Patents
Literature
172 results about "Secure Shell" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
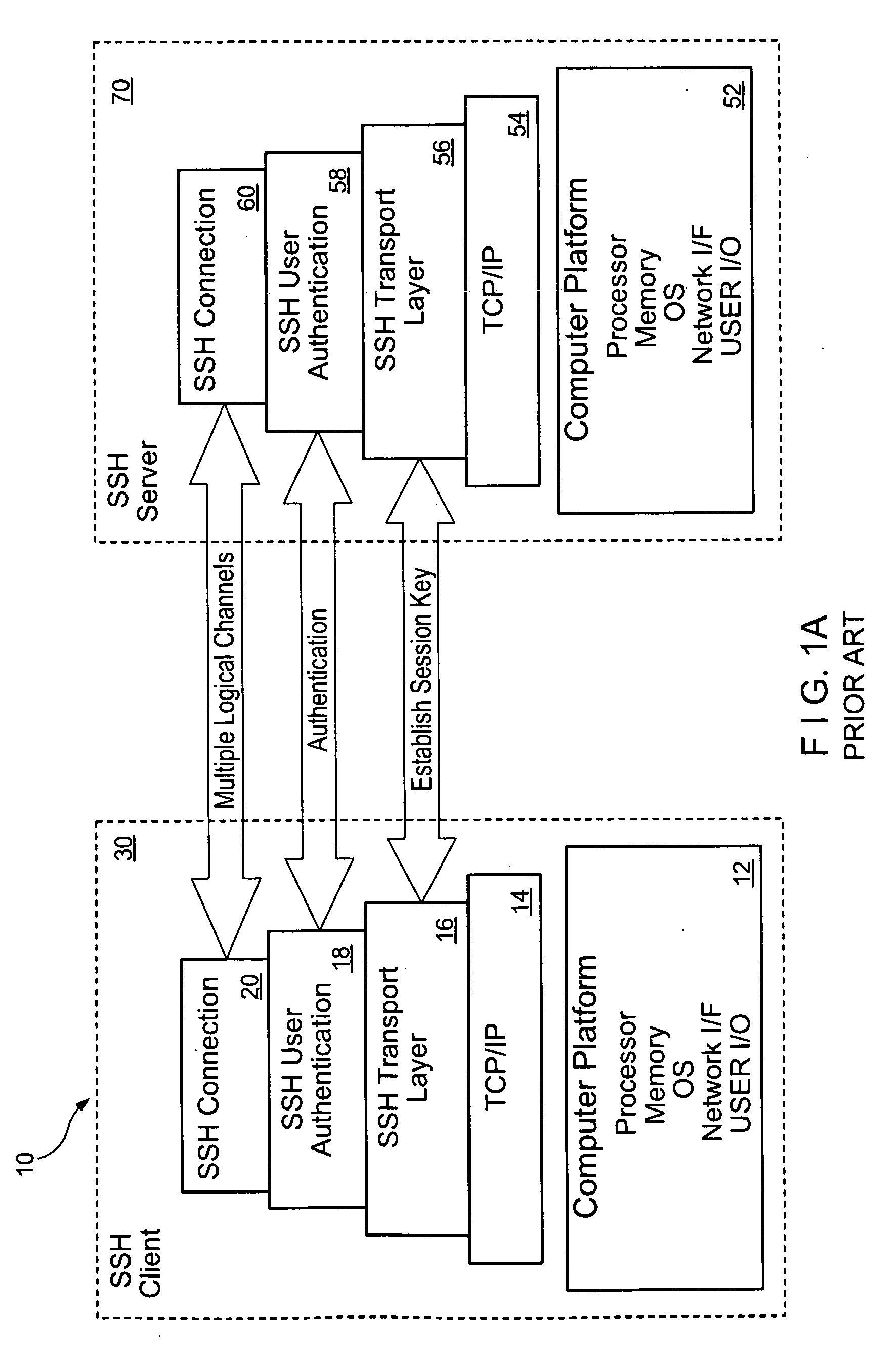
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Typical applications include remote command-line, login, and remote command execution, but any network service can be secured with SSH.
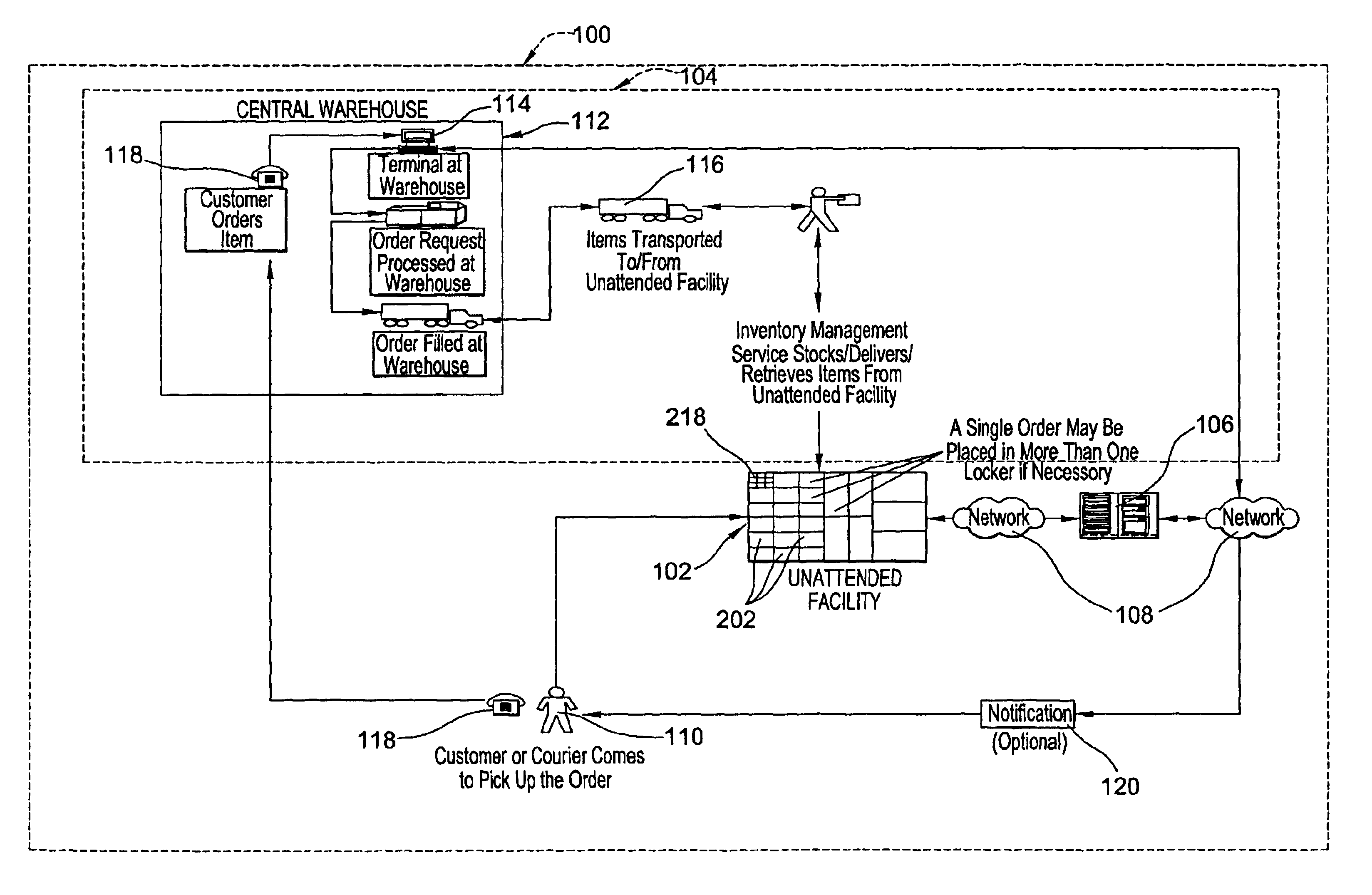
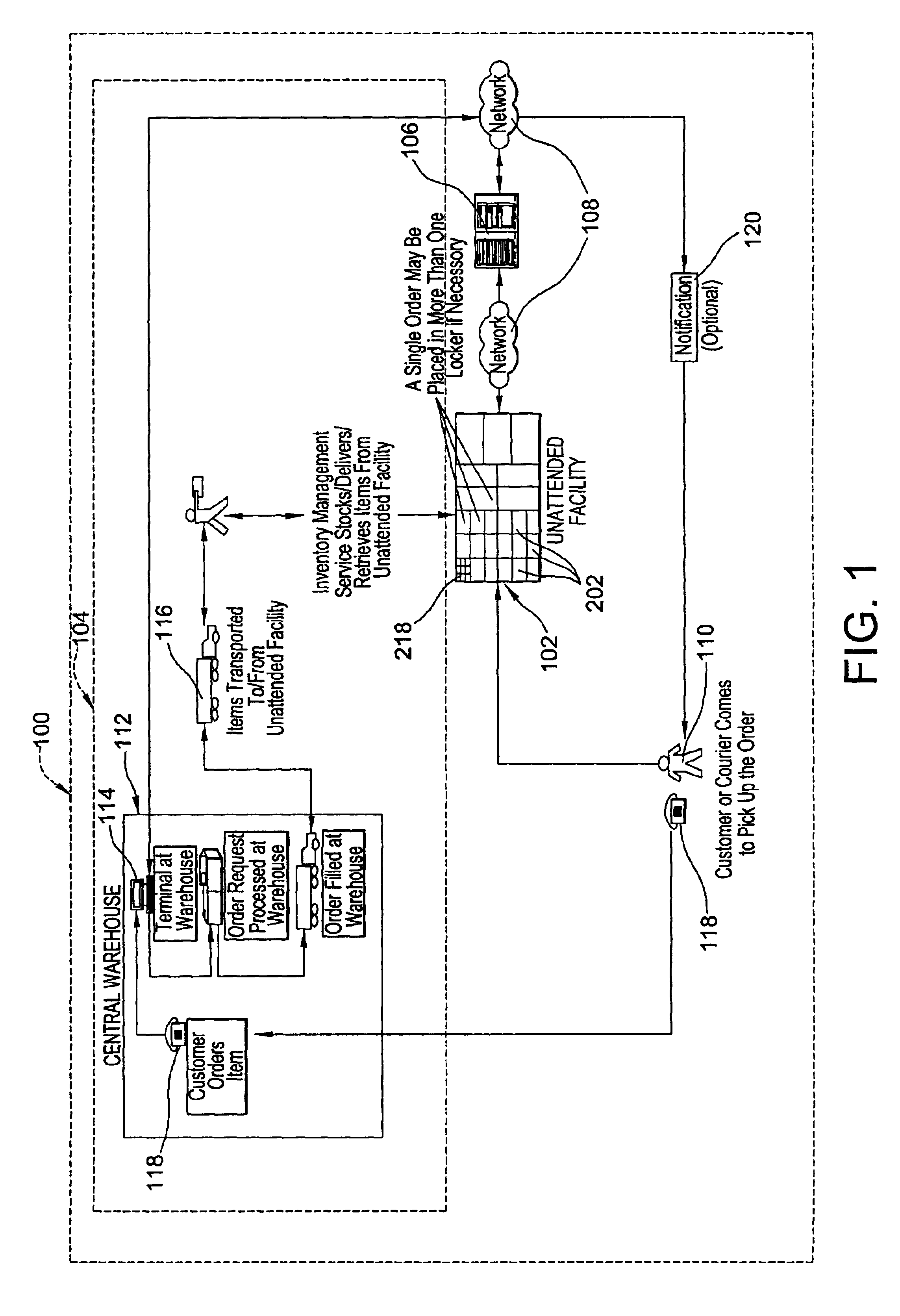
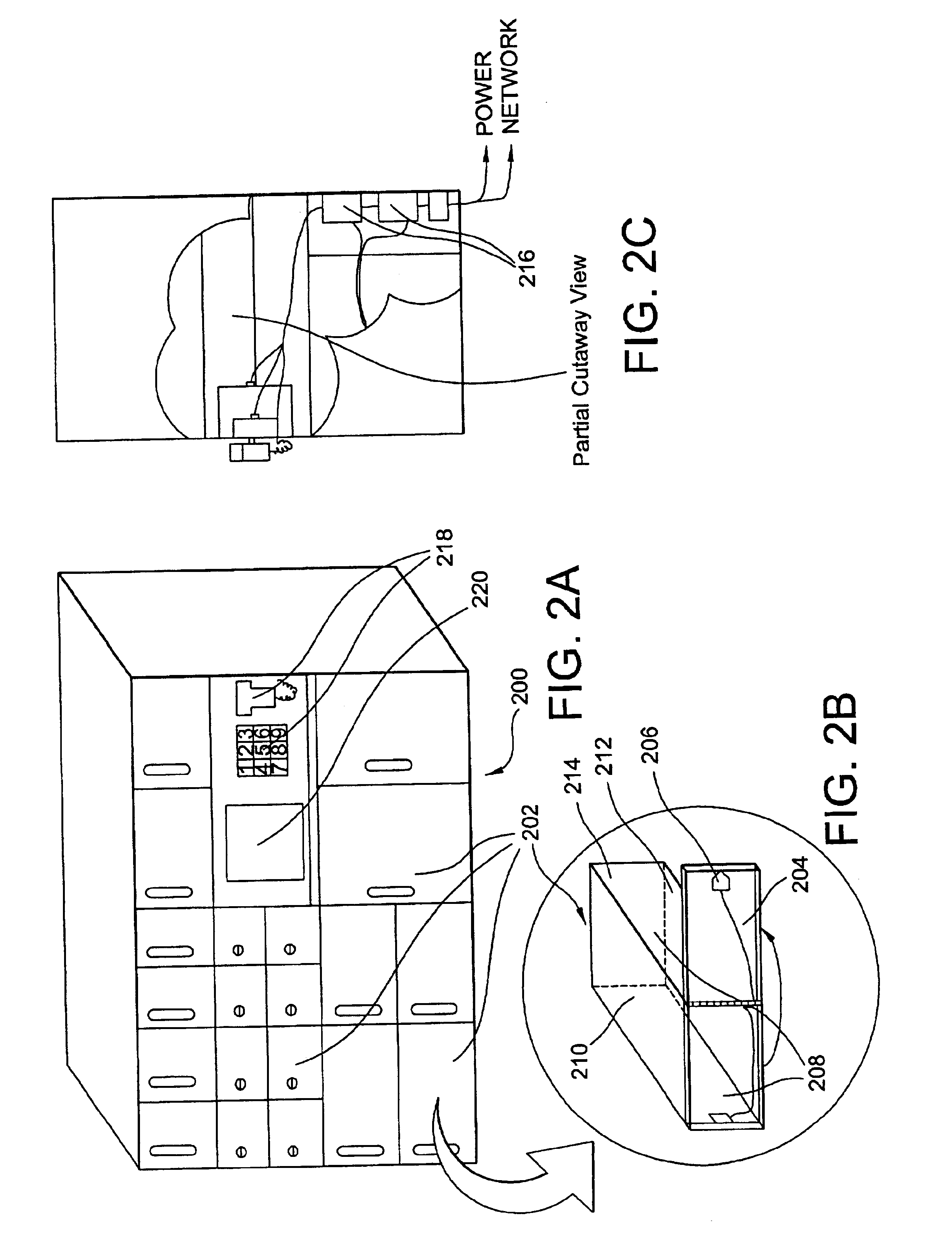
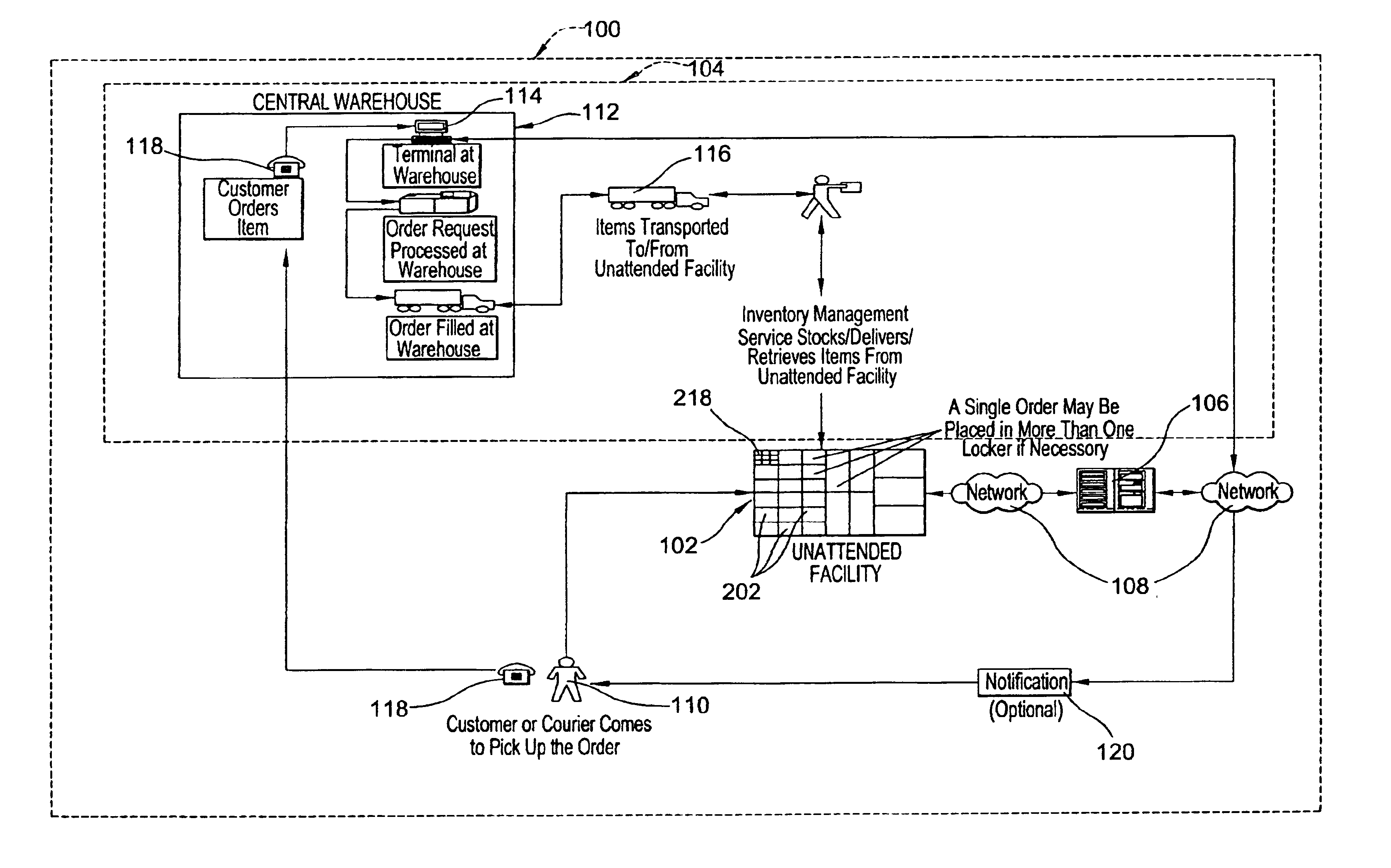
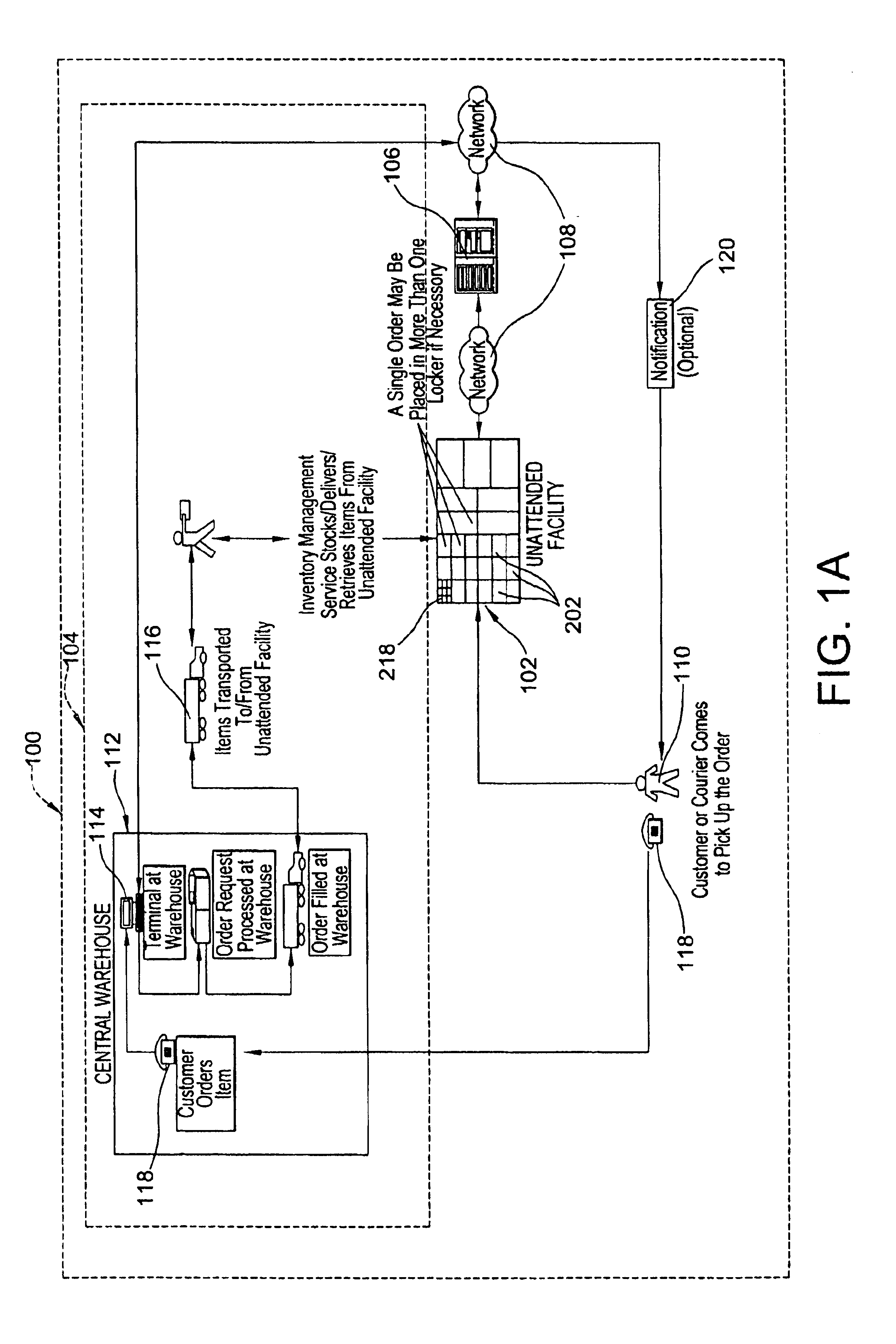
Systems and methods of inventory management utilizing unattended facilities
InactiveUS6866195B2Speed up the processLow costApparatus for meter-controlled dispensingVisual presentationLogistics managementSecure Shell
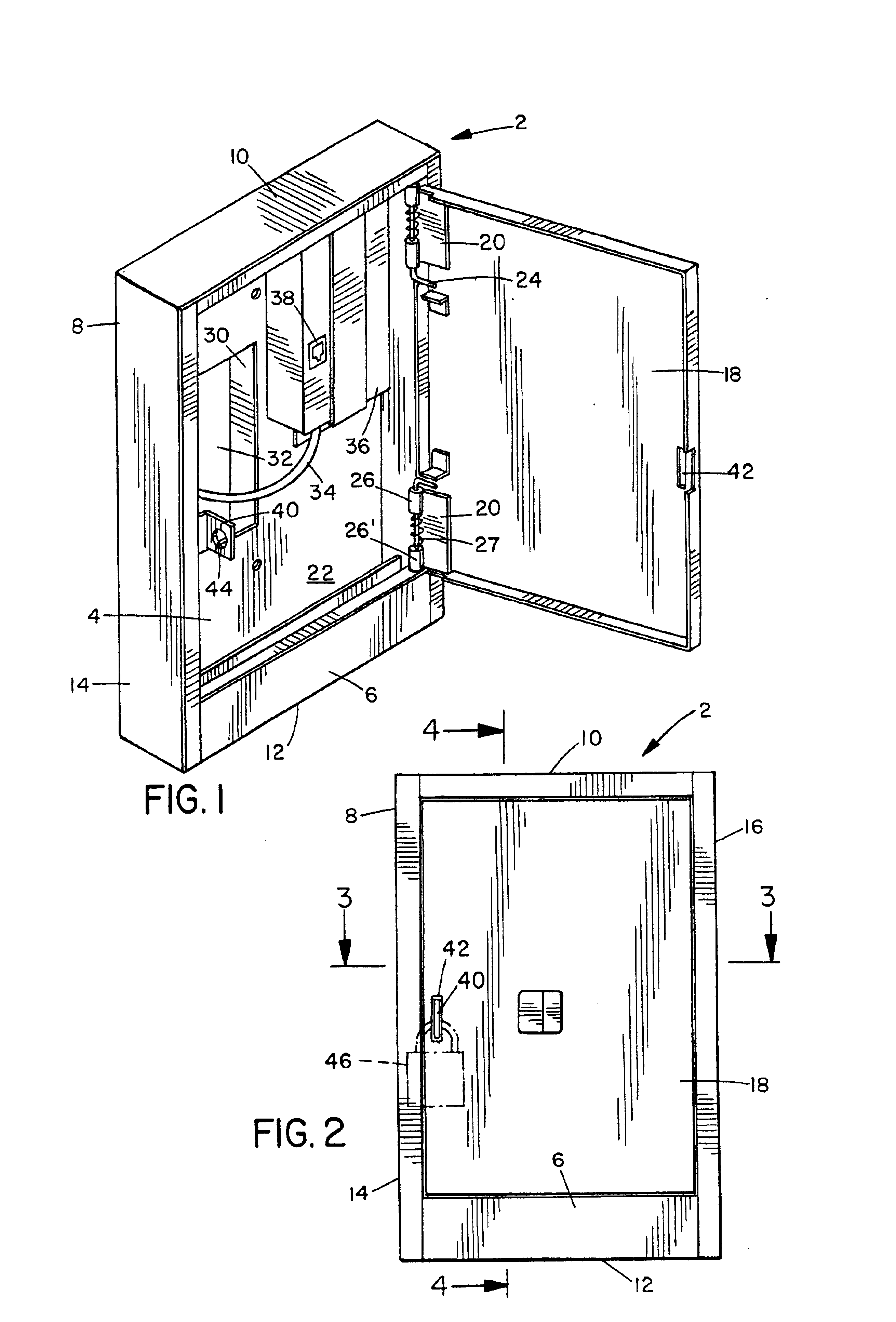
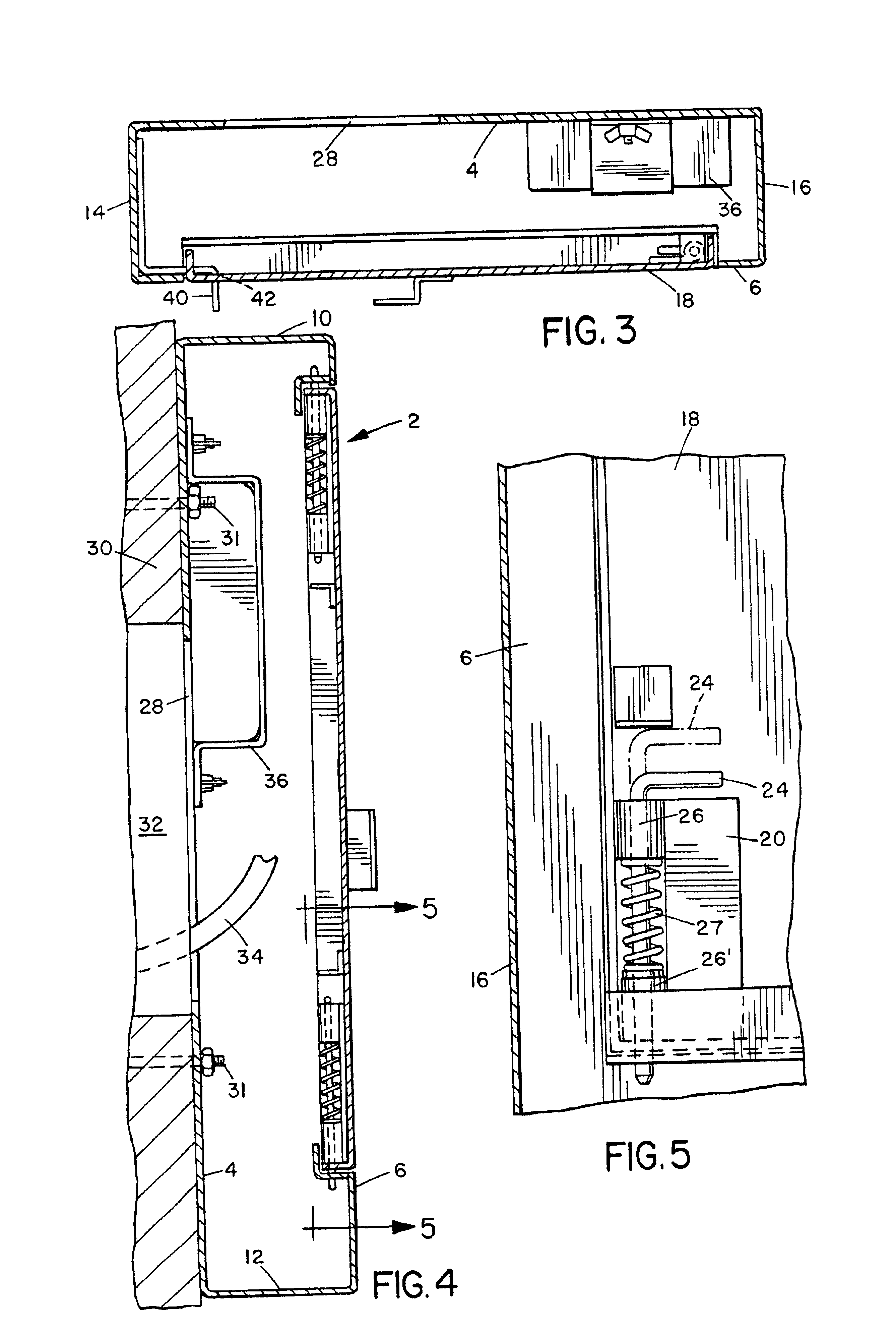
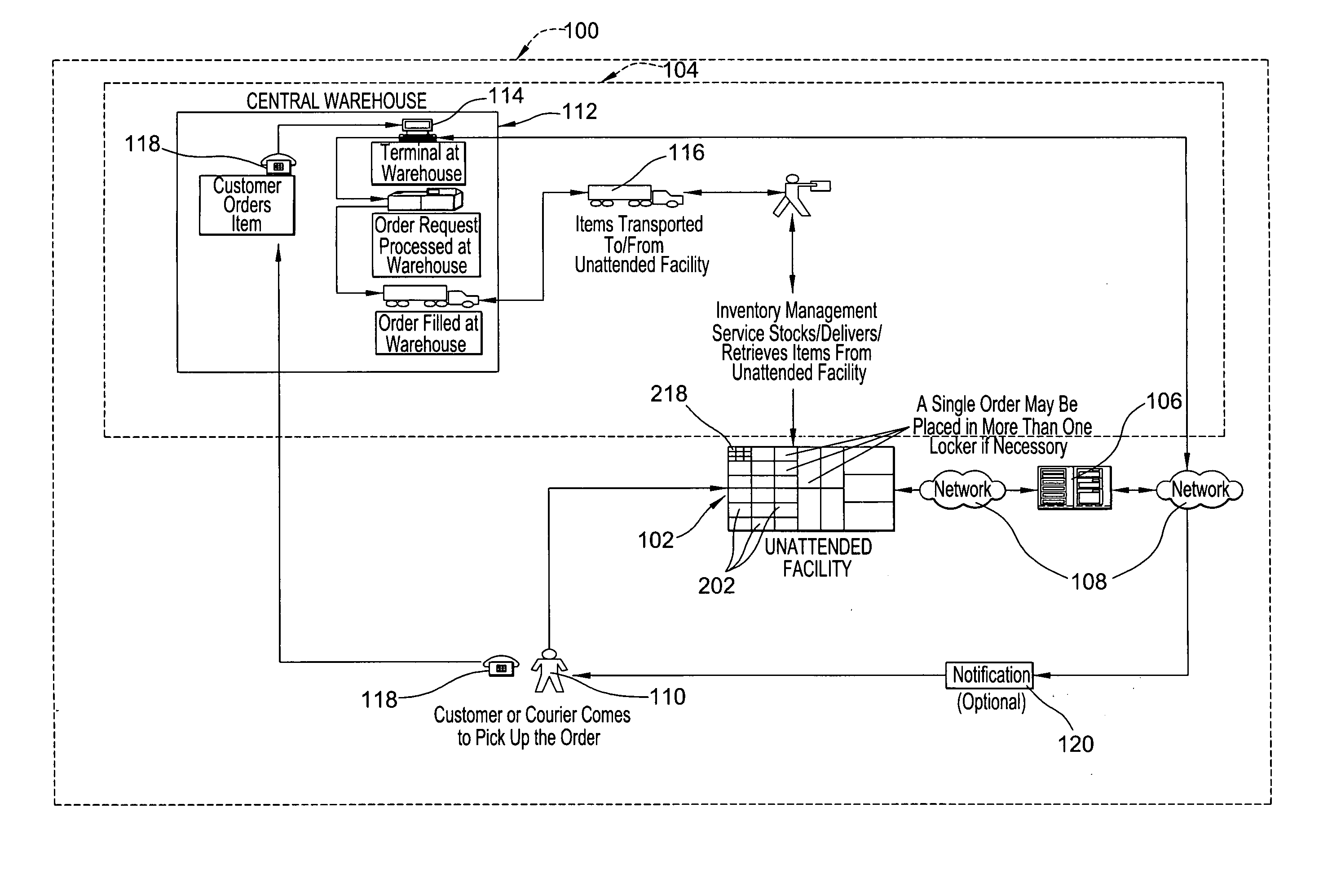
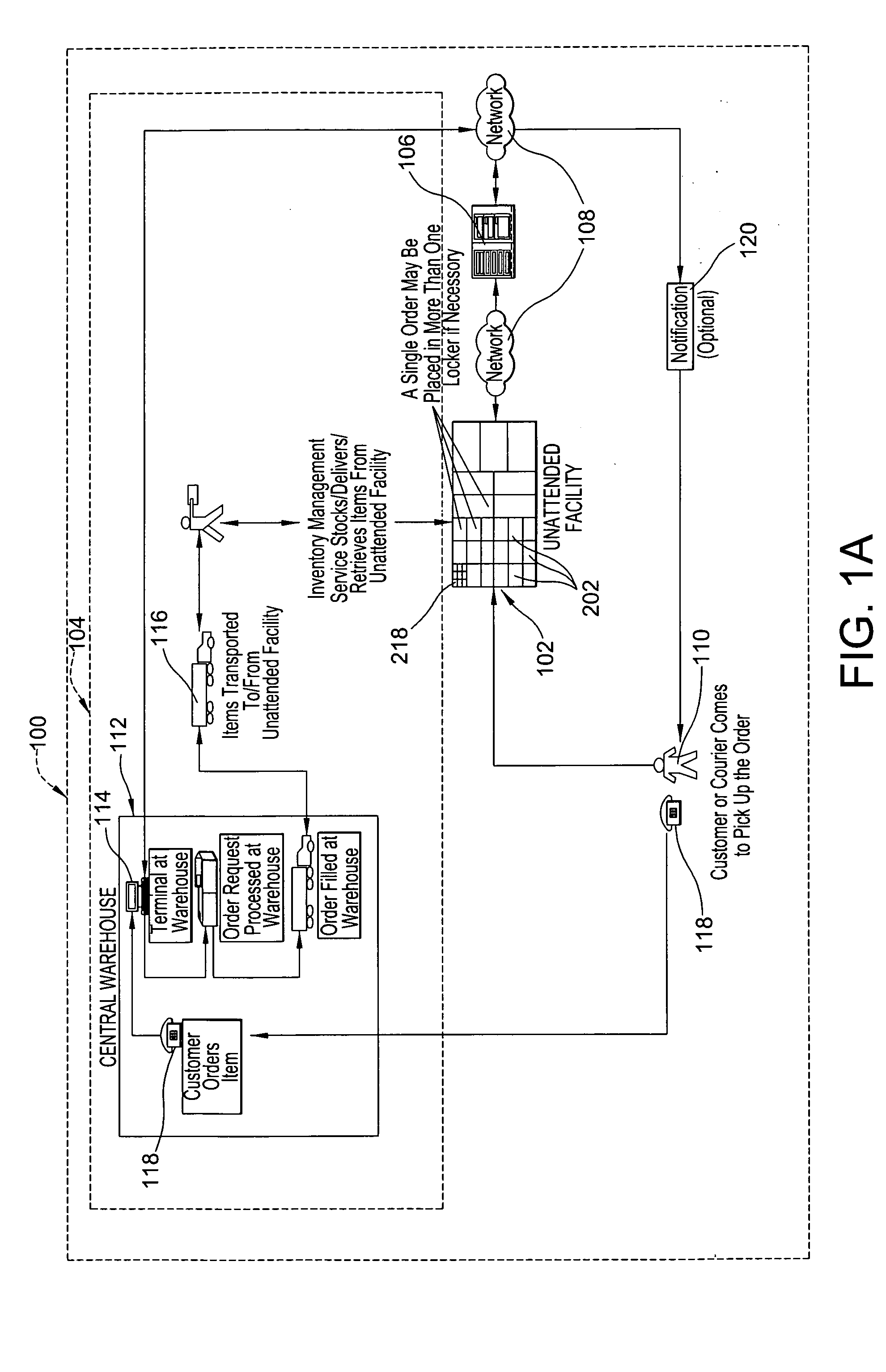
An inventory management system utilizes unattended facilities remote from a central warehouse for service parts logistics. Items are placed in inventory in secure enclosures at the unattended facilities by the inventory management service. The unattended facilities may be located near one or more customers to reduce a service technician's travel time and customers' inventory costs. A service technician utilizes a passcode to retrieve needed items. The service technician may order items that are not kept in the inventory of the unattended facility in which case the items may be delivered to the unattended facility and the service technician may receive a notification related to all the items that comprise an order that the order is ready for pick up at an unattended facility. Unused, used or damaged parts may be returned by a technician to a remote secure enclosure where such returned parts may be retrieved and disposed of, repaired or placed back into inventory if not damaged or after repair, and the processing of such returned parts begins by information entered into a data entry device at the remote secure enclosure location. Return items that are not damaged may be included in the inventory of an unattended facility.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
Systems and methods of inventory management utilizing unattended facilities
InactiveUS6845909B2Reduce inventory costsQuickly and inexpensively relocatedVisual presentationBuying/selling/leasing transactionsLogistics managementSecure Shell
An inventory management system utilizes unattended facilities remote from a central warehouse for service parts logistics. Items are placed in inventory in secure enclosures at the unattended facilities by the inventory management service or are delivered directly to the unattended facility. The unattended facilities may be located near one or more customers to reduce a service technician's travel time and customers' inventory costs. A service technician utilizes a passcode to retrieve needed items. The service technician may order items that are not kept in the inventory of the unattended facility in which case the items may be delivered to the unattended facility and the service technician may receive a notification related to all the items that comprise an order that the order is ready for pick up at an unattended facility. Unused, used or damaged parts may be returned by a technician to a remote secure enclosure where such returned parts may be retrieved and disposed of, repaired or placed back into inventory if not damaged or after repair, and the processing of such returned parts begins by information entered into a data entry device at the remote secure enclosure location. Return items that are not damaged may be included in the inventory of an unattended facility.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
