Cipher key negotiation method, system, customer terminal and server for cipher key negotiation
A key negotiation and client-side technology, applied in the key negotiation system, client and server fields, can solve the problems of low system security, difficult to implement, consuming storage and processor resources, etc., to save system resources, application The effect of a broad, streamlined process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
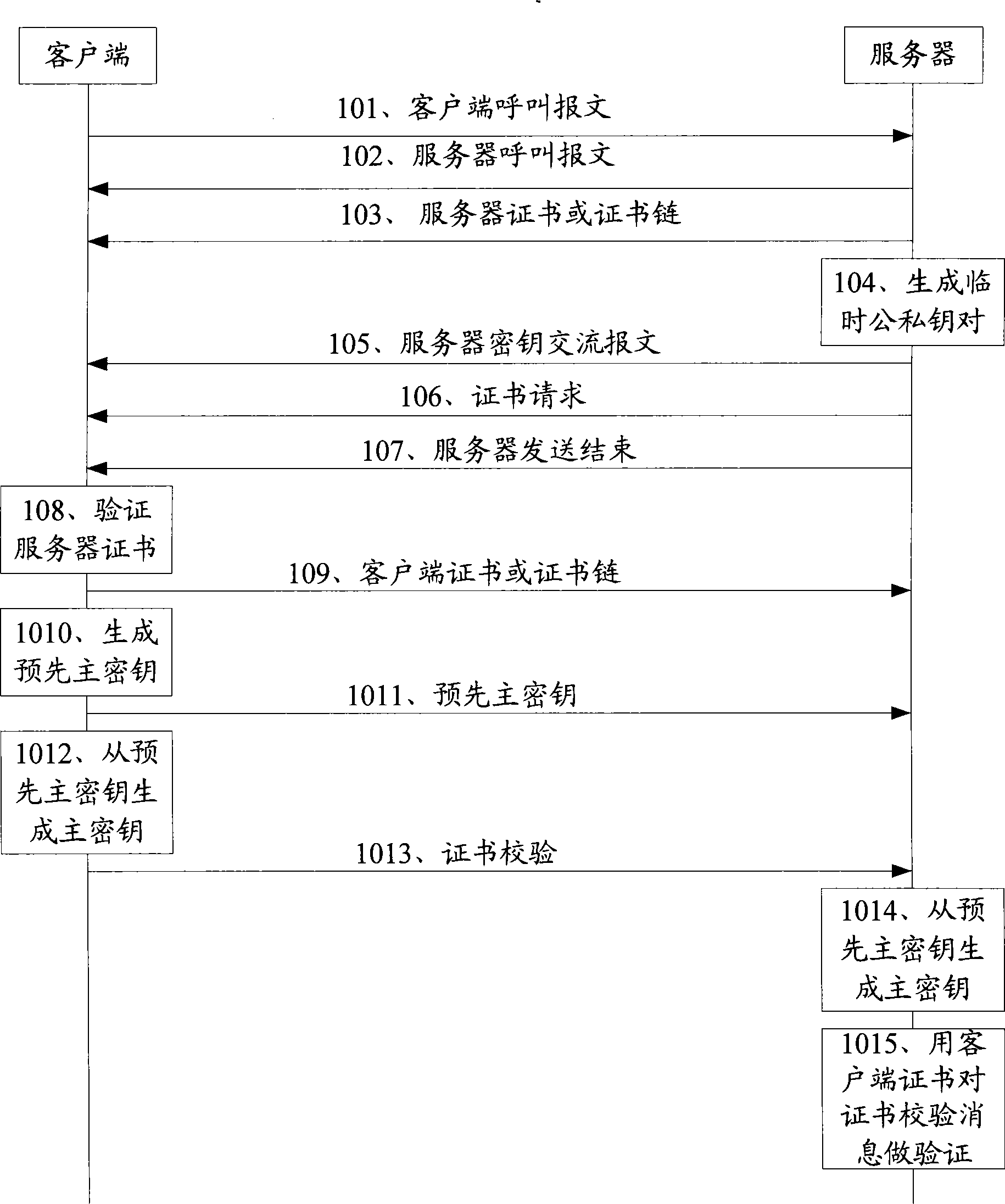
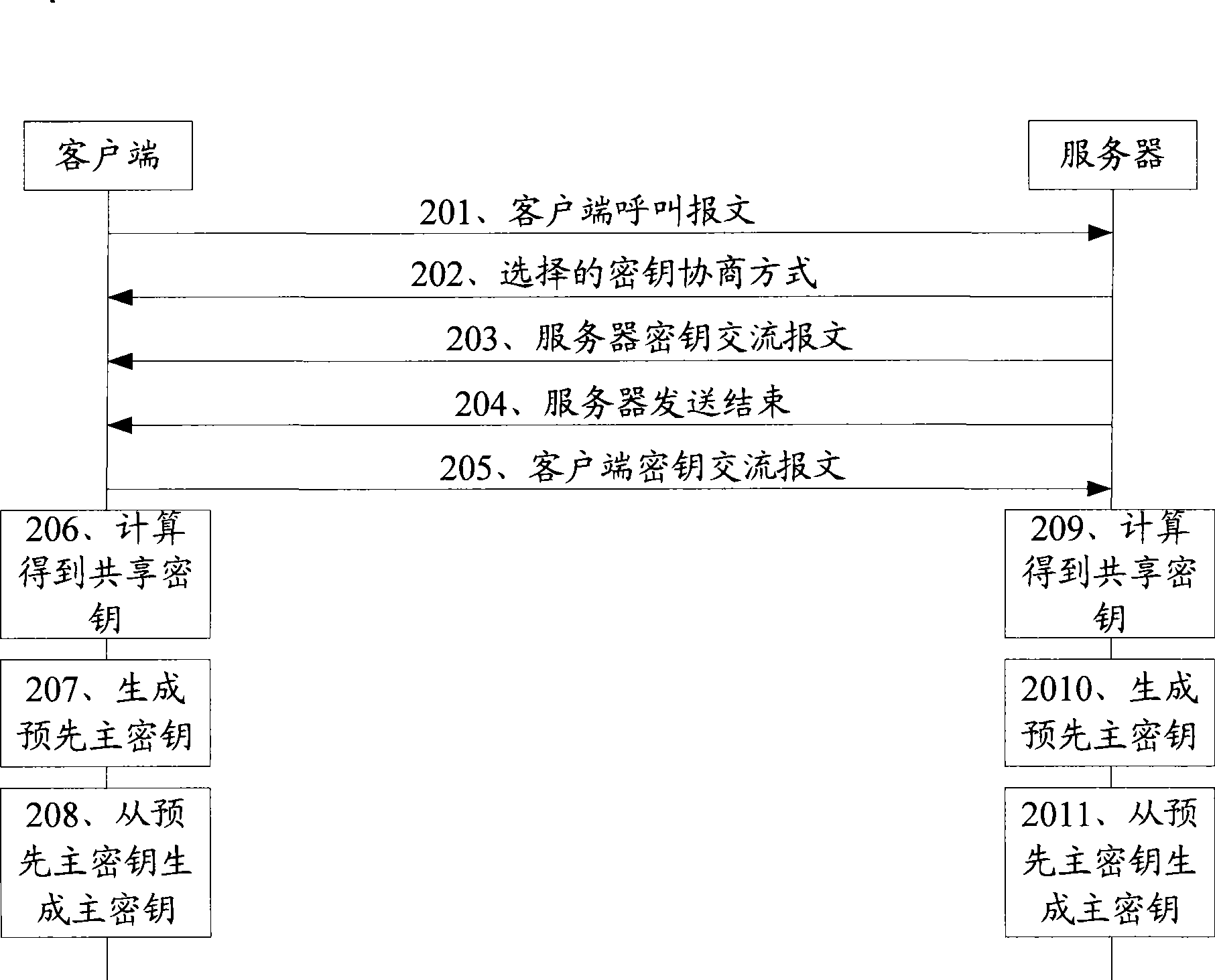
