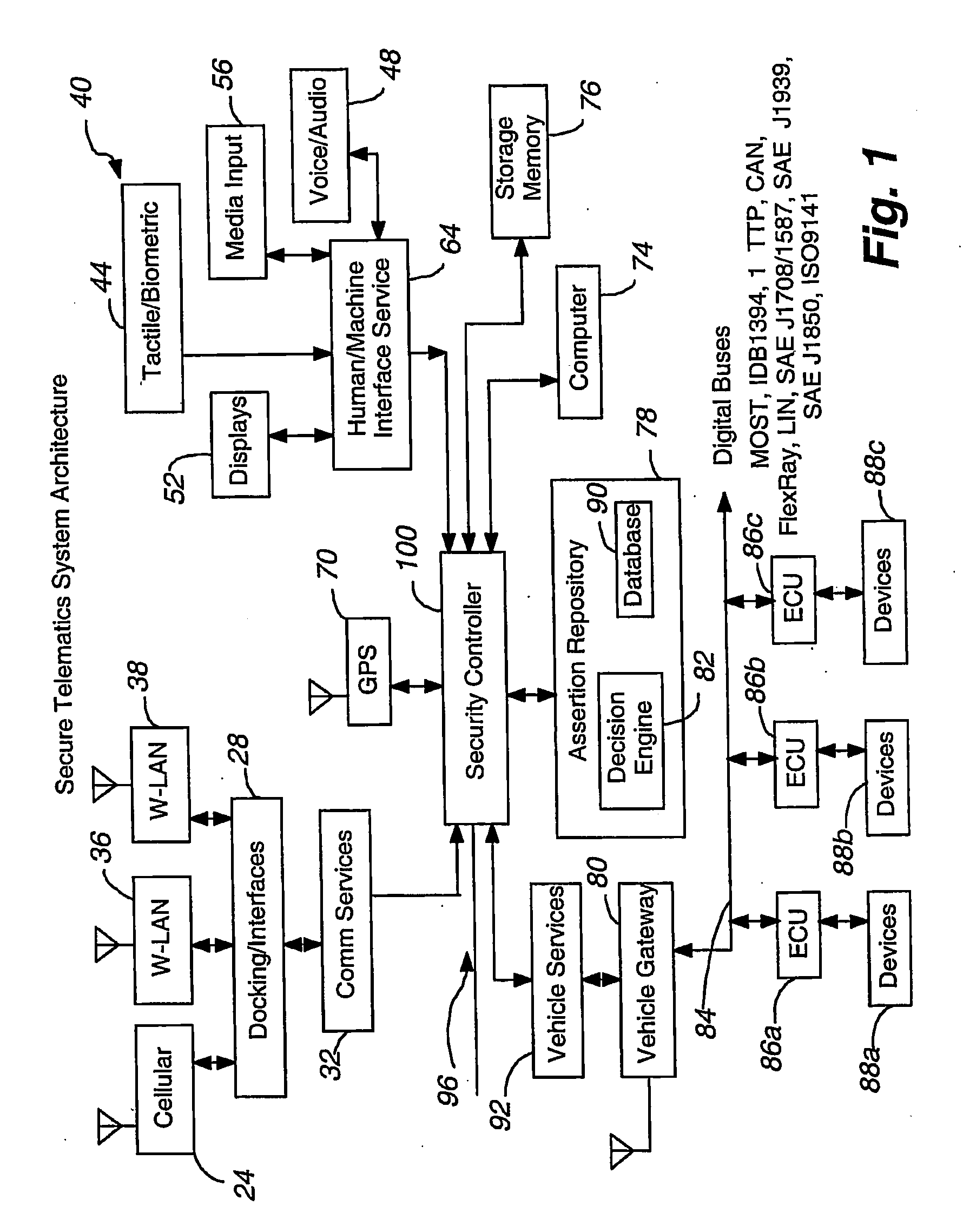
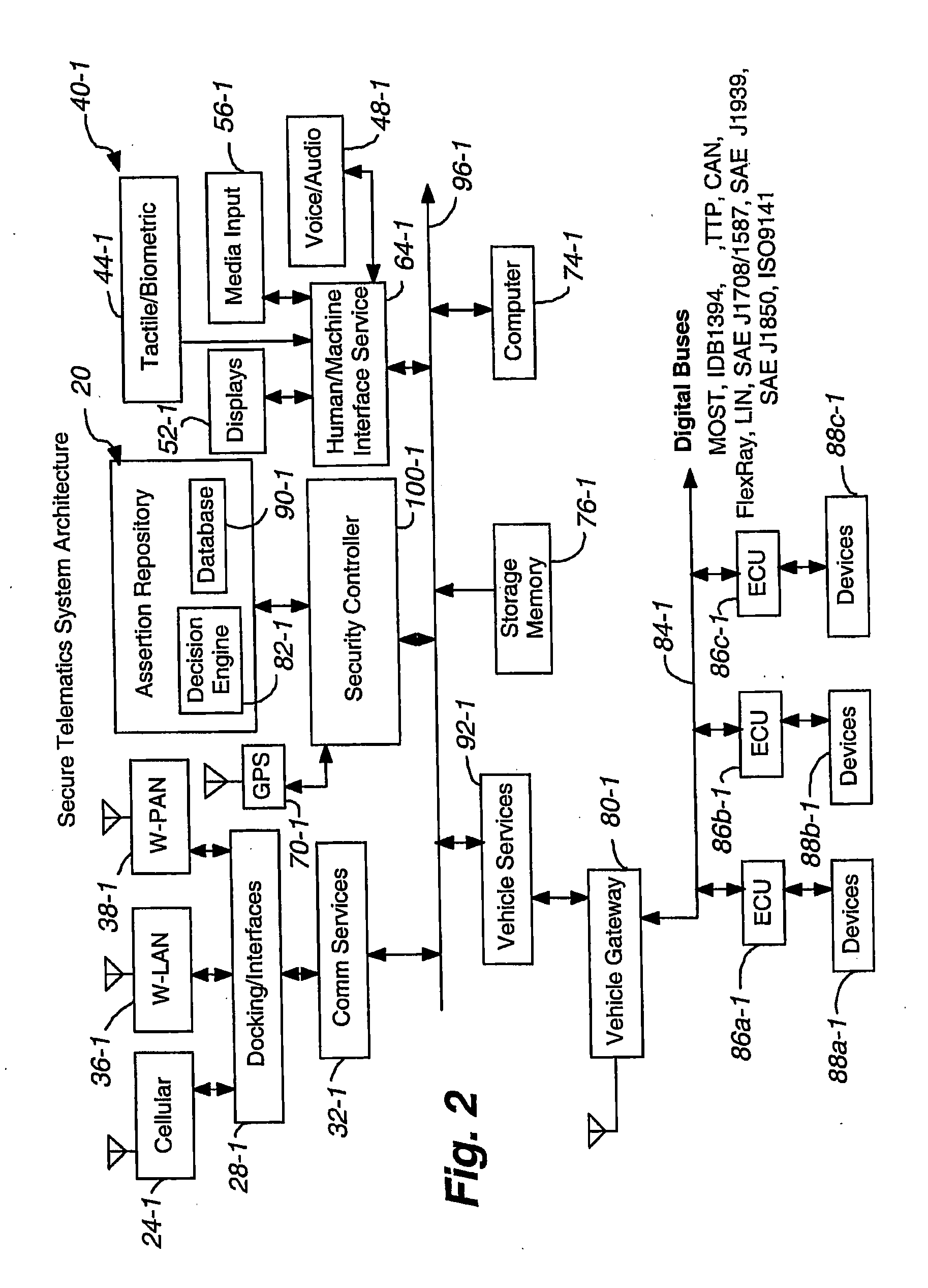
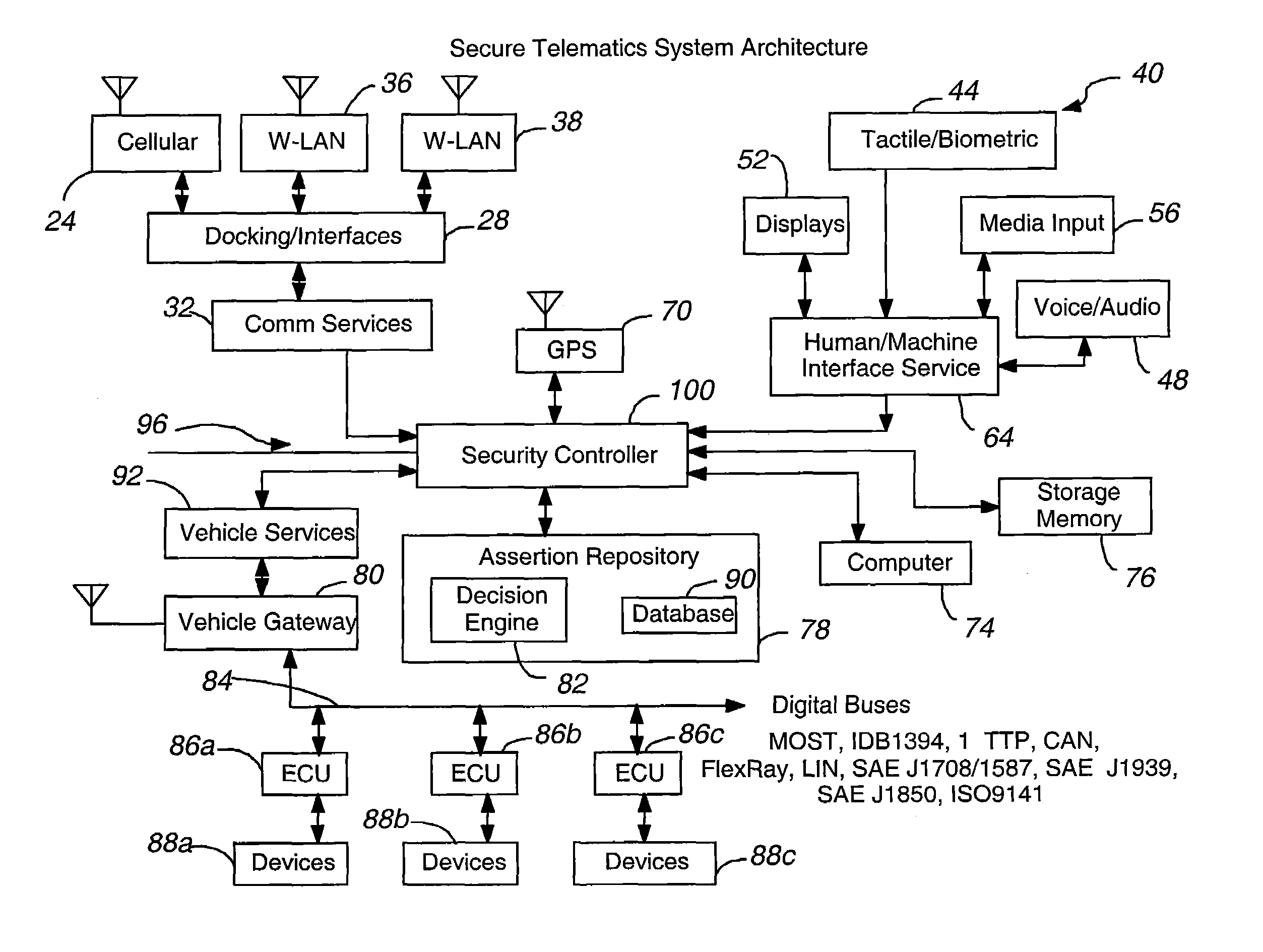
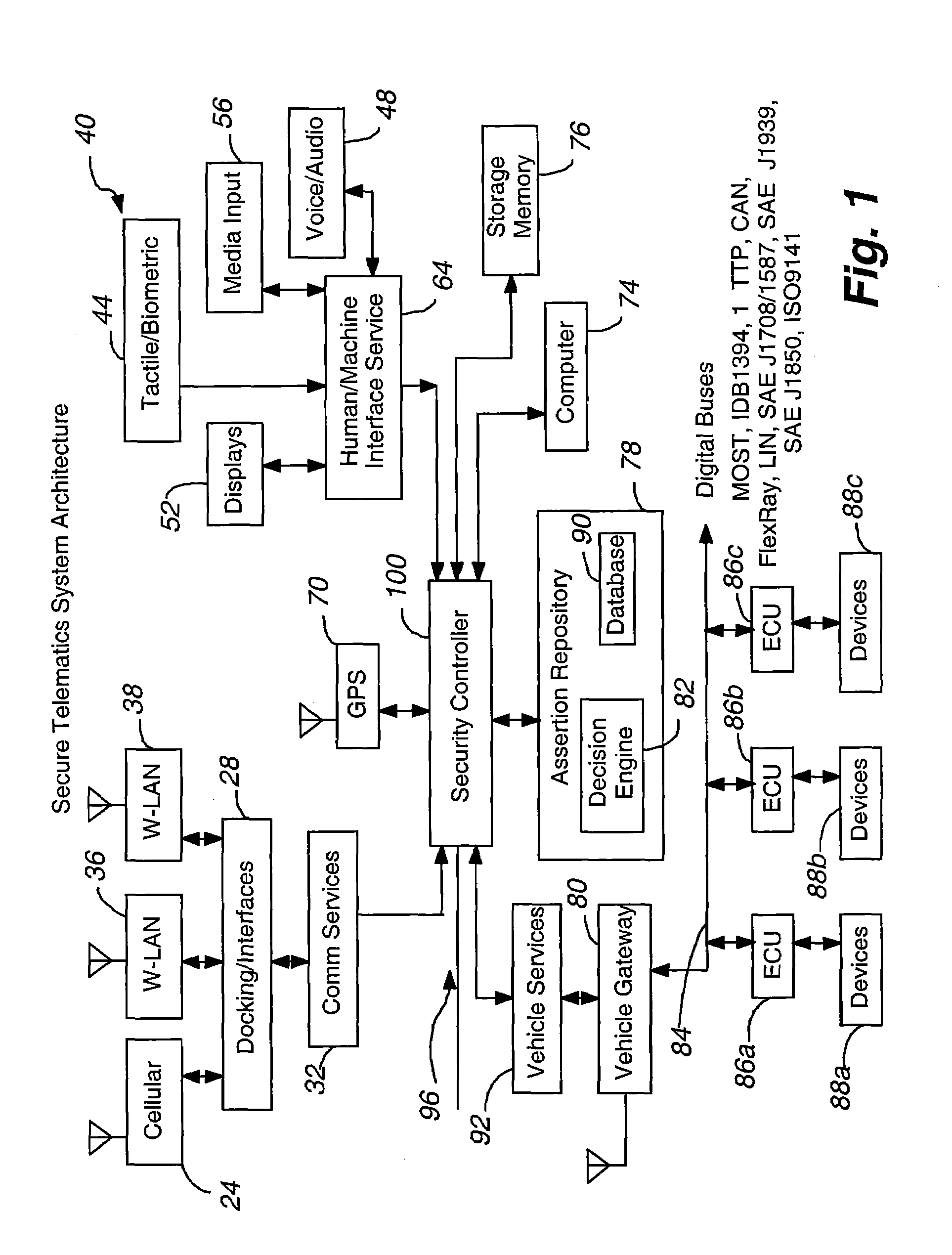
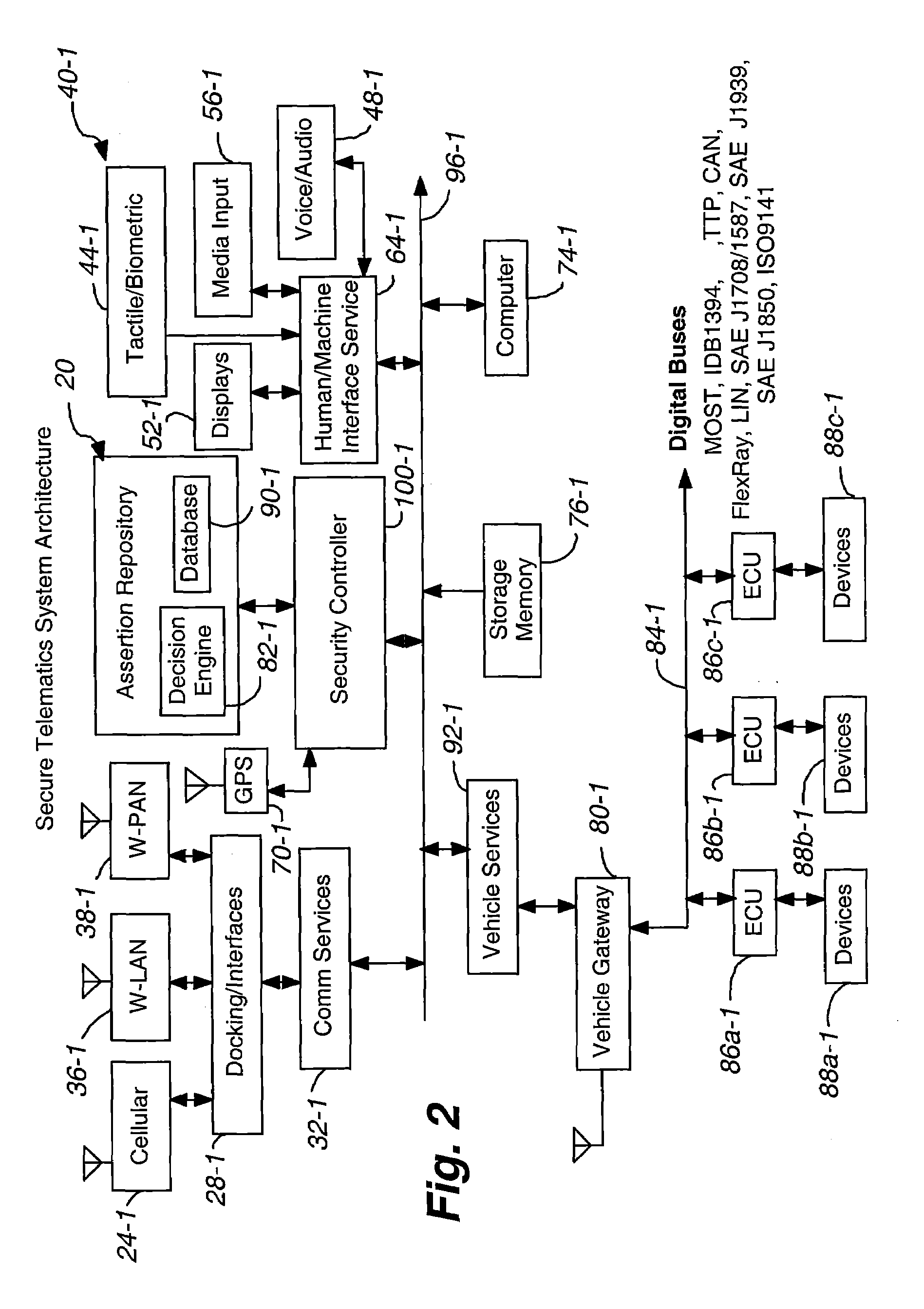
Secure telematics
InactiveUS20080148374A1Expands telematics usageImprove integrityVehicle testingRegistering/indicating working of vehiclesComputer networkService provision
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resources' security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
Secure telematics
ActiveUS7366892B2Expands telematics usageLow costUnauthorised/fraudulent call preventionRegistering/indicating working of vehiclesService provisionSecurity Measure
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resource'0 security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
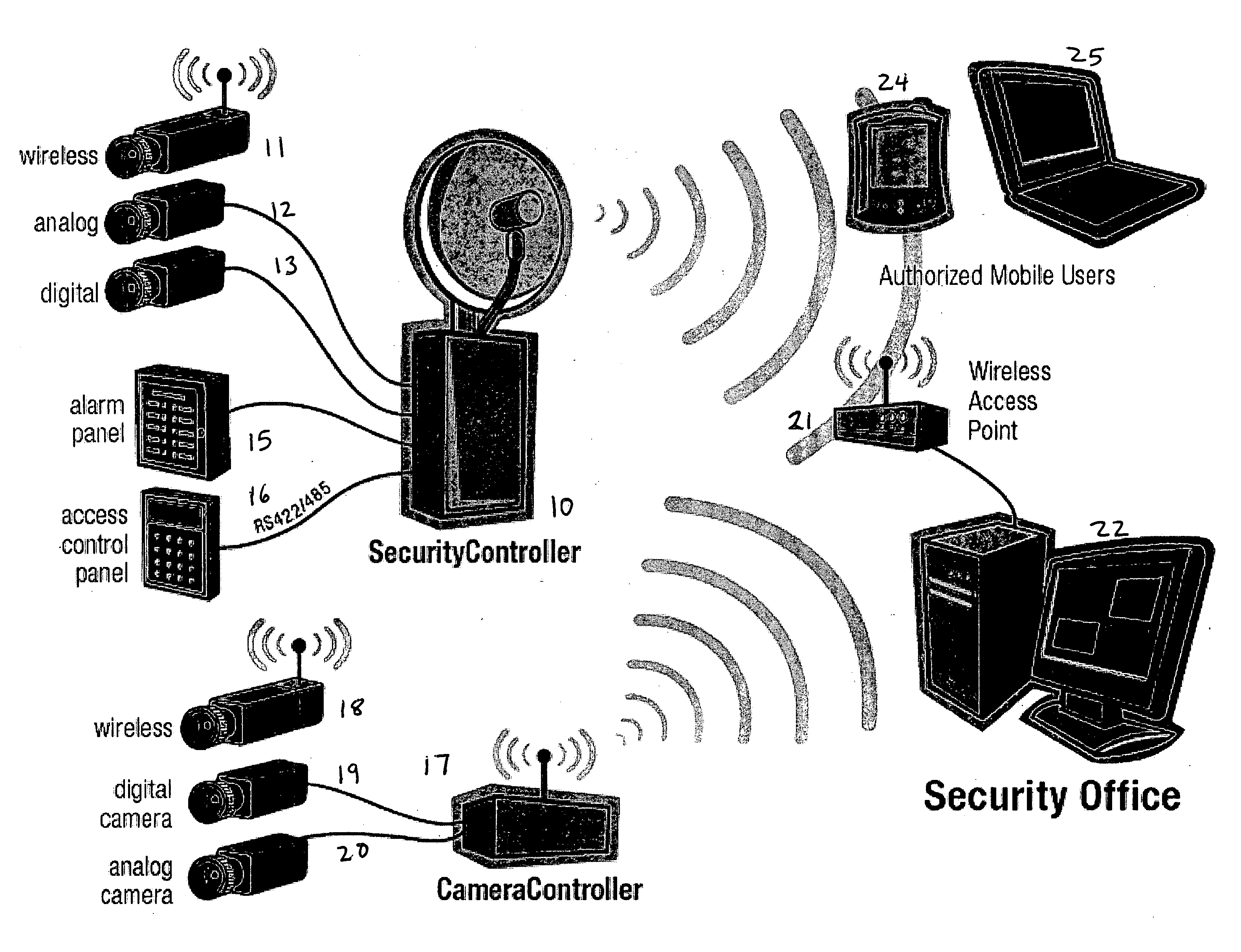
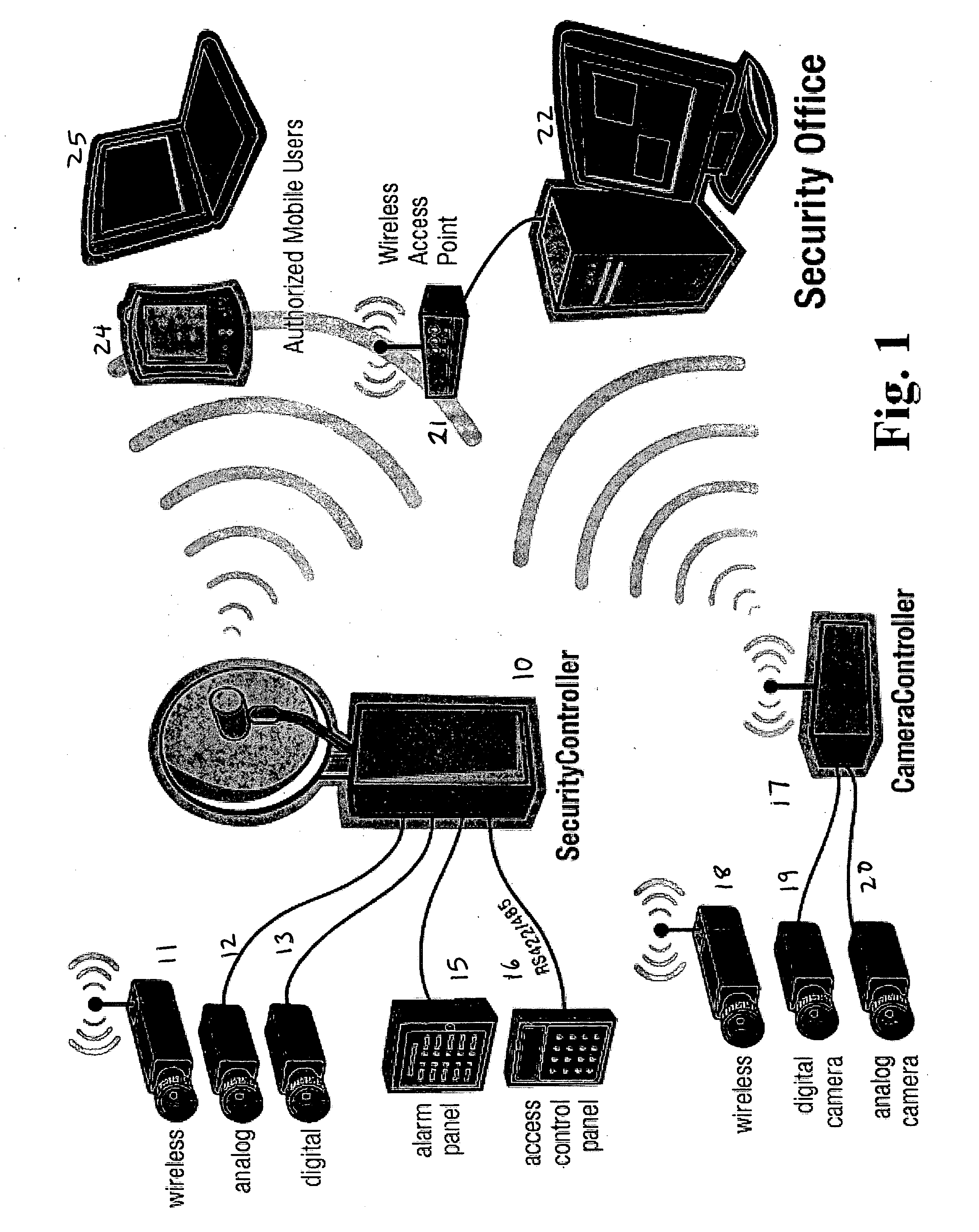
Wireless integrated security controller
InactiveUS20060200845A1Analogue secracy/subscription systemsColor television detailsDigital videoMulti camera
A system and method are disclosed for improved video transmission, particularly in security settings. An improved security controller combines the interfaces and functionality for high quality video delivery over often less-than-perfect wireless networks, multi-camera analog / digital video controllers and encoders, multi-frequency wireless camera support, connectivity for serial controllers, network switching, and distributed digital video recording with optional object and motion detection. The video transmission in enhanced using wireless adaptive video encoding, mobile viewing optimization, and wireless bandwidth improvement.
