Patents
Literature
25817 results about "Internet privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internet privacy involves the right or mandate of personal privacy concerning the storing, repurposing, provision to third parties, and displaying of information pertaining to oneself via the Internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large-scale computer sharing.
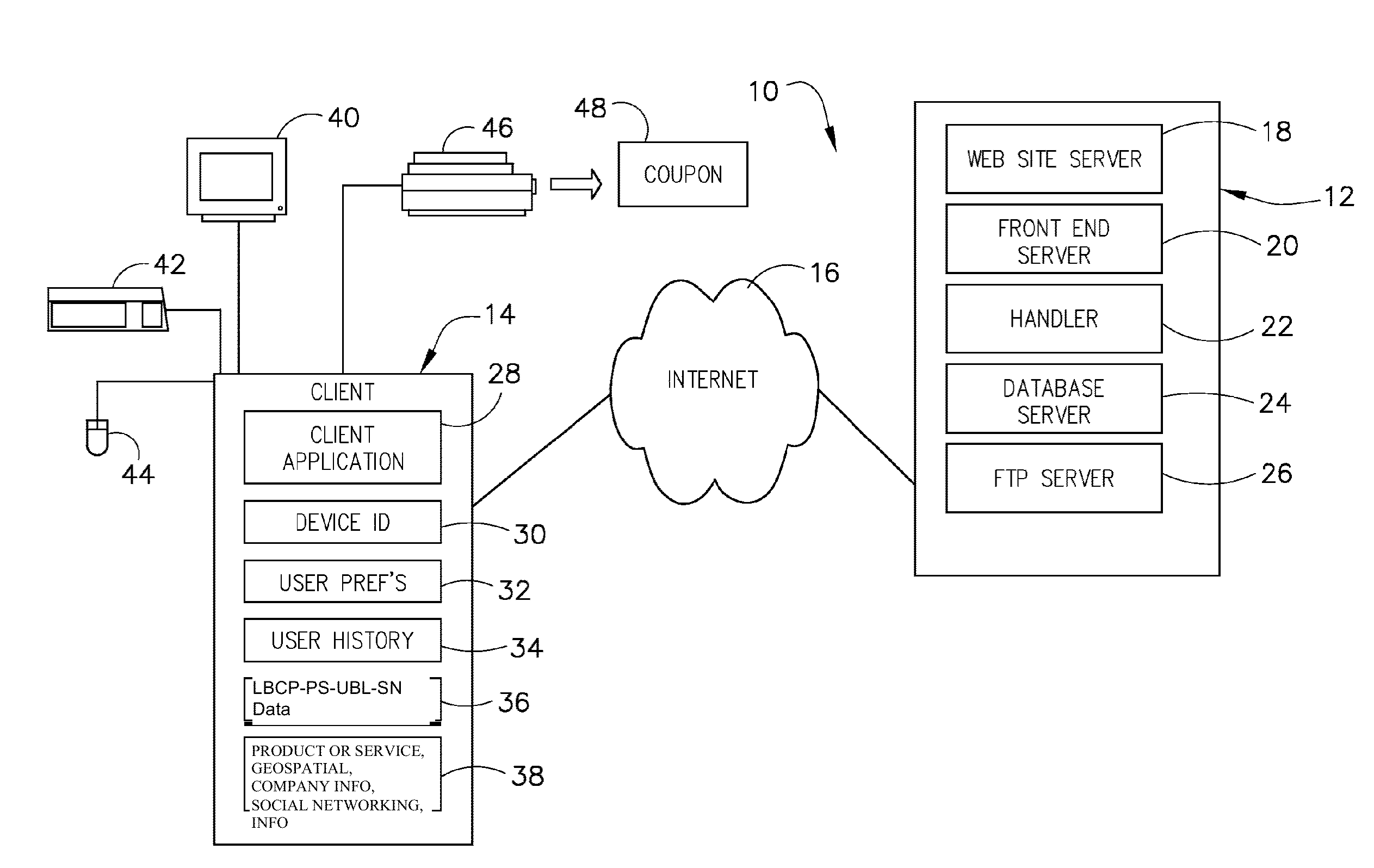
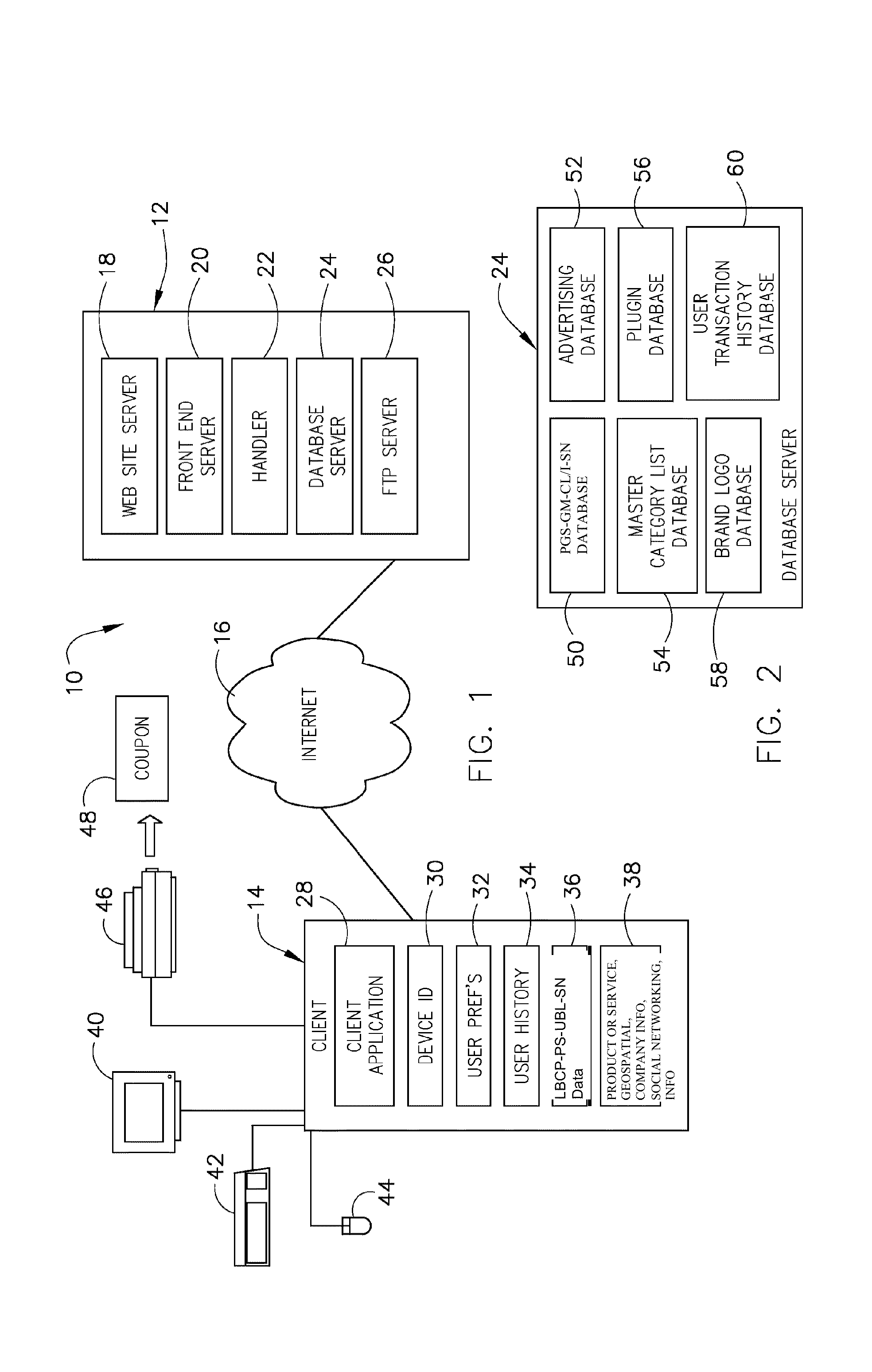
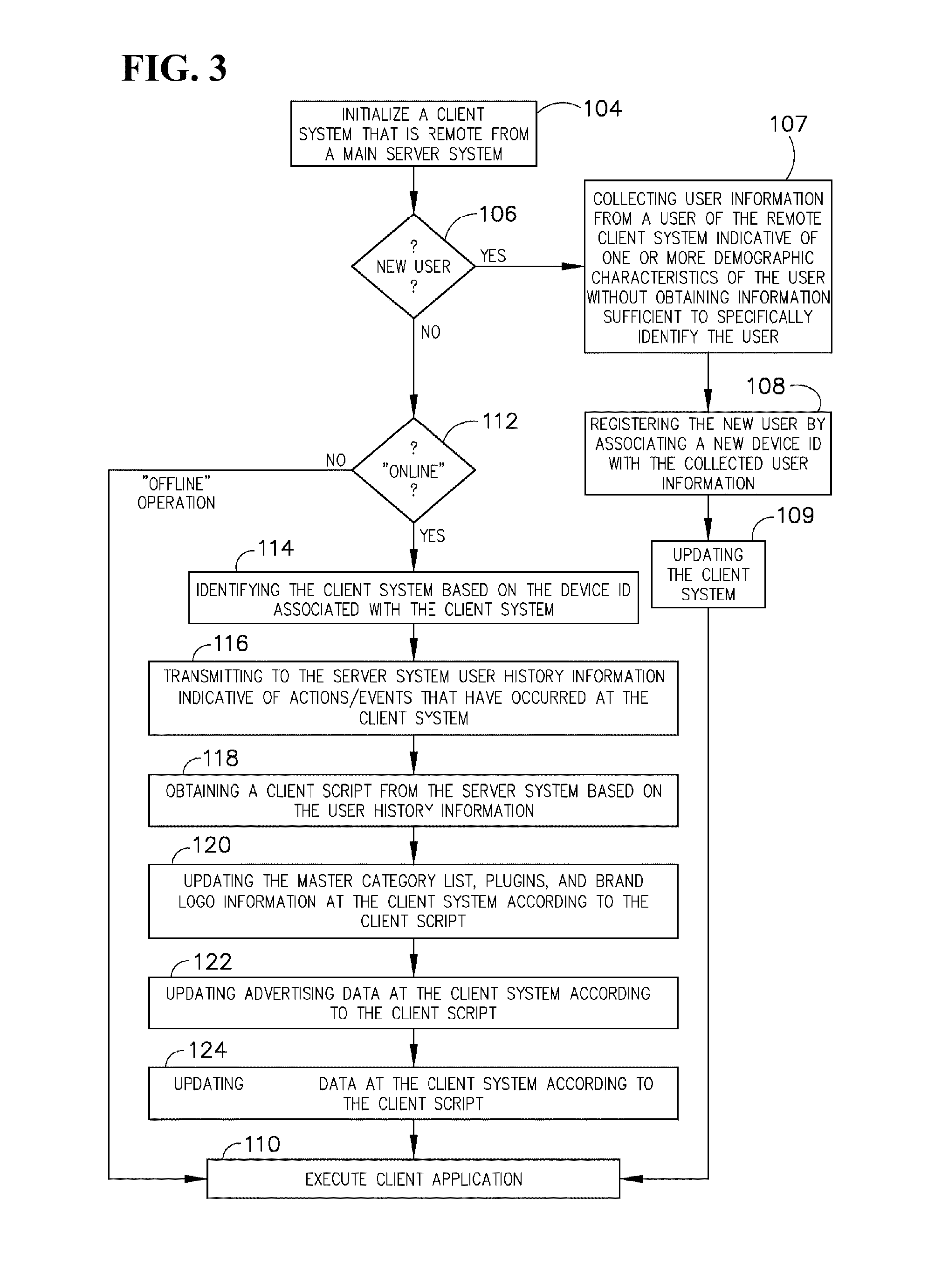
Database access system
ActiveUS7181438B1Increased formationGood user interfaceDigital data information retrievalAdvertisementsAnonymityPopulation statistics
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
Data security system and method for separation of user communities
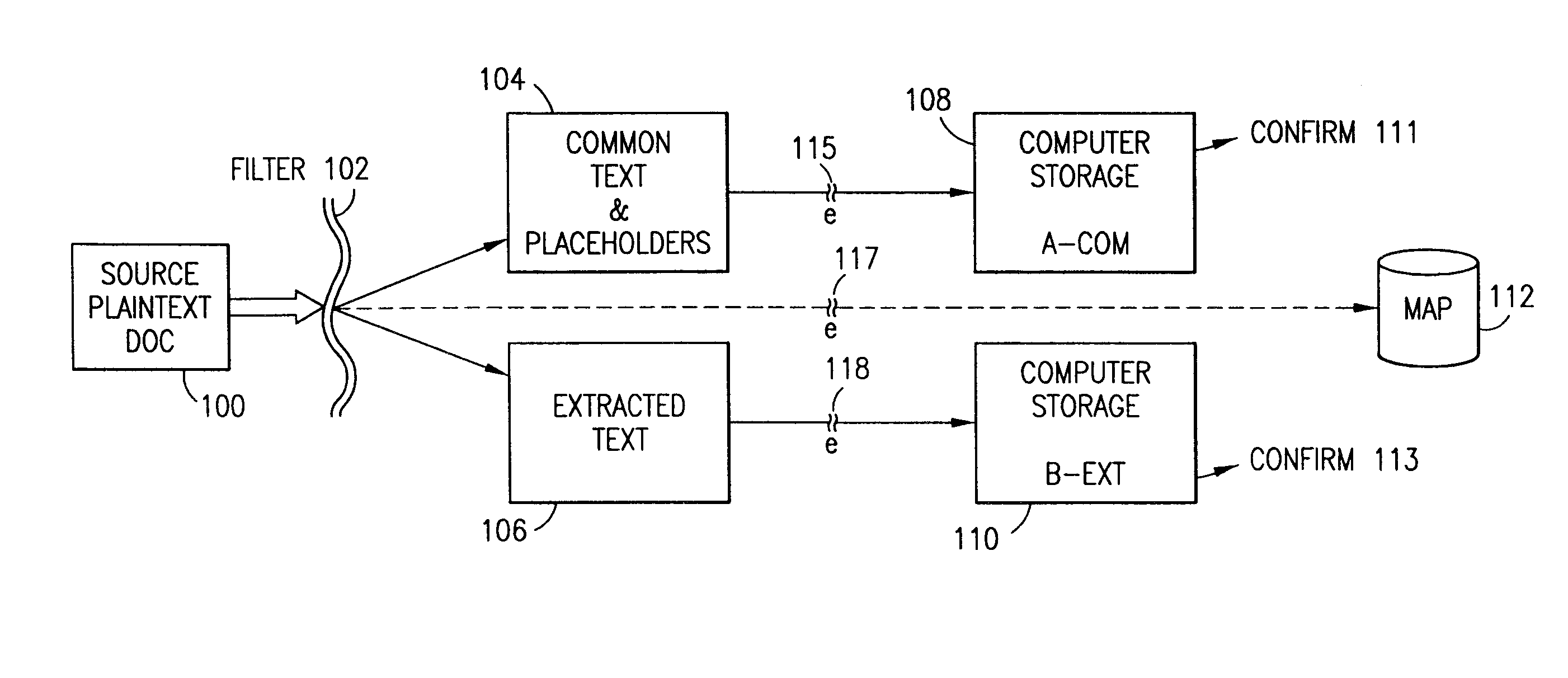
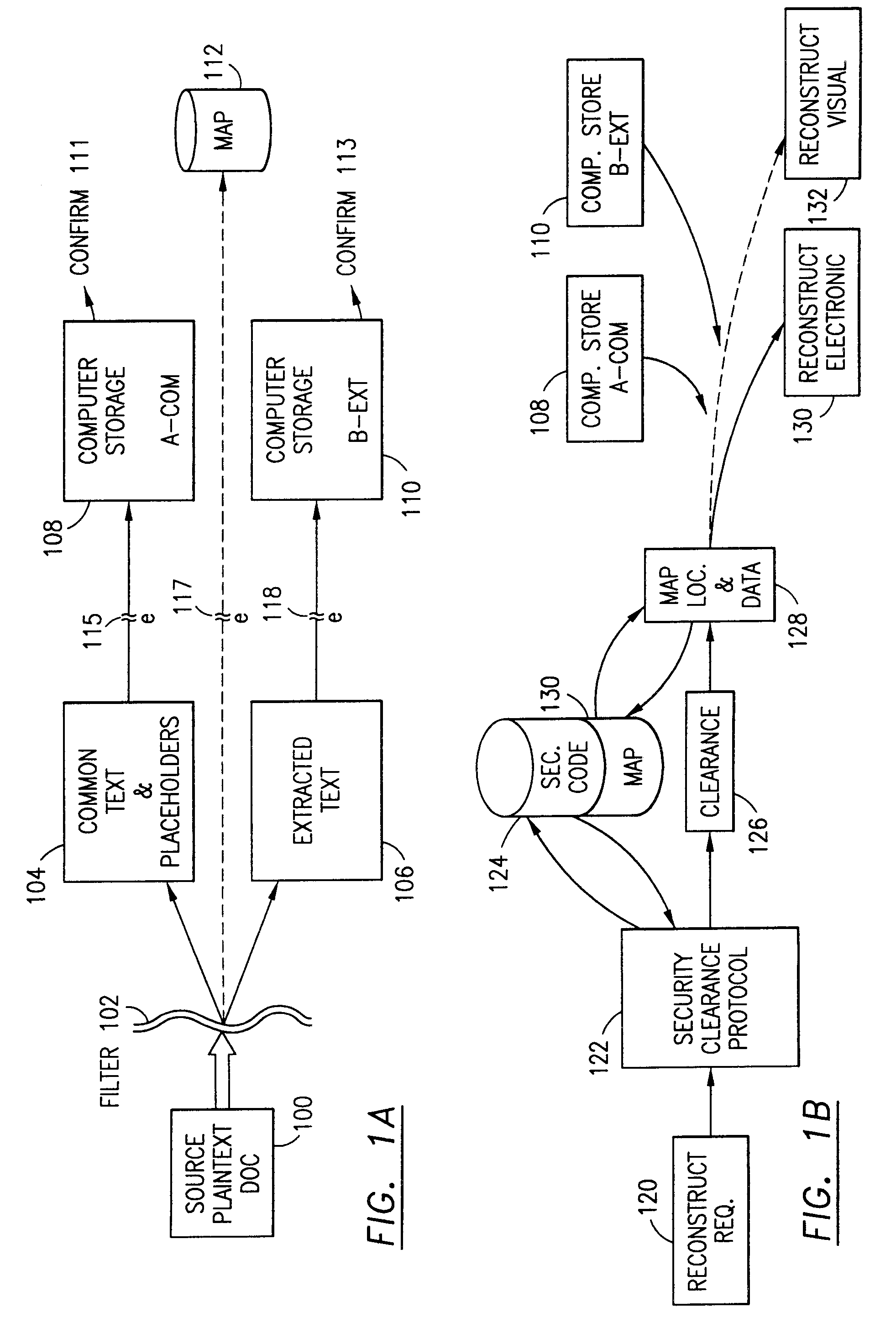
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
Secure data interchange
InactiveUS7630986B1Low pricePrivacy protectionMultiple digital computer combinationsOffice automationCommunications systemInternet privacy
A system for exchanging data includes a communication system, a first and a second party connected to the communication system, wherein each party has personal data, and each party has a disclosure policy to control dissemination of its data, and a secure intermediate party connected to the communication system, wherein the secure intermediate party exchanges data between the first and second parties in accordance with their respective disclosure policies.
