Patents
Literature
565 results about "Write buffer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A write buffer is a type of data buffer used in certain CPU cache architectures like Intel's x86 and AMD64. In multi-core systems, write buffers destroy sequential consistency. Some software disciplines, like C11's data-race-freedom, are sufficient to regain a sequentially consistent view of memory.
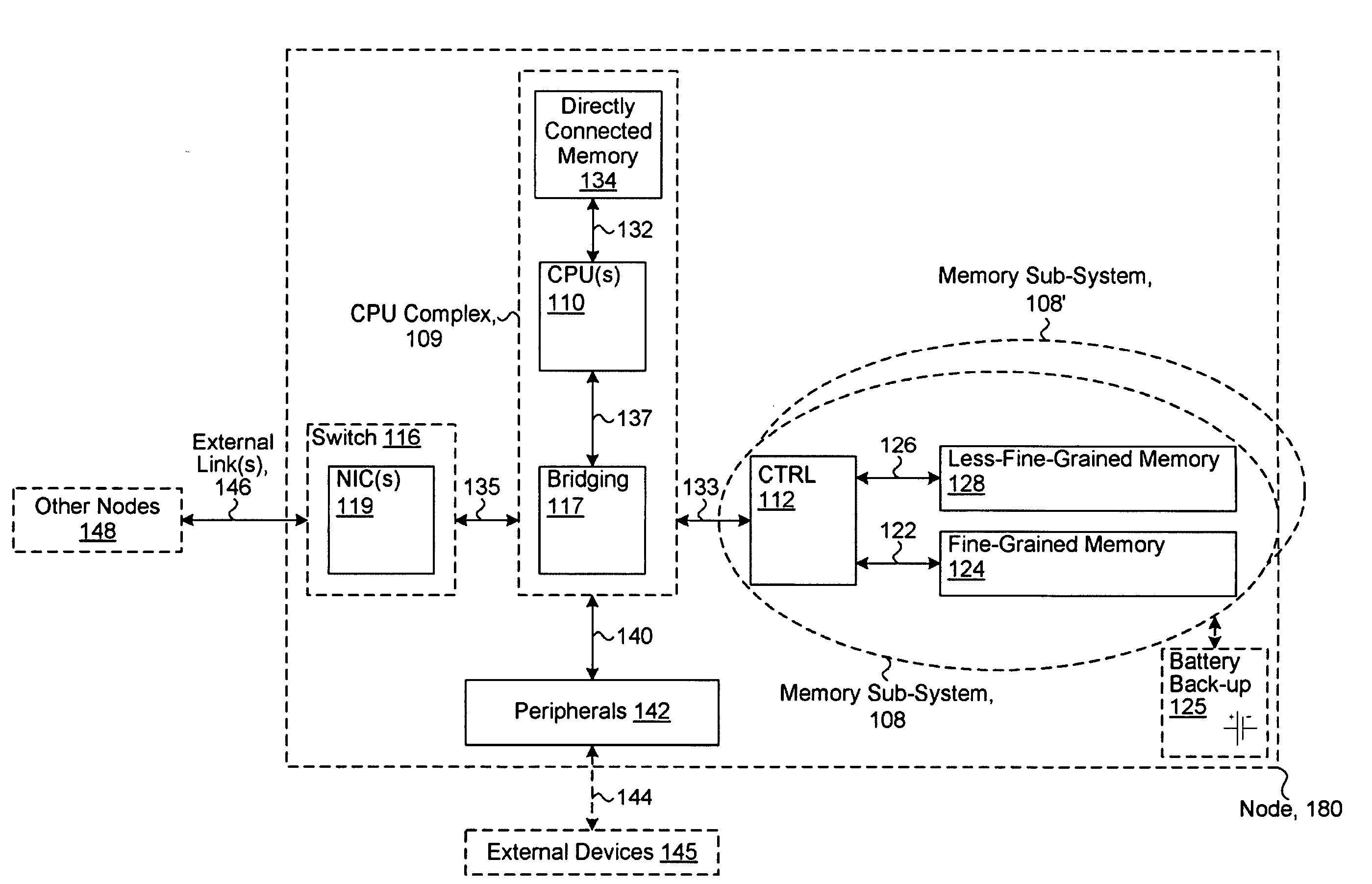
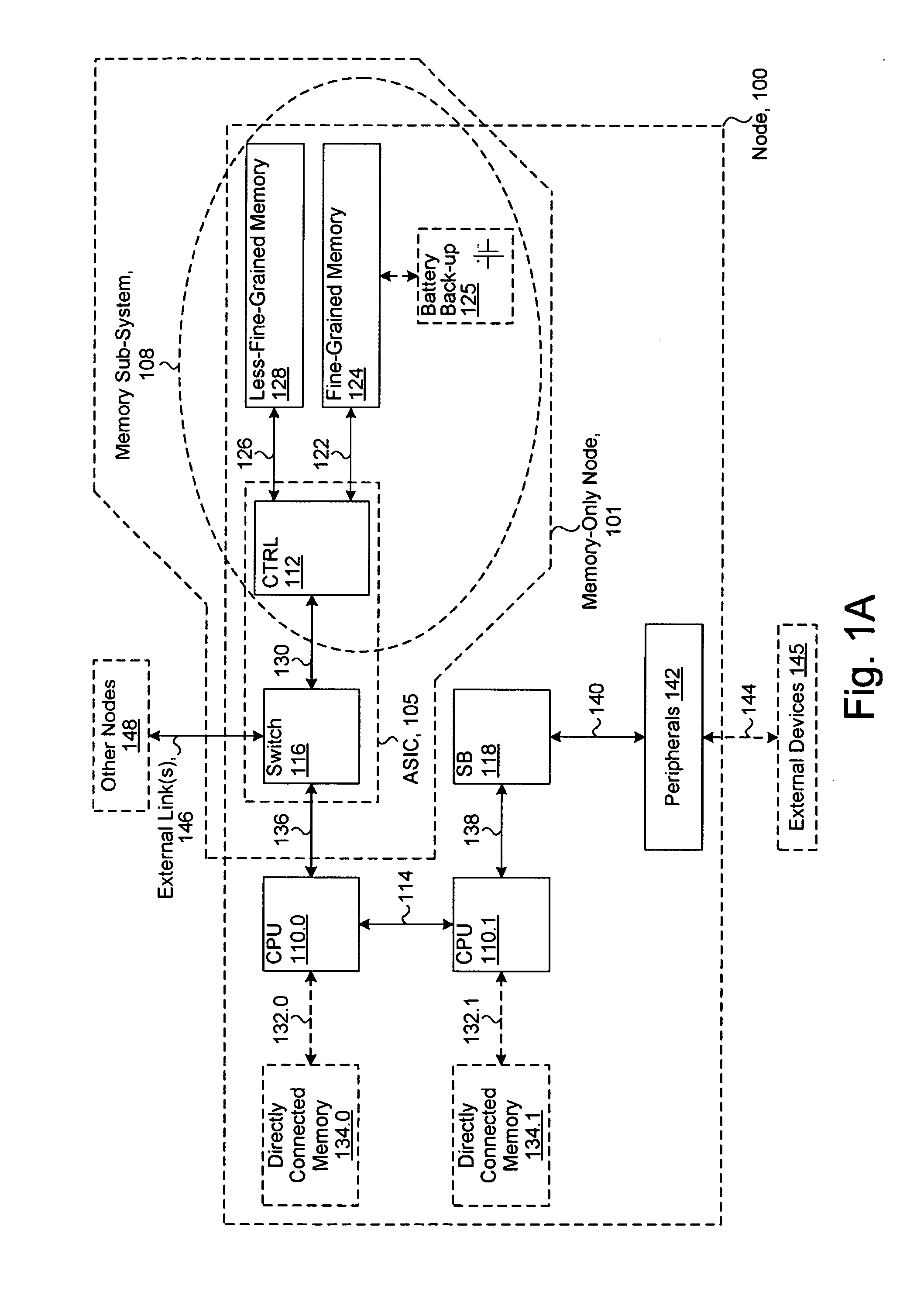
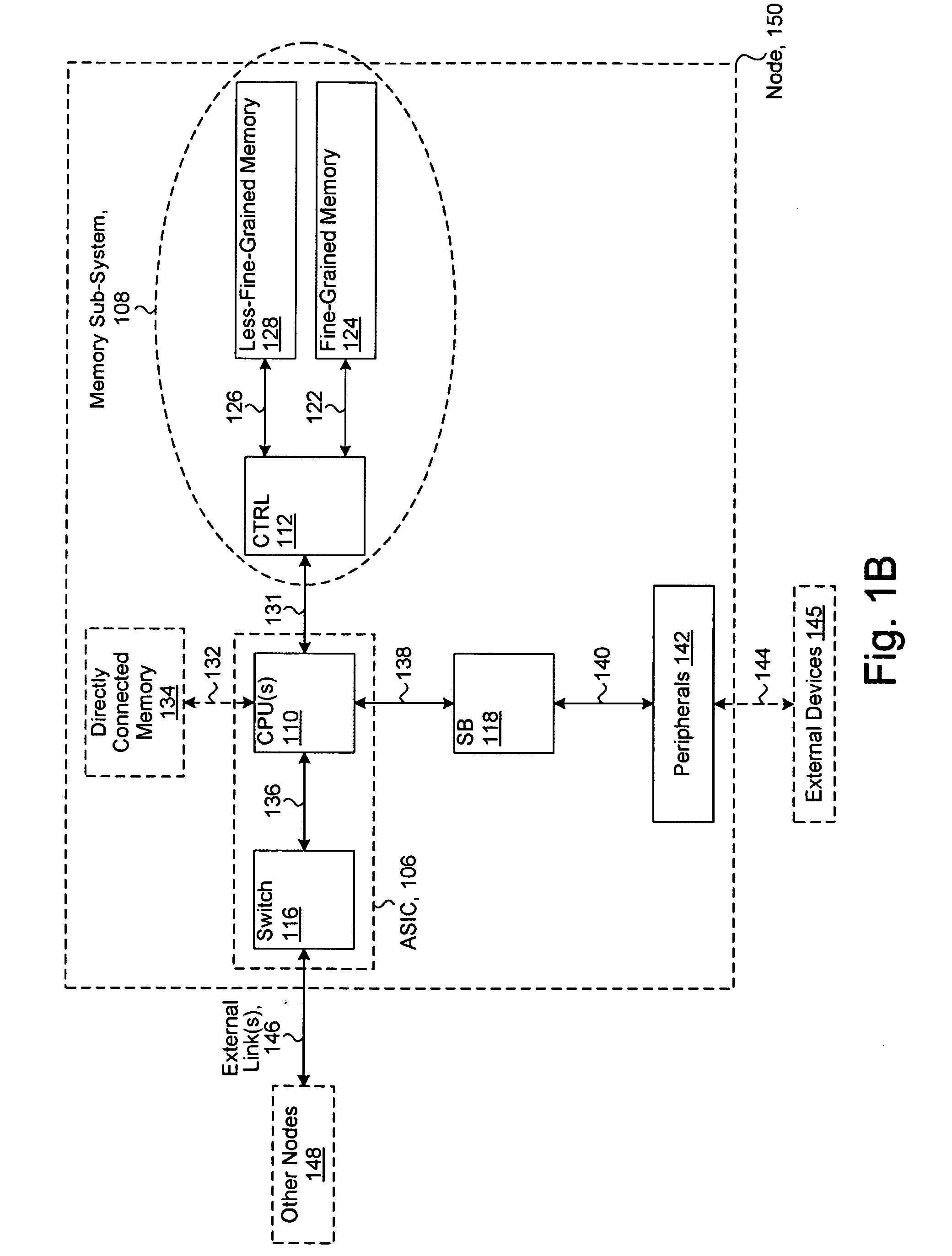
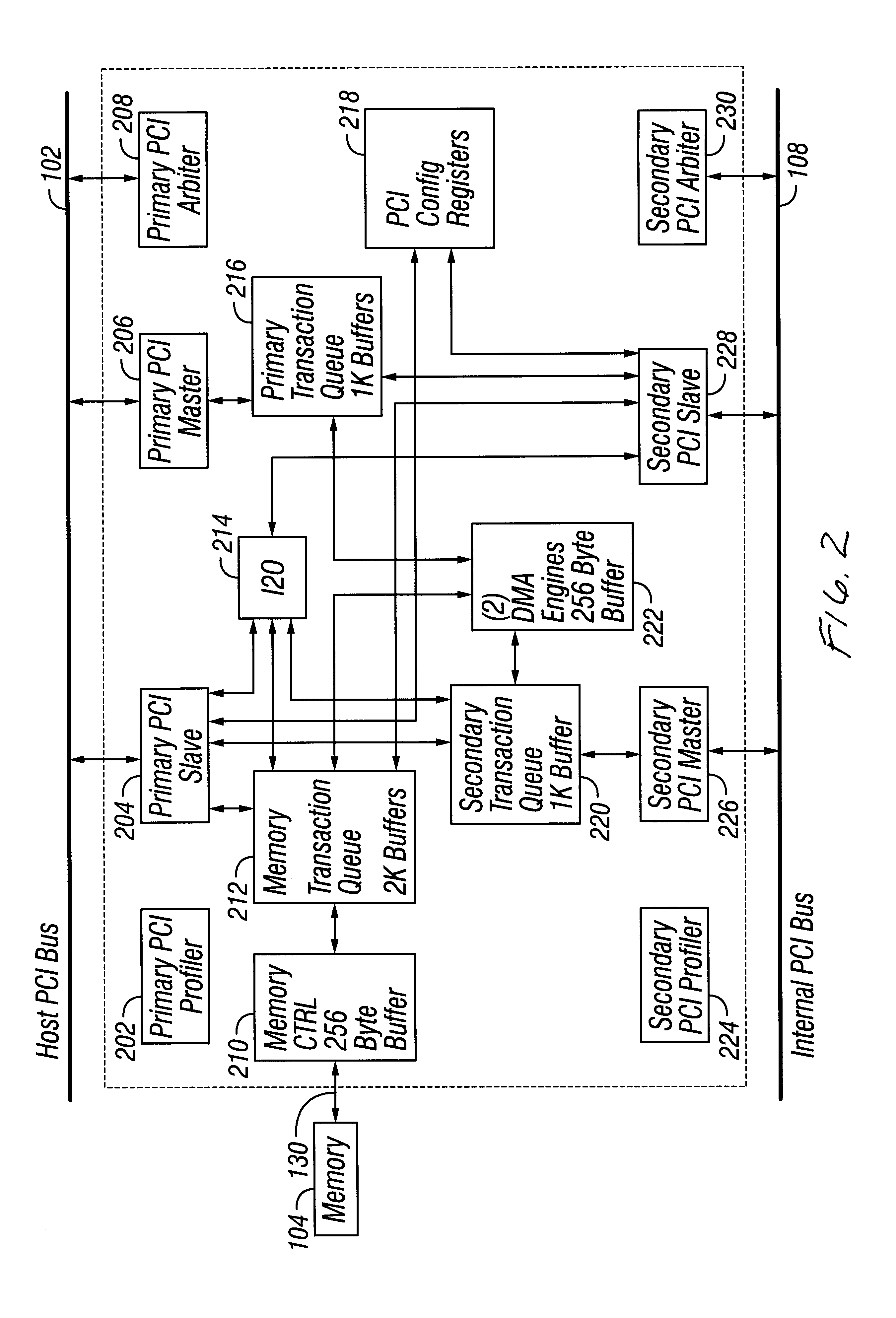
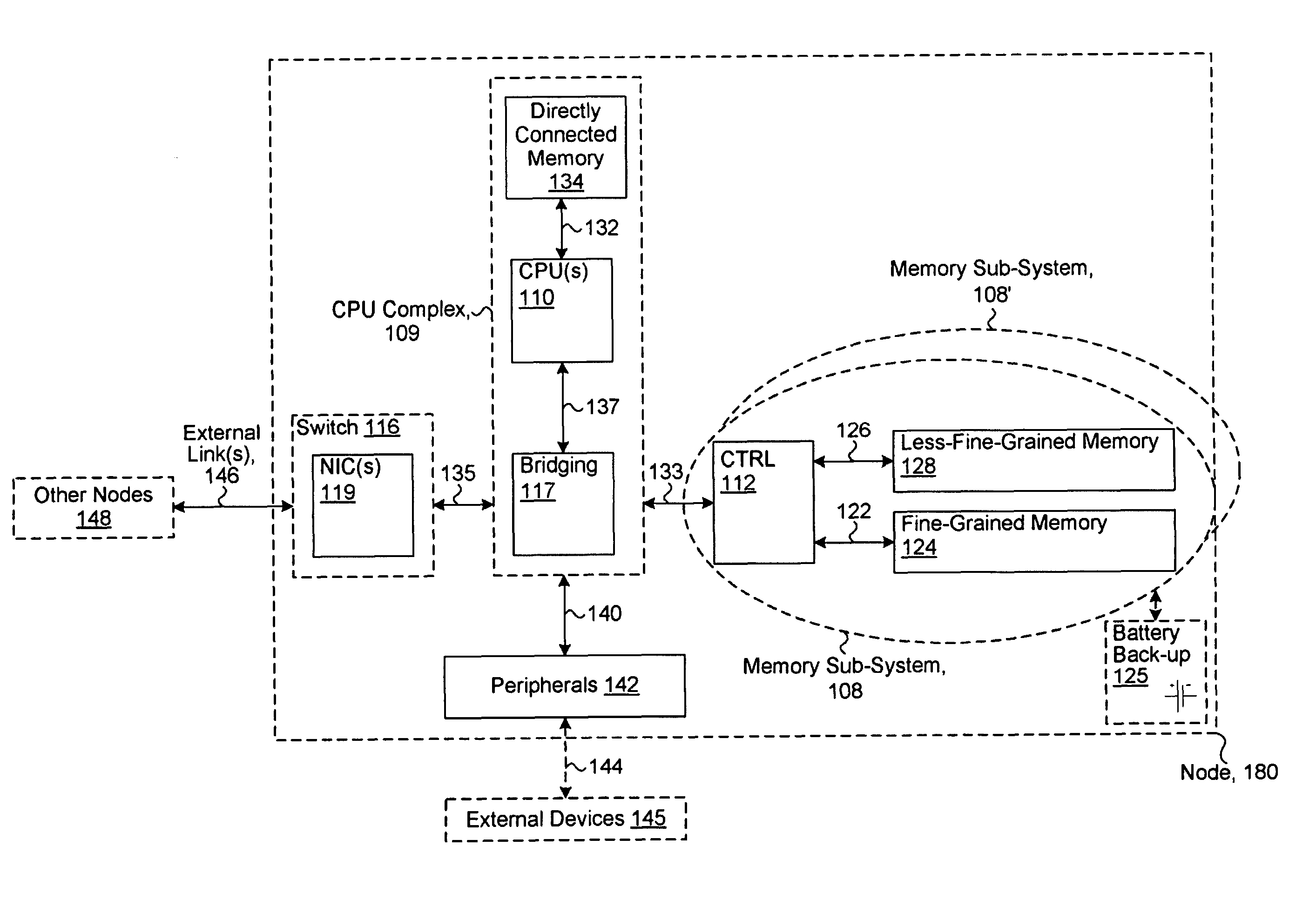
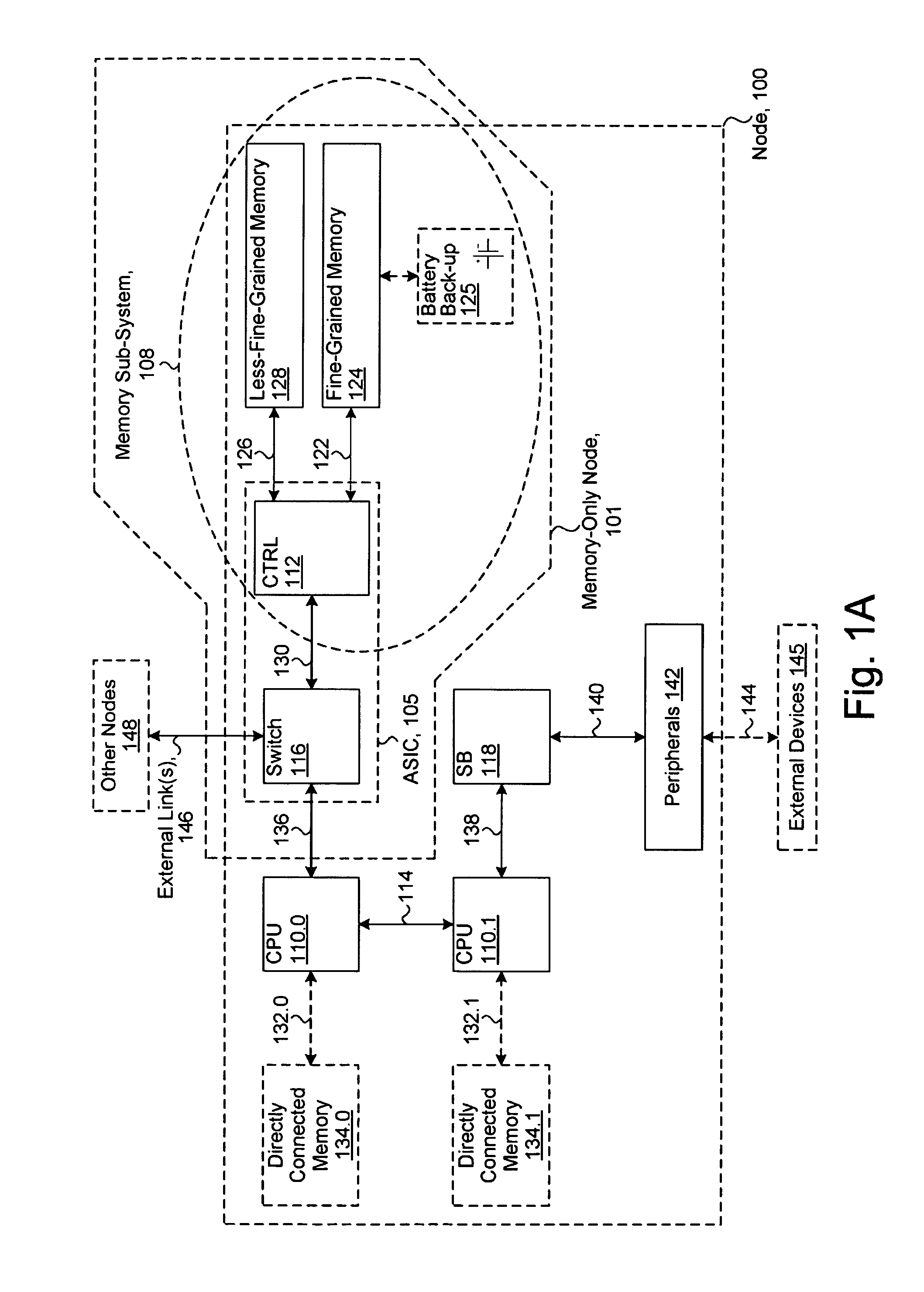
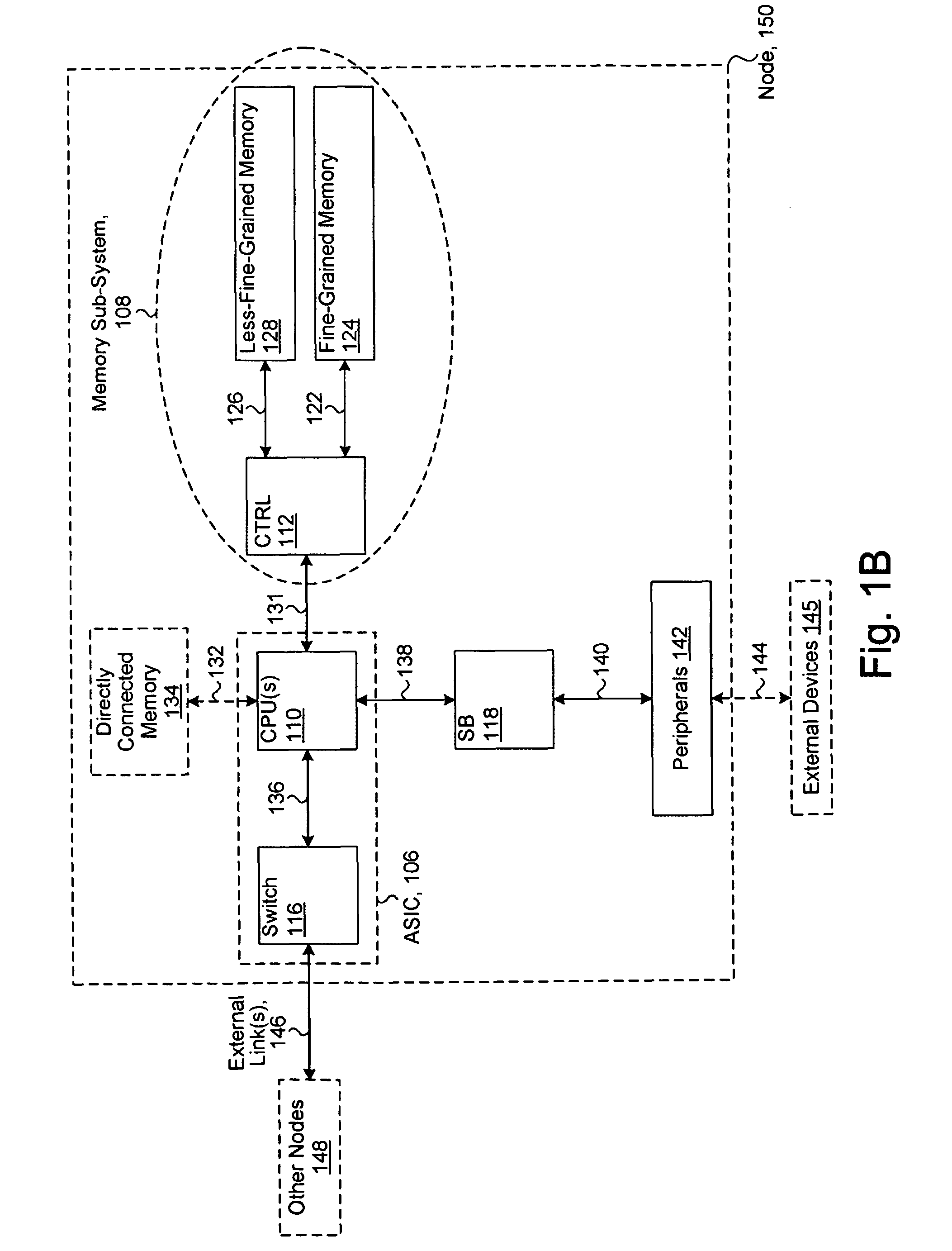
System including a fine-grained memory and a less-fine-grained memory
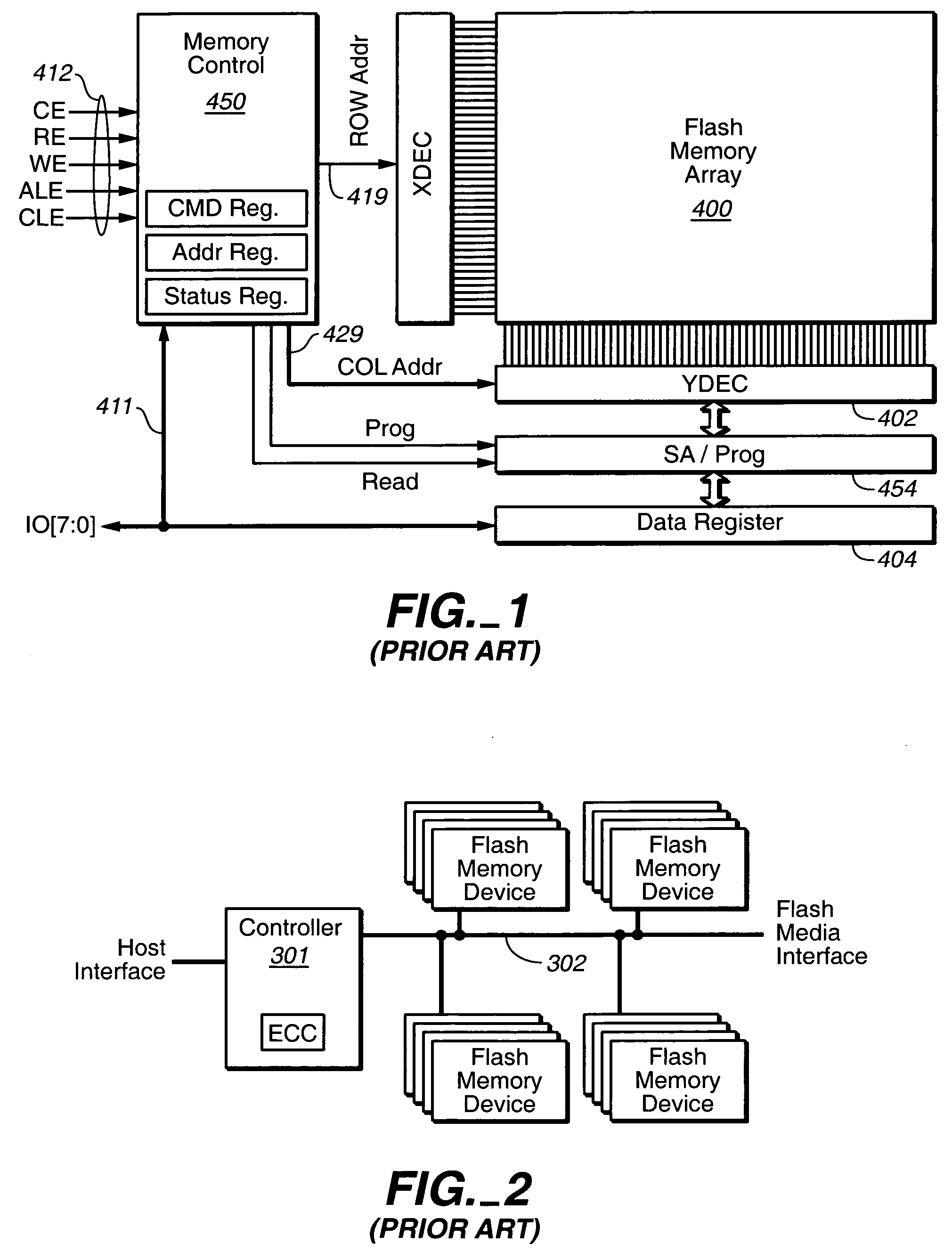
ActiveUS20080301256A1Memory architecture accessing/allocationEnergy efficient ICTData processing systemWrite buffer
A data processing system includes one or more nodes, each node including a memory sub-system. The sub-system includes a fine-grained, memory, and a less-fine-grained (e.g., page-based) memory. The fine-grained memory optionally serves as a cache and / or as a write buffer for the page-based memory. Software executing on the system uses n node address space which enables access to the page-based memories of all nodes. Each node optionally provides ACID memory properties for at least a portion of the space. In at least a portion of the space, memory elements are mapped to locations in the page-based memory. In various embodiments, some of the elements are compressed, the compressed elements are packed into pages, the pages are written into available locations in the page-based memory, and a map maintains an association between the some of the elements and the locations.
