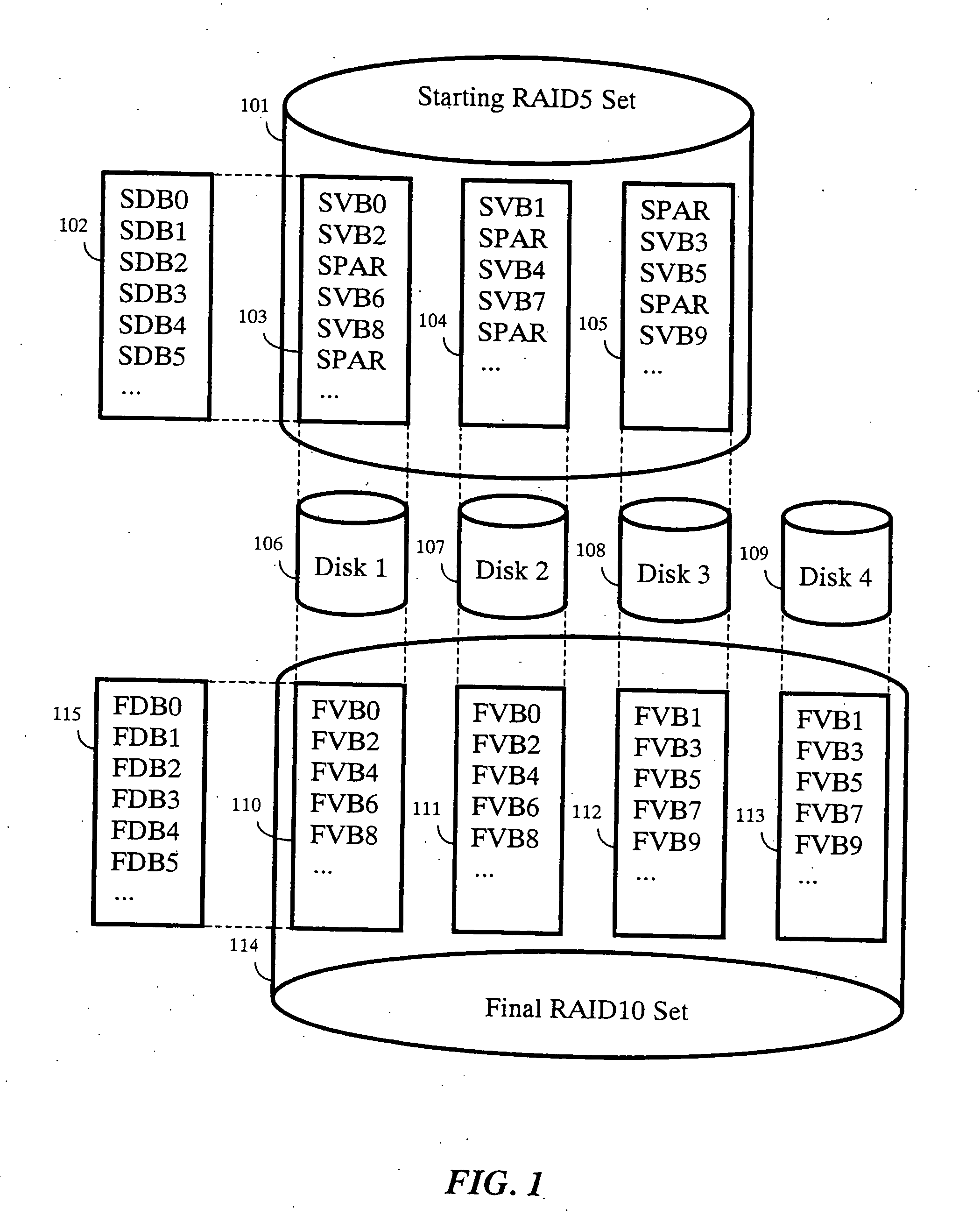
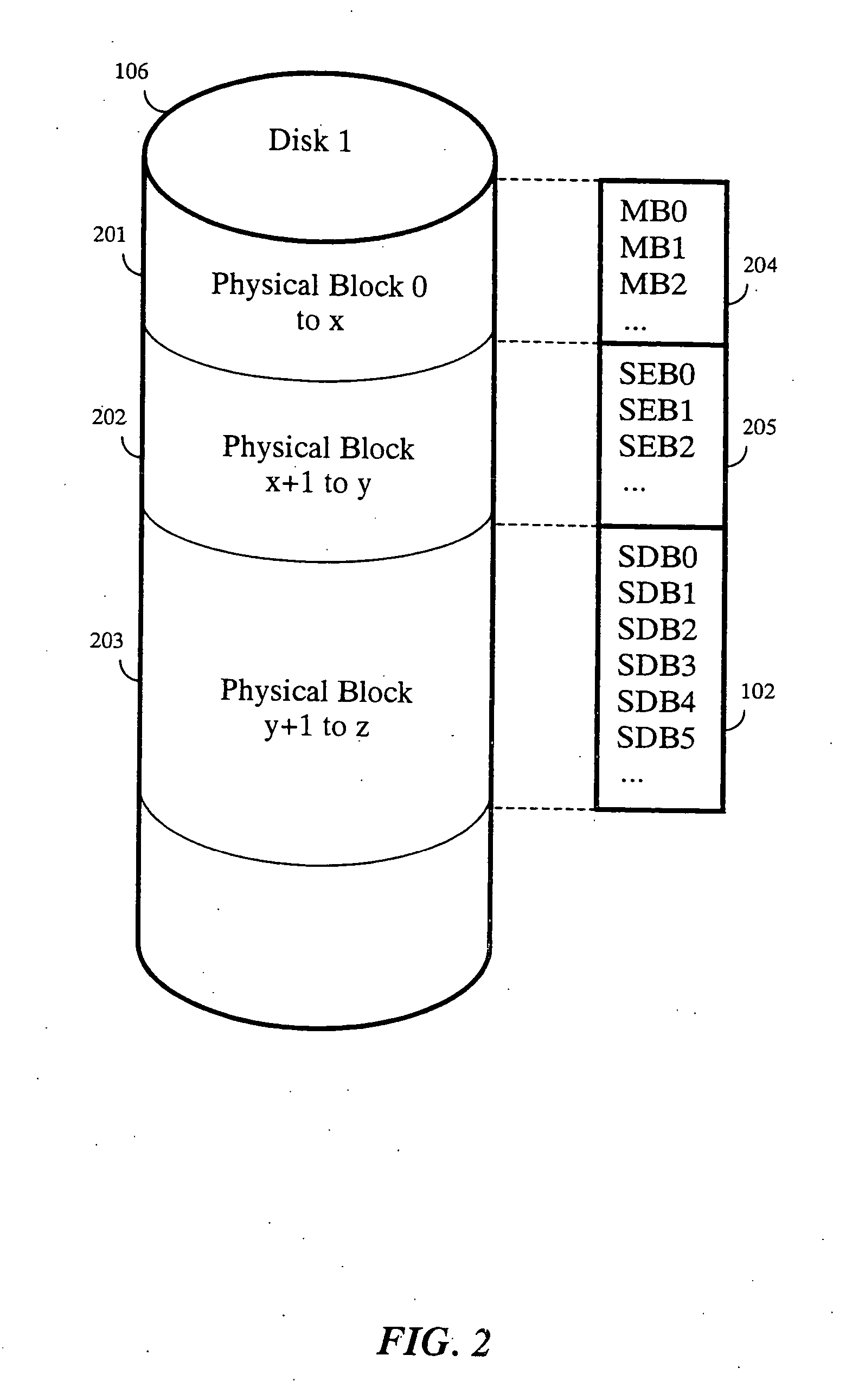
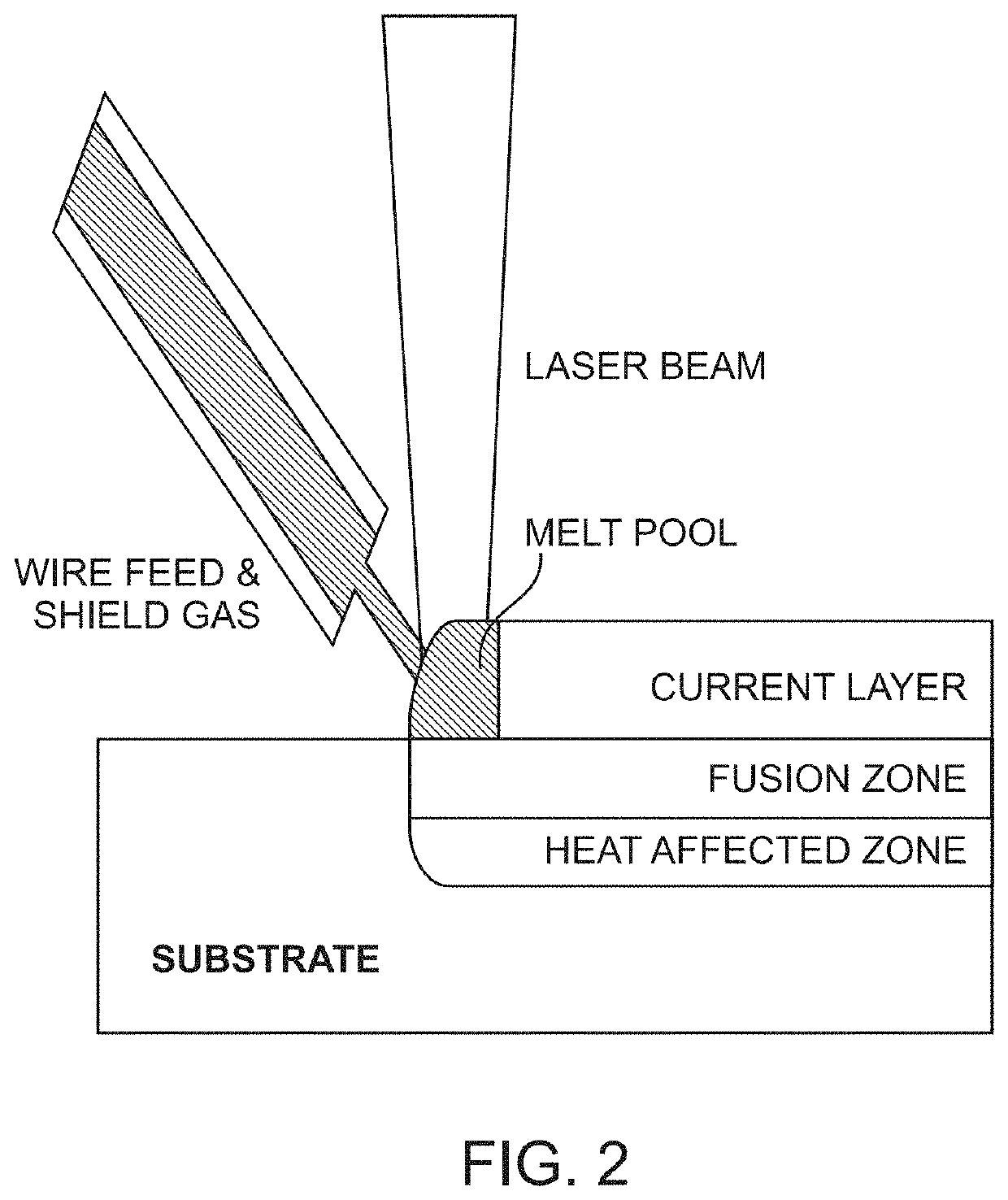
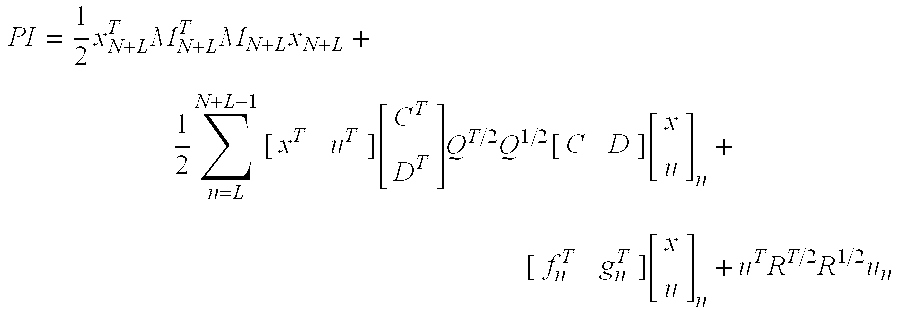Patents
Literature
172results about How to "Impact performance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
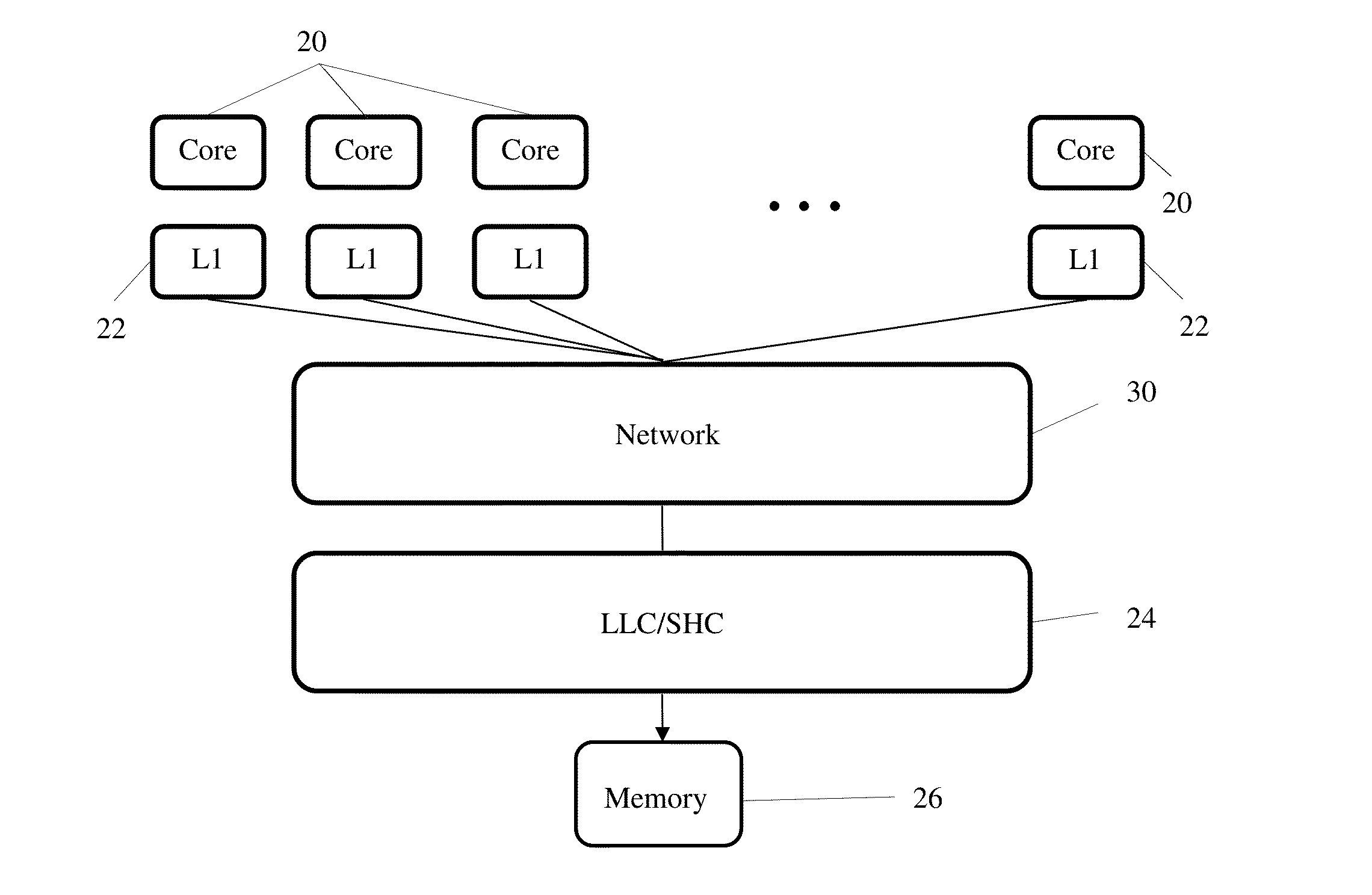
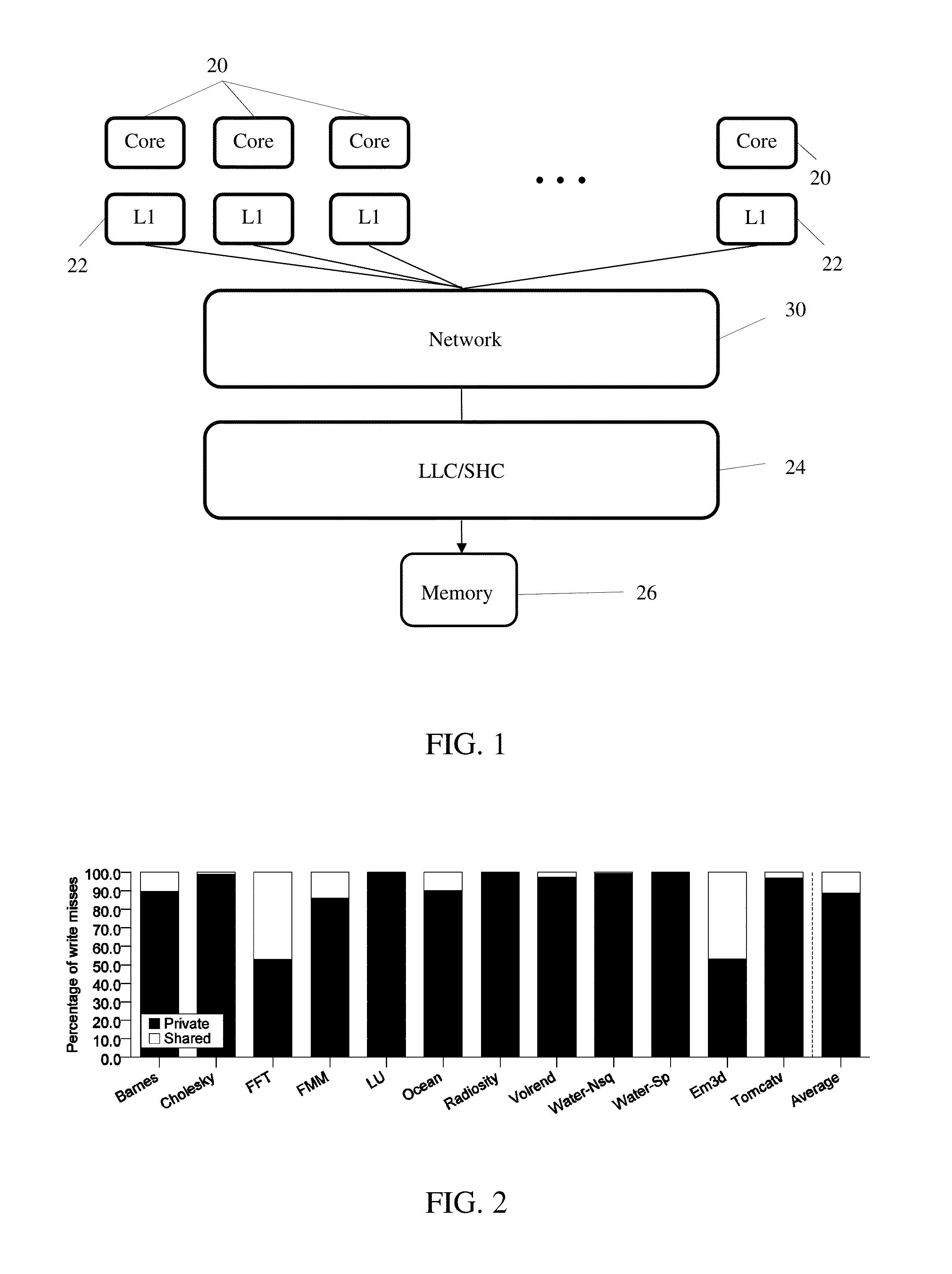
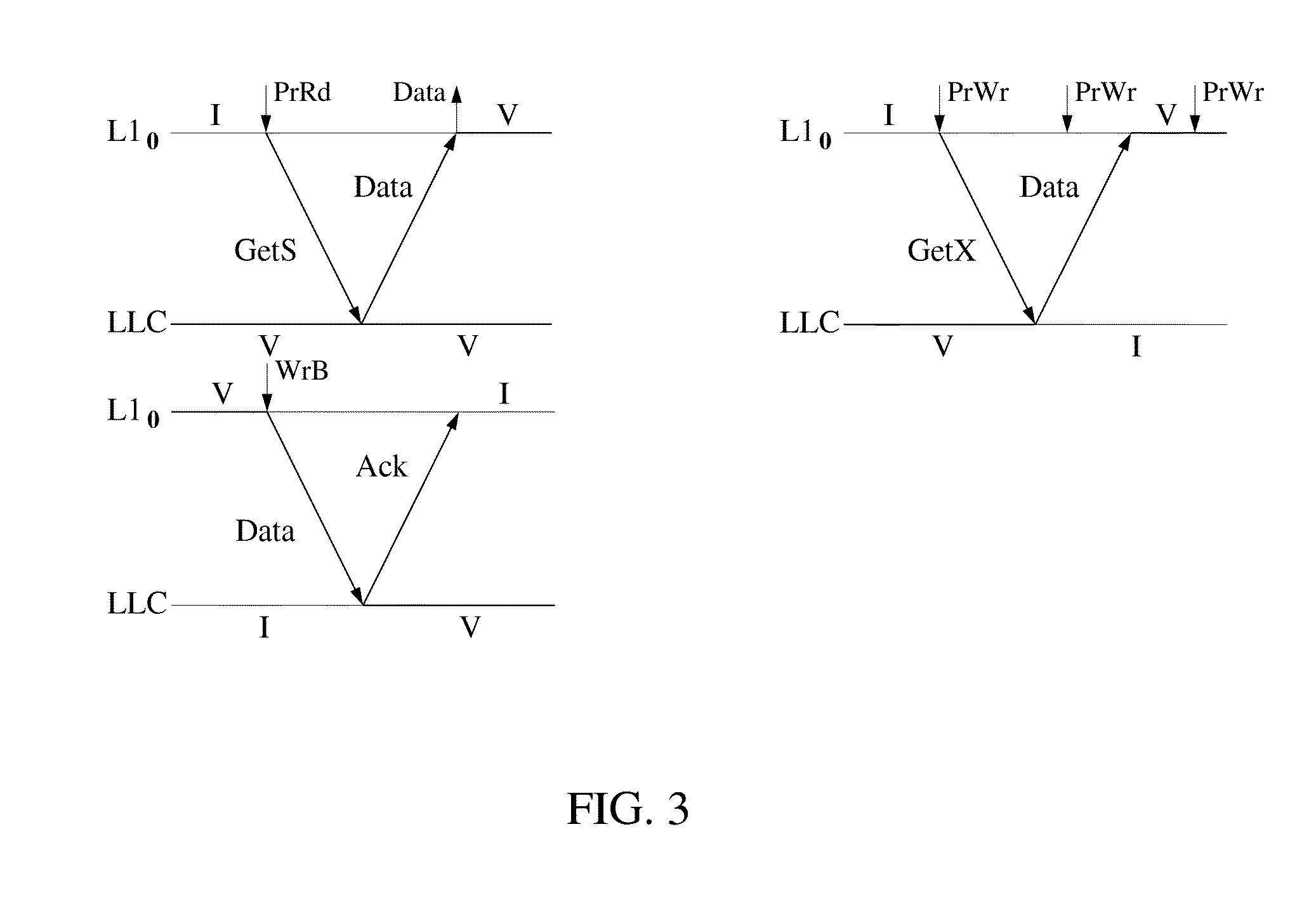
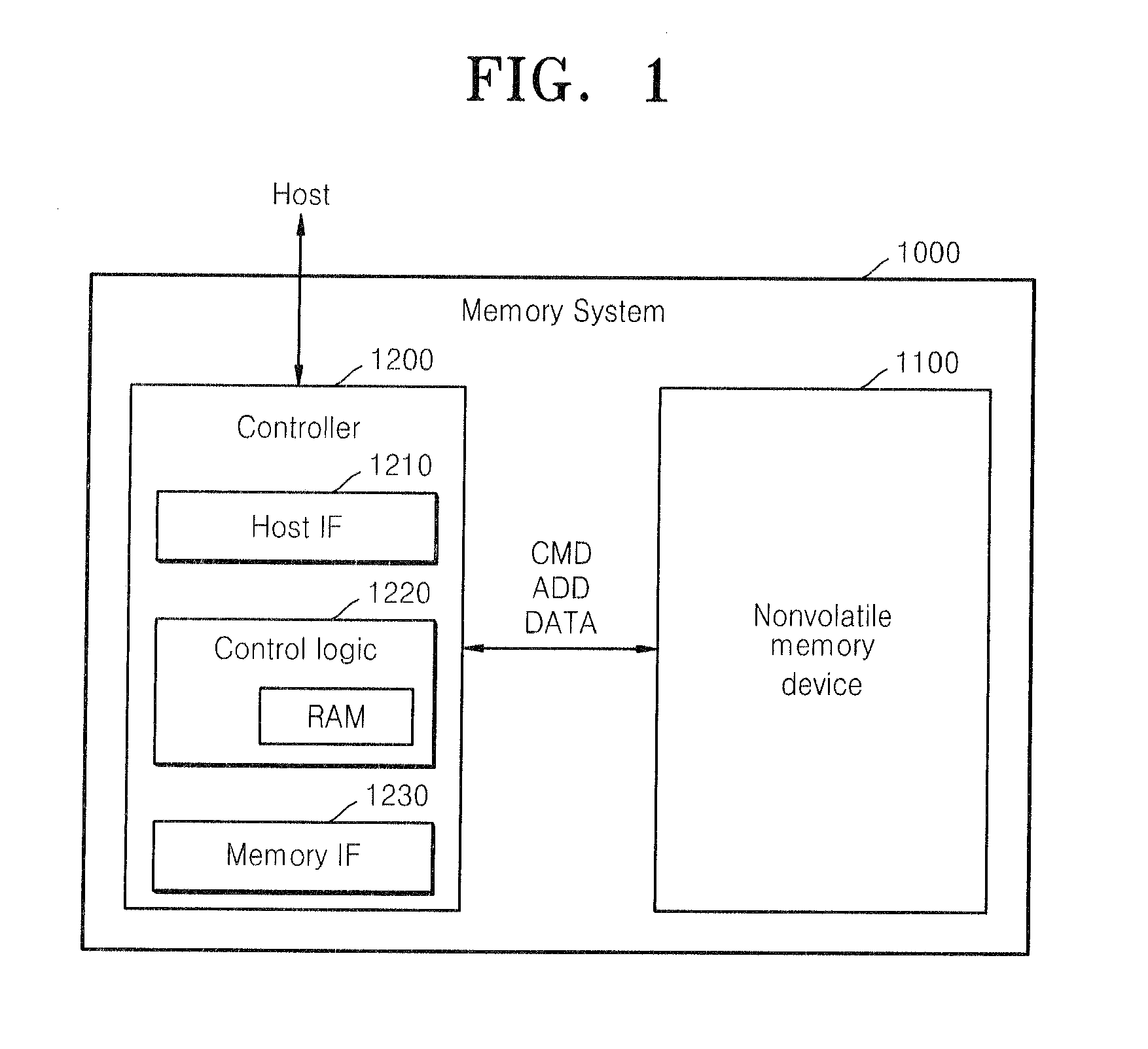
System and method for simplifying cache coherence using multiple write policies
ActiveUS20130254488A1Improve power efficiencyReduce hardware costsEnergy efficient ICTMemory adressing/allocation/relocationCache hierarchyCache coherence
System and methods for cache coherence in a multi-core processing environment having a local / shared cache hierarchy. The system includes multiple processor cores, a main memory, and a local cache memory associated with each core for storing cache lines accessible only by the associated core. Cache lines are classified as either private or shared. A shared cache memory is coupled to the local cache memories and main memory for storing cache lines. The cores follow a write-back to the local memory for private cache lines, and a write-through to the shared memory for shared cache lines. Shared cache lines in local cache memory enter a transient dirty state when written by the core. Shared cache lines transition from a transient dirty to a valid state with a self-initiated write-through to the shared memory. The write-through to shared memory can include only data that was modified in the transient dirty state.
Owner:ETA SCALE AB
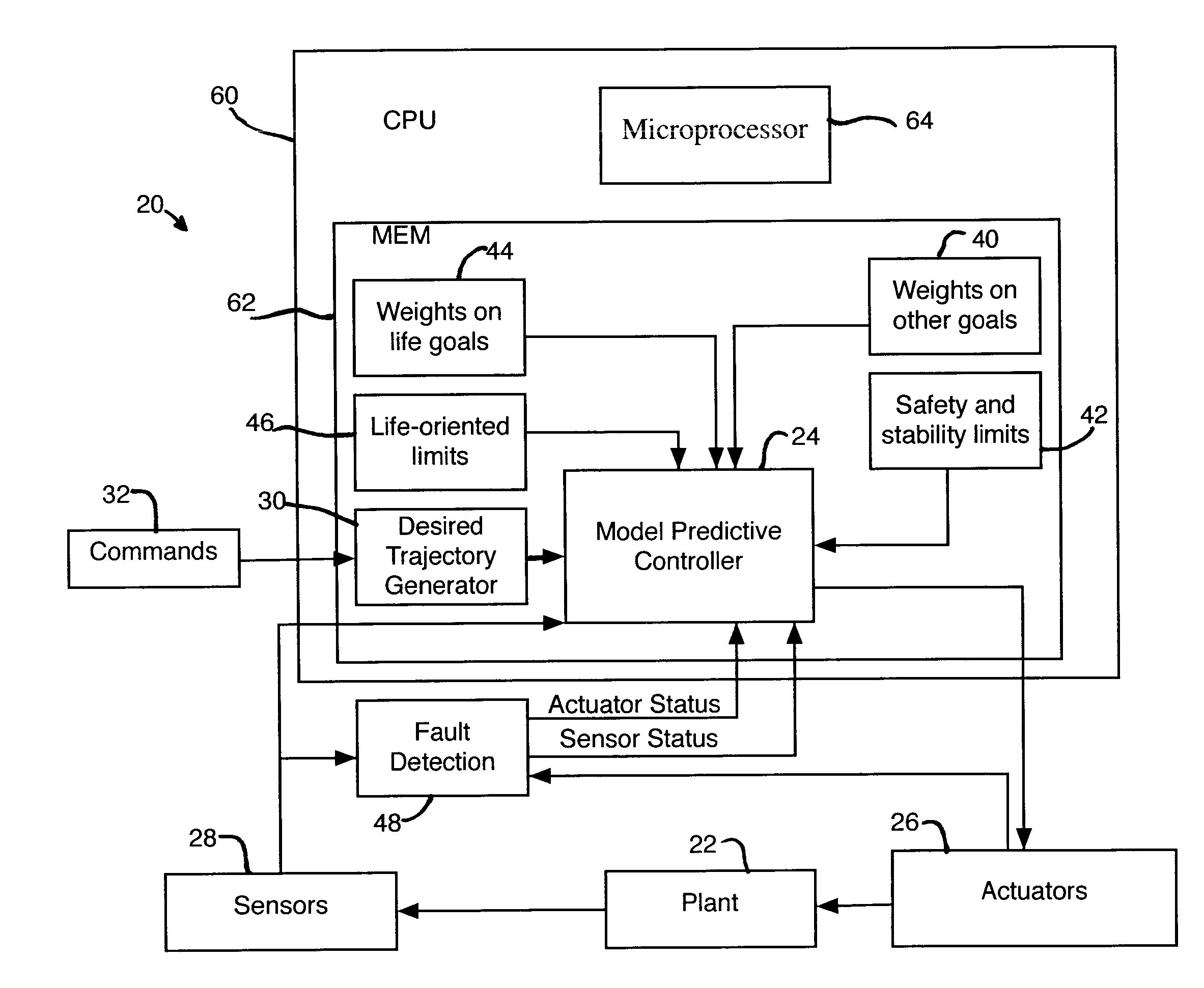
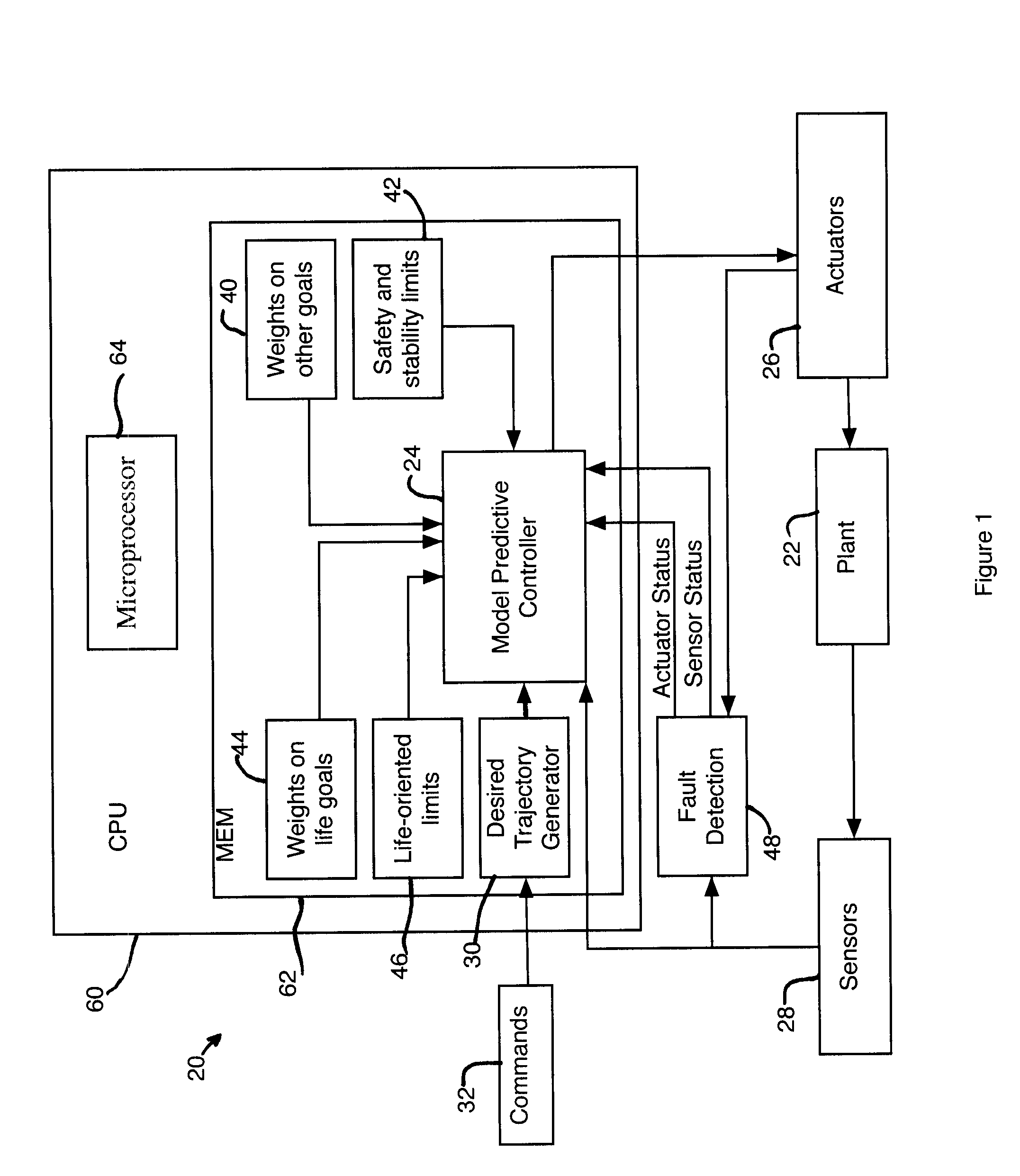
Model predictive controller with life extending control
ActiveUS7203554B2Reduce in quantityProlong lifeElectric testing/monitoringSpecial data processing applicationsControl systemPredictive controller
An MPC Control system provides a life extending control that includes life-extending goals in the performance index of the MPC controller and limits in the inequality equations. The MPC controller performs the normal functions of a control system for a physical system, but does so in a manner that extends the life or time-to-next maintenance or reduces the number of parts that need to be replaced. If the life extending functions do not degrade other control functions, they can be always enabled, making the system less expensive to maintain. If the life extending functions degrade some other control functions, they can be adjusted in-the-field or on-the-fly to stretch the time-until-maintenance until it is more convenient, but with some impact on performance.
