Patents
Literature
69 results about "Security compliance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
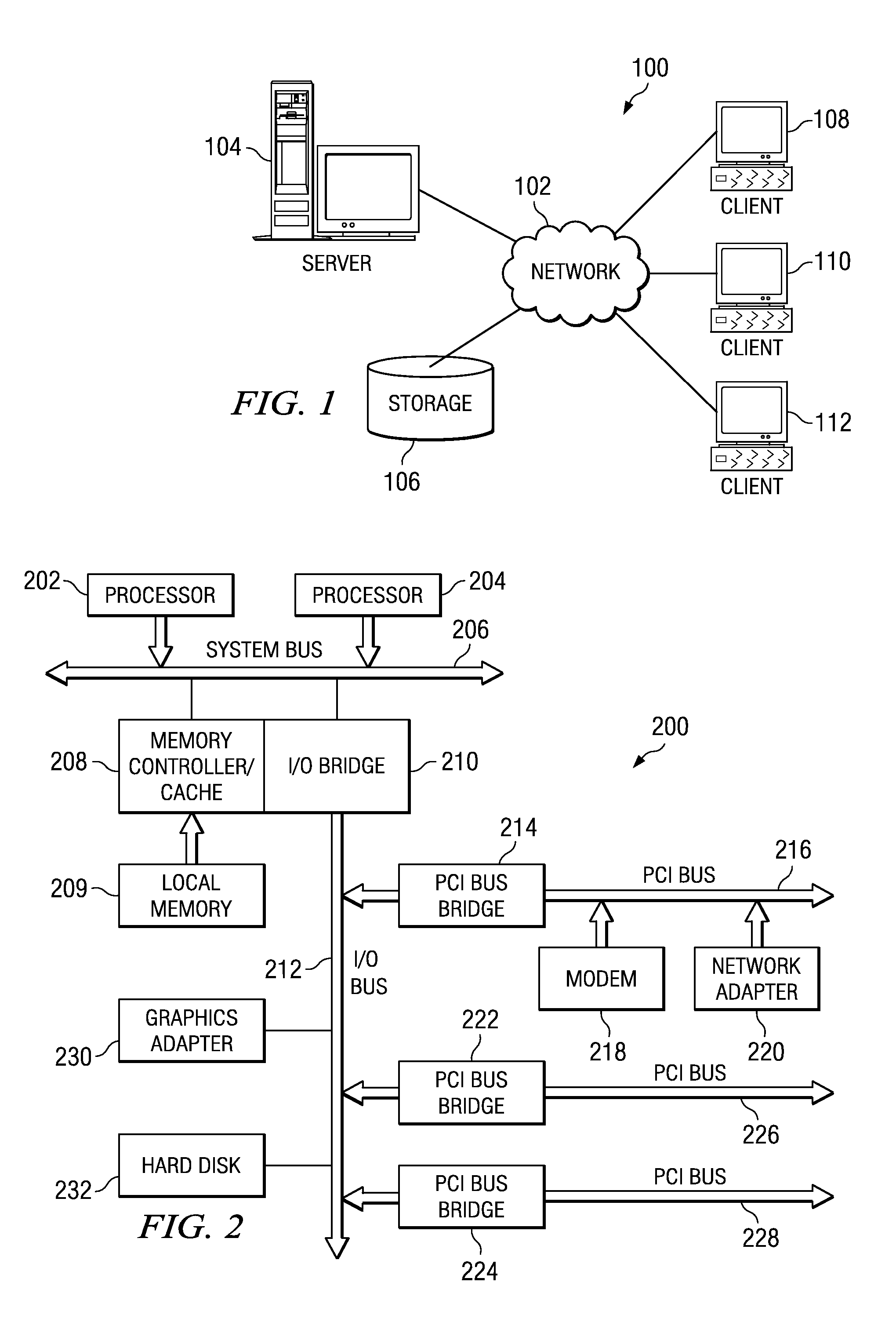
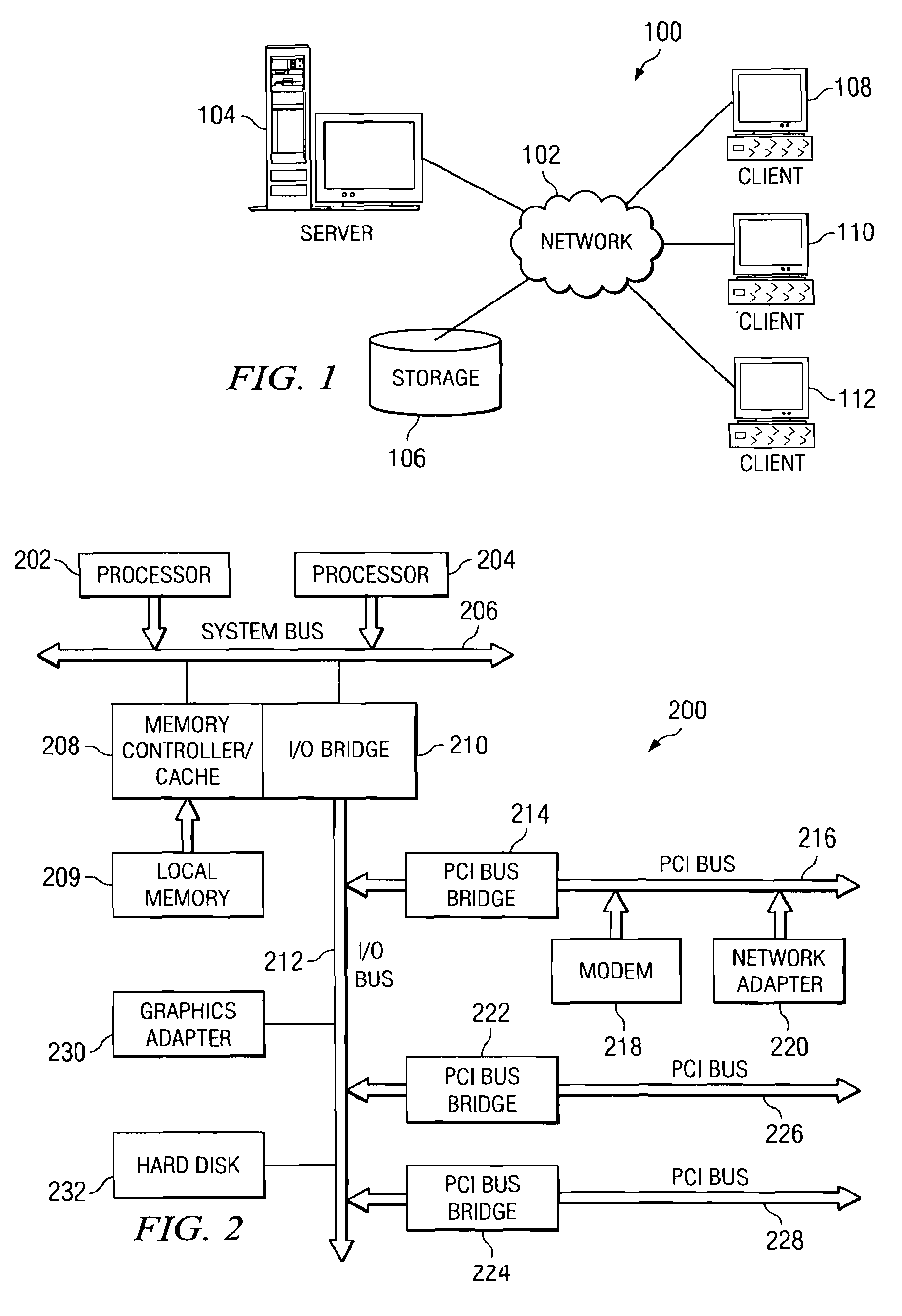
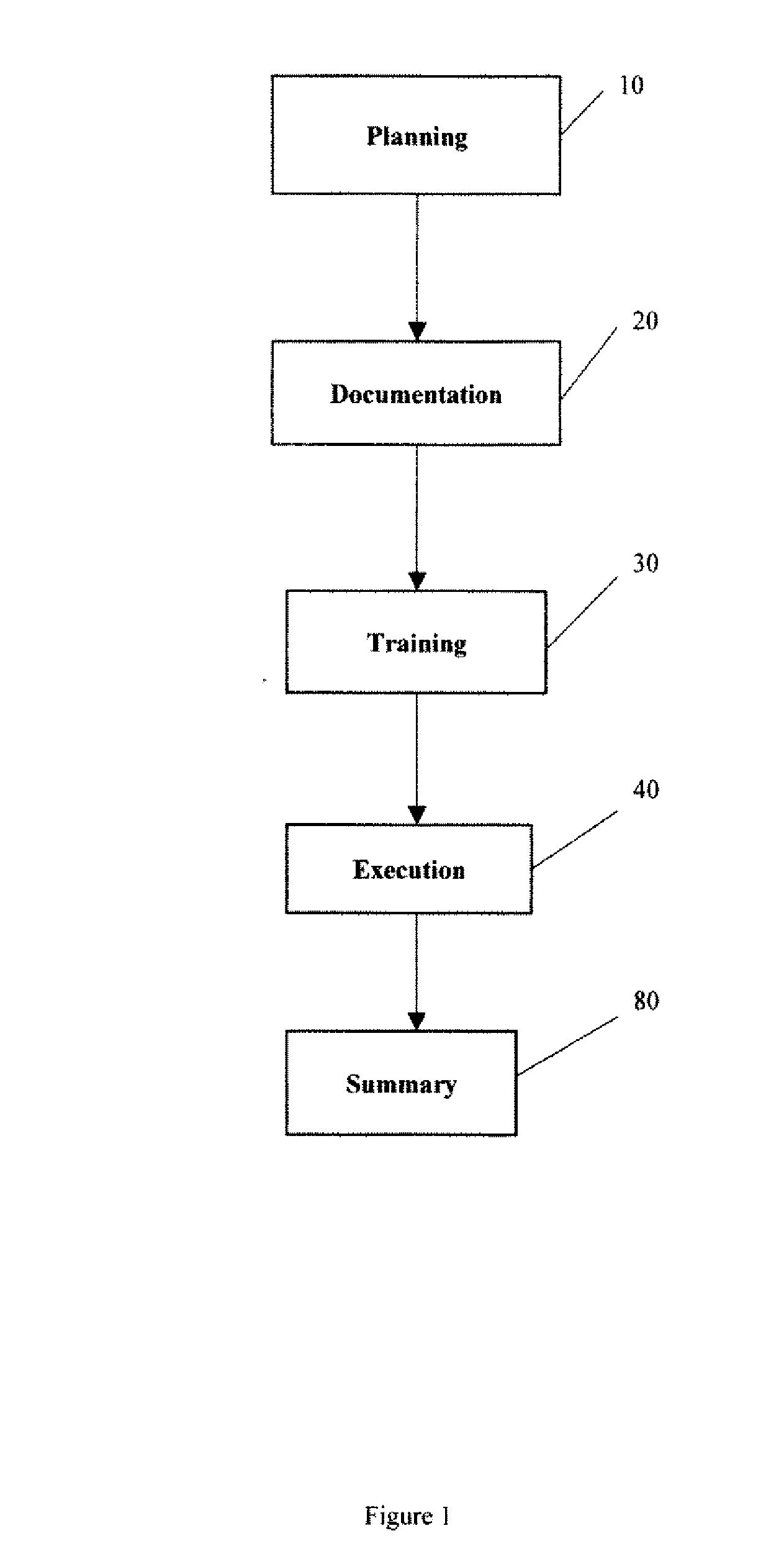
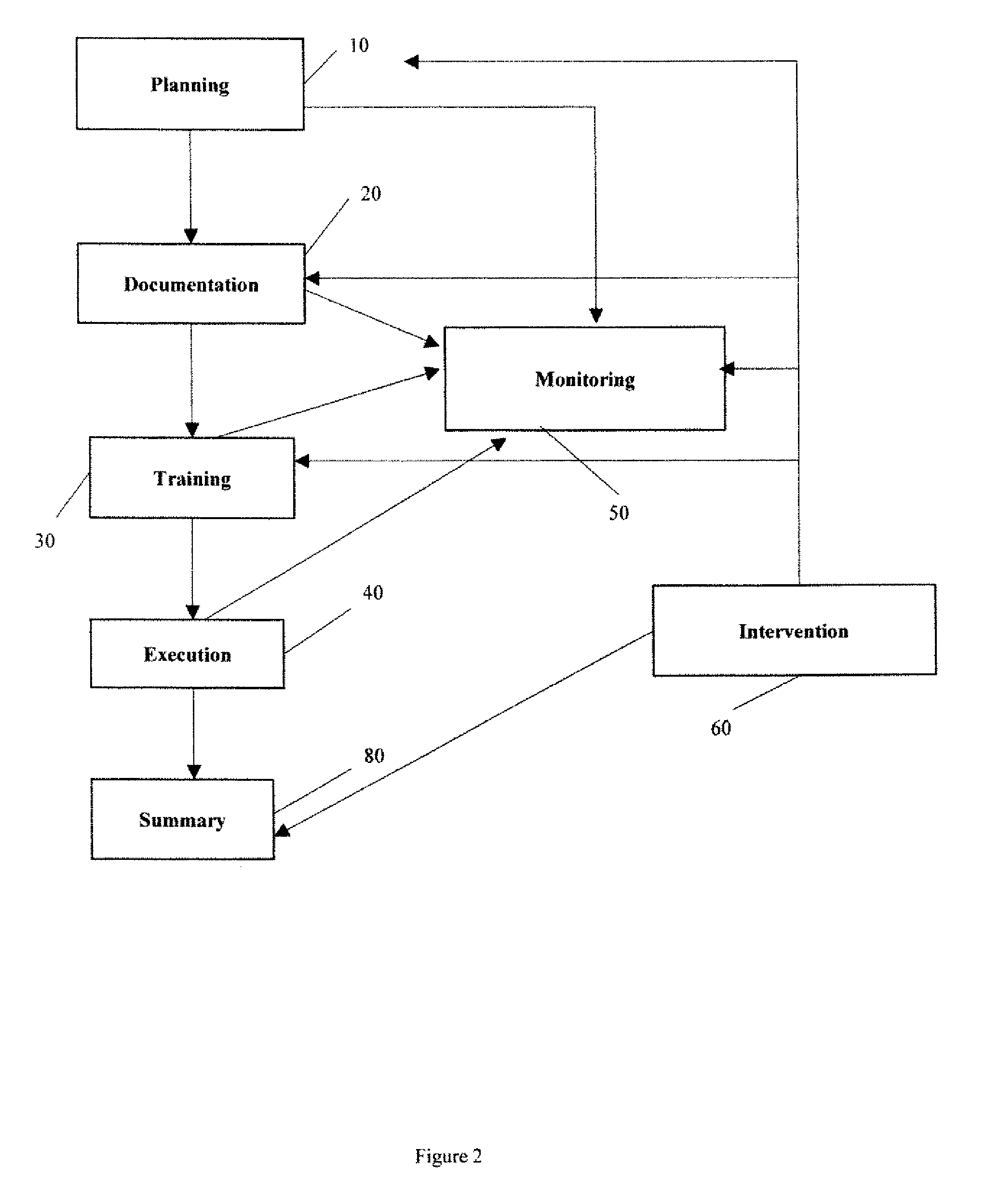
The Security Compliance Manager (SCM) is a free tool from Microsoft that enables you to quickly configure, and manage the computers in your environment using Group Policy and Microsoft System Center Configuration Manager.
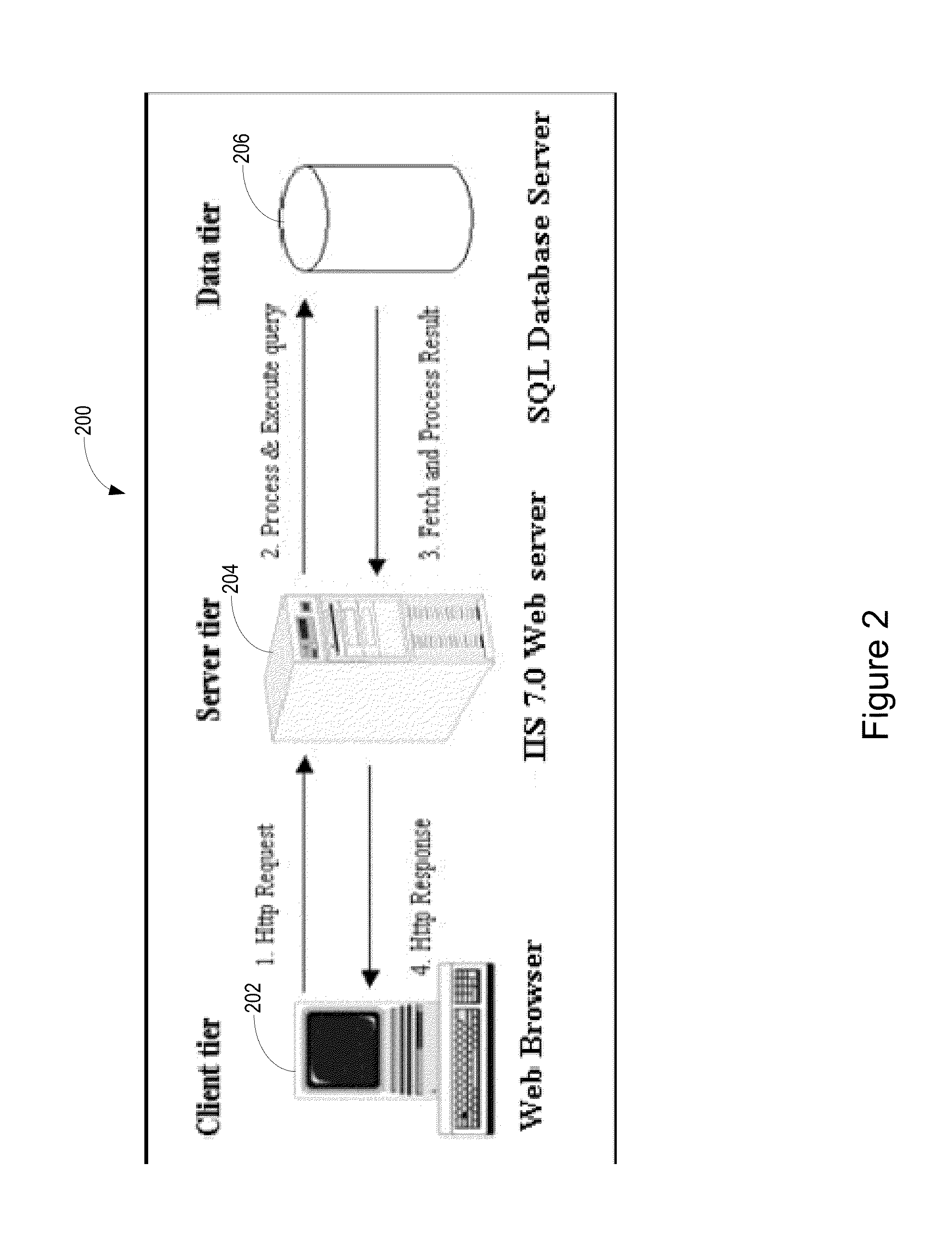
Security Compliance Methodology and Tool
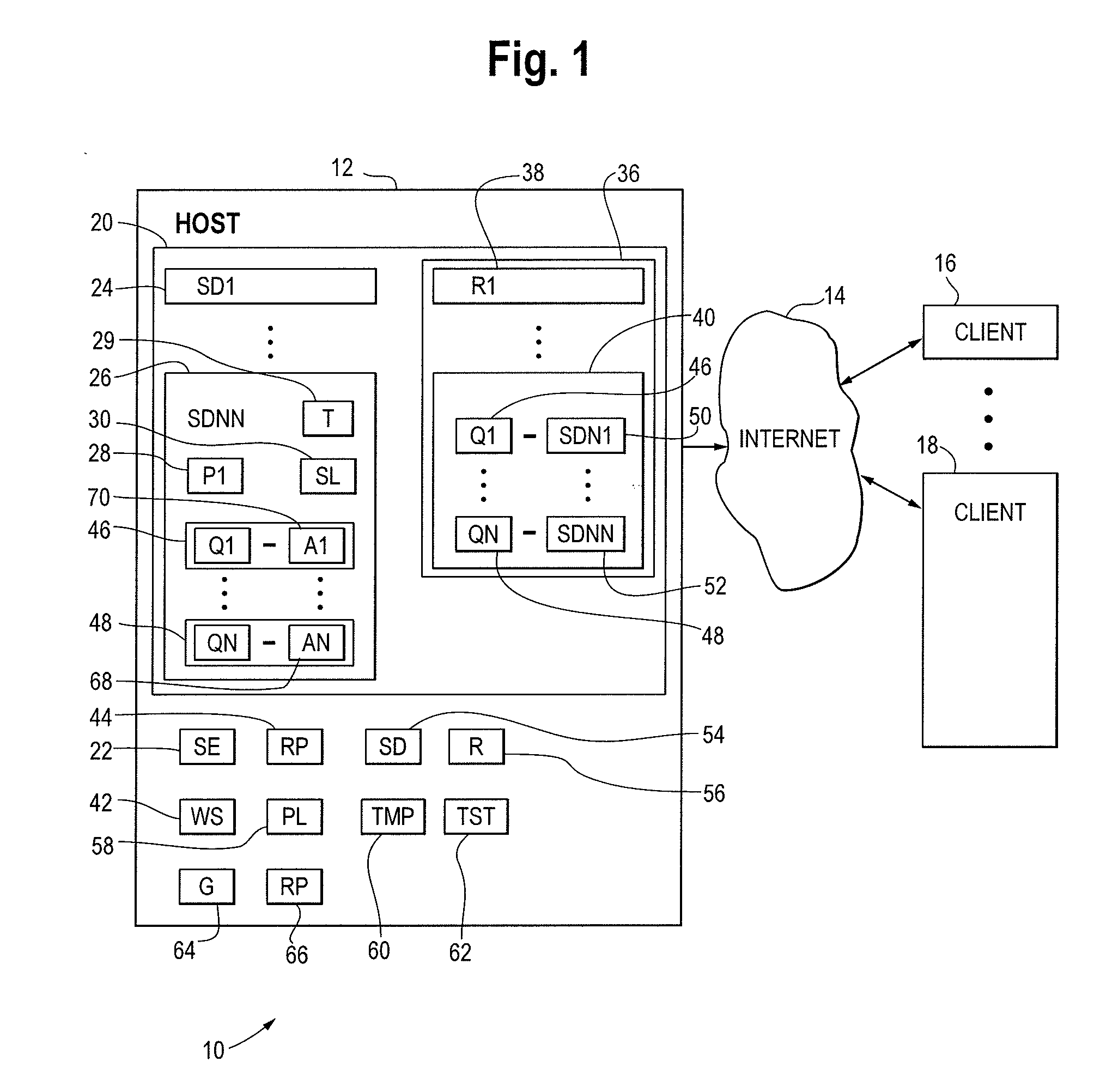
An apparatus is provided for evaluating risk to an organization. The apparatus includes a plurality of governmental rules directed to protecting shareholders, a plurality of security domains of the organization wherein each security domain is associated with a different asset of the organization and a request for an information risk assessment within at least one of the plurality of security domains of the organization formed under the plurality of governmental rules from a set of initializing inputs. The apparatus further includes a information risk assessment plan formed from the request for the information risk assessment, a set of information assessment templates and test cases formed from the information risk assessment plan, a set of information risk assessment tests conducted on the IT system using the assessment templates and test cases, a set of test results generated by the risk assessment tests, one or more security control gaps identified by the assessment responses and one or more gap remediation plans formed from the identified security gaps.
Owner:DENOVO ANDREW +1
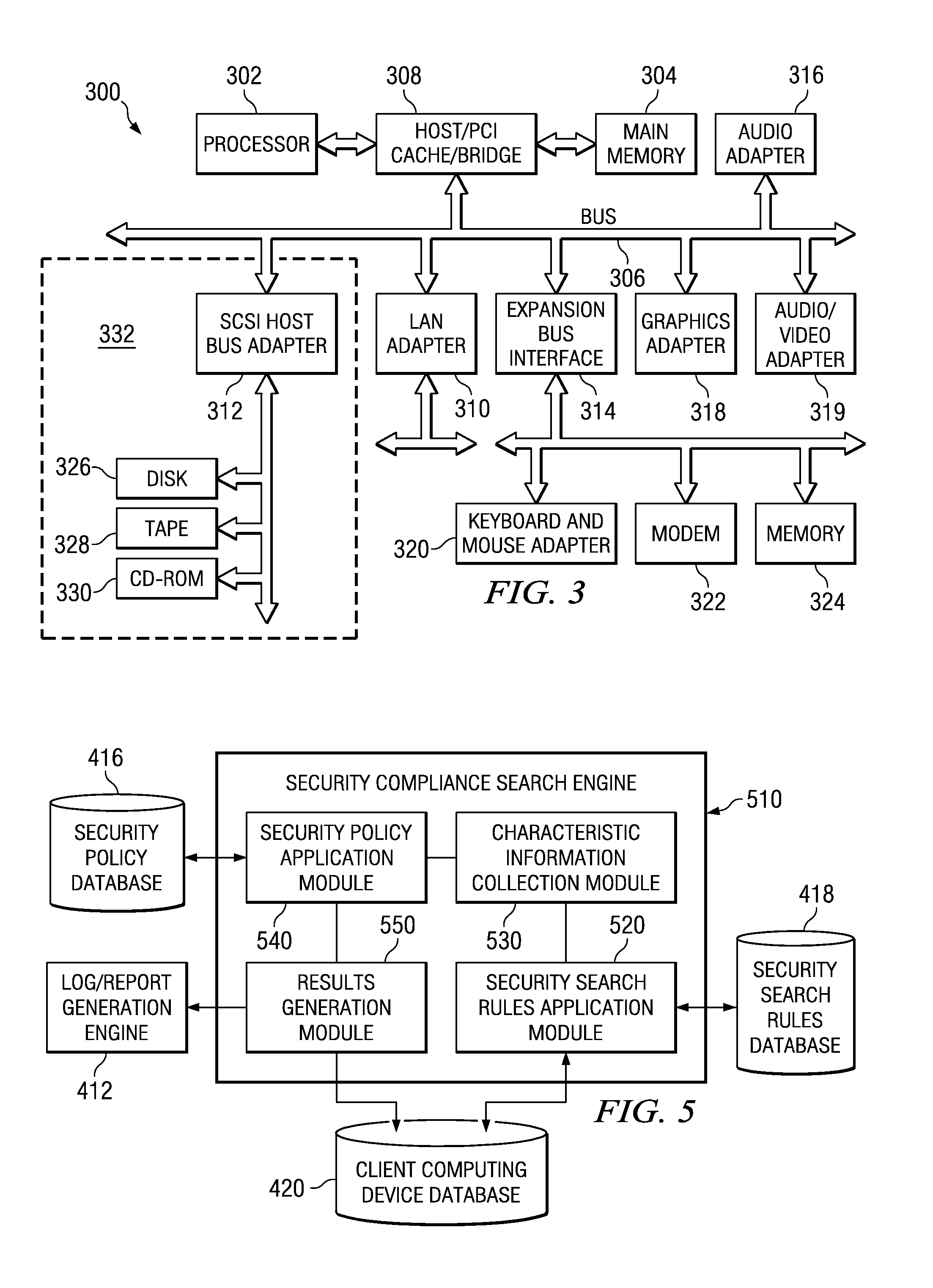
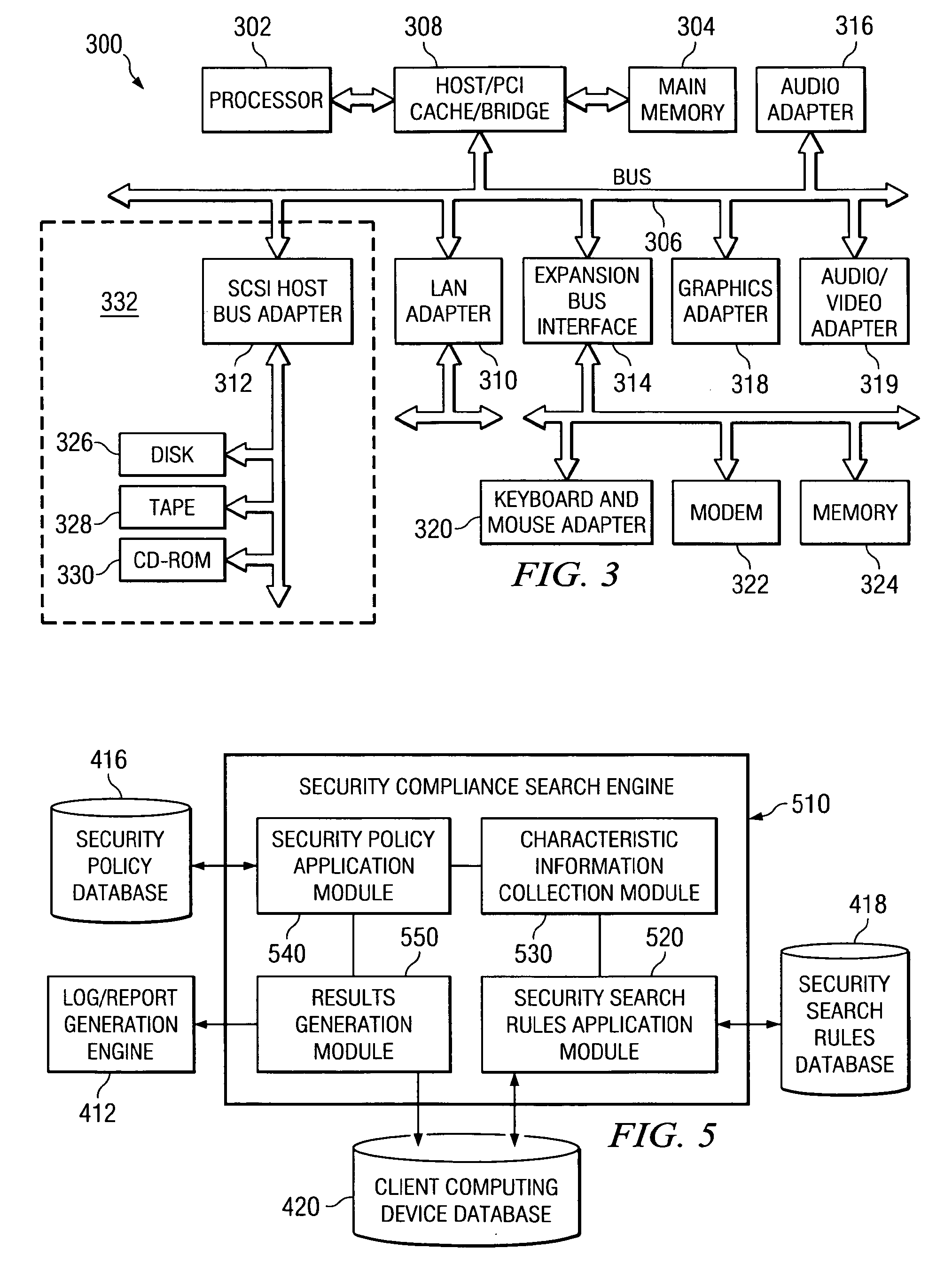
Confidential content reporting system and method with electronic mail verification functionality
InactiveUS20070261099A1Ensure complianceSpecial data processing applicationsSecuring communicationGraphicsGraphical user interface
A confidential content reporting system and method with electronic mail verification functionality are provided. With the system and method, a security compliance search engine is provided for searching items of information to identify items containing confidential content and security violations with regard to this confidential content. Results of the search may be reported to a user via a graphical user interface (GUI) that identifies the item of information, the security violations detected, and suggested corrective actions, such as encryption. A user may interact with the GUI to apply security mechanisms in accordance with the suggested corrective actions. Moreover, the searching and reporting mechanism may be used to search electronic mail messages and their attachments prior to distribution of the electronic mail messages. Automatic modification of the electronic mail message to modify distribution lists and / or content of the electronic mail message may be performed using the mechanisms of the illustrative embodiments.
