Patents
Literature
655 results about "Expiration Time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
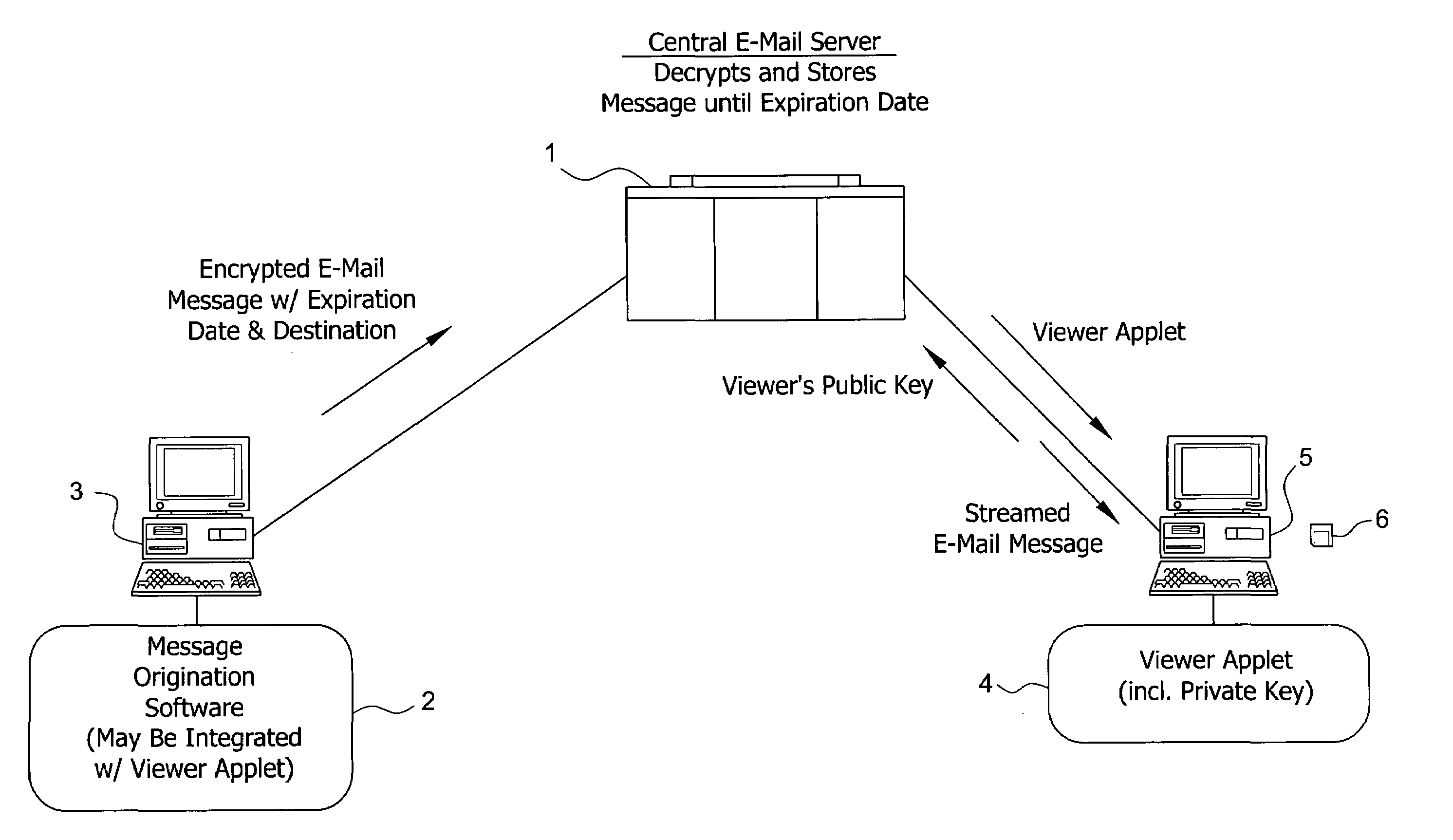
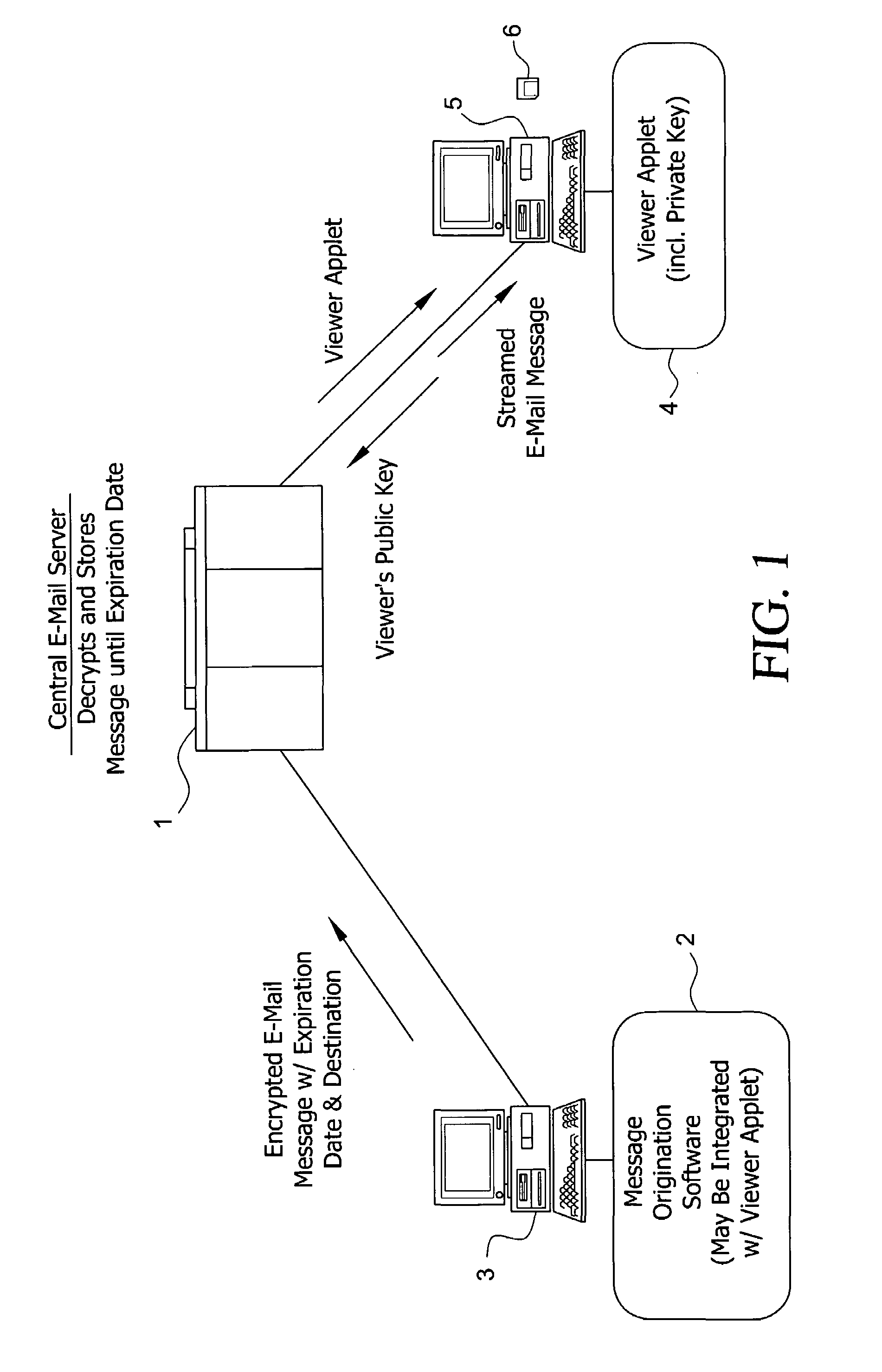
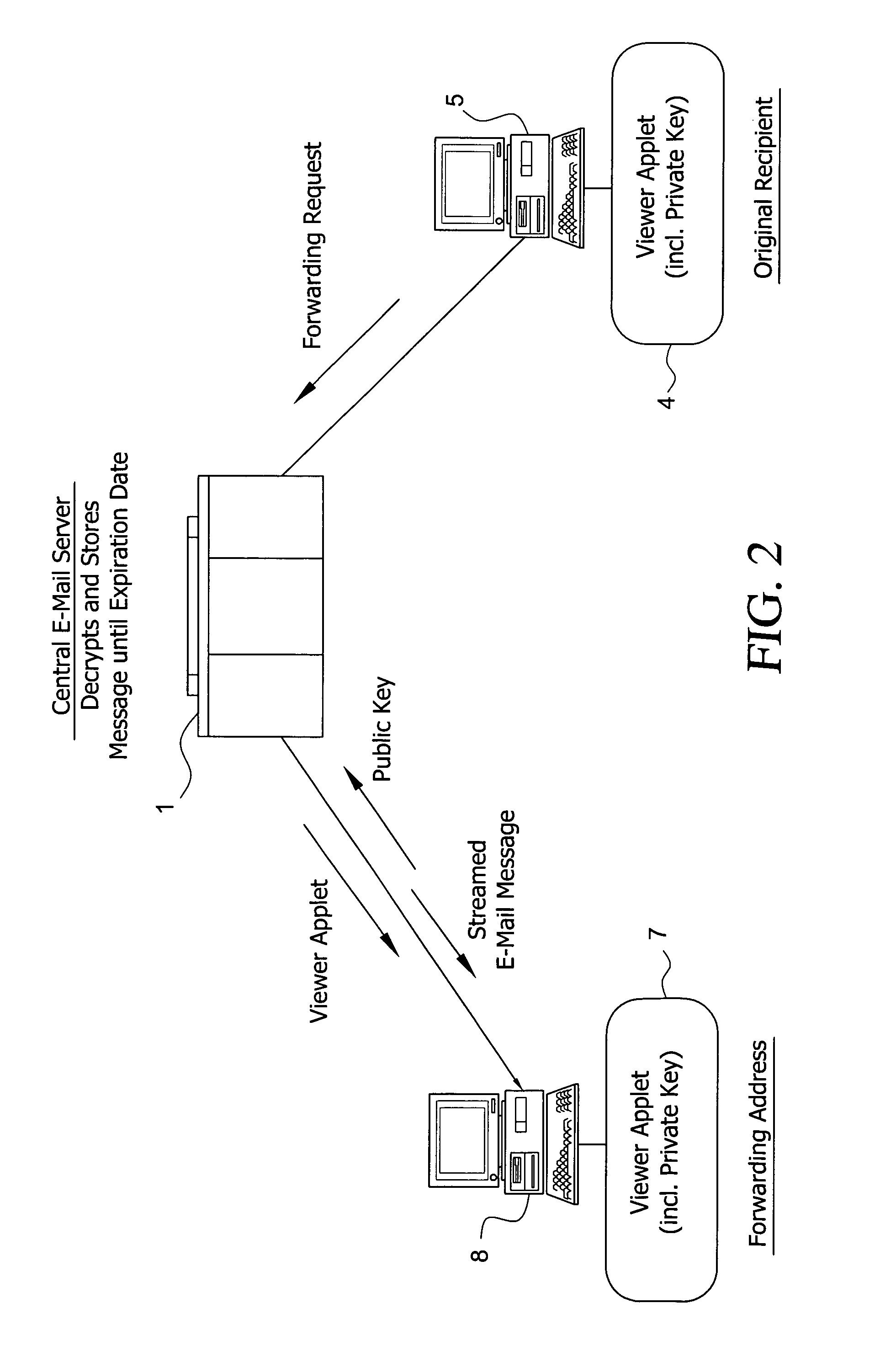
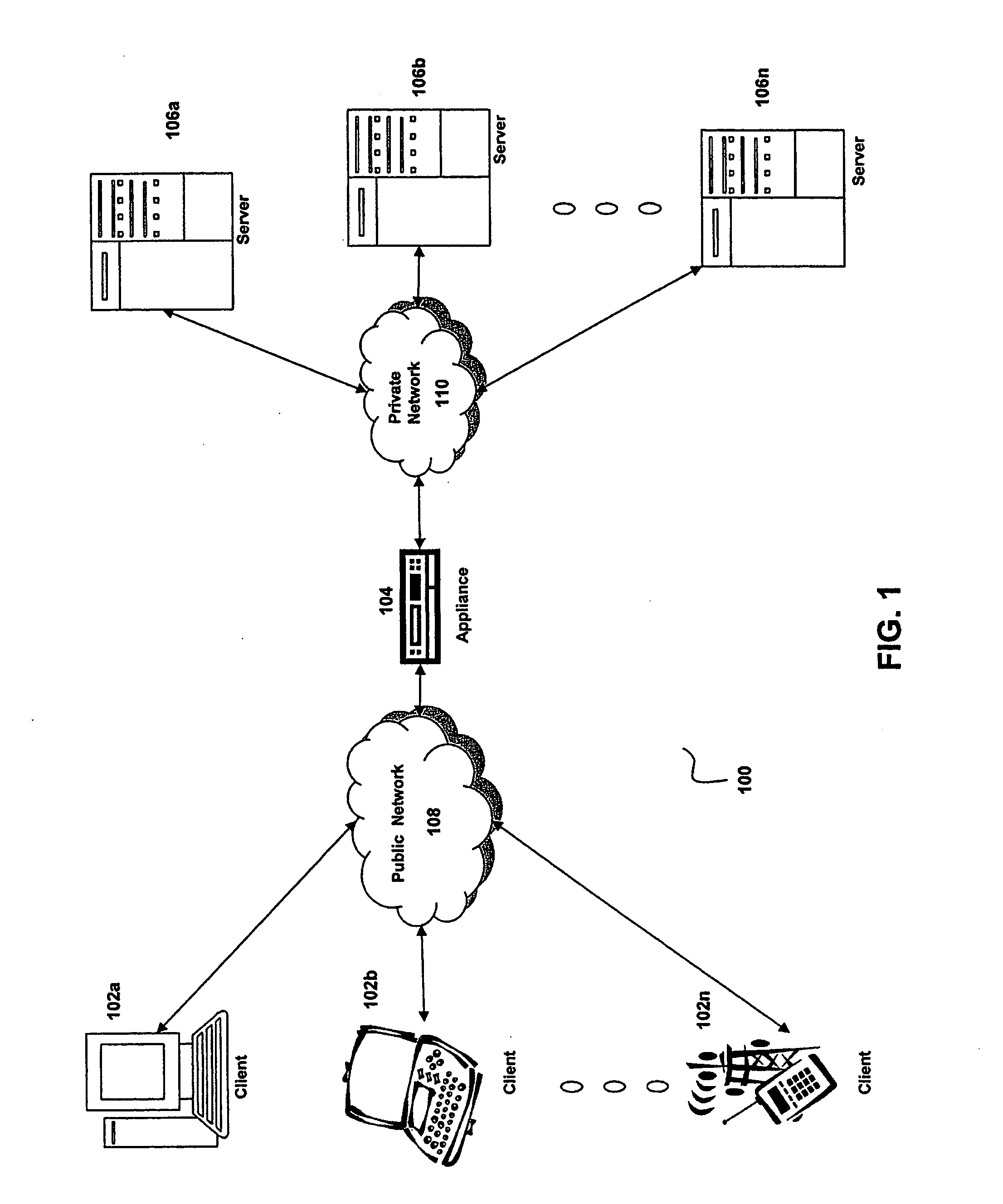
System and method for enabling the originator of an electronic mail message to preset an expiration time, date, and/or event, and to control processing or handling by a recipient
InactiveUS7149893B1Limited lifespanRapid and efficient mannerDigital data processing detailsAnalogue secracy/subscription systemsExpiration TimeComputer hardware
An electronic mail system and method enables the originator of a message sent by electronic mail to select a date, time, or event at which the message and all incarnations of the message to self-destruct, regardless of the number and types of computers or software systems that may have interacted with the message. The system and message also permits the originator to include processing and handling limitations. The necessary control over the message is achieved by encrypting the message and enabling viewing only through a viewer applet arranged to facilitate destruction of the message upon the occurrence of the selected expiration time, date, or event, and to implemented the handling and processing limitations. A central server can be used to exercise additional control over the message by serving as a proxy destination, and by streaming the encrypted message to the viewer applet. The viewer applet can be transmitted to new recipients with the message so that the system and method can direct mail to any electronic mail user.
Owner:RESOURCE CONSORTIUM LTD LLC
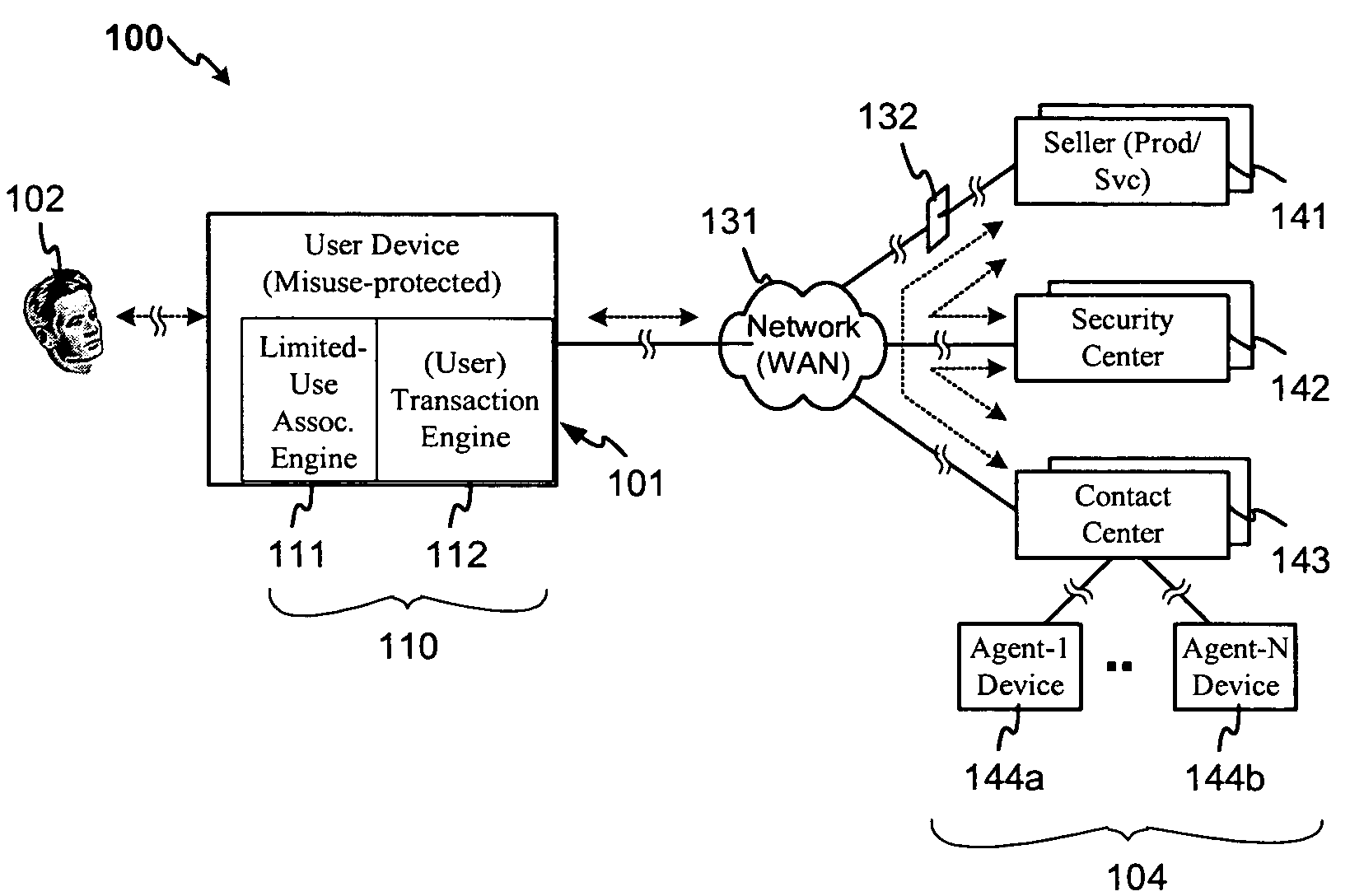
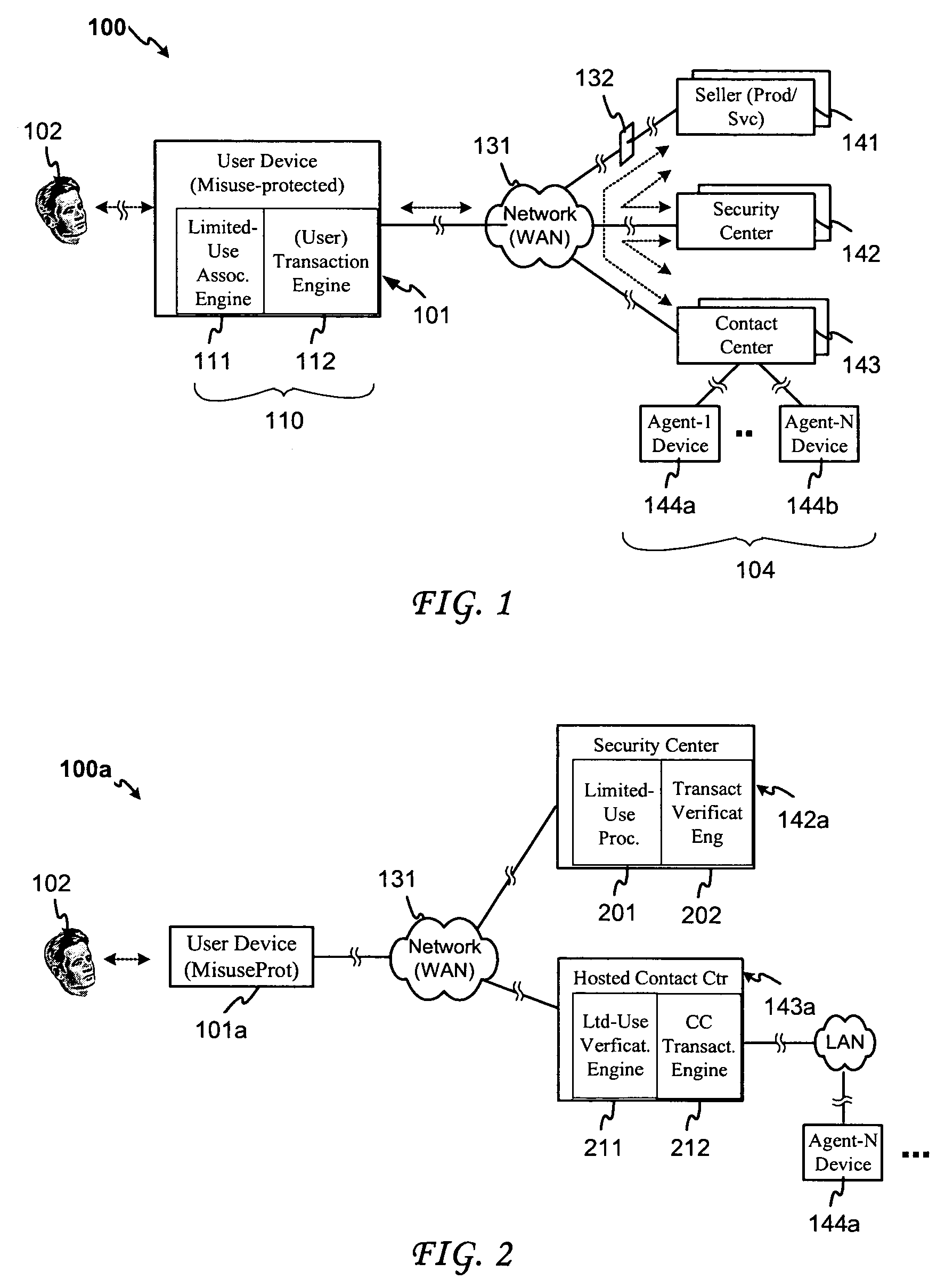
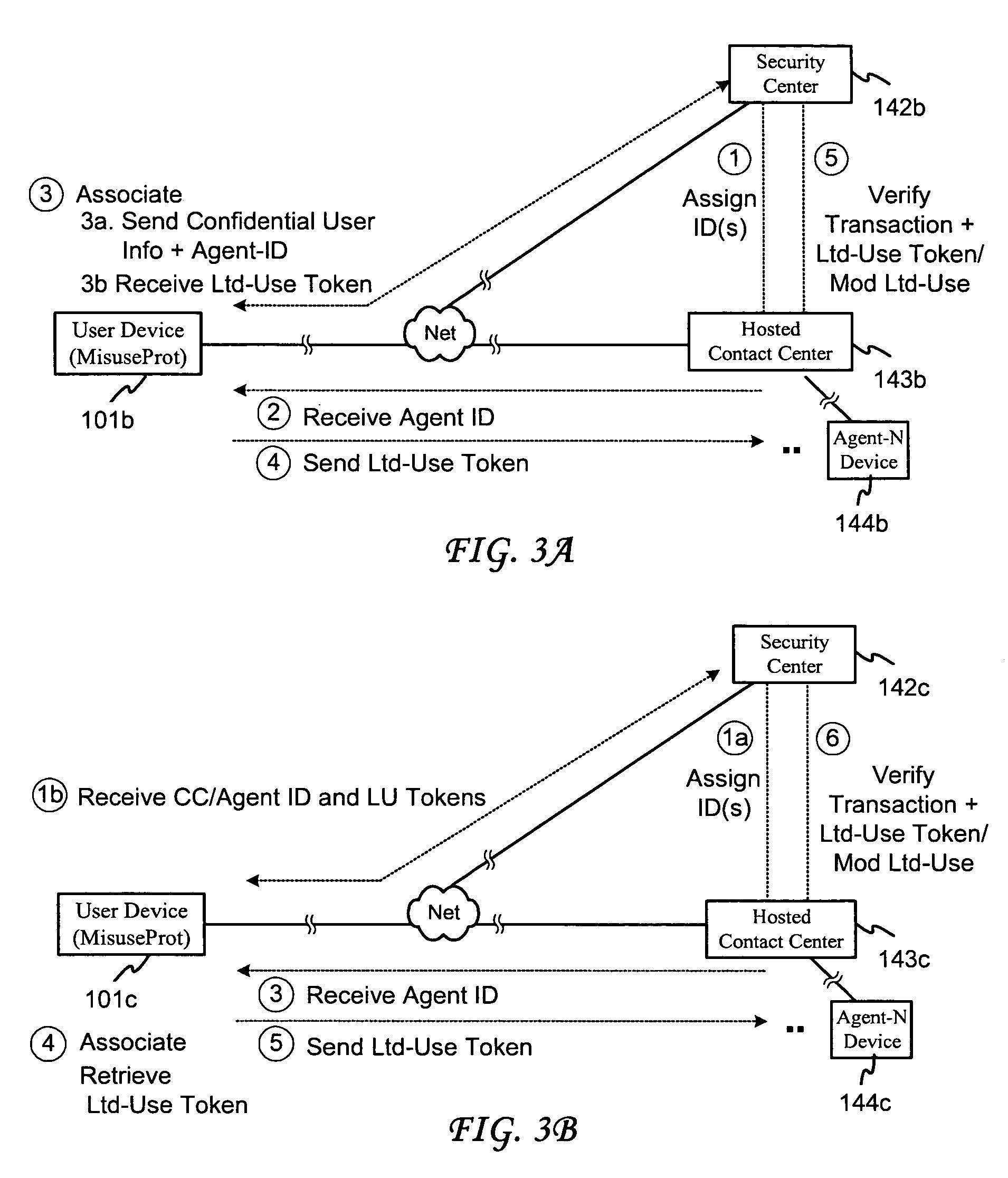
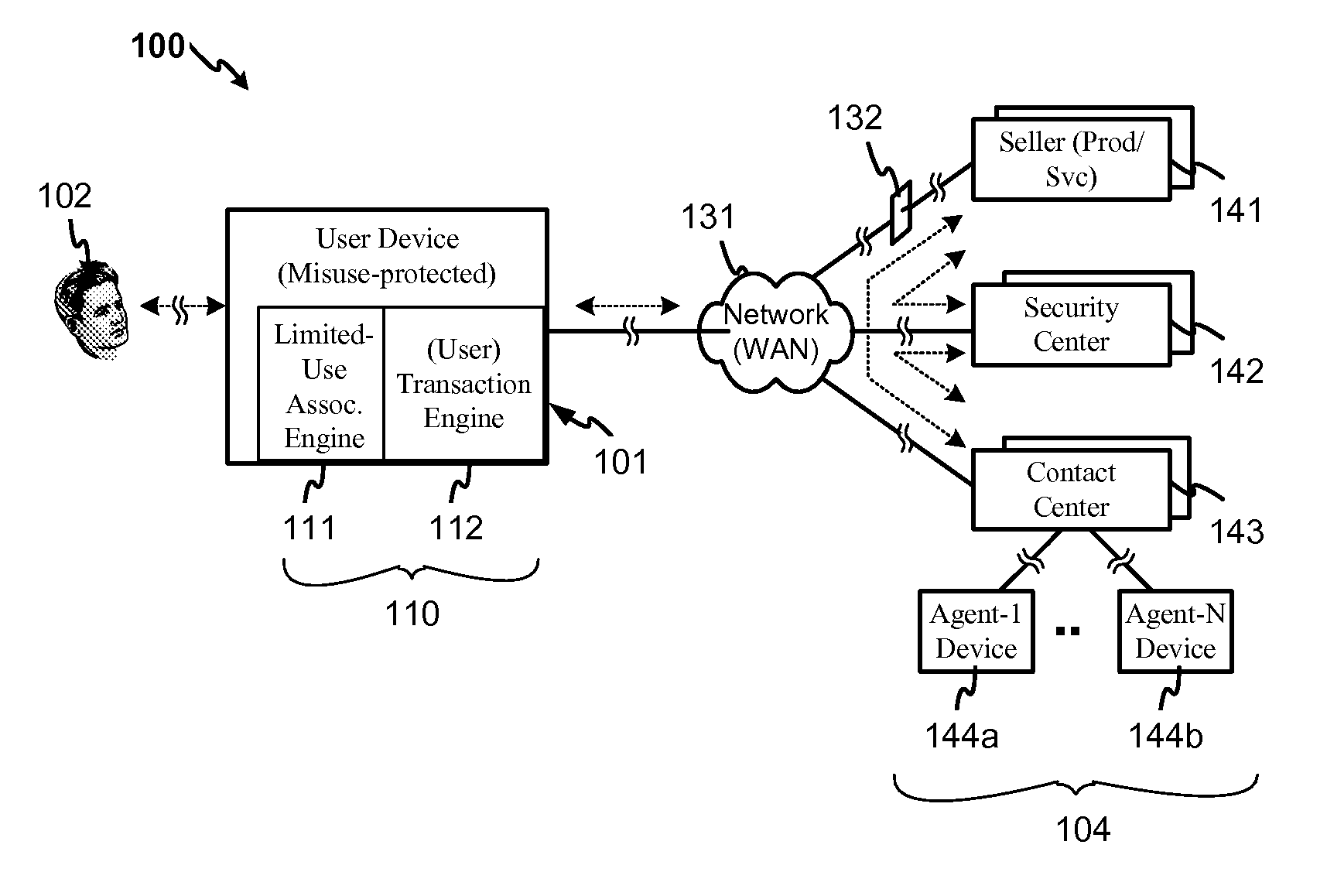
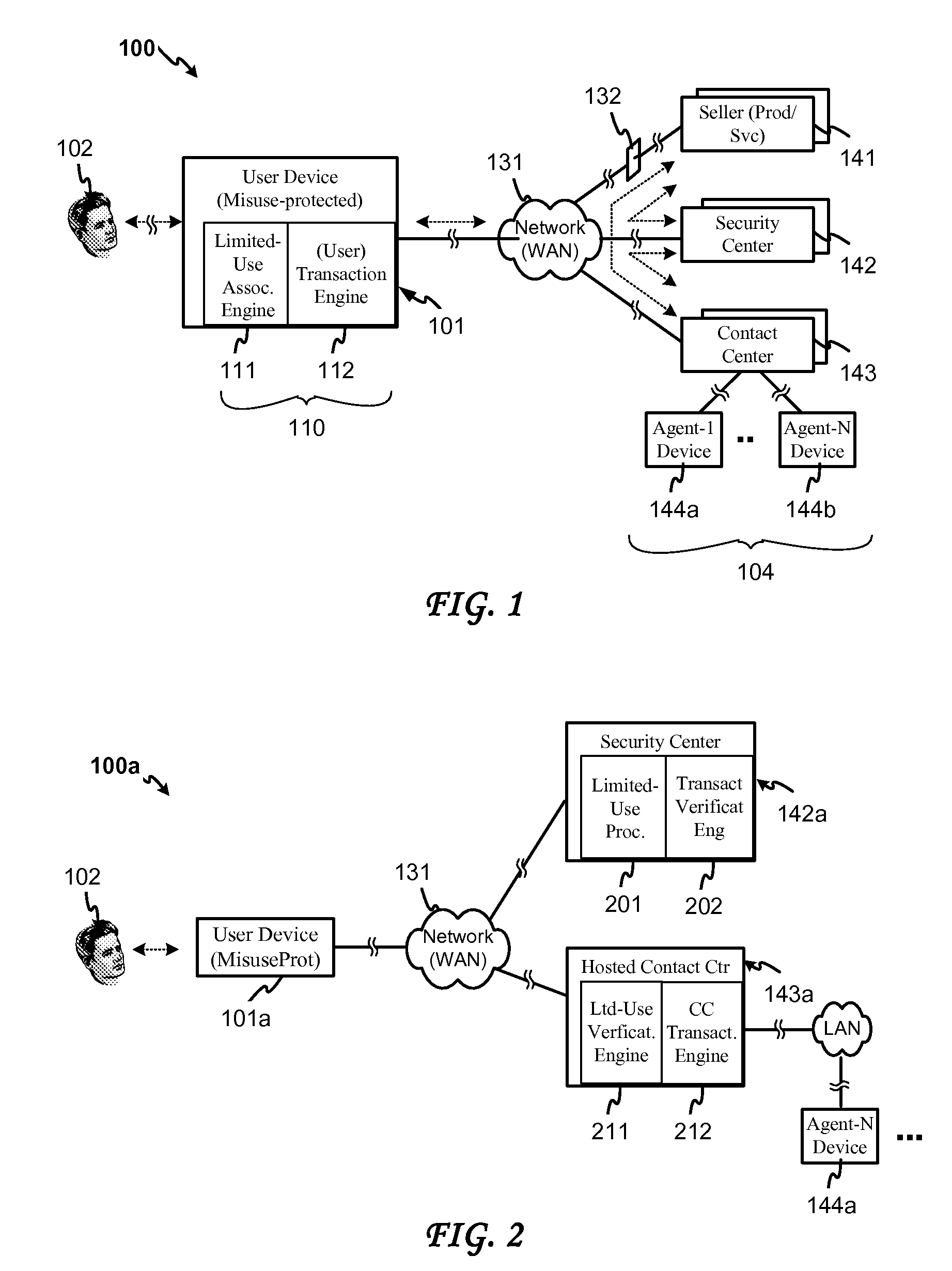
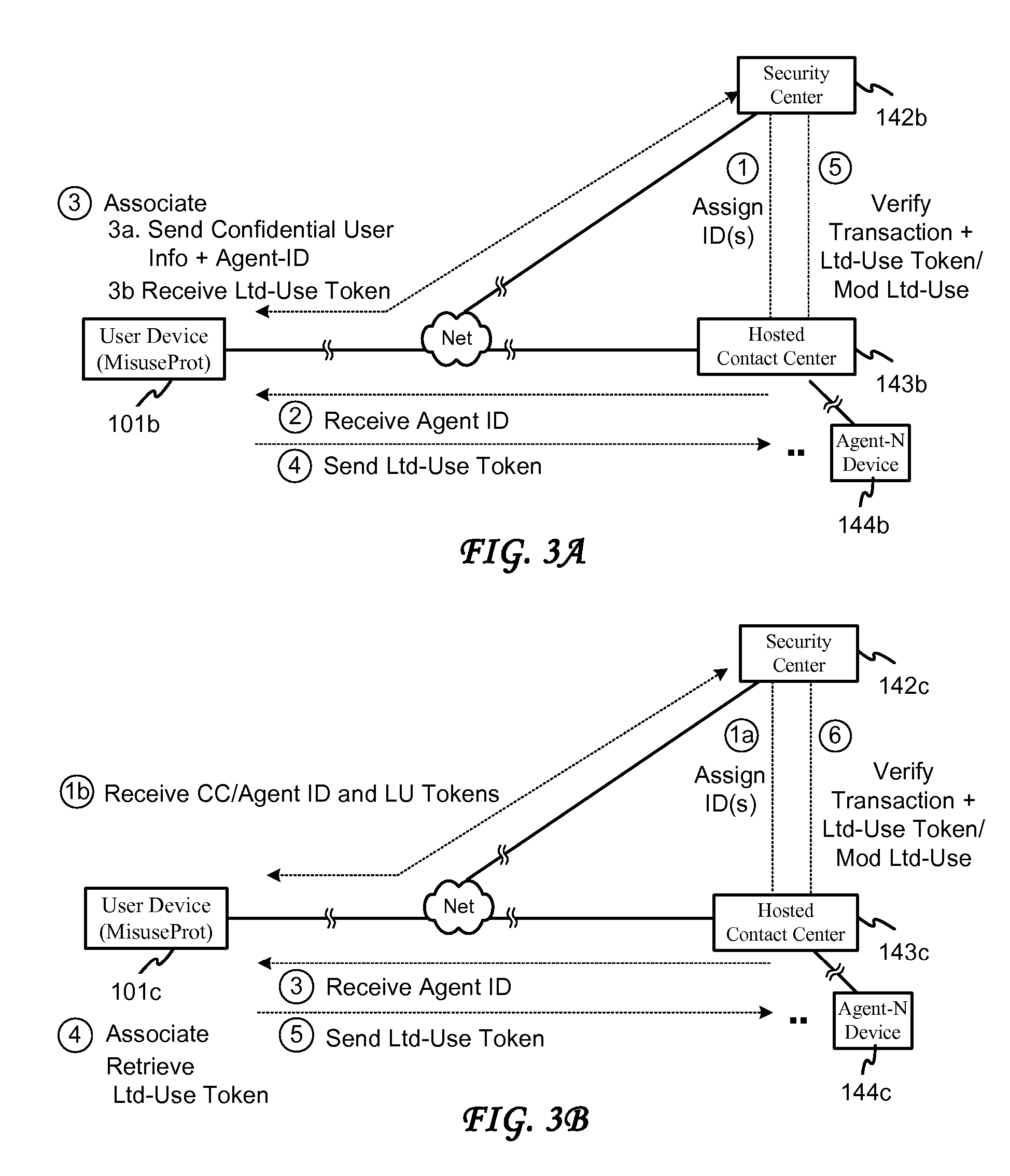
System and method for securing transactions in a contact center environment
ActiveUS7287692B1Avoid misuseGreat confidenceComplete banking machinesFinanceExpiration TimeAuthorization
A system and method for protecting confidential user information employed in an electronic transaction. The system and method provide for associating an expiration time / time period, use or other use-limiting authorization indicator with a credit card or other user information to be transferred to a user information recipient, in conjunction with a product / service payment or other business transaction with a hosted contact center. Embodiments of the invention further provide for forming a limited-use indicator, such as a use-limiting token, by associating a transaction agent indicator and a use-limiting indicator with the user information, and for verifying a limited use indicator received from a contact center agent and determining according to such indicator, in addition to any ordinary verification that might also be conducted, whether the use limitation has been met and whether the transaction should be authorized in accordance with the use limitation.
