Patents
Literature
905 results about "Key exchange" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Key exchange (also key establishment) is a method in cryptography by which cryptographic keys are exchanged between two parties, allowing use of a cryptographic algorithm. If the sender and receiver wish to exchange encrypted messages, each must be equipped to encrypt messages to be sent and decrypt messages received. The nature of the equipping they require depends on the encryption technique they might use. If they use a code, both will require a copy of the same codebook. If they use a cipher, they will need appropriate keys. If the cipher is a symmetric key cipher, both will need a copy of the same key. If it is an asymmetric key cipher with the public/private key property, both will need the other's public key.
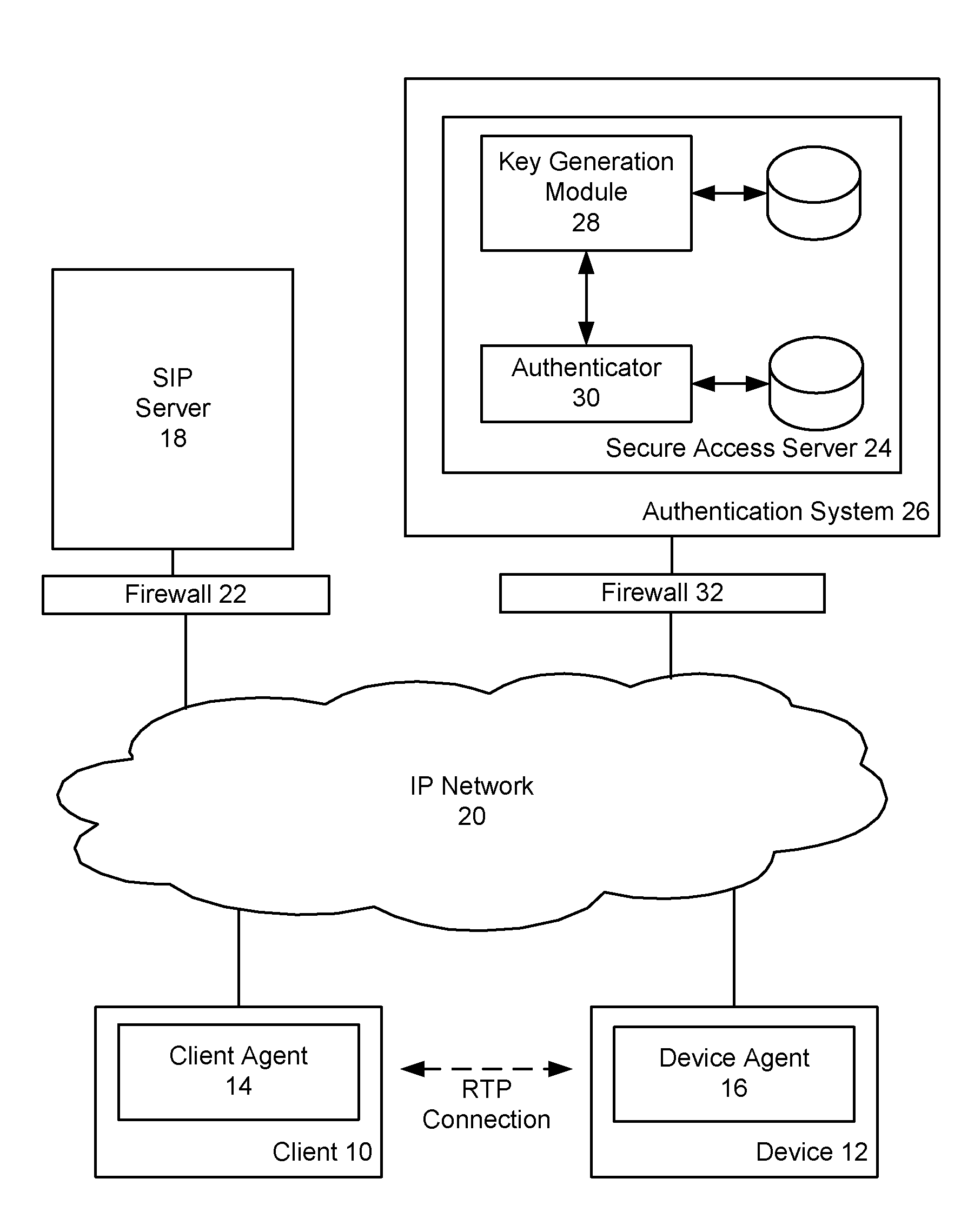
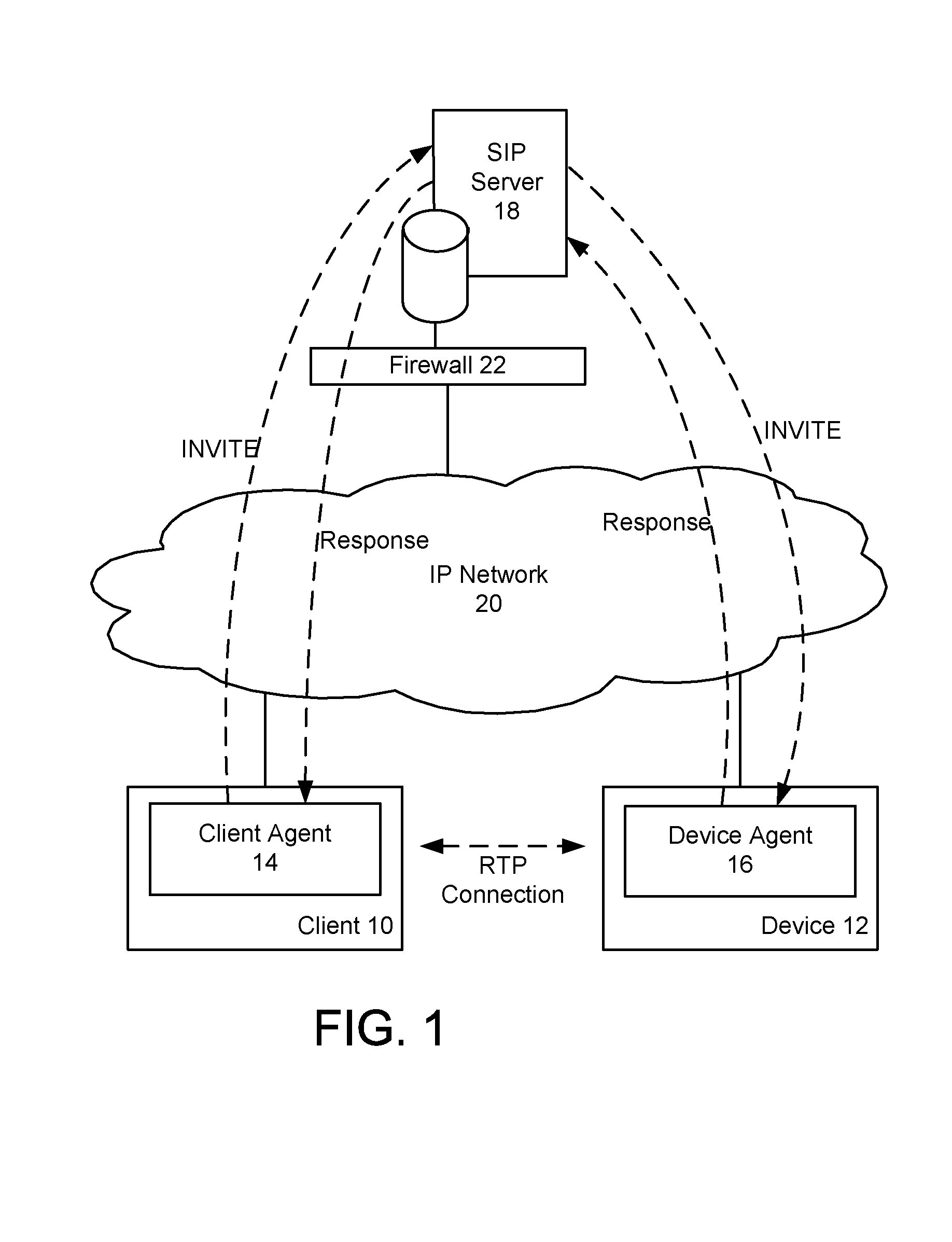
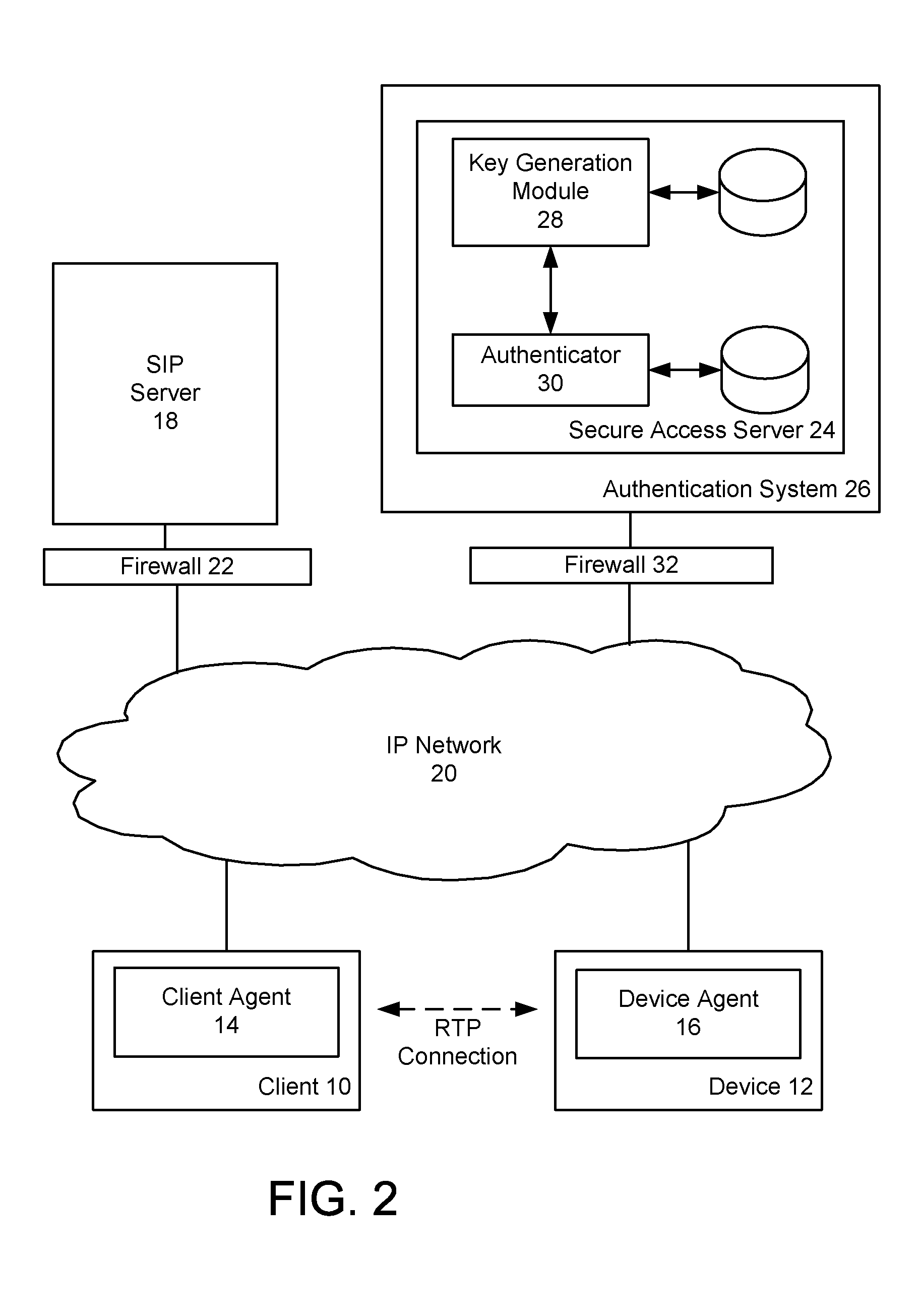
Device authentication and secure channel management for peer-to-peer initiated communications
ActiveUS20080235511A1Multiple keys/algorithms usageUser identity/authority verificationKey exchangeSignaling protocol
A method and system for providing secure access to a device initiating communications using a peer-to-peer signaling protocol, such as a SIP or H.323. In a device registration phase, the device contacts a secure access server, and authenticates to the secure access server by providing an identification, such as its factory ID. The secure access server then issues a device ID and private key to the authenticated device. A client can then initiate a further communication session and be authenticated by the secure access server. The secure access server returns the device identification and the device's public key to the client. The client and device can then perform a symmetrical key exchange for their current communication session, and can communicate with appropriate encryption. The device's private key can be set to expire after one or more uses.
Owner:BCE
Integrated system for network layer security and fine-grained identity-based access control
ActiveUS6986061B1Simple technologyUser identity/authority verificationDigital computer detailsKey exchangeMedia access control
Owner:TREND MICRO INC
Method and Apparatus for Hardware-Accelerated Encryption/Decryption
ActiveUS20090060197A1Avoid contactMaximize availabilityEncryption apparatus with shift registers/memoriesSecret communicationMultiple encryptionComputer hardware
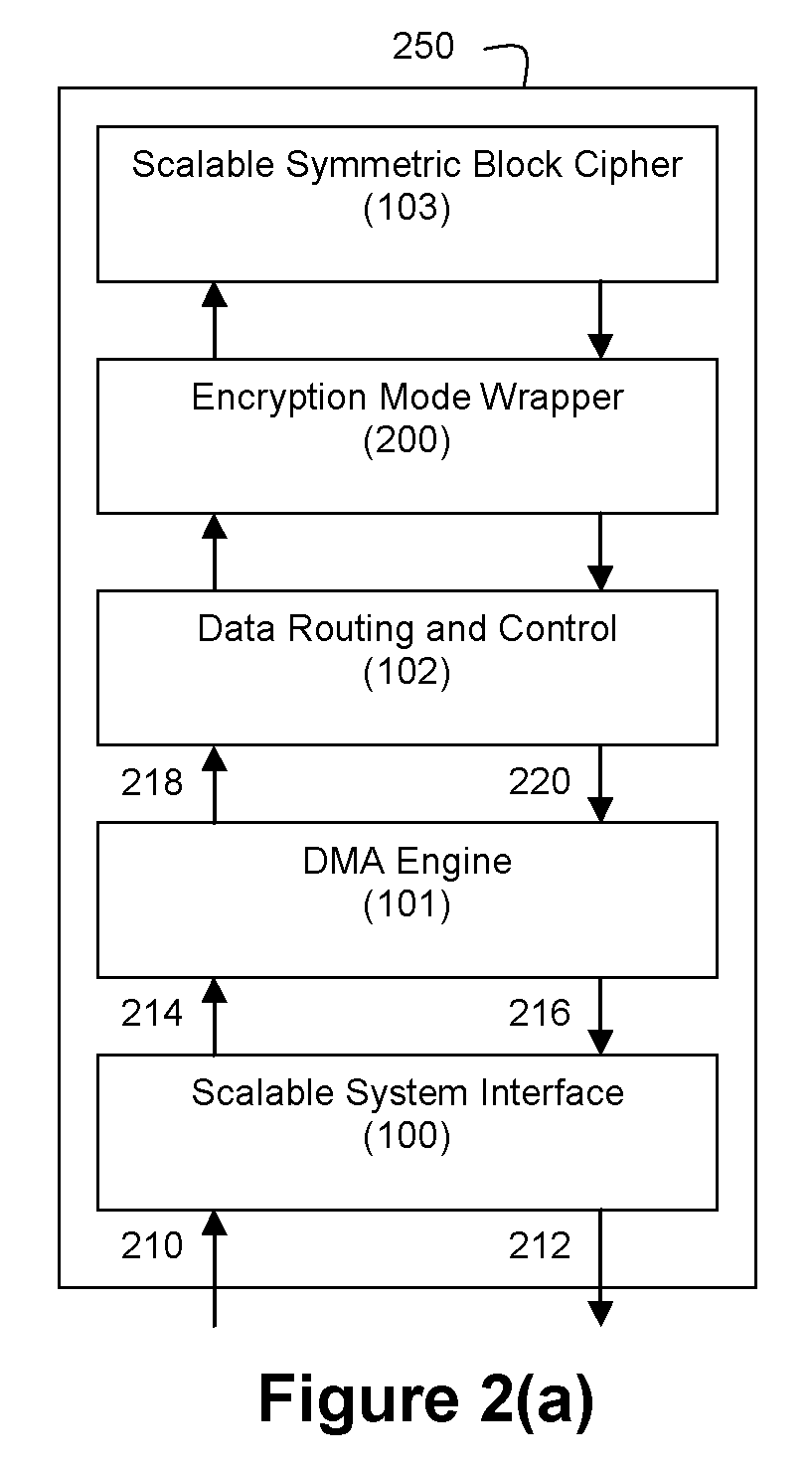
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
Systems and methods for authenticating communications in a network medium
InactiveUS20030149874A1Key distribution for secure communicationUser identity/authority verificationKey exchangeExchange protocol
Pre-authentication information of devices is used to securely authenticate arbitrary peer-to-peer ad-hoc interactions. In one embodiment, public key cryptography is used in the main wireless link with location-limited channels being initially used to pre-authenticate devices. Use of public keys in the pre-authenticate data allows for the broadening of types of media suitable for use as location-limited channels to include, for example, audio and infrared. Also, it allows a range of key exchange protocols which can be authenticated in this manner to include most public-key-protocols. As a result, a large range of devices, protocols can be used in various applications. Further, an eavesdropper is forced to mount an active attack on the location-limited channel itself in order to access an ad-hoc exchange. However, this results in the discovery of the eavesdropper.
Owner:CISCO TECH INC
System and method for secure three-party communications
InactiveUS7869591B1Reduce liabilityReduce riskKey distribution for secure communicationSecret communicationKey exchangeTranscoding
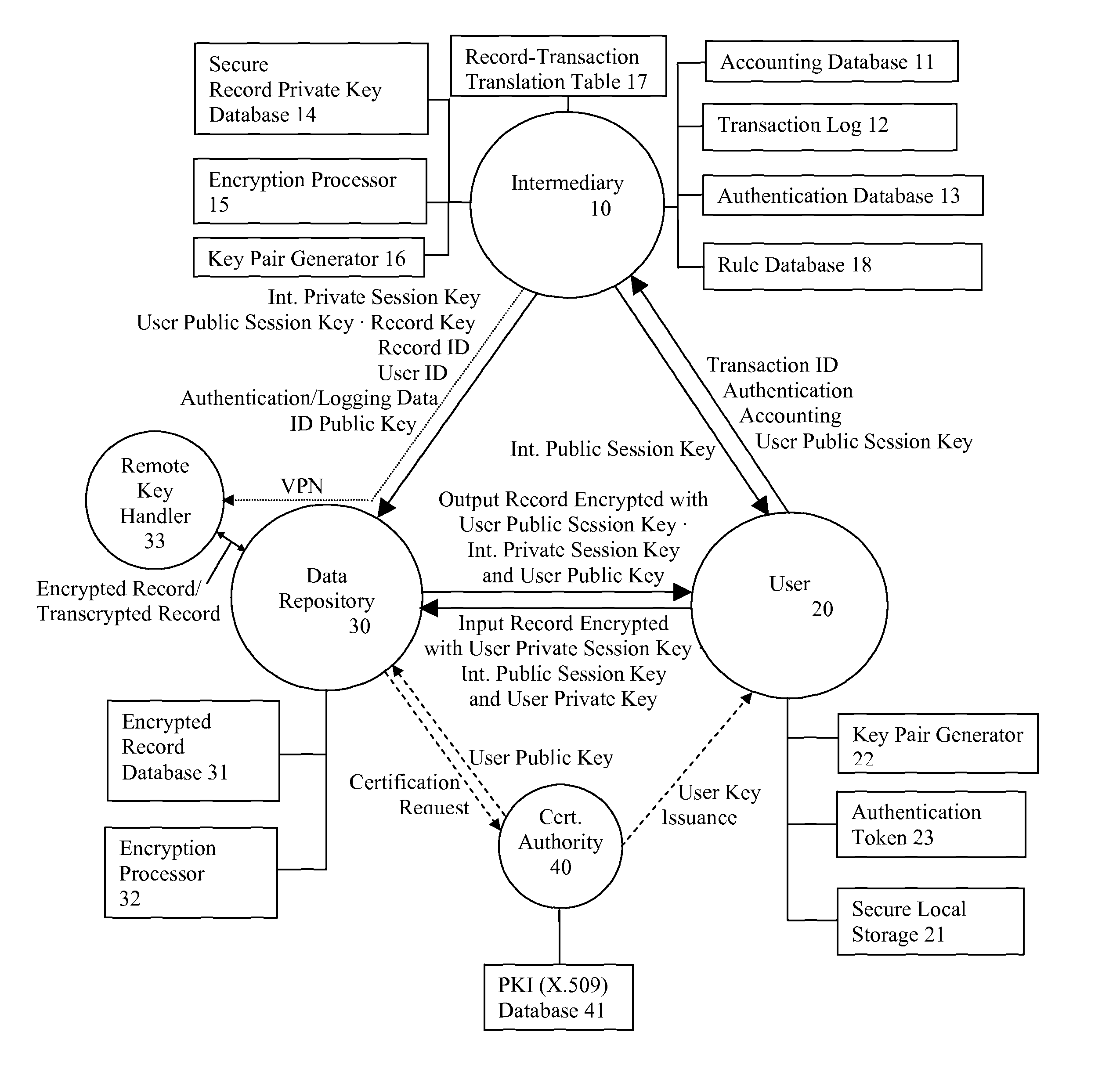
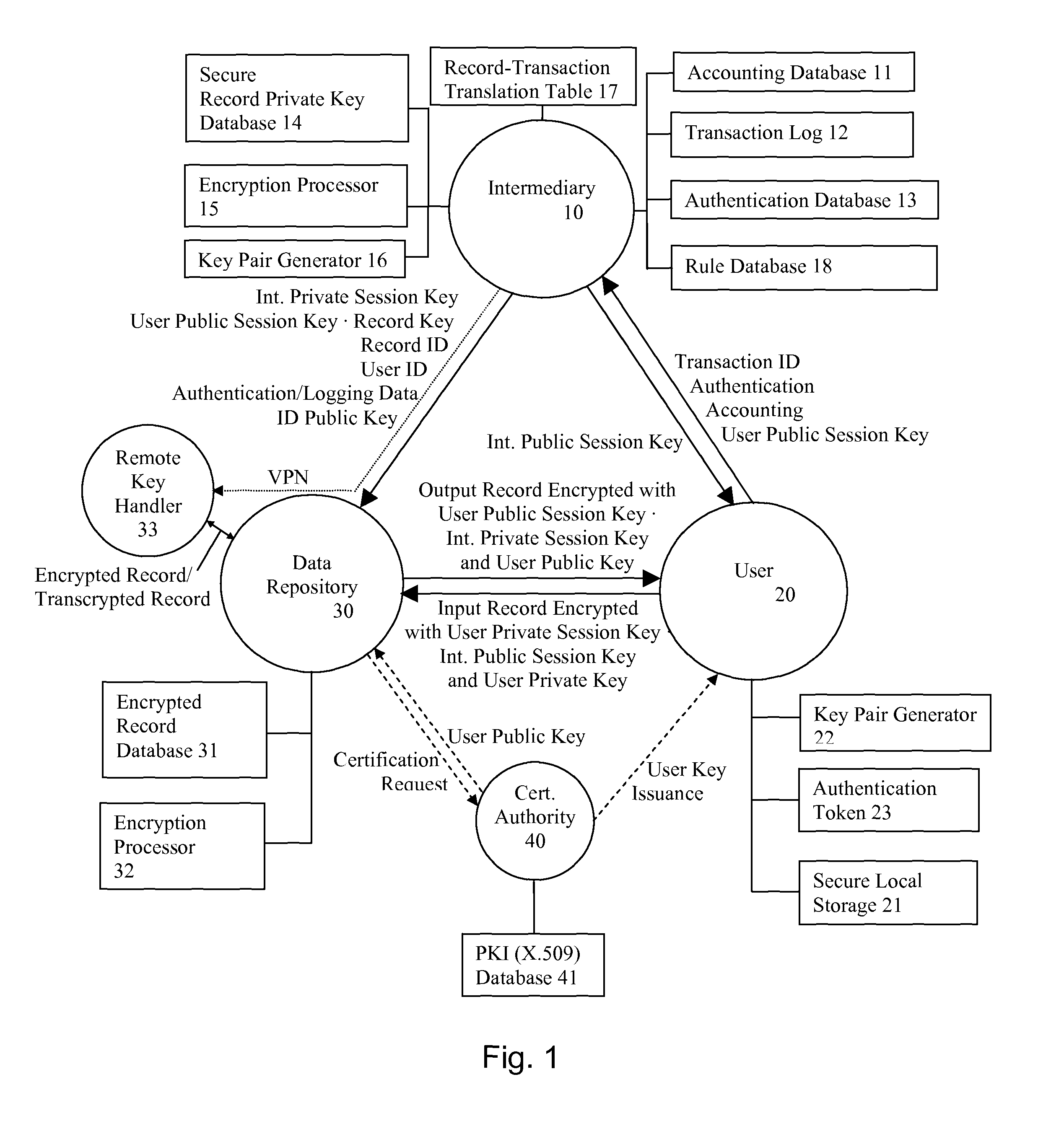
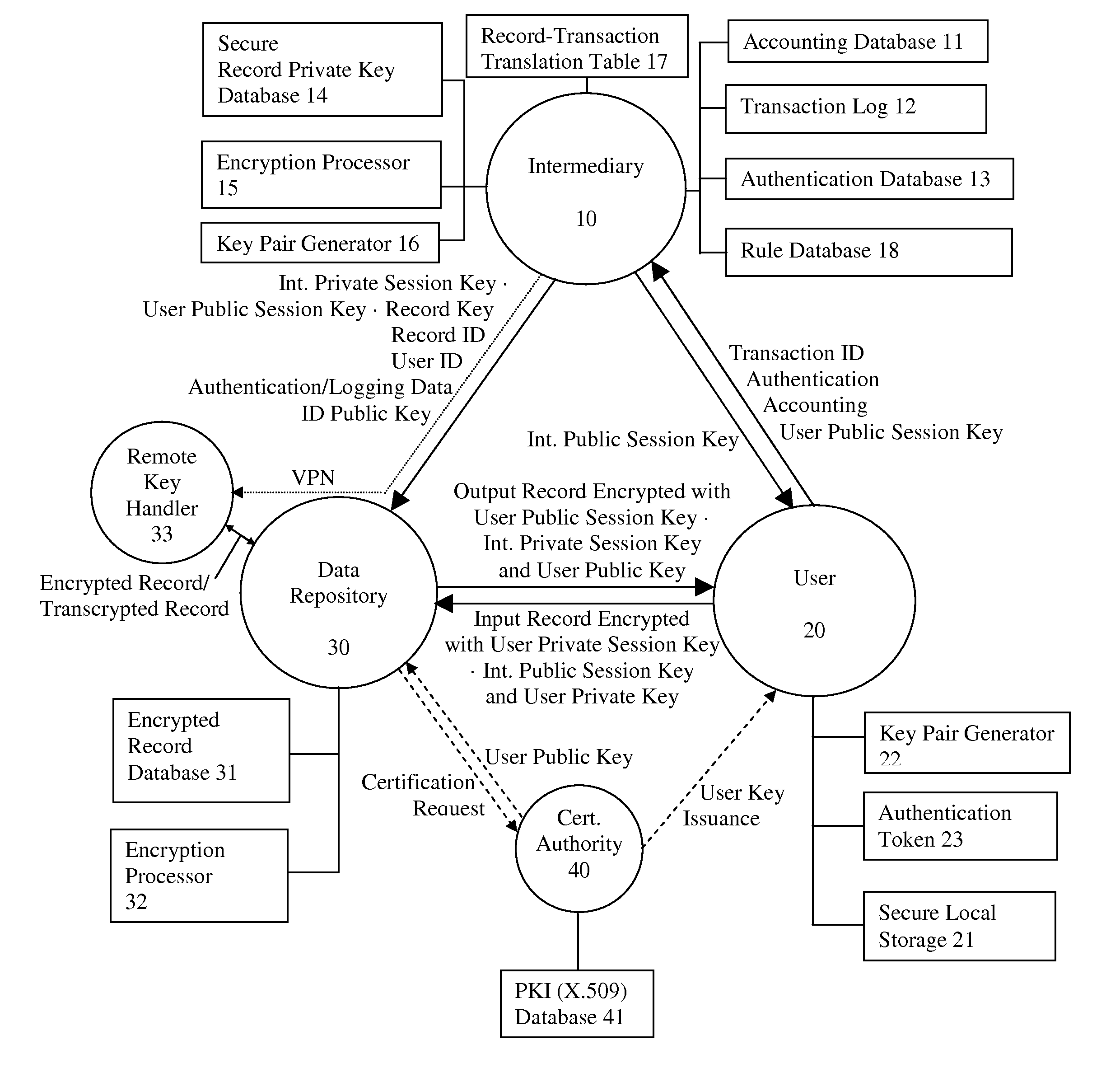
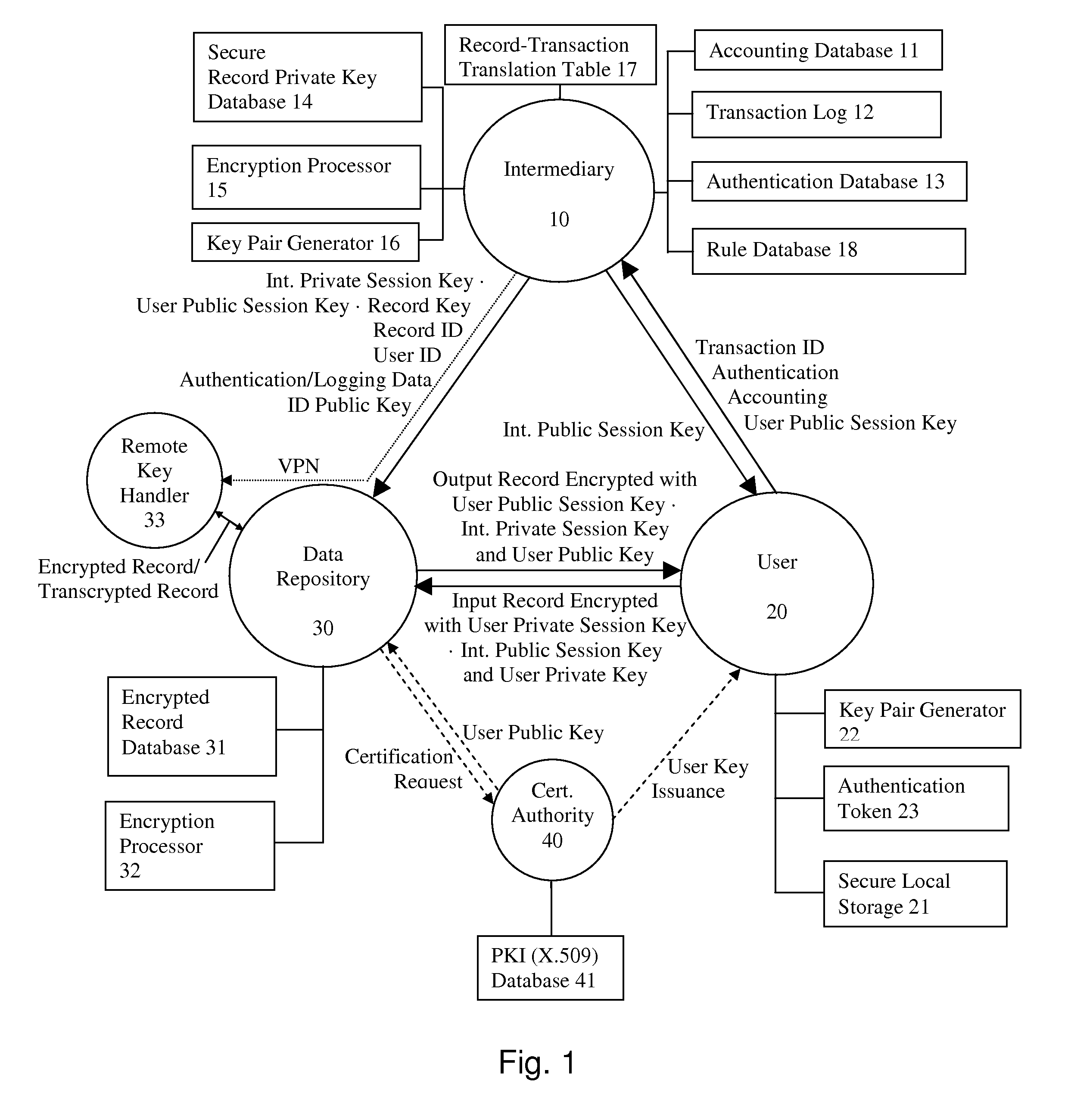
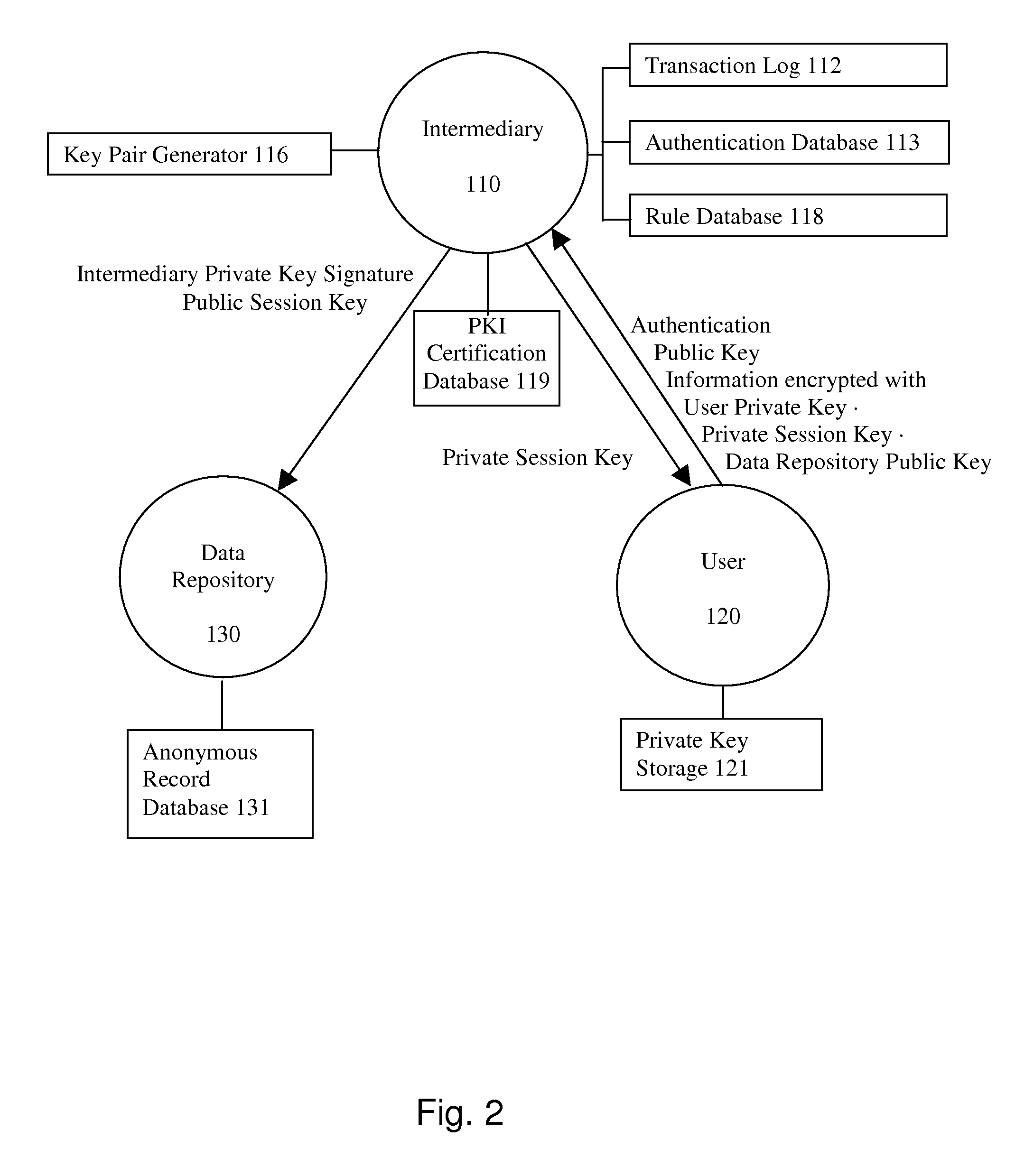
A system and method for communicating information between a first party and a second party, comprising the steps of receiving, by an intermediary, an identifier of desired information and accounting information for a transaction involving the information from the first party, transmitting an identifier of the first party to the second party, and negotiating, by the intermediary, a comprehension function for obscuring at least a portion of the information communicated between the first party and the second party. The data transmission may be made secure with respect to the intermediary by providing an asymmetric key or direct key exchange for encryption of the communication between the first and second party. The data transmission may be made secure with respect to the second party by maintaining the information in encrypted format at the second party, with the decryption key held only by the intermediary, and transmitting a secure composite of the decryption key and a new encryption key to the second party for transcoding of the data record, and providing the new decryption key to the first party, so that the information transmitted to the first party can be comprehended by it.
