Patents
Literature
296 results about "Globally unique identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Globally Unique Identifier is a unique reference number used as an identifier in computer software. The term GUID typically refers to various implementations of the universally unique identifier standard. GUIDs are usually stored as 128-bit values, and are commonly displayed as 32 hexadecimal digits with groups separated by hyphens, such as {21EC2020-3AEA-4069-A2DD-08002B30309D}. They may or may not be generated from random numbers. GUIDs generated from random numbers normally contain 6 fixed bits and 122 random bits; the total number of unique such GUIDs is 2¹²². This number is so large that the probability of the same number being generated randomly twice is negligible; however other GUID versions have different uniqueness properties and probabilities, ranging from guaranteed uniqueness to likely duplicates. Assuming uniform probability for simplicity, the probability of one duplicate would be about 50% if every person on earth as of 2014 owned 600 million GUIDs.
Internet profiling
InactiveUS6839680B1Quick applicationEasy to shareMarket predictionsSpecial data processing applicationsWeb serviceStandardization
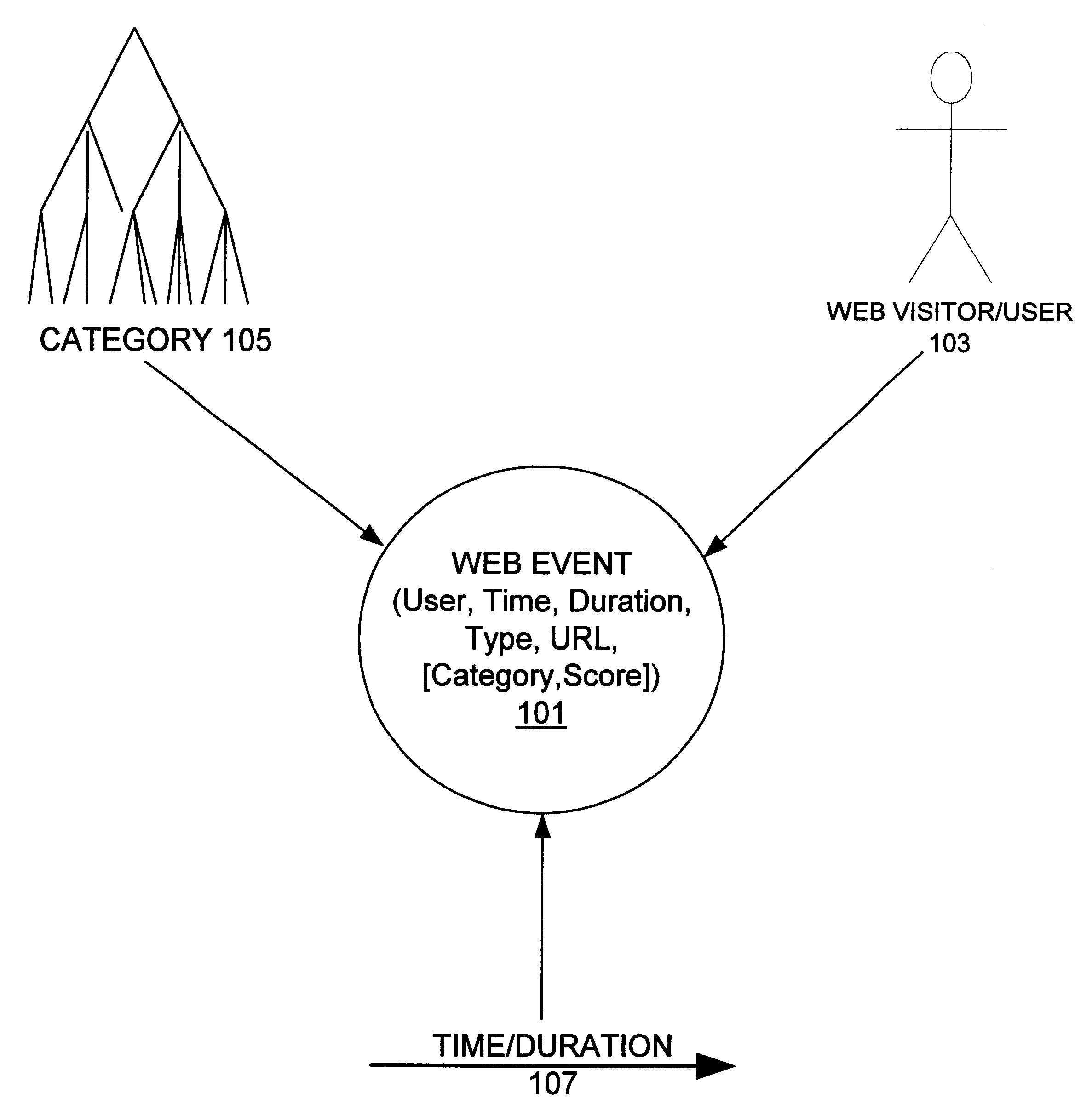
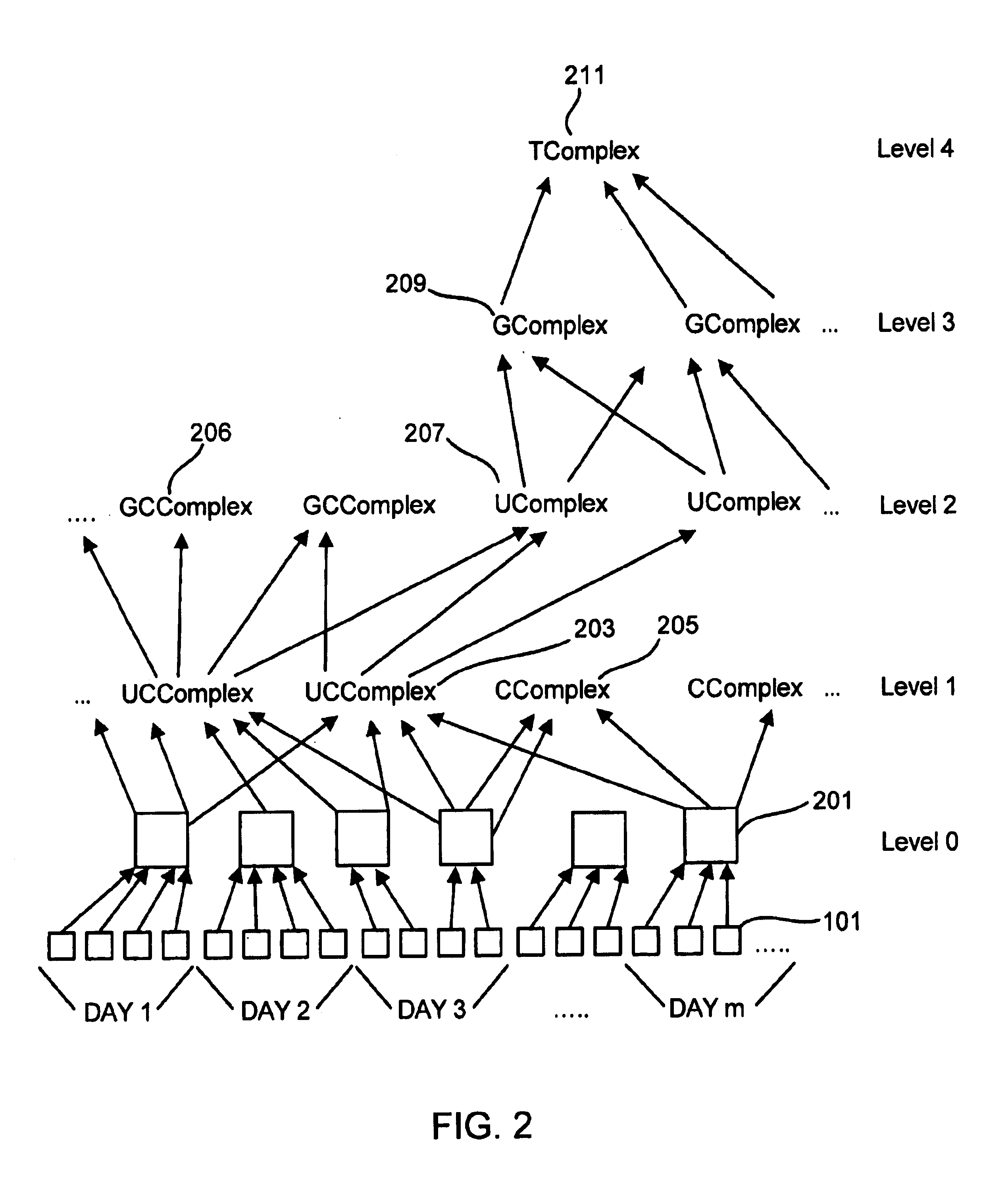
A system, method, and various software products provide for consistent identification of web users across multiple web sites, servers and domains, monitoring and capture of data describing the users' web activities, categorization of the web activity data, aggregation of the data into time dependent models describing interest of users and groups over time. Categorization is made with respect to a category tree which may be standardized or customized for each web site. User groups may be defined based on membership rules for category interest information and demographics. Individual user profiles are then created for users automatically based on satisfaction of the user group membership rules. As new data is collected on a user over time, the category interest information extracted from the user's web activity is updated to form a current model of the user's interests relative to the various categories. This information is also used to automatically update group membership and user profile information. Identification of users across multiple sites is provided by a global service that recognizes each user and provides a globally unique identifier to a requesting web server, which can use the identifier to accumulate activity data for the user. Client side user identification is provided to track user activity data on web servers that do not communicate with the global service and do not process activity for category information. User profiles may be shared among web sites that form alliances. User activity data may be aggregated along various dimensions including users / user groups, categorization, and time to provide robust models of interest at any desired time scale.
Owner:FUJITSU LTD
Content Metadata Directory Services
ActiveUS20070156726A1Improve interoperabilityIncrease the number ofMultimedia data indexingDigital data processing detailsContent IdentifierSystems management
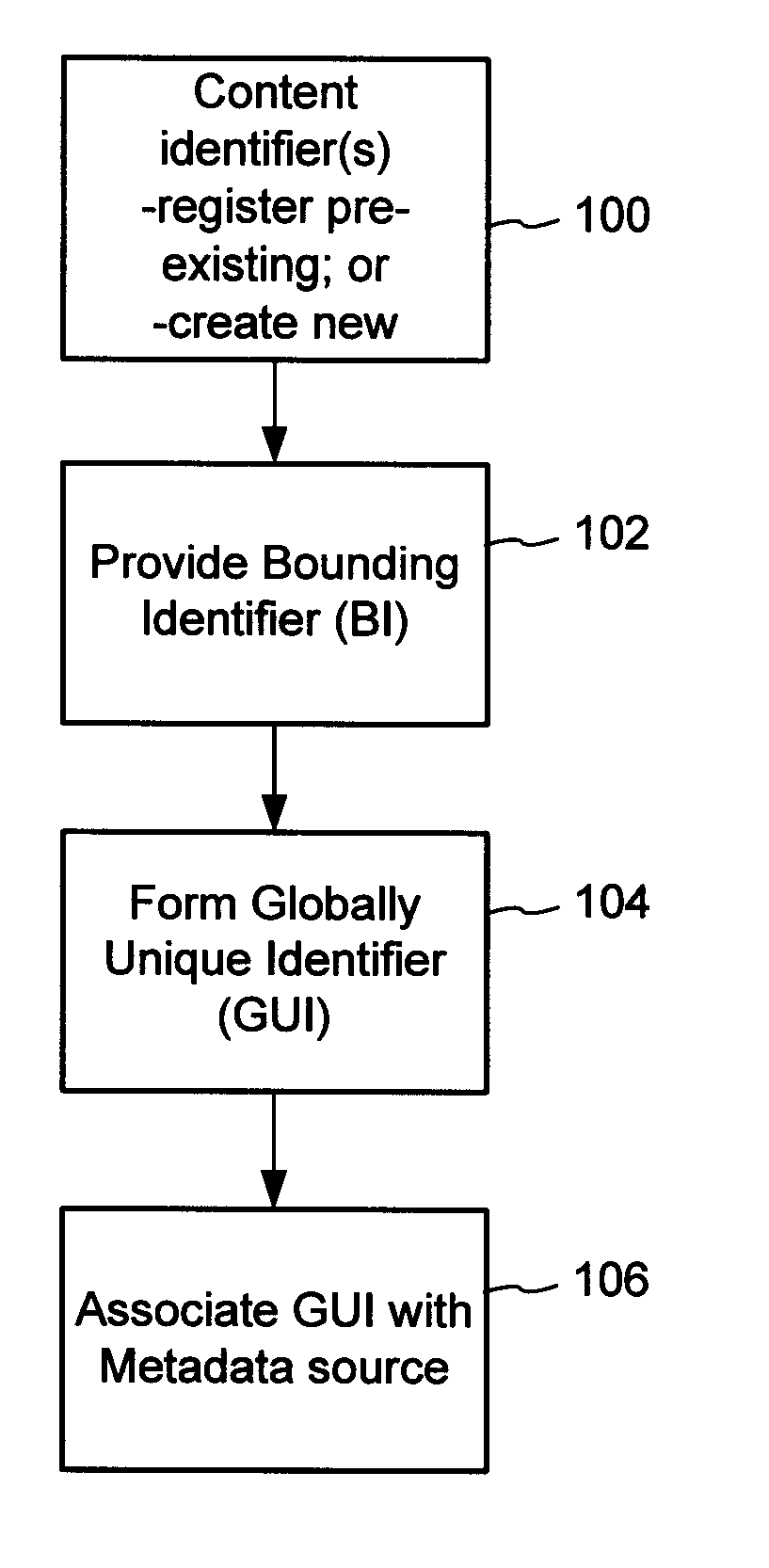
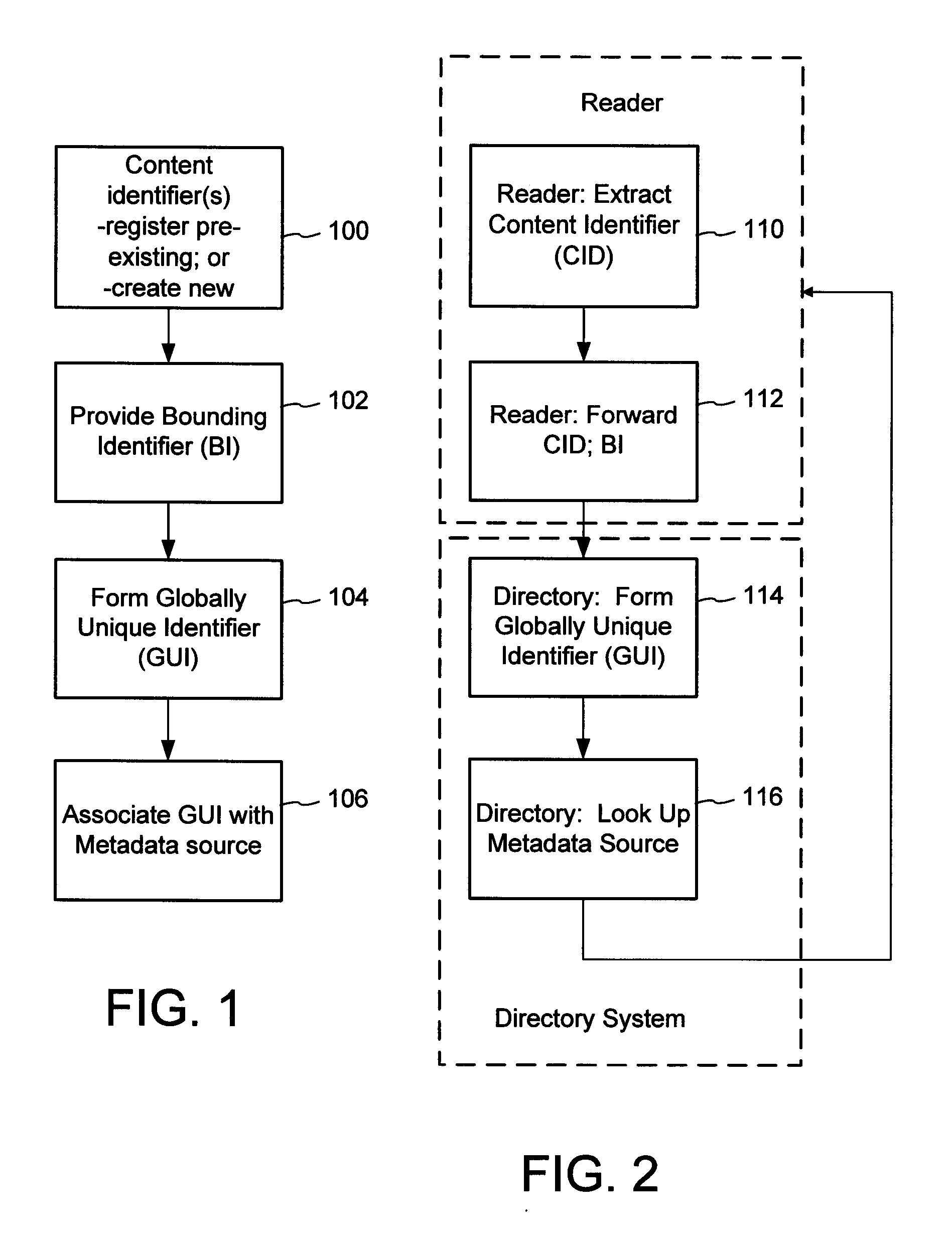
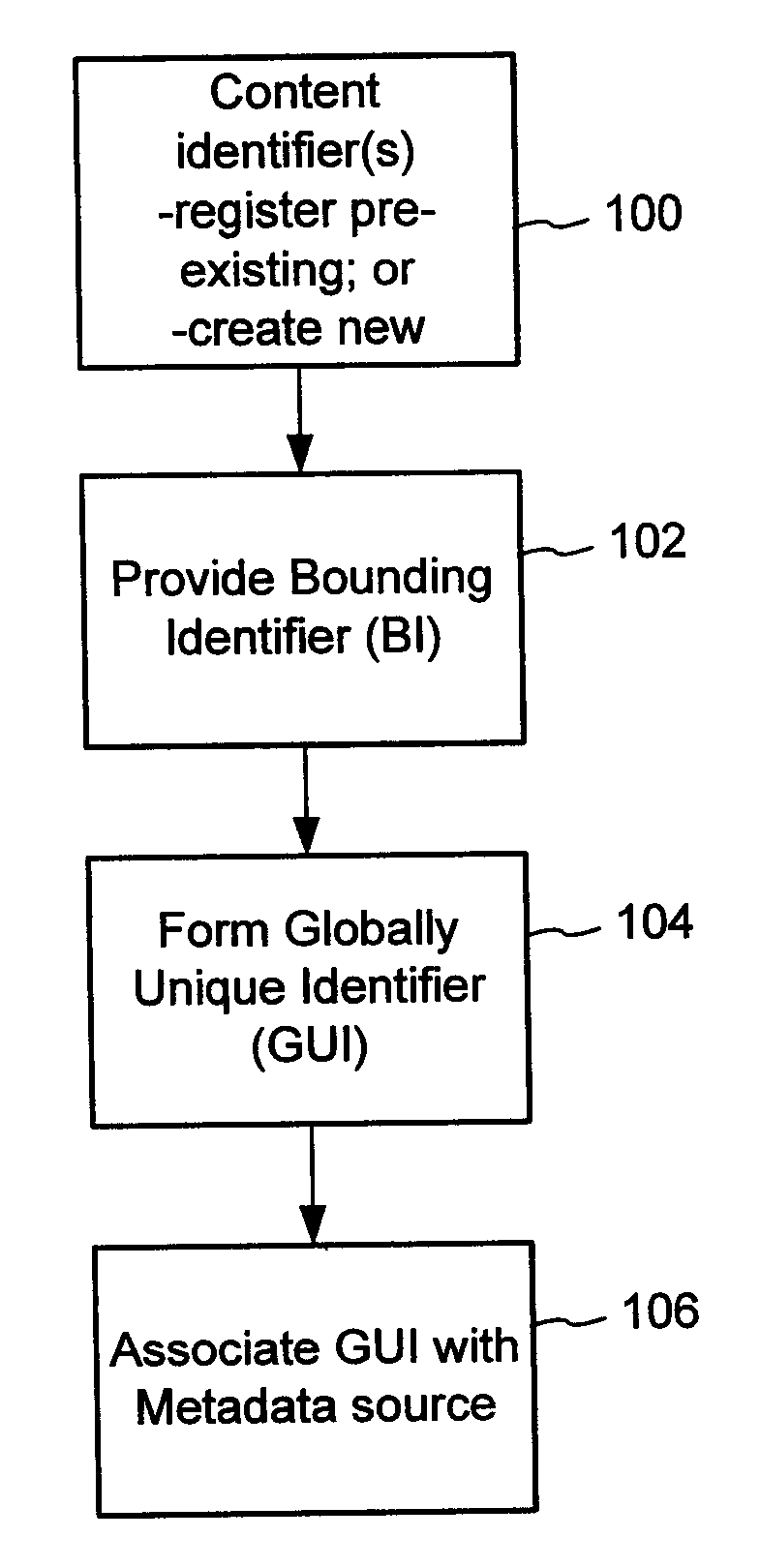
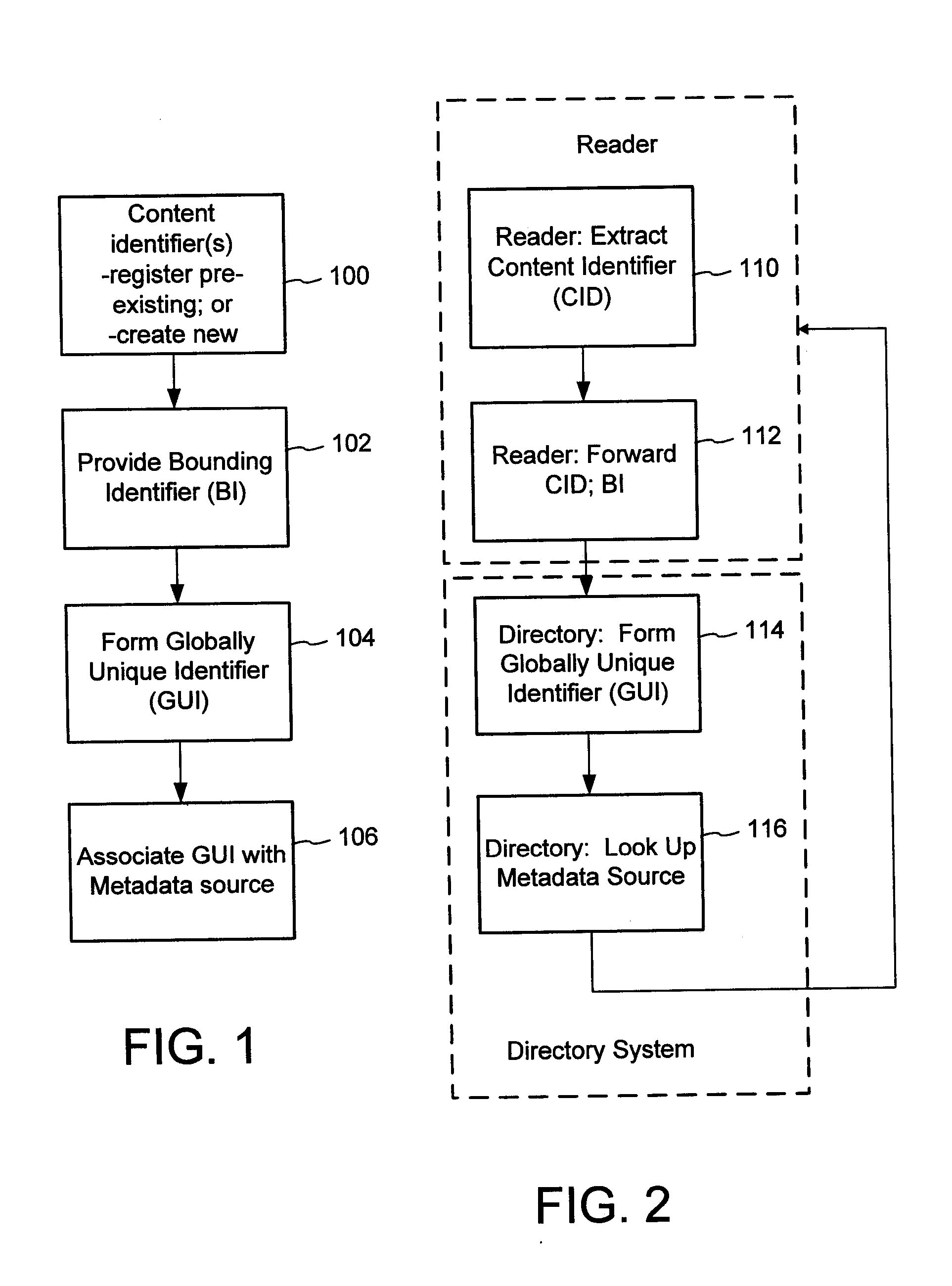
The content metadata directory system connects consumers of identified content to managed metadata databases and other digital resources. The system manages links between identifiers in content objects and metadata sources. It supports a variety of different type of content identifiers and allows for overlap among different content identification schemes. One method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers and provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source.
Owner:DIGIMARC CORP
Certificate-based search
InactiveUS20080005086A1Fine granularityImprove reusabilitySpecial data processing applicationsSecuring communicationGranularityReusability
The systems and methods disclosed herein provide for authentication of content sources and / or metadata sources so that downstream users of syndicated content can rely on these attributes when searching, citing, and / or redistributing content. To further improve the granularity and reusability of content, globally unique identifiers may be assigned to fragments of each document. This may be particularly useful for indexing documents that contain XML grammar with functional aspects, where atomic functional components can be individually indexed and referenced independent from a document in which they are contained.