Owner:IBM CORP
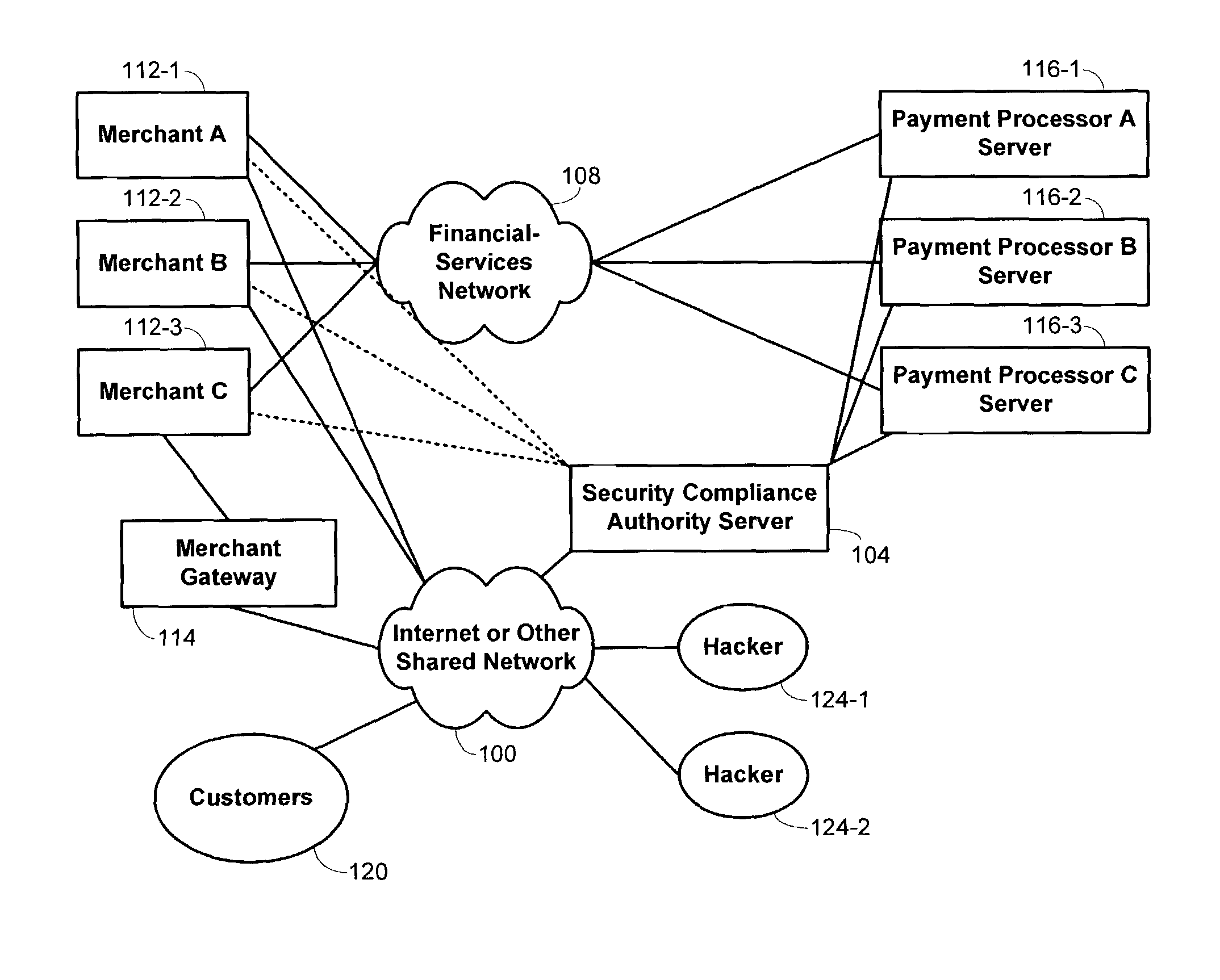
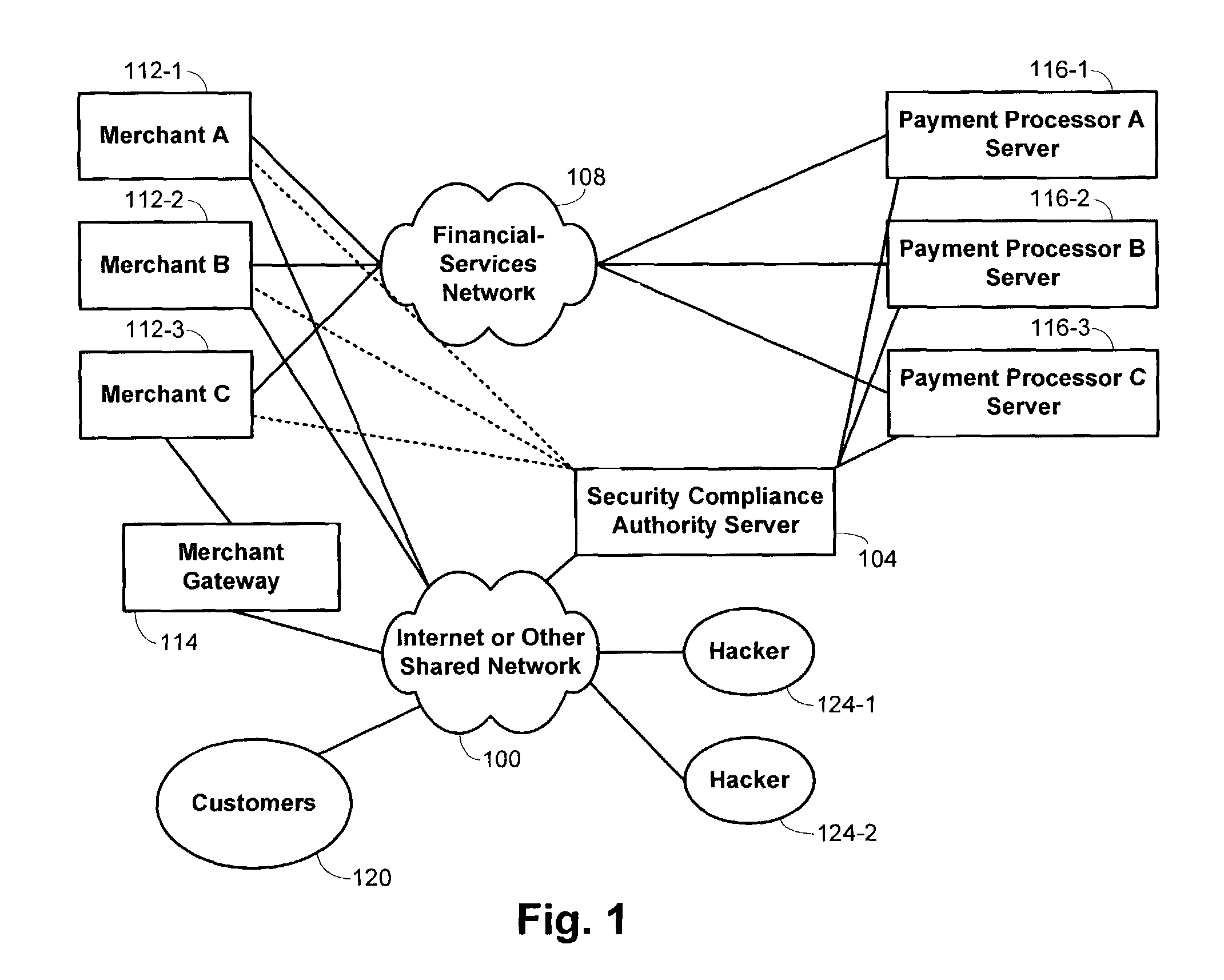
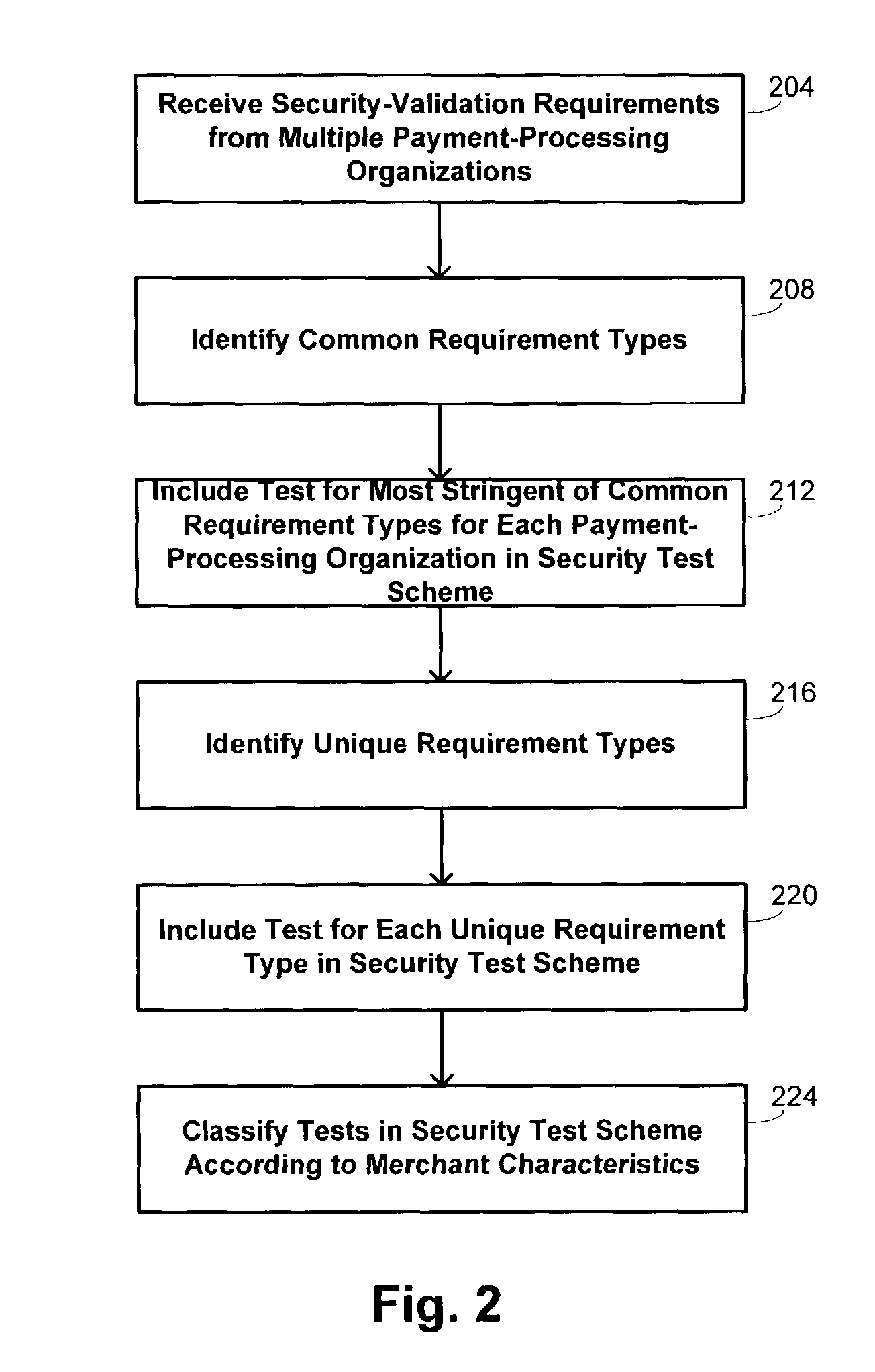
Methods and systems for performing security risk assessments of internet merchant entities
ActiveUS7930753B2Simplify complianceDigital data processing detailsAnalogue secracy/subscription systemsPaymentSecurity compliance
Methods and systems are provided for assessing a security risk for a merchant entity having connectivity to a shared network. Information describing characteristics of the merchant entity are received from the merchant entity. A determination is made which test requirements of a security test scheme are to be used in assessing the security risk for the merchant entity. The security test scheme includes a set of test requirements whose satisfaction by the merchant entity is sufficient to ensure compliance with a multiple sets of security requirements defined by multiple payment-processing organizations. The security test scheme is executed with a security compliance authority server in accordance with the determined test requirements.
Owner:FIRST DATA
Confidential Content Reporting System and Method with Electronic Mail Verification Functionality
InactiveUS20080235760A1Knowledge representationSpecial data processing applicationsGraphicsGraphical user interface
A confidential content reporting system and method with electronic mail verification functionality are provided. With the system and method, a security compliance search engine is provided for searching items of information to identify items containing confidential content and security violations with regard to this confidential content. Results of the search may be reported to a user via a graphical user interface (GUI) that identifies the item of information, the security violations detected, and suggested corrective actions, such as encryption. A user may interact with the GUI to apply security mechanisms in accordance with the suggested corrective actions. Moreover, the searching and reporting mechanism may be used to search electronic mail messages and their attachments prior to distribution of the electronic mail messages. Automatic modification of the electronic mail message to modify distribution lists and / or content of the electronic mail message may be performed using the mechanisms of the illustrative embodiments.
Owner:INT BUSINESS MASCH CORP
Method of assuring enterprise security standards compliance
ActiveUS20060156408A1Random number generatorsUser identity/authority verificationRisk impactSecurity compliance
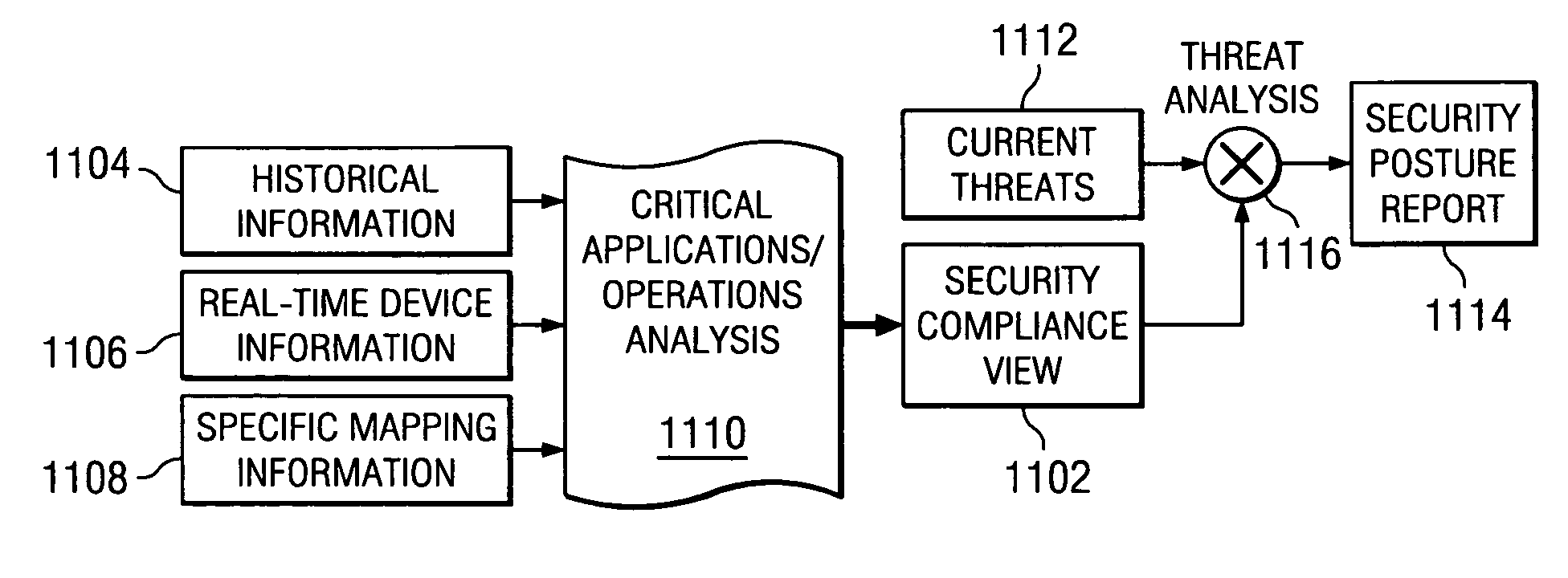
A method, apparatus, and computer instructions for providing a current and complete security compliance view of an enterprise system. The present invention provides the ability to gain a real-time security posture and security compliance view of an enterprise and to assess the risk impact of known threats and attacks to continued business operations at various levels is provided. Responsive to a change to an enterprise environment, a request, or an external threat, an administrator loads or updates at least one of a Critical Application Operations database, a Historical database, an Access Control database, a Connectivity database, and a Threat database. Based on a comparison of information in the databases against similar security data elements from company or external policies, the administrator may generate a Security Compliance view of the enterprise. A Security Posture view may also be generated by comparing the Security Compliance view against data in the Threat database.
Owner:TWITTER INC
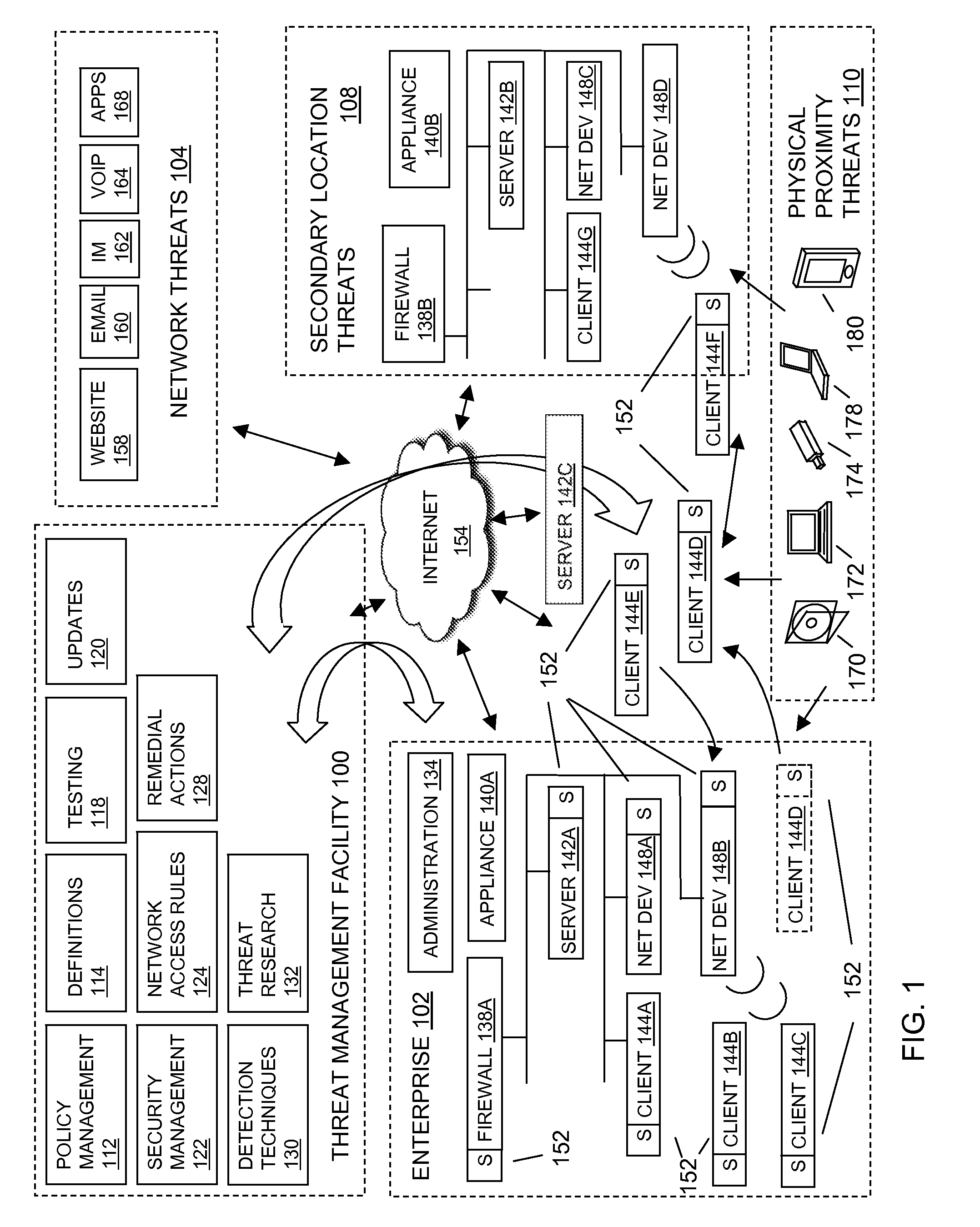
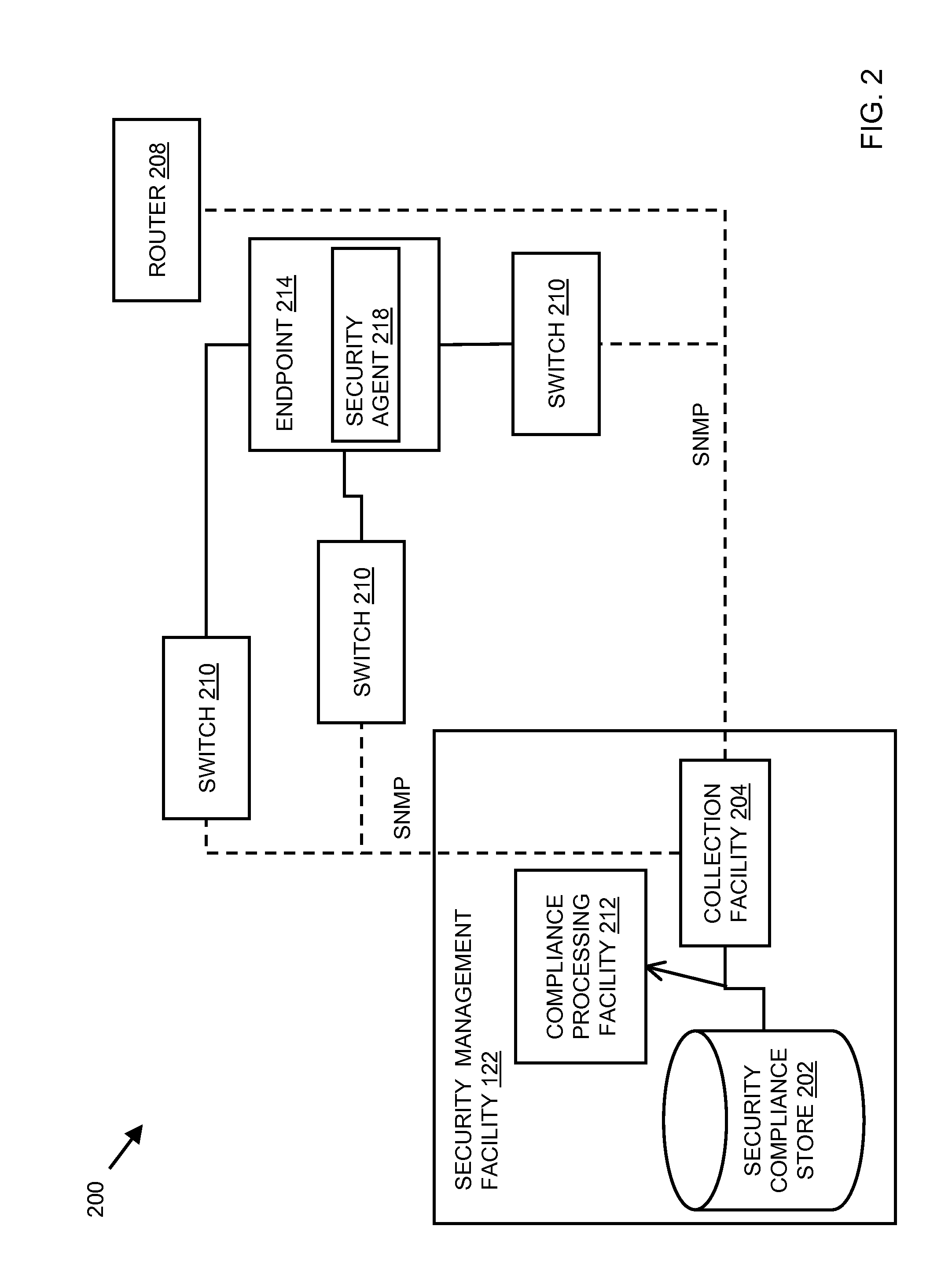
System and method for identifying unauthorized endpoints
ActiveUS8479267B2Digital data processing detailsUser identity/authority verificationSecurity complianceRemedial action
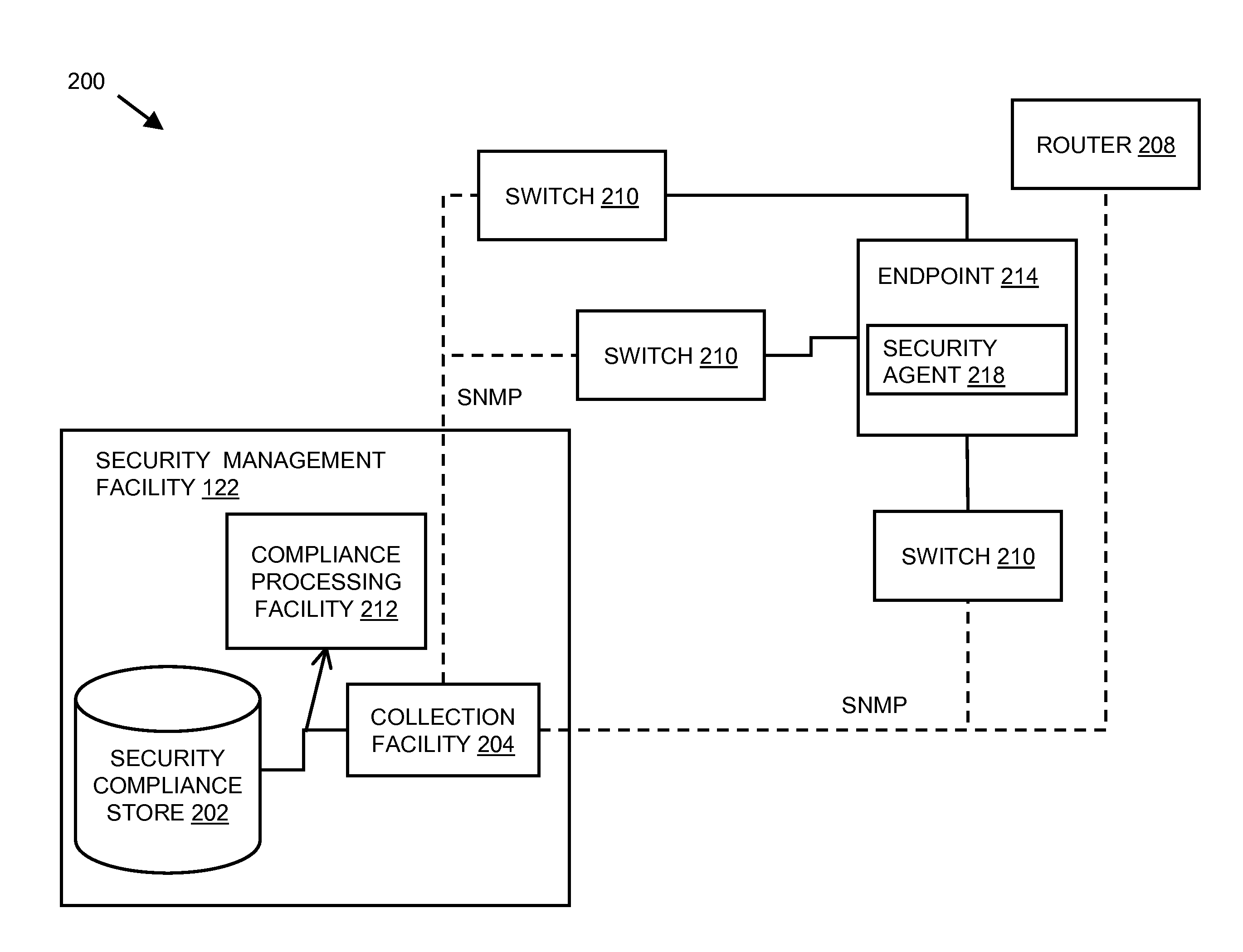
In embodiments of the present invention improved capabilities are described for identifying unauthorized endpoints. The present invention includes computer implemented methods and systems for actively polling and monitoring network devices, such as network routers and switches, to obtain information on any or all of the endpoints on a network with which the router or switch may have communicated. Address information acquired through polling is compared with an authorized endpoint list, which is generated from information reported to the store by security agents on the authorized endpoints and which is stored in a security compliance store, in order to identify unauthorized endpoints. Methods and systems disclosed herein also include remediation measures to be taken on the unauthorized endpoints. Related user interfaces, applications, and computer program products are disclosed.
