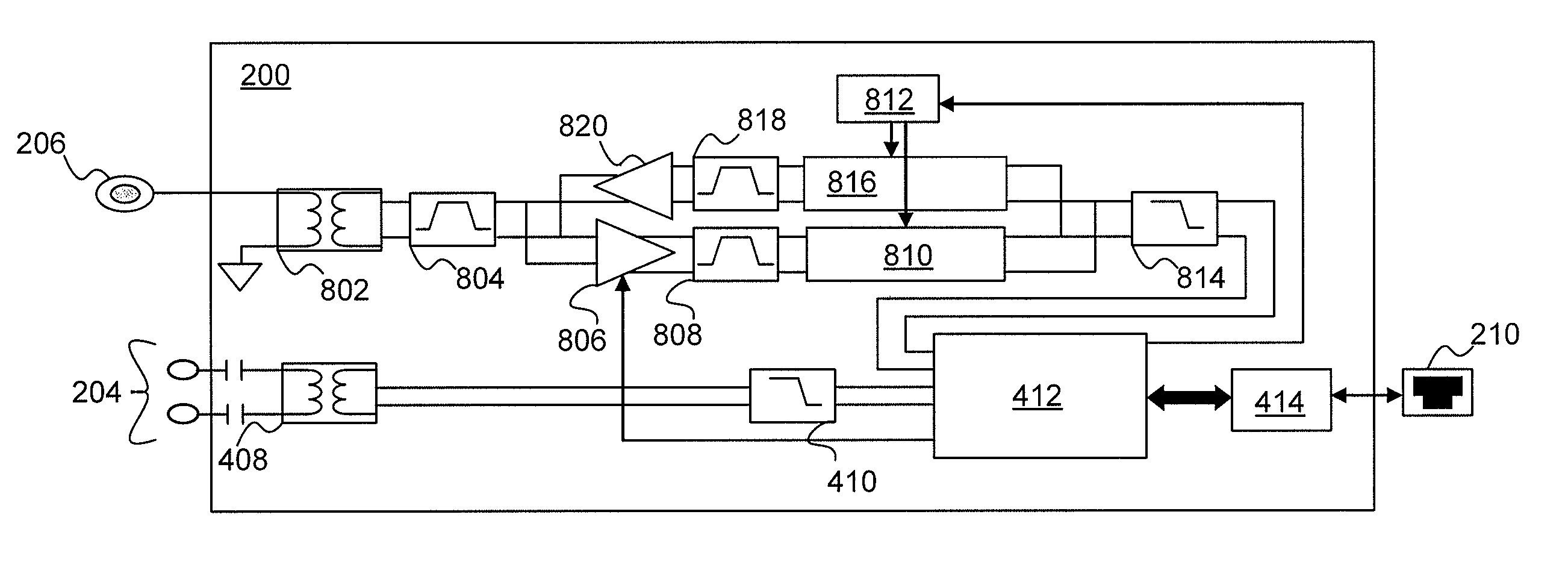
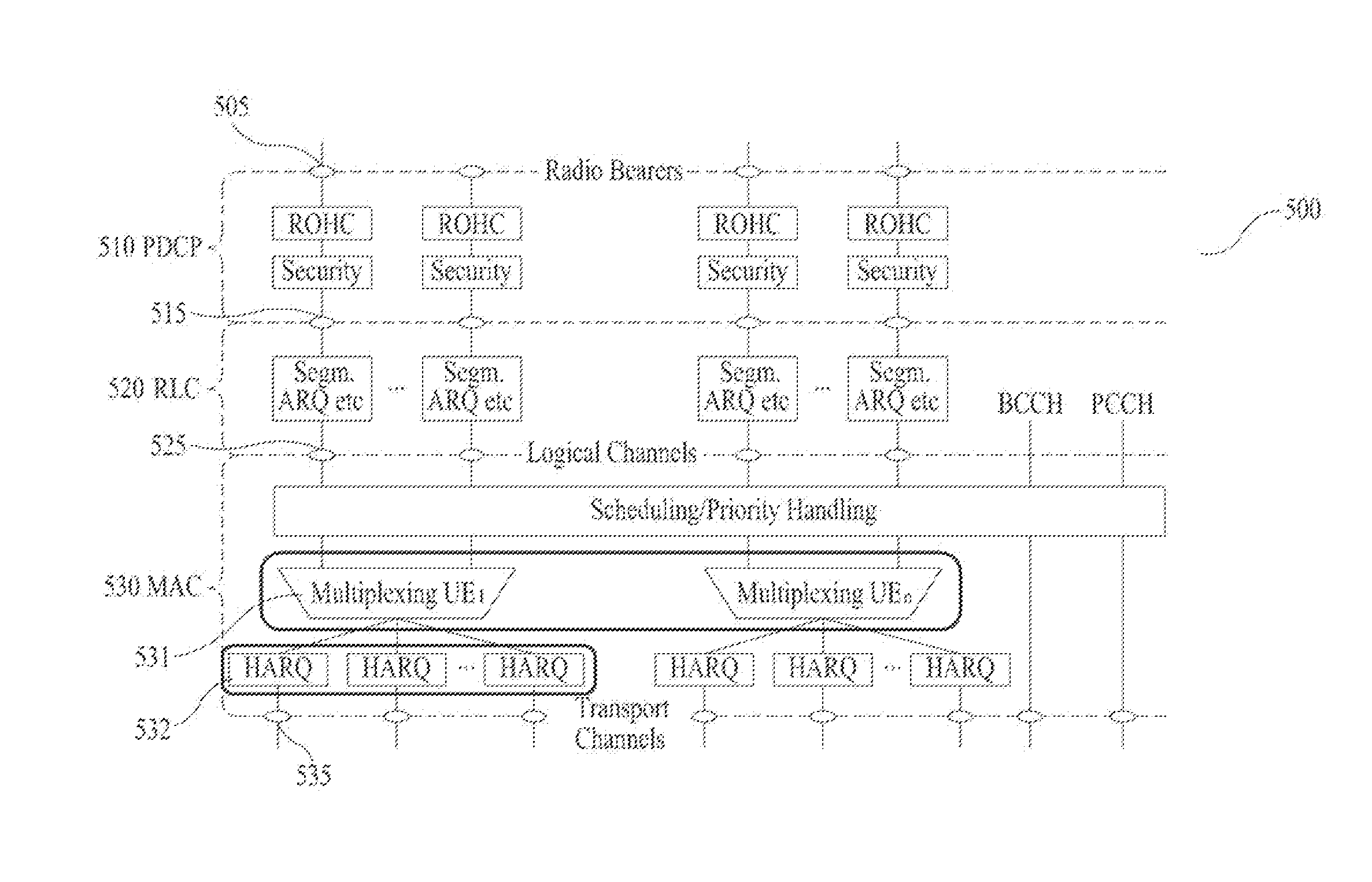
Patents
Literature
8914 results about "Media access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
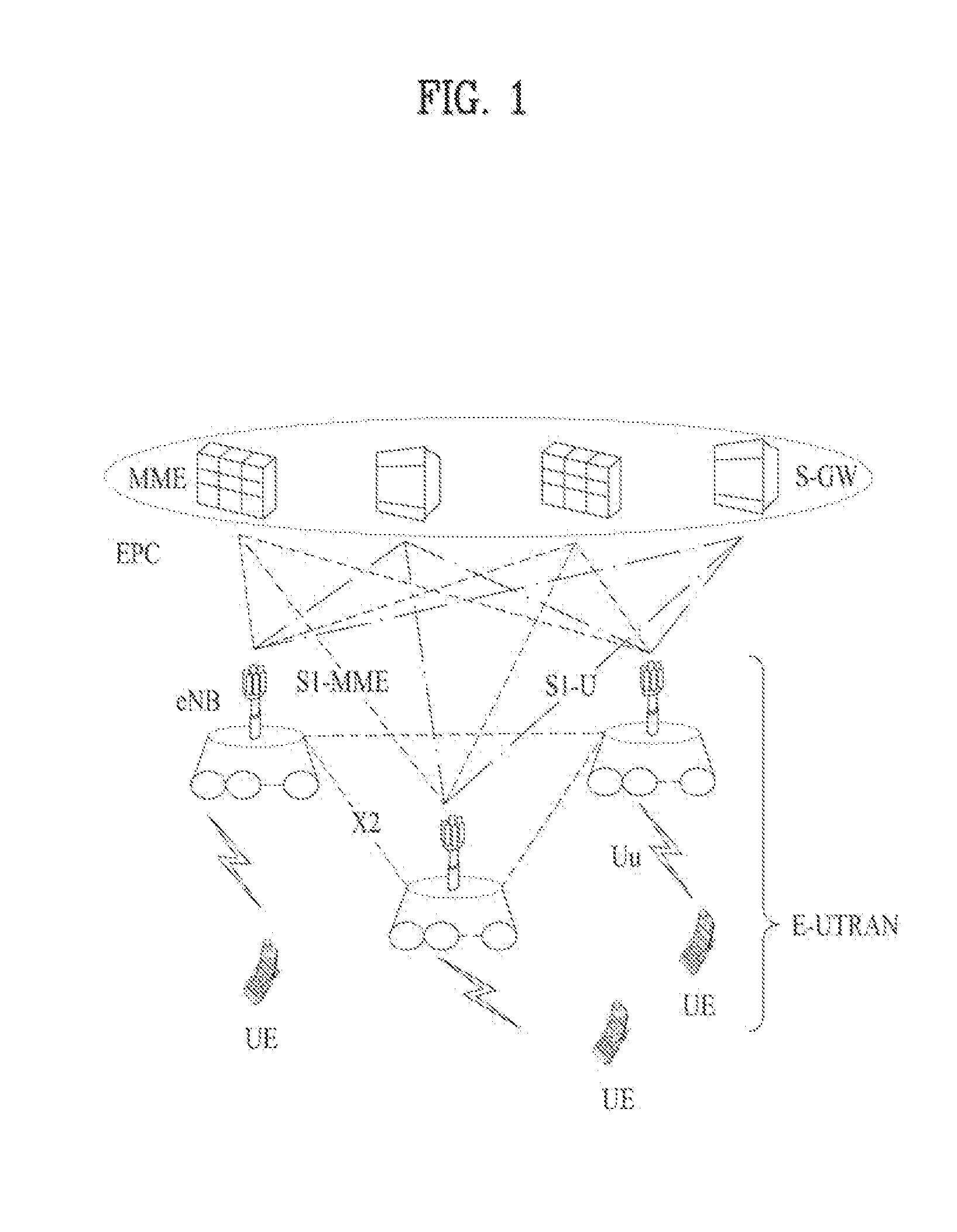
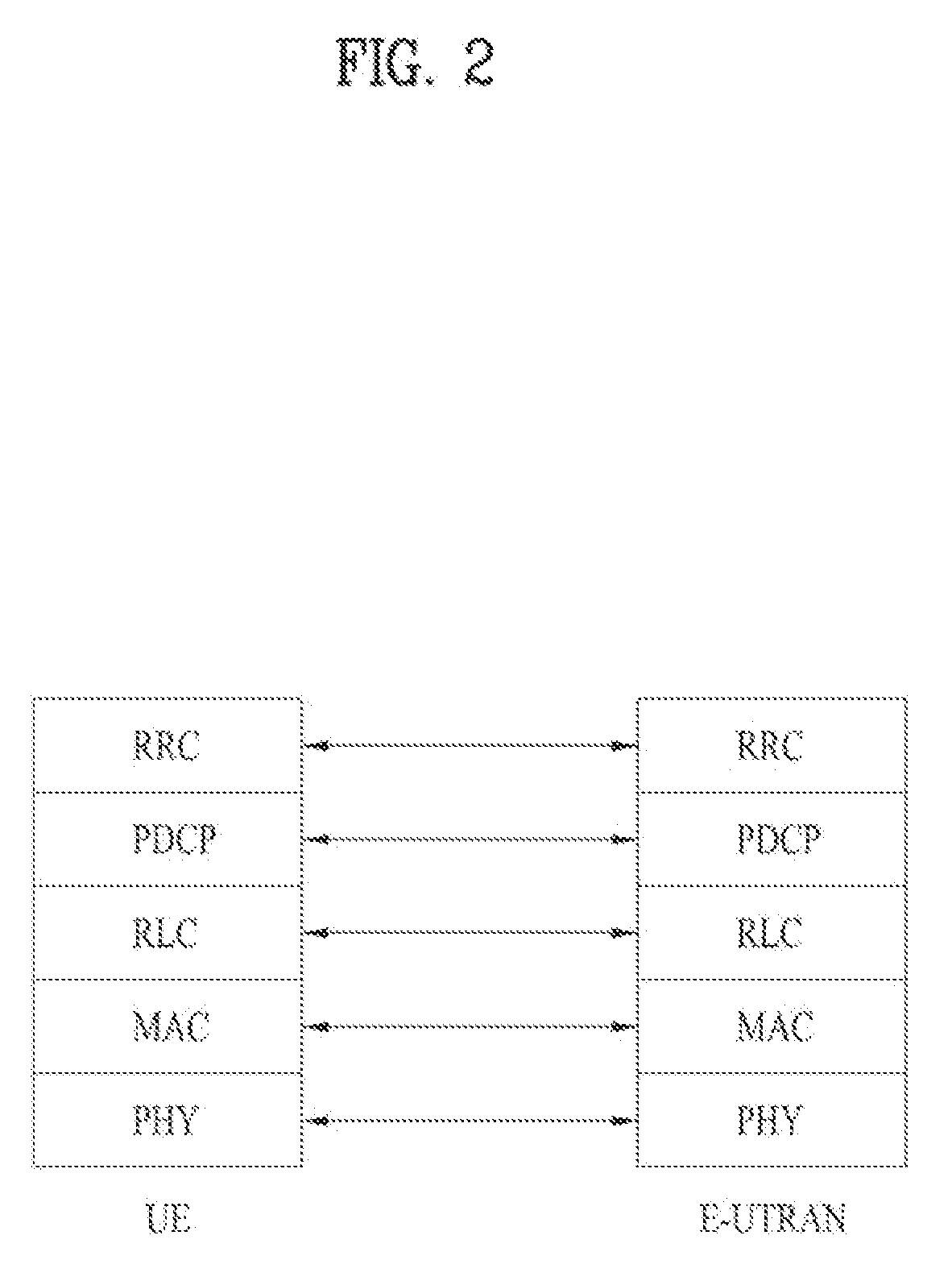
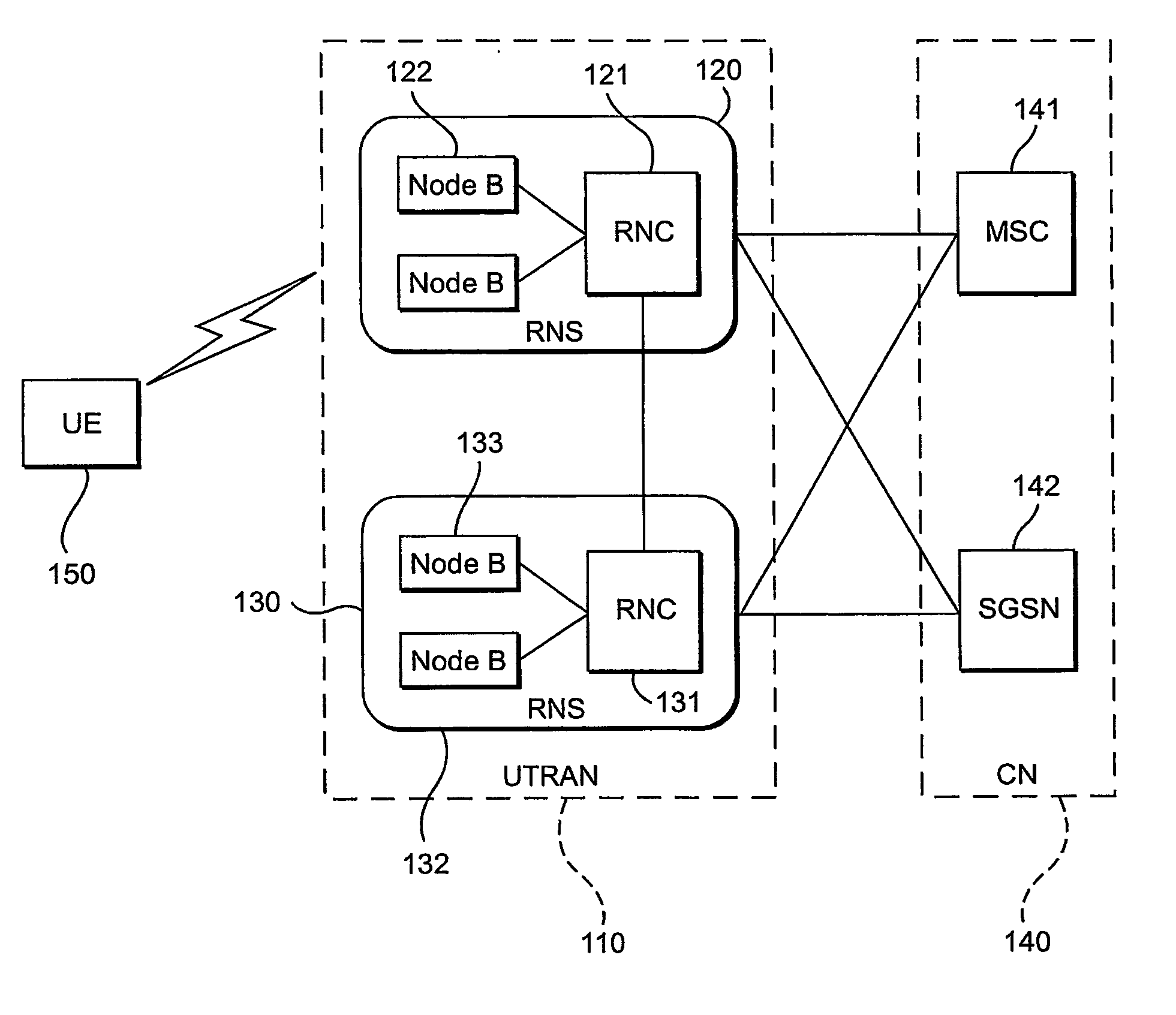
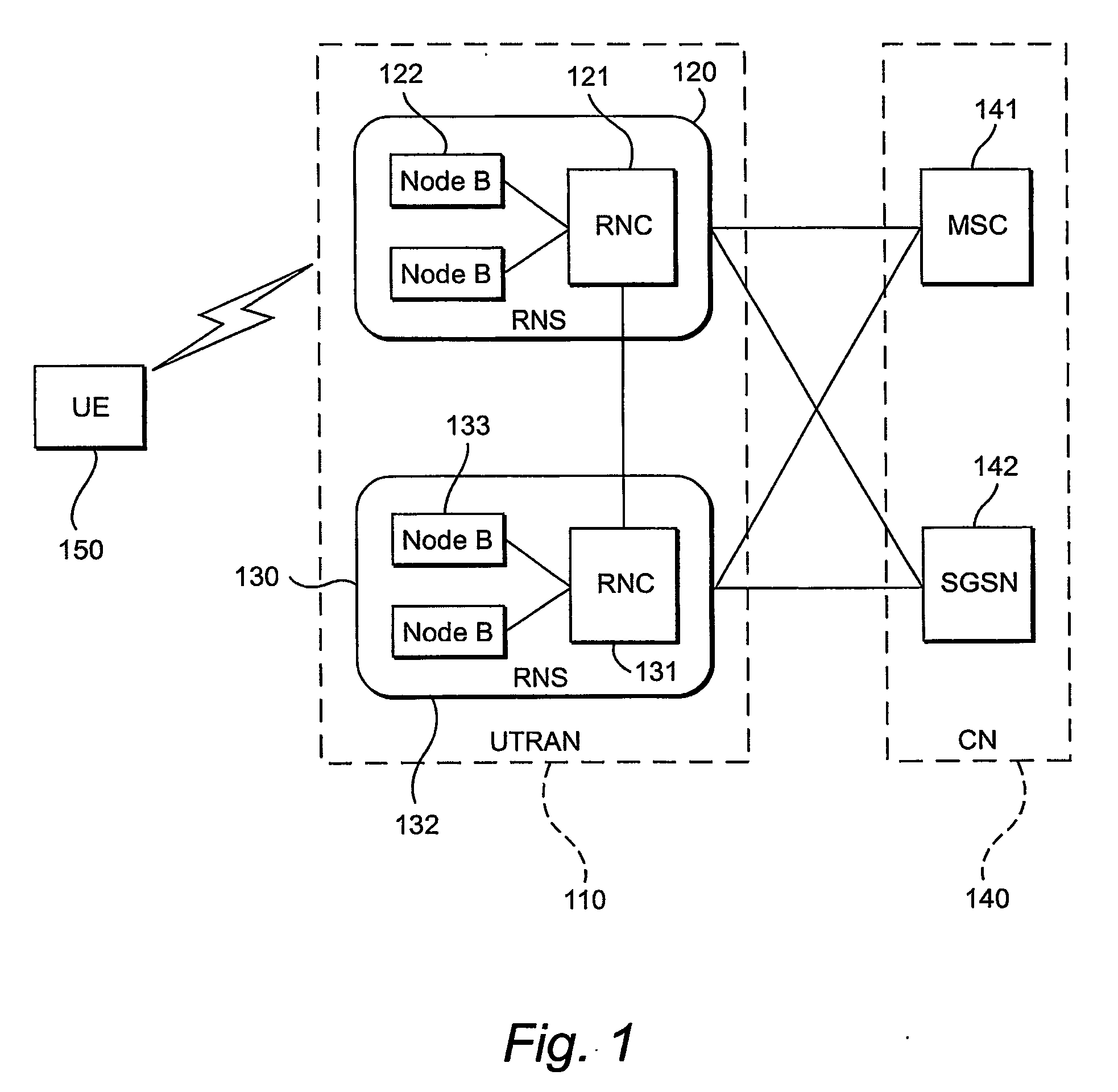
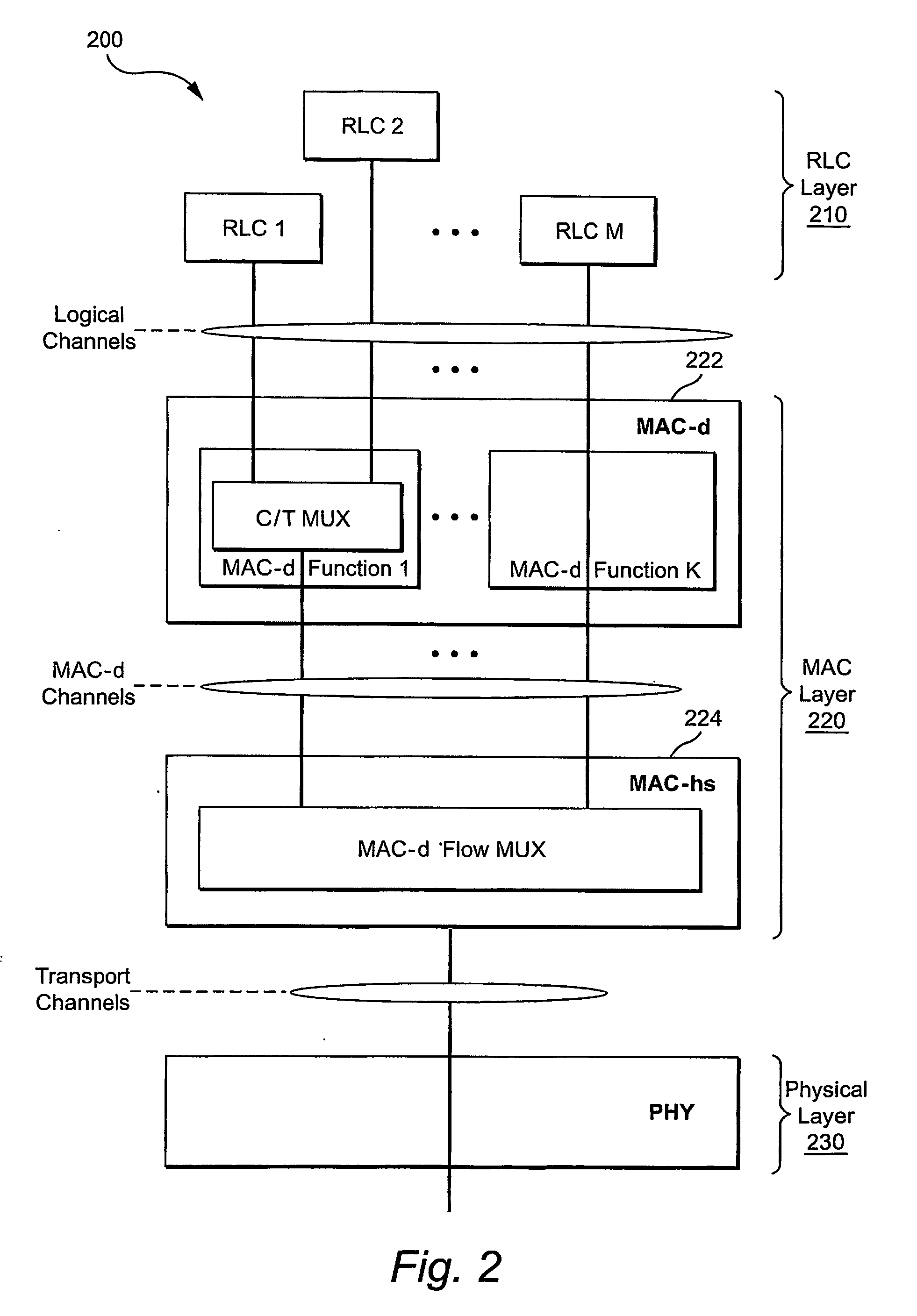
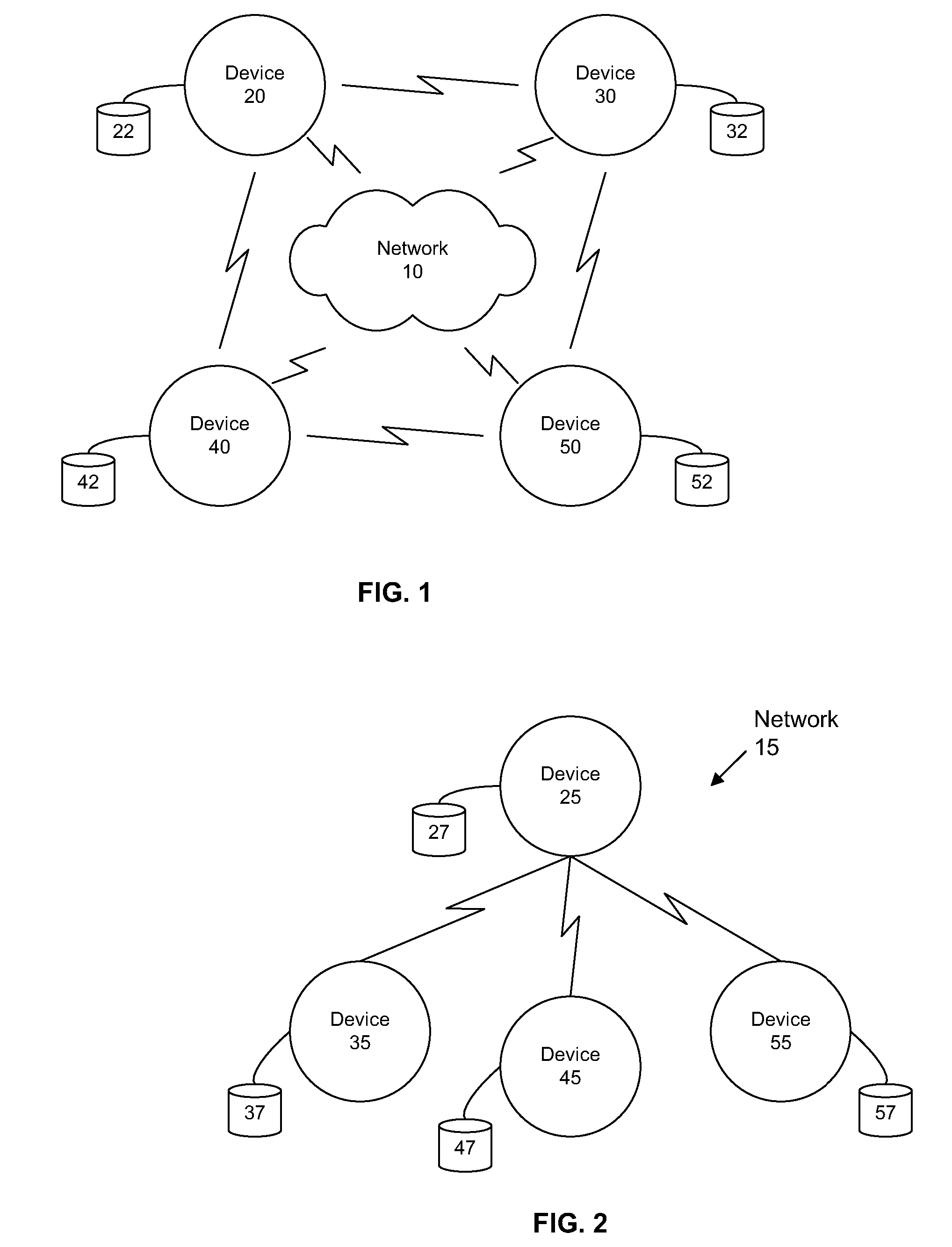
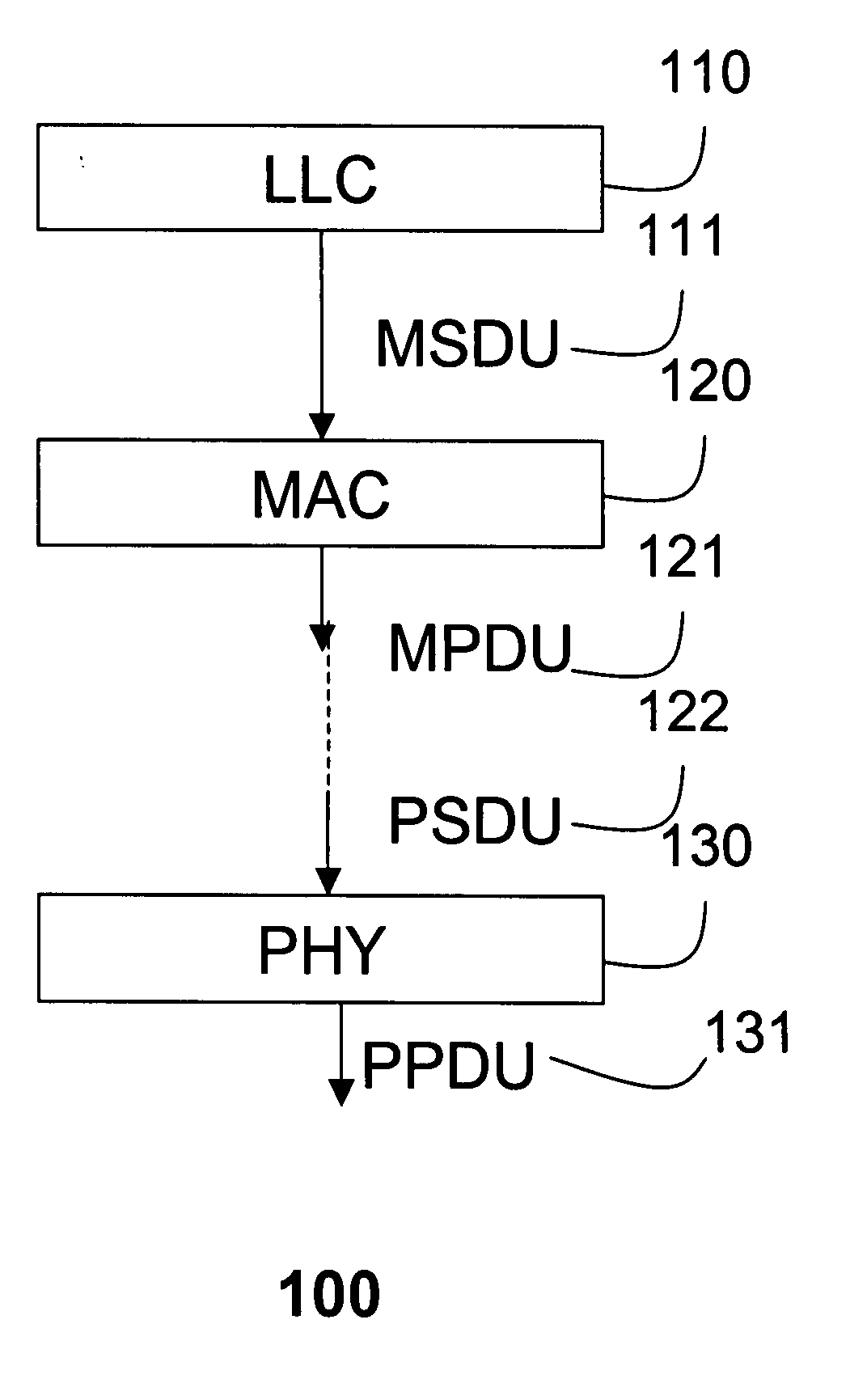
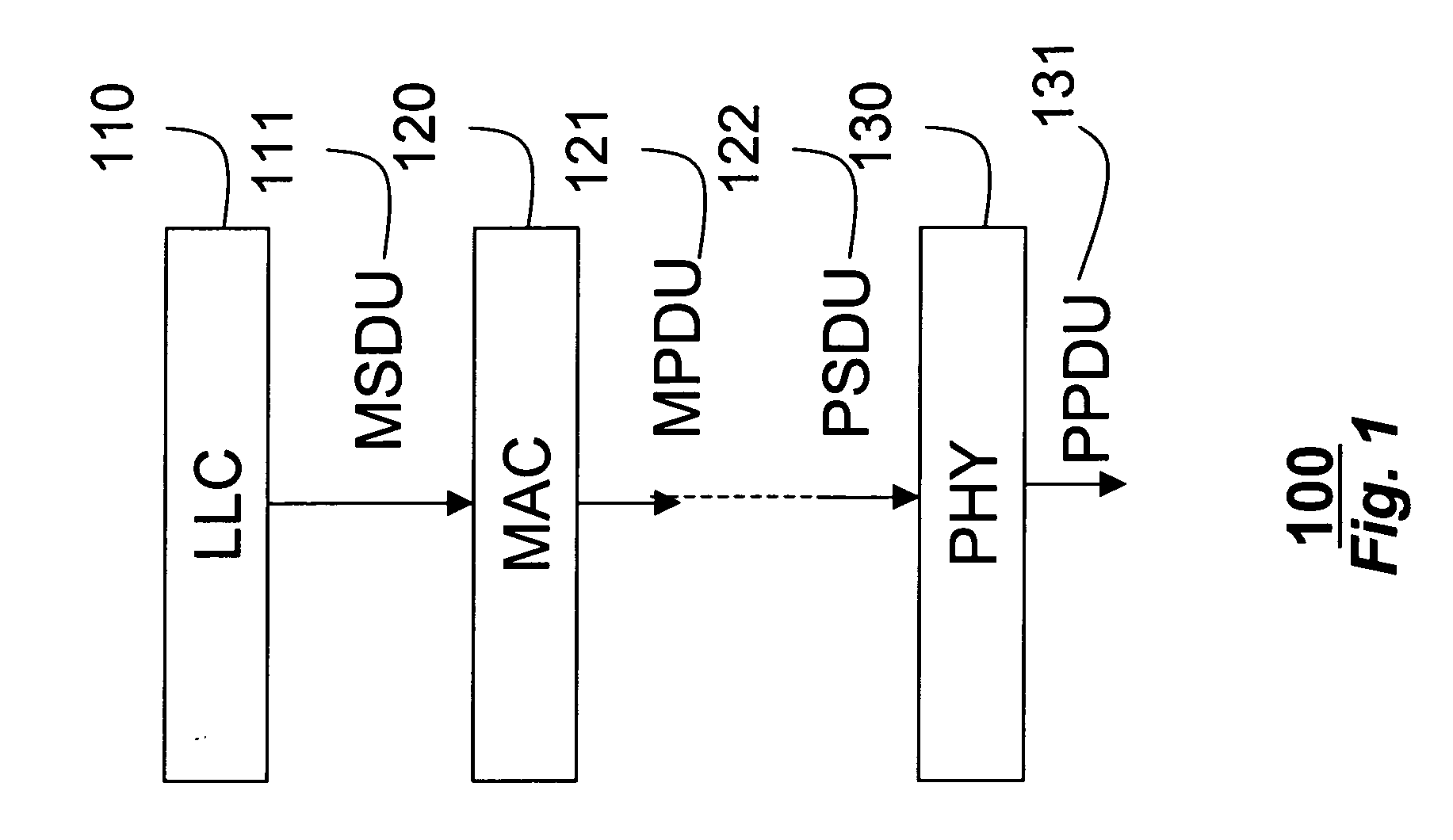
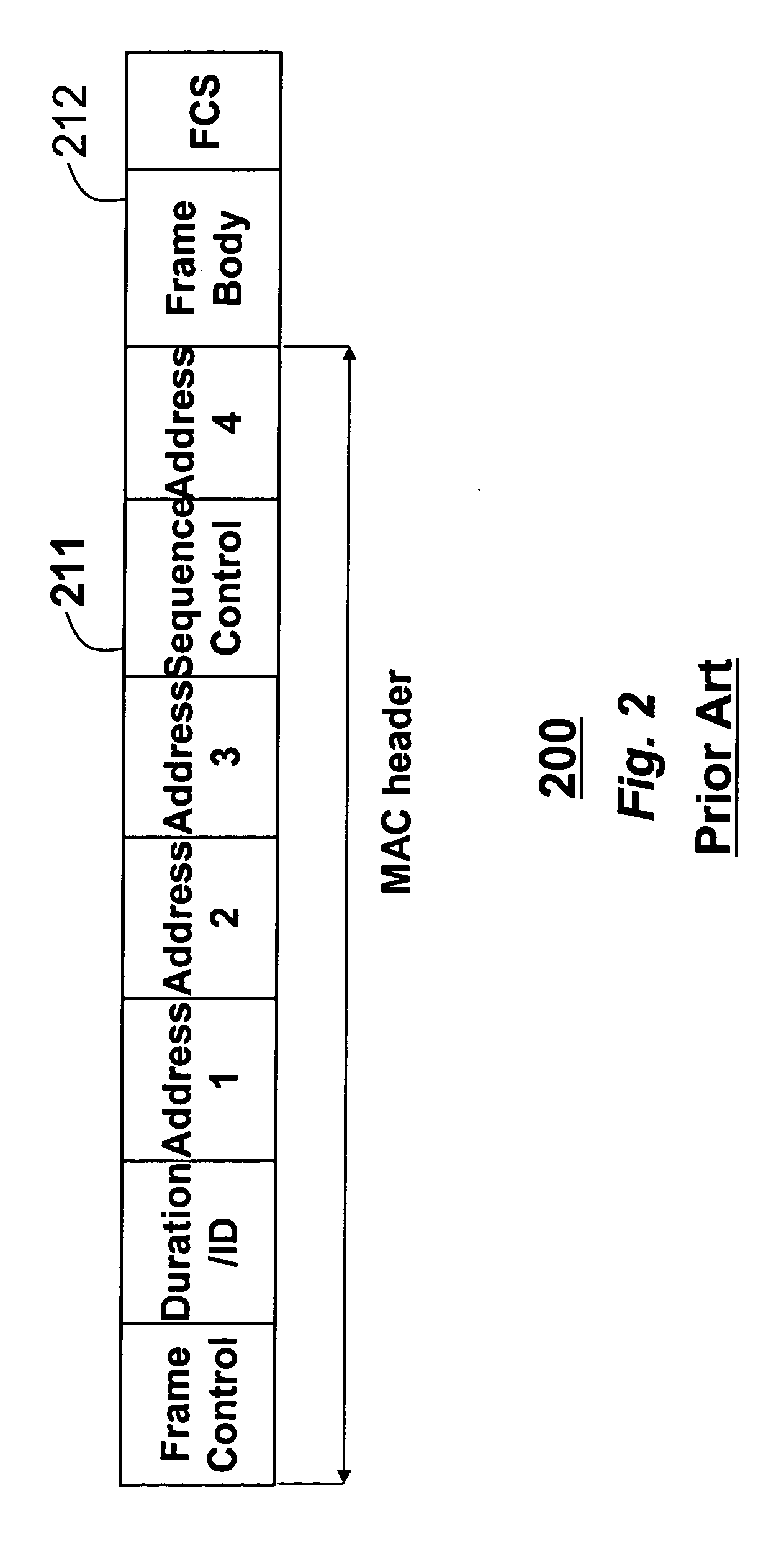
In IEEE 802 LAN/MAN standards, the medium access control (MAC, also called "media access protocol") sublayer is the layer that controls the hardware responsible for interaction with the wired, optical or wireless transmission medium. The MAC sublayer and the logical link control (LLC) sublayer together make up the data link layer. Within the data link layer, the LLC provides flow control and multiplexing for the logical link (i.e. EtherType, 802.1Q VLAN tag etc), while the MAC provides flow control and multiplexing for the transmission medium.
Secured data format for access control
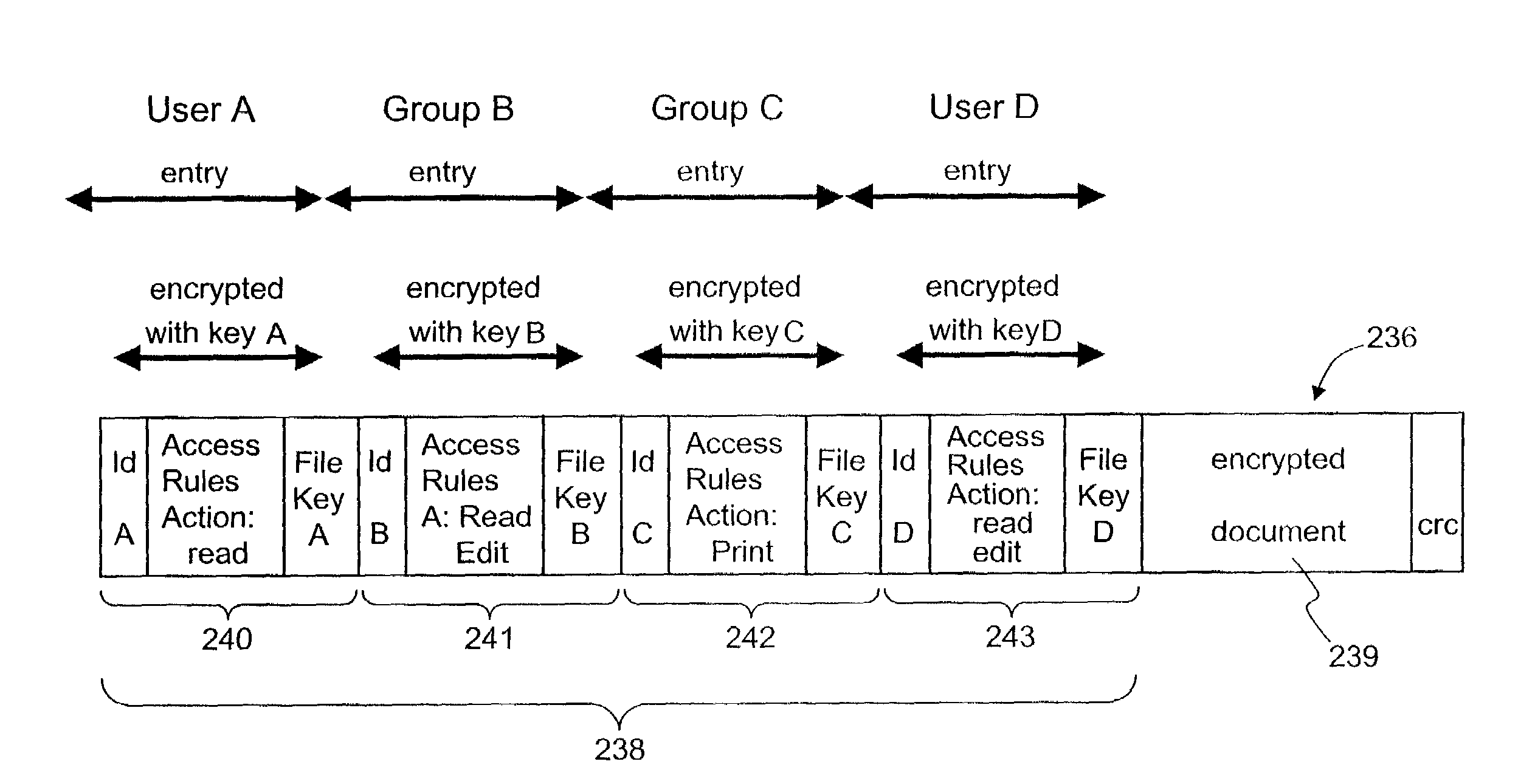
ActiveUS7380120B1Facilitate access control managementGood synchronizationDigital data processing detailsUser identity/authority verificationMedia access controlDocumentation
In a system for providing access control management to electronic data, techniques to secure the electronic data and keep the electronic data secured at all times are disclosed. According to one embodiment, a secured file or secured document includes two parts: an attachment, referred to as a header, and