Owner:STRIPE INC
System and method for providing content, management, and interactivity for client devices
InactiveUS7130616B2Data processing applicationsPicture reproducers using cathode ray tubesDigital dataInternet privacy
Owner:MUSICQUBED INNOVATIONS LLC
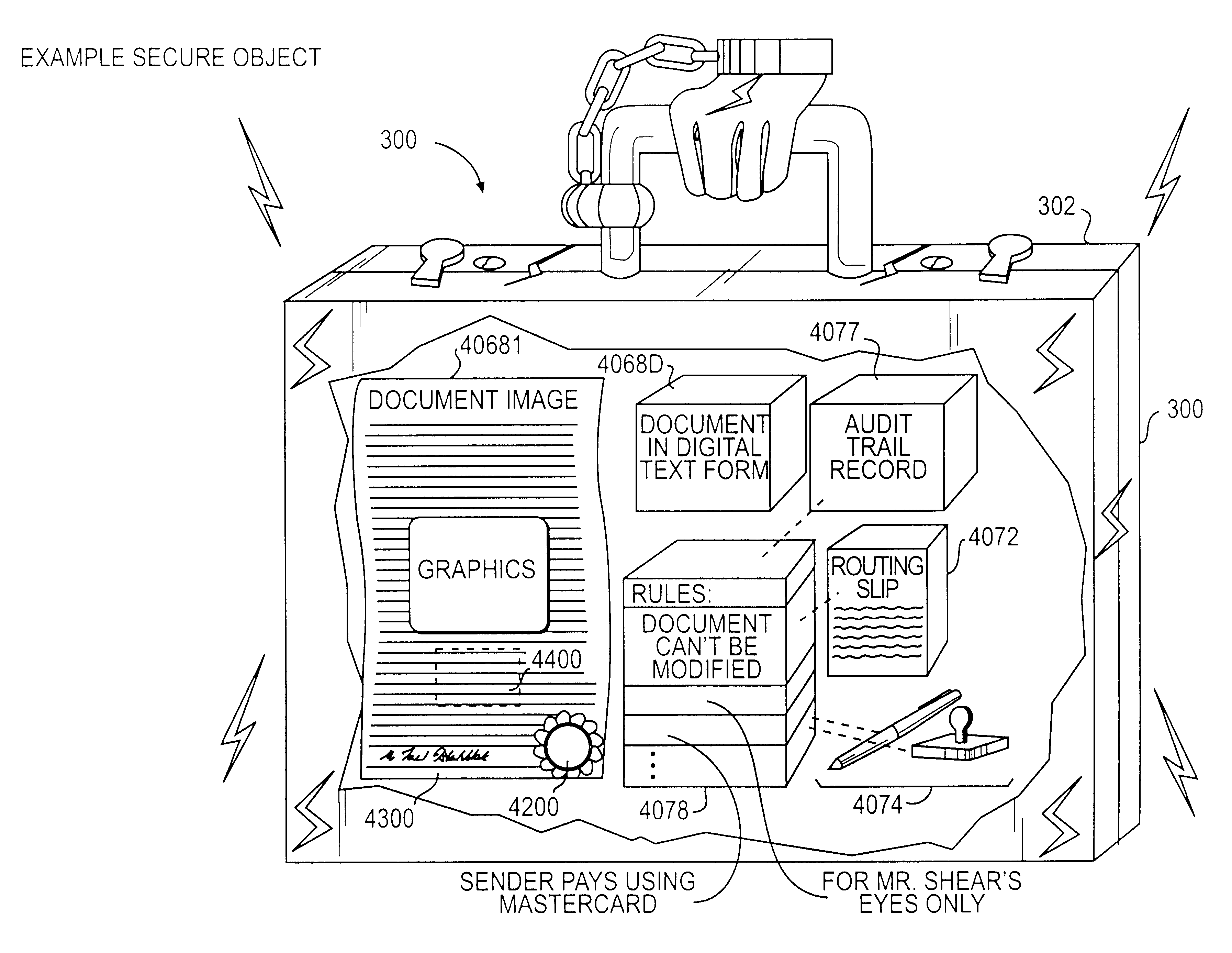
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
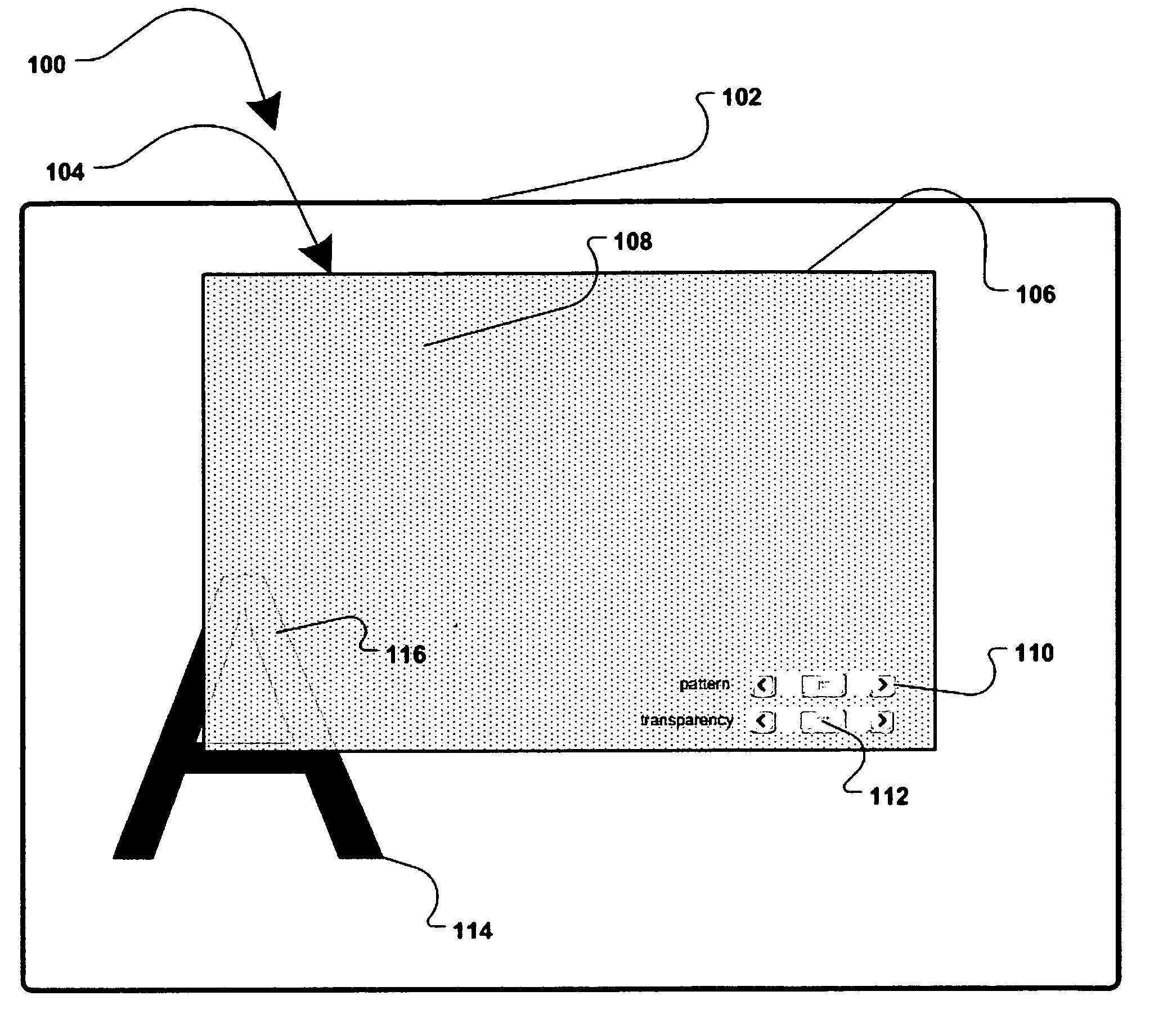
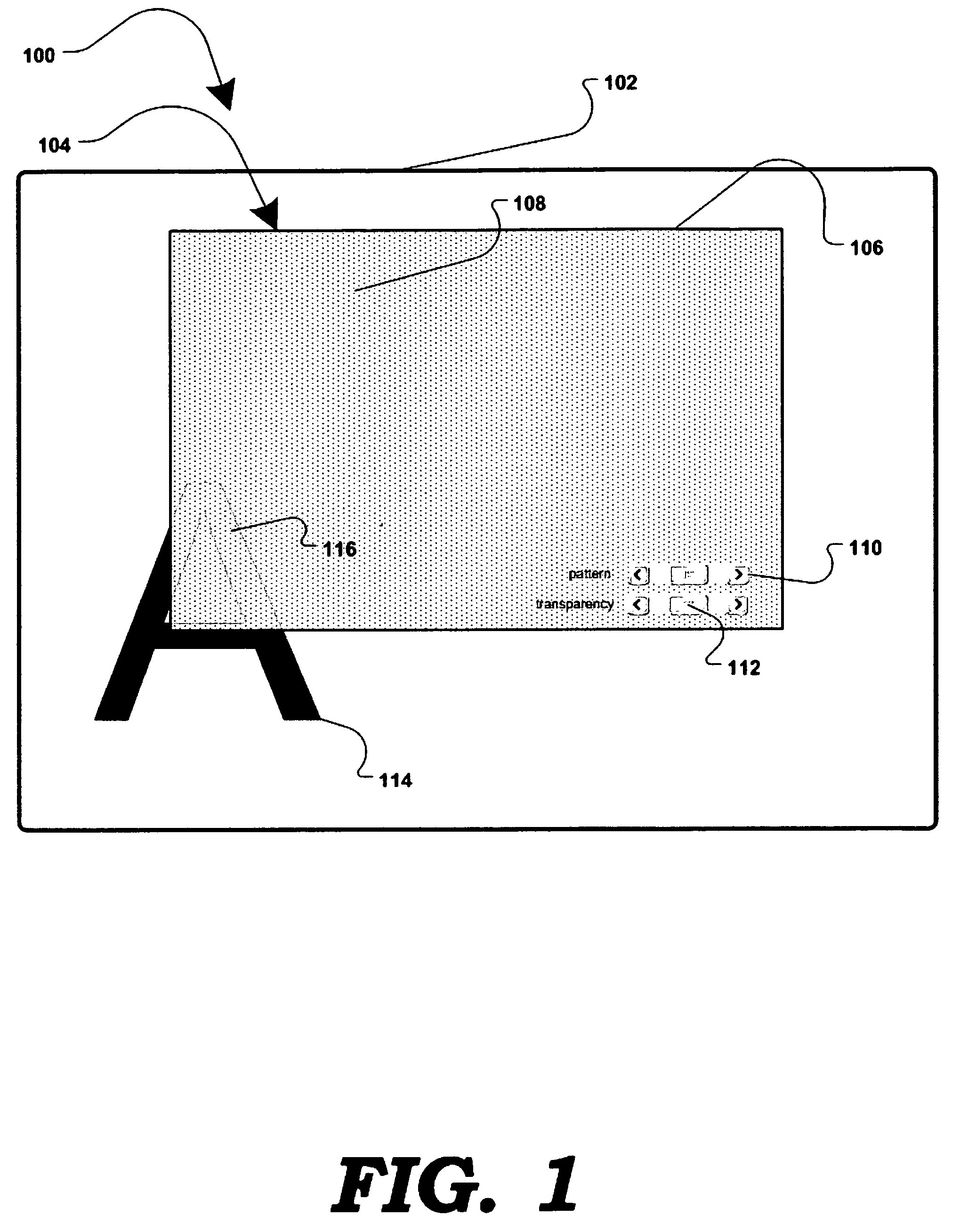
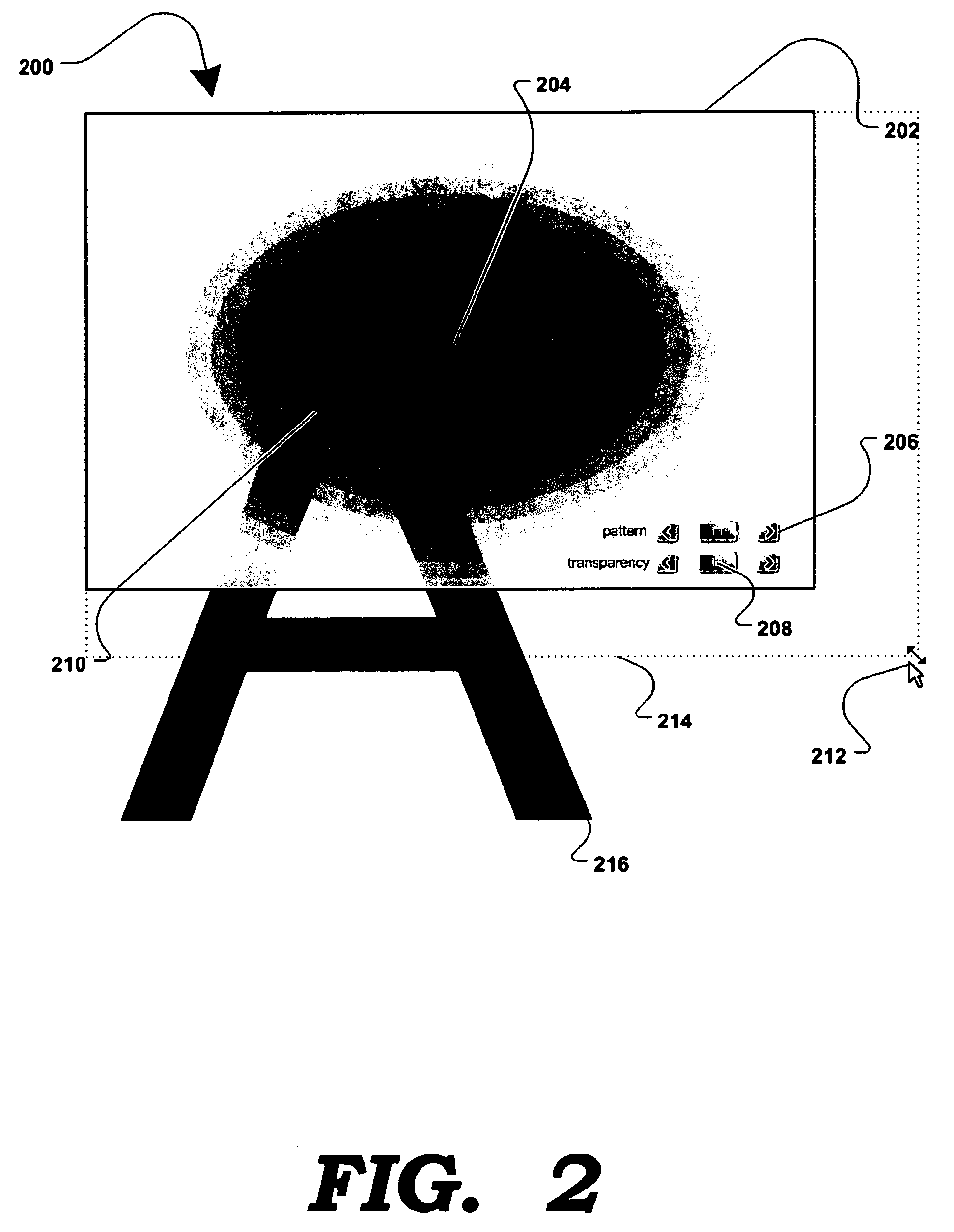
Software-based method for gaining privacy by affecting the screen of a computing device
InactiveUS7779475B2Improve privacyMinimal impactDigital data processing detailsUnauthorized memory use protectionGraphicsInternet privacy
A method and apparatus for allowing the user of an electronic device to enhance privacy over a display with the use of software, are disclosed. A security window including a translucent graphical effects region may be displayed on the electronic device such that it overlays content the user may choose to protect. The security window allows the protected content to remain discernable for the user of the device yet substantially indiscernible to a person at a further distance and / or greater viewing angle from the screen of the device. One or more security windows, each of which may be of any size, shape, texture, translucency level and any other graphical or behavioral properties may be displayed on the display associated with the electronic device. The user may control the size, shape, texture, translucency level and any other graphical or behavioral properties of the security window and graphical effects region. The user may invoke or terminate a security window with the single click of a button. Security windows may automatically attach to applications in focus, or be attached in response to a user command, and allow uninterrupted usability of those applications.
Owner:PETNOTE
Method and system for securing online identities
InactiveUS8646103B2Targeted optimizationDigital data processing detailsUser identity/authority verificationUser verificationElectronic communication
Owner:JAKOBSON GABRIEL +1
Database access system
InactiveUS20070156677A1Increased formationGood user interfaceDigital data information retrievalAdvertisementsPersonal detailsAnonymity
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
System and method for fraud monitoring, detection, and tiered user authentication
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
Social network systems and methods
InactiveUS20100306249A1Digital data processing detailsSpecial data processing applicationsInternet privacySocial web
Embodiments of computer-implemented methods and systems are described, including: in a computer network system, providing a user page region viewable by a user; providing to the user, in the user page region, indicators of each of three categories, the categories consisting essentially of: (i) what the user has, (ii) what the user wants, and (c) what the user has thought or is thinking; wherein the user page region accepts a post by the user; after the post by the user, displaying the post in a group page region, viewable by a set of one of more persons other than the user, the set of persons being separated from the user at locations on a network; before the displaying, requiring the user to select one of the three categories to be associated with the post; and displaying the category selected by the user, with the post, in the group page region.
Owner:FOSTER JOHN C
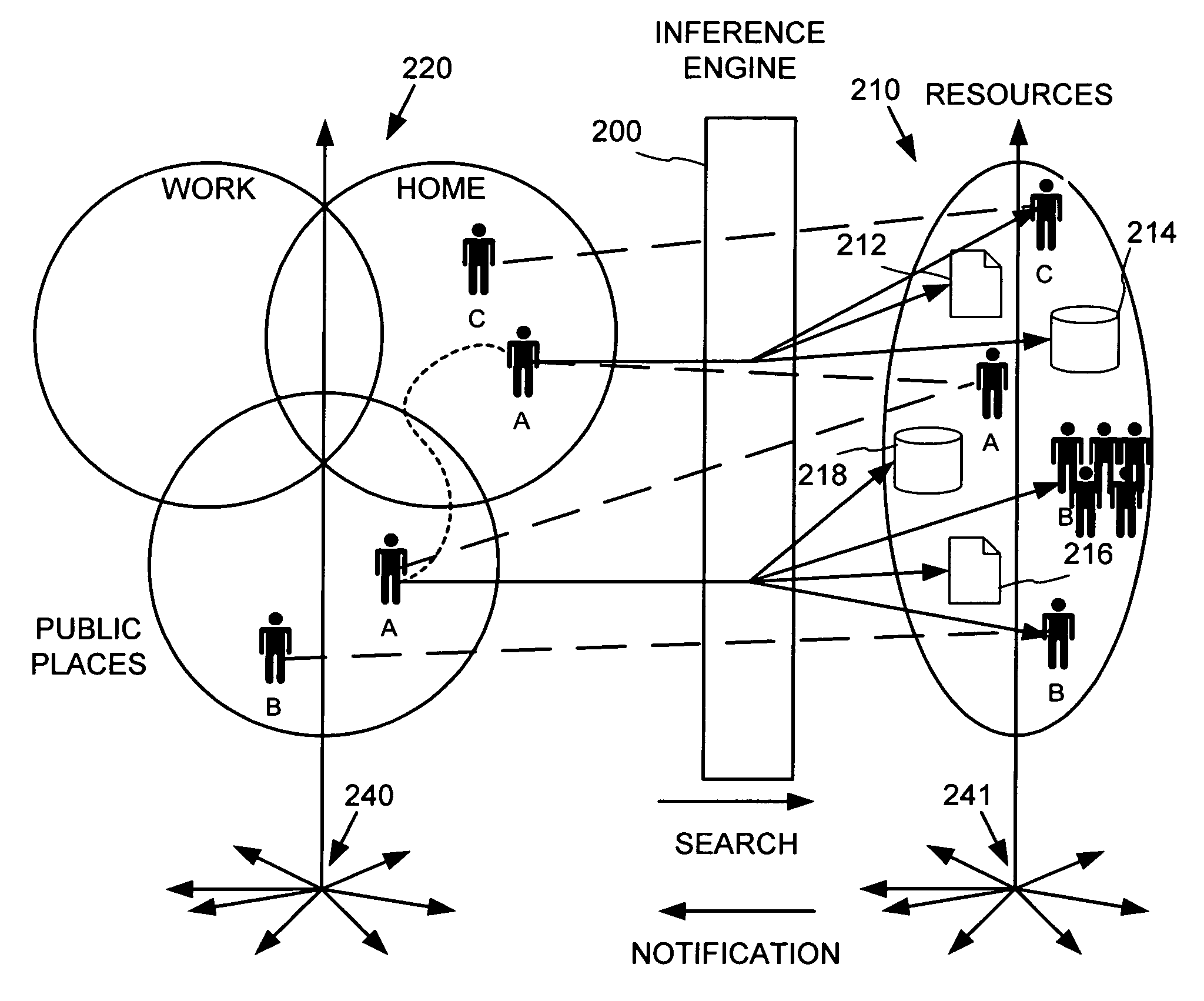
Place specific buddy list services
InactiveUS6968179B1Information formatSpecial service for subscribersWorld Wide WebPositioning equipment
An information service provides search and notifications to inform when certain people (e.g., friends, family, business contacts, etc.) are nearby so as to facilitate communications with those people. Users may define lists of people whose locations may be tracked by positioning equipment based on personal communications / computing devices carried by the people. The information service processes this people and place data to identify those of the listed people that are in the user's vicinity, and provide notifications and user-initiated search results informing the user such as via the user's personal communications / computing device.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for mobile and online payment systems for purchases related to mobile and online promotions or offers provided using impressions tracking and analysis, location information, 2d and 3D mapping, mobile mapping, social media, and user behavior and information for generating mobile and internet posted promotions or offers for, and/or sales of, products and/or services in a social network, online or via a mobile device
A method, apparatus, computer readable medium, computer system, network, or system is provided for mobile and online payment systems for mobile and online promotions or offers or daily deal coupons or daily deal coupons aggregation provided using impressions tracking and analysis, location information, 2D and 3D mapping, social media, and user behavior and information for generating mobile and internet posted promotions or offers or daily deal coupons or daily deal coupons aggregation for, and / or sales of, products and / or services in a social network, online or via a mobile device-for mobile and web based promotions or offers that connect information and user behavior data to a user or related demographic location or user specified or predicted demographic location(s) for targeted promotions or offers for products and / or services in a social network, online or via a mobile device.
Owner:HEATH STEPHAN
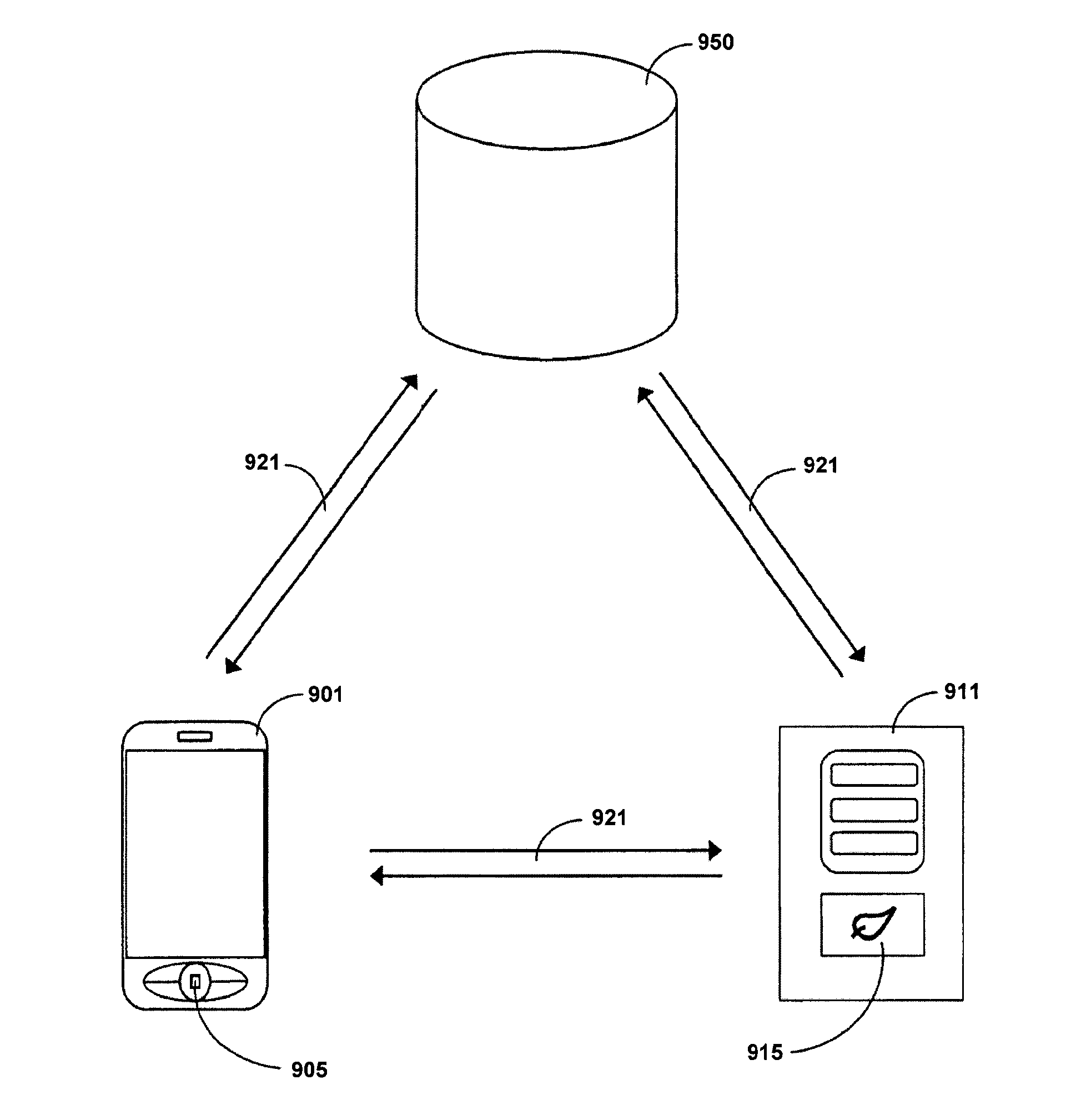
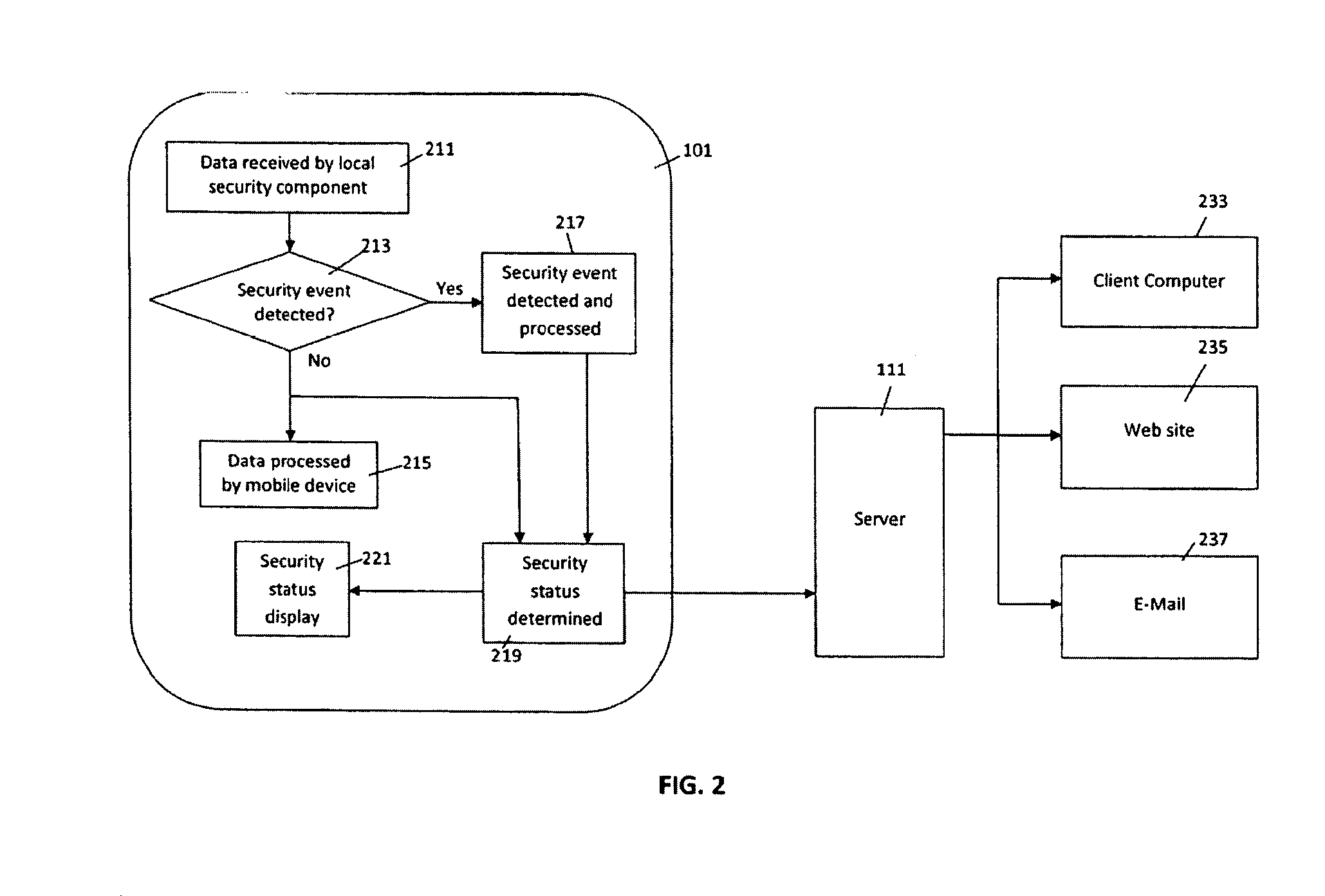
Methods and systems for sharing risk responses between collections of mobile communications devices
Methods are provided for determining an enterprise risk level, for sharing security risk information between enterprises by identifying a security response by a first enterprise and then sharing the security response to a second enterprise when a relationship database profile for the first collection indicates the security response may be shared. Methods are also provided for determining whether to allow a request from an originating device where the request may have been initiated by a remote device.
Owner:LOOKOUT MOBILE SECURITY
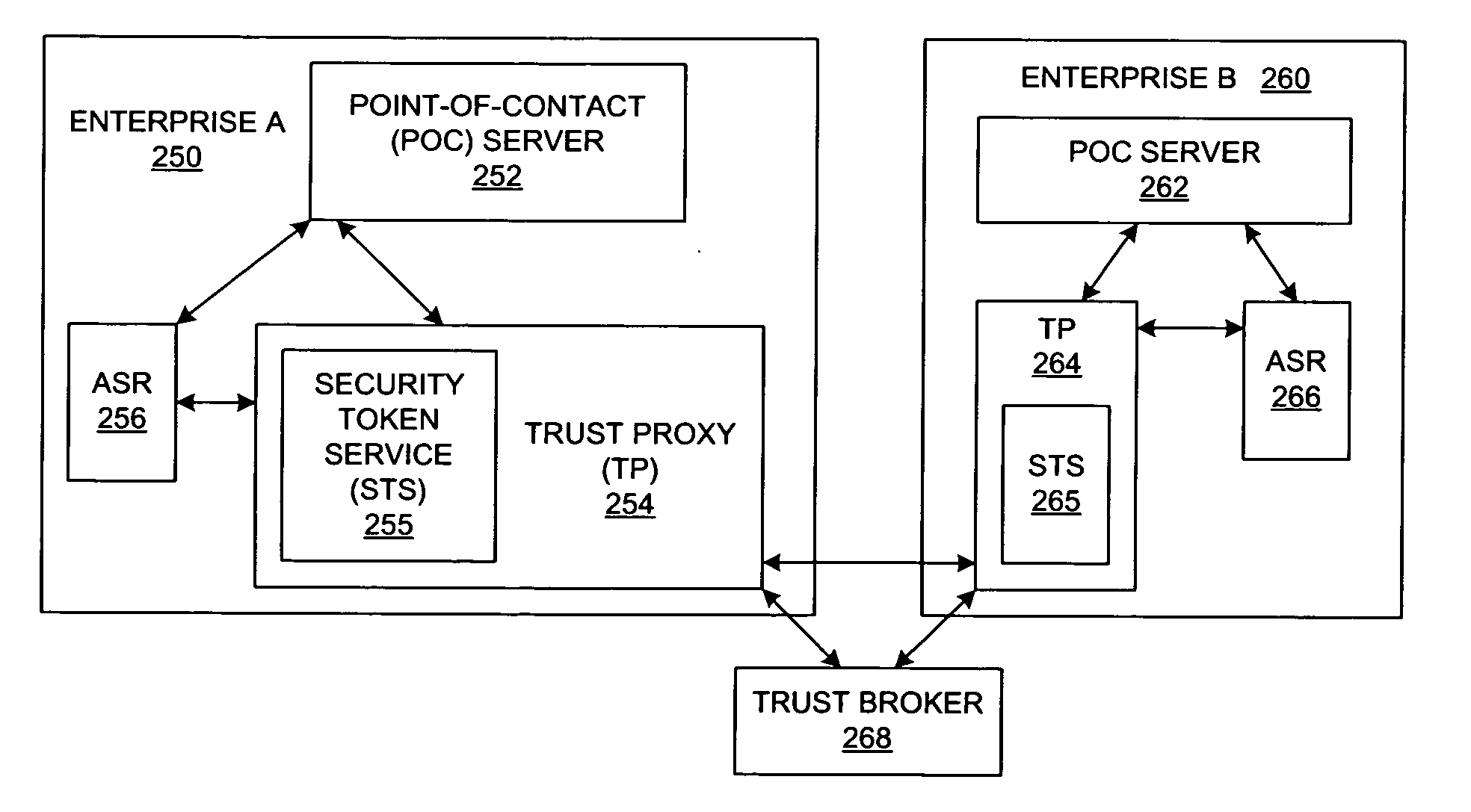
Method and system for federated provisioning
ActiveUS20060021019A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
A method and a system are presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated single-sign-on operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. Trust proxies interpret assertions from other federated domains as necessary. Trust proxies may have a trust relationship with one or more trust brokers, and a trust proxy may rely upon a trust broker for assistance in interpreting assertions. When a user is provisioned at a particular federated domain, the federated domain can provision the user to other federated domains within the federated environment. A provision operation may include creating or deleting an account for a user, pushing updated user account information including attributes, and requesting updates on account information including attributes.