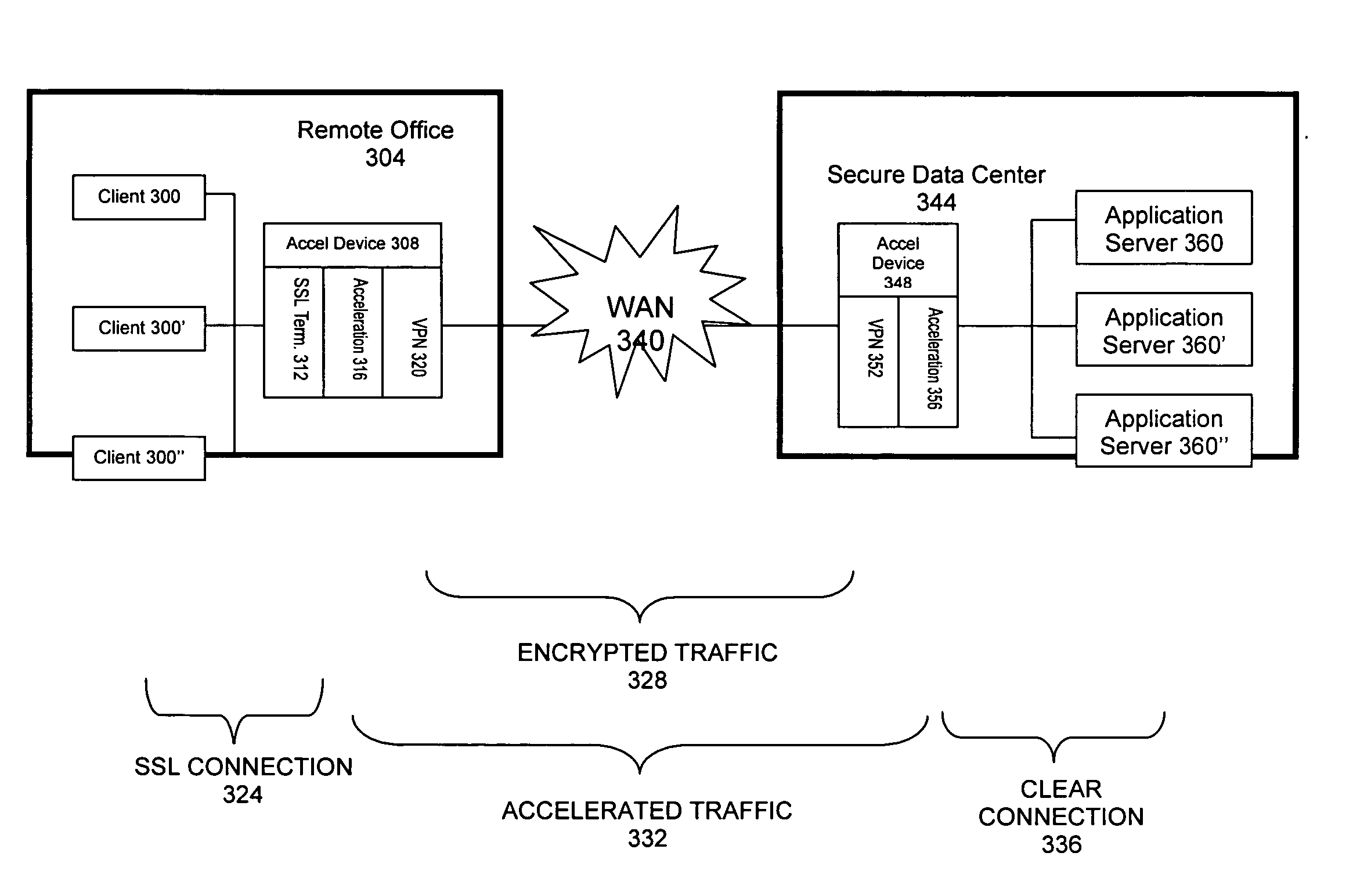
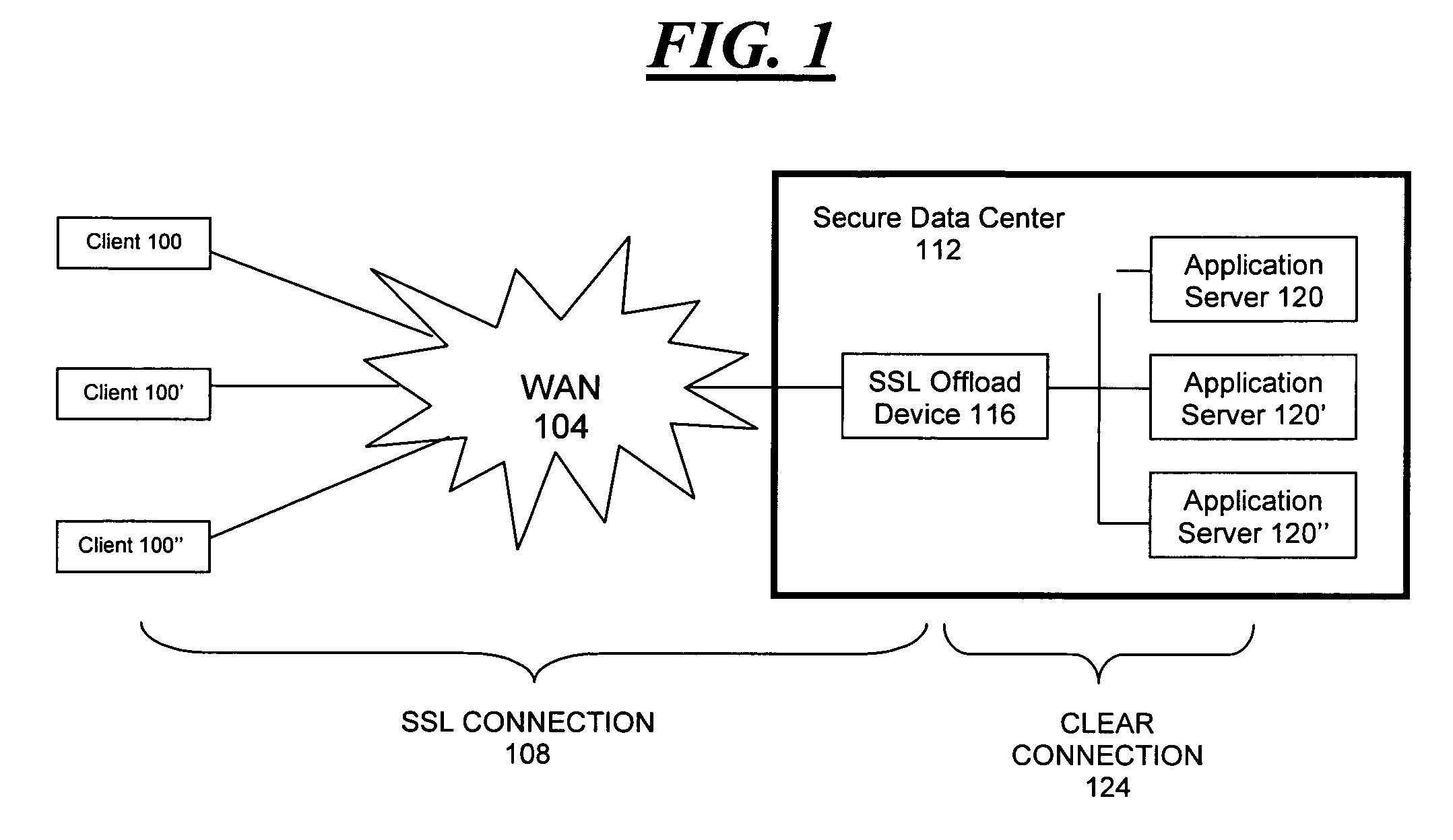
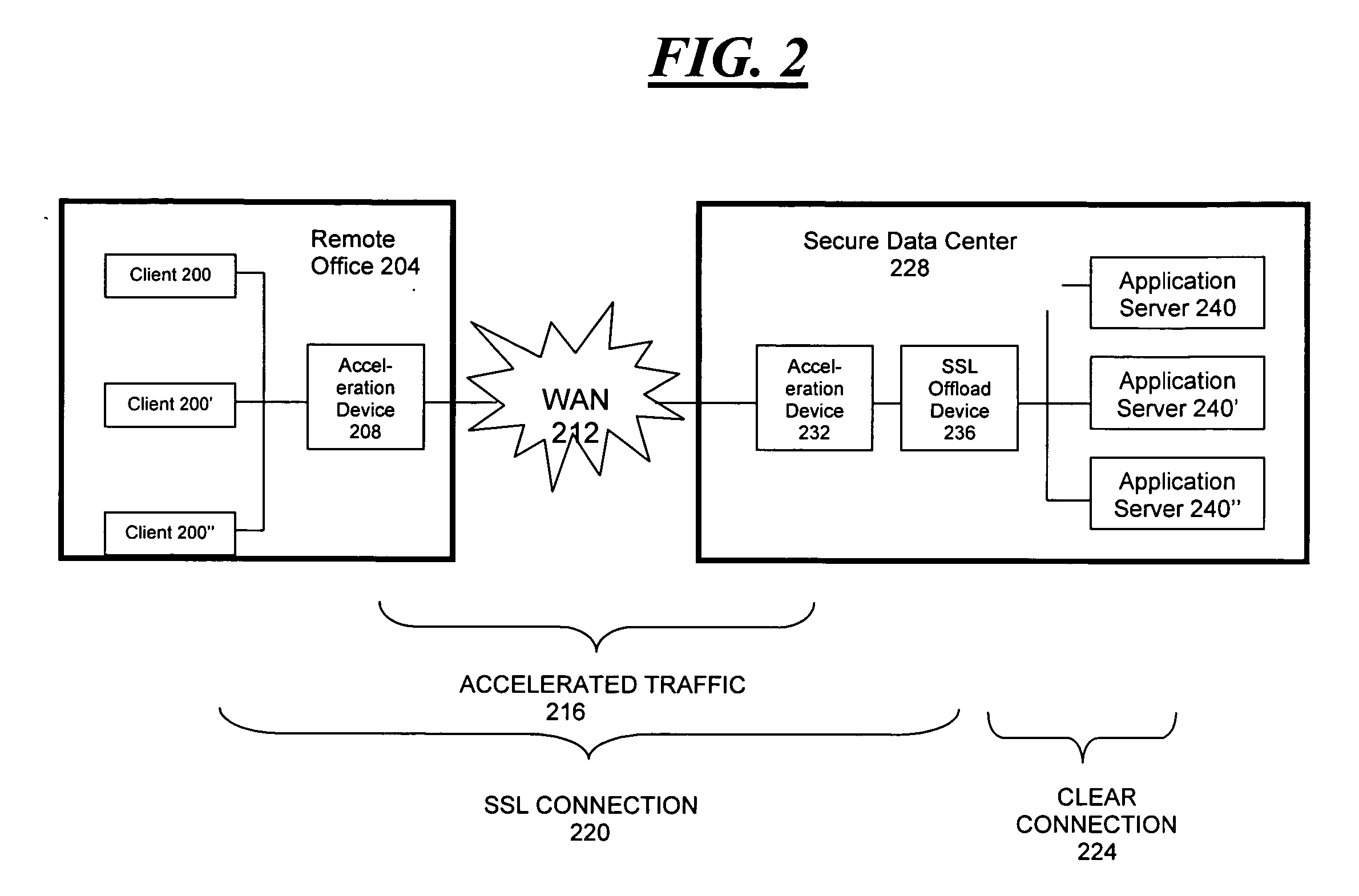
Distributed SSL processing
InactiveUS20070074282A1Improve scalabilityReduce certificate management complexityMultiple digital computer combinationsProgram controlApplication serverData center
Methods and systems for communicating data between a server and a remote client computer through a secure socket layer (“SSL”). In accordance with the present invention, server-side SSL functions are performed by a network device located remotely from a secure data center, while maintaining the secure use of centralized certificates and their associated private keys. The invention may be employed in conjunction with acceleration functions operating within coordinated network devices, facilitating acceleration of overall SSL traffic. The invention improves on the prior art by allowing the remotely located acceleration device to use the certificate and private key of the target application server, but without compromising the security of the server's private key.
Owner:CERTEON
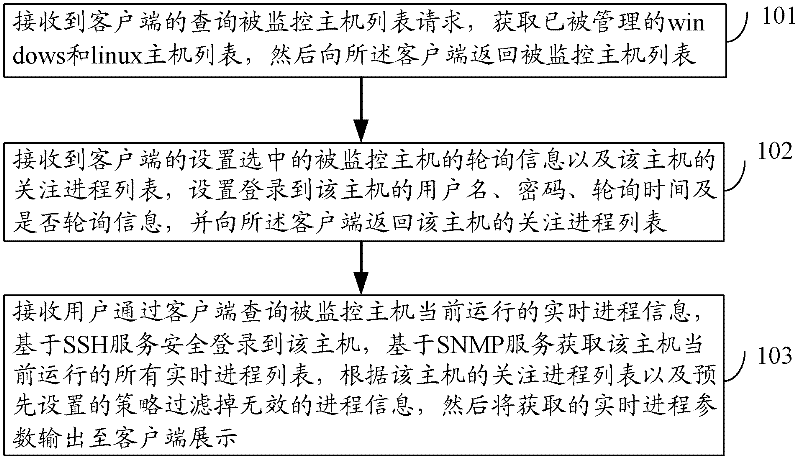
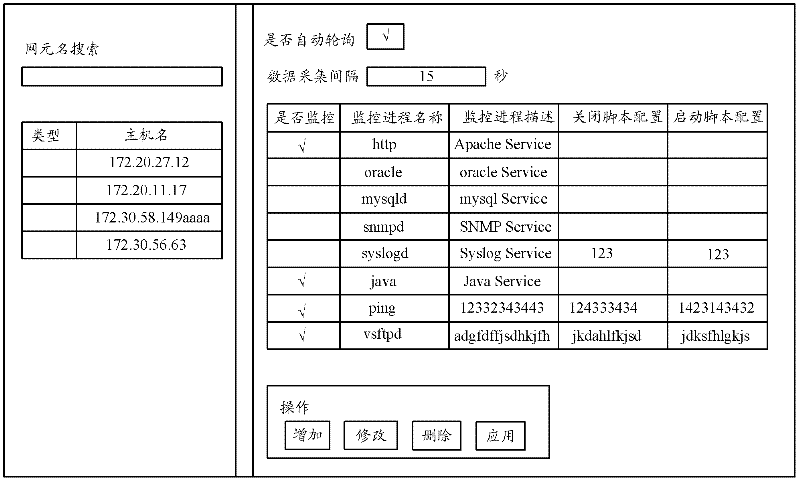
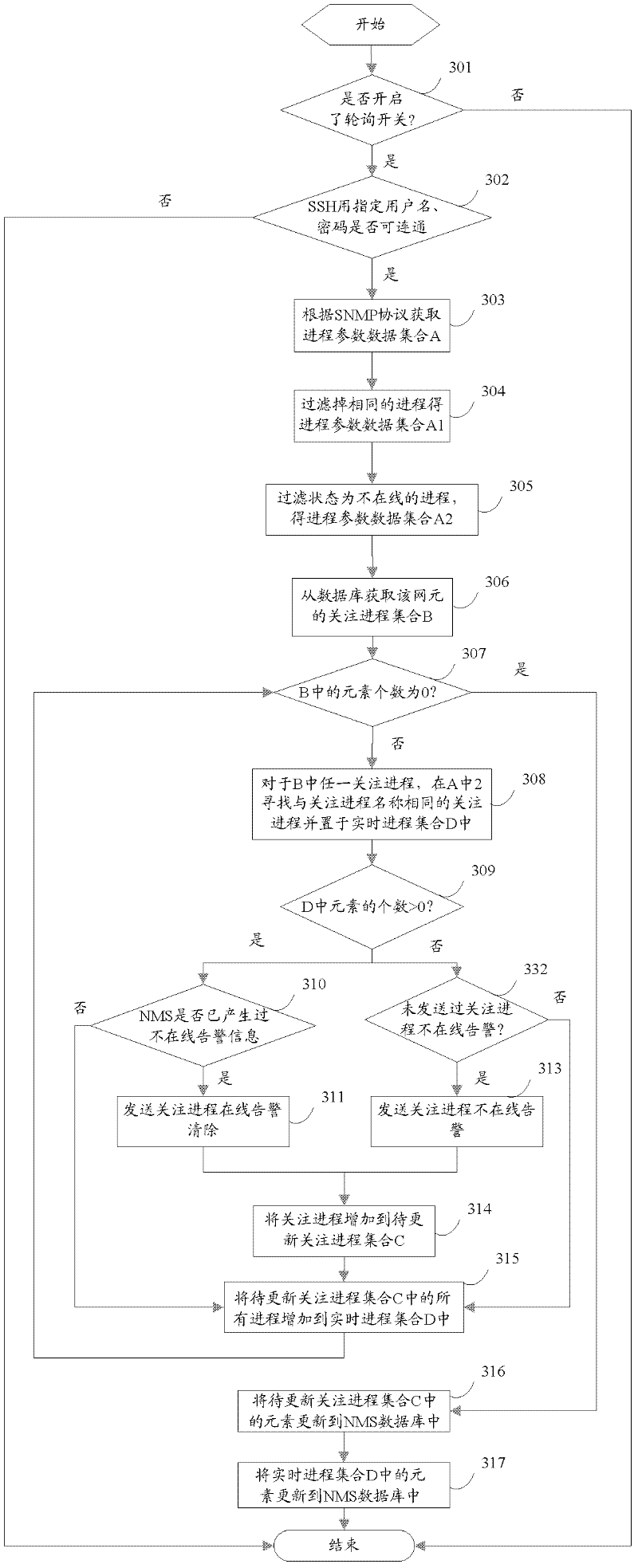
Process monitoring method and process monitoring system
InactiveCN102521099AReduce maintenance costsReduce development costsHardware monitoringTransmissionMonitoring systemSimple Network Management Protocol
The invention discloses a process monitoring method and a process monitoring system. The method comprises the following steps of: receiving a request for querying the list of monitored hosts from a client, acquiring the list of managed Windows and Linux hosts, and returning the list of the monitored hosts to the client; receiving information for polling a monitored host and the concerned process list of the host from the client, setting login information for logging in the host, and returning the concerned process list of the host to the client; and receiving information for querying the currently-running real-time process of the monitored host from the client, securely logging in the host based on SSH (Secure Shell) service, acquiring the list of all currently-running real-time processes of the host based on SNMP (Simple Network Management Protocol) service, filtering invalid process information according to the concerned process list of the host and a preset strategy, and outputting the acquired real-time process parameters to the client for exhibition. With the adoption of the process monitoring method and the process monitoring system, the cross-platform process monitoring can be achieved, and the cost for maintenance and development can be lowered.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
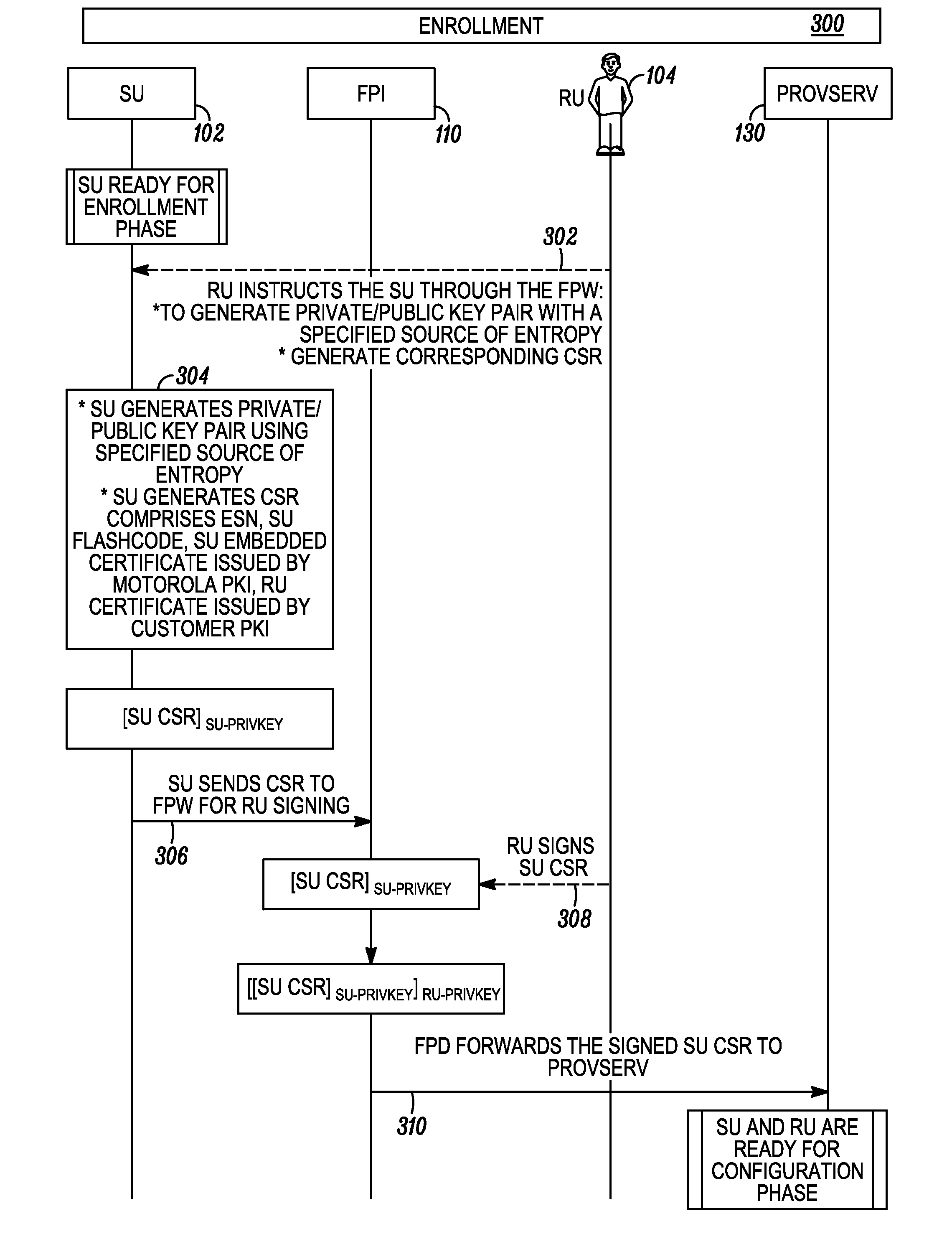
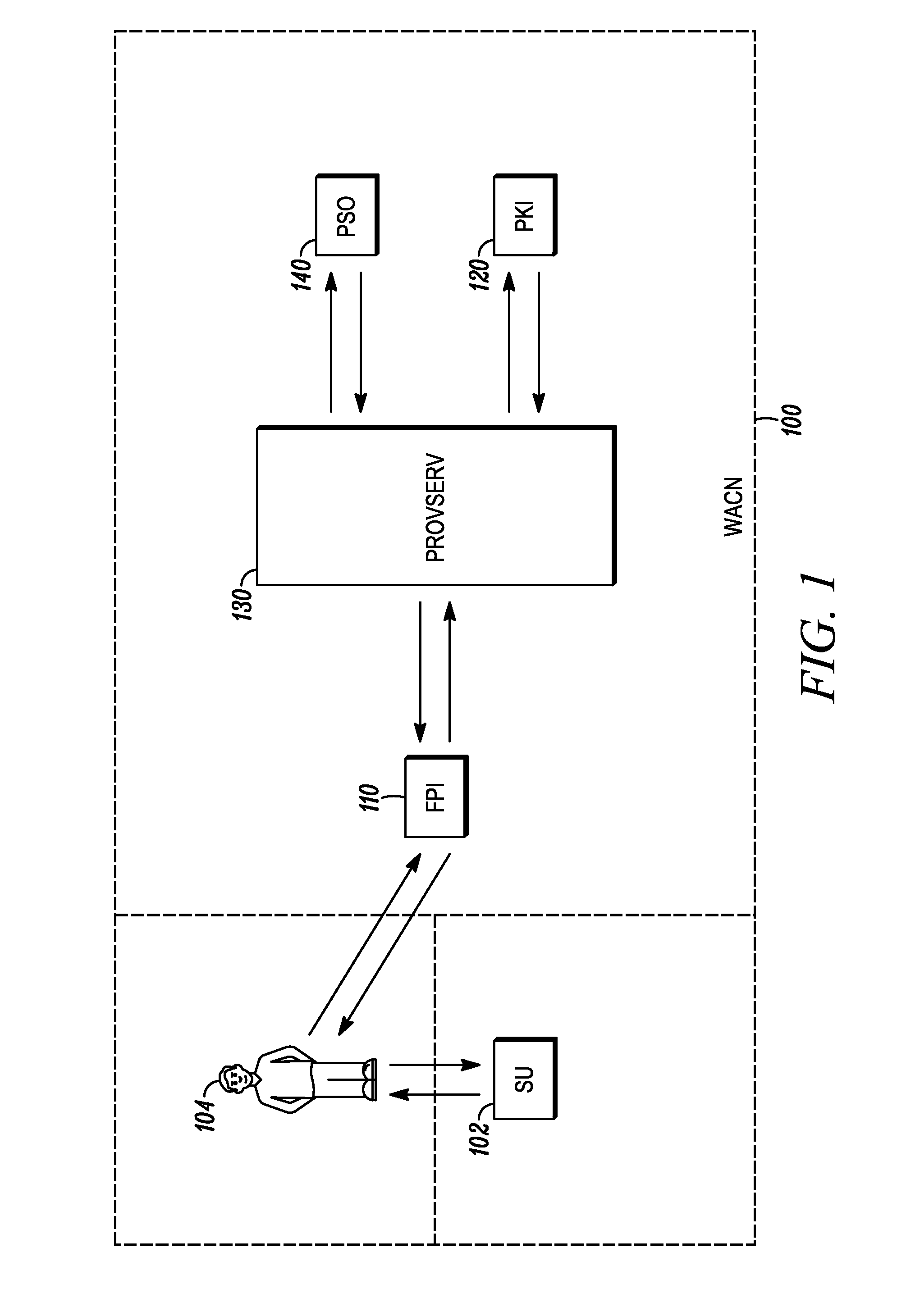
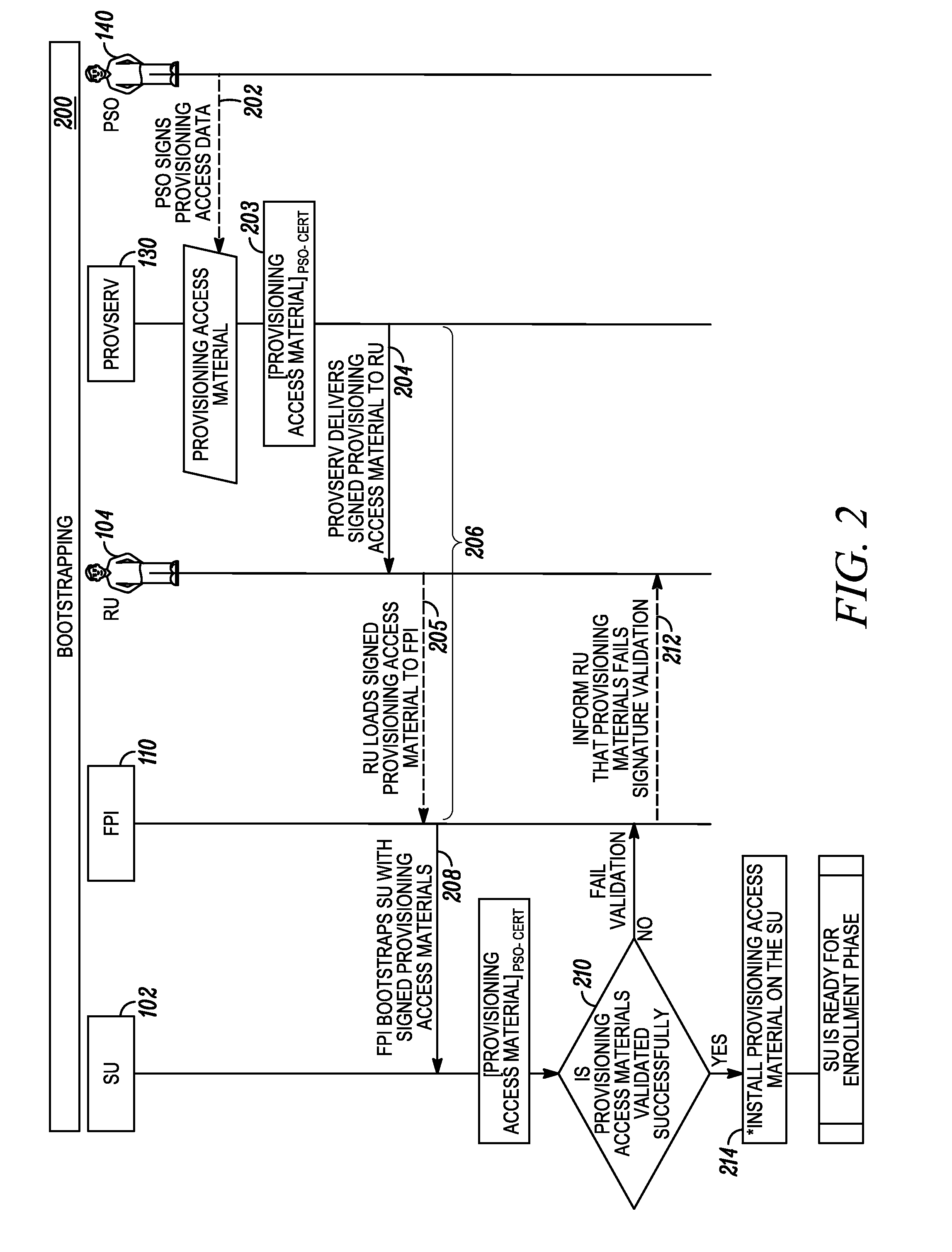
Method to enable secure self-provisioning of subscriber units in a communication system
InactiveUS20110161659A1Service provisioningDigital data authenticationCommunications systemCertificate signing request
A method to enable remote, secure, self-provisioning of a subscriber unit includes, a security provisioning server: receiving, from a subscriber unit, a certificate signing request having subscriber unit configuration trigger data; generating provisioning data for the subscriber unit using the subscriber unit configuration trigger data; and in response to the certificate signing request, providing to the subscriber unit the provisioning data and a subscriber unit certificate having authorization attributes associated with the provisioning data, to enable the self-provisioning of the subscriber unit.