Owner:RTX CORP
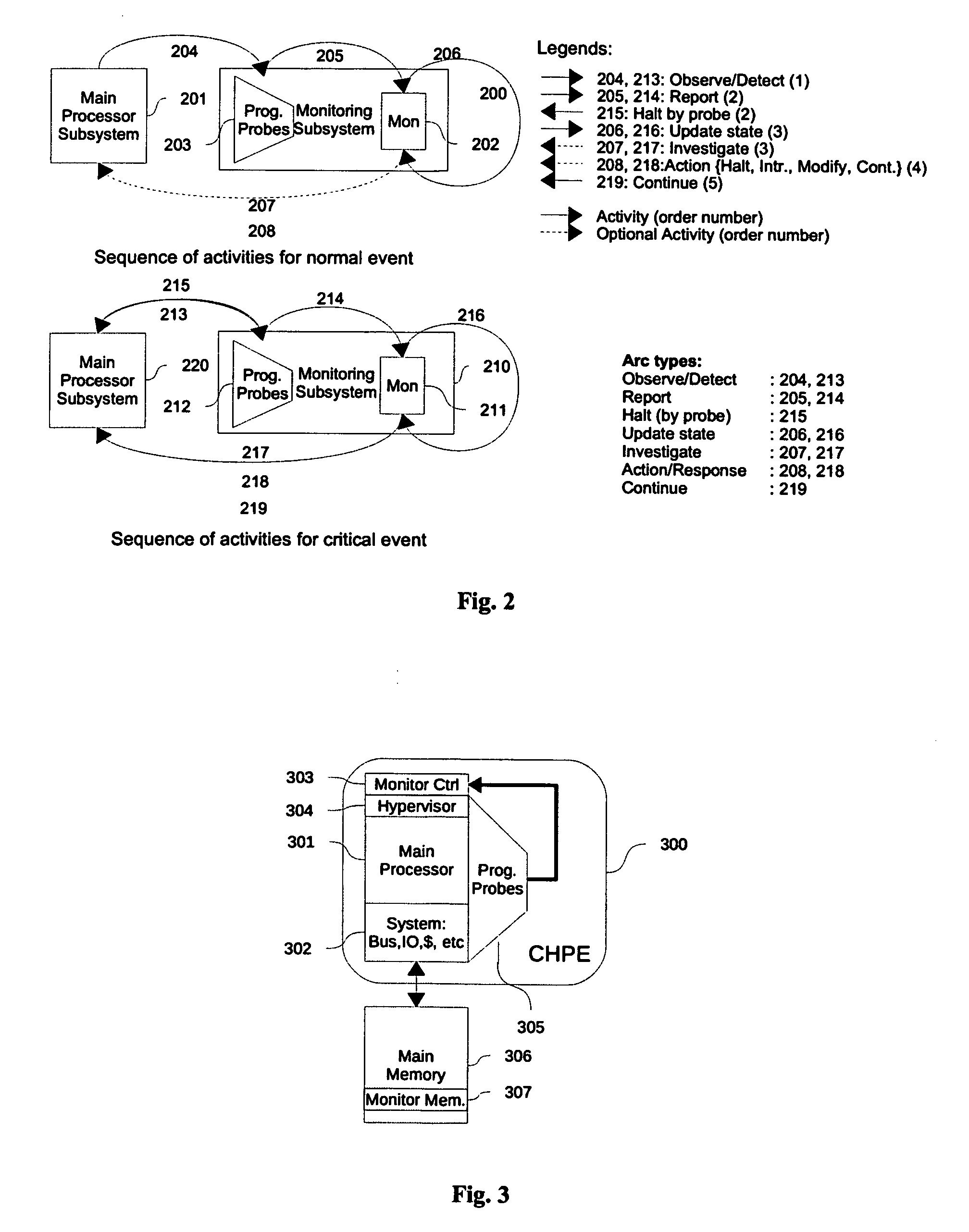
Cognizant engines: systems and methods for enabling program observability and controlability at instruction level granularity
ActiveUS20100107252A1Improve performanceEfficient powerMemory loss protectionError detection/correctionGranularityControllability
The present invention is directed to system for and methods of real time observing, monitoring, and detecting anomalies in programs' behavior at instruction level. The hardware assist design in this invention provides fine grained observability, and controllability. Fine grained observability provides unprecedented opportunity for detecting anomaly. Controllability provides a powerful tool for stopping anomaly, repairing the kernel and restoring the state of processing. The performance improvement over pure software approach is estimated to be many orders of magnitudes. This invention is also effective and efficient in detecting mutating computer viruses, where normal, signature based, virus detection is under performing.
Owner:MERTOGUNO SUKAMO
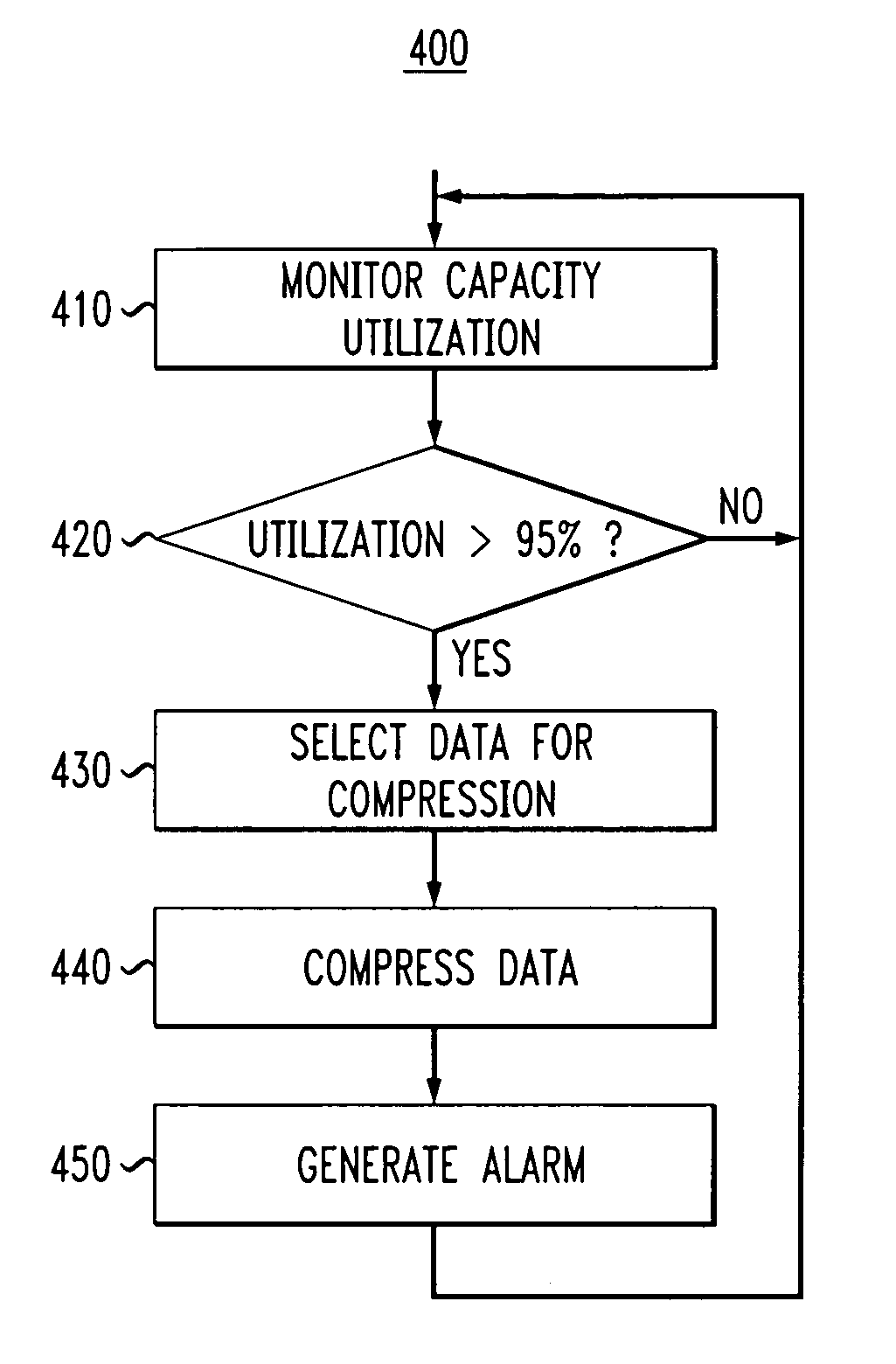
Method and apparatus for increasing virtual storage capacity in on-demand storage systems
InactiveUS20070150690A1Increasing virtual storage capacityReduce utilizationMemory systemsInput/output processes for data processingData compressionPhysical space
A method and apparatus are disclosed for increasing virtual storage capacity in on-demand storage systems. The method utilizes data compression to selectively compress data stored in a storage resource to reduce the utilization of physical storage space whenever such physical resources have been over committed and the demand for physical storage exceeds its availability. In one exemplary embodiment, the utilization of the capacity of a shared storage resource is monitored and data is selected for compression based on the utilization. The compression of the selected data is triggered in response to the monitoring results. In addition, policies and rules are defined that determine which data is selected for compression. For example, the selection of data may be based on one or more of the following: a degree of utilization of said capacity of said shared storage resource, a volume size of said data, an indicator of compressibility of said data, a frequency of use of said data, a manual selection of said data, and a predefined priority of said data. The disclosed methods improve the operation of virtual allocation by further enhancing the availability of physical space through data compression. Virtual allocation and block-based data compression techniques are utilized to improve storage efficiency with a minimal risk to system availability and reliability and with a minimal impact to performance (access time and latency).
Owner:IBM CORP
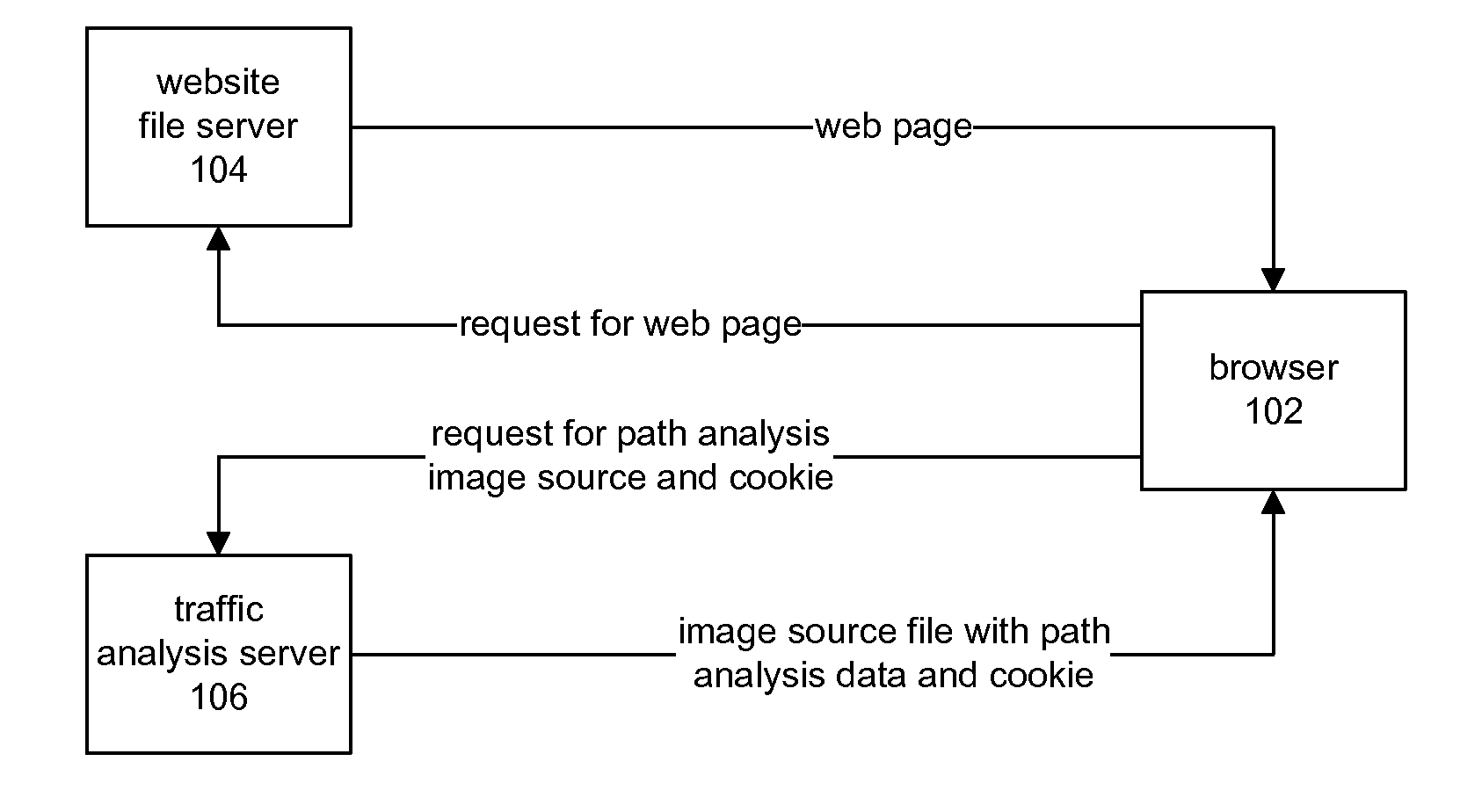
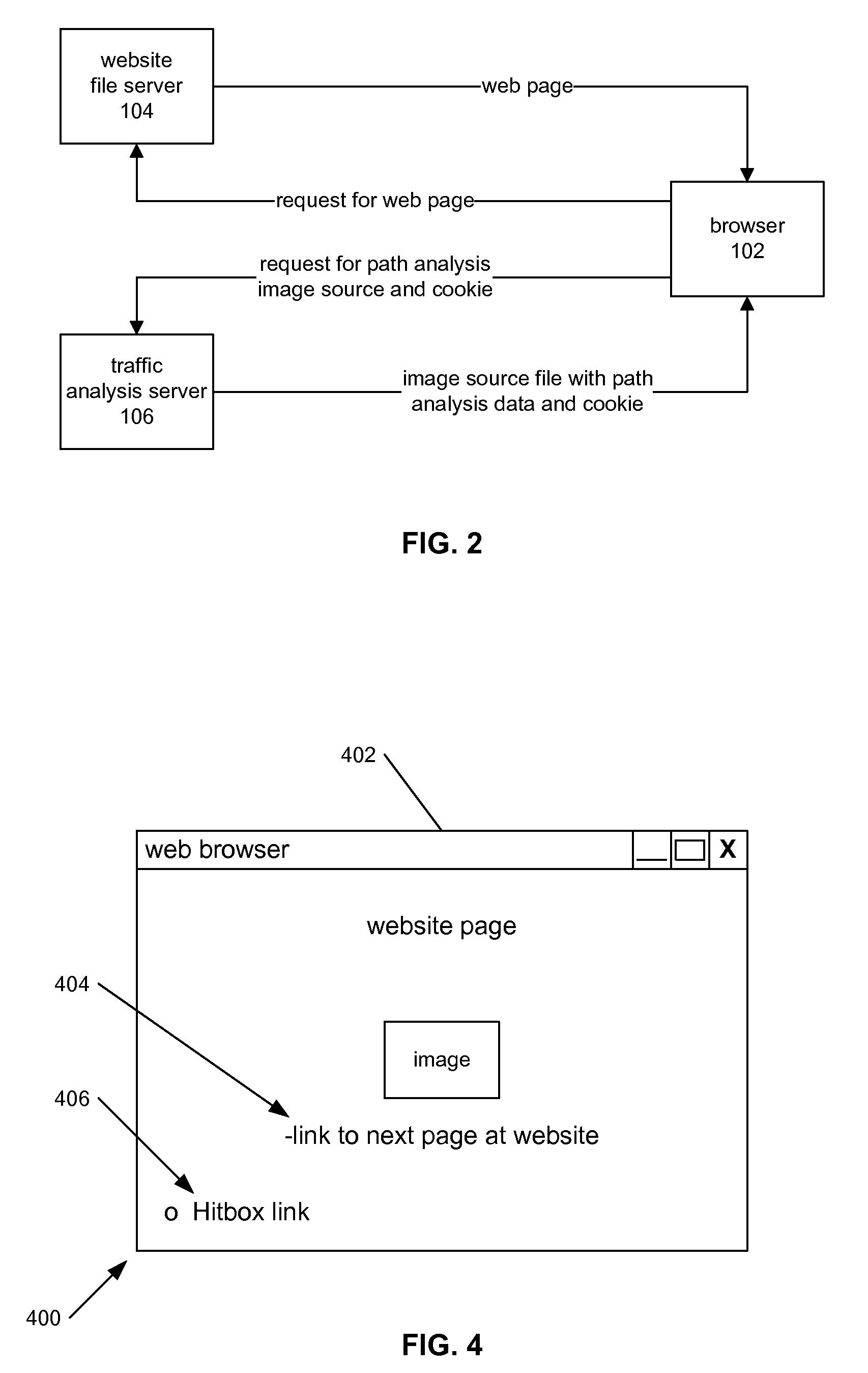
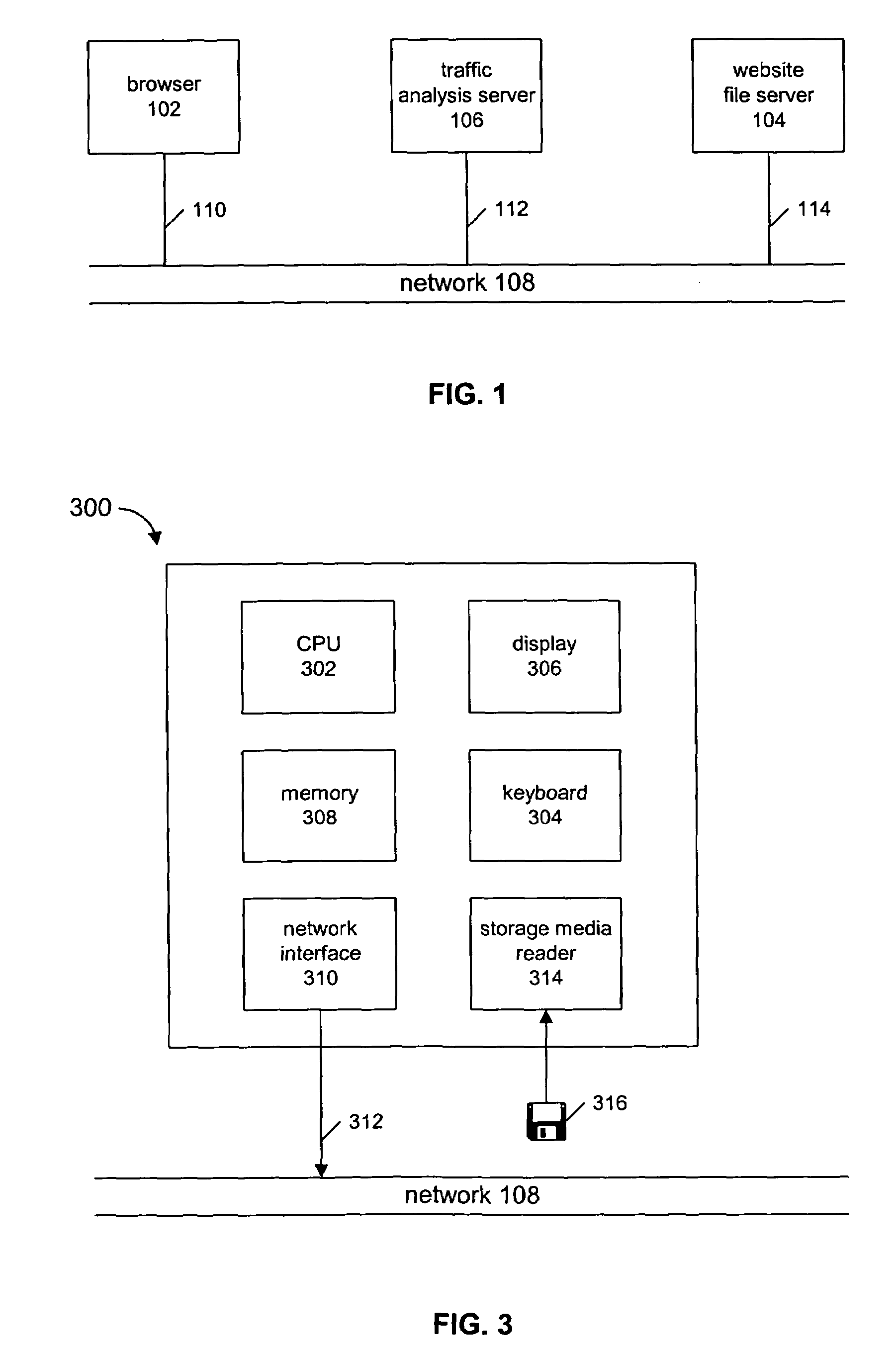
Internet Website Traffic Flow Analysis
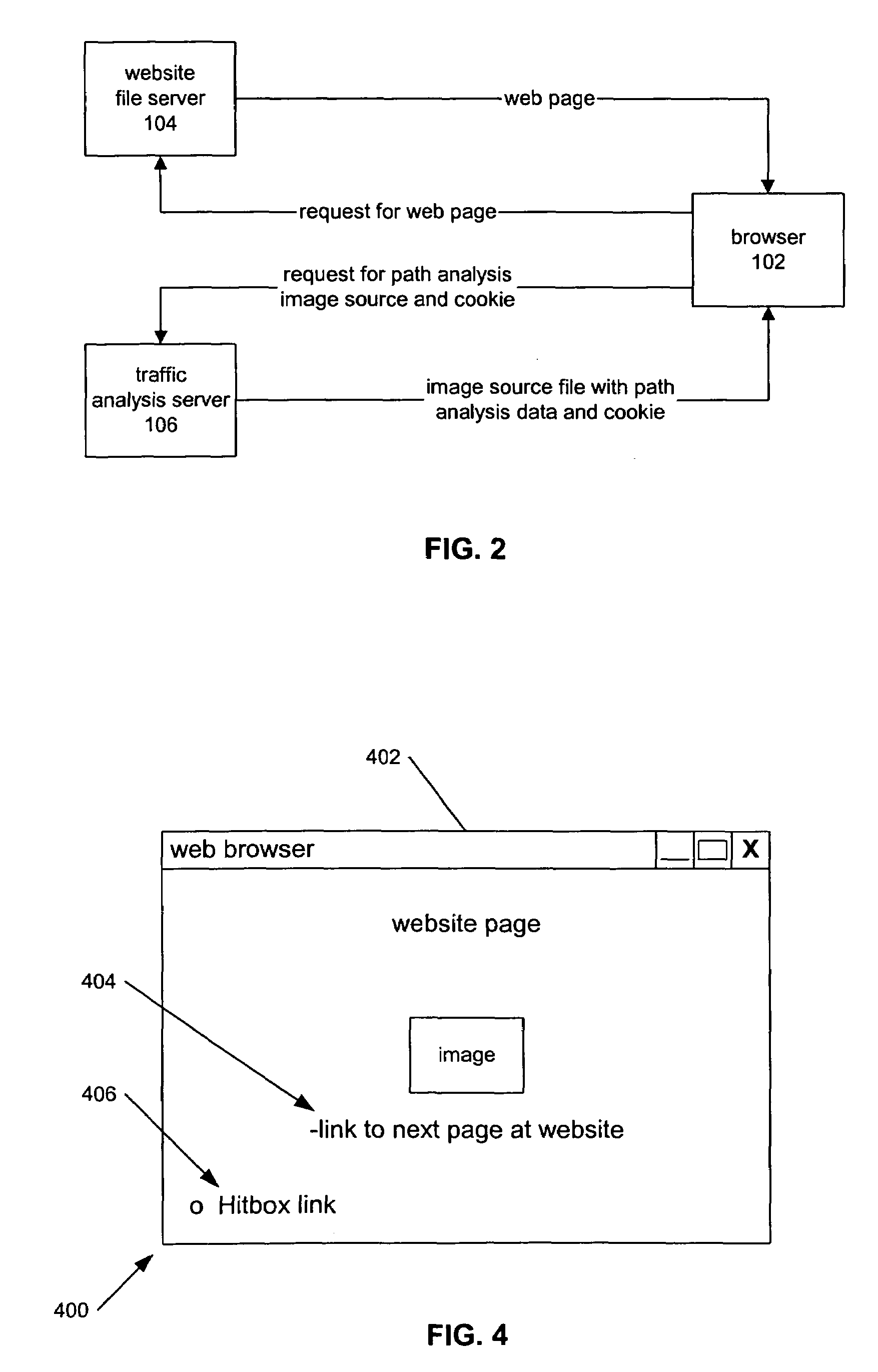
InactiveUS20090083421A1Accurate collectionAccurately studiedHardware monitoringMultiple digital computer combinationsWeb siteAnalysis tools
An Internet-based analysis tool follows, in real-time, the flow of traffic through a website. For every website page requested by a website visitor, the state of the visitor's browser is recorded and data relating to the path visitors take through the website is collected and studied. The state of the visitor's browser path is maintained in a traffic analysis cookie that is passed between a website file server and the visitor browser with every page requested for viewing. The cookie is maintained in a size that can be passed from server to browser and back again without negatively impacting server performance and without negatively impacting browser performance. The data in the cookie can follow the visitor browser through independent file servers, regardless of how the pages of a website might be distributed in storage.