Owner:SERVICENOW INC
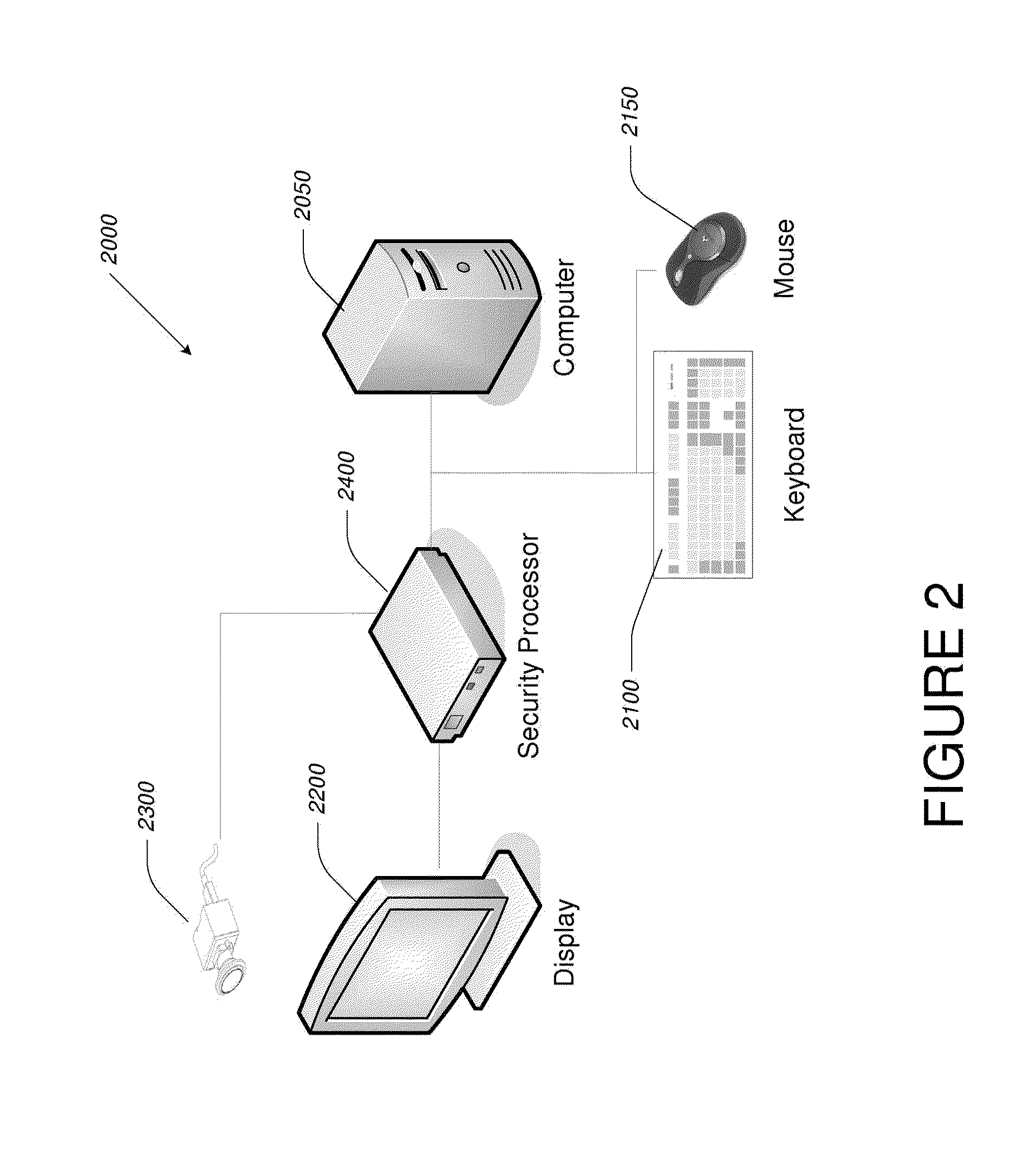
Video-Based Privacy Supporting System
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
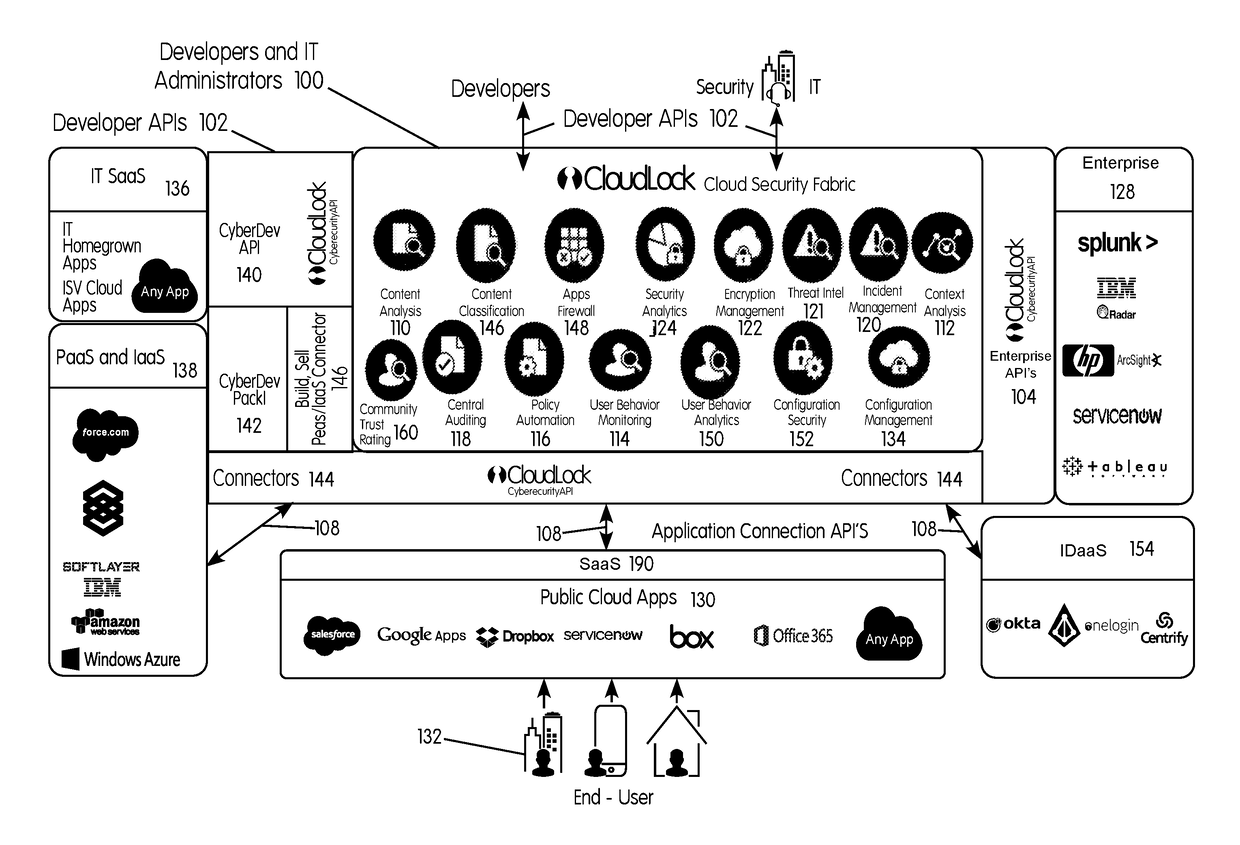
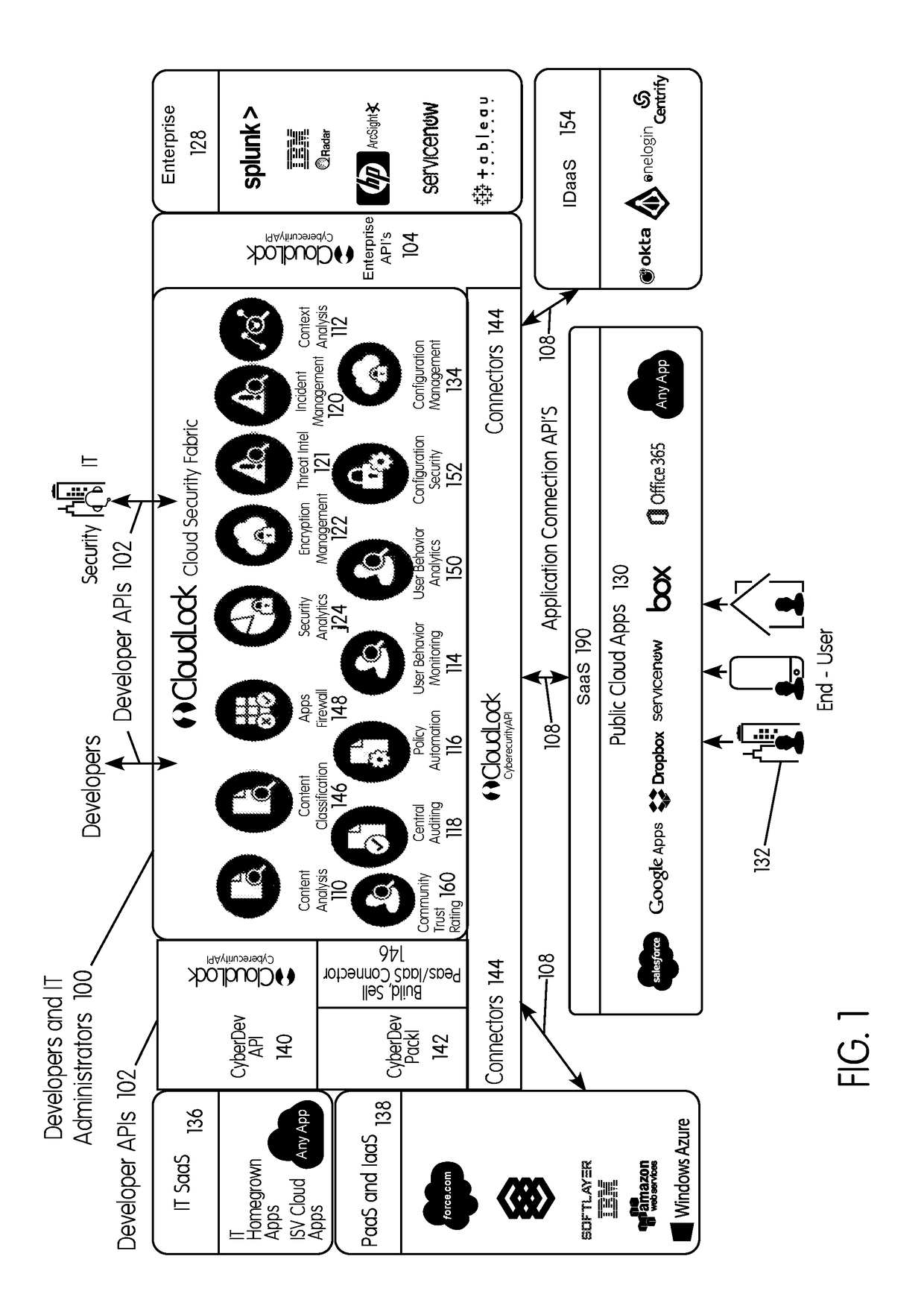
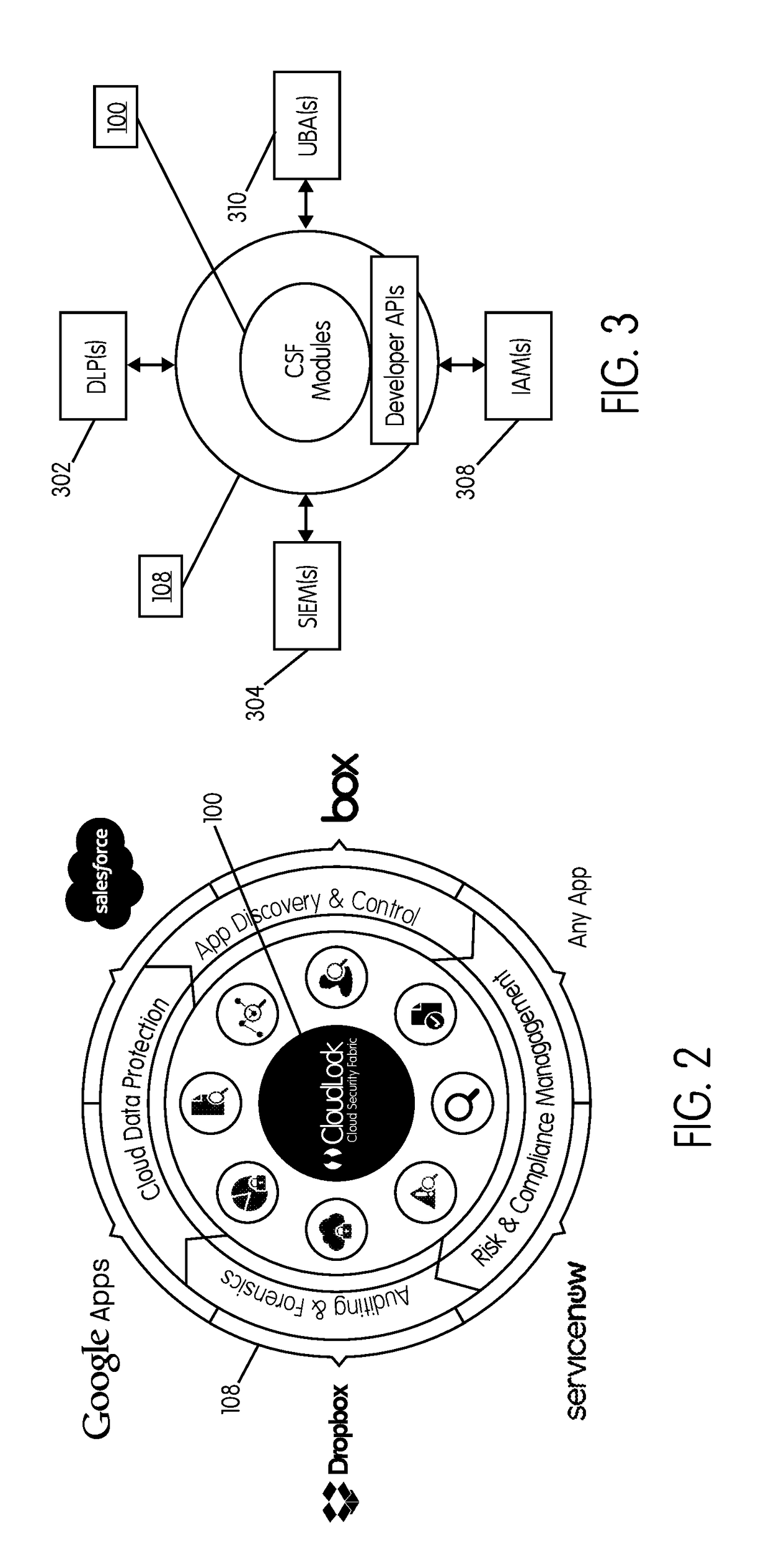
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
System and method for use of distributed electronic wallets
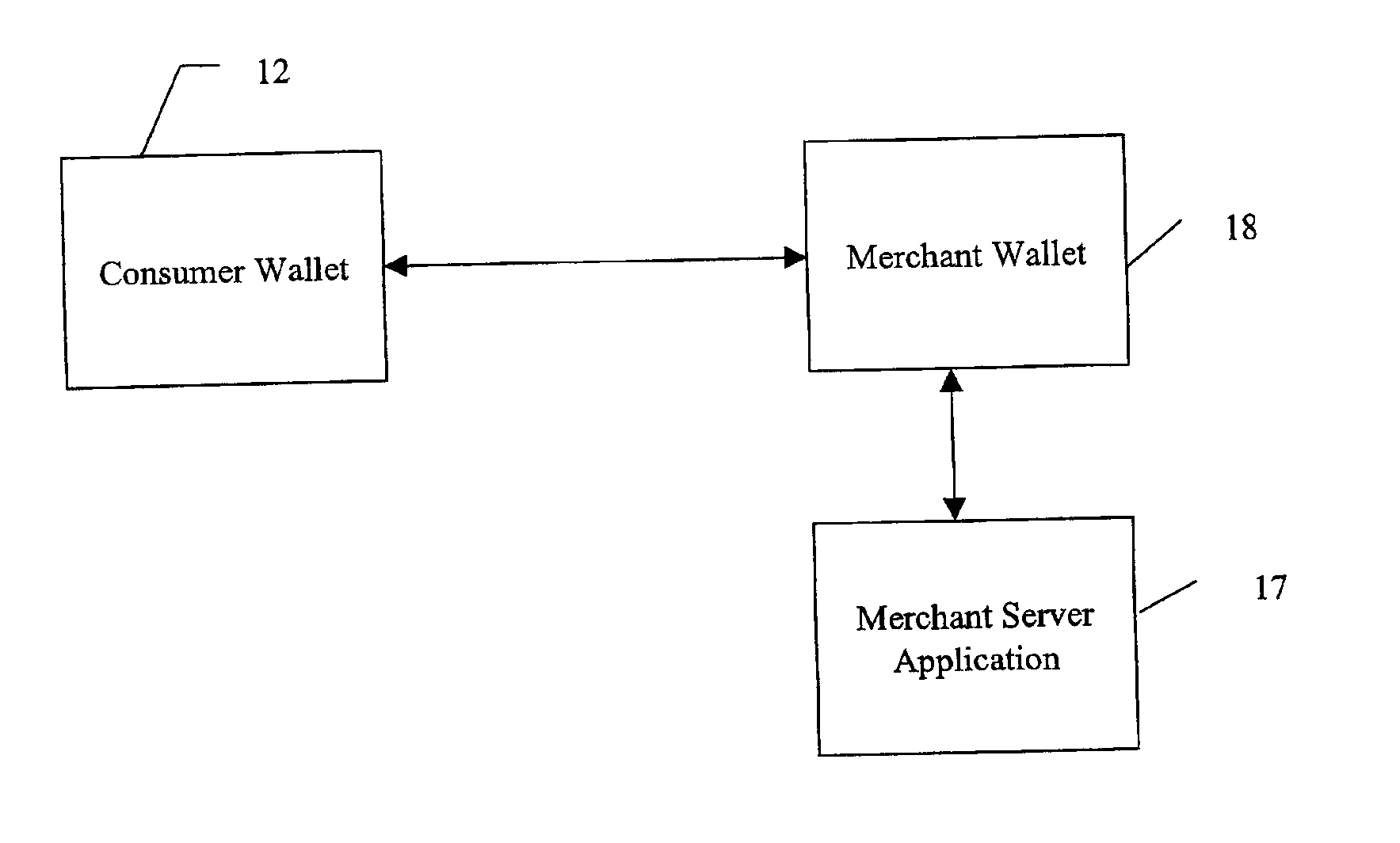
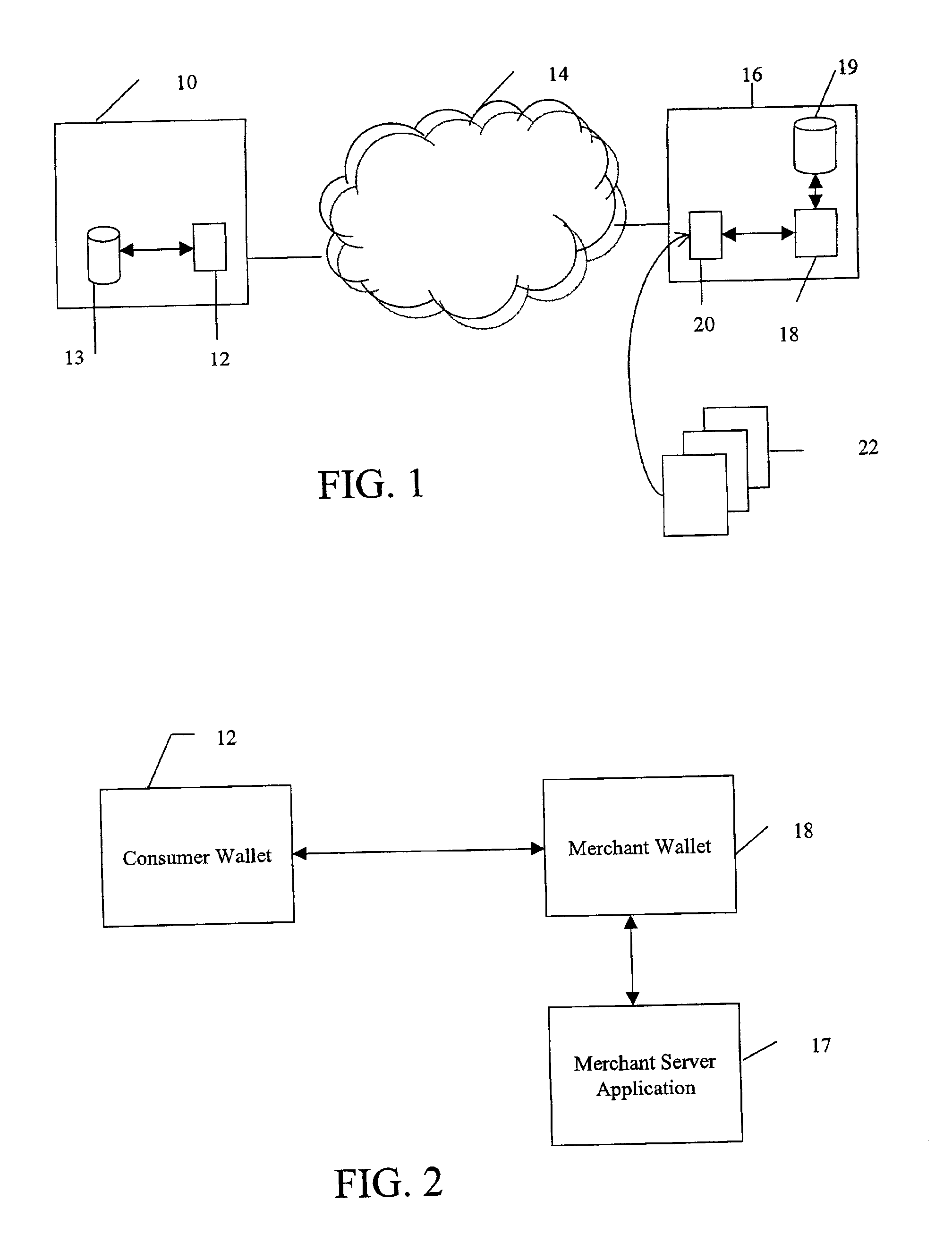
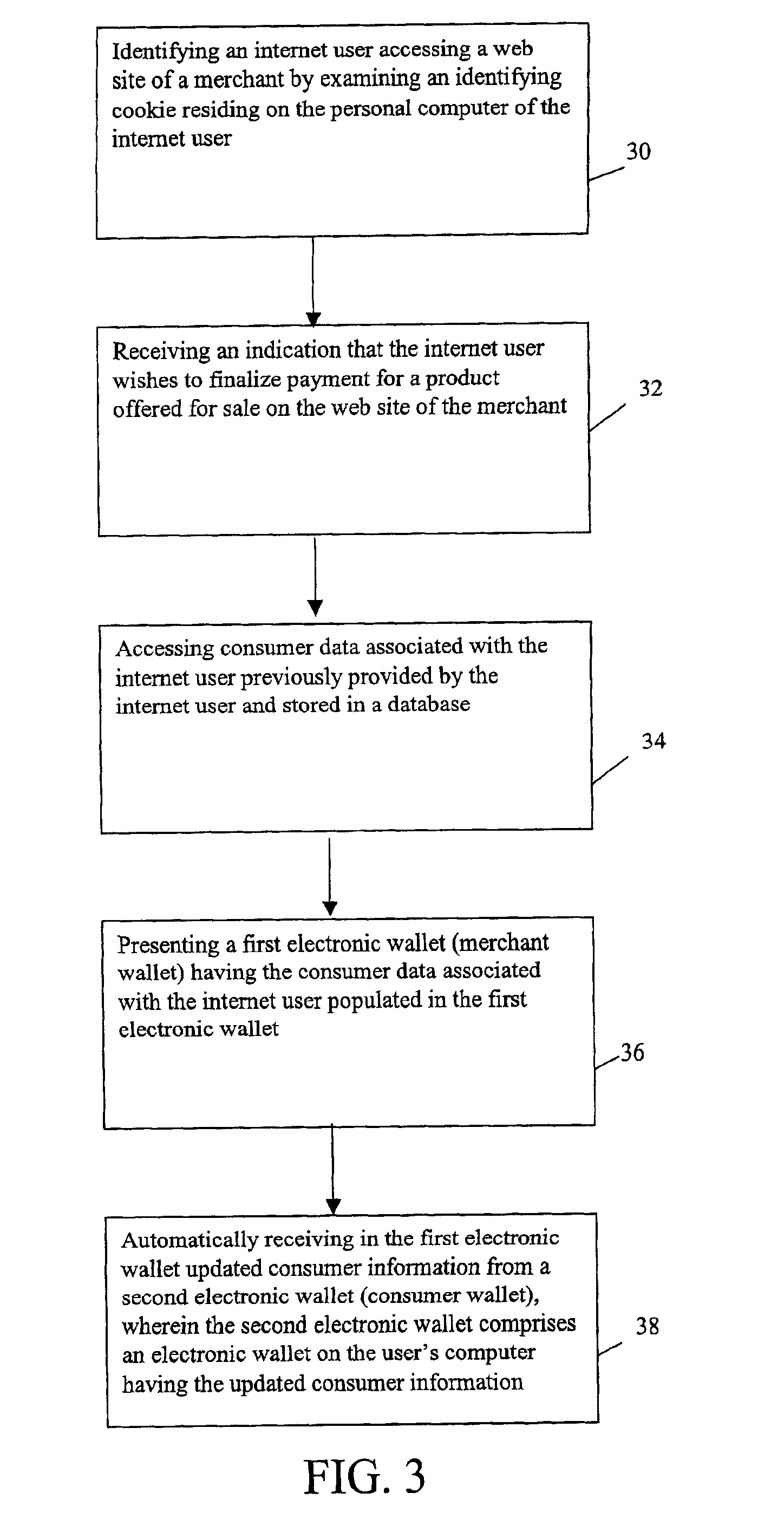
InactiveUS6873974B1Avoid burdenImprove efficiencyComplete banking machinesFinanceMerchant servicesCredit card
Methods and systems whereby two electronic wallets communicate and exchange information. In one such system, a consumer's personal electronic wallet communicates with the exclusive or preferred wallet of a web merchant. In one such system, an internet consumer registers with a web merchant's exclusive or preferred electronic wallet (“merchant wallet”) and provides consumer information (e.g., credit card number, mailing address, and other information) to the merchant wallet, which is stored by the merchant wallet in a database on the merchant server. Such information may be automatically populated by the consumer's personal electronic wallet. The consumer maintains current consumer information in a consumer electronic wallet on the consumer's personal computer. When the consumer visits the merchant site again, and orders goods or services, the merchant's preferred wallet can be automatically updated by the consumer's electronic wallet if any of the data in the merchant's wallet has changed. For example, the consumer wallet examines the information in the merchant wallet to determine if the information in the merchant wallet conforms to the current information in the consumer wallet. If the information does not conform, the consumer wallet communicates the current consumer information to the merchant wallet.