Owner:CISCO TECH INC
Secure content delivery system
InactiveUS20030097564A1Metering/charging/biilling arrangementsUser identity/authority verificationExpiration TimeRelevant information
A secure streaming content delivery system provides a plurality of content servers connected to a network that host customer content that can be cached and / or stored, e.g., images, video, text, and / or software. The content servers respond to requests for customer content from users. The invention load balances user requests for cached customer content to the appropriate content server. A user makes a request to a customer's server / authorization server for delivery of the customer's content. The authorization server checks if the user is authorized to view the requested content. If the user is authorized, then the authorization server generates a hash value using the authorization server's secret key, the current time, a time-to-live value, and any other information that the customer has configured, and embeds it into the URL which is passed to the user. A content server receives a URL request from the user for customer content cached on the content server. The request is verified by the content server creating its own hash value using the customer server's secret key, the current time, a time-to-live value, and any other related information configured for the customer. If the hash value from the URL matches the content server's generated hash value, then the user's request is valid and within the expiration time period and the content server delivers the requested content to the user.
Owner:AKAMAI TECH INC
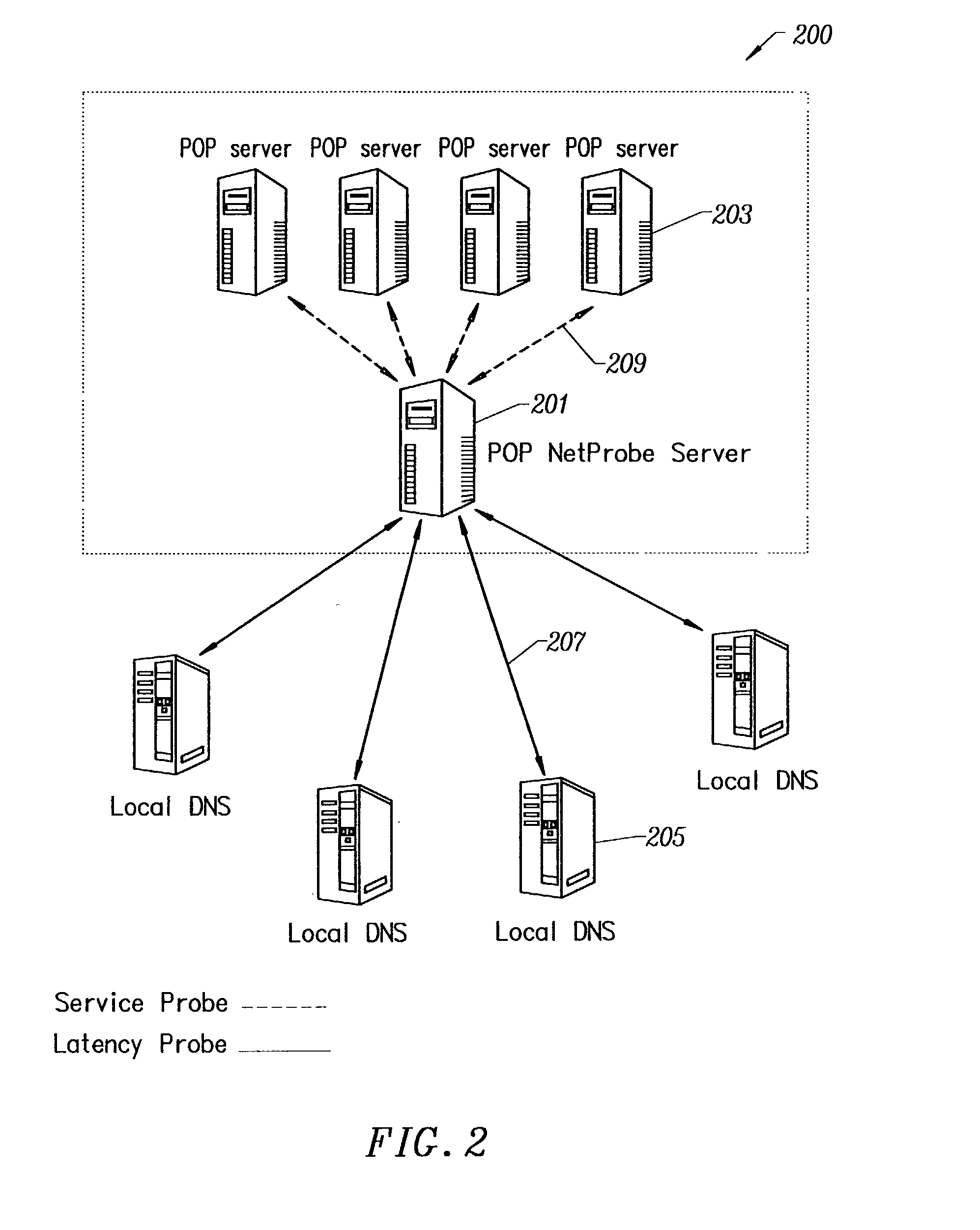
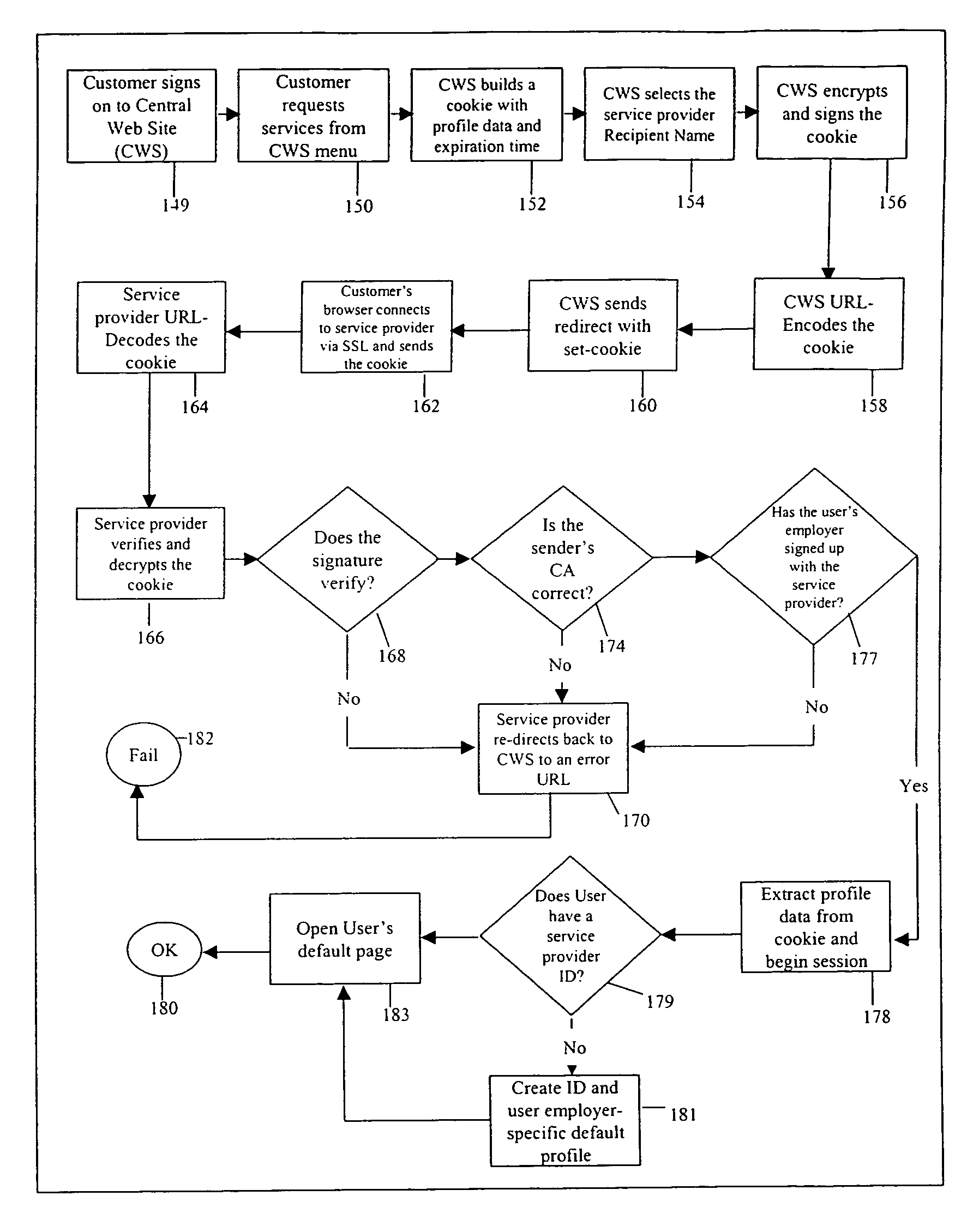
Method and system for single sign-on user access to multiple web servers
InactiveUS7137006B1User identity/authority verificationDigital data authenticationExpiration TimeHyperlink
Methods and systems for single sign-on user access to multiple web servers are provided. A user is authenticated at a first web server (e.g., by user name and password). The first web server provides a web page to the user having a service selector (e.g., a hyperlink comprising the URL of a second web server offering the service indicated by the selector). When the user activates the service selector, the first web server constructs and transmits an encrypted authentication token (e.g., a cookie) from the first web server to a second web server via the user client. The first and second web servers share a sub-domain. The authentication token comprises an expiration time and is digitally signed by the first web server and is authenticated at the second web server. Upon authentication, the second web server allows the user to conduct a session at the second web server.
Owner:CITICORP CREDIT SERVICES INC (USA)
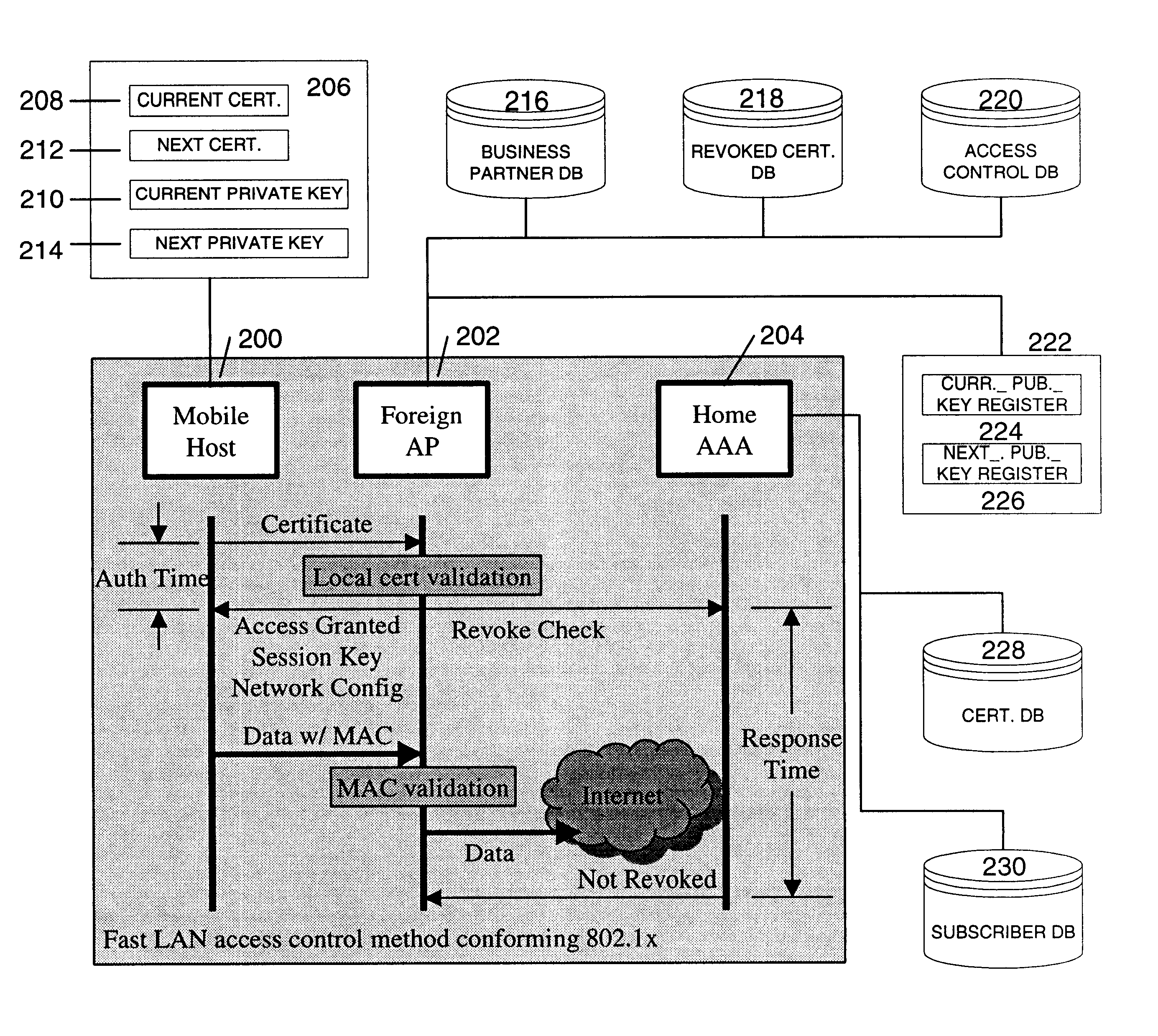
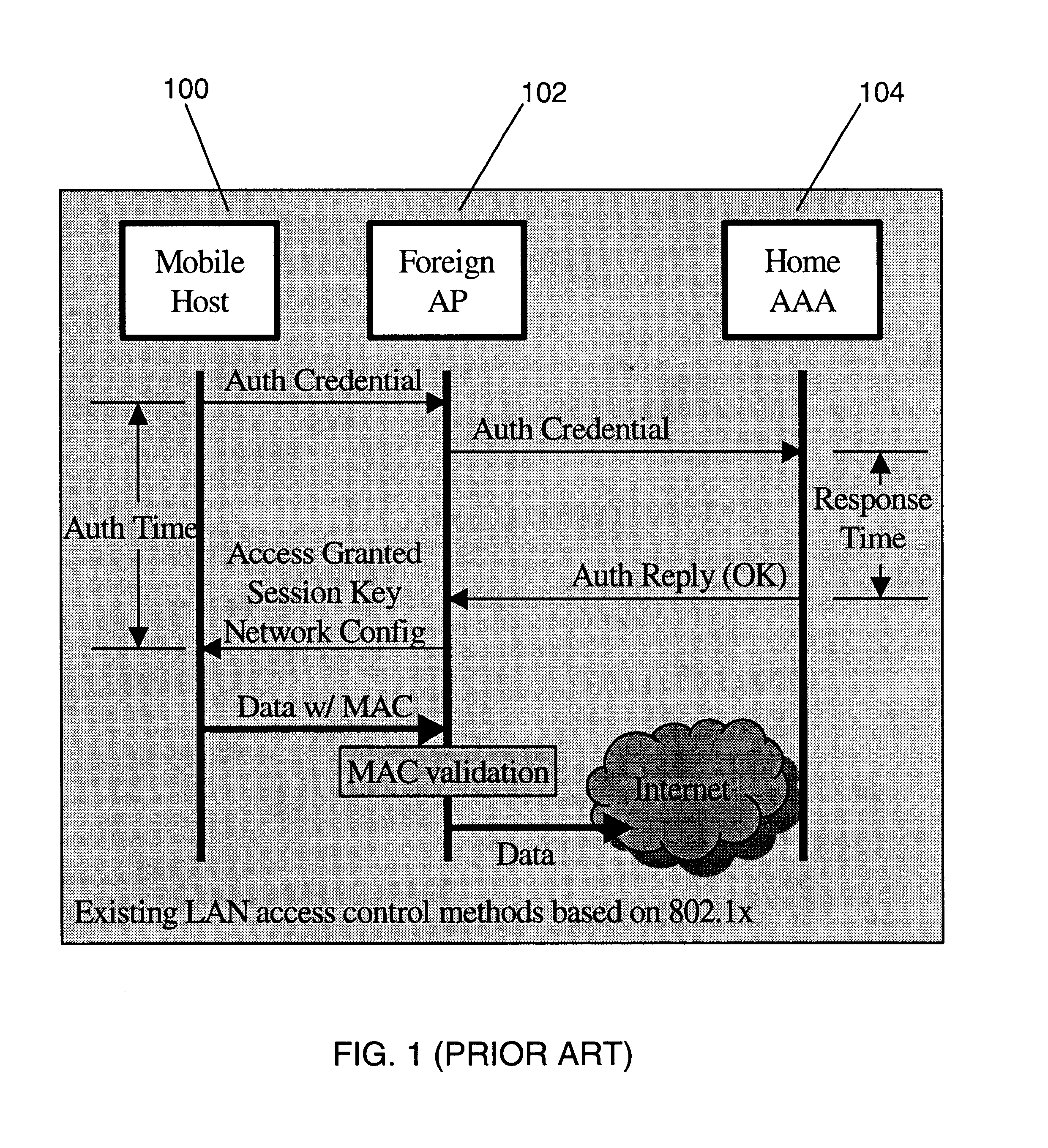
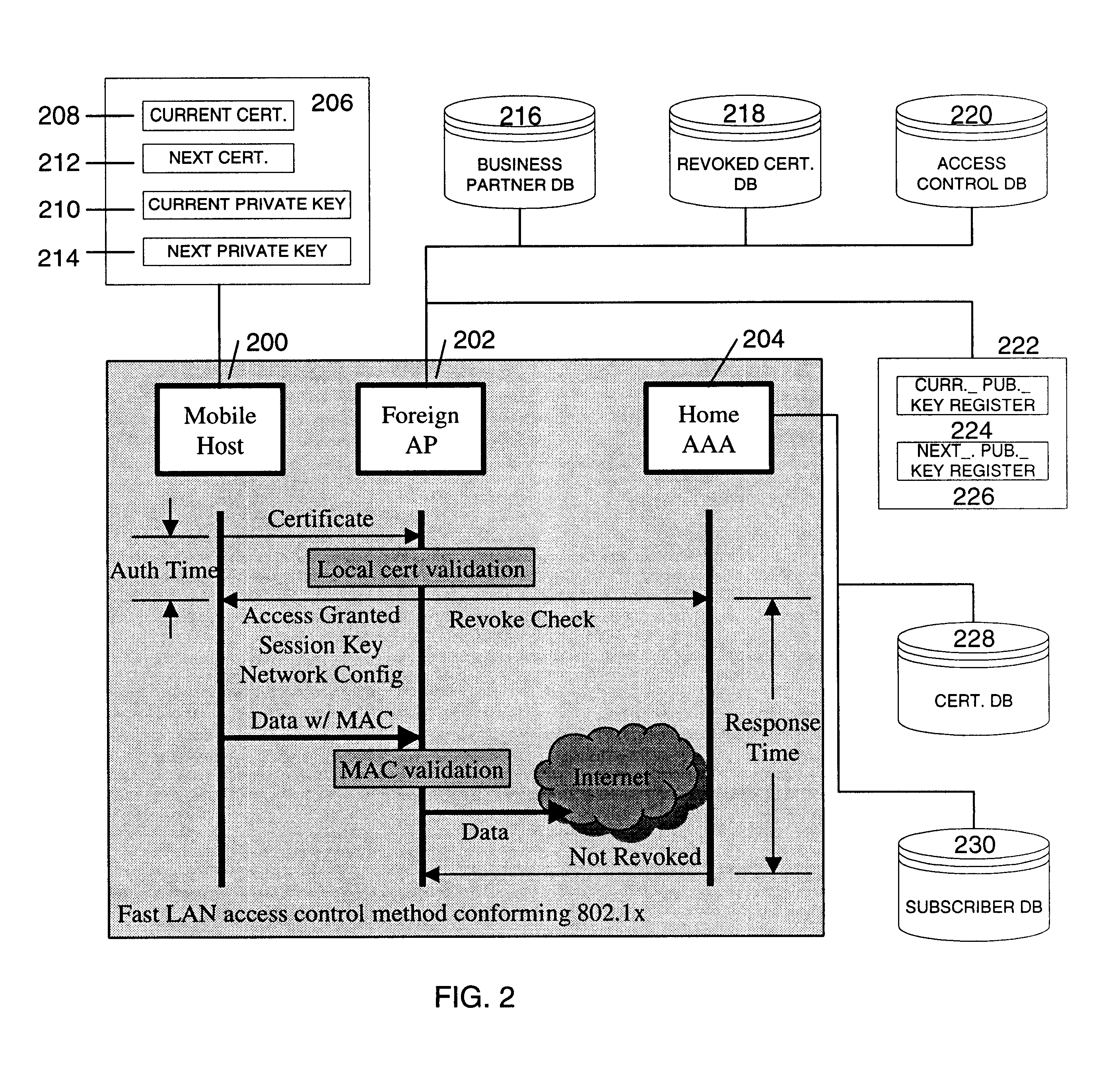
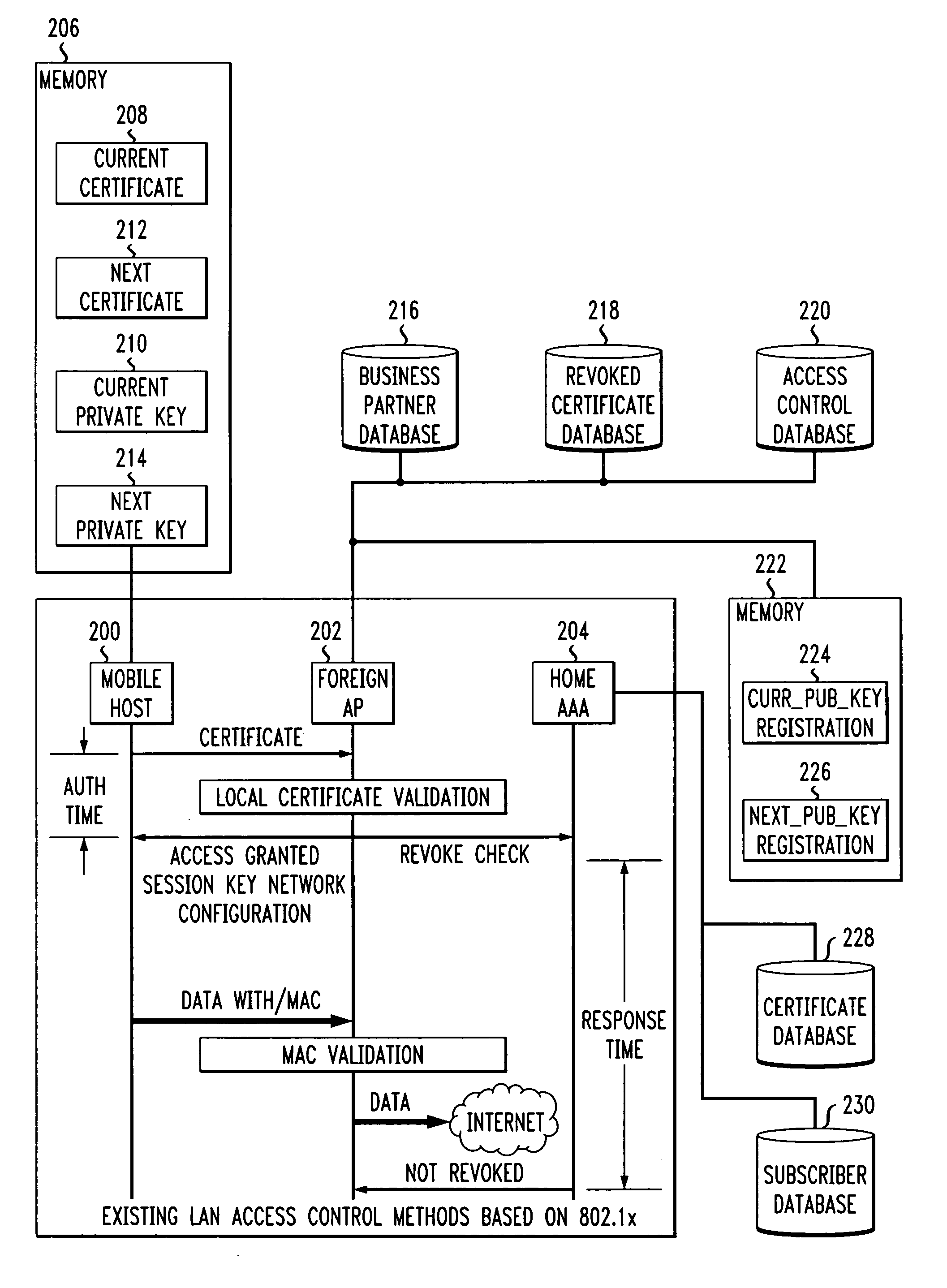
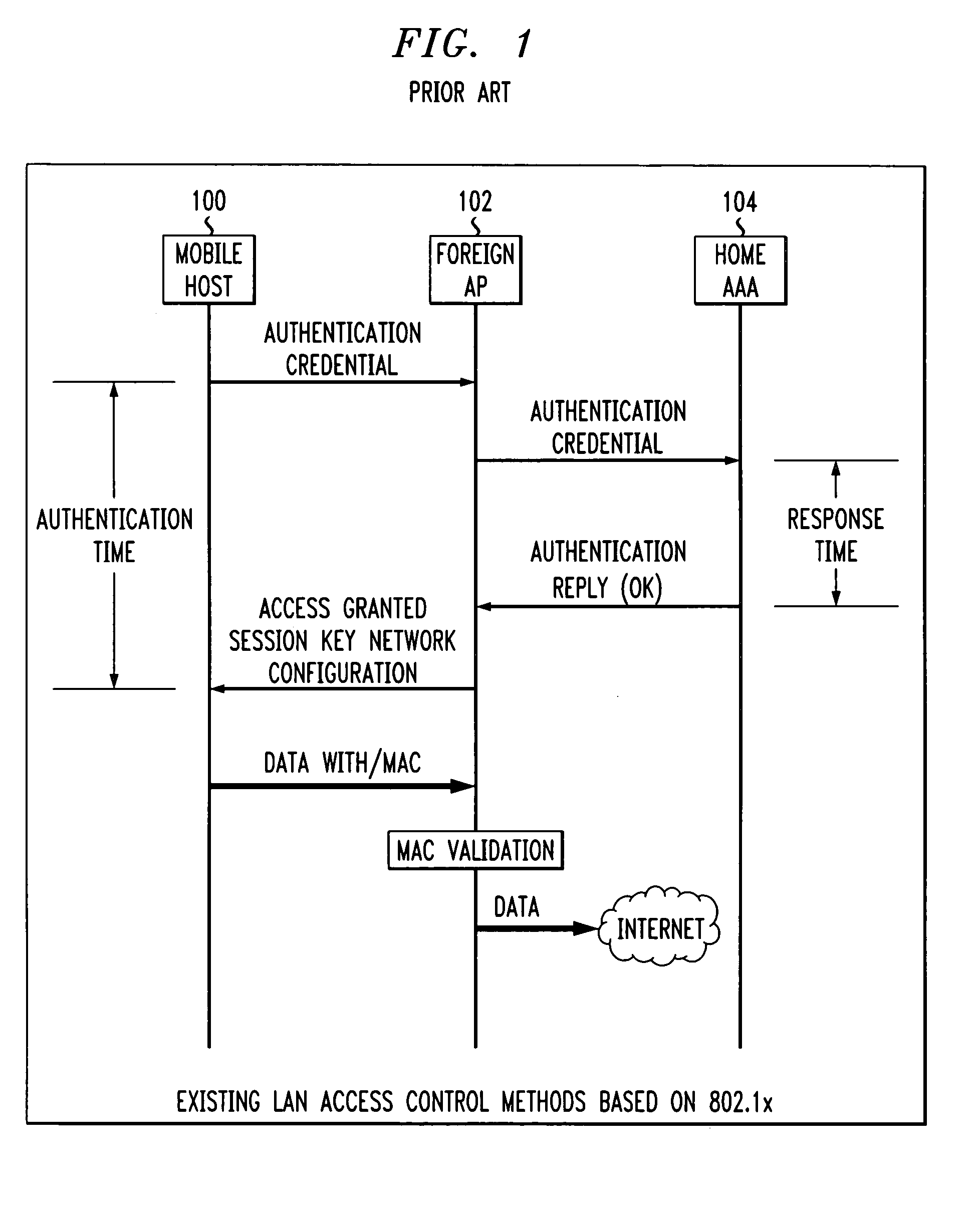
Fast authentication and access control system for mobile networking
InactiveUS6856800B1Easy to switchReduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
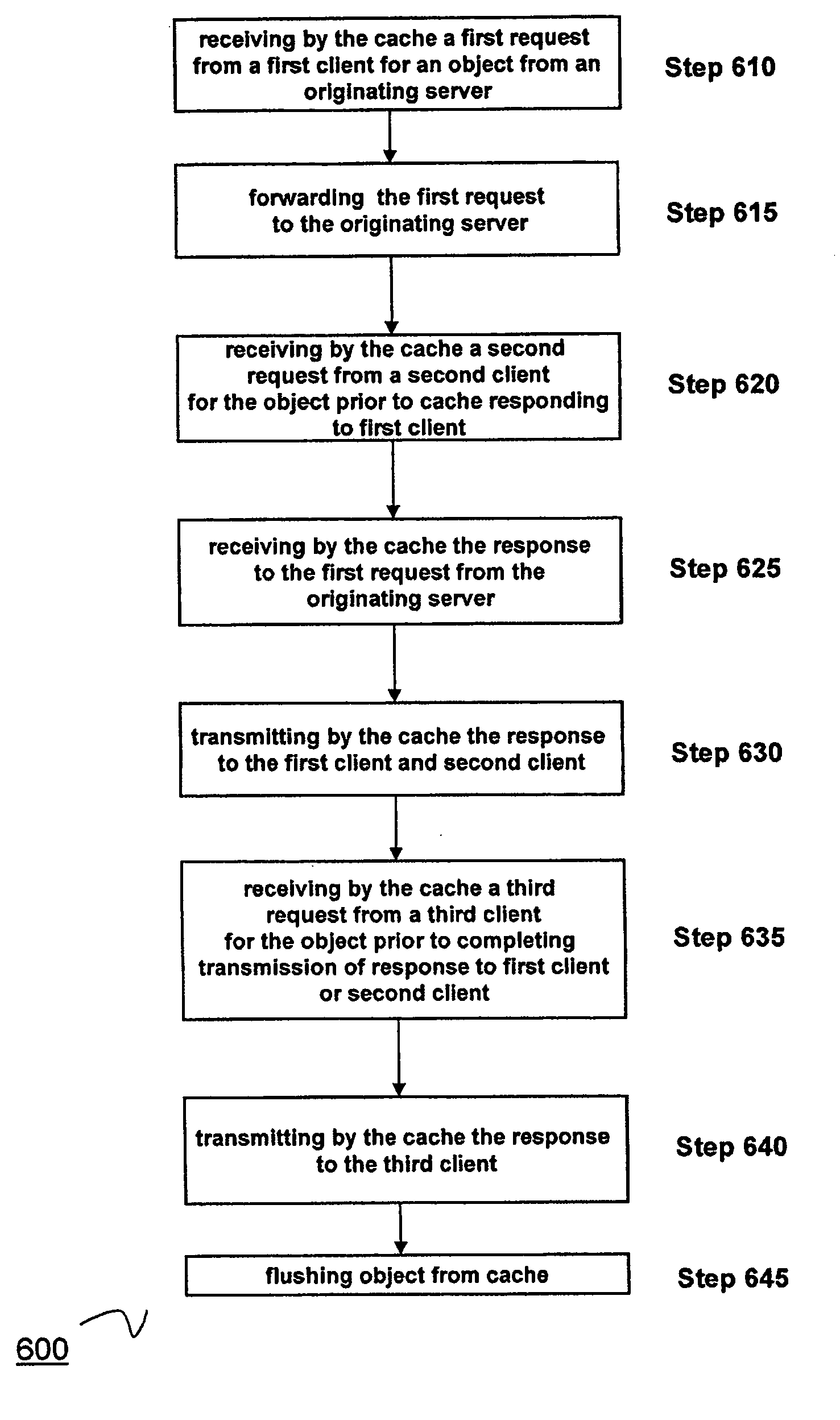
System and method for performing granular invalidation of cached dynamically generated objects in a data communication network
ActiveUS20070156966A1Great time intervalMemory architecture accessing/allocationMemory systemsExpiration TimeGranularity
The present invention is directed towards a method and system for providing granular timed invalidation of dynamically generated objects stored in a cache. The techniques of the present invention incorporates the ability to configure the expiration time of objects stored by the cache to fine granular time intervals, such as the granularity of time intervals provided by a packet processing timer of a packet processing engine. As such, the present invention can cache objects with expiry times down to very small intervals of time. This characteristic is referred to as “invalidation granularity.” By providing this fine granularity in expiry time, the cache of the present invention can cache and serve objects that frequently change, sometimes even many times within a second. One technique is to leverage the packet processing timers used by the device of the present invention that are able operate at time increments on the order of milliseconds to permit invalidation or expiry granularity down to 10 ms or less.