an encrypted document or data portion. The header includes security information that points to or includes the access rules and a file key. The access rules facilitate restrictive access to the secured document and essentially determine who / when / how / where the secured document can be accessed. The file key is used to encrypt / decrypt the encrypted data portion. Only those who have the proper access privileges are permitted to retrieve the file key to encrypt / decrypt the encrypted data portion.
Owner:INTELLECTUAL VENTURES I LLC
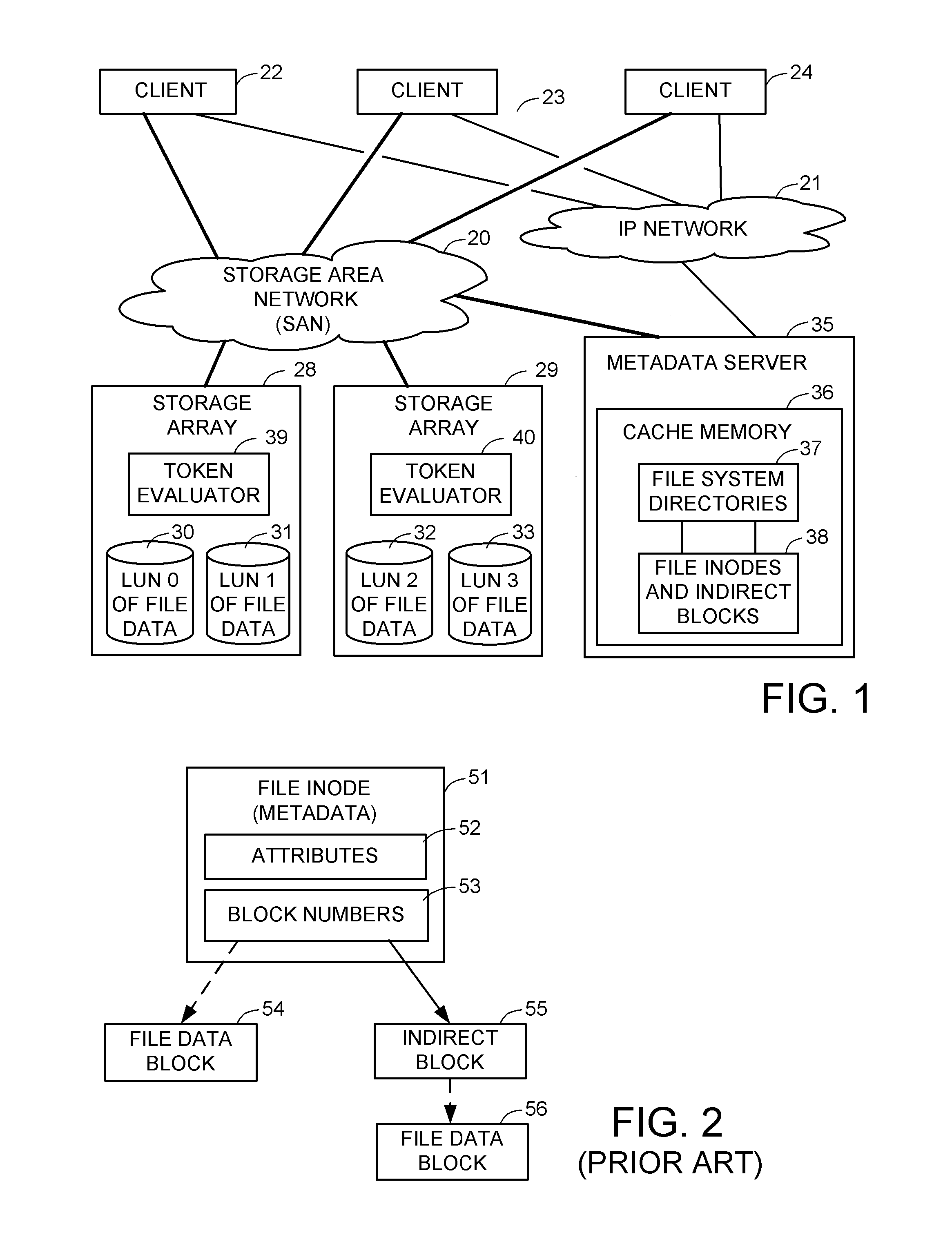
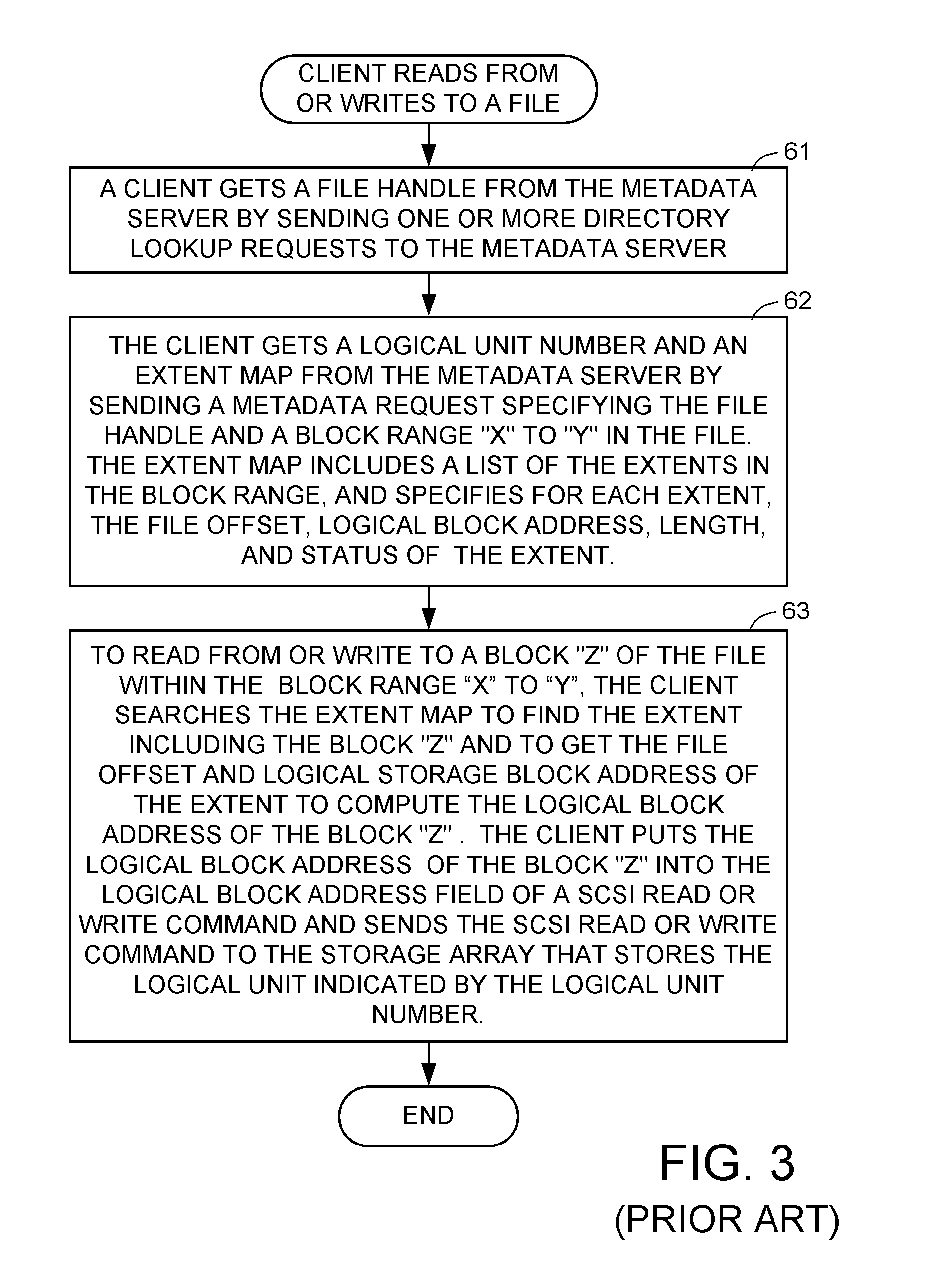
Access control to block storage devices for a shared disk based file system
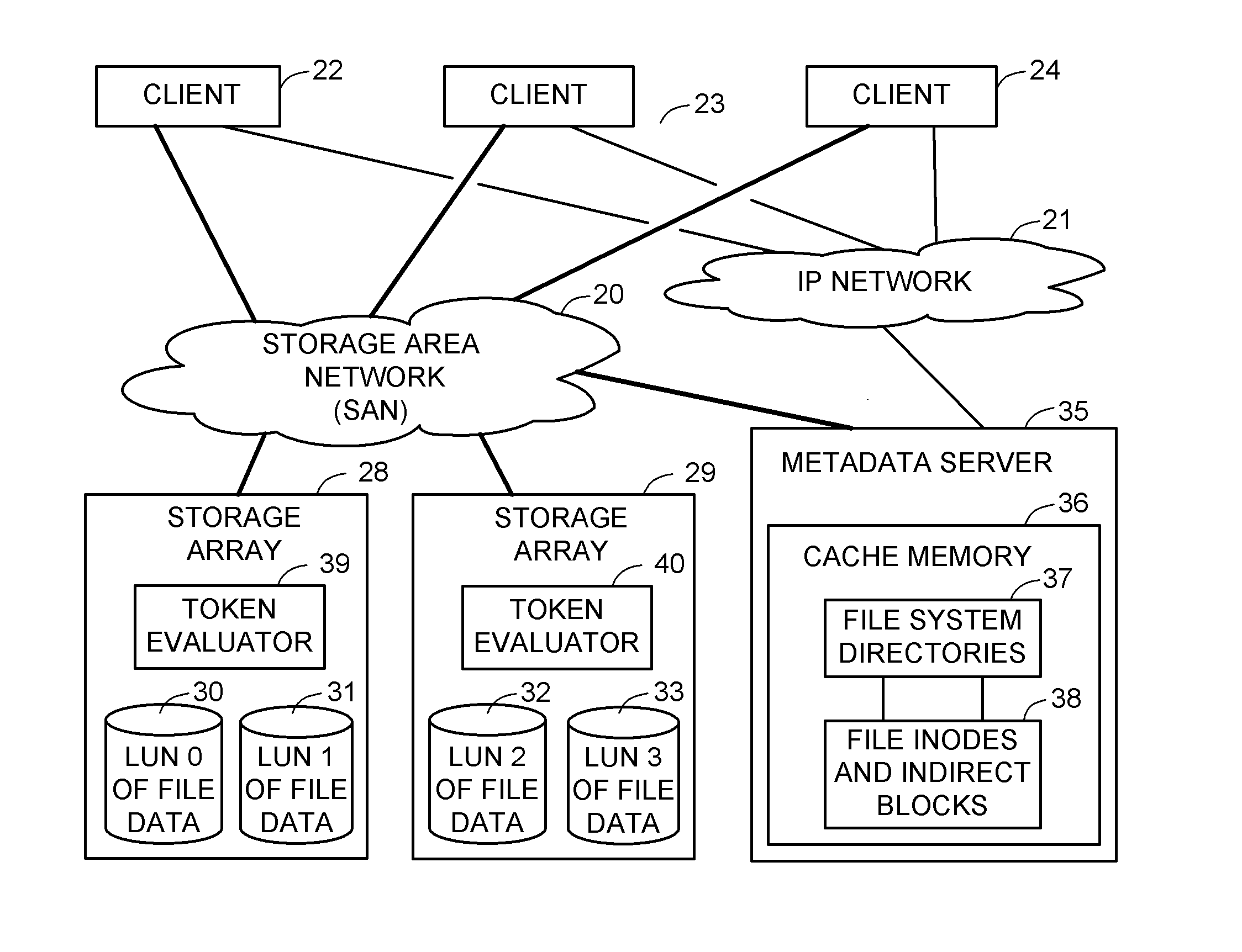
ActiveUS8086585B1Improve securityChangeDigital data information retrievalDigital data processing detailsSCSILogical block addressing
For enhanced access control, a client includes a token in each read or write command sent to a block storage device. The block storage device evaluates the token to determine whether or not read or write access is permitted at a specified logical block address. For example, the token is included in the logical block address field of a SCSI read or write command. The client may compute the token as a function of the logical block address of a data block to be accessed, or a metadata server may include the token in each block address of each extent reported to the client in response to a metadata request. For enhanced security, the token also is a function of a client identifier, a logical unit number, and access rights of the client to a particular extent of file system data blocks.
