Patents
Literature
22574results about How to "Improve integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
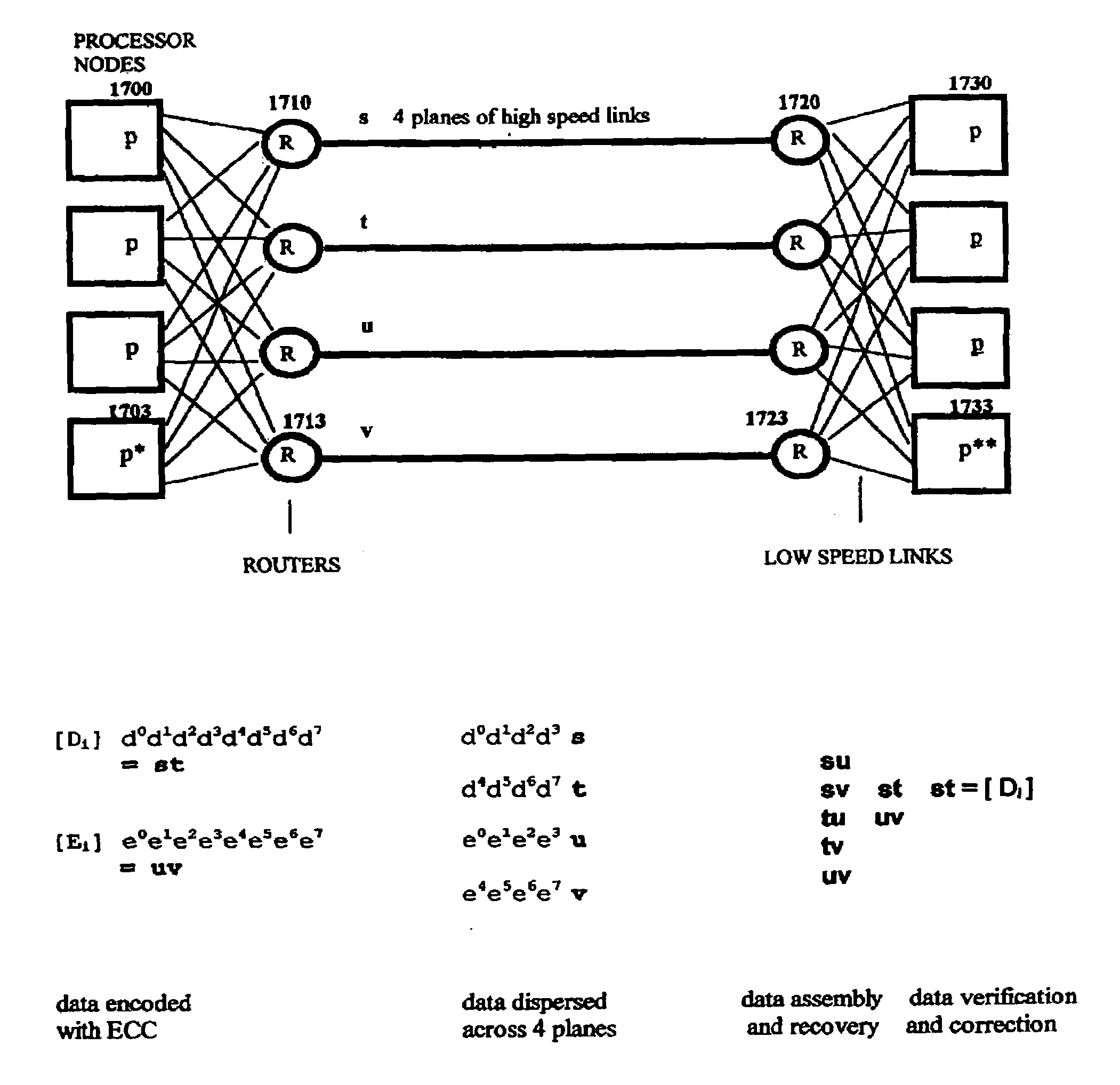
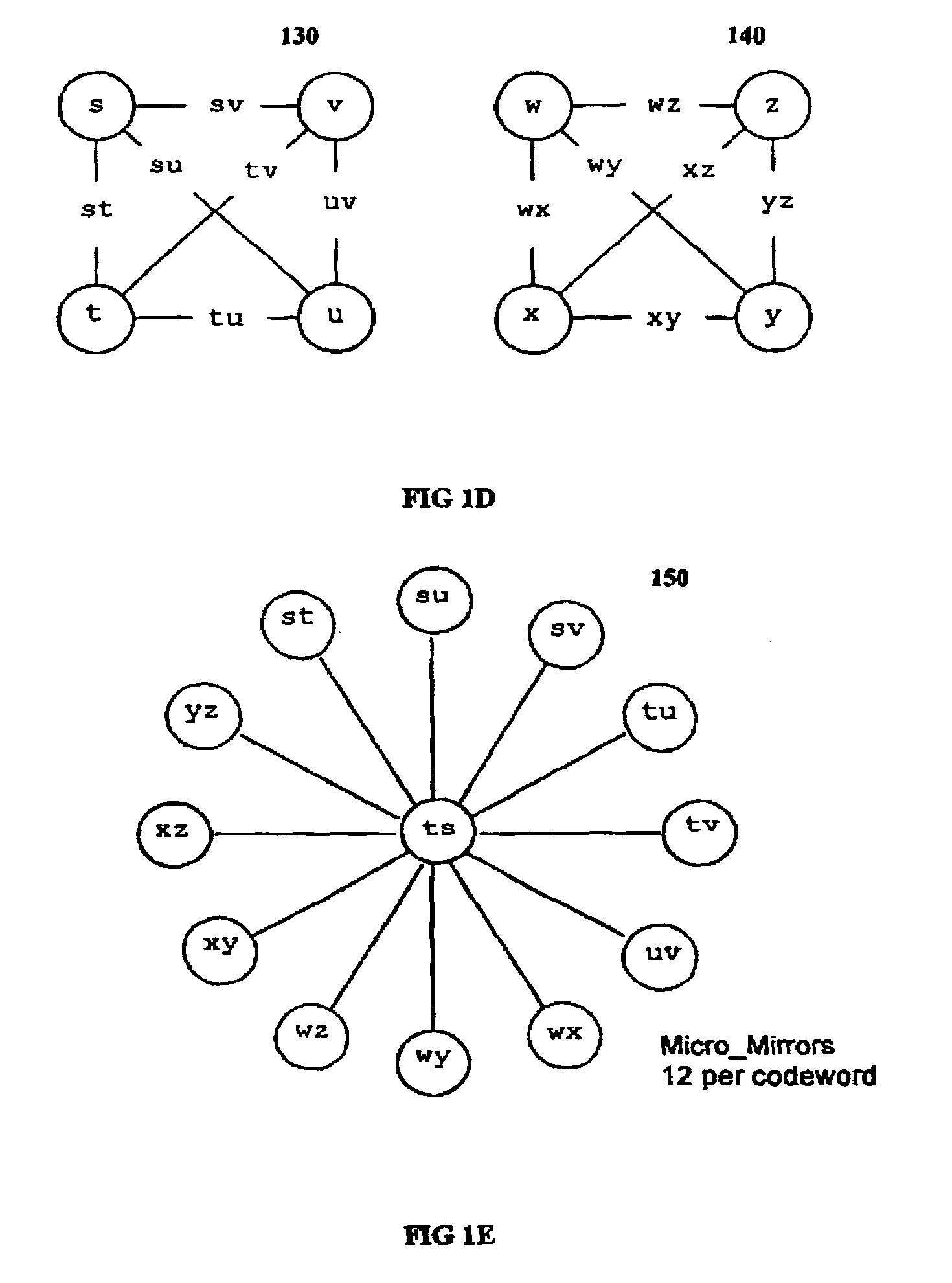
Multi-dimensional data protection and mirroring method for micro level data
ActiveUS7103824B2Detection errorLow common data sizeCode conversionCyclic codesData validationData integrity
The invention discloses a data validation, mirroring and error / erasure correction method for the dispersal and protection of one and two-dimensional data at the micro level for computer, communication and storage systems. Each of 256 possible 8-bit data bytes are mirrored with a unique 8-bit ECC byte. The ECC enables 8-bit burst and 4-bit random error detection plus 2-bit random error correction for each encoded data byte. With the data byte and ECC byte configured into a 4 bit×4 bit codeword array and dispersed in either row, column or both dimensions the method can perform dual 4-bit row and column erasure recovery. It is shown that for each codeword there are 12 possible combinations of row and column elements called couplets capable of mirroring the data byte. These byte level micro-mirrors outperform conventional mirroring in that each byte and its ECC mirror can self-detect and self-correct random errors and can recover all dual erasure combinations over four elements. Encoding at the byte quanta level maximizes application flexibility. Also disclosed are fast encode, decode and reconstruction methods via boolean logic, processor instructions and software table look-up with the intent to run at line and application speeds. The new error control method can augment ARQ algorithms and bring resiliency to system fabrics including routers and links previously limited to the recovery of transient errors. Image storage and storage over arrays of static devices can benefit from the two-dimensional capabilities. Applications with critical data integrity requirements can utilize the method for end-to-end protection and validation. An extra ECC byte per codeword extends both the resiliency and dimensionality.
Owner:HALFORD ROBERT
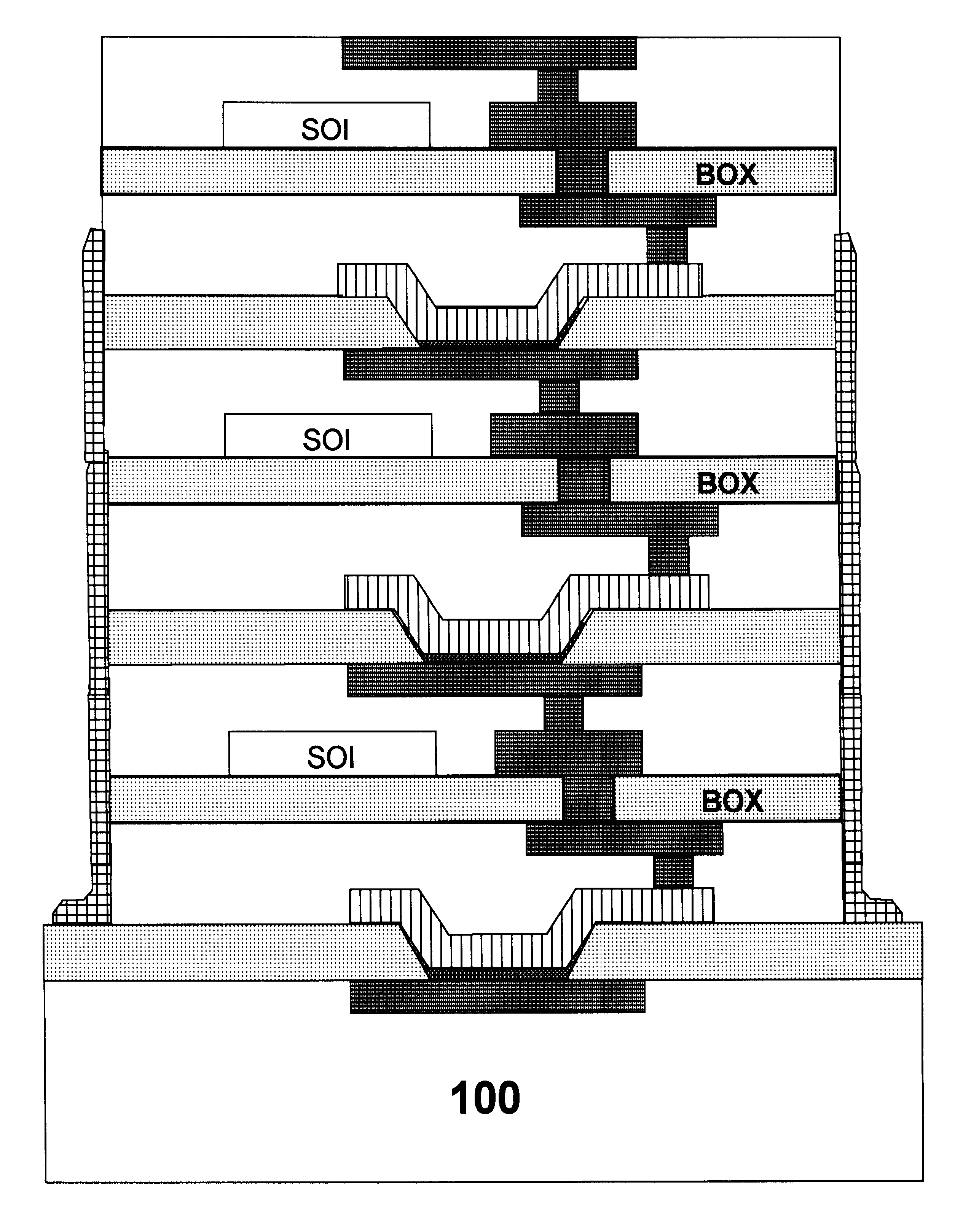
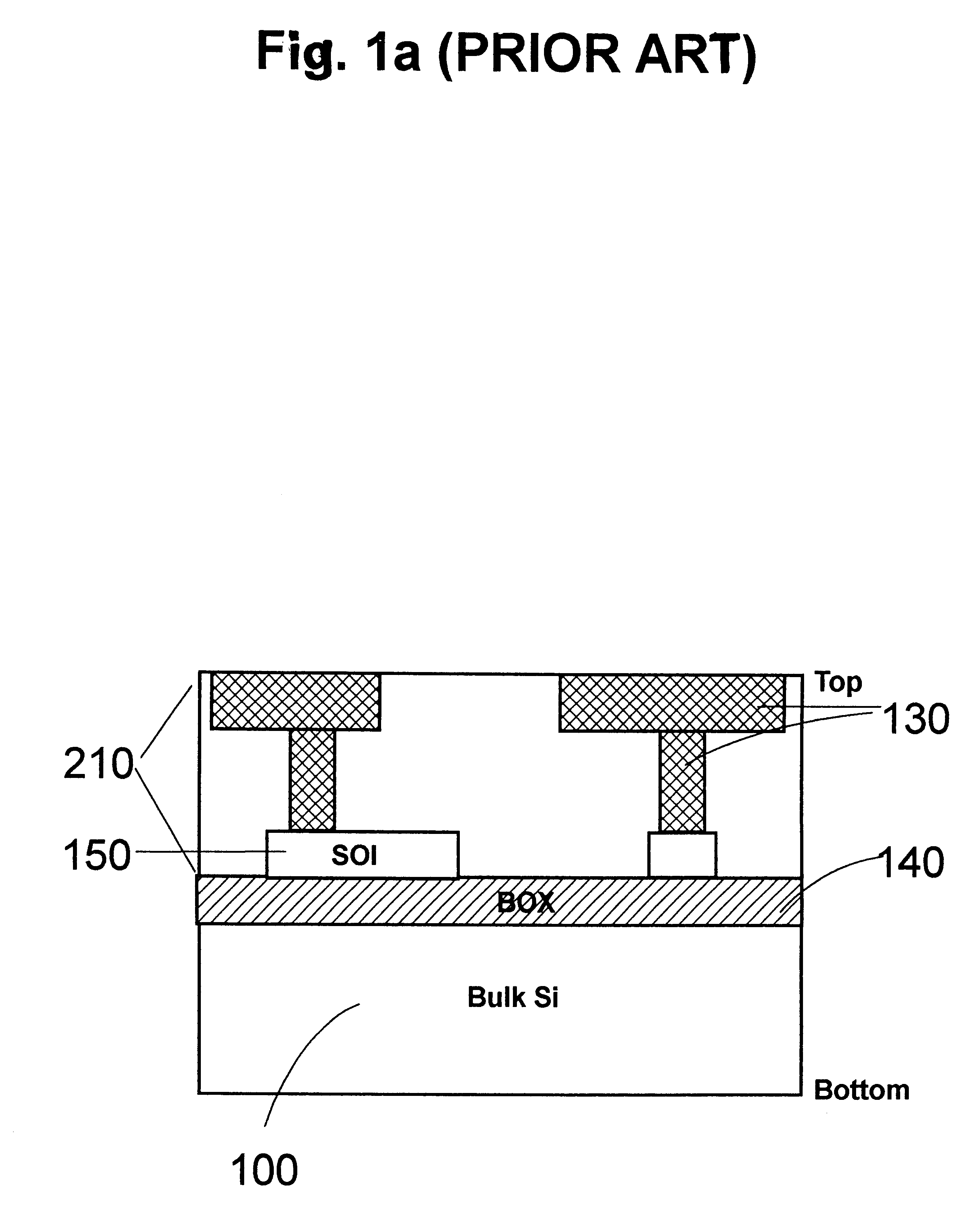
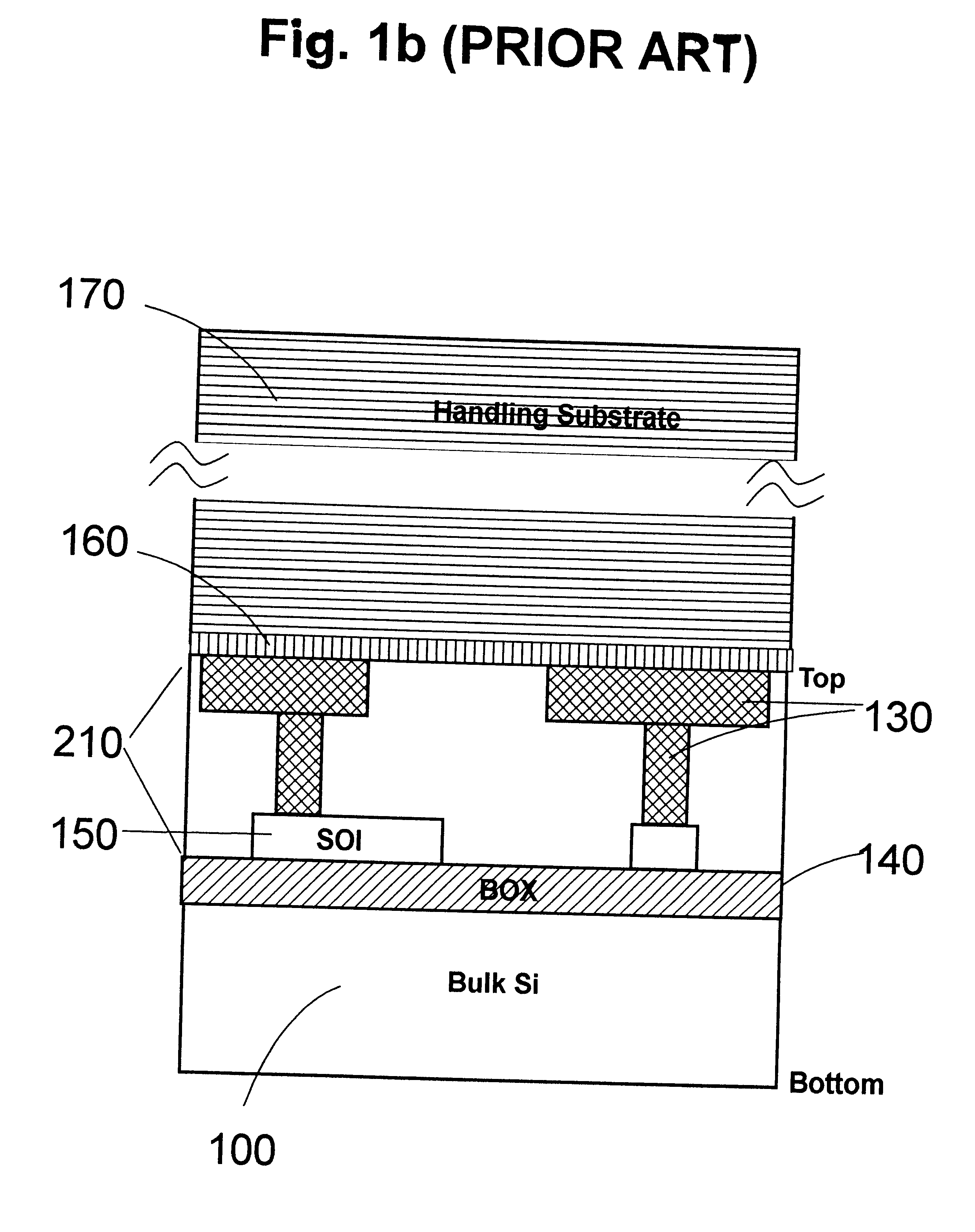
Three-dimensional chip stacking assembly
InactiveUS6355501B1Precise alignmentGood mechanical integritySolid-state devicesSemiconductor/solid-state device manufacturingEngineeringThree-dimensional integrated circuit
An assembly consisting of three dimensional stacked SOI chips, and a method of forming such integrated circuit assembly, each of the SOI chips including a handler making mechanical contact to a first metallization pattern making electrical contact to a semiconductor device. The metalized pattern, in turn, contacts a second metallization pattern positioned on an opposite surface of the semiconductor device. The method of fabricating the three-dimensional IC assembly includes the steps of: a) providing a substrate having a third metalized pattern on a first surface of the substrate; b) aligning one of the SOI chips on the first surface of the substrate, by having the second metallization pattern of the SOI chip make electrical contact with the third metalized pattern of the substrate; c) removing the handler from the SOI chip, exposing the first metallization pattern of the SOI chip; d) aligning a second one of the SOI chips with the first SOI chip, having the second metallization pattern of the second SOI chip make electrical contact to the exposed first metallization pattern of the first SOI chip; and e) repeating steps c) and d) for mounting subsequent SOI chips one on top of the other.
Owner:IBM CORP
Identifying and requesting data in network using identifiers which are based on contents of data
InactiveUS6415280B1Improve efficiencyImprove integrityData processing applicationsDigital data processing detailsHash functionData content
In a system in which a set of data items are distributed across a network of servers, at least some of the data items being cached versions of data items from a source server, a content delivery method includes determining a data identifier for a particular data item, the data identifier being determined using a given function of the data comprising the particular data item; and responsive to a request for the particular data item, the request including at least the data identifier of the particular data item, providing the particular data item from a given one of the servers of the network of servers. The request for the particular data item may be resolved based on a measure of availability of at least one of the servers, where the measure of availability may be a measurement of bandwidth to the server; a measurement of a cost of a connection to the server, and / or a measurement of a reliability of a connection to the server. The function used to determine the identifier may be a message digest function or a hash function.
