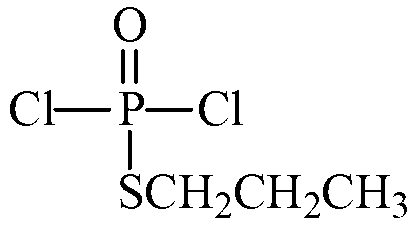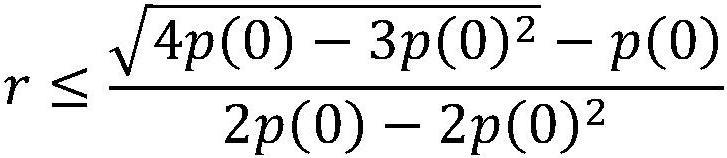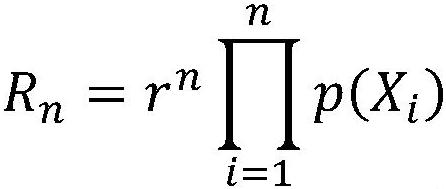Patents
Literature
50 results about "SAFER" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, SAFER (Secure And Fast Encryption Routine) is the name of a family of block ciphers designed primarily by James Massey (one of the designers of IDEA) on behalf of Cylink Corporation. The early SAFER K and SAFER SK designs share the same encryption function, but differ in the number of rounds and the key schedule. More recent versions — SAFER+ and SAFER++ — were submitted as candidates to the AES process and the NESSIE project respectively. All of the algorithms in the SAFER family are unpatented and available for unrestricted use.
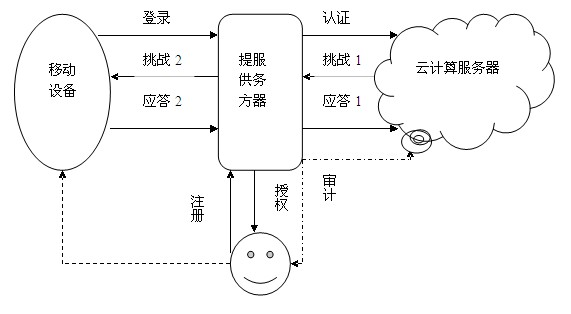
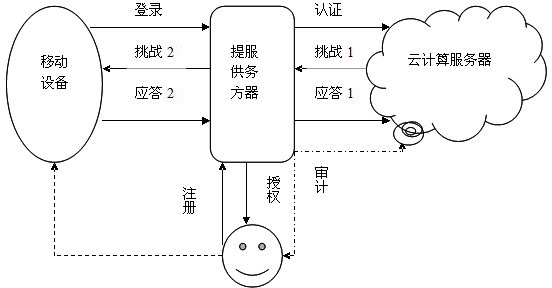
Identity authentication method based on biological feature encryption and homomorphic algorithm
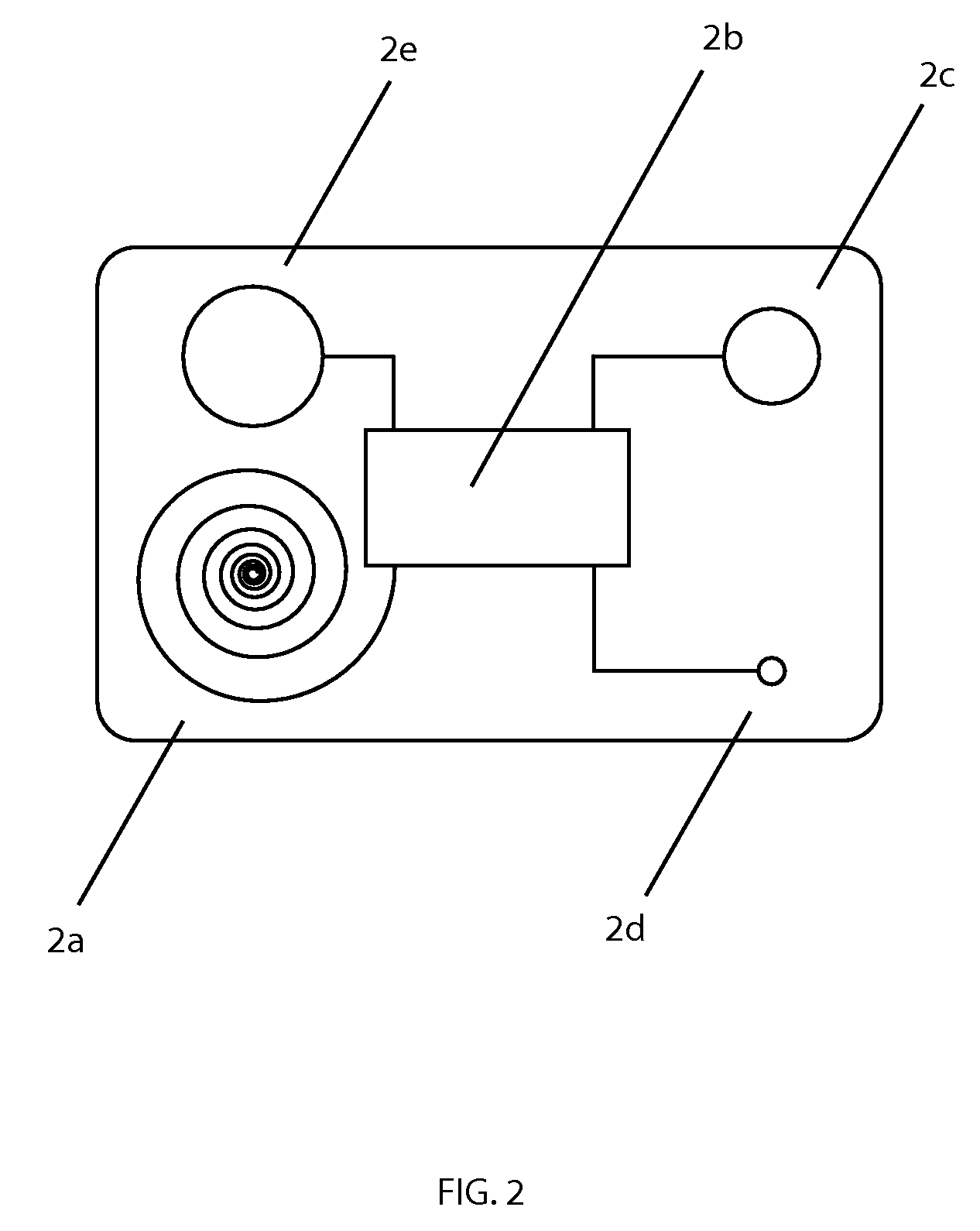
InactiveCN102664885AImprove privacyAvoid crackingUser identity/authority verificationTimestampAlgorithm
The invention discloses an identity authentication method based on biological feature encryption and a homomorphic algorithm. The method is quicker than a normal password method by using biological features of users as passwords to log in a system through a mobile device, using an encrypted biological template is safer, and privacy of the users can be guaranteed as information is transmitted in a ciphertext form. By adding factors such as timestamps, tri-party authentication among the users, a provider server and a cloud computing server is realized, and reliability among the three parties is enhanced. Legal users can be prevented from using resources in the cloud computing environment illegally to better manage the resources by means of user authentication operation according to attribution predicate encryption and real-time updating of permission information. Operation without encryption can be realized by the aid of the homomorphic algorithm, same effects as decrypting before operation can be achieved, time and space expenses can be saved, system efficiency is greatly improved, and the identity authentication method has high safety and efficiency.
Owner:南京邦普信息科技有限公司
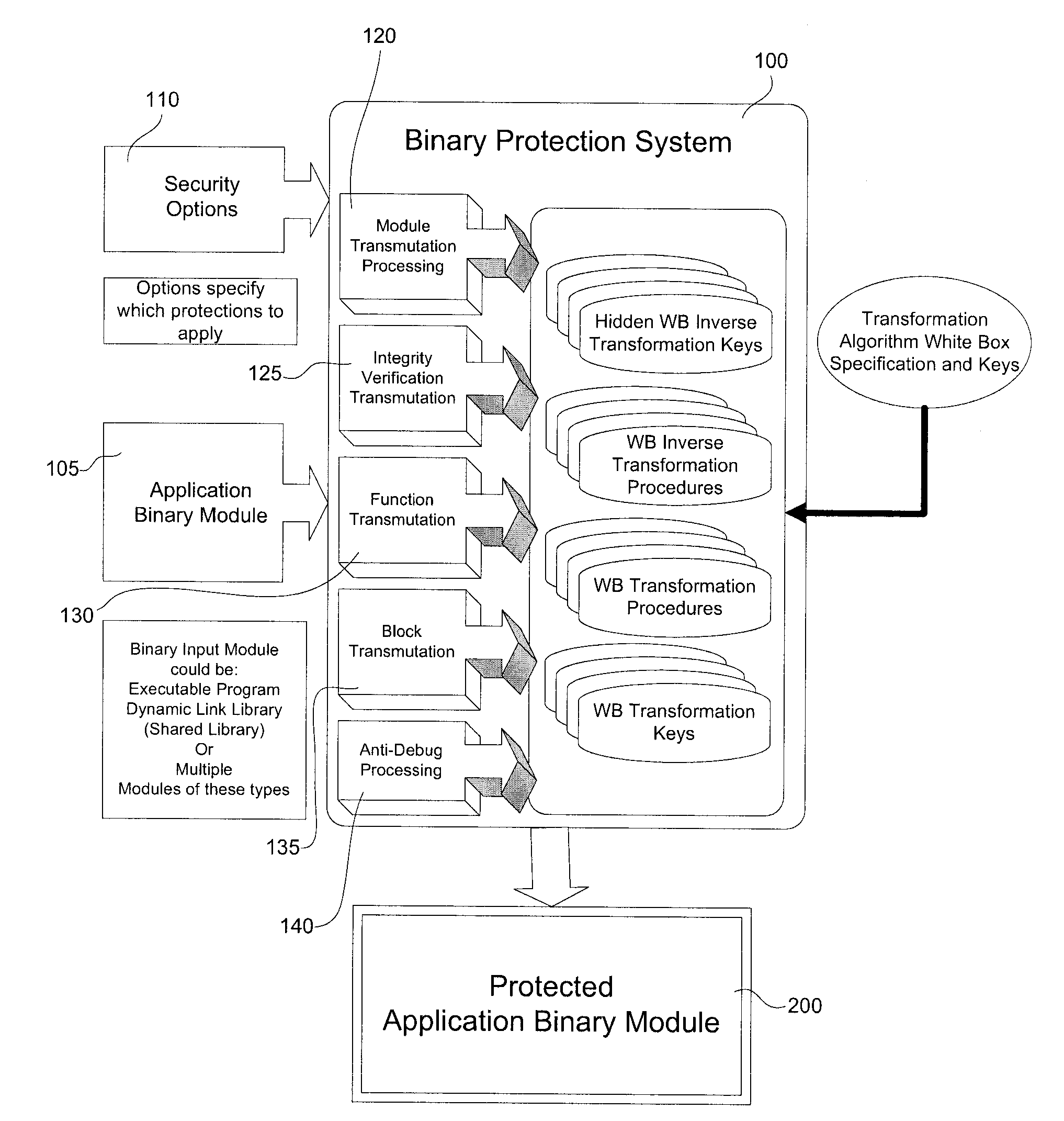
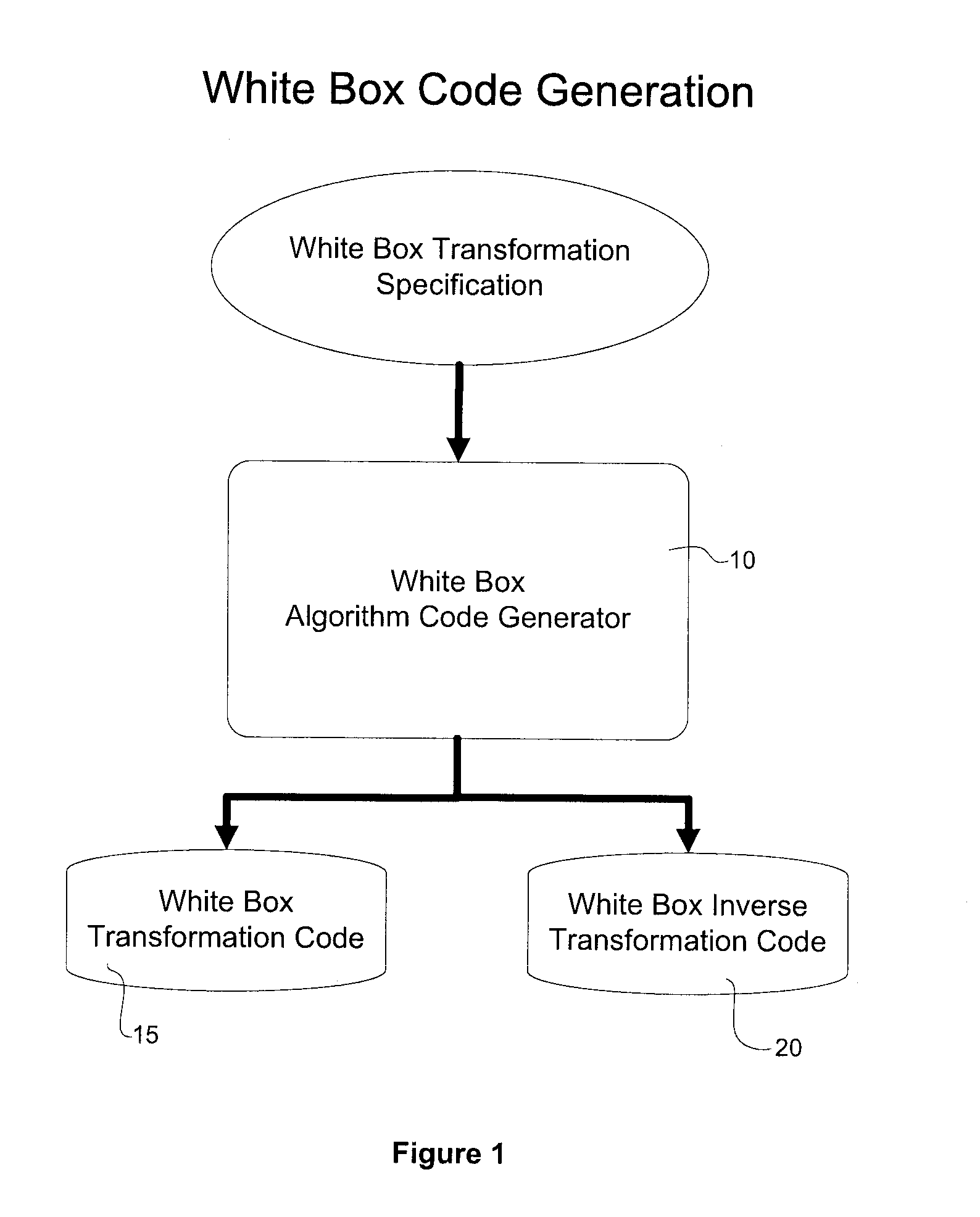
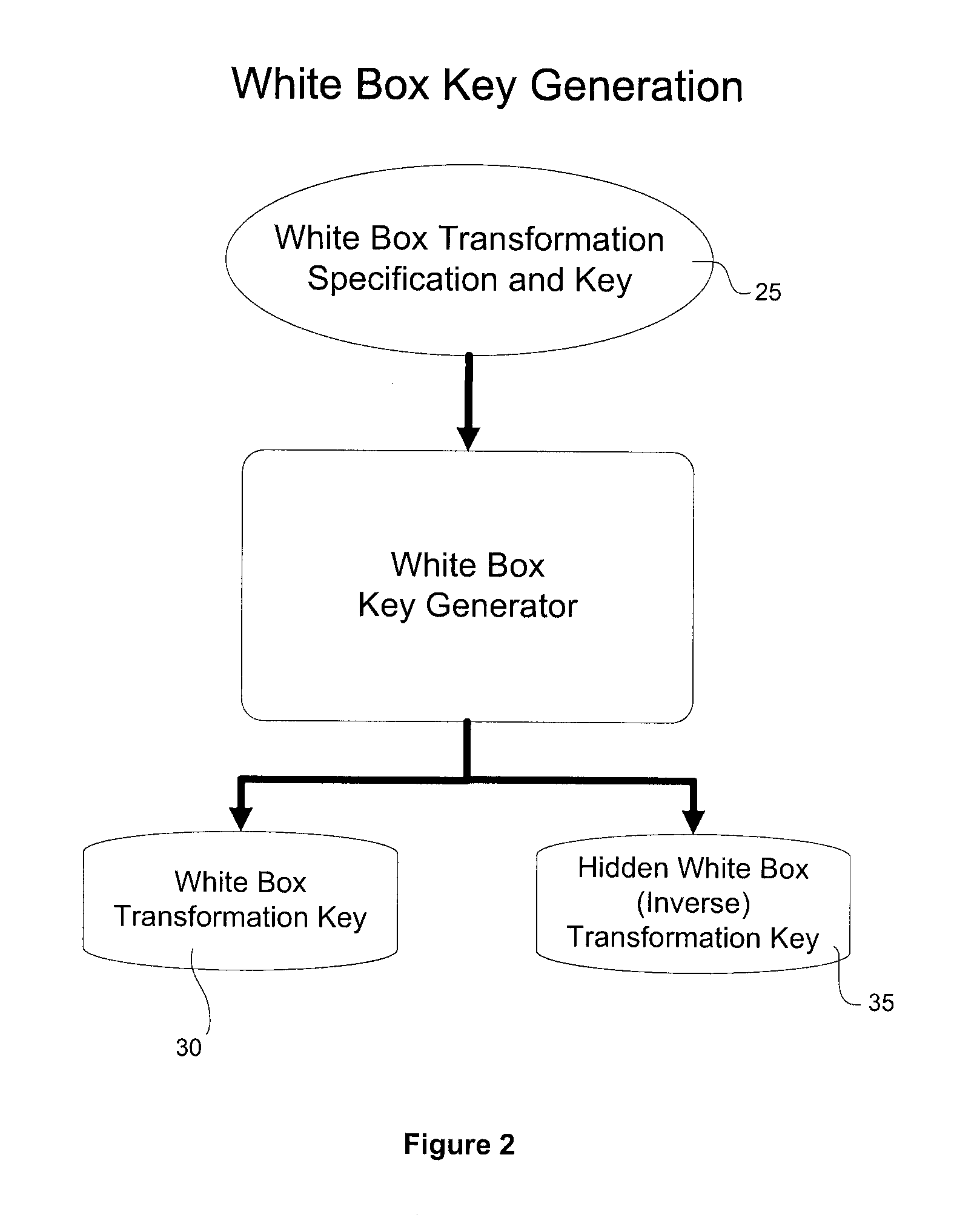
Interlocked Binary Protection Using Whitebox Cryptography
ActiveUS20120192283A1Digital data processing detailsAnalogue secracy/subscription systemsSAFERAttack
A system and method for transforming a software application comprising binary code and optionally associated data, from an original form to a more secure form. The method includes performing a combination of binary transmutations to the application, and interlocking the transmutations by generating and placing interdependencies between the transmutations, wherein a transmutation is an irreversible change to the application. Different types of the transmutations are applied at varied granularities of the application. The transmutations are applied to the application code and the implanted code as well. The result is a transformed software application which is semantically equivalent to the original software application but is resistant to static and / or dynamic attacks.