Owner:SANDISK TECH LLC
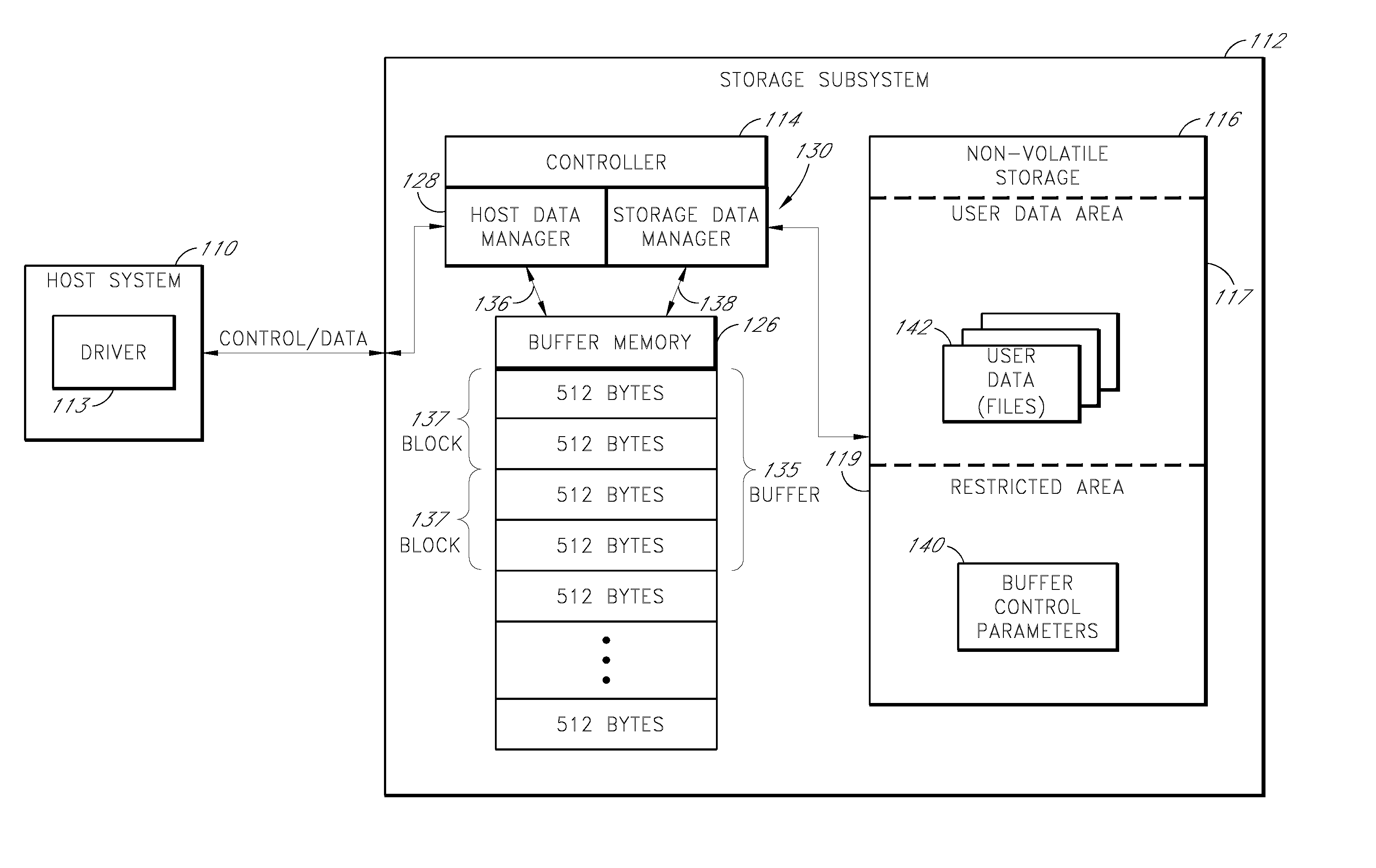
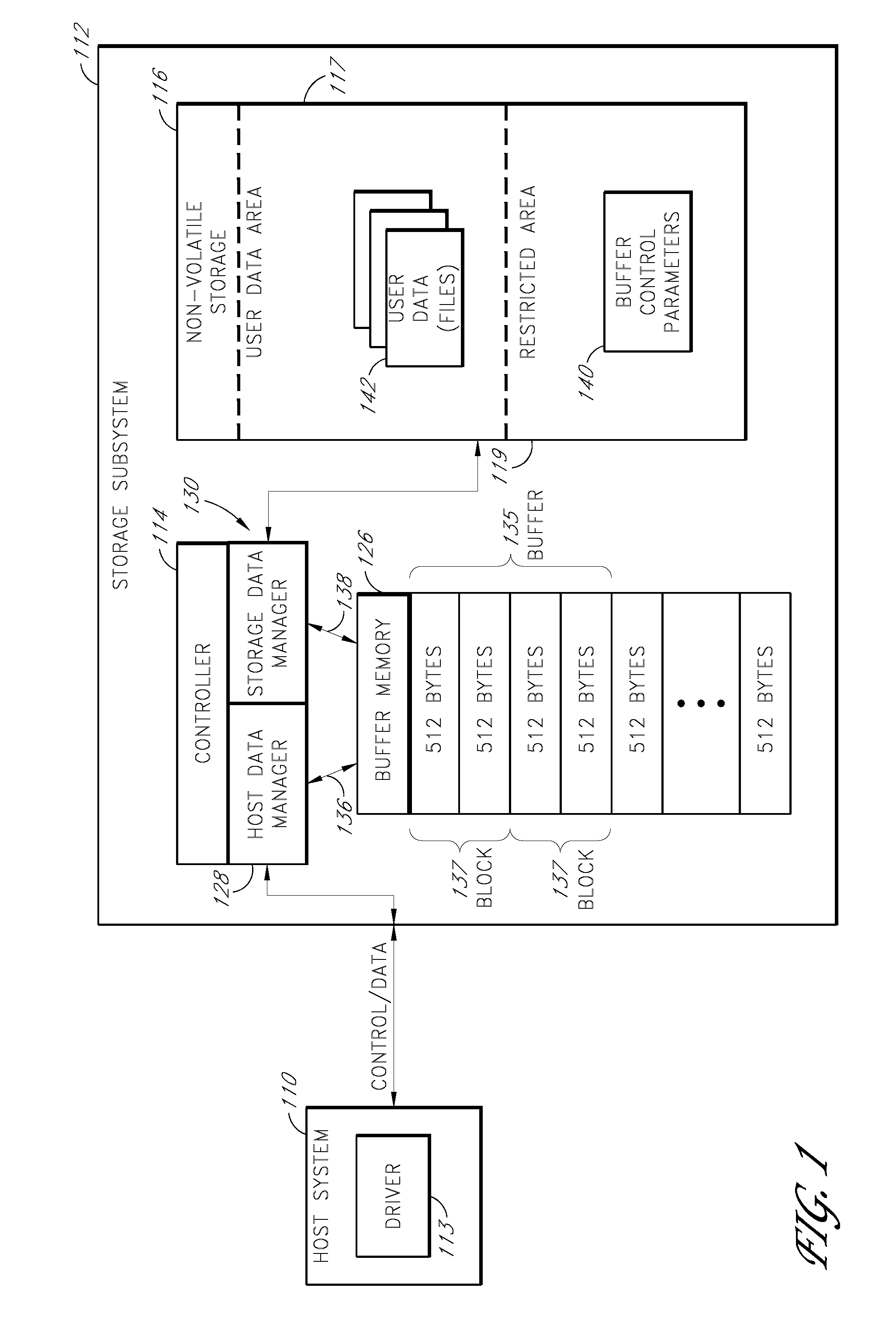
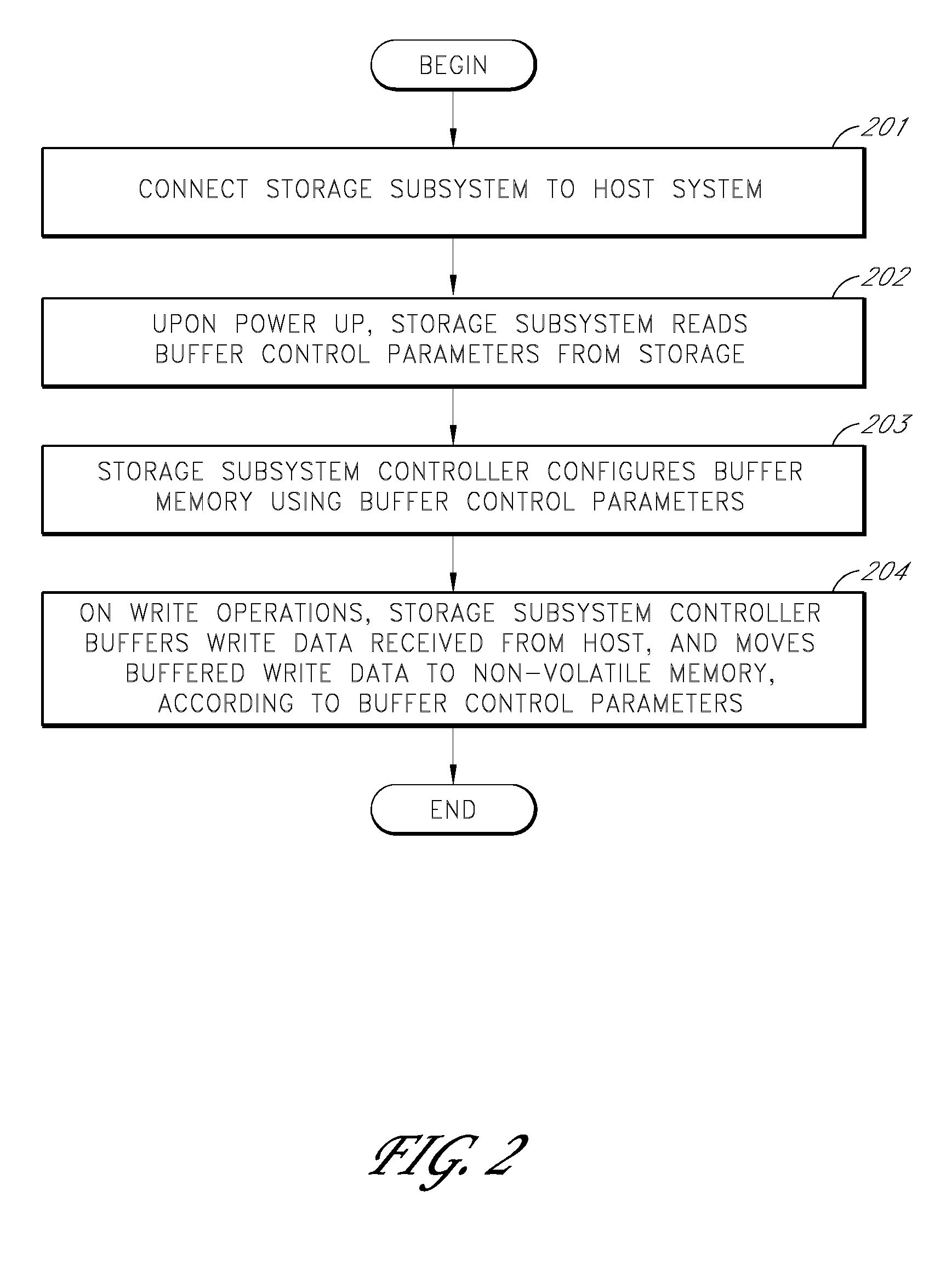
Storage subsystem with configurable buffer
ActiveUS7596643B2Reduce riskImprove performanceRecord information storageInput/output processes for data processingWrite bufferData loss
Owner:WESTERN DIGITAL TECH INC
In-line non volatile memory disk read cache and write buffer
ActiveUS20060248387A1Read/write performance of hardReduce the number of timesData buffering arrangementsError detection/correctionHard disc driveWrite buffer
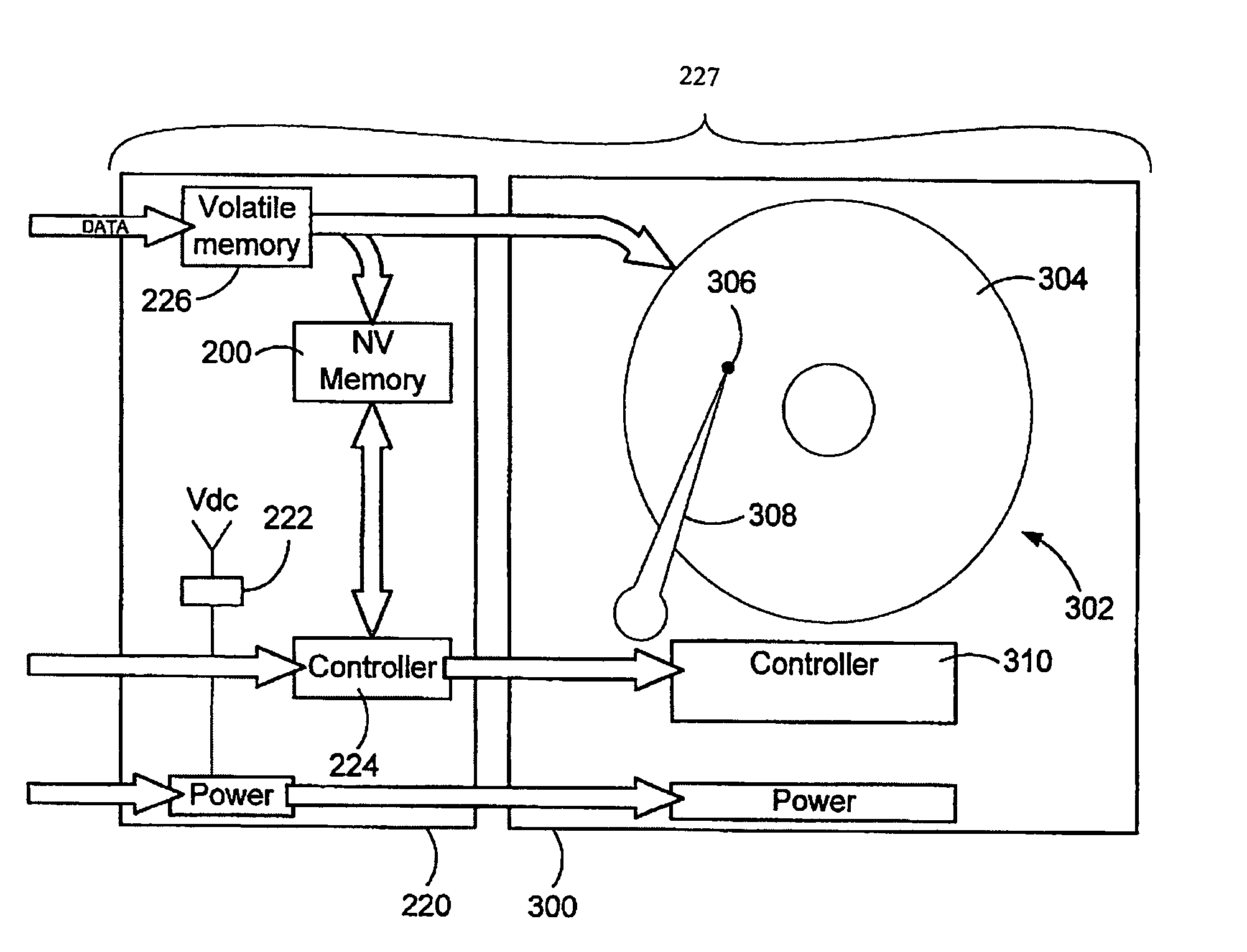
A method and apparatus to improve the read / write performance of a hard drive is presented. A device having solid state, non-volatile (NV) memory is added in-line to the conventional hard drive and acts as a read / write cache. Data specified by the operating system is stored in the NV memory. The operating system provides a list of data to be put in NV memory. The data includes data to be pinned in NV memory and data that is dynamic. Pinned data persists in NV memory until the operating system commands it to be flushed. Dynamic data can be flushed by the hard drive controller. Data sent by an application for storage is temporarily stored in NV memory in data blocks until the operating system commits it to the disk.
Owner:MICROSOFT TECH LICENSING LLC
Flash memory cache including for use with persistent key-value store
InactiveUS20110276744A1Memory architecture accessing/allocationMemory adressing/allocation/relocationWrite bufferEngineering
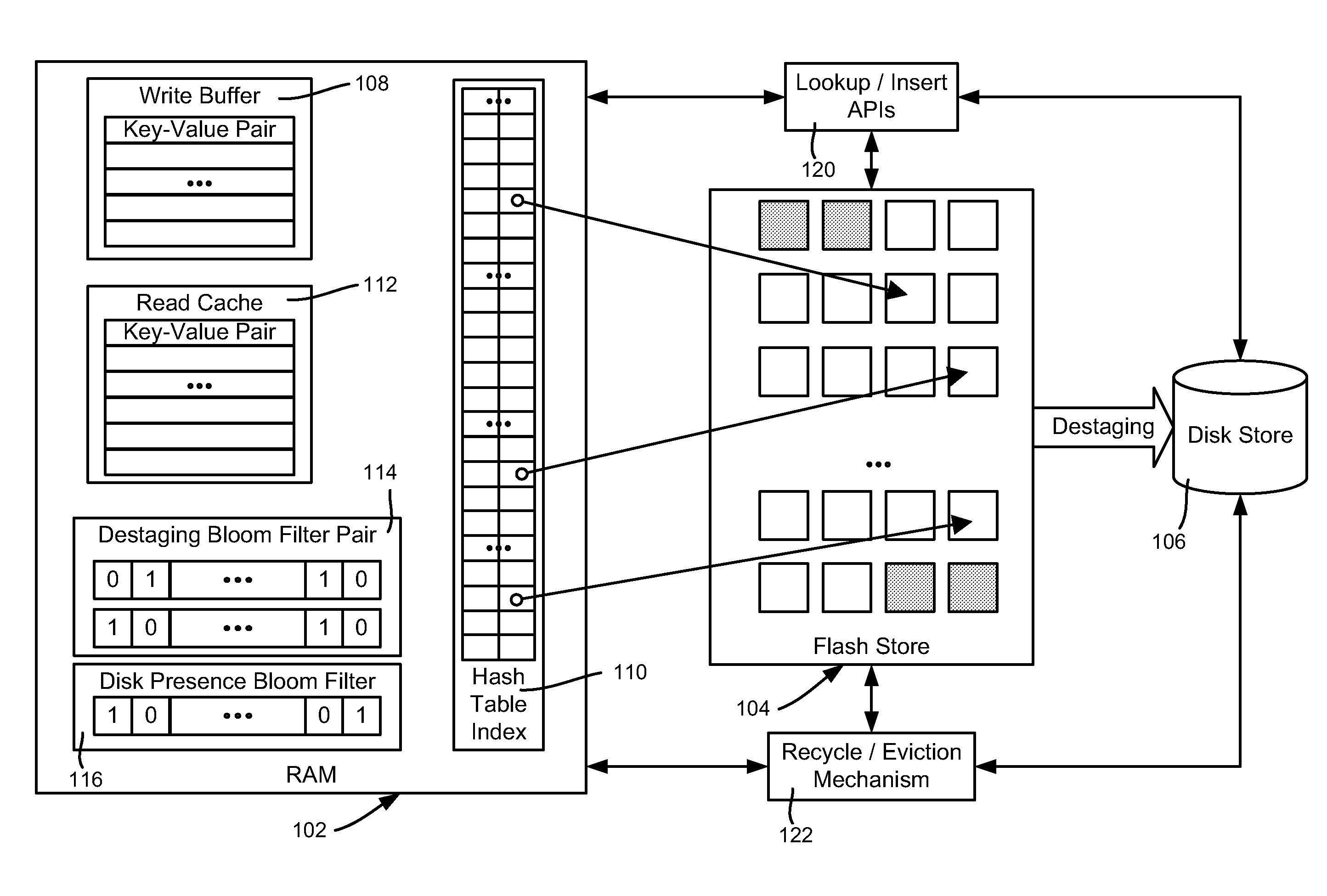
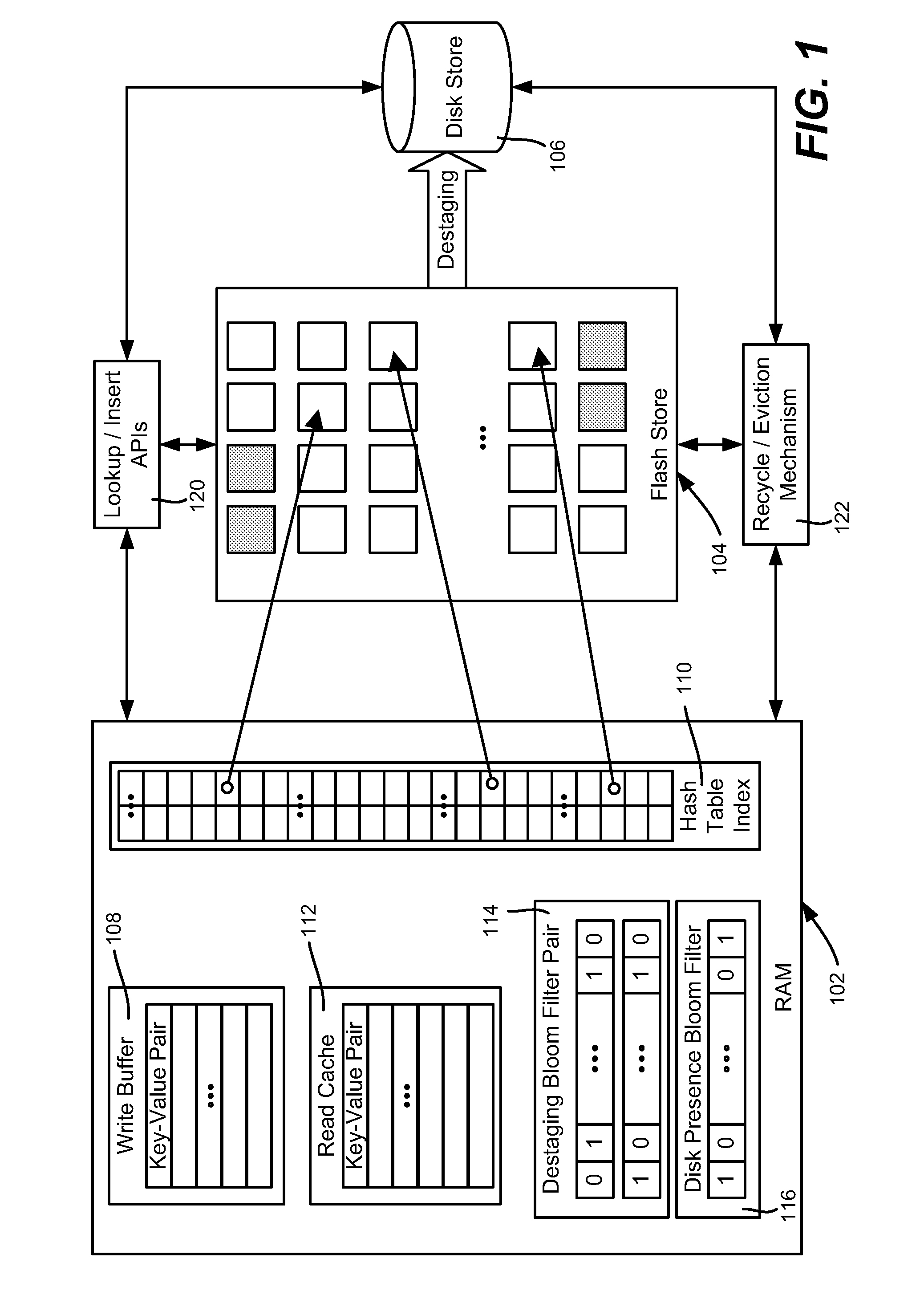
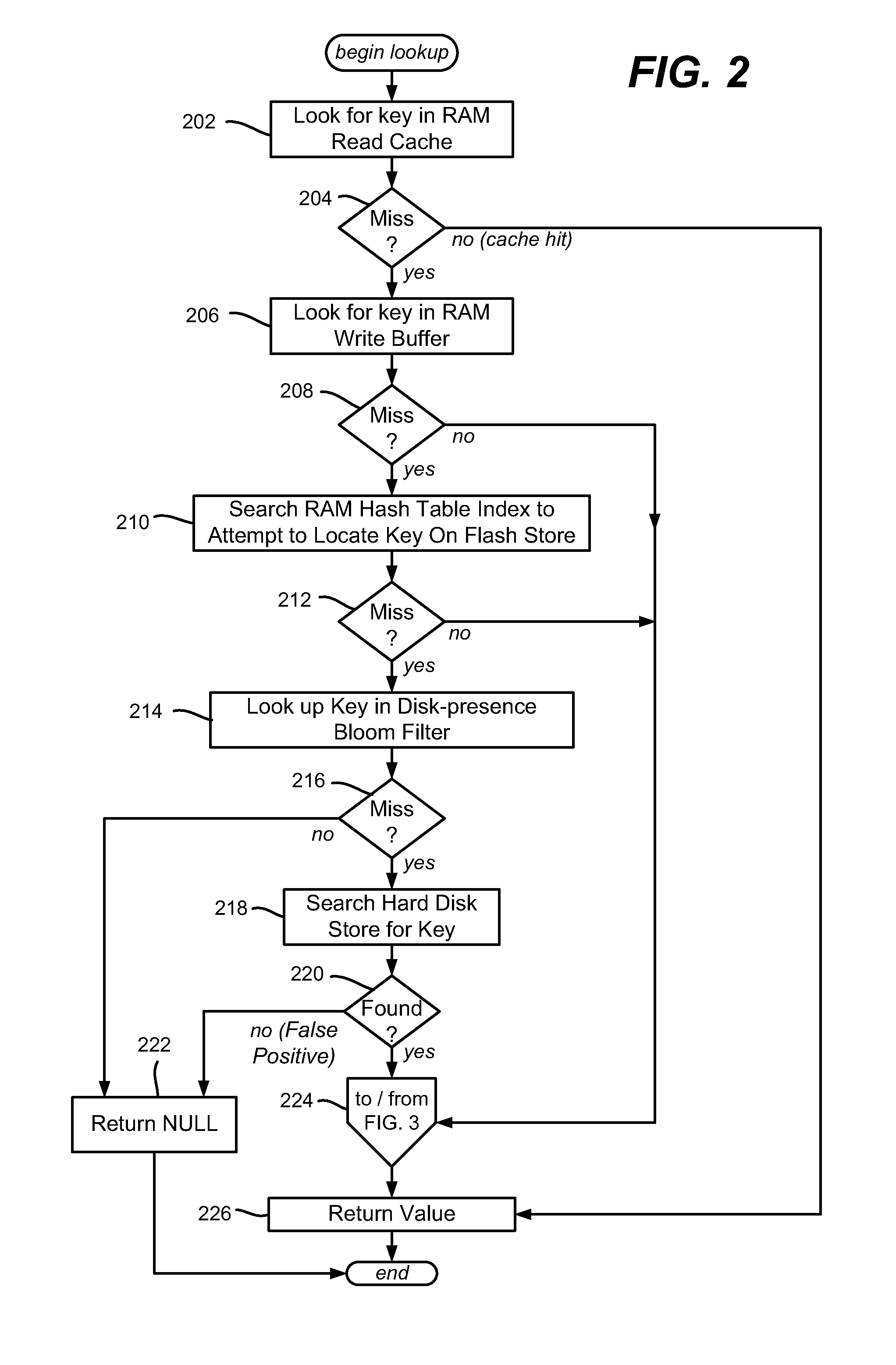
Described is using flash memory, RAM-based data structures and mechanisms to provide a flash store for caching data items (e.g., key-value pairs) in flash pages. A RAM-based index maps data items to flash pages, and a RAM-based write buffer maintains data items to be written to the flash store, e.g., when a full page can be written. A recycle mechanism makes used pages in the flash store available by destaging a data item to a hard disk or reinserting it into the write buffer, based on its access pattern. The flash store may be used in a data deduplication system, in which the data items comprise chunk-identifier, metadata pairs, in which each chunk-identifier corresponds to a hash of a chunk of data that indicates. The RAM and flash are accessed with the chunk-identifier (e.g., as a key) to determine whether a chunk is a new chunk or a duplicate.
Owner:MICROSOFT TECH LICENSING LLC
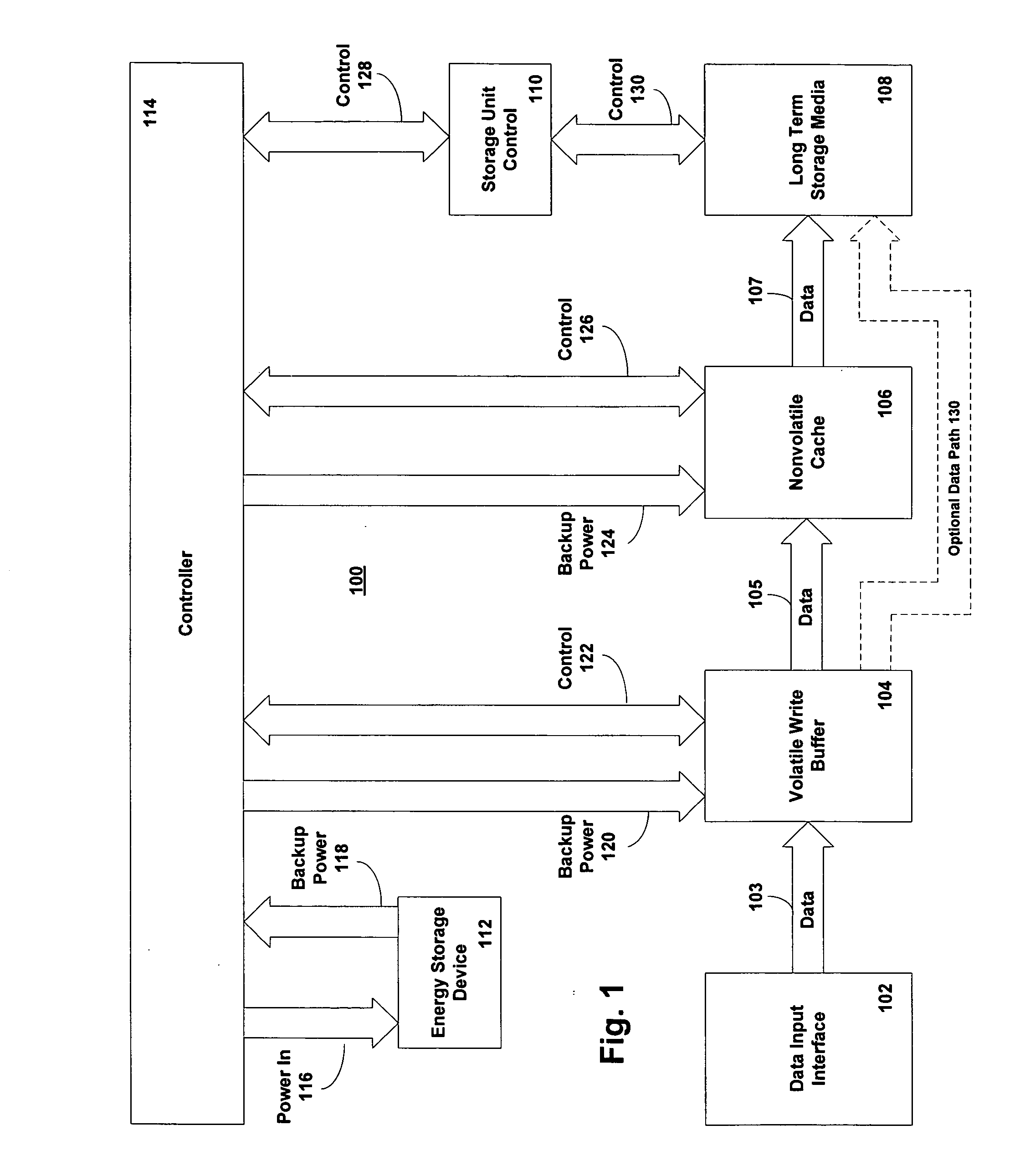
Non-volatile memory cache performance improvement
ActiveUS20050246487A1Improve efficiencyIncrease performance timeMemory architecture accessing/allocationEnergy efficient ICTWrite bufferData store
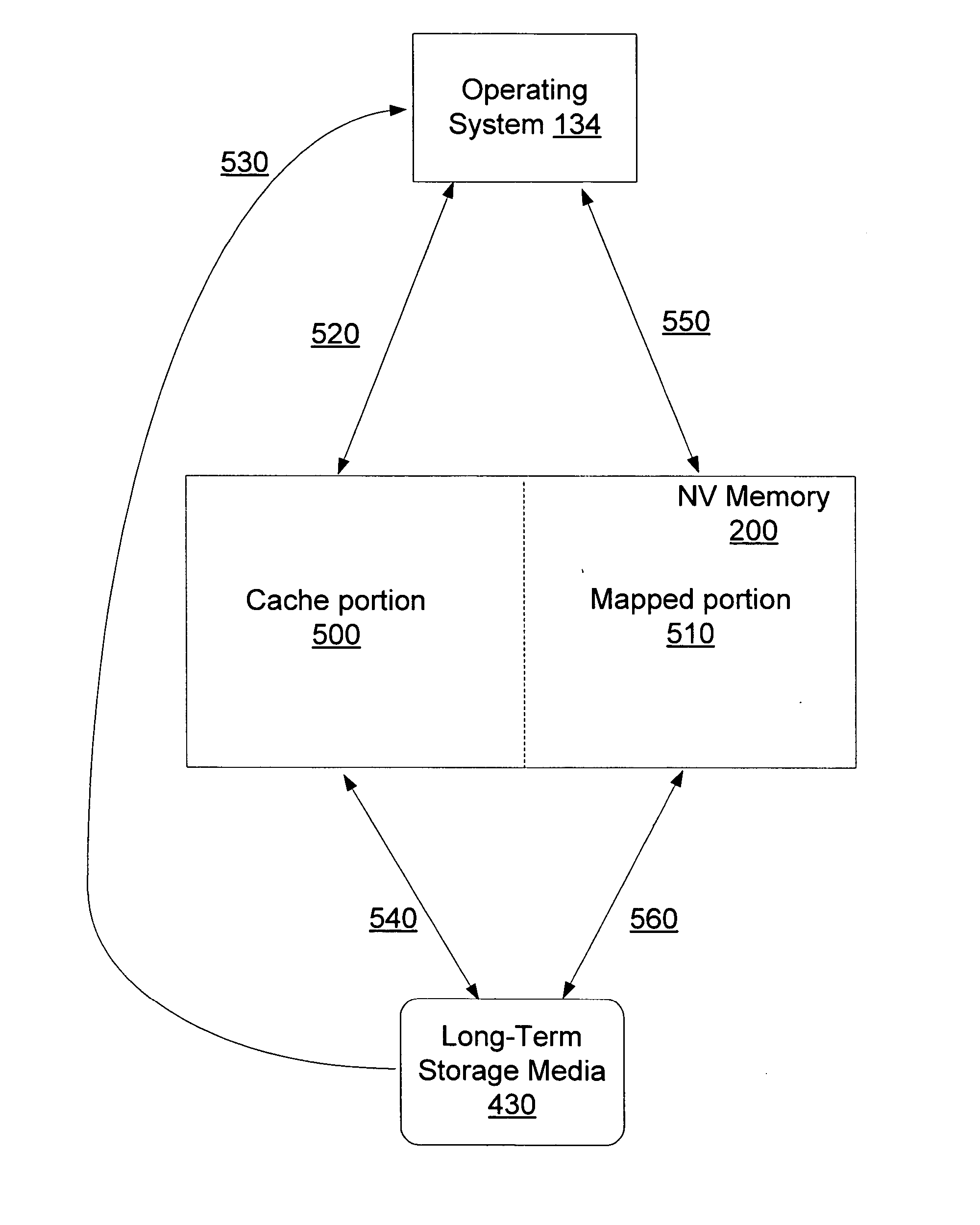
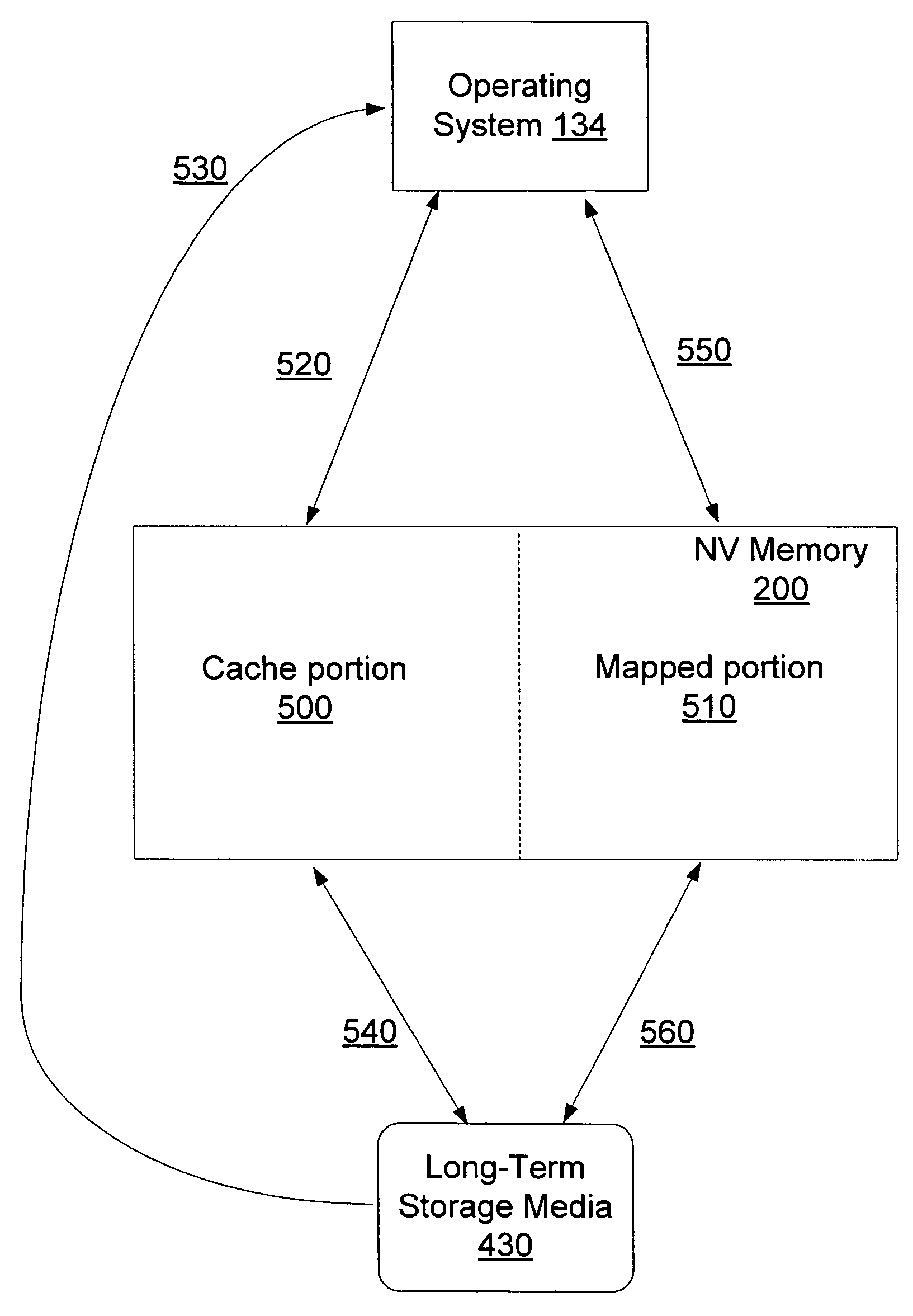
In order to provide a more efficient persistent storage device, one or more long-term storage media are included along with a non-volatile memory. In one embodiment, one portion of the non-volatile memory is used as a write buffer and a read cache for writes and reads to the long-term storage media. Interfaces are provided for controlling the use of the non-volatile memory as a write buffer and a read cache. Additionally, a portion of the non-volatile memory is used to provide a direct mapping for specified sectors of the long-term storage media. Descriptive data regarding the persistent storage device is stored in another portion of the non-volatile memory.