Owner:MOORE JAMES F
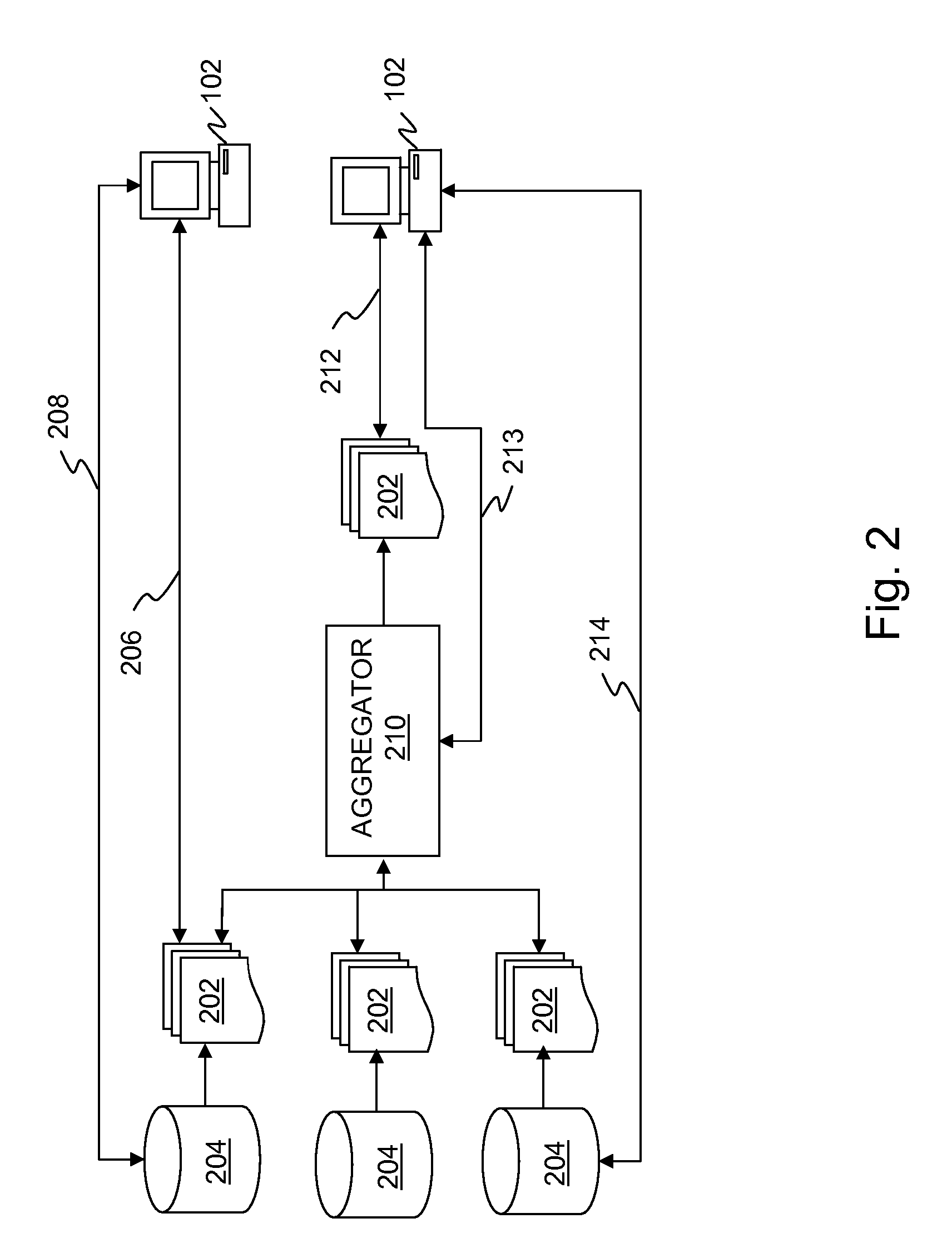
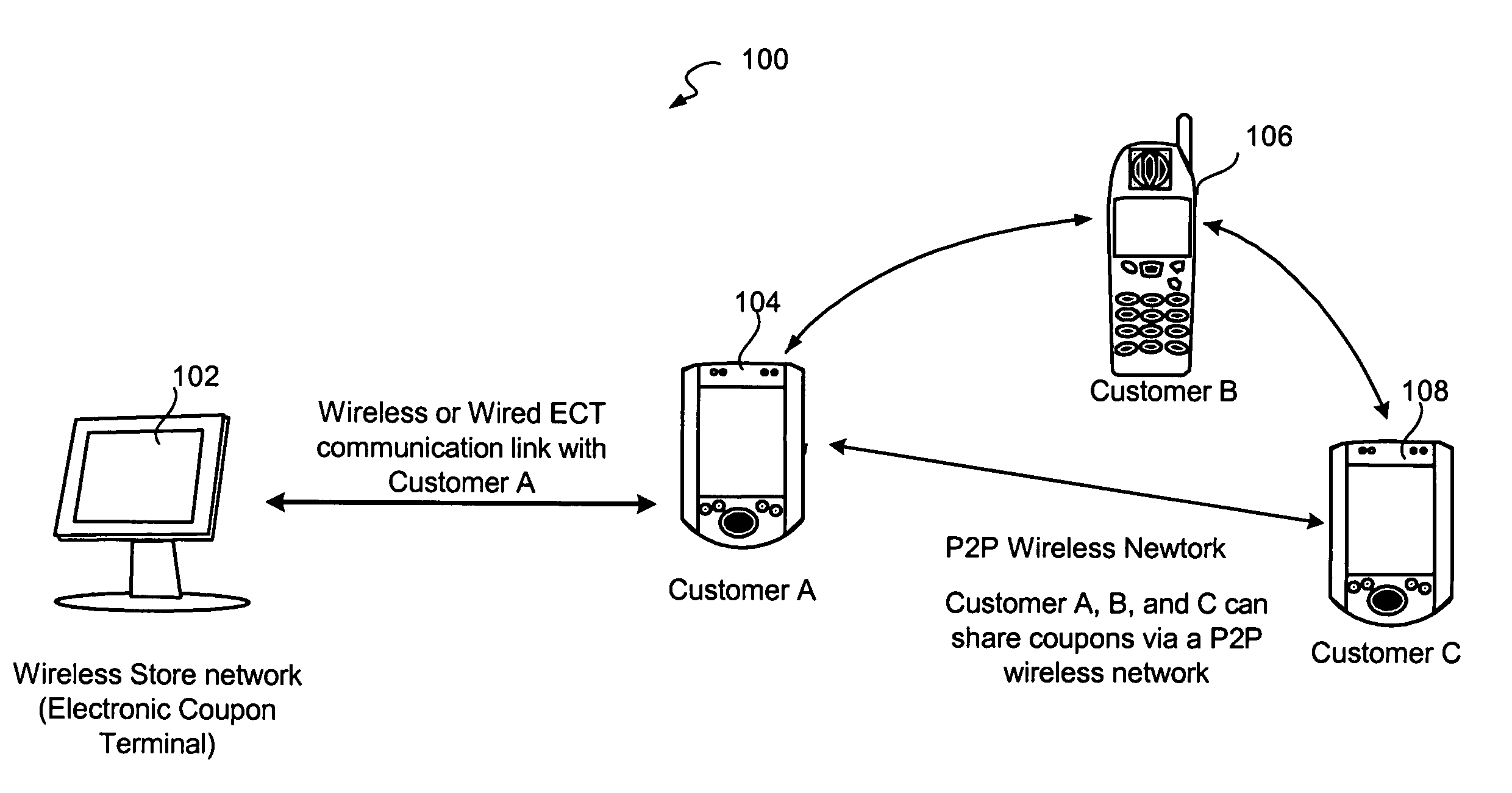
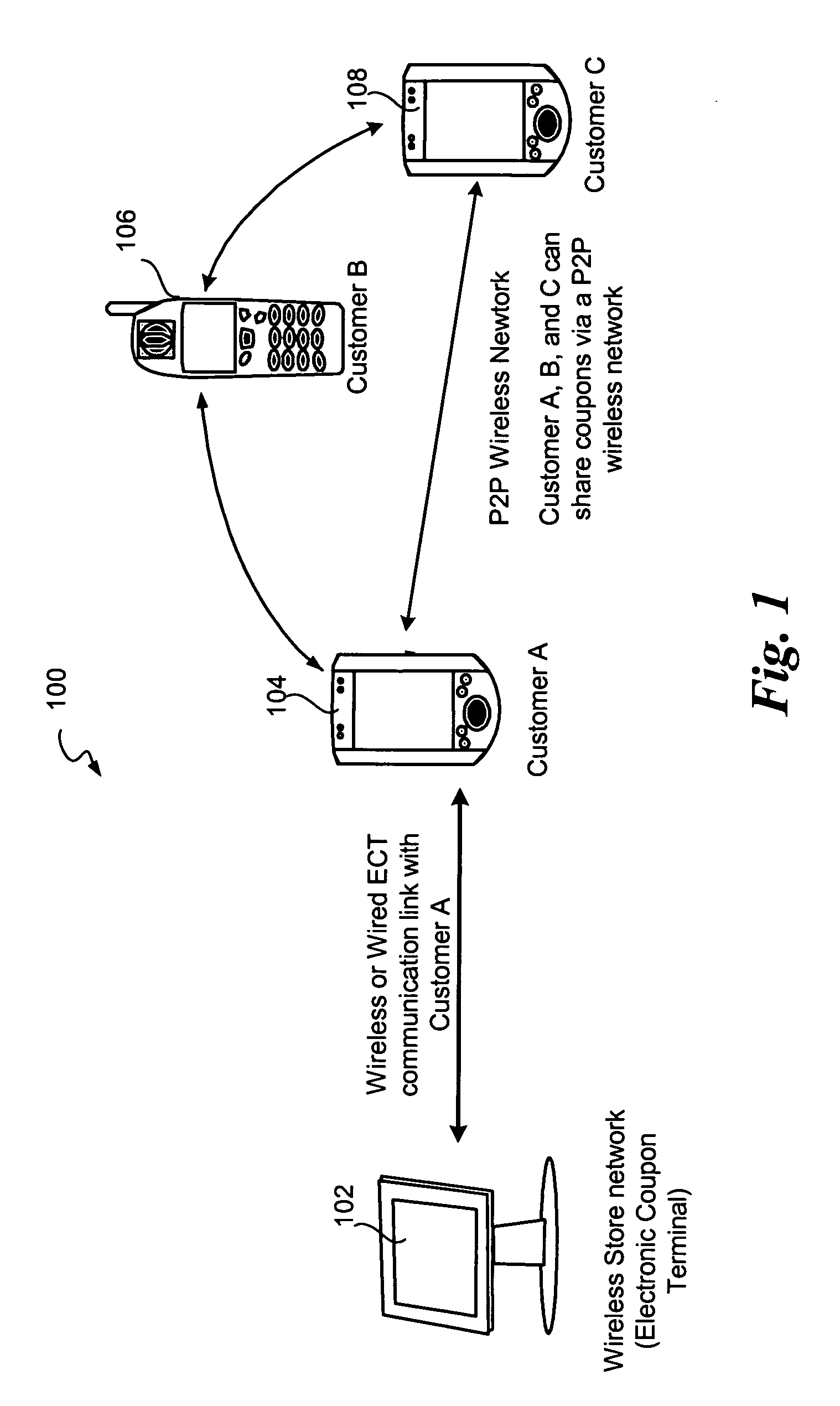
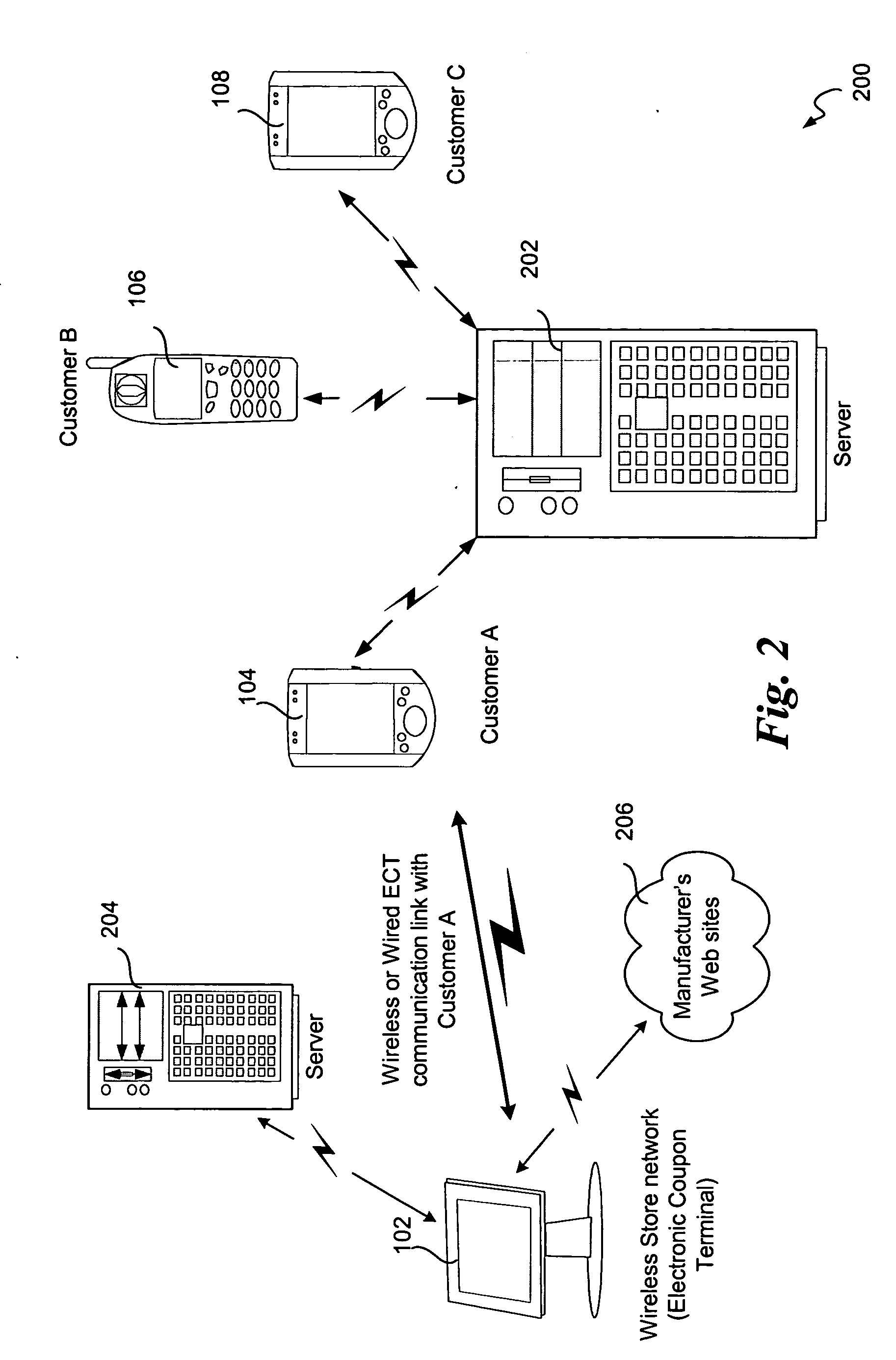
Mobile digital coupons
A system and method is disclosed for providing a reward-based digital mobile coupon environment, where the digital coupons may be shared among peers. Consumers utilize mobile digital coupon carriers having digital representations of coupons. Sharing of coupons among peers may be rewarded with additional discounts or points. The digital coupon carriers communicate with electronic coupon terminals at retail locations for automatic coupon redemption. A coupon may correspond to a globally unique identifier in order to track usage, sharing and redemption. Coupon use and sharing may be dependent upon stored user profiles, merchant profiles and policies, or programs embedded in the coupon.
Owner:INTEL CORP
Content Metadata Directory Services
ActiveUS20070192352A1Increase the number ofComplicate to identifyMultimedia data indexingDigital data processing detailsContent IdentifierWeb site
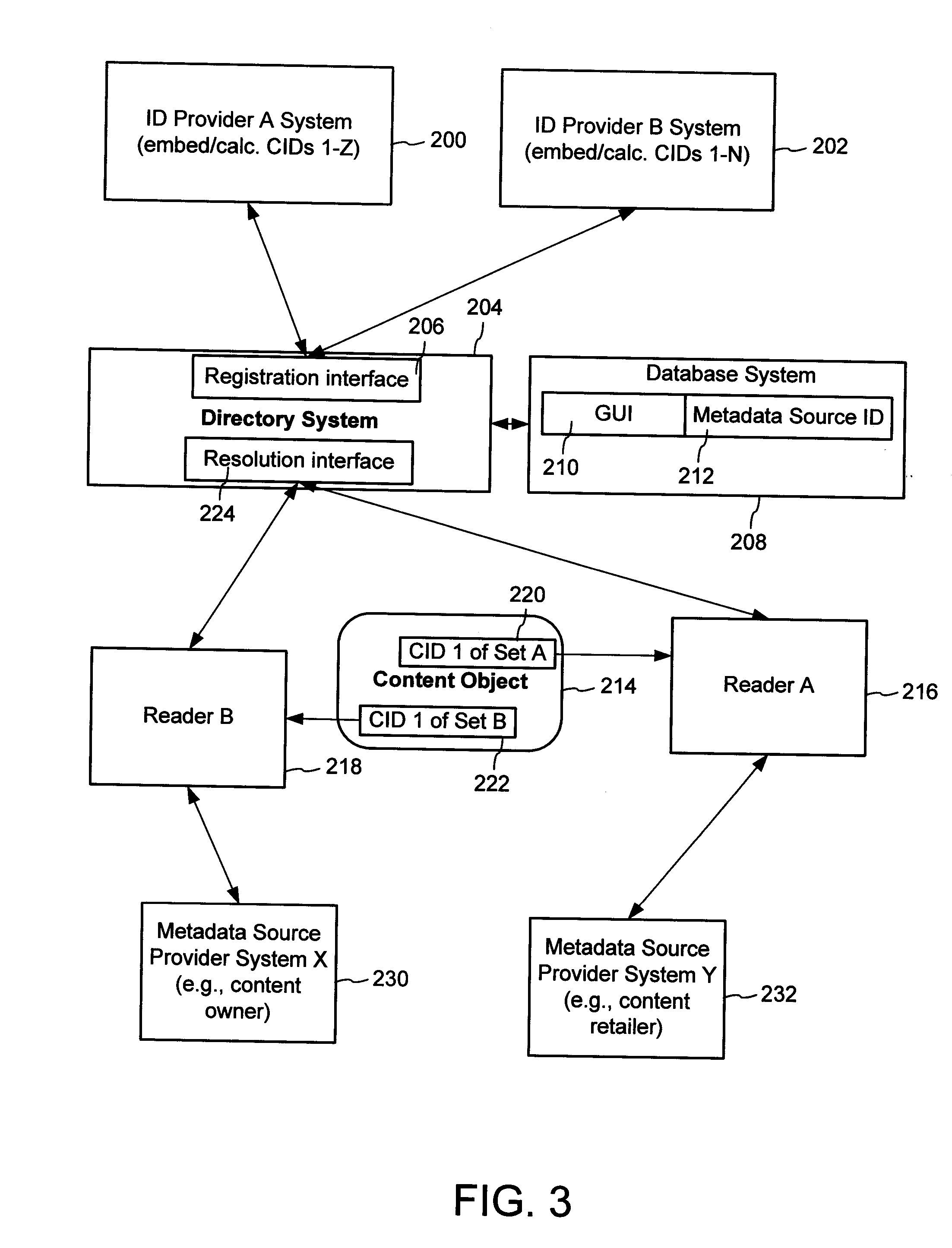
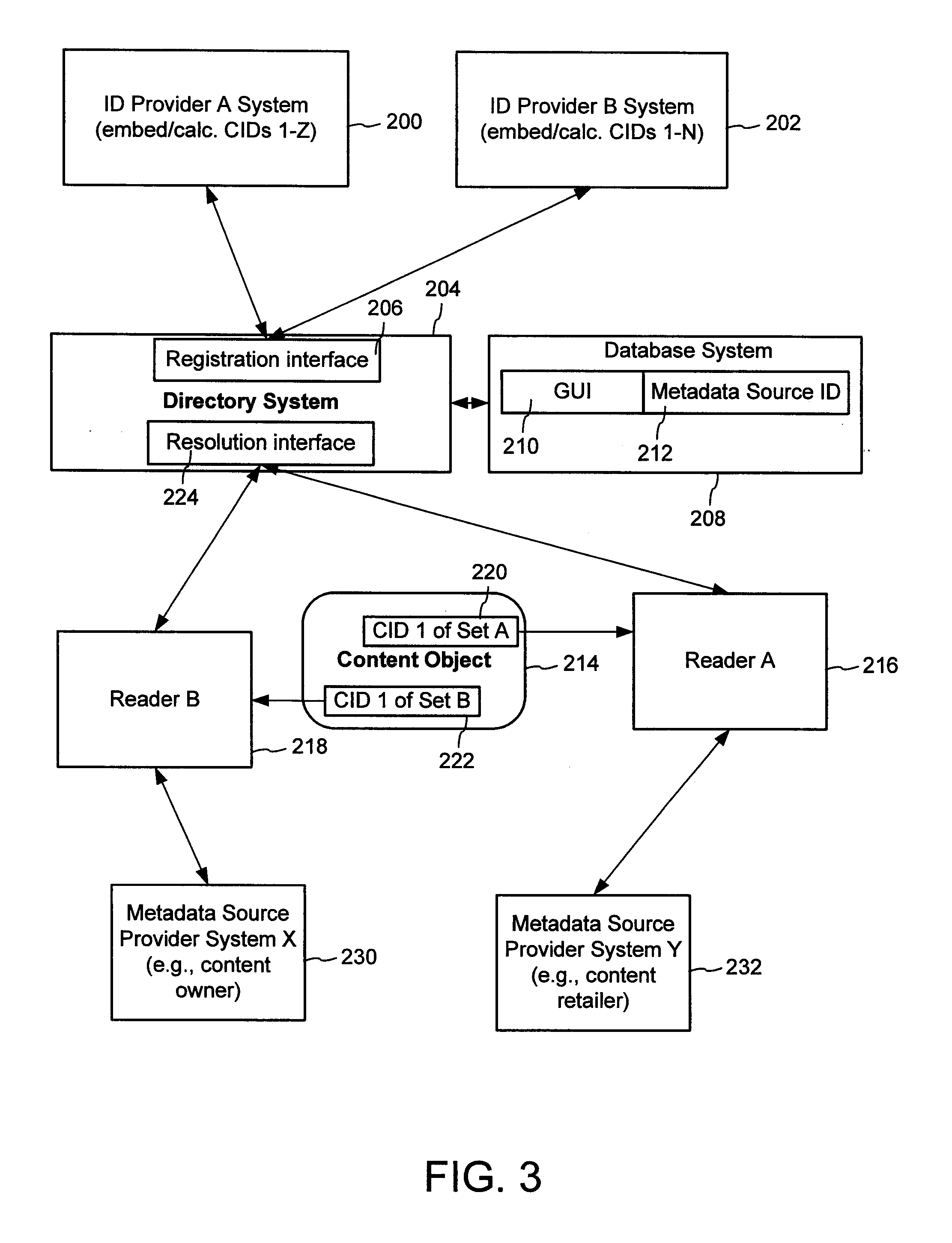
A method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers. It provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source. Another novel method addresses content objects with two or more content identifiers, potentially referencing different metadata sources. This method registers different globally unique identifiers for a content object. These globally unique identifiers each comprise a content identifier provided with the content object and a bounding identifier identifying a set of content identifiers of which the content identifier is a member. For each of the globally unique identifiers, information is maintained about a metadata source. The method receives a first content identifier for the content object, and uses a bounding identifier associated with the set of the first content identifier to determine the globally unique identifier for the first content identifier. The user is routed to the metadata source associated with globally unique identifier. This document describes a novel system that enables multiple identity providers (ID Providers) to register and use the system. The ID Provider registers with a metadata directory system, receives a unique bounding identifier, and uses this bounding ID (e.g., an ID provider ID) with subsequent interactions with the metadata directory system. Separately, metadata source providers register metadata sources with the metadata directory system. This enables many different participants to associate content objects with metadata sources using one or more identify providers. Examples of metadata source providers include content providers, like content owners or retailers that have the flexibility of working with different ID providers to associate content objects with metadata. Both content providers and ID providers can register and use the system. The metadata source is the system or device that provides the metadata, like a web site. The directory system uses an identifier for the metadata source, which enables it to maintain an association between a content object and its corresponding metadata source. For example, in some embodiments, a URL serves to identify the location of the source. The Content Metadata Directory Services (CMDS) is a global trusted directory service that connects consumers of identified content to content-provider authorized and managed metadata databases and other digital resources. It includes mostly links to metadata, forms globally unique IDs based upon overlapping content identifiers and unique bounding identifiers, enables multiple content identifiers within a content object, and enables multiple content identity technology providers, even when they are using different technology.
Owner:DIGIMARC CORP
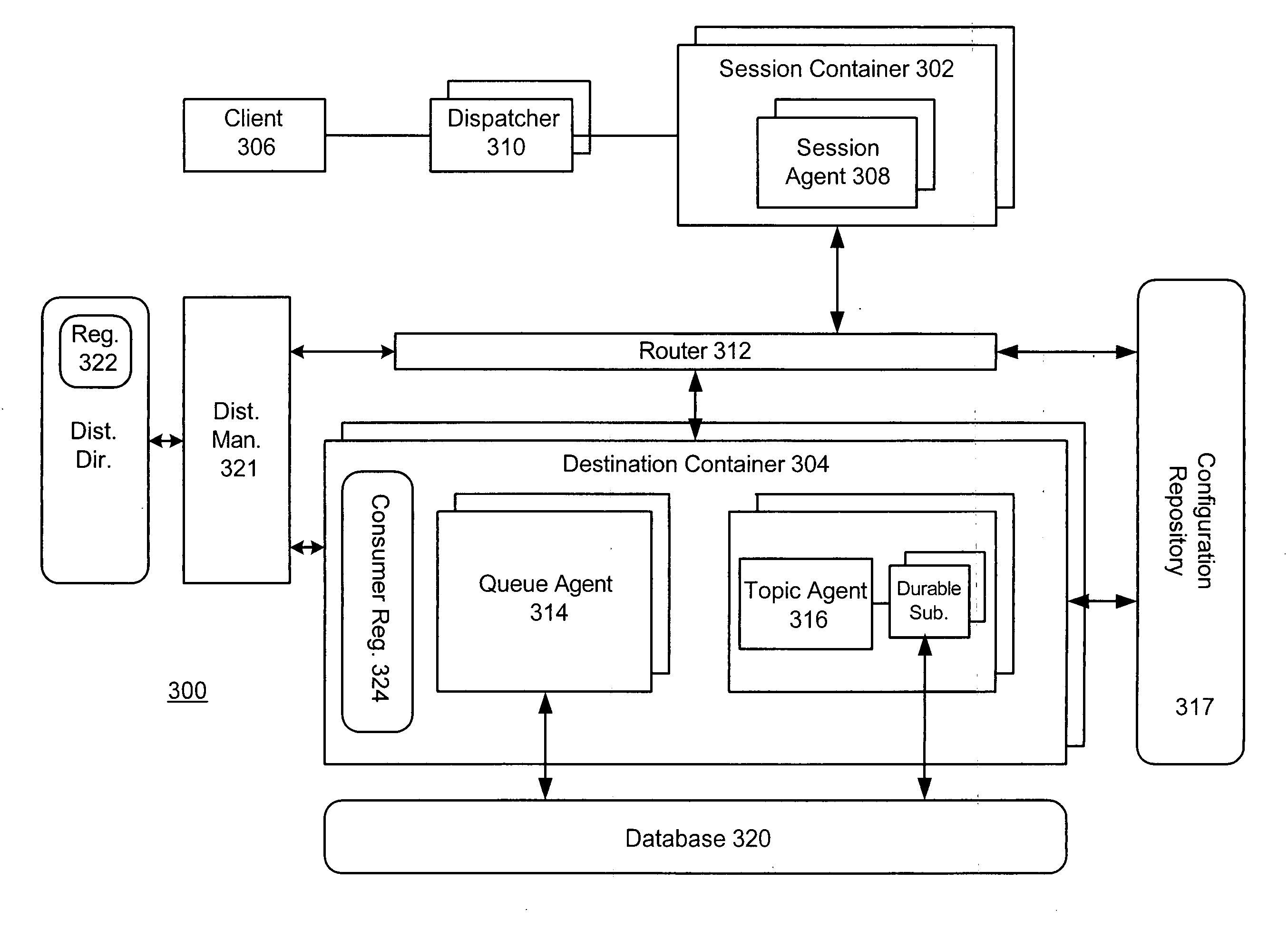
Message-oriented middleware provider having multiple server instances
ActiveUS20090217293A1Interprogram communicationDigital computer detailsApplication serverUnique identifier
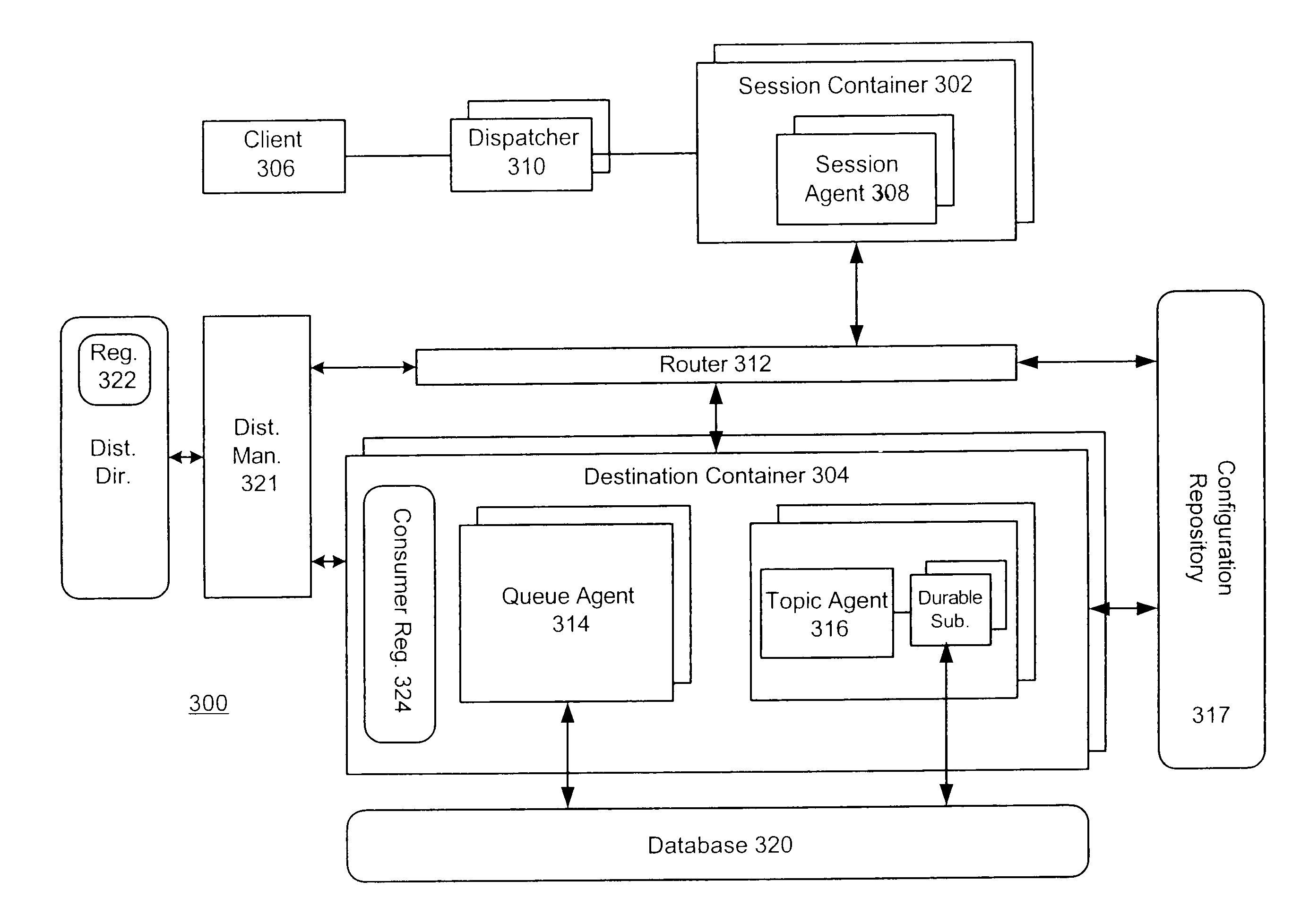
A method, apparatus, and system are provided for a Message-Oriented Middleware (MOM) provider having multiple logical MOM server instances. In an embodiment, the MOM provider having multiple logical MOM server instances is implemented on an application server. Each MOM server instance may include a session container to manage one or more sessions and a destination container to provide one or more destinations. In an embodiment, a globally unique identifier identifies each destination.