Owner:ADOBE SYST INC
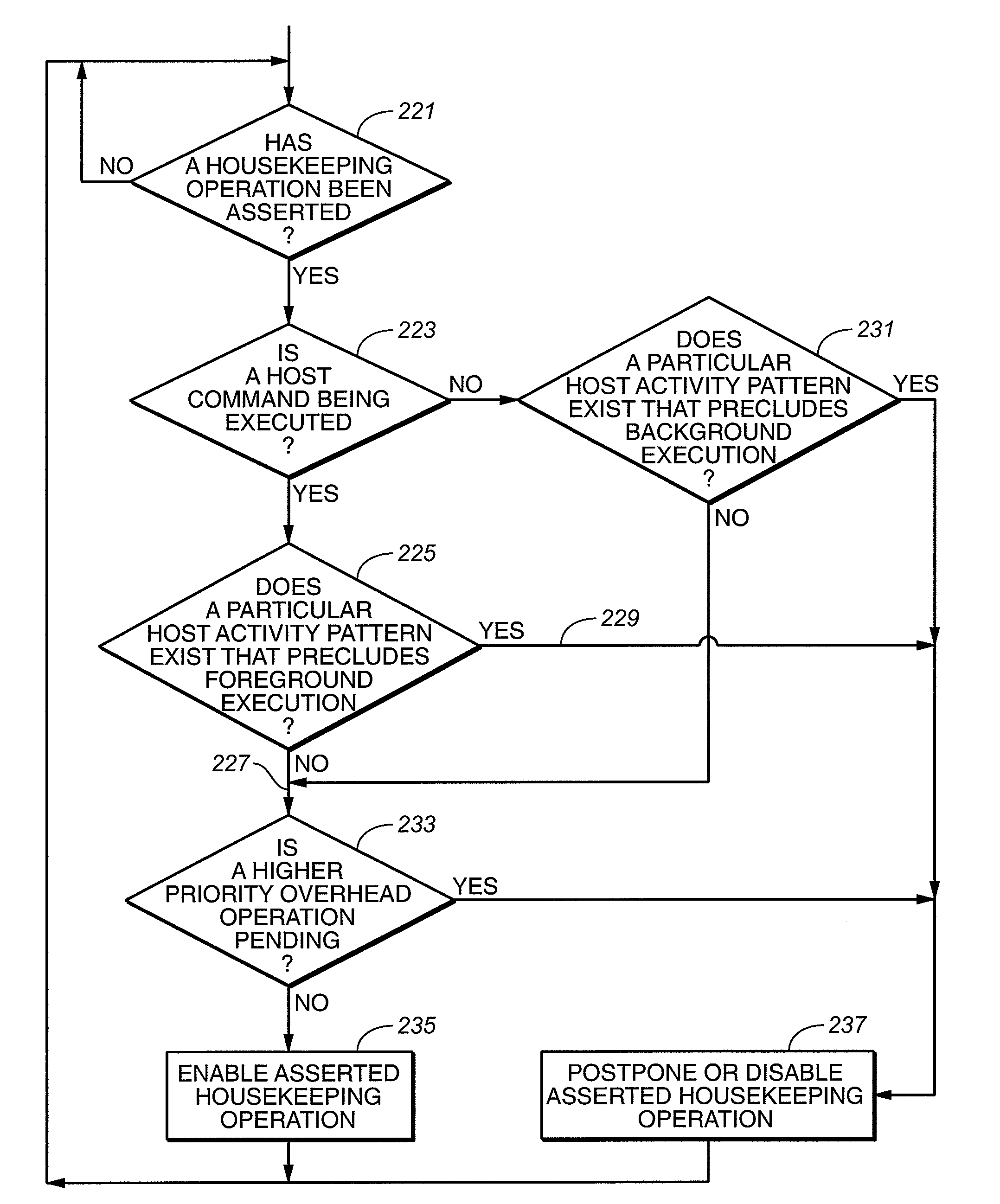
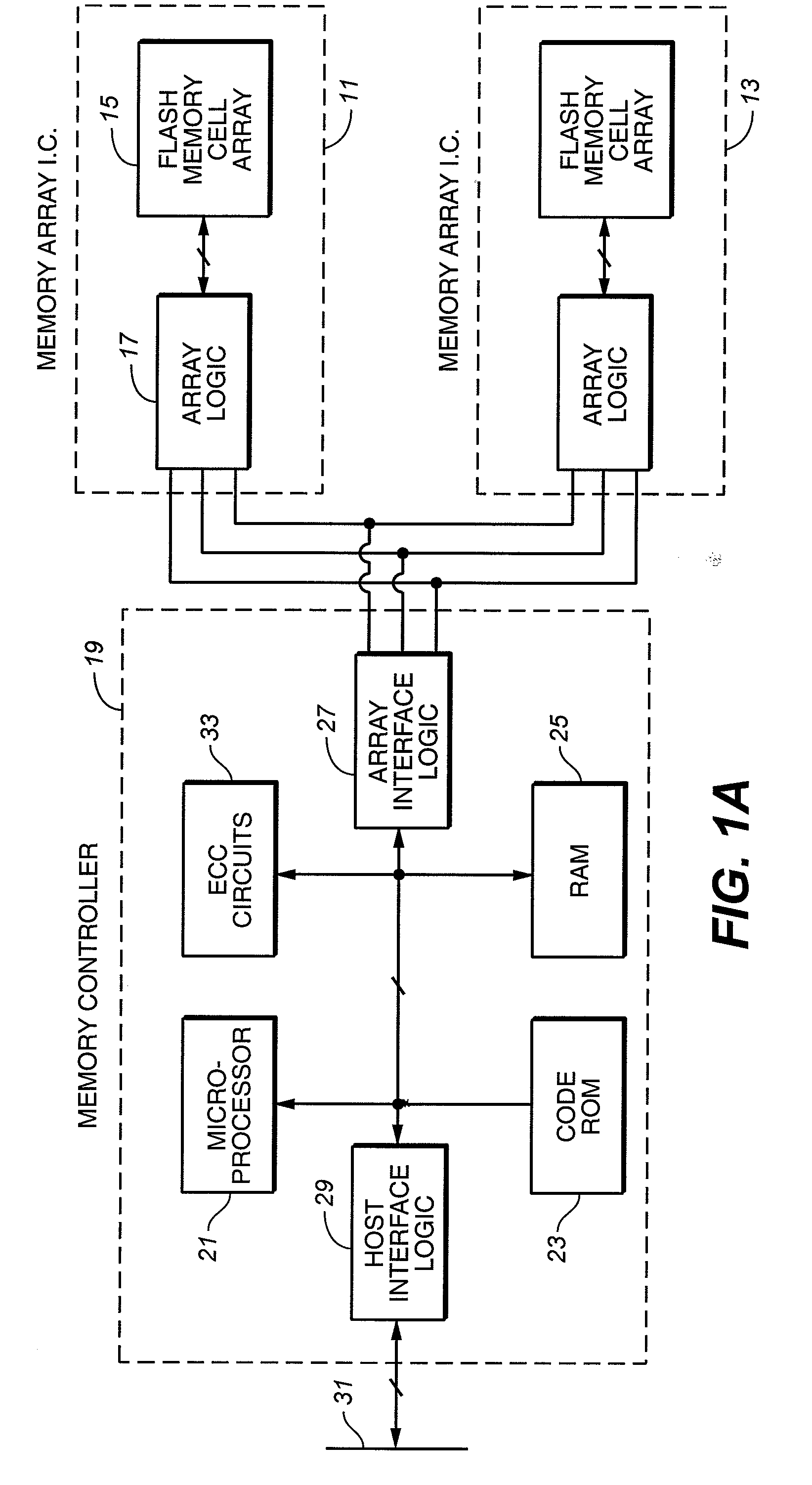
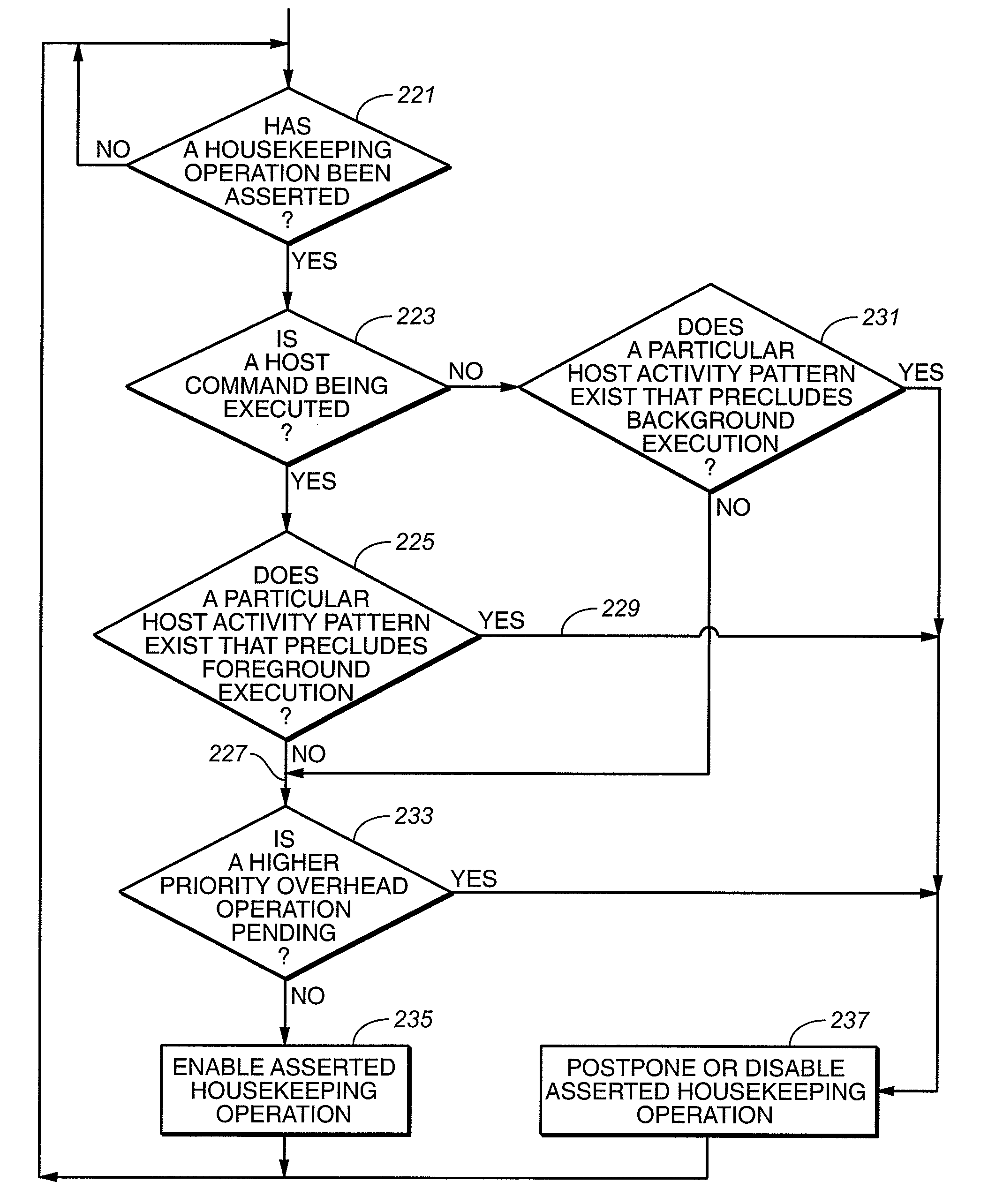
Flash Memory System with Management of Housekeeping Operations
InactiveUS20080294814A1Reduce transfer speedImpact performanceRead-only memoriesElectric digital data processingNon-volatile memoryMemory systems
A flash re-programmable, non-volatile memory system is operated to disable foreground execution of housekeeping operations, such as wear leveling and data scrub, in the when operation of the host would be excessively slowed as a result. One or more characteristics of patterns of activity of the host are monitored by the memory system in order to determine when housekeeping operations may be performed without significantly degrading the performance of the memory system, particularly during writing of data from the host into the memory.
Owner:SANDISK TECH LLC
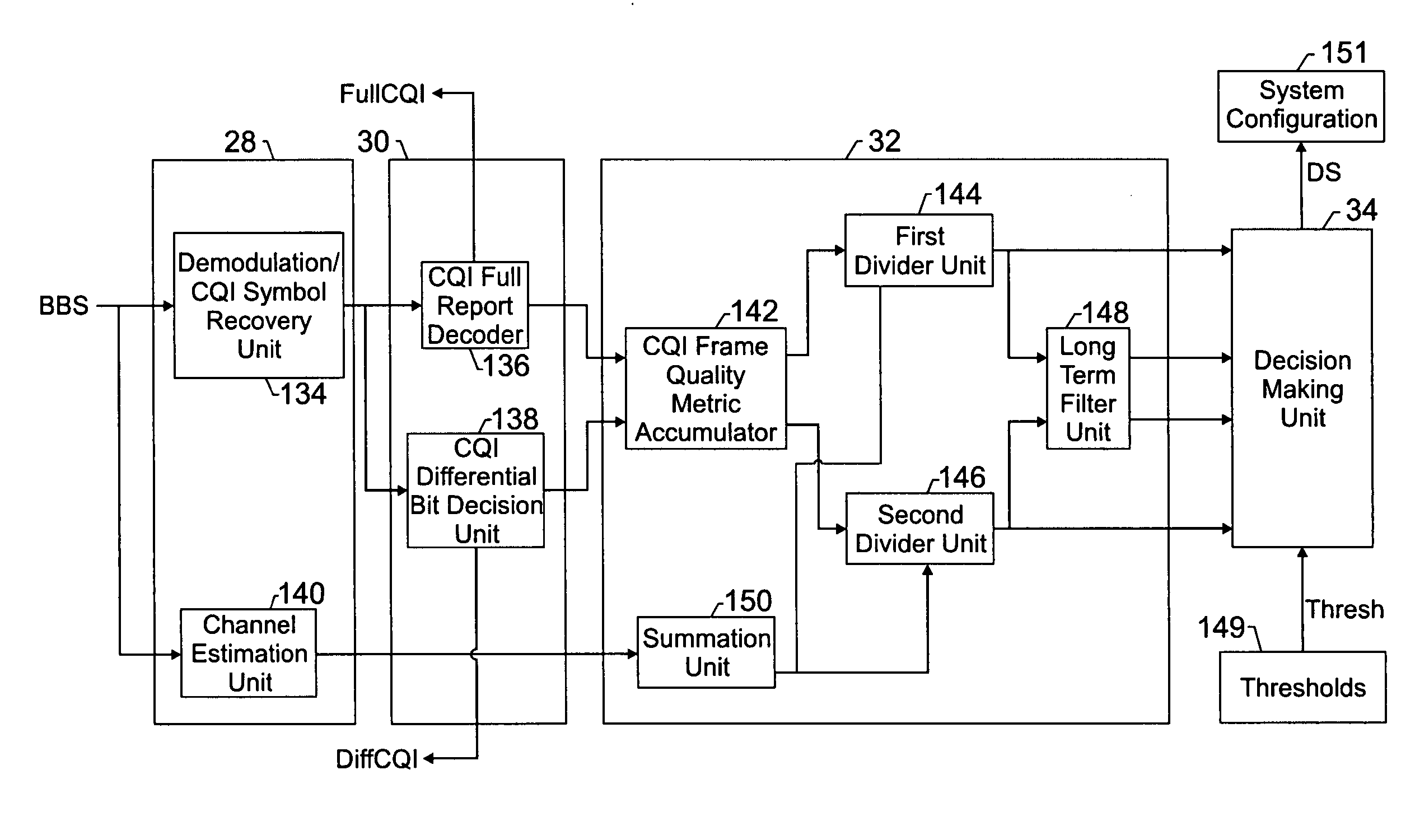
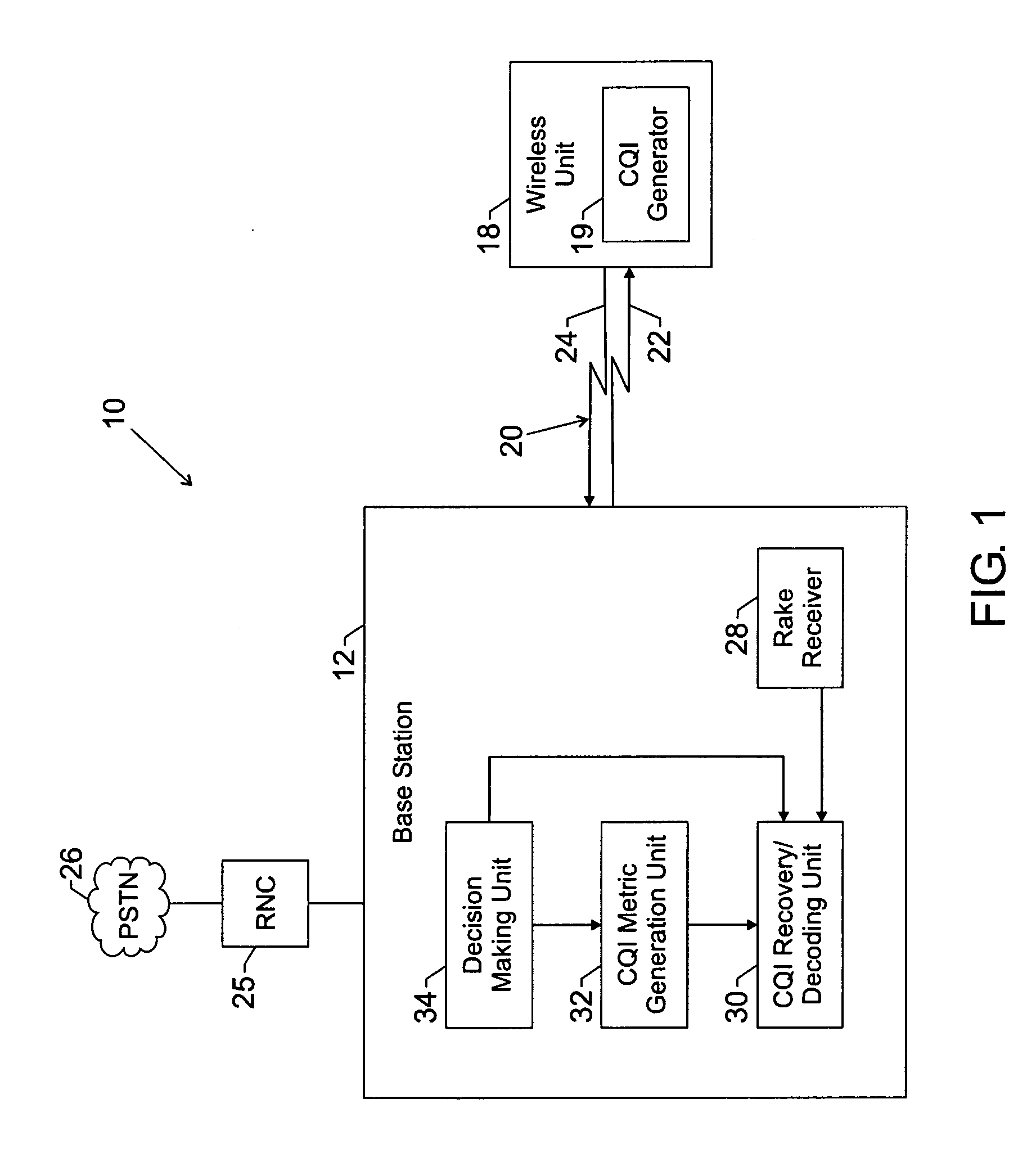
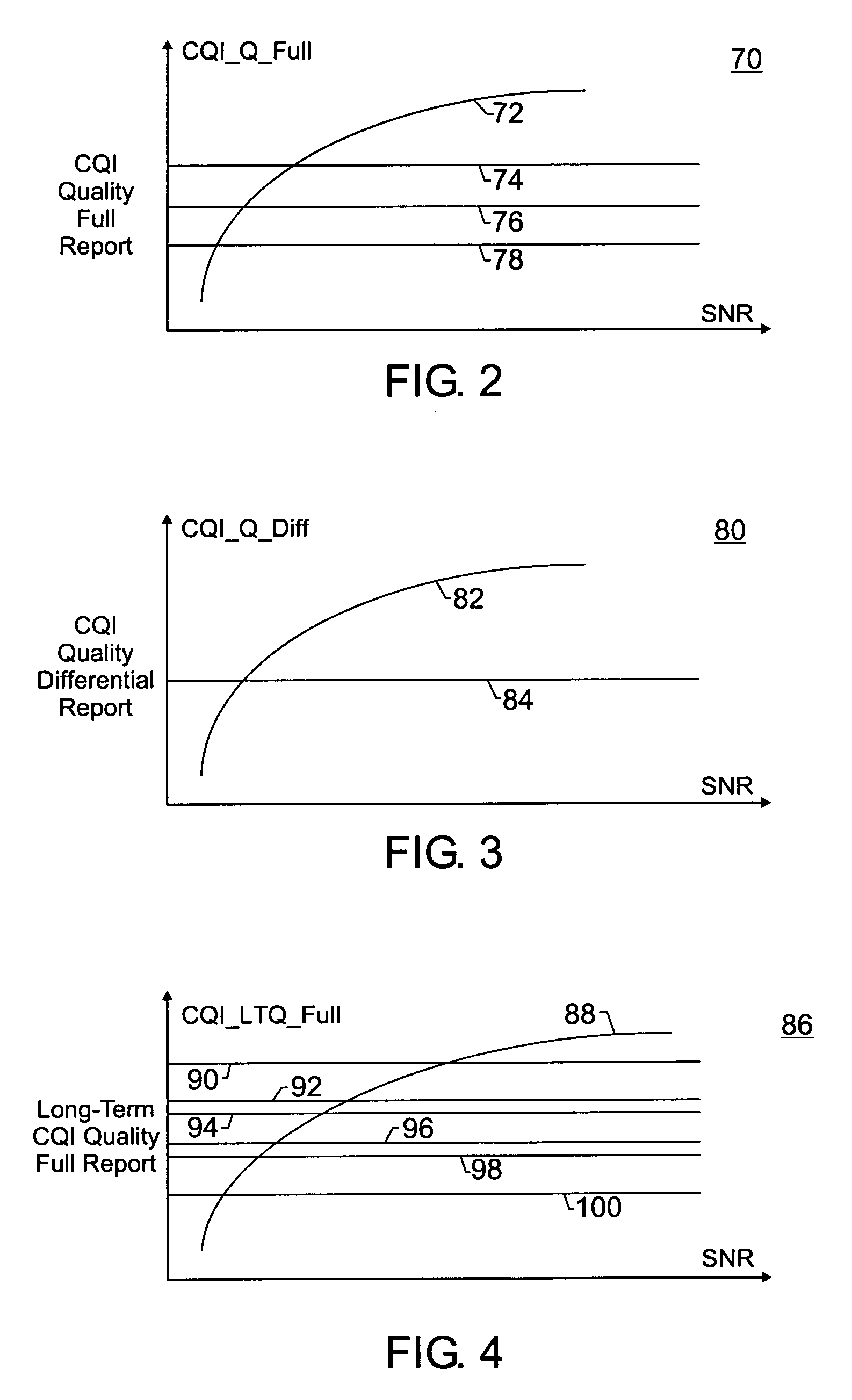
Utilization of overhead channel quality metrics in a cellular network
ActiveUS20060072508A1Maintain qualityReduce power consumptionPower managementNetwork traffic/resource managementData transmissionBase station
In a 3G cellular network, a Reverse Link Channel Quality Indicator Channel (R-CQICH) may be transmitted on a reverse link to support forward link high-speed data transmissions. Accordingly, the R-CQICH may be utilized to track the quality of the signal path between the wireless unit and the base station. The base station may include a CQI component that utilizes a received Channel Quality Indicator (CQI) signal from the wireless unit to generate CQI quality metrics based on the quality of the received signal. Also, the CQI quality metrics may be compared to different thresholds to adjust various system configurations in the base station. The base station may also provide feedback to the wireless unit with the updated system configurations. This technique allows CQI quality metrics to be utilized to adjust system configurations dynamically and enhance the operation of a wireless system.
Owner:WSOU INVESTMENTS LLC
Fused silica having high internal transmission and low birefringence
InactiveUS20040162211A1Increase transmissionLow absolute maximum birefringencePhotomechanical exposure apparatusMicrolithography exposure apparatusTransmittancePolymer chemistry
Fused silica members having high internal transmission and low birefringence are disclosed. Methods of making such fused silica members are also disclosed. According to the present invention, fused silica members having an internal transmission equal to or greater than 99.65% / cm at 193 nm and having an absolute maximum birefringence along the use axis of less than or equal to 0.75 nm / cm are provided.
Owner:DOMEY JEFFREY J +7
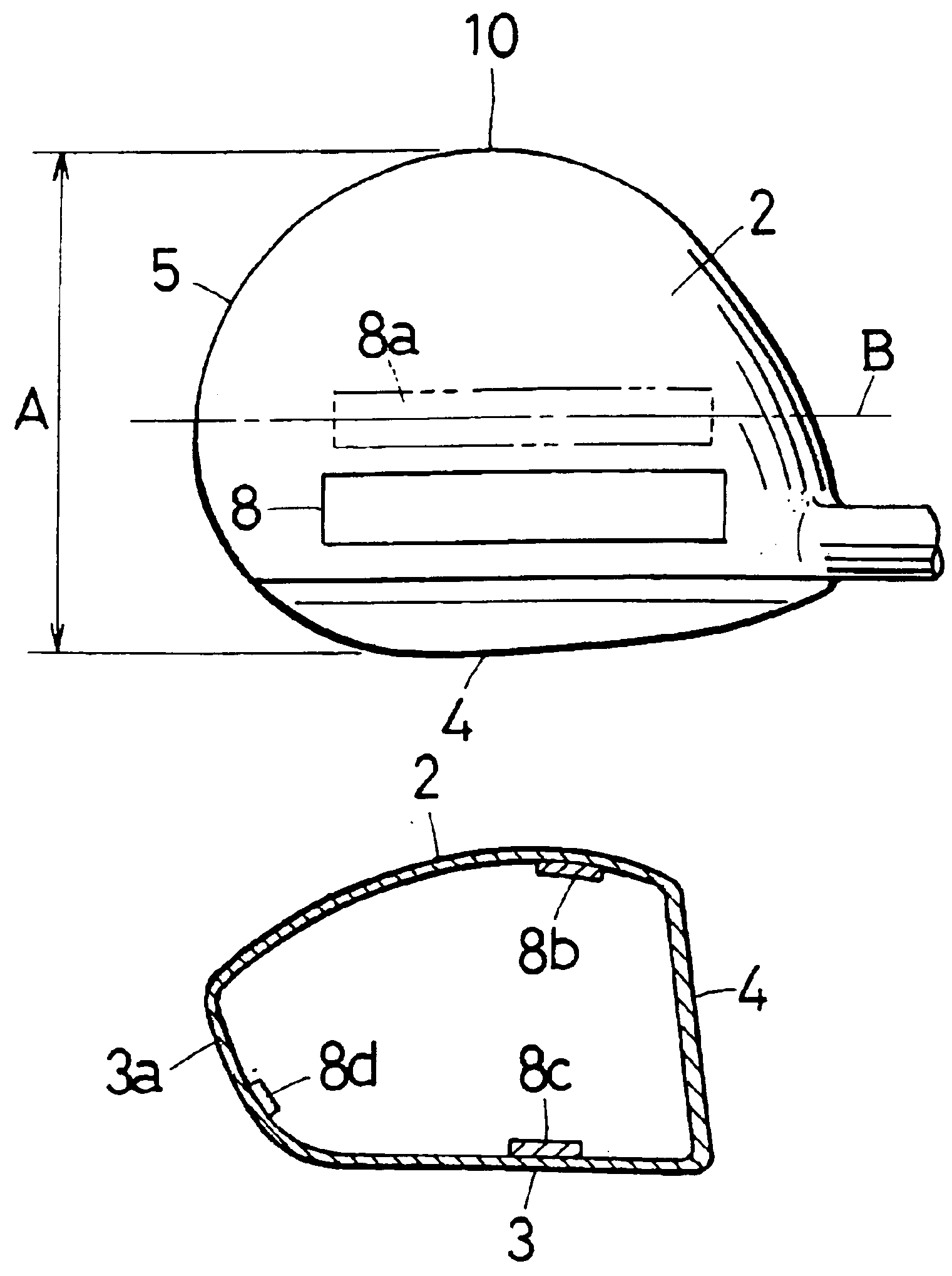
Golf club
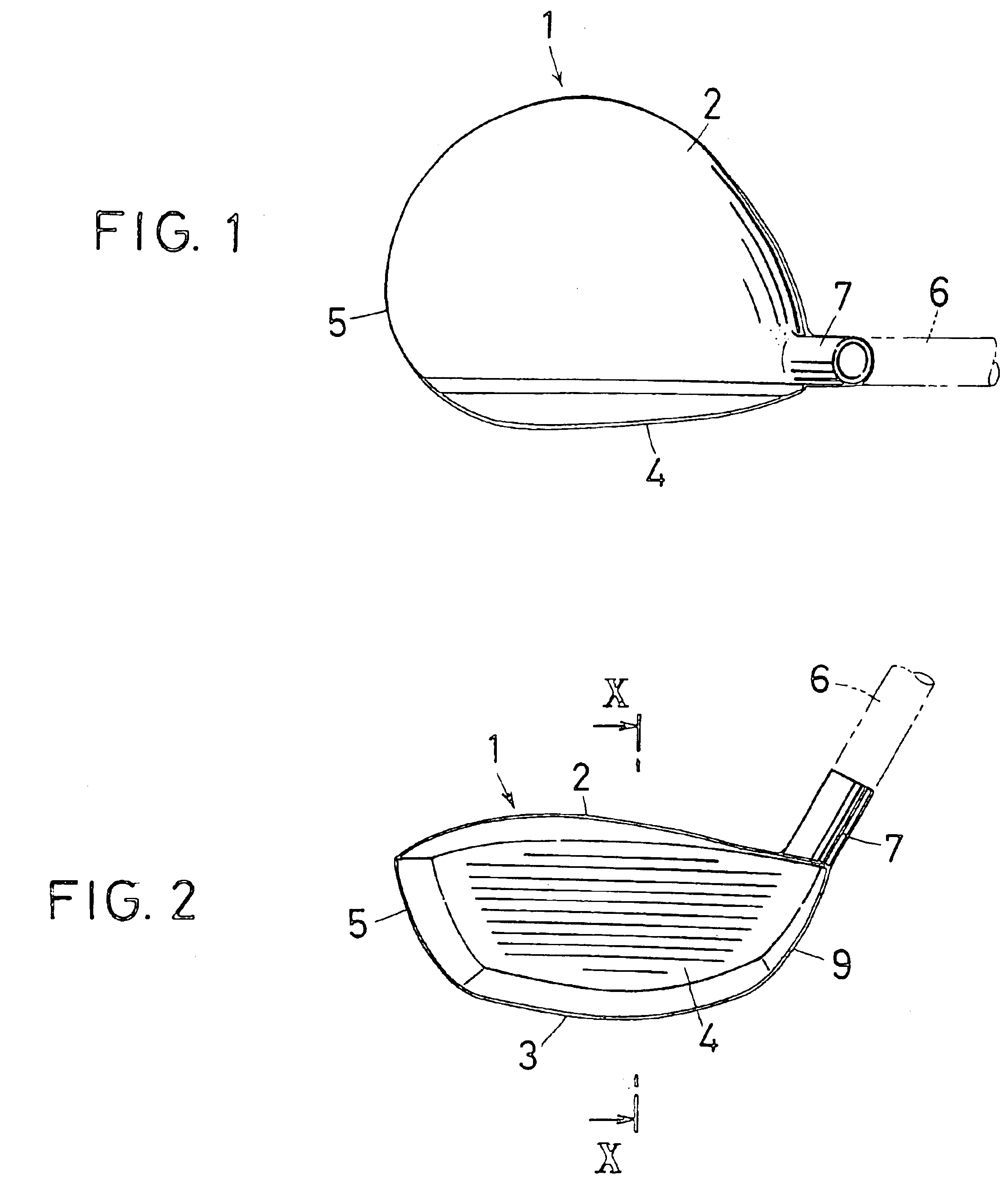
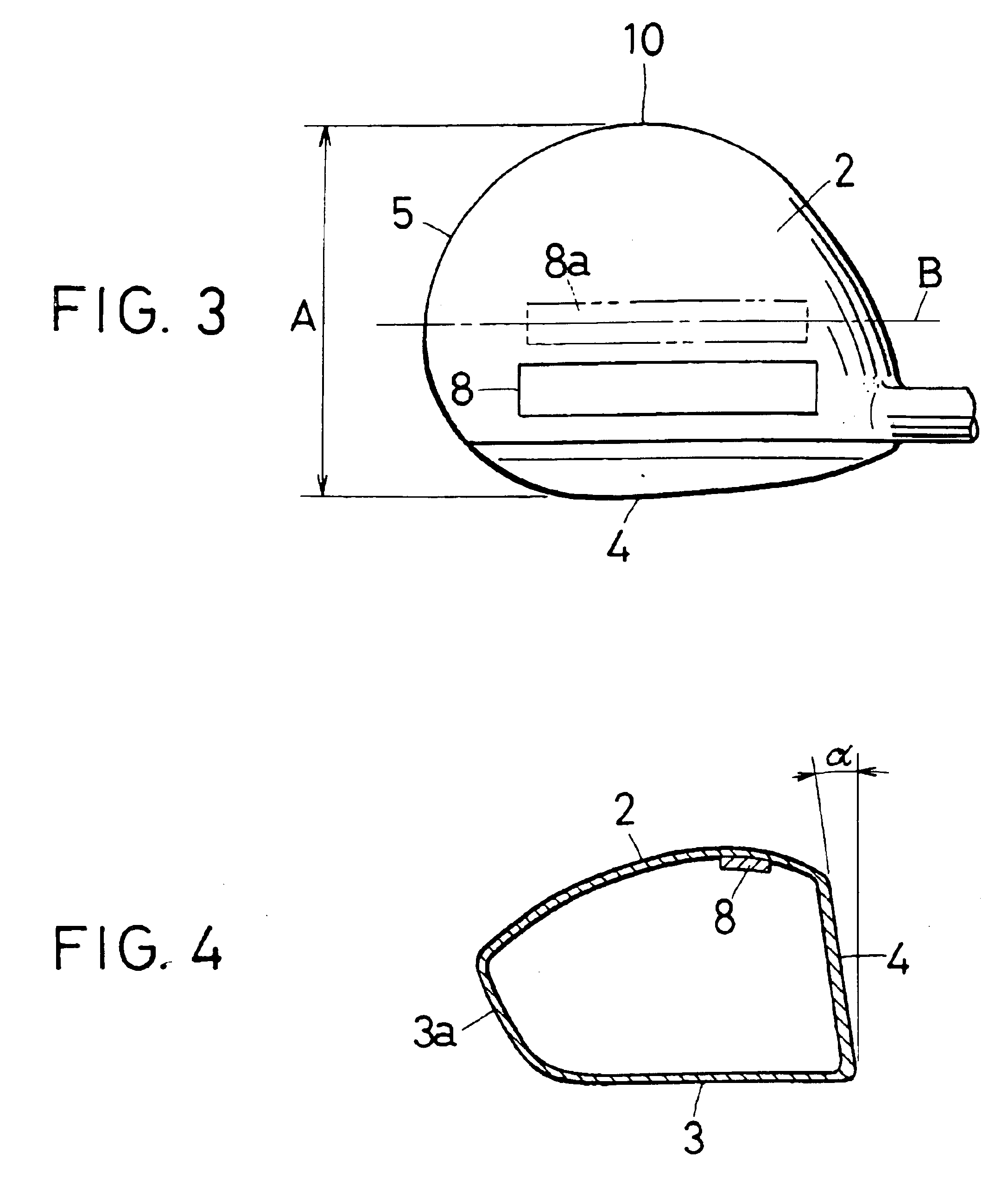
InactiveUS6945877B2Long carryAmount of backspin can be decreasedGolf clubsRacket sportsEngineeringGolf Ball
A golf club is provided in which, whether the loft angle is small or large, backspin is reduced and there is no decrease in carry. A golf club construction is obtained wherein, in a driver club head (1) comprising a face section 4 having a striking surface, a sole section (3) forming the bottom, a crown section (2) forming the top and a back section (3a) forming the back portion, when the loft angle is small, the amount of backspin is reduced and performance is maintained, and even when the loft angle is large, the amount of backspin is reduced and a good carry distance is achieved. For this purpose, the crown section (2) is improved, with the provision of a weight (8) on the inside surface thereof nearer to the face section than the center of the surface
