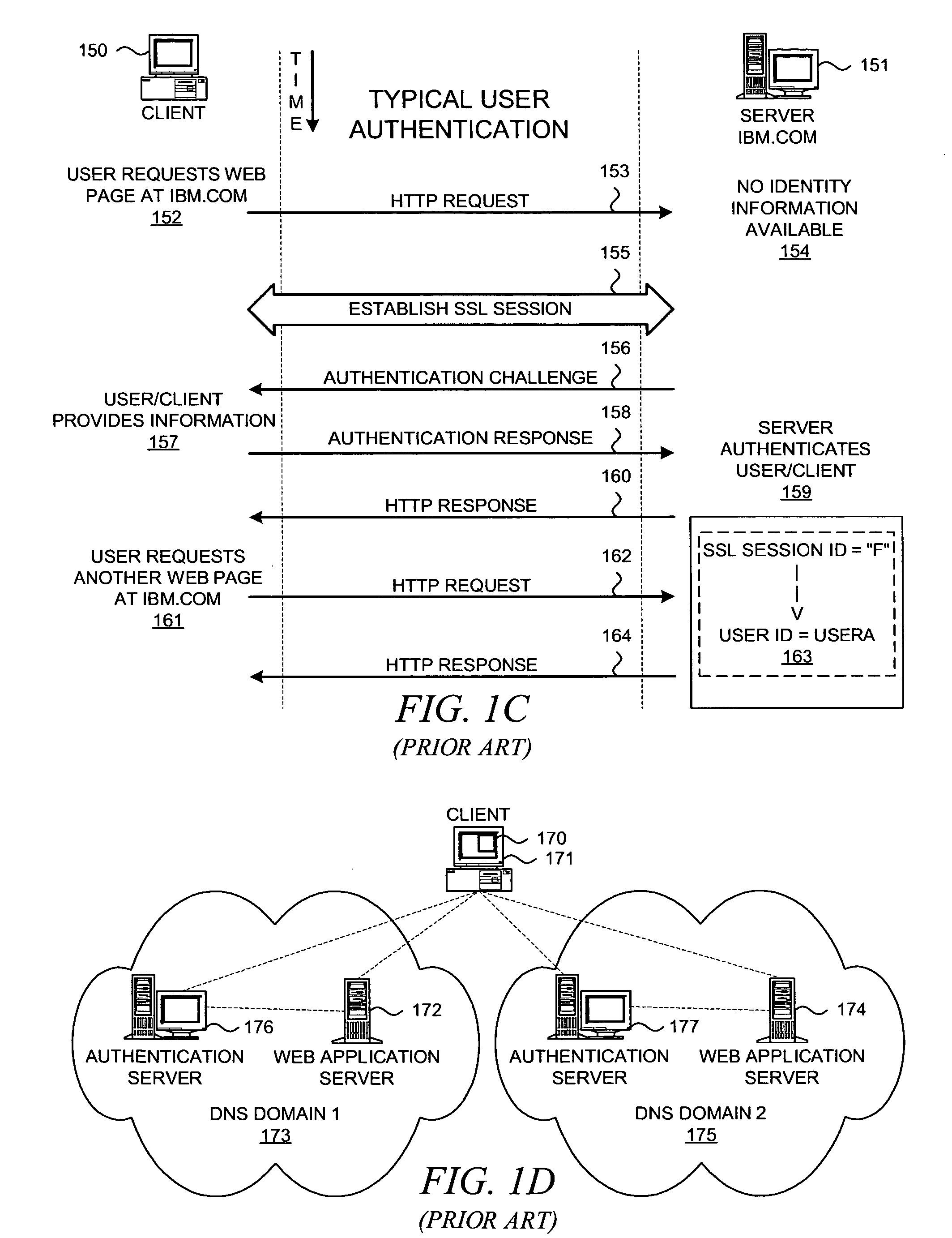
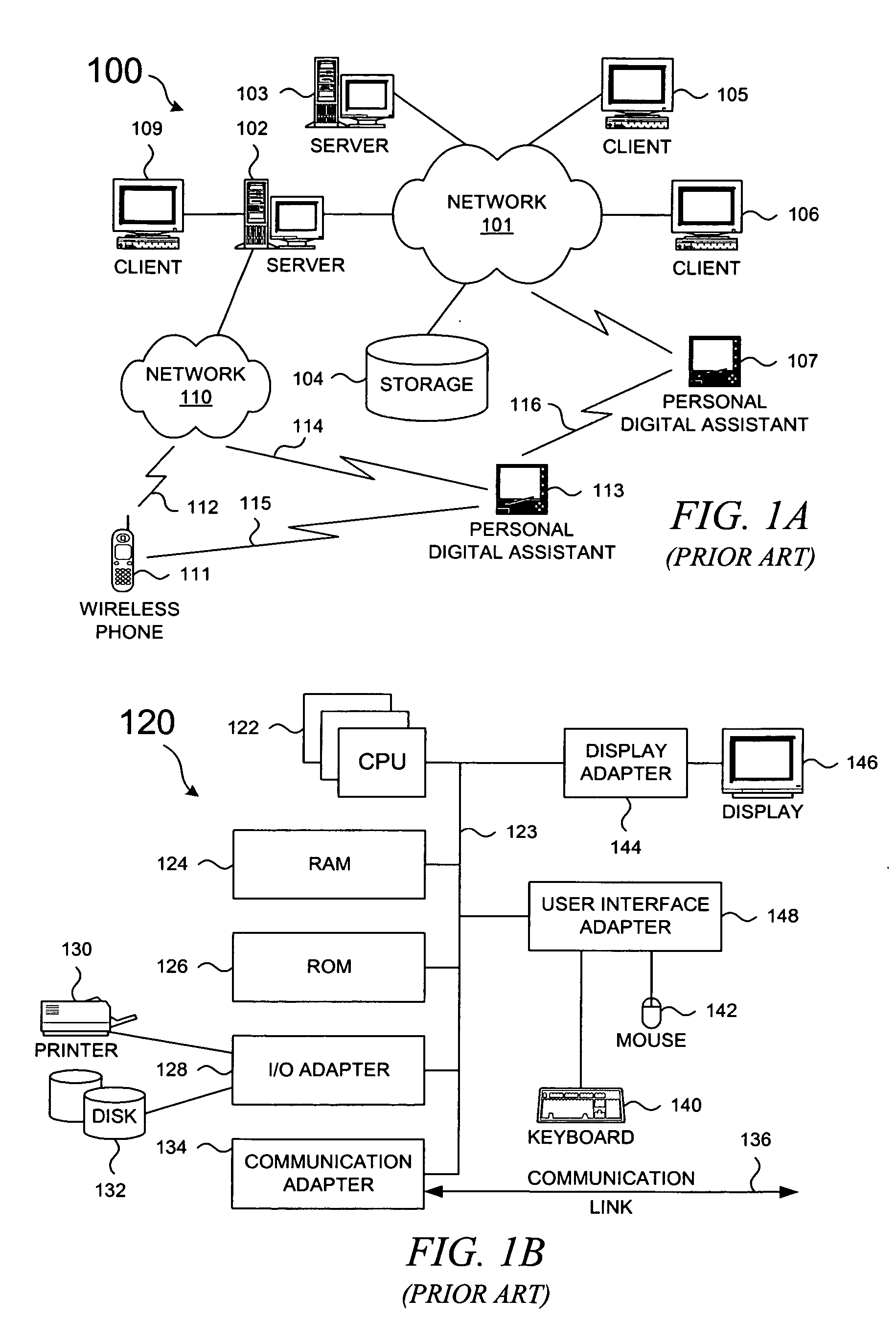
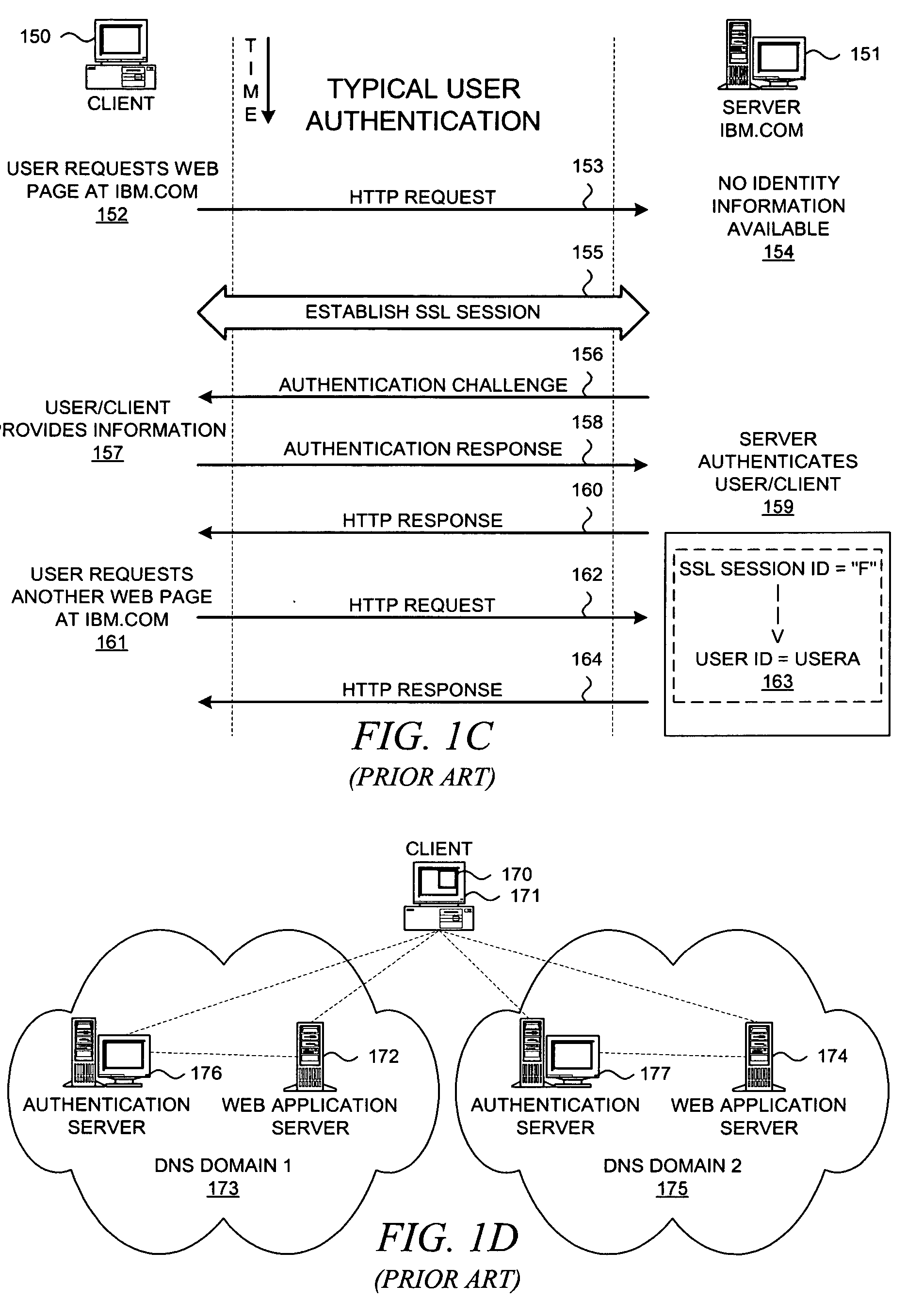
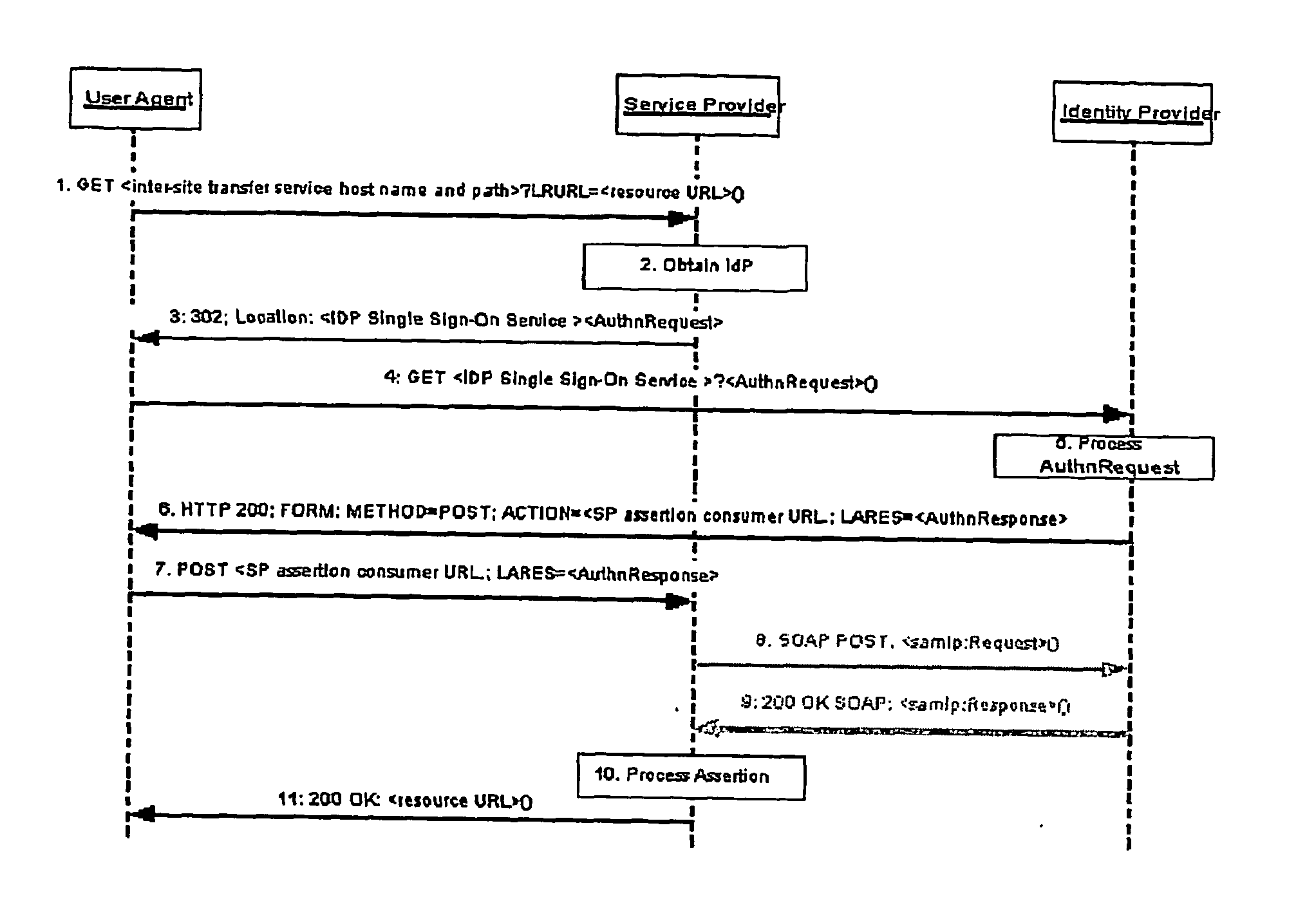
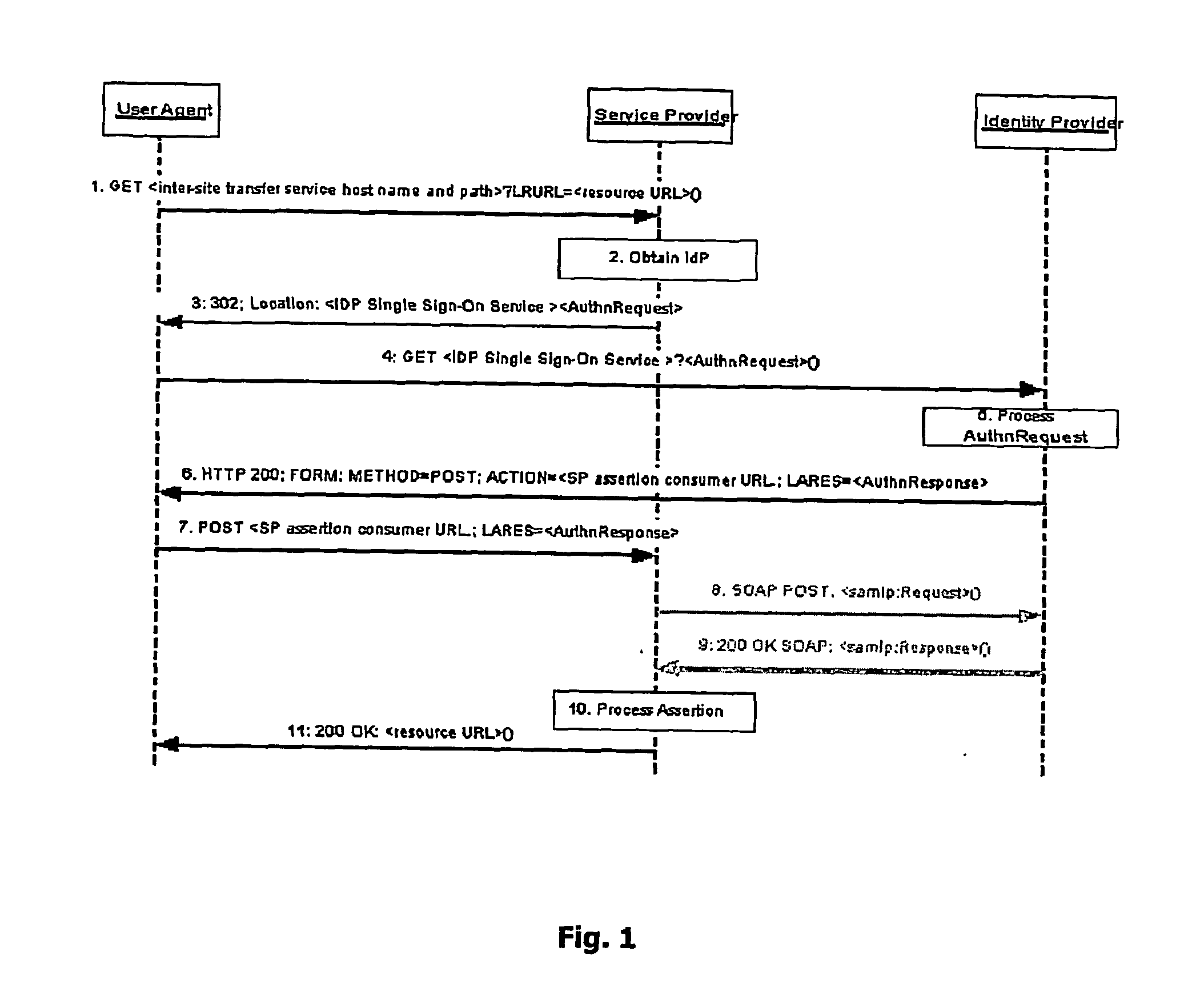
Patents
Literature
278 results about "Identity provider" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
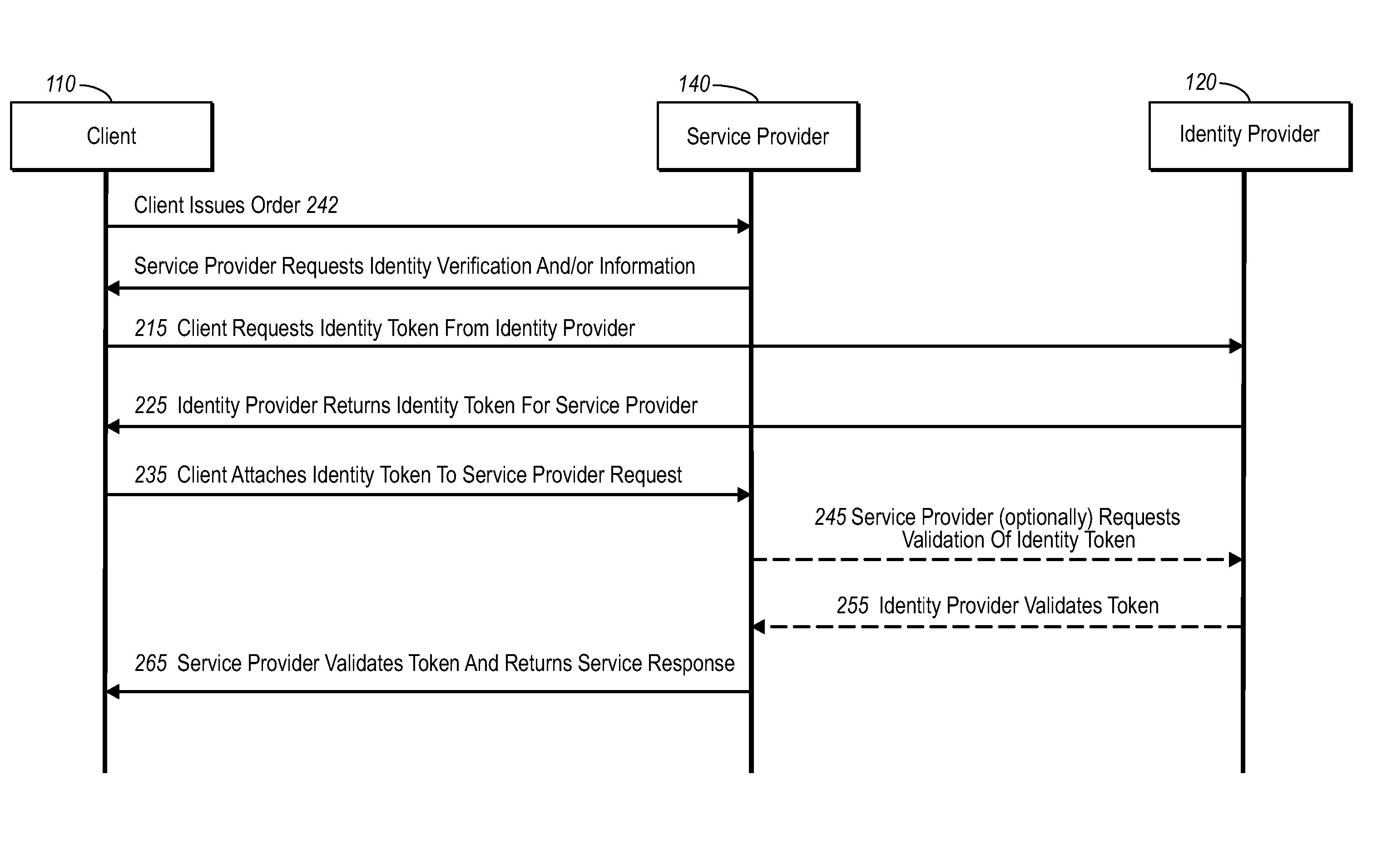
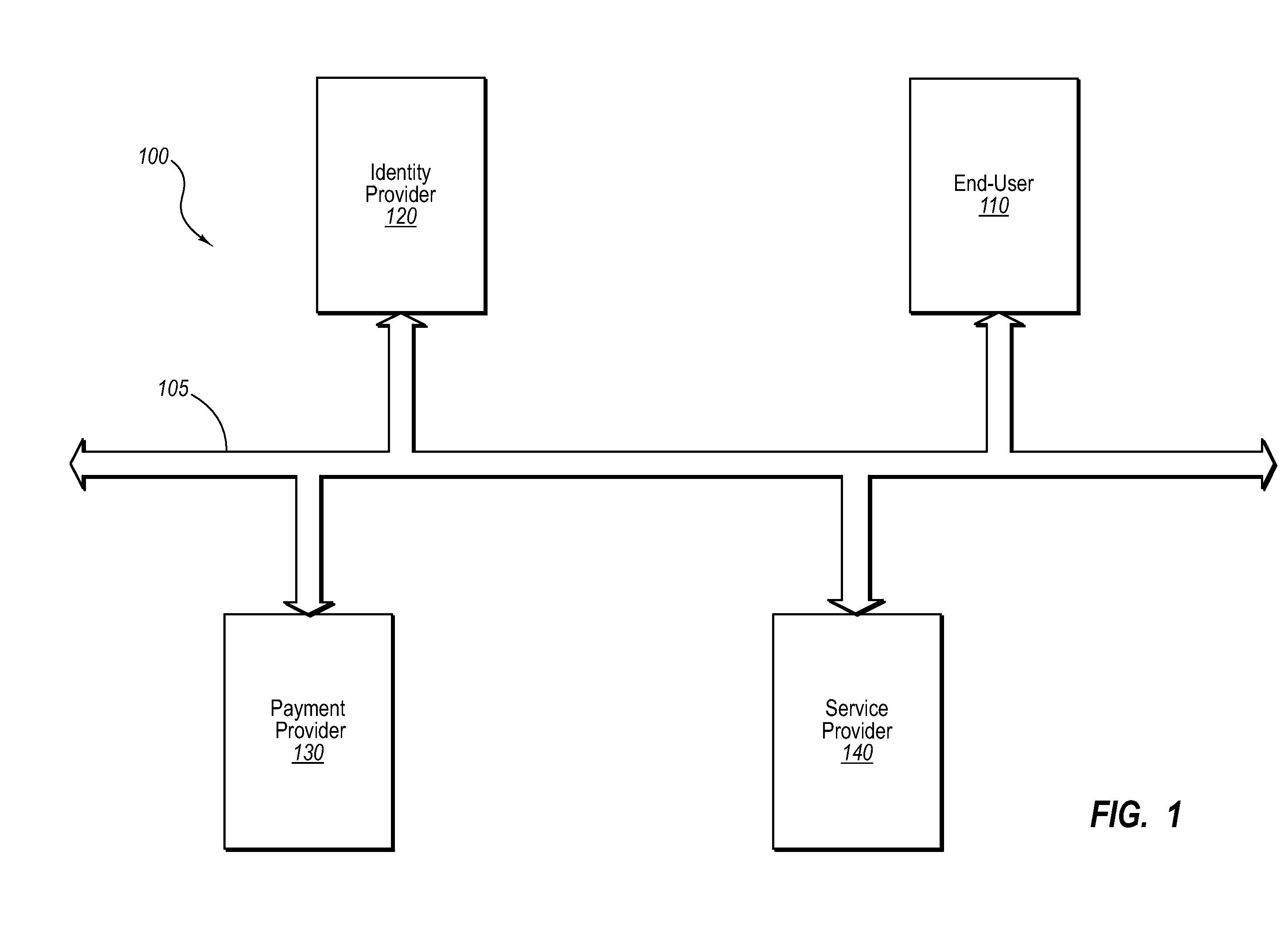
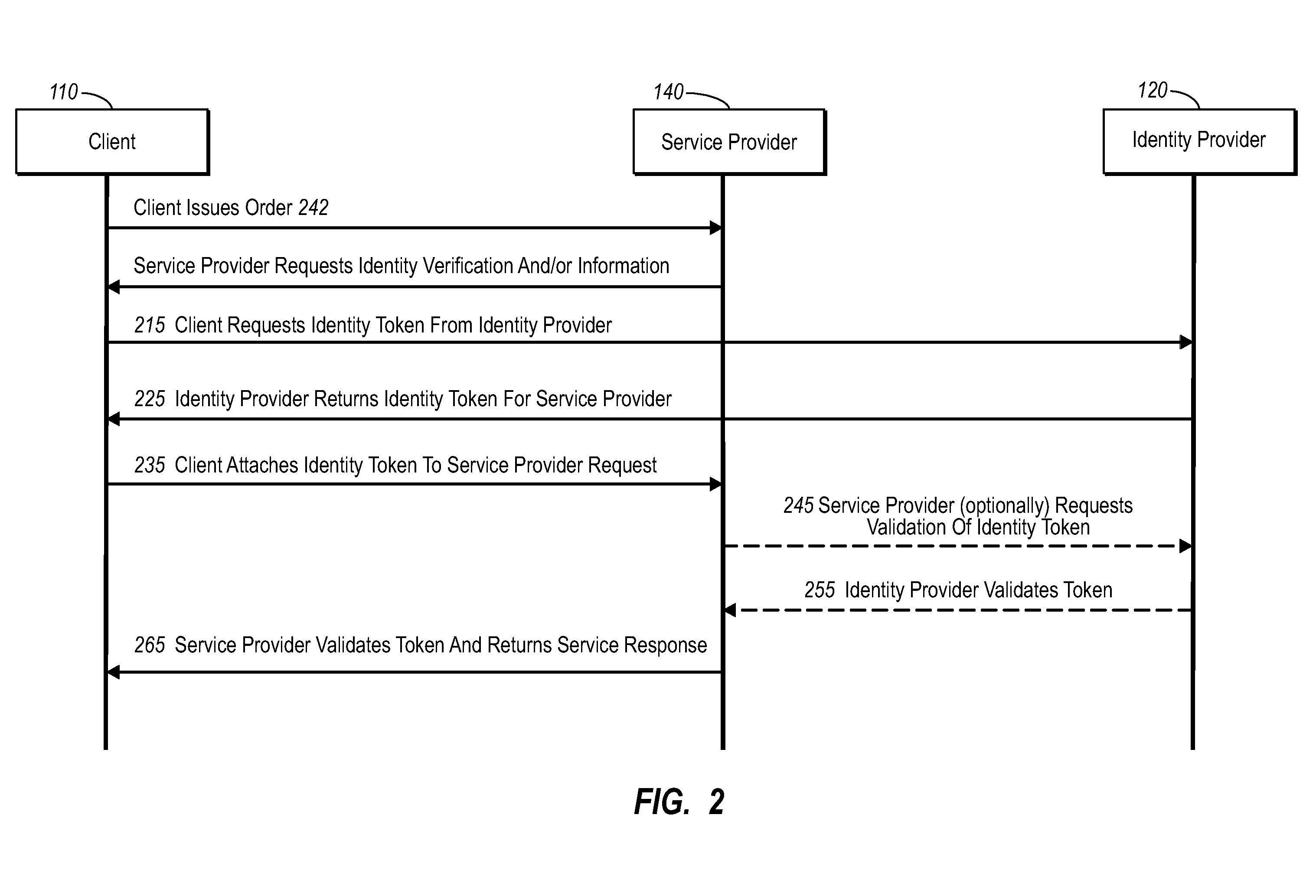
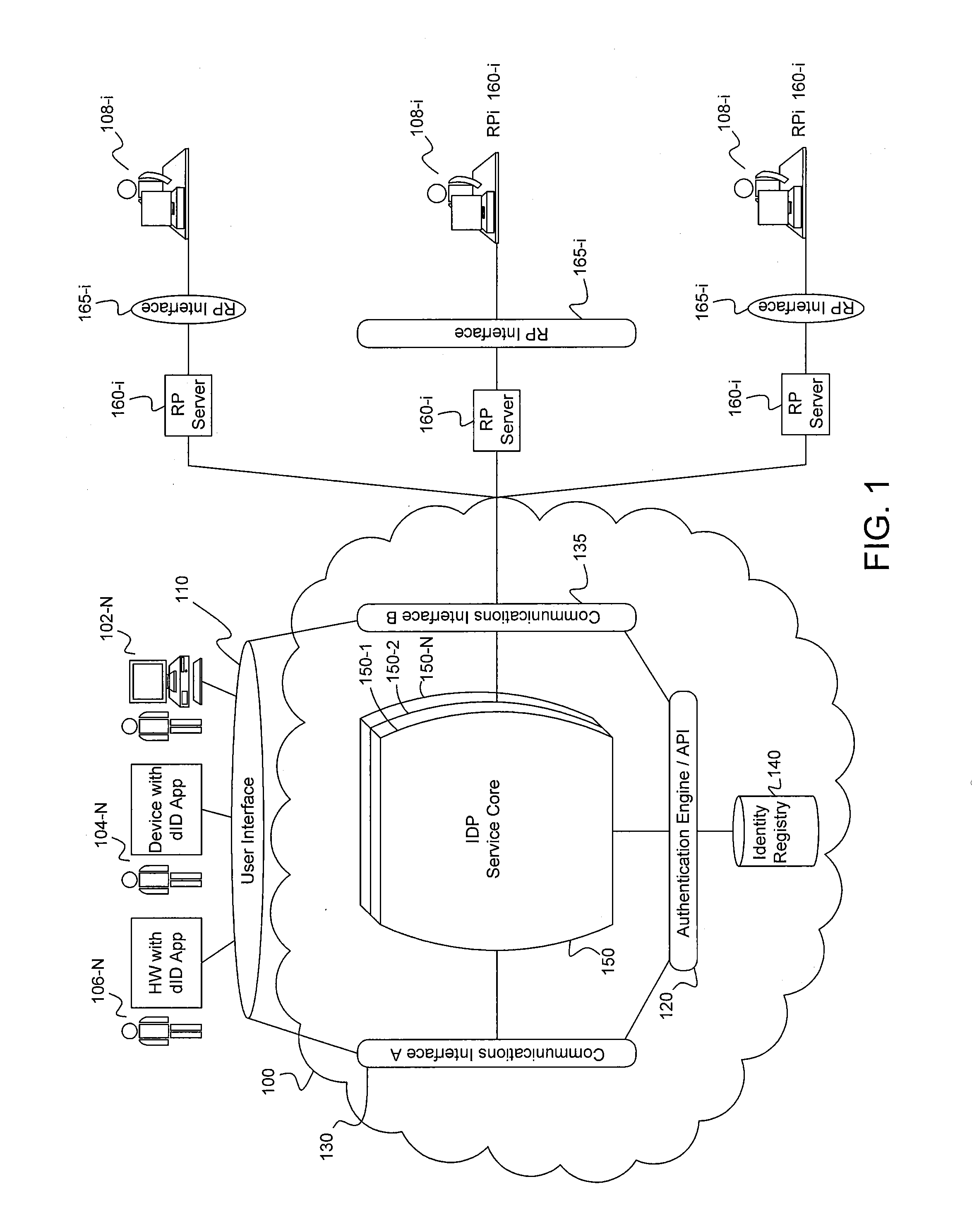
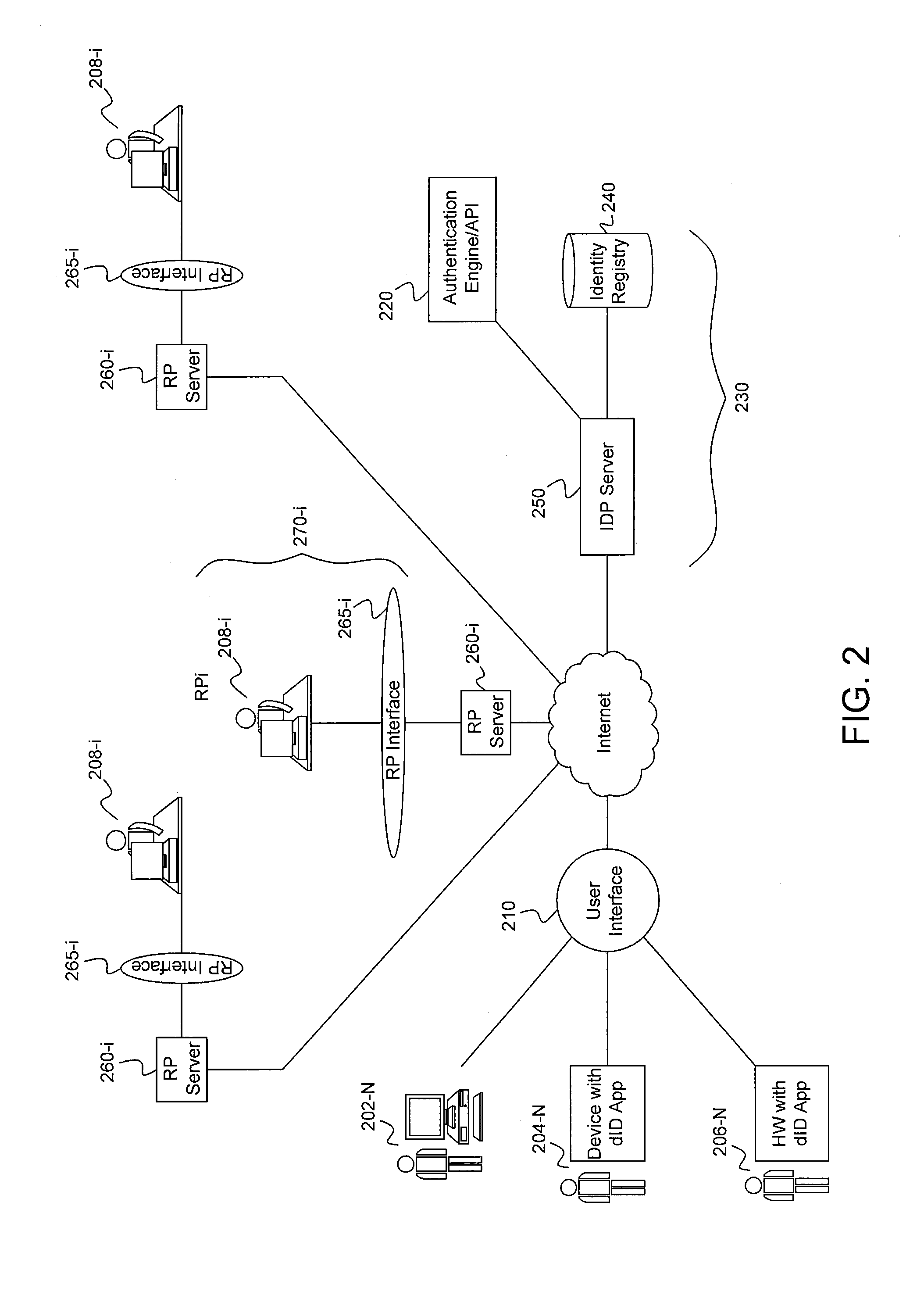