Owner:SAP AG
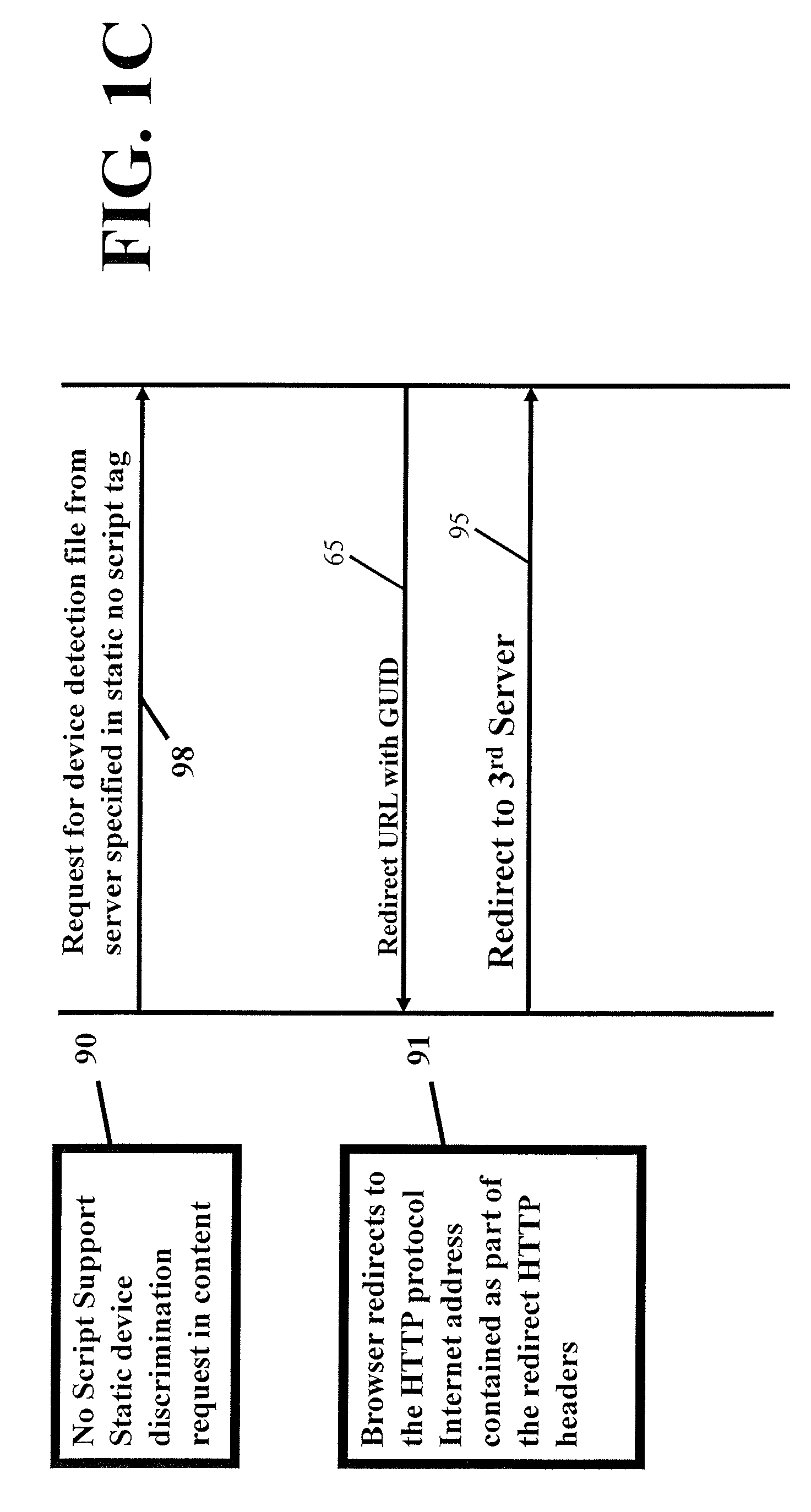
User-transparent system for uniquely identifying network-distributed devices without explicitly provided device or user identifying information
InactiveUS20100057843A1Overcome deficienciesEasy to catchMultiple digital computer combinationsTransmissionUnique device identifierUnique identifier
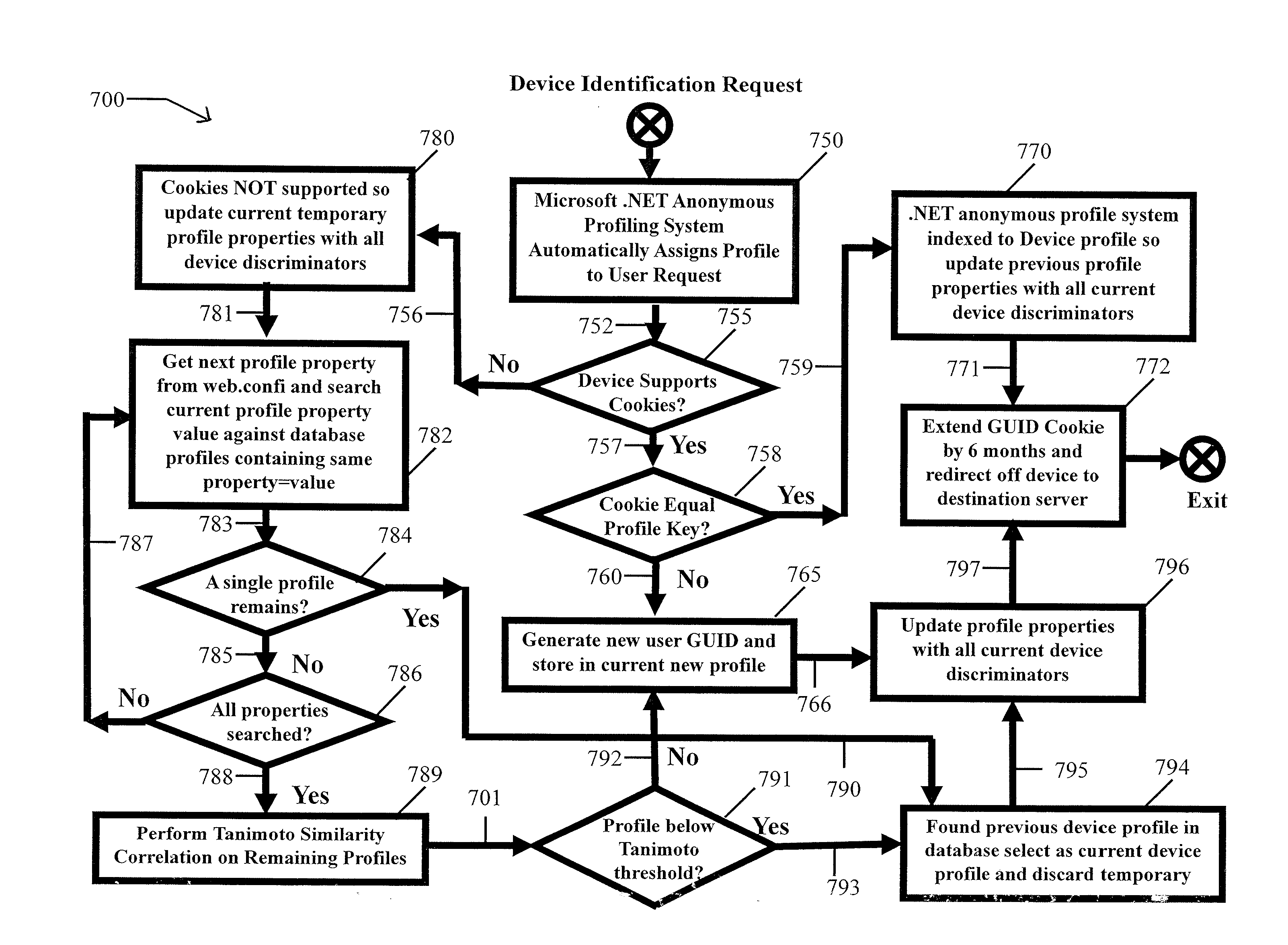
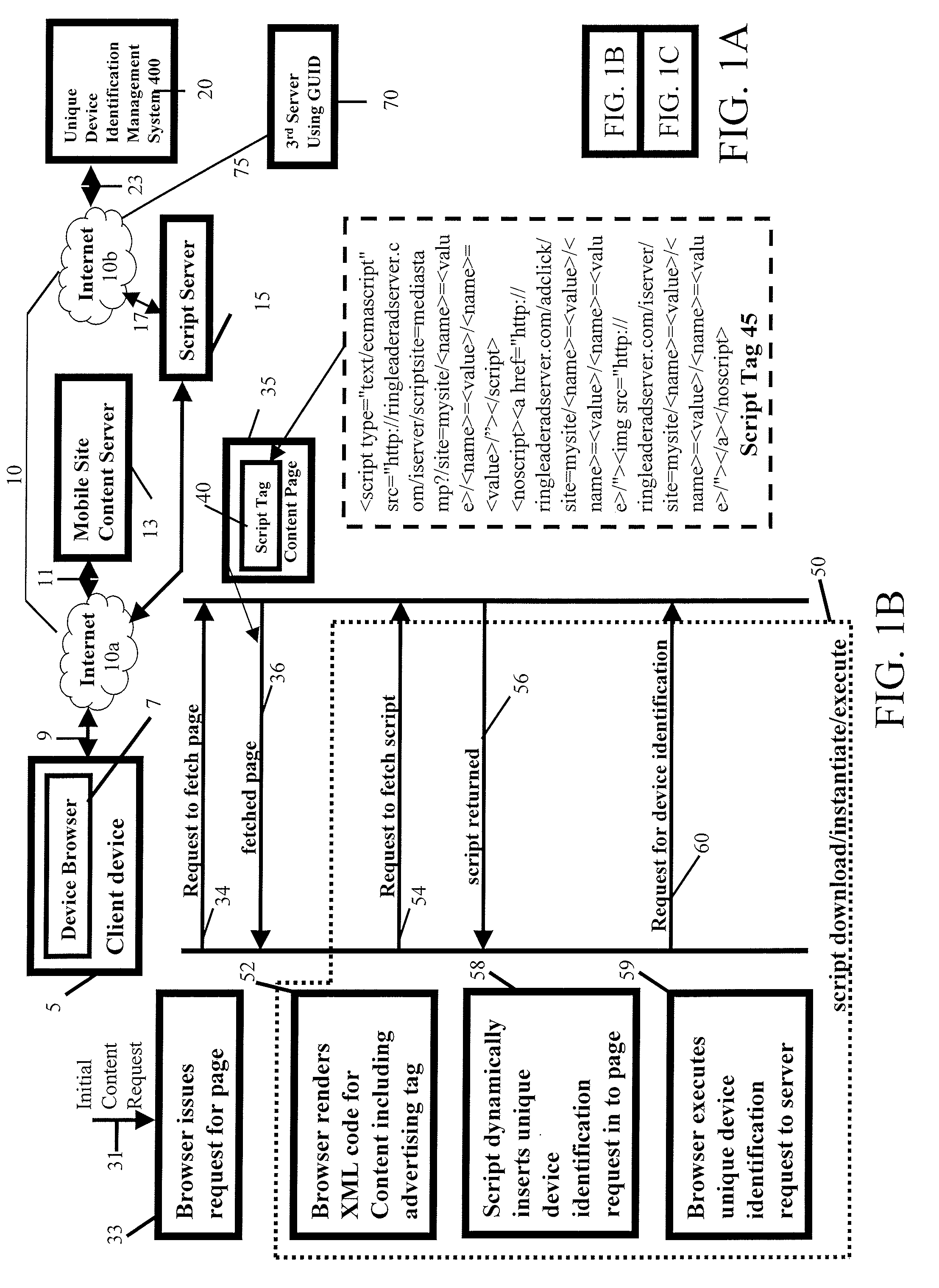
A technique for uniquely identifying devices without explicitly provided device or user identifying information in a networked client-server environment, e.g., the Mobile Internet, in which content is downloaded from a server to a device browser executing at a client device, and using static XML markup tags embedded in the content in a manner transparent to a user situated at the device browser, derives a globally unique device identifier. Device identifying information is captured and maintained in a device profile database associated with a globally unique device identifier. Specifically, mark up code embedded into a referring content page effectively downloads software from a distribution server, and then instantiates the software in the client device browser. The software transparently and dynamically inserts an Internet address request to a device identification management system. The device identification management system selects a device profile associated with a previously detected request from the device and retrieves its globally unique identifier from a database of all profiles for all previous devices requesting unique device identifications. If a matching profile is not found in the database, the device identifying information associated with the request is entered as a new device profile along with a globally unique identifier associated with that specific device in the database. The globally unique identifier is delivered back to the device or external systems for their own use, e.g., mobile Internet advertising management systems.
Owner:MEDIA STAMP
System and method enabling future messaging directives based on past participation via a history monitor
InactiveUS7461151B2Avoid the needEliminating flow of messageSpecial service provision for substationMultiple digital computer combinationsDocument handlingUnique identifier
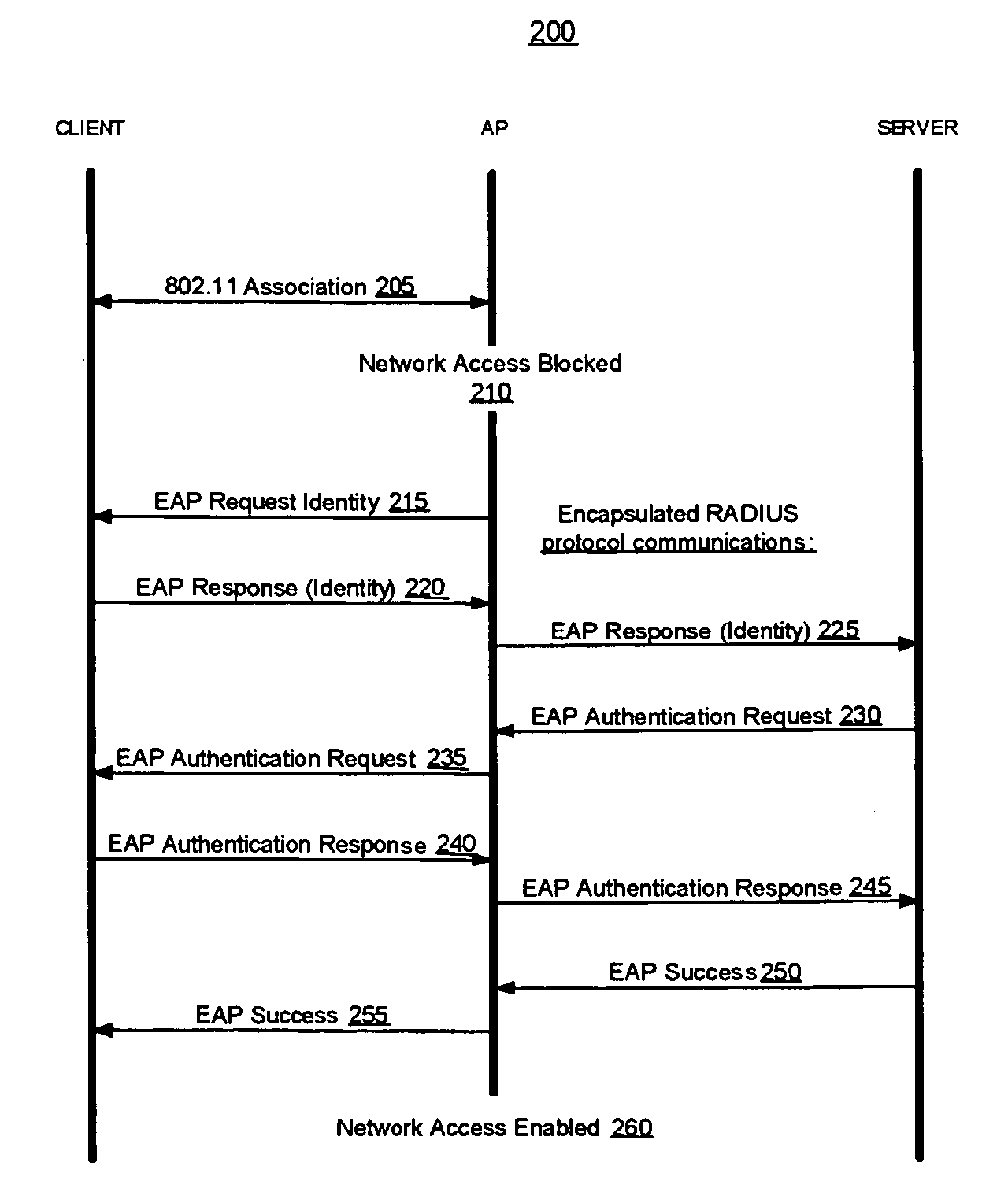
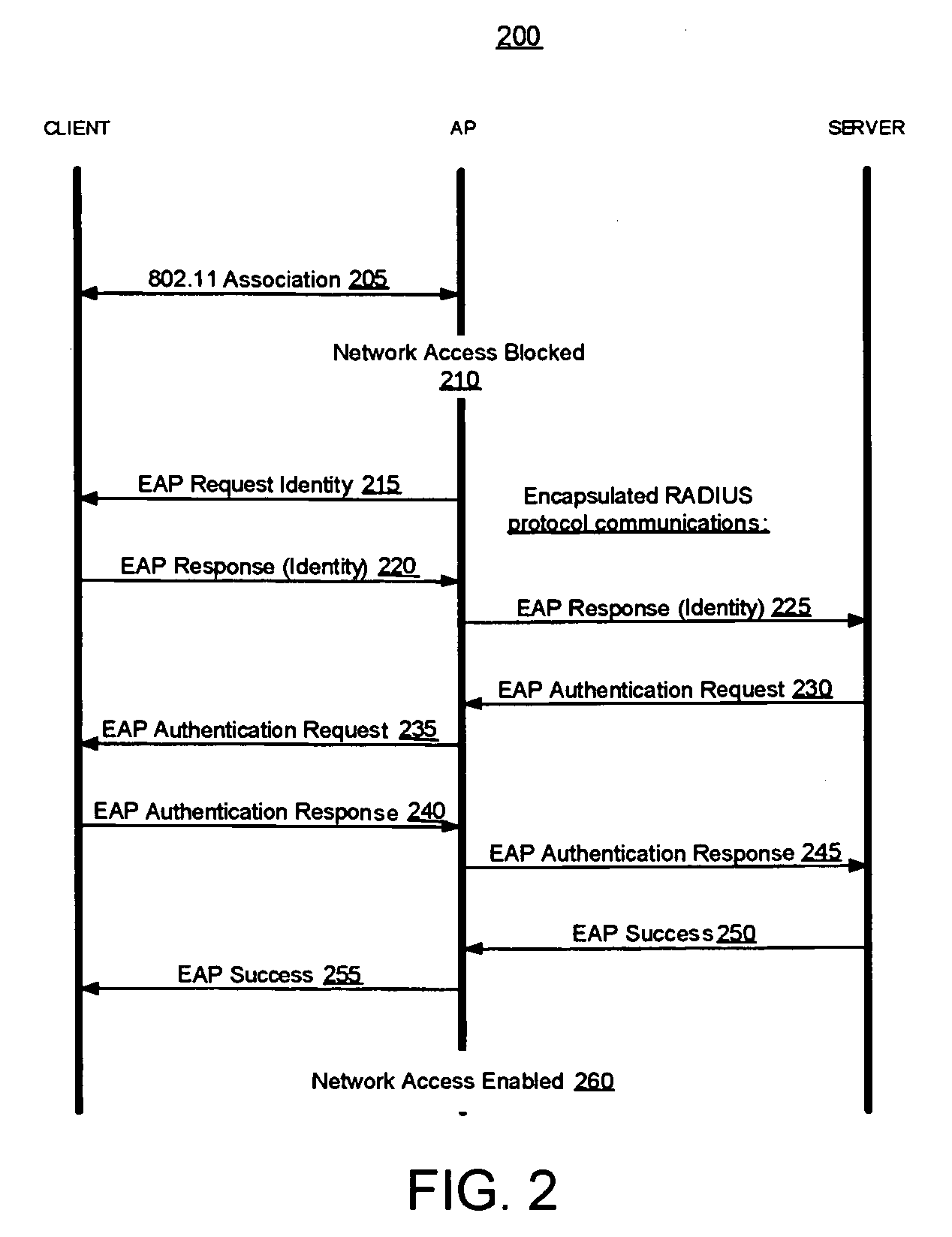
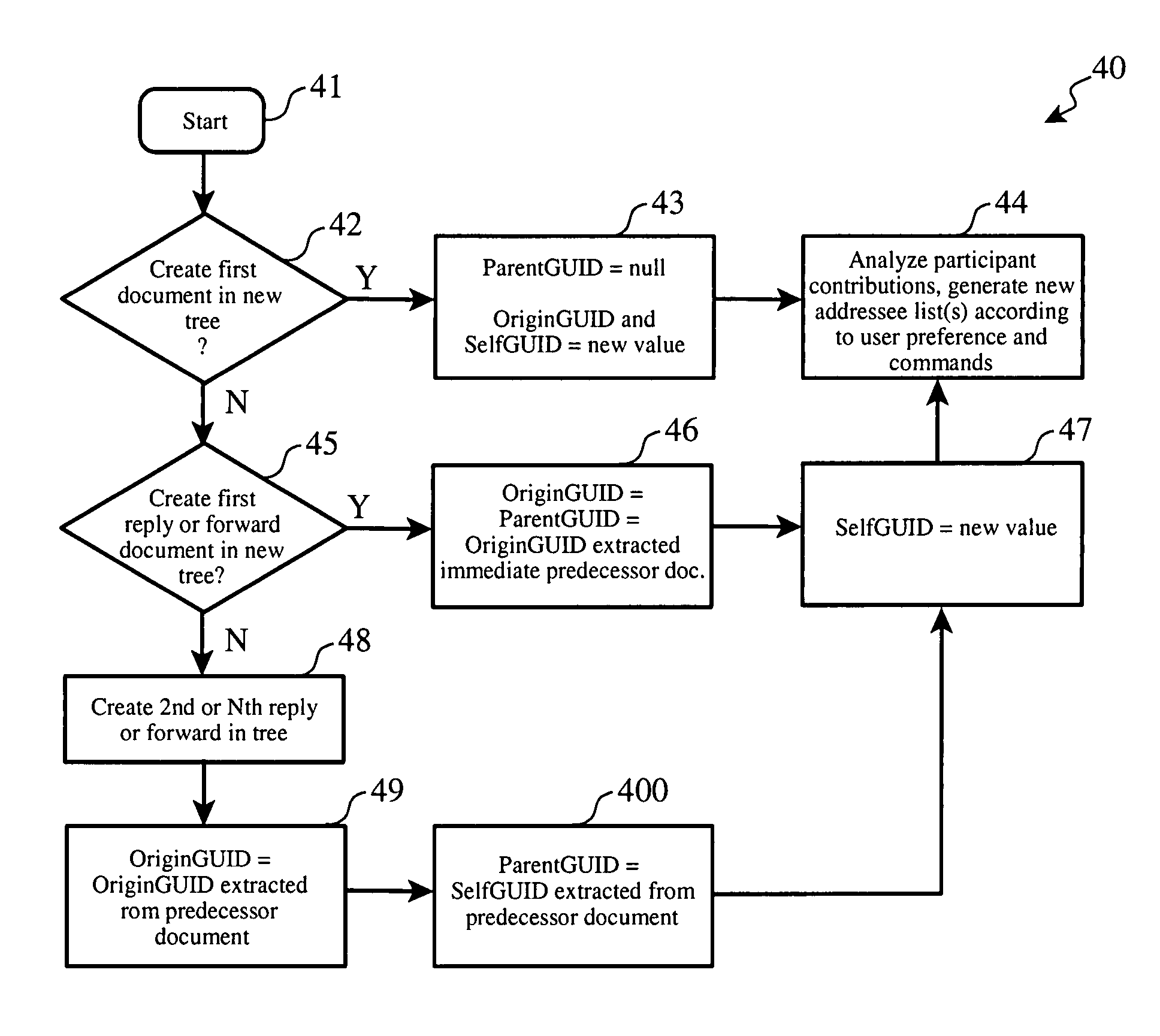
A system and method for controlling the flow of documents by associating Globally Unique Identifiers with each original document, each reply document, each copy document and each forwarded document, such as e-mail messages. Historical analysis is performed on a locally stored history records containing the Globally Unique Identifiers extracted from received documents to determine which recipients are active participants and which are inactive participants, according to user preferences and thresholds. Lists for direct recipients (e.g. “To” list), carbon copy recipients, and blind copy recipients are automatically proposed to a user of a document handling system when authoring a new document, replying to a document, or forwarding a document, according to the results of the historical participation analysis, thereby stemming information flow to participants who are not active in an ad hoc asynchronous conversation.
Owner:IBM CORP
Methods and systems of remote authentication for computer networks
InactiveUS20050021979A1Computer security arrangementsSecret communicationUnique identifierAuthentication server
As part of a network node authentication process, a MAC address or other globally unique identifier of an access point through which the network node will access a computer network is transmitted in an EAP or other authentication message to an authentication server to uniquely identify the access point to the authentication server.
Owner:MCAFEE LLC
System and method enabling future messaging directives based on past participation via a history monitor
InactiveUS20050108402A1Easy to mergeEasy to operateSpecial service provision for substationMultiple digital computer combinationsDocument preparationGlobally unique identifier
A system and method for controlling the flow of documents by associating Globally Unique Identifiers with each original document, each reply document, each copy document and each forwarded document, such as email messages. Historical analysis is performed on a locally stored history records containing the Globally Unique Identifiers extracted from received documents to determine which recipients are active participants and which are inactive participants, according to user preferences and thresholds. Lists for direct recipients (e.g. “To” list), carbon copy recipients, and blind copy recipients are automatically proposed to a user of a document handling system when authoring a new document, replying to a document, or forwarding a document, according to the results of the historical participation analysis, thereby stemming information flow to participants who are not active in an ad hoc asynchronous conversation.