Owner:REEDY CO TRUSTEE OF ARMIDA TECH LIQUIDATING TRUST MATTHEW C +1
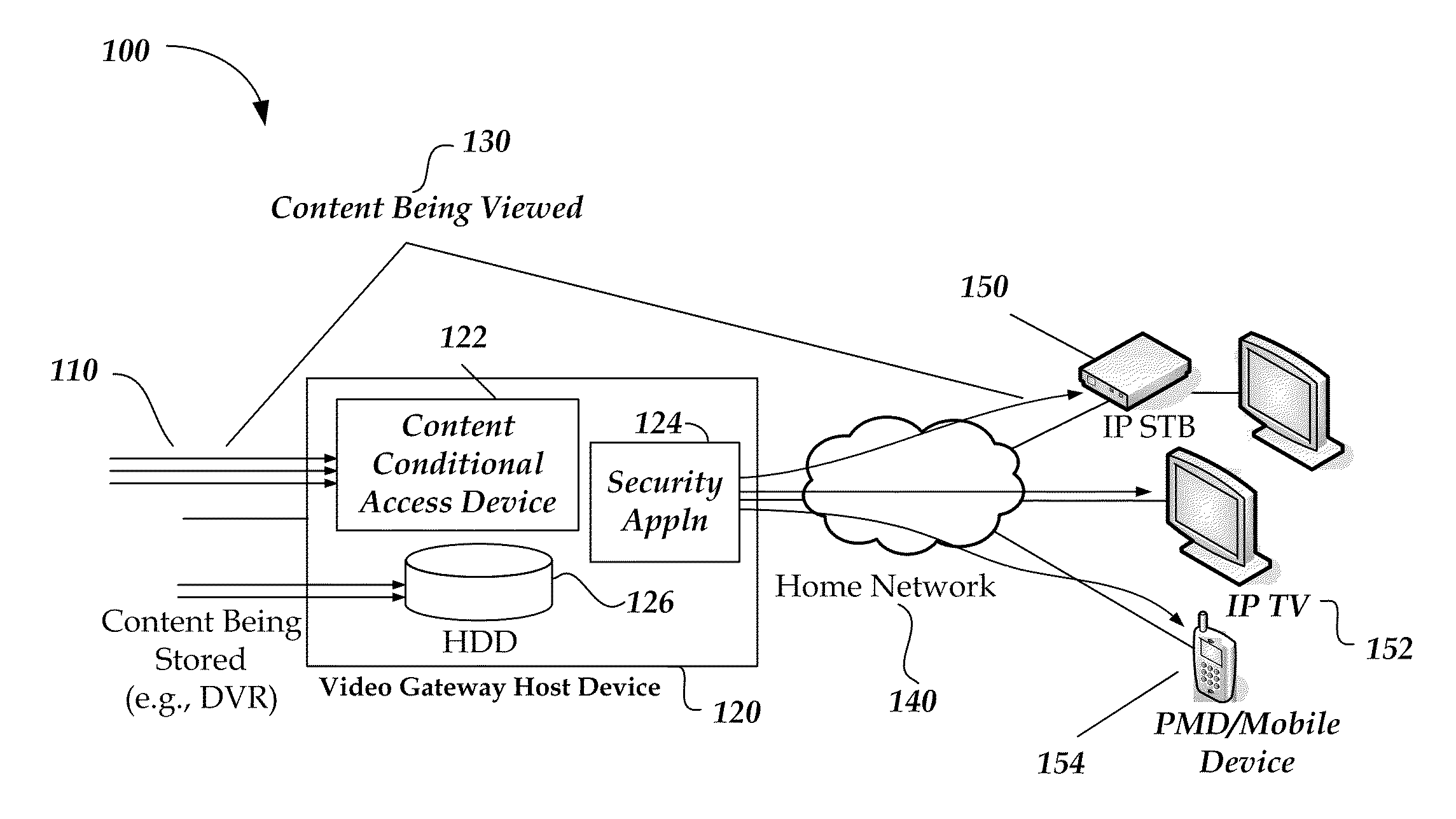
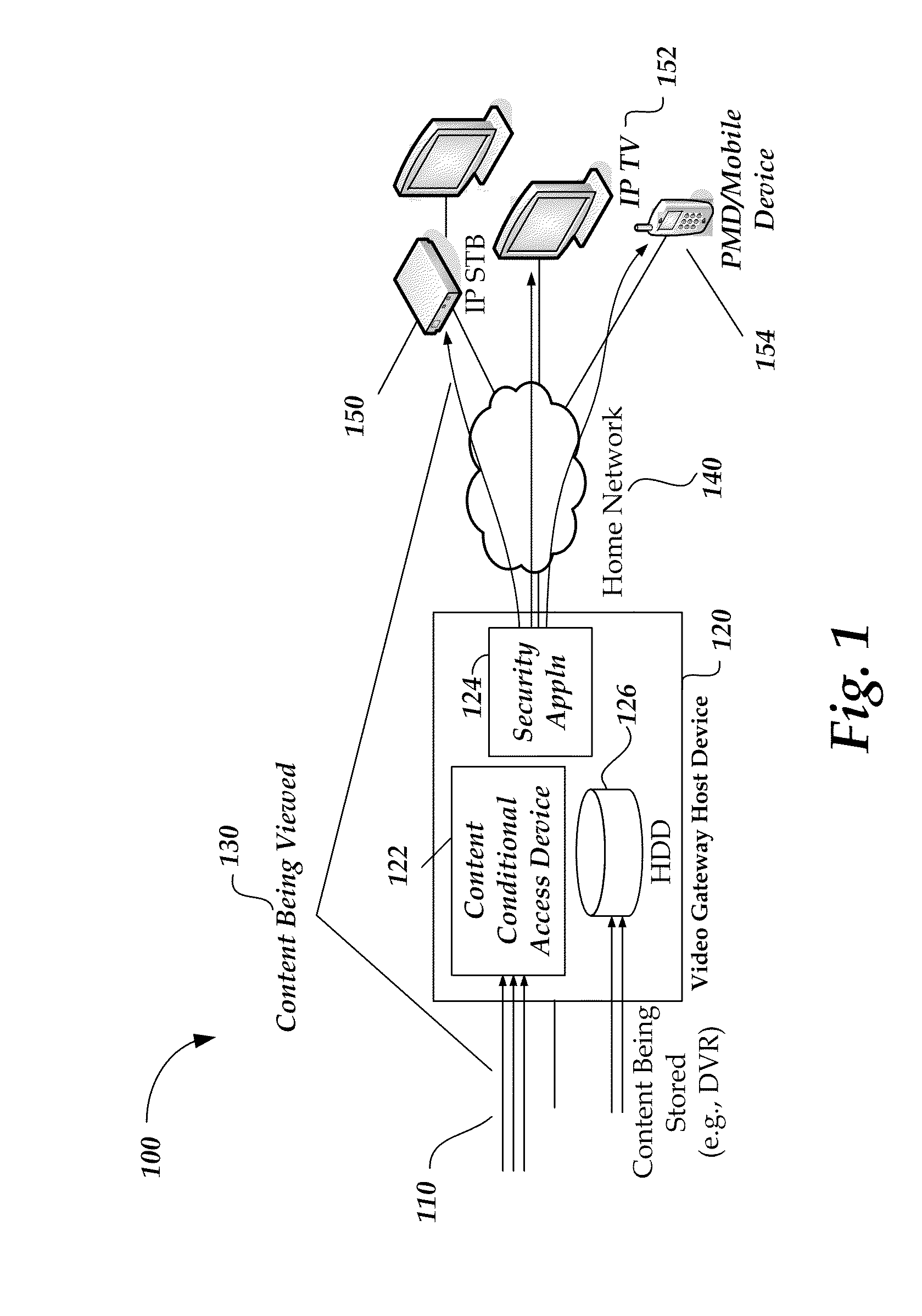
Content protection management system
ActiveUS20100287609A1Simple and consistent and reliableMultiple digital computer combinationsProgram controlSecurity domainContent security
A content protection management system that enables interoperability with other Content Protection and DRM technologies. A managed security domain provides a simple, consistent and reliable experience to whole-home network subscribers. The architectural concept for the whole-home network includes an underlying control plane with an overlaying content security control plane running a particular DRM technology.
Owner:COX COMMUNICATIONS
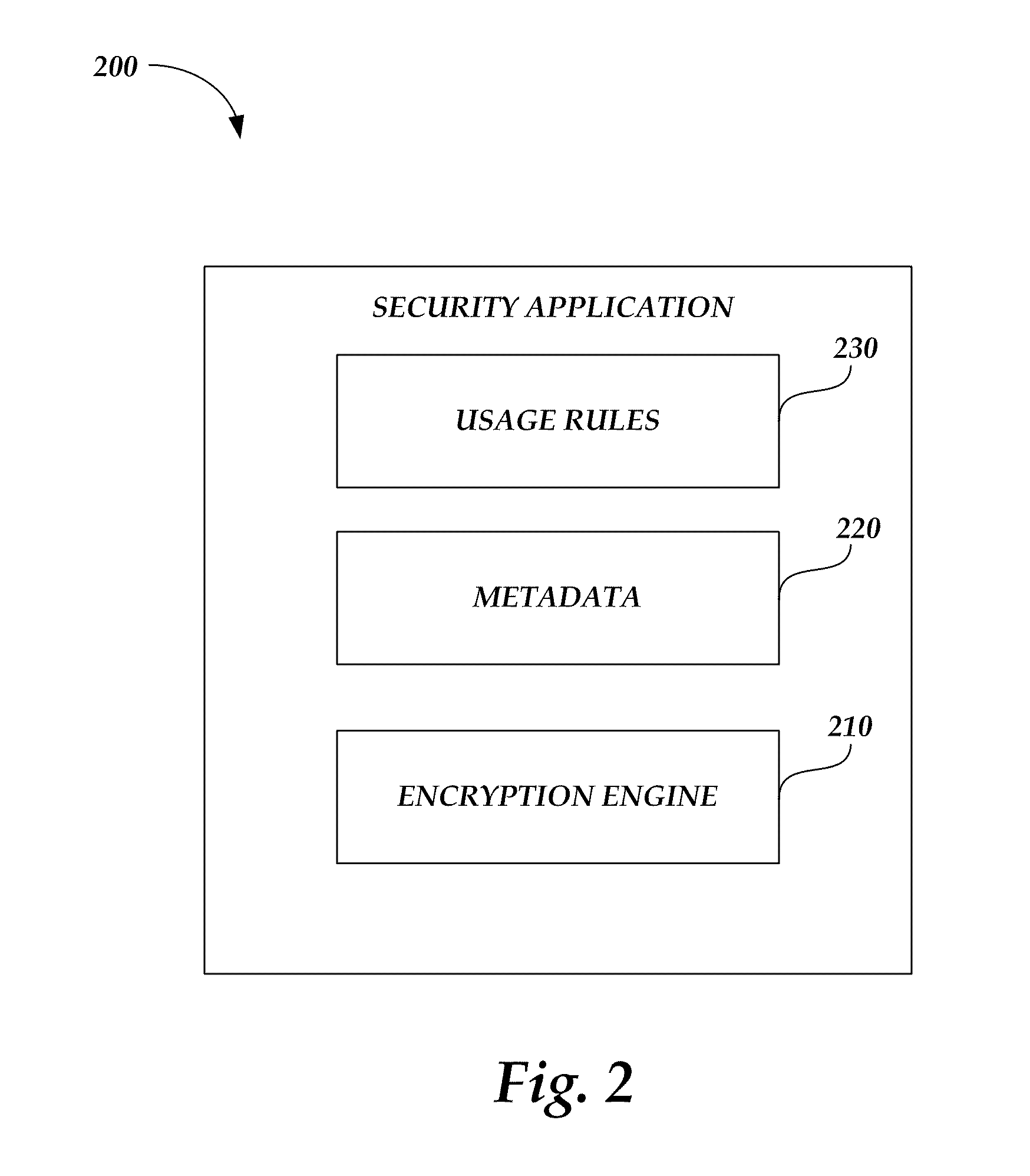
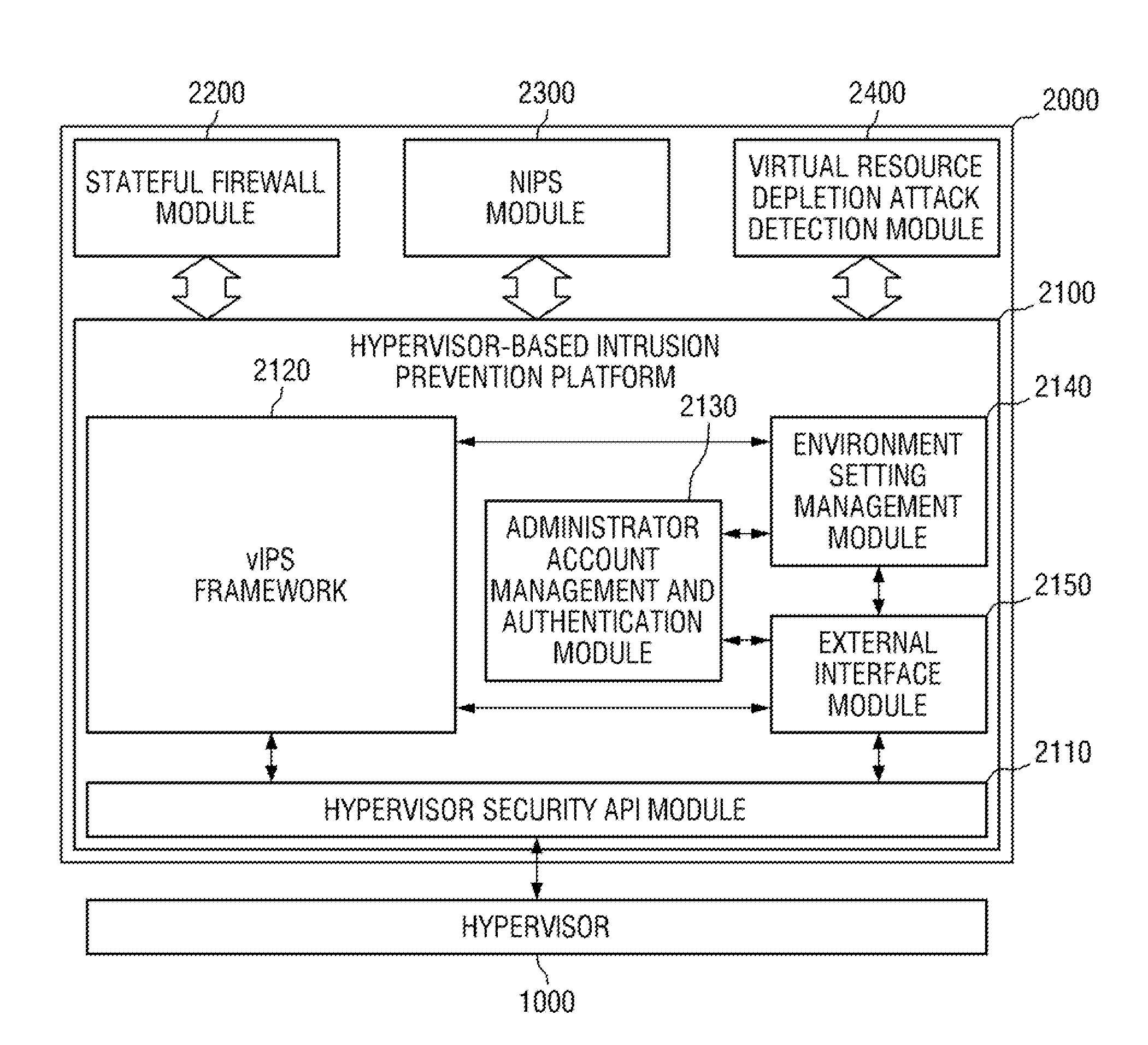
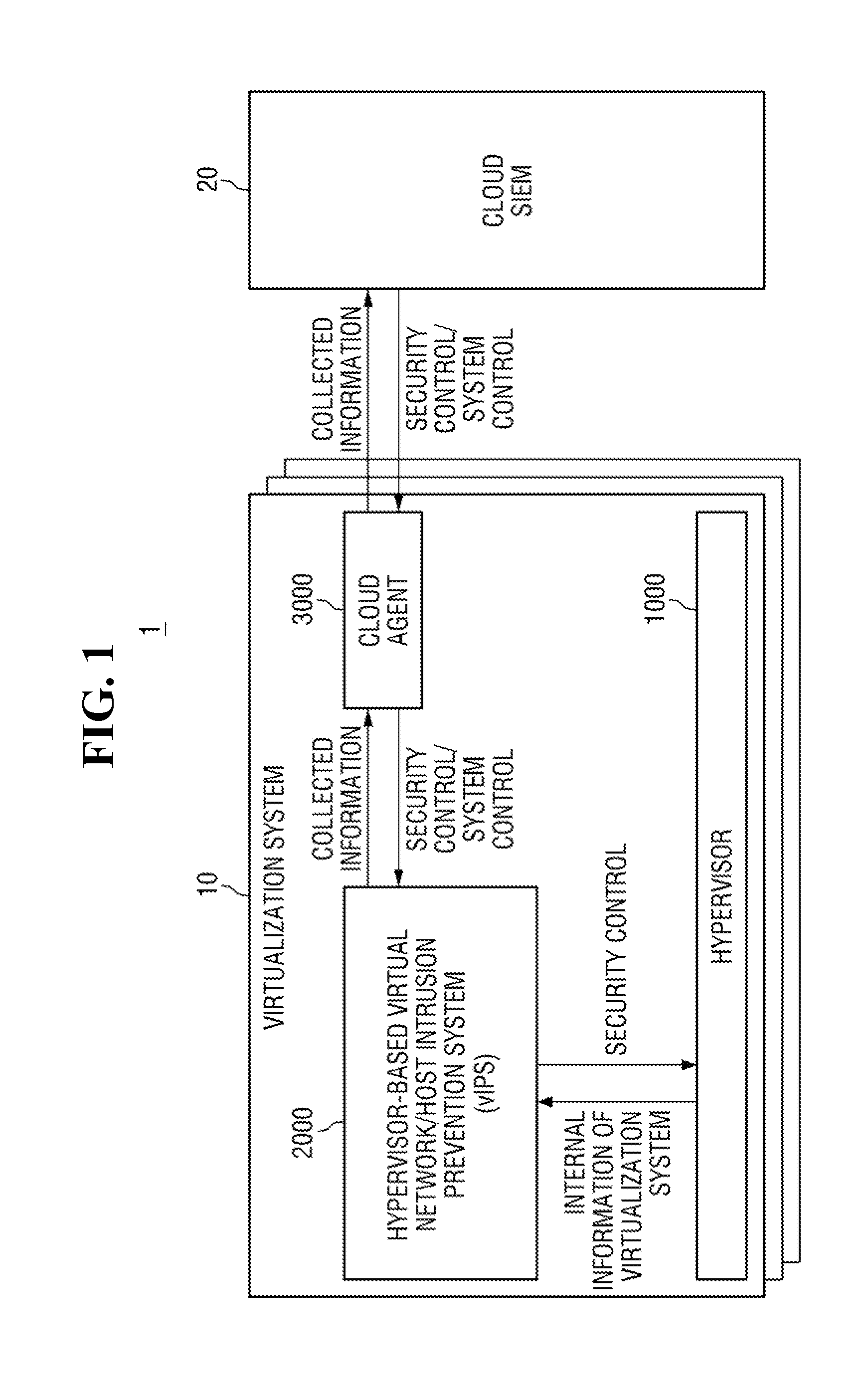
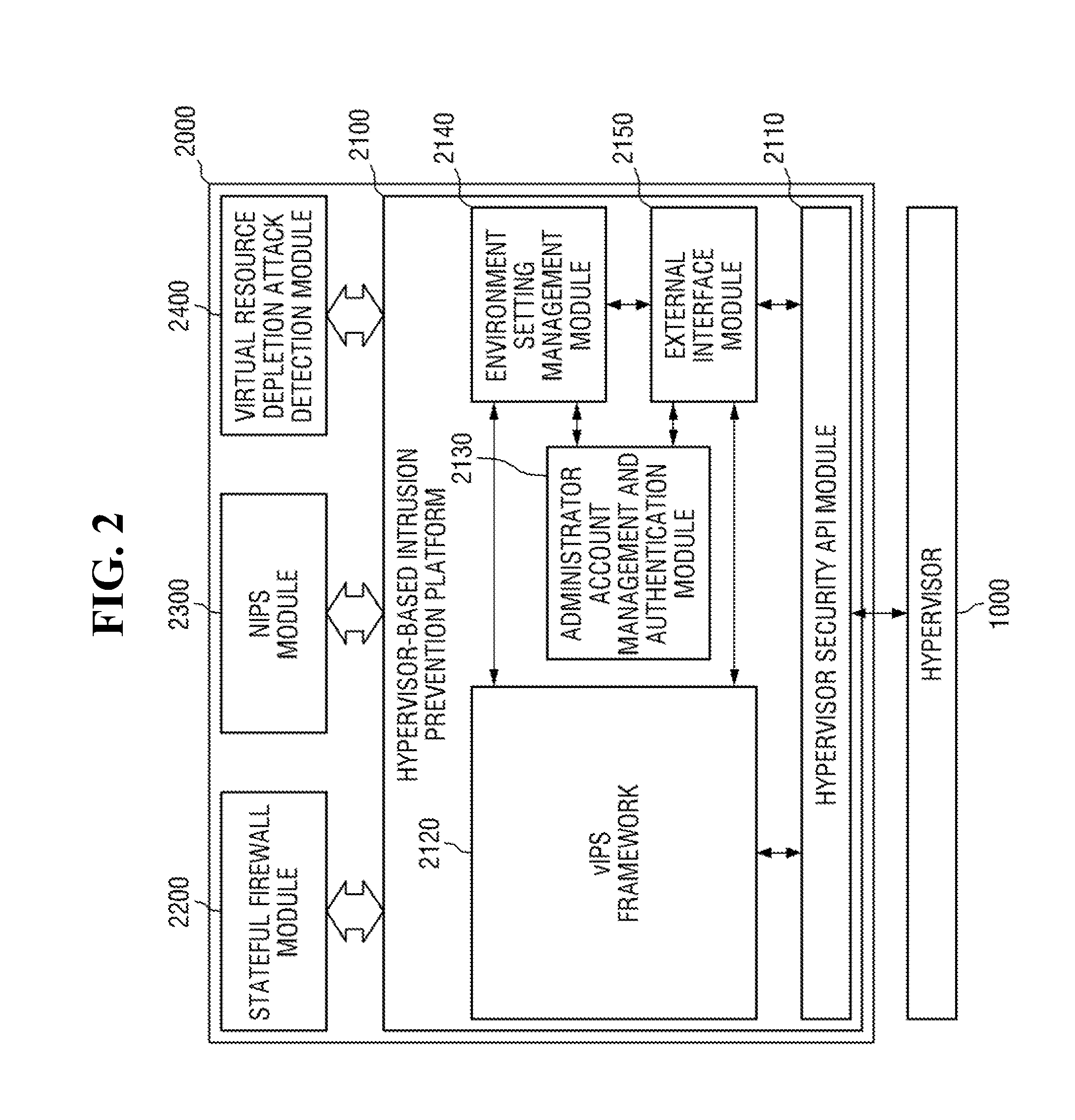
Hypervisor-based intrusion prevention platform and virtual network intrusion prevention system
InactiveUS20140317737A1Memory loss protectionData taking preventionApplication programming interfaceIntrusion prevention system
Hypervisor-based intrusion prevention platform is provided. The hypervisor-based intrusion prevention platform comprises a virtual network intrusion prevention system (vIPS) framework which obtains internal information of a virtualization system from a hypervisor and performs security control on the hypervisor in response to the result of intrusion detection carried out by using the internal information of the virtualization system, a hypervisor security application programming interface (API) module which provides an API used by the vIPS framework to access the hypervisor, an administrator account management and authentication module which manages an administrator account of a vIPS and authenticates the administrator account, an environment setting management module which manages environment setting values of modules within the vIPS, and an external interface module which provides an interface for system control and security control.