Owner:LEVEL 3 COMM LLC +1
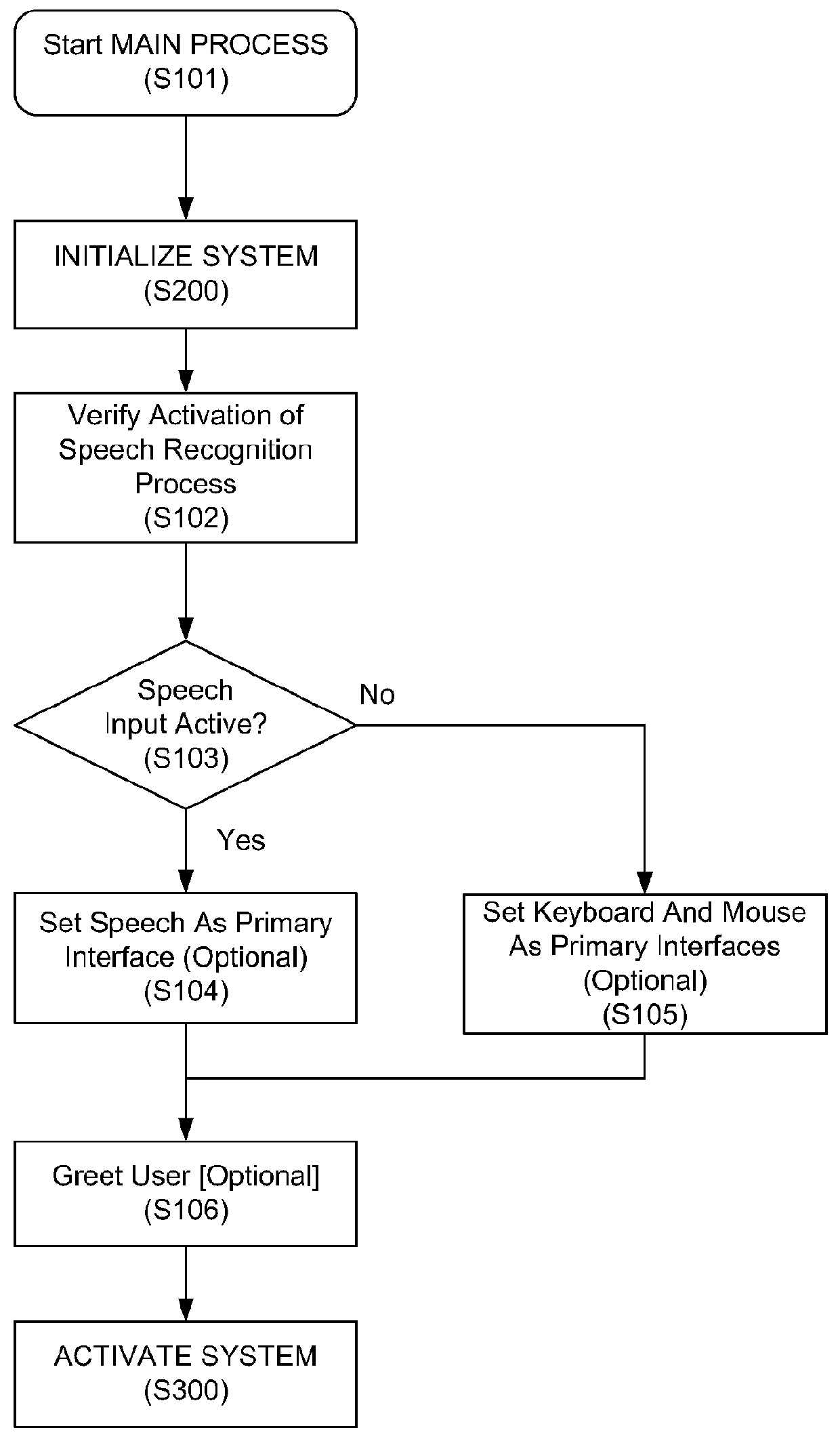
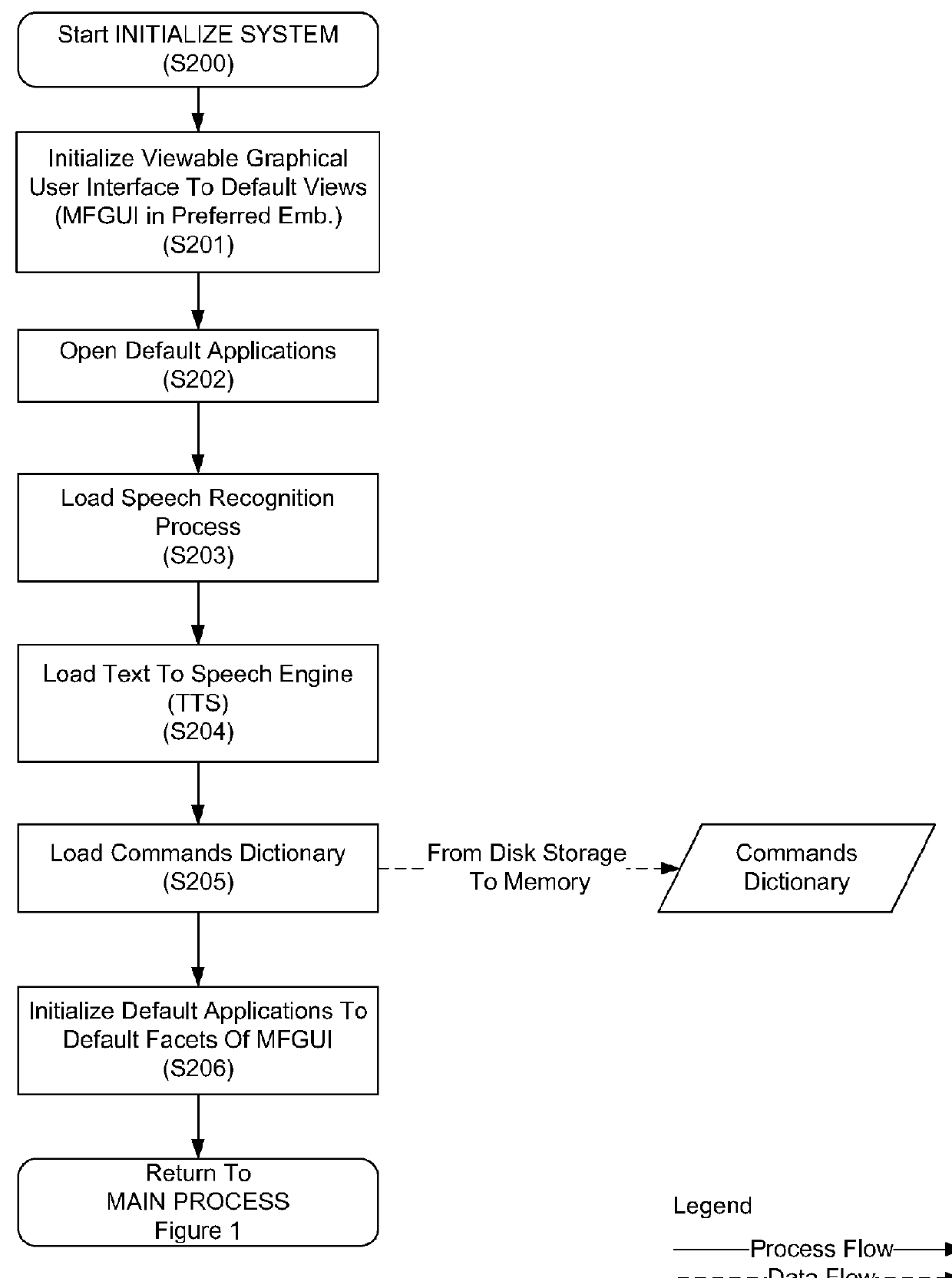
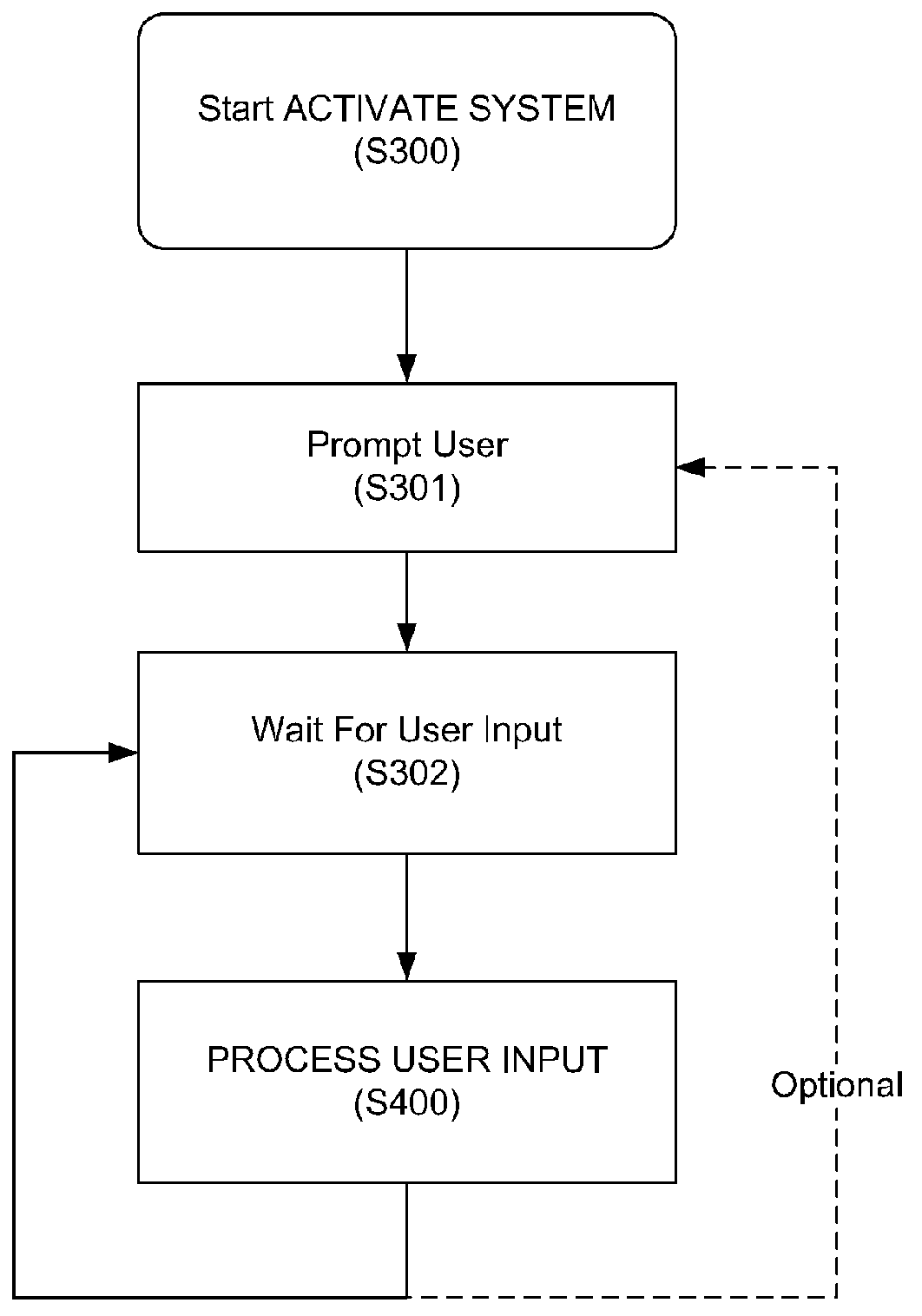
Speech interface system and method for control and interaction with applications on a computing system
ActiveUS8165886B1Reduce ambiguityImprove integritySound input/outputSpeech recognitionSpeech inputApplication software
A speech processing system which exploits statistical modeling and formal logic to receive and process speech input, which may represent data to be received, such as dictation, or commands to be processed by an operating system, application or process. A command dictionary and dynamic grammars are used in processing speech input to identify, disambiguate and extract commands. The logical processing scheme ensures that putative commands are complete and unambiguous before processing. Context sensitivity may be employed to differentiate data and commands. A multi faceted graphic user interface may be provided for interaction with a user to speech enable interaction with applications and processes that do not necessarily have native support for speech input.
Owner:SAMSUNG ELECTRONICS CO LTD
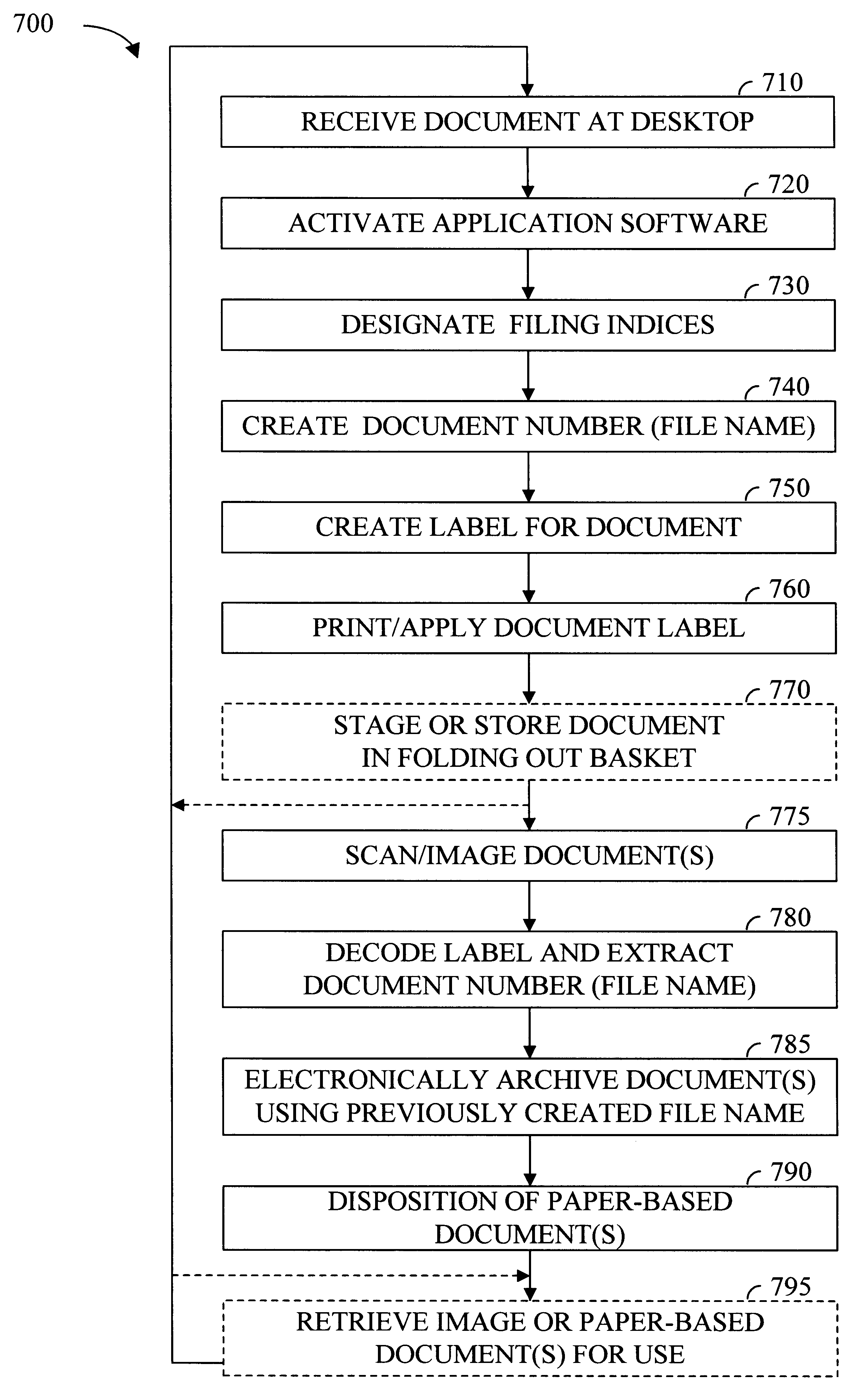
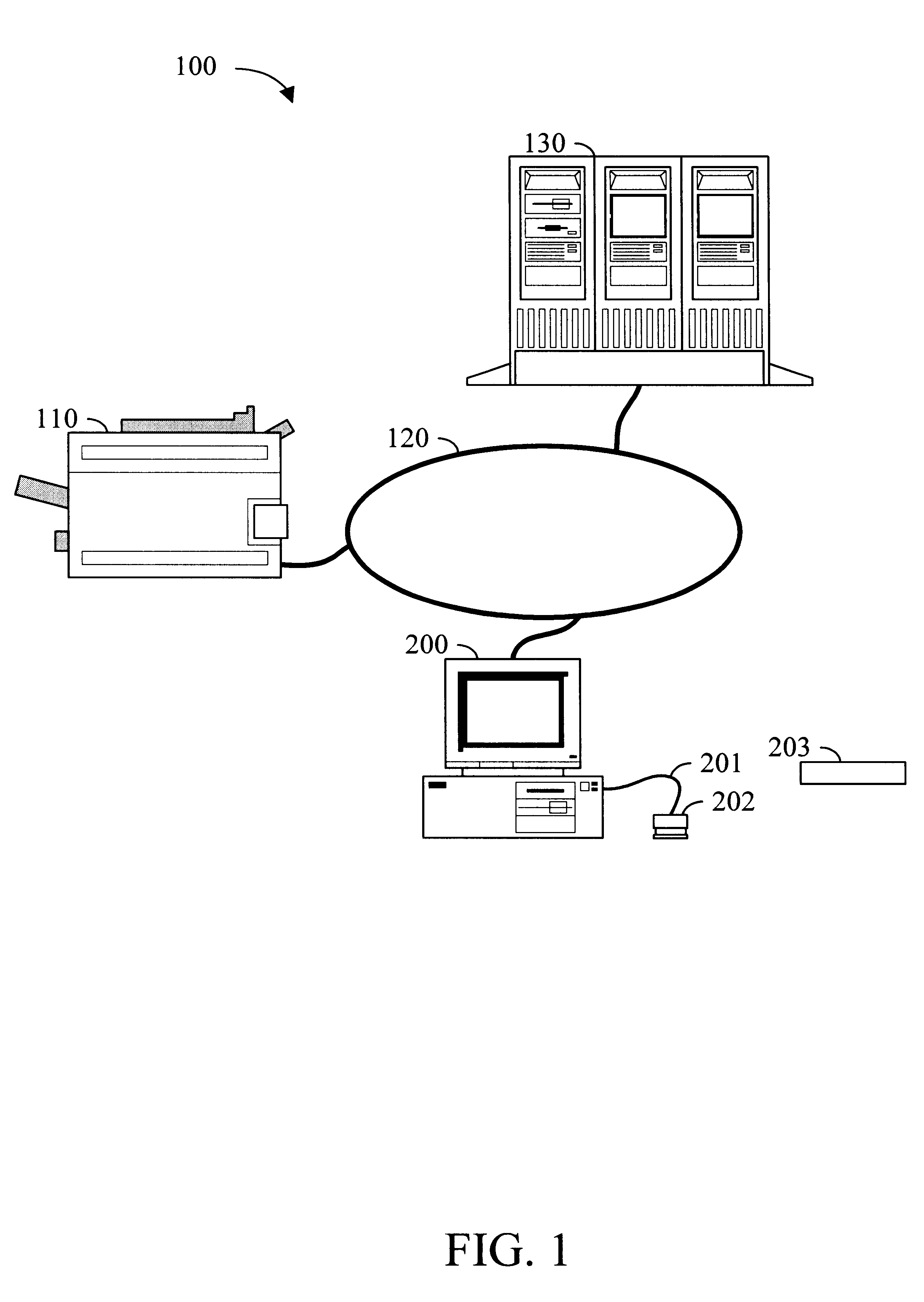
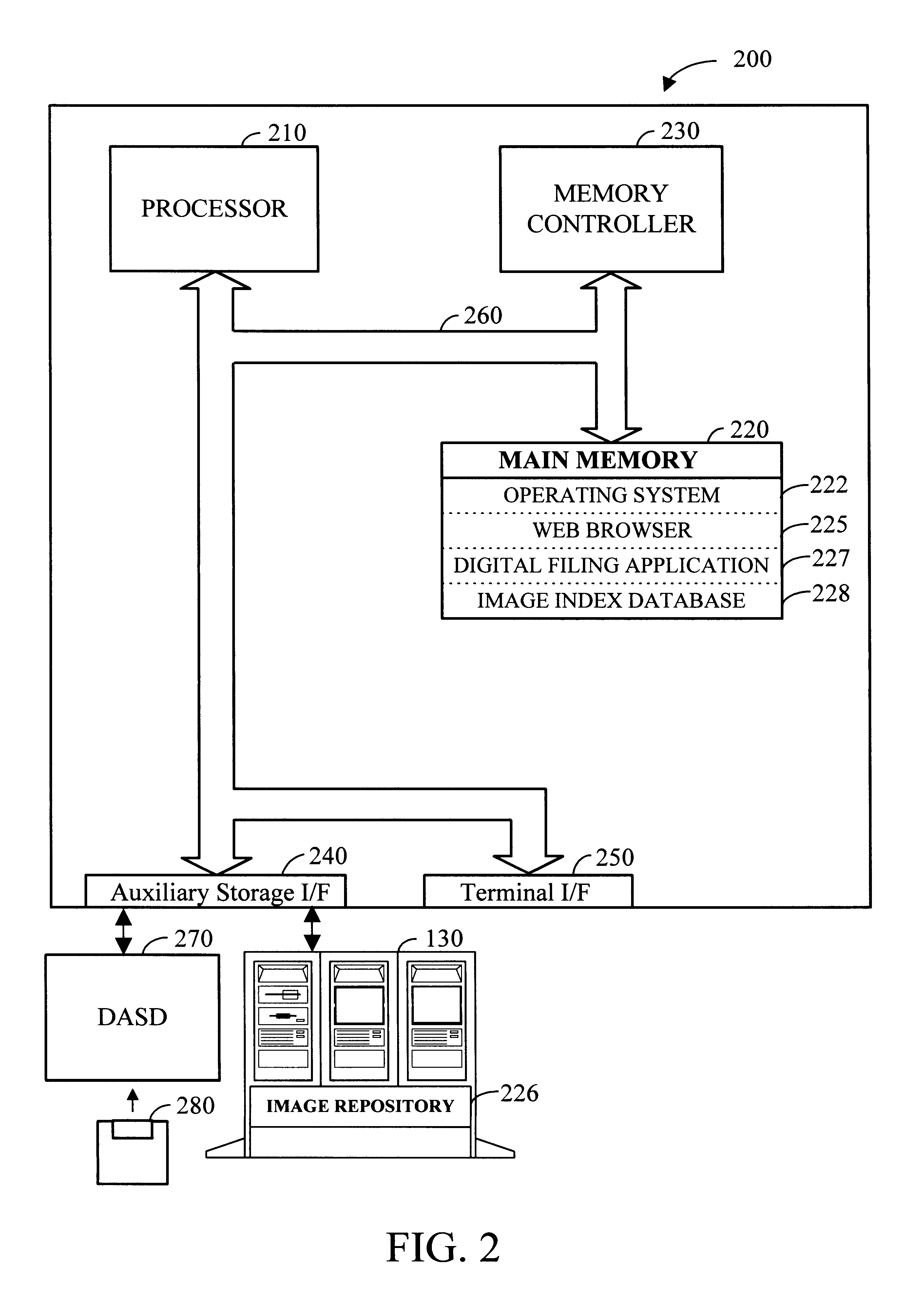
Apparatus and method for digital filing
InactiveUS6192165B1Easy and effective and imagingEasy and effective indexingData processing applicationsDigital computer detailsElectronic documentWeb browser
According to the preferred embodiments of the present invention, an apparatus and method for a digital filing system is disclosed. In this context, digital filing refers to the efficient management of paper-based information from its receipt at the desktop through an indexing, scanning, image storage and image retrieval process. The preferred embodiments of the present invention provide for easy and effective indexing, imaging, storing, retrieving and managing of paper-based documents, transforming them into electronic documents using a system which incorporates many existing office resources. The proposed system and method implements a desktop solution for digital filing, which can be made available to each worker. In one embodiment of the present invention, an individual has complete control over the electronic storage and retrieval of their documents from a standard desktop computer, using a standard web browser application. Uniquely, the digital filing system of the present invention also allows users to index and label documents prior to scanning / imaging by using a dedicated desktop labeling mechanism.
Owner:IMAGETAG
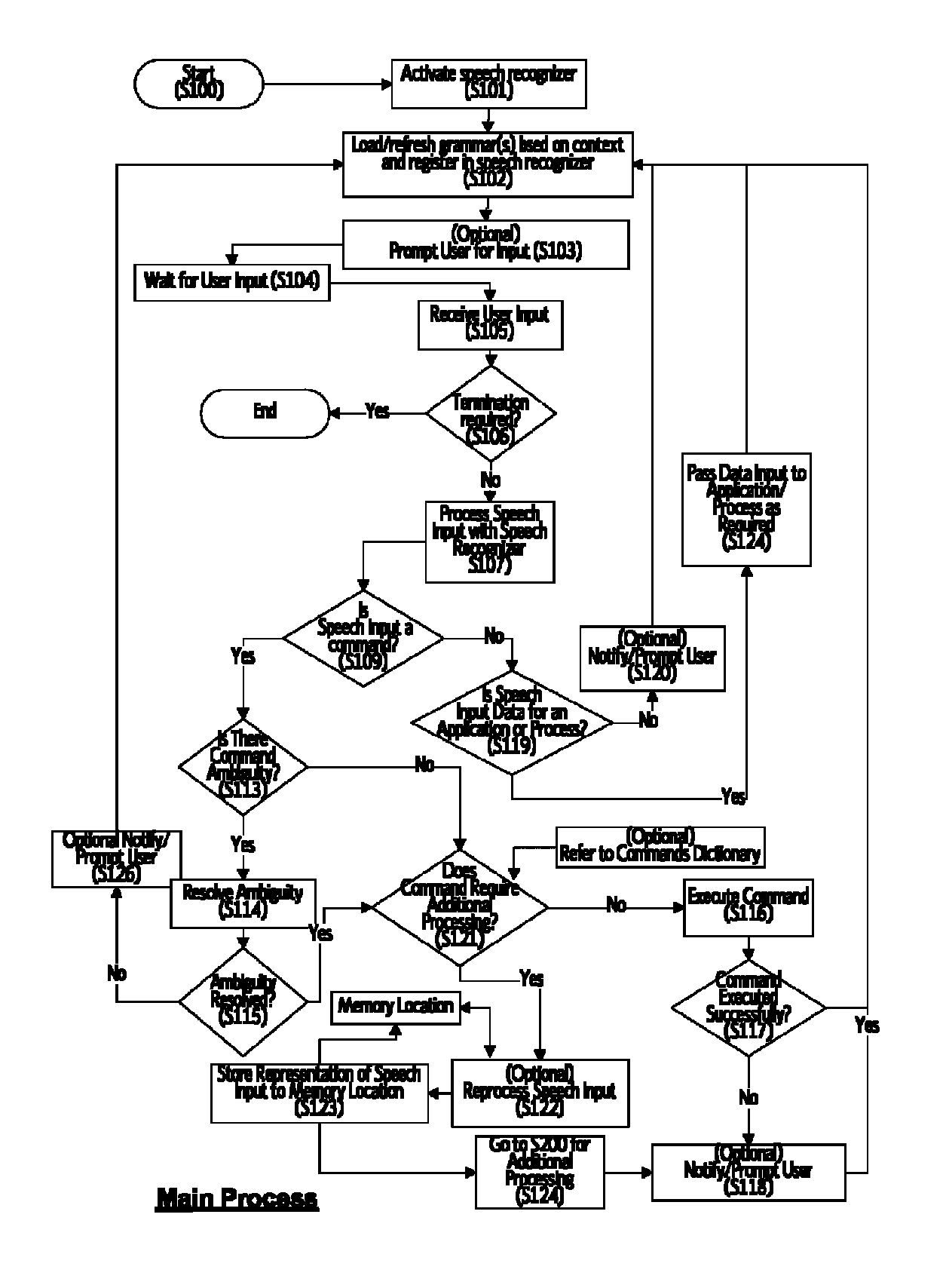
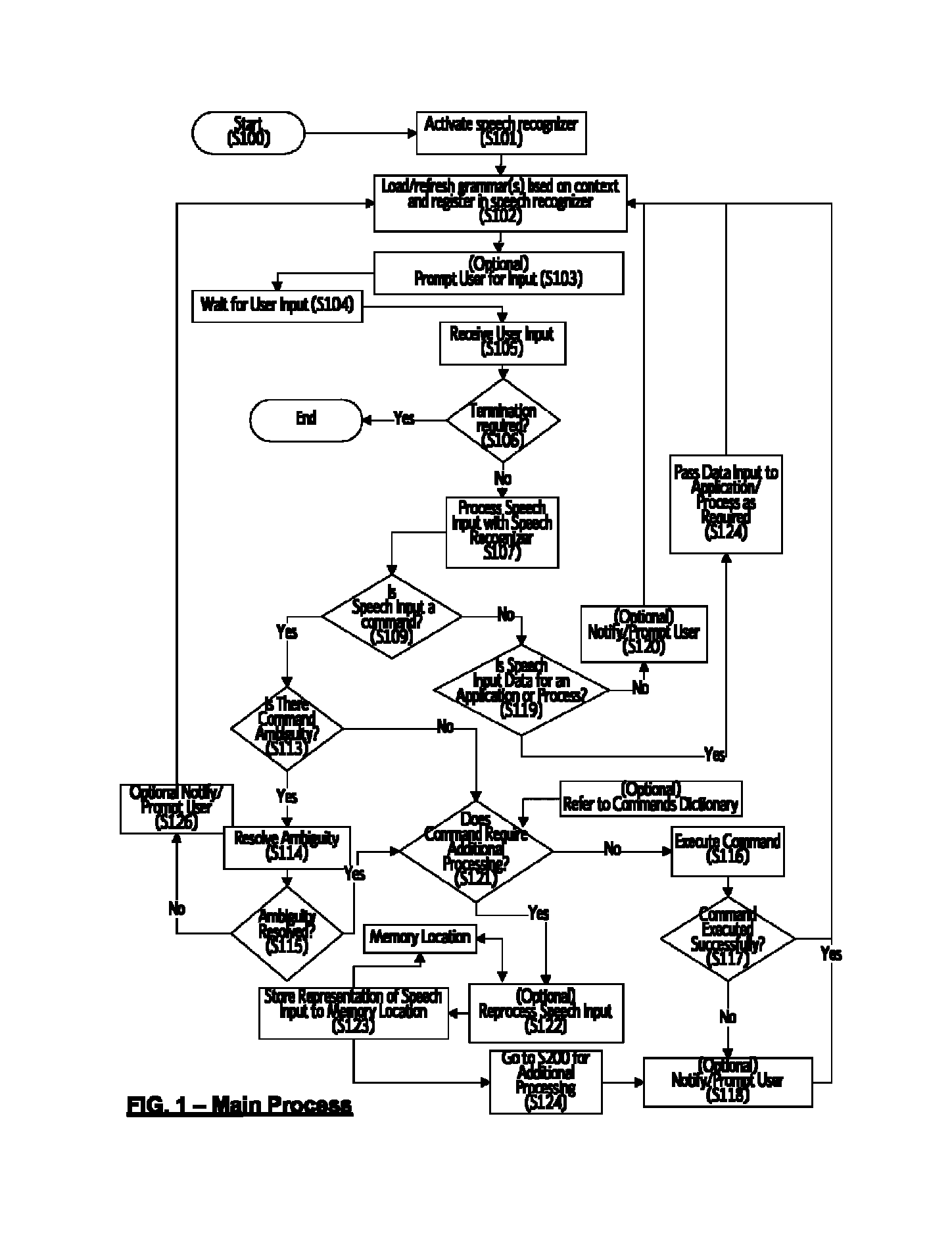
Method for processing the output of a speech recognizer
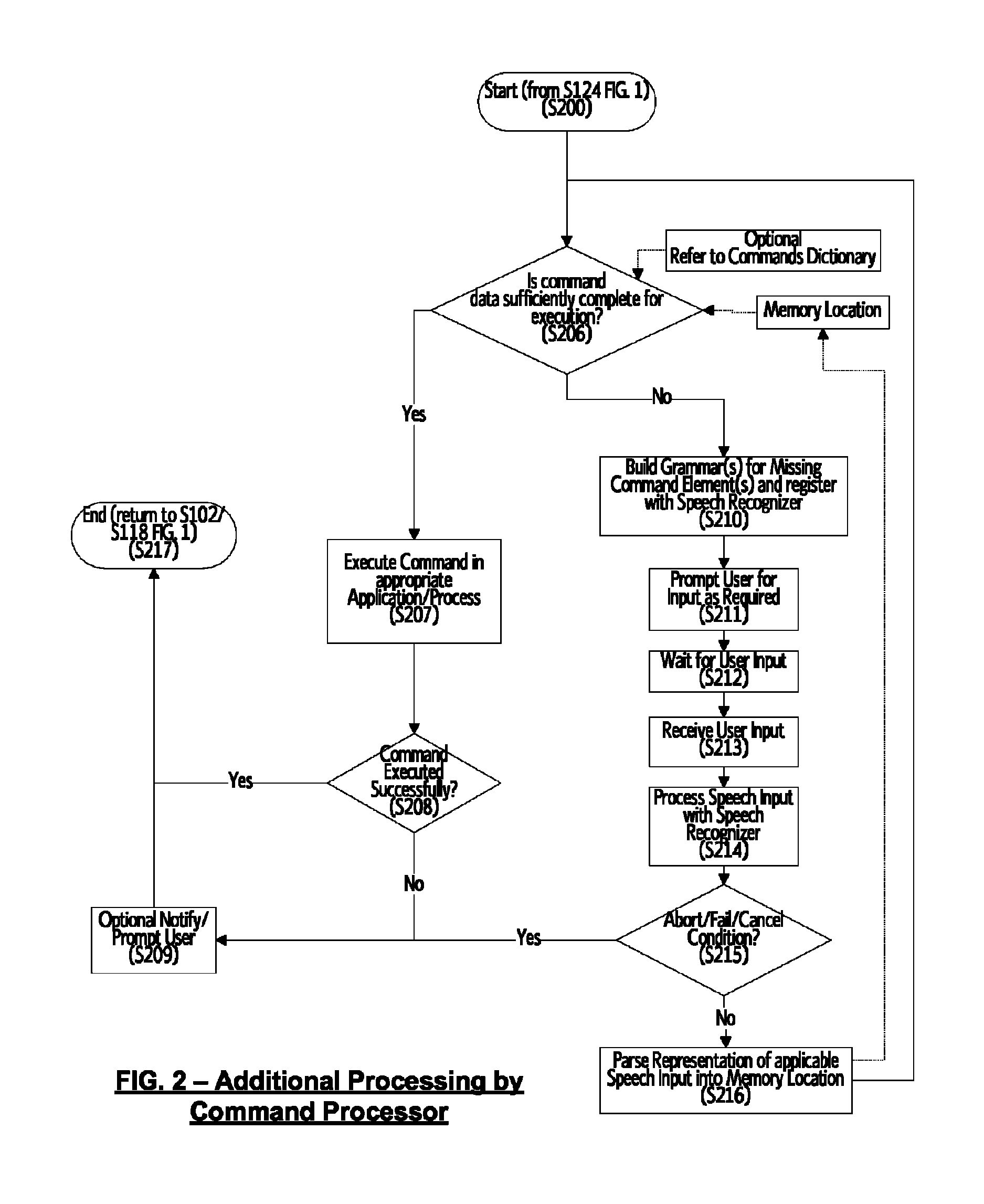
ActiveUS8219407B1Improve integrityReduce ambiguityEngine fuctionsBlade accessoriesUser inputSpeech identification
A system and method for processing speech input comprising a speech recognizer and a logical command processor which facilitates additional processing of speech input beyond the speech recognizer level. A speech recognizer receives input from a user, and when a command is identified in the speech input, if the command meets conditions that require additional processing, a representation of the speech input s stored for subsequent processing. A logical command processor performs additional processing of command input by analyzing the command and its elements, determining which elements are required for successful processing the command and which elements are present and lacking. The user is prompted to supply missing information, and subsequent user input is added to the command structure until the command input is aborted or the command structure reaches sufficient completeness to enable execution of the command. Thereby, speech input of complex commands in natural language in a system running a plurality of applications and processes is made possible.