Owner:RPX CORP
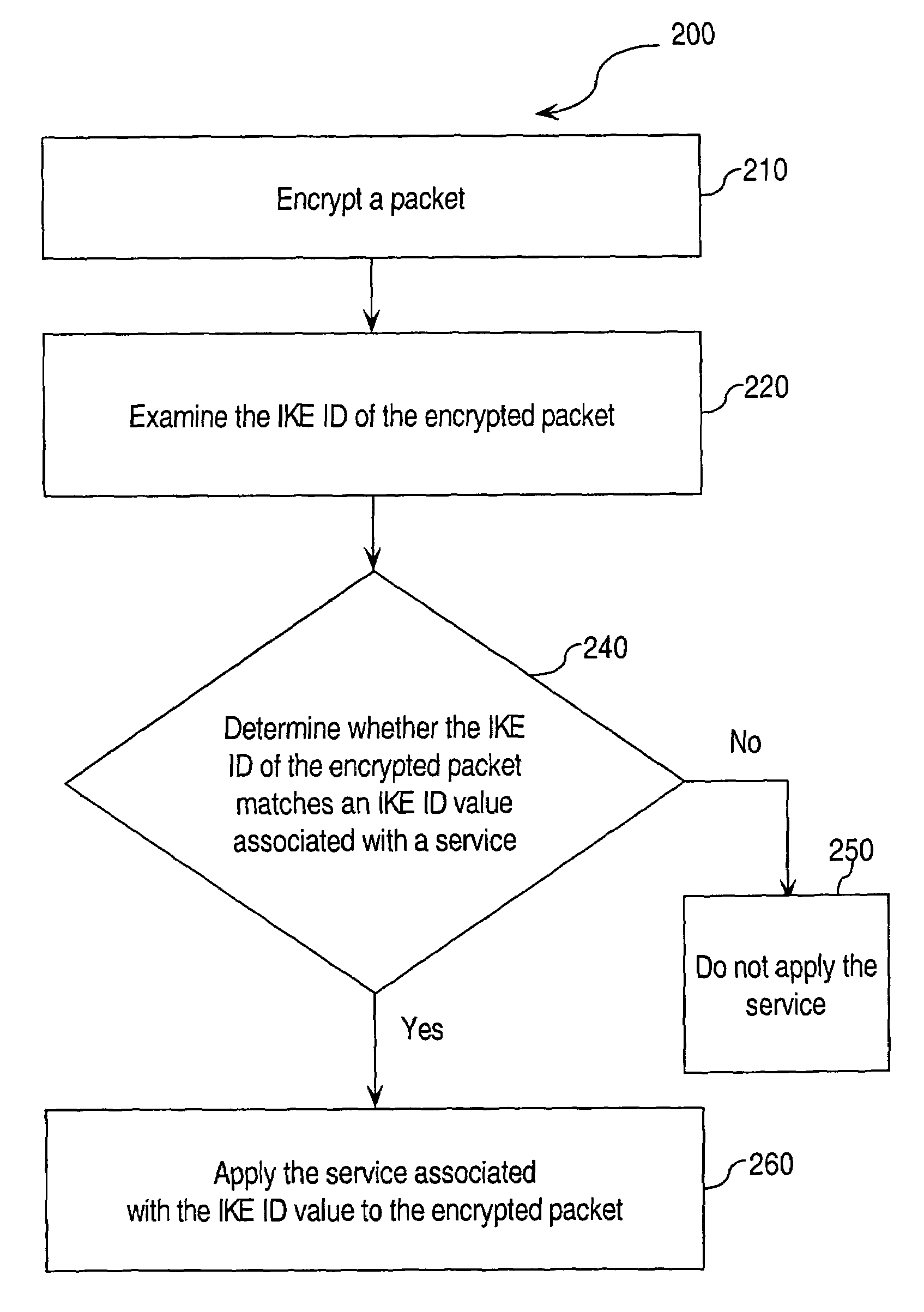
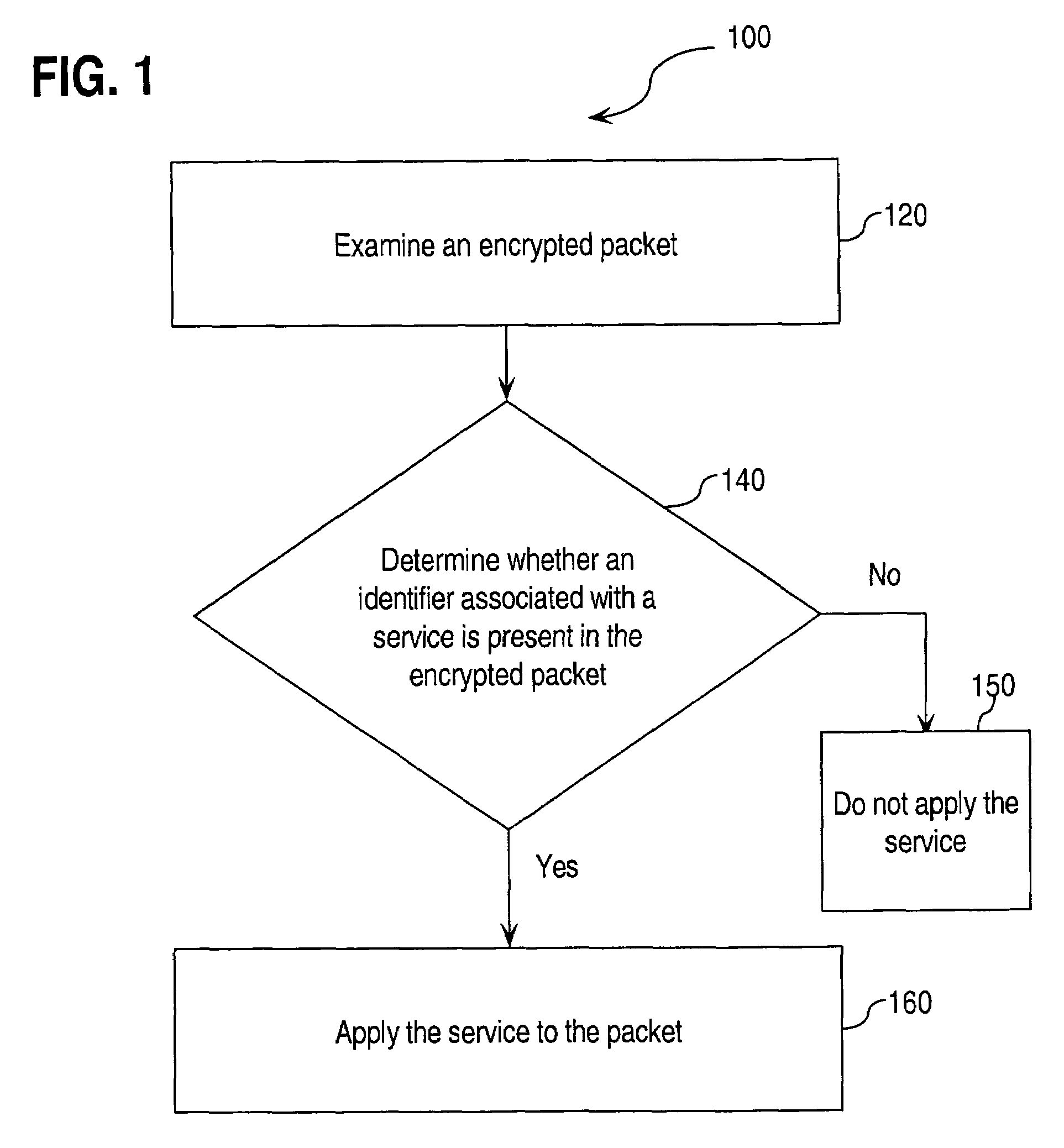
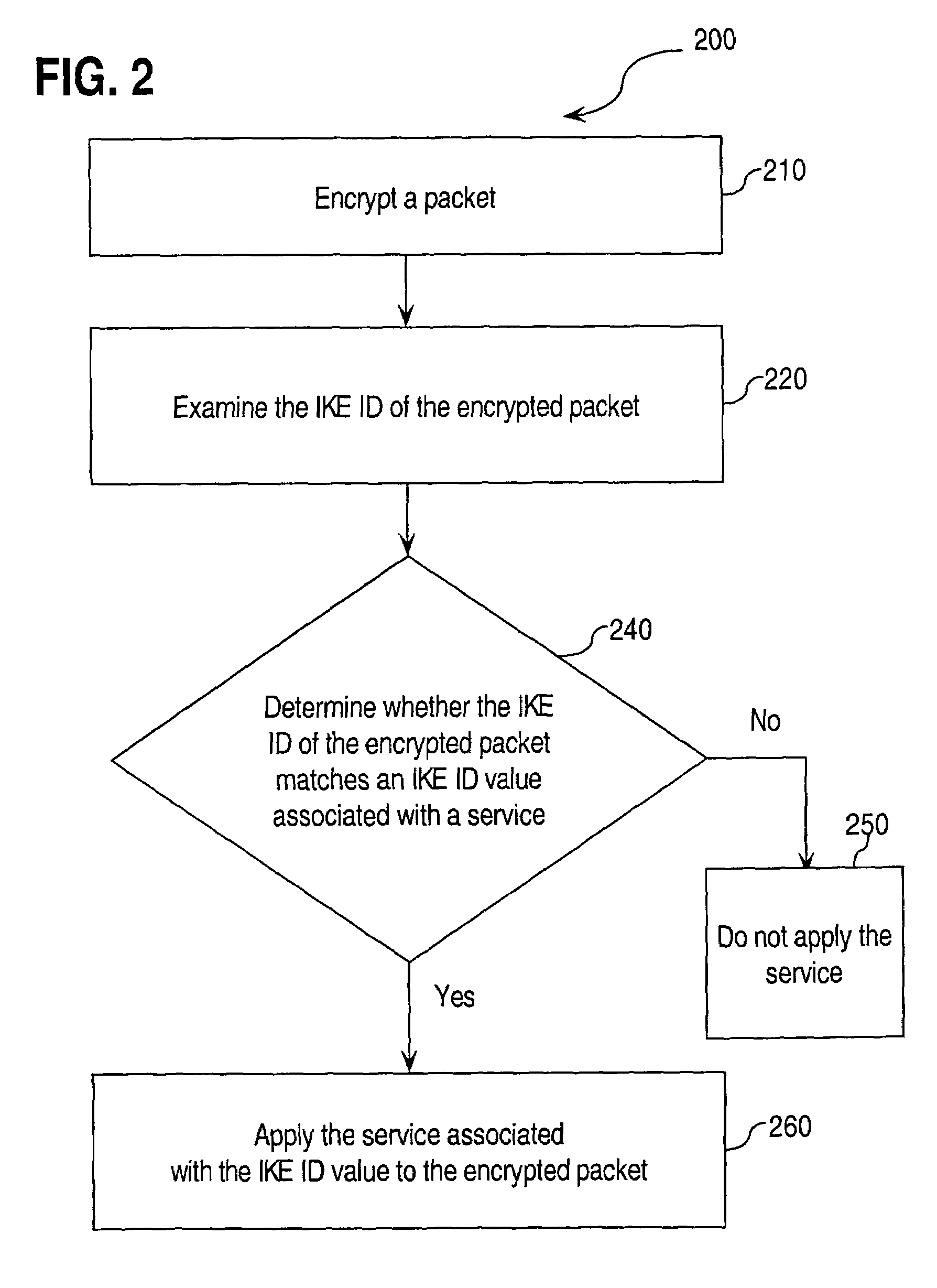
Approaches for applying service policies to encrypted packets
InactiveUS7562213B1Avoiding and reducing relianceSecuring communicationKey exchangeInternet Key Exchange
Approaches for applying service polices to encrypted packets are disclosed. One approach comprises examining an encrypted packet, determining whether an identifier associated with a service is present in an encrypted packet, and if it is determined that the identifier is present in the encrypted packet, applying the service to the encrypted packet. In an embodiment, the identifier is the Internet Key Exchange (IKE) ID of the encrypted packet.
Owner:CISCO TECH INC
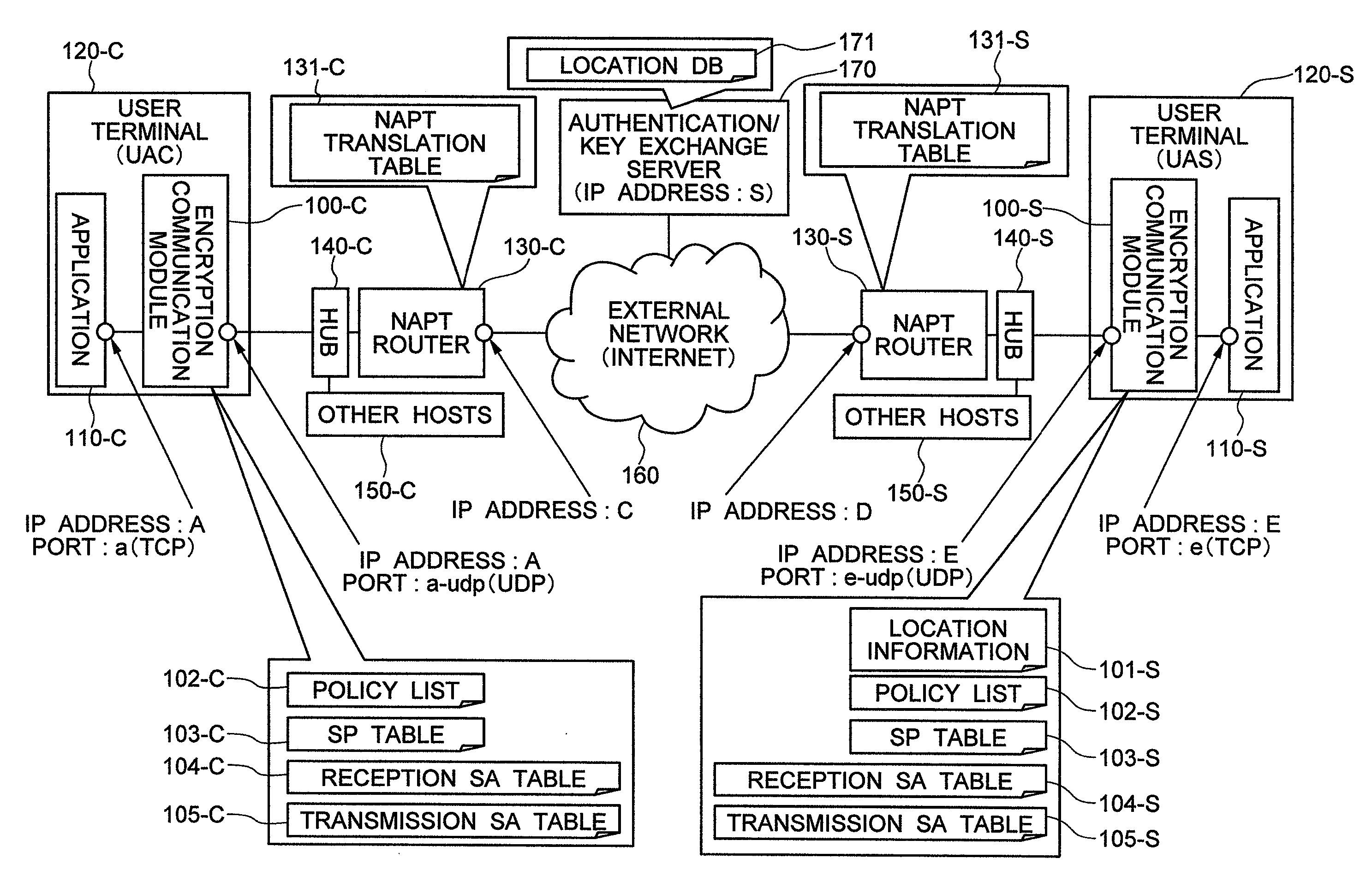
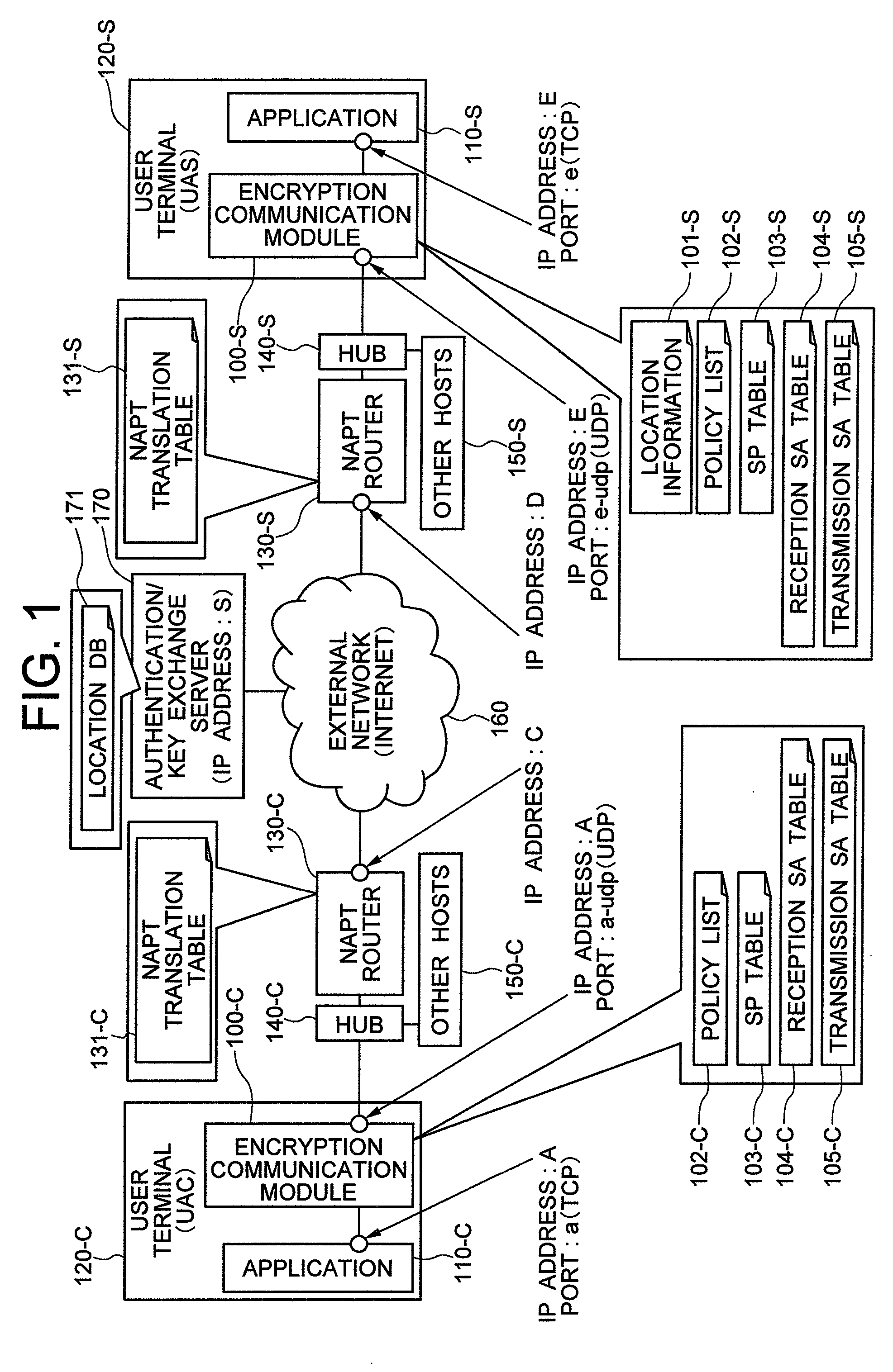
Network System
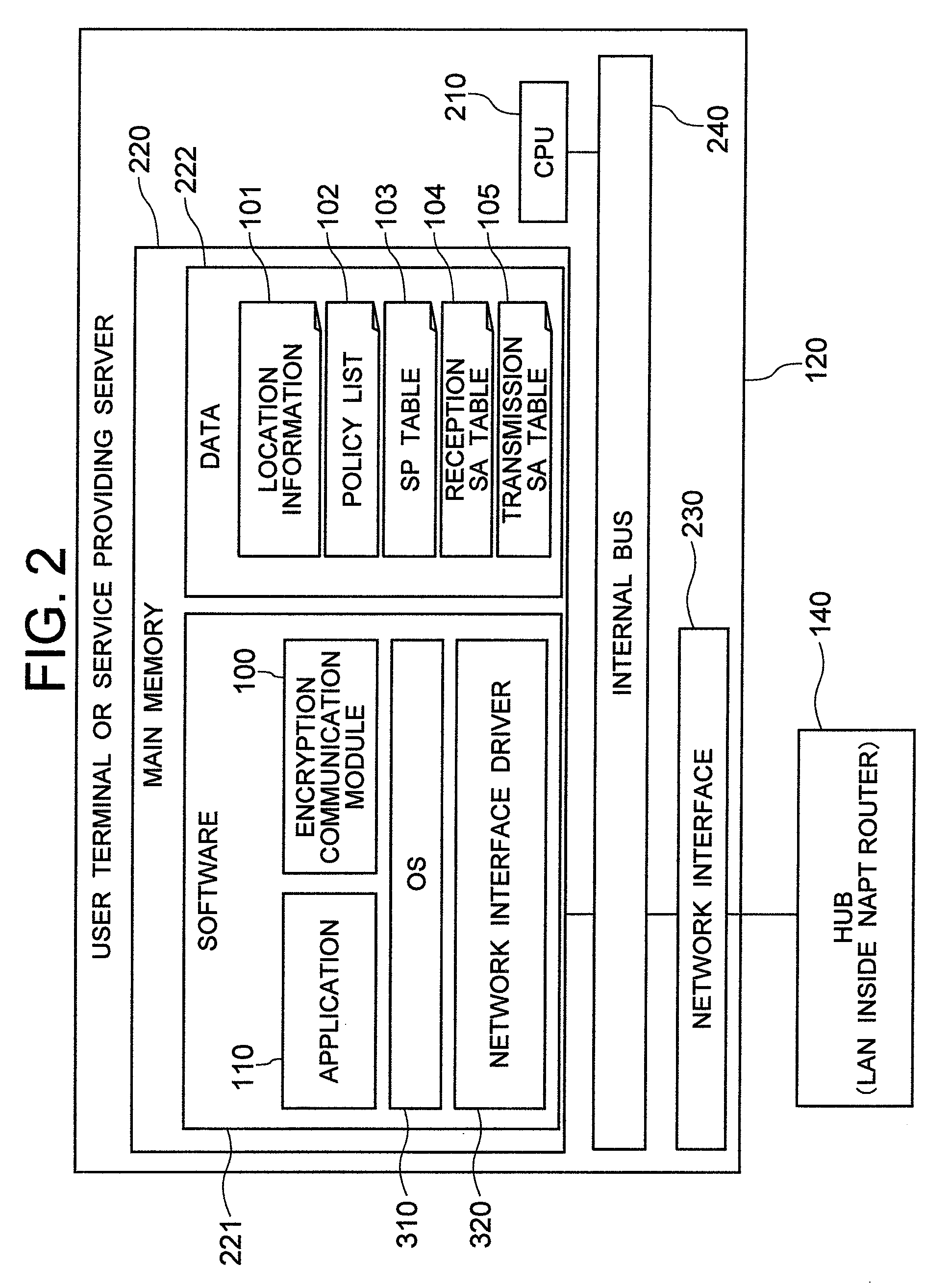
InactiveUS20090113203A1Accurate identificationRemove overlapKey distribution for secure communicationData taking preventionKey exchangeIp address
An encryption communication module on the side of a service providing server reports a global IP address allocated to an NAPT router on the service providing server side and a port number of an outside UDP header used on the global side to an authentication / key exchange server. When receiving an encryption packet from an encryption communication module on the user terminal side, the encryption communication module on the service providing server side overwrite a source / destination IP address of an inside IP header by a source / destination IP address of an outside IP header. The encryption communication module further changes a source port number of an inside TCP•UDP header to a unique value for each communication session in the encryption communication having the same source IP address in the outside IP header. The inverse header change is made when the packet is transmitted to the encryption communication module of the user terminal side.
Owner:HITACHI LTD
Methods and apparatus for delivering electronic identification components over a wireless network
ActiveUS20120108207A1Satisfies needService provisioningUnauthorised/fraudulent call preventionKey exchangeOperational system
Methods and apparatus enabling programming of electronic identification information of a wireless apparatus. In one embodiment, a previously purchased or deployed wireless apparatus is activated by a cellular network. The wireless apparatus connects to the cellular network using an access module to download operating system components and / or access control client components. The described methods and apparatus enable updates, additions and replacement of various components including Electronic Subscriber Identity Module (eSIM) data, OS components. One exemplary implementation of the invention utilizes a trusted key exchange between the device and the cellular network to maintain security.