Owner:MICROSOFT TECH LICENSING LLC
Non-volatile memory cache performance improvement
ActiveUS7644239B2Easy to useImprove efficiencyMemory architecture accessing/allocationEnergy efficient ICTWrite bufferData store
In order to provide a more efficient persistent storage device, one or more long-term storage media are included along with a non-volatile memory. In one embodiment, one portion of the non-volatile memory is used as a write buffer and a read cache for writes and reads to the long-term storage media. Interfaces are provided for controlling the use of the non-volatile memory as a write buffer and a read cache. Additionally, a portion of the non-volatile memory is used to provide a direct mapping for specified sectors of the long-term storage media. Descriptive data regarding the persistent storage device is stored in another portion of the non-volatile memory.
Owner:MICROSOFT TECH LICENSING LLC
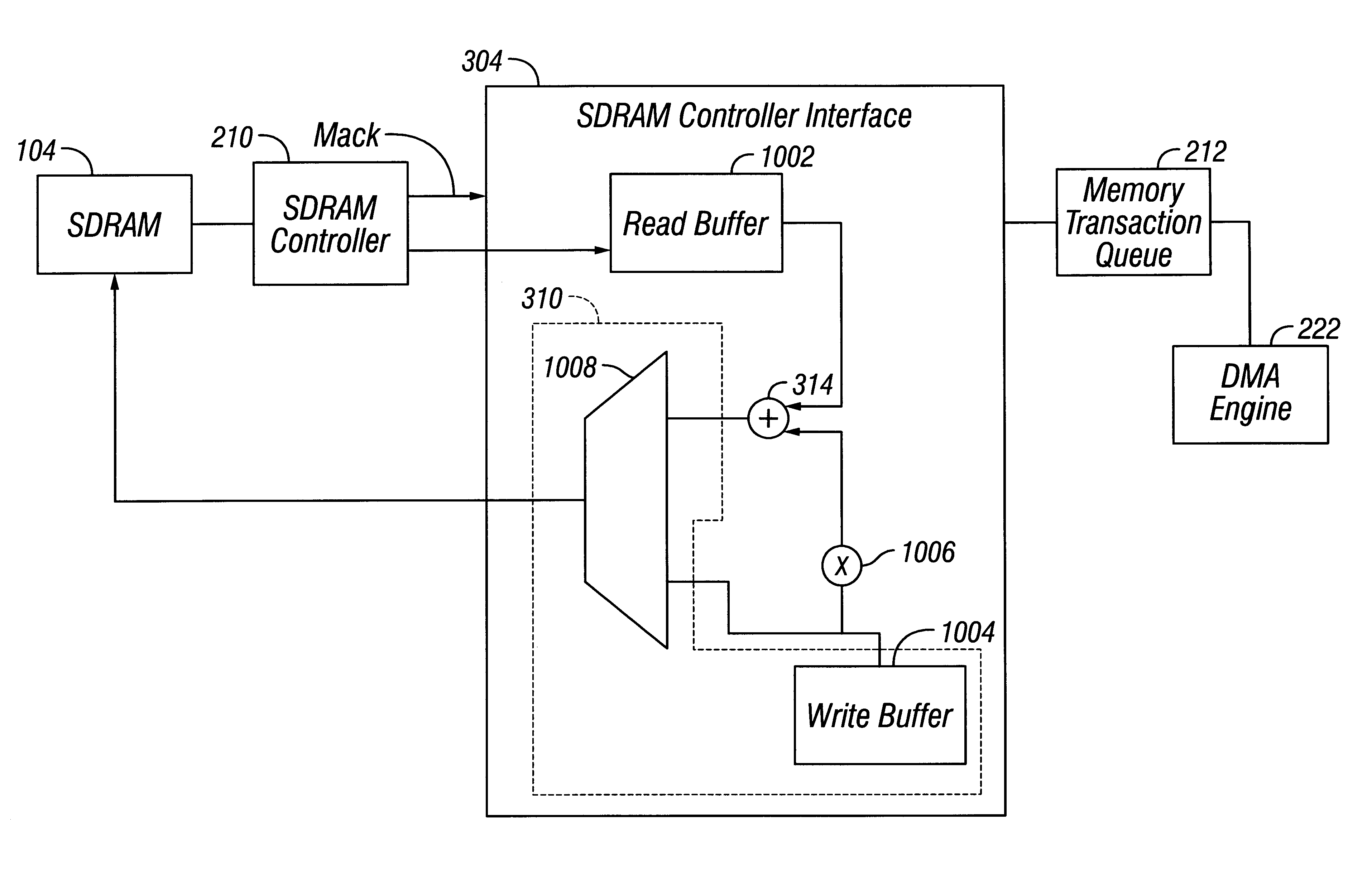
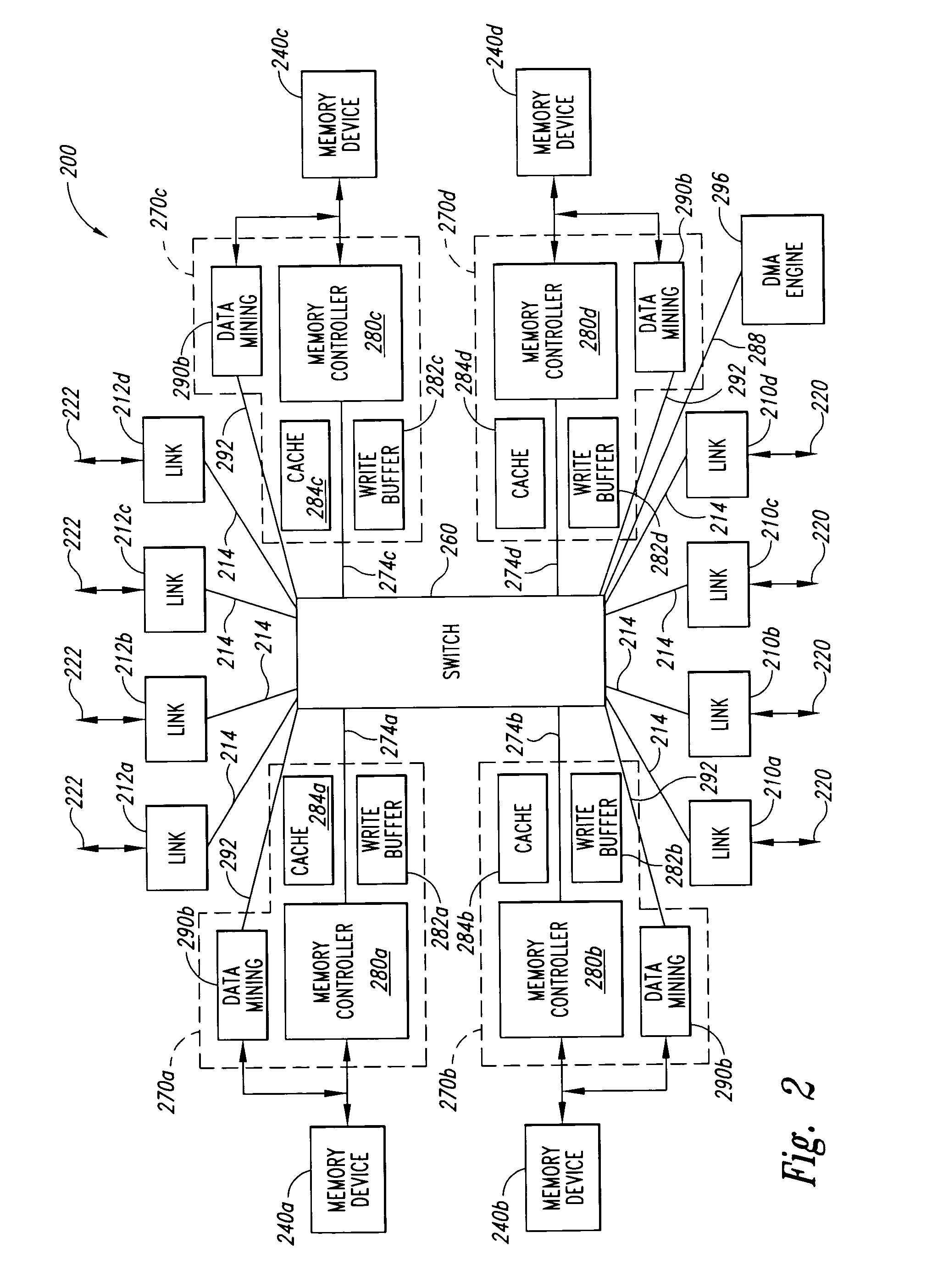
Raid XOR operations to synchronous DRAM using a read buffer and pipelining of synchronous DRAM burst read data
A memory interface controller includes a read buffer to pipeline data from a synchronous dynamic random access memory (DRAM) in response to a plurality of consecutive SDRAM burst read requests, a write buffer to store write data, an exclusive or (XOR) engine to XOR the write data with the data from the read buffer, and a write interface to write resulting data from XORing the write data and the data from the read buffer to the synchronous DRAM. Data is pipelined in the read buffer by repeatedly issuing an SDRAM burst read request before data is transferred out of the synchronous DRAM in response to a previous SDRAM burst read request until a desired amount of data is stored in the read buffer. The memory interface controller thus can perform an external read-modify-write cycle for the synchronous DRAM. The synchronous DRAM can serve as a RAID (Redundant Array s of Inexpensive Disks) memory.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
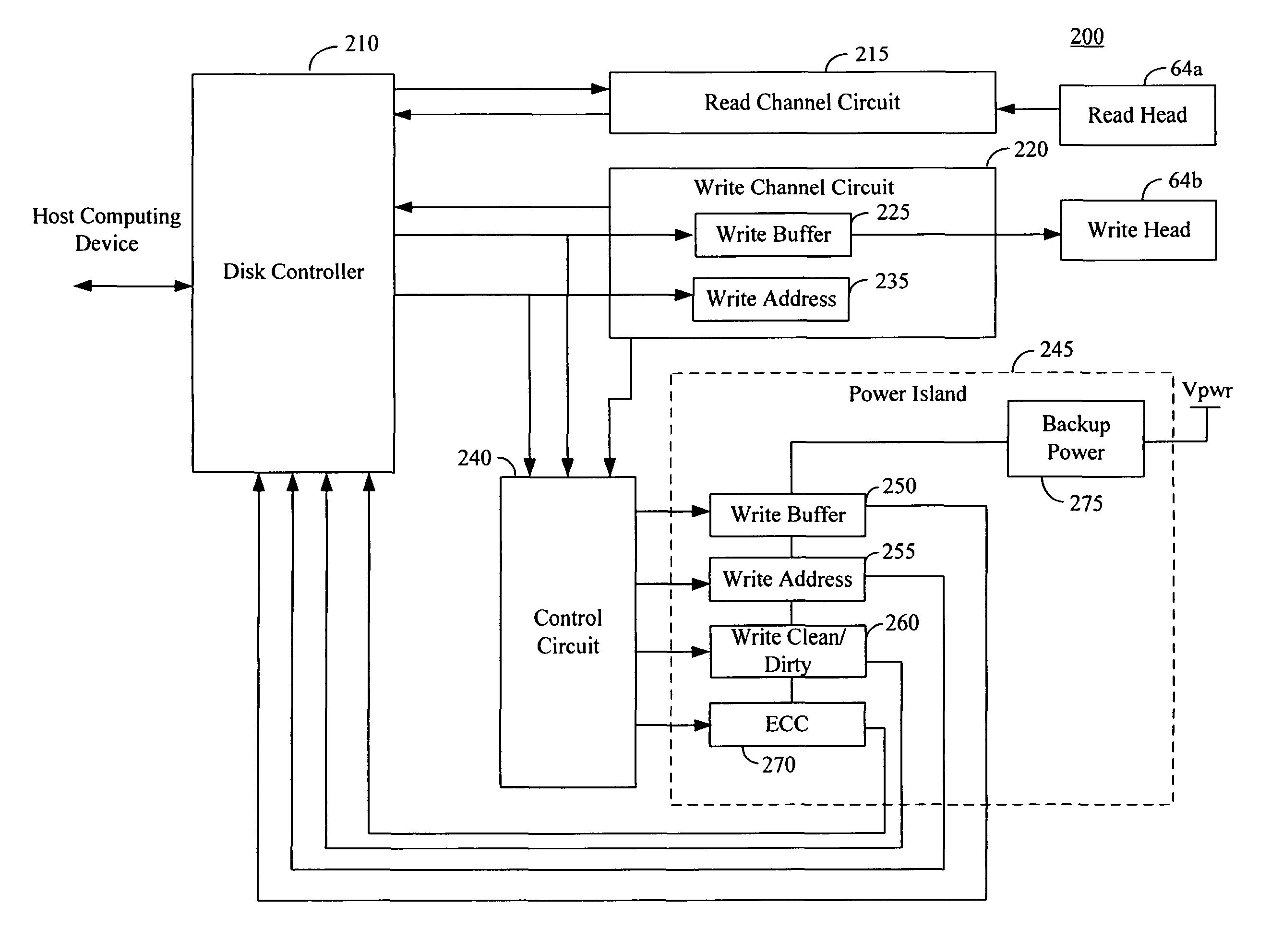
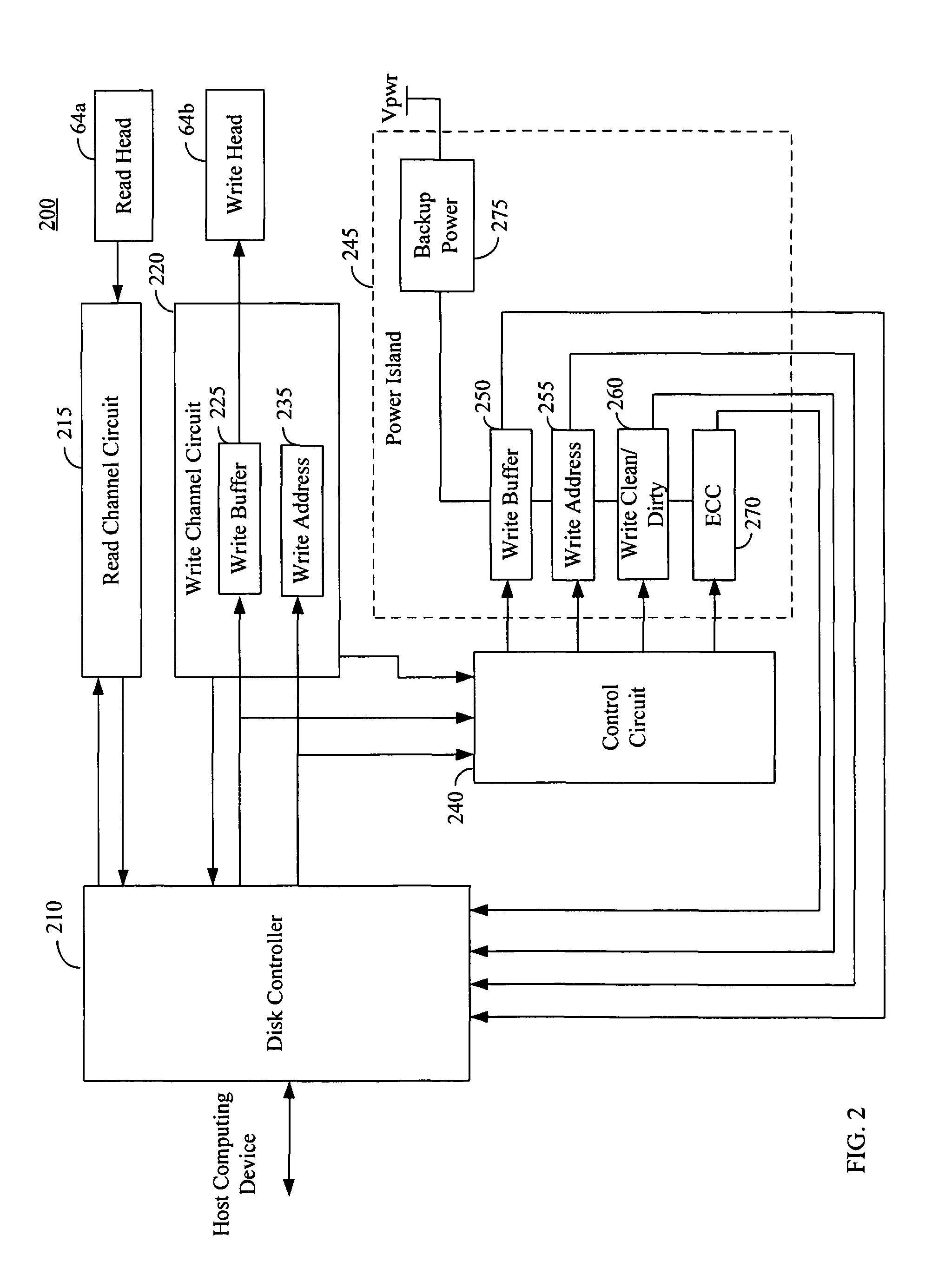
System and method to reduce write splice failures
Systems and methods are provided for reducing write splice failures. In one embodiment, a system for writing data to a media includes a write buffer for storing a data sector and a backup power device for providing power to the write buffer in the event of a power failure to hold the data sector in the write buffer. The next time the system is powered up after the power failure, the system reads the data sector from the write buffer and uses the read data sector to correct a write splice on the media that may have occurred due to the power failure.
Owner:WESTERN DIGITAL TECH INC
Off-chip data relocation
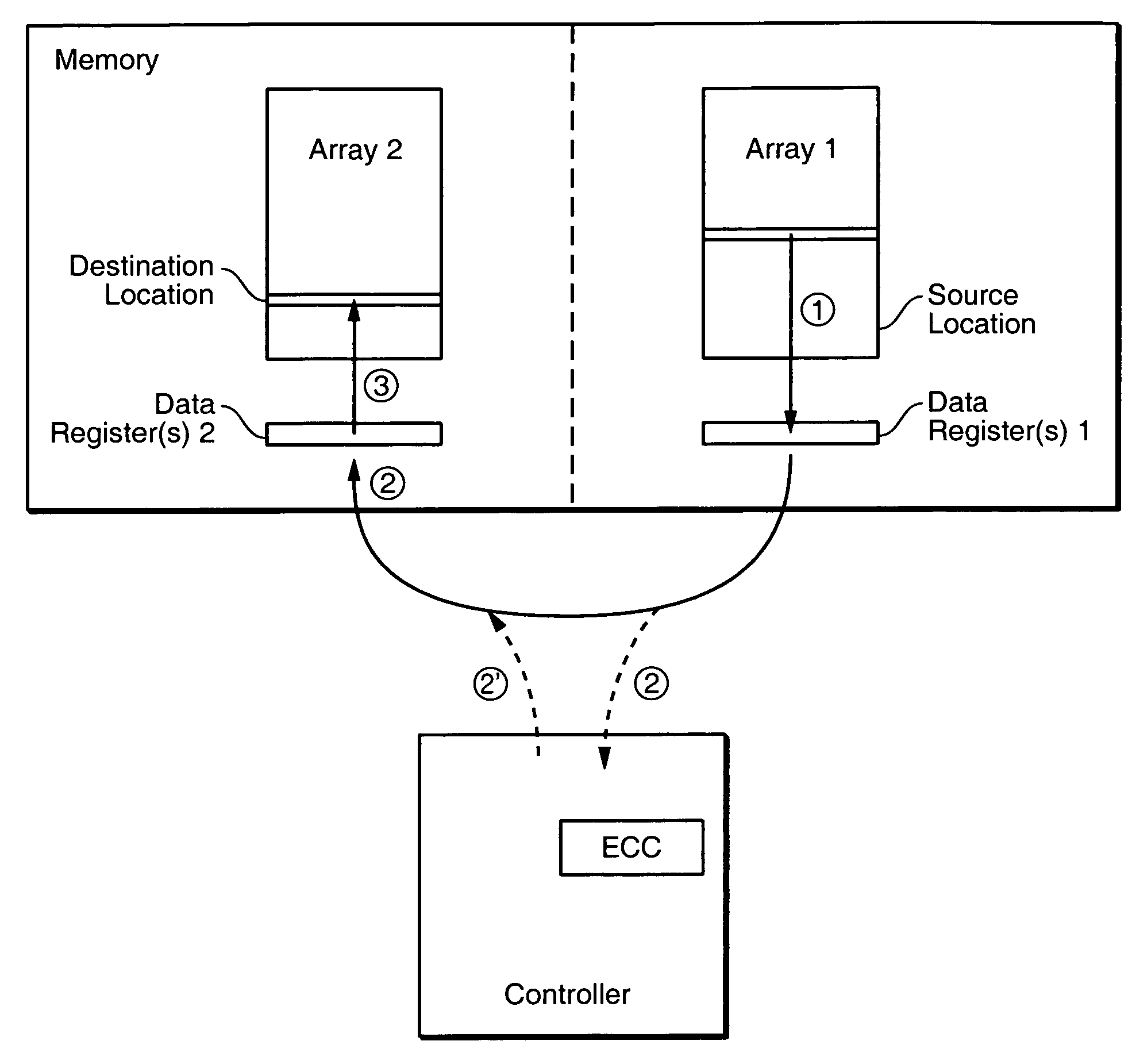
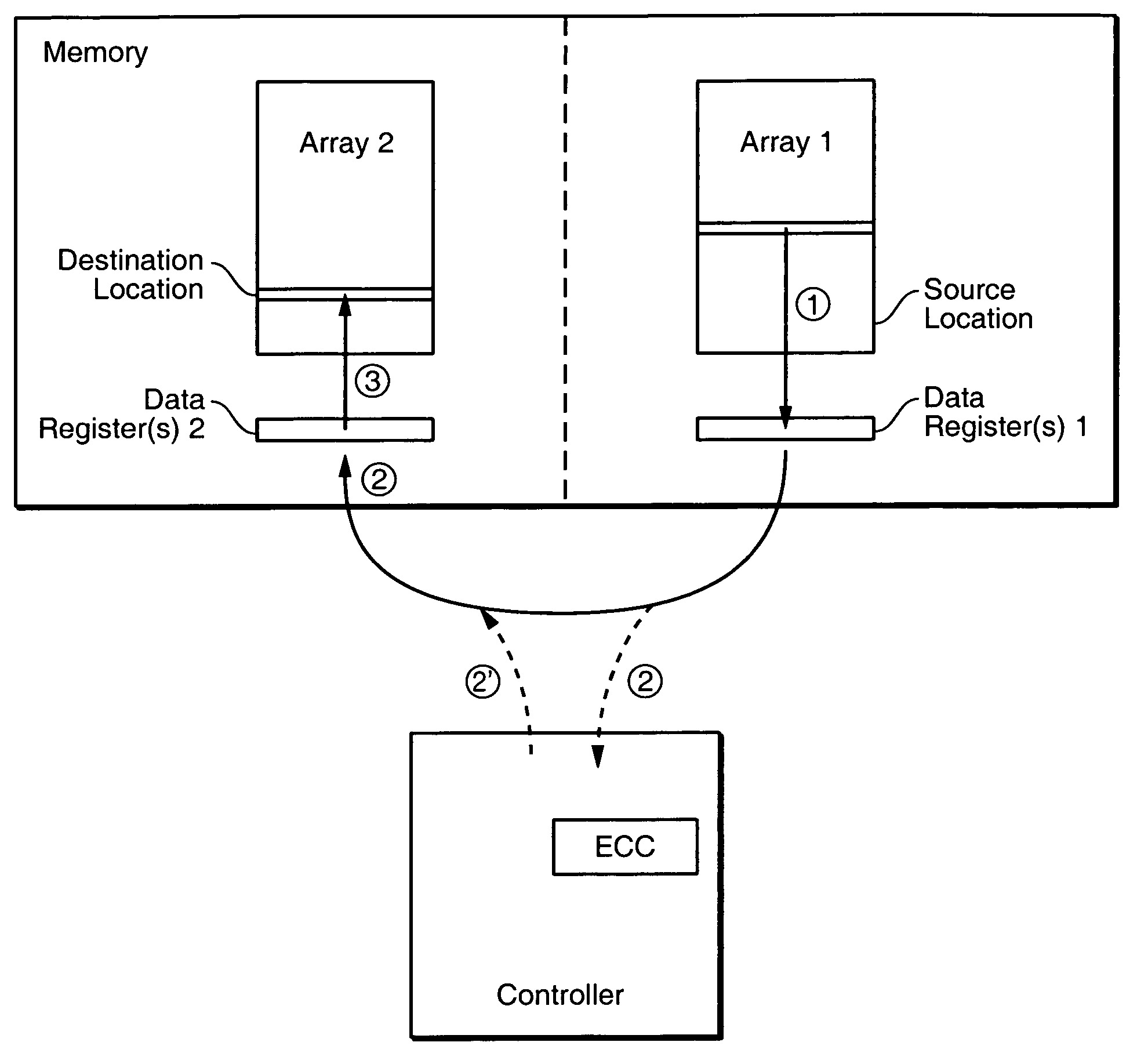
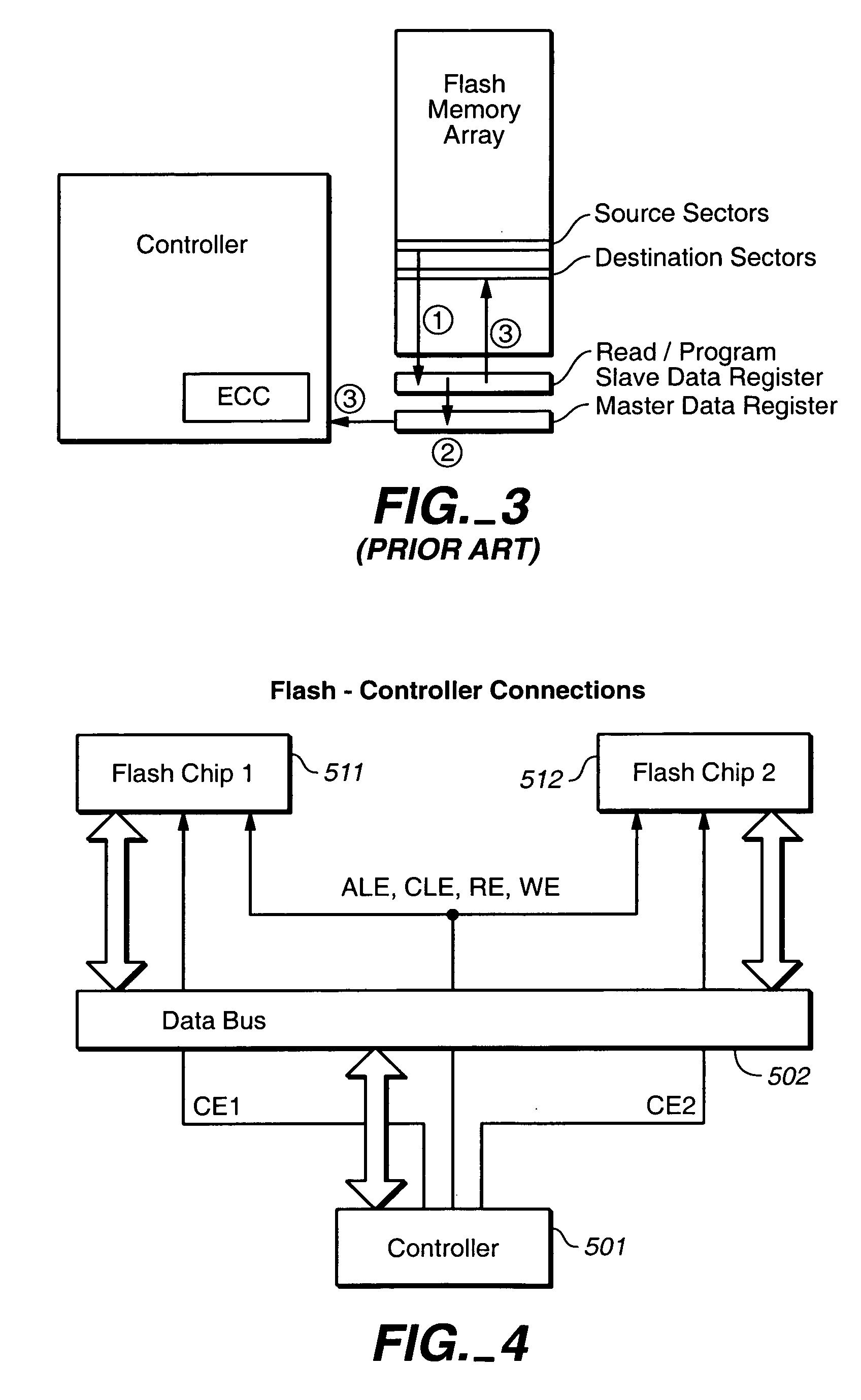
ActiveUS7409473B2Reduce frequencyEasy to operateRead-only memoriesDigital storageComputer hardwareData set
The on-chip copy process is extended so that the data may be copied between two blocks that may be on different chips, different planes on the same chip, or the same plane of the same chip. More specifically, the methods described here provide a single data copying mechanism that allows data to be copied between any two locations in a memory system. An exemplary embodiment uses an EDO-type timing. According to another aspect, selected portions of the relocated data, such as chosen words in a transferred page, can be updated in the controller on the fly. In addition to transferring a data set directly from a read buffer of a source array to a write buffer of a destination array, the data set can concurrently be copied, if desired, into the controller where an error detection and correction operation can be performed on it.
Owner:SANDISK TECH LLC
Off-chip data relocation
ActiveUS20060136687A1Reduce frequencyEasy to operateMemory loss protectionRead-only memoriesComputer hardwareData set
The on-chip copy process is extended so that the data may be copied between two blocks that may be on different chips, different planes on the same chip, or the same plane of the same chip. More specifically, the methods described here provide a single data copying mechanism that allows data to be copied between any two locations in a memory system. An exemplary embodiment uses an EDO-type timing. According to another aspect, selected portions of the relocated data, such as chosen words in a transferred page, can be updated in the controller on the fly. In addition to transferring a data set directly from a read buffer of a source array to a write buffer of a destination array, the data set can concurrently be copied, if desired, into the controller where an error detection and correction operation can be performed on it.
