Patents
Literature
619results about "Specific access rights" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
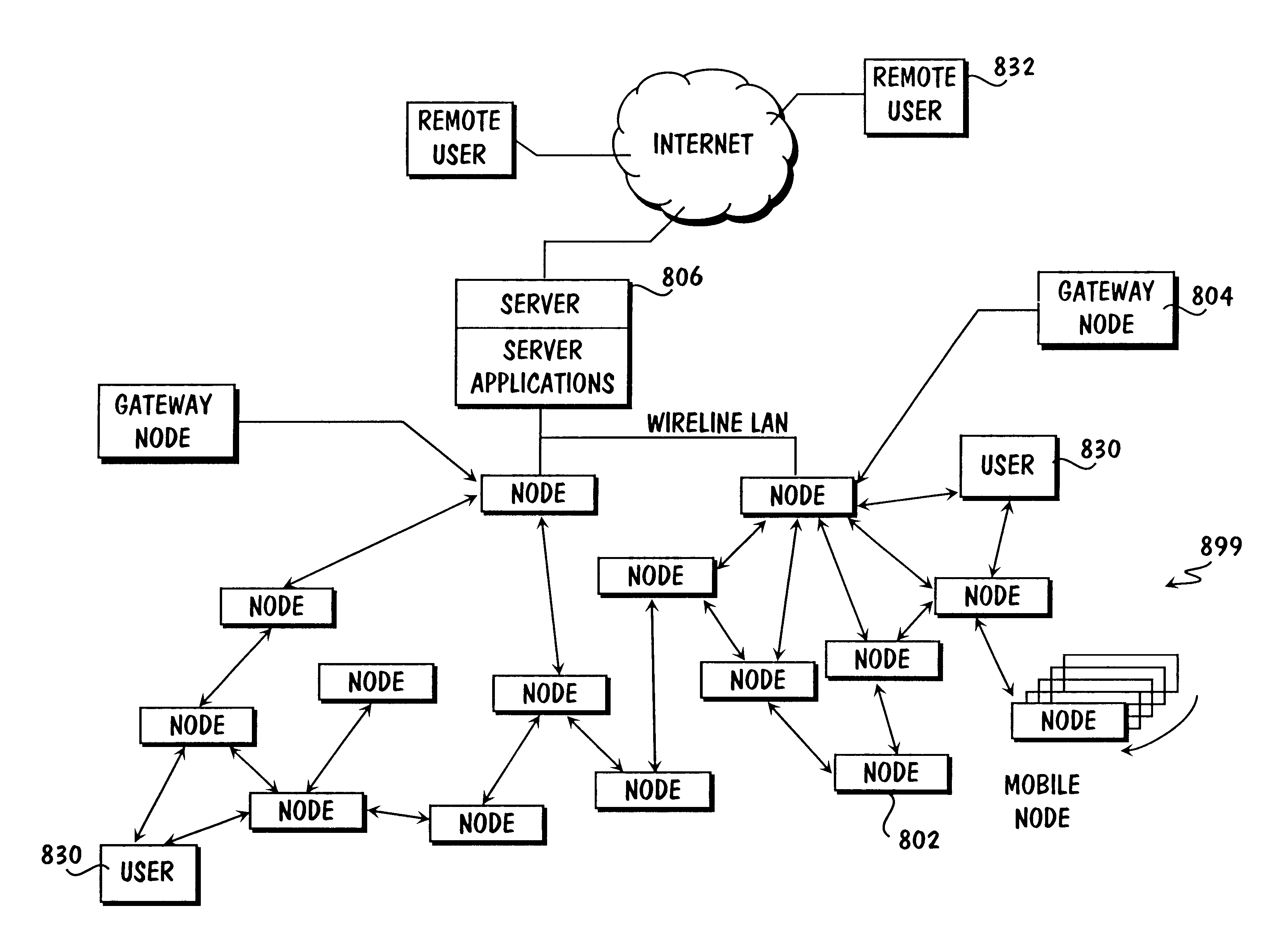
Method and apparatus for internetworked wireless integrated network sensor (WINS) nodes
InactiveUS6859831B1Ease real-time operating system issueImprove adaptabilitySpecific access rightsAnti-theft devicesReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
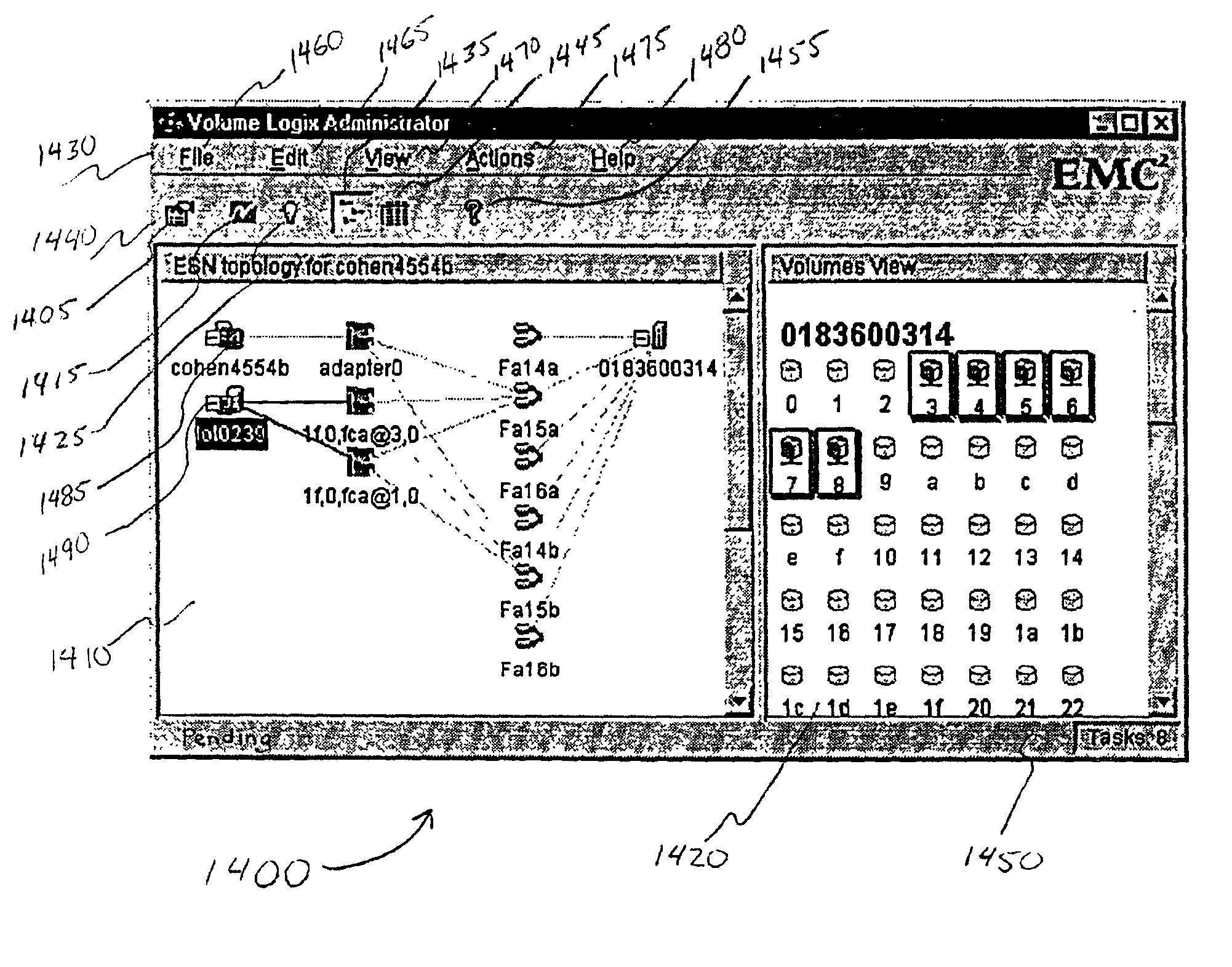
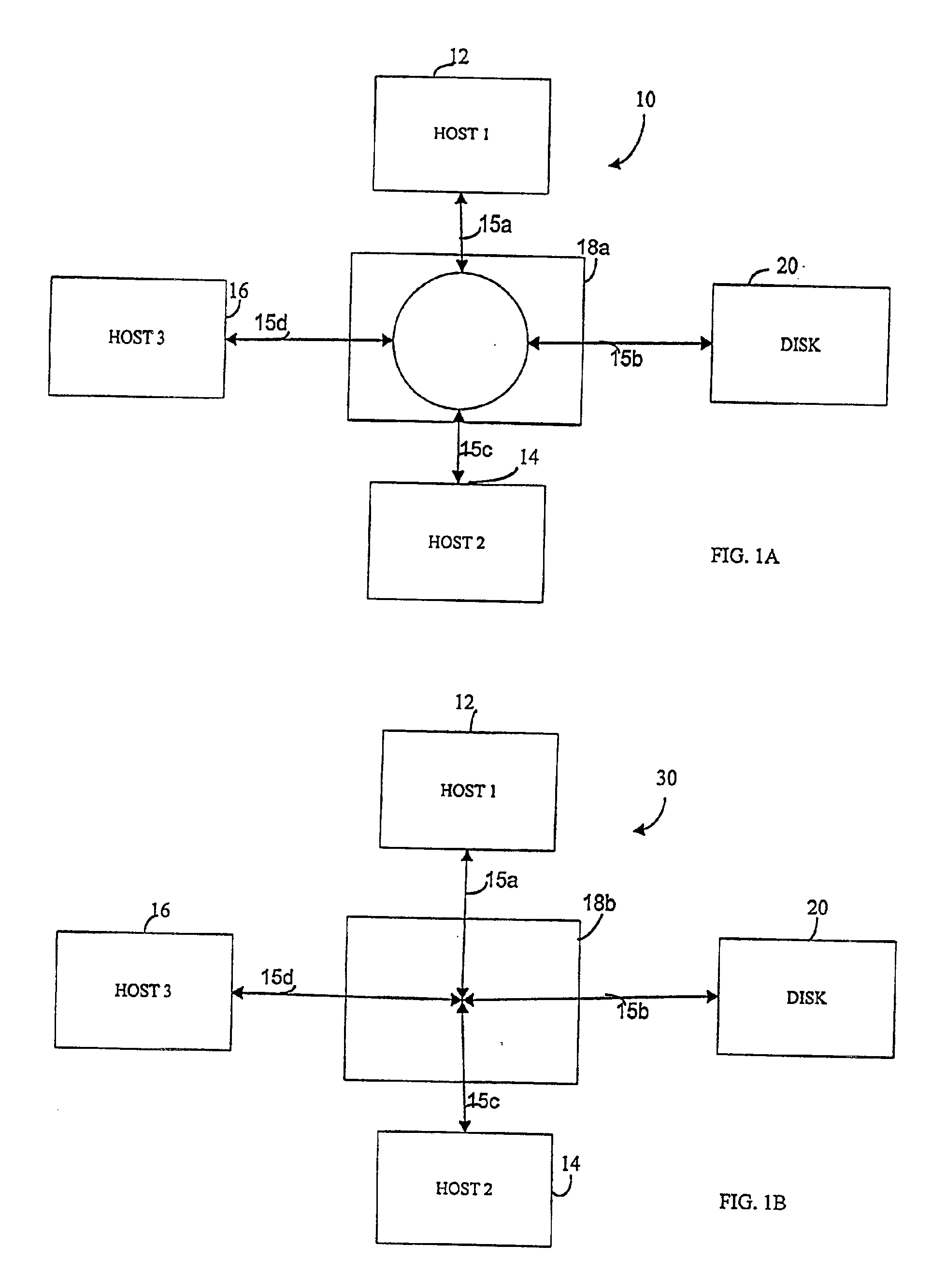
User interface for managing storage in a storage system coupled to a network
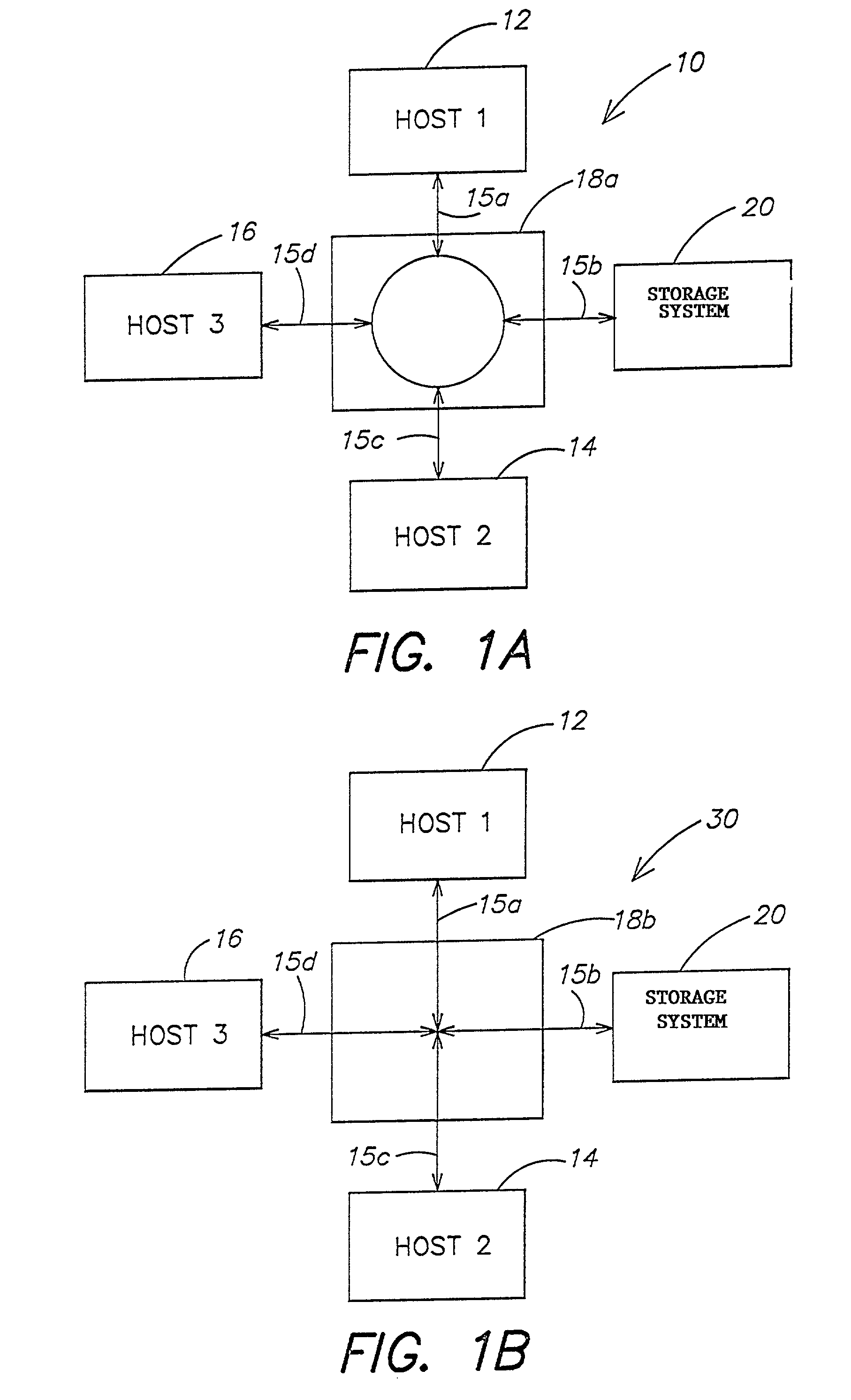
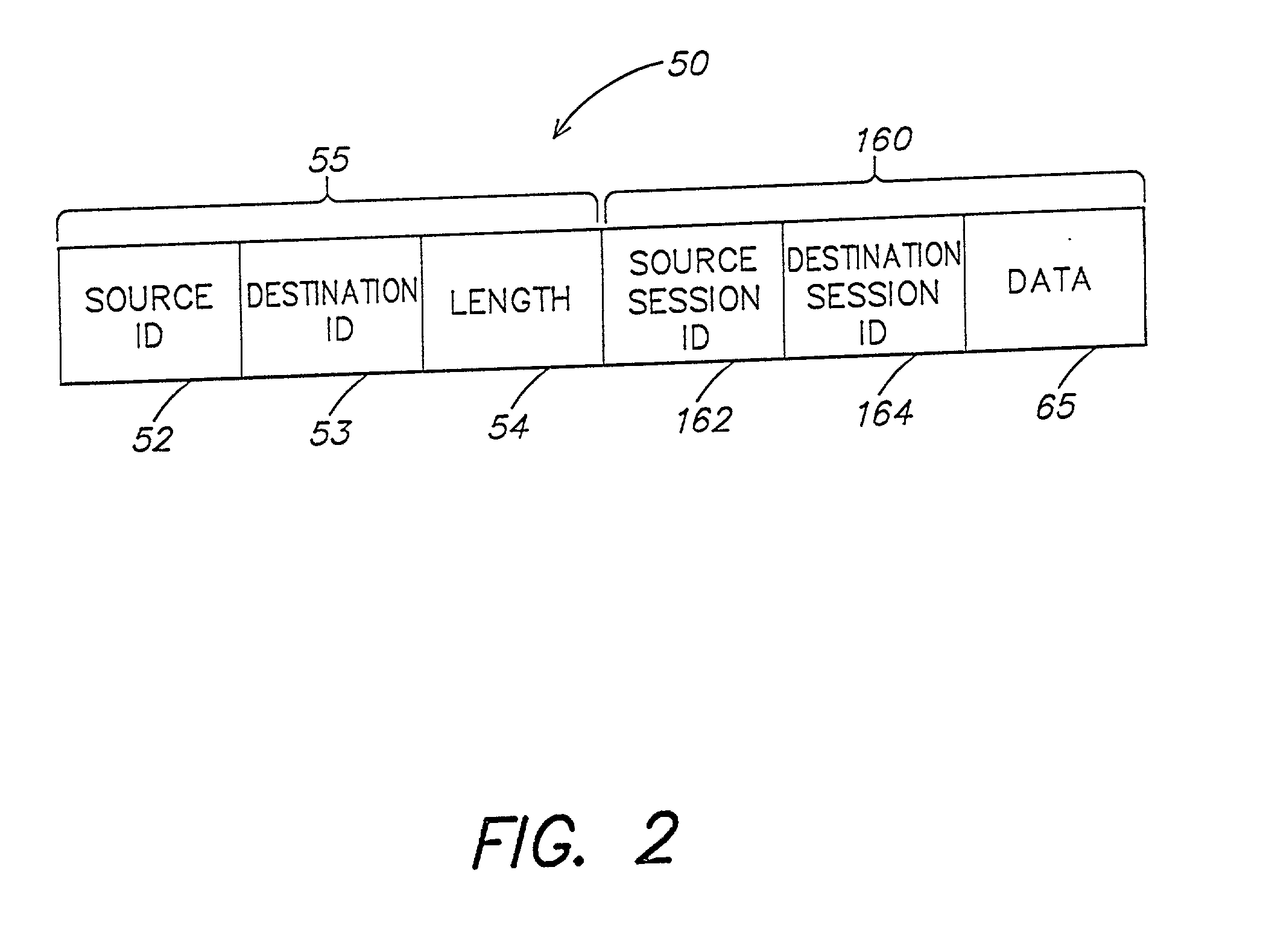
A method and apparatus for managing the availability and assignment of data in a storage system that is coupled to a network. A user interface is provided that executes on a host processor that is coupled to the storage system over the network. The user interface communicates with a configuration database in the storage system to identify host processors that are logged into the storage system over the network, to identify storage volumes on the storage system, to identify whether access to a particular storage volume on the storage system is permitted from a particular host processor, and to identify a network path by which host processors are logged into the storage system over the network. In one embodiment, a graphical user interface is provided that can be used to graphically represent host processors, host bus adapters, storage systems, and storage system adapters and storage volumes on the storage system. The graphical representation provided by the graphical user interface permits a user to graphically view a topology of the network at varying levels of detail, selectable by the user. The graphical user interface also permits a user to allow or deny access to storage systems or a particular storage volume on storage system from one or more of the host processors, host bus adapters, etc., by selecting and manipulating graphical representations thereof. In another embodiment, a command line user interface is provided with similar functionality.
Owner:EMC IP HLDG CO LLC
Method and System for Identity-Based Authentication of Virtual Machines
ActiveUS20140282889A1Specific access rightsDigital data processing detailsComputing systemsAuthentication
A cloud computing system configured to run virtual machine instances is disclosed. The cloud computing system assigns an identity to each virtual machine instance. When the virtual machine instance accesses initial configuration resources, it provides this identity to the resources to authenticate itself. This allows for flexible and extensible initial configuration of virtual machine instances.
Owner:RACKSPACE US
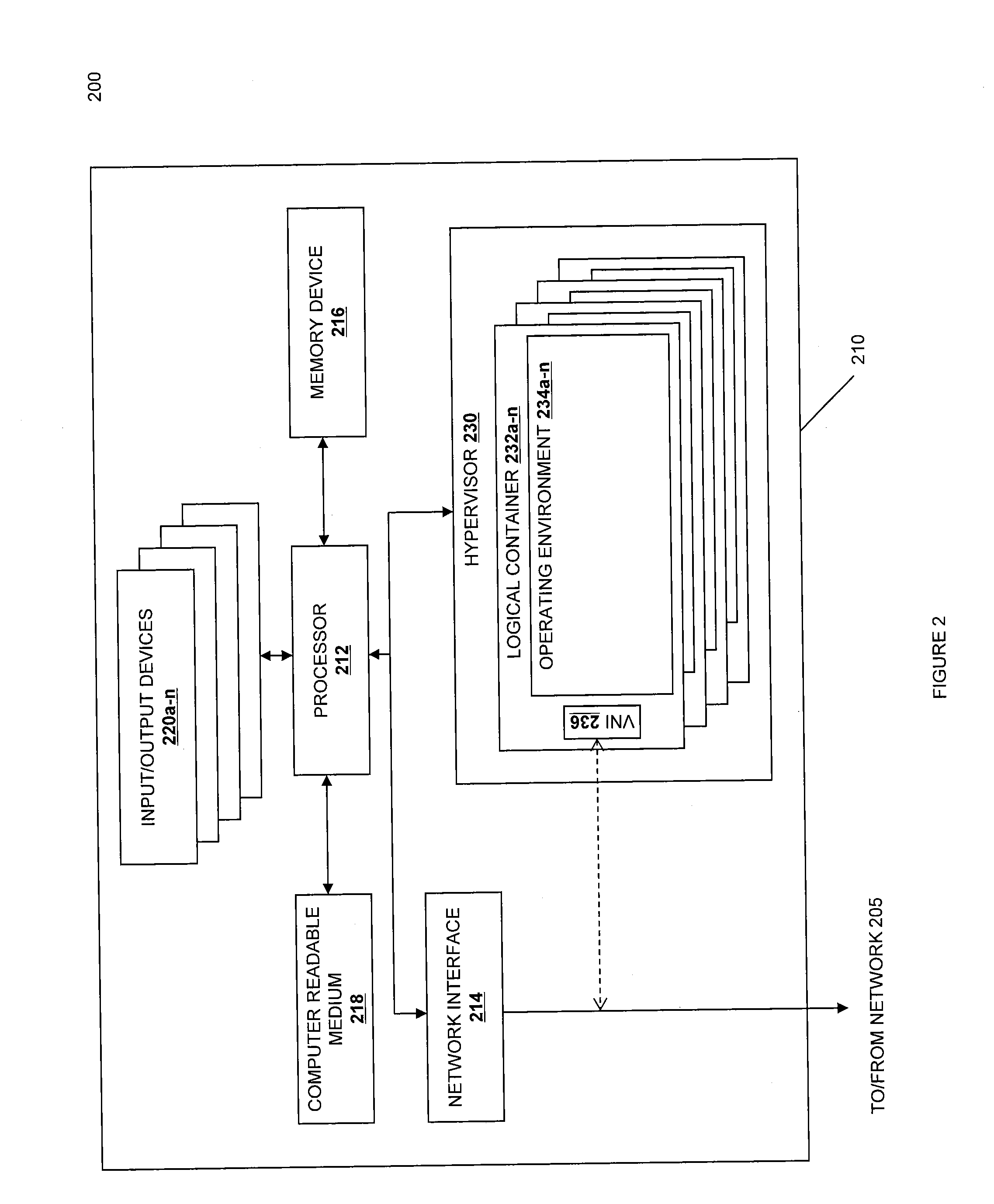
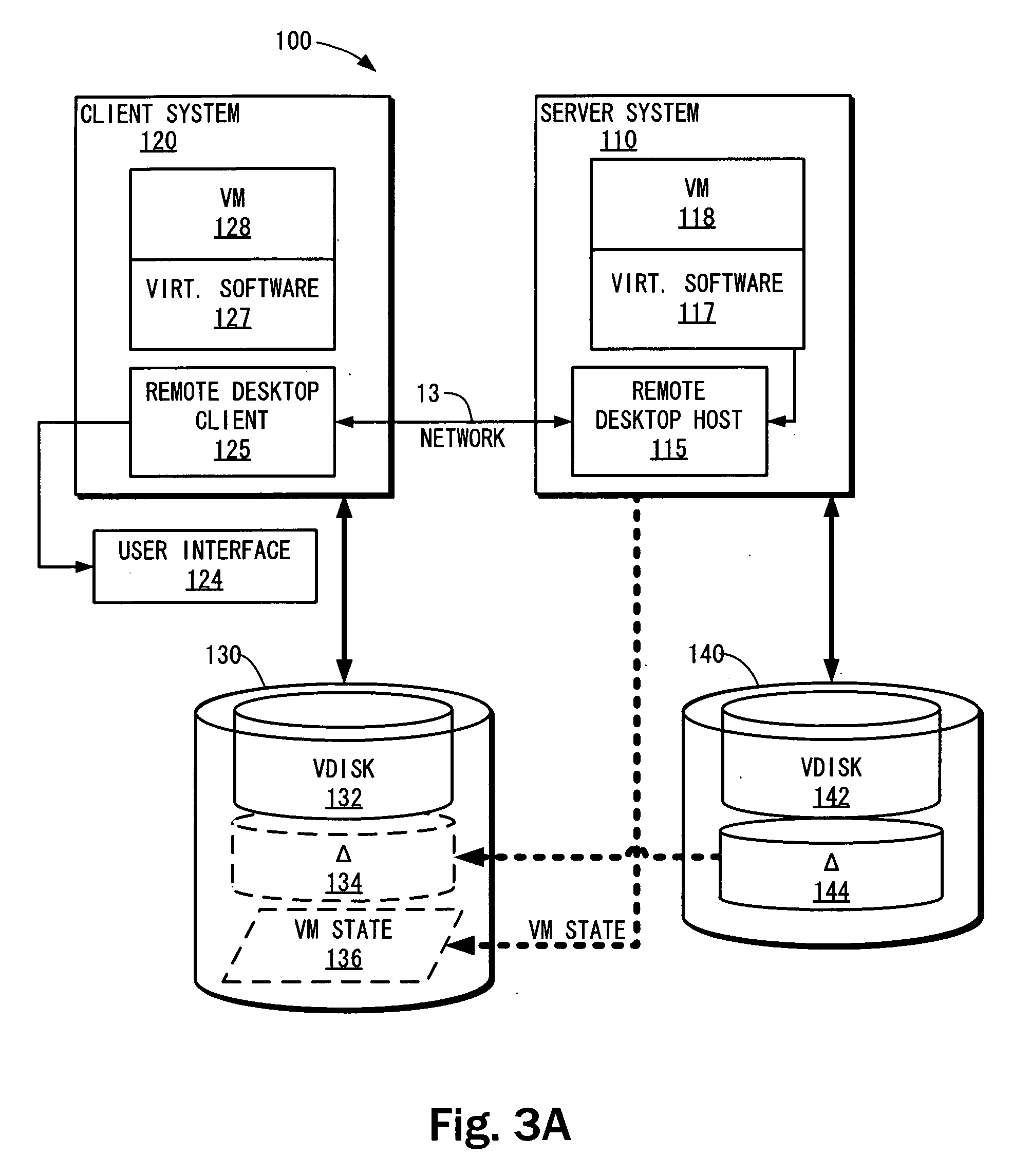
Extending server-based desktop virtual machine architecture to client machines
ActiveUS20090216975A1Address be challengeSpecific access rightsMemory loss protectionRemote desktopClient-side
A server-based desktop-virtual machines architecture may be extended to a client machine. In one embodiment, a user desktop is remotely accessed from a client system. The remote desktop is generated by a first virtual machine running on a server system, which may comprise one or more server computers. During execution of the first virtual machine, writes to a corresponding virtual disk are directed to a delta disk file or redo log. A copy of the virtual disk is created on the client system. When a user decides to “check out” his or her desktop, the first virtual machine is terminated (if it is running) and a copy of the delta disk is created on the client system. Once the delta disk is present on the client system, a second virtual machine can be started on the client system using the virtual disk and delta disk to provide local access to the user's desktop at the client system. This allows the user to then access his or her desktop without being connected to a network.