Owner:IBM CORP
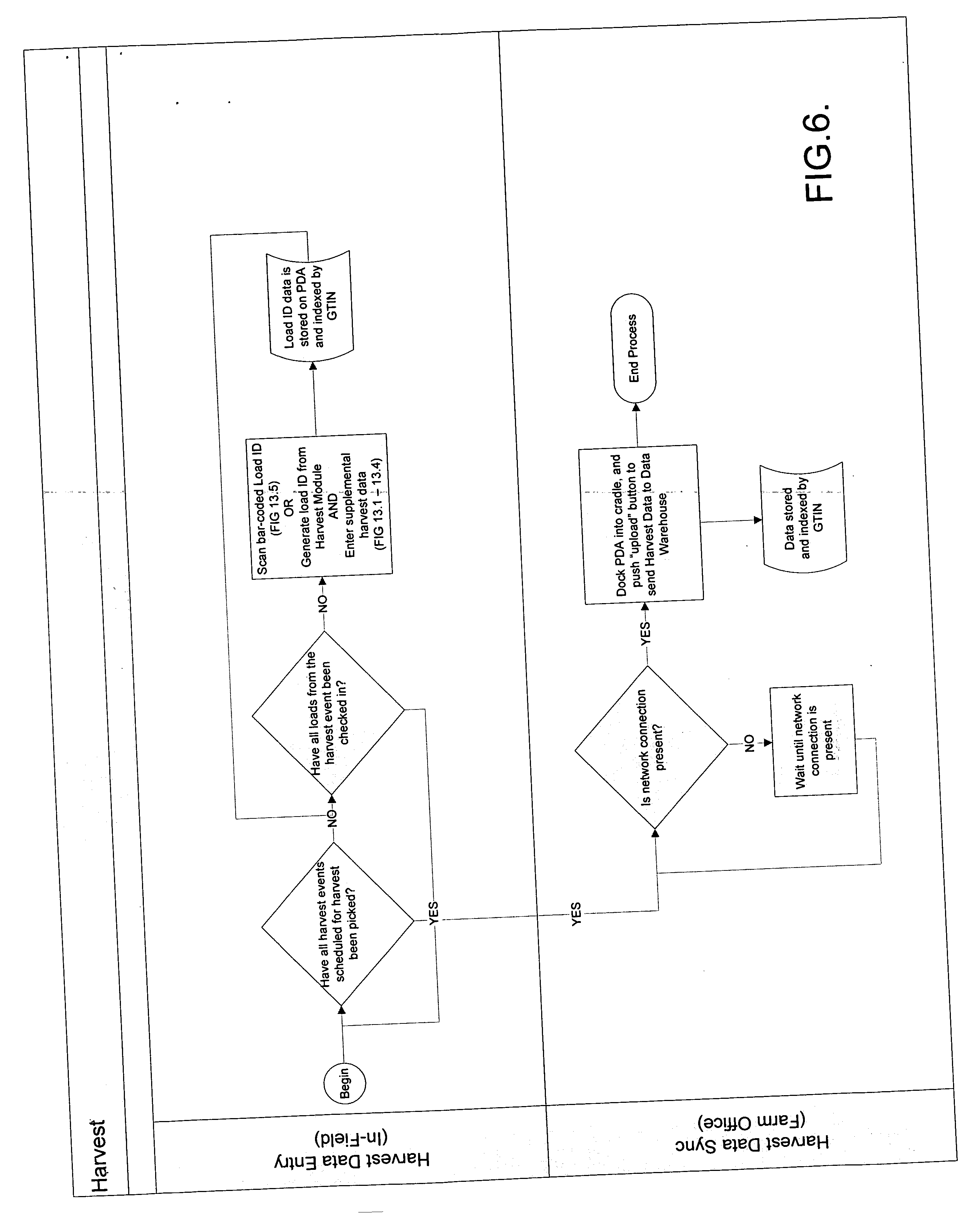
Method for managing agricultural produce inventories
InactiveUS20060111845A1Allowed to operatePractical implementationData processing applicationsBiological testingUnique identifierEngineering
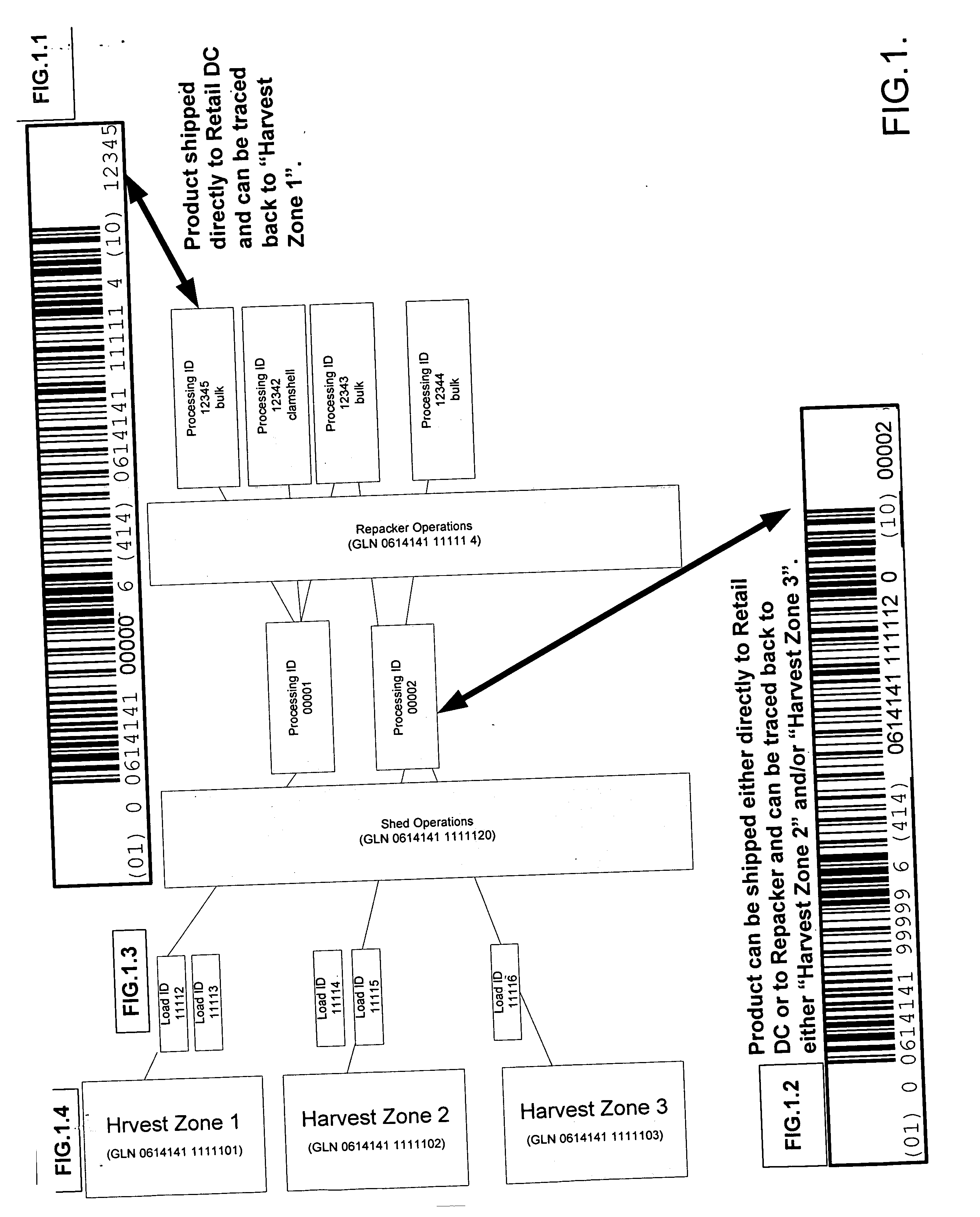
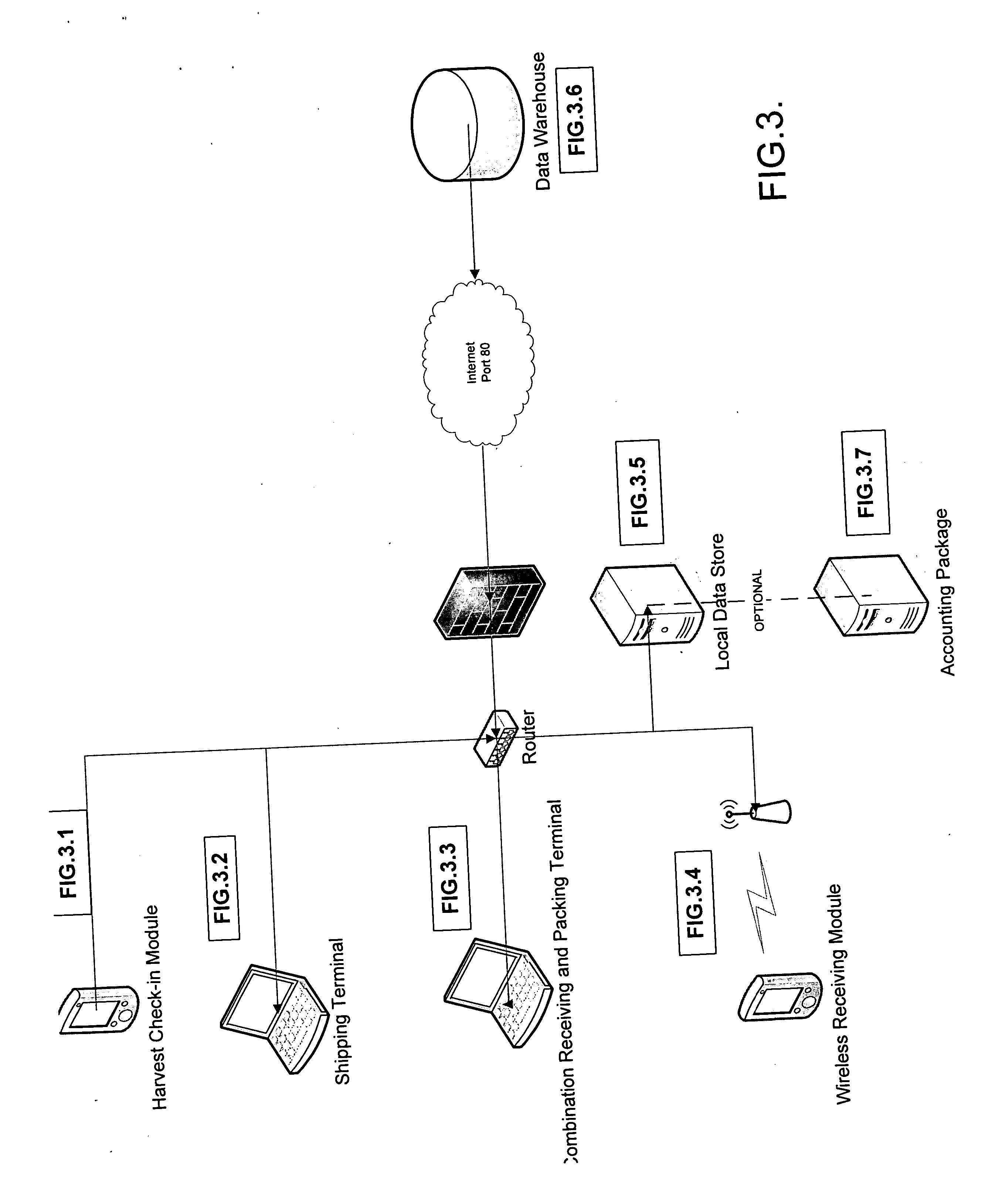
The present invention relates to a system and method for managing and monitoring agricultural produce inventories from harvest forward in the supply chain, including obtaining data points relating to activity and activity locations that bear on the produce as it moves along the supply chain, and further includes methods for tracing inventory histories. The invention includes three component parts; (1) management of variables that impact the crop prior to the farm gate, (2) tracking, tracing, and monitoring functions for the crop as it moves through the supply chain, and finally (3) crop-specific integration of the system and it's requisite control points into a wide variety of entities within the fresh produce supply chain with minimal impact on existing operations. Also included is a system and method for assigning a non-unique identifier to the segregated crop batch or product and associating a global location identifier indicating a point of origin of said crop batch with said non-unique identifier. This association transforms the non-unique product identifier into a globally unique identifier.
Owner:SYNGENTA CROP PROTECTION INC
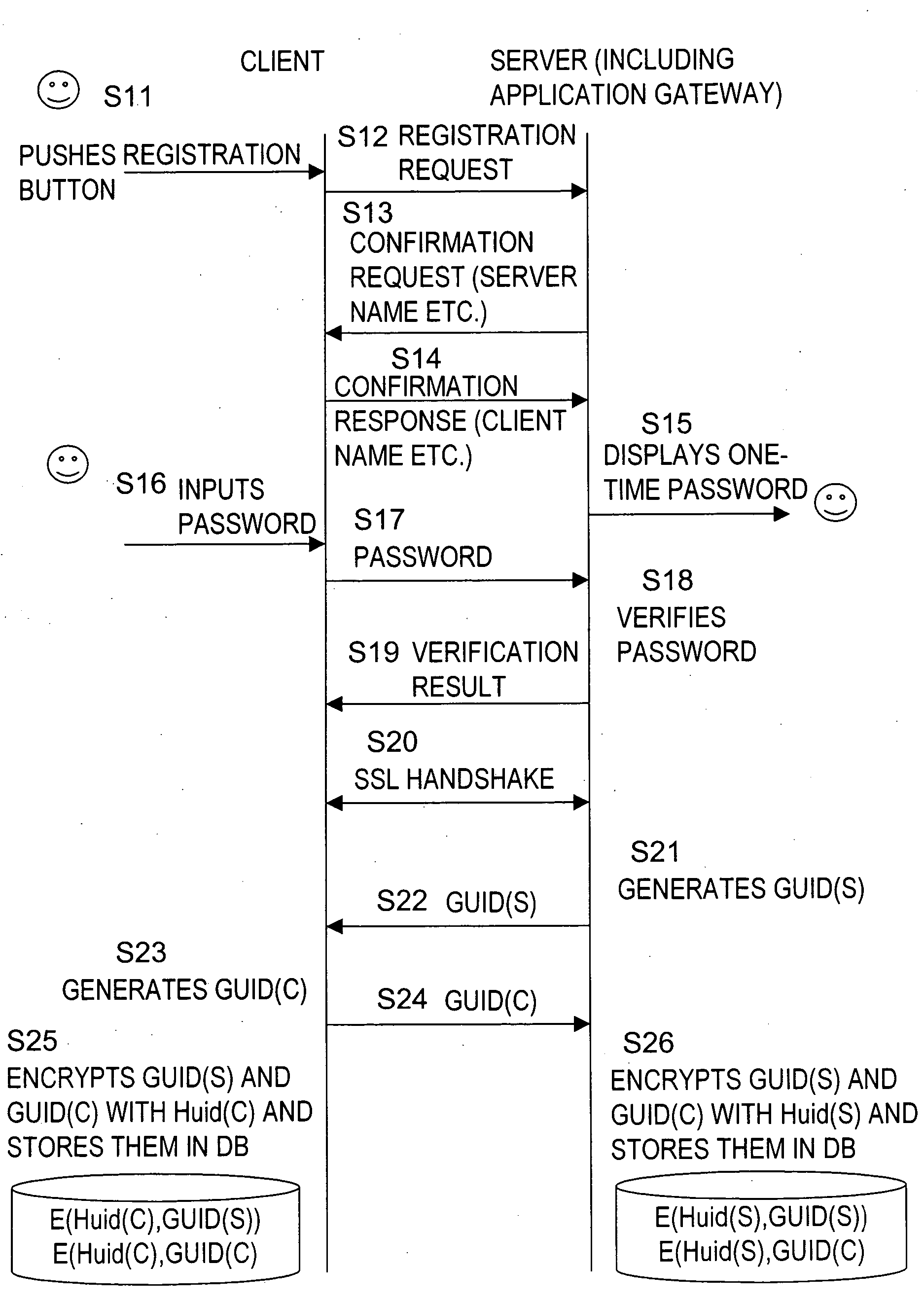
Access control processing method
ActiveUS20060168253A1Improve securityEasy accessUser identity/authority verificationDigital data protectionApplication softwareClient-side
The present invention provides a device and a method for accurately and efficiently controlling an access from an external network to an internal network. Both a client device connectable to the external network and an application gateway store shared secret information (Secret) including a client ID: GUID(C) as an ID generated by the client and a server ID: GUID(S) as an ID generated by the application gateway in respective storage units. In response to an access request from the client, the application gateway determines whether the client has appropriate shared secret information (Secret) so as to determine an access right. With this configuration, a right of access from the external network to the internal network, such as a home network, can be efficiently and accurately determined.
Owner:SONY CORP
Token based two factor authentication and virtual private networking system for network management and security and online third party multiple network management method
InactiveUS20070186099A1Efficient and effectiveNetwork topologiesDigital data authenticationBrute forcePrivate network
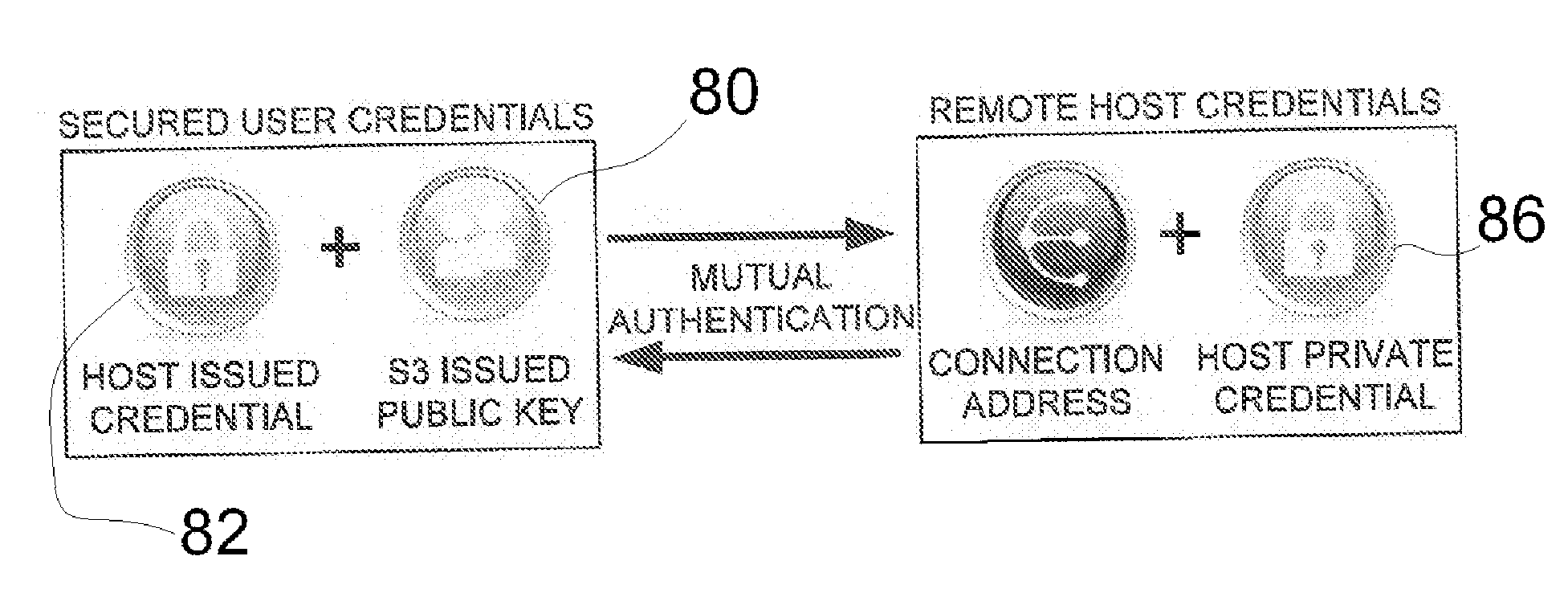
A two-factor network authentication system uses “something you know” in the form of a password / Pin and “something you have” in the form of a key token. The password is encrypted in a secure area of the USB device and is protected from brute force attacks. The key token includes authentication credentials. Users cannot authenticate without the key token. Four distinct authentication elements that the must be present. The first element is a global unique identifier that is unique to each key. The second is a private credential generated from the online service provider that is stored in a secure area of the USB device. The third element is a connection profile that is generated from the online service provider. The fourth element is a credential that is securely stored with the online service provider. The first two elements create a unique user identity. The second two elements create mutual authentication.
Owner:DIRECTPOINTE
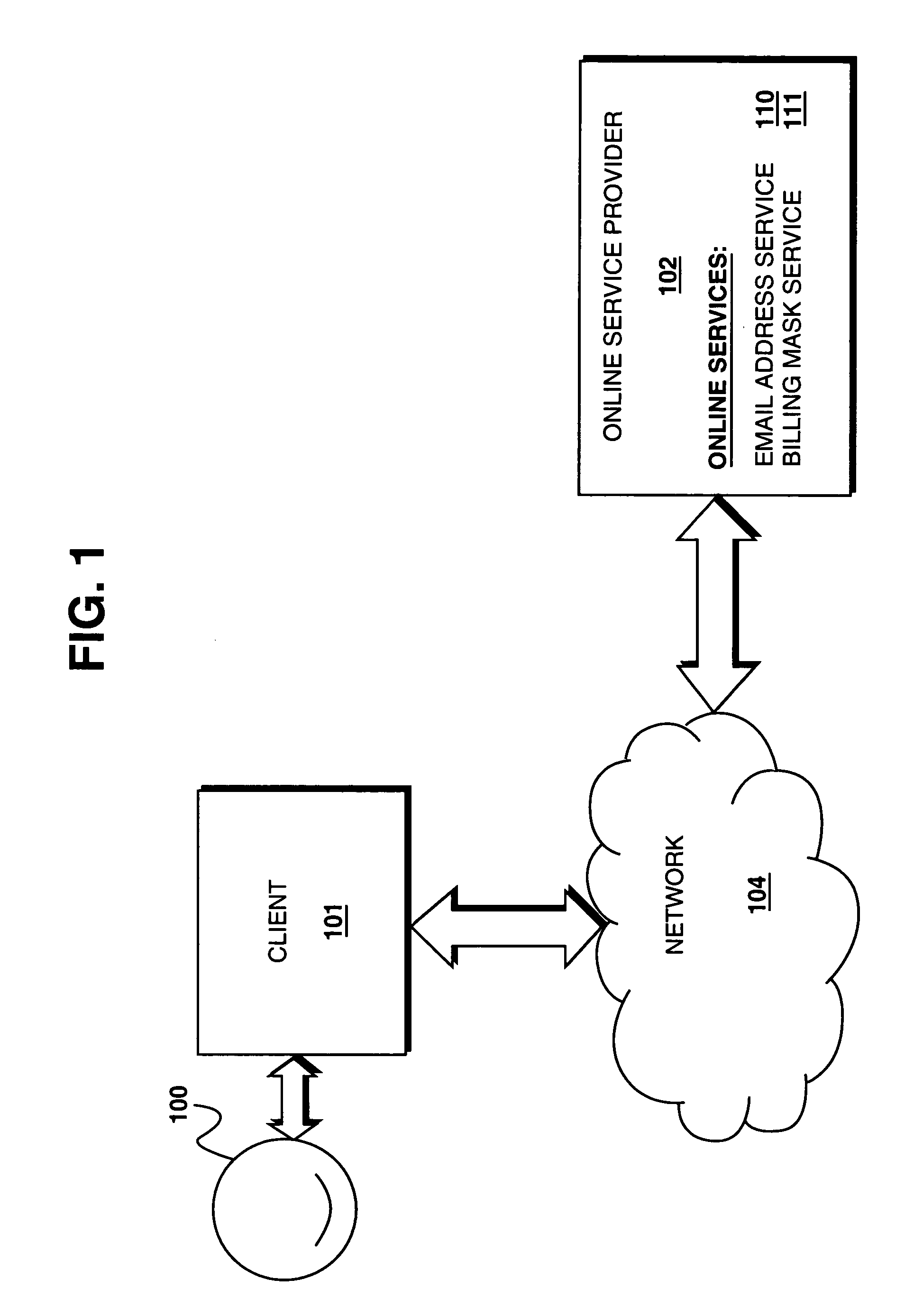
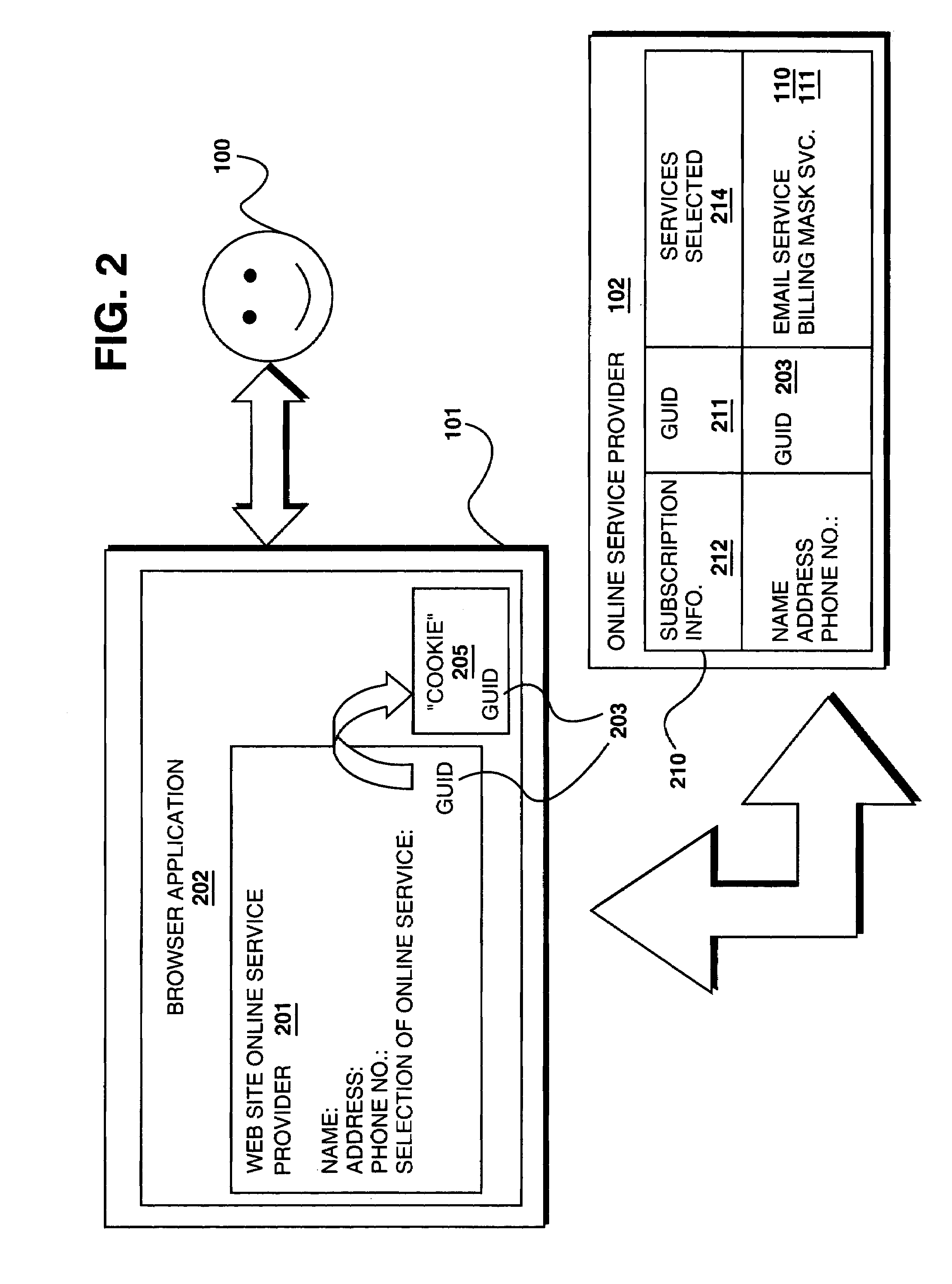
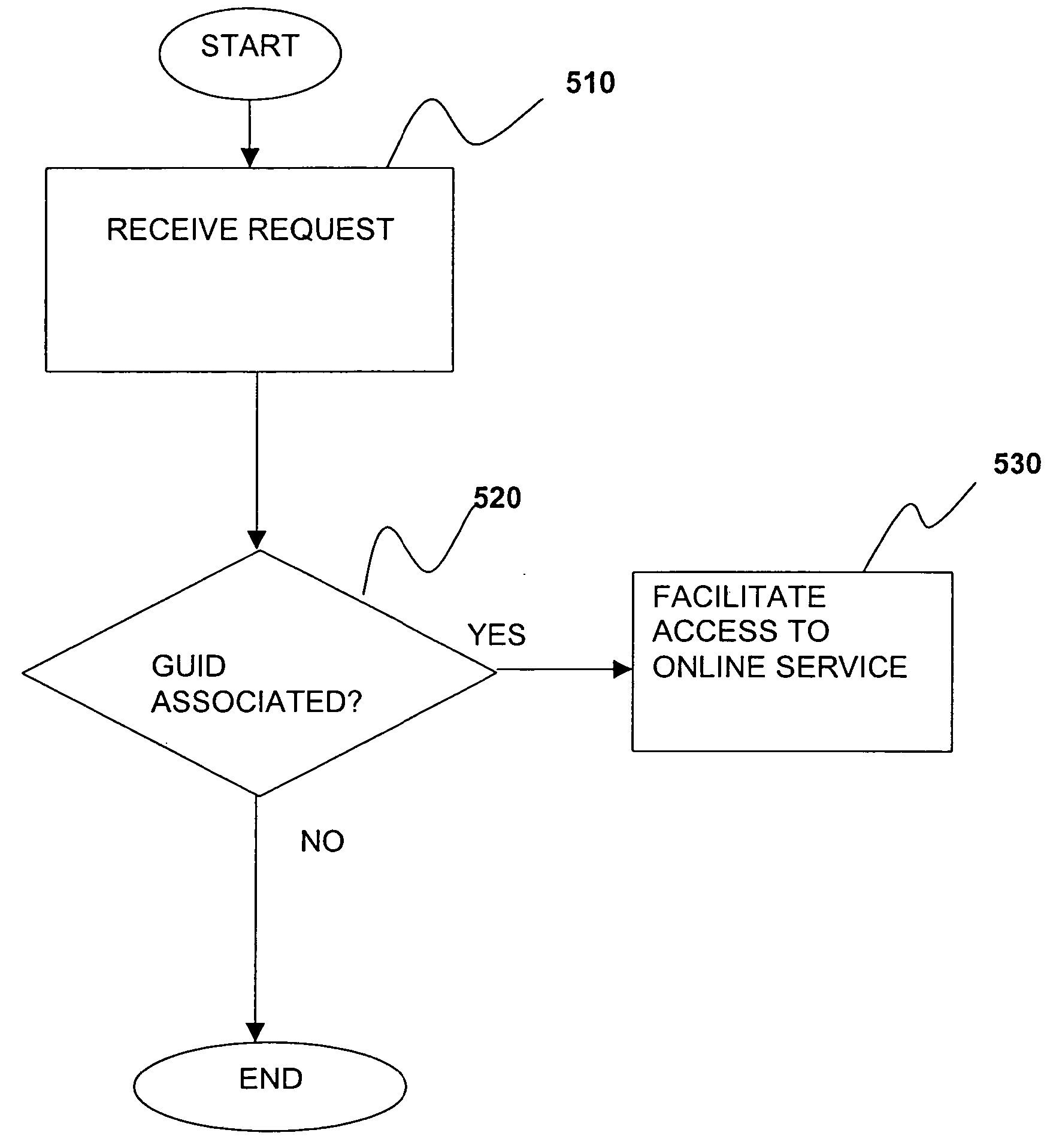
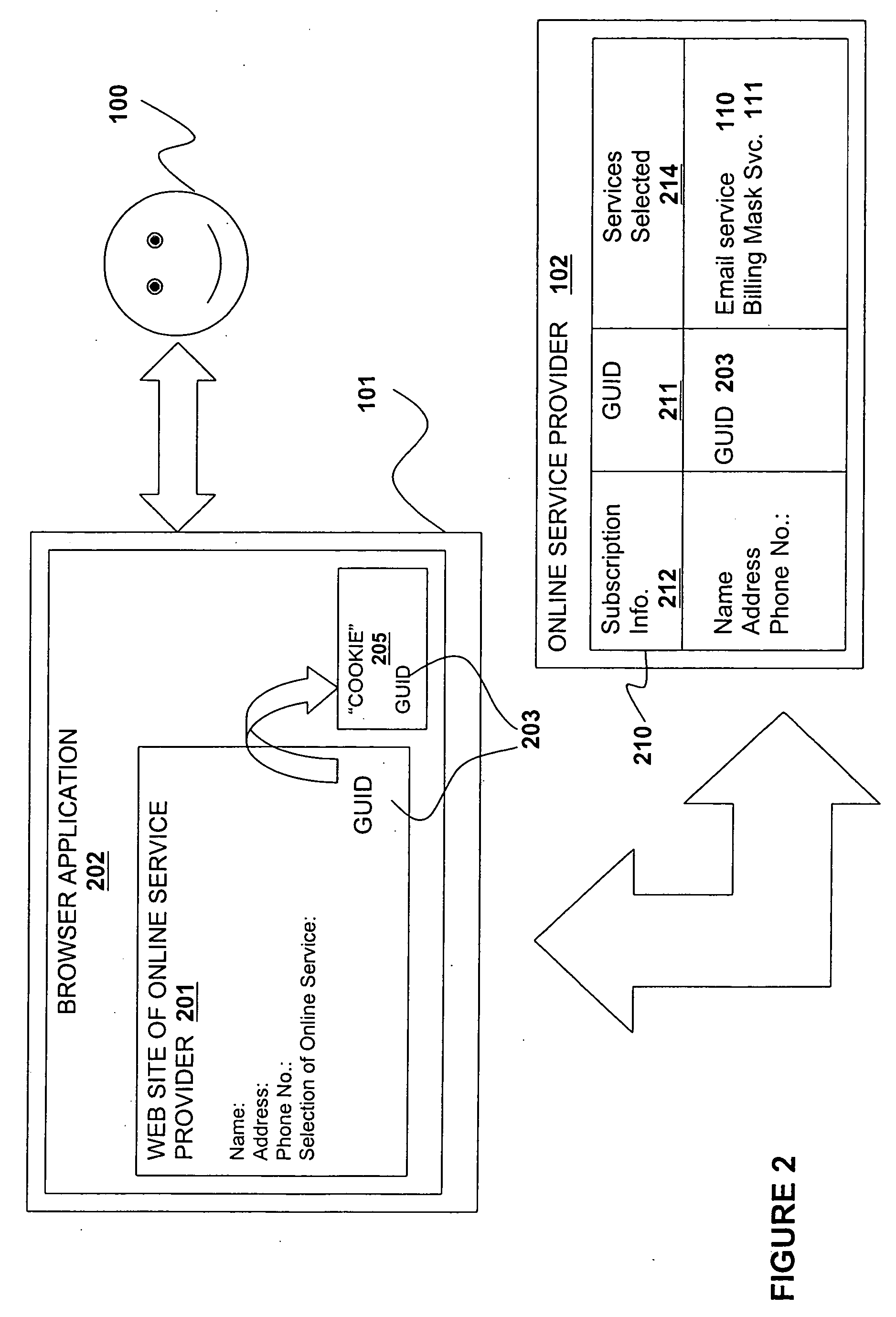
Method and apparatus for simplified access to online services
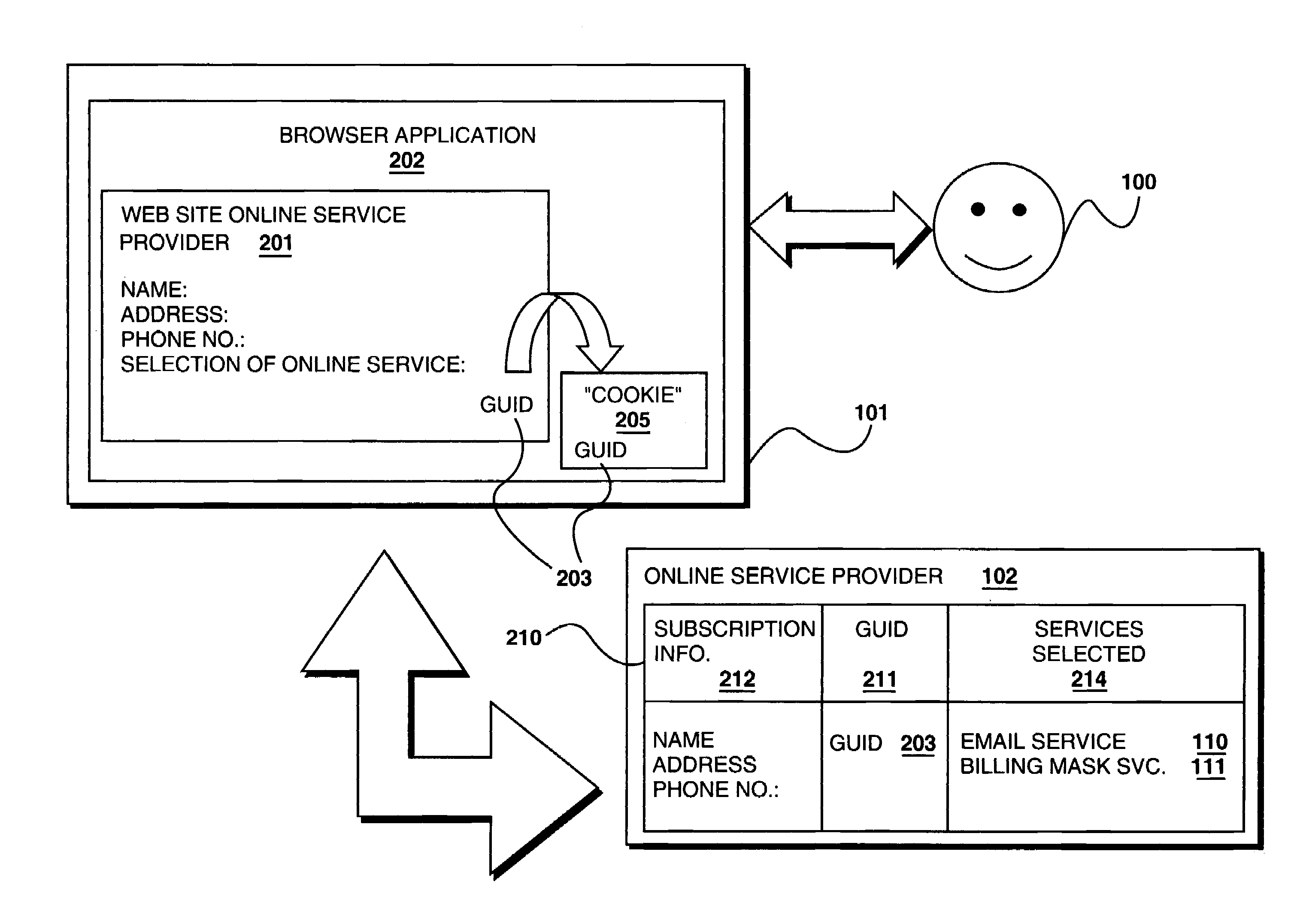
An online service provider is equipped to receive a request from a client to access a subscribed online service of a subscriber at the online service provider. Comprising the request is a globally unique identifier (GUID) of the subscriber. Once the request is received, the online service provider, determines if the GUID is associated with the subscriber, and if the GUID is associated with the subscriber, the online service provider facilitates access to the subscribed online service of the subscriber. As a result, a user is able to access online services without having to manage several a logon Id and password pair. In one embodiment, the GUID is also caused to be stored in an email with an email service provider. The novel storage enables the subscriber to access his / her subscribed services from another location, or even after the subscriber has reconfigured the original location.