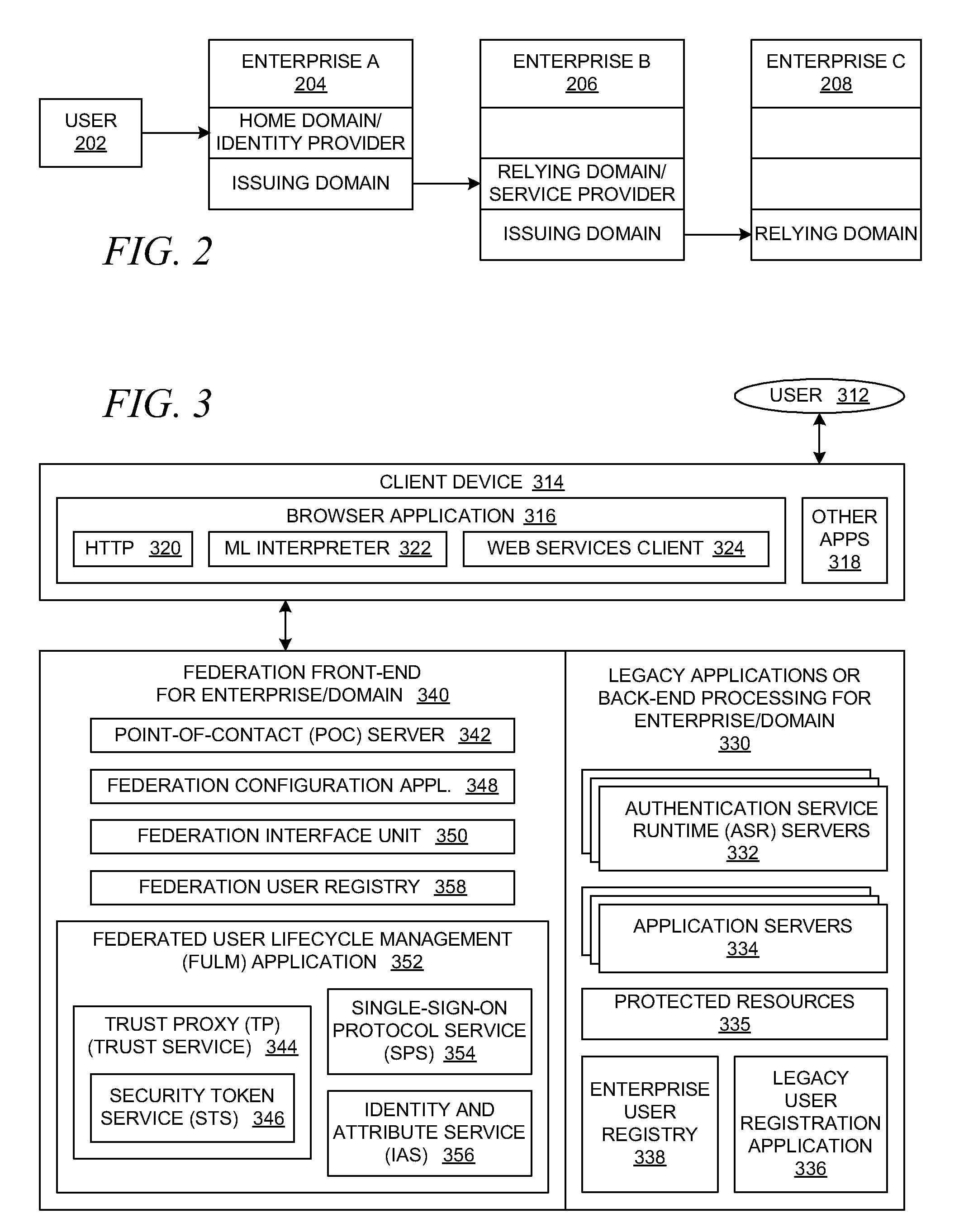
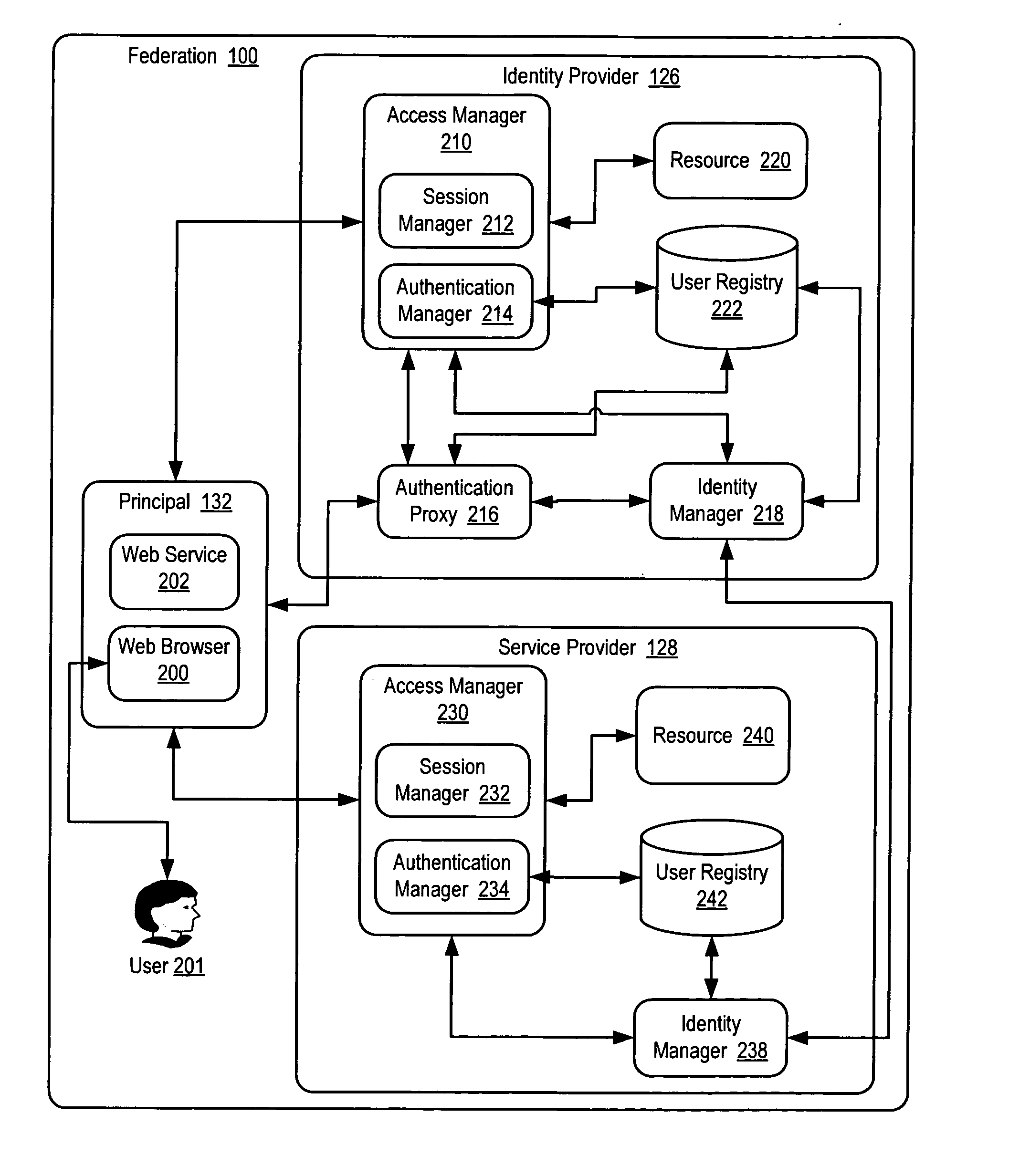
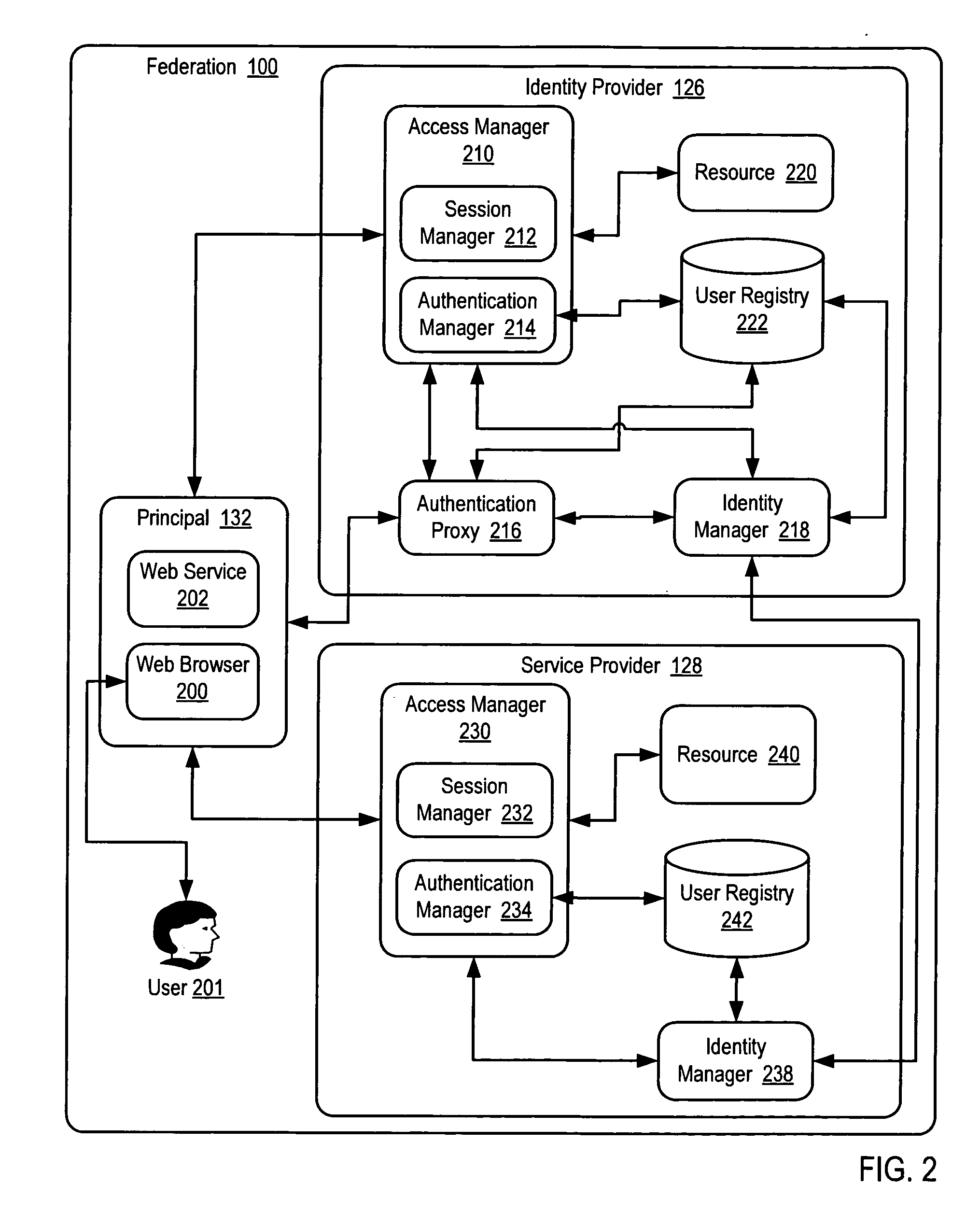
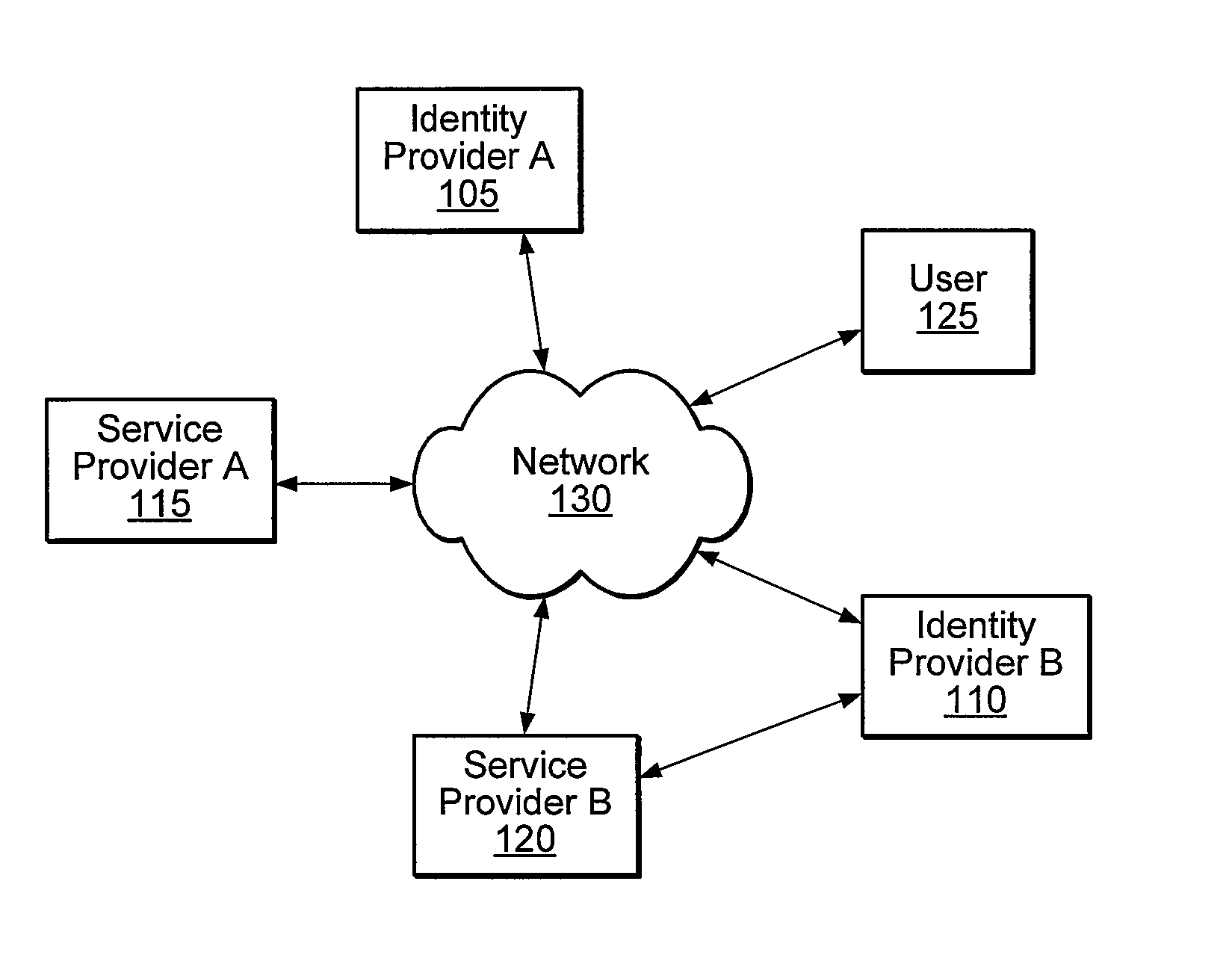
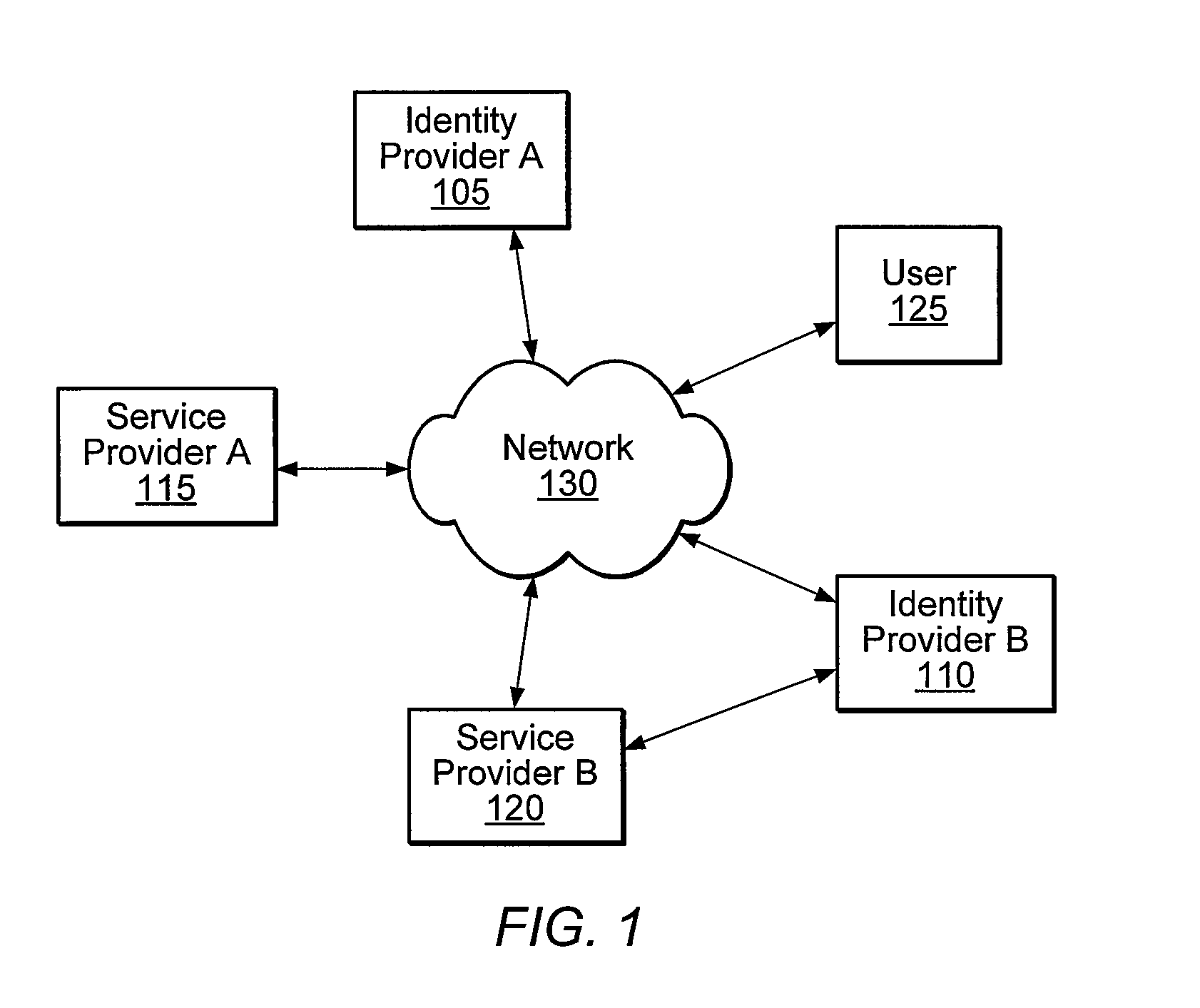
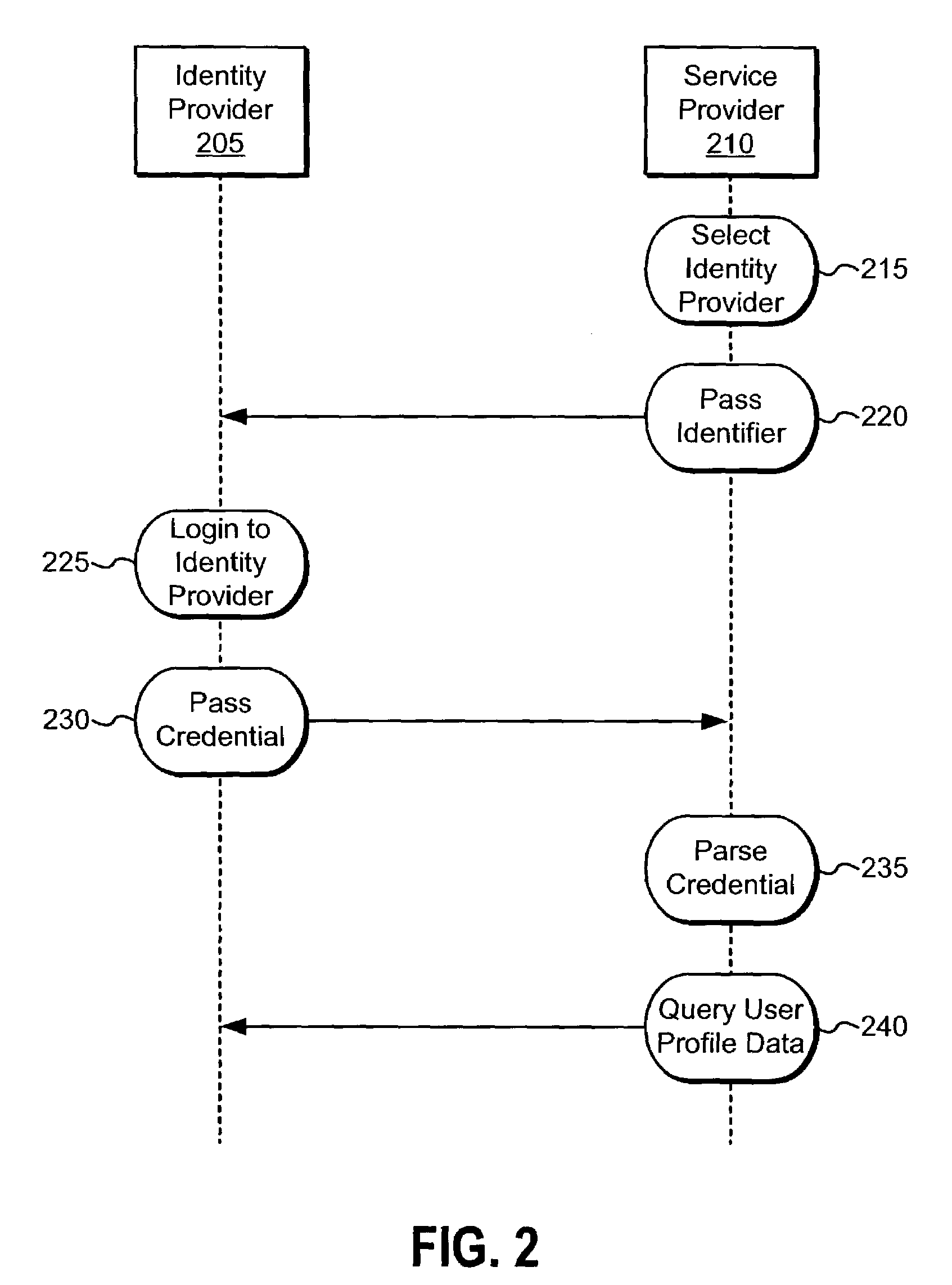
An identity provider (abbreviated IdP or IDP) is a system entity that creates, maintains, and manages identity information for principals while providing authentication services to relying applications within a federation or distributed network.