Owner:VMWARE INC
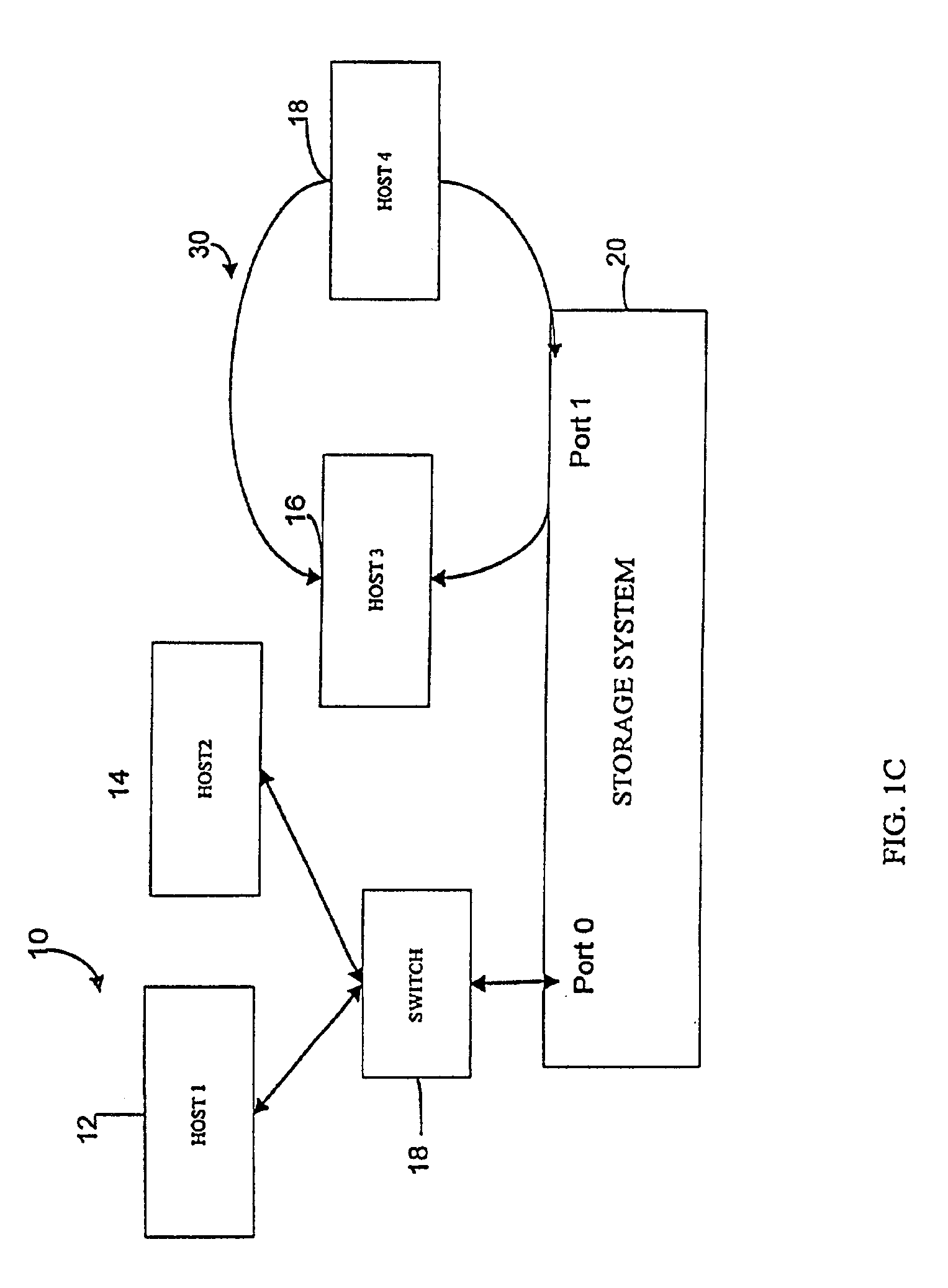
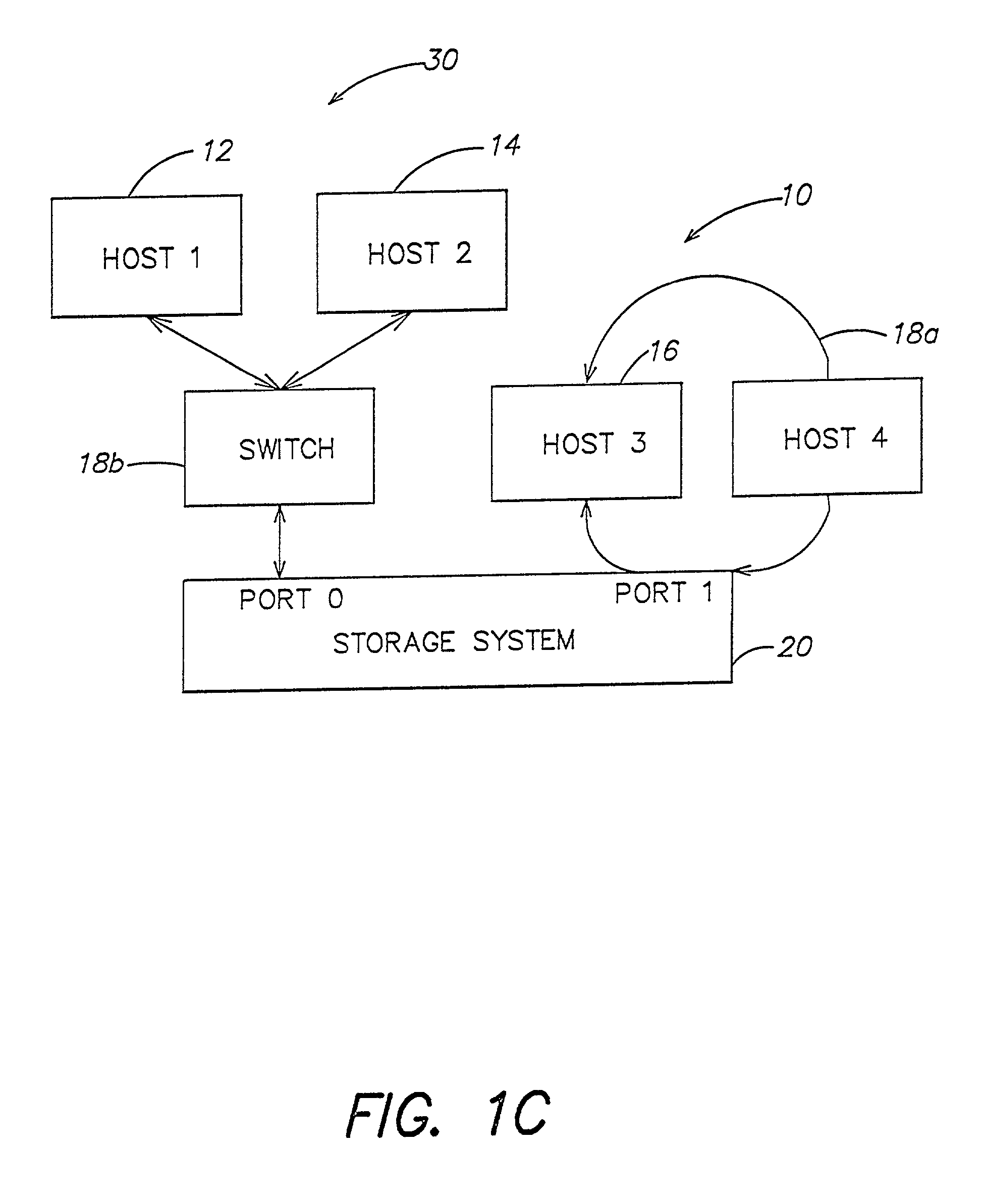
Method and apparatus for managing access to storage devices in a storage system with access control
A storage system is provided that includes a plurality of storage devices and a data structure, accessible to the storage system, that includes a plurality of records corresponding to a plurality of network devices that are coupled to the storage system. Each record includes configuration data that identifies each of the plurality of storage devices to which data access by a respective one of the plurality of network devices is authorized. Each record may further include visibility data that identifies whether certain types of non-data access, such as requests for general information relating to a respective storage device, by a respective one of the plurality of network devices is permitted, even though data access to the respective storage device by the respective one of the plurality of network devices is not authorized.
Owner:EMC IP HLDG CO LLC
Techniques of optimizing policies in an information management system
In an information management system, policies are optimized before they are associated to a device in order to increase evaluation speed or reduce space requirements, or both. Optimization techniques may include common subexpression elimination, constant folding, constant propagation, comparison optimization, dead code or subexpression removal, map or lookup table generation, policy rewriting, redundant policy elimination, heuristic-based policy ordering, or policy-format transformation, and combinations of these.
Owner:NEXTLABS
Integrating operating systems and run-time systems
InactiveUS6546546B1Specific access rightsMemory adressing/allocation/relocationOperational systemApplication software
The Virtual Machine is viewed by many as inherently insecure despite all the efforts to improve its security. This invention provides methods, apparatus, and computer products to implement a system that provides operating system style protection for code. Although applicable to many language systems, the invention is described for a system employing the Java language. Hardware protection domains are used to separate Java classes, provide access control on cross domain method invocations, efficient data sharing between protection domains, and memory and CPU resource control. Apart from the performance impact, these security measures are all transparent to the Java programs, even when a subclass is in one domain and its superclass is in another, when they do not violate the policy. To reduce the performance impact, classes are grouped and shared between protection domains and map data lazily as it is being shared. The system has been implemented on top of the Paramecium operating system used as an example of an extensible operating system application.
Owner:IBM CORP
Method and apparatus for an improved security system mechanism in a business applications management system platform
InactiveUS6850893B2Minimizing user input effortMinimize effortSpecific access rightsDigital data processing detailsSafety management systemsImproved method
The present invention provides a solution to the needs described above through an improved method and apparatus for an improved security system mechanism in a business applications management system platform. The security management system partitions a number of business objects into a number of hierarchical domains. A security list is then created and configured to grant a member the right to perform a security operation on the business object located within the hierarchical domain. The security list is created by adding the security operation to the security list, applying the security operation to one of the multiple domains, and adding members to the security list.
Owner:SABA SOFTWARE
Methods for providing cross-vendor support services
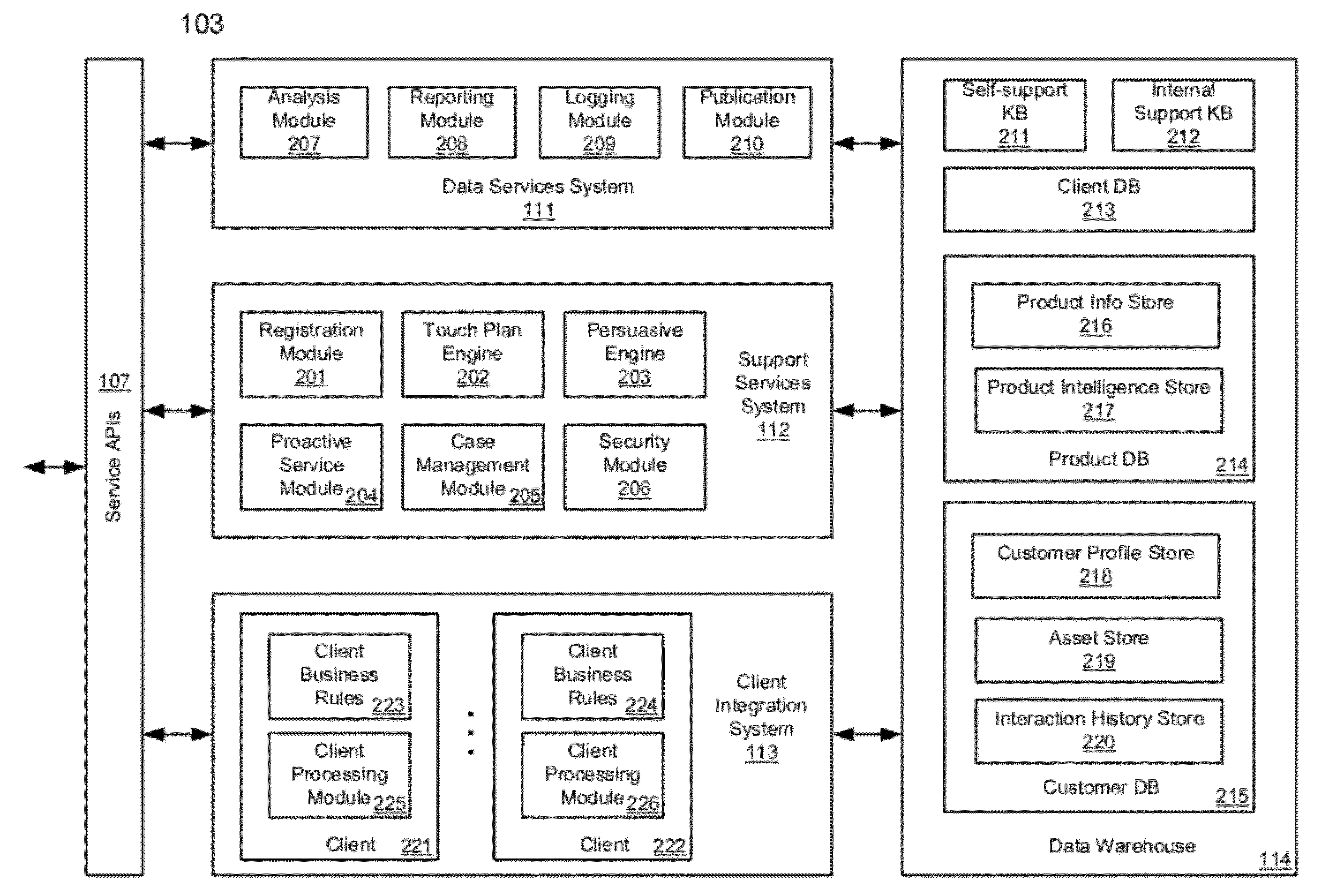
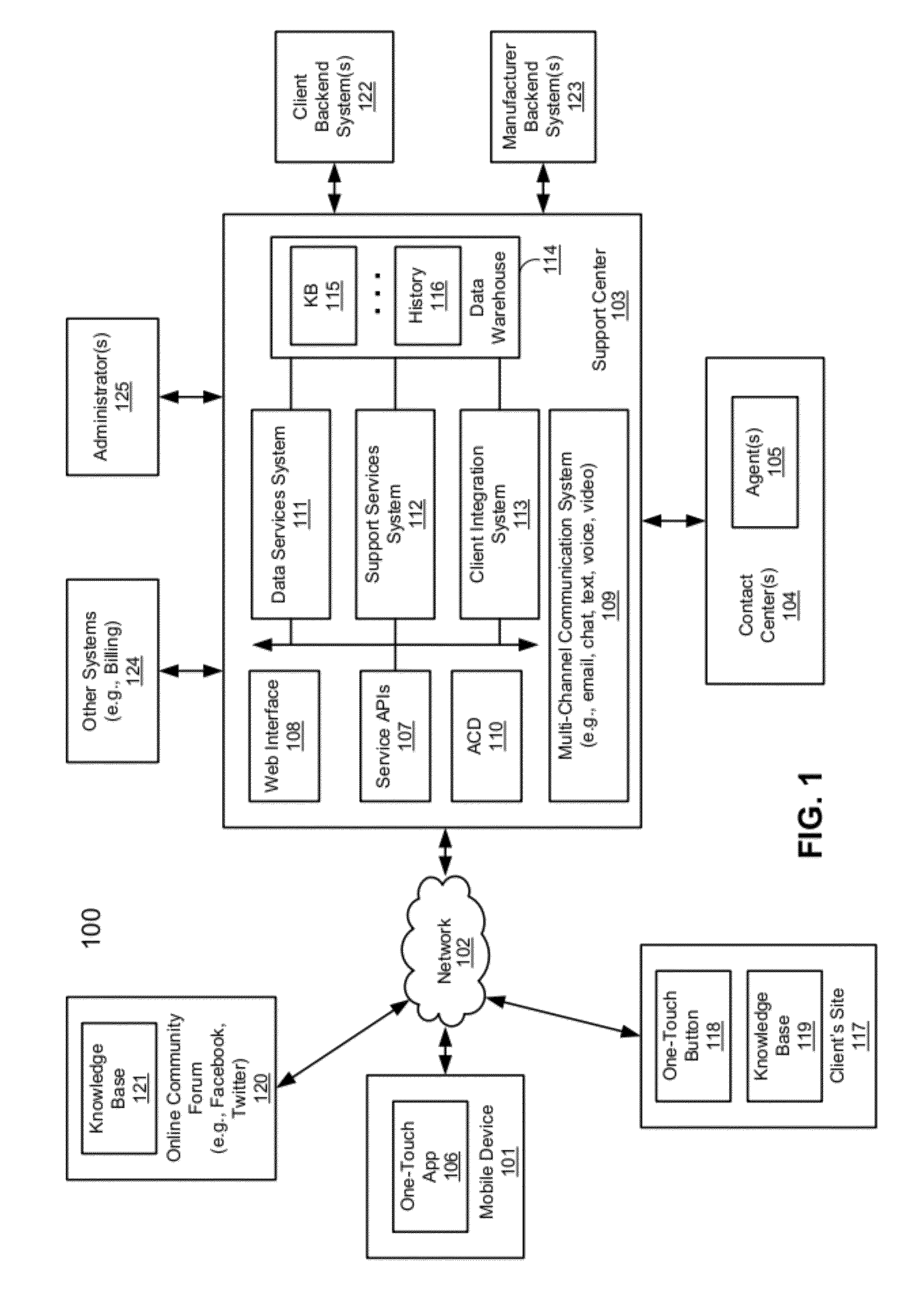
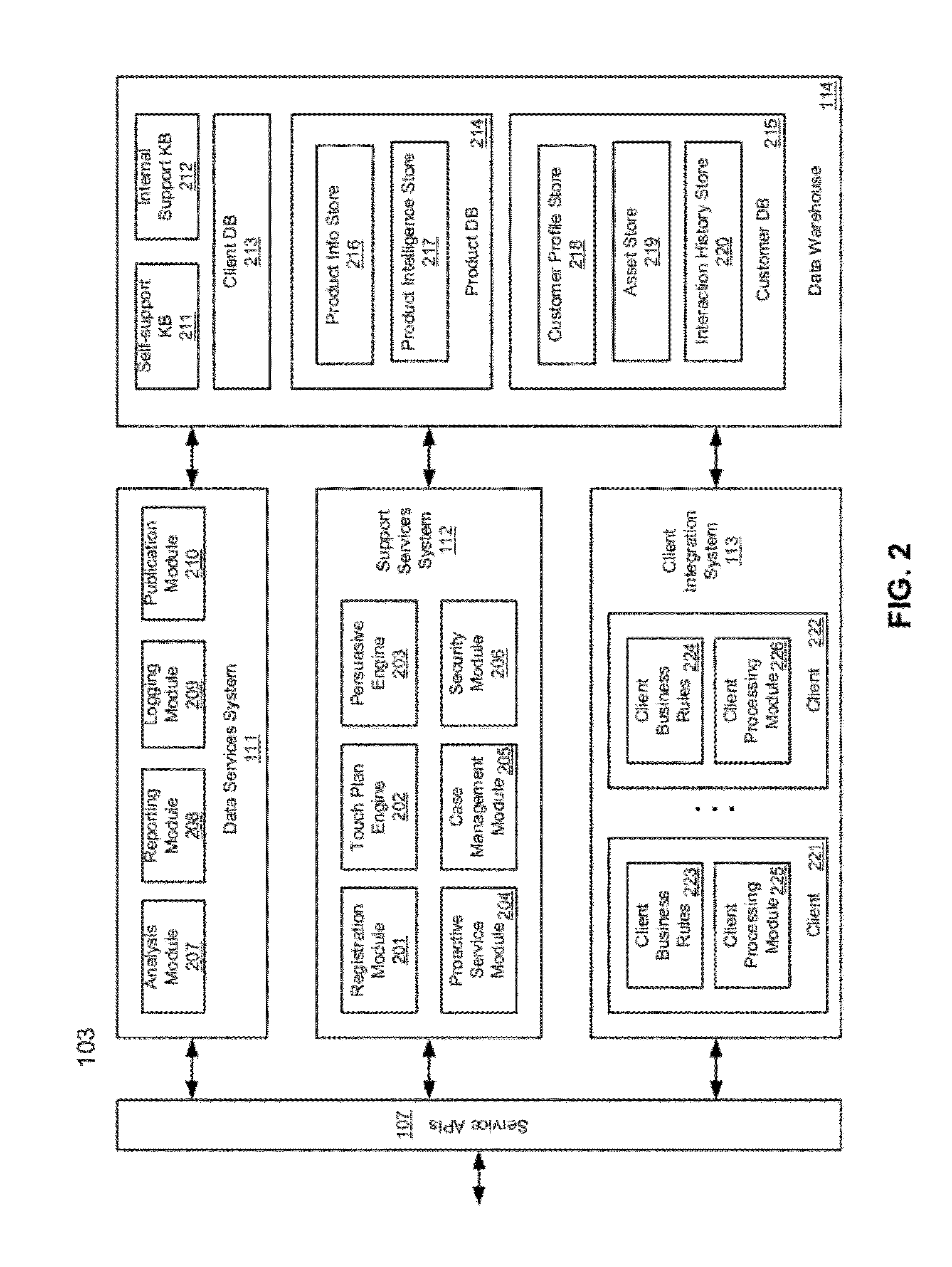
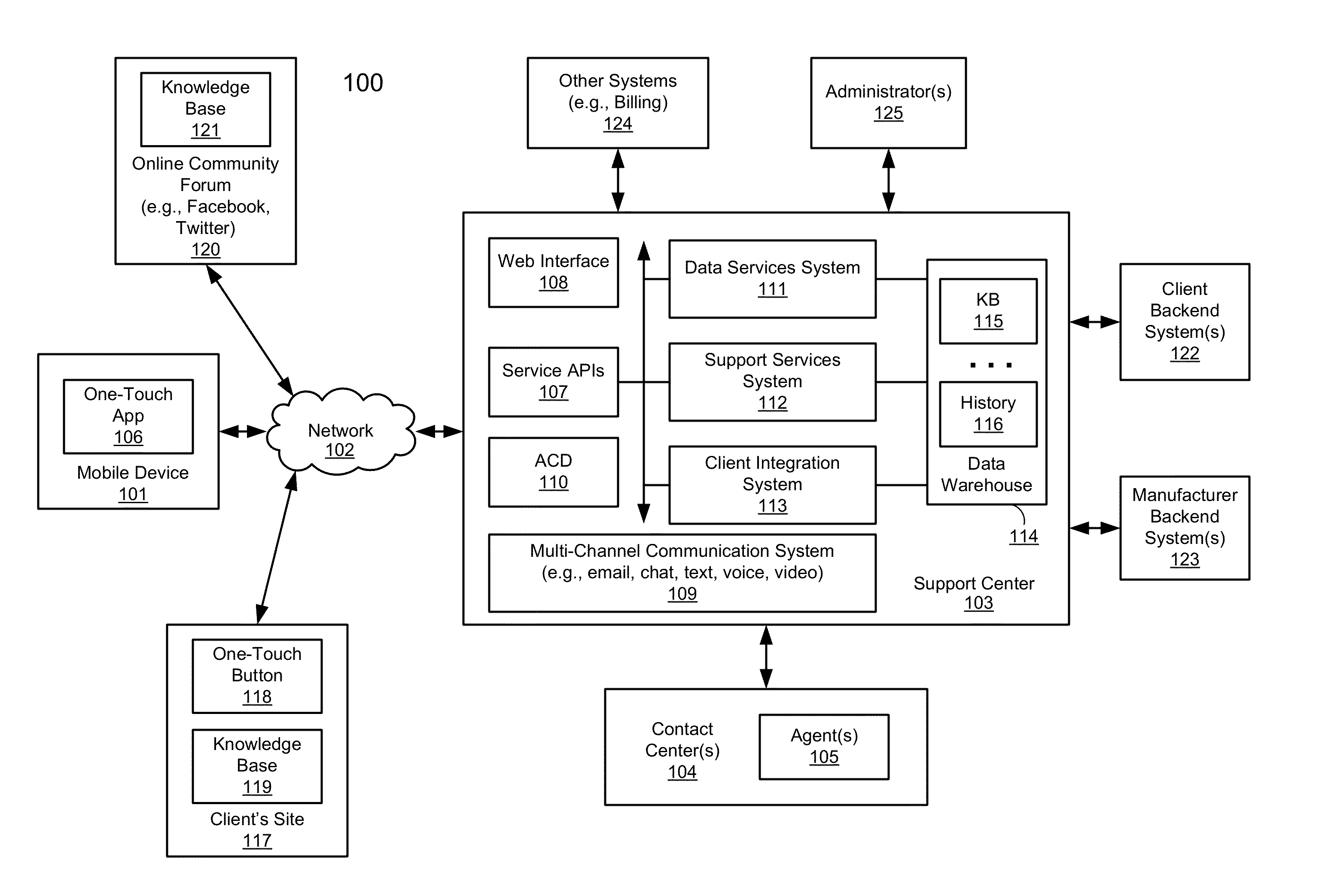
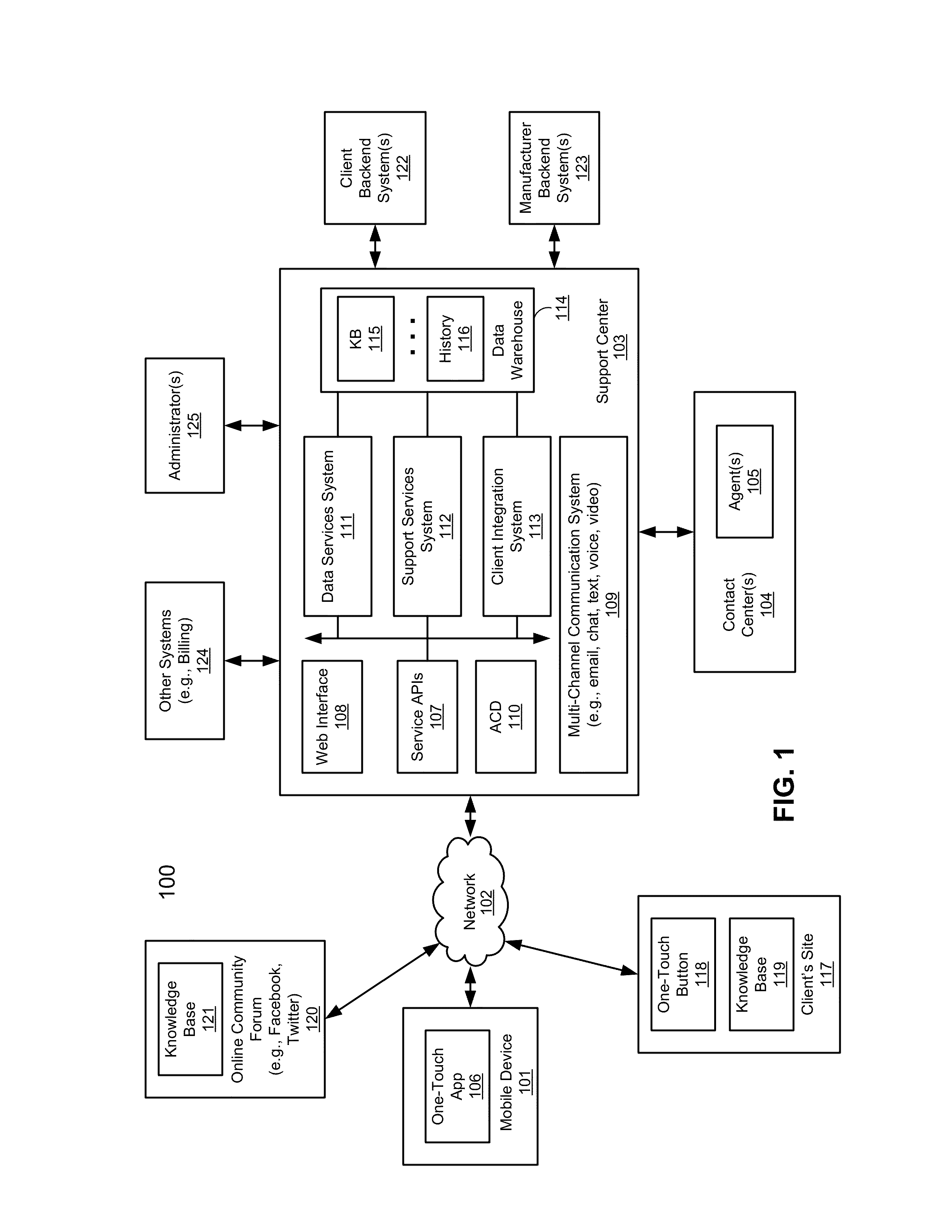
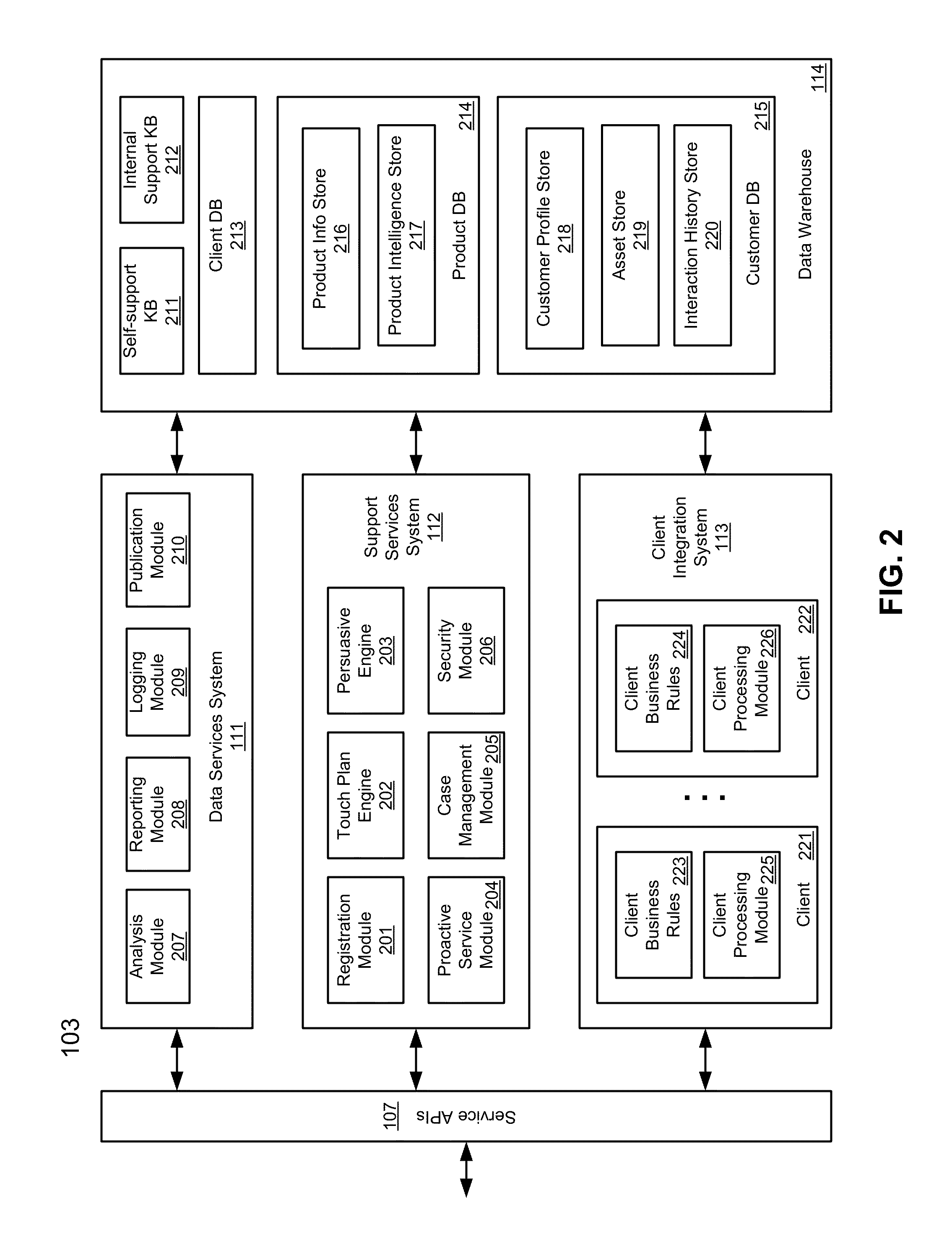
ActiveUS20120266258A1Specific access rightsDigital data processing detailsApplication programming interfaceClient-side
According to one aspect, a first request is received at a services application programming interface (API) of a support center from a first user for a first product provided by a first client. A second request is received at the services API of the support center from a second user for a second product provided by a second client. A first knowledgebase (KB) associated with the first client and a second KB associated with the second client are identified. A third KB that contains information common to the first product and the second product is identified. The first KB and the third KB are enabled to be accessible by a first agent assigned to provide support services of the first product. The second KB and the third KB are enabled to be accessible by a second agent assigned to provide support services of the second product.