Owner:MOTOROLA SOLUTIONS INC
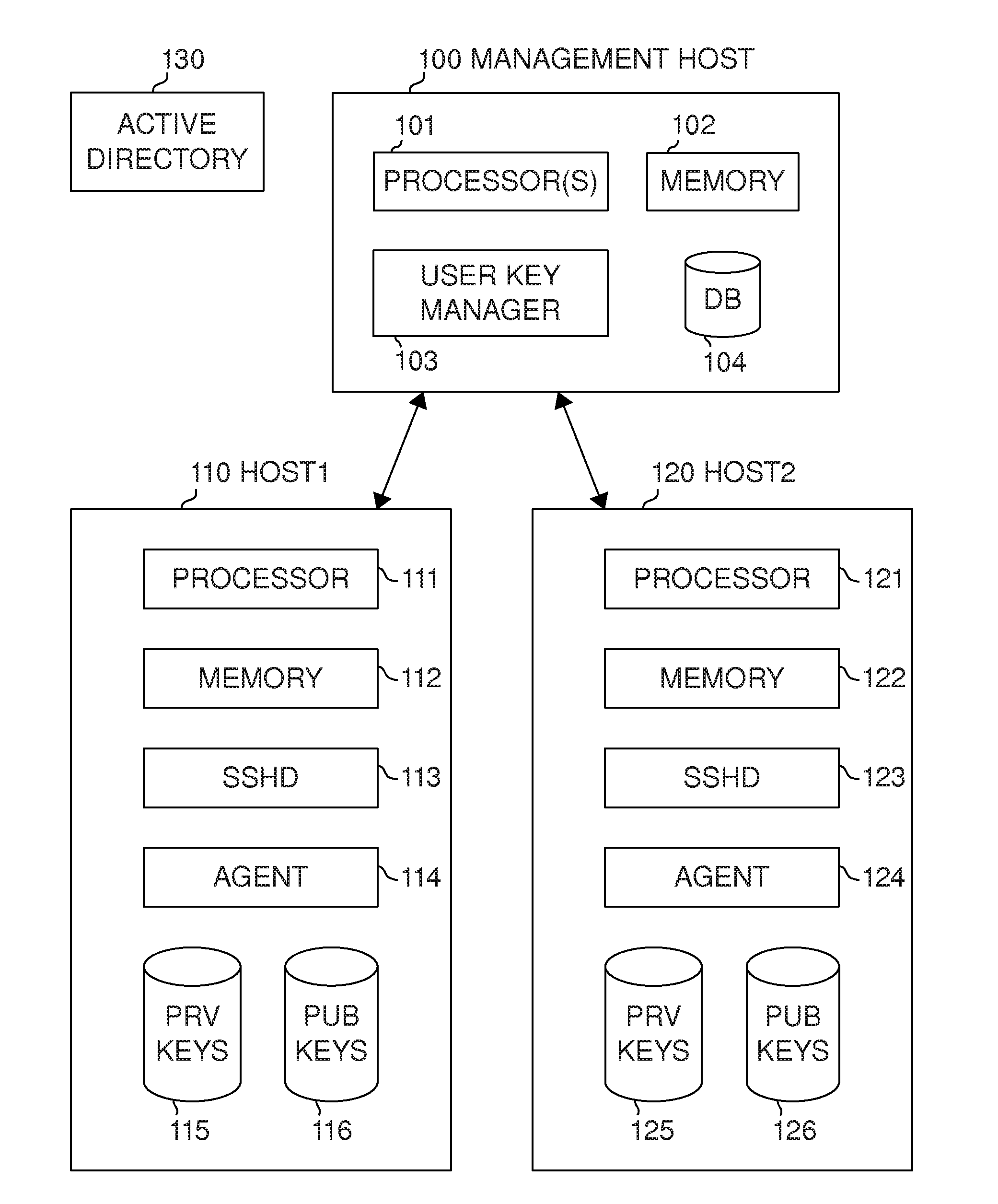
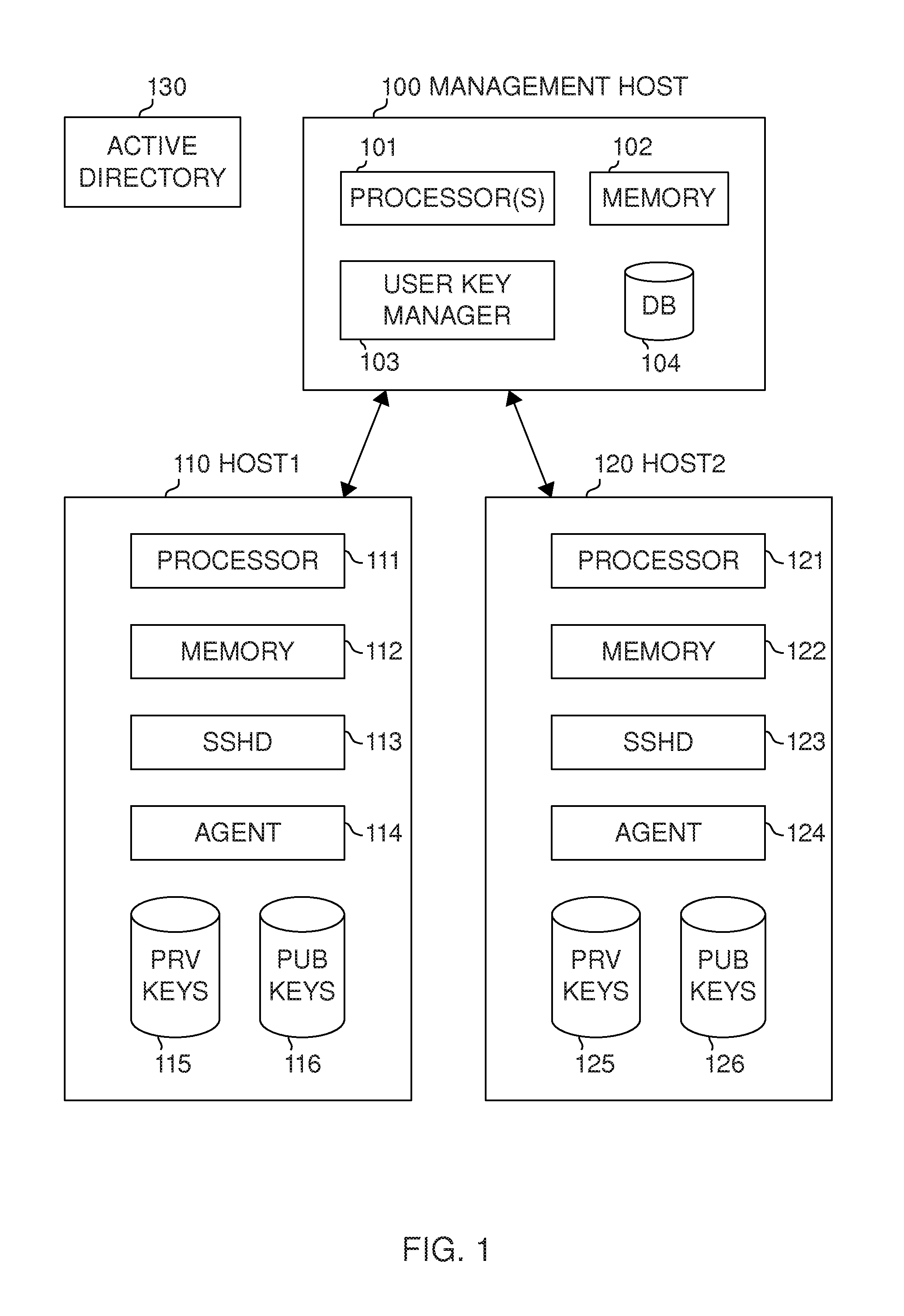
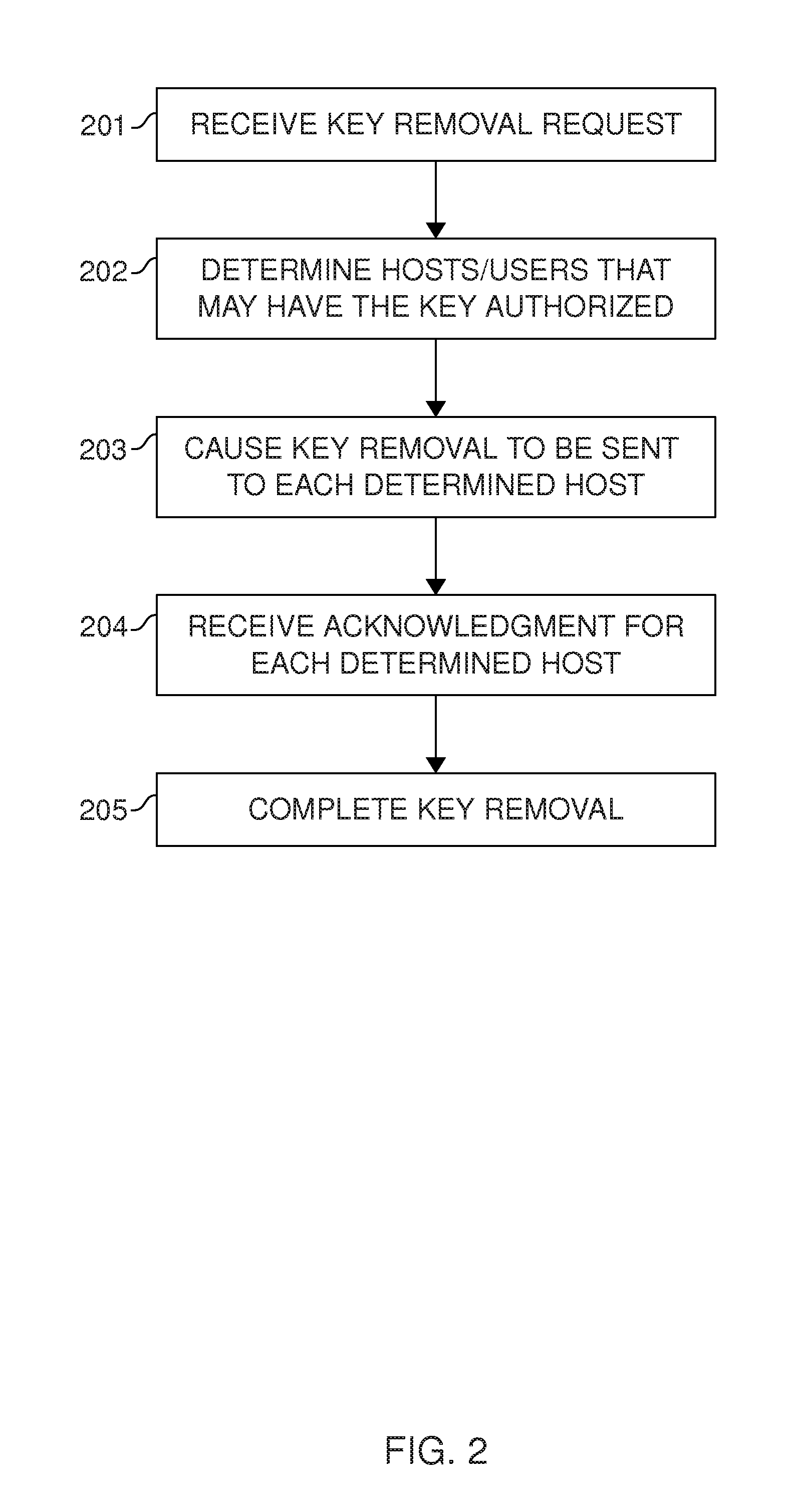
User key management for the Secure Shell (SSH)
ActiveUS20130117554A1Low costImprove securityKey distribution for secure communicationPublic key authenticationSecure Shell
Management of user keys for public key authentication using the SSH in large SSH deployments is automated by deploying a management system in the environment, discovering SSH identity keys and authorized keys, analyzing authorized connections between user accounts, and automatically managing the authorized connections and the key pairs used for authentication.
Owner:SSH COMMUNICATIONS SECURITY
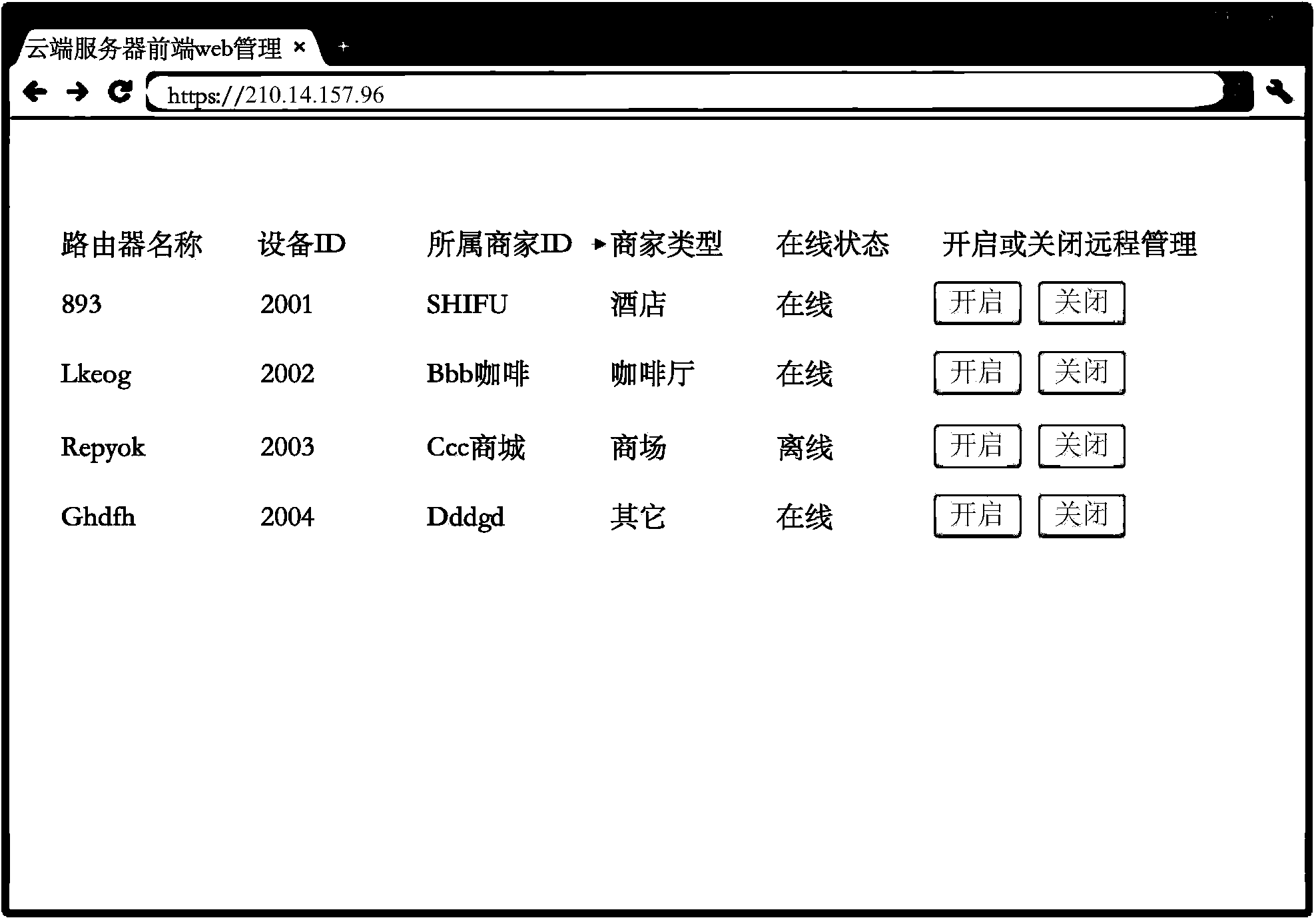
Method and system for remotely having access to administrative web pages of routers
ActiveCN104243210AReduce successEasy to operateData switching networksClient-sideProtocol for Carrying Authentication for Network Access
The invention discloses a method and system for remotely having access to administrative web pages of routers. The method comprises the steps that transmission control protocol (TCP) long connection is established between the routers and a cloud server and maintained; the cloud server determines monitoring port numbers corresponding to the routers, and the address of the cloud server and the monitoring port numbers are transmitted to the corresponding routers through TCP long connection; the routers turn on web ports, and a secure shell (SSH) reverse tunnel communicating the web ports, an SSH port of the cloud server and monitoring ports is established; a client-side browser has access to the administrative web pages of the routers through a web agent server of the cloud server and the SSH reverse tunnel. By means of the method and system, the software and hardware cost can be lowered, and the operating efficiency can be improved.