Owner:EMC IP HLDG CO LLC
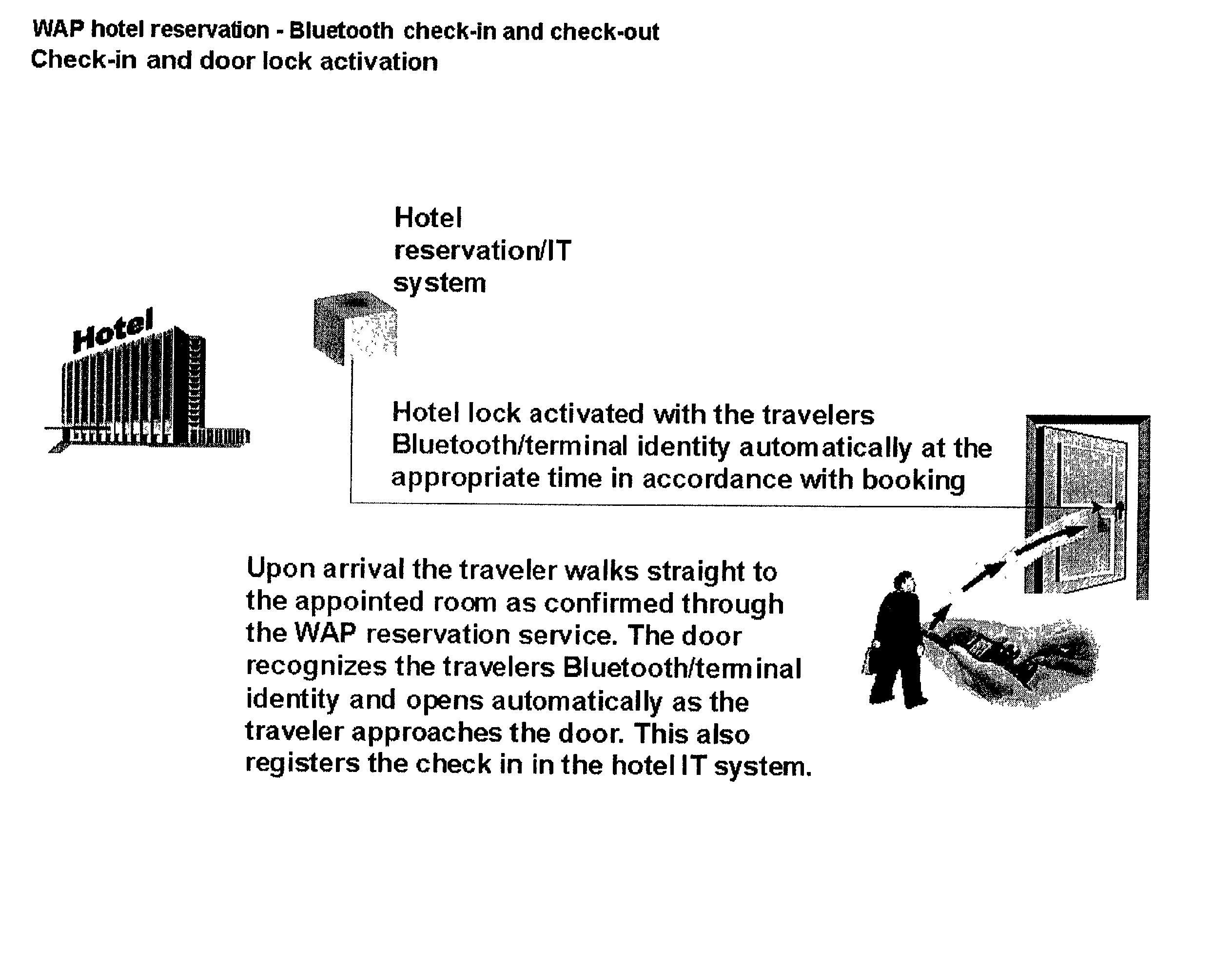
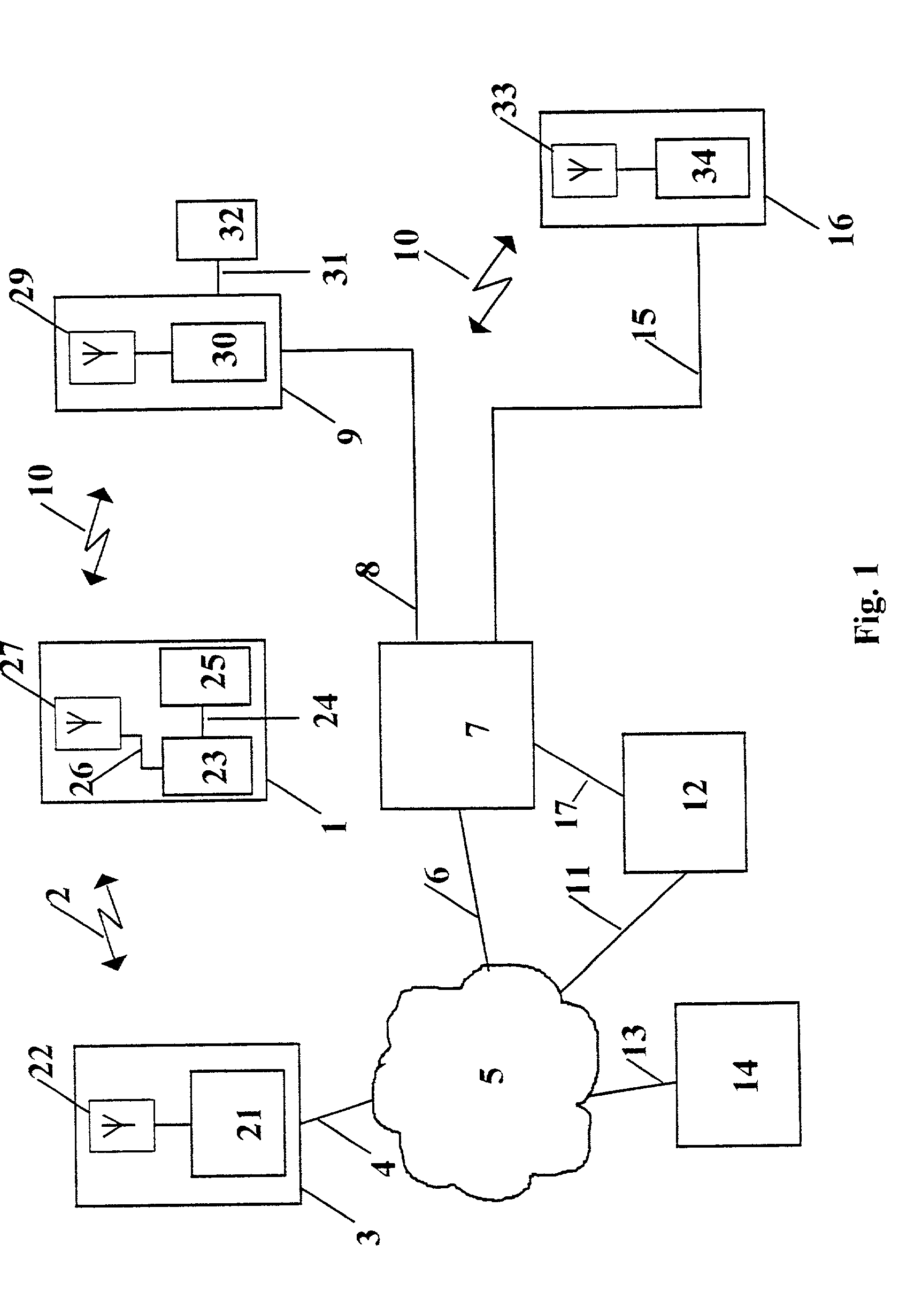
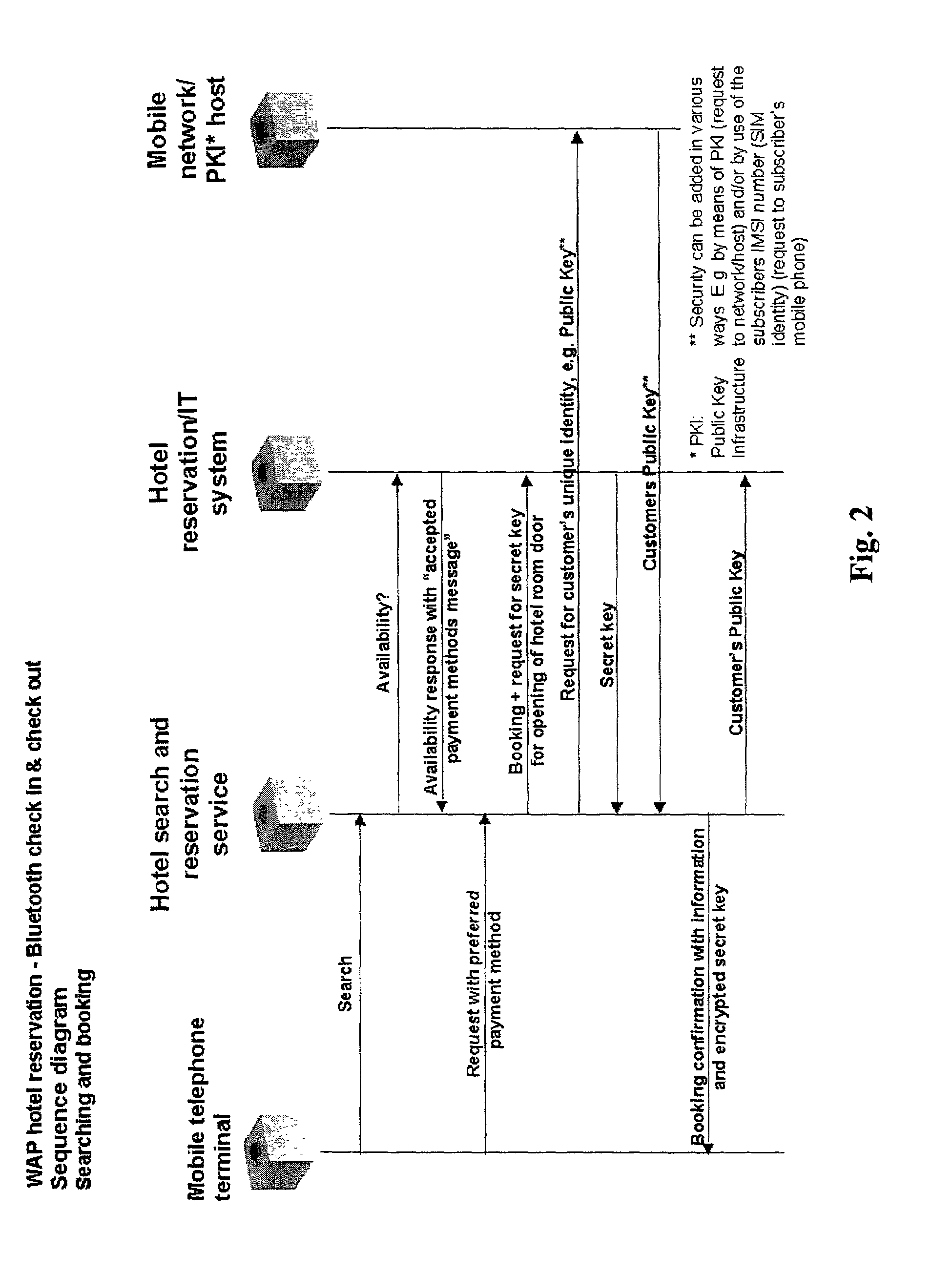
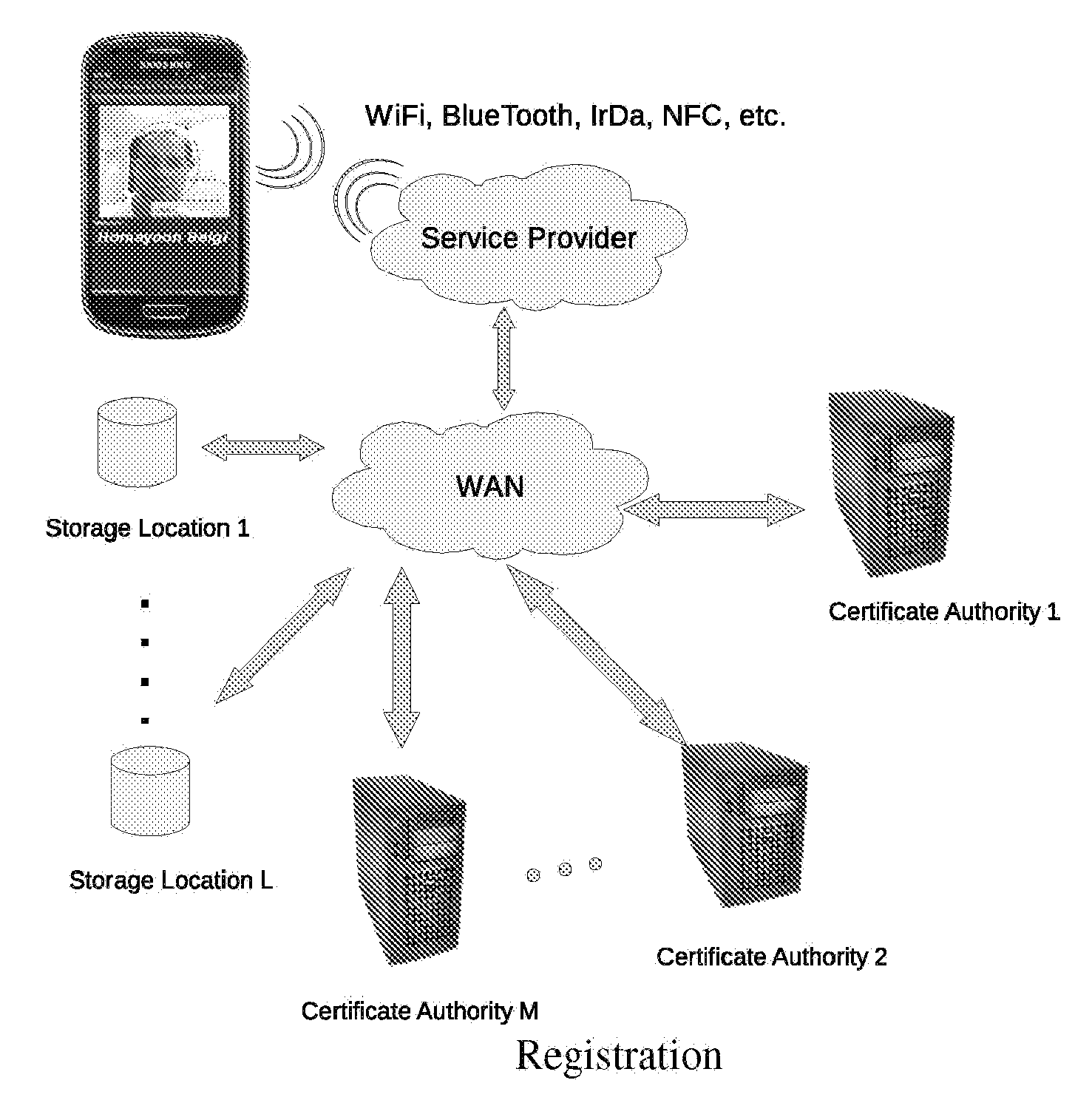
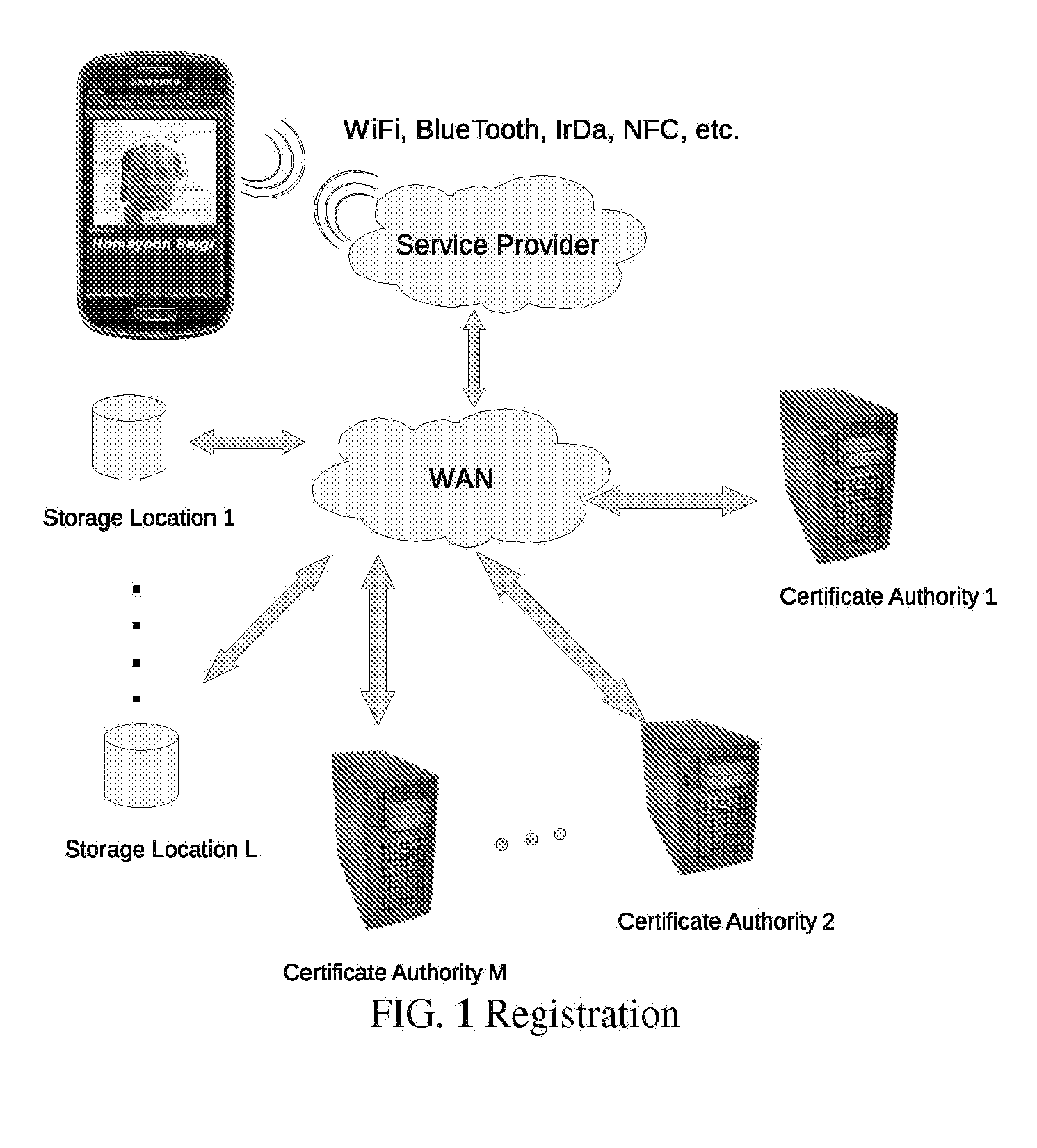
Wireless reservation, check-in, access control, check-out and payment
A system and method for, by means of a mobile terminal, wireless hotel search and selection, reservation / booking, check-in, room access control, check-out and payment services for hotel customers is disclosed. The mobile terminal (1) comprises a mobile telephone and processing unit (23), operating with wireless applications, for wireless communication (2) with a hotel search and reservation server (12) and a reservation / IT system (7) of a selected hotel, and a short-range wireless device (25) for wireless communication (10) with wireless devices (9,16) of door locks (32) and user locating arrangements, respectively. By means of the wireless application of the mobile terminal (1), the user reserves a hotel room. A hotel room key token is transferred from the reservation / IT system (7) to the wireless device (35) of the mobile terminal, and hence to the wireless door lock (9,32). When the terminal (1) and the wireless door lock (9,31) are in-range, the hotel room key token is transferred from mobile terminal (1) to the wireless door lock (9,32), the door is unlocked and check-in is registered. On departure, exit or expiration of the reservation period, the system provides wireless check-out and electronic bill settlement.
Owner:TELEFON AB LM ERICSSON (PUBL)
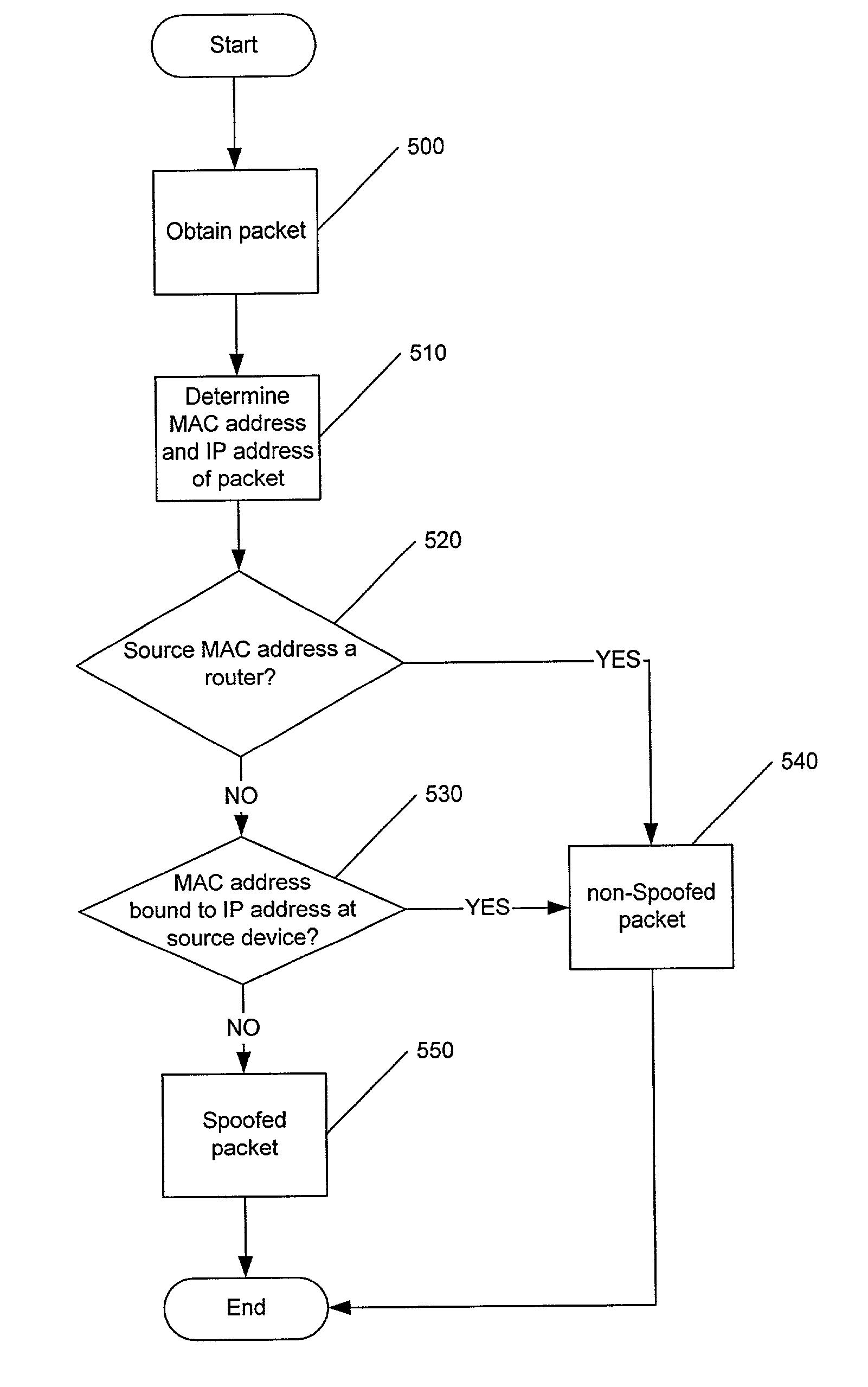
Methods, systems and computer program products for detecting a spoofed source address in IP datagrams
InactiveUS7134012B2Improve usabilityFrequency-division multiplexData switching by path configurationIp addressMedia access control
Methods, systems and computer program products are provided for determining if a packet has a spoofed source Internet Protocol (IP) address. A source media access control (MAC) address of the packet and the source IP address are evaluated to determine if the source IP address of the packet has been bound to the source MAC address at a source device of the packet. The packet is determined to have a spoofed source IP address if the evaluation indicates that the source IP address is not bound to the source MAC address. Such an evaluation may be made for packets having a subnet of the source IP address which matches a subnet from which the packet originated.
Owner:IBM CORP
Medium access control (MAC) protocol for wireless ATM
InactiveUS6198728B1Structure is limitedMinimize timePower managementNetwork traffic/resource managementNetwork communicationMedia access control
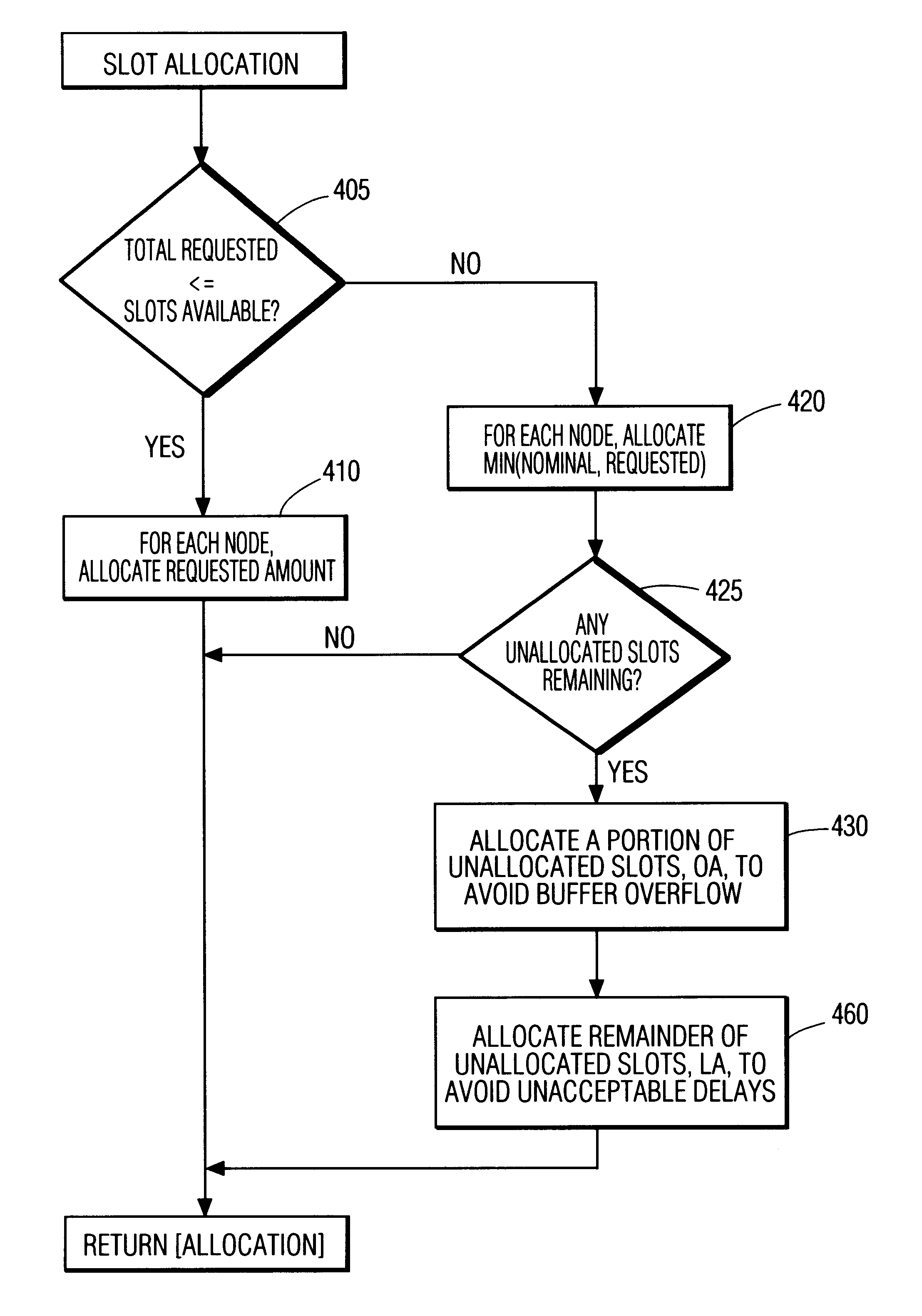
A protocol, method, and apparatus for managing network communications which are particularly well suited for ATM communications across a wireless medium. Contiguous time slots within a frame are allocated to each node having traffic to send. Each node is assured a nominal bandwidth, and excess bandwidth is distributed by demand. The allocation of excess bandwidth can be dependent upon the size of the buffer at each node, as well as the time-criticality of each message. Nodes communicate their requests for allocation by appending such control information to the first of their transmitted packets. The allocation, of each node's transmit and receive time slots, is transmitted to all the nodes at the beginning of each frame. Thereafter, each node need not participate on the network until their allocated time periods, thereby allowing portable devices to enter inactive states to conserve power. The network is operated in a connection mode; connections are established in a relatively non-interfering manner by the use of periodically occurring beacons. Inactive, unconnected, nodes need only monitor the network during these beacon periods, further allowing for power conservation.