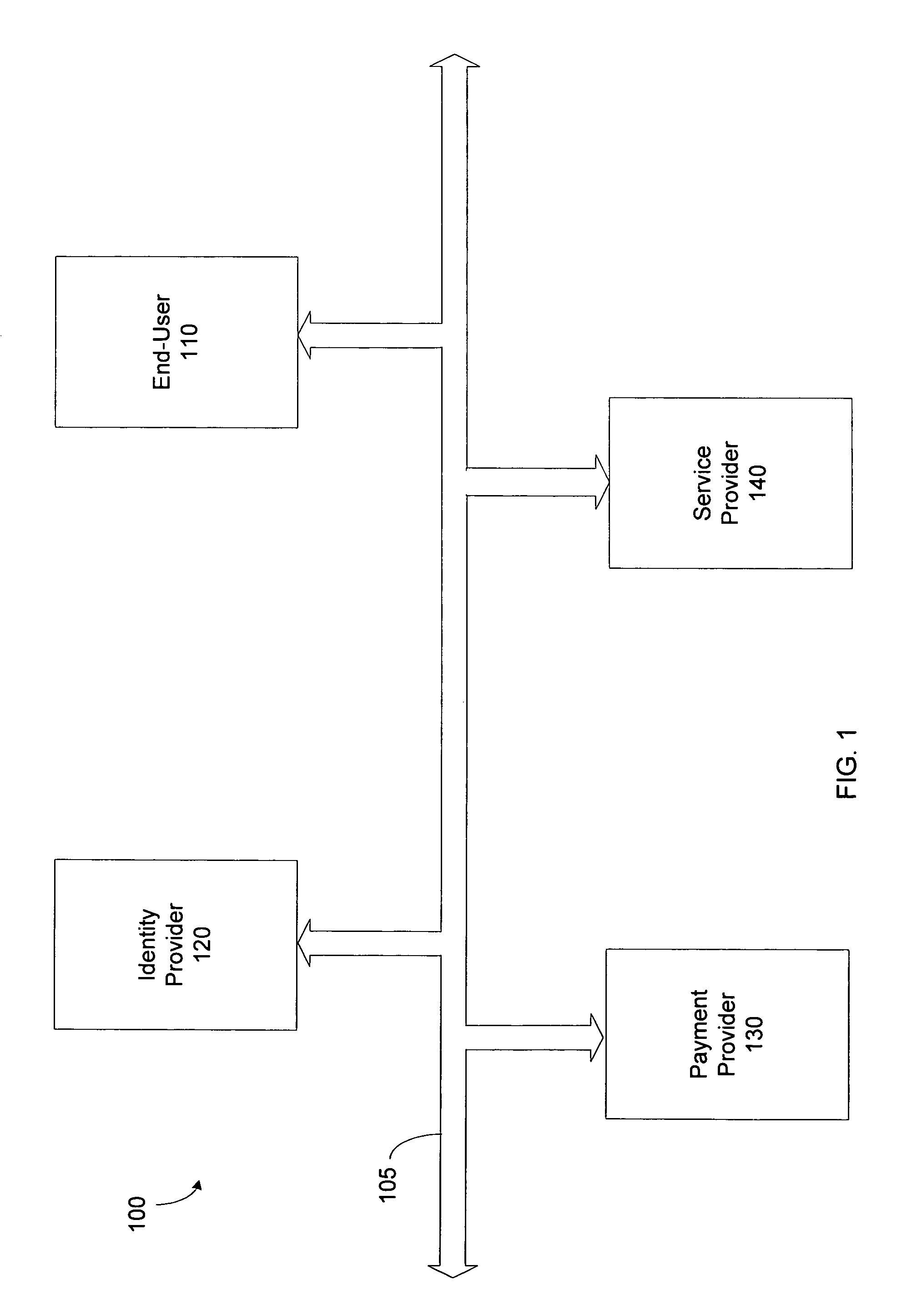
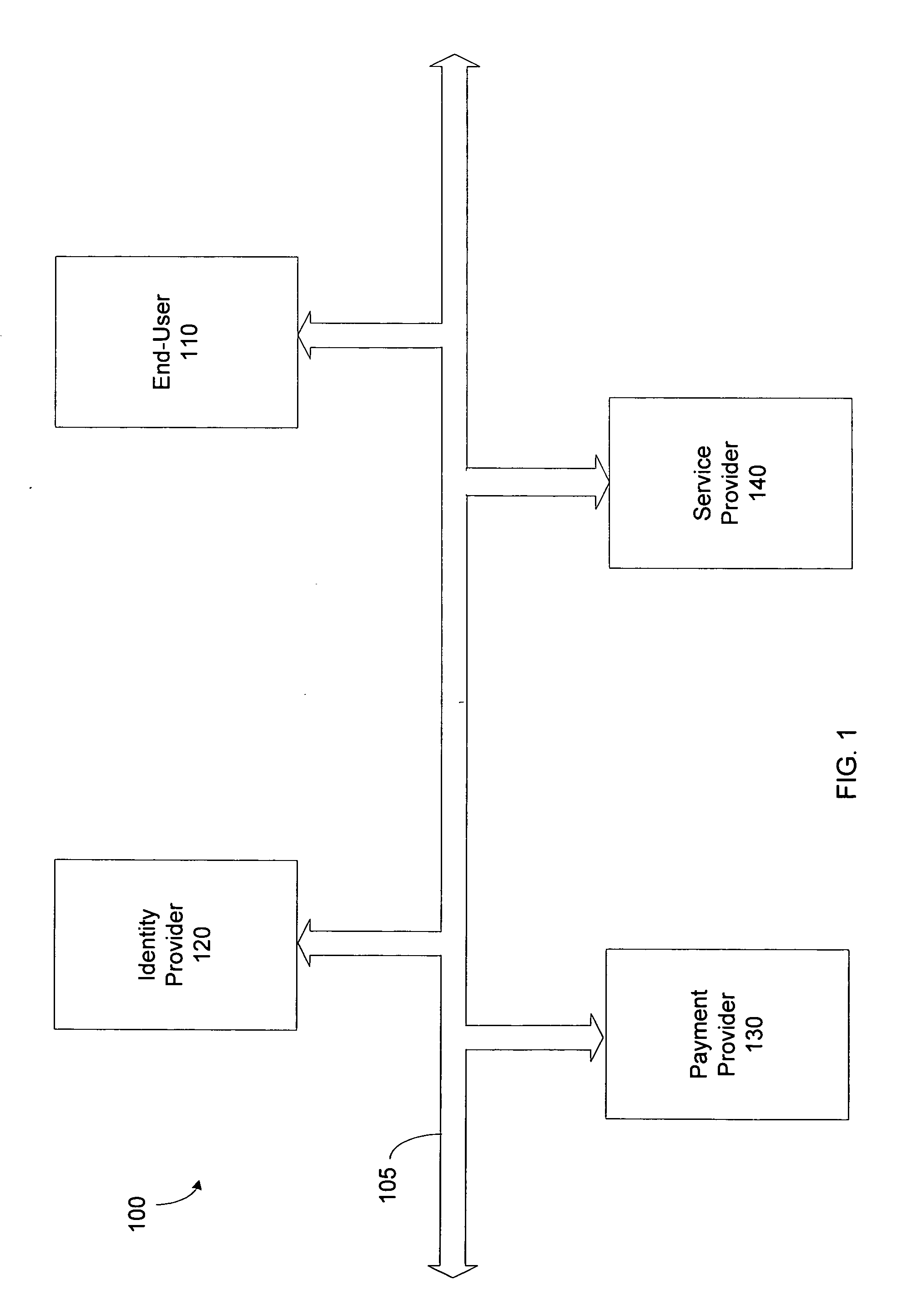
Secure network commercial transactions
InactiveUS20060235795A1Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceBuying/selling/leasing transactionsPaymentSecure communication
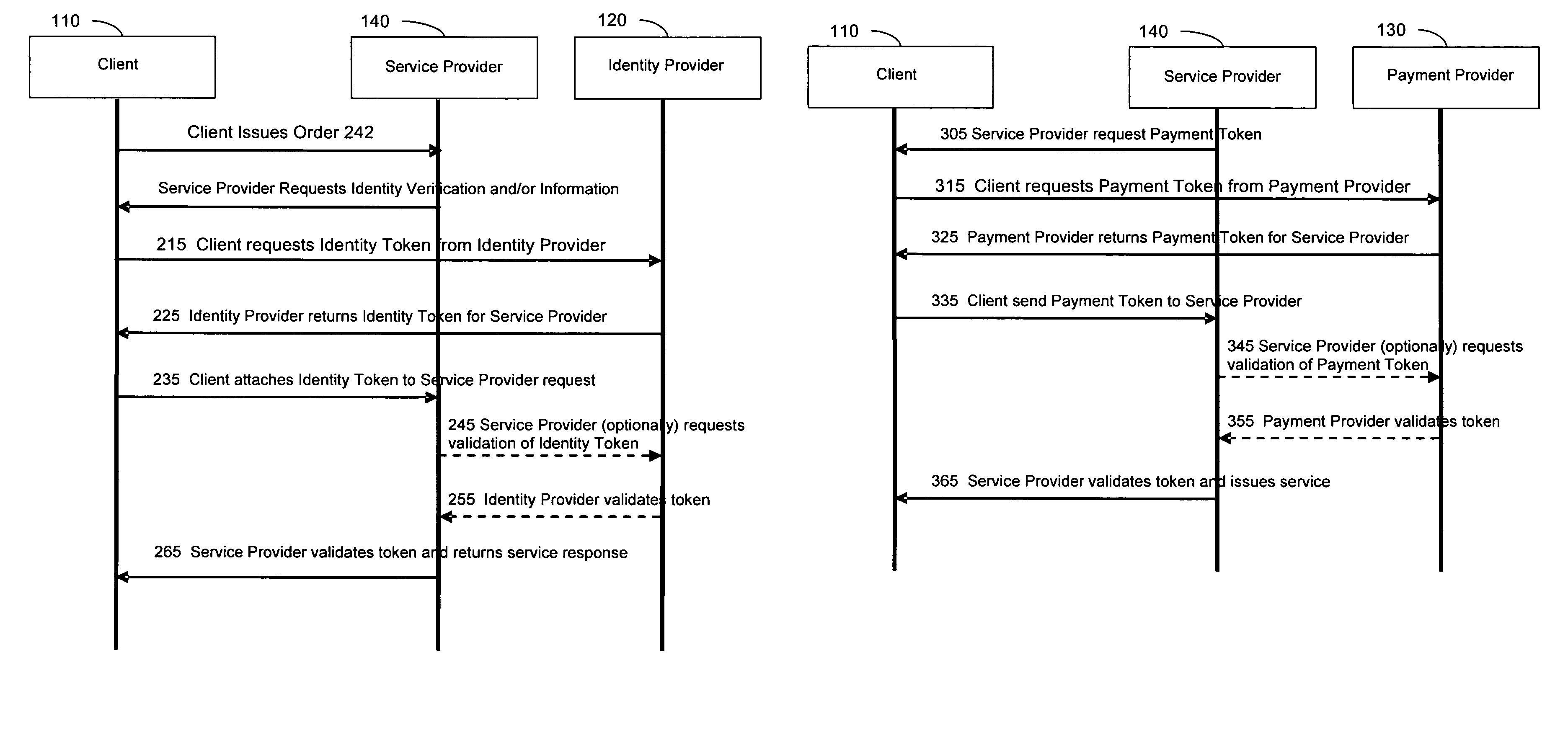
Current embodiments provide for authorization and payment of an online commercial transaction between a purchaser and a merchant including verification of an identity of the purchaser and verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are often different network entities. Other embodiments also provide for protocols, computing systems, and other mechanisms that allow for identity and payment authentication using a mobile module, which establishes single or multilevel security over an untrusted network (e.g., the Internet). Still other embodiments also provide for a three-way secure communication between a merchant, consumer, and payment provider such that sensitive account information is opaque to the merchant, yet the merchant is sufficiently confident of the consumer's ability to pay for requested purchases. In yet another embodiment, electronic billing information is used for authorization, auditing, payment federation, and other purposes.
Owner:MICROSOFT TECH LICENSING LLC
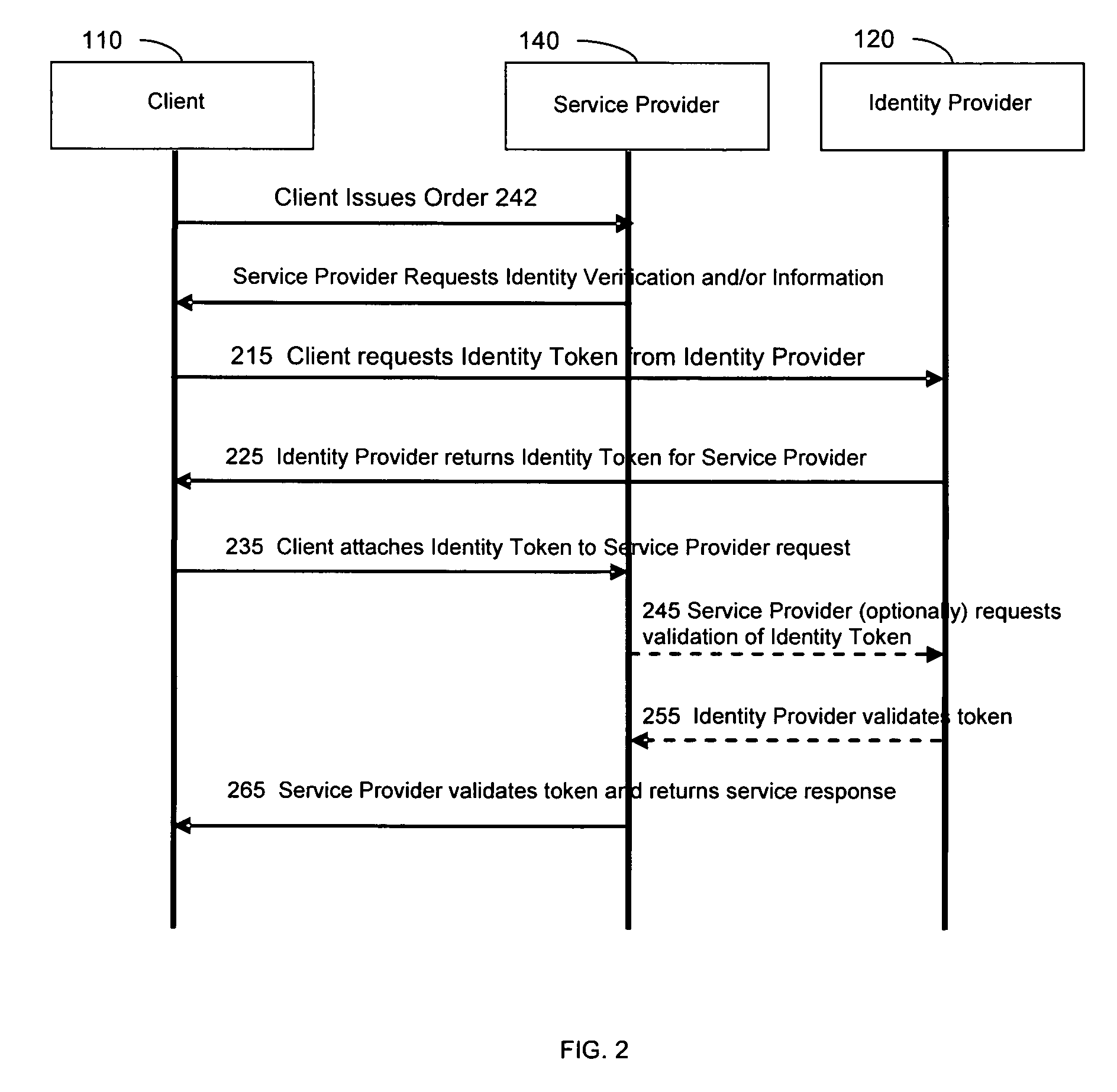
Method and apparatus for network transactions
InactiveUS7849020B2Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceDigital data processing detailsPaymentComputerized system
A method is provided to authorize an online transaction between a purchaser and a merchant. The method includes providing, via an identity provider, verification of an identity of the purchaser. The method also includes providing, via a payment provider, verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are different network entities. A computer system is also provided that can conduct an online transaction between a purchaser and a merchant providing one or more goods and / or services. The computer system includes a first node configured to provide verification of an identity of the purchaser, and a second node configured to provide verification of an ability of the purchaser to pay for the transaction, where the first node and the second node are associated with different network entities.
Owner:MICROSOFT TECH LICENSING LLC
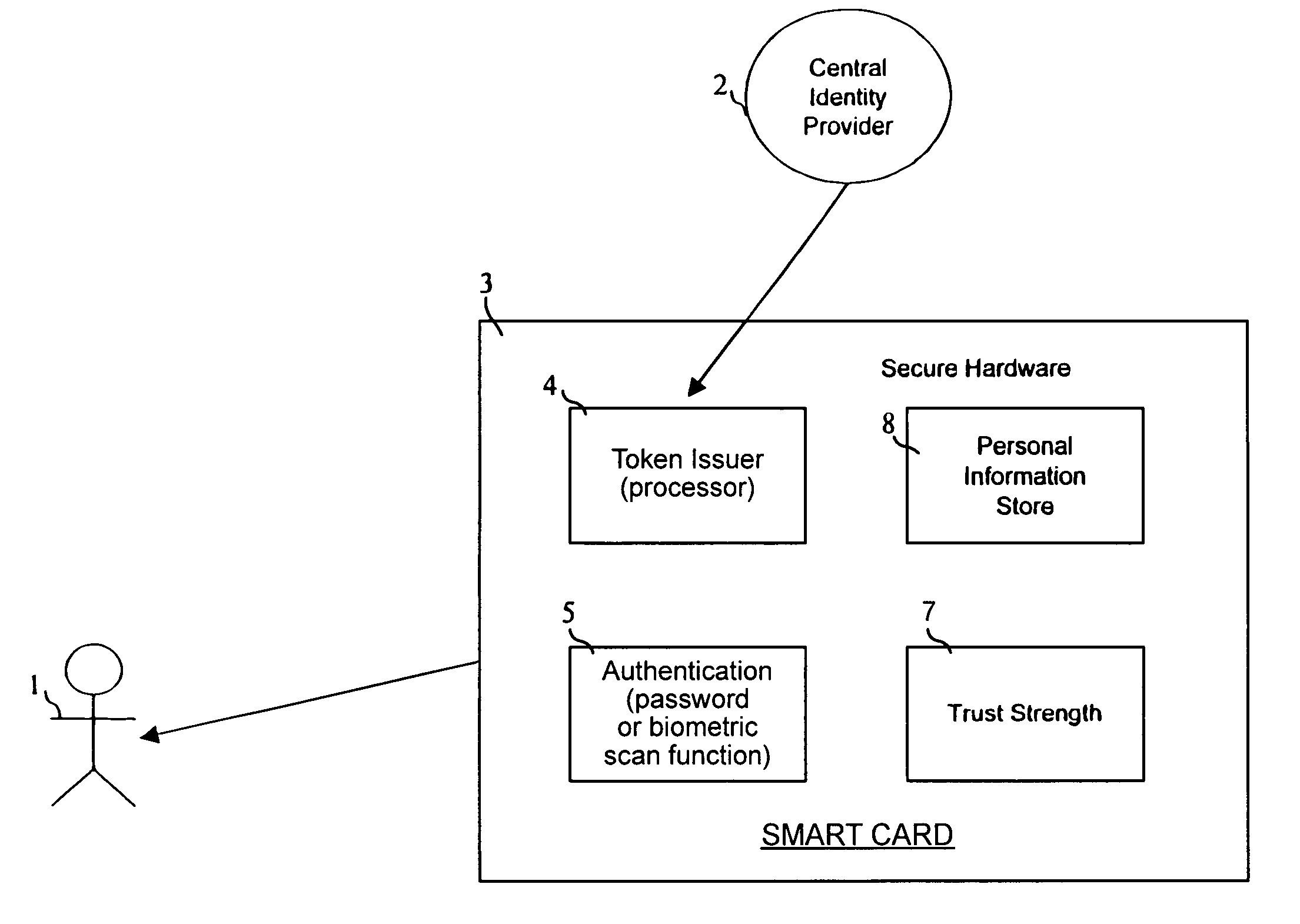
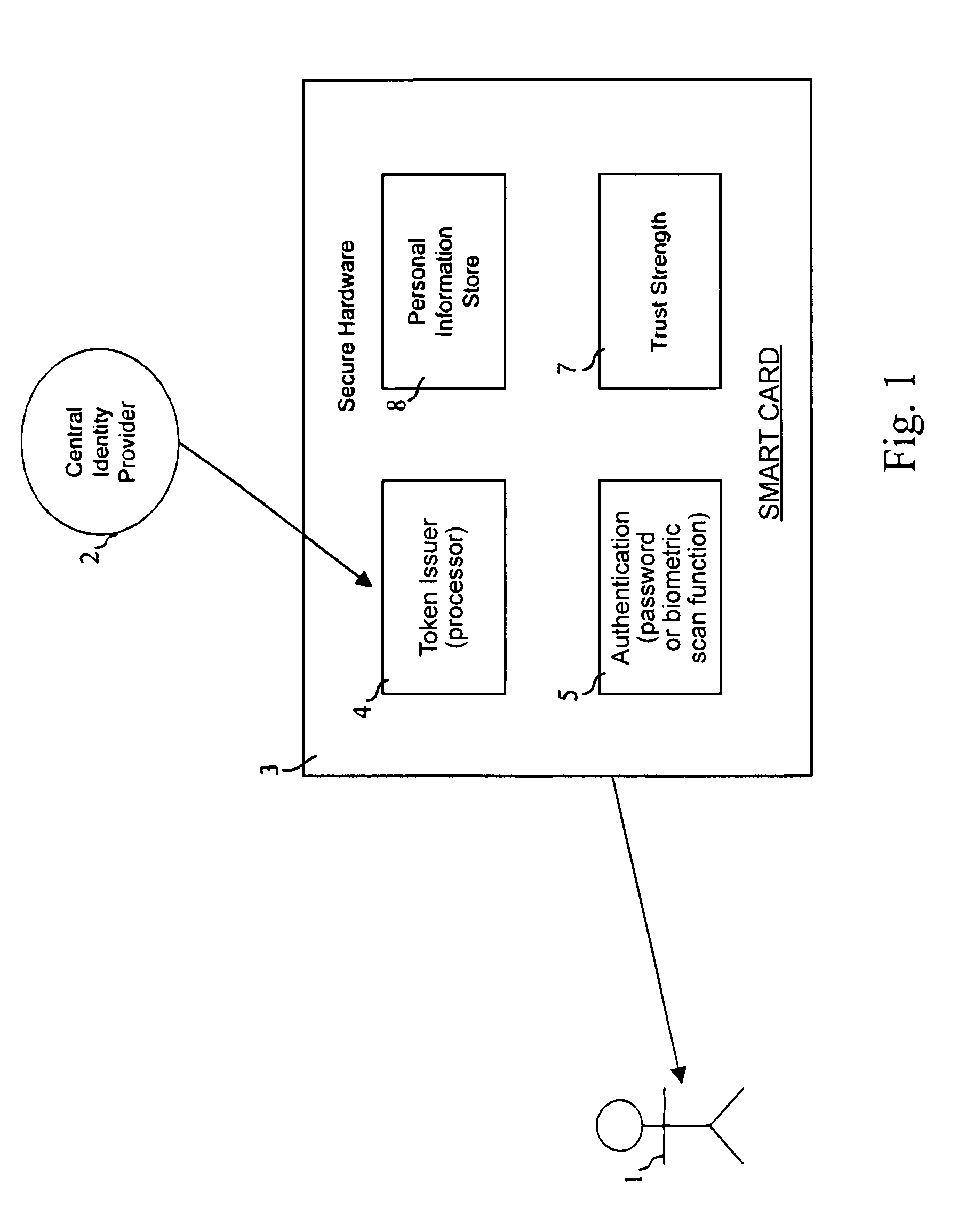
Trust tokens
InactiveUS7627895B2Eliminate needDigital data processing detailsUser identity/authority verificationInternet privacyE-commerce
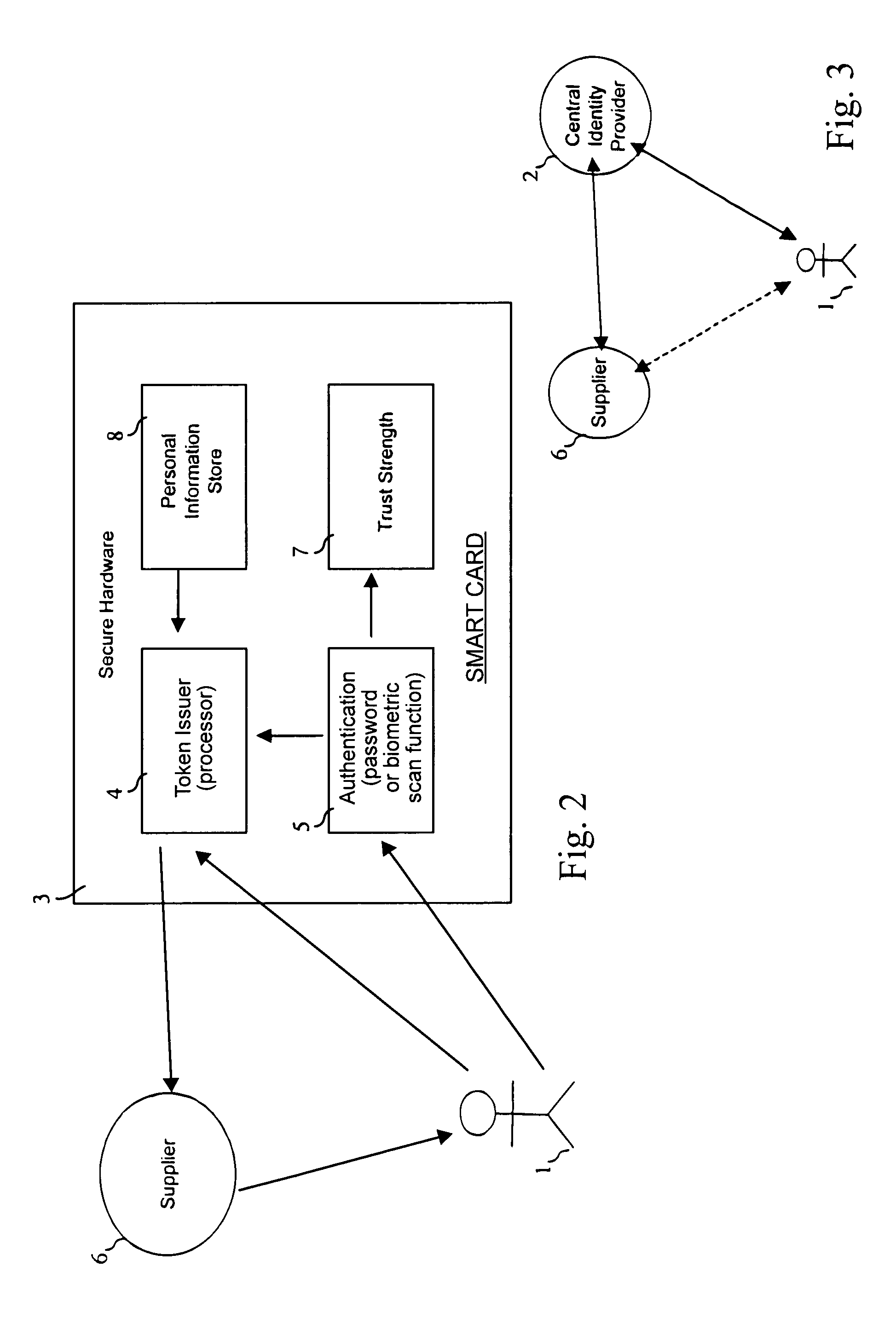
A token issuer and an authentication device provide an identity confirmation device. A token issuer is programmable by a central identity provider to issue certification tokens for use in e-commerce whereby transactions can be certified with suppliers without need for additional communication with a central server.
Owner:BRITISH TELECOMM PLC
Authentication & authorization of transactions using an external alias
Described herein is a transaction system (100) in which a transaction is authenticated using an external alias. When procuring an item from a supplier (120), a customer (110) needs to provide payment in some form or the other. Profiles relating to both the customer (110) and the supplier (120) are stored in an environment managed by a broker (130) and payment is effected by transfer of within that environment from a customer wallet to a supplier wallet. The customer (120) is represented as an alias as far as the supplier (120) is concerned, whereby the alias is provided by an external identity provider (140) such as a social network with which the customer (120) is associated. The anonymity of the customer (120) is maintained with respect to the supplier (120).