Owner:CITIBANK
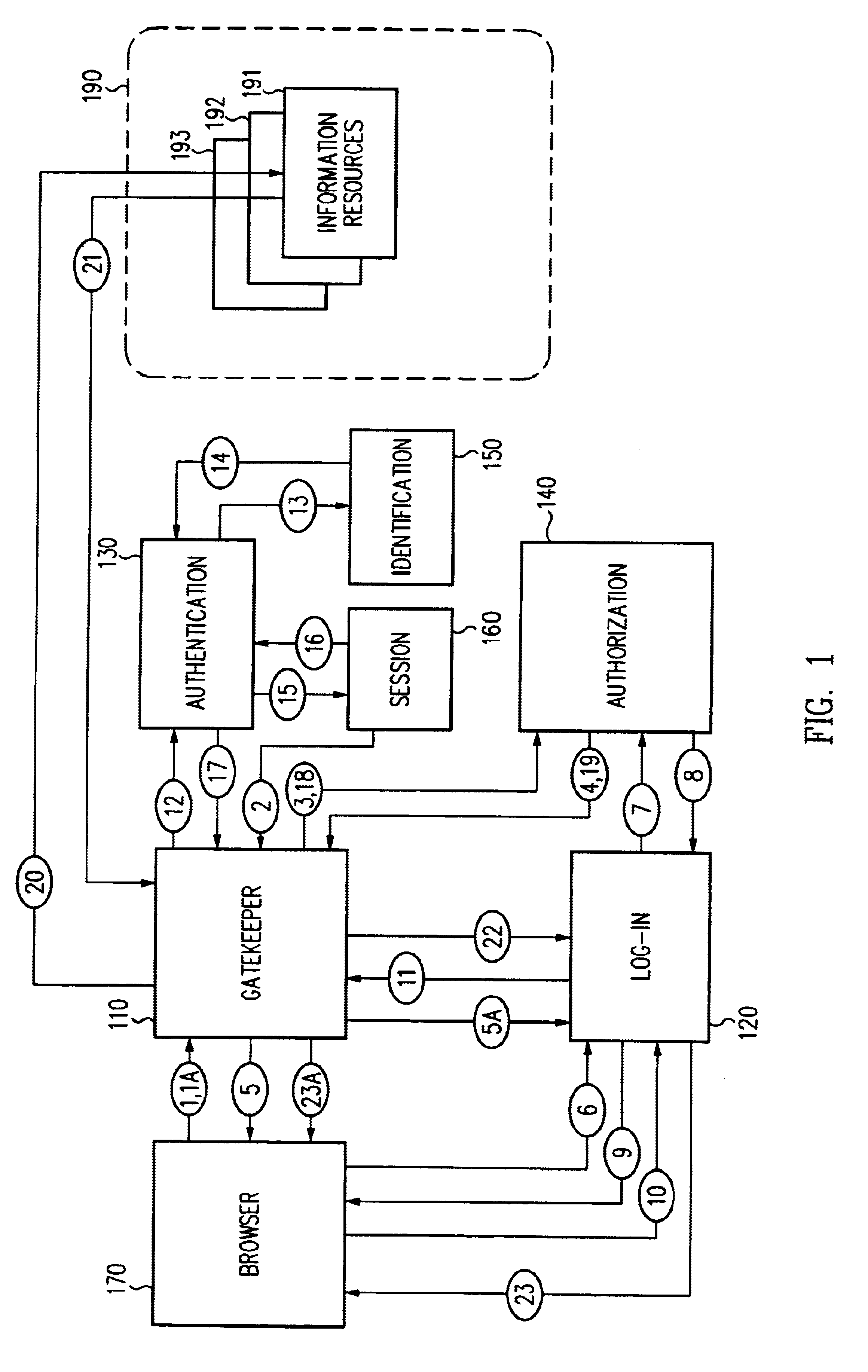
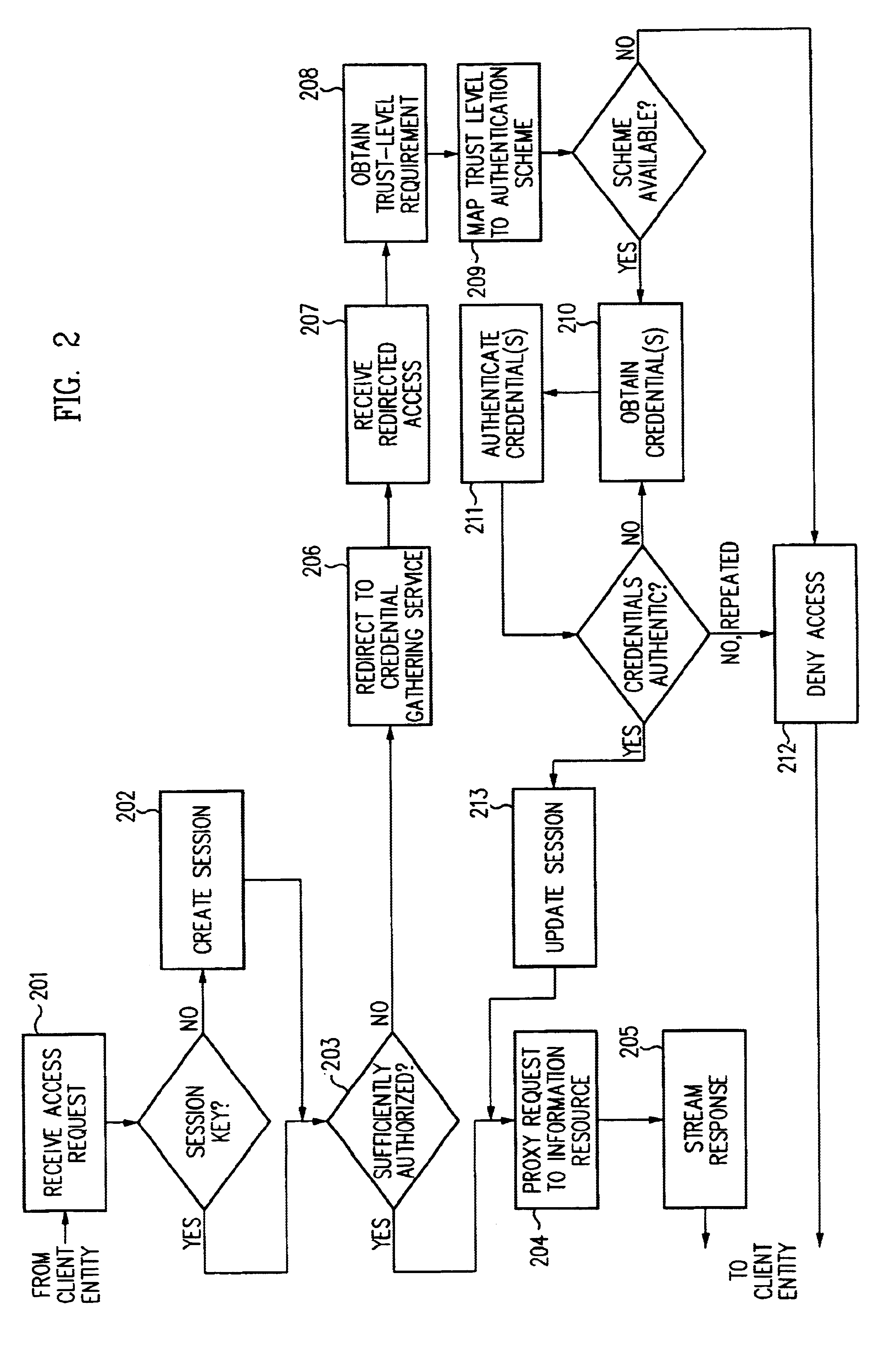
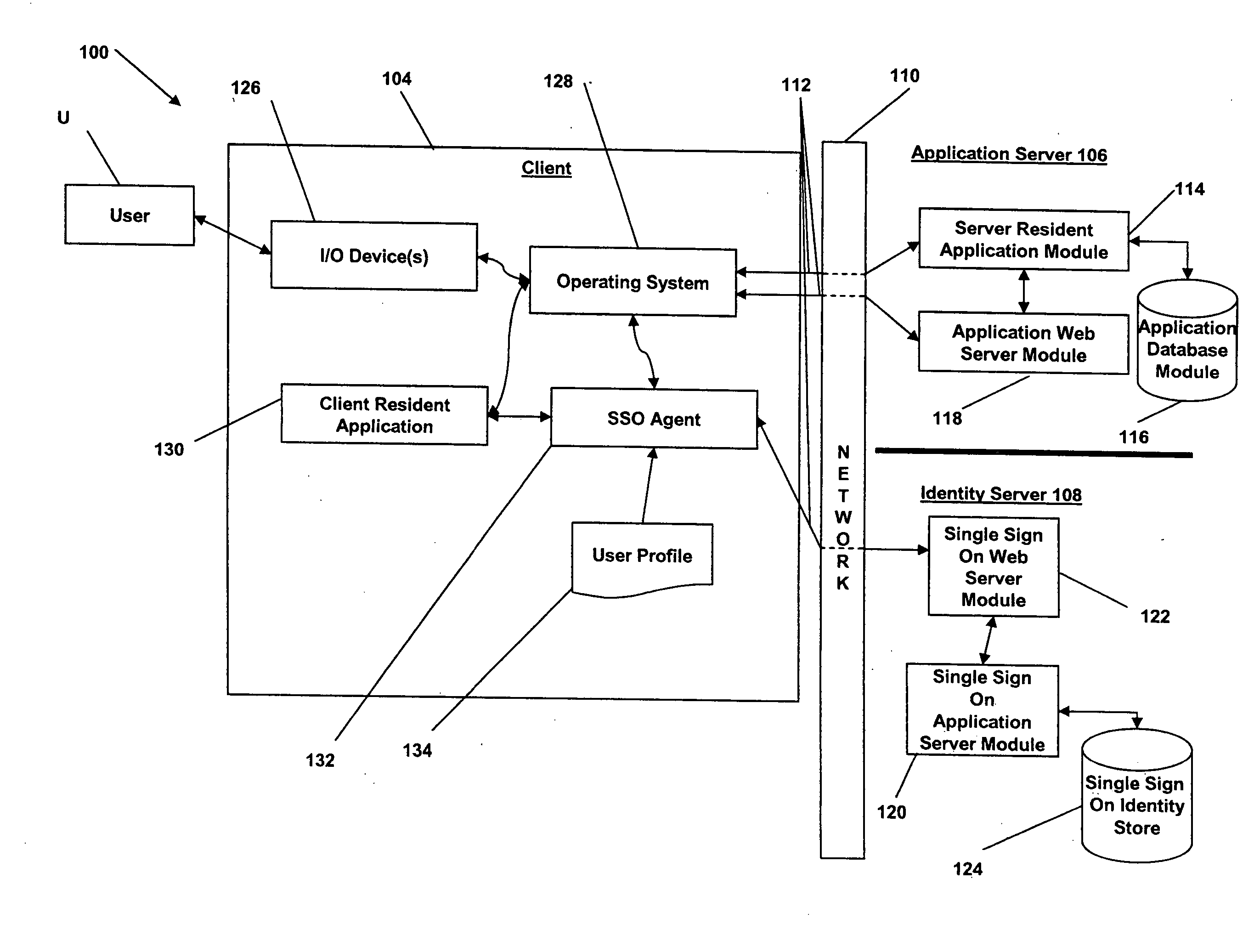
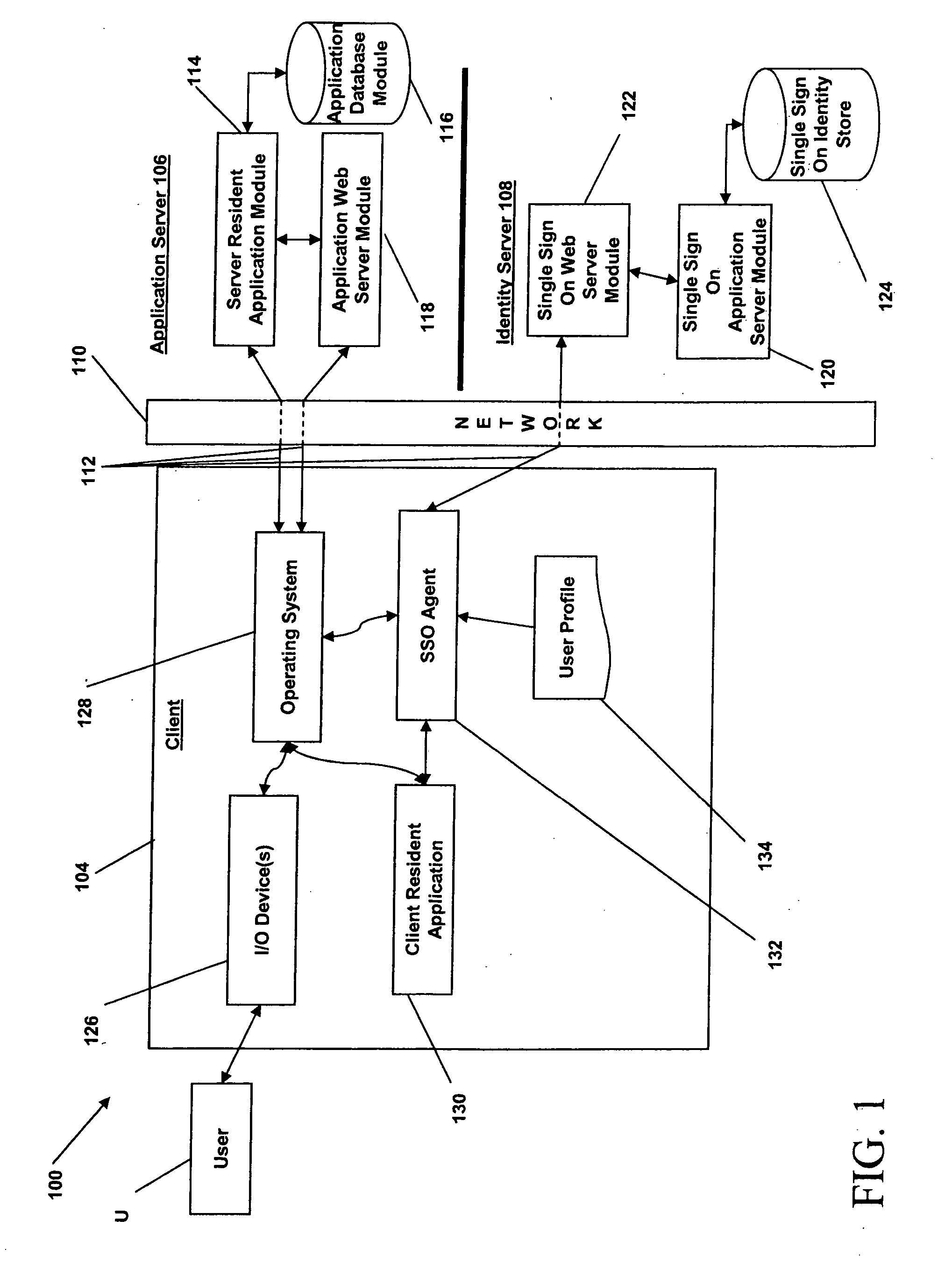
Access management system and method employing secure credentials
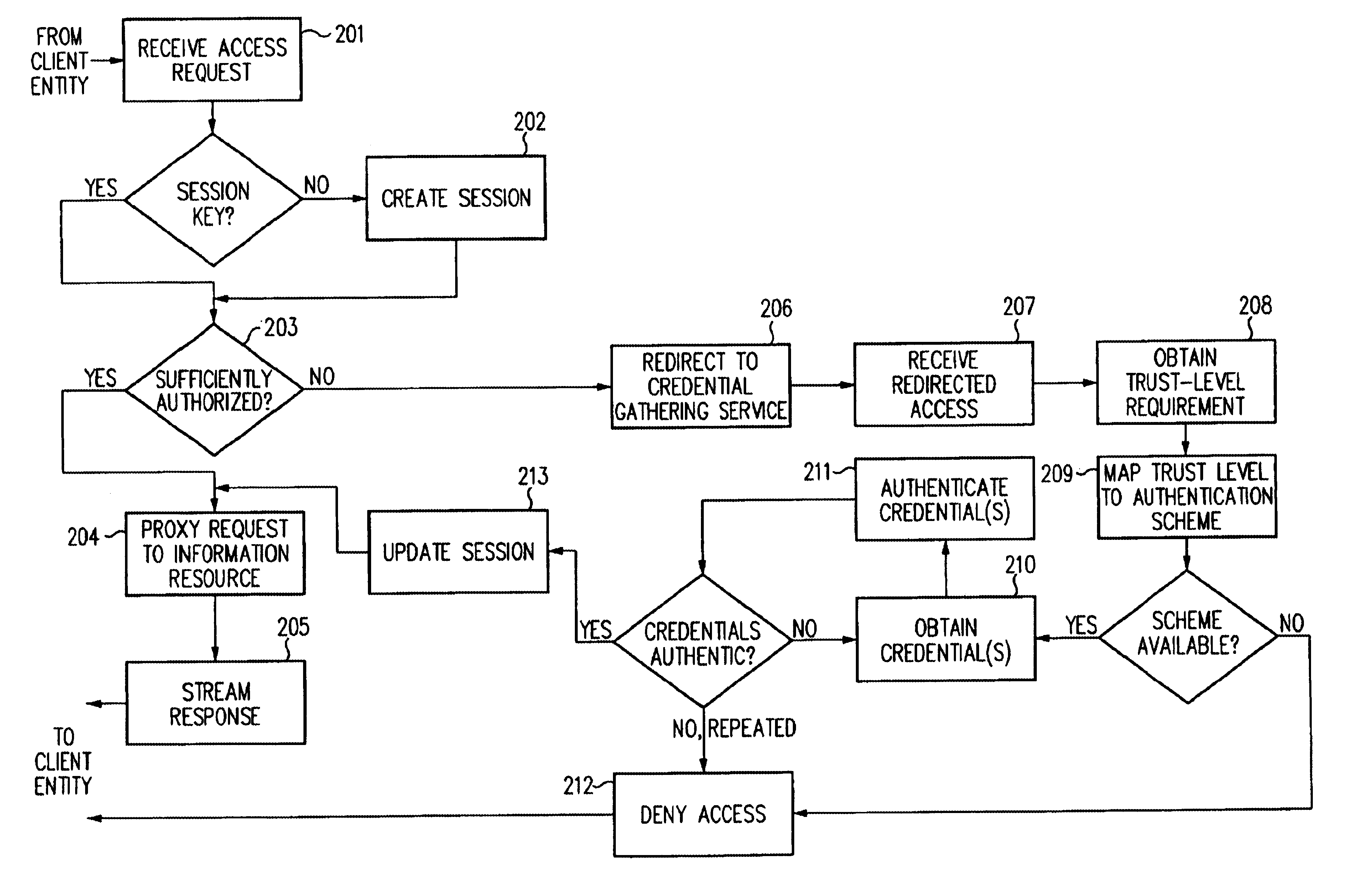
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
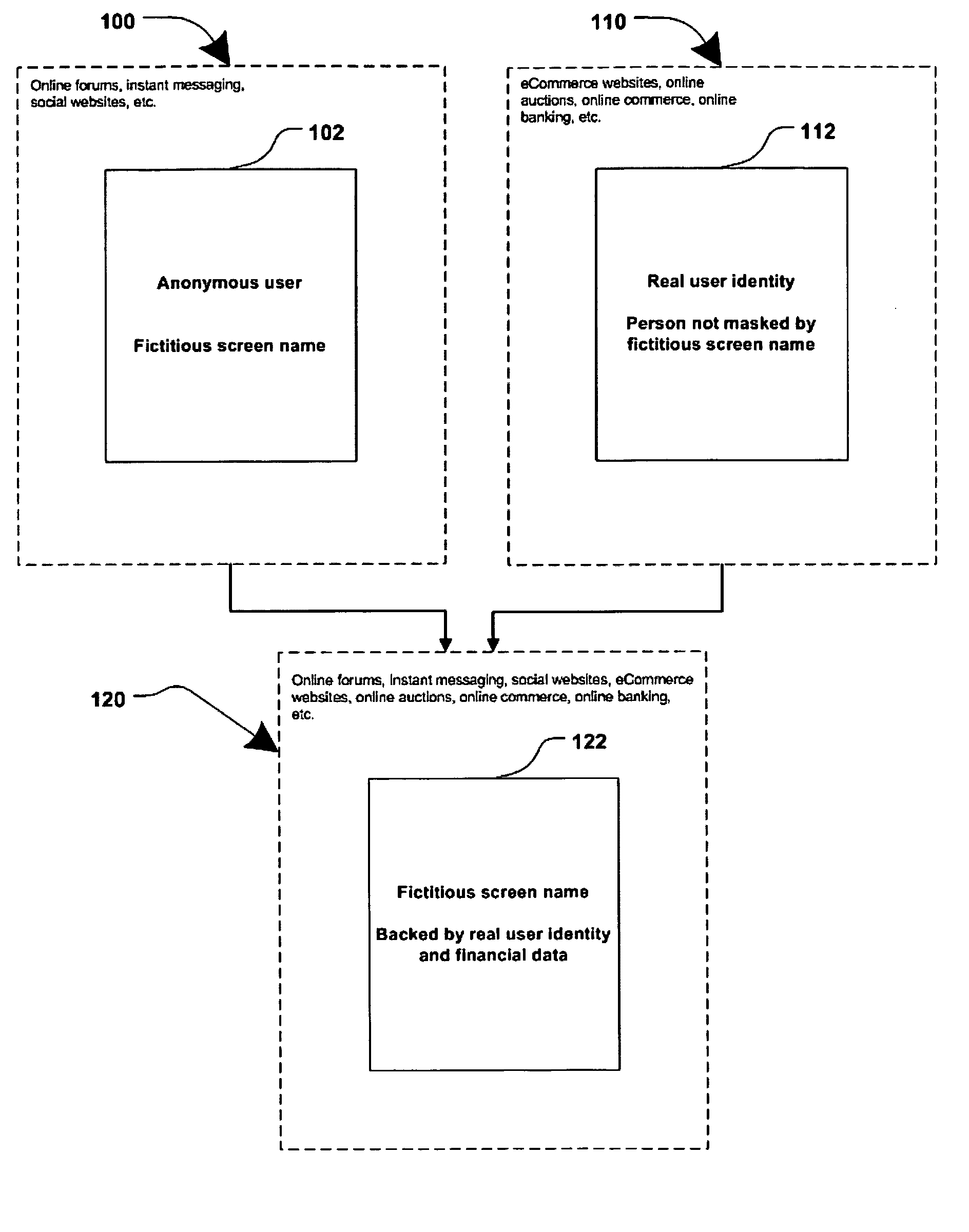
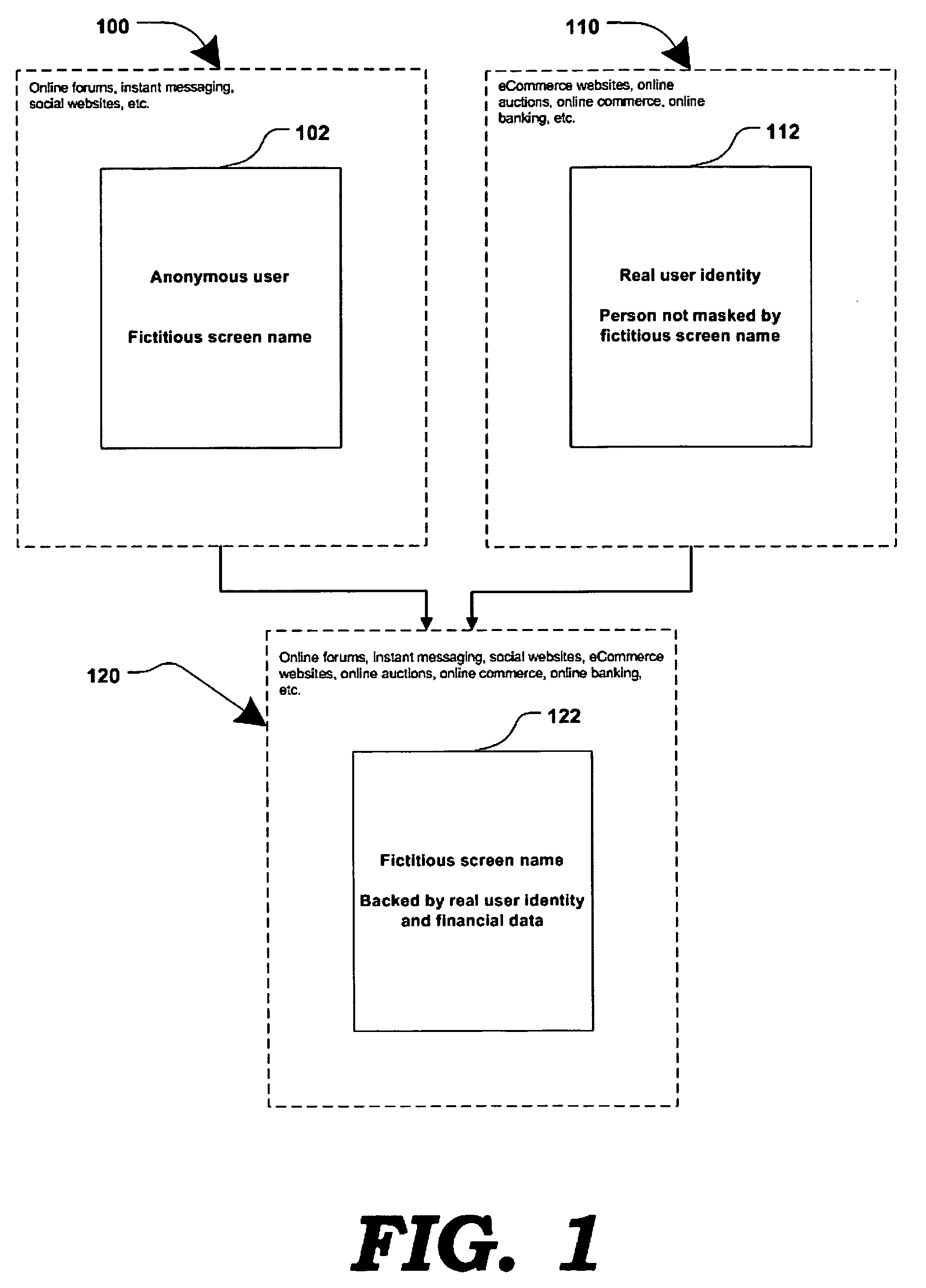
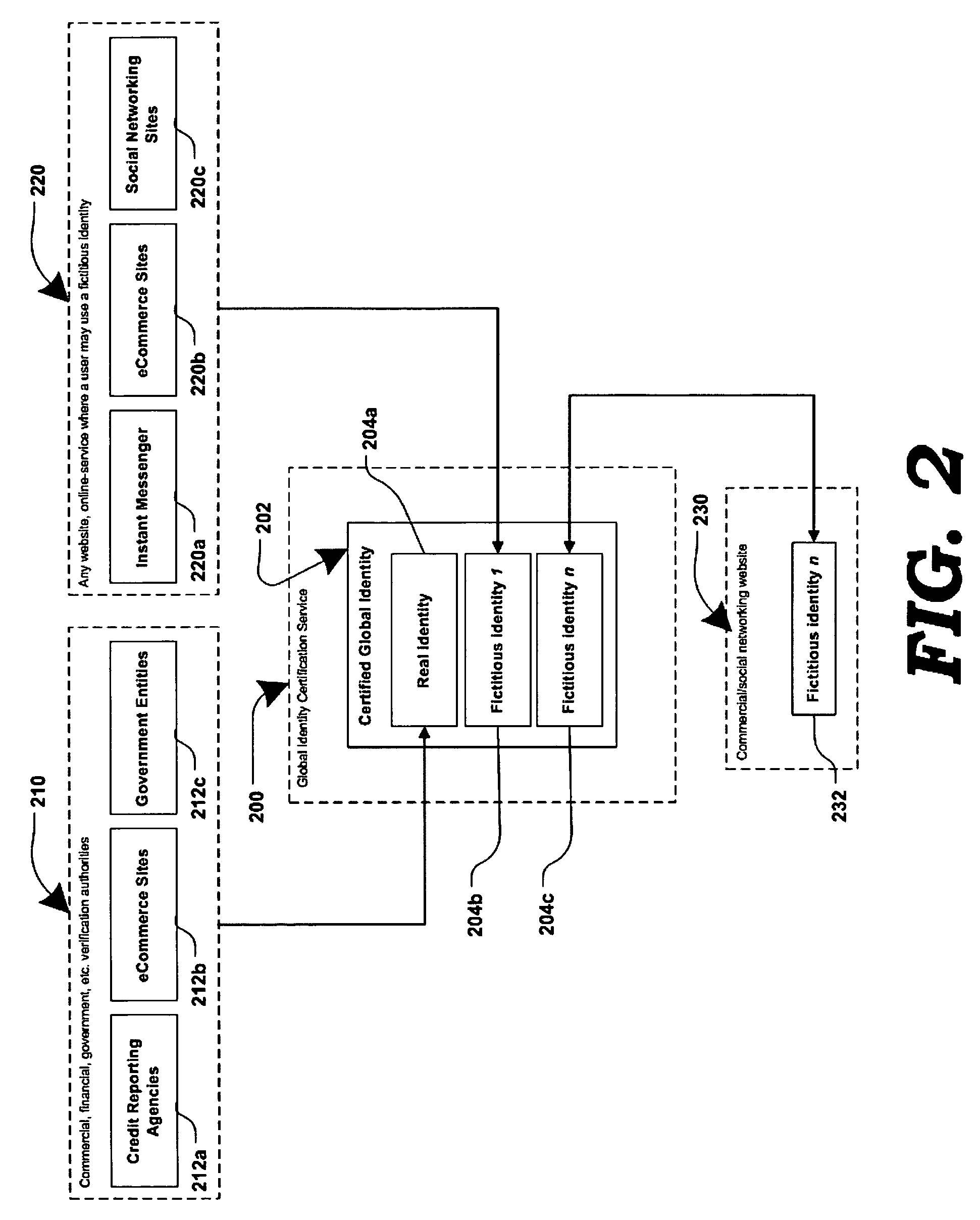
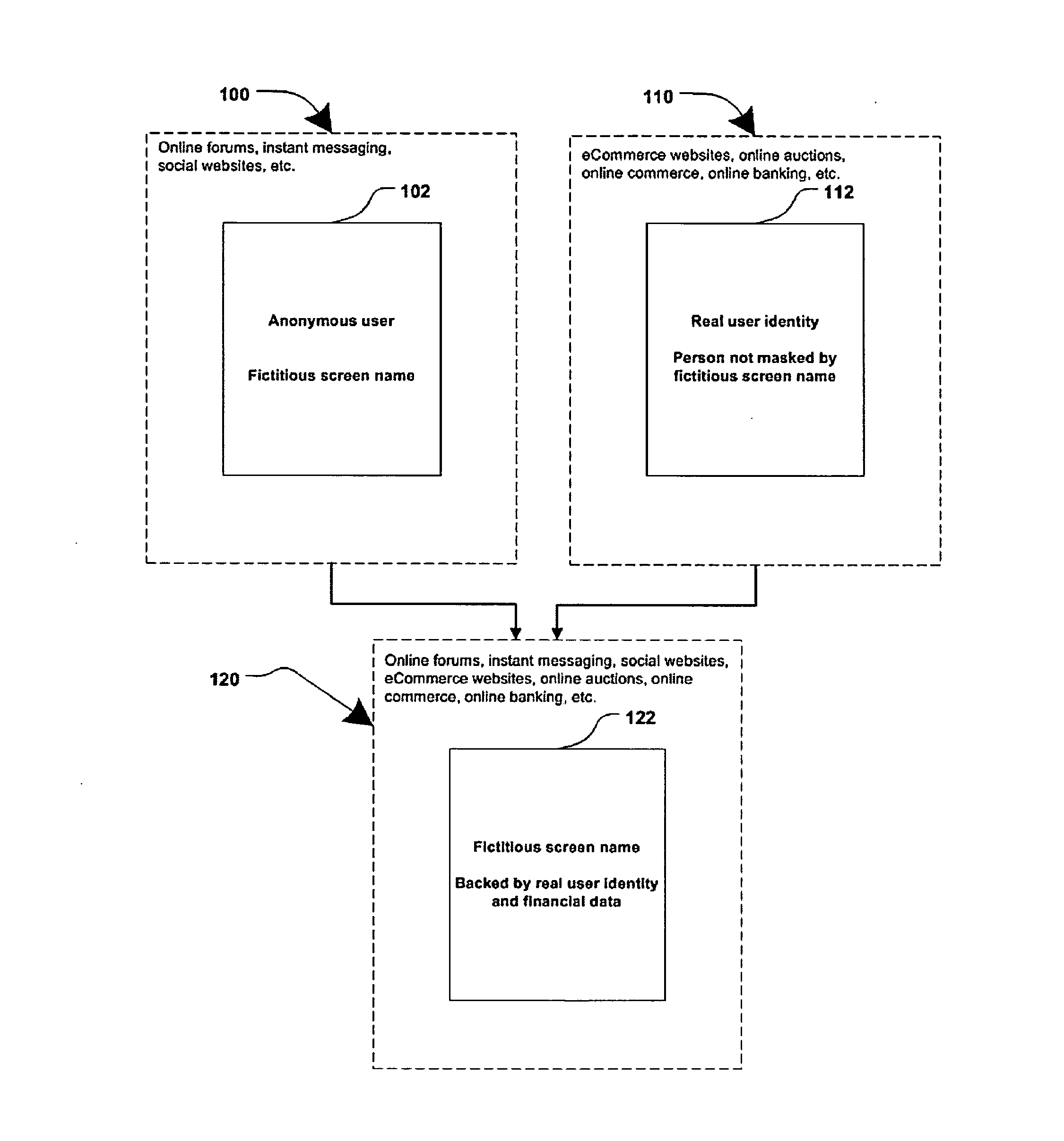
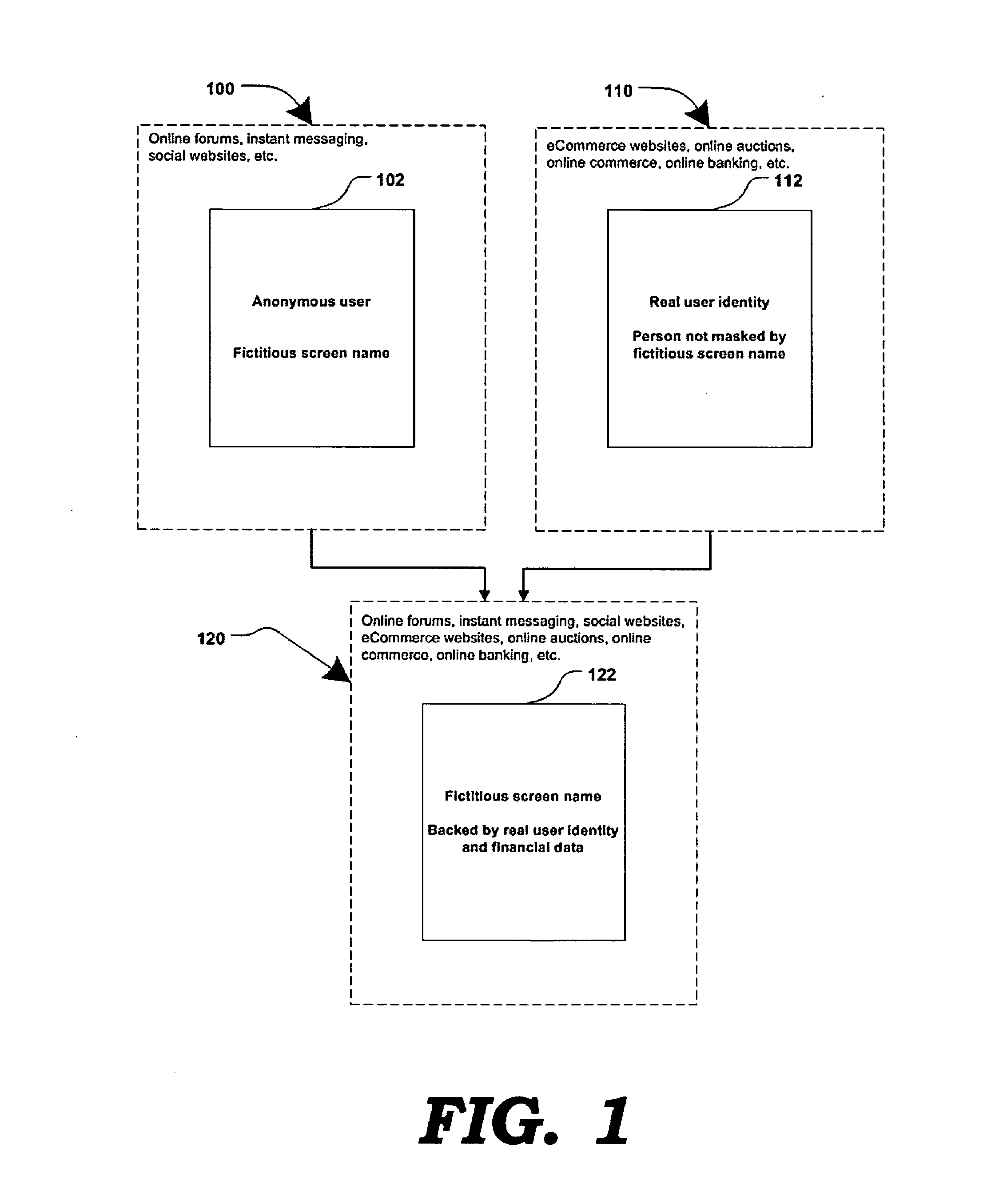
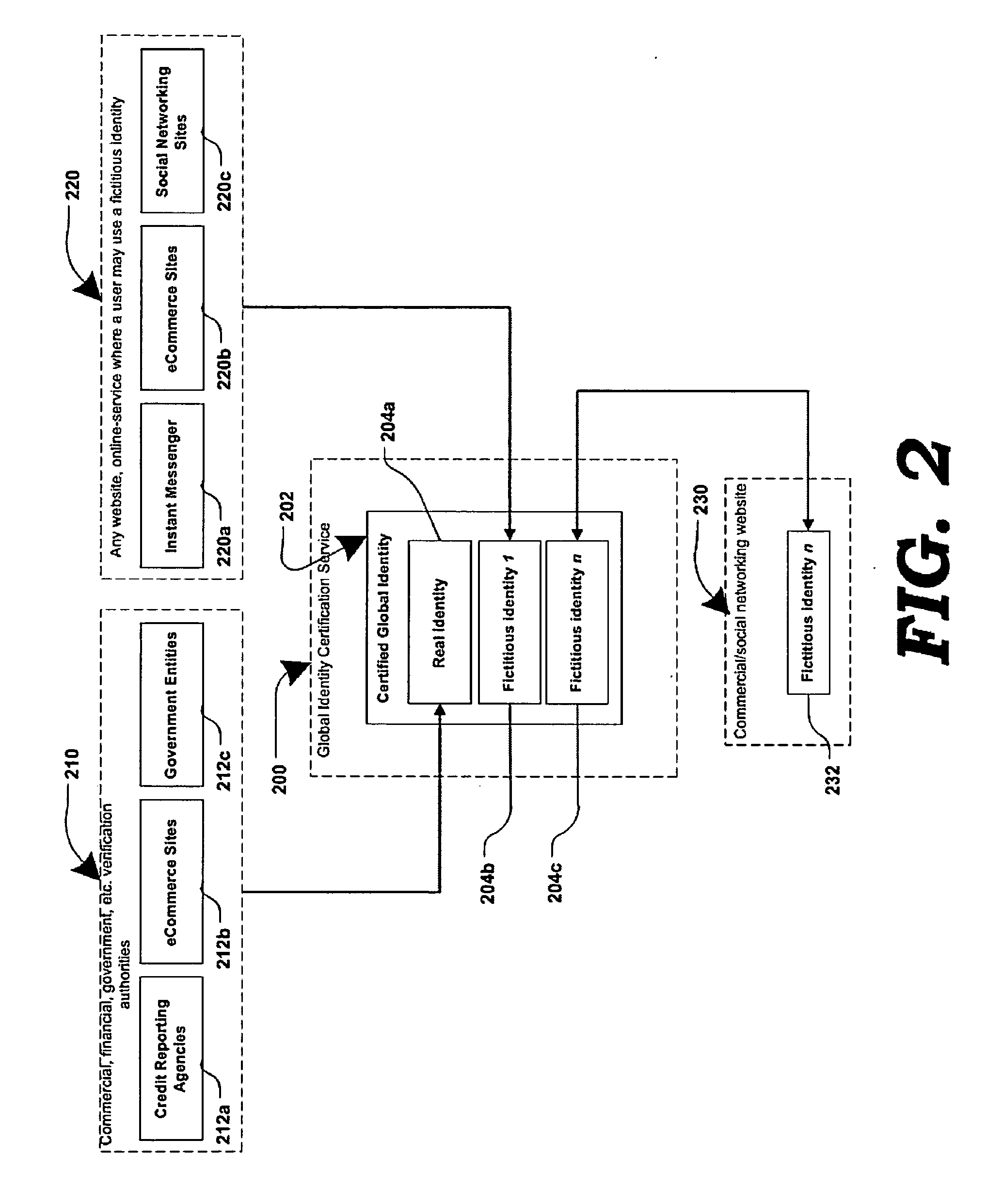
Method and systems for online advertising to users using fictitious user idetities
Various methods, systems and apparatus for associating fictitious user identities (e.g. screen names, user names, email addresses, handles, etc.) used in electronic communications (e.g. over the internet or mobile network via instant messenger, e-mail, social networks, ecommerce, auction websites, etc.) with real personal information (e.g. the true identity of an individual such as their name, address, credit score, driving record, mobile number, etc.) are disclosed. One such method may include discovering, verifying and storing real personal information, associated with fictitious user identities and email addresses. The method may further include allowing a remote user or service to submit a fictitious user identity and a query requesting real-user information associated with the submitted fictitious user identity. In one possible embodiment, a targeted-advertising service may utilize real user information, associated with a fictitious user name, to target advertisements at the user of the fictitious user name.
Owner:JAKOBSON GABRIEL +1
Systems and methods for multi-factor authentication
ActiveUS20070186106A1User identity/authority verificationElectric digital data processingInternet privacyControl system
Requests to gain access to secure resources are adjudicated according to authentication policies that include rules based on user-states derived from multiple heterogeneous access-control systems.
Owner:IMPRIVATA
Limited-use keys and cryptograms
ActiveUS20150178724A1Promote generationImprove securityMultiple keys/algorithms usageCryptography processingCryptogramCommunication device