Owner:UNILOC 2017 LLC
Internet-based shared file service with native PC client access and semantics and distributed access control
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
Integrated system for network layer security and fine-grained identity-based access control
ActiveUS6986061B1Simple technologyUser identity/authority verificationDigital computer detailsKey exchangeMedia access control
Owner:TREND MICRO INC
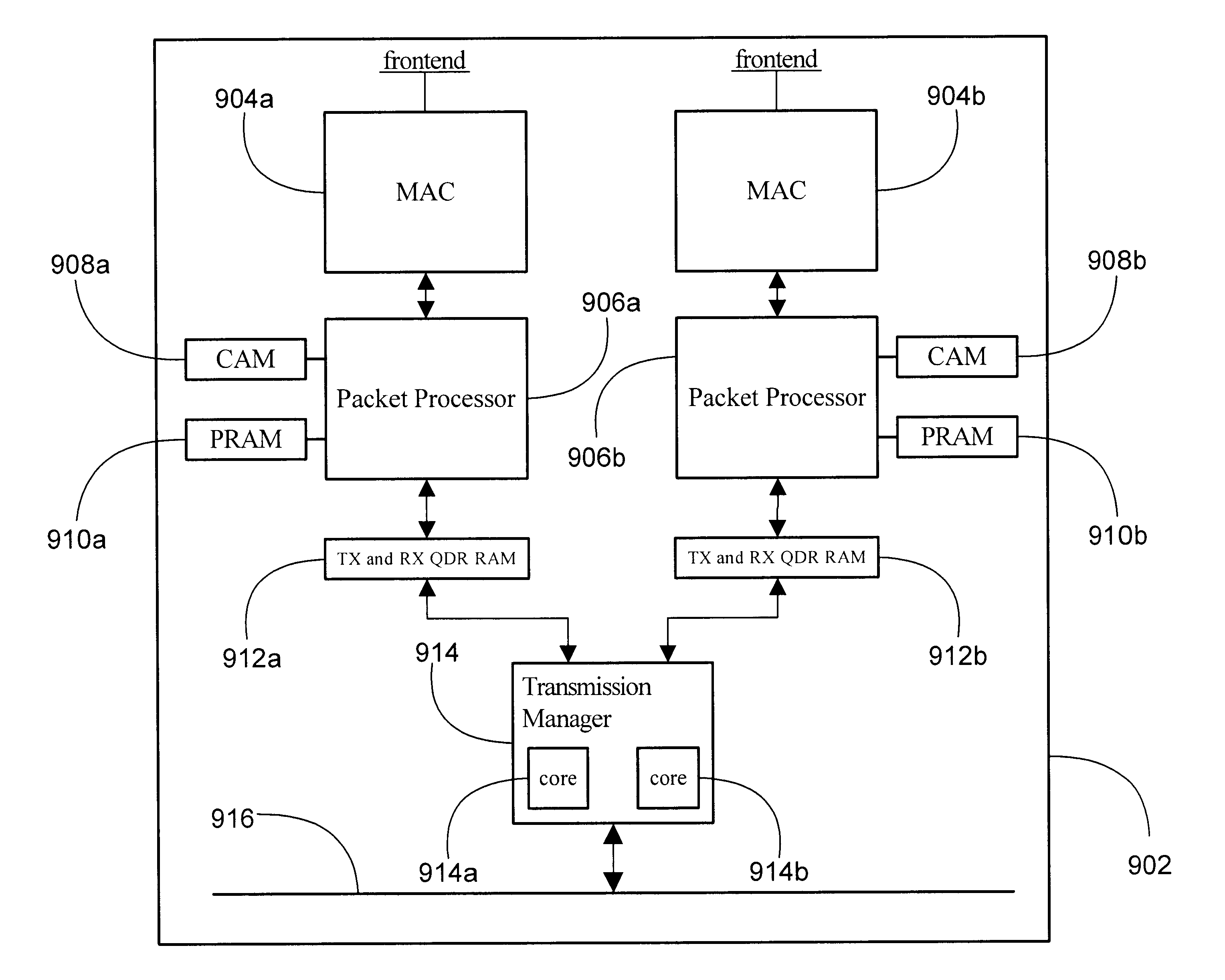
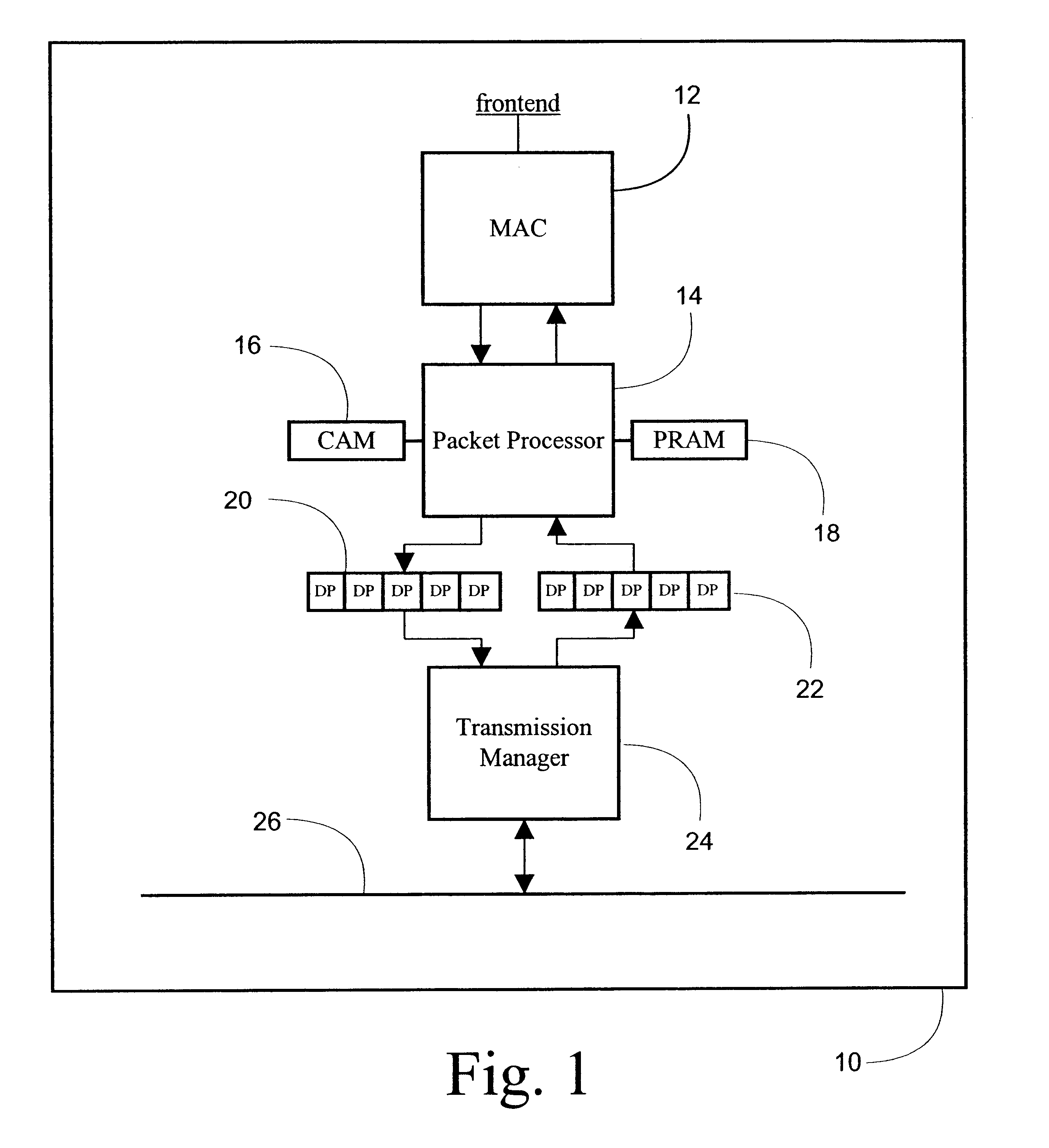
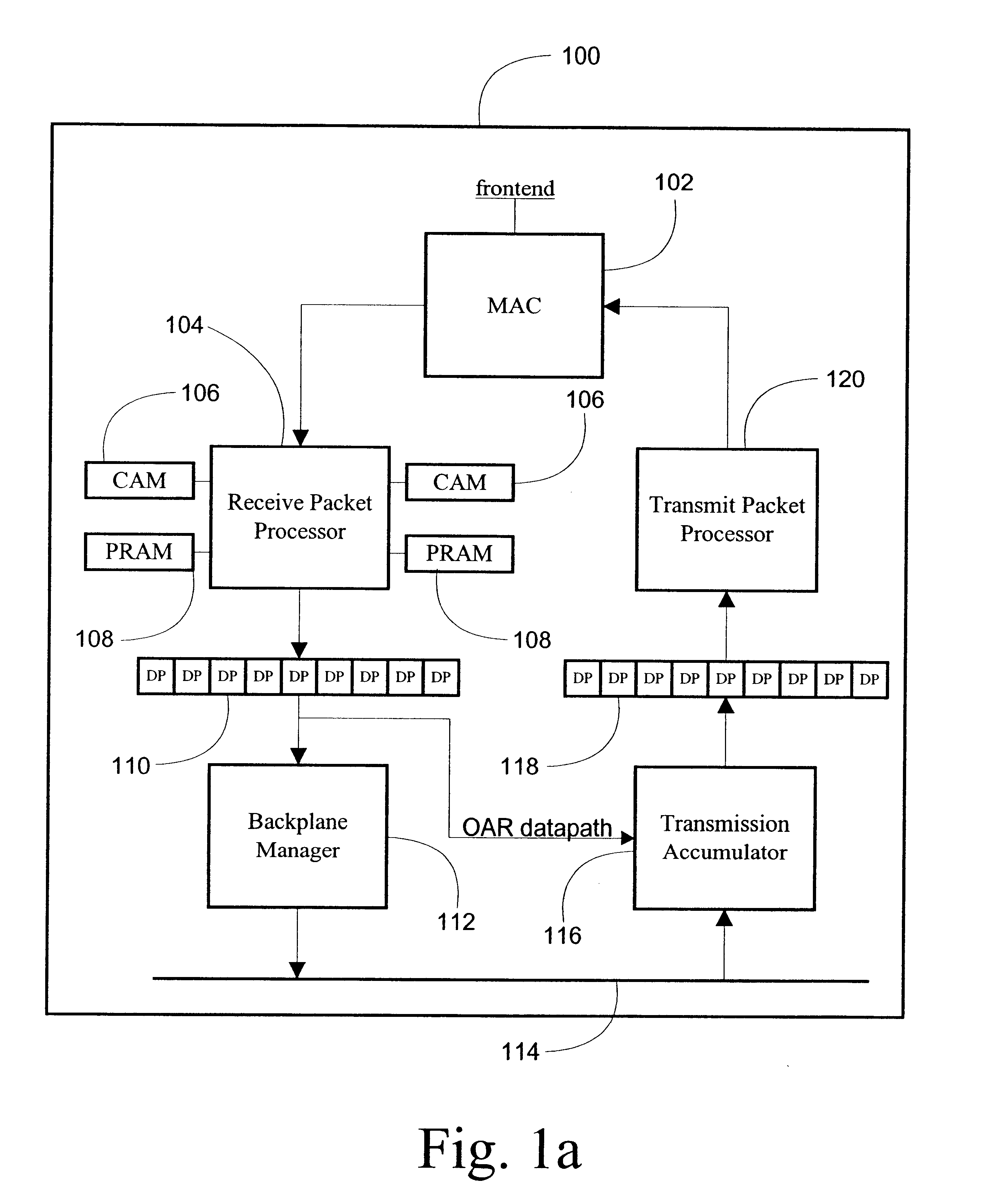
System and method for high speed packet transmission implementing dual transmit and receive pipelines
InactiveUS6901072B1Multiplex system selection arrangementsCircuit switching systemsGigabitStructure of Management Information
The present invention provides systems and methods for providing data transmission speeds at or in excess of 10 gigabits per second between one or more source devices and one or more destination devices. According to one embodiment, the system of the present invention comprises a first and second media access control (MAC) interfaces to facilitate receipt and transmission of packets over an associated set of physical interfaces. The system also contemplates a first and second field programmable gate arrays (FPGA) coupled to the MAC interfaces and an associated first and second memory structures, the first and second FPGAs are configured to perform initial processing of packets received from the first and second MAC interfaces and to schedule the transmission of packets to the first and second MAC interface for transmission to one or more destination devices. The first and second FPGAs are further operative to dispatch and retrieve packets to and from the first and second memory structures. A third FPGA, coupled to the first and second memory structures and a backplane, is operative to retrieve and dispatch packets to and from the first and second memory structures, compute appropriate destinations for packets and organize packets for transmission. The third FPGA is further operative to receive and dispatch packets to and from the backplane.
Owner:AVAGO TECH INT SALES PTE LTD
Multi-Wideband Communications over Multiple Mediums within a Network
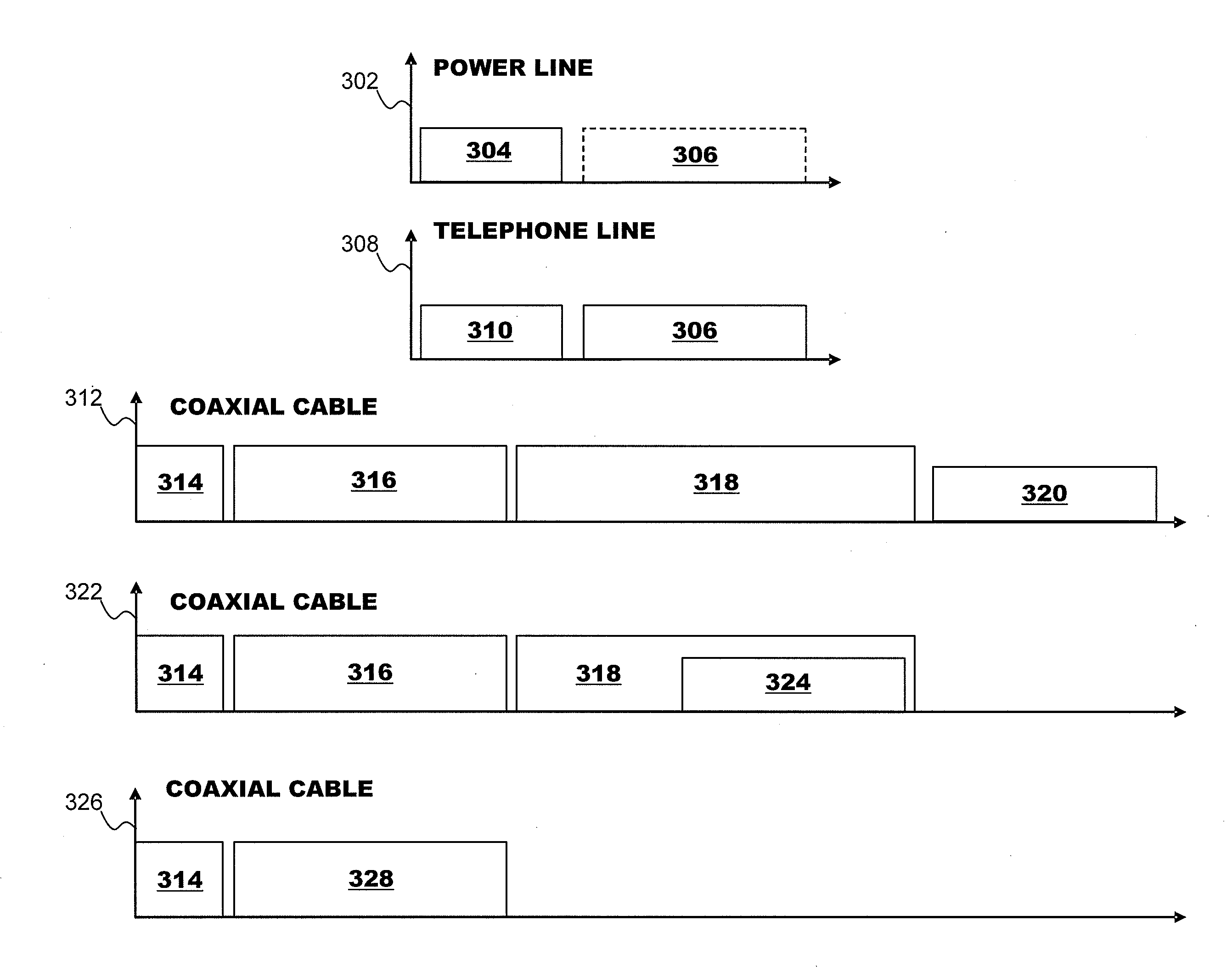
ActiveUS20070229231A1Systems using filtering and bypassingInterconnection arrangementsQuality of serviceMultiple frequency
A powerline communications device comprises a powerline communications interface and at least one other communications interface configured to communicate over a computing network. The powerline communications interface is further configured to receive electrical power. The computing network may comprise mediums including powerlines, telephone lines, and / or coaxial cables. In some embodiments, the powerline communications interface may communicate with a network apparatus, such as a personal computer, via an Ethernet interface. The powerline interface, the telephone line interface, and / or the coaxial cable interface may all be associated with the same media access control (MAC) address. The powerline communications device may receive a message via a first medium and repeat the message via a second medium based on a quality of service (QoS) metric. In some embodiments, the powerline communications device may communicate using multiple frequency bands.
Owner:AVAGO TECH INT SALES PTE LTD
User interface driven access control system and method
InactiveUS9003295B2Digital data processing detailsAnalogue secracy/subscription systemsGraphicsWeb browser
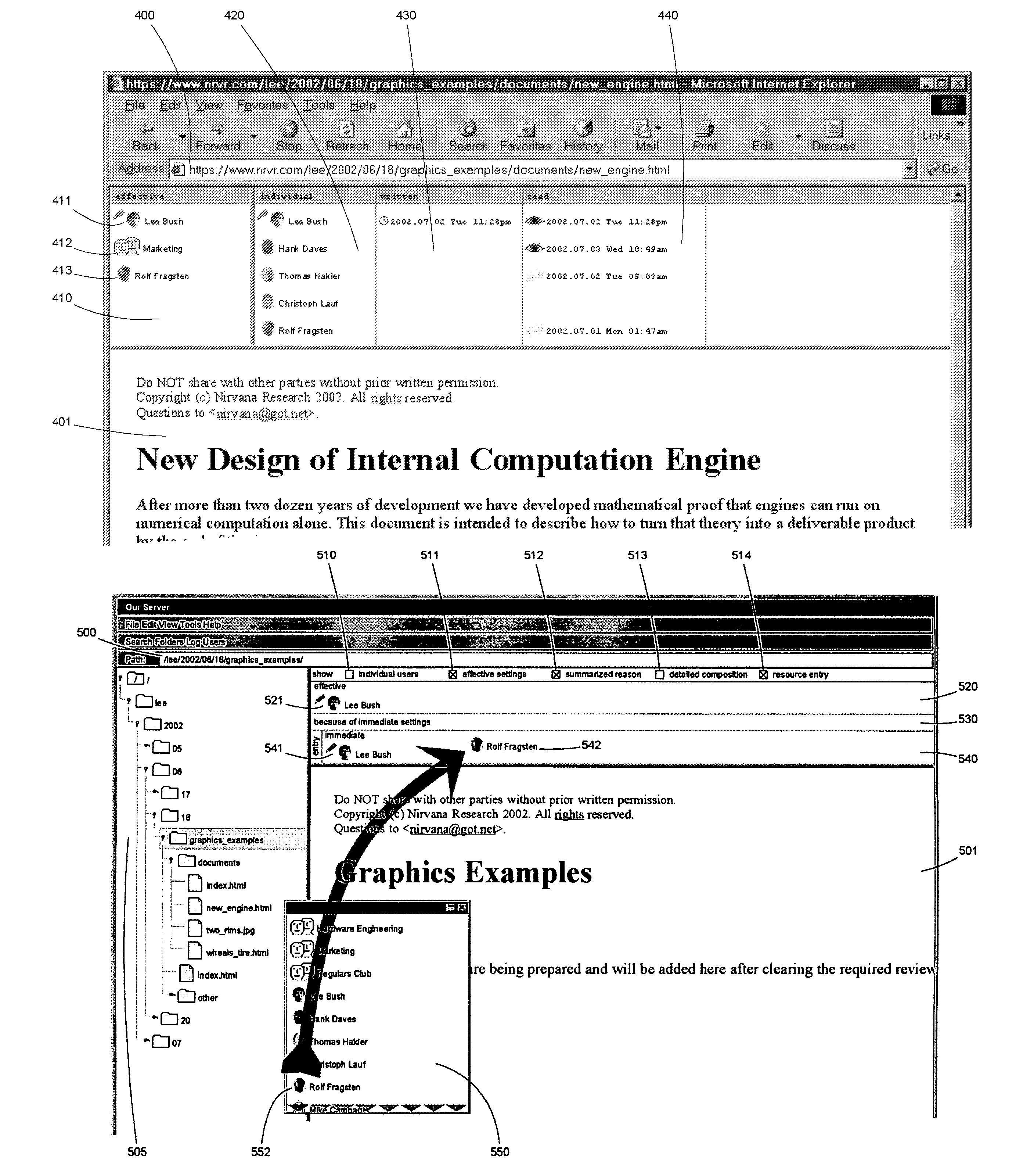
Display regions for representations of results of transformations applied to access control settings for a resource appear integrated with a familiar representation of the resource, e.g. word processor, or Web browser. A number of functions modify layout and transformations, and those functions are available for invocation, e.g. through mouse gestures or key combinations. Users are graphically represented by displays comprising photographic likenesses. Groups can be shown as individual users. Giving someone access to a resource can be as easy as dragging that person's likeness. Access log information can be shown together with access control settings. Reviewing the subset of resources available to a user is made easier. Overflow indicators replace scroll bars. Macros effect snapshots of volatile sets of users. Sections within documents can be omitted automatically if a user lacks authorization. Access control settings for one resource can be linked to be dependent on settings for other resources.
Owner:NIRESIP
Data link control proctocol for 3G wireless system
InactiveUS6542490B1Error prevention/detection by using return channelElectronic circuit testingTelecommunications linkDual mode
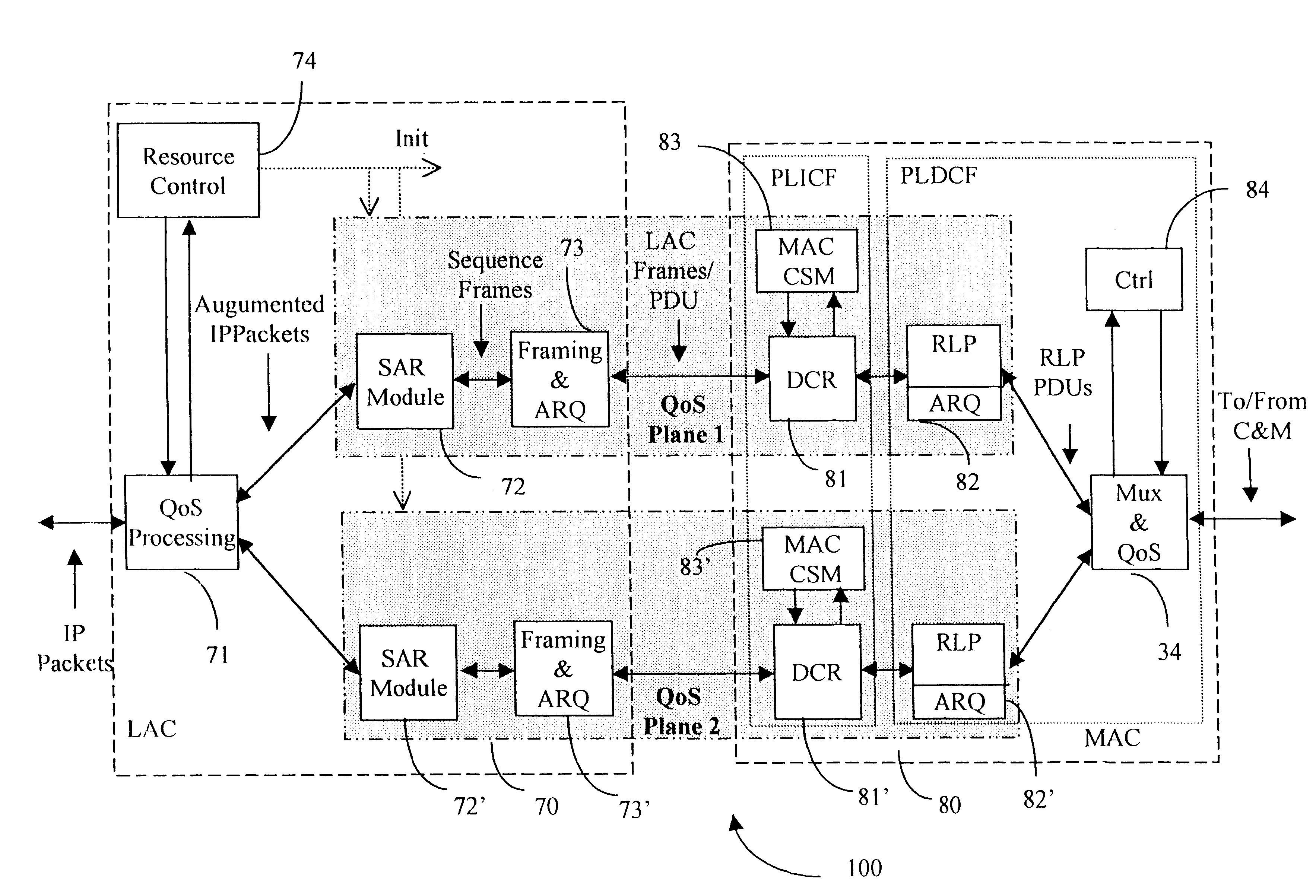
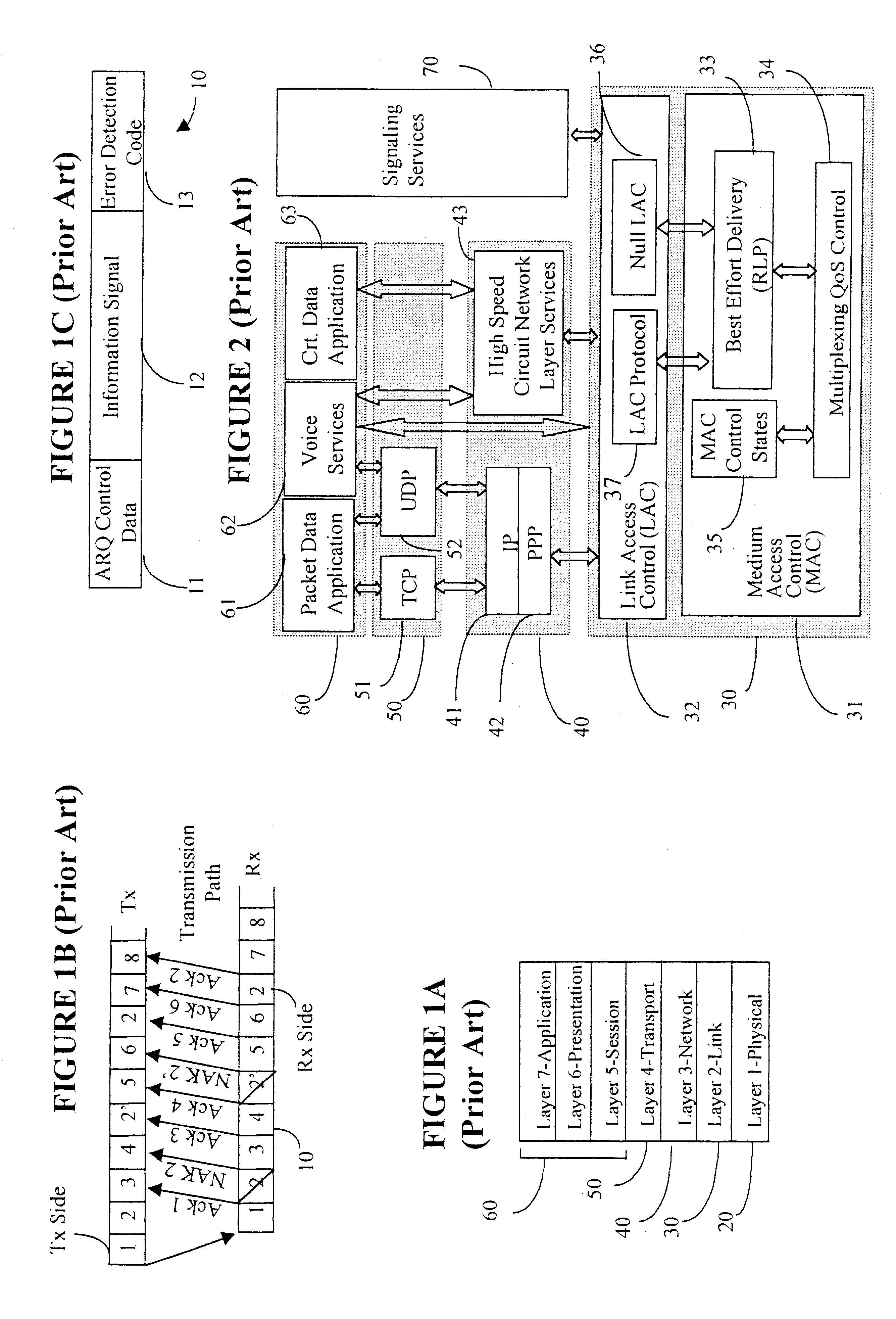
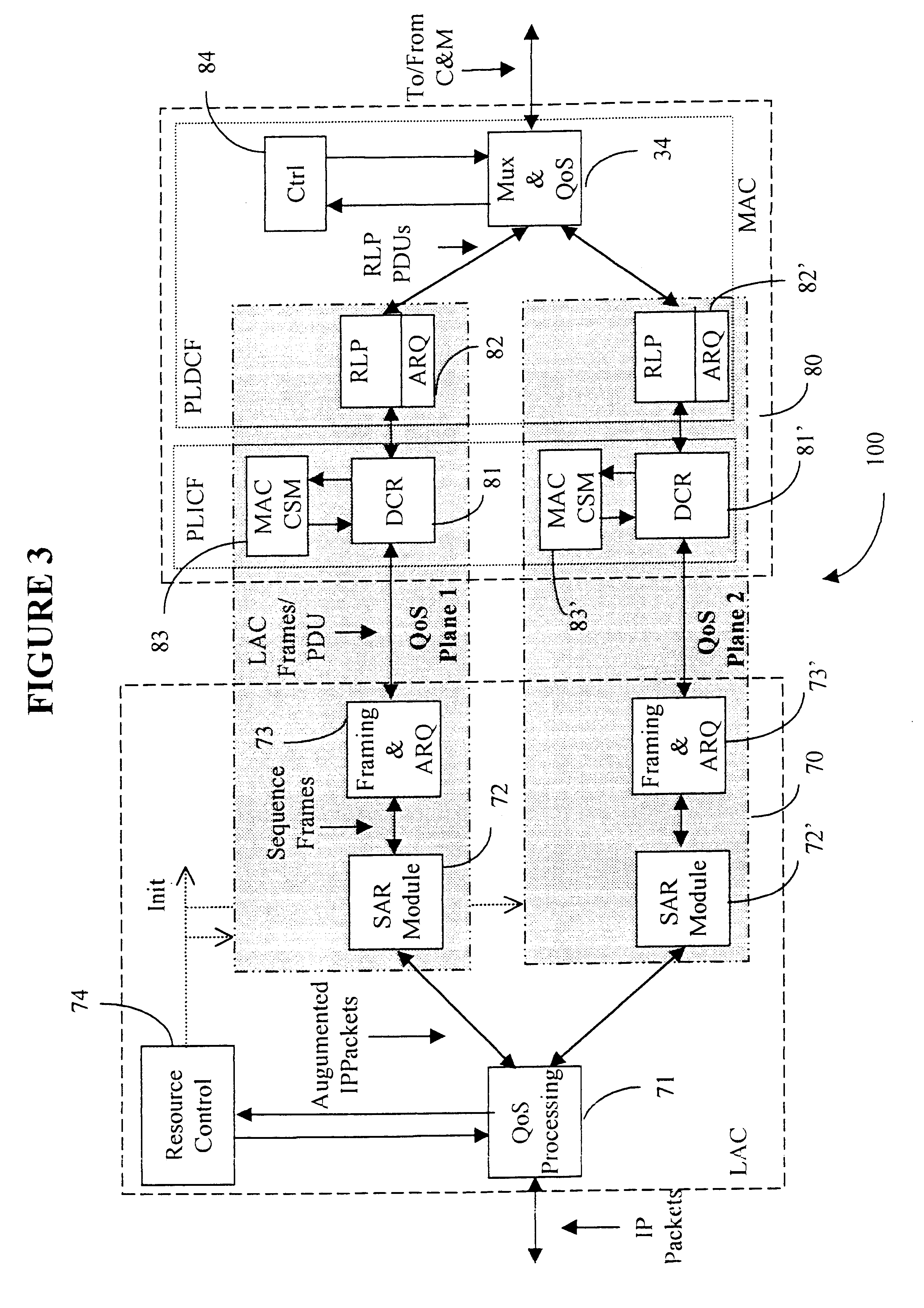
A Data Link Control protocol for 3G wireless communication system for direct support for network layer protocols, e.g. the Internet Protocol (IP), is provided. The Link Layer disclosed comprises a Link Access Control (LAC) sublayer and a Medium Access Control (MAC) sublayer. At a transmit end of the wireless system, a plurality of Quality of Service (QoS) data planes are created to directly support the IP QoS. Each QoS data plane is optimized to handle QoS requirements for a corresponding Class of Service (CoS). Data packets received at the LAC sublayer are directed to a QoS data plane according to the particular QoS information they contain and processed according to the particular QoS requirement to generate variable size LAC frames. The variable size LAC frames are transmitted to the MAC sublayer for generating radio link protocol data units (RLP PDUs) to be transmitted to a receiving end. A new level of error correction is provided at the LAC sublayer as the size of the LAC PDUs can be dynamically adjusted in response to the conditions of the communication link. A dual mode ARQ is provided at the MAC sublayer to improve the quality of the air transmission for bursty as well as non-bursty traffic conditions.