Owner:CITRIX SYST INC
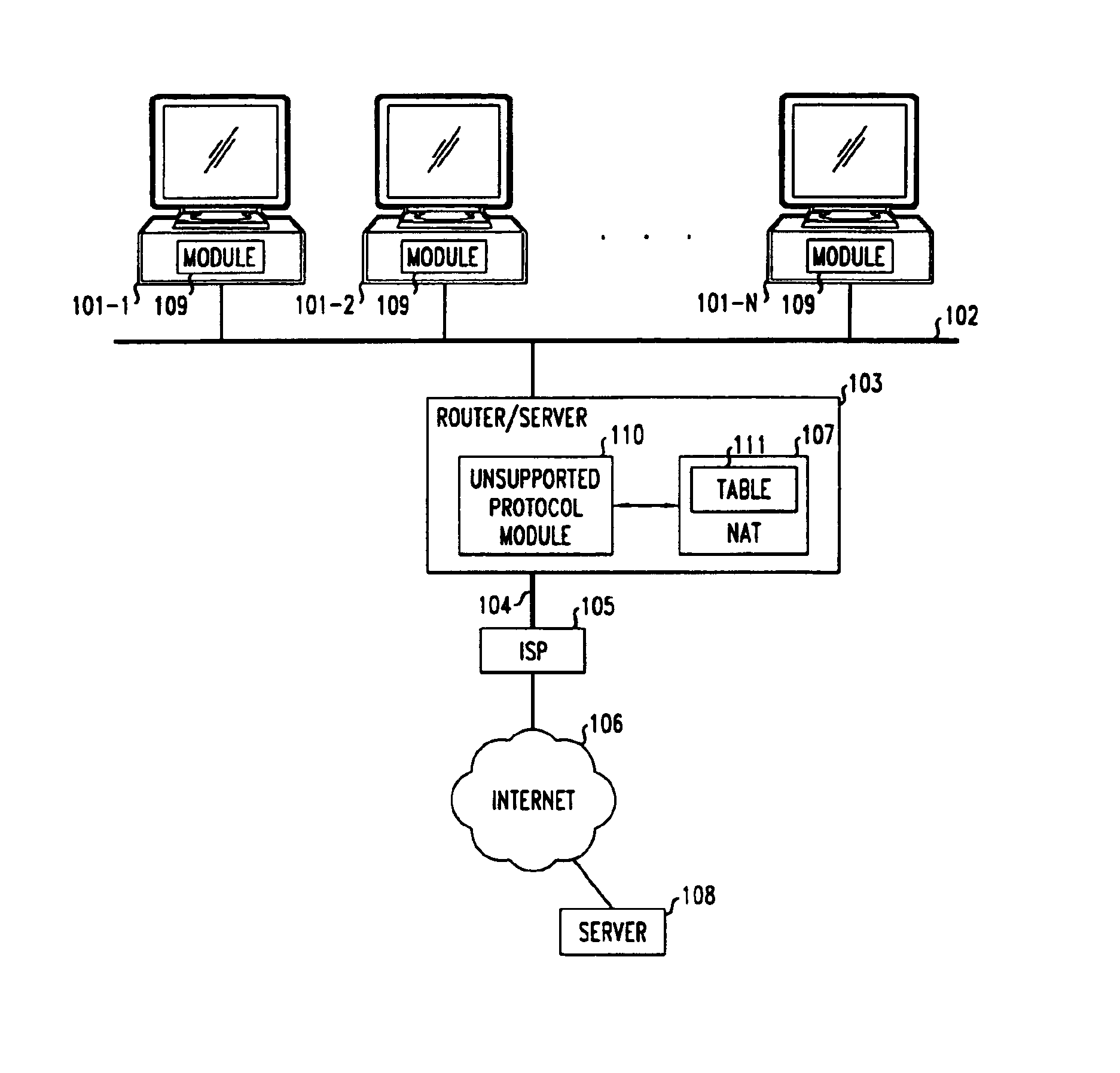
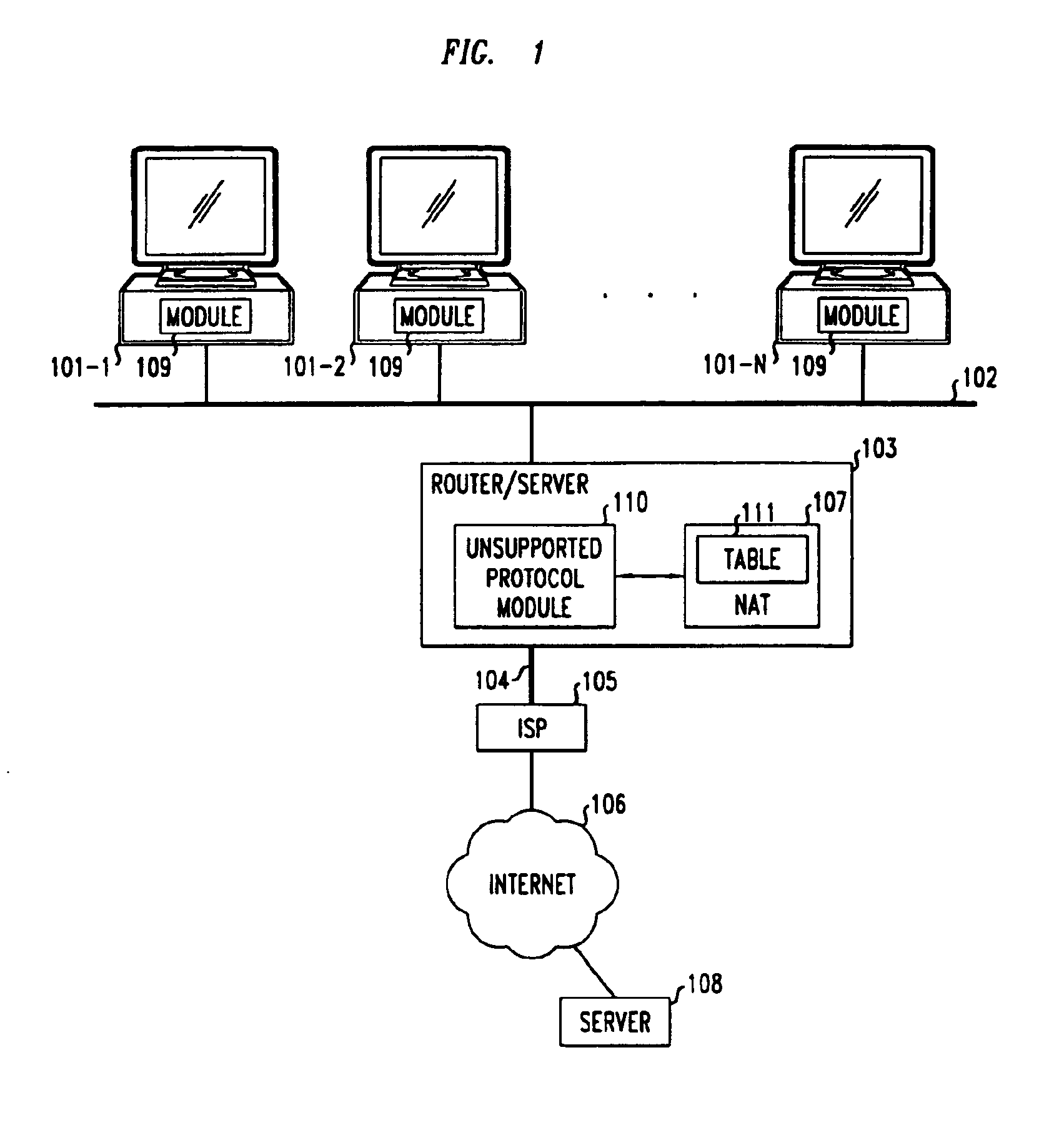
Method and apparatus for extending network address translation for unsupported protocols
InactiveUS6886103B1Ensure safetyMultiple digital computer combinationsProgram controlExpiration TimeIp address
Clients that are connected on a private network and which are assigned a private IP address that is not routable on the Internet can connect to the Internet through a router / server that includes a network address translator (NAT). For outgoing packets, the NAT translates the client's private source IP address and generalized port number (GPN) to the NAT's global IP address and GPN. For incoming packets sent to the NAT's global IP address and GPN, the NAT translates the global destination IP address and GPN to the client's private IP address and GPN. For protocols which cannot be directly supported by the NAT, such as those in the IPSec security protocol suite, the NAT is extended by creating in the NAT's translation table an entry that associates, for a specific unsupported protocol, a client's private IP address and GPN, the NAT's global IP address and GPN, and a foreign address on the Internet, that is valid until a specified or default expiration time. Outgoing packets from the client to that foreign address and incoming packets from that foreign address to the NAT's global IP address and GPN are translated according to the entry until the entry expires. In associations with these translations to outgoing and incoming packets, the client implements any Application Layer Gateway (ALG) that would otherwise be implemented at the NAT. Further, at the client, outgoing packets are modified before being transmitted so as to pre-compensate for the effects of the translations. Incoming packets at the client from the NAT are similarly modified so as to post-compensate for the effects of the translations. For the IPSec protocol, these modification include adjusting the checksum in the TCP or UDP header to account for IP address and TCP or UDP port number translations.
Owner:ALCATEL-LUCENT USA INC
Guaranteed exactly once delivery of messages
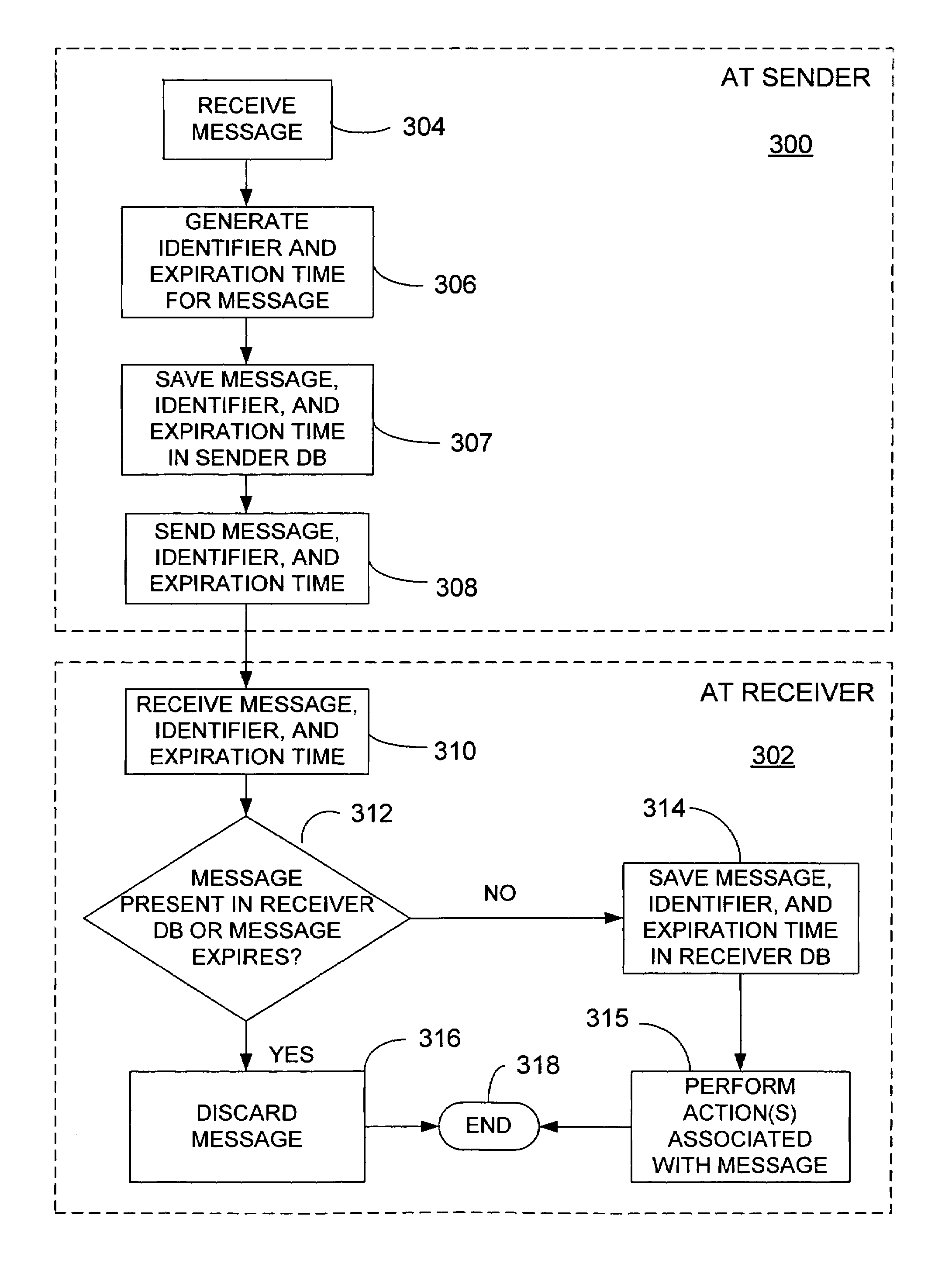
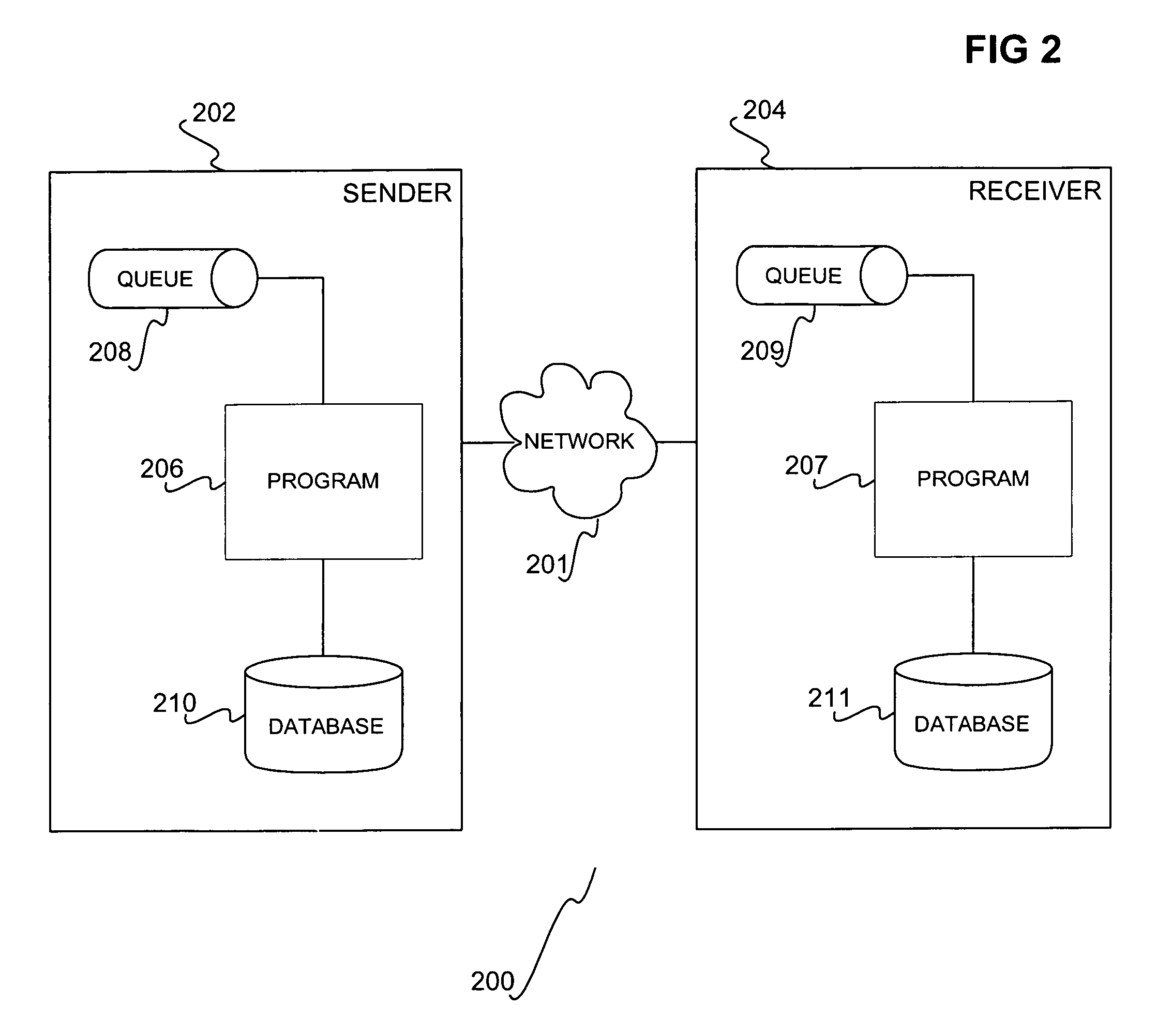
InactiveUS7162512B1Stable deliveryImprove performanceData processing applicationsMultiprogramming arrangementsExpiration TimeUnique identifier
Guaranteed, exactly once delivery of messages is disclosed. In one embodiment, there is a sender and a receiver. In a sender transaction, the sender does the following: receives a message from a sender queue; generates a substantially unique identifier and an expiration time for the message; and, saves the identifier, the expiration time, and the message in a sender database. The sender then sends the identifier, the expiration time, and the message to the receiver. In a receiver transaction, the receiver then does the following: receives the identifier, the expiration time, and the message from a receiver queue; determines whether the message has expired based on the expiration time and determines whether the message is present in a receiver database by its identifier; and, upon determining that the message has not expired and is not present in the receiver database, stores the message in the receiver database, and performs actions associated with the message.
Owner:MICROSOFT TECH LICENSING LLC
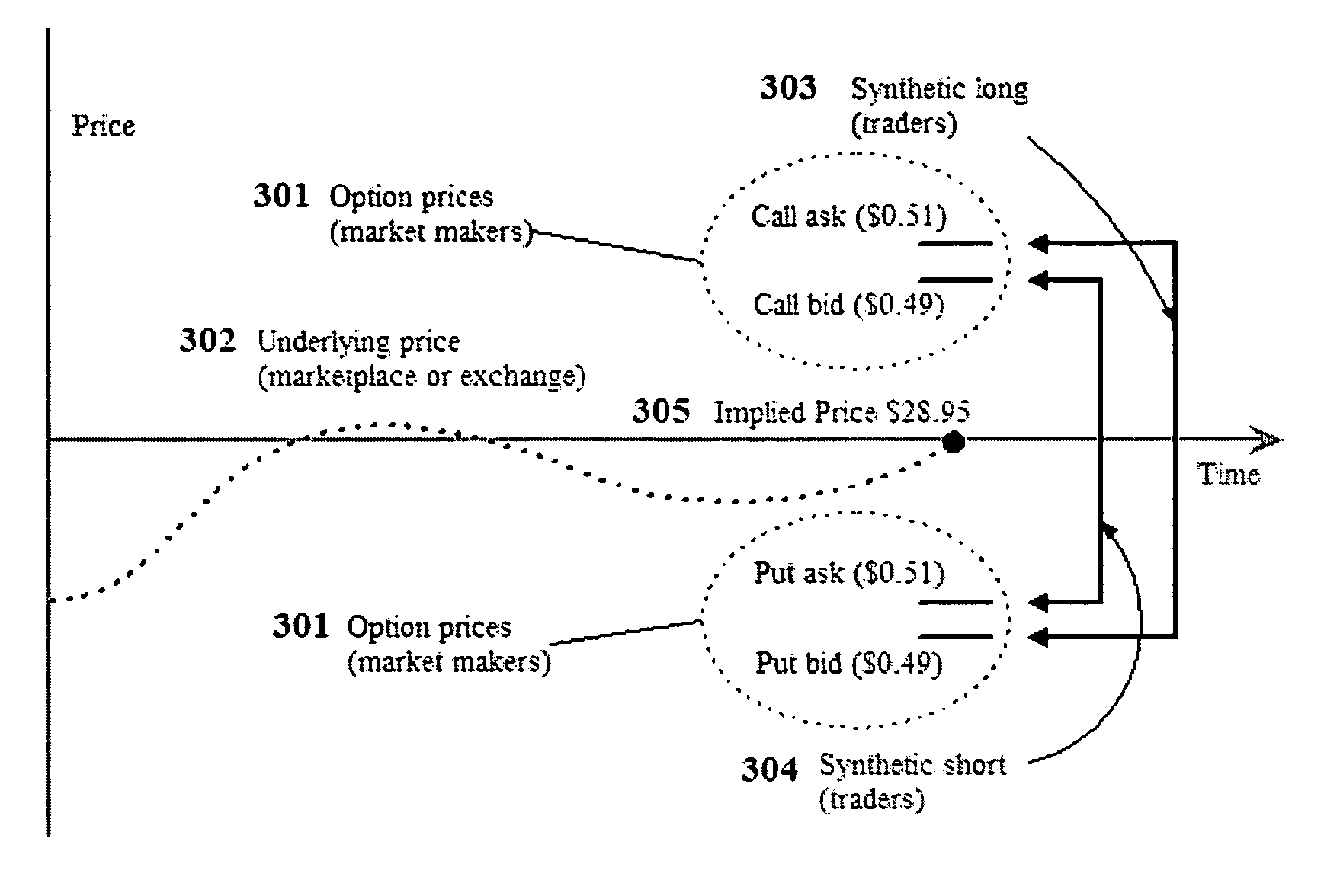
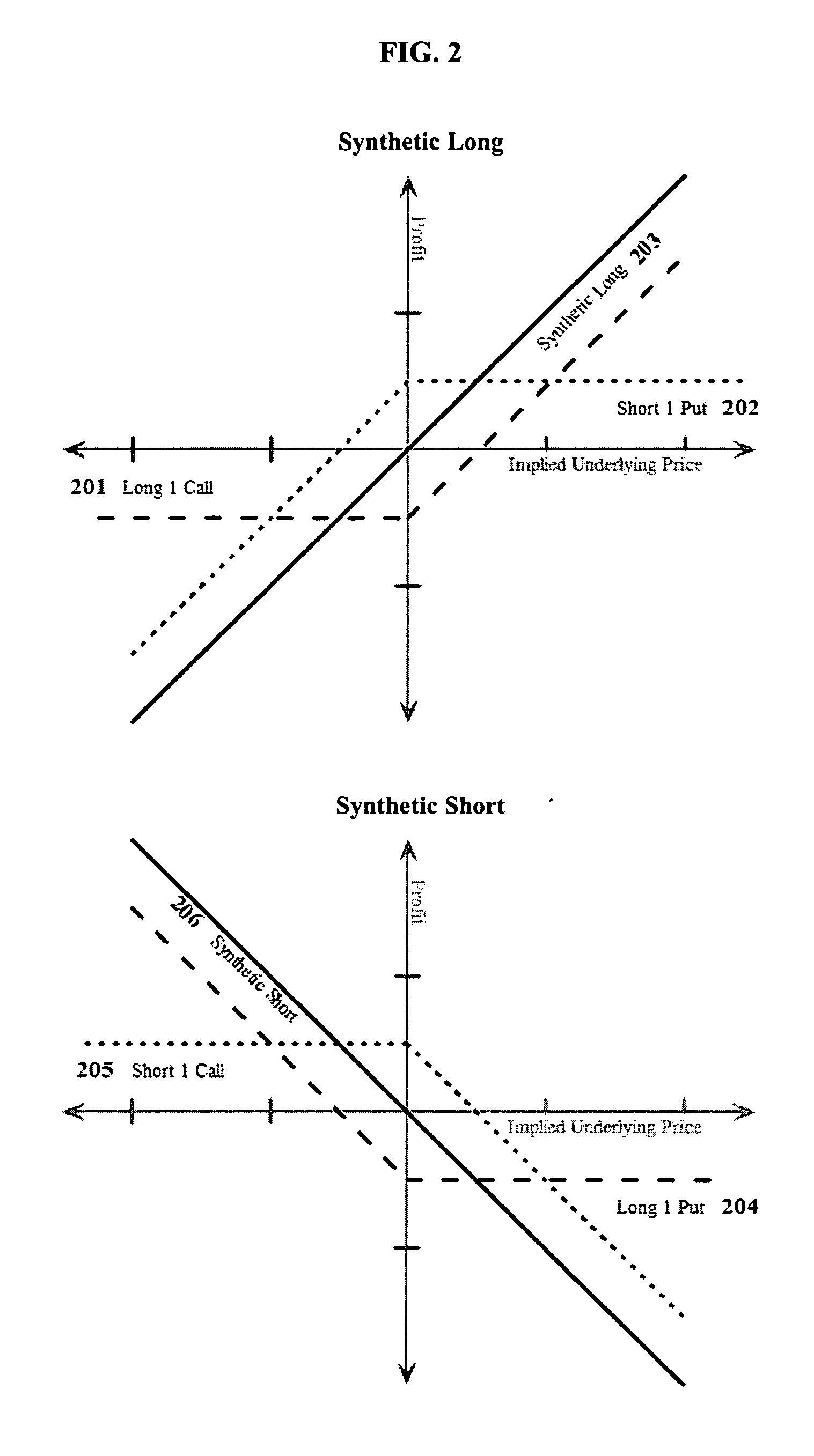
Short-term option trading system
InactiveUS20060036531A1High leverageTake advantage ofFinancePayment architectureExpiration TimeShort terms
Option contracts are traded by valuing an option that has at least one of a) strike price or b) expiration time unknown at the time the option is valued. The previously unknown values of the option are assigned at the time or after the time the trade is completed. An implied underlying price stream is generated from the option prices through the use of feedback between market participants and the marketplace. The resulting system is useful in trading option contracts of short time duration.