Owner:ENDO MFG COMPANY +1
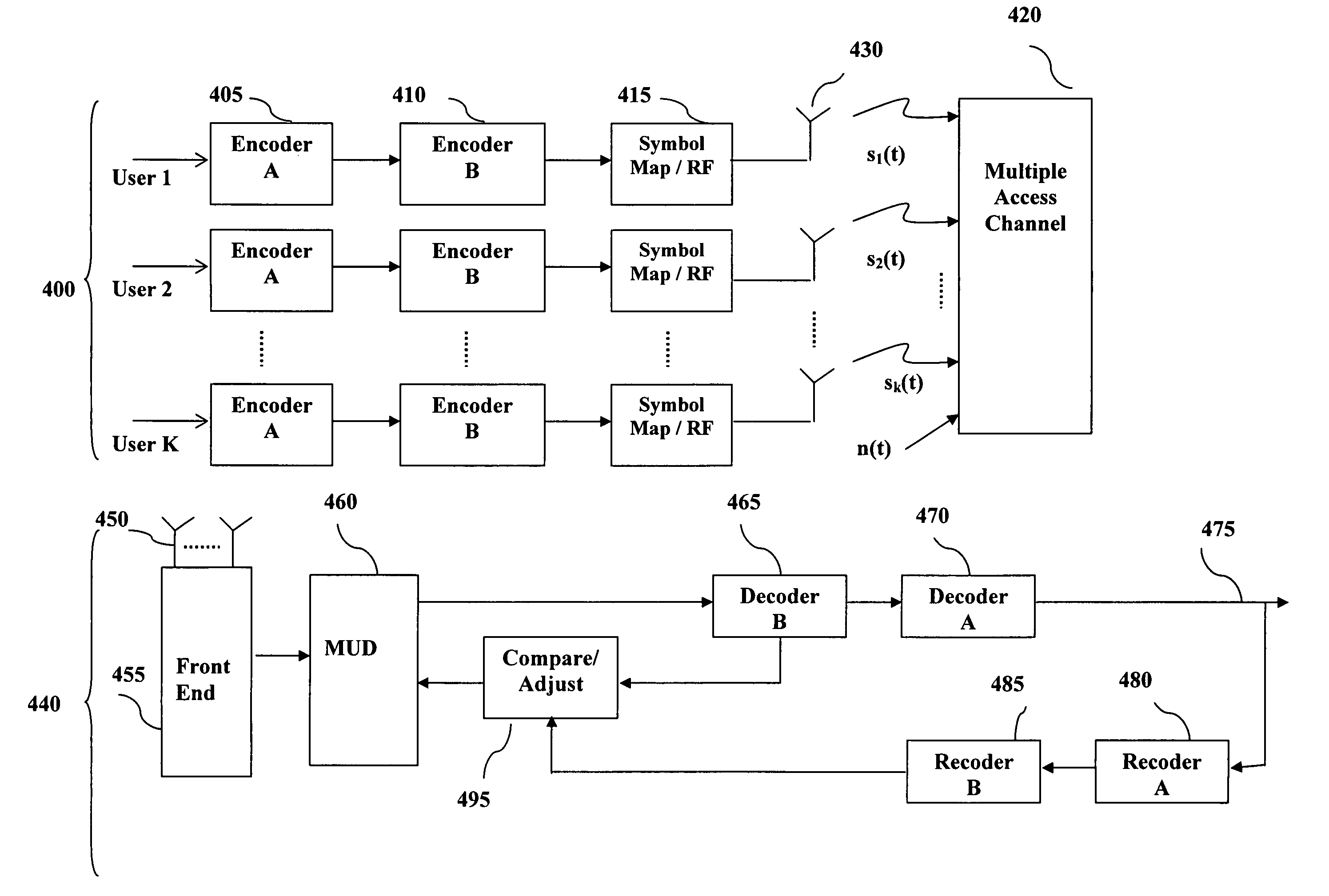
Reduced complexity multi-turbo multi-user detector
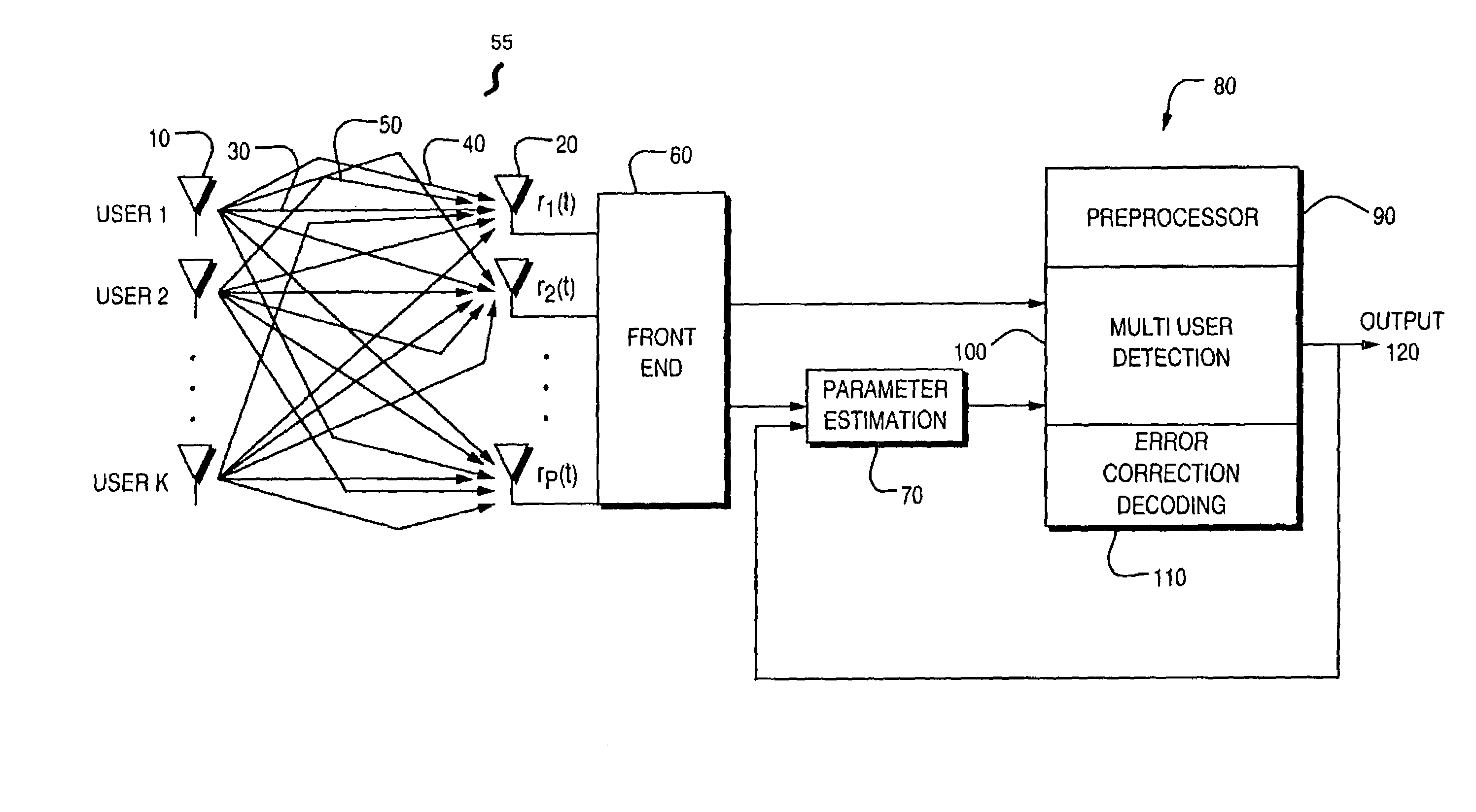
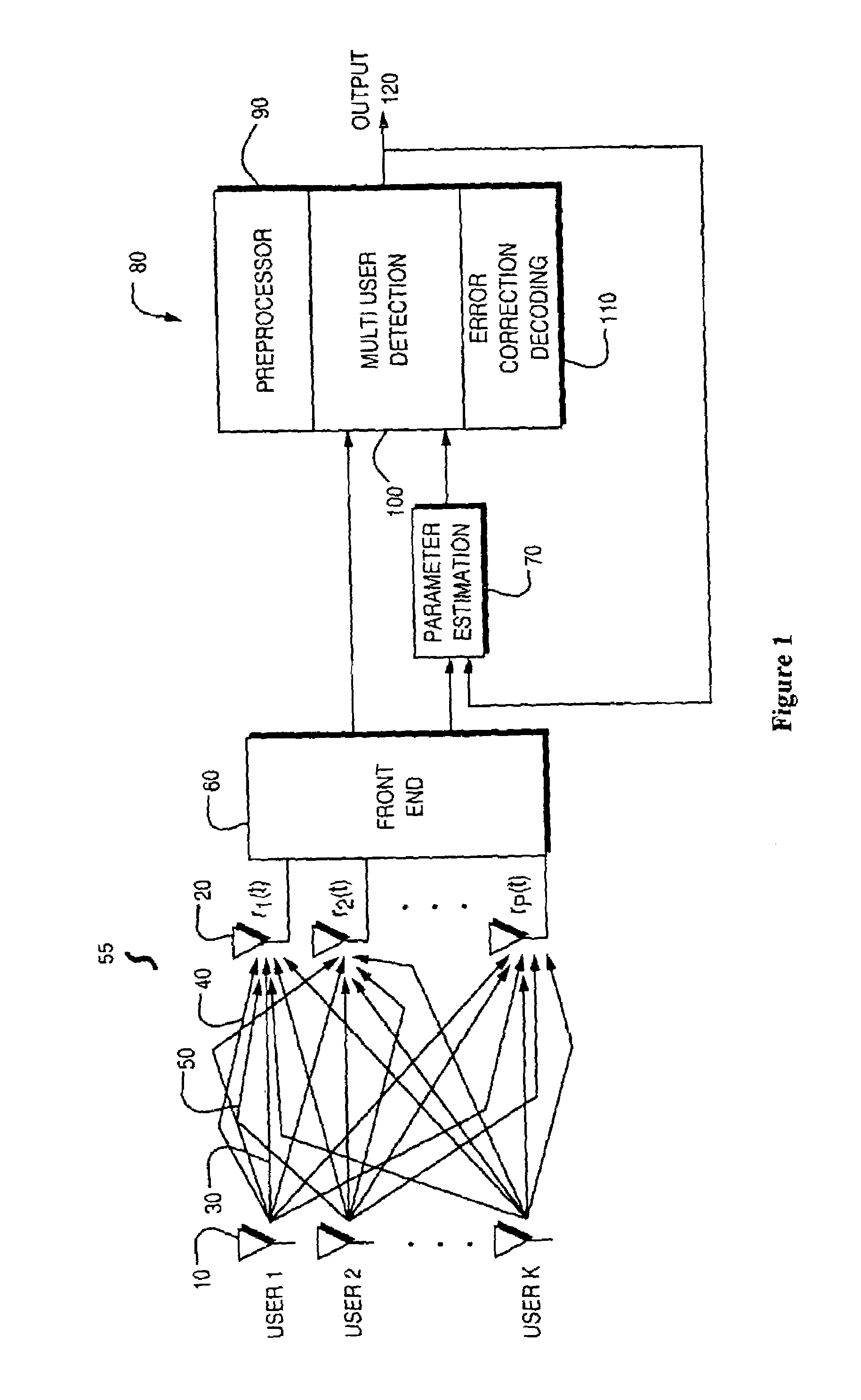
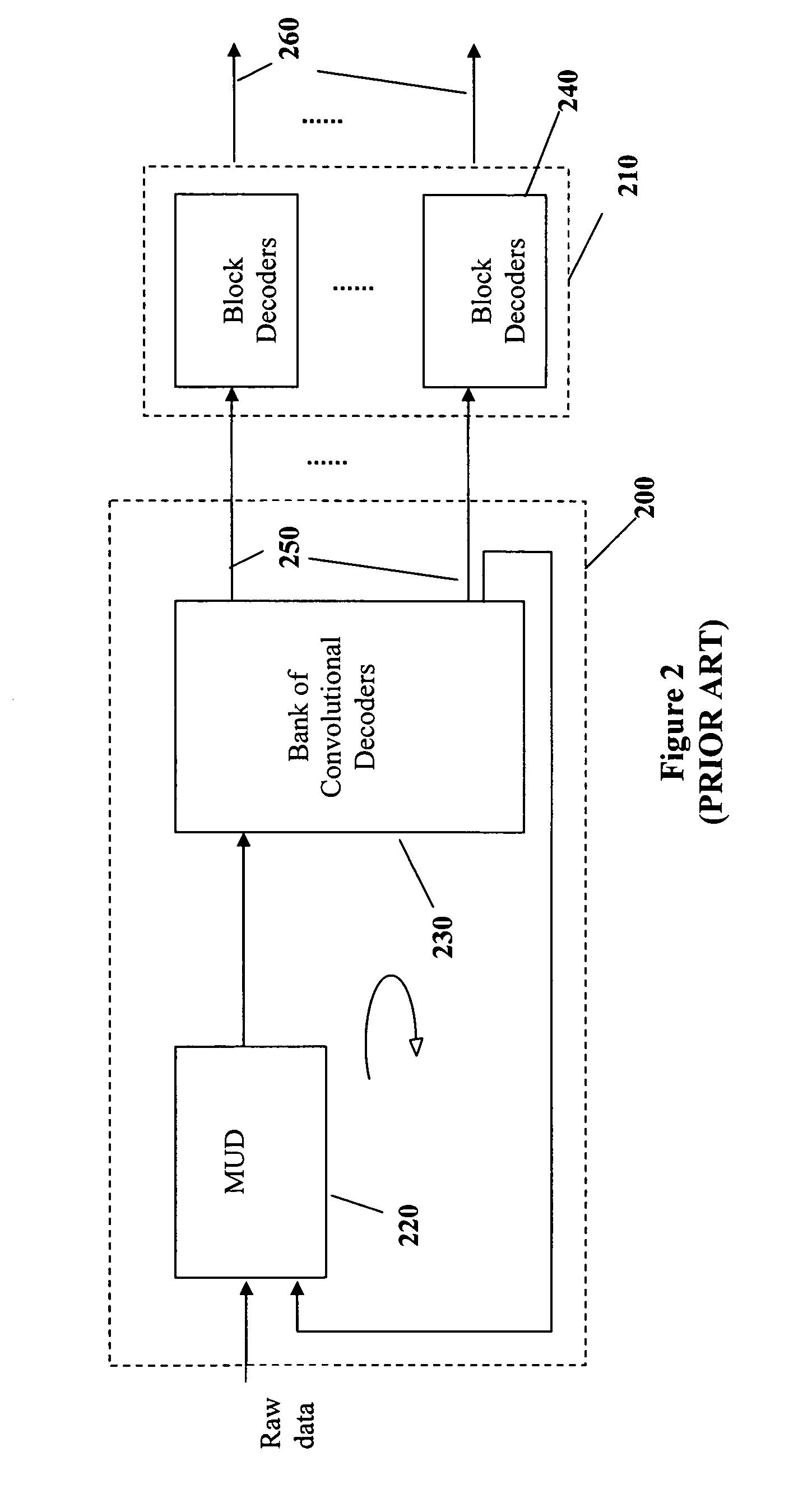
ActiveUS6967598B2Reduce the possibilityImprove performancePolarisation/directional diversityCode conversionPhase detectorRound complexity
A reduced complexity Turbo multi-user detector (MUD) processing system in multiple access communications channels that decreases the likelihood of improper decoding of the final values of interest and decreases the computation complexity for each iteration, thereby allowing for a reduction in the number of iterations performed and lowers the overall complexity without negatively impacting performance. In one form the present invention comprises a multi-user detector coupled to two or more decoder sections, two ore more recoders, and a compare and adjust section in such a manner that data flows iteratively to correct for errors in a computationally efficient manner.
Owner:COLLISION COMM INC
Age invariant face recognition using convolutional neural networks and set distances
ActiveUS20180293429A1Promote resultsEasy to identifyCharacter and pattern recognitionDigital data authenticationGeneralization errorNeural network learning
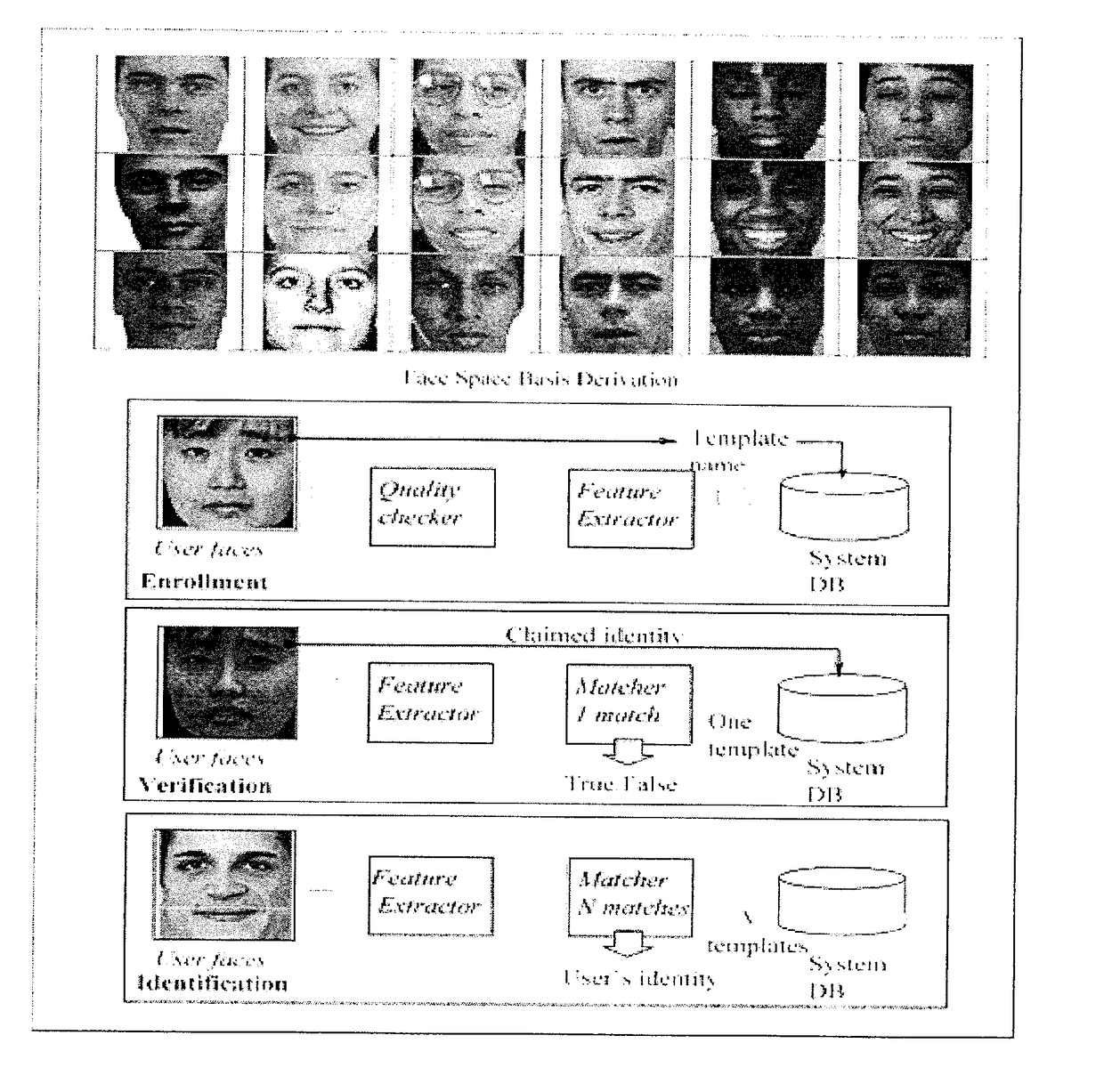
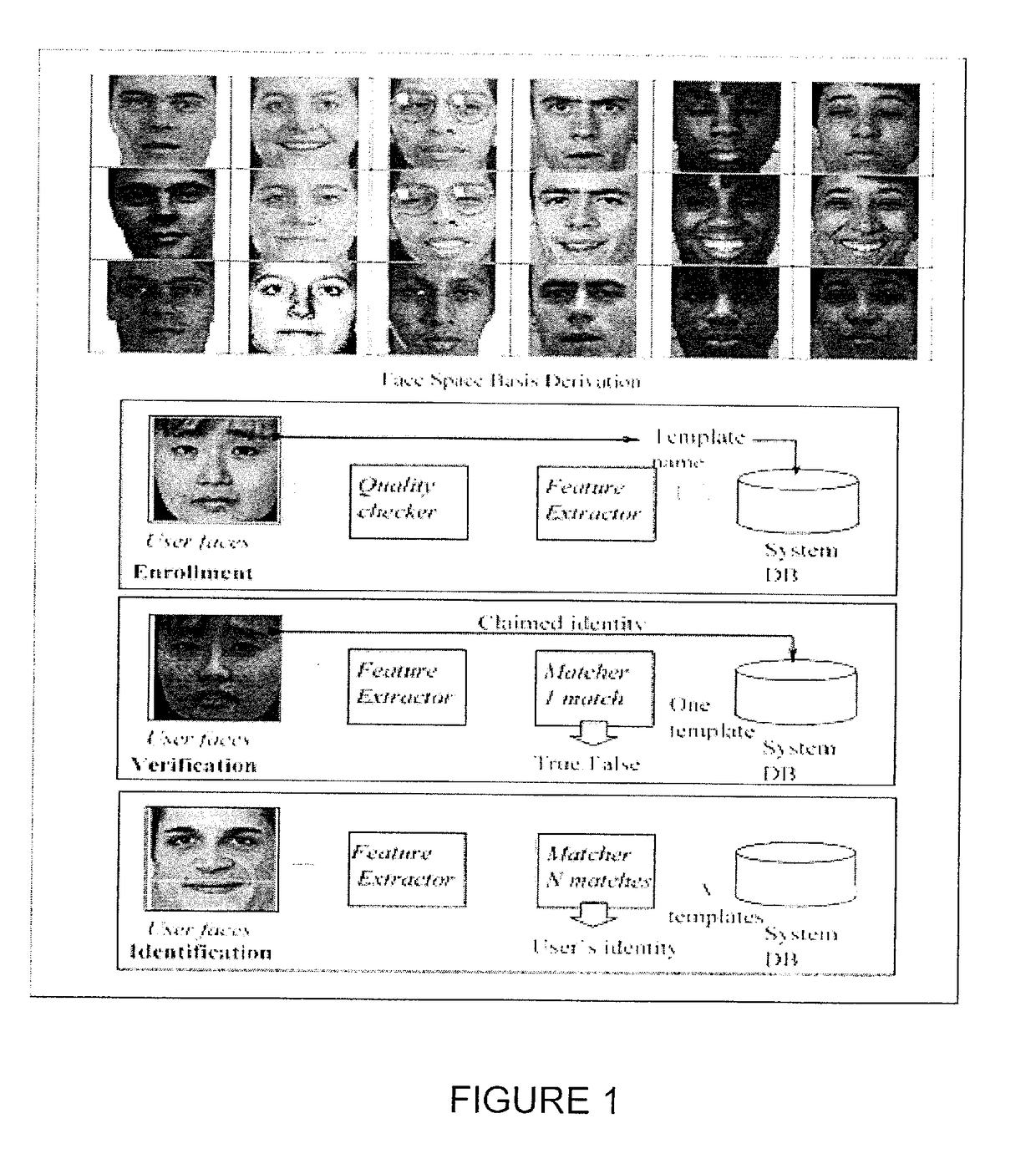
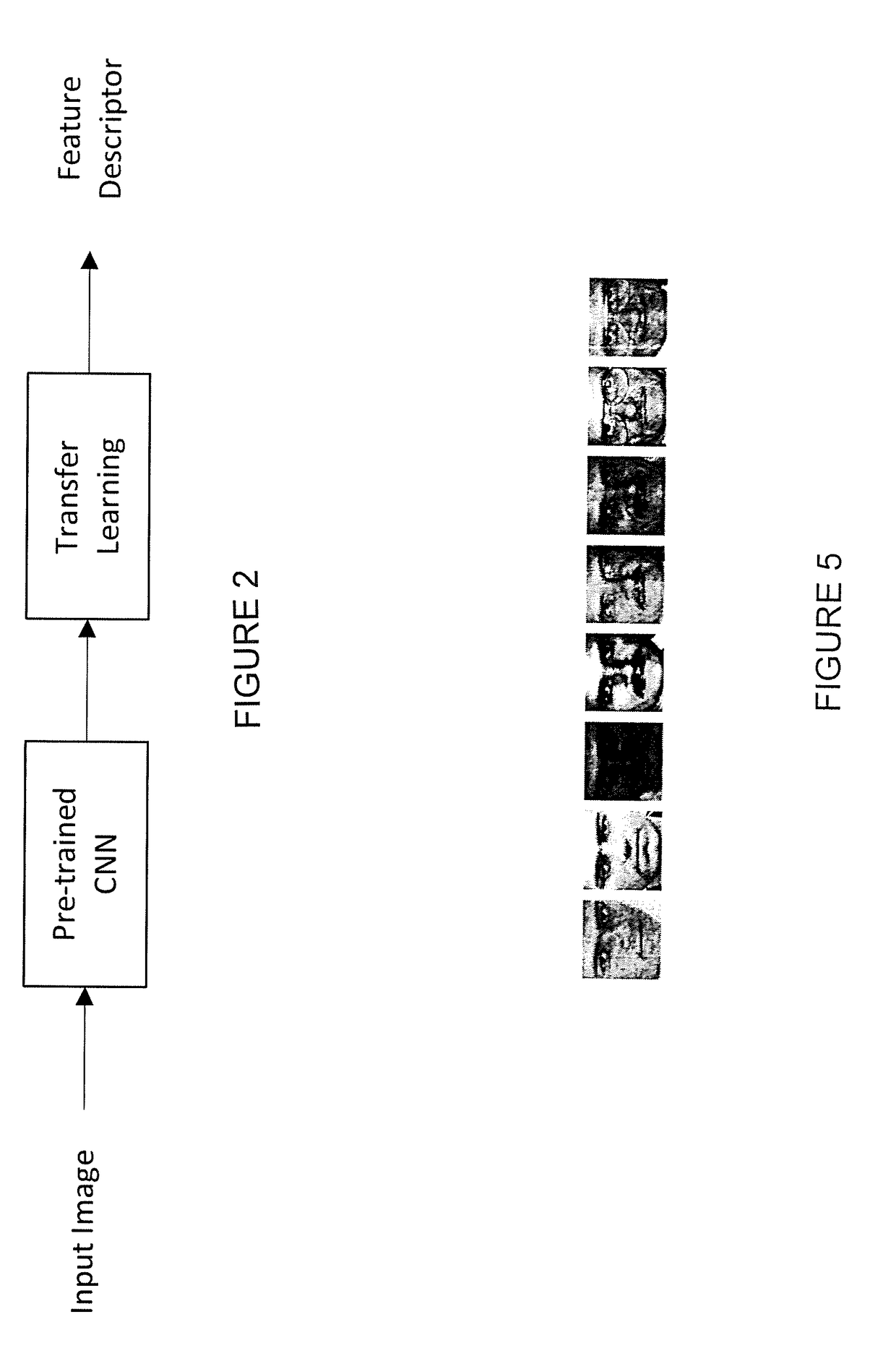
Time lapse, characteristic of aging, is a complex process that affects the reliability and security of biometric face recognition systems. Systems and methods use deep learning, in general, and convolutional neural networks (CNN), in particular, for automatic rather than hand-crafted feature extraction for robust face recognition across time lapse. A CNN architecture using the VGG-Face deep (neural network) learning produces highly discriminative and interoperable features that are robust to aging variations even across a mix of biometric datasets. The features extracted show high inter-class and low intra-class variability leading to low generalization errors on aging datasets using ensembles of subspace discriminant classifiers.
Owner:GEORGE MASON UNIVERSITY
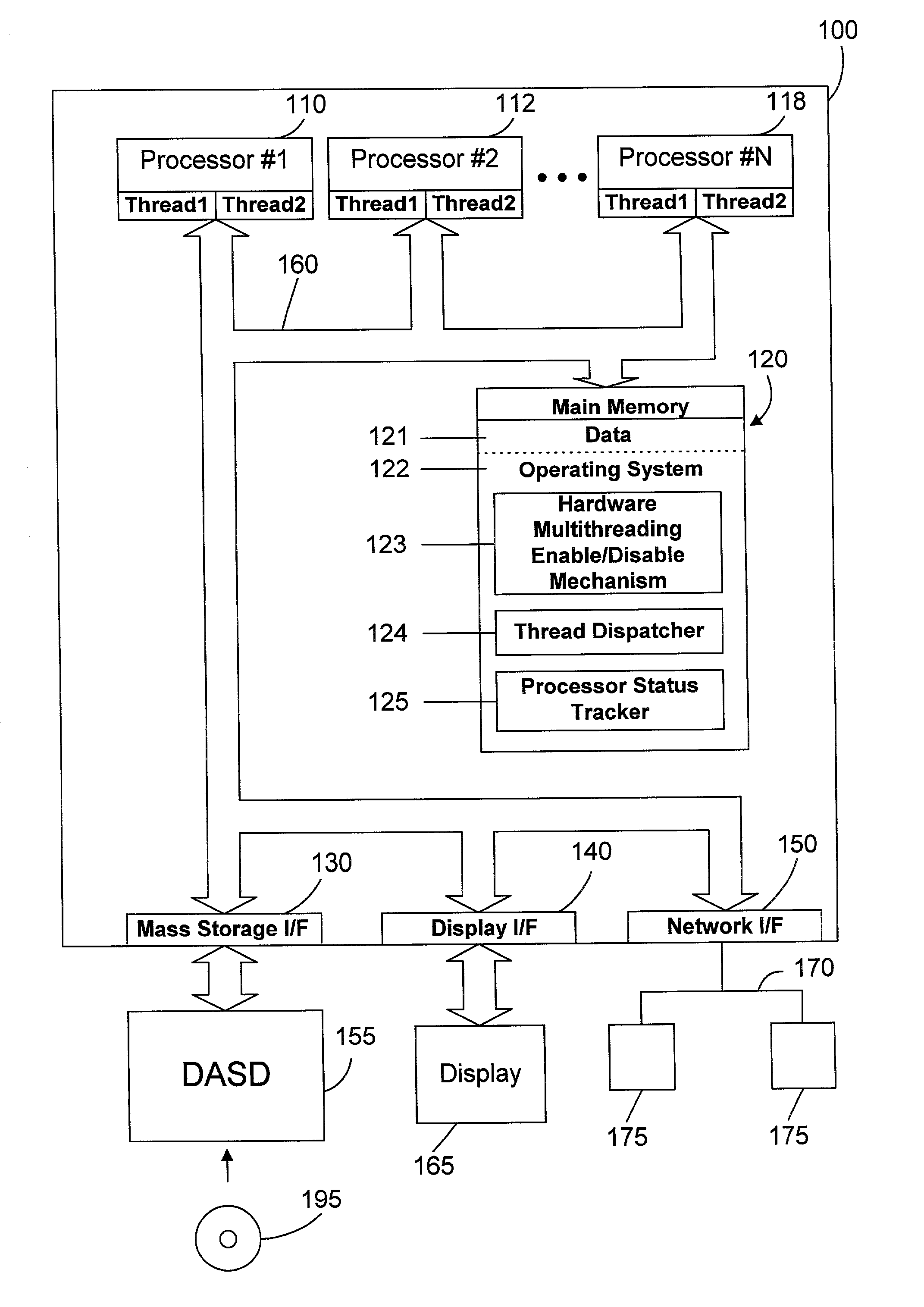
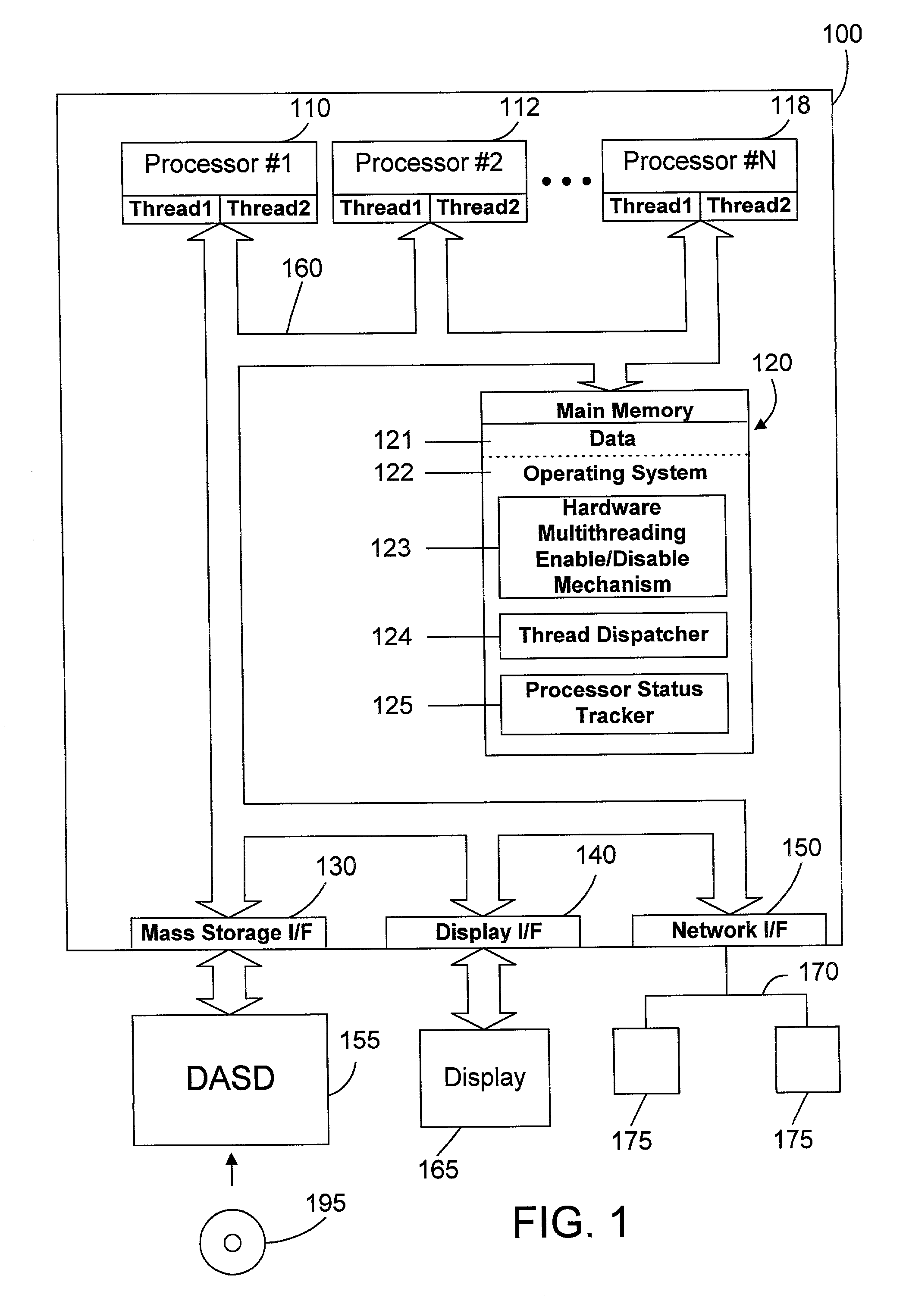
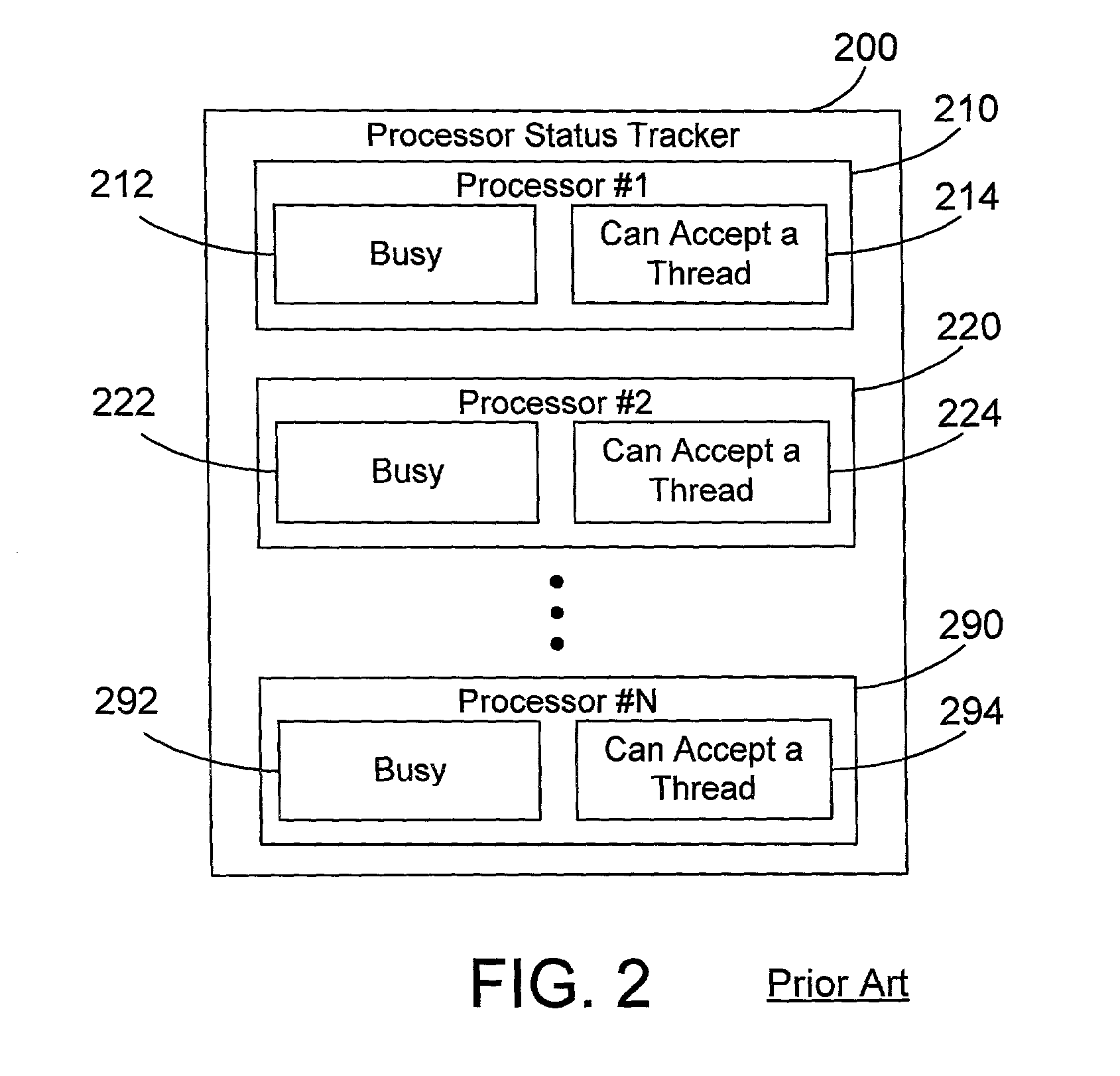
Thread dispatch mechanism and method for multiprocessor computer systems
InactiveUS20030149716A1Minimizing thread spreadHuman perceptionOperational speed enhancementResource allocationMulti processorThread scheduling
A thread dispatch mechanism dispatches threads in a multiprocessor computer system that has hardware multithreading enabled, thereby allowing each processor to execute multiple threads. The thread dispatch mechanism determines which processors are busy and cannot execute an additional thread, which processors are working on a thread but can still accept an additional thread, and which processors are idle. As threads are ready to be dispatched, each is dispatched to an idle processor instead of a processor that is already working on another thread. If there are no idle processors, the thread is dispatched to a processor working on one or more threads that can still process the new thread. In this manner the thread dispatch mechanism and method of the present invention provides greatly improved consistency in response times between threads and higher throughput compared to prior art methods of dispatching threads.