Owner:ALCATEL LUCENT SAS
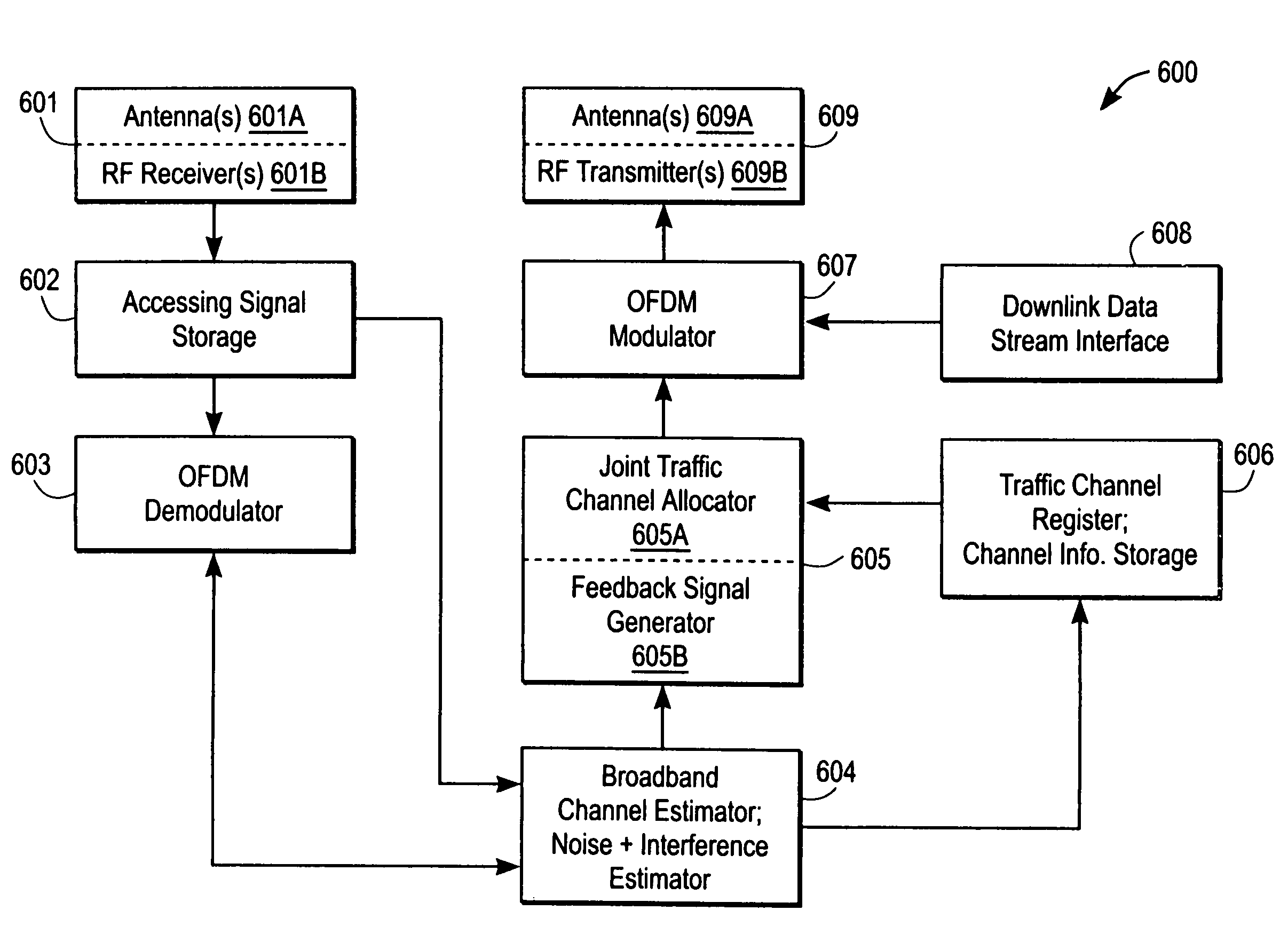
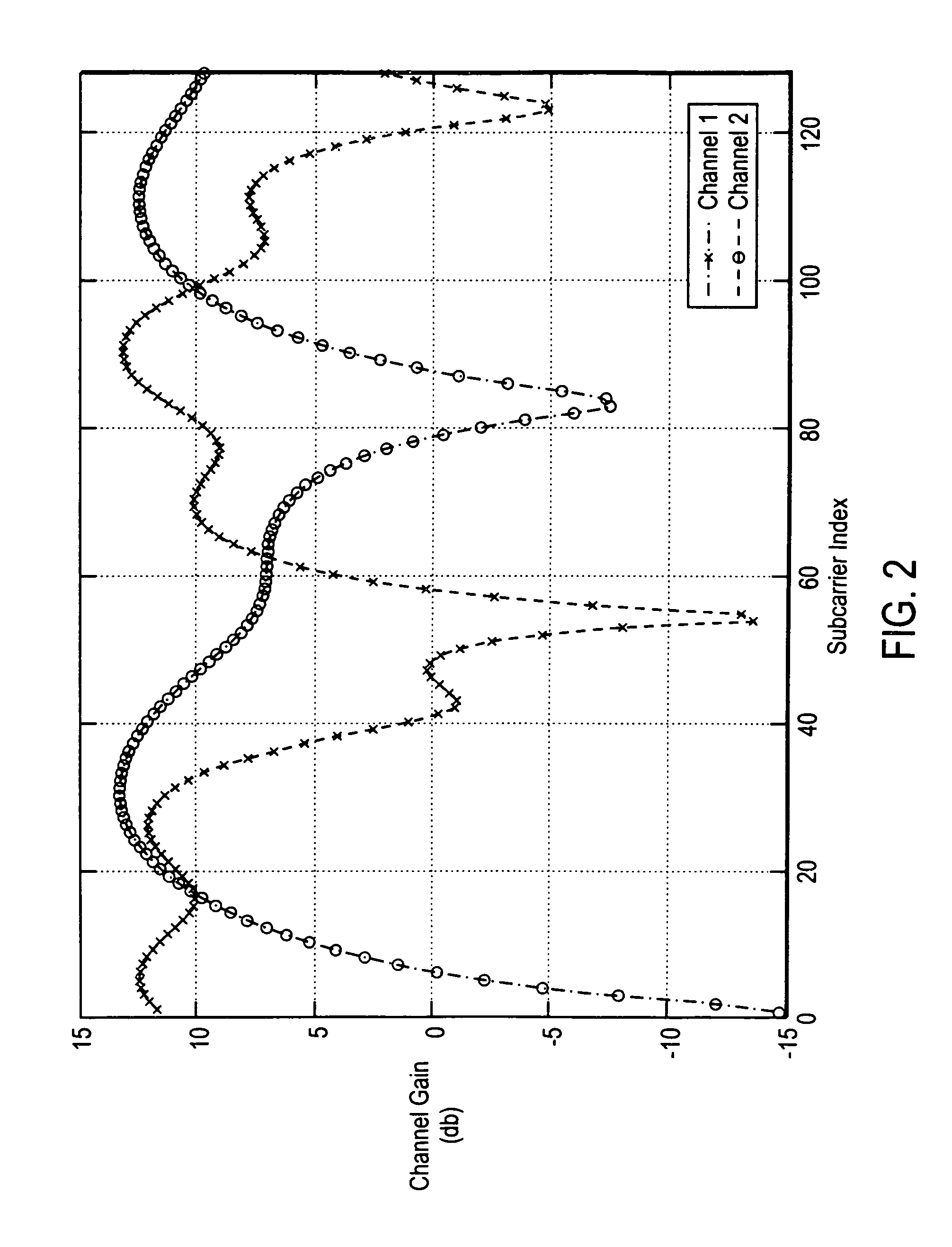
Medium access control for orthogonal frequency-division multiple-access (OFDMA) cellular networks
InactiveUS7072315B1Transmission path divisionCriteria allocationMedia access controlOrthogonal frequency-division multiple access
A method and apparatus for controlling OFDMA cellular networks is described. In one embodiment, the method comprises receiving channel characteristics and noise-plus-interference information measured at spatially distributed subscribers and assigning traffic channels for an orthogonal frequency-division multiple-access (OFDMA) network.
Owner:KAON SYST +1
Multi-wideband communications over multiple mediums
InactiveUS8406239B2Electric signal transmission systemsFrequency-division multiplex detailsQuality of serviceMultiple frequency
A powerline communications device comprises a powerline communications interface and at least one other communications interface configured to communicate over a computing network. The powerline communications interface is further configured to receive electrical power. The computing network may comprise mediums including powerlines, telephone lines, and / or coaxial cables. In some embodiments, the powerline communications interface may communicate with a network apparatus, such as a personal computer, via an Ethernet interface. The powerline interface, the telephone line interface, and / or the coaxial cable interface may all be associated with the same media access control (MAC) address. The powerline communications device may receive a message via a first medium and repeat the message via a second medium based on a quality of service (QoS) metric. In some embodiments, the powerline communications device may communicate using multiple frequency bands.
Owner:GIGLE SEMICON
Method and apparatus for transmitting and receiving duplicate data in a multicarrier wireless communication system
InactiveUS20120057560A1Increase probabilitySuccessful receptionTransmission path divisionData switching by path configurationCommunications systemCarrier signal
The present invention relates to a wireless communication system, and more particularly, discloses a method and an apparatus for transmitting and receiving duplicate data in a multicarrier wireless communication system. According to one embodiment of the present invention, a method in which a transmitter, which supports carrier aggregation for performing communication using N (N≧2) component carriers, transmits duplicate data, comprises the steps of: generating, in a media access control (MAC) layer of the transmitter, N duplicate data using radio link control (RLC) protocol data units (PDUs) from an RLC layer, and simultaneously transmitting, to a receiver, the respective N duplicate data on the N component carriers through respective N hybrid automatic repeat and request (HARQ) entities.
Owner:LG ELECTRONICS INC
Medium access control priority-based scheduling for data units in a data flow
InactiveUS20070081513A1Reduce delaysImprove efficiencyError prevention/detection by using return channelTransmission systemsData streamRadio networks
A data communication having at least one data flow is established over a wireless interface between a radio network and a user equipment node (UE). A medium access control (MAC) layer located in a radio network node receives data units from a higher radio link control (RLC) layer located in another radio network node. Some or all of a header of a RLC data units associated with the one data flow is analyzed at the MAC layer. Based on that analysis, the MAC layer determines a priority of the data unit relative to other data units associated with the one data flow. The MAC layer schedules transmission of higher priority data units associated with the one data flow before lower priority data units associated with the one data flow. The priority determination does not require extra priority flags or signaling.
Owner:TELEFON AB LM ERICSSON (PUBL)
Non-frequency translating repeater with detection and media access control
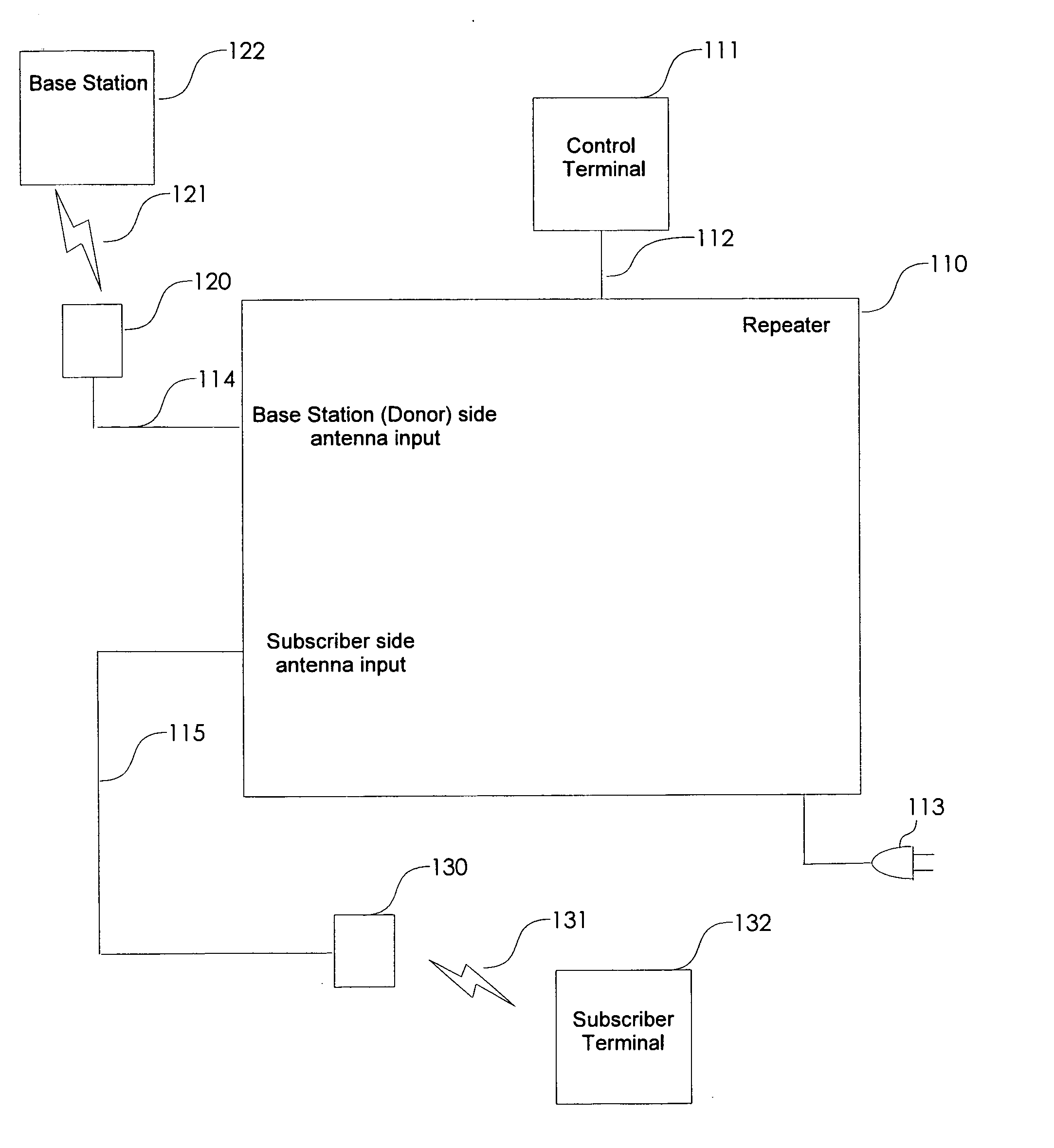
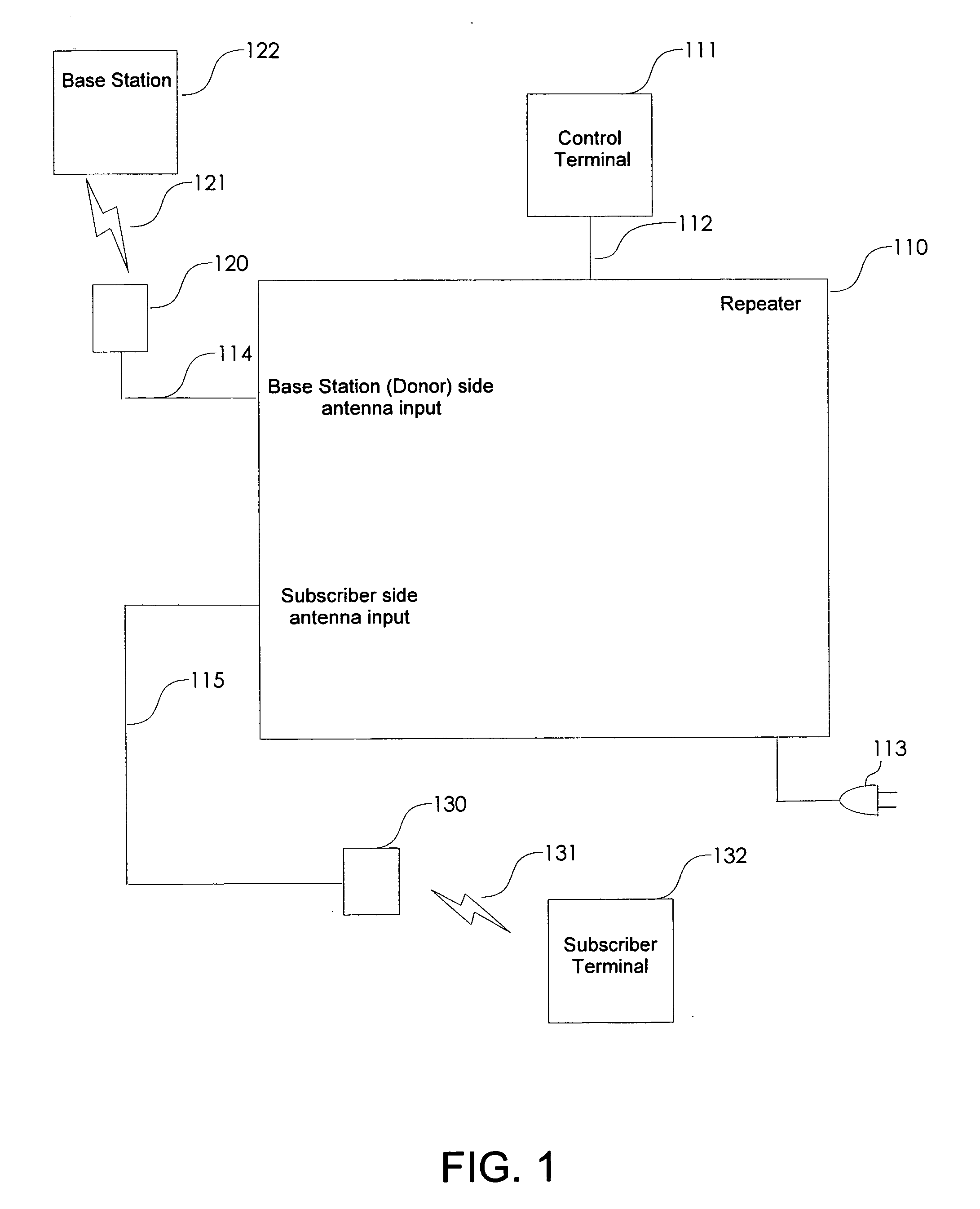
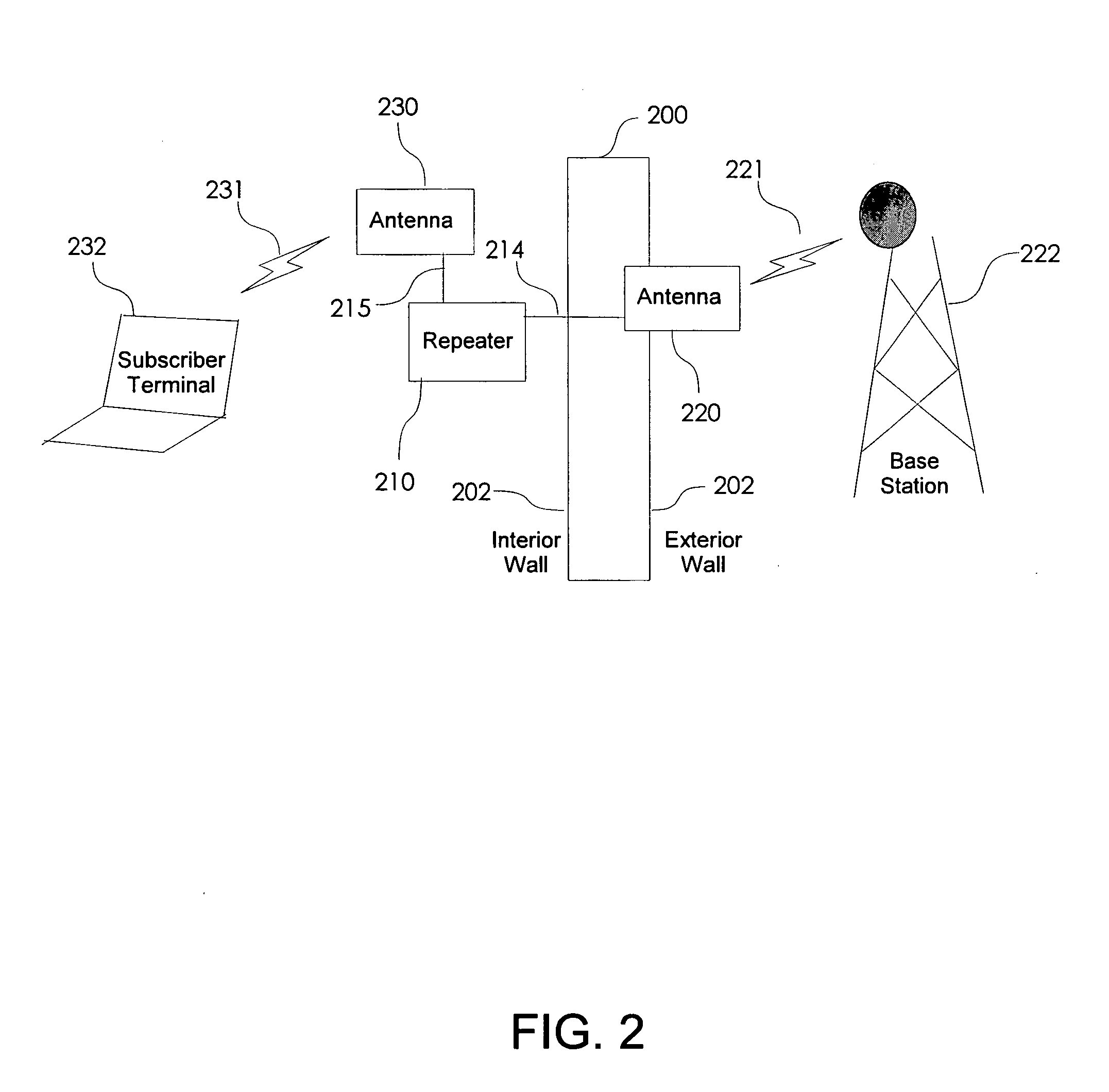
A non-frequency translating repeater (110, 210, 300) for use in a time division duplex (TDD) radio protocol communications system includes detection retransmission and automatic gain control. Detection is performed by detectors (309, 310) and a processor (313). Detection can be overridden by processor (313) using logic elements (314). Antennae (220, 230) having various form factors can be used to couple a base station (222) to a subscriber terminal (232) which can be located in a sub-optimal location such as deep inside a building or the like.
Owner:QUALCOMM INC
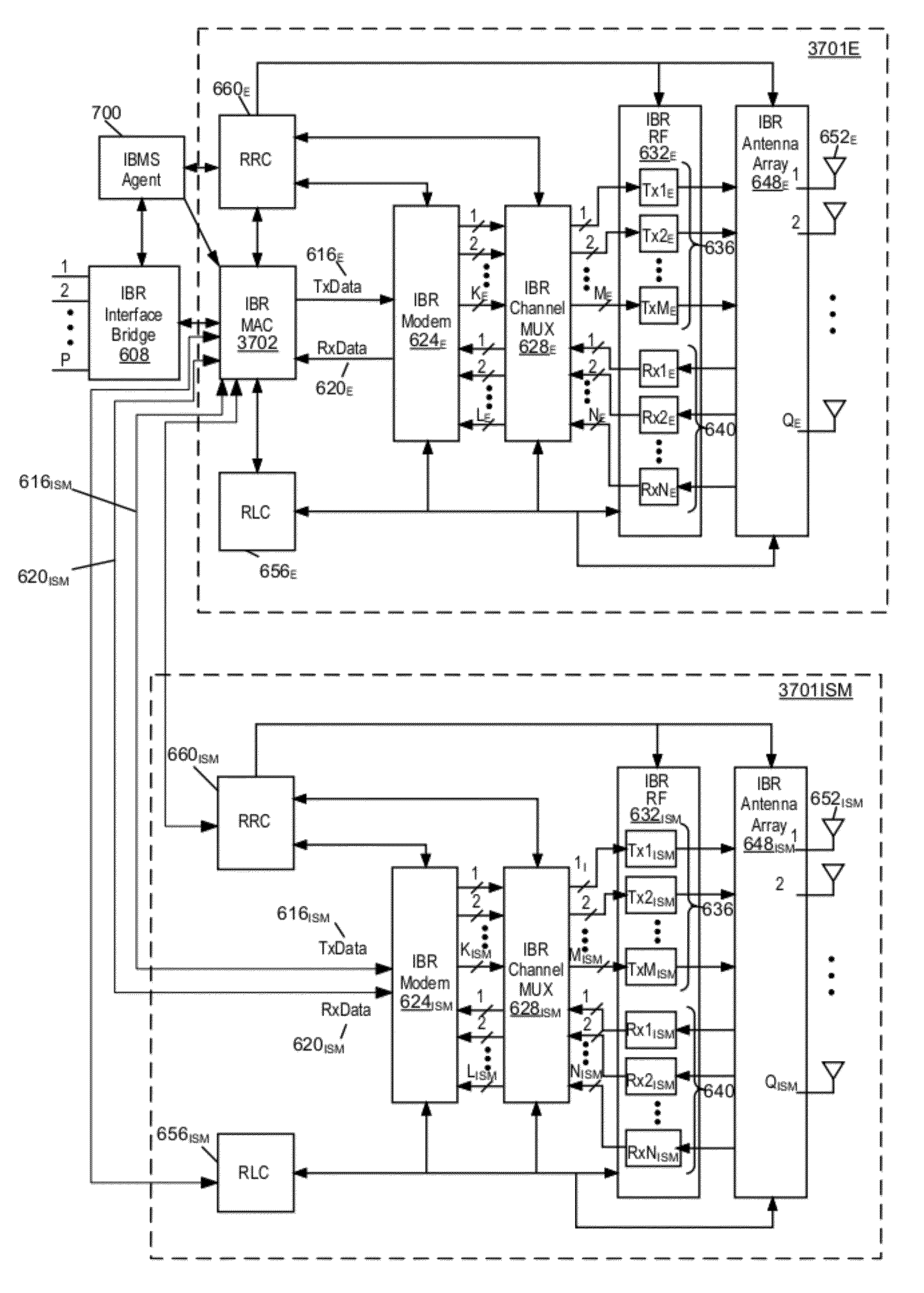
Hybrid band intelligent backhaul radio
ActiveUS8385305B1Reduce the time required for installationReduce installation costsNetwork topologiesFrequency-division multiplexRadio equipmentMedia access control
A hybrid band intelligent backhaul radio (HB-IBR) is disclosed that is a combination of two radios operating in different bands. Embodiments include a dual radio configuration wherein a first radio operates in a non-line of sight (NLOS) radio link configuration and a second ancillary radio operates in a near line of sight or line of sight configuration (n)LOS. For example, the HB-IBR may have an Intelligent Backhaul Radio (IBR) operating in the non-line of sight mode of operation within the 5.8 GHz unlicensed band, and have an ancillary radio link operating in the FCC part 101E band of operation at 60 GHz. A common medium access control (MAC) block may be utilized between the dual radios.
Owner:COMS IP HLDG LLC
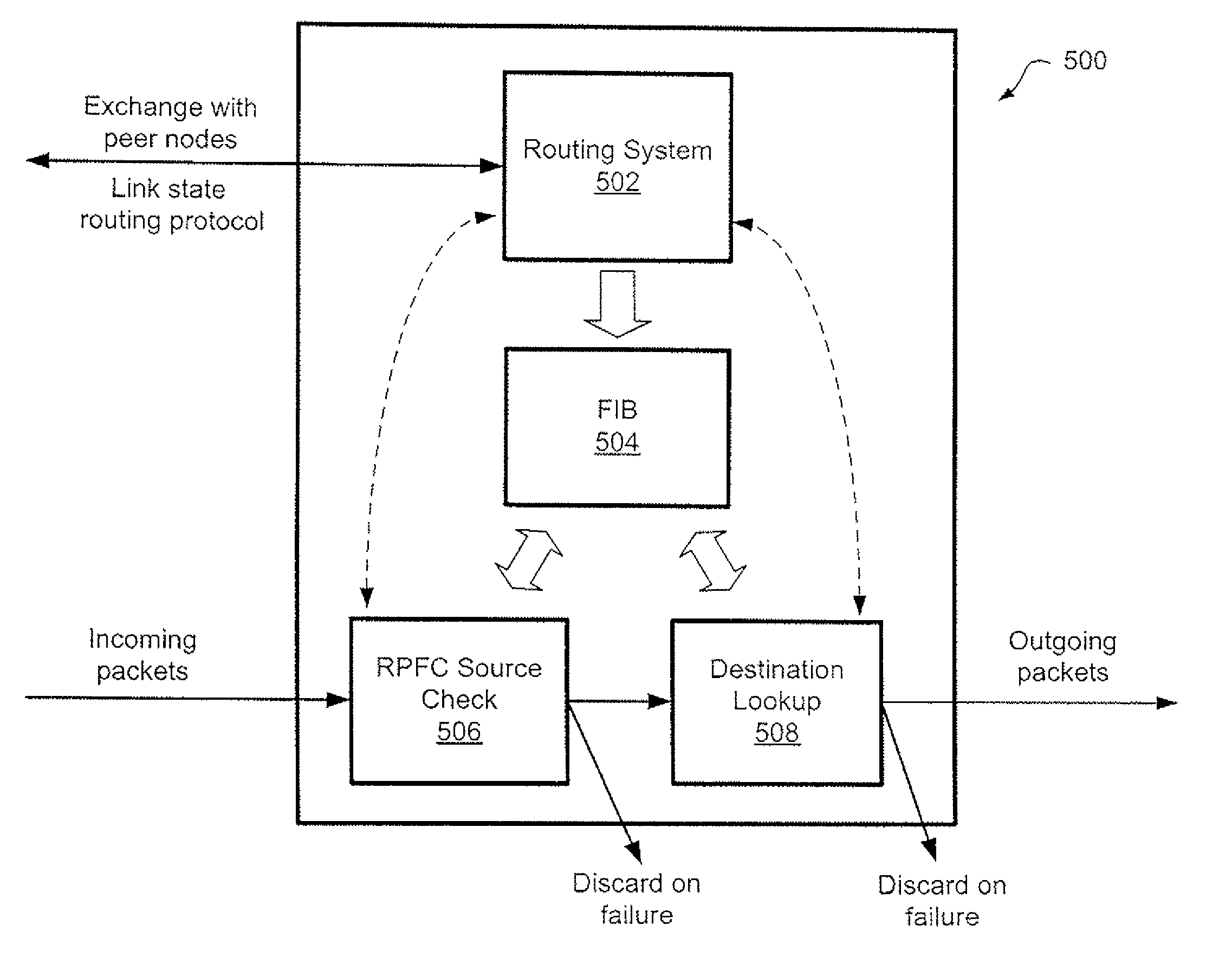
Provider link state bridging
InactiveUS20070086361A1Effective link utilizationMinimize impactSpecial service provision for substationData switching by path configurationMedia access controlInstability
Provider Link State Bridging (PLSB) expands static configuration of Ethernet MAC forwarding tables by the control plane and utilizes direct manipulation of Ethernet forwarding by a link state routing system. At least one media-access-control (MAC) address for unicast forwarding to the bridge and at least one MAC address for multicast forwarding from the bridge are assigned. Bridges exchange state information by a link state bridging protocol so that a synchronized configured view of the network is shared between nodes. Each node can calculate shortest path connective between peer bridging nodes and populated the appropriate forwarding tables. A reverse path forwarding check is performed on incoming packets to provide loop suppression. During times of network instability the loop suppression can be disabled for unicast packets as identified by the destination MAC address to buffer packets and minimize the impact on traffic flow.