Techniques for enhancing the security of a communication device when conducting a transaction using the communication device may include encrypting account information with a first encryption key to generate a second encryption key, and encrypting key index information using the second key to generate a limited-use key (LUK). The key index information may include a key index having information pertaining to generation of the LUK. The LUK and the key index can be provided to the communication device to facilitate generation of a transaction cryptogram for a transaction conducted using the communication device, and the transaction can be authorized based on the transaction cryptogram generated from the LUK.
Owner:VISA INT SERVICE ASSOC
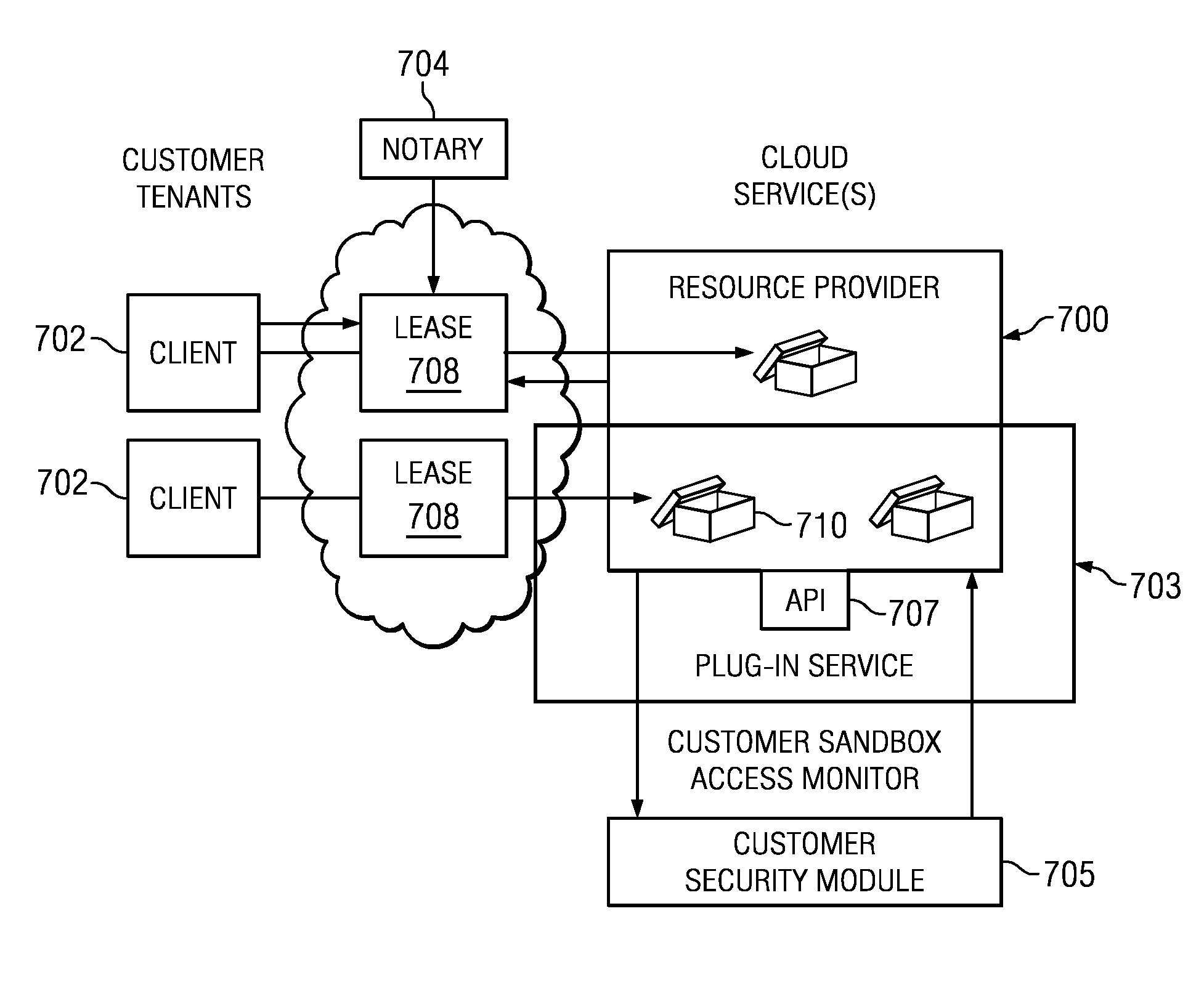
Authentication and authorization methods for cloud computing security
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
System and method for verifying delivery and integrity of electronic messages
InactiveUS20020144154A1Key distribution for secure communicationDigital data processing detailsDigital signatureThe Internet
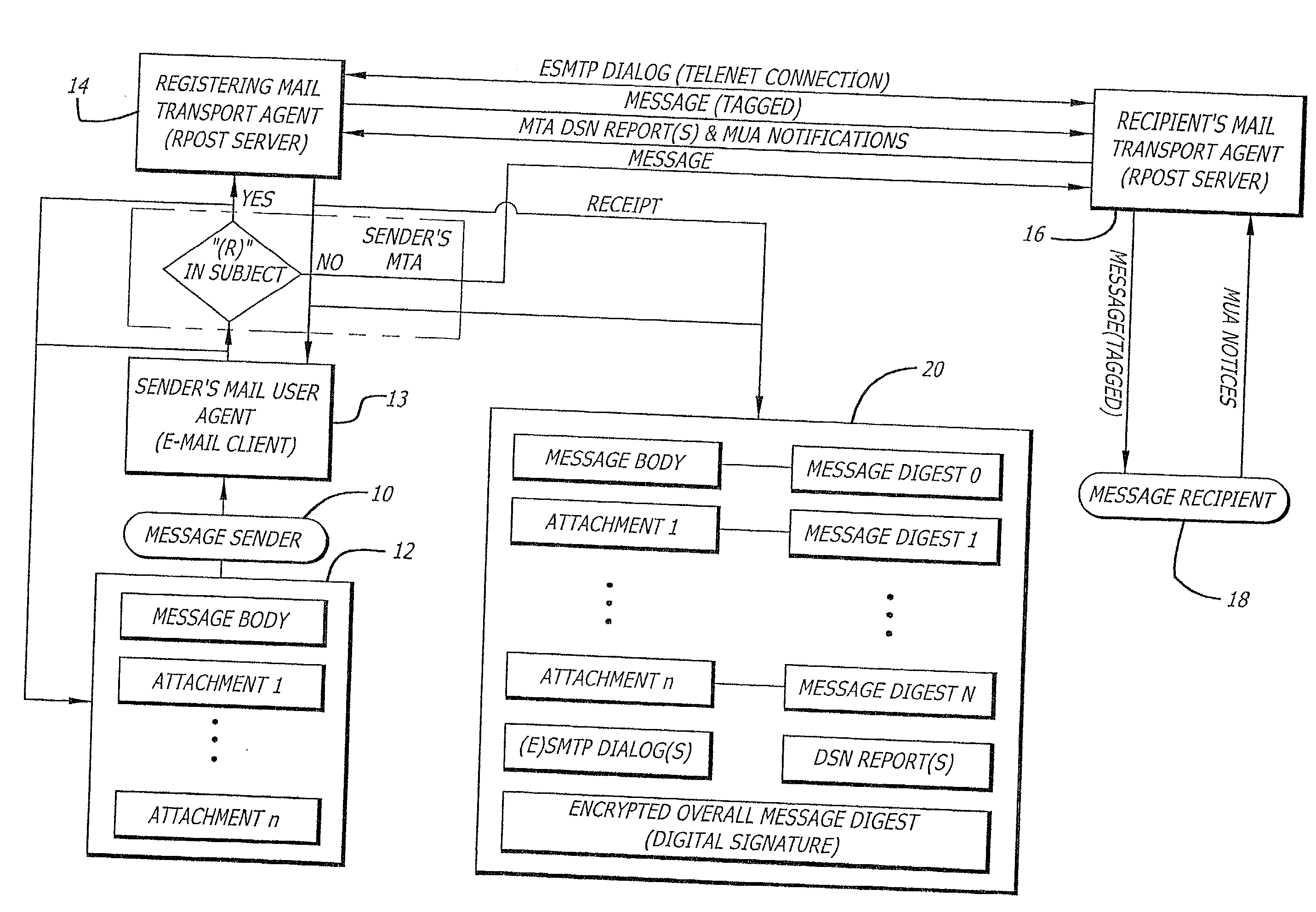
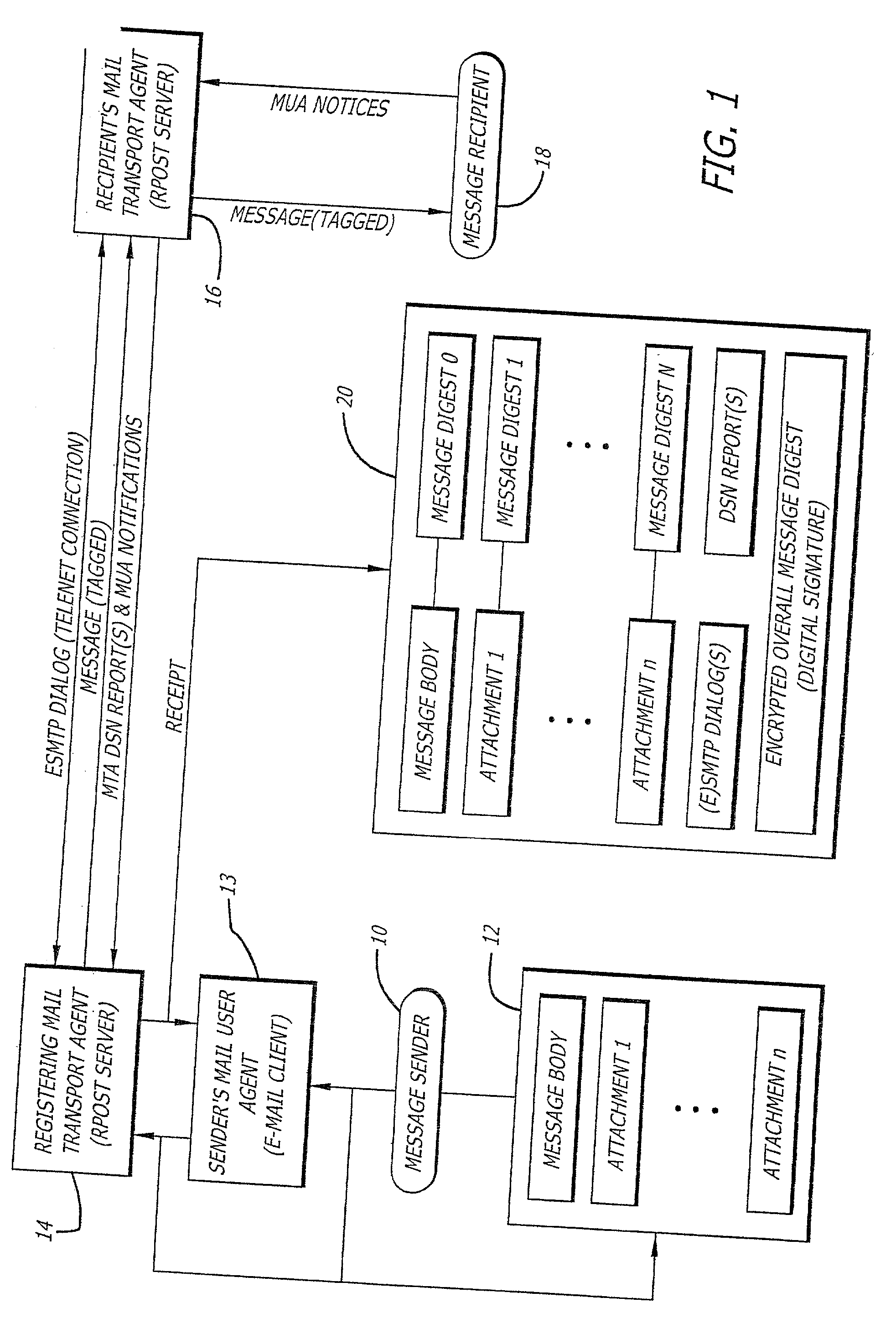
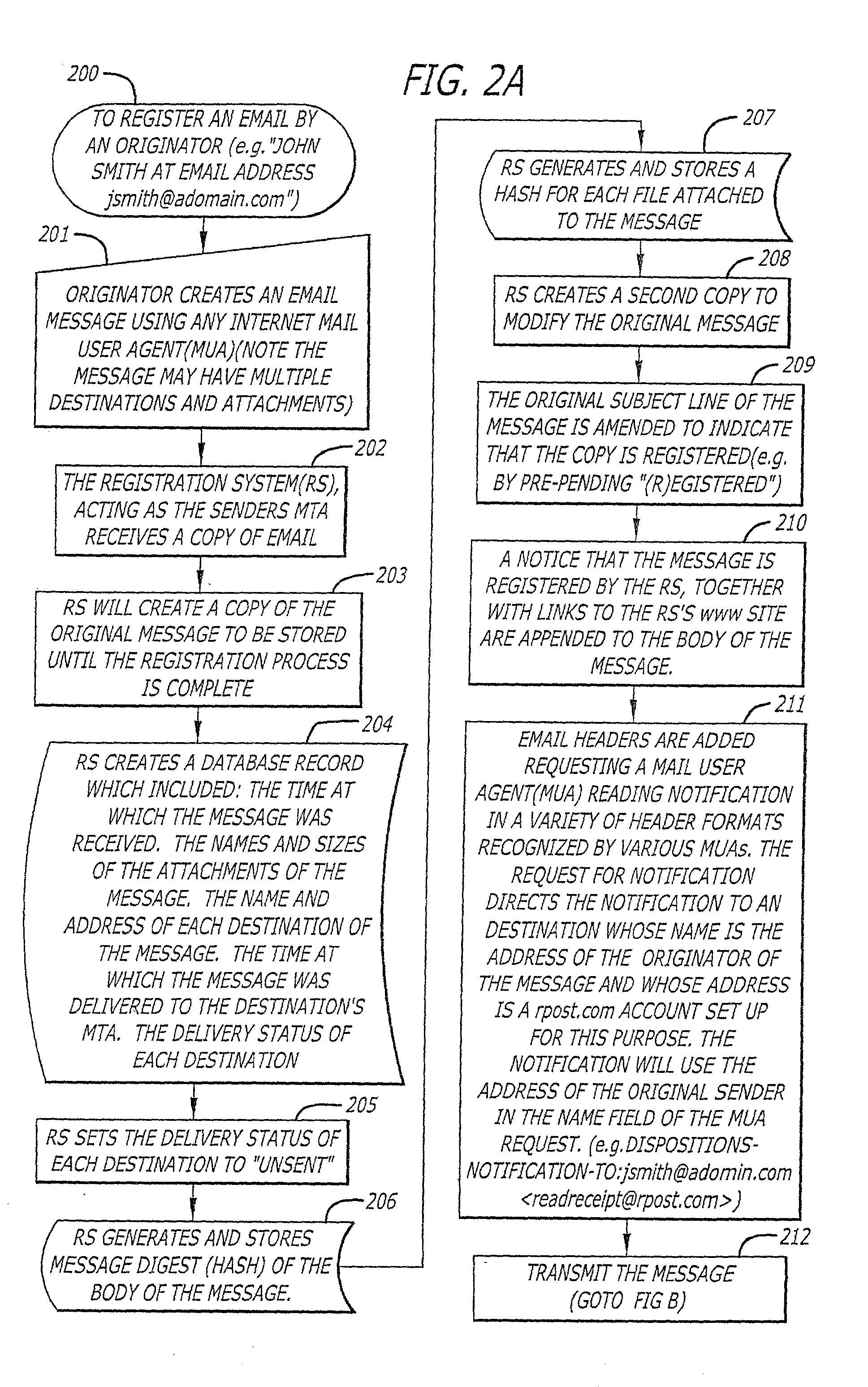
A server receives a message from a sender and transmits the message through the Internet to a recipient. The server normally transmits the message in a first path through the Internet to the recipient. When the sender indicates at a particular position in the message that the message is registered, the server transmits the message in a second path through the Internet to the recipient. The sender can also provide additional indications in the message to have the server handle the message in other special ways not normally provided by the server. After learning from the receipt or the recipient's agent through the Internet that the message was successfully received, the server creates, and forwards to the sender, an electronic receipt. The receipt includes at least one, and preferably all: the message and any attachments, a delivery success / failure table listing the receipts, and the receipt times, of the message by the recipient's specific agents, and the failure of other agents of the recipient to receive the message and a digital signature of the message and attachments subsequently. By verifying that the digital signature on the sender's receipt matches the digital receipt at the server, the server can verify, without retaining the message, that the receipt is genuine and that the message is accurate.