Owner:SOPHOS
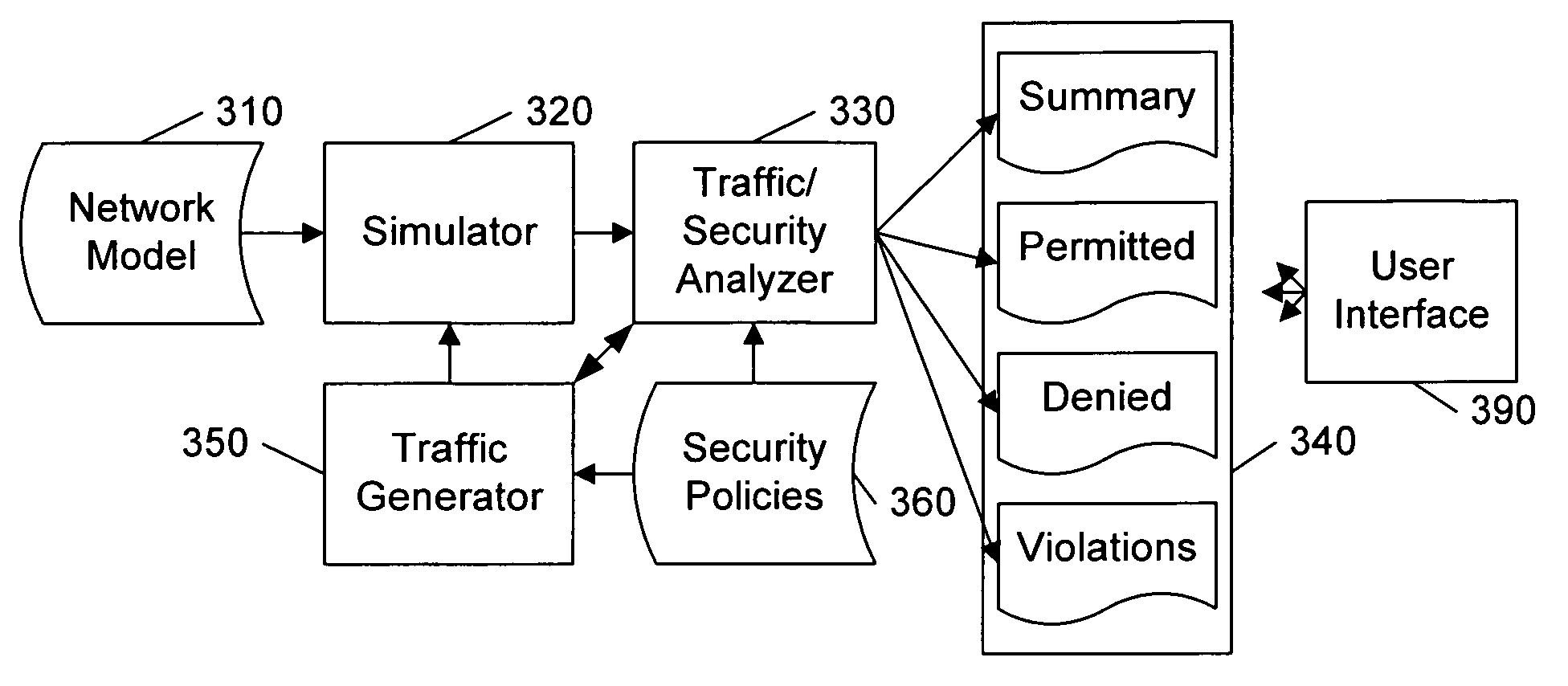
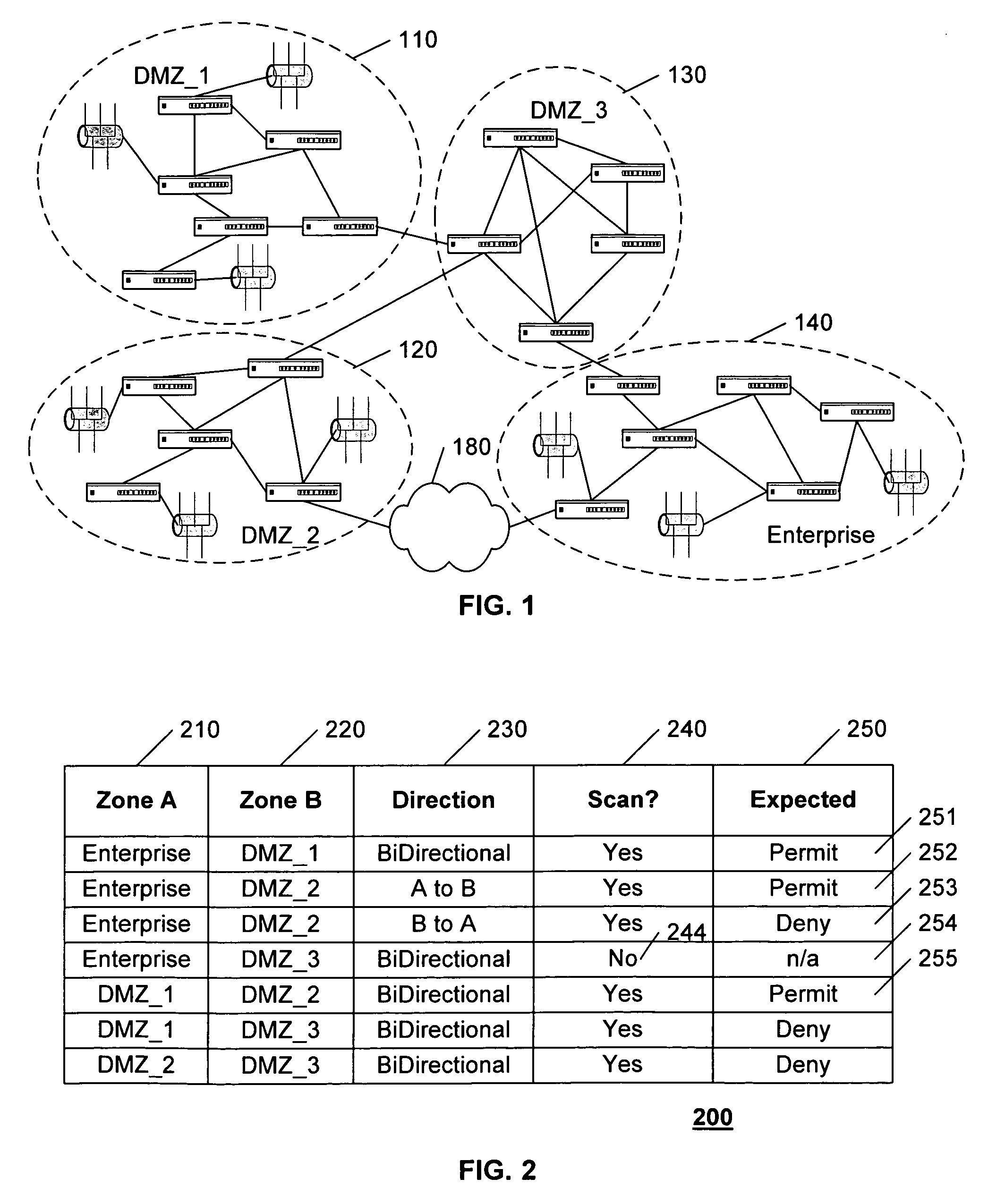
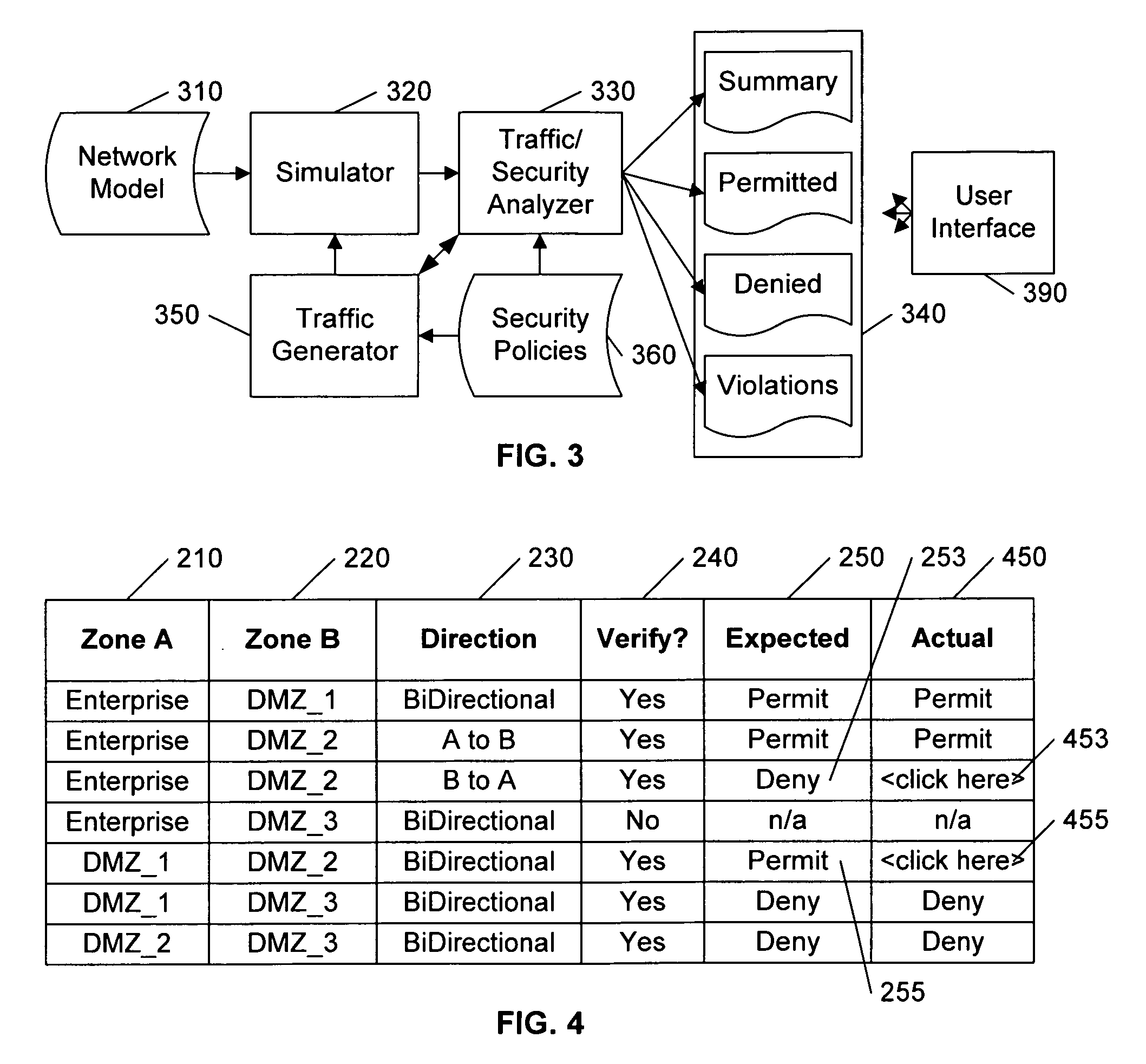
Analyzing security compliance within a network
ActiveUS20070157286A1Data switching networksSpecial data processing applicationsTraffic capacitySecurity compliance
A security policy database identifies the intended security policies within a network, a traffic generator provides test traffic that is configured to test each defined security policy, and a simulator simulates the propagation of this traffic on a model of the network. The model of the network includes the configuration data associated with each device, and thus, if devices are properly configured to enforce the intended security policies, the success / failure of the simulated test traffic will conform to the intended permit / deny policy of each connection. Differences between the simulated message propagation and the intended security policies are reported to the user, and diagnostic tools are provided to facilitate identification of the device configuration data that accounts for the observed difference. Additionally, if a network's current security policy is unknown, test traffic is generated to reveal the actual policy in effect, to construct a baseline intended security policy.
Owner:RIVERBED TECH LLC
DHCP centric network access management through network device access control lists
InactiveUS20090217346A1Improved security situationEasy to operateDigital data processing detailsComputer security arrangementsSecurity complianceSecure state
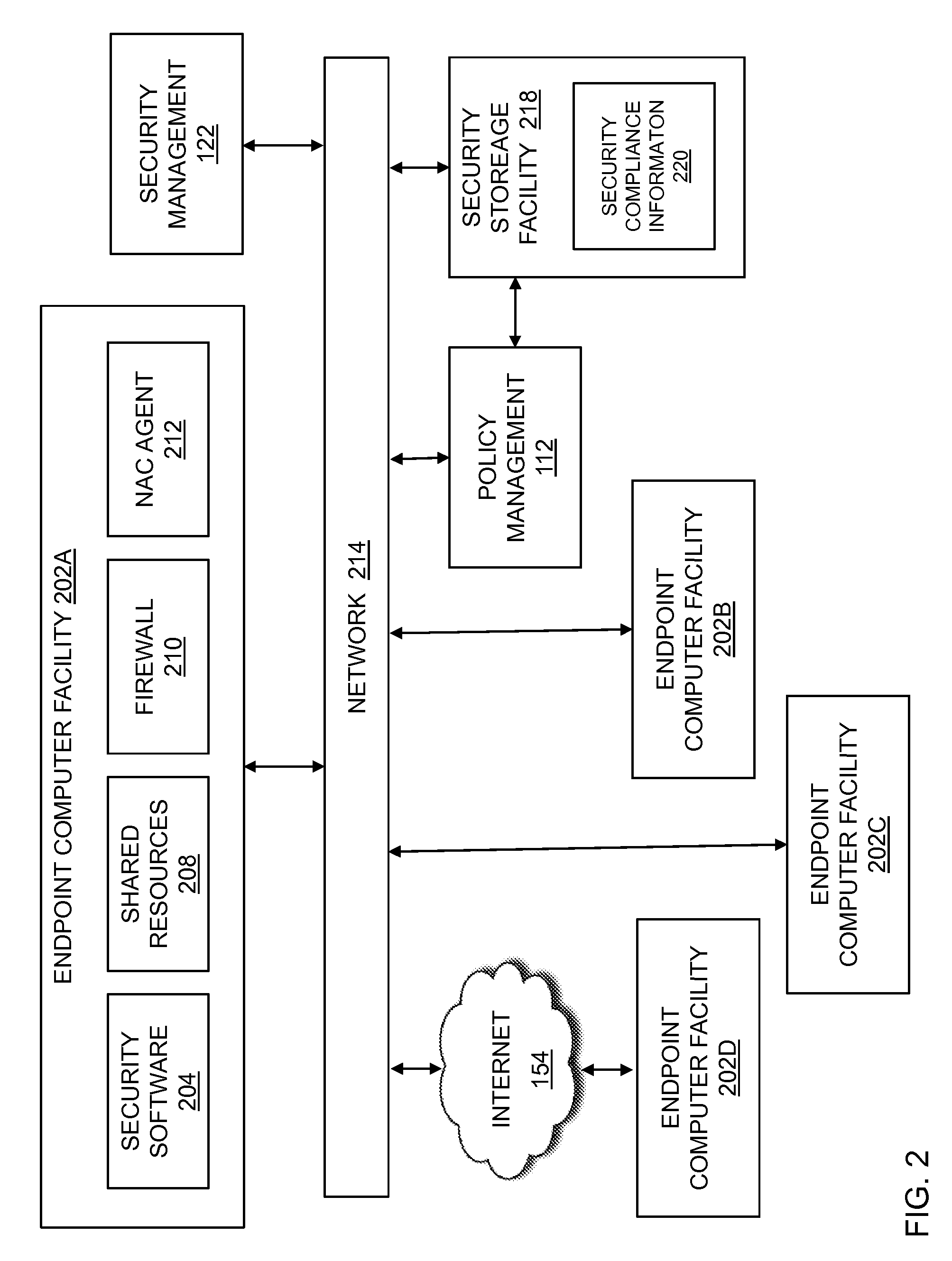
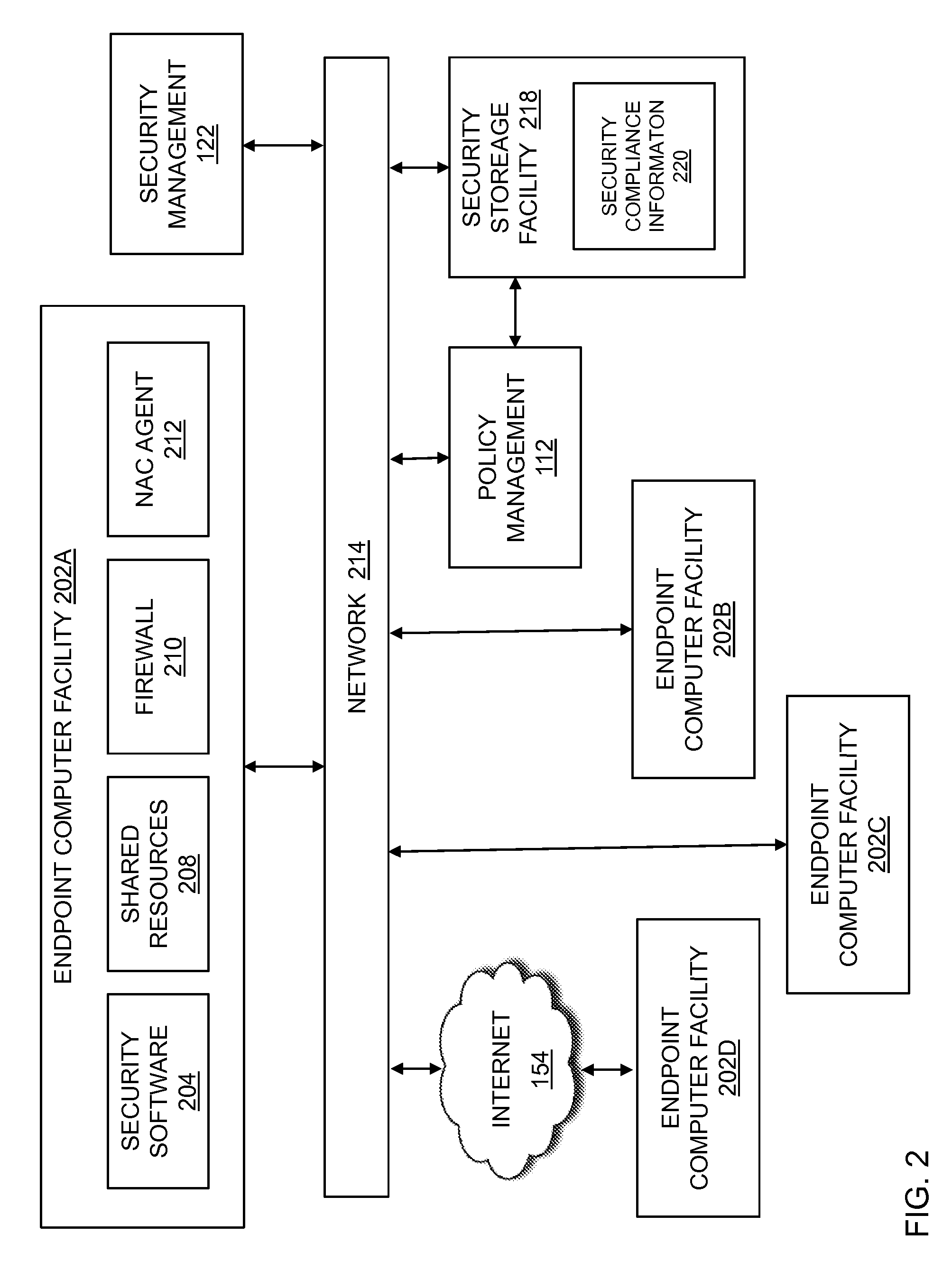
In embodiments of the present invention improved capabilities are described for the computer program product steps of serving a limited network connection to an endpoint computing facility via network device access control lists, where the limited network connection may enable the endpoint to communicate with a limited set of network resources; assessing security compliance information relating to the endpoint to determine a security state; and in response to receiving an indication that the security compliance information is acceptable, serving a managed network connection to the endpoint, where the managed connection may enable the endpoint to communicate with a larger set of network resources than the limited network connection.
Owner:SOPHOS
Protected access control method for shared computer resources
ActiveUS20100205657A1Improve protectionImprove integrityMemory loss protectionError detection/correctionComputer resourcesSecurity compliance
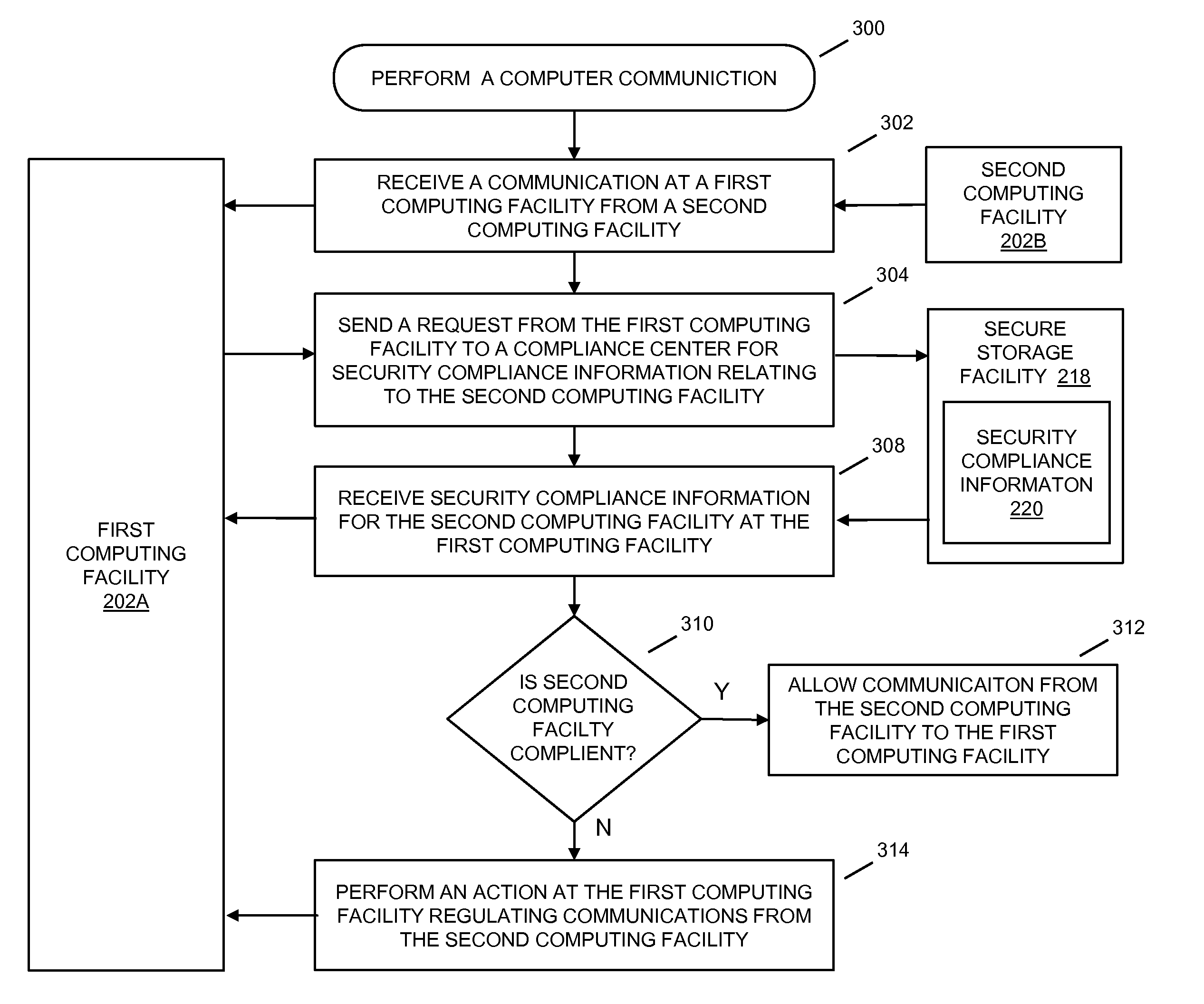
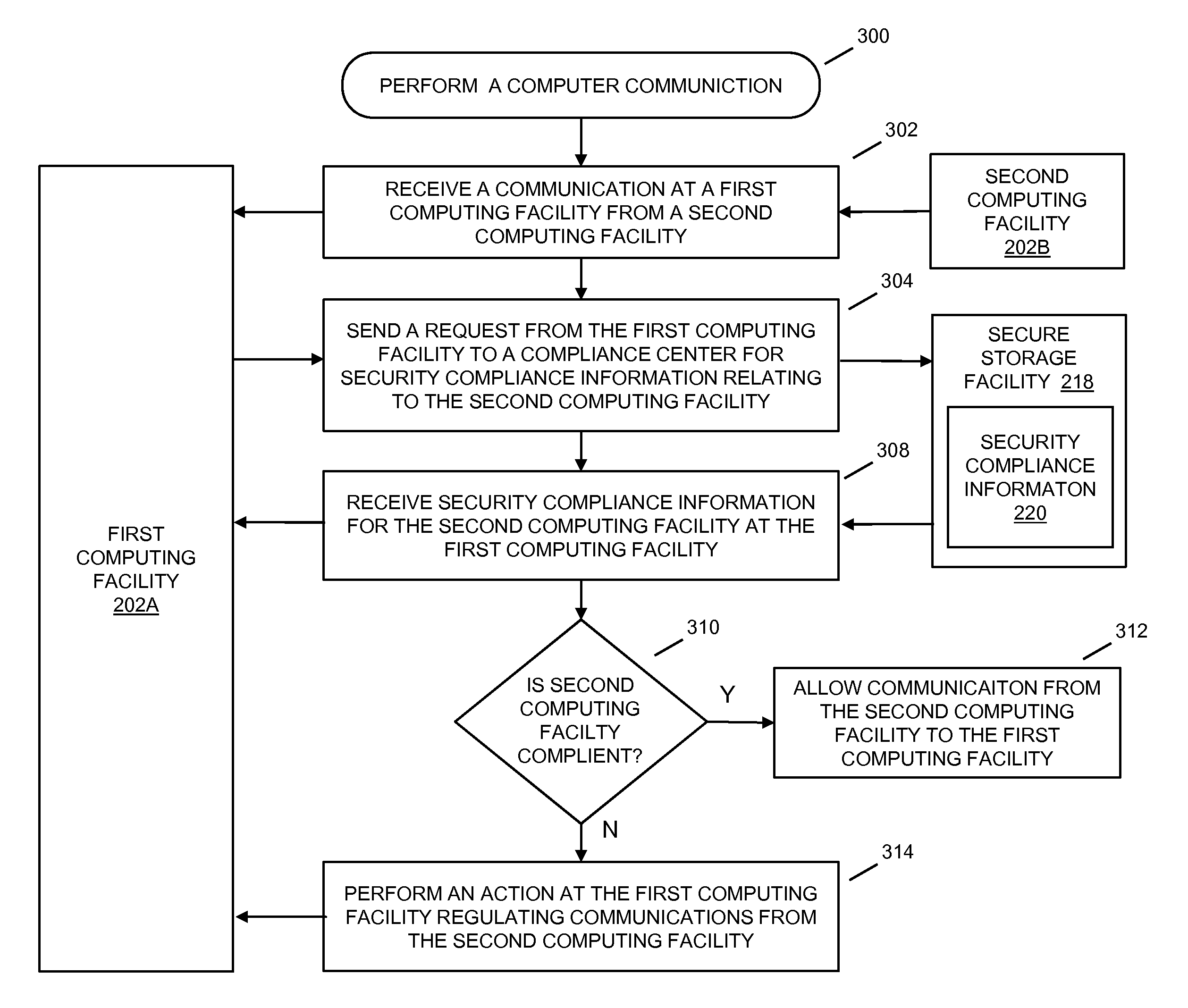
In embodiments of the present invention improved capabilities are described for providing protected computer communications. The present invention may provide for computer communications where in response to a receipt of a communication at a first computing facility from a second computing facility, the first computing facility may be caused to send a request to a compliance center for security compliance information relating to the second computing facility. In response to the request for security compliance information, the first computing facility may receive compliance information related to the second computing facility, which may cause the first computing facility to perform an action regulating further communications from the second computing facility if the second computing facility security compliance information indicates that the second client computing facility is not compliant with a current security policy.
