Information safety simulation model and terminal of industrial control system
An industrial control system and information security technology, applied in the field of network security, can solve problems that affect system operation, network instability, and failure to provide industrial control network security risk simulation and demonstration.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
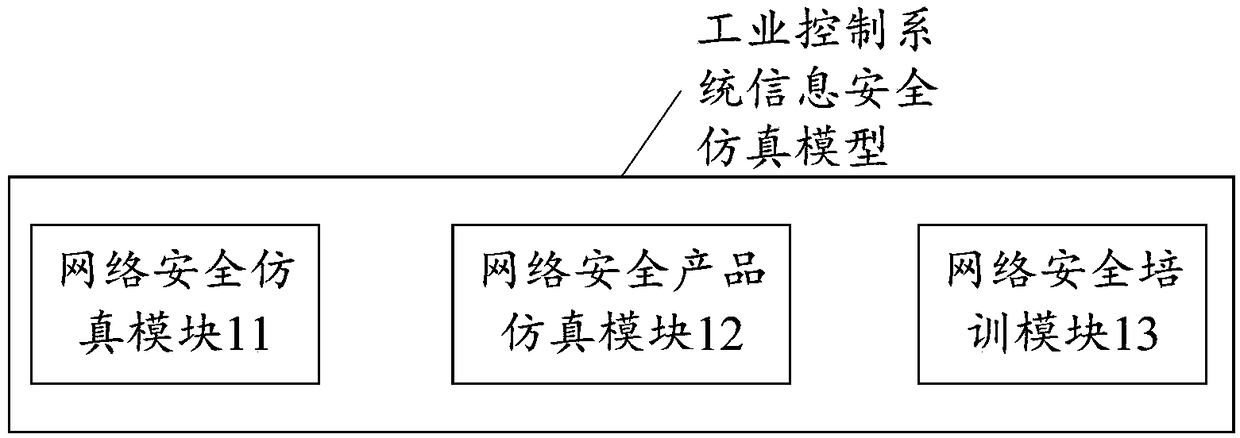
[0057] An industrial control system information security simulation model, reference figure 1 , the model is an independent information security simulation model, including: a network security simulation module 11, a network security product simulation module 12 and a network security training module 13;
[0058] The network security simulation module 11 is used to perform security compliance detection on the network structure of the industrial control system, perform security detection on the network traffic of the industrial control system, and perform security detection on the network host of the industrial control system;
[0059] The network security product simulation module 12 is used to test the function, vulnerability and performance of the network security product, obtain test information, and evaluate the conformity between the identification information of the network security product and the test information;
[0060] The network security training module 13 is use...
Embodiment 2
[0178] An industrial control system information security simulation terminal, on which the industrial control system information security simulation model in the first embodiment above is installed.
[0179] The computer program product of the industrial control system information security simulation model and the terminal provided by the embodiments of the present invention includes a computer-readable storage medium storing program codes, and the instructions included in the program codes can be used to execute the method described in the preceding method embodiments. For the specific implementation of the method, refer to the method embodiments, which will not be repeated here.
[0180] Those skilled in the art can clearly understand that for the convenience and brevity of description, the specific working process of the above-described system and device can refer to the corresponding process in the foregoing method embodiments, which will not be repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com