Owner:MICROTICK
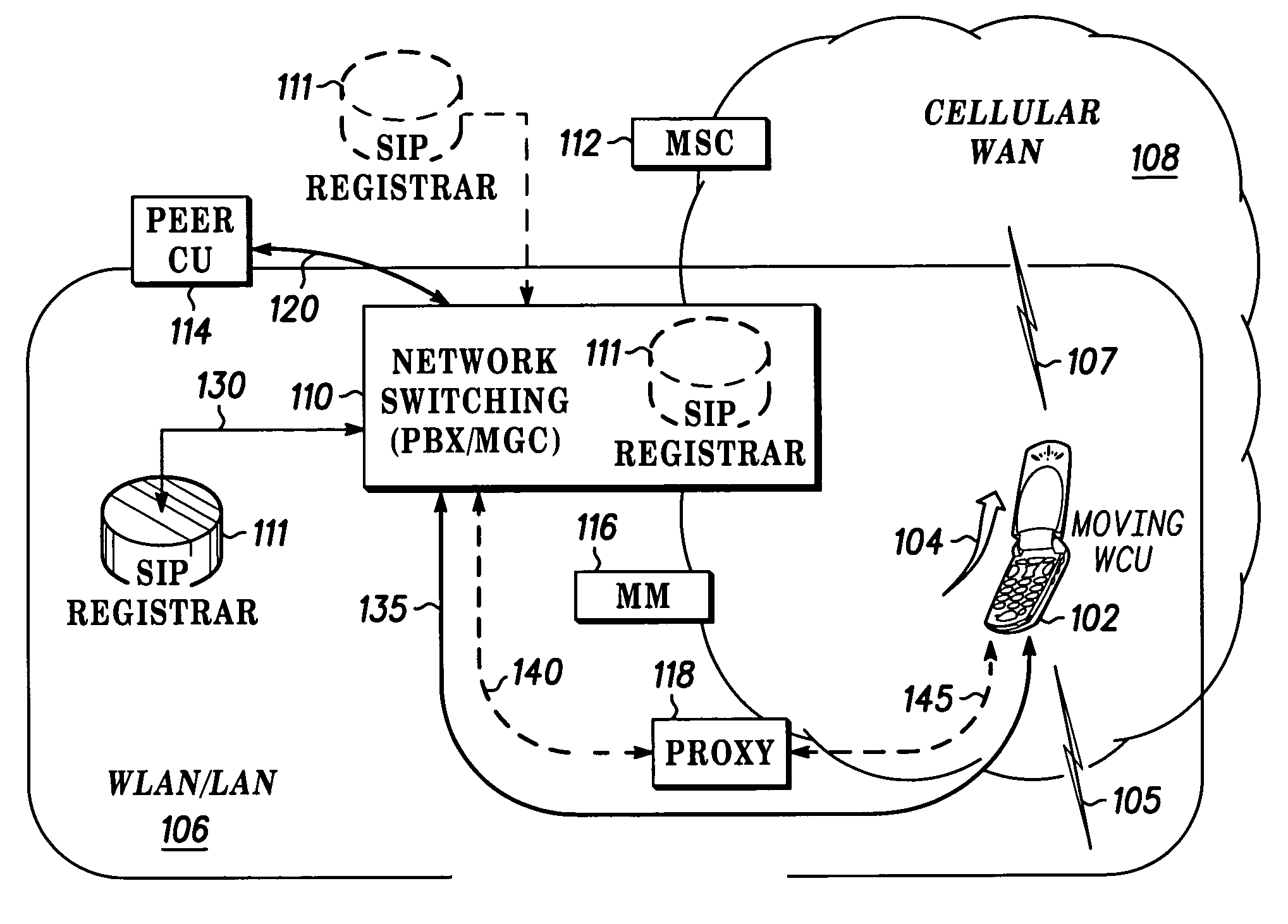
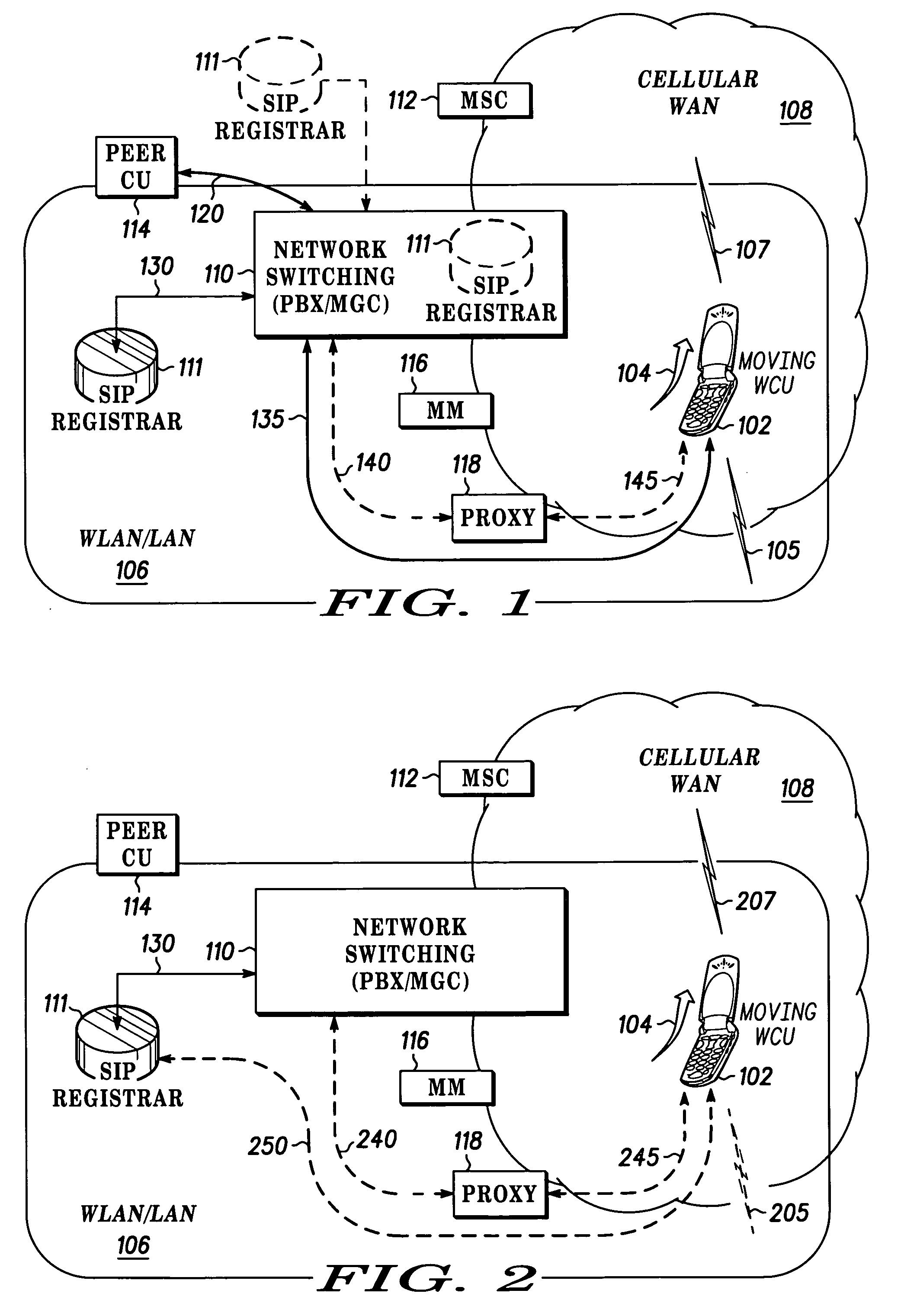
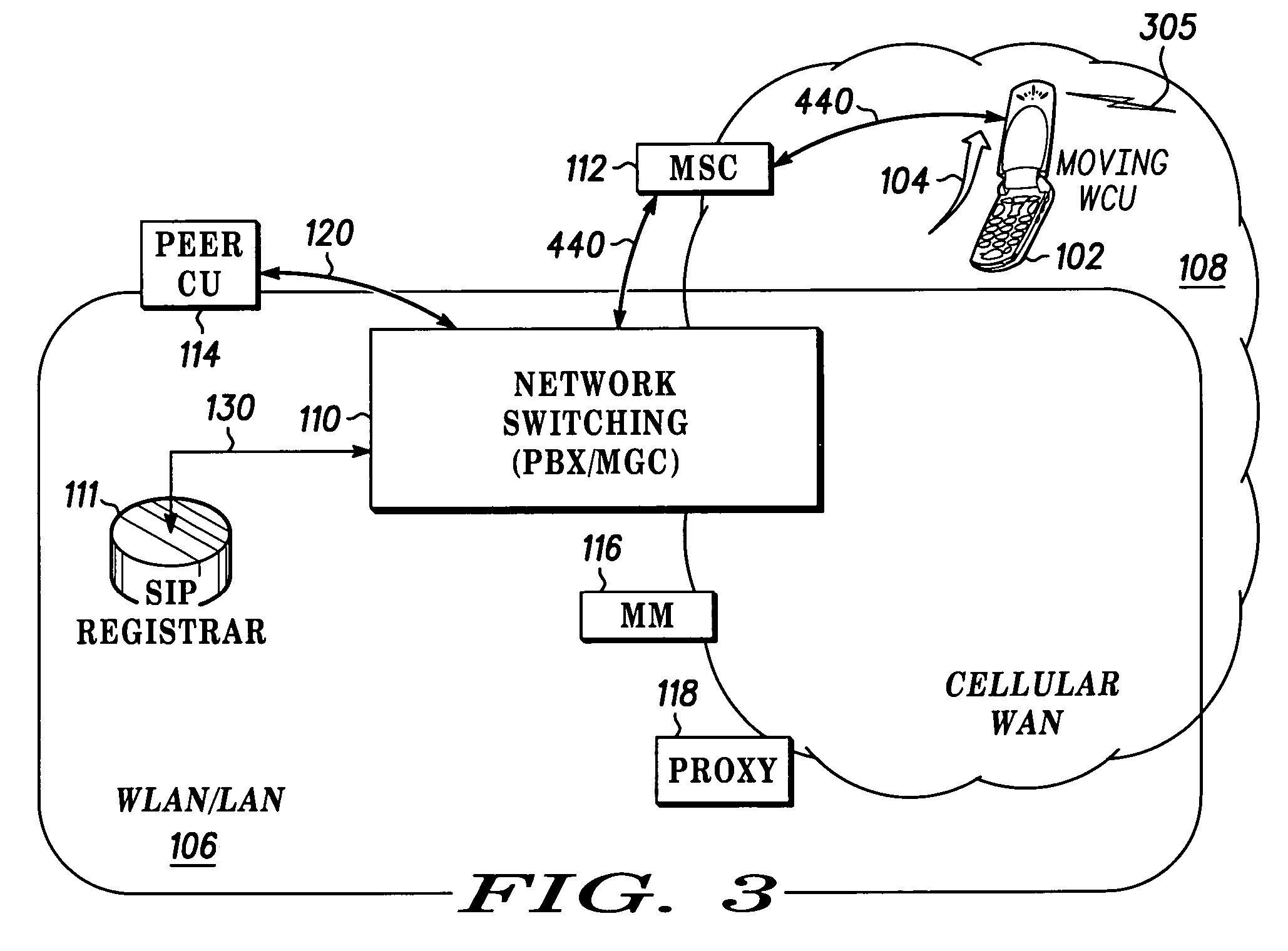
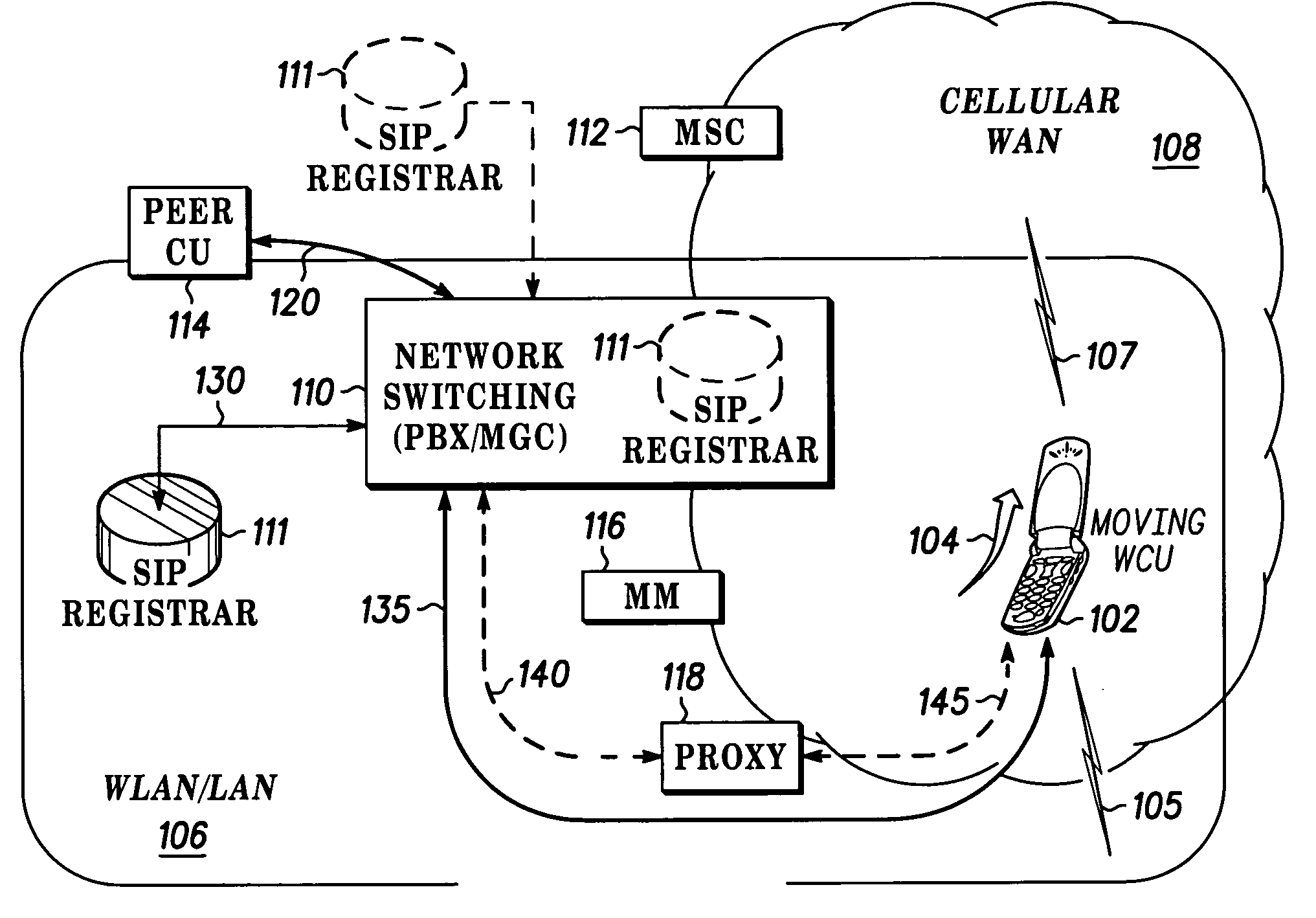
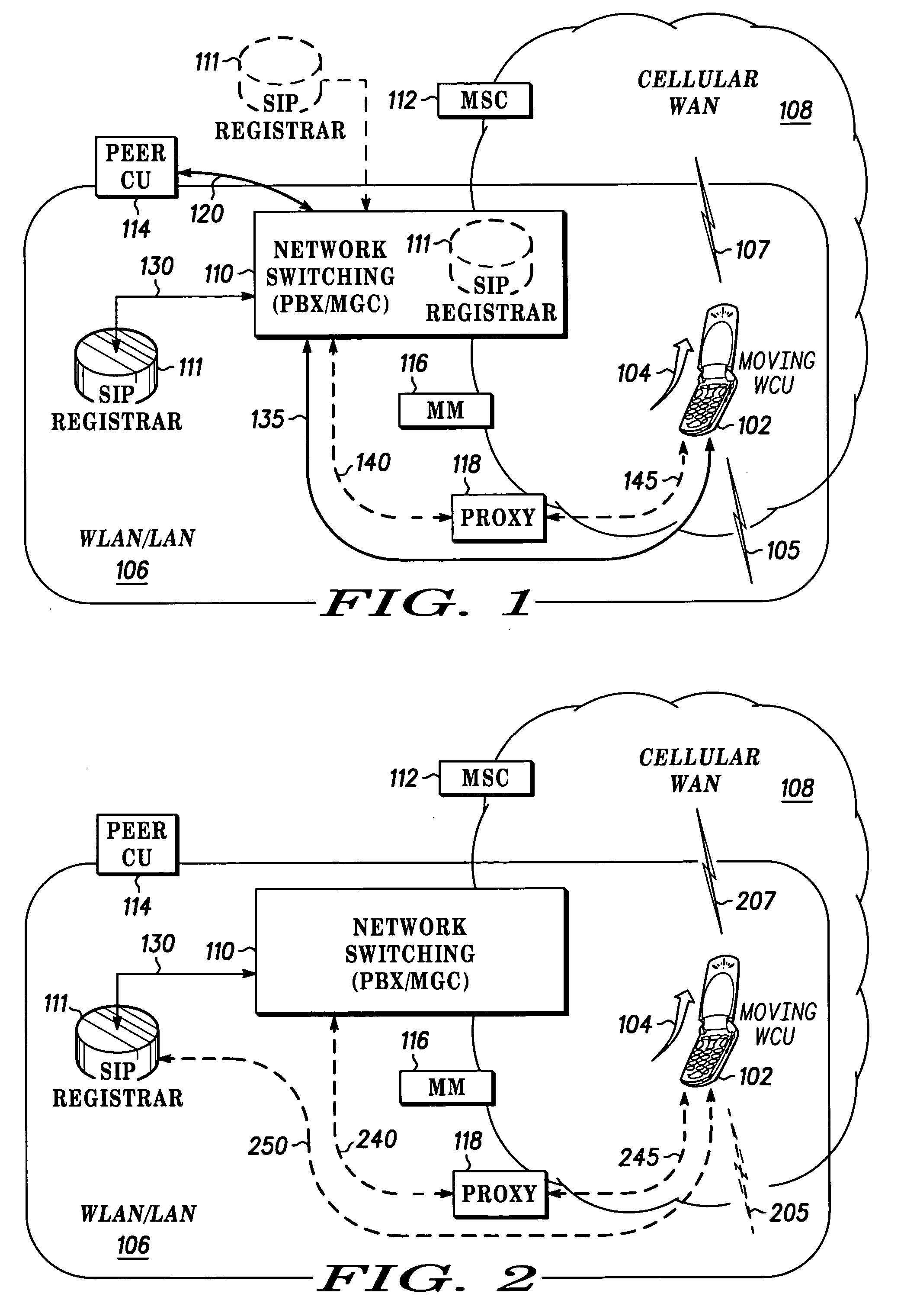
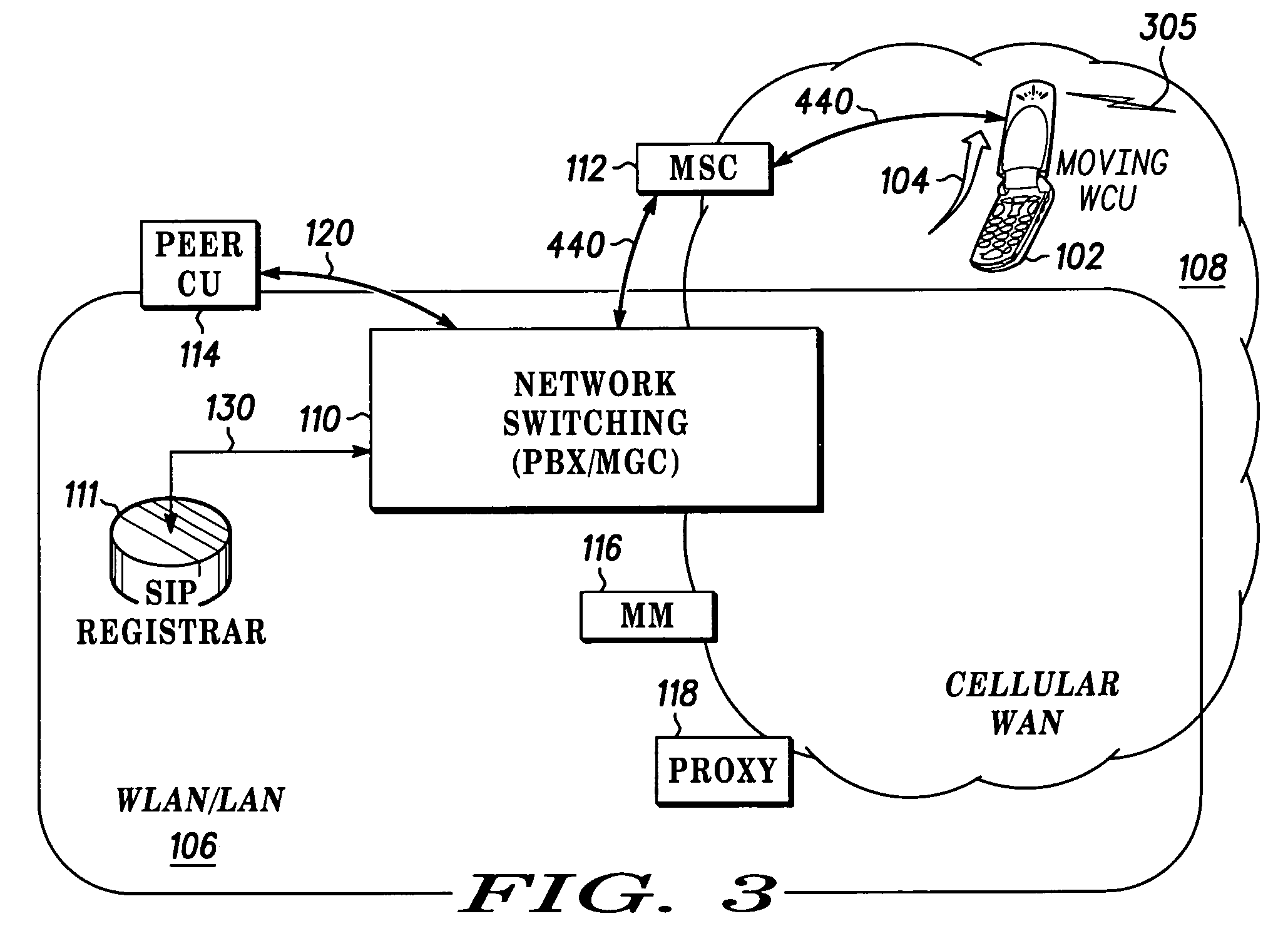
Fast call set-up for multi-mode communication
Owner:MOTOROLA SOLUTIONS INC
Fast call set-up for multi-mode communication
Fast call set-up for a call to a multi-mode communication unit (102) is facilitated by a method and apparatus for registering and re-registering priorities with a SIP registrar (111). A list of contacts with first priorities associated with a mode of operation in a first enterprise network (106) is established and used. A switch to second priorities is made when a probability of a switch from the first mode of operation to a second mode of operation in a second cellular network (108) satisfies a threshold. The list of contacts includes a contact having an expiration time for the first mode of operation. A quality factor is determined and the list of contacts is re-registered and the expiration time changed if the quality factor does not satisfy a threshold.
Owner:MOTOROLA SOLUTIONS INC
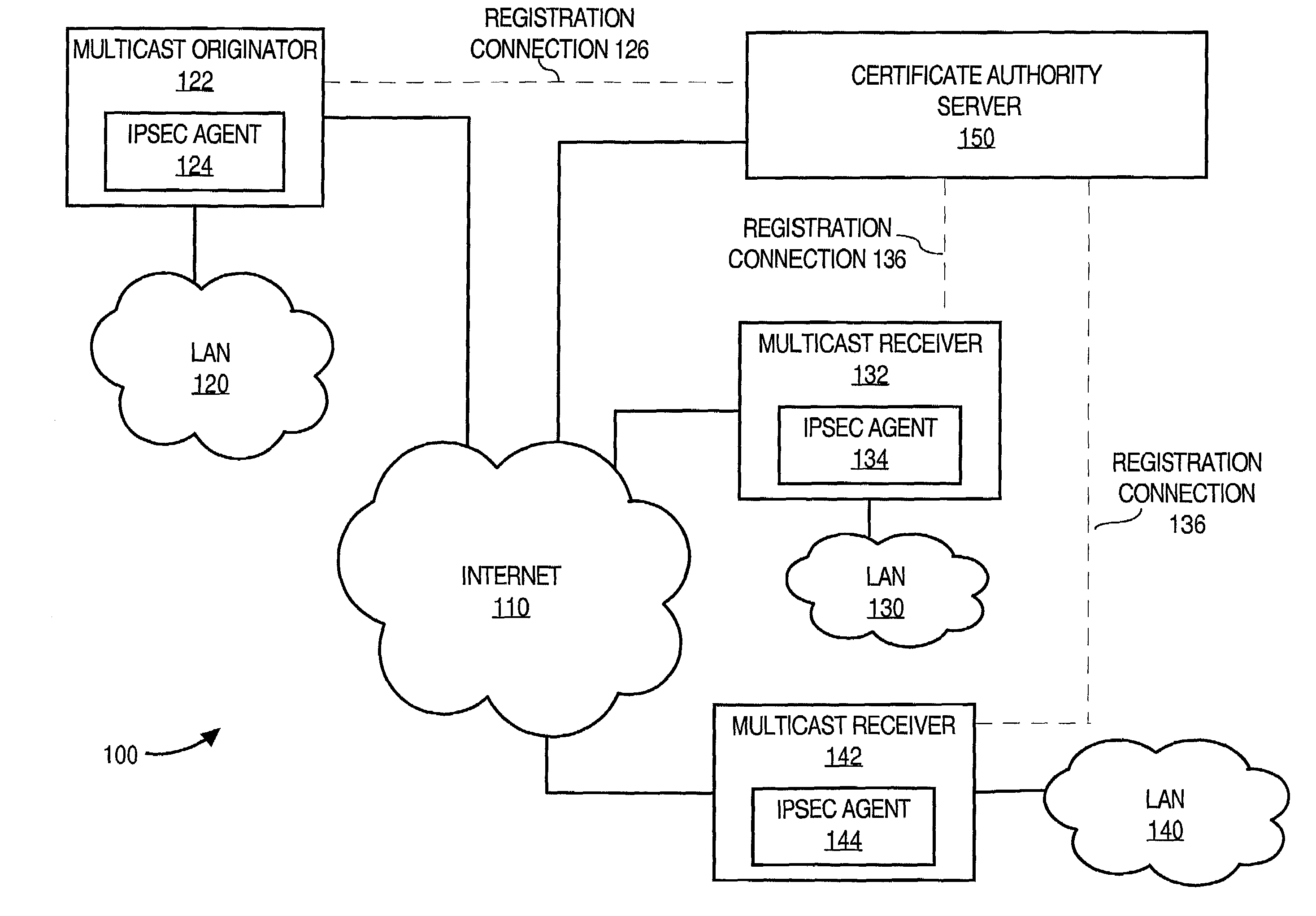
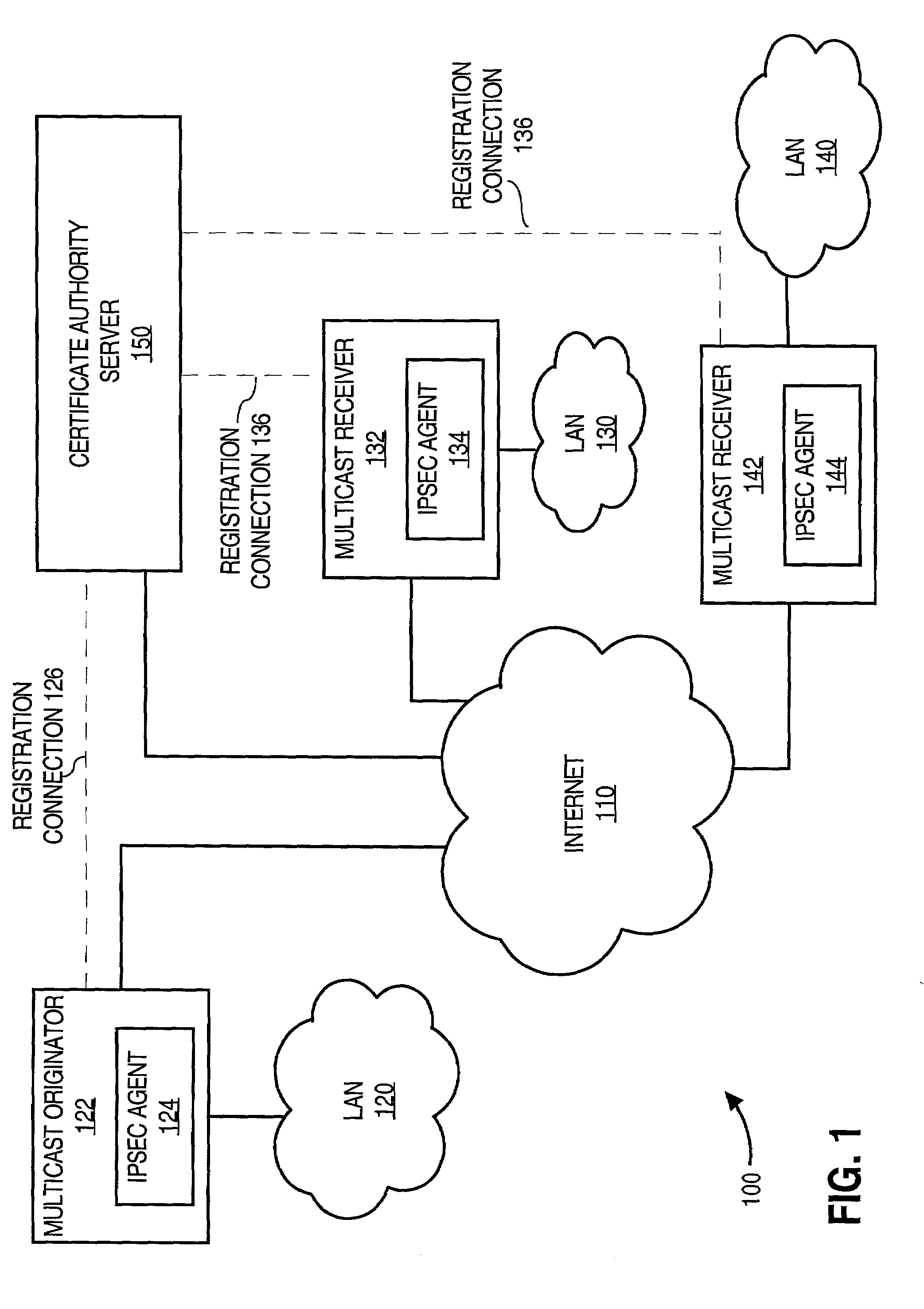
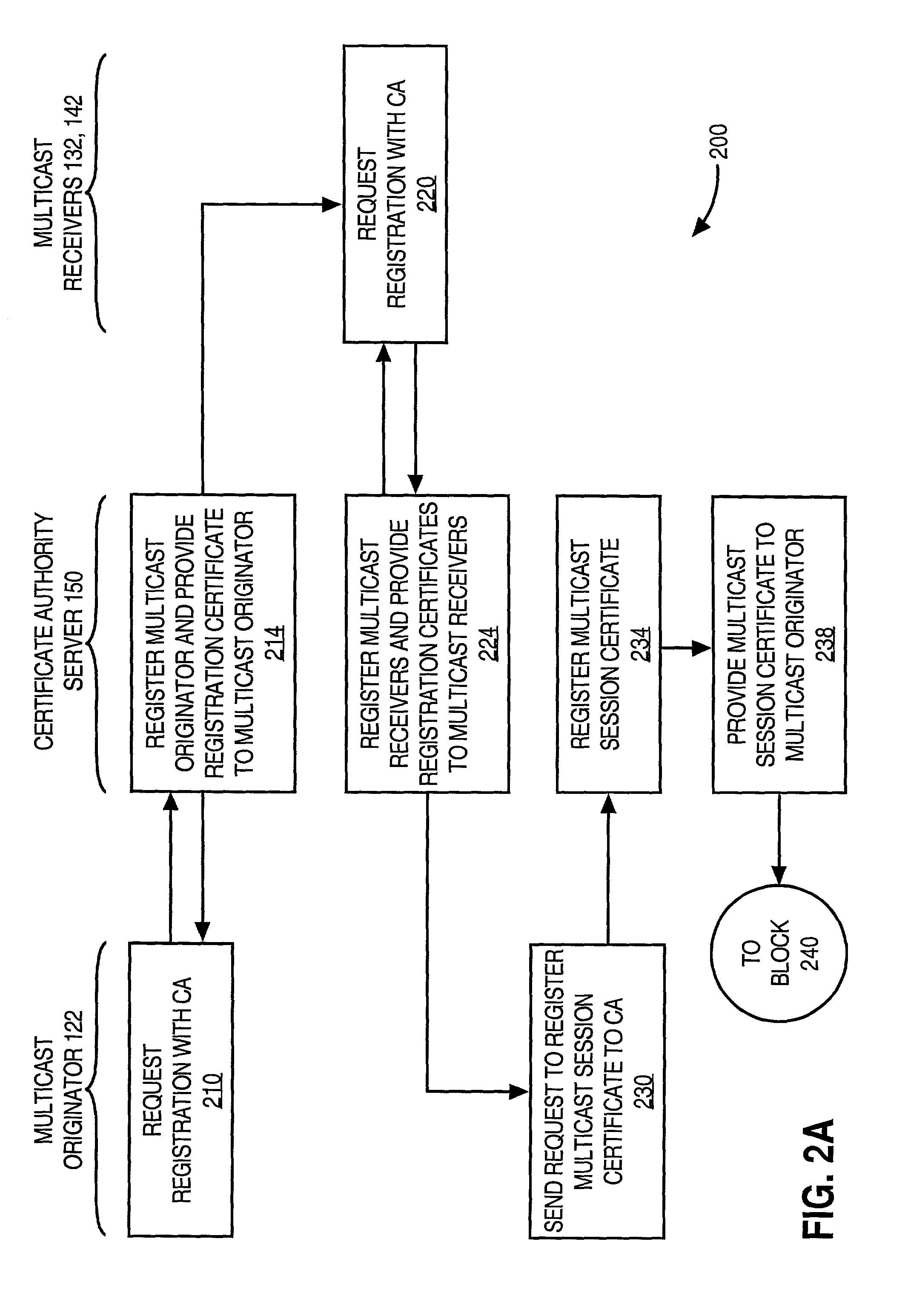
Facilitating secure communications among multicast nodes in a telecommunications network
An approach for facilitating secure communications among multicast nodes in a telecommunications network is disclosed. A source node sends an encryption key and an identifier to an authoritative node that stores the encryption key and associates the identifier with the encryption key. The source node encrypts data using the encryption key and sends the encrypted data with the identifier in a multicast. The multicast destination nodes retrieve the encryption key from the authoritative node based on the identifier and then decrypt the multicast. A list of administrative nodes, a list of authorized nodes, and an expiration time may be used to manage the encryption key. The authoritative node may be a certificate authority or key distribution center, and the source node may encrypt the multicast using the Internet security protocol (IPsec) or secure socket layer (SSL). Thus, communications among multicast nodes may be efficiently secured in a scalable manner.
Owner:CISCO TECH INC
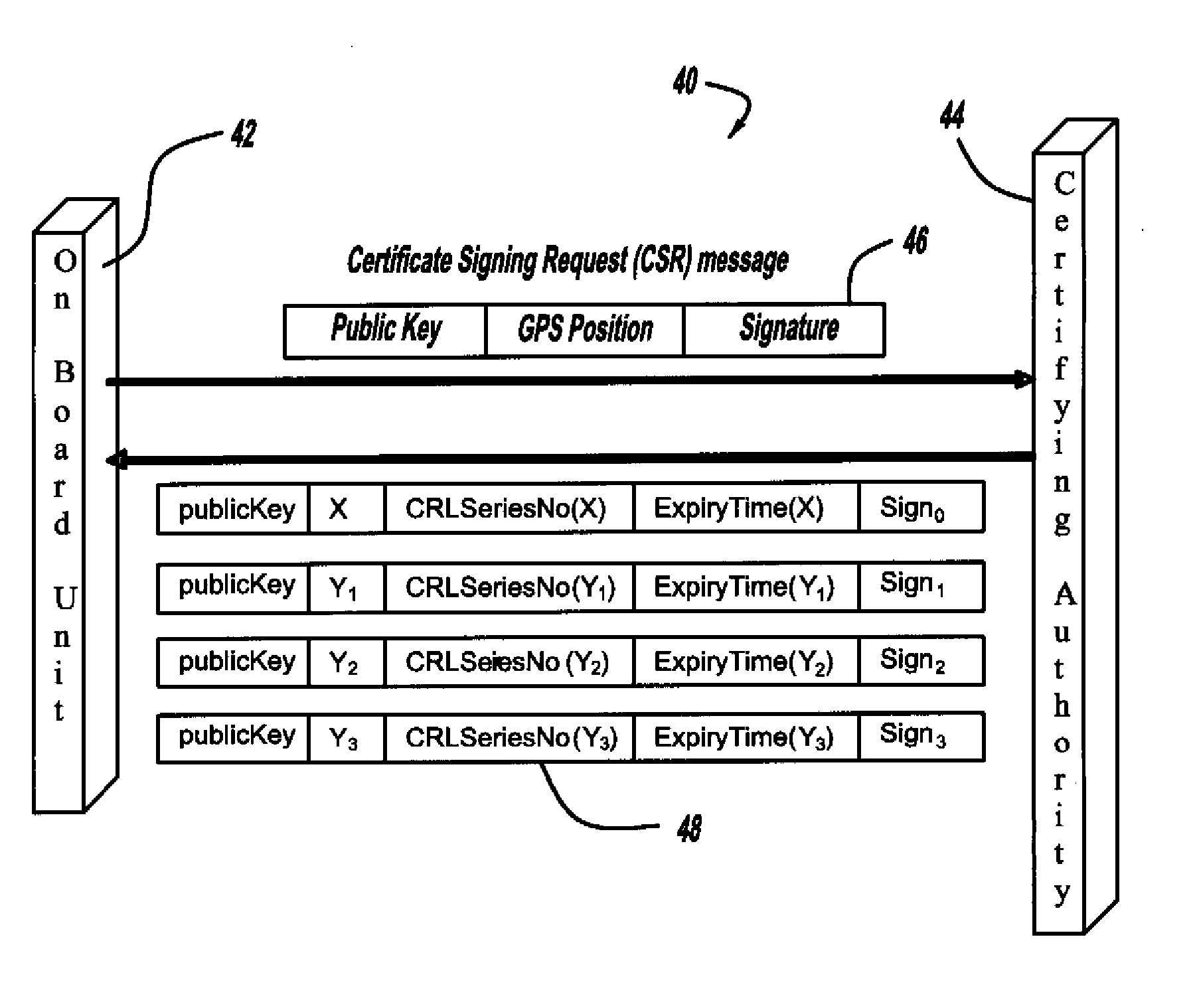
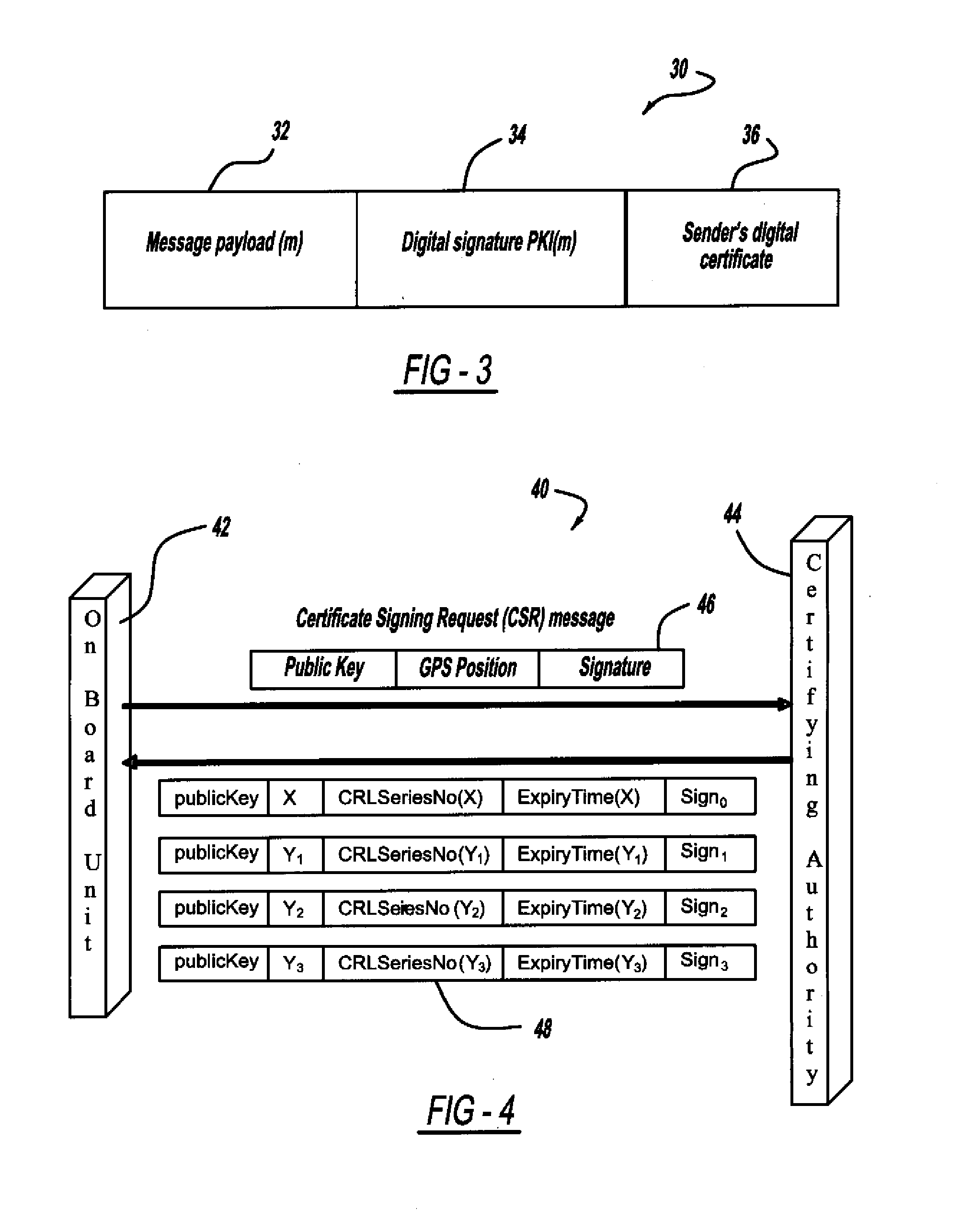
Certificate assignment strategies for efficient operation of the pki-based security architecture in a vehicular network
InactiveUS20090235071A1Small sizeReduce complexityTemperatue controlUser identity/authority verificationExpiration TimeCommunications system
A system and method for assigning certificates and reducing the size of the certificate revocation lists in a PKI based architecture for a vehicle wireless communications system that includes separating a country, or other area, into geographic regions and assigning region-specific certificates to the vehicles. Therefore, a vehicle need only process certificates and certificate revocation lists for the particular region that it is traveling in. Vehicles can be assigned multiple certificates corresponding to more than one region in the vehicles vicinity as advance preparation for possible travel or transmission into nearby regions. Further, the expiration time of certificates assigned to vehicles corresponding to a given geographic region can be tailored to be inversely proportional to the distance from a registered home region of the vehicle. A scalable design for a back-end certifying authority with region-based certificates can also be provided.