Owner:SOPHOS
Method for meeting U.S. government security controls under export control regimes
InactiveUS20100318475A1CommerceSpecial data processing applicationsMissile Technology Control RegimeSecurity compliance
Owner:ABRAHAMSON JAMES A
System, method and program product for dynamically performing an audit and security compliance validation in an operating environment
ActiveUS20100071066A1Secure transmissionMemory loss protectionError detection/correctionSecurity complianceApplication software
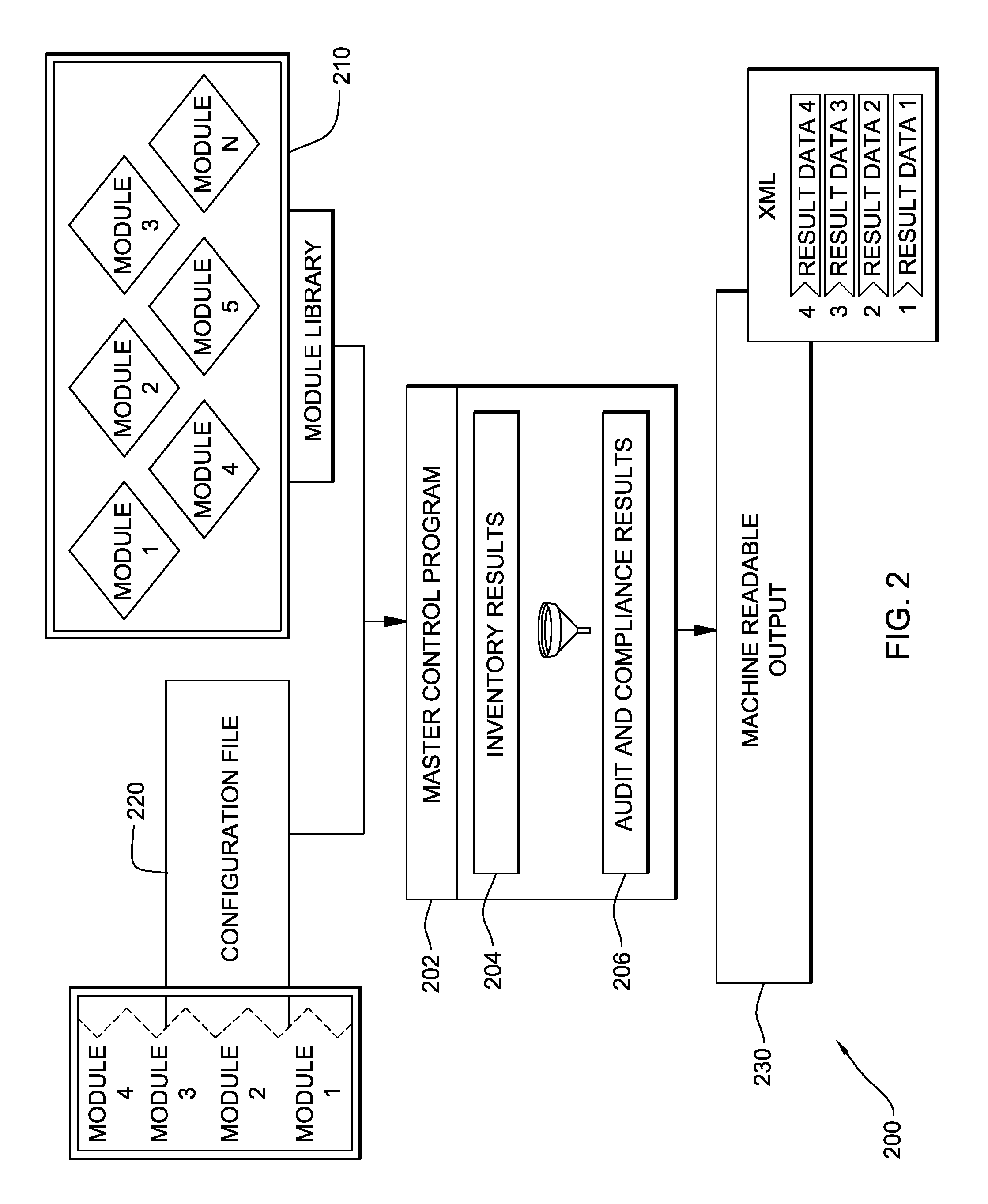
A system, method and program product for dynamically performing an audit and security compliance validation. The method includes providing a tool for performing a compliance check of installed computer applications running on a system, the tool including a first set and a second set of plug-ins. Further, the method includes scanning the system, using plug-ins selected from the first set to obtain a current inventory of applications currently installed on the system and selecting plug-ins from the second set to be run on the system in response to the current inventory of applications obtained, and automatically running the plug-ins selected from the second set for performing the compliance check on the system in response to a scheduling criteria identified for the system, where the second set of plug-ins perform the compliance check for only the applications currently installed on the system.
Owner:FINJAN BLUE INC
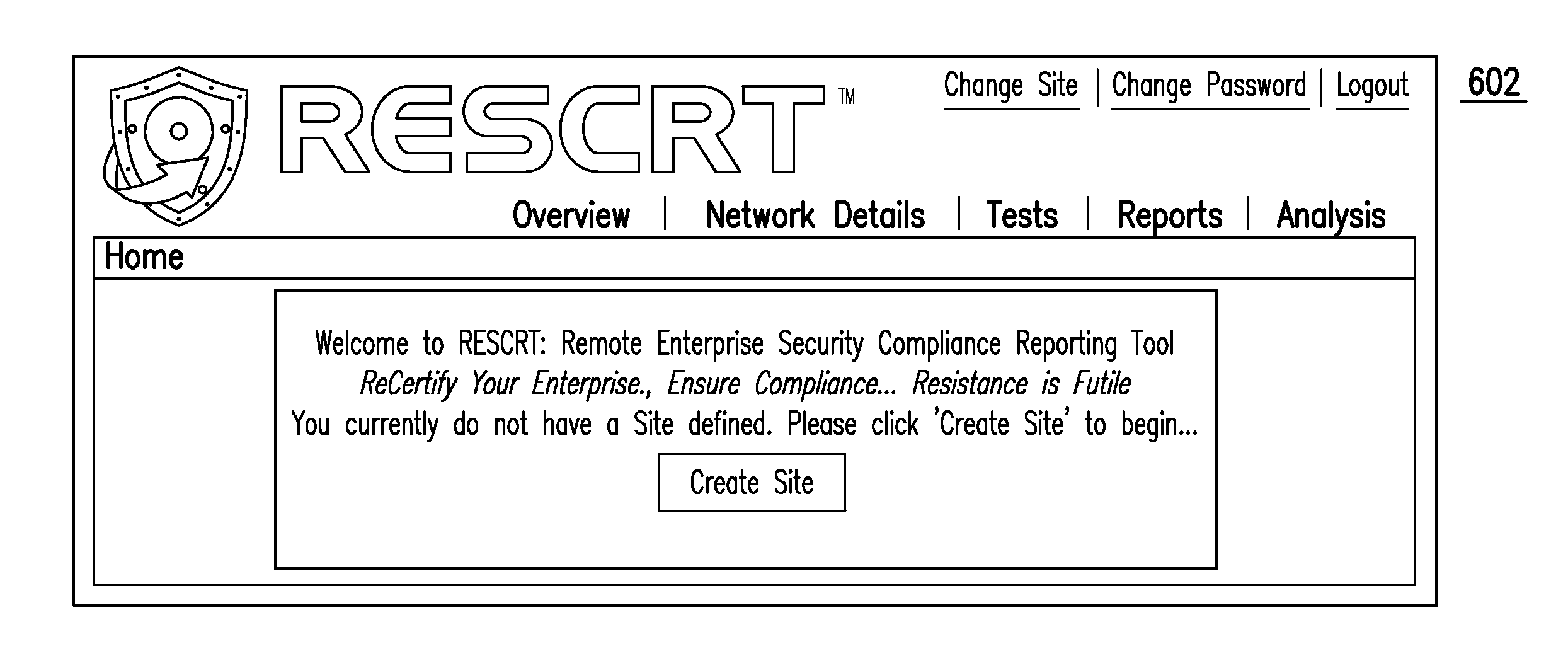
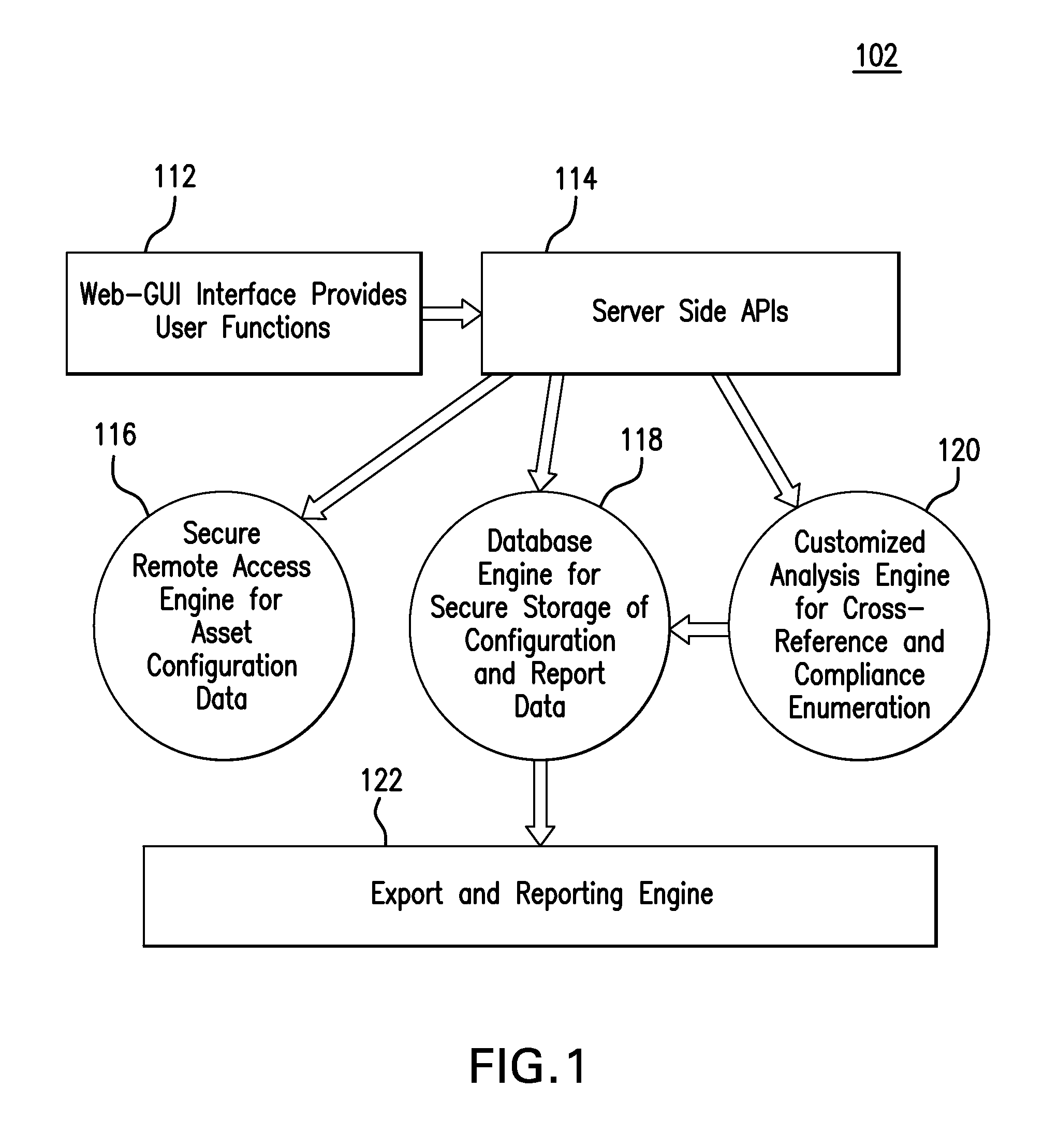
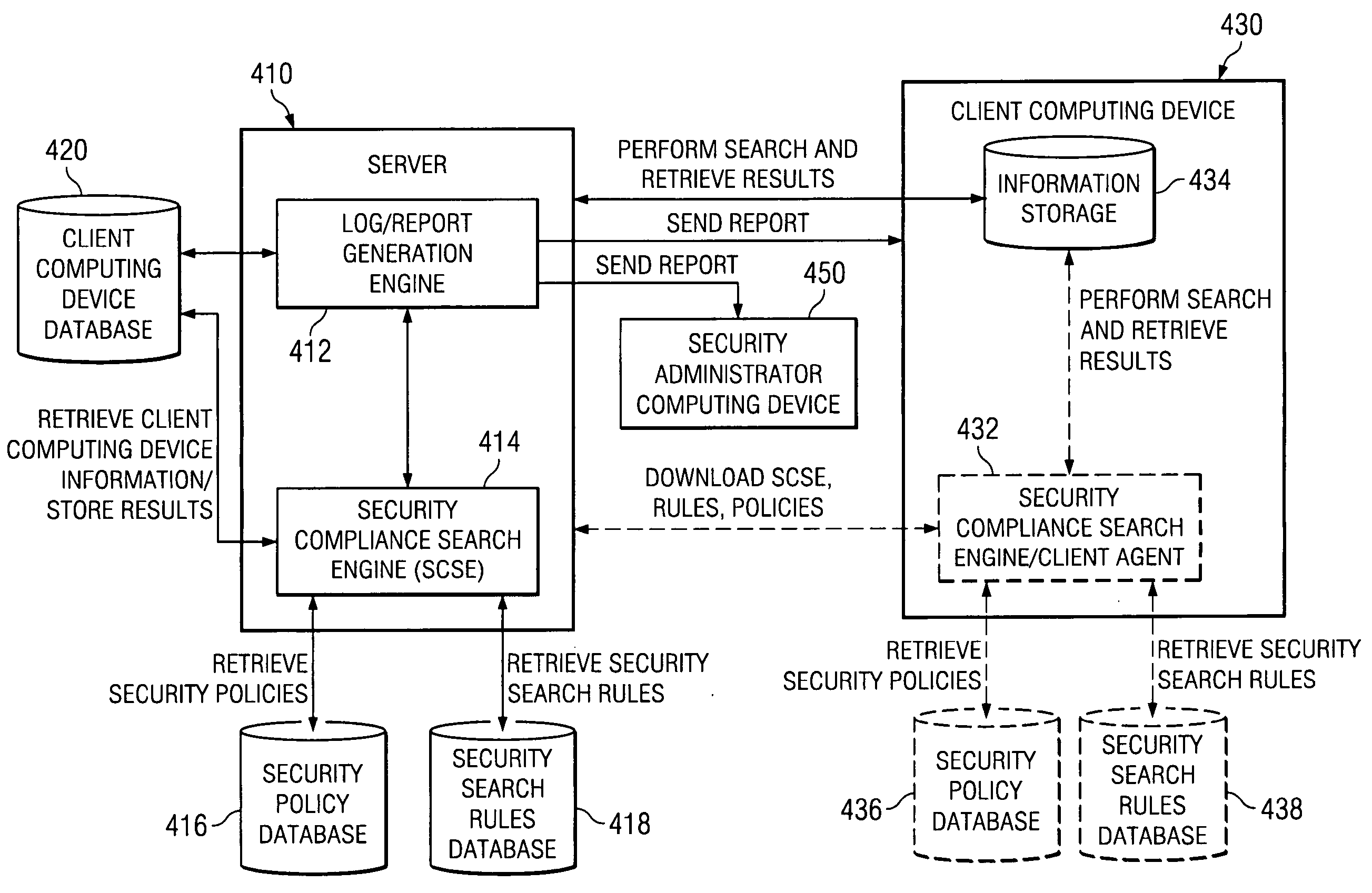
Remote enterprise security compliance reporting tool
Described is a method for cross-referencing one or more defined entities against a system configuration, system component configuration and / or system IT asset configuration to thereby validate applicability, non-applicability, compliance and / or non-compliance of a policy, set of policies, and / or policy checks with respect to the system, system component and / or system IT asset configuration. Also described are an apparatus and a machine-readable medium for performing this method.
Owner:SMARTRONIX
Data center station system
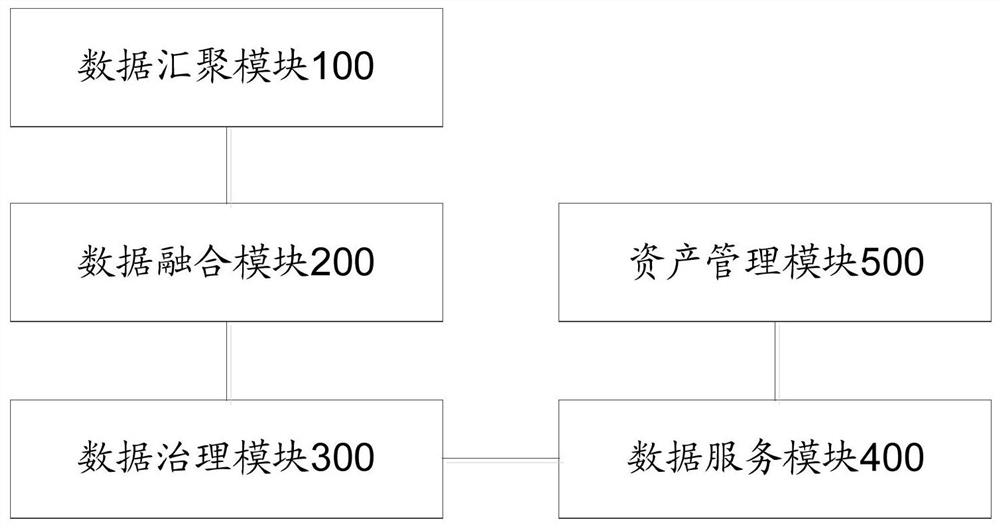
PendingCN112396404AImprove efficiencyImprove data qualityDatabase updatingDatabase management systemsSecurity complianceData aggregator
The invention discloses a data center station system, which comprises a data aggregation module used for collecting data of each service system to a data center; a data fusion module used for constructing a corresponding data model according to the business requirements so as to process the business data; a data processing module used for eliminating noise in the data of each business system; a data service module used for providing data sharing service for each department and each business system according to the data service catalogue and providing application management based on data assets; and an asset management module used for dynamically tracking and checking the data assets according to the data asset directory. According to the invention, a closed loop from data assets to business applications can be formed by constructing a data center station, data capitalization and asset business are realized, the data integration and utilization efficiency and data quality are improved,data islands are broken through, the data sharing performance is enhanced, the current situation of core data assets can be comprehensively mastered, and the data sharing security compliance is ensured.
Owner:广州光点信息科技股份有限公司
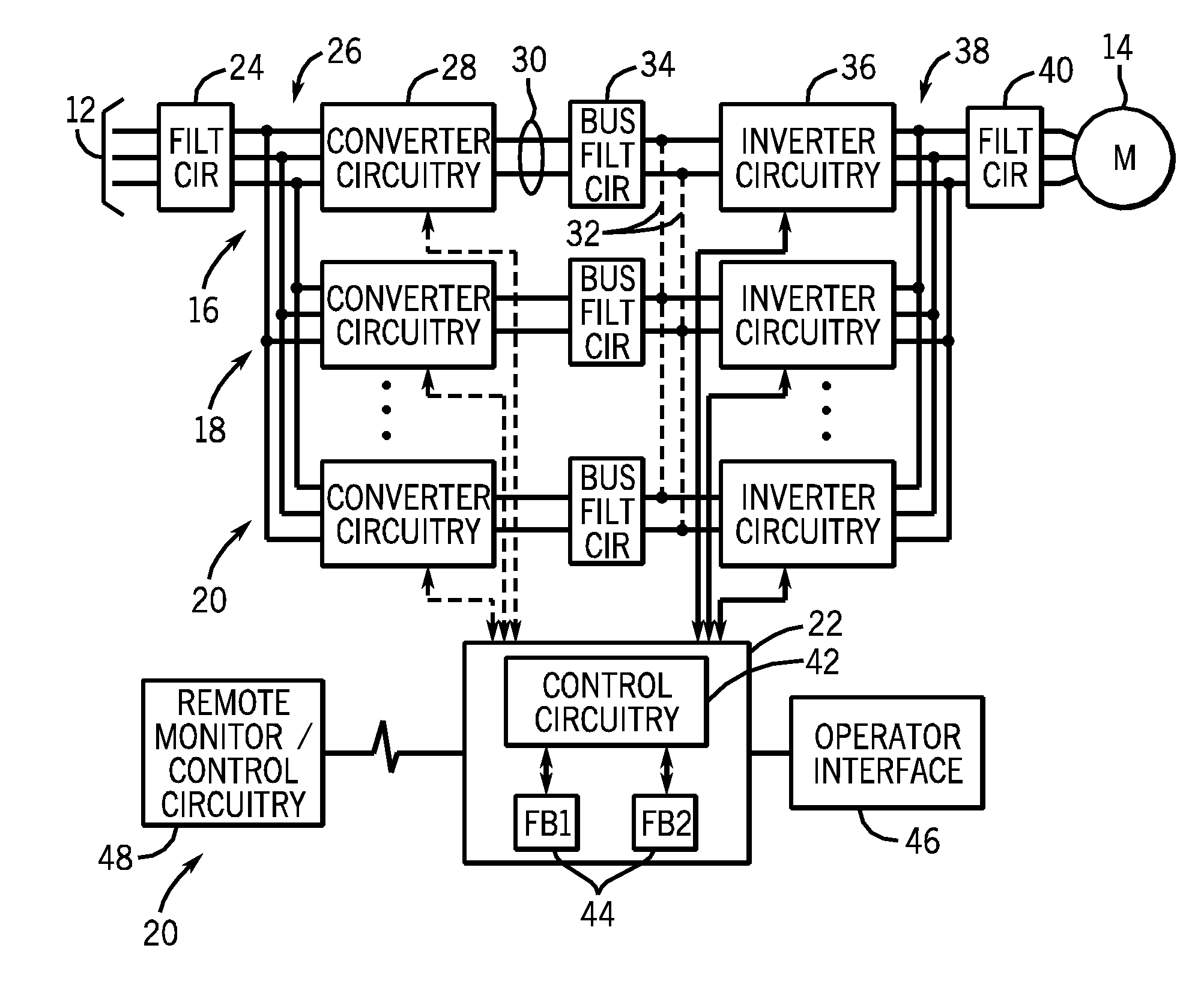
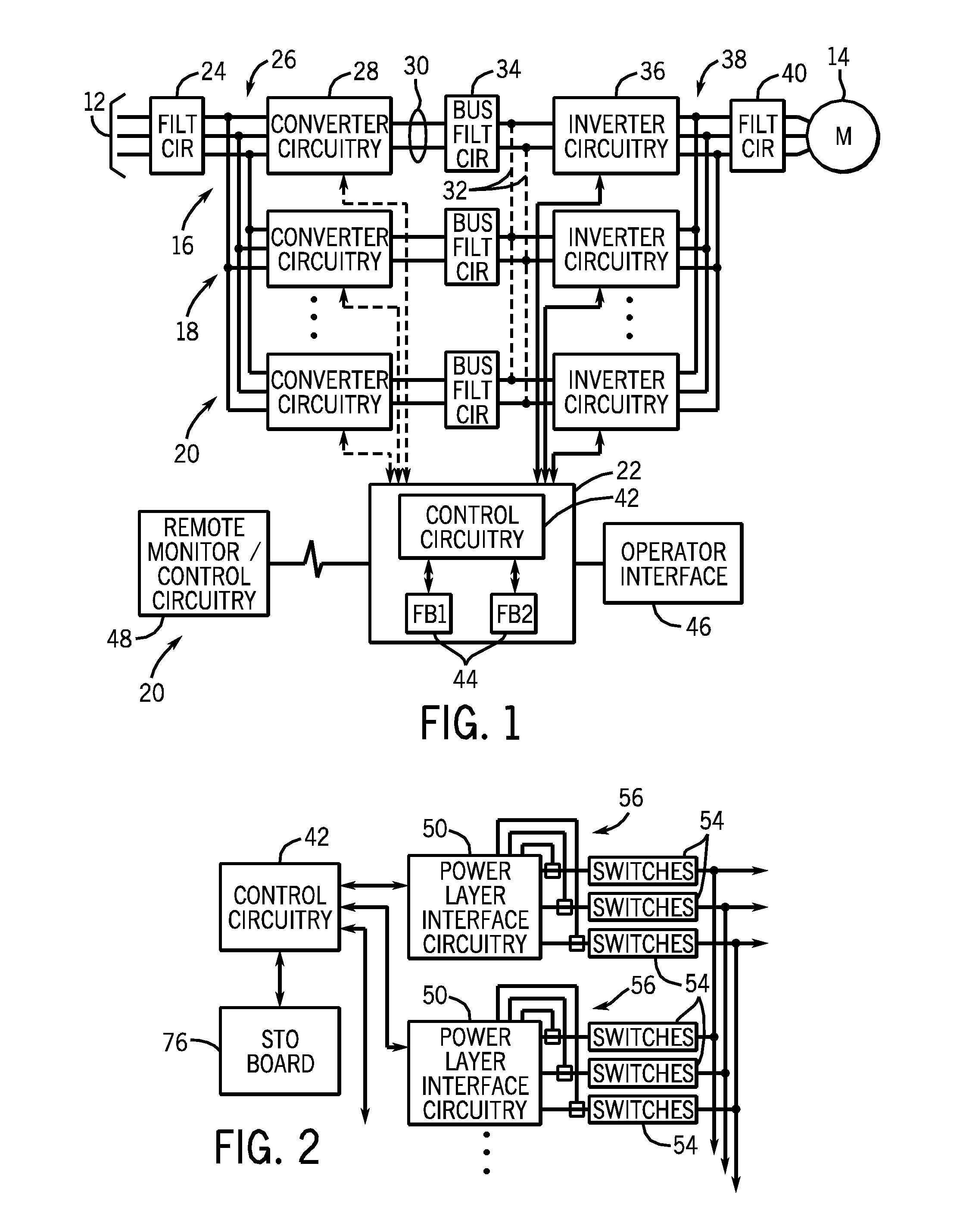
Parallel motor drive disable verification system and method
ActiveUS20120013284A1Relieve pressureMotor/generator/converter stoppersDC motor speed/torque controlMotor driveSecurity compliance
Systems and methods are provided for performing diagnostic testing for multiple motor drives operating in parallel. In one embodiment, the diagnostic testing may involve determining which of the multiple motor drives are in operation and communicating the active configuration of motor drives to testing circuitry. The testing circuitry generates an enable input signal transmitted to the transistor gates in each of the active motor drives. The testing circuitry also generates a power supply input signal transmitted to a DC to DC converter in each of the active motor drives. The responses to the enable input signal and the power supply input signal are measured to determine safety compliance.