Owner:TELETECH HLDG
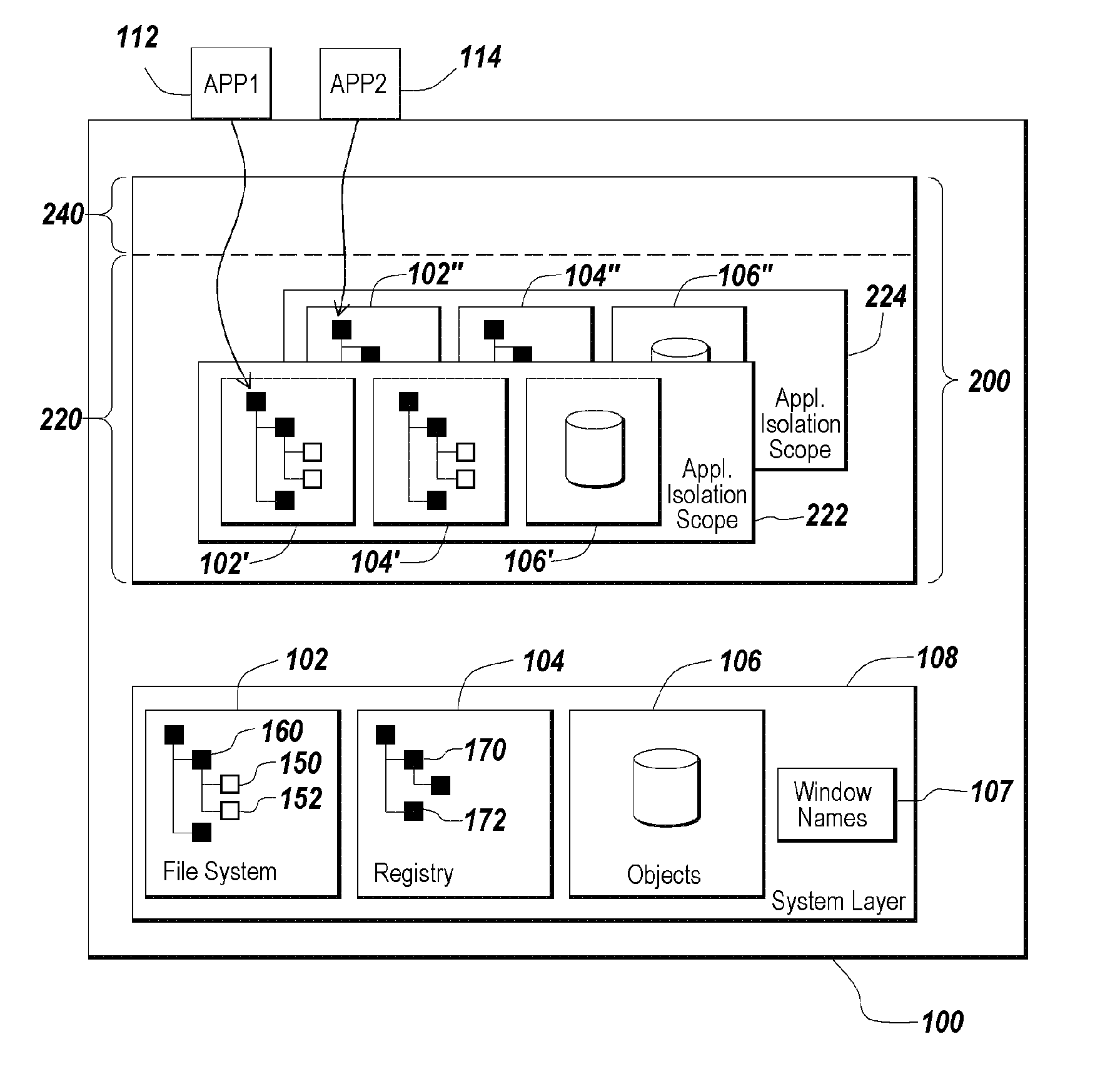
Method and apparatus for isolating execution of software applications
A method for isolating access by application programs to native resources provided by an operating system redirects a request for a native resource made by an application program executing on behalf of a user to an isolation environment. The isolation environment includes a user isolation scope and an application isolation scope. An instance of the requested native resource is located in the user isolation scope corresponding to the user. The request for the native resource is fulfilled using the version of the resource located in the user isolation scope. If an instance of the requested native resource is not located in the user isolation scope, the request is redirected to an application isolation scope. The request for the native resource is fulfilled using the version of the resource located in the application isolation scope. If an instance of the requested native resource is not located in the application isolation scope, the request is redirected to a system scope.
Owner:CITRIX SYST INC
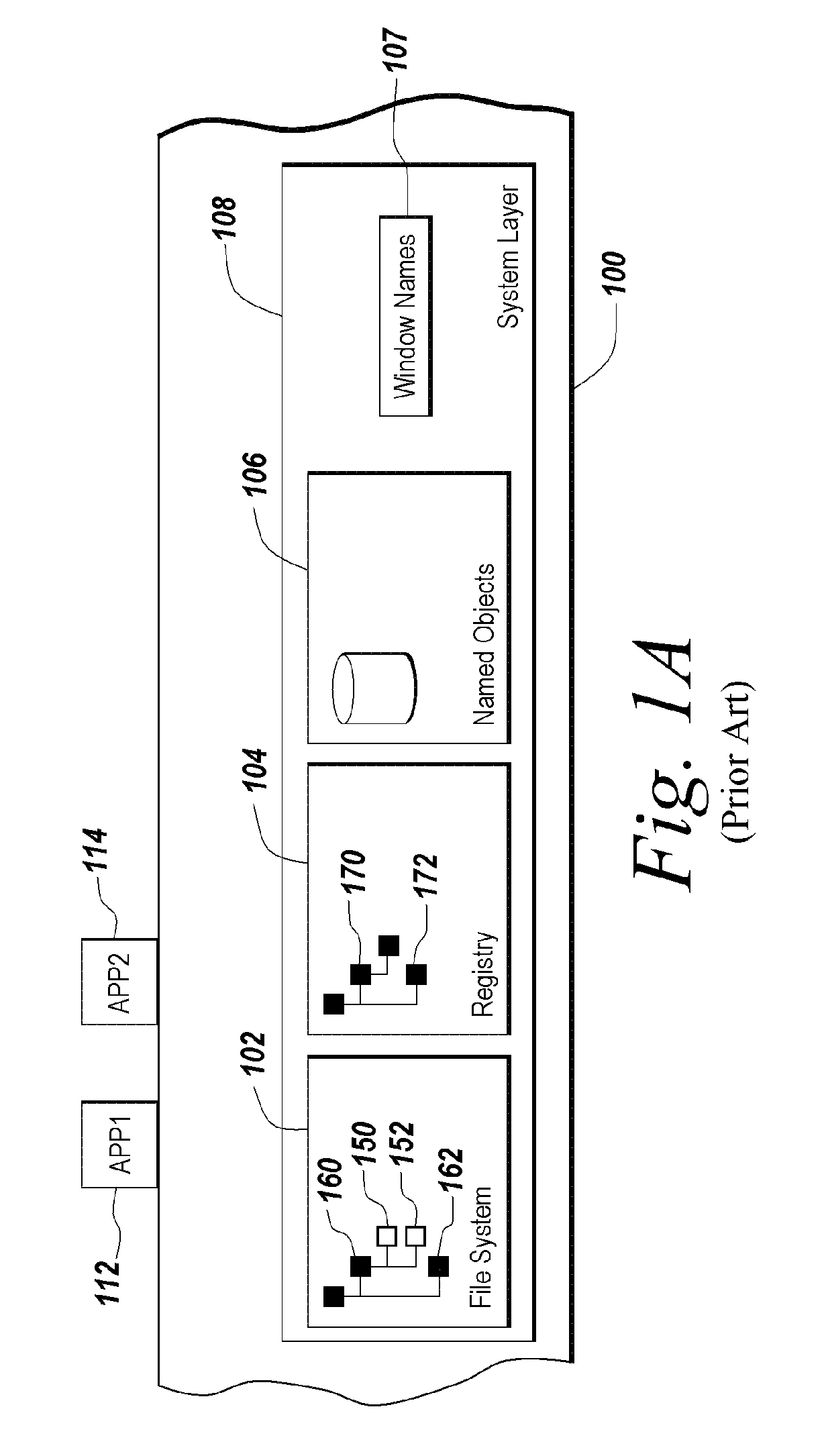
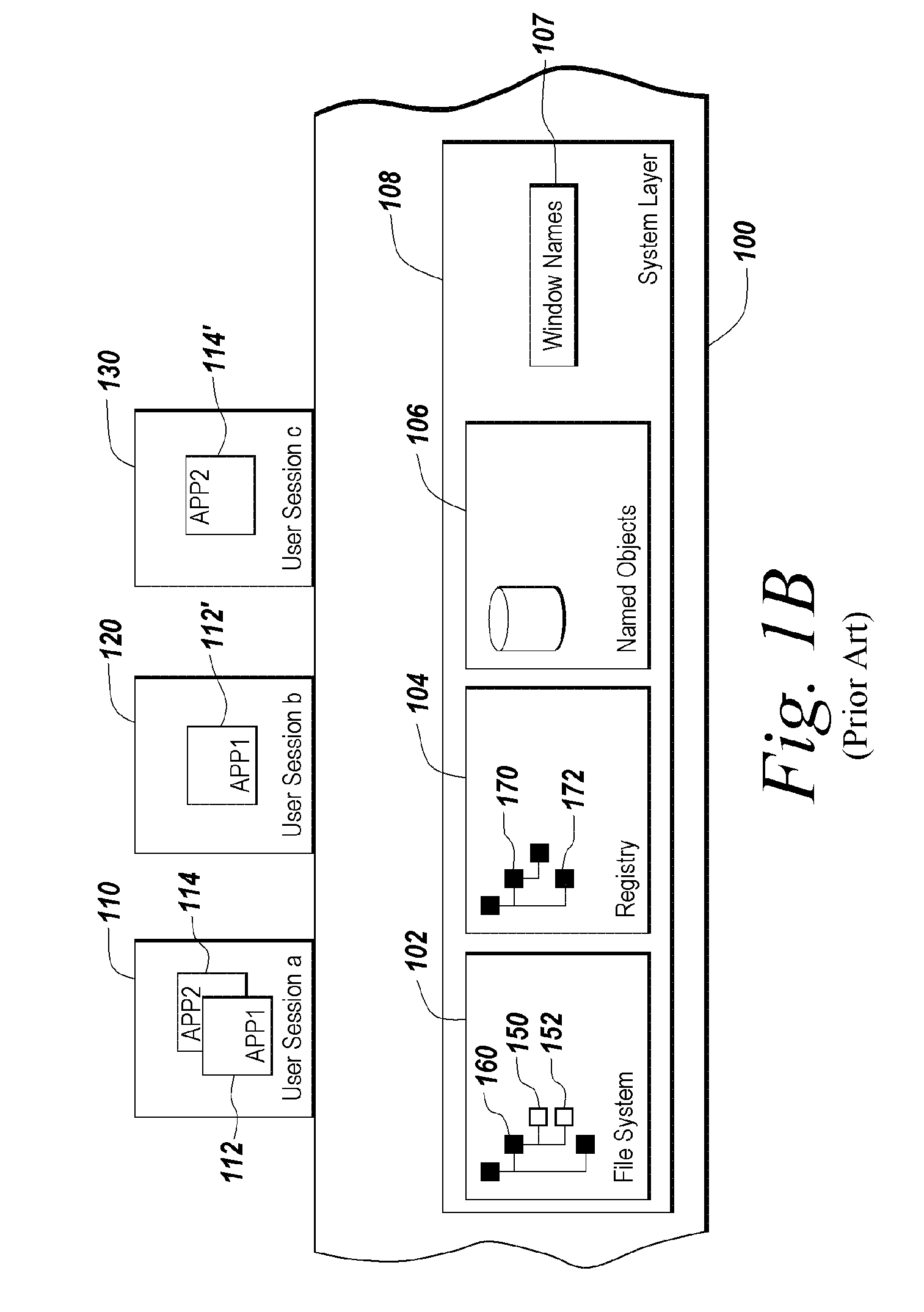
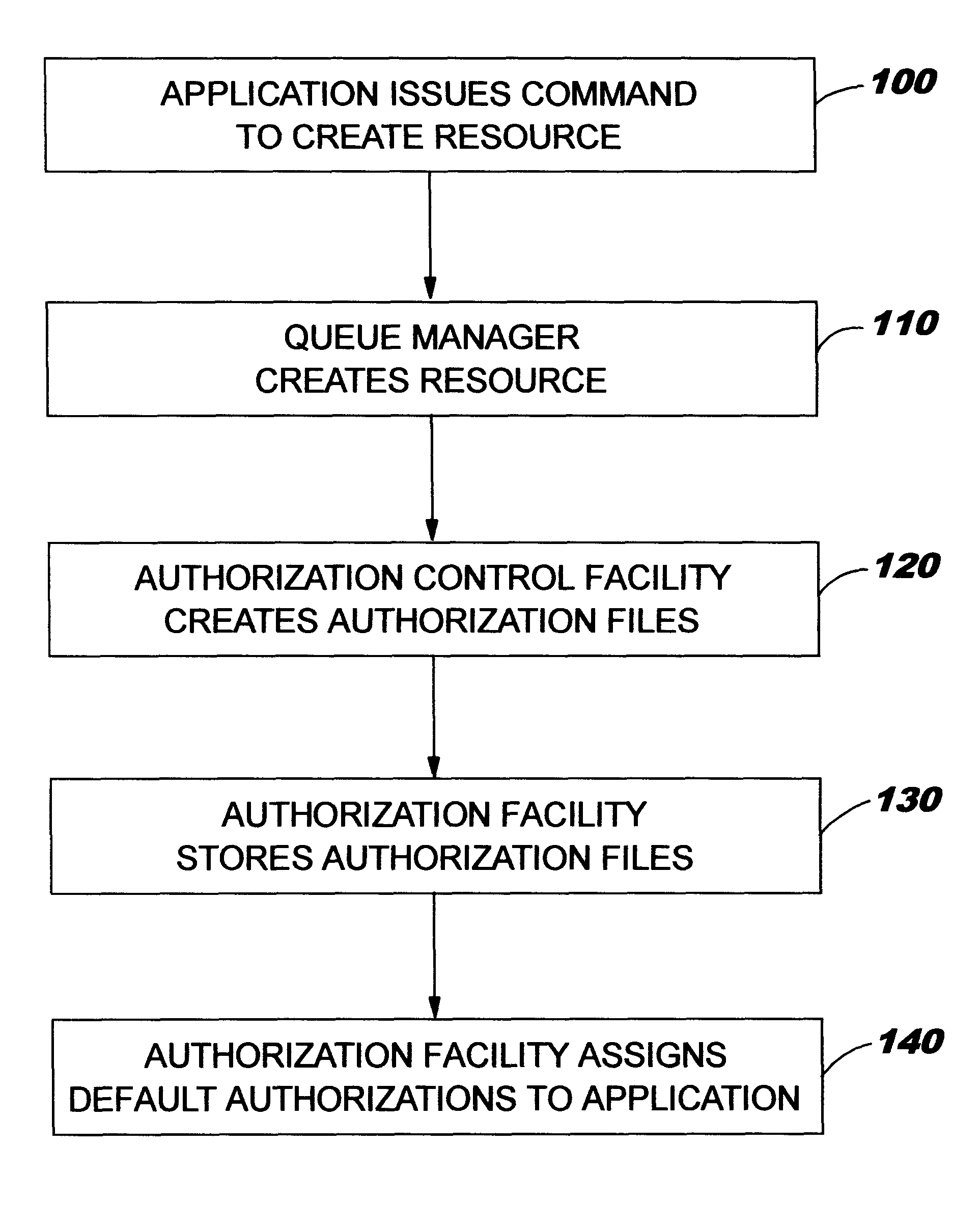
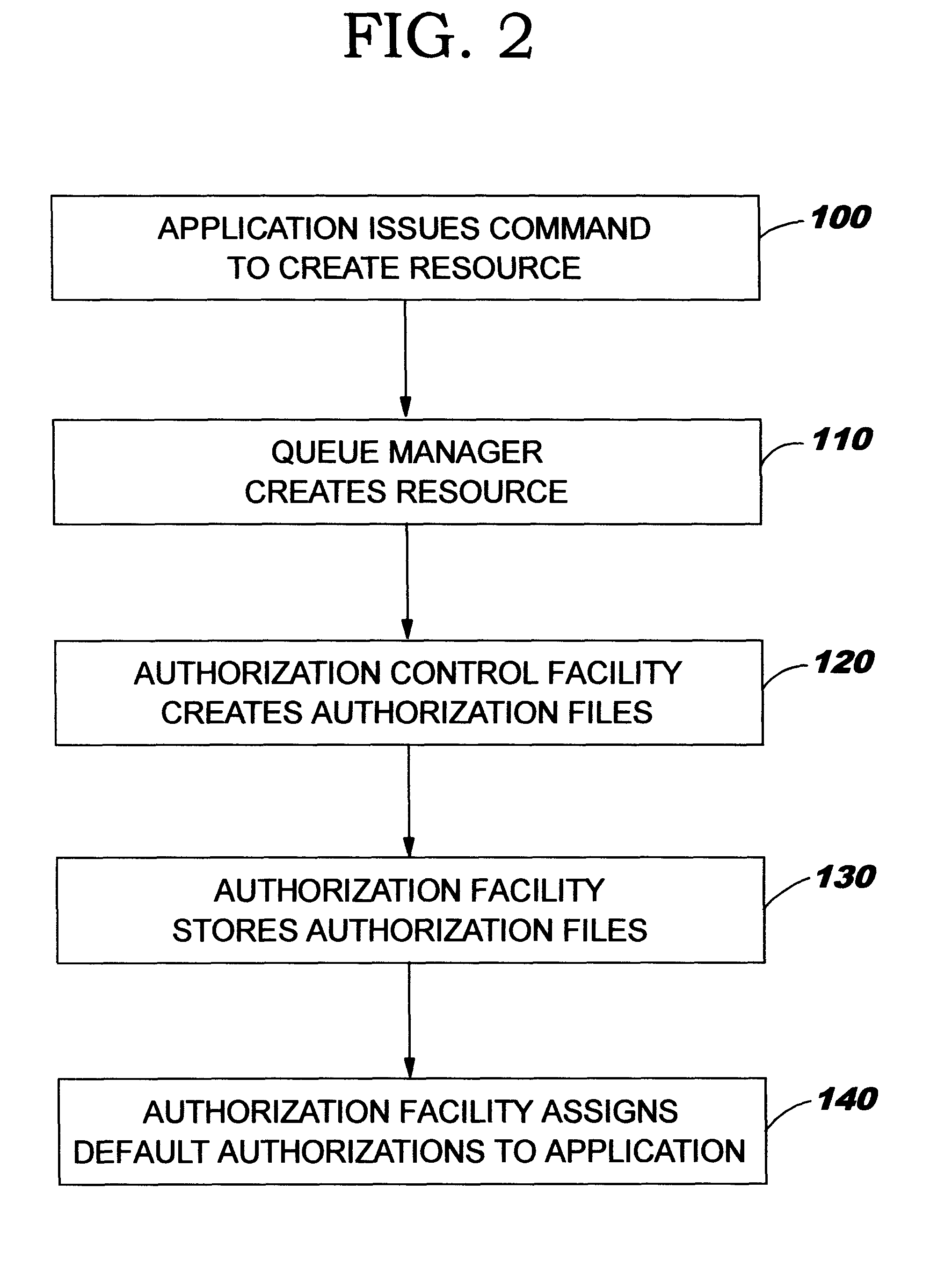
Enhanced security for computer system resources with a resource access authorization control facility that creates files and provides increased granularity of resource permission
InactiveUS6233576B1Provide flexibilitySpecific access rightsData processing applicationsComputer resourcesOperational system
Provided is a scheme for implementing flexible control of subject authorizations (i.e. the authorizations which users or processes have) to perform operations in relation to computer resources. The methods, computer systems and authorization facilities which are provided by the invention enhance the security provisions of operating systems which have only very limited authorization facilities, by mapping the available operating system permissions to specified resource authorities for each of a set of aspects or characteristics of a computer system resource. Thus, the standard operating system permissions (e.g. read, write, execute) can have different meanings for different resource aspects, and an individual subject can have separate authorization levels set for the different resource aspects. The mappings between authorities and the available permissions may be different for different types of resources. The invention provides great flexibility in setting the authorizations that a subject may have in relation to particular resources.