Owner:APPLE INC
Secure item identification and authentication system and method based on unclonable features
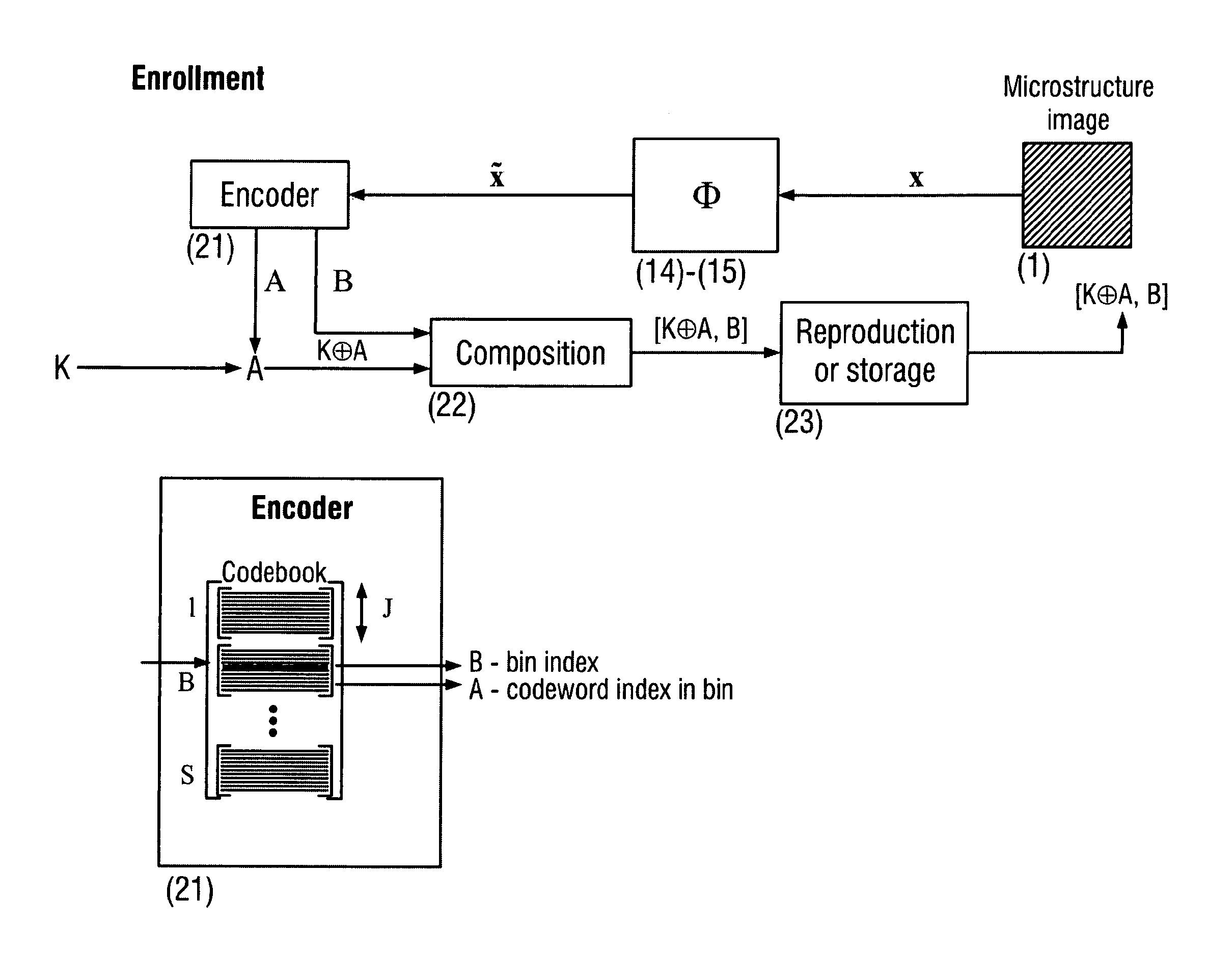
ActiveUS20110096955A1Improve efficiencyEasy to usePaper-money testing devicesCharacter and pattern recognitionKey exchangeDistributed source
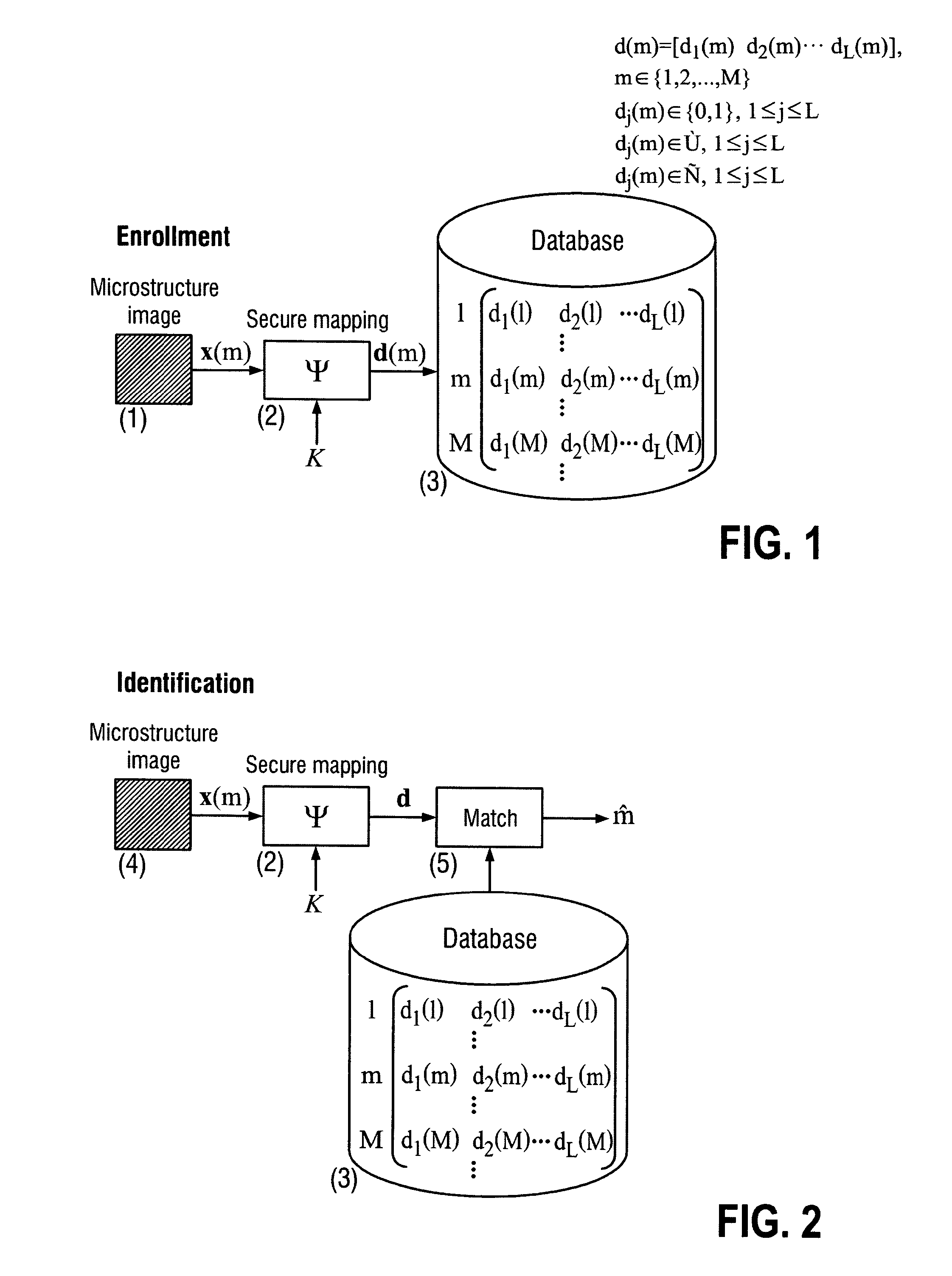
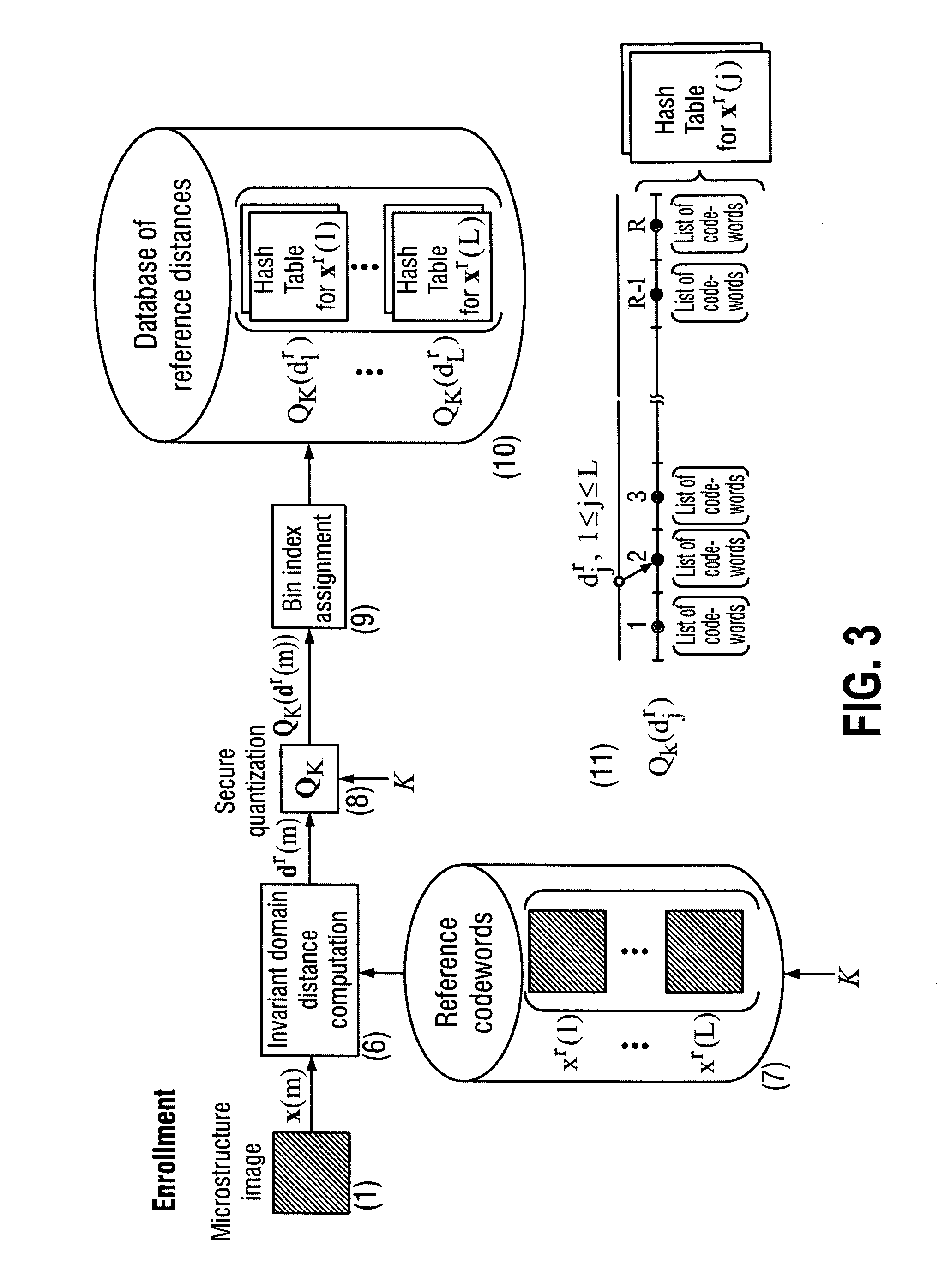
The present invention is a method and apparatus for protection of various items against counterfeiting using physical unclonable features of item microstructure images. The protection is based on the proposed identification and authentication protocols coupled with portable devices. In both cases a special transform is applied to data that provides a unique representation in the secure key-dependent domain of reduced dimensionality that also simultaneously resolves performance-security-complexity and memory storage requirement trade-offs. The enrolled database needed for the identification can be stored in the public domain without any risk to be used by the counterfeiters. Additionally, it can be easily transportable to various portable devices due to its small size. Notably, the proposed transformations are chosen in such a way to guarantee the best possible performance in terms of identification accuracy with respect to the identification in the raw data domain. The authentication protocol is based on the proposed transform jointly with the distributed source coding. Finally, the extensions of the described techniques to the protection of artworks and secure key exchange and extraction are disclosed in the invention.
Owner:UNIVERSITY OF GENEVA
Apparatus and method for establishing a VPN tunnel between a wireless device and a LAN
InactiveUS20070271606A1Communication latencyDelay minimizationMultiple digital computer combinationsProgram controlKey exchangeTelecommunications
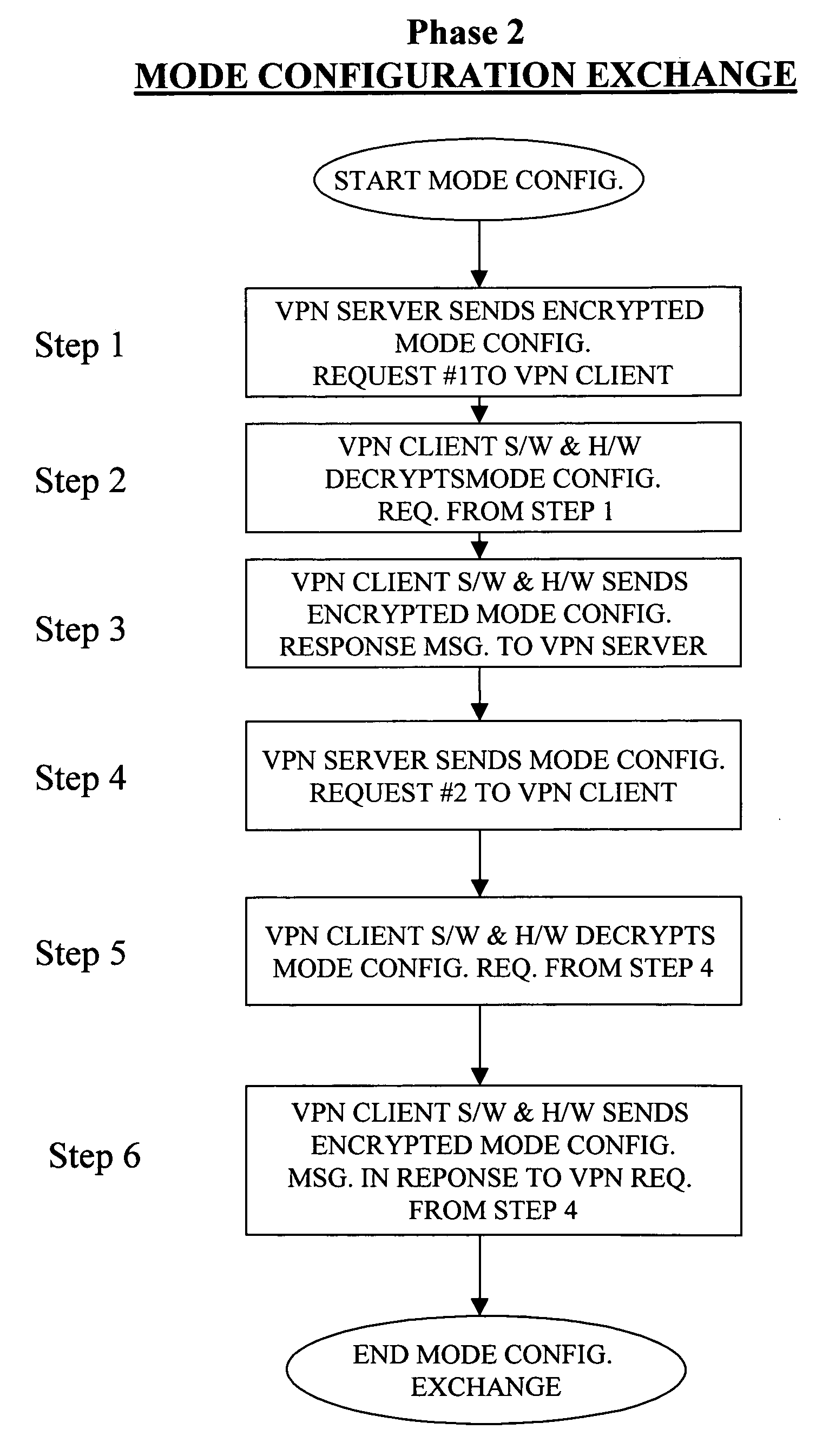
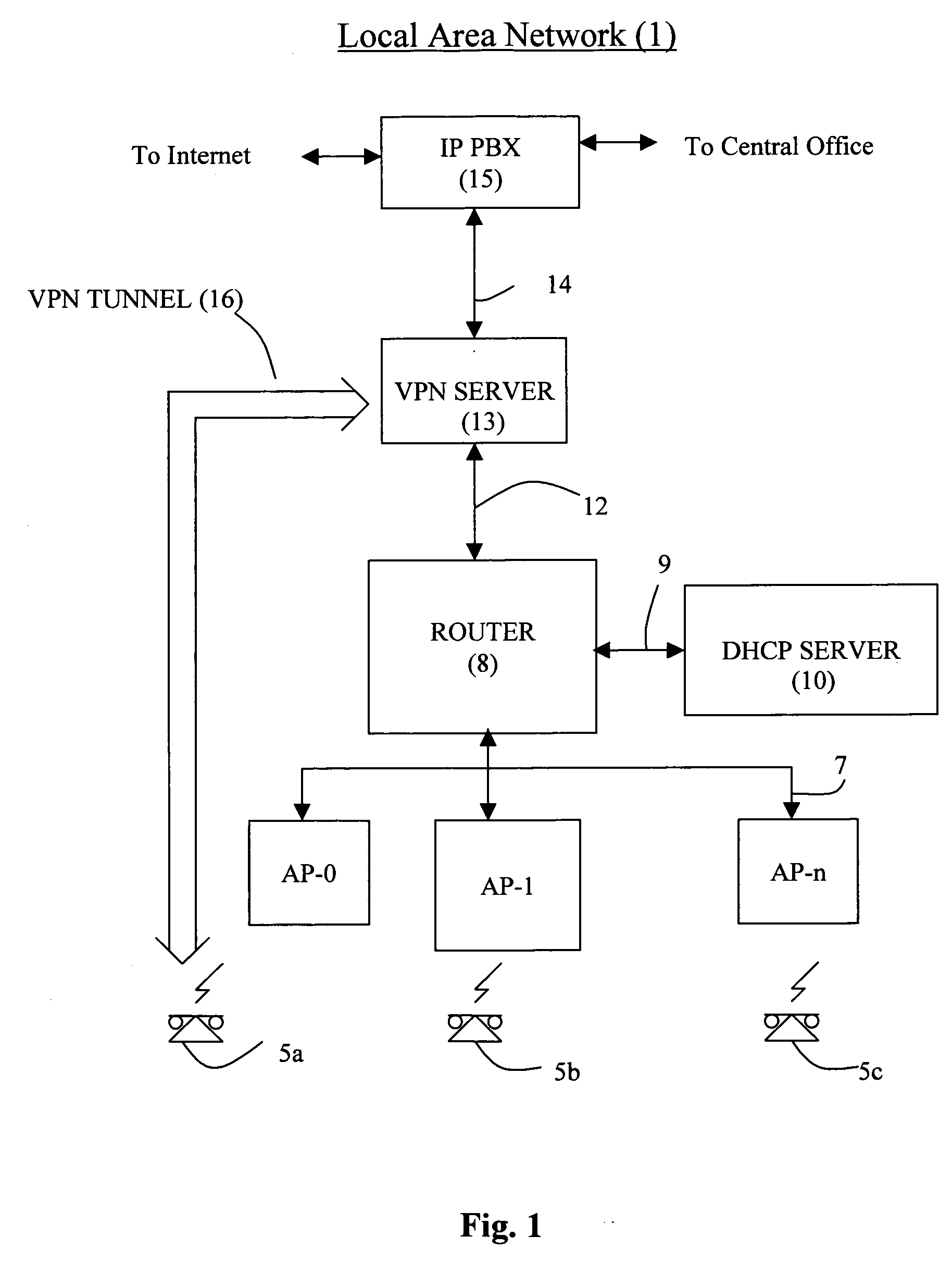
A local area network includes one or more wireless access points for receiving and sending voice and data messages from and to a mobile wireless communications device and a router to manage the delivery of messages to either a DHCP server, a VPN server, or the wireless access points. The DHCP server provides configuration parameters specific to a client requesting DHCP information. The VPN server operates, in conjunction with wireless communications devices to perform key exchange, mode configuration, client authentication, and to maintain the security of a VPN session. The wireless communications device includes a hybrid VPN client that operates, in conjunction with the LAN, to initiate the establishment of a VPN tunnel between the wireless communications device and the VPN server. The hybrid VPN client includes both software and hardware modules that operate together to limit communications latency during the establishment and maintenance of a VPN session.
Owner:SPECTRALINK
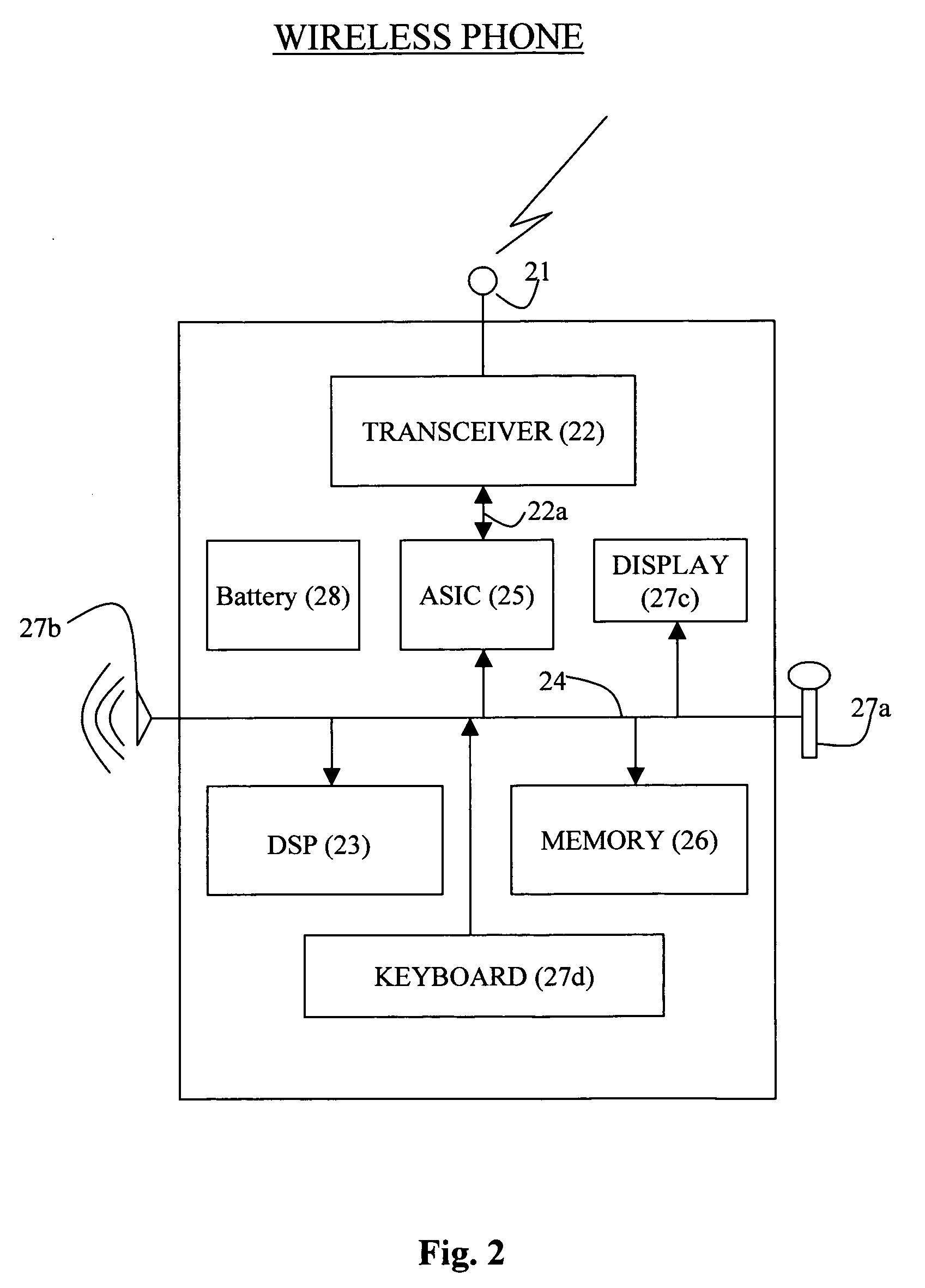
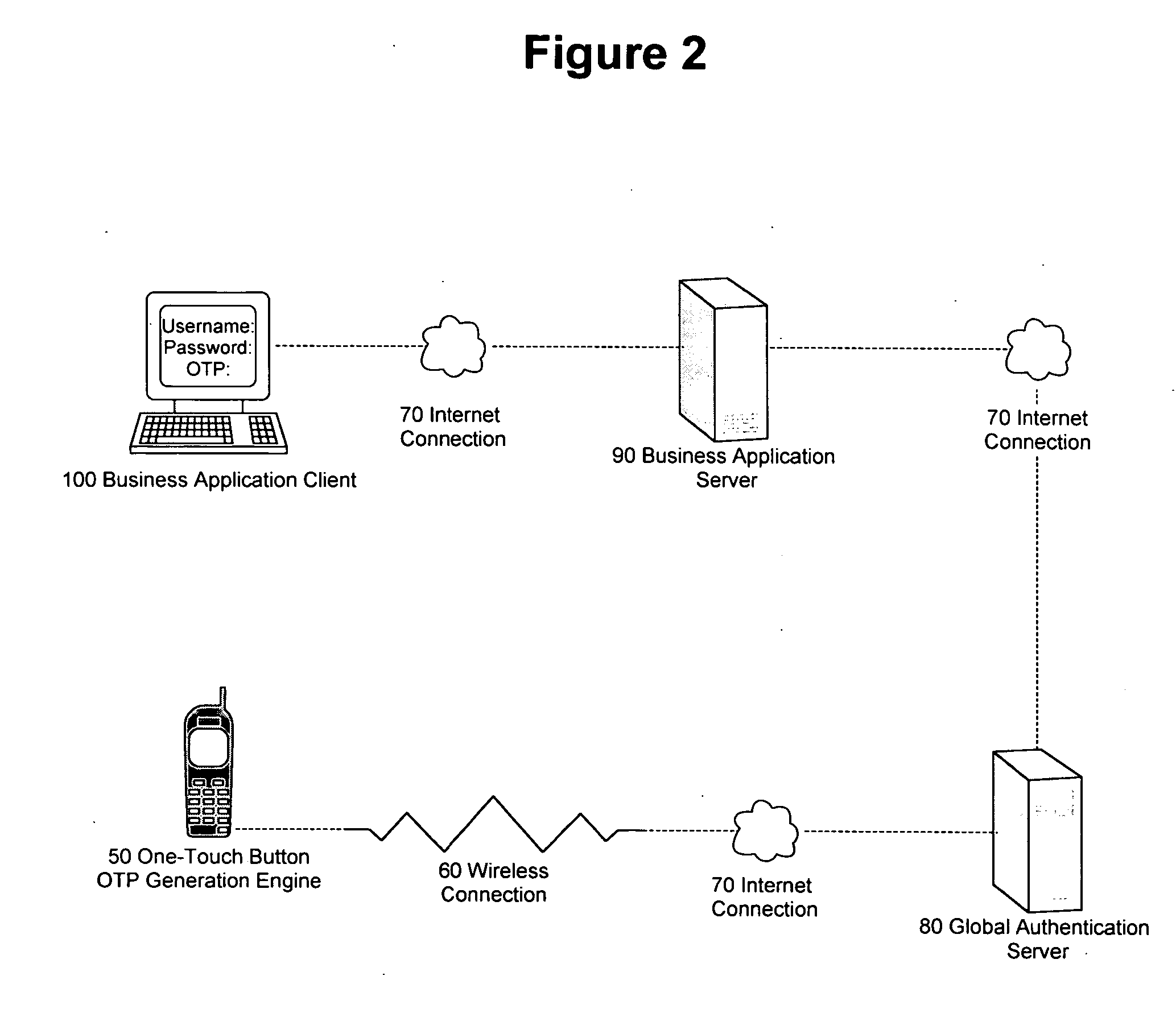
Method and apparatus for generating one-time password on hand-held mobile device
InactiveUS20060136739A1Easy to useSimple and easySynchronising transmission/receiving encryption devicesUnauthorised/fraudulent call preventionKey exchangeWeb service
According to the invention, a system and an apparatus to use the One-Touch button on a mobile hand-held device to generate one time passwords (OTP) are disclosed. Components of this system comprise: a mobile hand-held device, a built-in One-Touch button on the mobile device, a Global Authentication Server, and an OTP Generation engine installed and ran on the mobile device. The mobile device user only needs to push the One-Touch button and an OTP is generated. The OTP is generated on the mobile device by the OTP generation engine after a secure key exchange process is performed between the remote Global Authentication Server and the mobile device. The mobile device is registered to use online web services that recognize the OTP through the Global Authentication Service. Online web services require that the user enter a combination of the user's known password and OTP for identity assurance. As a result of this invention, users will quickly adopt the two-factor authentication method as a central means to identify themselves.
Owner:BROCK CHRISTIAN +1
Secure peer-to-peer messaging invitation architecture
ActiveUS20060101266A1Improve securityMaintaining the secrecy of the underlying address identityKey distribution for secure communicationUser identity/authority verificationKey exchangePersonal identification number
A system and methods providing immediate peer-to-peer messaging between mobile devices in a wireless system. An invitation architecture is disclosed which enables the exchange of personal identification numbers (PINs) without requiring a user to directly access or provide his or her PIN. A messaging application encrypts its associated PIN before providing it to a messaging application on another mobile device through an existing communication application. The invitation architecture automatically manages the encryption, any requisite key exchanges, the composition of invitation and acceptance messages, and the decryption and storage of PINs.