Owner:GM GLOBAL TECH OPERATIONS LLC
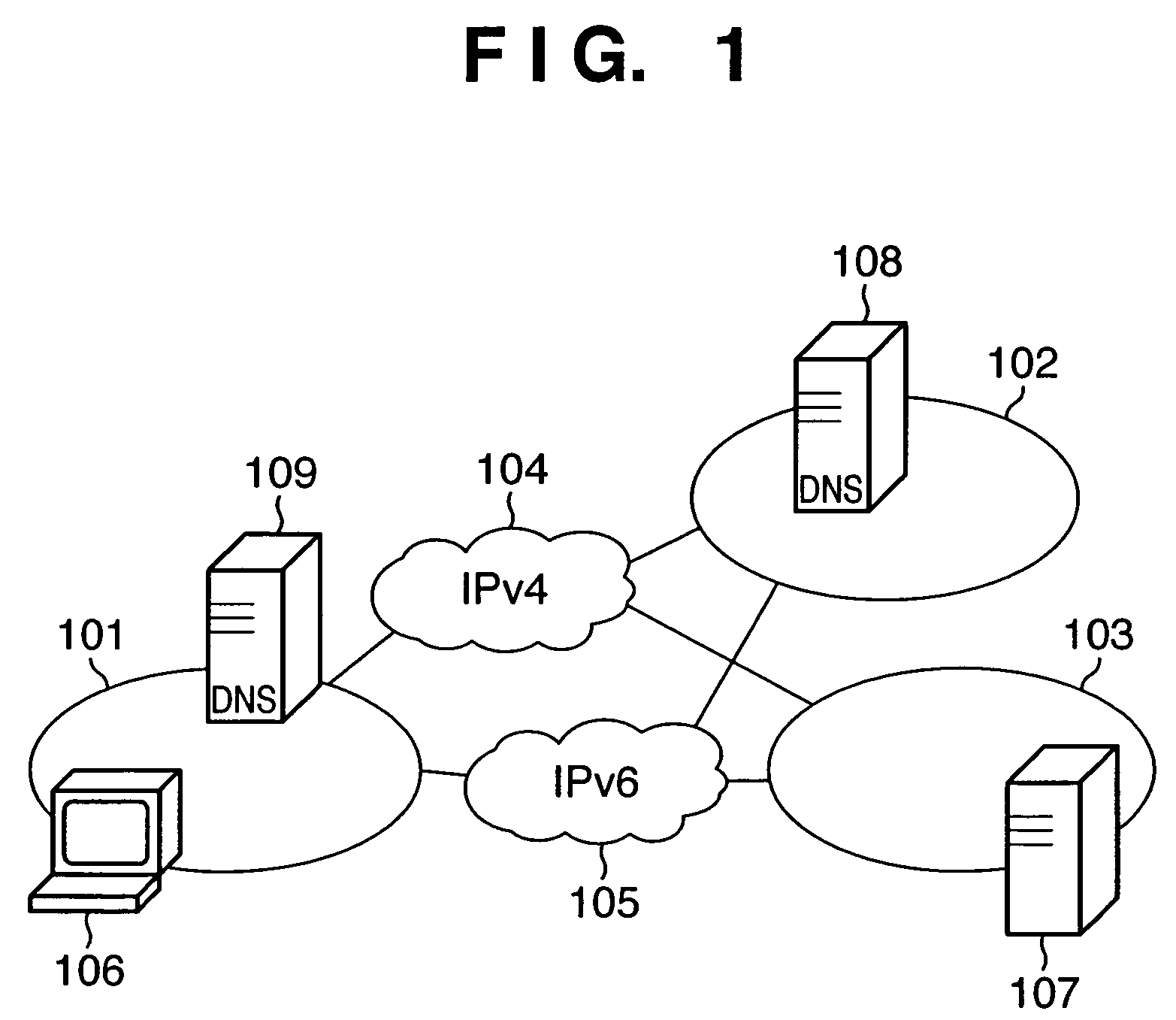
Address query response method, program, and apparatus, and address notification method, program, and apparatus
InactiveUS7415536B2Error prevention/detection by using return channelTransmission systemsExpiration TimeResponse method
Upon reception of a query about the address of a server from a client, a DNS server sends a query about the address of that server to an external DNS server. The DNS server checks based on the address obtained from the external DNS server if connection to the server can be established. If connection to the server cannot be established, and the DNS server receives a query about the address of the server, the DNS server returns a response indicating that the address is not available. When the address is returned before the check process, the DNS sever sets an expiration time shorter than that of the address of the server obtained from the external DNS server as the expiration time of the address of the server.
Owner:CANON KK
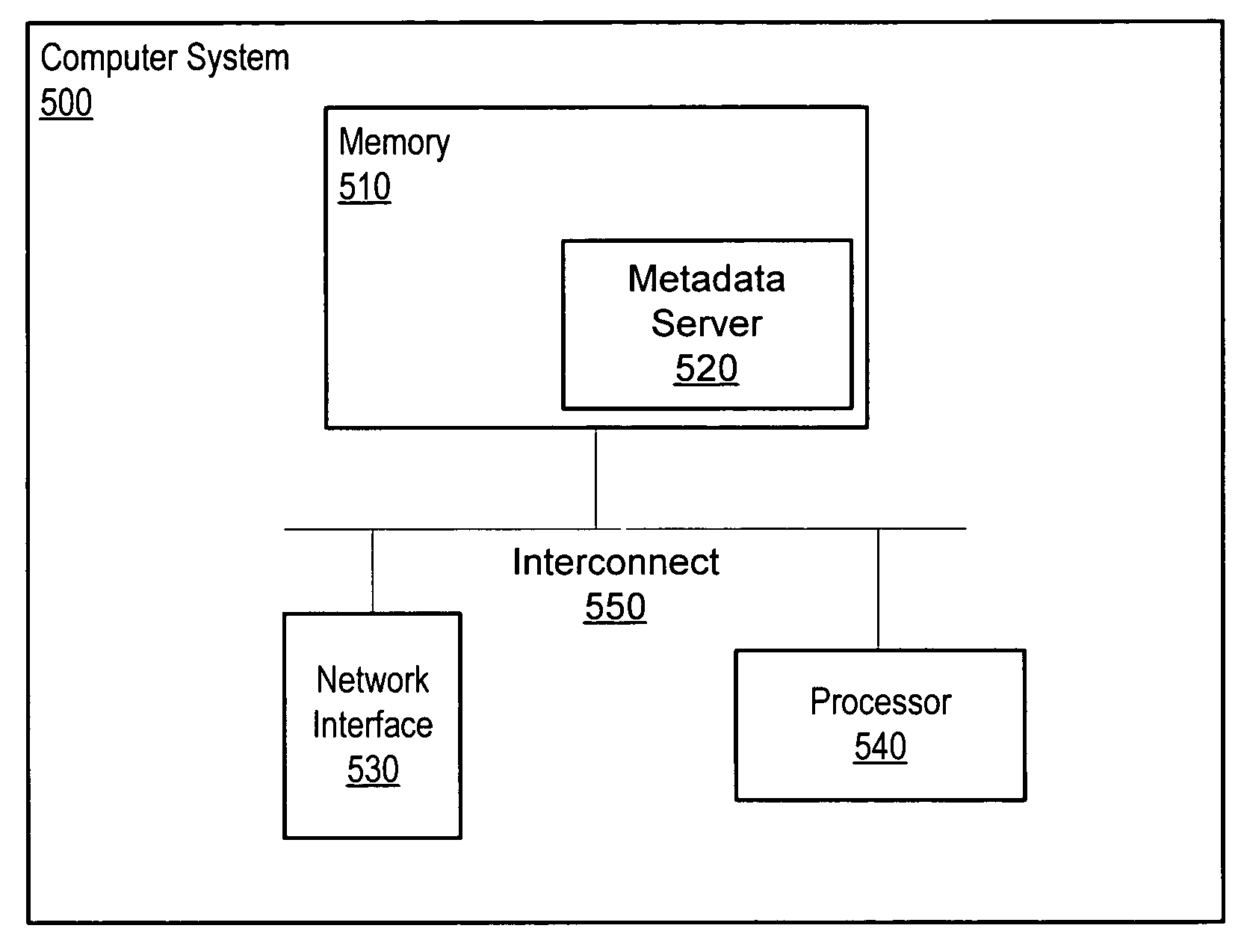
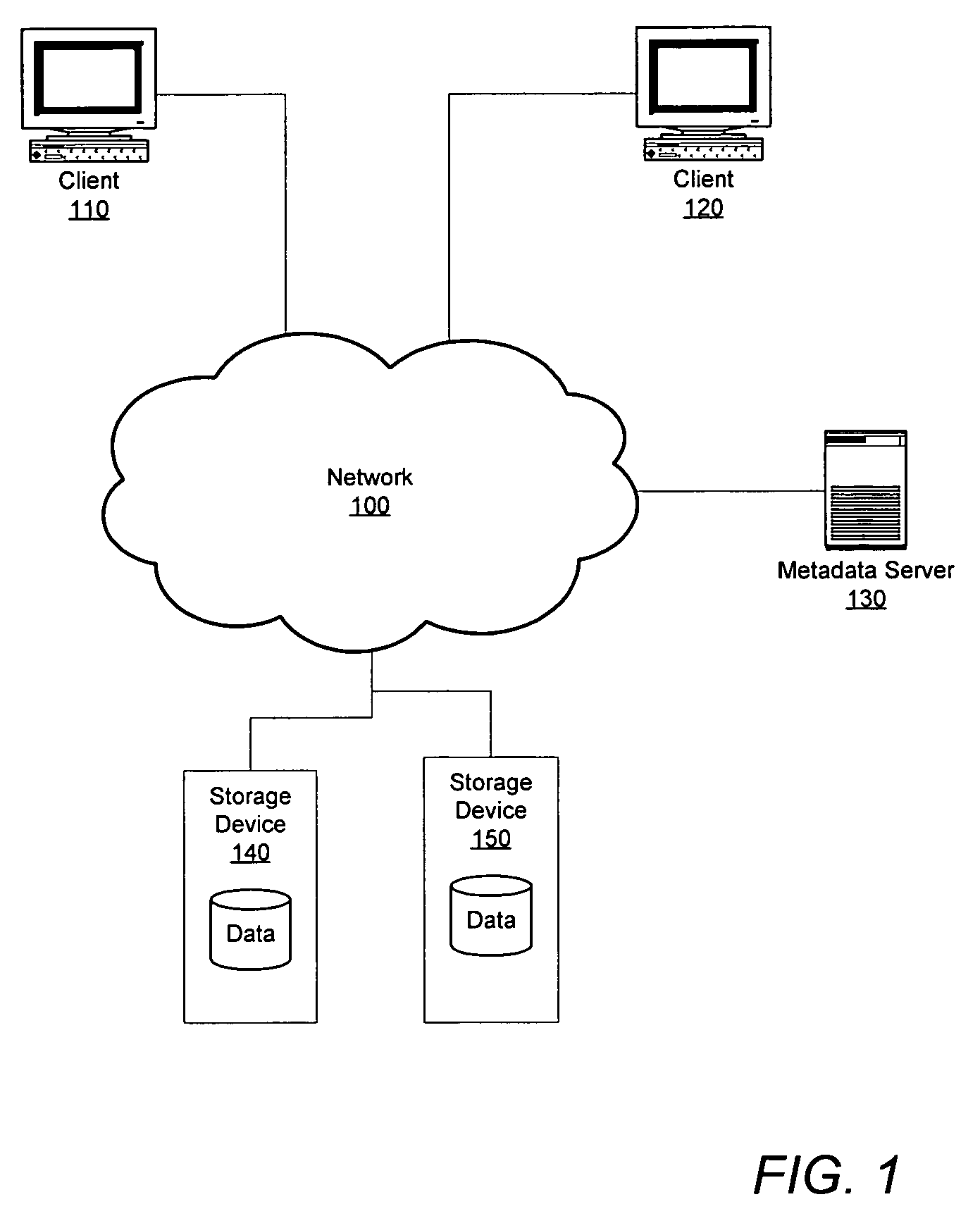
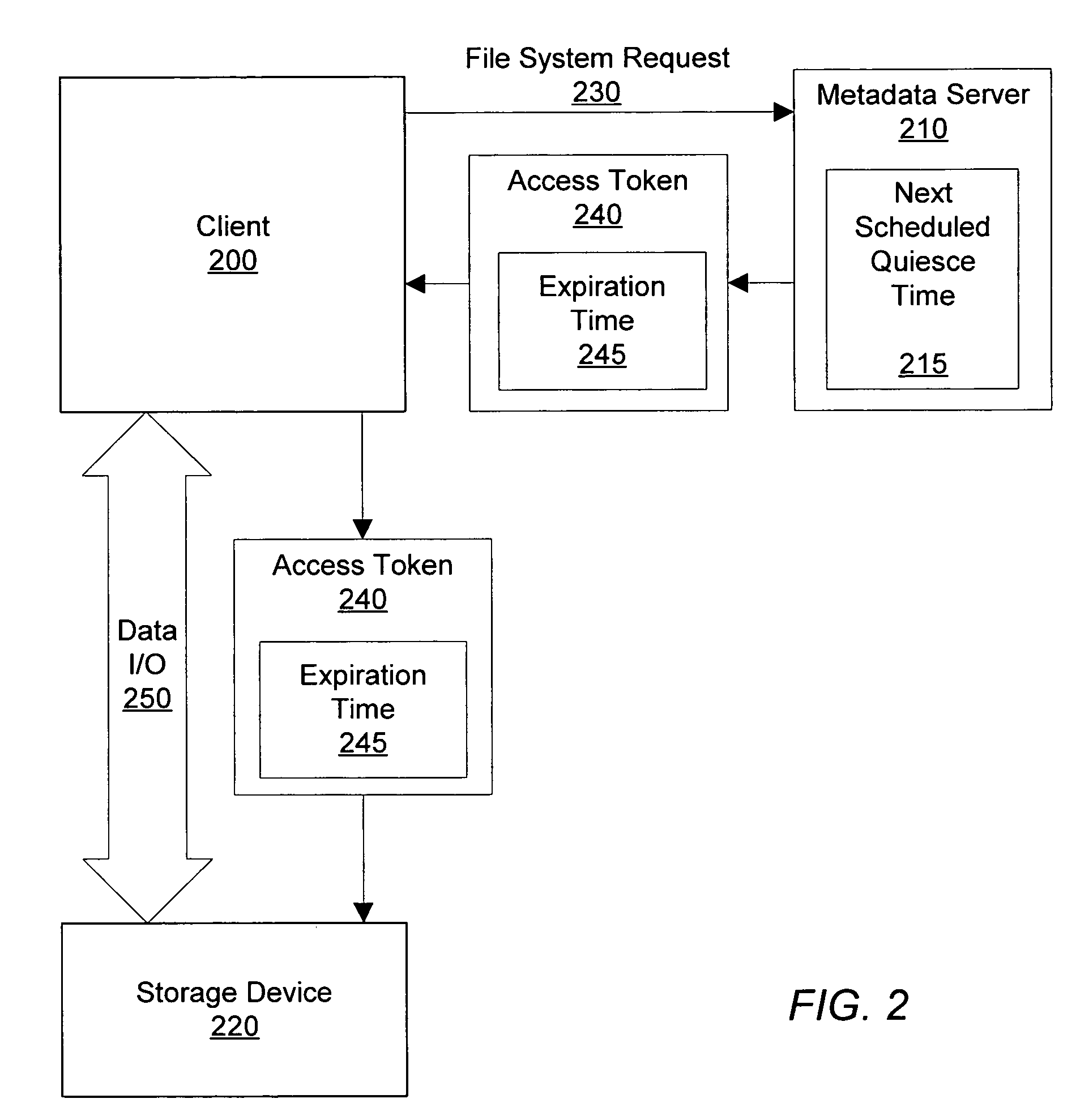
Expiration of access tokens for quiescing a distributed system
InactiveUS7720864B1Digital data information retrievalDigital data processing detailsExpiration TimeAccess token
A method, system and computer accessible medium for expiring access tokens in preparation for freezing file images. A metadata server may maintain a next scheduled quiesce time and may issue access tokens configured to expire before the next scheduled quiesce time. A metadata server may set an access token's expiration time to a maximum expiration time indicated by the next scheduled quiesce time or may set an access token's expiration time to a default expiration time if the default expiration time is earlier than the maximum expiration time. A storage device may recognize and enforce the access token's expiration time.
Owner:SYMANTEC OPERATING CORP
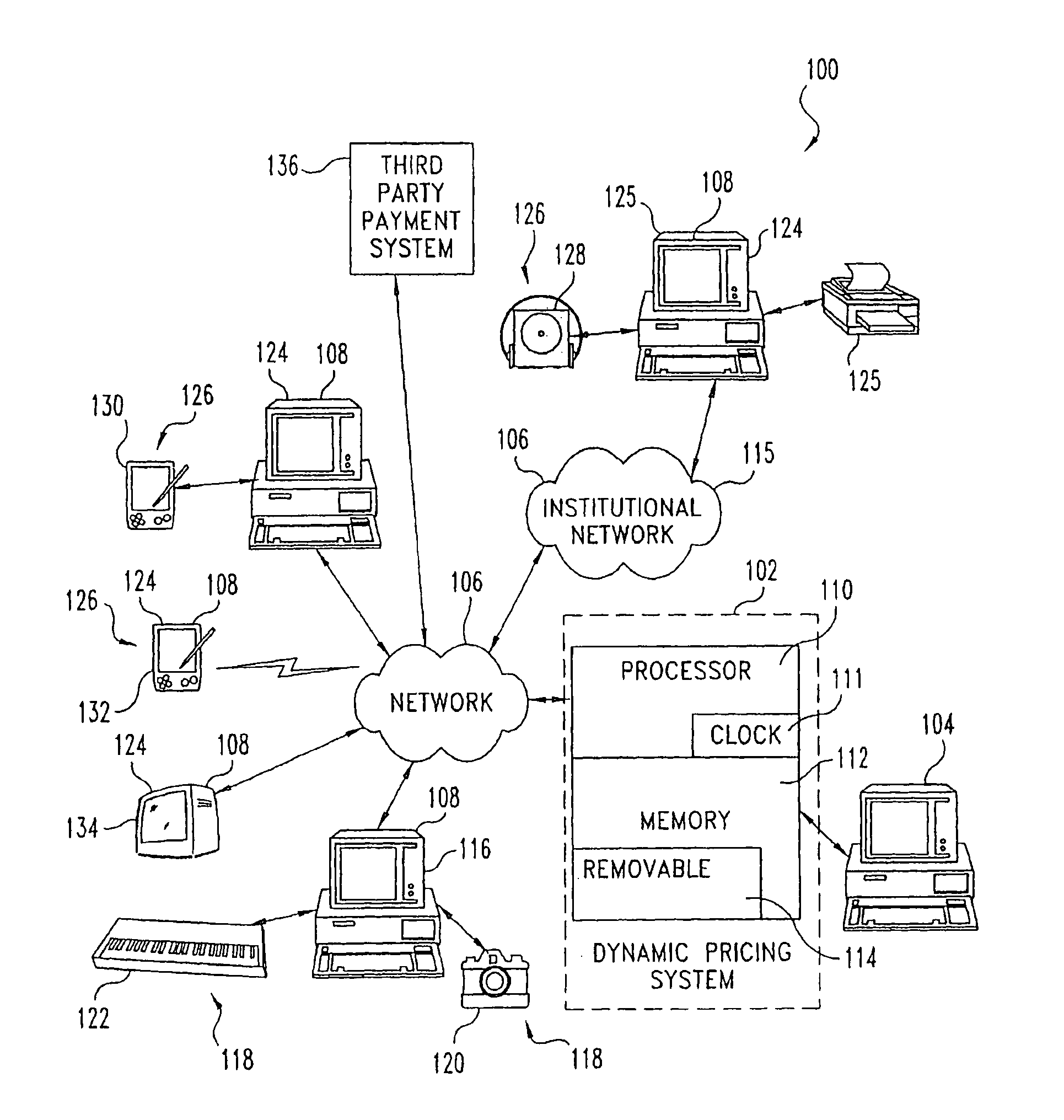
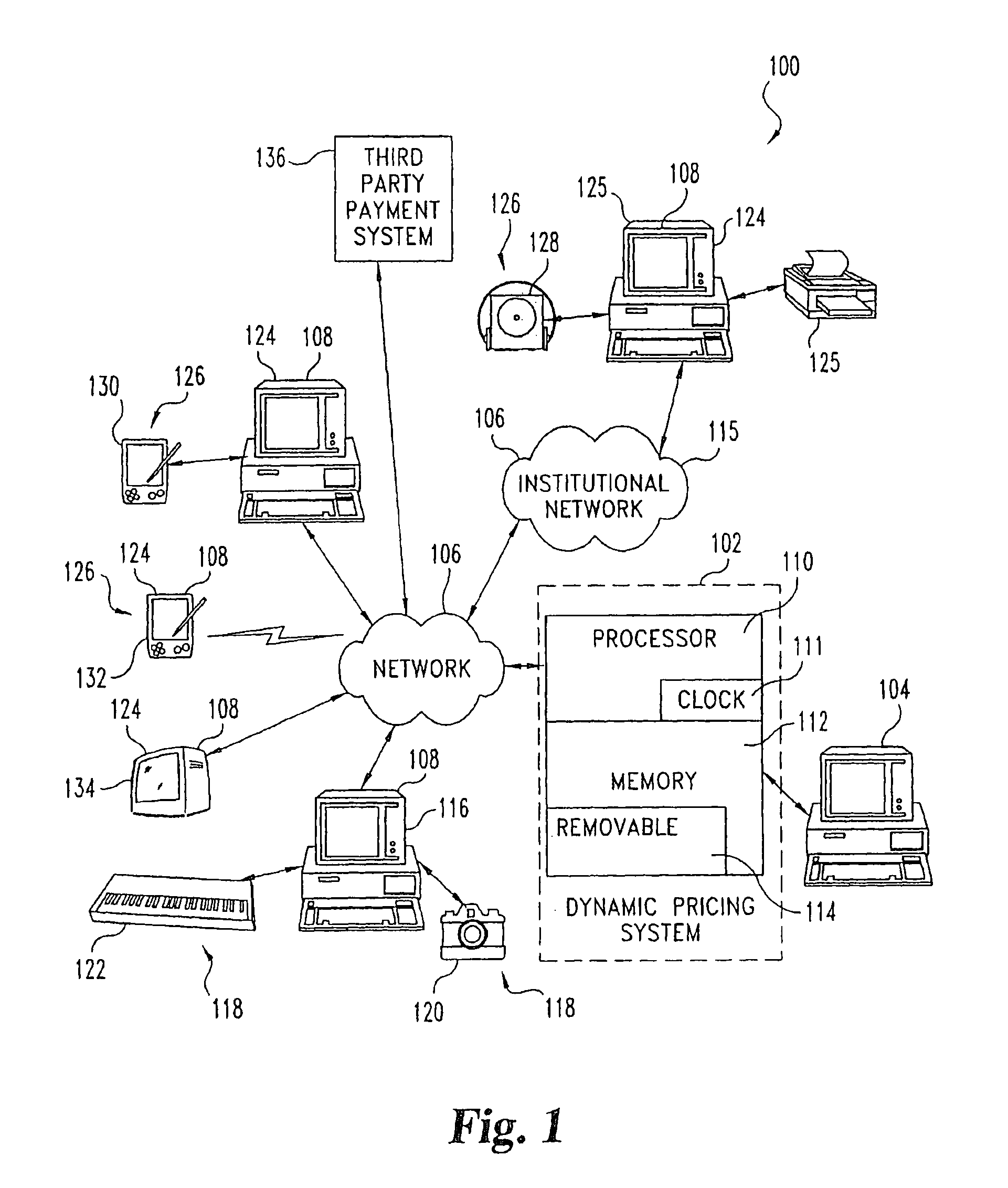
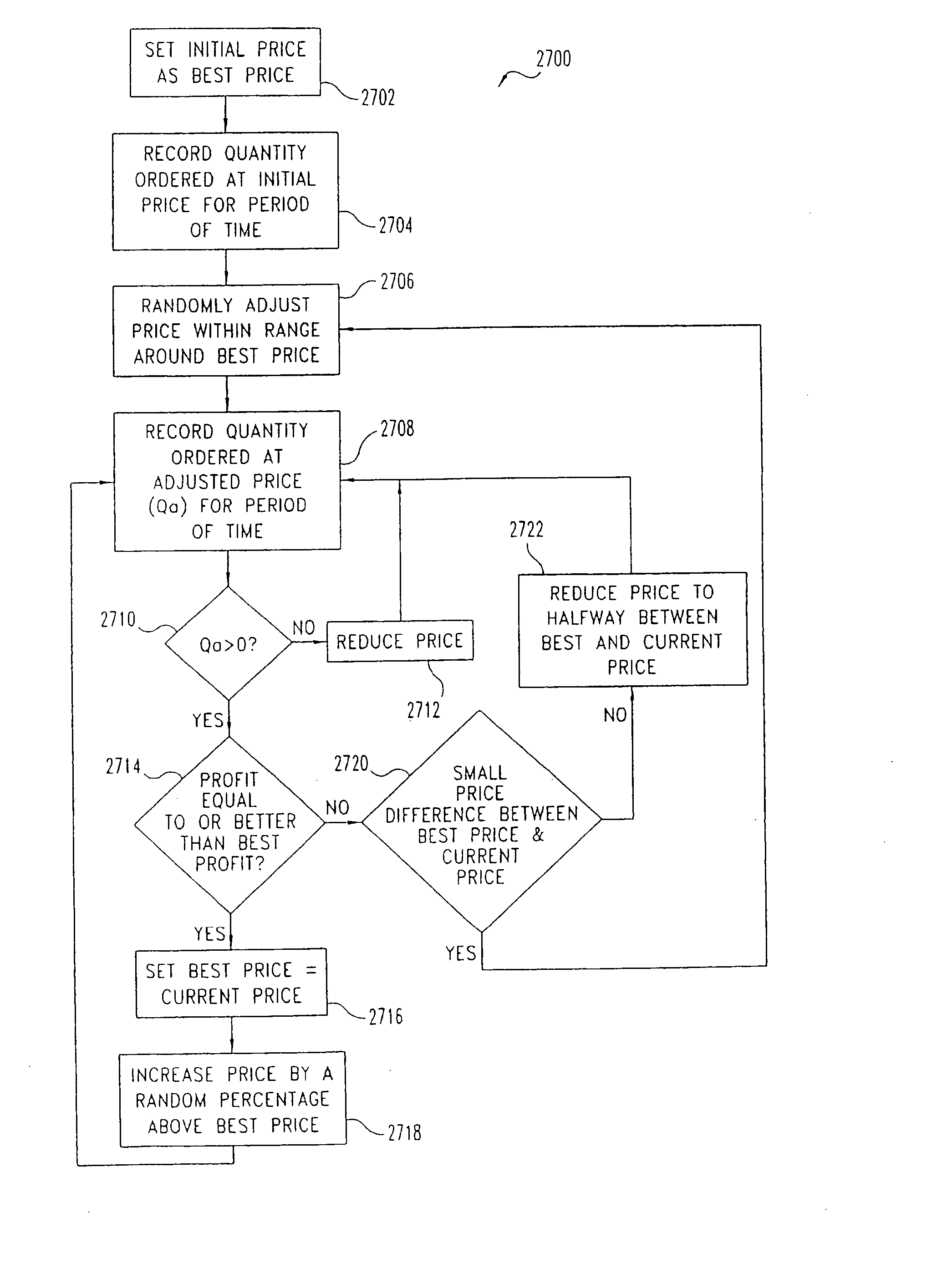
Digital online exchange for pricing items to exhaust inventory by an expiration time
InactiveUS8112303B2Network load increaseMarket predictionsBuying/selling/leasing transactionsExpiration TimeData storing
A dynamic pricing system for pricing items for sale by a seller which items are available in a limited quantity comprises a pricing server and various types of data stored in memory. The pricing server includes memory, a processor and a clock. One type of data stored in memory is indicative of the initial quantity of an item available in a limited quantity. Another type of data stored in memory is indicative of the current remaining quantity of the item available in a limited quantity. Yet another type of data stored in memory is indicative of an expiration time at which it is desired that all of the item available in a limited quantity be sold. The processor is configured to price the item available in a limited quantity so as to deplete the inventory of the item available in a limited quantity by the expiration date based in part by accessing the memory to retrieve the data indicative of the initial quantity, the current remaining quantity and the expiration time and accessing the clock.
Owner:DIGONEX TECH
Method and apparatus for conditioning access for a remotely-accessible device
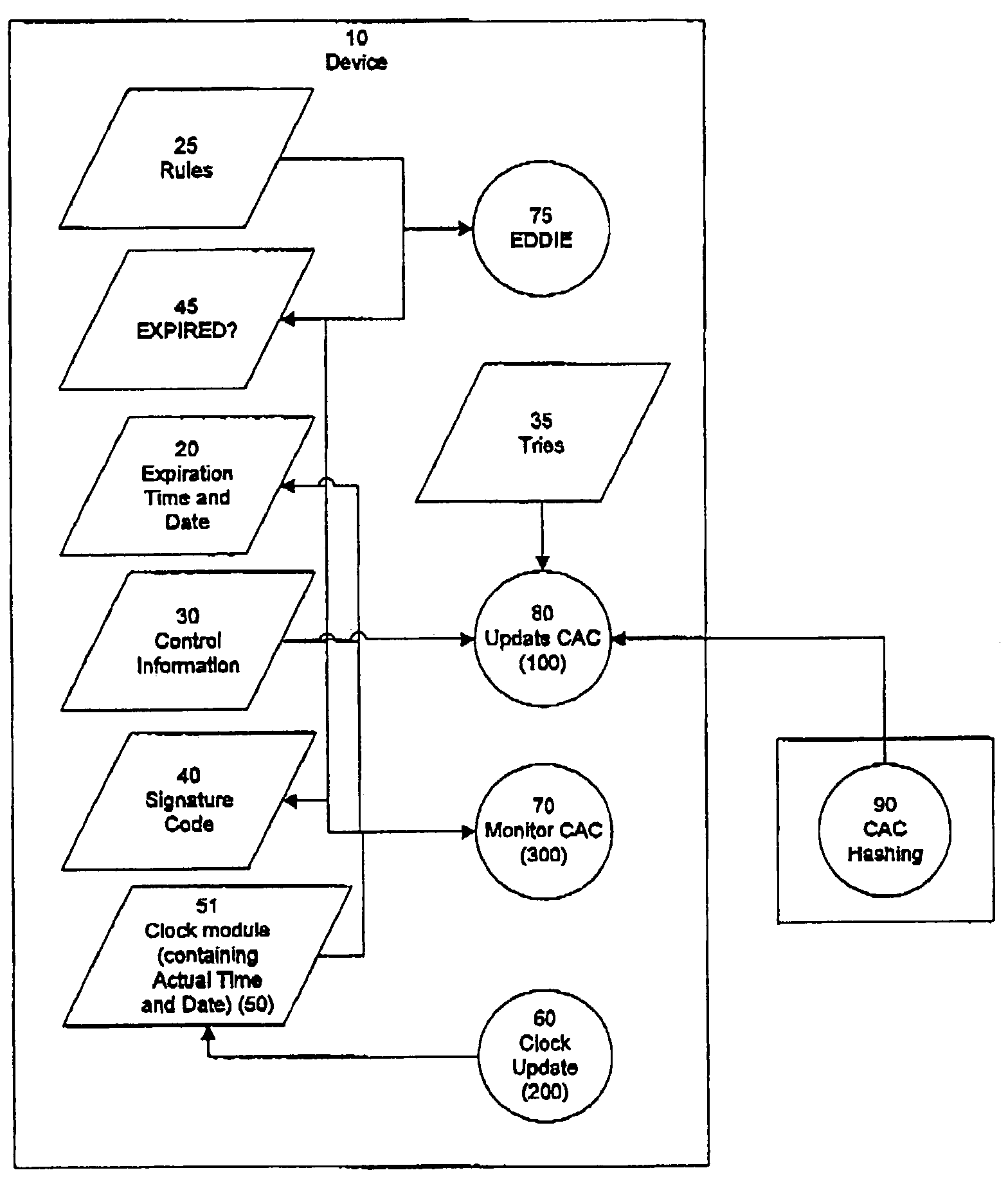
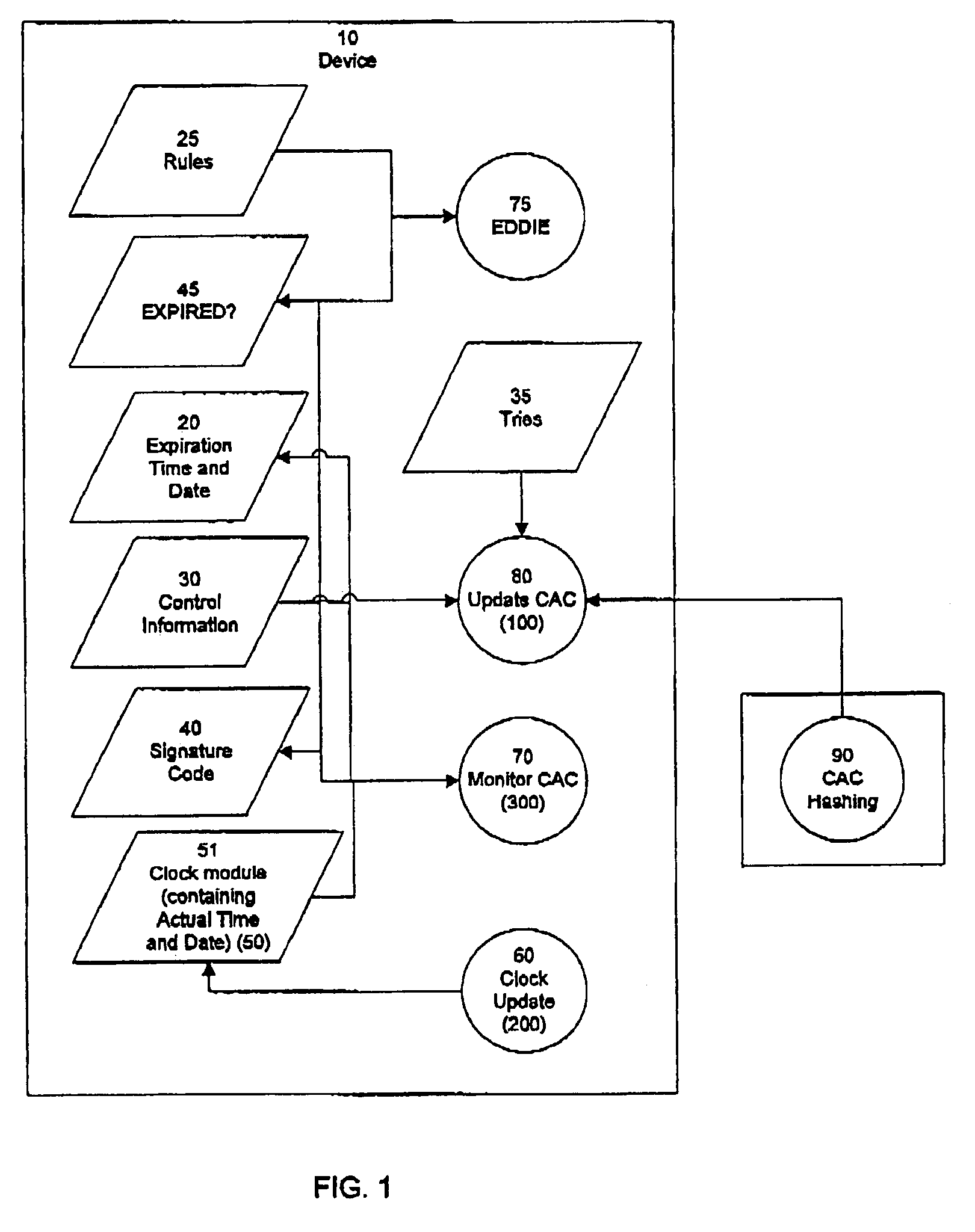
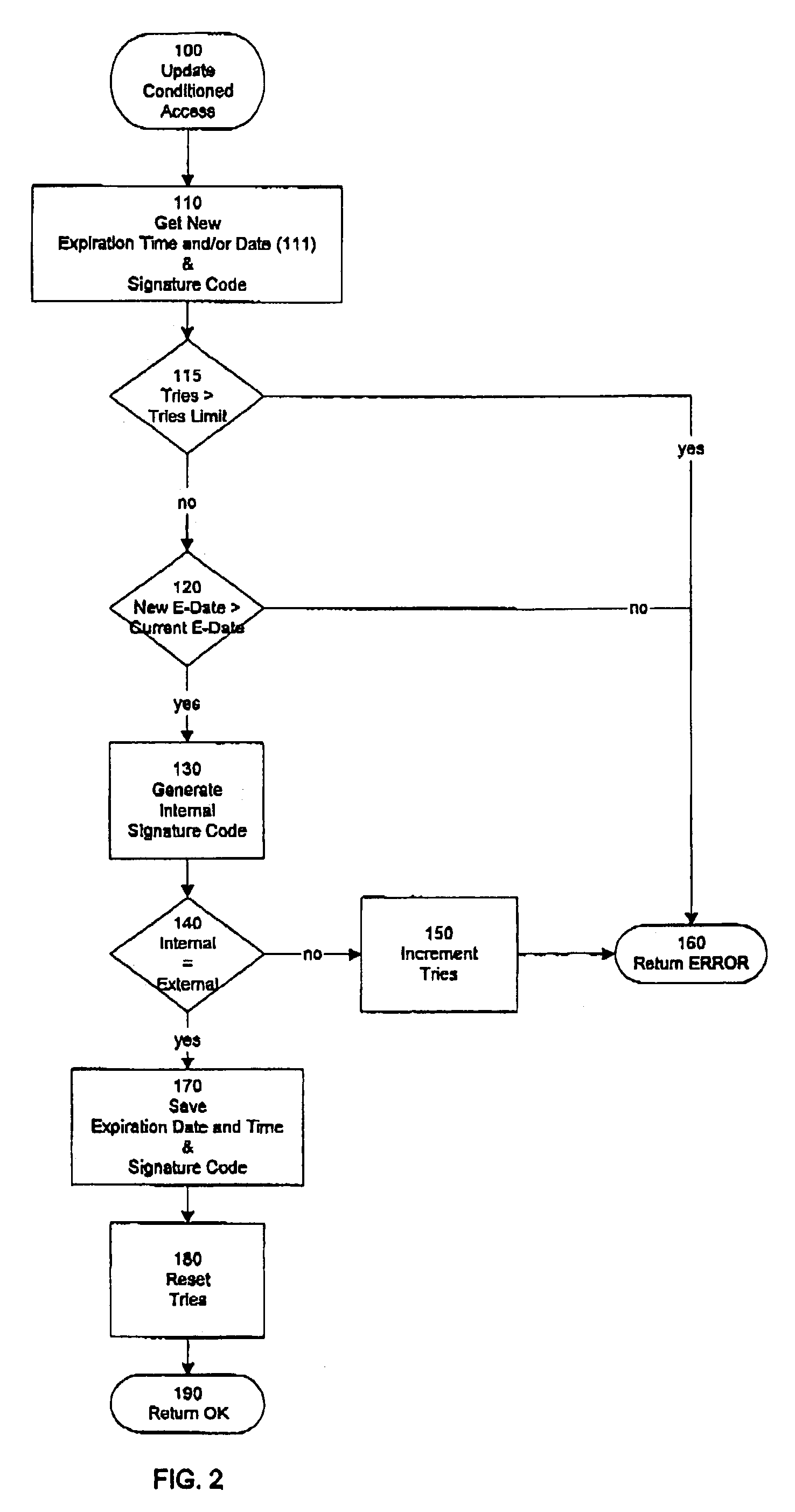
InactiveUS7170390B2Prevented from circumventingElectric signal transmission systemsMultiple keys/algorithms usageExpiration TimeGlobal positioning system receiver
A method and apparatus for conditioning the access of a user of a remotely-accessible device, which tracks and monitors objects, by using a preprogrammed expiration time and date and comparing that to a reliable time and date source, such as a time and date received from a global positioning system receiver, and disabling the processing of signals of the remotely-accessible device if the time and date comparison reveals that the license, service, lease, rental or commodity agreement has expired.