Owner:DUBOIS PIETER
System and architecture for merchant integration of a biometric payment system
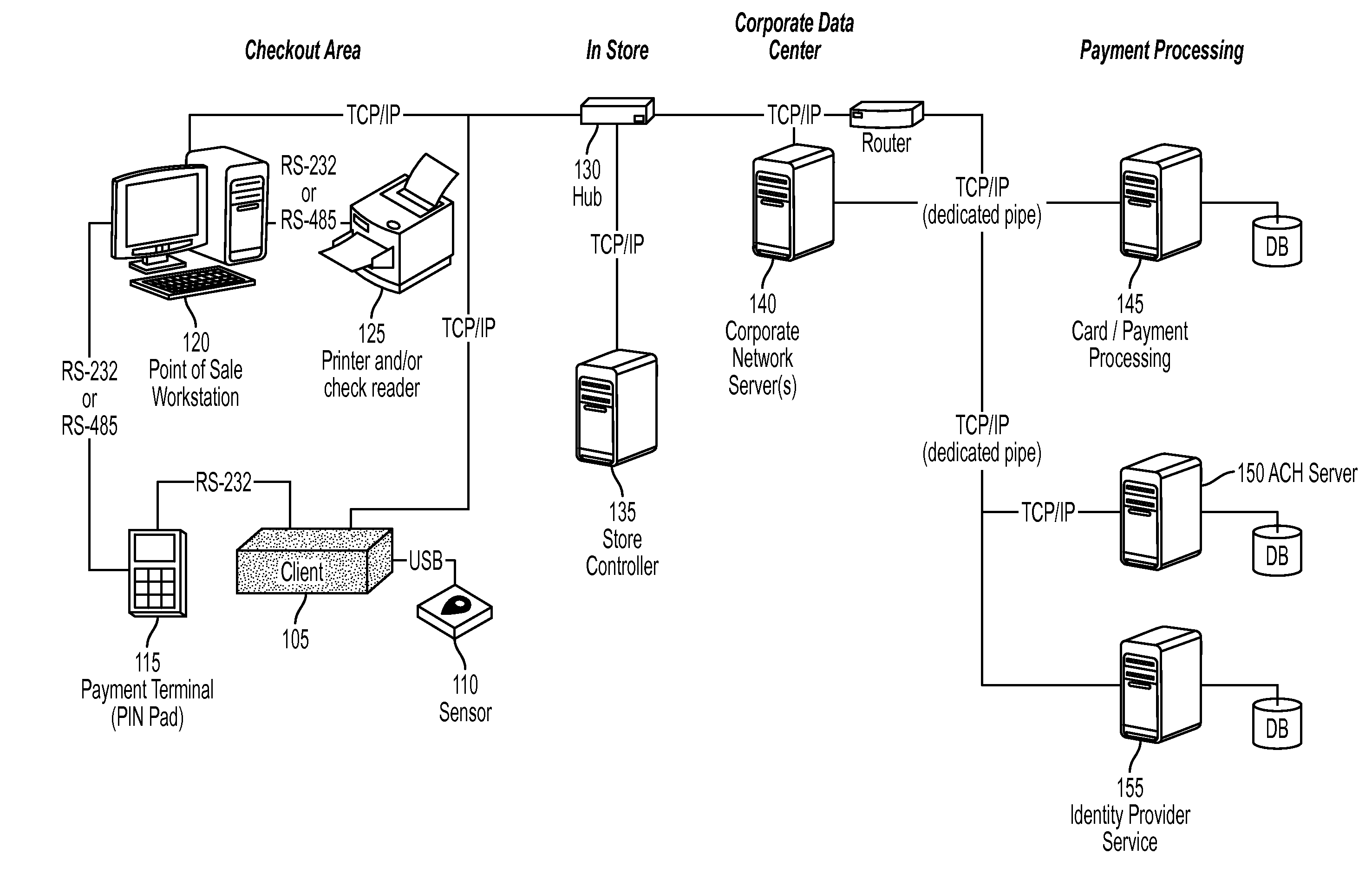
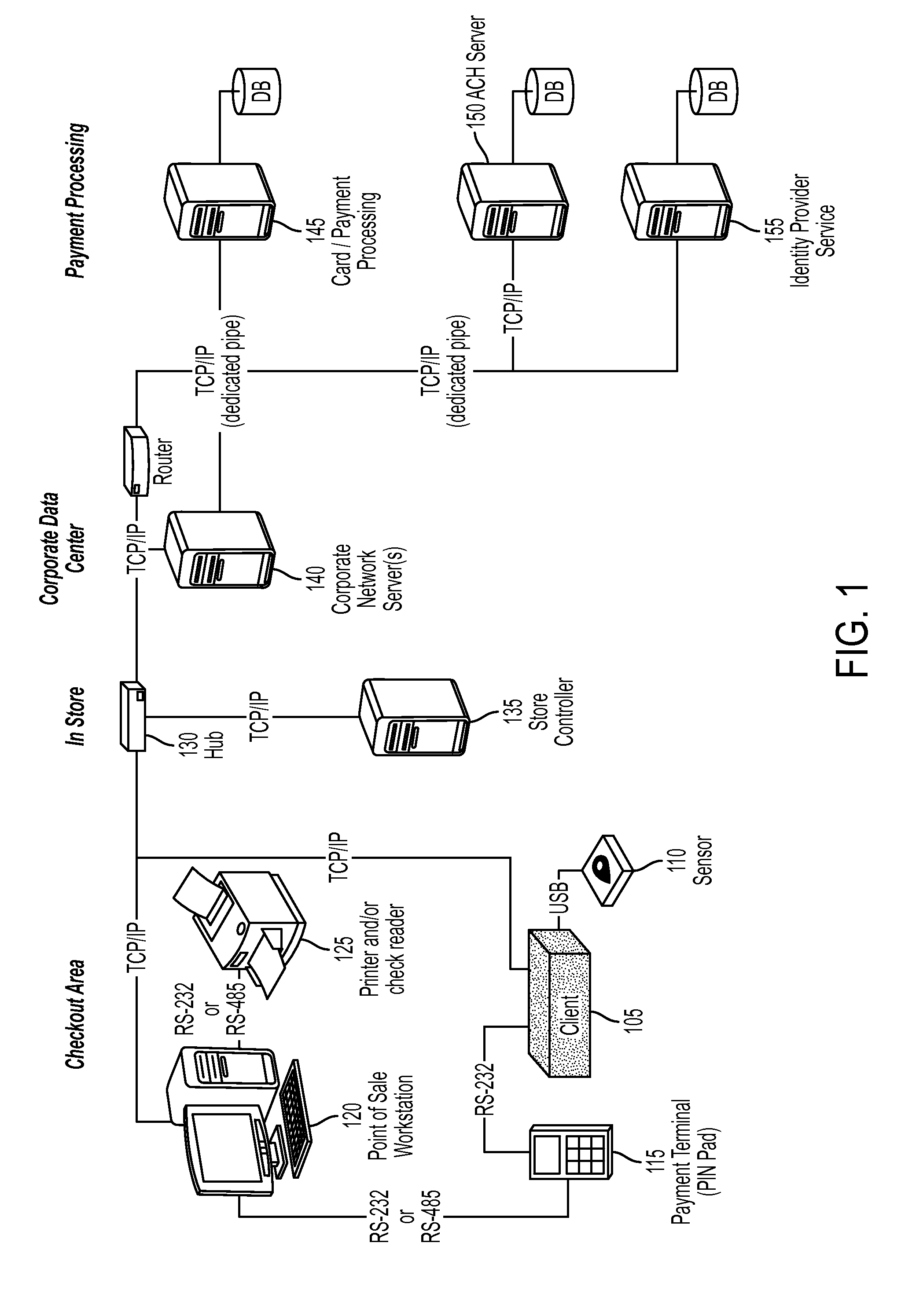
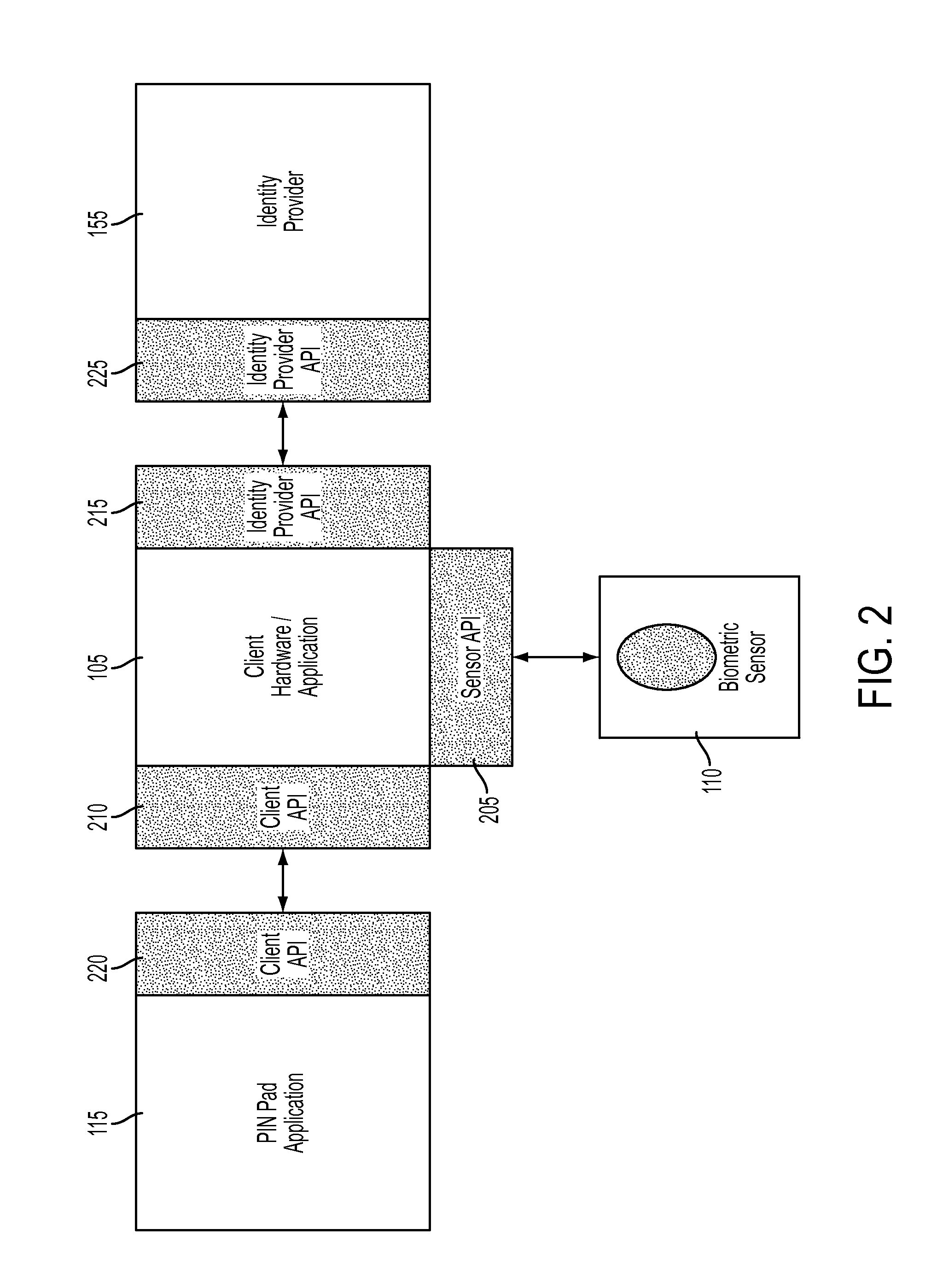
A system and method for performing authentication are disclosed. The system may include a shared central processing server, a plurality of software components each residing in a corresponding point-of-sale (POS) workstation and an identity provider service. The server may reside at a merchant location and communicate with multiple POS workstations at the merchant location. The server may be configured to receive biometric information from each POS workstation. Each software component may communicate with a biometric sensor in communication with the corresponding POS workstation to receive biometric information. The identity provider service may be configured to communicate with the server, store registered biometric information and compare biometric information received from the server with one or more of the stored registered biometric information. One of the biometric sensor, a POS workstation and the server may convert a biometric image into a biometric template for comparison with the stored registered biometric information.
Owner:YOUTECH
Trusted third party authentication for web services
InactiveUS20060206932A1Communication securityDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
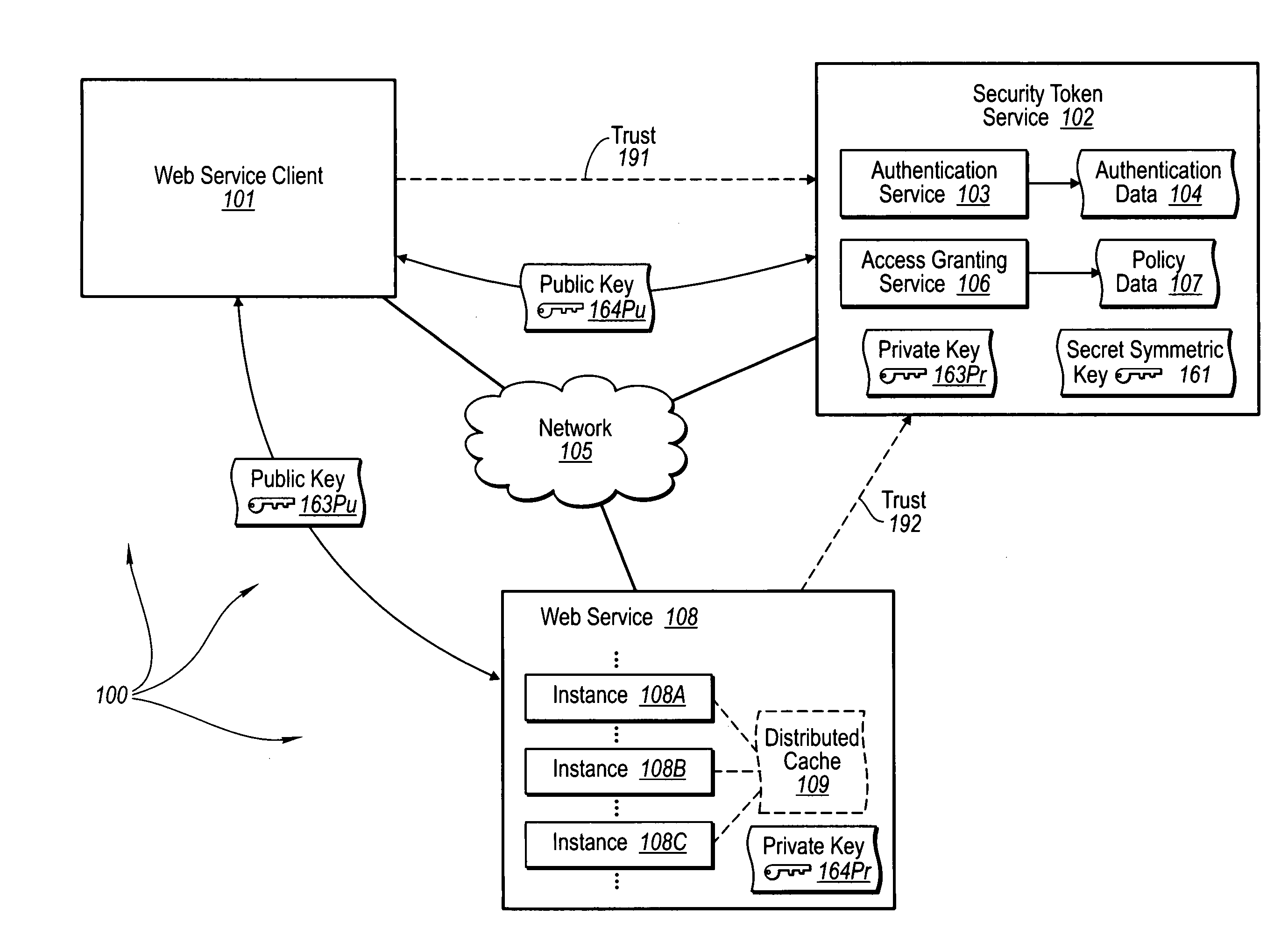
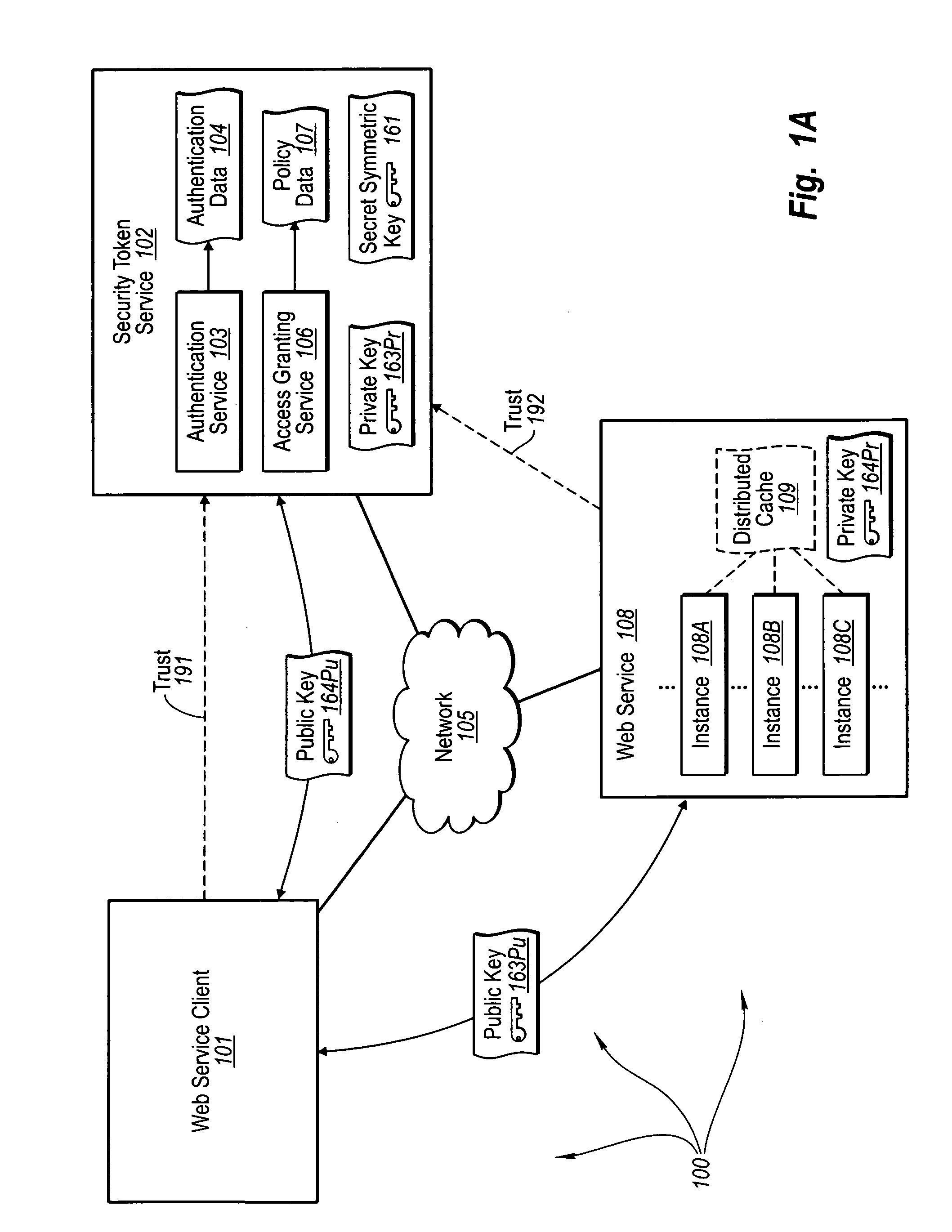
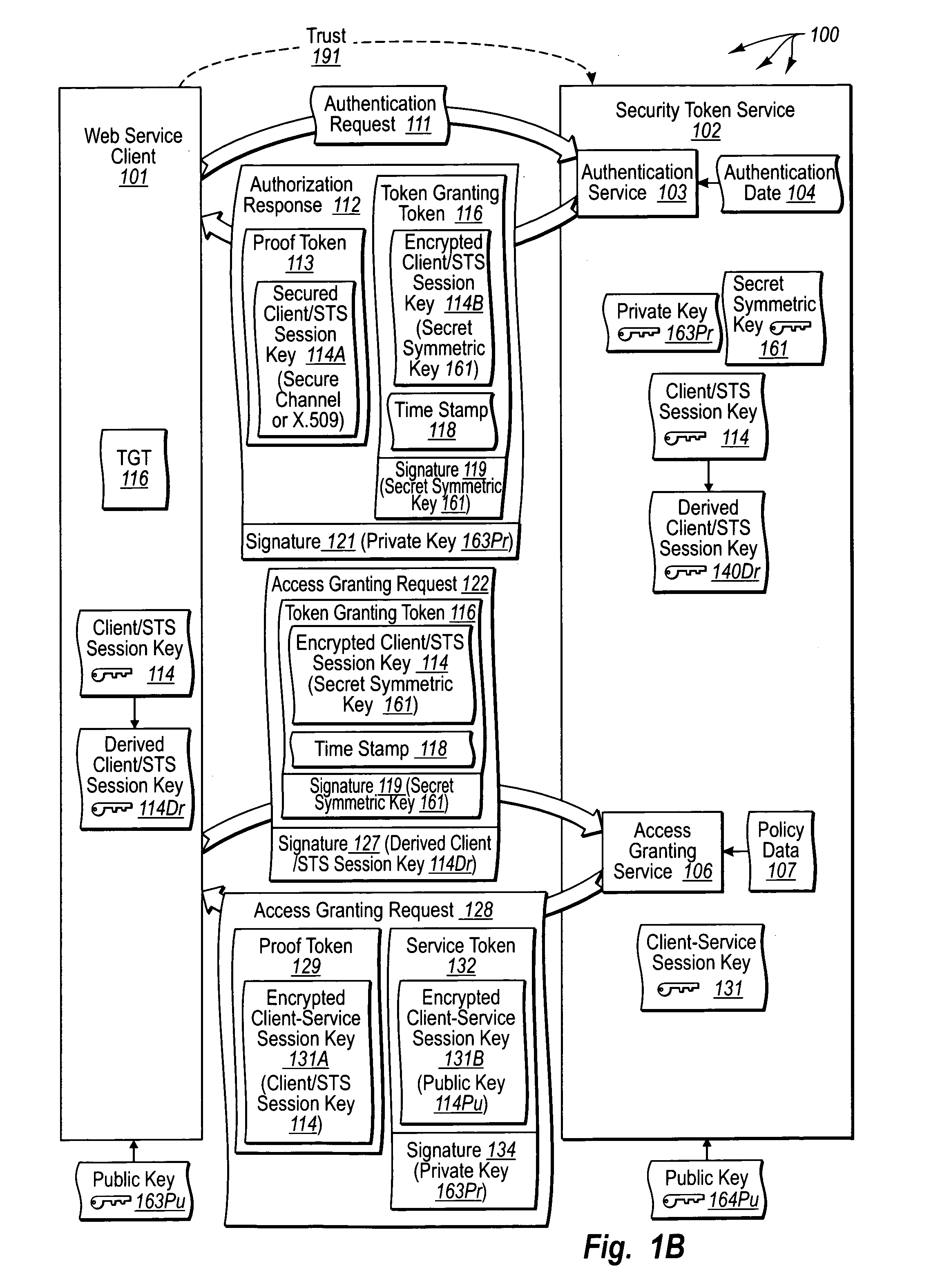
The present invention extends to trusted third party authentication for Web services. Web services trust and delegate user authentication responsibility to a trusted third party that acts as an identity provider for the trusting Web services. The trusted third party authenticates users through common authentication mechanisms, such as, for example, username / password and X.509 certificates and uses initial user authentication to bootstrap subsequent secure sessions with Web services. Web services construct user identity context using a service session token issued by the trusted third party and reconstruct security states without having to use a service-side distributed cache.