Owner:TREND MICRO INC
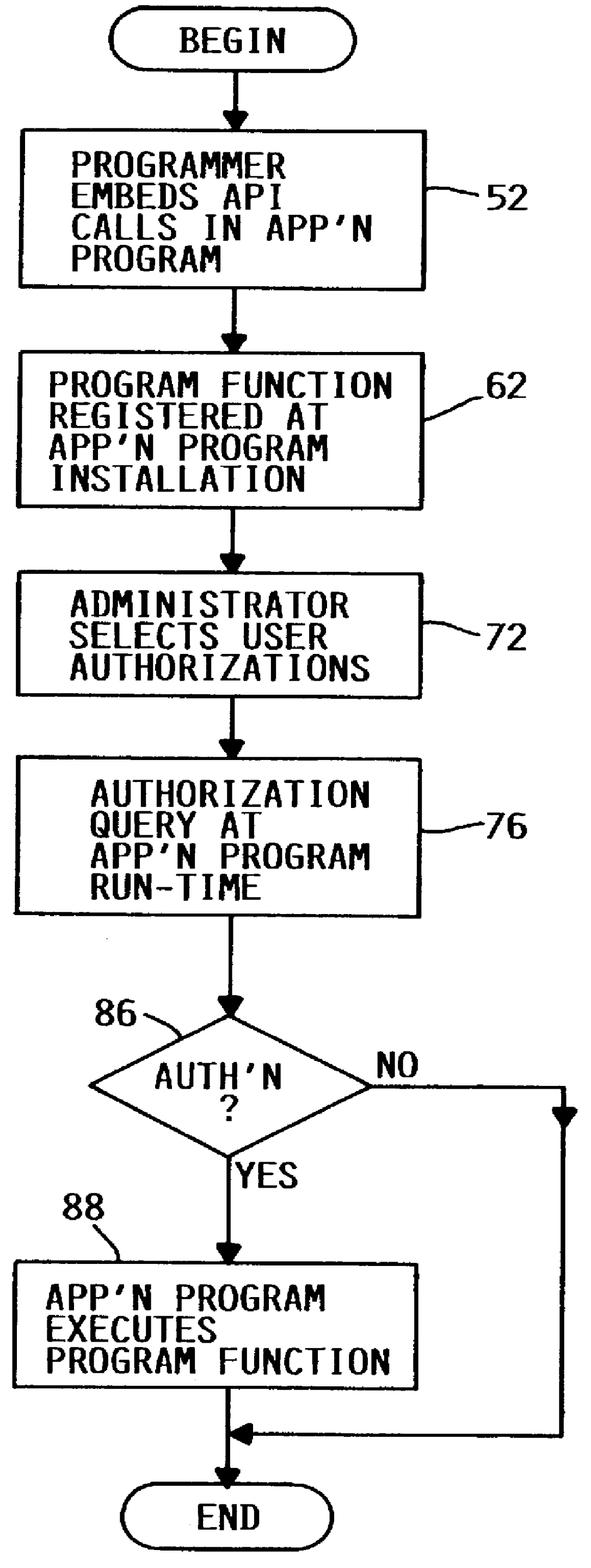
Limit access to program function
InactiveUS6101607ASpecific access rightsDigital data processing detailsOperational systemApplication programming interface
A method, system and computer program product for selectively restricting access to a program function in a computer system having an operating system security mechanism operates via an application programming interface (API) that includes a program function registration API function, an authorization selection API function, and an authorization query API function. In response to a call to the API registration function, the program function is registered in a repository in the computer system. After the program function has been registered, a system administrator can select user authorizations using a software tool that includes calls to the authorization selection API function. The system administrator may select whether a particular user or group of users is authorized to access each registered program function. A programmer can embed a call to the authorization query API function in an application program, which includes or calls the program function. When the application program reaches the call to the authorization query API function, the function is executed and returns an indicator or value indicating whether or not that user is allowed to access the program function.
Owner:IBM CORP
Techniques and System for Specifying Policies Using Abstractions
ActiveUS20070157287A1Specific access rightsError detection/correctionHuman languageComputer security
A policy language for an information management system allows specifying or more policies using policy abstractions. The policies and policy abstractions are decoupled from one another, so policies and policy abstractions may be specified and altered separately from each other. A policy may refer to any number of policy abstractions. Multiple policies may reference a single policy abstraction, and a change to that policy abstraction will result in multiple policies being changed. Further, policy abstractions may be nested, so one policy abstraction may reference another policy abstraction, and so forth.
Owner:BLUE JUNGLE
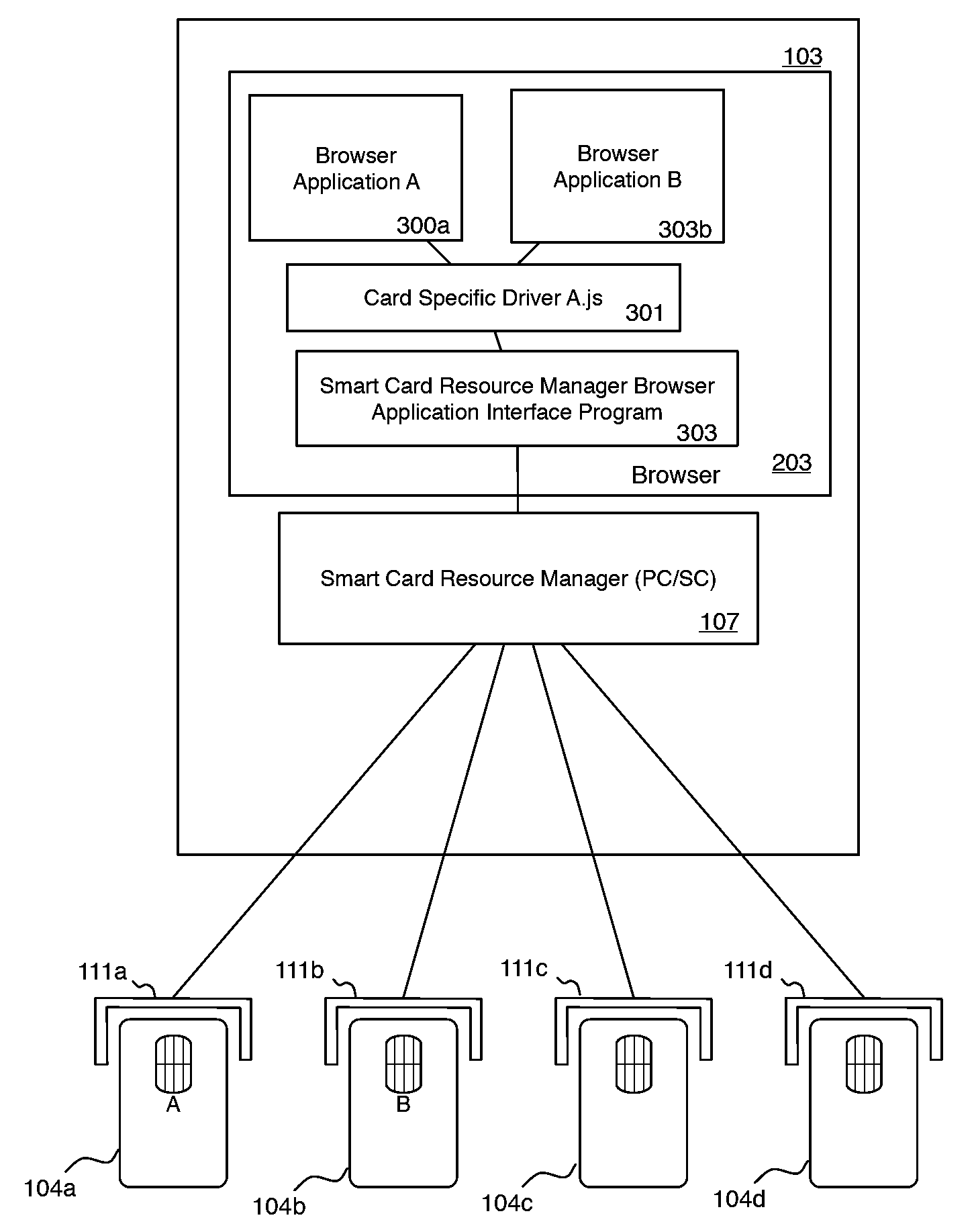
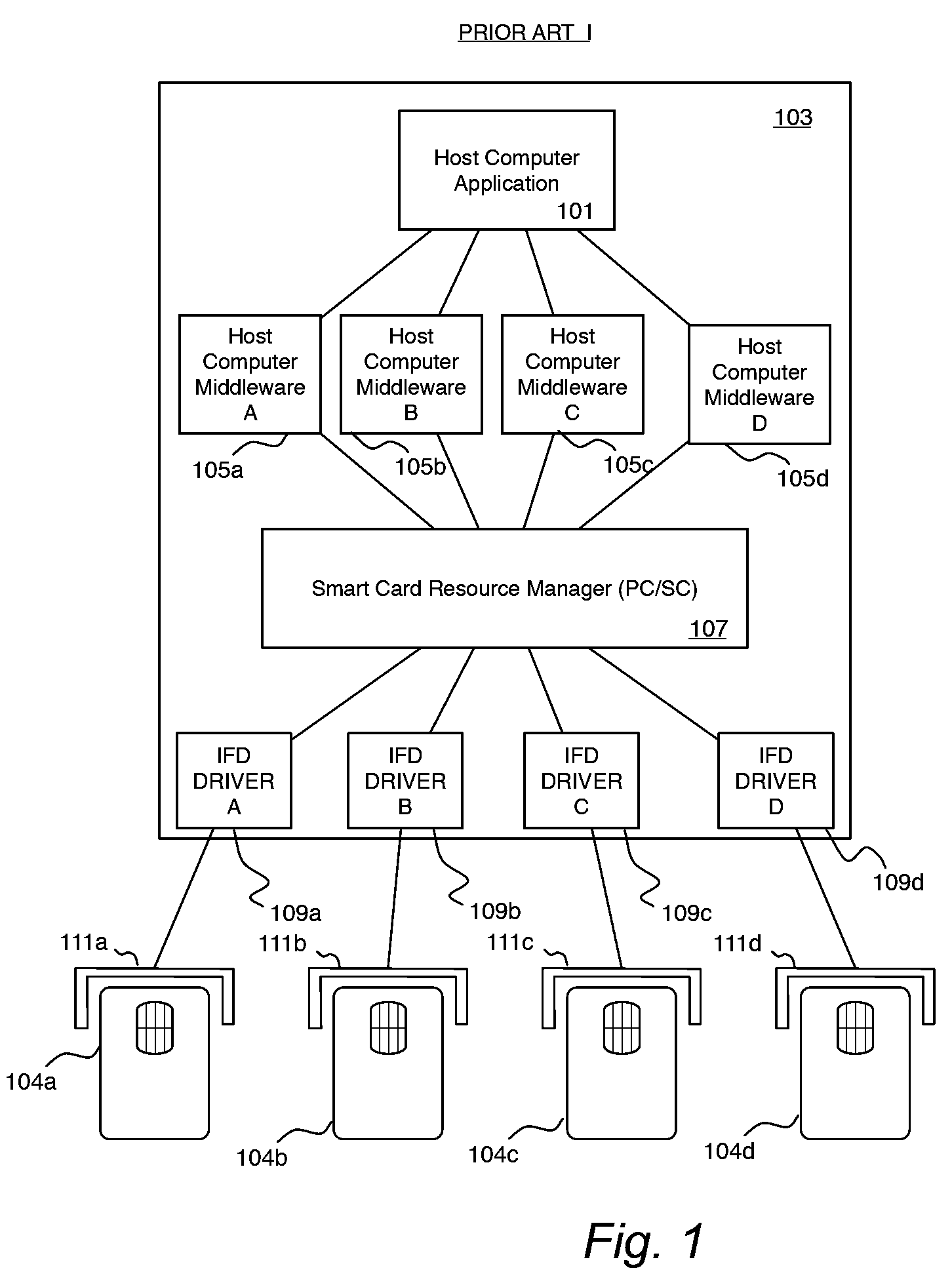
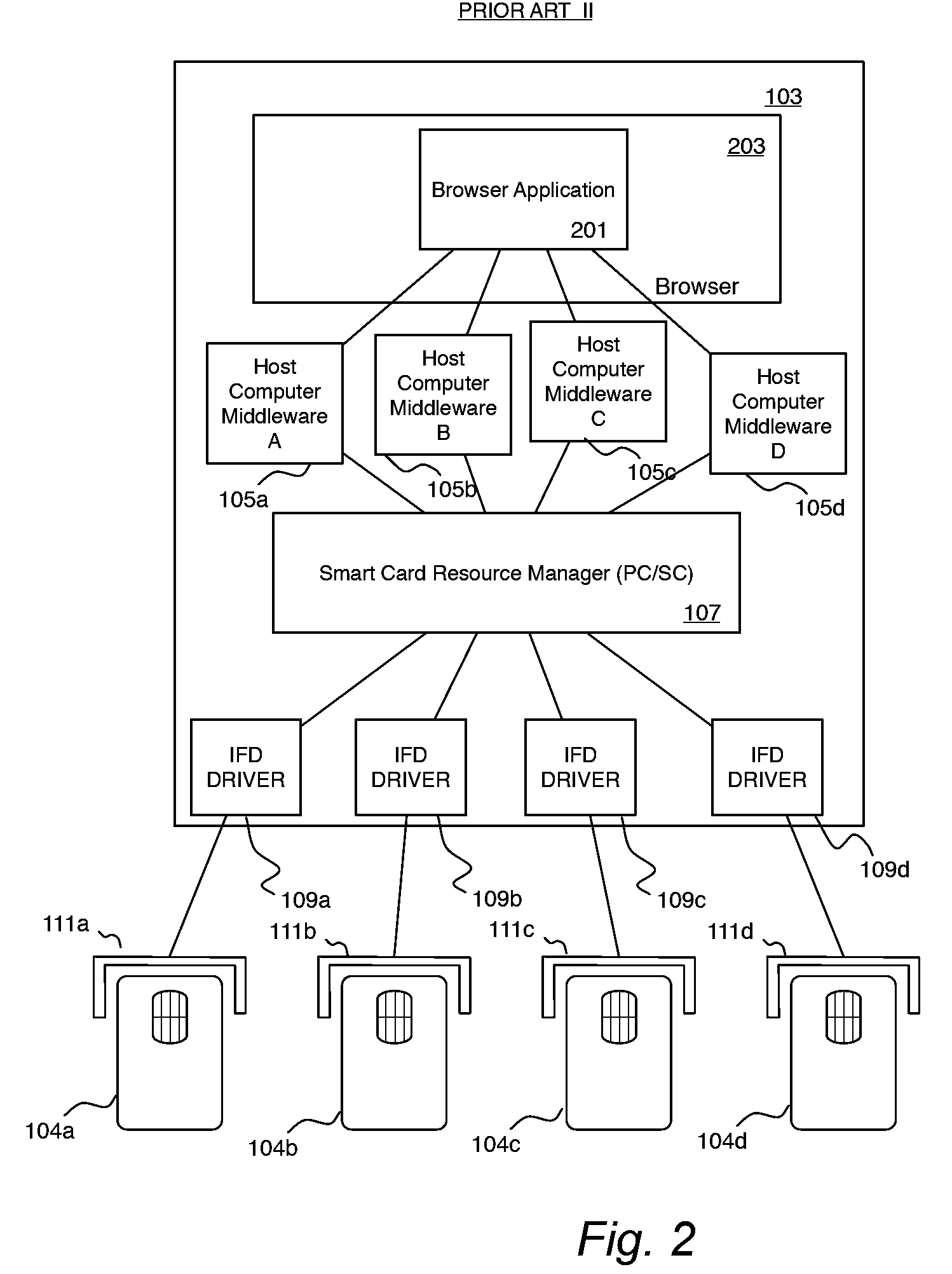
System and method for browser based access to smart cards
A client-side application extension executable on a host computer from within a web-browser having the capability of executing at least one web-browser add-on to provide a user access to a smart card, connected to the host computer having a smart card resource manager, via the web-browser. The web-browser extension has instructions to direct the central processing unit to access data on the smart card via a web-browser and platform independent interface module and a web-browser and platform dependent wrapper module connected to the web-browser and platform independent interface module and to the smart card resource manager having a function processing module operable to receive a call to the at least one function for accessing data on the smart card and for transforming the function call into a corresponding call to the smart card resource manager.
Owner:THALES DIS USA INC
Method and system for session based authorization and access control for networked application objects
Owner:PRISMTECH
By-pass and tampering protection for application wrappers
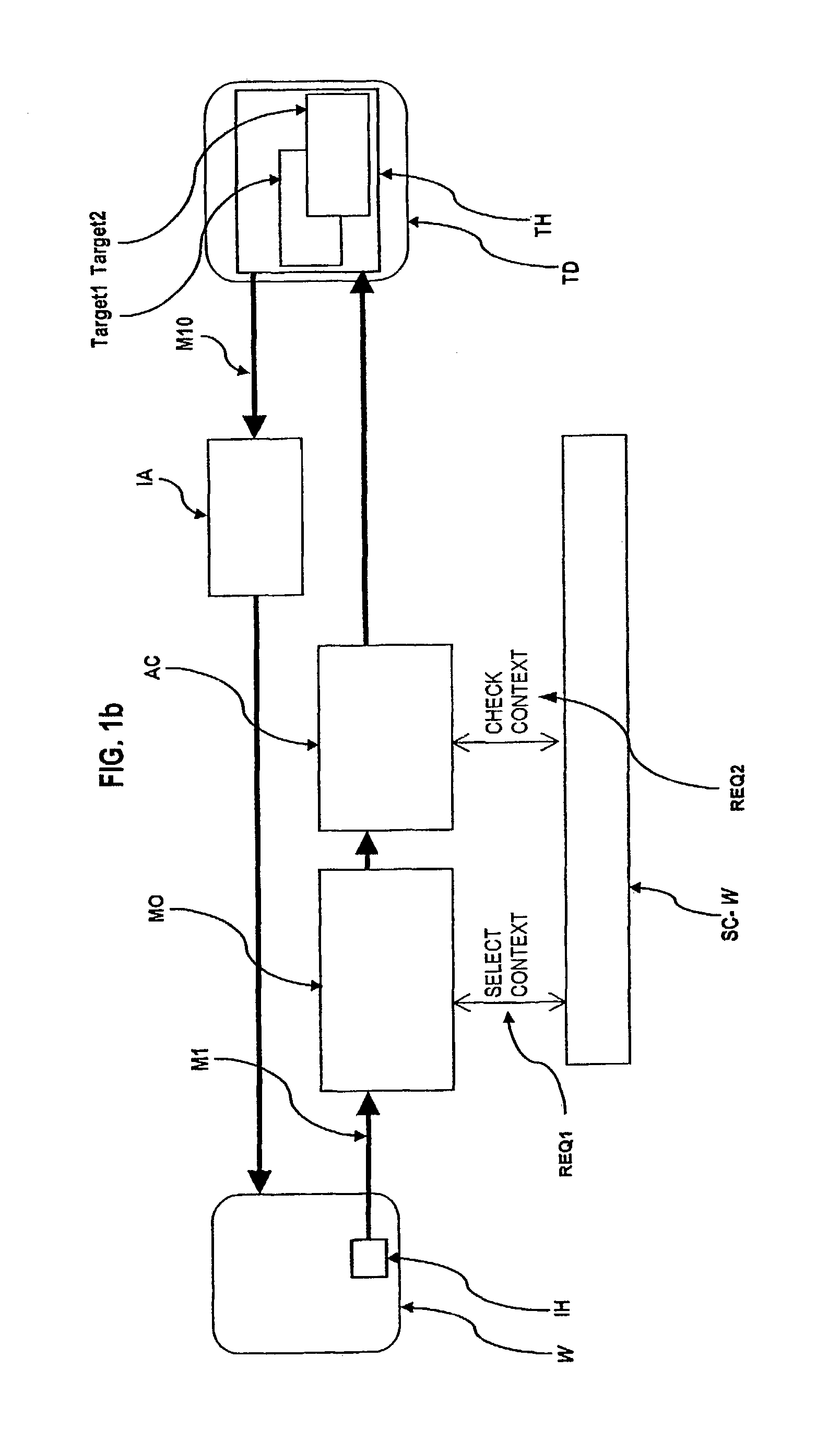
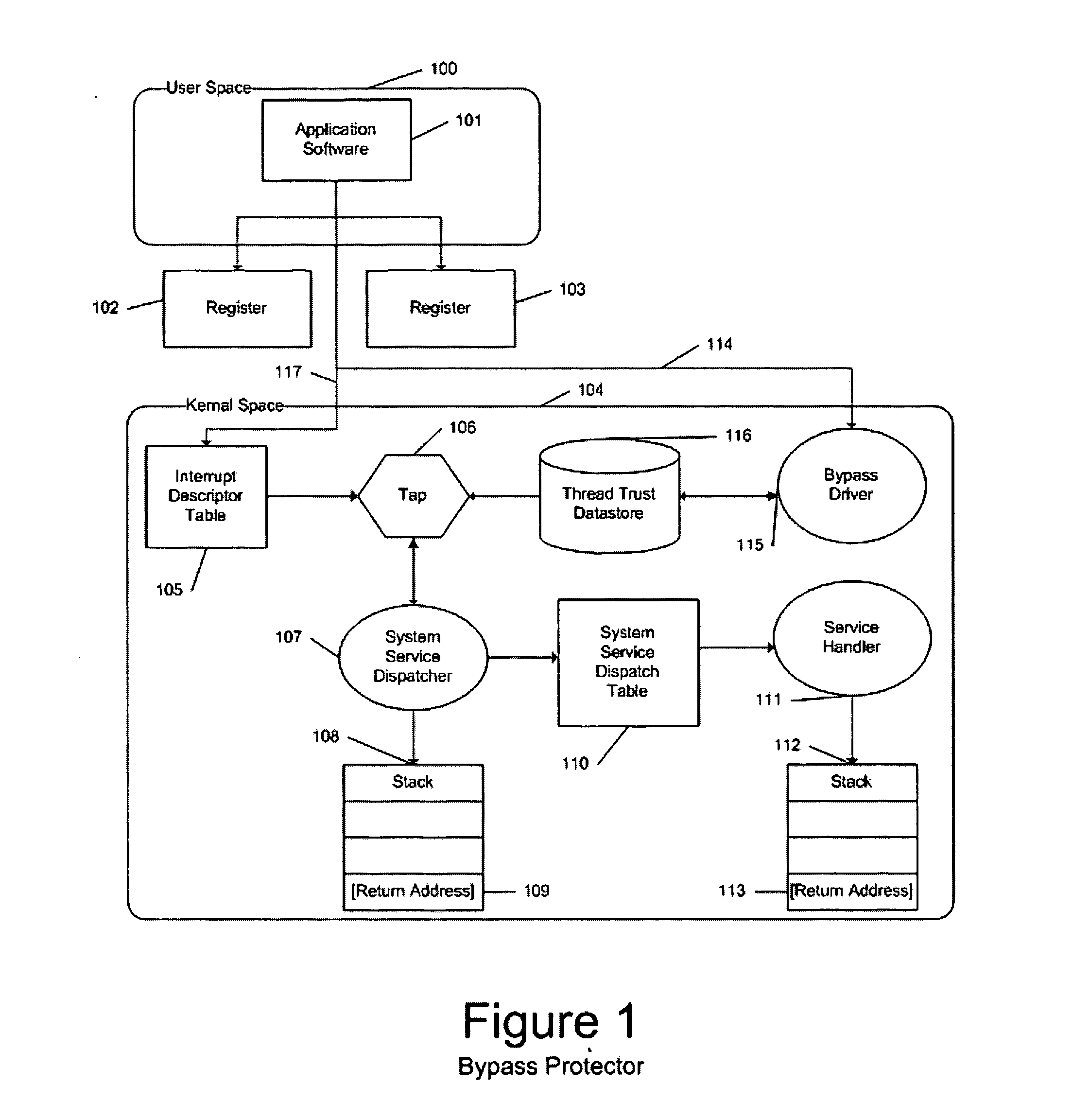
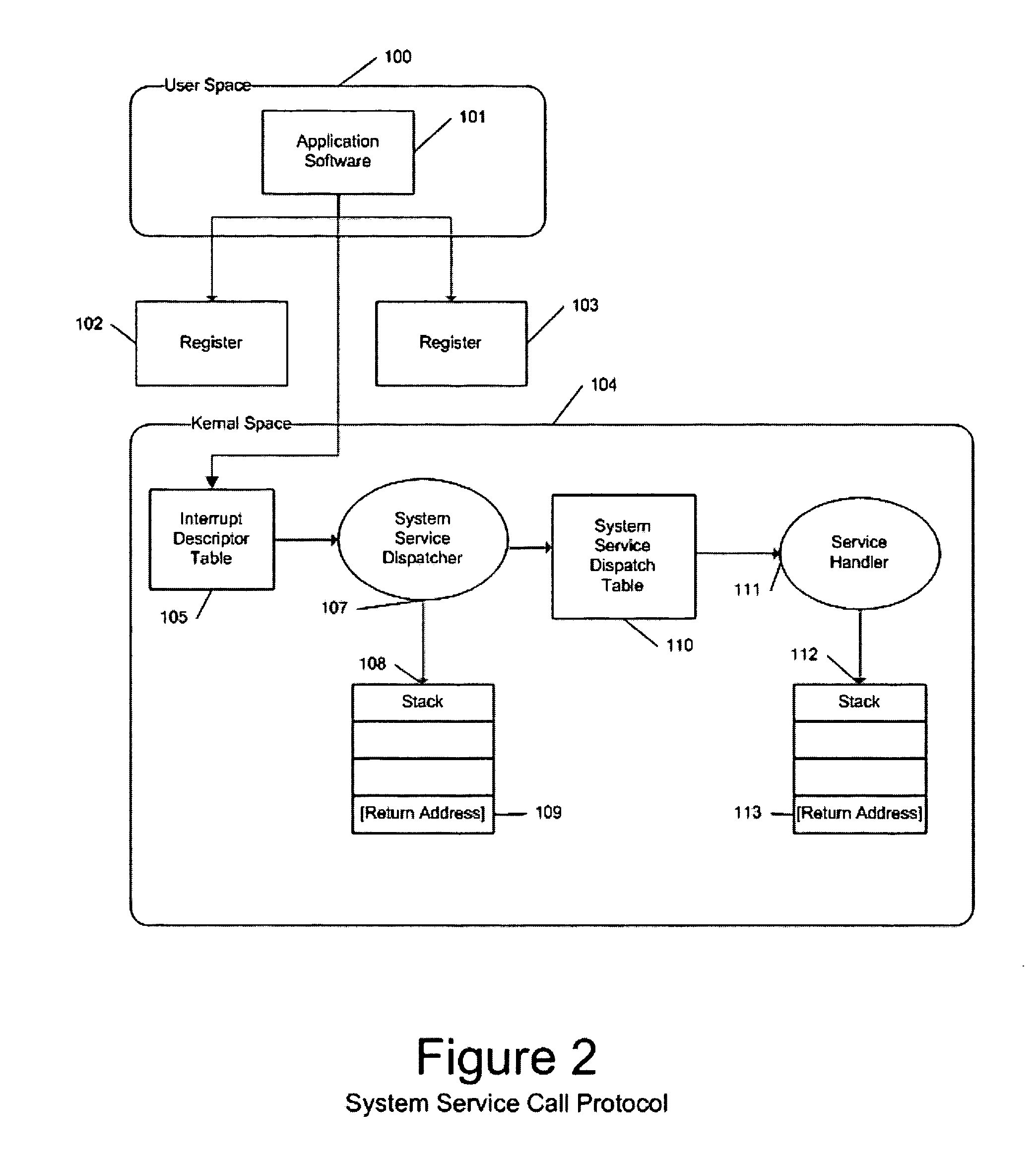
InactiveUS20050108516A1Restoration of protectionSpecific access rightsPlatform integrity maintainanceOperational systemHooking
In a computer system with an operating system that supports multiple levels of interfaces (APIs) that application programs (i.e. programs executing outside the operating system kernel in user mode) can invoke to obtain services from the operating system, and the employment of a hooking or mediation technology within a user-mode process (i.e. an instantiation of an application program) to intercept / mediate invocations of selected interfaces of some of those levels, the Tampering Protection protects the code and statically or heap allocated data of the mediators from corruption by the code of the user-mode process being mediated that resides and operates in the same address space as the code and data of the mediators (as such corruption would compromise the integrity of the mediator and could prevent it from accomplishing its intended mediation purpose). It does so by providing memory protection services that allow mediators to define data areas (both static segments and dynamic heaps) to be protected and to temporarily unprotect them during the execution of a mediator so that they can be modified during that execution, thus ensuring that the mediate application does not directly use the operating system services to override Tampering Protection management of these protected segments or protected.