Owner:GREAT NORTHERN RES
Device and method for forming hands of randomly arranged cards
The present invention provides an apparatus and method for moving playing cards from a first group of cards into plural hands of cards, wherein each of the hands contains a random arrangement of the same quantity of cards. The apparatus comprises a card receiver for receiving the first group of cards, a single stack of card-receiving compartments generally adjacent to the card receiver, the stack generally vertically movable, an elevator for moving the stack, a card-moving mechanism between the card receiver and the stack, and a microprocessor that controls the card-moving mechanism and the elevator so that an individual card is moved into an identified compartment. The number of compartments receiving cards and the number of cards moved to each compartment may be selected.
Owner:BALLY GAMING INC
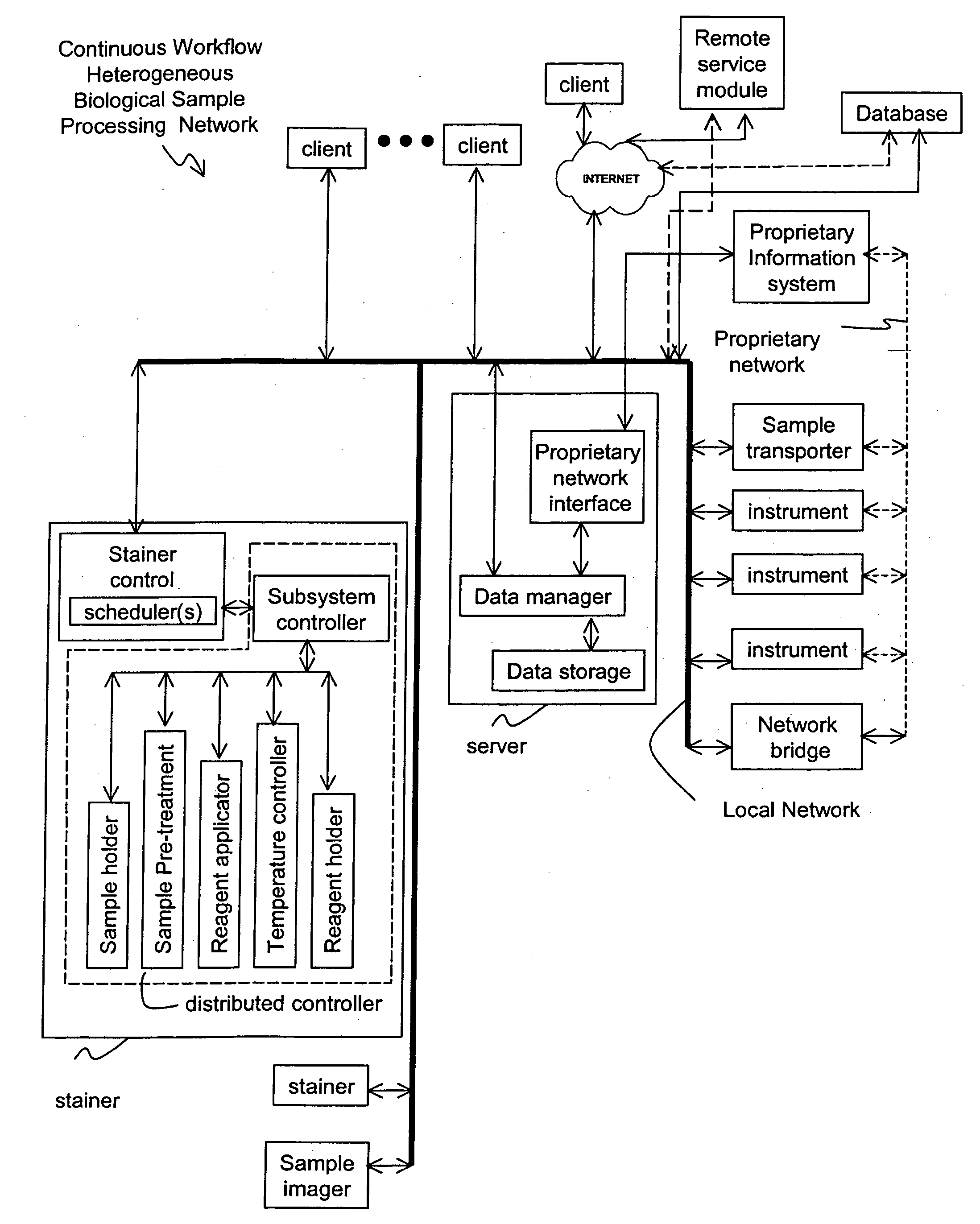
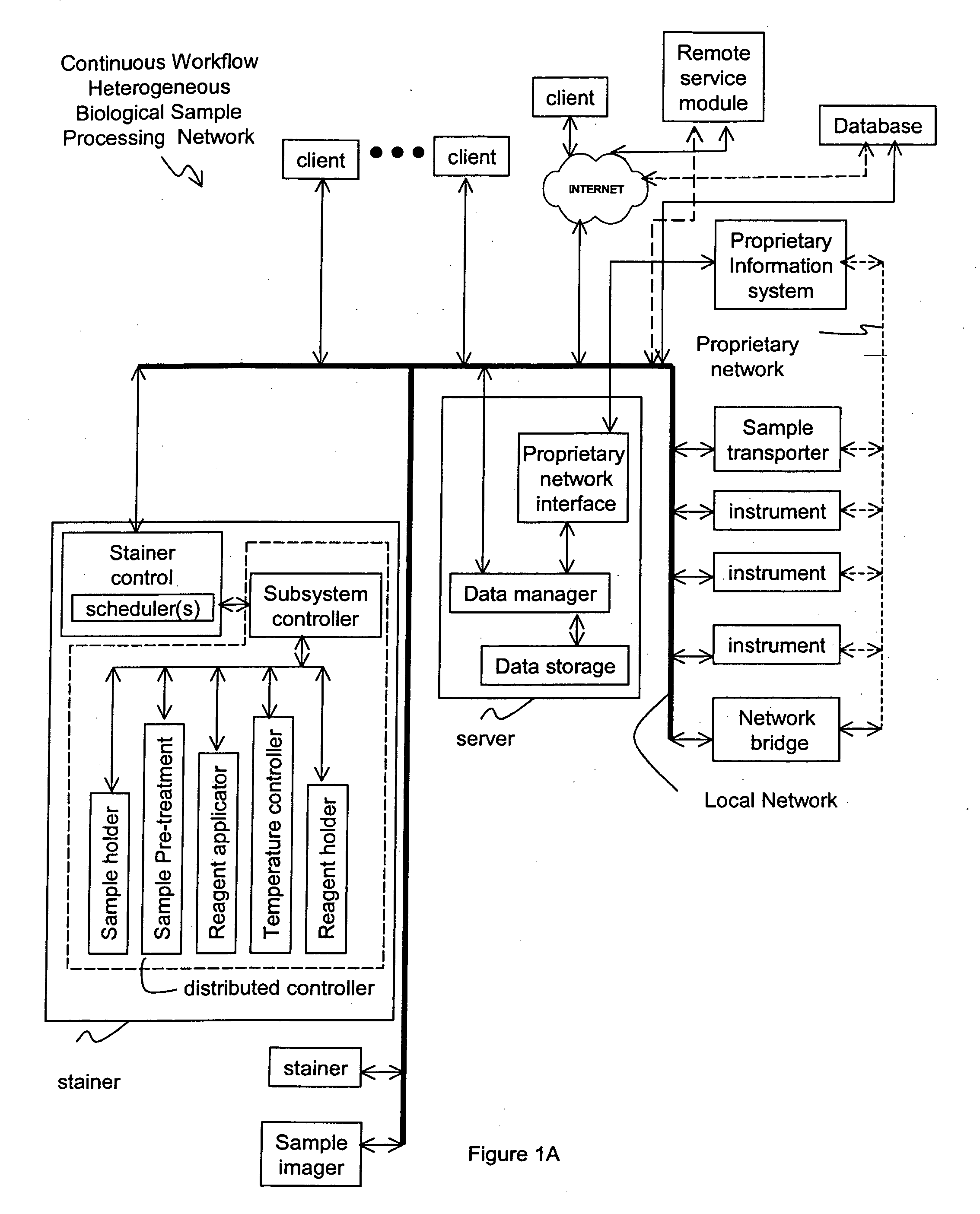
Method and apparatus for automated pre-treatment and processing of biological samples
ActiveUS20060148063A1Maximize throughputImprove efficiencyBioreactor/fermenter combinationsBiological substance pretreatmentsPre treatmentComputer science
A method and apparatus for continuous workflow processing of biological samples. In one embodiment, the appratus includes a probe for dispensing one or more reagents from one or more reagent containers onto one or more biological sample carriers. The method and apparatus includes processing each biological sample according to a respective sequence of protocol steps which may be ordered by a scheduler protocol. The method and apparatus also includes network capability for connectivity with additional equipment for receiving or transmitting pertinent data via the network.
Owner:AGILENT TECH INC
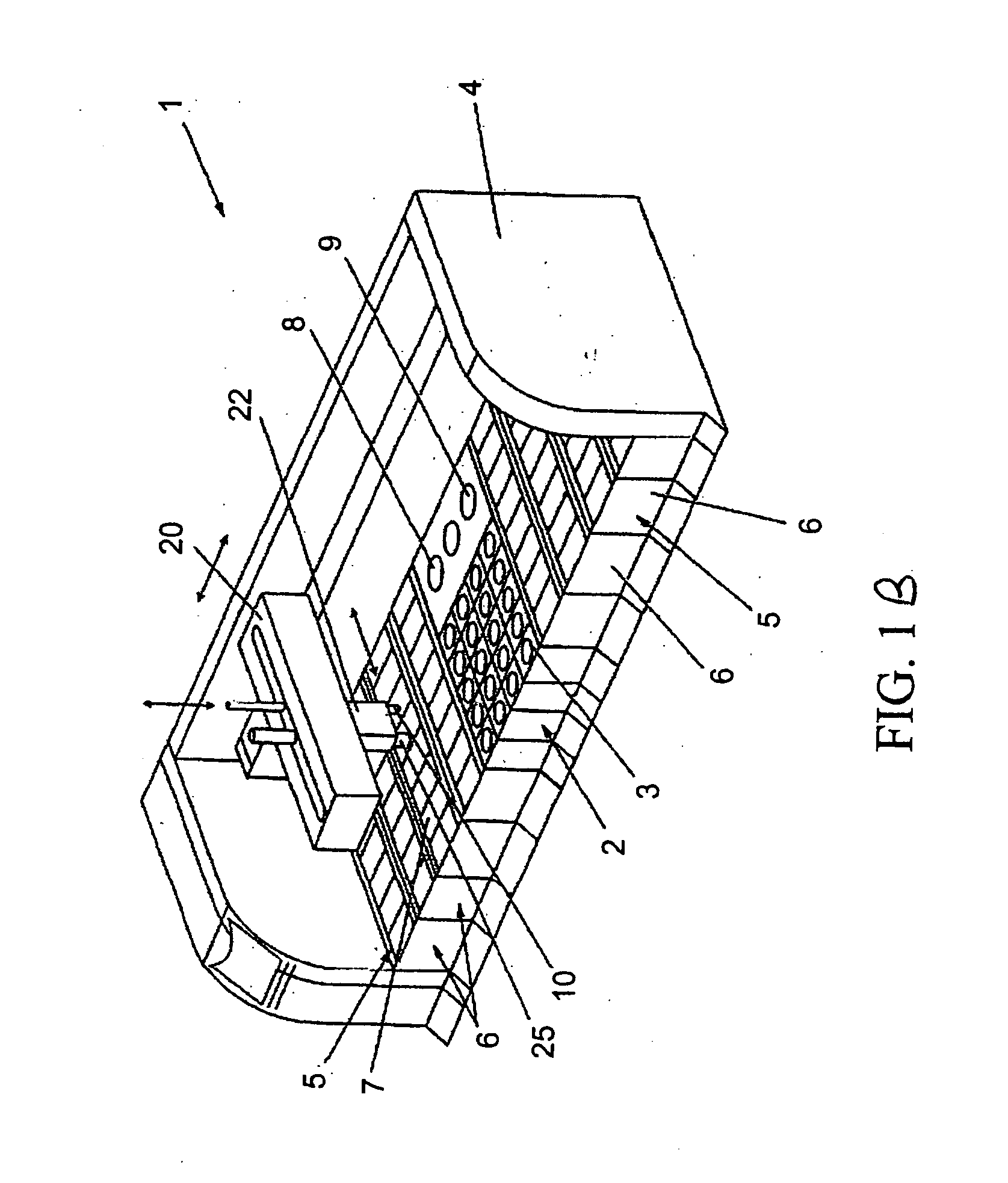
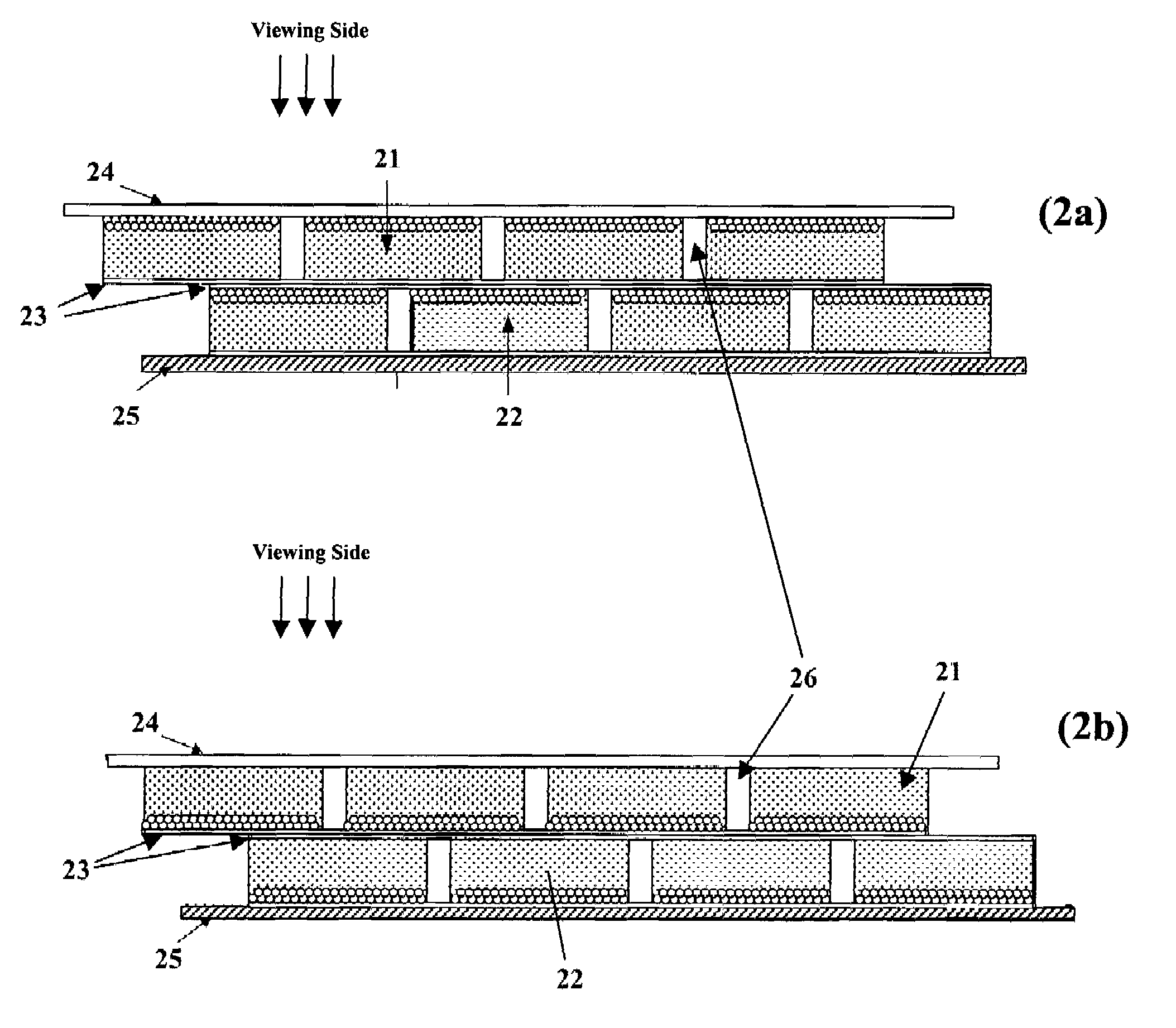
Electrophoretic display and novel process for its manufacture
ActiveUS7072095B2Improve contrast ratioImprove switching performanceStatic indicating devicesElectrographic processes using photoelectrophoresisElectrophoresisDisplay device
This invention relates to an electrophoretic display with improved contrast ratio, switching performance, reflectivity at the Dmin state and structural integrity, and methods for its manufacture.
Owner:E INK CALIFORNIA
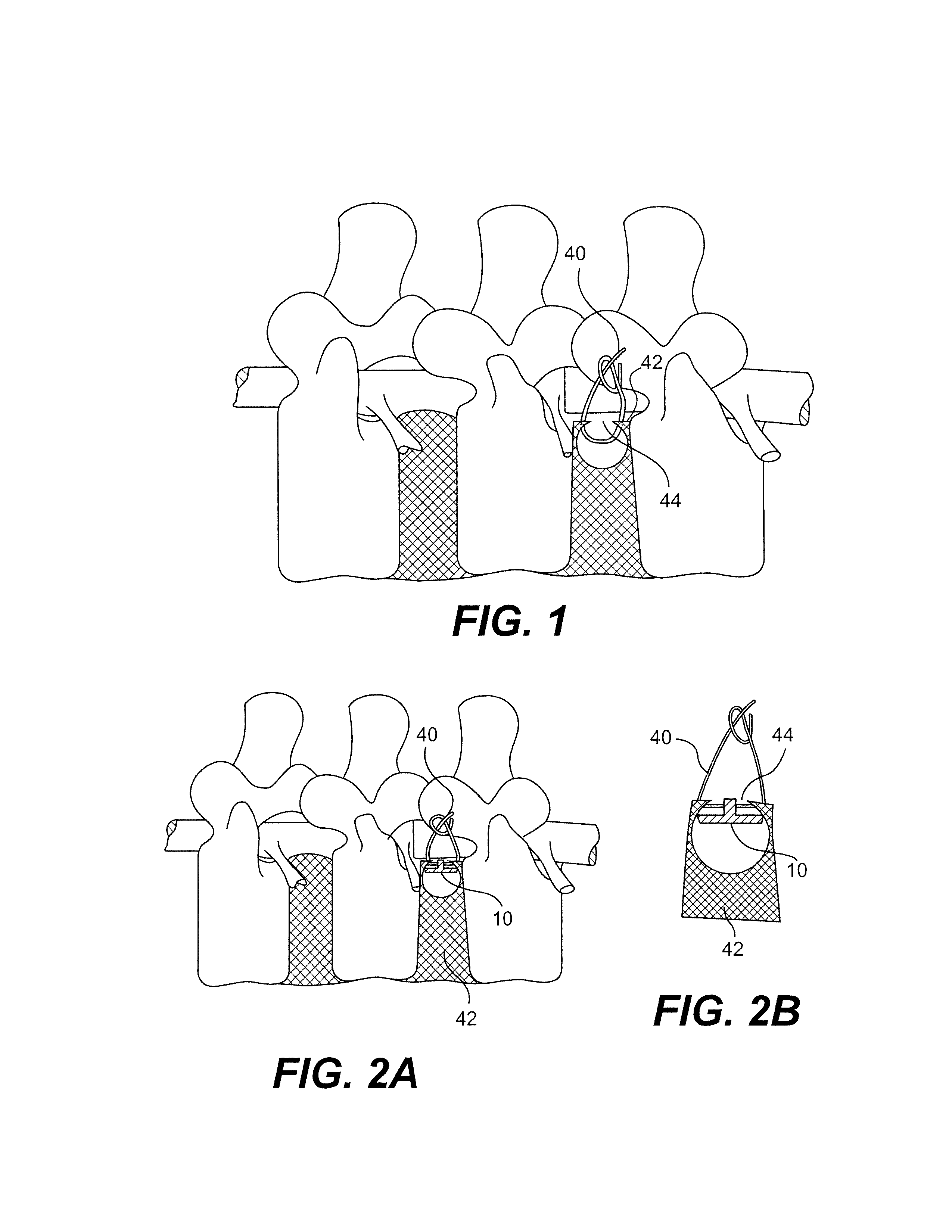
Intervertebral disc treatment devices and methods
InactiveUS7318840B2Promote tissue growthFunction increasePeptide/protein ingredientsBone implantFibrous bodyIntervertebral disk
Intervertebral disc treatment devices and methods are provided. An intervertebral disc treatment device includes a fibrous body sized for introduction into a disc cavity of a damaged disc wherein the body incorporates an effective amount of a tissue growth factor. Intervertebral disc treatment apparatuses are also described that include such a disc treatment device in combination with a delivery apparatus for retaining and selectively releasing the device into the disc cavity. Methods for treatment include providing a disc treatment device as described above and inserting the device into an opening in an annulus fibrous and into the disc cavity. The methods further include stimulating tissue growth within the disc cavity of the intervertebral disc.