Owner:MICROSOFT TECH LICENSING LLC
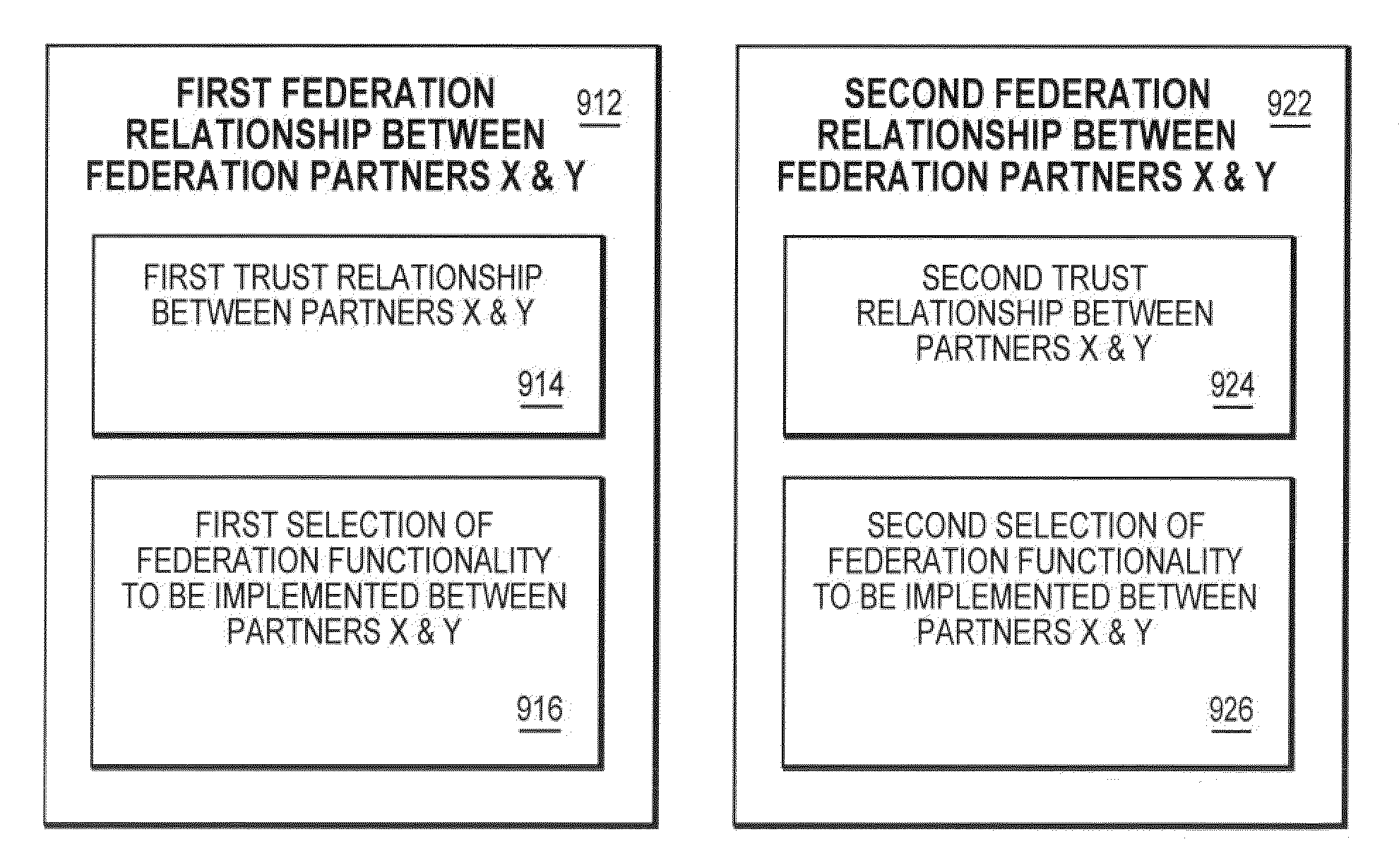
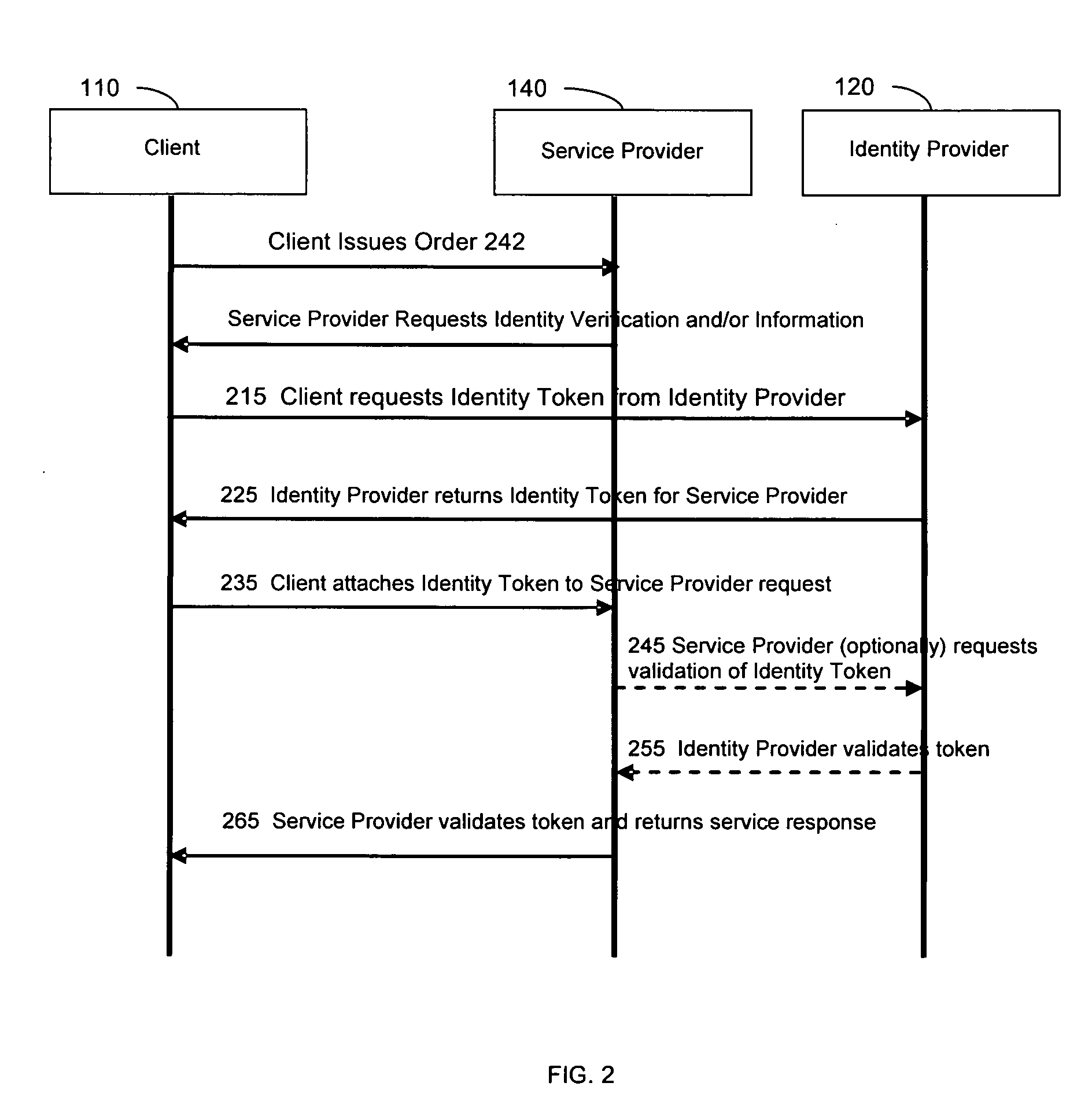
Method and system for a runtime user account creation operation within a single-sign-on process in a federated computing environment
ActiveUS20060236382A1Key distribution for secure communicationDigital data processing detailsComputer networkService provision
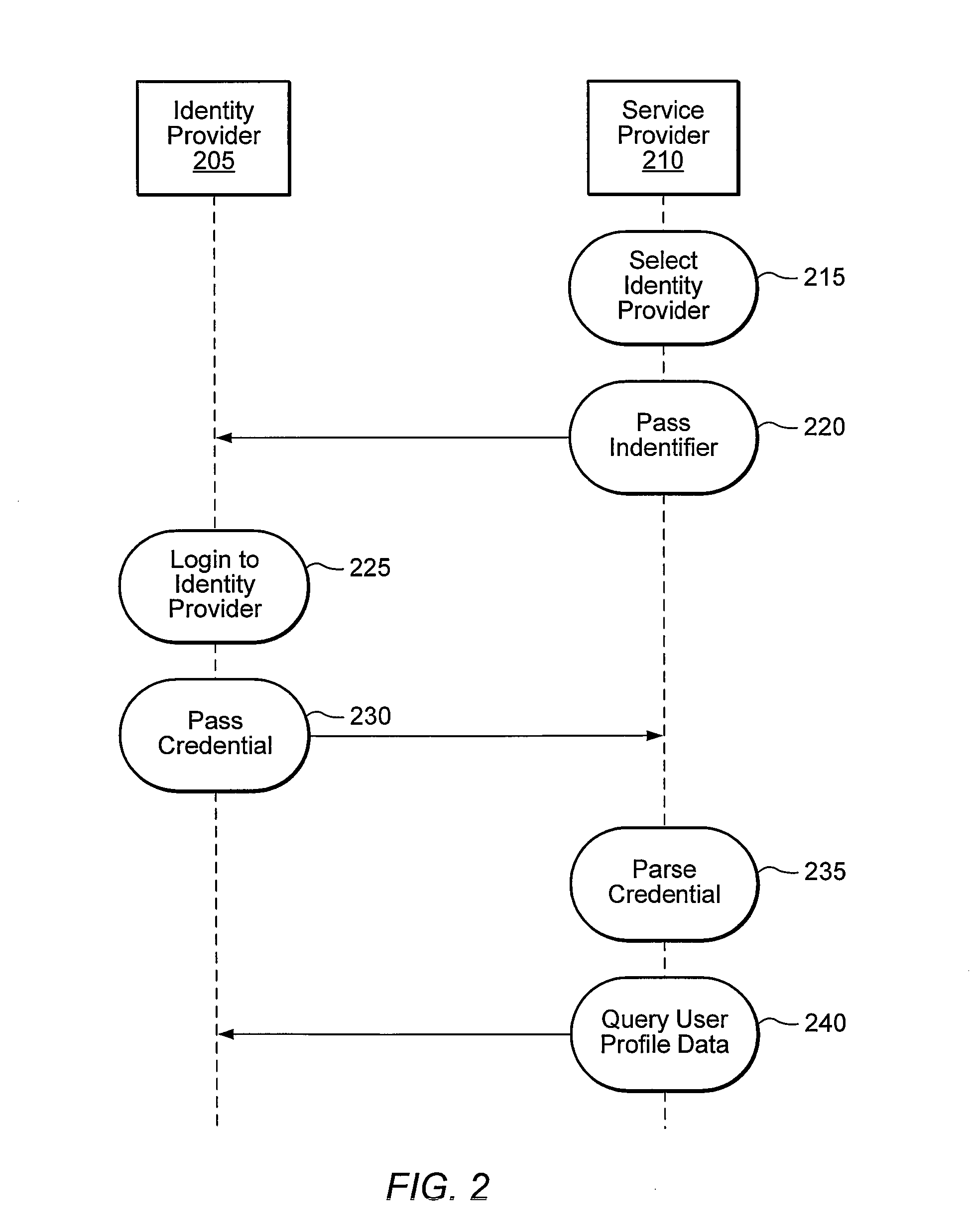
A method, system, apparatus, and computer program product are presented to support computing systems of different enterprises that interact within a federated computing environment. Federated single-sign-on operations can be initiated at the computing systems of federation partners on behalf of a user even though the user has not established a user account at a federation partner prior to the initiation of the single-sign-on operation. For example, an identity provider can initiate a single-sign-on operation at a service provider while attempting to obtain access to a controlled resource on behalf of a user. When the service provider recognizes that it does not have a linked user account for the user that allows for a single-sign-on operation with the identity provider, the service provider creates a local user account. The service provider can also pull user attributes from the identity provider as necessary to perform the user account creation operation.
Owner:IBM CORP
Content Metadata Directory Services
ActiveUS20070192352A1Increase the number ofComplicate to identifyMultimedia data indexingDigital data processing detailsContent IdentifierWeb site
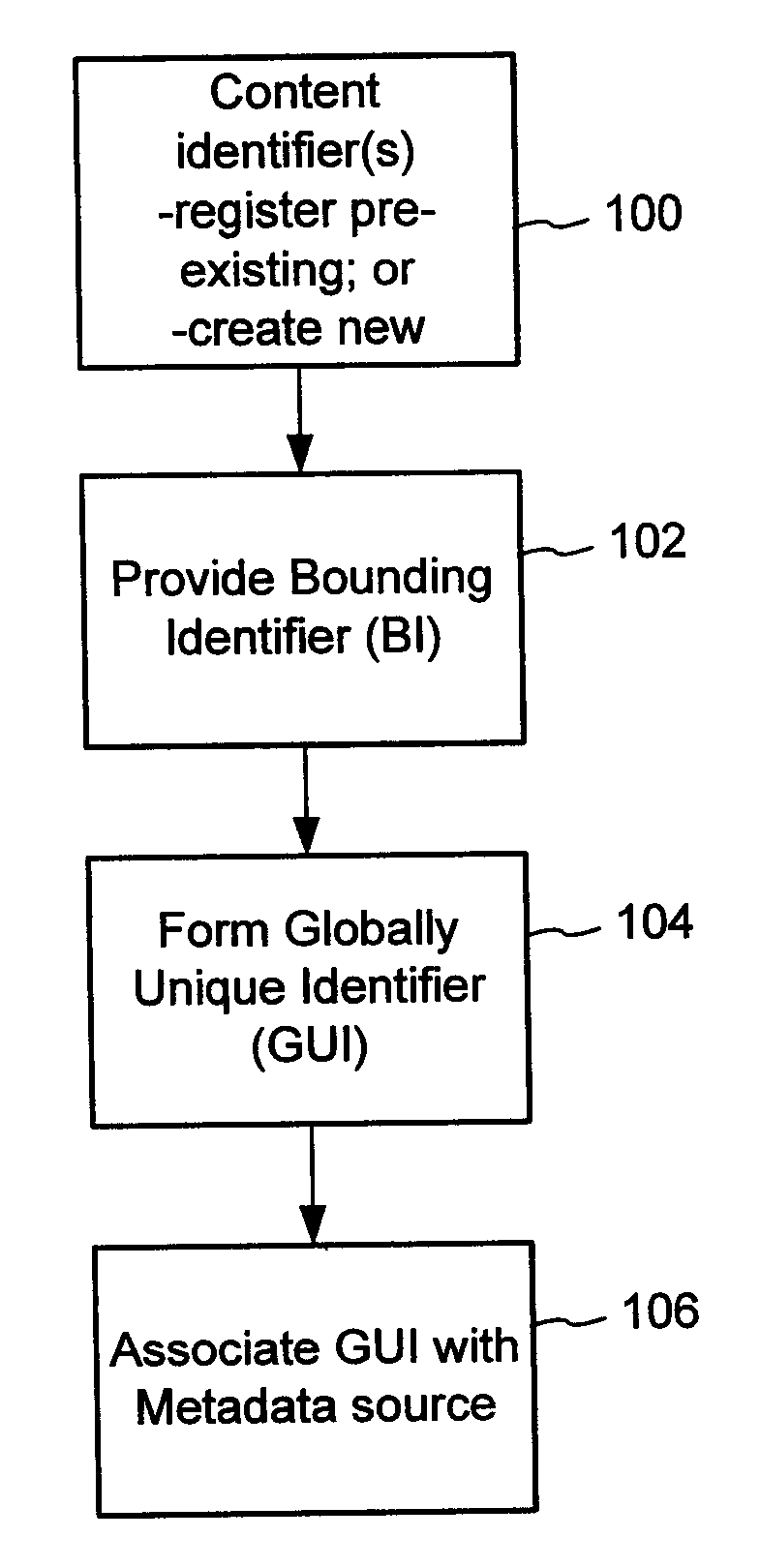
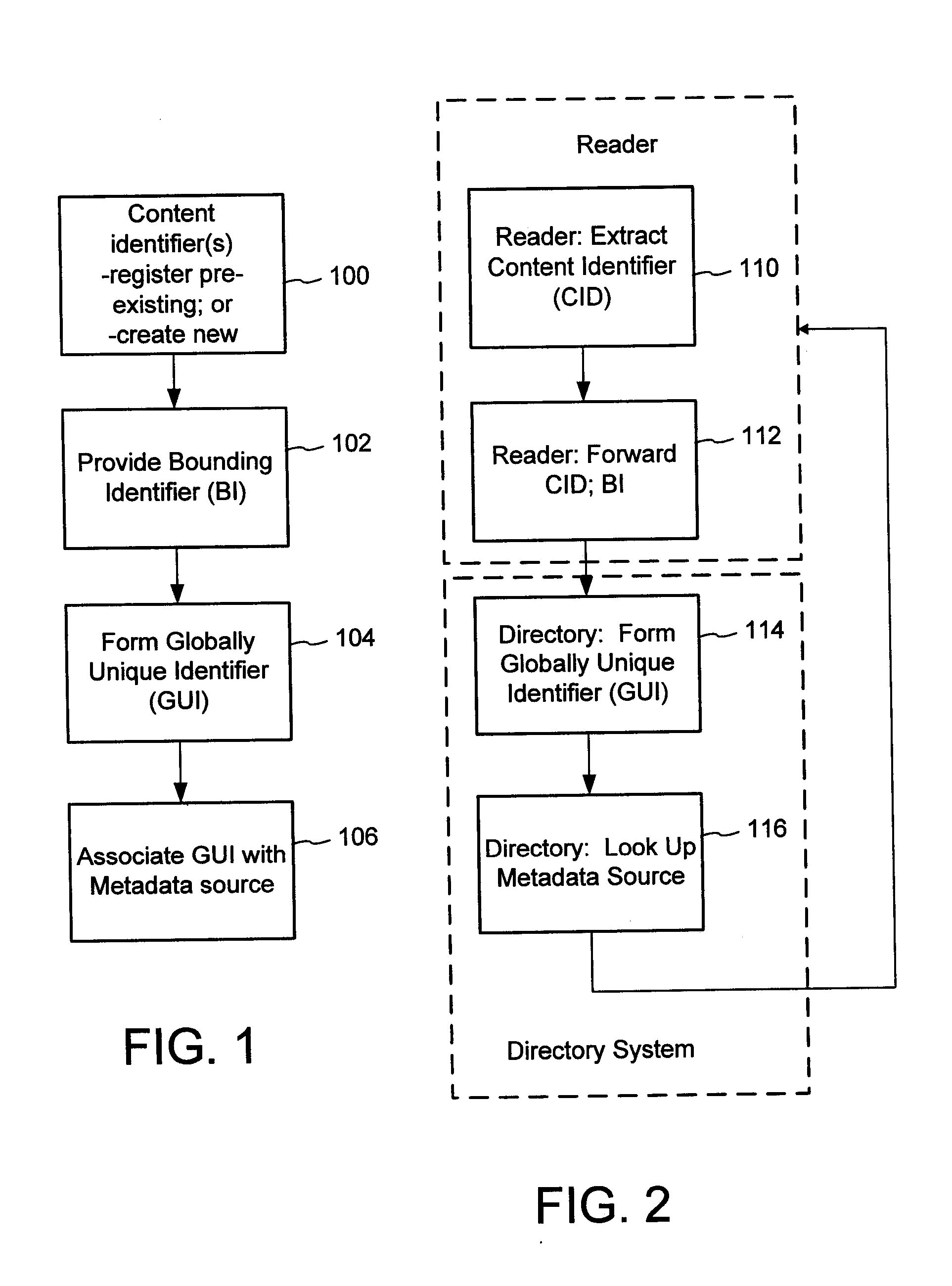
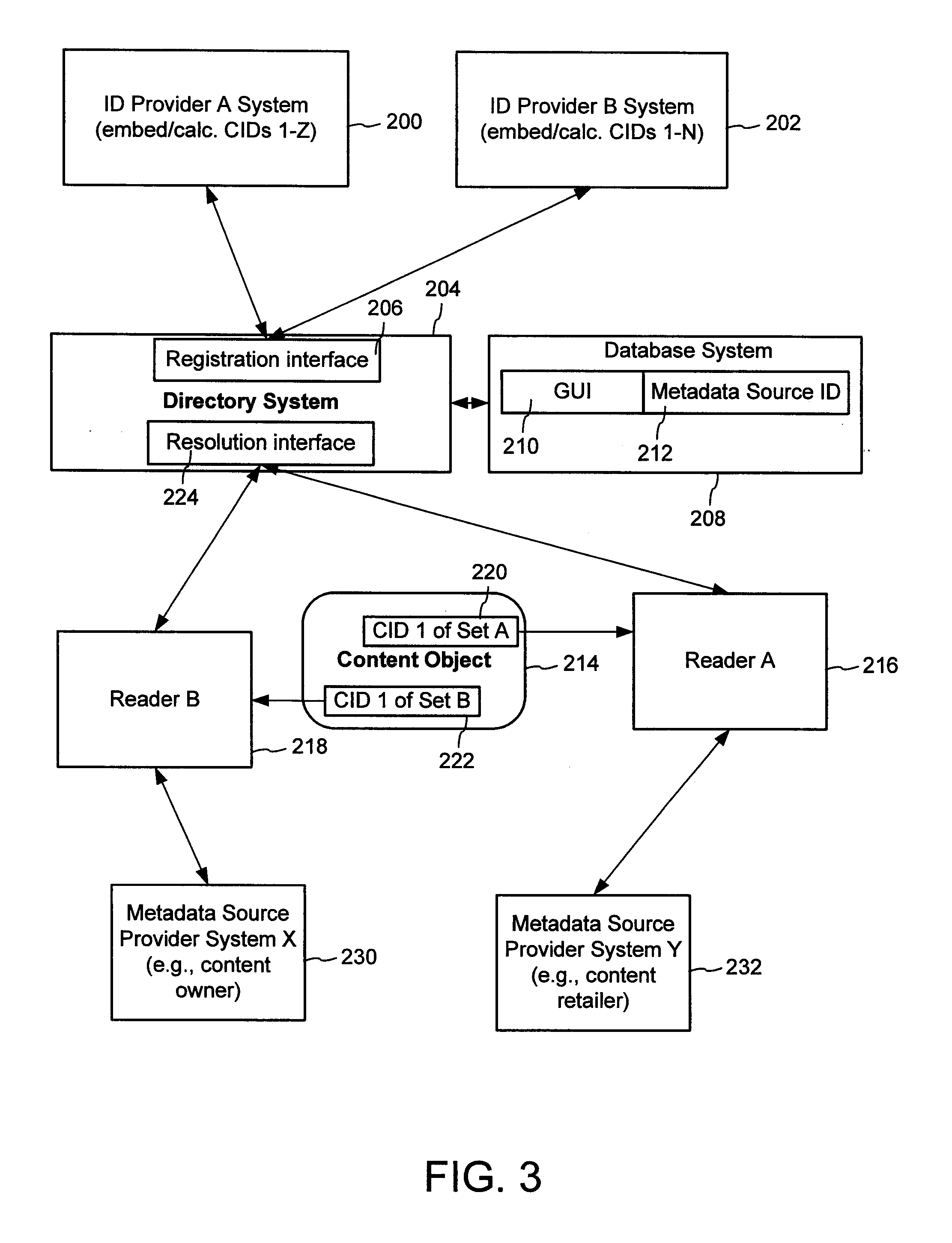
A method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers. It provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source. Another novel method addresses content objects with two or more content identifiers, potentially referencing different metadata sources. This method registers different globally unique identifiers for a content object. These globally unique identifiers each comprise a content identifier provided with the content object and a bounding identifier identifying a set of content identifiers of which the content identifier is a member. For each of the globally unique identifiers, information is maintained about a metadata source. The method receives a first content identifier for the content object, and uses a bounding identifier associated with the set of the first content identifier to determine the globally unique identifier for the first content identifier. The user is routed to the metadata source associated with globally unique identifier. This document describes a novel system that enables multiple identity providers (ID Providers) to register and use the system. The ID Provider registers with a metadata directory system, receives a unique bounding identifier, and uses this bounding ID (e.g., an ID provider ID) with subsequent interactions with the metadata directory system. Separately, metadata source providers register metadata sources with the metadata directory system. This enables many different participants to associate content objects with metadata sources using one or more identify providers. Examples of metadata source providers include content providers, like content owners or retailers that have the flexibility of working with different ID providers to associate content objects with metadata. Both content providers and ID providers can register and use the system. The metadata source is the system or device that provides the metadata, like a web site. The directory system uses an identifier for the metadata source, which enables it to maintain an association between a content object and its corresponding metadata source. For example, in some embodiments, a URL serves to identify the location of the source. The Content Metadata Directory Services (CMDS) is a global trusted directory service that connects consumers of identified content to content-provider authorized and managed metadata databases and other digital resources. It includes mostly links to metadata, forms globally unique IDs based upon overlapping content identifiers and unique bounding identifiers, enables multiple content identifiers within a content object, and enables multiple content identity technology providers, even when they are using different technology.
Owner:DIGIMARC CORP
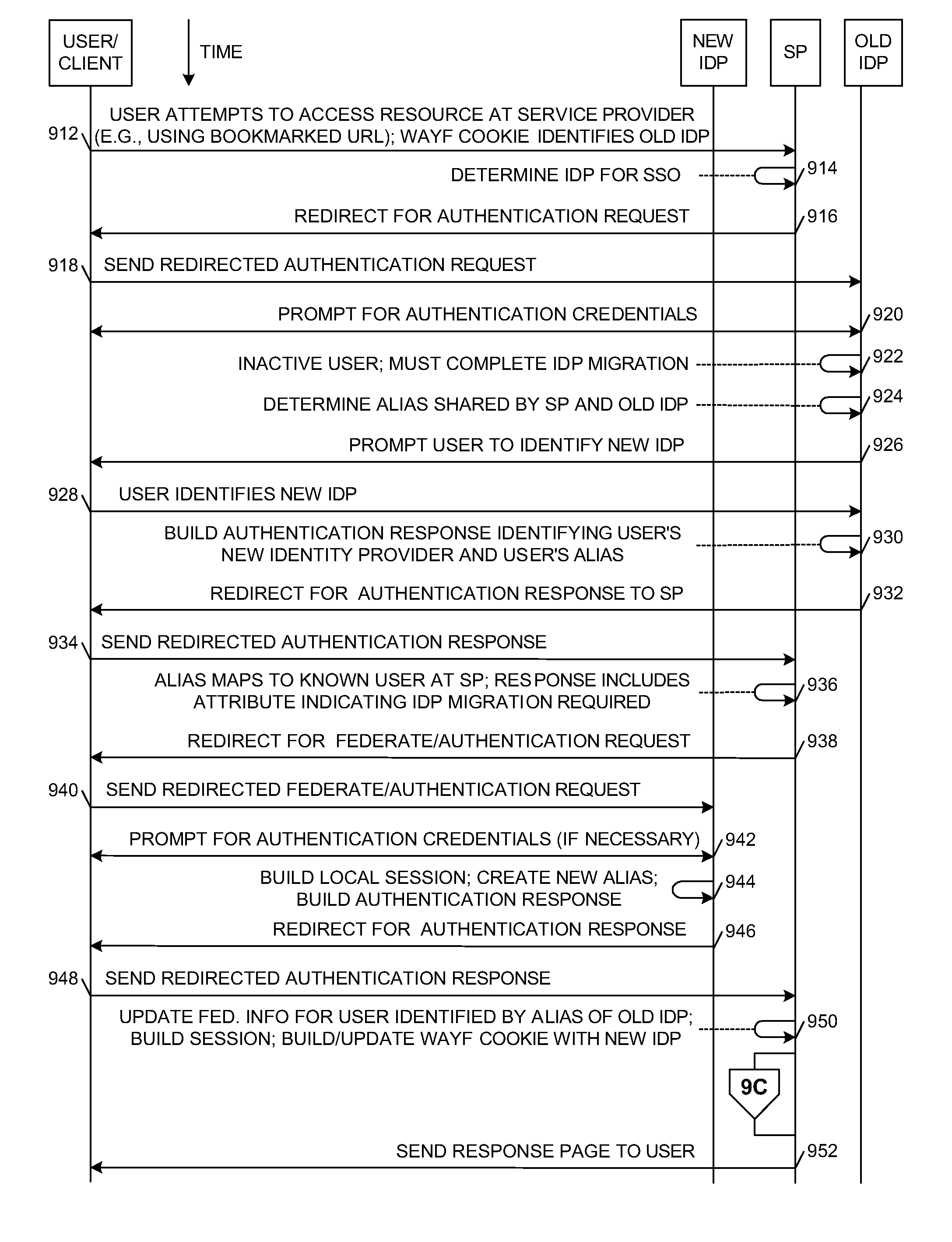
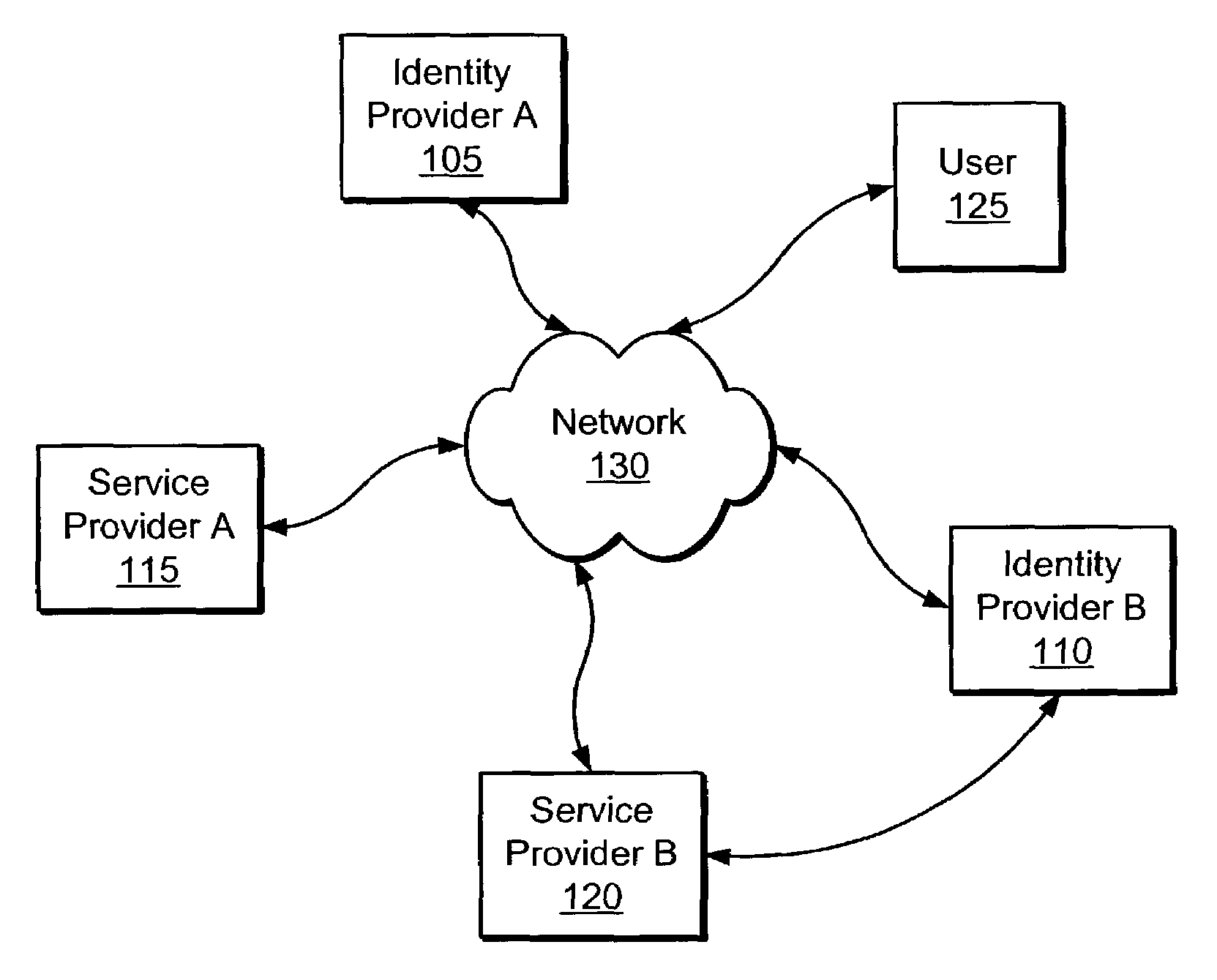
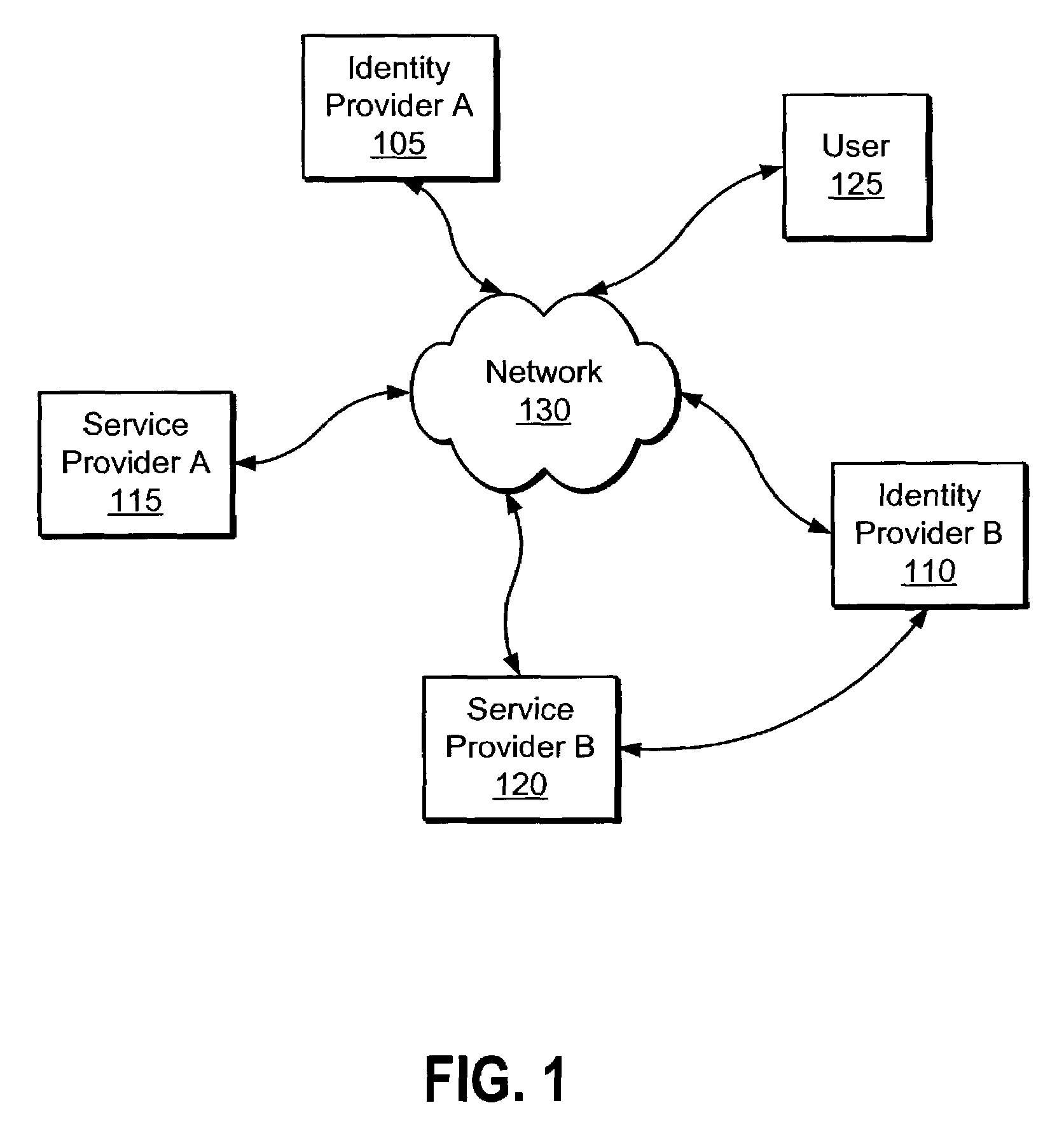
Method and system for identity provider migration using federated single-sign-on operation
ActiveUS20080021997A1Digital data processing detailsMultiple digital computer combinationsInternet privacyIdentity provider
A method is presented for performing an identity provider migration operation with respect to a user within a federated computational environment, wherein the user has a first user account at a first identity provider, a second user account at a second identity provider, and a third user account at a service provider. A request to access a resource is received by the service provider, after which a federated single-sign-on operation for the user is performed between the service provider and the first identity provider. Prior to sending a response to the request to access the protected resource, information in the third user account is modified to indicate that the service provider relies upon the second identity provider to authenticate the user on behalf of the service provider rather than the first identity provider. A response for the request to access the resource is then returned by the service provider.