Owner:HUBEI CENTURY NETWORK TECHNOLOGY CO LTD
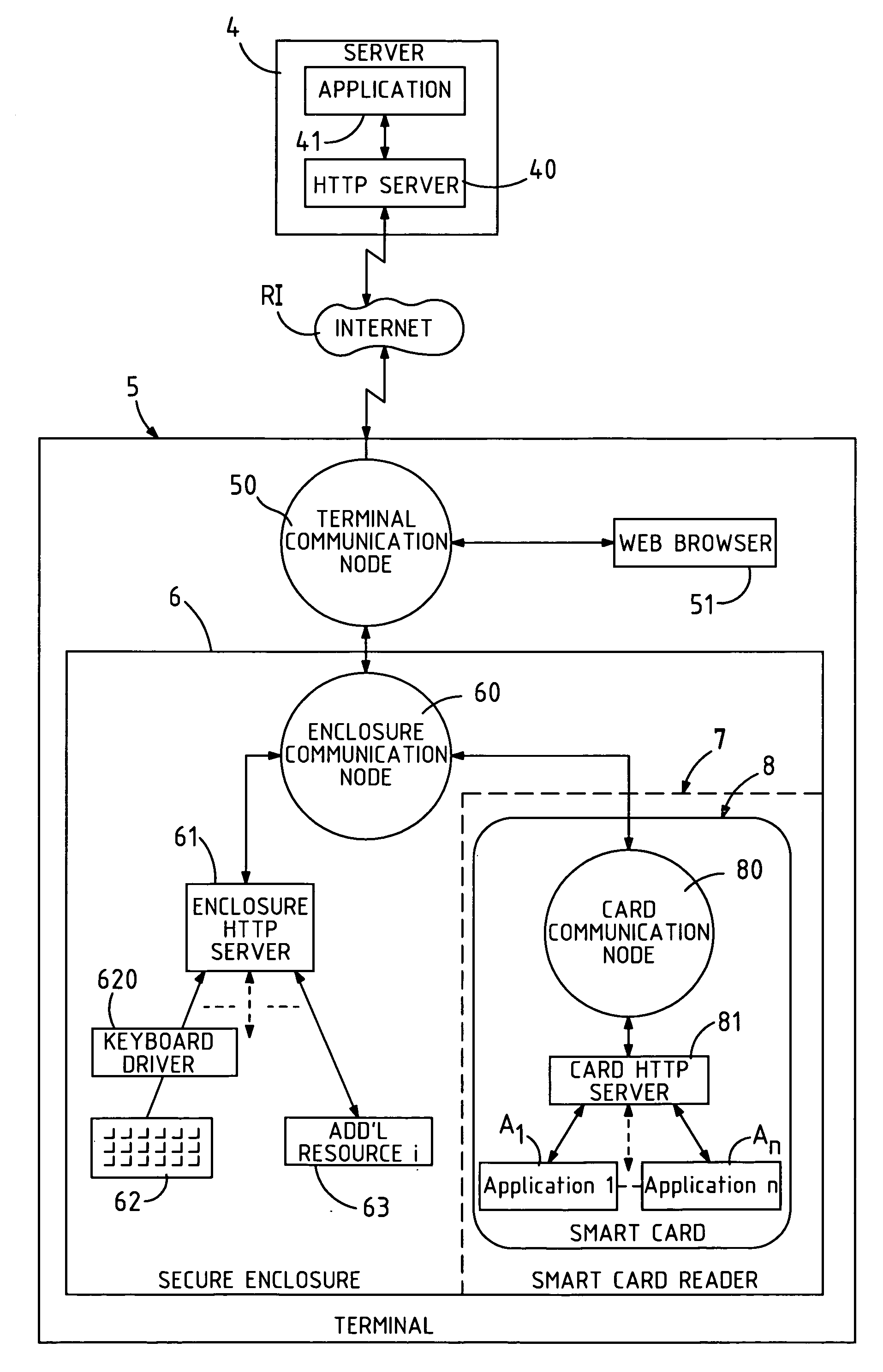
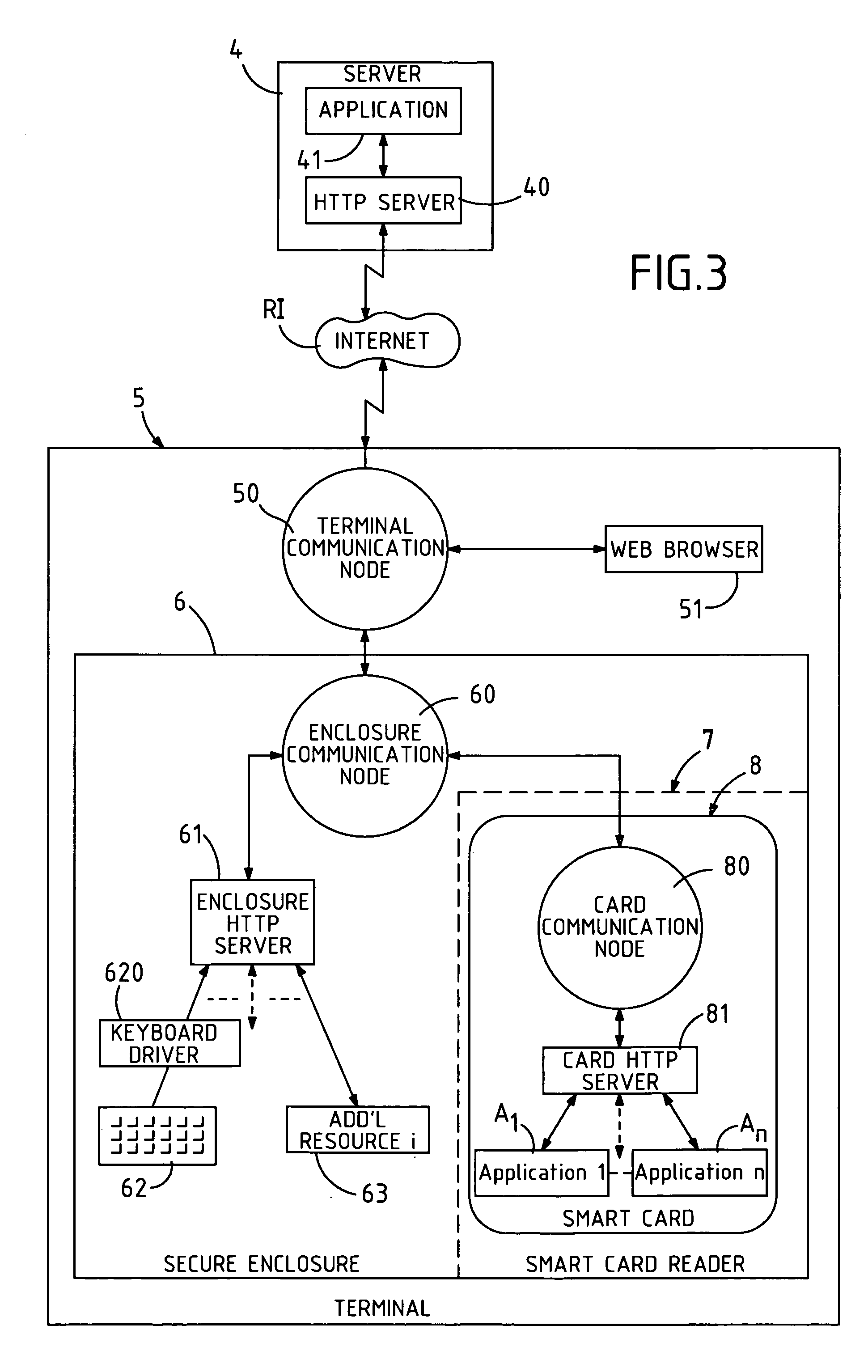
Secure terminal provided with a smart card reader designed to communicate with a server via an internet network
InactiveUS7047558B1Improve utilizationMaximum safetyDigital data processing detailsCo-operative working arrangementsWeb browserInternet network
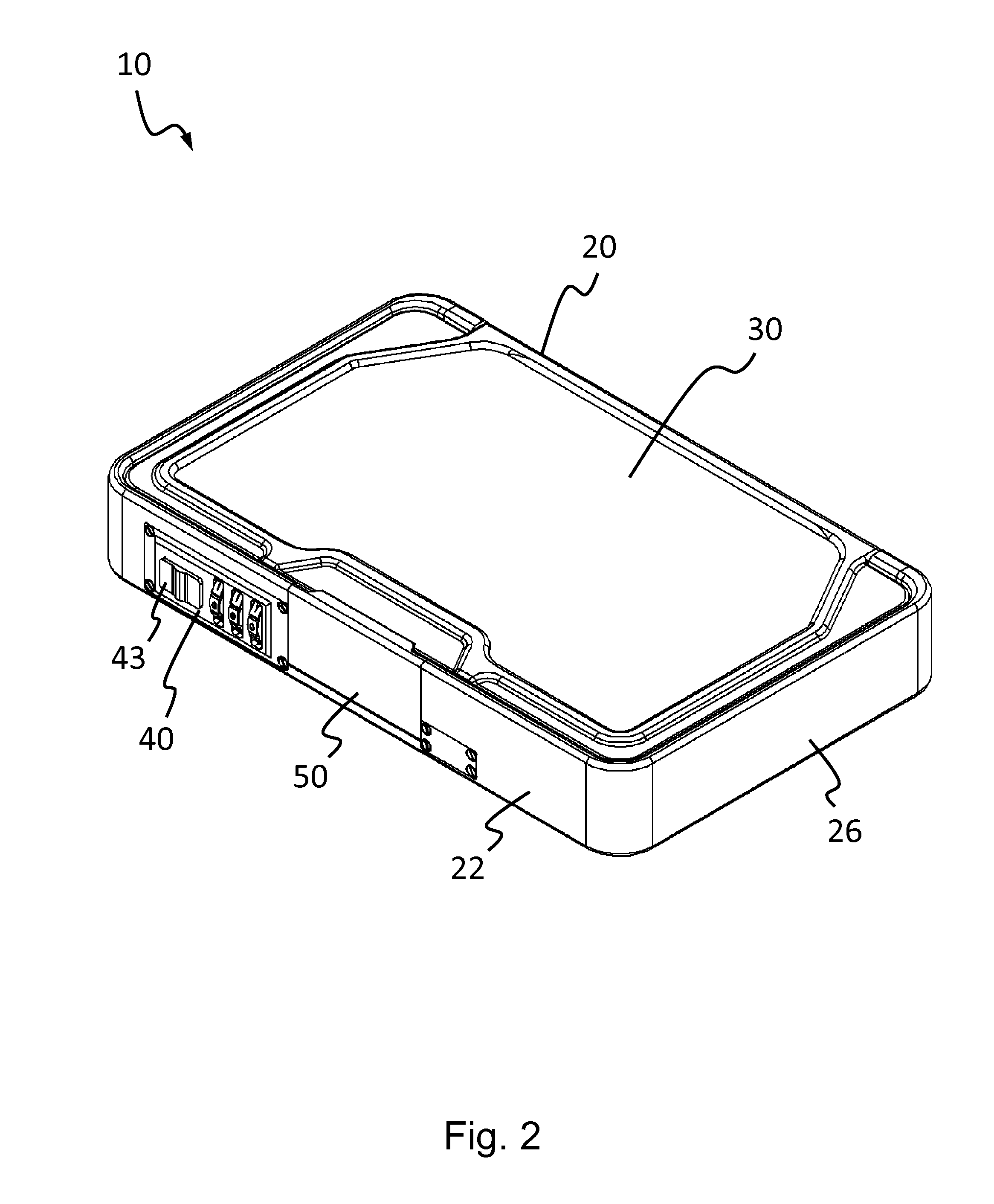
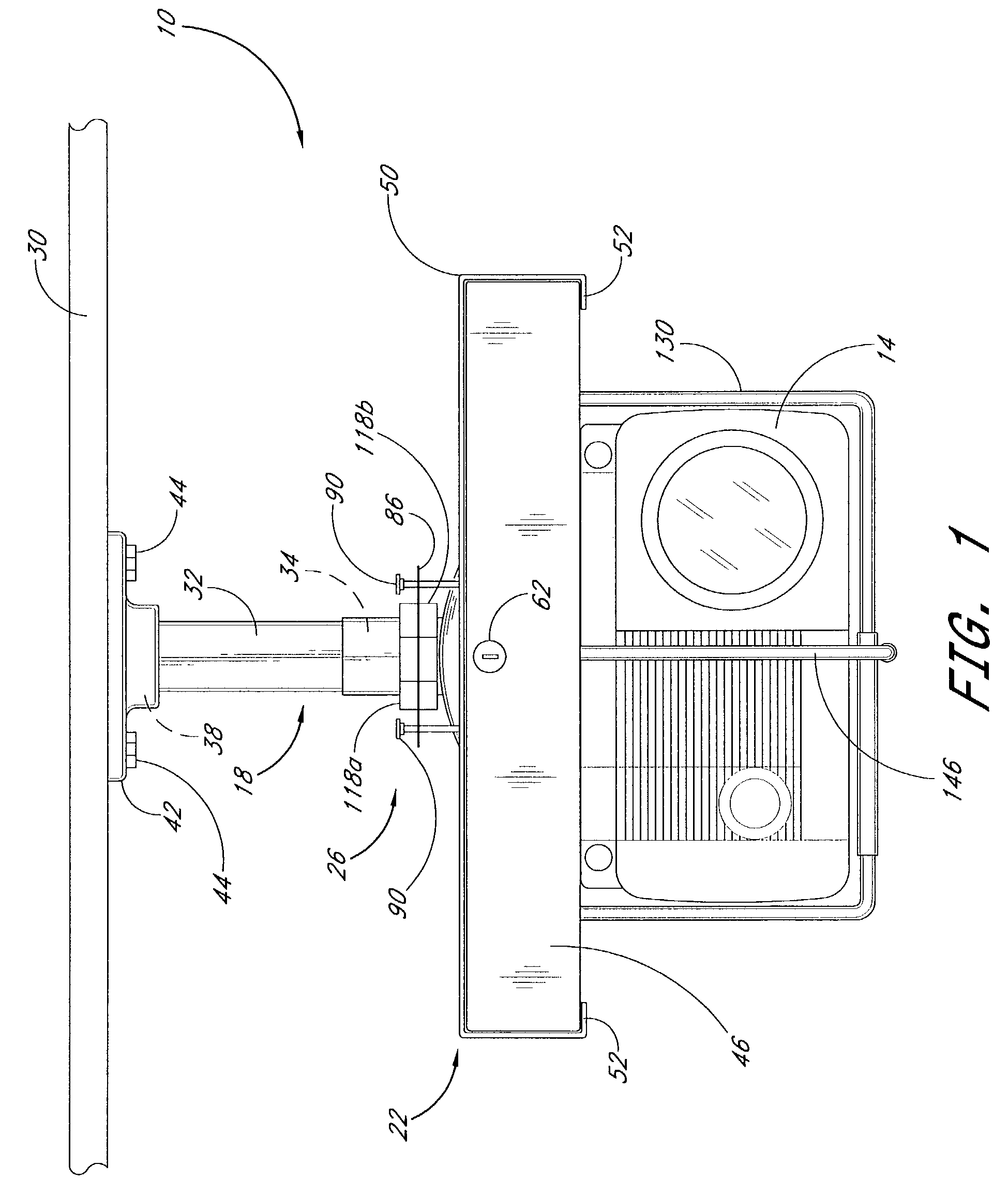
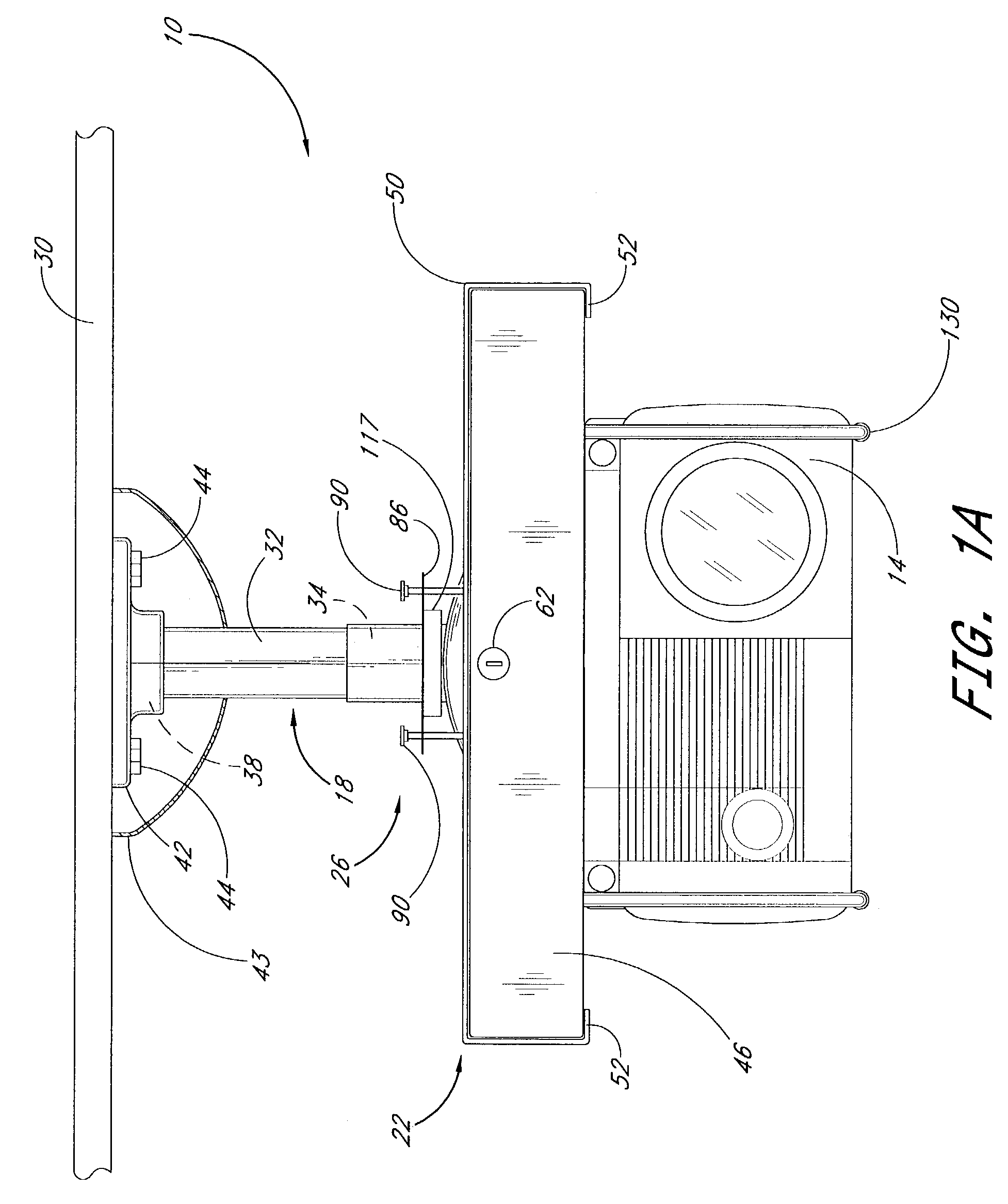
The invention concerns an architecture of a terminal (5) allowing communications between a smart card (8) and a web server (4), via an internet network (RI). The terminal (5) is equipped with a secure enclosure (6) comprising a smart card reader (8), a keyboard (62), and optionally, other computing resources (63). The non-secure part of the terminal (5) comprises a web browser (51) and a first communication node (50) that routes the requests received to the browser (51) or to the secure enclosure (6). The secure enclosure (6) comprises a second communication node (60) and an HTTP server (61). The smart card (8) comprises a third communication node (80) and an HTTP server (81). The web server (4) comprises a merchant application (41) that can be placed in communication with the smart card (8) and activate software applications (A1–An) of the latter.
Owner:CP8 TECH SA
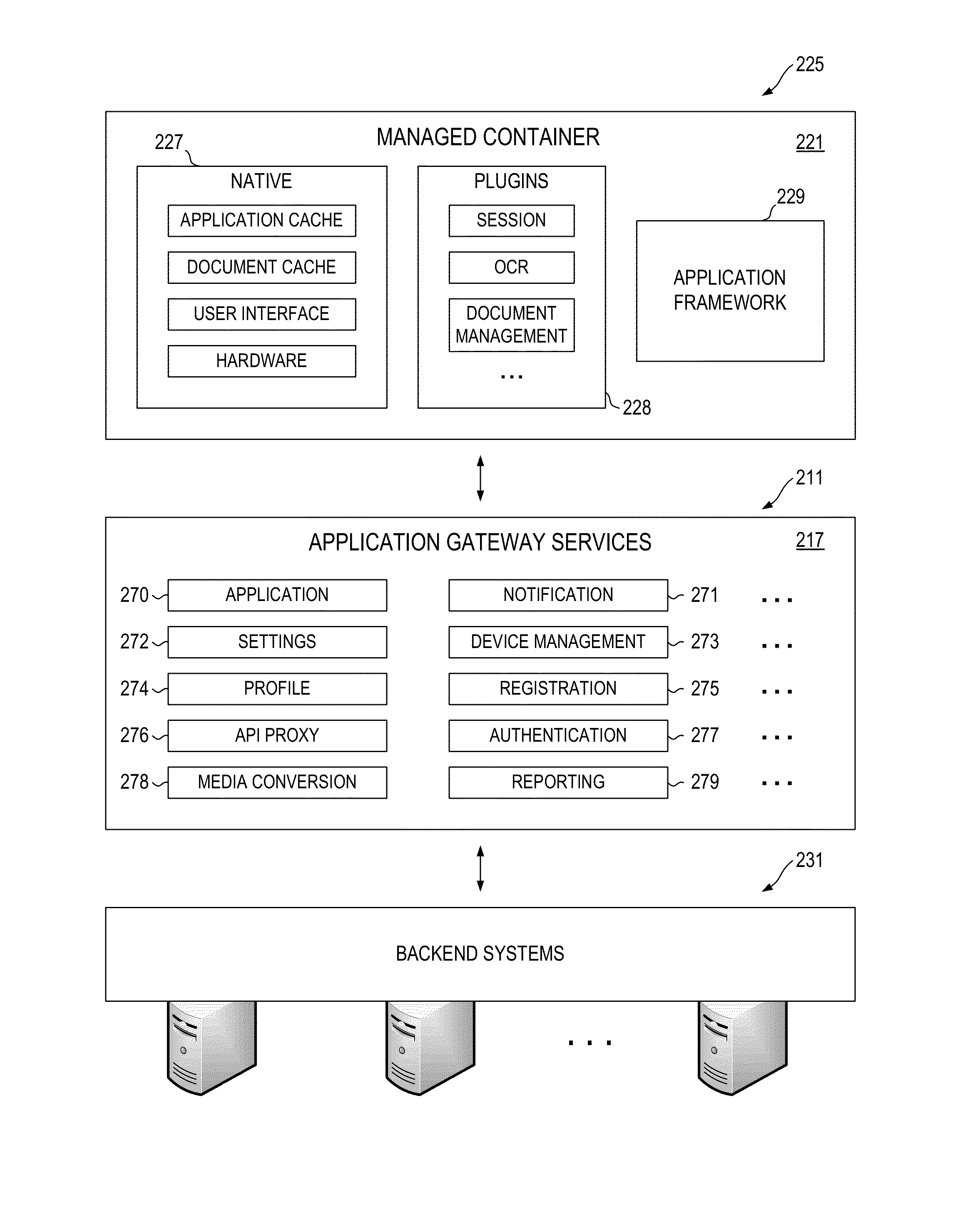
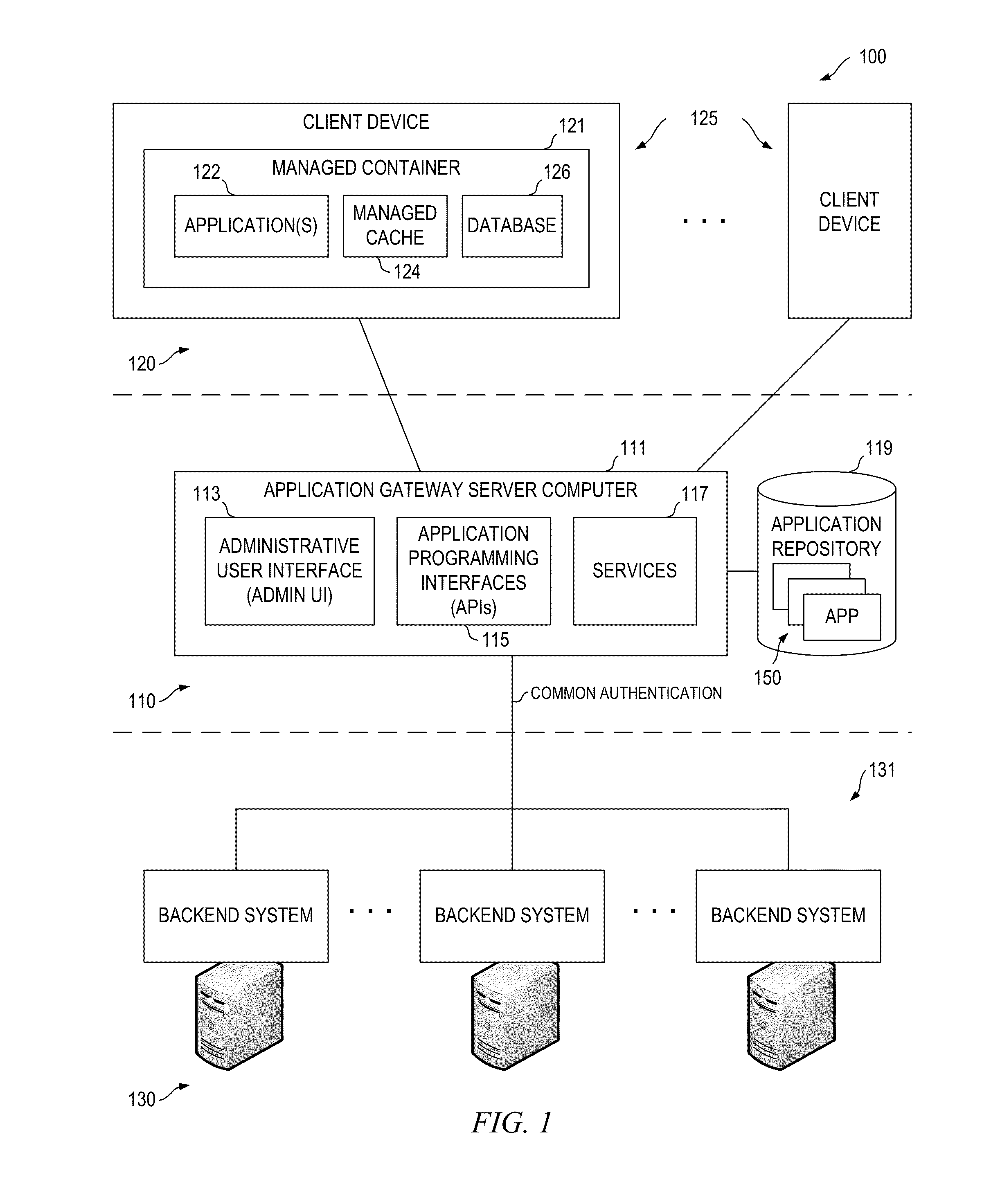
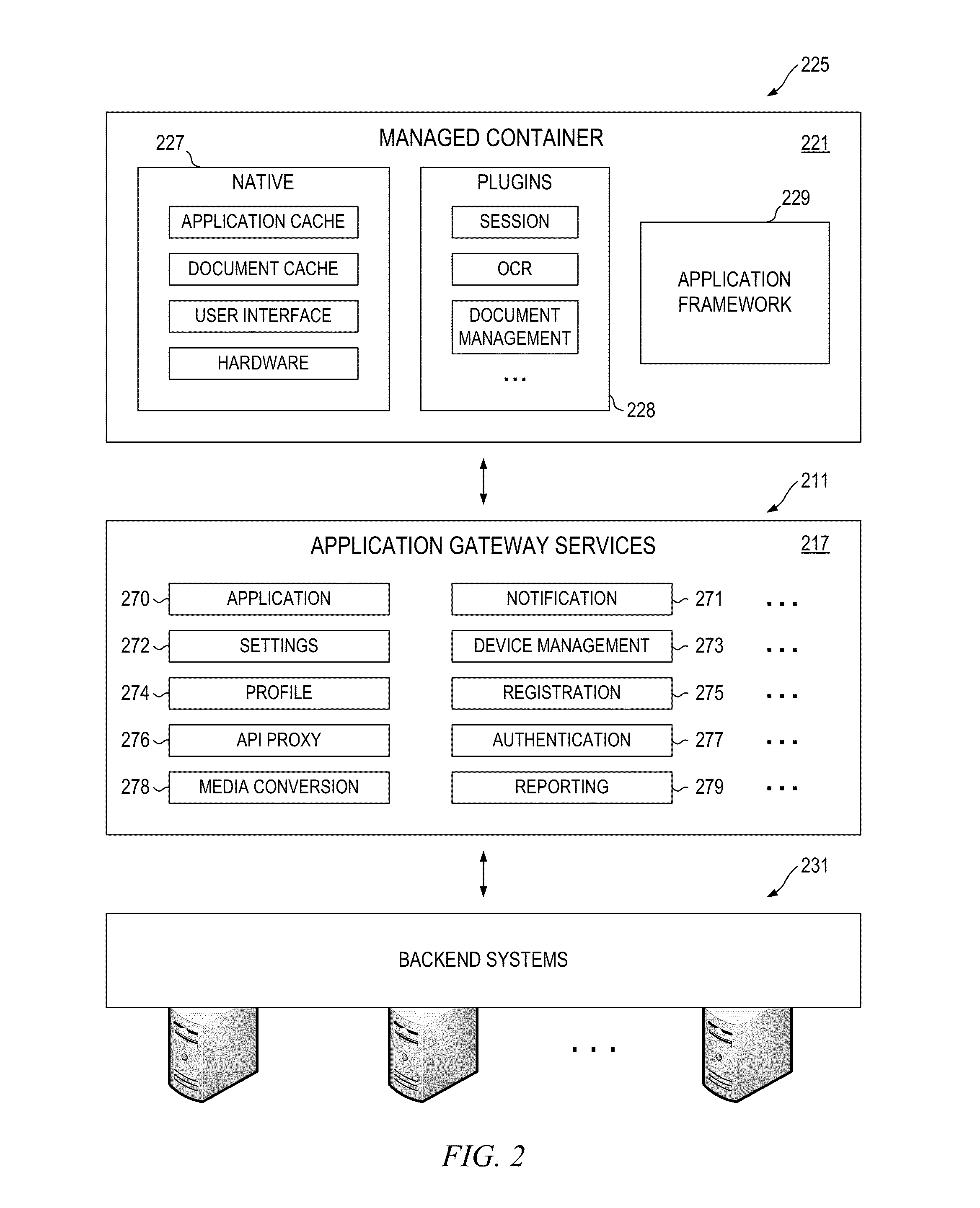
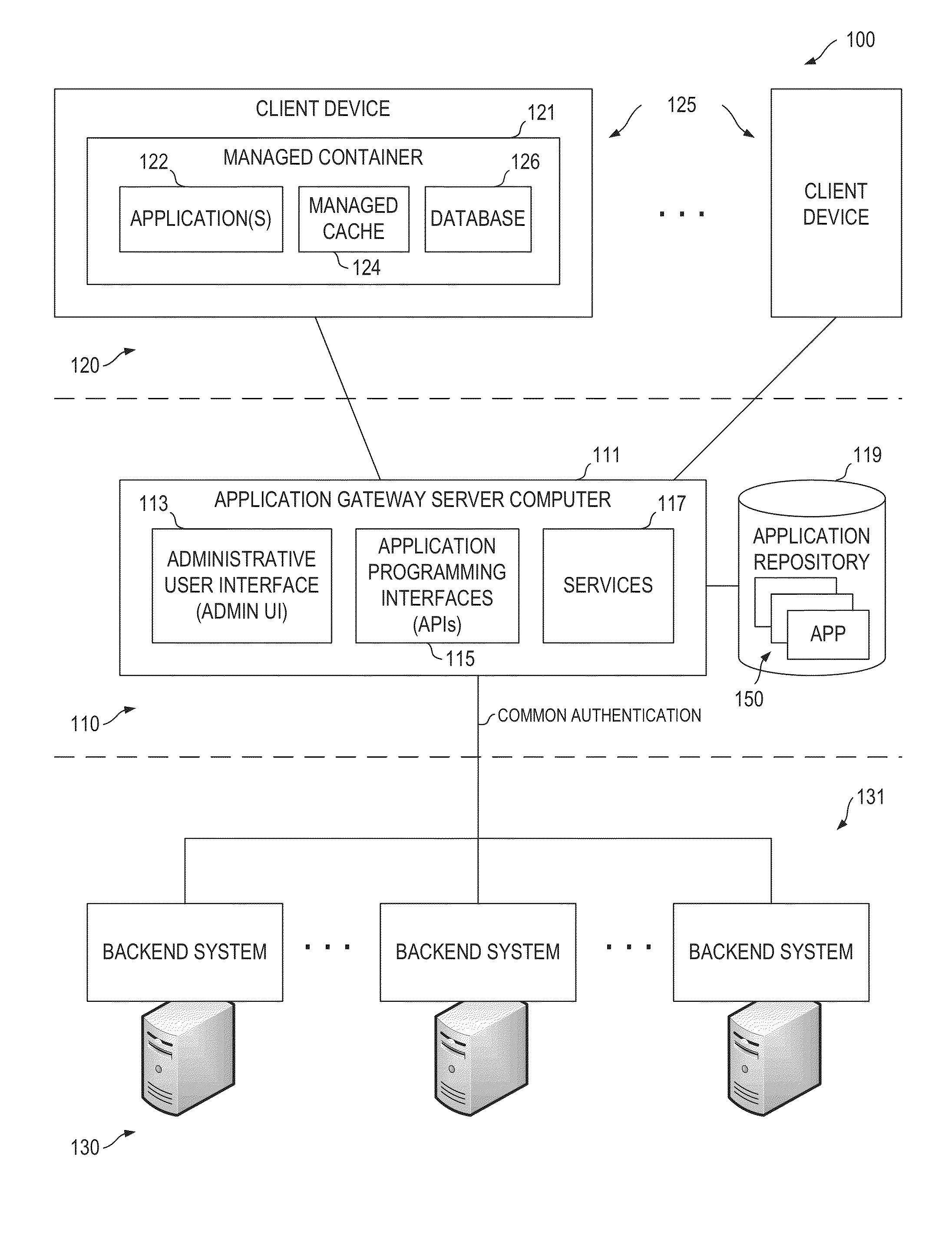
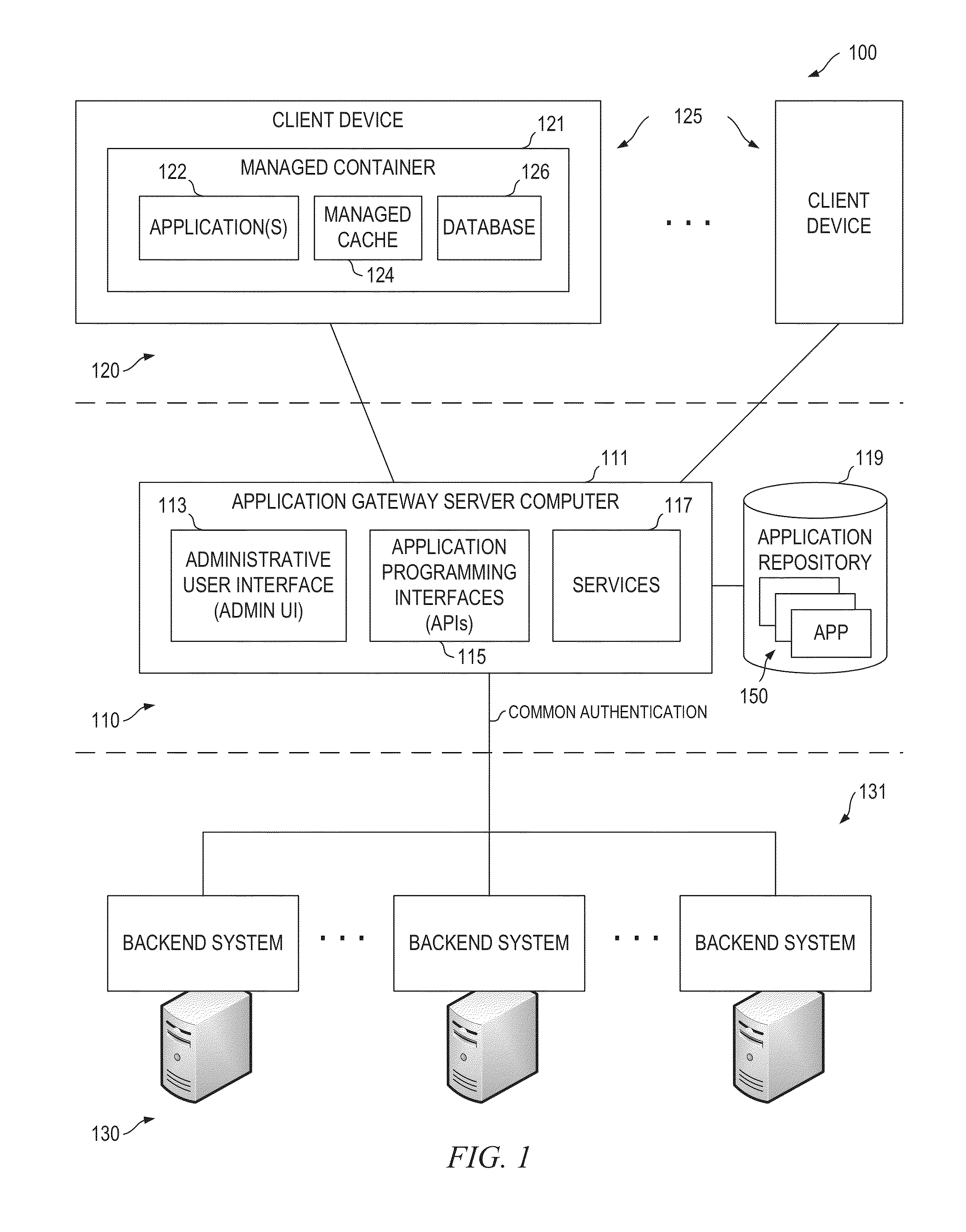
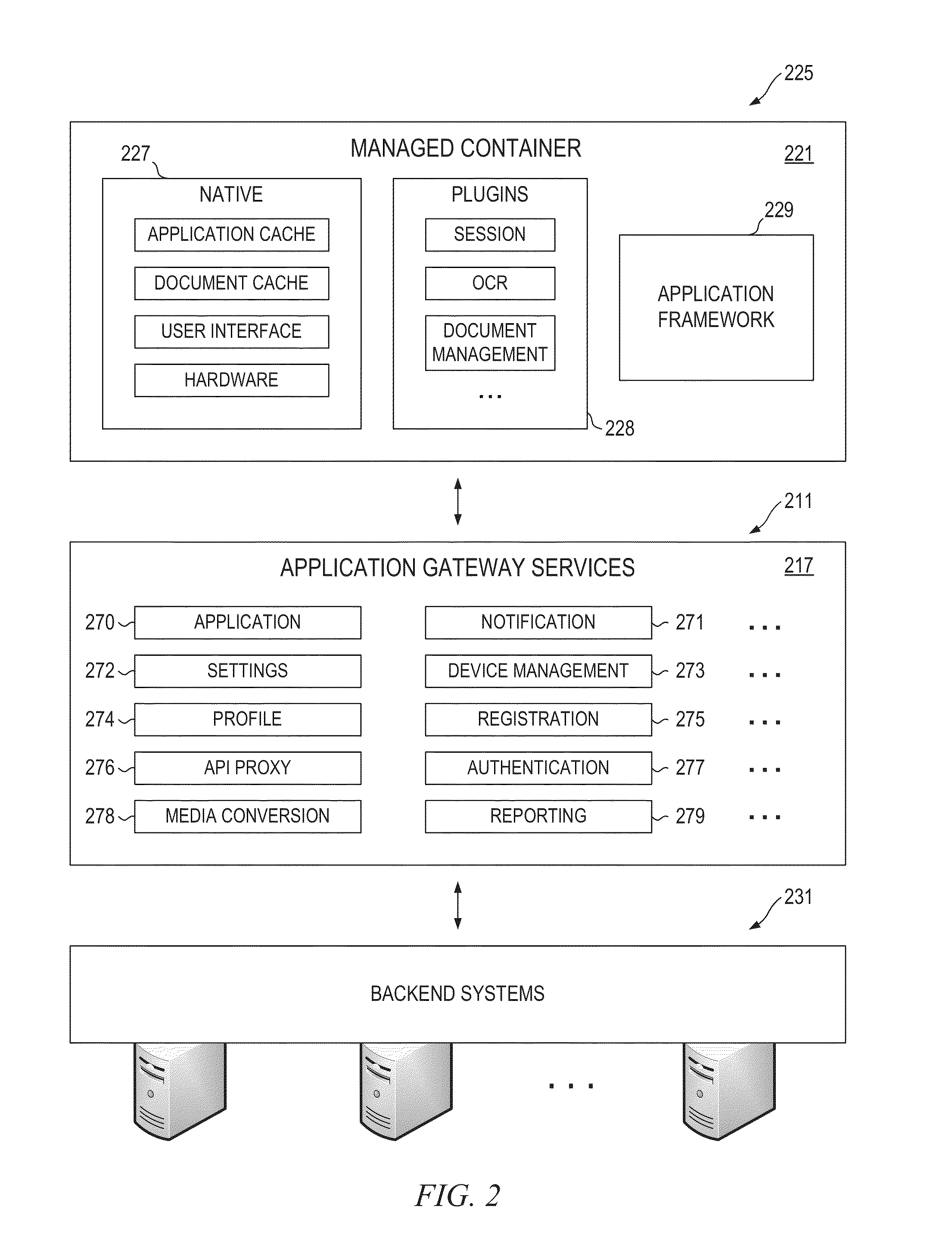
Application Gateway Architecture with Multi-Level Security Policy and Rule Promulgations
ActiveUS20150089224A1Retain controlSafe storageUser identity/authority verificationDigital computer detailsApplication programming interfaceCentralized management
Embodiments of an application gateway architecture may include an application gateway server computer communicatively connected to backend systems and client devices operating on different platforms. The application gateway server computer may include application programming interfaces and services configured for communicating with the backend systems and managed containers operating on the client devices. The application gateway server computer may provide applications that can be centrally managed and may extend the capabilities of the client devices, including the ability to authenticate across backend systems. A managed container may include a managed cache and may provide a secure shell for applications received from the application gateway server computer. The managed container may store the applications in the managed cache and control access to the managed cache according to rules propagated from at least one of the backend systems via the application gateway server computer.