Owner:IRDETO ACCESS
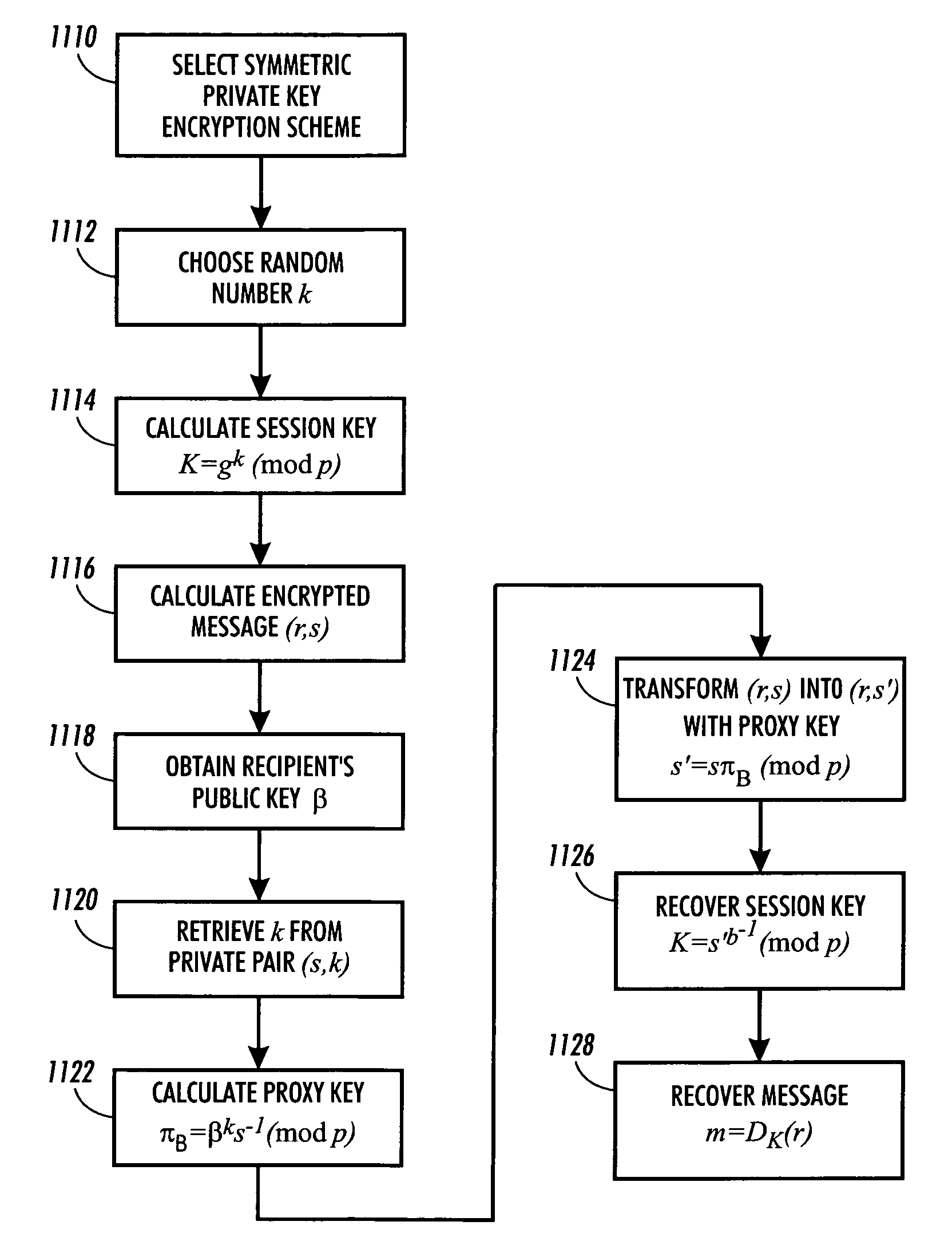
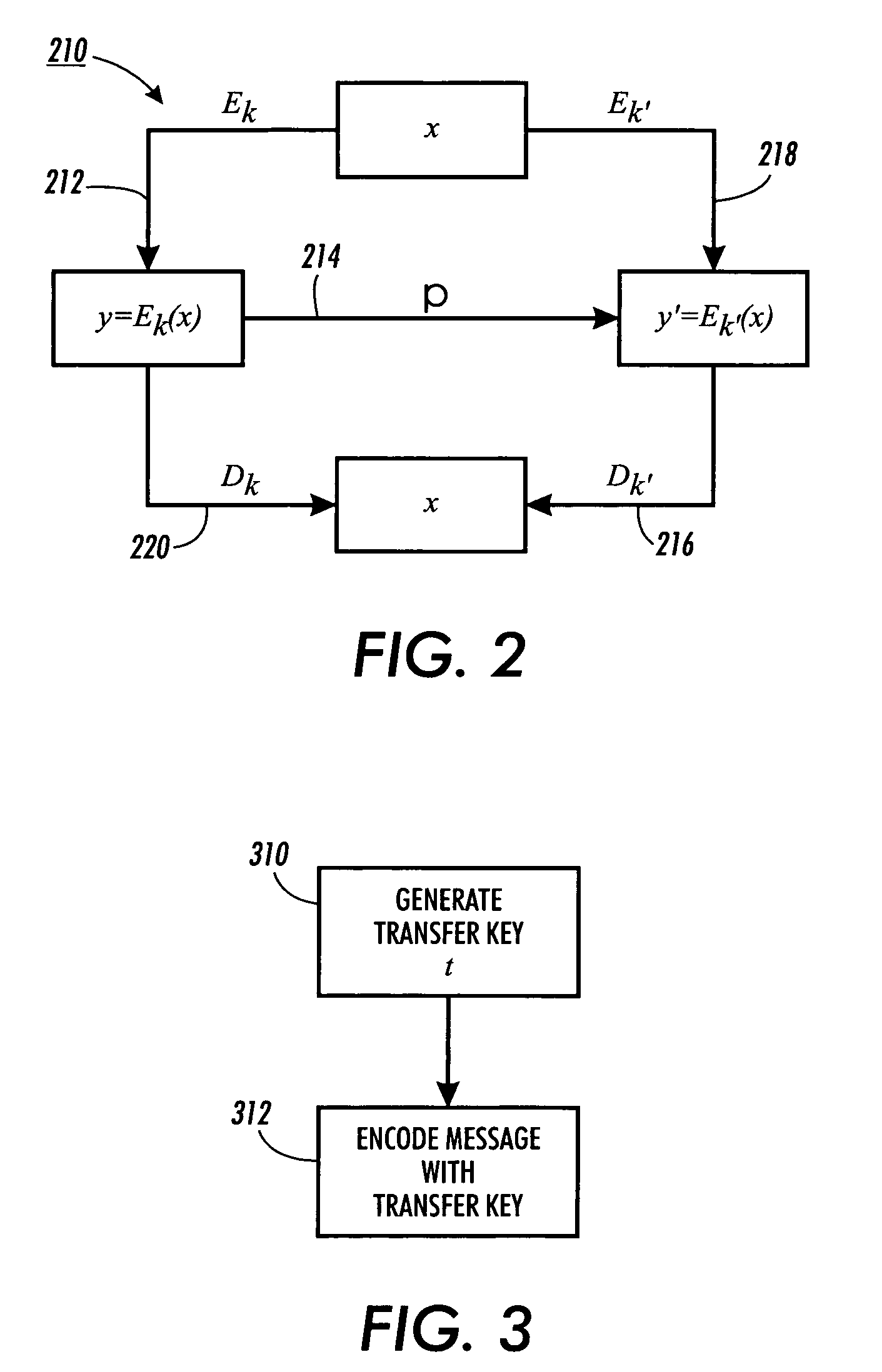
System and method for transferring the right to decode messages
InactiveUS7286665B1Improve efficiencyEliminate disadvantagesKey distribution for secure communicationPublic key for secure communicationSAFERTheoretical computer science
Methods for transferring among key holders in encoding and cryptographic systems the right to decode and decrypt messages in a way that does not explicitly reveal decoding and decrypting keys used and the original messages. Such methods are more secure and more efficient than typical re-encoding and re-encryption schemes, and are useful in developing such applications as document distribution and long-term file protection.
Owner:CONTENTGUARD HLDG
Identity-based conferencing systems and methods
InactiveUS20080259824A1More experienceLess codeSpecial service provision for substationMultiplex system selection arrangementsSAFERSystem identification
Described in this paper are systems and methods of providing conferencing services where a conference participant is identified by the conferencing system when calling into the system. The system and methods focus on individual users instead of groups of participants. Instead of using a conference identity as the driver, embodiments herein invoke a user identity, and services are personalized for each user. The user has far fewer codes to juggle and all participants enjoy a quicker, richer, and more secure experience.
Owner:ZIPDX
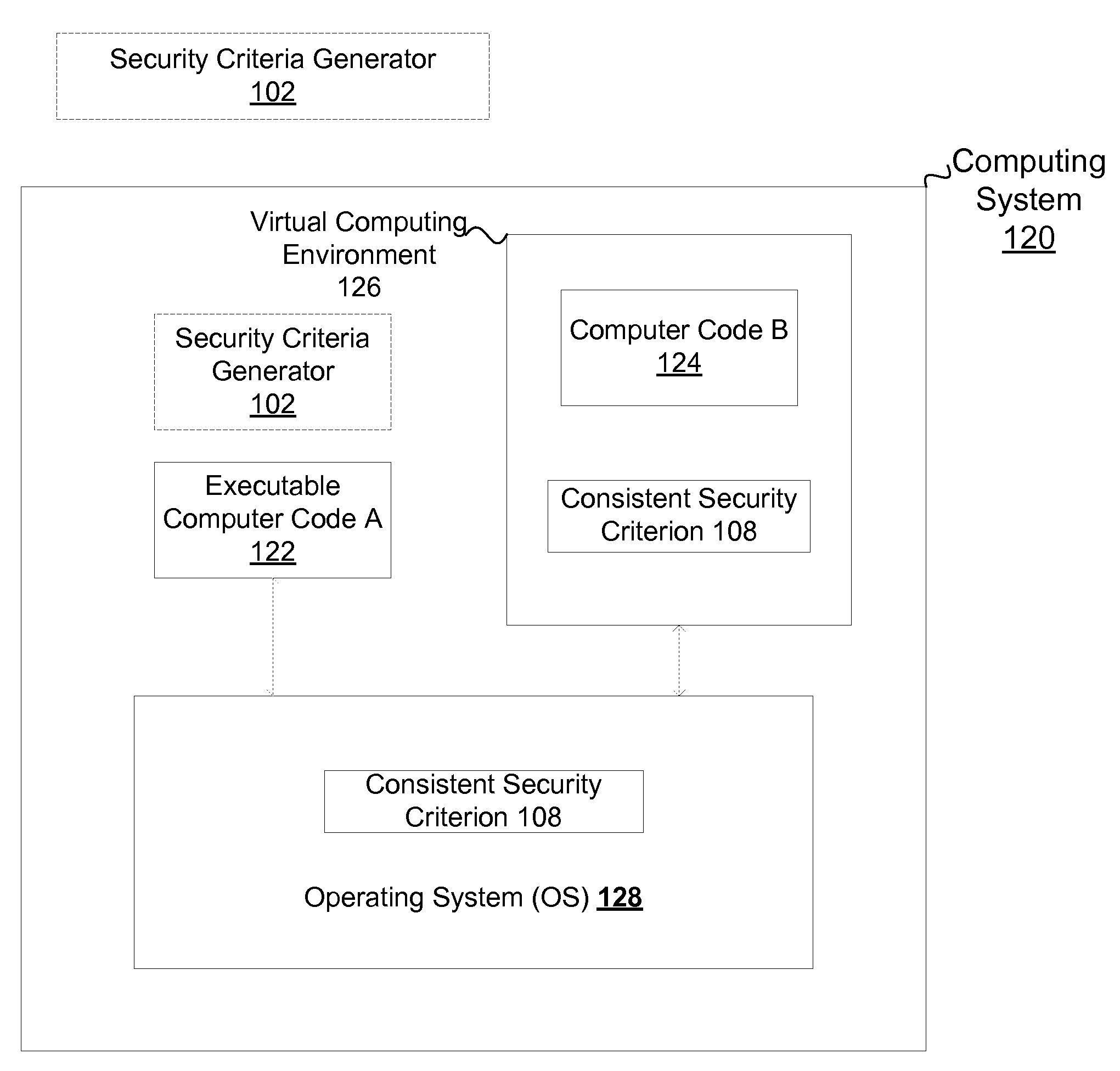
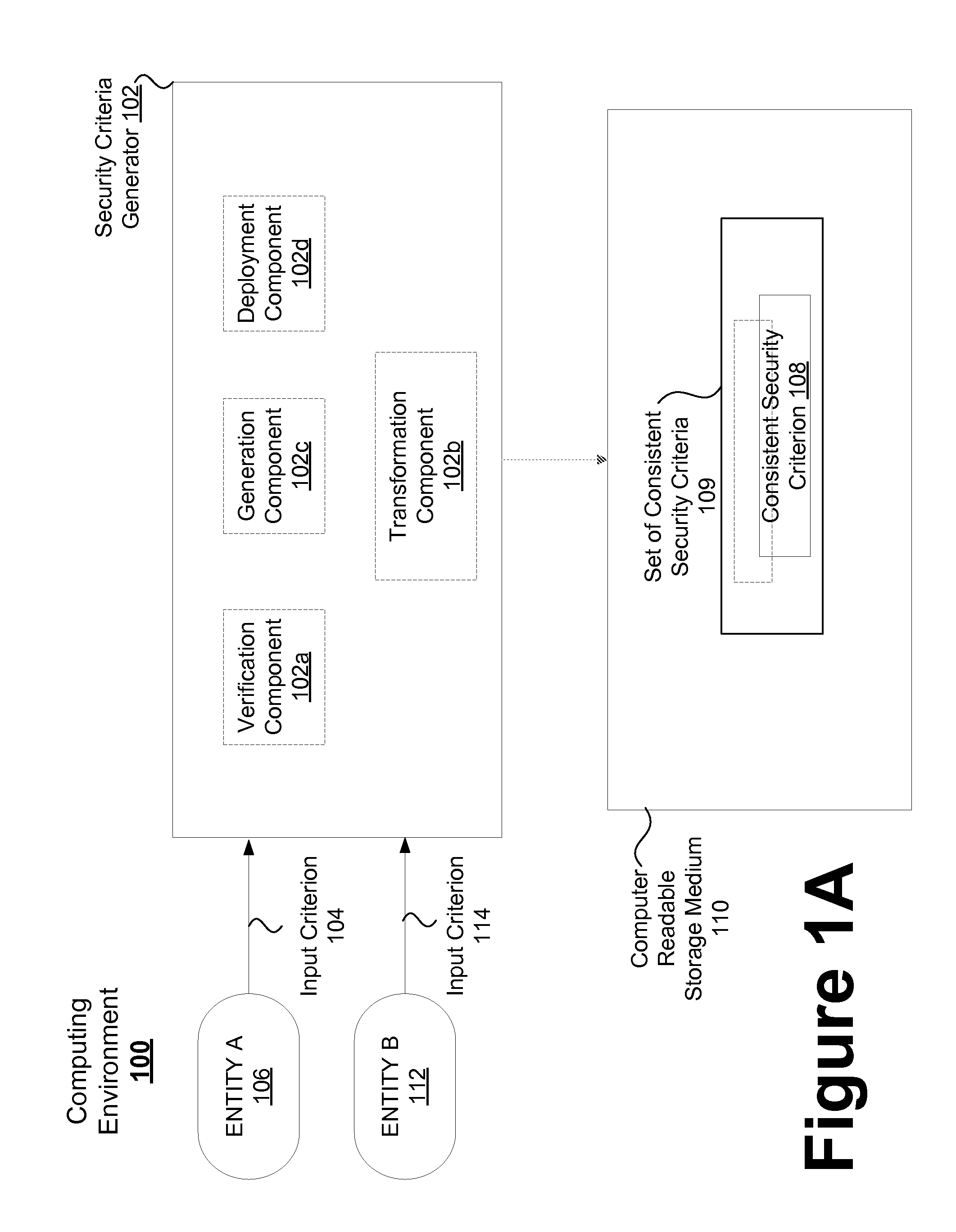
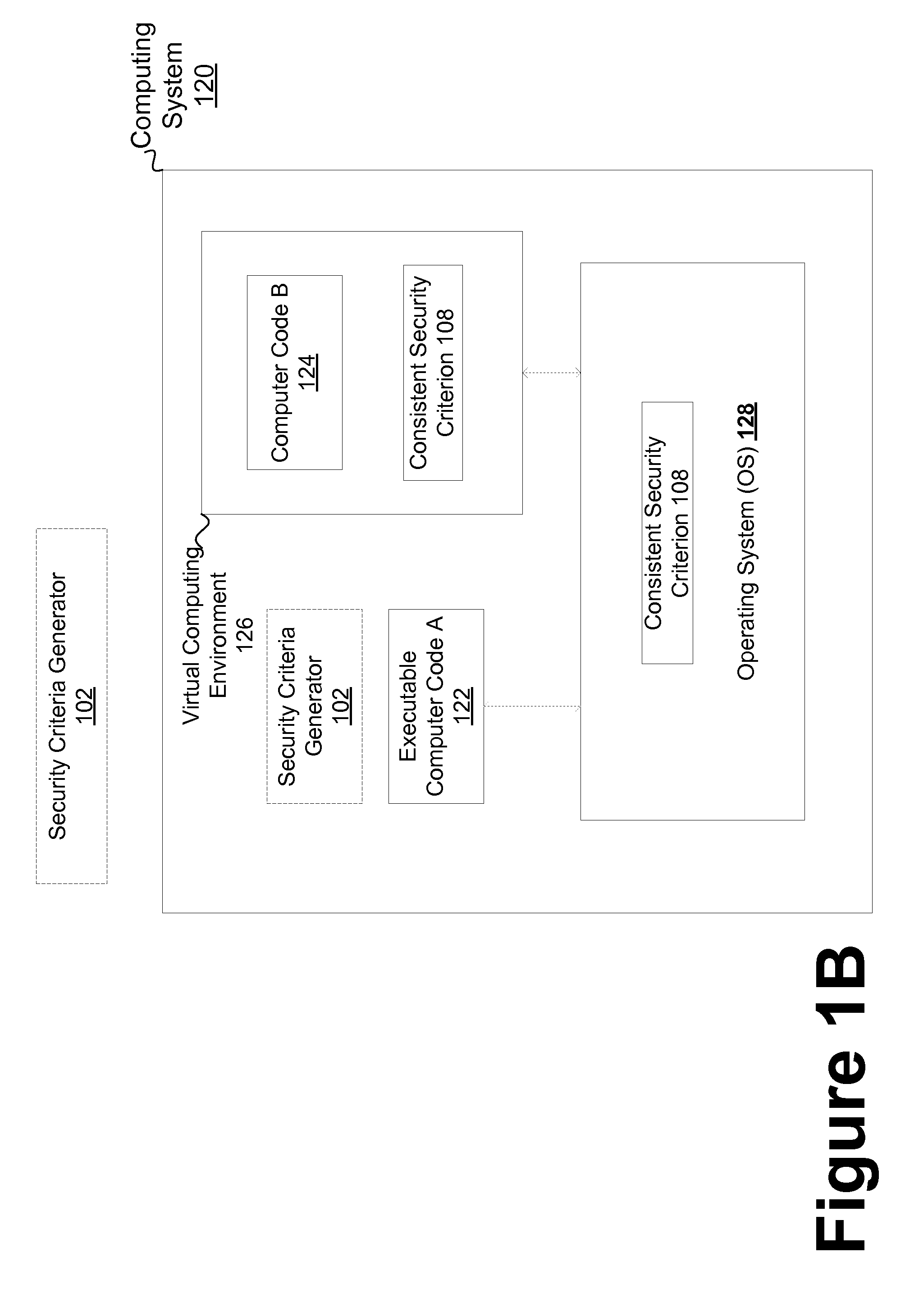
Consistent security enforcement for safer computing systems
InactiveUS20100162240A1Efficiently provideProvide securityComputer security arrangementsSoftware simulation/interpretation/emulationOperational systemTrusted components
Security can be enforced in a consistent manner with respect to various computing environments that may be operable in a computing system. Consistent security criteria can be generated, based on input security criterion, in a computer readable and storable form and stored in a computer readable storage medium, thereby allowing the consistent security criterion to be effectively provided to a computing system for enforcement of the input security criterion in a consistent manner with respect to, for example, (a) a first executable computer code effectively supported by an Operating System (OS), and (b) a second computer code effectively supported by the Virtual Computing Environment (VCE). A Trusted Component (TC) can effectively provide a consistent security criterion as a part and / or form that is suitable for a particular computing environment. The TC can, for example, be an automated tool that performs various functions including: verifying the consistency of security criteria, generation and deployment of consistent security criteria, and transformation of security criteria to parts and / or forms suitable for various computing environments. In addition, a Virtual Computing Environment (VCE) can obtain from the Operating System (OS) one or more security criteria. The Virtual Computing Environment (VCE) can be operable in a Trusted Computing Environment (TCE) and interface with a Trusted Operating System (TOS) that effectively enforces Mandatory Access Control (MAC), thereby allowing the Virtual Computing Environment (VCE) to leverage the security provided by the OS. The OS can, for example, be a Security-Enhanced Linux (SELinux) Operating System operating as a Trusted Component in a Trusted Environment that includes a Trusted Security Agent (TSA) operable to deploy consistent security criteria.