Owner:INTELLECTUAL VENTURES I LLC
Method and apparatus for simplified access to online services
InactiveUS20060143188A1Data processing applicationsDigital data processing detailsService provisionPassword
Owner:INTELLECTUAL VENTURES I LLC
Real-time authorization software License control method
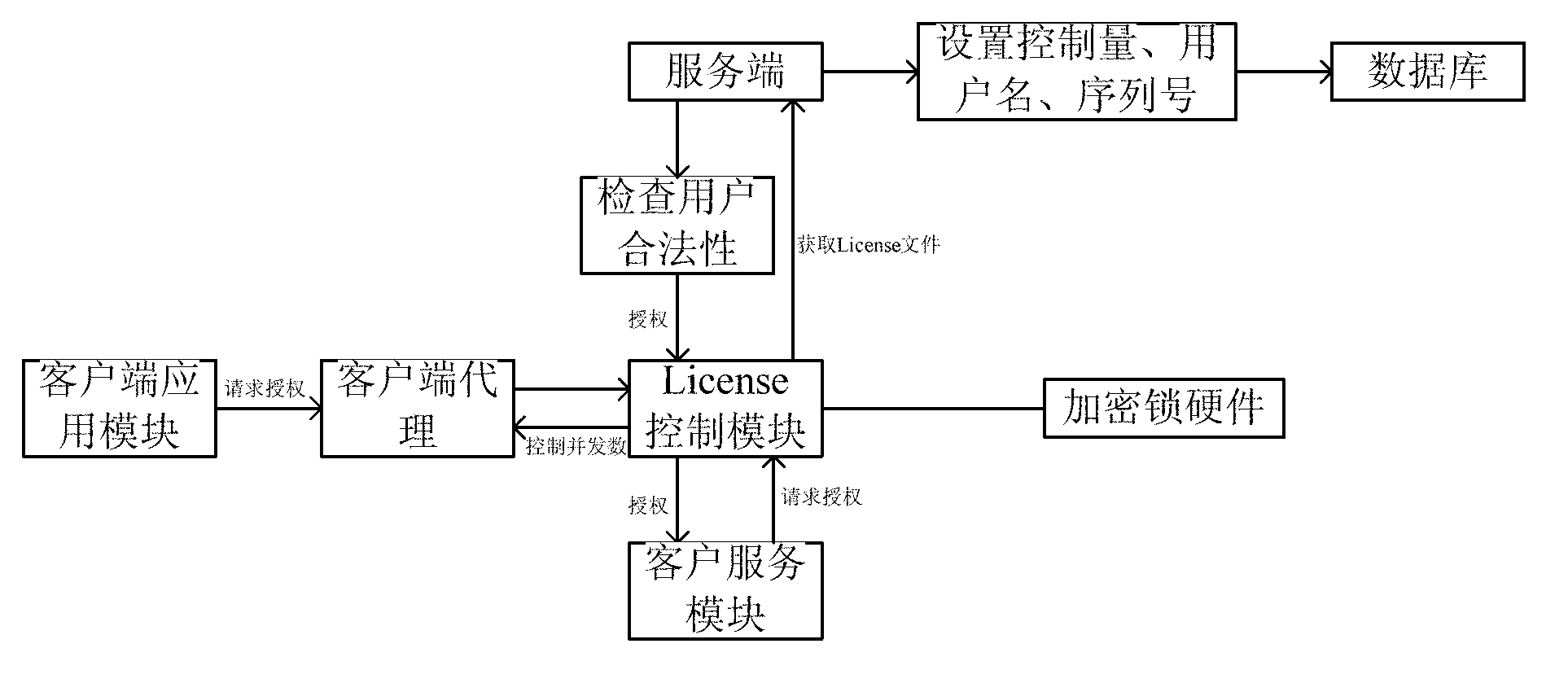
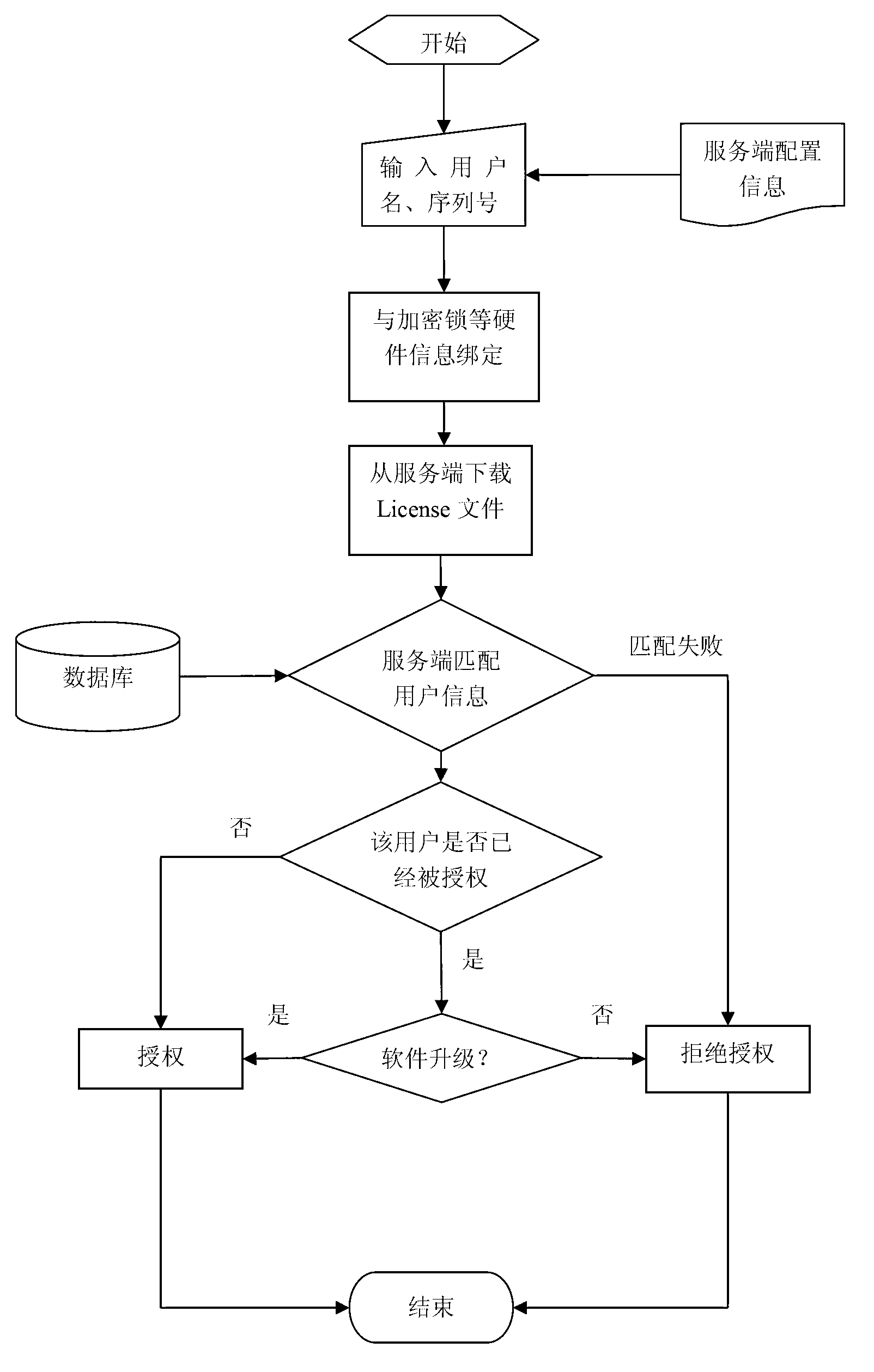
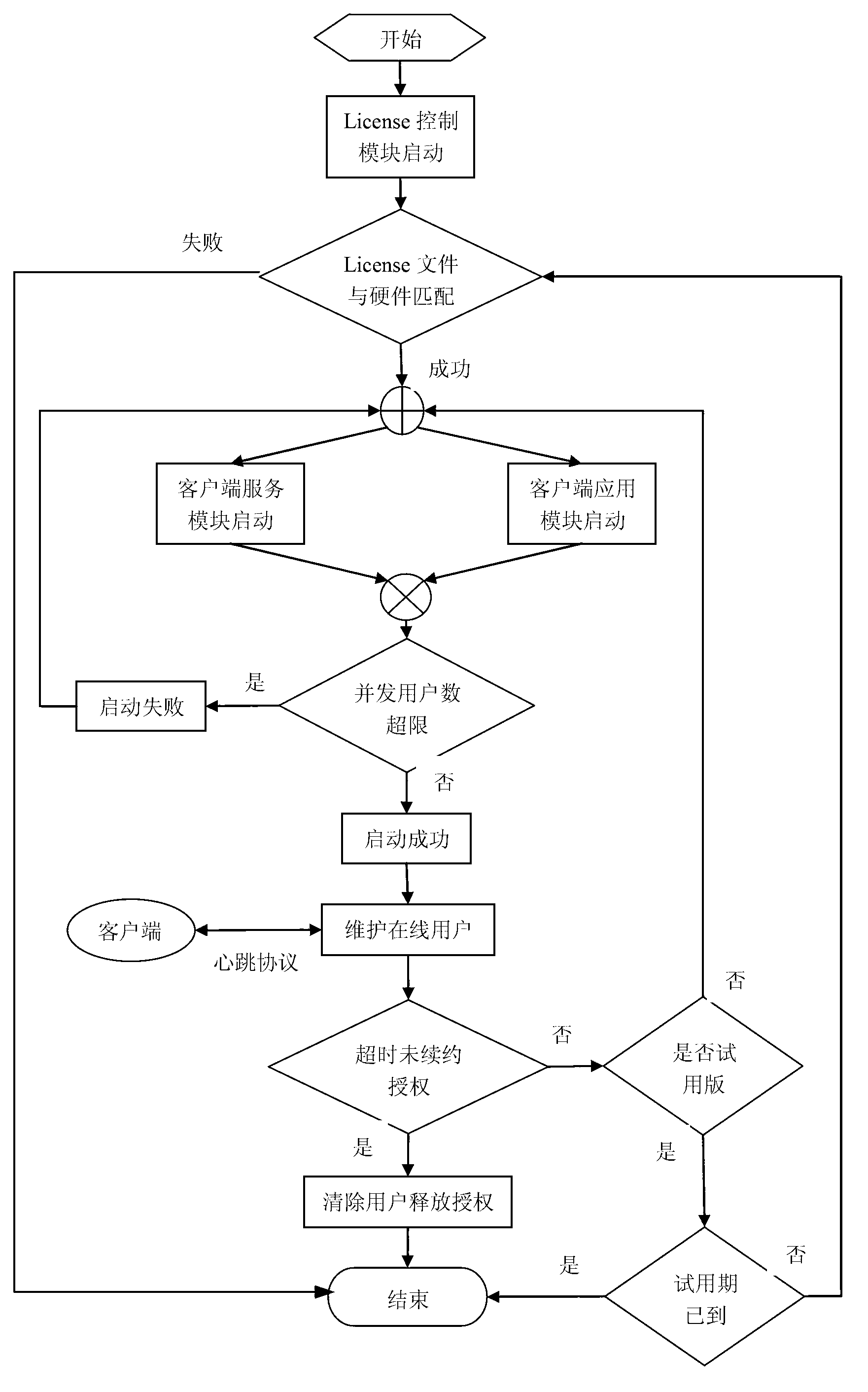
ActiveCN103258151ARealize managementEasy to controlProgram/content distribution protectionLicense controlSoftware system
The invention provides an enterprise software License control method implementing real-time authorization. The method includes the steps of using an SOA (service oriented architecture) for software, setting controlled quantities, such as the number of client application module concurrent users and the number of servers simultaneously published by a client service module, on a server, and binding the controlled quantities with user names and an automatically generate GUID (globally unique identifier) serial number; after a client binds the user names and the serial number with hardware information such as encryption lock (including computer CPU (central processing unit) serial number, network card serial number and hard disk drive serial number), allowing the client to acquire an encrypted License file from the server; and allowing a License control module to analyze the License file to allow for real-time control of authorization to the whole software system. According to the method, authorization of software can be controlled effectively as the client is communicated with the server in real time, whether the software runs in a virtual machine or not can be detected, and control of versions such as trial version and official version can be performed. The enterprise software License control method implementing real-time authorization is widely applicable to the field of authorization control for computer enterprise software.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
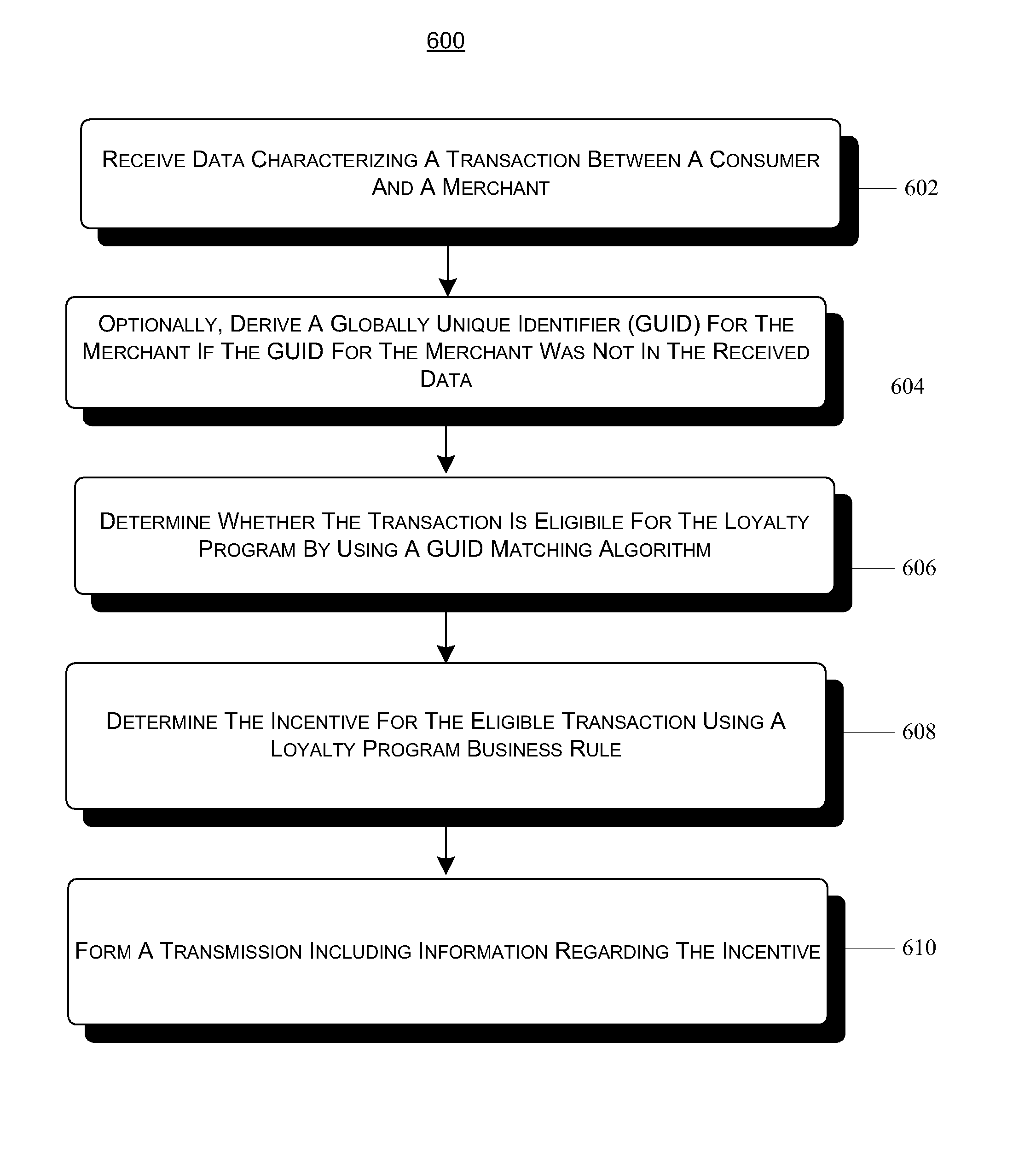
Loyalty program incentive determination
Owner:VISA USA INC (US)
System and method for identifying a product
InactiveUS20050197926A1Disadvantages and and reduced eliminatedMethods reduced eliminatedBuying/selling/leasing transactionsPoint-of-sale network systemsUnique identifierProduct Identifier
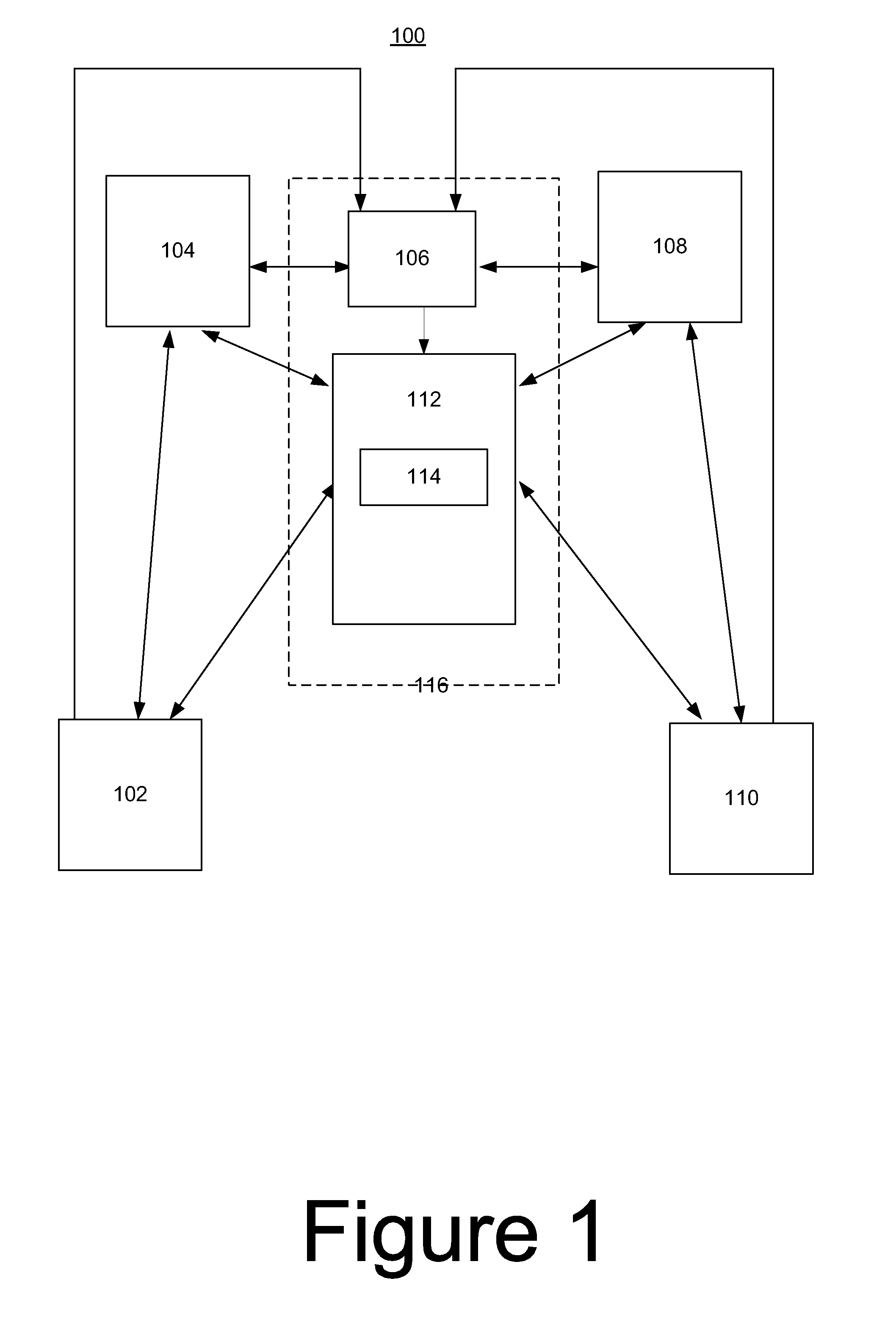
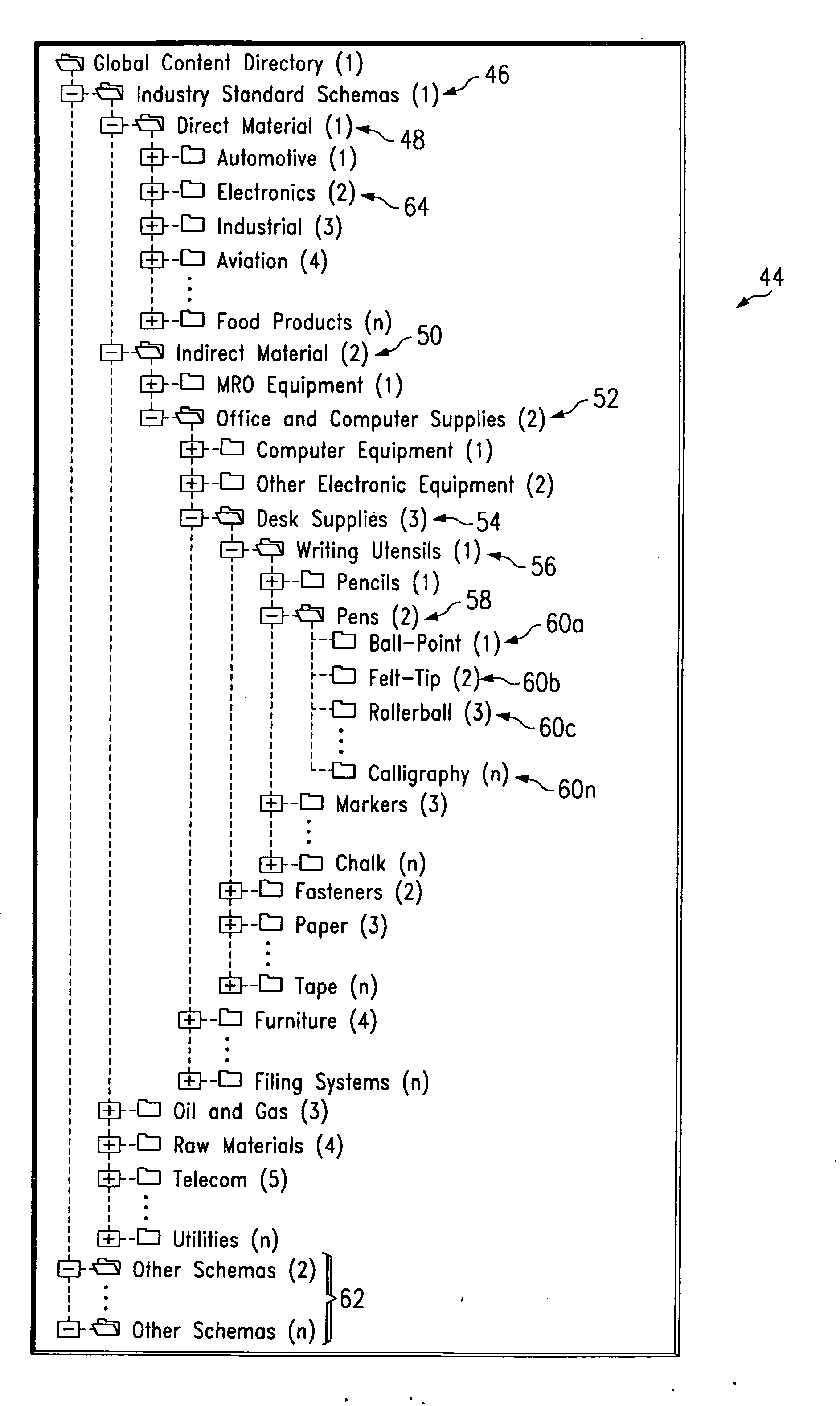
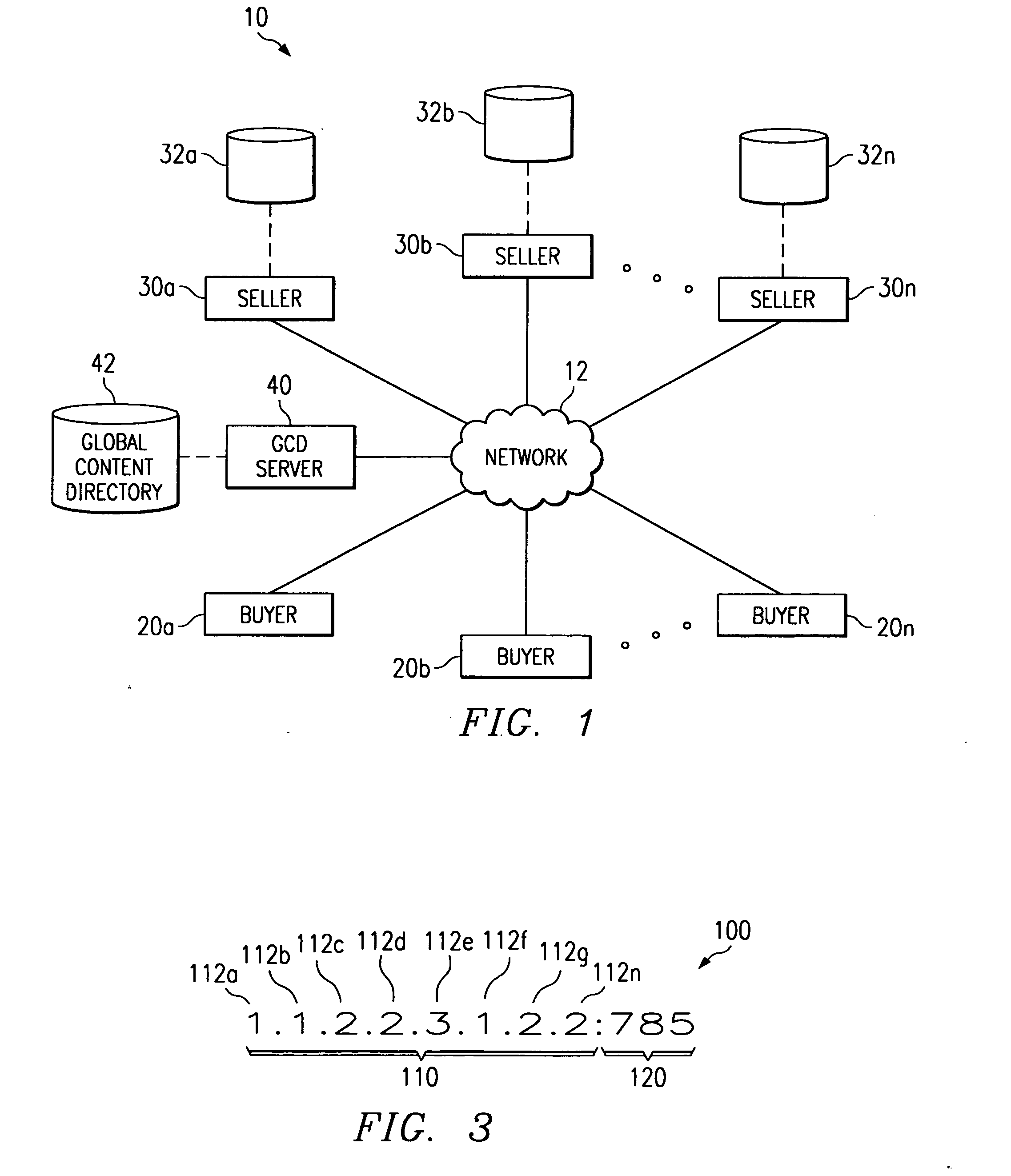
A product that is uniquely identifiable according to a globally unique identifier (GUID) (100) includes a class identifier (CID) (110) that uniquely identifies at least one product class in which the product is categorized (along with a plurality of other products) within a class hierarchy of a global content directory (42). The product class defines one or more attributes of the products categorized in the class. The product also includes a product identifier (PID) (120) that uniquely identifies the particular product from among the plurality of products categorized in the product class uniquely identified by the CID (110). The CID (110) and PID (120) collectively provide the GUID (100), which may be specified or determined to facilitate a commercial transaction involving the product.