Owner:SDGI HLDG
Composition and process for the sealing of microcups in roll-to-roll display manufacturing
InactiveUS7144942B2Improve adhesionQuality improvementLamination ancillary operationsLaminationCrystallographyElectrophoresis
Owner:E INK CALIFORNIA
System using leo satellites for centimeter-level navigation
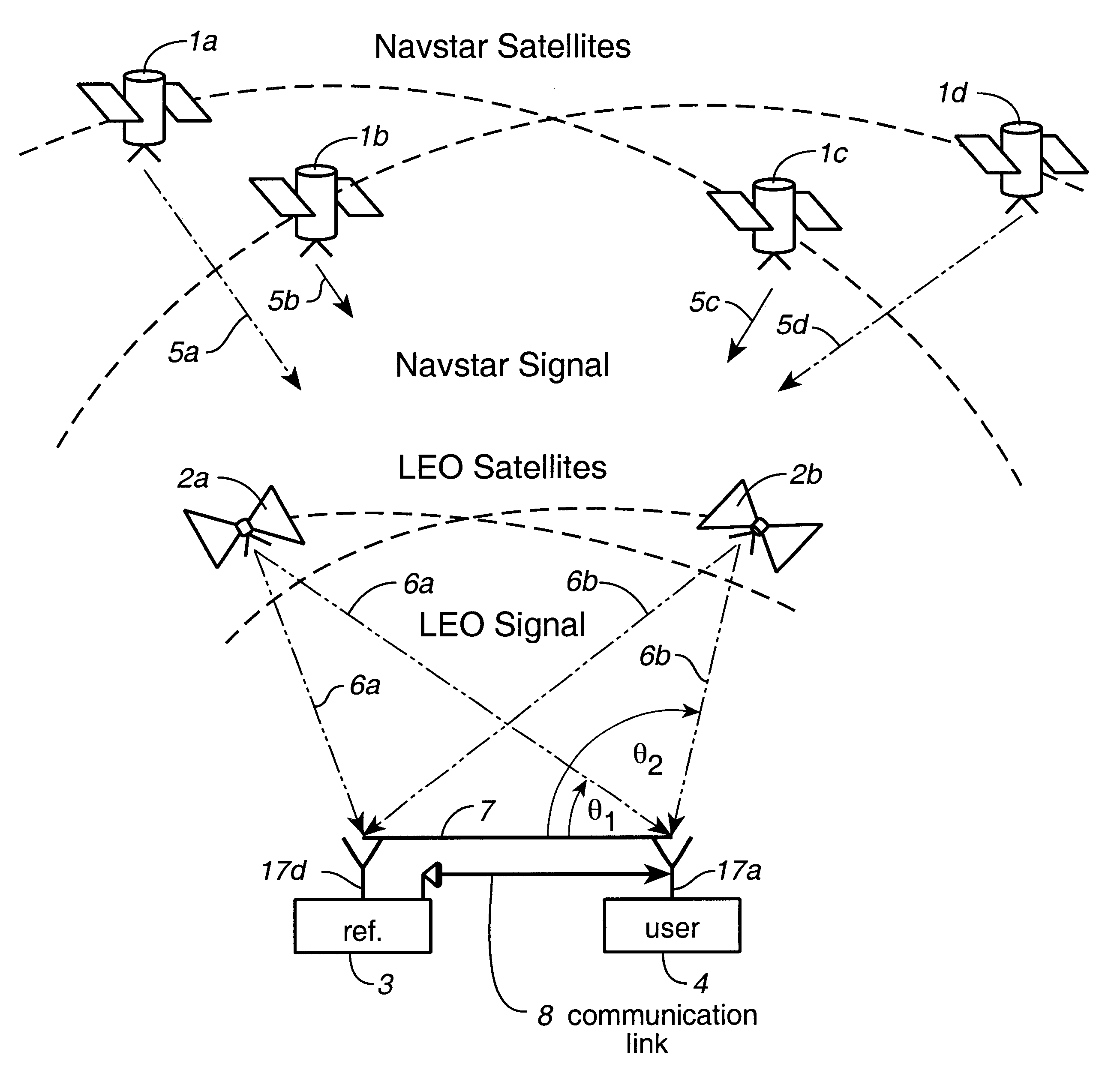
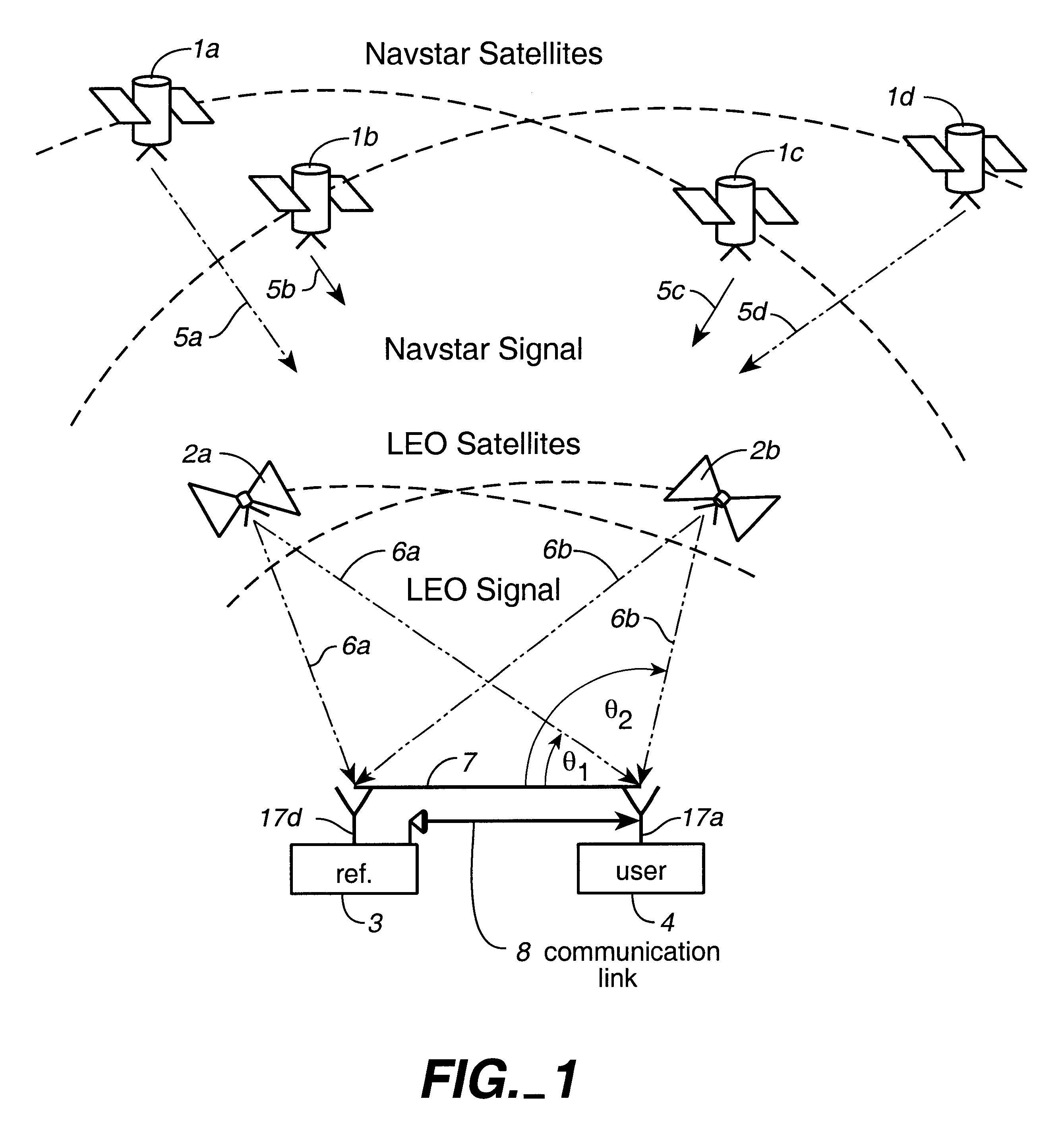
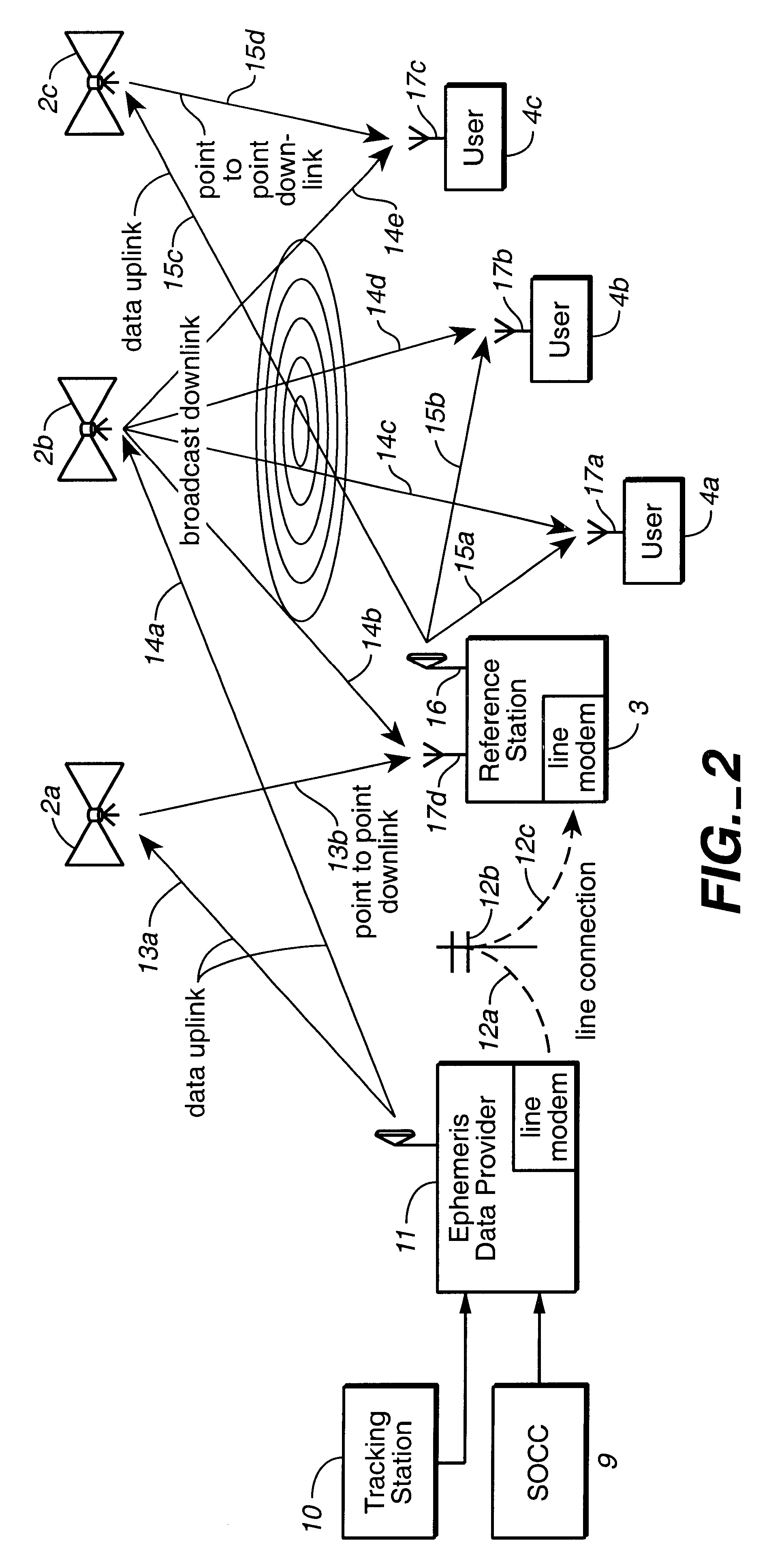
InactiveUS6373432B1Improve reliabilityEasy accessPosition fixationNavigation instrumentsNatural satelliteAmbiguity
Disclosed herein is a system for rapidly resolving position with centimeter-level accuracy for a mobile or stationary receiver [4]. This is achieved by estimating a set of parameters that are related to the integer cycle ambiguities which arise in tracking the carrier phase of satellite downlinks [5,6]. In the preferred embodiment, the technique involves a navigation receiver [4] simultaneously tracking transmissions [6] from Low Earth Orbit Satellites (LEOS) [2] together with transmissions [5] from GPS navigation satellites [1]. The rapid change in the line-of-sight vectors from the receiver [4] to the LEO signal sources [2], due to the orbital motion of the LEOS, enables the resolution with integrity of the integer cycle ambiguities of the GPS signals [5] as well as parameters related to the integer cycle ambiguity on the LEOS signals [6]. These parameters, once identified, enable real-time centimeter-level positioning of the receiver [4]. In order to achieve high-precision position estimates without the use of specialized electronics such as atomic clocks, the technique accounts for instabilities in the crystal oscillators driving the satellite transmitters, as well as those in the reference [3] and user [4] receivers. In addition, the algorithm accommodates as well as to LEOS that receive signals from ground-based transmitters, then re-transmit frequency-converted signals to the ground.
Owner:INTEGRINAUTICS
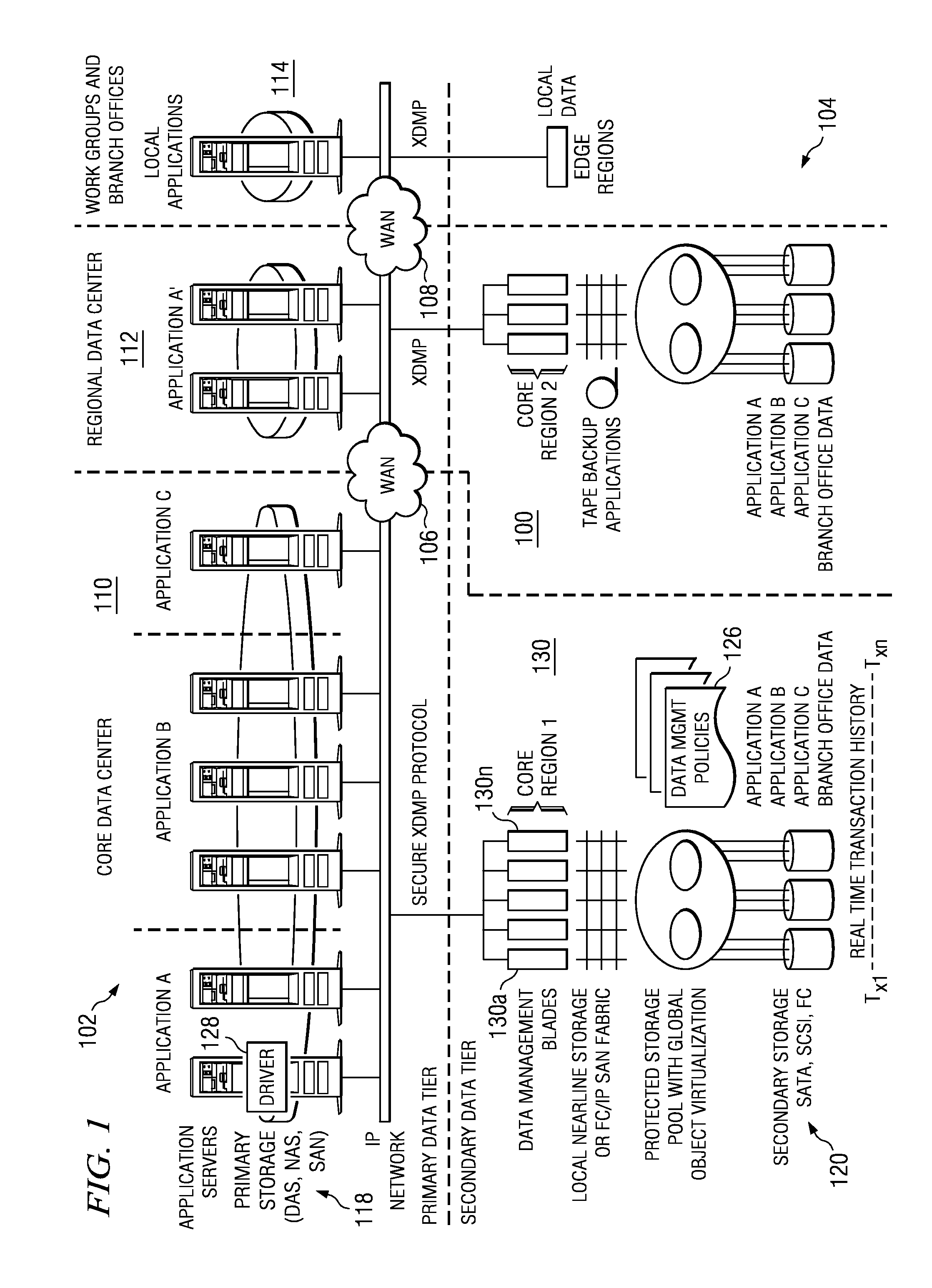
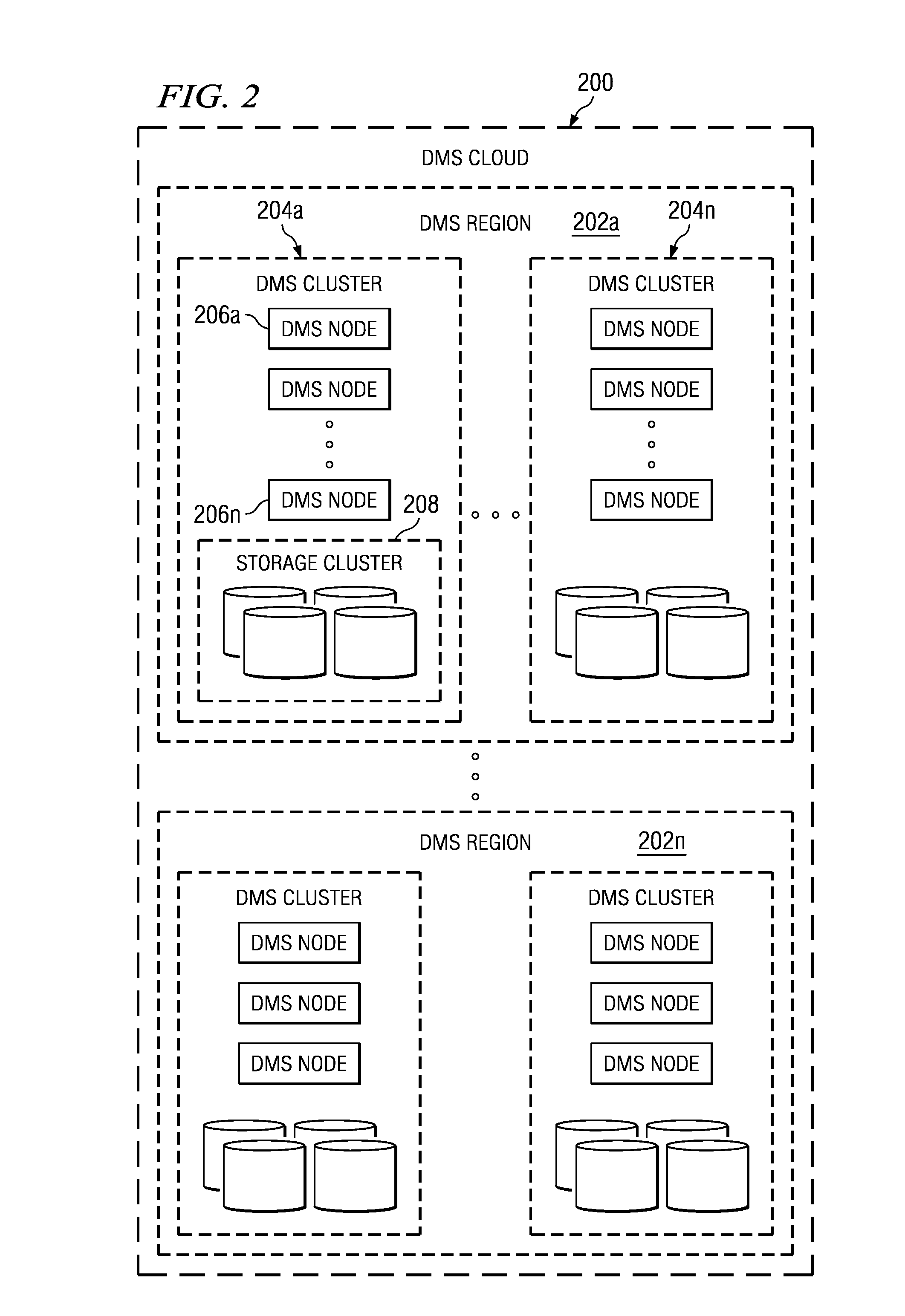
Recovering a file system to any point-in-time in the past with guaranteed structure, content consistency and integrity
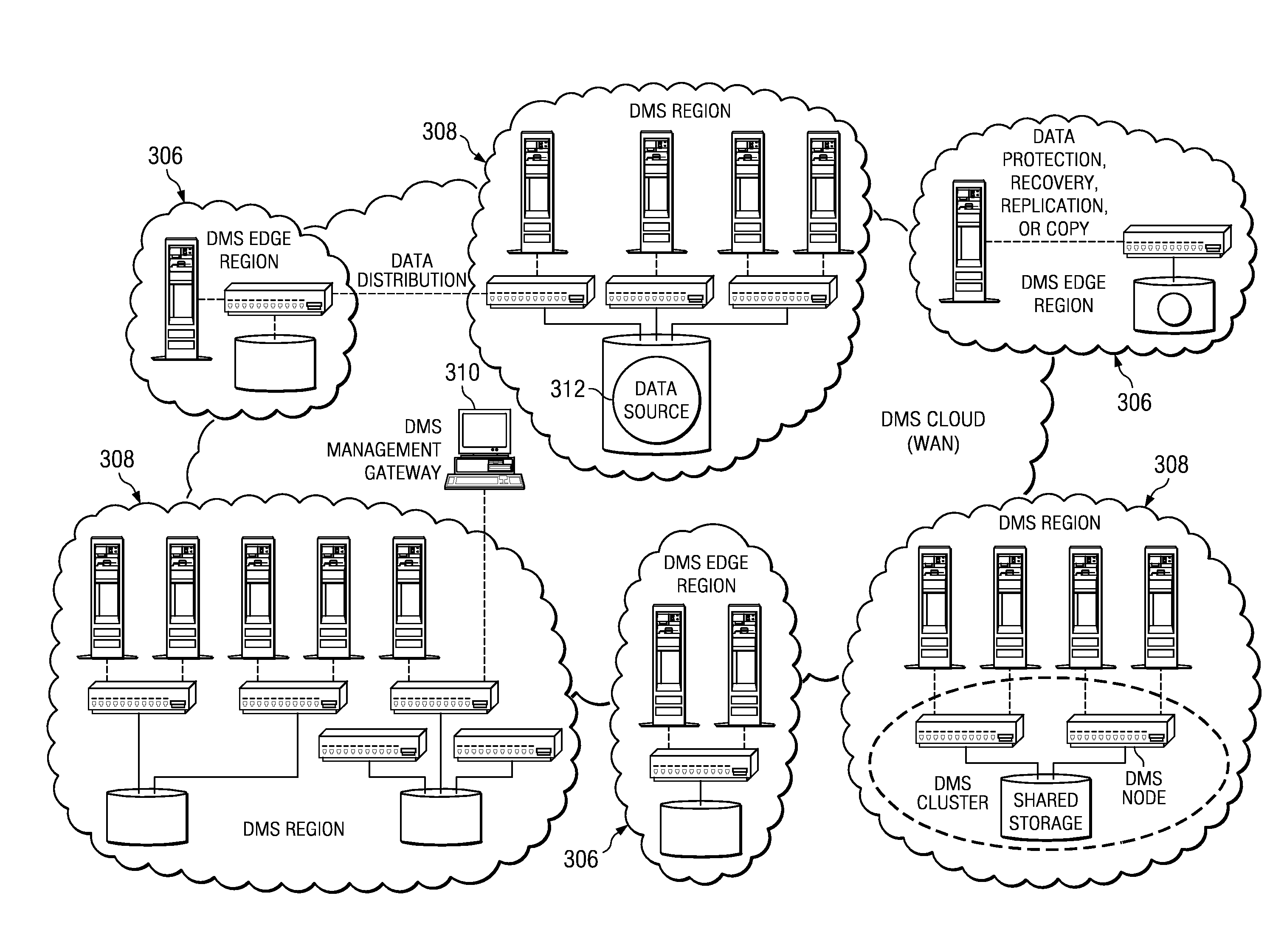
InactiveUS20080256138A1Improve integrityDigital data information retrievalDigital data processing detailsFile systemData management
A data management system (DMS) includes a continuous real-time object store that captures all real-time activities, with associated object metadata information. The DMS is capable of reintroducing any point-in-time view of data ranging from a granular object to an entire file system. A set of algorithms (for creation of a file or directory, modification of a file or directory, deletion of a file or directory, and relocation / renaming of a file or directory) are used to generate and maintain a file system history in the DMS and to ensure that a latest version of a directory always refers to a latest version of its children until the directory changed. Any point-in-time recovery is implemented using the file system history in one of various ways to provide strong individual file integrity, exact point-in-time crash consistency, and / or recovery of last version of all files in the file system.