Owner:KOREA INTERNET & SECURITY AGENCY
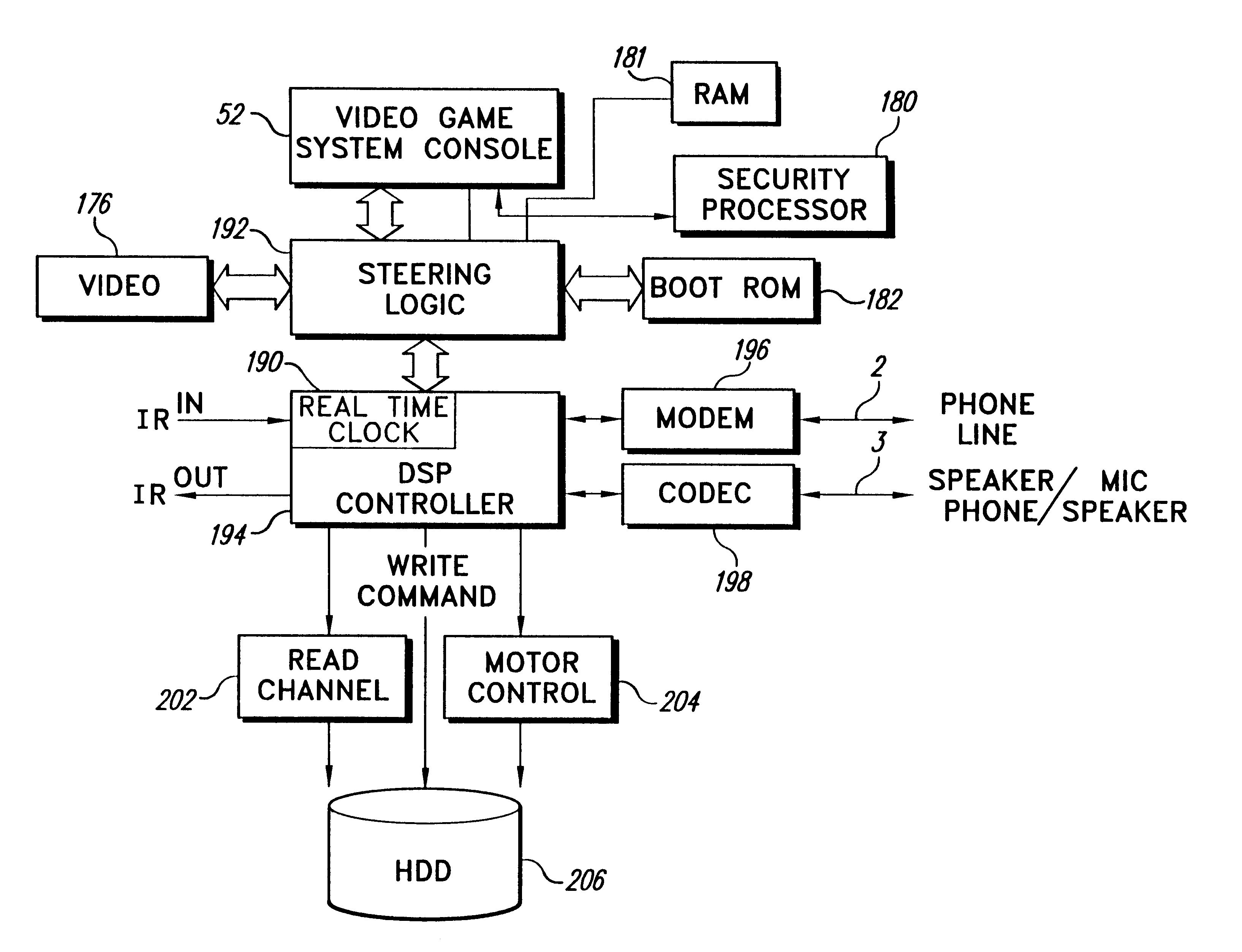
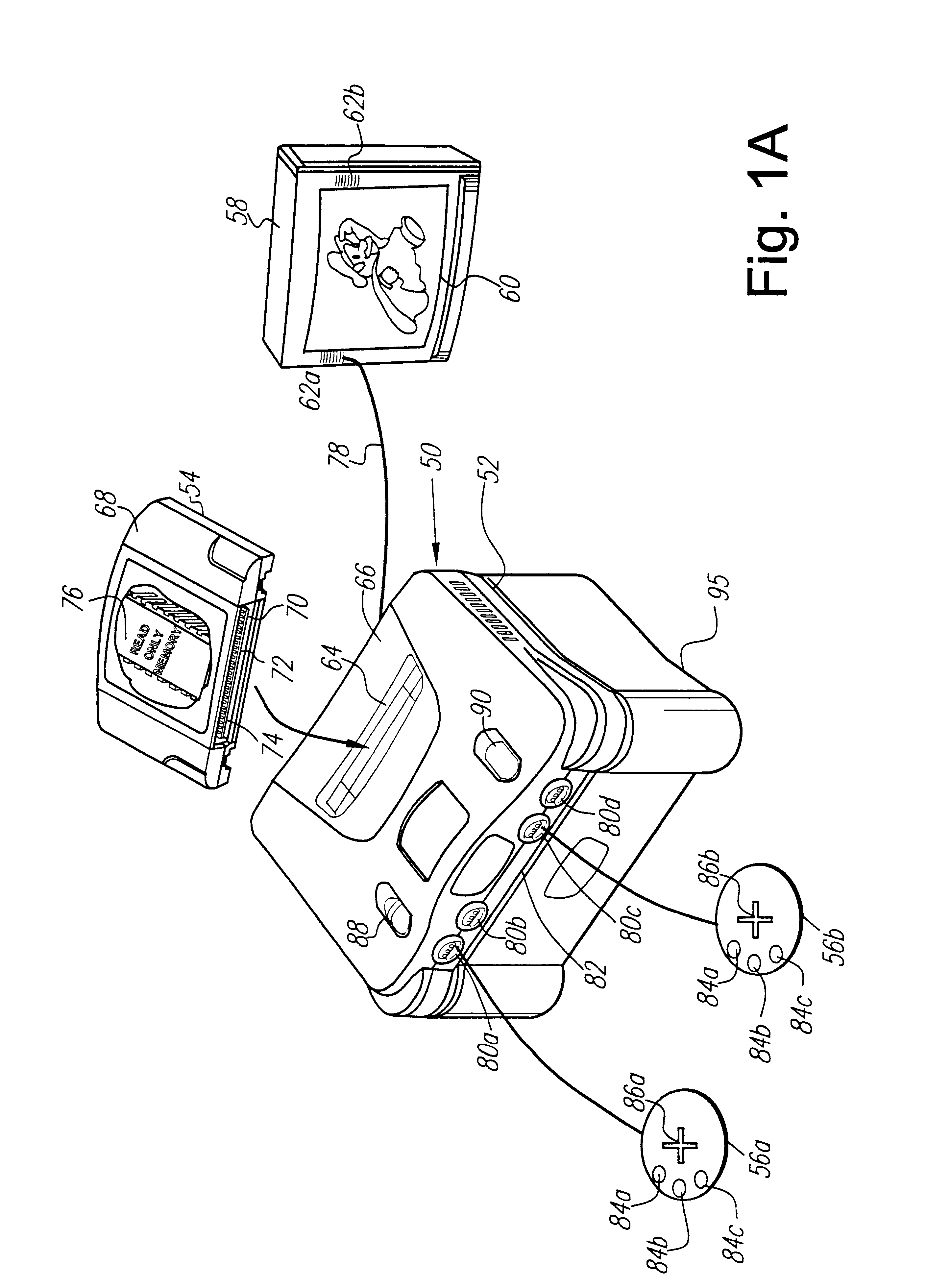
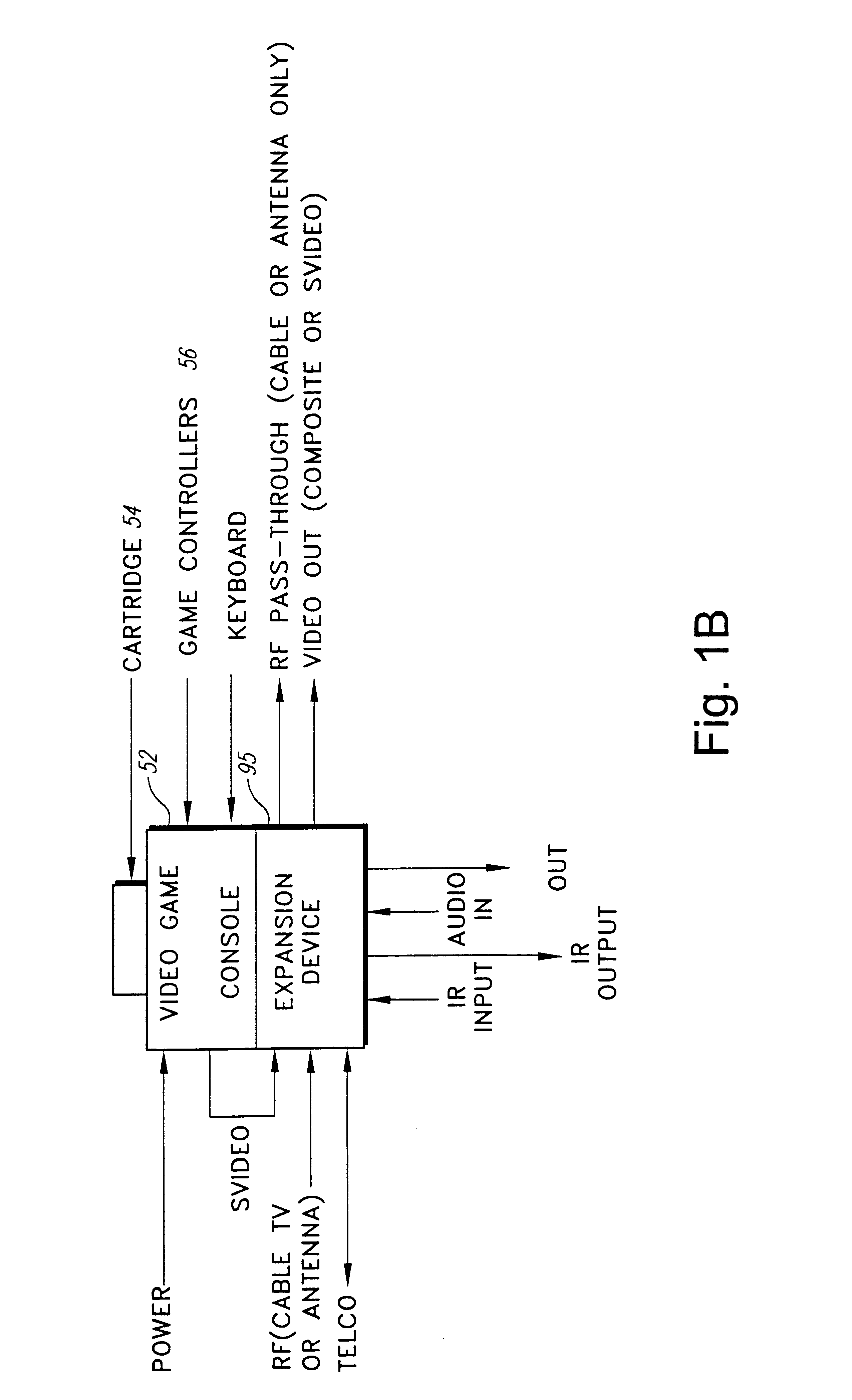
Security system for video game system with hard disk drive and internet access capability
An existing video game system is modified to include additional communication and storage capability via a modem and hard disk drive. In accordance with one embodiment of the present invention, the primary system security features are incorporated into a video game system expansion device having a hard disk drive. The security system does not rely on the relatively insecure video game system. The present exemplary embodiment focuses security control in a disk drive / mass media controlling engine which is physically disposed within the expansion device housing as close as possible to the hard disk drive and the downloaded video games and other data it is designed to protect. Security features are incorporated into, for example, a disk drive controlling processing engine to provide security features which extend far beyond simplistic password systems which have heretofore been utilized in conjunction with disk drive controllers. In accordance with an exemplary embodiment of the present invention, the disk controller also incorporates an encrypting engine which encrypts in accordance with a highly secure encrypting algorithm. A further level of security is provided in the illustrative embodiments by partitioning the hard drive into various partitions whose security / accessibility is tightly controlled. Each application program, e.g., a video game, has a predetermined number of private partitions, including a read only encrypted partition.