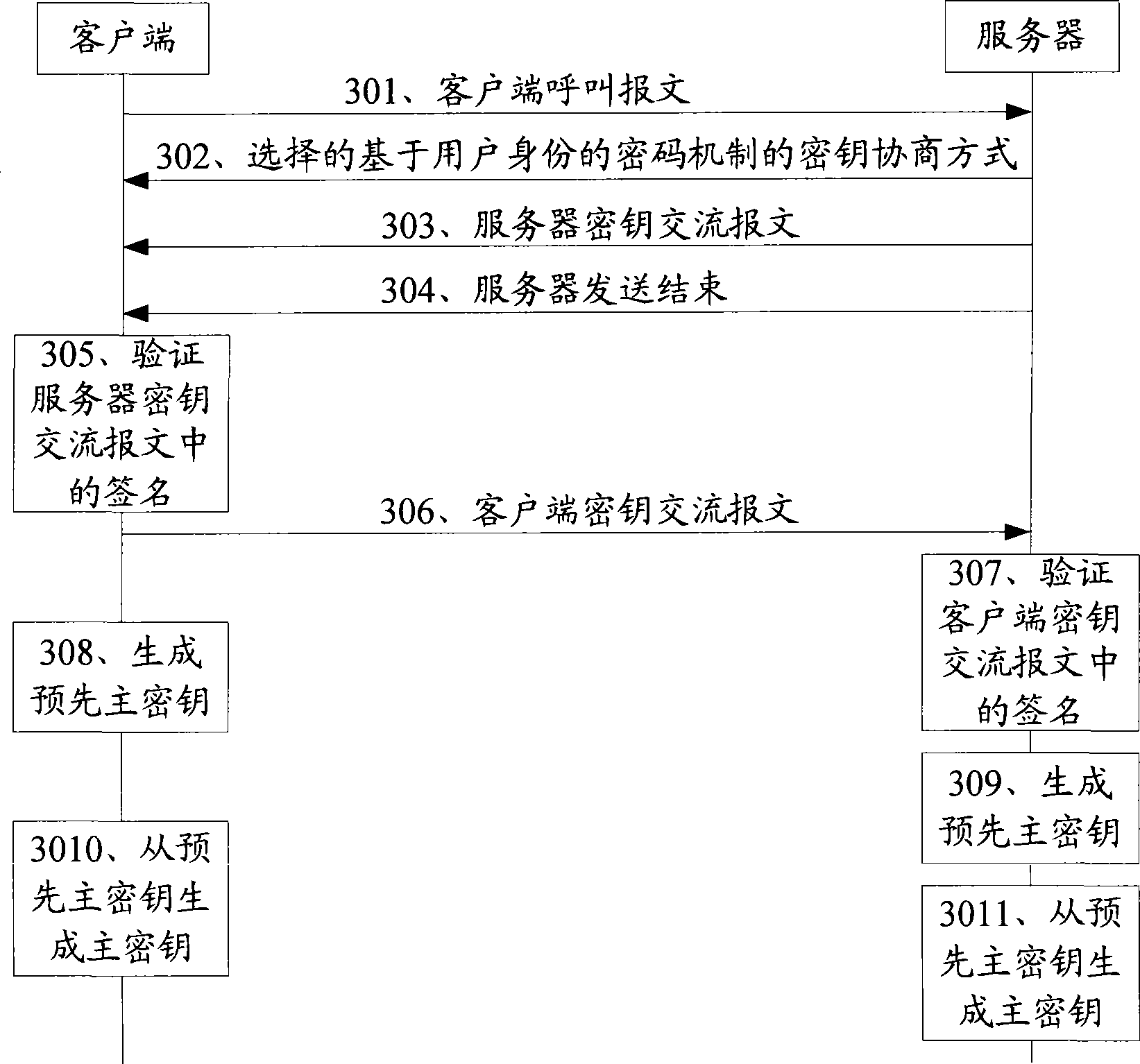
[0082] Embodiments of the present invention provide a key negotiation method applicable to the TLS protocol, a system for key negotiation, a client and a server, so that the key negotiation process is more convenient, has a wide application range, and is safe.
[0083] In the embodiment of the key agreement method provided in the embodiment of the present invention, an asymmetric key mechanism that can be called an identity-based cryptographic mechanism (IBC, Identity-Based Cryptograph) is used to negotiate the key. The user public key used in this method can be the user ID or the hash value of the user ID after hashing, and the private key can be further derived by using the public key through a certain algorithm.
[0084] Since the hash formula used for hashing is a public parameter that can be obtained by any terminal, calling the hash value of the user ID a public key has the same meaning as directly calling the user ID a public key , so it is usually collectively referred...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com