Owner:IBM CORP
Ultraviolet light treatment chamber
ActiveUS20100078574A1Easy and economical implementationHigher effective treatment dosMaterial analysis using wave/particle radiationWater/sewage treatment by irradiationUltravioletEngineering
An apparatus for the treatment of a liquid that includes a chamber having at least one inner surface, the chamber adapted for passage of a fluid therethrough. The chamber is at least 80 percent enclosed. The apparatus also includes an optional ultraviolet-transmissive tube disposed within the chamber and also adapted for the passage of the liquid therethrough. The apparatus further includes an ultraviolet lamp disposed within the chamber and, optionally, within the ultraviolet-transmissive tube. A reflective material is interposed between the chamber and the transmissive tube. The reflective material is adapted so as to reflect at least a portion of light emitted by the ultraviolet lamp, wherein the reflective material is at least 80 percent reflective.
Owner:NEO TECH AQUA SOLUTIONS
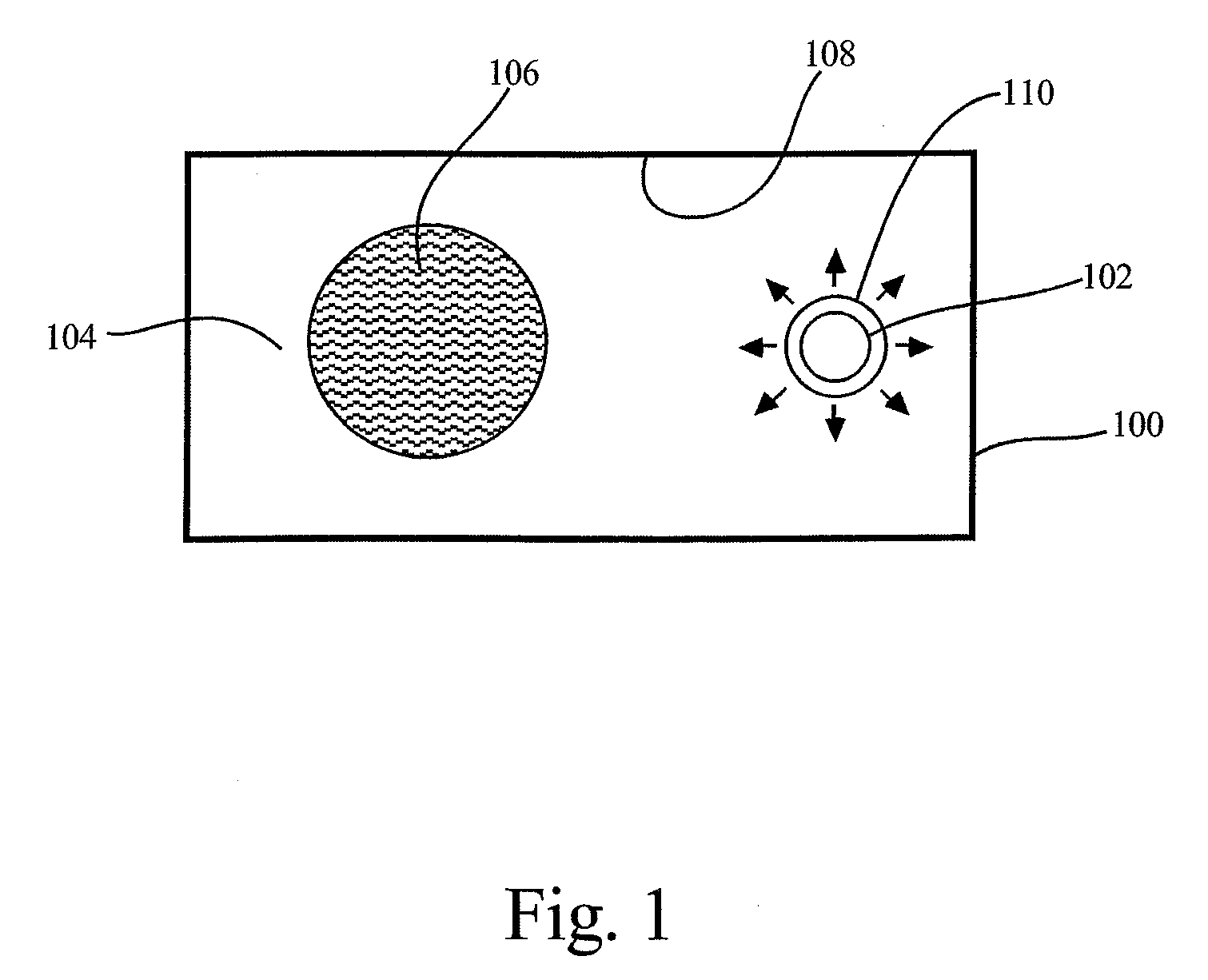
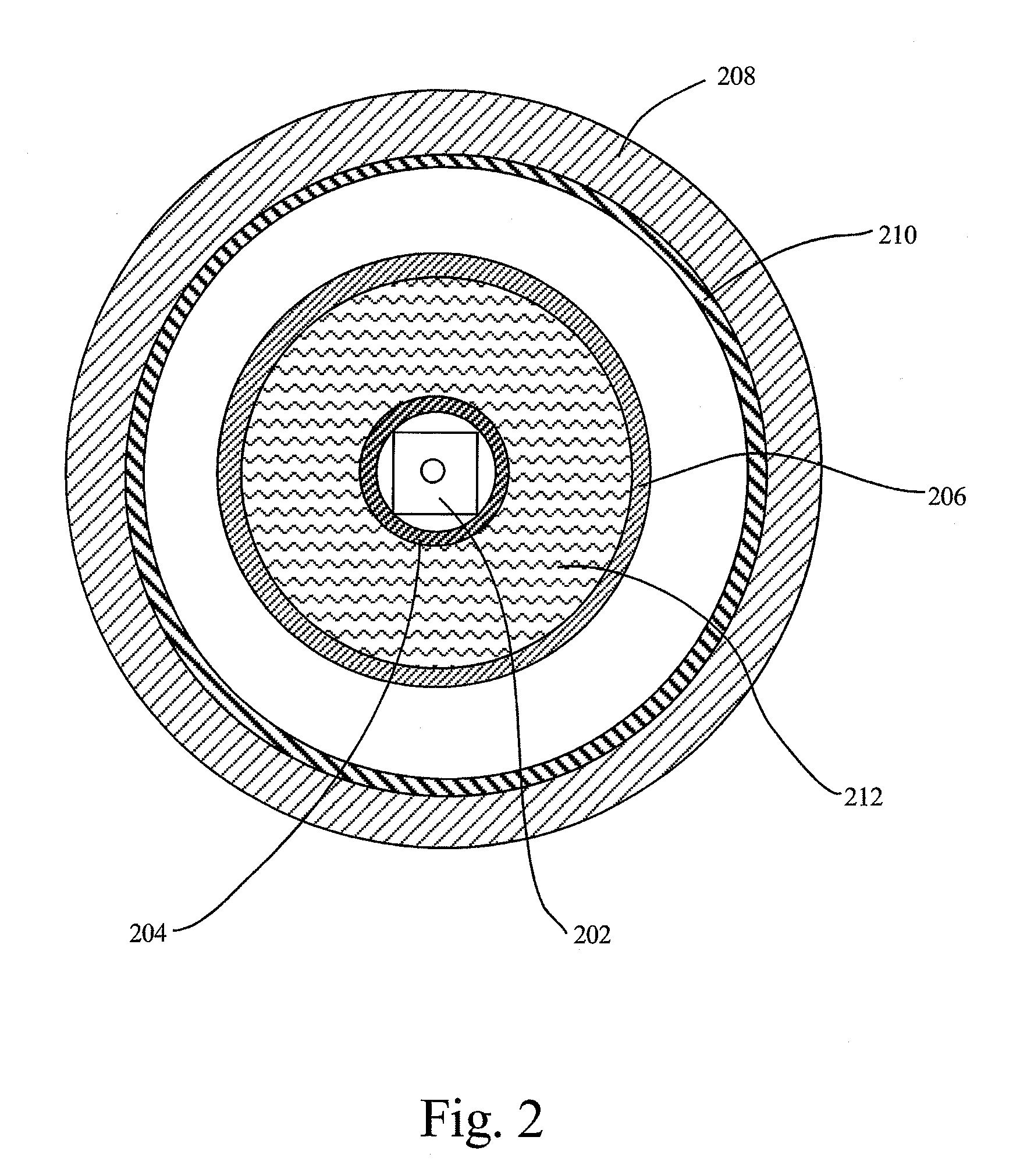
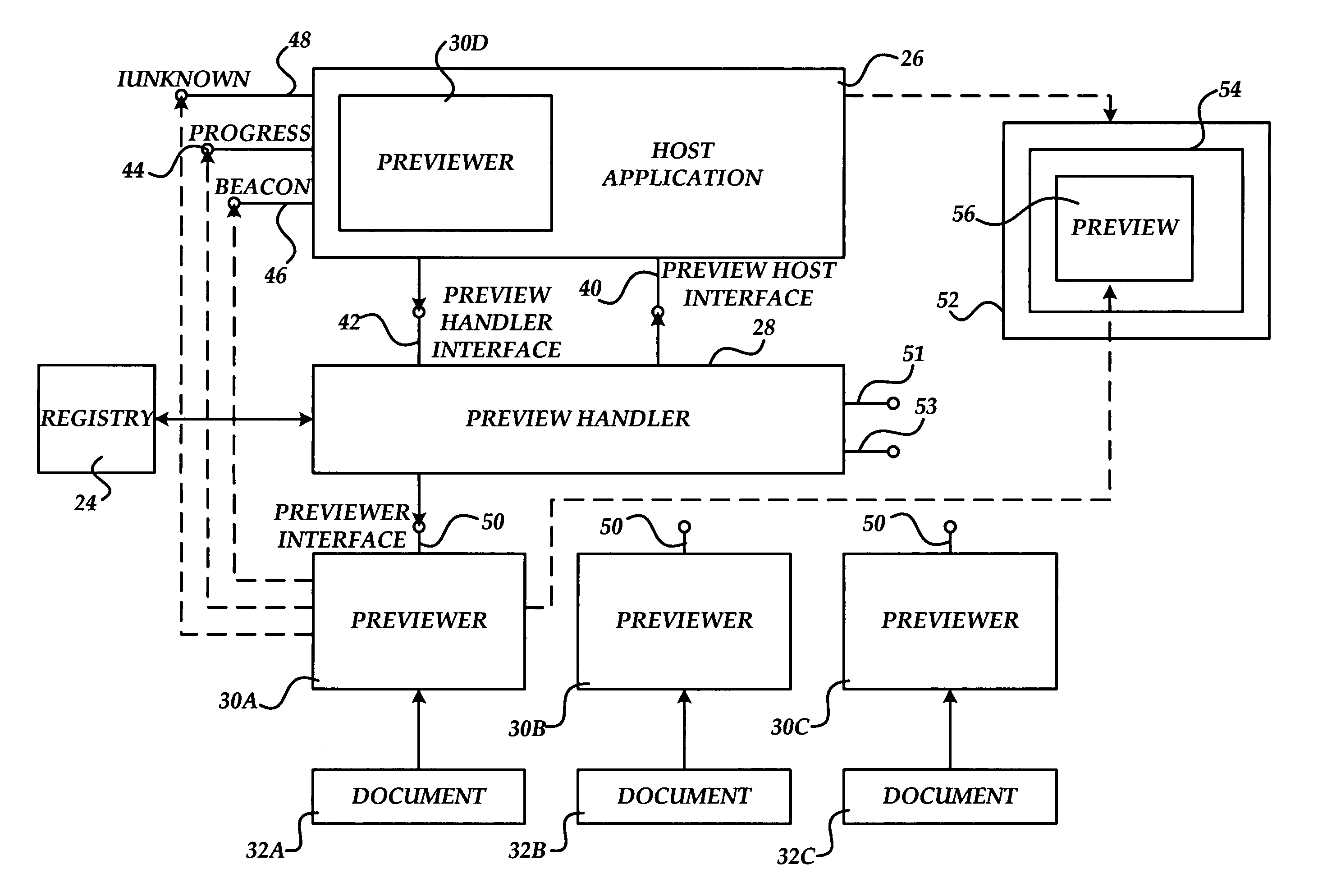
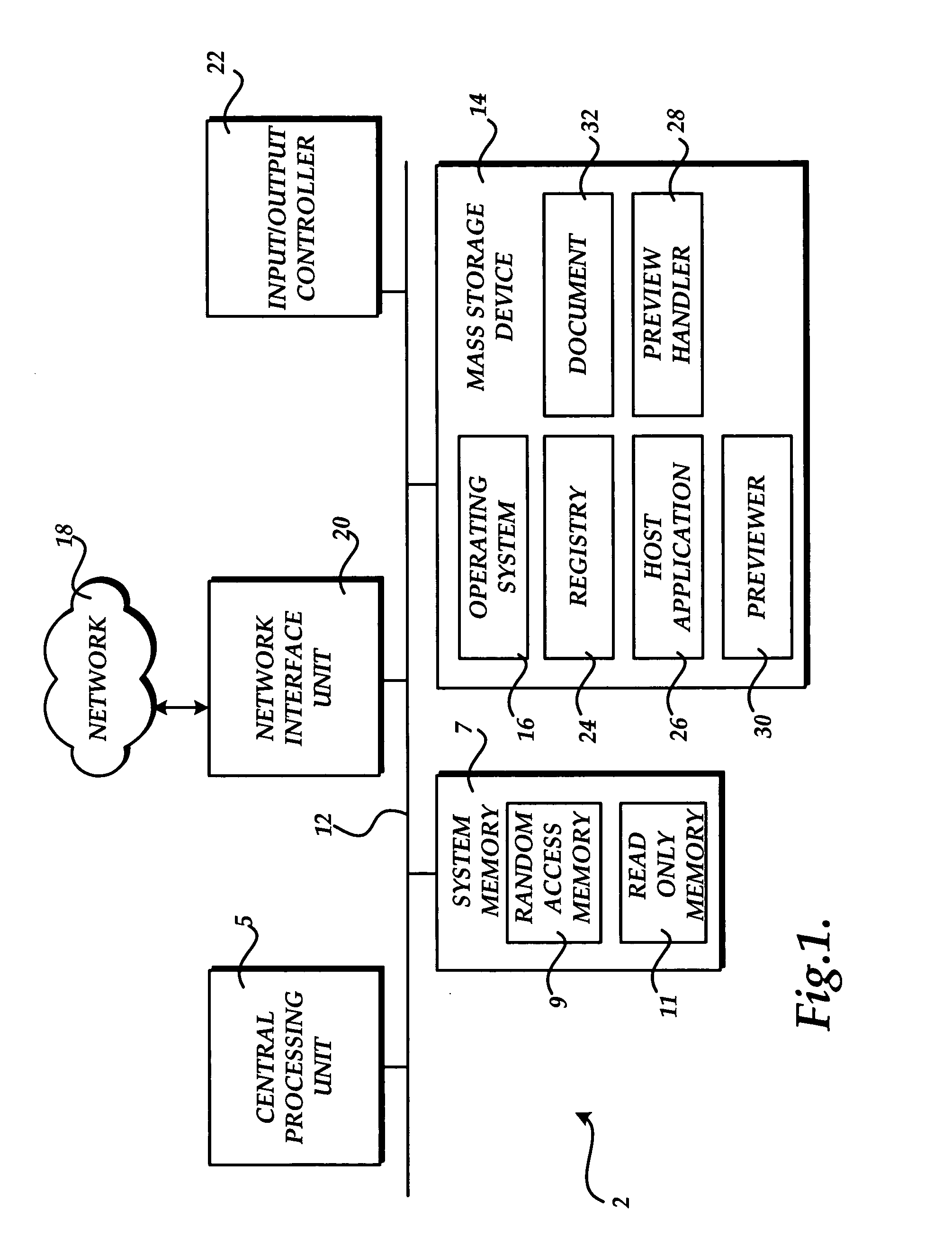
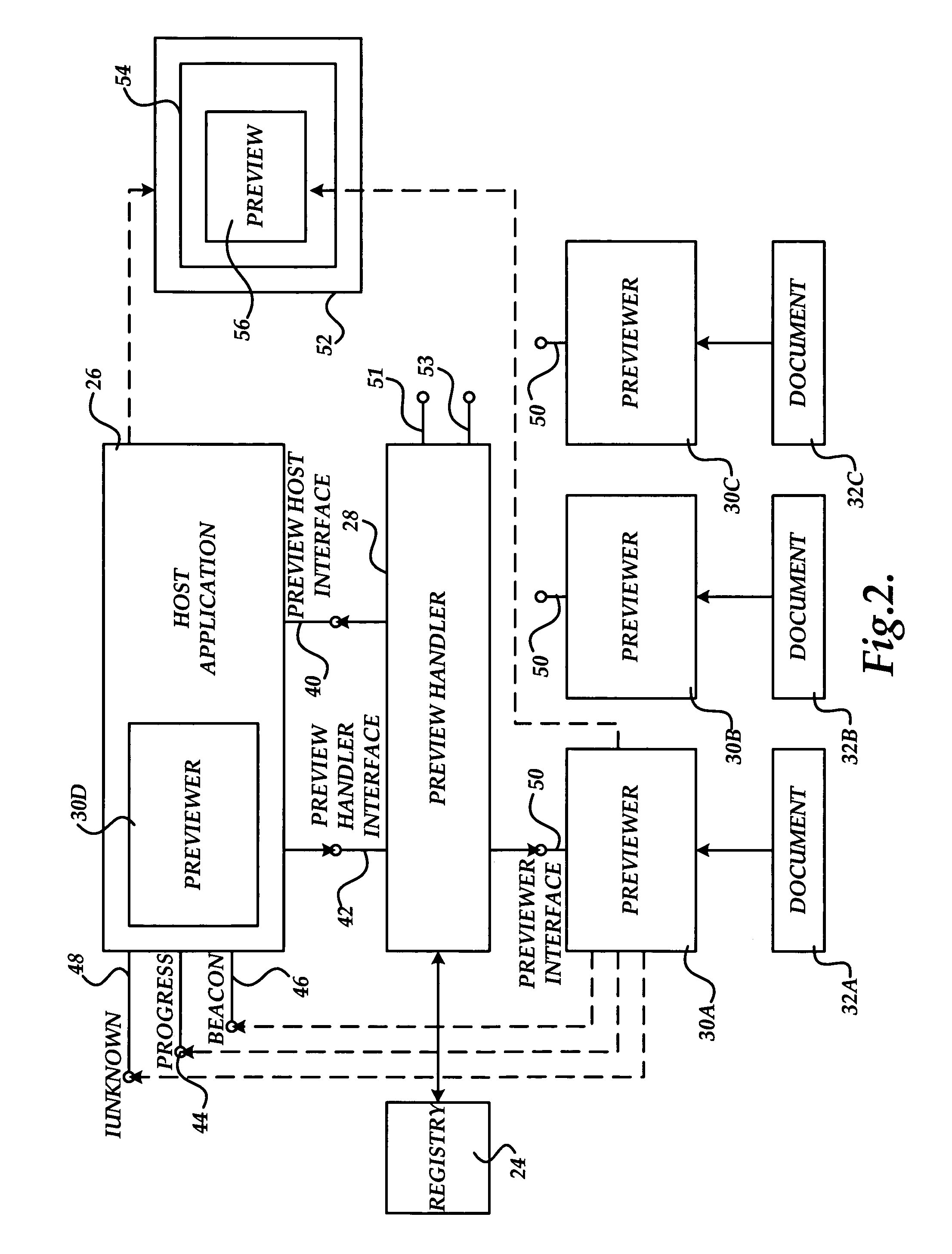
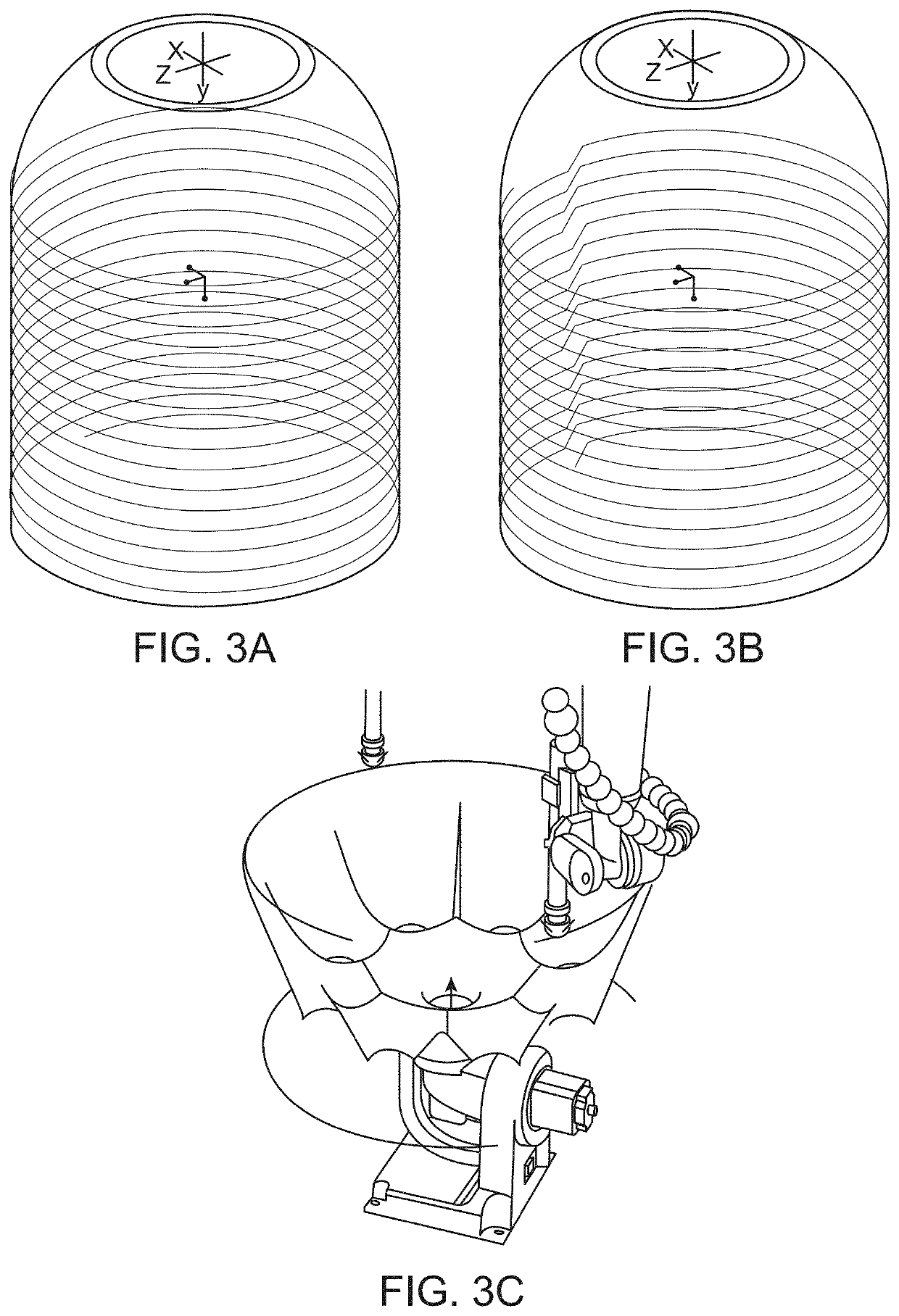
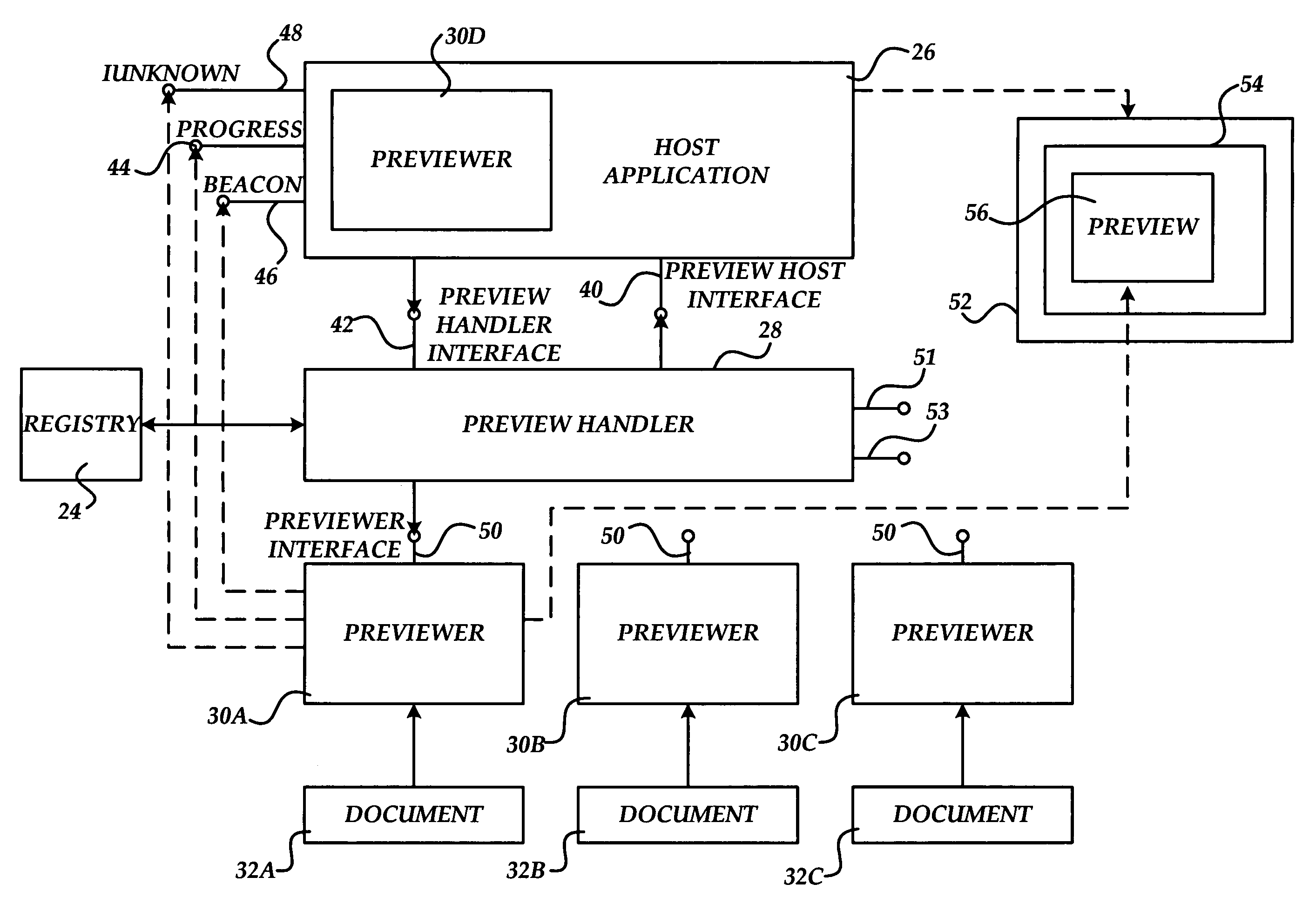
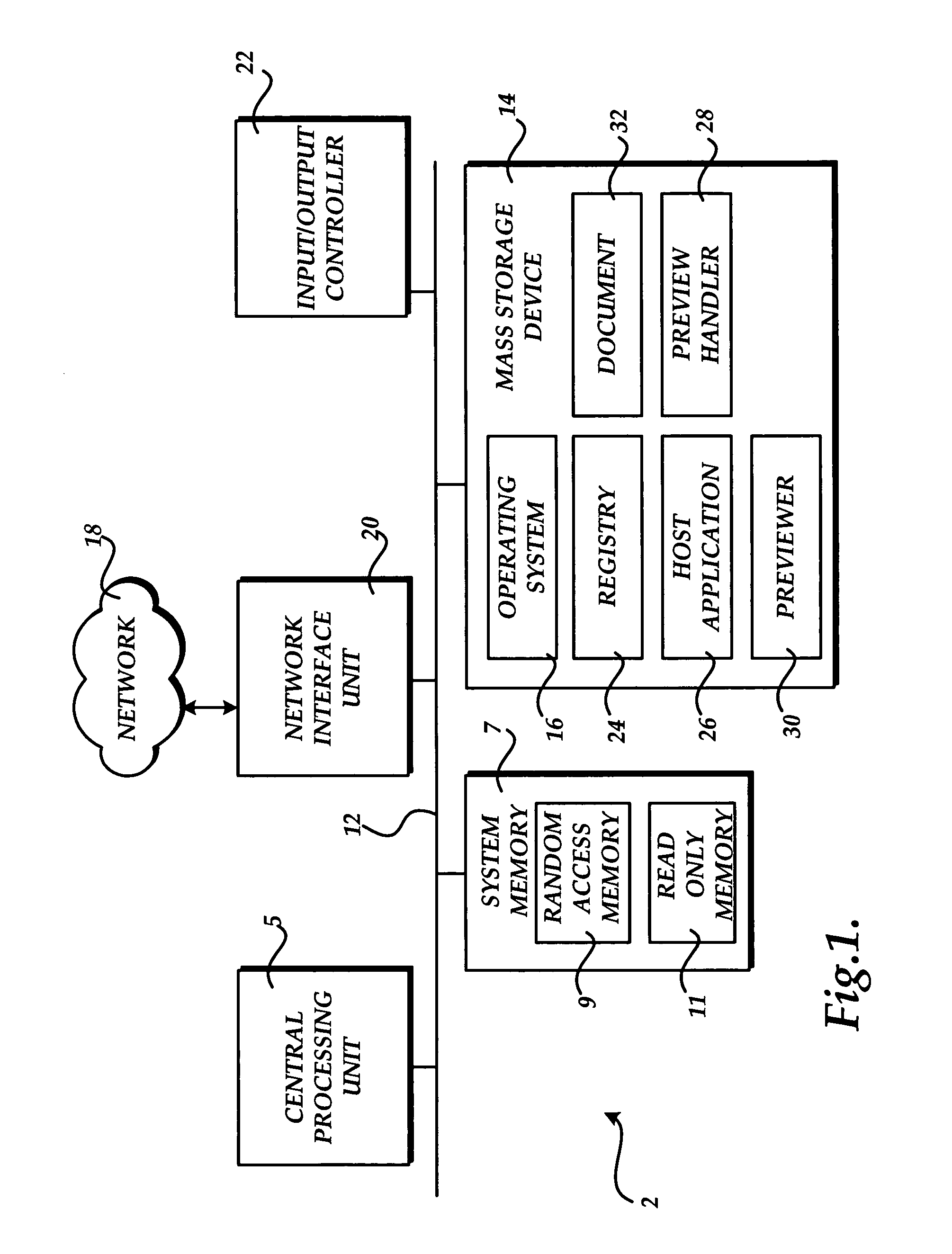
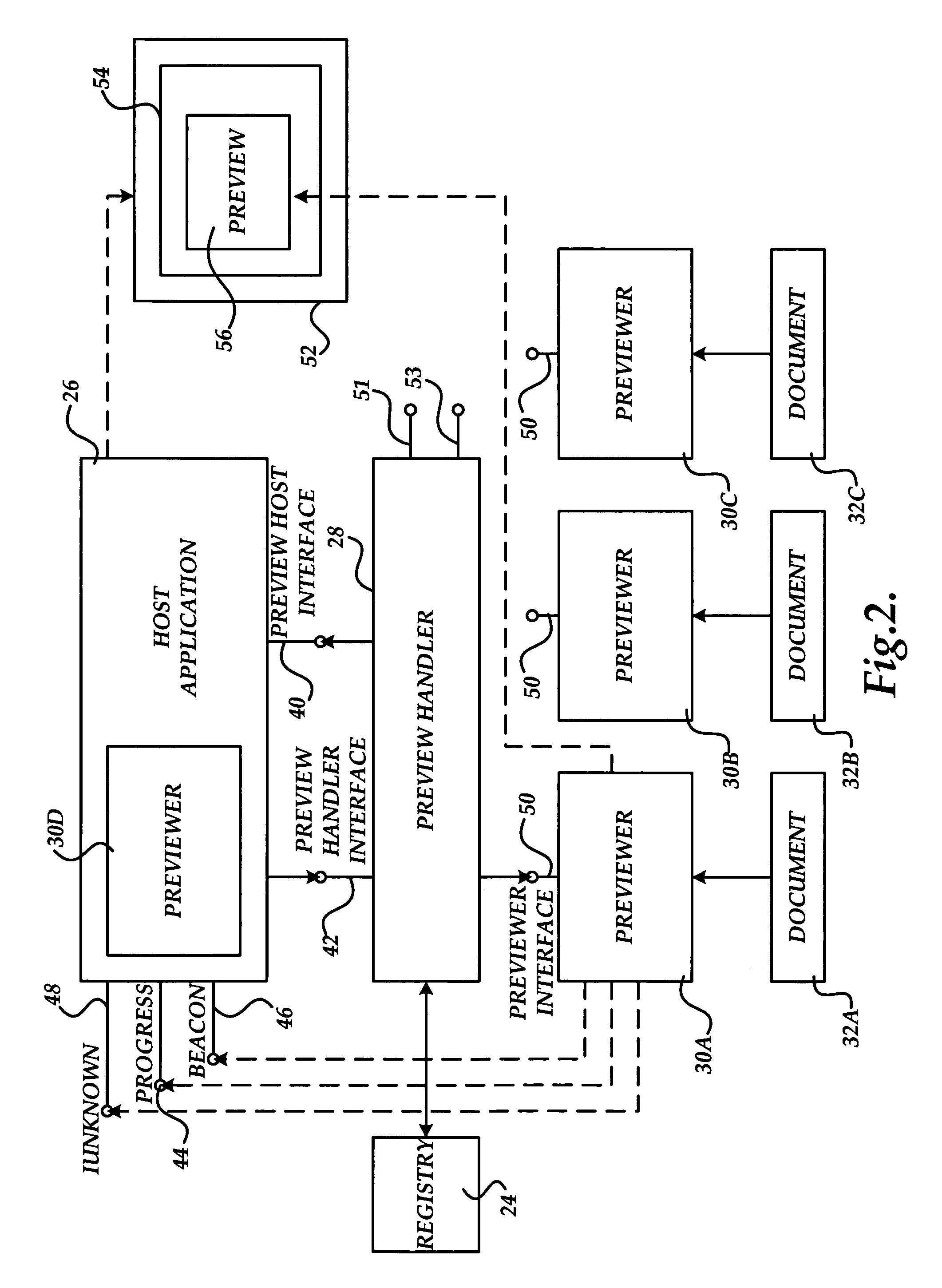
Method, system, and apparatus for providing a document preview
ActiveUS20060074869A1Impact stabilityImpact system performanceData processing applicationsDigital data processing detailsApplication softwareInformation retrieval
A method and apparatus are provided for generating a document preview. According to the method, a preview handler provides an interface to one or more previewers. The previewers are software components capable of generating a visual preview for one or more document types. In response to a request from a host application to generate a preview for a document, the preview handler is operative to identify the appropriate previewer for generating a preview for the document. The preview handler may then call the previewer and instruct the previewer to load the document and to show the preview in a sub-window of a window provided by the calling host application.