Owner:TOPP GROUP
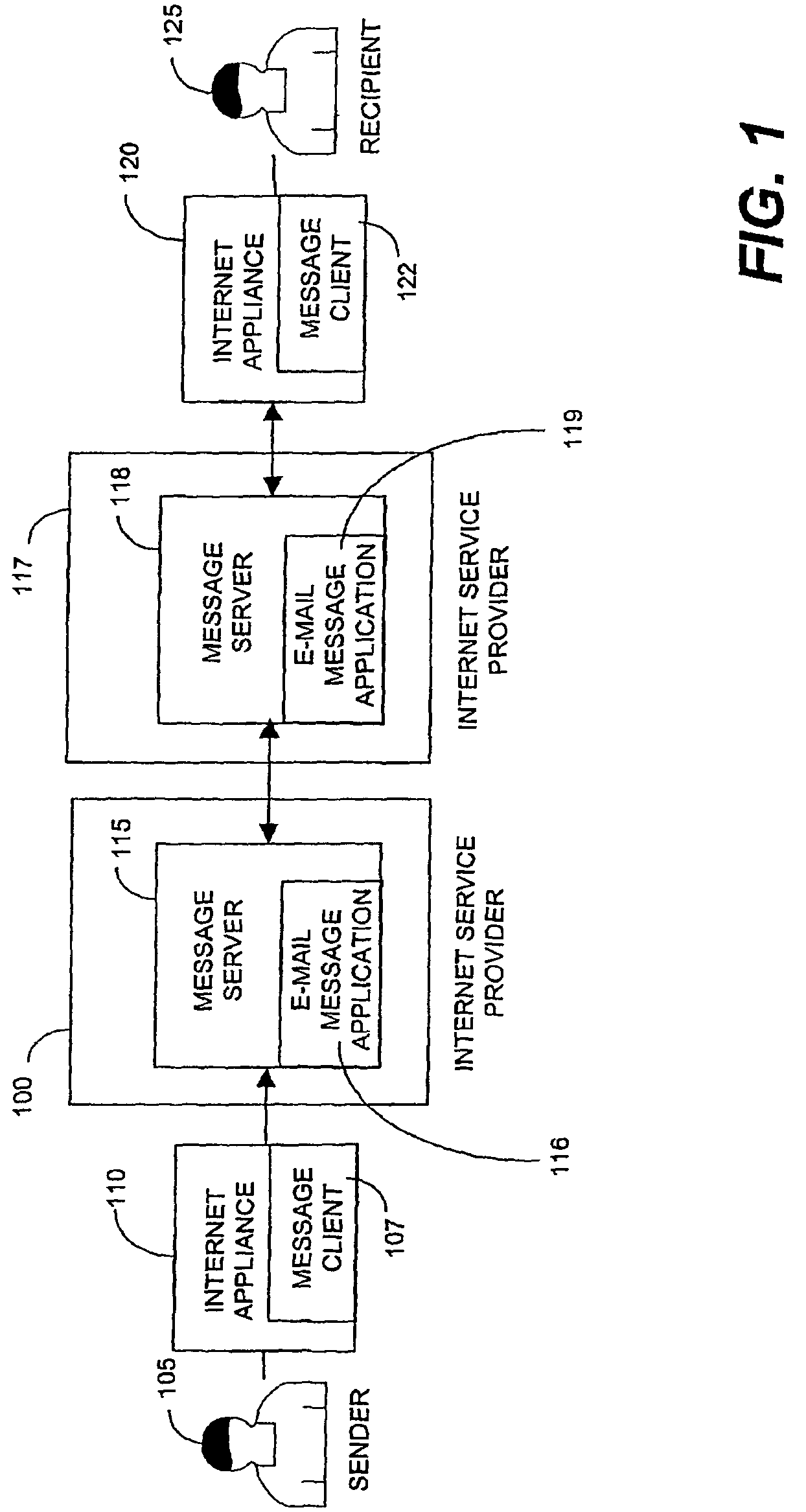
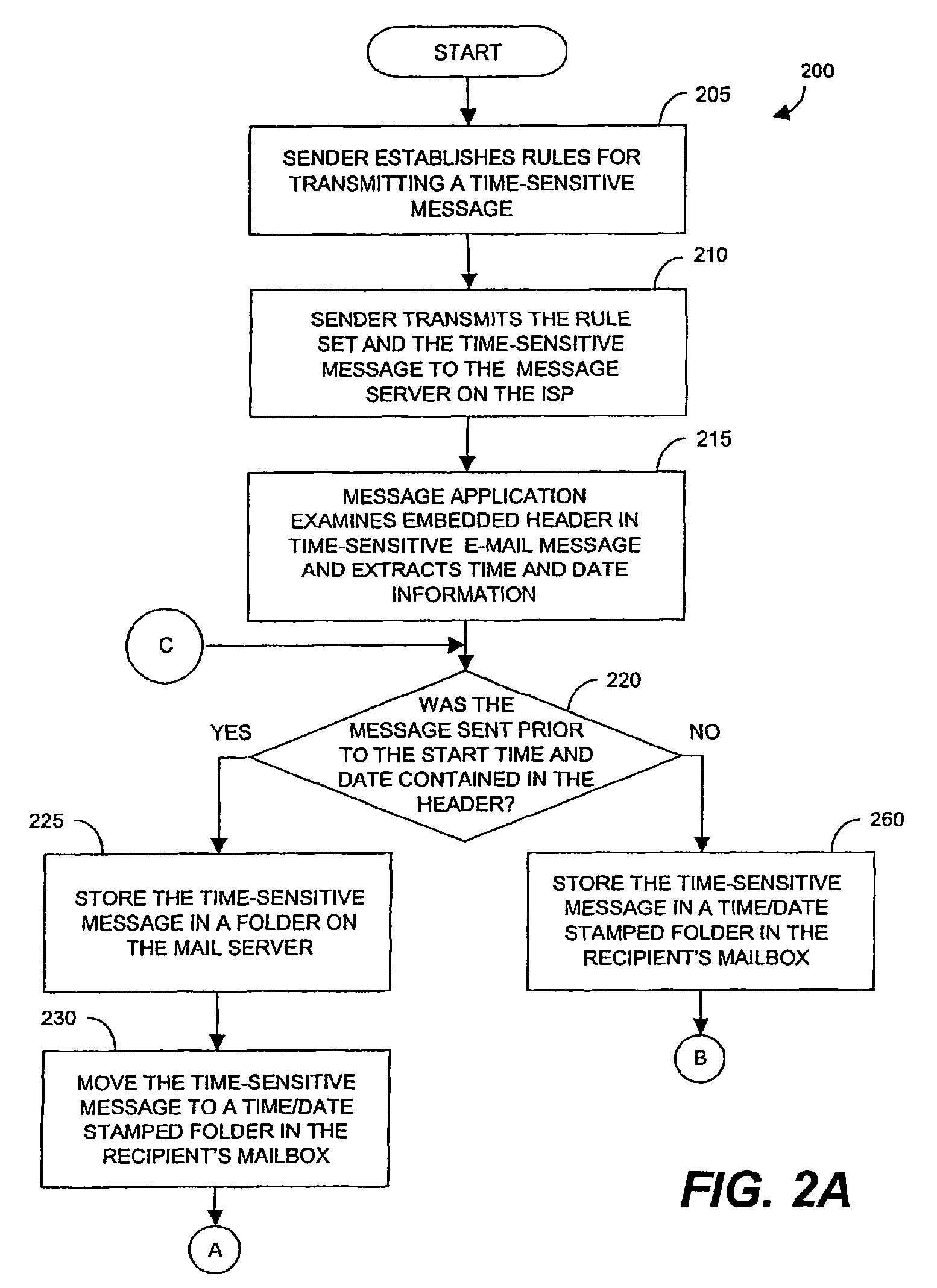
Methods, systems, and computer program products for delivering time-sensitive content
A method for delivering a time-sensitive message to a recipient includes receiving the time-sensitive message, the time-sensitive message having a rule set for delivering the time-sensitive message. The rule set is extracted from the time-sensitive message. The rule set specifies a starting time and an expiration time for the time-sensitive message. The time-sensitive message is provided to the recipient based on the starting time. A determination is made if a current time is within a threshold of the expiration time. An extension message is sent to a source of the time-sensitive message if the current time is within a threshold of the expiration time.
Owner:UBER TECH INC
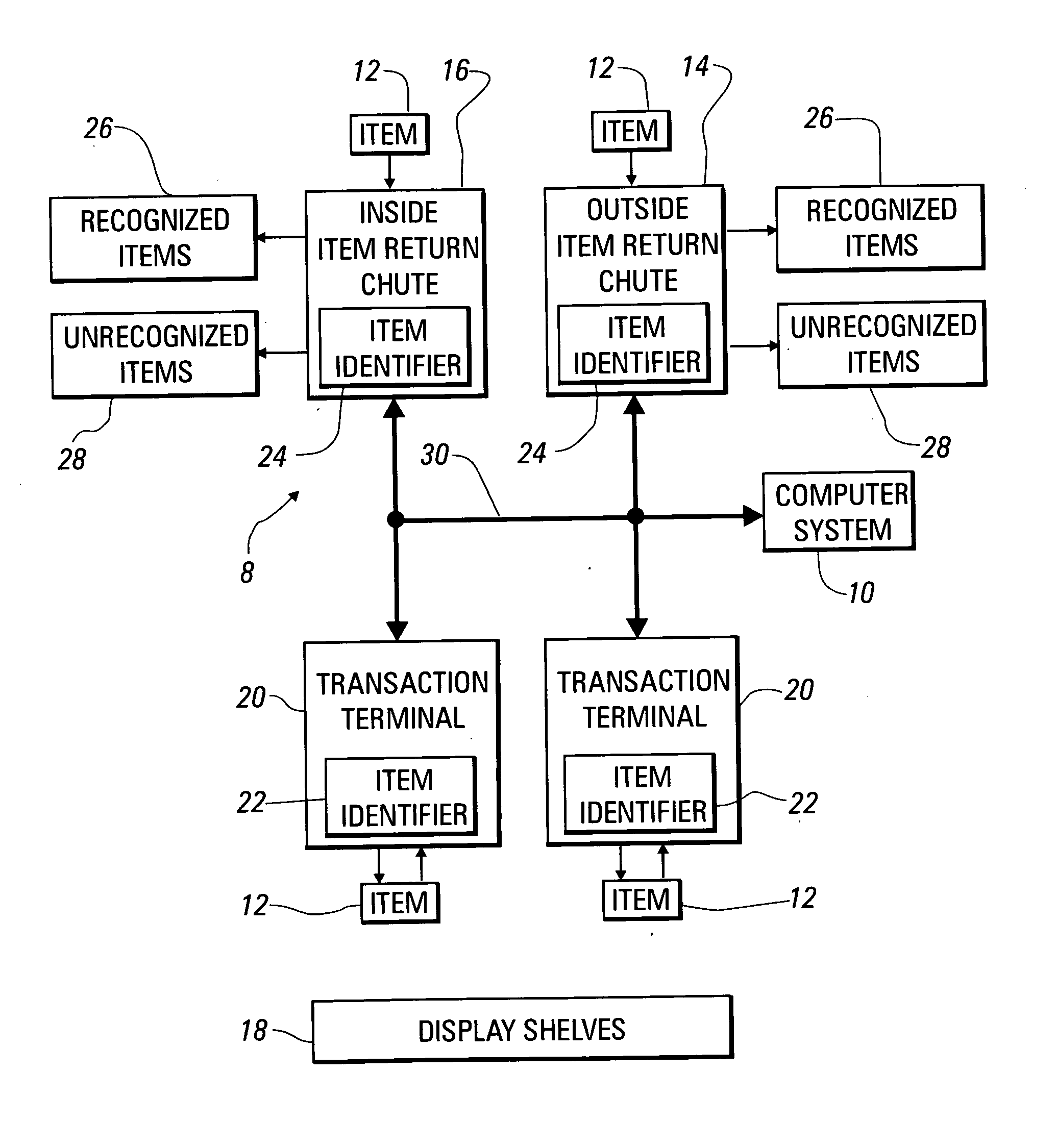
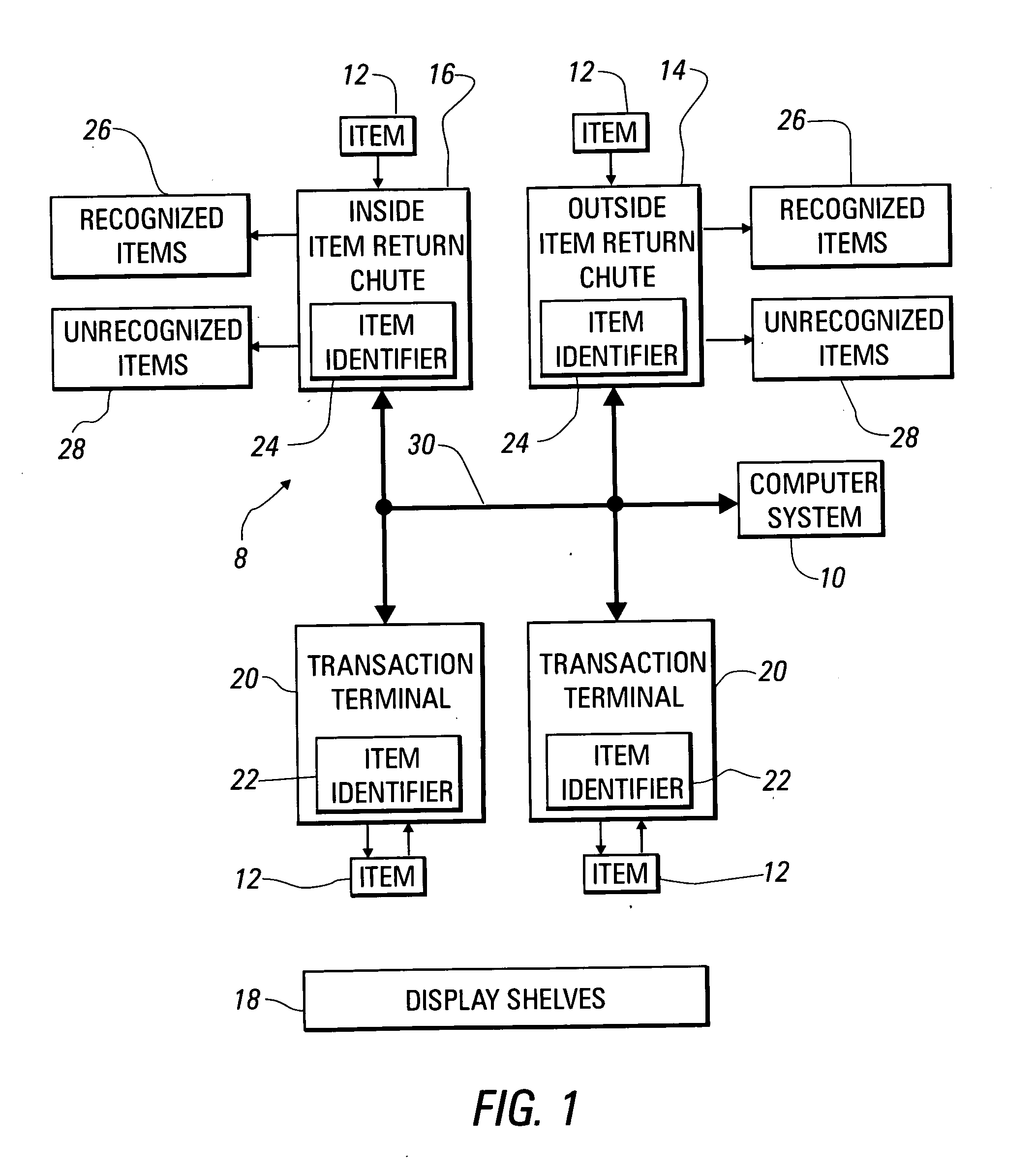
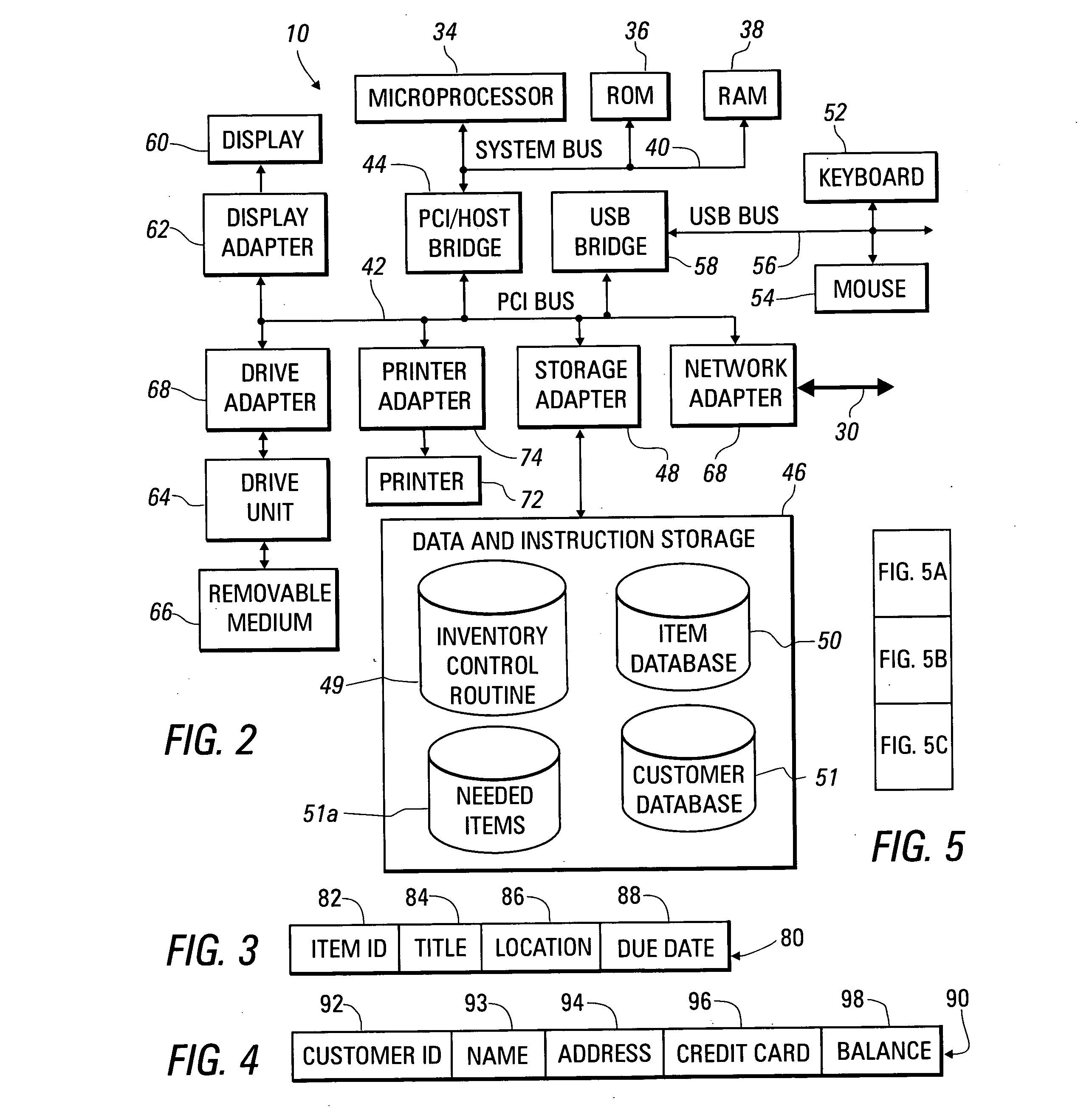
System and method for tracking the return of loaned or rented items
A system for tracking a number of items borrowed or rented by customers includes a chute reading identification data from each item as the item is returned through the chute by the customer. Data records associated with the returned items are updated to indicate the items are available, even before the items can be restocked. The time at which an item is returned may be compared with a time at which it is due, with an additional fee being added to an account of a customer borrowing or renting an item that is returned late.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
System and associated terminal, method and computer program product for controlling memory for storage of content
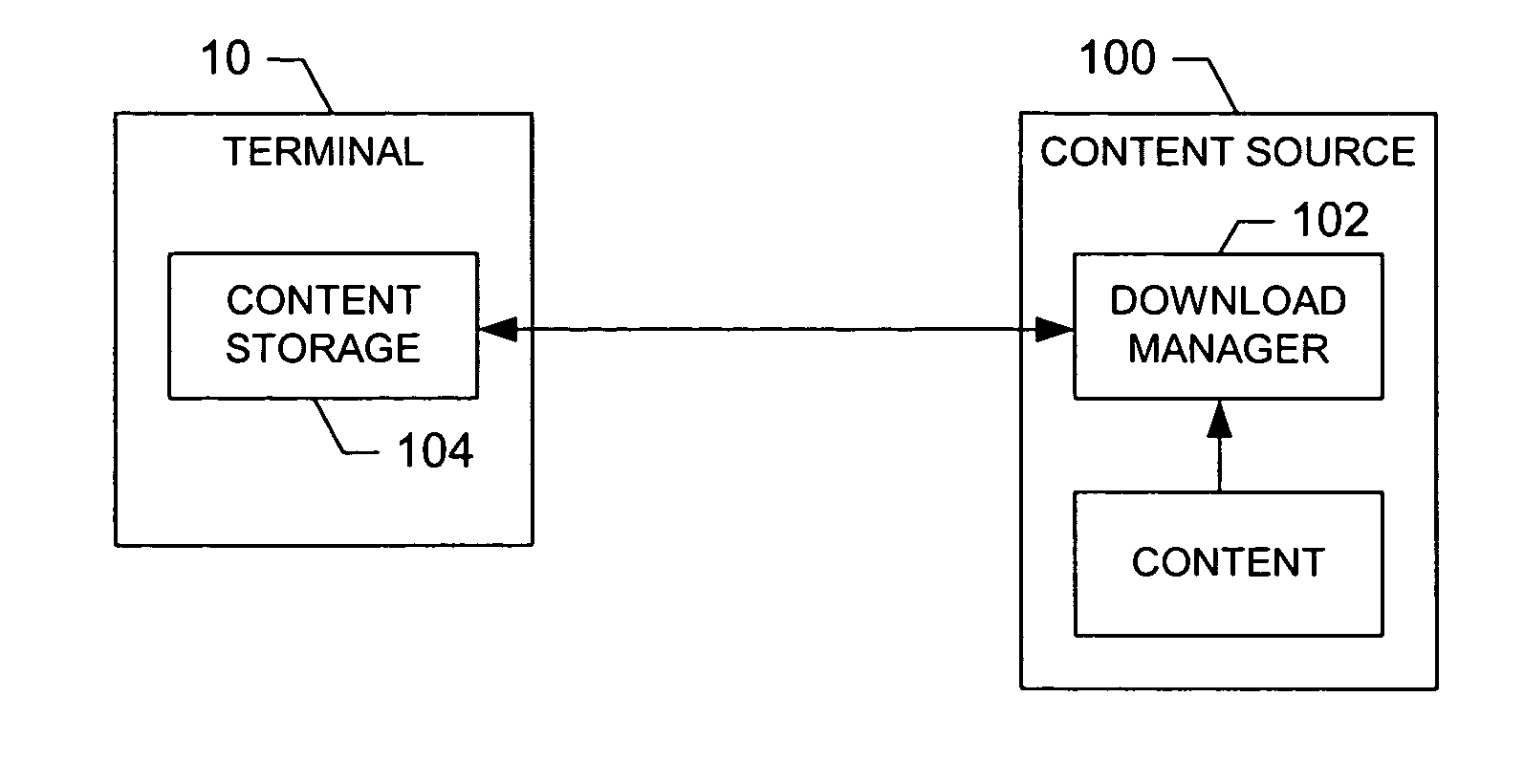
InactiveUS20050129042A1Increase storage capacityReduce the burden onAccumulation-type receiver broadcastData switching by path configurationExpiration TimeControl memory
A system for controlling memory for storage of content includes a network entitiy, such as a terminal or a content source. The network entity includes a download manager capable of receiving a selection of at least one piece of content. The download manager is also capable of reserving at least a portion of a storage capacity of memory of a terminal for at least one of the selected piece(s) of content such that the terminal can thereafter receive and store the selected piece(s) of content into the reserved storage capacity. To facilitate reserving storage capacity, the selected piece(s) of content and / or content stored in memory of the terminal includes a set of one or more parameters, such as an expiration time, a deletion priority value and / or a download priority value.
Owner:NOKIA CORP
Fast authentication and access control method for mobile networking
InactiveUS7174456B1Easy to switchReduce certification timeDigital data processing detailsUser identity/authority verificationExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
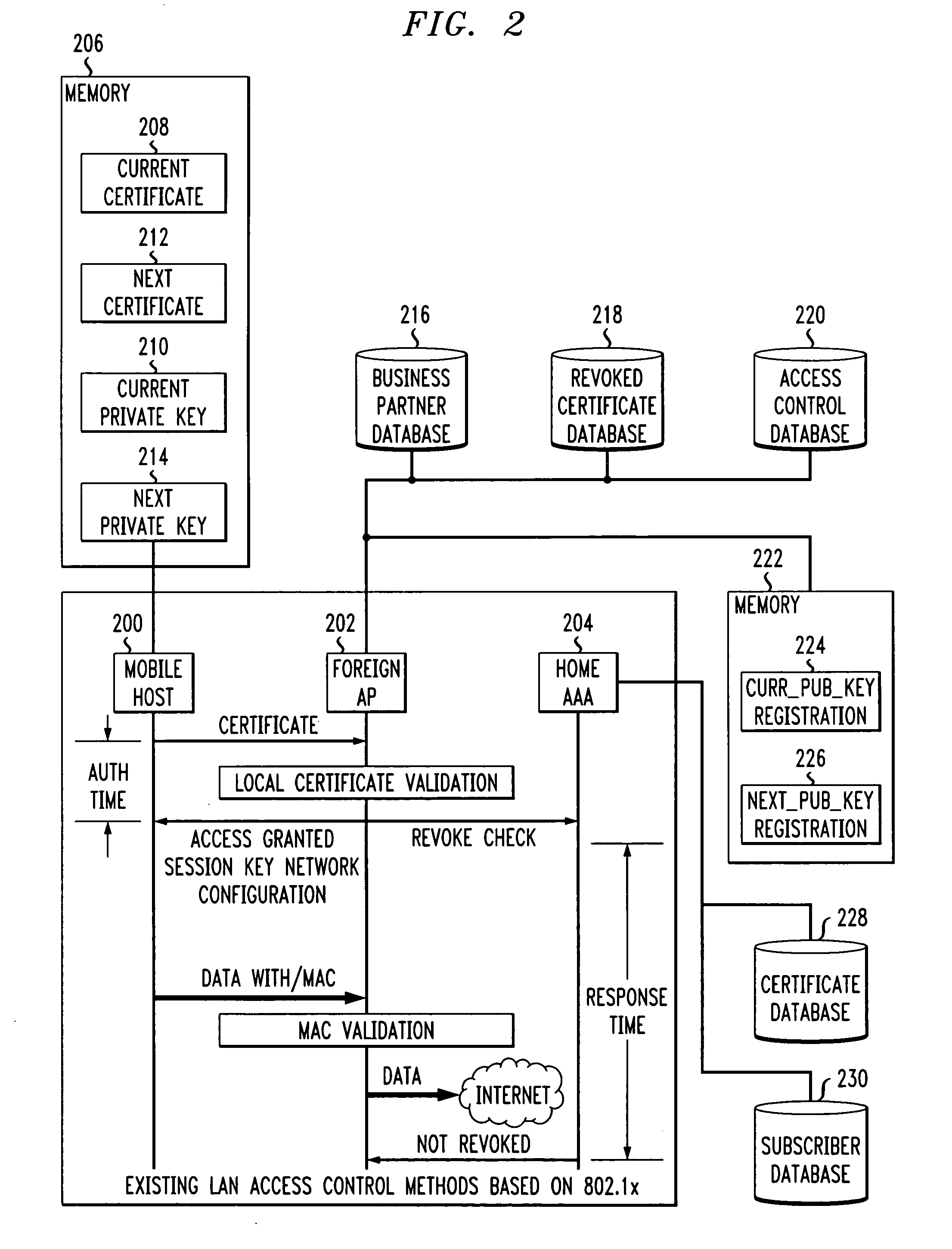
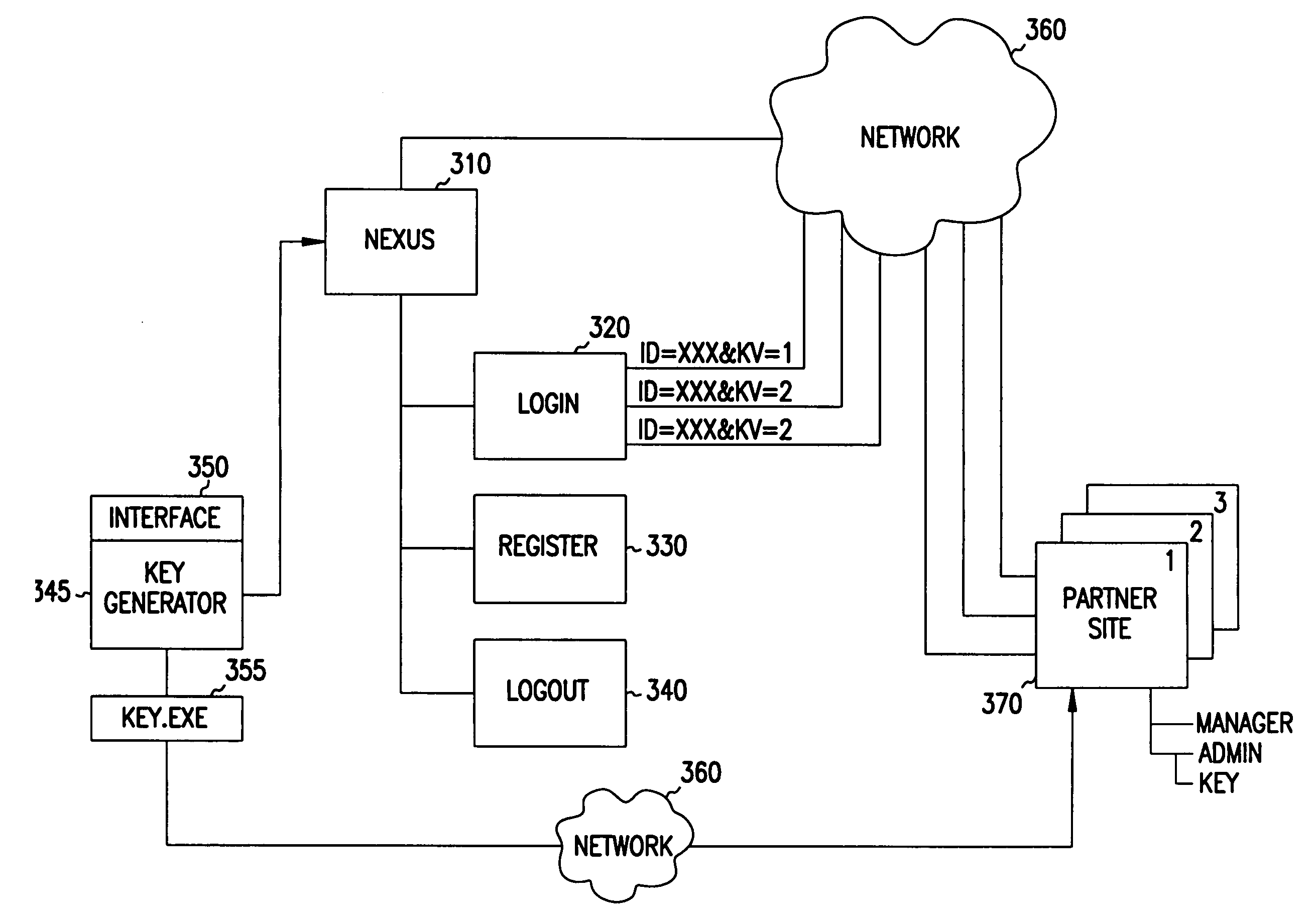
Encryption key updating for multiple site automated login
ActiveUS6950522B1Minimum level of safetyKey distribution for secure communicationDigital data processing detailsExpiration TimeEncryption
A version number is associated with an encrypted key executable to allow real time updating of keys for a system which facilitates users signing on to multiple websites on different domains using an encrypted ticket. Two keys may be used at each site during updating of keys, each having an associated one digit Hex version tag. When a key is to be updated with a new key, the existing or old key is provided an expiration time. A second key is provided from the system in a secure manner with a new version number and made the current key which provides decryption of the encrypted ticket. The system tracks both keys while they are concurrent. After the existing key expires, only the second, or updated key is used to provide login services for users. The system periodically flushes old keys.