Owner:RPOST COMM
Privacy firewall
ActiveUS20140047551A1Impact efficiencyImpact performanceDigital data processing detailsRelational databasesSupplicantInternet privacy
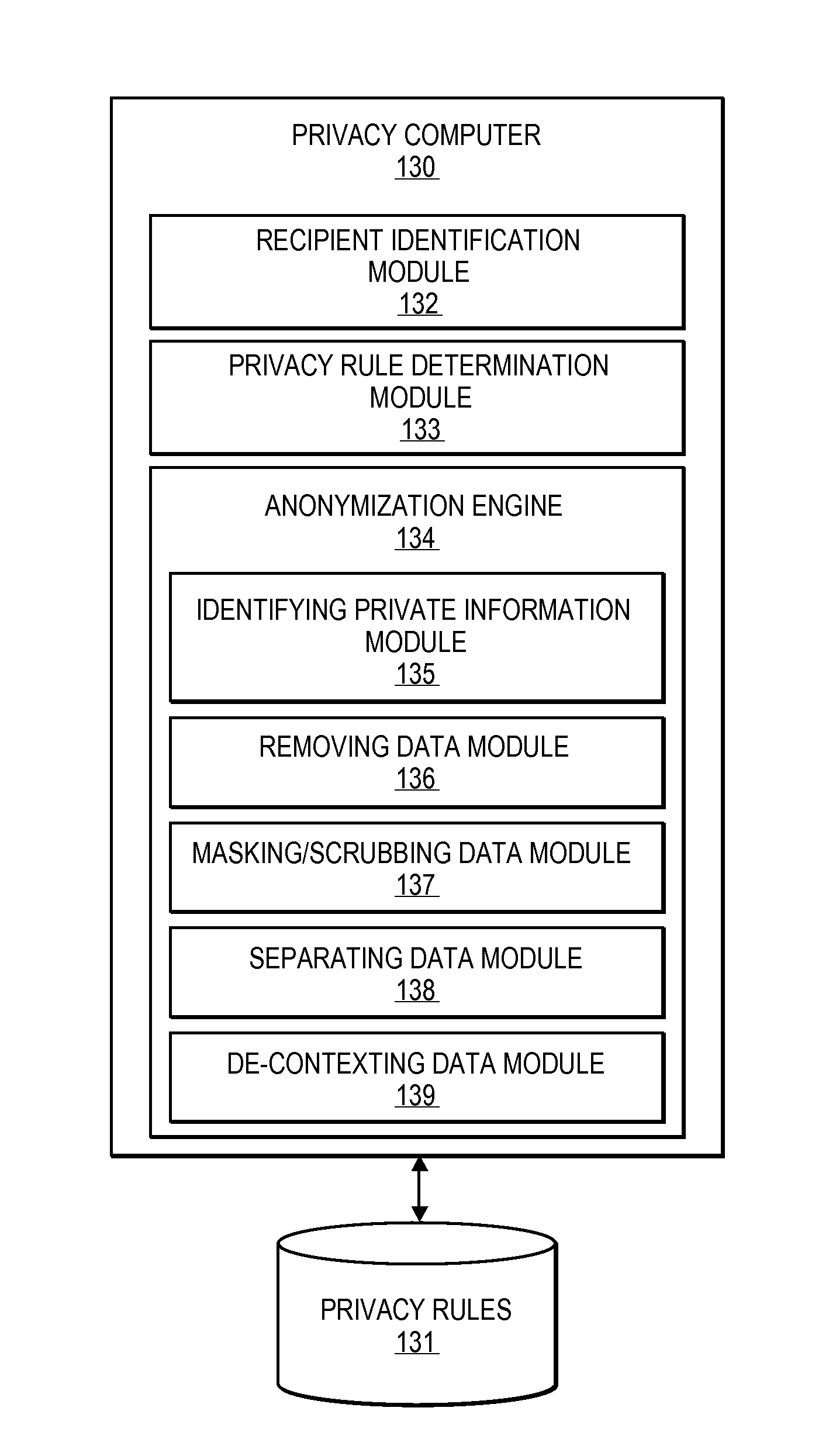
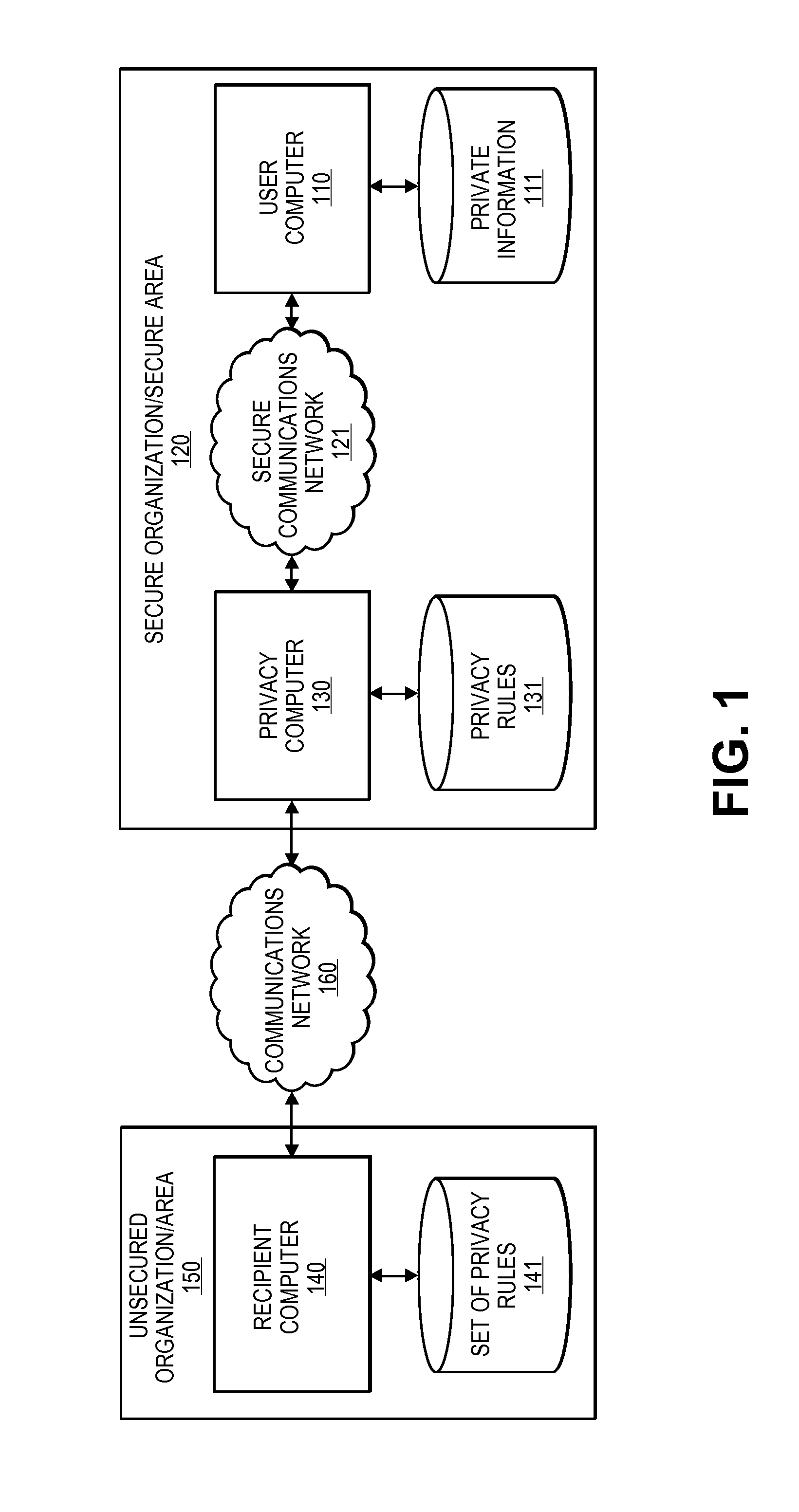
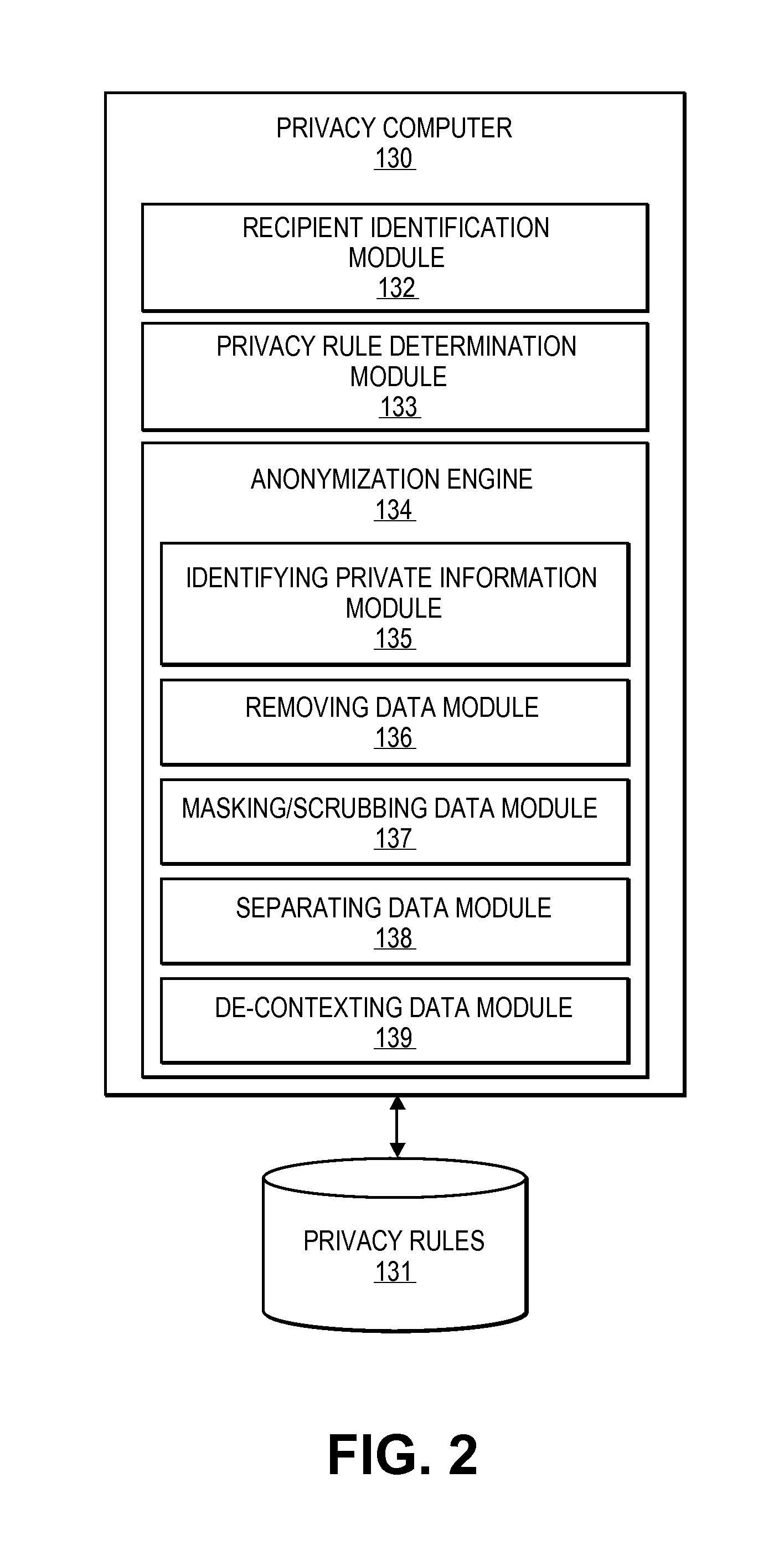
Embodiments of the invention relate to systems and methods for providing an anonymization engine. One embodiment of the present invention relates to a method comprising receiving a message directed at a recipient computer located outside a secure area by a privacy computer located within a secure area. The privacy computer may identify private information using a plurality of privacy rules and anonymize the message according to the plurality of privacy rules. Another embodiment may be directed to a method comprising receiving a request for sensitive data from a requesting computer. An anonymization computer may determine a sensitive data record associated with the request and may anonymize the sensitive data record by performing at least two of: removing unnecessary sensitive data entries from the sensitive data record, masking the sensitive data entries to maintain format, separating the sensitive data entries into associated data groupings, and de-contexting the data.
Owner:VISA INT SERVICE ASSOC
Smart Device User Authentication
InactiveUS20110219427A1Little and no burdenImprove securityDigital data processing detailsComputer security arrangementsUser deviceWeb service
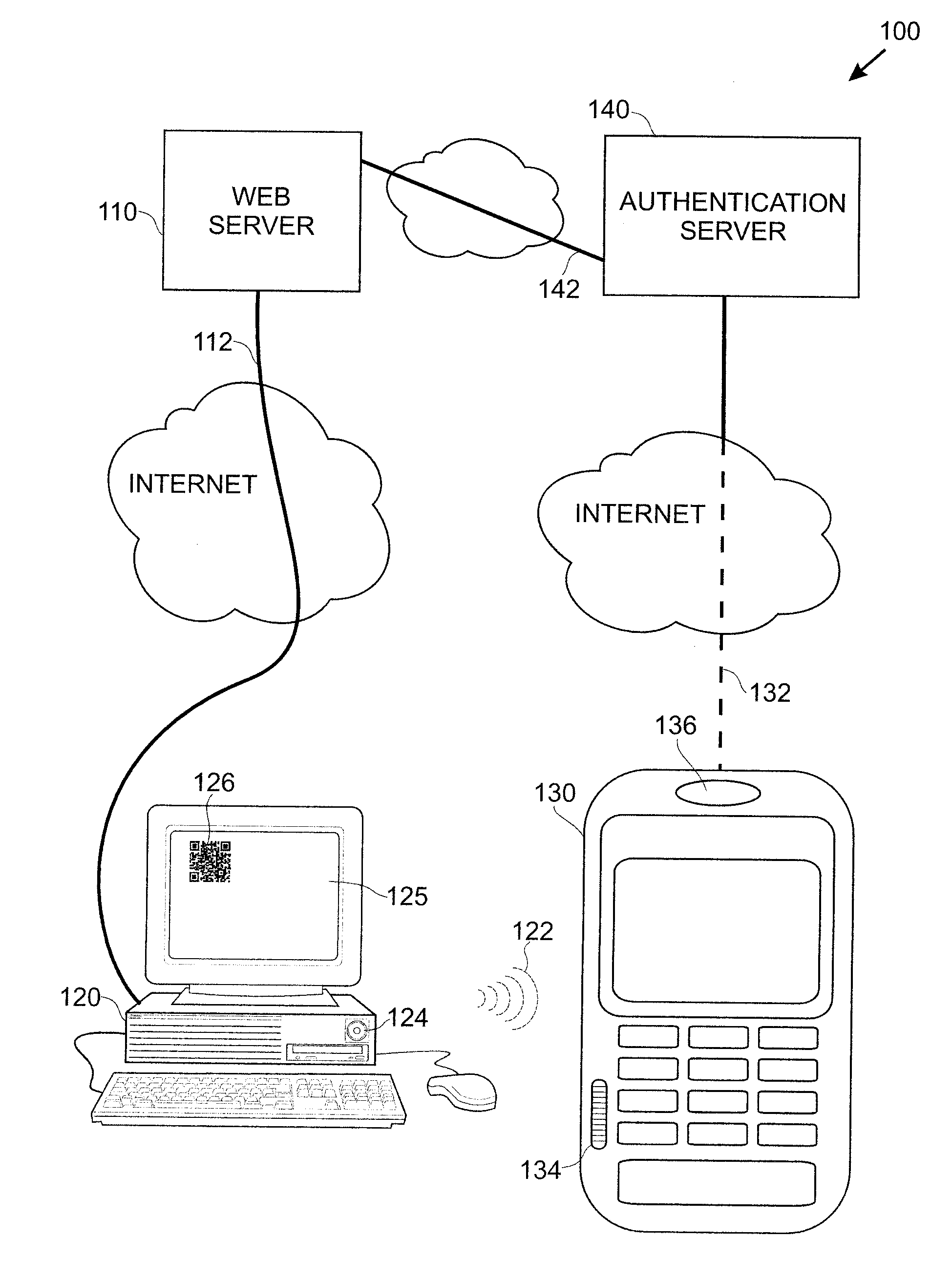
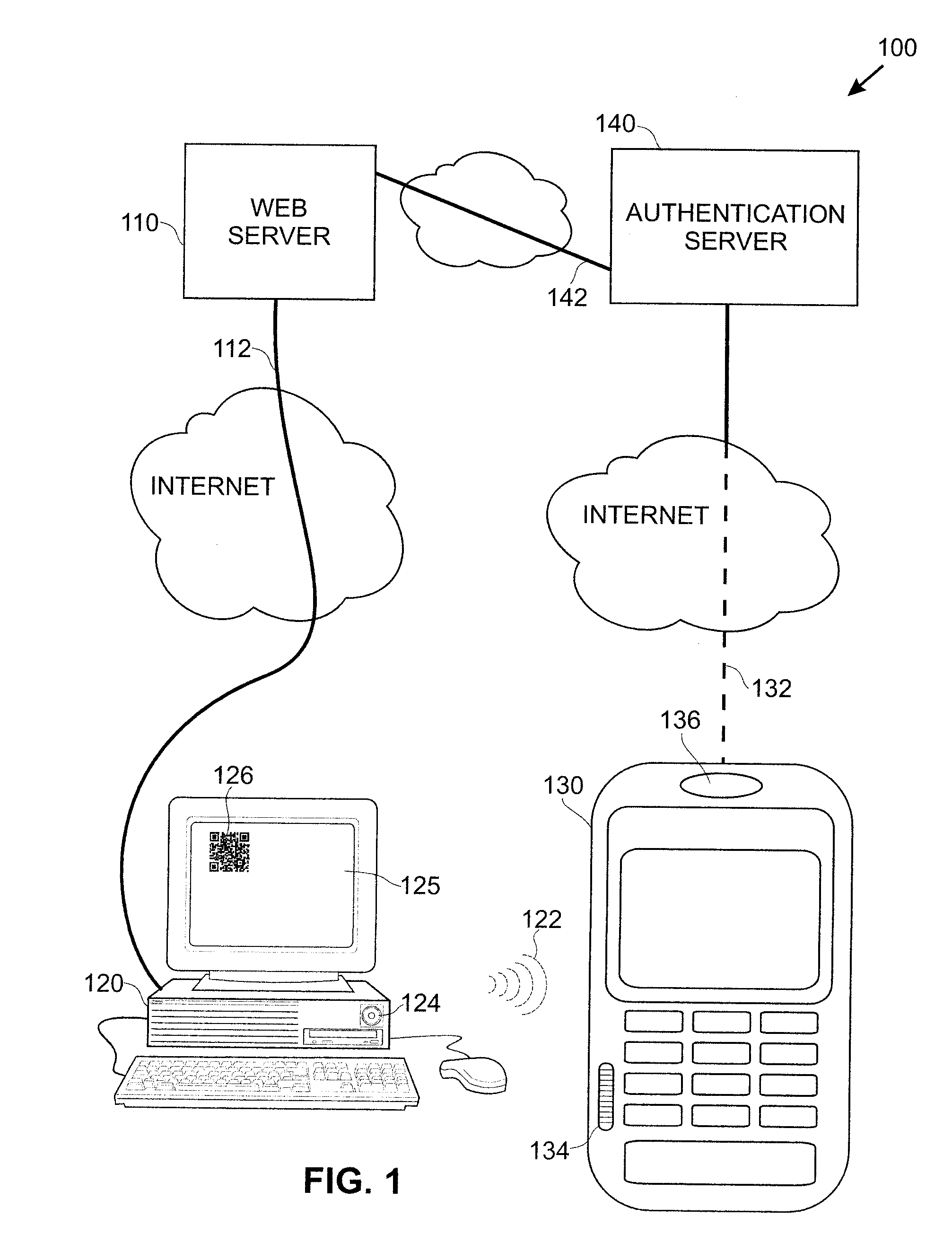
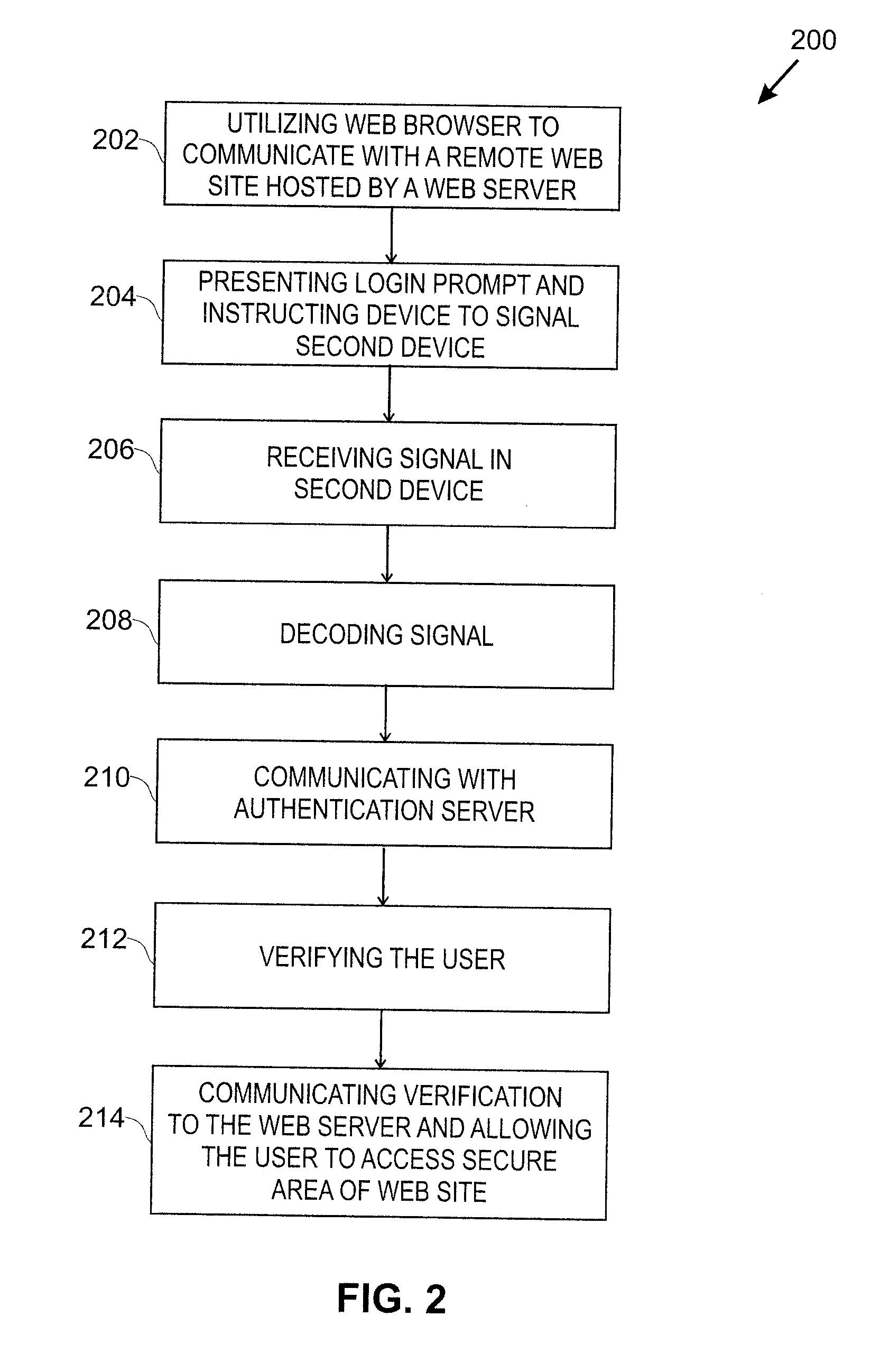
Techniques for simplifying an authentication process from the viewpoint of a user while providing improved security to the many users currently employing no or weak security techniques. In logging into a web site hosted by a web server, a session begins by a user connecting and logging in with a device, such as a personal computer. Rather than a user name and password approach which is presently typical, the personal computer communicates with another user device, such as a smart phone. In one approach, an encoded acoustic signal is employed for this communication. The smart phone securely communicates with an authentication server which informs the web server whether the user has been authenticated or not.