Owner:OPEN TEXT SA ULC
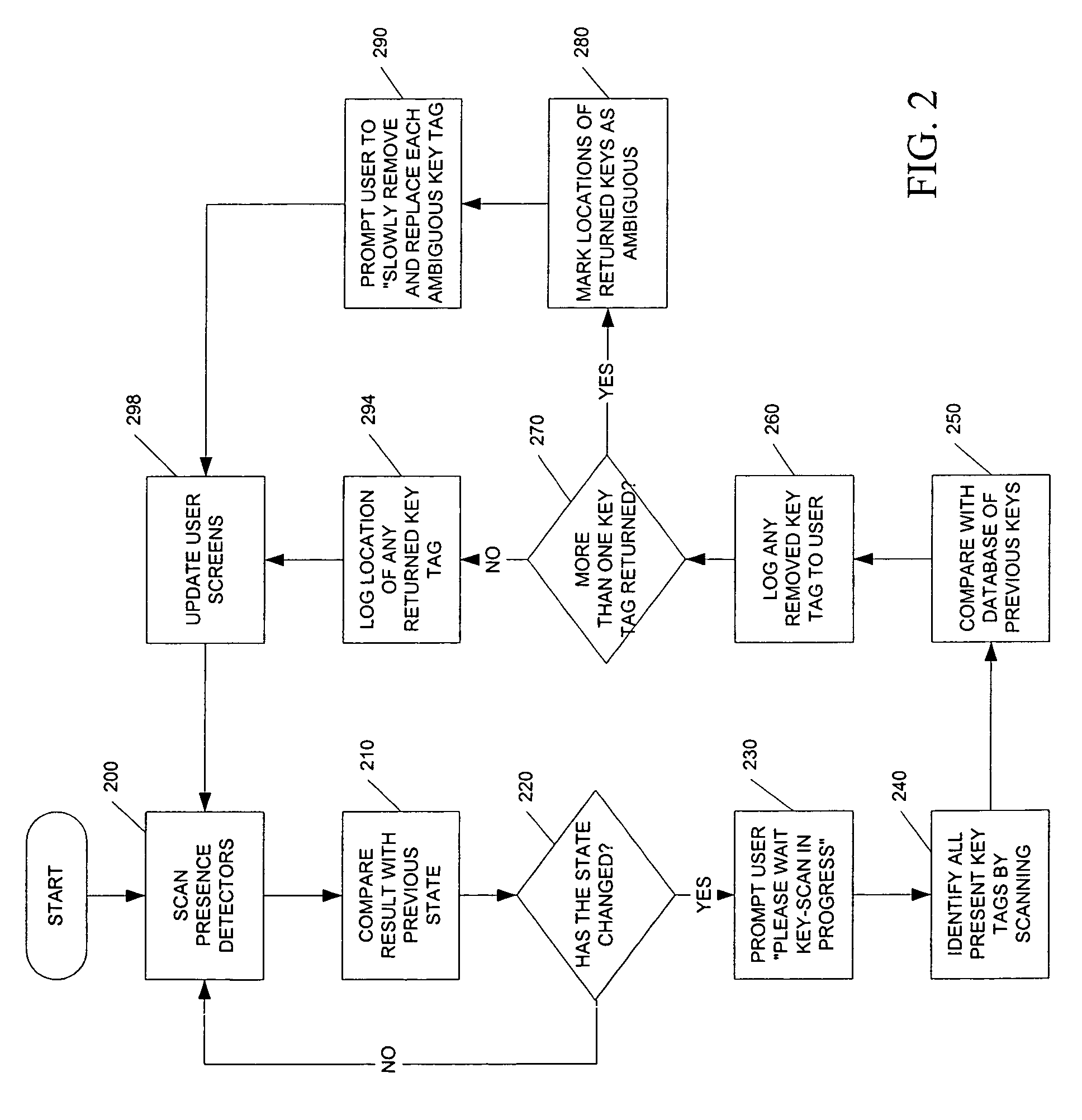
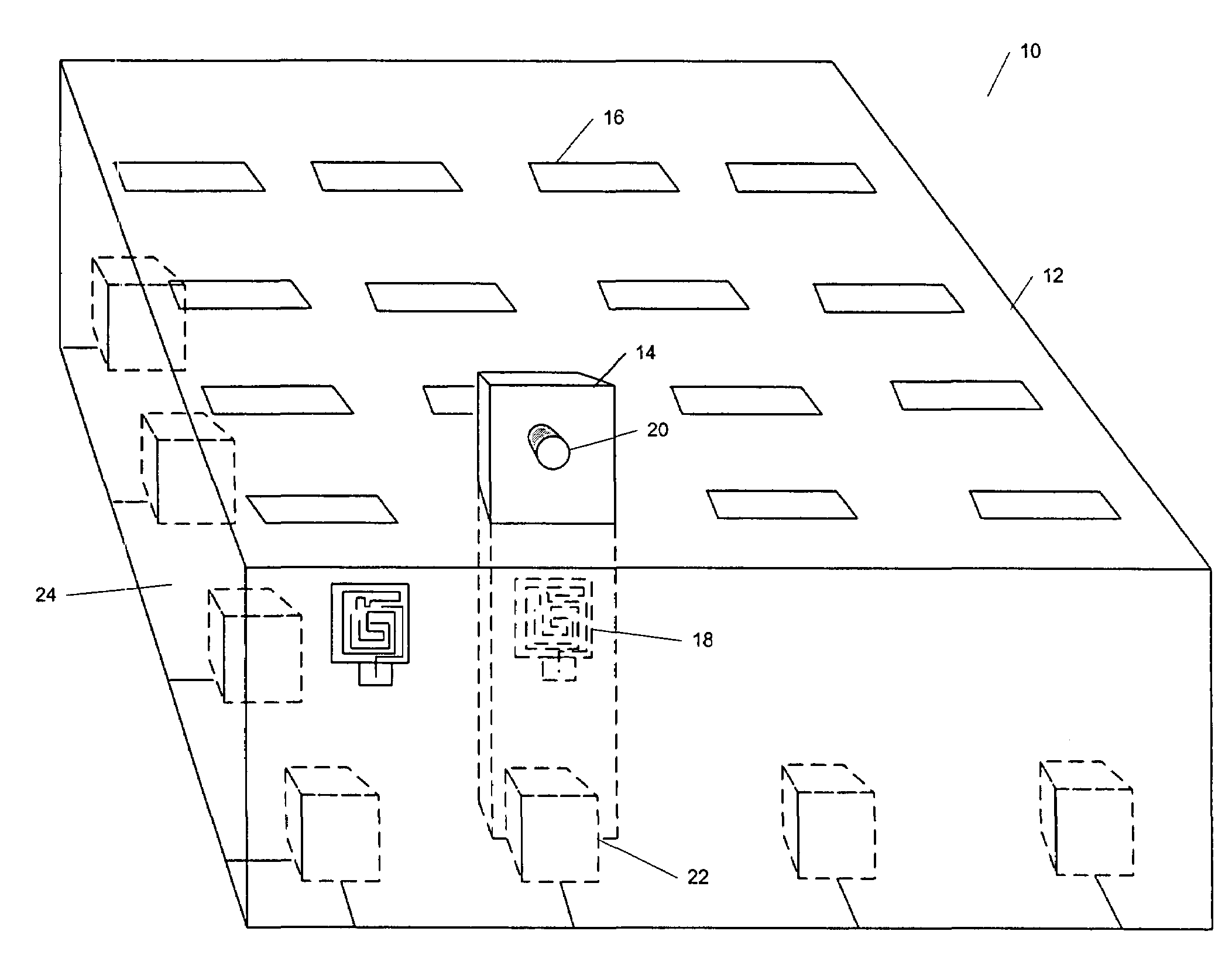
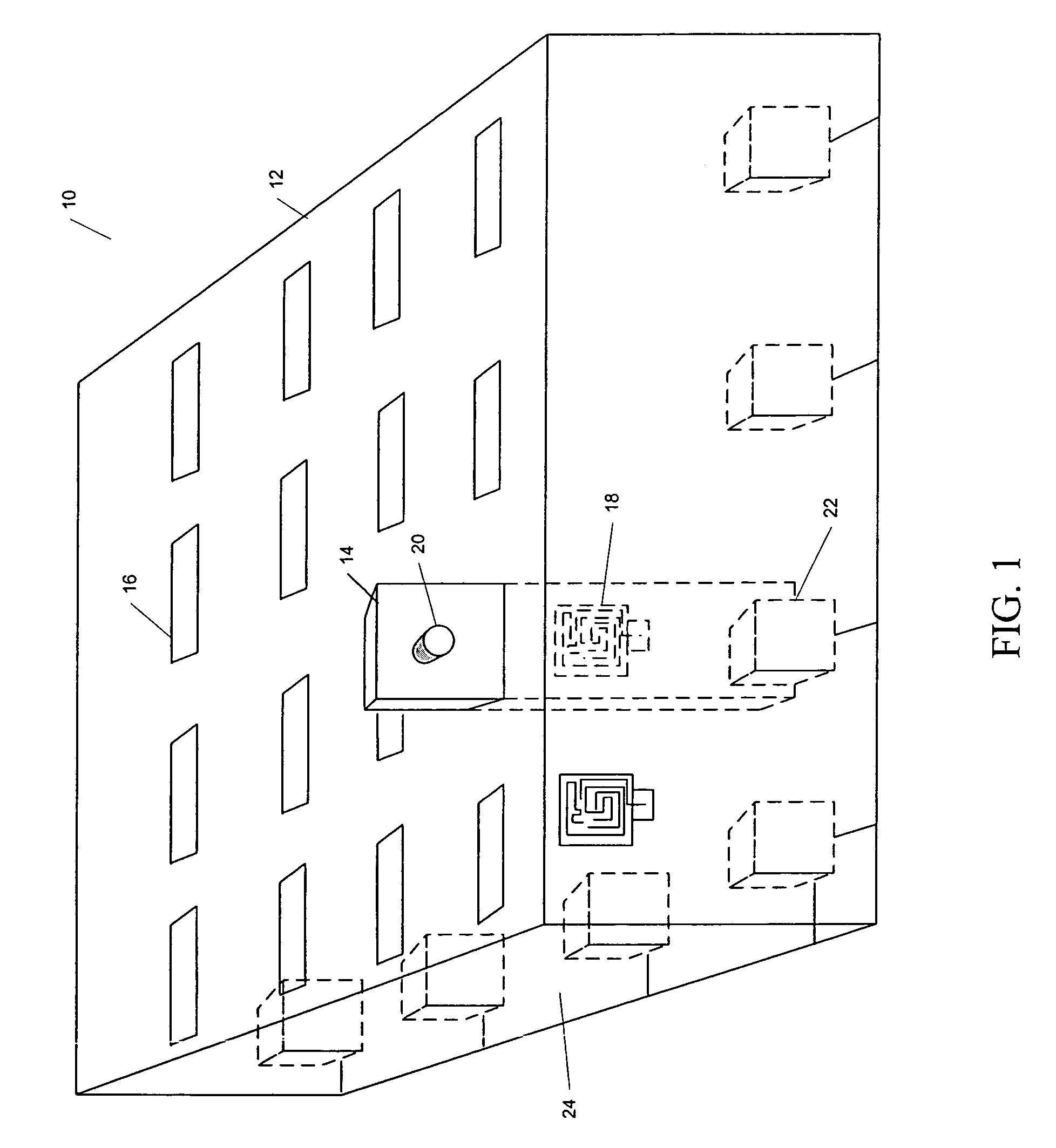
Key control system using separated ID and location detection mechanisms
InactiveUS20050024211A1Avoid detectionCo-operative working arrangementsSensing record carriersLocation detectionControl system
An object control and tracking system and related methods using separate object identification and location detection mechanisms for objects, such as keys, that are maintained in a secure enclosure, such as a key drawer. A plurality of object slots are located on the top tray of the enclosure to receive object tags that include both an RFID tag and an object to be tracked. The objects (e.g., keys) are attached to a portion of the object tags that are outside of the enclosure. Presence detectors are used to determine if an object tag is present in the corresponding slot of the enclosure. RFID sensors located on opposite interior side walls of the enclosure interrogate each RFID tag to determine the presence of each RFID tag within the enclosure. The object control and tracking system includes a controller, a memory for storing an object control database, and related processing logic operating on the controller to control scanning of the presence detectors to determine an object tag's presence in a corresponding slot, to identify each object present in the enclosure and to compare the identified objects with an object control database to determine each object removed or replaced since the previous database update.
Owner:DEUT BANK AG NEW YORK BRANCH
System and method for geofencing
ActiveUS20150089673A1Digital data processing detailsAnalogue secracy/subscription systemsGeographic siteGeolocation
A managed container may have a managed cache storing content managed by or through an application gateway server computer. The managed container may receive a request for content from an application running in a secure shell provided by the managed container on a client device. The managed container may determine whether the client device is within a specified geographical location. If not, the managed container may deny or restrict the application access to the requested content. The access denial or restriction may continue until a connection is made to the application gateway server computer or until the client device has returned to within the specified geographical location. If the client device is within the specified geographical location, the managed container may provide or restore access to requested content. Embodiments of the managed container can therefore perform geofencing by disabling or limiting access to content based on predetermined secure / insecure designations.
Owner:OPEN TEXT SA ULC
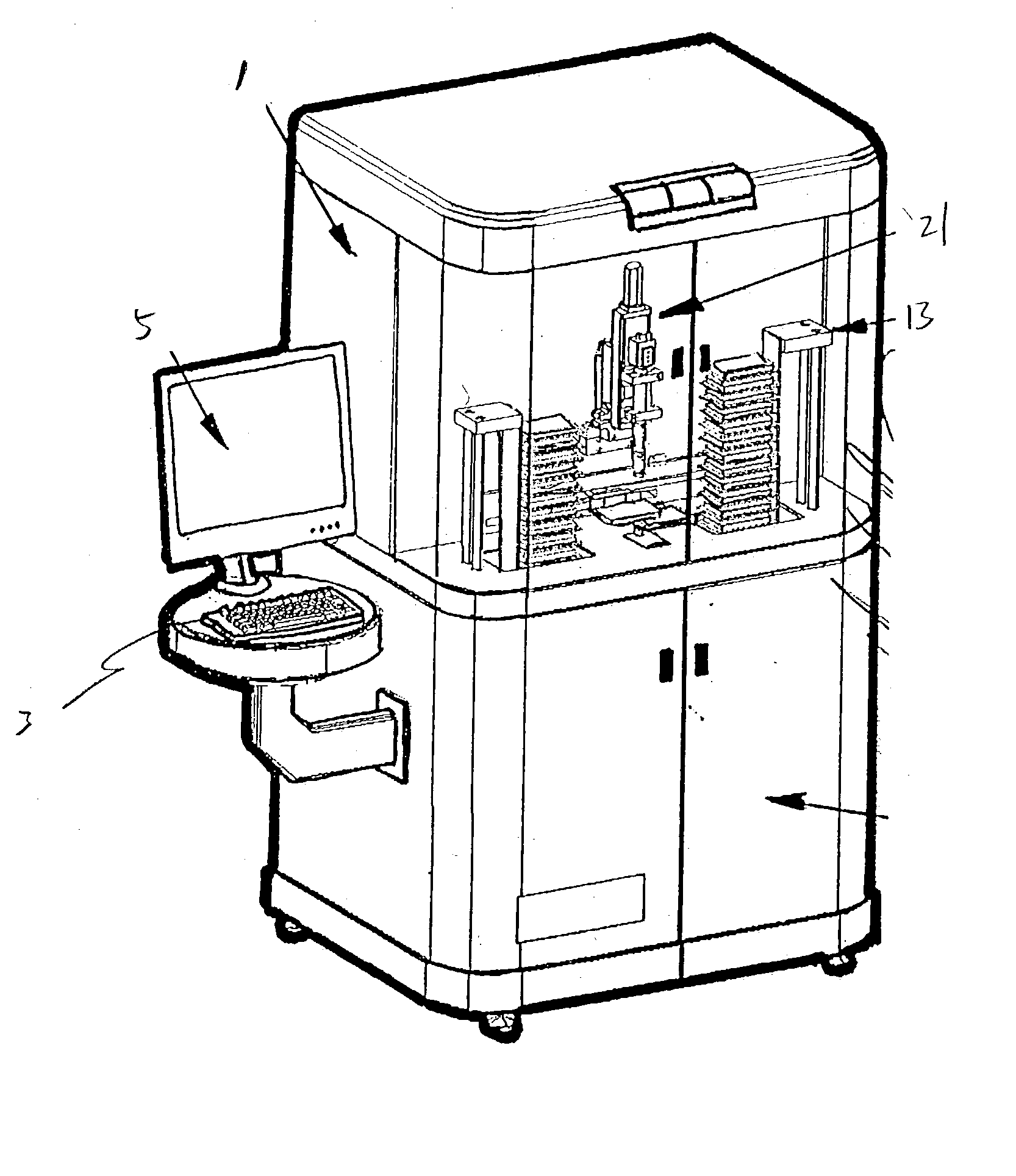
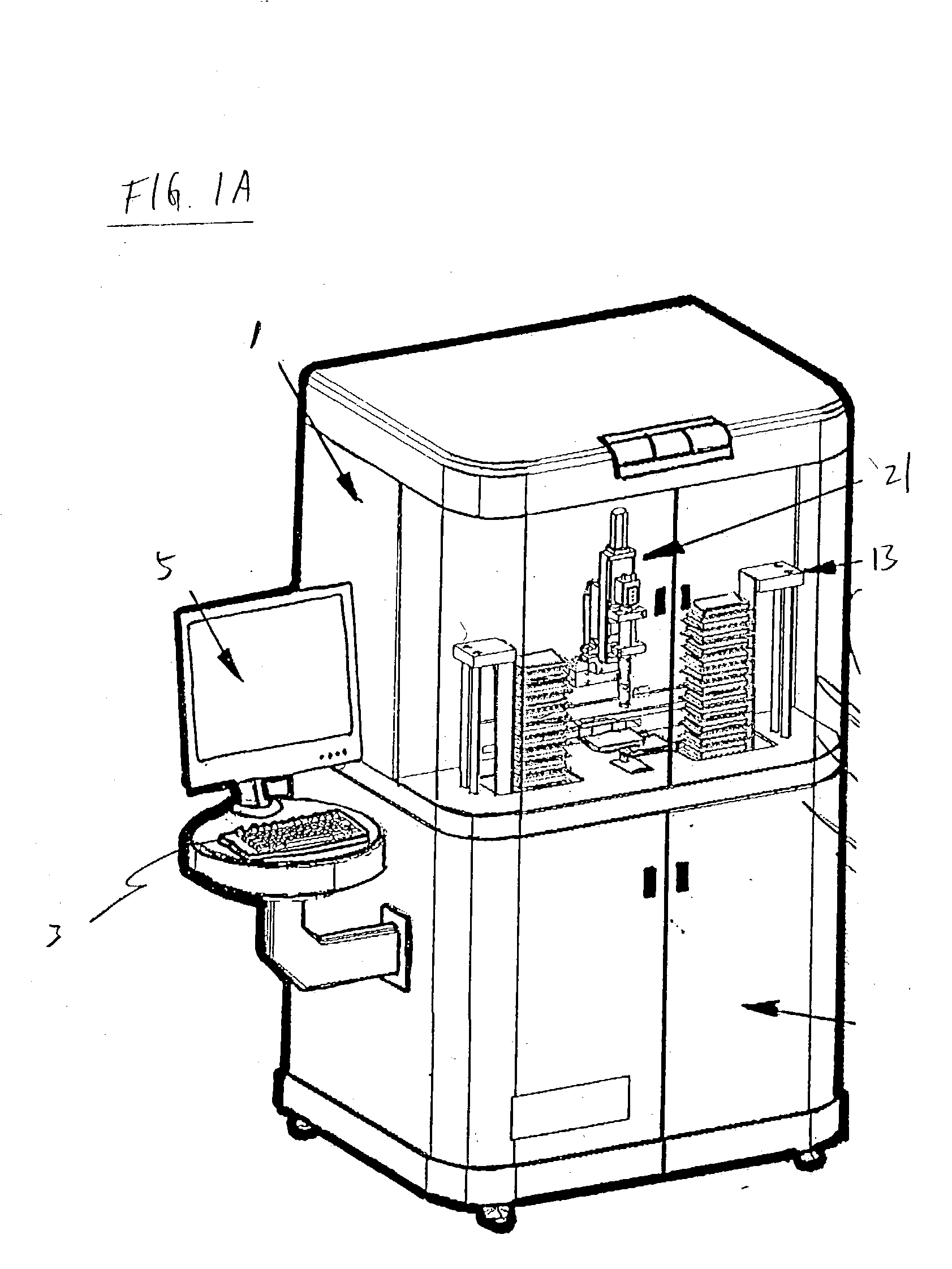
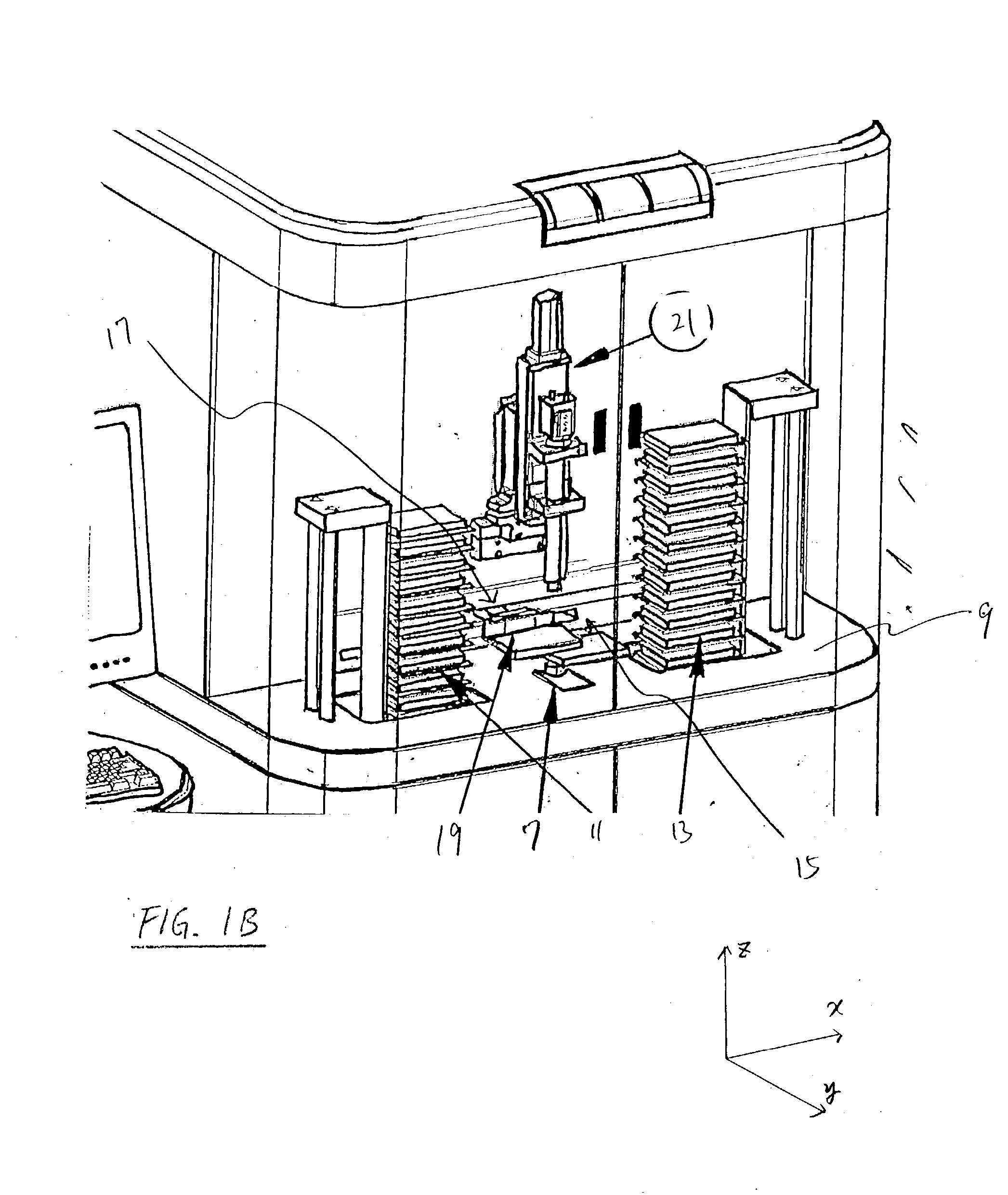
Apparatus for high-throughput non-contact liquid transfer and uses thereof
Disclosed is an apparatus for high-throughput non-contact liquid transfer. The high-throughput non-contact liquid transfer apparatus may be implemented for high-throughput biological, chemical and biochemical, synthesis and / or screening. In one variation, the apparatus comprise of an acoustic emitter, one or more X / Y linear stage with associated handling device, one or more storage queue, and an image detection system. The apparatus may be controlled by a centralized system controller with associated electronic and / or software. The apparatus may further be integrated within a frame with environment and safety enclosure. The system controller may control positioning of source vessel and target device relative to an acoustic emitter device. The system controller may also track the location of all the source well plates and target well plates, thus providing for user-defined association of any well on any source well plate with any well on any target well plate for liquid transfer.
Owner:EDC BIOSYST
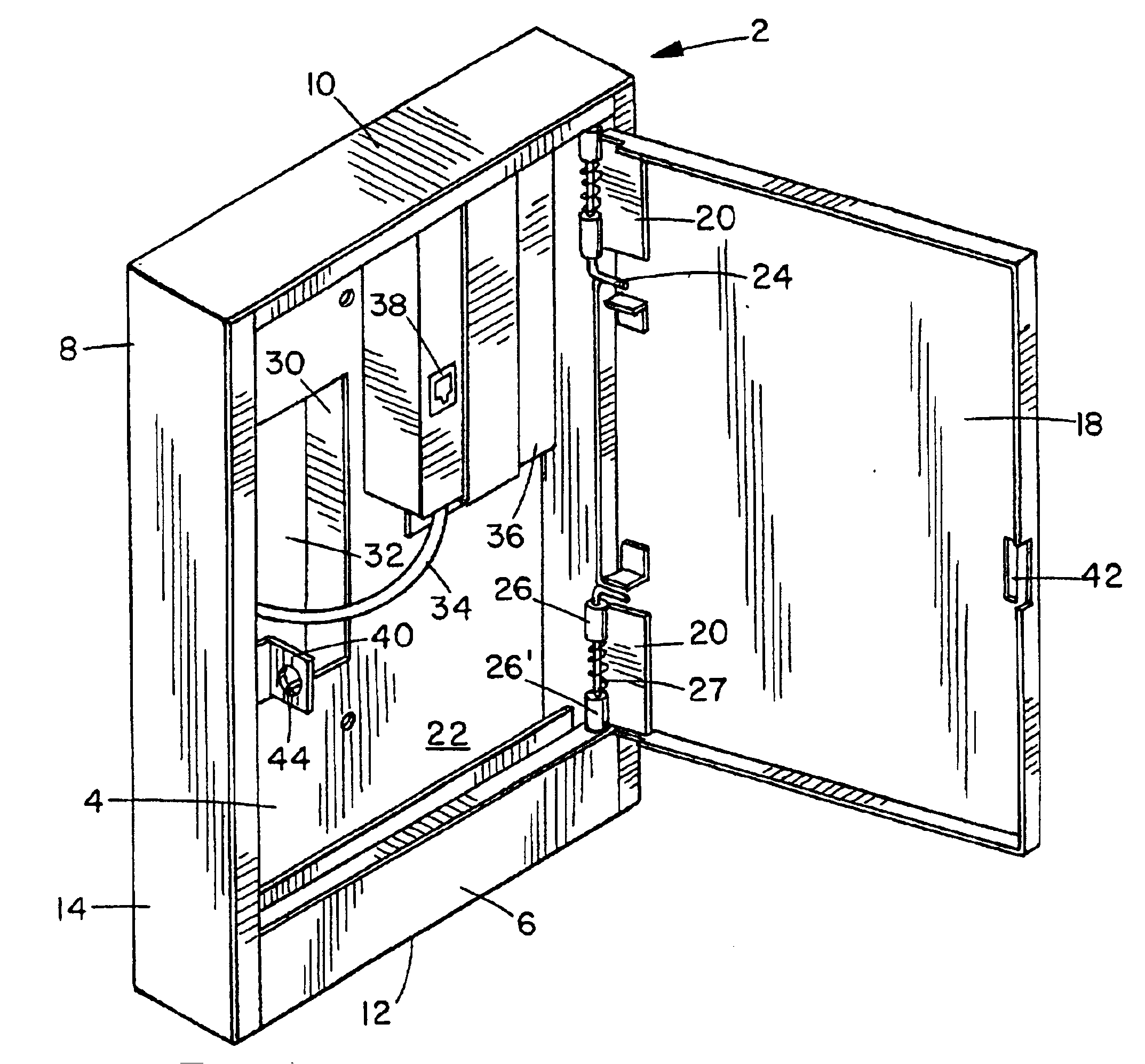
Secure enclosure for access to cabled systems
An enclosure is disclosed which is highly secure, permits access to a cabled network system only by one user at a time, permits visual and unequivocal observation of the security status of the enclosure, and prevents access to the interior thereof only by authorized persons. The enclosure has back, front and side walls and an interior, with all connections being internal. Limited interior access is provided only through a door and a service opening. Within the enclosure is a system connection device to the system, which is configured for access thereto by only a single user at a time. A lock secures door closure. Thus access to the cabled system through the enclosure is available only to one user at a time and must be obtained through the open door, with usage thereby being visually identifiable, and the door prevents unauthorized access.