Owner:SANDISK TECH LLC
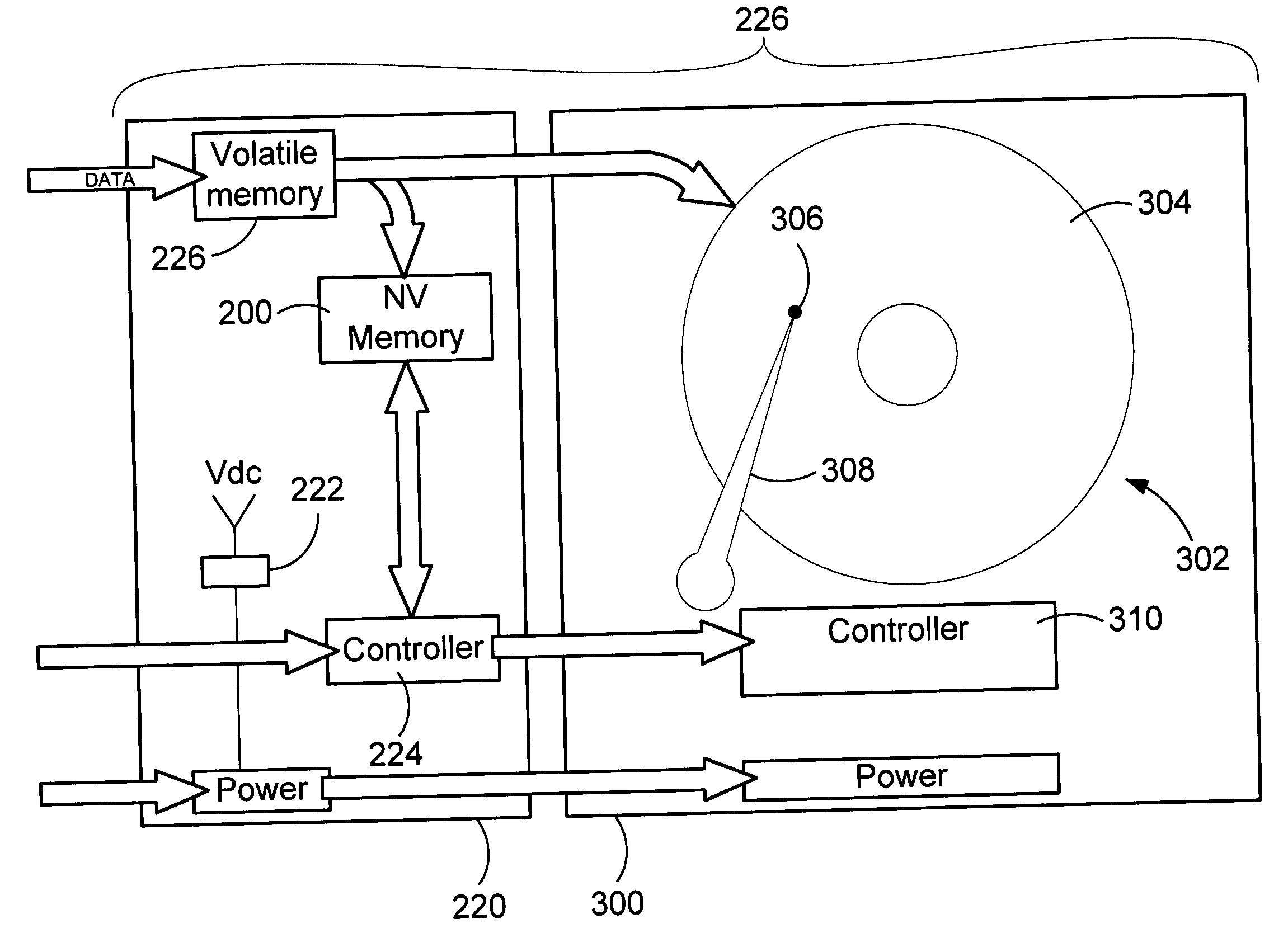
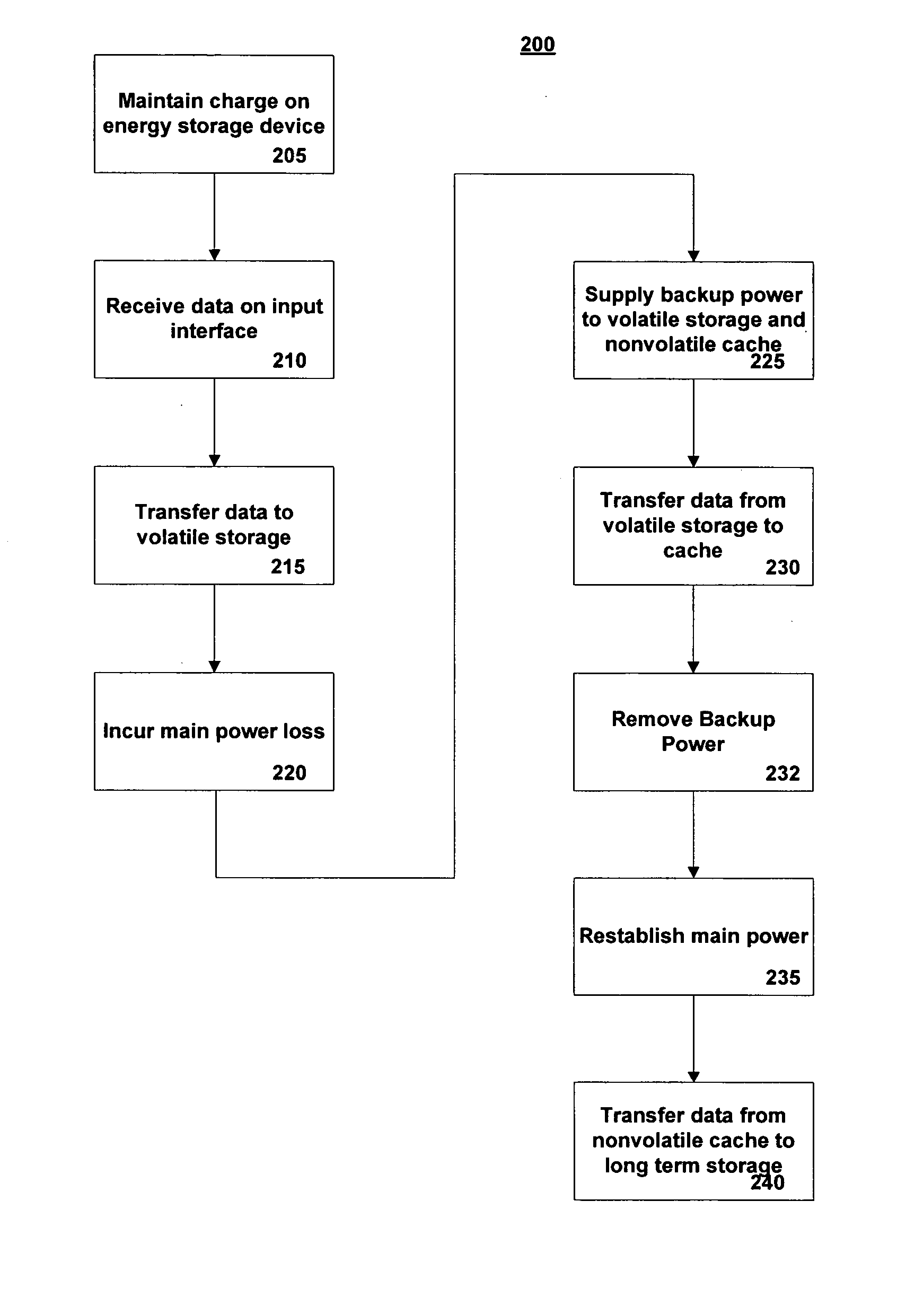
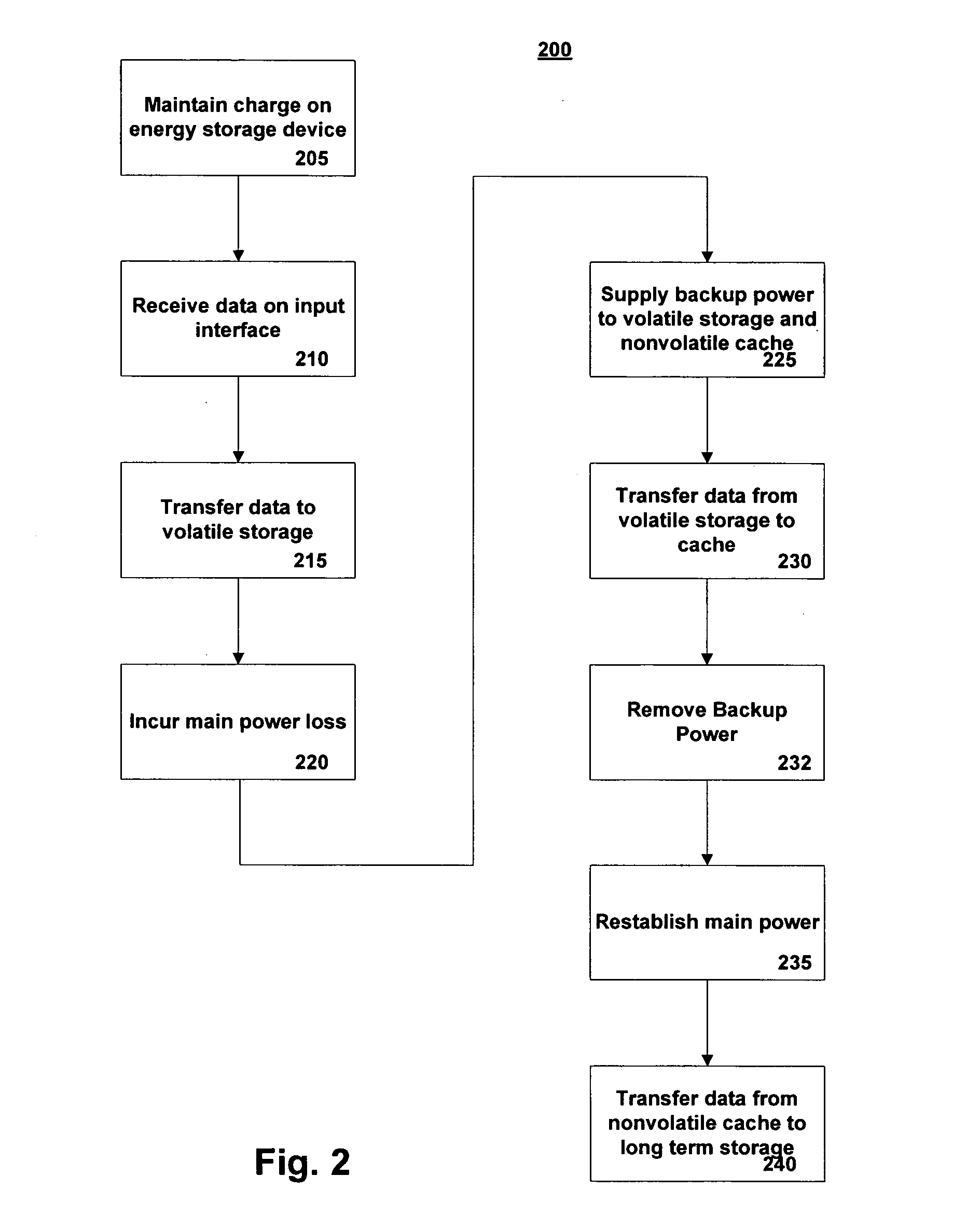
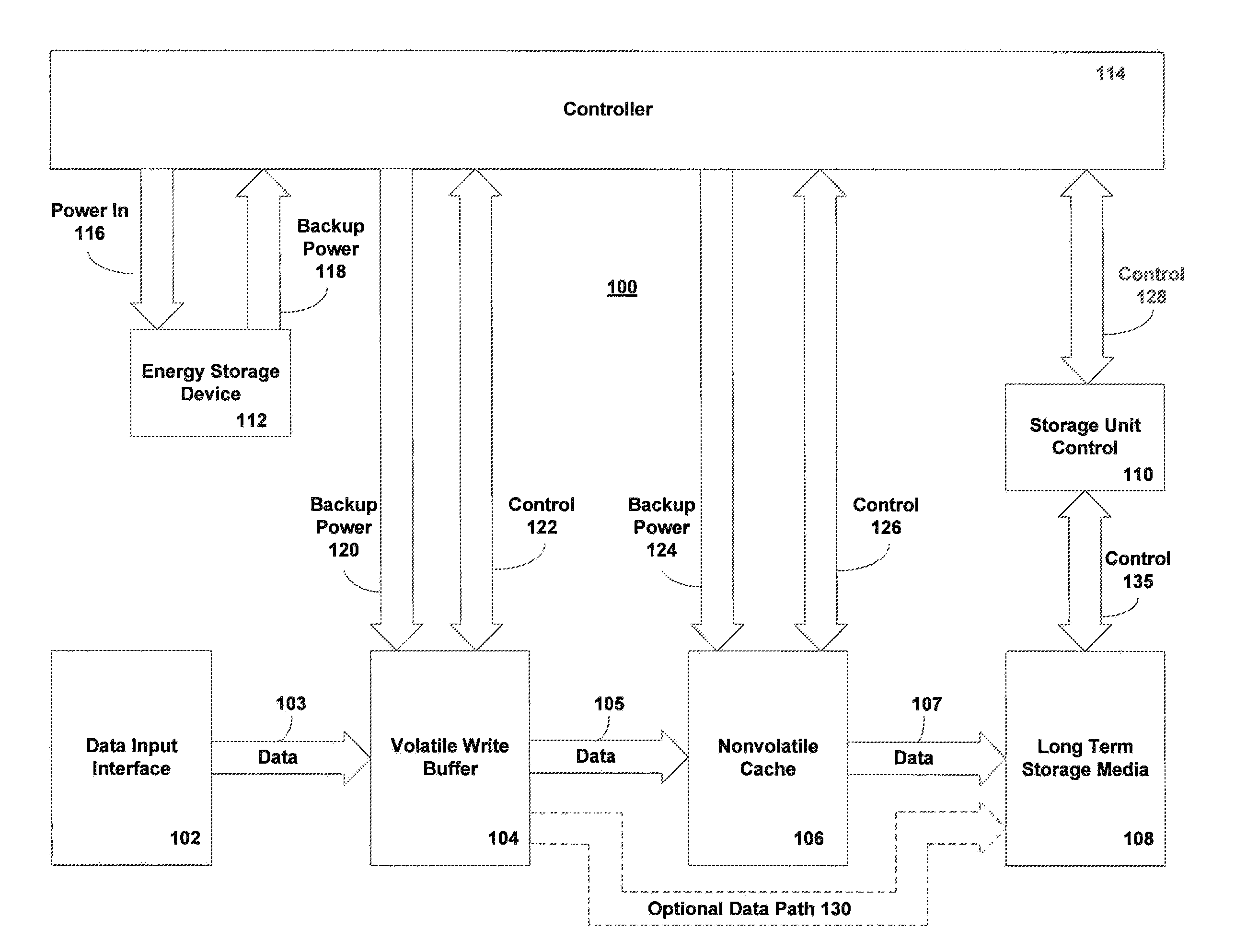
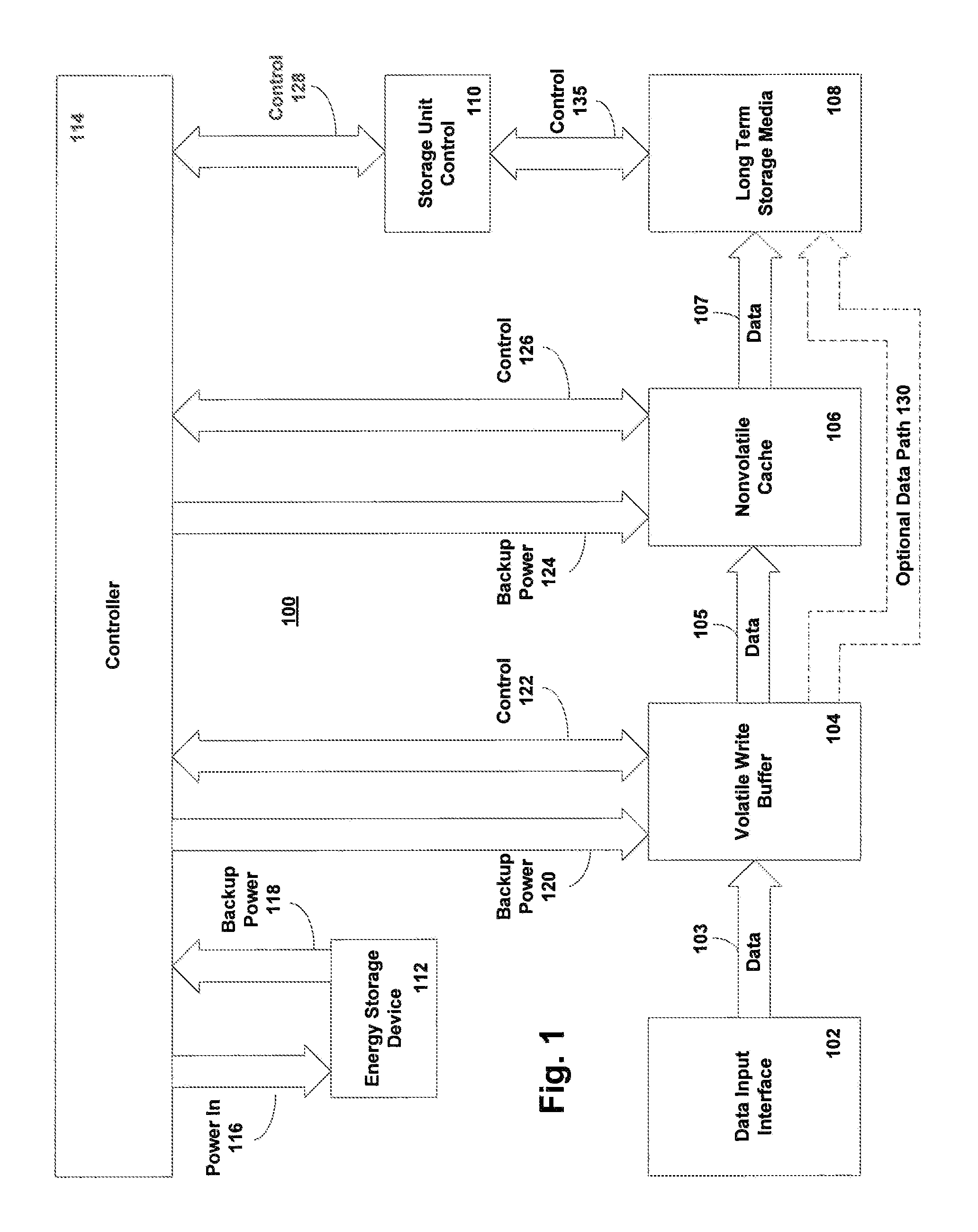
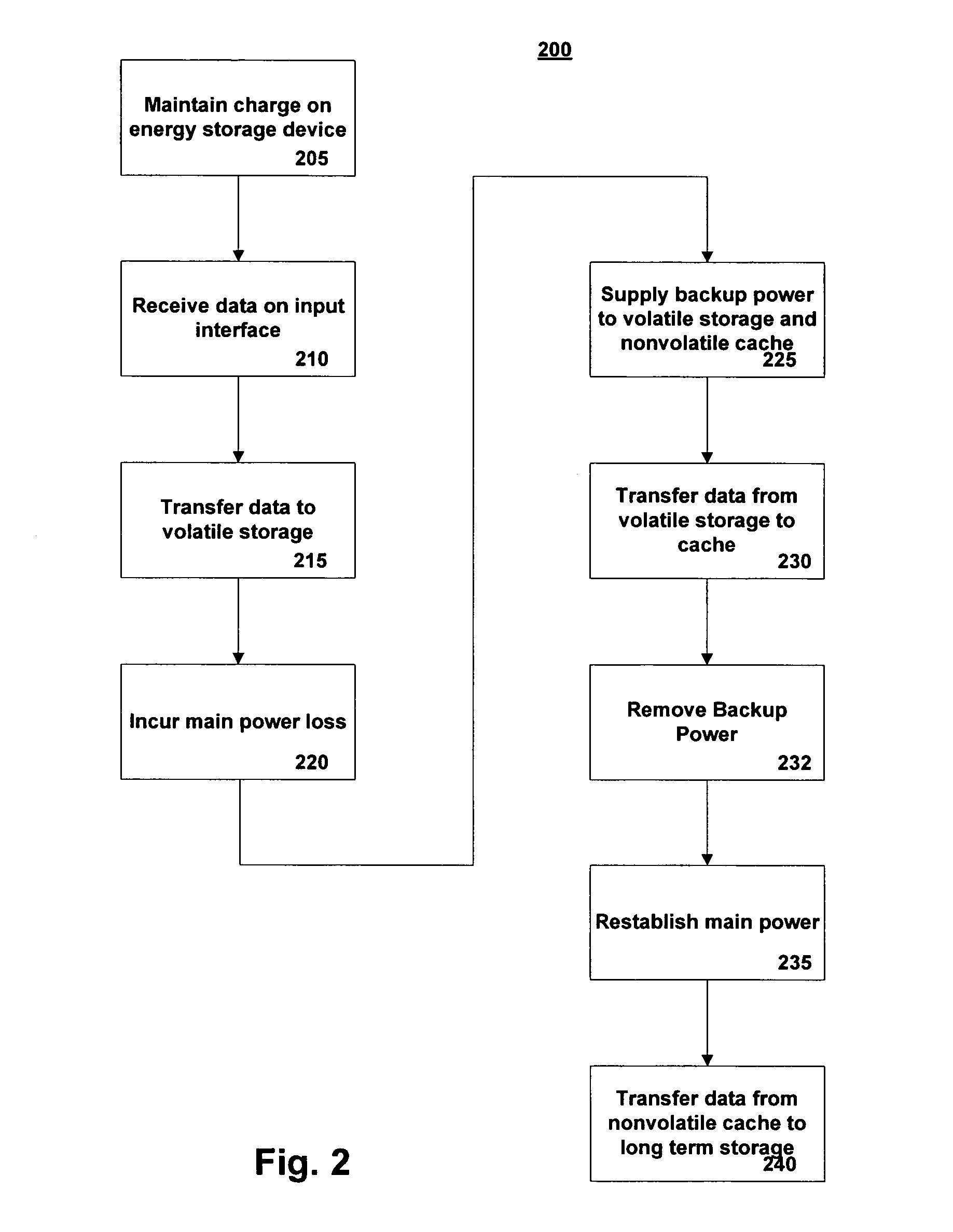
Method and system for improved reliability in storage devices
ActiveUS20060069870A1Memory architecture accessing/allocationEnergy efficient ICTWrite bufferPower cycle
A method of preventing data loss in a data storage system includes supplying write data to a high speed volatile write buffer and supplying electrical power from an energy storage device upon detection of a primary power loss event. The backup electrical power is supplied to the write buffer and nonvolatile cache. Under backup power, the write data is transferred into the nonvolatile cache and the backup power is removed. Upon regaining main power, a data presence indication triggers a transfer of the write data from the nonvolatile cache to the long term storage media. The method may be implemented for a system to protect it from inadvertent power losses or it may implemented in a system where the long term storage device is power cycled to save power. The energy storage device is not necessarily needed in the power cycled system unless power failure protection is also desired.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for improved reliability in storage devices
ActiveUS7395452B2Memory architecture accessing/allocationEnergy efficient ICTWrite bufferPower cycle
A method of preventing data loss in a data storage system includes supplying write data to a high speed volatile write buffer and supplying electrical power from an energy storage device upon detection of a primary power loss event. The backup electrical power is supplied to the write buffer and nonvolatile cache. Under backup power, the write data is transferred into the nonvolatile cache and the backup power is removed. Upon regaining main power, a data presence indication triggers a transfer of the write data from the nonvolatile cache to the long term storage media. The method may be implemented for a system to protect it from inadvertent power losses or it may implemented in a system where the long term storage device is power cycled to save power. The energy storage device is not necessarily needed in the power cycled system unless power failure protection is also desired.
Owner:MICROSOFT TECH LICENSING LLC
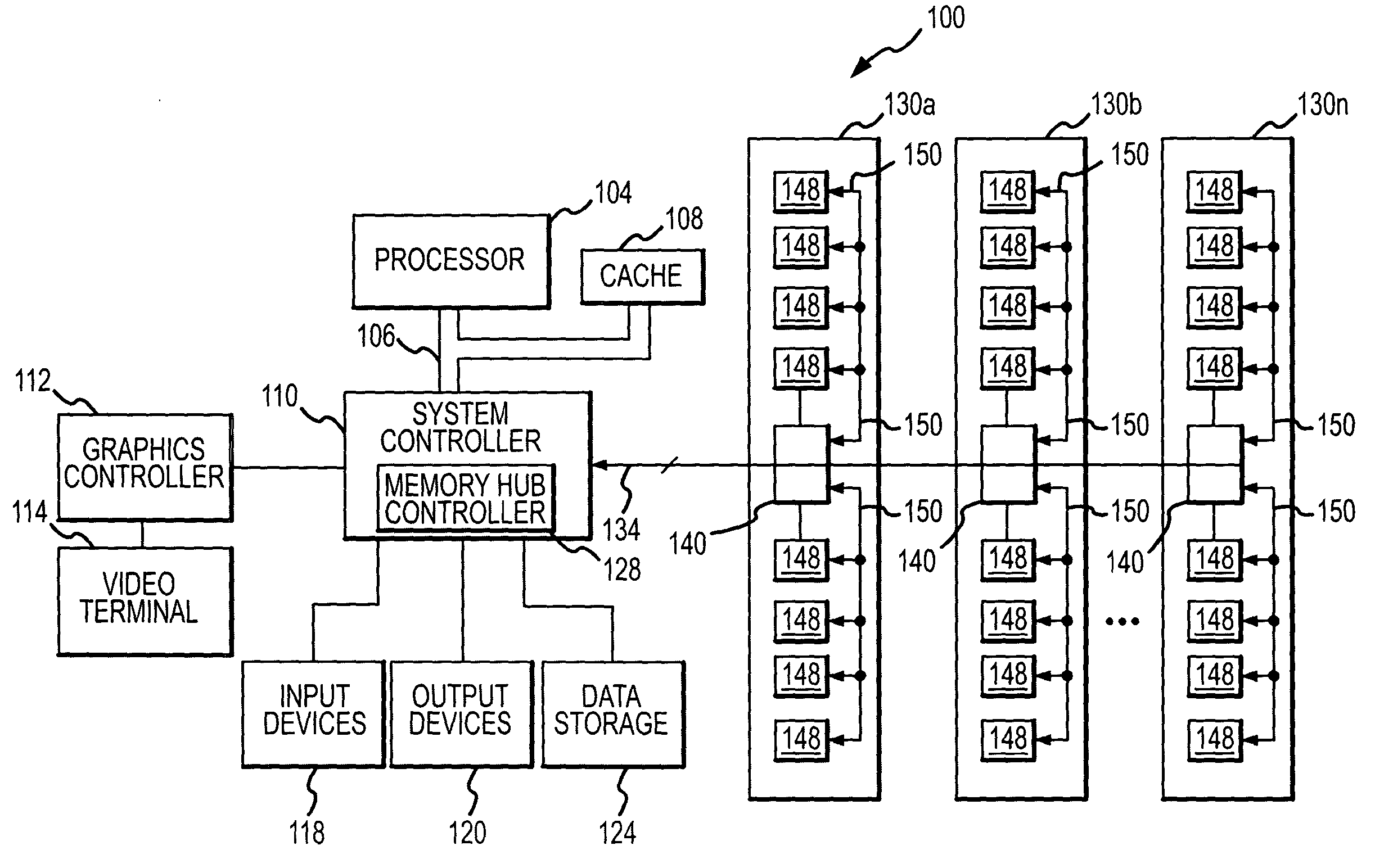
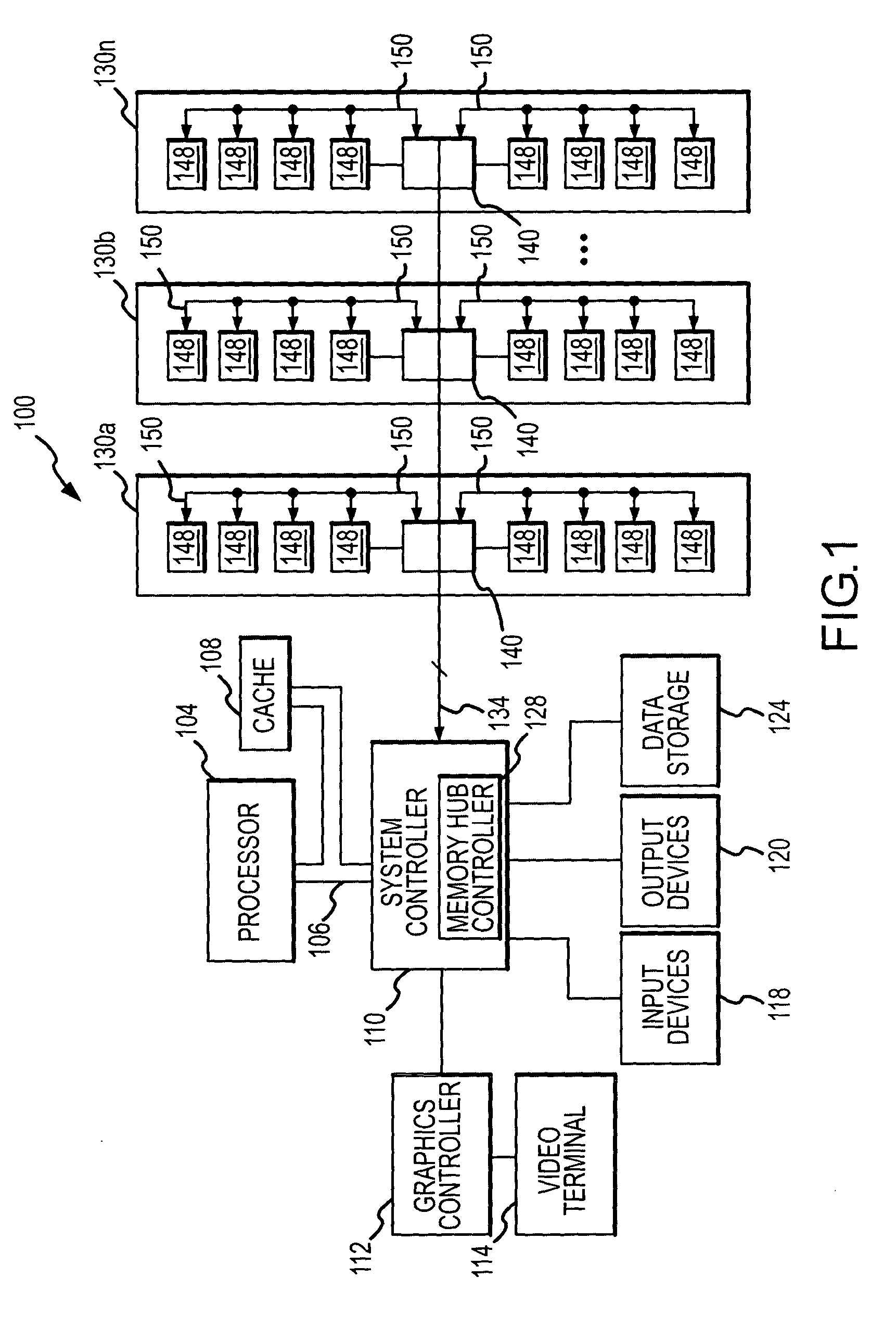
Memory module and method having on-board data search capabilities and processor-based system using such memory modules
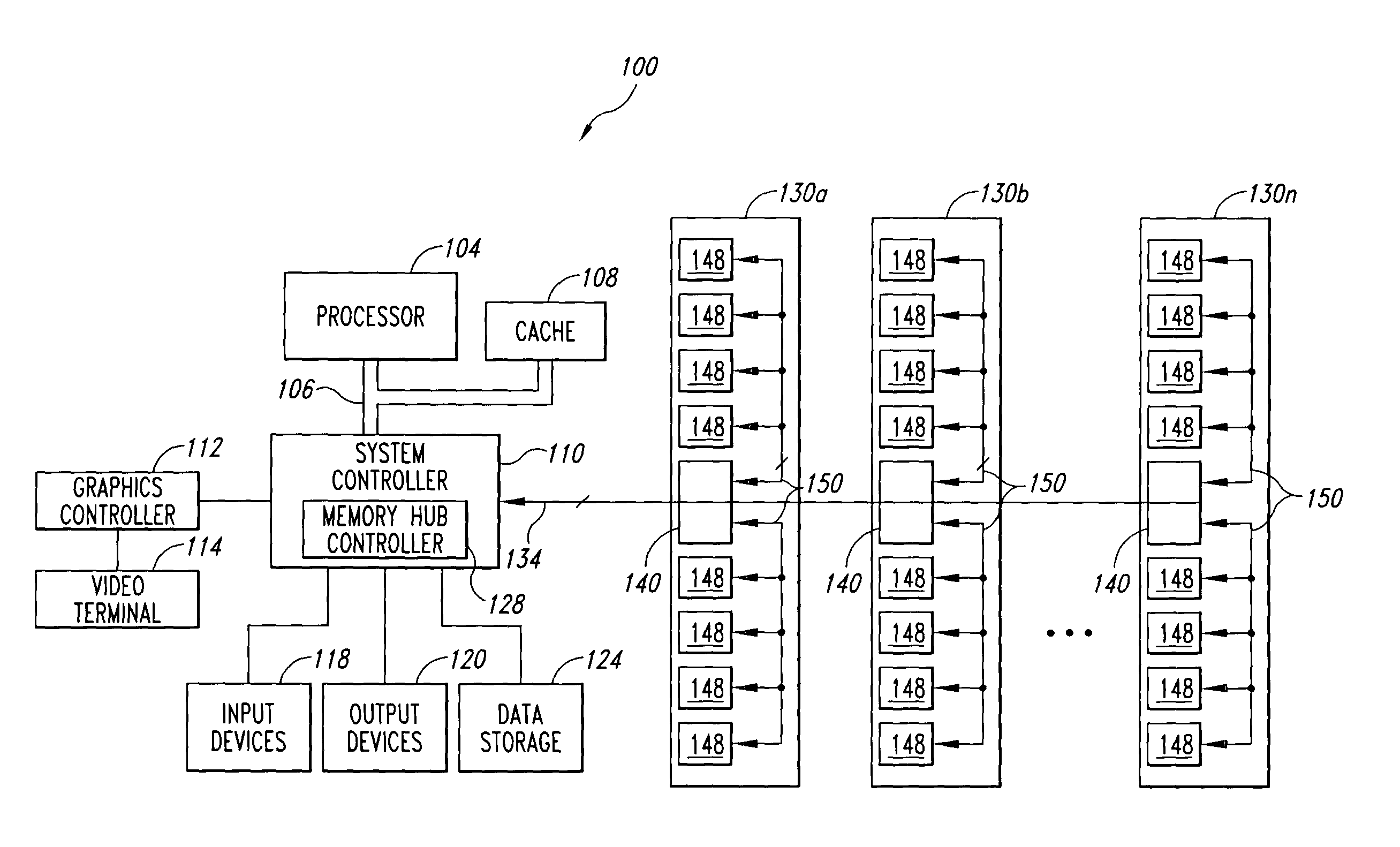
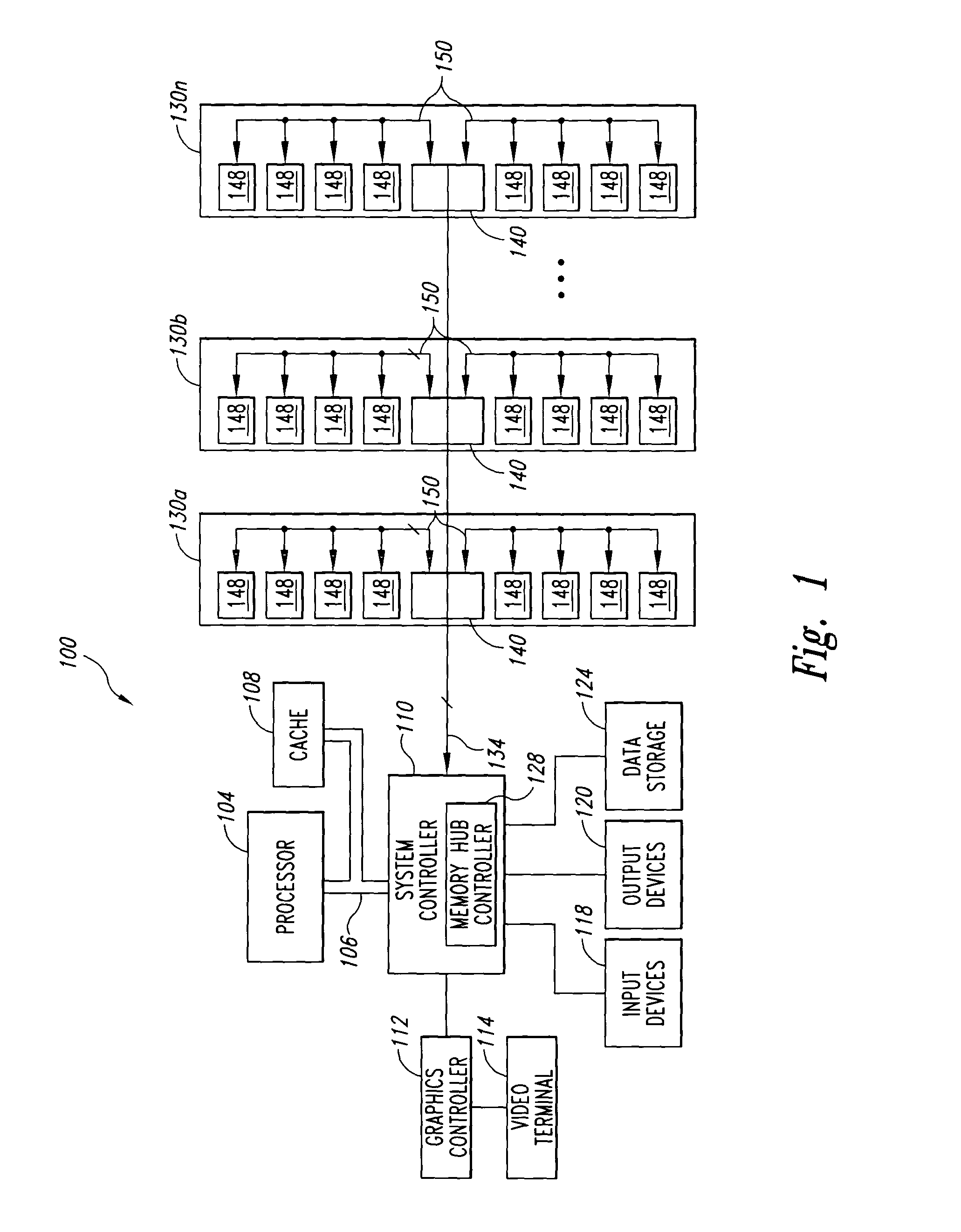
InactiveUS20050050237A1Faster rateDigital data information retrievalStatic storageCrossbar switchWrite buffer
A memory module includes several memory devices coupled to a memory hub. The memory hub includes several link interfaces coupled to respective processors, several memory interfaces coupled to respective memory devices, and a cross-bar switch coupling any of the link interfaces to any of the memory interfaces. Each memory interface includes a memory controller, a write buffer, a read cache, and a data mining module. The data mining module includes a search data memory that is coupled to the link interface to receive and store at least one item of search data. A comparator receives both the read data from the memory device and the search data. The comparator then compares the read data to the respective item of search data and provides a hit indication in the event of a match.