Owner:NINTENDO OF AMERICA
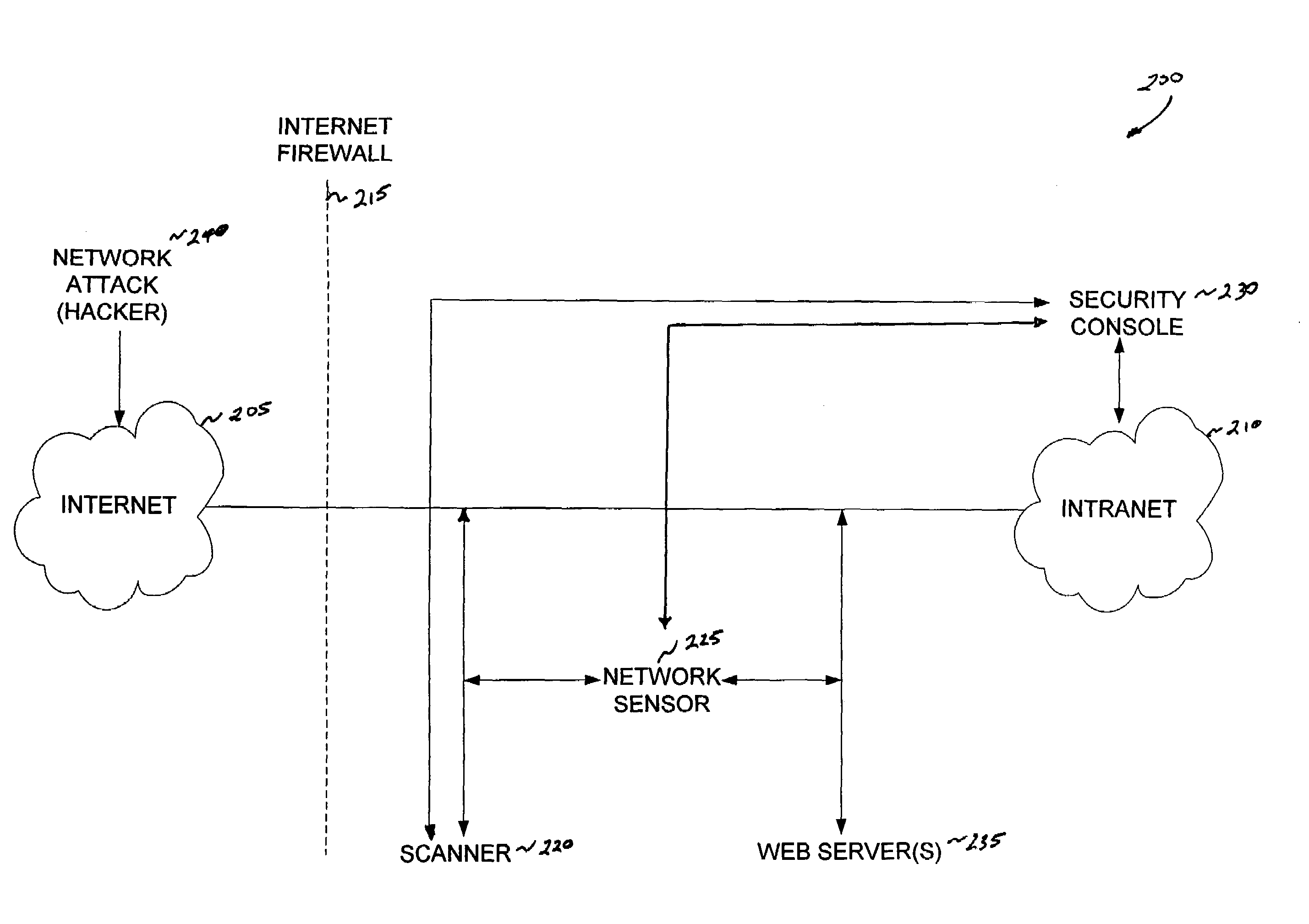
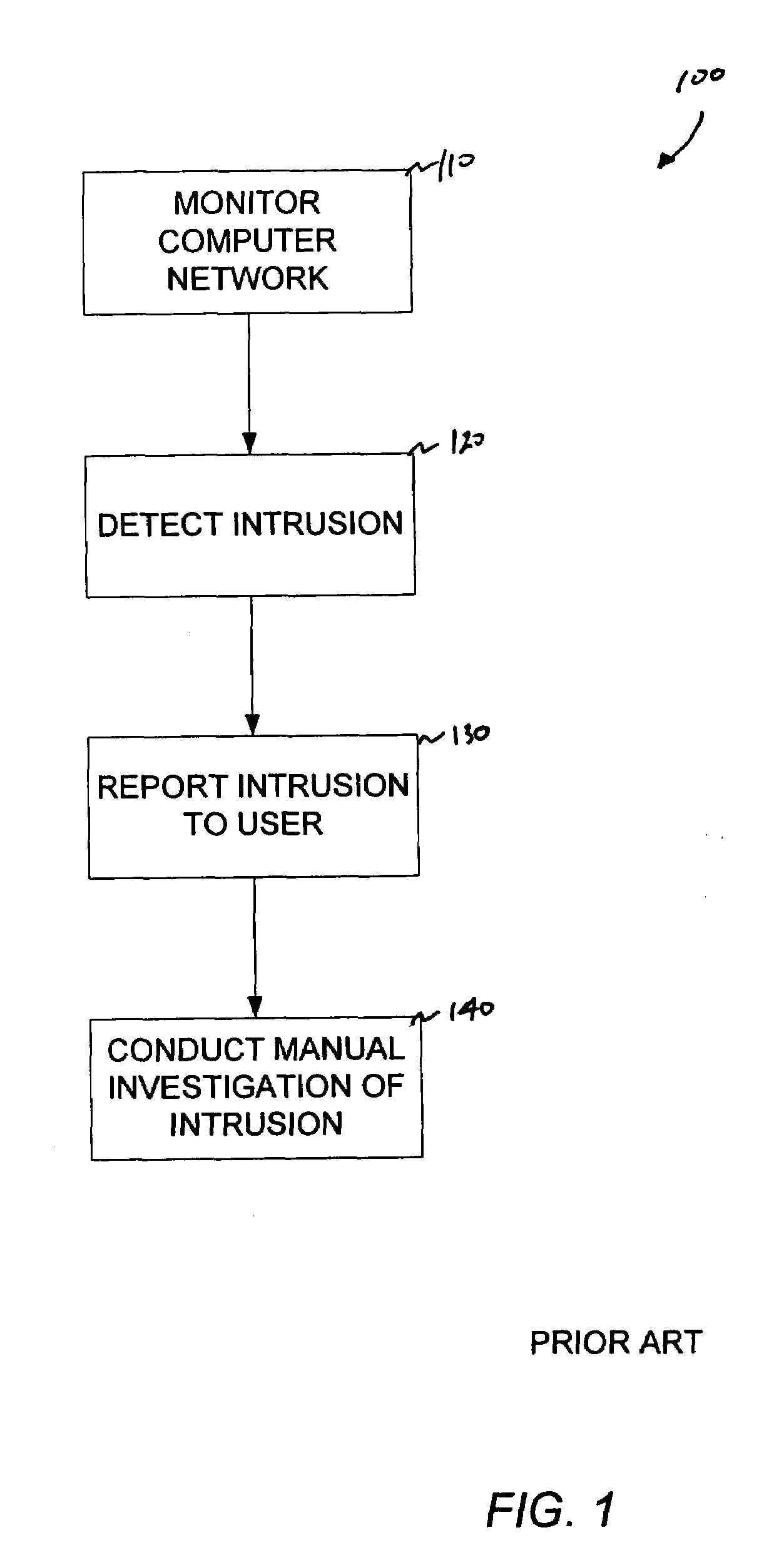
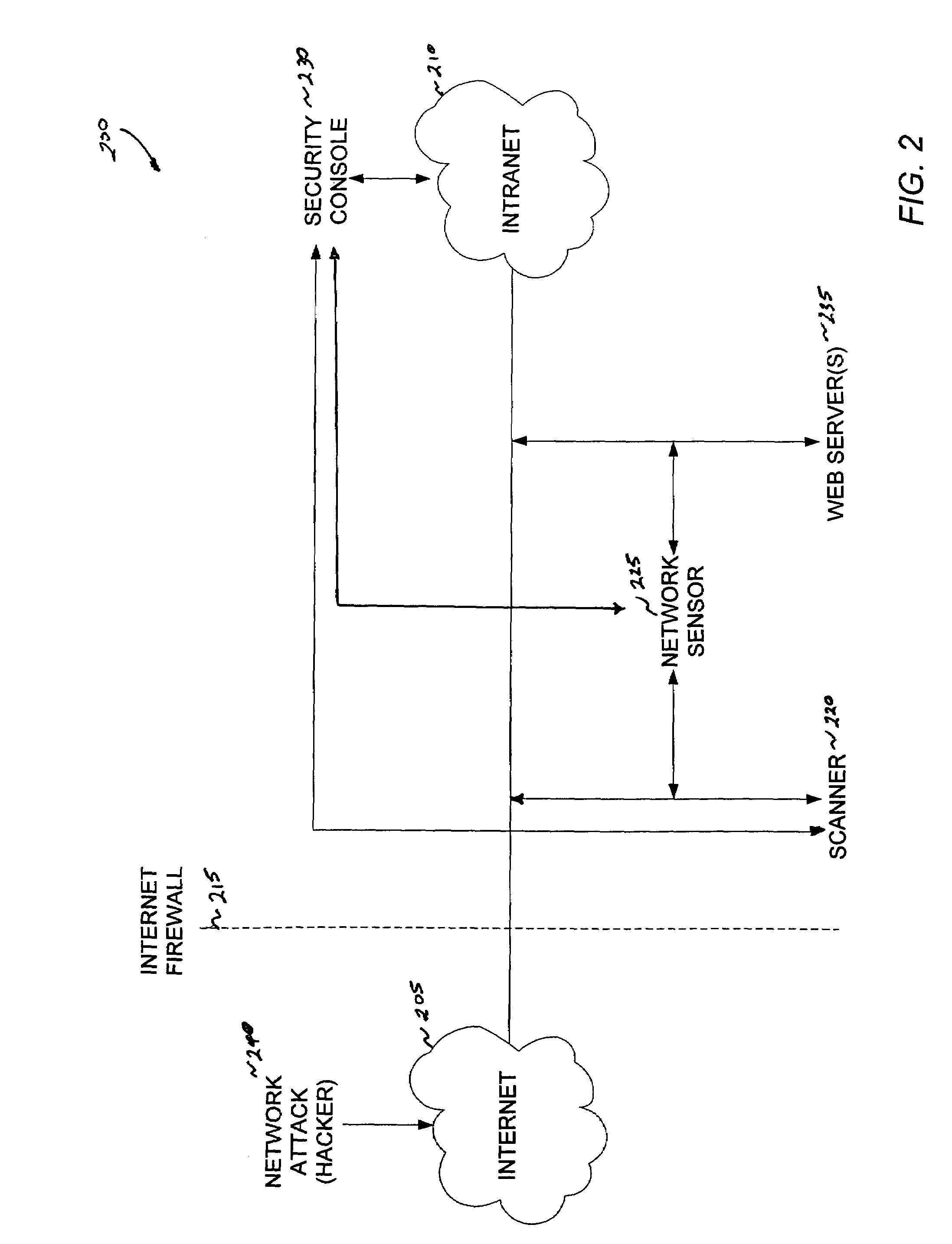
Method and system for intrusion detection in a computer network
InactiveUS7574740B1Memory loss protectionError detection/correctionDatabase intrusion detectionVulnerability
An intrusion detection system for detecting intrusion events in a computer network and assessing the vulnerability of the network components to the detected events. The intrusion detection system comprises a scanner, one or more sensors and a security console for operation within a networked computing environment. A sensor of the inventive intrusion detection system can monitor the networked computing environment for possible intrusion events representing an unauthorized access or use of the network resources. In response to detecting an intrusion event, the sensor can generate a scan request for handling by a scanner. This request initiates a scan of the target computer by the scanner to determine the vulnerability of the target to the attack. Based on this vulnerability analysis, the inventive intrusion detection system can evaluate the severity of the detected intrusion event and issue an alert having a priority corresponding to the severity of the intrusion.
Owner:IBM CORP
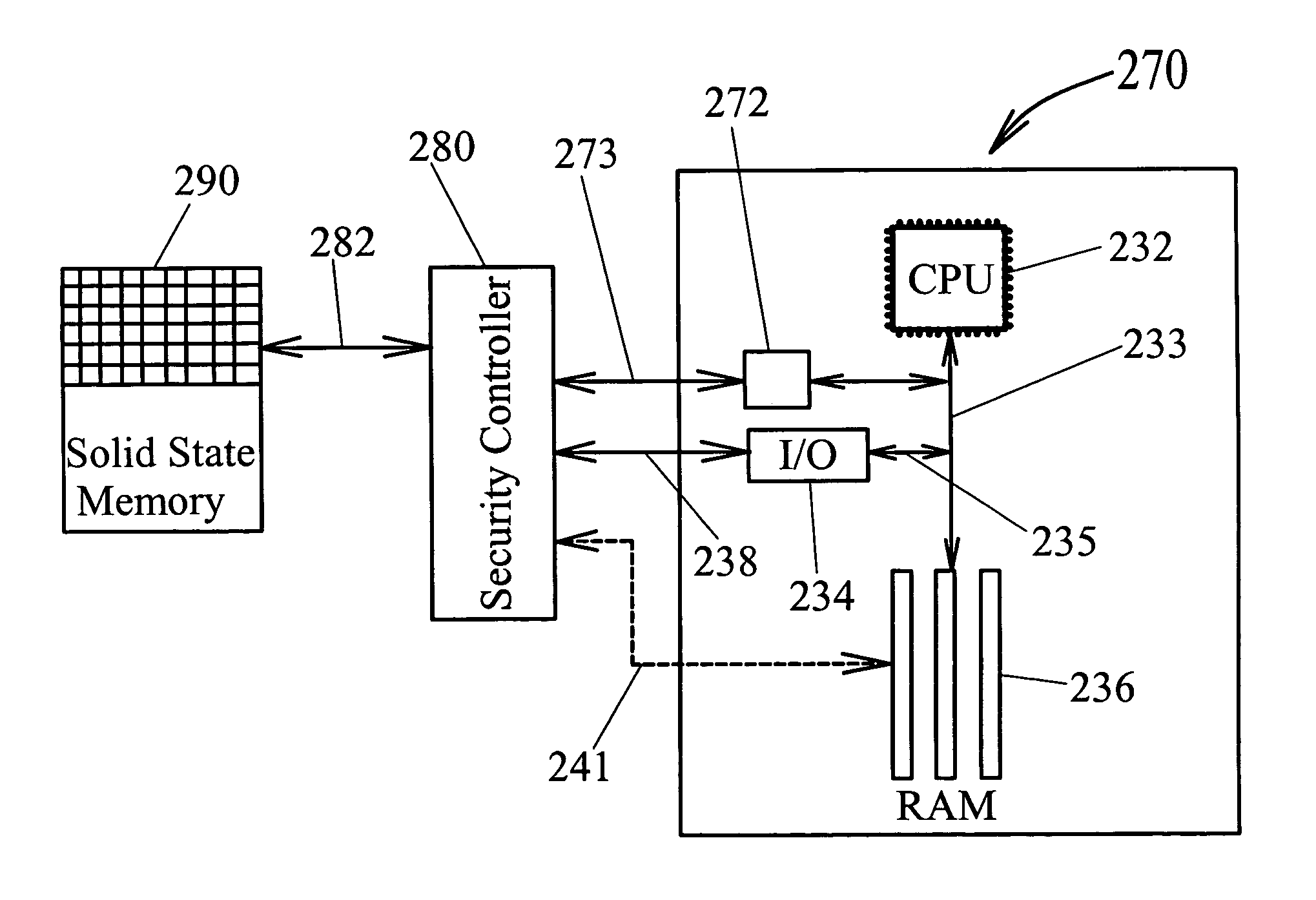
Dynamic associative storage security for long-term memory storage devices
InactiveUS7814554B1Improve protectionSignificant to useDigital data processing detailsUnauthorized memory use protectionStorage securityProgram Thread
A hierarchical folder security system for mapping files into and out of alias directories and / or real directories depending on: 1) the directory of the specific file being accessed, 2) the program thread requesting access to a memory storage device (114), and 3) the type of access request being made (i.e. load, save, run, etc.). For write access requests (i.e. save, modify, paste, delete, cut, move, rename, etc.), security controller (180) determines if the requested folder access address (150a) is associated with the requesting program's folder address (168). If it is, the file is written at absolute address (156b) on disk platter (160) through real folder map (152). If requested address (150a) is not associated with program folder address (168), then an alias directory address is created and the file is written at alias address (156a) through alias folder address map (154).
Owner:RAGNER GARY DEAN
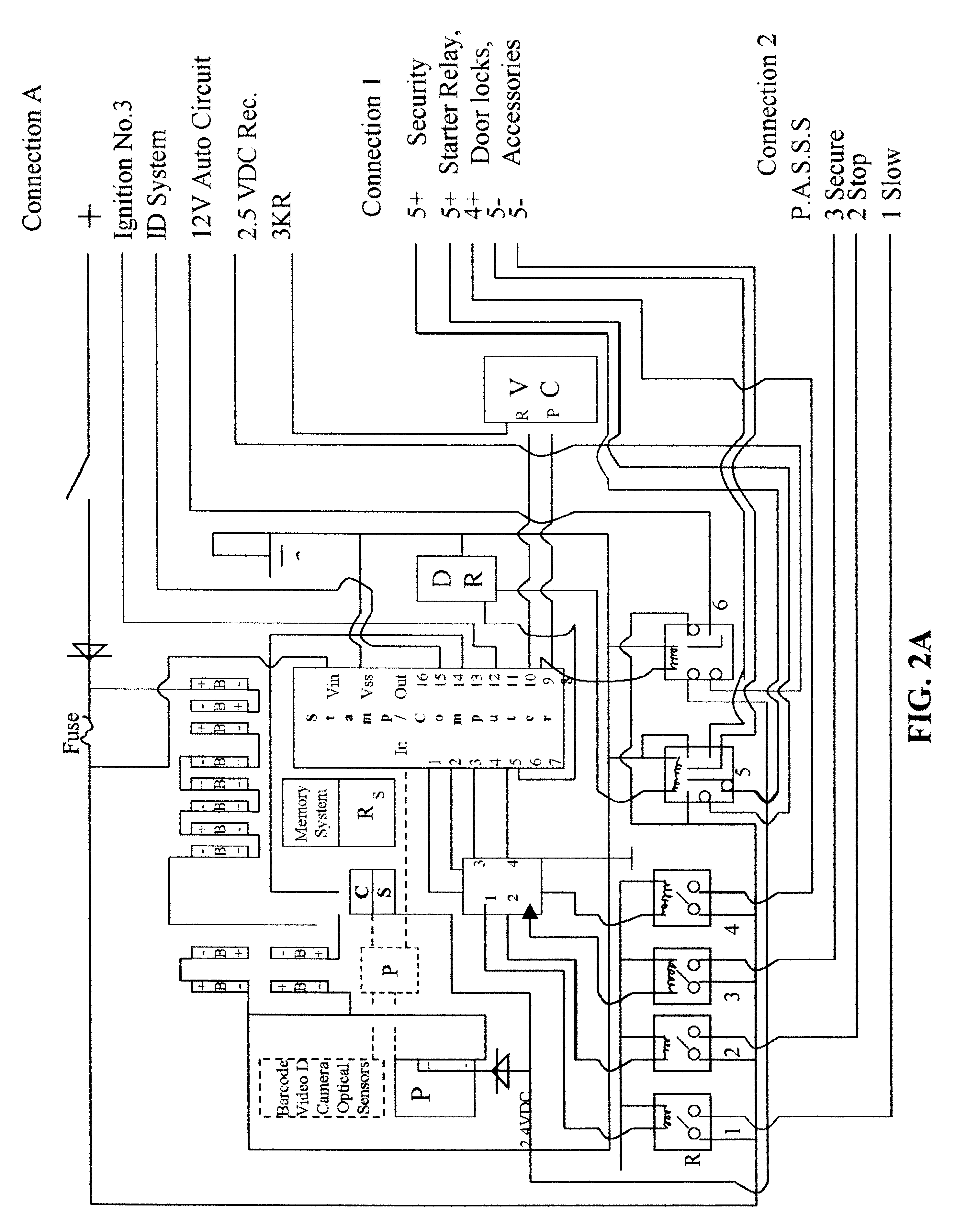
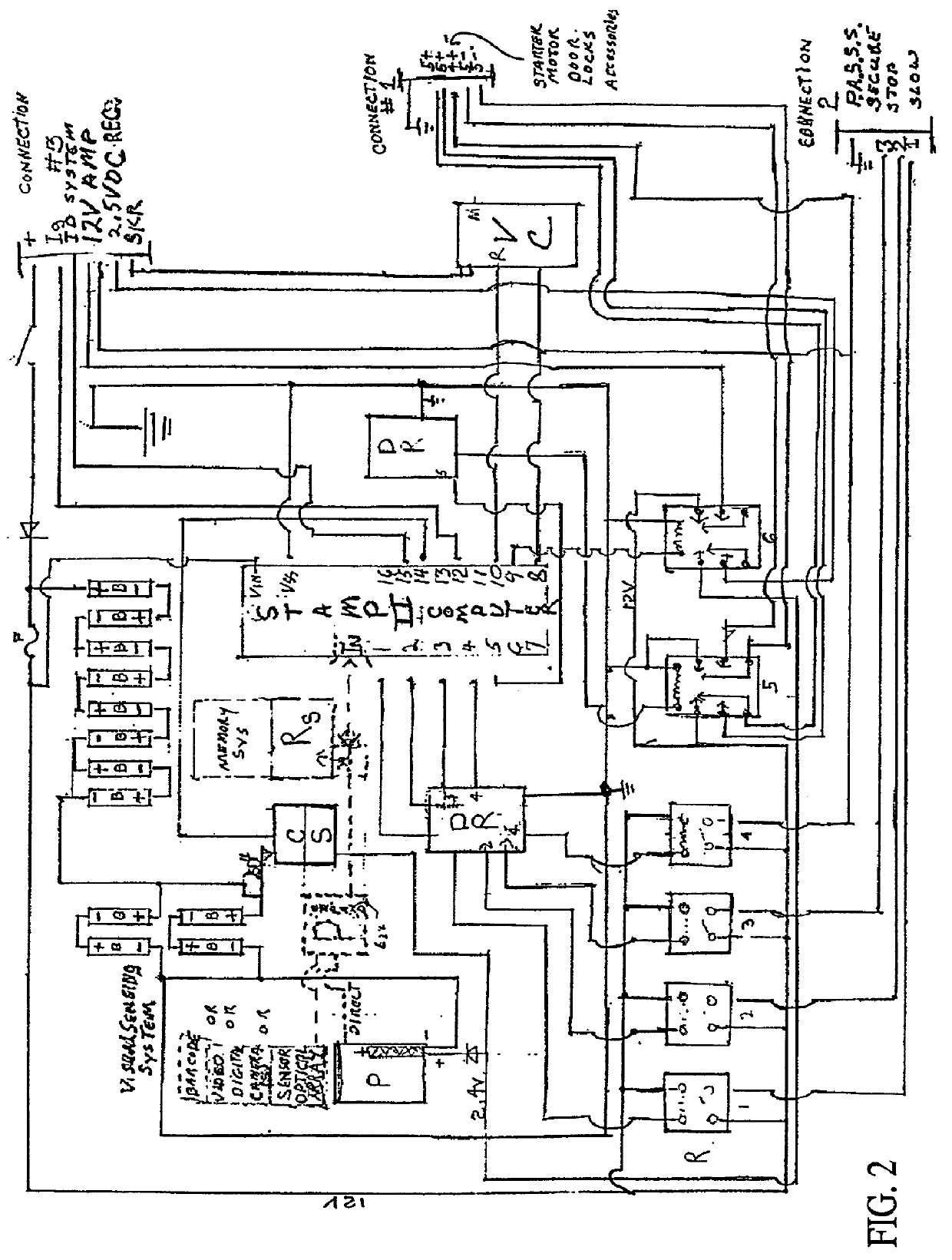
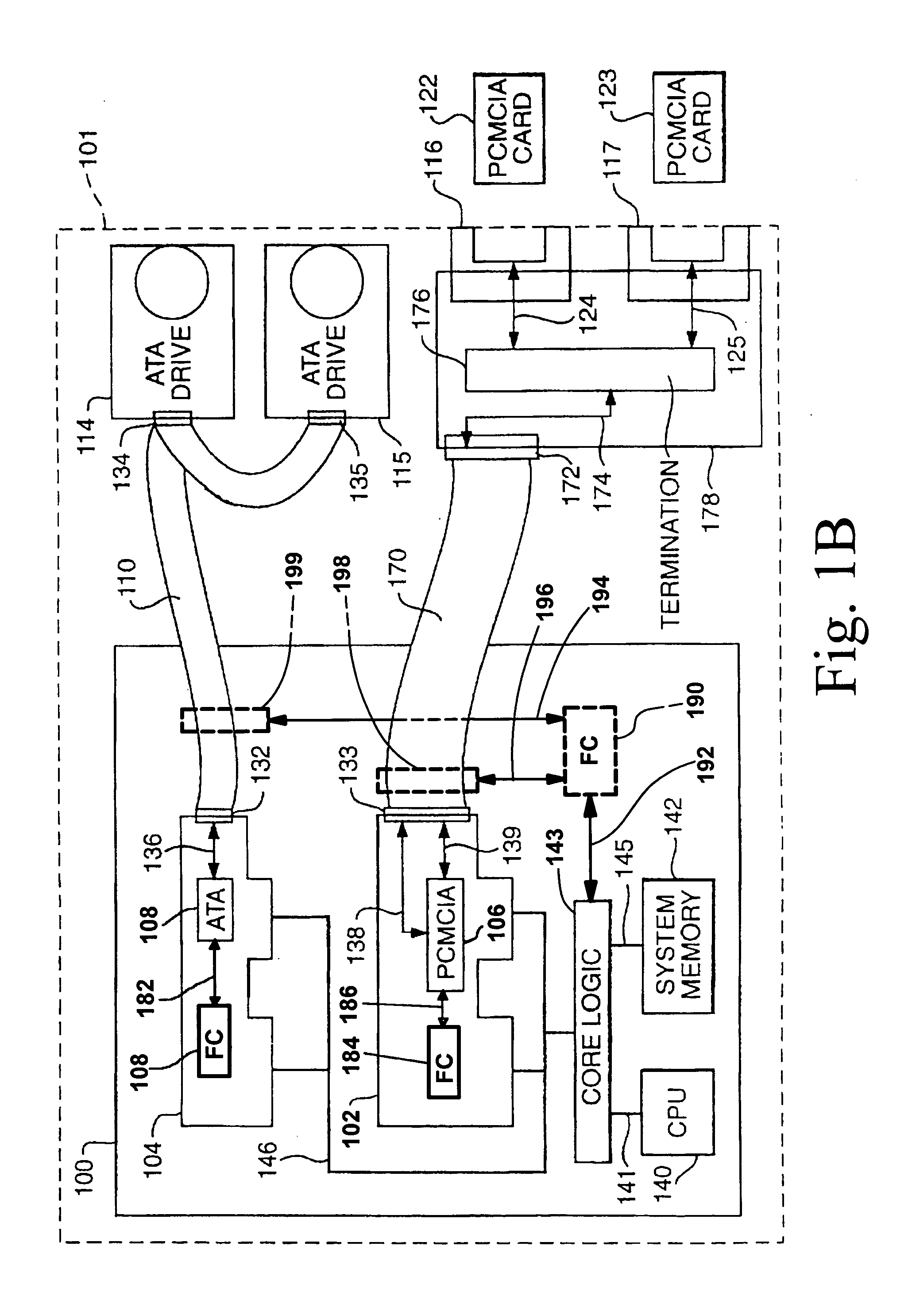
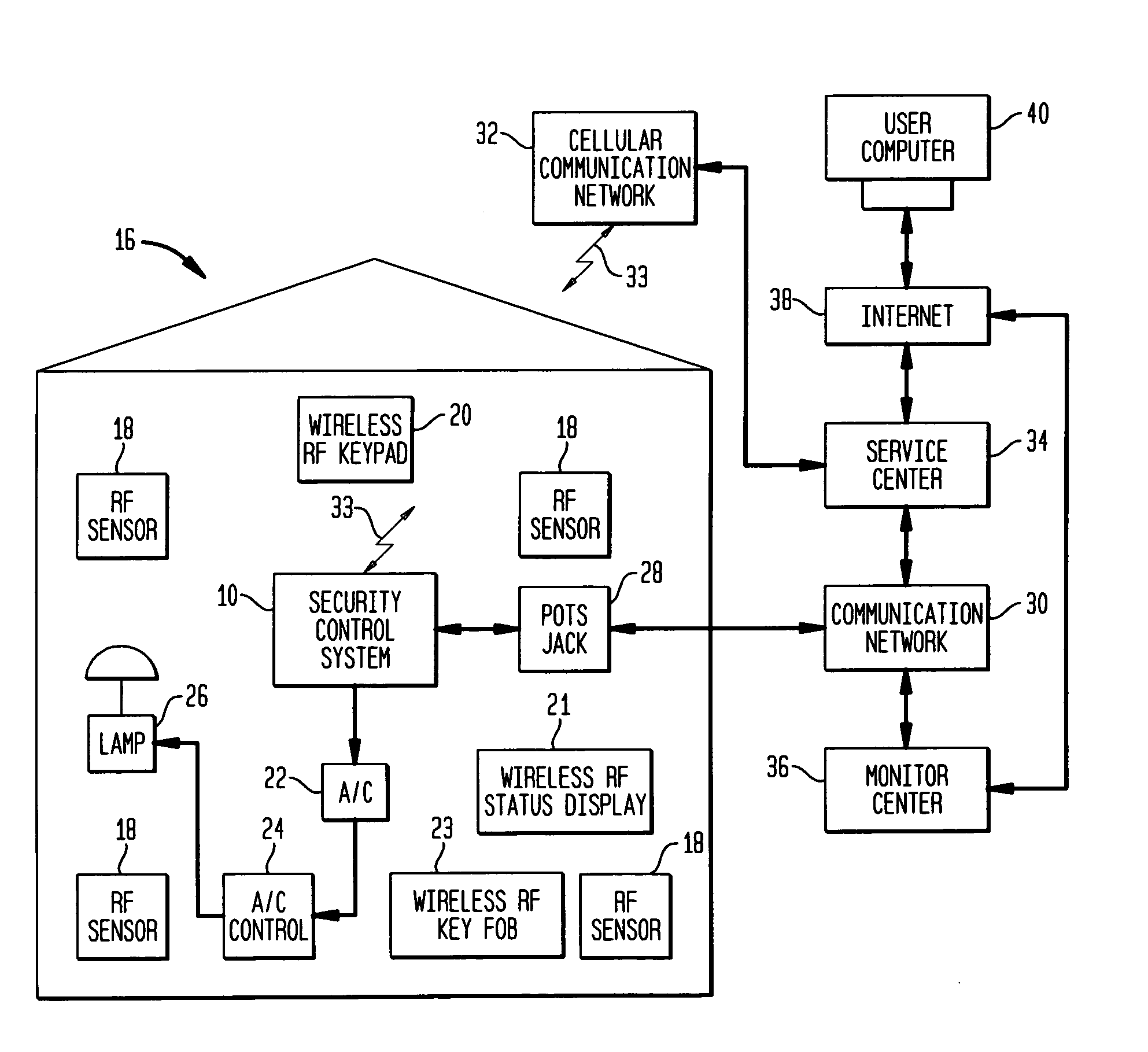