Owner:SERVICENOW INC
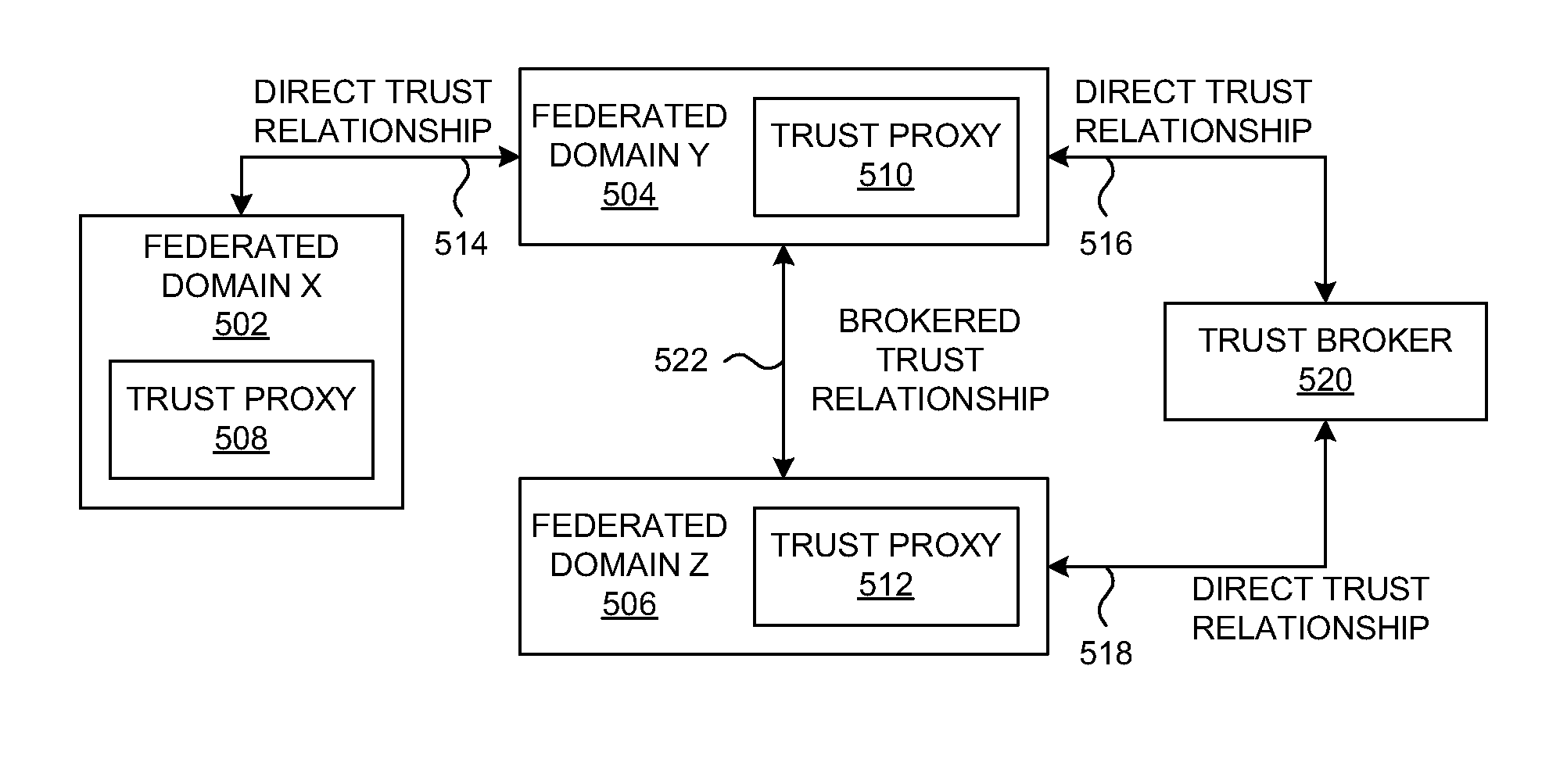
Specializing support for a federation relationship
ActiveUS7562382B2Change is minimalDigital data processing detailsUser identity/authority verificationData processing systemIdentity provider
The invention provides federated functionality within a data processing system by means of a set of specialized runtimes. Each of the plurality of specialized runtimes provides requested federation services for selected ones of the requestors according to configuration data of respective federation relationships of the requestors with the identity provider. The configuration data is dynamically retrieved during initialization of the runtimes which allows the respective runtime to be specialized for a given federation relationship. Requests are routed to the appropriate specialized runtime using the first requestor identity and the given federation relationship. The data which describes each federation relationship between the identity provider and each of the plurality of requesters is configured prior to initialization of the runtimes. Configuration data is structured into global specified data, federation relationship data and requestor specific data to minimize data change, making the addition or deletion of requestors very scalable.
Owner:IBM CORP
User impersonation/delegation in a token-based authentication system
ActiveUS20120254957A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
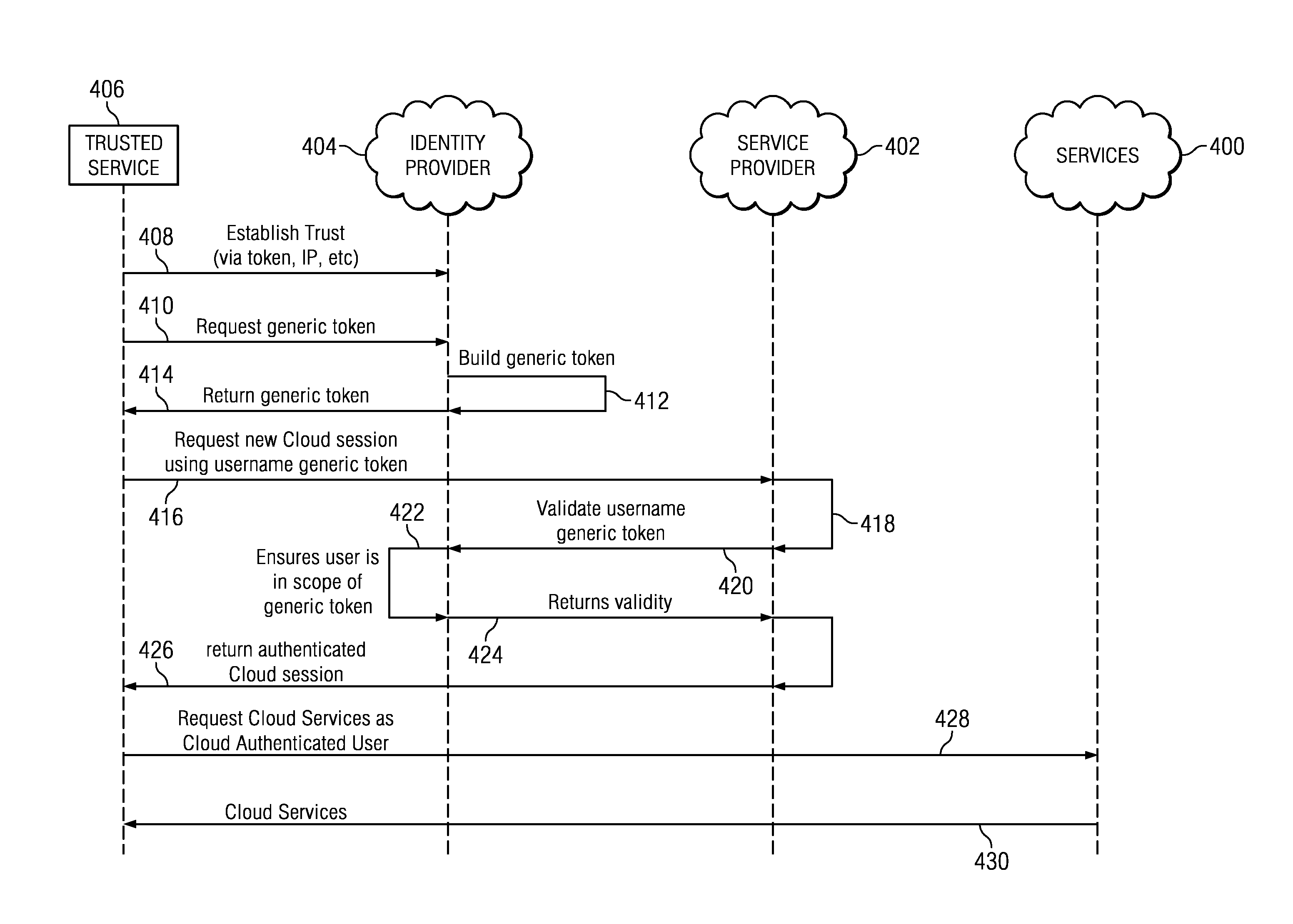
A “trusted service” establishes a trust relationship with an identity provider and interacts with the identity provider over a trusted connection. The trusted service acquires a token from the identity provider for a given user (or set of users) without having to present the user's credentials. The trusted service then uses this token (e.g., directly, by invoking an API, by acquiring another token, or the like) to access and obtain a cloud service on a user's behalf even in the user's absence. This approach enables background services to perform operations within a hosted session (e.g., via OAuth-based APIs) without presenting user credentials or even having the user present.
Owner:IBM CORP
Methods and systems for identity creation, verification and management
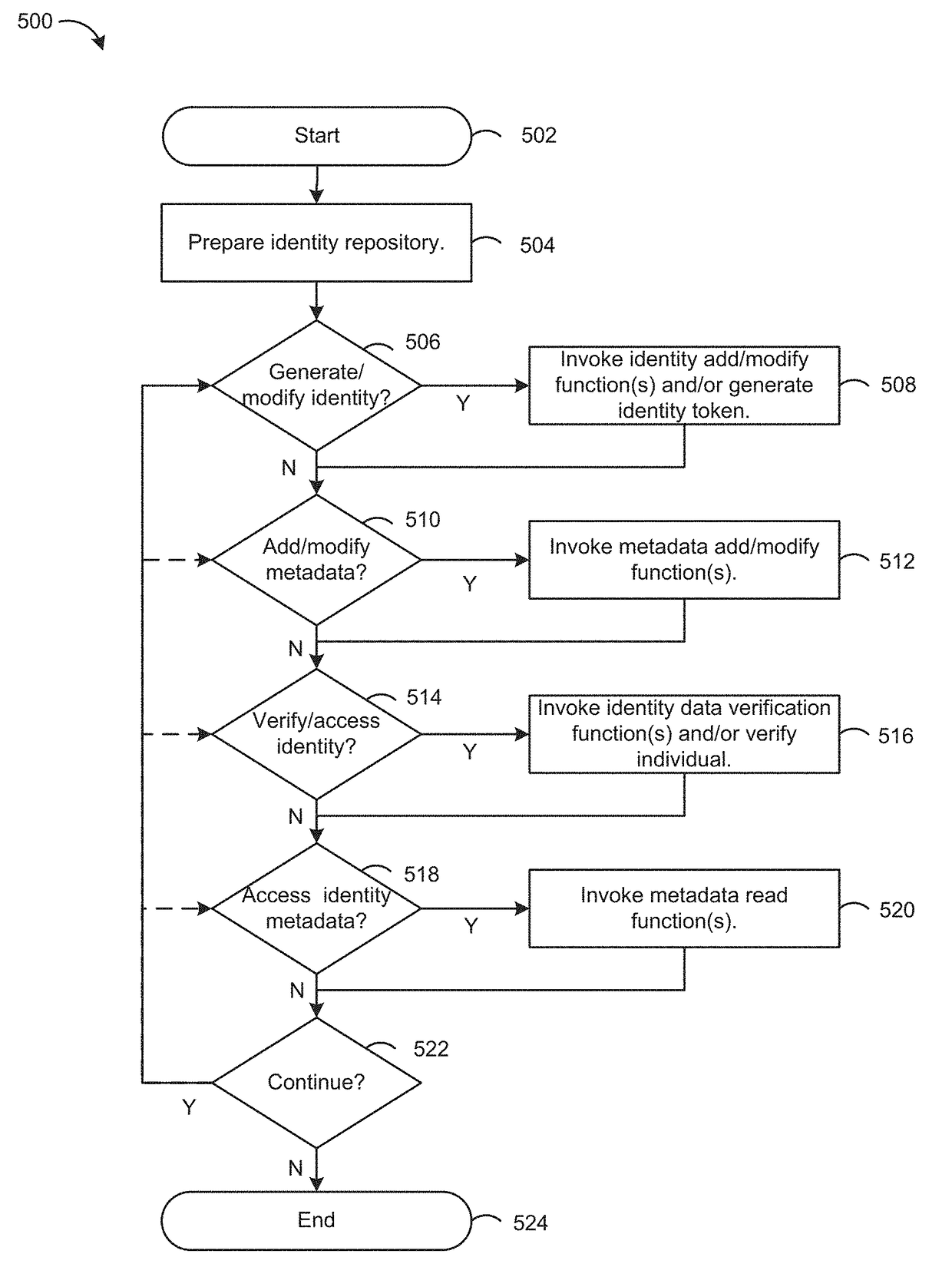
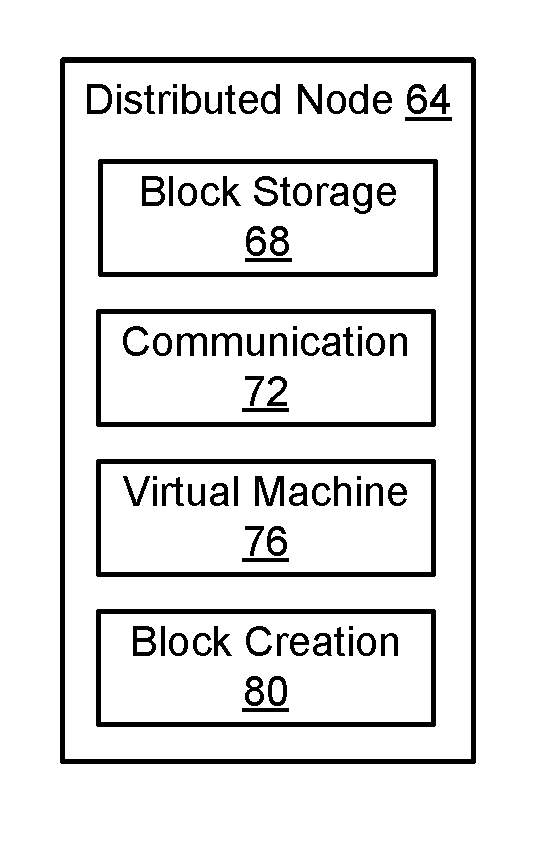
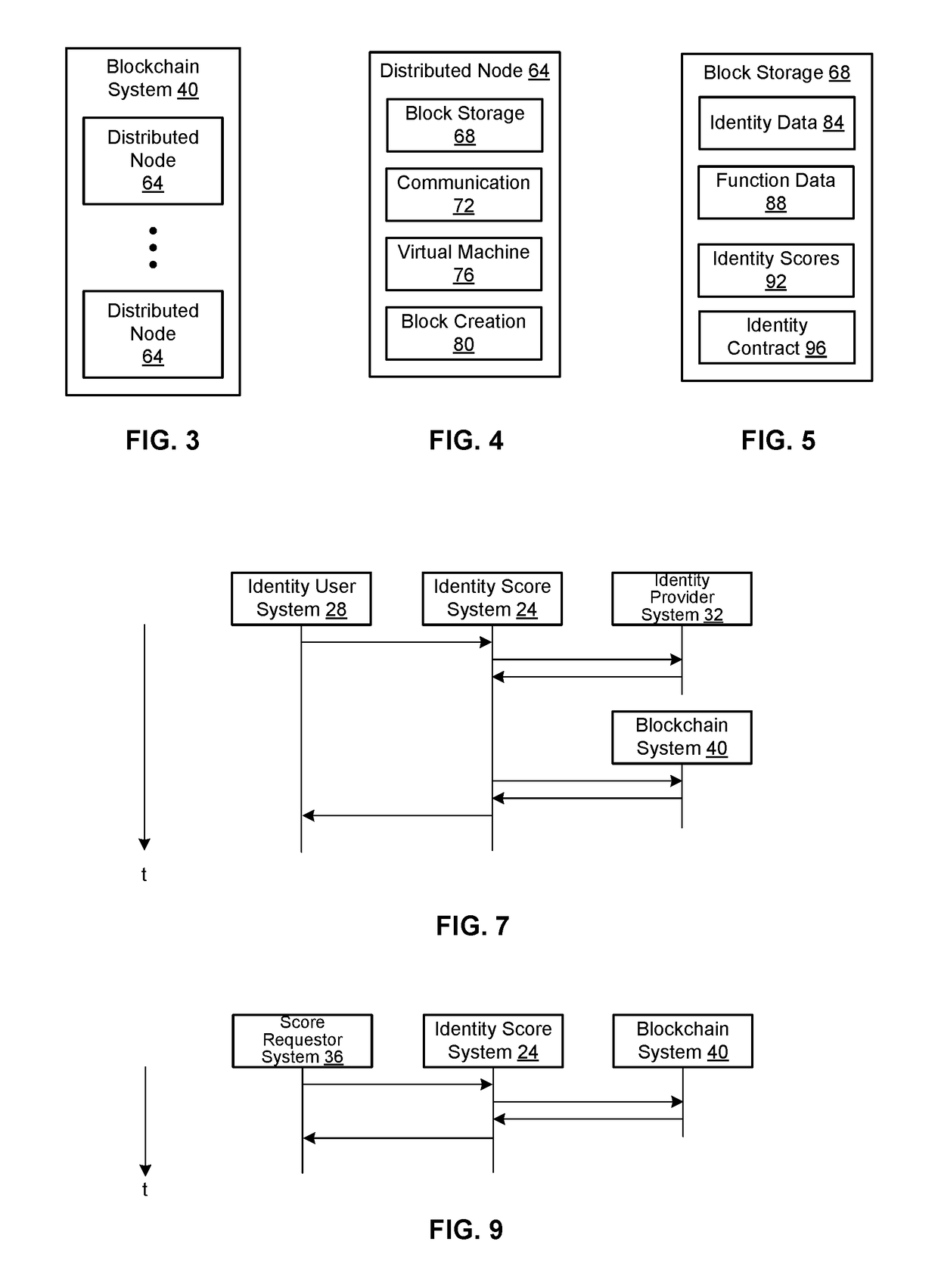
ActiveUS20170177855A1User identity/authority verificationDigital data authenticationBlockchainIdentity provider
An embodiment of a method of providing identity services includes: receiving identity data for an individual for which the identity provider has provided an identity; generating a transaction to store an identifier representing the identity data in a data structure on a blockchain of a distributed system; sending the transaction to at least one node of the distributed system; and generating an identity token incorporating the identifier representing the identity data. An embodiment of a method of verifying an identity includes: receiving data extracted from the identity token, wherein the extracted data includes an identifier representing the identity data; determining whether a data structure containing the extracted identifier representing the identity data is stored on a blockchain of a distributed system; and outputting an indication of a validity of an identity associated with the identity data based on the determination.
Owner:REFINITIV US ORG LLC
Specializing support for a federation relationship
ActiveUS20060136990A1Change is minimalDigital data processing detailsUser identity/authority verificationData processing systemIdentity provider
The invention provides federated functionality within a data processing system by means of a set of specialized runtimes. Each of the plurality of specialized runtimes provides requested federation services for selected ones of the requestors according to configuration data of respective federation relationships of the requestors with the identity provider. The configuration data is dynamically retrieved during initialization of the runtimes which allows the respective runtime to be specialized for a given federation relationship. Requests are routed to the appropriate specialized runtime using the first requestor identity and the given federation relationship. The data which describes each federation relationship between the identity provider and each of the plurality of requesters is configured prior to initialization of the runtimes. Configuration data is structured into global specified data, federation relationship data and requestor specific data to minimize data change, making the addition or deletion of requesters very scalable.
Owner:IBM CORP
Computer-implemented systems and methods of device based, internet-centric, authentication
ActiveUS20160134599A1User identity/authority verificationDigital data authenticationInternet usersIdentity provider
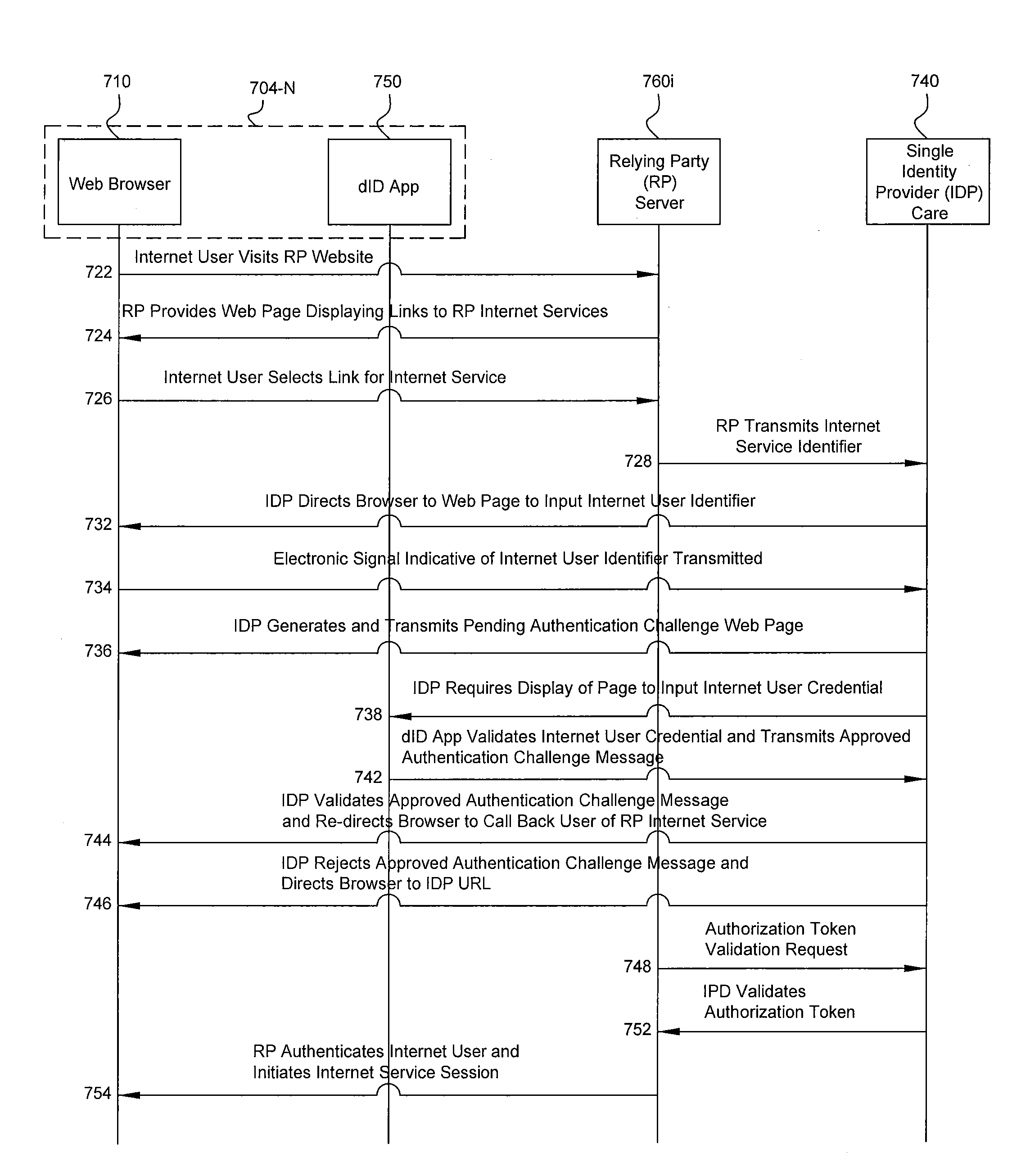
Systems and computer-implemented methods for authorizing respective access by each of a plurality of Internet users to a respective one or more Internet services provided by each of a plurality of Internet service providers. A system includes a processor, and non-transient computer readable storage media, at a single identity provider. The storage media is encoded with program code executable by the processor for requiring an identity provider application residing on each of a plurality of devices to create a respective authentication token that is specific to a respective identifier and user credential of a respective Internet user, a respective device identifier, and the respective identity provider application, and for authorizing respective access by the plurality of Internet users to a respective requested one of the Internet services provided by each Internet service provider using the respective created authentication tokens and respective identifiers for each of the respective requested Internet services.
Owner:PRIVAKEY INC
Method and system for identity provider migration using federated single-sign-on operation
ActiveUS7657639B2Digital data processing detailsMultiple digital computer combinationsInternet privacyIdentity provider
A method is presented for performing an identity provider migration operation with respect to a user within a federated computational environment, wherein the user has a first user account at a first identity provider, a second user account at a second identity provider, and a third user account at a service provider. A request to access a resource is received by the service provider, after which a federated single-sign-on operation for the user is performed between the service provider and the first identity provider. Prior to sending a response to the request to access the protected resource, information in the third user account is modified to indicate that the service provider relies upon the second identity provider to authenticate the user on behalf of the service provider rather than the first identity provider. A response for the request to access the resource is then returned by the service provider.
Owner:SERVICENOW INC
Authentication of a principal in a federation
InactiveUS20070143829A1Increase flexibilityRandom number generatorsUser identity/authority verificationIdentity providerAuthentication
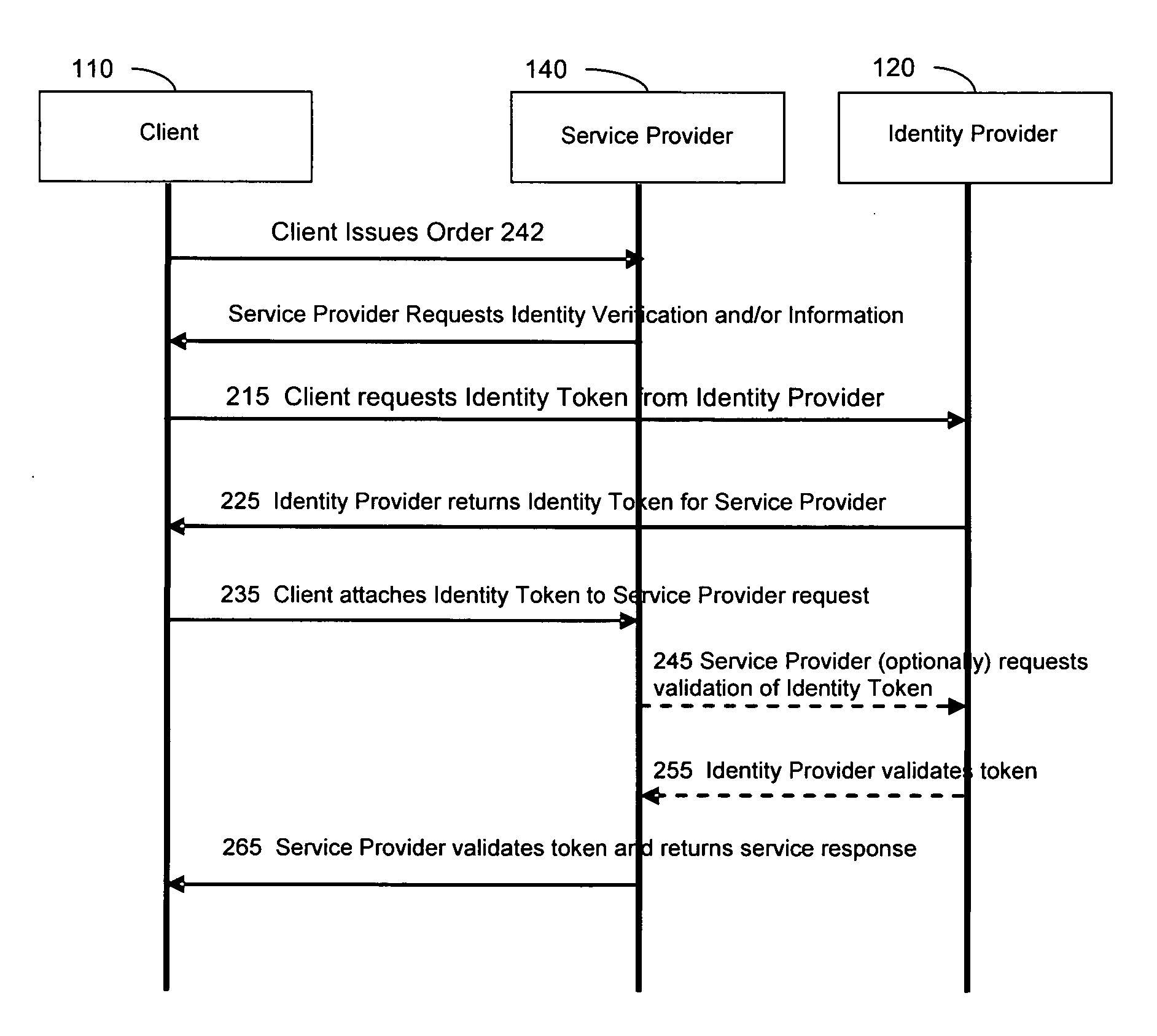
Methods, systems, and computer program products are disclosed that give entities flexibility to implement custom authentication methods of other entities for authentication of a principal in a federation by authenticating the principal by an identity provider according to a service provider's authentication policy and recording in session data of the identity provider an authentication credential satisfying the service provider's authentication policy. Authentication of a principal in a federation is also carried out by authenticating the principal by the identity provider according to an identity provider's authentication policy. Authentication of a principal in a federation is further carried out by receiving in the identity provider an authentication request from the service provider, the authentication request specifying the service provider's authentication policy.