Owner:HOLOCOM
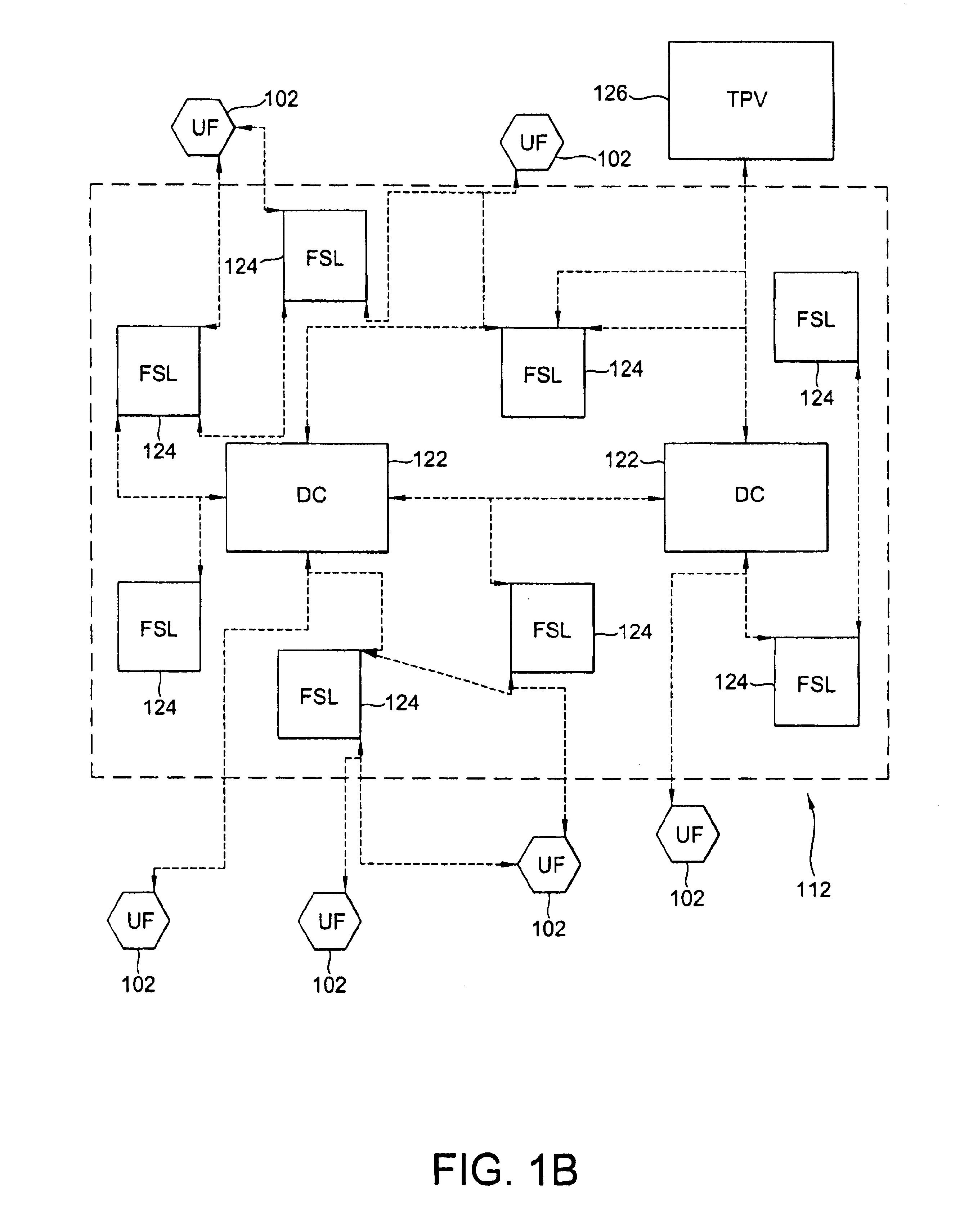
Systems and methods of inventory management utilizing unattended facilities
InactiveUS20050103842A1Improve efficiencyLow costSensing detailsDigital computer detailsLogistics managementSecure Shell
An inventory management system utilizes unattended facilities remote from a central warehouse for service parts logistics. Items are placed in inventory in secure enclosures at the unattended facilities by the inventory management service or are delivered directly to the unattended facility. The unattended facilities may be located near one or more customers to reduce a service technician's travel time and customers' inventory costs. A service technician utilizes a passcode to retrieve needed items. The service technician may order items that are not kept in the inventory of the unattended facility in which case the items may be delivered to the unattended facility and the service technician may receive a notification related to all the items that comprise an order that the order is ready for pick up at an unattended facility. Unused, used or damaged parts may be returned by a technician to a remote secure enclosure where such returned parts may be retrieved and disposed of, repaired or placed back into inventory if not damaged or after repair, and the processing of such returned parts begins by information entered into a data entry device at the remote secure enclosure location. Return items that are not damaged may be included in the inventory of an unattended facility.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
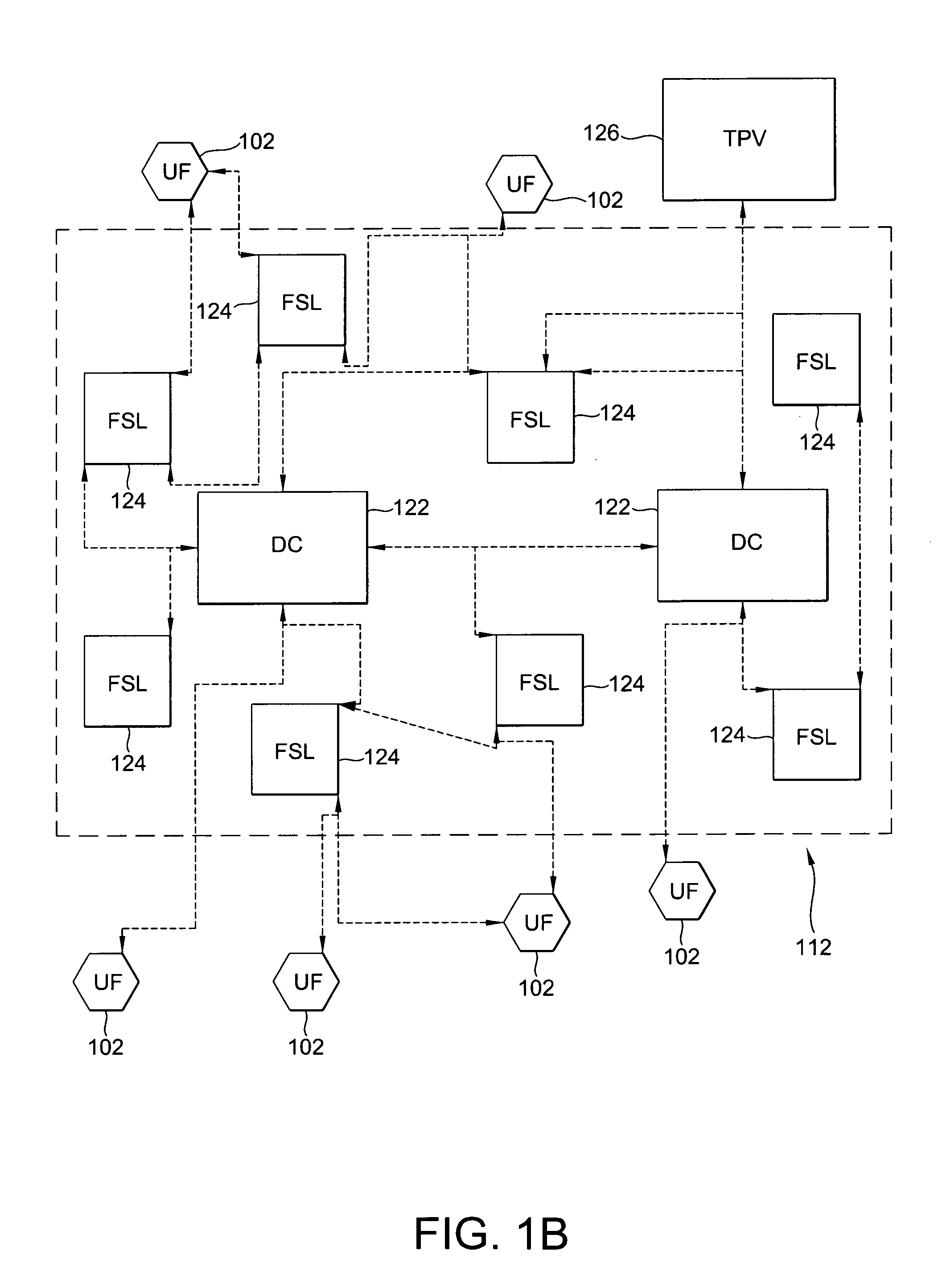
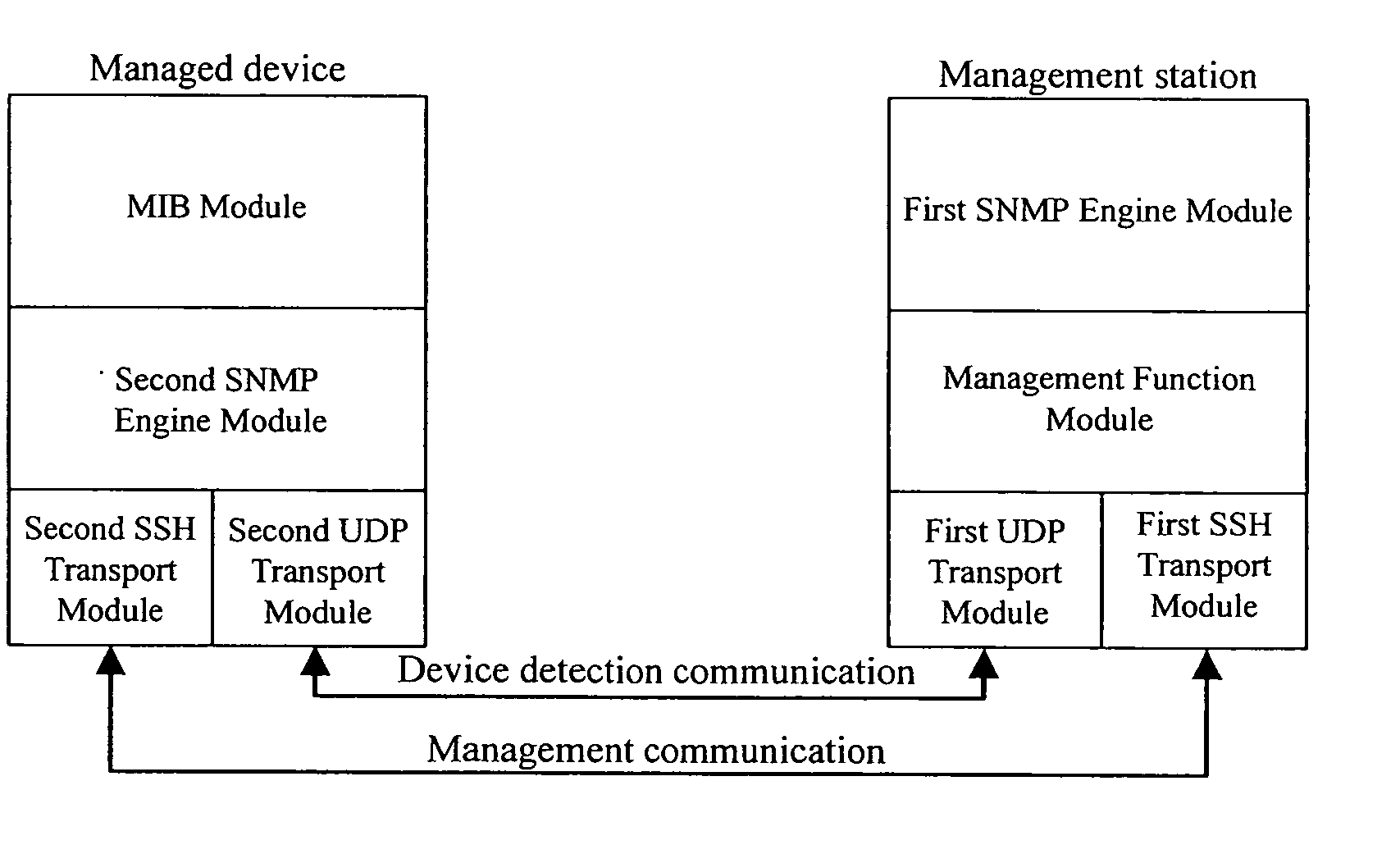
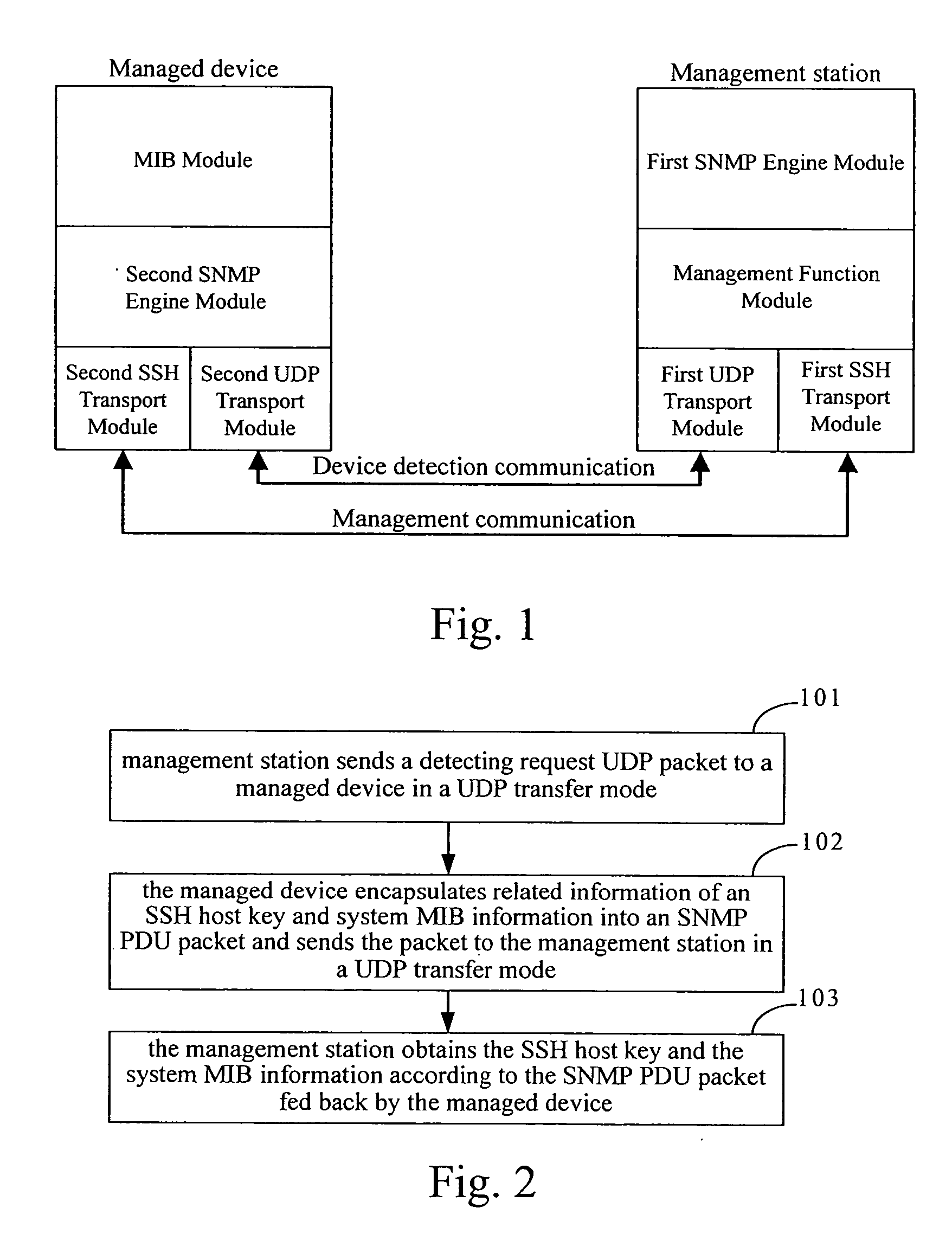
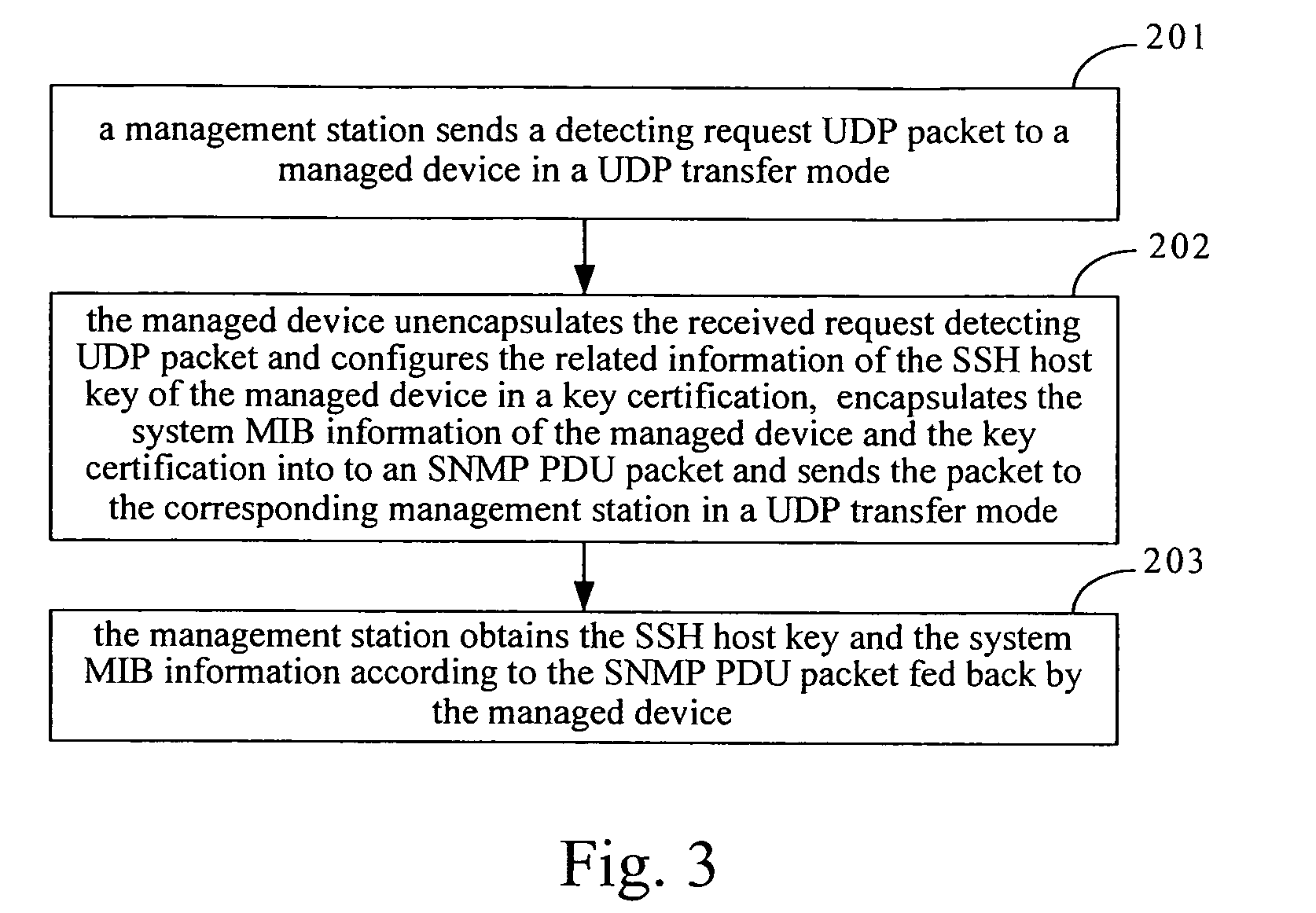
Method and system for obtaining secure shell host key of managed device
ActiveUS20070083665A1Conveniently implementedReduce managementDigital data processing detailsMultiple digital computer combinationsRelevant informationKey distribution
Owner:HUAWEI TECH CO LTD
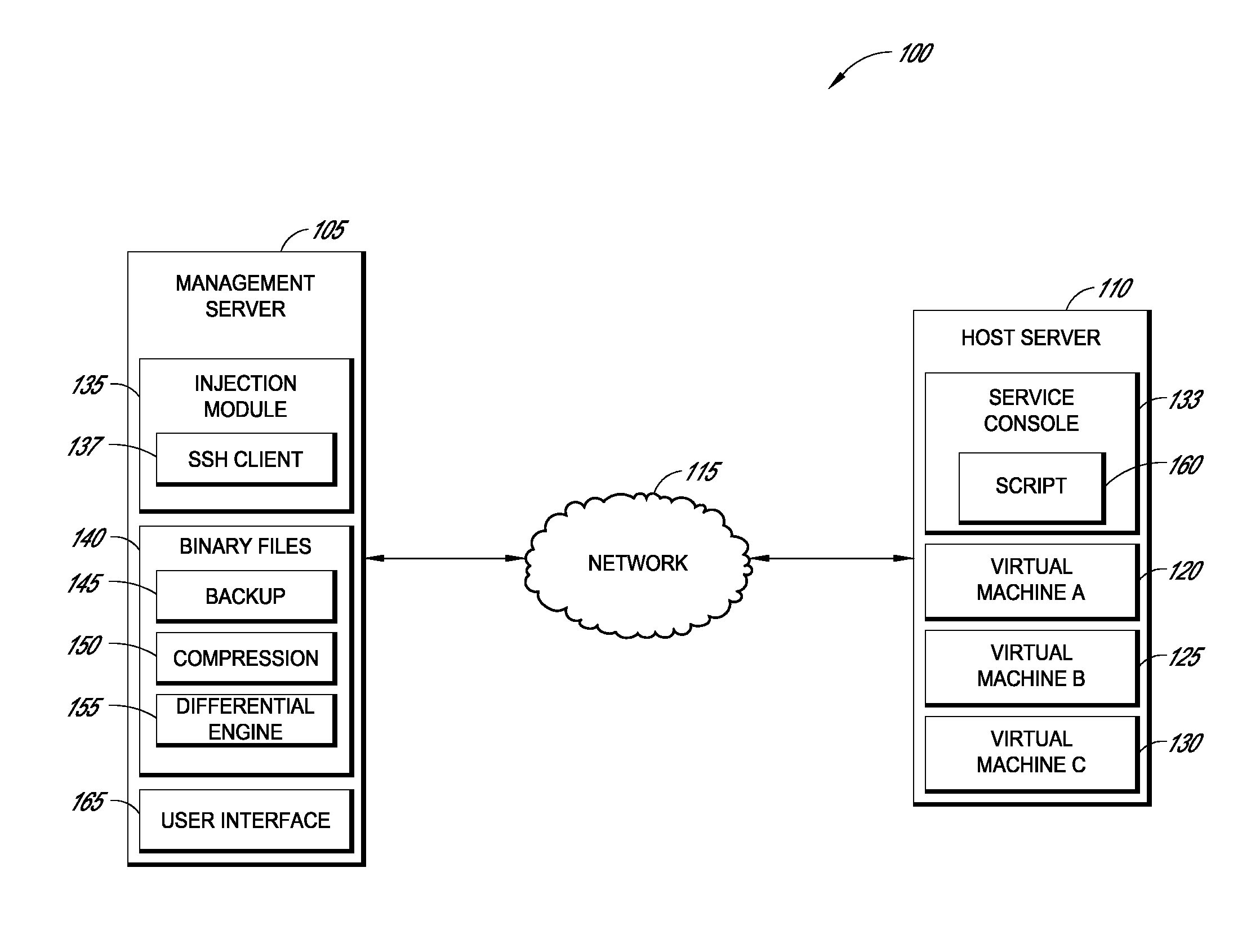
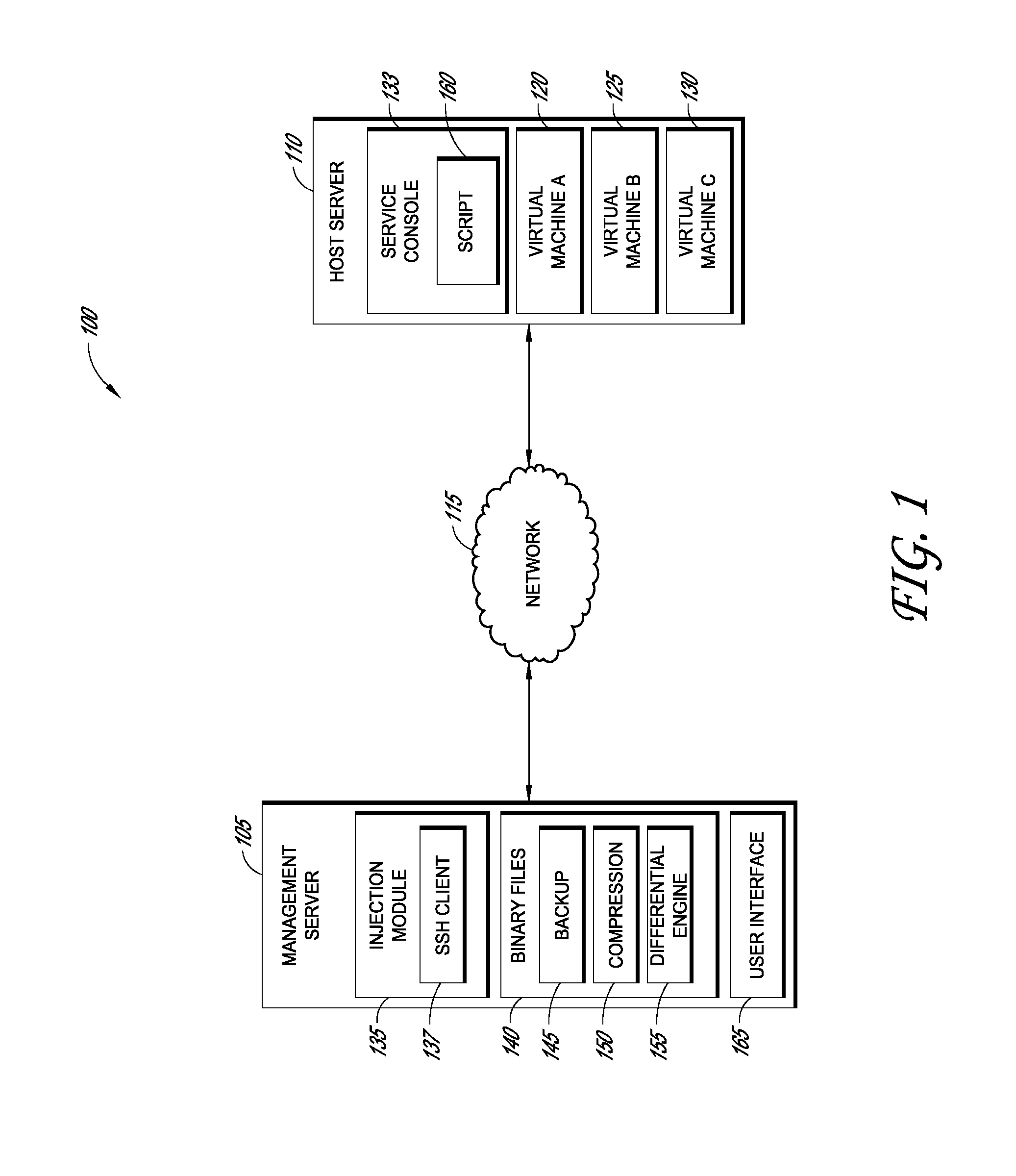
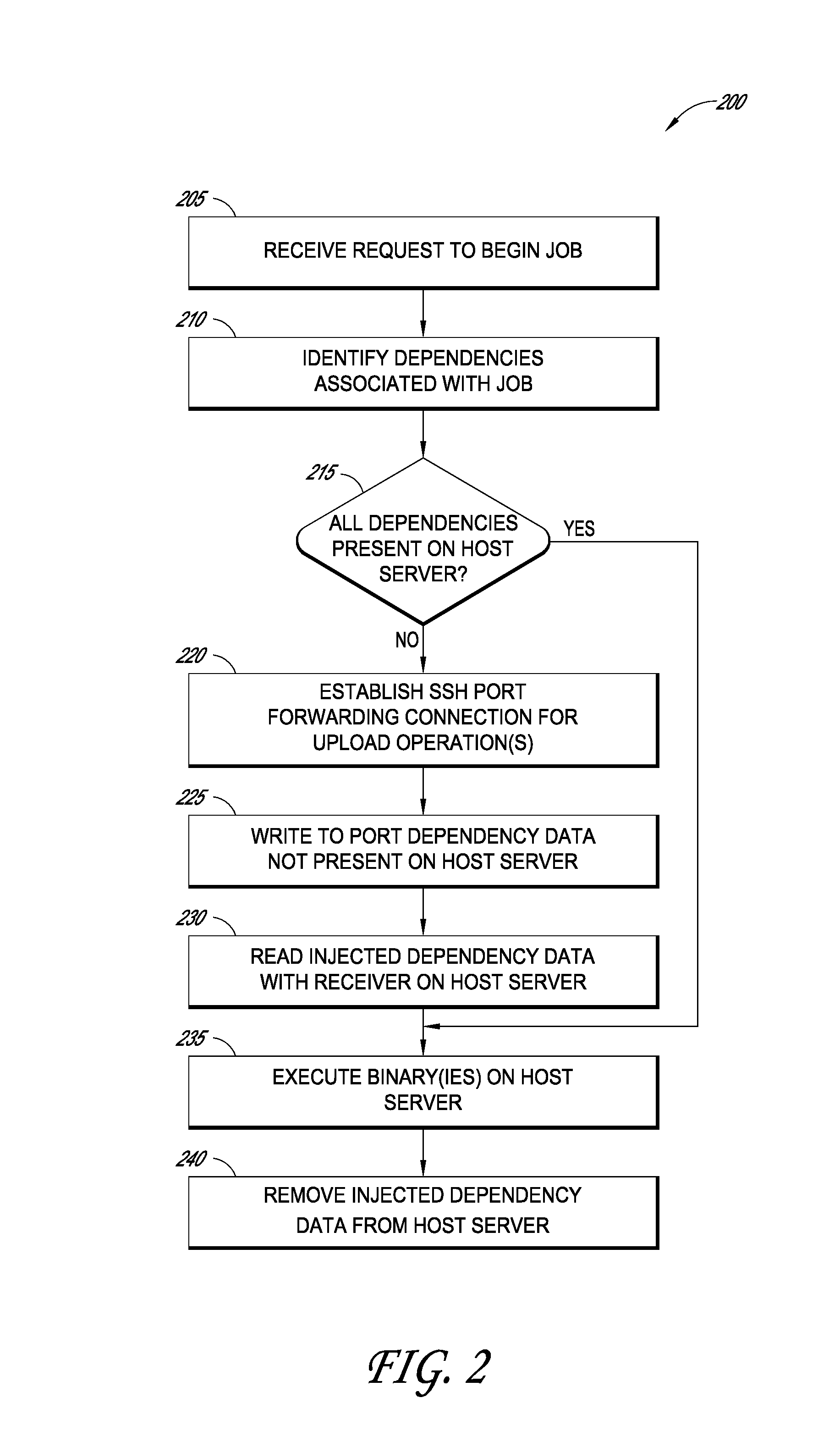
Systems and methods for data management in a virtual computing environment
ActiveUS8429649B1Improved data management operationFacilitate improved version controlMultiprogramming arrangementsSoftware simulation/interpretation/emulationData managementVirtual computing
Systems and methods are disclosed for performing operations on a host system with one or more virtual machines without persistently storing an agent or daemon thereon. In certain examples, a management server is configured to inject dependencies, such as binary data, over a network to the host system for performing a requested operation. For instance, systems and methods can establish a secure shell (SSH) port forwarding connection through which dependencies stored on the management server are injected into a service console of the host system. The injected dependencies can then be executed and / or used to perform the requested operation, such as a backup or compression operation on virtual machine data. Once the requested operation has completed, the injected binaries are preferably removed from the host system so as to conserve system resources.