Owner:BLUE YONDER GRP INC
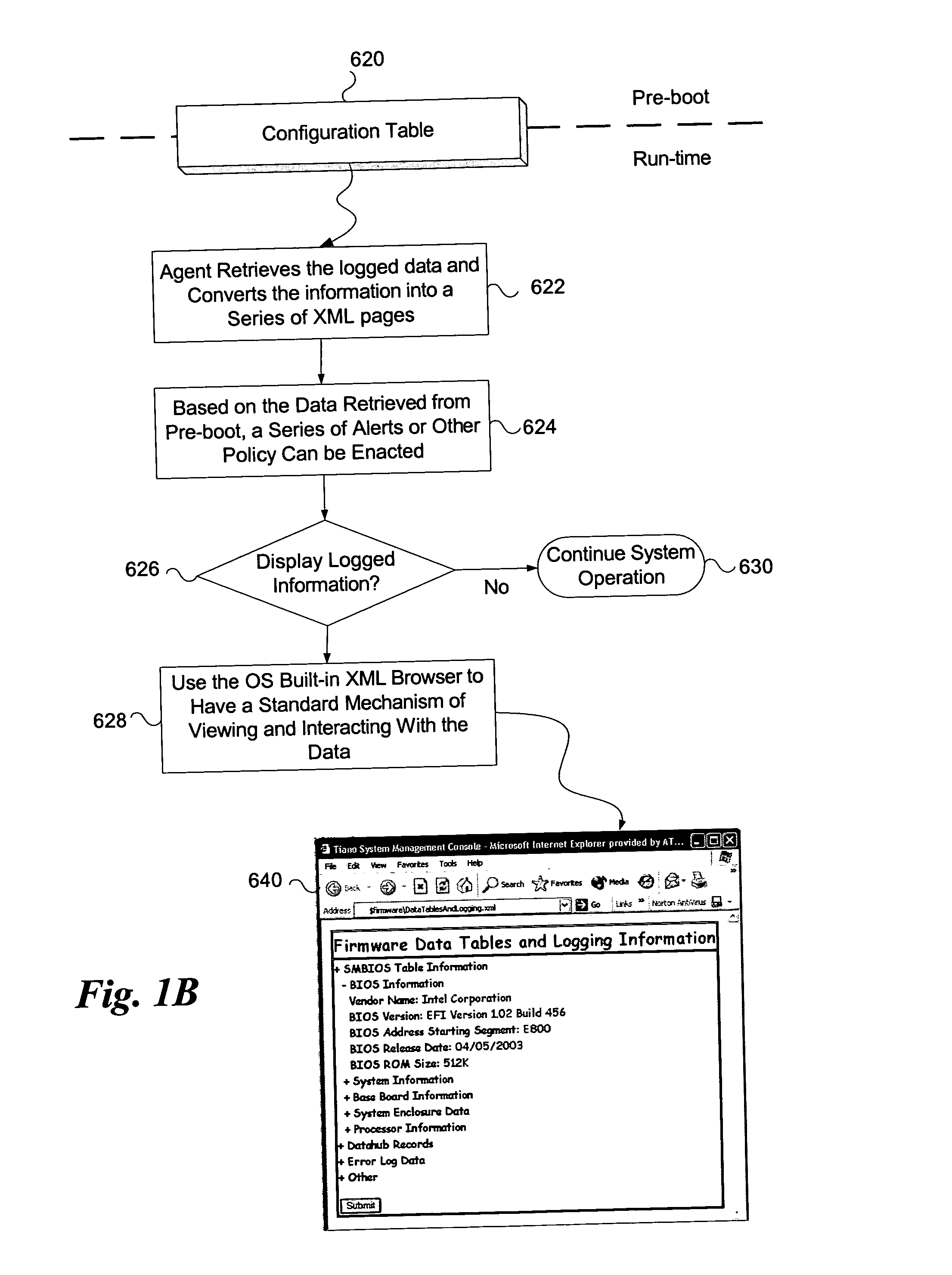
System and method for firmware to export pre-boot data into the operating system runtime environment
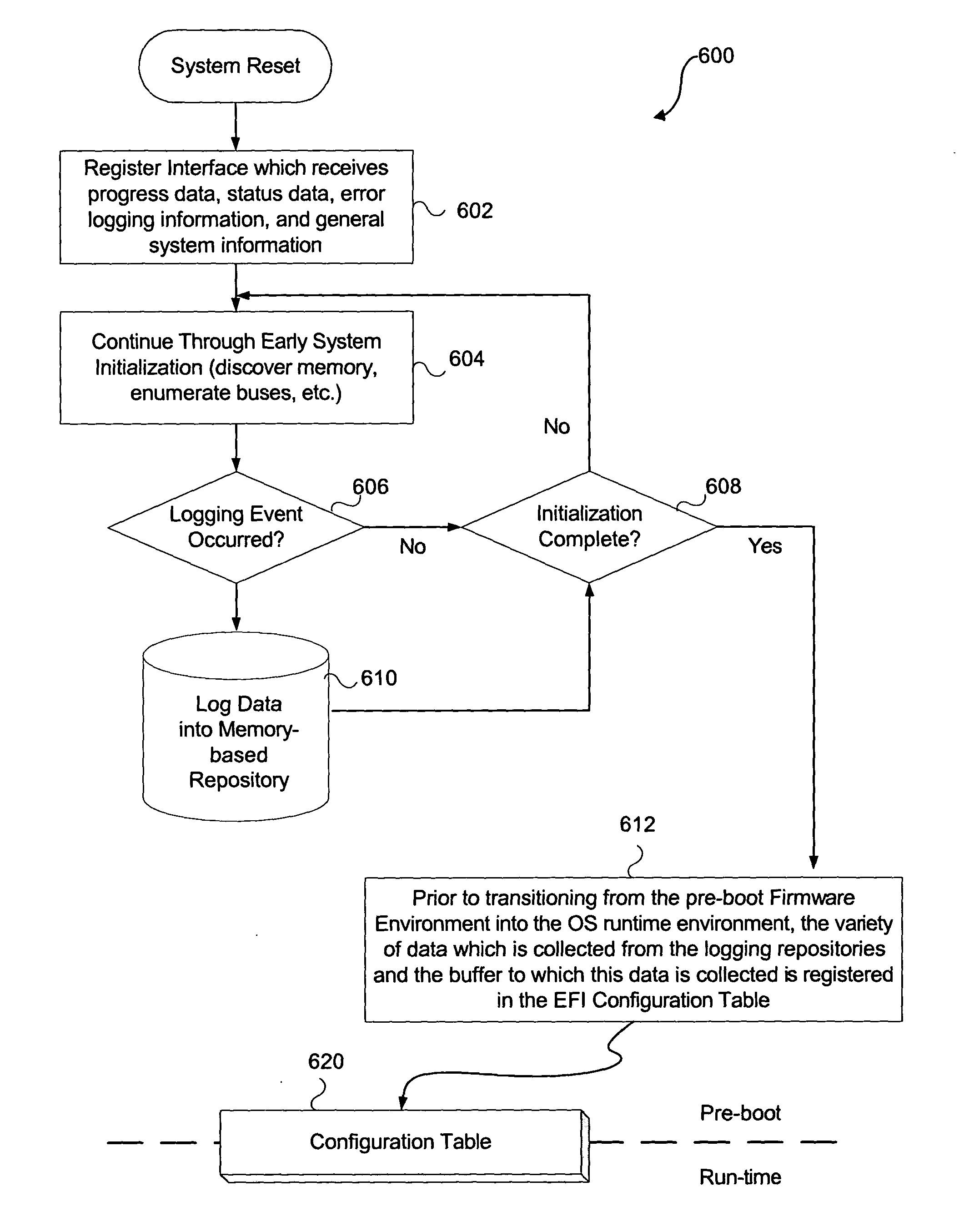
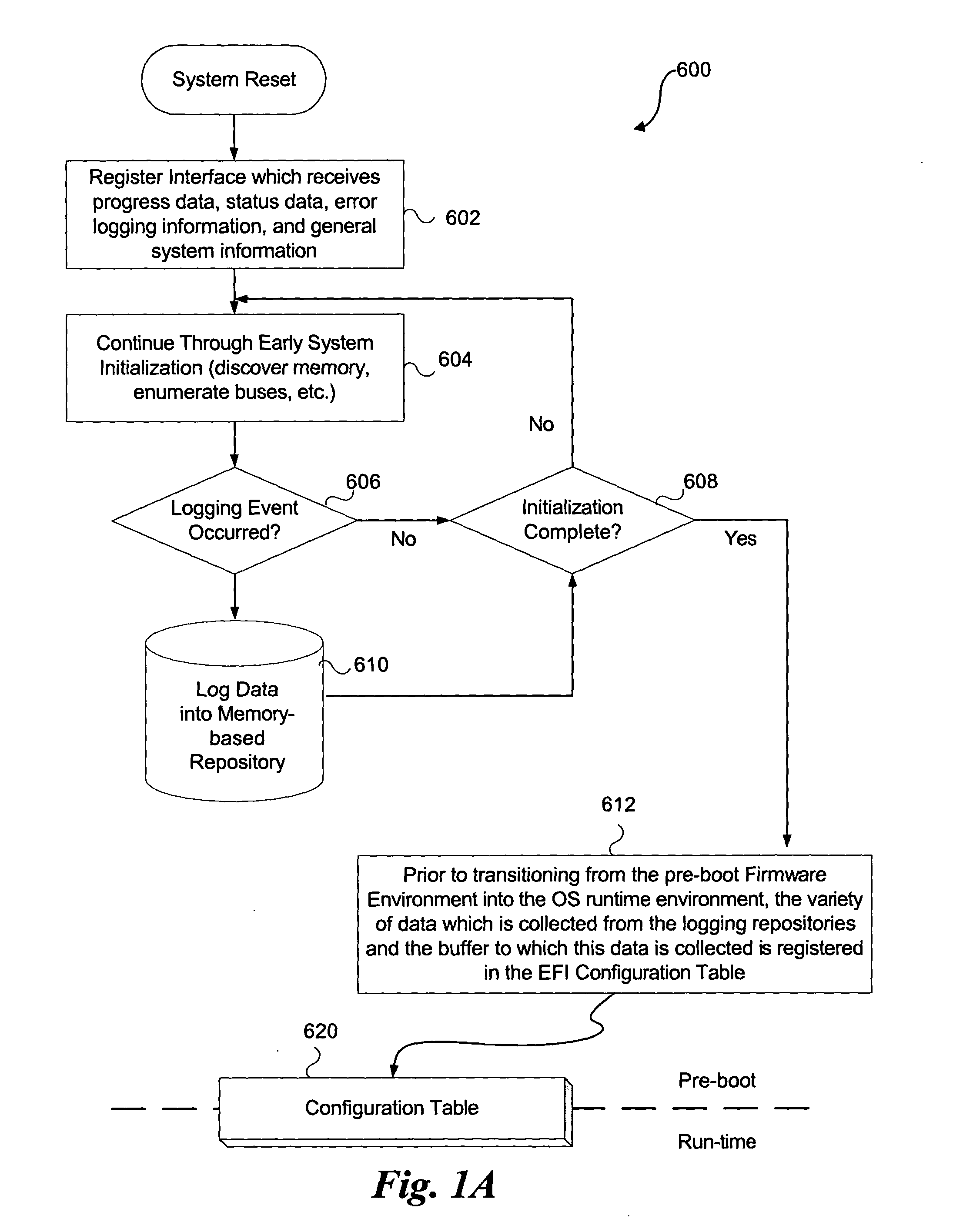
ActiveUS20050060526A1Fault responseDetecting faulty hardware by configuration testOperational systemEvent data
An embodiment of the present invention bridges event data from the pre-boot environment to the operating system runtime environment. Event logs are stored in a memory buffer during pre-boot. Prior to launching the operating system (OS), the event log is registered to a known memory location accessible to the OS. A preferred embodiment uses the extensible firmware interface (EFI) configuration table to store the event log. A globally unique identifier (GUID) may be used to identify the memory buffer location. Once accessible to the OS, the event data may be displayed using standard extensible Markup Language (XML) forms, or via any other desired method.
Owner:INTEL CORP
Message-oriented middleware provider having multiple server instances integrated into a clustered application server infrastructure
ActiveUS20050240654A1Multiple digital computer combinationsDistributed object oriented systemsApplication serverUnique identifier
A method, apparatus, and system are provided for a Message-Oriented Middleware (MOM) provider having multiple logical MOM server instances. In an embodiment, a number of application servers are communicatively coupled on an enterprise network. In an embodiment, the MOM provider includes an MOM server instance implemented on each of the plurality of application servers. Each MOM server instance may include a session container to manage one or more sessions and a destination container to provide one or more destinations. In an embodiment, each destination is identified by a globally unique identifier.
Owner:SAP AG
User authentication system
ActiveUS20110246764A1Public key for secure communicationDigital data processing detailsThird partyRoot certificate
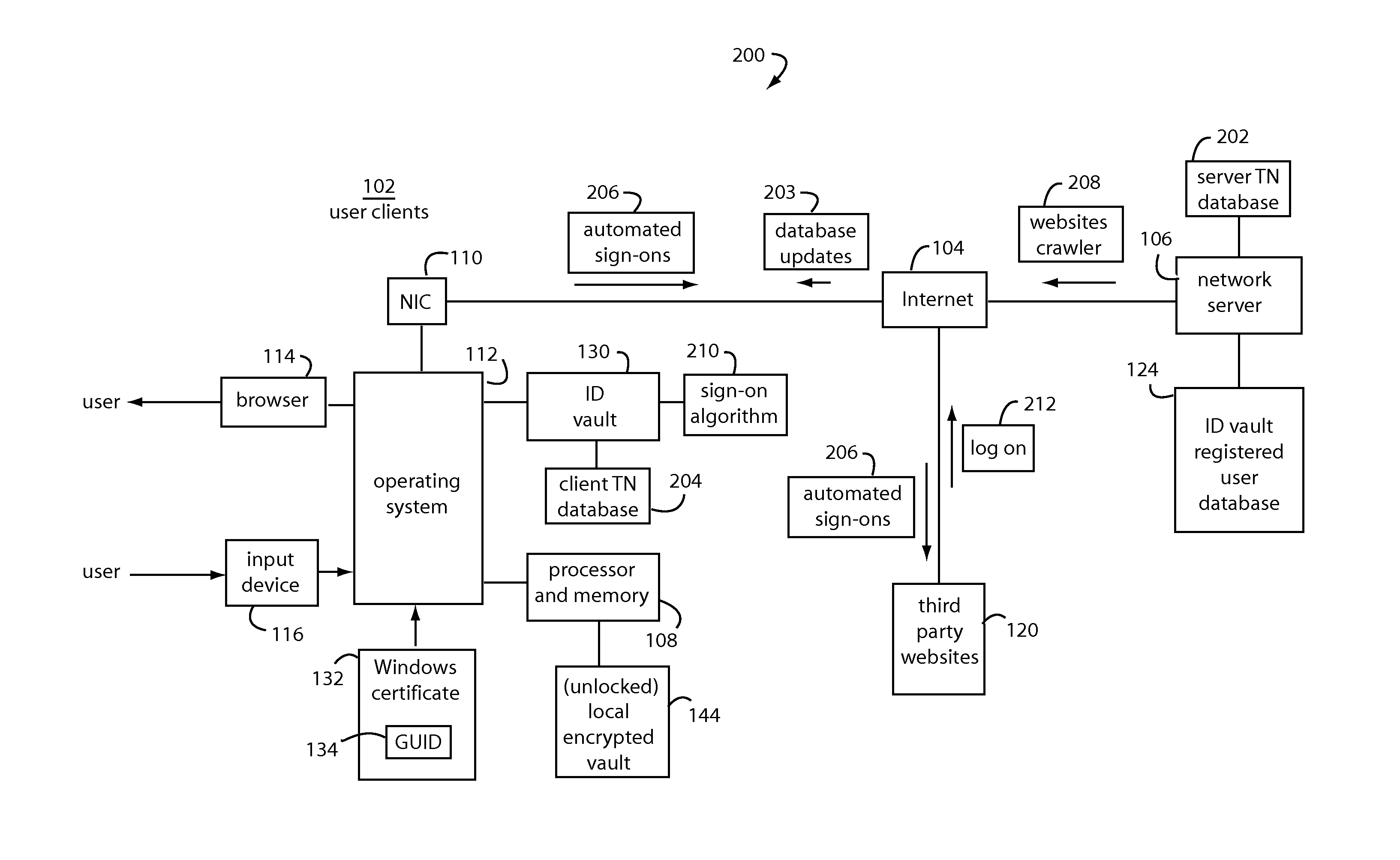
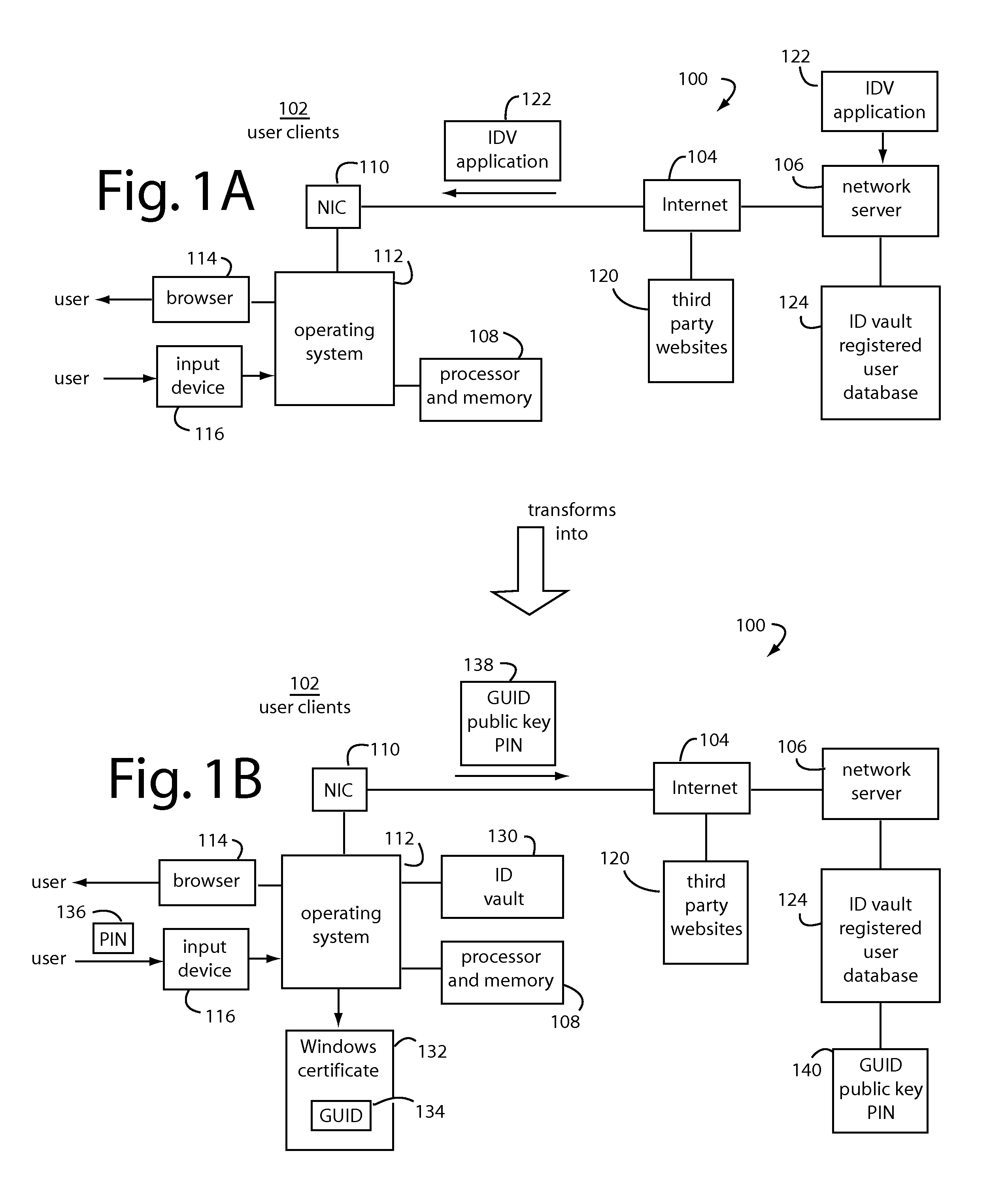
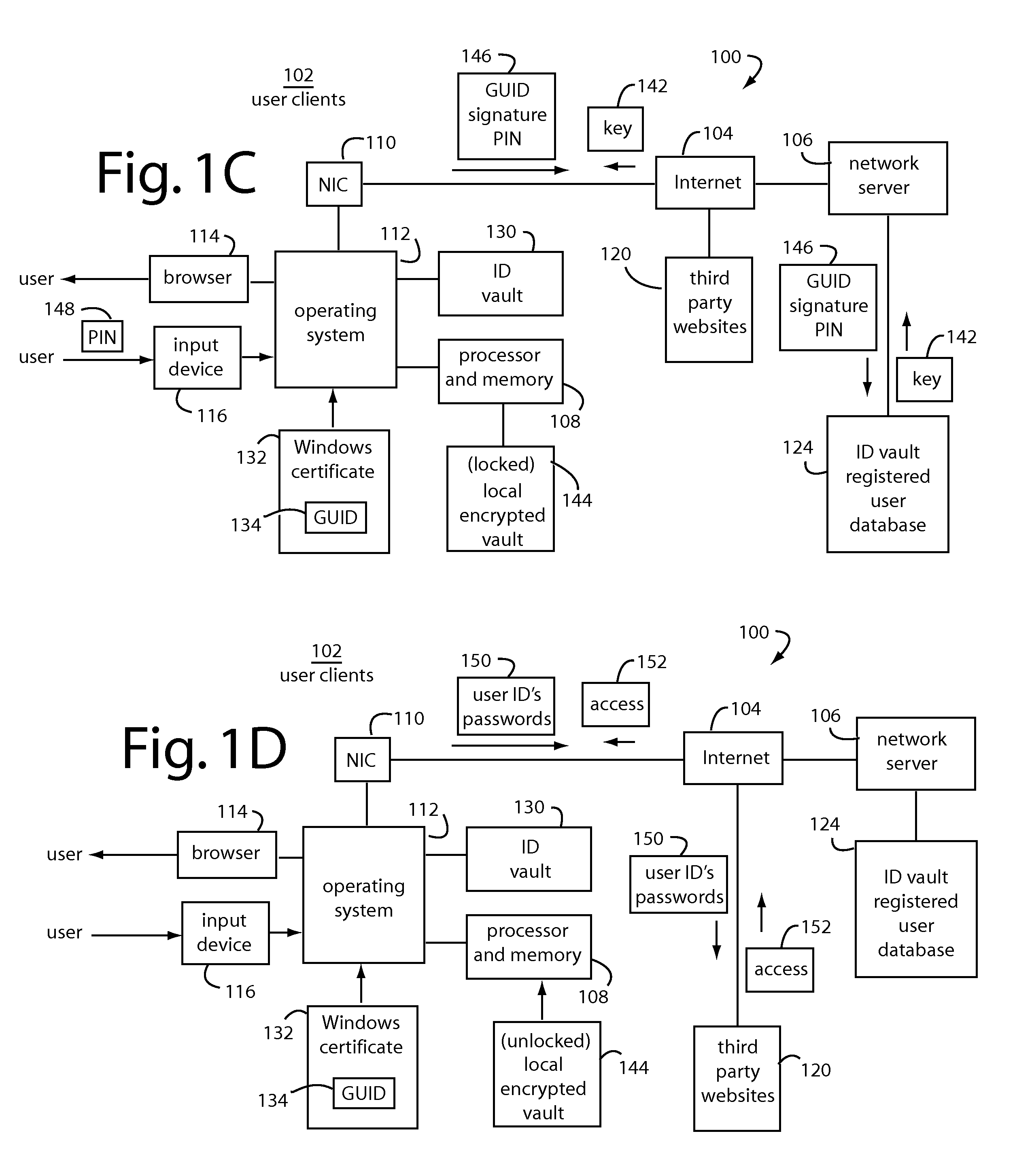
An ID vault computer control program detects when a user's browser navigates to a third-party website that requires a user ID and password. If it hasn't done so already, it automatically requests a decryption key for a local encrypted vault file from a network server by supplying a personal identification number (PIN) from the user through the input device, a copy of the GUID, and a signature of GUID using a private key for the root certificate. If a decryption key is returned from the network server, the local encrypted vault file is unlocked and automatically supplies a corresponding user ID and password to log-on to the third-party website without the user.