Owner:MICRON TECH INC
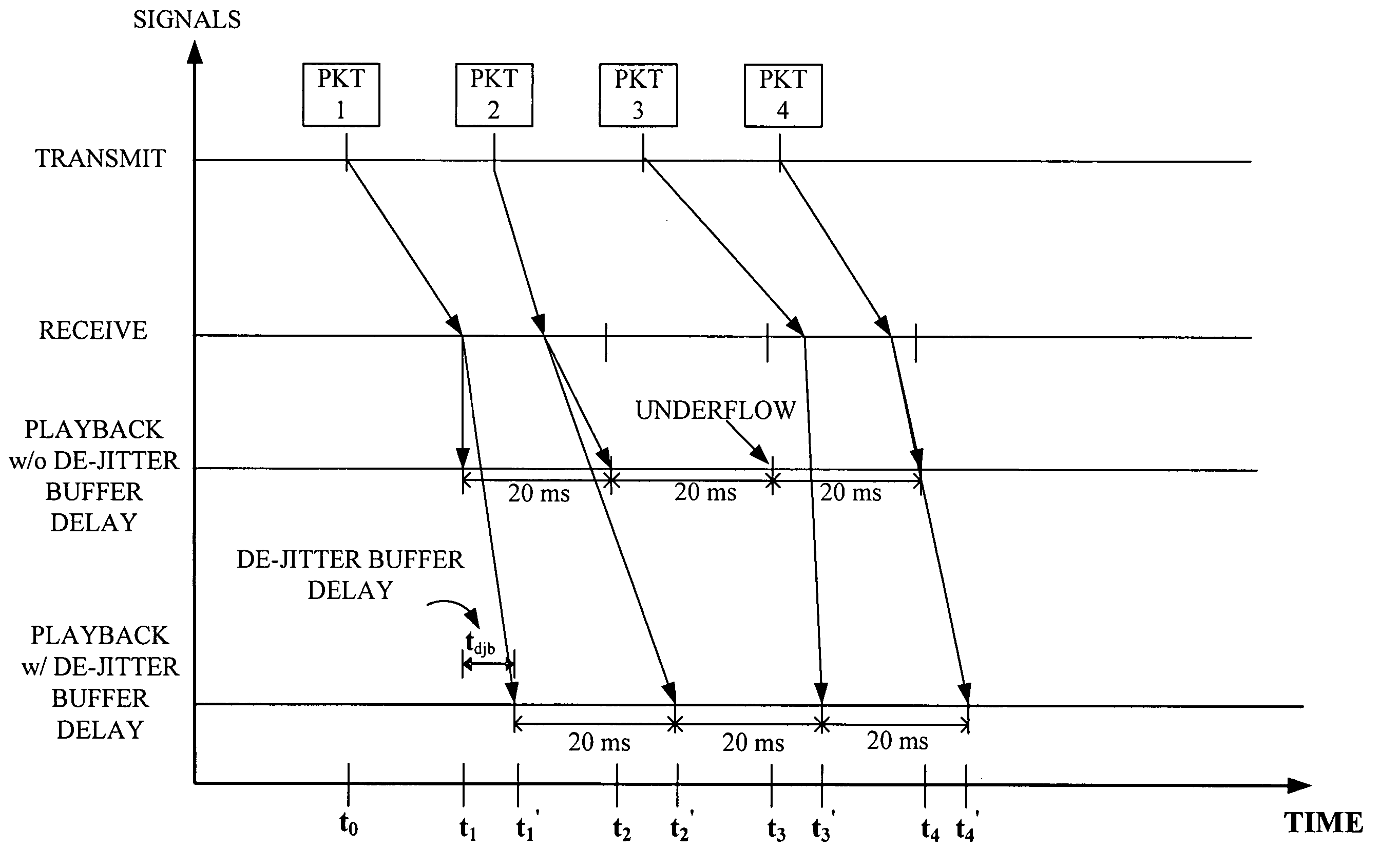
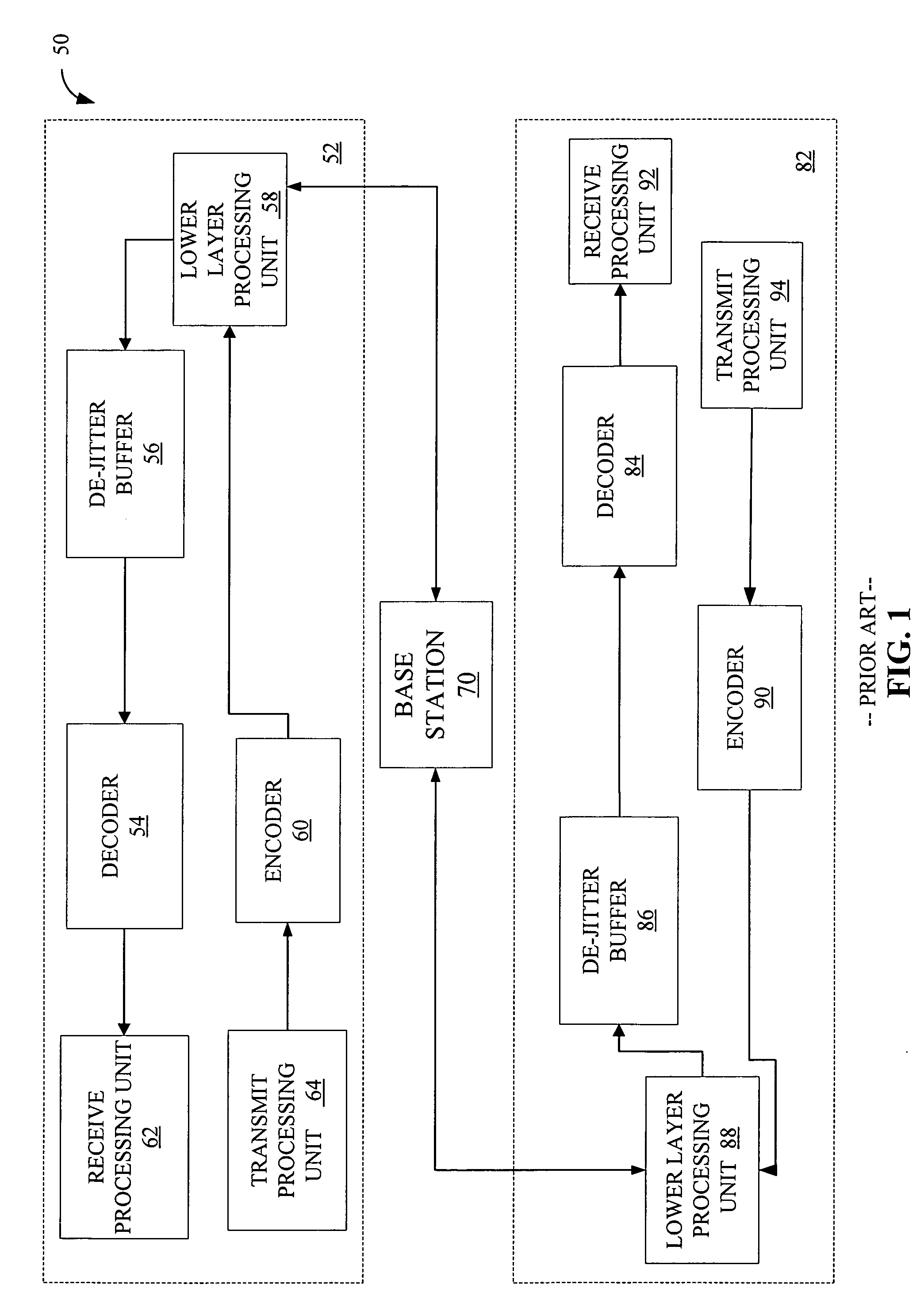
Method and apparatus for an adaptive de-jitter buffer
Adaptive De-Jitter Buffer for Voice over IP (VoIP) for packet switch communications. The de-jitter buffer methods and apparatus presented avoid playback of underflows while balancing end-to-end delay. In one example, the de-jitter buffer is recalculated at the beginning of each talkspurt. In another example, talkspurt packets are compressed upon receipt of all remaining packets.
Owner:QUALCOMM INC
System including a fine-grained memory and a less-fine-grained memory
ActiveUS7975109B2Memory architecture accessing/allocationEnergy efficient ICTData processing systemWrite buffer
A data processing system includes one or more nodes, each node including a memory sub-system. The sub-system includes a fine-grained, memory, and a less-fine-grained (e.g., page-based) memory. The fine-grained memory optionally serves as a cache and / or as a write buffer for the page-based memory. Software executing on the system uses a node address space which enables access to the page-based memories of all nodes. Each node optionally provides ACID memory properties for at least a portion of the space. In at least a portion of the space, memory elements are mapped to locations in the page-based memory. In various embodiments, some of the elements are compressed, the compressed elements are packed into pages, the pages are written into available locations in the page-based memory, and a map maintains an association between the some of the elements and the locations.
Owner:SANDISK TECH LLC
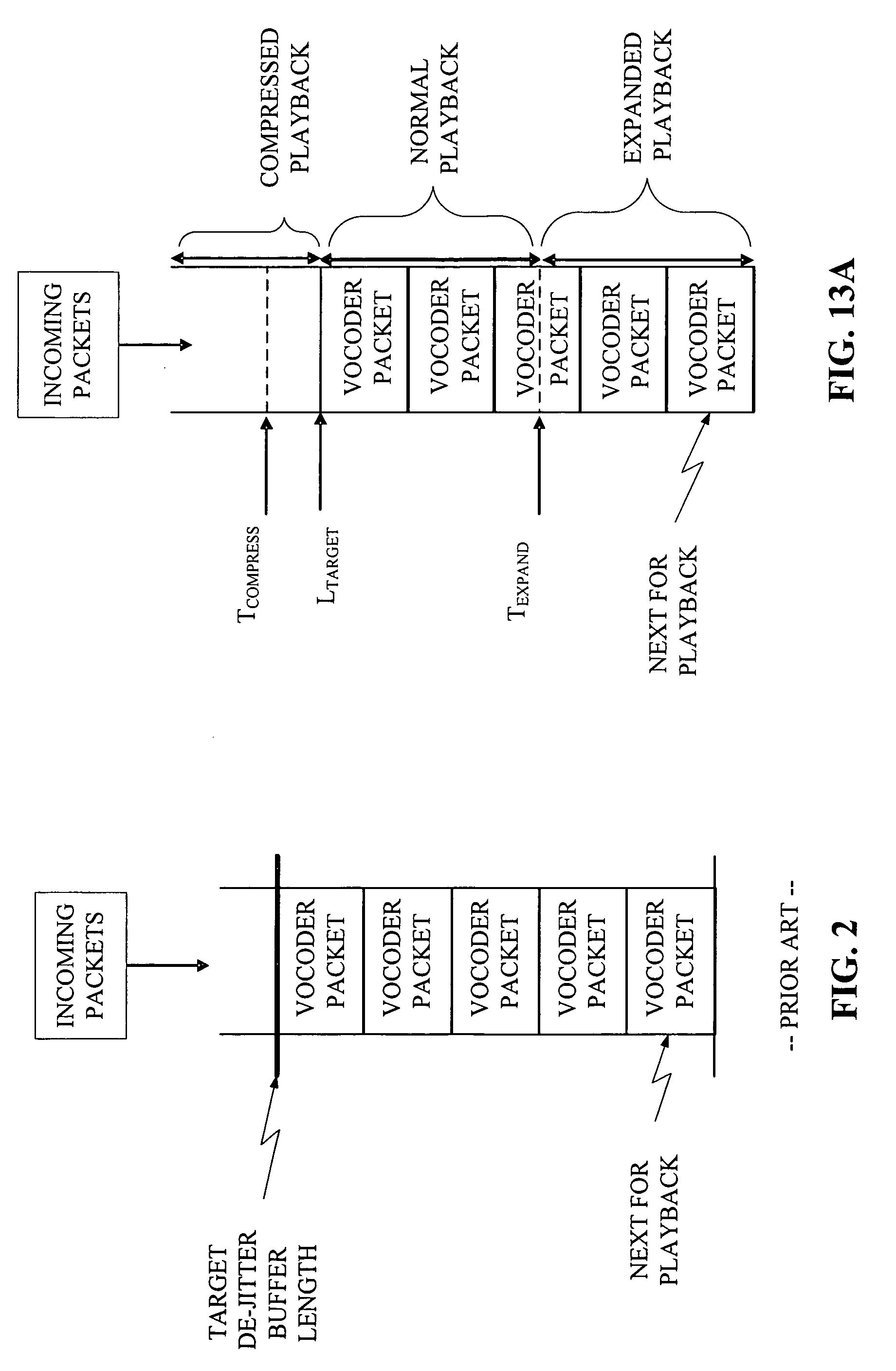
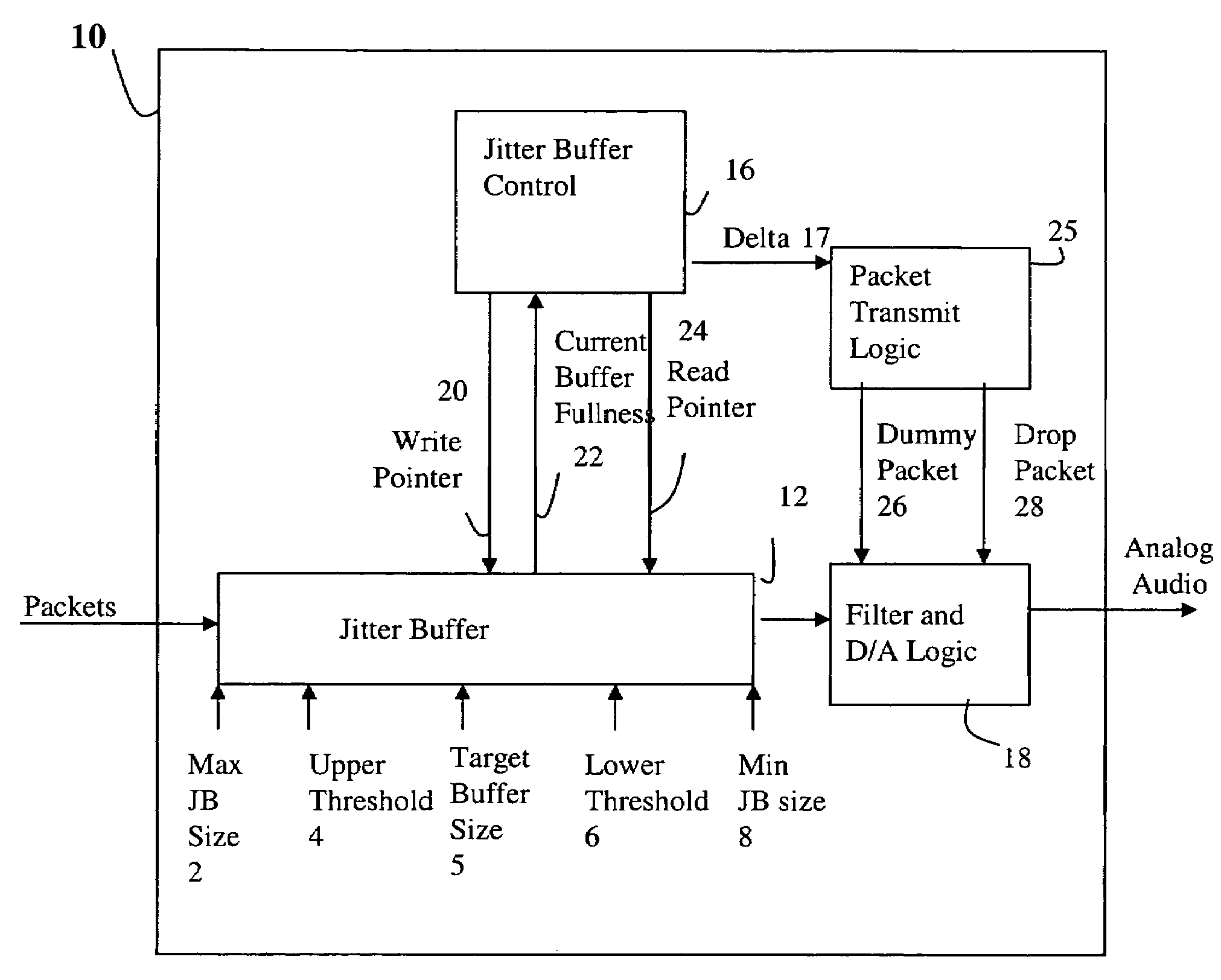
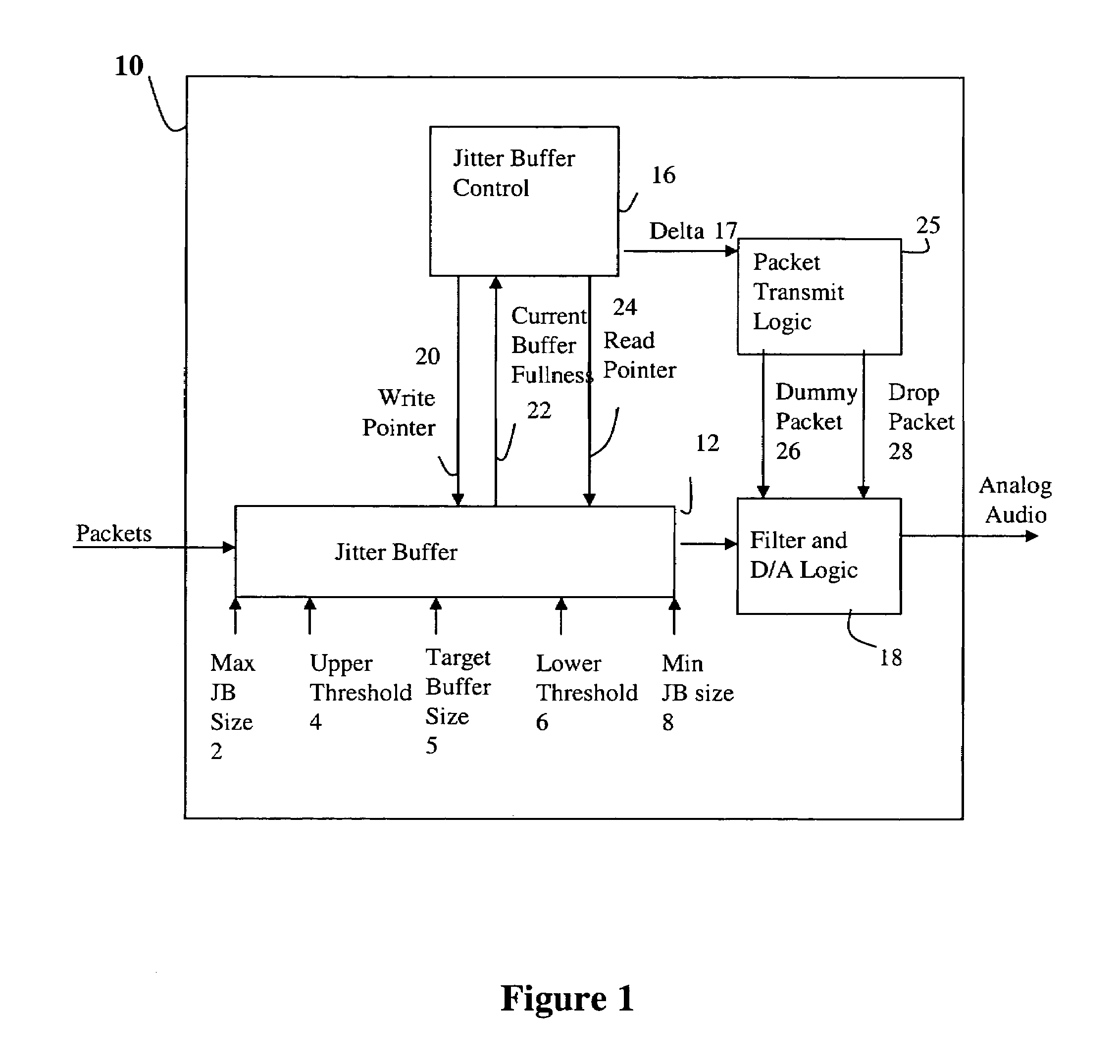
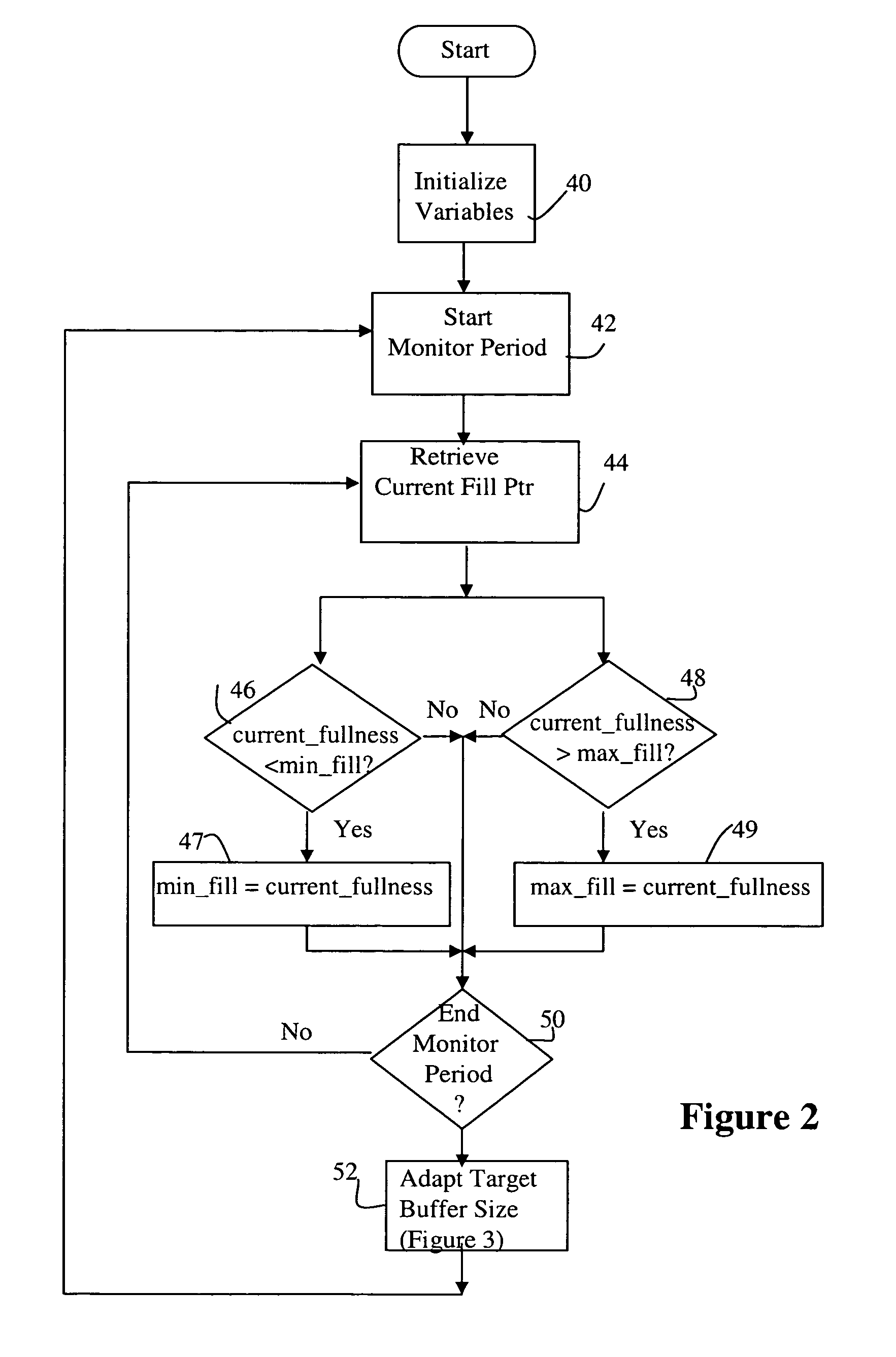
Adaptive jitter buffer control
ActiveUS7359324B1Reducing playout time offsetShorten the timeError preventionTransmission systemsWrite bufferSelf adaptive
A method for dynamically adjusting jitter buffer size according to buffer fill dynamics is disclosed. In one embodiment, an upper threshold and lower threshold for the jitter buffer are identified, wherein the lower buffer threshold identifies a minimum desirable number of packets in the jitter buffer, and the upper buffer threshold identifies a maximum desirable number of packets in the jitter buffer. Operating characteristics of the jitter buffer are monitored to identify instances when the jitter buffer size falls below or exceeds the desired thresholds. When a threshold is crossed, the adaptive algorithm alters the playback offset time, by introducing or deleting packets into the transmission path, to allow the jitter buffer size to return to a desirable target size within the threshold boundaries.
Owner:CIENA
DMA descriptor queue read and cache write pointer arrangement
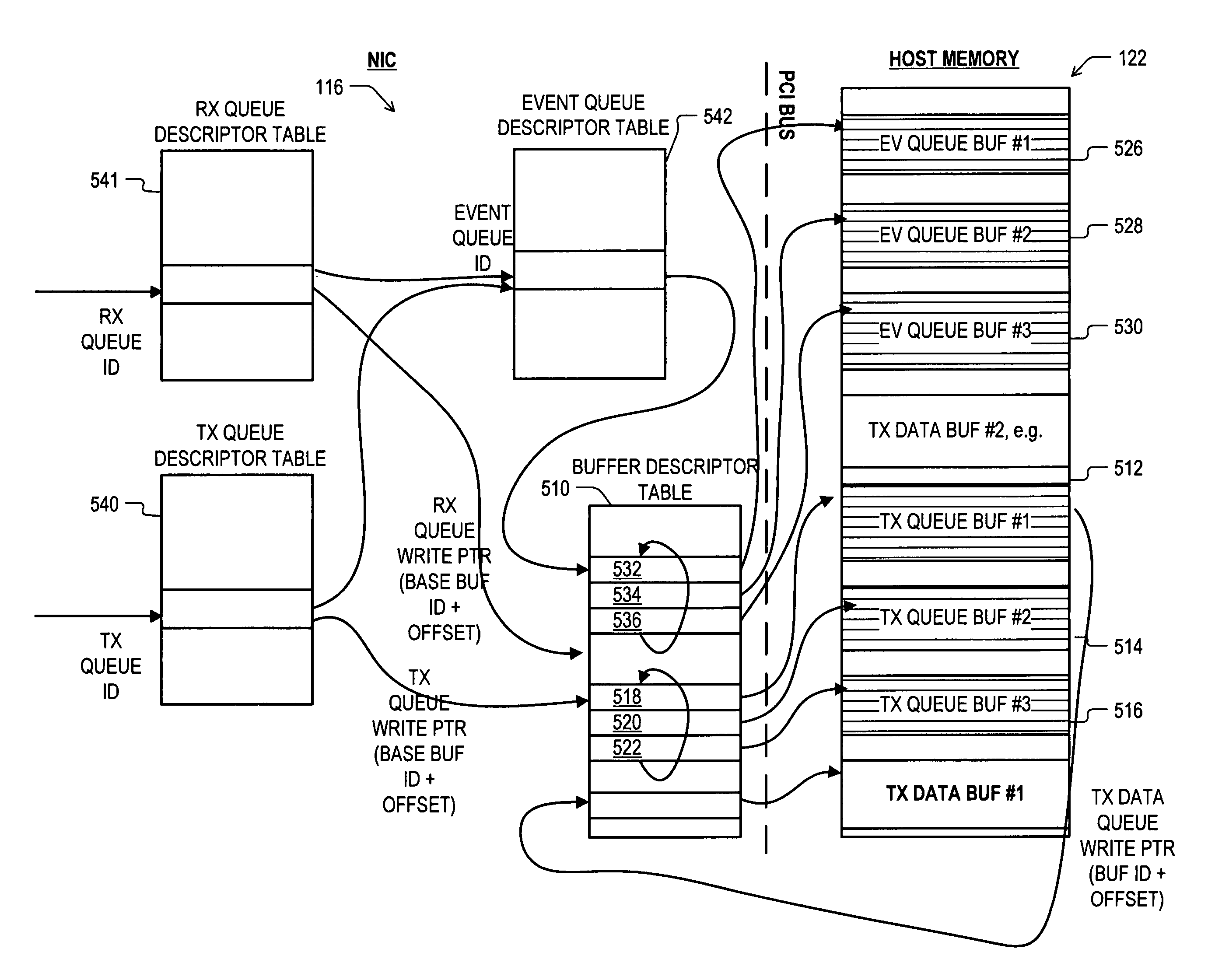
Method and apparatus for retrieving buffer descriptors from a host memory for use by a peripheral device. In an embodiment, a peripheral device such as a NIC includes a plurality of buffer descriptor caches each corresponding to a respective one of a plurality of host memory descriptor queues, and a plurality of queue descriptors each corresponding to a respective one of the host memory descriptor queues. Each of the queue descriptors includes a host memory read address pointer for the corresponding descriptor queue, and this same read pointer is used to derive algorithmically the descriptor cache write addresses at which to write buffer descriptors retrieved from the corresponding host memory descriptor queue.