Owner:RSSBUS
Systems and Methods for Providing a Single Click Access to Enterprise, SAAS and Cloud Hosted Application
ActiveUS20110277027A1Input/output for user-computer interactionDigital data processing detailsThird partyGraphics
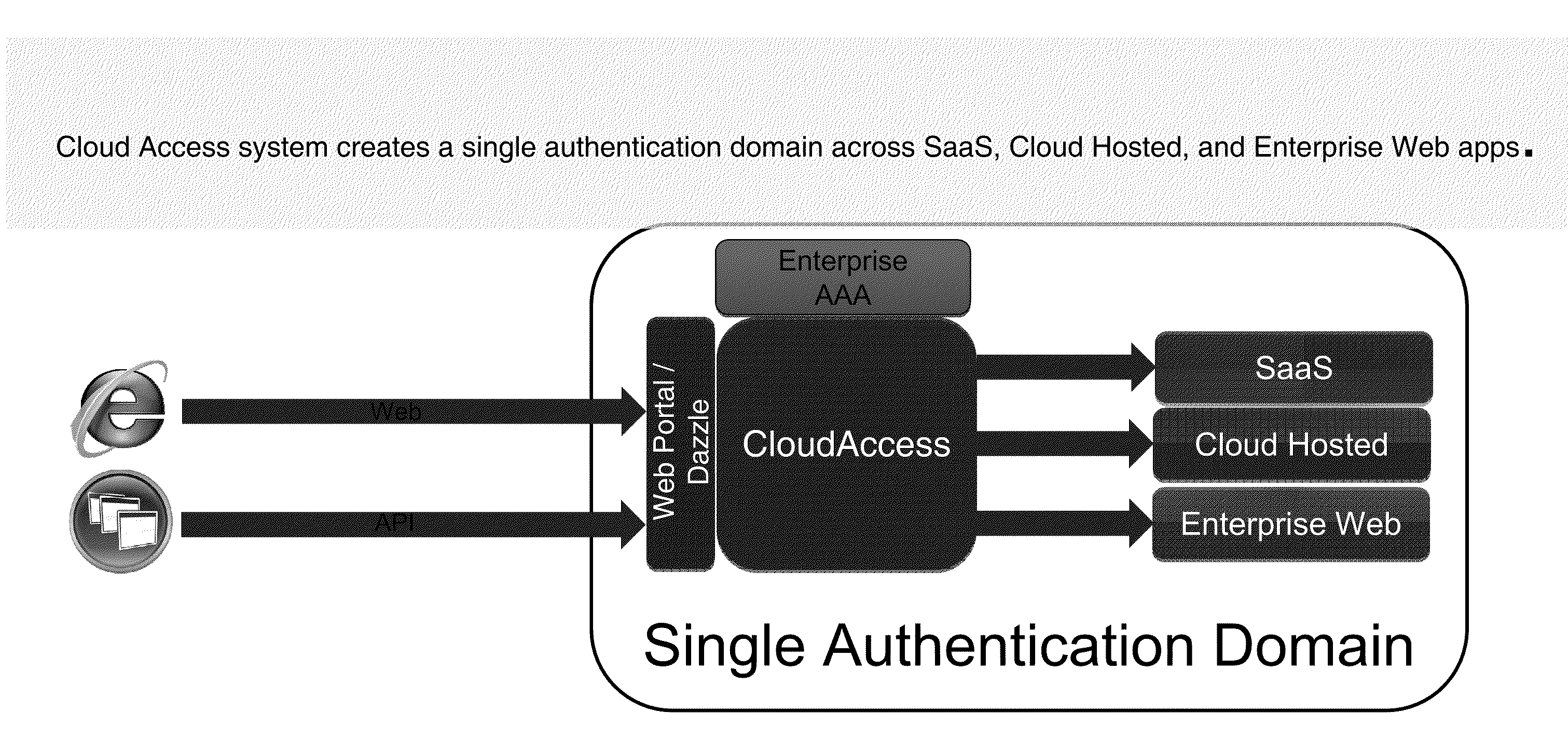
The present disclosure is directed to methods and systems of providing a user-selectable list of disparately hosted applications. A device intermediary to a client and one or more servers may receive a user request to access a list of applications published to the user. The device may communicate to the client the list of published applications available to the user, the list comprising graphical icons corresponding to disparately hosted applications, at least one graphical icon corresponding to a third-party hosted application of the disparately hosted applications, the third party hosted application served by a remote third-party server. The device may receive a selection from the user of the at least one graphical icon. The device may communicate, from the remote third party server to the client of the user, execution of the third party hosted application responsive to the selection by the user.
Owner:CITRIX SYST INC
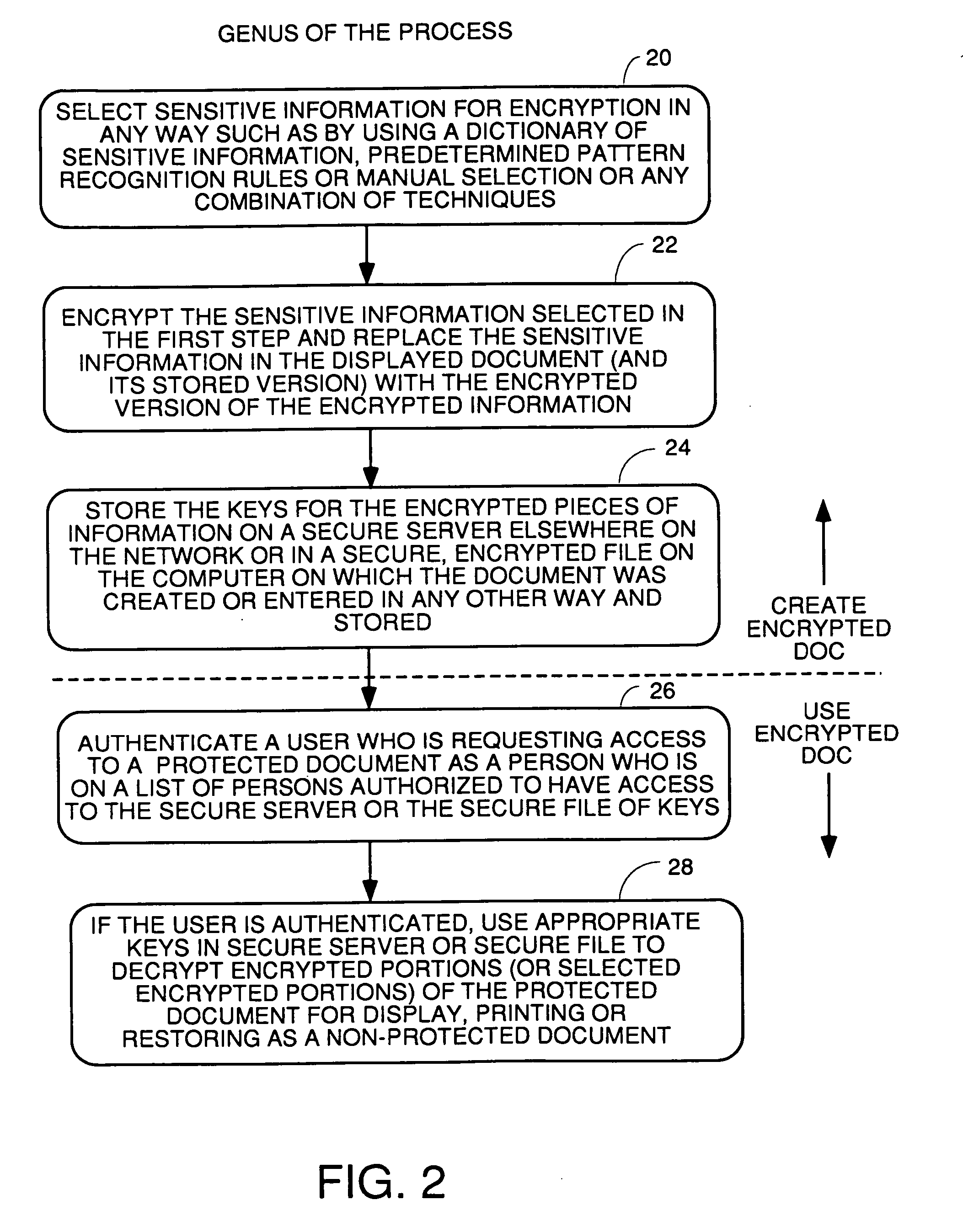
Method and apparatus for recognition and real time protection from view of sensitive terms in documents
InactiveUS20060075228A1Computer security arrangementsSecuring communicationInternet privacyClient-side
A process for automatically selecting sensitive information in any form of document being displayed and / or generated on a computer to select sensitive information for protection by encryption, redaction or removal of only the sensitive text. Selection is done by using pattern recognition rules, dictionaries of sensitive terms and / or manual selection of text. The sensitive text is automatically protected on the fly in the same manner as a spell checker works so that the sensitive information immediately is removed and replaced with the encrypted or redacted version or a space and a pointer to where the decryption key or the original of the redacted or removed text is stored. Other embodiments require manual approval of automatically selected text prior to protection. For encryption embodiments, the keys used to encrypt the sensitive information in each document are stored in a table or database, preferably on a secure key server so that they do not reside on the computer on which the partially redacted document is stored. Embodiments to protect the body of emails and attachments in either the email client or web mail environment are also disclosed.
Owner:INFOSAFE
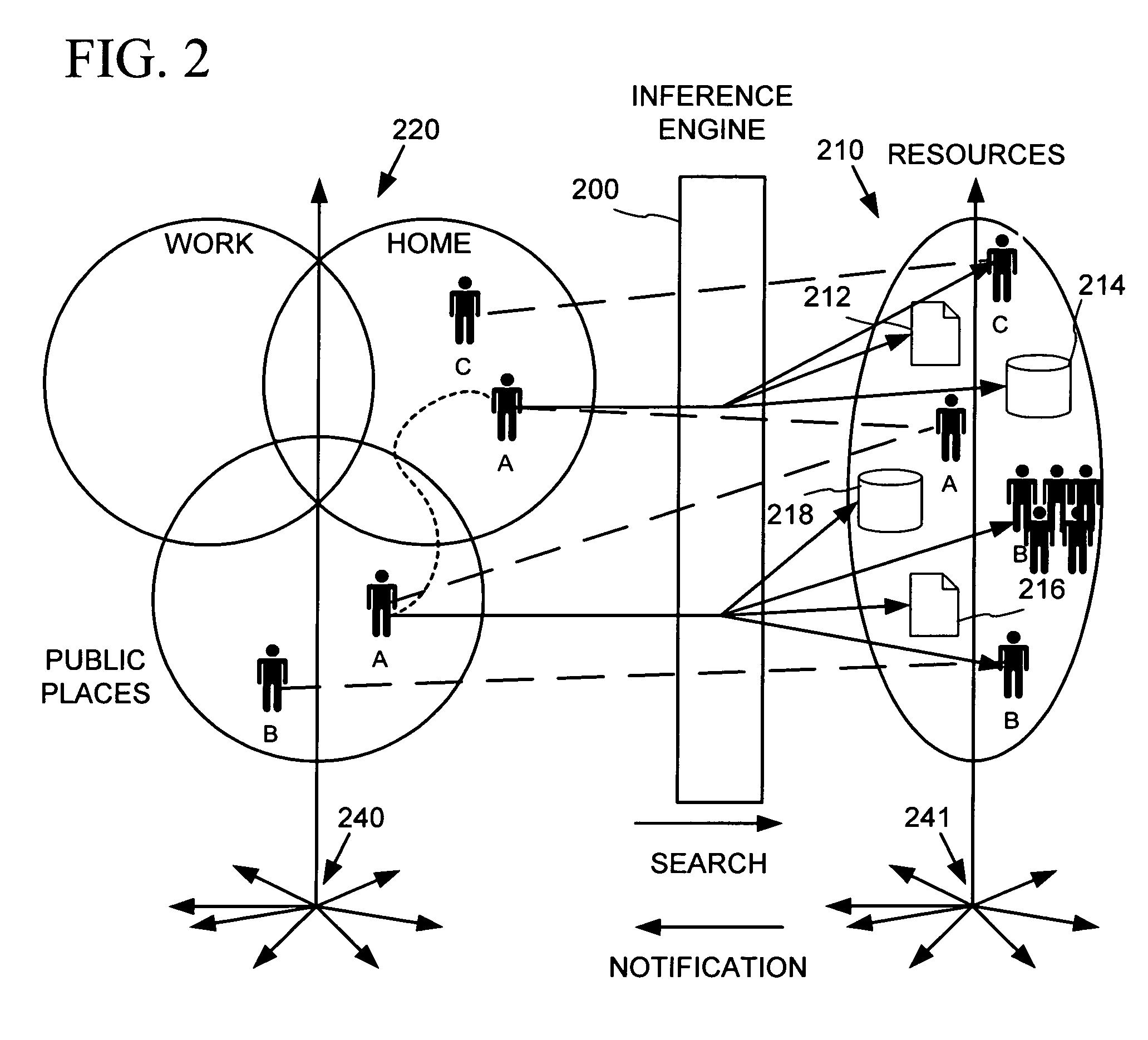
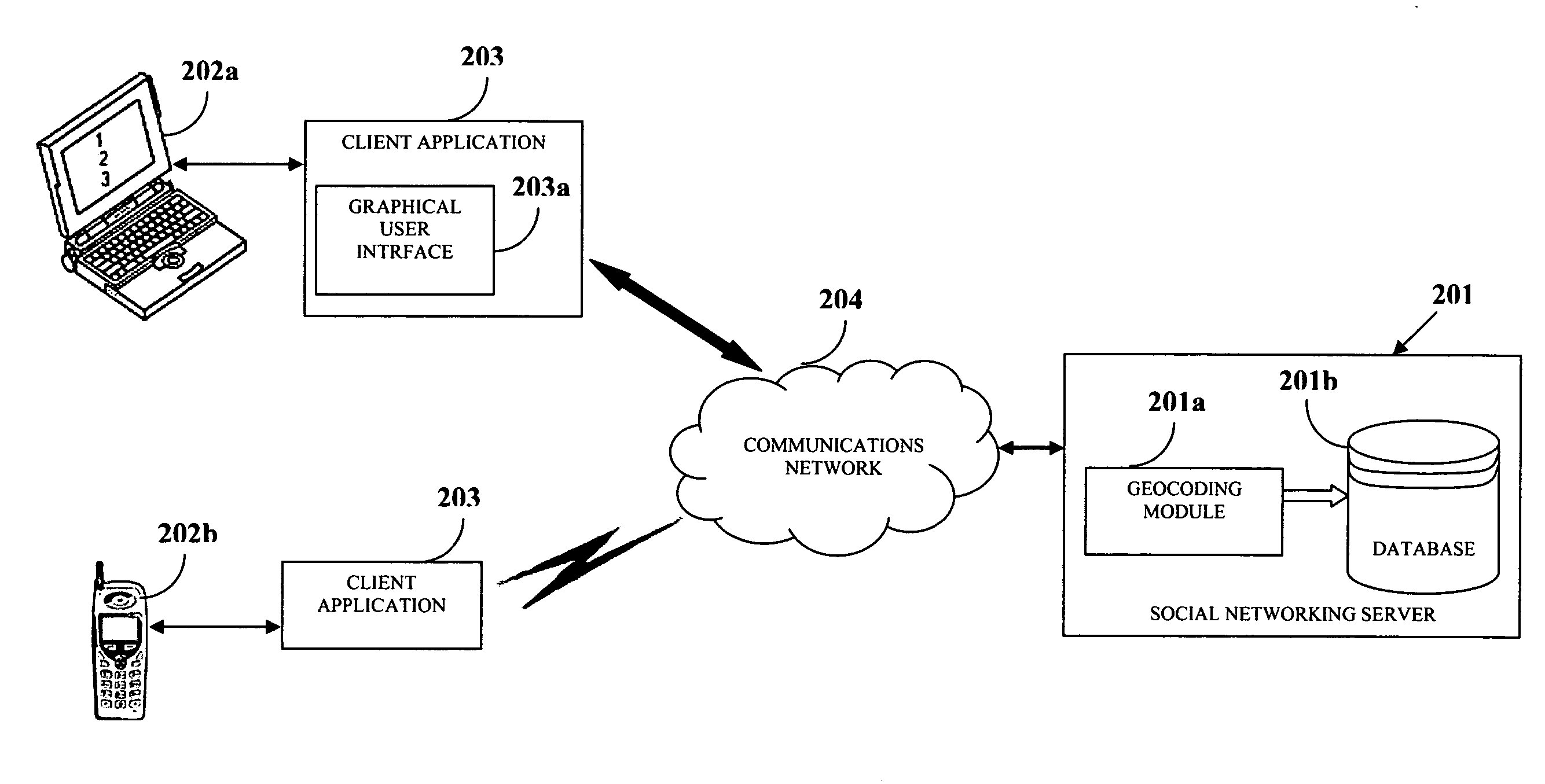
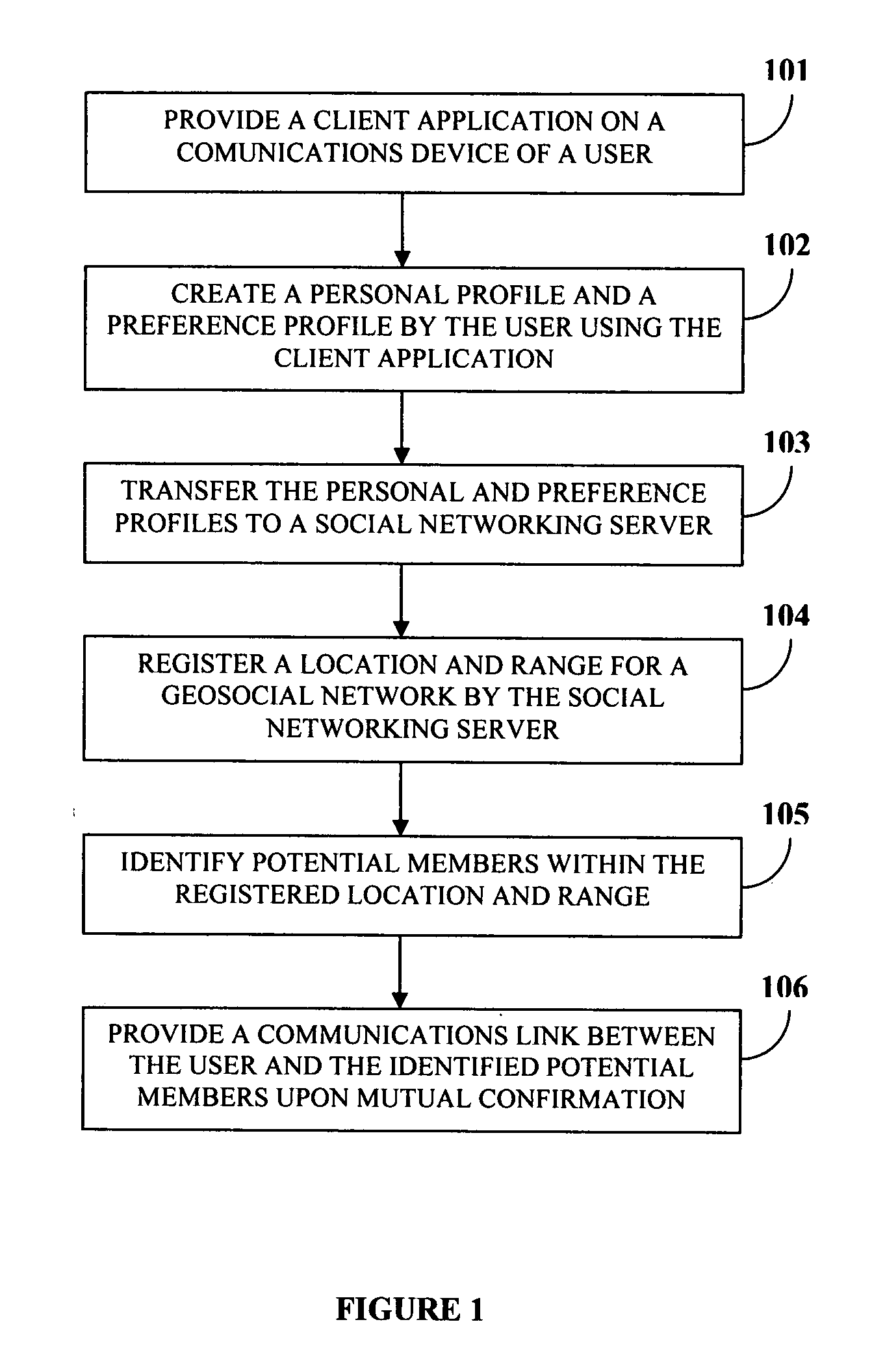
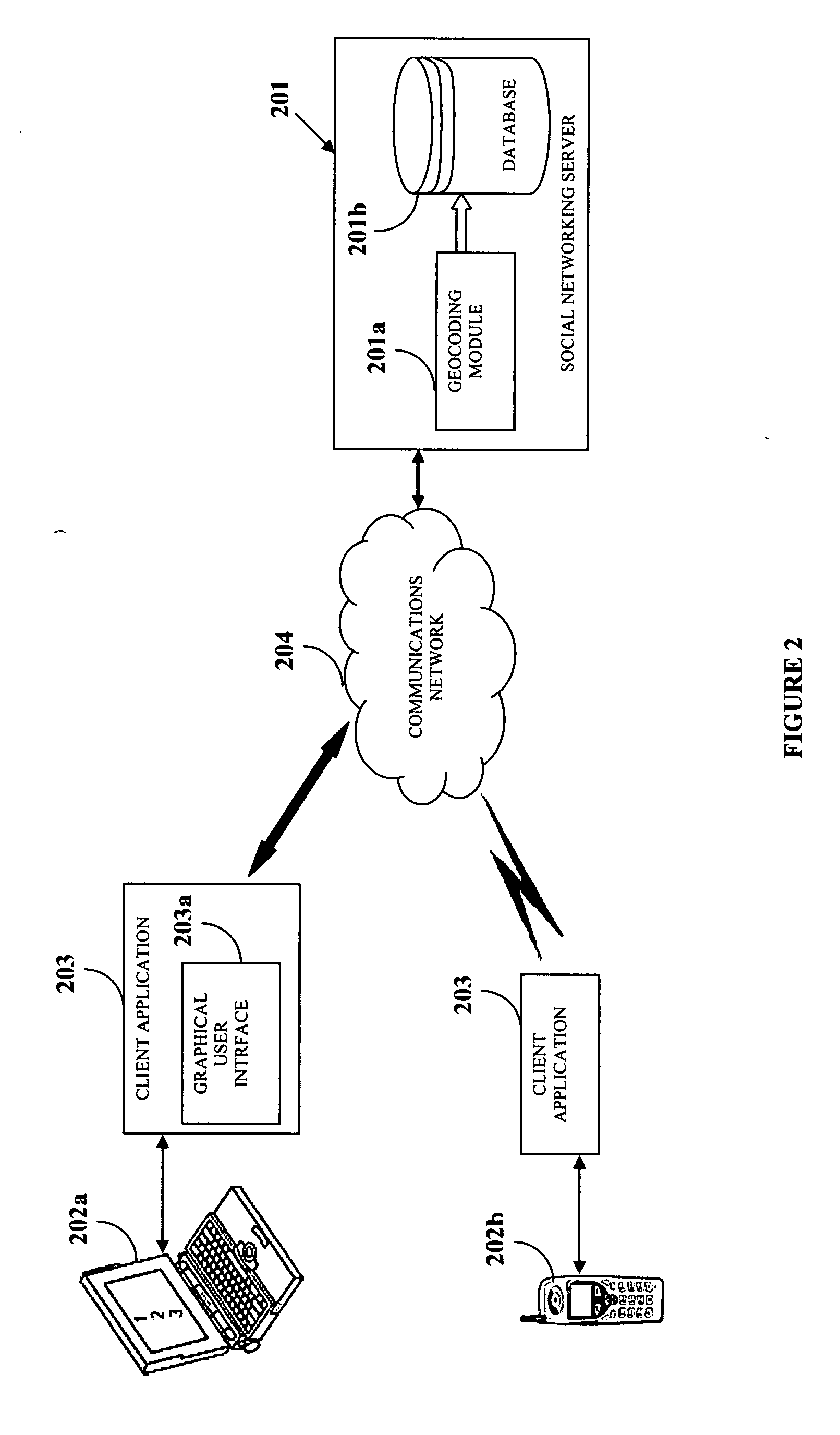
Dynamic geosocial networking
InactiveUS20080140650A1Save effortShorten the timeDigital data information retrievalServices signallingInternet privacyCommunication link
Disclosed herein is a method and system for establishing a geosocial network. A client application is provided on a communications device of a user seeking to establish the geosocial network. The user creates a personal profile and a preference profile using the client application. The preference profile refers to characteristics the user seeks in potential members of the geosocial network. The user transfers the personal and preference profiles to the social networking server. The social networking server registers a location and range selected by the user for the geosocial network. The social networking server identifies potential members within the registered location and range by matching the personal profile of each of the potential members with the preference and personal profiles of the user. The social networking server provides communications link between the user and the identified potential members upon mutual confirmation between the user and the identified potential members.