Owner:INTERSECTIONS LLC +1
System, method, and computer program product for sending remote device configuration information to a monitor using e-mail
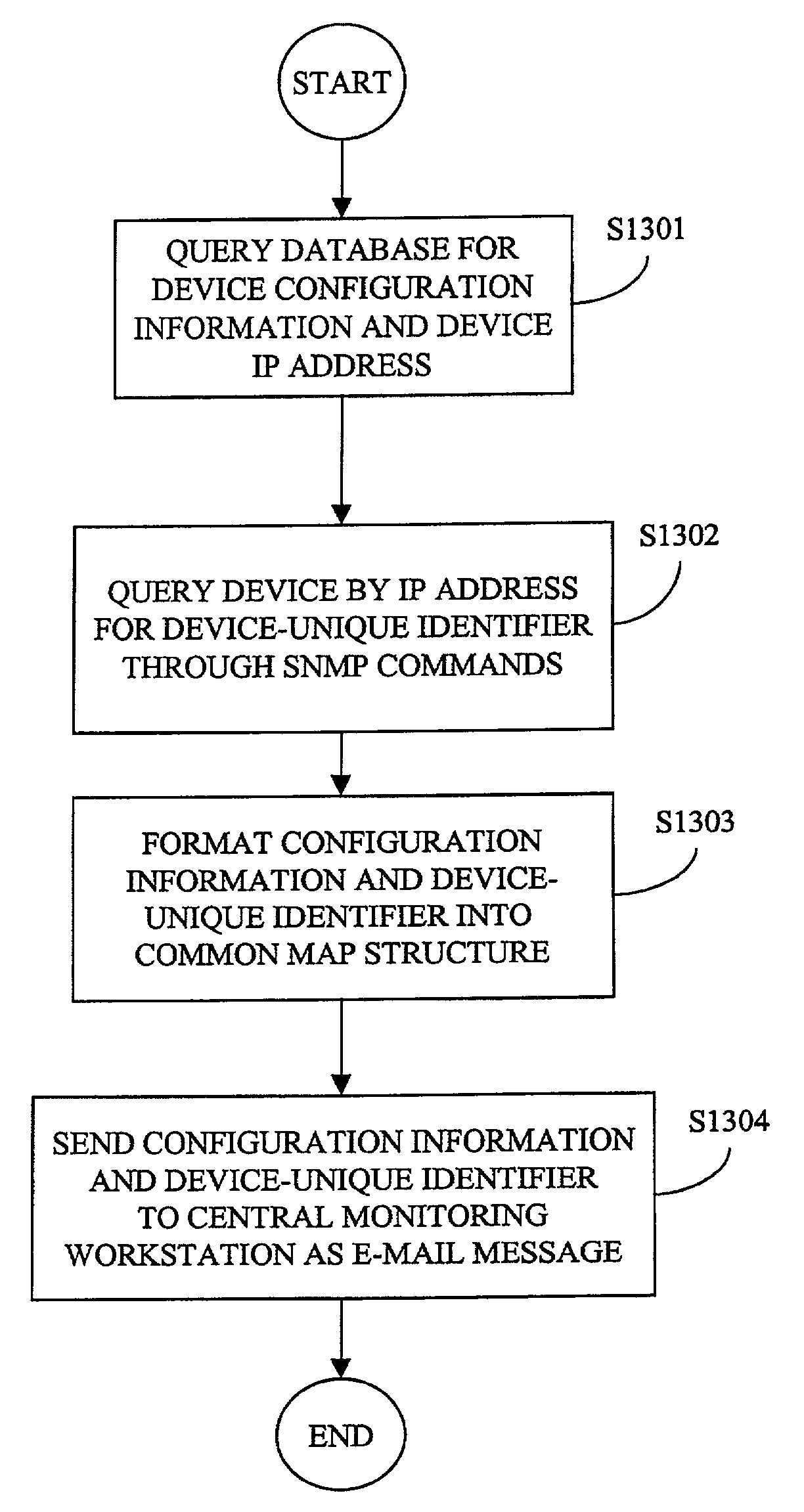
InactiveUS7536450B2Digitally marking record carriersMultiple digital computer combinationsIp addressUnique device identifier
In a monitoring system for networked devices, a system, method, and computer program product for obtaining a globally-unique identifier for a network device, and sending the same to a central monitor responsible for monitoring devices on multiple networks. A remote monitoring workstation monitors devices connected to a network using IP-based SNMP commands and stores the device monitoring information in a database. The remote monitoring workstation queries the database to obtain an IP address and the collected monitoring information for a device, uses the IP address to request a globally-unique identifier (e.g., a MAC address) from a device using SNMP commands, then sends the monitoring information including the globally-unique device identifier to a central monitoring workstation via an e-mail message.
Owner:RICOH KK
System and method for incremental and reversible data migration and feature deployment
InactiveUS7165088B2Scope can be broadened and narrowedLimited resourceMultiple digital computer combinationsWebsite content managementWeb siteWeb service
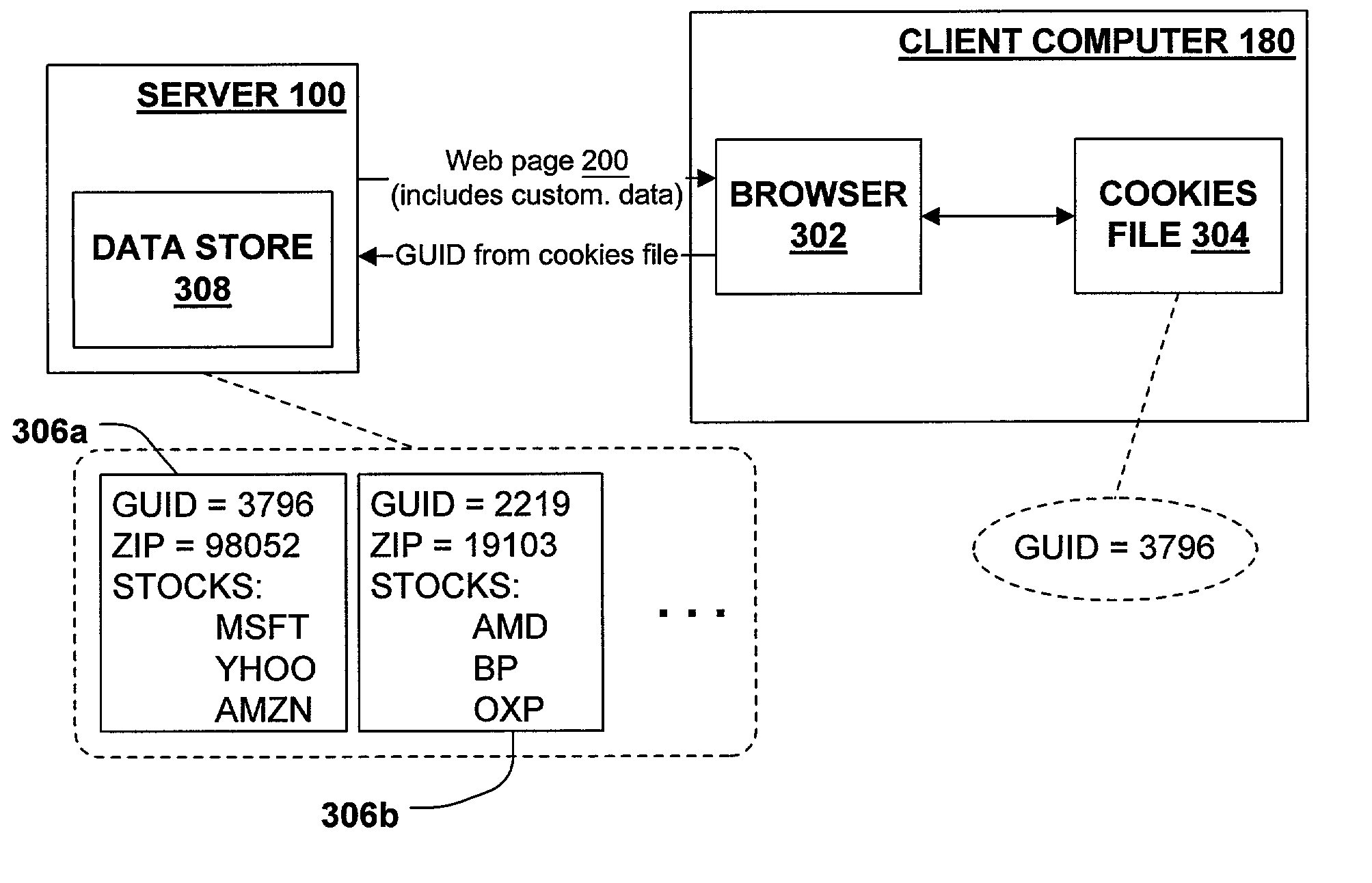
A data migration throttle that supports the incremental and reversible migration of web site customization data from a client-side data store to a server-side data store. Initially, each user of the web site stores customization data, such as the user's zip code, in a cookies file together with a globally unique identifier (GUID) which identifies the user. In order to migrate data to a server side store, the throttle is set to a value. Each time a user contacts the web server a hash of the user's GUID is compared with the throttle value, and the user's data is migrated to the server if the hash value is less than the throttle value. The throttle may be lowered, thereby causing some users to revert to client-side storage of customization data.
Owner:MICROSOFT TECH LICENSING LLC
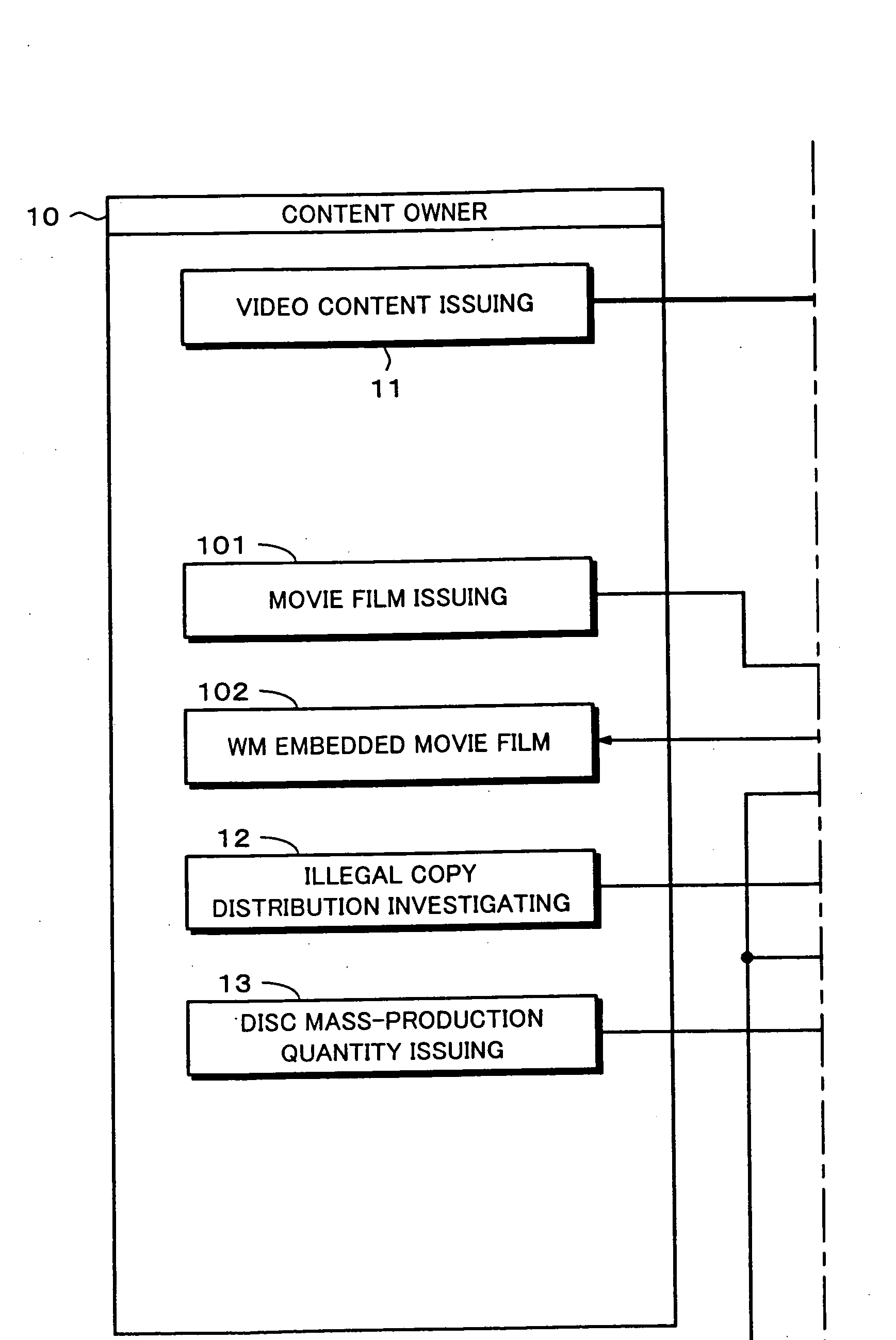
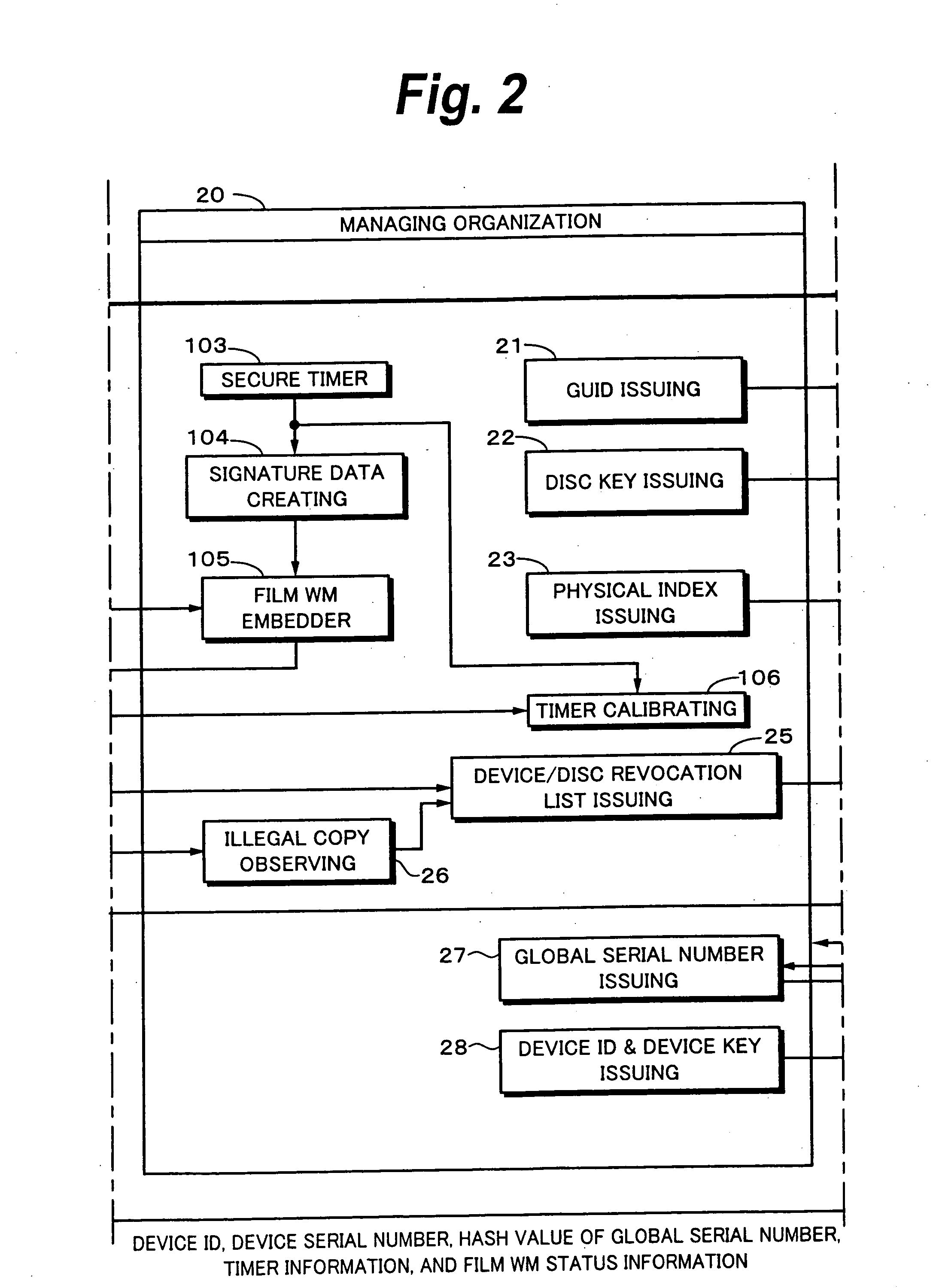
Recording medium and producing method thereof, reproducing method and reproducing apparatus, and copyright managing method
InactiveUS20060062073A1Controlled reproductionTelevision system detailsDisc-shaped record carriersDigital videoSerial code
A GUID as title information and a global serial number are recorded in a BCA of a digital video disc 60. A hash value of the GUID is embedded as an electronic watermark in a data area 64. When content data is reproduced from the digital video disc 60, a match of information of the two GUIDs is checked so as to prevent the digital video disc 60 from being illegally copied. A lead-in area 63 and a managing organization 20 provide disc revocation lists. With a global serial number and a disc revocation list, content data can be prevented from being reproduced from an illegally distributed disc. A film WM detector 84 detects data embedded in a movie shown in a theater so as to prevent content data from being reproduced from a disc on which the embedded data is recorded. Thus, content data can be prevented from being reproduced from an illegally distributed disc before a copyright supervisor of the content authorizes the disc to be distributed.
Owner:SONY CORP +1
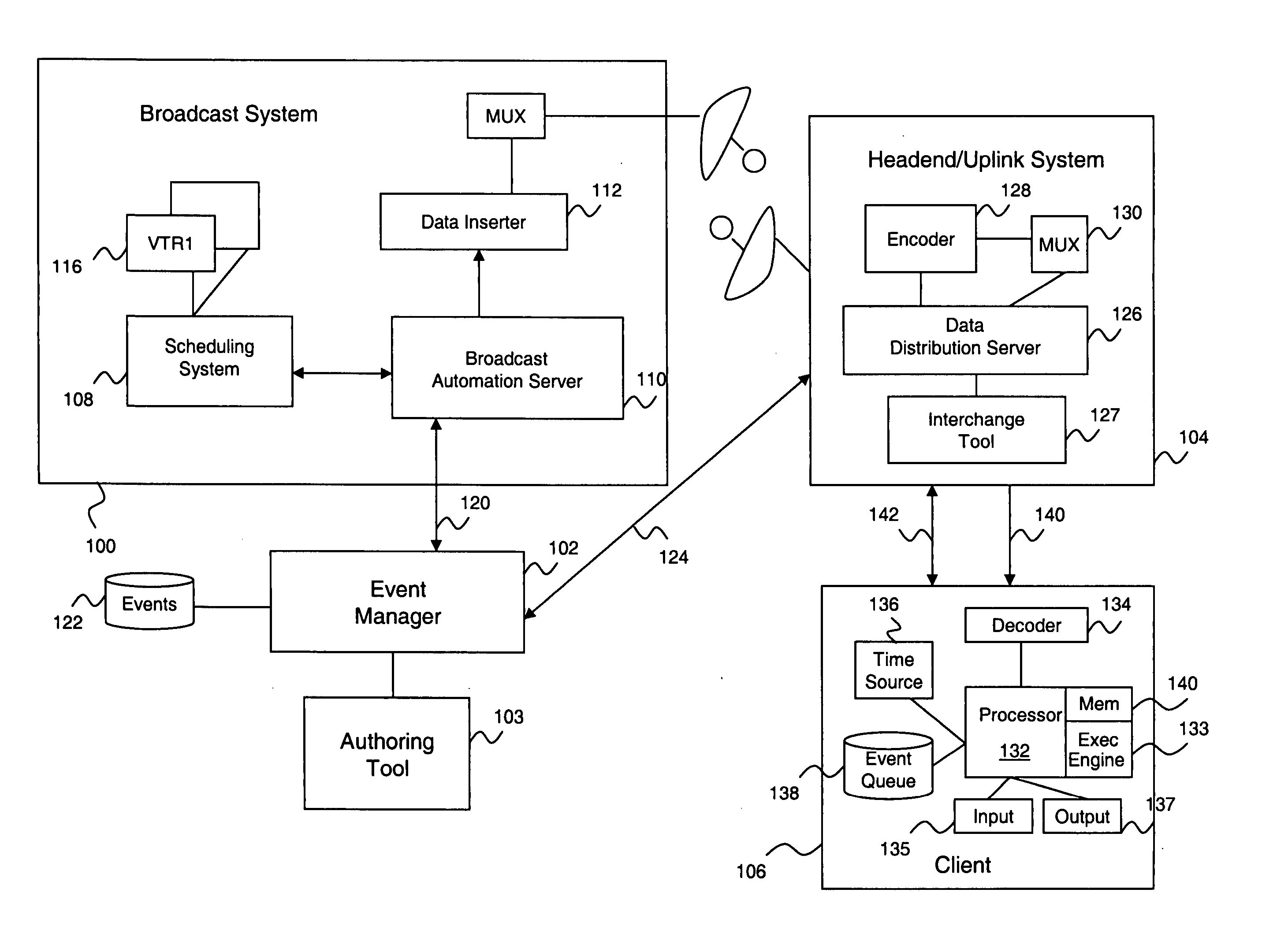
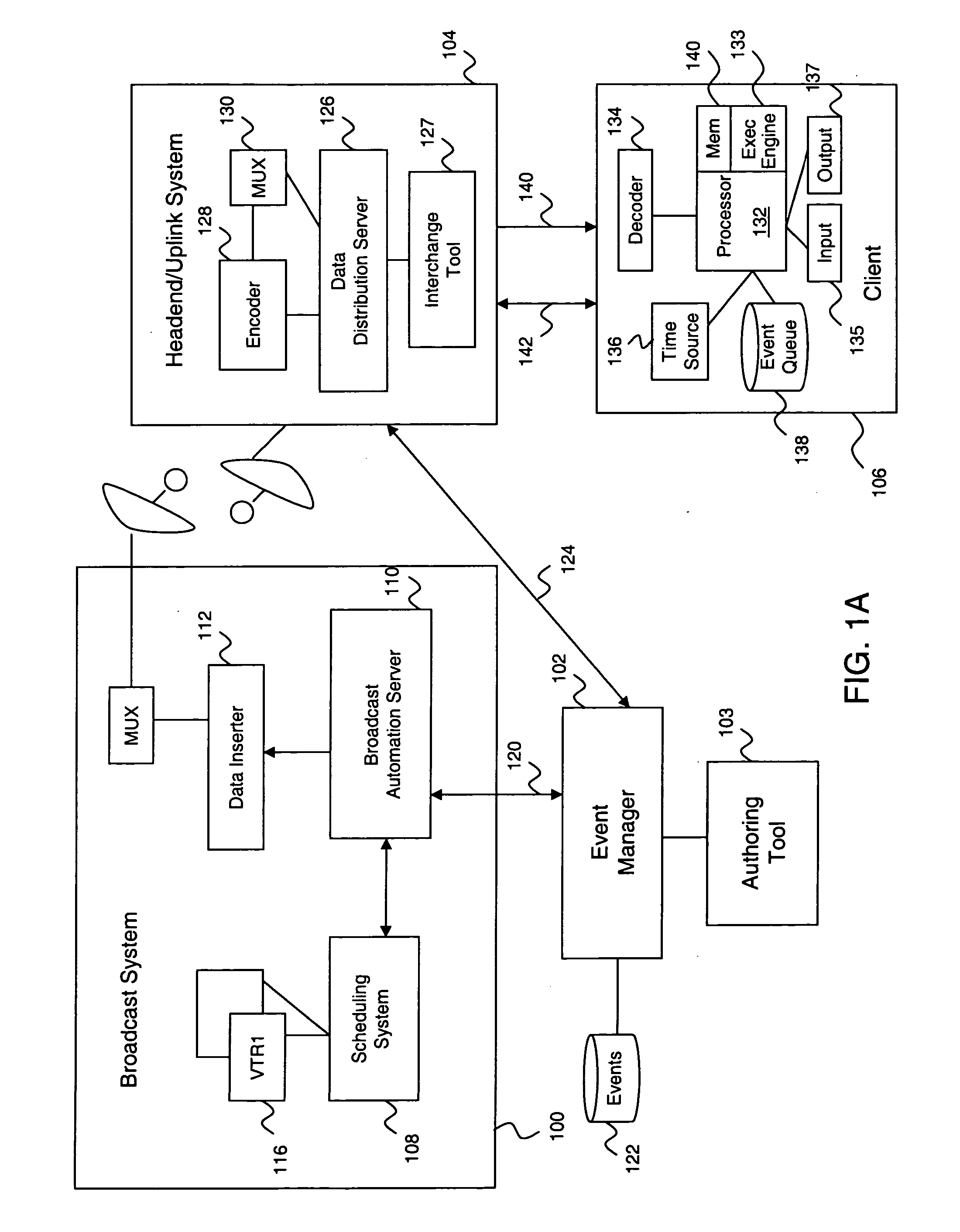
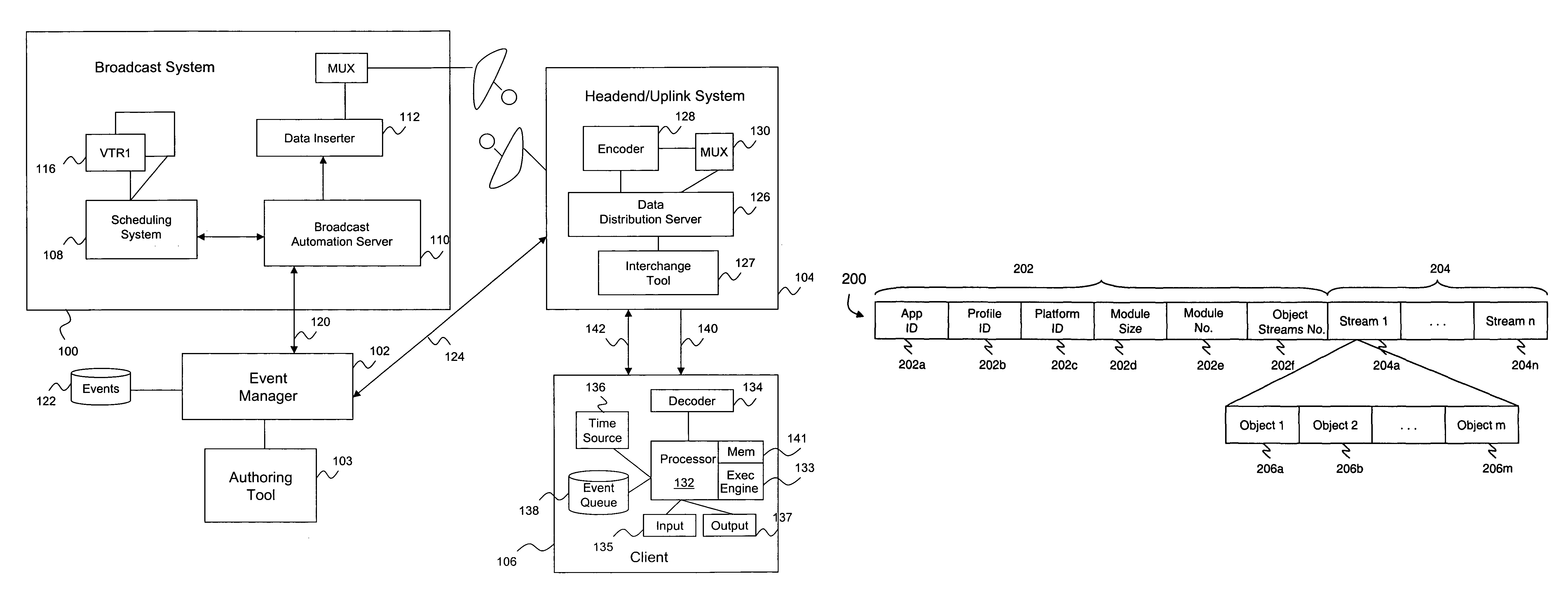
System and method for describing presentation and behavior information in an ITV application
ActiveUS20060031918A1Television system detailsAnalogue secracy/subscription systemsExpiration TimeComputer module
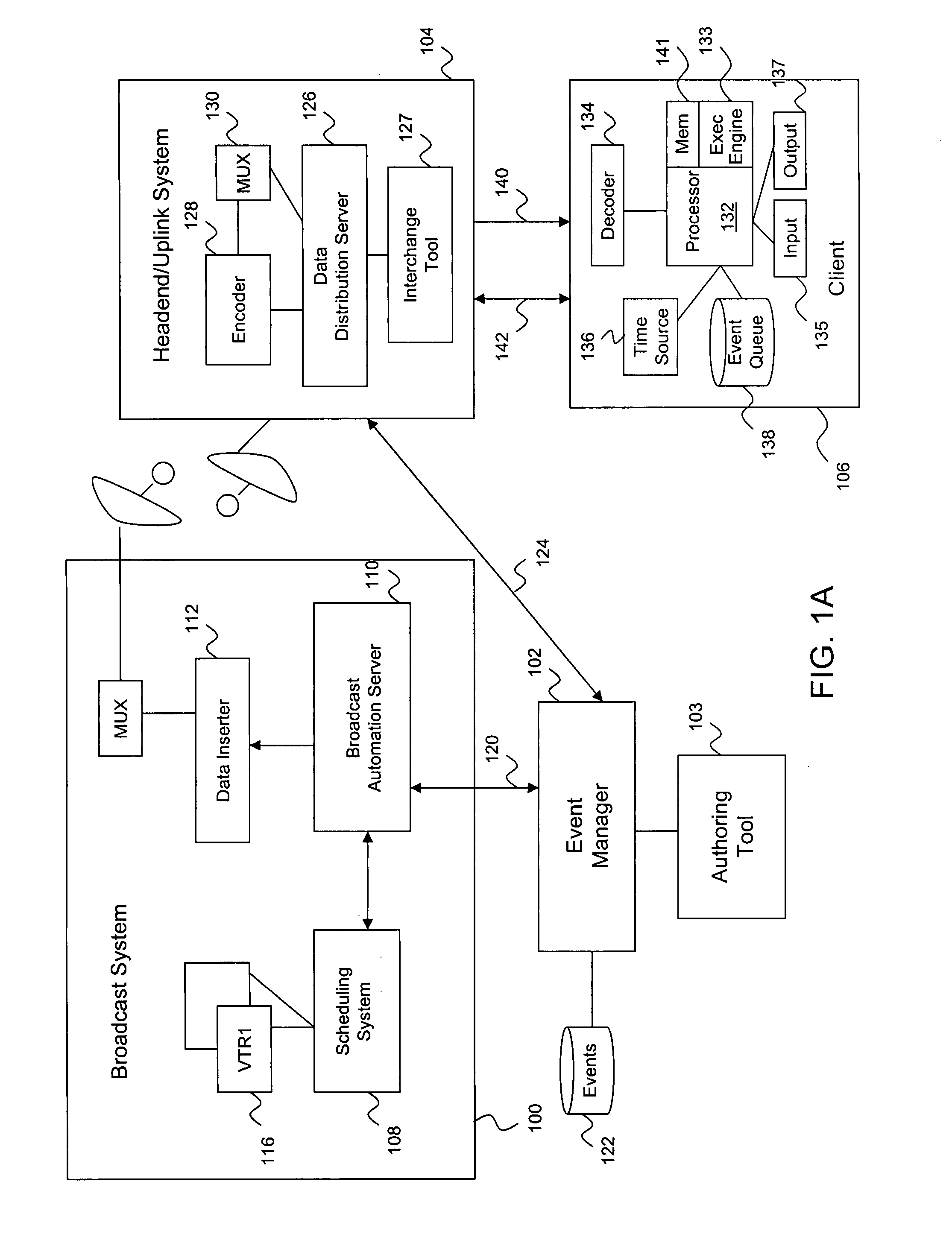
An ITV application definition language (ADL) used to generate ITV applications for different types of target platforms and devices. The ADL provides a plurality of core data structure types upon which one or more data structures may be built. Data structures storing ITV content presentation and behavior information are referred to as resources. A resource is associated with a globally unique identifier that allows the data structure to be efficiently stored and retrieved from a hash table. A resource is also associated with an expiration time stamp that indicates when the resource is to be freed from memory. A resource is of arbitrary length, and contains values that differ from the default values stored at a receiving client device. Resources are also packaged into a module that may be catered to a platform and / or profile of a receiving client. The client may quickly determine whether the module is relevant to it by examining the platform and / or profile If) contained in a header of the module.