Owner:XILINX INC
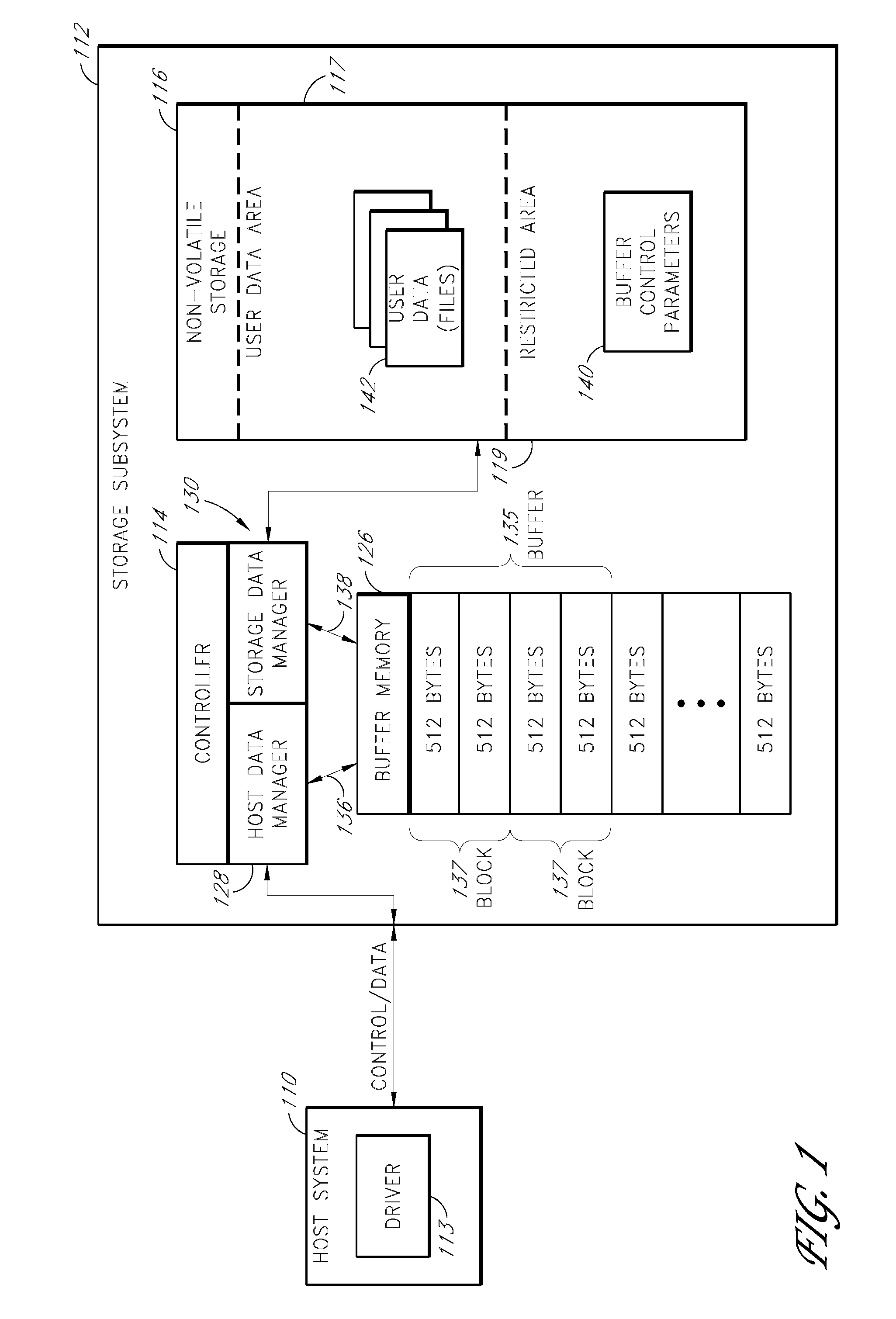
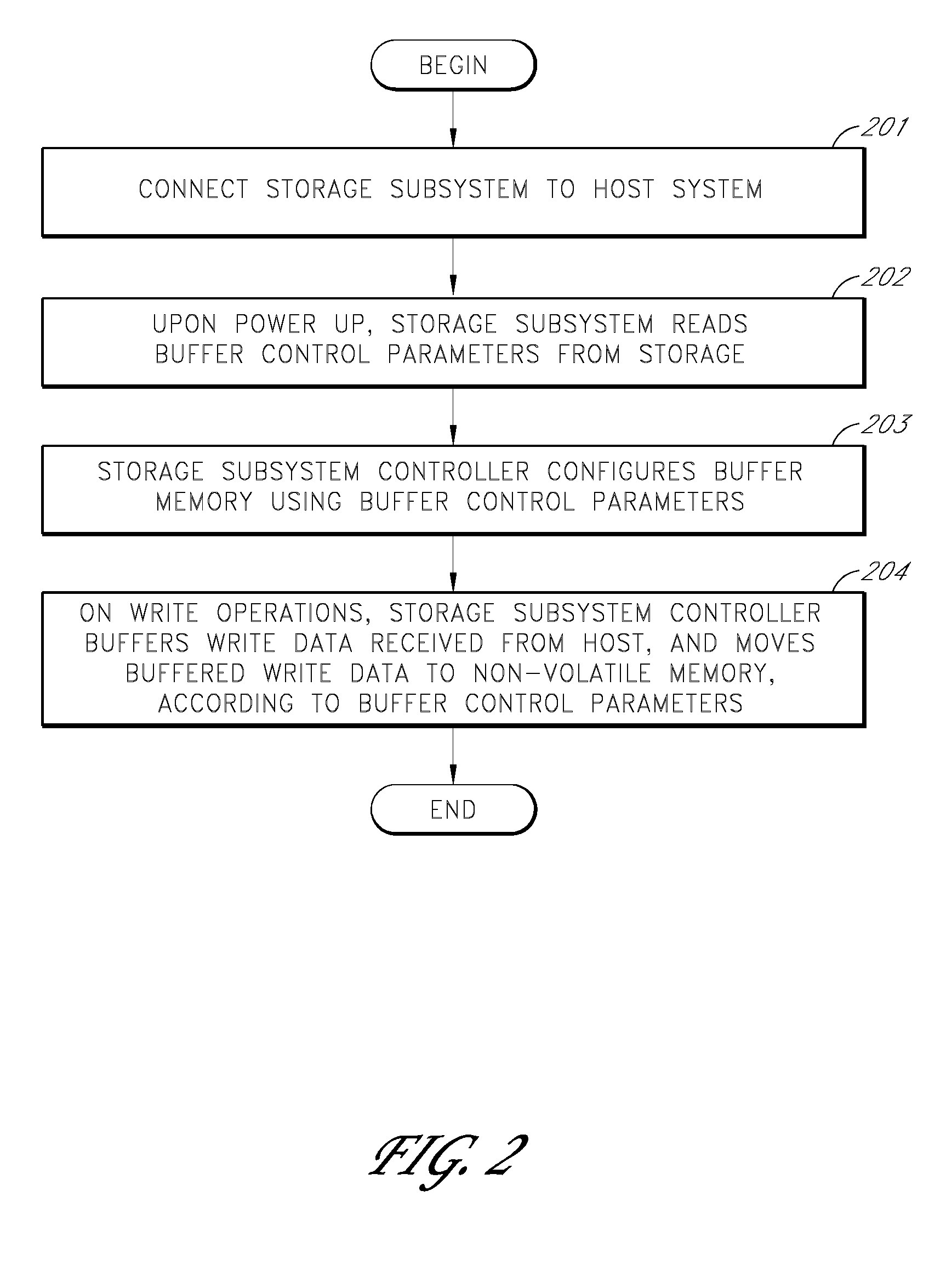
Storage subsystem with configurable buffer
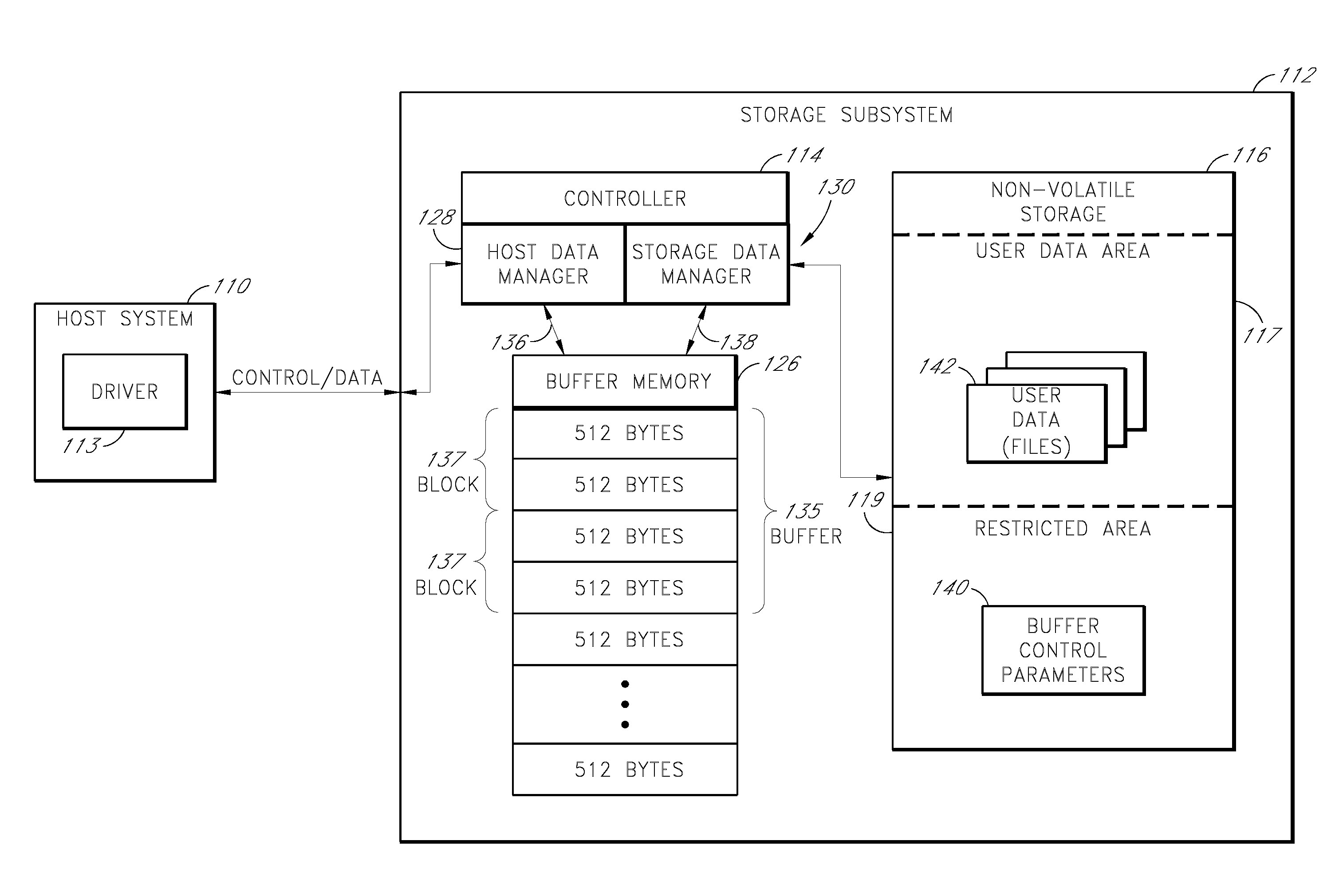
ActiveUS20080189452A1Improve performanceReduce riskRecord information storageInput/output processes for data processingWrite bufferData loss
A storage subsystem includes a variable-size write buffer that temporarily stores write data received from a host system. The storage subsystem is capable of adjusting the size of the write buffer so as to vary both the performance (e.g., sustained write speed) of the storage subsystem and a risk of data loss. In one embodiment, the storage subsystem implements a command set that enables the host system to directly control the size of the write buffer. The storage subsystem may additionally or alternatively be capable of adjusting the size of the write buffer based on monitored operating conditions, such as the temperature, the stability / consistency of a power signal received from the host system, and / or the elapsed time since the storage subsystem was last powered up.
Owner:WESTERN DIGITAL TECH INC
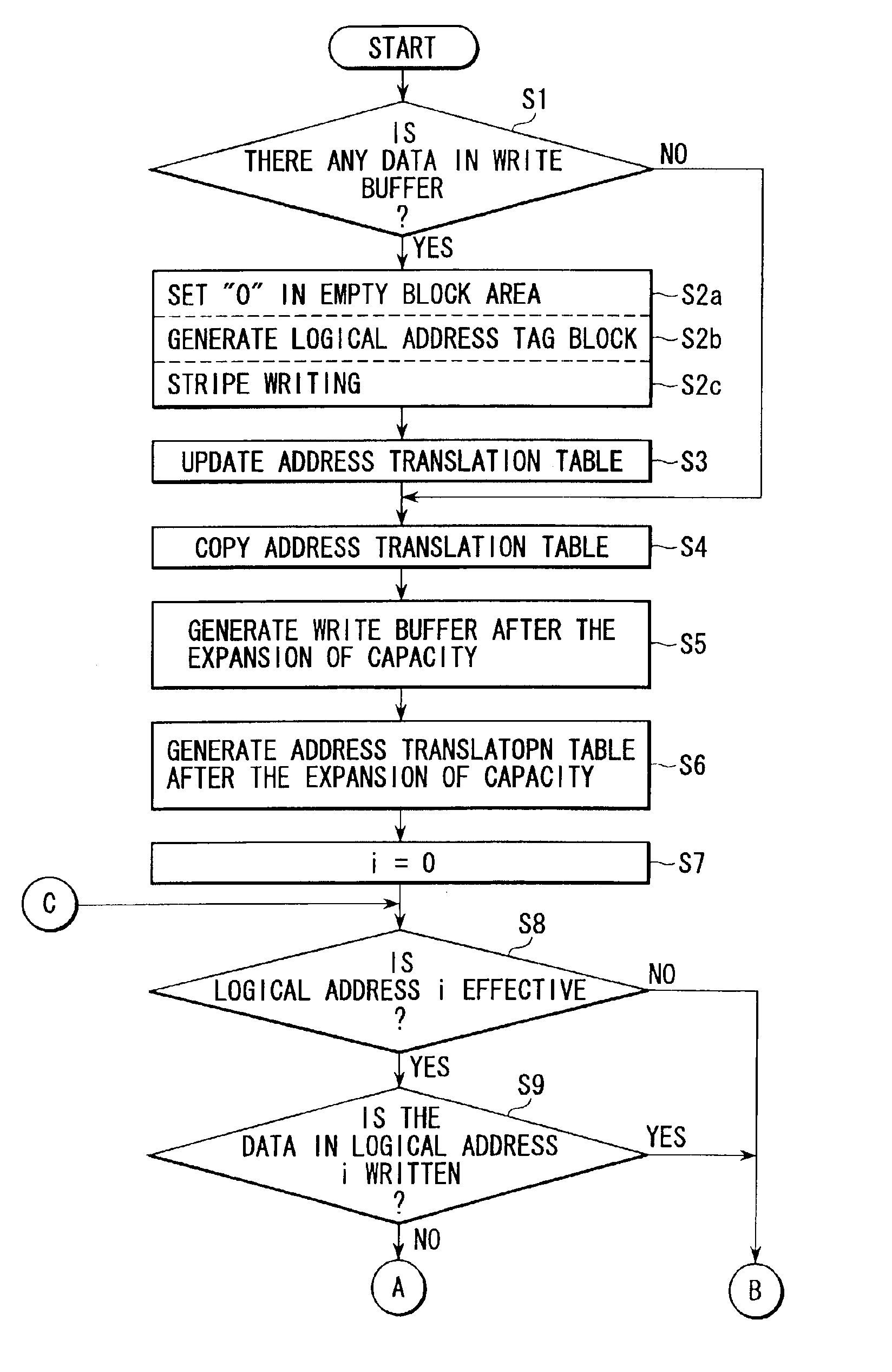
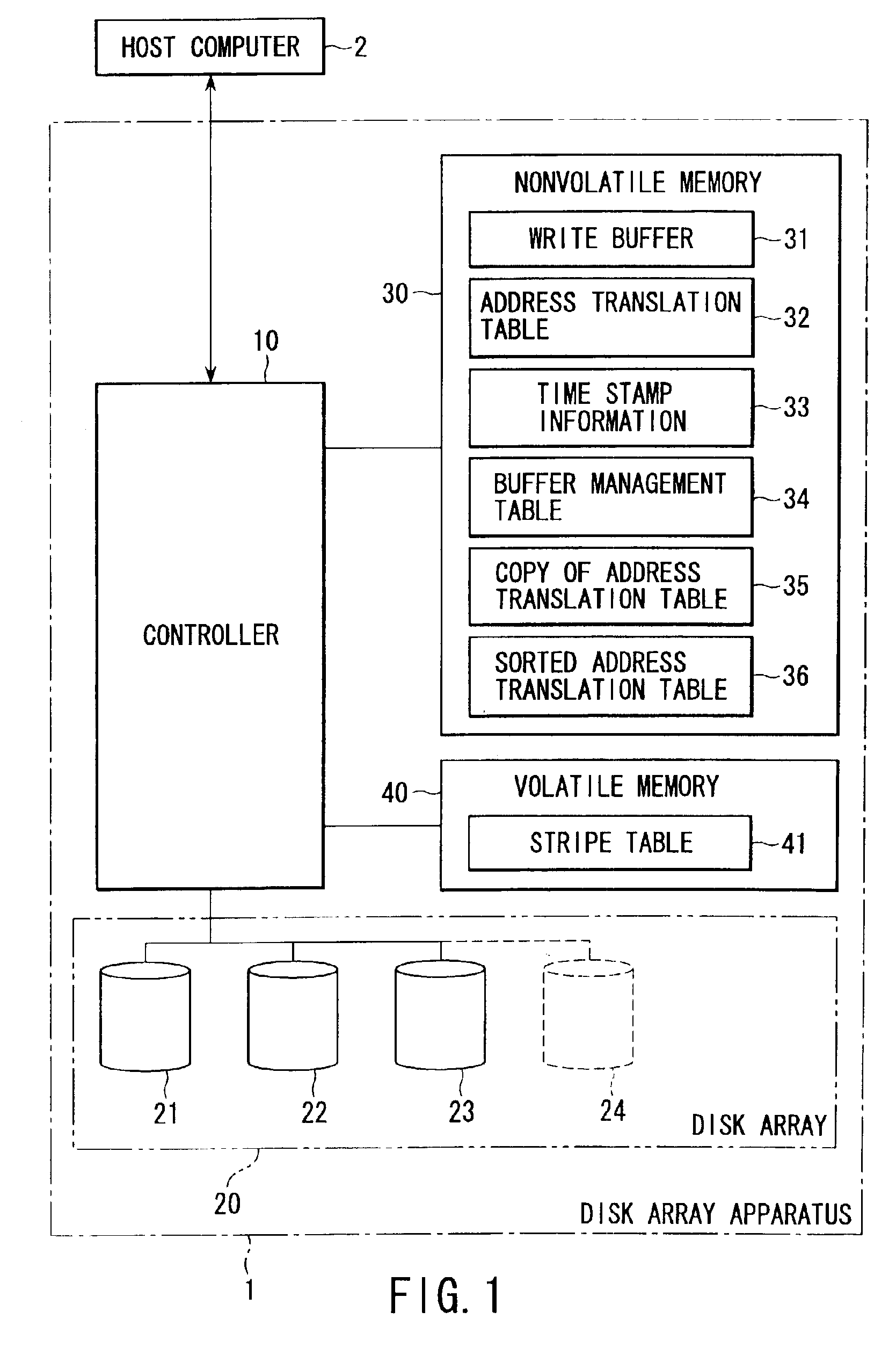
Disk array apparatus for and method of expanding storage capacity dynamically
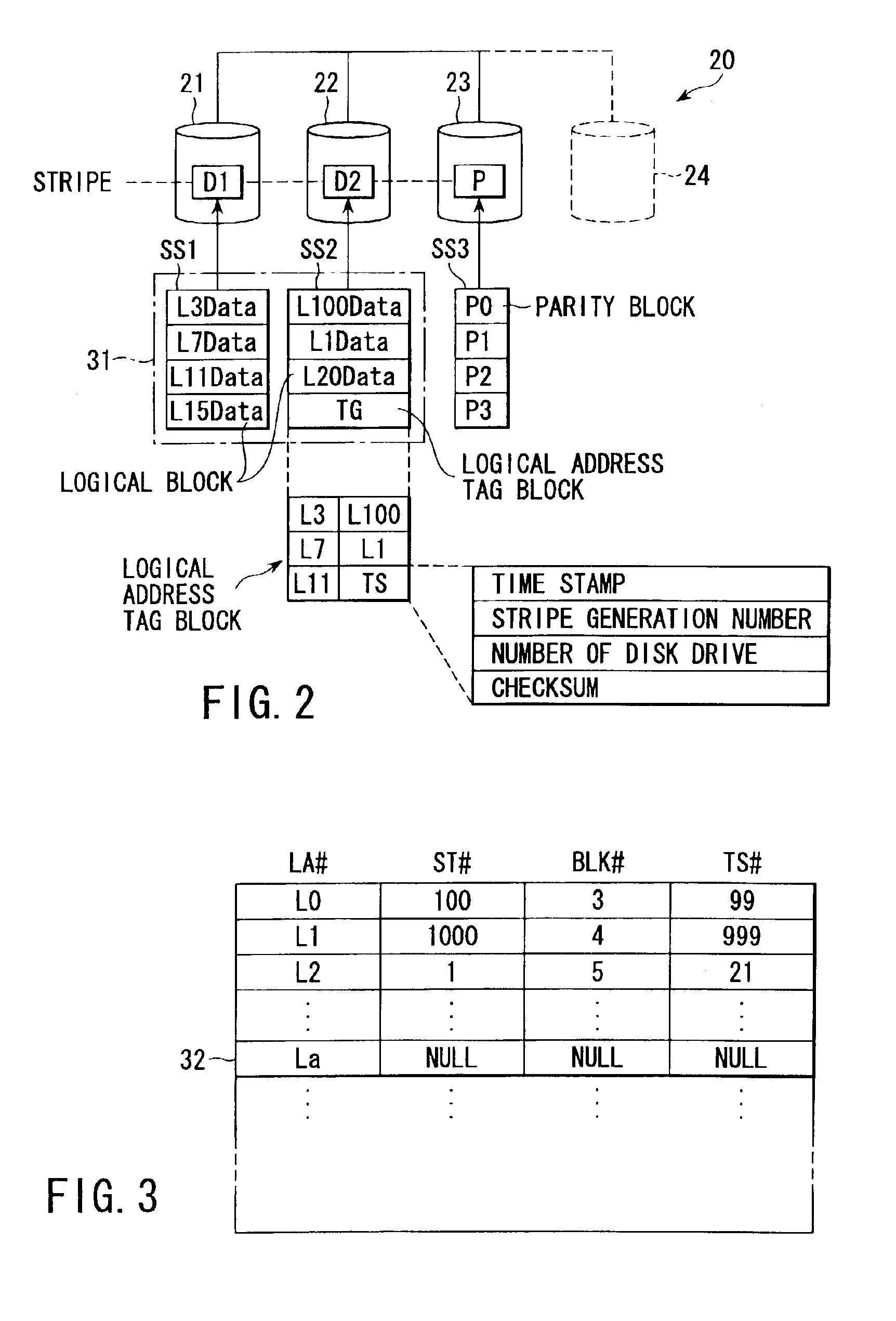
InactiveUS6901479B2Shorten the timeIncrease storage capacityInput/output to record carriersError detection/correctionWrite bufferDisk array
A controller retrieves effective logical addresses sequentially according to a copy of an address translation table at the time of the start of storage capacity expansion in the process of expanding the storage capacity of a disk array by adding a disk drive to the disk array. The controller stores the data in the logical address into a restructured write buffer each time an effective logical address is retrieved. The controller writes one stripe worth of data blocks including one stripe of logical blocks and a logical address tag block into an empty area different from the area in which the data to be updated has been stored in the data array each time one stripe worth of logical blocks of data is accumulated in the write buffer.
Owner:KK TOSHIBA
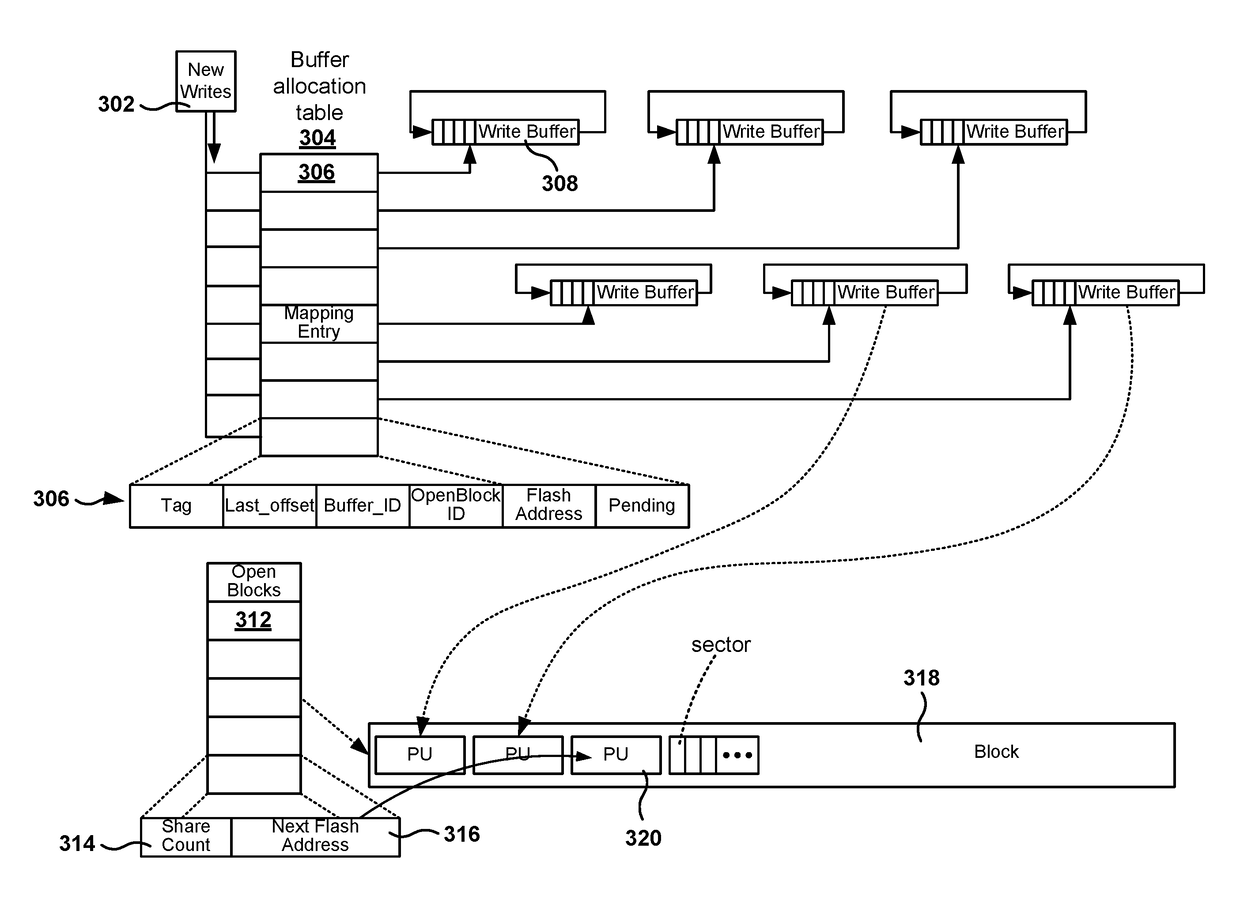
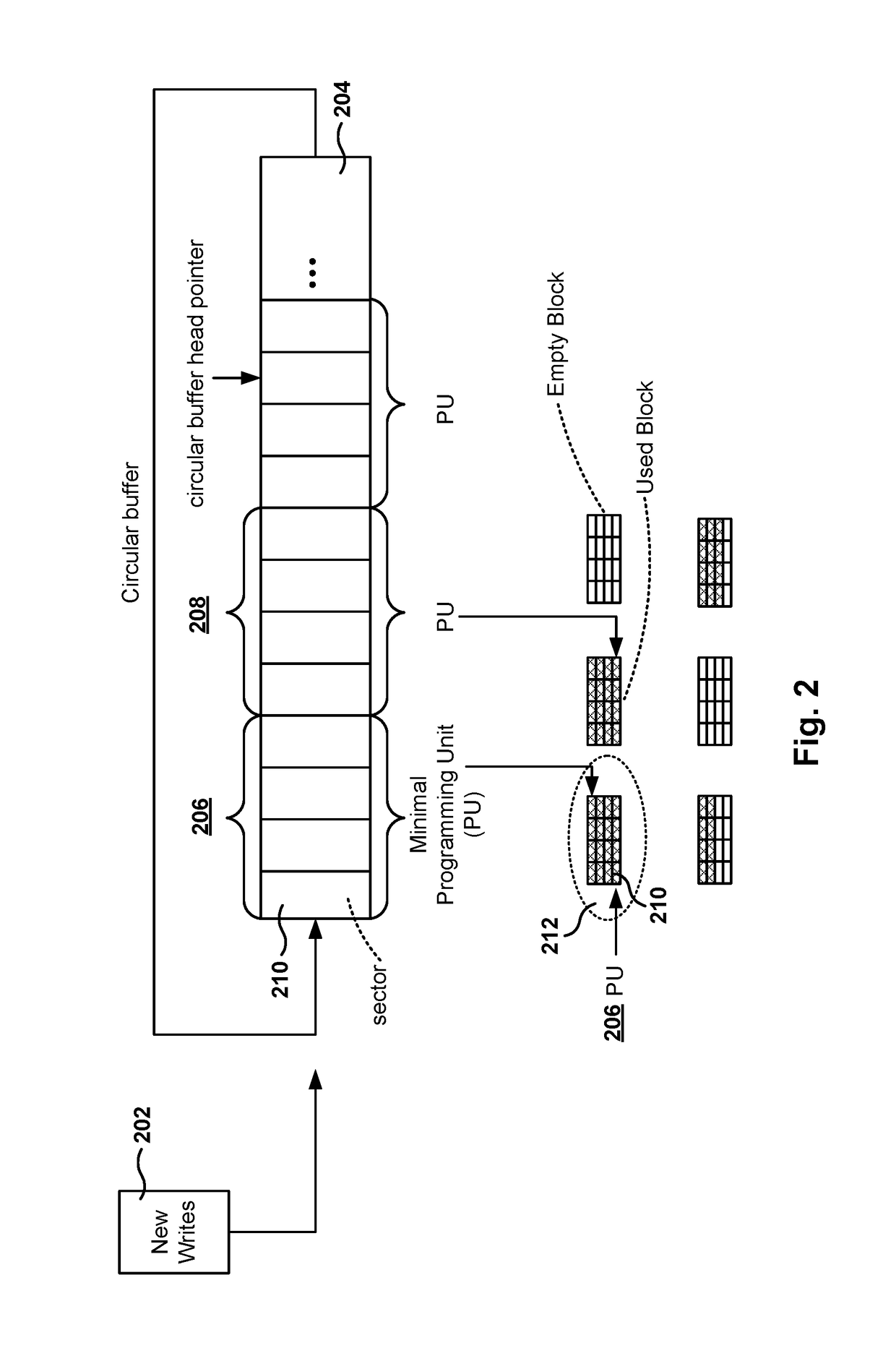
Low write amplification in solid state drive
Methods, systems, and computer programs are presented for storing data in a solid state drive (SSD). One method includes an operation for detecting a plurality of streams writing to the SSD, each stream writing in sectors, a page including a plurality of sectors and a block including a plurality of pages. A write operation includes writing at least one complete page, and an erase operation includes erasing at least one complete block. The method further includes operations for allocating a write buffer for each stream in RAM memory, and for storing each received sector of a stream in the corresponding write buffer. When a write buffer stores enough sectors to fill a page, content of the write buffer is written to a page in flash memory such that the page is filled. Further, the write buffer is freed after writing the content of the write buffer to the flash memory.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
In-line non volatile memory disk read cache and write buffer
ActiveUS7620773B2Read/write performance of hardReduce the number of timesData buffering arrangementsError detection/correctionHard disc driveWrite buffer
A method and apparatus to improve the read / write performance of a hard drive is presented. A device having solid state, non-volatile (NV) memory is added in-line to the conventional hard drive and acts as a read / write cache. Data specified by the operating system is stored in the NV memory. The operating system provides a list of data to be put in NV memory. The data includes data to be pinned in NV memory and data that is dynamic. Pinned data persists in NV memory until the operating system commands it to be flushed. Dynamic data can be flushed by the hard drive controller. Data sent by an application for storage is temporarily stored in NV memory in data blocks until the operating system commits it to the disk.