Owner:RPX CLEARINGHOUSE
Resource exchange discovery in a cellular communication system
ActiveUS20090161614A1Efficient disseminationEasy to useConnection managementWireless commuication servicesAir interfaceStructure of Management Information
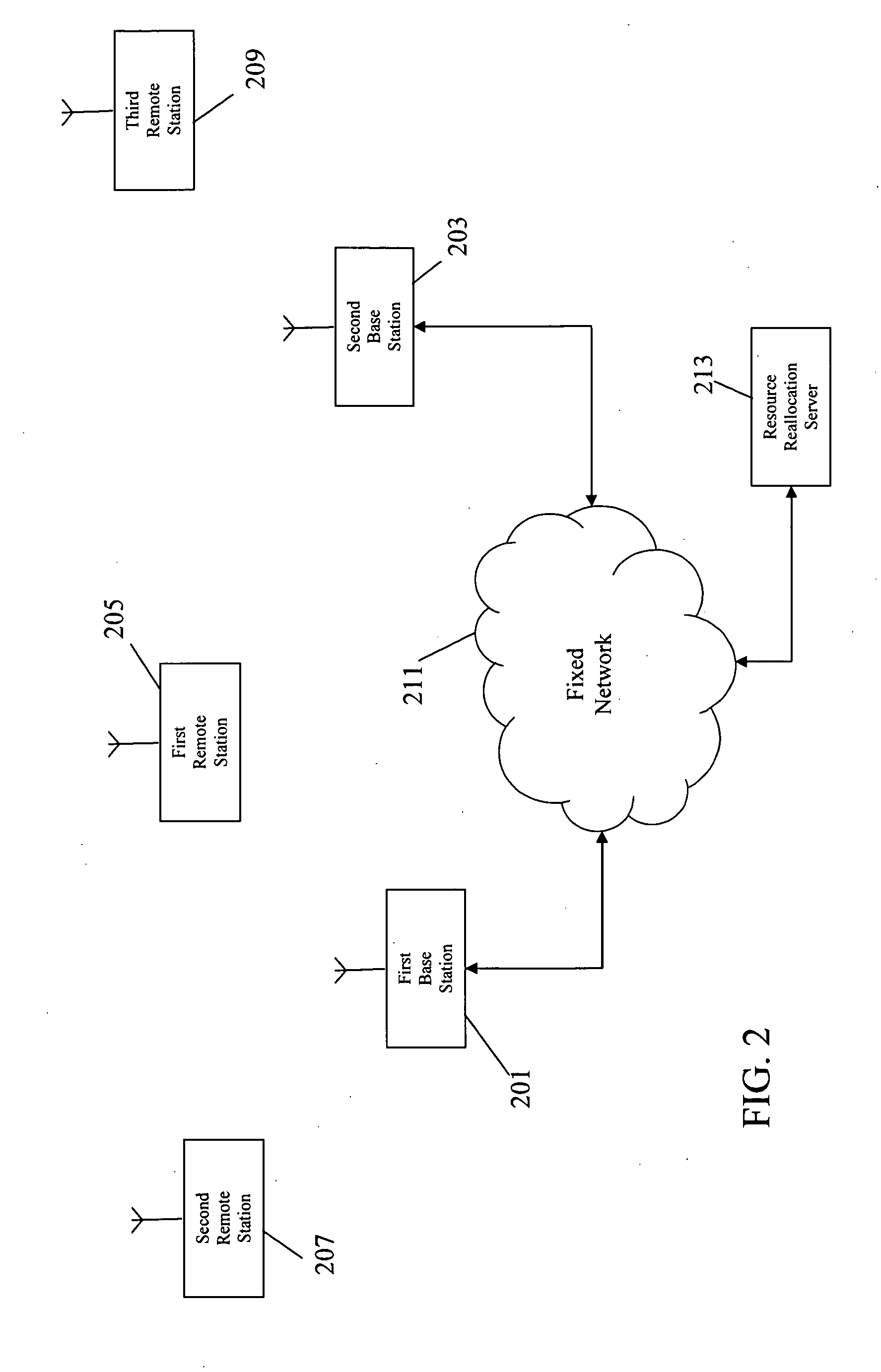
A cellular communication system comprises a set of base stations (201,203) which transmit downlink resource exchange discovery messages to remote terminals in resource allocations of a Media Access Control, MAC, frame structure. The discovery messages may indicate that a base station has resource available for reallocation to another base station or that a base station is seeking resource to be allocated from another base station. A remote terminal (205) comprises a receiver (401, 403) which receives a first message of the downlink resource exchange discovery messages from at least a first base station (201). A discovery message transmit processor (407) generates a second message, which is an uplink resource exchange message comprising resource exchange data determined from the first message, and transmits this to a second base station (203). The second base station (203) then initiates a temporary air interface resource reallocation with the first base station in response to receiving the second message.
Owner:MOTOROLA SOLUTIONS INC
Fast authentication and access control system for mobile networking
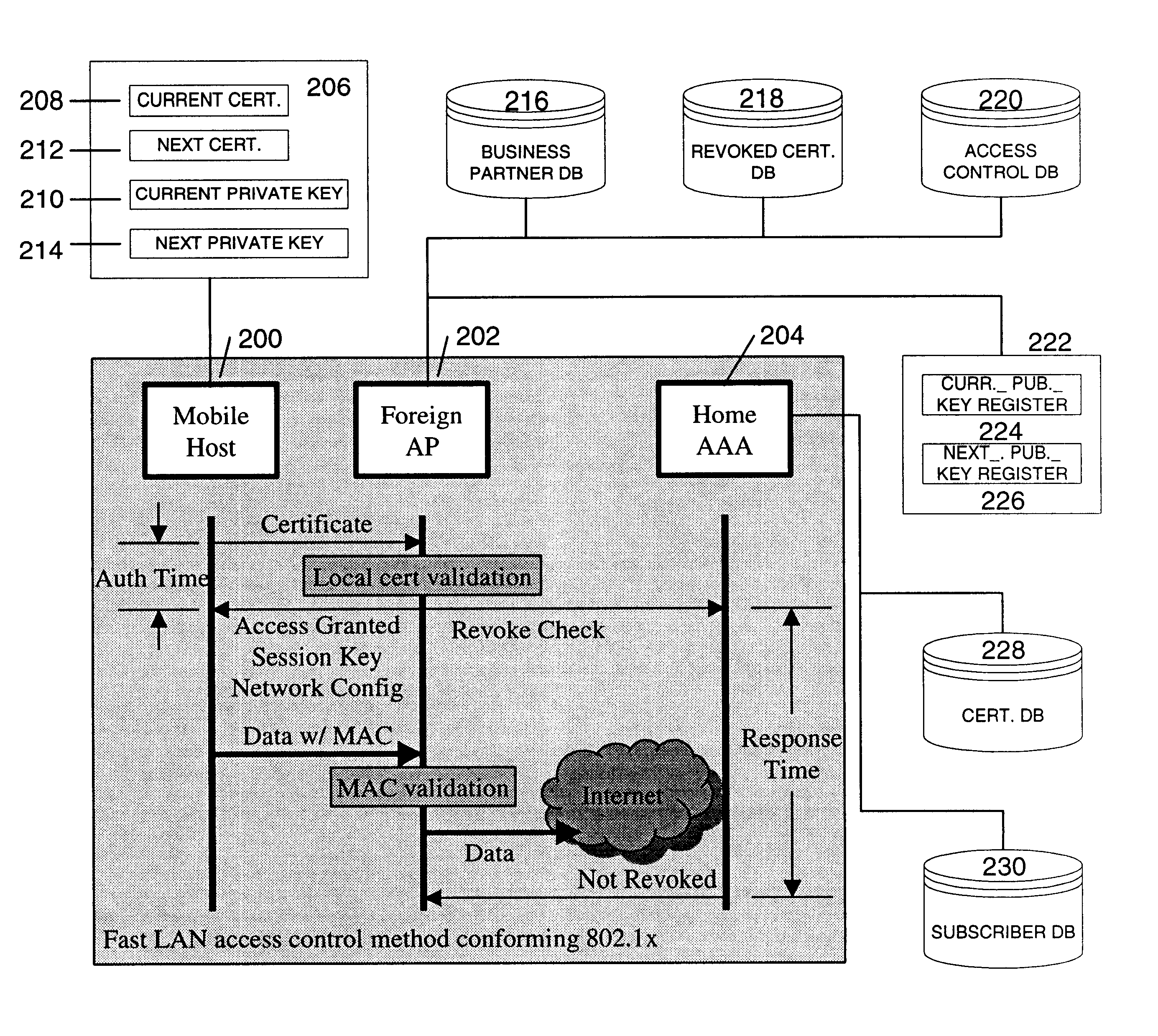
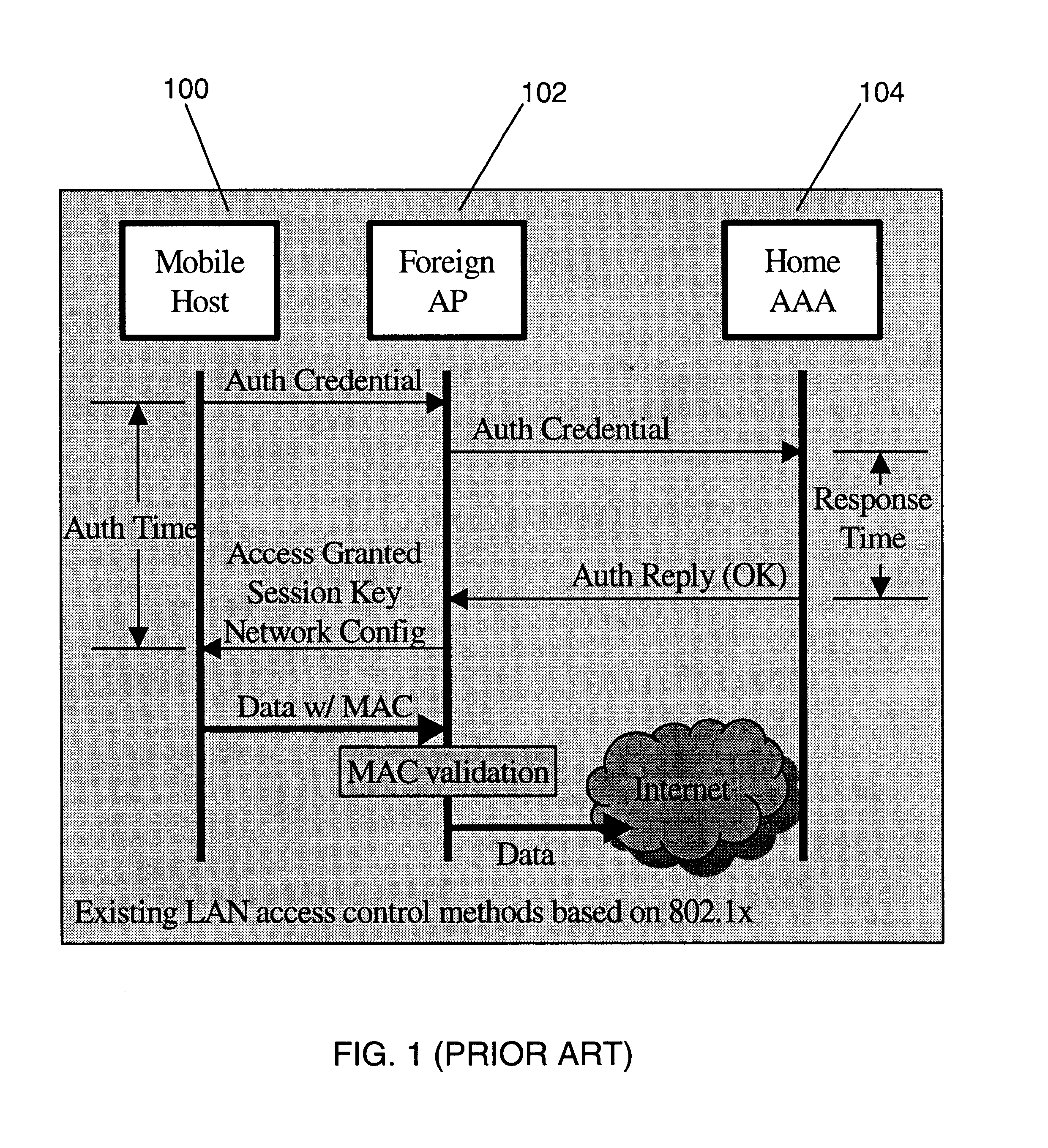
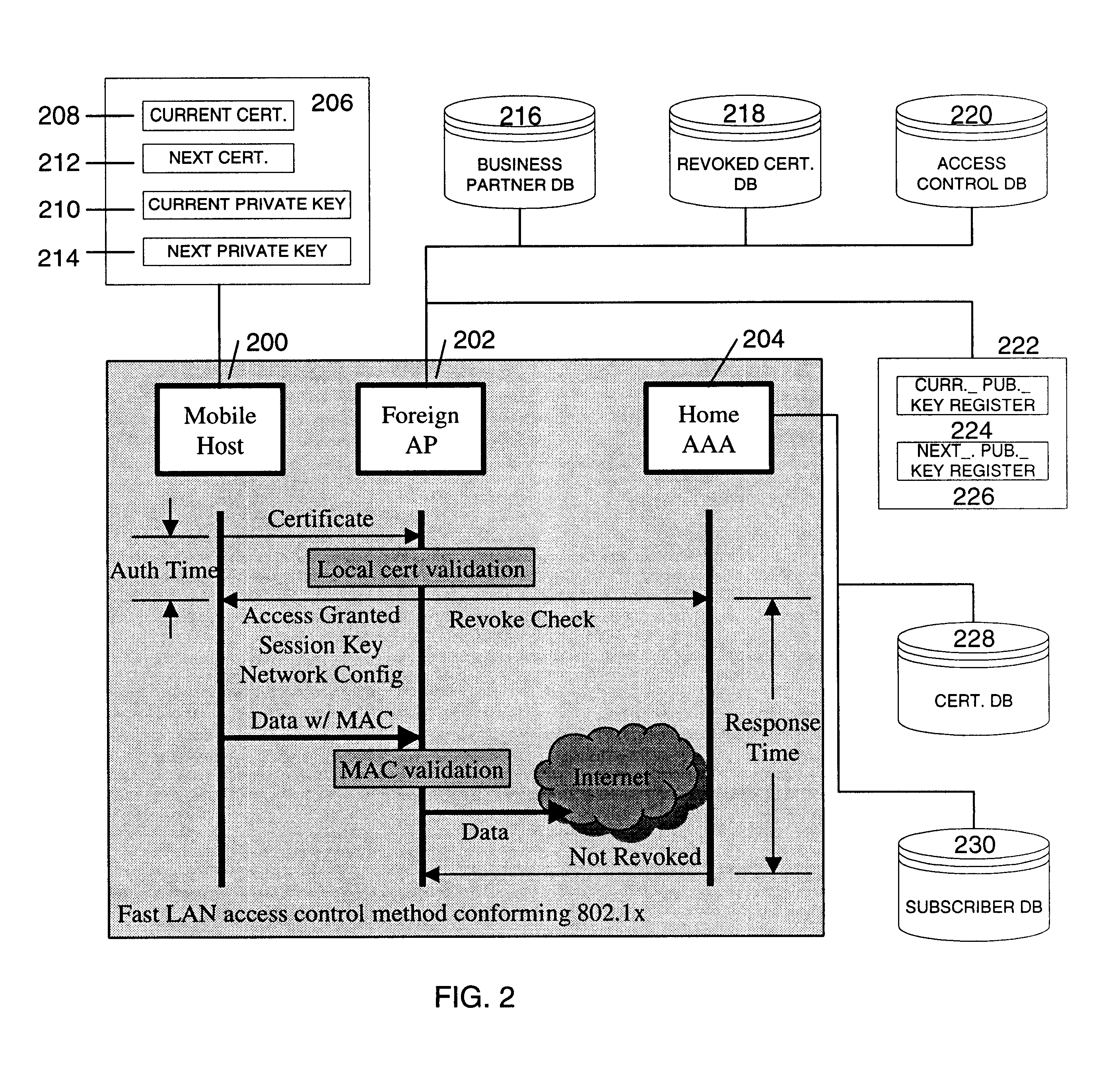
InactiveUS6856800B1Easy to switchReduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
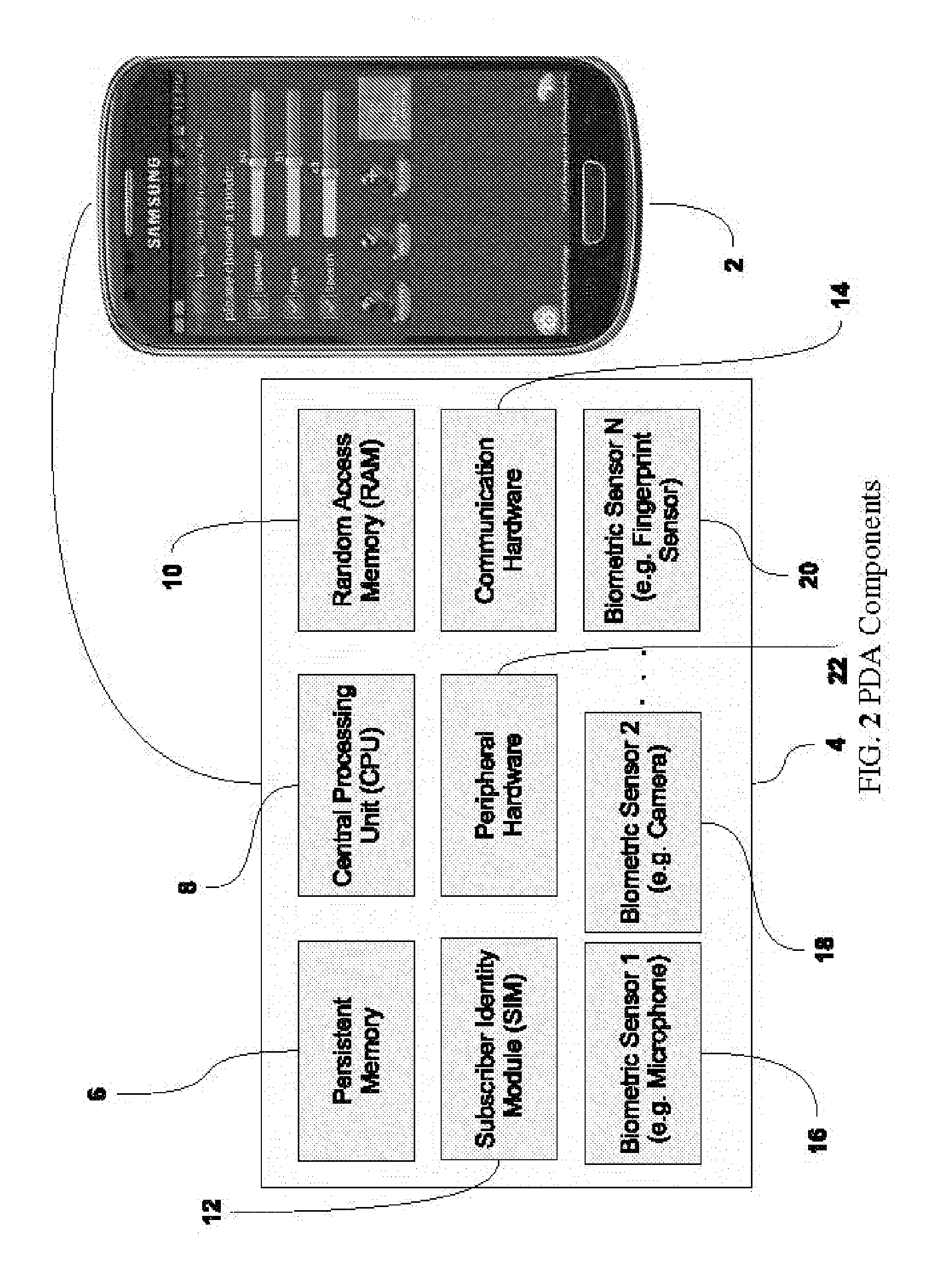
Access Control Through Multifactor Authentication with Multimodal Biometrics
ActiveUS20150347734A1Safe storageImprove securityDigital data processing detailsUser identity/authority verificationThe InternetFinancial transaction
A system is provided in which a person may use a Cellular (Mobile) Telephone, a PDA or any other handheld computer to make a purchase. This is an example only. The process may entail any type of transaction which requires authentication, such as any financial transaction, any access control (to account information, etc.), and any physical access scenario such as doubling for a passport or an access key to a restricted area (office, vault, etc.). It may also be used to conduct remote transactions such as those conducted on the Internet (E-Commerce, account access, etc.). In the process, a multifactor authentication is used.
Owner:BEIGI HOMAYOON
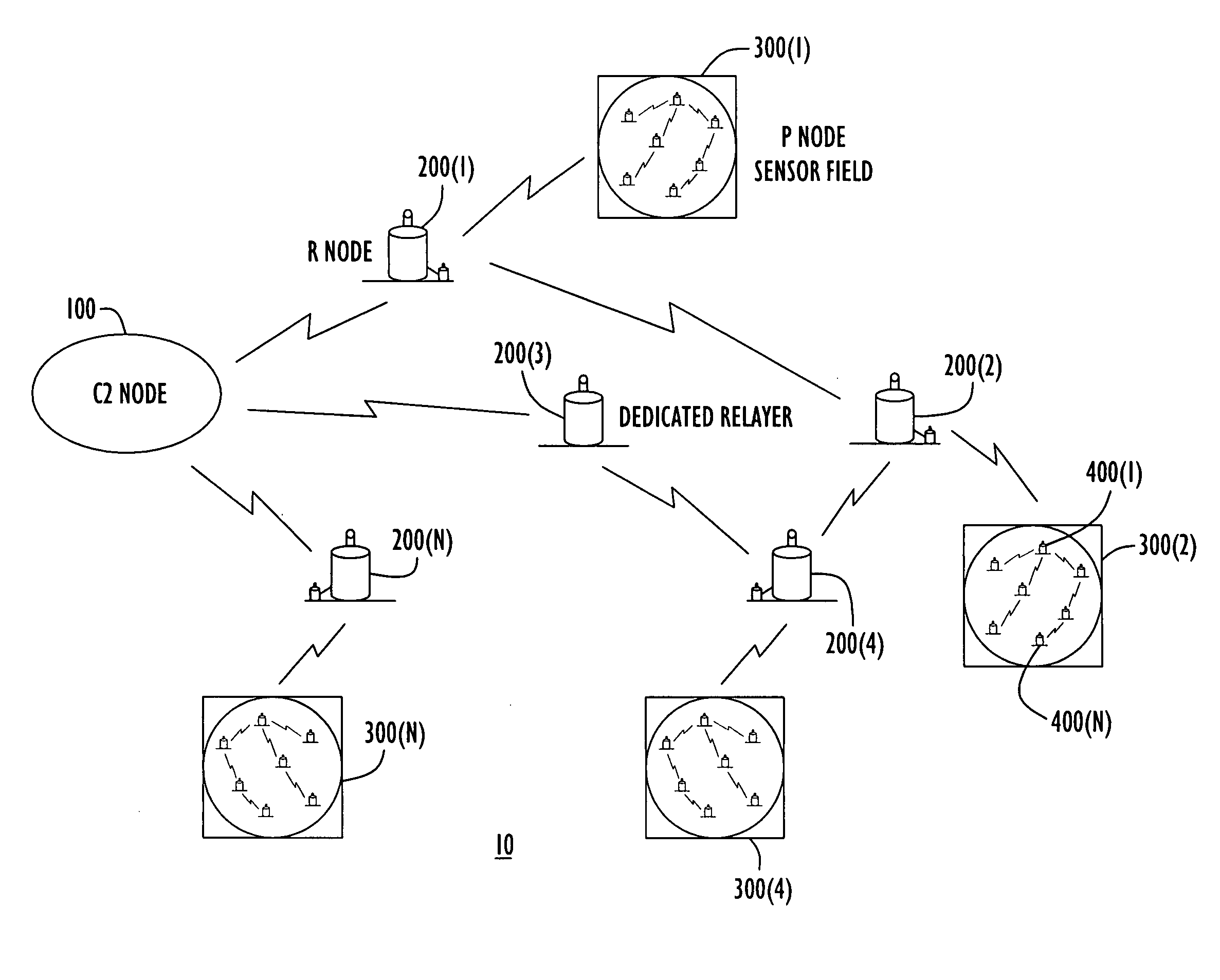
Multi-Hop Ultra Wide Band Wireless Network Communication
InactiveUS20070104215A1Avoid bandwidth reservation conflictImprove utilizationNetwork traffic/resource managementAssess restrictionFrequency spectrumCommunication device
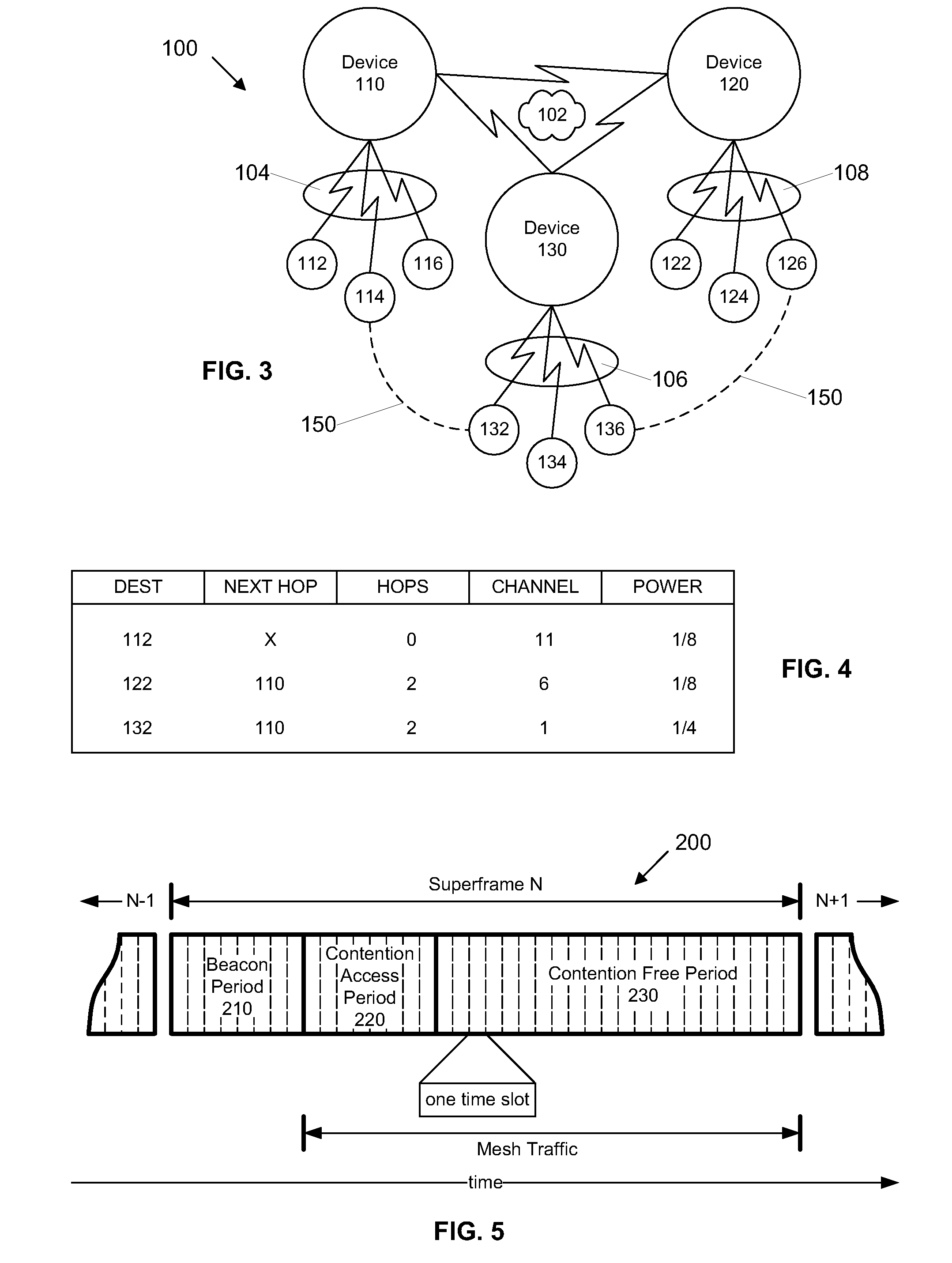
A wireless communication system is provided that has at least three nodes arranged in a multi-hop ultra wide band (UWB) communication network such that communications from a first node destined for a third node pass through a second node. Each of the devices in the system includes a radio and a media access control (“MAC”) module that is configured to establish multi-hop UWB wireless communications between the three or more wireless communication devices that enables high bandwidth applications such as Voice Over Internet Protocol (“VoIP”); multiplayer gaming; Wireless High Definition Television; and Internet Protocol Television (“IPTV”) among others. The MAC module is configured to avoid bandwidth reservation conflicts so that network performance does not degrade as the number of hops or the number of nodes in the wireless communication system increases. The MAC also facilitates utilization of multiple channels to maximize the available spectrum and is further configured to dynamically switch between channels to maximize throughput and meet or exceed quality of service (“QoS”) requirements such that QoS is guaranteed and network resources are efficiently utilized.