Owner:IBM CORP
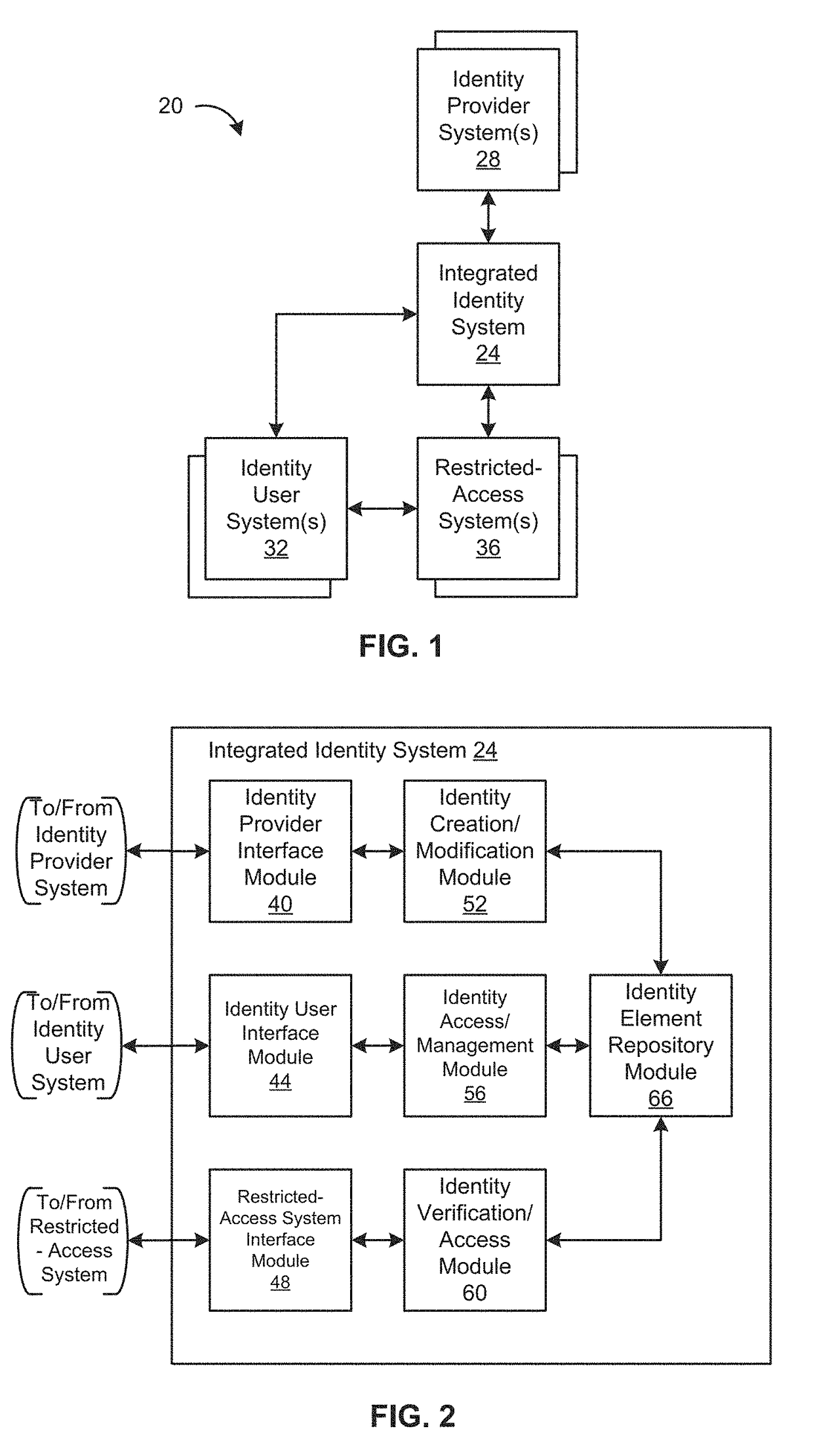
Distributed Network Identity
ActiveUS20080016232A1Improve user interactionAssure integrityMultiple digital computer combinationsDigital data authenticationInformation sharingInternet privacy
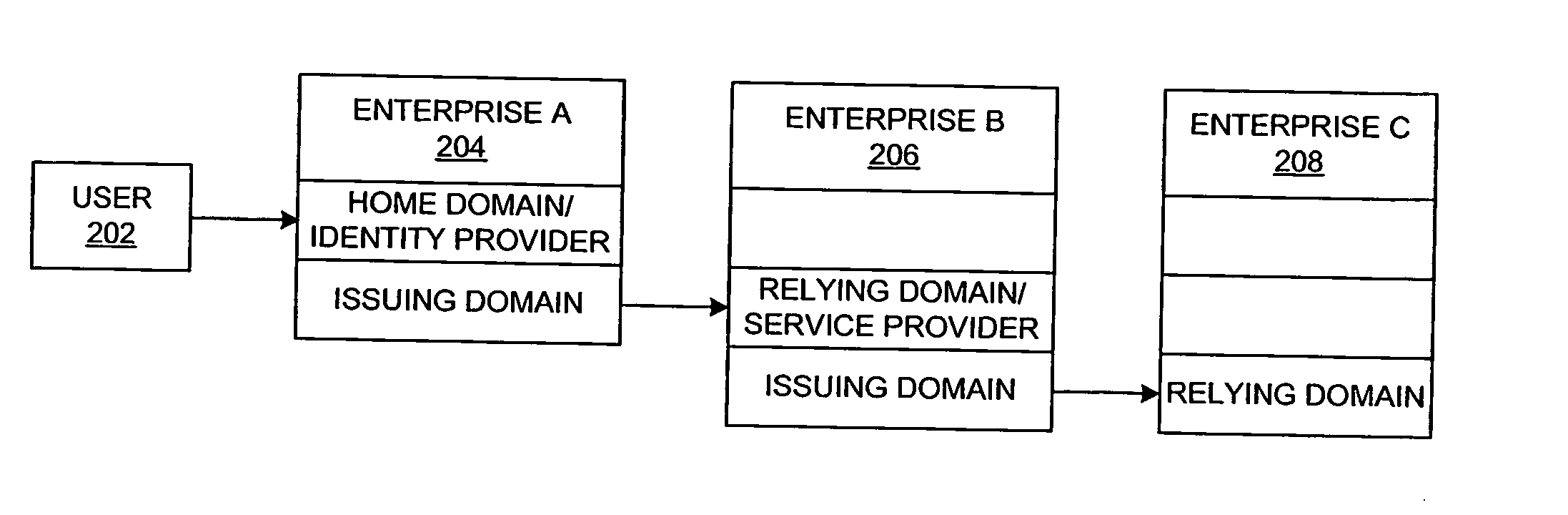
A distributed network identity is provided. An identity provider stores a portion of a user's personal information. A service provider accesses user information from one or more identity providers. System entities such as identity providers and service providers can be linked to enable information sharing and aggregation. User policies and privacy preferences are provided to control how information is shared. A single sign-on architecture is provided where an identity provider is used to facilitate cross-domain authentication and to enhance user convenience. Service delegation features are also provided.
Owner:ORACLE INT CORP
Method and apparatus for network transactions
InactiveUS20060235761A1Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceDigital data processing detailsPaymentIdentity provider
A method is provided to authorize an online transaction between a purchaser and a merchant. The method includes providing, via an identity provider, verification of an identity of the purchaser. The method also includes providing, via a payment provider, verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are different network entities. A computer system is also provided that can conduct an online transaction between a purchaser and a merchant providing one or more goods and / or services. The computer system includes a first node configured to provide verification of an identity of the purchaser, and a second node configured to provide verification of an ability of the purchaser to pay for the transaction, where the first node and the second node are associated with different network entities.
Owner:MICROSOFT TECH LICENSING LLC
Distributed network identity
ActiveUS7610390B2Improve user interactionAssure integrityMultiple digital computer combinationsDigital data authenticationInformation sharingInternet privacy
A distributed network identity is provided. An identity provider stores a portion of a user's personal information. A service provider accesses user information from one or more identity providers. System entities such as identity providers and service providers can be linked to enable information sharing and aggregation. User policies and privacy preferences are provided to control how information is shared. A single sign-on architecture is provided where an identity provider is used to facilitate cross-domain authentication and to enhance user convenience. Service delegation features are also provided.
Owner:ORACLE INT CORP
Method and system for a runtime user account creation operation within a single-sign-on process in a federated computing environment
ActiveUS7631346B2Key distribution for secure communicationDigital data processing detailsComputer networkService provision
A method, system, apparatus, and computer program product are presented to support computing systems of different enterprises that interact within a federated computing environment. Federated single-sign-on operations can be initiated at the computing systems of federation partners on behalf of a user even though the user has not established a user account at a federation partner prior to the initiation of the single-sign-on operation. For example, an identity provider can initiate a single-sign-on operation at a service provider while attempting to obtain access to a controlled resource on behalf of a user. When the service provider recognizes that it does not have a linked user account for the user that allows for a single-sign-on operation with the identity provider, the service provider creates a local user account. The service provider can also pull user attributes from the identity provider as necessary to perform the user account creation operation.
Owner:INT BUSINESS MASCH CORP
Means and method for generating a unique user's identity for use between different domains
InactiveUS20070130343A1Multiple digital computer combinationsTransmissionComputer networkIdentity provider
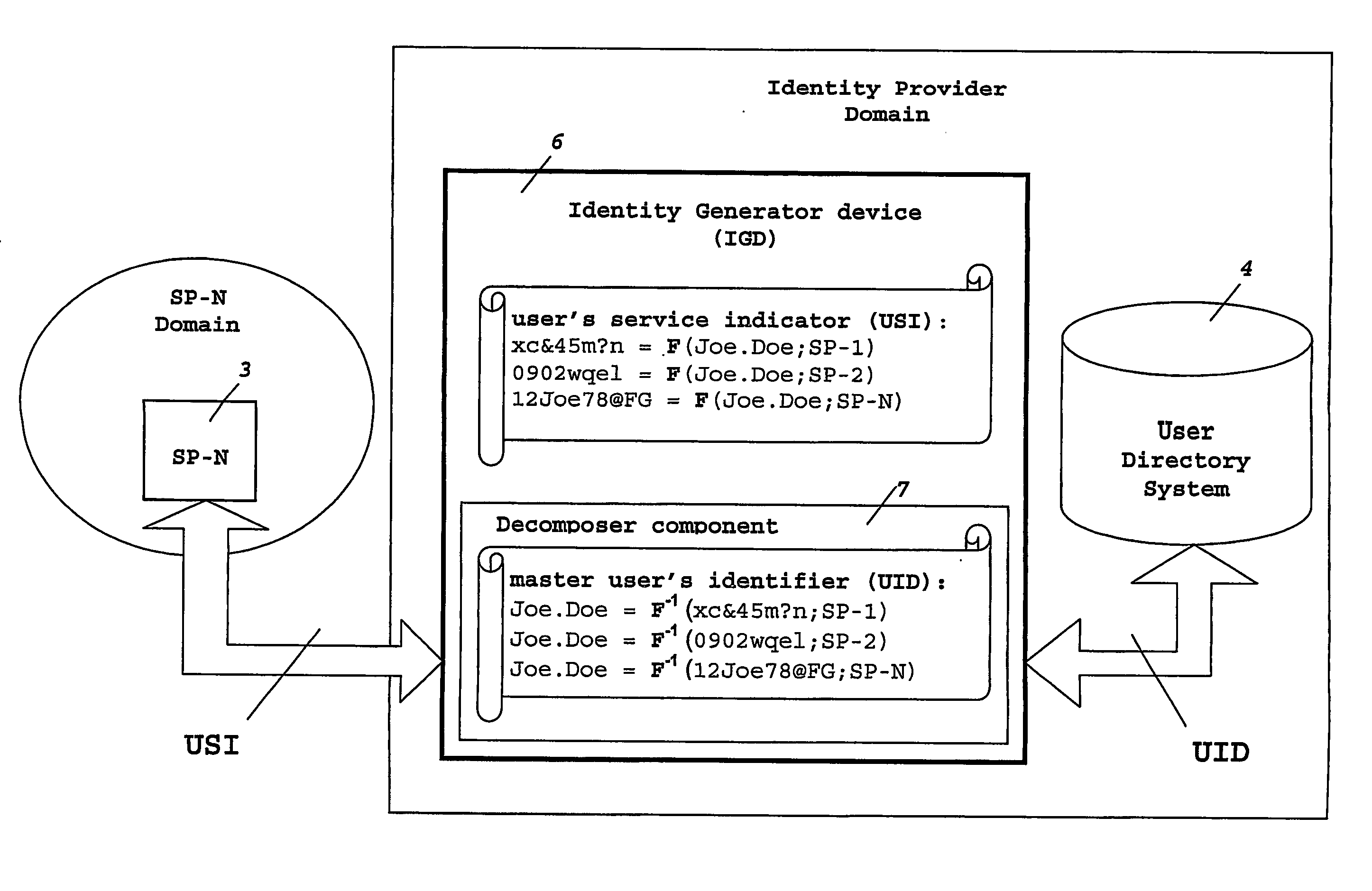
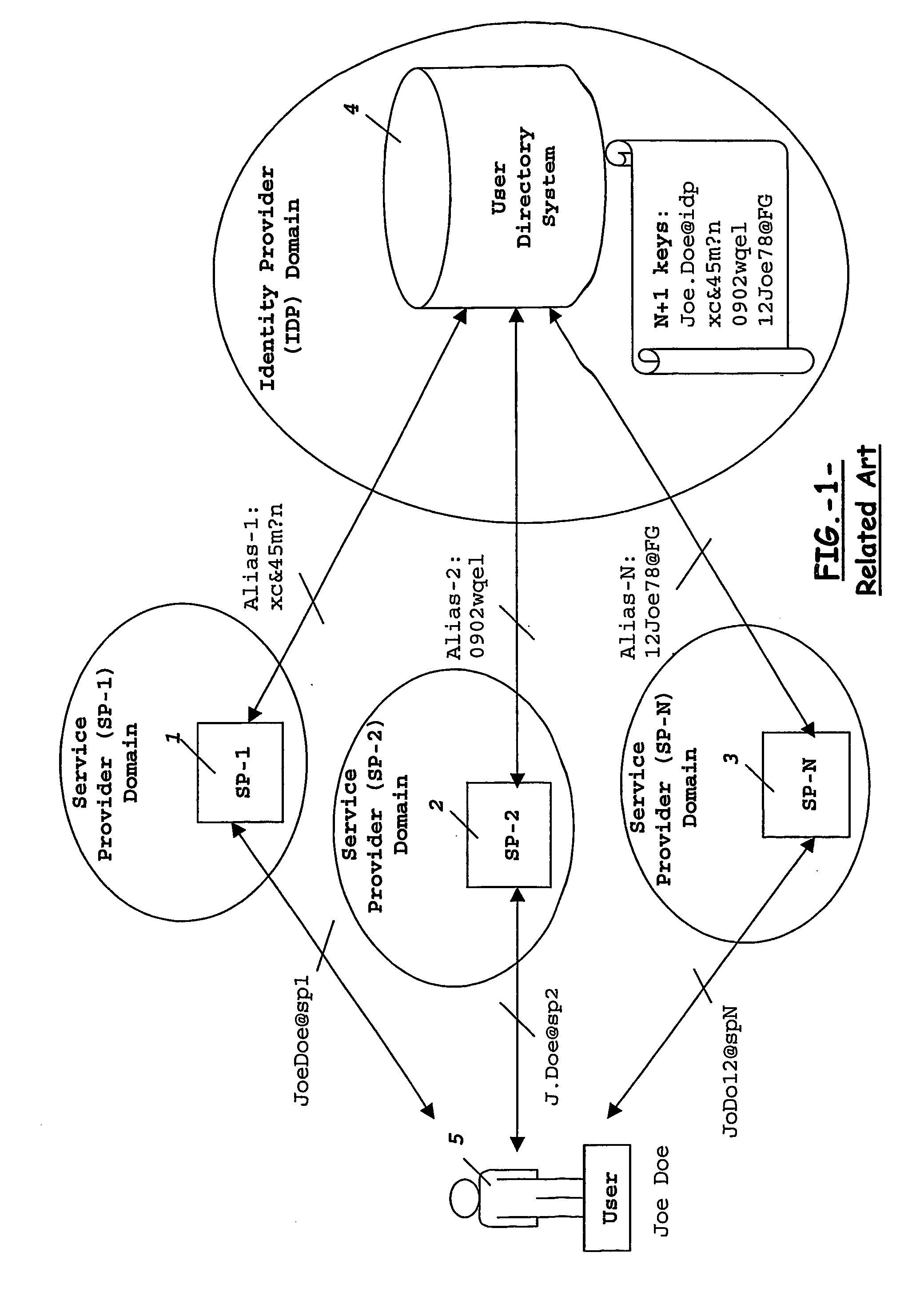
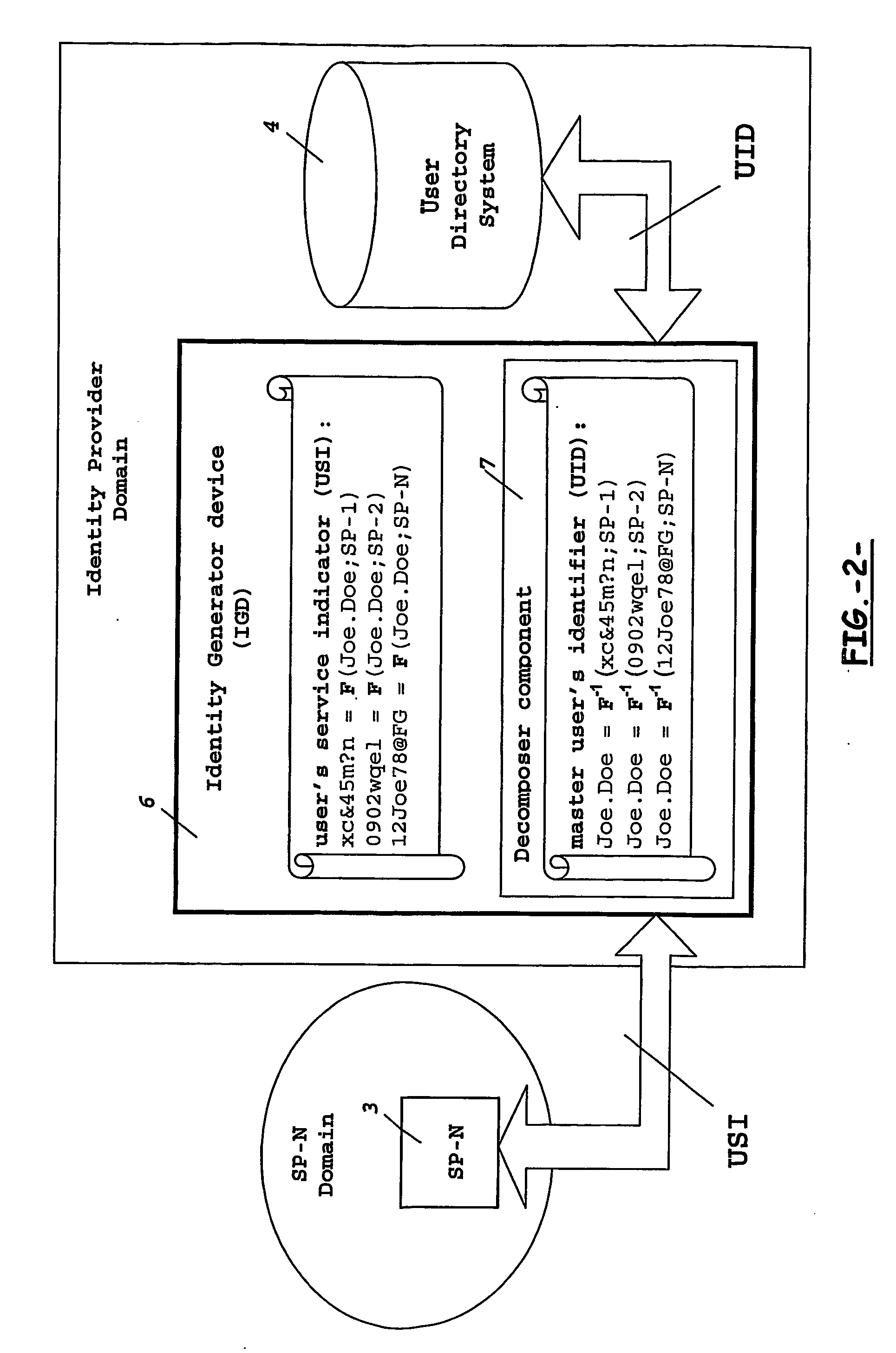
Mobile operators presently offer services on behalf of service providers where such services are really carried out for the users. Mobile operators act as identity providers in this scenario, wherein service provider and identity provider share a unique identity to identify each particular user accessing a number of services. As the number of users accessing these services, and the number of services offered from different service providers increase, the storage required at the operator's network for such amount of user's identities becomes a problem. To overcome this and other problems, the present invention provides an identity Generator device arranged to generate a user's service indicator to identify the user between the service provider and the identity provider, the user's service indicator comprising a master user's identifier for identification of the user at the identity provider, and a service identifier indicating the services to be accessed at a given service provider.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and system for secure binding register name identifier profile
ActiveUS20060129816A1Enhance the imageUser identity/authority verificationDigital data authenticationIdentity providerAuthentication
A method, a system, an apparatus, and a computer program product are presented for improving a register name identifier profile within a federated computing environment such that the register name identifier profile is enhanced to be more securely binding between two federated entities within the federated computing environment, such as an identity provider and a service provider. After the first federated entity sends a register name identifier request for a principal to the second federated entity, the second federated entity performs an authentication operation for the principal. In response to successfully completing the authentication operation, the second federated entity registers or modifies a name identifier for the principal that has been extracted from the received register name identifier request.
Owner:IBM CORP
Service provider anonymization in a single sign-on system
InactiveUS20060155993A1User identity/authority verificationDigital computer detailsInternet privacyService provision
A method for sign-on in a network based communications environment is described. Authentication of a first entity is requested by a second entity for accessing a service to be provided by the second entity to the first entity. The authentication is provided by a third entity. Data that identify the second entity are blinded towards the third entity. Blinding means that data identifying the second entity are modified such that the blinded data do not provide any information on the basis of which the second entity can be identified preferably except for the entity which has at least initiated data blinding, here the first entity. Examples for blinding include the use of a pseudonym or alias for the data identifying the second entity. According to a preferred embodiment, the method according to the present invention is used for a single sign-on. Referring to the above description of single sign-on, e.g. in line with the LAP specifications, the present invention provides a method for blinding the identity of the service provider SP towards the identity provider IdP.
Owner:TELEFON AB LM ERICSSON (PUBL)
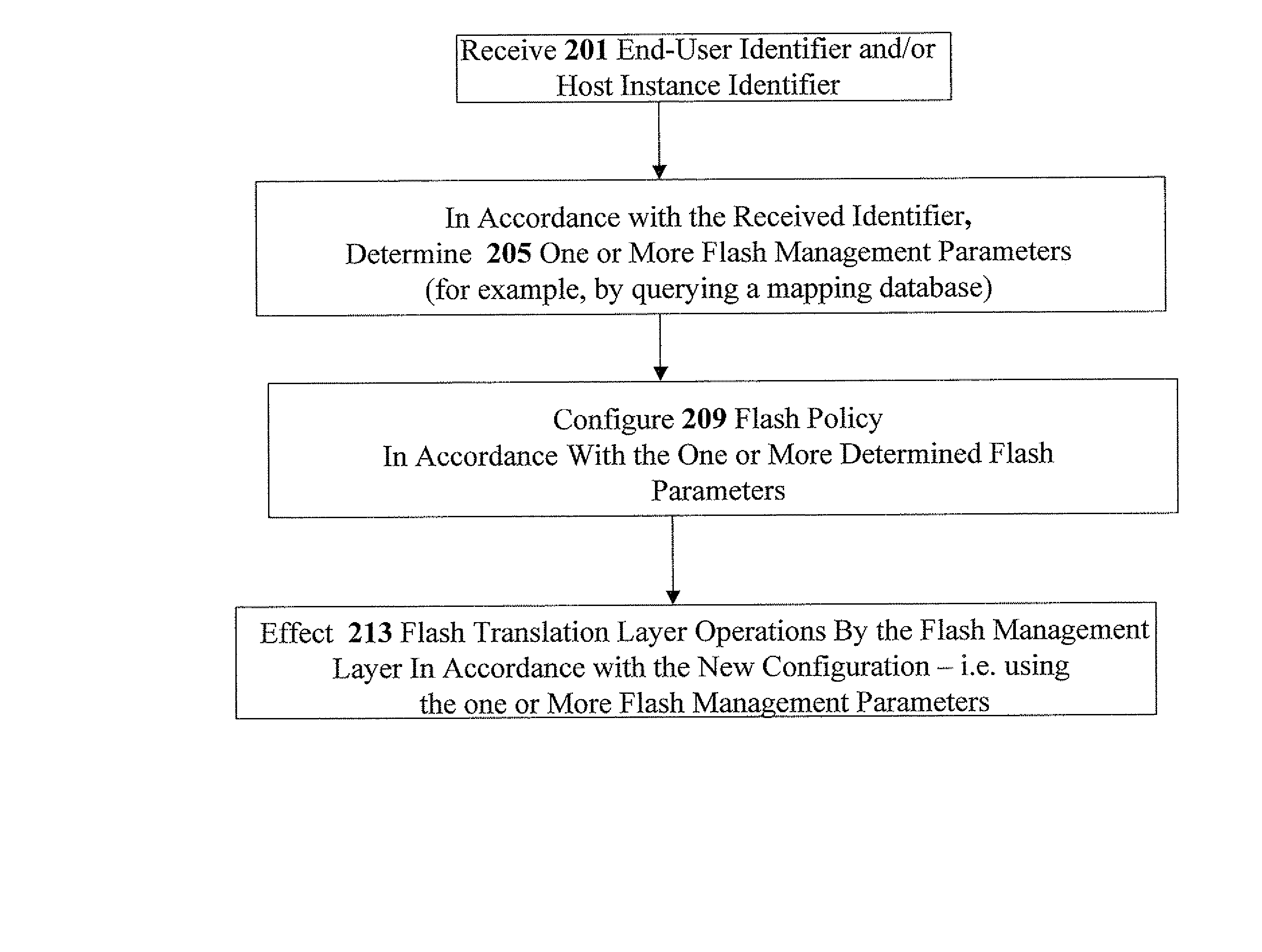
Identity-based flash management
Methods, apparatus, and computer code for effecting flash policy configuration operations in accordance with an end-user identifier and / or a host-instance identifier are disclosed herein. Exemplary flash policy configuration operations include (i) configuring a flash error-correction policy, (ii) configuring a flash-management table storage policy; (iii) configuring a wear-leveling policy; (iv) configuring a bad-block management policy and (v) configuring a flash-programming voltage parameter. Exemplary end-user identifiers include but are not limited to email account identifiers, logon user names, and International Mobile Subscriber Identities (IMSI). Exemplary host-instance identifiers may include but are not limited to International Mobile EQUIPMENT Identifiers (IMEI). Optionally, the flash policy configuration is contingent on authentication context data—for example, strength of the authentication (e.g. login / password vs. smartcard authentication or biometric authentication), date of the authentication, and identity provider information.