Owner:MICROSOFT TECH LICENSING LLC
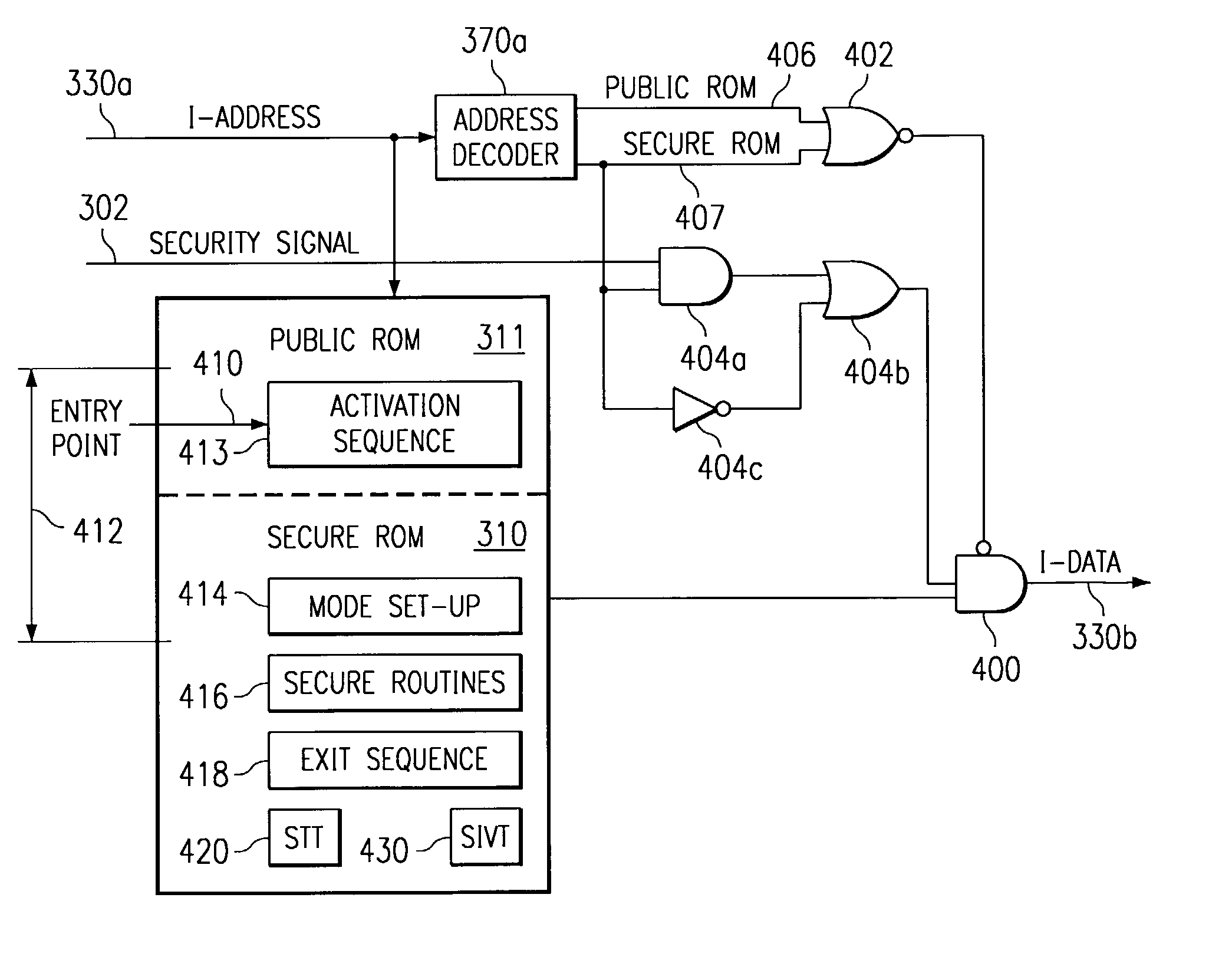
Secure mode for processors supporting interrupts
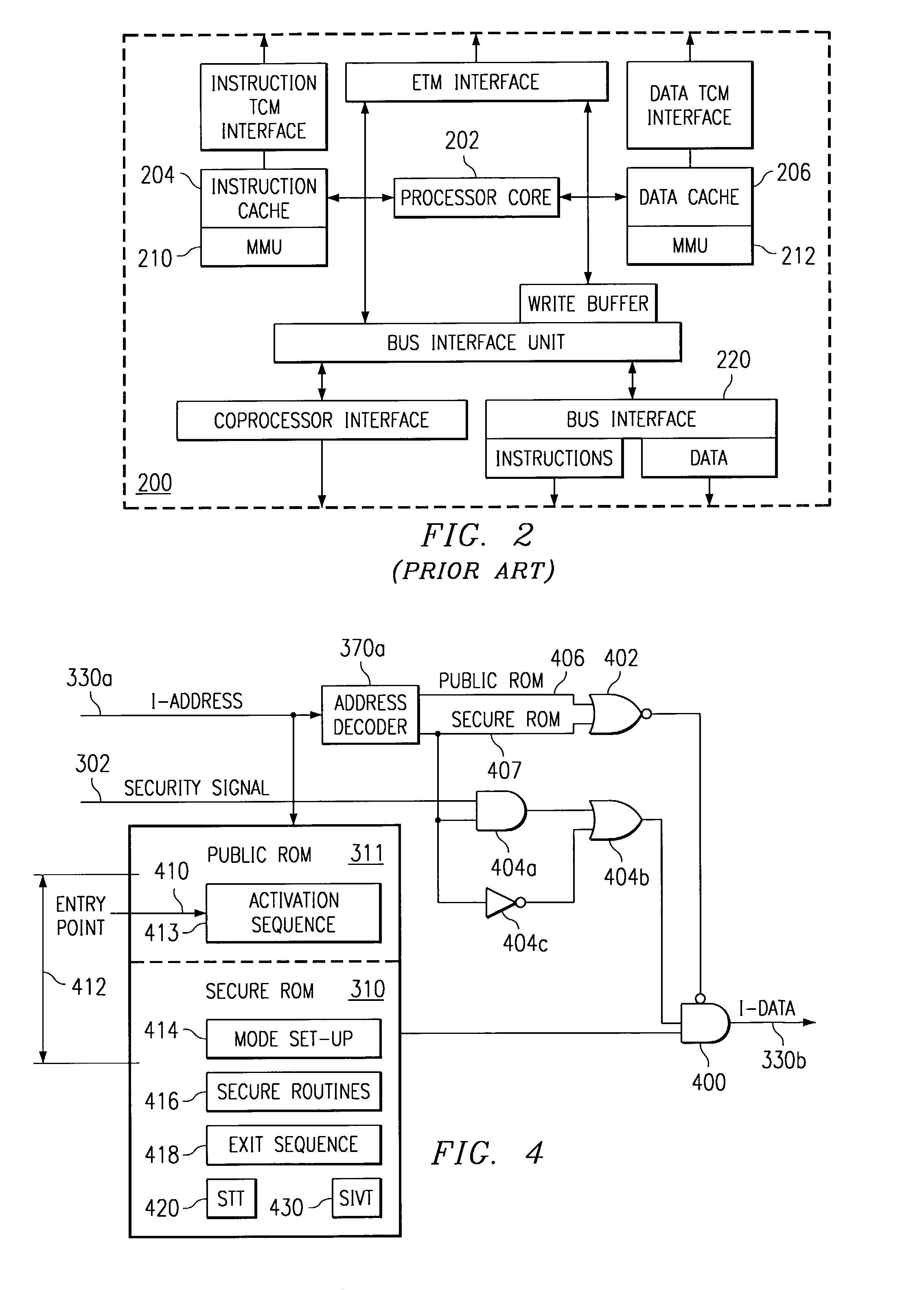
ActiveUS7237081B2Specific access rightsDigital data processing detailsOperational systemManagement unit
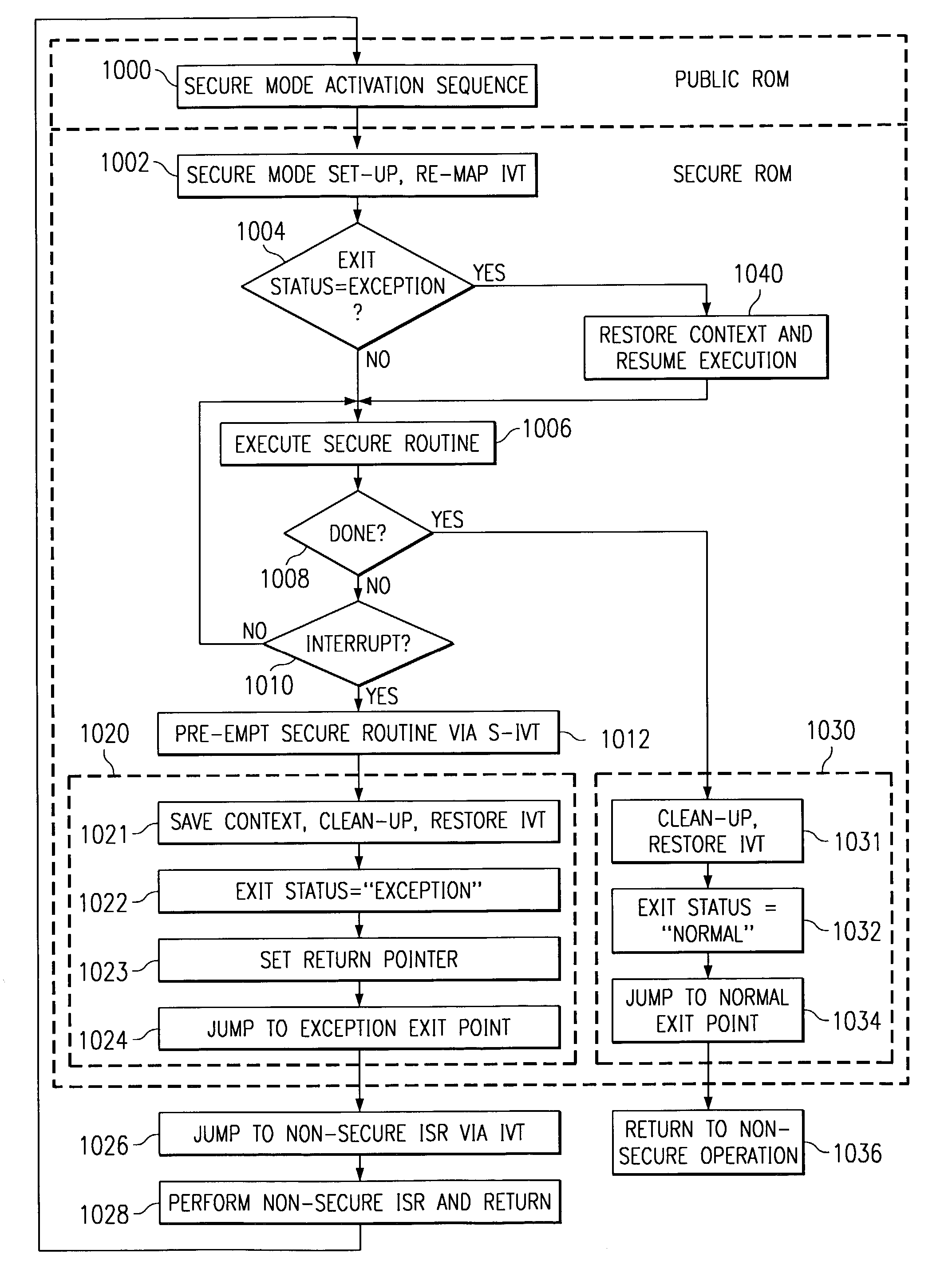
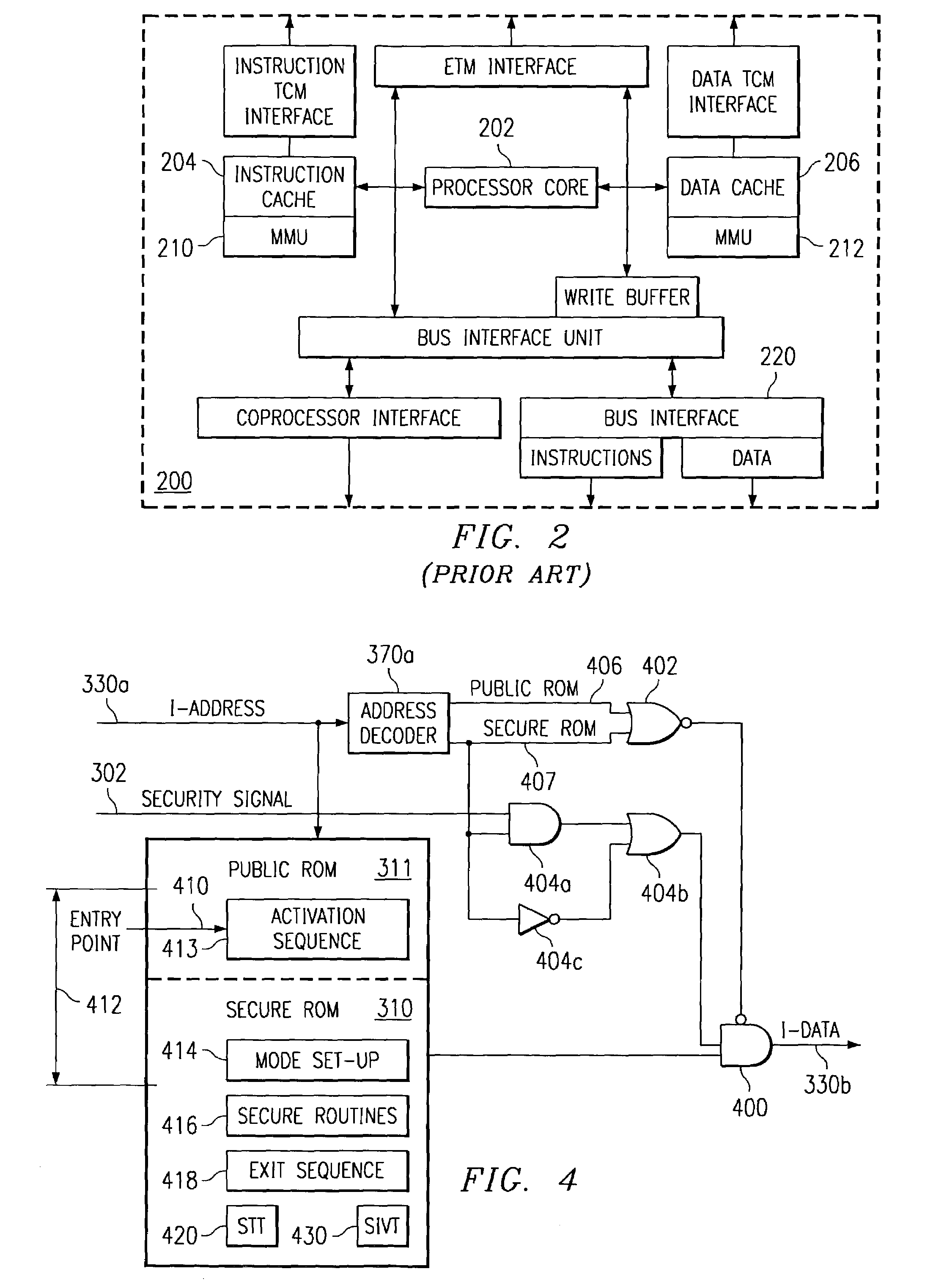
A digital system is provided with a secure mode (3rd level of privilege) built in a non-invasive way on a processor system that includes a processor core, instruction and data caches, a write buffer and a memory management unit. A secure execution mode is thus provided on a platform where the only trusted software is the code stored in ROM. In particular the OS is not trusted, all native applications are not trusted. A secure execution mode is provided that allows virtual addressing when a memory management unit (MMU) is enabled. The secure execution mode allows instruction and data cache to be enabled. A secure execution mode is provided that allows all the system interruptions to be unmasked. The secure mode is entered through a unique entry point. The secure execution mode can be dynamically entered and exited with full hardware assessment of the entry / exit conditions. A specific set of entry conditions is monitored that account for caches, write buffer and MMU being enabled. The structure of the activation sequence code accounts for caches, write buffer and MMU being enabled. The structure of the exit sequences code accounts for caches, write buffer and MMU being enabled. A specific way is provided to manage a safe exit of secure mode under generic interruptions and allows return from interruption through entry point and activation sequence and a proper resuming of the secure execution. A specific way is provided to manage the MMU in secure mode and provide data exchange between secure and non-secure environment.
Owner:TEXAS INSTR INC
System and method for improving data integrity and memory performance using non-volatile media
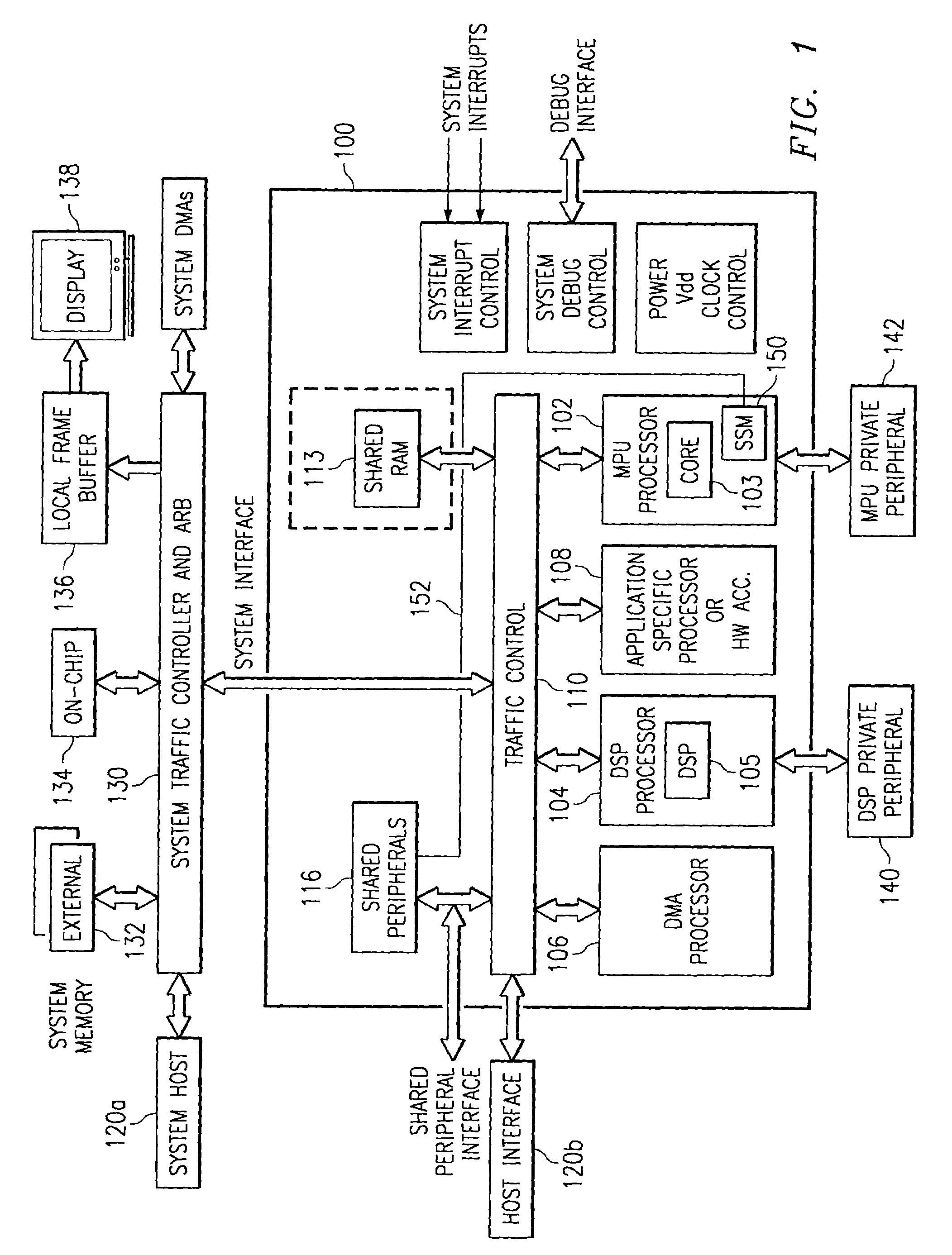
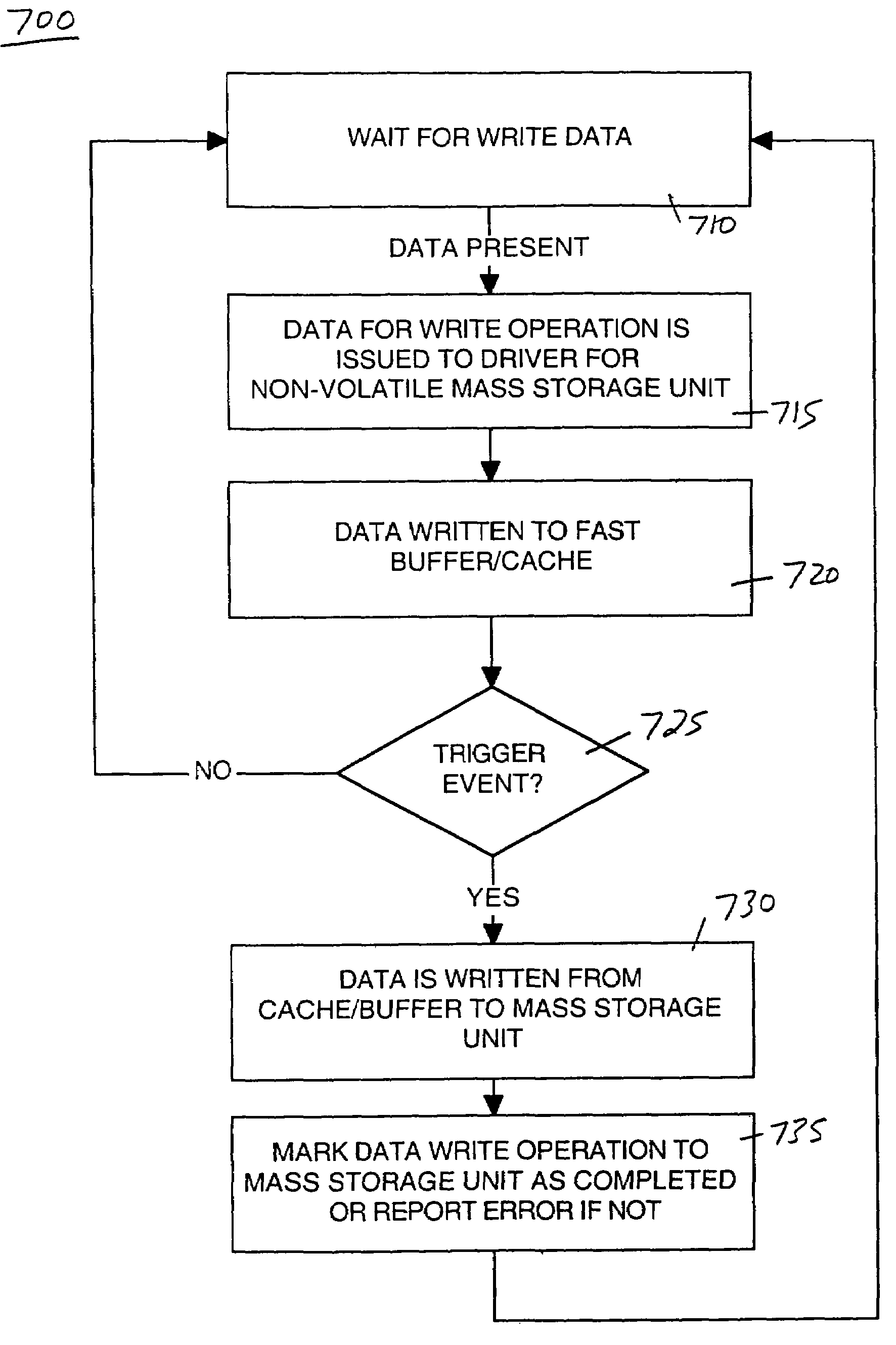
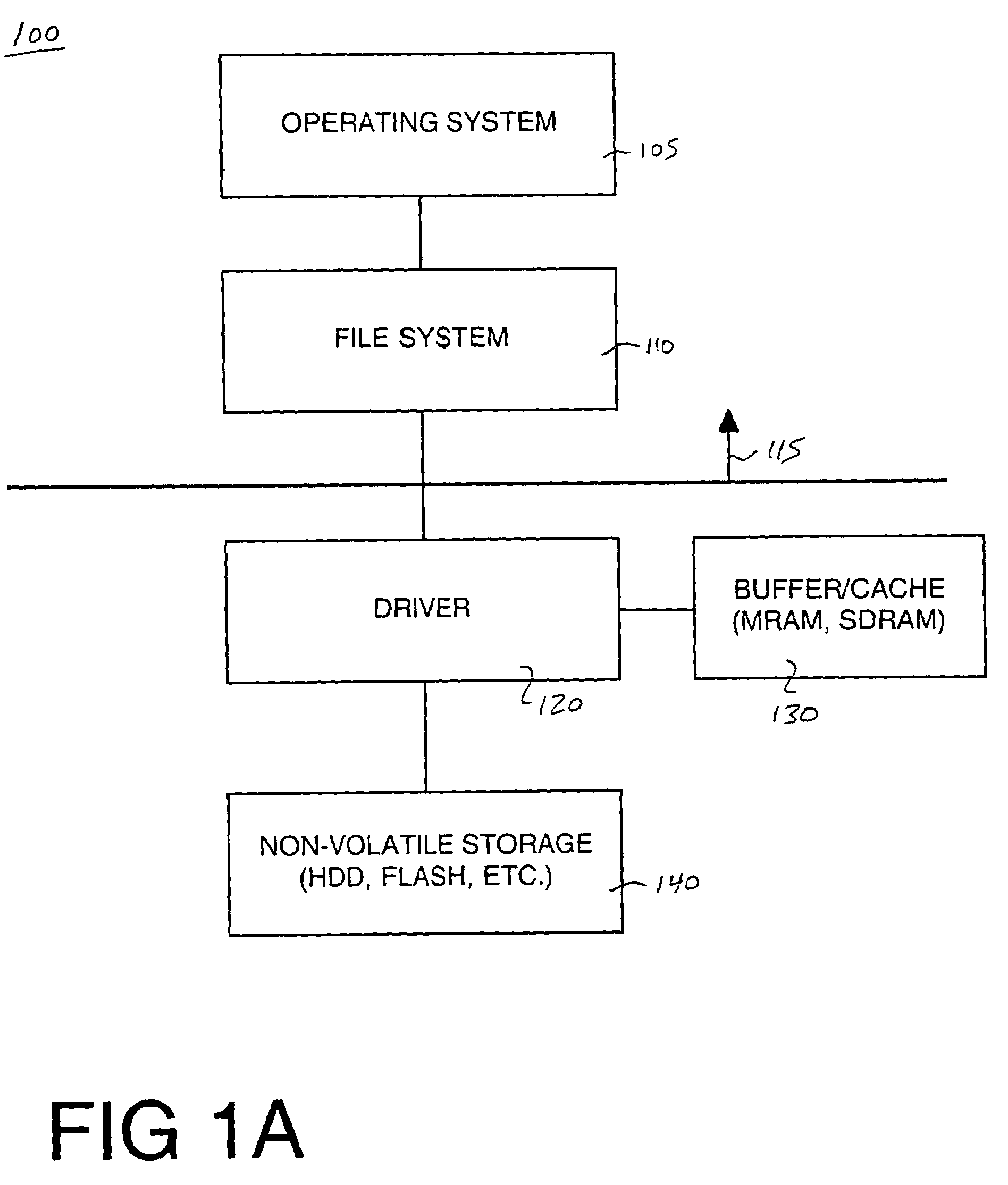
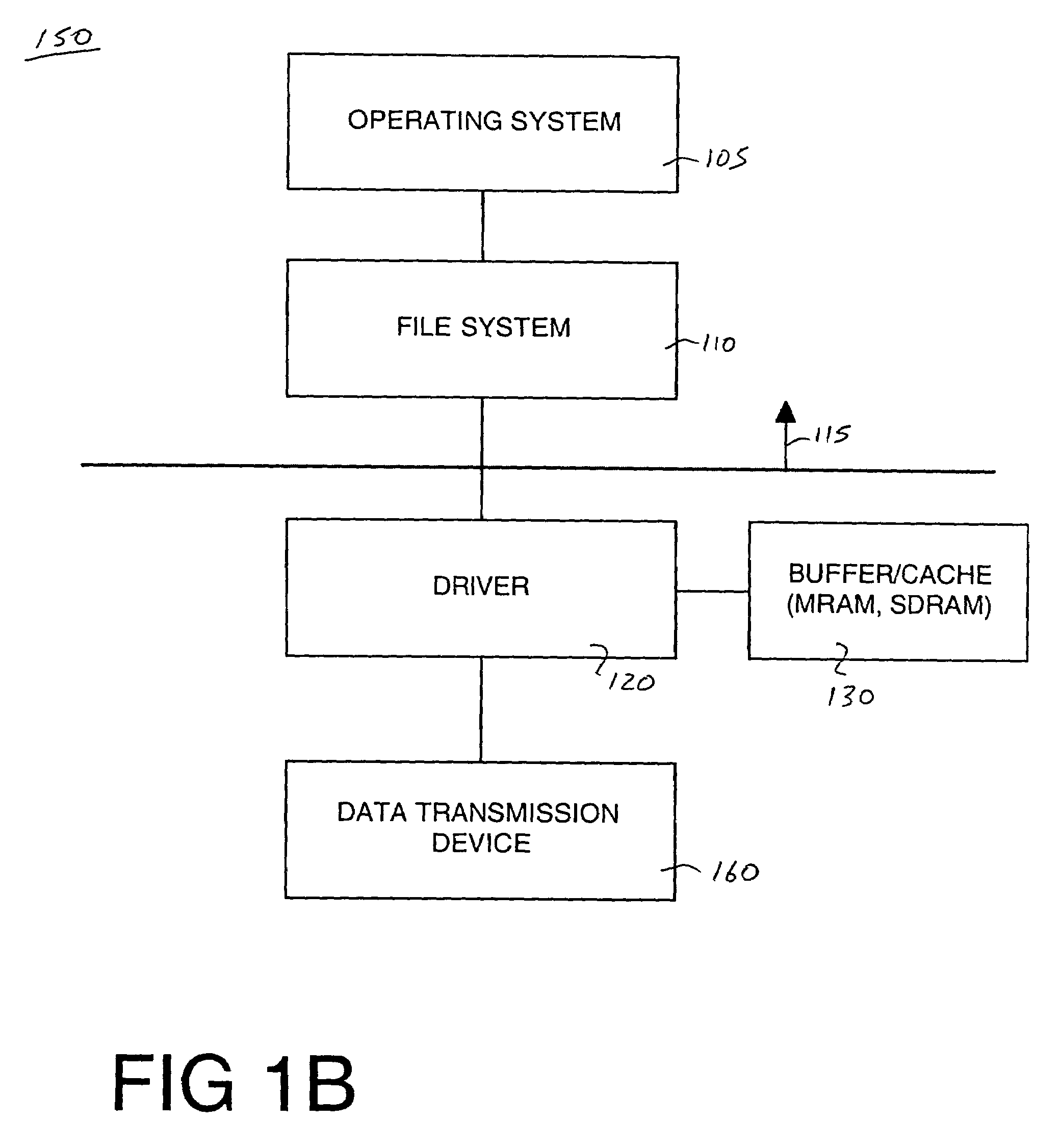
A system and computer system for improving data integrity and memory performance using non-volatile media. A system includes a non-volatile mass storage unit, e.g., a flash memory device and / or a hard drive unit for instance. A memory device is used as a high speed data buffer and / or cache for the non-volatile storage unit. The memory device may be non-volatile, e.g., magnetic random access memory (MRAM) or volatile memory, e.g., synchronous dynamic random access memory (SDRAM). By buffering and / or caching the write data, fewer accesses are required to the mass storage device thereby increasing system performance. Additionally, mechanical and electrical degradation of the mass storage device is reduced. Certain trigger events can be programmed to cause data from the memory device to be written to the mass storage device. In one embodiment, the write buffer contents are preserved across reset or power loss events. In one embodiment, the mass storage unit may be a data transport layer, e.g., Ethernet, USB, Bluetooth, etc.
Owner:QUALCOMM INC
Synchronous double data rate DRAM
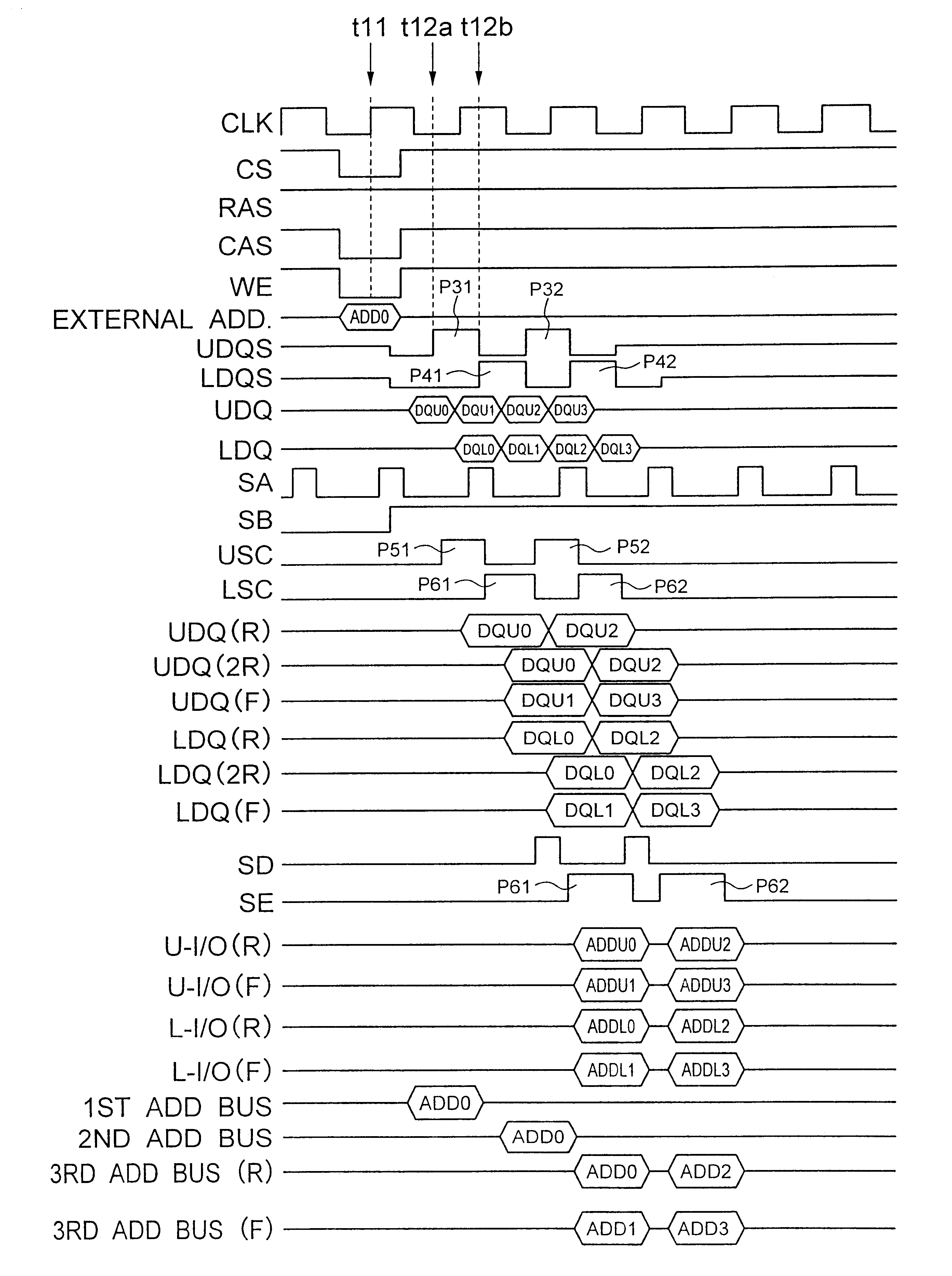
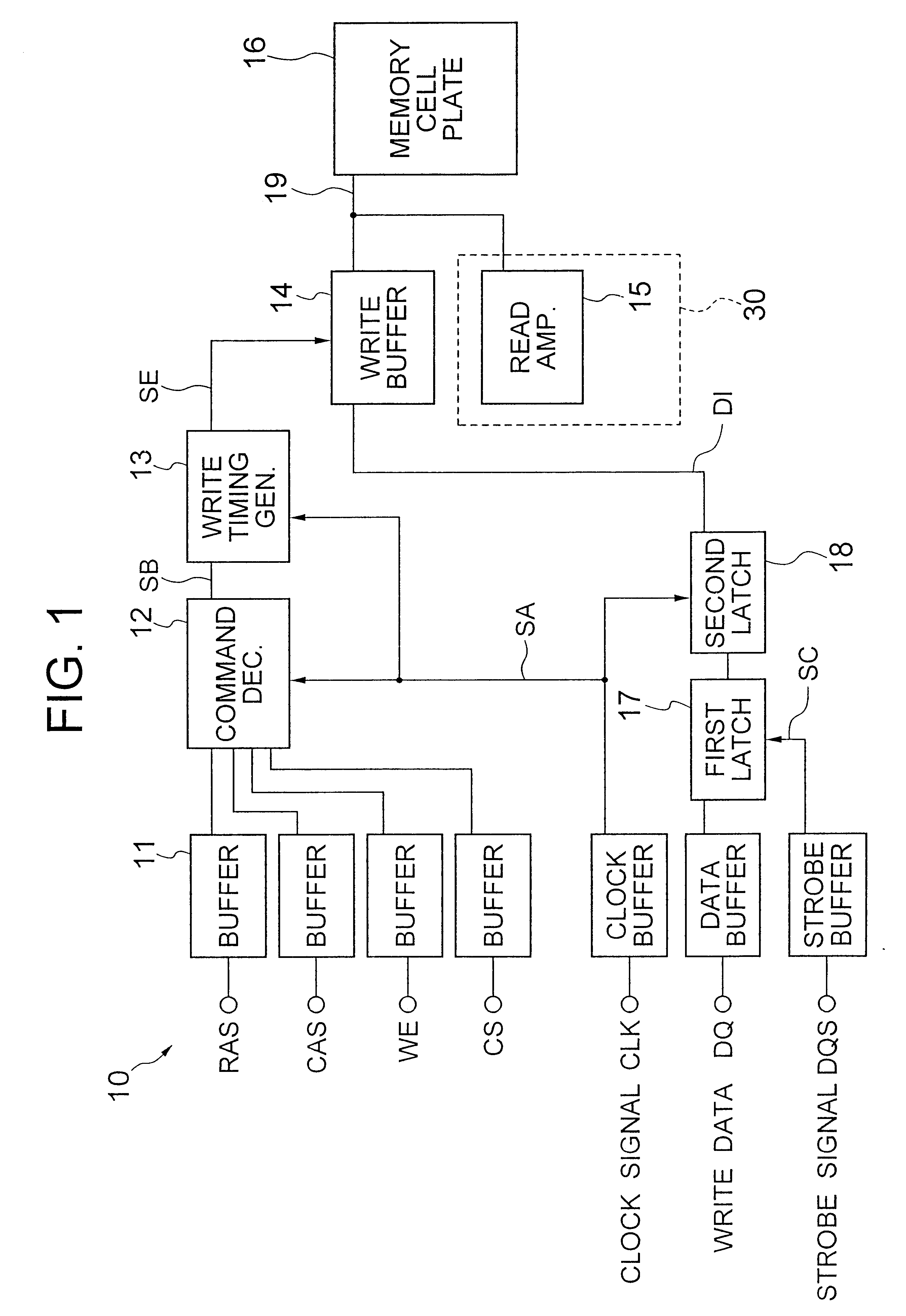
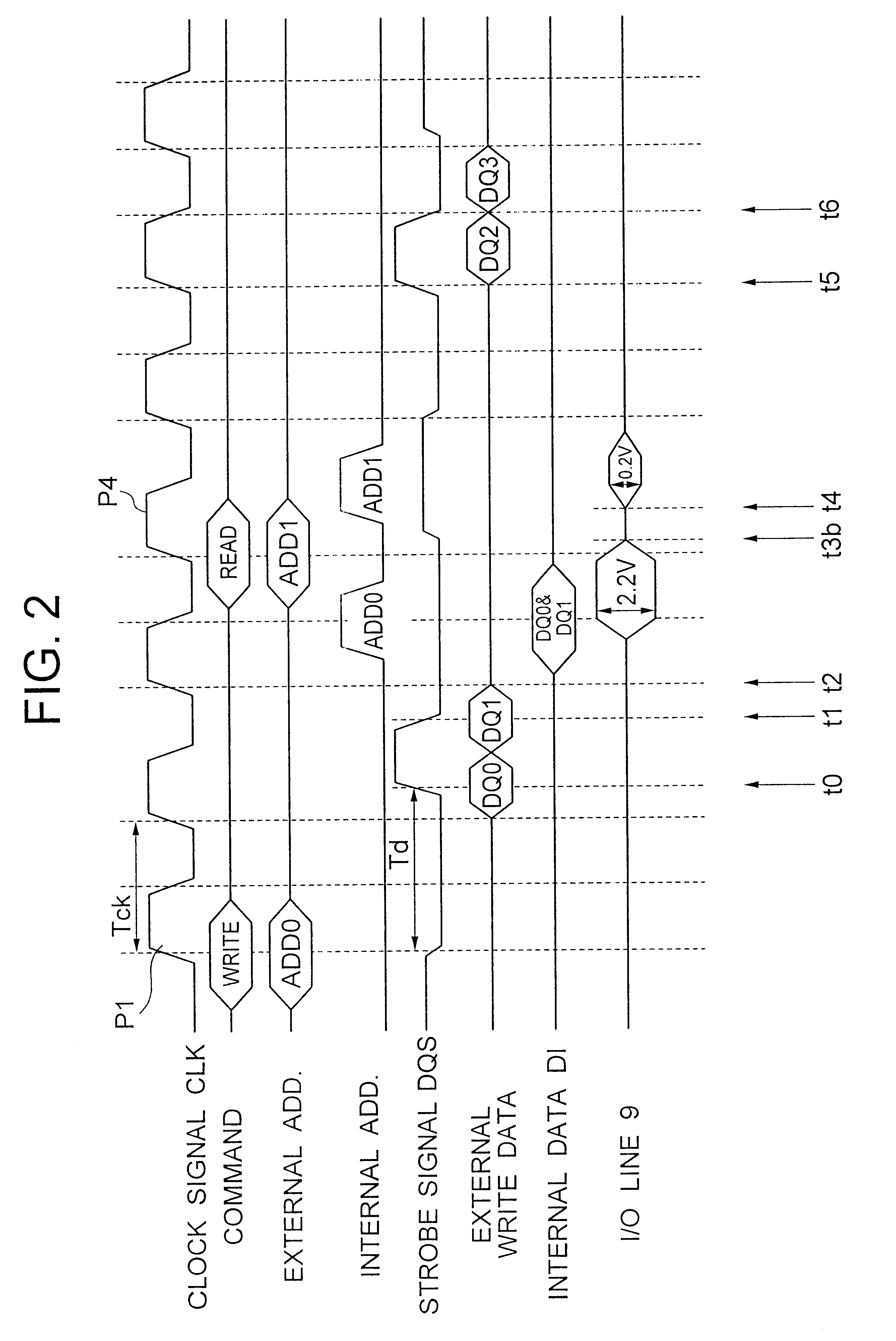
A DDR-SDRM includes a data write section including a latch section for latching first write data at a rising edge of a data strobe signal and second write data at a falling edge of the data strobe signal, and a write buffer section for writing the first write data and the second write data at a time based on the signals generated from the data strobe signal. A read operation is conducted based on the system clock signal.