Owner:BALZER ROBERT +1
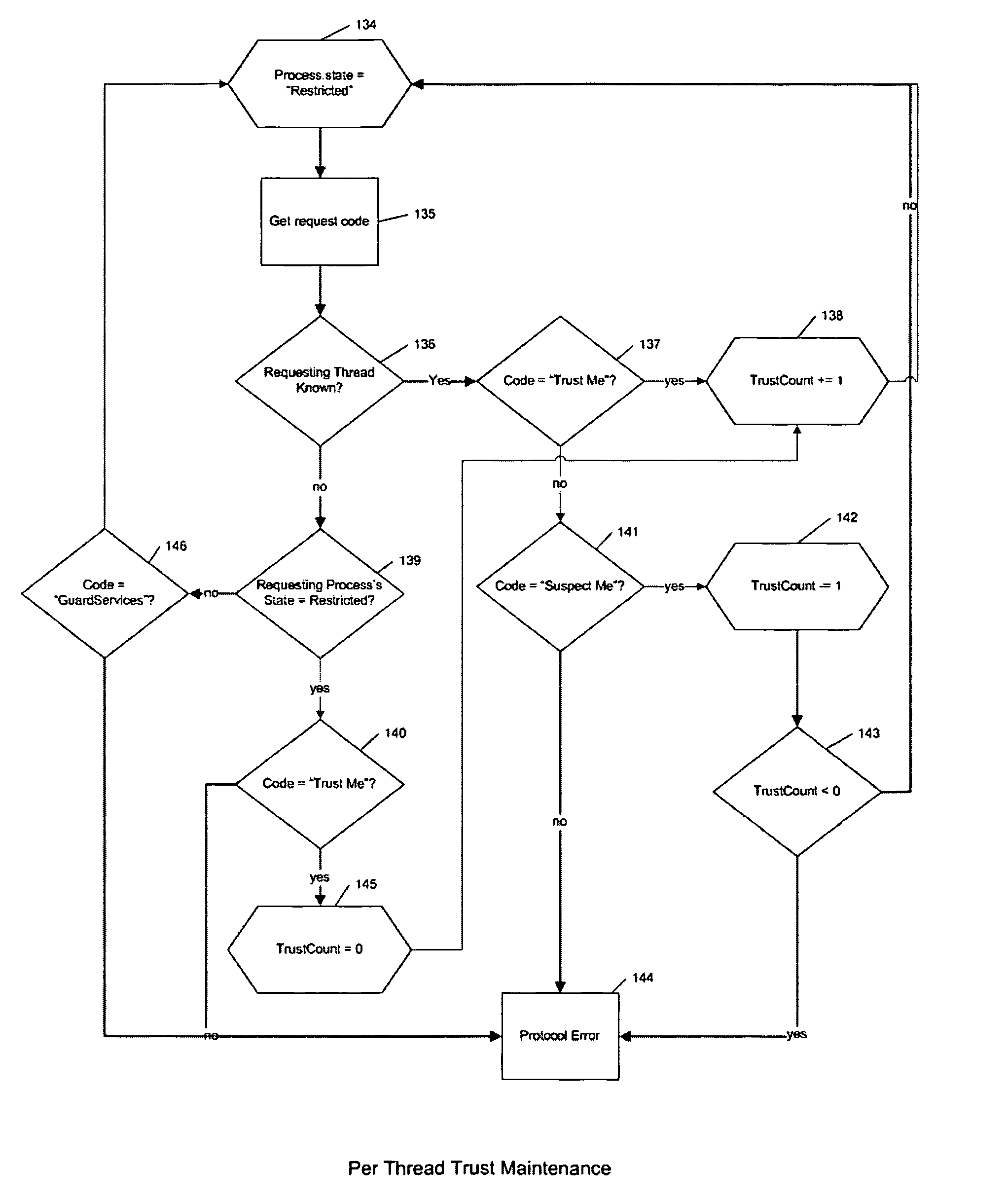
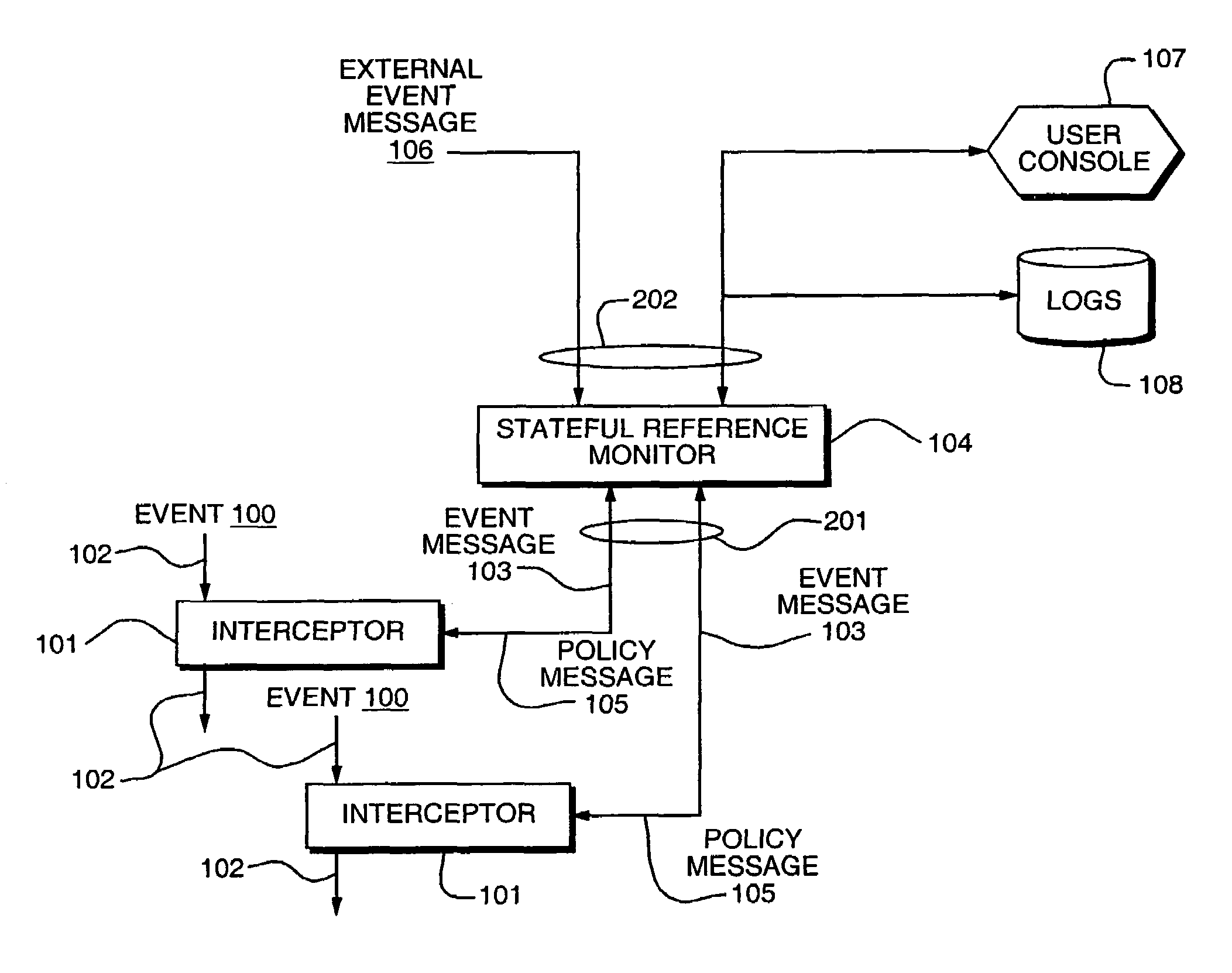
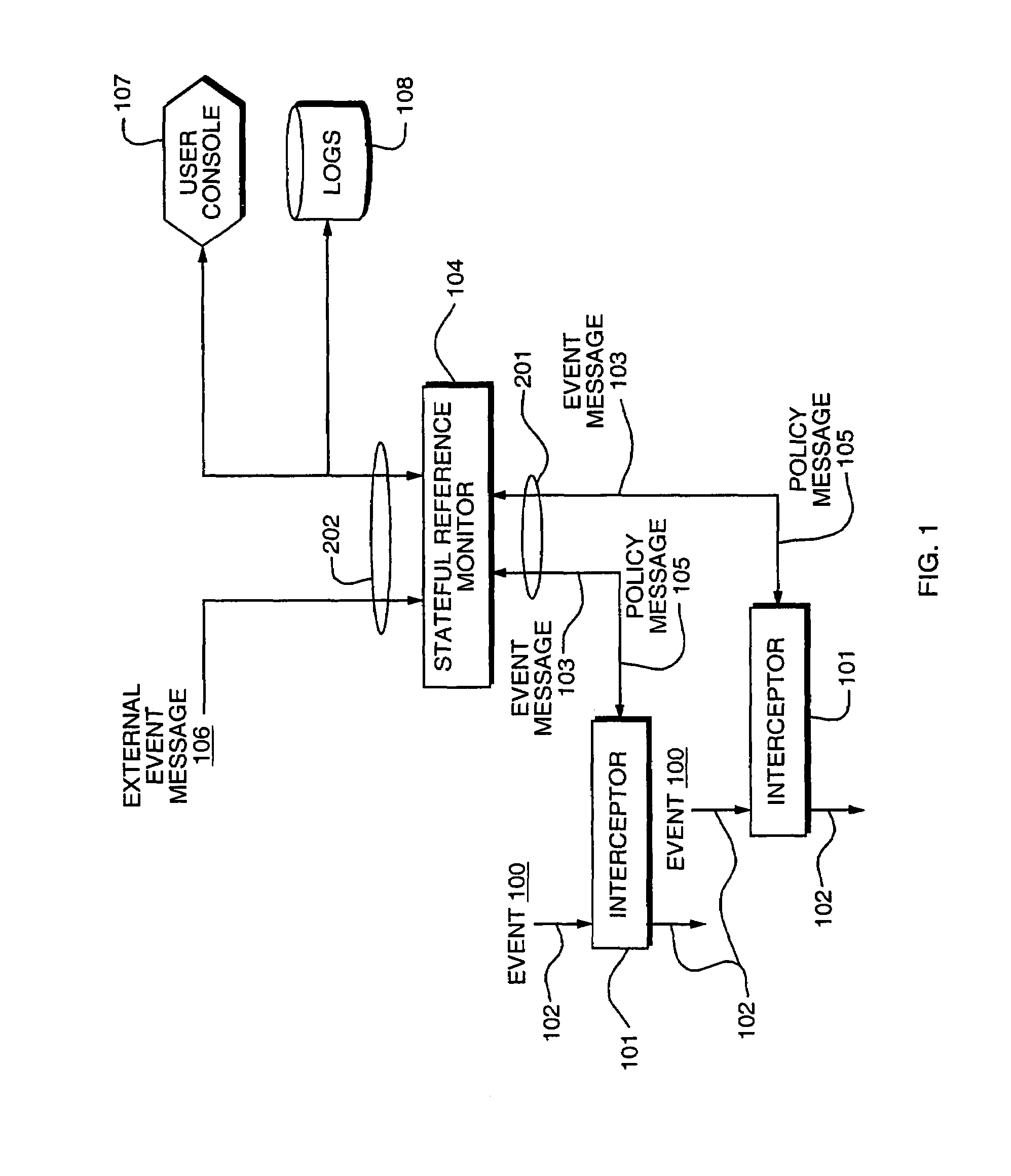
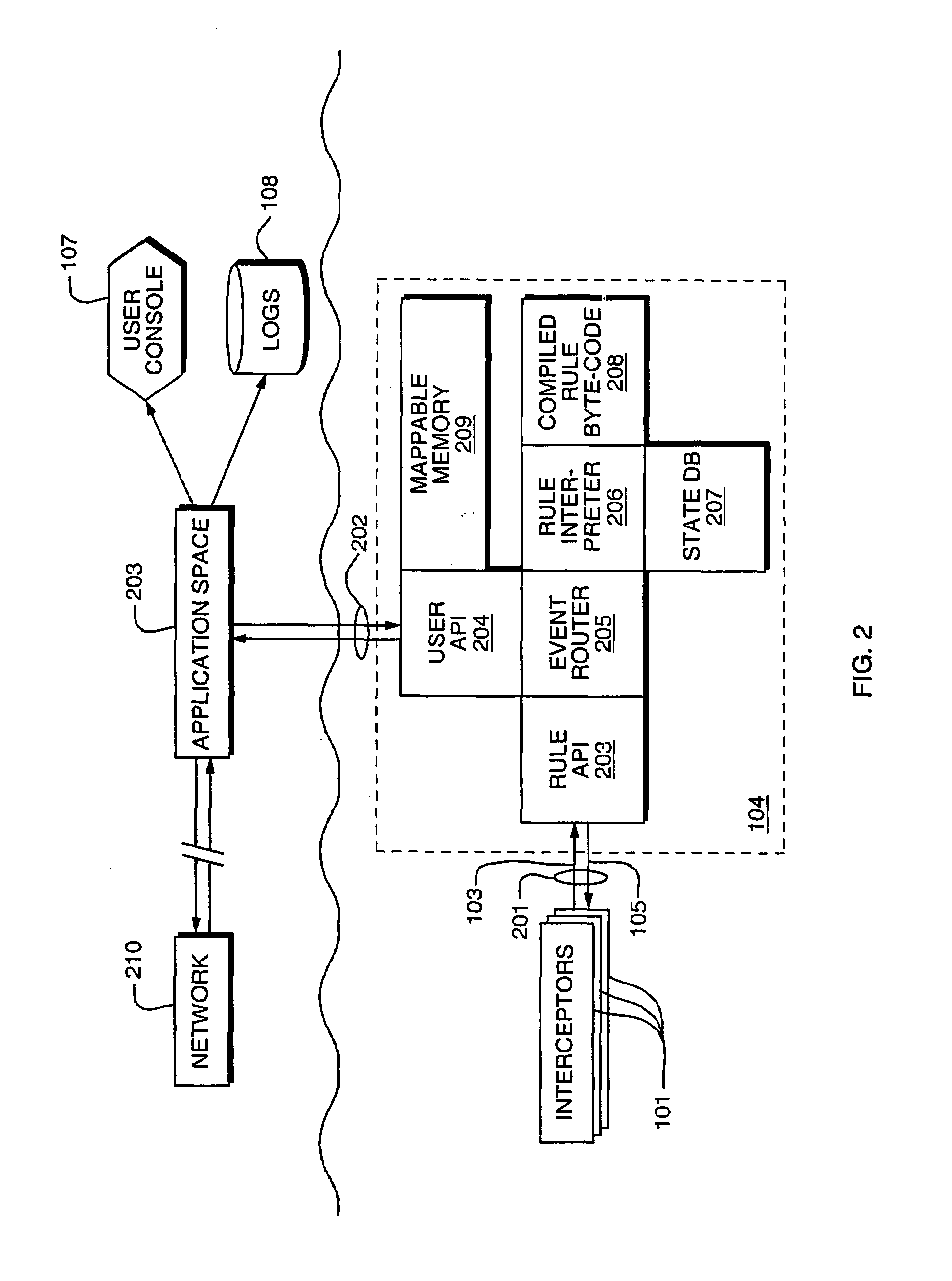
Access control by a real-time stateful reference monitor with a state collection training mode and a lockdown mode for detecting predetermined patterns of events indicative of requests for operating system resources resulting in a decision to allow or block activity identified in a sequence of events based on a rule set defining a processing policy
ActiveUS7290266B2Access control difficultSpecific access rightsDigital data processing detailsOperational systemRule sets
A Stateful Reference Monitor can be loaded into an existing commercial operating system, and then can regulate access to many different types of resources. The reference monitor maintains an updateable storage area whose contents can be used to affect access decisions, and access decisions can be based on arbitrary properties of the request.
Owner:CISCO TECH INC
Techniques and system to manage access of information using policies
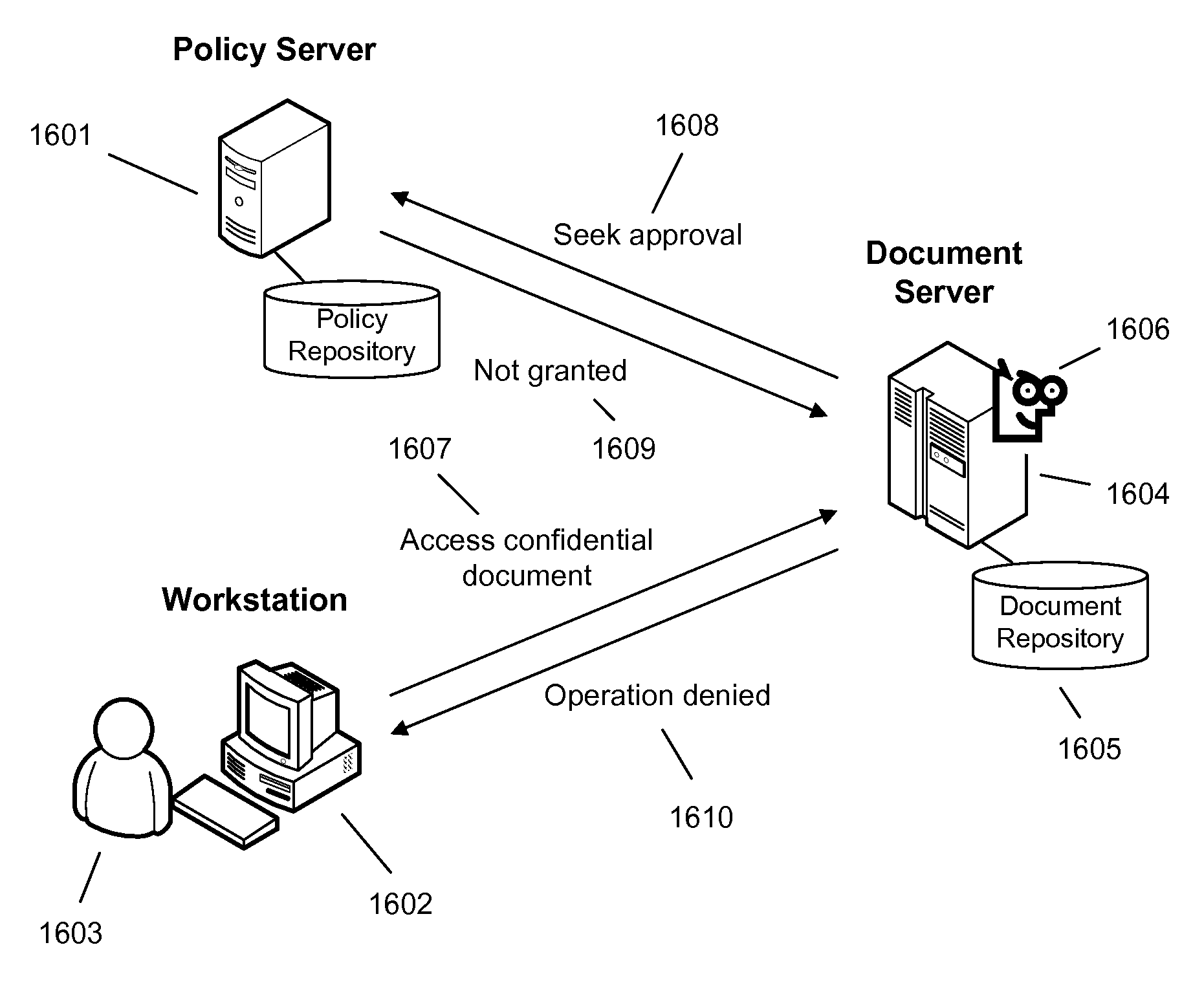
ActiveUS20070156694A1Specific access rightsError detection/correctionApplication softwareDocumentation
An information management system approves or denies user requests to access information of the system. The information includes all types of information including documents and e-mail. The information management system is driven using a policy language having policies and policy abstractions. The information management system may approve or deny many different types of requests including opening a document or file, copying a file, printing a file, sending an e-mail, reading an e-mail, cut and paste of a portion of a document, saving a document, executing an application on a file, and many others.
Owner:NEXTLABS
Method and system for identity-based authentication of virtual machines
A cloud computing system configured to run virtual machine instances is disclosed. The cloud computing system assigns an identity to each virtual machine instance. When the virtual machine instance accesses initial configuration resources, it provides this identity to the resources to authenticate itself. This allows for flexible and extensible initial configuration of virtual machine instances.