Owner:QUEST SOFTWARE INC
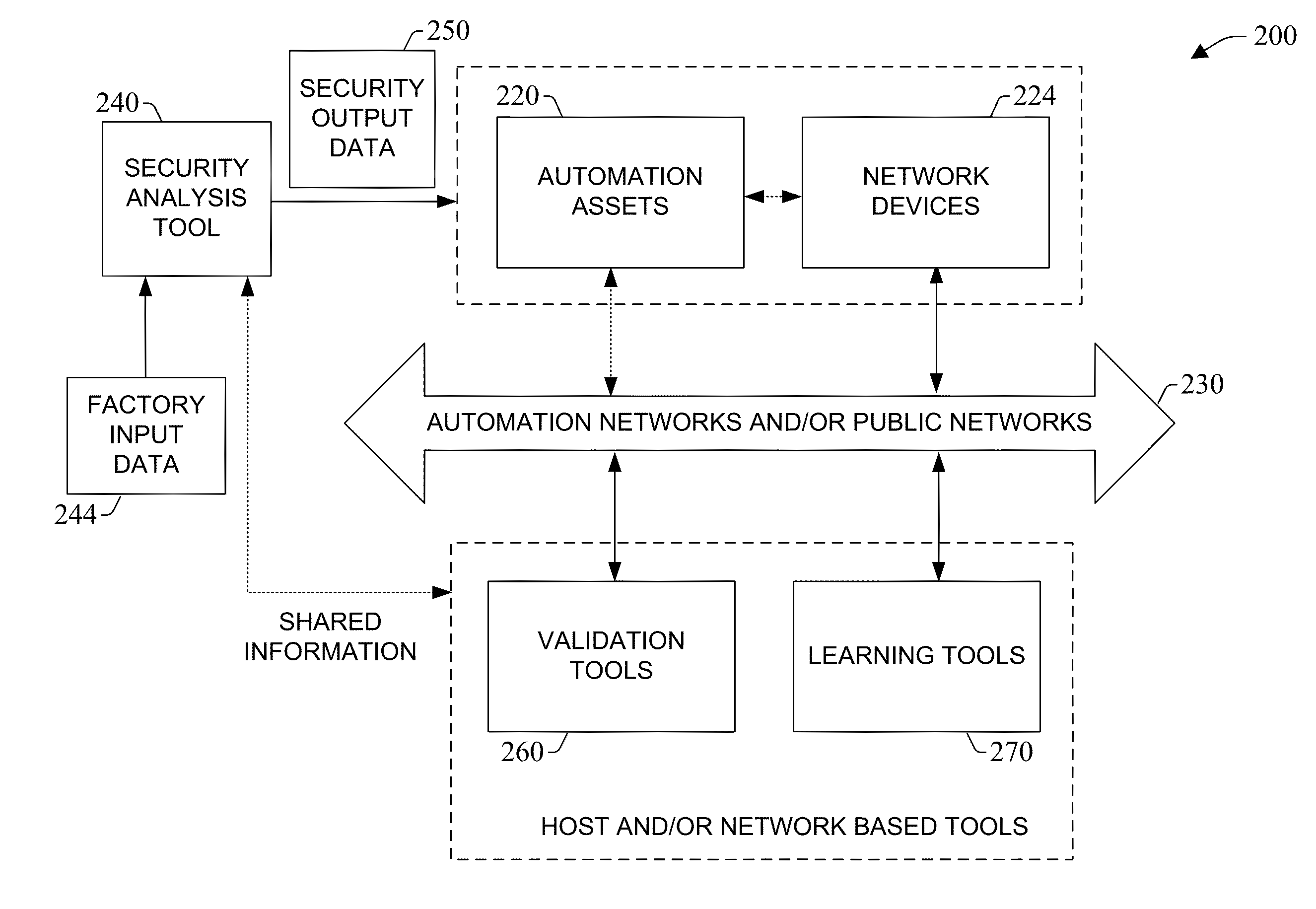
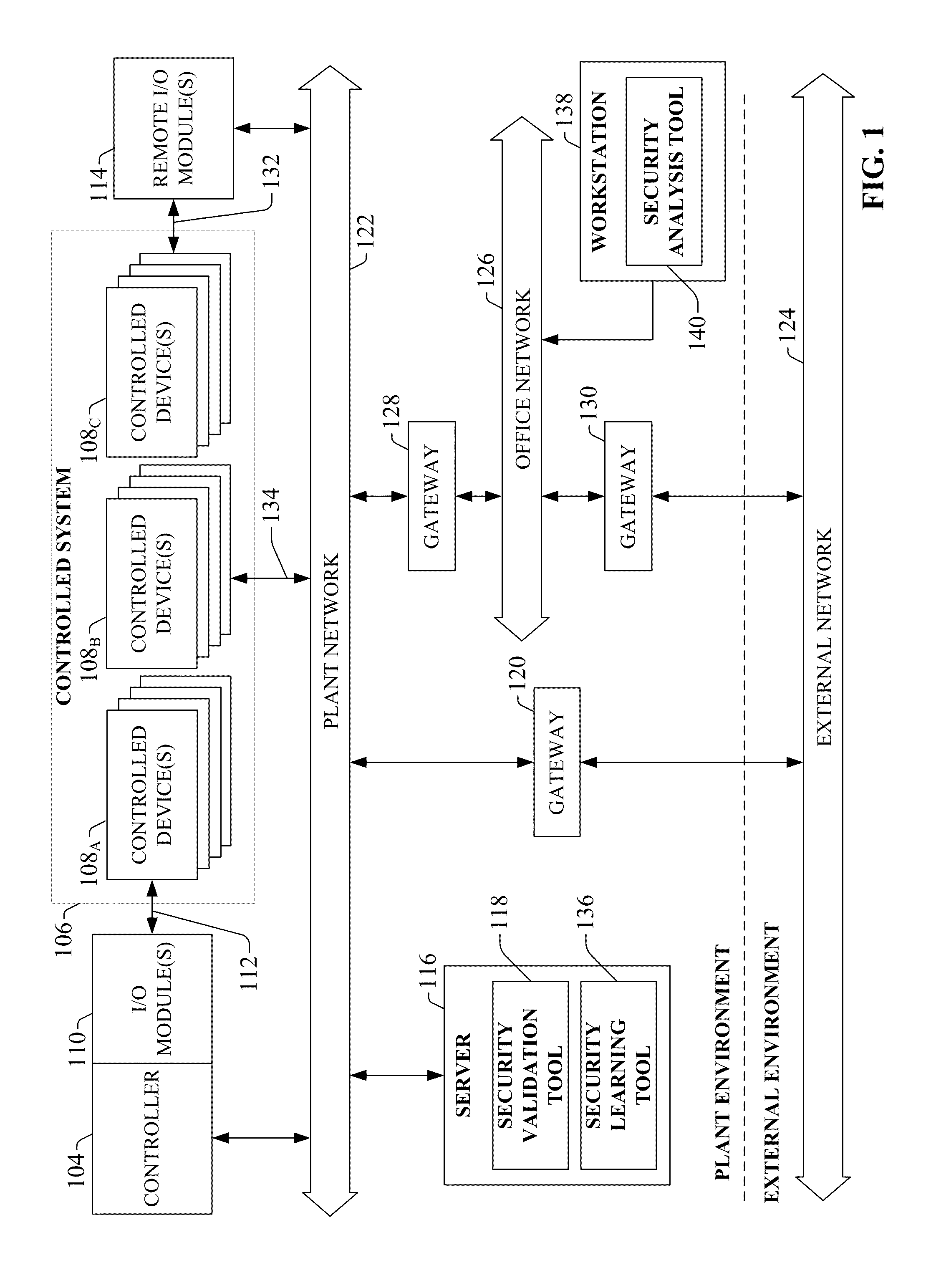
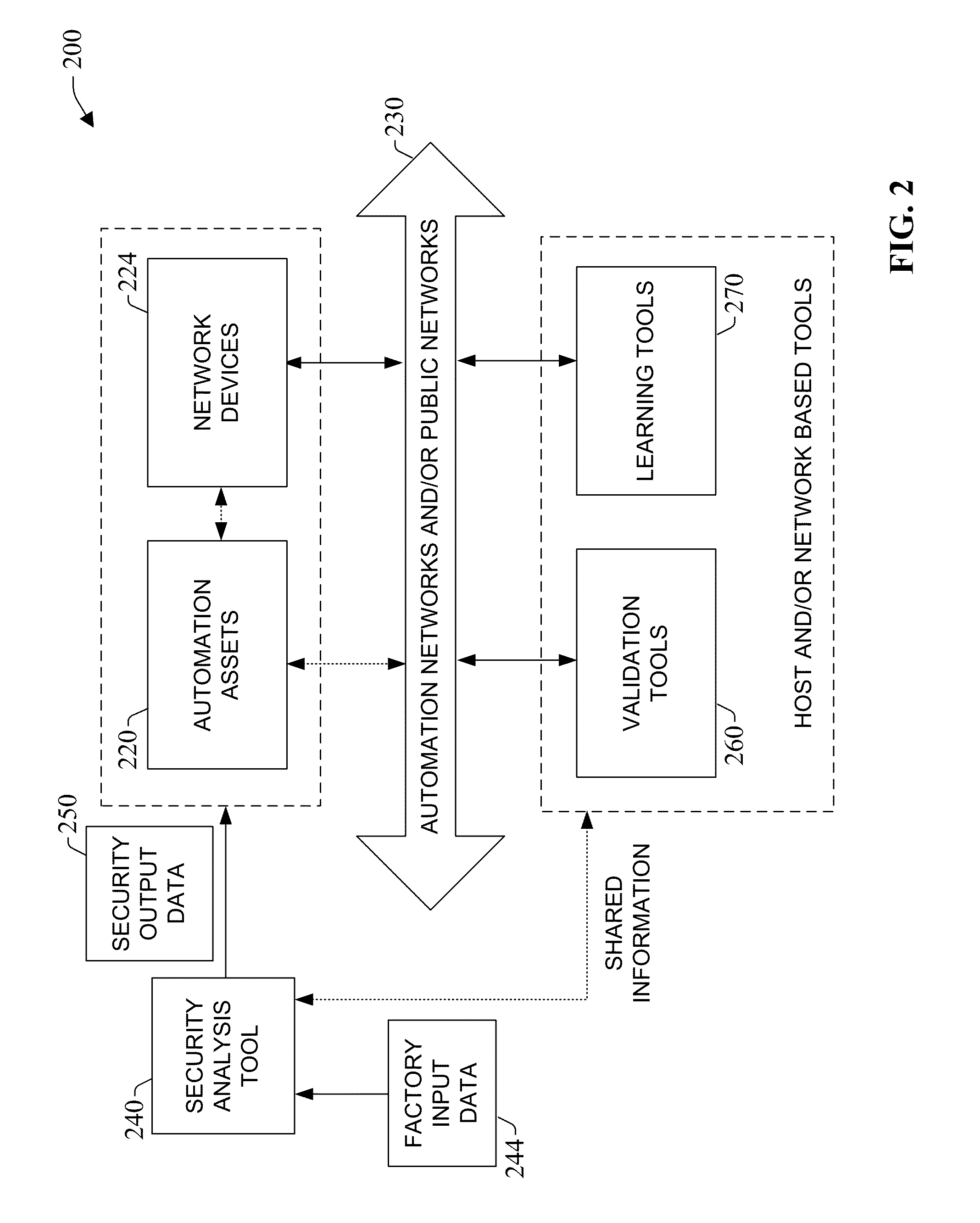
System and methodology providing automation security analysis and network intrusion protection in an industrial environment
ActiveUS20130031037A1Improve integrityFacilitate privacyProgramme controlComputer controlGuidelineEngineering
The present invention relates to a system and methodology facilitating automation security in a networked-based industrial controller environment. Various components, systems and methodologies are provided to facilitate varying levels of automation security in accordance with security analysis tools, security validation tools and / or security learning systems. The security analysis tool receives abstract factory models or descriptions for input and generates an output that can include security guidelines, components, topologies, procedures, rules, policies, and the like for deployment in an automation security network. The validation tools are operative in the automation security network, wherein the tools perform security checking and / or auditing functions, for example, to determine if security components are in place and / or in suitable working order. The security learning system monitors / learns network traffic patterns during a learning phase, fires alarms or events based upon detected deviations from the learned patterns, and / or causes other automated actions to occur.
Owner:ROCKWELL AUTOMATION TECH
Lighting device and method of making
ActiveUS20070274063A1Reduced optical degradationGood mechanical integrityOptical articlesSemiconductor/solid-state device manufacturingEffect lightEngineering
A lighting device comprises a solid state light emitter, first and second electrodes connected to the emitter, an encapsulant region comprising a silicone compound and a supporting region. The encapsulant region extends to an external surface of the lighting device. At least a portion of the first electrode is surrounded by the supporting region. The encapsulant region and the supporting region together define an outer surface which substantially encompasses the emitter. A method of making a lighting device, comprises electrically connecting first and second electrodes to an emitter; inserting the emitter into mold cavity; inserting an encapsulant composition comprising a one silicone compound; and then inserting a second composition to substantially surround at least a portion of the first electrode.
Owner:CREELED INC
Security framework and protocol for universal pervasive transactions
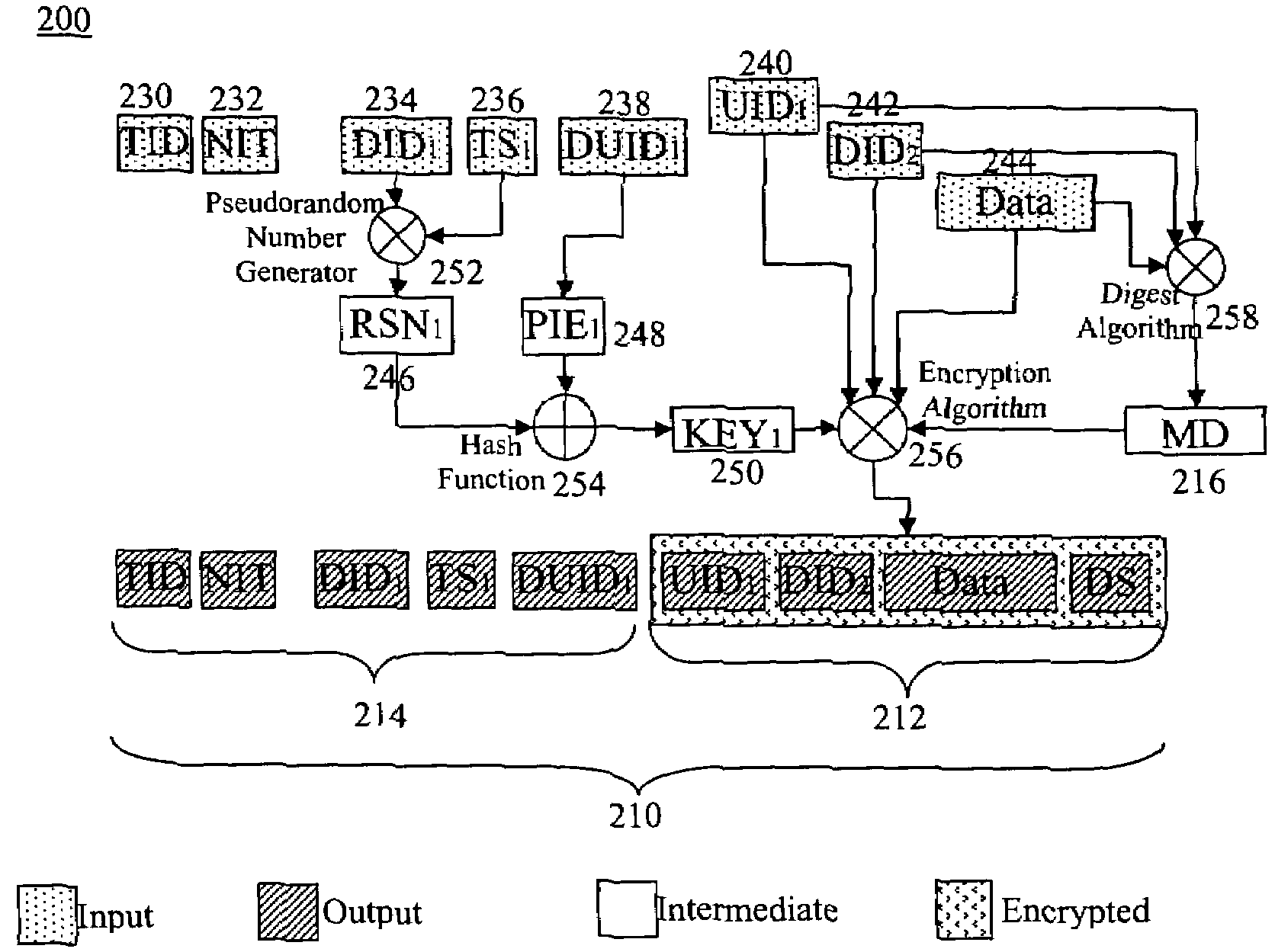
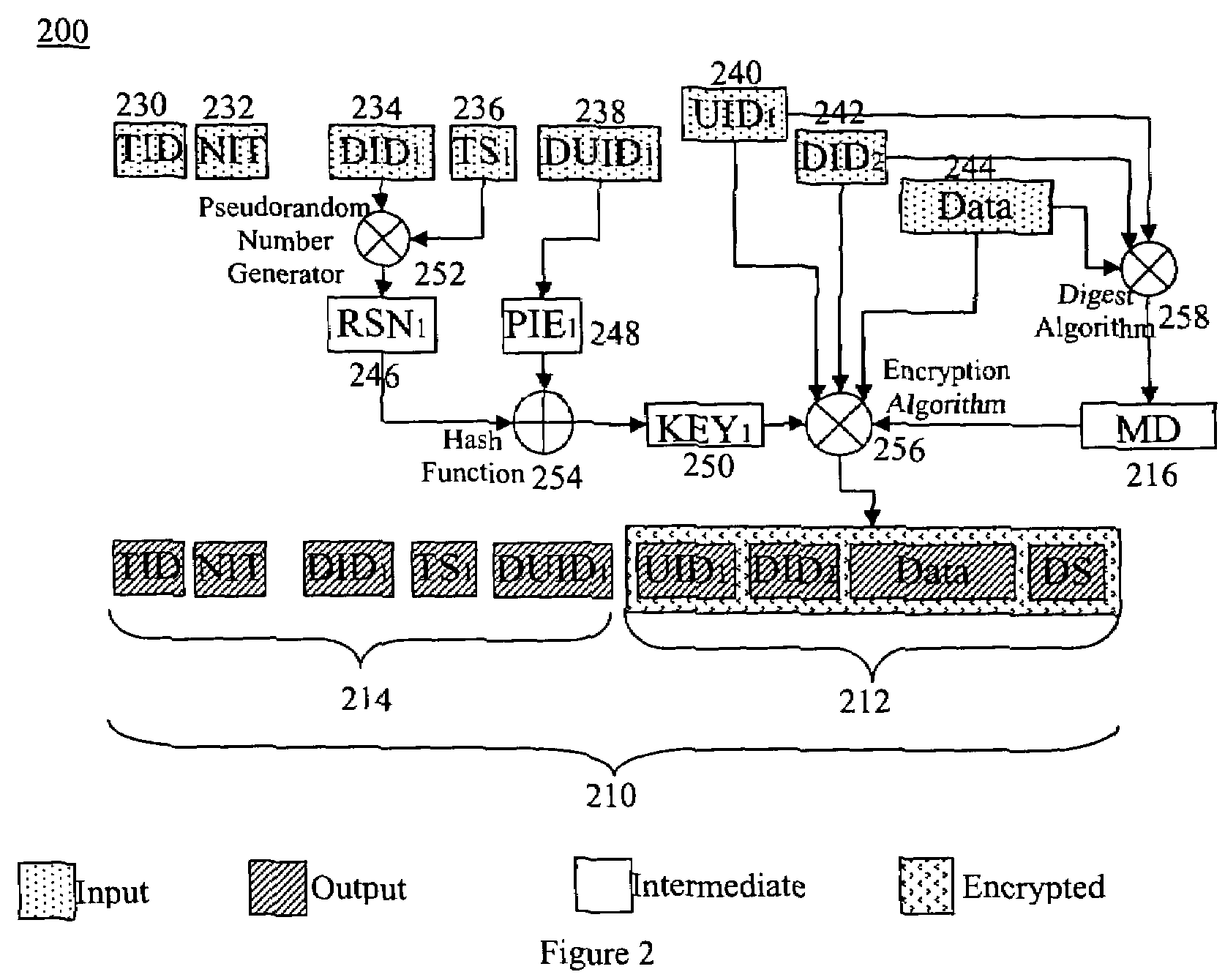
ActiveUS7353382B2Improve integrityAvoid communicationKey distribution for secure communicationMultiple keys/algorithms usageInternet privacyComputerized system
A computer system, a method of a computer system and a computer-readable medium securely transmit and verify a multiparty agreement. The method, the computer system, and the computer readable medium include developing and transmitting views of the multi-party agreement by each party to a separate verification party. The verification party authenticates the participants and determines whether the views of the agreement are mutually consistent, and notifies the partys of the results of the comparison.
Owner:INTERDIGITAL PATENT HLDG INC
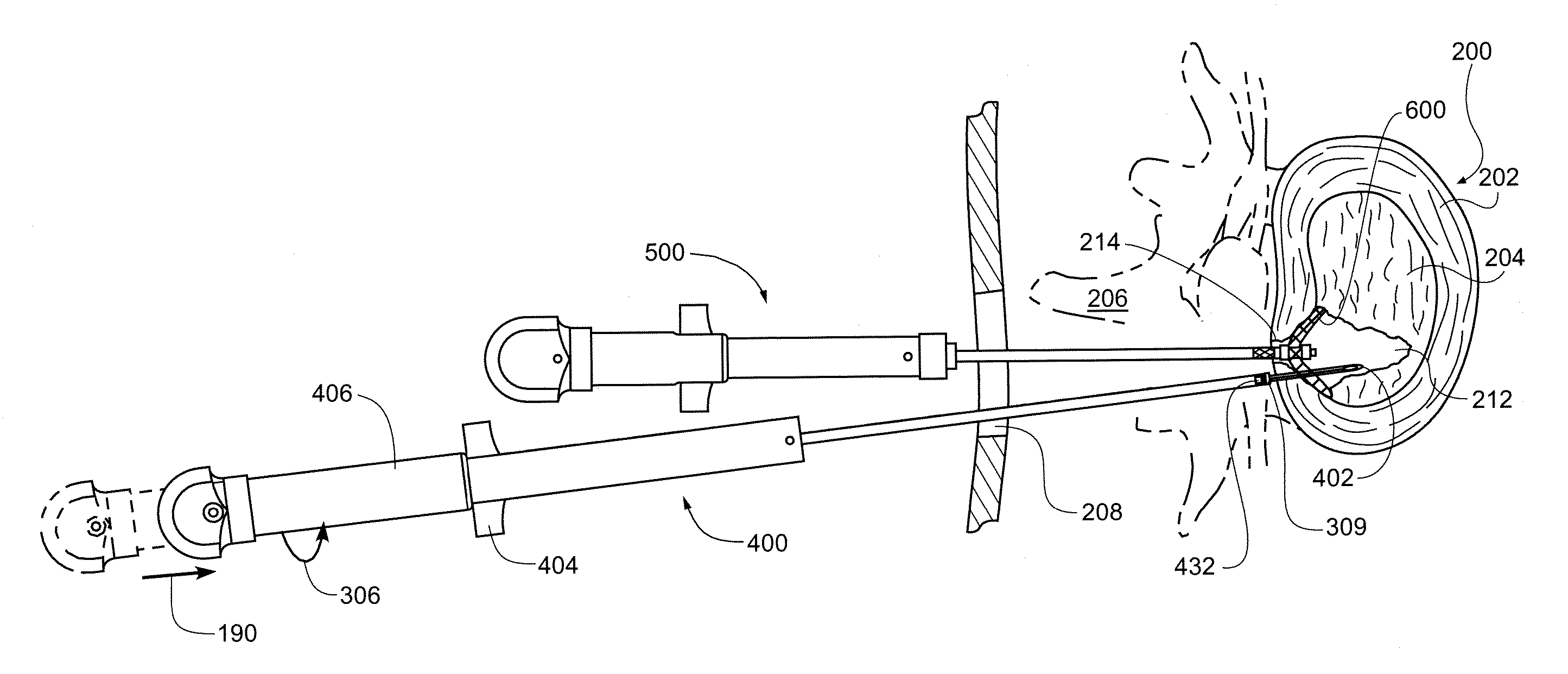
Method and apparatus for the treatment of the intervertebral disc annulus
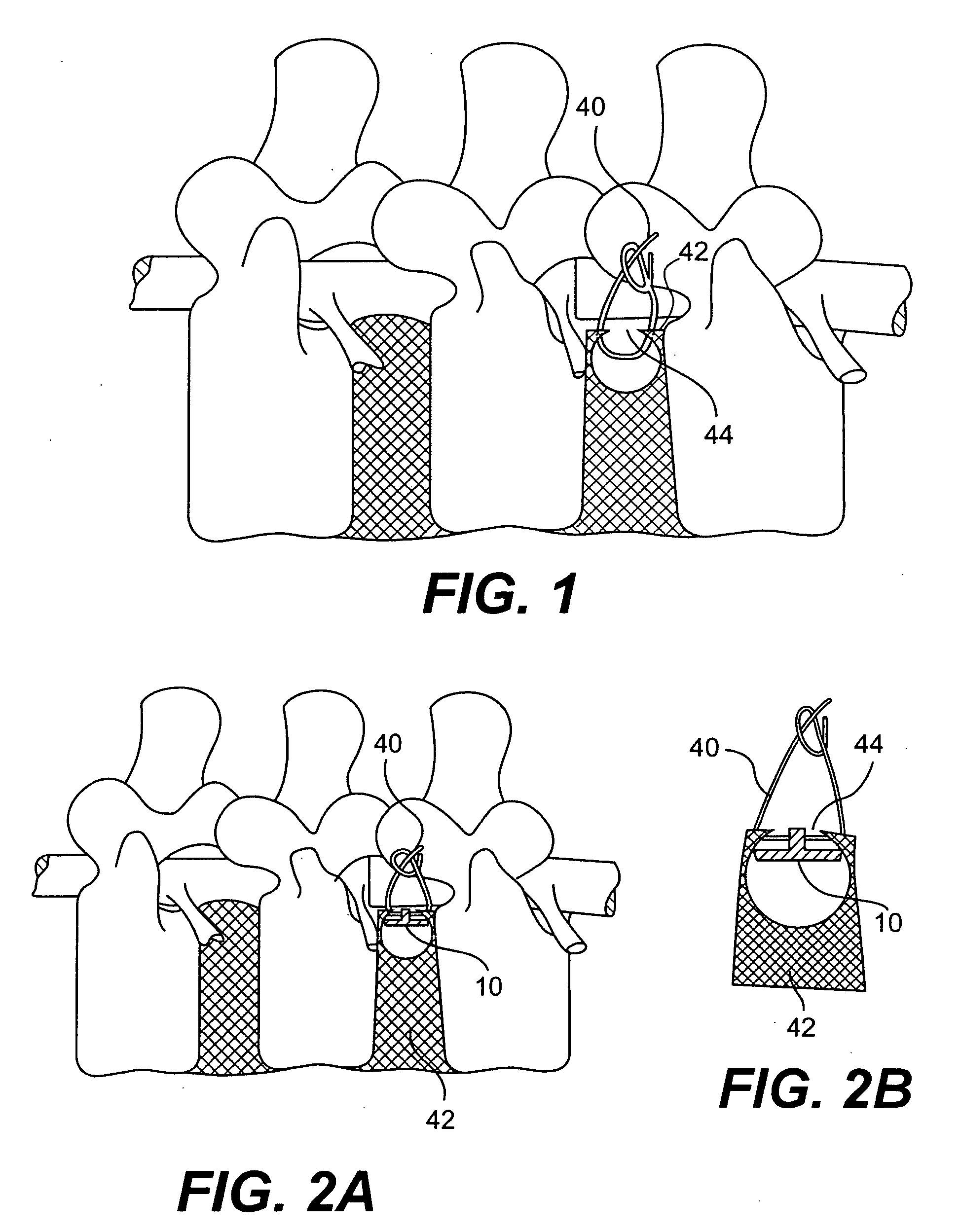
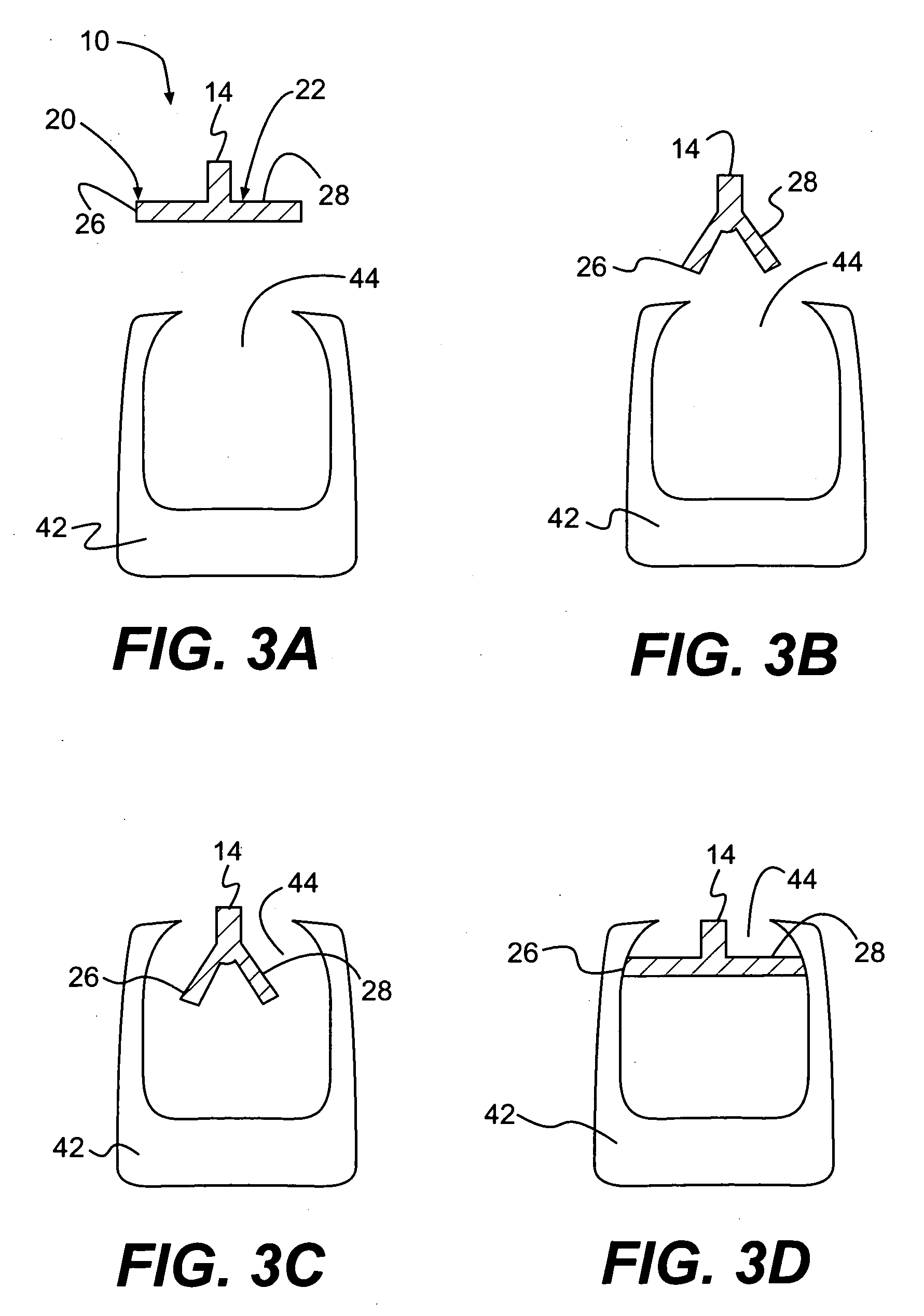
InactiveUS20050283246A1Reduce riskImprove integritySuture equipmentsDiagnosticsBiomedical engineeringIntervertebral disc
The present invention provides methods and devices for treating the annulus of an intervertebral disc. The methods and devices can employ an expandable treatment device which is deployed at least partially in the subannular space. Fixation devices and methods are also disclosed, which help to secure the treatment device in place.