Owner:QUEST SOFTWARE INC
System and Method for Managing Access to a Plurality of Servers in an Organization
InactiveUS20100325717A1Computer security arrangementsMultiple digital computer combinationsOperational systemCentralized database
A system for managing access to resources in a plurality of servers by a plurality of client computers by using an operating system independent Secure Shell (SSH) protocol running in each server and using a central policy database that centrally stores access rules which specify access to the servers for a plurality of users / accounts. Each time a target server receives a user request to establish an SSH session, it retrieves associated access rules from the central policy database to obtain the latest access rules. Based on the retrieved rules and the identity of the user and the identity of the client computer, the target server determines whether the user has permission to establish the SSH session with the target server. Using a centralized database and requiring the servers to always retrieve the latest access rules from a central database provides consistent application of the access rules across all servers and all client computers.
Owner:VISA USA INC (US)
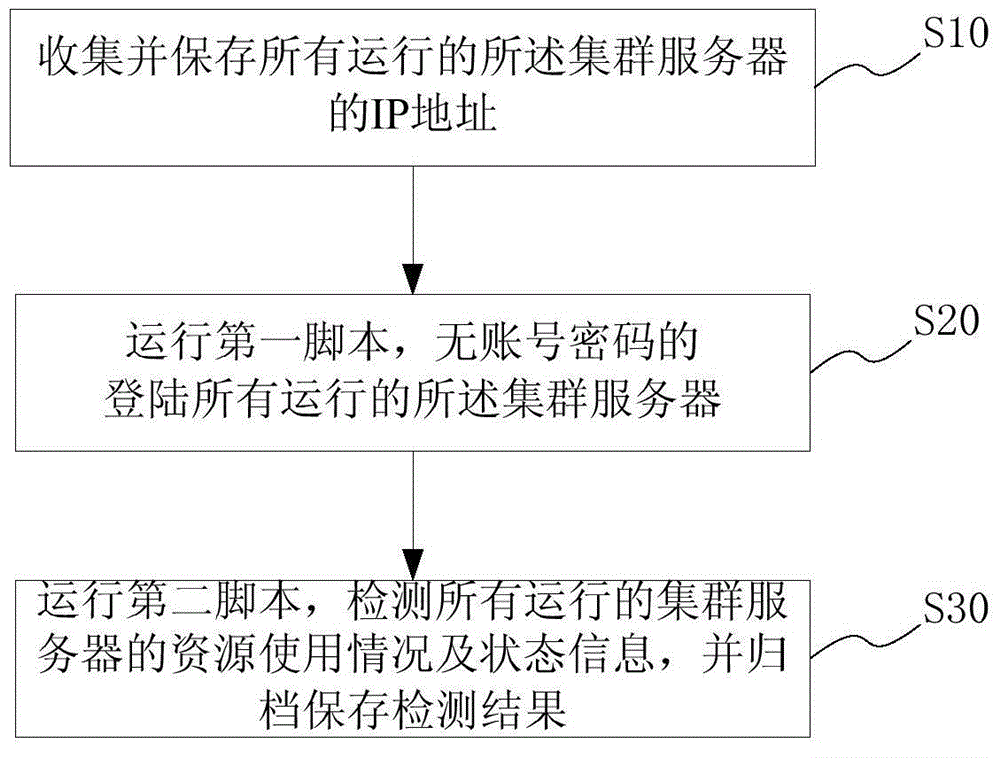
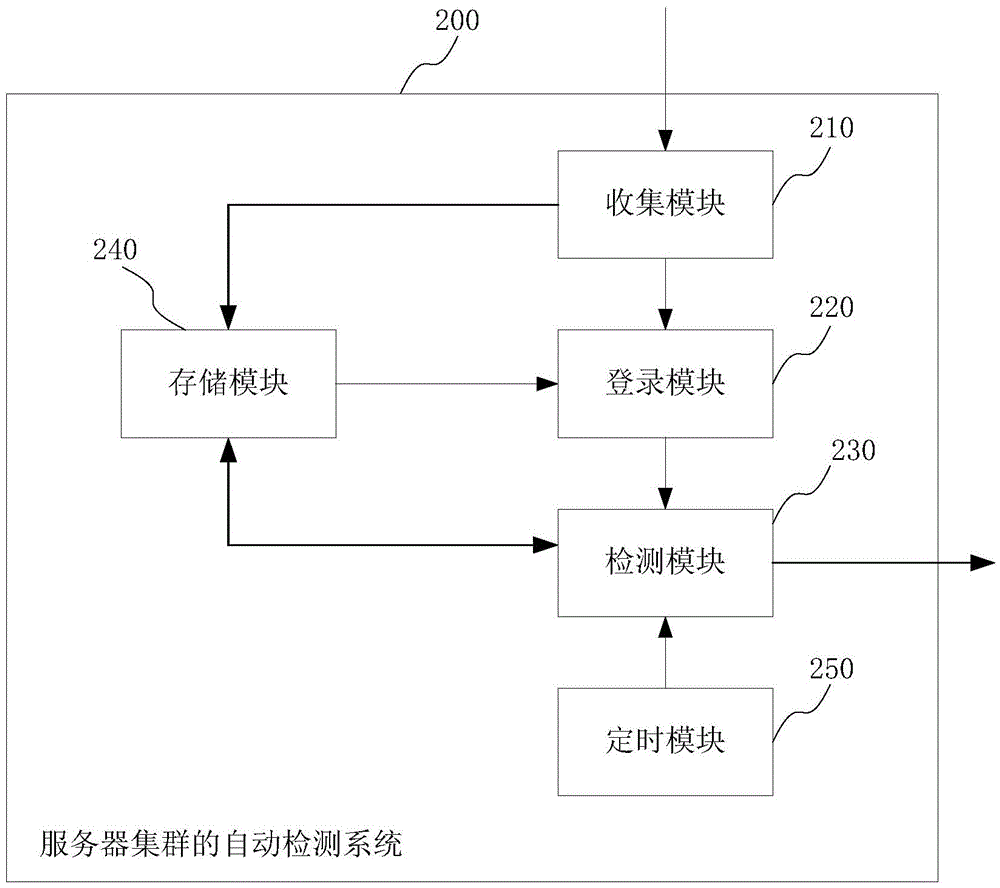
Automatic server cluster detecting method and system
The invention provides an automatic server cluster detecting method and system. The method comprises steps as follows: IP addresses of all operating cluster servers are collected and saved; a first script is operated according to the collected IP addresses, and all the cluster servers are logged in without account passwords; a second script is operated, the resource use condition and the state information of all the operating cluster servers are detected, and a detecting result is filed and saved. The first script is used for logging in the cluster servers without passwords and is pre-written with an SSH (secure shell) remote login authentication method; the second script is used for detecting the operating cluster servers and is pre-written through SHELL. According to the method and the system, no server is required to be purchased alone for deployment, no third-party business software is adopted, automatic detection is used to replace manual operation, the workload of a system administrator is reduced, the working efficiency is improved, and the cost is lower.
Owner:PHICOMM (SHANGHAI) CO LTD
Code generator based on SSH (secure shell) architecture and method
ActiveCN102591654AQuality improvementImprove efficiencySpecific program execution arrangementsProgramming languageComputer module
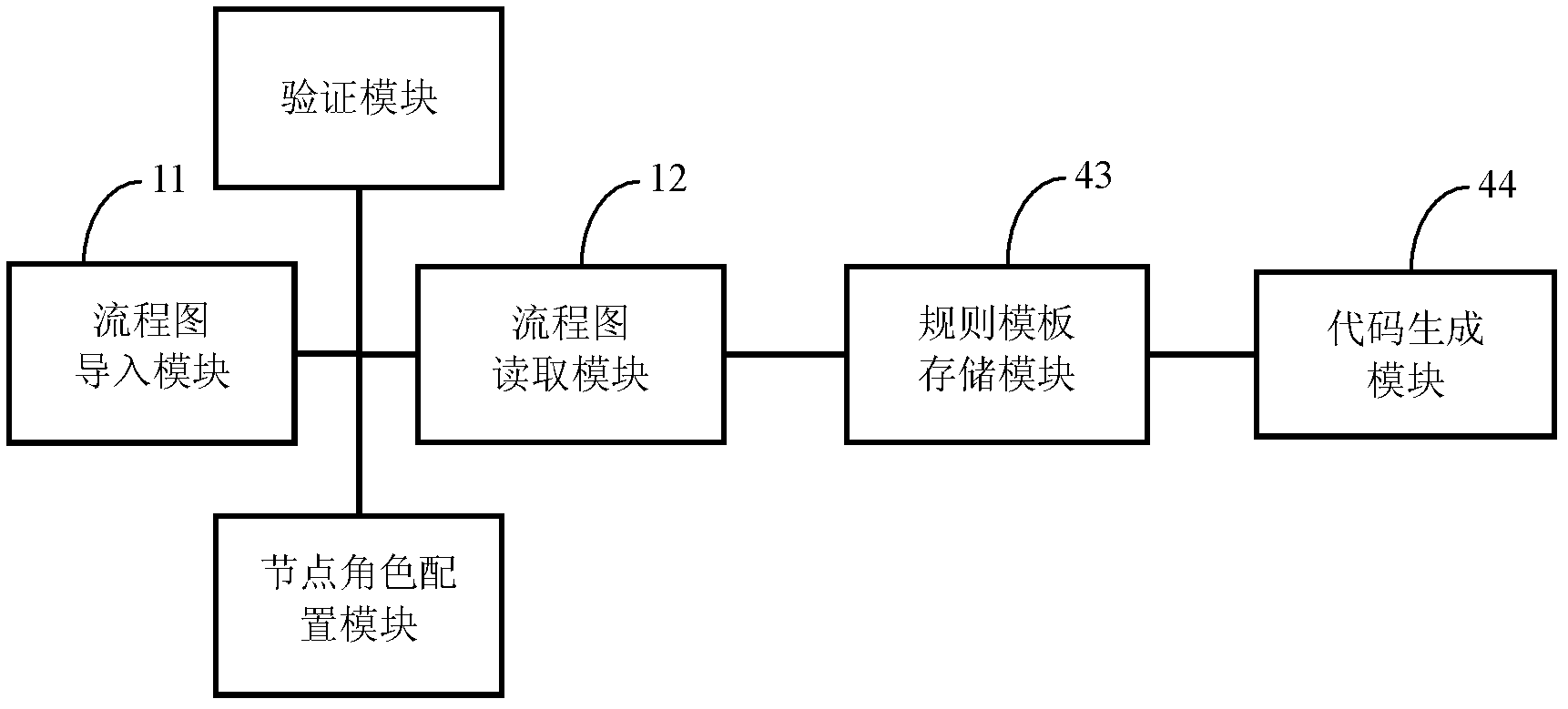
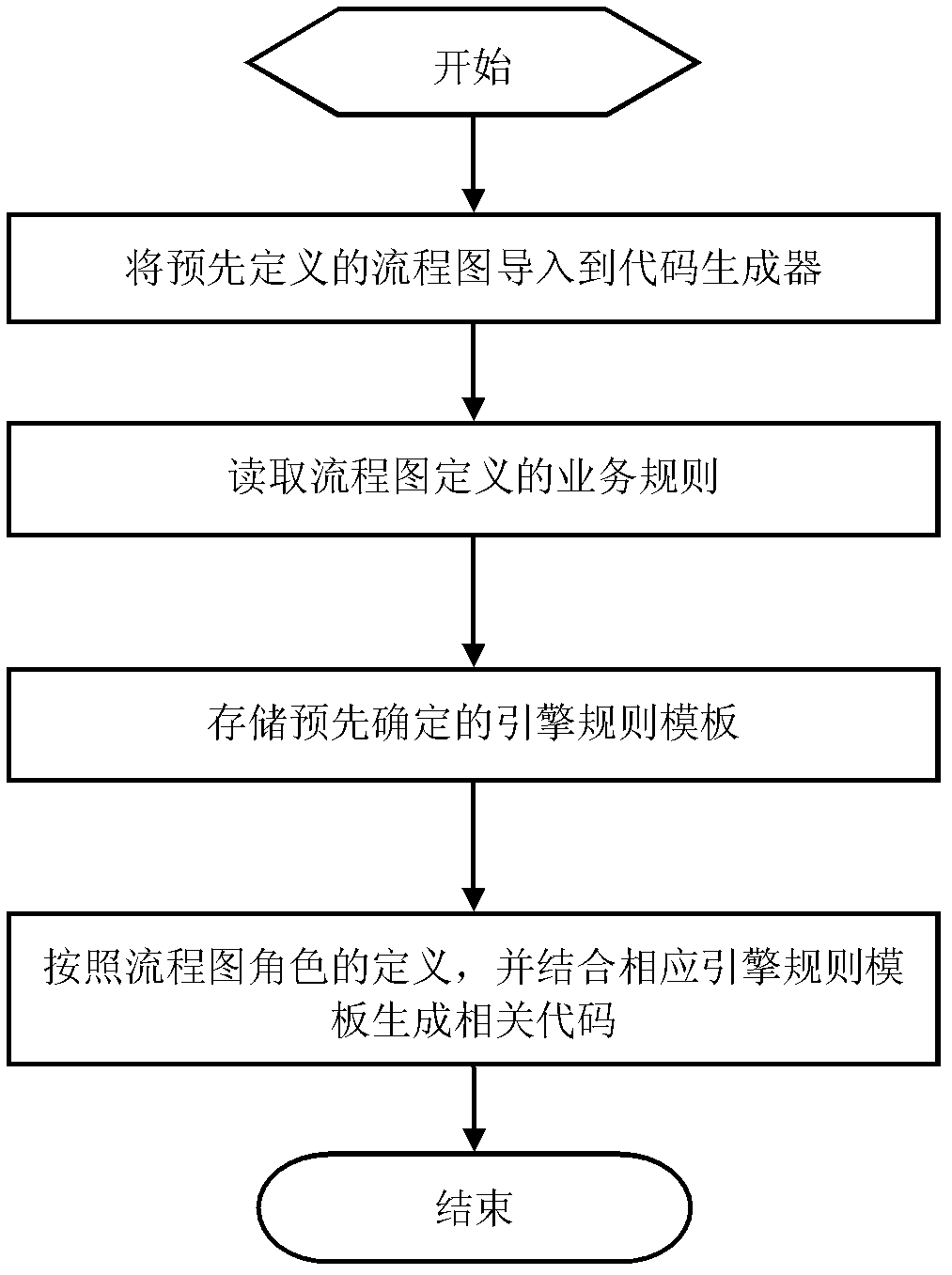
The invention relates to a code generator based on an SSH (secure shell) architecture. The code generator comprises a flow chart lead-in module (11), a flow chart reading module (12), a rule template storage module (13) and a code generation module (14), the flow chart lead-in module (11) is used for leading a flow chart into the code generator, the flow chart reading module (12) is used for reading business rules defined by the flow chart, the rule template storage module (13) is used for storing predetermined engine rule templates, the engine rule templates are called by the code generation module, and the code generation module (14) is used for generating relevant codes according to combination of definition of roles of the flow chart and the corresponding engine rule templates. The invention further relates to a code generating method based on the SSH architecture. By the aid of the code generator and the code generating method, operability, the quality of the codes and efficiency are improved to a great extent.
Owner:FOUNDER INTERNATIONAL CO LTD
Method and device for logging in Docker container by Web end
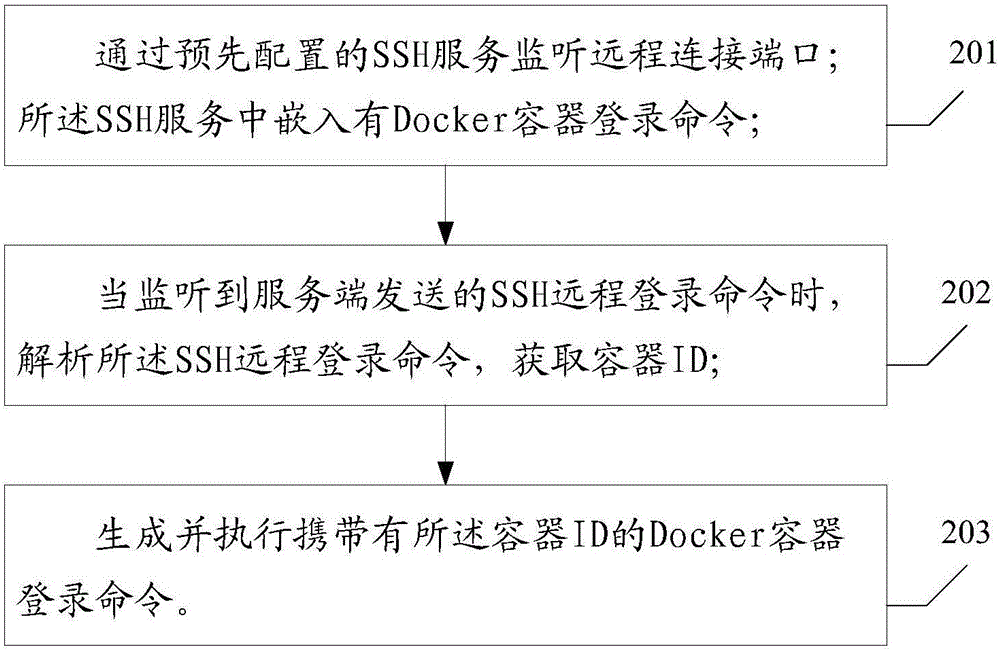
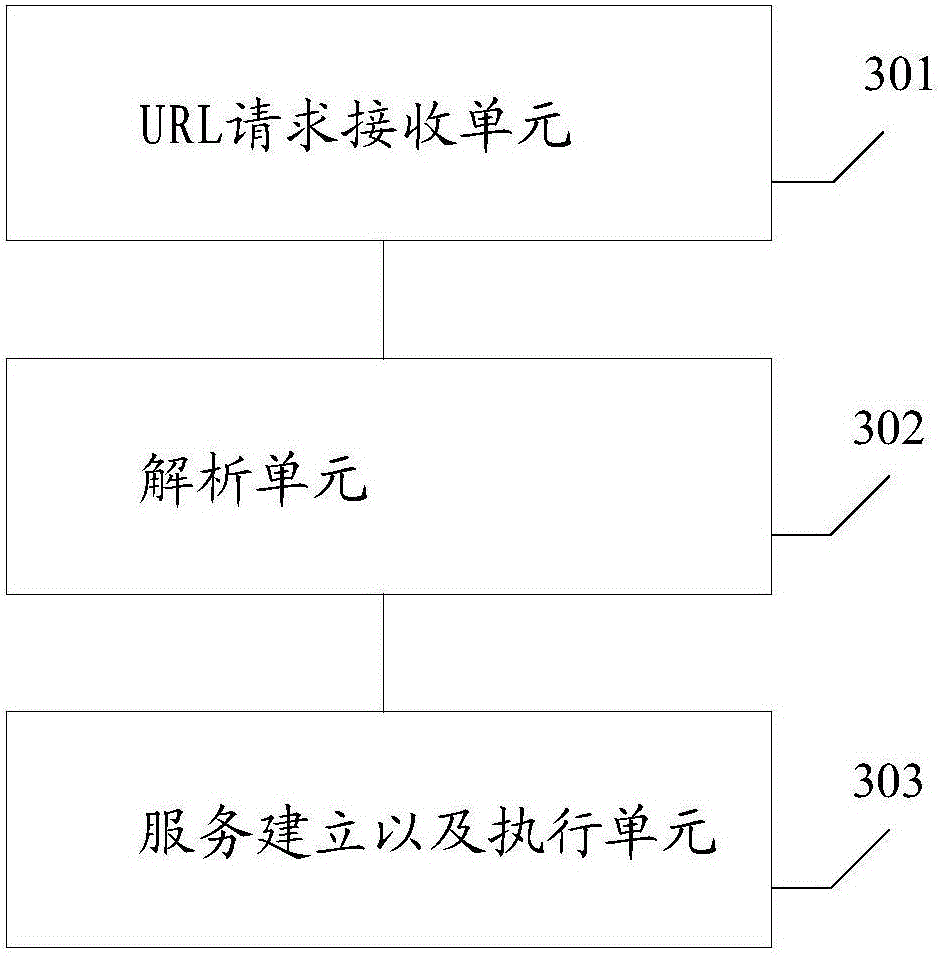
ActiveCN105872019AImprove the efficiency of development and maintenanceEasy and fast direct accessTransmissionUniform resource locatorSecure Shell
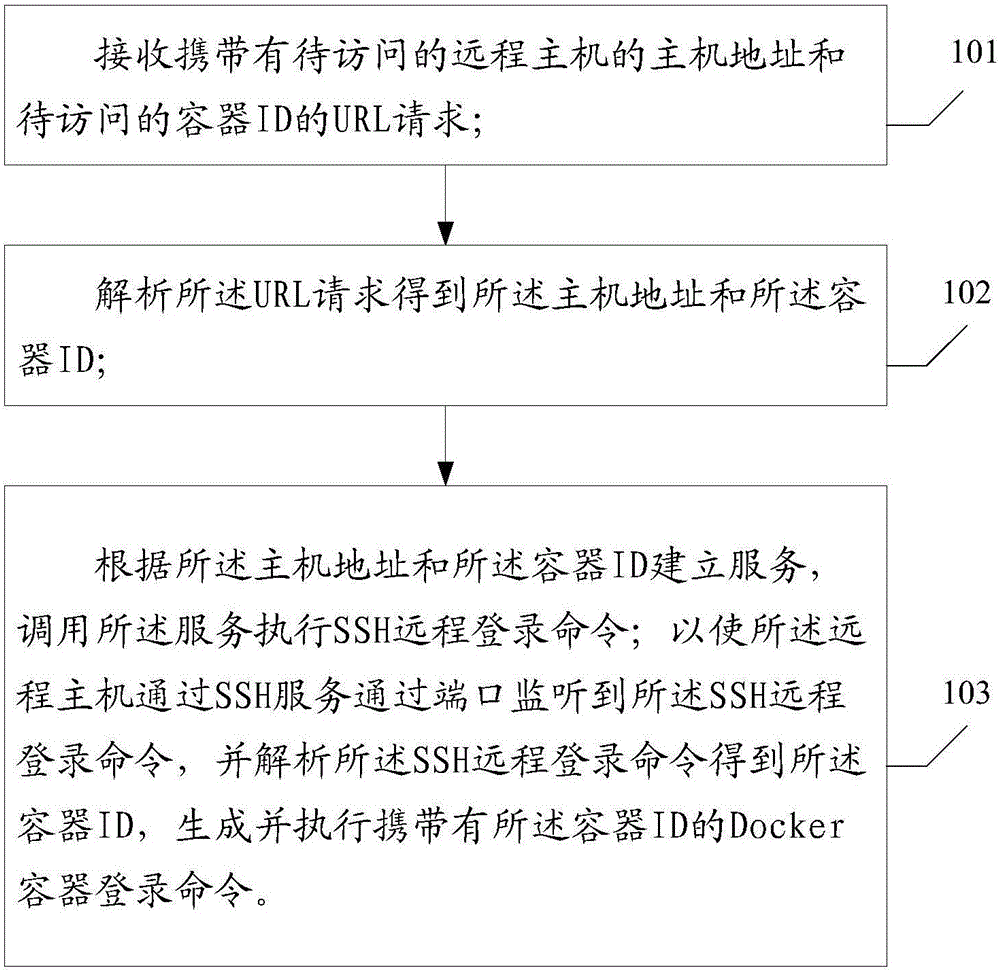
The invention provides a method and device for logging in a Docker container by a Web end, wherein the method comprises following steps of receiving a URL (Uniform Resource Locator) request in which the host address of a to-be-accessed remote host and a to-be-accessed container ID are carried; analyzing the URL request, thus obtaining the host address and the container ID; establishing service according to the host address and the container ID; invoking the service to execute an SSH (Secure Shell) remote login command; monitoring the SSH remote login command by the remote host through the SSH service and a port; analyzing the SSH remote login command, thus obtaining the container ID; and generating and executing a Docker container login command in which the container ID is carried. According to the method and the device, the Docker container in the remote host can be directly logged in by the Web end; the development, operation and maintenance complexity in the field of the Docker container can be reduced; the development, operation and maintenance efficiency can be improved; and a more convenient access mode is provided for a user.
Owner:BEIJING SOHU NEW MEDIA INFORMATION TECH
Secure Shell for Electronic Devices
InactiveUS20160042202A1Avoid overall overheatingMinimize damageBatteries circuit arrangementsScreening casingsLocking mechanismRadio frequency signal
An apparatus serving as a portable, lockable secure shell that prevents unauthorized physical and electrical signal access to a device enclosed within the shell. The apparatus comprises a case, a lid, a locking mechanism, cooling means, and charging means. When closed, the apparatus provides Faraday cage protection to an enclosed device to block external electronic, electromagnetic, and radio frequency signals from reaching the enclosed device, which preserves data stored in the device in its original form. In addition, the apparatus prevents clandestine access to an electronic device, which creates an obstacle to unauthorized access of information stored on the device.
Owner:MURRAY KENNETH +3
Network terminal management method
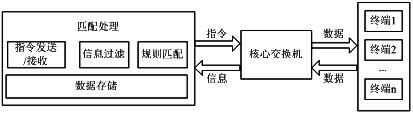
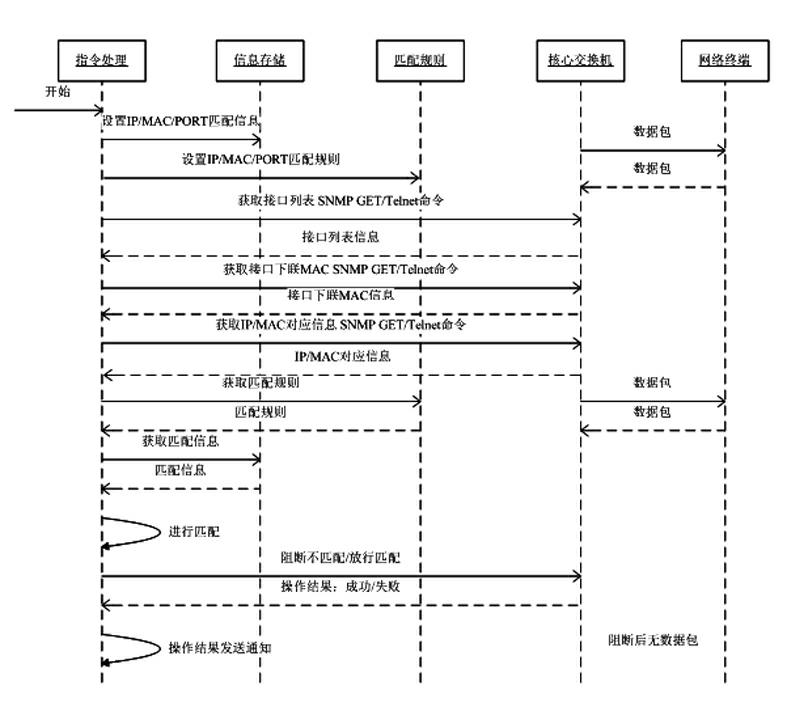
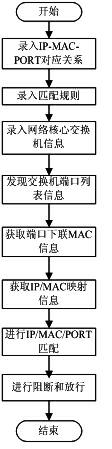
InactiveCN102123050AComplete managementAutomate managementData switching networksIp addressTerminal equipment
The invention discloses a network terminal management method, which comprises the following steps of: 1) inputting a correspondence relationship between a port of a switch and an Internet protocol (IP) address and a media access control (MAC) address of a terminal; 2) setting a terminal matching rule; 3) inputting simple network management protocol (SNMP) network related information required to be managed, or inputting the Telnet / secure shell (SSH) related information of each core switch manually; 4) acquiring the port list information of the core switch; 5) acquiring the downlink information of the MAC address of each port of the core switch; 6) acquiring a correspondence relationship list of the IP address and the MAC address in a network; 7) matching the port of the core switch, the IP address and the MAC address according to the configured terminal matching rule; and 8) blocking the terminal which does not accord with the matching rule, releasing the terminal which accords with the matching rule, and giving an alarm for an operation result.
Owner:勤智数码科技股份有限公司
Automated multi-platform configuration tool for master data management systems using secure shell protocol
InactiveUS20100162201A1Consistent environmentSimple and reliable processDigital data processing detailsUser identity/authority verificationMulti platformSecure Shell
Various embodiments of a method, apparatus and article of manufacture provide an automated multi-platform configuration tool for master data management systems using secure shell protocol.
Owner:SAP AG
Equipment security apparatus
InactiveUS7481410B2Improve securityEasy to operateClothing locksLocks for portable objectsEngineeringSecure Shell
A security apparatus connects an electronic device to a structure. The security apparatus includes a structural mount, a security enclosure, and a swivel mechanism. The structural mount extends from the structure. The security enclosure has a tray that can mount a variety of electronic devices externally to the security enclosure. The security enclosure also has a security housing that slidably receives the tray. The tray and the security housing define a substantially secure fastening volume wherein at least one electronic device fastener is located. The swivel mechanism, which is at least partially located within the fastening volume, engages the security housing and orients the security enclosure and the electronic device attached thereto with respect to the structure.