Owner:SAMSUNG ELECTRONICS CO LTD
Triple length passwords composed of memorizeable synthetic and natural pronounceable words
InactiveUS20050144462A1Easy to rememberDigital data authenticationSecret communicationPasswordComputer science
This paper introduces a design of a longer than normal, vastly more secure, password, which is composed of smaller pronounceable words, enabling the password to be easily memorized. The password is actually a pass phrase, or pass sentence. This pass phrase may be composed of English dictionary words, words not in the dictionary, or even computer generated, synthetic (but still pronounceable) words.
Owner:LAGARDE VICTOR JUSTIN
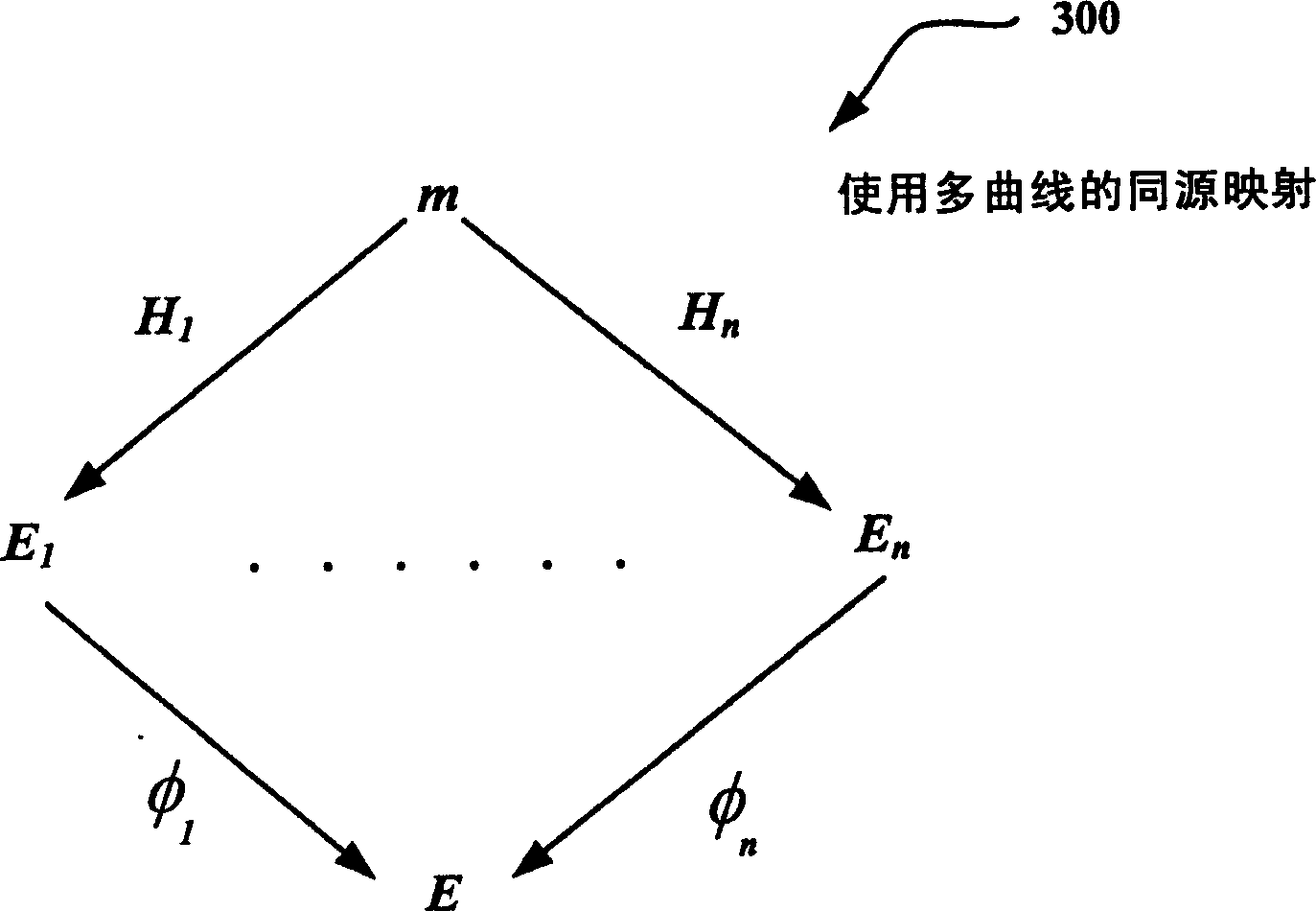
Use of isogenies for design of cryptosystems
ActiveCN1614922AKey distribution for secure communicationPublic key for secure communicationID-based encryptionSAFER
Techniques for providing public key cryptography systems are revealed. More specifically, public key cryptography systems are provided using homologs of Abelian varieties (eg, elliptic curves in the one-dimensional case). For example, homology allows the use of multiple curves instead of a single curve to provide more secure encryption. The technology can be applied to digital signing and / or identity-based encryption (IBE) solutions. Additionally, same origins can be used in other applications such as blind signing, rating systems, etc. In addition, the solution for generating homology is revealed.
Owner:MICROSOFT TECH LICENSING LLC
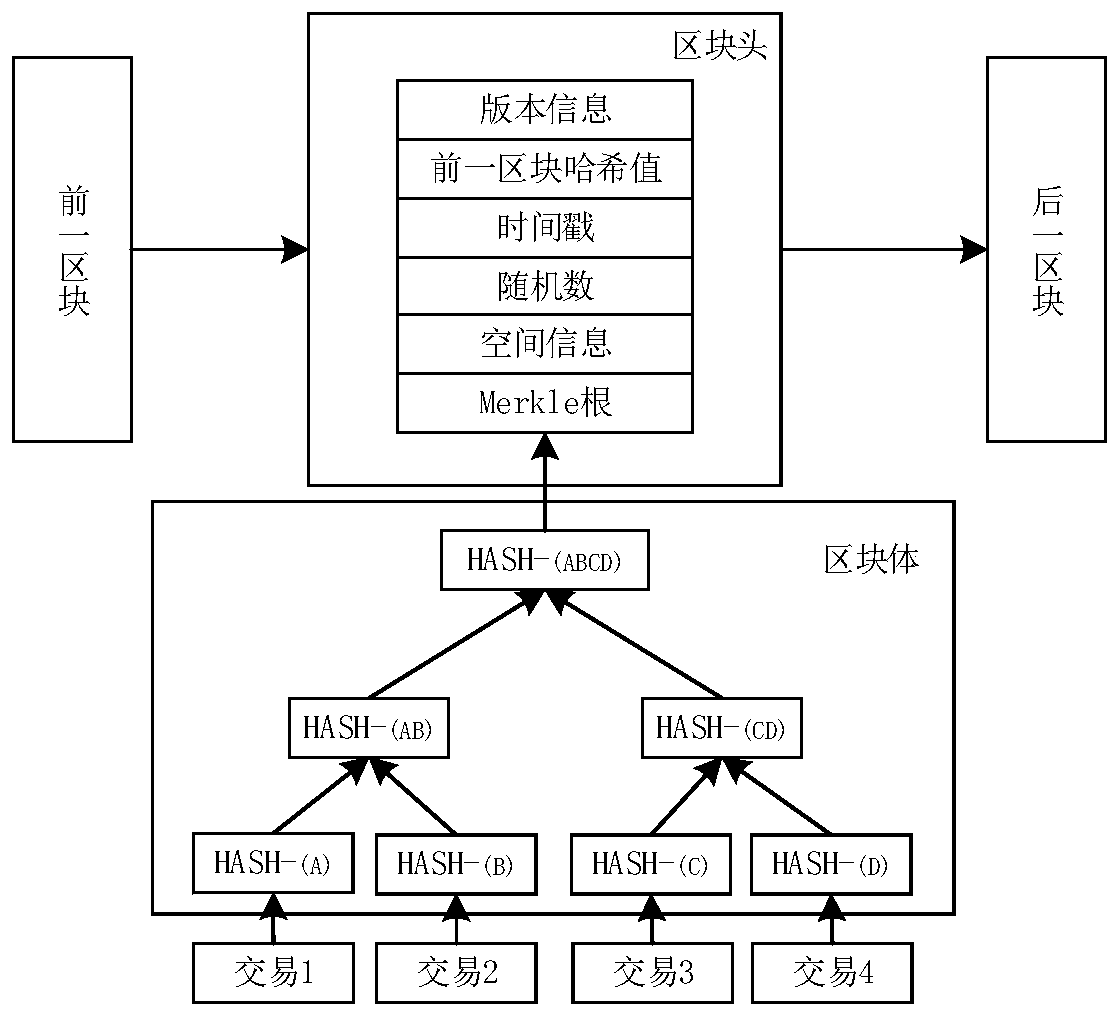
Communication method and communication platform based on block chain
ActiveCN111147227AMilitary Data SecurityReliable military dataEncryption apparatus with shift registers/memoriesUser identity/authority verificationDigital signatureSAFER
The invention provides a communication method and a communication platform based on a block chain. The method comprises the steps that military data serves as transaction information to be stored in distributed nodes of a block chain network in a block mode, and each block comprises a block head and a block body; in the data transmission process, each distributed node verifies the legality of thedata in a digital signature mode, and the block chain storage process calculates the HASH value through the SM3 cryptographic algorithm. According to the invention, the communication is safer, more reliable, more flexible and more intelligent.
Owner:HANGZHOU INST OF ADVANCED TECH CHINESE ACAD OF SCI
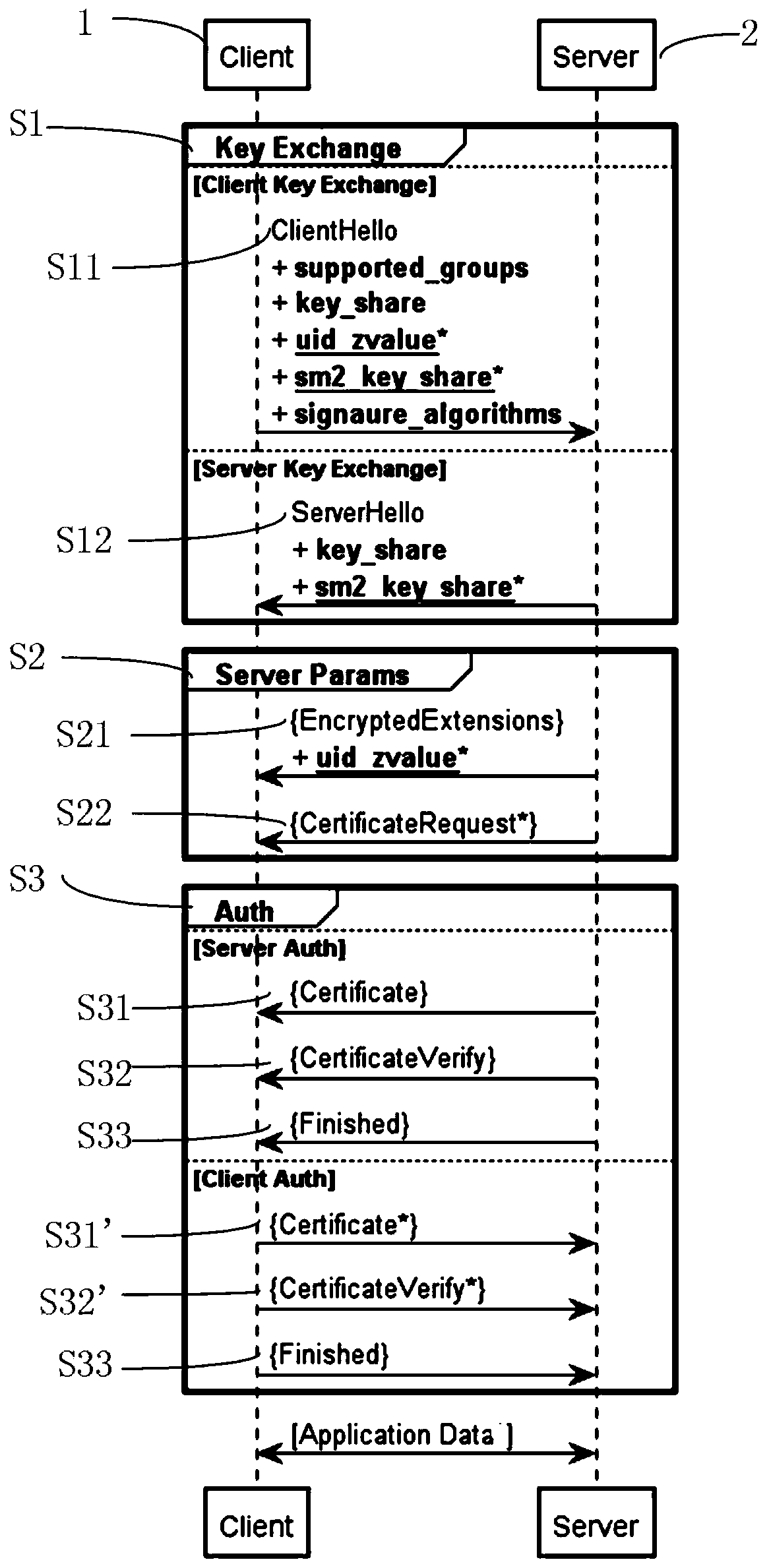
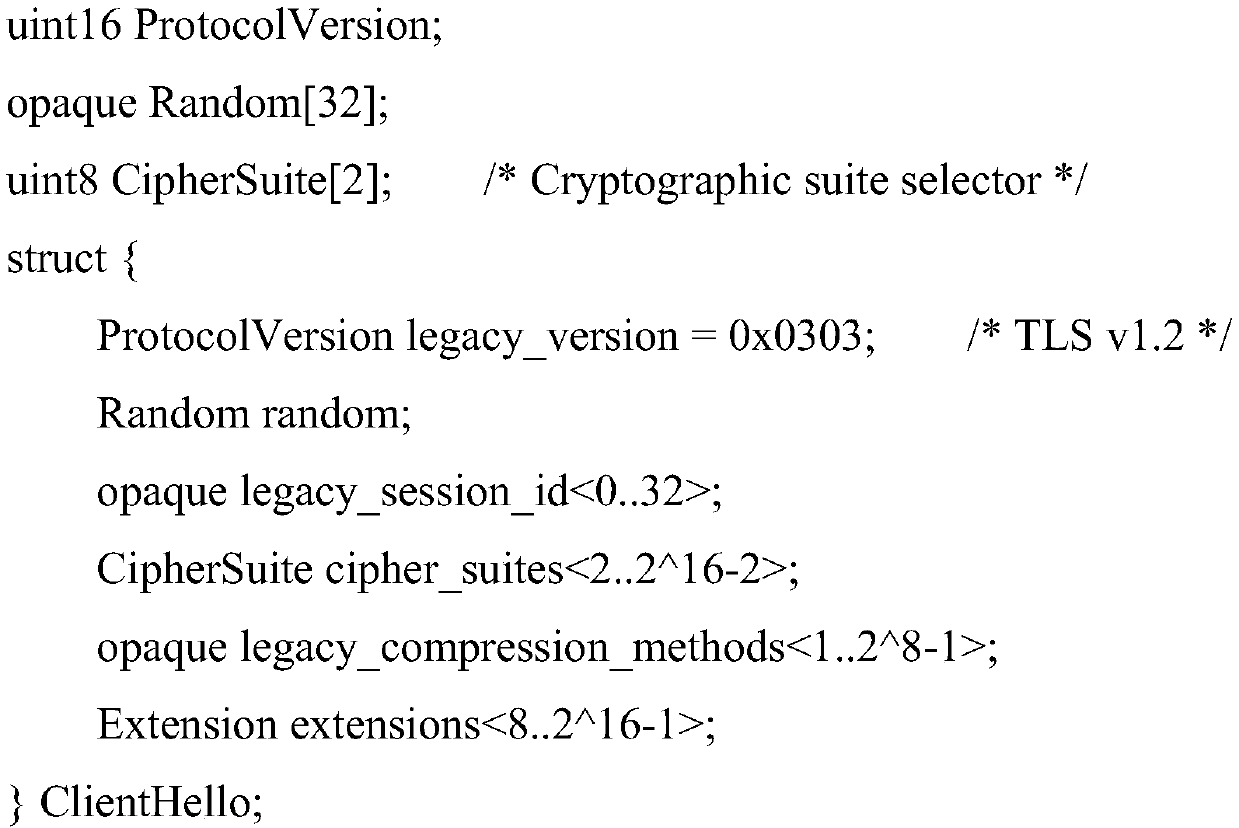
Method for establishing channel in TLS1_3 protocol based on national cryptographic algorithm
ActiveCN110995414AShorten the lengthPrevent theftEncryption apparatus with shift registers/memoriesPublic key for secure communicationKey exchangeKey size
The invention discloses a method for establishing a channel in a TLS1_3 protocol based on a national cryptographic algorithm. The method comprises a key exchange stage, a server parameter stage and anidentity authentication stage. In the key exchange phase, an SM2 key exchange algorithm is introduced to negotiate a shared key, and compared with international algorithms such as ECDH and ECDSA, a safer mechanism is adopted; in the identity authentication stage, compared with an RSA algorithm, the SM2 algorithm has the advantages that the encryption strength is similar to the safety performanceof a 3072-bit RSA algorithm when the key length of the SM2 algorithm is 256 bits, two message words are used in each round of a compression function of the SM3 algorithm, and the SM3 algorithm has higher word completeness than an existing SHA256 algorithm. In a symmetric encryption algorithm, an SM4 algorithm is introduced, a 32-round nonlinear iterative structure is adopted, the number of roundsof calculation is far larger than that of an AES algorithm, and safety is higher. According to the method, by improving the encryption algorithm serving as a data transmission safety core, secret keyleakage in the transmission process is avoided, and the safety of establishing a TLS1_3 channel is improved to a great extent.