Owner:UNWIRED BROADBAND INC
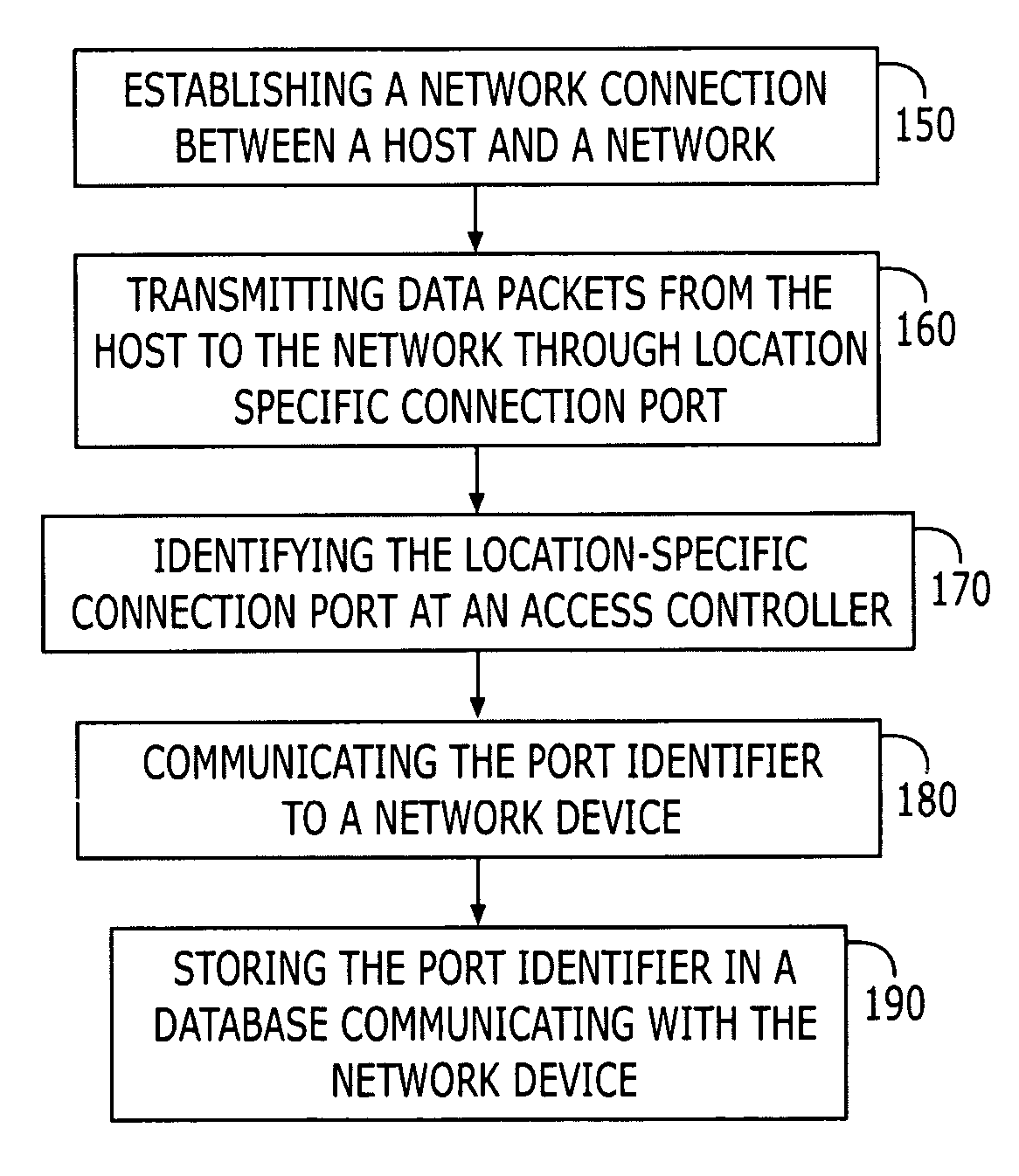
Location-based identification for use in a communications network
A method and apparatus for implementing location-based identification in a communication network. The method comprises establishing a network connection between a host and a network, transmitting network data packets from the host through a connection port, transmitting data packets from the host through a location-specific connection port and identifying the port at an access concentrator in the form of a port identifier. The port identifier is then communicated to a network device, typically a gateway device, and stored in a database in communication with the network device. The method may include tagging the network packets at the access concentrator with a port identifier that corresponds to a media access control (MAC) address. The access concentrator and the network device will tag and communicate port numbers by assigning VLAN (Virtual Local Area Network) identifiers to the ports.
Owner:NOMADIX INC
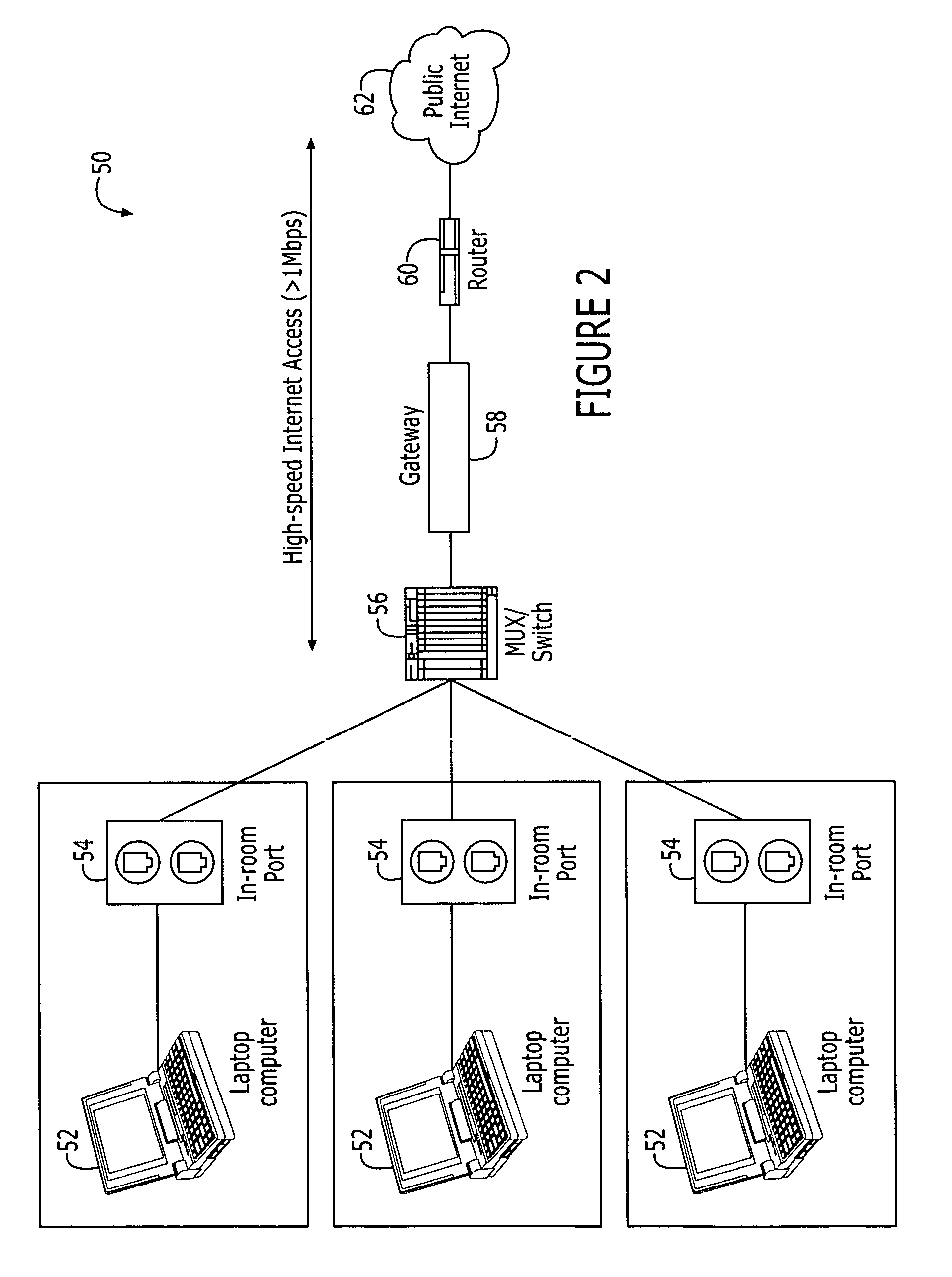
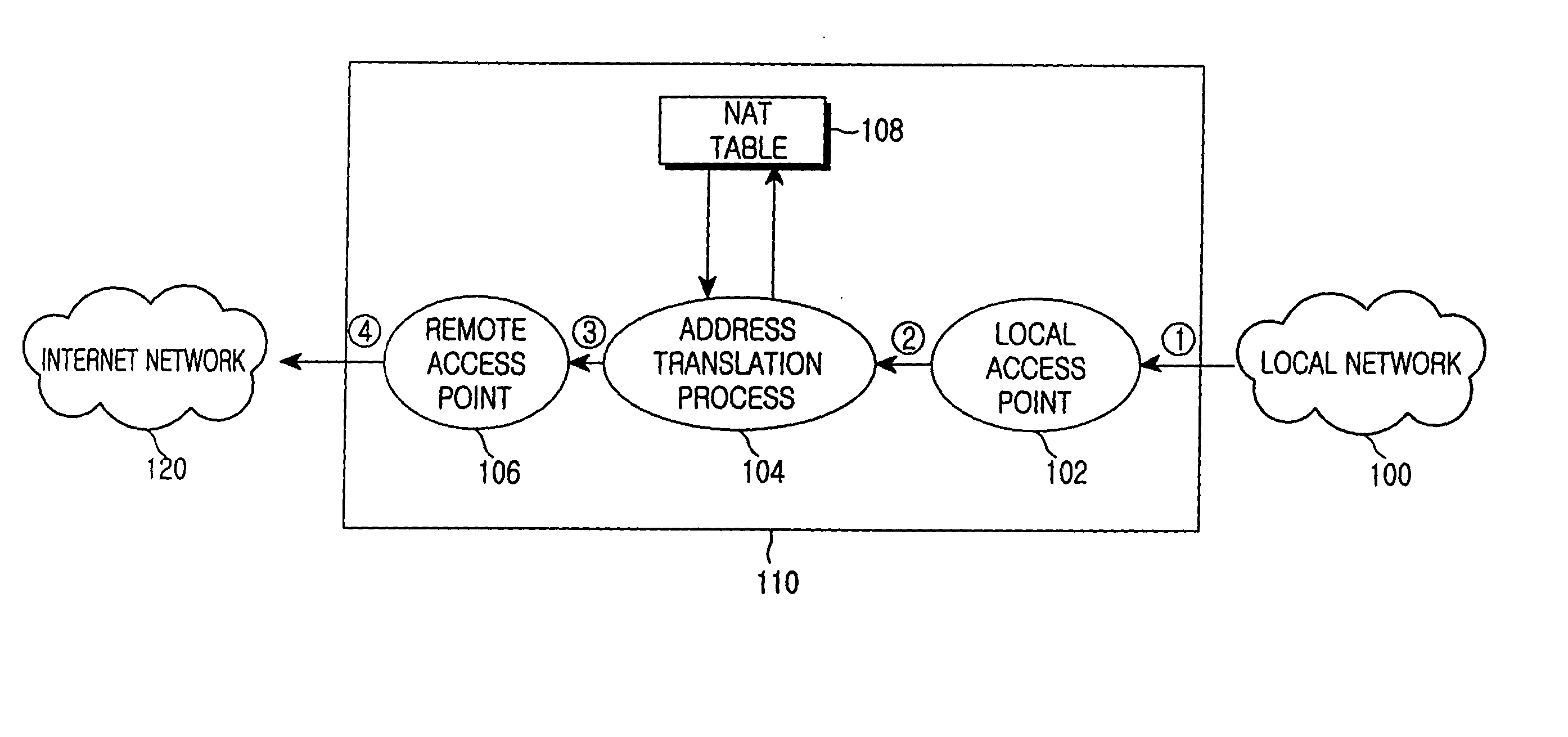
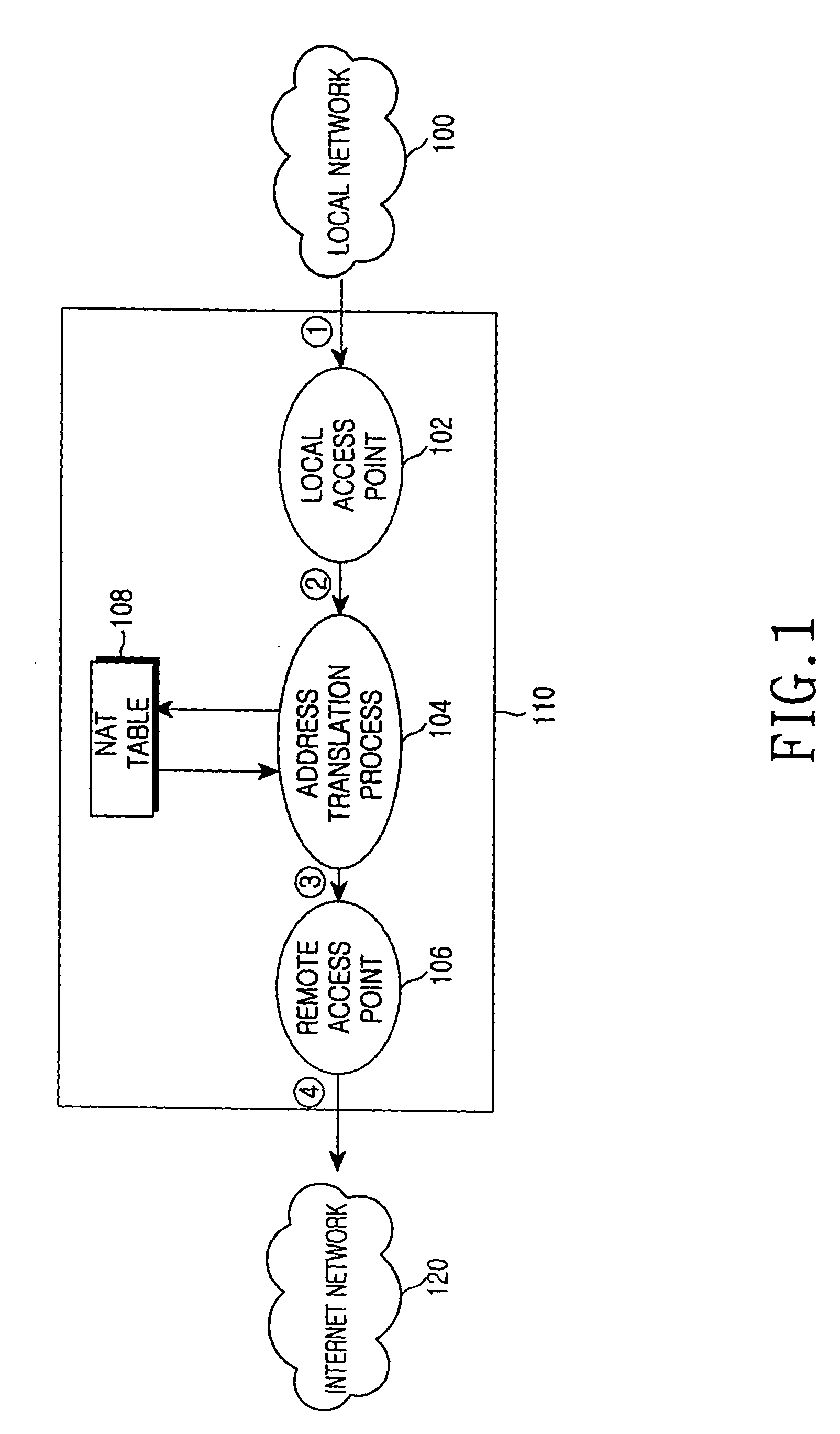
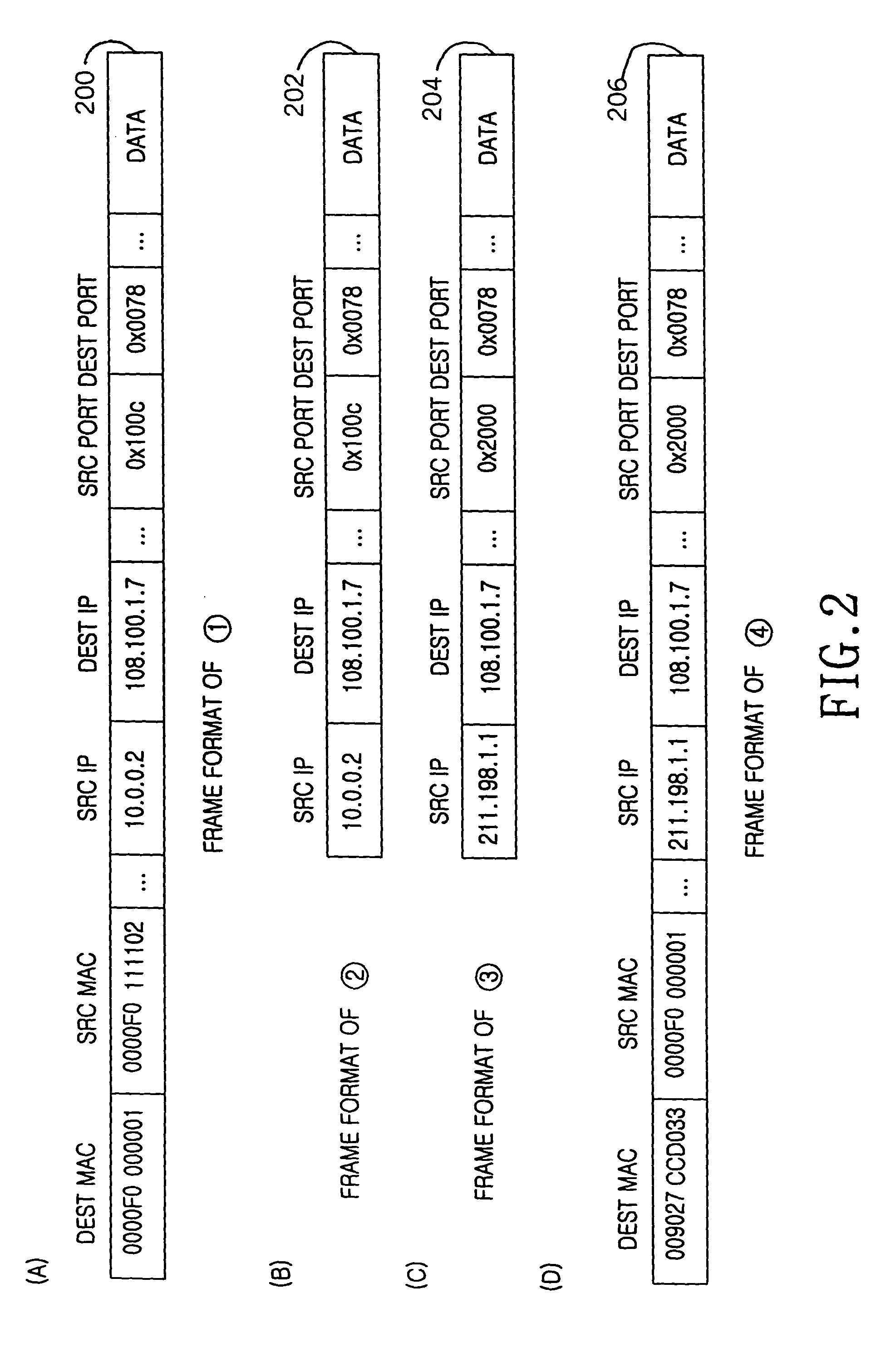
Internet protocol address allocation device and method
InactiveUS20040052216A1Error preventionFrequency-division multiplex detailsService provisionInternet access
A device and method for allocating the same Internet protocol (IP) address to all information terminals or hosts connected to a specific local network, which allows the hosts in the local network to gain access to the Internet while the hosts share a single IP address. The device includes a dynamic host configuration protocol (DHCP) client, a local access point, and a DHCP server spoofer. The DHCP client is allocated an IP address through a DHCP message communication with an Internet service provider. The Internet service provider includes a DHCP server for allocating IP addresses to the hosts and an Internet access gateway. The local access point includes a hardware address port translation (HAPT) module and a local IP address translation (LIAT) module. The HAPT module modifies a source medium access control (MAC) II address and port number of a frame received from each host, stores the modified result in a HAPT table, and recovers a destination MAC address and port number of a frame received from the Internet service provider, referring to the HAPT table. The LIAT module prevents a collision occurring because the hosts have the same public IP address. The DHCP server spoofer implements a DHCP server function to allocate an IP address to each host.
Owner:SAMSUNG ELECTRONICS CO LTD
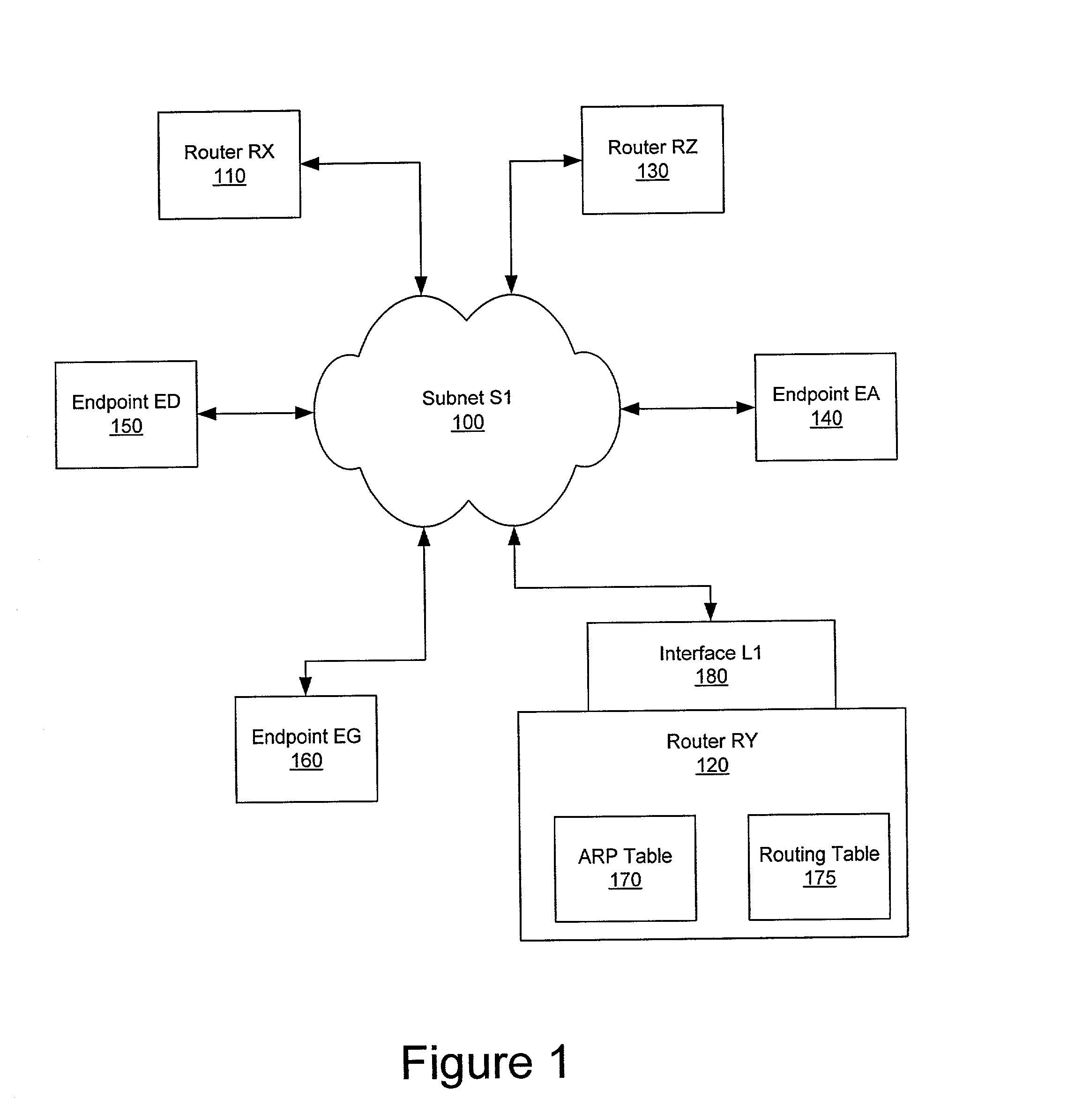
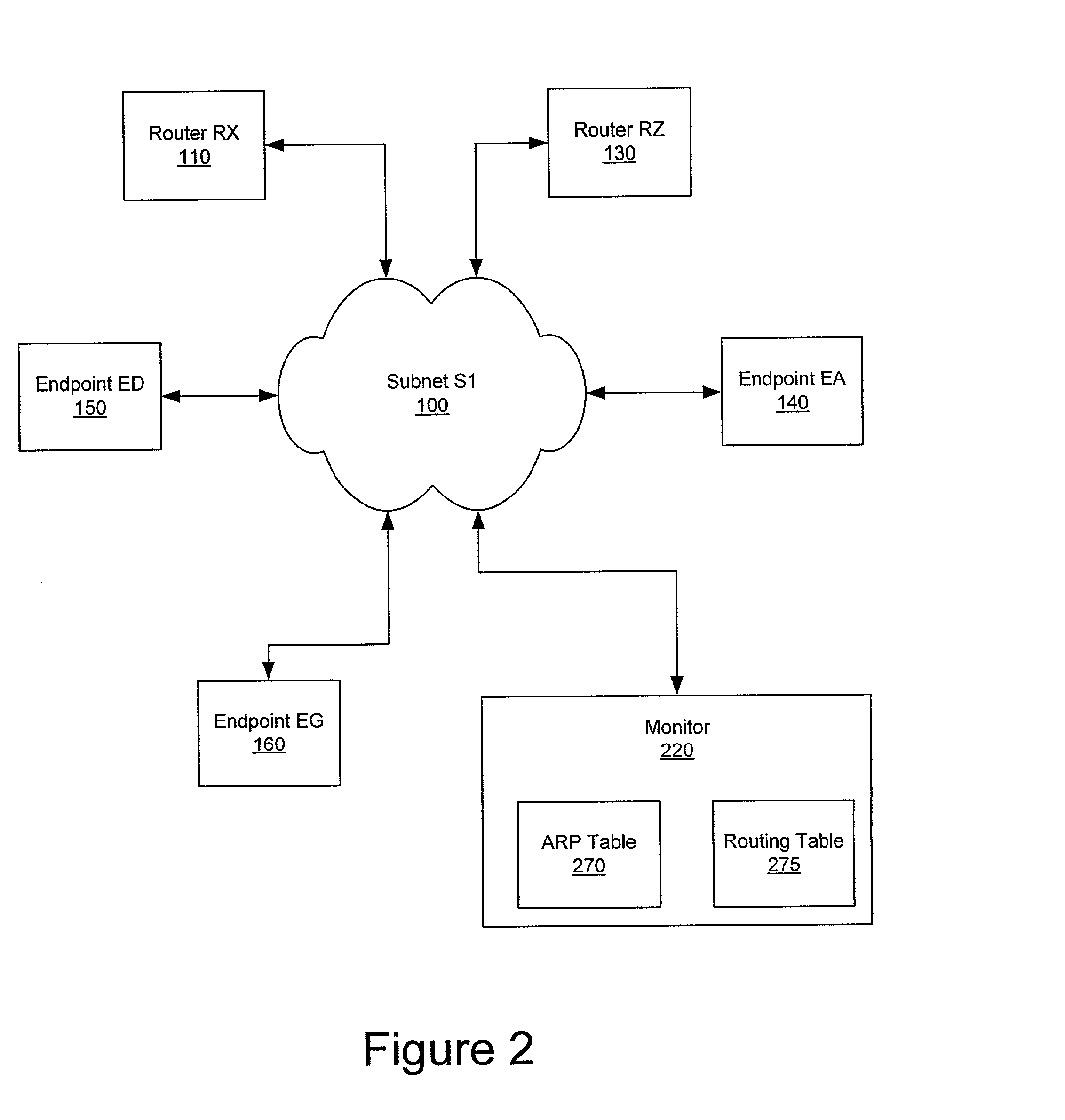
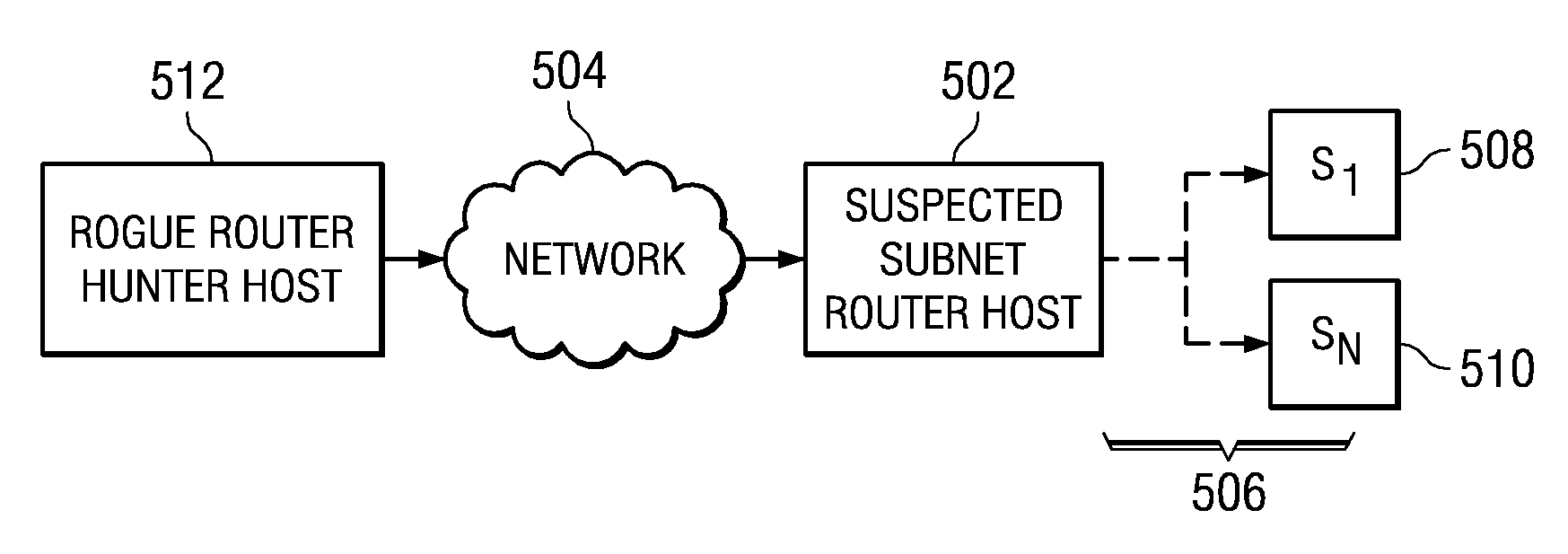
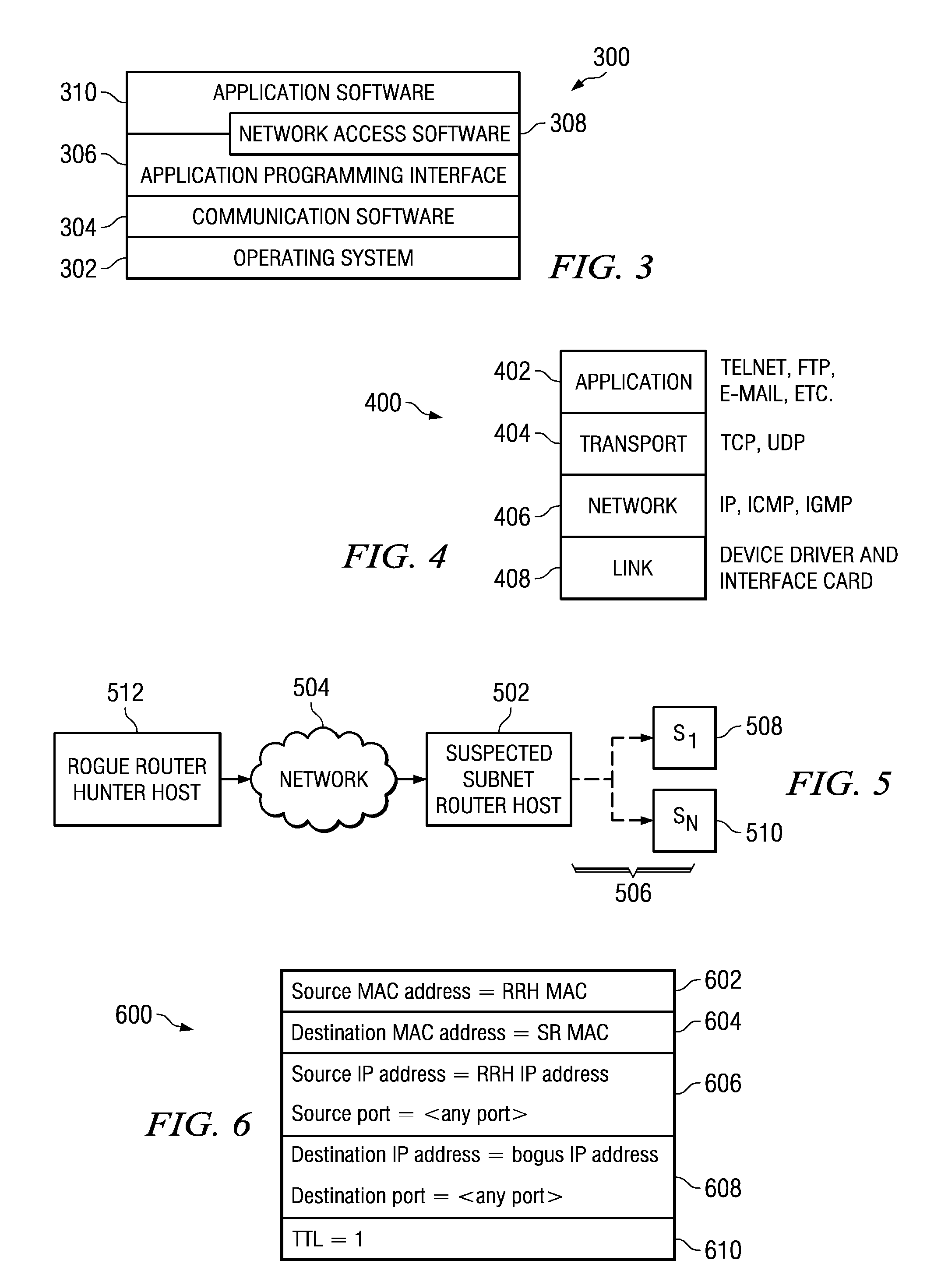
Rogue router hunter
InactiveUS7991877B2Digital computer detailsPlatform integrity maintainanceData processing systemTime limit
A computer implemented method, data processing system, and computer program product for discovering an unauthorized router in a network. The process in the illustrative embodiments first obtains a physical address of a suspected router or destination device. A data packet is created which comprises at least a destination media access control field, a destination internet protocol field, and a time-to-live field, wherein the destination media access control field comprises the physical address of the destination device, wherein the destination internet protocol field comprises a bogus internet protocol address, and wherein the time-to-live field comprises a value indicating the data packet has exceeded a time limit. The data packet is sent to the destination device using the physical address in the destination media access control field. If a time exceeded message is received from the destination device, the destination device is determined to be enabled for routing.