Owner:RACKSPACE US
Managing processing within computing environments including initiation of virtual machines
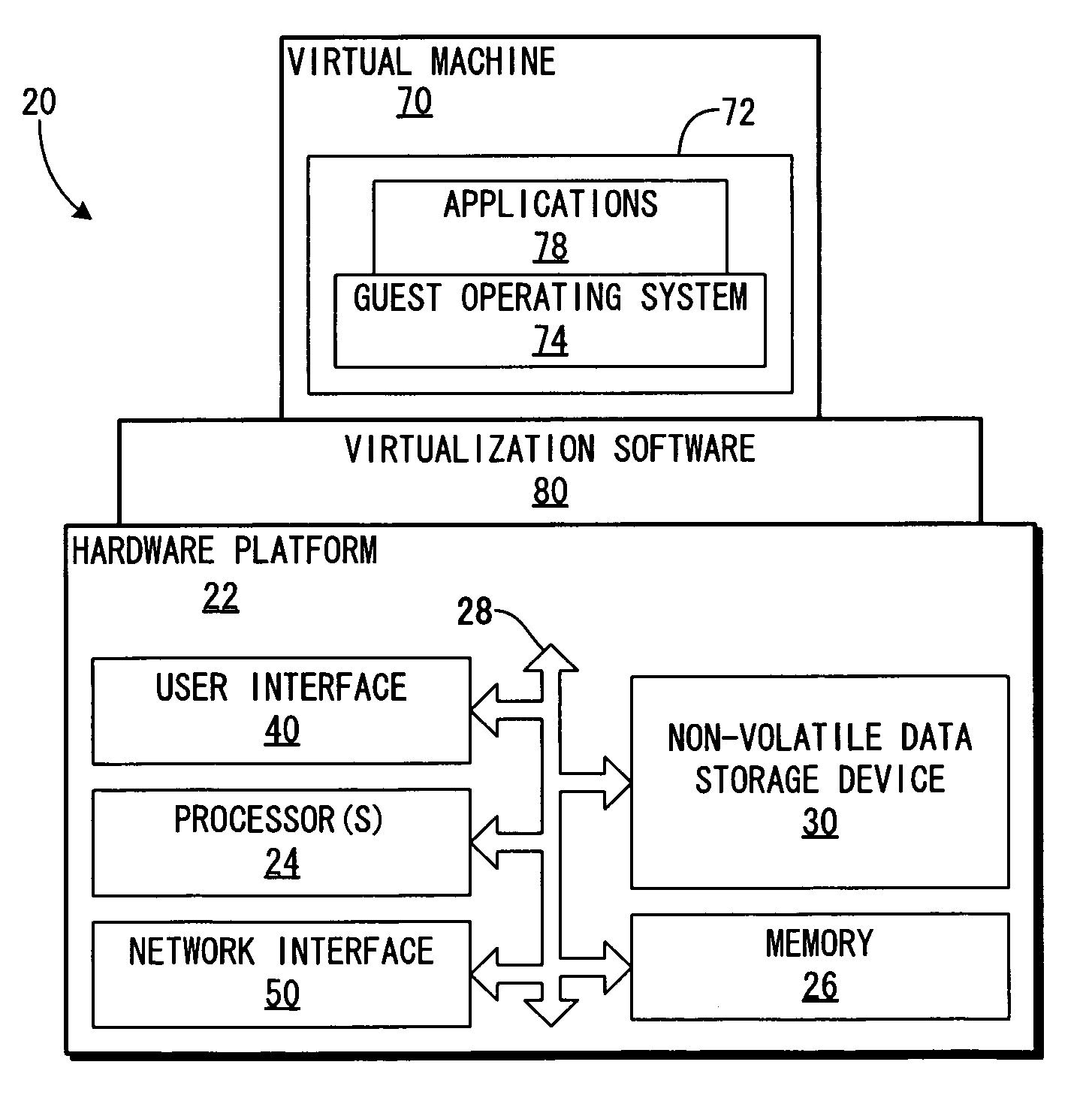
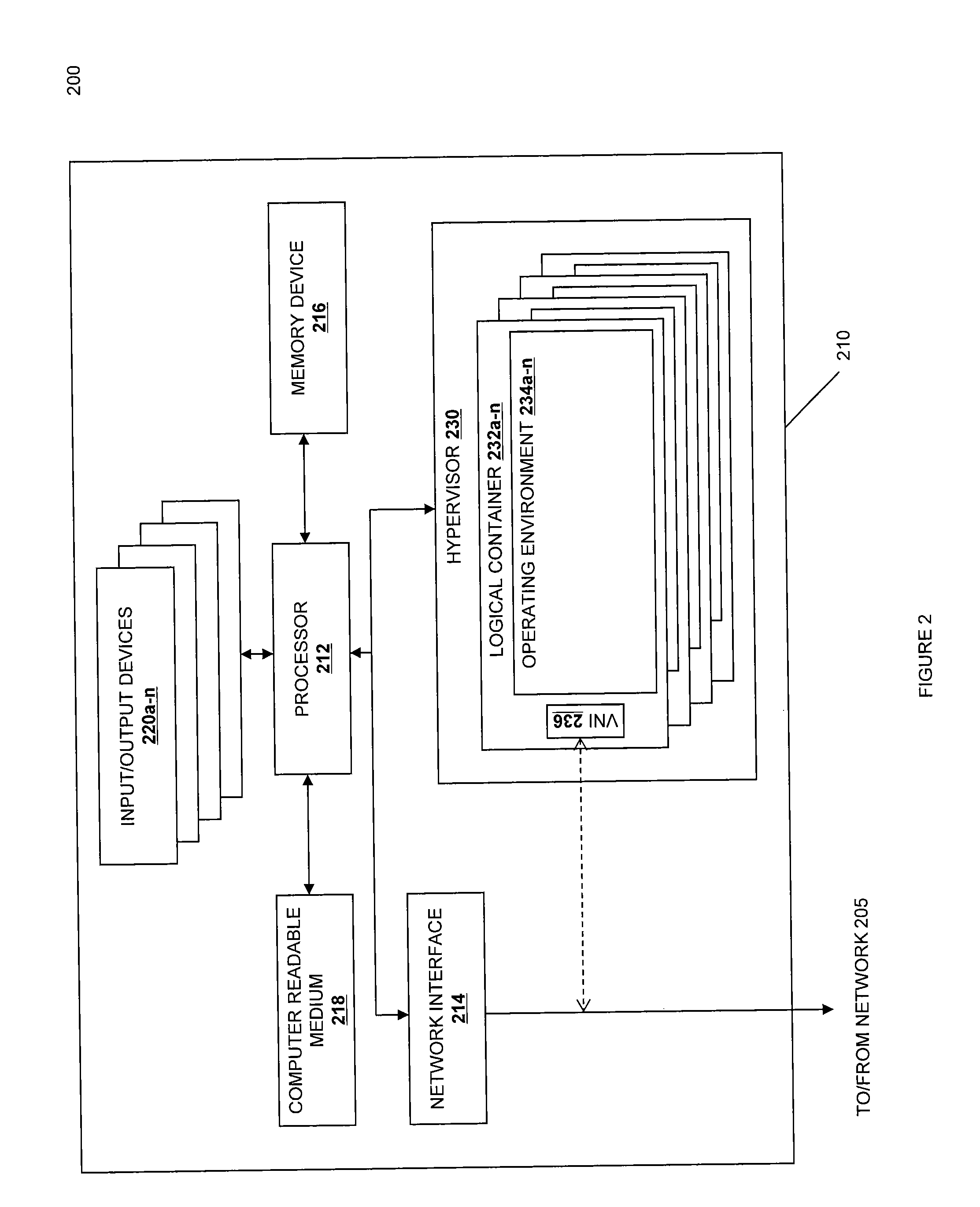
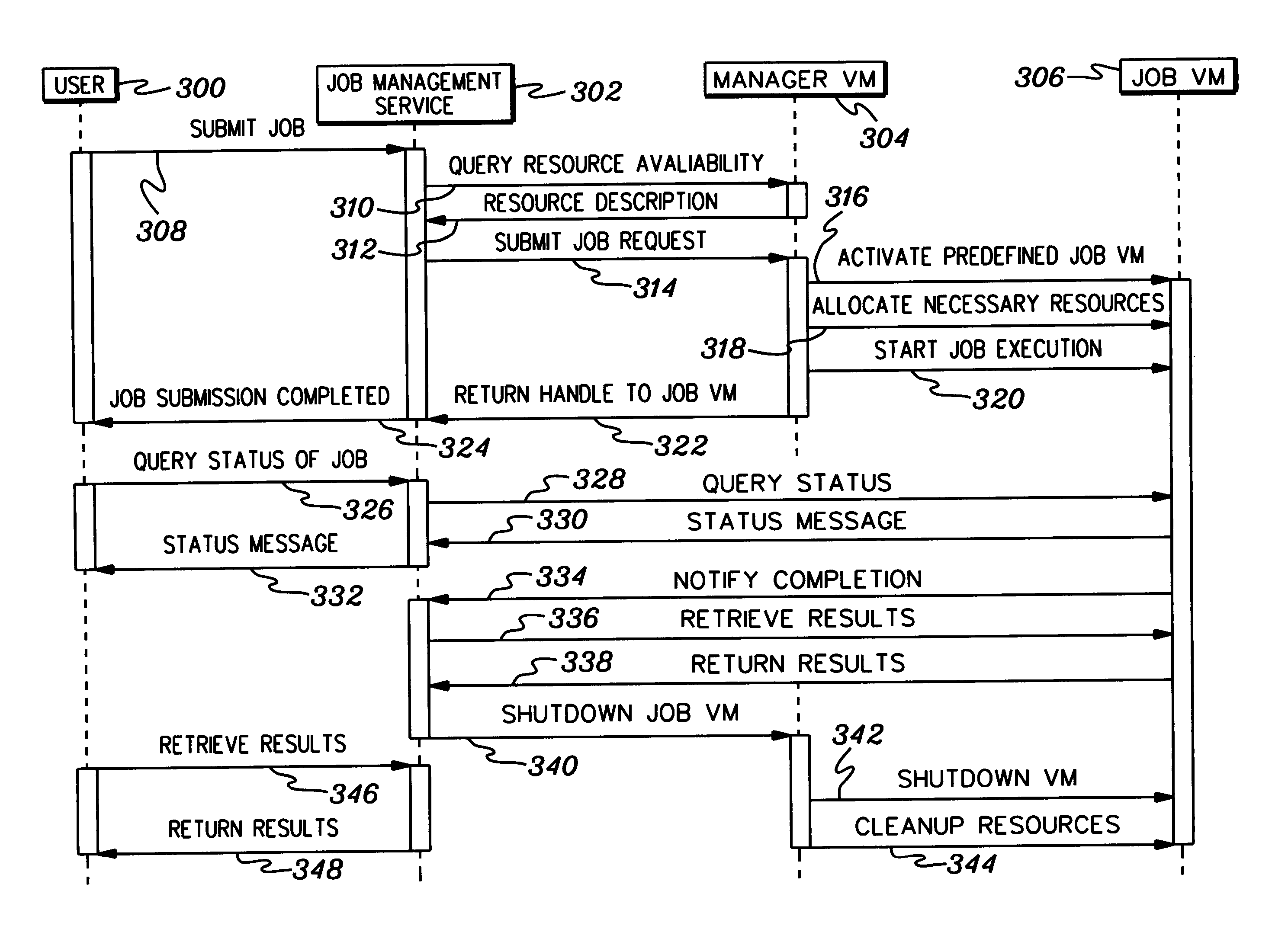
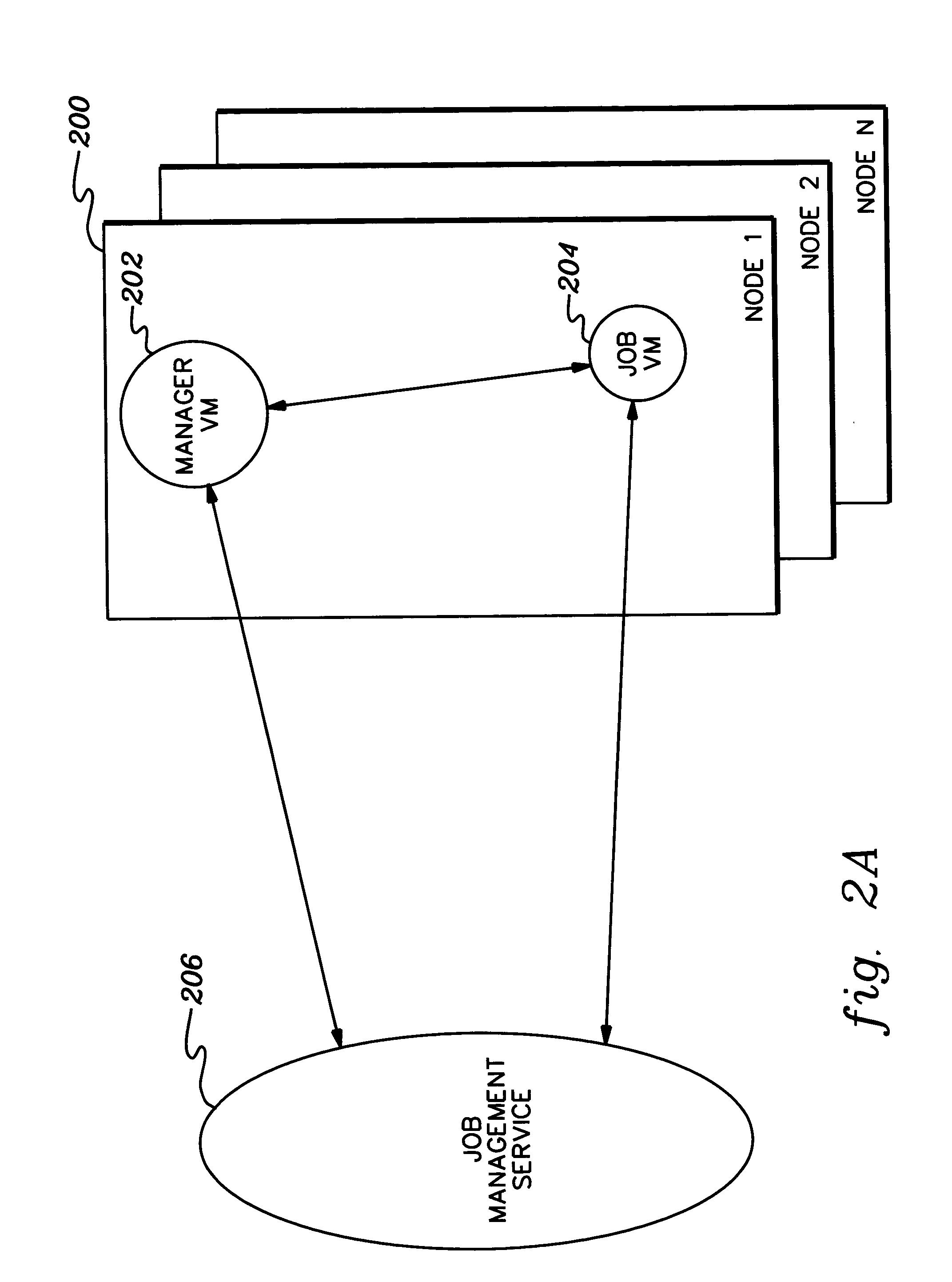
InactiveUS20050060704A1Specific access rightsProgram control using stored programsVirtual machineStart up
Virtual machines are provided on-demand. This on-demand service is beneficial in many situations, including, for instance, providing a virtual machine on-demand to process a request. The virtual machine provided to process the request is exclusive to the request. The on-demand virtual machine is automatically activated by another virtual machine, which has control over the on-demand virtual machine. The controlling virtual machine manages the start-up, provision of resources, and the shut-down of the on-demand virtual machine.
Owner:IBM CORP
Deploying Policies and Allowing Off-Line Policy Evaluations
ActiveUS20070157288A1Specific access rightsError detection/correctionOperating systemInformation management
In an information management system, policies are deployed to targets and targets can evaluate the policies whether they are connected or disconnected to the system. The policies may be transferred to the target, which may be a device or user. Relevant policies may be transferred while not relevant policies are not. The policies may have policy abstractions.
Owner:NEXTLABS
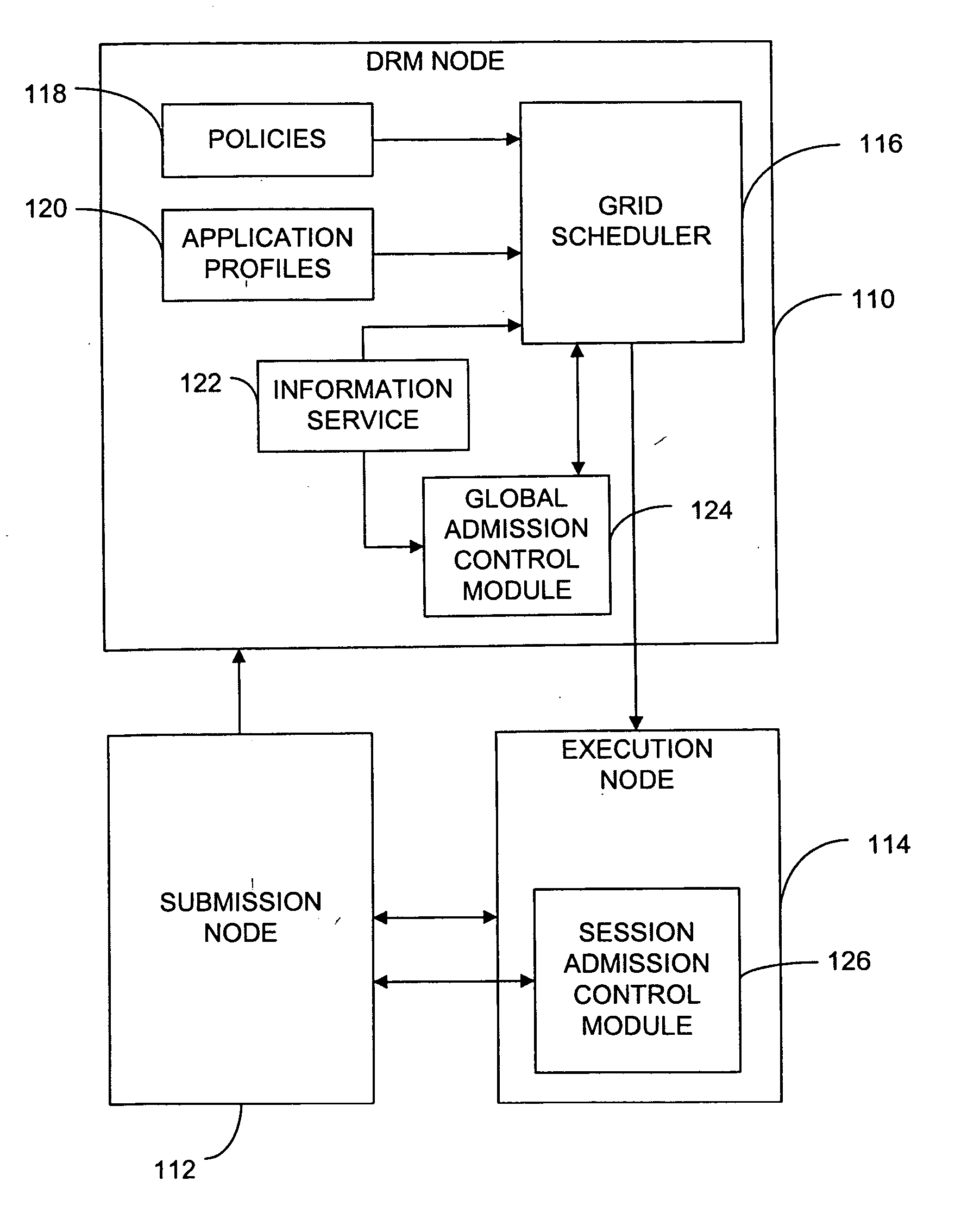
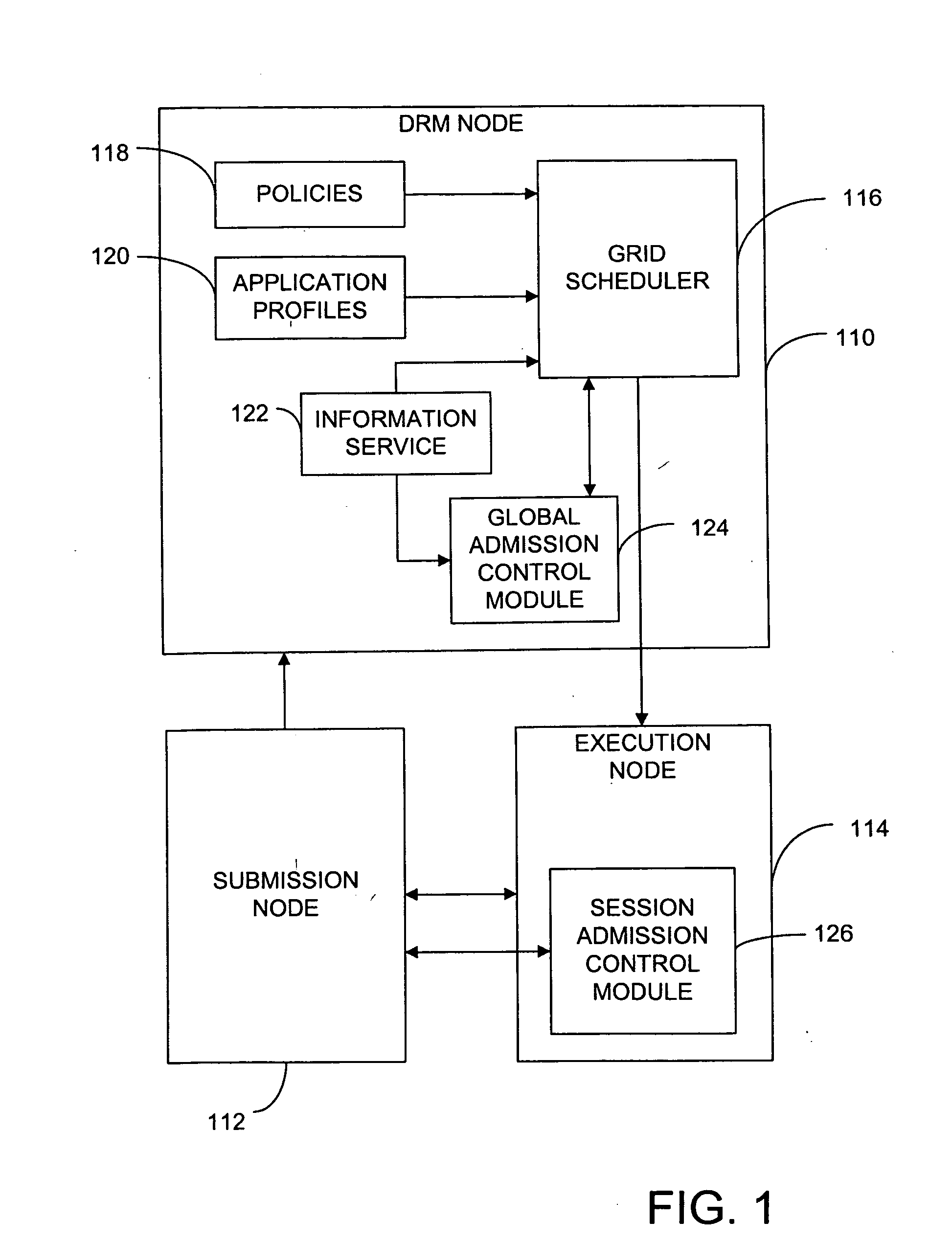
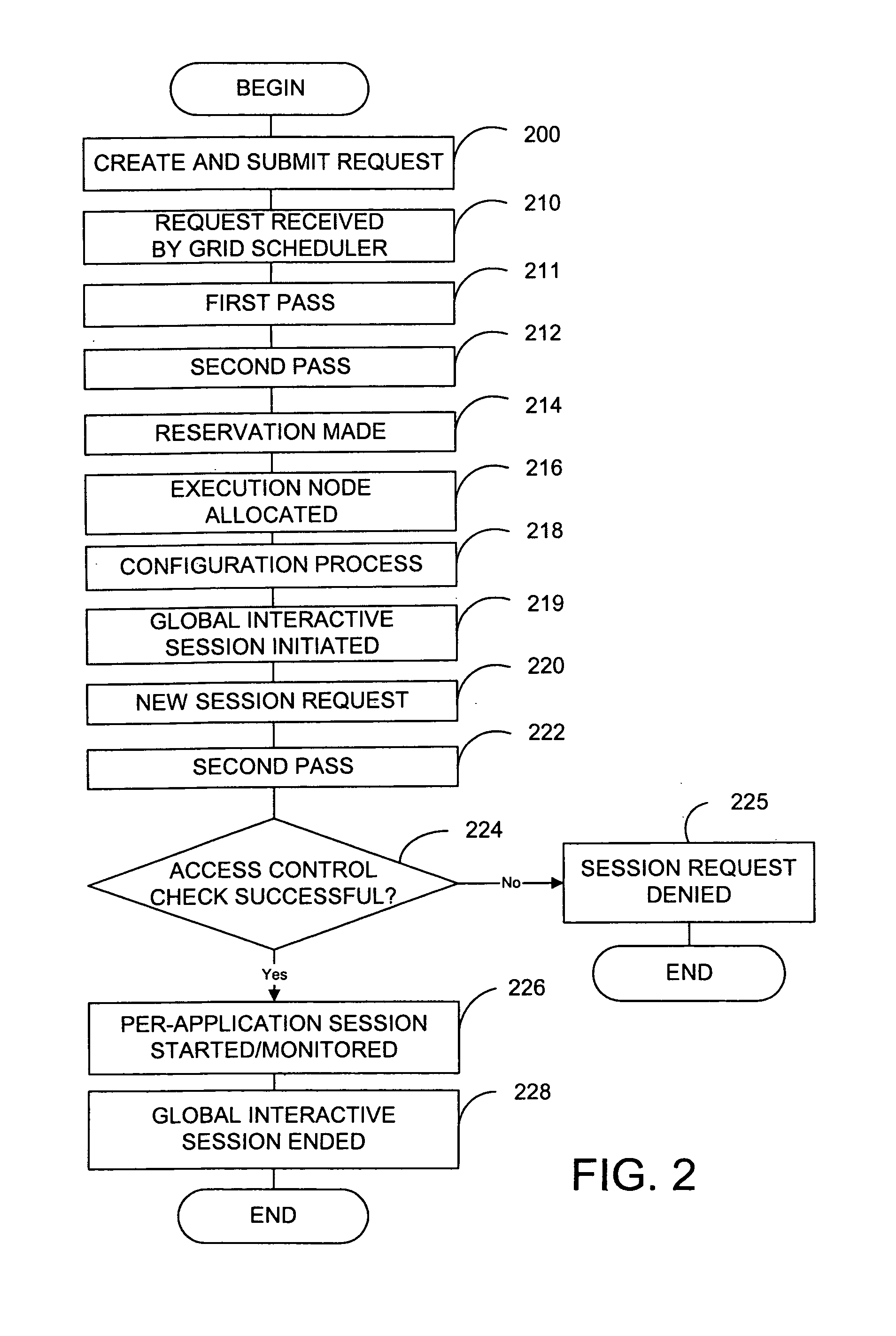
Method and system using admission control in interactive grid computing systems
In brief, the invention provides a method and system for admission control in a grid computing environment. When a user request for a global session is received from a submission node, applications to be launched through the global session are identified, and resource requirements are determined. A execution node is then allocated, and the global session is established between the execution node and the submission node. A user then requests an application session through the established global session, and the application session is established with the execution node.