Owner:CHINA FINANCIAL CERTIFICATION AUTHORITY
Method and system for generating passwords
InactiveUS7434061B2More secure passwordDigital data authenticationSecuring communicationThird partyPresent method
An improved method and system of generating passwords wherein Internet search engines are provided a random query and the search results are used to generate a mnemonic password. The password is memorable, yet non-user generated, and the use of search engines allows for a very large set of potential results. The password is more secure than most conventional passwords because it is memorable and not likely to be written down and because it is random. A large set of potential results ensures that the password is unlikely to be determined by a third party. The present method can be used with any device that has access to the Internet. The system can be customized to limit results to a specific language, filter offensive content, and incorporate encryption to limit eavesdropping.
Owner:MOSELEY BRETT E
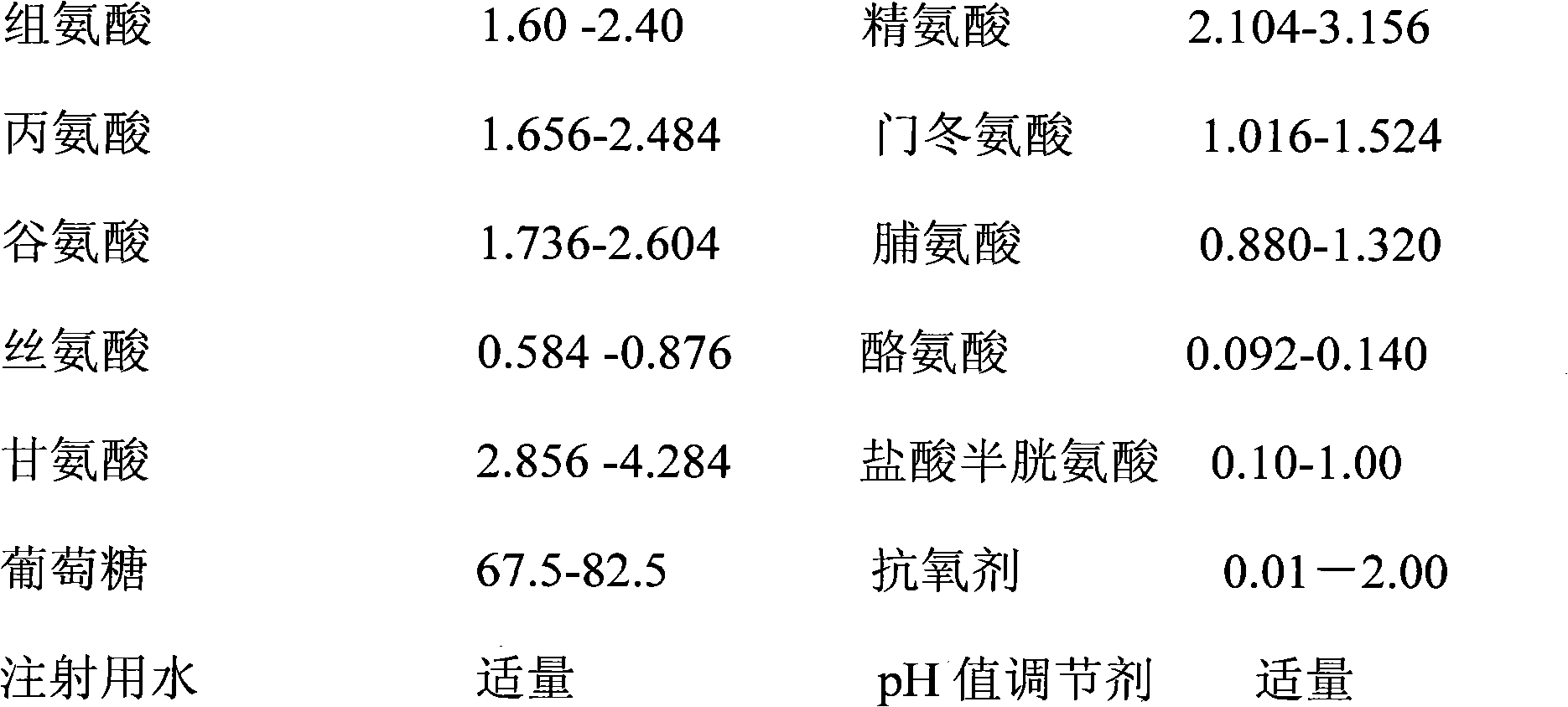
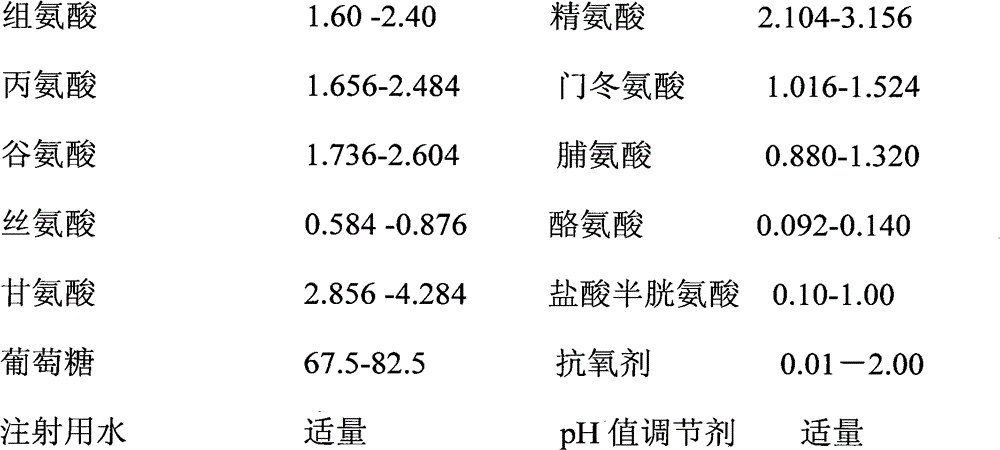
Pharmaceutical composition containing 18 amino acids
InactiveCN102626409AReduce residual oxygenAvoid huge investment in transformationOrganic active ingredientsPeptide/protein ingredientsSAFERAntioxidant
The invention discloses a pharmaceutical composition containing 18 amino acids. The pharmaceutical composition containing 18 amino acids is characterized in that raw materials of 18 amino acids and auxiliary materials of an antioxidant and a pH conditioning agent are prepared into compound amino acid injections (18AA-IV) having different concentrations, wherein the compound amino acid injection is the pharmaceutical composition containing 18 amino acids and has a pH value of 3.5 to 5.5. The pharmaceutical composition containing 18 amino acids does not contain a sulfite antioxidant and thoroughly prevents the damage of sulfites on the human body. Products of the pharmaceutical composition containing 18 amino acids are safer in clinical use. An accelerated stability test proves that the pharmaceutical composition (18AA-IV) containing 18 amino acids has the stability the same as or superior to the stability of commercial sulfite-containing like products.
Owner:郑飞雄
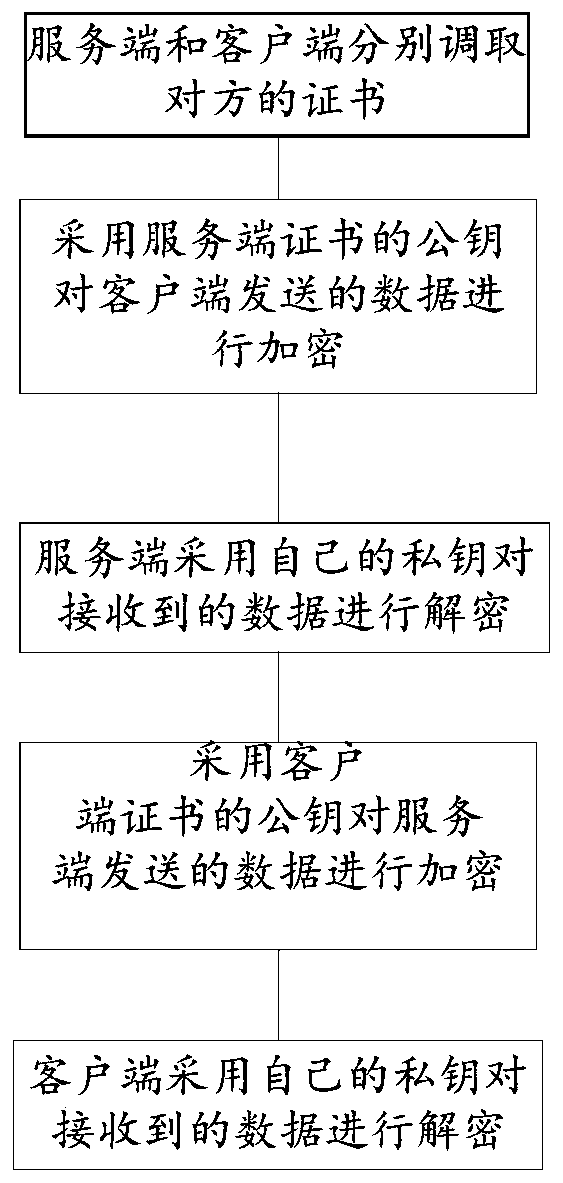
TLS secure communication method and system
ActiveCN111064738AEnsure safetyEffective isolationKey distribution for secure communicationKey exchangeSecure communication
The invention discloses a TLS secure communication method. The method comprises the following steps: a server and a client call certificates of each other; encrypting an encryption suite and key exchange information sent by the client by adopting the public key of the server certificates; encrypting the encryption suite selection and key exchange information sent by the server by adopting the public keys of the client certificates; allowing the client to decrypt the received encryption suite selection and key exchange information sent by the server by using the private key of the client; and allowing the server to decrypt the received encryption suite selection and key exchange information sent by the client by using the private key of the server. The TLS secure communication method has the beneficial effects that the secure communication method is suitable for occasions with relatively high data transmission security requirements; synchronous updating of certificates of the two parties can also be included in the ciphertext, and safety is higher.
Owner:TIH MICROELECTRONIC TECH CO LTD +1
Student And Faculty Emergency Response System (SAFERS)
An emergency response system that is used by schools to alert students, faculty, and staff on the school campus of critical situations. The system utilizes ID cards that are issued to the students, faculty, and staff at the beginning of each new school year, and issued to visitors as needed. The ID cards each have a miniature receiver, control circuitry, antenna and battery embedded into them along with a flat speaker and an LED light. If an emergency on the grounds of the school is imminent or ongoing, a master transmitter box is triggered by an administrator. The triggering of the transmitter sends coded RF signals out to ID cards and repeaters that are strategically placed through the school property. Signals received by the receivers embedded into the ID cards and decoded by the control circuitry trigger the speaker and LED in the ID cards to alert persons carrying the ID cards.
Owner:STAPLEFORD SCOTT
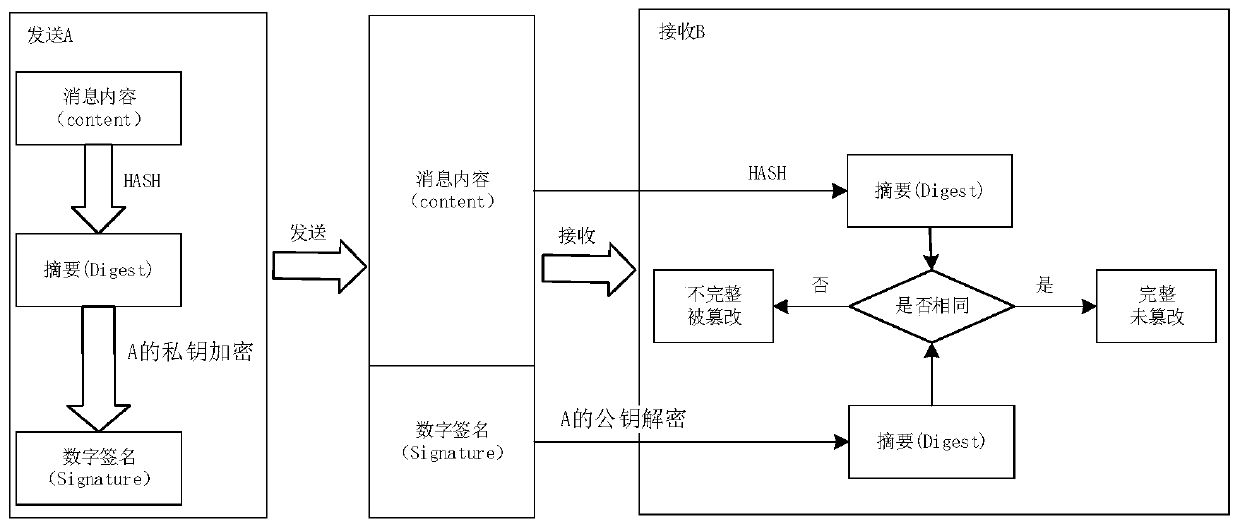
Data encryption method and system, client and computer readable storage medium
PendingCN109918877AKeep safeHigh encryption strengthDigital data protectionDigital data authenticationClient-sideEncryption system
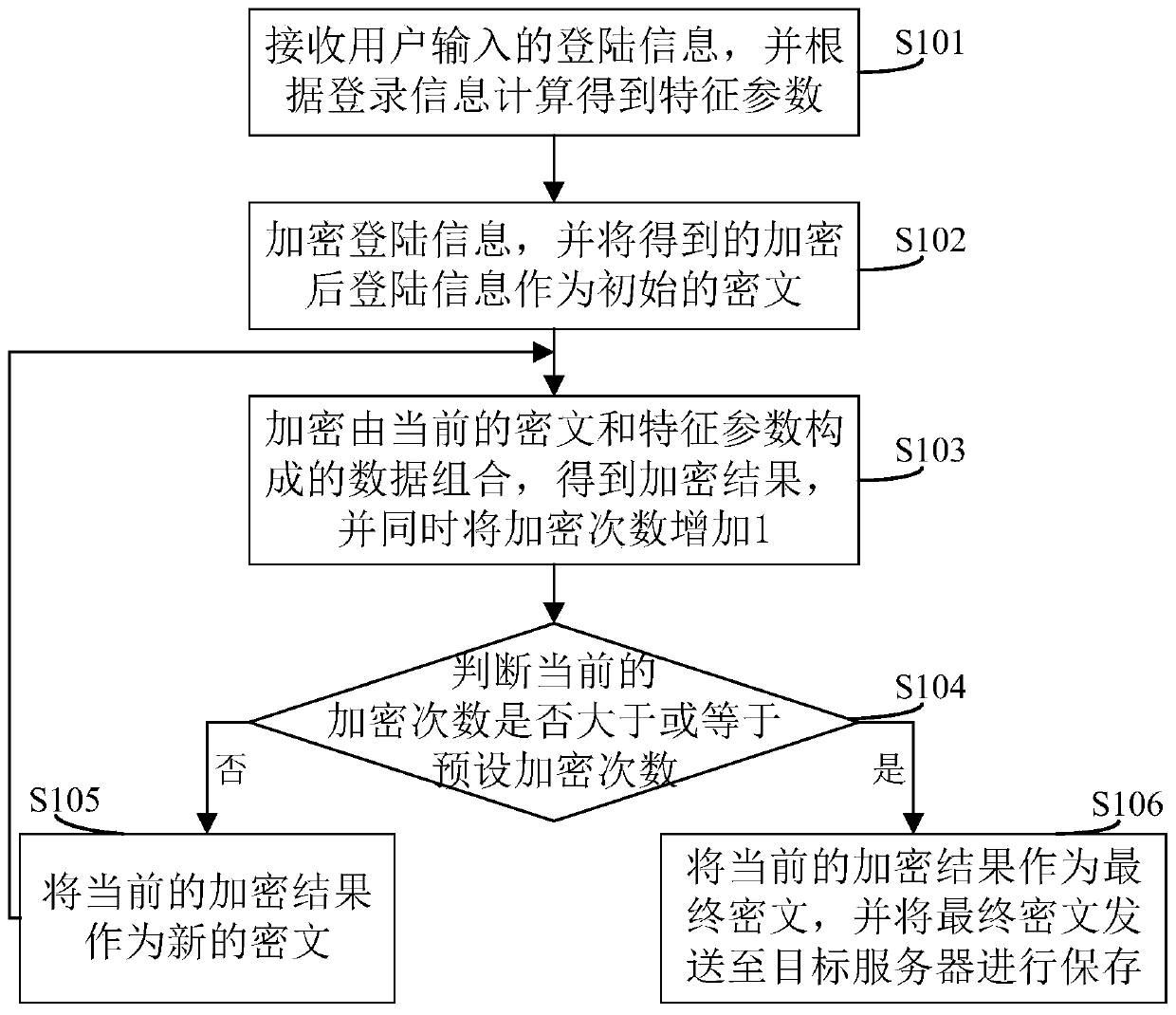
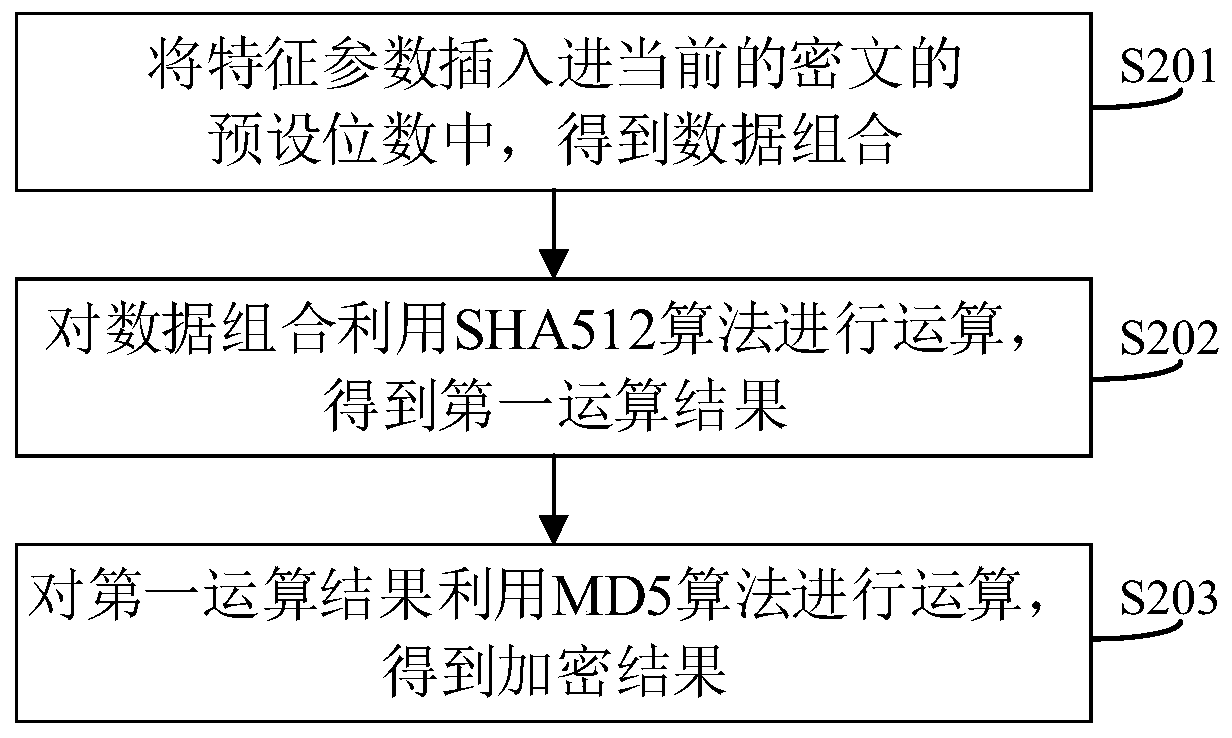
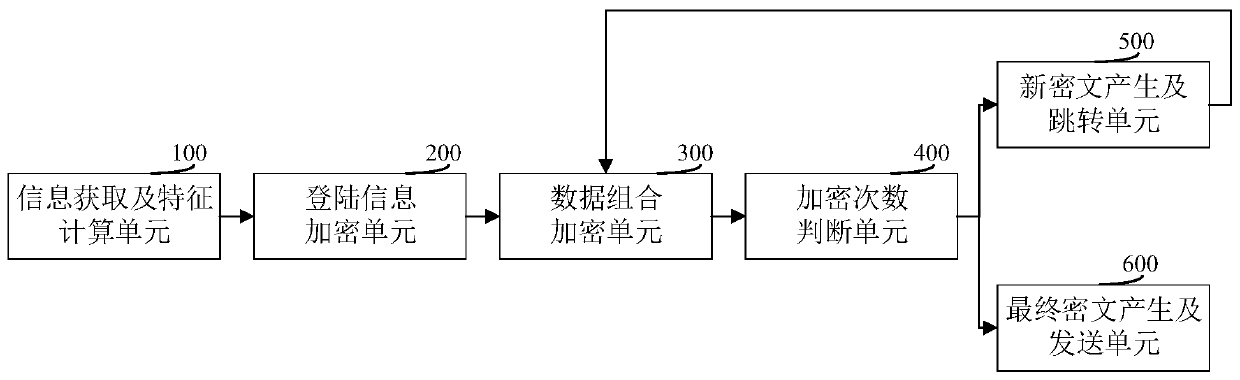
The invention discloses a data encryption method. The method is different from a conventional cyclic encryption mode. The basic data encrypted each time are inconsistent in a mode of adding the characteristic parameters on the basis of the encryption result obtained after each time of encryption. Even if the algorithm which is encrypted circularly is guessed, a cracker cannot finally obtain real and available user login information from the ciphertext obtained from the dragging library through reverse cracking, so that the user login information can be stored more safely under the protection of higher encryption intensity. The invention also discloses a data encryption system, a client and a computer readable storage medium, which have the above beneficial effects.