Owner:KRT INVESTORS
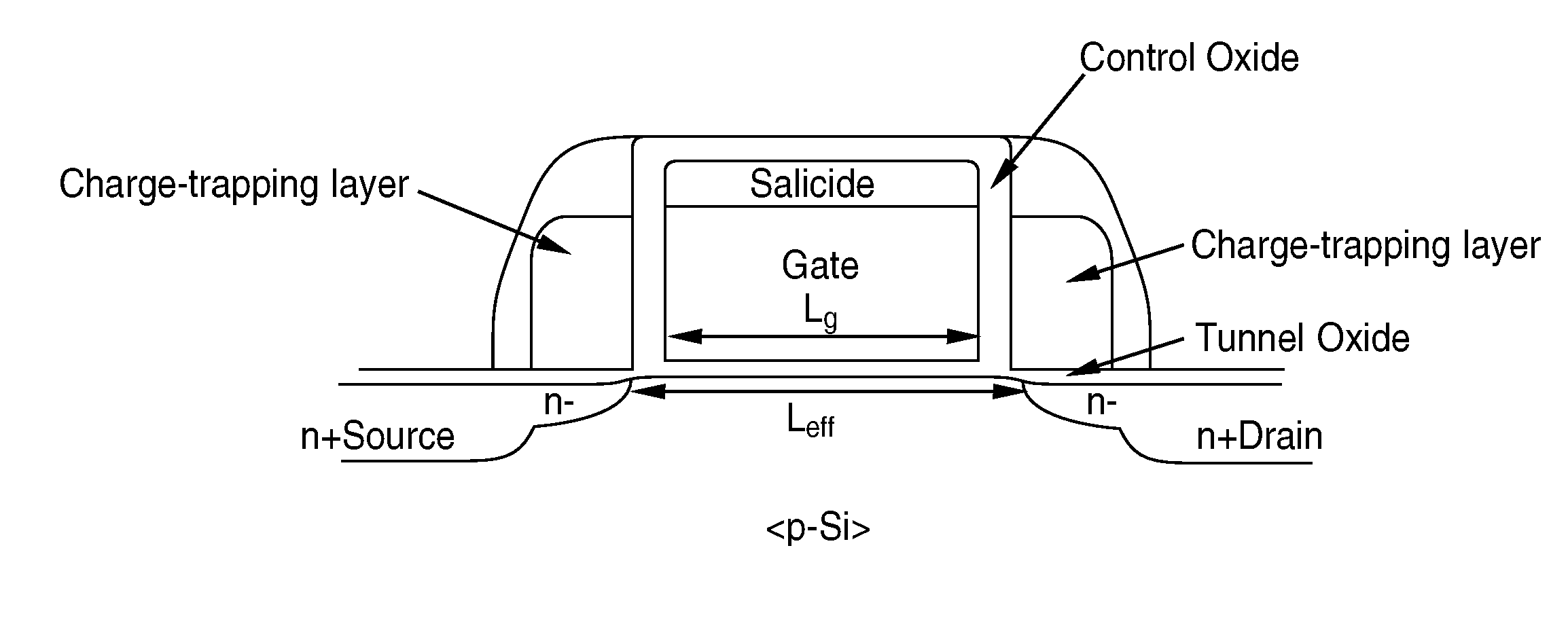
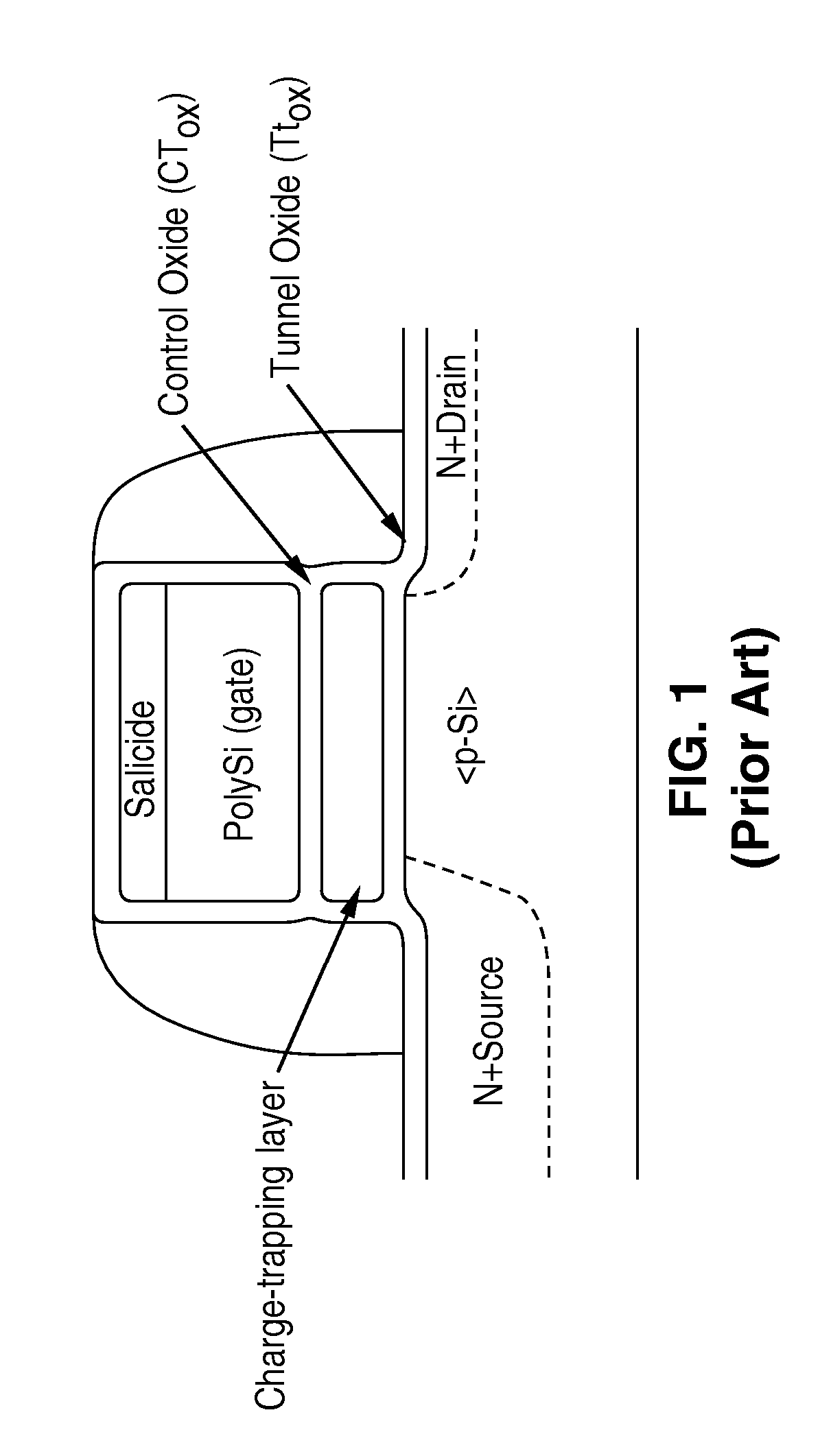
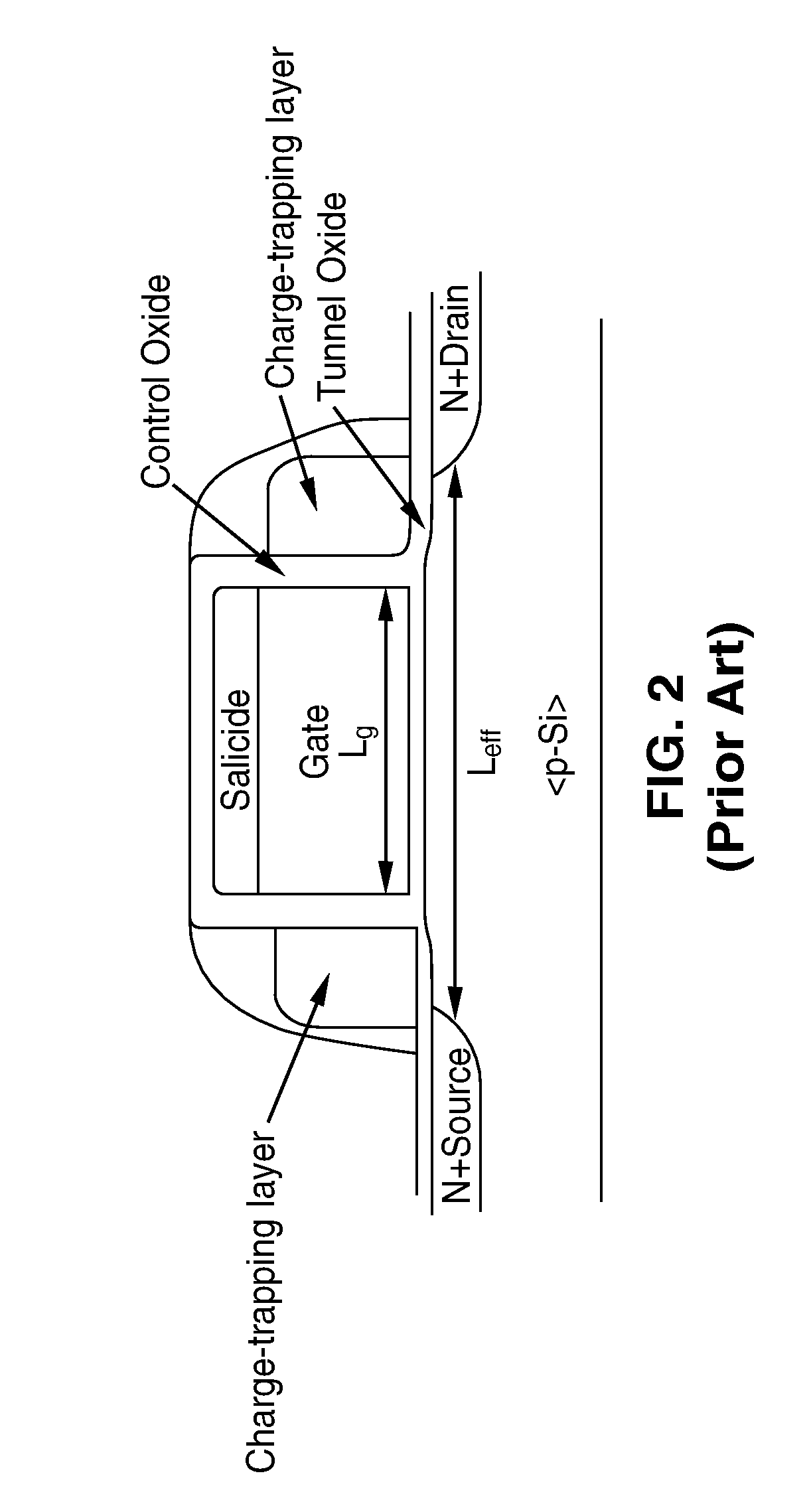
Multi-bit-per-cell nvm structures and architecture
InactiveUS20070164352A1High sensitivityReduce sensitivitySolid-state devicesRead-only memoriesGate dielectricEngineering
A transistor structure, such as a Double-gated FET (DG FET), that has been modified to include a charge-trapping region used to store either 2- or 4-bits of information. The charge-trapping region can, for example, be embedded in the gate dielectric stack underneath each gate electrode, or placed on the sidewalls of each gate electrode.
Owner:RGT UNIV OF CALIFORNIA
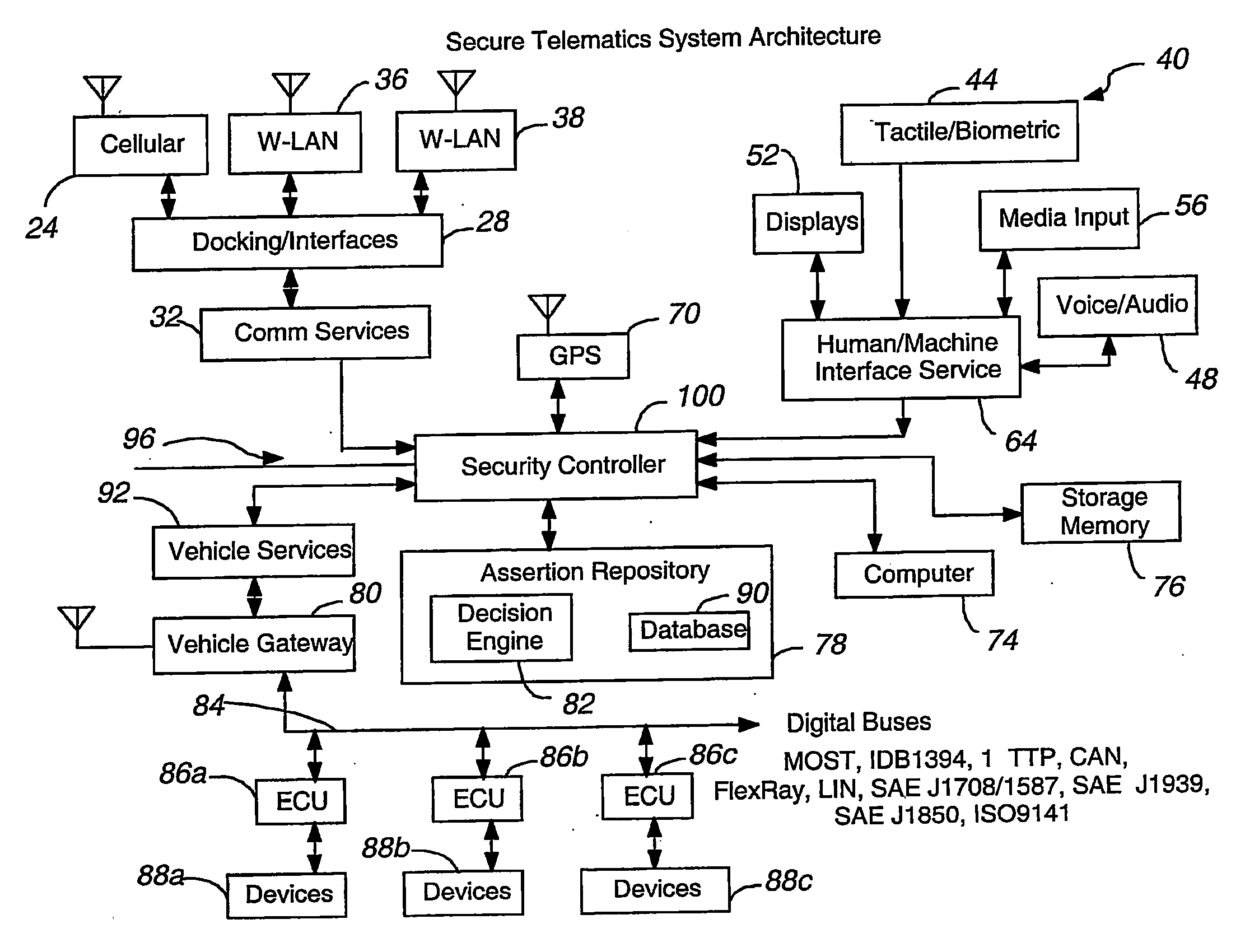
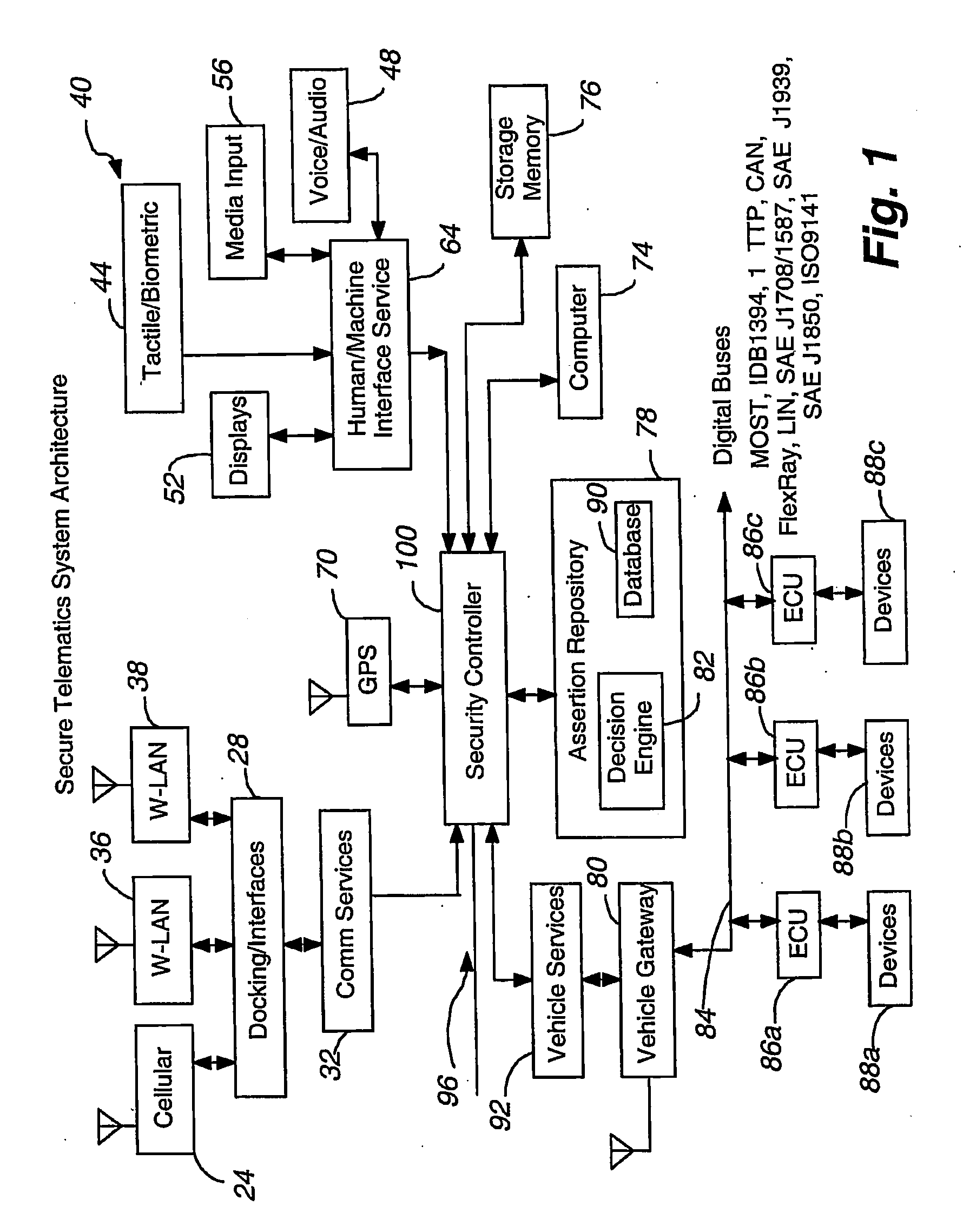
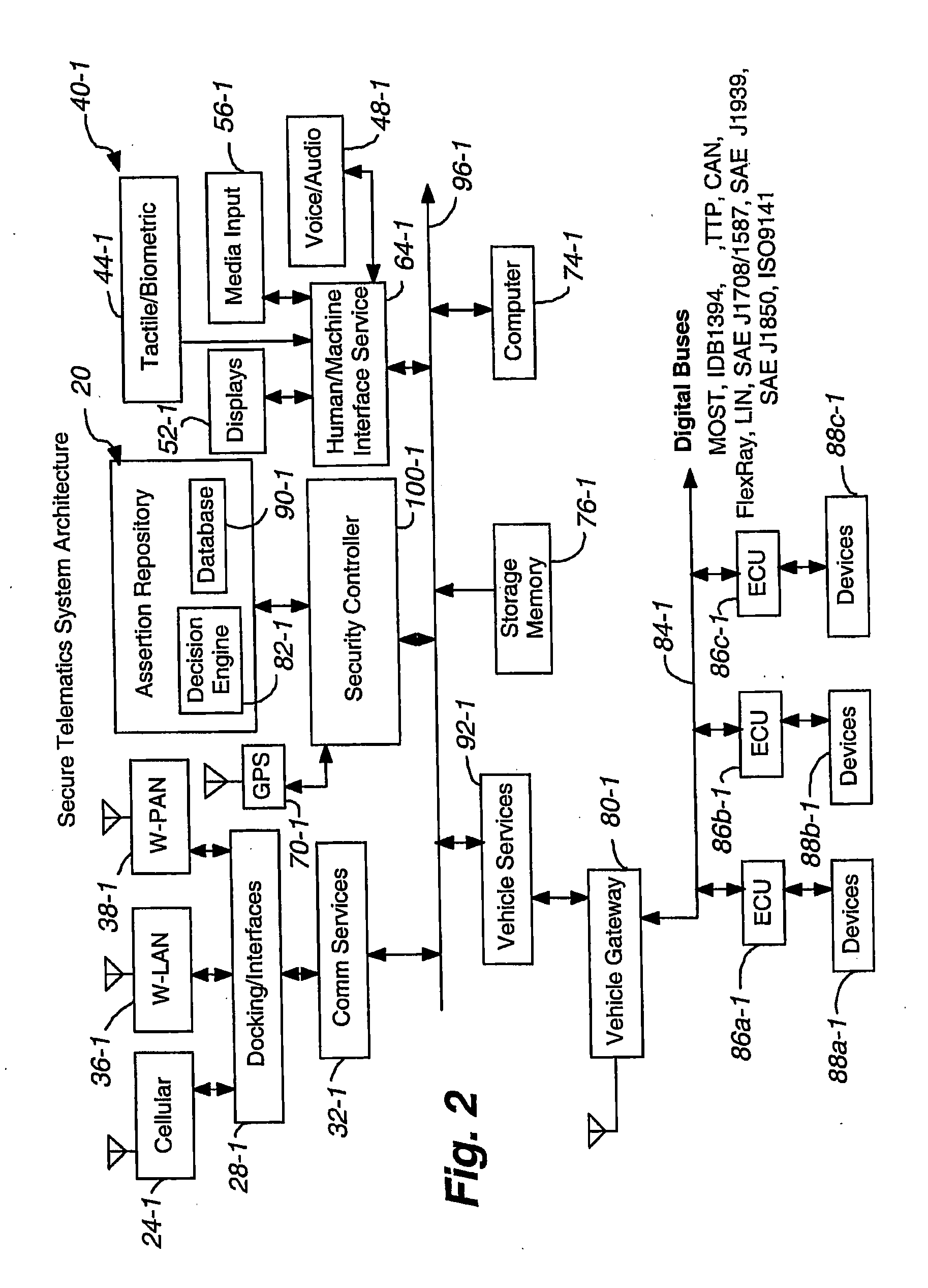
Secure telematics
InactiveUS20080148374A1Expands telematics usageImprove integrityVehicle testingRegistering/indicating working of vehiclesComputer networkService provision
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resources' security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
System and method for managing and updating information relating to economic entities
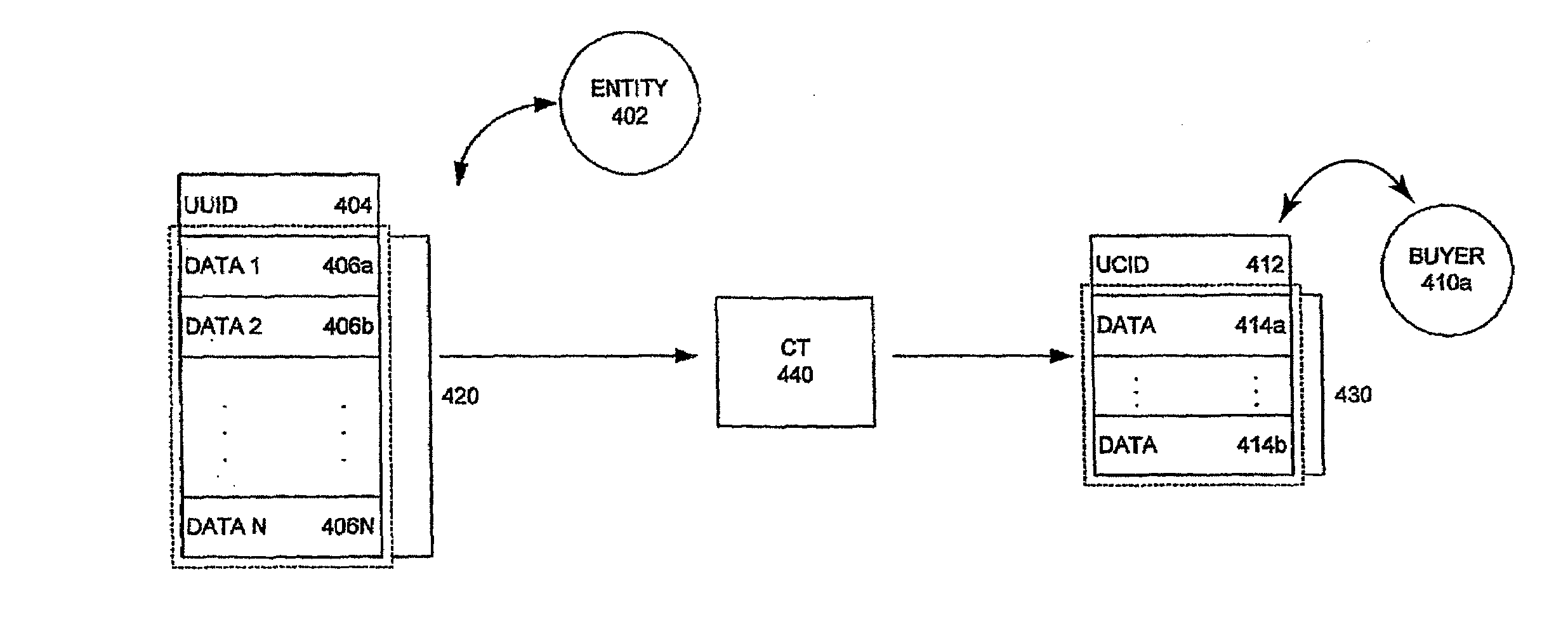
InactiveUS7370044B2Efficiently transfer informationImprove integrityDigital data information retrievalDigital data processing detailsUnique identifierDatabase
Methods and systems for managing and updating information relating to economic entities using sets of unique identifiers. A universe database contains record entries. Each of the record entries is associated with a unique universe identifier. A customer database contains customer record entries. Each customer record entry is associated with a unique customer identifier. A conversion table provides a mapping between the unique universe identifiers and the unique customer identifiers. The information contained in the customer database is updated using the unique universe identifiers, unique customer identifiers and the conversion table. The unique universe identifiers and the unique customer identifiers are stable over a period of time.