Owner:GEOFRIEND LLC
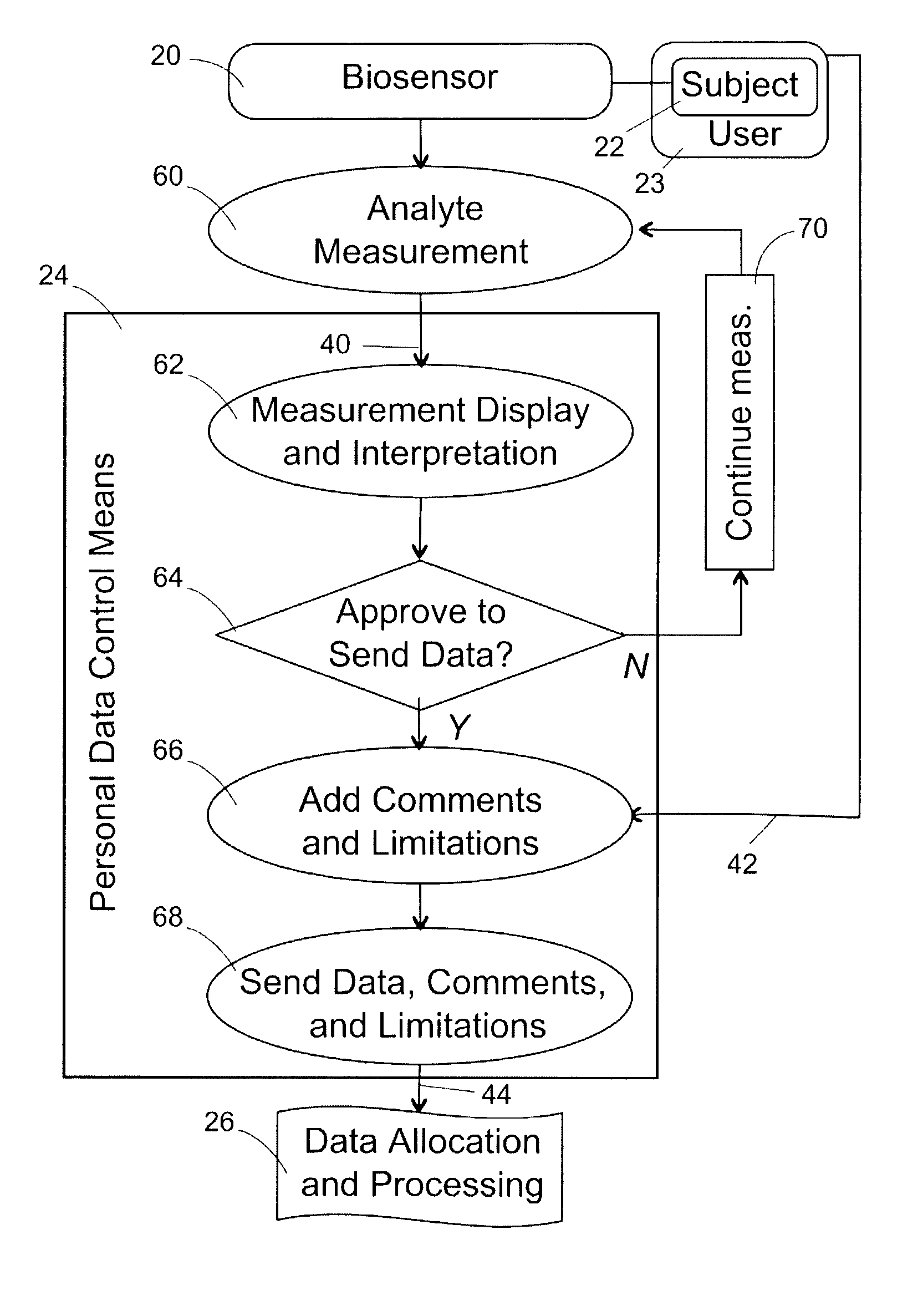
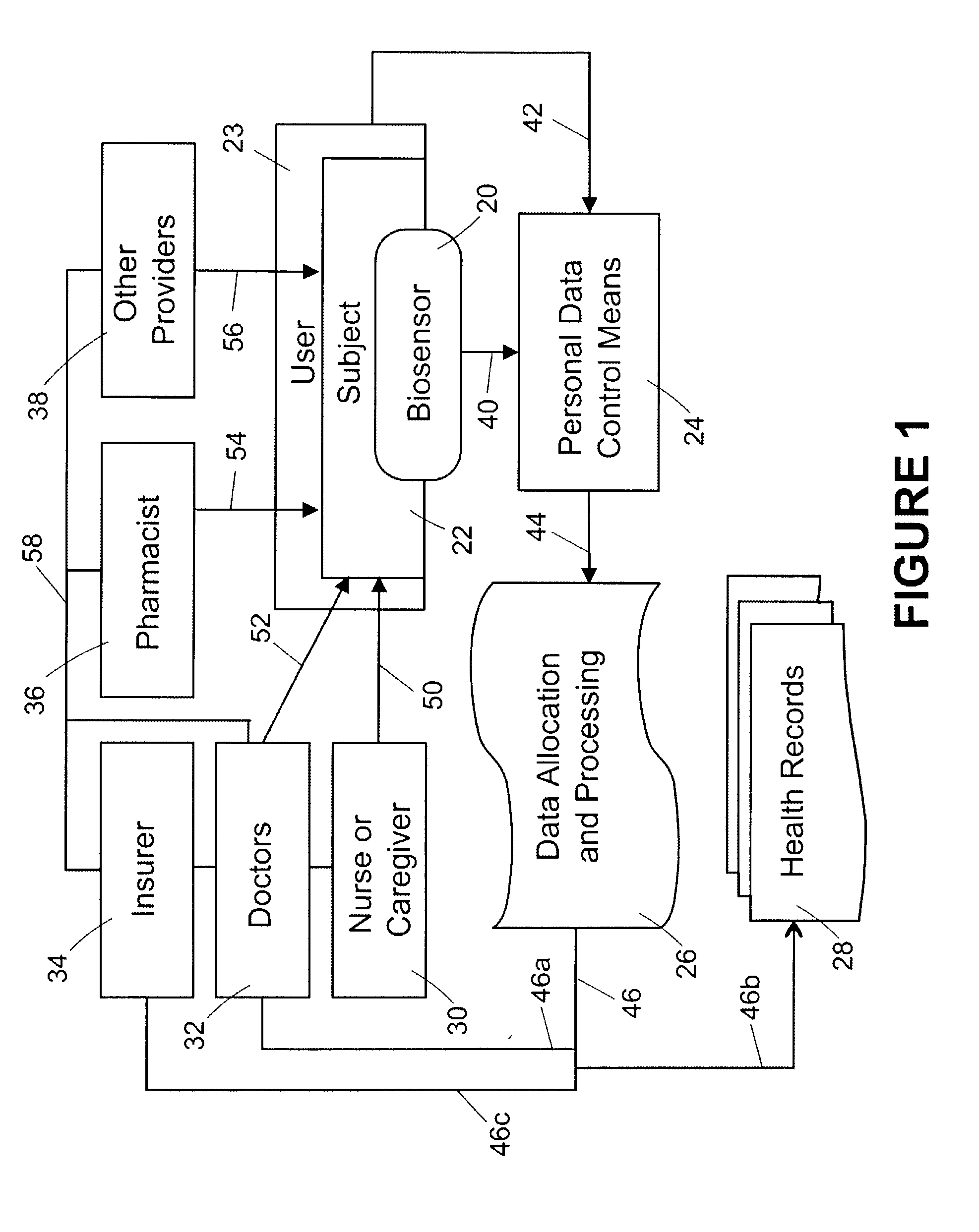
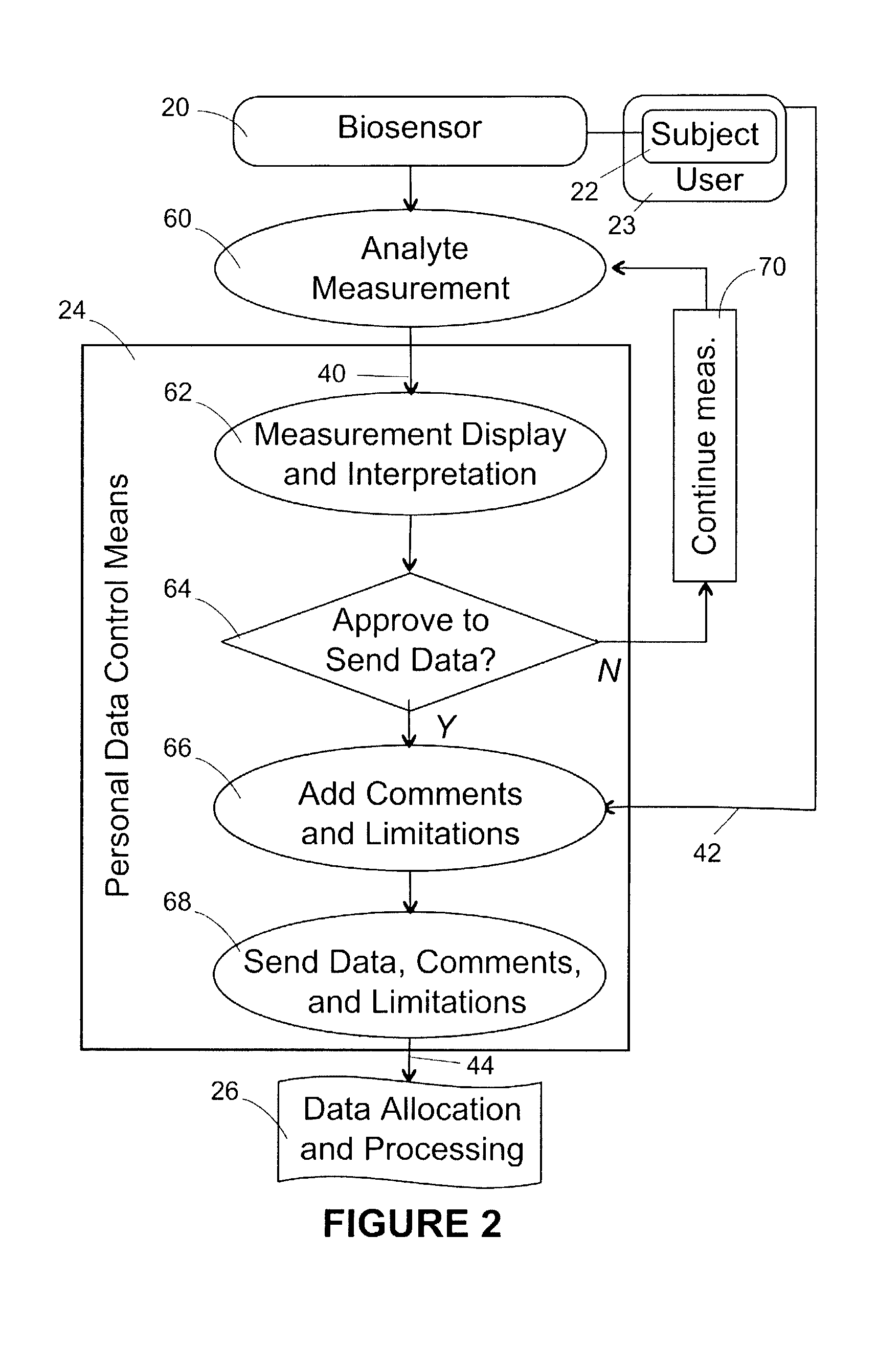
Healthcare networks with biosensors
InactiveUS20050101841A9Privacy protectionElectrotherapyData processing applicationsData controlInternet privacy
A healthcare network is provided for sharing information concerning the health of a user with at least one outside source, the network including a biosensor associated with the user that generates a biosensor signal containing the information; and a personal data control means including receiving means for receiving the biosensor signal, input means for receiving a privacy input from the user, and output means for generating a response signal based on the biosensor signal and privacy input. The network also includes a data allocation and processing module including means for receiving the response signal, and means for generating and directing an output signal to the at least one outside source, wherein the module is responsive to the response signal, and wherein the availability of the information to the at least one outside source is responsive to the privacy input.
Owner:BINFORMA GROUP LIABILITY
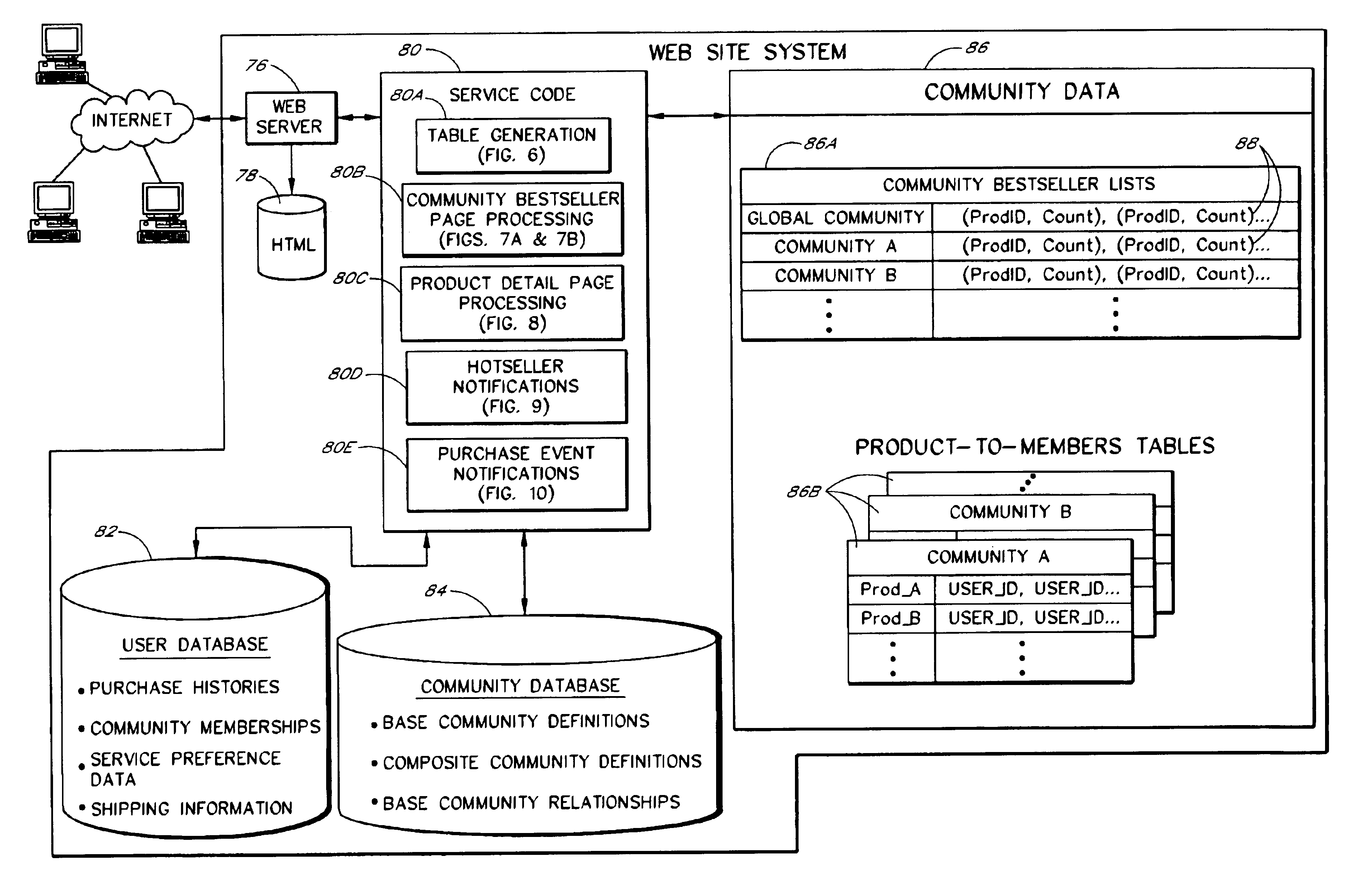
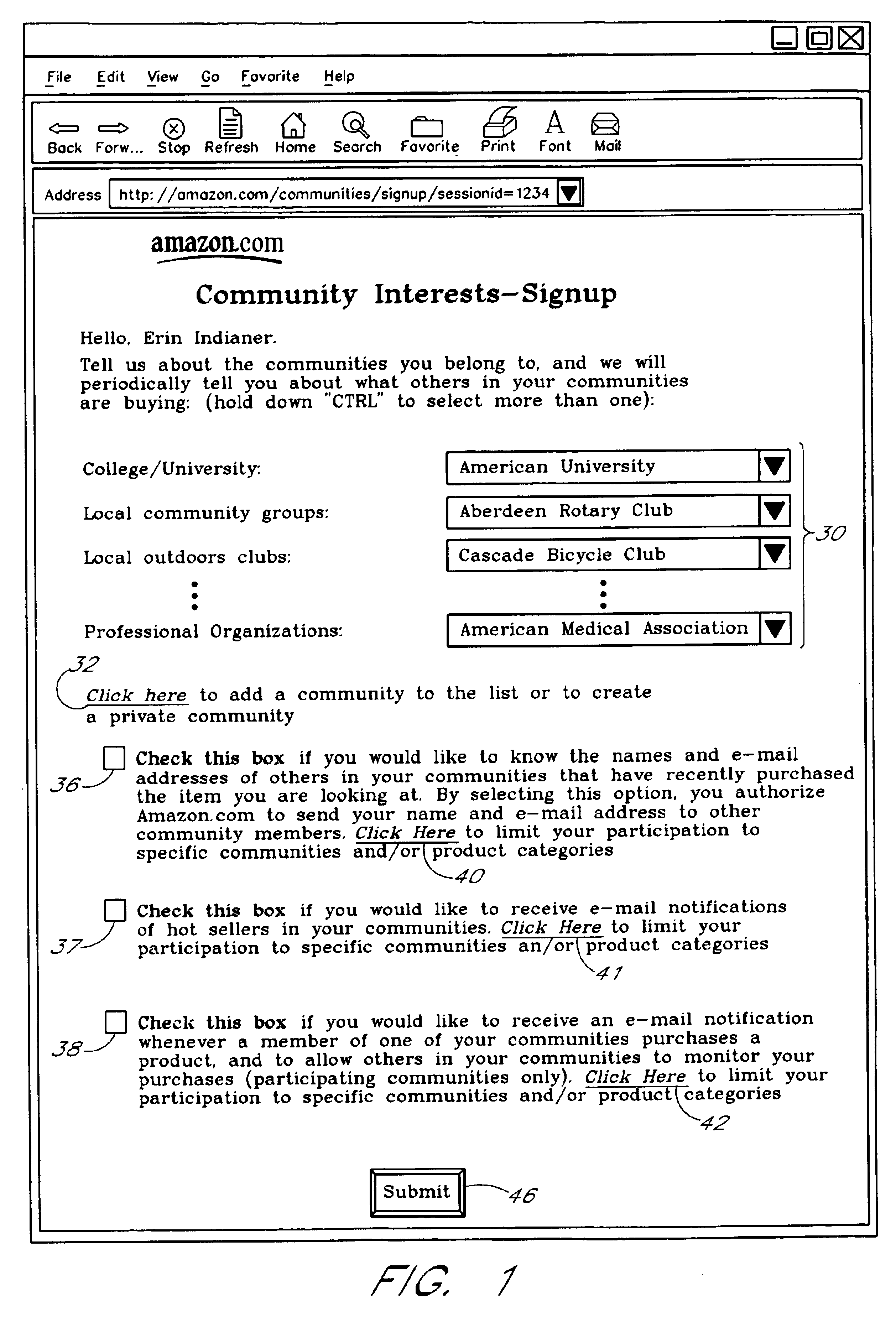
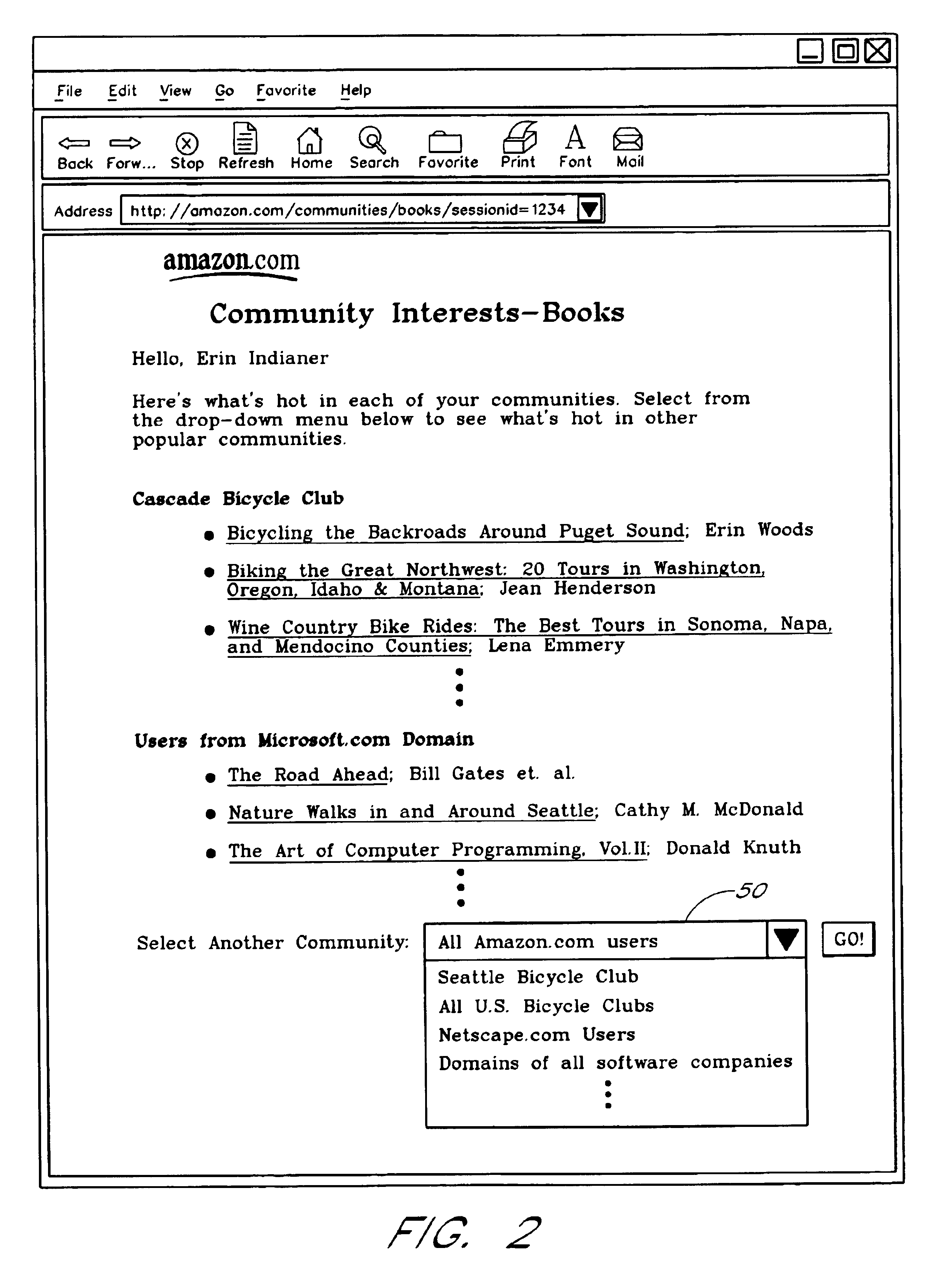
Computer services for assisting users in locating and evaluating items in an electronic catalog based on actions performed by members of specific user communities
A Web based system provides informational services for assisting customers in selecting products or other types of items from an electronic catalog of a merchant. Users of the system can create and join user communities, such as communities based on user hobbies, localities, professions, and organizations. The system also supports implicit membership communities that are based on email addresses (e.g., all users having a “nasa.com” email address), shipping / billing addresses, and other known user information. Using purchase history data collected for online users, the system automatically identifies and generates lists of the most popular items (and / or items that are becoming popular) within particular communities, and makes such information available to users for viewing. For example, in the context of an online book store users of the nasa.com community may automatically be presented a Web page which lists the bestselling book titles among nasa.com users, or may be sent email notifications of purchase events or hotselling books within the community. Another feature involves automatically notifying users interested in particular products of other users (preferably other members of the same community) that have purchased the same or similar products. For example, in one embodiment, when a user accesses a book detail page, the detail page is customized to include the names and email addresses of other members of the user's community that recently purchased the same book.
Owner:AMAZON TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com