Owner:INT BUSINESS MASCH CORP
Frame aggregation in wireless communications networks
InactiveUS20060056443A1Improve throughputReduce complexityError preventionNetwork traffic/resource managementTelecommunicationsMedia access control
A method aggregates frames to be transmitted over a channel in a wireless network into a single frame. Multiple MSDU frames having identical destination addresses and identical traffic classes, received in the media access control layer from the logical link layer in a transmitting station are aggregated into a single aggregate MPDU frame, which can be transmitted on the channel to a receiving station. In addition, aggregate MSDU frames with different destination addresses and different traffic classes received from the media access control layer can be further aggregated into a single aggregate PPDU frame before transmission.
Owner:MITSUBISHI ELECTRIC RES LAB INC
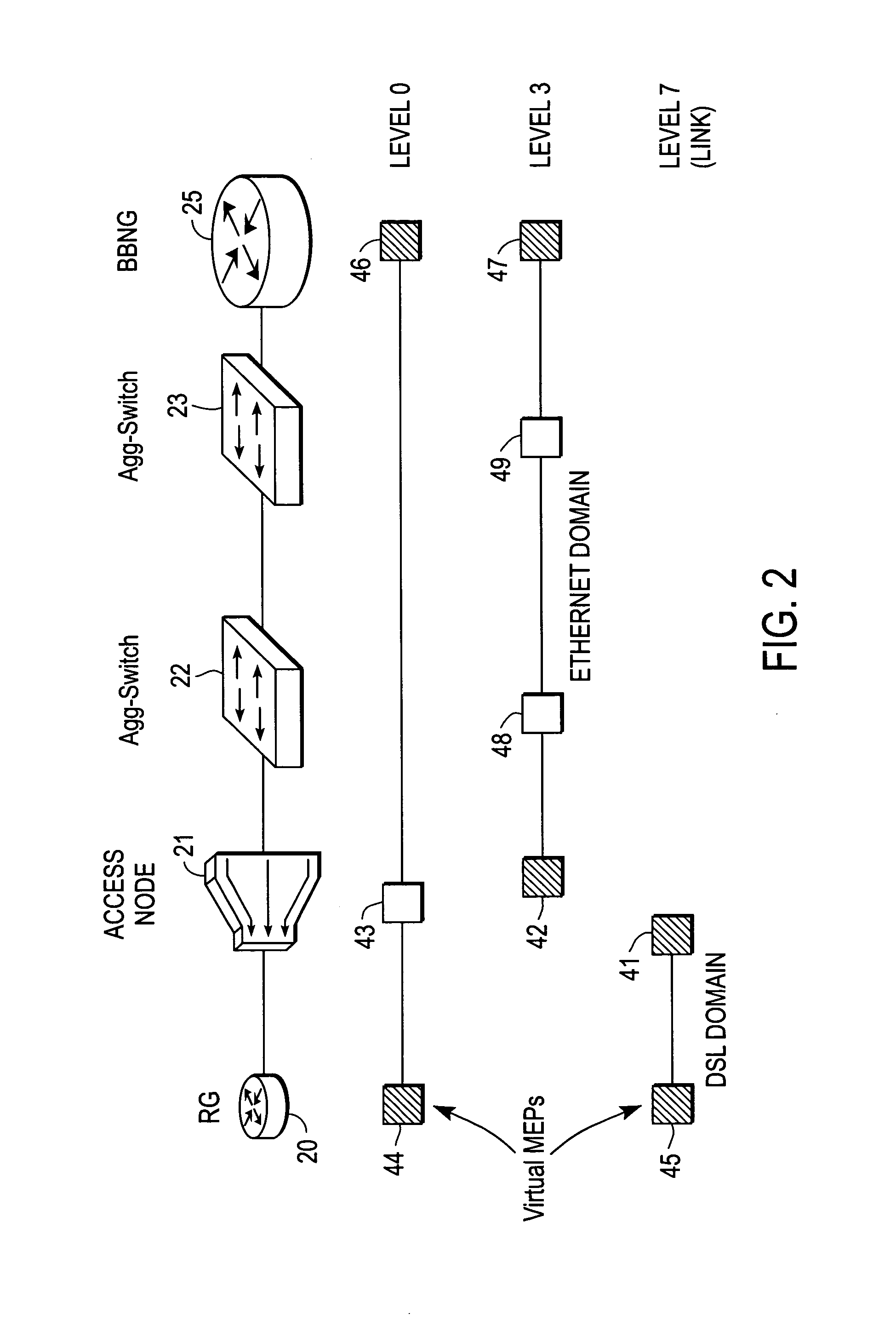
Address resolution mechanism for ethernet maintenance endpoints
A method of operation for a node of an Ethernet access network includes issuing a multicast message on the Ethernet access network by a maintenance end point (MEP) of the node. The multicast message contains a name of a target MEP. The node is further operable to receive a unicast reply message from the target MEP, the unicast message reply containing a MEP identifier (MEP-ID) and a MEP Media Access Control (MAC) address of the target MEP. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
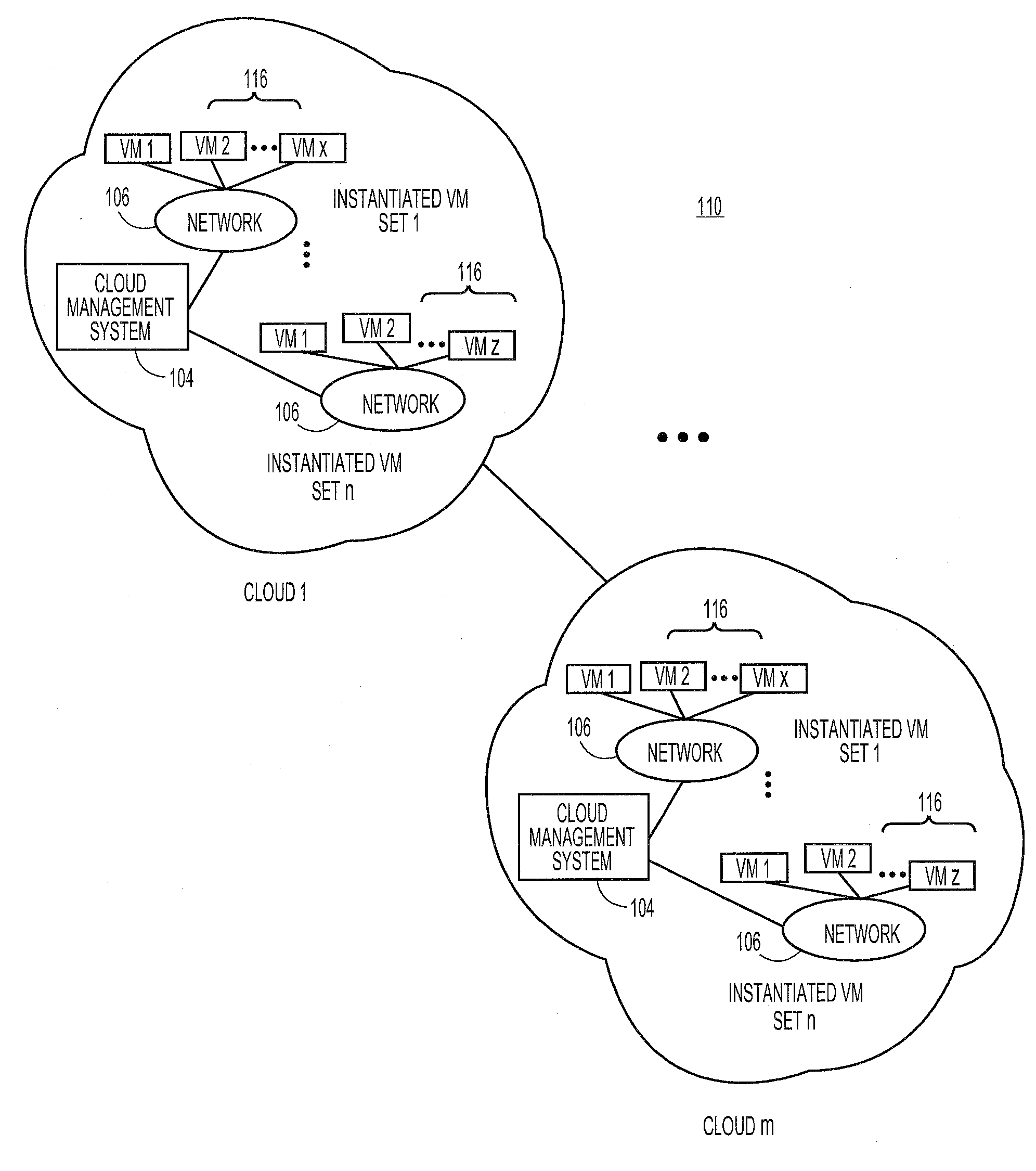
Methods and systems for providing access control to user-controlled resources in a cloud computing environment
A cloud computing environment can be configured to allow third party, user-controlled resources to be included in the pool of resources available in the cloud. The user-controlled resources can include a cloud application to communicate with a cloud management system to coordinate access to the user-controlled resources. The cloud application allows the user to specify the specific set of resources that the cloud can access, such as specific hardware and software resources.
Owner:RED HAT
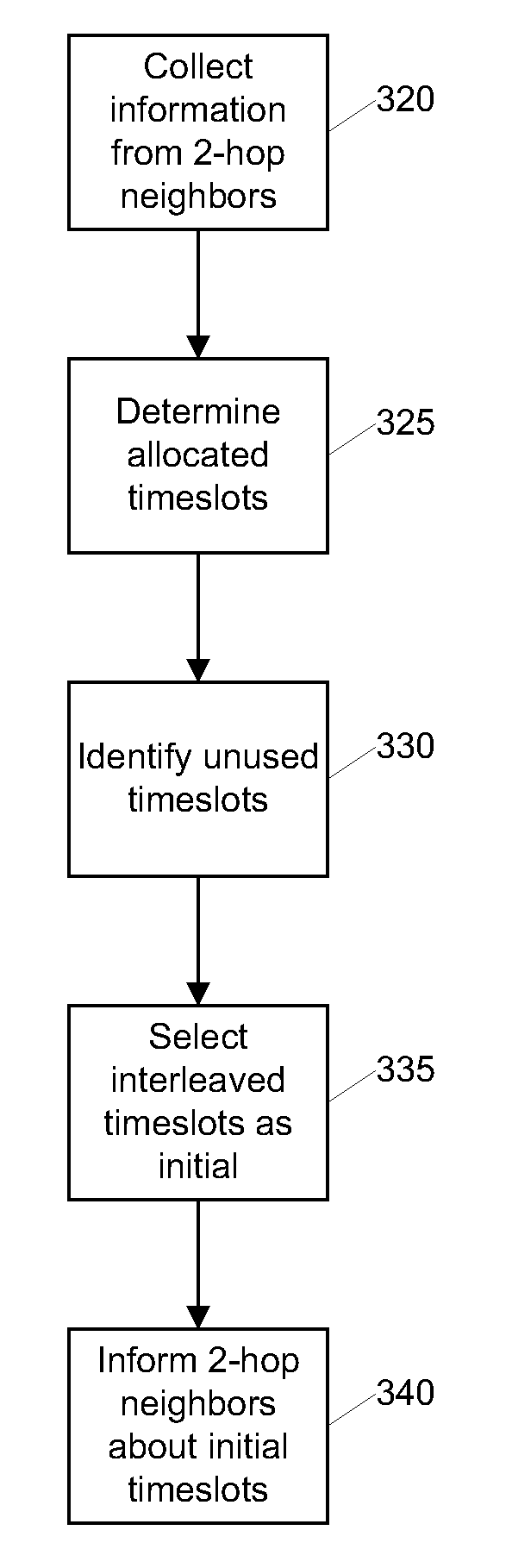
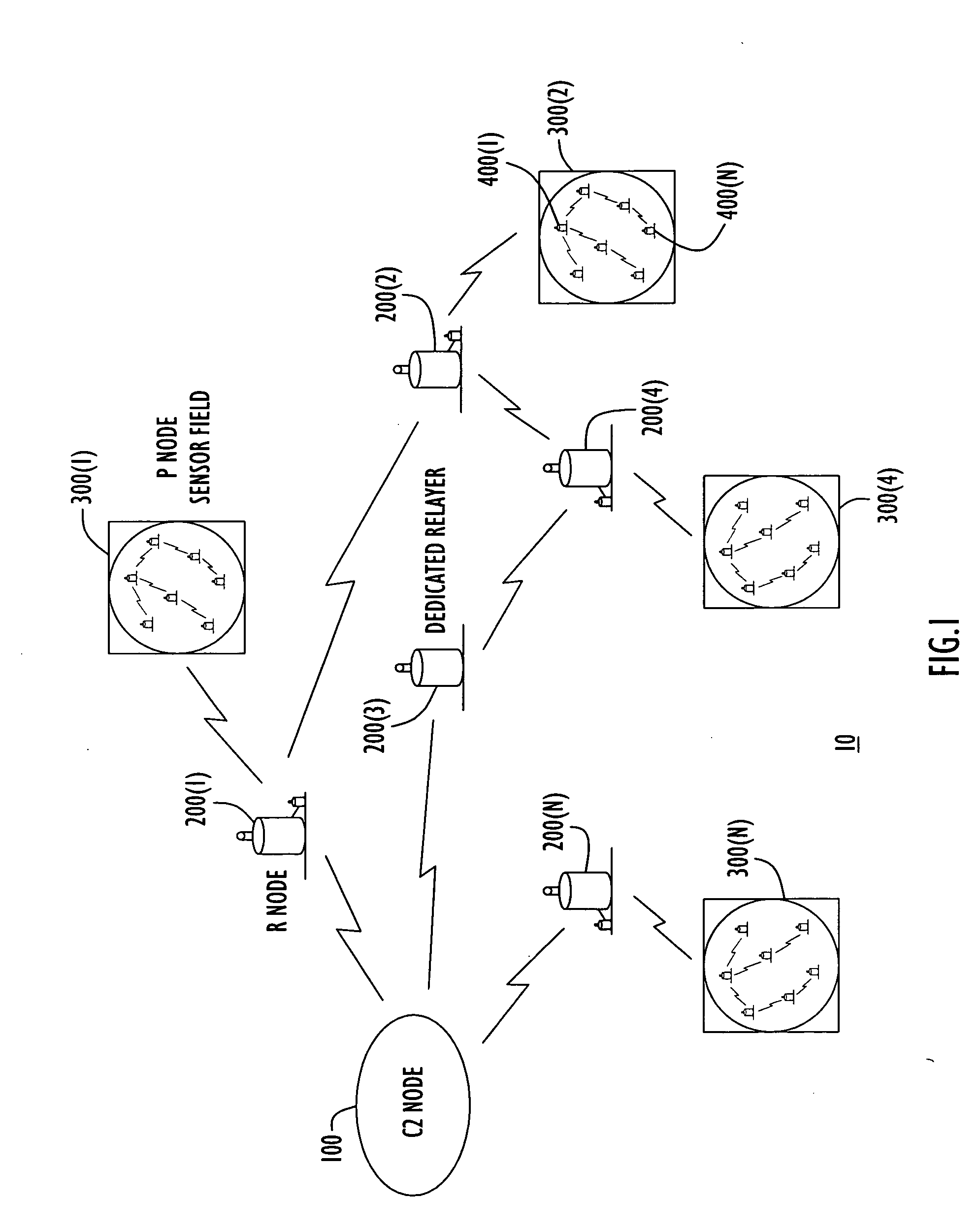
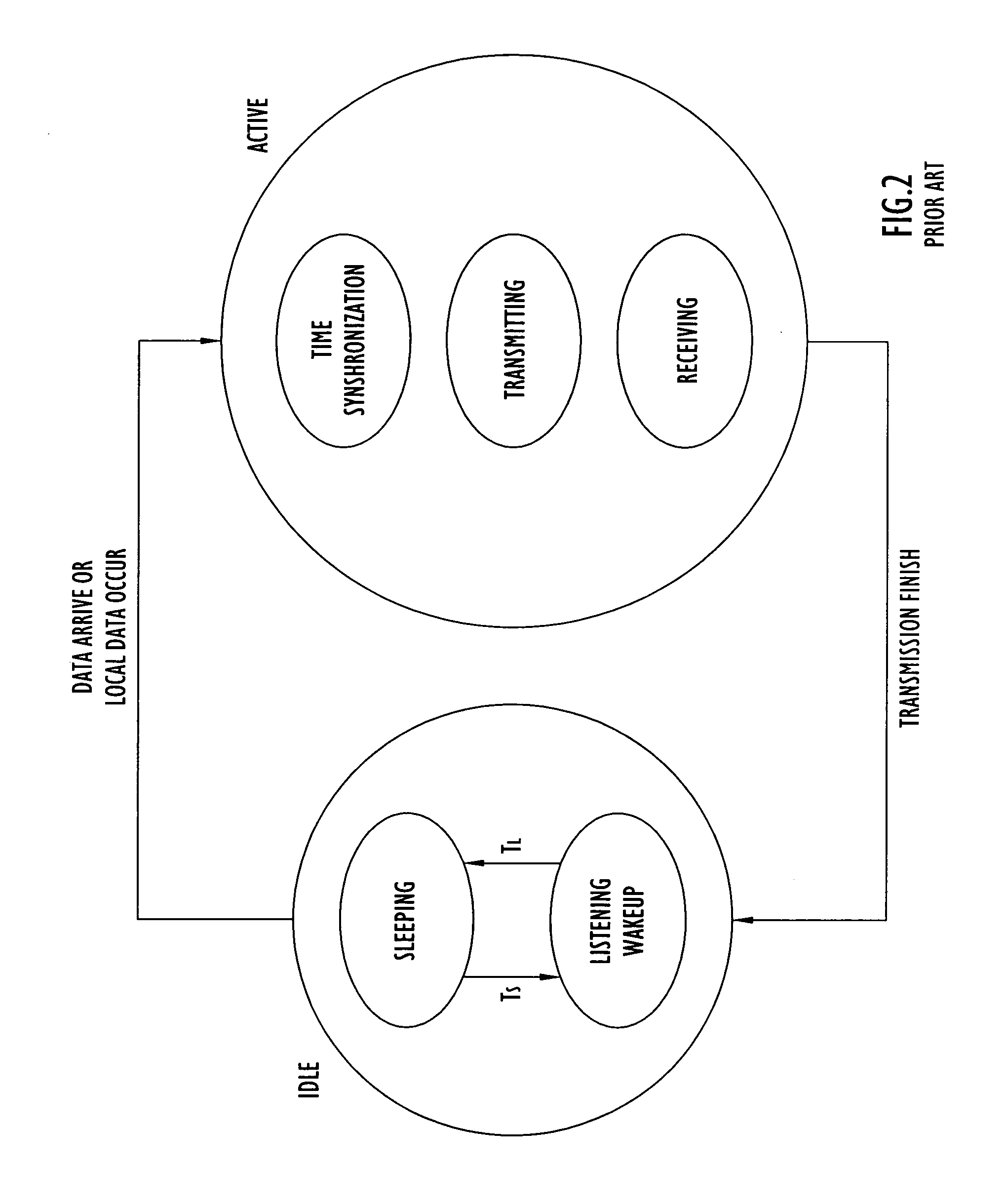
Energy-efficient medium access control protocol and system for sensor networks
ActiveUS20060128349A1Extend battery lifeMore processing gainEnergy efficient ICTPower managementMedia access controlReal-time computing
An energy efficient MAC protocol for a sensor network that extends the battery life of remotely located wireless nodes by employing MAC operations involving transmission of a wake-up signal with more processing gain, dynamic adjustment of a transmission rate of synchronization messages for fast time synchronization and an energy efficient neighboring node discovery technique.
Owner:HARRIS GLOBAL COMMUNICATIONS INC
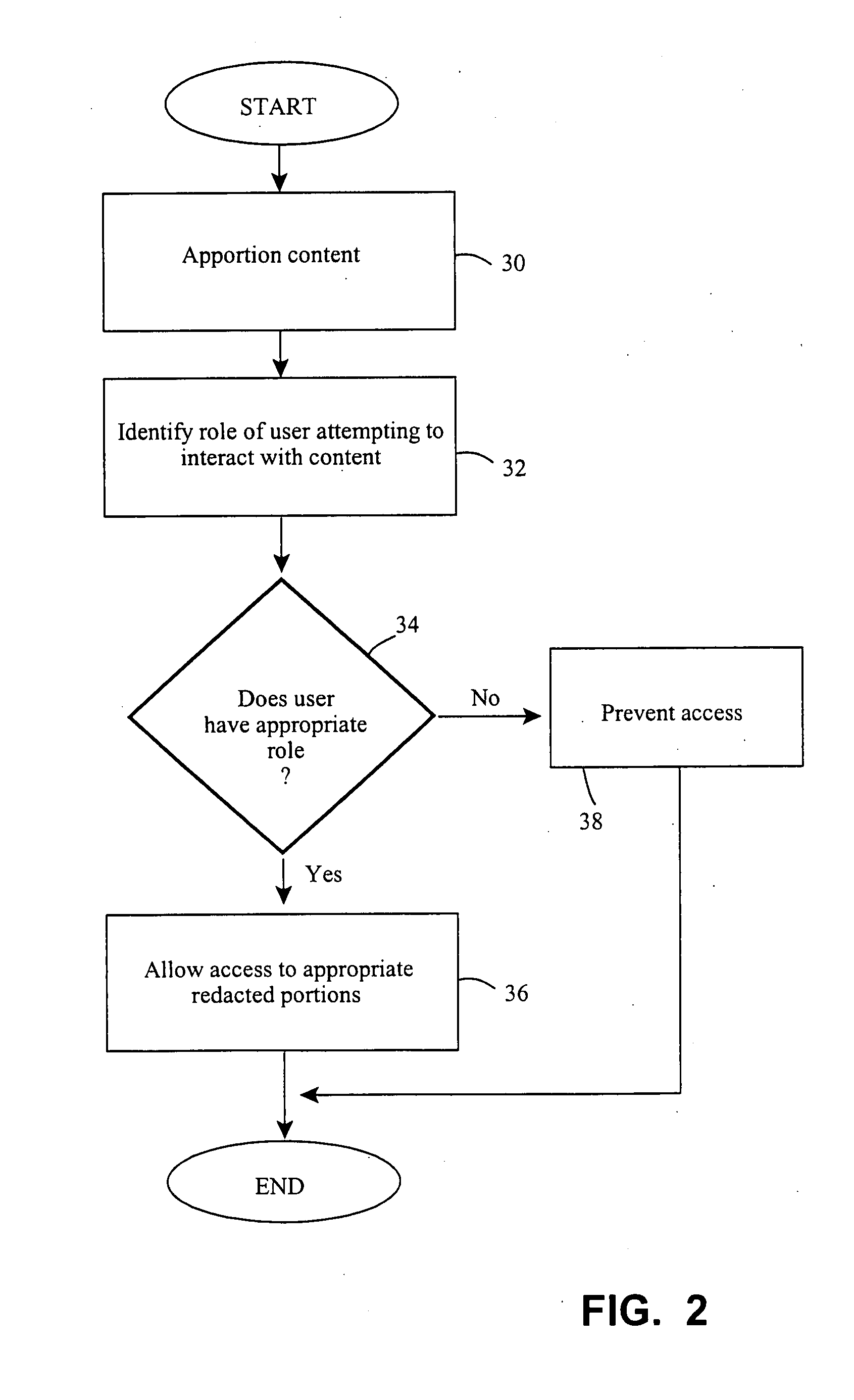
Role-based access control for redacted content
InactiveUS20090025063A1Digital data processing detailsComputer security arrangementsMedia access controlUser interface
Apparatus and methods are described for accessing redacted material based on user roles. An author designates portions of content as to-be-redacted. The author establishes various users roles able to access it and defines attributes or time constraints affecting the viewing / using. Upon electronically saving the content, the to-be-redacted portion is encrypted. An intermediary, such as a keytable service, mediates access between later users and the content. Upon identification of a role of a user attempting to interact with the content, and matching the role to one of the author-established roles, the encrypted redacted portion is decrypted. In this manner, users gain access to content based only on their role. The surrounding events are also loggable, traceable, and verifiable. A monitored connection between the user and the content, as well as various user interface options, are other noteworthy features. Computer program products and computing network interaction are also defined.
Owner:NOVELL INTPROP HLDG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com