Owner:ROCKWELL AUTOMATION TECH
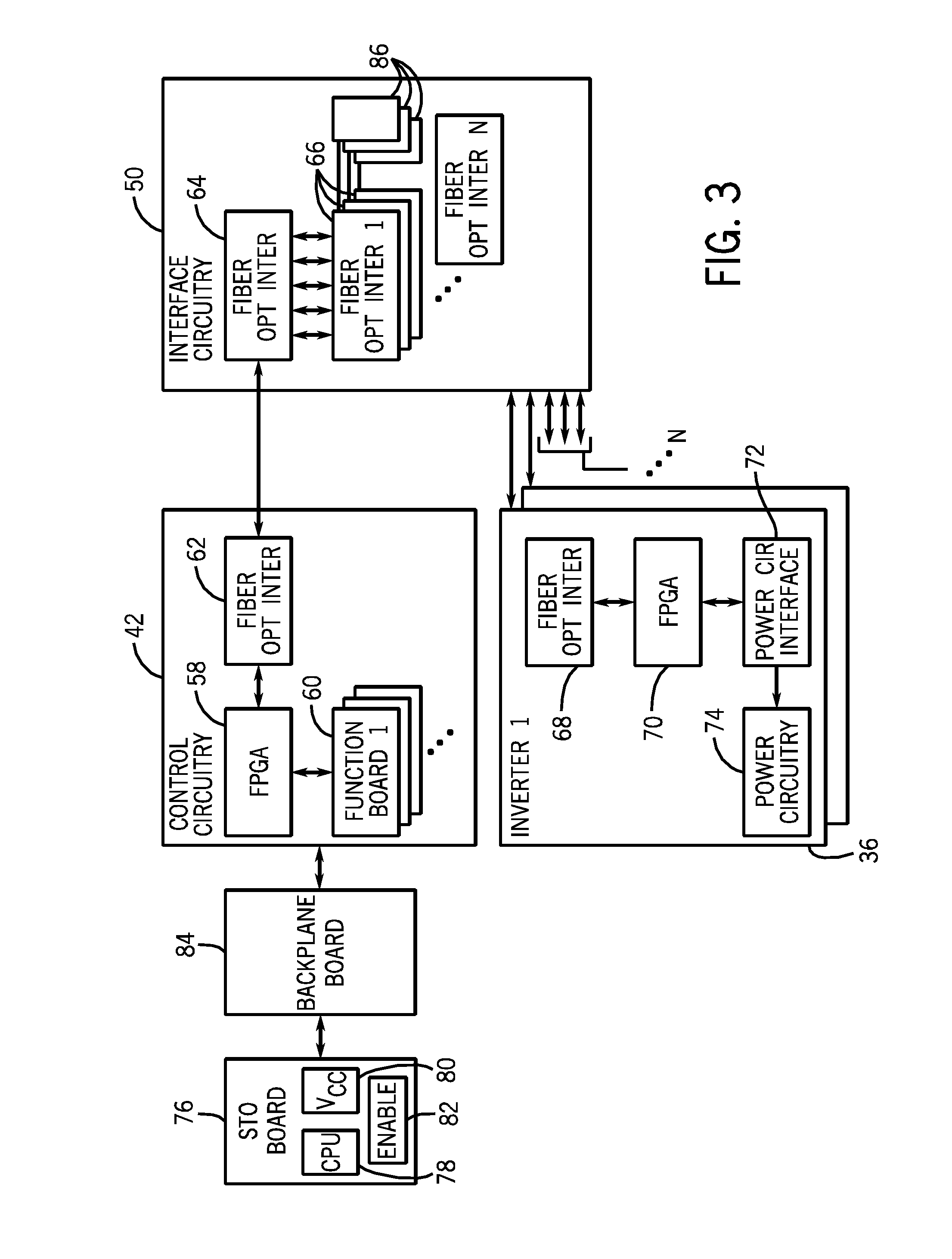
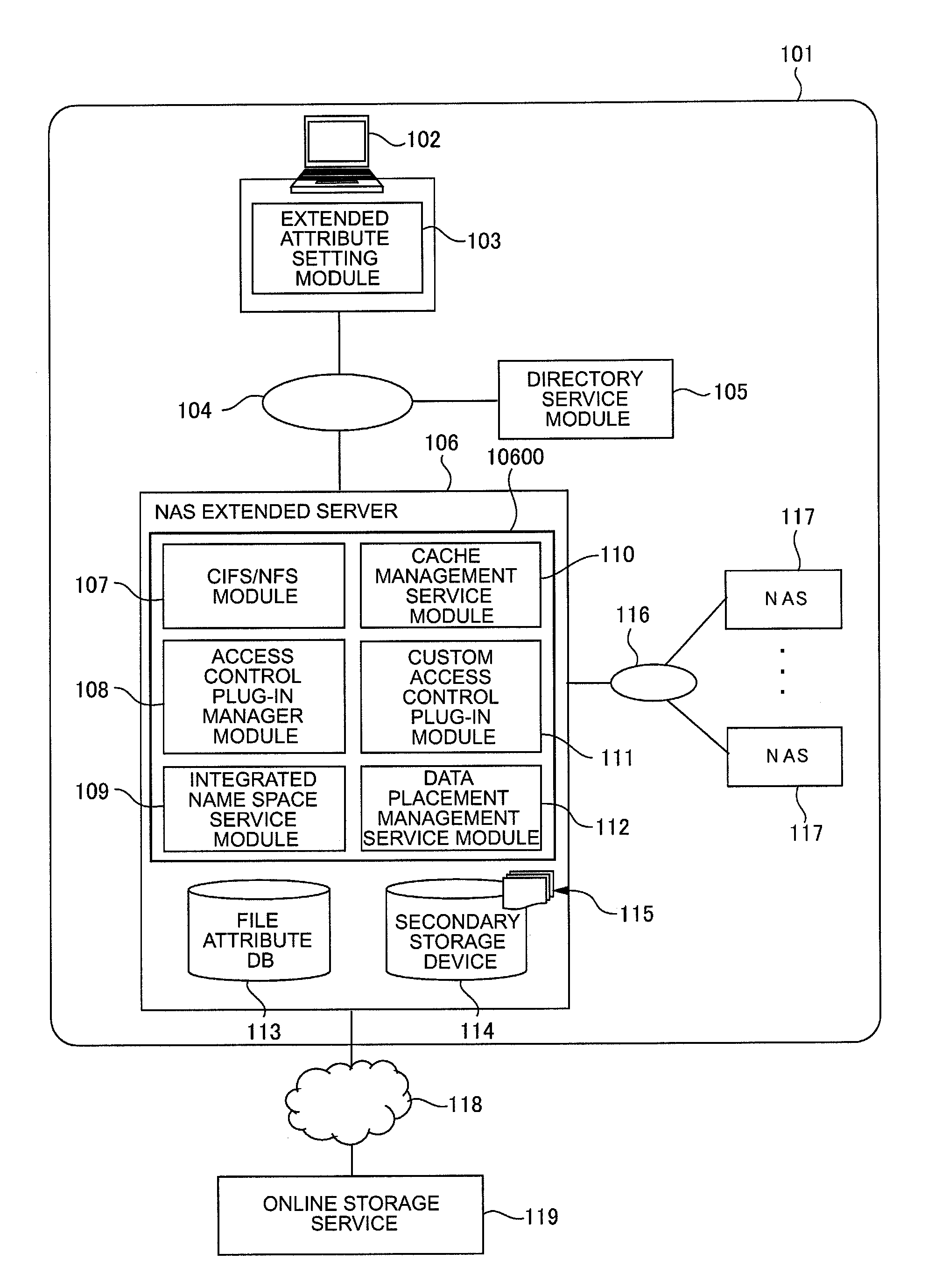
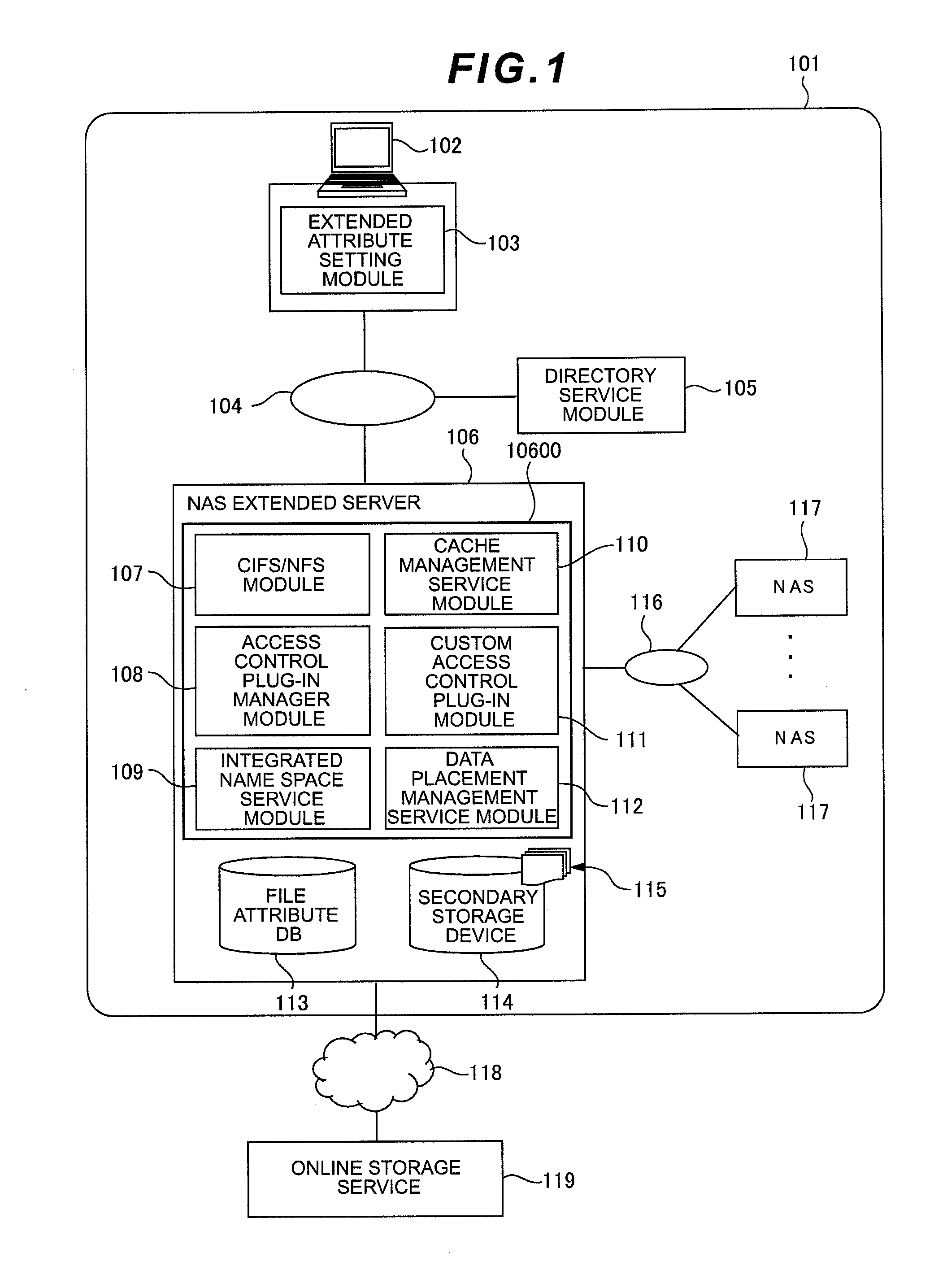
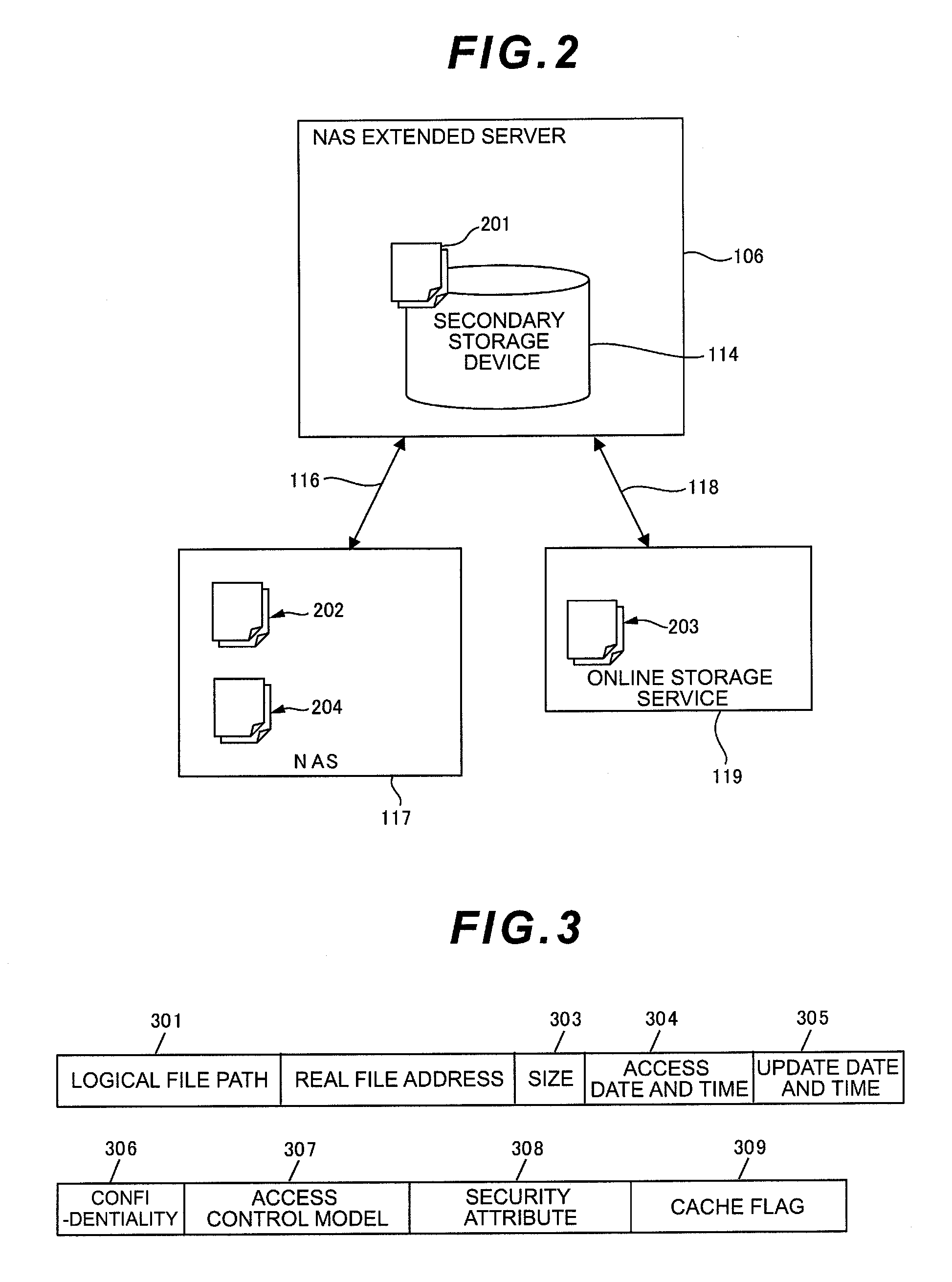
Computer system and storage capacity extension method
InactiveUS20120102080A1Security problem can be avoidedProcess safetyDigital data information retrievalDigital data protectionExternal storageConfidentiality
Provided is a computer system configured so that security compliance problems can be avoided and an access control model which can be uniquely customized can be implemented by extending the storage capacity to an external storage service by means of integrated management of an existing NAS(s) and the external storage service, and controlling the optimum data placement according to the confidentiality and importance level of data.In a computer system according to this invention, a local storage system includes an extended server for integrating a NAS(s) existing in the local storage system with an external storage service and thereby providing a client with a storage area as a single virtual NAS.
Owner:HITACHI LTD +1
Method for meeting u.s. government security controls under export control regimes
InactiveUS20080065401A1Improve securityProcess safetyCommerceSecurity complianceMissile Technology Control Regime
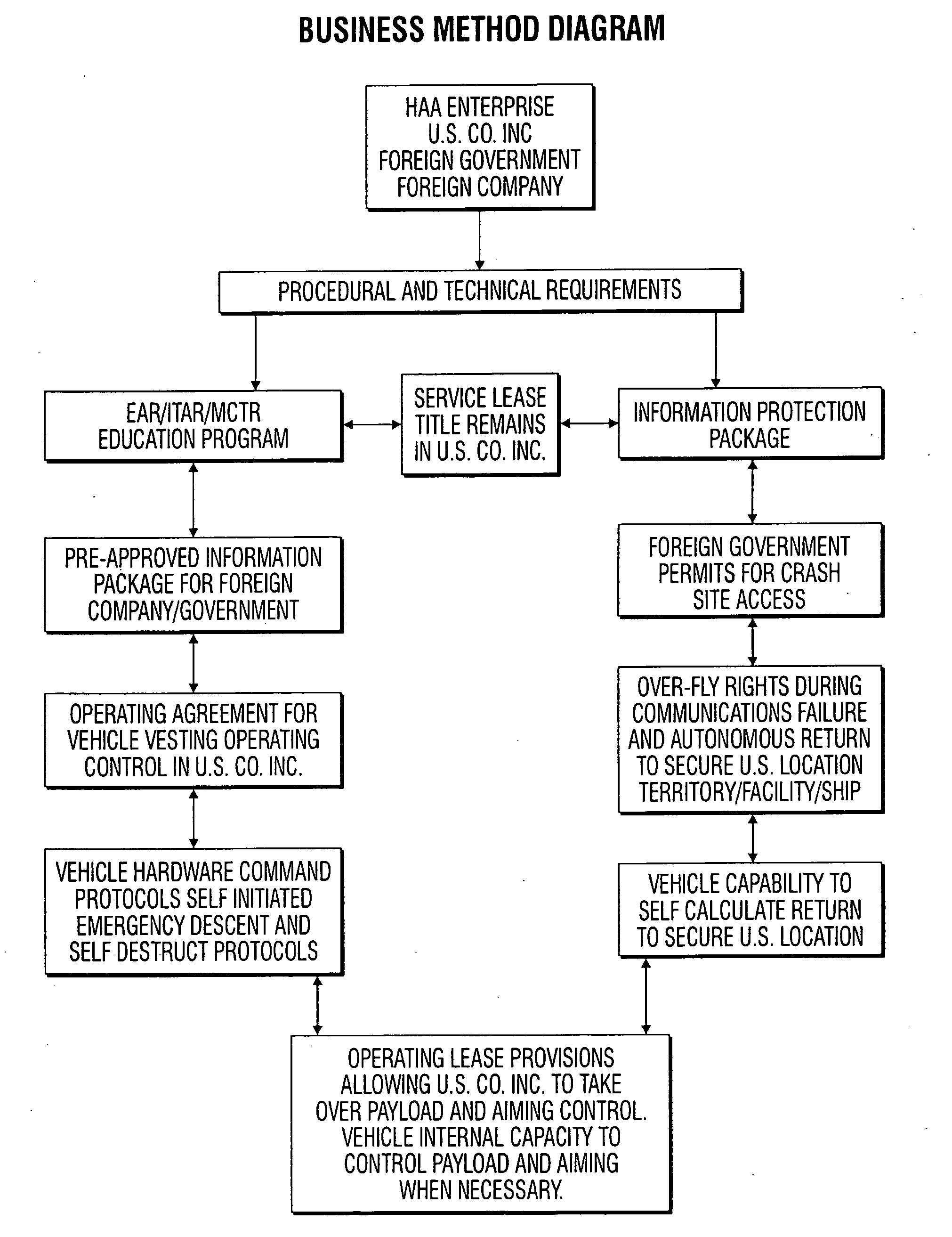
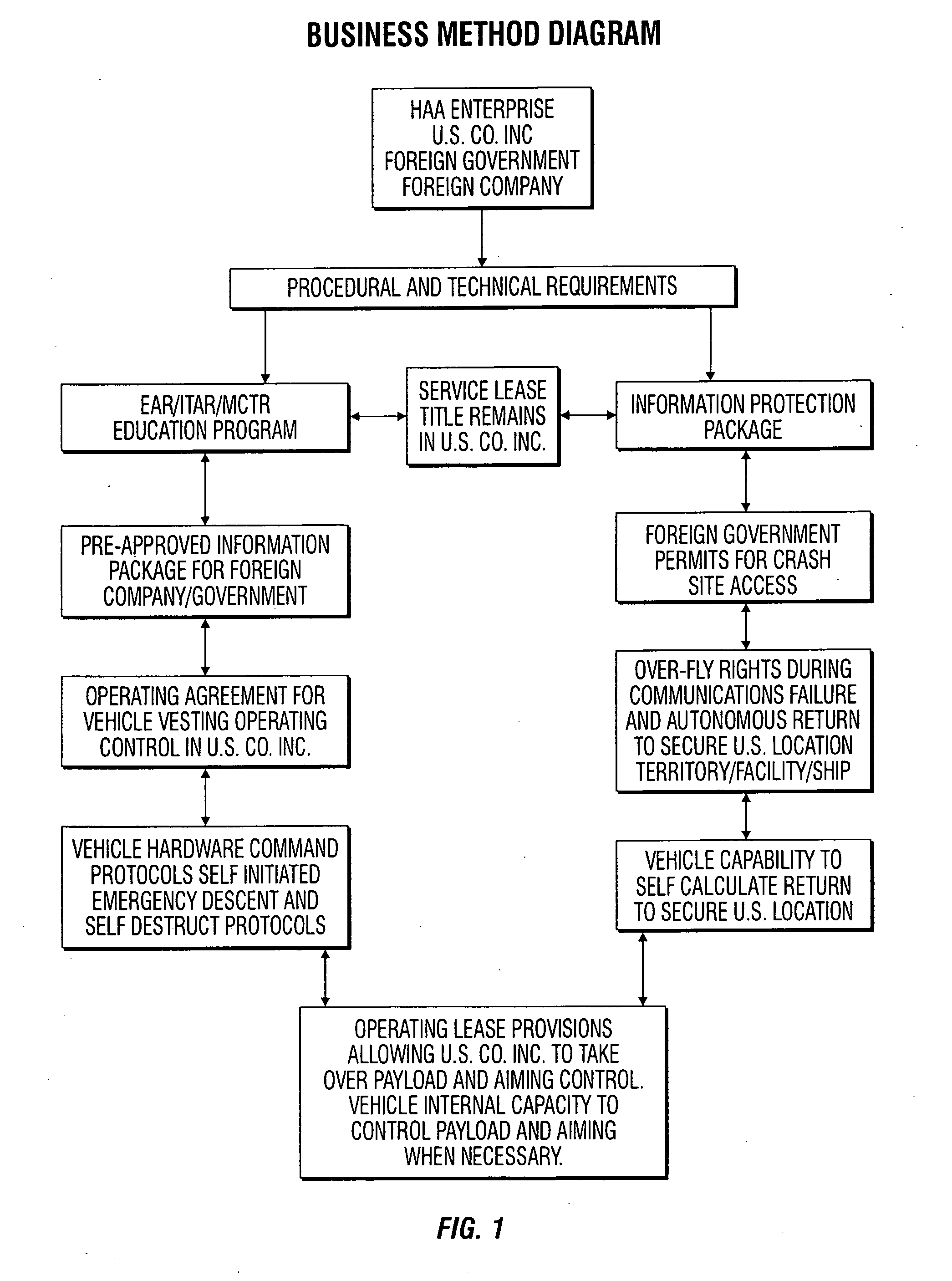
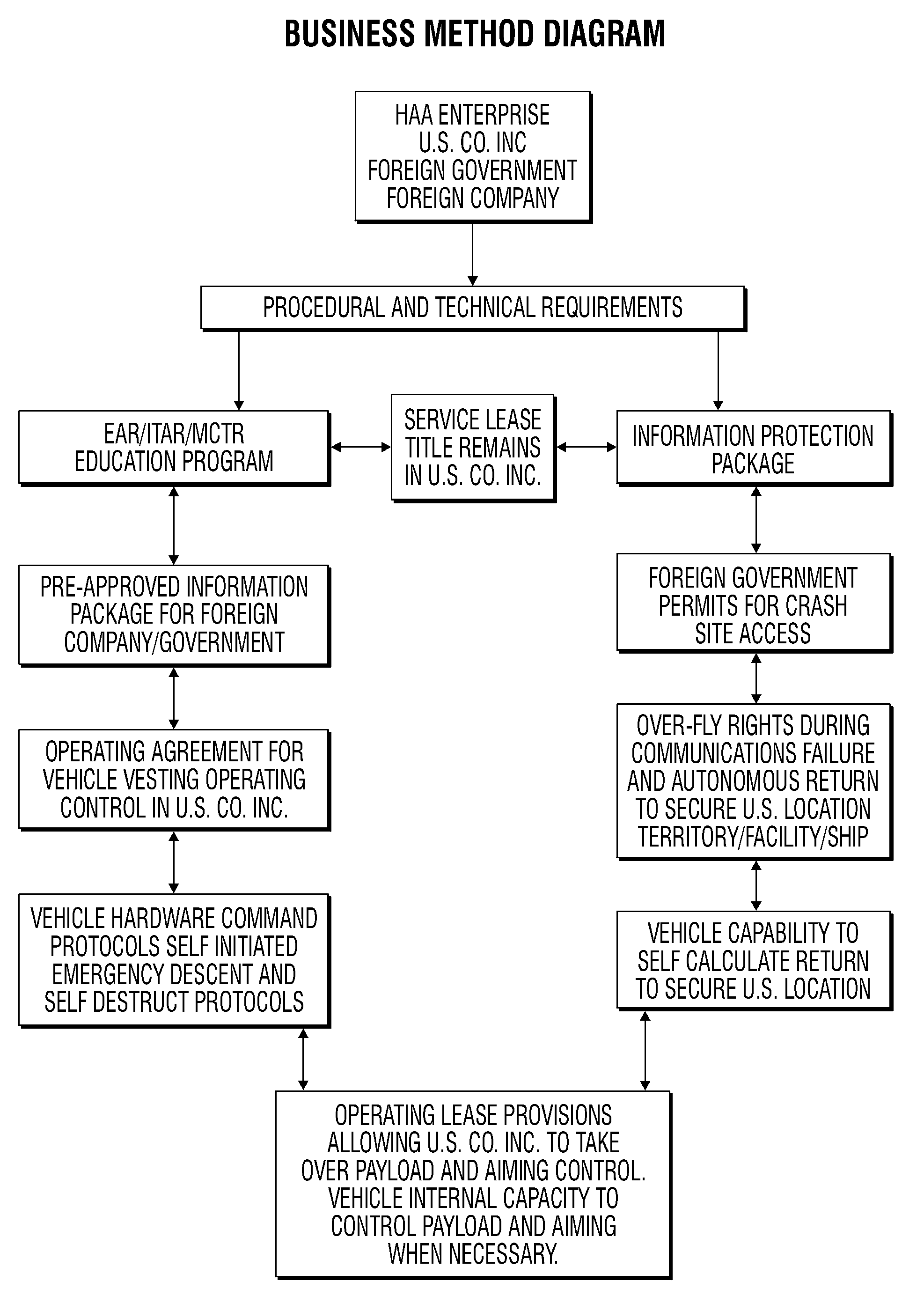
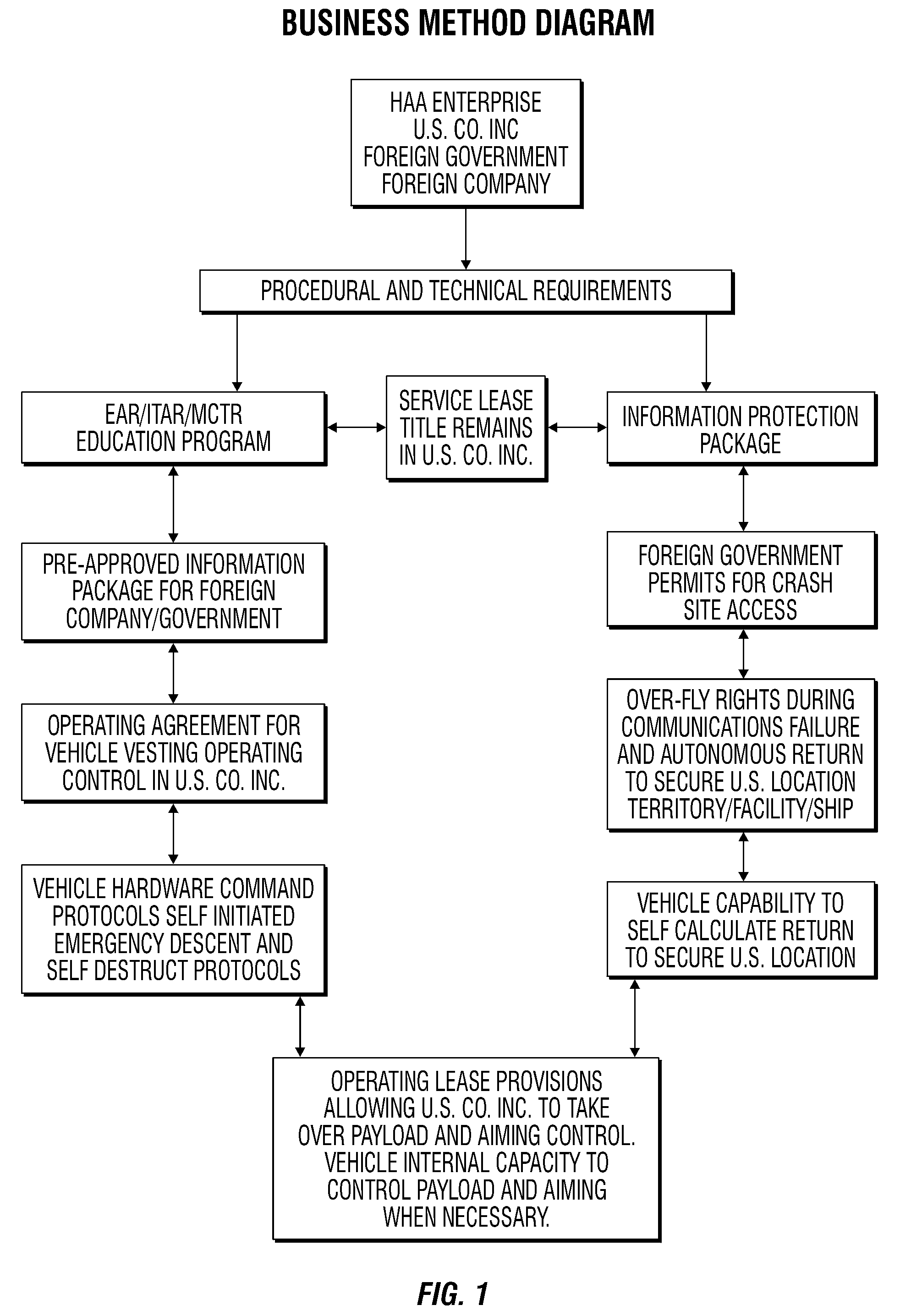
A business method which enables full conformance and probable approval within the U.S. International Export Controls, such as the Export Administration Regulation (EAR); the International Traffic in Arms Regulation (ITAR); and the international Missile Technology Control Regime (MTCR) even though the item may normally be precluded from export. The method includes filing an application for a license to exploit the technology; and including in the application commitments by the participants to comply with and follow certain security related procedures, including a service lease, security compliance training; pre-approval of technical disclosures; and operations and task compartmentalization among the parties.