Owner:WESTERN DIGITAL ISRAEL LTD
Systems and methods for providing identity scores
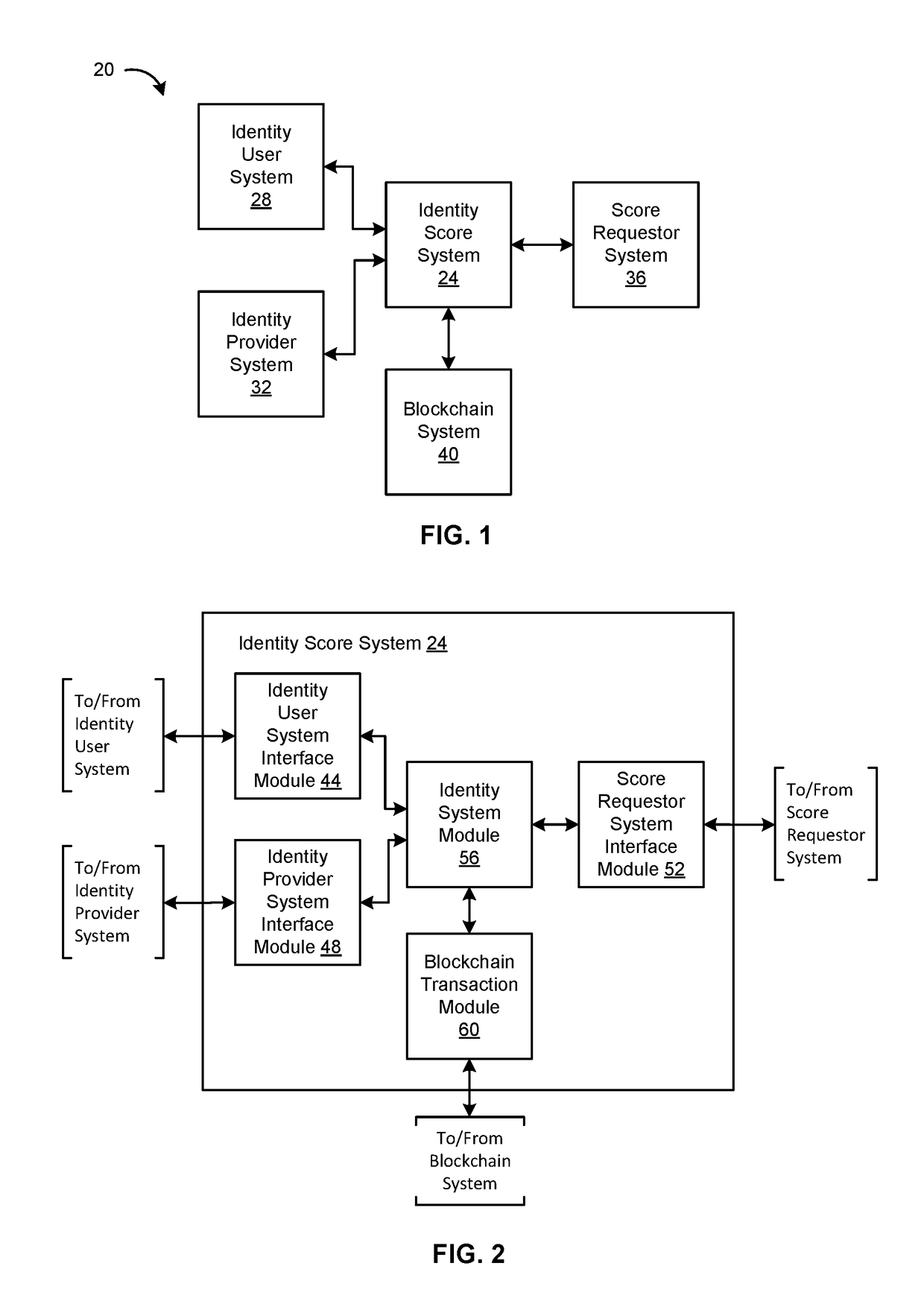
ActiveUS20170353311A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationIdentity scoreInternet privacy
An embodiment of a method of providing identity services includes receiving identity data from an identity user, the identity data related to an identity of the identity user; receiving validation data from an identity provider, the validation data related to the identity data; if the validation data indicates that the identity data is valid, generating a transaction to store data related to the identity of the identity user on a blockchain of a blockchain system, the data to be stored including a representation of at least one of: the identity data, or the validation data; and transmitting the transaction to at least one distributed node of the blockchain system. An embodiment of a method of providing an identity score includes receiving an identity score request for an identity user from an identity score requestor; executing a read to at least one distributed node of a blockchain system to retrieve data related to one or more identities of the identity user stored on a blockchain of the blockchain system; for each of the one or more identities, determining a weight; and determining the identity score as a function of the weights for each of identities.
Owner:REFINITIV US ORG LLC
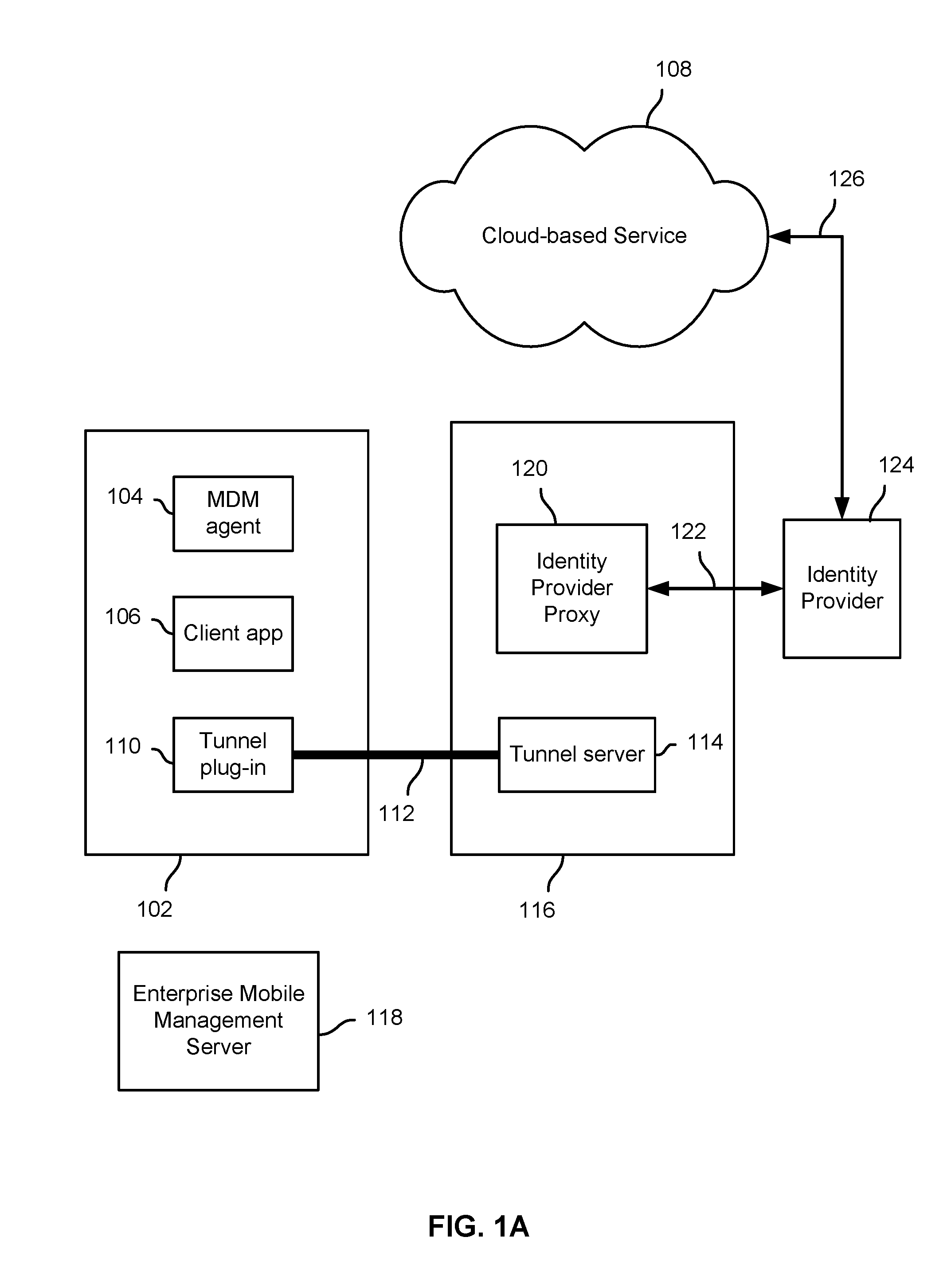
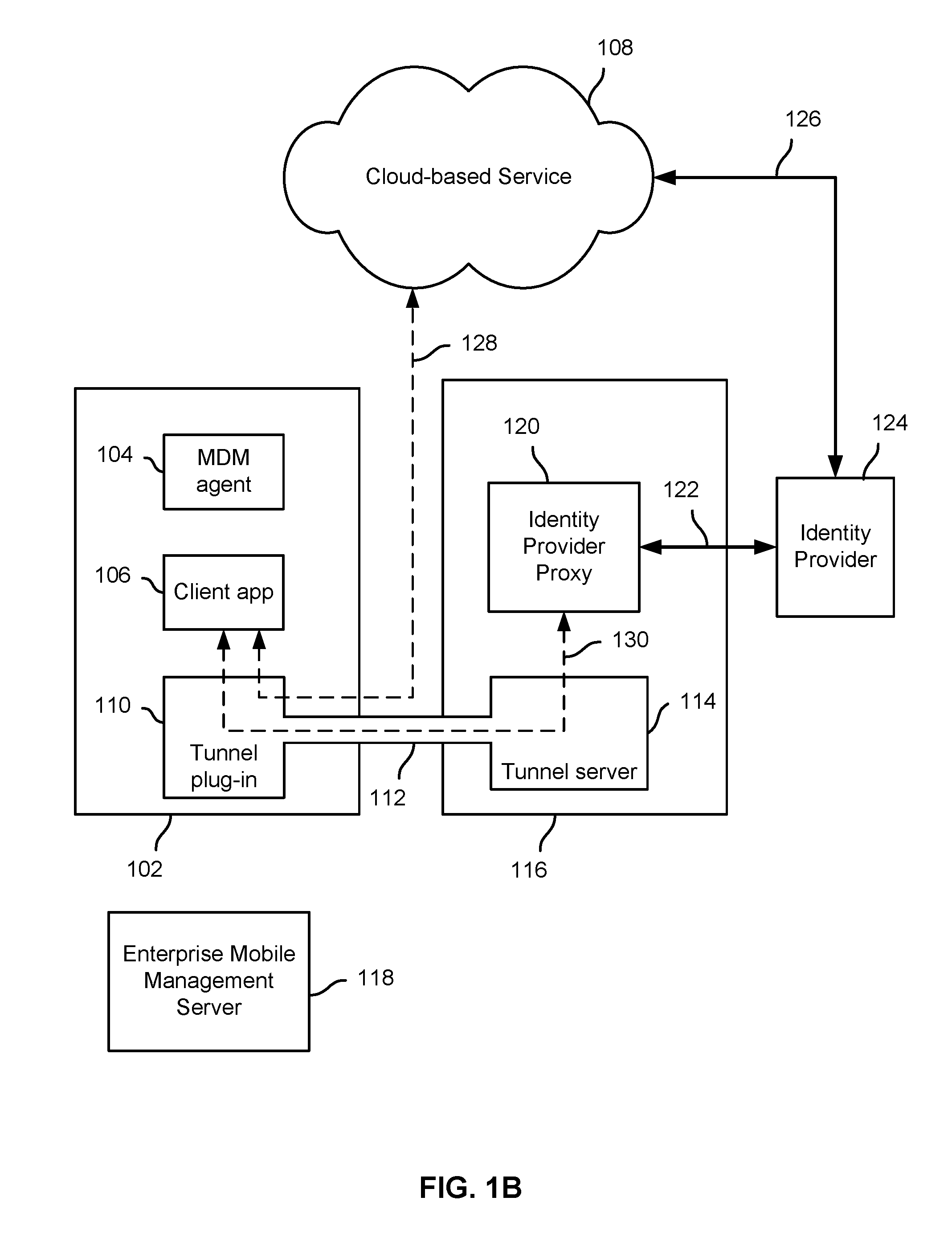
Identity proxy to provide access control and single sign on
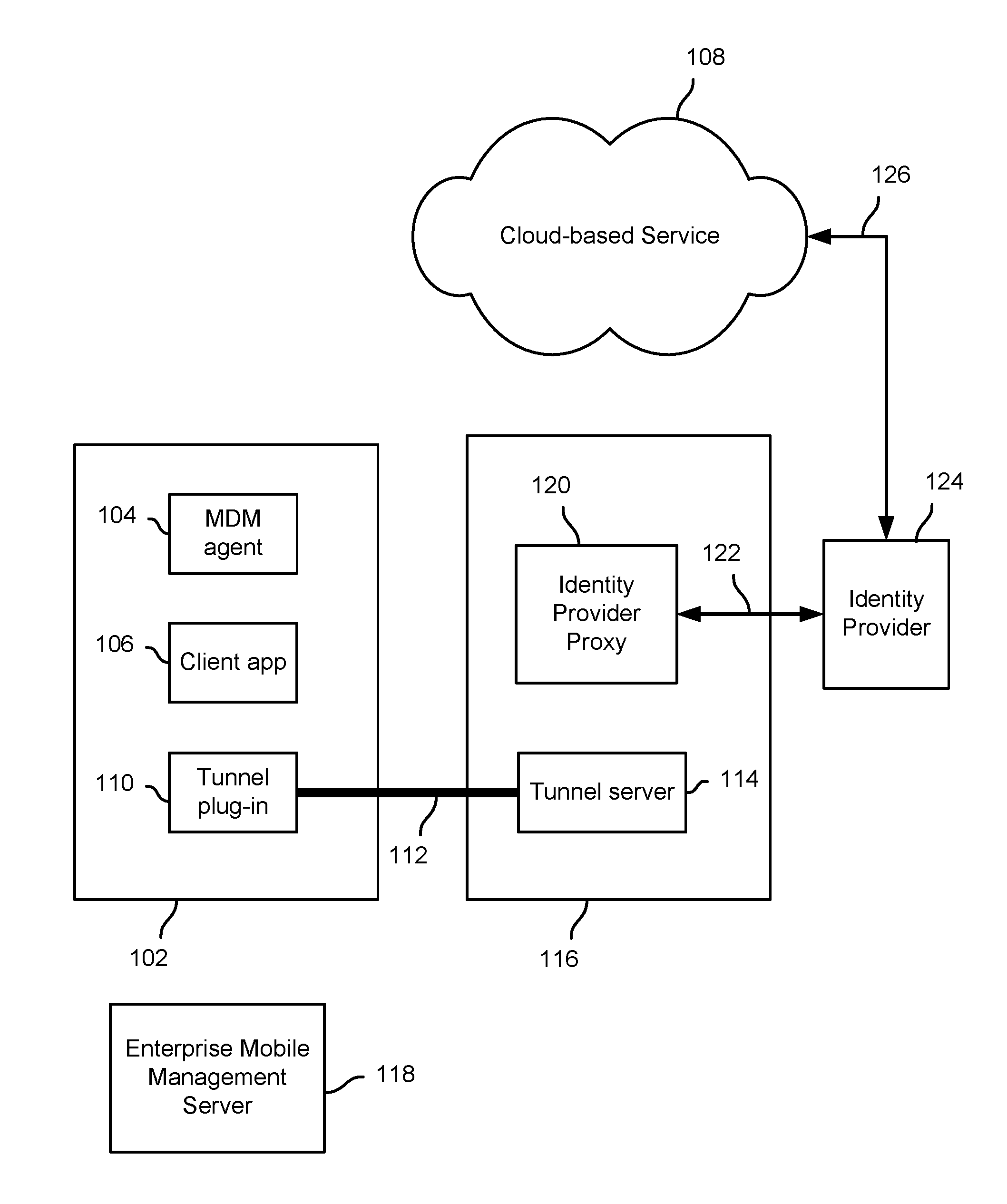
Techniques to provide secure access to a cloud-based service are disclosed. In various embodiments, a request is received from a client app on a device to connect to a security proxy associated with the cloud-based service. A secure tunnel connection between the device and a node with which the security proxy is associated is used to establish the requested connection to the security proxy. Information associated with the secure tunnel is used to determine that the requesting client app is authorized to access the cloud-based service from the device and to obtain from an identity provider associated with the cloud-based service a security token to be used by the client app to authenticate to the cloud-based service.
Owner:IVANTI INC
Methods and Systems for Distributing Cryptographic Data to Authenticated Recipients
ActiveUS20120179905A1Digital data authenticationSelective content distributionIdentity providerClient-side
A method for distributing cryptographic data to authenticated recipients includes receiving, by an access control management system, from a first client device, information associated with an encrypted data object. The method includes receiving, by the access control management system, from a second client device, a request for the information associated with the encrypted data object. The method includes verifying, by the access control management system, that a user of the second client device is identified in the received information associated with the encrypted data object. The method includes authenticating, by the access control management system, with an identity provider, the user of the second client device. The method includes sending, by the access control management system, to the second client device, the received information associated with the encrypted data object.
Owner:VIRTRU
Redundant multifactor authentication in an identity management system
InactiveUS20100132019A1Digital data processing detailsUser identity/authority verificationIdentity providerDependability
A redundant multifactor identity authentication system provides users with a secure mechanism for providing identity information through the use of redundant independent identity providers in concert with each other so that resources are accessed only through a combination of providers. By eliminating reliance on a single provider, security is increased as is reliability. Similarly, redundant credentials can be provided to relying parties to ensure that the relying party receives proof of a credential without requiring a specific credential.
Owner:BLAME CANADA HLDG
System and method for application-integrated information card selection
InactiveUS20090205014A1Digital data processing detailsUnauthorized memory use protectionInformation CardIdentity provider
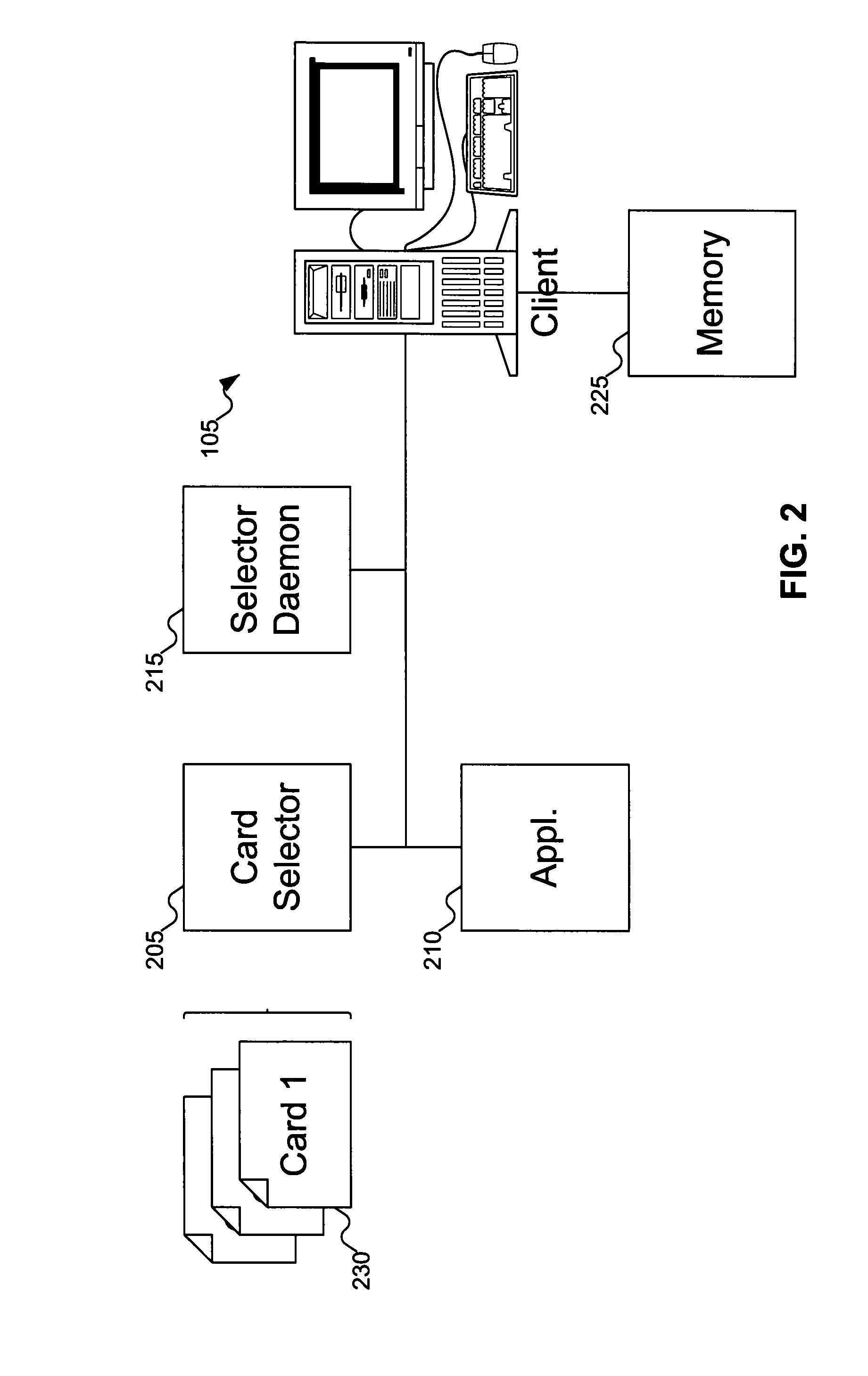
A selector daemon can run in the background of a computer. Applications that are capable of processing information cards directly, without requiring the use of a card selector, can request the selector daemon to list information cards that satisfy security policy. Upon receiving such a request, selector daemon can determine the information cards available on the computer that satisfy the security policy, and can identify these information cards to the requesting application. The applications can then use the identified information cards in any manner desired, without having to use a card selector: for example, by requesting a security token based on one of the information cards directly from an identity provider.
Owner:WORDPERFECT CORP +1
Use of device risk evaluation to manage access to services
A method includes: receiving a request regarding access by a first computing device (e.g., a mobile device of a user) to a service; in response to the request, performing, by a second computing device (e.g., a device risk evaluation server, or a server of an identity provider), an evaluation of the first computing device; and performing, by the second computing device, an action (e.g., authorizing access to the service) based on the evaluation.
Owner:LOOKOUT MOBILE SECURITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
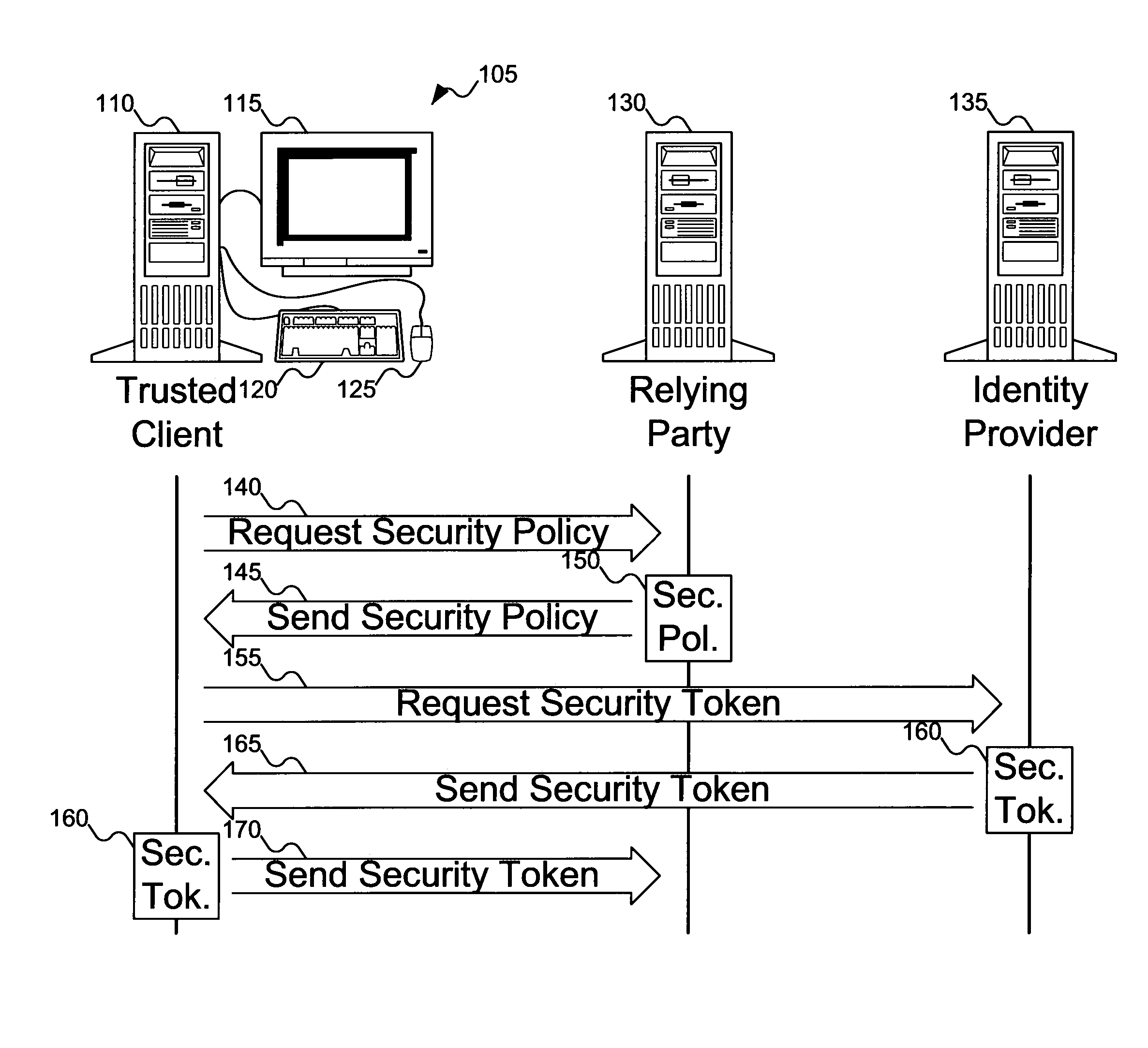
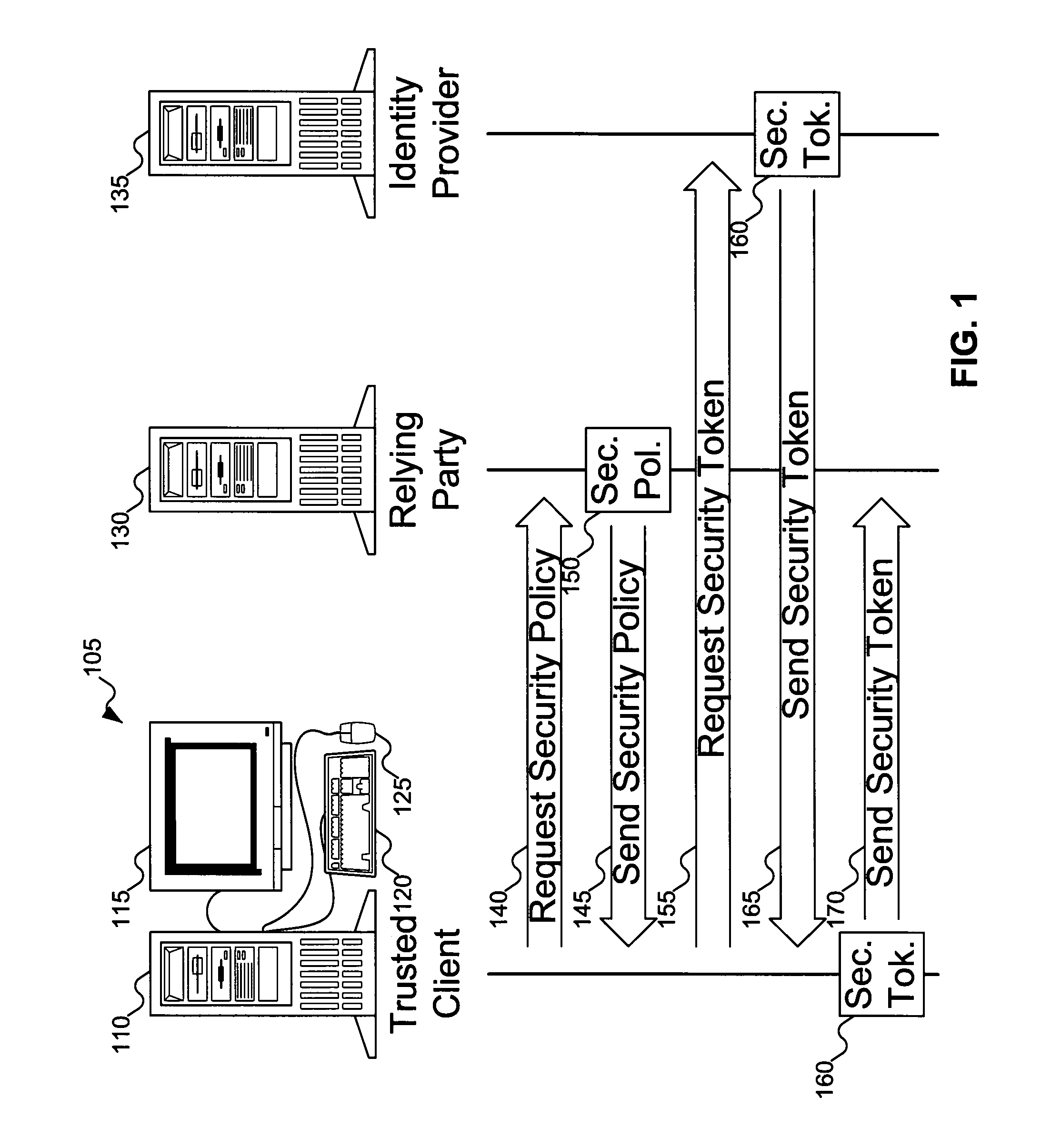
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com