Owner:EQUIFAX INC
Enforcing Geographic Constraints in Content Distribution
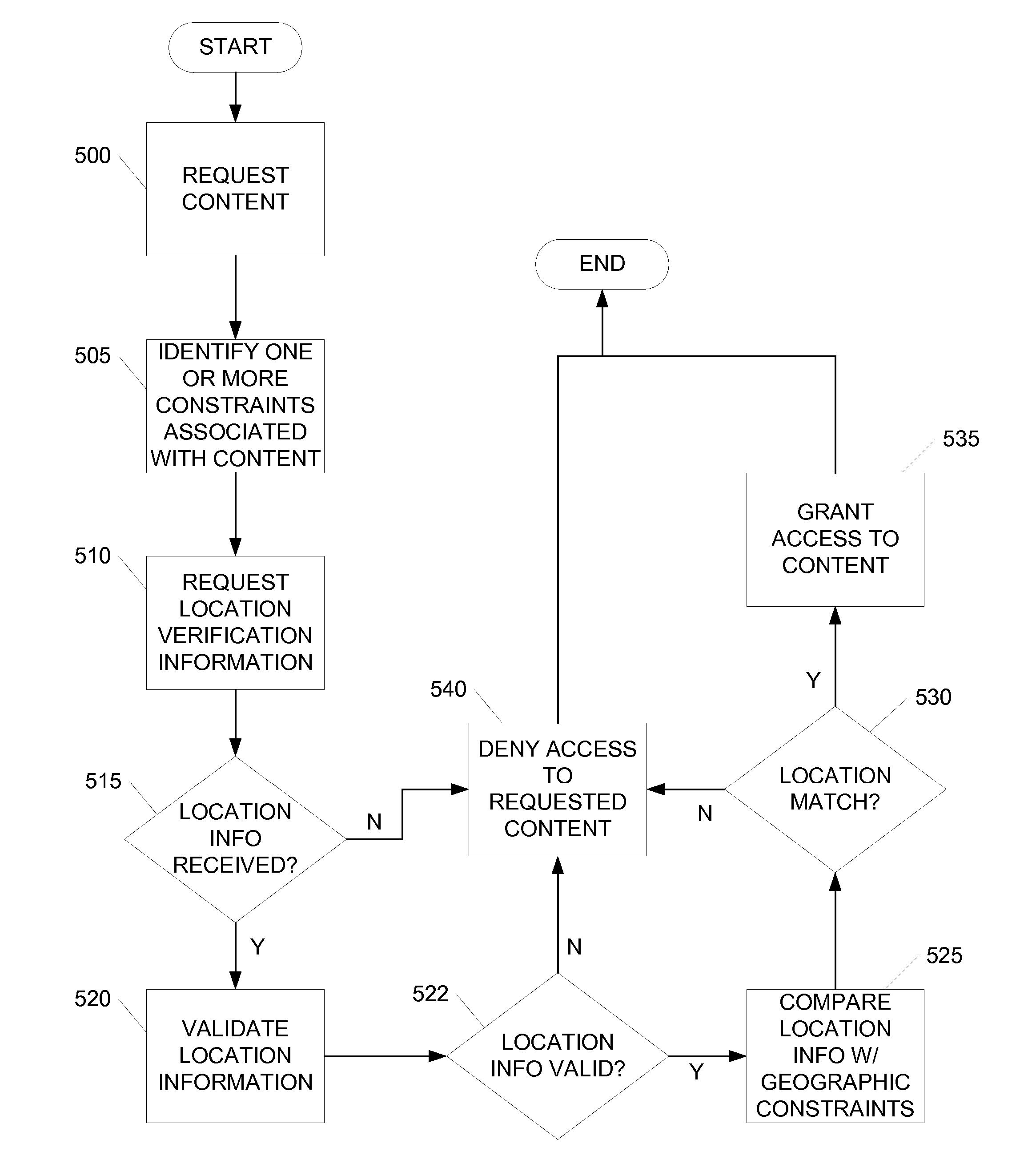
ActiveUS20080022003A1Improve integrityInhibition of informationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsContent distributionProtection mechanism
Enforcement of geographic and location based constraints on content distribution is provided to allow distribution of content to remote devices while preventing unauthorized use and consumption of the content. Content requested by a device may be protected using a variety of content protection mechanisms that support geographic constraints. The requesting device may be required to validate and / or obtain the device's physical location prior to being granted access to the protected content. The requesting device may validate and / or obtain its physical location by requesting location information from a location server or another geographic aware device. The distribution of the location information from the location server may be limited to a predefined proximity. The proximity limit on the dissemination of the location information prevents remote devices from fraudulently using the location information. Location information may be encapsulated and may be formatted as a content file.
Owner:NOKIA TECHNOLOGLES OY
Techniques for secure channelization between uicc and a terminal
InactiveUS20090209232A1Improve integrityReduce needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemThird generation
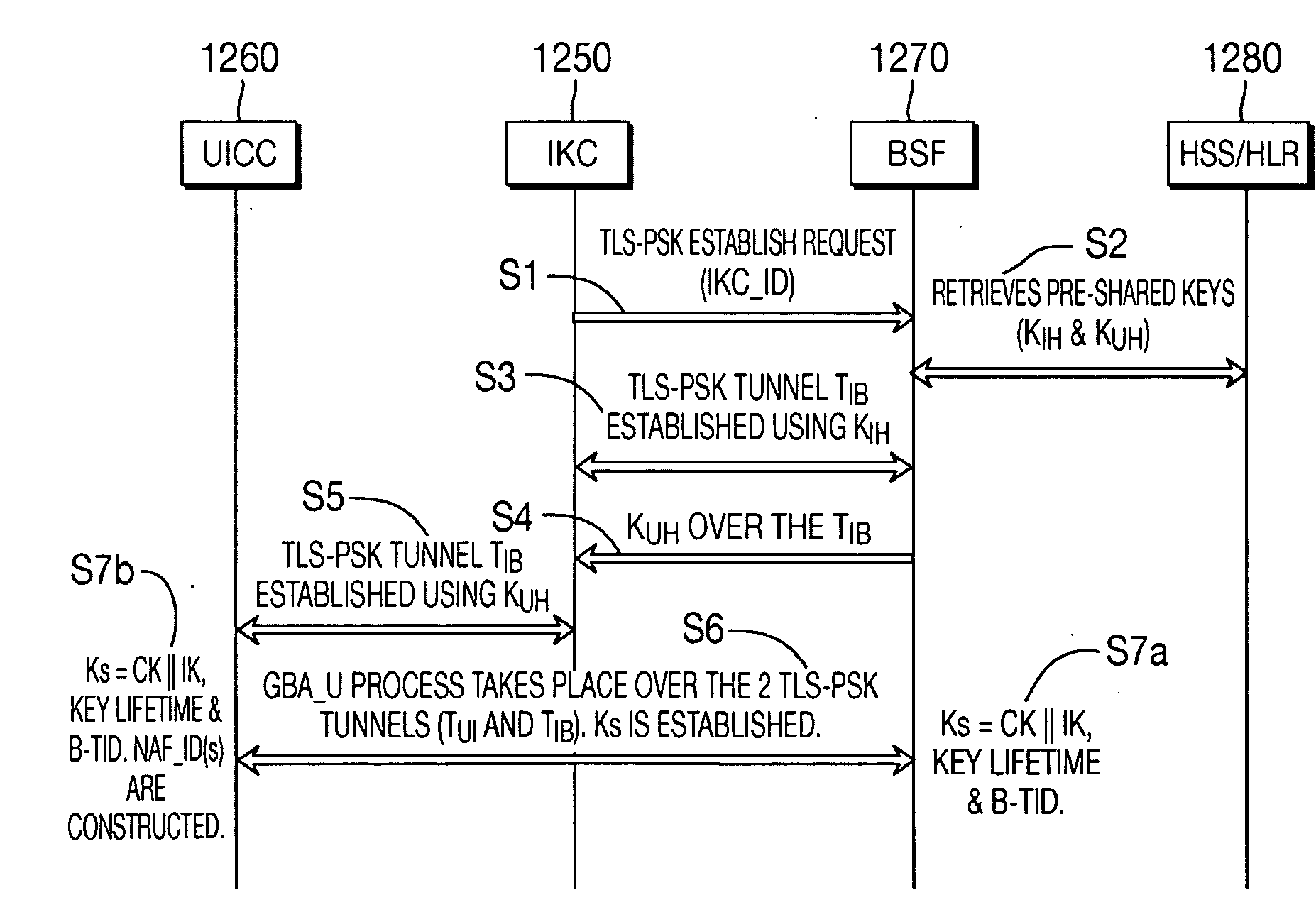
The present invention is related to a wireless communication system. 3G UMTS mobile phone systems rely on a protected smart card called the UMTS integrated circuit card (UICC) that provides UMTS subscriber identity module (USIM) applications as a basis or root of various security measures protecting the communication path between the 3G mobile terminal and the UMTS wireless network (or UTRAN). Disclosed is a method by which the UICC exchanges information with a terminal, such as an Internal Key Center (IKC 1250) and a Bootstrapping Server Function (BSF 1270) enables a procedure where multiple local keys specific to applications and Network Application Functions (NAFs) (Ks_local) are used for authentication and to encrypt and decrypt messages.
Owner:INTERDIGITAL TECH CORP
Physiological sensor device
InactiveUS20110237922A1Improve reliabilityImprove accuracyElectrocardiographySensorsElectricityElectrical conductor
A physiological sensor device is attachable to the skin of a person for collecting physiological signals generated by the person's body. The device includes a flexible front layer made of a material that does not conduct electricity and a flexible back layer made of a material that does not conduct electricity. A flexible intermediate layer made of a material that does not conduct electricity is sandwiched between and fixed to the front layer and the back layer. Electrodes and electrical conductors are fixed to a back side of the intermediate layer. Each of the electrodes is attached to one of the electrical conductors and all of the electrical conductors are attached to a single common connector that protrudes through a portal in the front layer. A conductive gel pad is adhered to and aligned with each of the electrodes and protrudes through a portals in the back layer to contact the skin of a person when the physiological sensor device is attached to the skin of a person. Each layer of the physiological sensor device has, when attached to a standing person's chest, a vertically extending portion with a horizontally extending portion located at a lower end of the vertically extending portion to give the physiological sensor device a shape like an inverted T. The vertically extending portion is intended to overly a person's sternum and is sized to comfortably fit either a male or female patient.
Owner:HALTHION MEDICAL TECH INC
Method and apparatus for seismic data acquisition
InactiveUS20050052951A1Avoid entrapmentMinimize the possibilityTransducer detailsSeismic signal receiversOcean bottomRubidium
A marine seismic exploration method and system comprised of continuous recording, self-contained ocean bottom pods characterized by low profile casings. An external bumper is provided to promote ocean bottom coupling and prevent fishing net entrapment. Pods are tethered together with flexible, non-rigid, non-conducting cable used to control pod deployment. Pods are deployed and retrieved from a boat deck configured to have a storage system and a handling system to attach pods to cable on-the-fly. The storage system is a juke box configuration of slots wherein individual pods are randomly stored in the slots to permit data extraction, charging, testing and synchronizing without opening the pods. A pod may include an inertial navigation system to determine ocean floor location and a rubidium clock for timing. The system includes mathematical gimballing. The cable may include shear couplings designed to automatically shear apart if a certain level of cable tension is reached.
Owner:MAGSEIS FF LLC
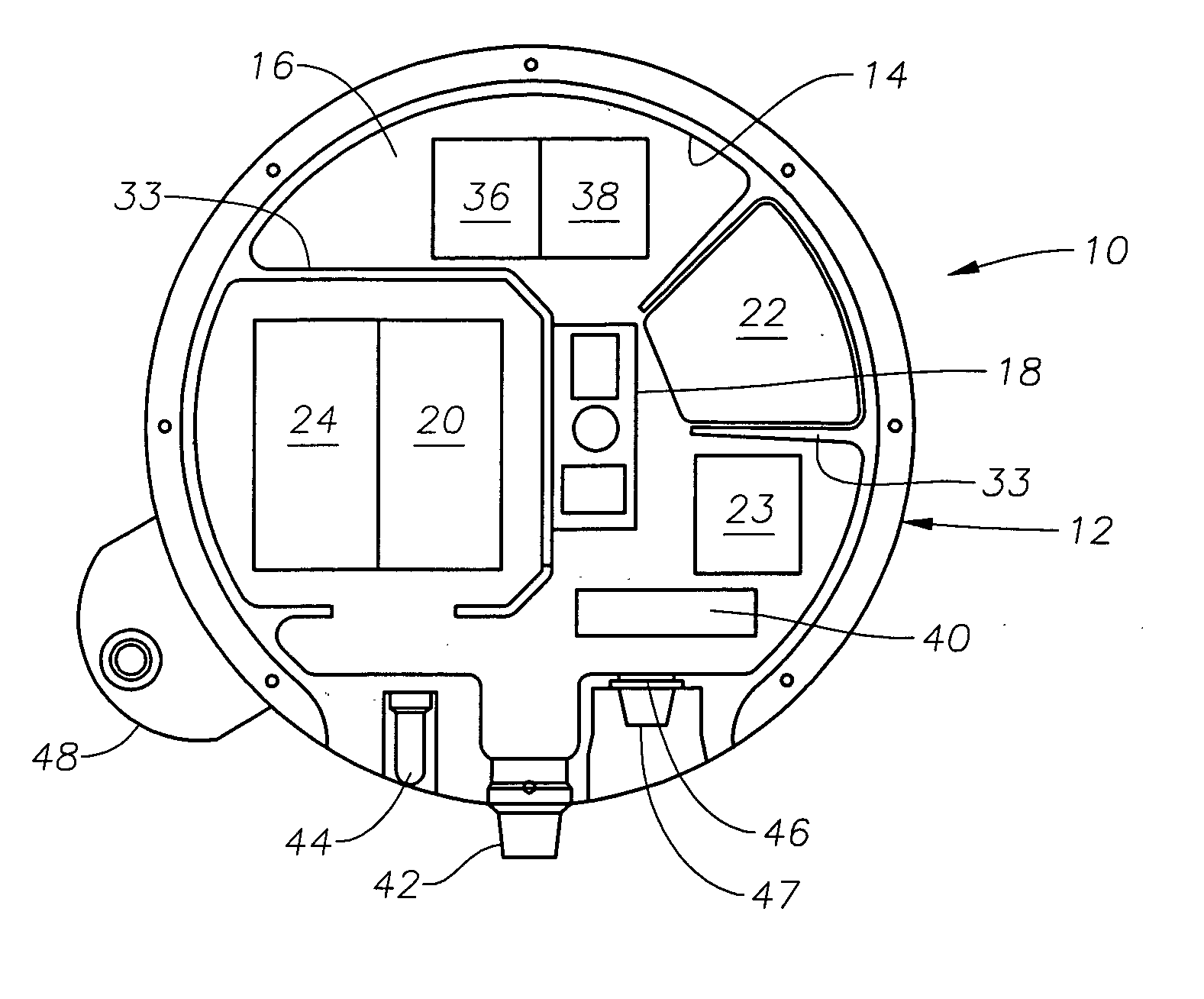
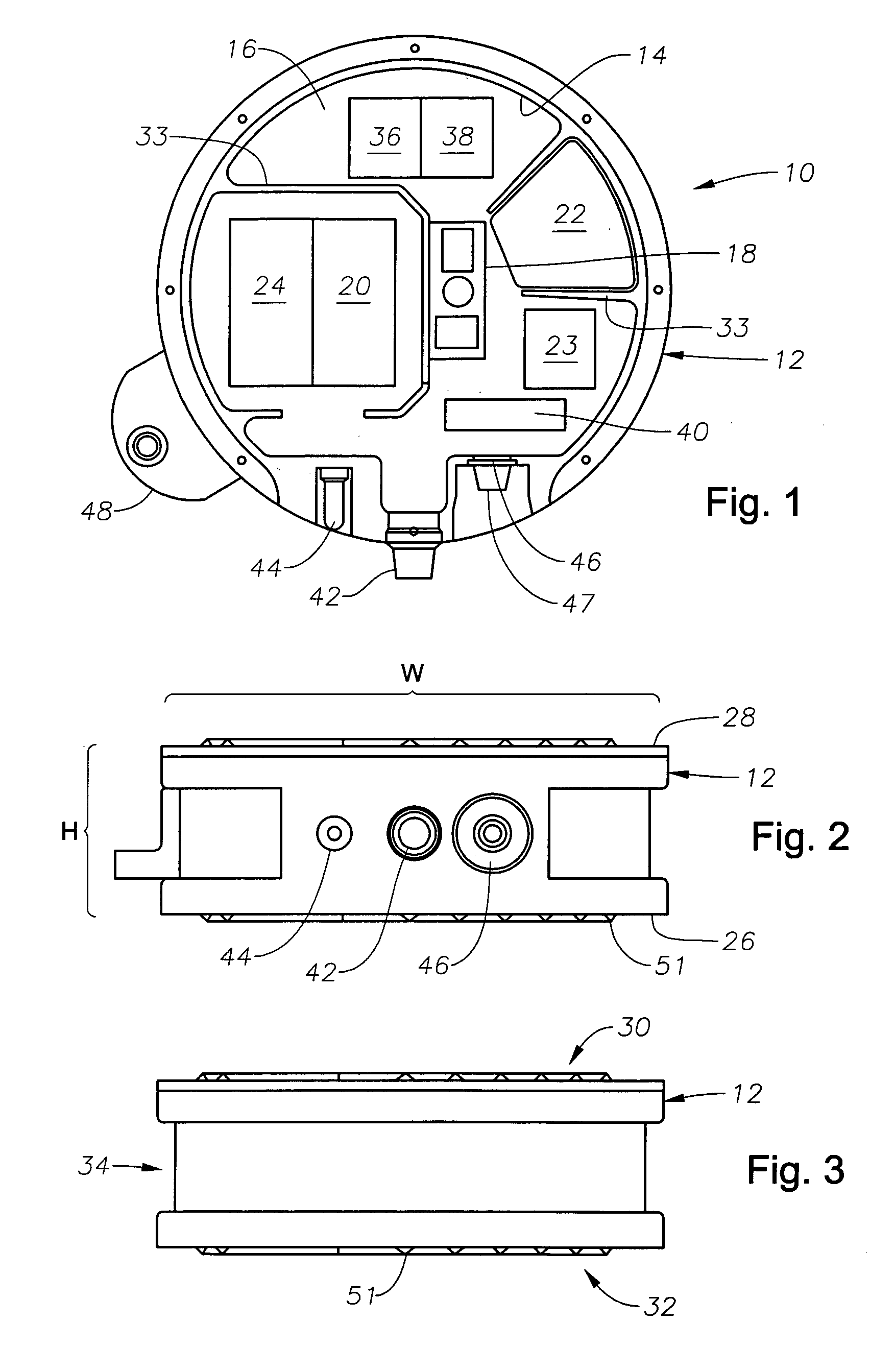
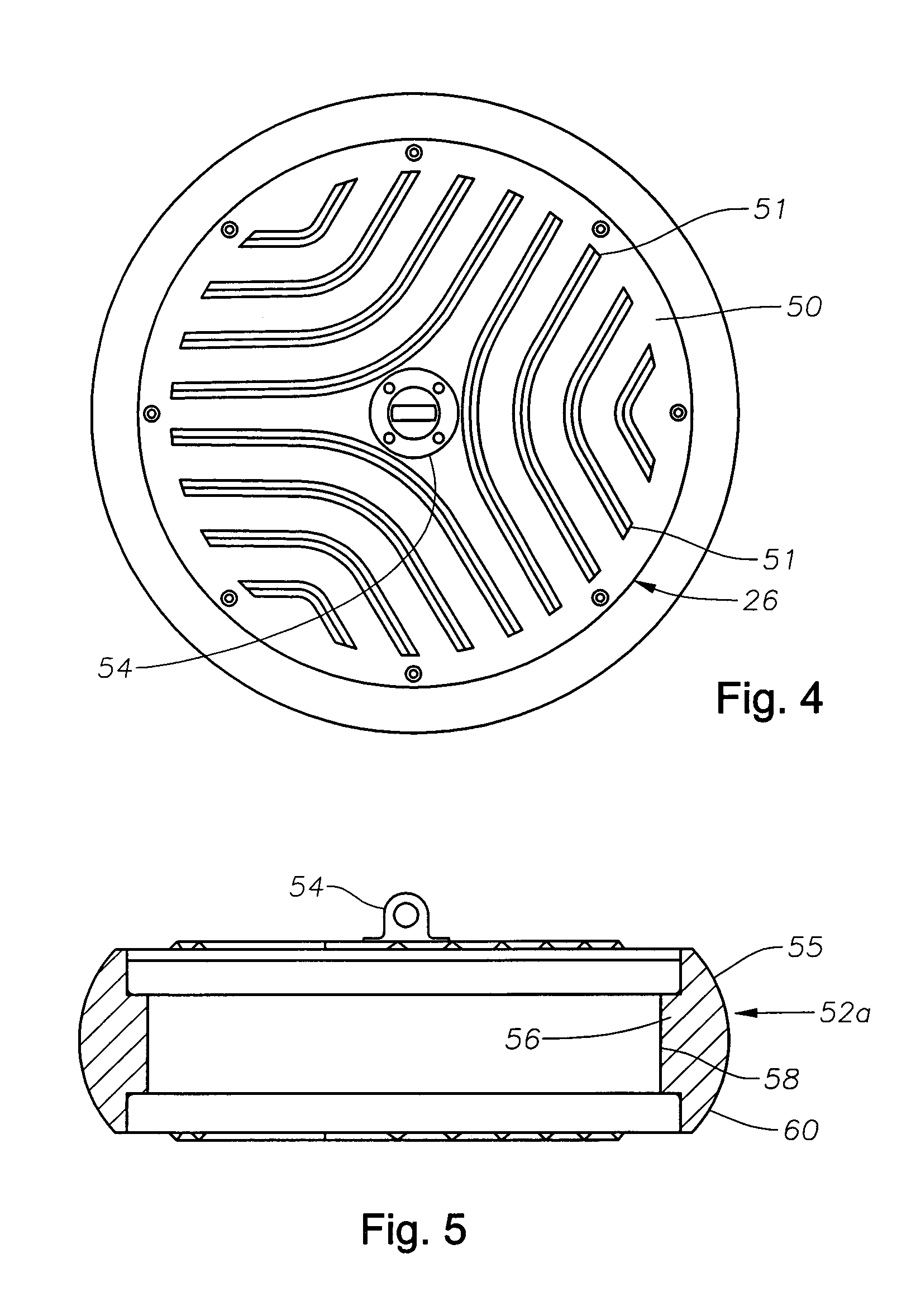
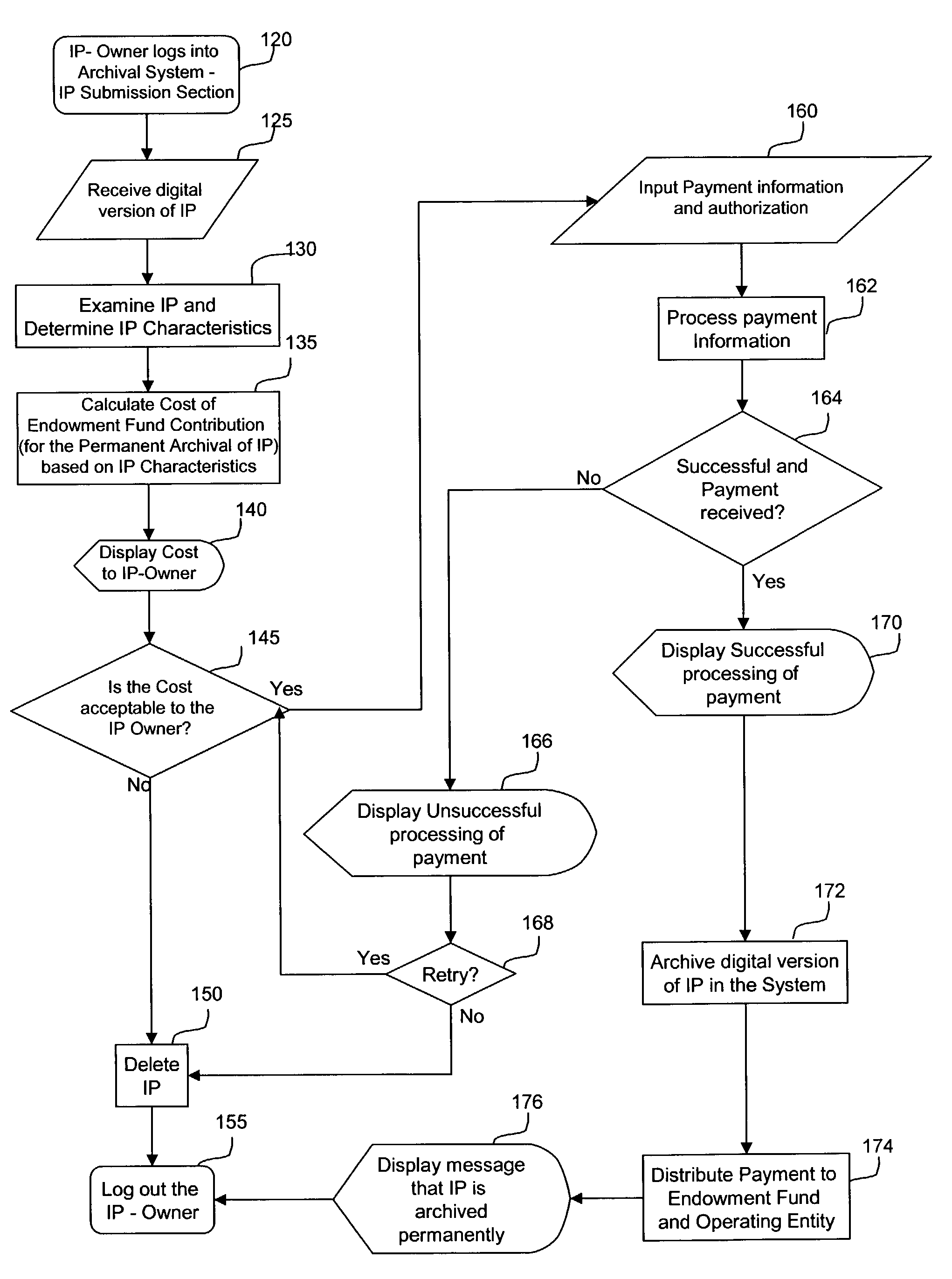
Assured archival and retrieval system for digital intellectual property
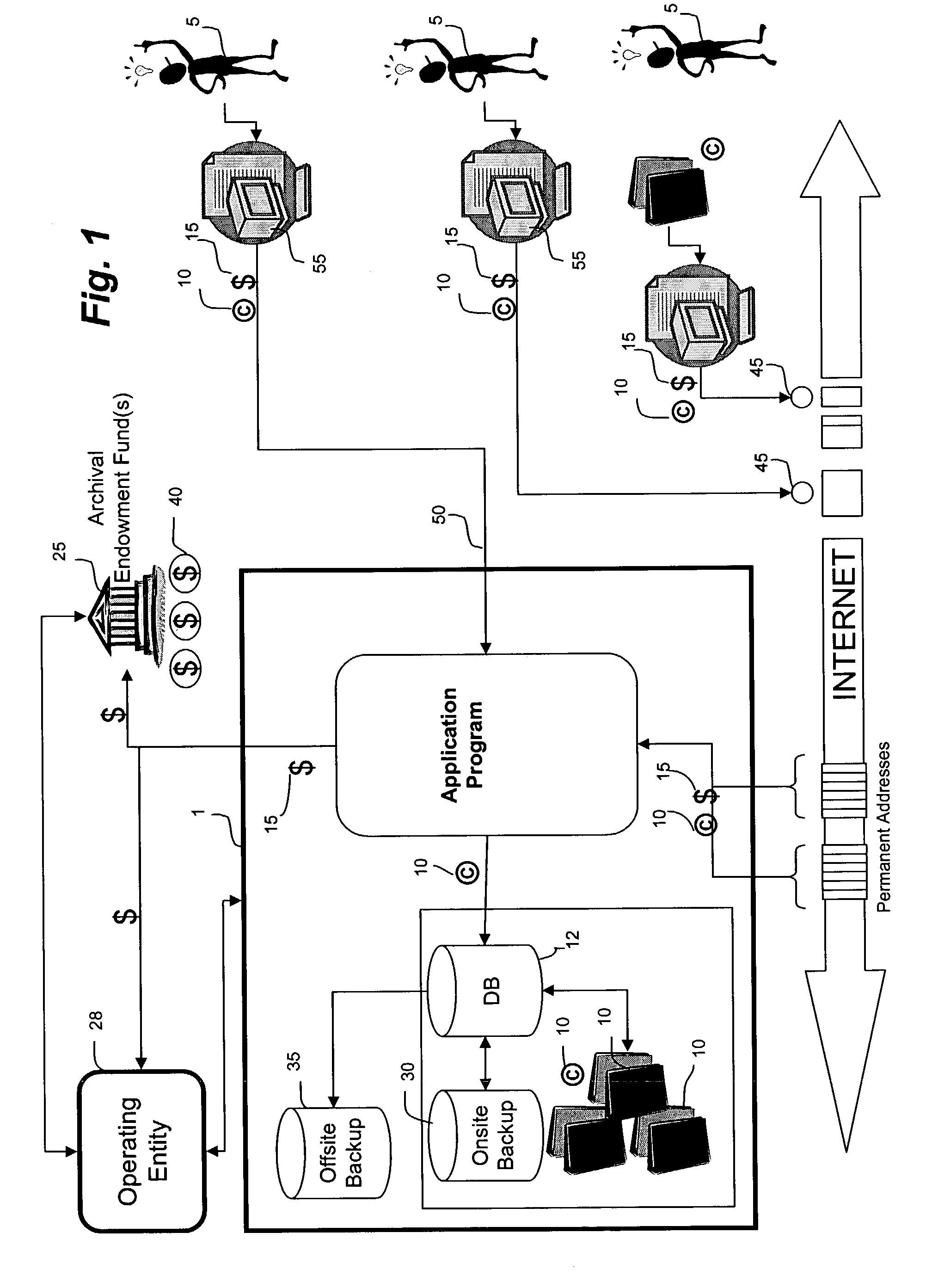
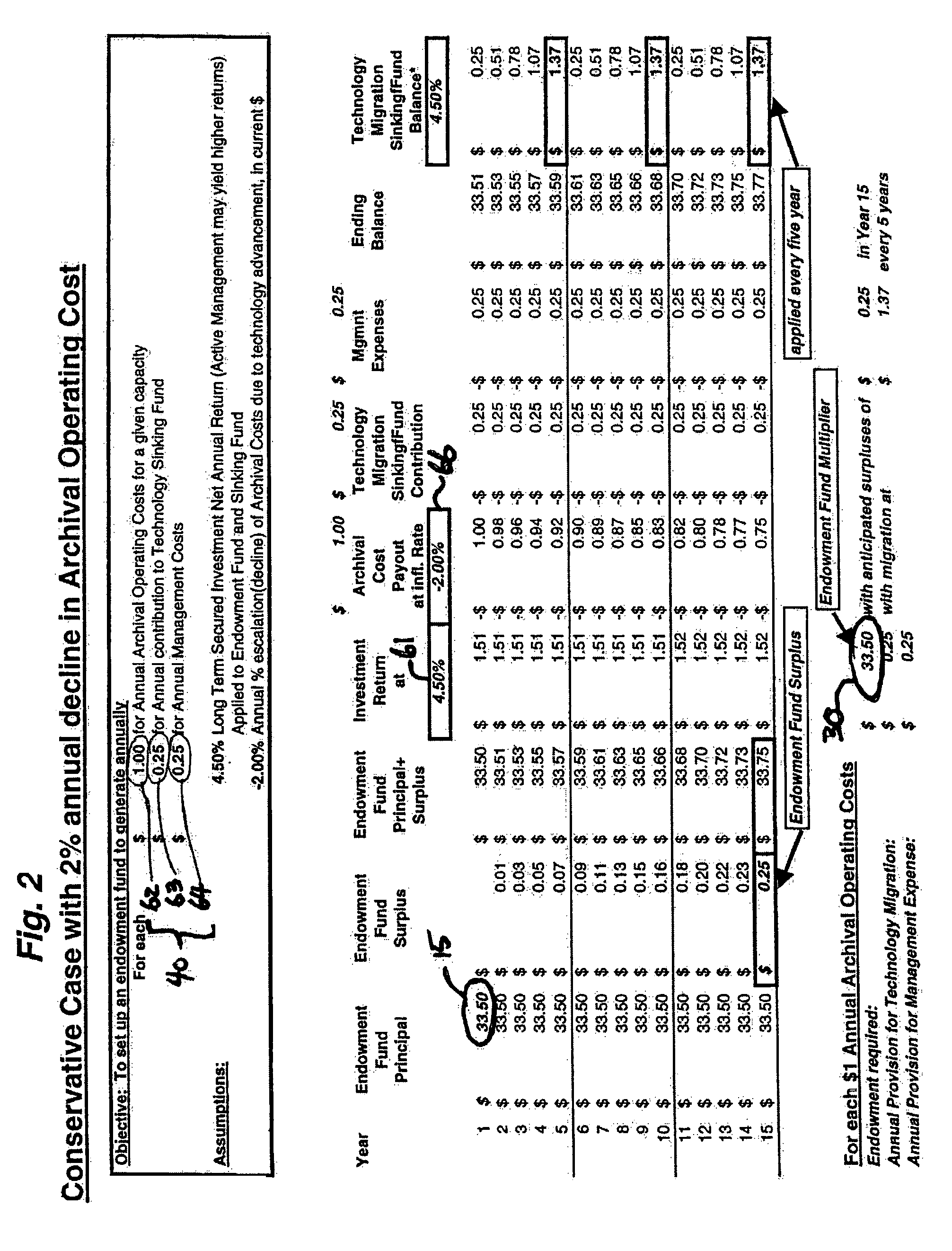
ActiveUS7856414B2Economy of scaleImprove integrityFinanceDigital data processing detailsIntellectual propertyDigital rights management
A system and method of use for permanently archiving intellectual properties (IP) in a digital archival system. An owner contributes each IP with an initial financial contribution including a discrete archival endowment which is sufficient to fund archival of the IP for an assured archival period. A plurality of discrete archival endowments can be pooled into one or more archival endowment funds, jointly managed for the maintenance of each archived IP. The endowment funds can be managed by a trustee separate from the management of the digital archive. Retrieval can be funded through retrieval fees or an endowment maintained separate from the archival endowment fund. Digital rights management can remunerate owners and revenue tracking can capitalize the value of each IP. Access to the archive system is preferably through a variety of membership options including owners, users, and partners.