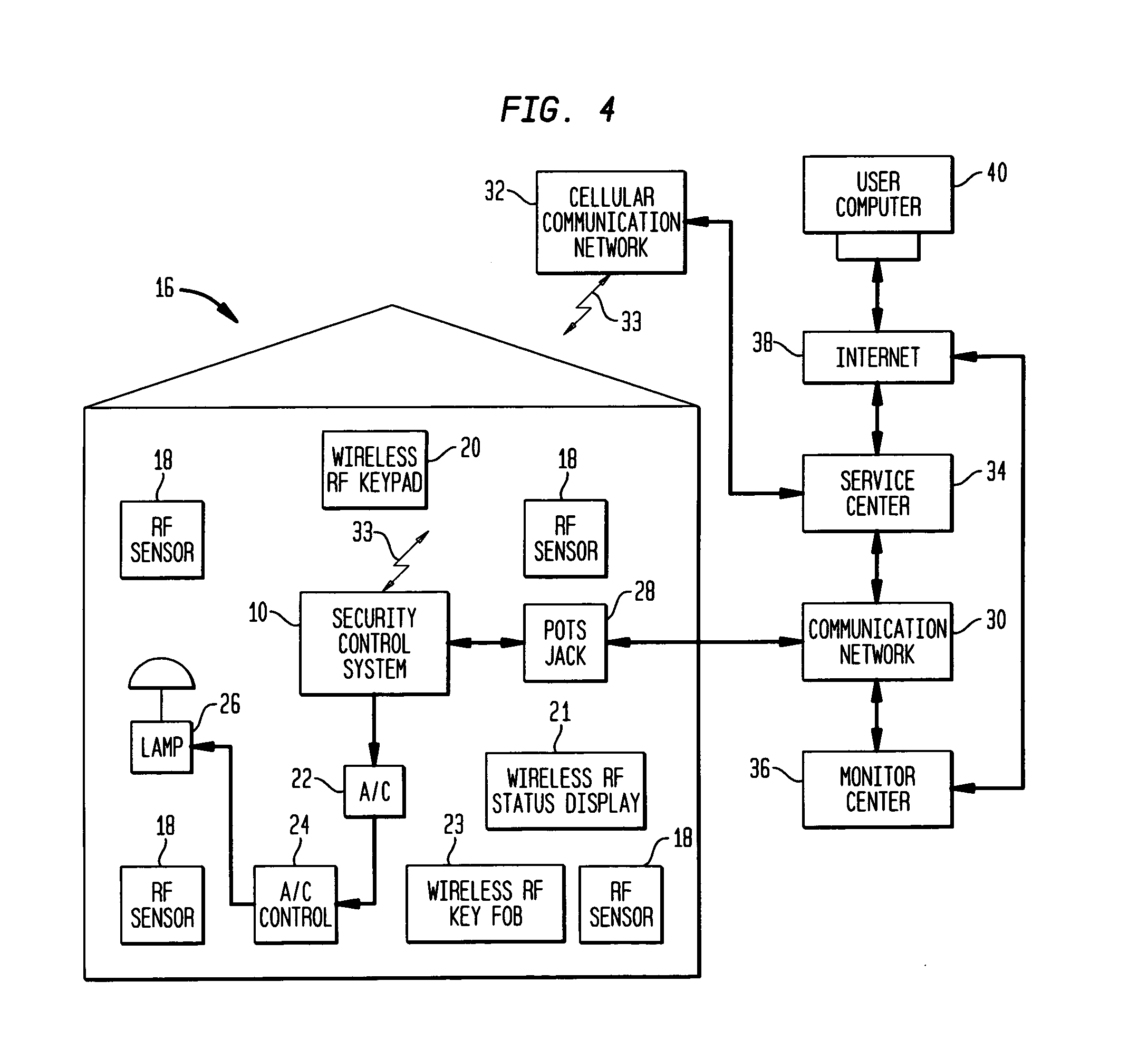
Security control and communication system and method
ActiveUS6999562B2Convenient programmingEasy to installFrequency-division multiplex detailsTelephonic communicationTransceiverDisplay device
An integrated security control system and method which integrate the functions of a wireless security system control panel and a radio transceiver in an integrated security control system unit. The integrated control unit includes a first telephone communication system for communicating security system data by wired telephone communications, and a second radio frequency (RF) cellular communication system for communicating security system data by communications through an RF communication network. The cellular communication system is the primary communication network for reporting a security event, thereby leaving the first telephone communication system open for telephone communications during the reporting of a security event. A separate unit of the security system, such as a wireless RF status display or a wireless RF keypad, is provided with a beeper transducer for sounding entry and exit beeps. The separate unit is positioned at a separate location from the integrated security control system unit, such that the entry beeps do not alert an entering person to the location of the integrated security control system unit. When a security event is triggered, the control unit delays activating a security alarm sounder in the control unit until after the second RF communication system has finished transmitting the alarm message.
Owner:ADEMCO INC
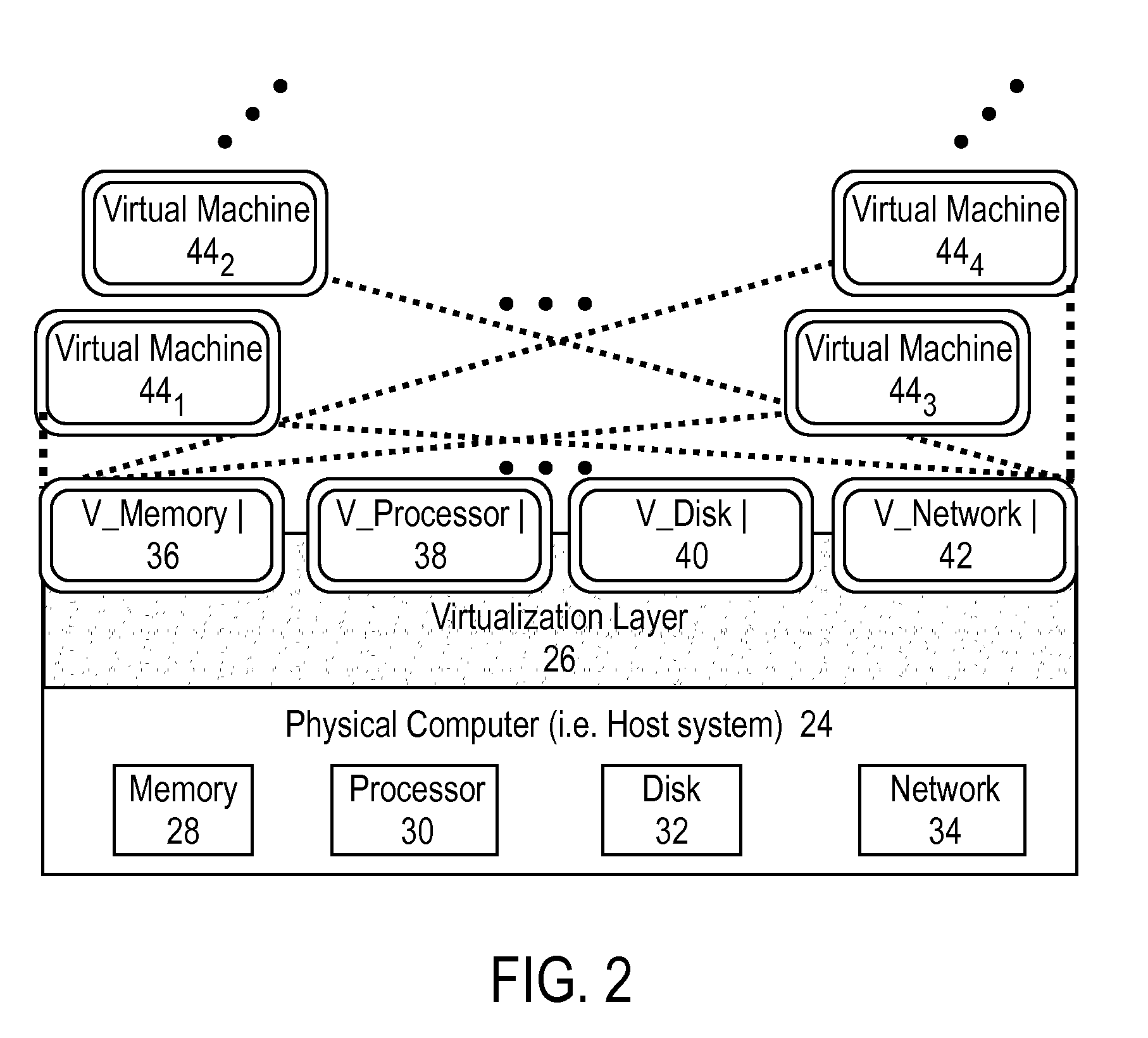
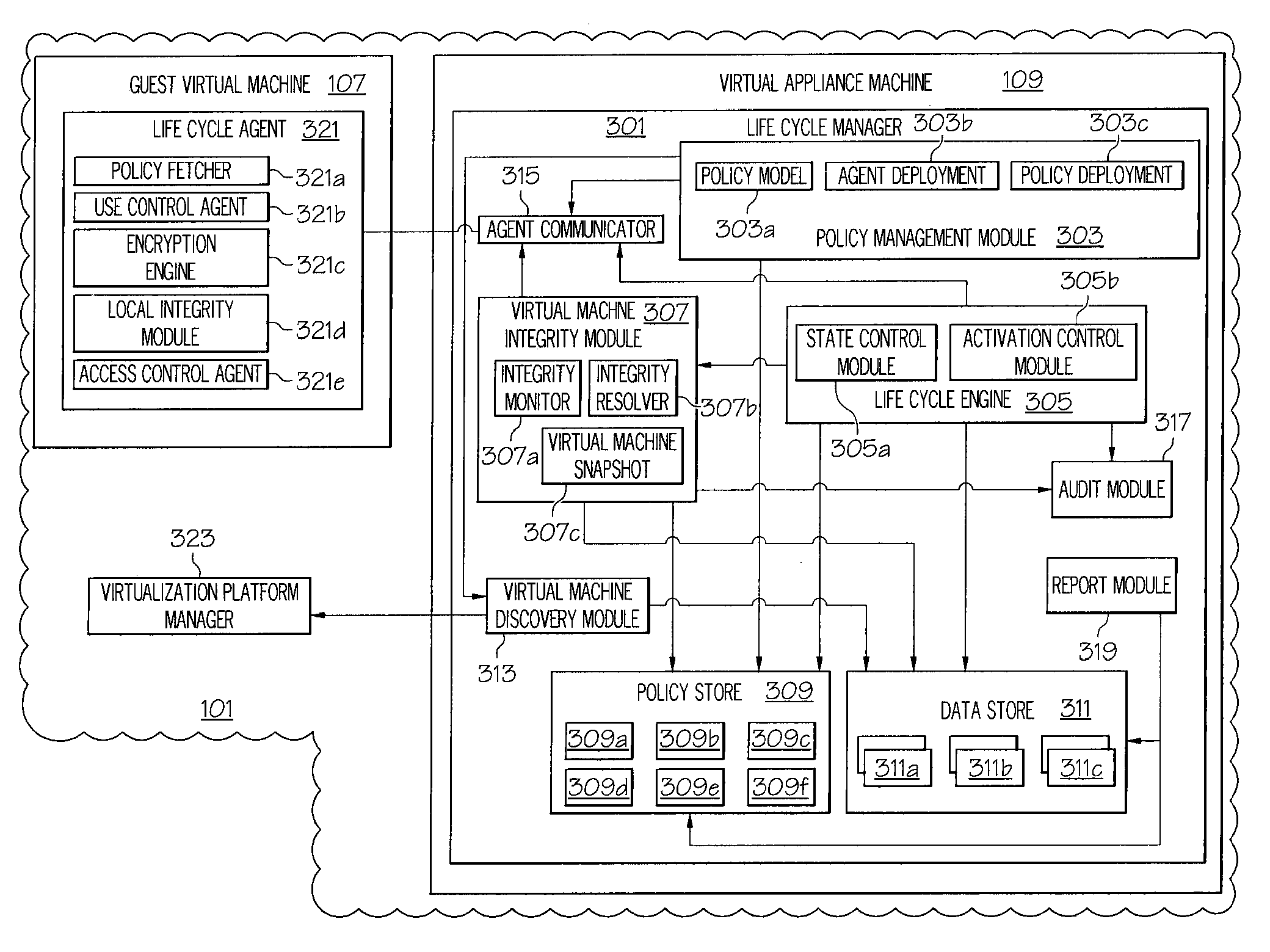
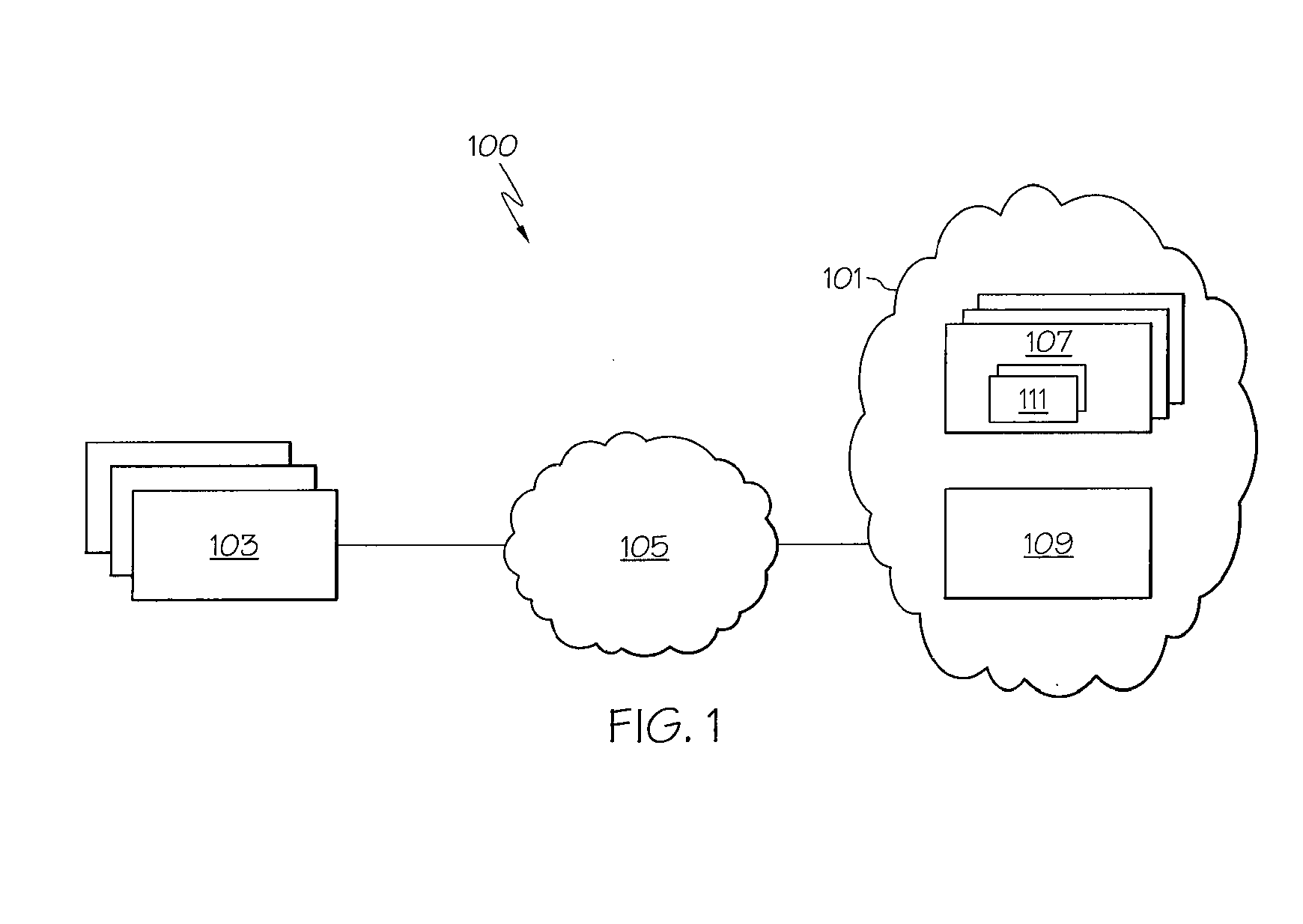
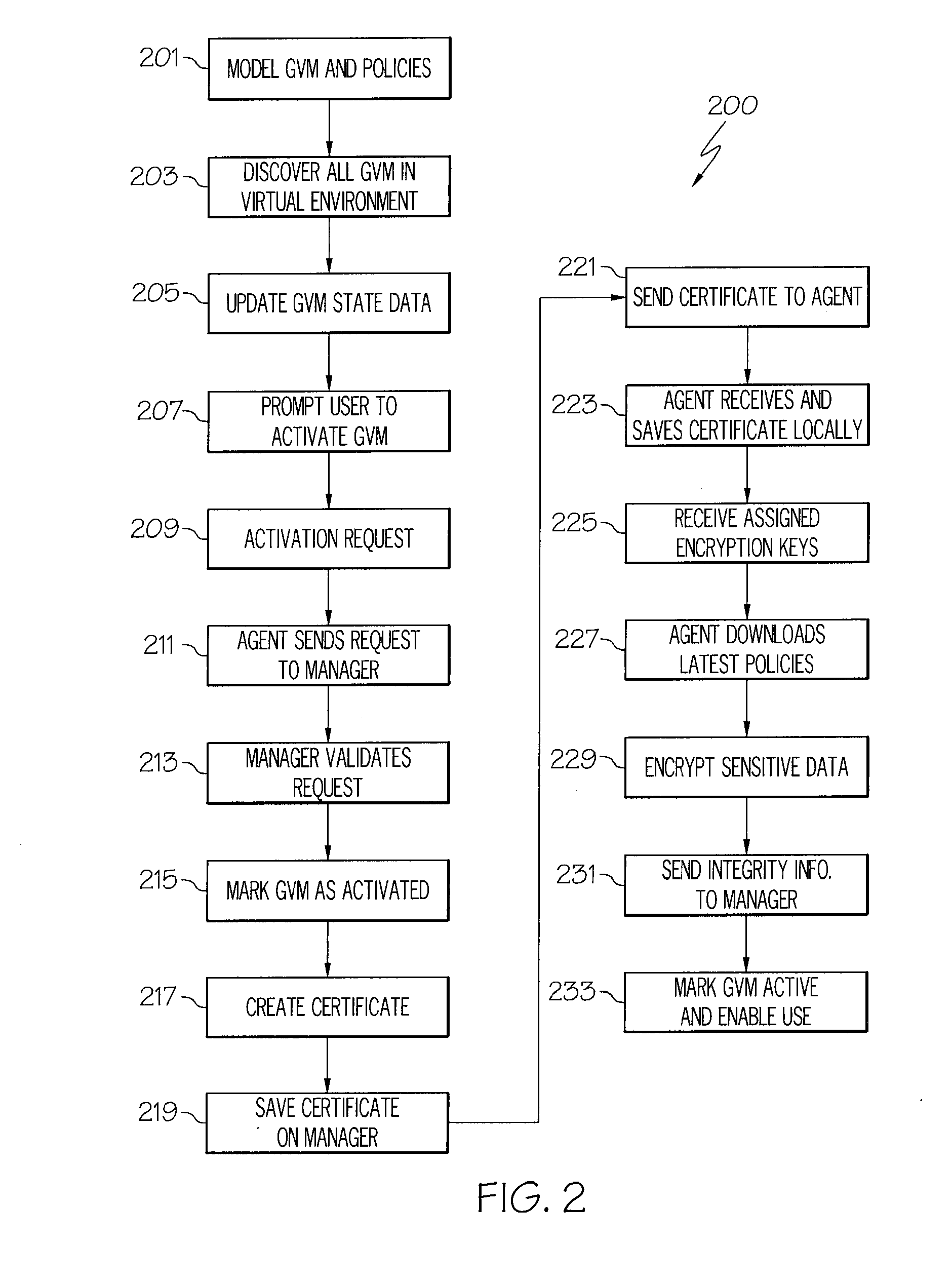
System and method for enforcement of security controls on virtual machines throughout life cycle state changes
ActiveUS20140096134A1Improve securityStrong security policyPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtual computingData storing
Systems and methods associated with virtual machine security are described herein. One example method includes instantiating a guest virtual machine in a virtual computing environment. The method also includes installing a life cycle agent on the guest virtual machine, assigning an identifying certificate, a set of policies, and an encryption key to the guest virtual machine, and providing the certificate, policies, and encryption key to the guest virtual machine. The certificate, policies, and encryption key may then be used by the guest virtual machine to authenticate itself within the virtual computing environment and to protect data stored on the guest virtual machine.