Owner:MALIKIE INNOVATIONS LTD
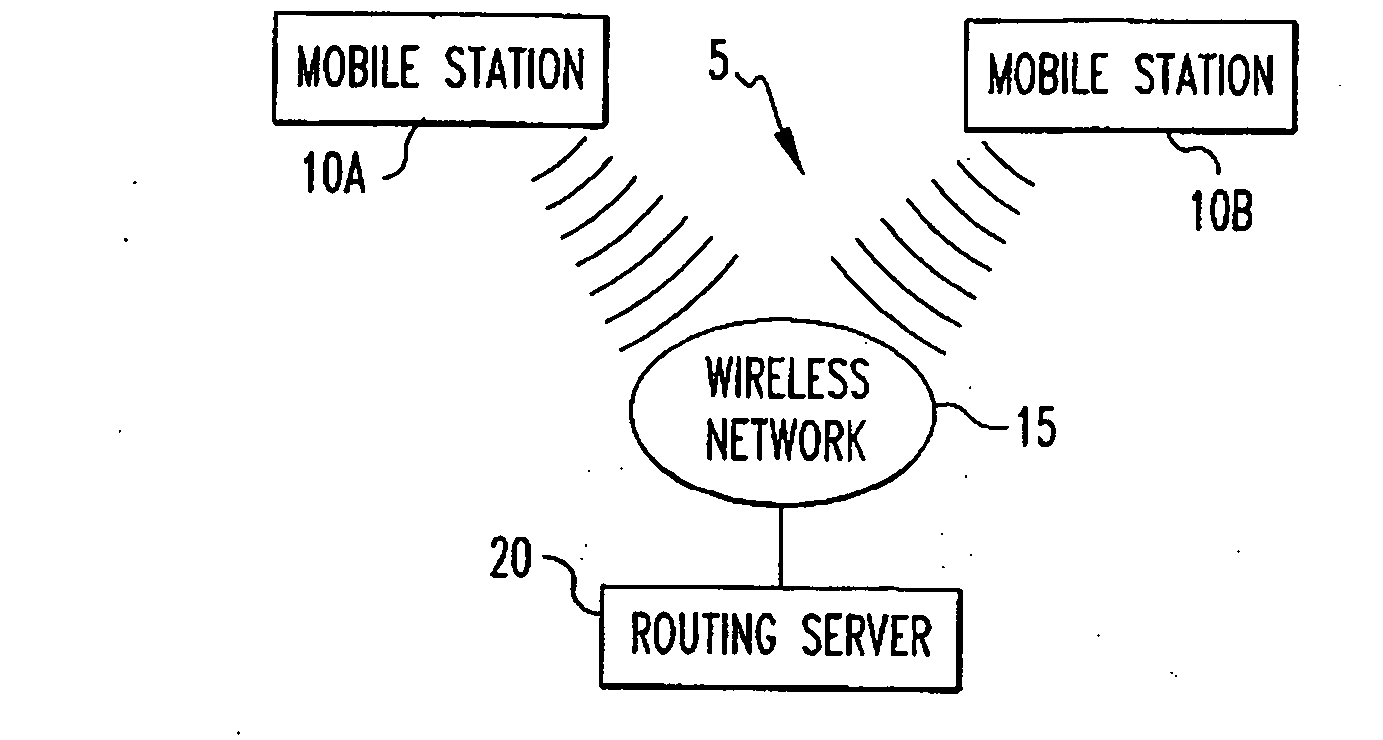
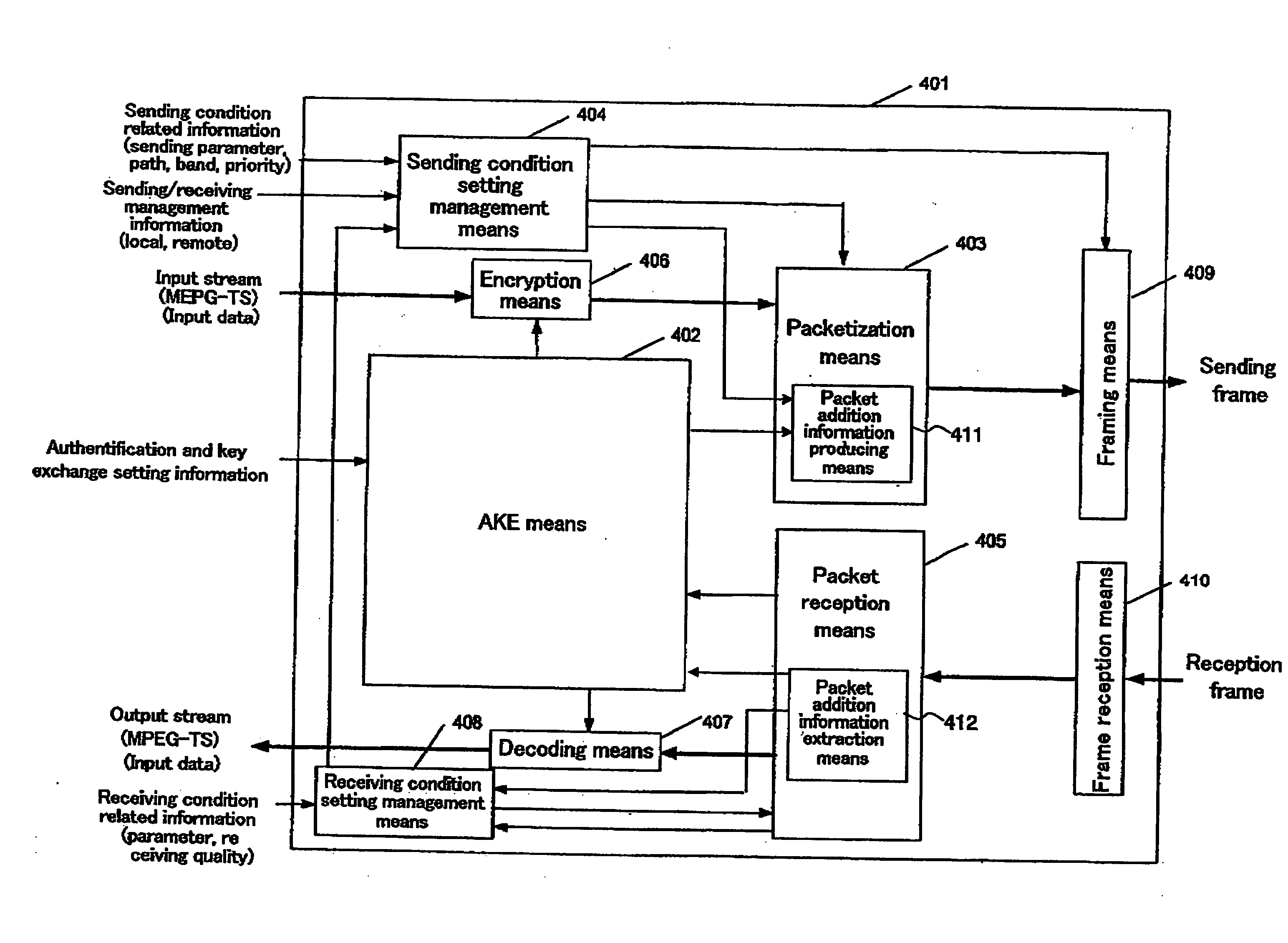
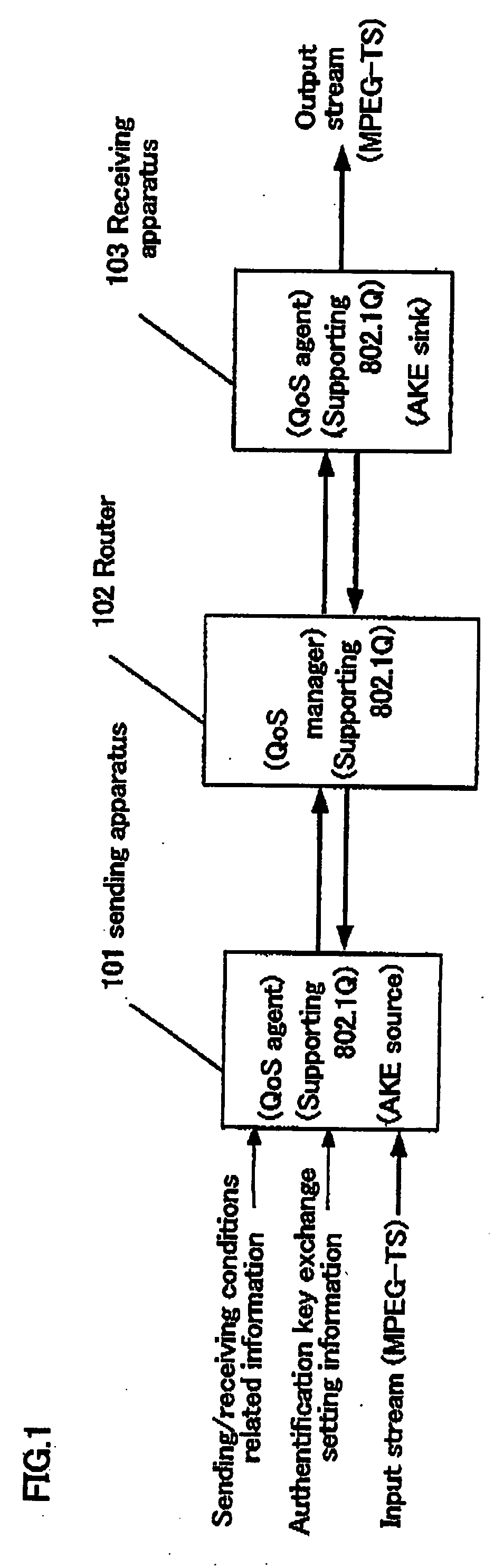
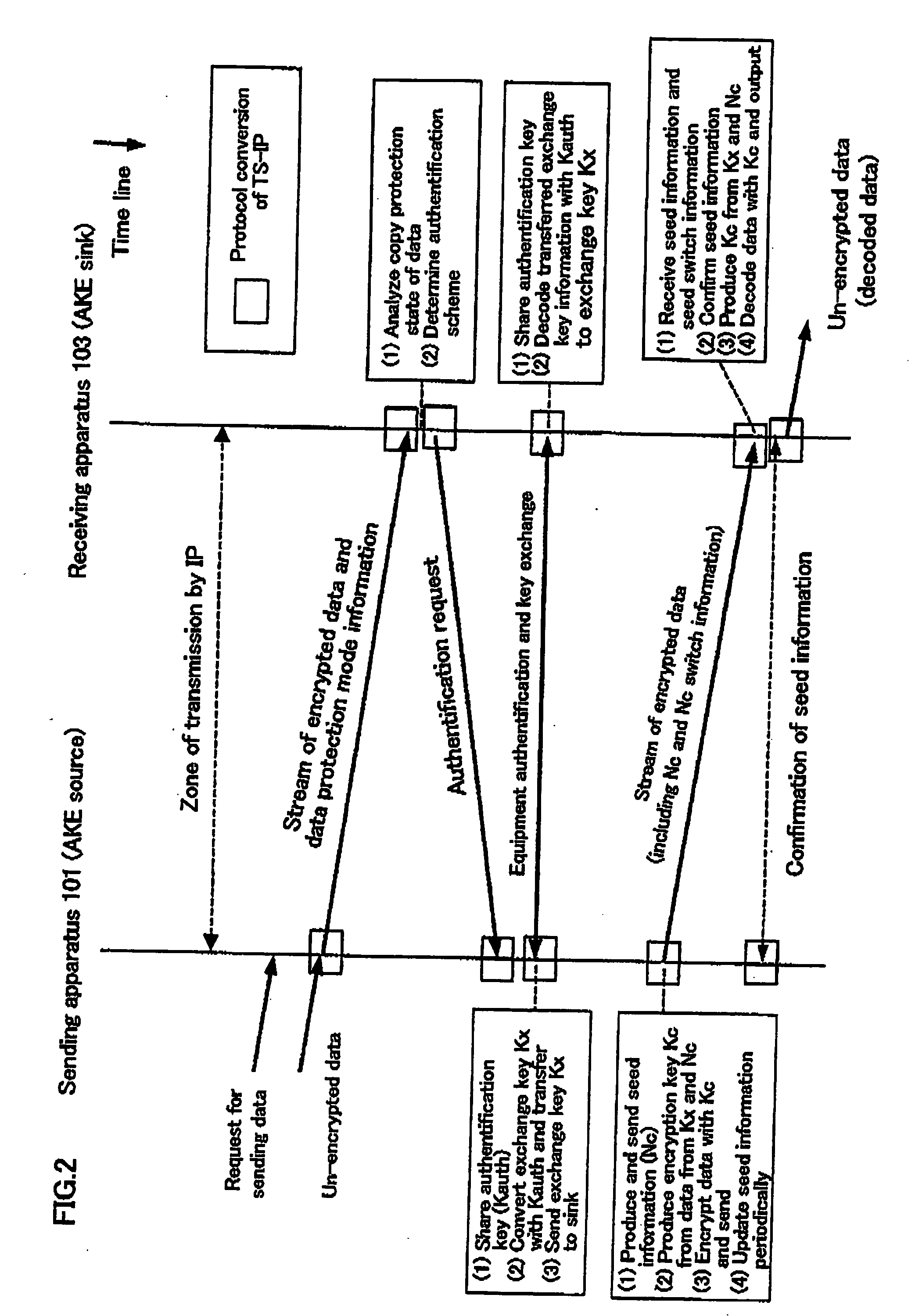
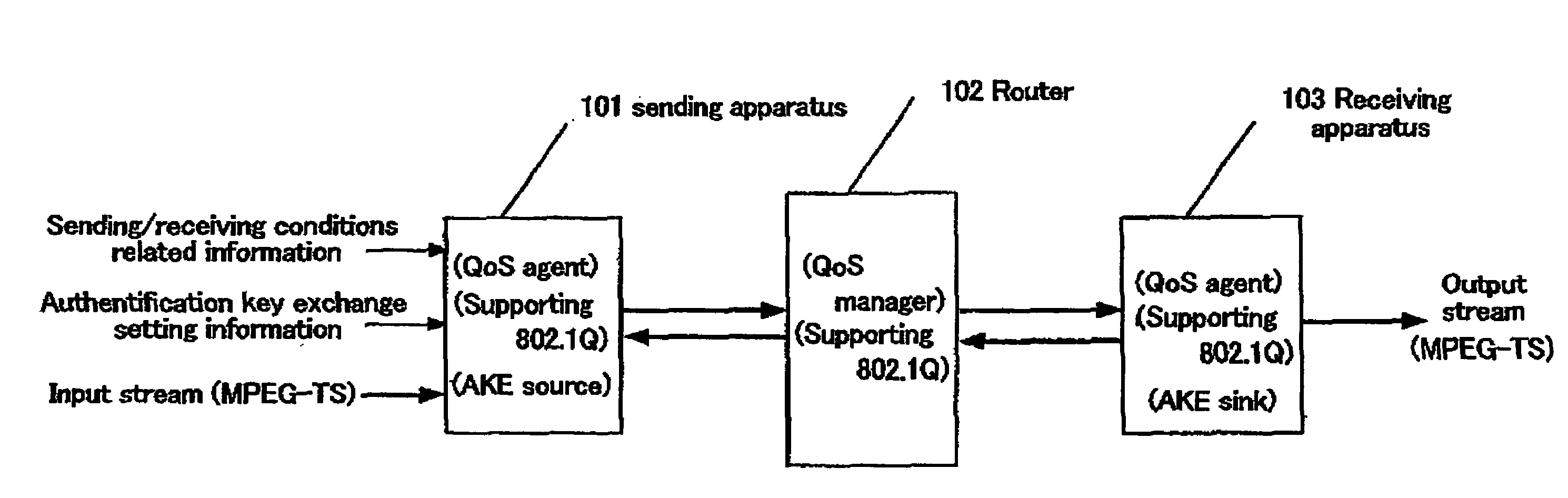
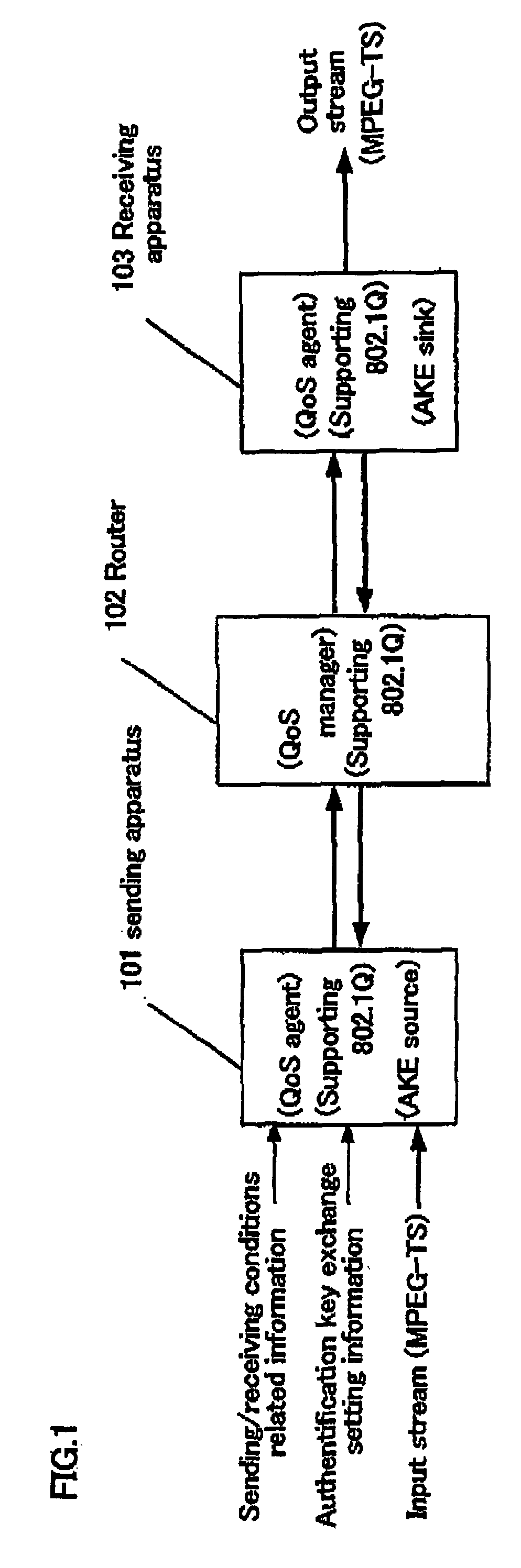
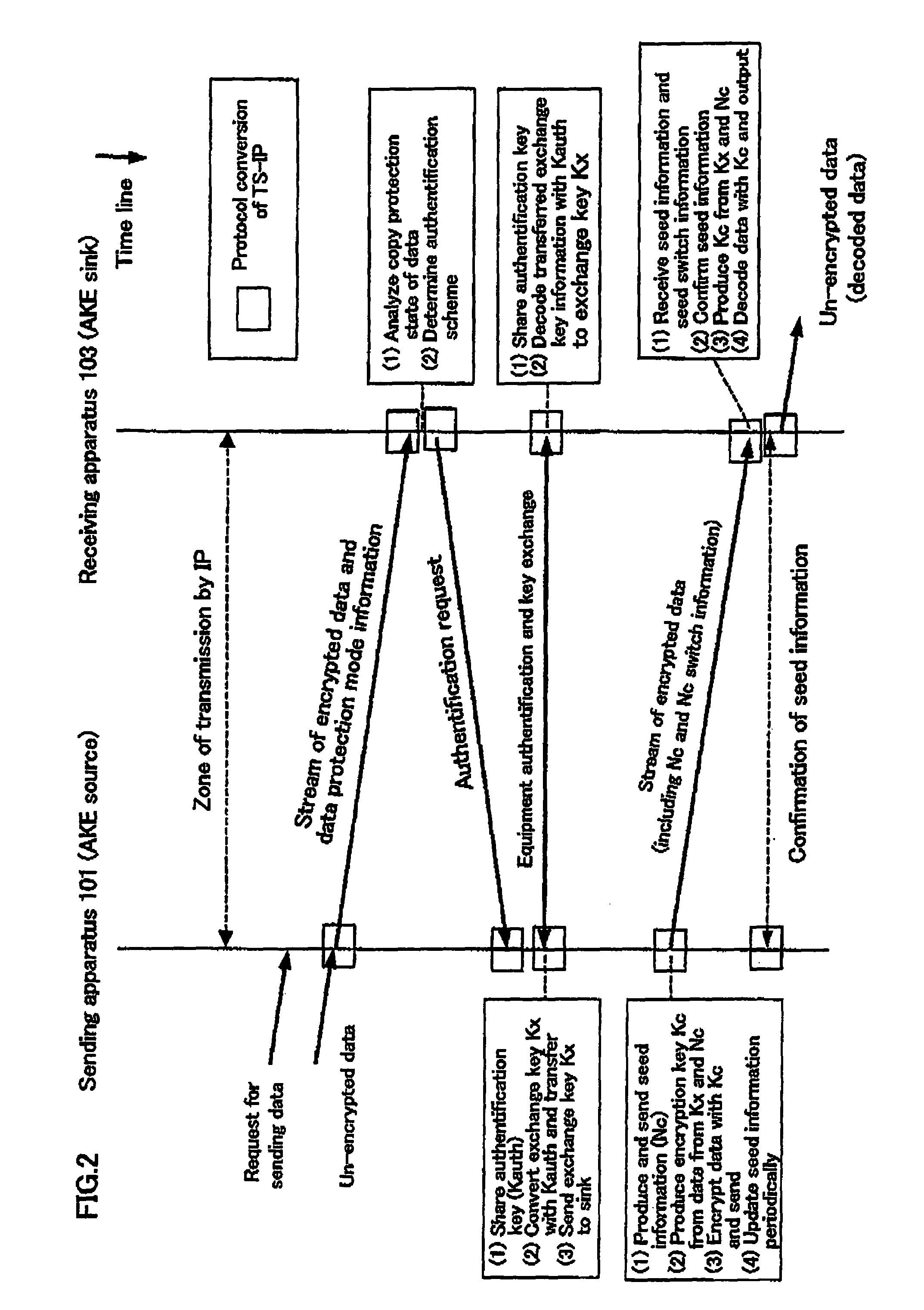
Packet transmission/reception device
InactiveUS20060112272A1Simple structurePrevent eavesdroppingUser identity/authority verificationTelevision systemsComputer hardwareKey exchange
A packets sending / receiving apparatus, comprising: authentication and key exchange means; encryption means for producing an encryption sending data; sending condition setting management means for producing sending condition setting information for setting sending condition of the sending packets; packetization means for producing the sending packets using the encryption sending data; receiving condition setting management means for producing receiving condition setting information for setting receiving condition of the receiving packets; packets reception means for receiving the reception packets; and decoding means for decoding the reception data using the decoding key.
Owner:GK BRIDGE 1
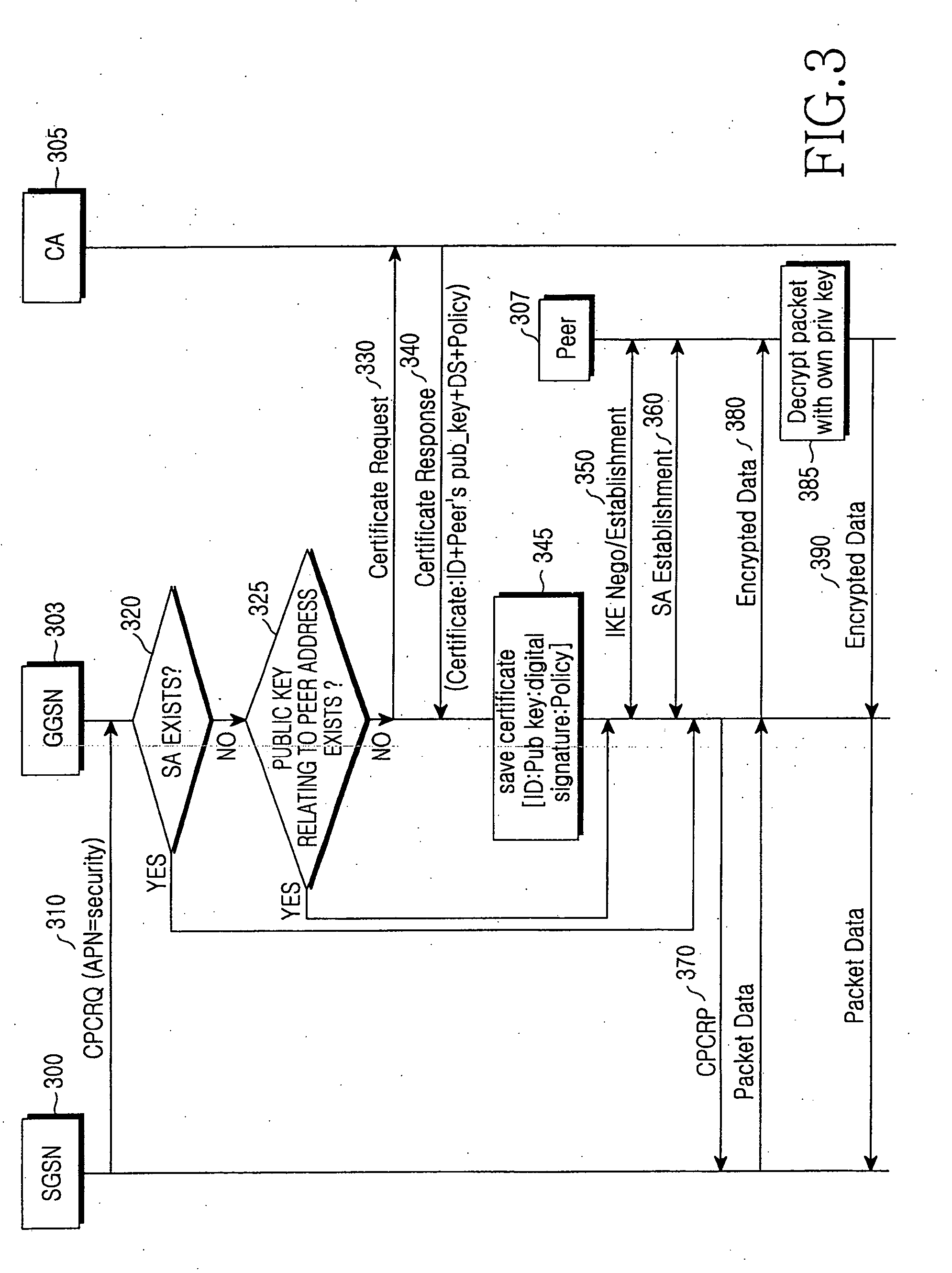
Method and apparatus for security of IP security tunnel using public key infrastructure in mobile communication network
InactiveUS20060105741A1Applied load reductionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsKey exchangeInternet Key Exchange
A method and apparatus is provided for security of an IP security tunnel using public key infrastructure, including the steps of receiving a request message which relates to a security service requested by a mobile node, determining if there is security association (SA) for the security service and determining if there is a public key related to a peer address when the SA does not exist, sending a certificate request message to a certificate authority (CA) when the public key does not exist and receiving a certificate response message which has a certificate that includes a public key. The method further includes the steps of performing an internet key exchange and SA establishment procedure with a peer corresponding to the peer address by using the certificate, completing the internet key exchange and the SA establishment, and encrypting a packet received from the mobile node, transmitting the encrypted packet to the peer, decrypting a packet received from the peer, and transmitting the decrypted packet to the mobile node.
Owner:SAMSUNG ELECTRONICS CO LTD
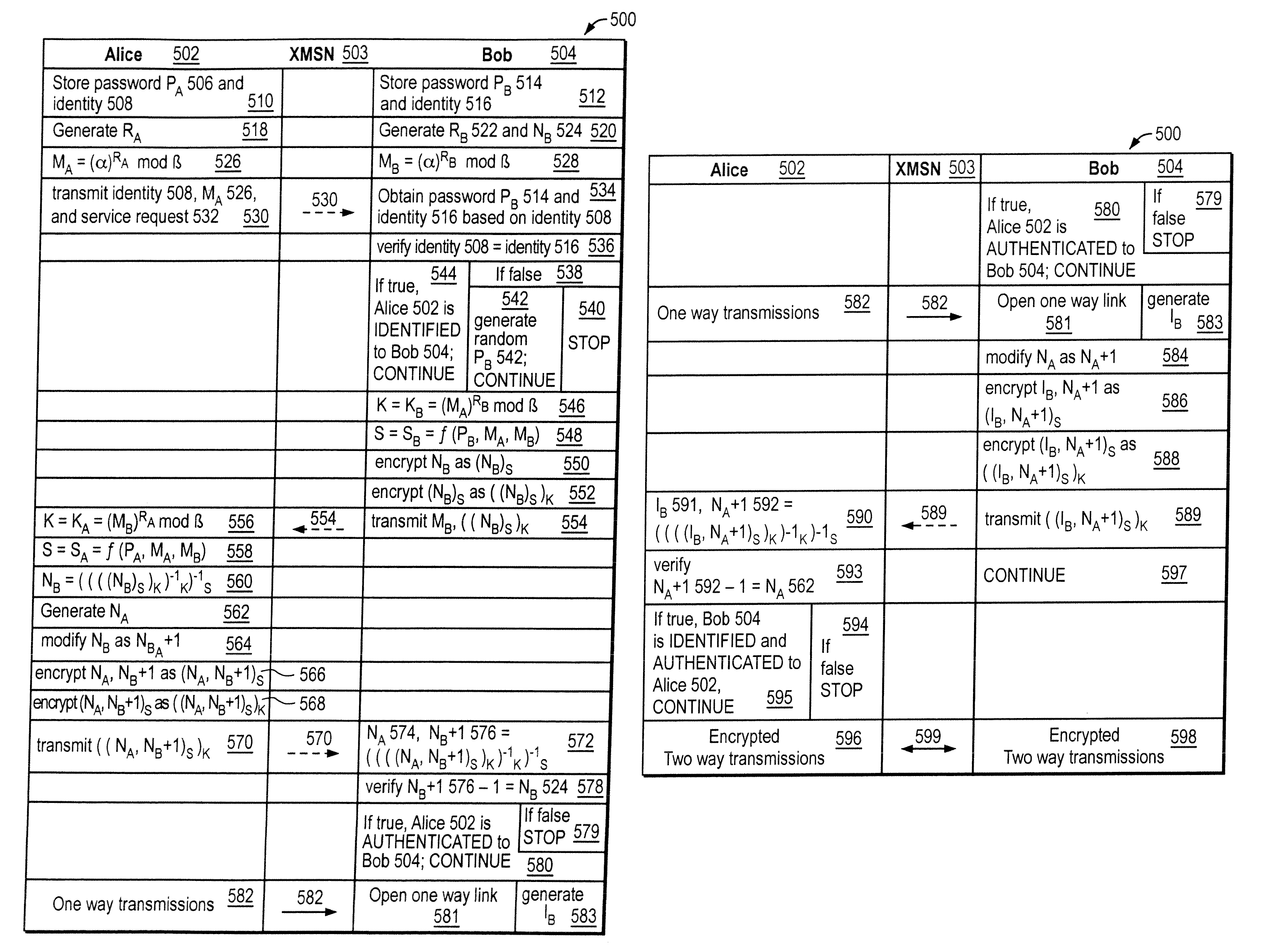
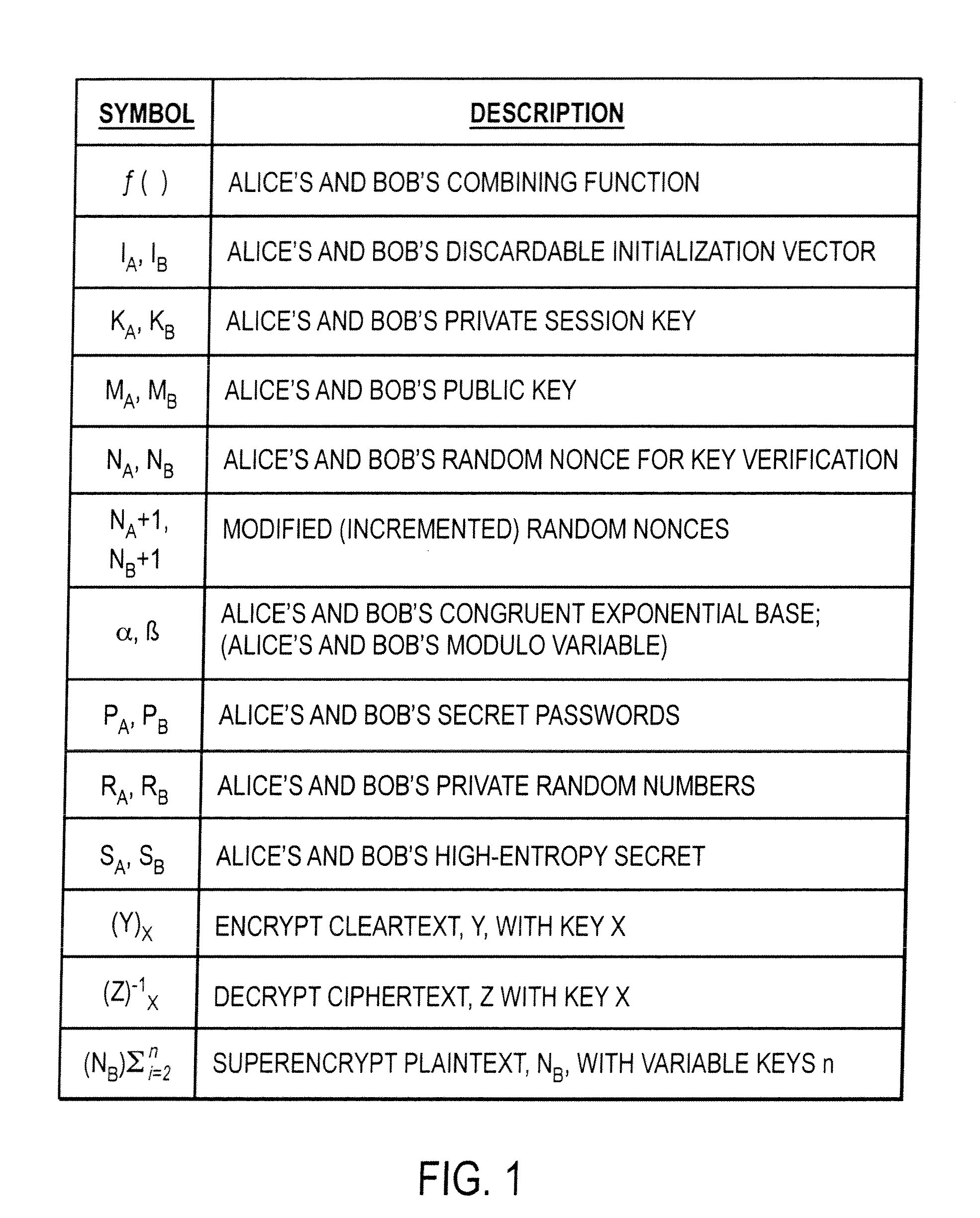
Mutually authenticated secure key exchange (MASKE)
InactiveUS7424615B1Key distribution for secure communicationUser identity/authority verificationKey exchangeTelecommunications link
The invention provides a cryptographic method which includes receiving at a first entity a second public key MA. At least one of a first session key KB and a first secret SB may be generated based on the second public key MA. A first random nonce NB may be generated which may be encrypted with at least one of the first session key KB and the first secret SB to obtain an encrypted random nonce. The encrypted random nonce may be transmitted from the first entity. In response to transmitting the encrypted random nonce, the first computer may receive a data signal containing a modification of the first random nonce NB+1. If the modification of the first random nonce NB+1 was correctly performed, then at least one of (i) opening a communication link at the first computer, and (ii) generating a first initialization vector IB is performed.