Owner:MICROSOFT TECH LICENSING LLC
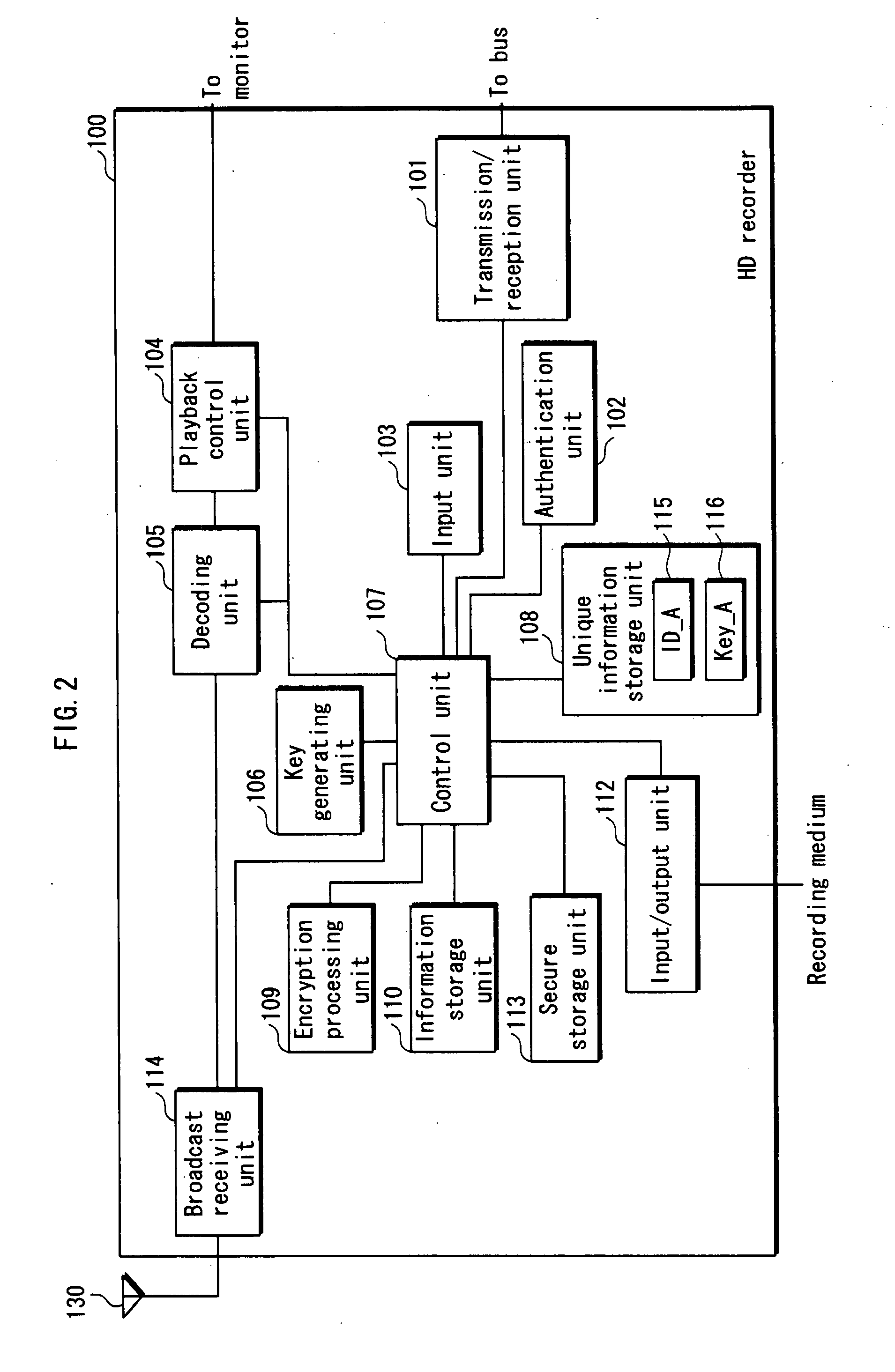
Backup System, Recording/Reproduction Device, Backup Device, Backup Method, Program, and Integrated Circuit
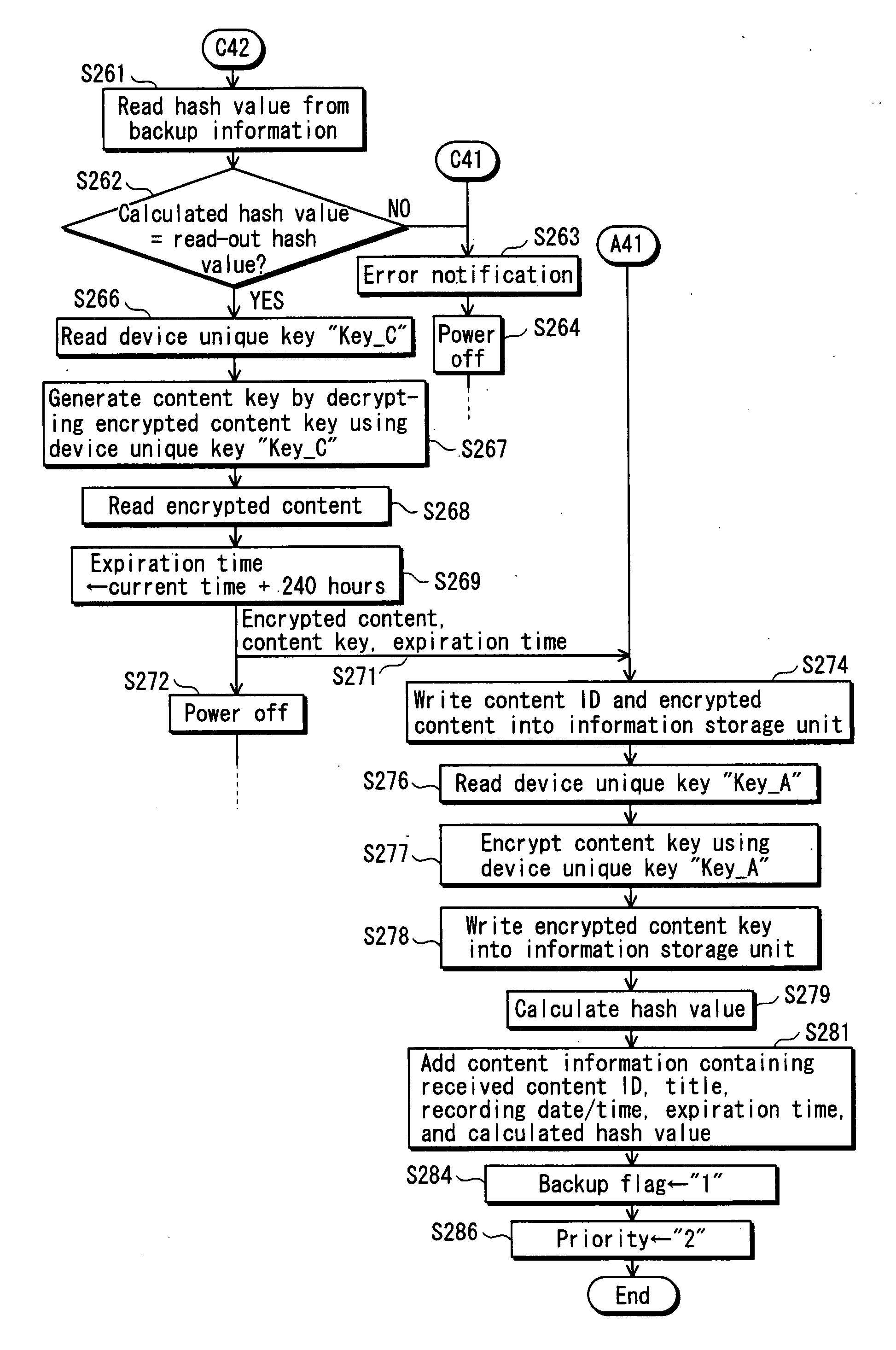
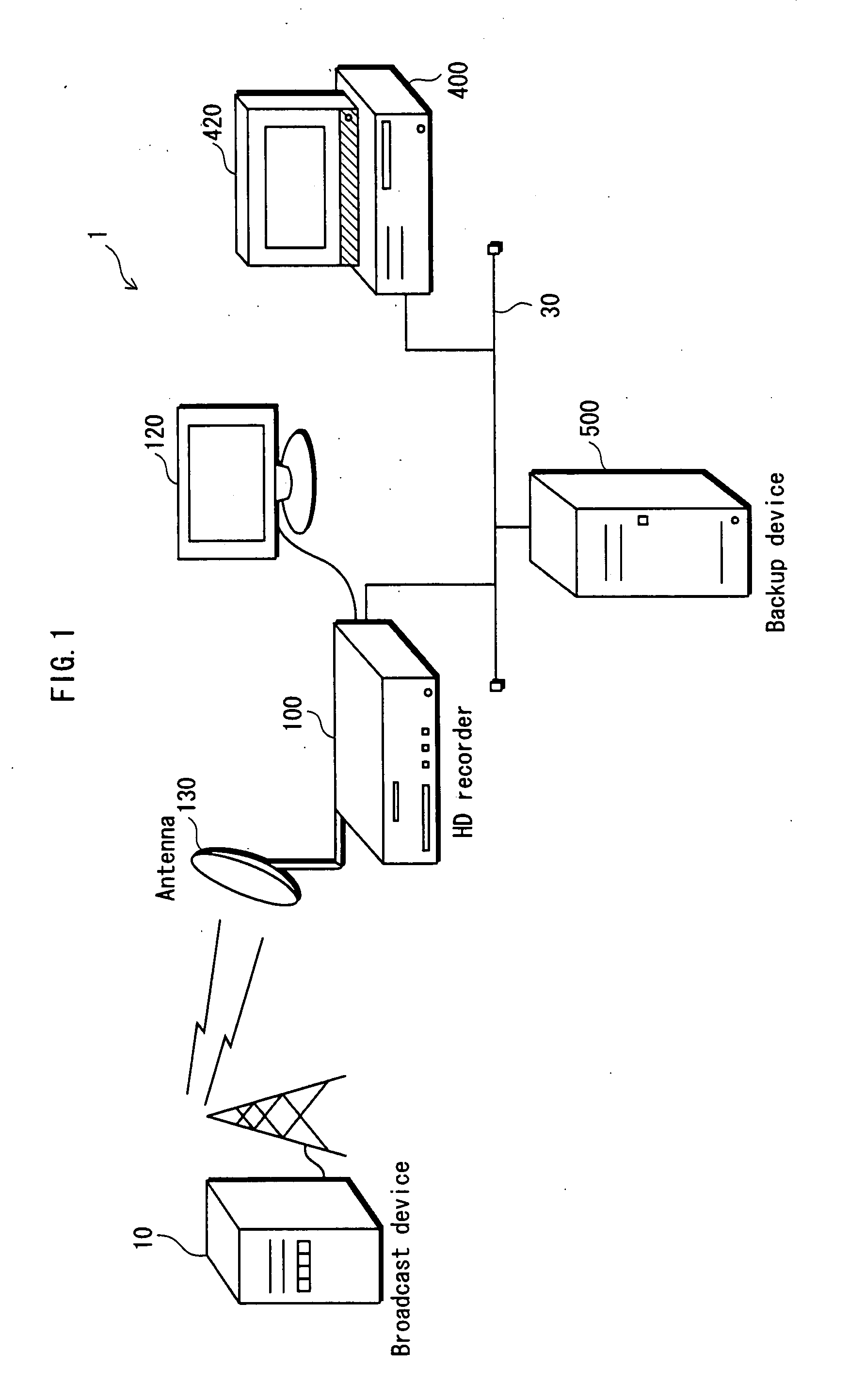
InactiveUS20080022061A1Secure convenienceTelevision system detailsMemory loss protectionExpiration TimeHard disk recorder
A content of Copy Once cannot be copied to an external device or the like, even for the purpose of making a backup. This is inconvenient for the user. However, if copying to another device for the purpose of making a backup is permitted, the content may be copied in an unauthorized manner. The present invention provides the hard disk recorder 100 that transmits the content to the backup device 500, sets an expiration time in the content stored in the hard disk recorder 100 itself, and deletes the content stored in the hard disk recorder 100 itself after the expiration time expires.
Owner:PANASONIC CORP
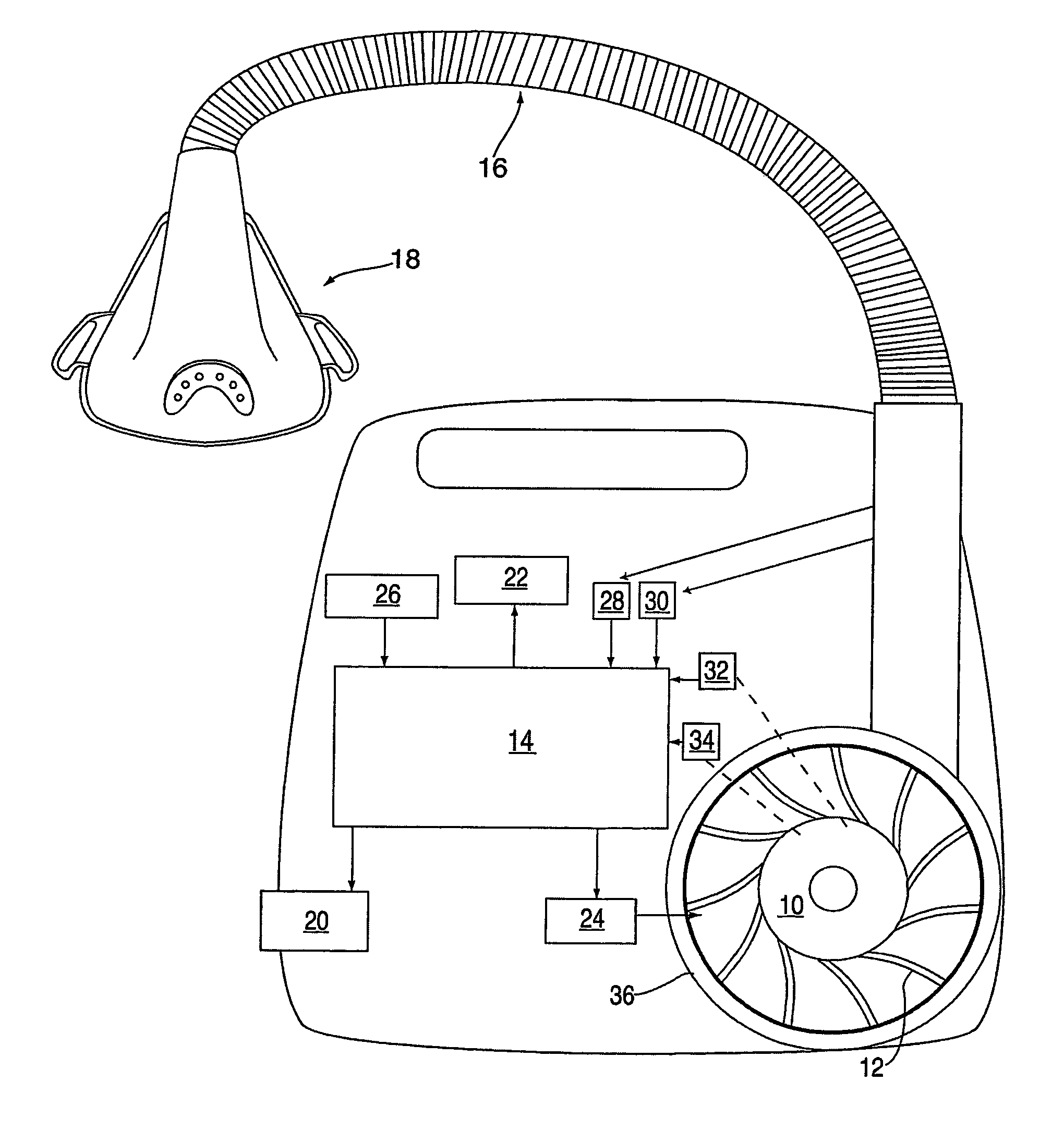
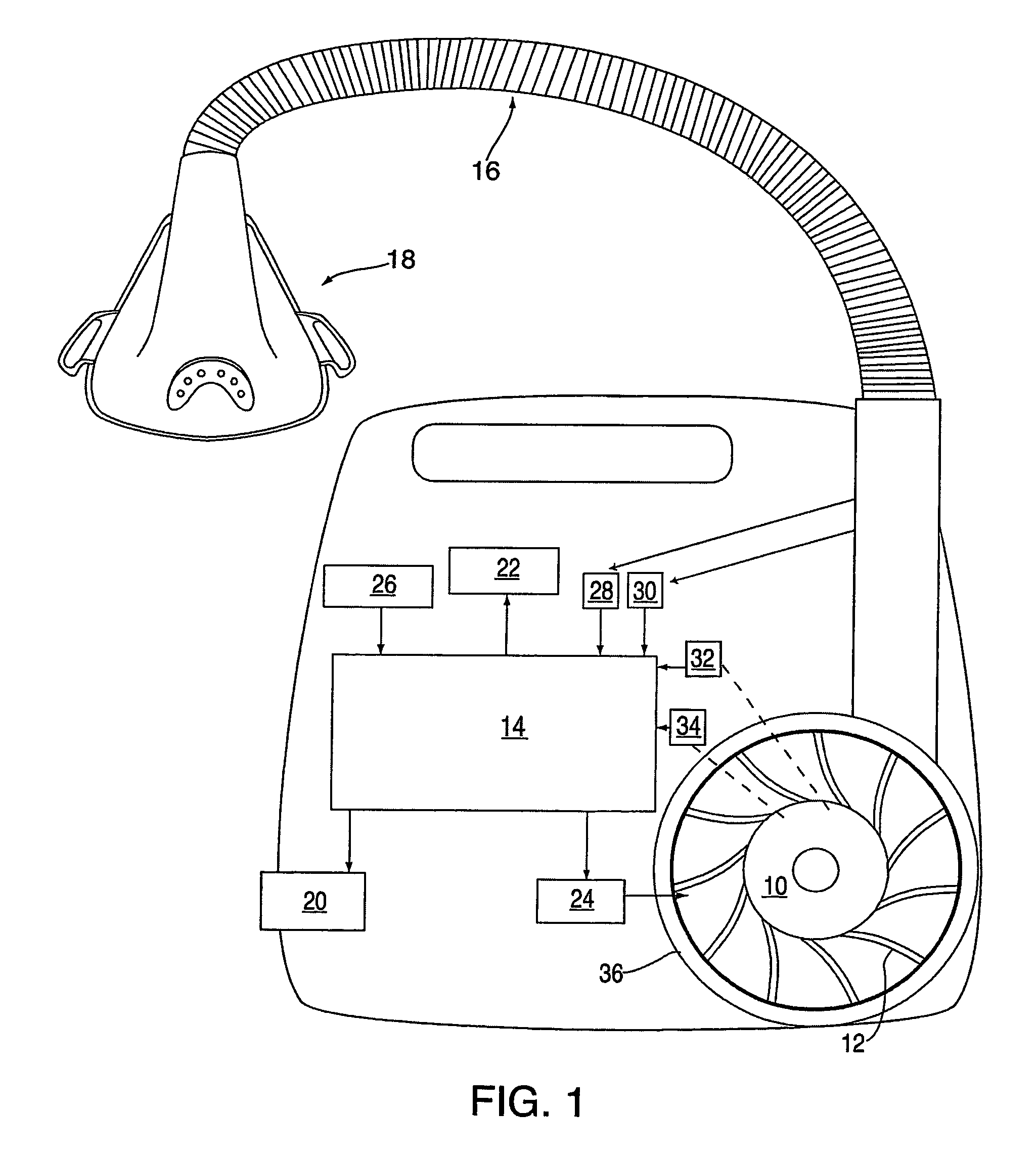
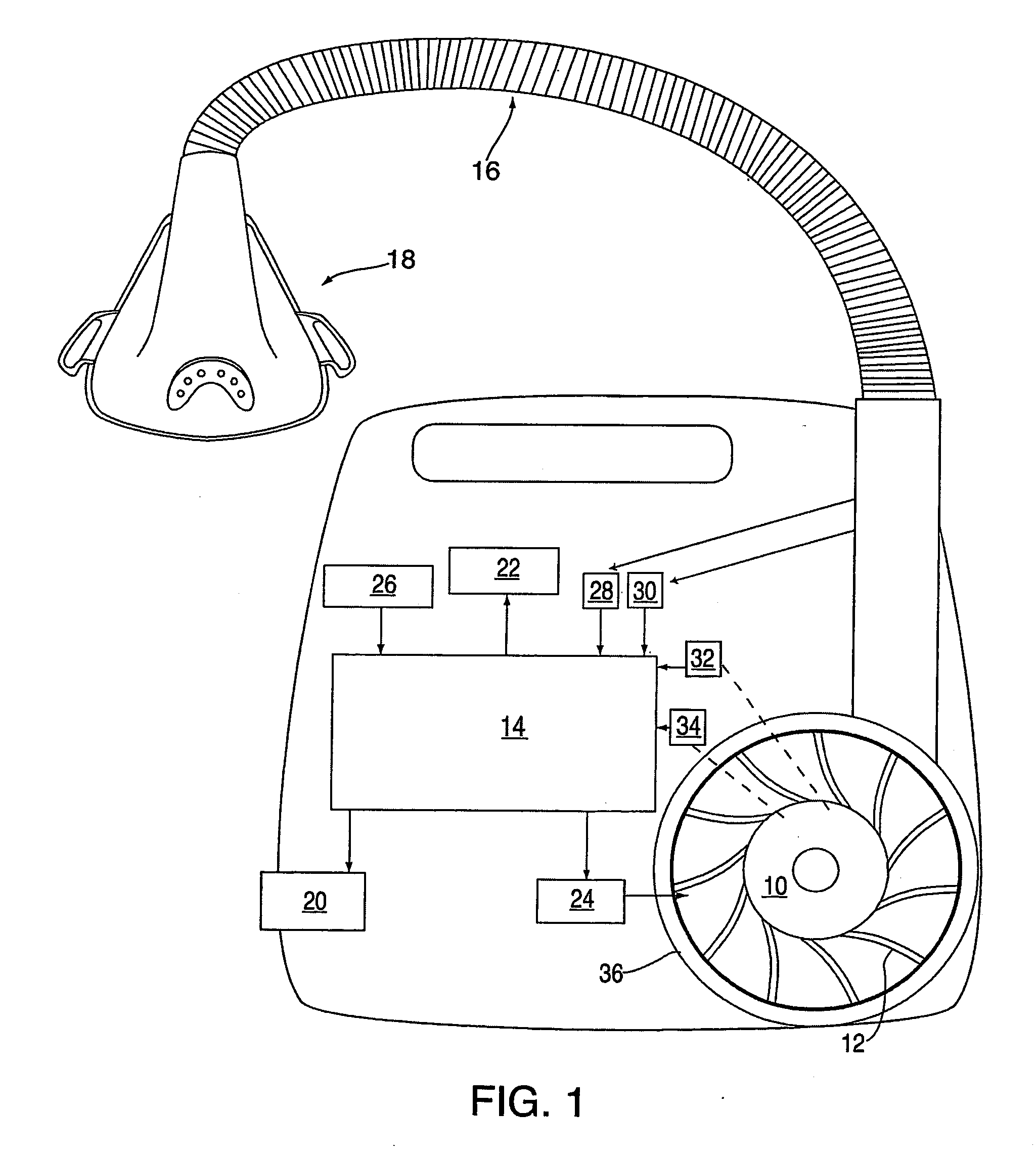
Methods for providing expiratory pressure relief in positive airway pressure therapy
InactiveUS7866318B2Stable changeOperating means/releasing devices for valvesRespiratory masksRespiratory flowExpiration Time
Owner:RESMED LTD
Digital online exchange for pricing items to exhaust inventory by an expiration time
InactiveUS20080059384A1Network load increaseMarket predictionsBuying/selling/leasing transactionsExpiration TimeData storing
A dynamic pricing system for pricing items for sale by a seller which items are available in a limited quantity comprises a pricing server and various types of data stored in memory. The pricing server includes memory, a processor and a clock. One type of data stored in memory is indicative of the initial quantity of an item available in a limited quantity. Another type of data stored in memory is indicative of the current remaining quantity of the item available in a limited quantity. Yet another type of data stored in memory is indicative of an expiration time at which it is desired that all of the item available in a limited quantity be sold. The processor is configured to price the item available in a limited quantity so as to deplete the inventory of the item available in a limited quantity by the expiration date based in part by accessing the memory to retrieve the data indicative of the initial quantity, the current remaining quantity and the expiration time and accessing the clock.
Owner:DIGONEX TECH
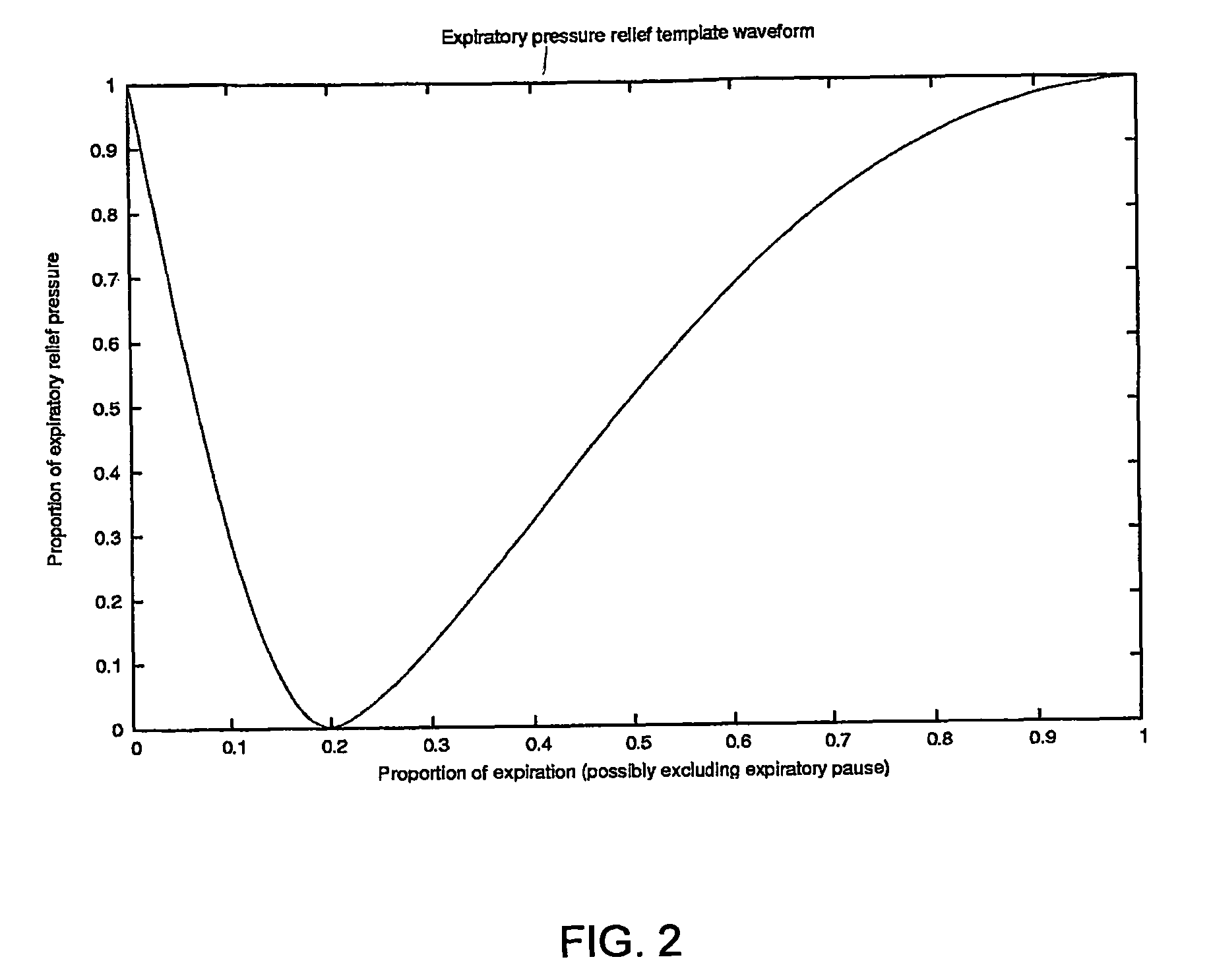
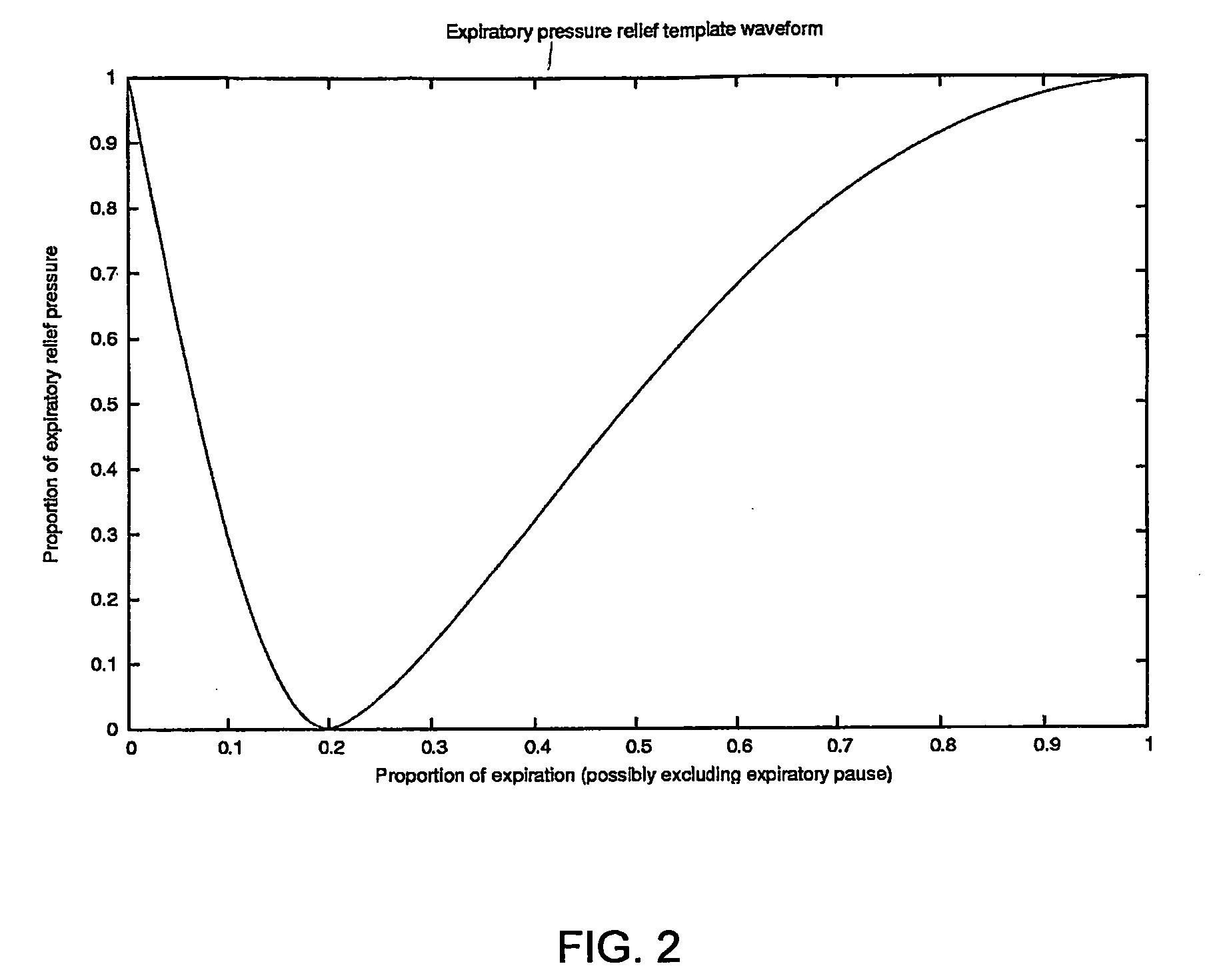
Methods for providing expiratory pressure relief in positive airway pressure therapy
InactiveUS20090020121A1Stable changeOperating means/releasing devices for valvesRespiratory masksExpiration TimePositive airway pressure
A method of operating a CPAP apparatus in which the interface pressure is controlled to rapidly drop at the start of expiration by an expiratory relief pressure (ERP) that is independent of instantaneous respiratory flow, following which the pressure rises to an inspiratory level at or shortly before the end of expiration, or at the onset of an expiratory pause, if any. The ERP is an increasing function of the inspiratory pressure. The expiratory pressure follows a template that is a function of the expected expiration time, the magnitude of the template being equal to the ERP. The current estimated proportion of expiration is determined by comparing the expiration time of the breath in progress to low-pass filtered expiratory durations measured for a number of the preceding breaths.