Owner:ABRAHAMSON JAMES A
Method and system of auditing databases for security compliance
ActiveUS8095962B2Digital data processing detailsAnalogue secracy/subscription systemsInternet privacySecurity compliance
Method and system of auditing databases for security compliance. The method and system relating to querying databases for security parameters and auditing the queried parameters against authorized security parameters to determine security compliance of the databases.
Owner:SBC KNOWLEDGE VENTURES LP
Protected access control method for shared computer resources
ActiveUS8392972B2Improve protectionImprove integrityMemory loss protectionDigital data processing detailsComputer resourcesSecurity compliance
In embodiments of the present invention improved capabilities are described for providing protected computer communications. The present invention may provide for computer communications where in response to a receipt of a communication at a first computing facility from a second computing facility, the first computing facility may be caused to send a request to a compliance center for security compliance information relating to the second computing facility. In response to the request for security compliance information, the first computing facility may receive compliance information related to the second computing facility, which may cause the first computing facility to perform an action regulating further communications from the second computing facility if the second computing facility security compliance information indicates that the second client computing facility is not compliant with a current security policy.
Owner:SOPHOS
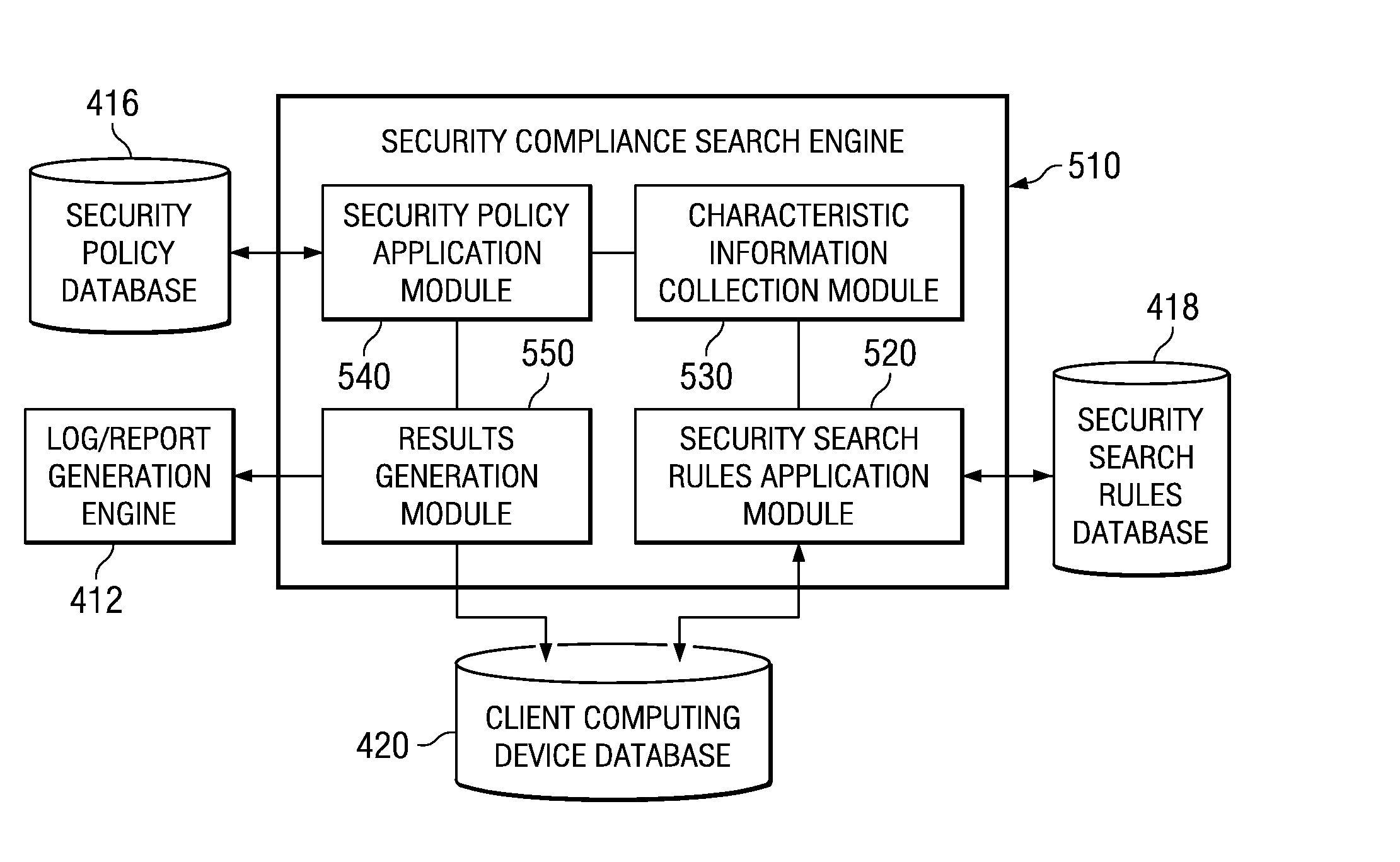
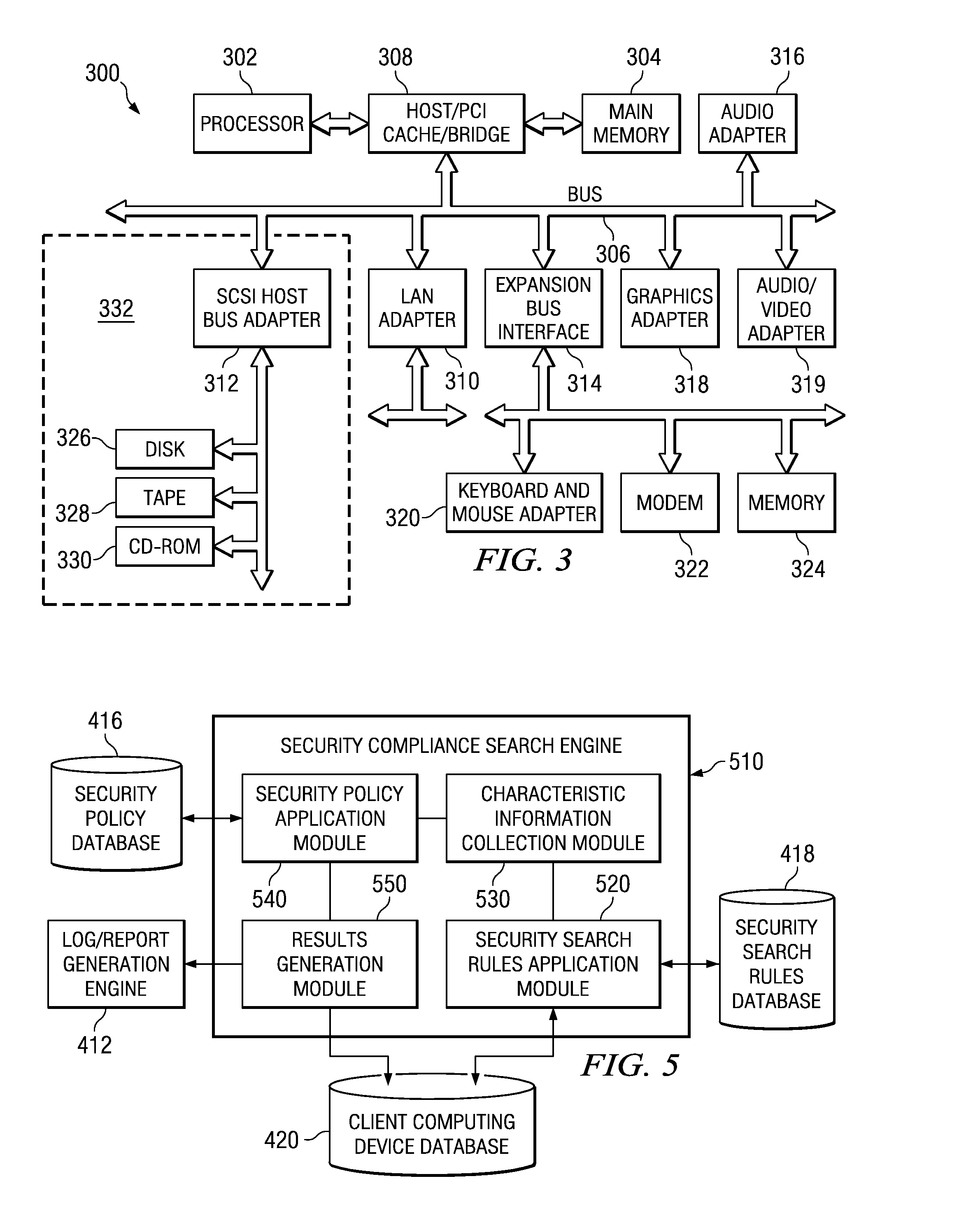
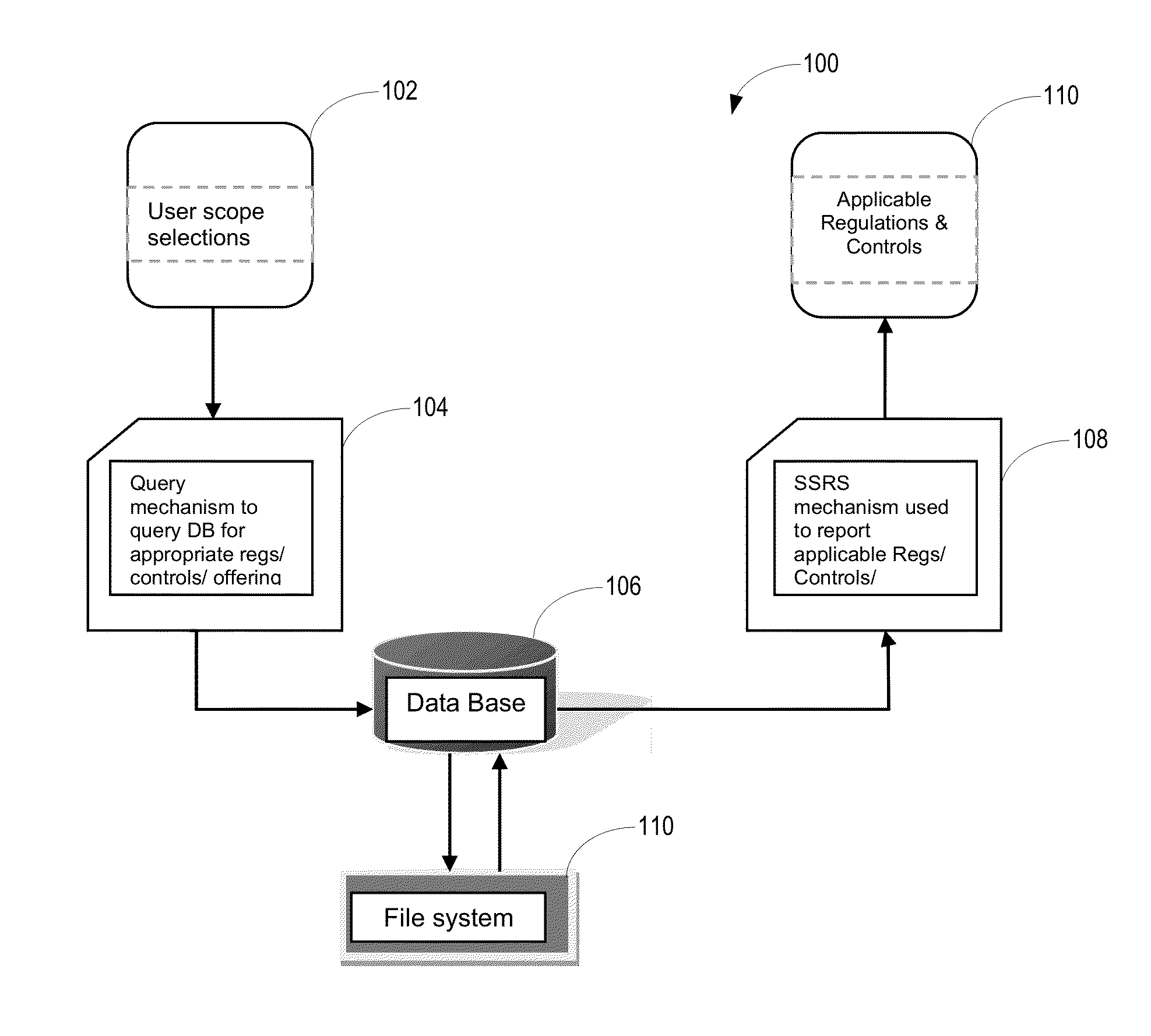
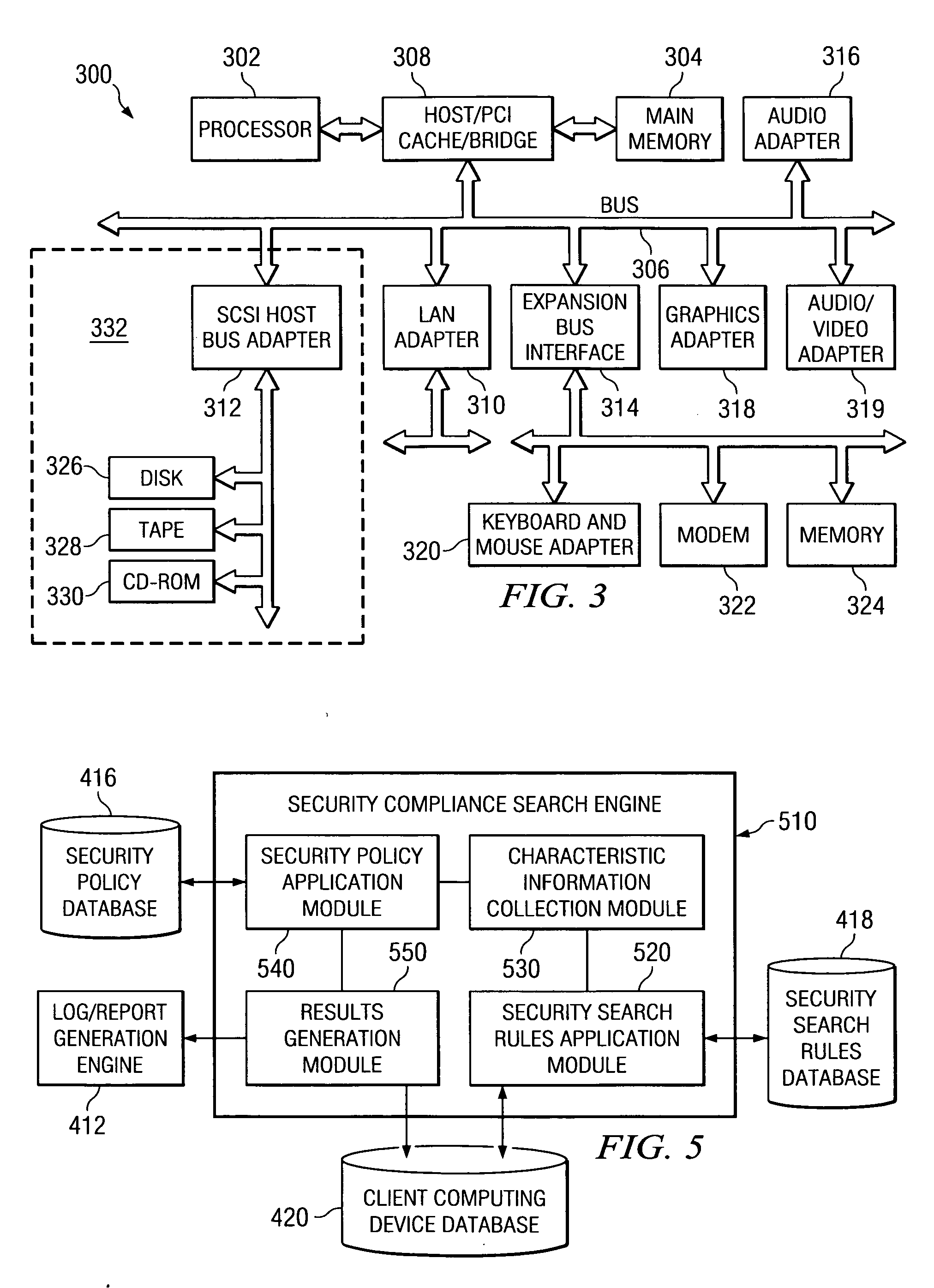
Confidential Content Search Engine
InactiveUS20080235196A1Computer security arrangementsSpecial data processing applicationsInternet privacyConfidentiality
A security compliance search engine is provided for searching one or more client computing devices for items of information that meet a security criteria identifying items of information containing confidential content. Results of the search are provided to an analysis engine for determining if the items of information identified by the search are being maintained in accordance with a security policy for ensuring the confidentiality of the confidential content. Results of the analysis may be used to generate a report or log and to generate a notification to the client computing device identifying any violations of the security policy and possible solutions for bringing the item of information into compliance with the security policy. In addition, an administrator may be notified of any violations so that corrective action may be taken.
Owner:INT BUSINESS MASCH CORP
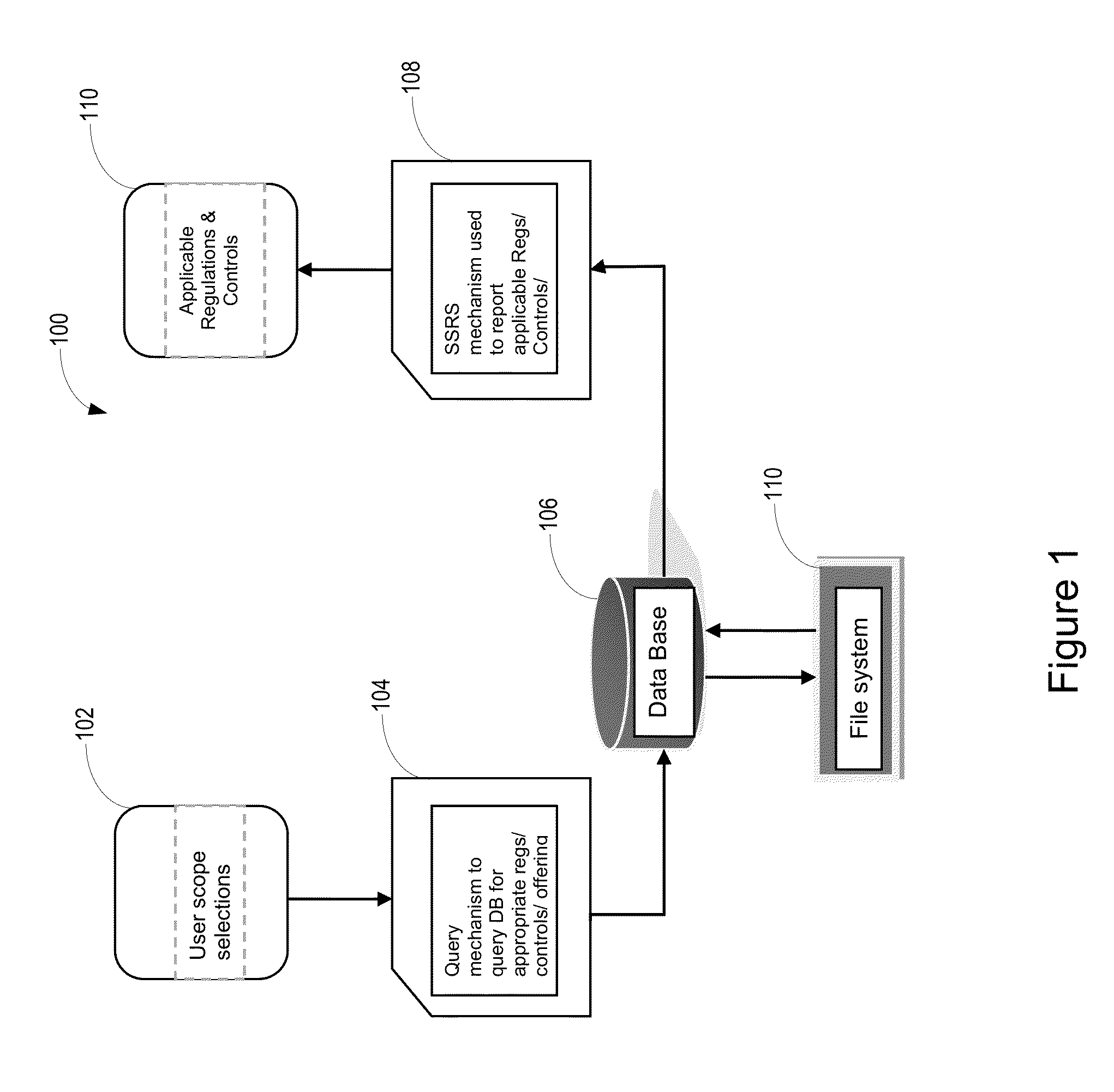
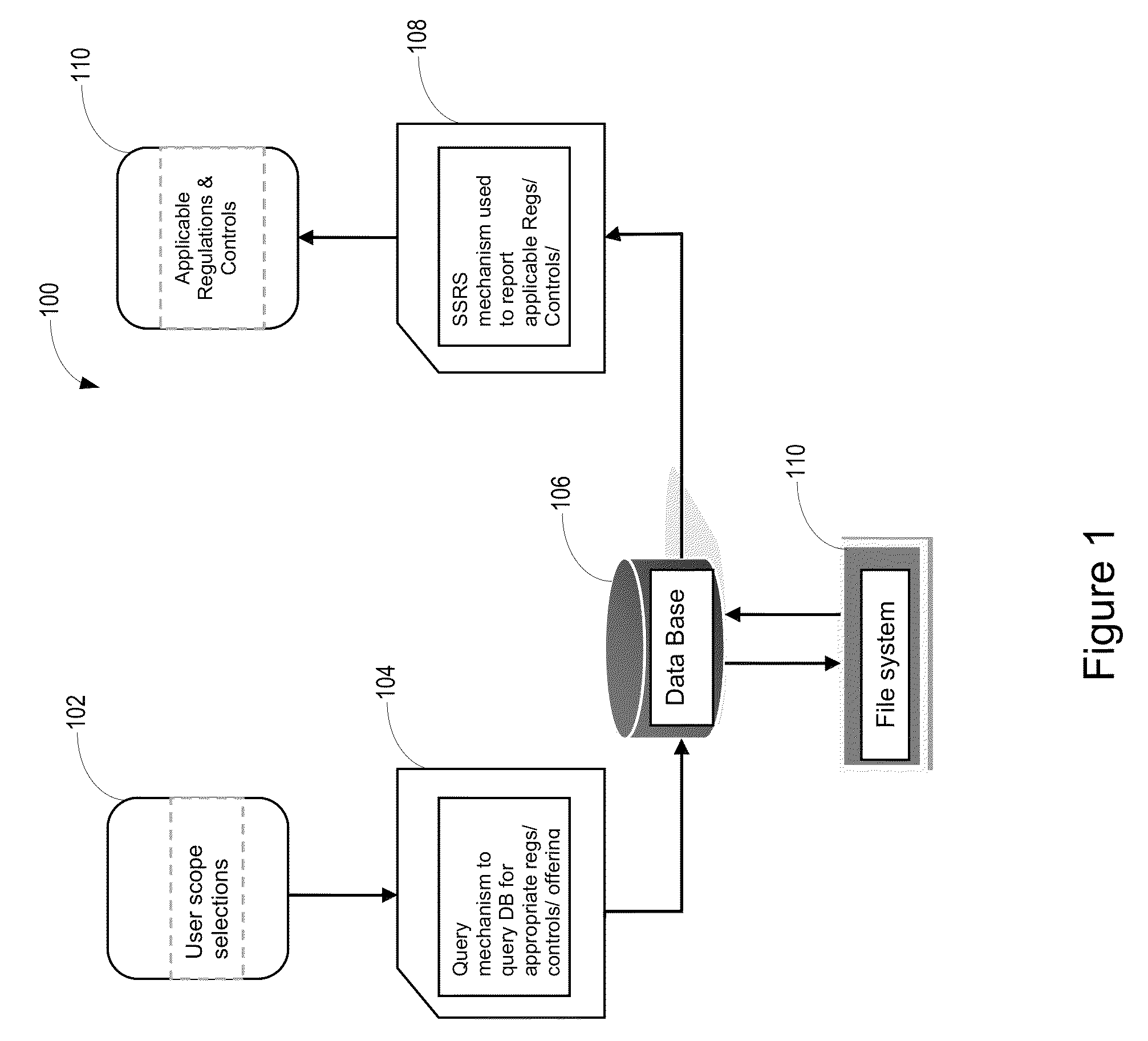
System for analyzing security compliance requirements
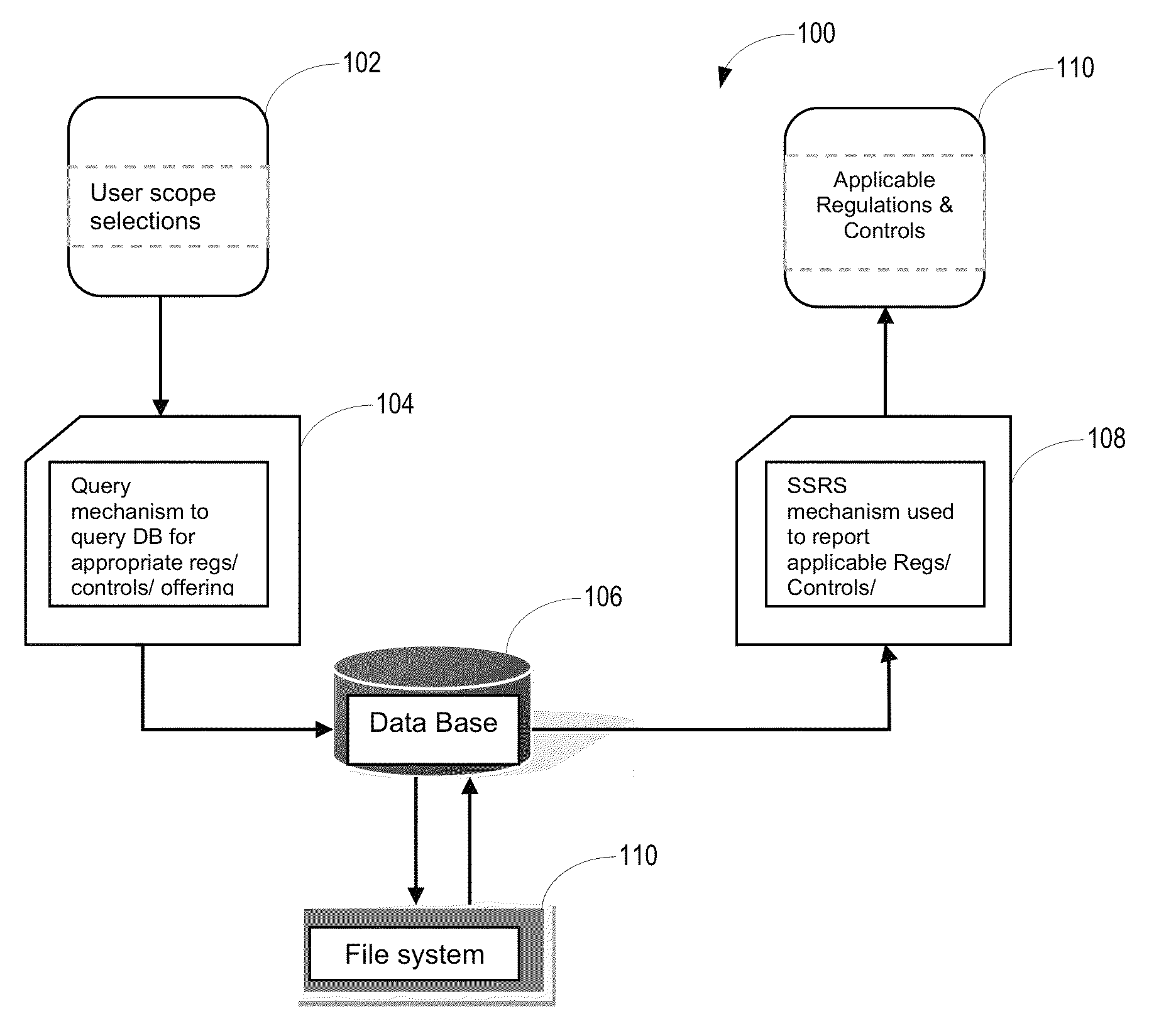
A system for analyzing security compliance requirements analyzes a linked database that includes data from the Unified Compliance Framework™. The system generates a tiered question structure to obtain information about a particular business offering, wherein questions of a particular tier are based on answers to questions of a preceding tier. Based on the information, the system generates a query and submits the query to the linked database. The query results provide a list of security compliance requirements, leading practices, and / or regulations applicable to the business offering.