Owner:CA TECH INC
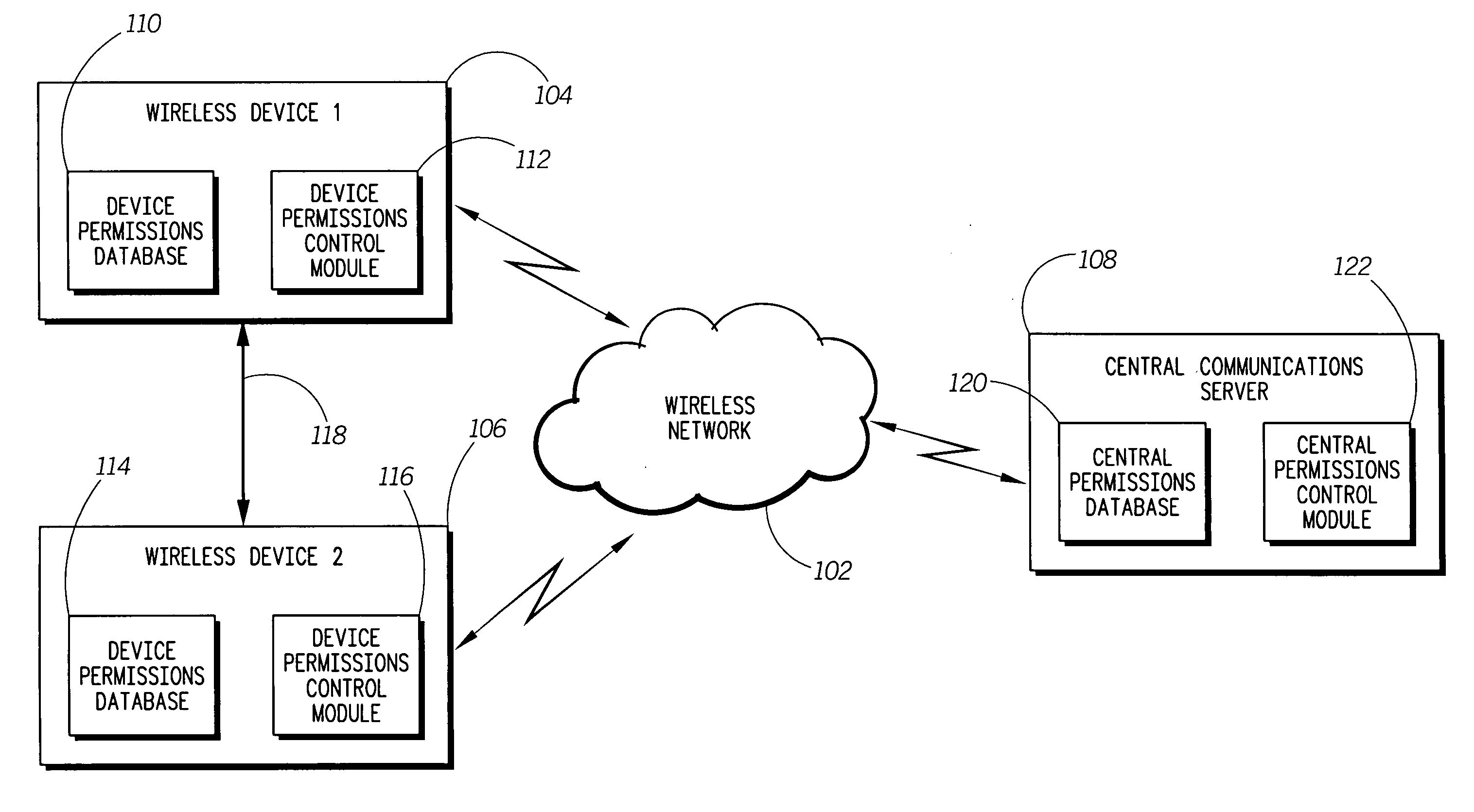
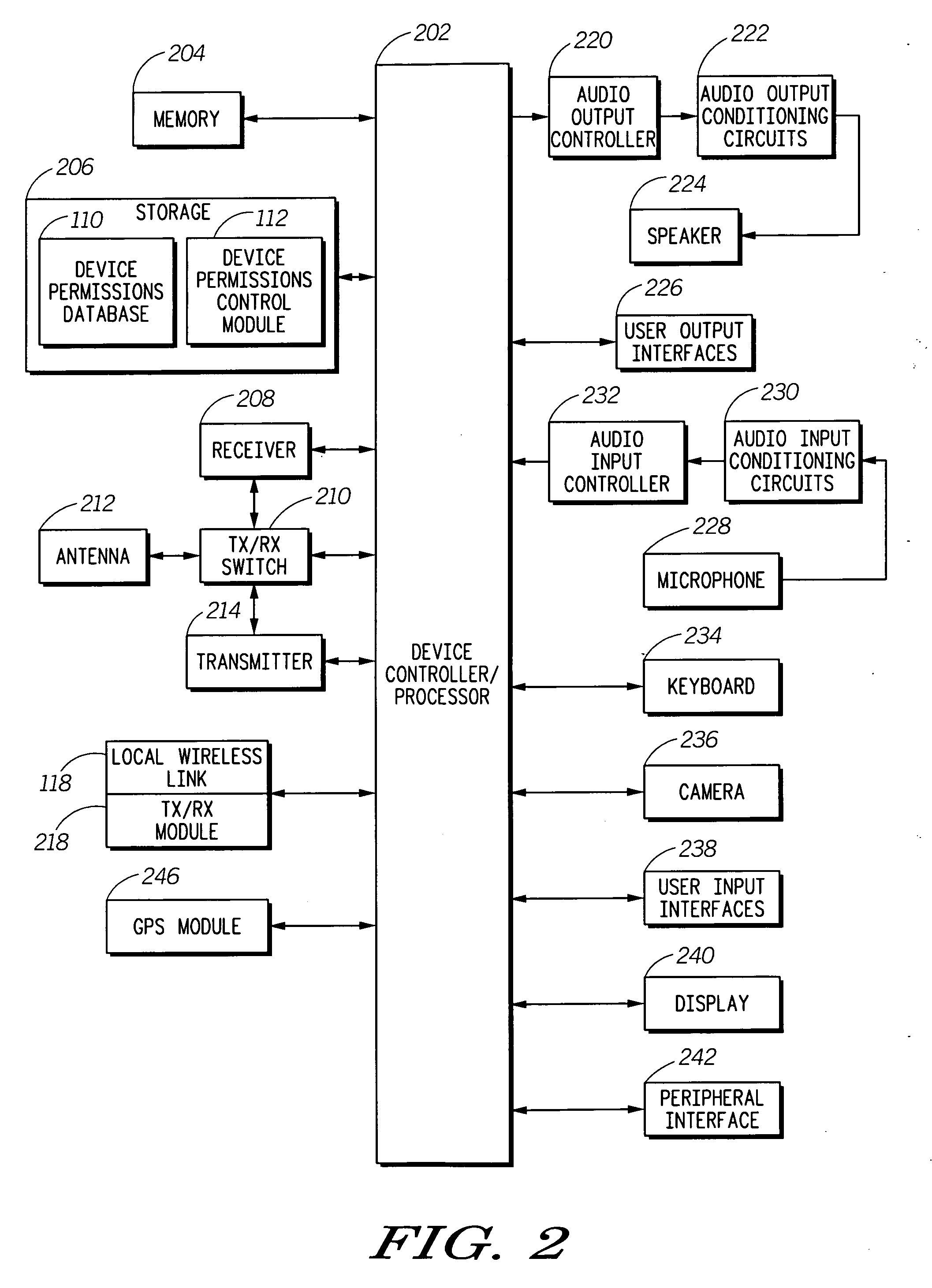
Dynamic management for interface access permissions
InactiveUS20060141985A1Efficient managementSafe operating environmentUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTime informationComputer network
A system, device, and method, for managing application interface access permissions for an application (302) in an electronic device, such as a wireless device (104), is disclosed. The method includes associating a security policy with an application (302). The method further includes creating a history log (324) associated with the application (302). The history log (324) includes time information associated with permission information indicating permission for an application to access at least one application interface in the electronic device (104). The method further includes dynamically adjusting the security policy for the application (302) when a security control signal associated with the application (302) is detected.
Owner:MOTOROLA INC
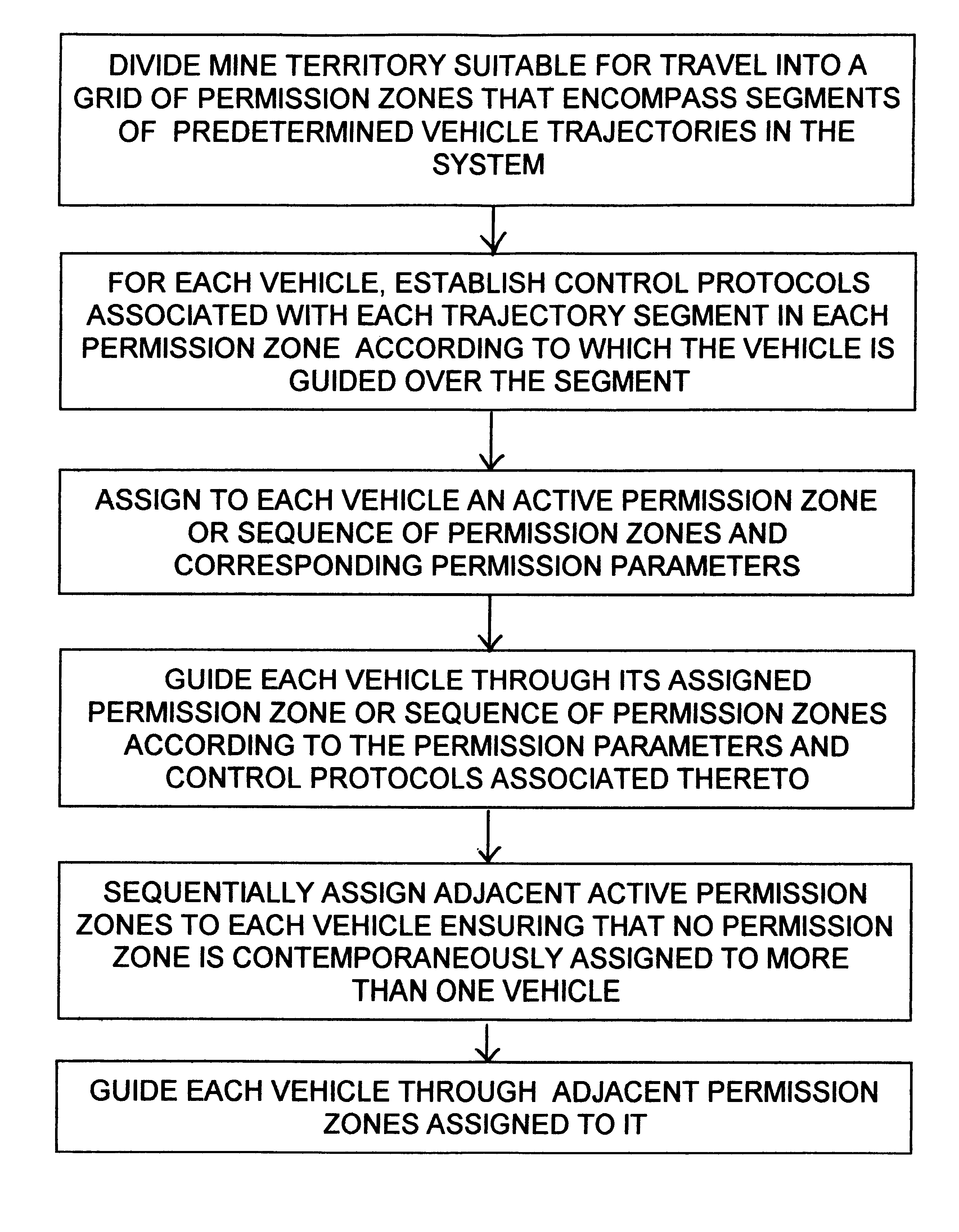
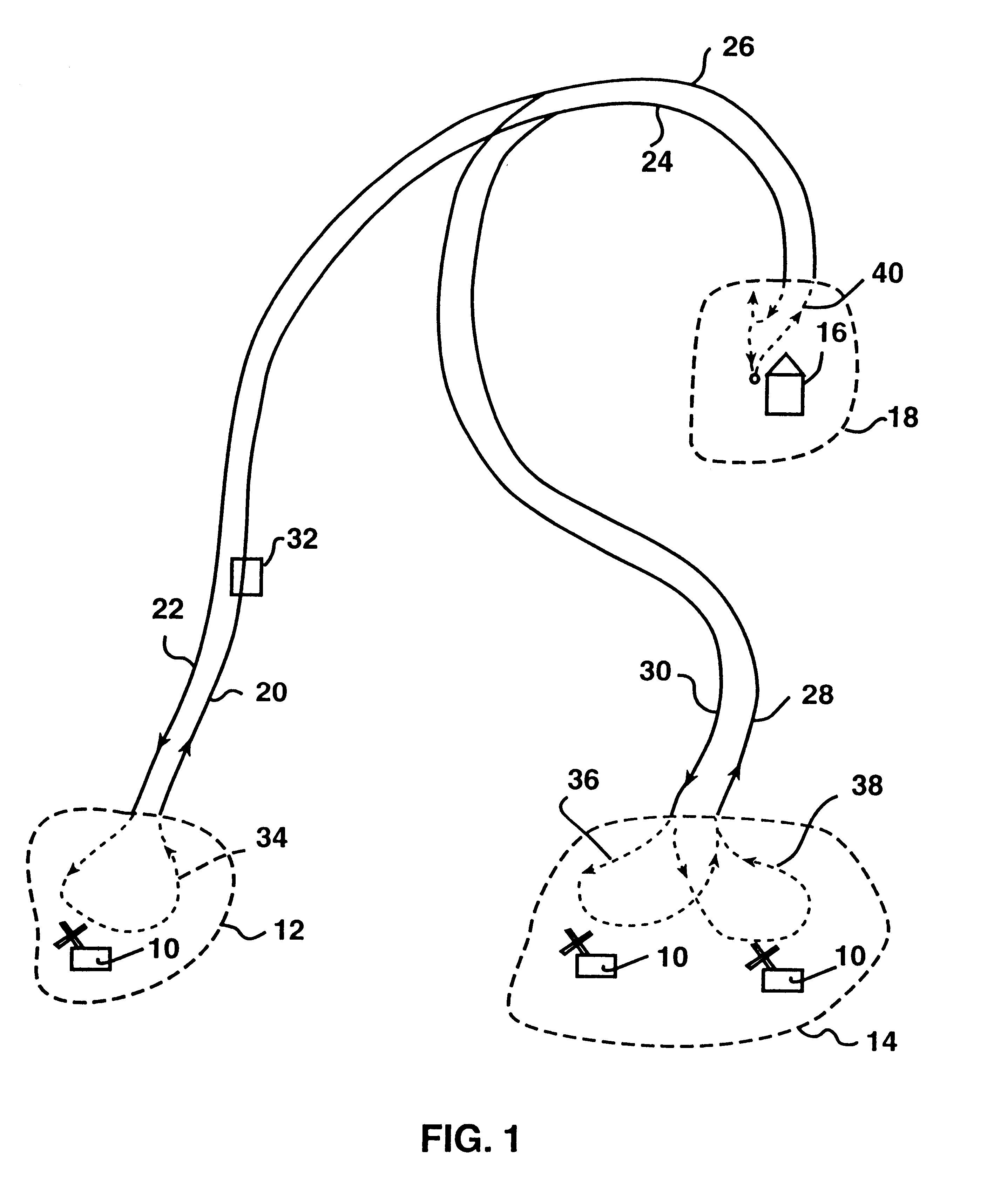
Permission system for controlling interaction between autonomous vehicles in mining operation
InactiveUS6799100B2Analogue computers for vehiclesAnalogue computers for trafficGuidance systemControl system
A supervisory safety-control system is implemented by dividing a mine's territory into zones of free operation ("permission zones") wherein a vehicle is allowed to move according to predetermined permission parameters but unhindered by other system constraints. Traffic of autonomous vehicles in each permission zone is controlled by the supervisory system in conjunction with and in addition to conventional safety constraints associated with the guidance system that effects the vehicle's tracking of predetermined trajectories. Permission zones are assigned and activated using criteria that ensure the vehicle will remain entirely within active zones so long as the vehicle acts within such predetermined permission parameters. Each permission zone is also associated with a maximum velocity profile that overrides guidance-system safety controls, if necessary, and ensures stoppage of the vehicle at the end of the permission zone.