Owner:APPLE INC
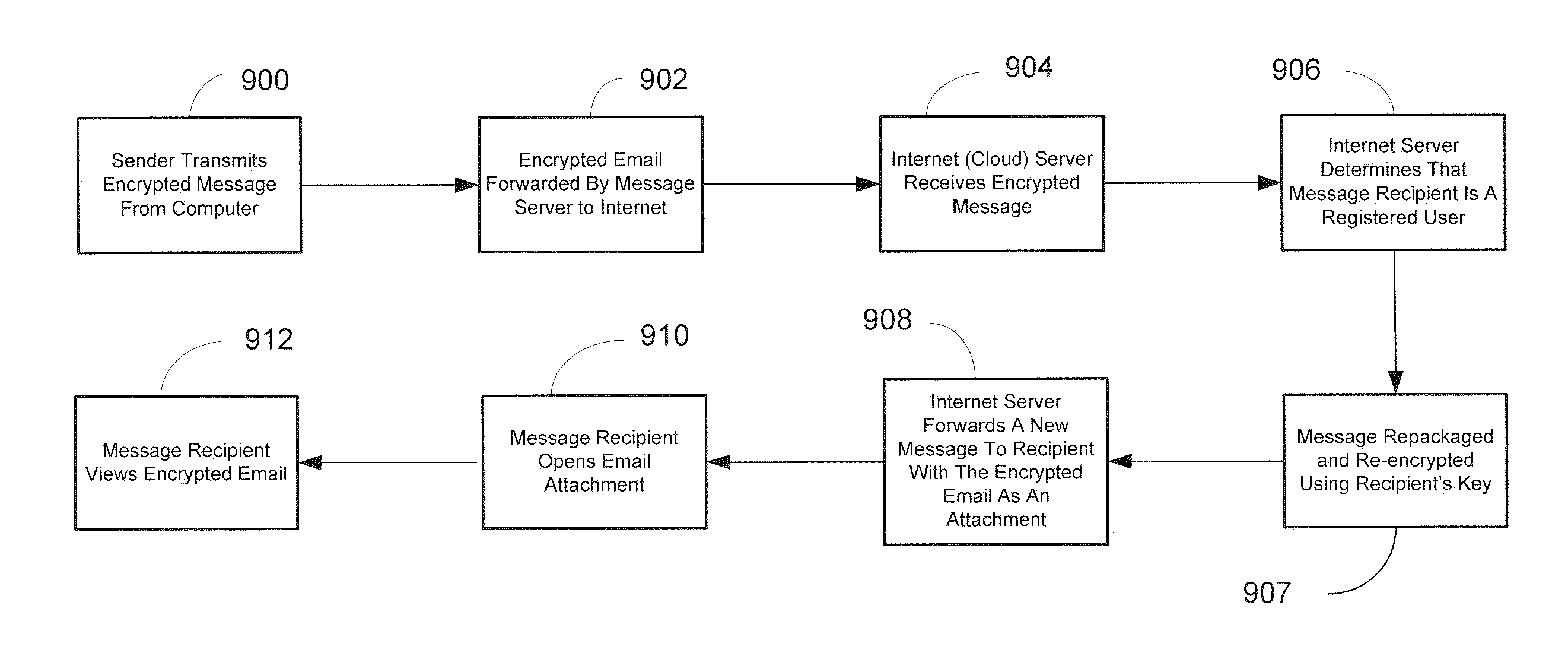
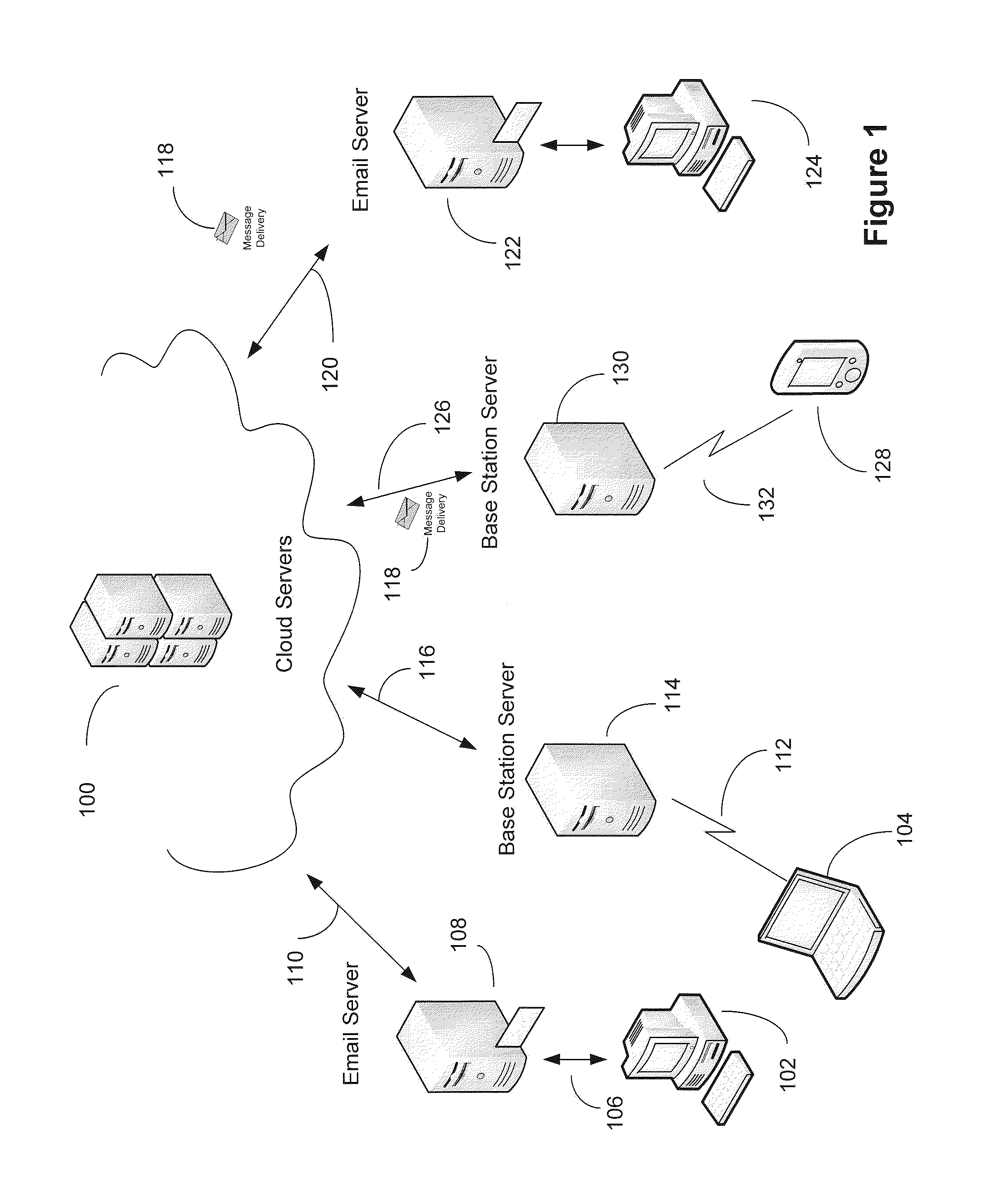
Encryption messaging system
ActiveUS8837739B1Easy to useRaise the level of confidentialityKey distribution for secure communicationPublic key for secure communicationKey exchangeS/KEY
This invention provides a user friendly, email encryption system allowing users to send and receive encrypted messages for registered and unregistered users. Encrypted messages can be sent to registered or non-registered users by transmitting the encrypted message to cloud system servers. The cloud system servers acquire certificates from certificate authorities or any end-to-end exchange of keys between the sender and the recipient of the encrypted message. For registered users, messages sent by senders are encrypted by the sender and sent to the cloud system servers which decrypt the message and re-encrypt the message with the recipient's key. For non-registered users, once the encrypted message is decrypted at the cloud system servers, another message is sent to the non-registered informing them that an encrypted message awaits them if they select a link in the message which allows them to log into the cloud system servers and view the original message.
Owner:IDENTILLECT TECH
Packet transmission/reception device
InactiveUS7228422B2Easy to processUser identity/authority verificationTelevision systemsComputer hardwareKey exchange
A packets sending / receiving apparatus, comprising: authentication and key exchange means; encryption means for producing an encryption sending data; sending condition setting management means for producing sending condition setting information for setting sending condition of the sending packets; packetization means for producing the sending packets using the encryption sending data; receiving condition setting management means for producing receiving condition setting information for setting receiving condition of the receiving packets; packets reception means for receiving the reception packets; and decoding means for decoding the reception data using the decoding key.
Owner:GK BRIDGE 1
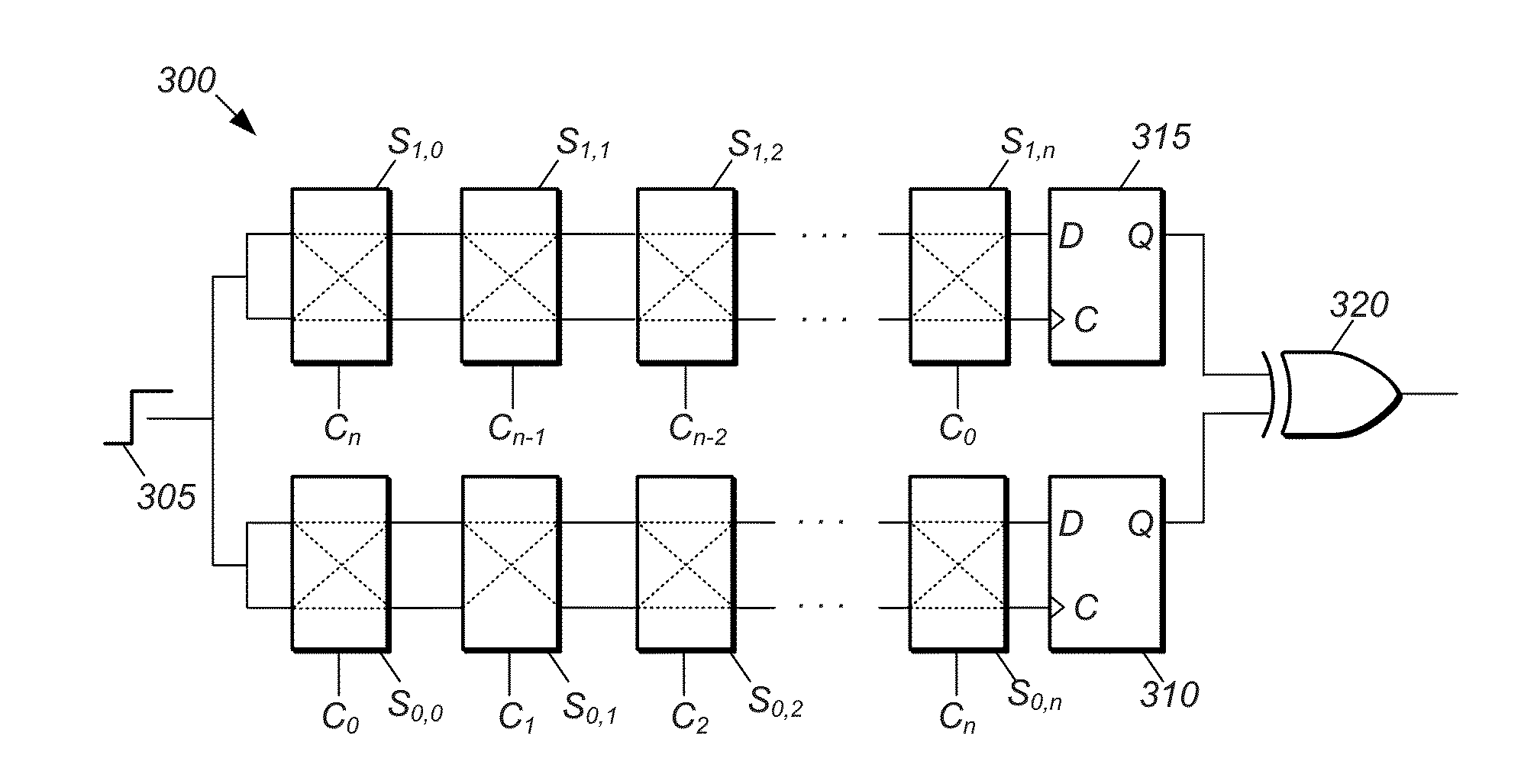
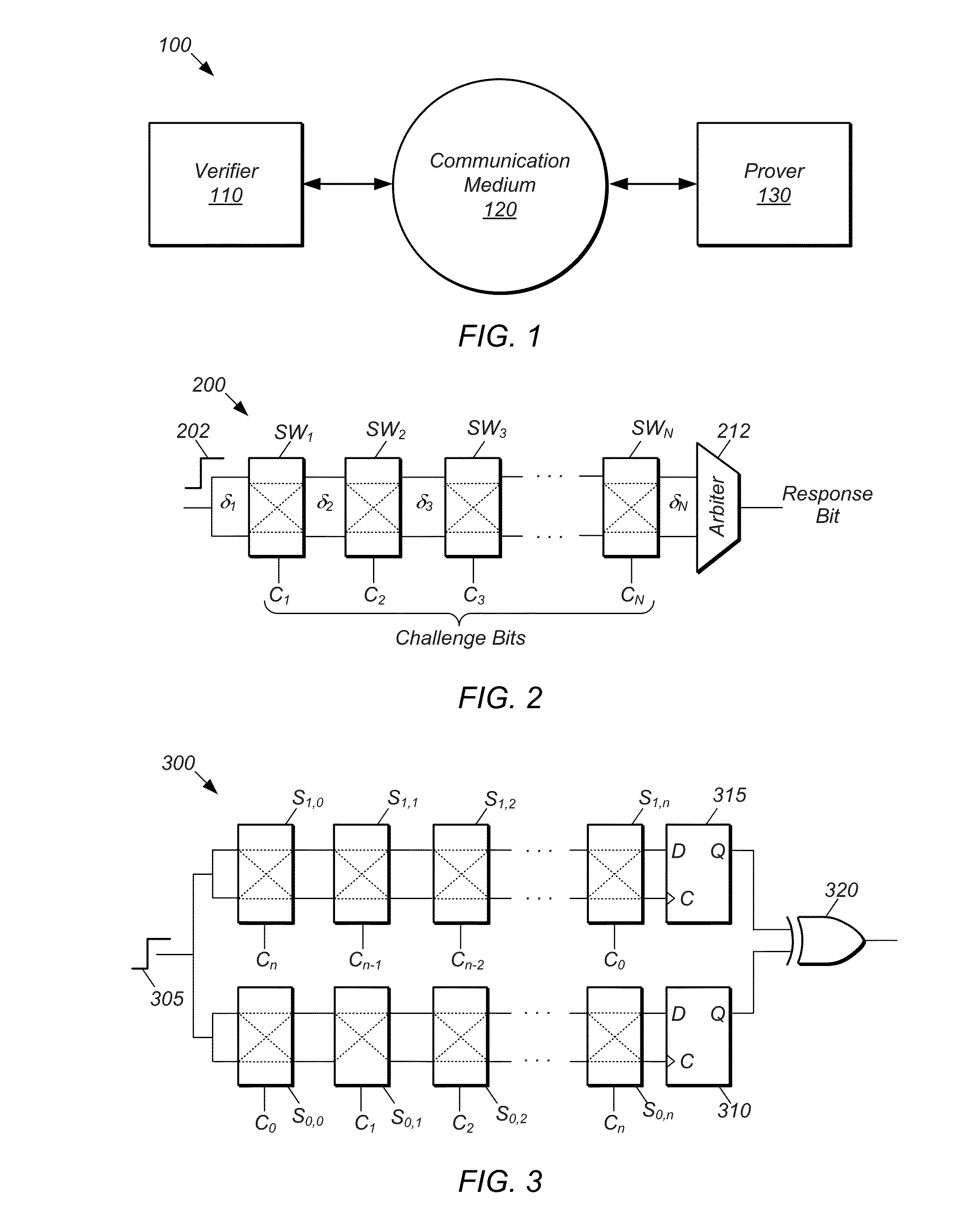
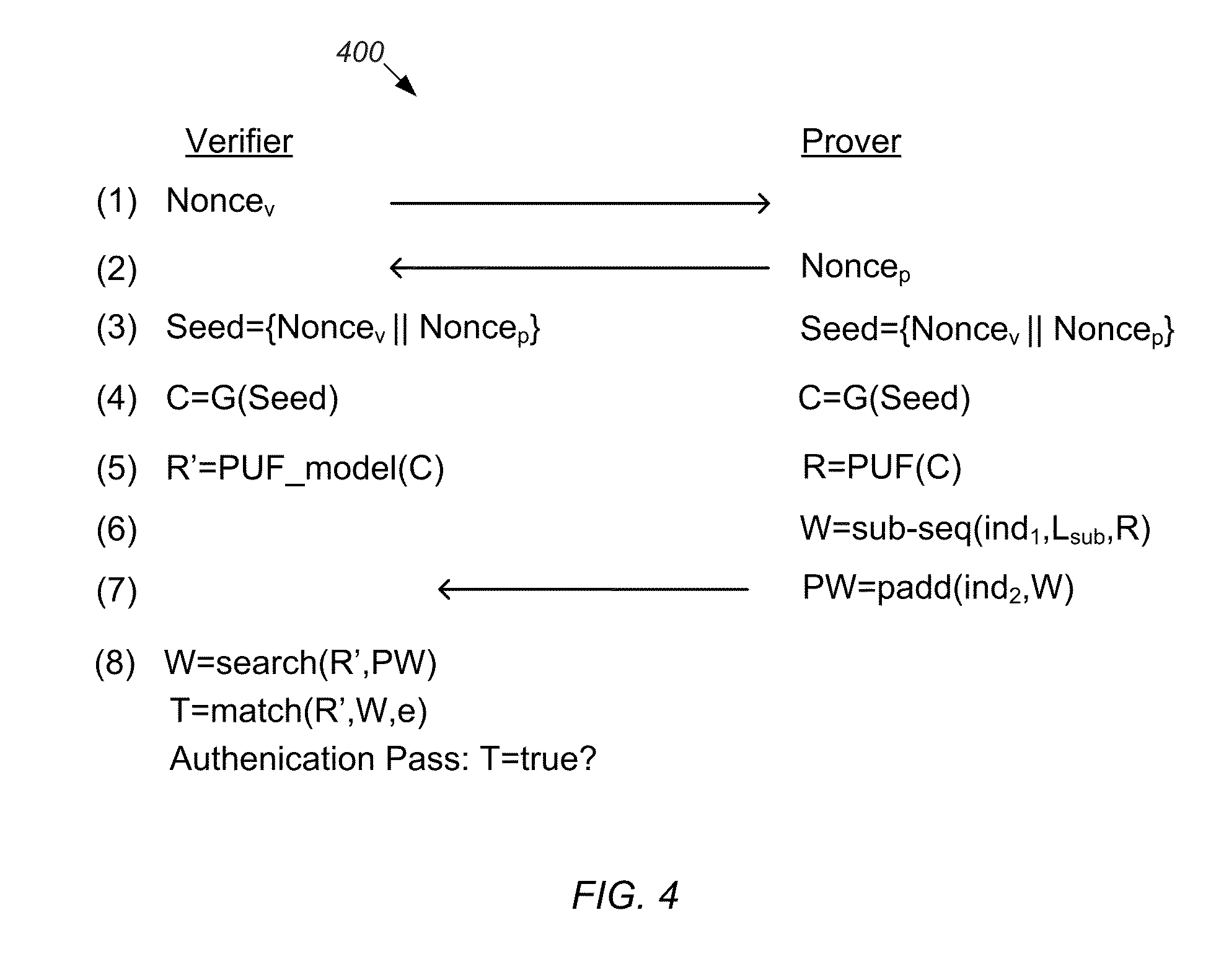
PUF Authentication and Key-Exchange by Substring Matching
ActiveUS20150195088A1Key distribution for secure communicationSecret communicationKey exchangeComputational model
Mechanisms for operating a prover device and a verifier device so that the verifier device can verify the authenticity of the prover device. The prover device generates a data string by: (a) submitting a challenge to a physical unclonable function (PUF) to obtain a response string, (b) selecting a substring from the response string, (c) injecting the selected substring into the data string, and (d) injecting random bits into bit positions of the data string not assigned to the selected substring. The verifier: (e) generates an estimated response string by evaluating a computational model of the PUF based on the challenge; (f) performs a search process to identify the selected substring within the data string using the estimated response string; and (g) determines whether the prover device is authentic based on a measure of similarity between the identified substring and a corresponding substring of the estimated response string.
Owner:RICE UNIV +1
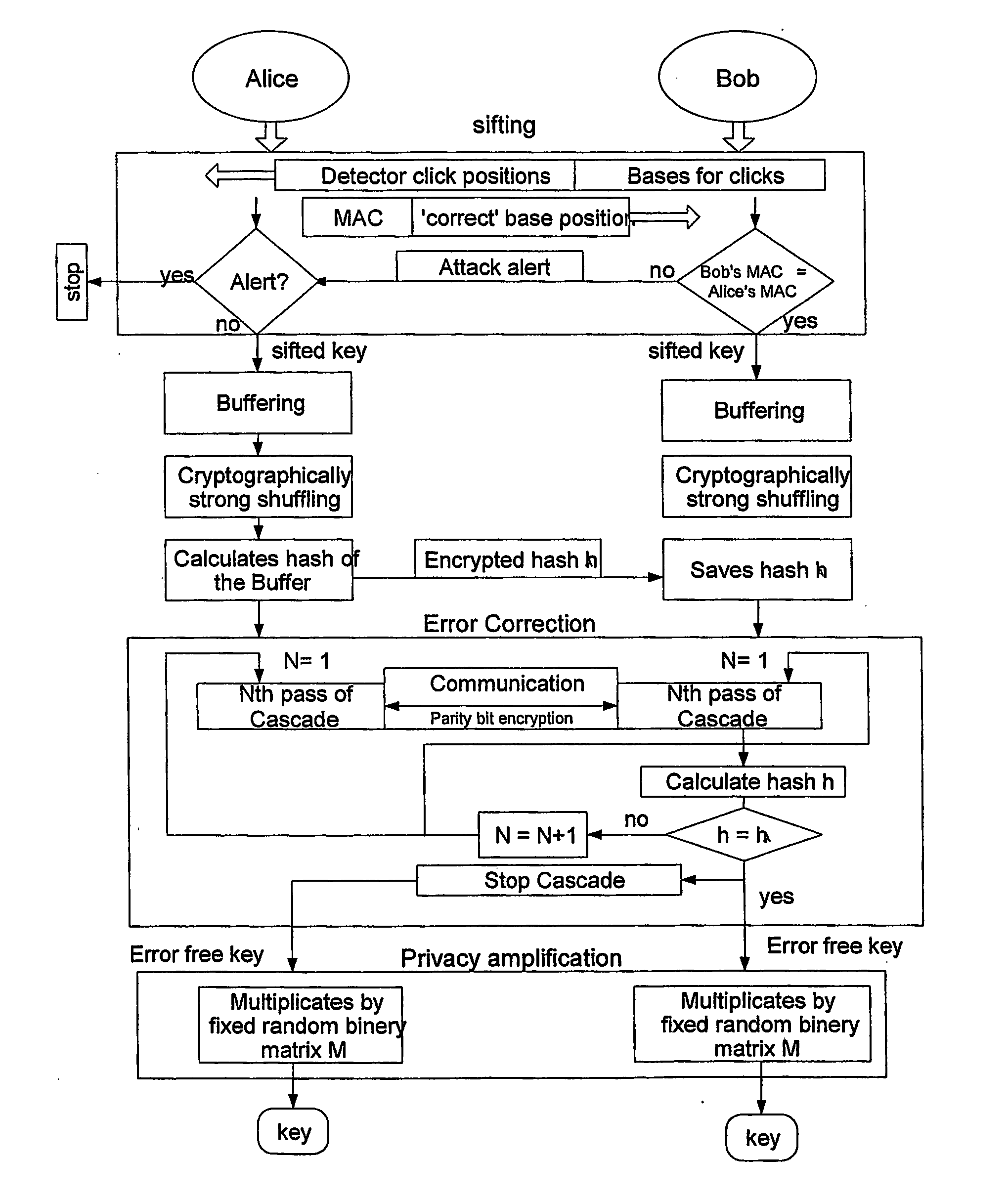
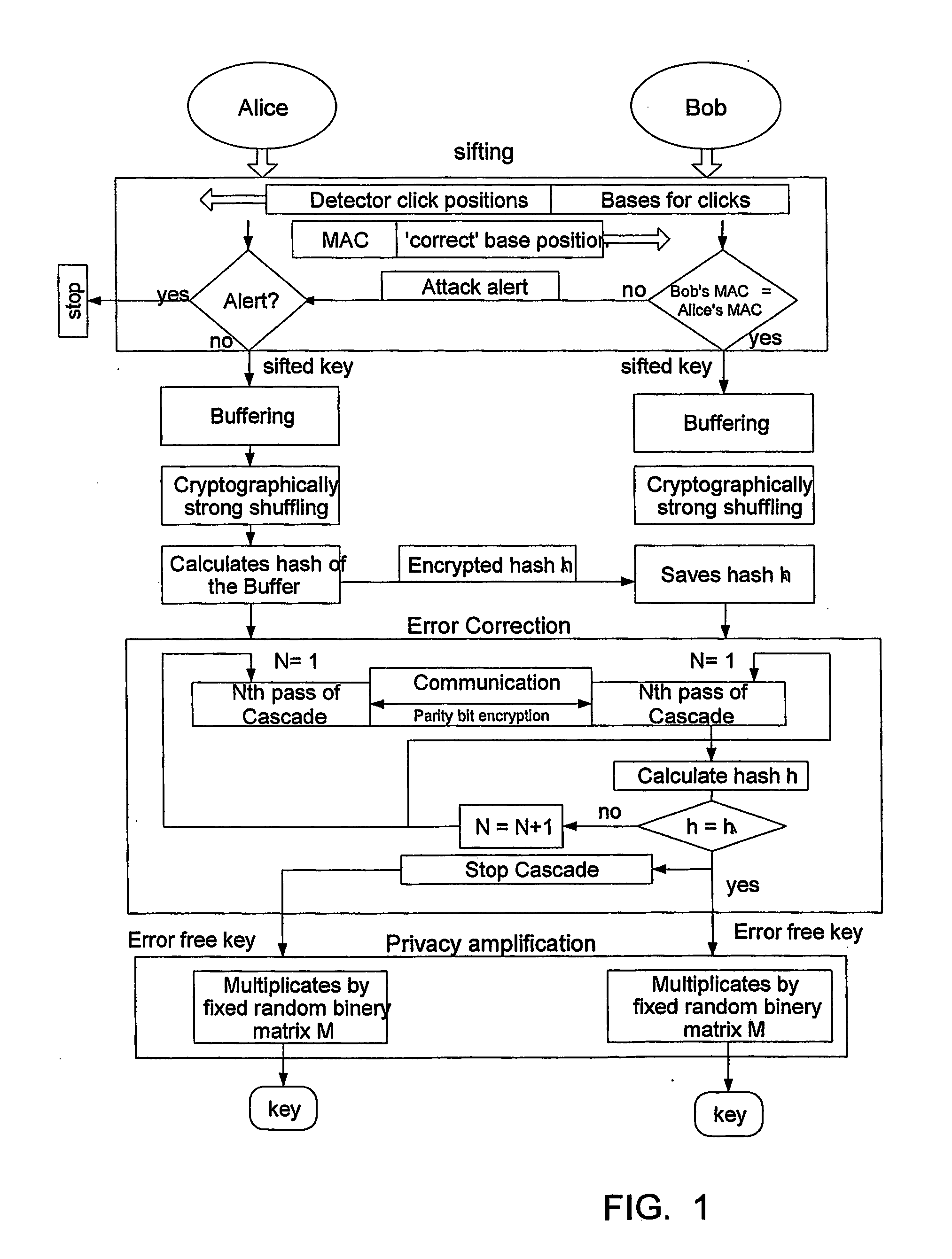
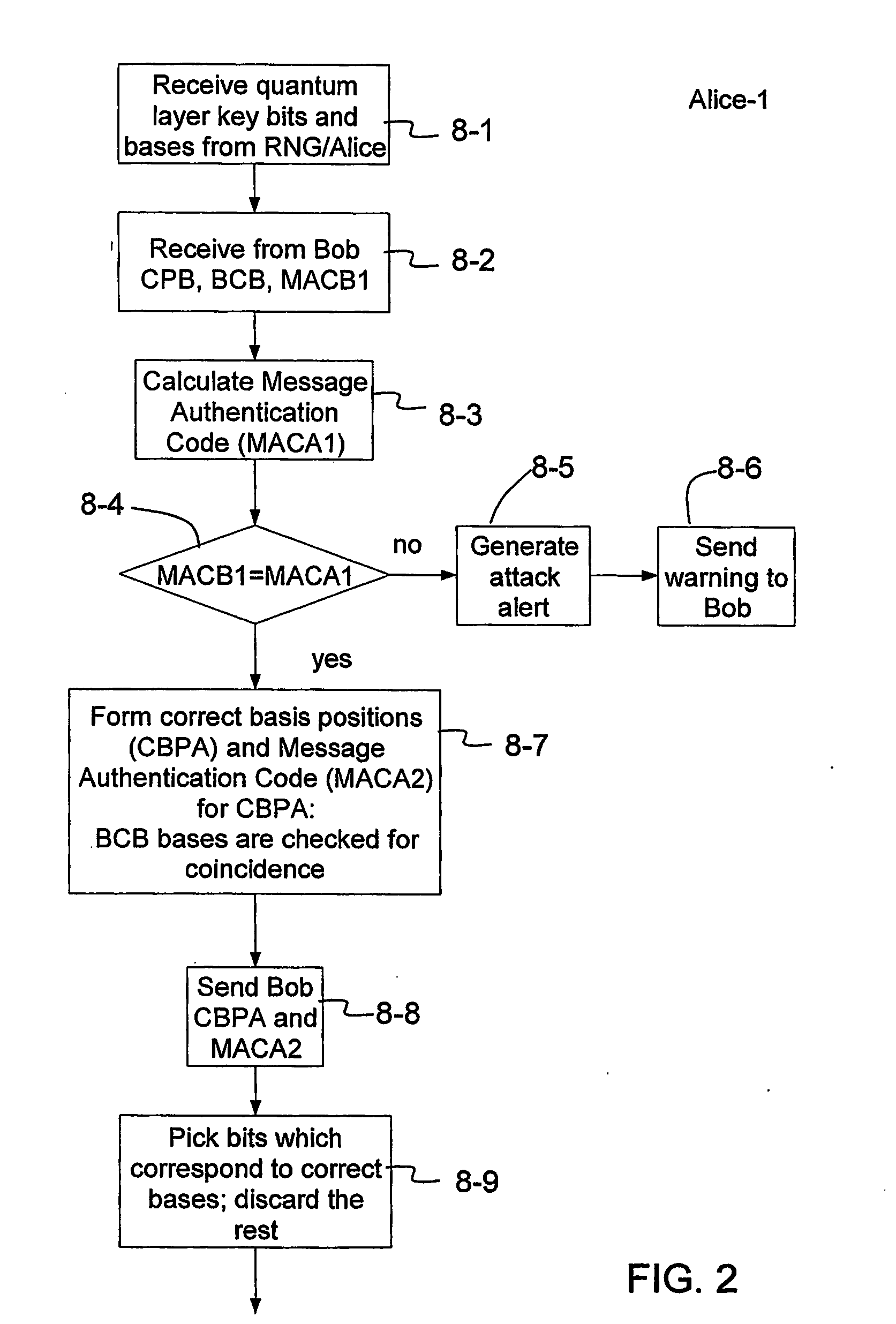
Key expansion for qkd
InactiveUS20060059343A1Key distribution for secure communicationSynchronisation information channelsKey exchangeKey schedule
A method of encrypting information using an encryption pad based on keys exchanged between quantum key distribution (QKD) stations is disclosed. The method includes establishing raw keys between two stations using QKD, processing the keys to establish a plurality of matching privacy amplified keys at each station and buffering the keys in a shared key schedule. The method also includes the option of expanding one or more of the keys in the shared key schedule using a stream cipher to create a supply of expanded keys that serve as pads for one-time-pad encryption.
Owner:MAGIQ TECH INC
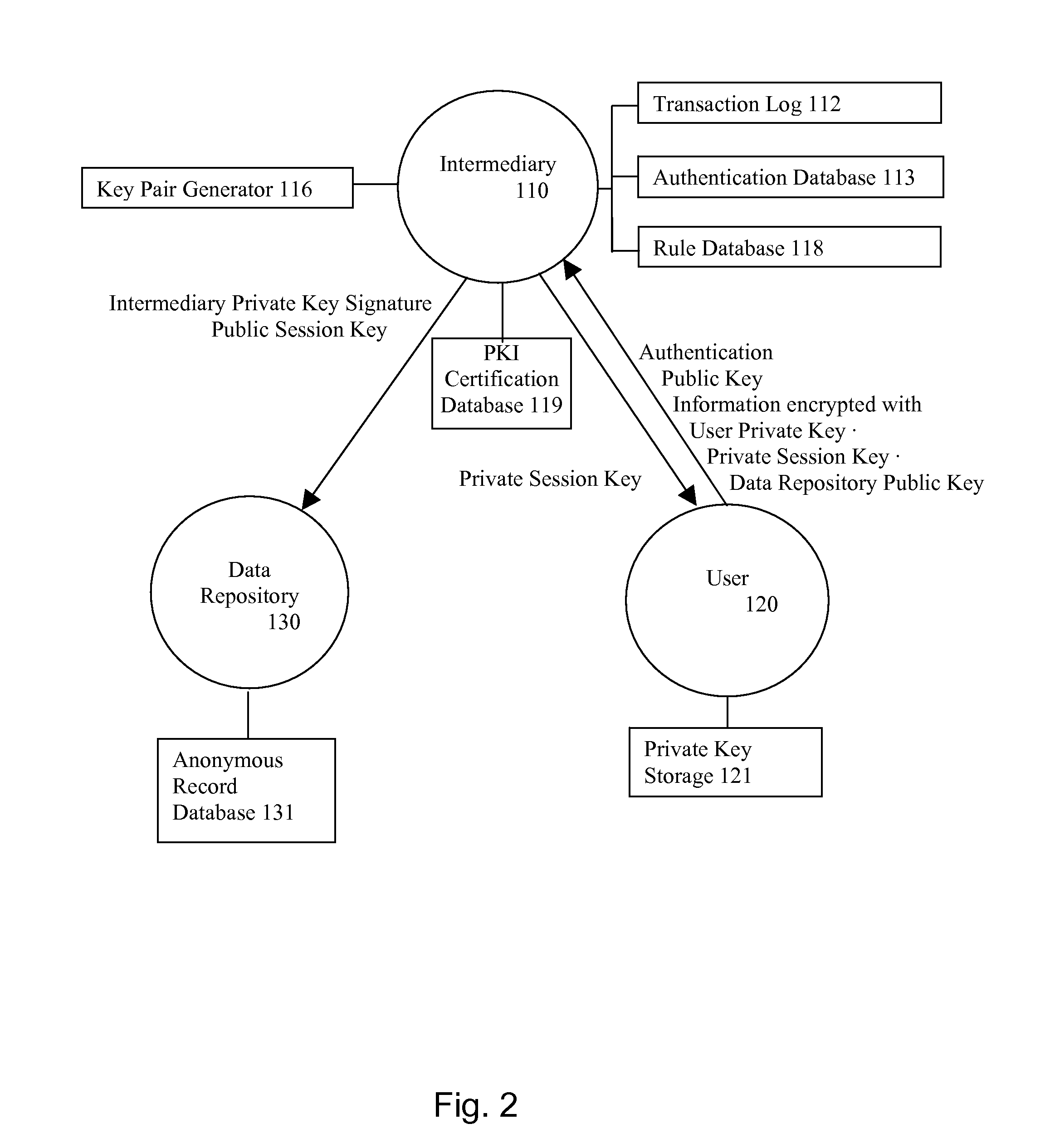
System and method for secure communications involving an intermediary
ActiveUS8566247B1Reduce liabilityReduce riskPublic key for secure communicationInformation retrieval from punched cardsSecure communicationKey exchange
A system and method for communicating information or a cryptographic key therefore between a first party and a second party, comprising the steps of receiving, by an intermediary, an identifier of desired information and accounting information for a transaction involving the information from the first party, transmitting an identifier of the first party to the second party, and negotiating, by the intermediary, a comprehension function for obscuring at least a portion of the information communicated between the first party and the second party. The data transmission may be made secure with respect to the intermediary by providing an asymmetric key or direct key exchange for encryption of the communication between the first and second party. The data transmission may be made secure with respect to the second party by maintaining the information in encrypted format at the second party, with the decryption key held only by the intermediary, and transmitting a secure composite of the decryption key and a new encryption key to the second party for transcoding of the data record, and providing the new decryption key to the first party, so that the information transmitted to the first party can be comprehended by it. According to the present invention, asymmetric key encryption may be employed to provide the establishment of secure communications channels involving an intermediary, without making the intermediary privy to the decryption key or the message.