Owner:HEWLETT PACKARD DEV CO LP
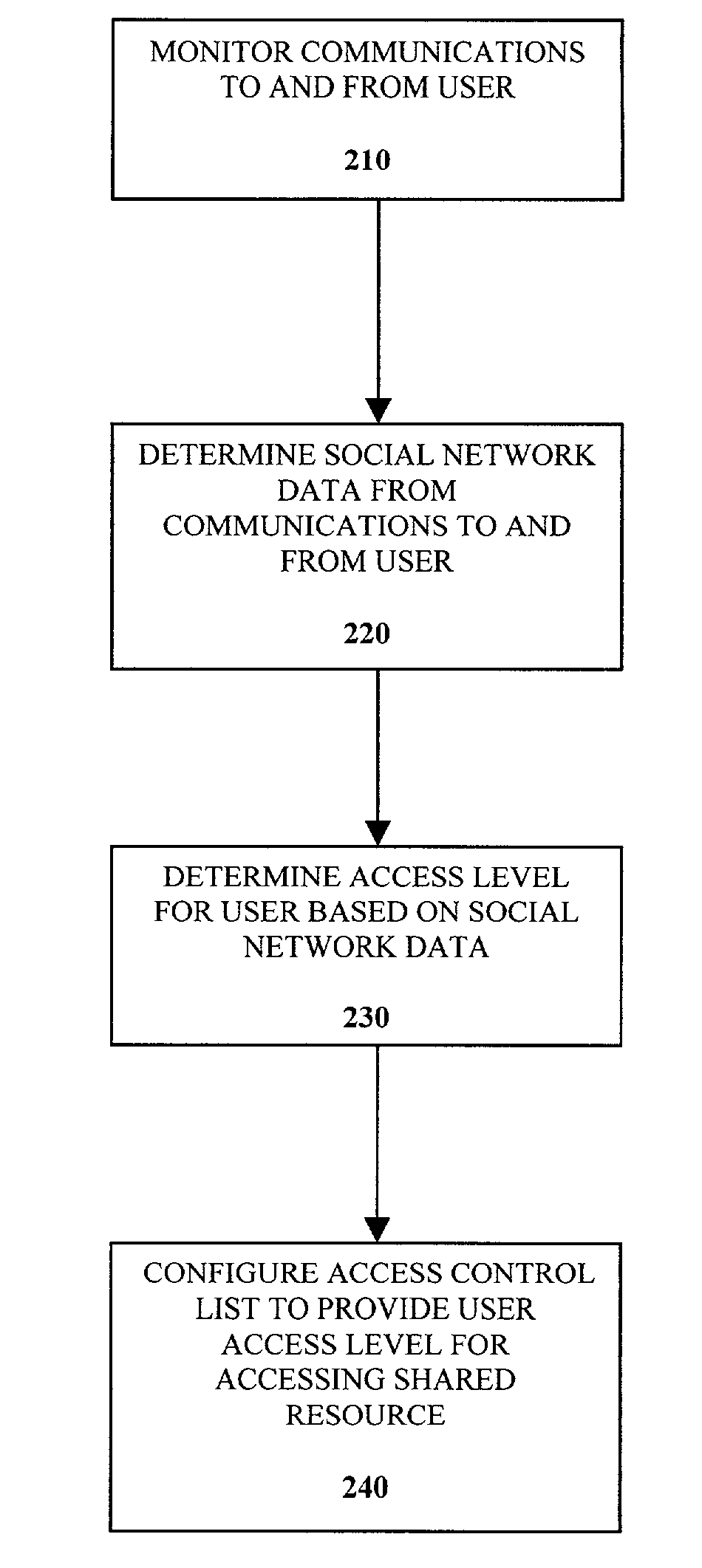
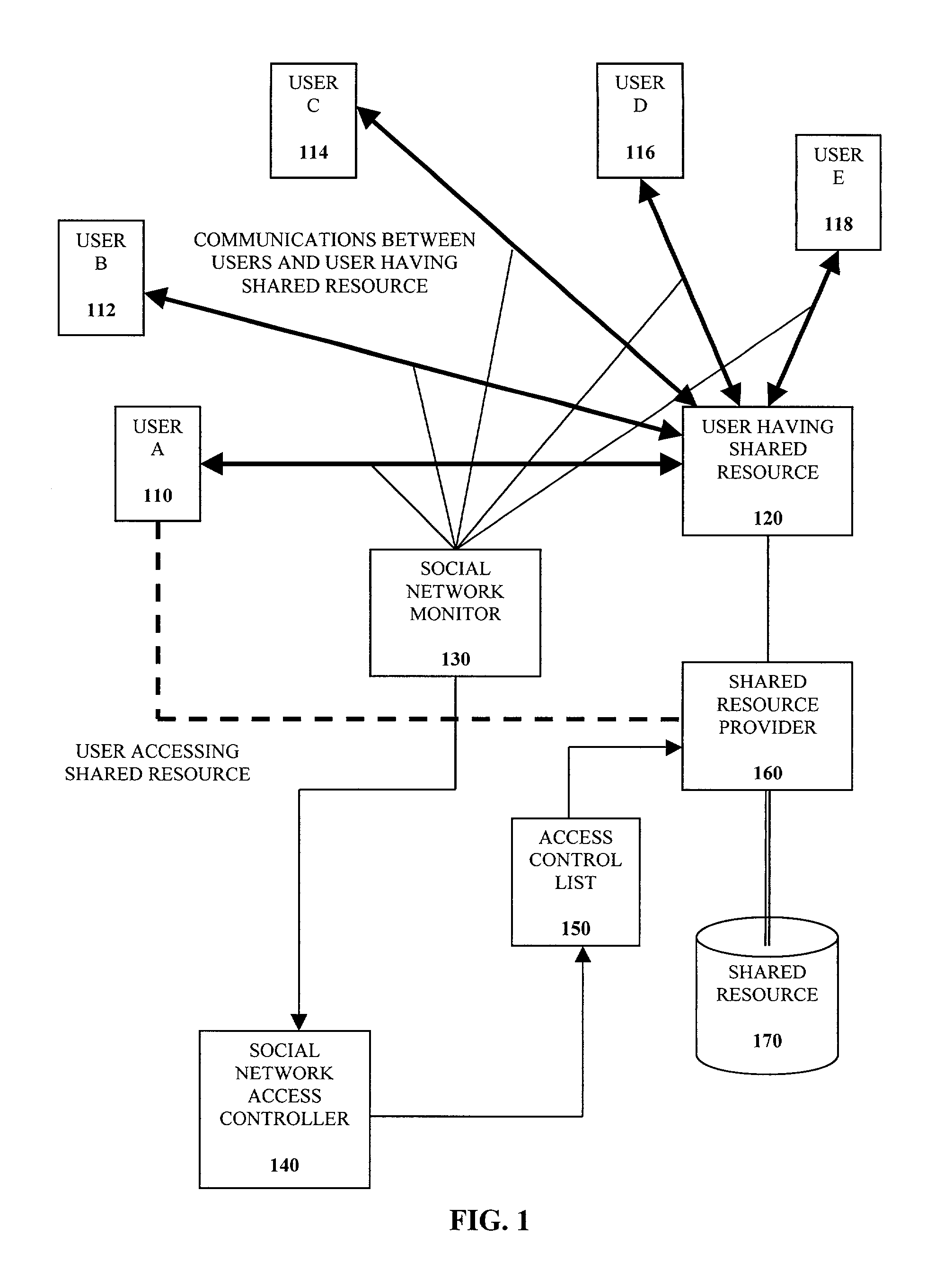
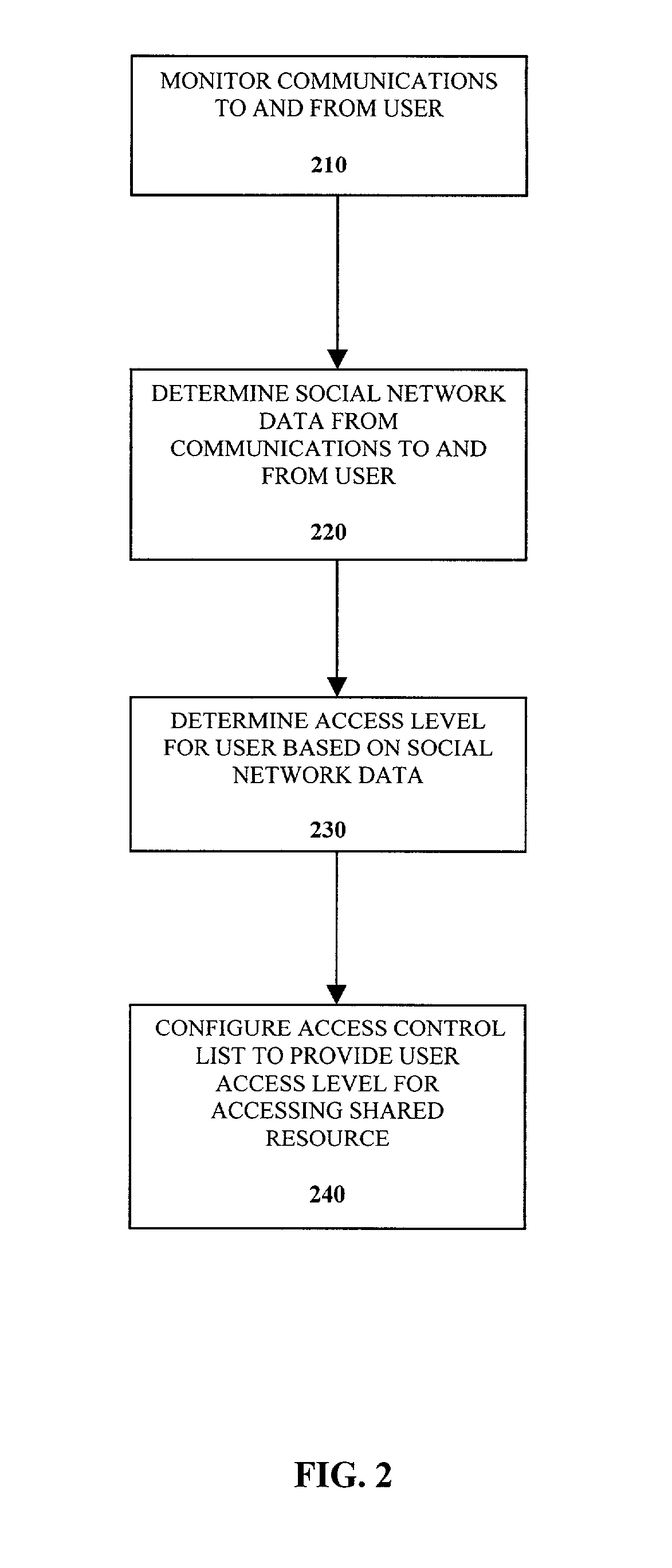
Control of access control lists based on social networks
InactiveUS7467212B2Specific access rightsDigital data processing detailsVLAN access control listSocial web
A method of controlling a social network access control list (ACL) for a shared resource includes monitoring communications to and from a user. Social network data from the communications to and from the user is determined. An access level for the user is determined based on the social network data. The access control list is configured to provide the user the access level determined for accessing the shared resource.
Owner:INTEL CORP
Method and apparatus for an improved security system mechanism in a business applications management system platform
InactiveUS20050154699A1Minimize effortSpecific access rightsDigital data processing detailsImproved methodSafe operation
Owner:SABA SOFTWARE
Methods for providing cross-vendor support services
ActiveUS8533857B2Specific access rightsDigital data processing detailsApplication programming interfaceClient-side
According to one aspect, a first request is received at a services application programming interface (API) of a support center from a first user for a first product provided by a first client. A second request is received at the services API of the support center from a second user for a second product provided by a second client. A first knowledgebase (KB) associated with the first client and a second KB associated with the second client are identified. A third KB that contains information common to the first product and the second product is identified. The first KB and the third KB are enabled to be accessible by a first agent assigned to provide support services of the first product. The second KB and the third KB are enabled to be accessible by a second agent assigned to provide support services of the second product.
Owner:TELETECH HLDG
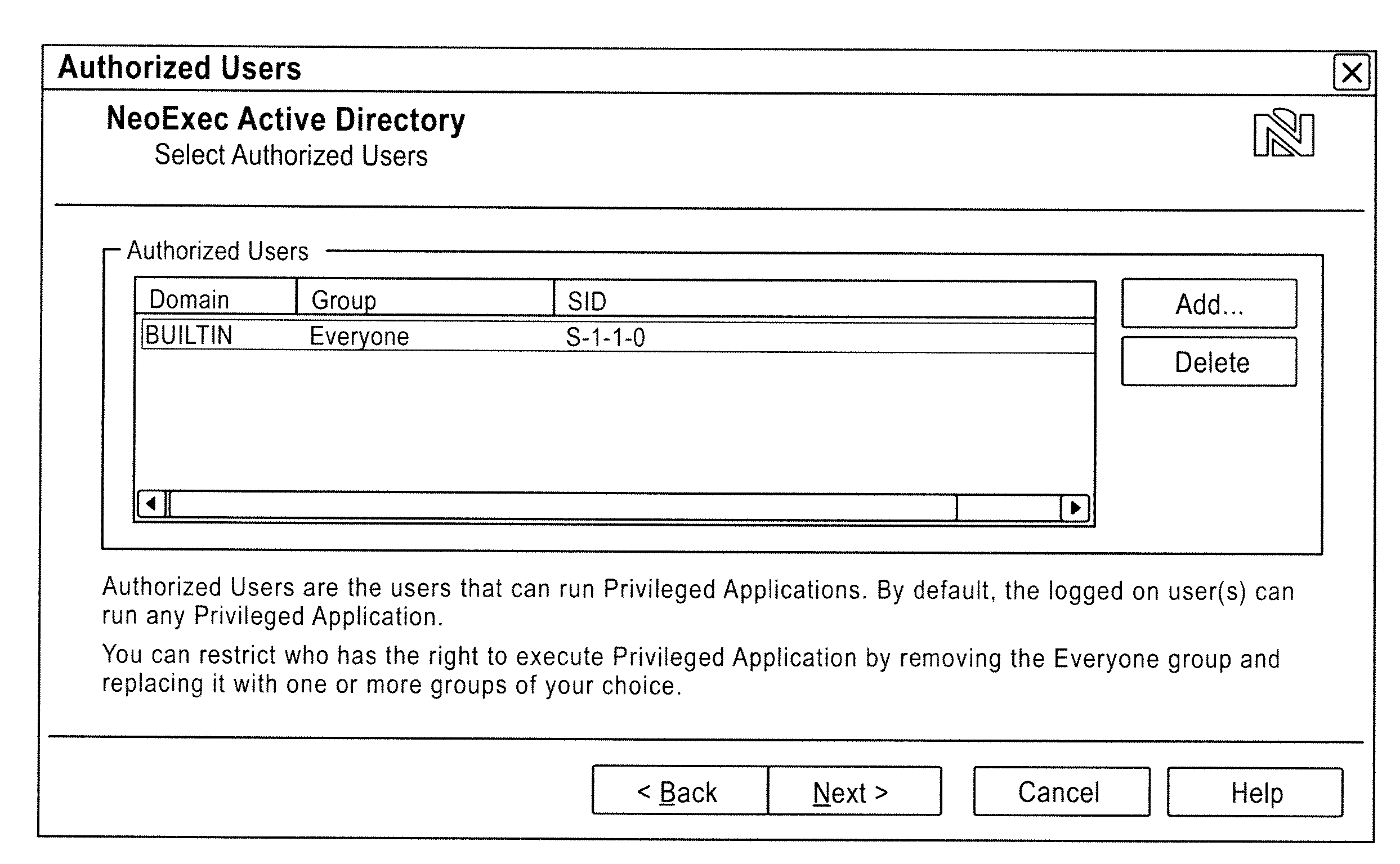
Methods and Systems for Controlling Access to Resources and Privileges Per Process
ActiveUS20110030045A1Specific access rightsDigital data processing detailsGroup PolicyWorld Wide Web
To control privileges and access to resources on a per-process basis, an administrator creates a rule that may be applied to modify a token of a process. The rule may include an application-criterion set and changes to be made to the groups and / or privileges of the token. The rule may be set as a policy within a group policy object (GPO), where a GPO is associated with one or more groups of computers or users. When a GPO containing a rule is applied to a computer, a driver installed on the computer may access the rule(s) anytime a logged-on user executes a process. If the executed process satisfies the criterion set of a rule, the changes contained within the rule are made to the process token, and the user has expanded and / or contracted access and / or privileges for only that process.
Owner:BEYONDTRUST SOFTWARE INC
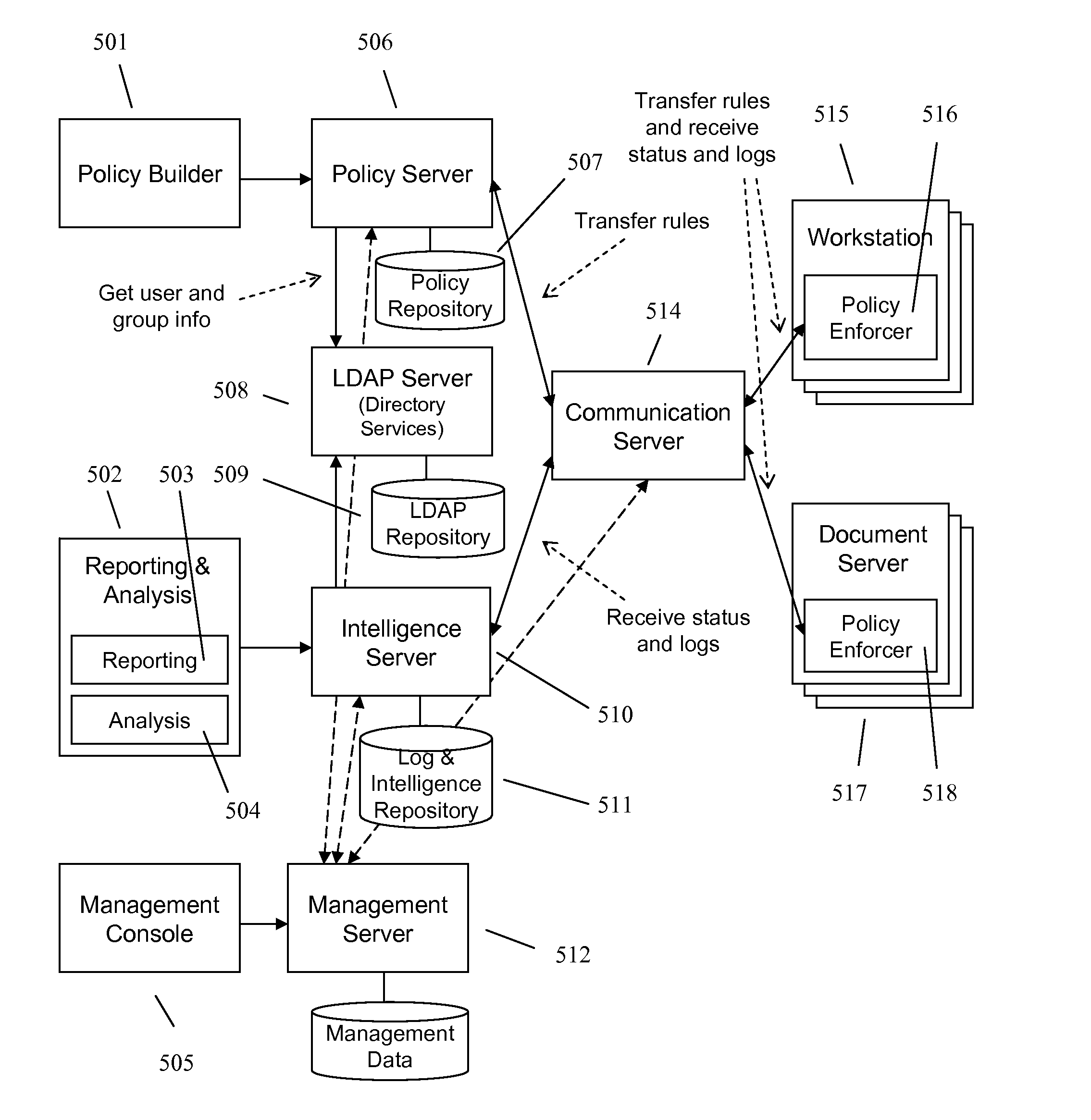
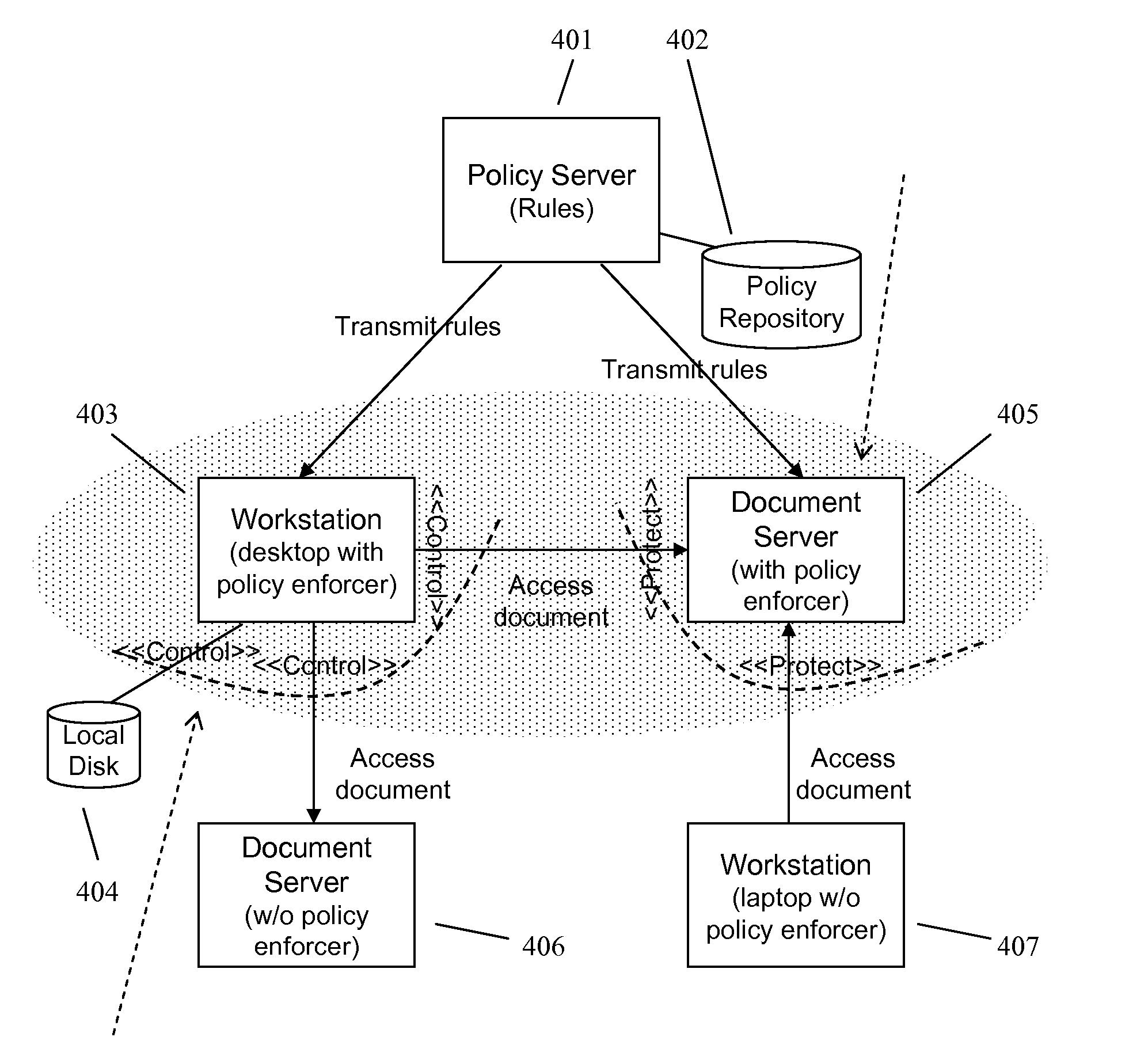
Information Management System with Two or More Interactive Enforcement Points
ActiveUS20070157203A1Specific access rightsComputer security arrangementsClient-sideCentralized management
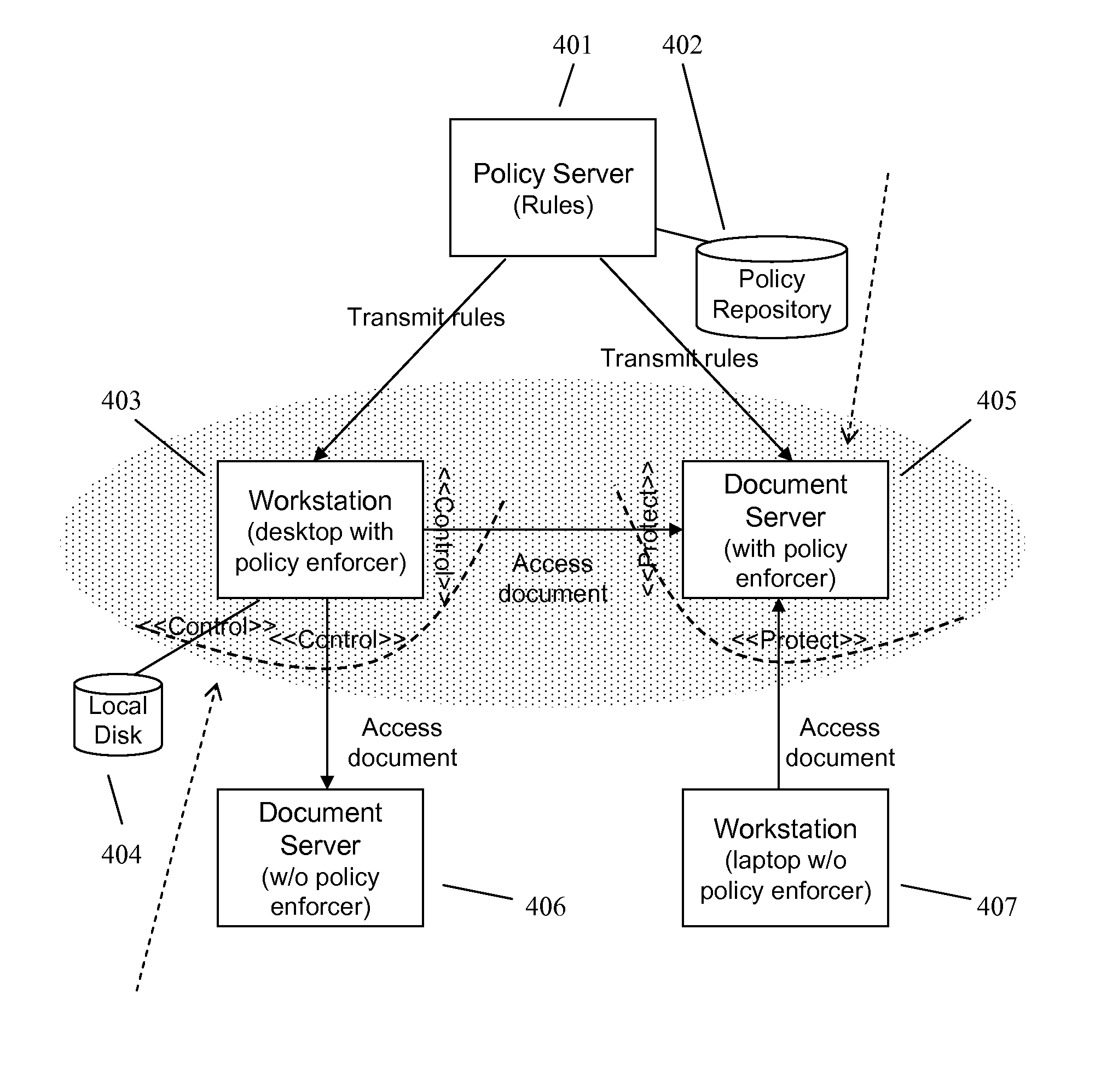
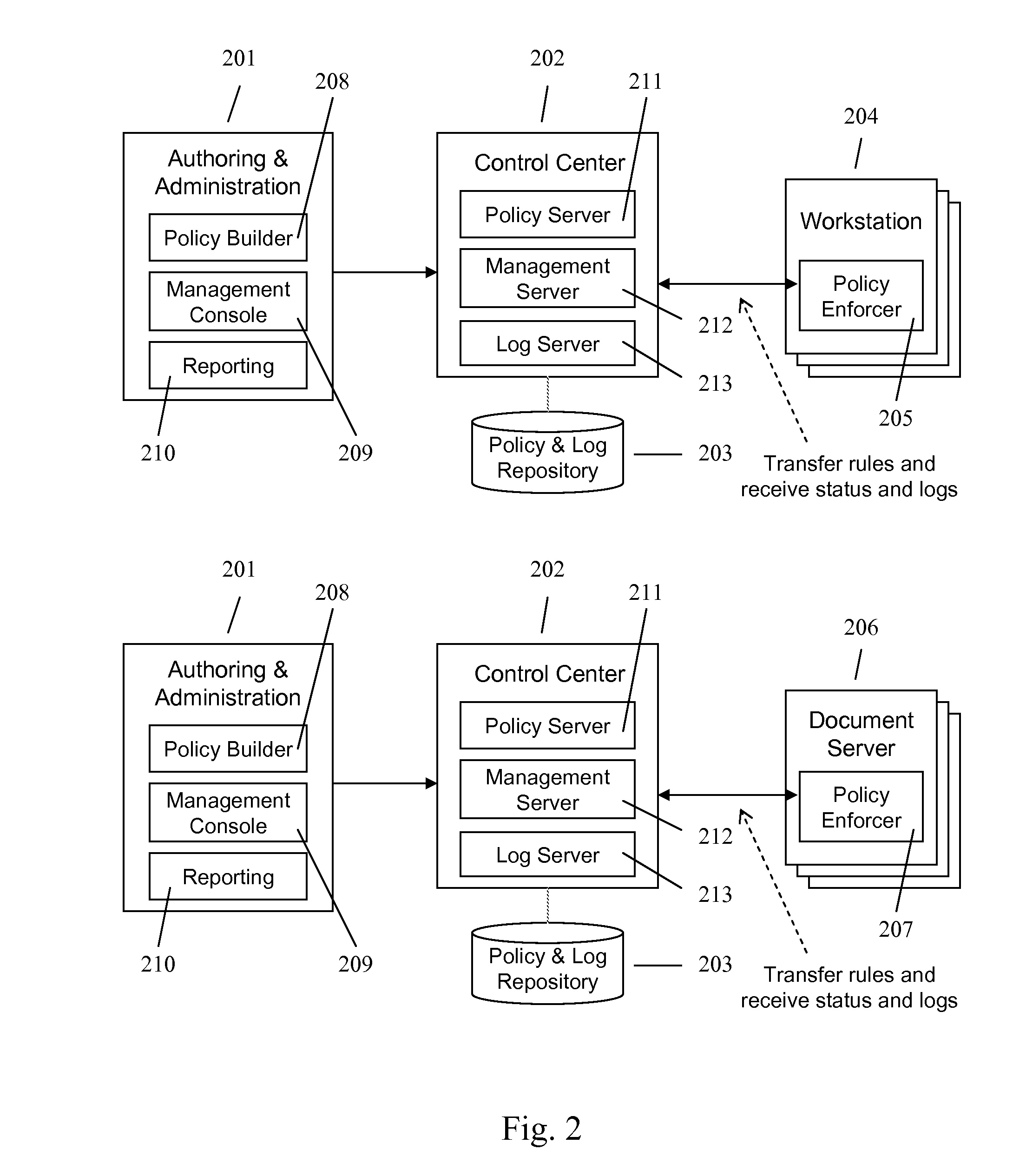
A method and apparatus for controlling document access and application usage using centrally managed rules. The rules are stored and manipulated in a central rule database via a rule server. Policy enforcers are installed on client systems and / or on servers and perform document access and application usage control for both direct user document accesses and application usage, and application program document accesses by evaluating the rules sent to the policy enforcer. The rule server decides which rules are required by each policy enforcer. A policy enforcer can also perform obligation and remediation operations as a part of rule evaluation. Policy enforcers on client systems and servers can operate autonomously, evaluating policies that have been received, when communications have been discontinued with the rule server.