Owner:MODULAR MINING SYSTEMS
Security system and method
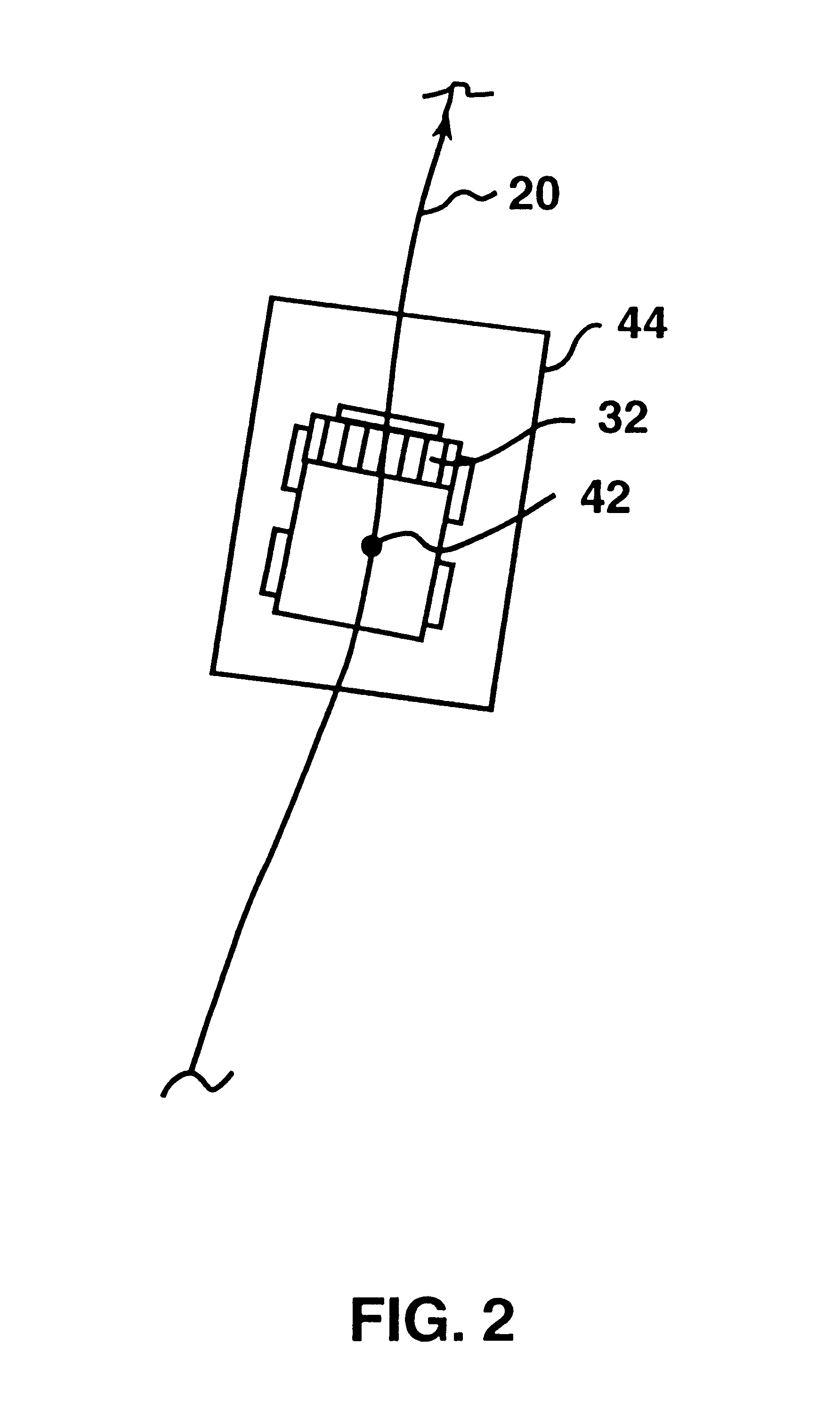
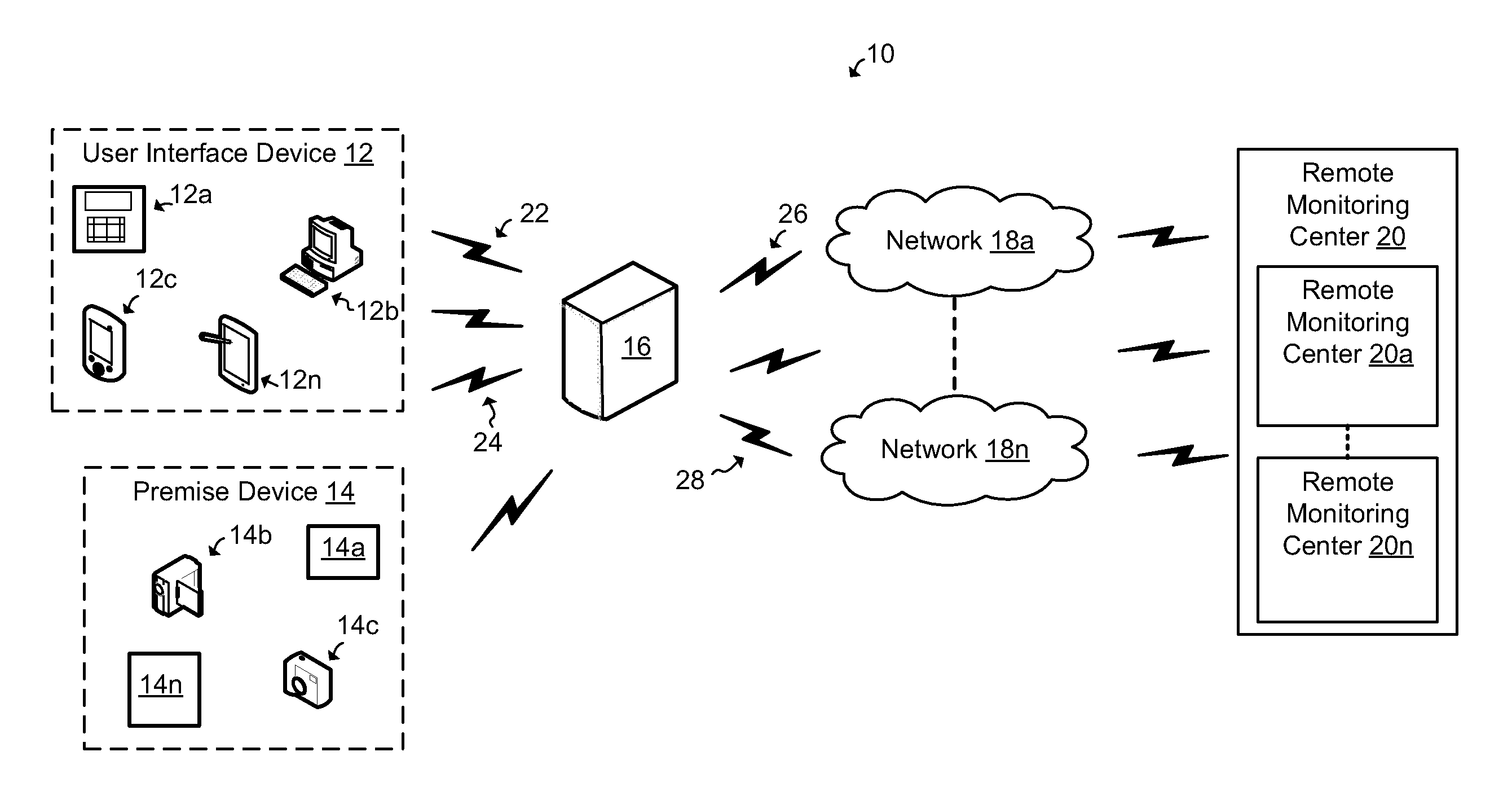
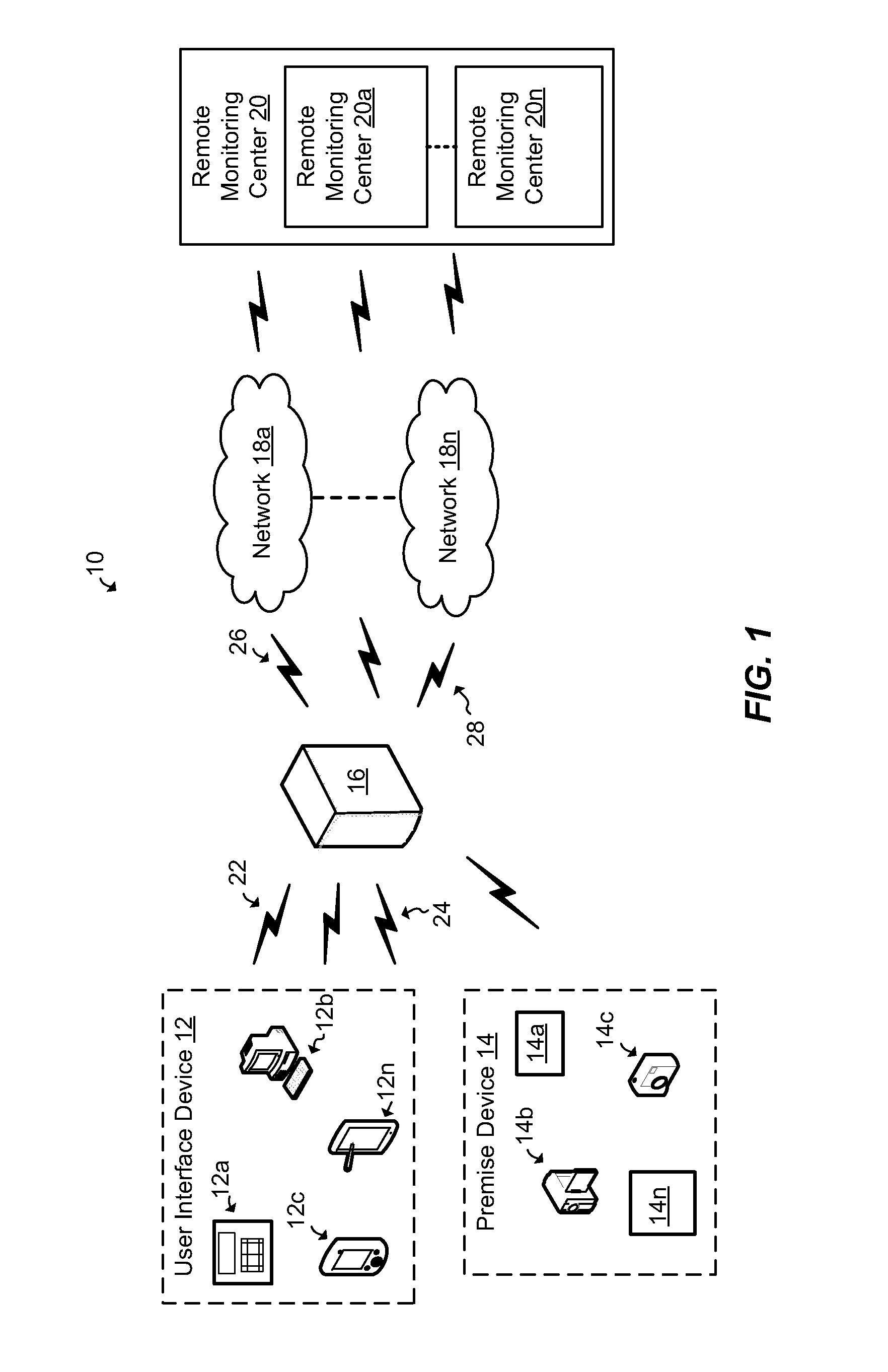
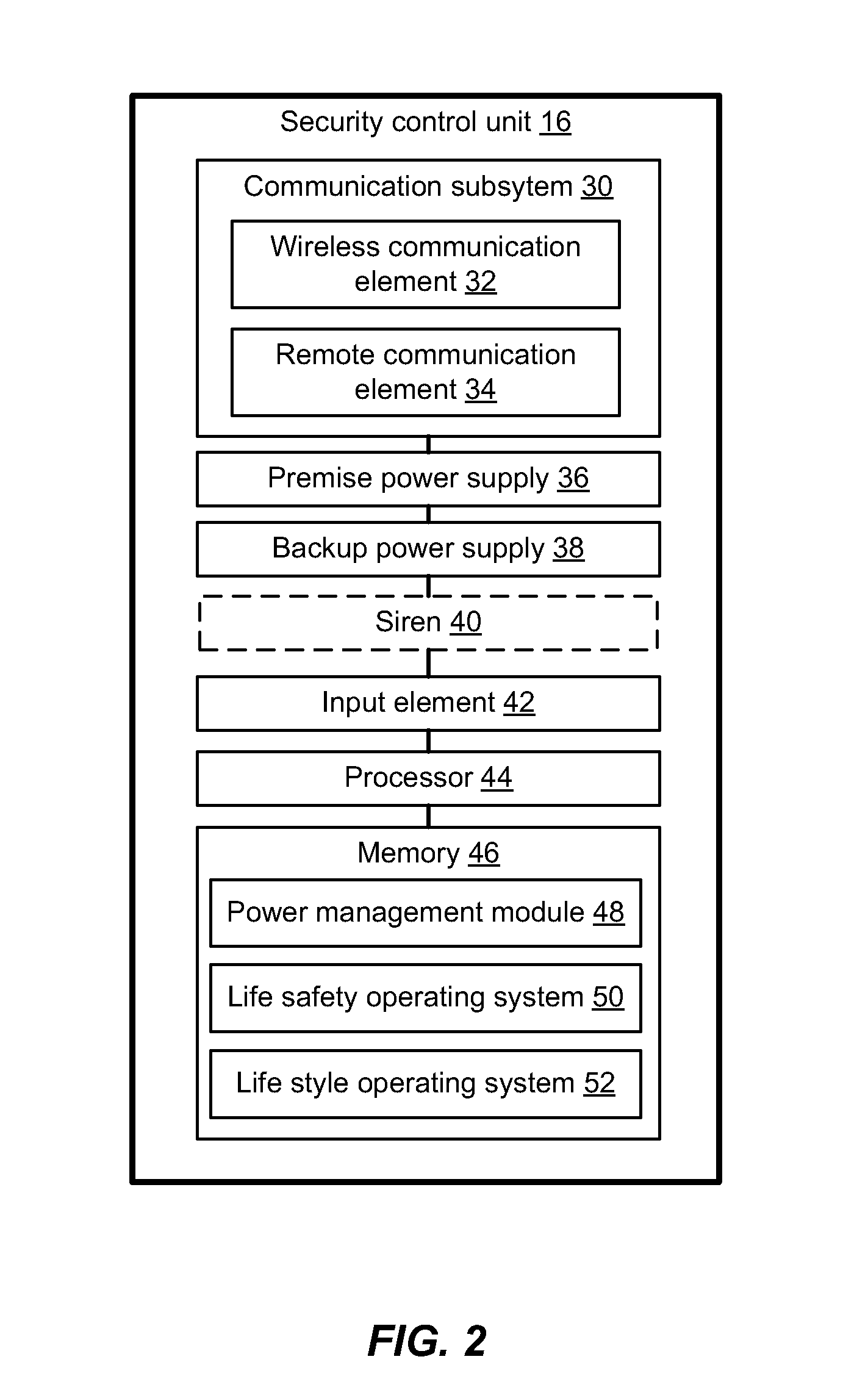
ActiveUS20130082835A1Management is restrictedPower supply for data processingBurglar alarmWireless communication protocolTelecommunications
A security control apparatus, system and method are provided. The security control apparatus includes a wireless communication element that supports a plurality of wireless communication protocols. The wireless communication element is configured to provide wireless communications with a user interface device and at least one premise-based device. A remote communication element is configured to provide remote communications with a monitoring center. A processor is in communication with the local wireless communication element and the remote communication element. The processor is configured to use the wireless communication element to communicate with the user interface device to receive local control and configuration data. The processor is also configured to use the remote communication element to communicate data associated with at least one of a life safety feature and life style feature with the monitoring center.
Owner:ADT US HLDG INC
Method and apparatus for the zonal transmission of data using building lighting fixtures
InactiveUS20060275040A1Breech mechanismsElectric light circuit arrangementCommunications systemEffect light
This invention relates to the zonal transmission of data by optical means through the modulation of light from common building light fixtures, including the light output of fluorescent, mercury vapor, and other arc or discharge lamps and fixtures; a system for the reuse of radio frequencies by smart radios, and the accurate locating and tracking of objects or persons as they move through a building; by means of creating a communications system which exploits the existing infrastructure of a building to facilitate the transmission of relatively secure control and communications data via creation of a multiplicity of area-limited interference-free communication zones. The system facilitates the transmission of wide-area as well as zonal-specific data. The system facilitates the creation of a database that contains present location and history location and movement data of persons and objects as they move through a building.
Owner:CONVERGENCE WIRELESS A CALIFORNIA CORP
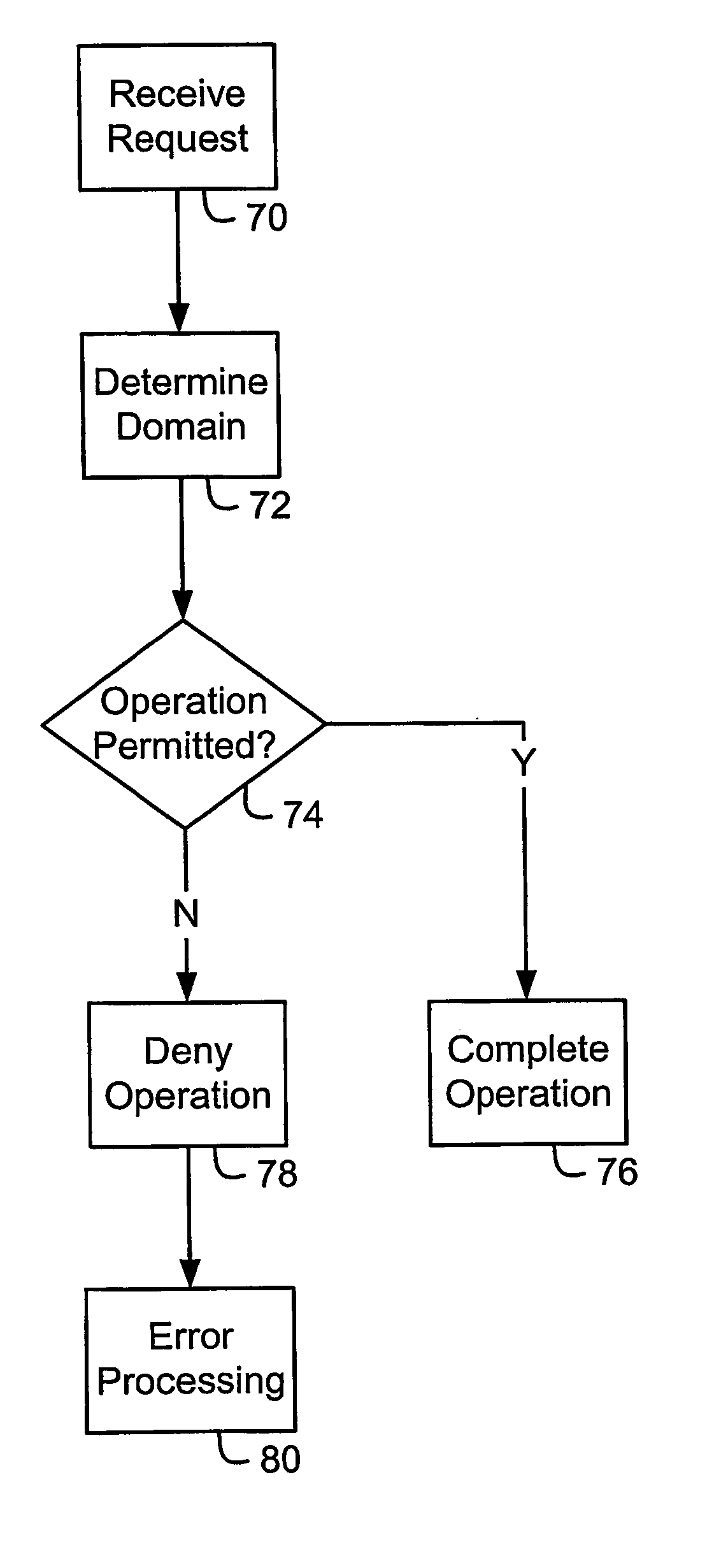
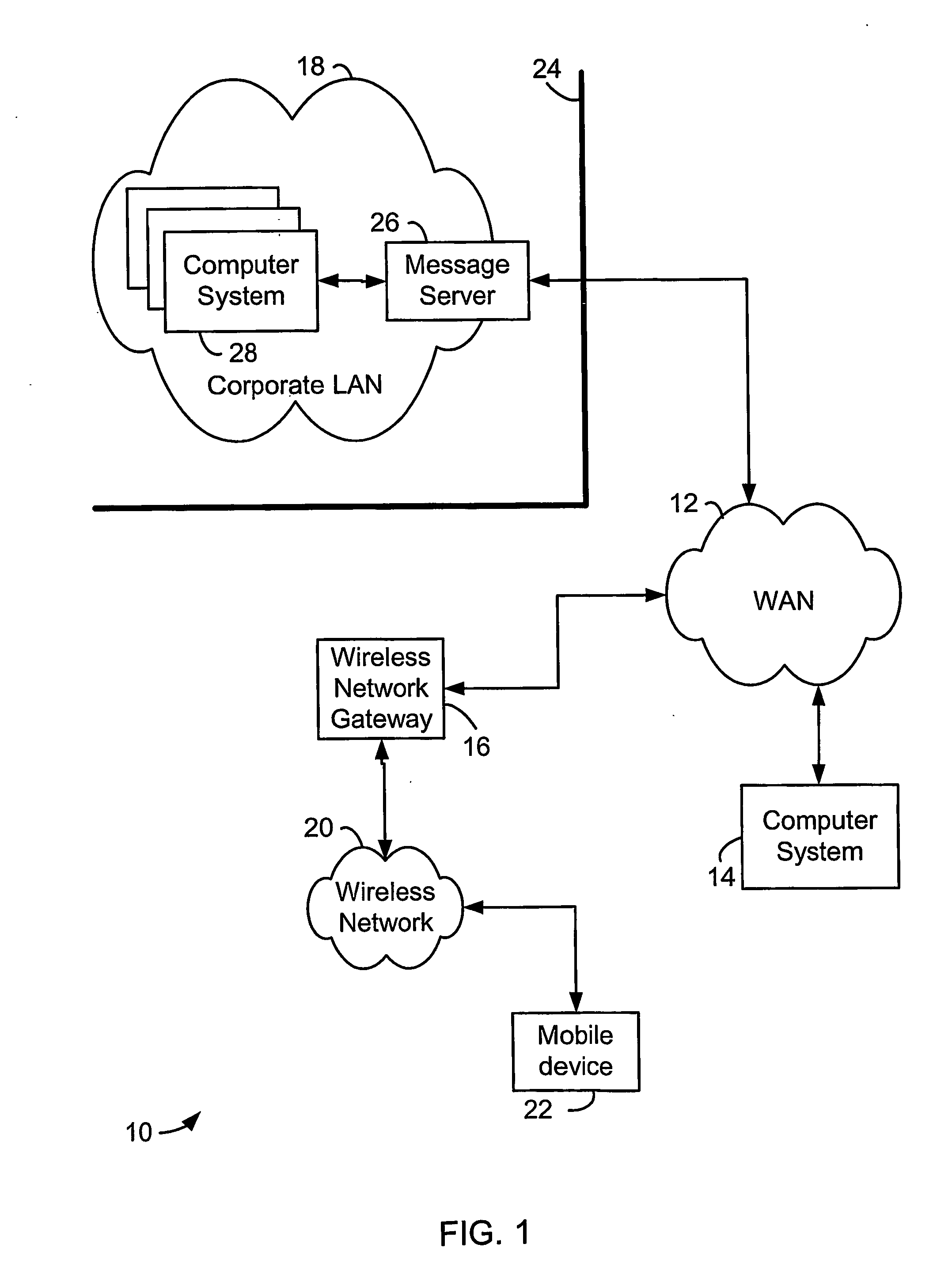
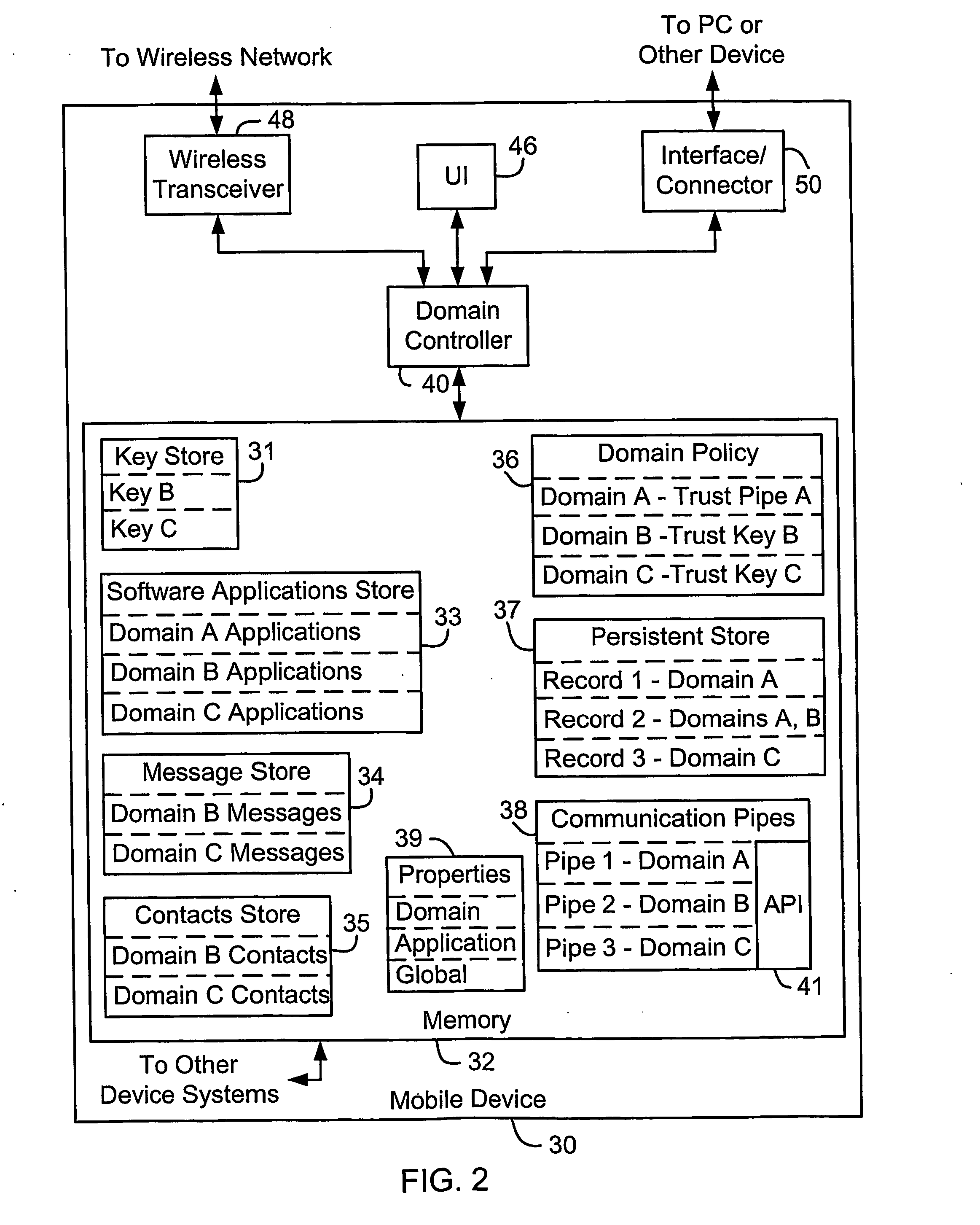
System and method for secure control of resources of wireless mobile communication devices
ActiveUS20050213763A1Digital data processing detailsUser identity/authority verificationTrust relationshipCommunication device
Systems and methods for secure control of a wireless mobile communication device are disclosed. Each of a plurality of domains includes at least one wireless mobile communication device asset. When a request to perform an operation affecting at least one of the assets is received, it is determined whether the request is permitted by the domain that includes the at least one affected asset, by determining whether the entity with which the request originated has a trust relationship with the domain, for example. The operation is completed where it is permitted by the domain. Wireless mobile communication device assets include software applications, persistent data, communication pipes, and configuration data, properties or user or subscriber profiles.