Owner:RESMED LTD
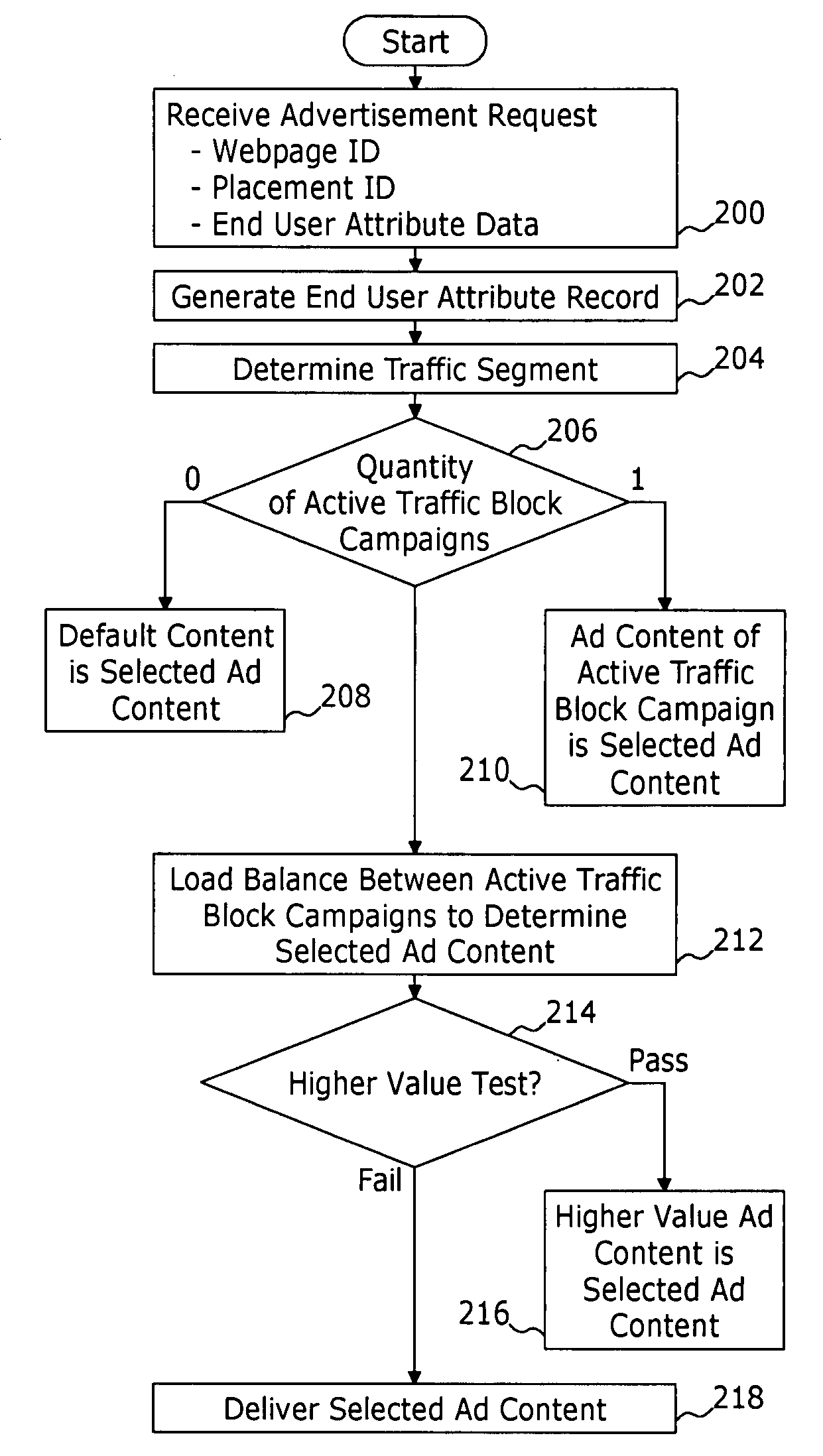
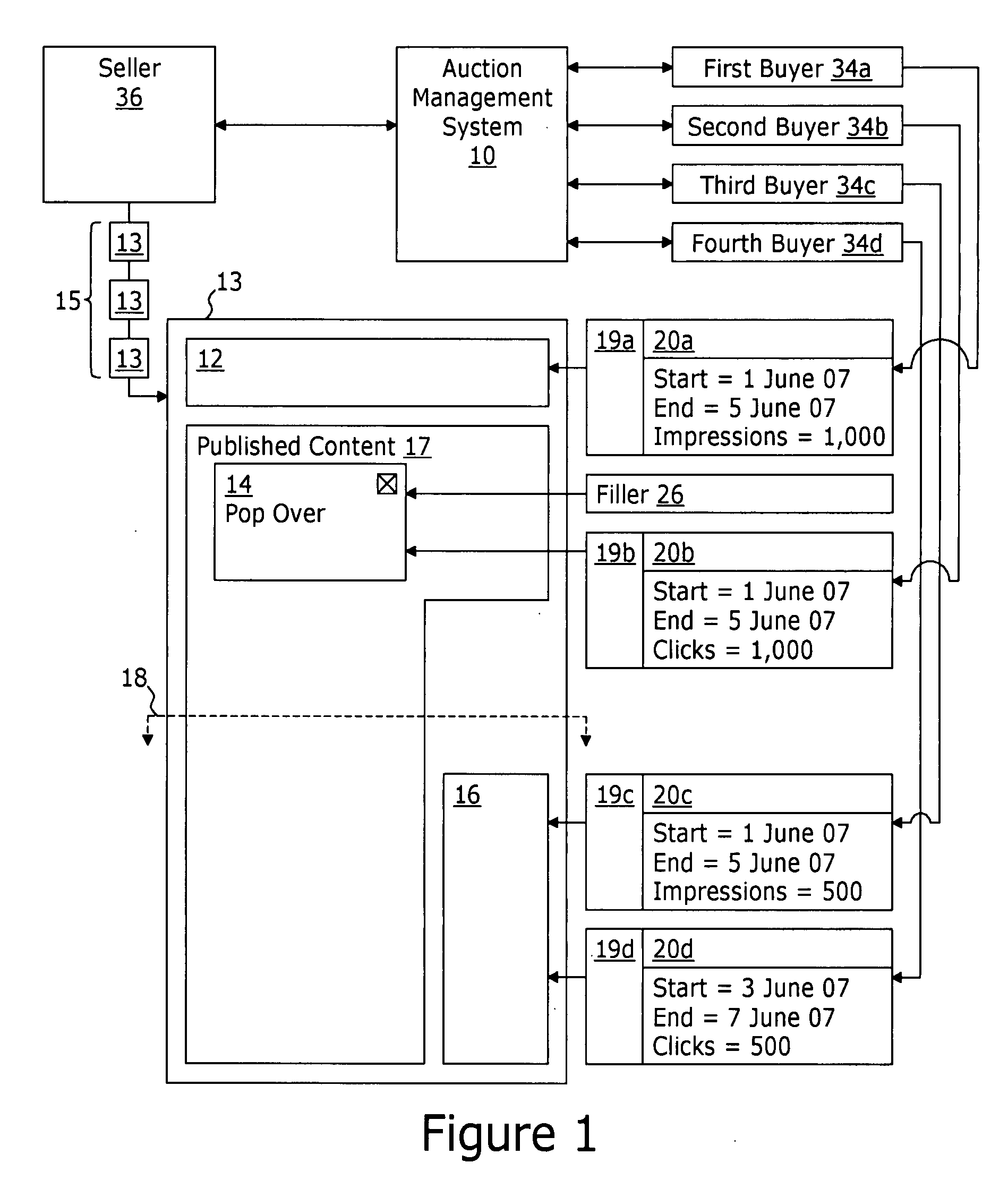
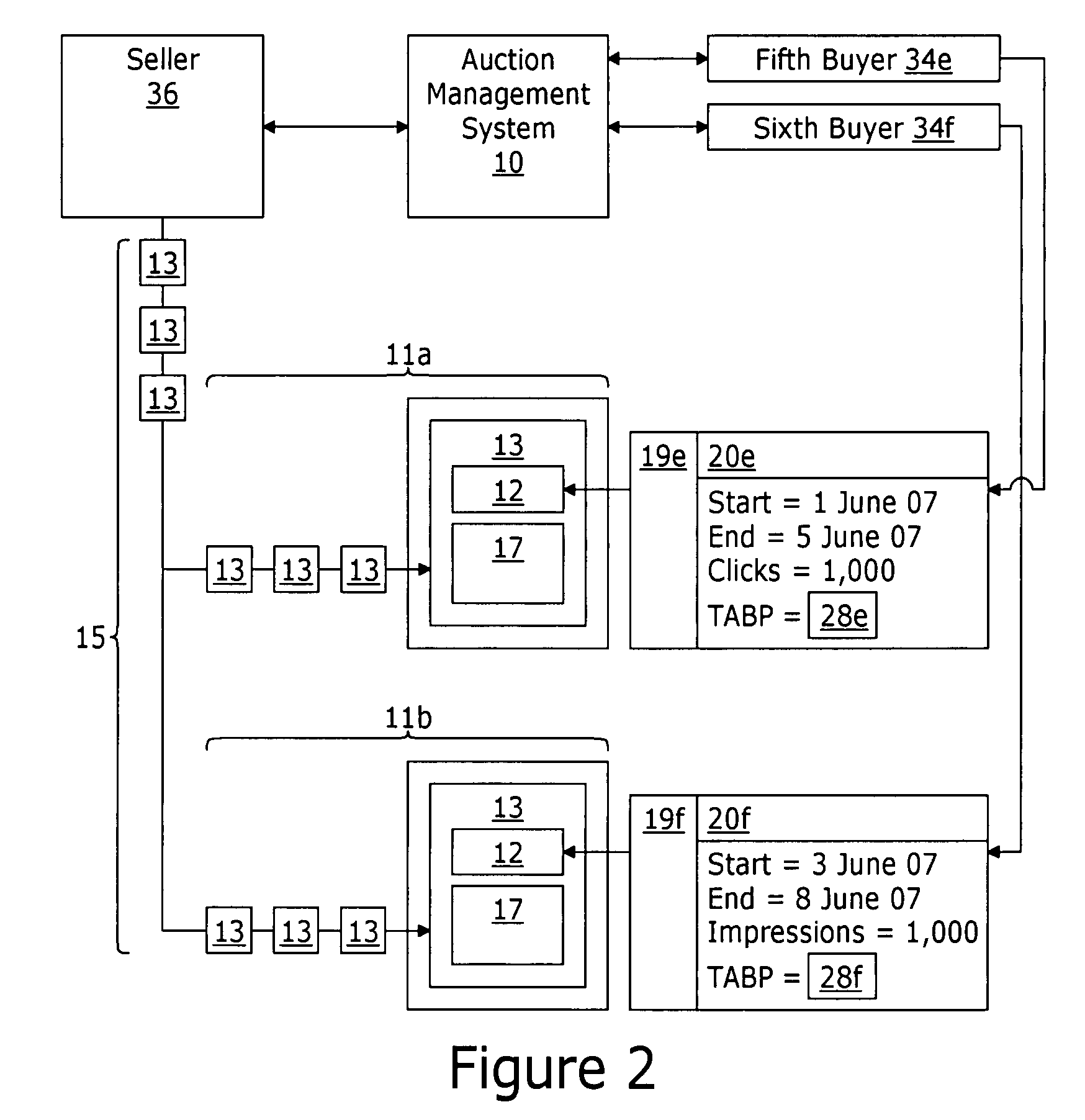
System and method for brokering the sale of internet advertisement inventory as discrete traffic blocks of segmented internet traffic
An auction management system brokers, between a seller and a buyer, a discrete traffic block of an ad placement. The auction management system comprises a traffic block definition tool providing workflows for obtaining traffic block parameters defining the discrete traffic block, the traffic block parameters comprising: i) an identification of the ad placement; ii) a volume parameter defining the volume of traffic included in the discrete traffic block; iii) at least one duration parameter defining an active time period during which the volume of traffic included in the discrete traffic block will be provided; and iv) an auction parameter defining an expiration time before which buyers submit offers to purchase the discrete traffic block. A listing search tool provides web pages displaying a listing of a plurality of listed discrete traffic blocks. Each listed discrete traffic block comprises a discrete traffic block with an expiration time that has not yet passed. The listing includes, for each listed discrete traffic block, the traffic block parameters associated therewith. An auction management tool provides for: i) obtaining a buyer compensation parameter from each of a plurality of buyers bidding for purchase of the discrete traffic block; and ii) designating the buyer that that provided a compensation parameter meeting selection criteria as the winning buyer. An order management system directs placement of buyer advertisement content designated by the winning bidder within the ad placement for the volume of traffic defined by the volume parameter and during the time period defined by the at least one duration parameter.
Owner:TRAFFIQ
System and method for securing transactions in a contact center environment
ActiveUS20080011823A1Avoid misuseGreat confidenceComplete banking machinesFinanceCredit cardExpiration Time
A system and method for protecting confidential user information employed in an electronic transaction. The system and method provide for associating an expiration time / time period, use or other use-limiting authorization indicator with a credit card or other user information to be transferred to a user information recipient, in conjunction with a product / service payment or other business transaction with a hosted contact center. Embodiments of the invention further provide for forming a limited-use indicator, such as a use-limiting token, by associating a transaction agent indicator and a use-limiting indicator with the user information, and for verifying a limited use indicator received from a contact center agent and determining according to such indicator, in addition to any ordinary verification that might also be conducted, whether the use limitation has been met and whether the transaction should be authorized in accordance with the use limitation.
Owner:CISCO TECH INC
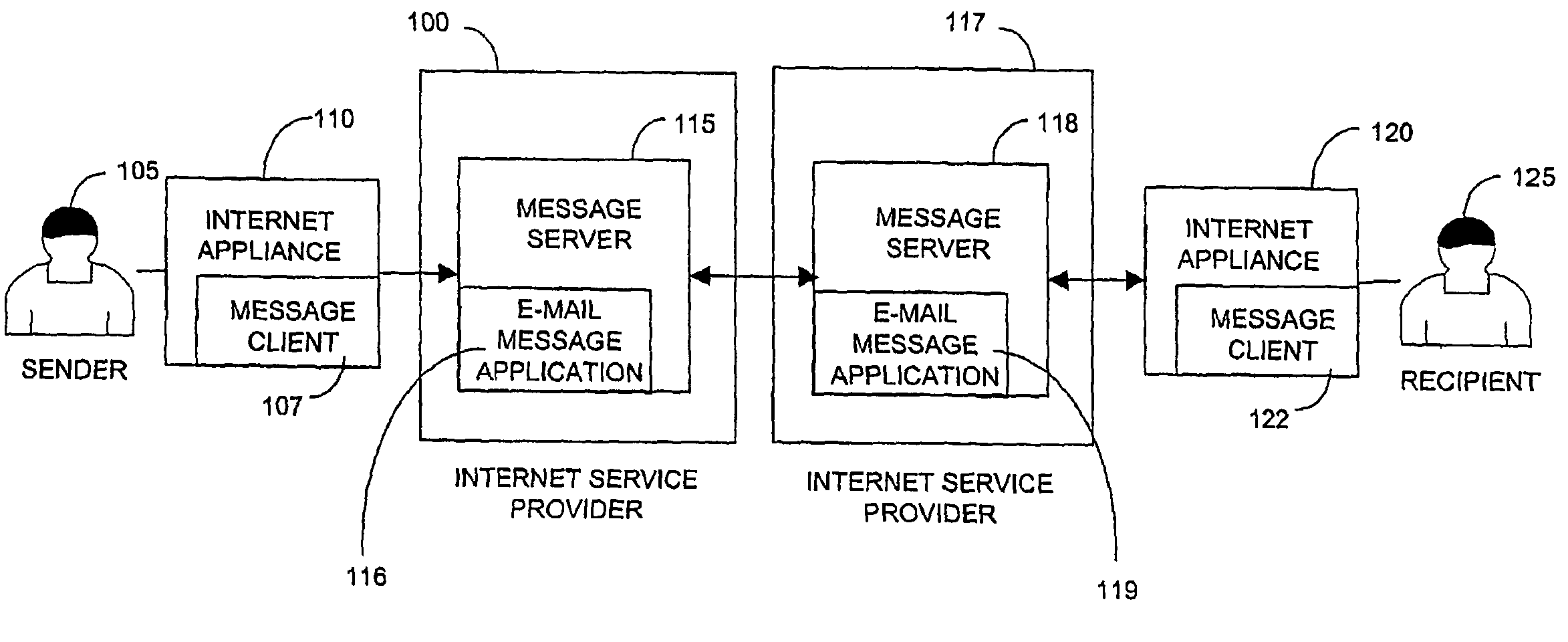
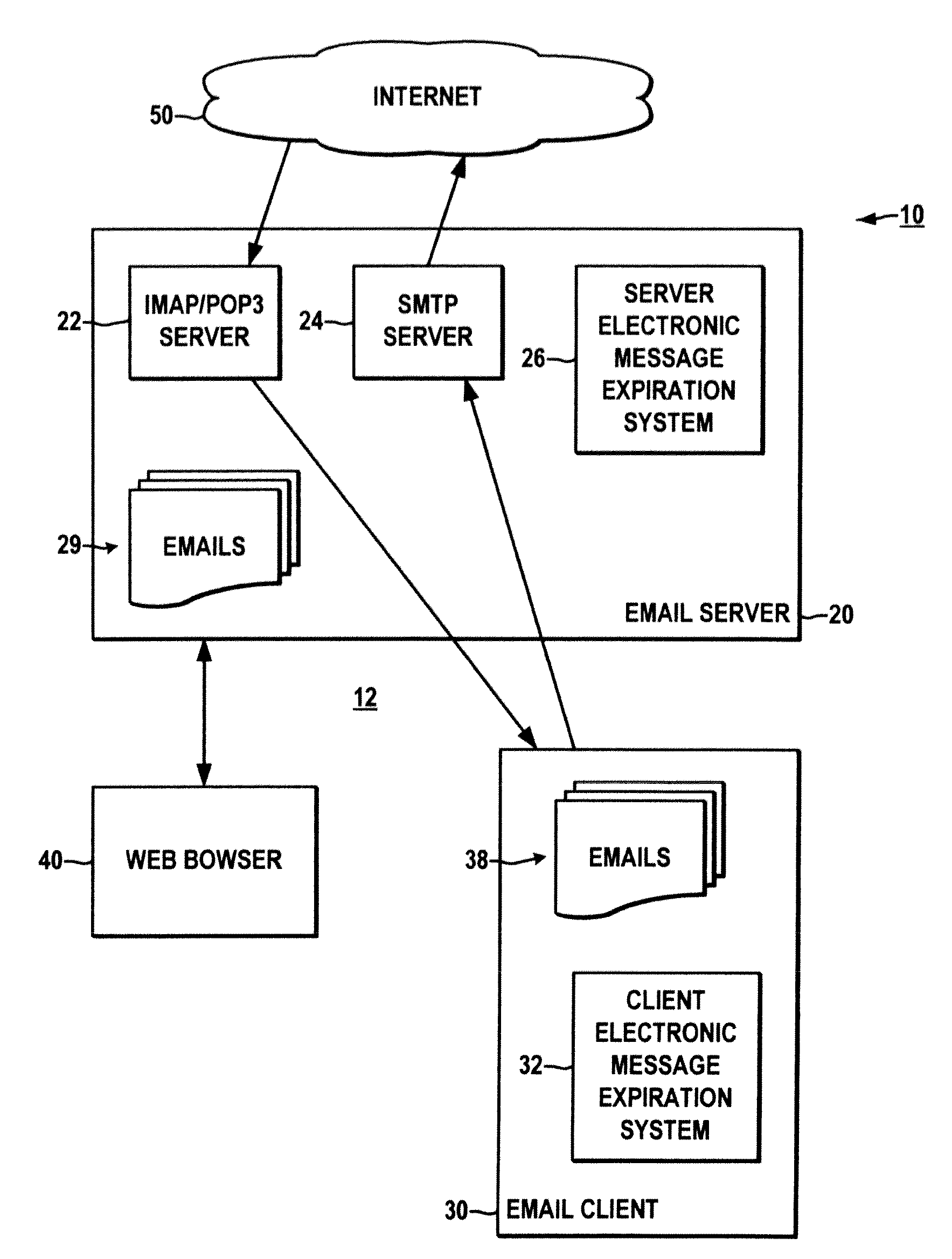
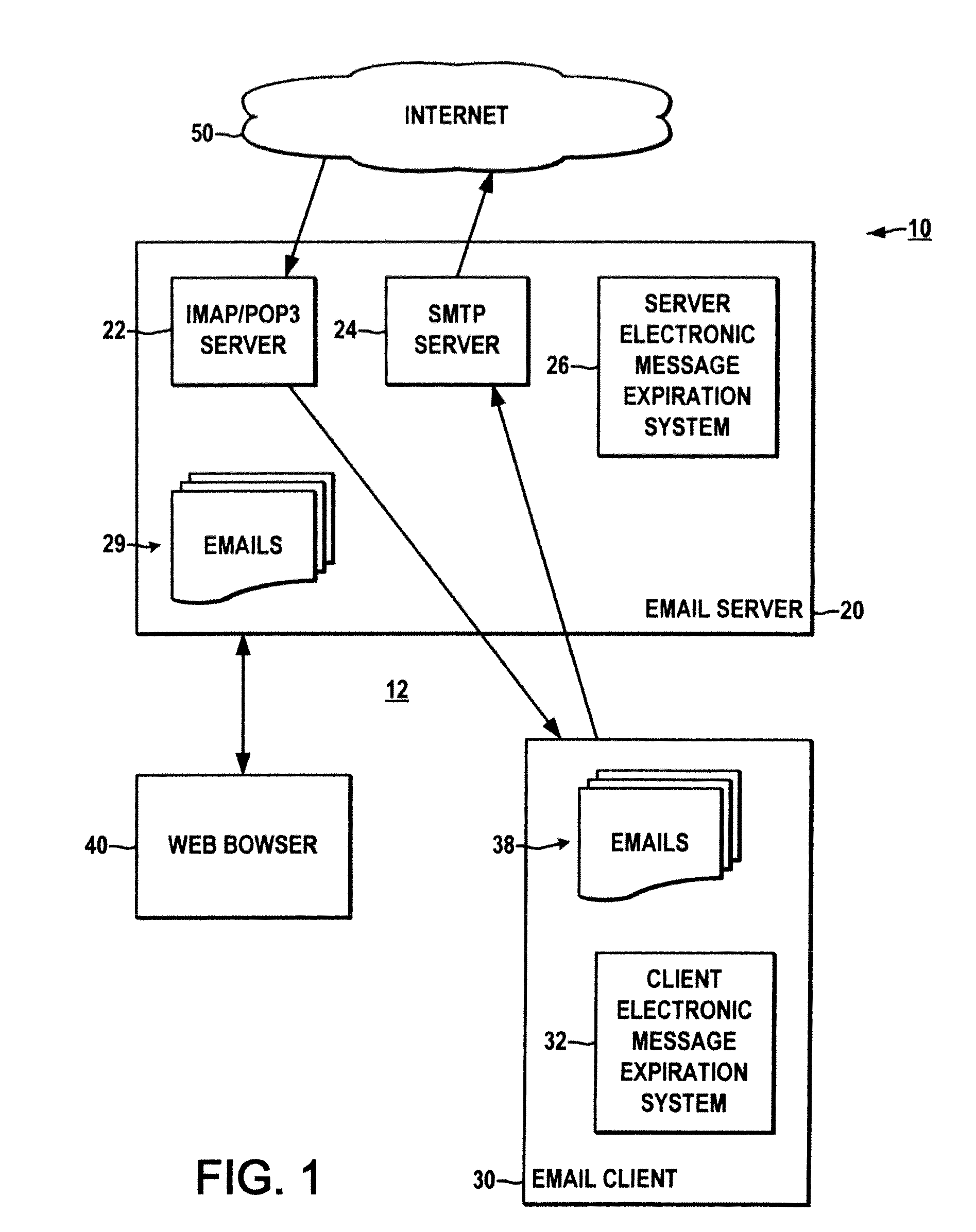
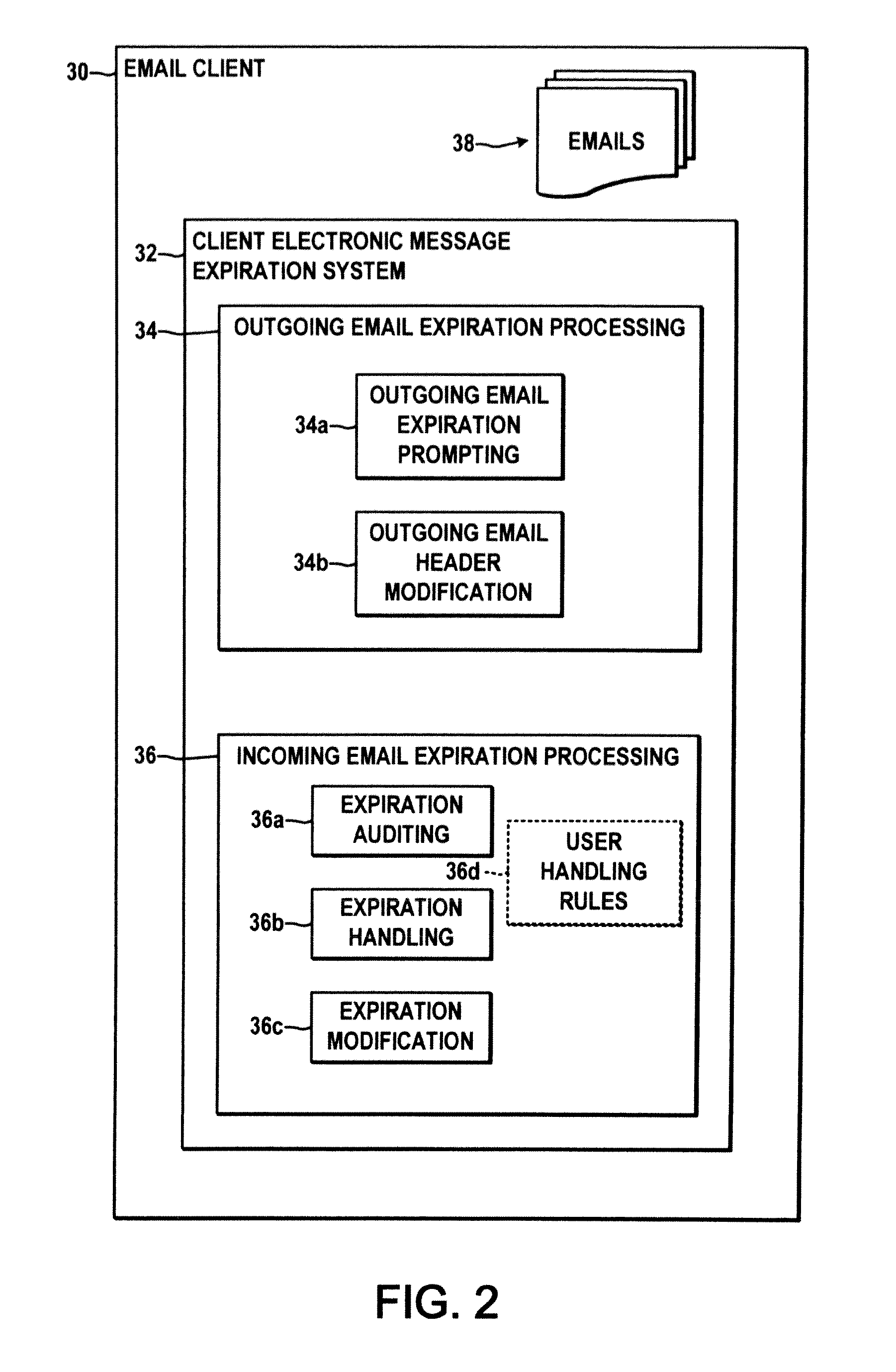
Methods and systems for expiration handling in electronic message systems
ActiveUS20100287249A1Easy to understandMinimize space occupationMultiple digital computer combinationsExpiration TimeComputer science
Systems and methods are described for electronic message expiration processing, in which a message originator or recipient can set an expiration time / date attribute for individual emails, short messages, or other electronic messages, and the messages are automatically deleted from the recipient's system or handled according to other user-selected processing rules when the expiration time / date has past.
Owner:ALCATEL LUCENT SAS
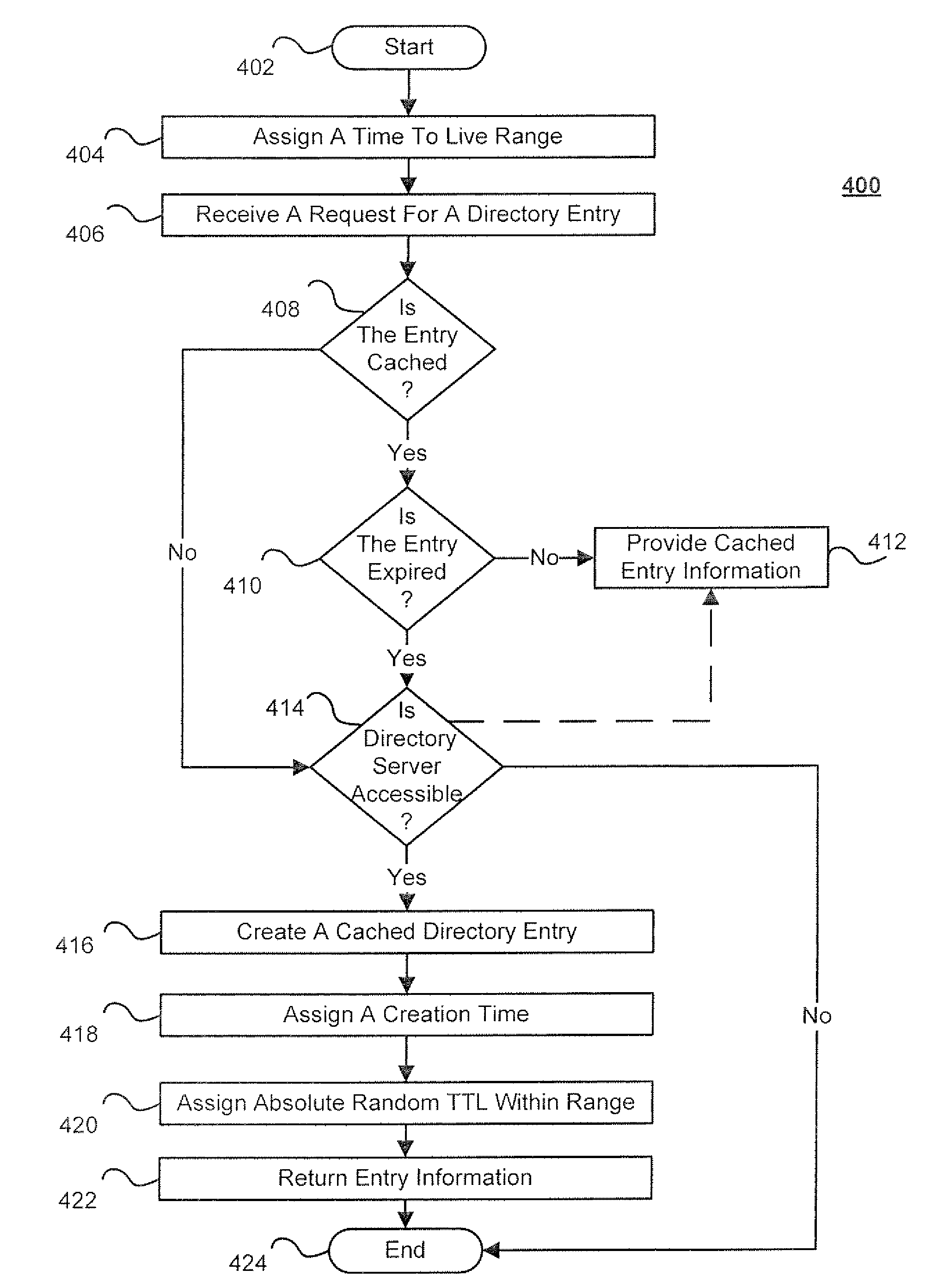
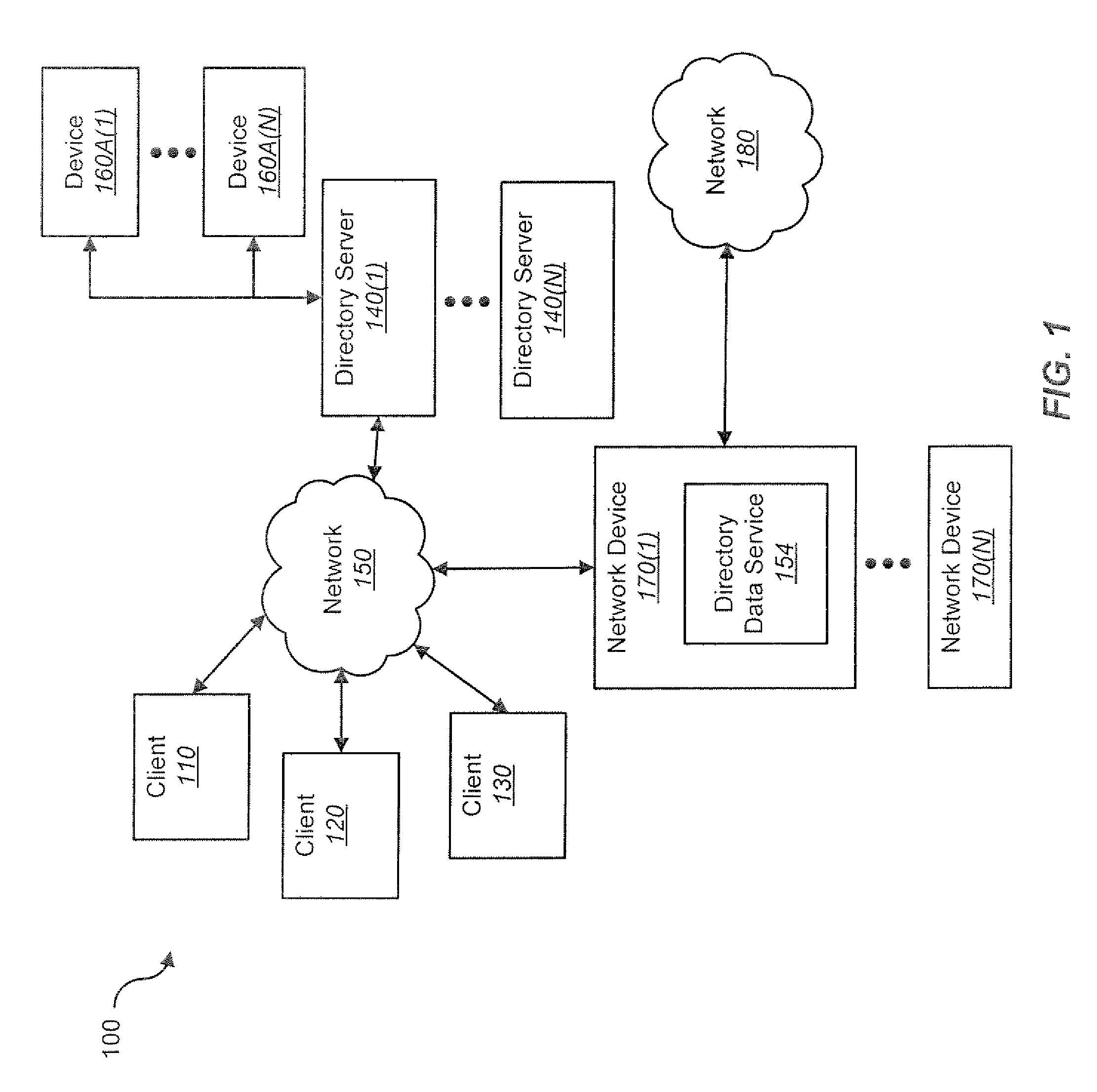
Techniques for directory server integration
ActiveUS8209491B2Reduce the amount requiredSpecial data processing applicationsMemory systemsExpiration TimeTime range
Techniques for directory server integration are disclosed. In one particular exemplary embodiment, the techniques may be realized as a method for directory server integration comprising setting one or more parameters determining a range of permissible expiration times for a plurality of cached directory entries, creating, in electronic storage, a cached directory entry from a directory server, assigning a creation time to the cached directory entry, and assigning at least one random value to the cached directory entry, the random value determining an expiration time for the cached directory entry within the range of permissible expiration times, wherein randomizing the expiration time for the cached directory entry among the range of permissible expiration times for a plurality of cached directory entries reduces an amount of synchronization required between cache memory and the directory server at a point in time.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com