Owner:ZEE CHRISTOPHER
Surgical instrument seal assembly
InactiveUS7056303B2Easy to produceImprove integrityOperating means/releasing devices for valvesCannulasEngineeringSurgical department
A surgical instrument valve assembly is provided with a valve seal where the upper portion of the valve seal is rigidly mounted to the body of the valve assembly. The lower portion of the valve seal is configured to allow some radial movement while the upper portion of the valve seal remains rigidly mounted within the valve assembly. The valve seal may be provided with stay that prevents the valve seal from inverting when an instrument in withdrawn from the valve assembly.
Owner:CONMED CORP
Device and method for continuously shuffling and monitoring cards
The present invention provides an apparatus and method for moving playing cards from a first group of cards into a second group of cards, wherein the second group of cards is randomly arranged or shuffled. The apparatus comprises a card receiver for receiving the first group of cards, a single stack of card-receiving compartments generally adjacent to the card receiver, the stack generally vertically movable, an elevator for moving the stack, a card-moving mechanism between the card receiver and the stack for moving cards one at a time into a selected one of the compartments, another card moving mechanism for moving cards from one of the compartments to a second card receiver and a microprocessor that controls the card-moving mechanisms and the elevator. A count of cards within specified areas of the card handling system is maintained and card handling is halted and all cards counted by adding a count of all cards not within the specified areas to the total of cards counted within the specified areas.
Owner:BALLY GAMING INC
Secure Biometric Verification of Identity
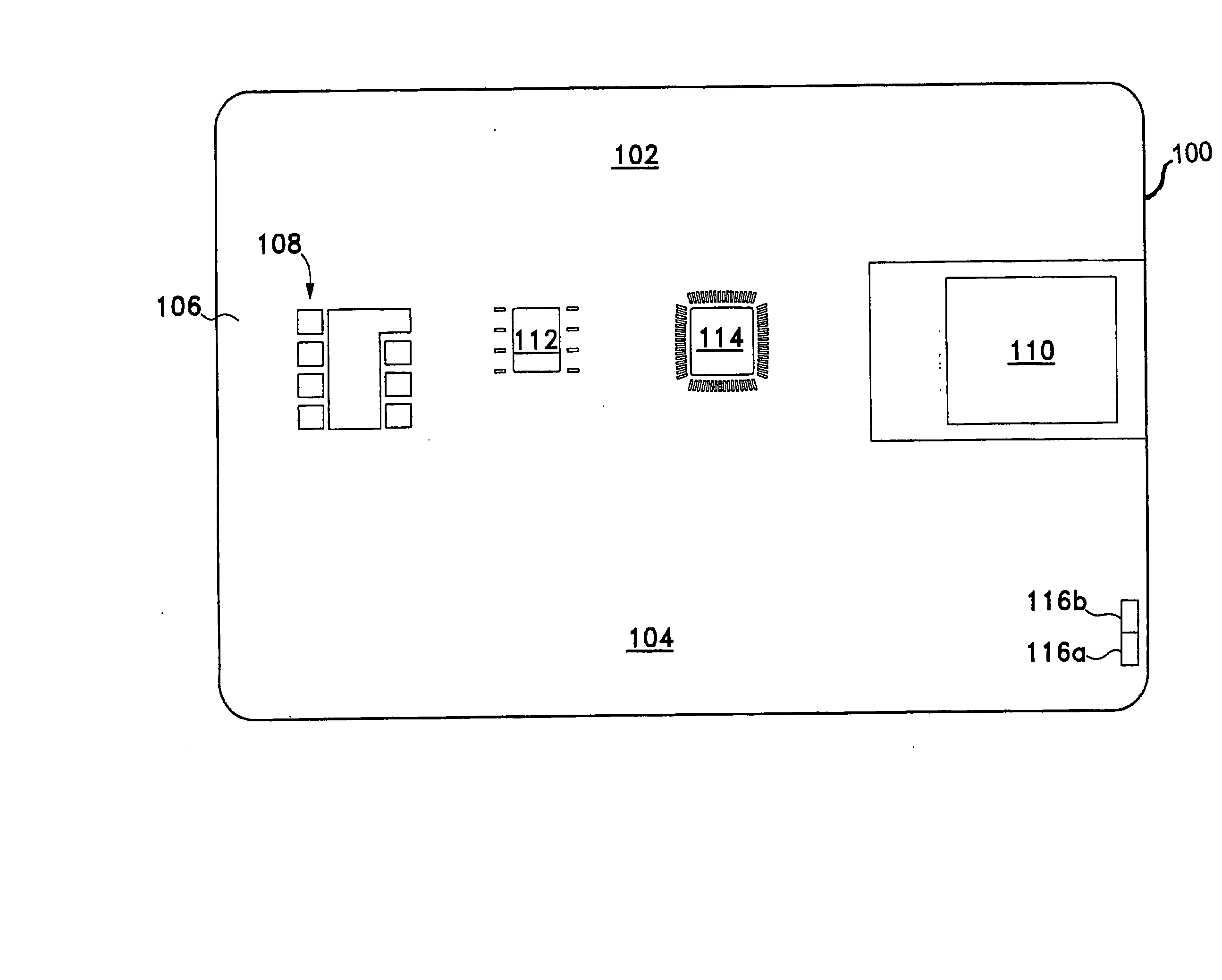
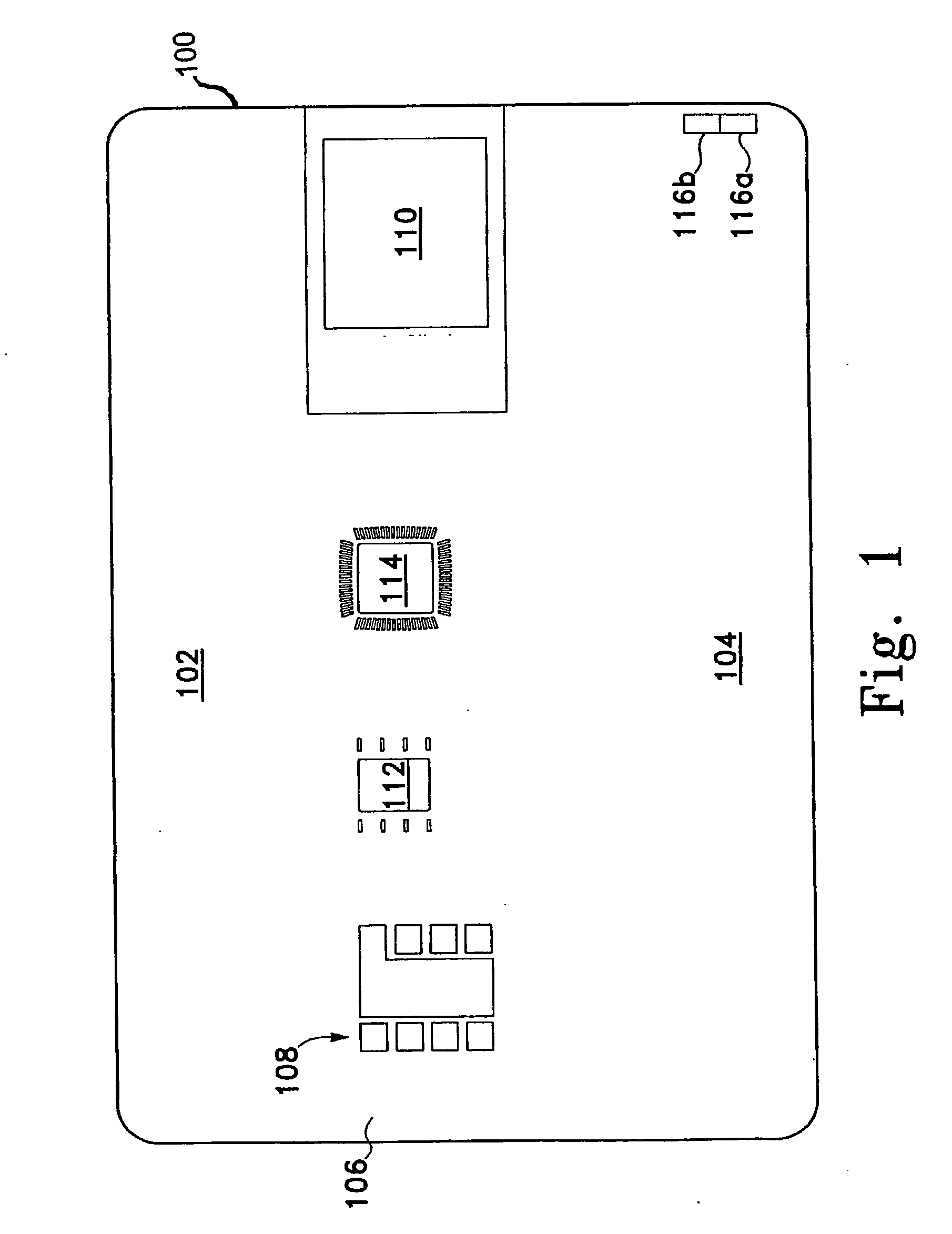
InactiveUS20080019578A1Reduce computational complexityReduce probabilityImage analysisCharacter and pattern recognitionComputer hardwareData matching
A high security identification card includes an on-board memory for stored biometric data and an on-board sensor for capturing live biometric data. An on-board processor on the card performs a matching operation to verify that the captured biometric data matches the locally stored biometric data. Only if there is a positive match is any data transmitted from the card for additional verification and / or further processing. Preferably, the card is ISO SmartCard compatible. In one embodiment, the ISO SmartCard functions as a firewall for protecting the security processor used for storing and processing the protected biometric data from malicious external attack via the ISO SmartCard interface. In another embodiment, the security processor is inserted between the ISO SmartCard Interface and an unmodified ISO SmartCard processor and blocks any external communications until the user's fingerprint has been matched with a previously registered fingerprint. Real-time feedback is provided while the user is manipulating his finger over the fingerprint sensor, thereby facilitating an optimal placement of the finger over the sensor. The card may be used to enable communication with a transactional network or to obtain physical access into a secure area.
Owner:IVI HLDG
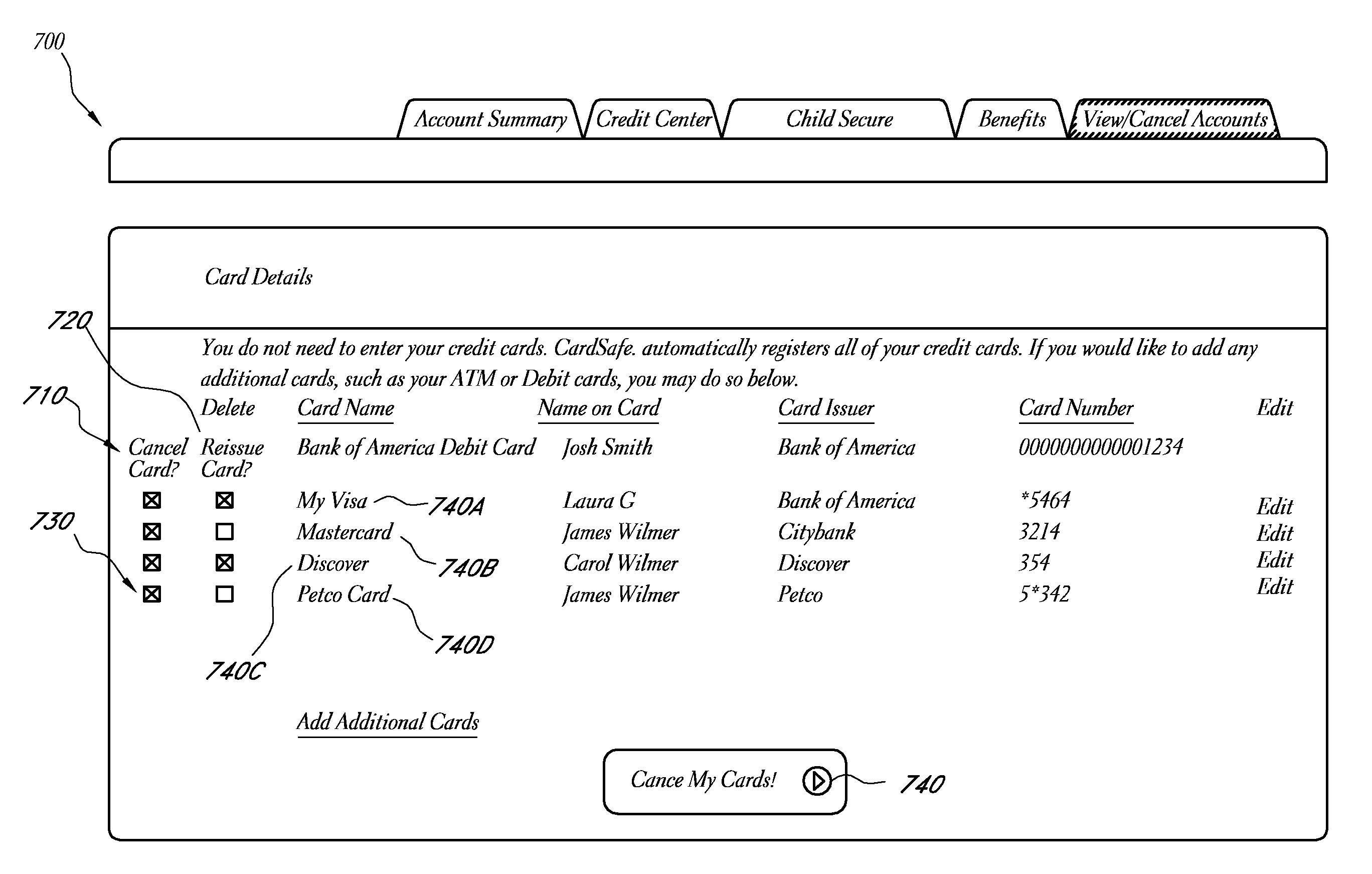
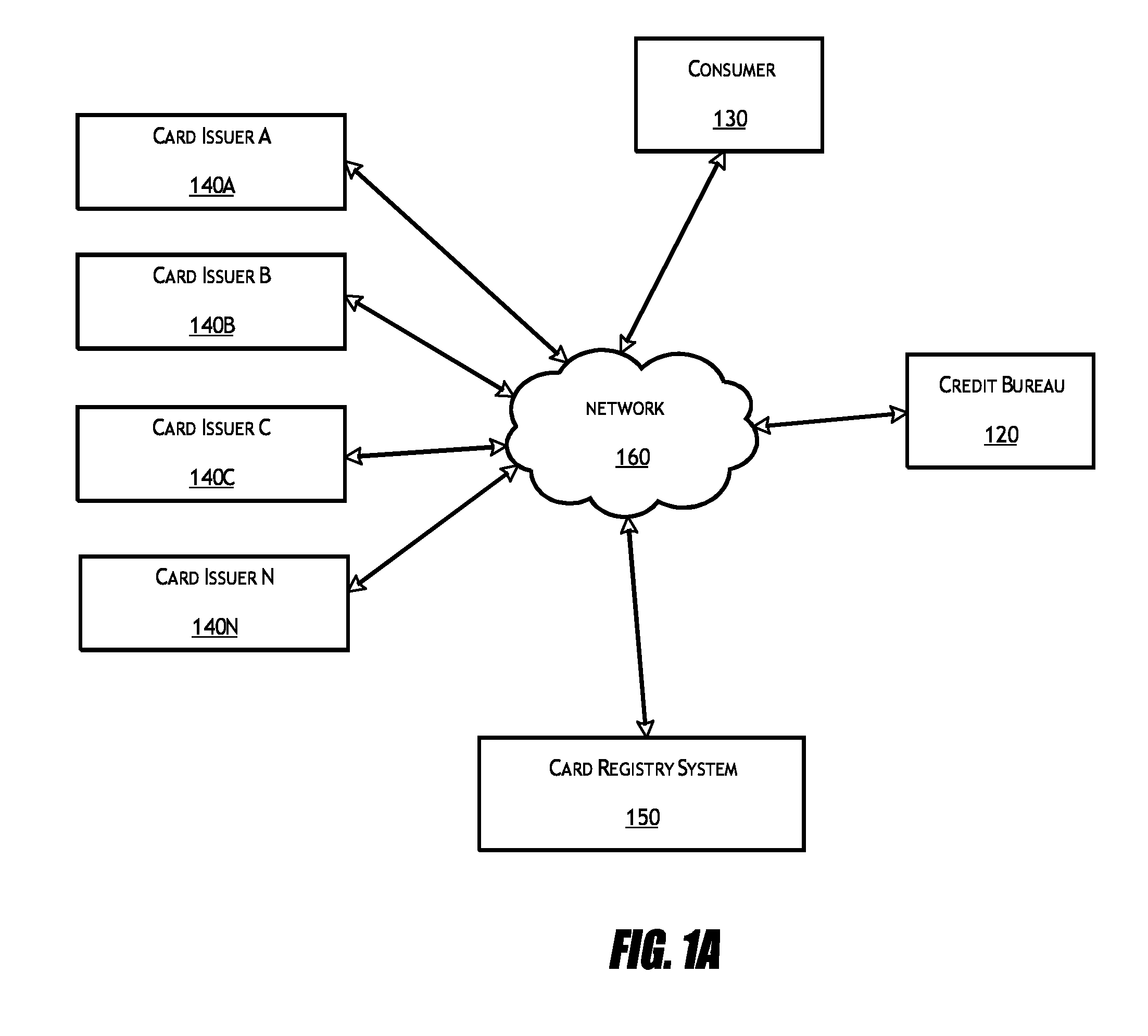
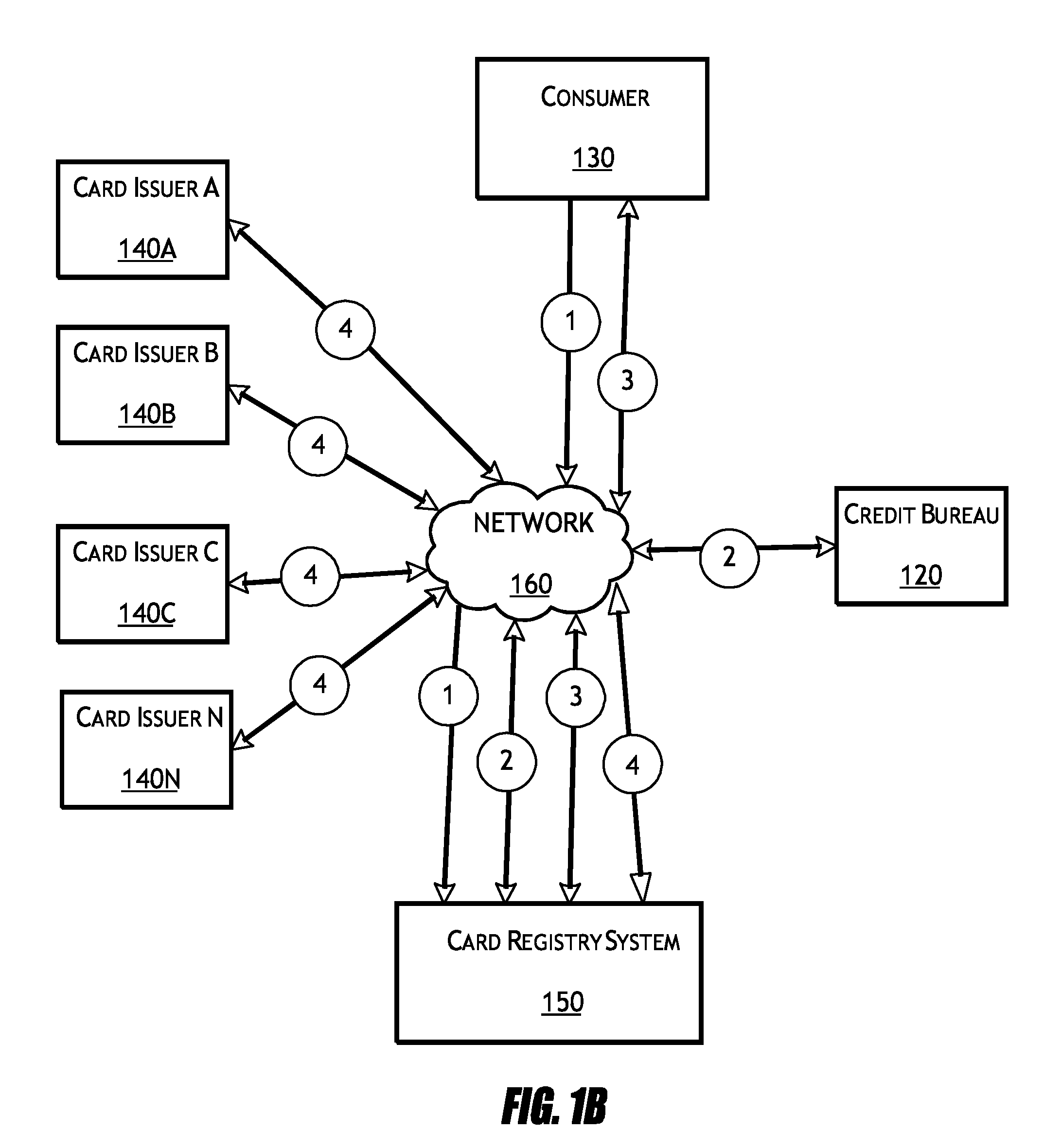
Card registry systems and methods
A card registry system is configured to automatically identify financial card information in one or more credit files associated with a consumer and populate a card registry account of the consumer with the identified financial card information. Once the financial card information has been obtained from the credit file(s), the card registry system may transmit cancellation and / or reissuance requests to the respective card issuers in the instance that one or more cards are compromised, so that the financial cards may be easily and efficiently cancelled and / or reissued at the request of the consumer.
Owner:CONSUMERINFO COM
Method and apparatus for the treatment of the intervertebral disc annulus
InactiveUS20070185497A1Reduce riskImprove integritySuture equipmentsInternal osteosythesisBiomedical engineeringIntervertebral disk
The present invention provides methods and devices for treating the annulus of an intervertebral disc. The methods and devices employ a fixation device delivery tool having a curved body portion. Fixation devices and methods are also disclosed for placement in intervertebral disc tissue.
Owner:KRT INVESTORS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com