Owner:RENESAS ELECTRONICS CORP
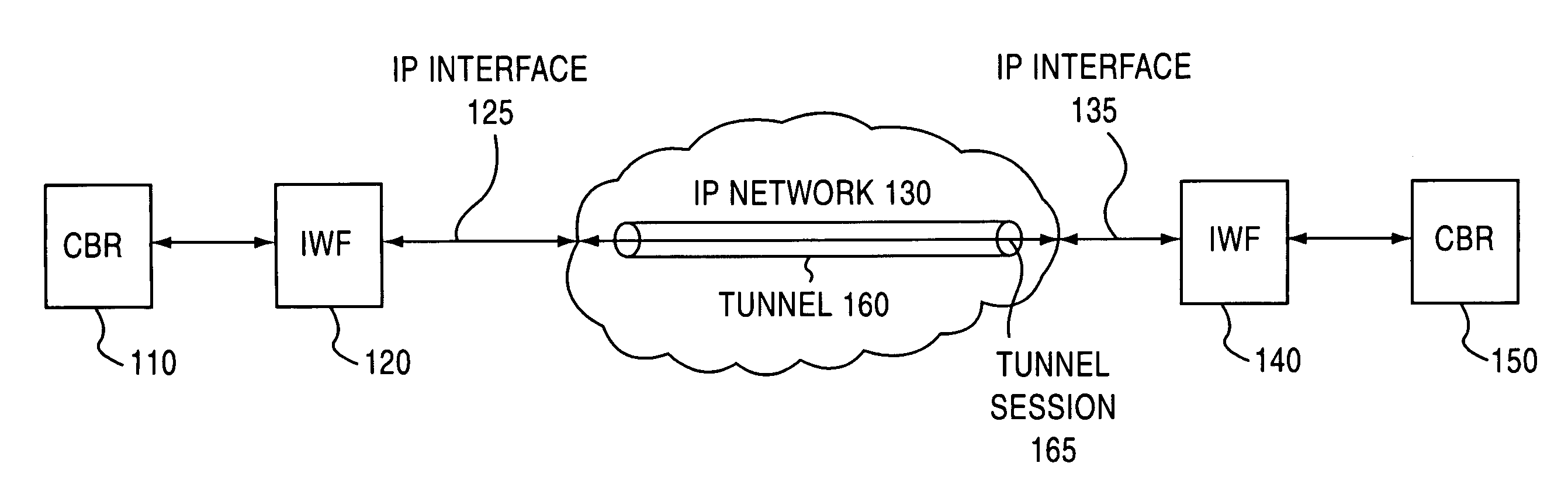
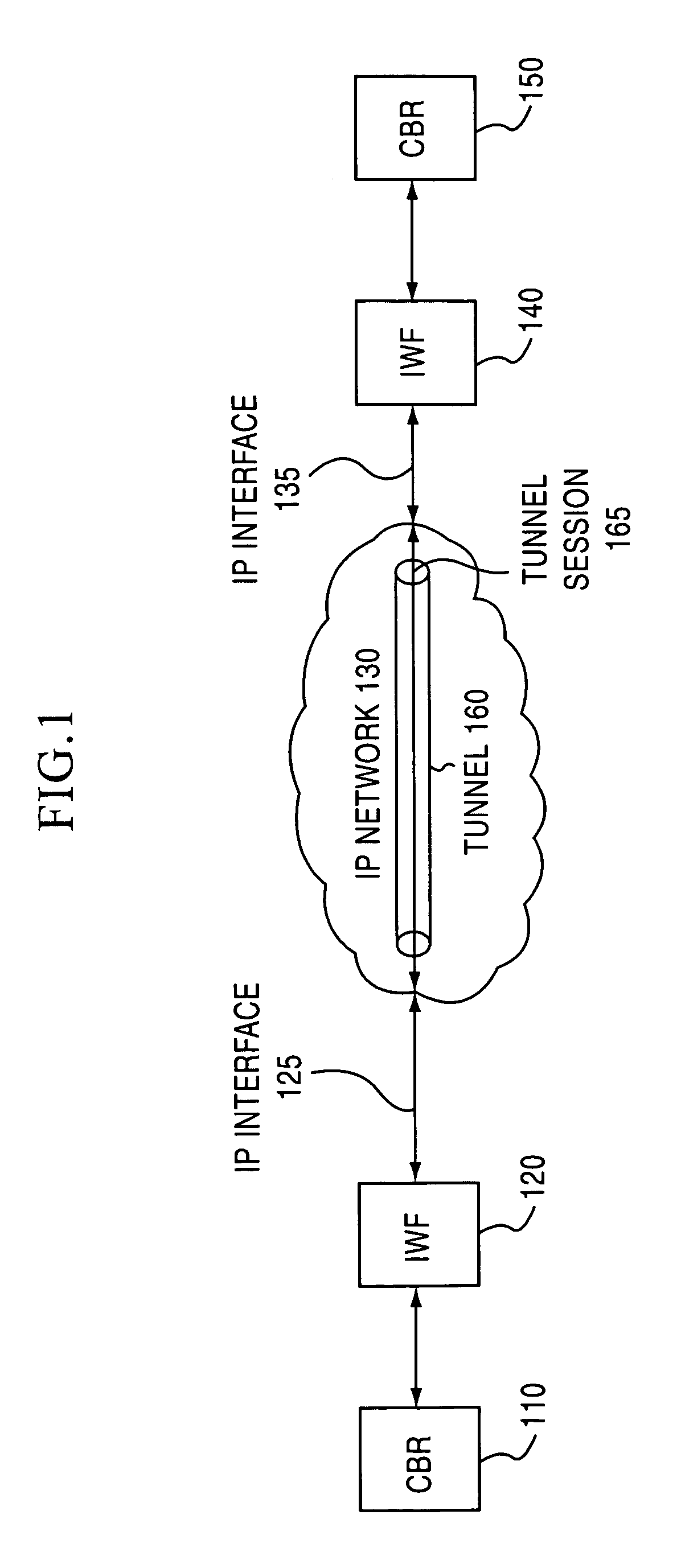
Jitter buffer for a circuit emulation service over an internet protocol network
A jitter buffer receives a plurality of data packets comprising a circuit emulation service over internet protocol (CESIP), buffers the plurality of data packets, and plays data from the plurality of data packets at a constant bit rate corresponding to the CESIP.
Owner:NOKIA TECHNOLOGLES OY
System and method for on-board timing margin testing of memory modules
InactiveUS20050060600A1Increase computing speedElectronic circuit testingError detection/correctionOn boardCrossover switch
A memory module includes several memory devices coupled to a memory hub. The memory hub includes several link interfaces coupled to respective processors, several memory controller coupled to respective memory devices, a cross-bar switch coupling any of the link interfaces to any of the memory controllers, a write buffer and read cache for each memory device and a self-test module. The self-test module includes a pattern generator producing write data having a predetermined pattern, and a flip-flop having a data input receiving the write data. A clock input of the flip-flop receives an internal clock signal from a delay line that receives a variable frequency clock generator. Read data are coupled from the memory devices and their pattern compared to the write data pattern. The delay of the delay line and frequency of the clock signal can be varied to test the speed margins of the memory devices.
Owner:ROUND ROCK RES LLC
Secure mode for processors supporting MMU
A digital system is provided with a secure mode (3rd level of privilege) built in a non-invasive way on a processor system that includes a processor core, instruction and data caches, a write buffer and a memory management unit. A secure execution mode is thus provided on a platform where the only trusted software is the code stored in ROM. In particular the OS is not trusted, all native applications are not trusted. A secure execution mode is provided that allows virtual addressing when a memory management unit (MMU) is enabled. The secure execution mode allows instruction and data cache to be enabled. A secure execution mode is provided that allows all the system interruptions to be unmasked. The secure mode is entered through a unique entry point. The secure execution mode can be dynamically entered and exited with full hardware assessment of the entry / exit conditions. A specific set of entry conditions is monitored that account for caches, write buffer and MMU being enabled. The structure of the activation sequence code accounts for caches, write buffer and MMU being enabled. The structure of the exit sequences code accounts for caches, write buffer and MMU being enabled. A specific way is provided to manage a safe exit of secure mode under generic interruptions and allows return from interruption through entry point and activation sequence and a proper resuming of the secure execution. A specific way is provided to manage the MMU in secure mode and provide data exchange between secure and non-secure environment.
Owner:TEXAS INSTR INC
Circuit implementations for asynchronous processors
InactiveUS6152613AGeneral purpose stored program computerConcurrent instruction executionWrite bufferProcessor register
An asynchronous and delay-insensitive data processor comprises a plurality of components communicating with each other and synchronizing their activities by communication actions on channels and buses. Each component consists of a control part and a data part. All control parts are implemented with a lazy-active-passive handshake protocol and a sequencing means called a left / right buffer that provides the minimal sequencing constraints on the signals involved. The data parts comprise novel asynchronous ALU, buses, and registers. The control parts and data parts are connected together in an asynchronous and delay-insensitive manner.
Owner:CALIFORNIA INST OF TECH
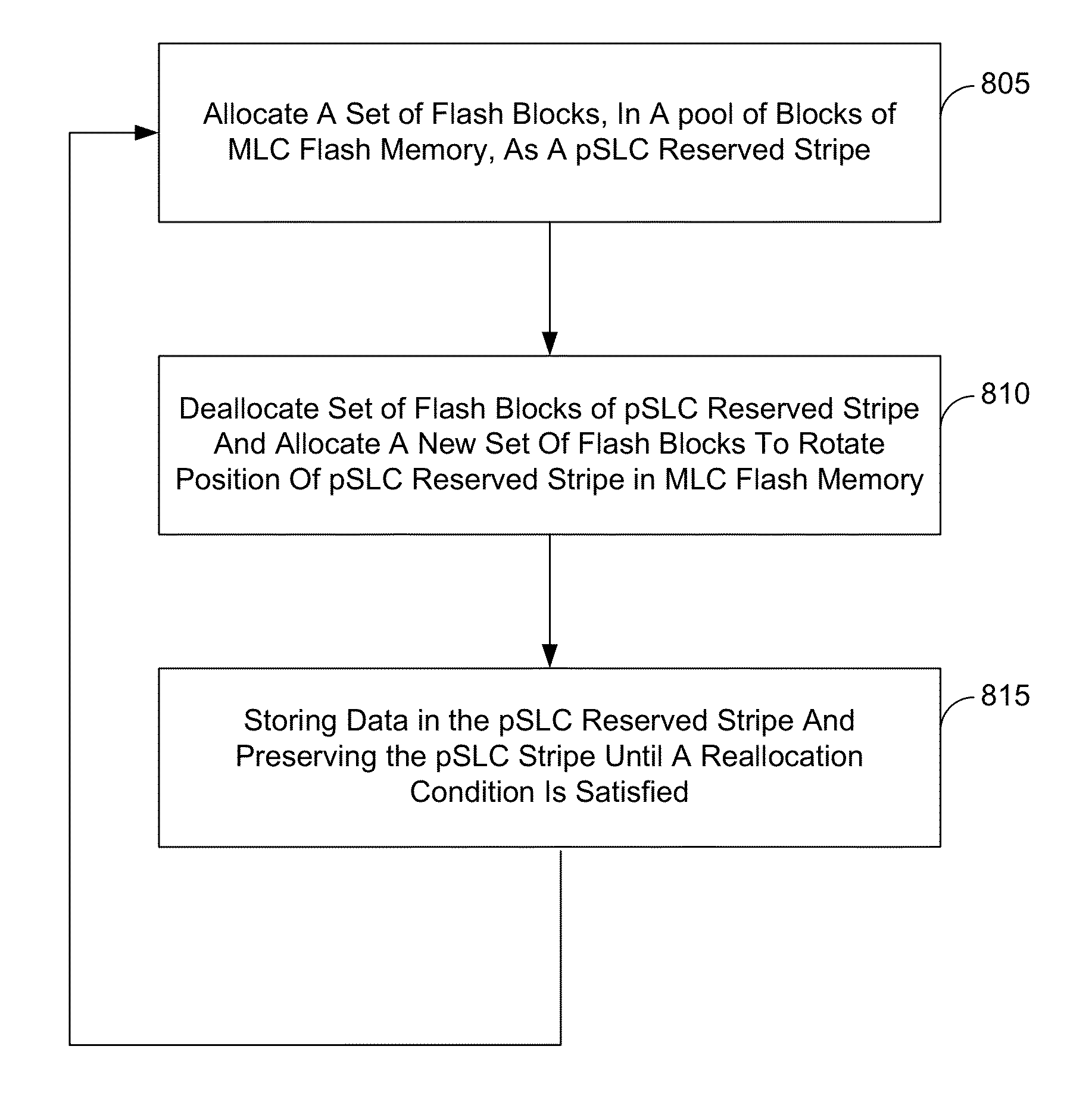
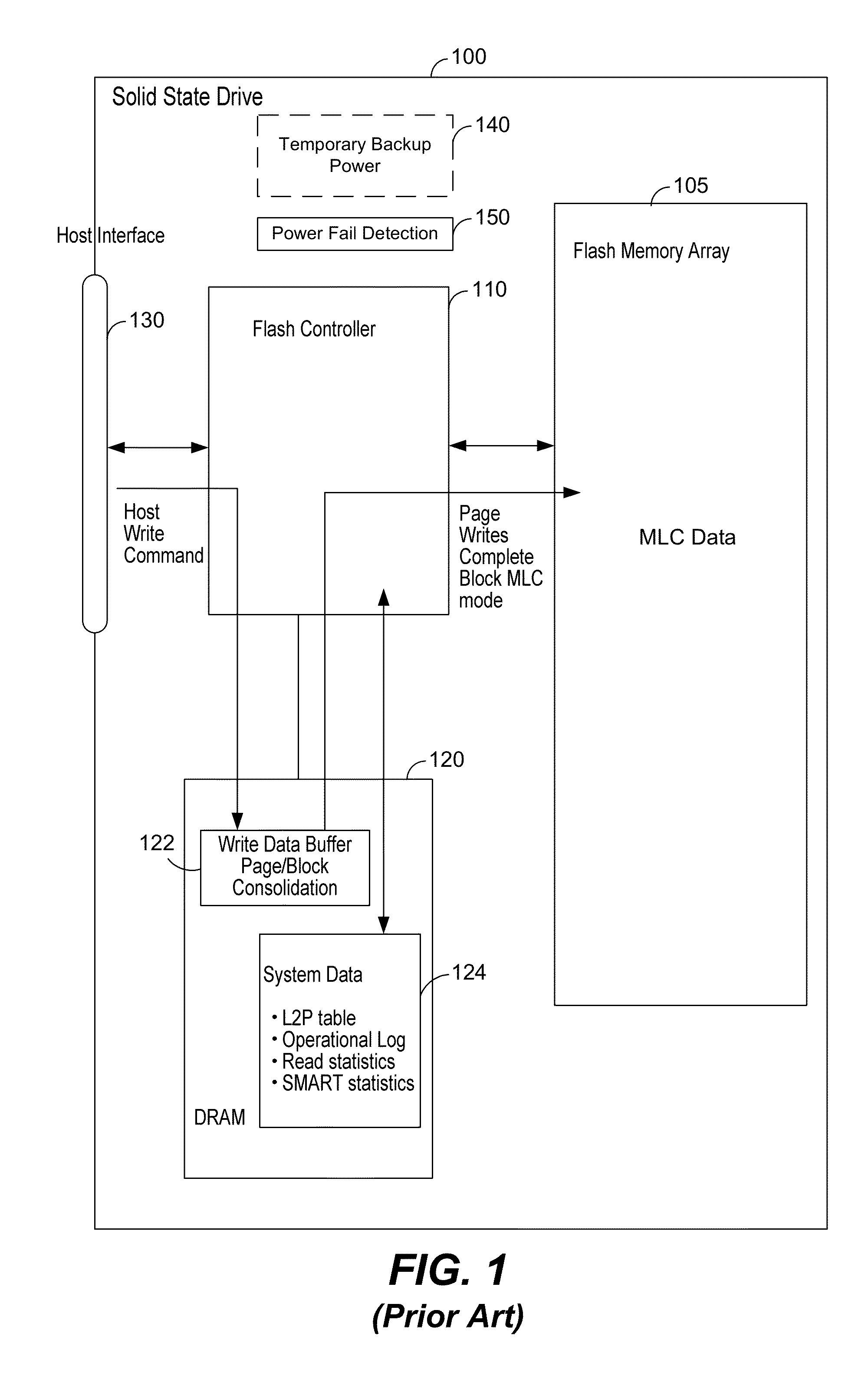
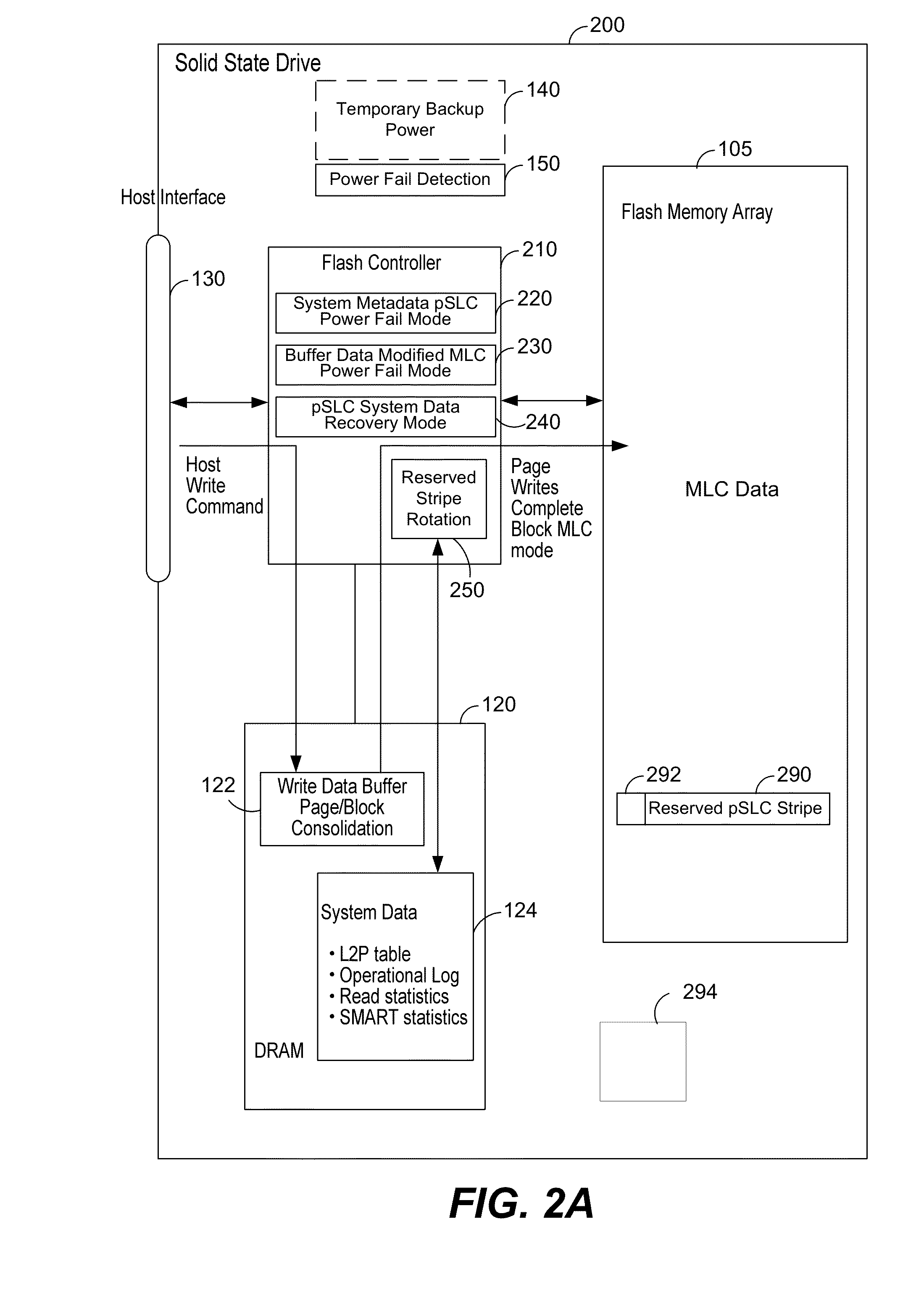
Power fail saving modes in solid state drive with mlc memory
ActiveUS20160268000A1Reduce dwell timePrevent corruptionRead-only memoriesDigital storageWrite bufferStandby power
A solid state drive has a power failure savings mode that permits a reduction in holdup time for a temporary backup power supply. The solid state drive stores data in a multi-level cell (MLC) mode. In a power fail saving mode system metadata is written in a pseudo Single Level Cell (pSLC) mode. In the normal operating mode page writes are performed in complete blocks. In the power fail save saving mode data from a write buffer is written and additional dummy pages written to reduce the total number of pages that must be written to below a complete block size with the dummy pages providing protection from data corruption.
Owner:KIOXIA CORP
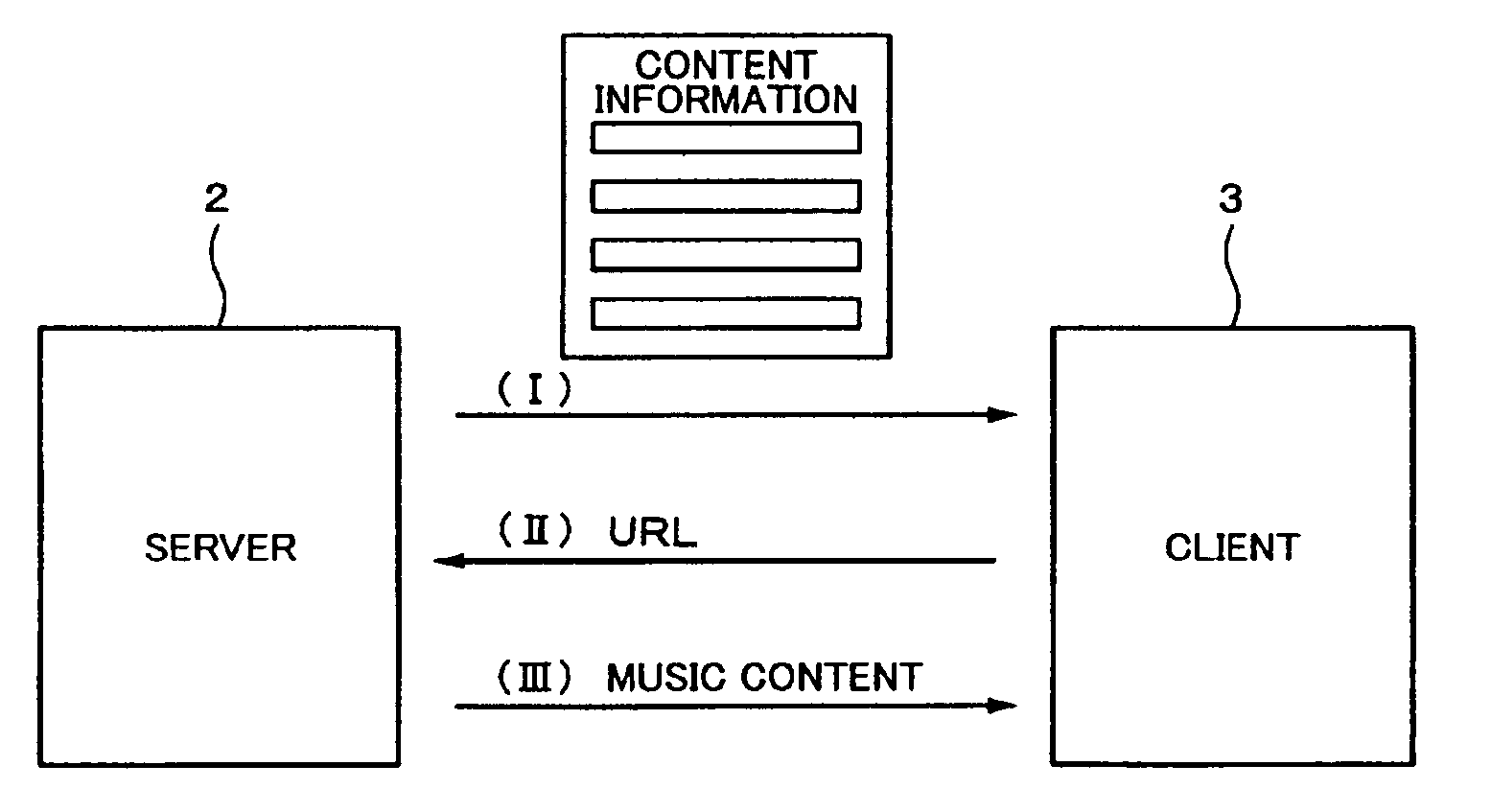
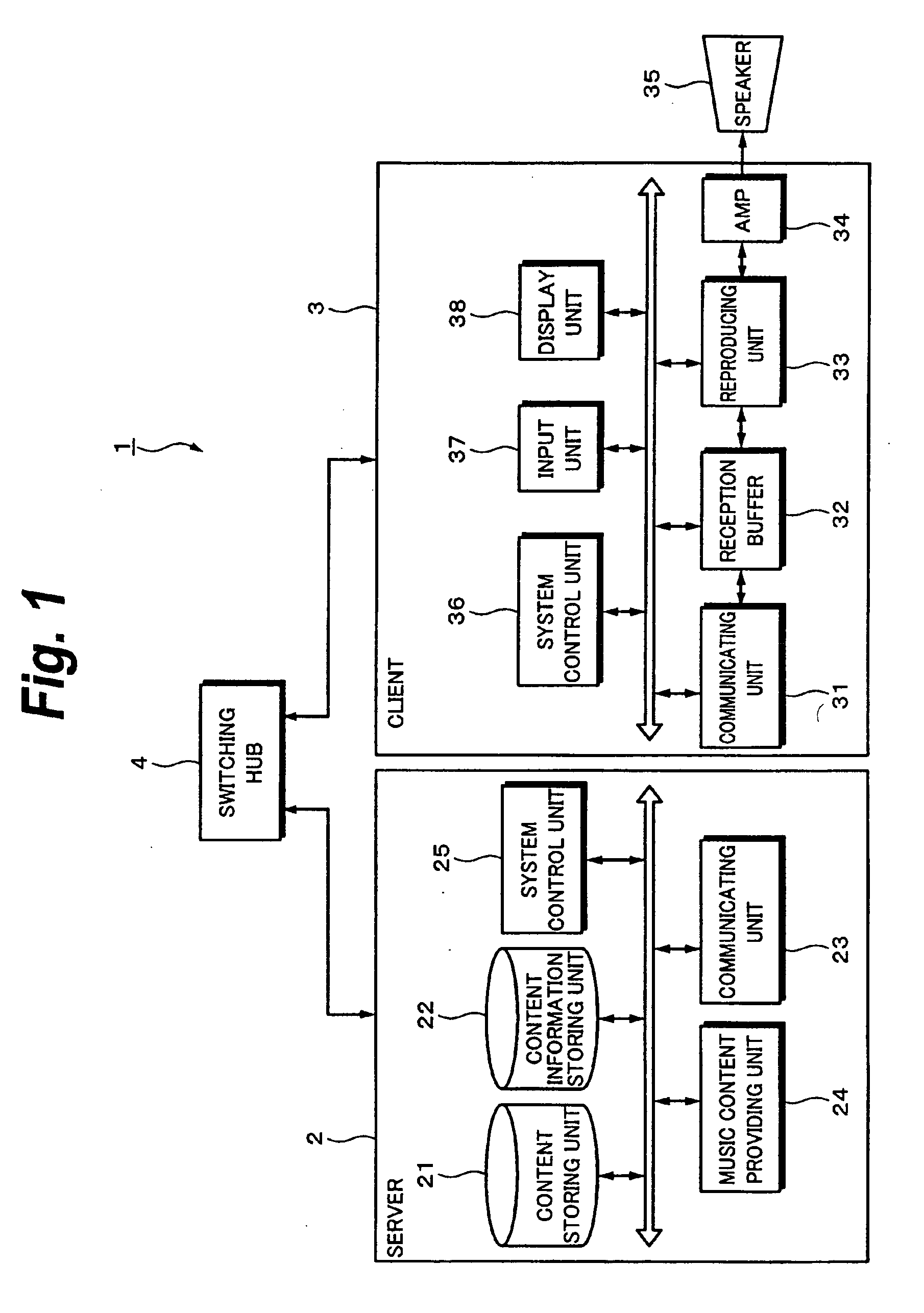
Content receiving apparatus and content receiving method
InactiveUS20070050479A1Avoid disturbanceMultiple digital computer combinationsTwo-way working systemsComputer hardwareWrite buffer
A content receiving apparatus has: a communicating unit connecting to a server; a reception buffer receiving and storing transmitted content data; a content reproducing unit reproducing the read-out content data; a controller controlling the communicating unit and the reception buffer; and an operating unit supplying an operation signal to the control unit. The data reception and the data output to the reproducing unit from the buffer are stopped by a reproduction temporary stop instruction. The data reception is restarted by a reproduction temporary stop cancellation instruction. The received content data is written into the buffer. The reception of a disconnection signal from the server is discriminated after the restart of the data reception. If the signal is not received, a predetermined amount of received data is written into the buffer, the reading is started, the data is outputted to the reproducing unit, and the reproduction is restarted.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com