Owner:BLUE JUNGLE
Method and apparatus for authenticating an open system application to a portable IC device
InactiveUS20060036851A1Specific access rightsUser identity/authority verificationSecure communicationApplication software
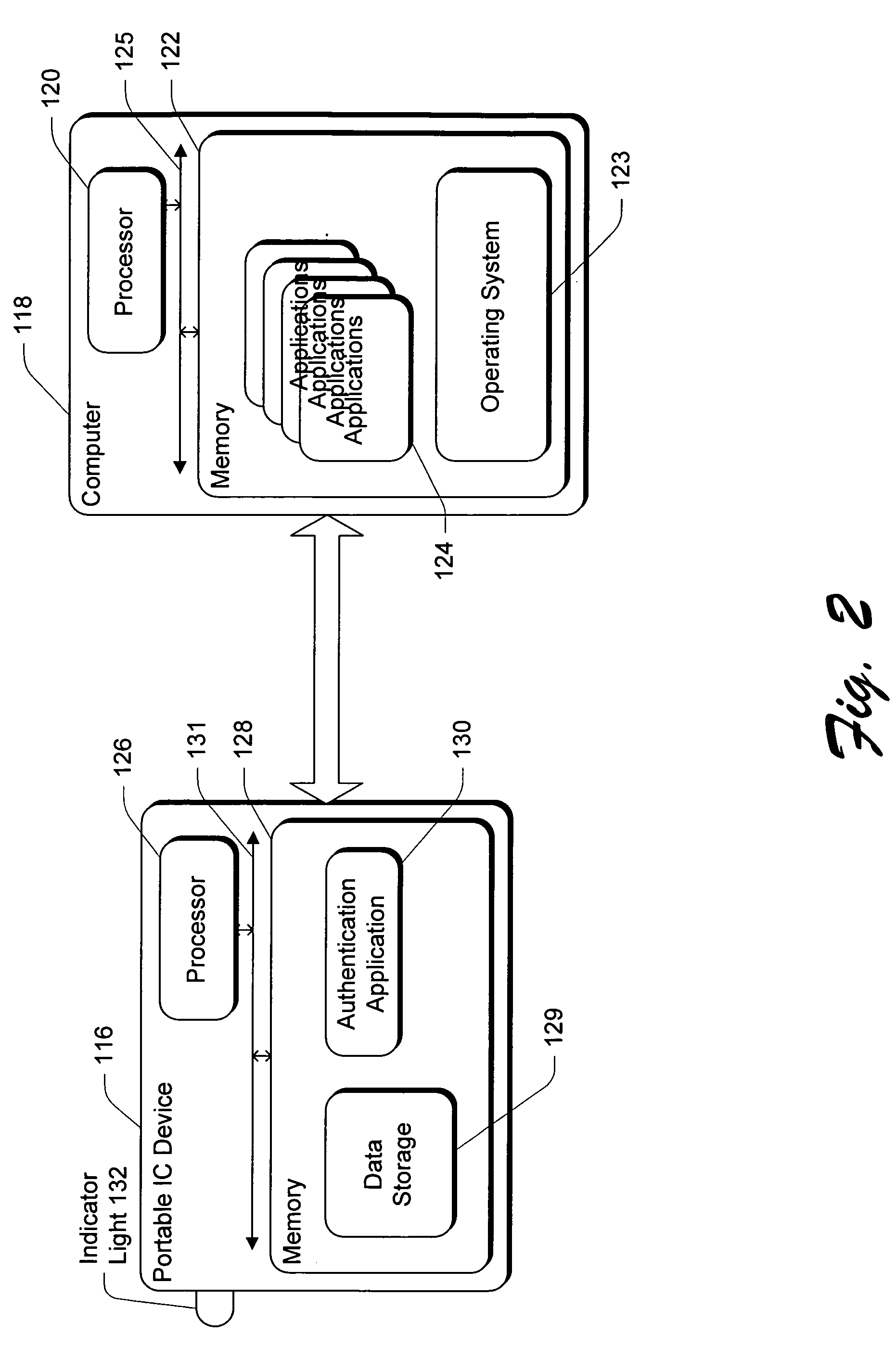
A secure communication channel between an open system and a portable IC device is established. An application running on the open system desiring access to the information on the portable IC device authenticates itself to the portable IC device, proving that it is trustworthy. Once such trustworthiness is proven, the portable IC device authenticates itself to the application. Once such two-way authentication has been completed, trusted communication between the open system and the portable IC device can proceed, and private information that is maintained on the portable IC device can be unlocked and made available to the application.
Owner:MICROSOFT TECH LICENSING LLC
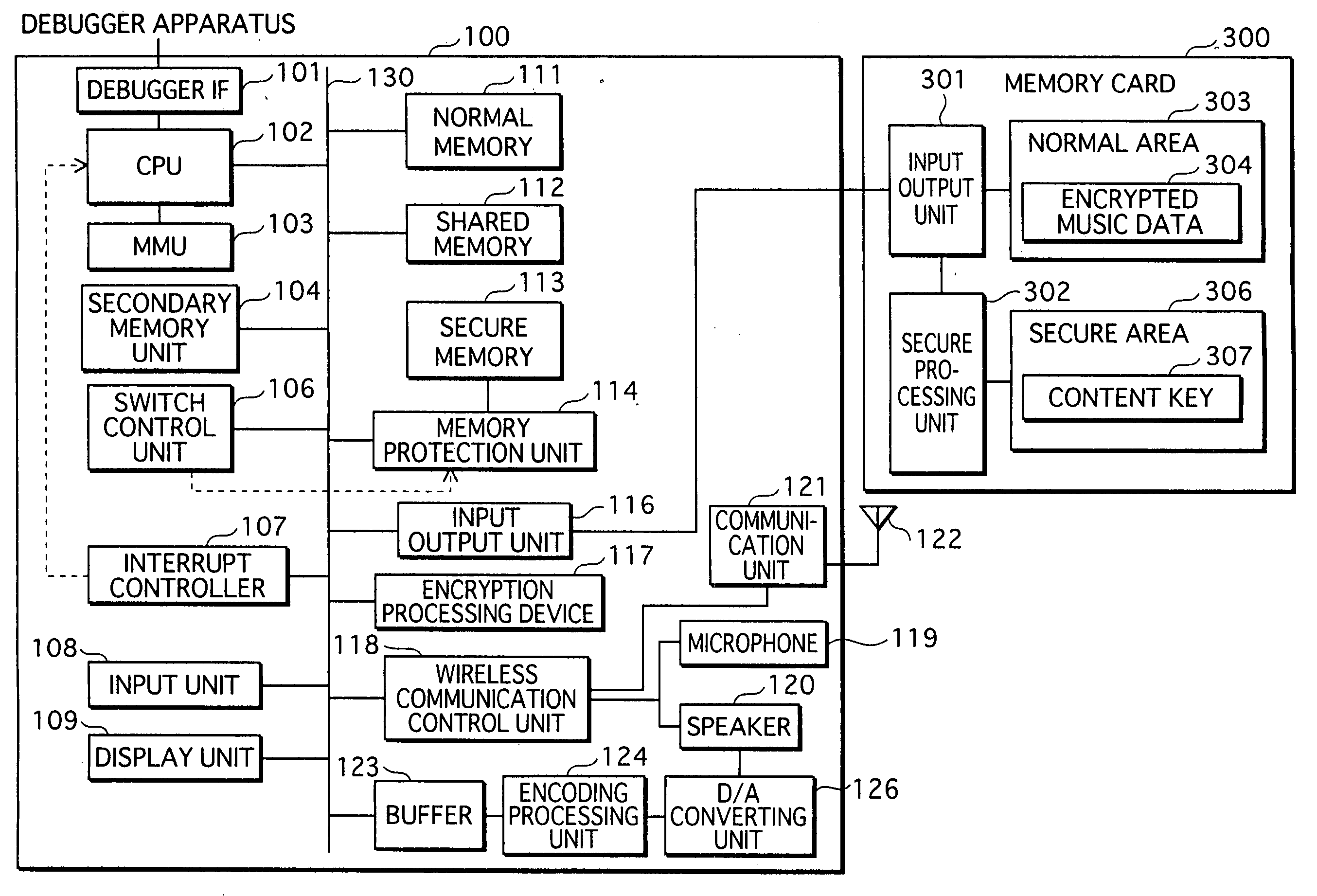
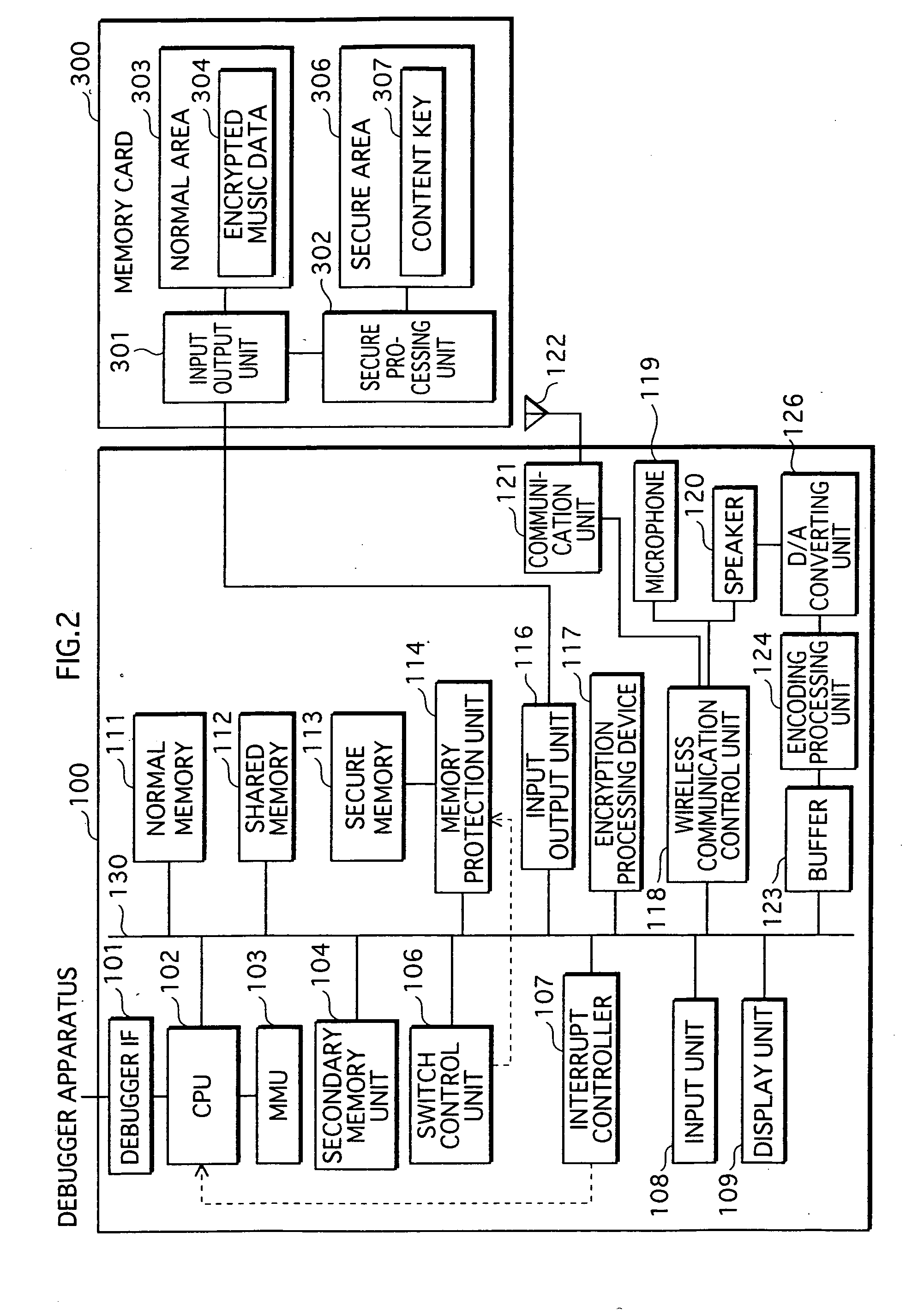
Data processing apparatus
ActiveUS20070113079A1Reduce memorySmall sizeSpecific access rightsProgram initiation/switchingComputer hardwareProtection mechanism
In a data processing apparatus that switches between a secure mode and a normal mode during execution, the secure mode allowing access to secure resources to be protected, the normal mode not allowing access to the secure resources, when the secure resources increase in the secure mode, the load on a protection mechanism for protecting the resources becomes large. Thus, there is a demand for data processing apparatuses that are able to reduce secure resources. The present invention relates to a data processing apparatus that stores therein a secure program including one or more processing procedures which use secure resources and a call instruction for calling a normal program to be executed in a normal mode. While executing the secure program, the data processing apparatus calls the normal program with the call instruction and operates according to the called normal program.
Owner:SK HYNIX INC
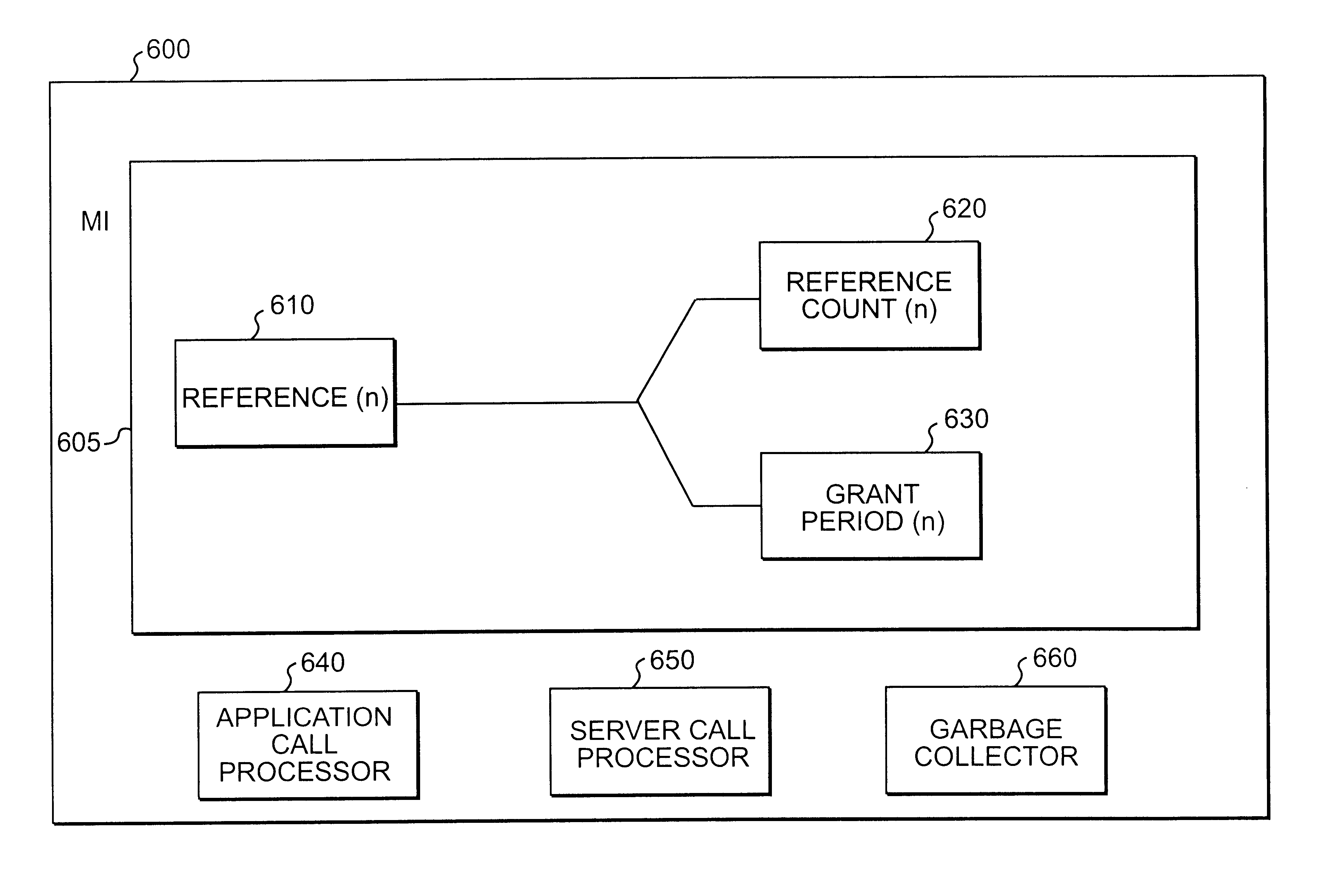
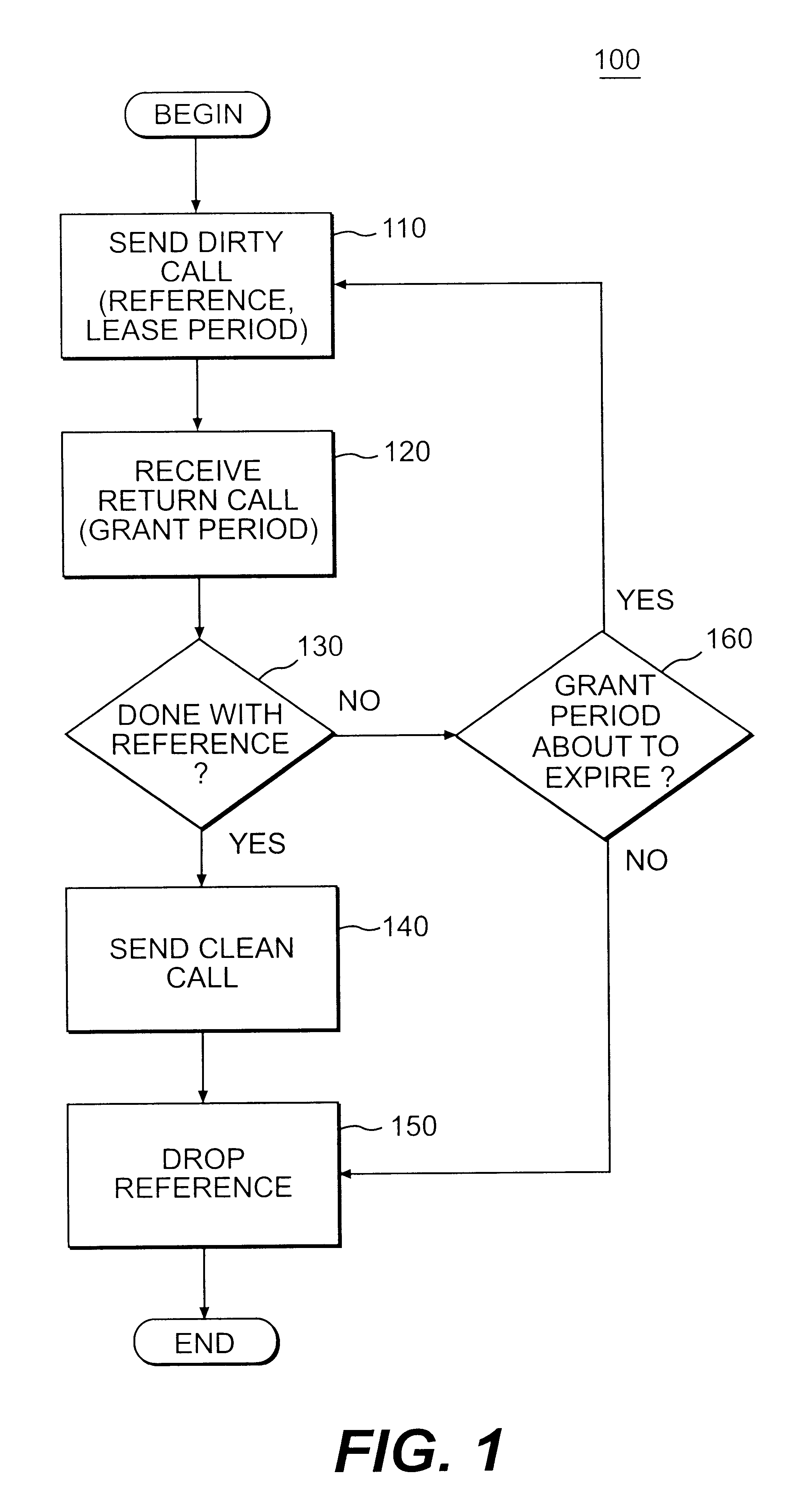
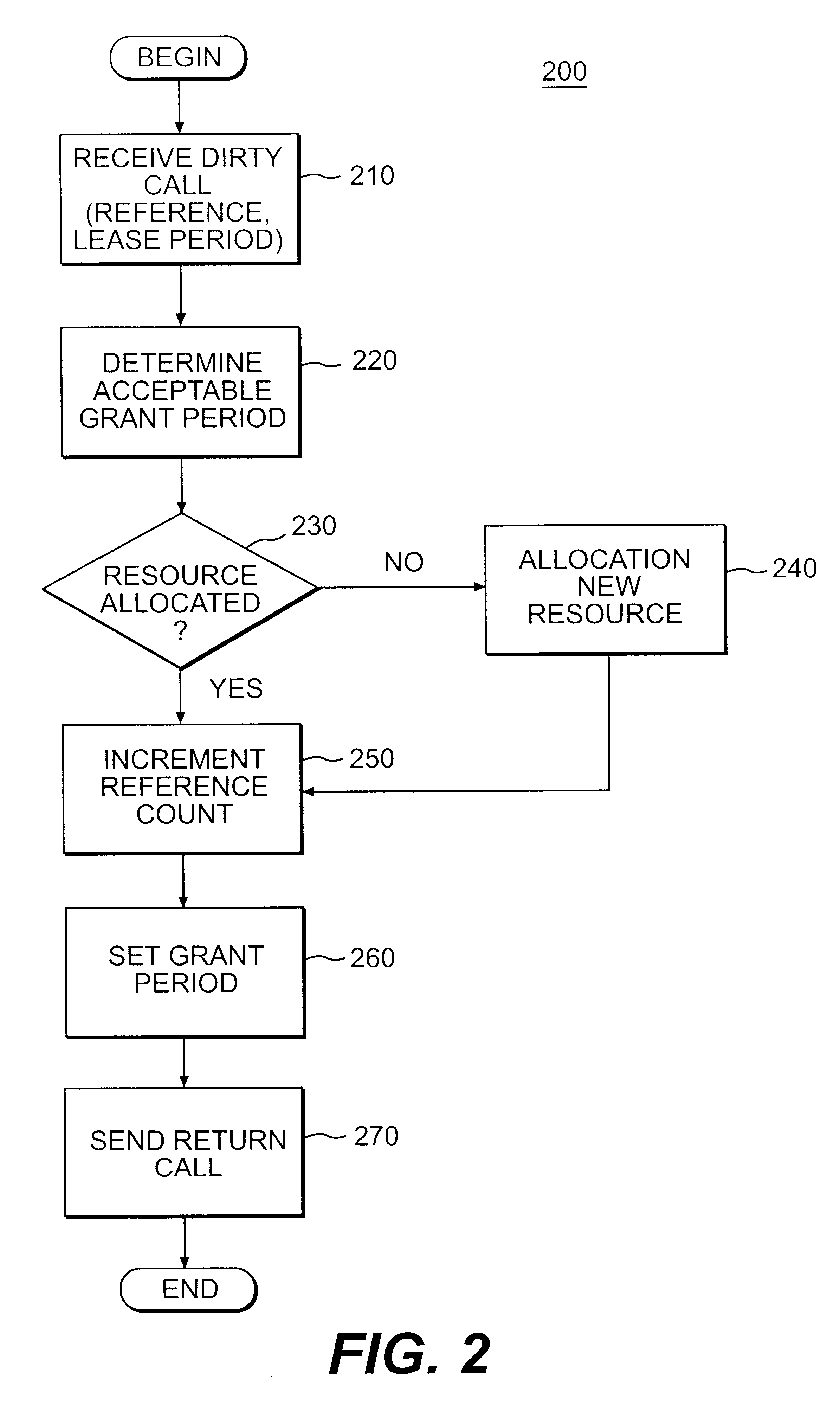
Method, apparatus, and product for leasing of delegation certificates in a distributed system
InactiveUS6247026B1Specific access rightsData processing applicationsHandling systemComputer science
A method, apparatus, and product for leasing a delegation certificate in a distributed processing system is provided. Consistent with this method, apparatus, and product, a delegatee requests from a delegator access to a resource for a period of time that the delegator has authority to access. Responsive to this request, the delegator determines an appropriate lease period during which time the delegatee has authority to access to the resource.
Owner:SUN MICROSYSTEMS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com