Owner:BLACKBERRY LTD
Automated monitoring and control of safety in a production area
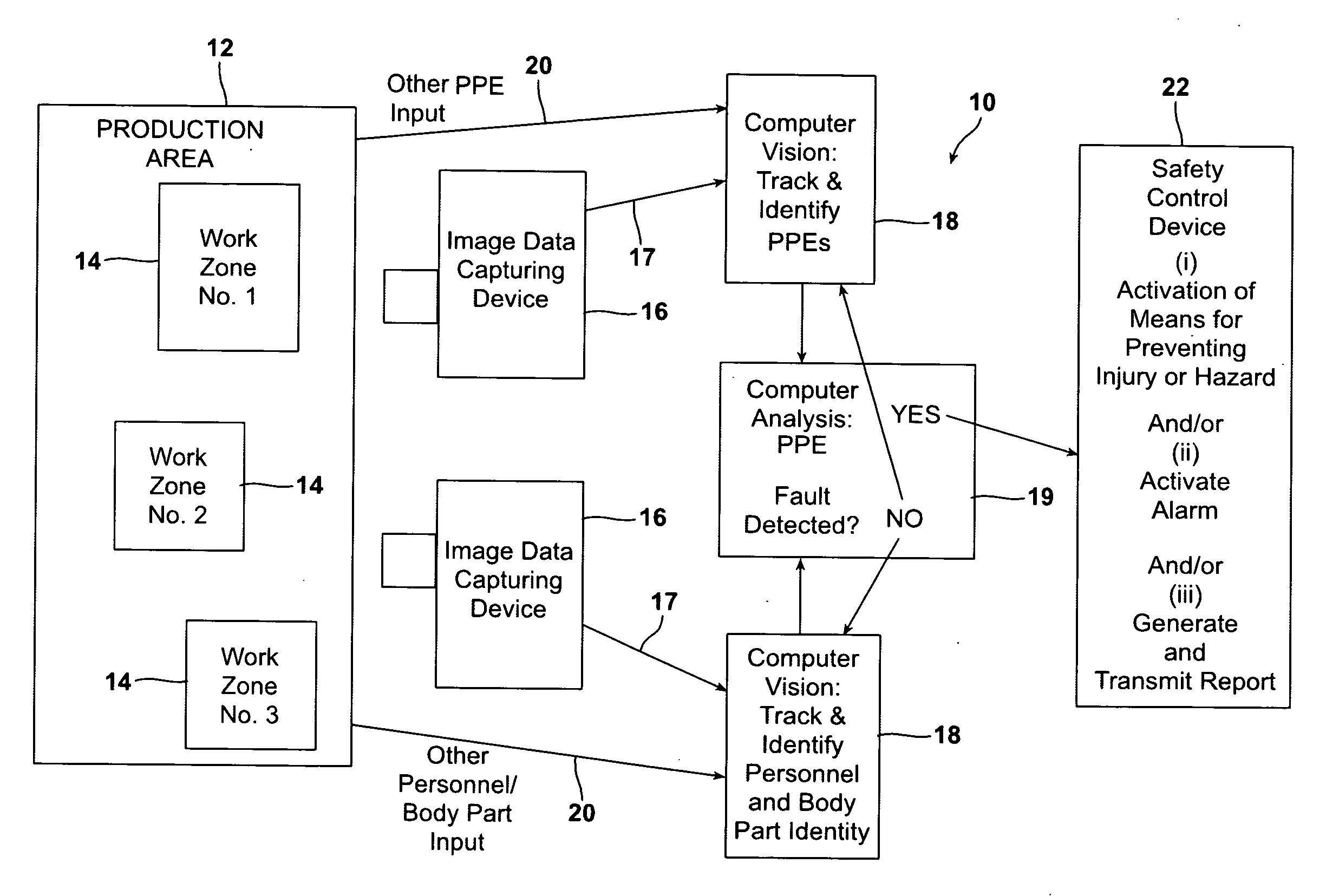
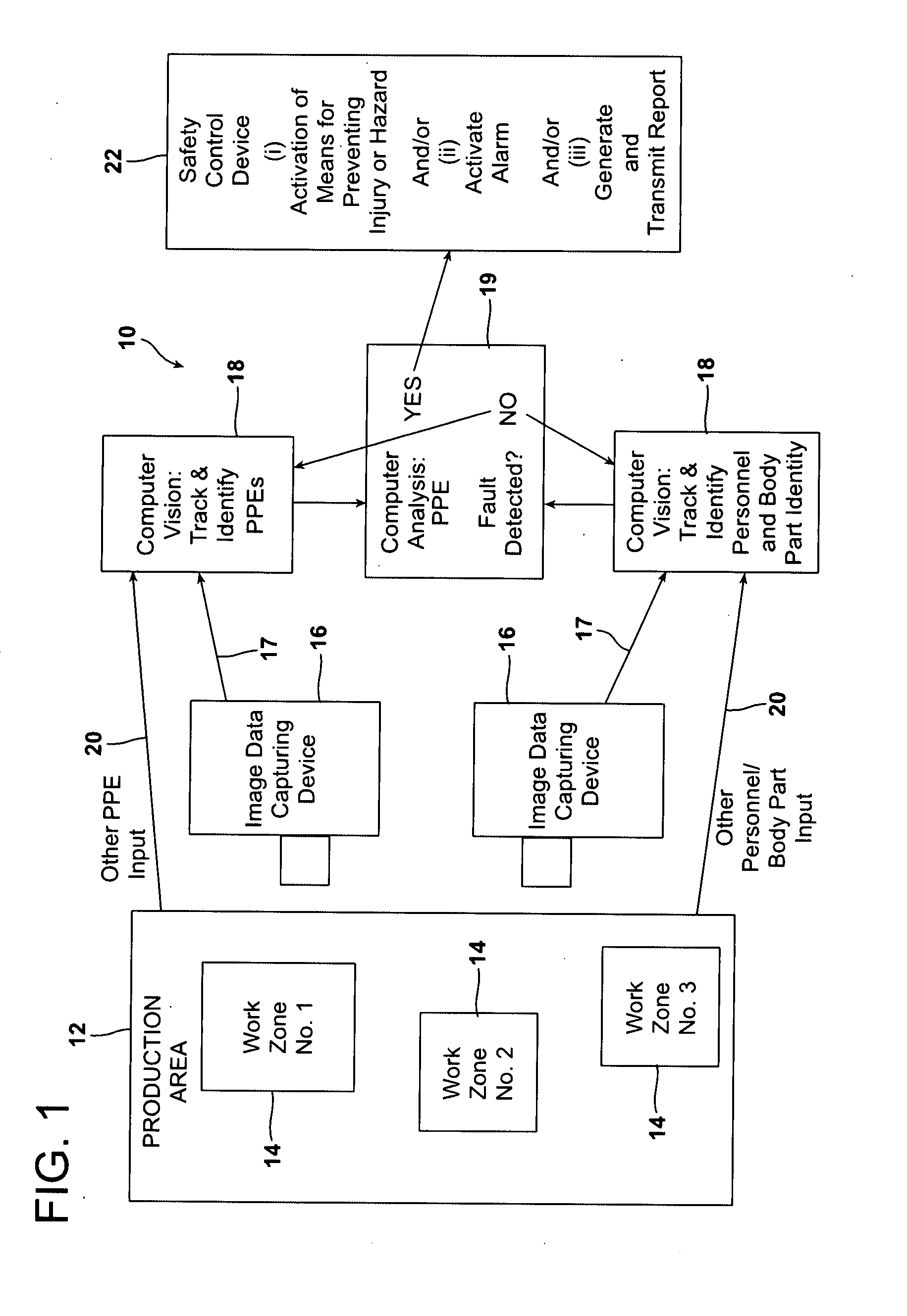
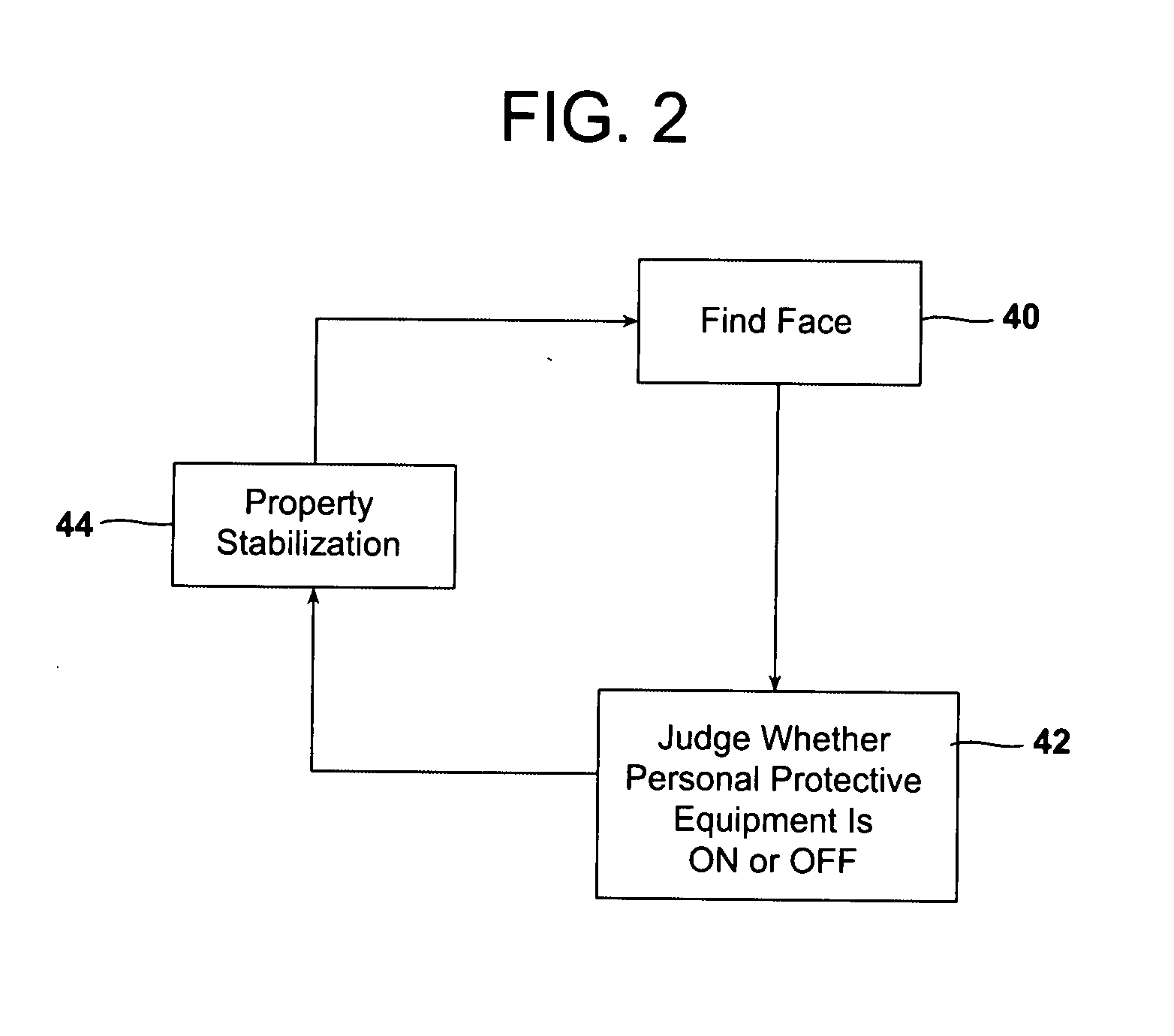
ActiveUS20120146789A1Avoid injuryAvoid damageTelevision system scanning detailsWireless architecture usageMachine visionPersonal protective equipment
A machine vision process monitors and controls safe working practice in a production area by capturing and processing image data relative to personal protective equipment (PPE) worn by individuals, movement of various articles, and movement-related conformations of individuals and other objects in the production area. The data is analyzed to determine whether there is a violation of a predetermined minimum threshold image, movement, or conformation value for a predetermined threshold period of time. The determination of a safety violation triggers computer activation of a safety control device. The process is carried out using a system including an image data capturing device, a computer and computer-readable program code, and a safety control device.
Owner:SEALED AIR U S
Method and apparatus for operating resources under control of a security module or other secure processor
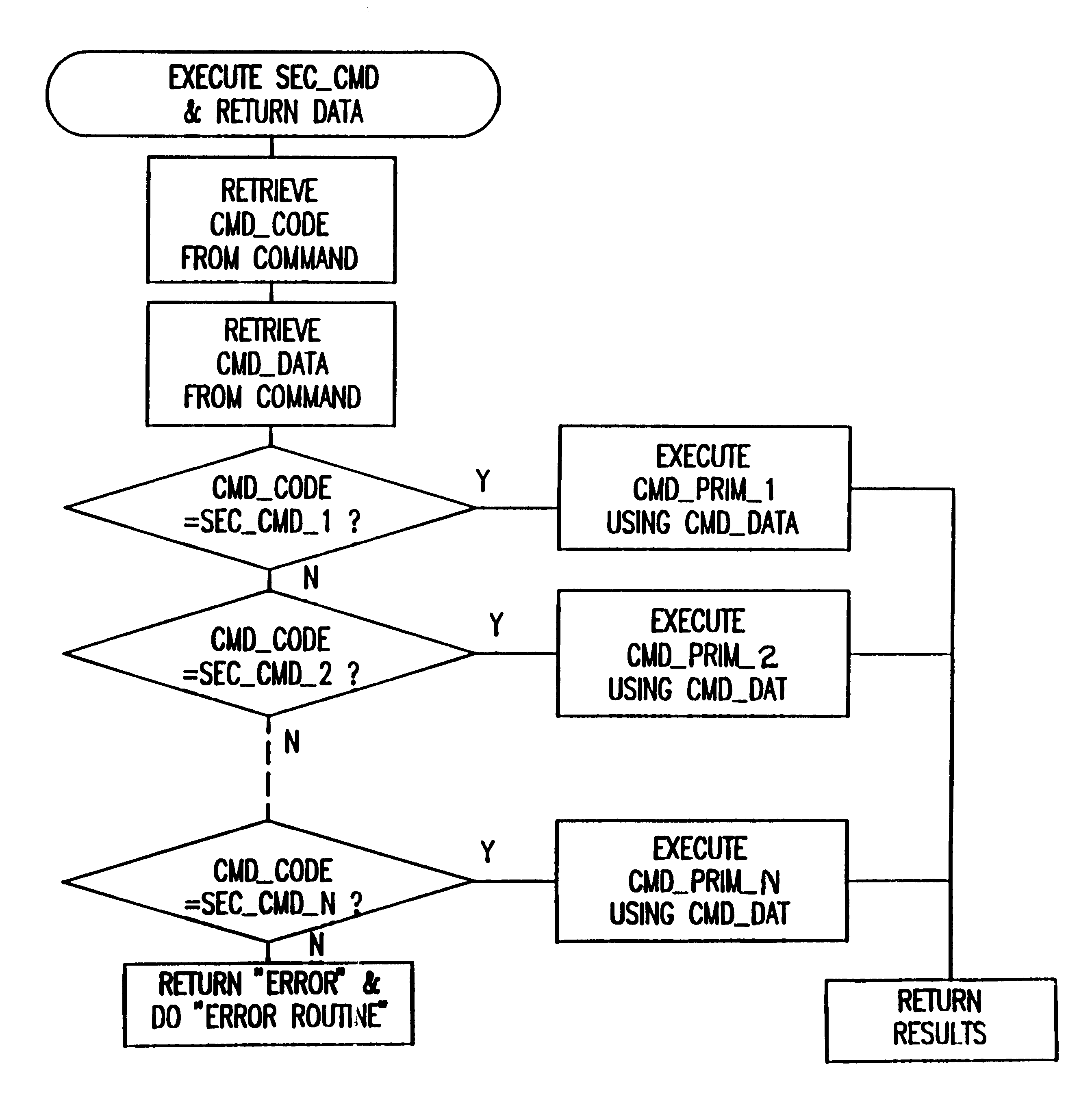
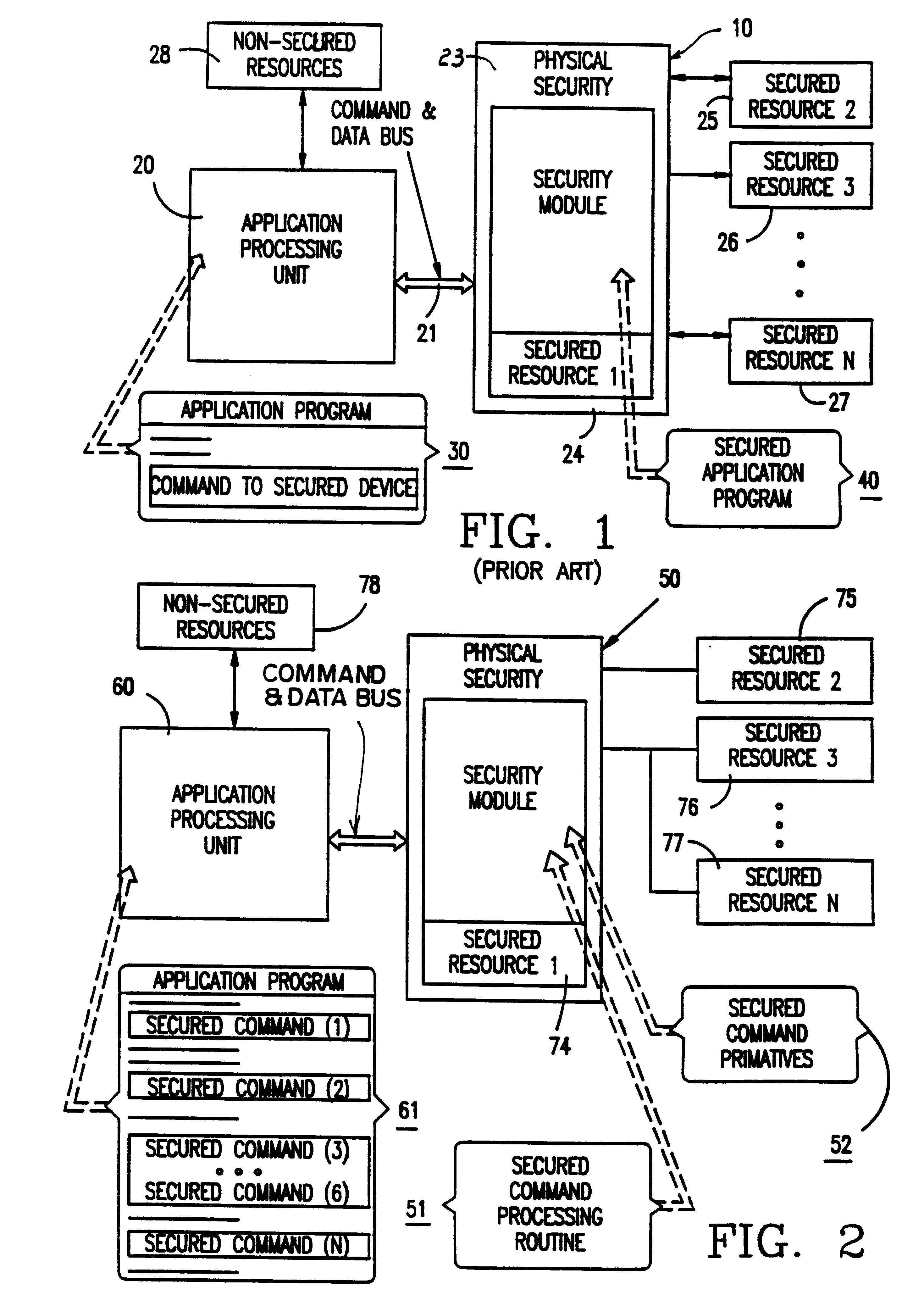
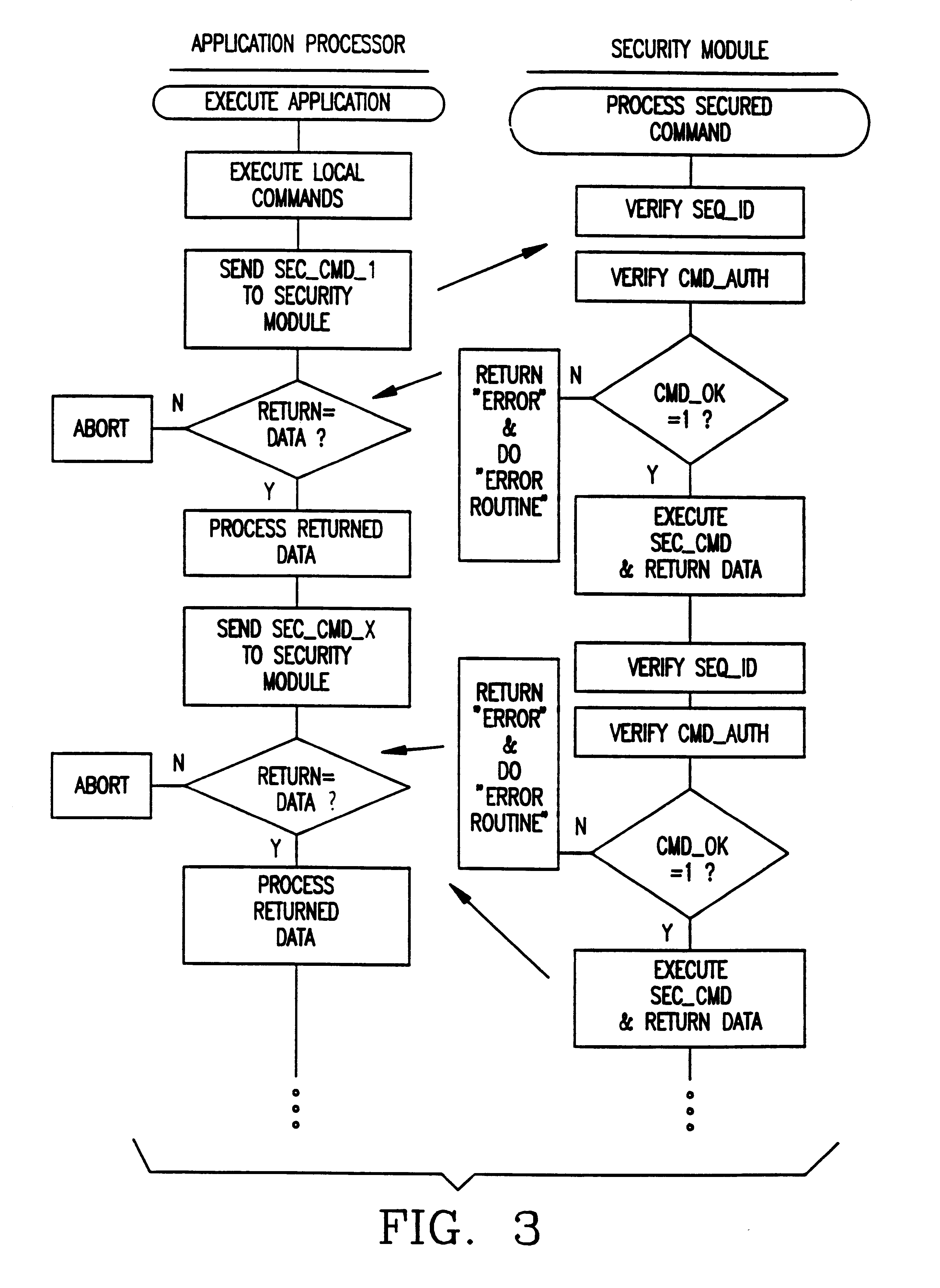
InactiveUS6226749B1Improve operational flexibilityDigital data processing detailsDigital data protectionComputer hardwareSequence ID
A method and apparatus for operating a set of resources under the control of a secure processor, e.g. security module, having a command authentication means and a command execution means, to achieve secure control of the resources. The secure processor stores a set of command primitives for functional control of the resources. A set of defined commands for invoking command primitives has either a secured command format including a command sequence ID, a command code, and a set of command data items or a non-secured command format including a command code and a set of command data items. The secure processor stores a command set up table including command type flags to designate each command as a secured command or a non-secured command. An application program running in an external device includes a plurality of the defined commands in either secured command format or the non-secured command format and these are sent one at a time to the secure processor for execution. The secure processor looks up each received command in the command set up table, and if the command is a non-secured command it immediately executes associated command primitives. If the command is a secured command, the secure processor tests both its authenticity and regularity and only executes the associated command primitives if the command passes both tests.
Owner:HEWLETT PACKARD DEV CO LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com