Owner:RPX CORP
Cipher key negotiation method, system, customer terminal and server for cipher key negotiation
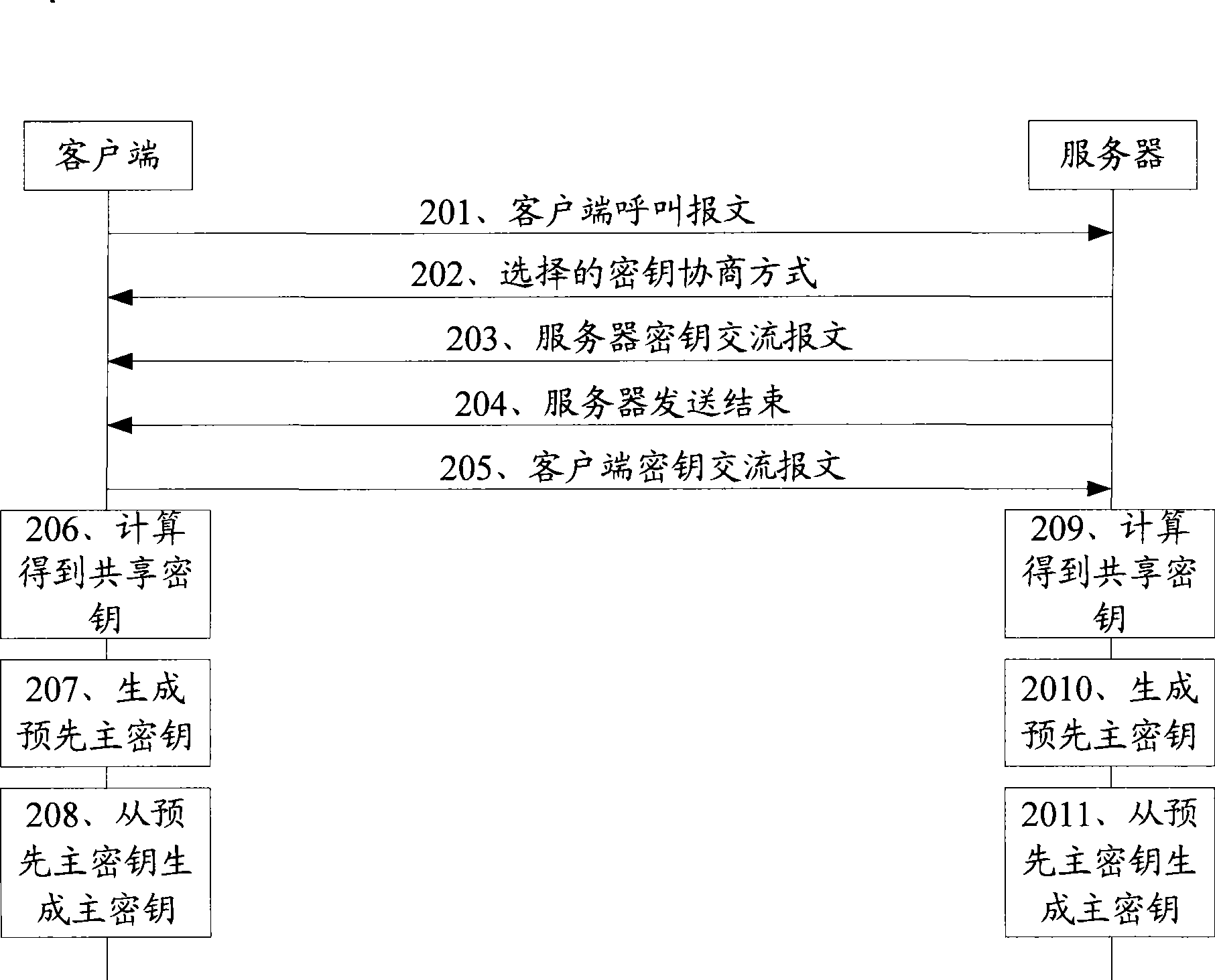
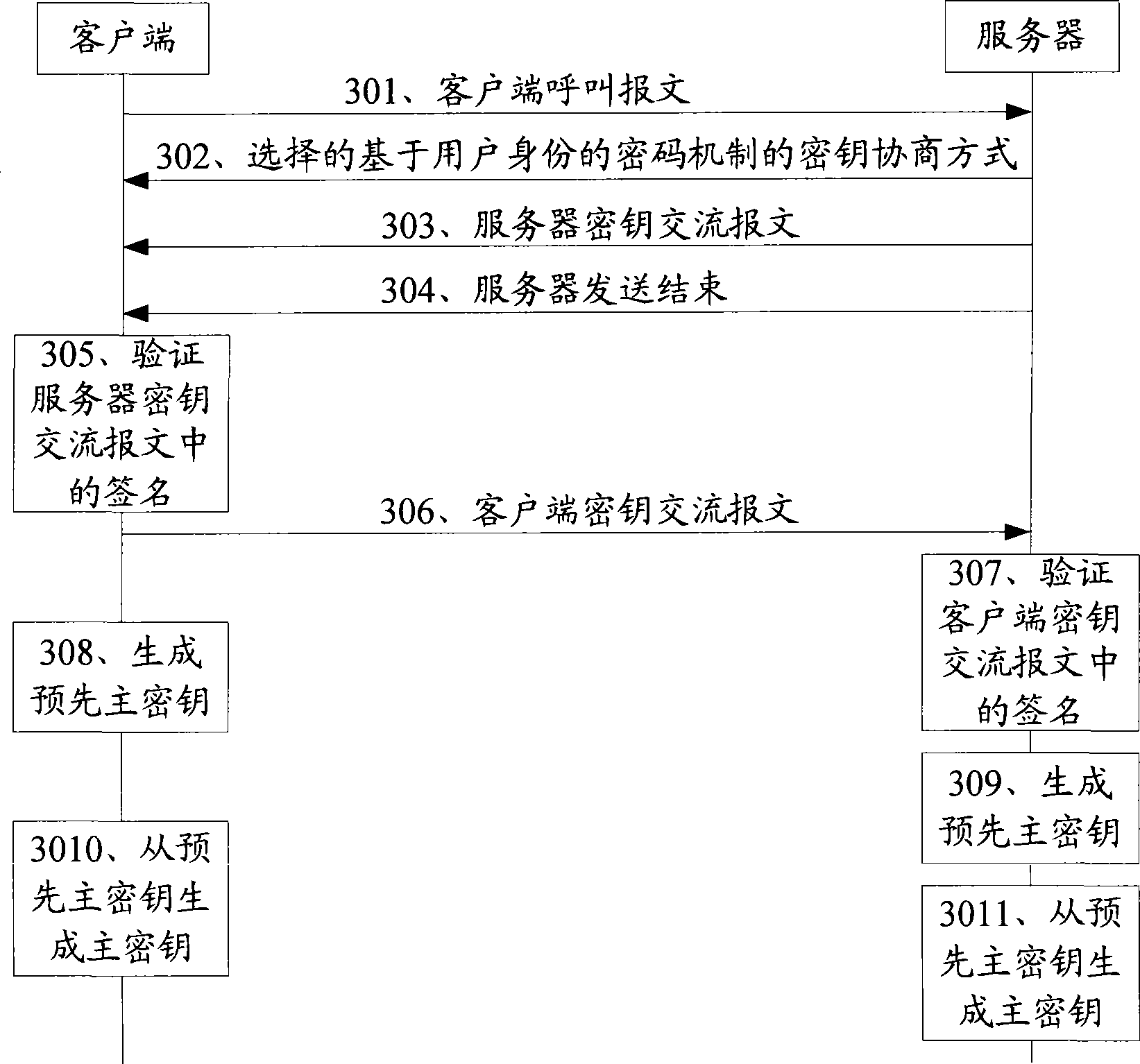
InactiveCN101459506ASimple processAvoid attackKey distribution for secure communicationData switching networksComputer hardwareKey exchange
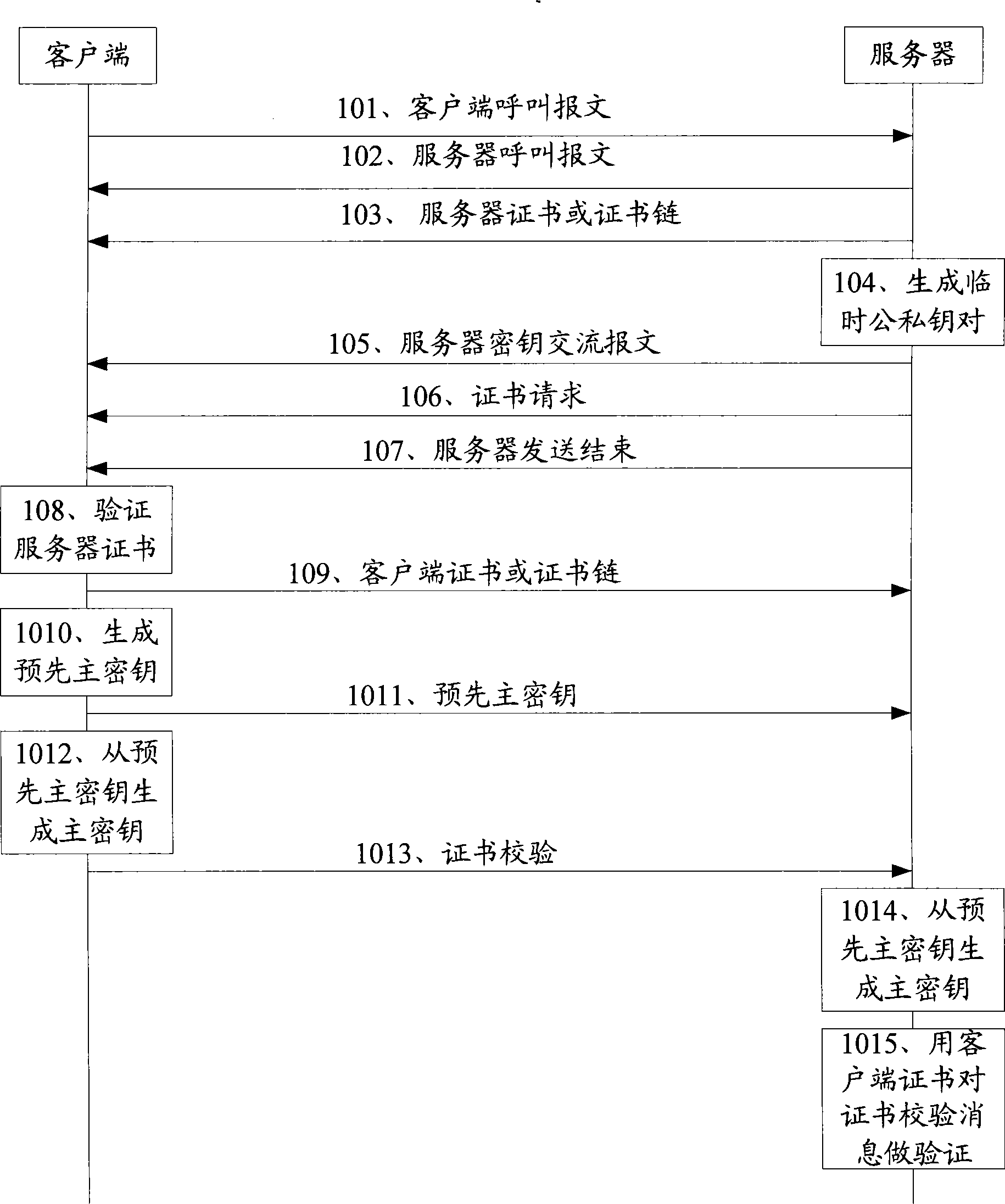
The embodiment of the invention discloses a key agreement method, which comprises sending a client calling message to a server, receiving information returned by the server, including key agreement mode of a code mechanism based on user's identity, receiving a server key exchange message sent by the server, obtaining a master key, and sending a client key exchange message to the server. The embodiment of the invention further discloses an another key agreement method, which comprises receiving a client calling message sent by a client terminal, selecting ciphertex family using the key agreement mode of the code mechanism based on user's identity from a ciphertext family list, and then sending to a client, sending a server key exchange message to the client, receiving a client key exchange message sent by the client, and obtaining a master key according to information carried in the client key exchange message. The invention further discloses a system used for the key agreement, and a relative client and a server, which can make the process of the key agreement more rapid, safer and more highly-effective.
Owner:HUAWEI TECH CO LTD
Information communication device, information communication system, and computer program product for transmission control
ActiveUS20050027984A1Transmission controlTelevision system detailsKey distribution for secure communicationKey exchangeCommunications system
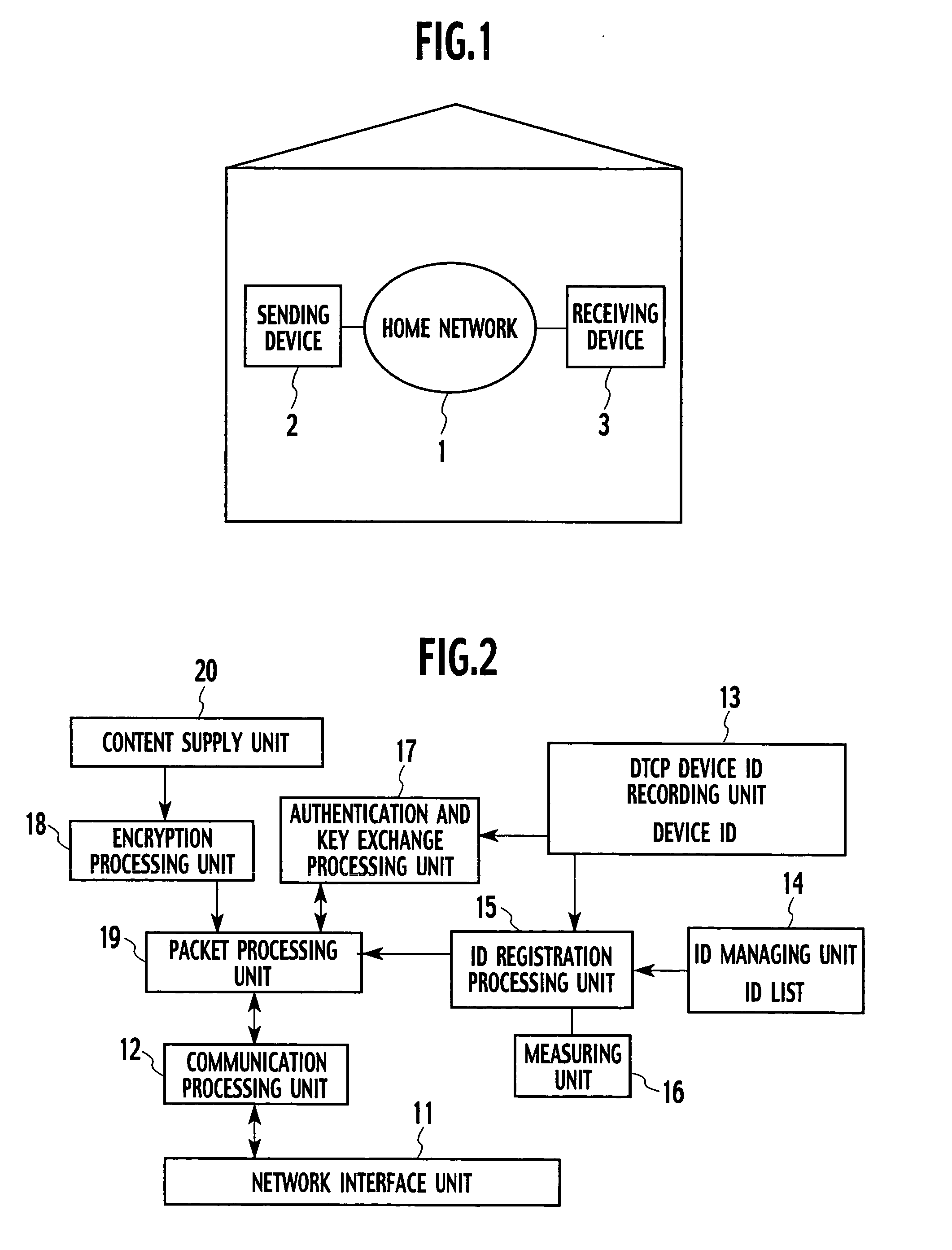
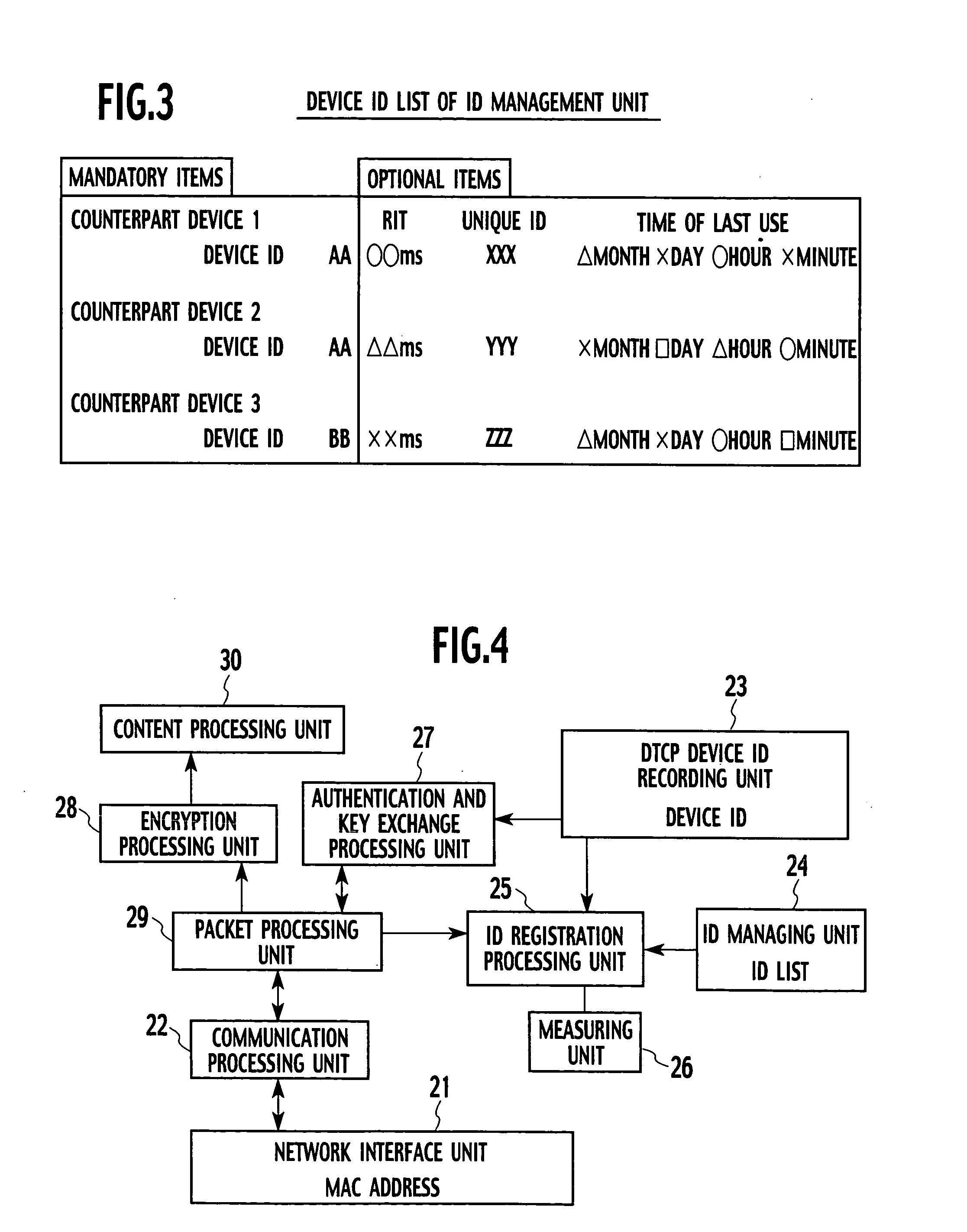
An aspect of the present invention provides an information communication device for transmitting electronic data encrypted for the purpose of copyright protection, the device includes that an identification information managing unit configured to hold device identification information in connection with other information communication devices acquired through a network, an ID registration processing unit configured to register the device identification information of another connection device when the other communication device satisfies a predetermined distance condition or when common identification information that is held by both information communication devices is received from a portable device, and an authentication and key exchange processing unit configured to, for the purpose of copyright protection, complete authentication and key exchange process (AKE process) only when another information communication device whose device identification information is registered in the identification information managing unit.
Owner:KK TOSHIBA
Encryption storage system for block chains and method for applying encryption storage system
InactiveCN106055993AStop out of capacity issuesAvoid the hassle of contactDigital data protectionKey exchangeComputer hardware
The invention provides an encryption storage system for block chains. The encryption storage system comprises file groups (S) (1), open file systems (2) and lock box devices (3). The file groups (S) are used for reducing the amounts of secret key exchange between users, differentiating file reading and writing, effectively processing and revoking access rights of the users and allowing authorization files of a distrusted server to carry out write operation; the open file systems are used for embedding encryption storage system prototypes of the block chains and comprise authentication databases; the lock box devices comprise a plurality of secrete key distribution schemes, and safety strategies and authentication mechanisms can be customized for files of each user by the aid of one of multiple client-based secret key distribution schemes. The invention further discloses a method for applying the encryption storage system for the block chains. The encryption storage system and the method have the advantages that the problem of possibly insufficient capacity of server sides due to expensive cipher computation can be solved by the aid of the encryption storage system and the method; the files can be accessed when file owners are offline, and accordingly the trouble of the requirement on contact with the corresponding file owner when each file needs to be accessed can be prevented.
Owner:SHENZHEN FANXI ELECTRONICS CO LTD
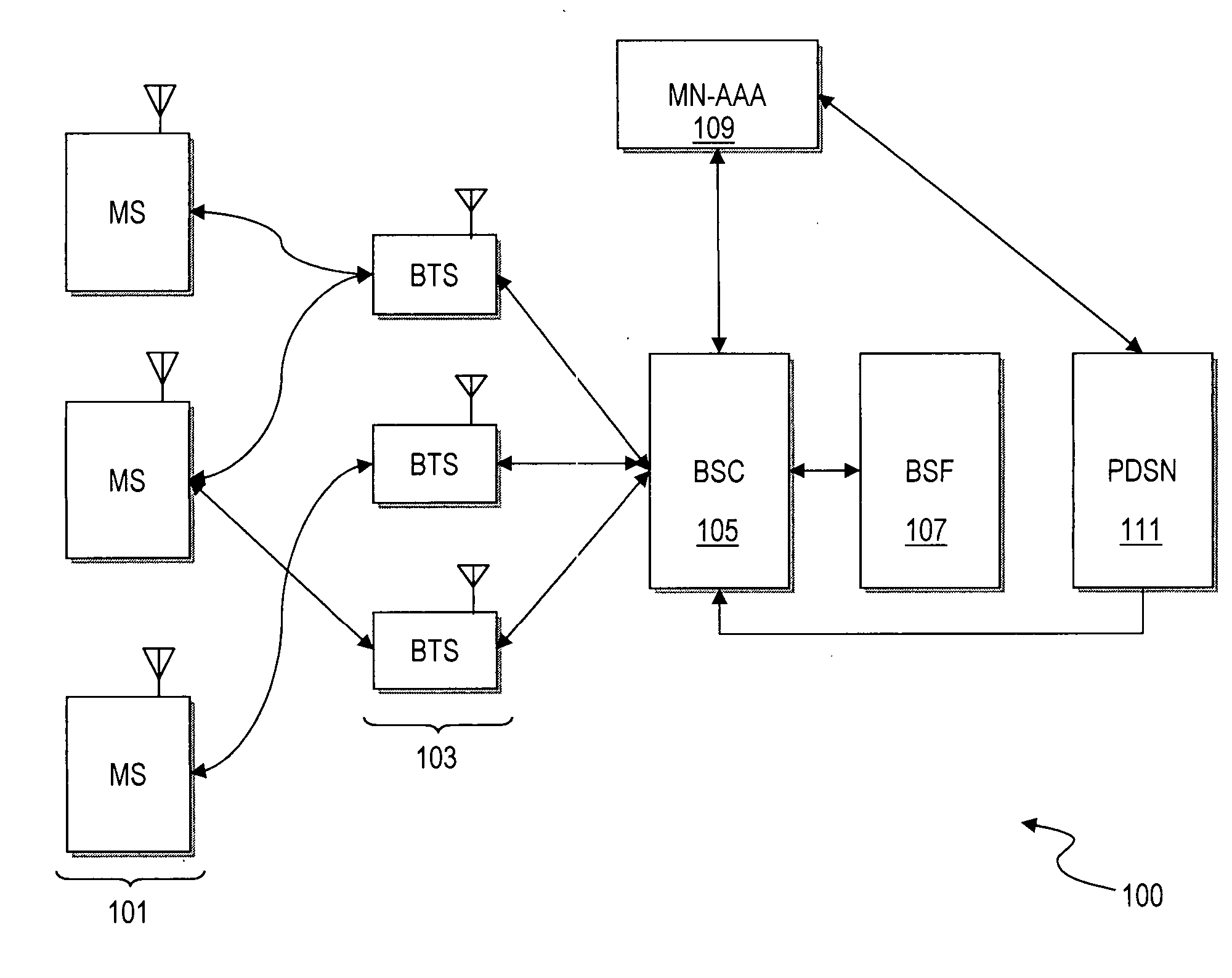
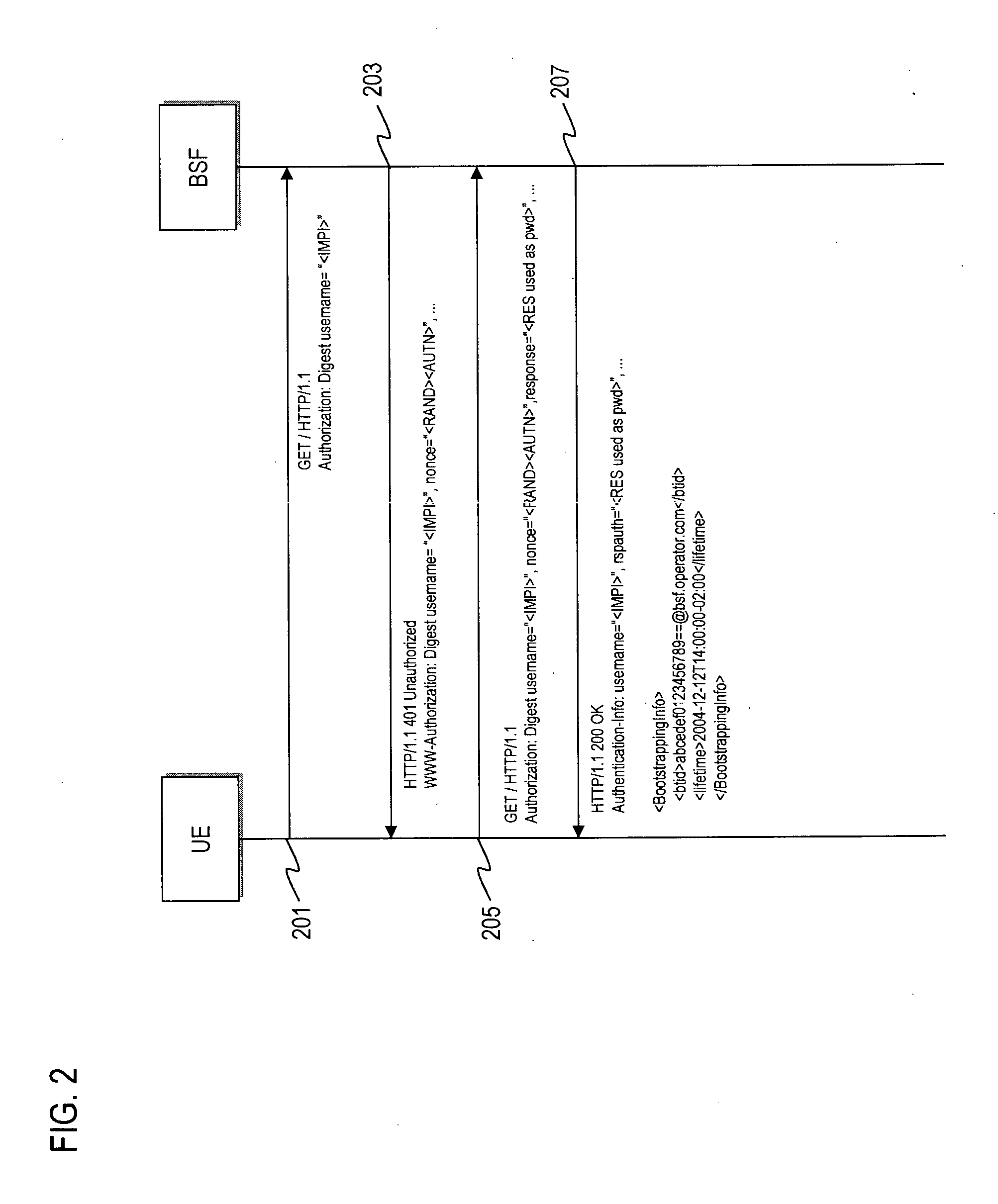
Method and apparatus for providing bootstrapping procedures in a communication network
ActiveUS20060182280A1Efficient executionSecret communicationProgram controlComputer hardwareKey exchange
An approach is provided for performing authentication in a communication system. In one embodiment, a key is established with a terminal in a communication network according to a key agreement protocol. The agreed key is tied to an authentication procedure to provide a security association that supports reuse of the key. A master key is generated based on the agreed key. In another embodiment, digest authentication is combined with key exchange parameters (e.g., Diffie-Hellman parameters) in the payload of the digest message, in which a key (e.g., SMEKEY or MN-AAA) is utilized as a password. In yet another embodiment, an authentication algorithm (e.g., Cellular Authentication and Voice Encryption (CAVE)) is employed with a key agreement protocol with conversion functions to support bootstrapping.