Owner:MICROSOFT TECH LICENSING LLC
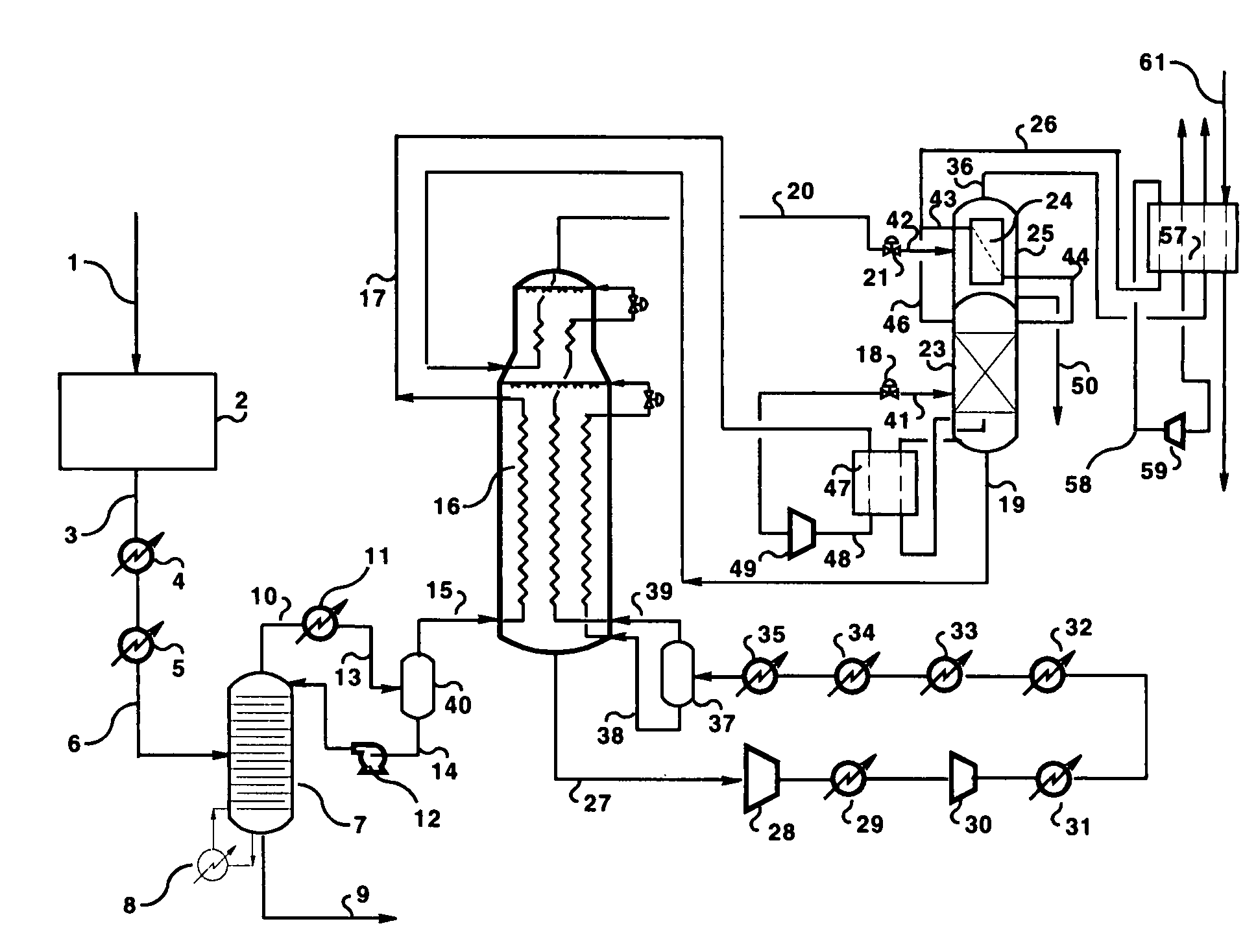
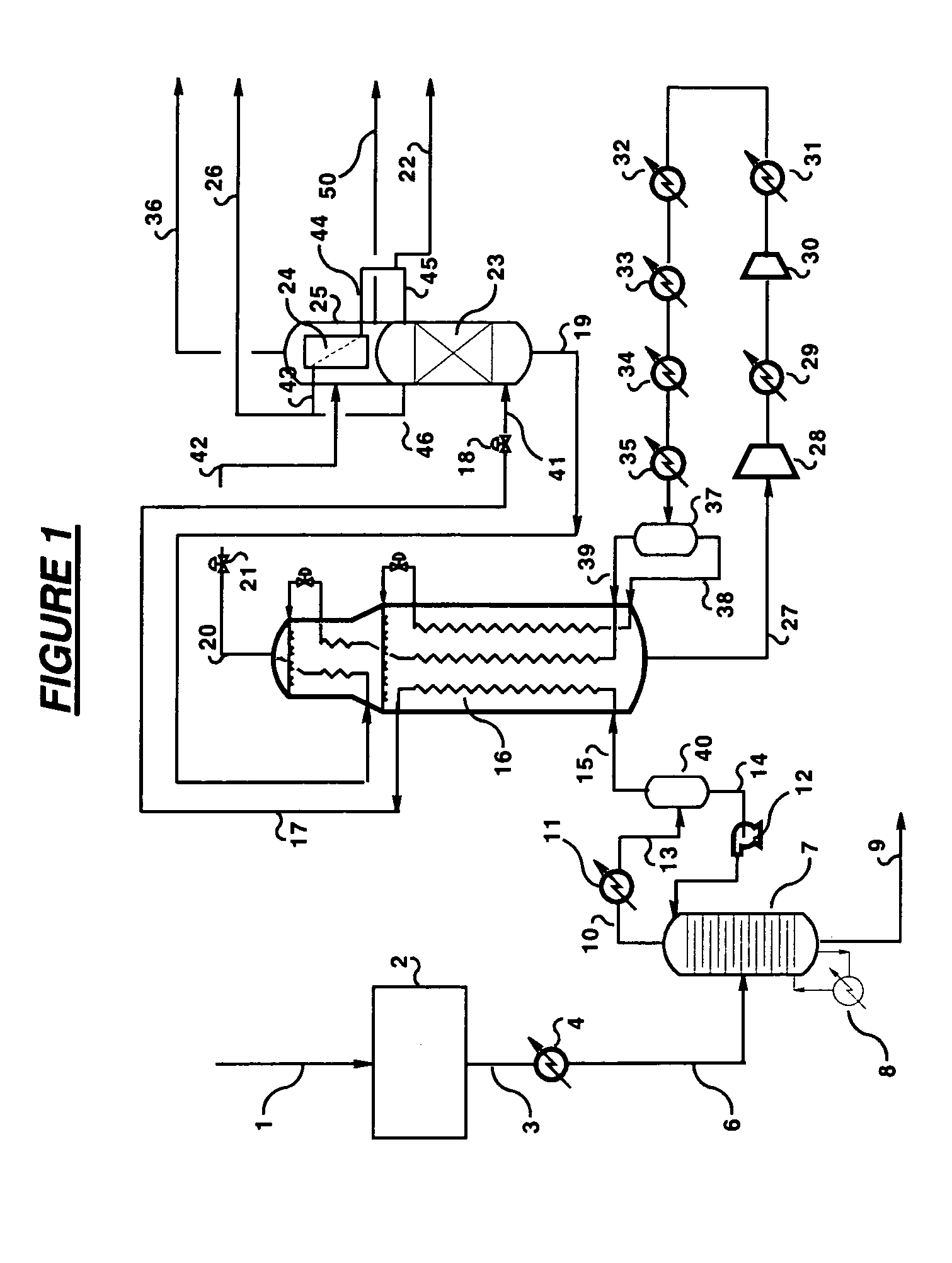
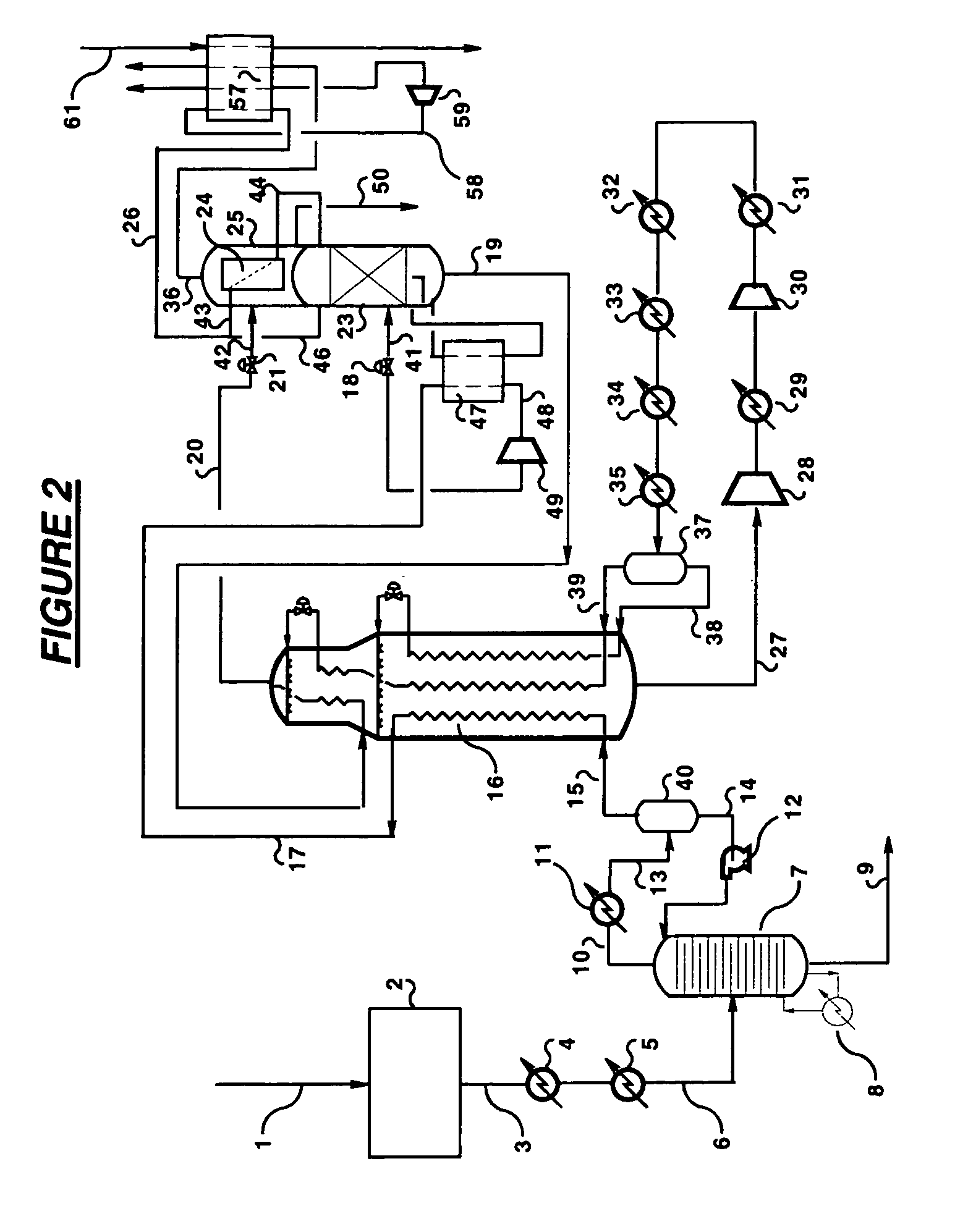
Dual stage nitrogen rejection from liquefied natural gas
Nitrogen is removed from a liquefied natural gas feed (41) by a two stage separation in which the liquefied natural gas (41) is first fractionated (23) to provide a first nitrogen-enriched overhead vapour stream (46) and a nitrogen-containing bottoms liquid stream (19) and then at least a portion of said bottoms liquid stream (19) is fractionated (25) to provide a second nitrogen-enriched overhead vapour stream (36) that is of lower purity than said first overhead vapour stream (46) and a purified liquefied natural gas stream (50). The first fractionation is conducted in a distillation column (23) refluxed (45) with nitrogen overhead (43) condensed in a condenser (24) located in a flash drum (25) in which the second fractionation is conducted. The second nitrogen-enriched overhead vapour stream (36) provides fuel gas for use in the natural gas liquefaction plant.
Owner:AIR PROD & CHEM INC
Managing Housekeeping Operations in Flash Memory
InactiveUS20080294813A1Reduce transfer speedImpact performanceMemory architecture accessing/allocationMemory systemsWear levelingVolatile memory
A flash re-programmable, non-volatile memory system is operated to disable foreground execution of housekeeping operations, such as wear leveling and data scrub, in the when operation of the host would be excessively slowed as a result. One or more characteristics of patterns of activity of the host are monitored by the memory system in order to determine when housekeeping operations may be performed without significantly degrading the performance of the memory system, particularly during writing of data from the host into the memory.
Owner:SANDISK TECH LLC
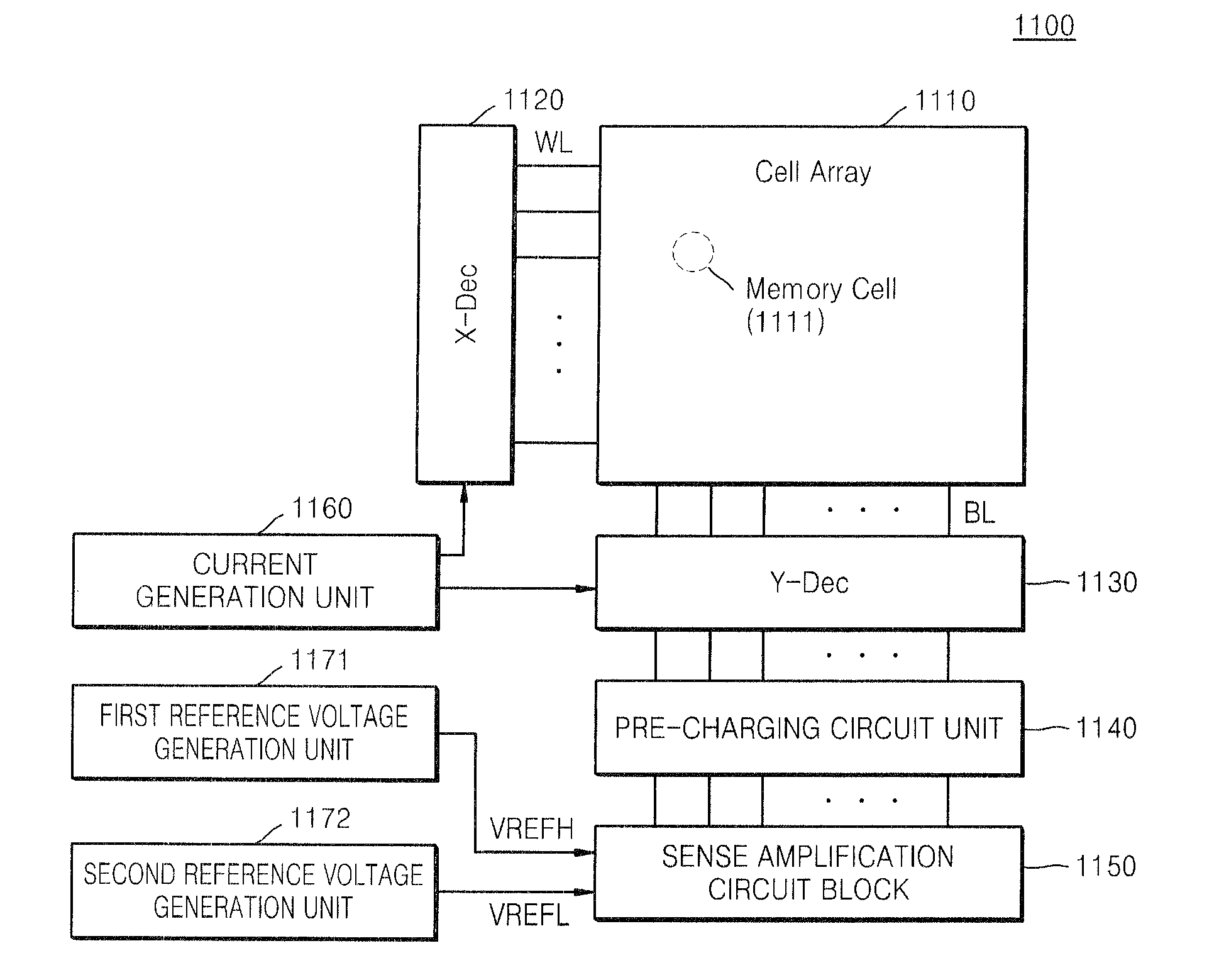
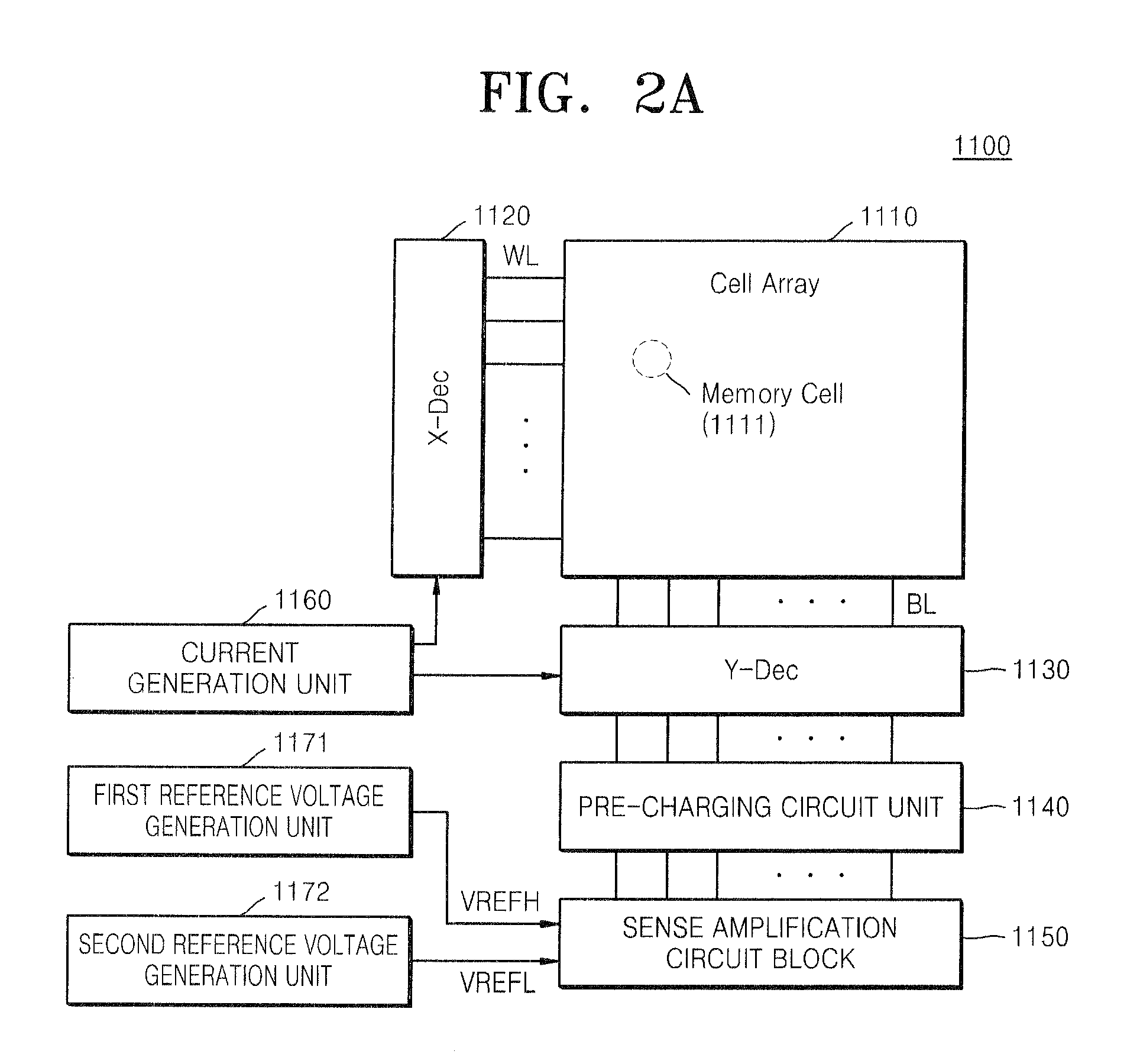
Data read circuit, a non-volatile memory device having the same, and a method of reading data from the non-volatile memory device
ActiveUS20130051114A1Improve performanceGood semiconductor performanceDigital storageVoltage referenceHemt circuits
A non-volatile memory device including a cell array, which includes a plurality of memory cells, and a sense amplification circuit. The sense amplification circuit is configured to receive a data voltage of a memory cell, a first reference voltage and a second reference voltage during a data read operation of the memory cell, generate differential output signals based on a voltage level difference between the data voltage and the first and second reference voltages, and output the differential output signals as data read from the memory cell.
Owner:SAMSUNG ELECTRONICS CO LTD
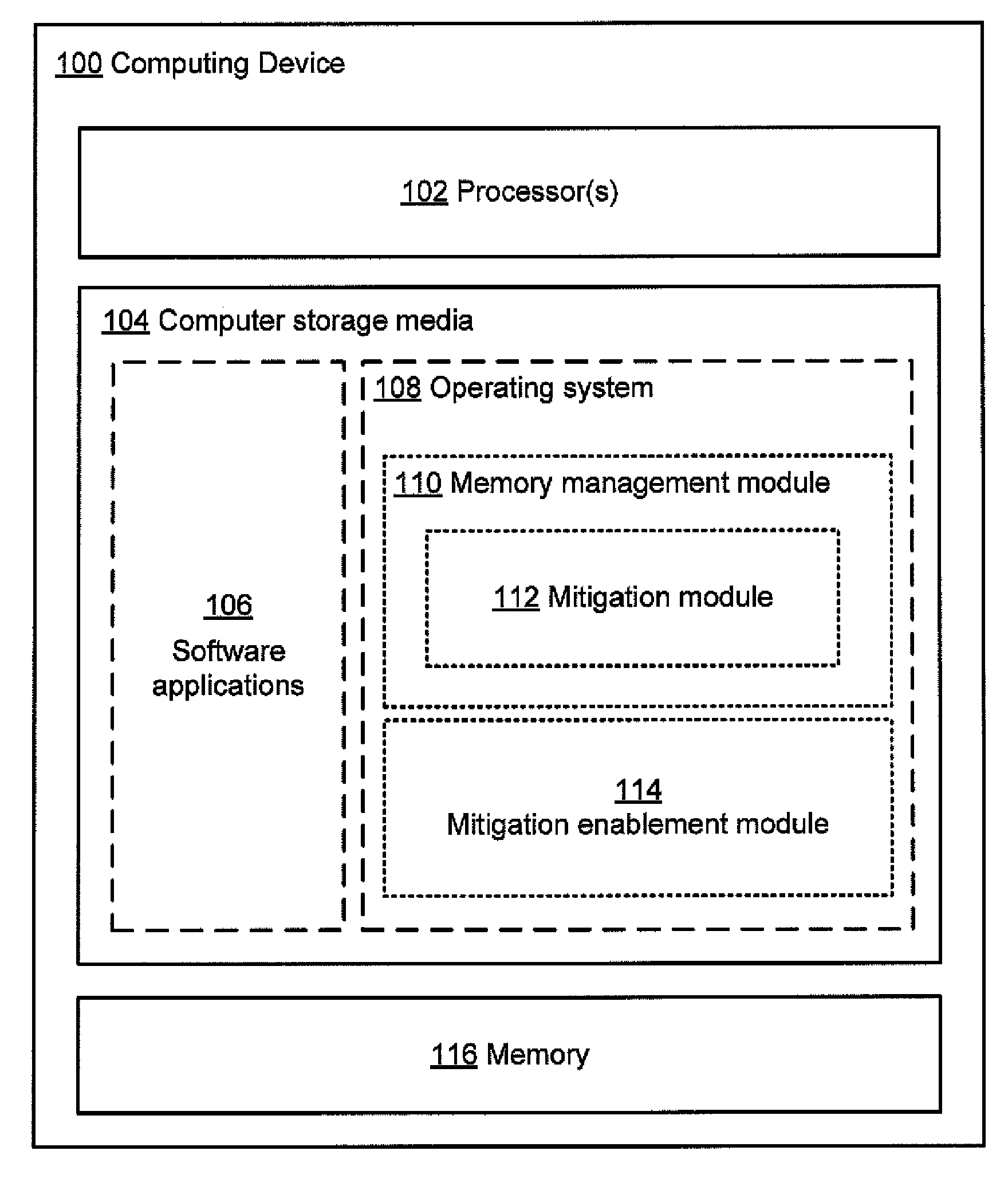
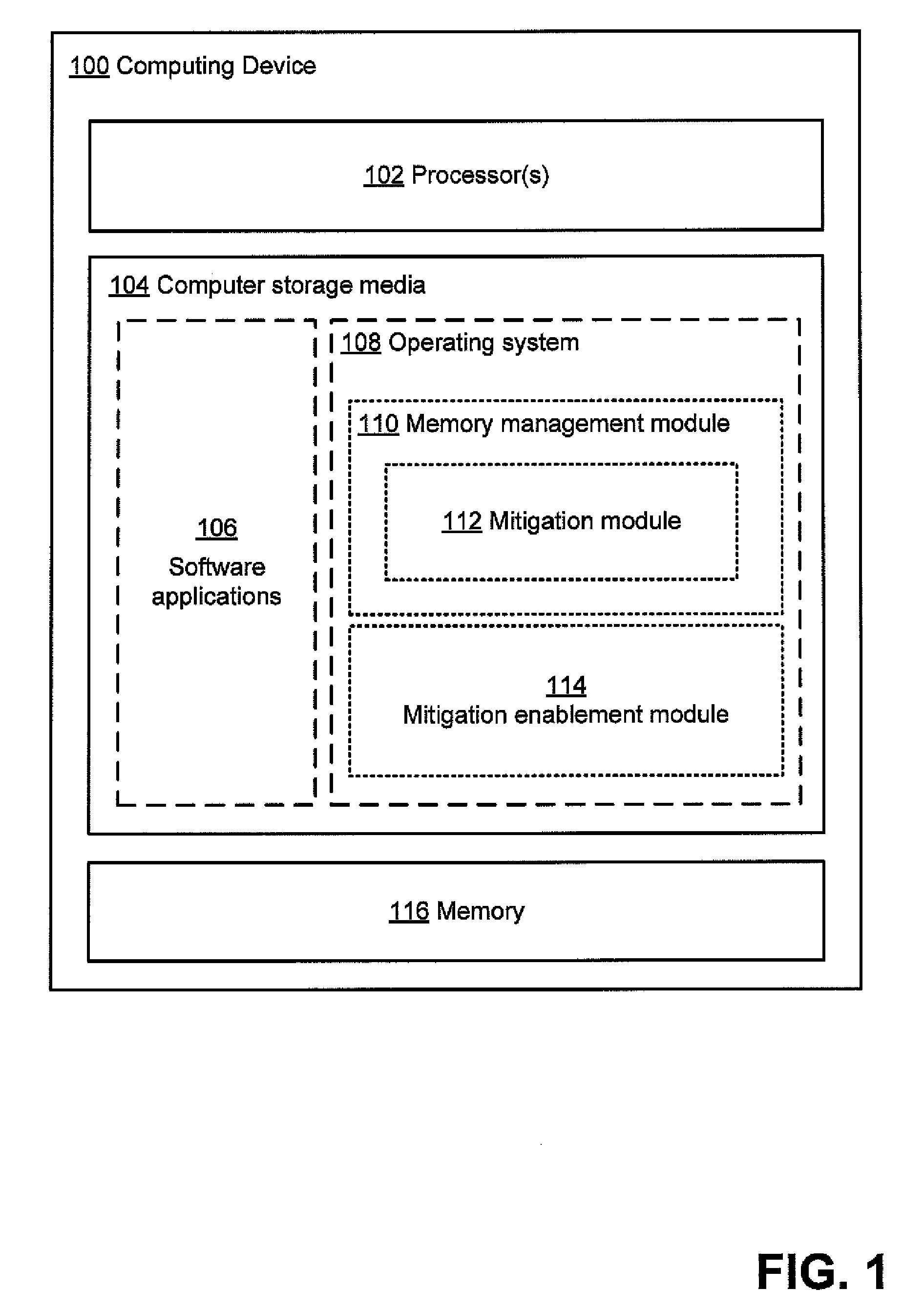
Evaluating effectiveness of memory management techniques selectively using mitigations to reduce errors
InactiveUS20100083048A1Improve user experienceReduce errorsSoftware testing/debuggingNon-redundant fault processingError reductionError prevention
A mitigation enablement module for a computer that improves application reliability. When performing memory management operations, the mitigation enablement module and associated memory manager selectively use mitigations that are intended to prevent an application bug from cause an application error. The memory manager may selectively apply mitigations for each of one or more applications based on the likelihood that such mitigations are successful at preventing bugs from causing application errors. The likelihood is determined from historical information on whether the mitigations, when applied, prevented bugs from causing memory operations that could cause application errors. This historical information can be gathered on a single computer over multiple invocations of the application or may be aggregated from multiple computers, each invoking the application. The determined likelihood may then be used to determine whether or for how long to apply the mitigation actions for memory operations requested by the application.