Owner:SHENZHEN ONETHING TECH CO LTD
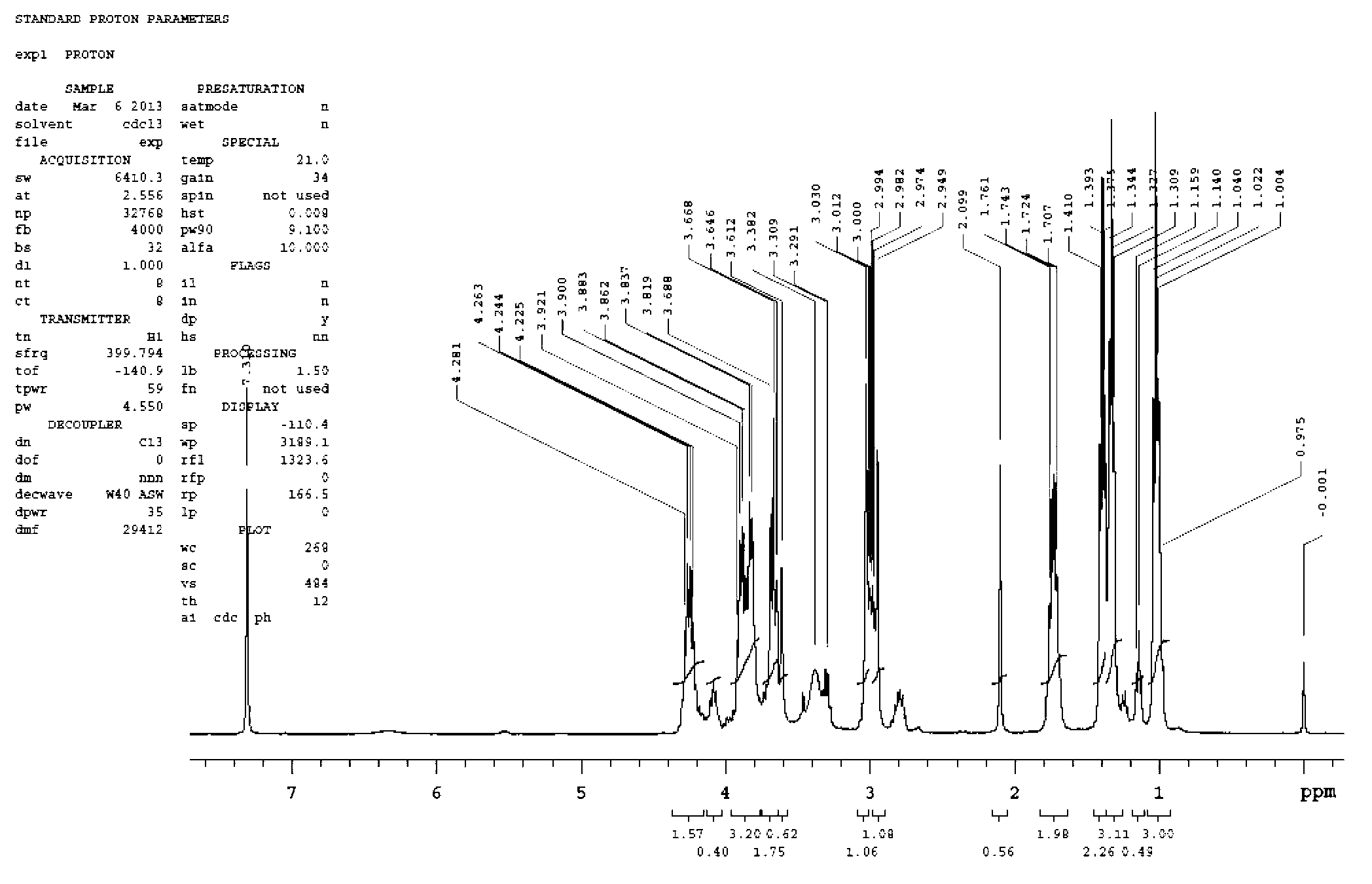
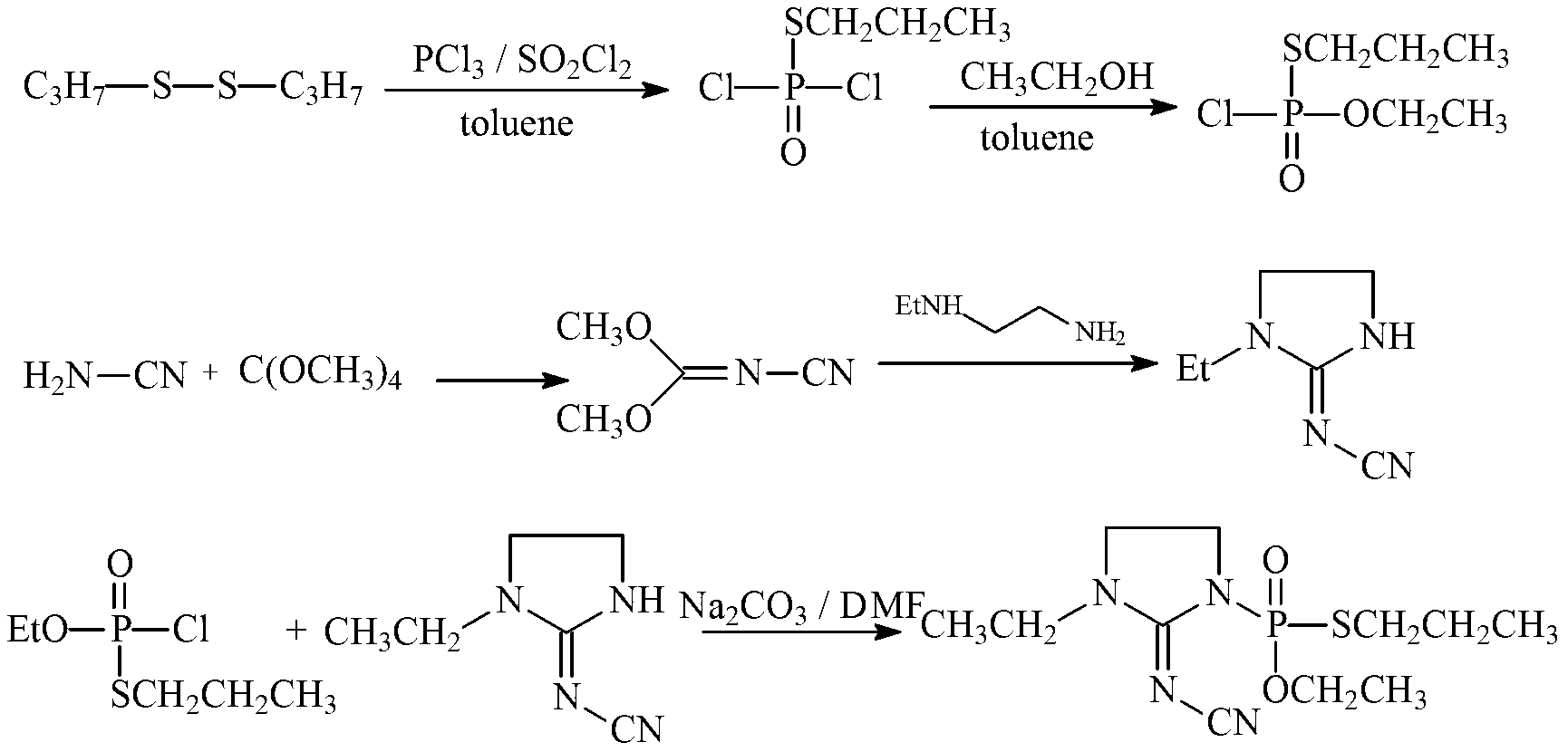
Synthetic process of O-ethyl-S-n-proply-(3-ethyl-2-cyano imine-1-imidazole) phosphate
InactiveCN103214519AHigh yieldReduced responseGroup 5/15 element organic compoundsEthyl groupPhosphorus trichloride
The invention relates to a synthetic process of O-ethyl-S-n-proply-(3-ethyl-2-cyano imine-1-imidazole) phosphate. The process comprises the following steps of: 1) synthesis of O-ethyl-S-n-proply-S-propyl phosphoryl chloride; 2) synthesis of 1-ethyl-2-(N-cyano imine) imidazole; and 3) synthesis of O-ethyl-S-n-proply-(3-ethyl-2-cyano imine-1-imidazole) phosphate. The process provided by the invention has the beneficial effects that the reaction step and time are shortened, the yield is improved from 50% to over 70%, and the total yield is improved; according to the process, potassium carbonate replaces flammable and combustible sodium hydride, so that the reaction condition is more mild and the production process is safer; based on dipropyl dithio and phosphorus trichloride as initial raw materials, S-n-proply phosphoryl dichloride is synthesized and reacted with ethanol to obtain O-ethyl-S-n-propyl-phosphoryl chloride; the line is short and the raw material is easy to get with less wastewater, and the method is suitable for industrialization.
Owner:WUHAN INSTITUTE OF TECHNOLOGY
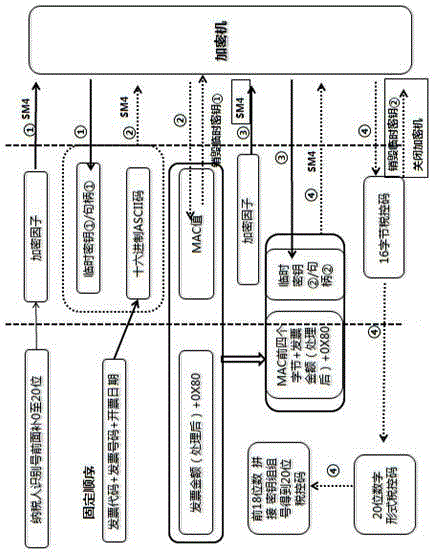
Anti-fake code generation and verification method based on cipher machine and universal serial bus key (USBKey)
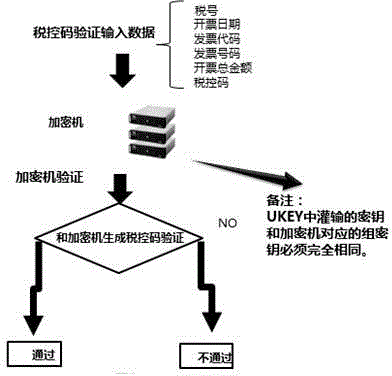
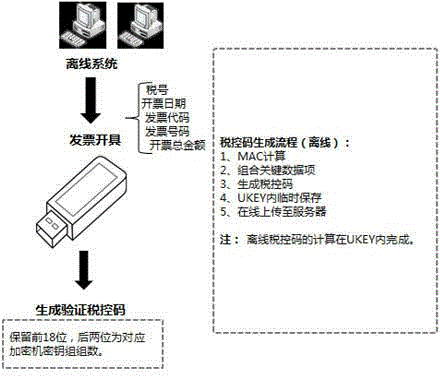
ActiveCN104318461AThere is no timelinessSafeguard hidden dangersFinanceUser identity/authority verificationSource Data VerificationSAFER
The invention provides an anti-fake code generation and verification method based on a cipher machine and a universal serial bus key (USBKey). Calculation is performed to generate a specific anti-fake code according to parameters such as tax number, sum and code of an invoice, an invoice number and an invoice-making-out date, and a verification method is supported. USBKey data verification is synchronously provided, the problem of low USBKey timeliness is solved, effective, safe and timely 'one invoice one code' can be achieved, the cipher machine is applied, an algorithm which can support SM1 / SM2 / SM3 / SM4 / 3DES / SSF33 encryption is provided, an anti-fake code with national standard rule is generated according to invoice information of identify number of invoice maker taxpayer, invoice sum, invoice code, invoice number and invoice making date, hidden dangers that exist in network security can be avoided, and the problem of timeliness can not be solved if secret keys that are instilled by the USBKey are different from any group of secret keys of the cipher machine.