Owner:NOKIA TECHNOLOGLES OY
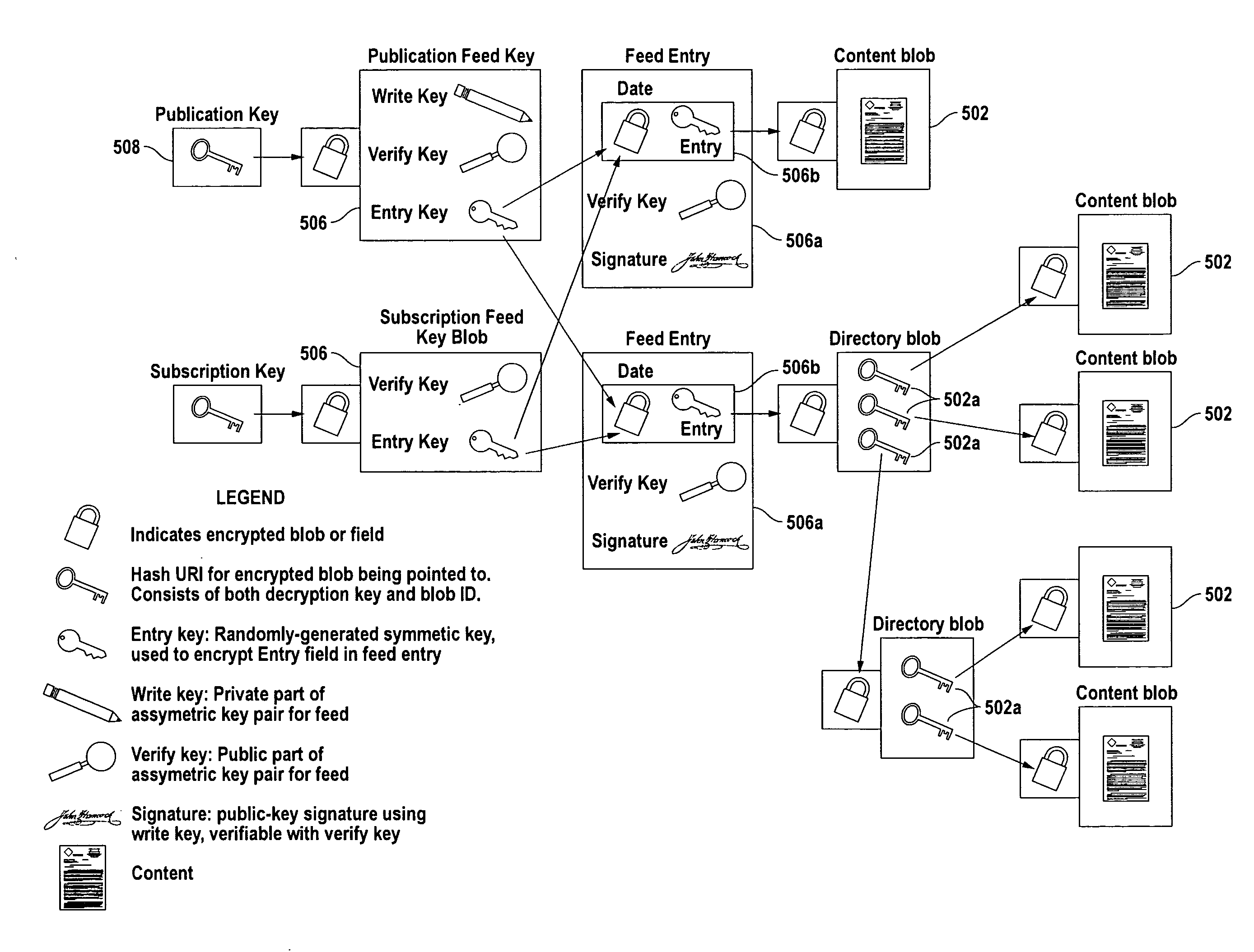
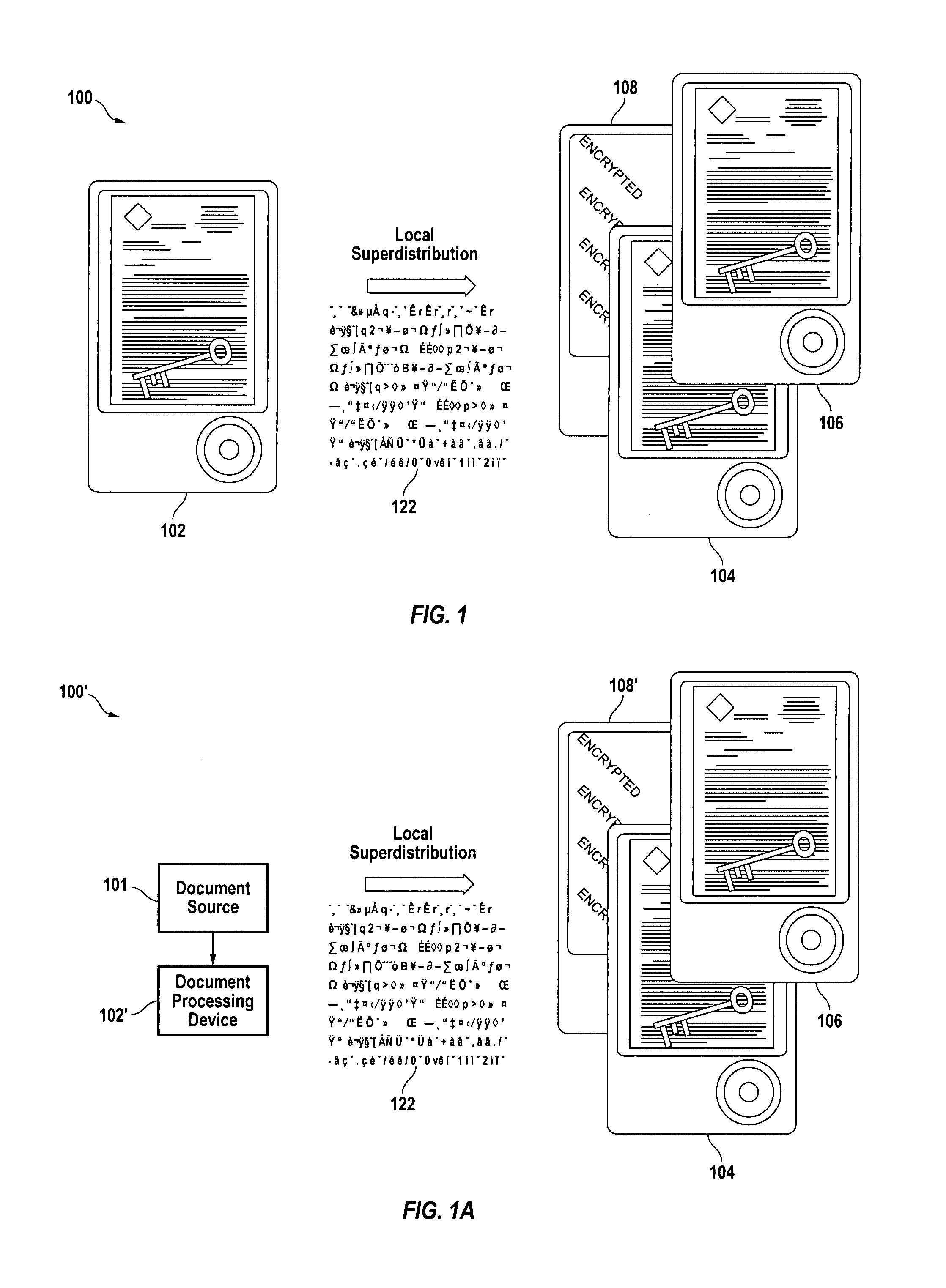
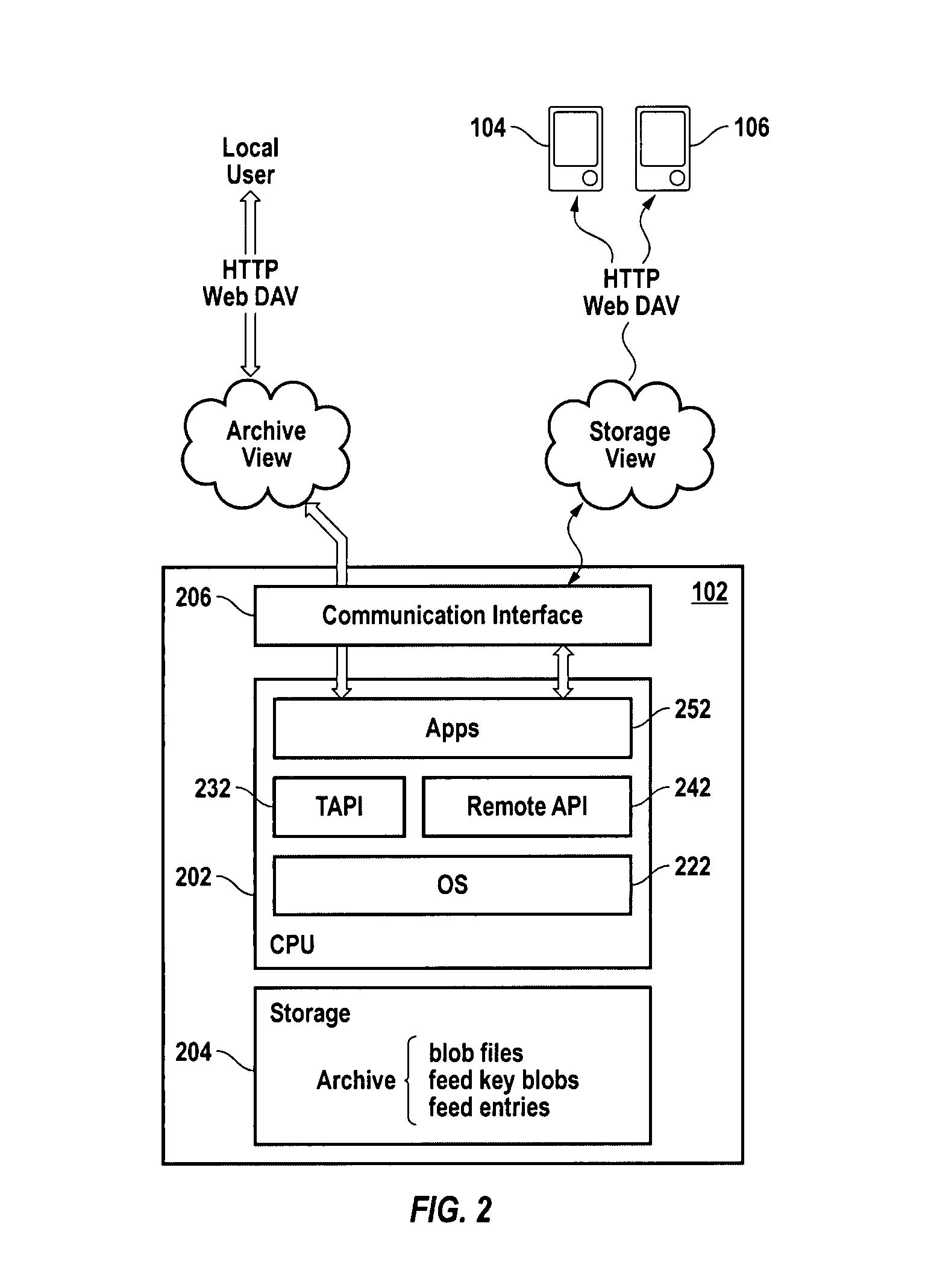
Secure pre-caching through local superdistribution and key exchange
InactiveUS20090327729A1Improve balanceDigital data processing detailsUser identity/authority verificationPersonalizationKey exchange
A distributed peer-to-peer document archival system provides the version-control, security, access control, linking among stored documents and remote access to documents usually associated with centralized storage systems while still providing the simplicity, personalization and robustness to network outages associated with personal and peer-to-peer storage systems.
Owner:RICOH KK
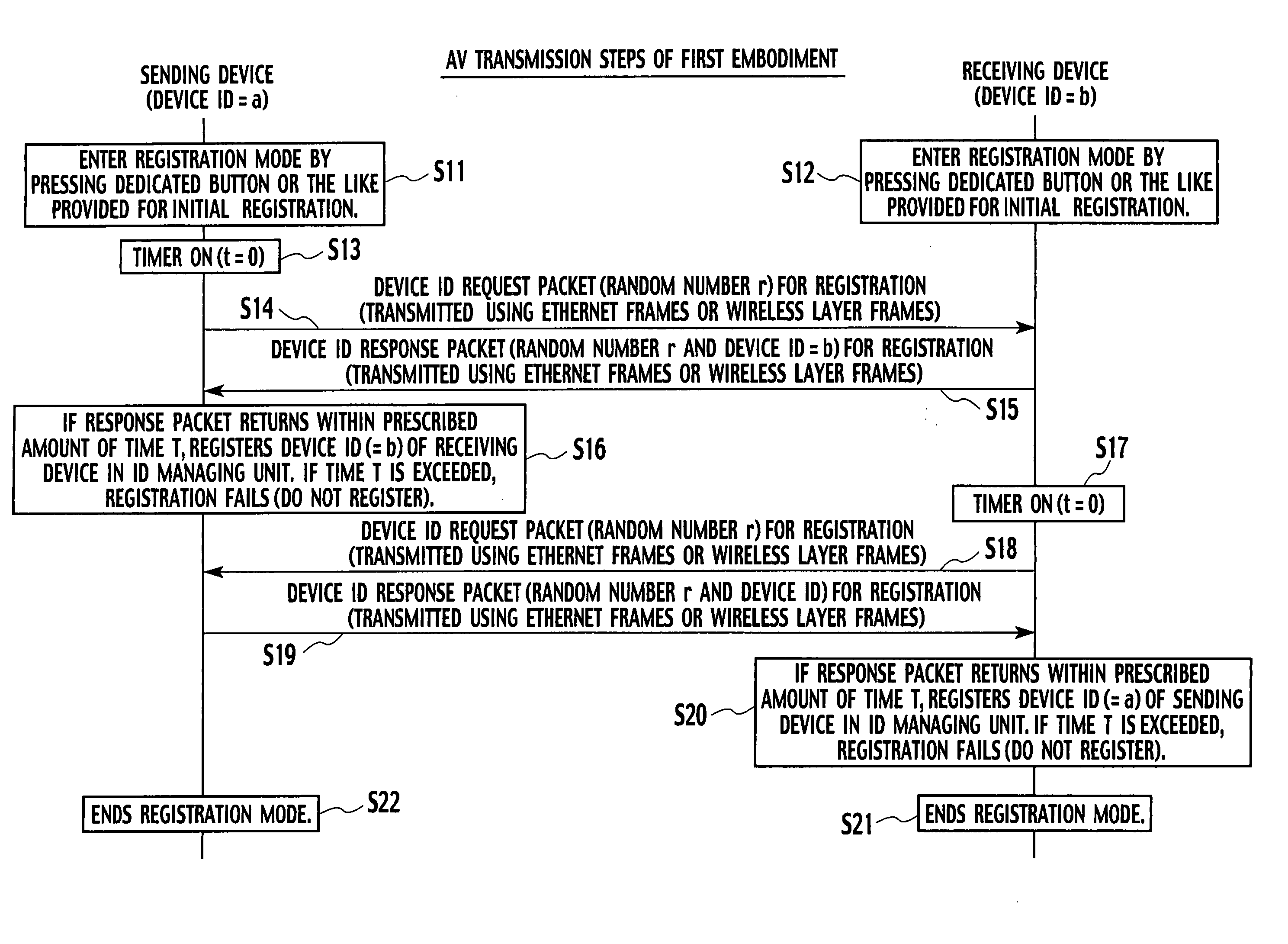
Av data receiving device, av data receiving method, and av data transmission and receiving system
InactiveUS20110293090A1Reduce frequencyReduce resultTelevision systemsSelective content distributionKey exchangeComputer hardware
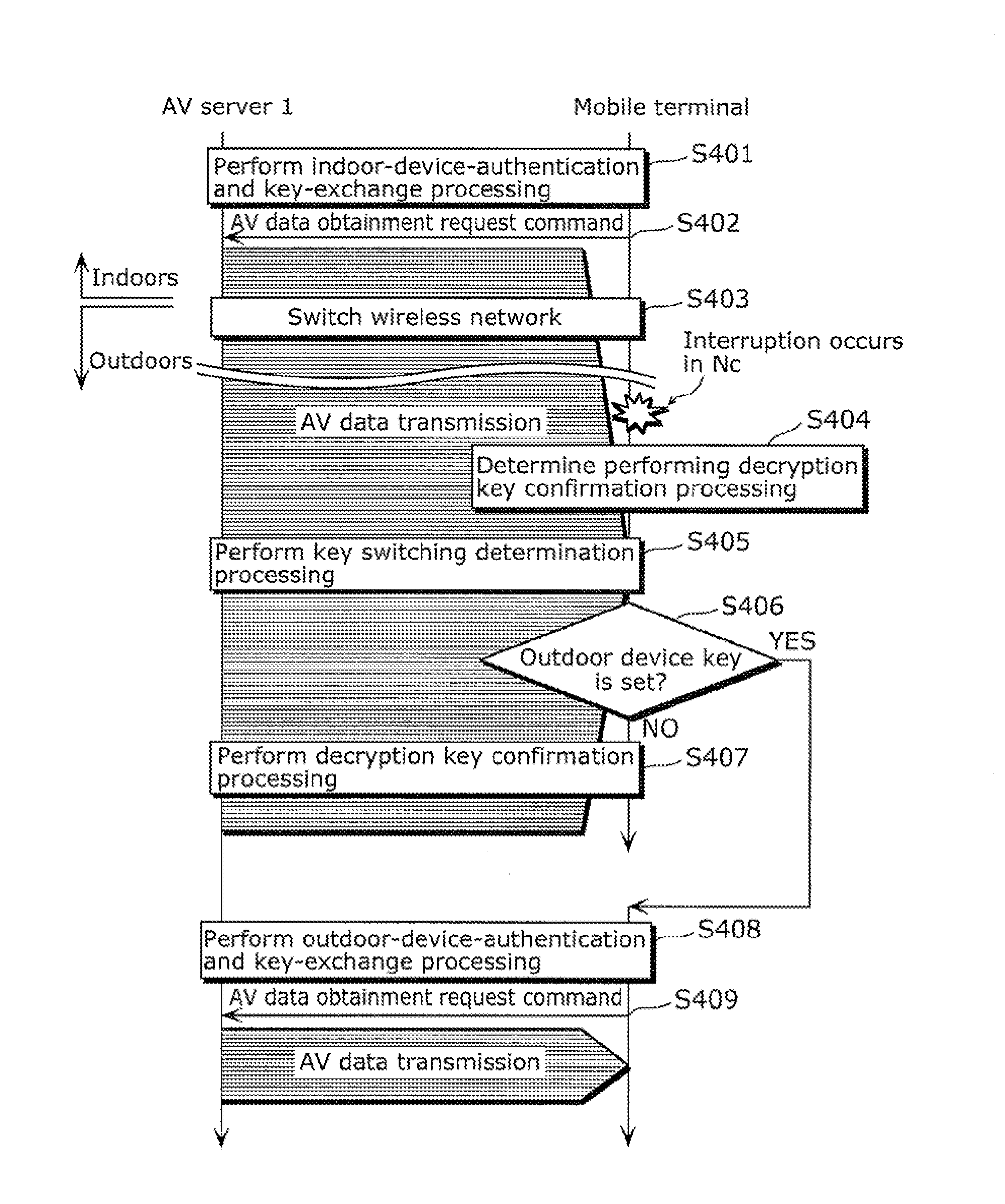
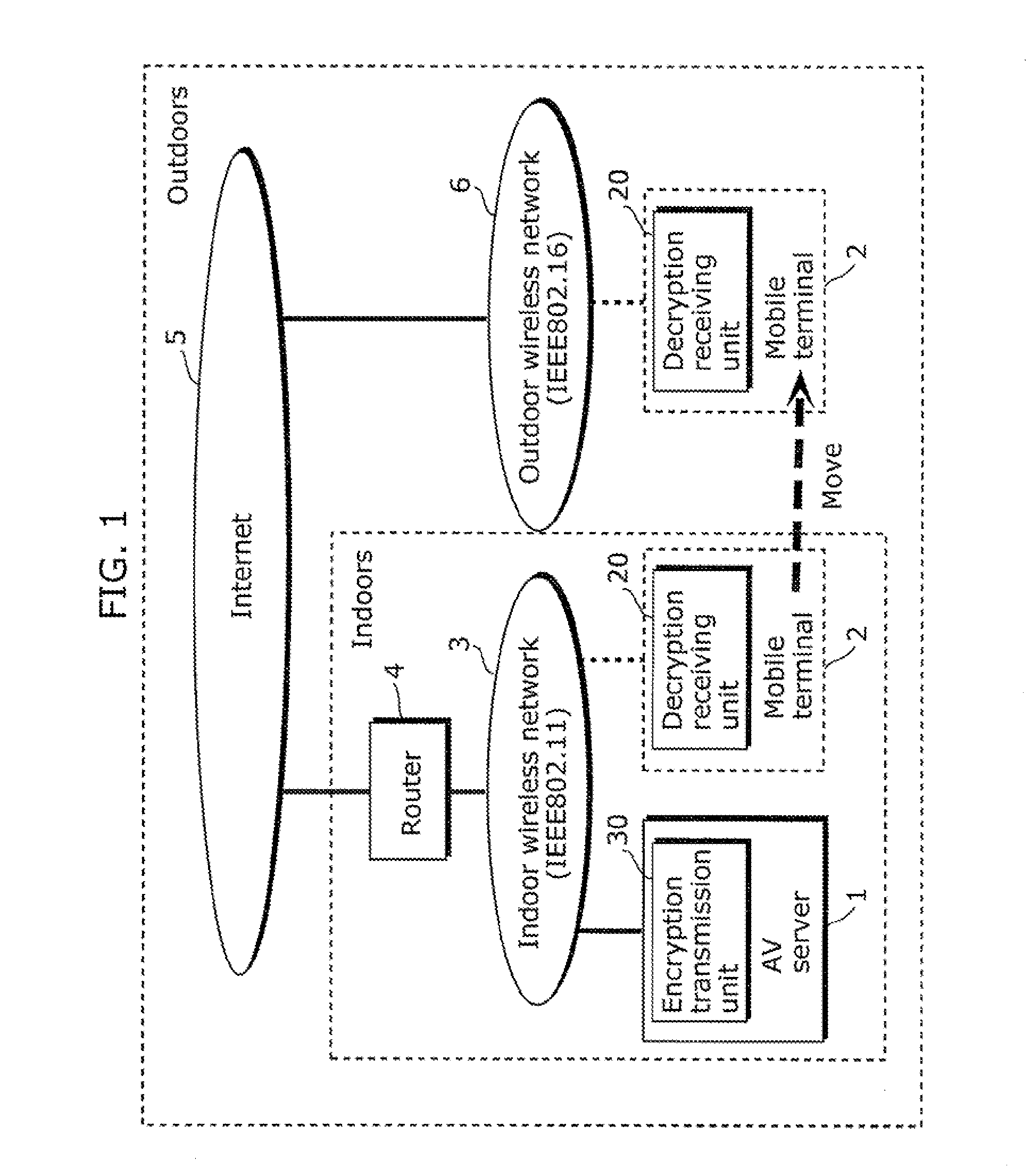
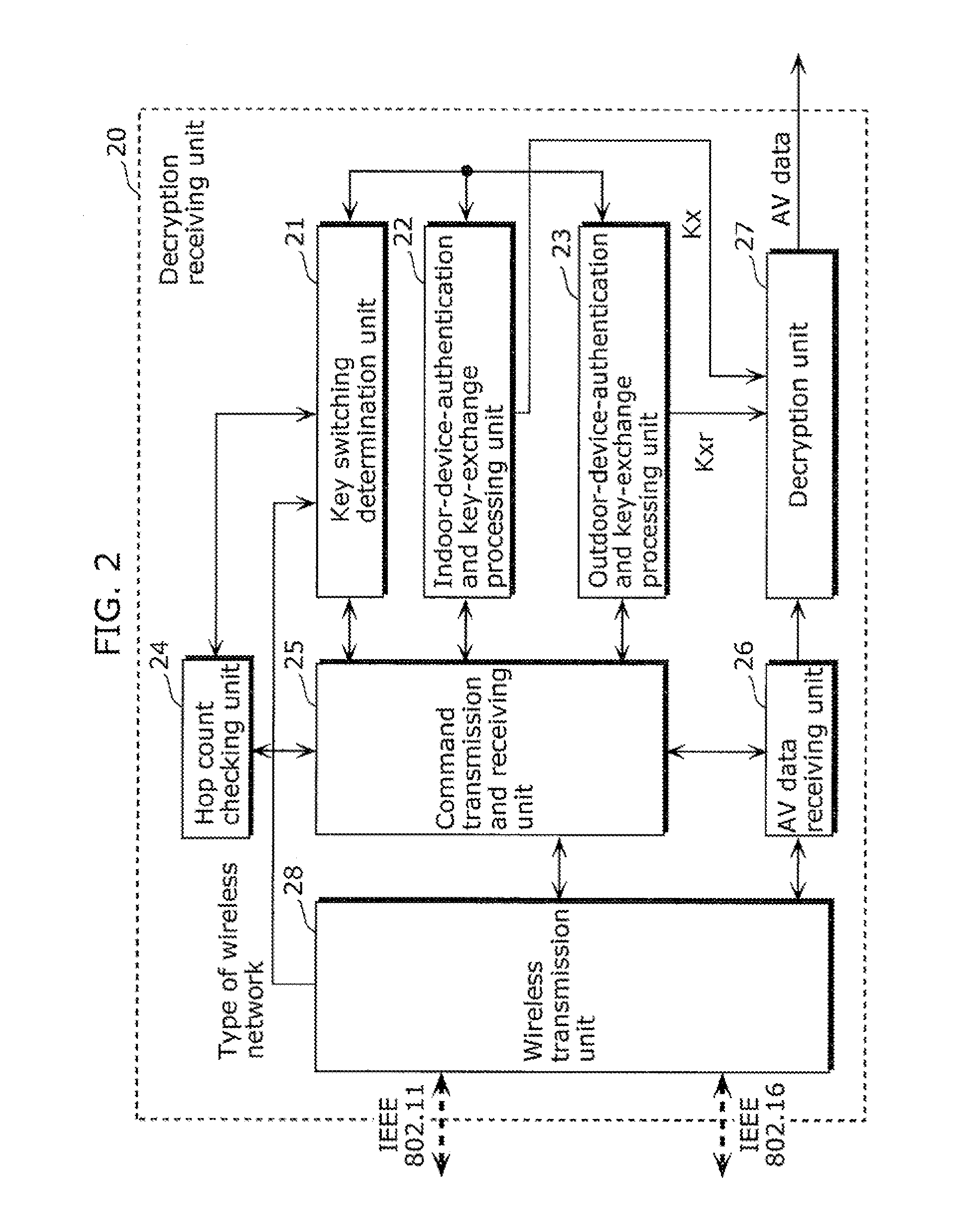
A conventional AV data receiving device switches to a key for distribution to an outdoor device when a network environment is switched to an outdoor network environment, thus resulting in high key switching frequency. In view of this, an AV data receiving device according to the present invention determines, after switching the network environment from indoors to outdoors as a result of moving the AV data receiving device, whether or not key switching should be performed, before a command for restricting a hop count on a route from an AV data transmission device located indoors is transmitted, and performs authentication and key exchange processing for outdoor device distribution, so as to switch to the key for outdoor device distribution.
Owner:PANASONIC CORP
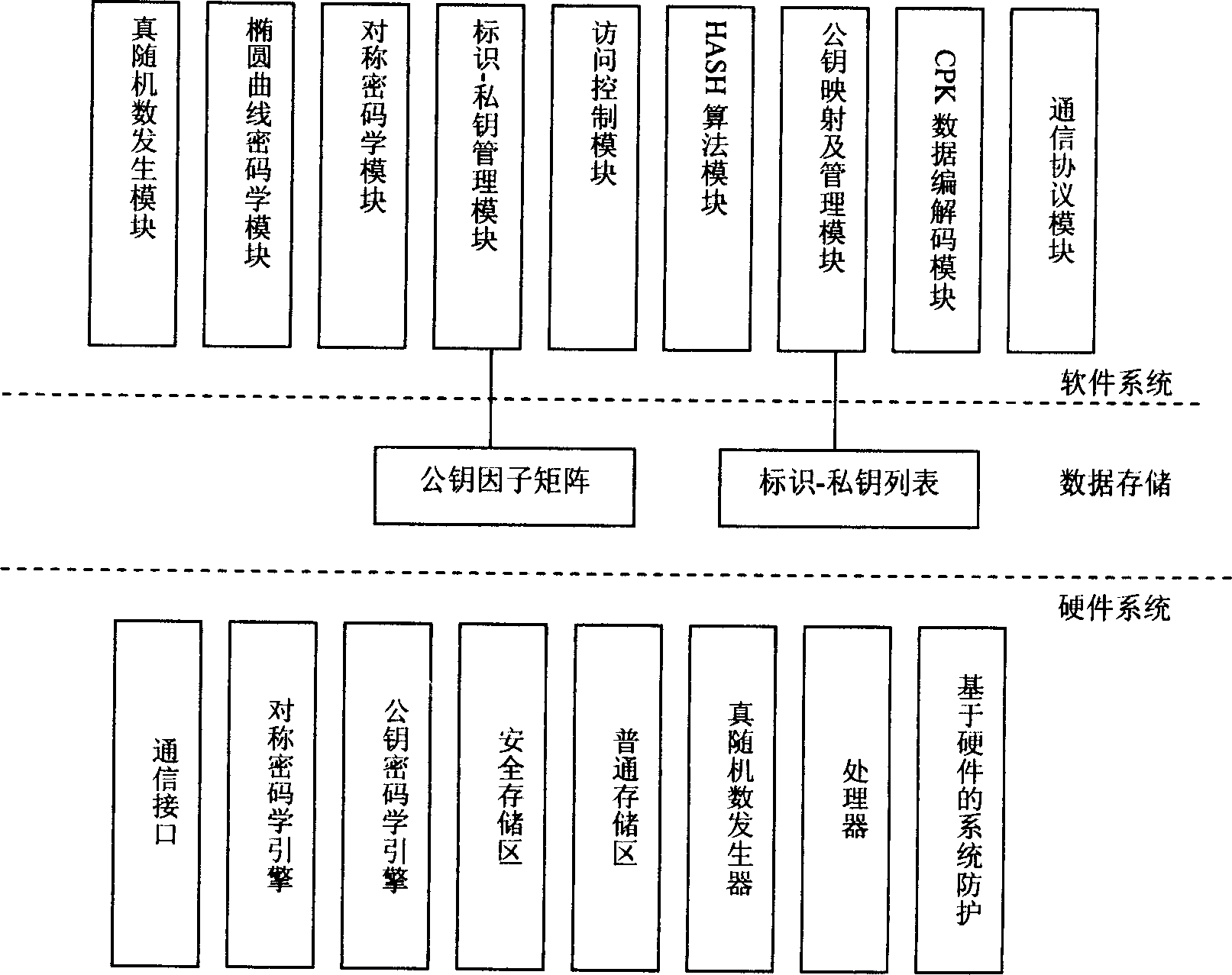
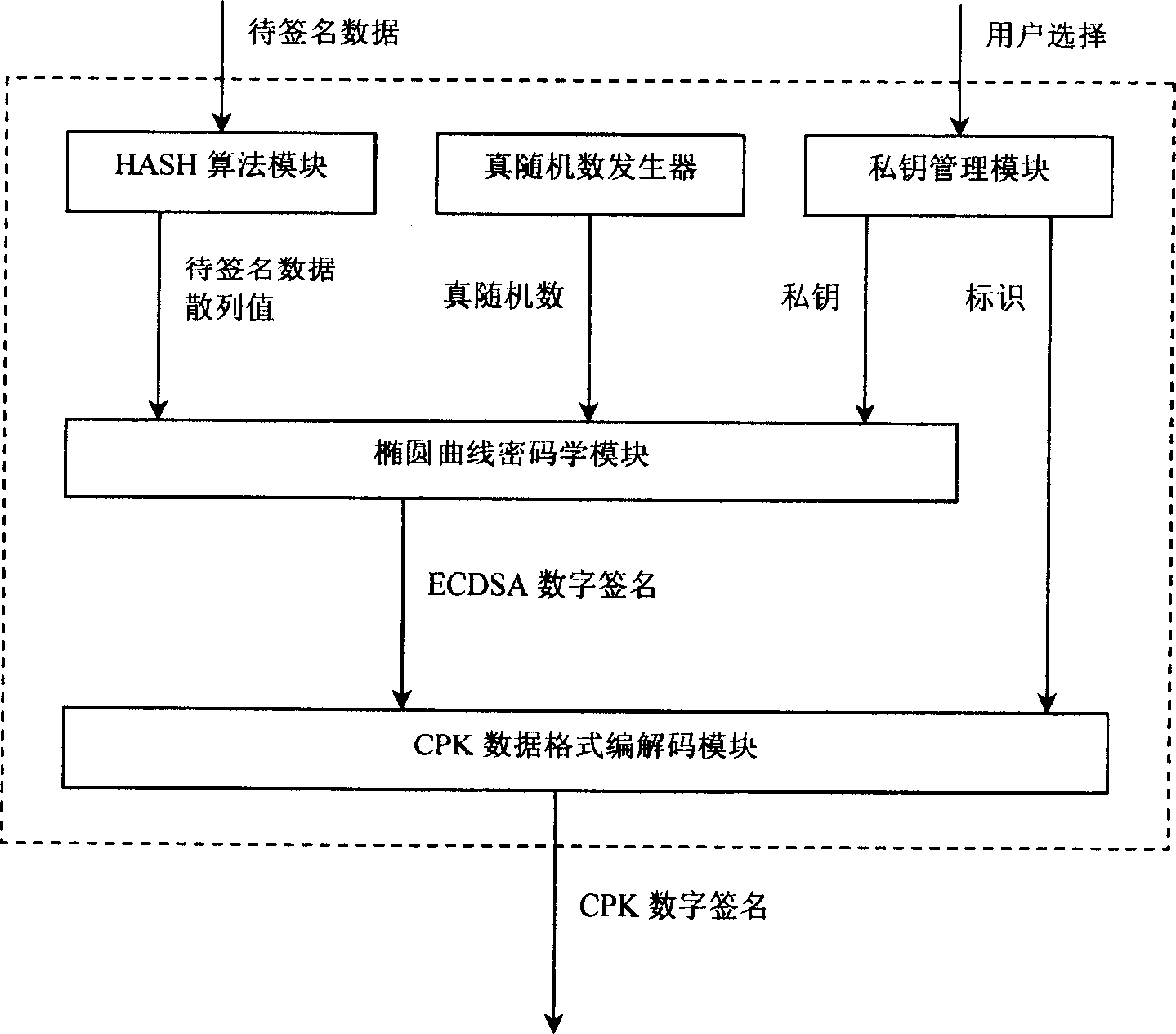
CPK credibility authorization system
InactiveCN1832403AEliminate Collusion AttacksImprove securityUser identity/authority verificationKey exchangeHash function
This invention discloses a CPK trustable certification system with a chip including special COS, CPK algorithm, ID certificates, signature protocol, a cryptographic key exchange protocol, a ciphering algorithm and HASH function and divided into intelligent card, USB Key, Flash card and cell phone SIM card. One chip can bear the functions of a cipher machine, signature verification, cryptographic key storage and management.