Owner:ACCENTURE GLOBAL SERVICES LTD
Confidential content search engine system and method
InactiveUS20070180258A1Ensure complianceDigital data processing detailsError detection/correctionInternet privacyConfidentiality
A confidential content search engine system and method are provided. With the system and method, a security compliance search engine is provided for searching one or more client computing devices for items of information that meet a security criteria identifying items of information containing confidential content. Results of the search are provided to an analysis engine for determining if the items of information identified by the search are being maintained in accordance with a security policy for ensuring the confidentiality of the confidential content. Results of the analysis may be used to generate a report or log and to generate a notification to the client computing device identifying any violations of the security policy and possible solutions for bringing the item of information into compliance with the security policy. In addition, an administrator may be notified of any violations so that corrective action may be taken.
Owner:IBM CORP
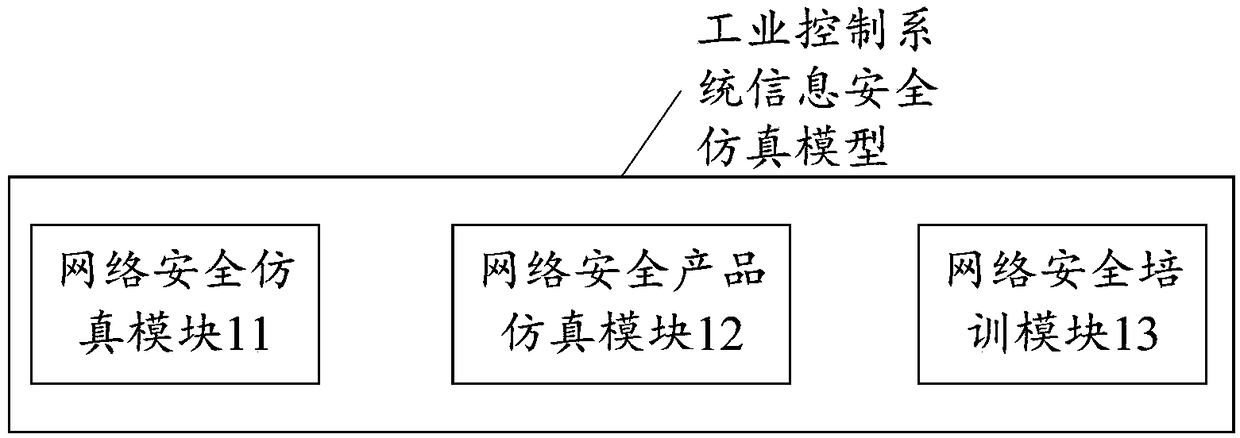
Information safety simulation model and terminal of industrial control system
ActiveCN108646722AReduce limitationsVersatileProgramme controlElectric testing/monitoringSecurity complianceStructure of Management Information
The invention provides an information safety simulation model and terminal of an industrial control system. The information safety simulation model comprises a network safety simulation module,a network safety product simulation module and a network safety training module; the network safety simulation module conducts safety compliance detection on the network structure of the industrial control system,conducts safety detection on the network flow of the industrial control system and conducts safety detection on a network host of the industrial control system; the network safety product simulation module tests the function,loopholes and performance of a network safety product,obtains testing information,and evaluates the conformity of identification information and the testing informationof the network safety product; the network safety training module simulates the usage scenario,the operating scenario and the emergency response scenario of the industrial control system. The information safety simulation model is more professional and diversified in function in the aspect of network safety simulation and wide in applicable range,and does not rely on a power simulation system,so that the technical problems of dependence on a network safety attack simulation technology of the industrial control system,limitation and non-professional performance of an existing information safetysimulation model are solved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
System for analyzing security compliance requirements
A system for analyzing security compliance requirements analyzes a linked database that includes data from the Unified Compliance Framework™. The system generates a tiered question structure to obtain information about a particular business offering, wherein questions of a particular tier are based on answers to questions of a preceding tier. Based on the information, the system generates a query and submits the query to the linked database. The query results provide a list of security compliance requirements, leading practices, and / or regulations applicable to the business offering.
Owner:ACCENTURE GLOBAL SERVICES LTD
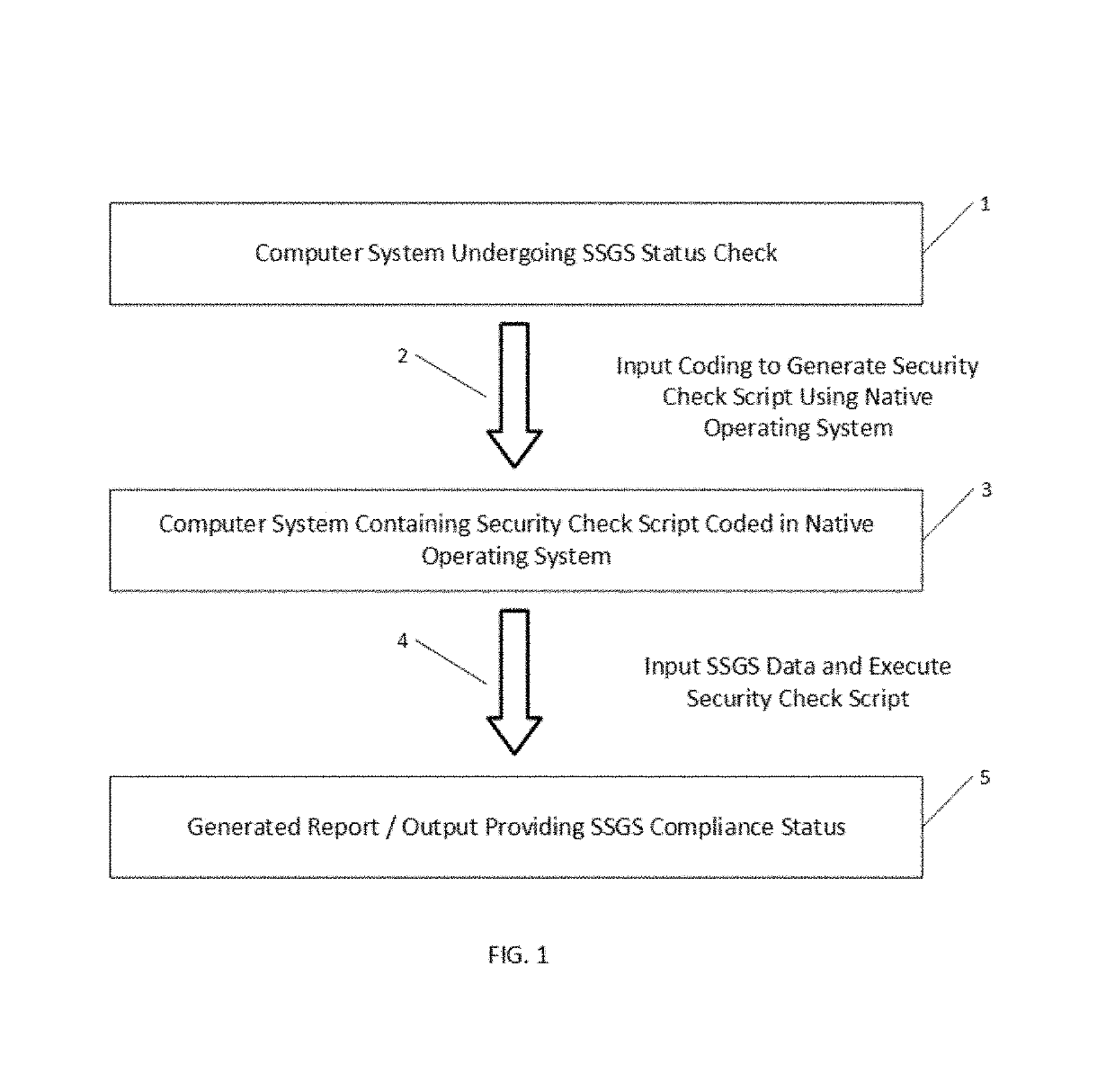
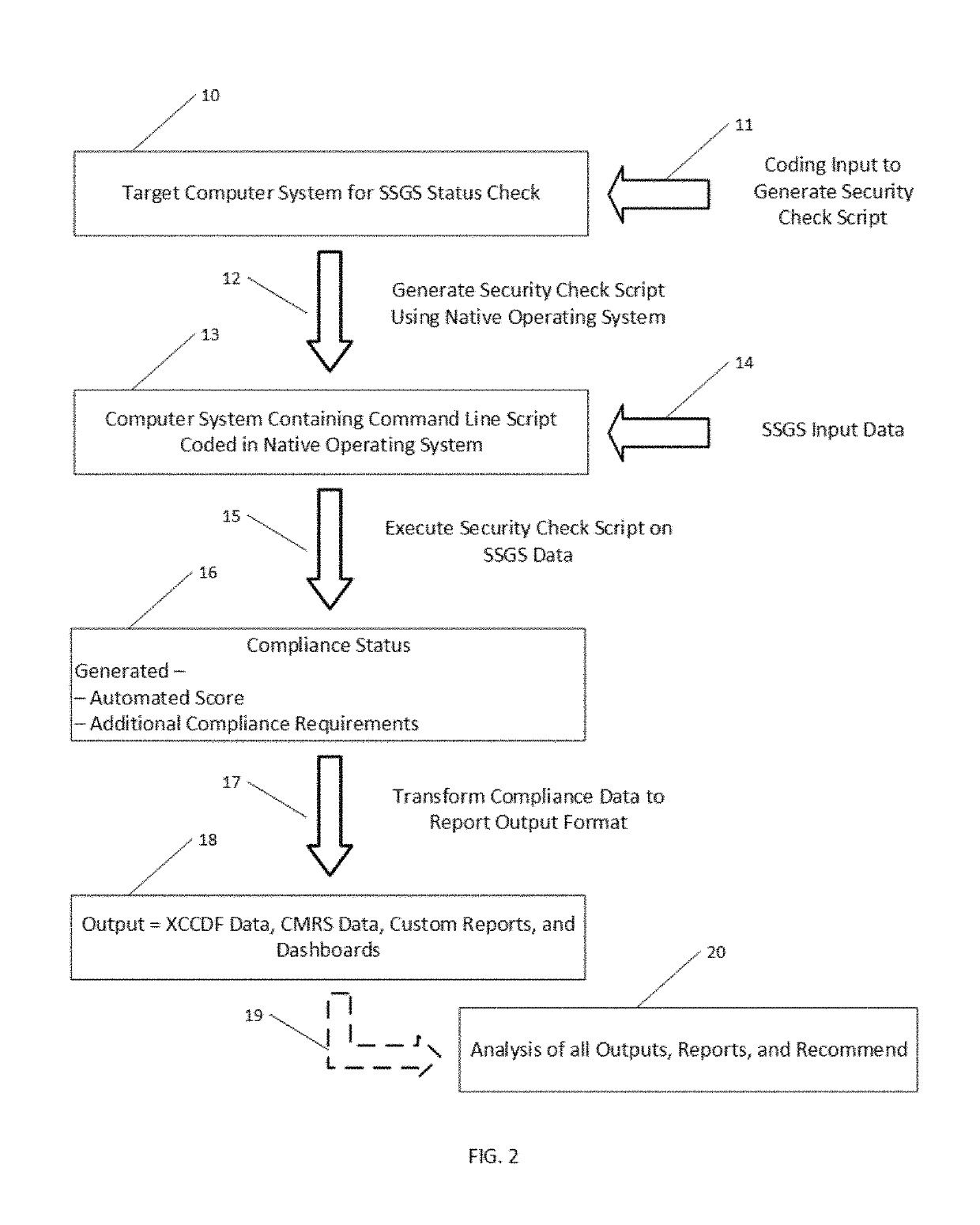
Method and system for computer self-determination of security protocol compliance
ActiveUS10360408B1Shorten the timeIncrease heightDigital data protectionPlatform integrity maintainanceGuidelineOperational system
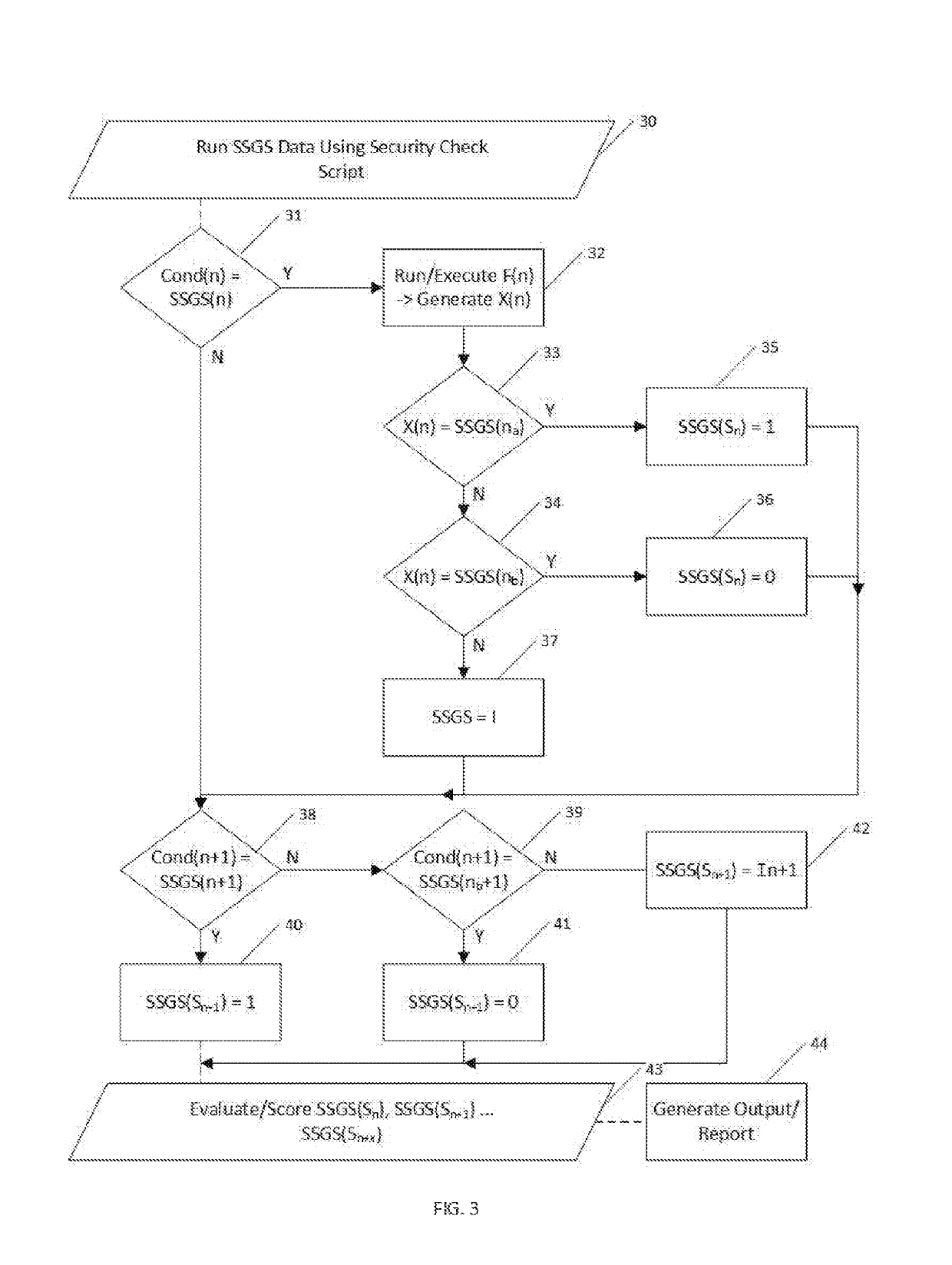
A method and system for automating the evaluation of a computer system under a Software Security Guideline Set (SSGS) using the internal scripts and the script generating capability of the computer system under evaluation to perform much of the evaluation of the SSGS. The method and systems arranged in accordance therewith generate a security check script that adds automation to the otherwise laborious process of checking for compliance with an SSGS. By using the systems own software and script generating capabilities the computer system under review is in one sense using its own capability to check itself for compliance with an SSGS. The use of the software and data from the operating system of the computer system under review greatly simplifies the complexity of the programming necessary for such automation of SSGS compliance check, dramatically reducing the lines of code to perform such compliance evaluations. The information provided by this invention enables the owners of such systems to put them in a better state of operation.
Owner:SECURESTRUX LLC
Discovery, deployment, and security systems and methods
InactiveUS20060153208A1Data switching by path configurationNetwork connectionsSecurity complianceThe Internet
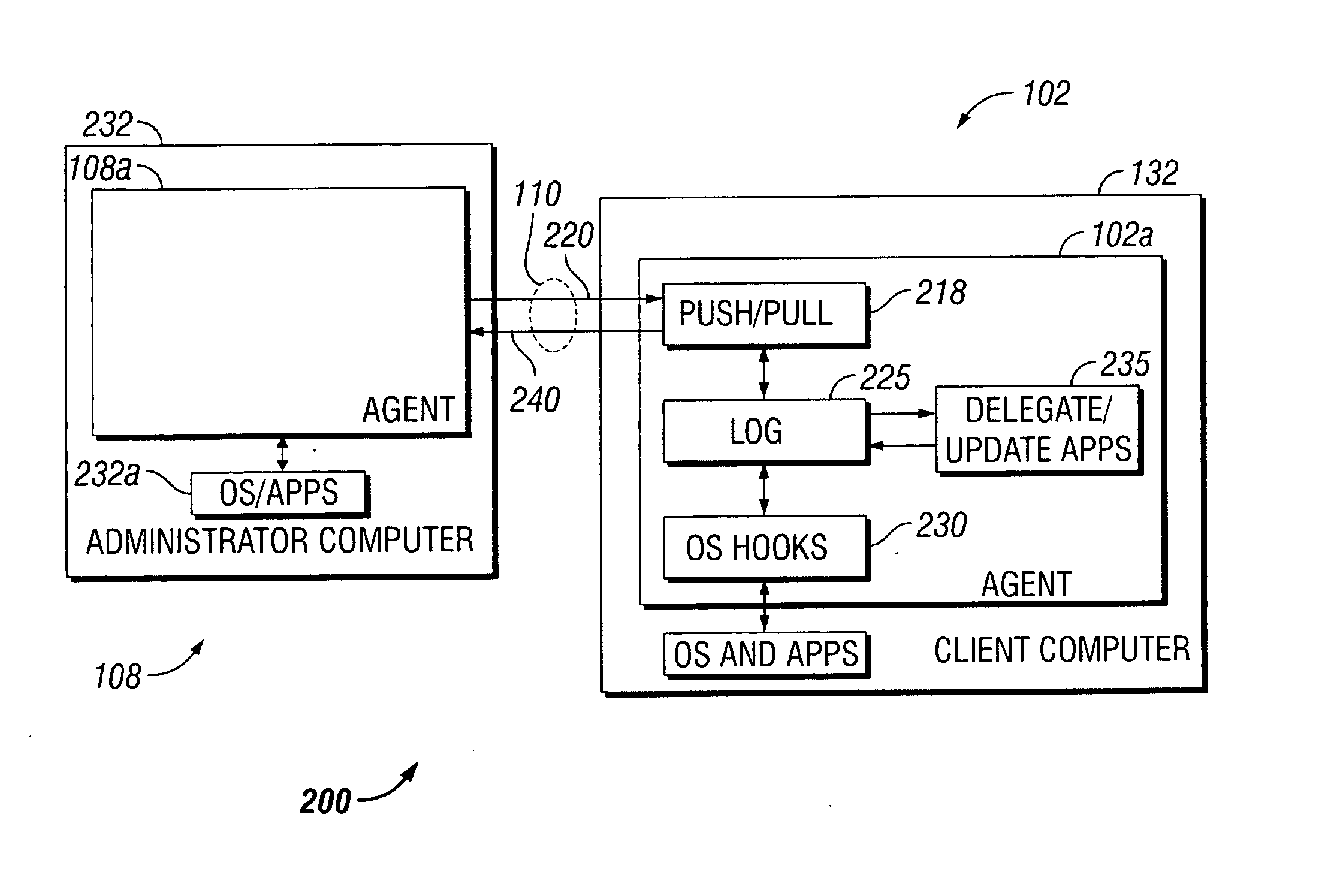
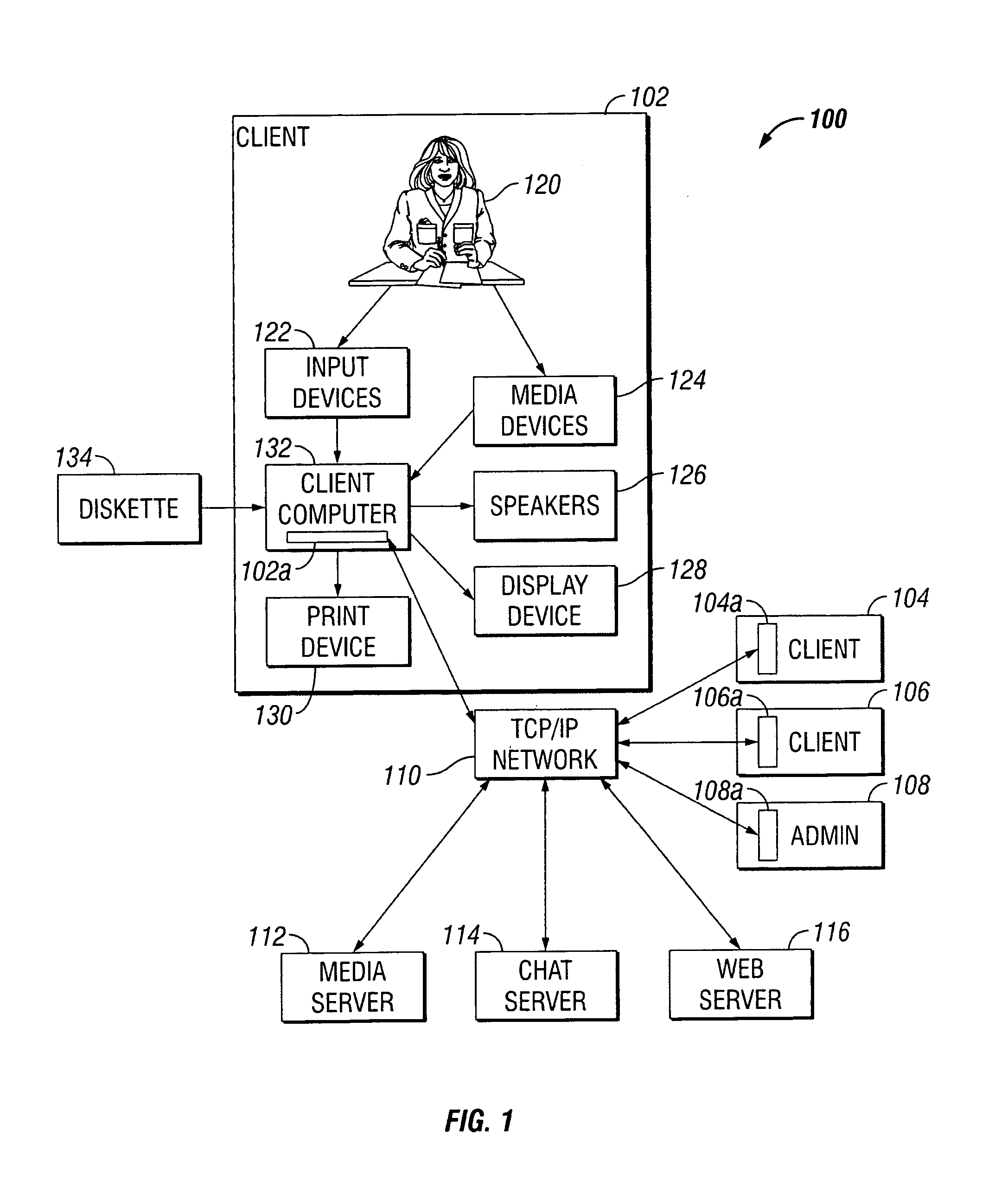
A system and method for discovering devices connected to a communications network, such as the Internet, includes an agent and installation of the agent on a communications device of the network. The agent is installed on a delegate device, which may, but need not necessarily, be an administration device for the network. The delegate device discovers all other devices of the network, via the agent. The agent is also installed on each other networked device, either by direct installation or by pushing the agent to each other device by communications over the network from the delegate device after discovery. The delegate device, which may be the same device that discovers or another device so designated by delegation, deploys the agent on the other devices, including by delegating authority and capabilities to dictate operations by the other devices. The delegate device can delegate to each other device the ability to discover other networked devices, or not, and also can delegate other functions of the agent once deployed on the other devices. The delegate device (or devices, as the case may be), and the other devices on which are deployed the agent, are linked in communication over the network, for example, to communicate via TCP / IP protocols. The agent of the delegate device controls by delegation to the agent of the other devices, the permissible operations of the agent on the other devices. The agent of each device can be delegated authority and capability, by communications from the delegate device (which may, but need not necessarily be, an administration device for the network), to automatedly or otherwise download software patches and perform security compliance operations at each device.
Owner:TRIACTIVE
Software protection using an installation product having an entitlement file
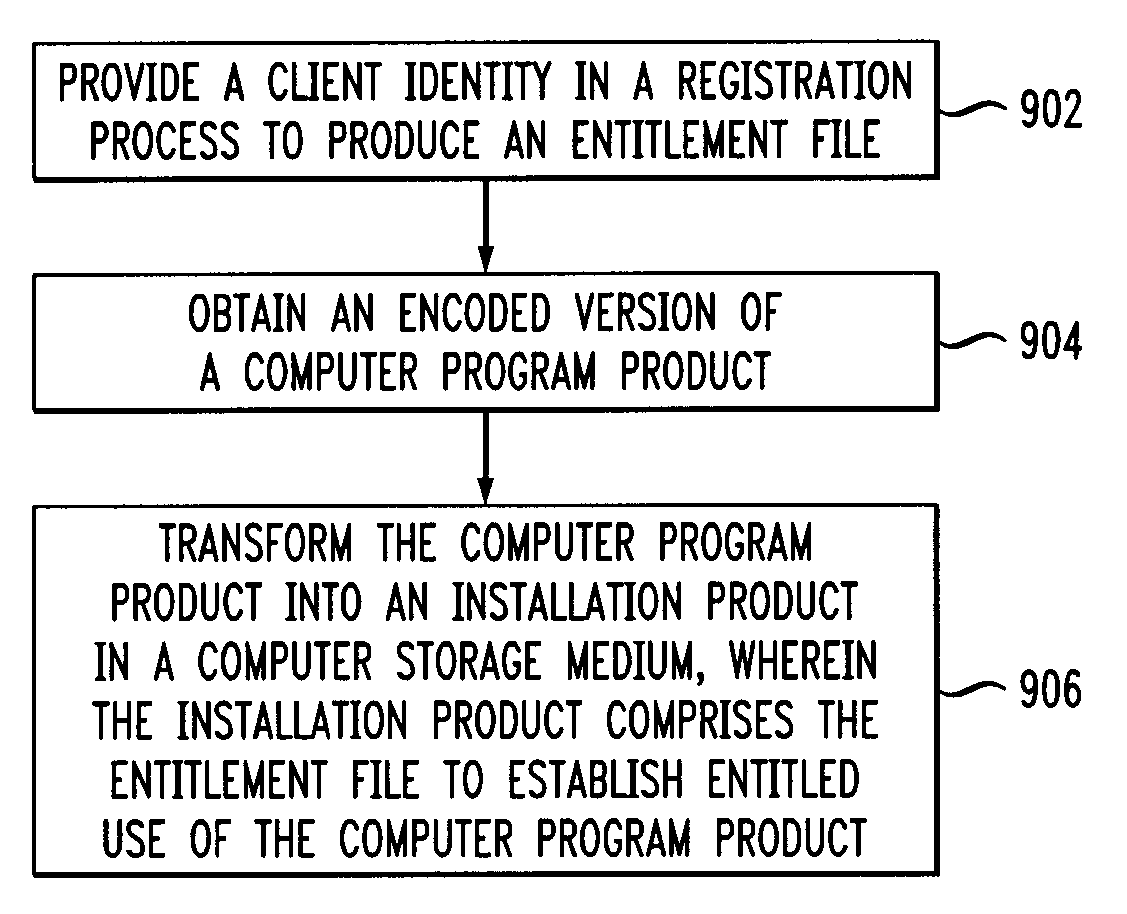
ActiveUS20100218182A1Facilitating security complianceDigital data processing detailsUser identity/authority verificationSecurity complianceClient-side
Techniques for establishing entitlement to a computer program product are provided, and include providing a client identity in a registration process to produce an entitlement file, obtaining an encoded version of a computer program product, and transforming the computer program product into an installation product in a computer storage medium, wherein the installation product comprises the entitlement file to establish entitled use of the computer program product. Also, techniques for facilitating security compliance of a computer program product include providing an encoded version of a computer program product, and providing an installation product builder for the computer program product, wherein the installation product builder creates an installation product in a computer storage medium using a client identity and the encoded version of the computer program product during a registration process, and wherein the created installation product comprises an entitlement file to facilitate security compliance of the computer program product.