Owner:BUSINESS MACHINE SECURITY
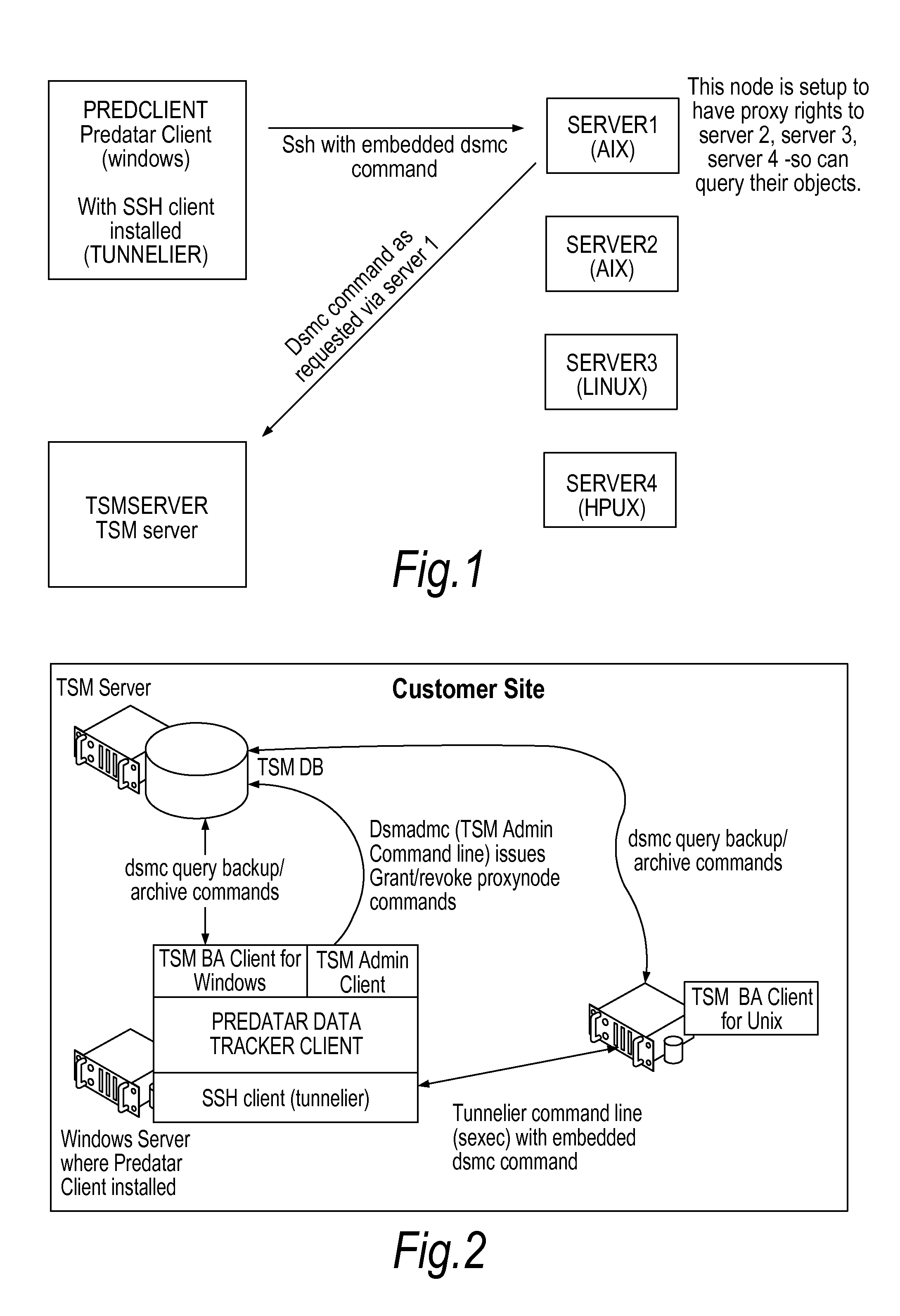
Data Storage Management
InactiveUS20110196893A1Avoid restrictionsEfficient collectionDigital data information retrievalDigital data processing detailsOperational systemStorage management
Apparatus is disclosed for managing the use of storage devices on a network of computing devices, the network comprising a plurality of computing devices each running different operating systems, at least one data storage device, and a management system for controlling archival of data from the computing devices to the data storage device, the management system including a database of data previously archived; the apparatus comprising an agent running on a first computing device attached to the network, the first computing device running a first operating system, the agent being adapted to issue an instruction to a second computing device being one of the plurality of computing devices via a remote administration protocol, the second computing device running a second operating system that differs from the first operating system, and the instruction comprising a query to the database concerning data archived from computing devices running the second operating system. The remote administration protocol is preferably Secure Shell (SSH), but other protocols can be employed. A corresponding method and software agent are also disclosed. In addition, a data storage resource management system is disclosed, comprising a query agent and an analysis agent, the query agent being adapted to issue at least one query to a database of backed up or archived objects in order to elicit information relating to the objects; the analysis agent being adapted to organise the query results and display totals of objects meeting defined criteria.
Owner:SILVERSTRING
Key control system using separated ID and location detection mechanisms
InactiveUS7049961B2Co-operative working arrangementsSensing record carriersLocation detectionControl system
An object control and tracking system and related methods using separate object identification and location detection mechanisms for objects, such as keys, that are maintained in a secure enclosure, such as a key drawer. A plurality of object slots are located on the top tray of the enclosure to receive object tags that include both an RFID tag and an object to be tracked. The objects (e.g., keys) are attached to a portion of the object tags that are outside of the enclosure. Presence detectors are used to determine if an object tag is present in the corresponding slot of the enclosure. RFID sensors located on opposite interior side walls of the enclosure interrogate each RFID tag to determine the presence of each RFID tag within the enclosure. The object control and tracking system includes a controller, a memory for storing an object control database, and related processing logic operating on the controller to control scanning of the presence detectors to determine an object tag's presence in a corresponding slot, to identify each object present in the enclosure and to compare the identified objects with an object control database to determine each object removed or replaced since the previous database update.
Owner:DEUT BANK AG NEW YORK BRANCH
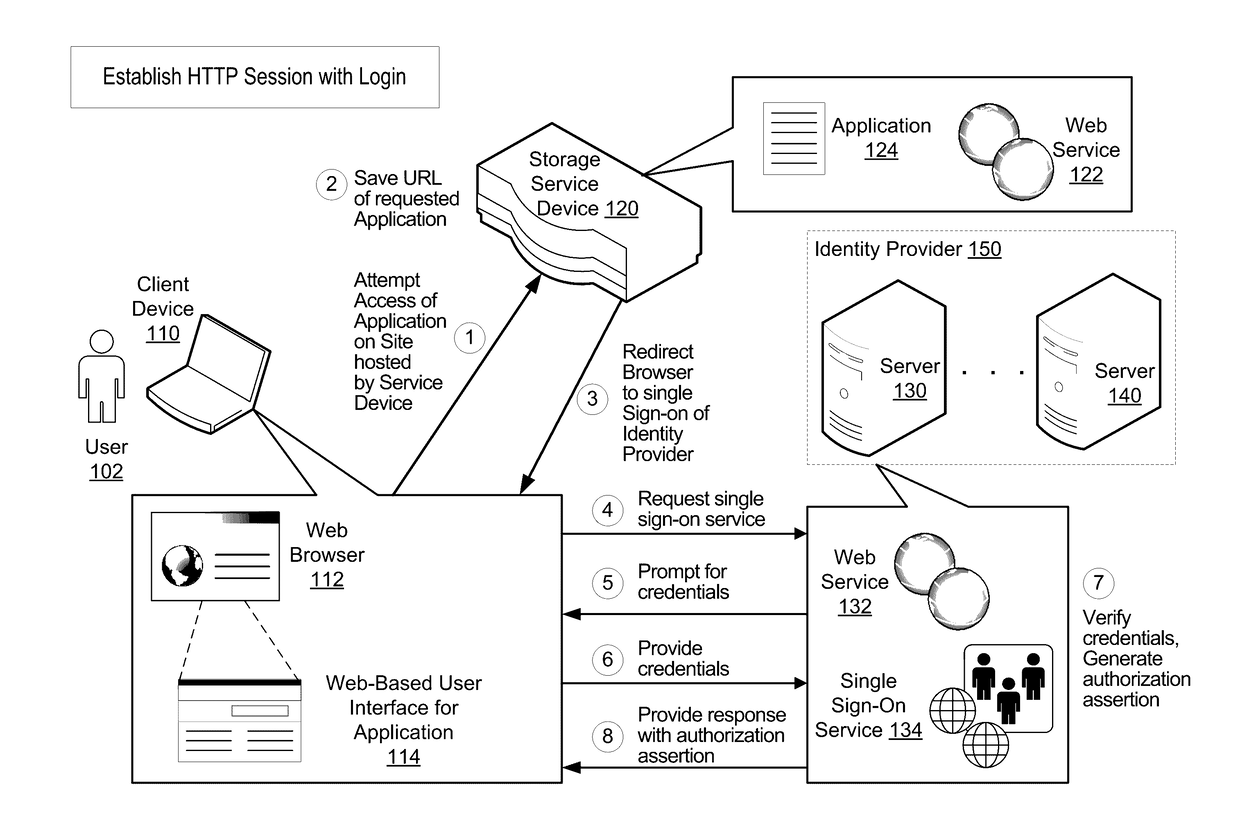
Single Sign-On Method for Appliance Secure Shell
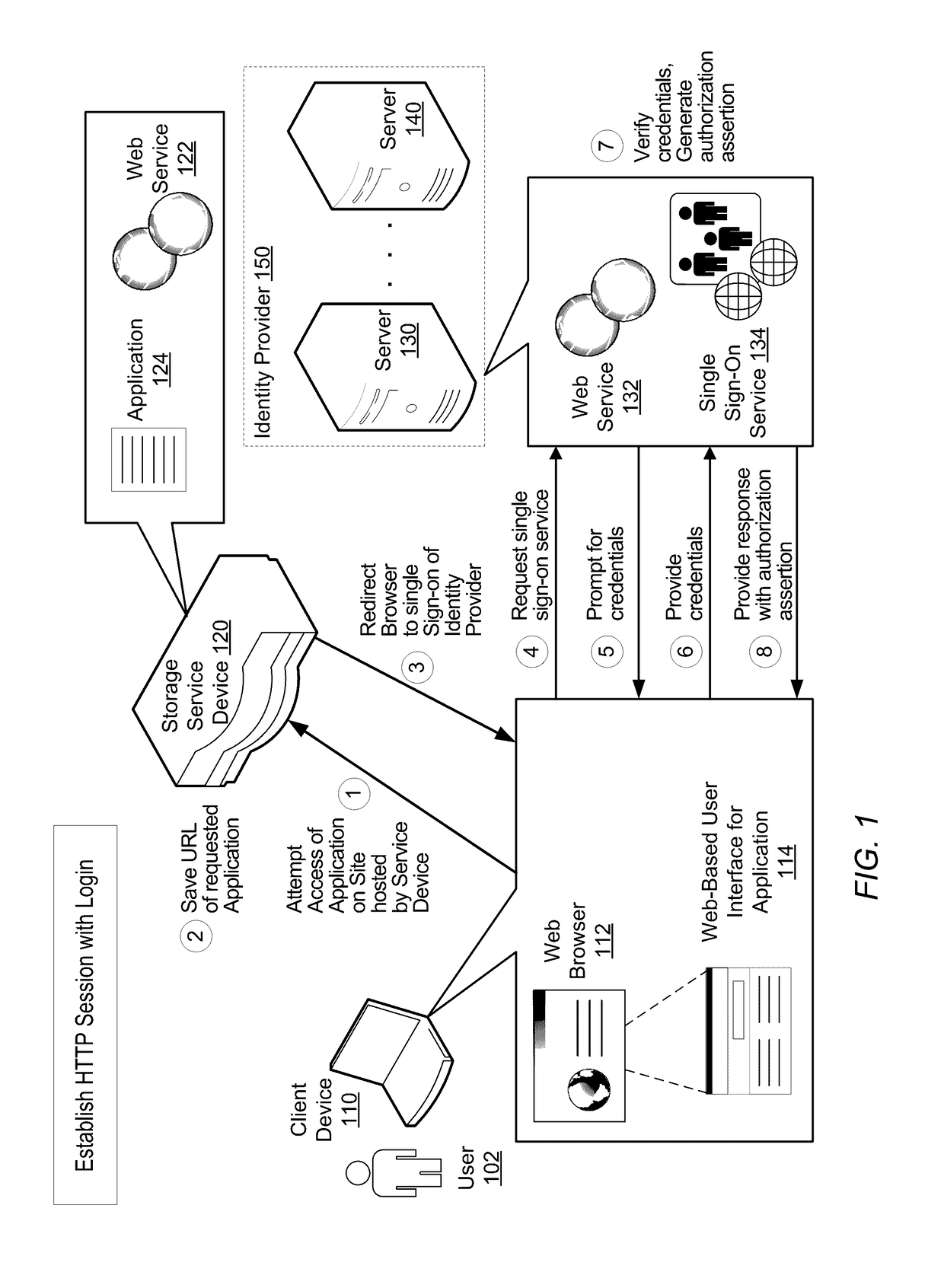
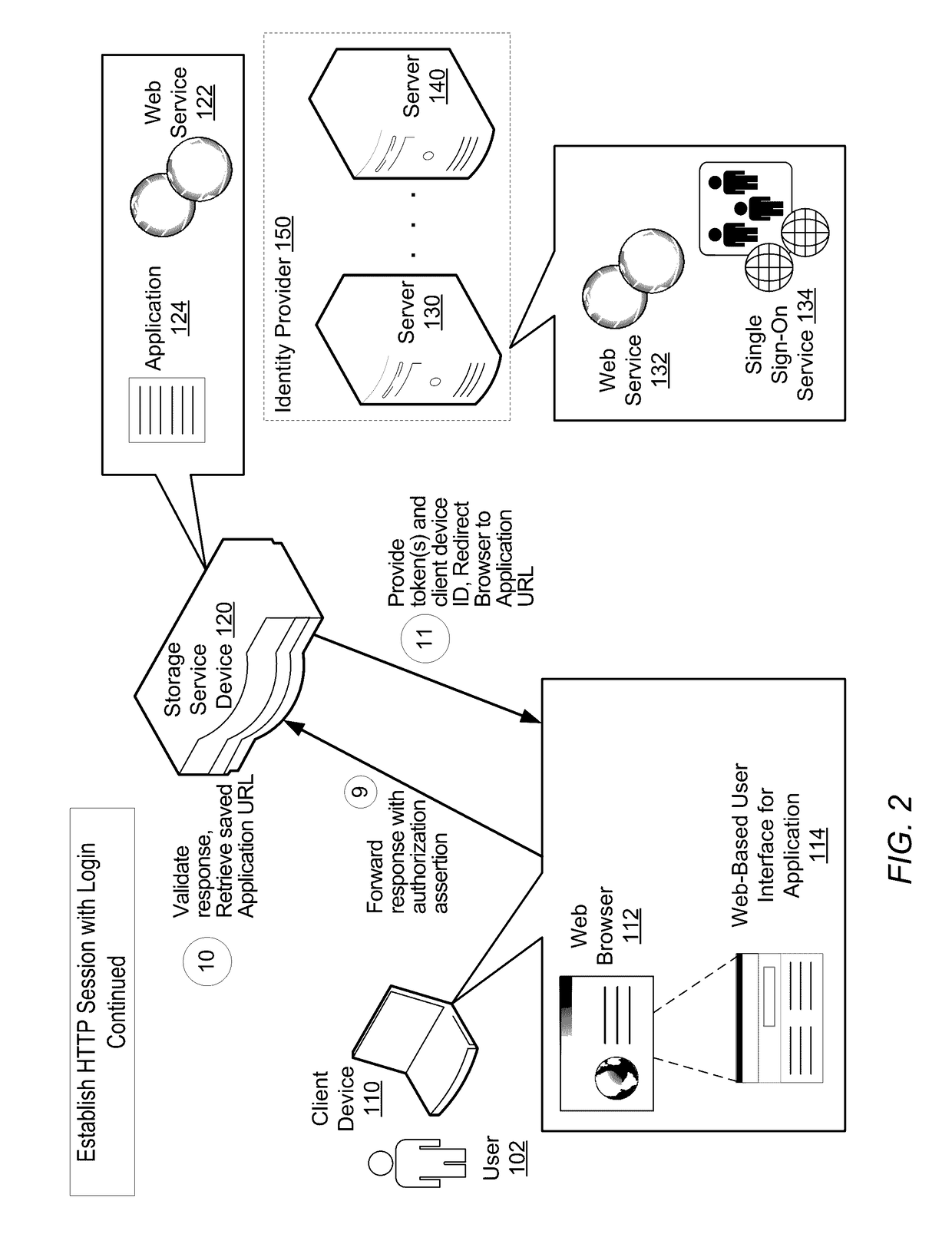
ActiveUS20170099280A1Efficiently establishedComputer security arrangementsTransmissionThird partyWeb browser
A system and method for efficiently establishing a secure shell connection for accessing Web resources. A user attempts to establish a secure Hypertext Transfer Protocol (HTTP) session between a client computing device and a remote storage device. The storage device redirects the Web browser of the client computing device to a single sign-on (SSO) third-party identity provider for authorizing the user. After successful authorization, the client computing device receives information to use to maintain a secure HTTP session. This information is stored on the storage device. The user attempts to establish a text-based secure shell session. The user is not prompted for login credentials. However, the user is authenticated using the previously stored information and a text-based secure shell session is established.
Owner:VERITAS TECH
Docker container safety management method, system and equipment and storage medium
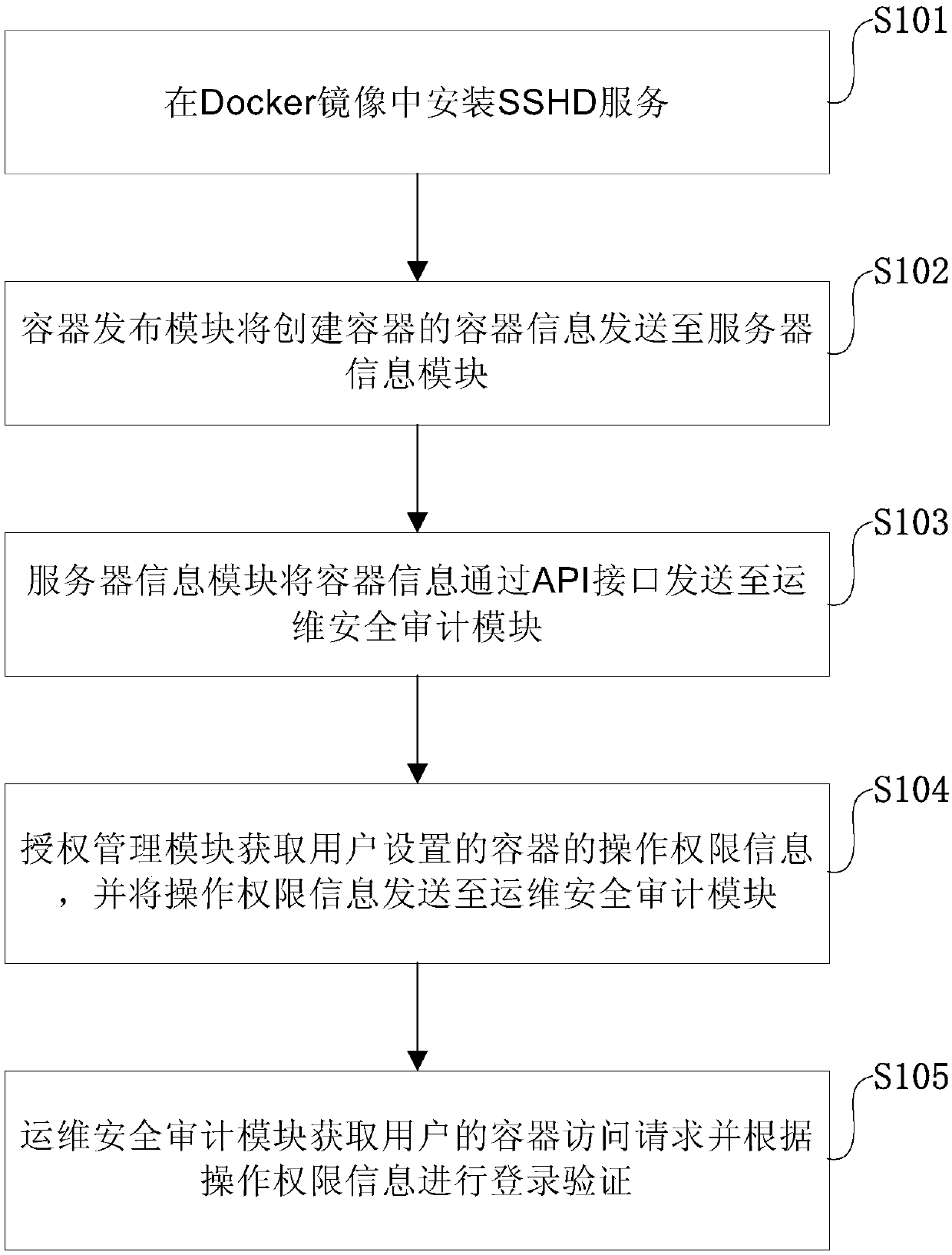
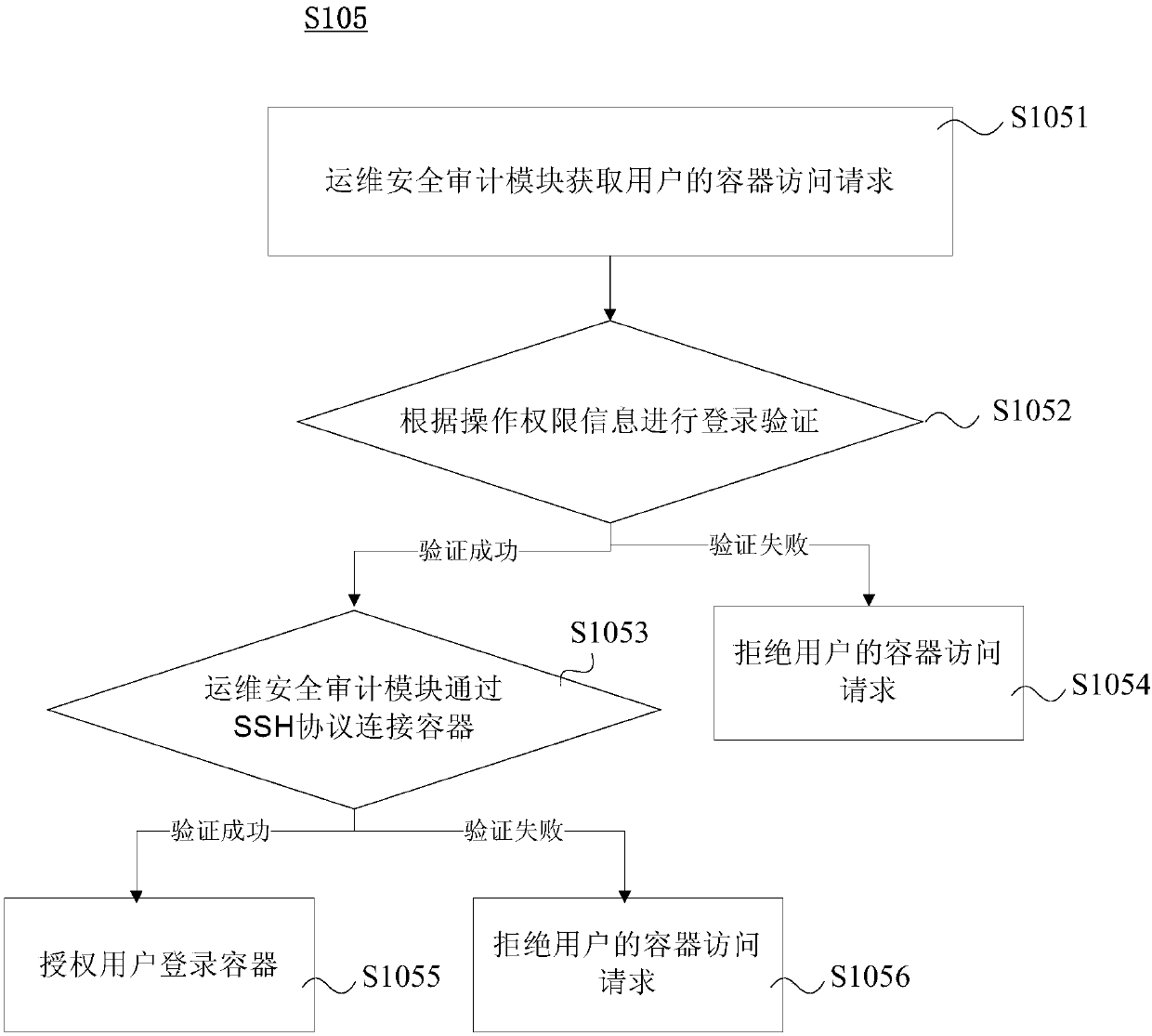
InactiveCN107634951AEnsure safetyTransmissionSoftware simulation/interpretation/emulationSafety controlComputer module
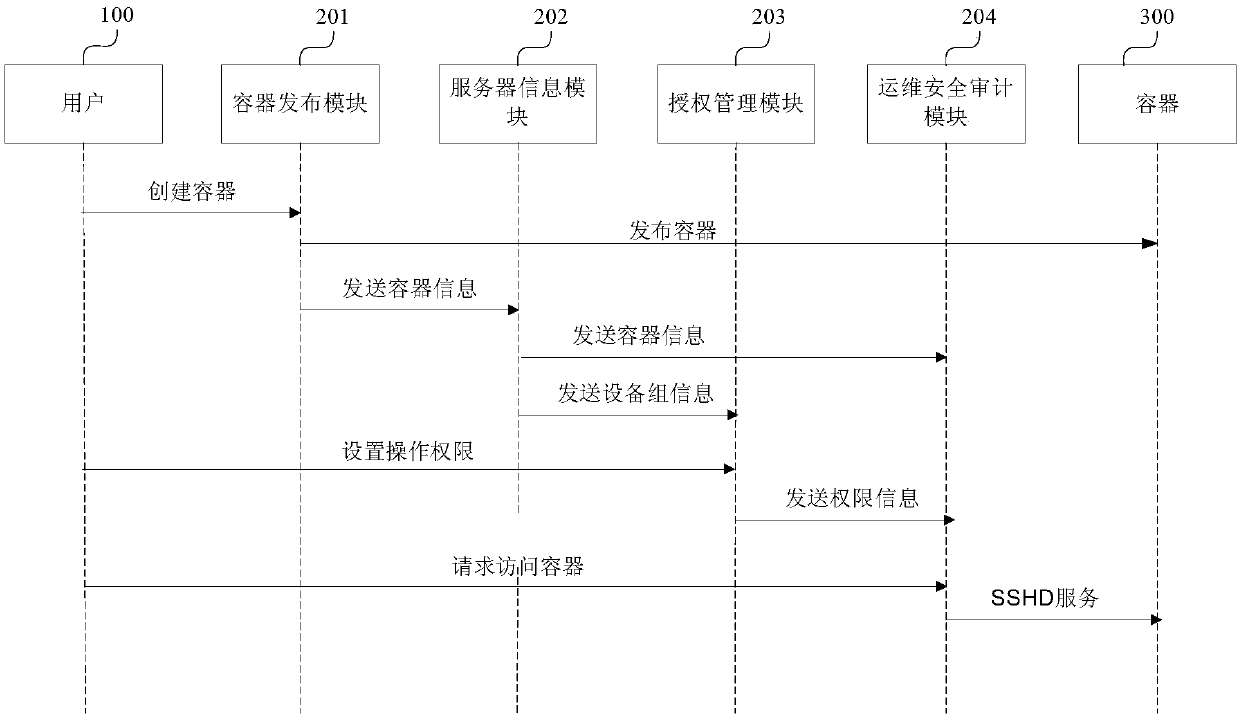
The invention provides a Docker container safety management method. The Docker container safety management method comprises the following steps: an SSHD (Solid State Hybrid Drive) service is installedin a Docker mirror; a container publishing module transmits container information of a creating container to a server information module; the server information module transmits the container information to an operation-maintenance safety audit module through an API (Application Programmable Interface); an authorization management module acquires operation permission information of the containerset by a user, and transmits the operation permission information to the operation-maintenance safety audit module; and the operation-maintenance safety audit module acquires a container access request of the user, performs login verification according to the operation permission information, is connected with the container through an SSH (Secure Shell) protocol if the verification is passed, so that the user logs in the container through the operation-maintenance safety audit module, and the operation-maintenance safety audit module denies the container access request of the user if the verification fails. Container authorization, safety control of login and operation audit are all finished by the operation-maintenance safety audit module, so that the safety of the container in a using process is ensured fully.
Owner:CTRIP TRAVEL NETWORK TECH SHANGHAI0
SSH protocol behavior pattern recognition and alarm method based on total traffic of bypass network
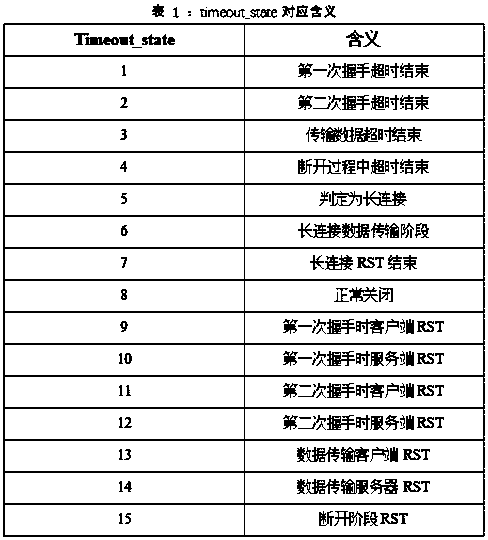
ActiveCN109587179AImprove work efficiencyProtection securityData switching networksTraffic capacitySecure Shell
The invention relates to an SSH (Secure Shell) protocol behavior pattern recognition and alarm method based on the total traffic of a bypass network. User network traffic is received through switch bypass mirroring, TCP (Transmission Control Protocol) traffic is separated out, and the key features of SSH protocol traffic are extracted for behavior judgment. The behavior pattern of the traffic dataof each SSH protocol is judged according to the key feature information, the SSH protocol data is aggregated according to the source address and the destination address, and the overall communicationbehavior pattern of the current source address and destination address is considered and judged according to the behavior pattern of each piece of traffic data. Different patterns correspond to different alarm information, and the same type of alarms has different alarm levels. The invention provides an SSH protocol behavior pattern recognition and alarm method based on the total traffic of a bypass network, which has the advantages of simple acquisition of basic data, avoidance of the tedious traditional identification, wide application range, fast and simple identification and judgment andhigh accuracy.
Owner:广州广电研究院有限公司
Secure access logic control method based on terminal access behavior and platform server
ActiveCN102984159ASimplify the difficulty of resource managementAvoid log audit complexityUser identity/authority verificationDot matrixFree interface
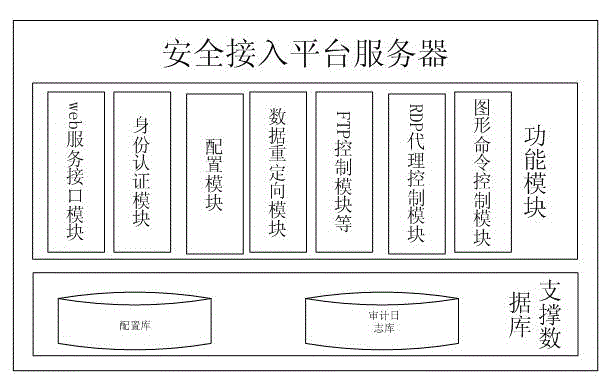
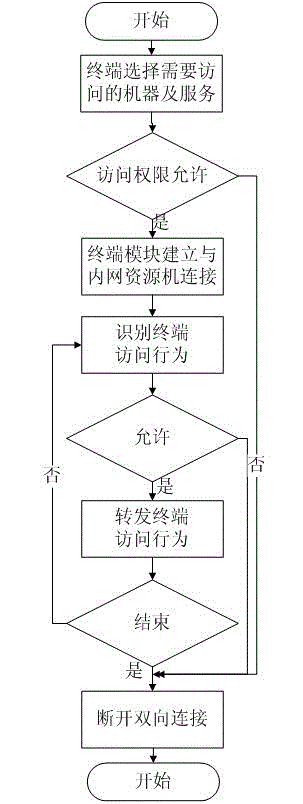
The invention discloses a secure access logic control method based on a terminal access behavior and a secure access platform server. A logic control module of the terminal access behavior is arranged at a secure access platform server terminal; information, such as terminal access authority, scene judging parameters, a dot matrix area command comparison table and the like is configured; each data package of terminal access intranet resource is redirected into an agent program which corresponds to the logic control module; and the logic control module identifies the terminal access behavior in various modes to control forwarding or discard. The method of the invention executes classification and identification of character commands, such as FTP (File Transfer Protocol), TELNET, SSH (Secure Shell) and the like, RDF (Resource Description Framework) graphical interface operation and user free interface system operation for the terminal access behavior on the secure access platform server terminal, and judges whether the execution is permitted or not according to identified commands and user authority logic control, so that the difficulty of resource management is simplified, the repeated authentication of each system is avoided; and the identification and the logic control of the character commands, the graphical interface operation and the like are solved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com