Owner:MICROSOFT TECH LICENSING LLC
Reduced complexity multi-turbo multi-user detector
ActiveUS20050185729A1Reduce the possibilityImprove performancePolarisation/directional diversityCode conversionPhase detectorRound complexity
A reduced complexity Turbo multi-user detector (MUD) processing system in multiple access communications channels that decreases the likelihood of improper decoding of the final values of interest and decreases the computation complexity for each iteration, thereby allowing for a reduction in the number of iterations performed and lowers the overall complexity without negatively impacting performance. In one form the present invention comprises a multi-user detector coupled to two or more decoder sections, two ore more recoders, and a compare and adjust section in such a manner that data flows iteratively to correct for errors in a computationally efficient manner.
Owner:COLLISION COMM
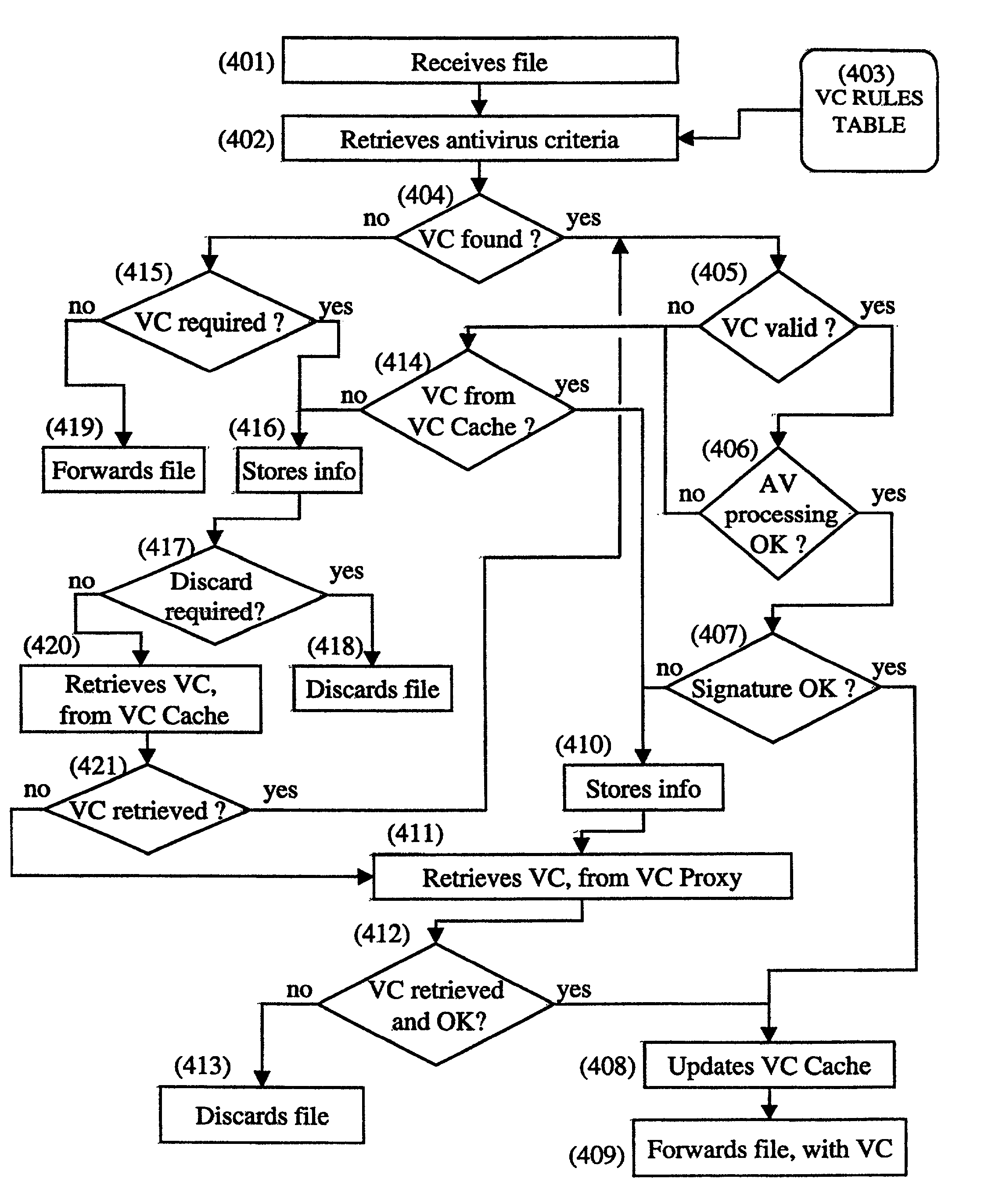
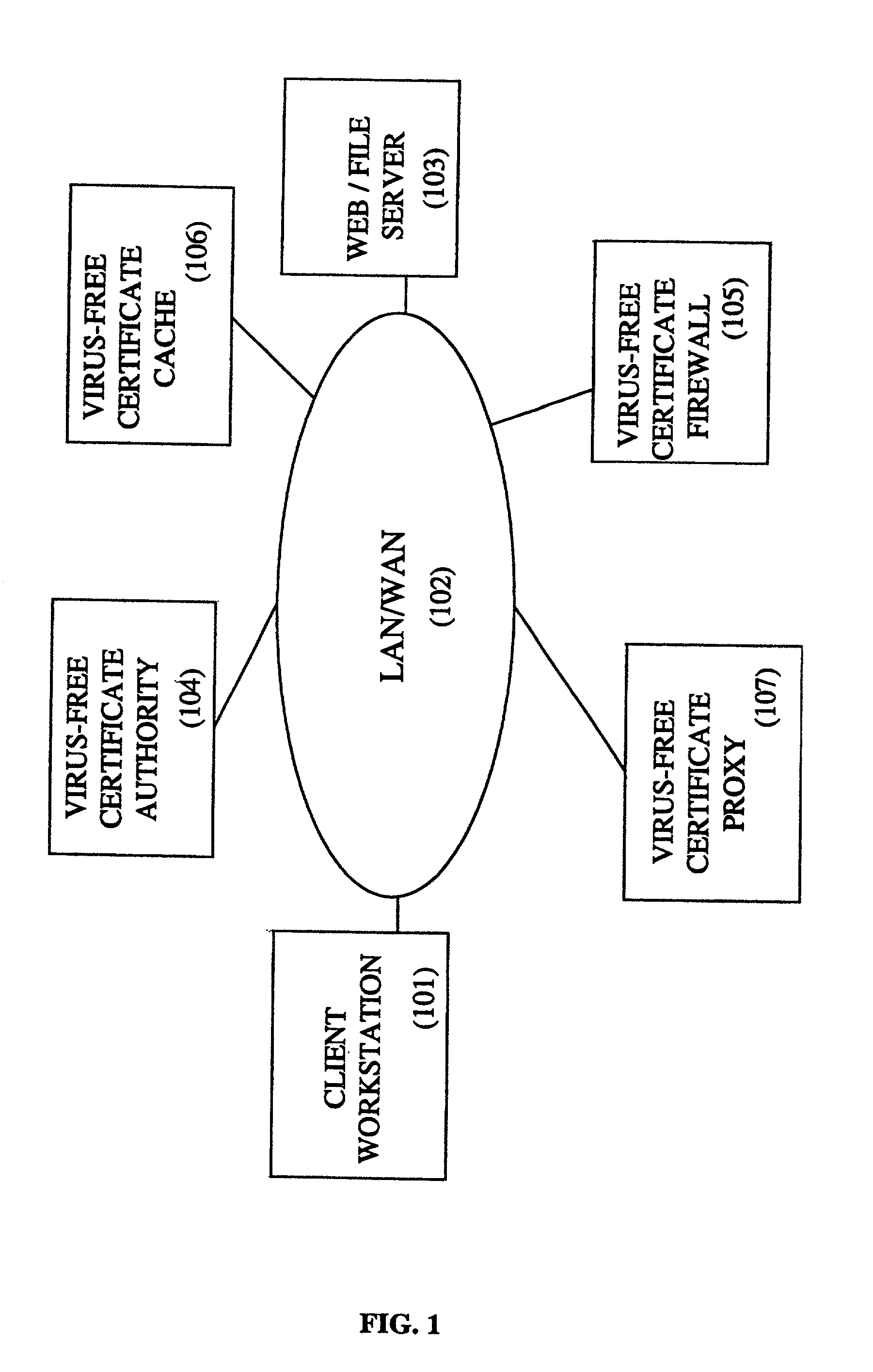
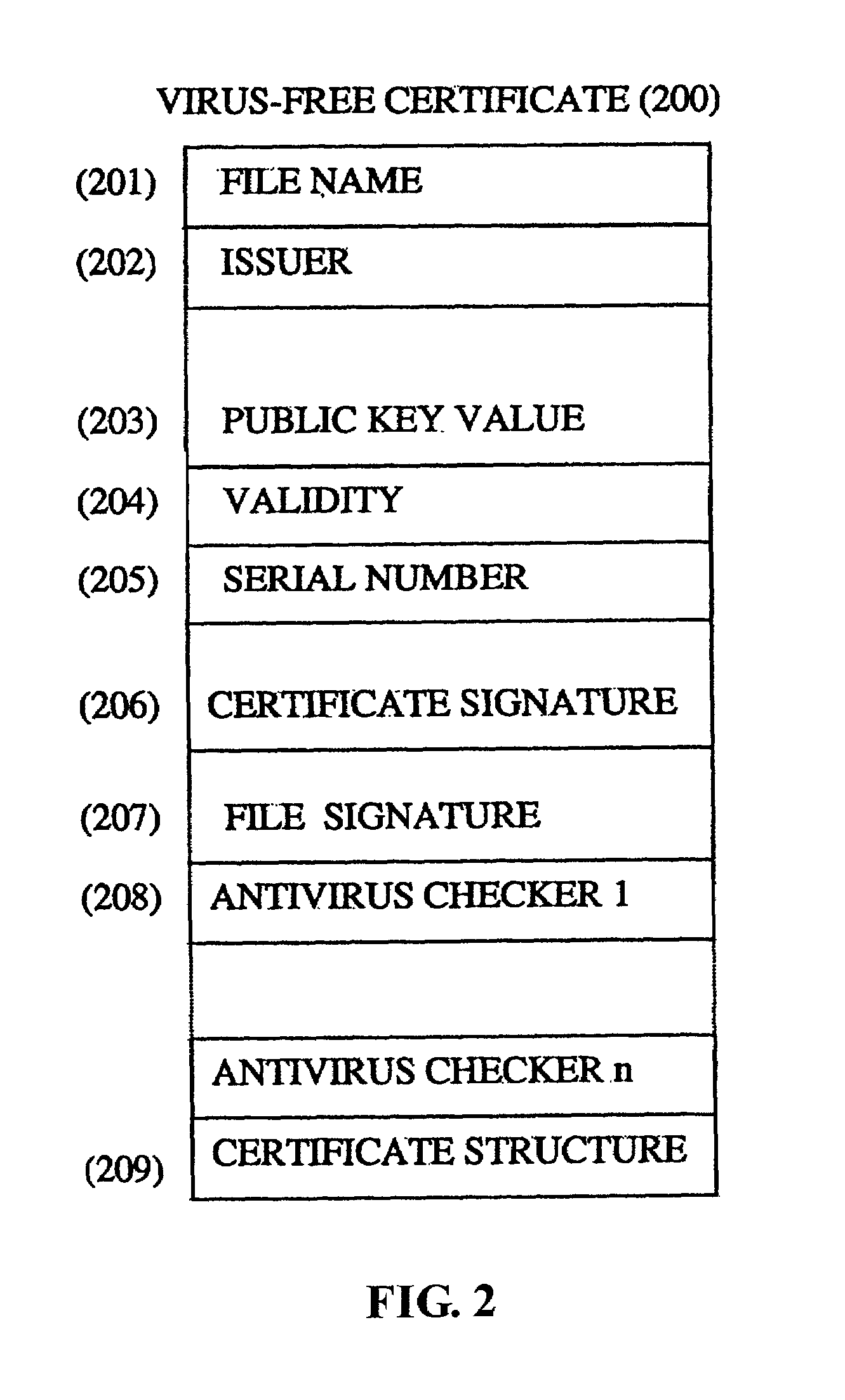
Method and system for controlling and filtering files using a virus-free certificate
InactiveUS6986051B2Simple methodEasy to detectMemory loss protectionDigital data processing detailsVirusAuthentication
The present invention is directed to computer viruses and more particularly to a method and system for use in a virus-free certificate firewall, of controlling and filtering files using a virus-free certificate. An example embodiment of the method comprises the steps of: receiving a file; if a virus-free certificate (200) is required for the file: determining whether the a virus-free certificate is already associated with the file; if a virus-free certificate is already associated with the file: authenticating the associated virus-free certificate, said virus-free certificate comprising a certificate signature; if the virus-free certificate is authenticated, determining whether the file is virus-free or not; if the file is virus-free, forwarding the file with the associated virus-free certificate; if the virus-free certificate is not authenticated or if no virus-free, certificate is associated with the file; determining whether the file is virus-free or not, if the file is virus-free, associating with the file a new virus-free certificate; and forwarding the file with the new virus-free certificate.
Owner:TREND MICRO INC
In-place data transformation for fault-tolerant disk storage systems
InactiveUS20050138286A1Minimizing performance impactShort amount of timeTransmissionMemory systemsData transformationComputer science
Owner:AVAGO TECH INT SALES PTE LTD
Real-time adaptive control of manufacturing processes using machine learning
InactiveUS20200166909A1Fast optimizationEasy to adjustProgramme controlComputer controlLearning machineProcess engineering
Machine learning-based methods and systems for automated object defect classification and adaptive, real-time control of manufacturing processes are described.
Owner:RELATIVITY SPACE INC
Method, system, and apparatus for providing a document preview
ActiveUS8032482B2Impact performanceImpact stabilityData processing applicationsDigital data processing detailsApplication softwareDocumentation
A method and apparatus are provided for generating a document preview. According to the method, a preview handler provides an interface to one or more previewers. The previewers are software components capable of generating a visual preview for one or more document types. In response to a request from a host application to generate a preview for a document, the preview handler is operative to identify the appropriate previewer for generating a preview for the document. The preview handler may then call the previewer and instruct the previewer to load the document and to show the preview in a sub-window of a window provided by the calling host application.
Owner:MICROSOFT TECH LICENSING LLC
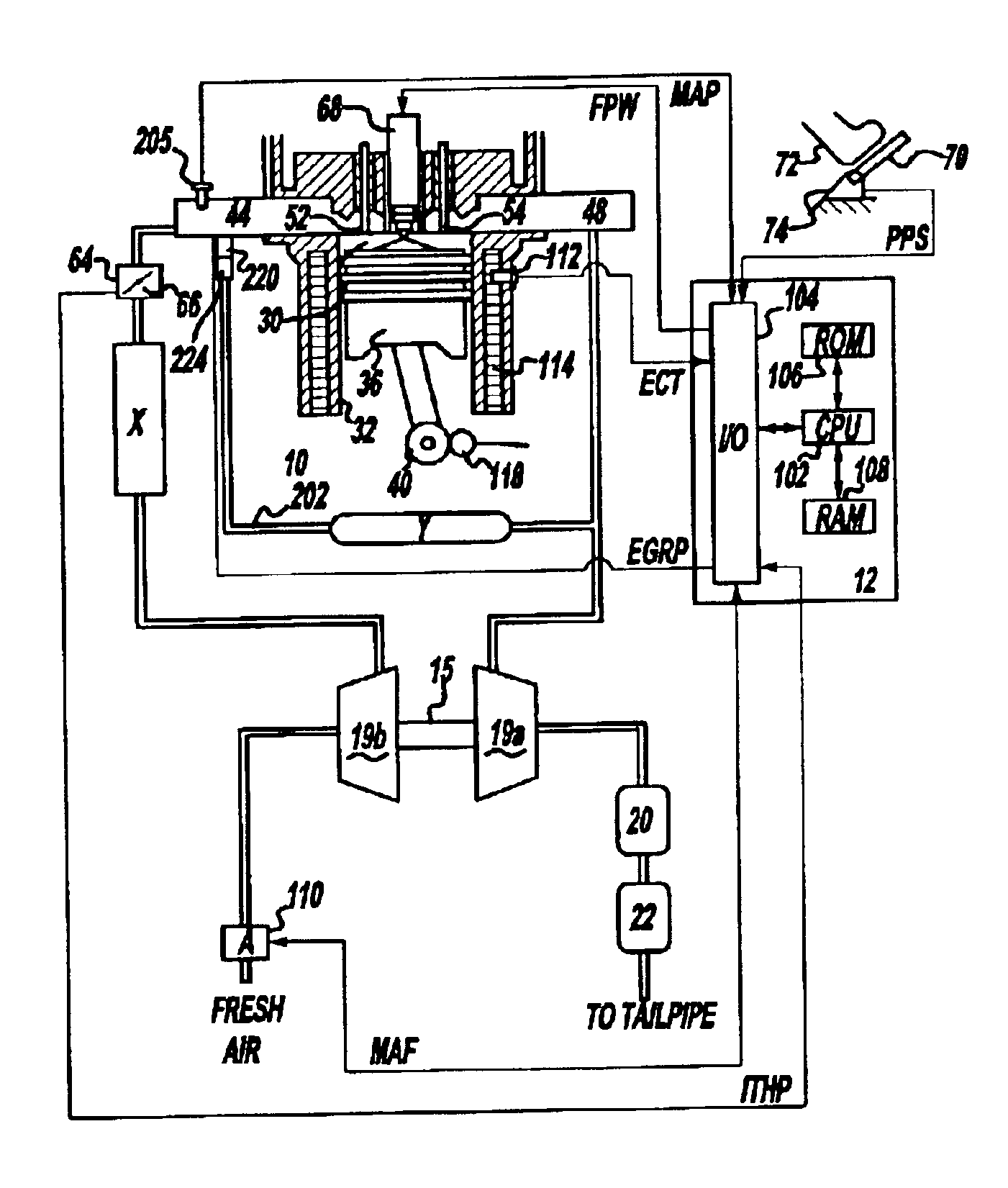
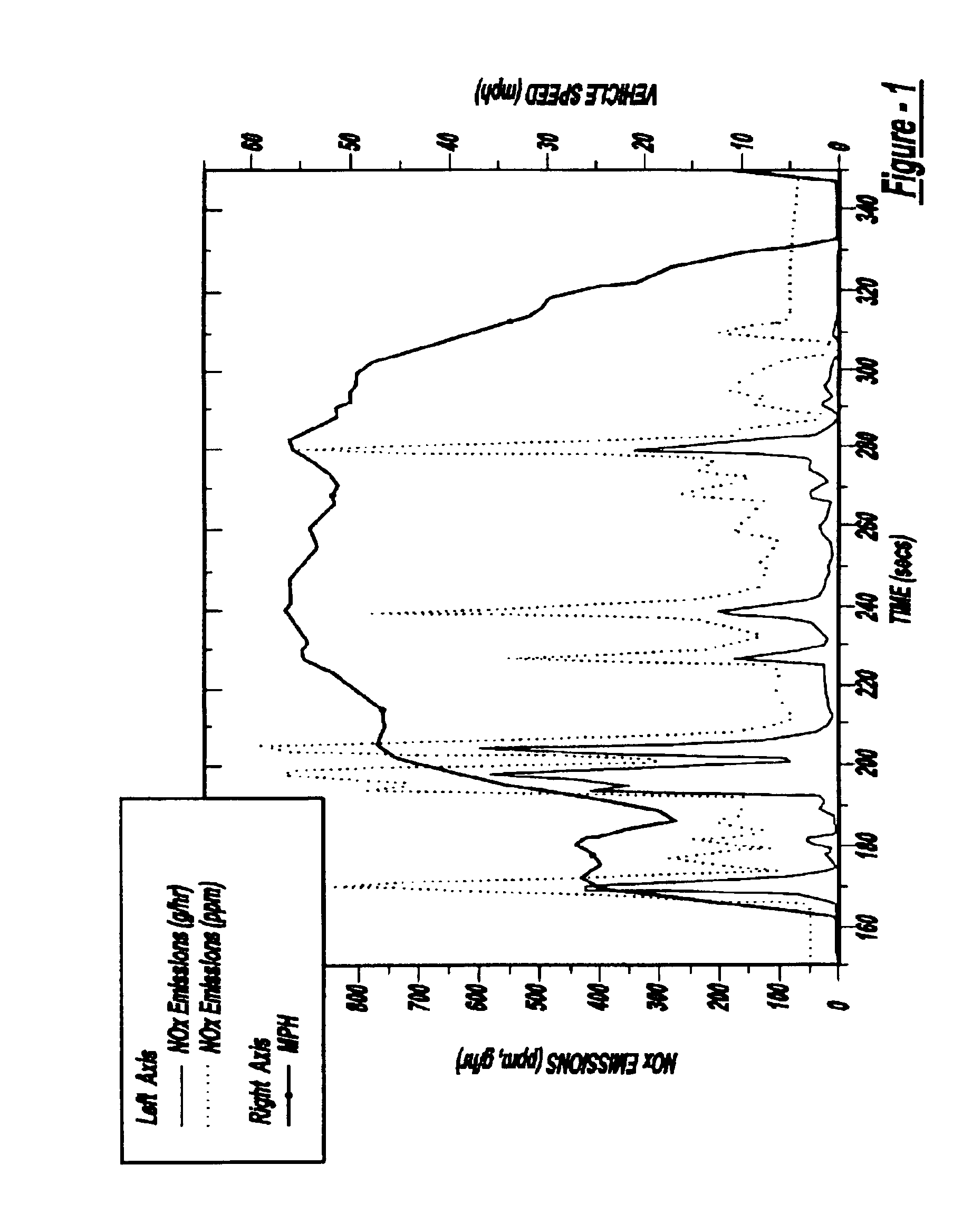
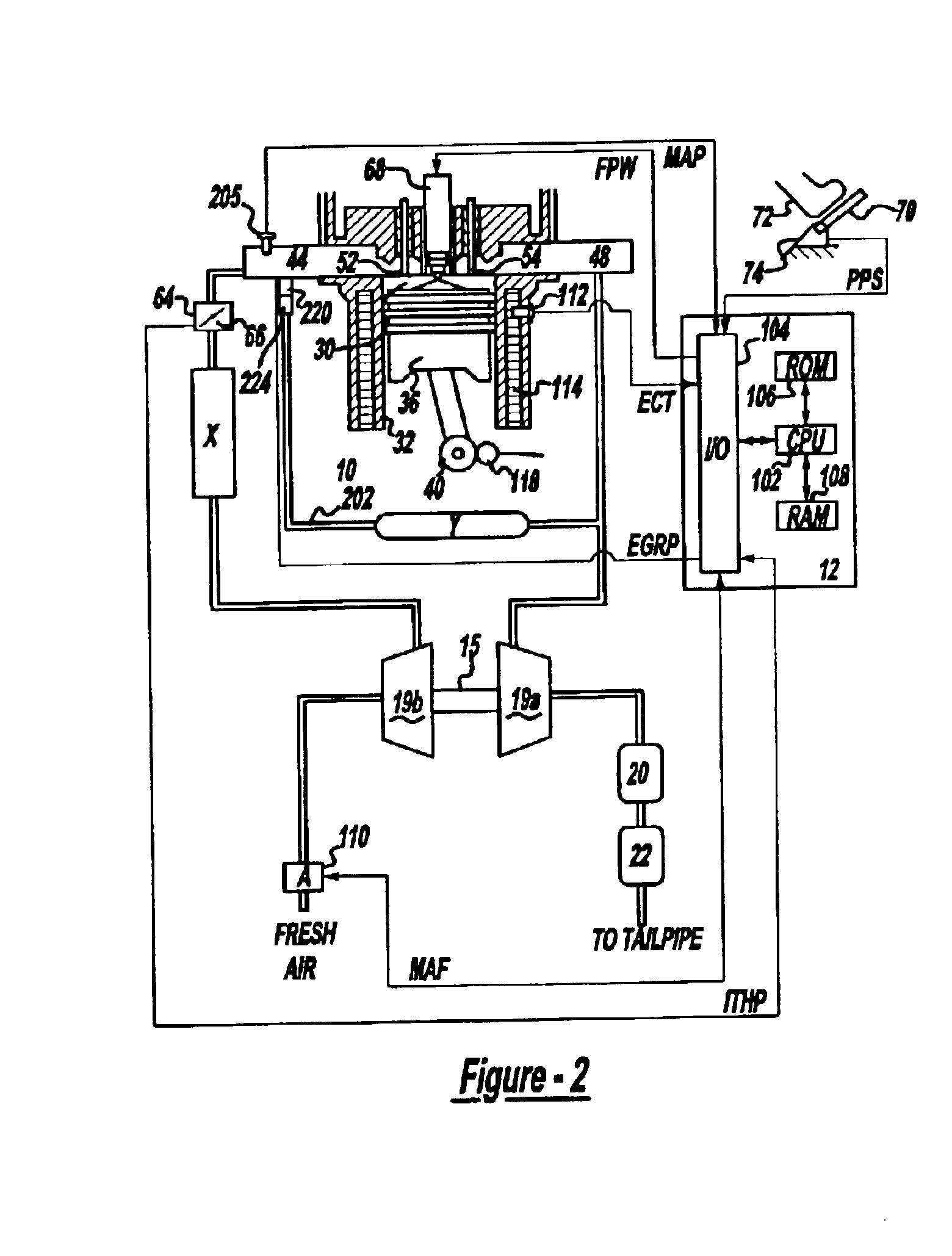
System and method for reducing NOx emissions during transient conditions in a diesel fueled vehicle
InactiveUS6863058B2Accurately controlReduce nitrogen oxide emissionsElectrical controlNon-fuel substance addition to fuelCombustion chamberManifold vacuum
The present invention is a dual-stage fuel injection strategy for compression ignition engines in which 15-40% of the fuel is injected into the combustion chamber no later than about −20 to −30 CA ATDC and as early as IVC. The rest of the fuel is then injected in one or more fuel pulses, none of which start before about −20 to −30 CA ATDC. The fuel injected early in the compression stroke forms a lean mixture that burns with low soot and low NOx emissions. The combustion of that fuel serves to increase in-cylinder temperature such that the ignition delay of subsequent fuel injection pulses is short. This mode is utilized when it is predicted that a NOx spike is imminent. Various other alternative methods for reducing NOx spikes are also disclosed such as specialized EGR systems that can provide EGR with low manifold vacuum.
Owner:FORD GLOBAL TECH LLC
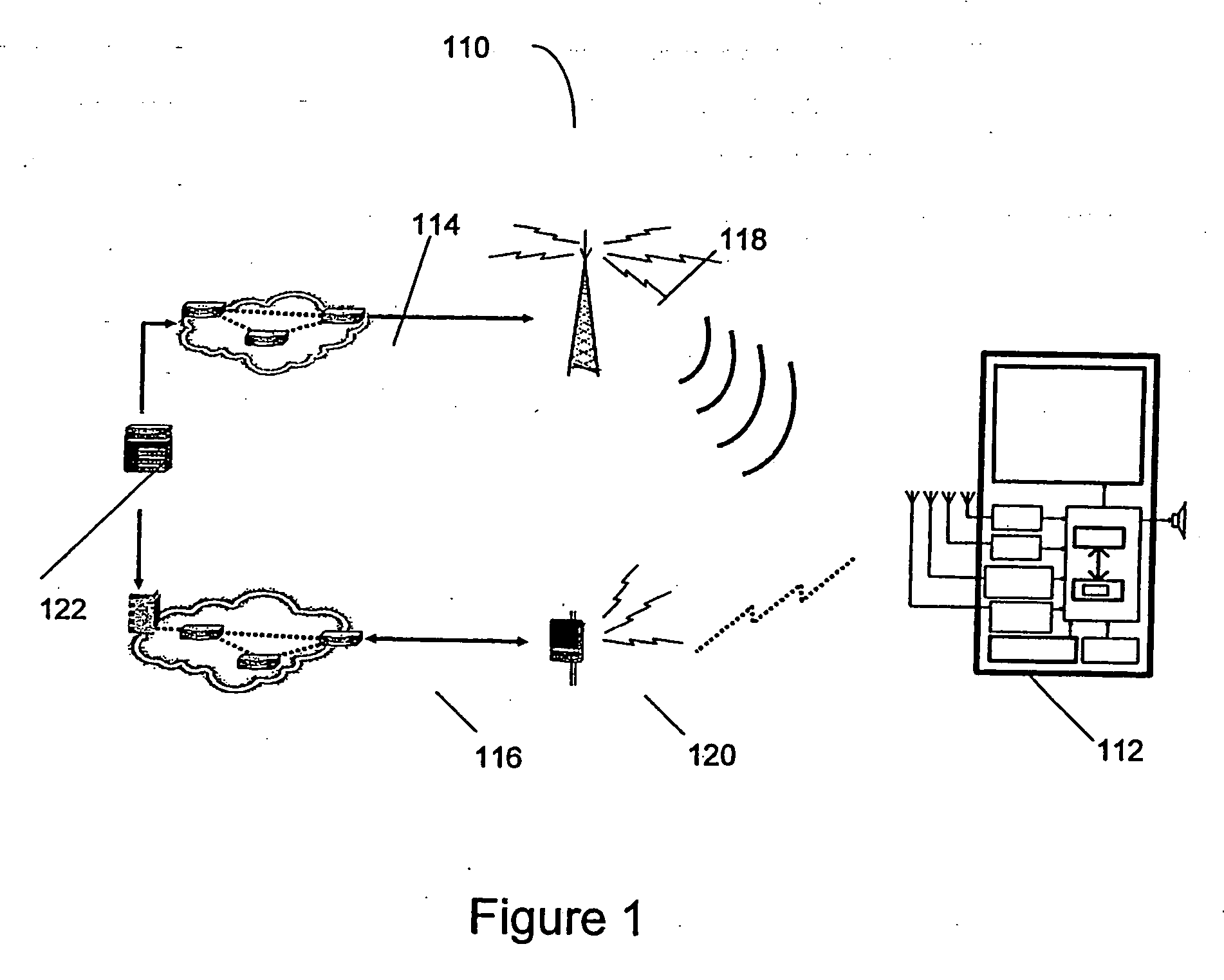
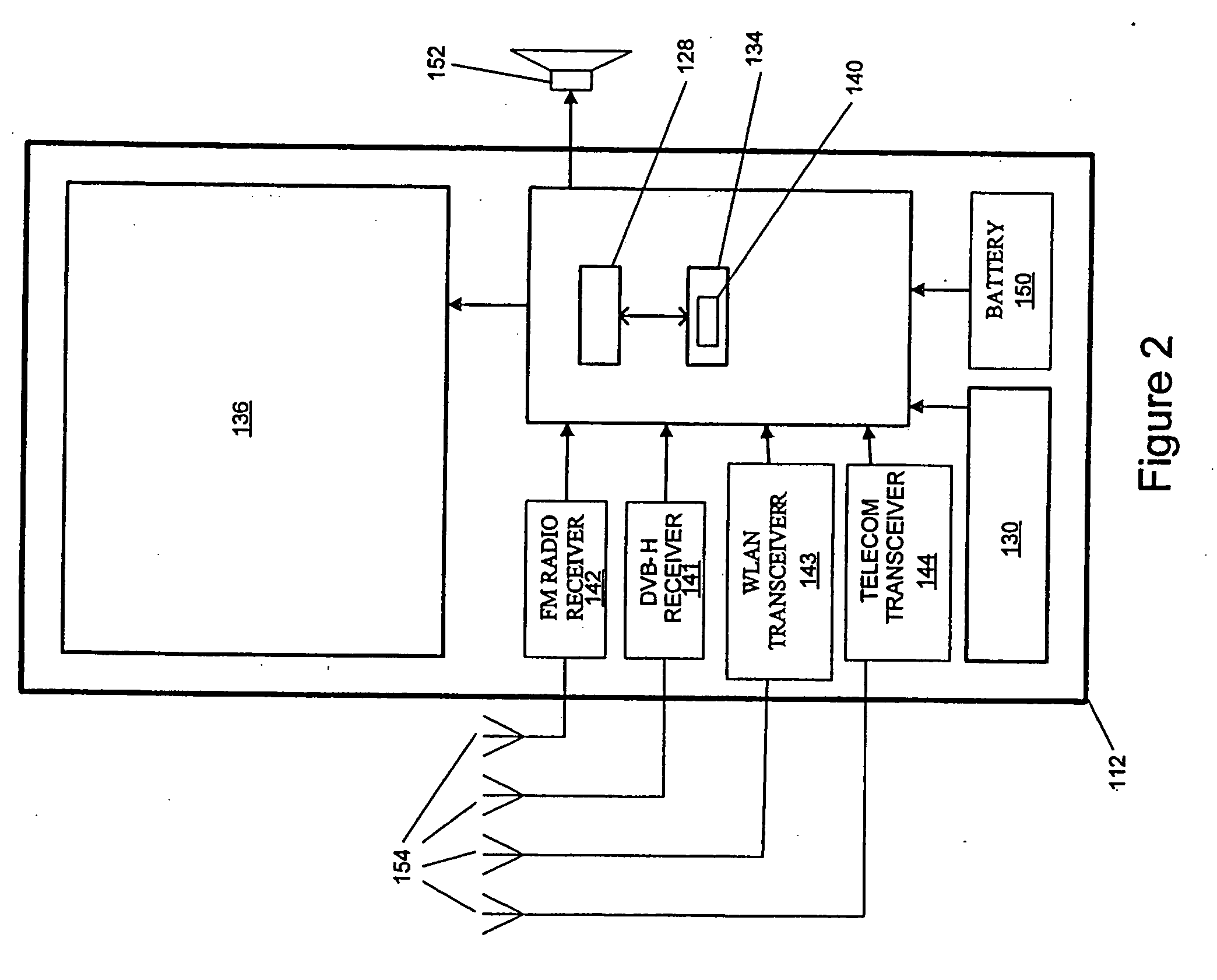
Prioritization of data
InactiveUS20060242091A1Simple and extensibleEfficient transportTelevision system detailsSpecific information broadcast systemsClient-sideMobile device
Prior art methods of receiving, organizing, and implementing the data transmitted to mobile devices, such as ESG fragments, have a great impact on mobile device performance and battery lifetime. Furthermore, in order to keep server side and client side ESG fragments in synch, any change in content of ESG fragments needs to be indicated. Additionally, any change in how ESG fragments are distributed requires the client side to verify if all the fragments are still available and valid in any new distribution set up and if their content has not changed. Aspects of the invention provide a protocol for prioritizing the ESG fragments to ensure the end user of a destination device receives more pertinent ESG data in a timely manner. Other aspects of the invention minimize the number of updates required on a client side or destination device caused by the re-distribution of the “unchanged” ESG fragments into different carousels.