Owner:INSPUR SOFTWARE TECH CO LTD
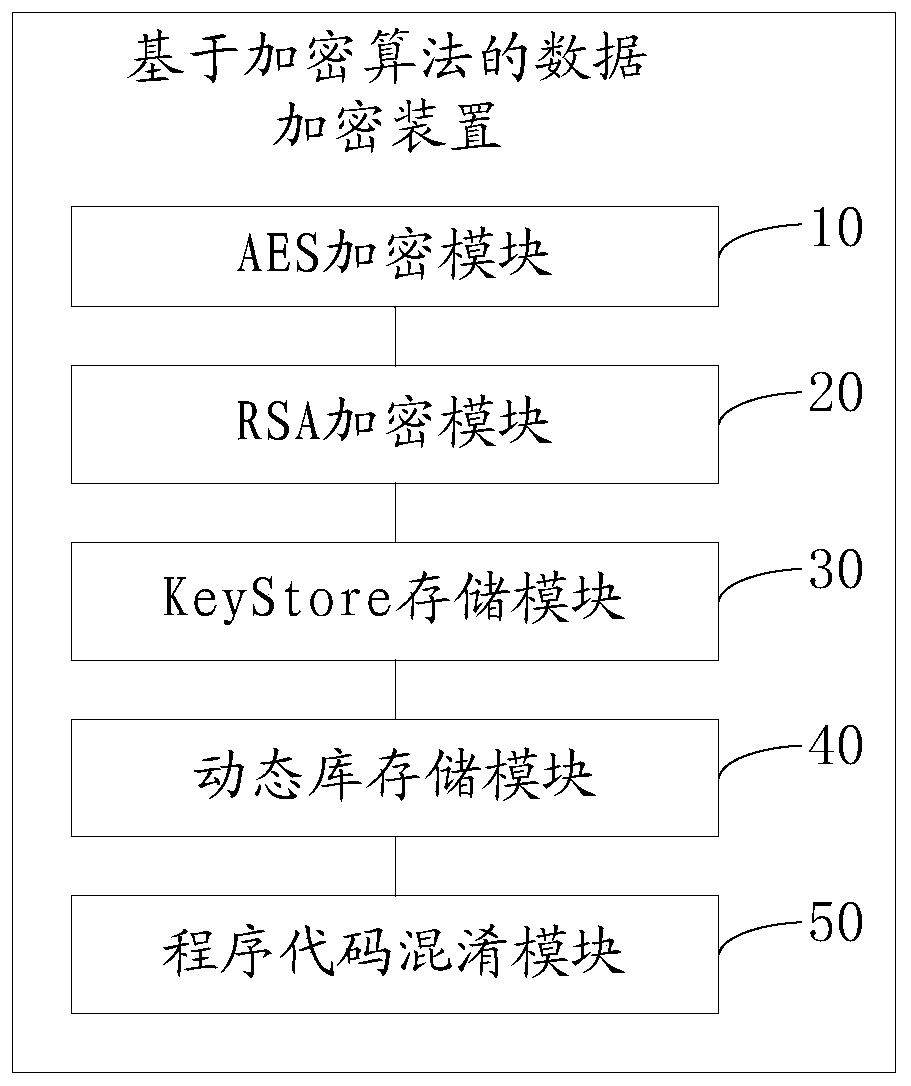
Data encryption method and device based on encryption algorithm and computer equipment
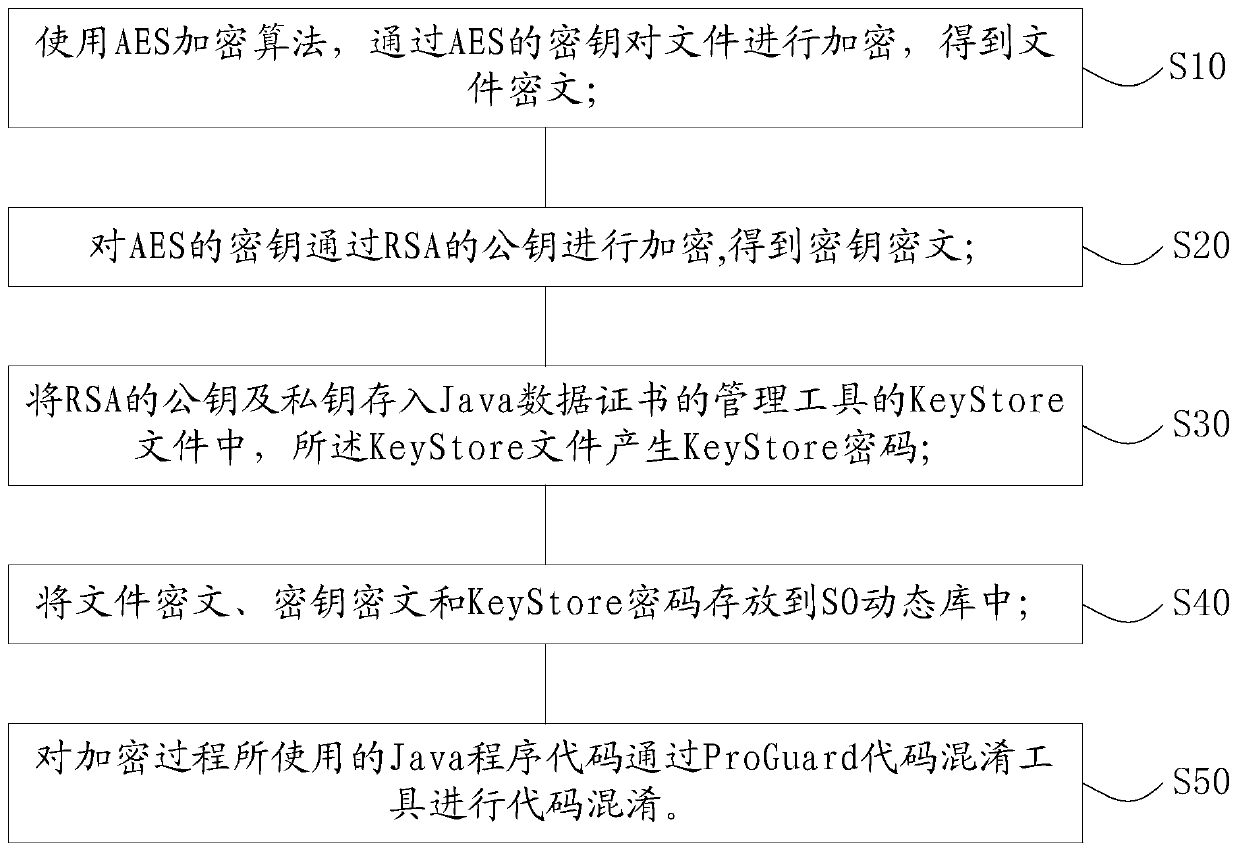
ActiveCN110855433ADifficult to analyzeDifficult to obtainKey distribution for secure communicationEncryption apparatus with shift registers/memoriesManagement toolAlgorithm
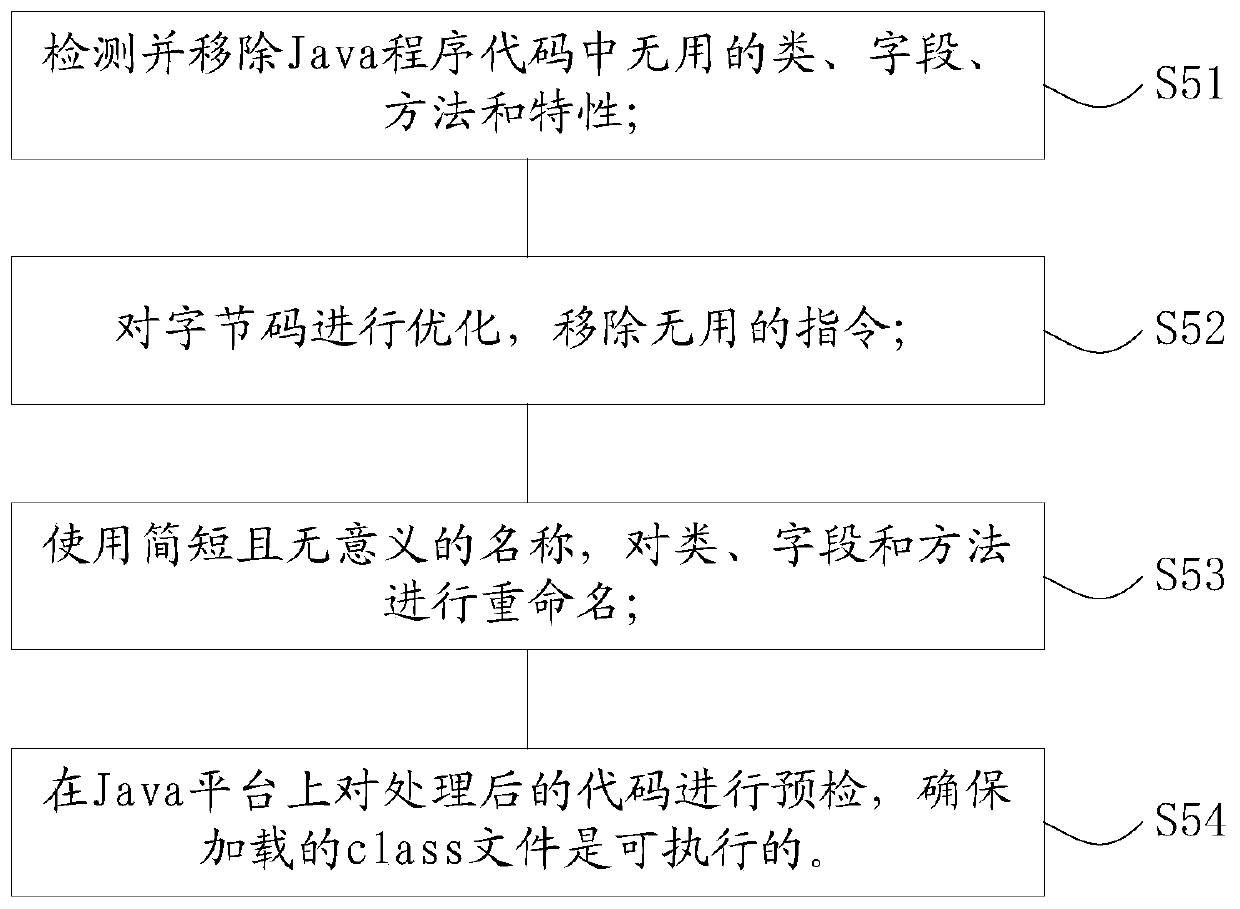
The invention provides a data encryption method and device based on an encryption algorithm and computer equipment, and the method comprises the steps: carrying out the encryption of a file through anAES encryption algorithm and an AES secret key, and obtaining a file ciphertext; encrypting the secret key of the AES through the public key of the RSA to obtain a secret key ciphertext; storing thepublic key and the private key of the RSA into a KeyStore file of a management tool of the Java data certificate, wherein the KeyStore file generates a KeyStore password; storing the file ciphertext,the key ciphertext and the KeyStore password into an SO dynamic library; and performing code obfuscation on Java program codes used in the encryption process through a ProGuard code obfuscation tool.The method has the beneficial effects that the RSA private key is stored by using the KeyStore key, so that the RSA private key is safer and cannot be violently cracked. And the SO dynamic inventory KeyStore password and the encrypted ciphertext of the RSA are used, so that the KeyStore password and the encrypted ciphertext of the RSA are more difficult to analyze and obtain. Code obfuscation is carried out by using a ProGuard tool, so that the code implementation process cannot be effectively decompiled.
Owner:深圳市信联征信有限公司
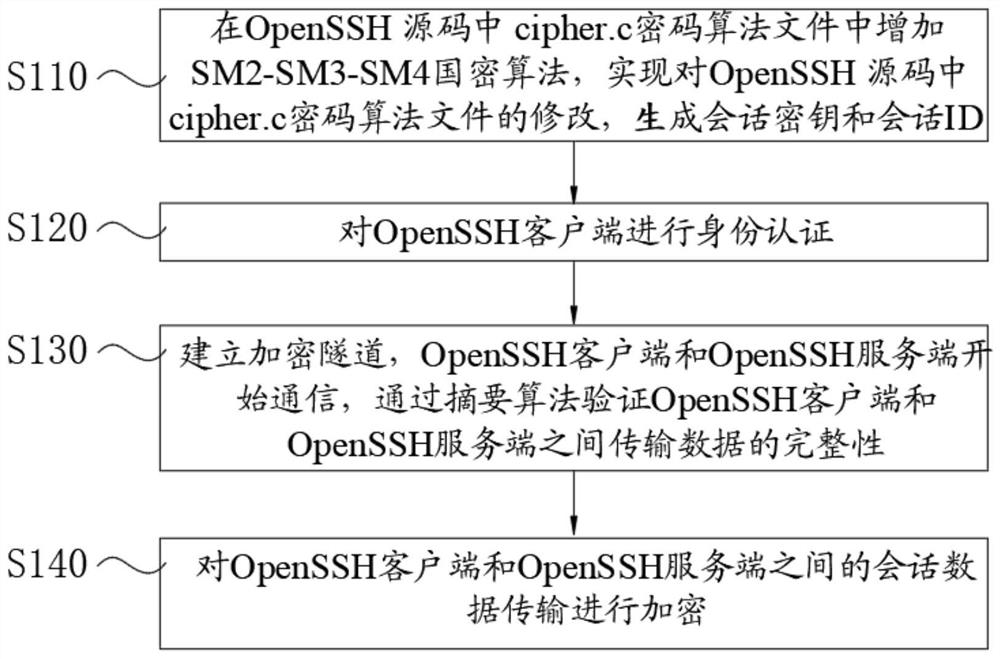
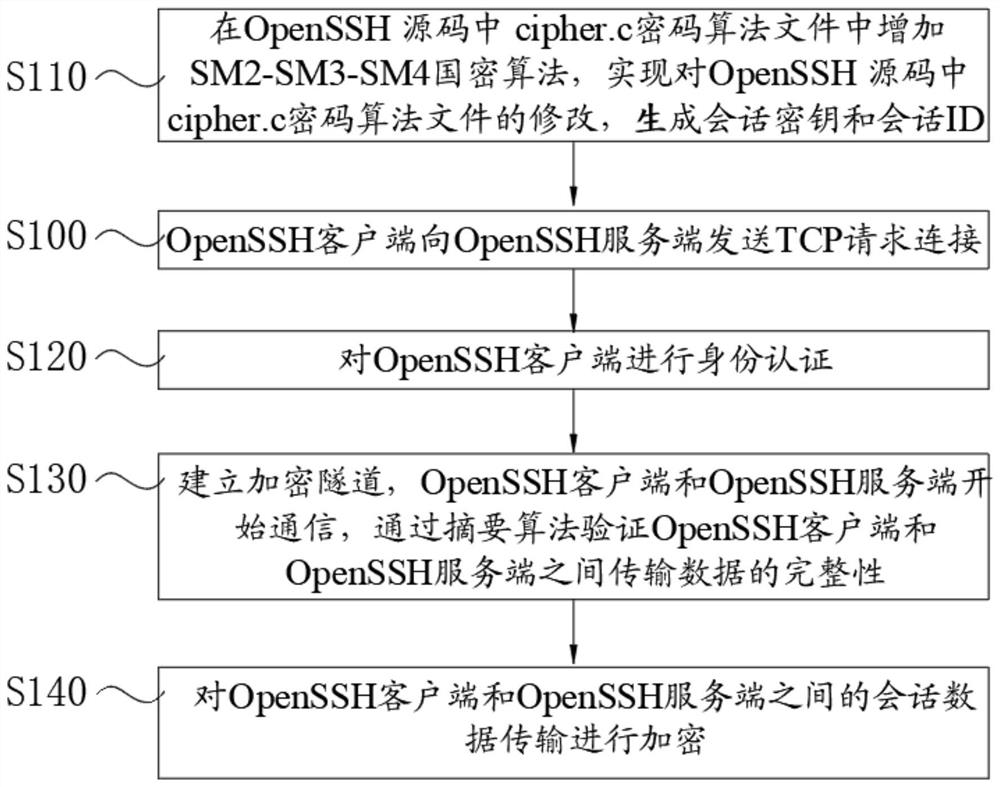
Method for realizing secure transmission of data based on SM2-SM3-SM4 cryptographic algorithm
PendingCN113572741AEnhanced adaptationIncrease the amount of encryption calculationTransmissionAlgorithmTheoretical computer science
The invention discloses a method for realizing secure transmission of data based on a national cryptographic SM2-SM3-SM4 algorithm, which comprises the following steps of: adding the SM2-SM3-SM4 national cryptographic algorithm in a cipher.c cryptographic algorithm file in an OpenSSH (Open Secure Shell) source code, modifying the cipher.c cryptographic algorithm file in the OpenSSH source code, and generating a session key and a session ID (Identity); carrying out identity authentication on the OpenSSH client; establishing an encryption tunnel, the OpenSSH client and the OpenSSH server starting to communicate, and the integrity of data transmission between the OpenSSH client and the OpenSSH server being verified through a digest algorithm; and session data transmission between the OpenSSH client side and the OpenSSH server side being encrypted. According to the method, the source codes of the OpenSSH client side and the OpenSSH server side are modified, the adaptation of the SM2-SM3-SM4 cryptographic algorithm is increased, a safer mechanism is adopted, the information encryption calculation amount and complexity are improved, and an encryption communication tunnel is established, so that the attack on the block cipher algorithm can be effectively resisted when the OpenSSH client side accesses the OpenSSH server side.
Owner:深圳市证通云计算有限公司 +1
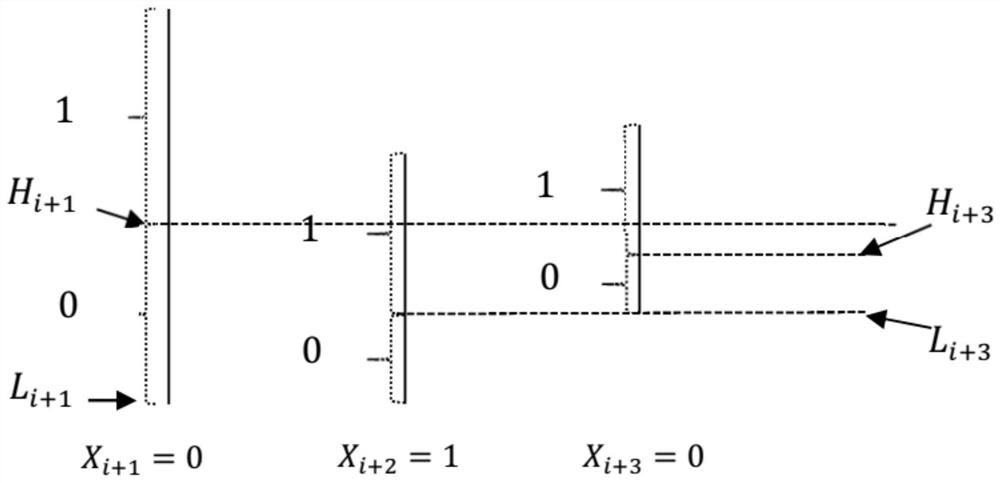
Linear piecewise symmetric encryption encoding and decoding method
The invention provides a linear piecewise symmetric encryption coding and decoding method, which comprises the following steps of: segmenting any binary sequence by taking 1 bit as a unit, and implanting a weight coefficient (symmetric key) into a password (or binary information corresponding to the password) set by a user at the first section as a parameter to carry out weighted probability modelcoding. Starting from the second segment, implanting the last segment of uncoded binary system end s (s > 0) bits into the weight coefficient, and performing weighted probability model coding on thesecond segment, and so on. It is proved that when l is long enough, any bit error of the weight coefficient or any bit error of the coded ciphertext will cause that the binary sequence cannot be decoded successfully. Compared with the prior art, the method has the advantages that segmented encryption is adopted, different secret keys are adopted for encoding in all the segments, the cracking difficulty is higher, safety is higher, and data can be encrypted in a streaming mode in a segmented and secret-key-divided mode.