Owner:IBM CORP
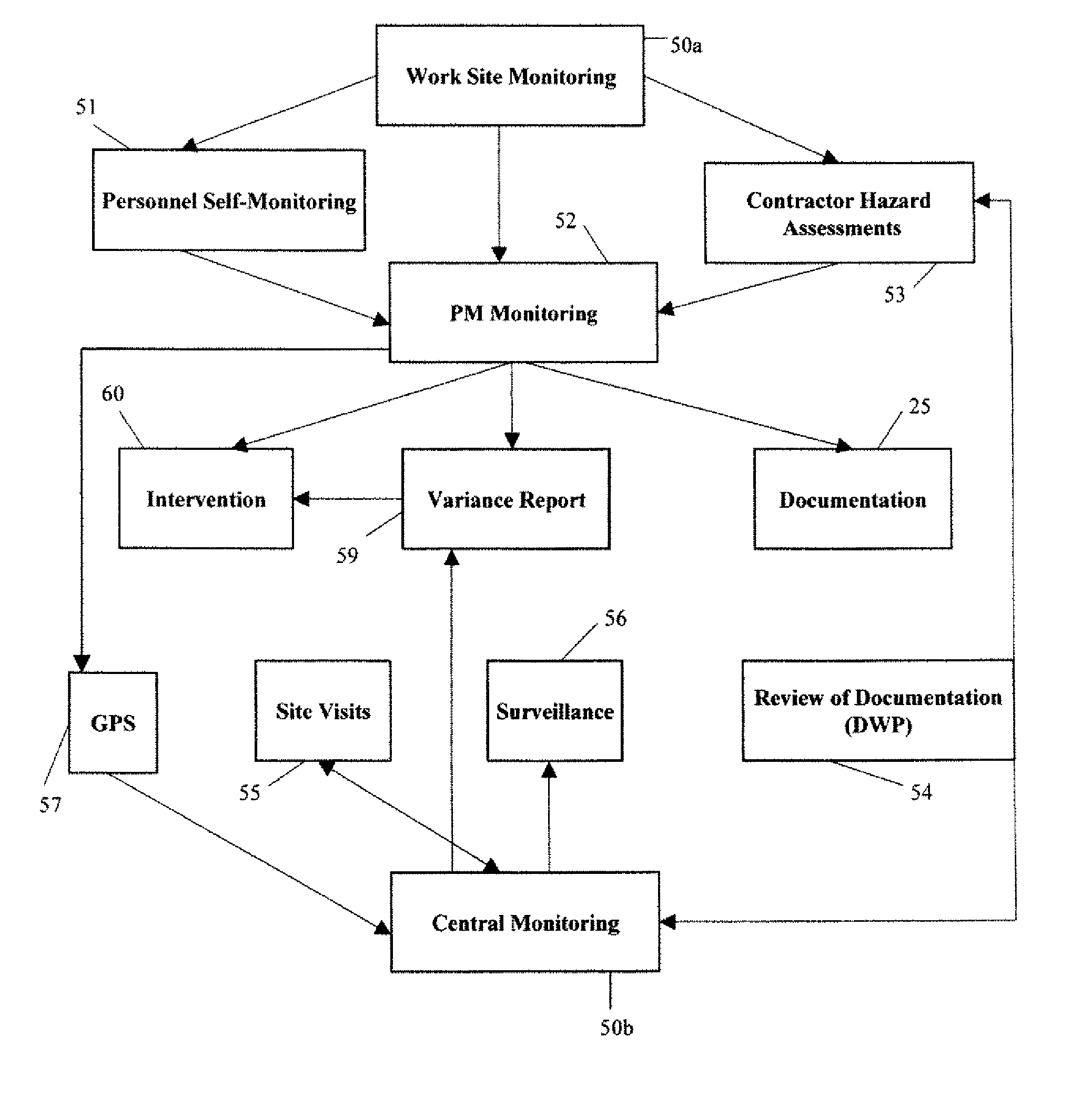
Compliance management system
A system is provided for central monitoring of operational and safety compliance at remote work sites.
Owner:MERCHANT NEIL
Targeted anti-piracy system and methodology
A movie anti-piracy system with sensing and reporting is provided. A movie projector projects a light image to reflect off of a screen, while an infrared energy projection source generates an infrared energy pattern which is reflected off the screen (or otherwise projected) in the same field of view as the light images reflecting from the screen. Infrared energy sensors are positioned in the seating area of the theater. The infrared sensors provide sensed signals respectively to a sensor response controller. The controller is responsive to the sensor signals to provide an infrared status (and other data) signal output to a control center. The control center responds to the infrared status and other data signals, from one or a plurality of theaters, and provides for reporting of information (such as security compliance, attendance, etc.) to one or multiple reporting sites (such as movie distribution studios, etc.). In a preferred embodiment, the control center determines whether the infrared sensors or other data indicate violation of anti-piracy protection within a theater and provides reporting on the status and data. If a violation is indicated, then the control center sends a violation signal such as to the sensor response controller which can trigger an alarm and / or activate a violation inhibit output to shut down the movie projector. This shut down of the projector is an optional feature. In a preferred embodiment, the shut down can be overridden with the entry of an appropriate security code. A data entry subsystem permits entry of additional data, which is communicated as signal to the sensor response controller. The controller provides for processing the data from the data entry and communicating to the control center. The additional data can include ticket sales for one or more movies, attendance data, security code, etc. In a preferred embodiment, there are a plurality of theater systems, each of which has an equivalent anti-piracy system installed, each providing reporting back to the control center which provides overall system control.
Owner:DIGIMEDIA TECH LLC +1
Client computer for protecting confidential file, server computer therefor, method therefor, and computer program
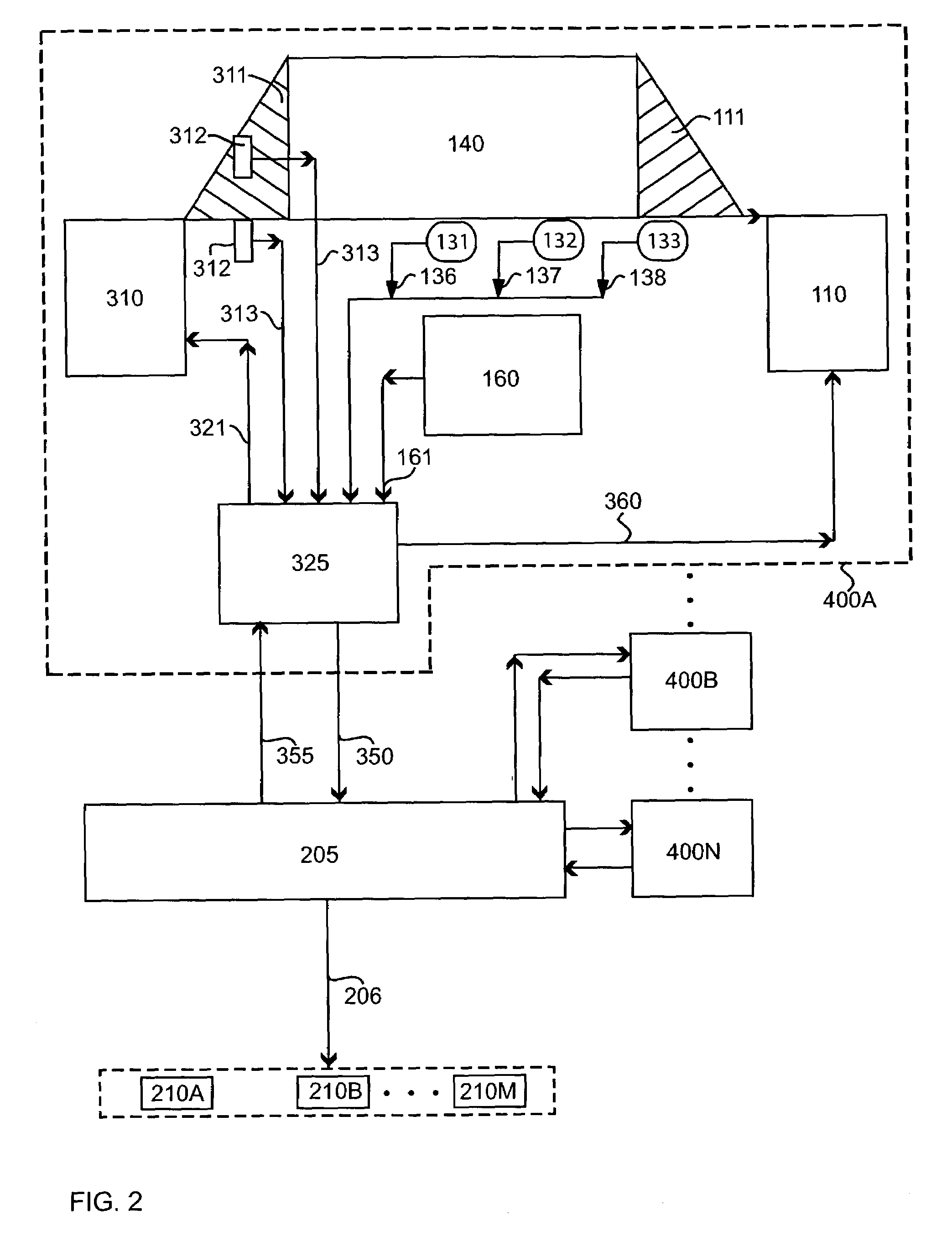
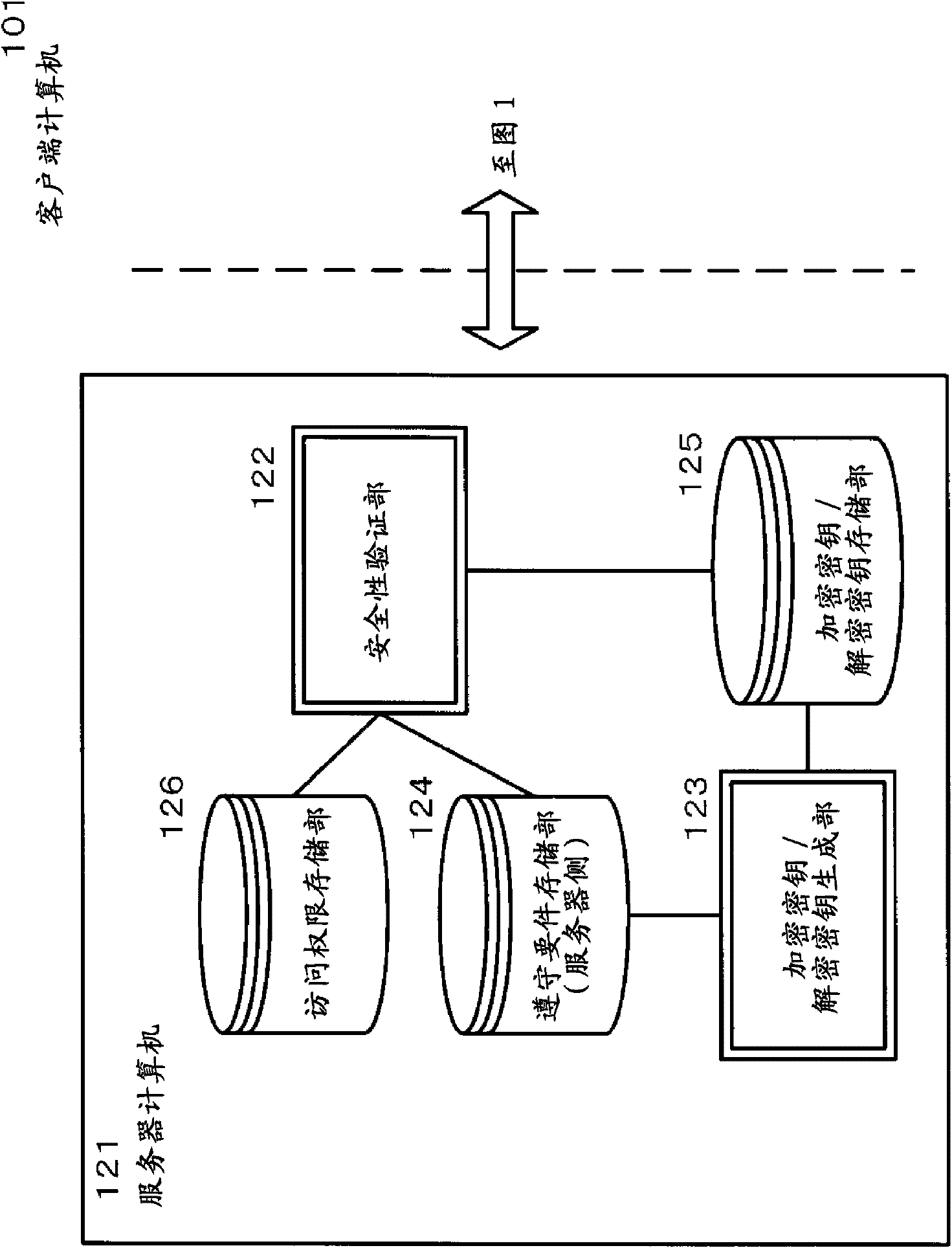
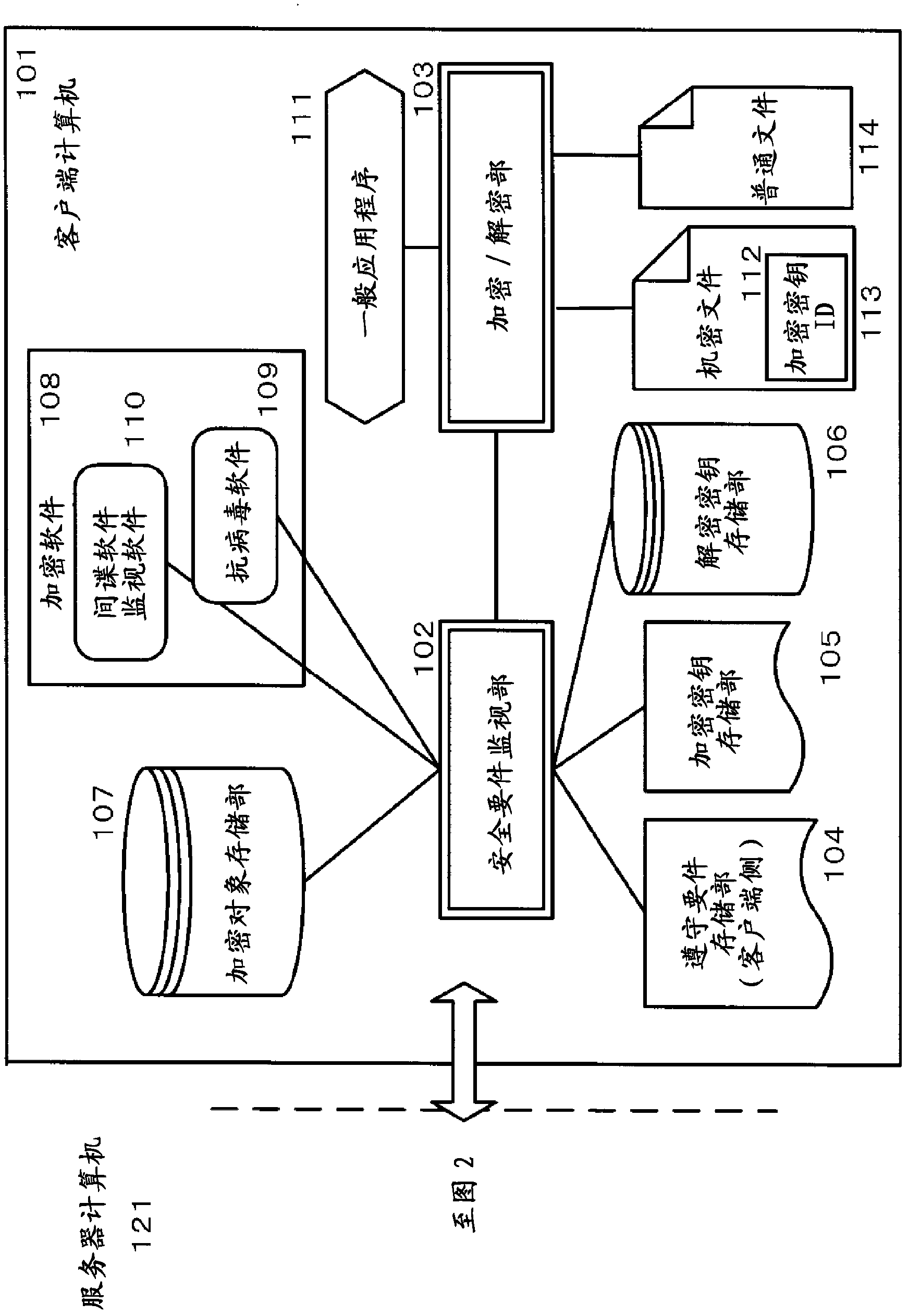
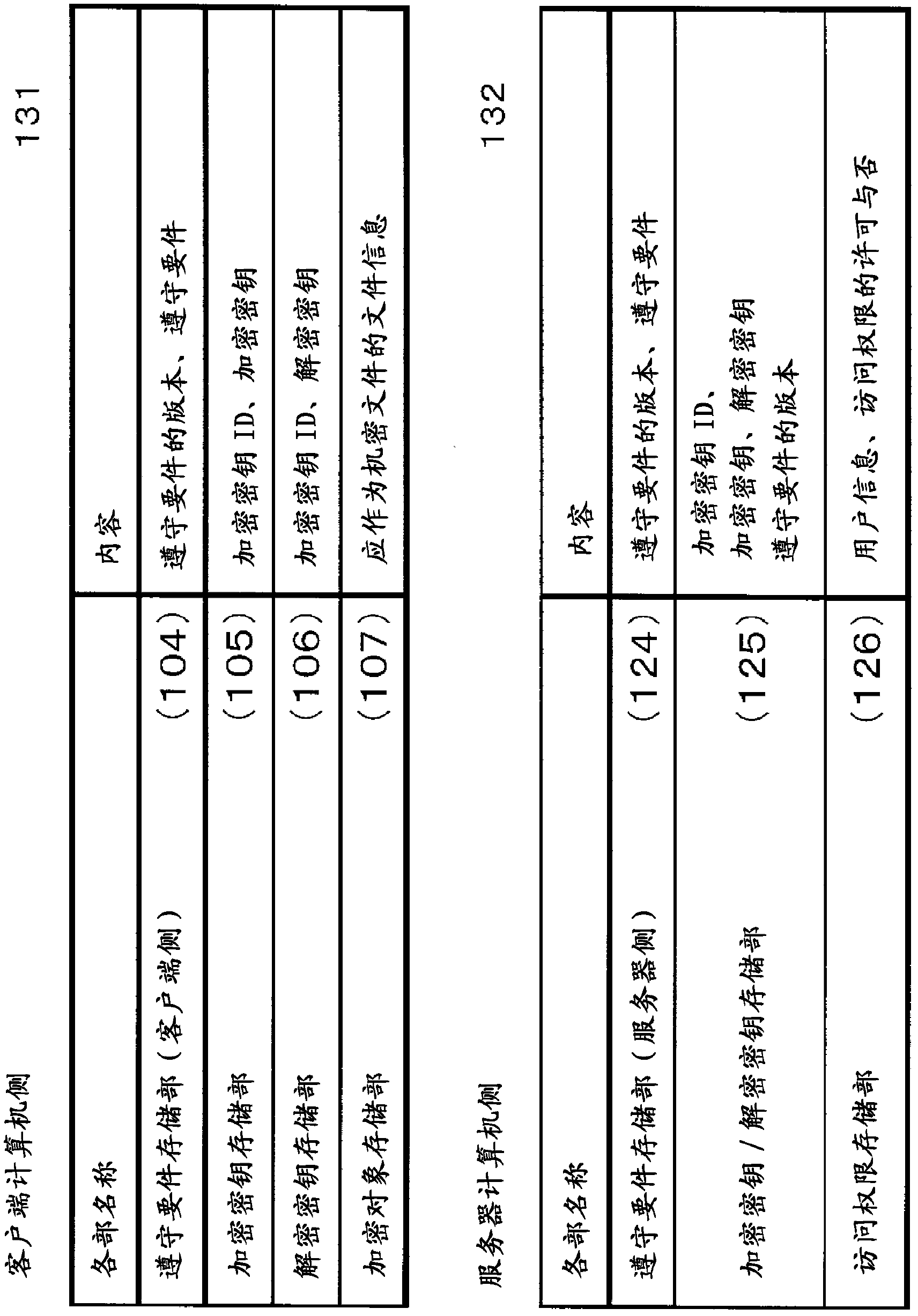
ActiveCN102227734APrevent proliferationEnsure operabilityKey distribution for secure communicationUser identity/authority verificationComputer hardwareSecurity compliance
A client computer includes an encryption / decryption unit for encrypting a confidential file in which an encryption key ID is embedded using an encryption key corresponding to the encryption key ID and decrypting the confidential file using a decryption key corresponding to the encryption key ID, an encryption key storage unit for storing the encryption key, a decryption key storage unit for storing the decryption key, a compliance requirement storage unit for storing security compliance requirements for the client computer transmitted from a server computer, and a security requirement monitoring unit for determining, according to a read command or a write command for the confidential file issued by application software, whether the client computer complies with the security compliance requirements, and, when the requirements are complied with, passing the encryption key and the encryption key ID corresponding to the encryption key from the encryption key storage unit to the encryption / decryption unit in response to the write command or passing the decryption key corresponding to the encryption key ID embedded in the encrypted confidential file from the decryption key storage unit to the encryption / decryption unit in response to the read command.
Owner:IBM CORP
Multi-channel network payment method and system
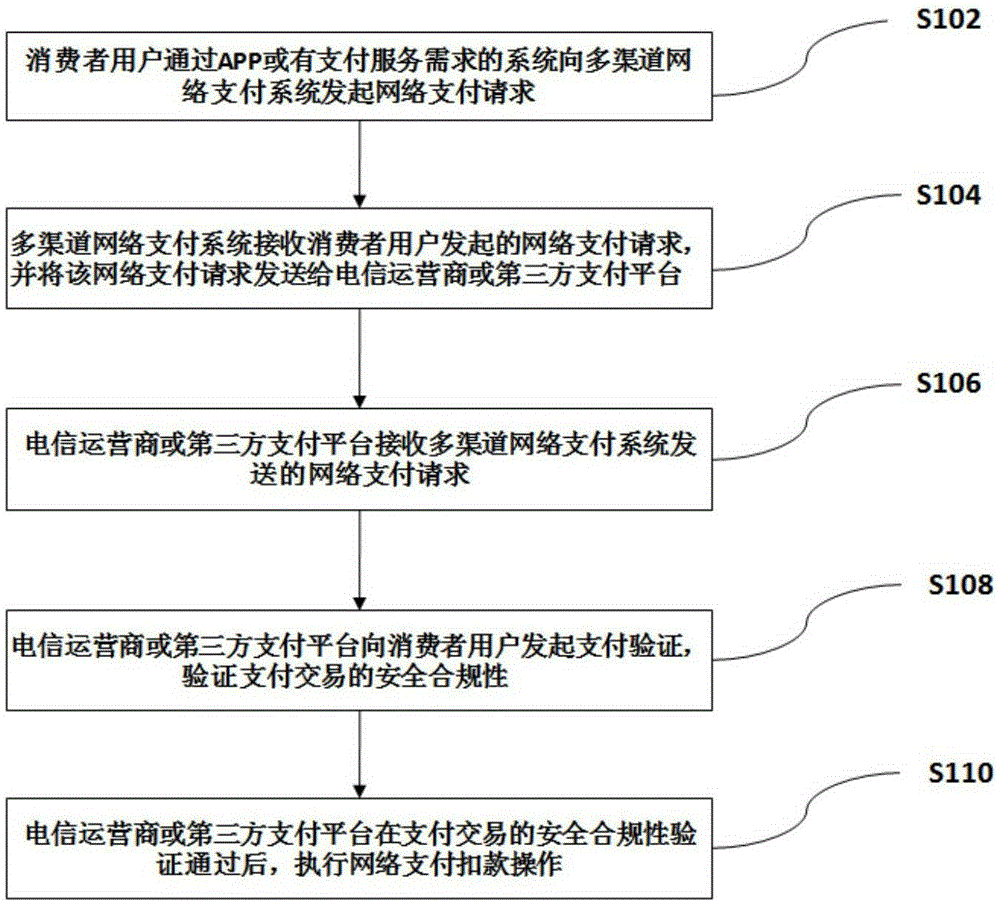
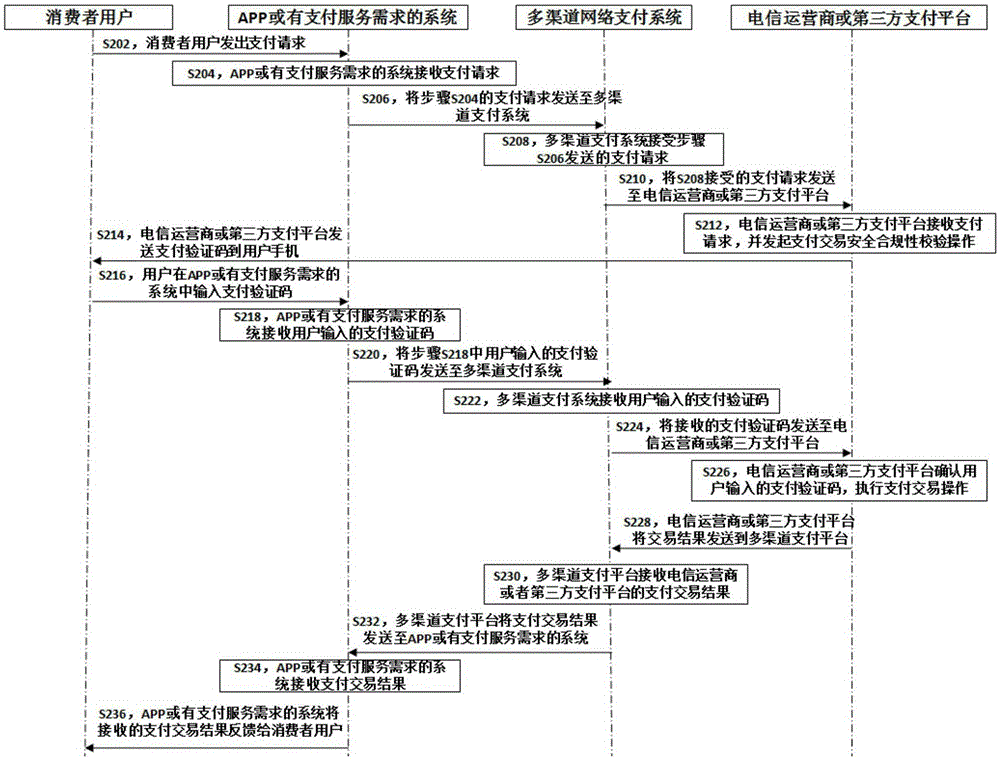
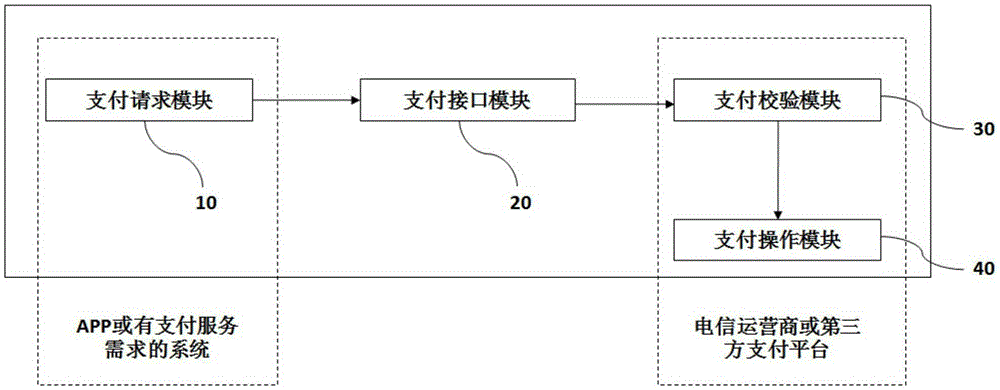
InactiveCN105389695AReduce business complexityPayment circuitsPayments involving neutral partyTelecommunications networkSecurity compliance
The present invention discloses a multi-channel network payment method. The method comprises the following steps that: (1) a consumer user initials a network payment request to a multi-channel network payment system through an APP or a system with a payment service requirement, (2) the multi-channel network payment system receives the network payment request initiated by the consumer user and sends the network payment request to a telecommunications network operator or a third-party payment platform, (3) the telecommunications network operator or the third-party payment platform initiates payment verification to the consumer user, and (4) after the security compliance verification of the telecommunications network operator or the third-party payment platform is passed, a network payment deduction operation is executed. The invention also provides a multi-channel network payment system with the application of the above method. According to the multi-channel network payment method and system, the network payment can be completed through the multi-channel network payment system, the service complexity of the network payment is reduced, and thus the network payment is more convenient and fast.
Owner:江西掌中无限网络科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com