Owner:WSOU INVESTMENTS LLC
Internet website traffic flow analysis
InactiveUS7464187B2Accurate collectionAccurately studiedHardware monitoringMultiple digital computer combinationsWeb siteAnalysis tools
An Internet-based analysis tool follows, in real-time, the flow of traffic through a website. For every website page requested by a website visitor, the state of the visitor's browser is recorded and data relating to the path visitors take through the website is collected and studied. The state of the visitor's browser path is maintained in a traffic analysis cookie that is passed between a website file server and the visitor browser with every page requested for viewing. The cookie is maintained in a size that can be passed from server to browser and back again without negatively impacting server performance and without negatively impacting browser performance. The data in the cookie can follow the visitor browser through independent file servers, regardless of how the pages of a website might be distributed in storage.
Owner:ADOBE SYST INC
Coherency coverage of data across multiple packets varying in sizes
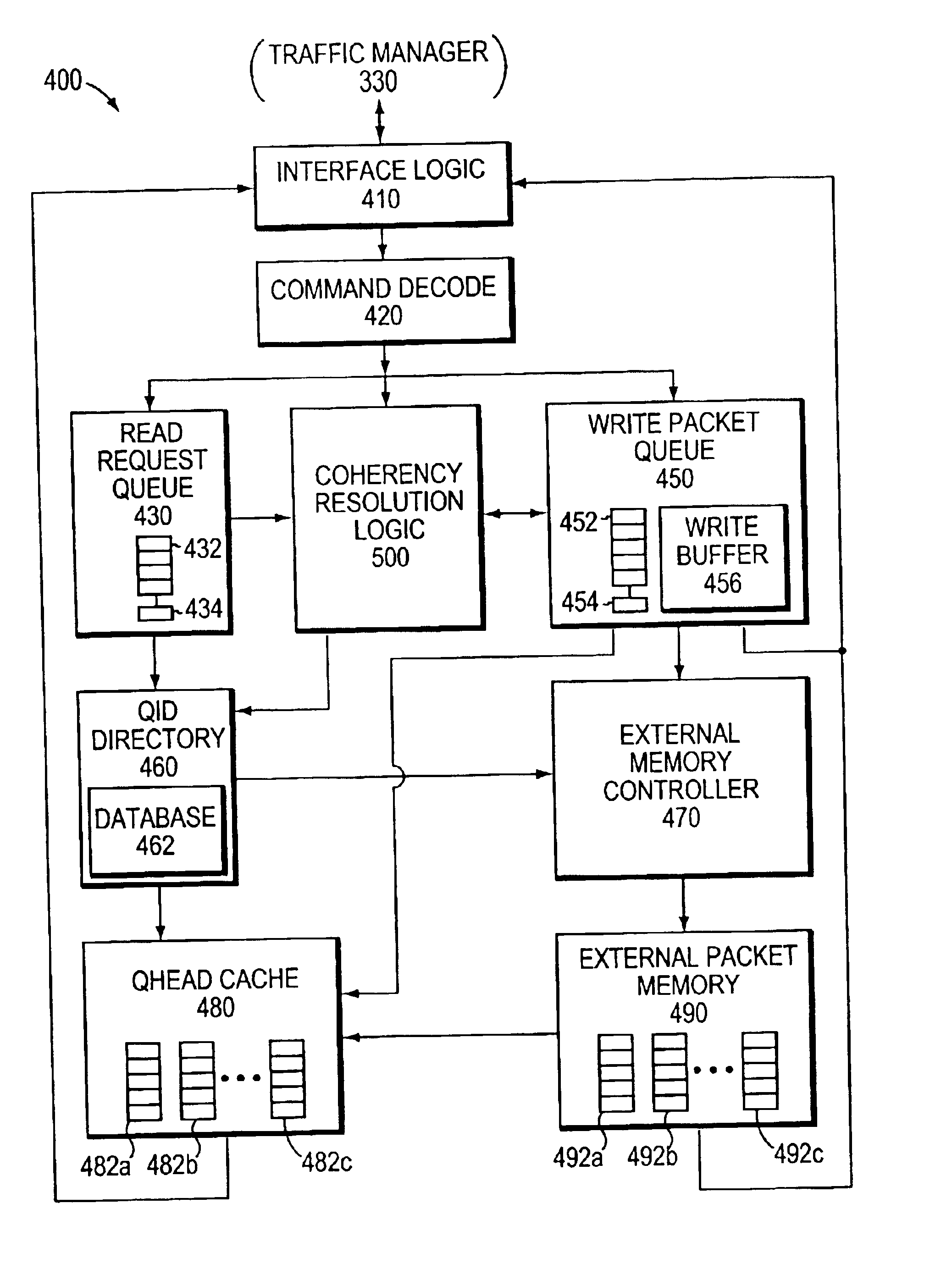
ActiveUS6850999B1Simplifies data coherencyReduce the impactMemory adressing/allocation/relocationDigital computer detailsWrite bufferNetwork packet
A coherency resolution technique enables efficient resolution of data coherency for packet data associated with a service queue of an intermediate network node. The packet data is enqueued on a write buffer prior to being stored on an external packet memory of a packet memory system. The packet data may be interspersed among other packets of data from different service queues, wherein the packets are of differing sizes. In response to a read request for the packet data, a coherency operation is performed by coherency resolution logic on the data in the write buffer to determine if any of its enqueued data can be used to service the request.
Owner:CISCO TECH INC
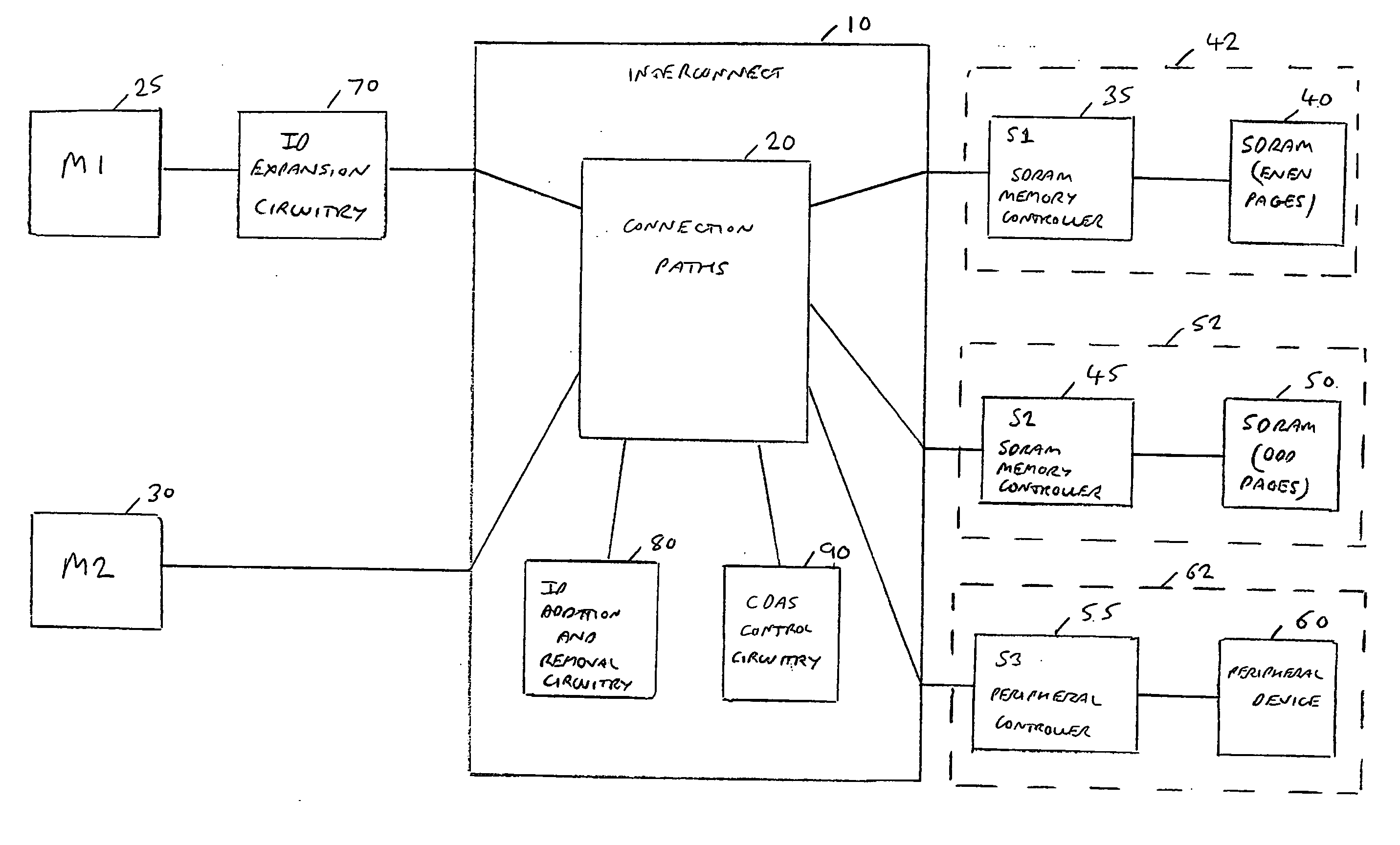
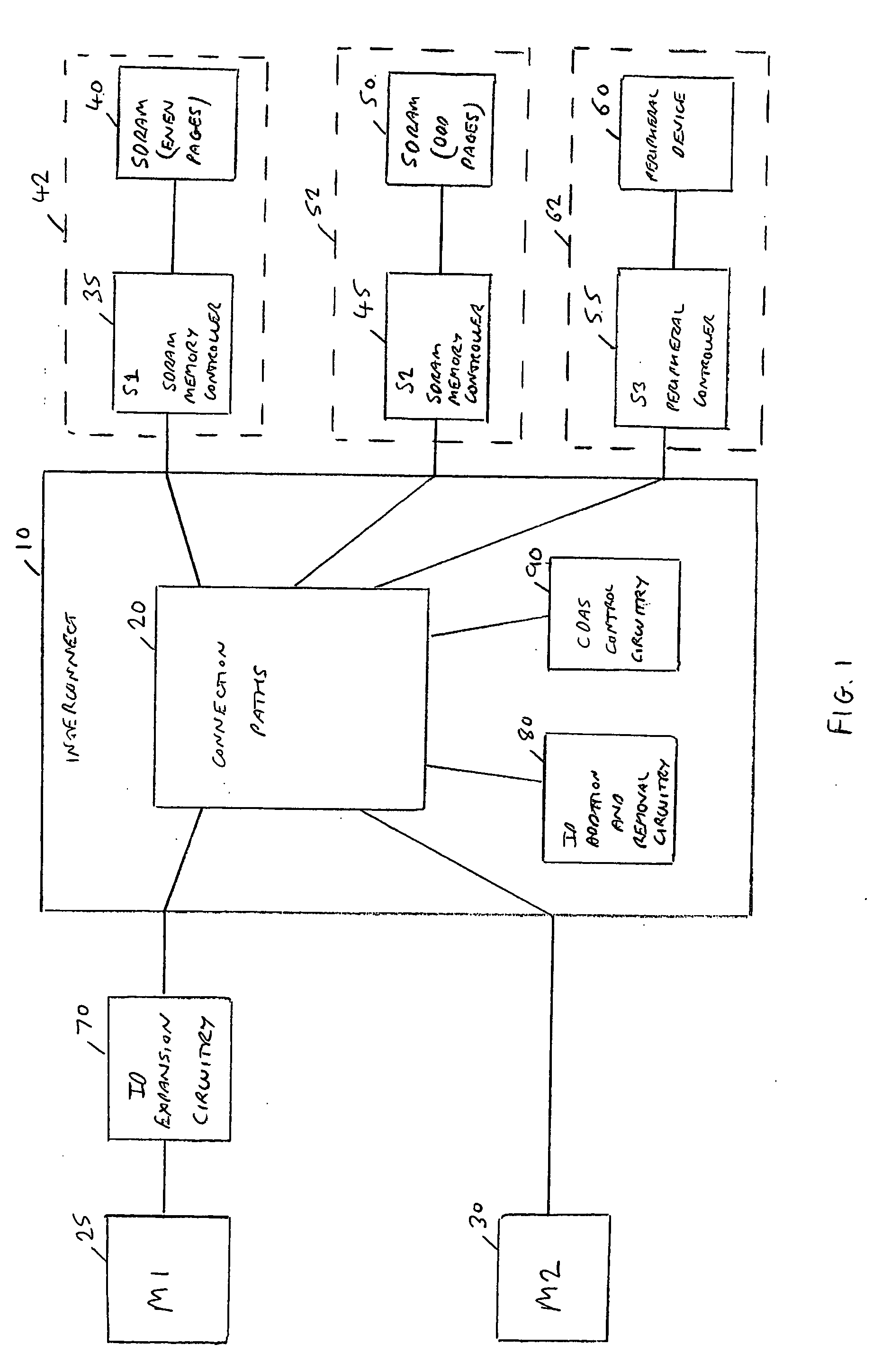
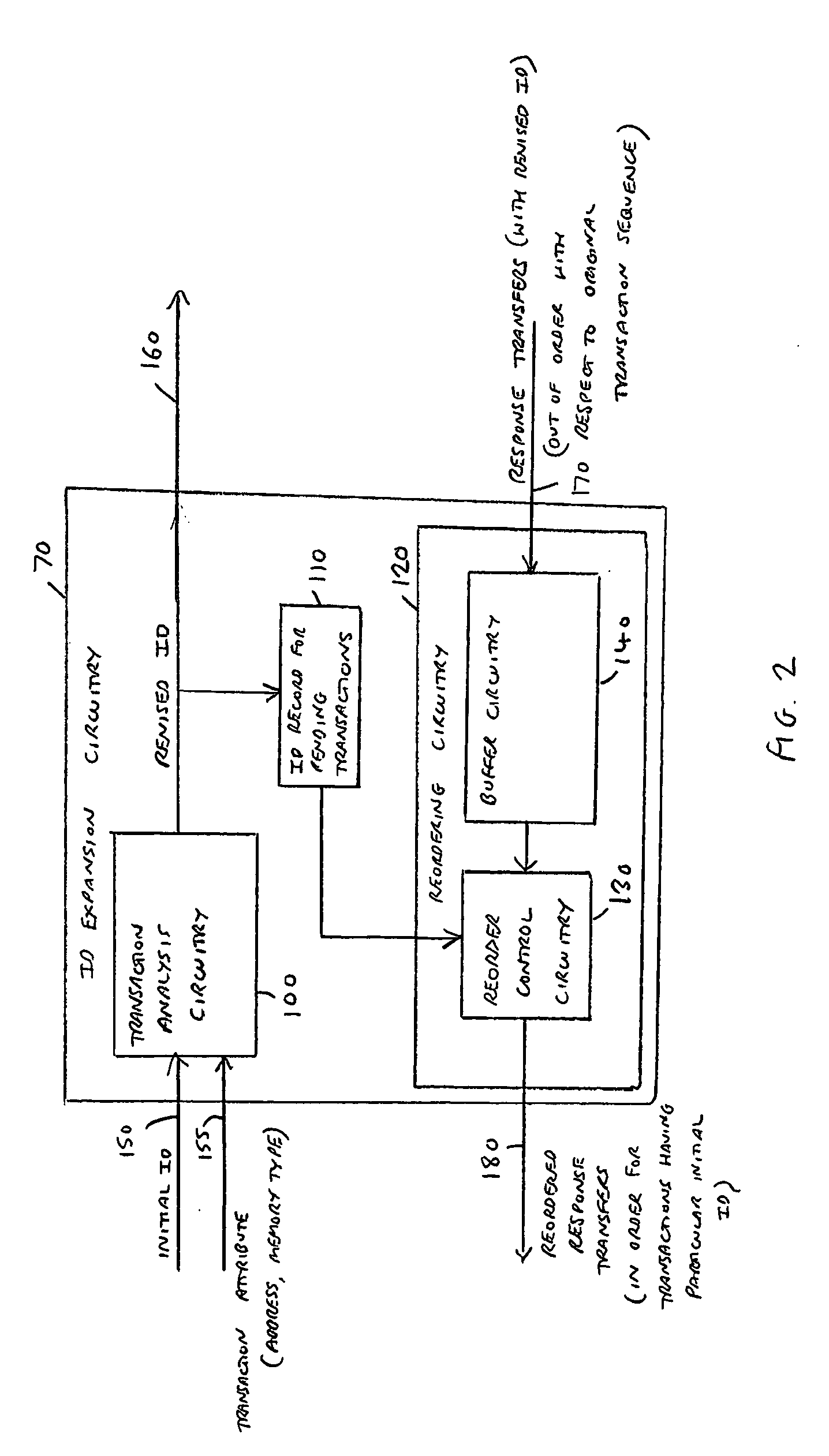
Transaction indentifier expansion circuitry and method of operation of such circuitry
ActiveUS20120290752A1Work wellSimple techniqueElectric digital data processingIdentifier ExtensionDeadlock
Transaction identifier expansion circuitry is provided, along with a method of operating such circuitry. The transaction identifier expansion circuitry interfaces between a master device and interconnect circuitry used to couple the master device with a plurality of slave devices to enable transactions to be performed. Transaction analysis circuitry is responsive to each transaction in a sequence of transactions initiated by the master device, to compare at least one attribute of the transaction with predetermined attributes indicative of the target slave device for that transaction. Based on the comparison, an initial transaction identifier is then mapped to one of a plurality of revised transaction identifiers, such that the revised transaction identifier is dependent on the target slave device. Reordering circuitry is then arranged to buffer response transfers received from the interconnect circuitry destined for the master device, with each response transfer having the revised transaction identifier associated therewith. The reordering circuitry then re-orders the response transfers having regard to the original transaction order of those transactions within the sequence of transactions that had the same initial transaction identifier, prior to provision of each response transfer to the master device. By such an approach, the performance of a high performance master device can be maintained, by ensuring that for at least the transactions targeted to a particular subset of the slave devices, no intervention by deadlock avoidance circuitry within the interconnect is required when routing transactions to those slave devices, due to the use of different transaction identifiers when accessing those slave devices.
Owner:ARM LTD
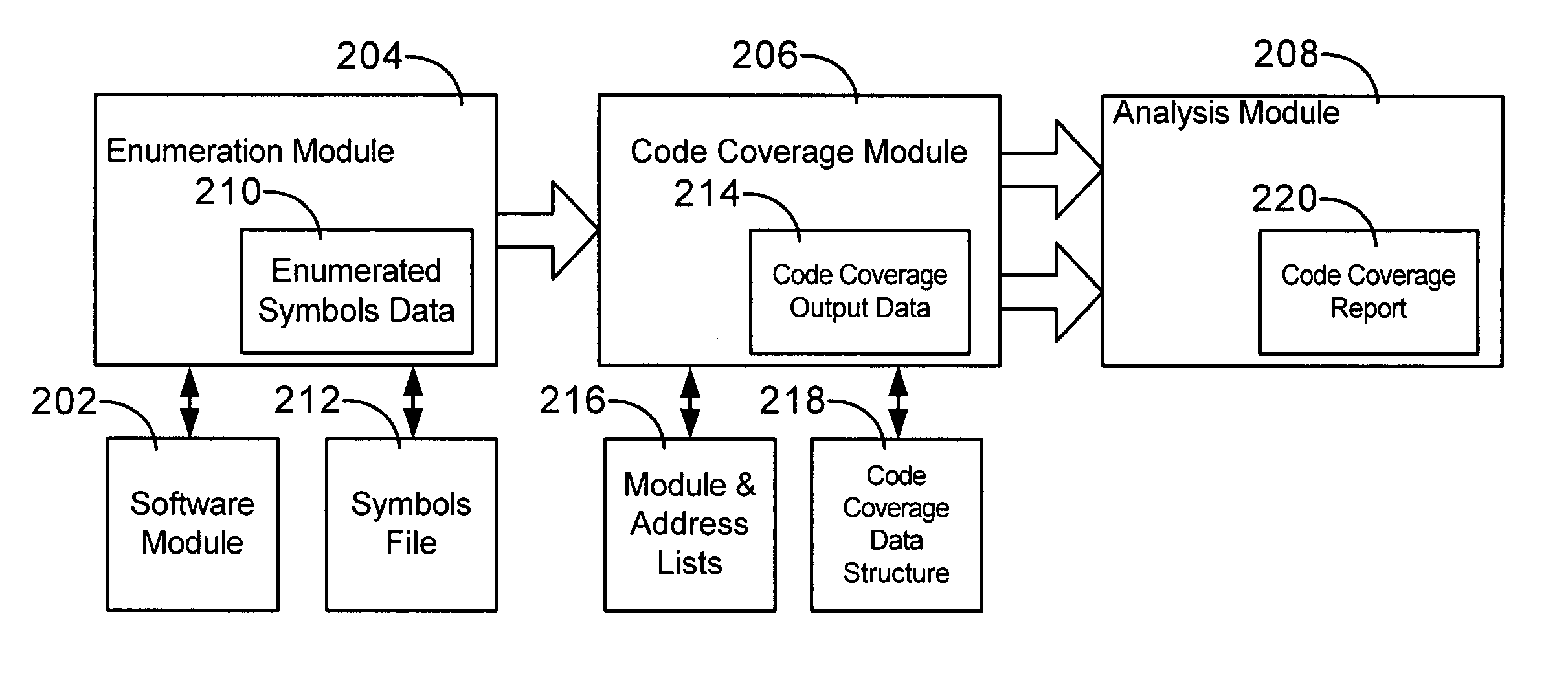
Method for determining code coverage
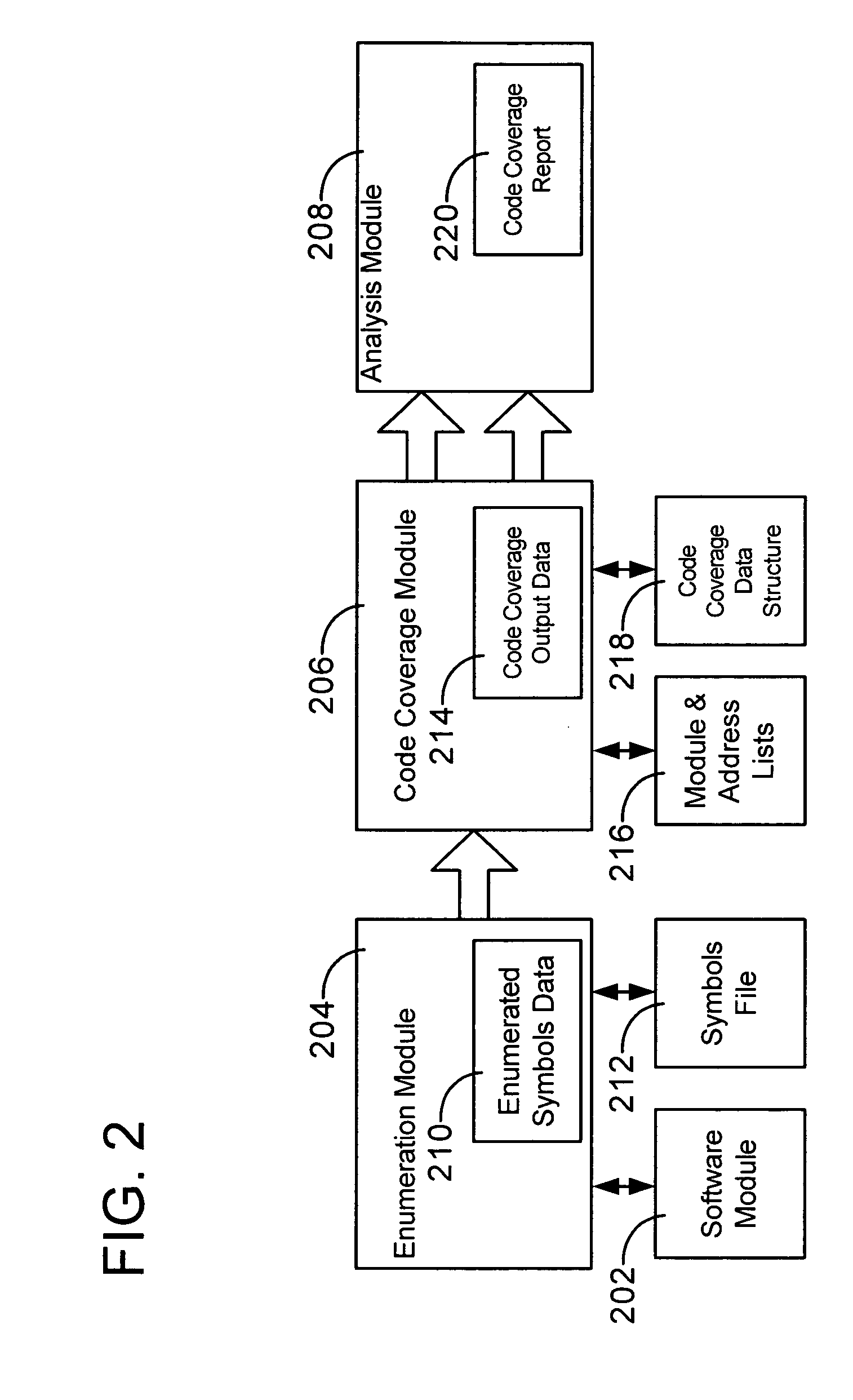
InactiveUS20060195724A1Minimize impactSuitable for useError detection/correctionSpecific program execution arrangementsCode coverageSystem usage
A method and system for determining code coverage of one or more software modules is disclosed. The disclosed method and system uses an enumeration module, a code coverage module and an analysis module. The enumeration module is used to identify portions of the code in the software module for which code coverage data is desired. The code coverage module collects code coverage data when the software module is loaded. The analysis module summarizes and reports results of the collected code coverage data.
Owner:MICROSOFT TECH LICENSING LLC
Lenses, systems and methods for providing custom aberration treatments and monovision to correct presbyopia
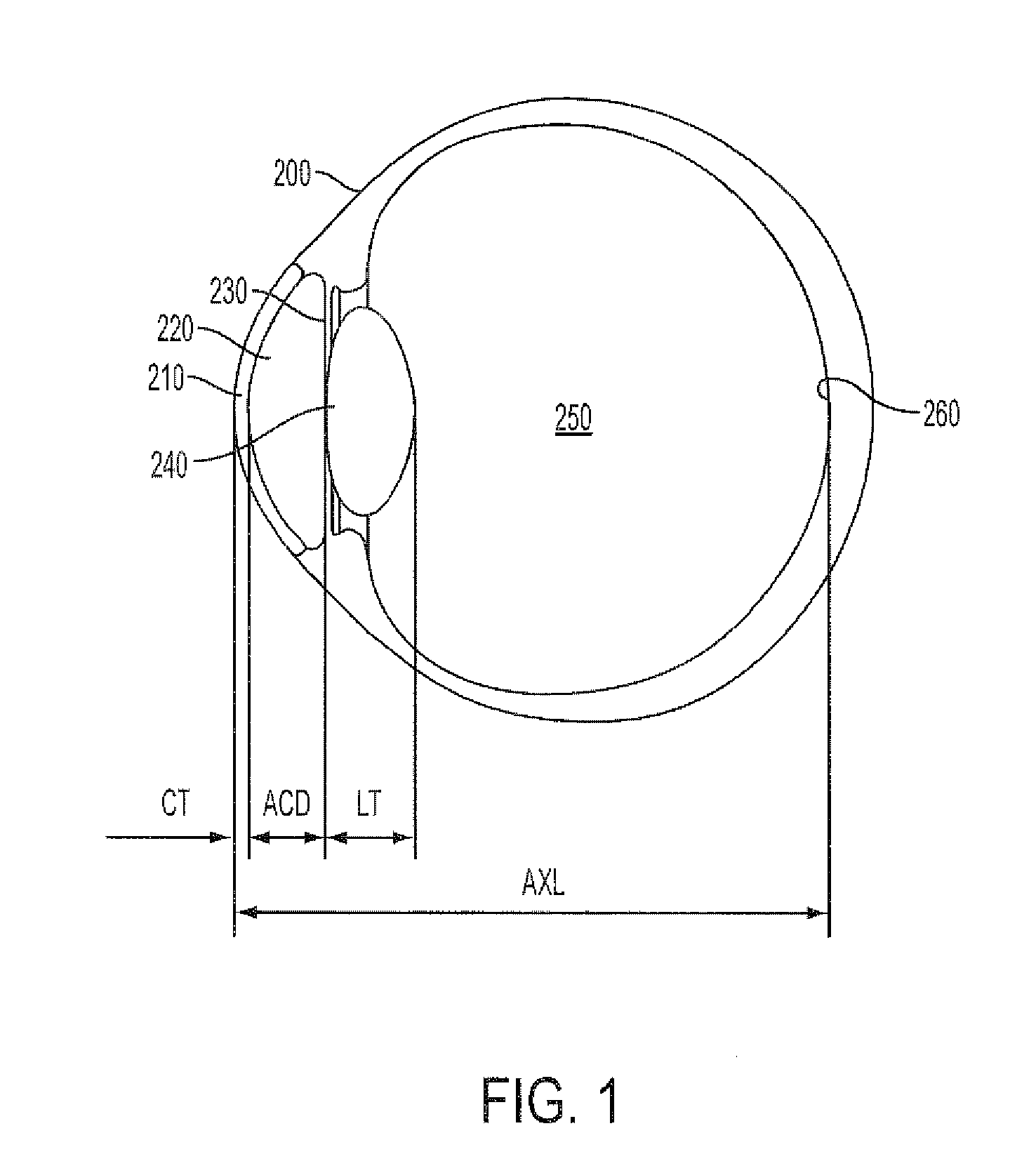
InactiveUS20130335701A1Improve eyesightIncrease depth of focusSpectales/gogglesEye diagnosticsFar-sightednessAberrations of the eye
A lens, system and / or method for providing custom ocular aberrations for enhanced higher visual acuity. Scaled versions of a patient's aberration pattern may either attenuate or amplify the overall amount of ocular aberrations, to either correct or partially correct a patient's aberrations leading to enhanced visual acuity and / or extended depth of focus. This may be binocularly applied in order to provide high visual acuity in a patient at least at near, far and intermediate distances. The method may include obtaining an optimized binocular summation of both eyes of the patient; designing a first lens solution to correct or partially correct the dominant eye's aberrations according to an attenuated scaled version of a patient's ocular aberrations in the dominant eye; and designing a second lens solution to provide an additional customized extension of depth of focus by the induction of scaled patterns of ocular aberrations in the non dominant eye.
Owner:AMO GRONINGEN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com