Owner:湖南瑞利德信息科技有限公司
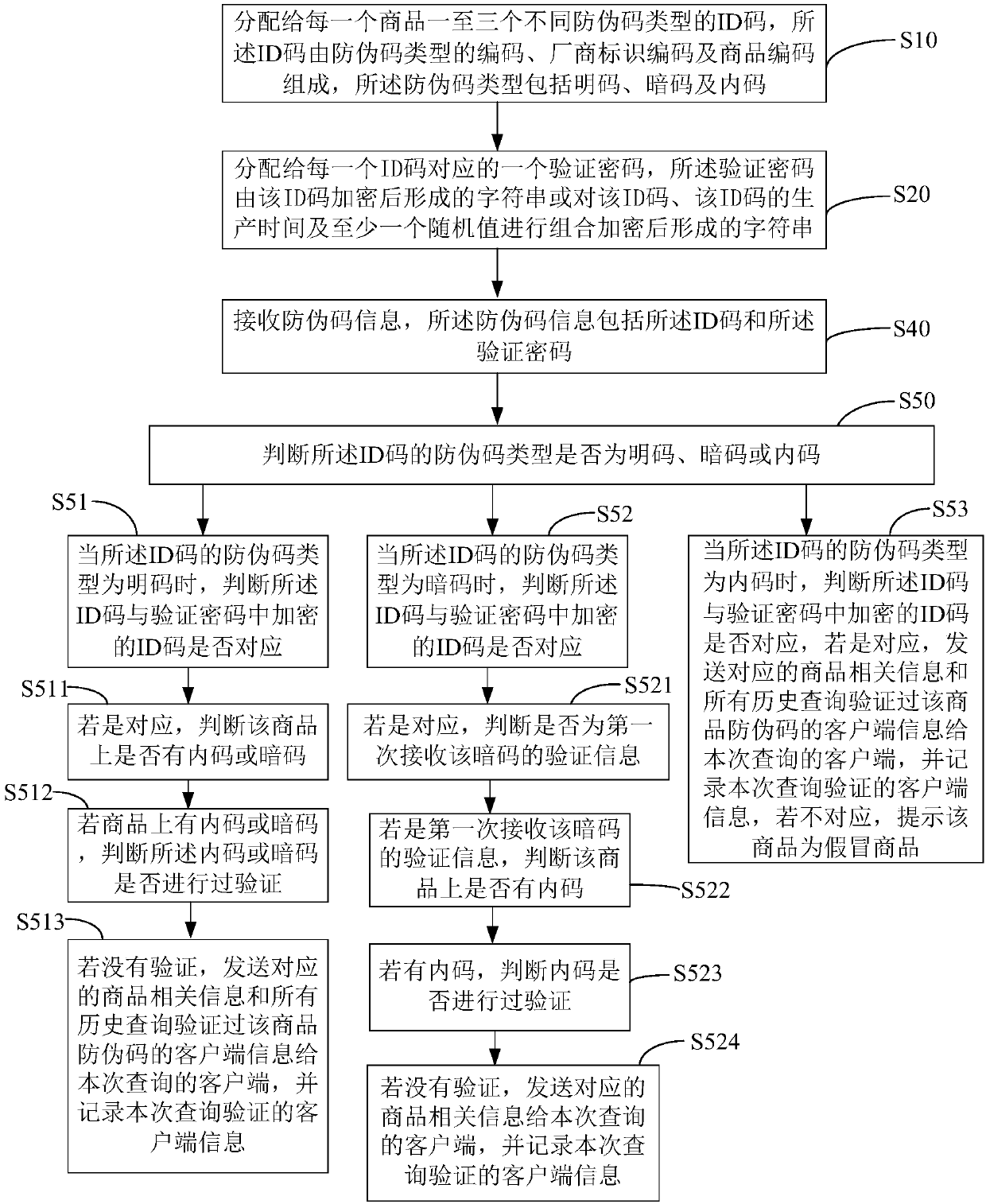
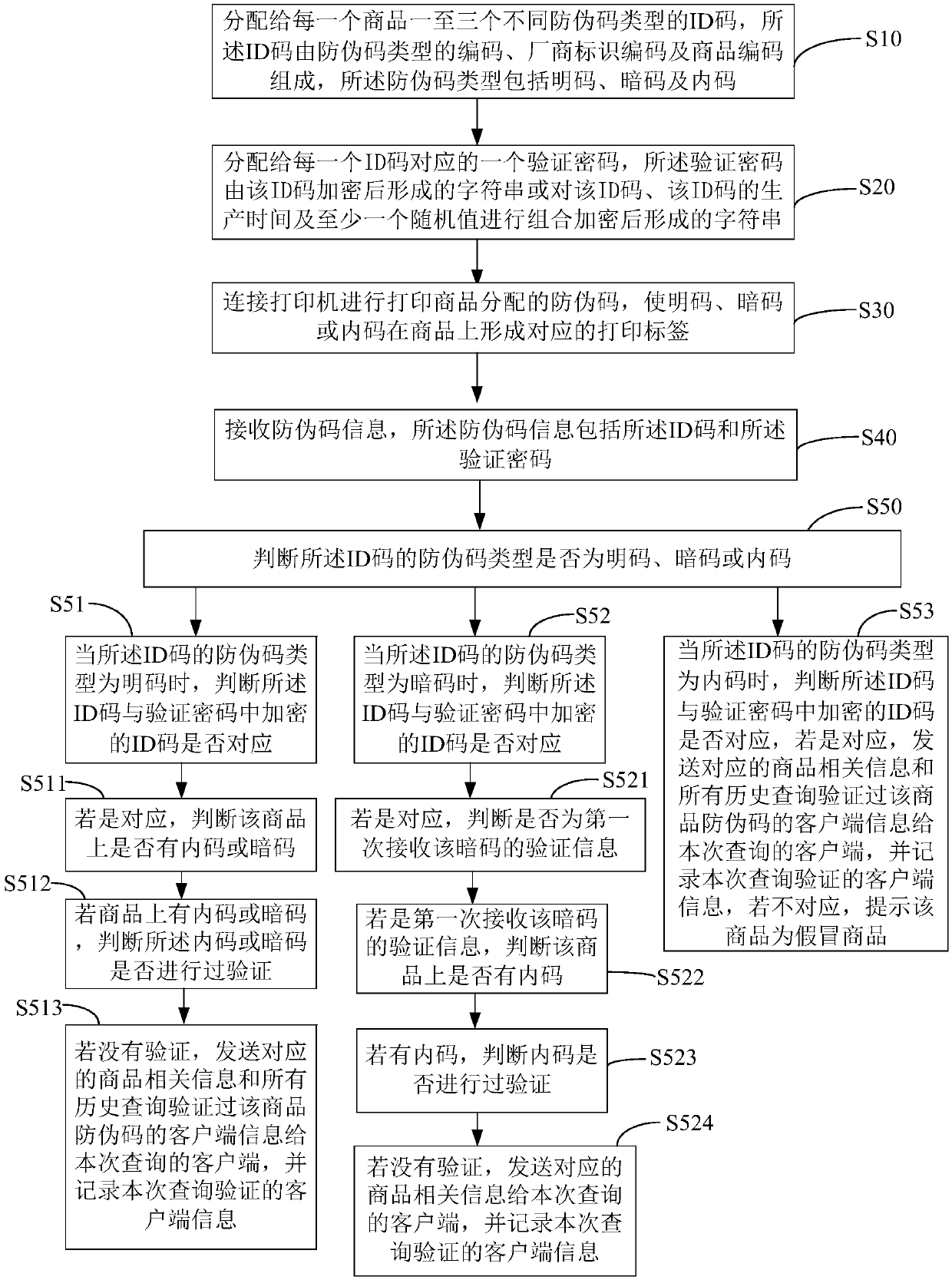
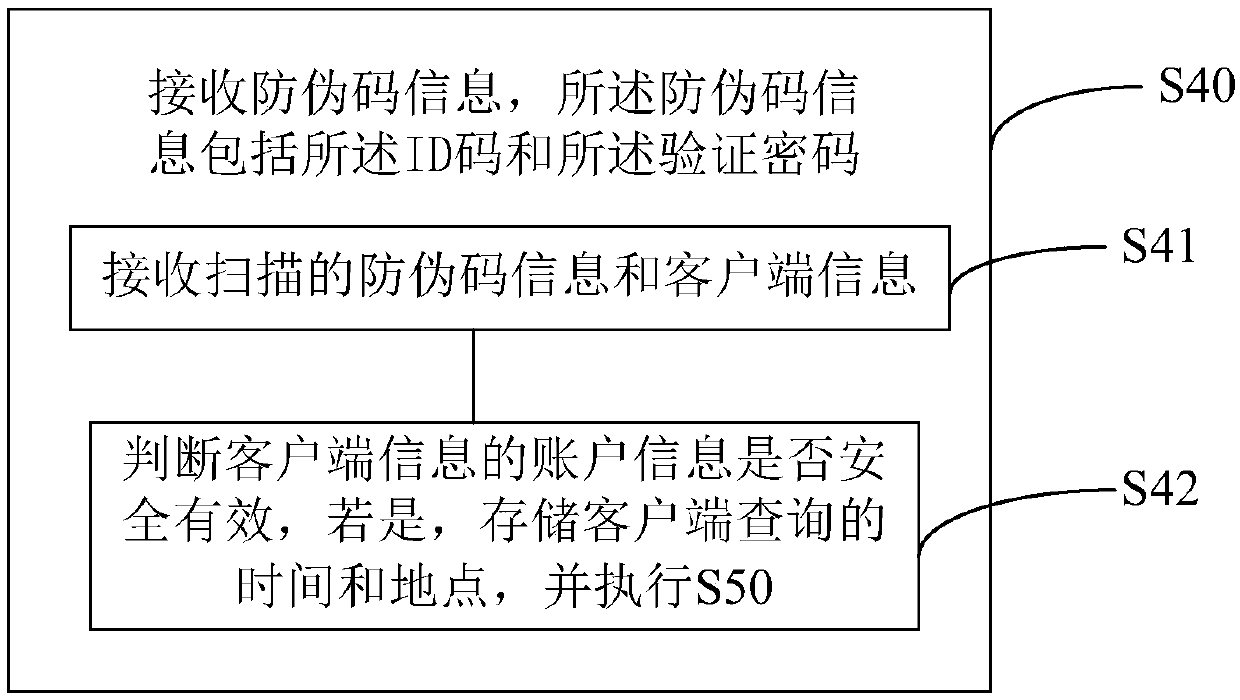
Commodity anti-counterfeiting code generation and verification method and system and computer readable storage medium
PendingCN111311268AImprove safety and reliabilityDigital data protectionCommerceProgramming languagePassword
The invention discloses a commodity anti-counterfeiting code generation and verification method, and the method comprises the steps: distributing one to three ID codes of different anti-counterfeitingcode types to each commodity, enabling the ID codes to be composed of codes of the anti-counterfeiting code types, manufacturer identification codes and commodity codes, and enabling the anti-counterfeiting code types to comprise a plain code, a secret code and an internal code; and allocating a verification password corresponding to each ID code, wherein the verification password is a characterstring formed by encrypting the ID code or a character string formed by combining and encrypting the ID code, the production time of the ID code and at least one random value. The commodity anti-counterfeiting code verification method comprises the following steps: receiving anti-counterfeiting code information, wherein the anti-counterfeiting code information comprises the ID code and the verification password; and judging whether the anti-counterfeiting code type of the ID code is a plain code, a secret code or an internal code. According to the commodity anti-counterfeiting code generationand verification method, commodity anti-counterfeiting is safer and more reliable.
Owner:深圳市节点加科技有限责任公司
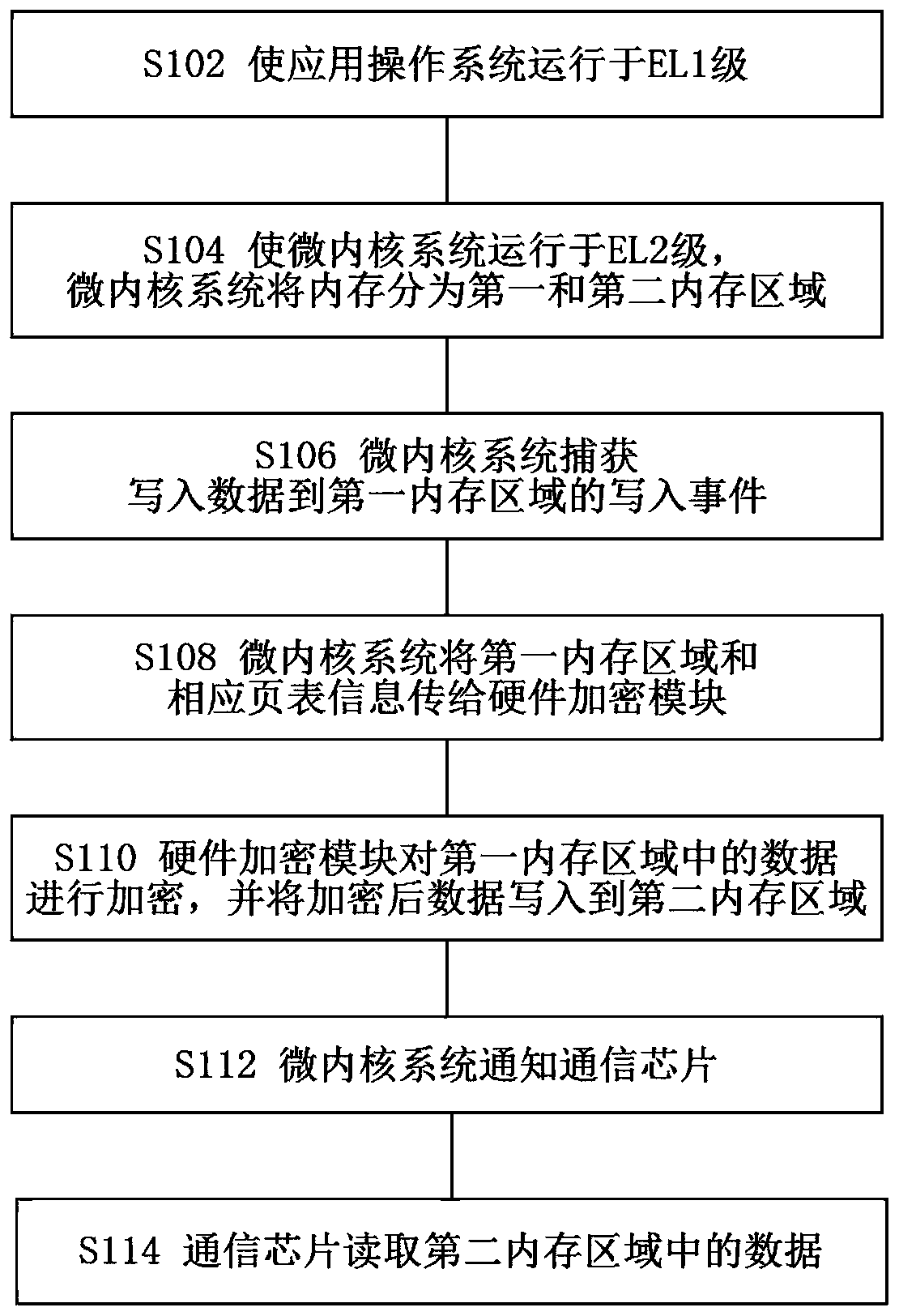
Encryption communication method and system of Arm architecture application processor
ActiveCN111246466AImprove securityCommunication securityTransmissionSecurity arrangementComputer architectureSAFER
The invention discloses an encryption communication method and system of an Arm architecture application processor. The method comprises: an application operating system being made to run at a first-level exception level of the application processor; a microkernel system which at least performs memory allocation management and control running in a second-level exception level, higher than the first-level exception level, of the application processor, wherein the microkernel system divides a memory into a first memory area and a second memory area; the microkernel system enabling the application operating system to only read and write the first memory area, the communication chip only reading and writing the second memory area, and performing reading and writing between the first memory area and the second memory area through a hardware encryption module arranged outside the application processor. According to the invention, the risk that encryption is bypassed can be greatly reduced, so that communication is safer.
Owner:BEIJING YUANXIN SCI & TECH
Split binary data encryption method
PendingCN112165380AKey distribution for secure communicationDigital data protectionAlgorithmOriginal data
The invention relates to a split binary data encryption method, which solves the problem that the development of the information communication industry is restricted due to the fact that the space occupied by encrypted binary data is increased or the encrypted binary data is easy to crack. According to the method, binary data is encrypted in a split mode, the space occupied by original data is notincreased any more except a small number of simple keys after data encryption, and the encrypted data and the original data have no logical relation, so that the purpose of safer data transmission and storage is achieved.
Owner:吕志强
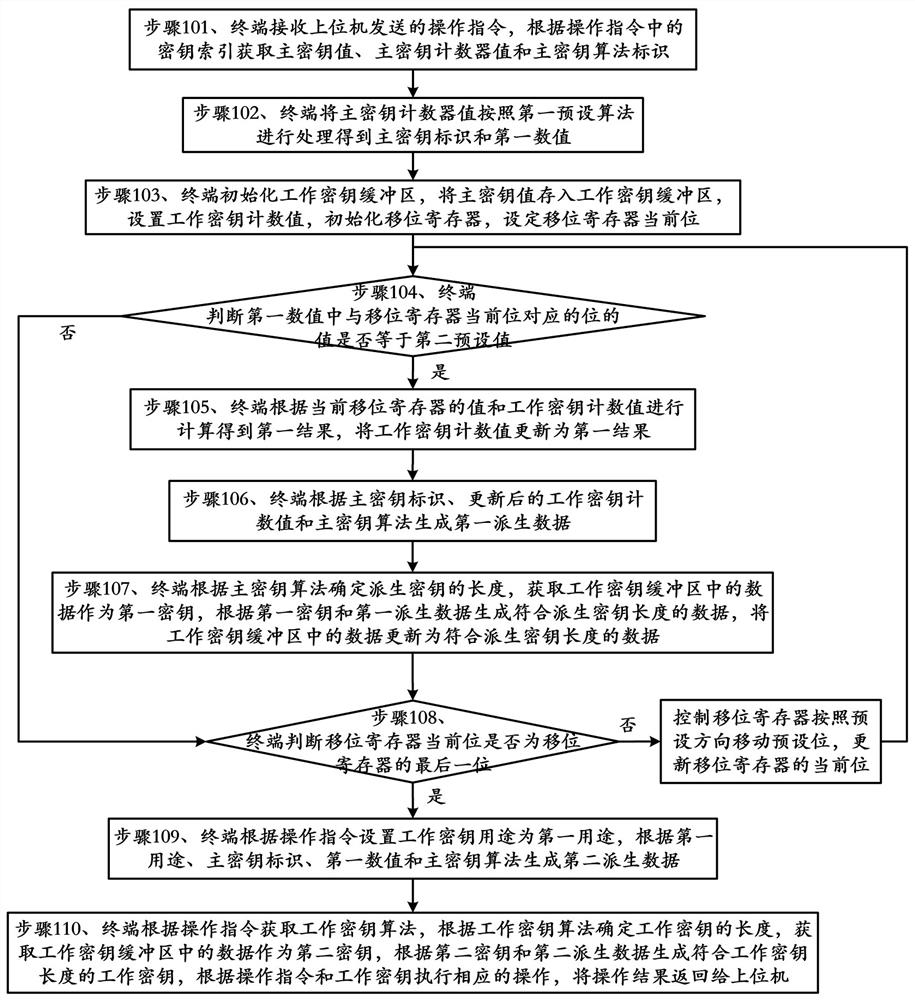
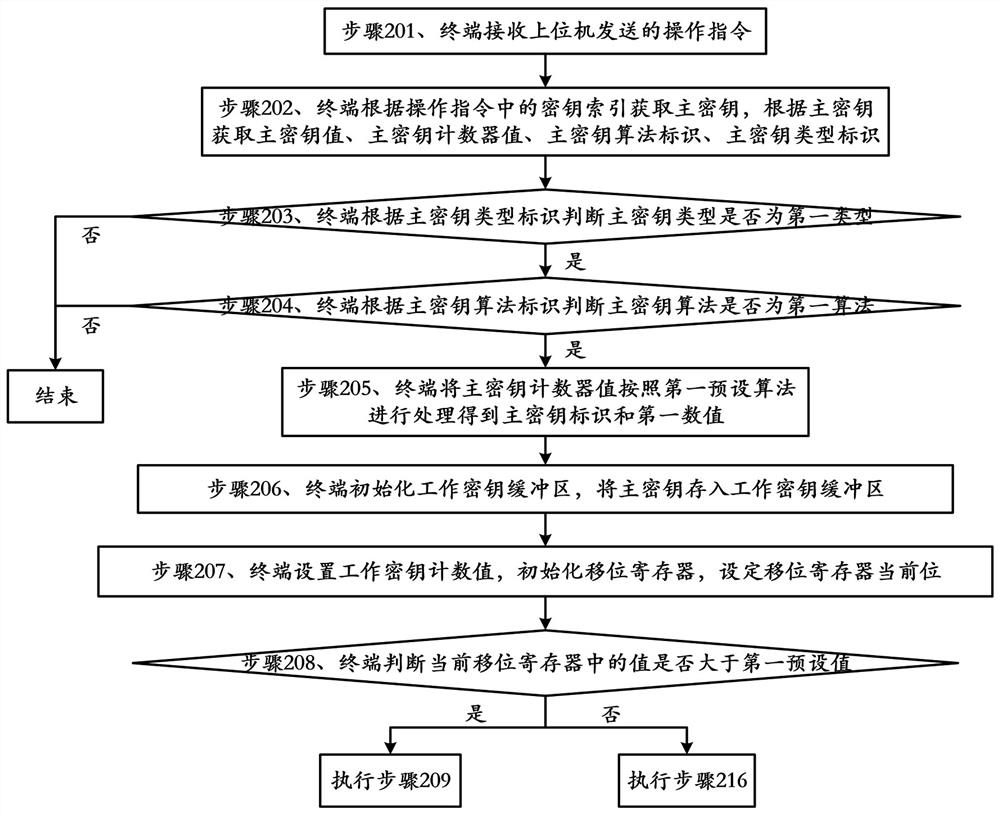
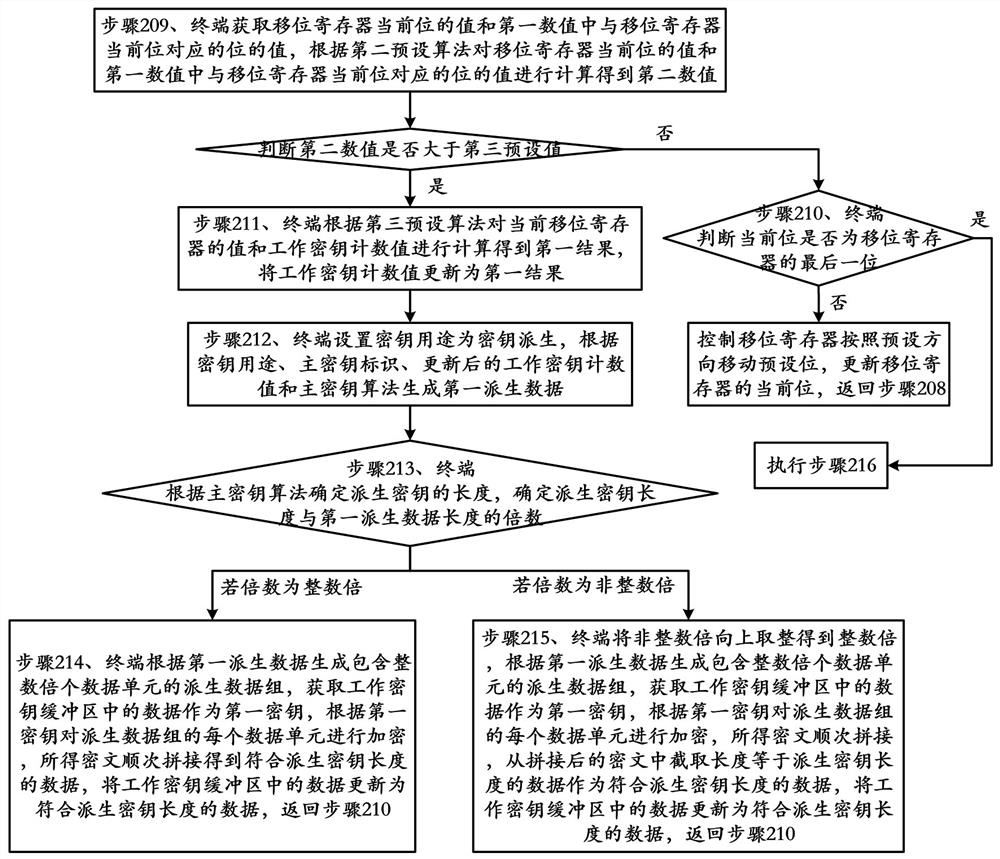
Working key generation method and device and computer readable storage medium
The invention provides a working key generation method and device and a computer readable storage medium, and belongs to the technical field of information security. The method comprises the following steps: the terminal receiving an operation instruction sent by an upper computer, obtaining a working key purpose and a working key algorithm according to the operation instruction, setting the working key purpose as a first purpose by the terminal, generating derived data according to the first purpose, a master key identifier, a first numerical value and a master key algorithm, determining the length of a working key according to the working key algorithm, obtaining data in a working key buffer area as a key, generating the working key according with the length of the working key according to the key and the derived data, executing corresponding operation according to the operation instruction and the working key, and returning an operation result to the upper computer. Compared with an encryption scheme in the prior art, the method provided by the invention is safer and wider in application range.