Owner:BEIJING E HENXEN AUTHENTICATION TECH
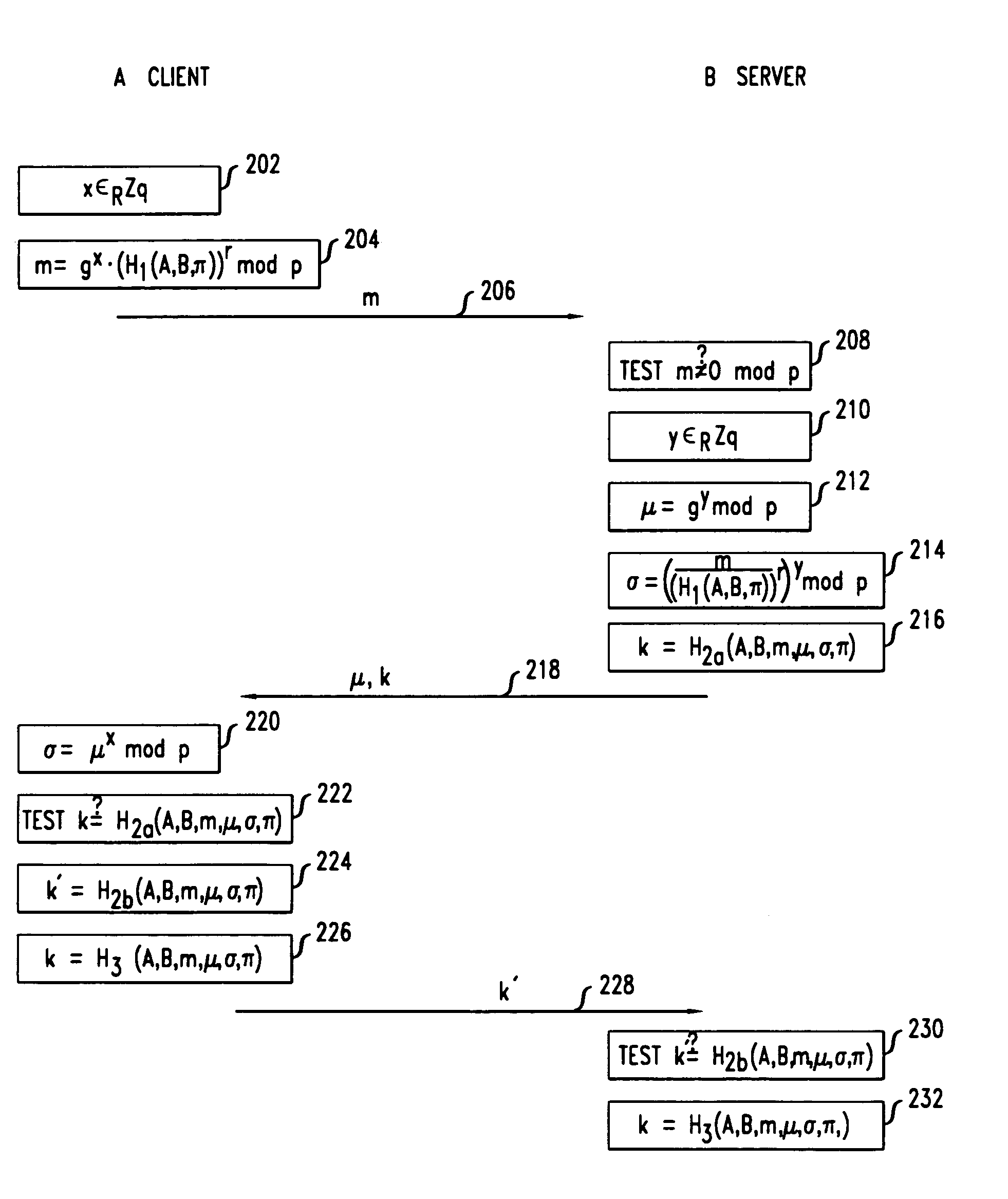
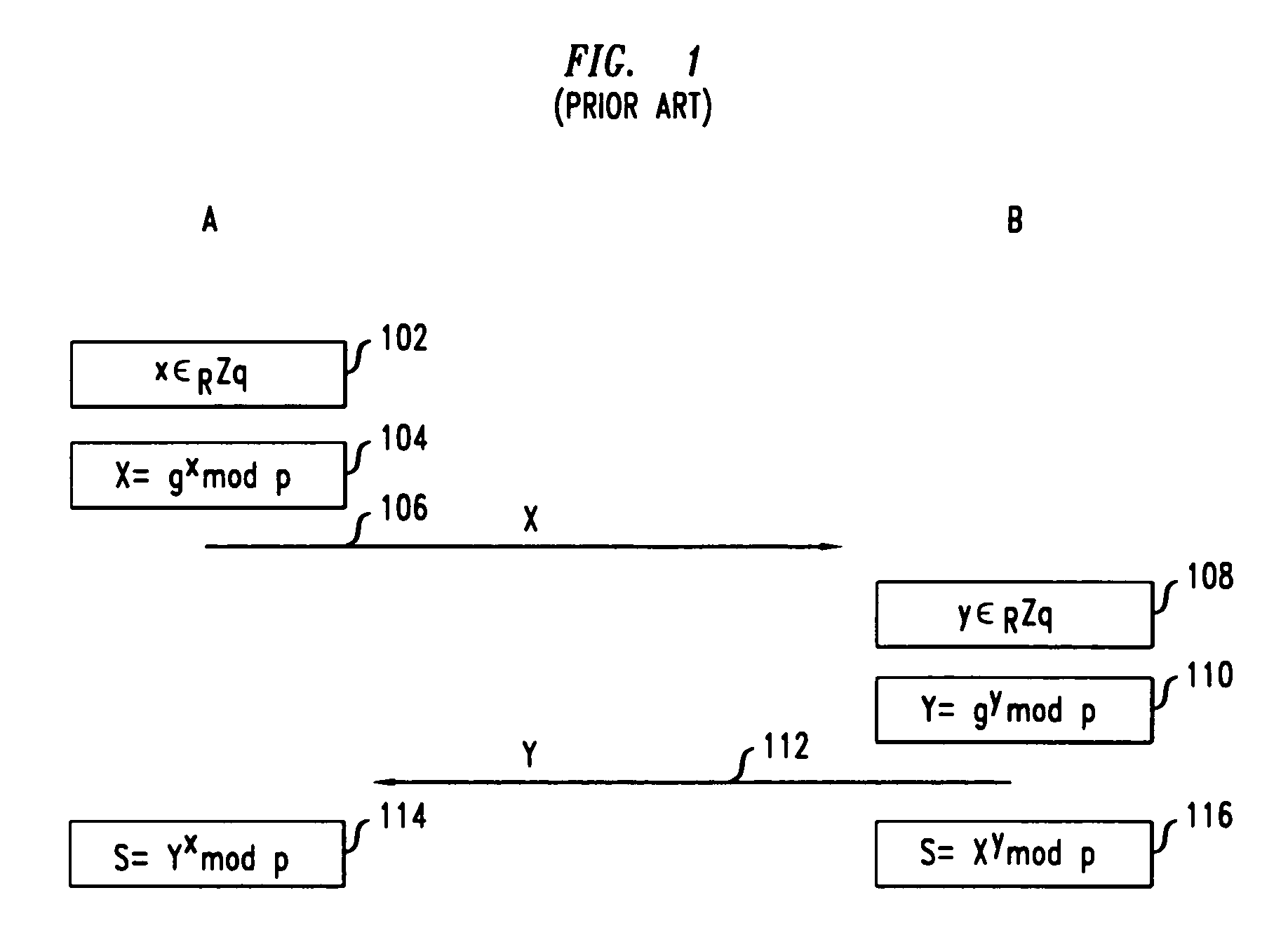
Secure mutual network authentication and key exchange protocol
InactiveUS7047408B1Key distribution for secure communicationUser identity/authority verificationKey exchangeSecure communication
Secure communication protocols are disclosed in which two parties generate a shared secret which may be used as a secure session key for communication between the parties. The protocols are based on Diffie-Hellman type key exchange in which a Diffie-Hellman value is combined with a function of at least a password using the group operation such that the Diffie-Hellman value may be extracted by the other party using the inverse group operation and knowledge of the password. In one embodiment, each of the parties explicitly authenticates the other party, while in another embodiment, the parties utilize implicit authentication relying on the generation of an appropriate secret session key to provide the implicit authentication. Typically, the parties will be a client computer and a server computer. In accordance with other embodiments of the invention, in order to protect against a security compromise at the server, the server is not in possession of the password, but instead is provided with, and stores, a so-called password verifier which is a function of the password and where the password itself cannot be determined from the value of the password verifier.
Owner:ALCATEL-LUCENT USA INC
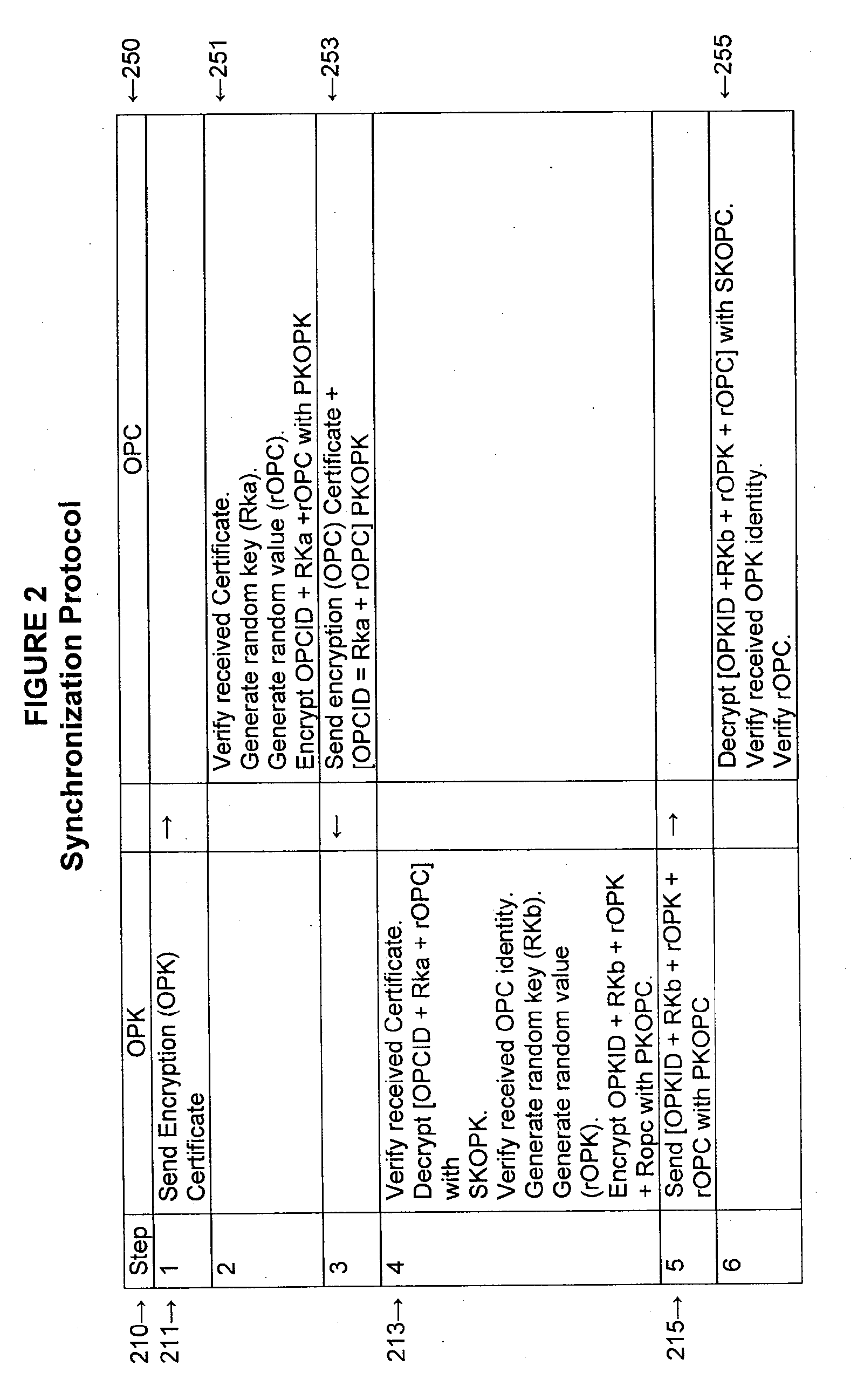
Methods and systems for security authentication and key exchange
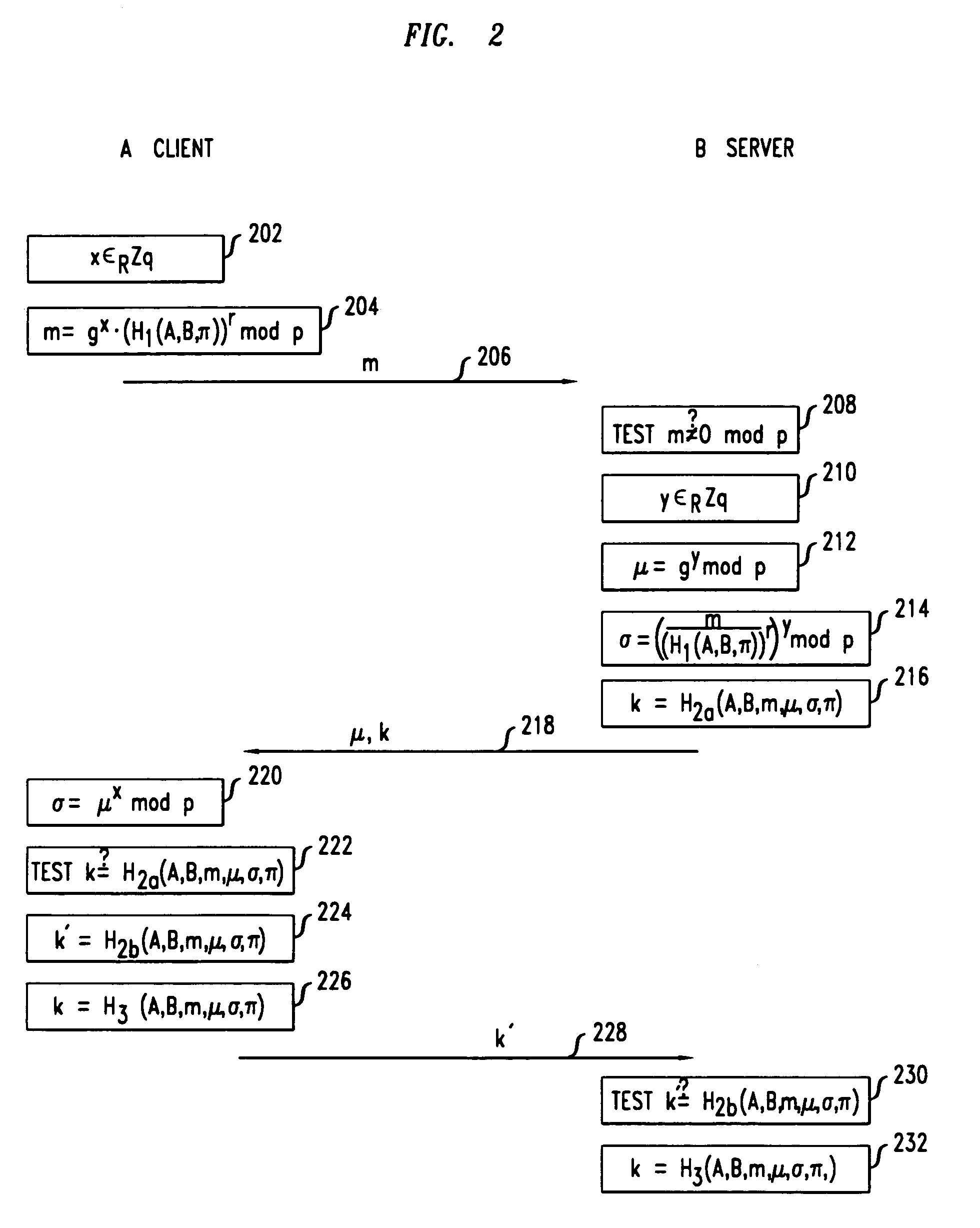
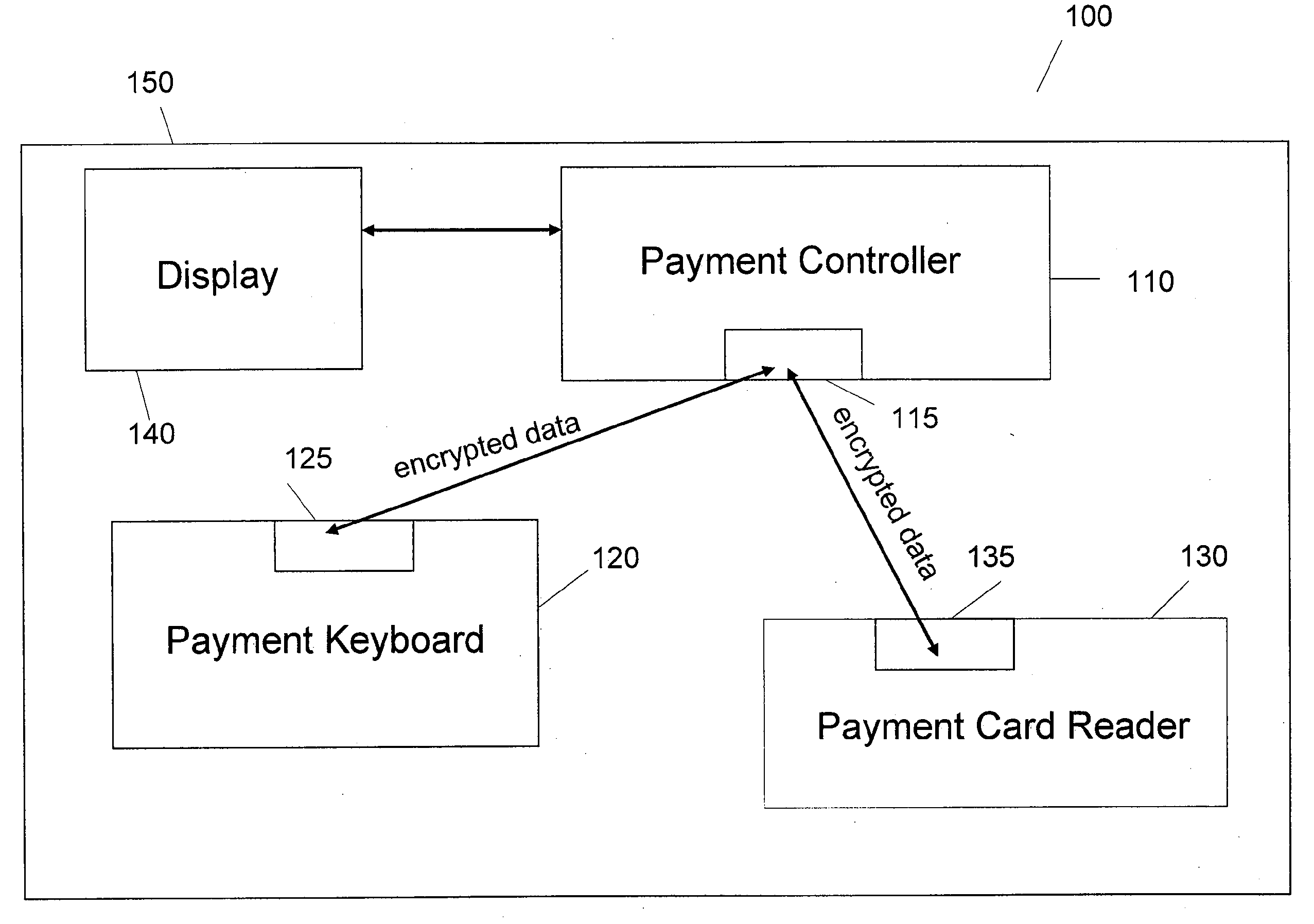
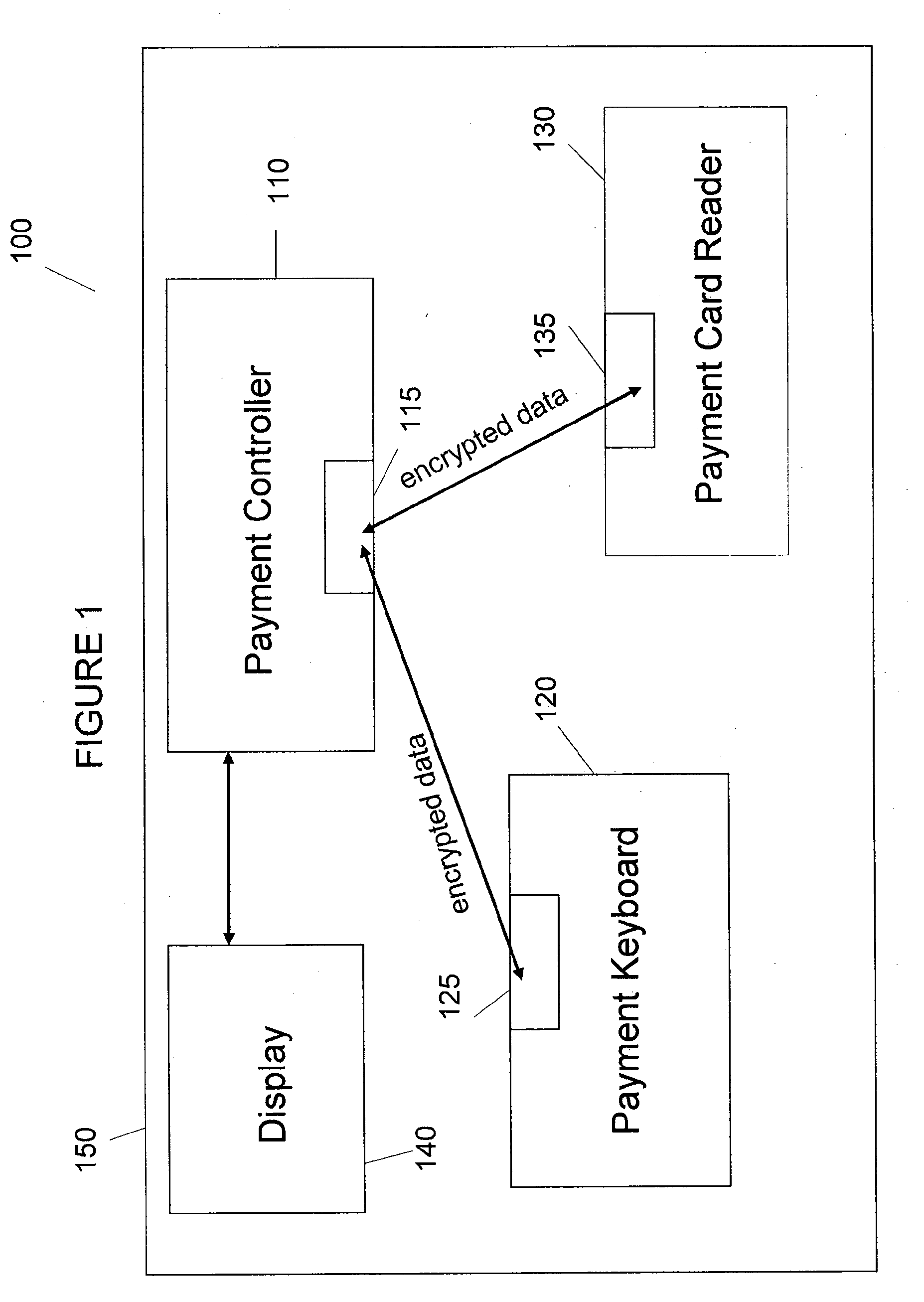
This is for a payment device that may be constructed from separate modules in a secure fashion such that the aggregation of the modules constitutes an overall secure device without the use of additional covers, cases, or tamper-resistant housings. The methods and system are provided whereby the devices within a modular payment system can exchange data between each-other in a secure fashion. While data encryption is being used elsewhere, the present invention extends the security zone from each secure payment module within a modular device out over the cable to the next device. This allows the user to purchase payment device components, place them as they see fit, and not have to obtain certification on their end product as a POS-A level payment device.
Owner:HYPERCOM CORP
System, apparatus, method and computer program for transferring content
ActiveUS20070162753A1Reduce usageEasy to useData processing applicationsUser identity/authority verificationKey exchangeTransfer system
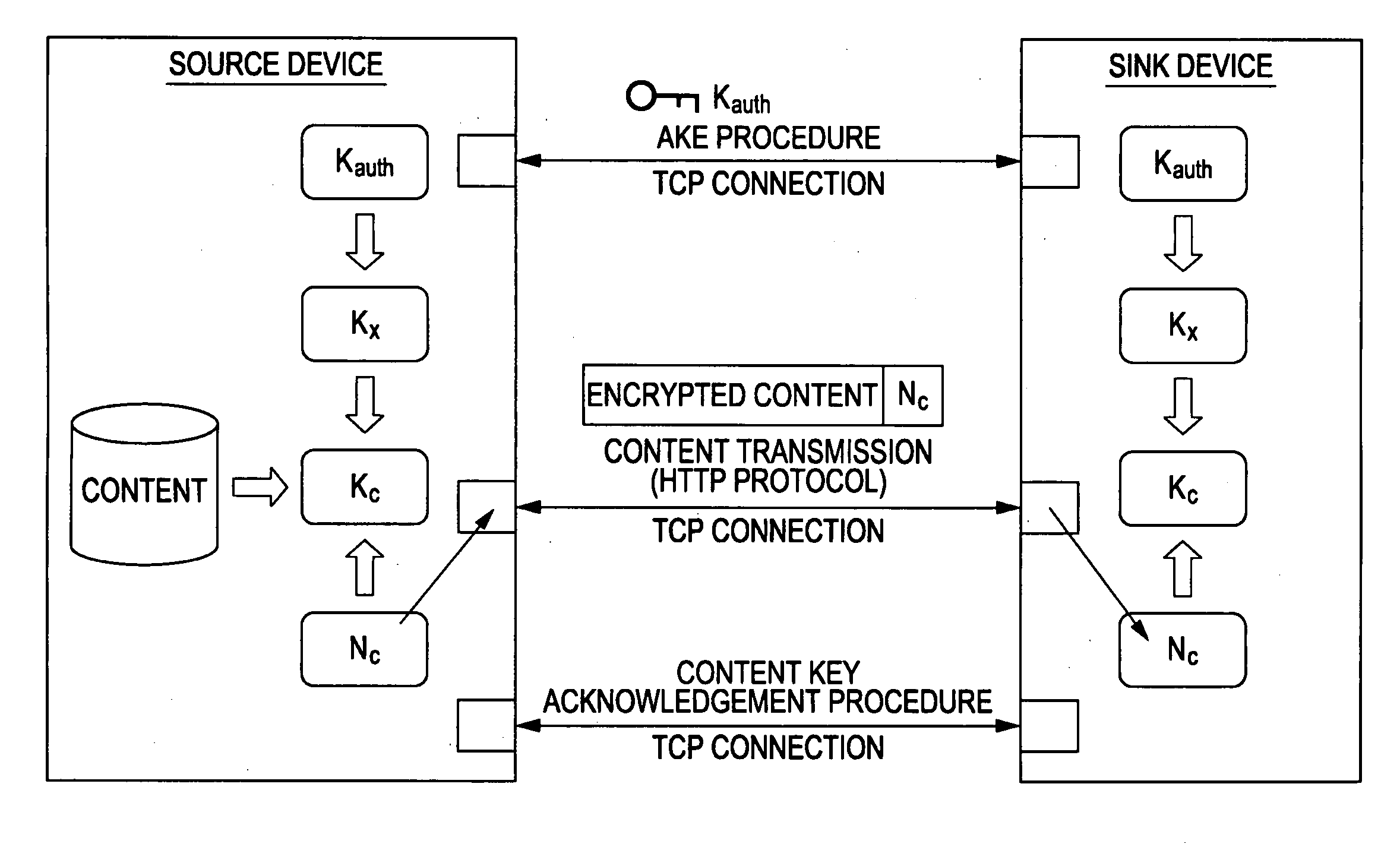
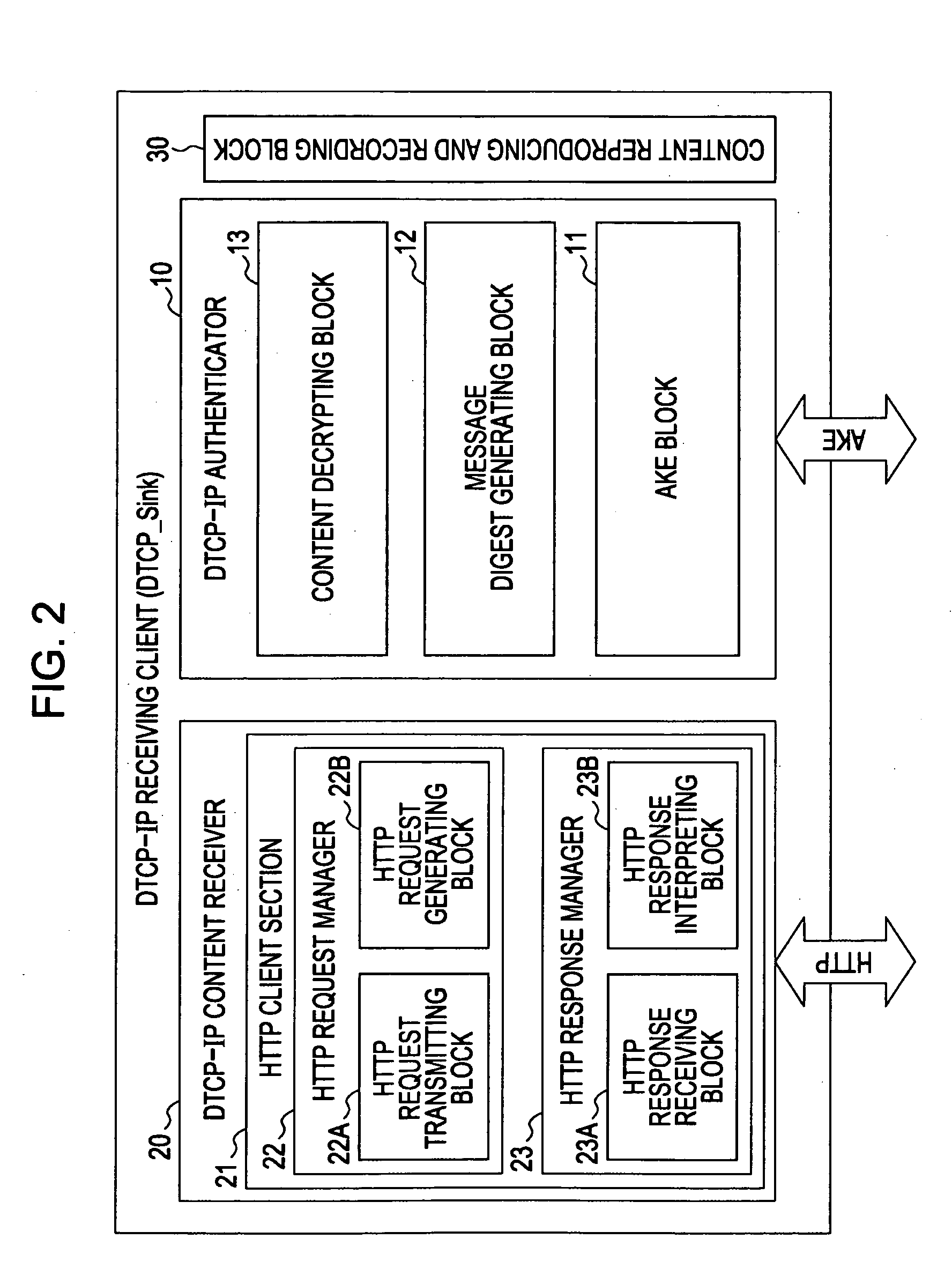
A content transfer system for transferring content between a source device transmitting the content and a sink device receiving the content, includes a content specifying unit for specifying the content to be transferred between the source device and the sink device, an authentication unit for performing an authentication exchange key process between the source device and the sink device, a content transfer unit for performing a content transfer process by encrypting and transferring the content specified by the content specifying unit from the source device to the sink device using the key exchanged by the authentication unit, and a content transfer finalizing unit for performing a content transfer finalizing process by validating the content at the sink device and invalidating the original content at the source device in response to the end of the content transfer process performed by the content transfer unit, the content thus being moved from the source device to the sink device.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com