Owner:MK SYST USA INC
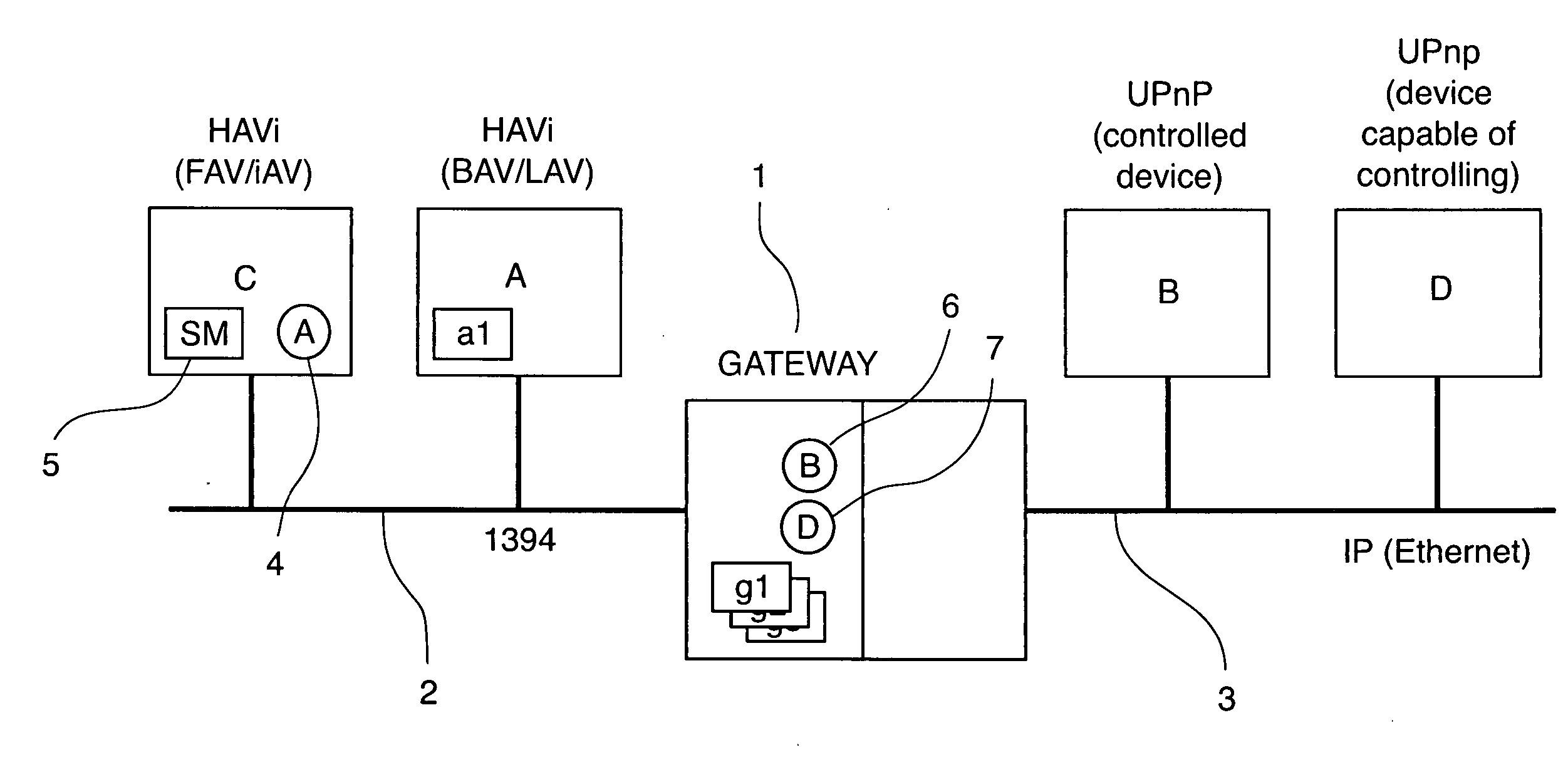
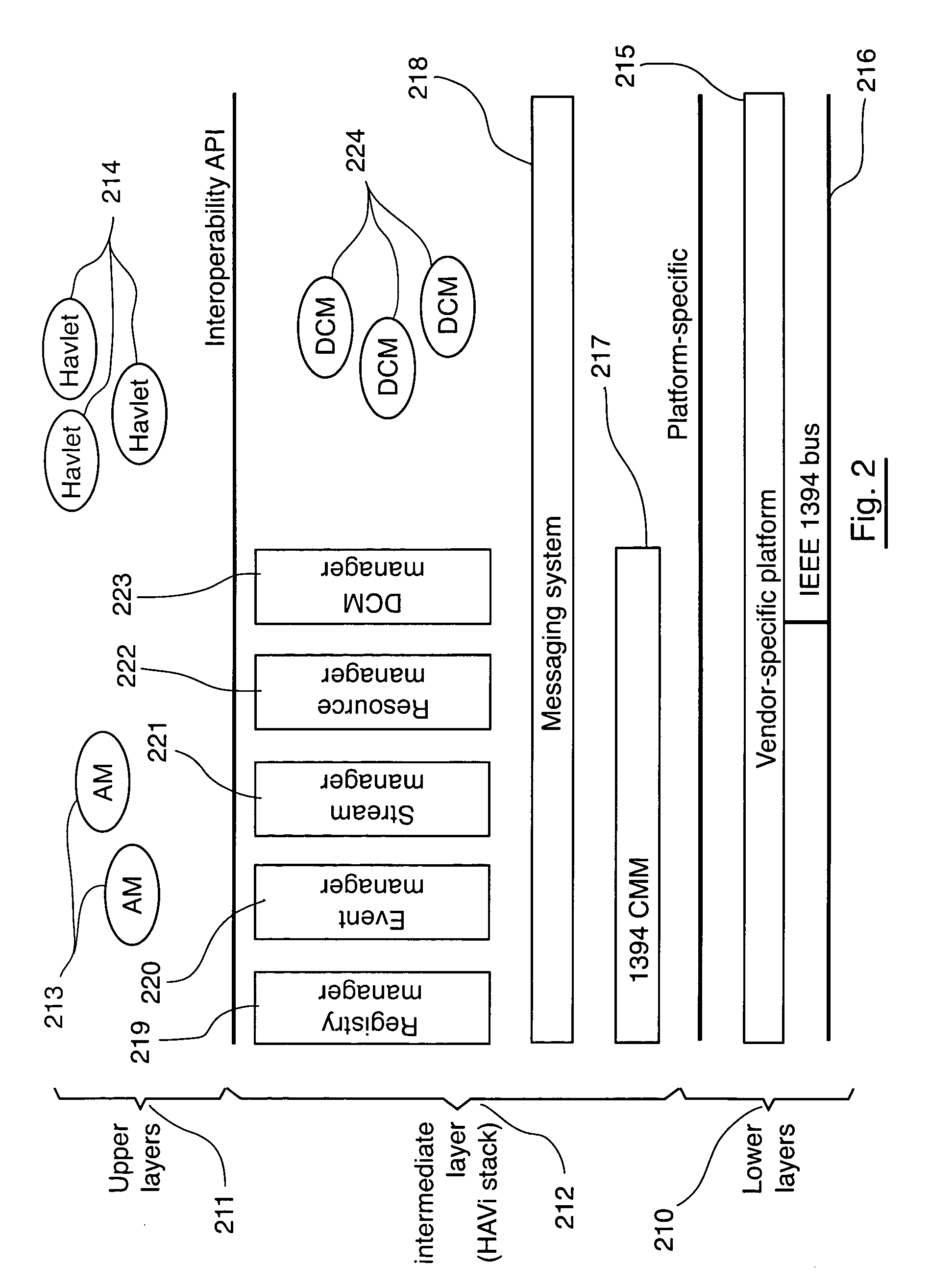
Gateway and method for the interconnection of two networks, especially a HAVi network and an UPnP network
InactiveUS20050021852A1Optimized bandwidth consumptionSimple processHybrid switching systemsMultiple digital computer combinationsUnique identifierInterconnection
A method of interconnection, through a gateway, between a first network of type IEEE 1394 enabling communications between a plurality of HAVi compliant devices and a second network enabling communications between a plurality of devices comprising the steps of: determining a global unique identifier for each device from the second network; determining a distinct IEEE 1394 address for each device from the second network; representing each device from the second network by a HAVI compliant software element hosted by the gateway; managing communication between devices from the first network and devices from the second network, using for each device from the second network, its corresponding software element associated with the global unique identifier and the IEEE1394 address.
Owner:CANON RES CENT FRANCE +1
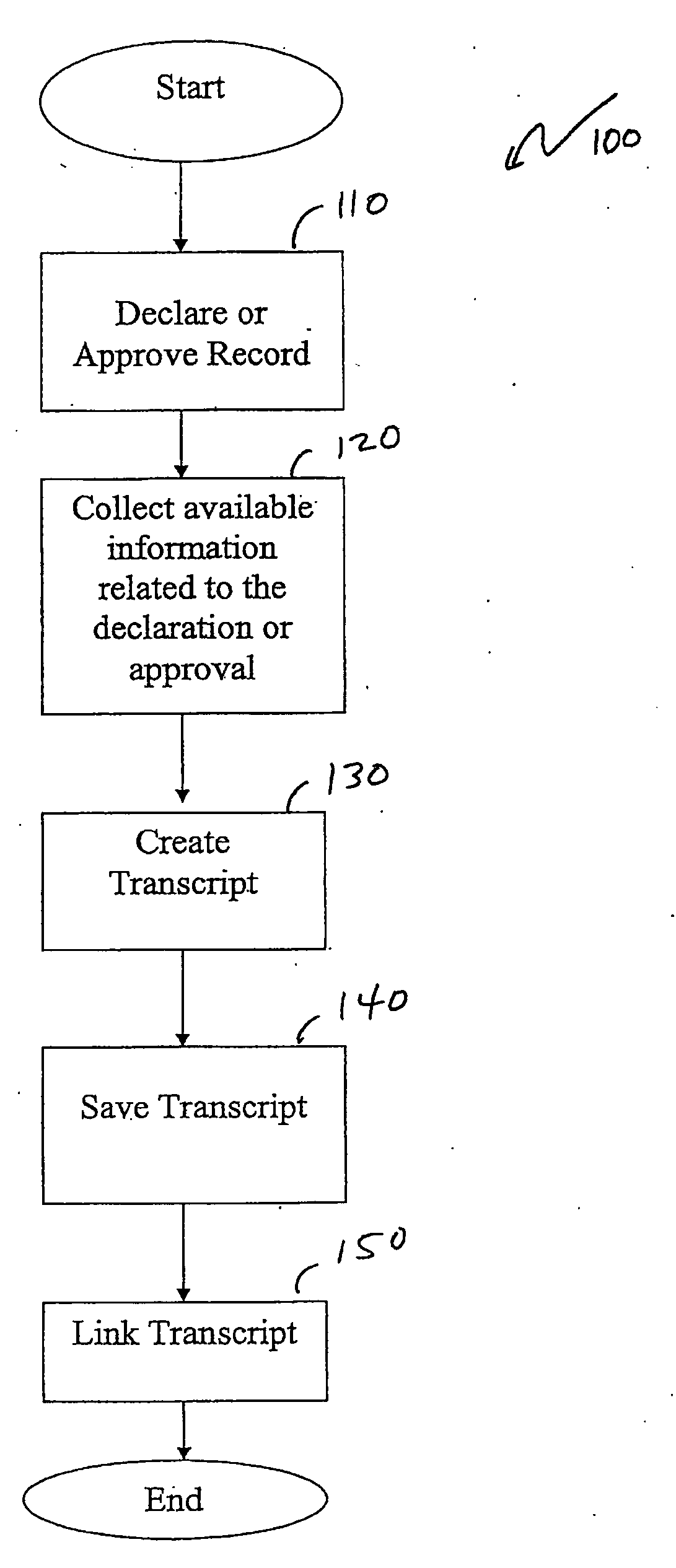
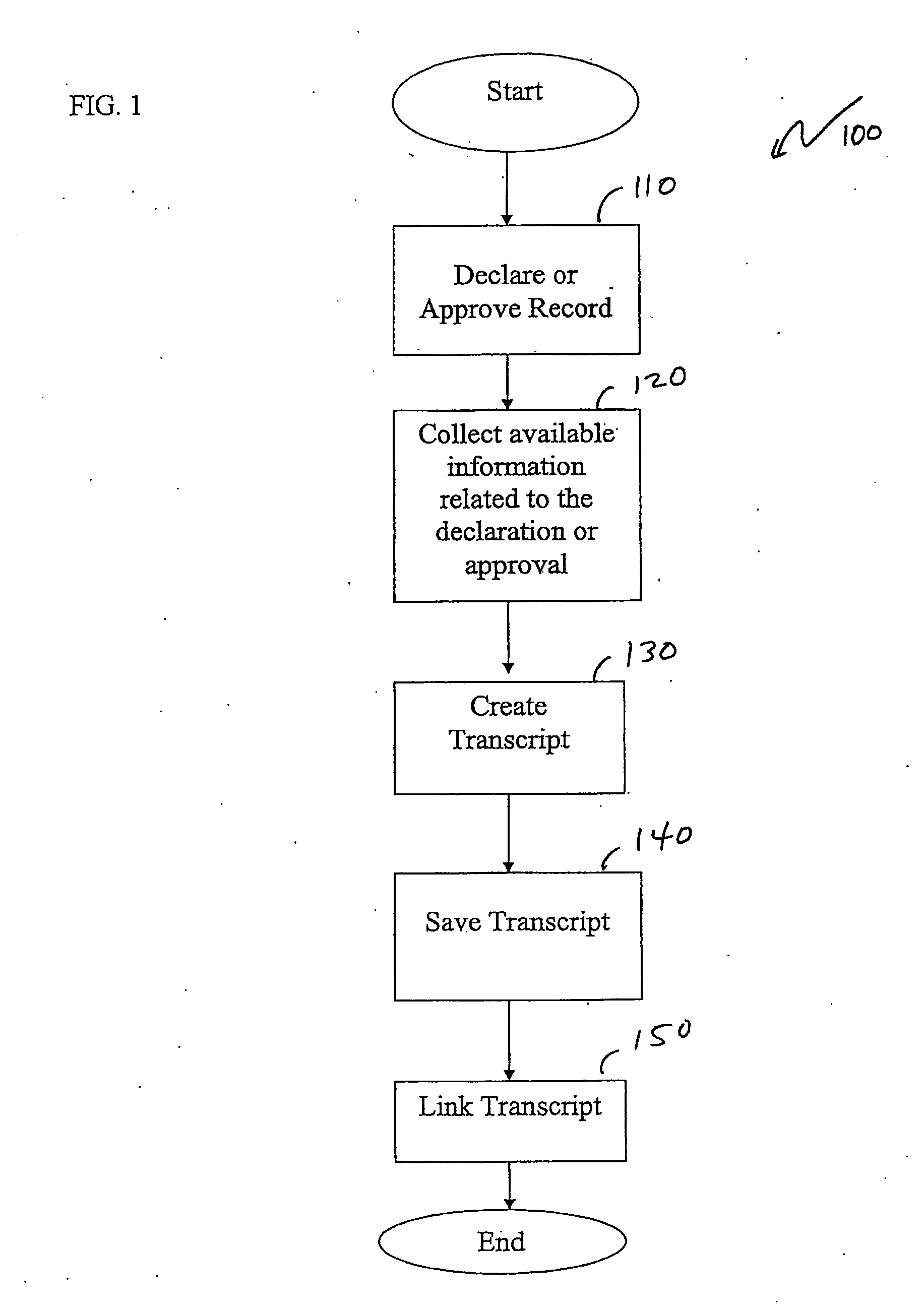
Record authentication and approval transcript
Authenticating a declared or approved record and creating a transcript related to the declaration or approval. The transcript is created based on available information at the time of declaration. The collected available information may include the user / program declaring the record, the method used to declare and / or approve the record and record content, any log or audit entries generated during the declaration, the document and record metadata (including globally unique identifiers for the record and content objects), and / or a hash of the record. The collected information may also include user information, e.g., the user's IP address or MAC address. The transcript may be saved, and linked to the record. Additionally, the hash may be revalidated at various times to ensure the accuracy of the record. Moreover, related logs may be archived and declared as records.
Owner:IBM CORP
System and method for software product test modularization
InactiveUS20060048100A1Error detection/correctionSpecific program execution arrangementsComputer hardwareTest document
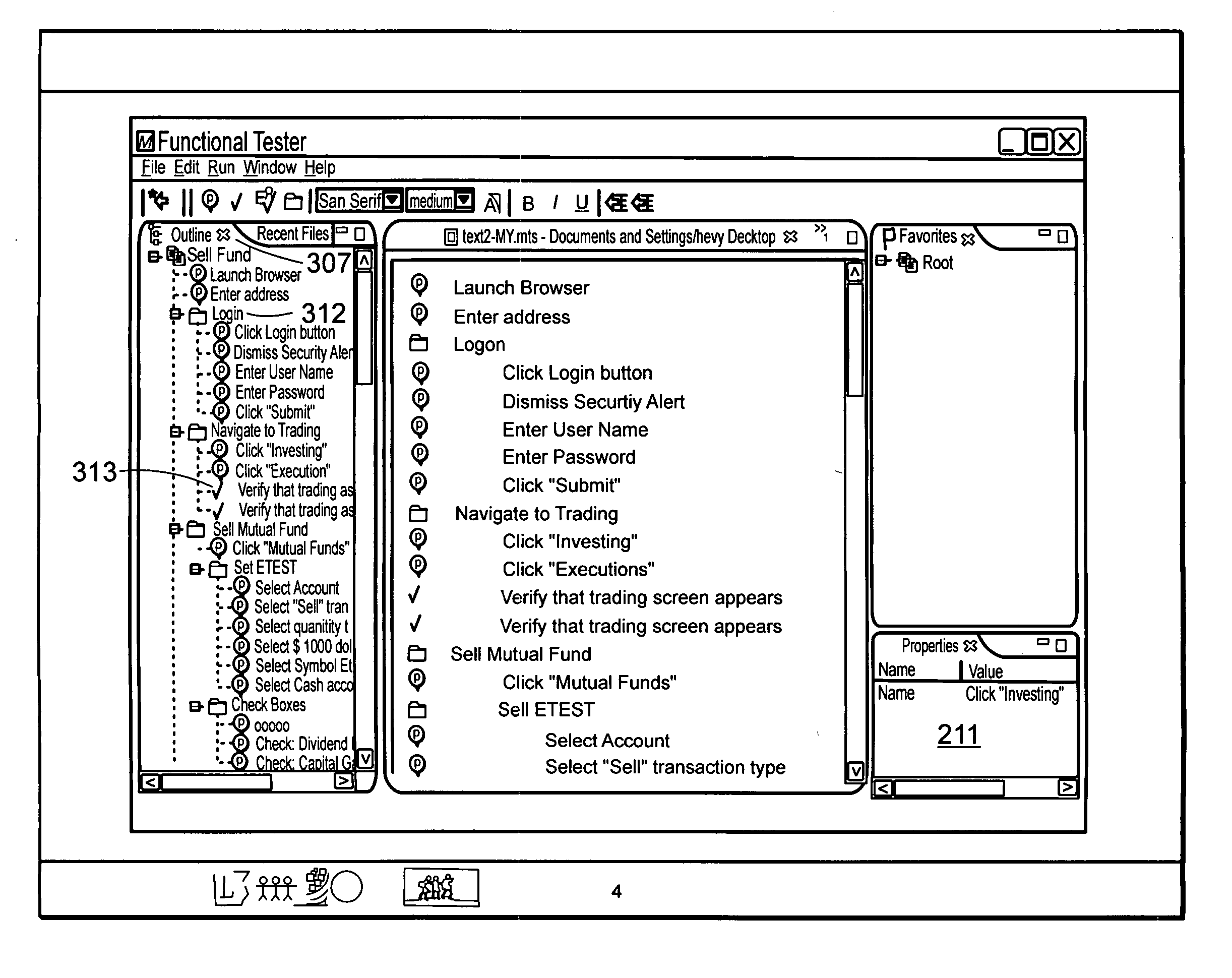
In accordance with one embodiment of the invention, there is provided a method for modularizing testing of a software product. The method comprises receiving user input indicating a source and a destination of test content; and linking modification of the test content at the destination to modification of the test content at the source. In further related embodiments, receiving the user input may comprise receiving input of a copy / paste gesture for the test content, or a drag / drop gesture for the test content. The linking may comprise using a globally unique identifier to identify each test step of a test document; and using the globally unique identifier as a pointer from the destination to the source of the test content. The method may also comprise rendering the test content to the user as if the test content was in-line at the destination.
Owner:IBM CORP
System and method for describing presentation and behavior information in an ITV application
ActiveUS7913286B2Television system detailsAnalogue secracy/subscription systemsExpiration TimeTerm memory
An ITV application definition language (ADL) used to generate ITV applications for different types of target platforms and devices. The ADL provides a plurality of core data structure types upon which one or more data structures may be built. Data structures storing ITV content presentation and behavior information are referred to as resources. A resource is associated with a globally unique identifier that allows the data structure to be efficiently stored and retrieved from a hash table. A resource is also associated with an expiration time stamp that indicates when the resource is to be freed from memory. A resource is of arbitrary length, and contains values that differ from the default values stored at a receiving client device. Resources are also packaged into a module that may be catered to a platform and / or profile of a receiving client. The client may quickly determine whether the module is relevant to it by examining the platform and / or profile ID contained in a header of the module.
Owner:MK SYST USA INC
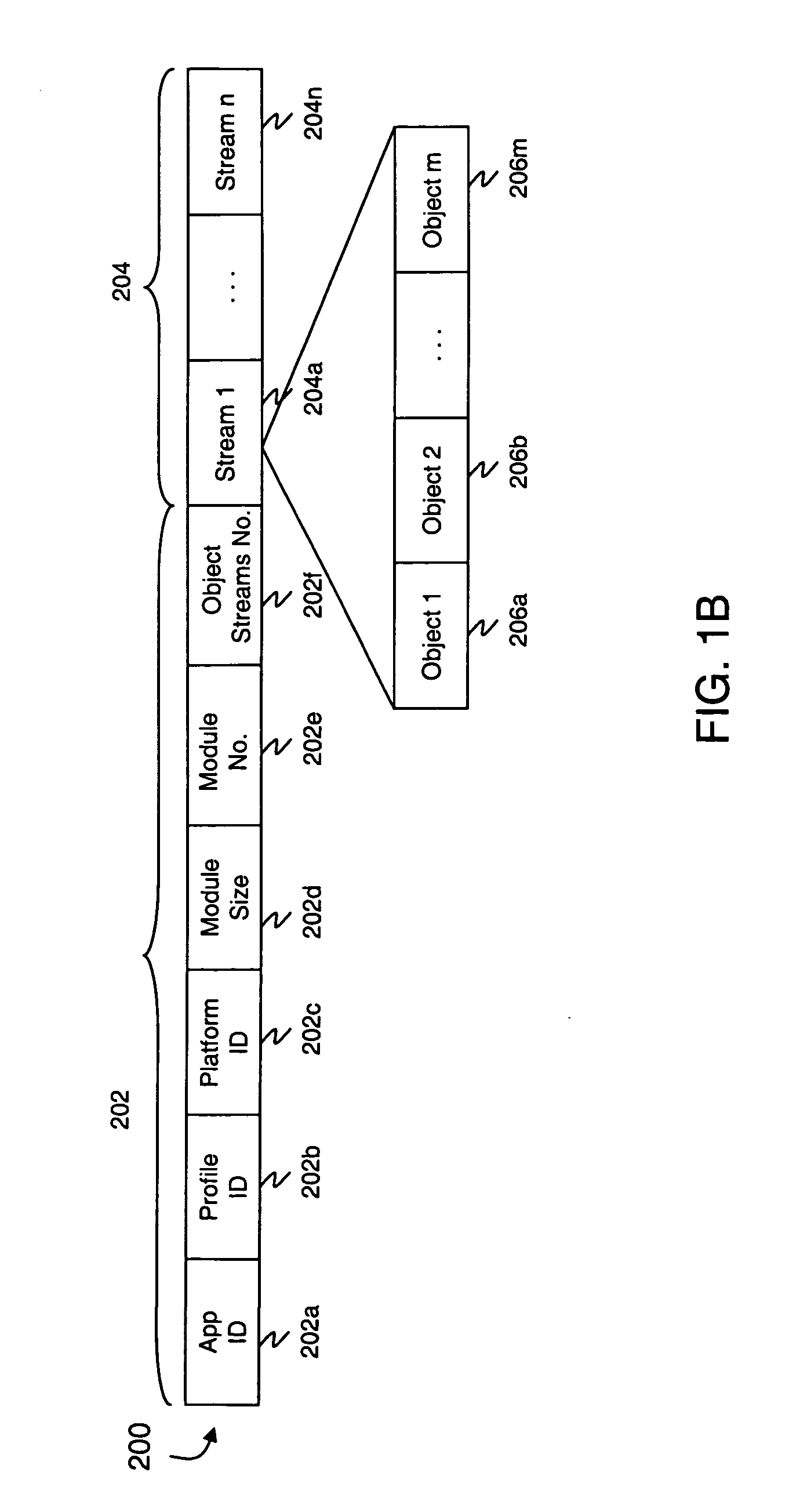
Global metadata embedding and decoding
InactiveUS7421439B2Increase flexibilityDigital data processing detailsCharacter and pattern recognitionDocument IdentifierUnique identifier
Global metadata, such as a document identifier, which may be a globally unique identifier, is embedded into an embedded interactive code document by combining a first m-array and a plurality of copies of the first m-array to generate a combined m-array with encoded global metadata such that respective start positions (xd,yd)i of the plurality of copies of the first m-array in the combined m-array are each shifted, by respective amounts that are based on respective portions of the global metadata, relative to a start position of the first m-array in the combined m-array. Global metadata may be decoded from the combined m-array by determining the respective amounts by which the plurality of copies of the first m-array are shifted, relative to the first m-array, in the combined m-array and by combining the respective amounts to produce a decoded value of the global metadata.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com