Owner:FEITIAN TECHNOLOGIES
Glyoxylic acid continuous oxidation process
InactiveCN109678693AHigh selectivityHigh yieldOrganic compound preparationCarboxylic compound preparationChemical synthesisGlyoxylic acid
The invention relates to a glyoxylic acid production process, in particular to a glyoxylic acid continuous oxidation process, and belongs to the technical field of chemical synthesis. The process comprises the following steps: fully and evenly mixing glyoxal, a cocatalyst and an initiator which are accurately measured to obtain a mixture A; after preheating by a preheater, feeding the mixture A into an initiation kettle for reaction with nitric acid to obtain a reaction solution; then feeding the reaction solution into a first oxidation kettle, a second oxidation kettle and a thermal insulation kettle which are connected in series sequentially to complete oxidation reaction; after cooling by a cooler, obtaining an oxidation solution, and performing concentration dehydration, crystallization for oxalic acid removal and dechlorination to obtain teh glyoxylic acid finished product, wherein the molar ratio of glyoxal, nitric acid, the cocatalyst and the initiator is 1:0.3-0.4:0.2-0.3:0.01-00.2. The process is safer and more efficient, can reduce the production cost and improve stability of product quality, and is an industrial glyoxylic acid production process which is easy to operatecontinuously.
Owner:BROTHER ENTERPRISES HLDG CO LTD
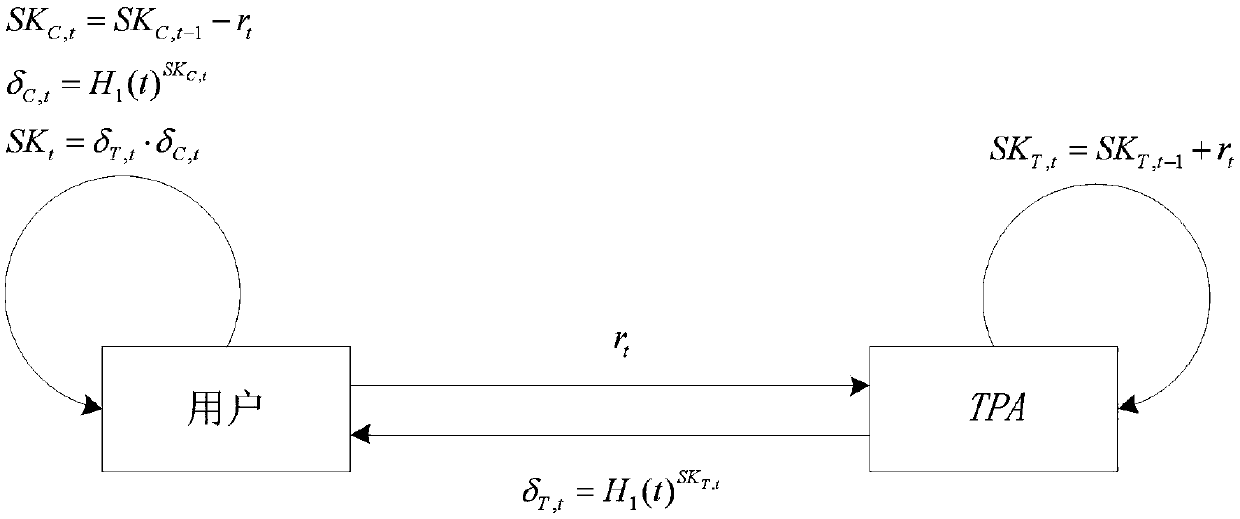
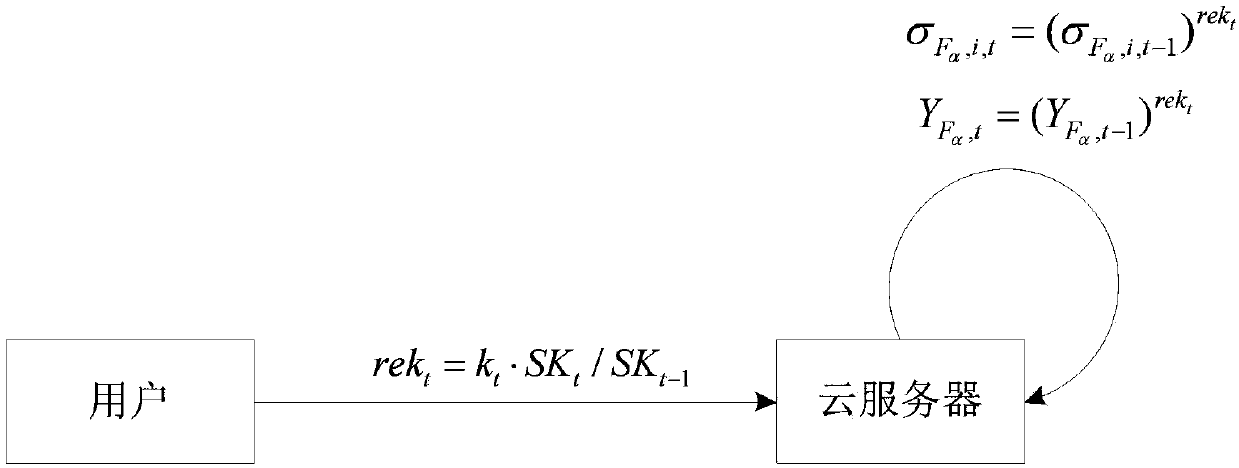
A security cloud audit method and system with updatable verification label
ActiveCN109040058AImprove securityOvercoming security issues caused by unfixedKey distribution for secure communicationUser identity/authority verificationSAFERCloud server
The invention discloses a security cloud audit method and a security cloud audit system with updatable verification label, comprising the following steps: 1, initializing; 2, updating the key; 3, verifying the update of the tag; 4, verifying the generation of the tag; 5, generating evidence; 6: auditing. The invention can effectively protect the audit key of the user and the file saved by the useron the cloud server, thereby making the audit key and the file of the user more secure.
Owner:ANHUI UNIVERSITY
Automated encryption degradation detection, reporting and remediation
Communication security is an ongoing problem. Over time, various protocols have been used and then replaced due to insufficient protection. For example, some client / server web communication used to rely on Secure Socket Layers (SSL) to protect communication, but was replaced with a more secure Transport Layer Security (TLS) protocol. TLS itself has undergone several revisions, and TLS 1.0 is now considered not secure. TLS and other protocols provide backwards compatibility, so while a higher security level is desired, communication may fallback to an undesirable level, e.g., TLS 1.0, if required by either communication endpoint. An intermediary to communication with an organization may capture data to facilitate analyzing it to determine what caused a fallback, and to decide if and how to remediate it. Remediation may vary depending on, for example, whether the cause was from within the organization, or external, such as from a client.
Owner:SALESFORCE COM INC
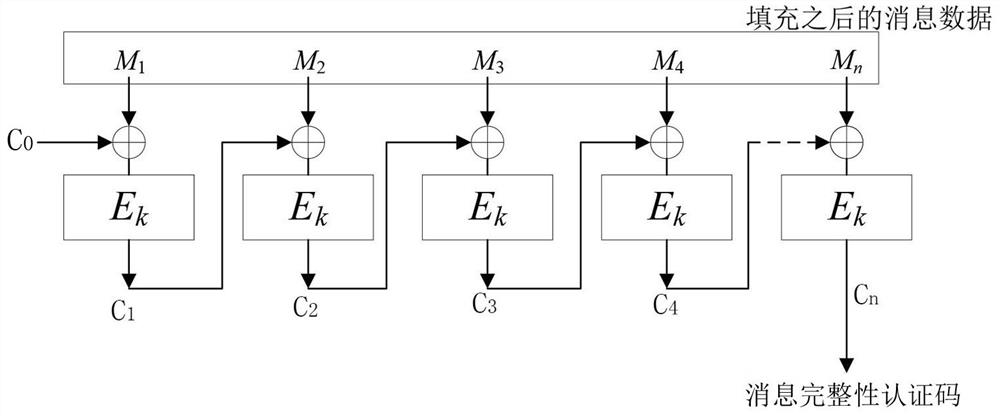
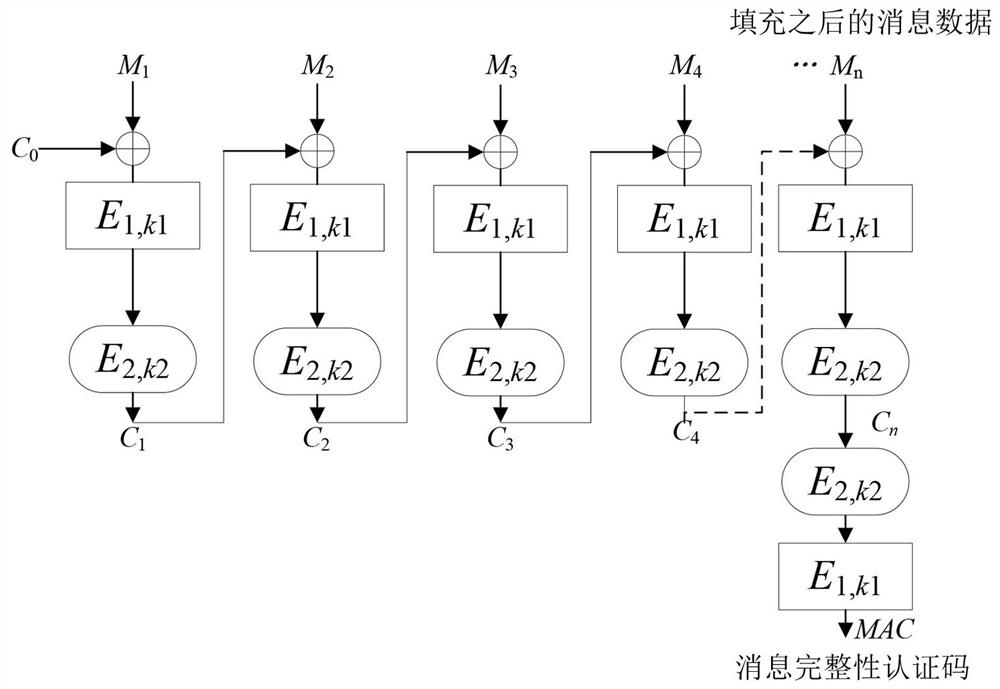
Generation method of a new keyed message integrity authentication code
ActiveCN108599922BIntegrity securityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesKey (cryptography)Data integrity
The invention belongs to the technical field of cryptography and in particular relates to a method for generating a novel key-containing message integrity authentication code, which comprises the following steps: firstly, pre-processing to separately obtain block cipher algorithms E1, k1, E2 and k2; filling a message to be processed, selecting a random number C0, and dividing the filled message into formula according to single processing length by the block cipher algorithms; using the formula to process formula to obtain intermediate data Cn, wherein i is not greater than n and not smaller than 1; finally, using the formula to process the intermediate data Cn so as to obtain a message authentication code MAC. The method for generating a novel key-containing message integrity authentication code in the invention can be used for data integrity verification, and the traditional CBC-MAC mode and various variants thereof are improved from calling of only one block cipher algorithm to calling of two block cipher algorithms simultaneously, so that the message integrity authentication code is more secure.
Owner:成都盛拓源科技有限公司
A Linear Segmented Symmetric Encryption and Decoding Method
The present invention provides a linear segmented symmetric encryption, encoding and decoding method. In the method, any binary sequence is segmented in units of l bits, and the password (or binary information corresponding to the password) set by the user is used for the first segment to be implanted into the right Coefficients (symmetric keys) are used as parameters for weighted probabilistic model encoding. Starting from the second segment, the uncoded binary end s (s>0) bits of the previous segment are implanted into the weight coefficients and the second segment is encoded with a weighted probability model, and so on. It has been proved that when l is long enough, any bit error in the weight coefficient or any bit error in the encoded ciphertext will cause the binary sequence to fail to be successfully decoded. Therefore, if the correct s bits at the end of the first paragraph cannot be obtained, the second paragraph cannot be decoded correctly. Compared with the prior art, the present invention uses segmented encryption, and each segment is encoded with a different key, which is difficult to crack. Larger, more secure, and segmented key-encrypted data that can be streamed.
Owner:湖南瑞利德信息科技有限公司
A pharmaceutical composition containing 18 kinds of amino acids
InactiveCN102626409BReduce residual oxygenAvoid huge investment in transformationOrganic active ingredientsPeptide/protein ingredientsSAFERAntioxidant
Owner:郑飞雄
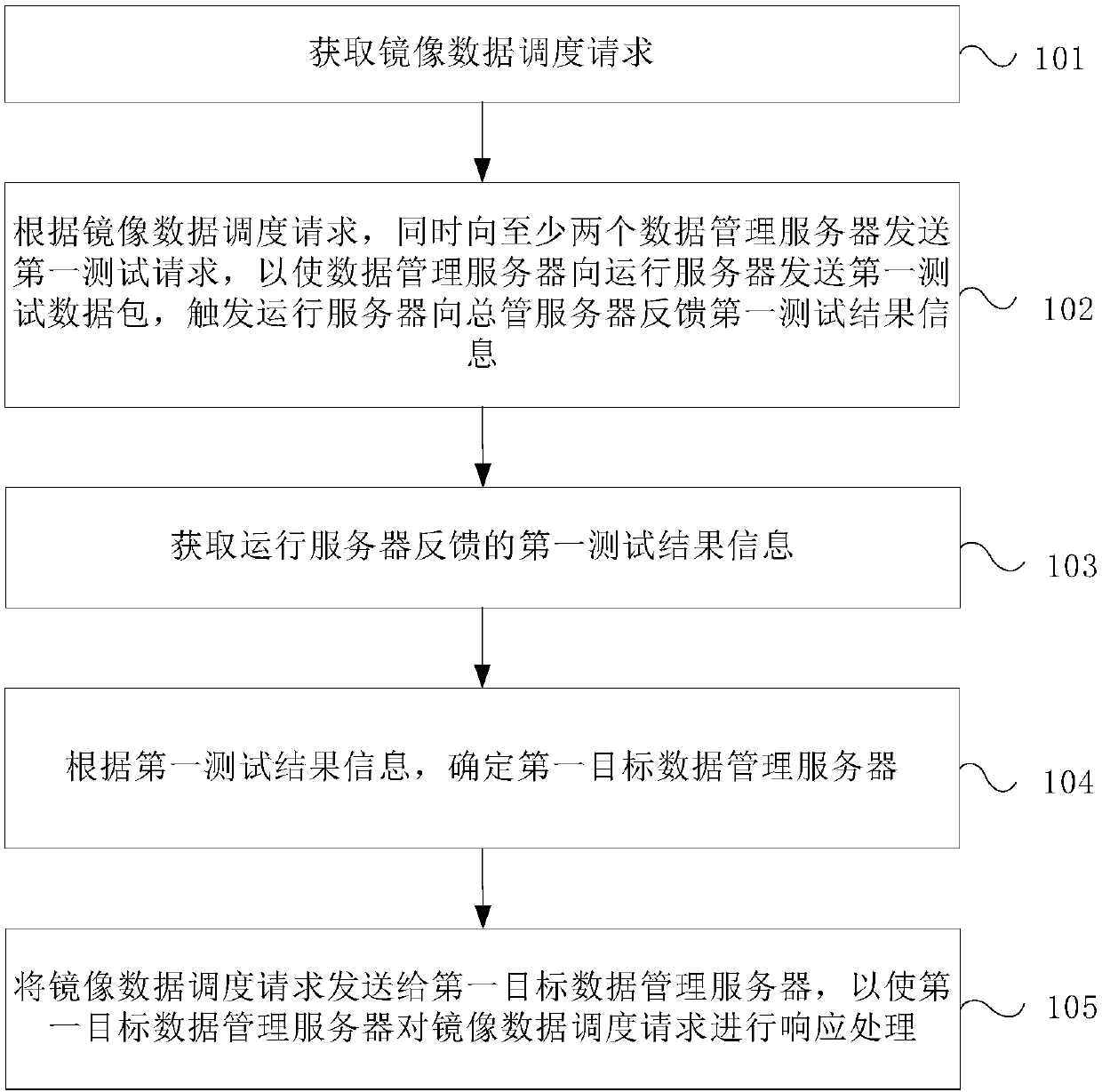
Container image data management method, device and system
The invention provides a container image data management method, device and system. The method comprises the steps of acquiring an image data scheduling request; sending a first test request to at least two data management servers simultaneously according to the image data scheduling request; acquiring first test result information fed back by a running server; according to the first test result information, determining a first target data management server; and sending the image data scheduling request to the first target data management server, so as to enable the first target data management server to respond to the image data scheduling request. According to the method, at least two data management servers are adopted for storing image data for backup, so that the image data is safer.In the prior art, only one data management server is adopted, once image data fails, containers corresponding to the image data cannot be created. The invention solves the problem in the prior art.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com